Patents
Literature
33results about How to "Avoid the Risk of Privacy Leakage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
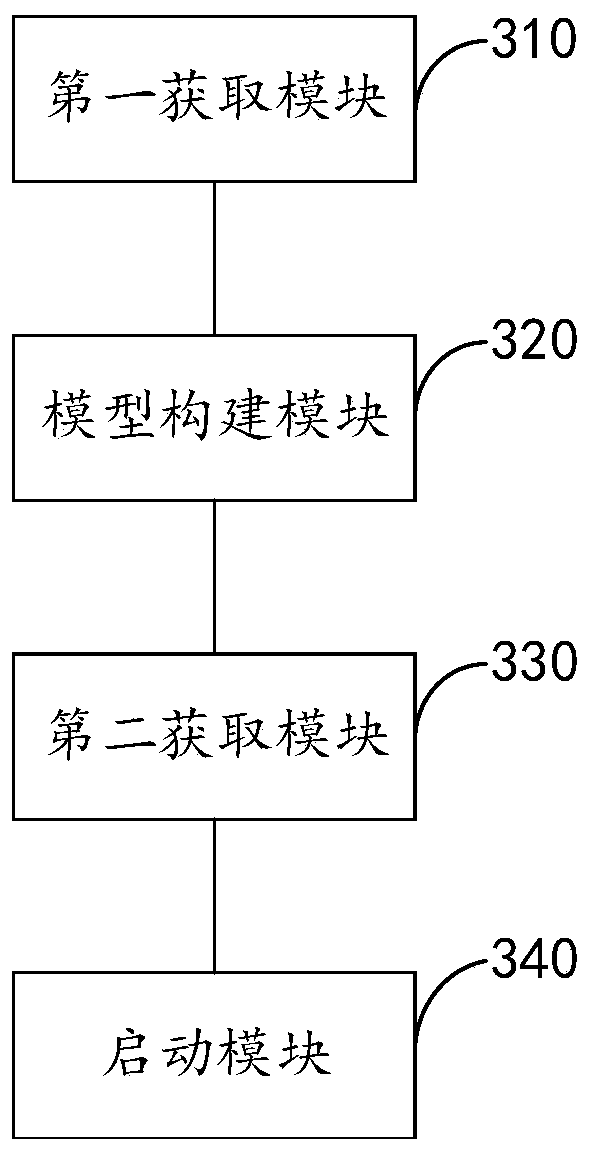
Multi-party safety calculation method and device, and electronic equipment
ActiveCN109255247AAvoid the Risk of Privacy LeakageDigital data processing detailsDigital data protectionInternet privacyElectric equipment
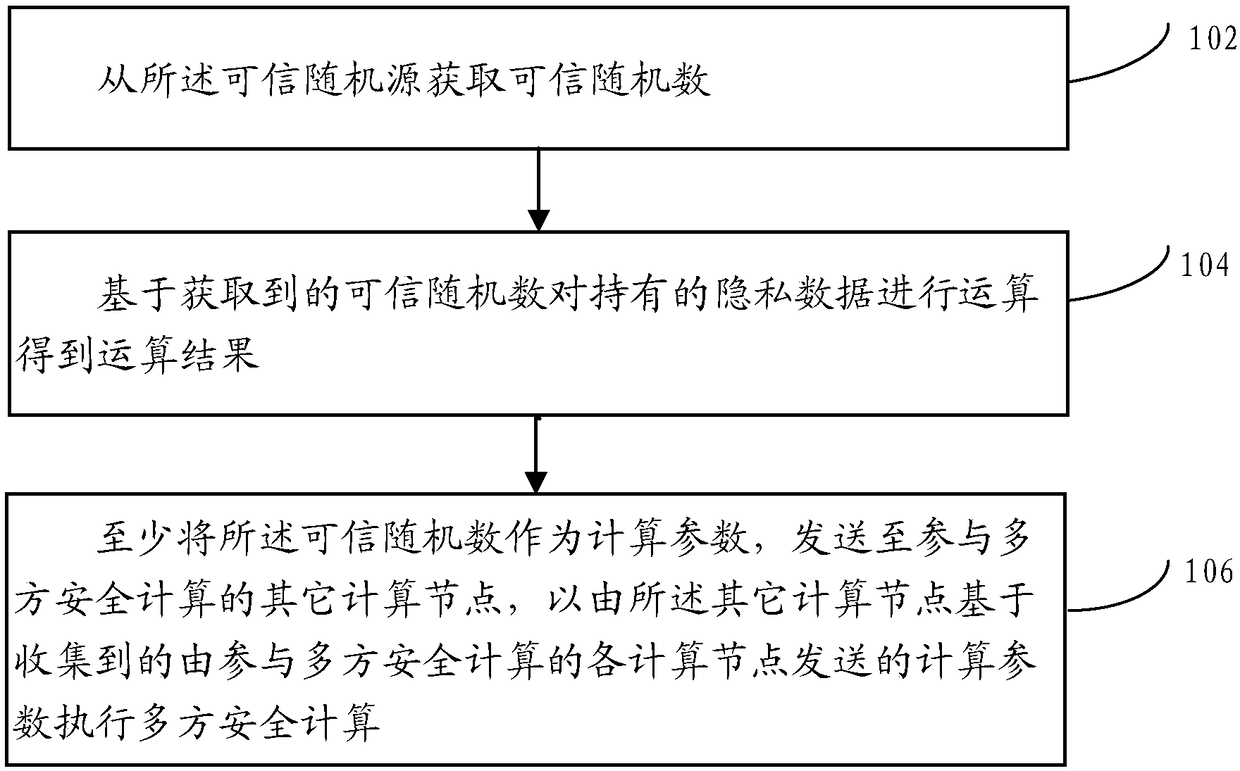
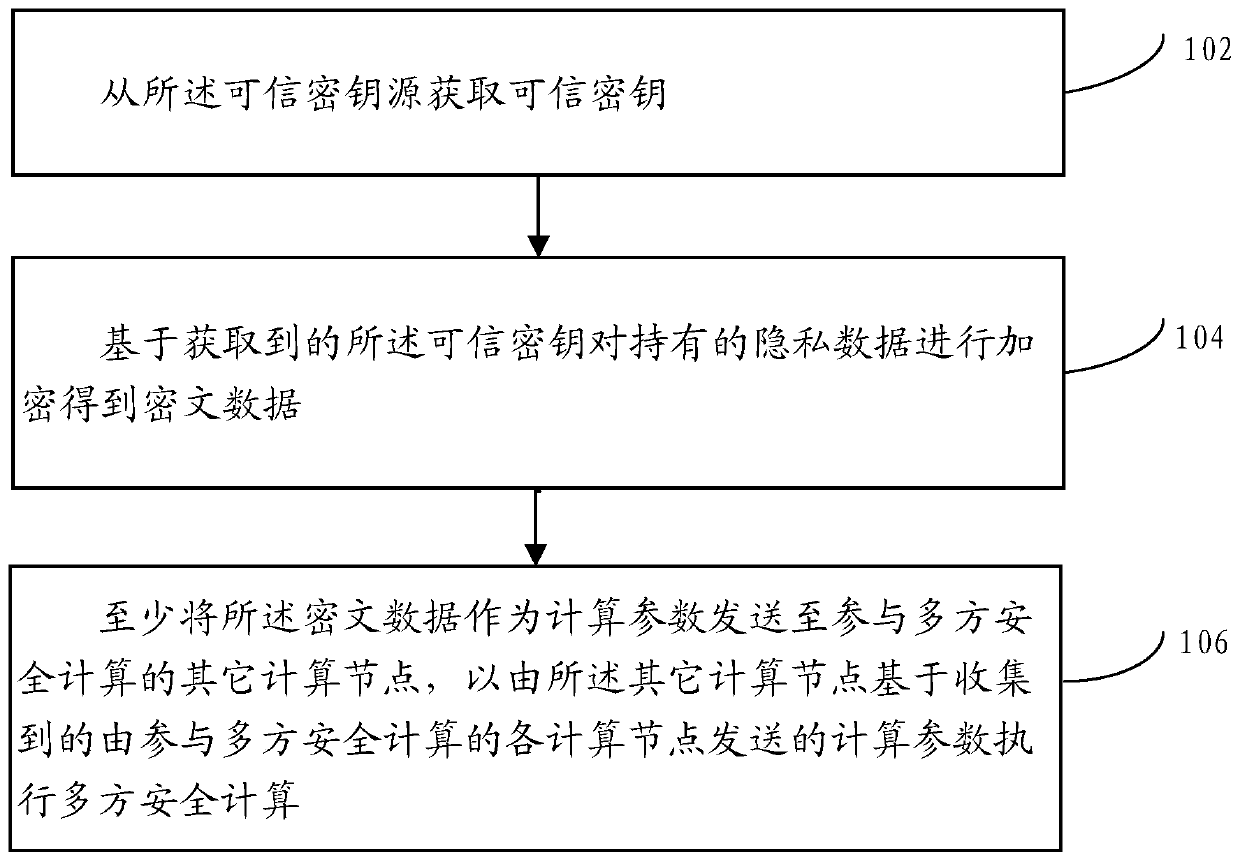
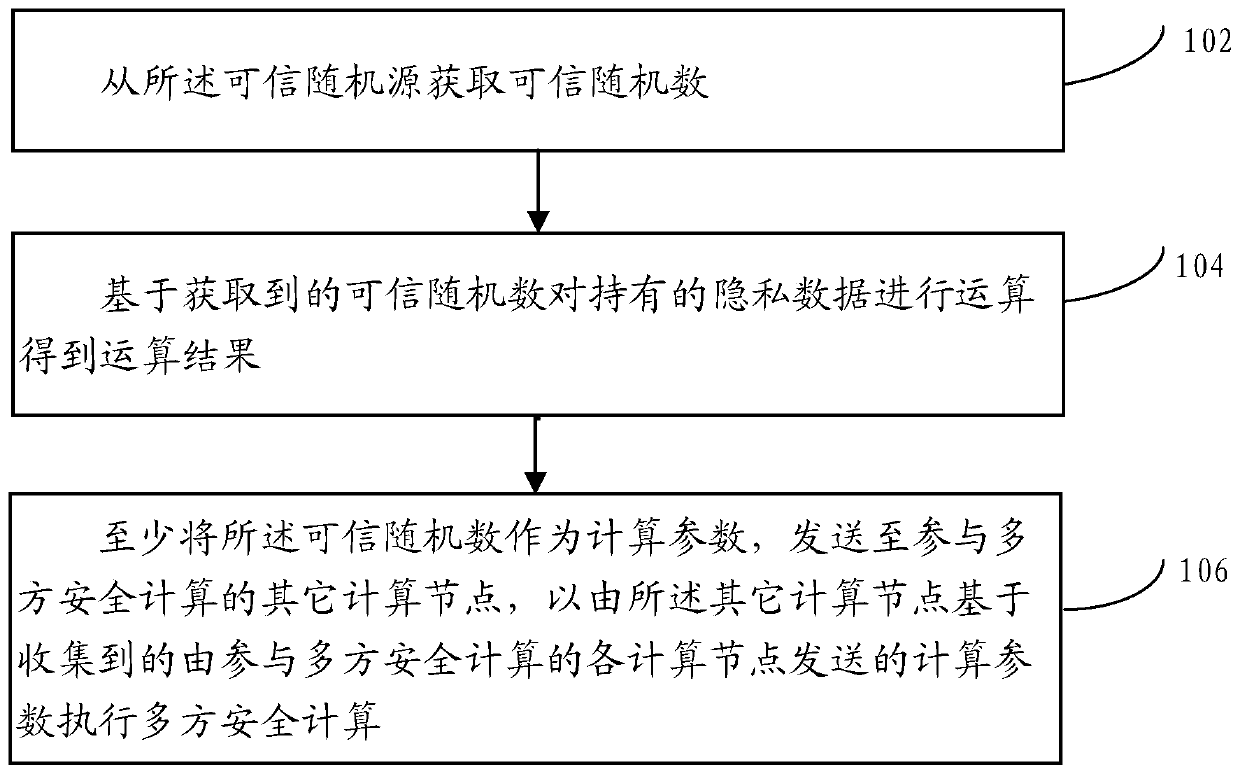
A multi-party secure computing method is applied to any computing node deployed in a distributed network. A plurality of computing nodes are deployed in the distributed network, and the plurality of computing nodes participate in the multi-party secure computing together based on the privacy data held by the plurality of computing nodes respectively; Wherein the computing node is docked with a trusted random source. The method comprises: obtaining a trusted random number from the trusted random source; Calculating the held privacy data based on the obtained trusted random number to obtain an operation result; sending at least the trusted random number as a computational parameter to other computational nodes participating in the multi-party security computation to perform the multi-party security computation by the other computational nodes based on the collected computational parameters sent by each computational node participating in the multi-party security computation.
Owner:ADVANCED NEW TECH CO LTD
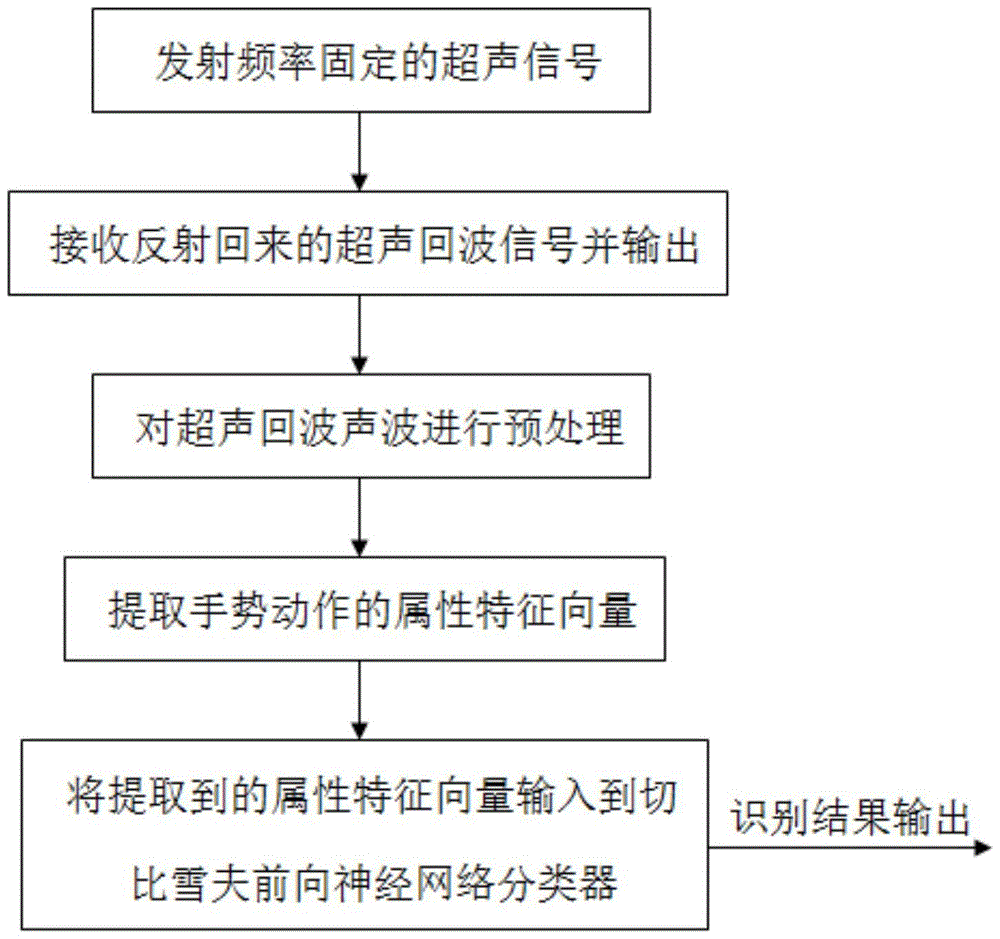
Gesture identification system and method based on Chebyshev feed forward neural network
InactiveCN105760825AAvoid the Risk of Privacy LeakageReduce complexityInput/output for user-computer interactionCharacter and pattern recognitionPattern recognitionNerve network
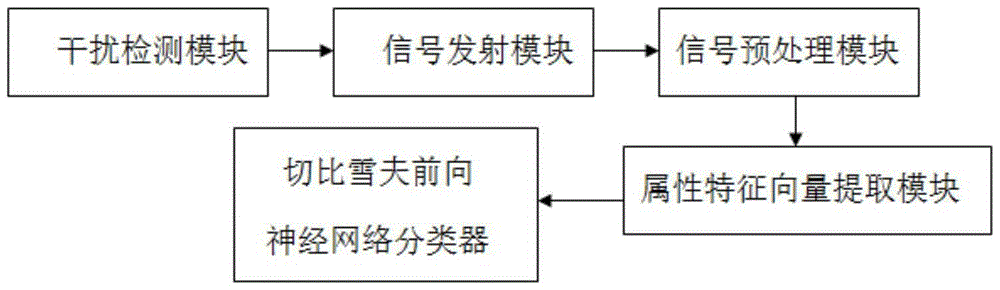
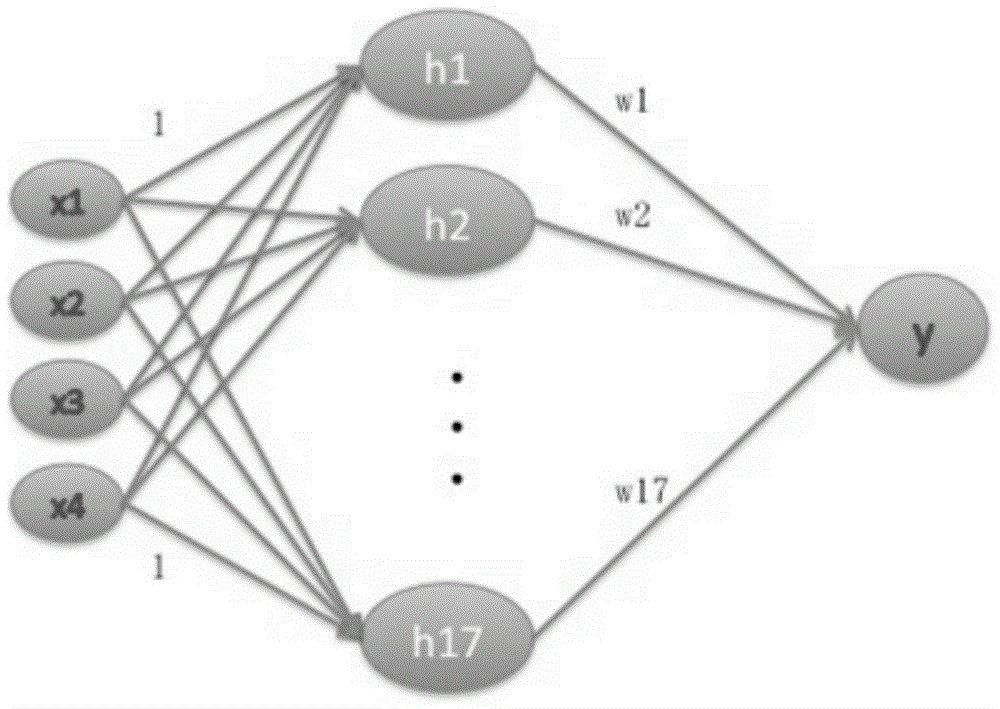
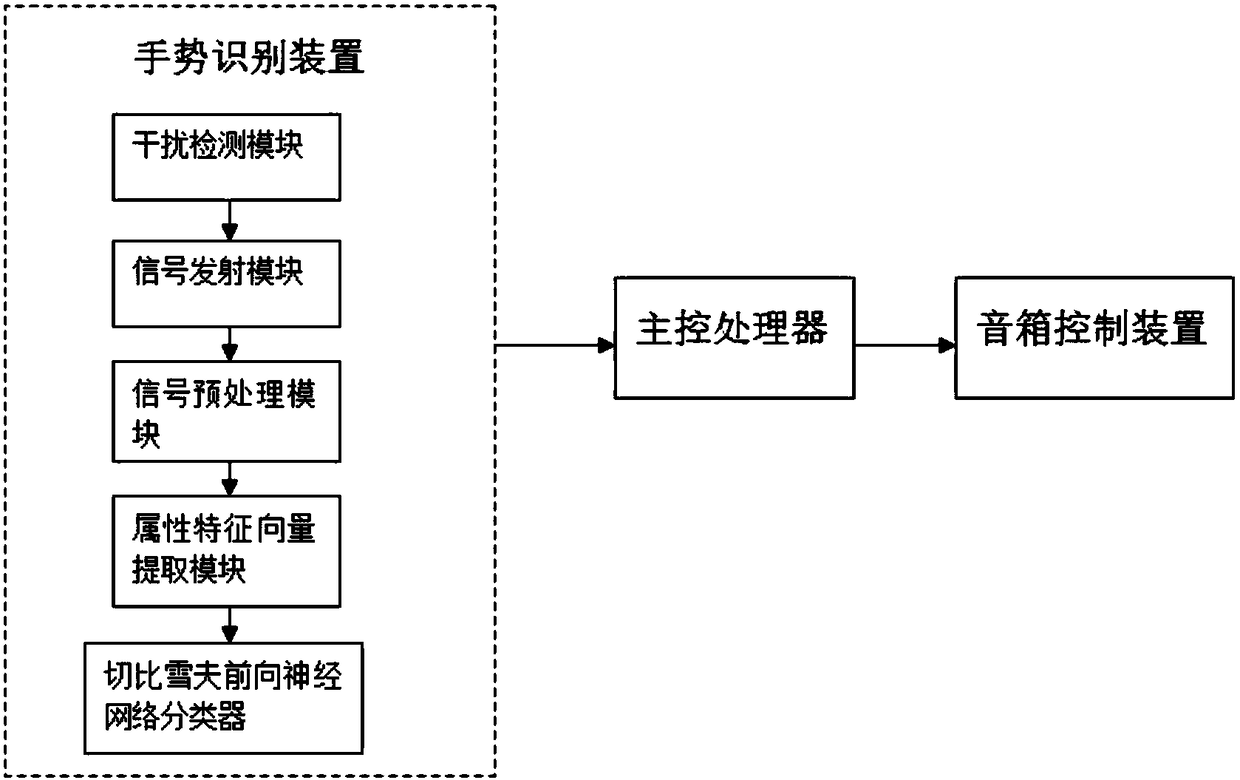
The present invention discloses a gesture identification system based on a Chebyshev feed forward neural network. The system comprises a signal emission module, a signal receiving module and a signal pre-processing module which are connected in order, and an attribute characteristic vector extraction module connected with the signal pre-processing module. The attribute characteristic vector extraction module is connected with a Chebyshev feed forward neural network classifier; the signal emission module is configured to emit ultrasonic signals; the signal receiving module is configured to receive the reflected ultrasonic echo signals; the signal pre-processing module is configured to perform pre-processing of the received ultrasonic echo signals; and the attribute characteristic vector extraction module is configured to extract the attribute characteristic vectors of the gesture motions; and the Chebyshev feed forward neural network classifier is configured to identify the attribute characteristic vectors and output identification results. The gesture identification system and method based on a Chebyshev feed forward neural network are able to perform accurate identification of different users' gestures at different environments.
