Identity authentication method and device based on temporary identifier
An identity verification method and a temporary identifier technology, applied in the field of communication technology and Internet advertising, can solve the problems of privacy information leakage, untrustworthy behavior, etc., and achieve the effect of effective monitoring and avoiding the risk of user privacy leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
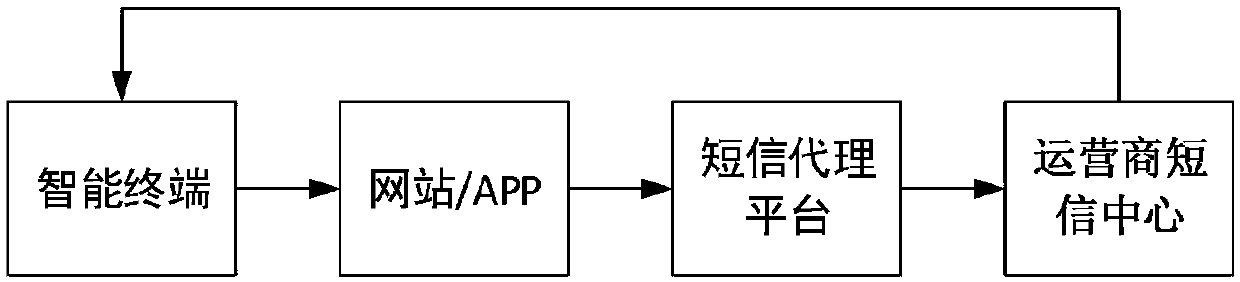
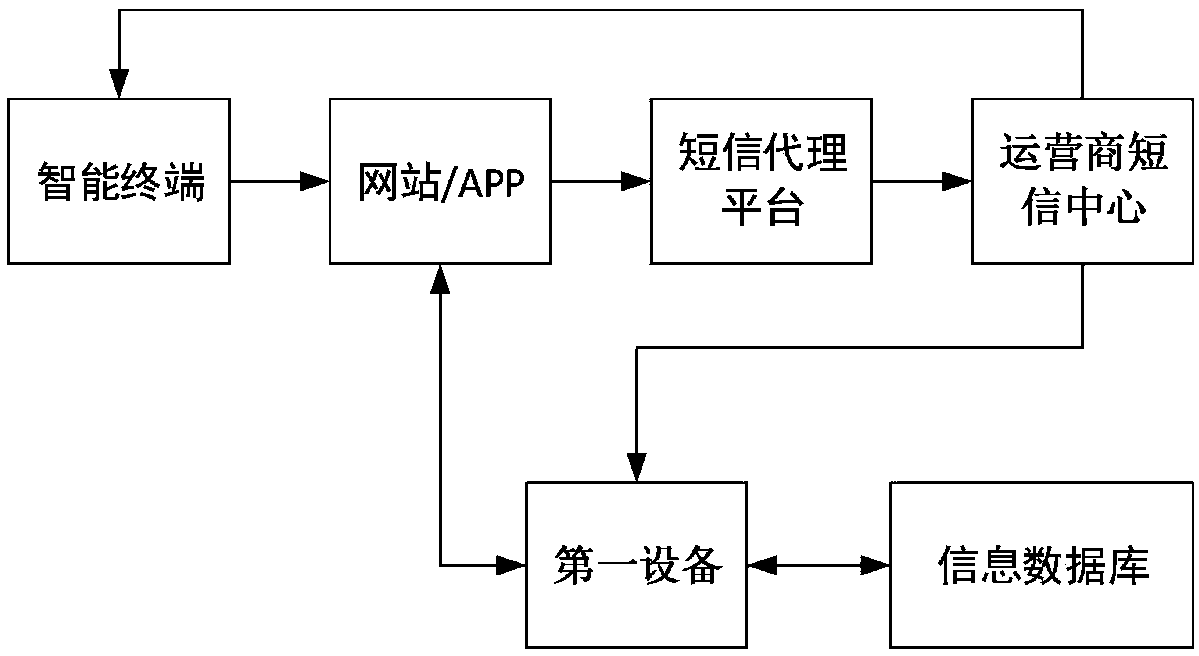
[0054] Embodiment 1 of the present invention provides an identity verification method based on a temporary identifier, which is used to solve the problem in the prior art that when a user applies for an operation on a website or APP, the website or APP cannot combine user history information to determine whether the user is allowed to perform the operation. The above operation is effectively verified, and the user identity is described by a fixed user identifier in the prior art, and carrying a fixed user identifier in a message transmitted over the network will involve leakage of user privacy. The embodiment of the present invention is a solution designed to this technical problem.