Owner:SHENZHEN MAXUSTECH CO LTD
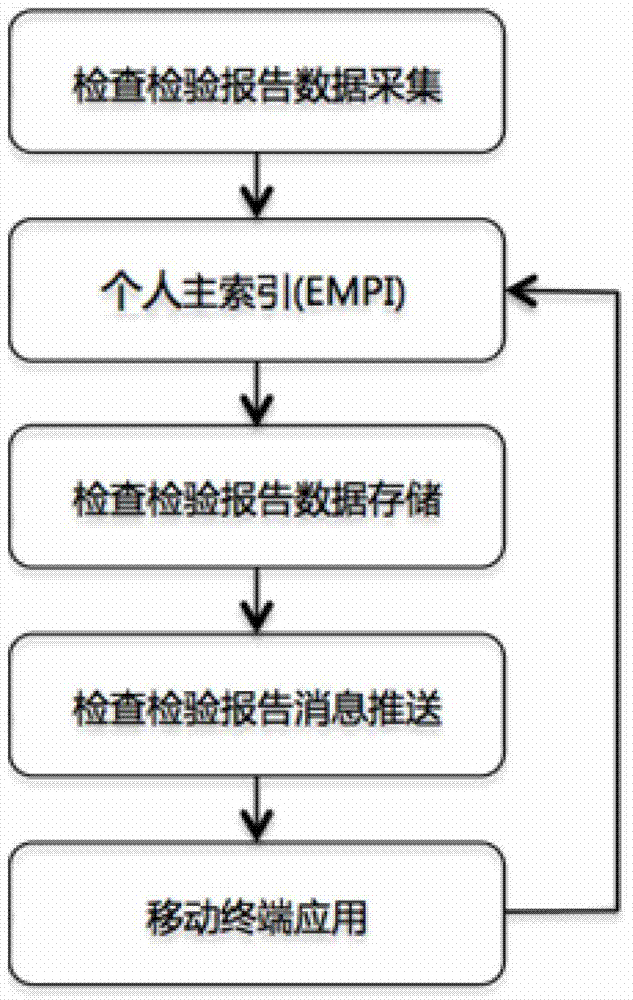
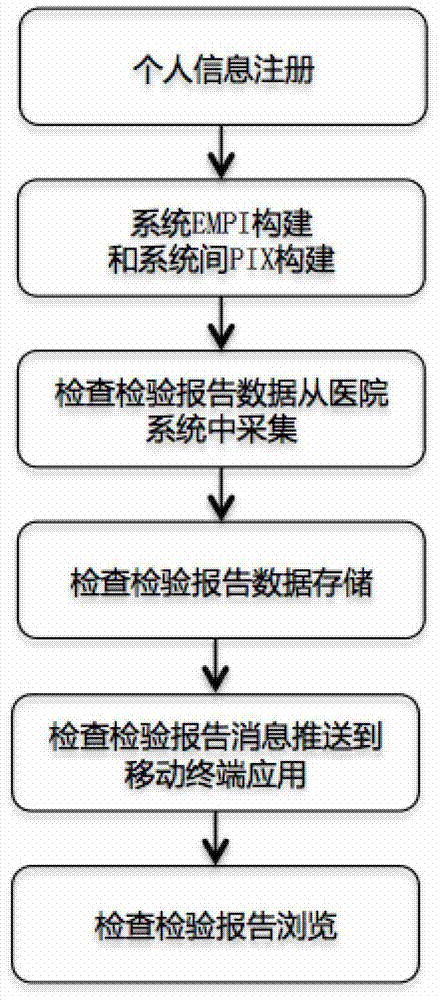
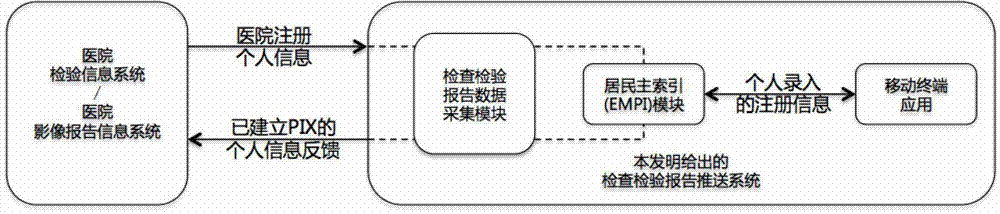
Check inspection report push system and method
InactiveCN102968752AGuaranteed objective presentationAvoid the Risk of Privacy LeakageData processing applicationsSpecial data processing applicationsPersonalizationInformation system
The invention discloses a check inspection report push system and a method. The system comprises a data acquisition module, an individual primary index module, a check inspection report push module and a mobile terminal application. The data acquisition module is connected with a hospital inspection information system and an image report information system mutually to acquire individual check inspection reports from a hospital end; the individual primary index module confirms individual identification and achieves cross system individual identification cross indexes; the check inspection report push module completes pushing of the check inspection reports according to identification matching conditions; and the mobile terminal application receives the check inspection reports and produces report browse pages to help individuals browse the check inspection reports. According to the check inspection report push system and the method, original check inspection report data of the hospital end are collected completely, and any data element mapping which changes or may lead to changes is not performed. According to the check inspection report push system and the method, original complete check inspection reports are pushed to individuals, personalized characteristics of check inspection reports of various mechanisms are preserved, and the individuals are helped to obtain the individual check inspection reports timely through mobile internets.
Owner:段缨
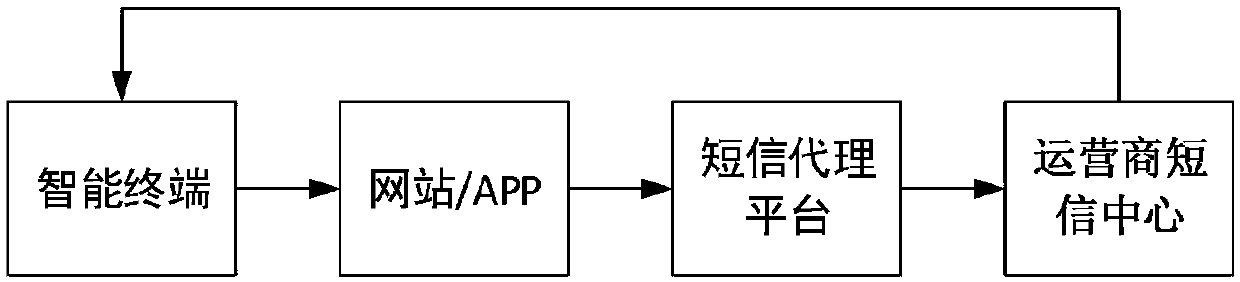
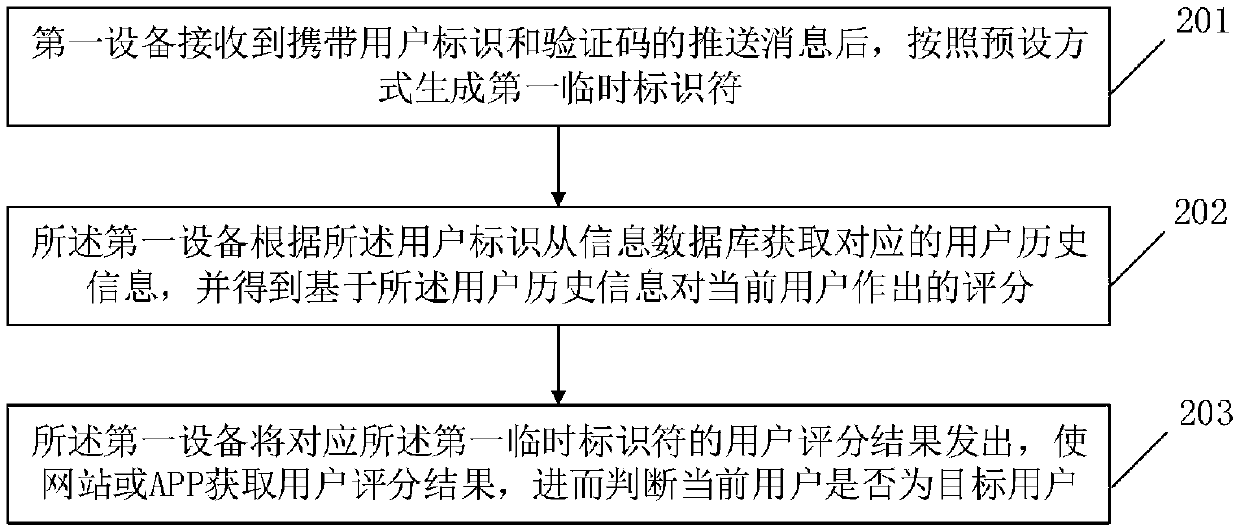
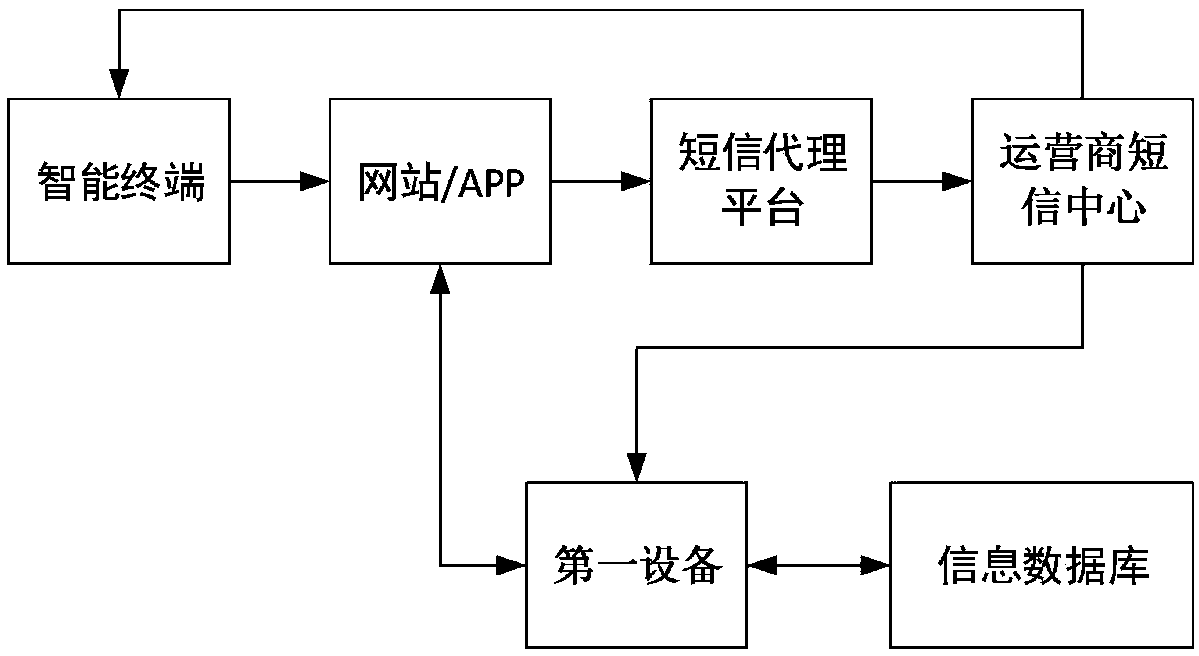
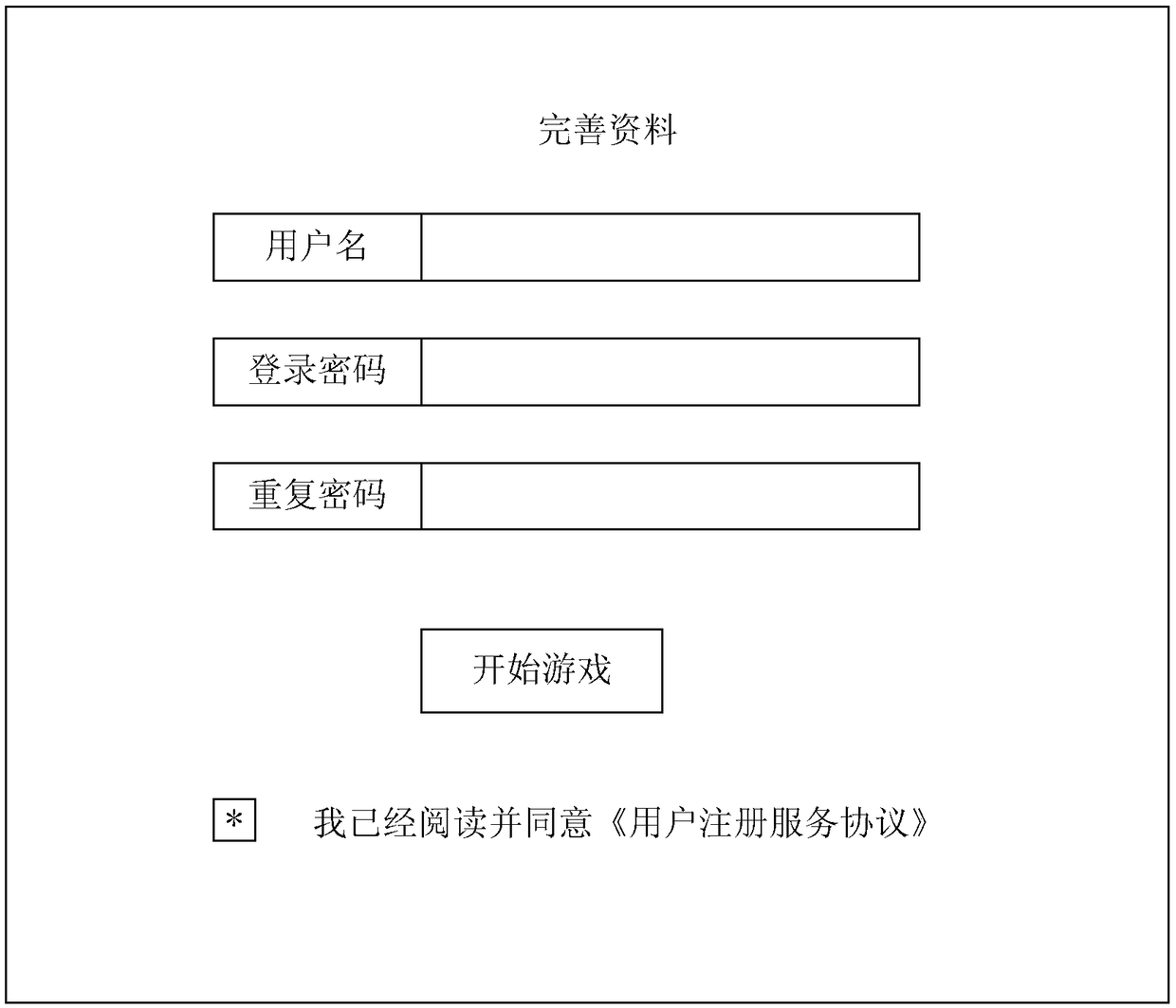
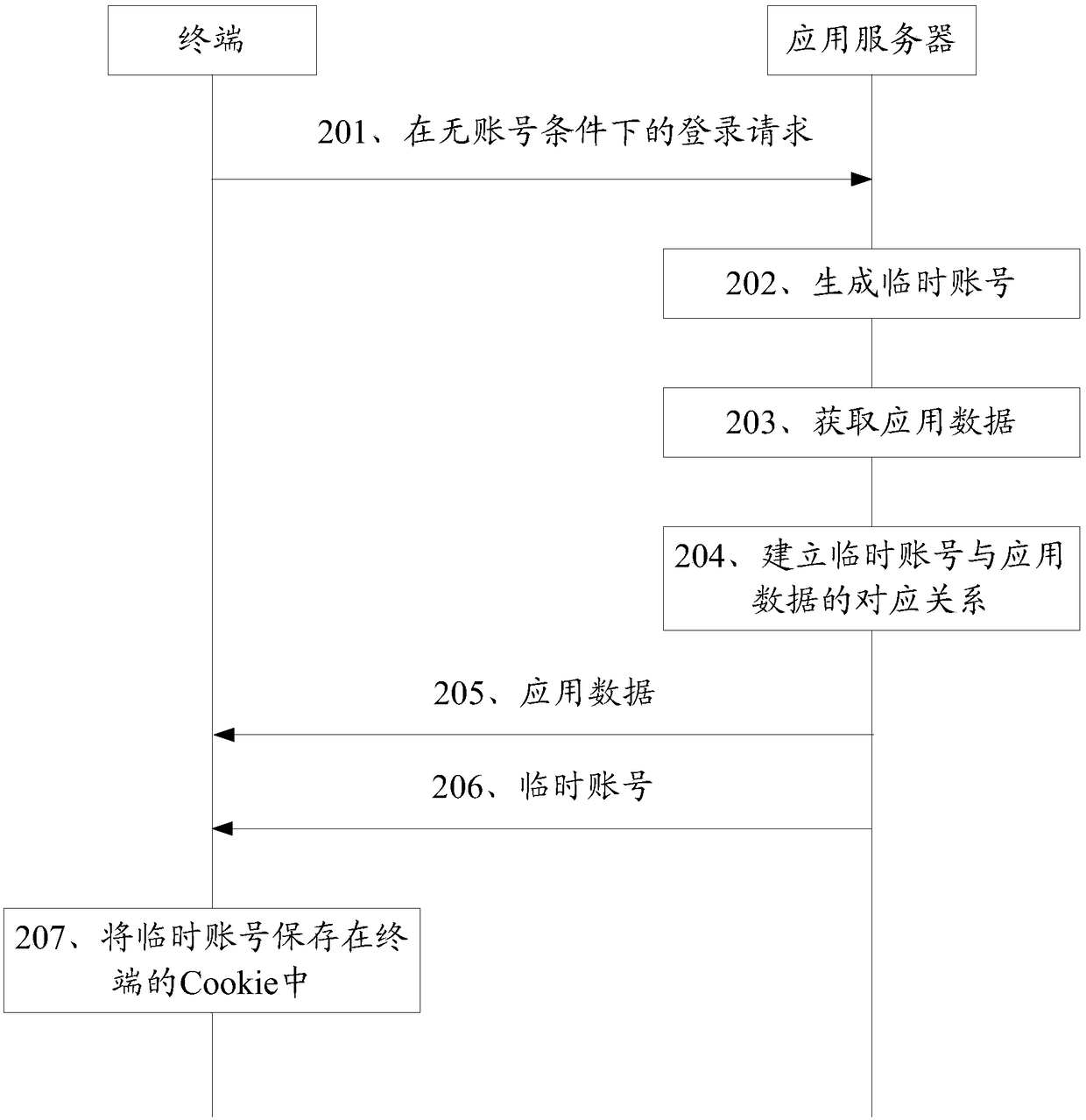
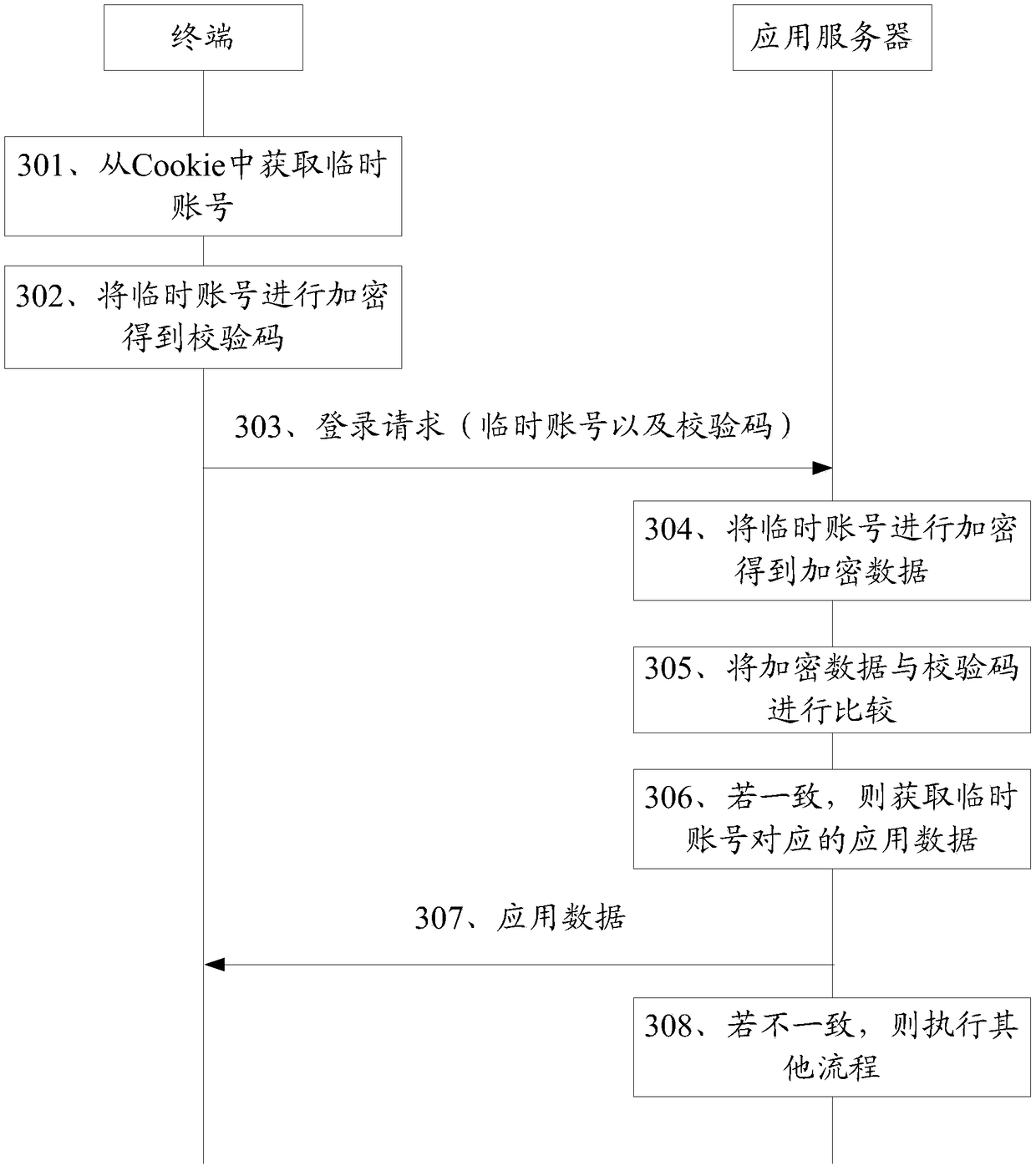
Identity authentication method and device based on temporary identifier
ActiveCN109639719AAvoid the Risk of Privacy LeakageEffective monitoringKey distribution for secure communicationUser identity/authority verificationInternet privacyUser privacy
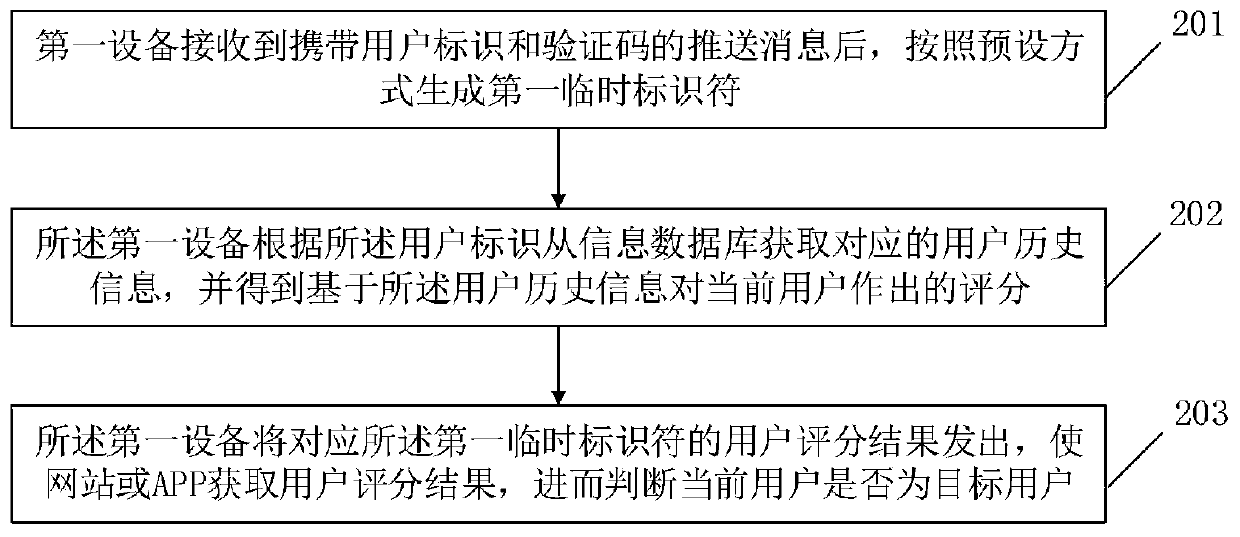
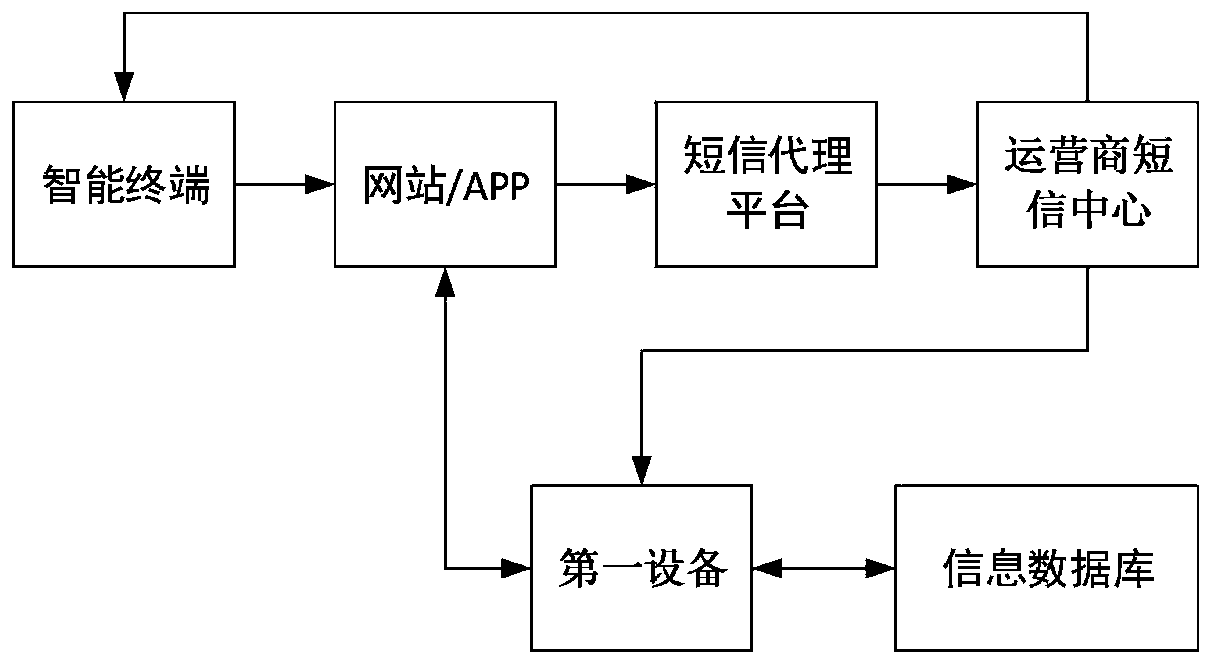
The invention relates to the technical field of communication technology and personal information services and provides an identity authentication method and device based on a temporary identifier, wherein the method comprises the following steps: receiving a push message carrying a user identifier and a verification code and generating a first temporary identifier according to a preset mode; acquiring corresponding user historical information from an information database according to the user identifier, and obtaining a score made by the current user based on the user historical information;sending out a user grading result corresponding to the first temporary identifier so that the website or an APP can obtain the user grading result and judge whether the current user is a target user or not. According to the method and the device in the invention, the user can be effectively verified and screened according to the user historical information, which facilitates effective monitoring of the website or the APP and avoids a potential user privacy leakage risk caused by the fact that the fixed user identifier is used in the network.
Owner:武汉稀云科技有限公司
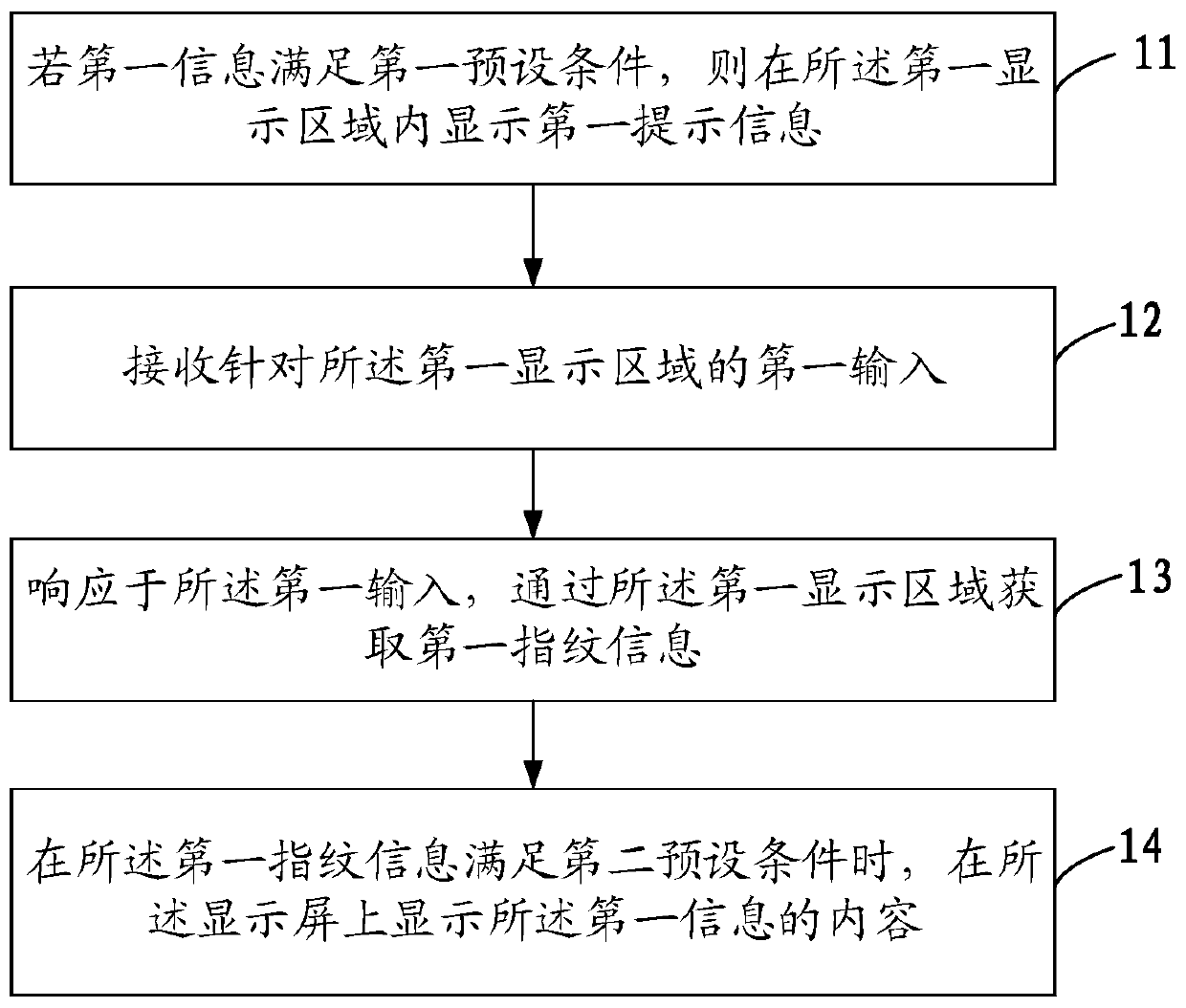
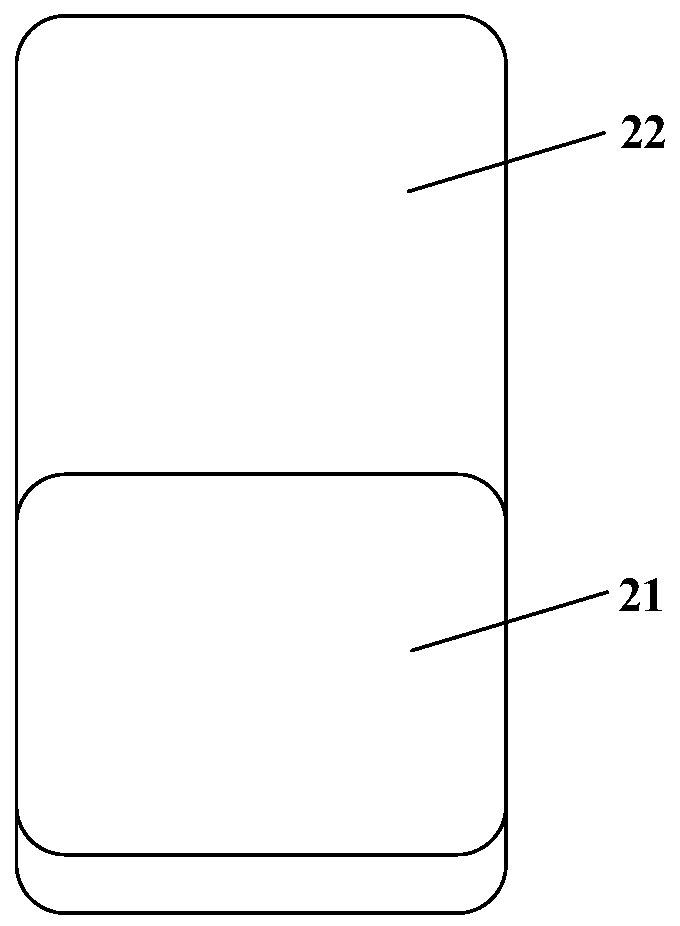
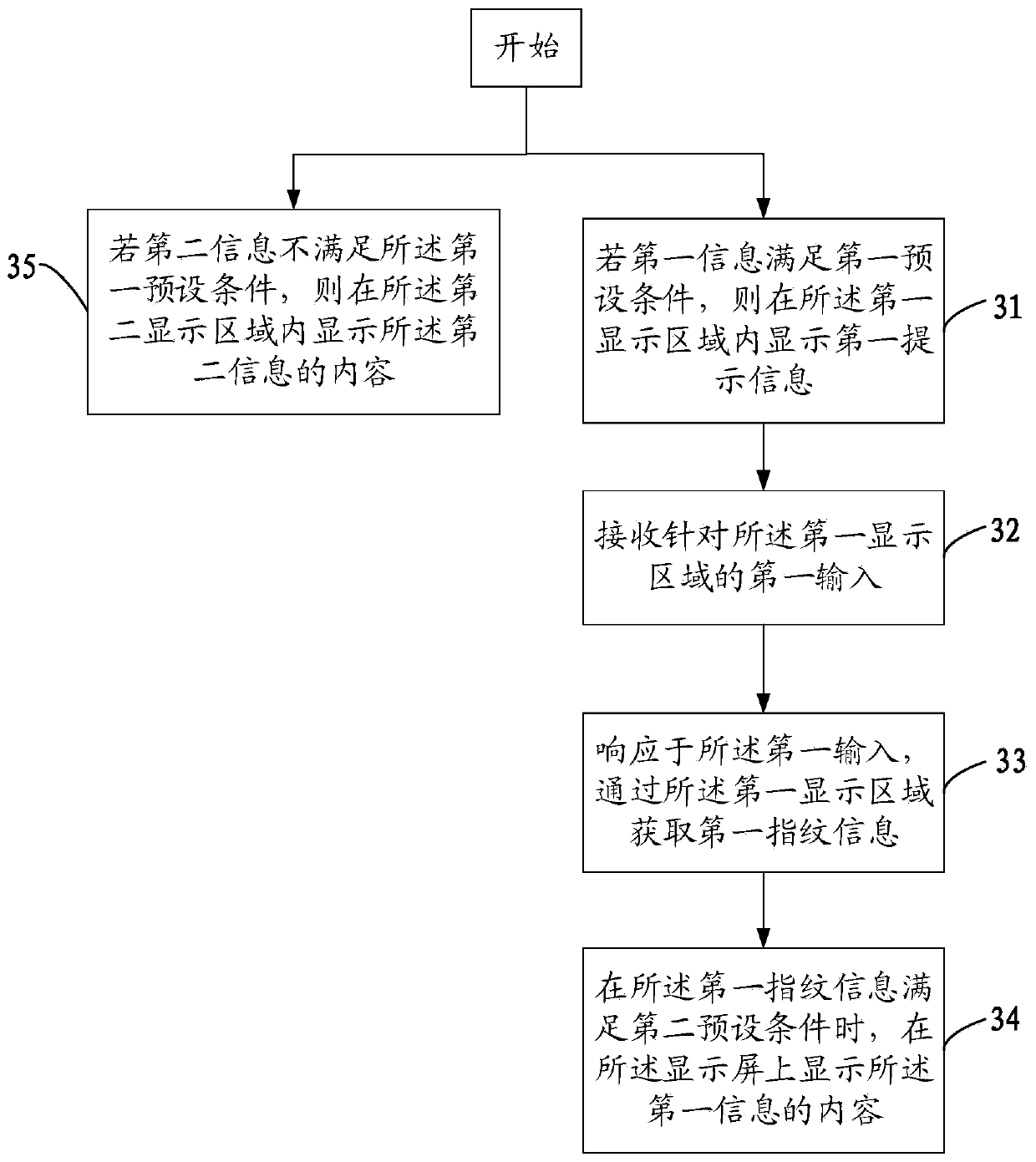
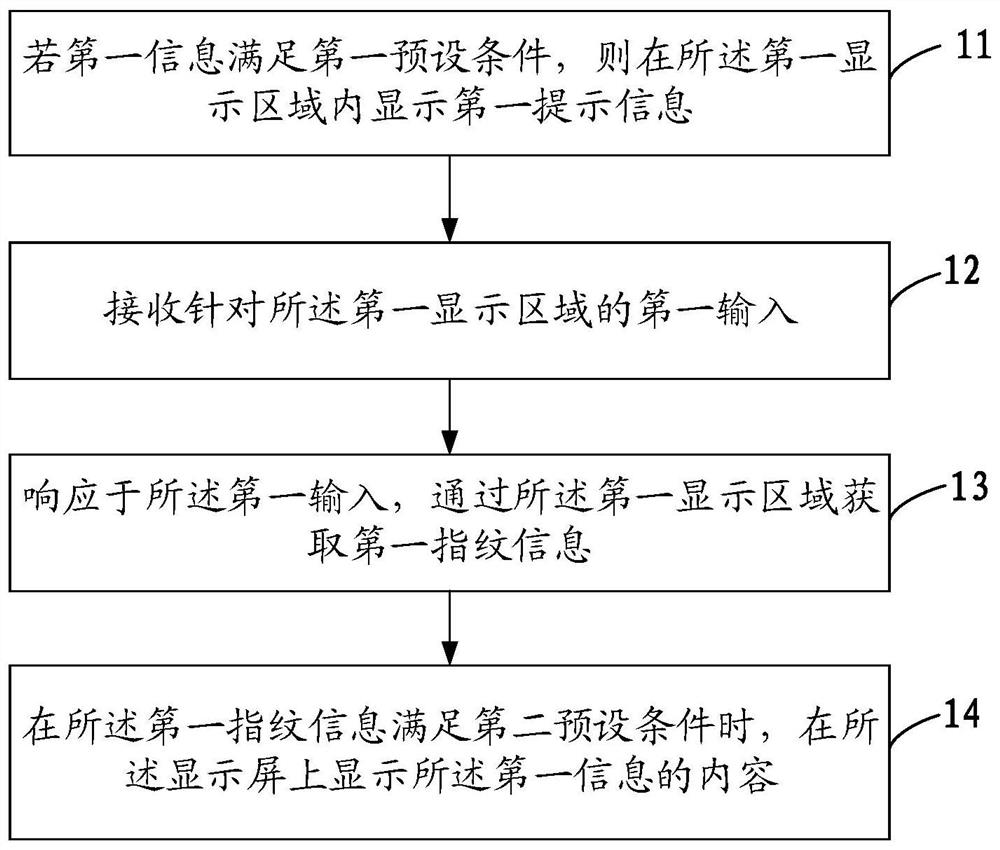
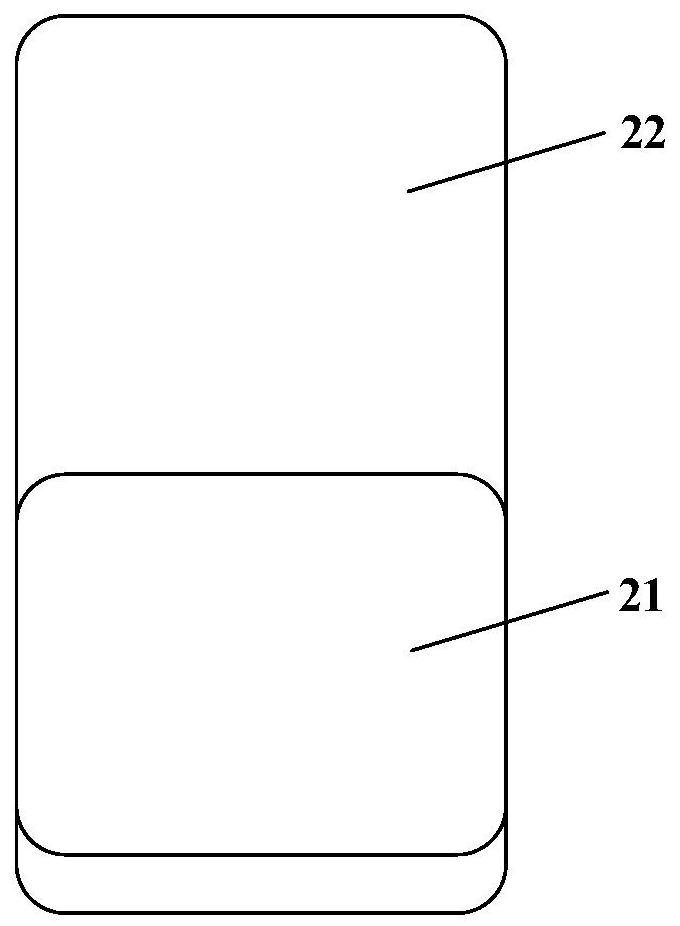
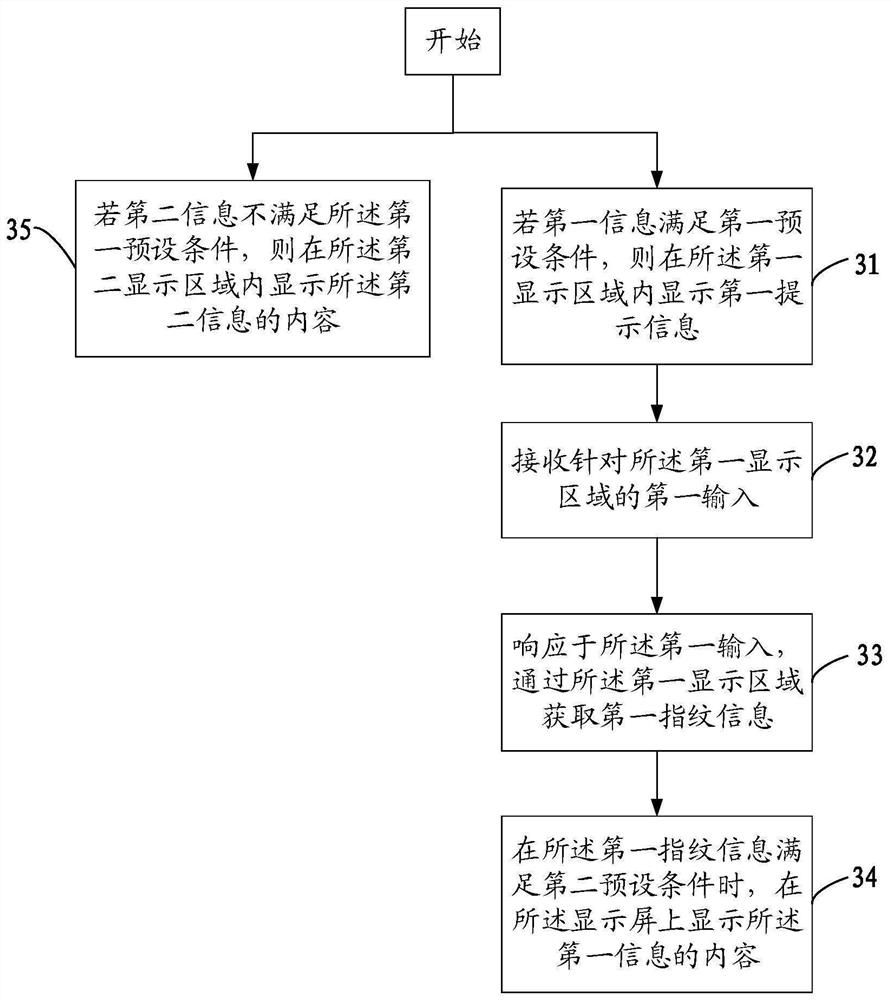
Information display method and mobile terminal
ActiveCN109993010AImprove securityEnsure safetyStatic indicating devicesDigital data protectionInformation securityComputer science
The invention discloses an information display method and a mobile terminal, the method is applied to the mobile terminal with a display screen, and the display screen comprises a first display area;the method comprises the steps that if first information meets a first preset condition, first prompt information is displayed in a first display area; receiving a first input for the first display area; obtaining first fingerprint information through the first display area in response to the first input; and when the first fingerprint information satisfies a second preset condition, displaying the content of the first information on the display screen. According to the invention, the information display security can be ensured, and the risk of privacy disclosure is avoided.