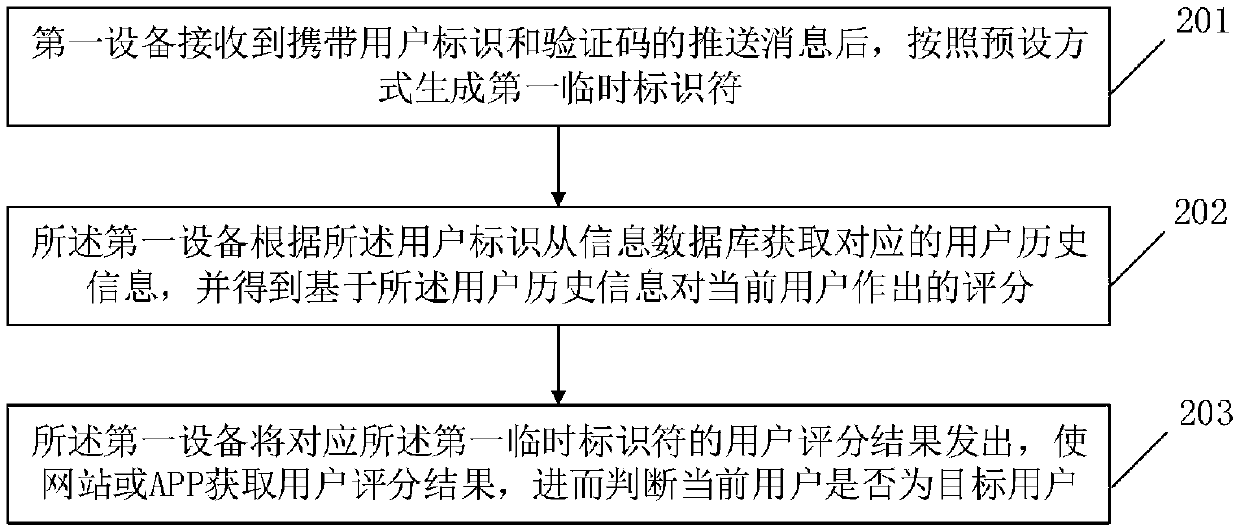
[0055] like figure 2 As stated, methods include:
[0056] In step 201, after receiving a push message carrying a user ID and a verification code, the first device generates a first temporary identifier in a preset manner.
[0057] In a specific implementation manner, the first device may be a ...
Embodiment 2
[0140] The embodiment of the present invention combines as Figure 15 The signaling diagram shown illustrates a specific implementation process of an identity verification method based on a temporary identifier. In the scenario described in the embodiment of the present invention, the enhanced proxy and processing engine described in Embodiment 1 are not introduced, the first device acts as an enhanced gateway; the information database includes a first information database and a second information database, The first information database is represented as a telecommunications database, and the second information database is embodied as a financial information database; the operation is embodied as applying for registration on a website or App; Mobile phone number; the verification code is randomly generated by the website or APP.
[0141] In step 501, the user uses the smart terminal and uses the corresponding mobile phone number to apply for registration on the website or Ap...
Embodiment 3
[0160] The embodiment of the present invention combines as Figure 16 The signaling diagram shown illustrates a specific implementation process of an identity verification method based on a temporary identifier. Compared with Embodiment 2, the enhanced agent described in Embodiment 1 is introduced into the scenario described in the embodiment of the present invention, then the interaction between each website and / or APP and the enhanced gateway can be centrally processed through the enhanced agent, The network bandwidth occupation in the network can be saved, the signaling interaction process in the network environment can be simplified, and the message processing load of the first device can be reduced.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com