Owner:VIVO MOBILE COMM CO LTD
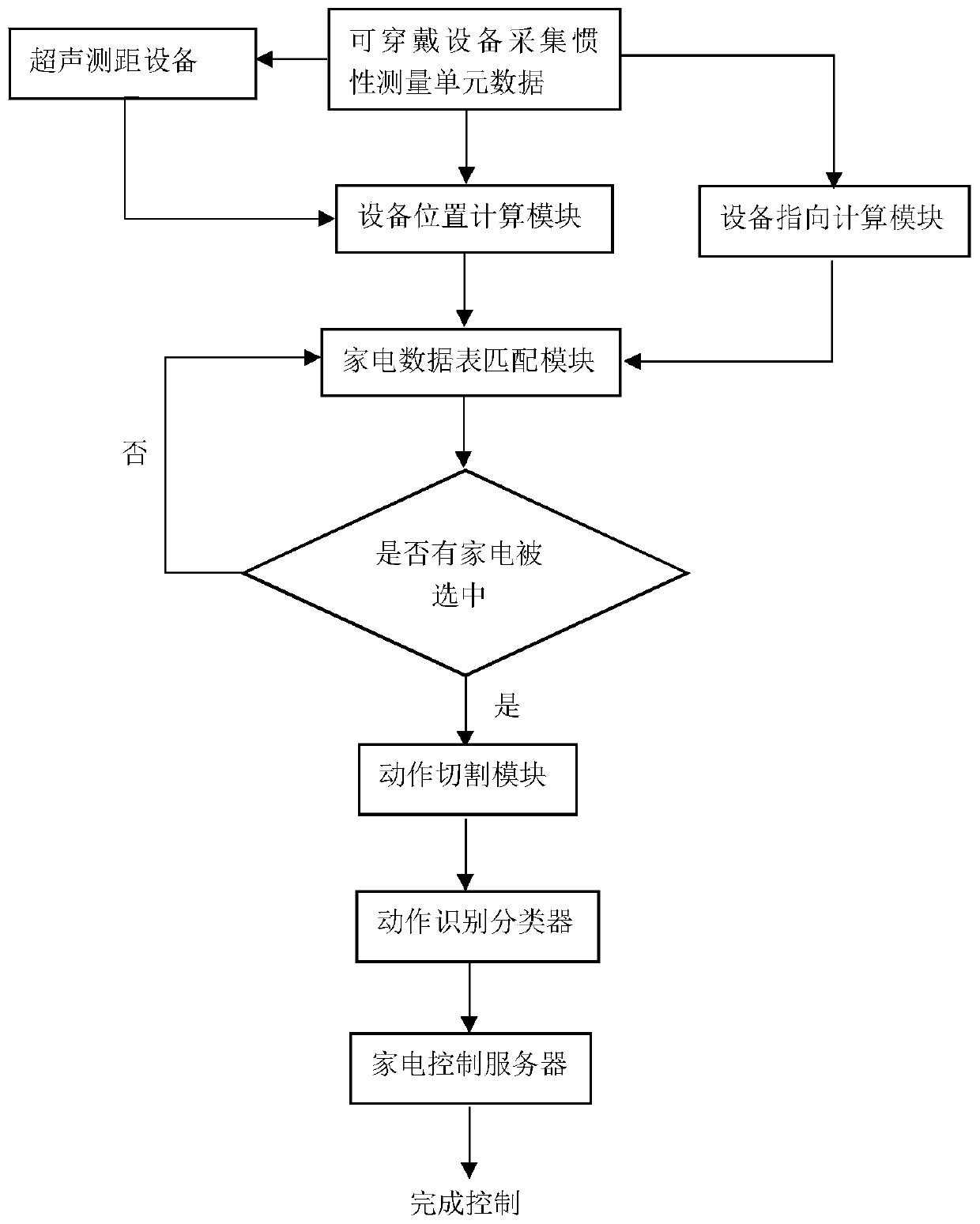
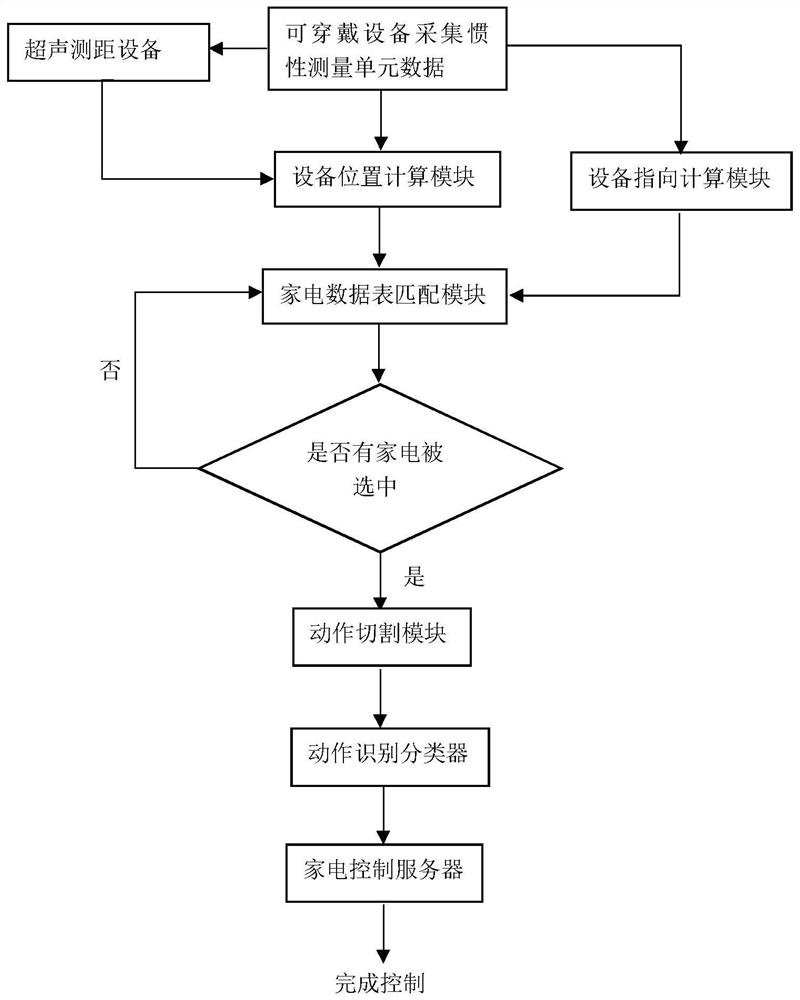
Multi-home appliance control method based on wearable device
ActiveCN109870984ASimple controlAvoid Privacy LeakageComputer controlNavigation by speed/acceleration measurementsEmbedded systemInertial measurement unit
A multi-home appliance control method based on a wearable device comprises the following steps of: step 1, obtaining three-dimensional spatial information of a room of the user and locations of home appliances; step 2, placing an ultrasonic ranging device for positioning in the room; step 3, obtaining information of a sensor on the wearable device; step 4, during the training phase, extracting data feature values of the sensor and establishing a feature database and a classifier; and step 5, during the control phase, acquiring and executing a user instruction according to the information of the sensor returned by the wearable device and an auxiliary positioning device. The multi-home appliance control method is simple and natural, avoids the risk of privacy leakage, can calculate the position and orientation of the wearable device by analyzing the inertial measurement unit and the ultrasonic ranging information, and improves the reliability of the control system by accurately determining devices selected by the user in the multi-home appliance scene by using the previously established data table.
Owner:ZHEJIANG UNIV +1
Data processing method, device and equipment and computer readable storage medium
InactiveCN110365685AAvoid Security-Compromised IssuesAvoid the abuse of personal privacyUser identity/authority verificationRelevant informationChain network
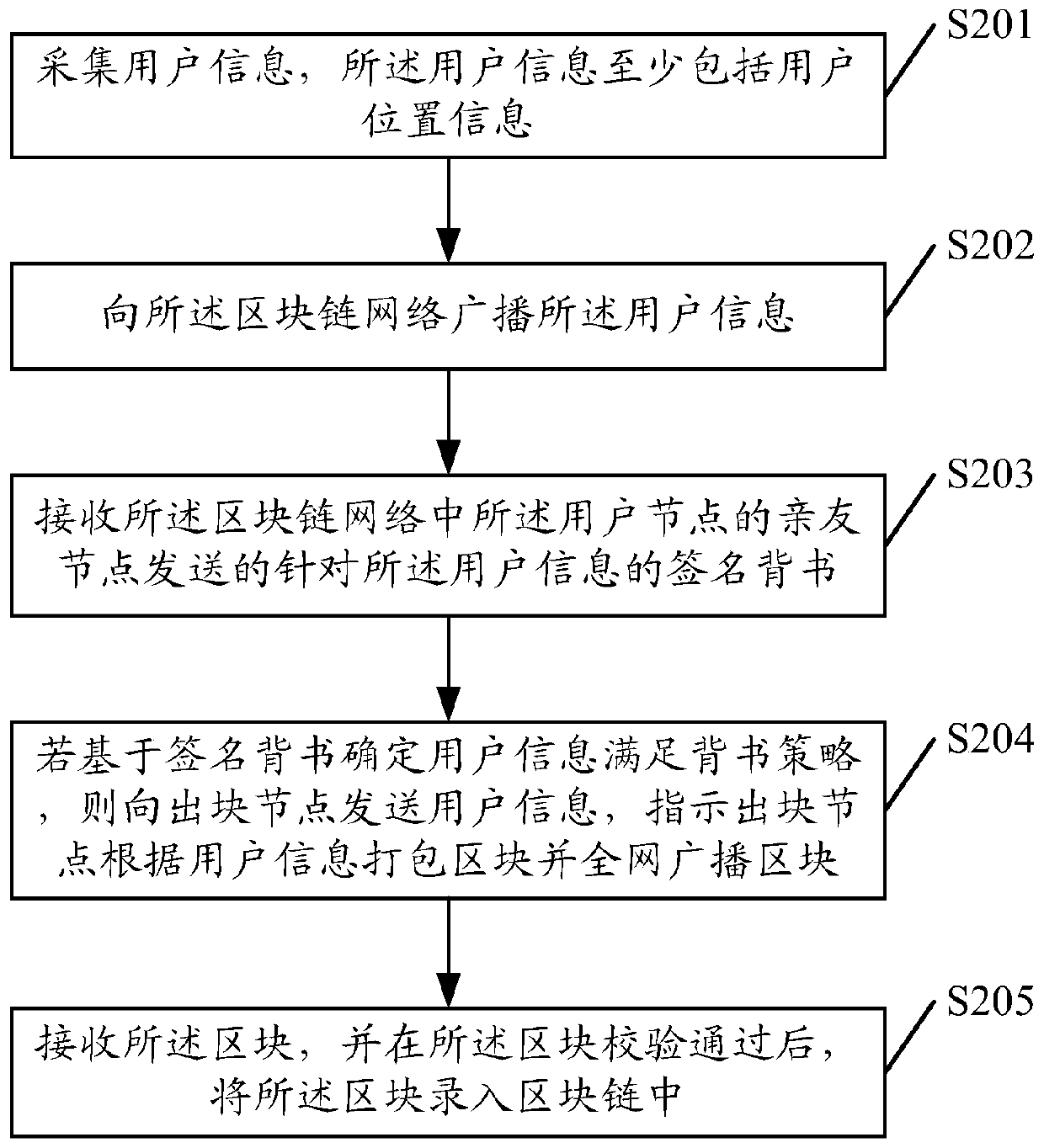
The invention discloses a data processing method, comprising: acquiring user information, and the user information at least comprising user position information; broadcasting user information to a block chain network; receiving signature endorsement of the user information sent by relatives and friends of user nodes in the block chain network; if it is determined that the user information meets anendorsement strategy based on a signature endorsement, sending the user information to an outgoing block node, and indicating the outgoing block node to package a block according to the user information and broadcast the block in the whole network; and receiving the block, and inputting the block into a block chain after the block passes the verification. Thus, each node of the block chain network maintains the user travel related information, when the user is in danger, any node can provide travel related data to ensure the user safety, and the user travel related data only circulates in theblock chain network and the security party, thereby avoiding the risk of privacy disclosure. The invention further discloses a corresponding device, equipment and a medium.
Owner:HUNDSUN TECH
Monitoring method and device and computer equipment
PendingCN111460886AAvoid Privacy LeakageMeet various needsDiagnostic recording/measuringSensorsMicrowave radarUser privacy
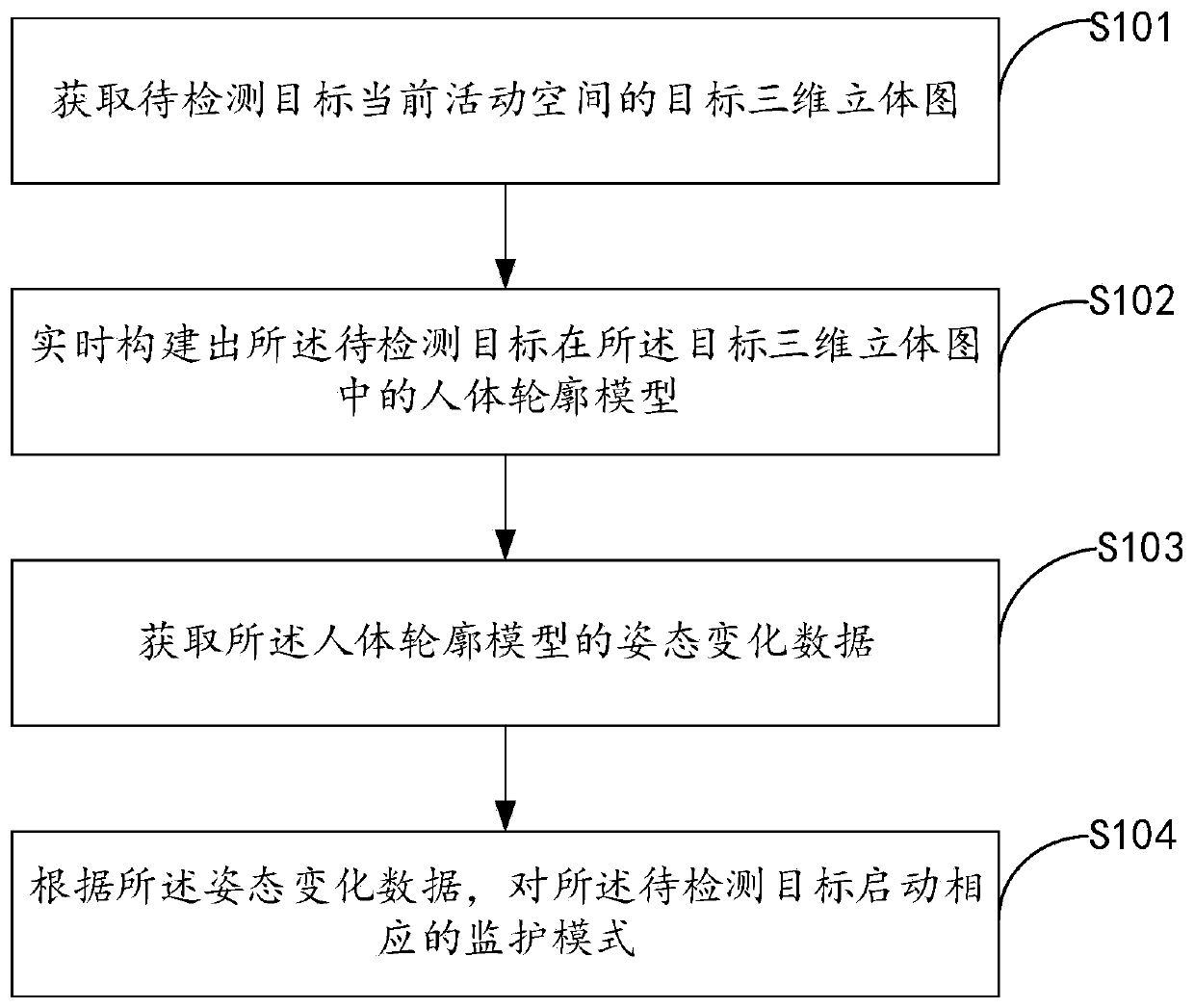
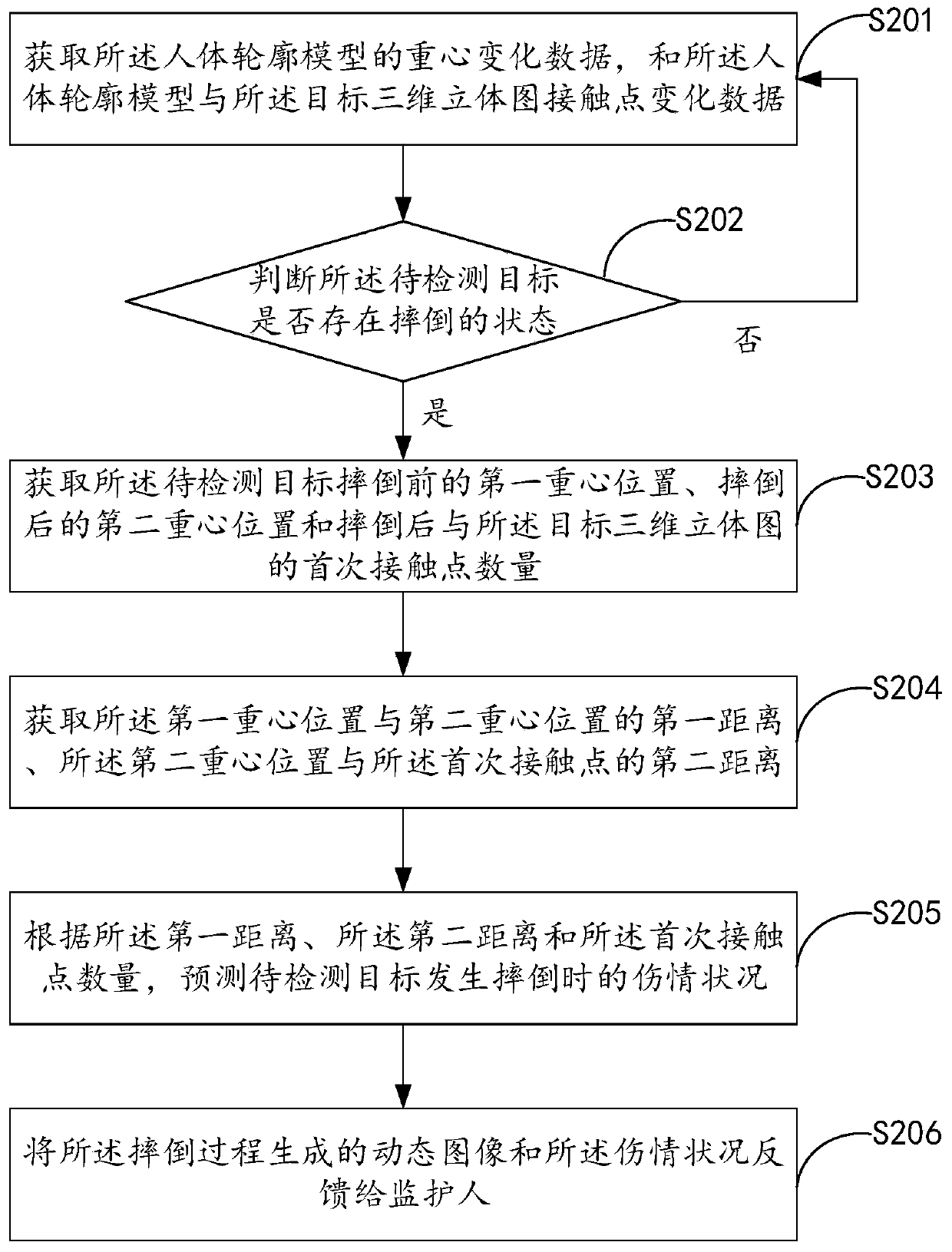
The invention relates to a monitoring method and device and computer equipment, which are applied to a monitoring system based on a microwave radar, and the method comprises: obtaining a target three-dimensional stereogram of a current activity space of a to-be-detected target, constructing a human body contour model of the to-be-detected target in the target three-dimensional diagram in real time, acquiring posture change data of the human body contour model, and starting a corresponding monitoring mode for the to-be-detected target according to the posture change data. According to the monitoring method, the problems that in the prior art, due to the privacy problem of a user, a monitoring missing area occurs, and all activity areas of the elderly at home cannot be effectively monitoredare solved, corresponding monitoring modes can be carried out according to different field conditions, and the multi-aspect requirements of the user are met.
Owner:GREE ELECTRIC APPLIANCES INC +1
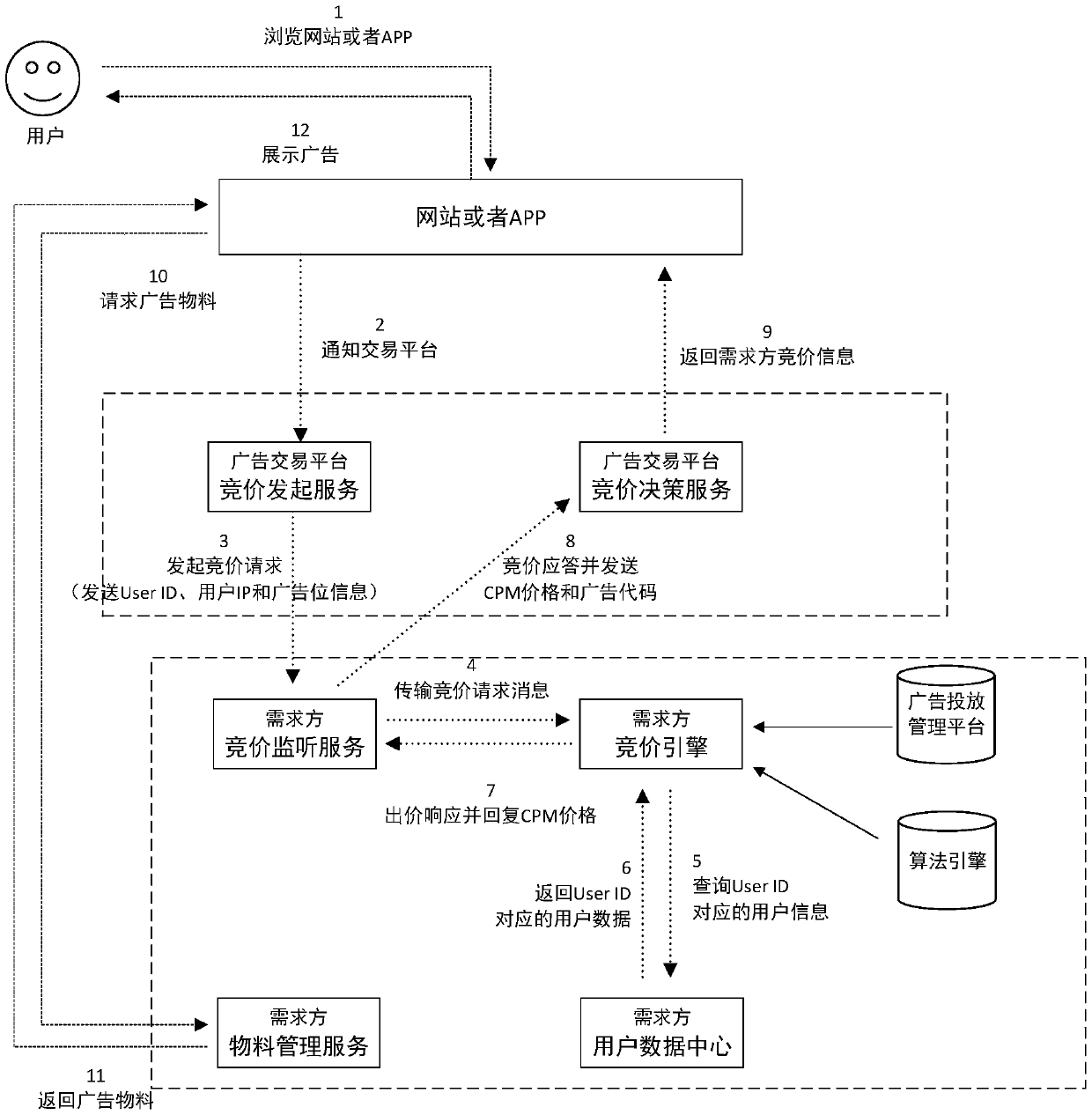
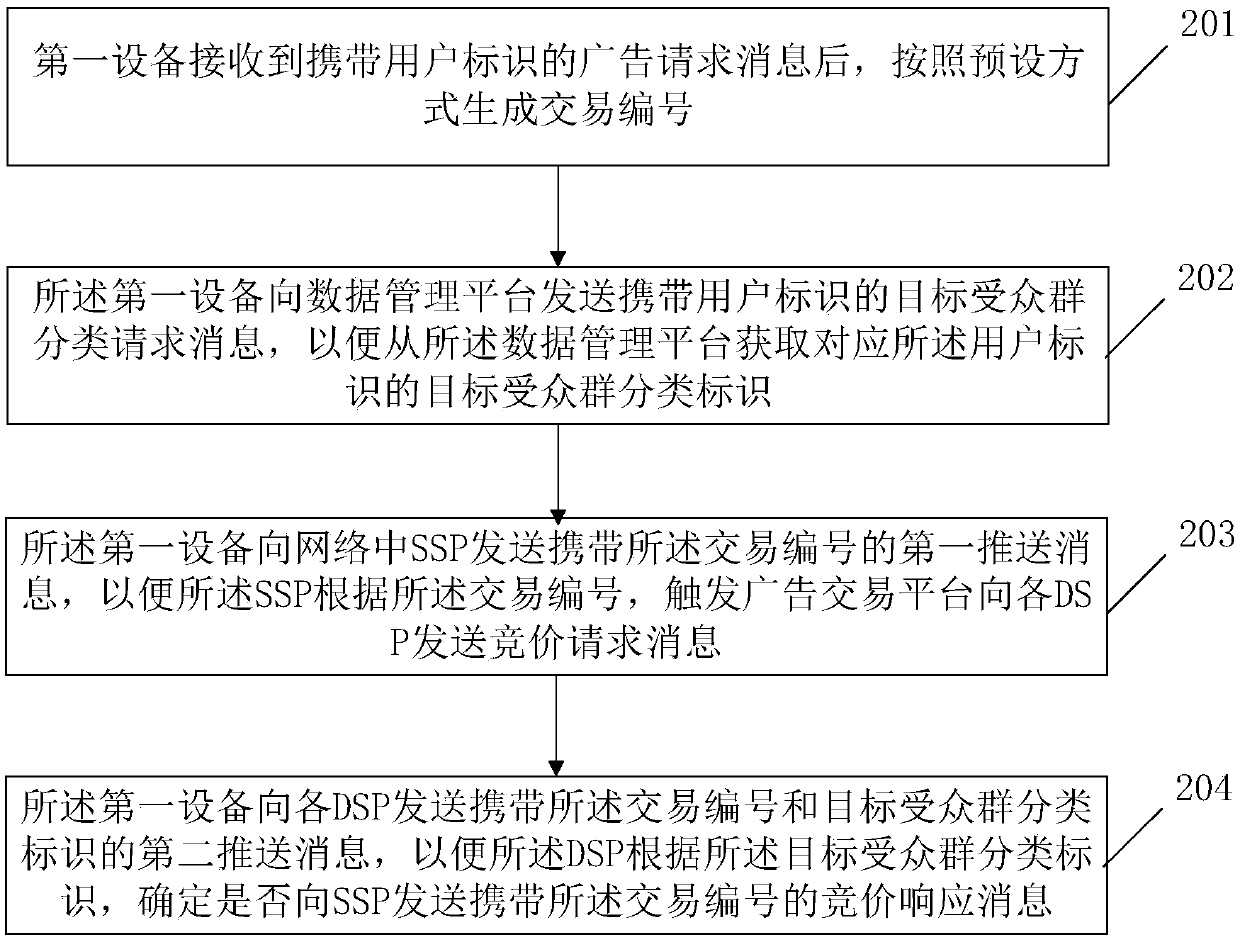
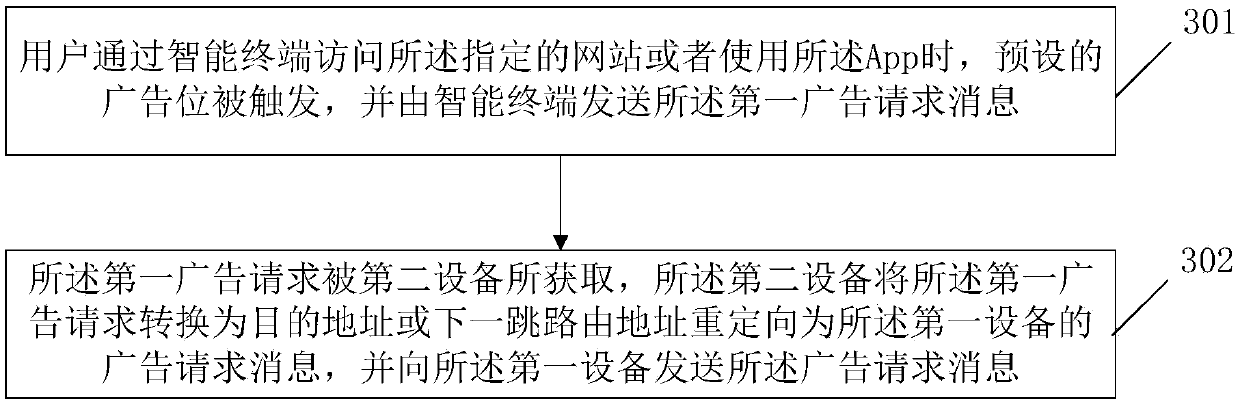
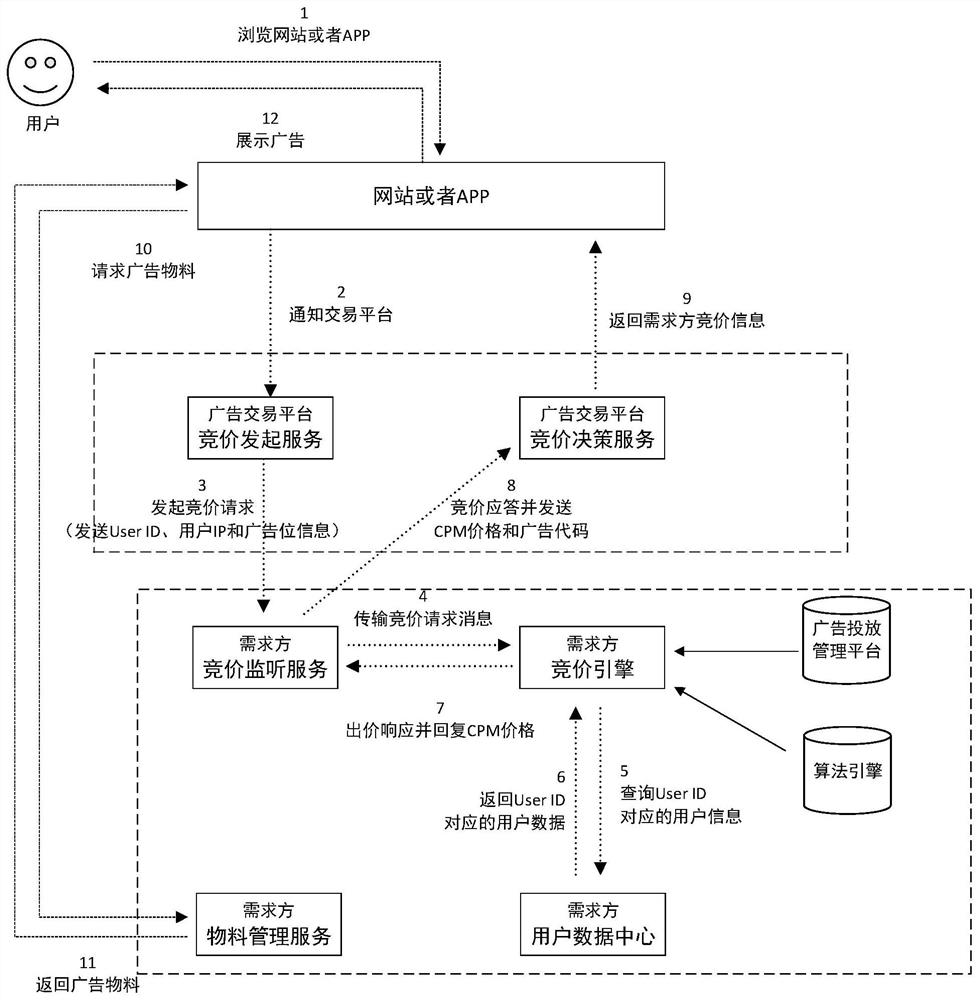
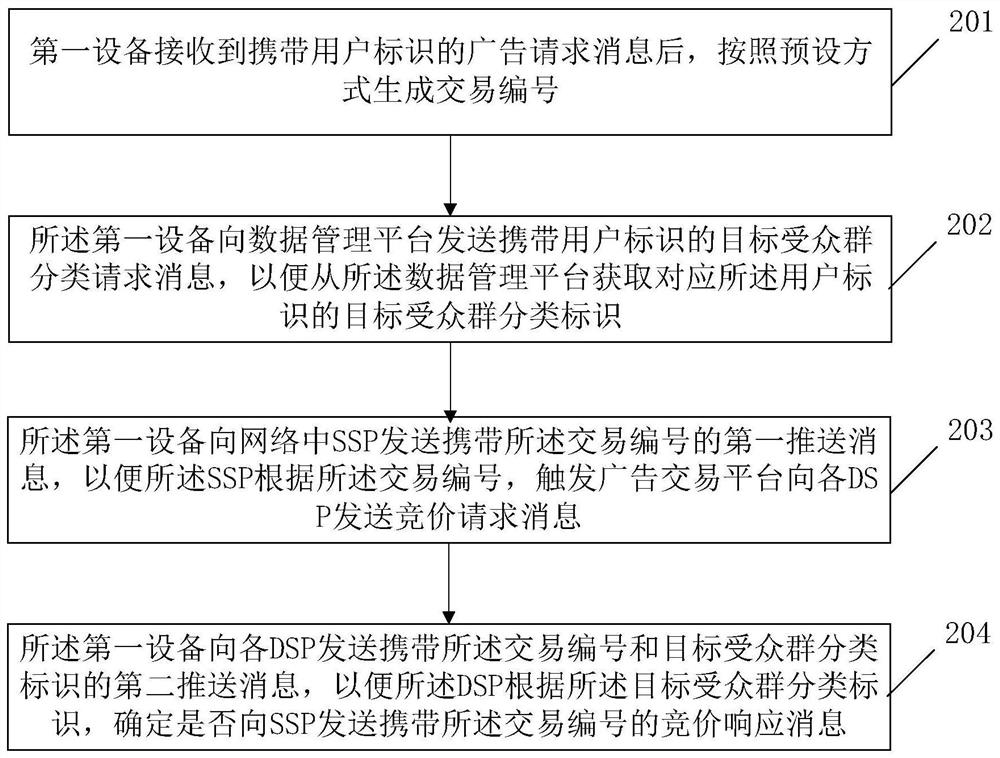
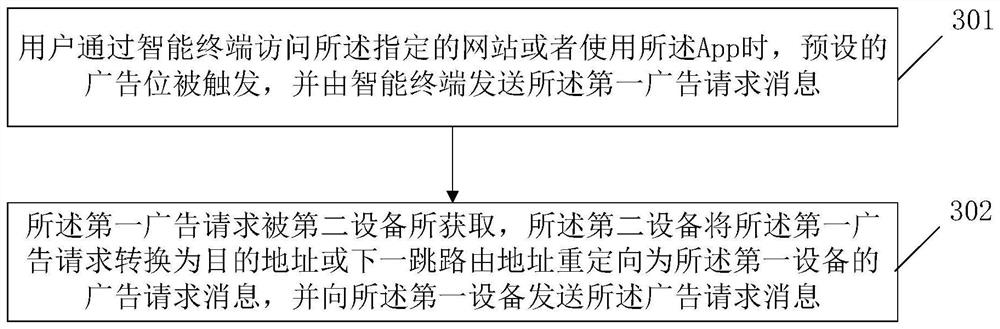
An Internet advertisement putting method and device
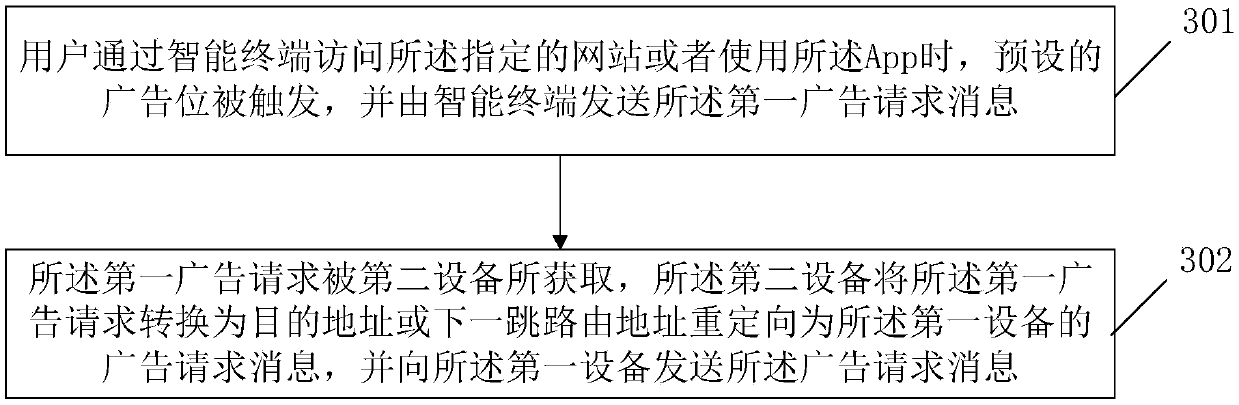
ActiveCN109598550AAvoid the risk of potential privacy leakageAvoid the Risk of Privacy LeakageDigital data information retrievalAdvertisementsThe InternetData management
The invention relates to the technical field of communication technologies and Internet advertisements, and provides an Internet advertisement putting method and device. The method comprises the following steps: after receiving an advertisement request message carrying a user identifier, a first device generates a transaction number according to a preset mode; The first device sends a target audience group classification request message carrying a user identifier to a data management platform; The first device sends a first push message carrying the transaction number to an SSP in a network; And the first device sends a second push message carrying the transaction number and the target audience group classification identifier to each DSP. According to the invention, the potential privacy leakage risk caused by using the user identifier in the advertisement bidding network where the DSP and the SSP are located is avoided.
Owner:武汉稀云科技有限公司
Authentication method and device, electronic equipment and storage medium
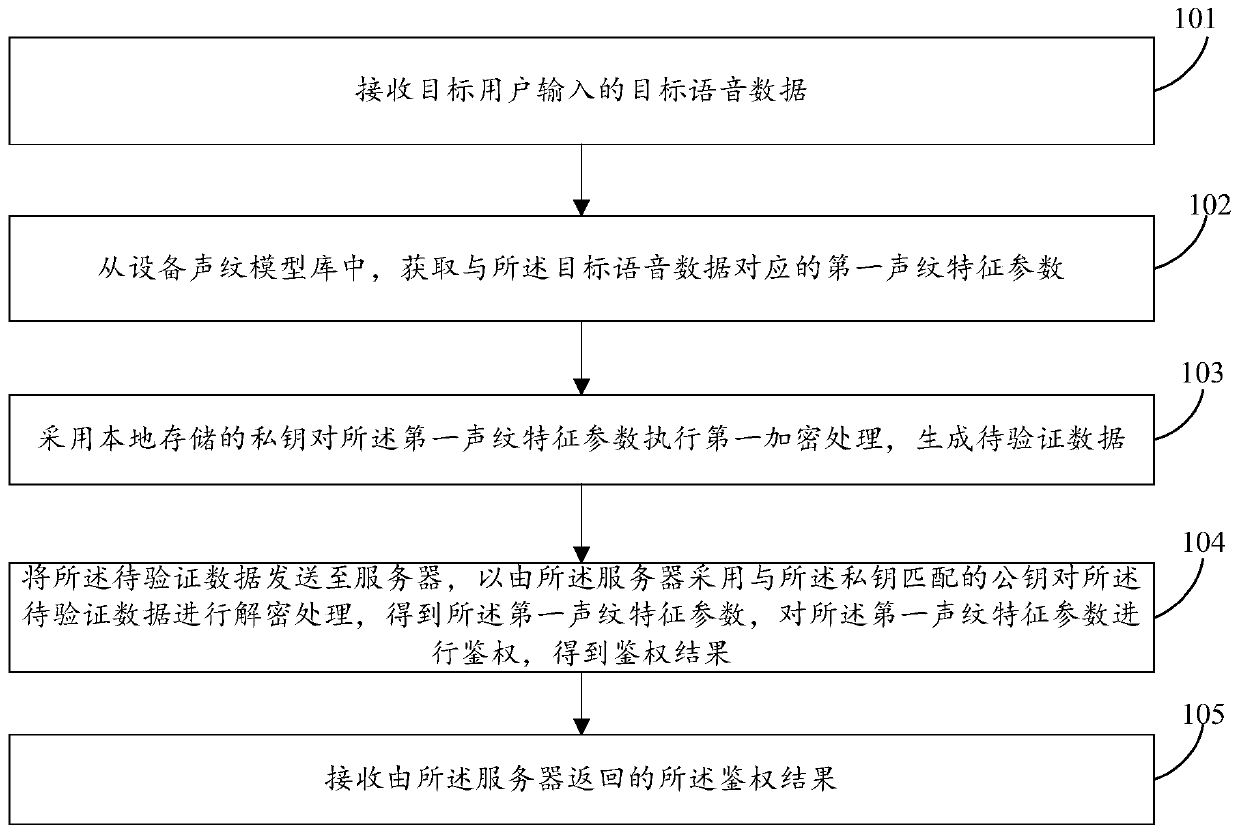
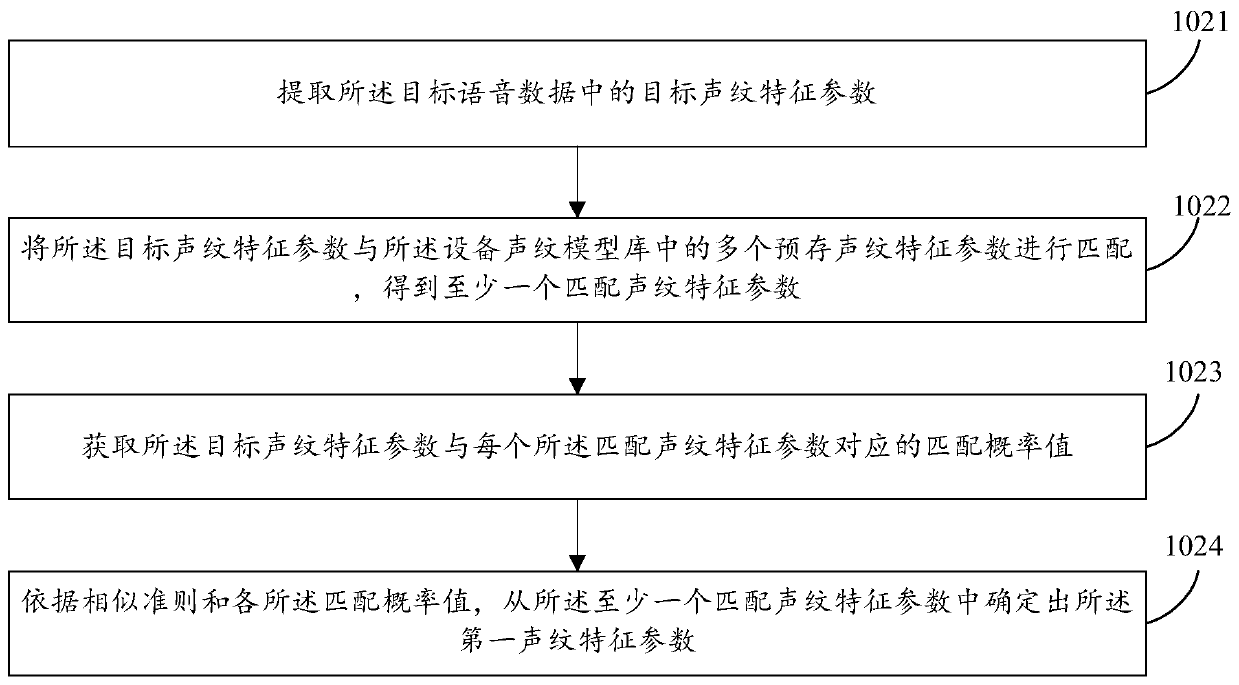
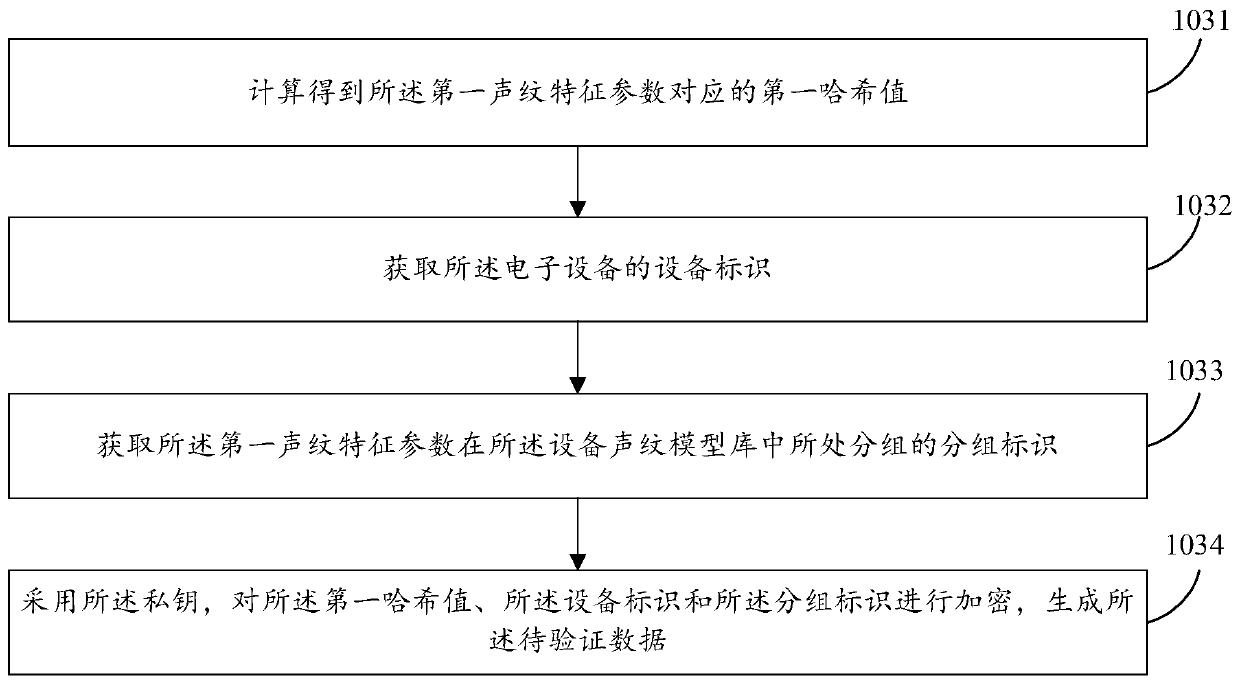
ActiveCN110677260AAvoid the Risk of Privacy LeakageUser identity/authority verificationSpeech analysisUser privacySpeech sound
The invention provides an authentication method and device, electronic equipment and a storage medium. The method comprises the following steps: receiving target voice data input by a target user; obtaining a first voiceprint characteristic parameter corresponding to the target voice data from a device voiceprint model library; executing first encryption processing on the first voiceprint characteristic parameter by adopting a locally stored private key to generate to-be-verified data; sending the to-be-verified data to a server, so that the server decrypts the to-be-verified data by adoptinga public key matched with the private key to obtain the first voiceprint characteristic parameter, and authenticating the first voiceprint characteristic parameter to obtain an authentication result;and receiving the authentication result returned by the server. According to the invention, an authentication mode of combining voiceprint characteristic parameters and public and private keys is adopted, so that the risk of user privacy leakage can be avoided.
Owner:BOE TECH GRP CO LTD
Internet advertisement putting method and device
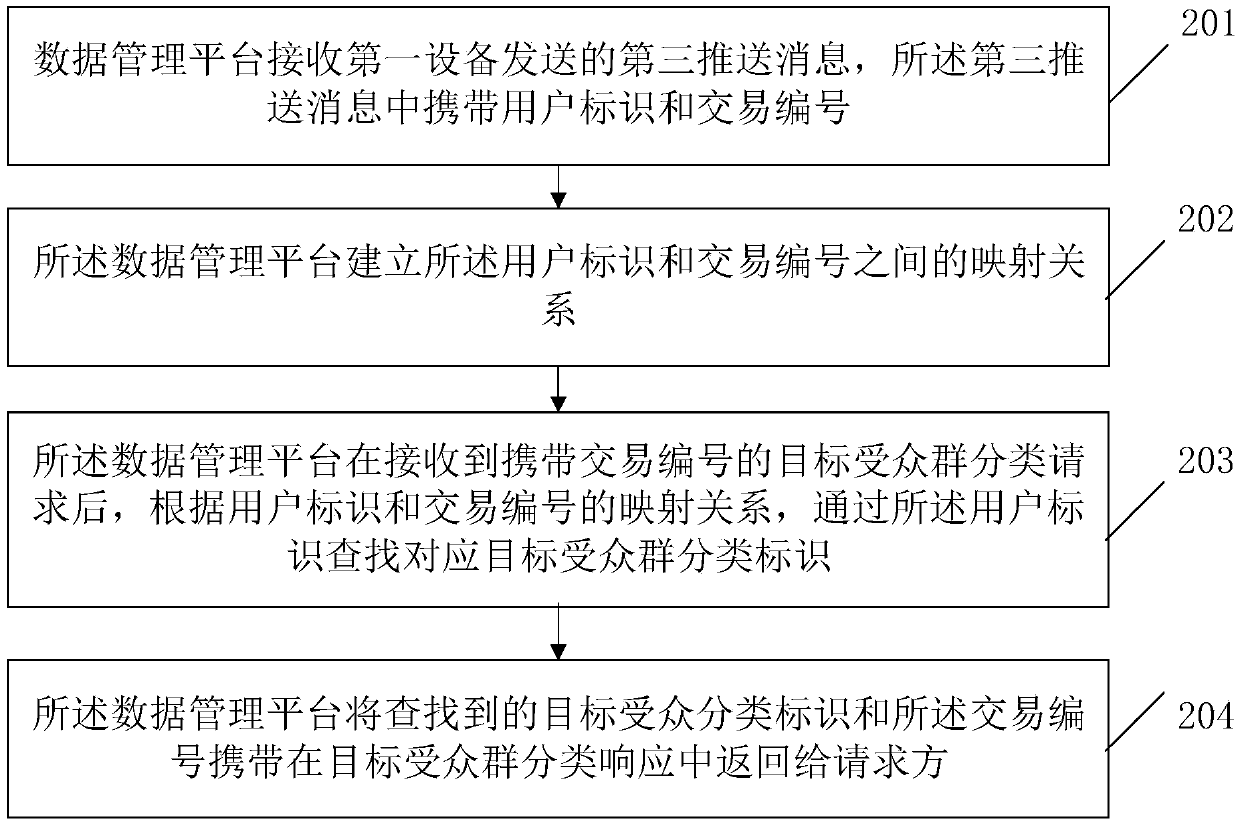
ActiveCN110796466AAvoid the risk of potential privacy leakageAvoid the Risk of Privacy LeakageAdvertisementsInternet privacyThe Internet
The invention relates to the technical field of communication technologies and internet advertisements, and provides an internet advertisement putting method and device. The method comprises: a data management platform receiving a third push message sent by a first device, wherein the third push message carries a user identifier and a transaction number; establishing a mapping relationship betweenthe user identifier and the transaction number; after a target audience group classification request carrying the transaction number is received, searching a corresponding target audience group classification identifier through the user identifier according to a mapping relationship between the user identifier and the transaction number; and carrying the searched target audience classification identifier and the transaction number in a target audience group classification response, and returning the target audience group classification response to the requester. According to the invention, the potential privacy leakage risk caused by using the user identifier in the advertisement bidding network where the DSP and the SSP are located is avoided.
Owner:武汉稀云科技有限公司
Secret state data access protection method for db2 data
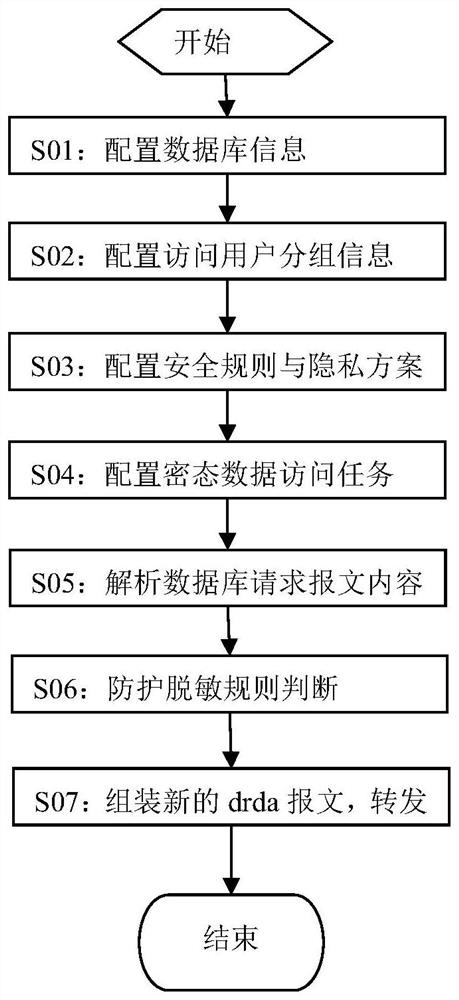
ActiveCN112906048AOptimizationEasy to useDigital data protectionTransmissionData connectionInternet privacy
The invention relates to the technical field of information security, in particular to a secret state data access protection method for db2 data, which comprises the following steps: step S01, configuring target db2 data connection information to authorize the device to access a target db2 database, obtaining all privacy field information of the db2 database by performing privacy discovery on the db2 database, and according to the actual situation, finishing incremental privacy discovery; s02, configuring grouping information of the access users; s03, setting a secret state data access protection rule, namely a security rule and a privacy scheme, of the target database, and controlling the access permission of the target database; and step S04, setting a secret state data access protection task, selecting a protected target database, an access group, a specific secret state data access protection rule and a forwarding port, and enabling a user to access a target db2 database through a proxy port monitored by the device. The invention is simple in deployment and can be transparently used.
Owner:上海凯馨信息科技有限公司
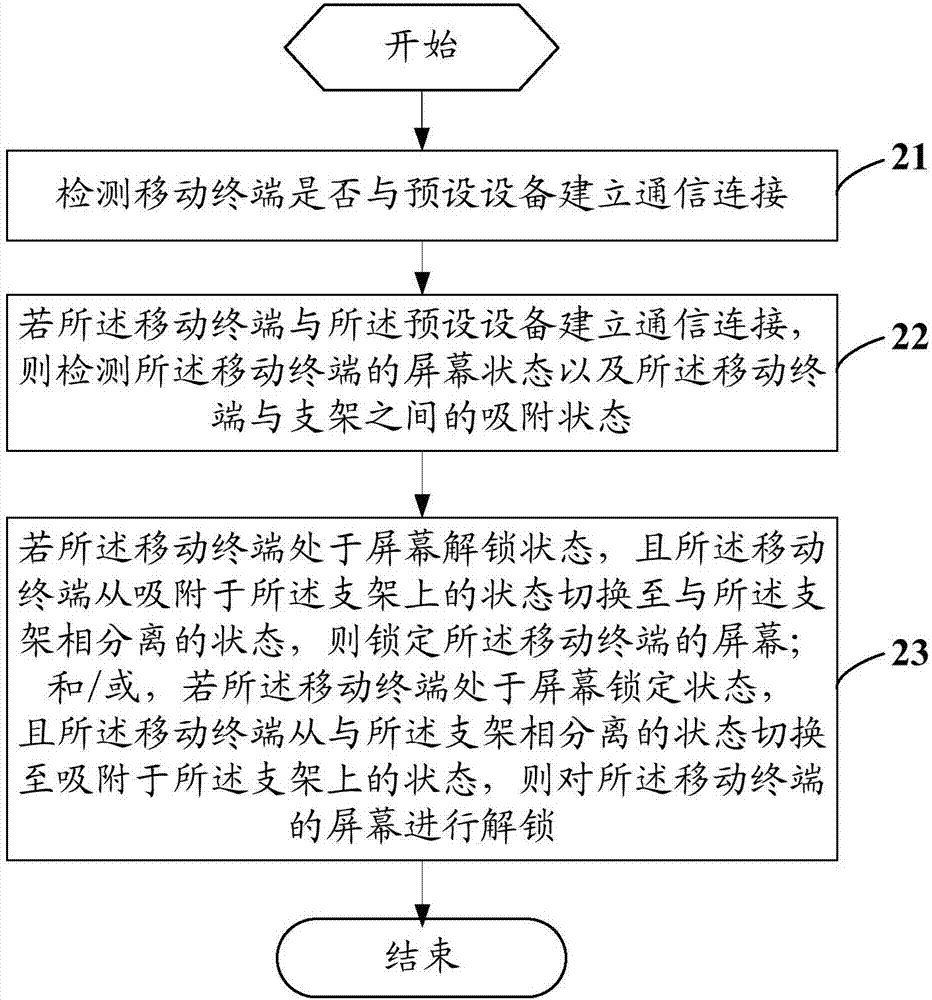
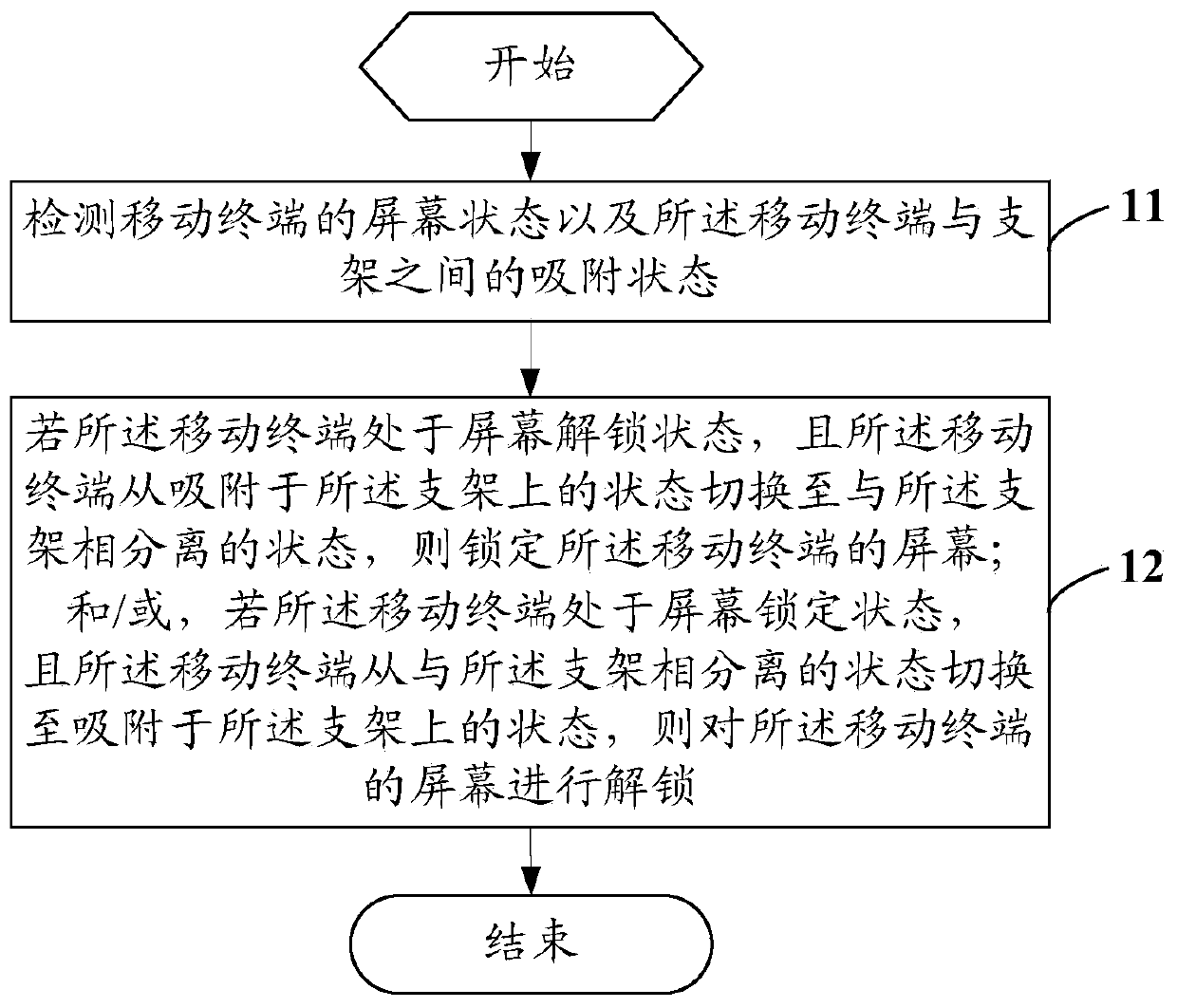
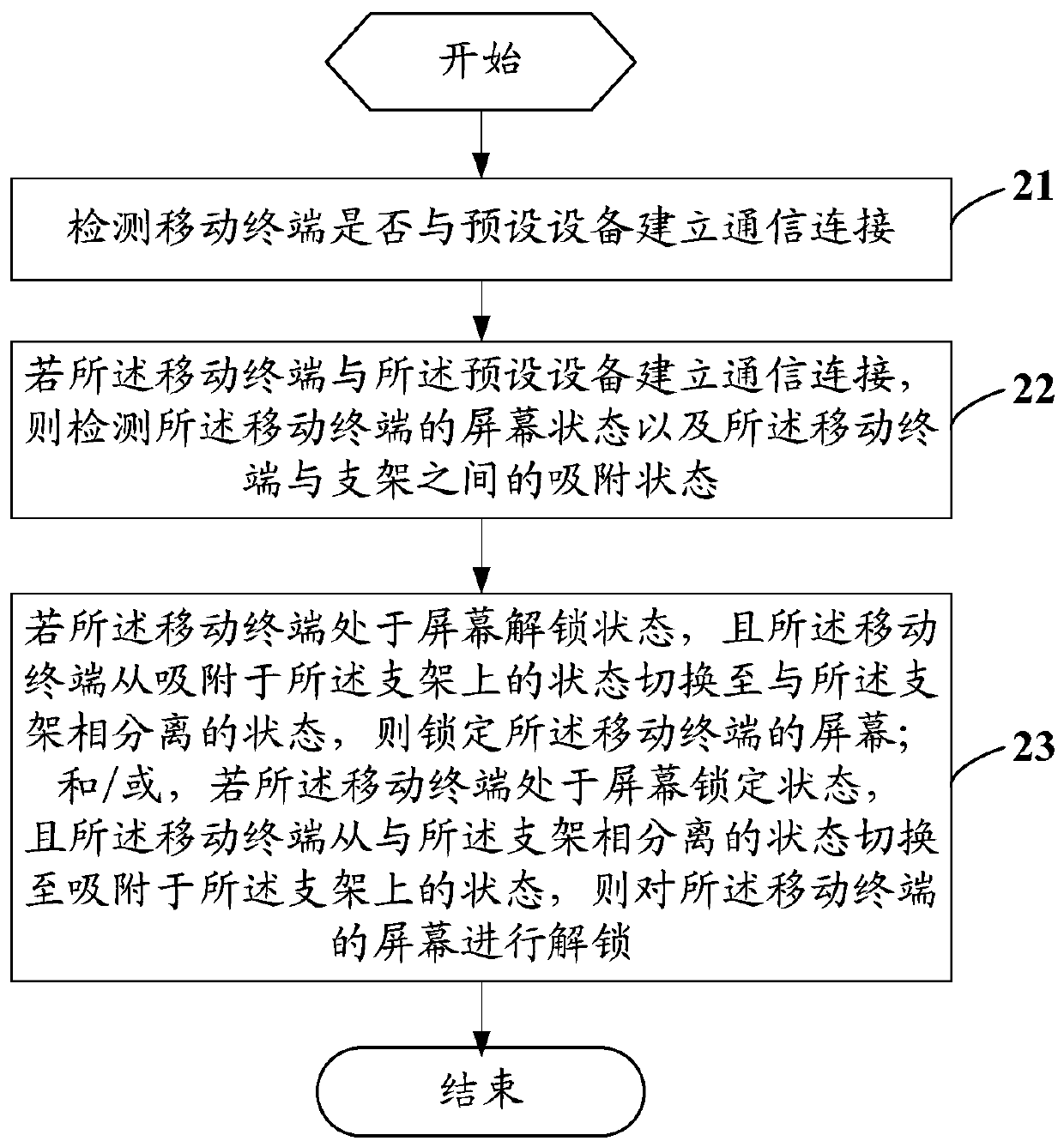
Unlocking control method, mobile terminal and computer readable storage medium
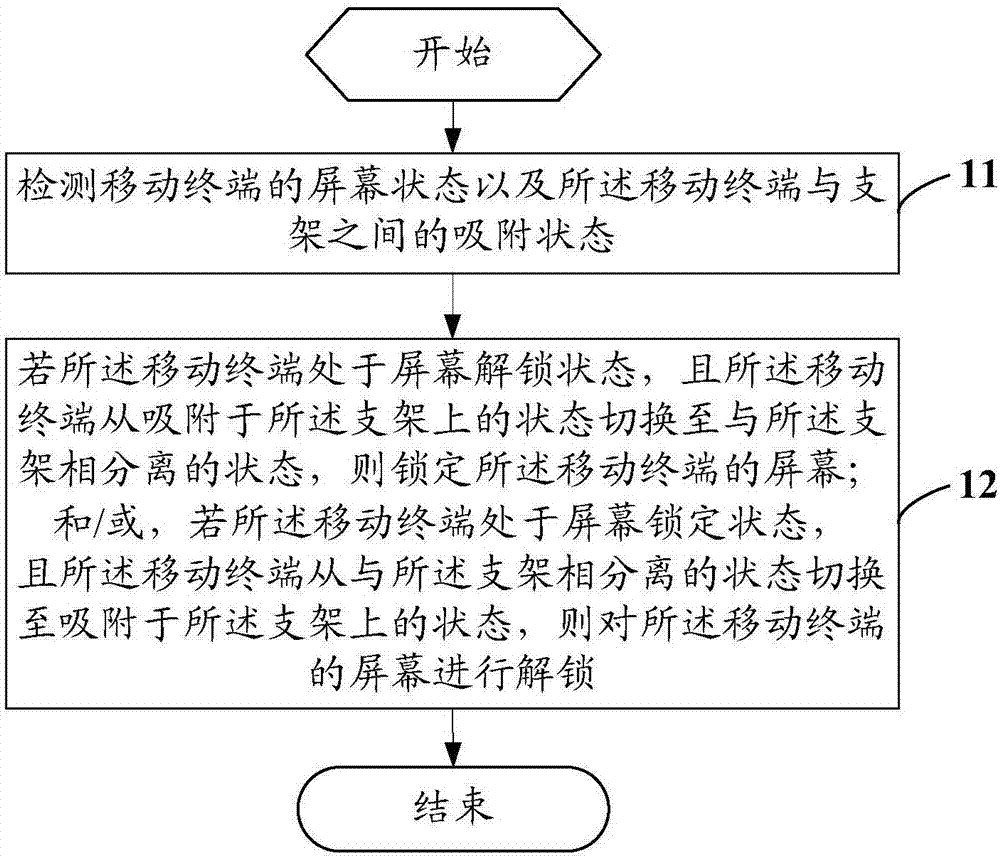
ActiveCN107885405AAvoid Privacy LeakageSimplify the screen unlock processDigital output to display deviceComputer engineeringComputer terminal
Owner:VIVO MOBILE COMM CO LTD
Iris feature hiding method based on random noise mechanism
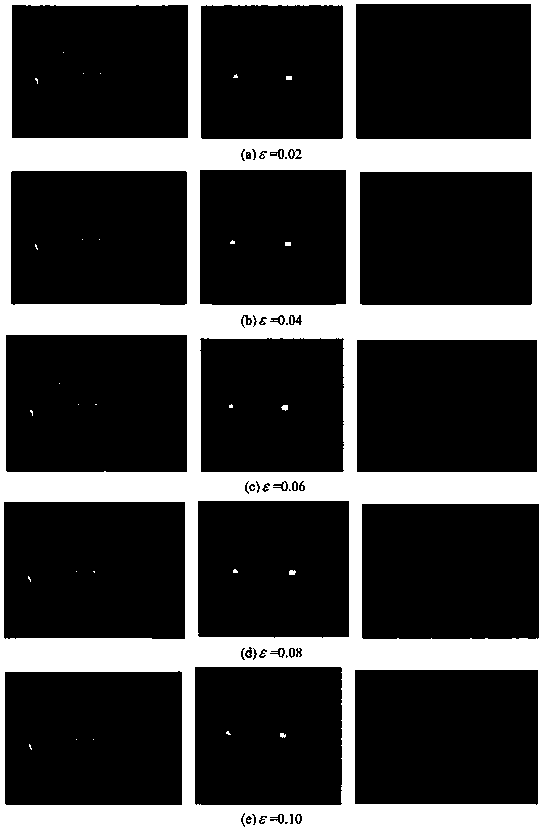
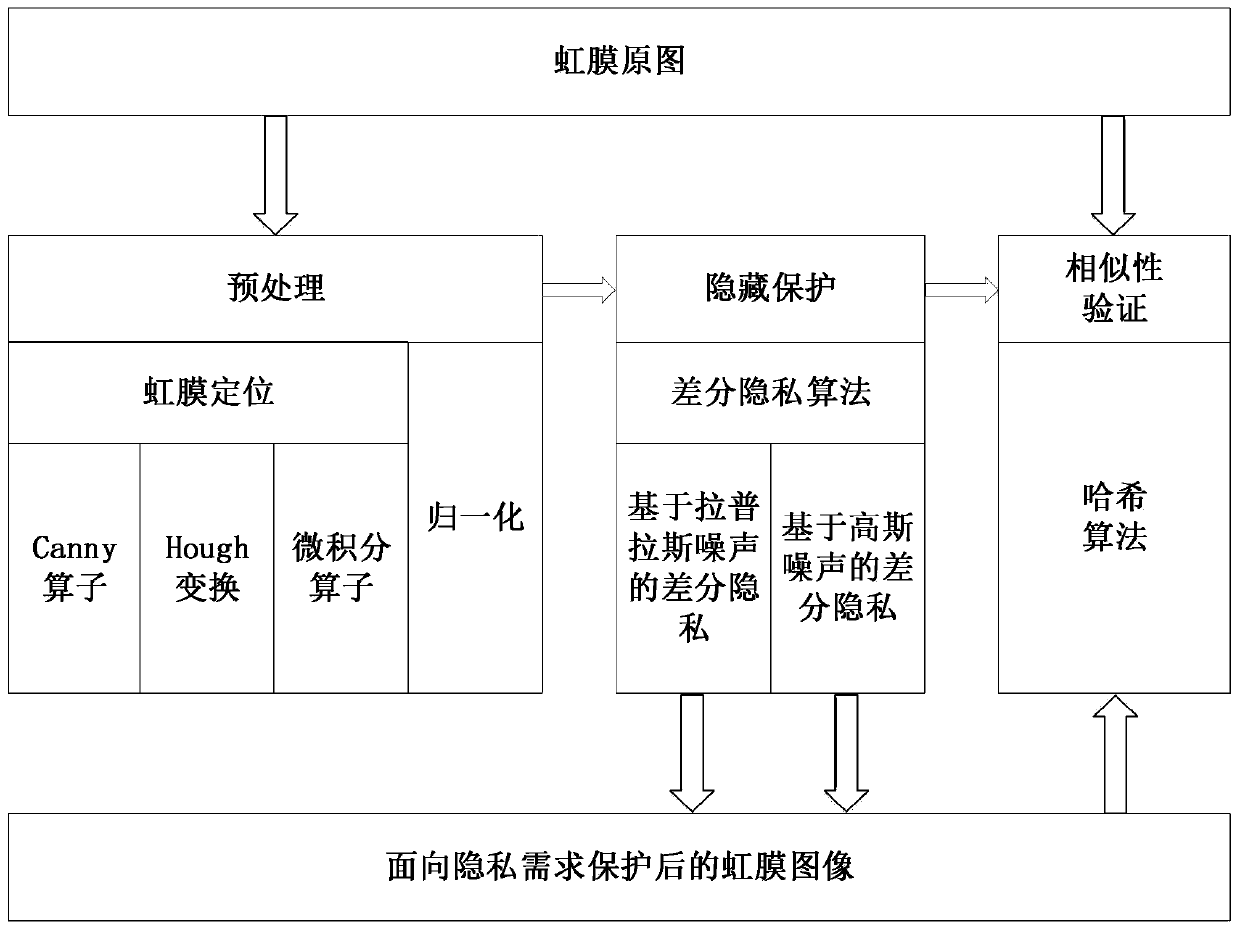
ActiveCN110503697APrivacy protectionPrevent theftAcquiring/recognising eyesImage codingOriginal dataPrivacy protection
The invention discloses an iris feature hiding method based on a random noise mechanism. The iris feature hiding method comprises the following specific steps of extracting and preprocessing iris features by using a wavelet-change-based zero-crossing detection and coding method; realizing iris biological feature hiding based on a differential privacy algorithm of a controllable noise adding mechanism; and verifying the similarity between the iris image after differential privacy protection and the original data based on a hash algorithm. The invention provides a privacy protection method basedon differential privacy measurement, so as to protect the privacy of iris images, improve the safety of iris image publishing and avoid the risk of privacy leakage. The hash algorithm-based iris image similarity verification method is used for comparing the similarity between an iris image to which a random noise mechanism is applied and an original iris image.
Owner:JIANGSU OCEAN UNIV
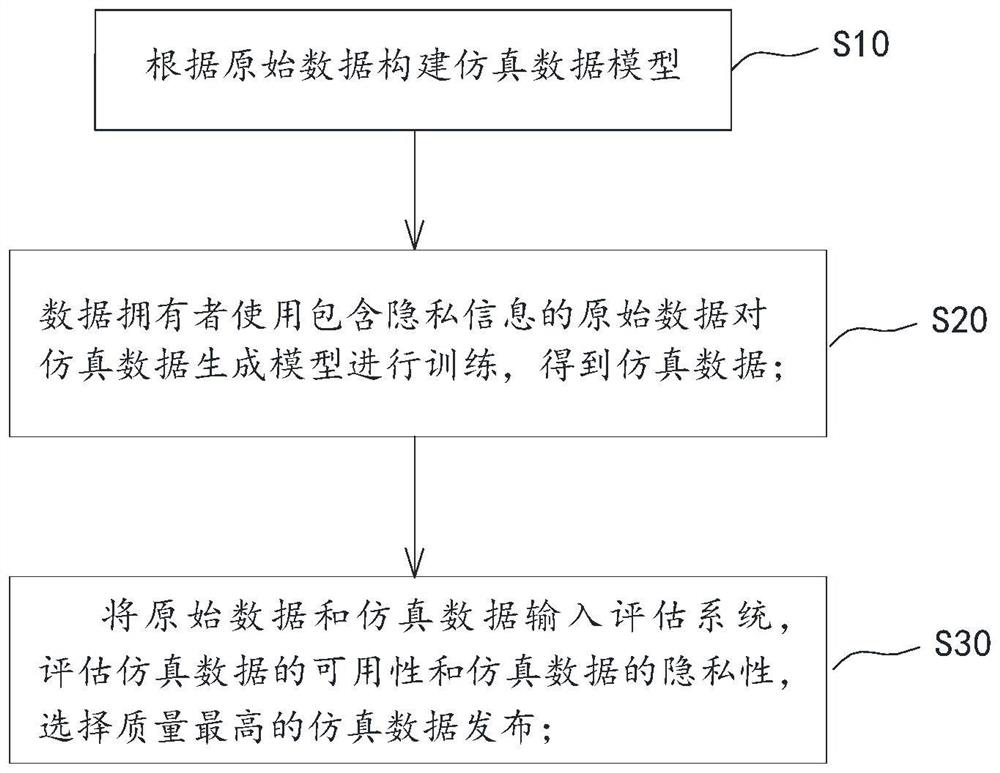
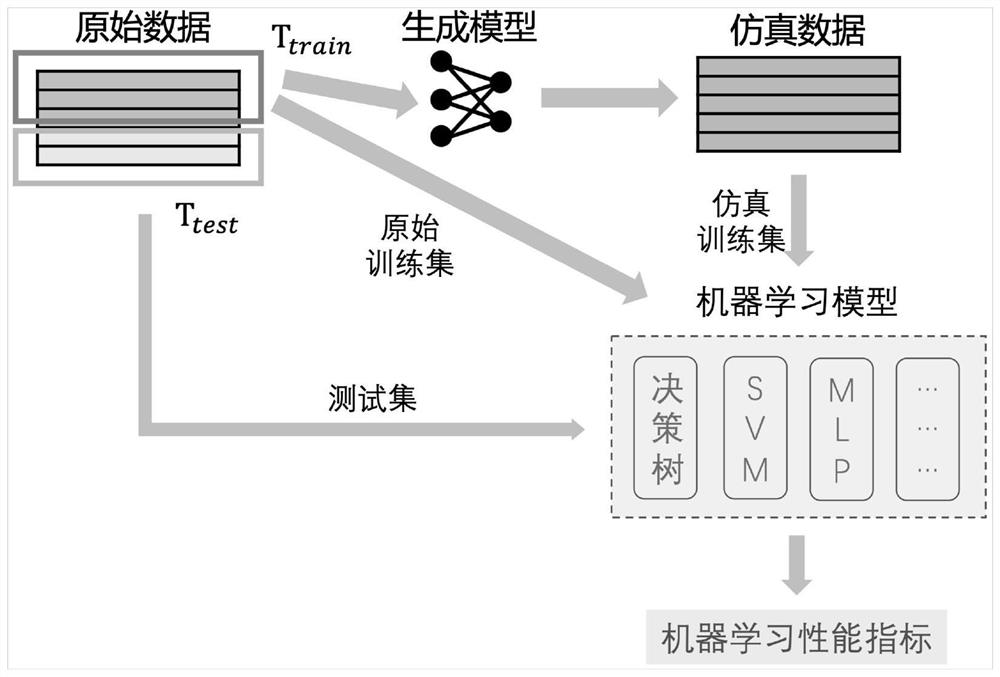
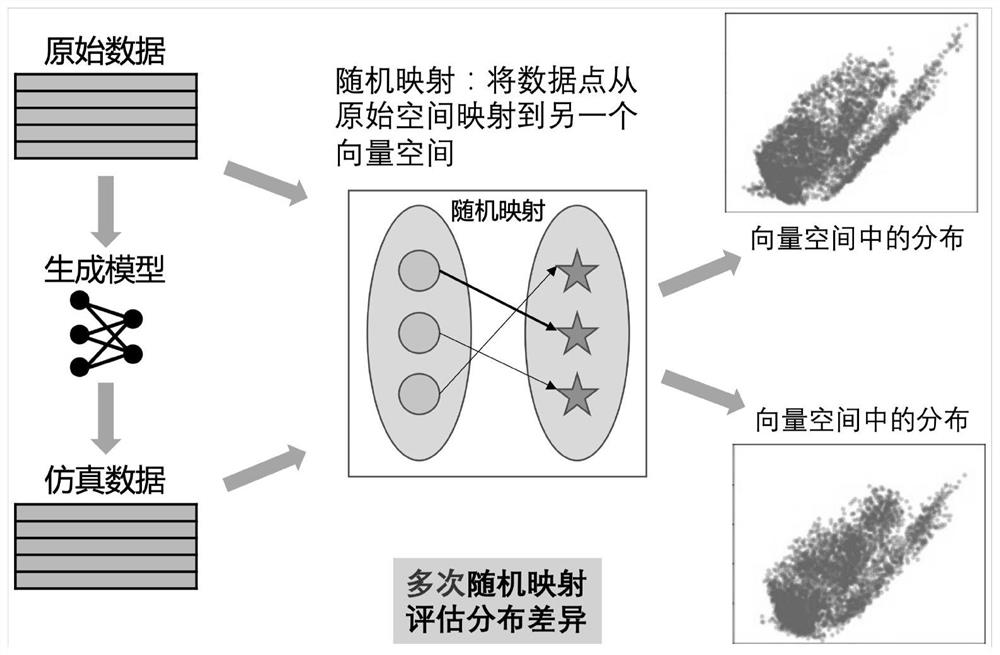
Structured simulation data-oriented quality evaluation method, system and equipment
PendingCN114357714AEnough privacy protectionAvoid the Risk of Privacy LeakageDigital data protectionDesign optimisation/simulationData streamOriginal data
The invention provides a structured simulation data-oriented quality evaluation method and system. The method comprises the steps of constructing a simulation data generation model according to original data; the data owner uses original data containing privacy information to train a simulation data generation model to obtain simulation data; the original data and the simulation data are input into an evaluation system, the availability and privacy of the simulation data are evaluated, and the simulation data with the highest quality is selected to be published; the original data and the simulation data are structured data and are composed of a plurality of data records, each record has a plurality of fields, and the fields of the simulation data are completely the same as the fields of the original data. According to the method, the simulation data is used for replacing the original data to participate in data circulation for quality evaluation, the data items of the simulation data are synthesized and are not associated with any entity in reality, and other hypotheses or priori knowledge are not needed, so that the risk of privacy disclosure is effectively avoided, the evaluation is comprehensive and reliable, and the universality is good.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
An authentication method and device based on a temporary identifier
ActiveCN109639719BAvoid the Risk of Privacy LeakageEffective monitoringKey distribution for secure communicationUser identity/authority verificationWeb siteInternet privacy
The invention relates to the technical field of communication technology and personal information services and provides an identity authentication method and device based on a temporary identifier, wherein the method comprises the following steps: receiving a push message carrying a user identifier and a verification code and generating a first temporary identifier according to a preset mode; acquiring corresponding user historical information from an information database according to the user identifier, and obtaining a score made by the current user based on the user historical information;sending out a user grading result corresponding to the first temporary identifier so that the website or an APP can obtain the user grading result and judge whether the current user is a target user or not. According to the method and the device in the invention, the user can be effectively verified and screened according to the user historical information, which facilitates effective monitoring of the website or the APP and avoids a potential user privacy leakage risk caused by the fact that the fixed user identifier is used in the network.
Owner:武汉稀云科技有限公司
Air conditioner control method and device, storage medium and air conditioner
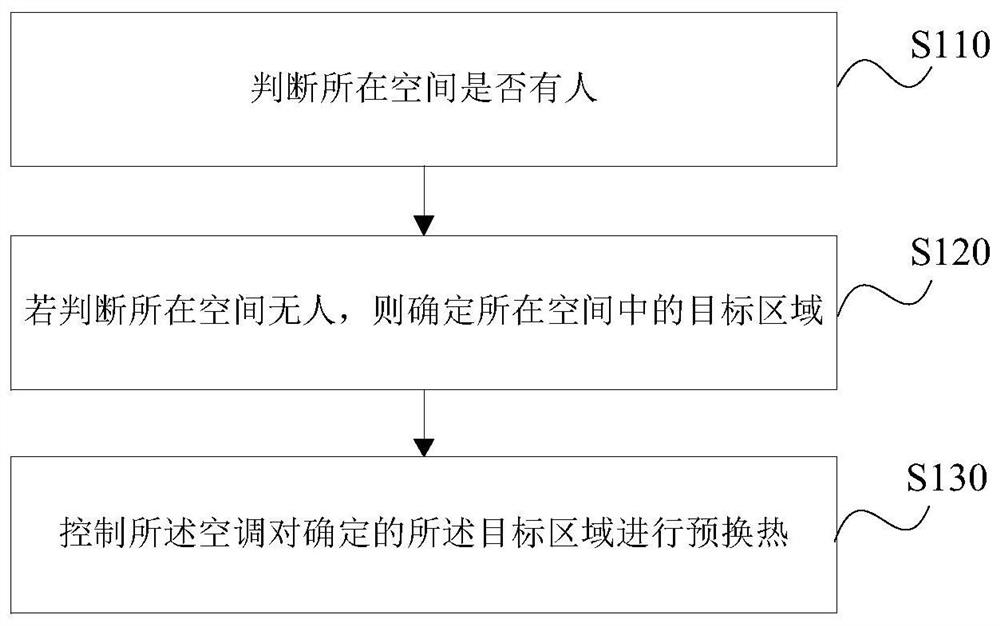
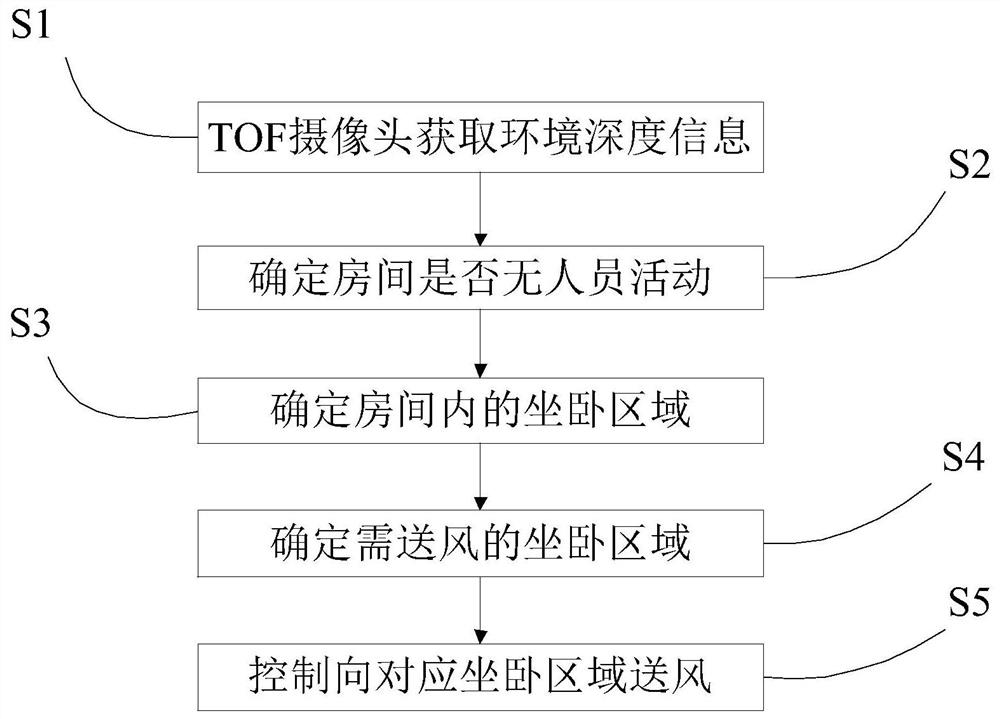
ActiveCN113188232AAvoid the Risk of Privacy LeakageFast and efficient warm-upMechanical apparatusSpace heating and ventilation safety systemsEngineeringProcess engineering
The invention provides an air conditioner control method and device, a storage medium and an air conditioner. The method comprises the steps that whether a person is in the space or not is judged; if it is judged that no person is in the space, a target area in the space is determined; the target area comprises an area which has a preset attribute and / or where the user staying time in a preset time period is larger than a preset time threshold value; and the air conditioner is controlled to conduct pre-heat exchange on the determined target area. According to the scheme, rapid preheating and precooling effects can be realized.
Owner:GREE ELECTRIC APPLIANCES INC
An unlocking control method, mobile terminal and computer-readable storage medium
ActiveCN107885405BEasy to unlockEasy to operateDigital output to display deviceComputer hardwareEmbedded system
Owner:VIVO MOBILE COMM CO LTD
Multi-party secure computing method and device, electronic equipment
ActiveCN109241016BAvoid the Risk of Privacy LeakageKey distribution for secure communicationData stream serial/continuous modificationNetwork deploymentComputer network
A multi-party secure computing method, applied to any computing node deployed in a distributed network; the distributed network deploys multiple computing nodes, and the multiple computing nodes jointly participate in multi-party secure computing based on private data held by them ; Wherein, the computing node is connected to a trusted key source; the method includes: obtaining a trusted key from the trusted key source; based on the acquired private data held by the trusted key pair Encrypt to obtain ciphertext data; at least send the ciphertext data as calculation parameters to other computing nodes participating in the multi-party secure computing, so that the other computing nodes can use the data collected by the computing nodes participating in the multi-party secure computing. Computational parameters perform multi-party secure computations.
Owner:ADVANCED NEW TECH CO LTD
Communication platform and method for providing commercial communication for partitioned mobile telecommunication clients
InactiveCN110996252AImplement automatic repairAvoid the Risk of Privacy LeakageAccounting/billing servicesAutomatic exchangesInformation processingTelecommunications
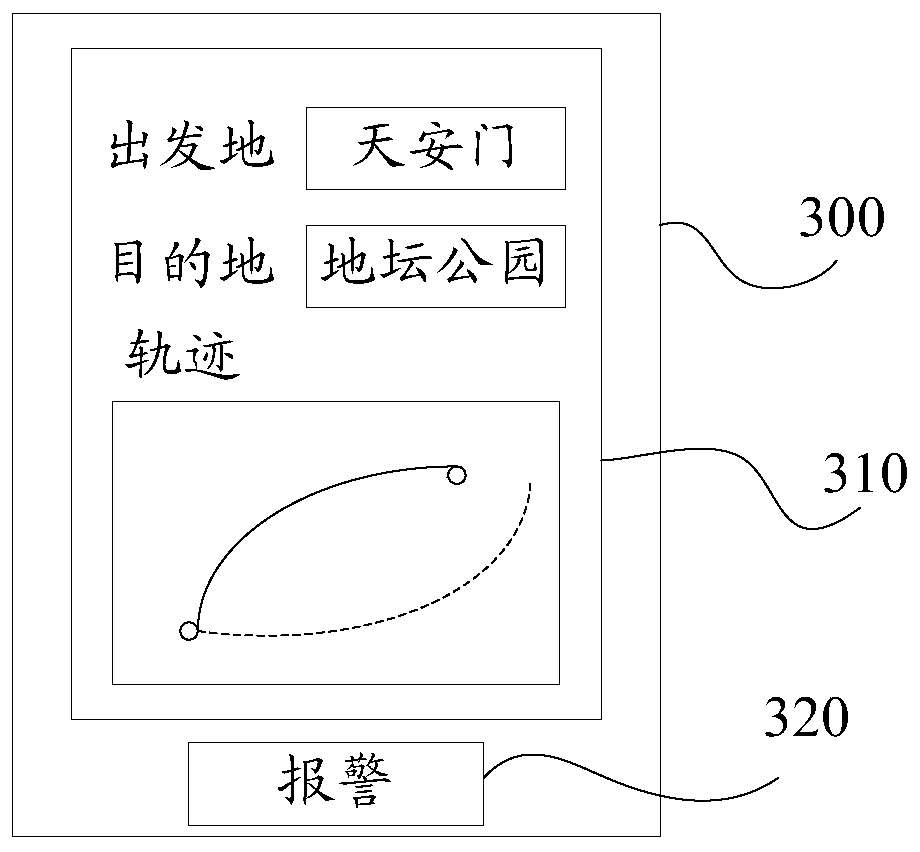
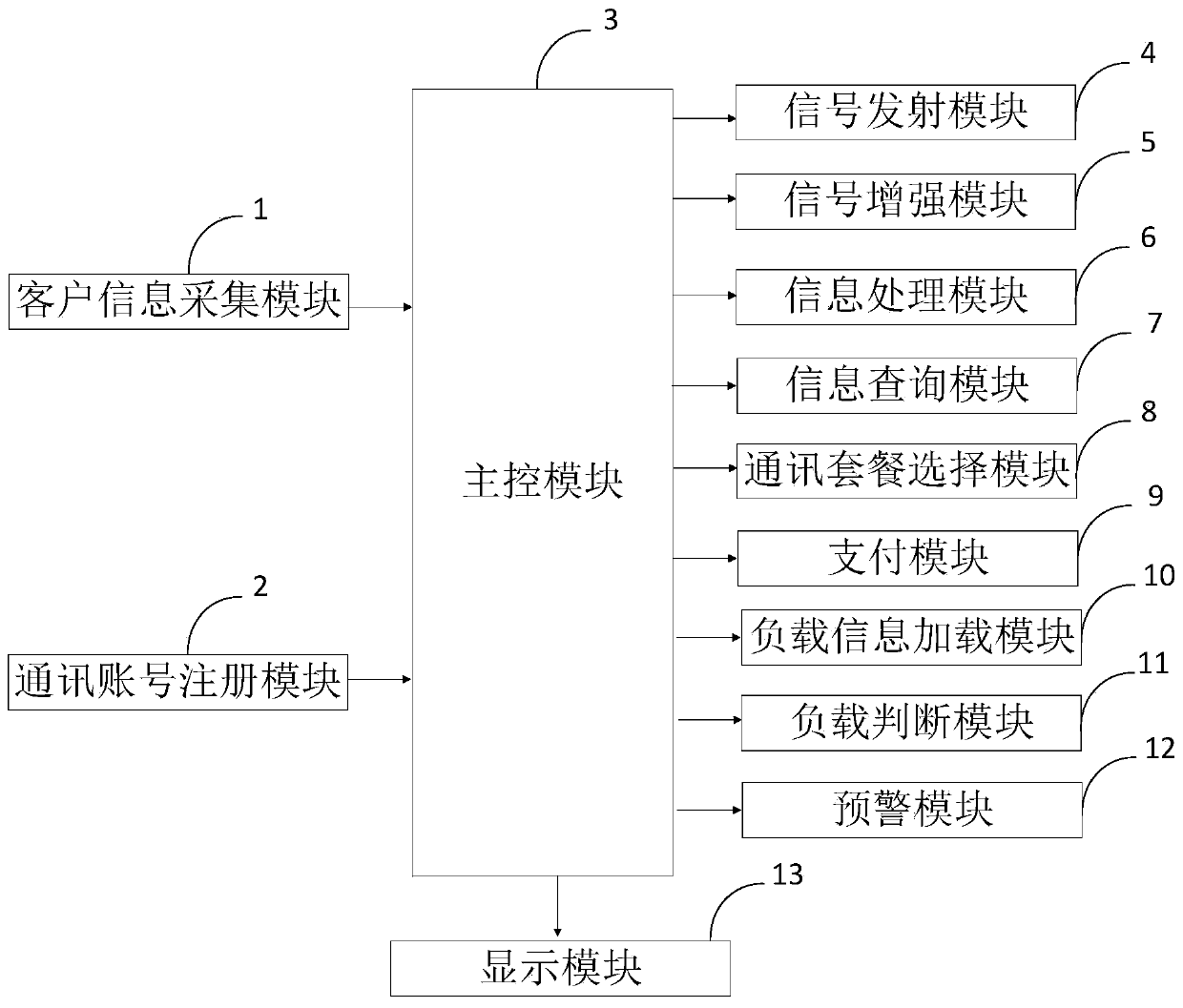
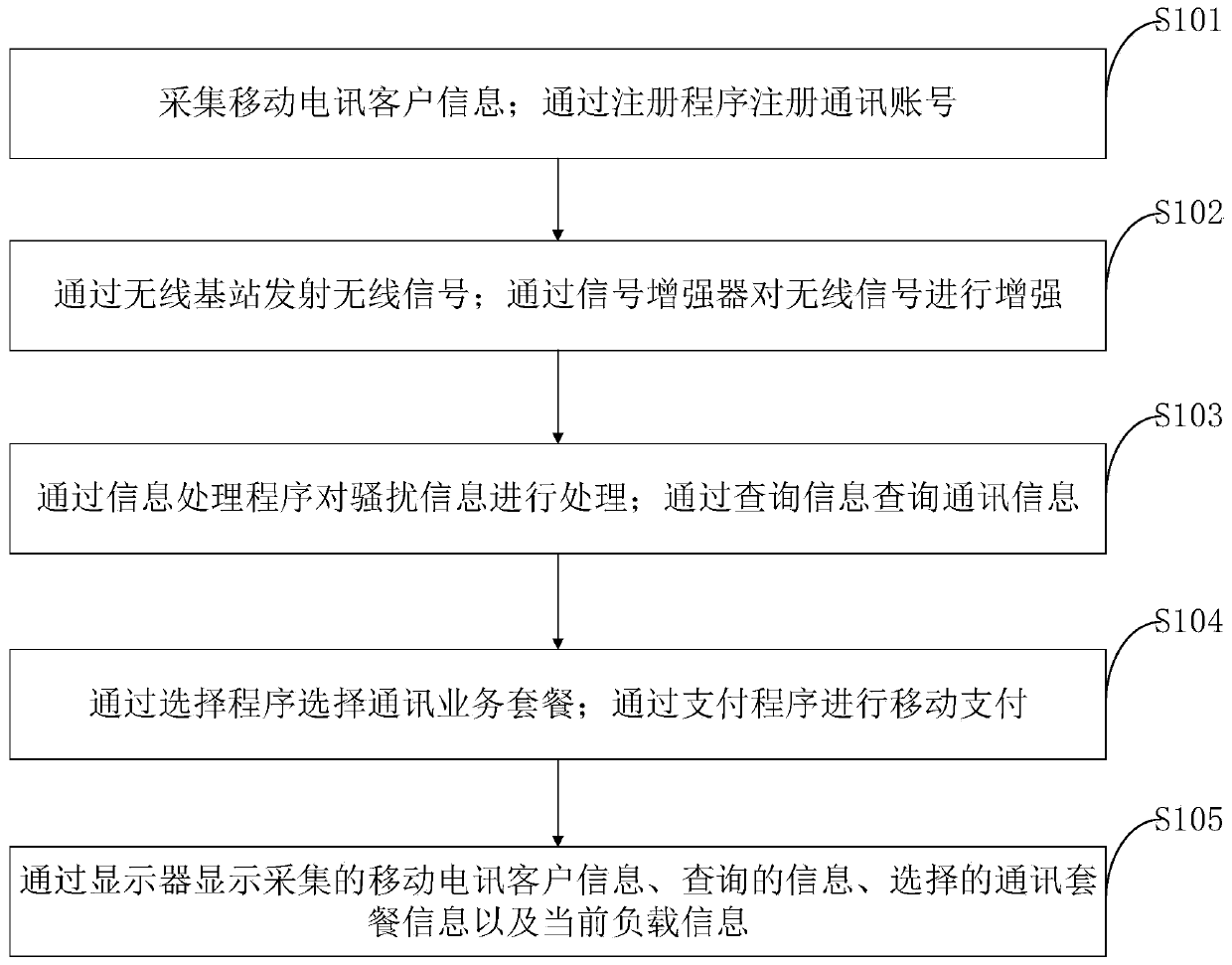
The invention belongs to the technical field of commercial communication. The invention discloses a communication platform and method for providing commercial communication for partitioned mobile telecommunication customers. The communication platform comprises a client information collection module, a communication account registration module, a main control module, a signal emission module, a signal enhancement module, an information processing module, an information query module, a communication package selection module, a payment module, a load information loading module, a load judgment module, an early warning module and a display module. According to the invention, automatic repair of the wrong label in the address book is realized through the information processing module, and thesituation that the incoming call which is not the crank call is mistakenly considered as the crank call and is hung up by the user after the common network address is mistakenly modified is avoided; meanwhile, the position privacy and the query range privacy of the moving object are protected through the information query module, the privacy leakage risk possibly occurring in the information queryprocess is avoided, and the safety of the moving object during information query based on the position is improved.
Owner:武汉微分享互动科技有限公司
Data privacy protection aggregation method under secondary network of smart power grid based on block chain
ActiveCN112887095AAvoid the Risk of Privacy LeakageImprove privacy protectionKey distribution for secure communicationData processing applicationsData privacy protectionCiphertext
The invention discloses a data privacy protection aggregation method under a secondary network without a trusted third party in a smart power grid based on a block chain. According to the method, data aggregation under the secondary network without a trusted third party is realized by utilizing the Hough rule and the ElGamal cryptographic algorithm, so that the trusted third party does not need to be introduced into the intelligent power grid system, and the risk of privacy disclosure when the trusted third party is not trusted is avoided. Meanwhile, the Hough parameters are embedded into the first-level aggregation ciphertext of each first-level fog node to achieve data aggregation under the second-level network, stronger privacy protection is achieved, large-scale users are supported, and calculation overhead is reduced. In addition, a transaction relationship between the user and the electric power company is established through the smart contract, and the transaction relationship between the user and the electric power company is written into the block chain. The method has the advantages of good expandability and small calculation overhead, and is suitable for a large-scale smart power grid.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
A smart speaker control method and system based on gesture recognition
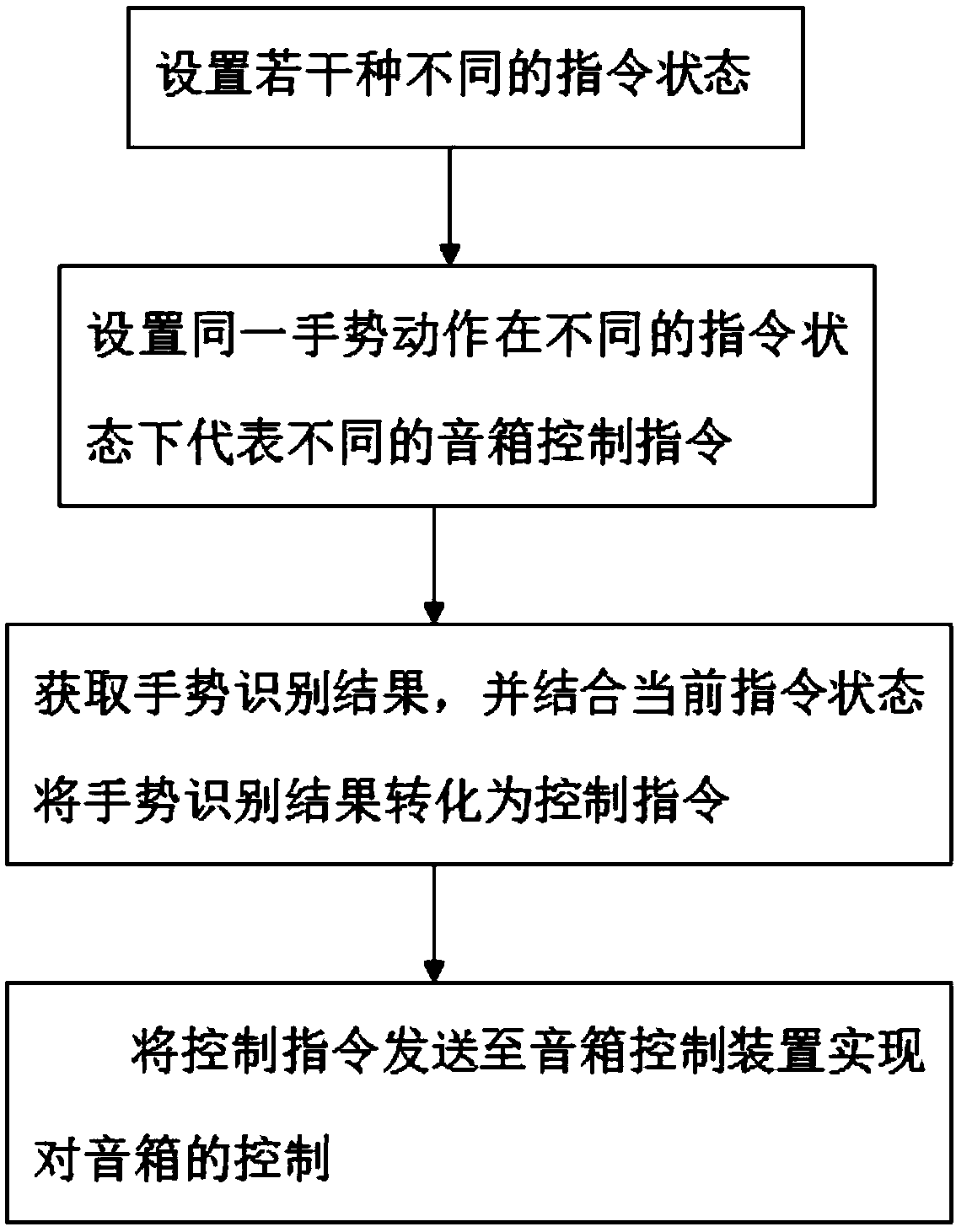
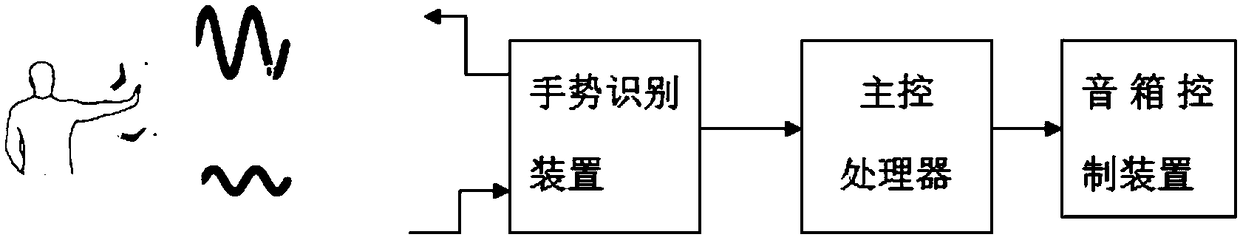
ActiveCN105744434BIncreased complexityWill not reduce the experienceFrequency/directions obtaining arrangementsTransducer circuitsSonificationControl system
The invention discloses an intelligent loudspeaker box control method based on gesture recognition. The method comprises the steps of setting several different kinds of command states; setting a same gesture action to represent different loudspeaker box control commands under different command states; acquiring a gesture recognition result, and converting the gesture recognition result into a control command through combining with the current command state; and sending the control command to the loudspeaker box control device to achieve the control on the loudspeaker box. Also disclosed is an intelligent loudspeaker box control system based on gesture recognition, the loudspeaker box control system comprises a gesture recognition device, a master control processor and a loudspeaker box control device. According to the method and system, the several different kinds of command states are set, thus the same gesture action is converted into different operations on the loudspeaker box under the different command states, the reuse of the simple gesture action is achieved, the ultrasonic signal is used as a gesture action detection and recognition carrier, the risk that the privacy of the user is leaked can be effectively avoided, meanwhile the signal processing complexity is smaller, fewer resources are required, and the recognition rate is also improved.
Owner:SHENZHEN MAXUSTECH CO LTD
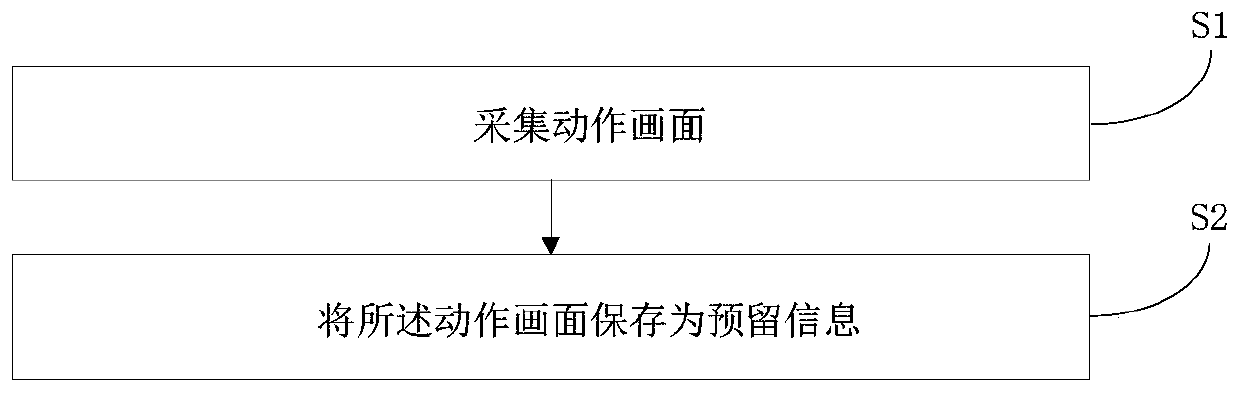
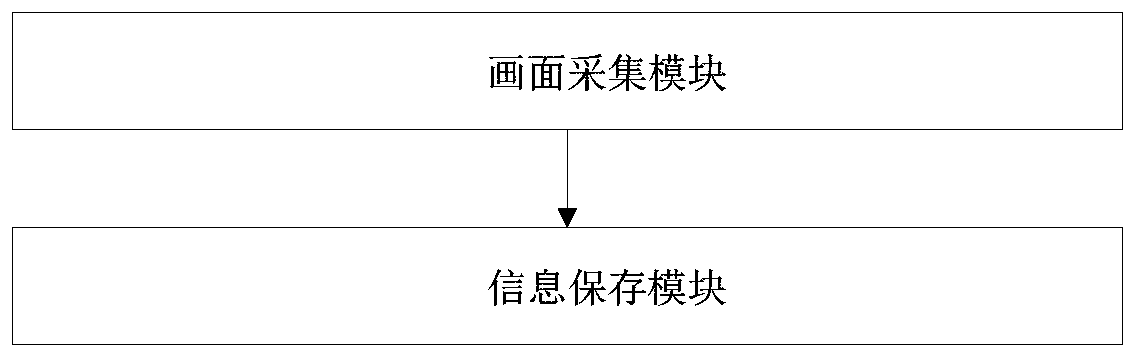
Reserved information processing method, system, device and storage medium
PendingCN110472394AAvoid the Risk of Privacy LeakageAvoid muddling throughCharacter and pattern recognitionDigital data authenticationData compressionInformation processing
The invention discloses a reserved information processing method, a reserved information processing system, a reserved information processing device and a storage medium. The method comprises the steps of collecting an action picture, storing the action picture as reserved information and the like. According to the invention, an action picture containing limb actions, facial expressions and voicesignals is used for replacing traditional personal information as reserved information, so that the risk of personal privacy leakage can be avoided; limb actions, facial expressions, voice signals andcombinations thereof can form a large number of combinations. Limb actions, facial expressions and voice signals can be included in forms of small videos and the like through a data compression technology; therefore, a large amount of reserved information can be stored with only a small amount of data, and due to the complexity of body movements, facial expressions and voice signals, the reservedinformation stored through the method has uniqueness, and lawbreakers are prevented from being mixed in a guessing mode and the like. The method is widely applied to the technical field of the Internet.
Owner:北京拉近众博科技有限公司
Method and device for placing an Internet advertisement
ActiveCN109598550BAvoid the risk of potential privacy leakageAvoid the Risk of Privacy LeakageDigital data information retrievalAdvertisementsInternet privacyThe Internet
The invention relates to the fields of communication technology and Internet advertisement technology, and provides an Internet advertisement placing method and device. The method includes that the first device generates a transaction number according to a preset method after receiving the advertisement request message carrying the user ID; the first device sends a target audience group classification request message carrying the user ID to the data management platform; the first The device sends a first push message carrying the transaction number to an SSP in the network; the first device sends a second push message carrying the transaction number and target audience classification identifiers to each DSP. The invention avoids the potential privacy leakage risk caused by using the user identification in the advertising bidding network where the DSP and the SSP are located.
Owner:WUHAN CIRROST (XIYUN) TECH CO LTD
Information display method and mobile terminal
ActiveCN109993010BImprove securityEnsure safetyStatic indicating devicesDigital data protectionComputer hardwareEmbedded system
The invention discloses an information display method and a mobile terminal. The method is applied to a mobile terminal with a display screen, and the display screen includes a first display area; the method includes: if the first information satisfies a first preset condition, then displaying first prompt information in the first display area; receiving a first input for the first display area; in response to the first input, acquiring first fingerprint information through the first display area; When the first fingerprint information satisfies a second preset condition, the content of the first information is displayed on the display screen. The invention can ensure the safety of information display and avoid the risk of privacy leakage.
Owner:VIVO MOBILE COMM CO LTD
Application data processing method, terminal and server
ActiveCN106339613BAvoid the Risk of Privacy LeakageShorten the timeDigital data authenticationApplication serverComputer terminal
Owner:TENCENT TECH (SHENZHEN) CO LTD
A multi-appliance control method based on wearable devices
ActiveCN109870984BImprove reliabilitySimple controlComputer controlNavigation by speed/acceleration measurementsDatasheetRoomba
A multi-home appliance control method based on a wearable device comprises the following steps of: step 1, obtaining three-dimensional spatial information of a room of the user and locations of home appliances; step 2, placing an ultrasonic ranging device for positioning in the room; step 3, obtaining information of a sensor on the wearable device; step 4, during the training phase, extracting data feature values of the sensor and establishing a feature database and a classifier; and step 5, during the control phase, acquiring and executing a user instruction according to the information of the sensor returned by the wearable device and an auxiliary positioning device. The multi-home appliance control method is simple and natural, avoids the risk of privacy leakage, can calculate the position and orientation of the wearable device by analyzing the inertial measurement unit and the ultrasonic ranging information, and improves the reliability of the control system by accurately determining devices selected by the user in the multi-home appliance scene by using the previously established data table.
Owner:ZHEJIANG UNIV +1
Multi-party secure computing method and device, electronic equipment
ActiveCN109255247BAvoid the Risk of Privacy LeakageDigital data processing detailsDigital data protectionNetwork deploymentComputer network
A multi-party secure computing method, applied to any computing node deployed in a distributed network; the distributed network deploys multiple computing nodes, and the multiple computing nodes jointly participate in multi-party secure computing based on private data held by them ; Wherein, the computing node is connected to a trusted random source; the method includes: obtaining a trusted random number from the trusted random source; performing an operation on the held private data based on the obtained trusted random number to obtain an operation Result; at least the trusted random number is sent as a calculation parameter to other computing nodes participating in the multi-party secure computing, so that the other computing nodes can execute the calculation based on the collected computing parameters sent by the computing nodes participating in the multi-party secure computing Multi-party secure computing.
Owner:ADVANCED NEW TECH CO LTD
Electronic equipment
ActiveCN111726489AAvoid Privacy LeakageAvoid Dust ProblemsTelevision system detailsStatic indicating devicesStopwatchUser privacy
The invention relates to the technical field of electronic equipment, and discloses electronic equipment, which comprises a front camera; a dimming component which covers the light incident side of the front-facing camera, is in a transparent state when powered on, and is in a non-transparent state when powered off; a switch component which is used for controlling the power-on and power-off of thedimming component, is connected with the dimming component and the power supply respectively, and is used for realizing the conduction and disconnection by pushing the sliding block to slide betweenthe conduction station and the disconnection station; and the mechanical timer is located beside the switch part, is used for controlling the conduction time of the switch component, and can push thesliding block to move from the conduction station to the disconnection station in the timing process. According to the electronic equipment, the problem of privacy leakage caused by the fact that a user forgets to reset the shielding structure in the prior art can be avoided, the privacy of the user is protected, and the problem that ash enters the front camera can be avoided.
Owner:SHANGHAI CHUANGGONG COMM TECH
A blockchain-based federated learning system and method
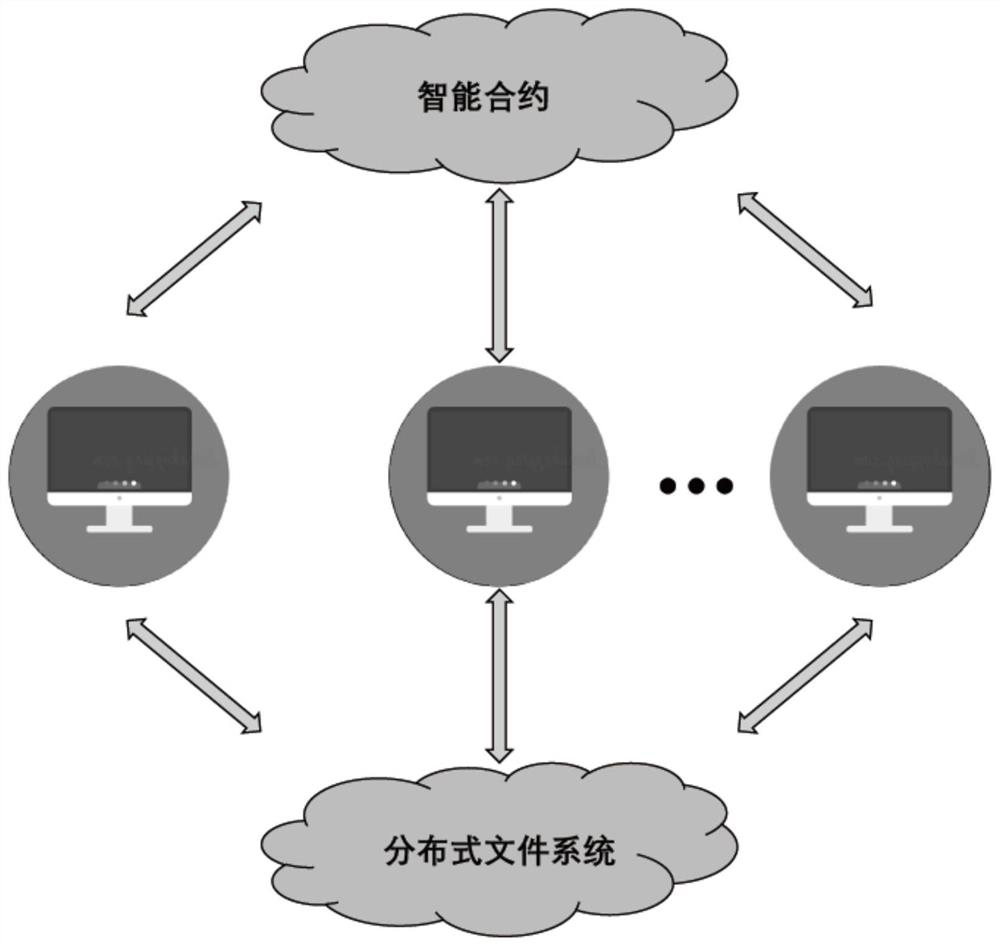
ActiveCN111212110BAchieve decentralizationImprove robustnessMachine learningTransmissionEngineeringSmart contract
The present invention provides a blockchain-based federated learning system and method. The system includes: a model training module for updating machine learning models in the federated learning process and aggregation of change values of the machine learning models; The contract module is used to provide decentralized control functions and key management functions in the process of the federated learning; the storage module based on the IPFS protocol is used to provide decentralized Information storage mechanism: The model training module, the smart contract module based on blockchain technology, and the storage module based on the IPFS protocol are simultaneously run on each node participating in federated learning. To achieve complete decentralization of the entire system, the failure and exit of any node will not affect other nodes to continue federated learning, which is more robust.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com