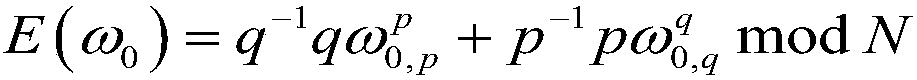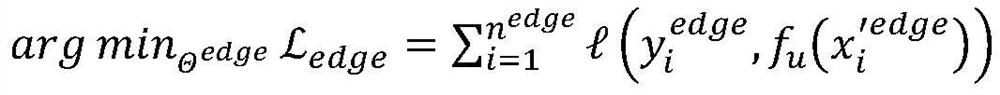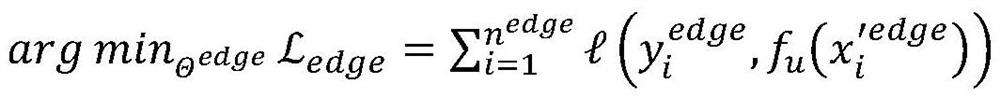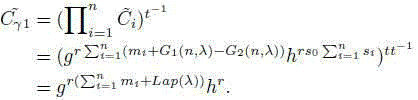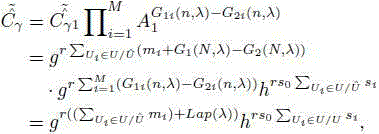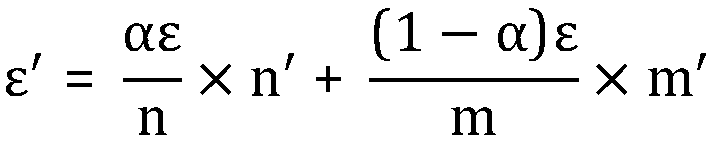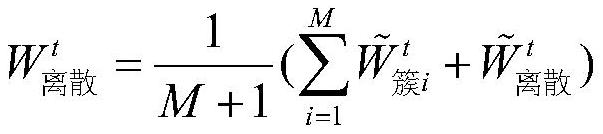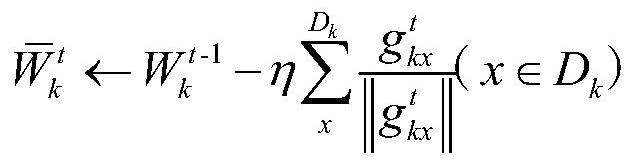Patents
Literature
677 results about "Differential privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
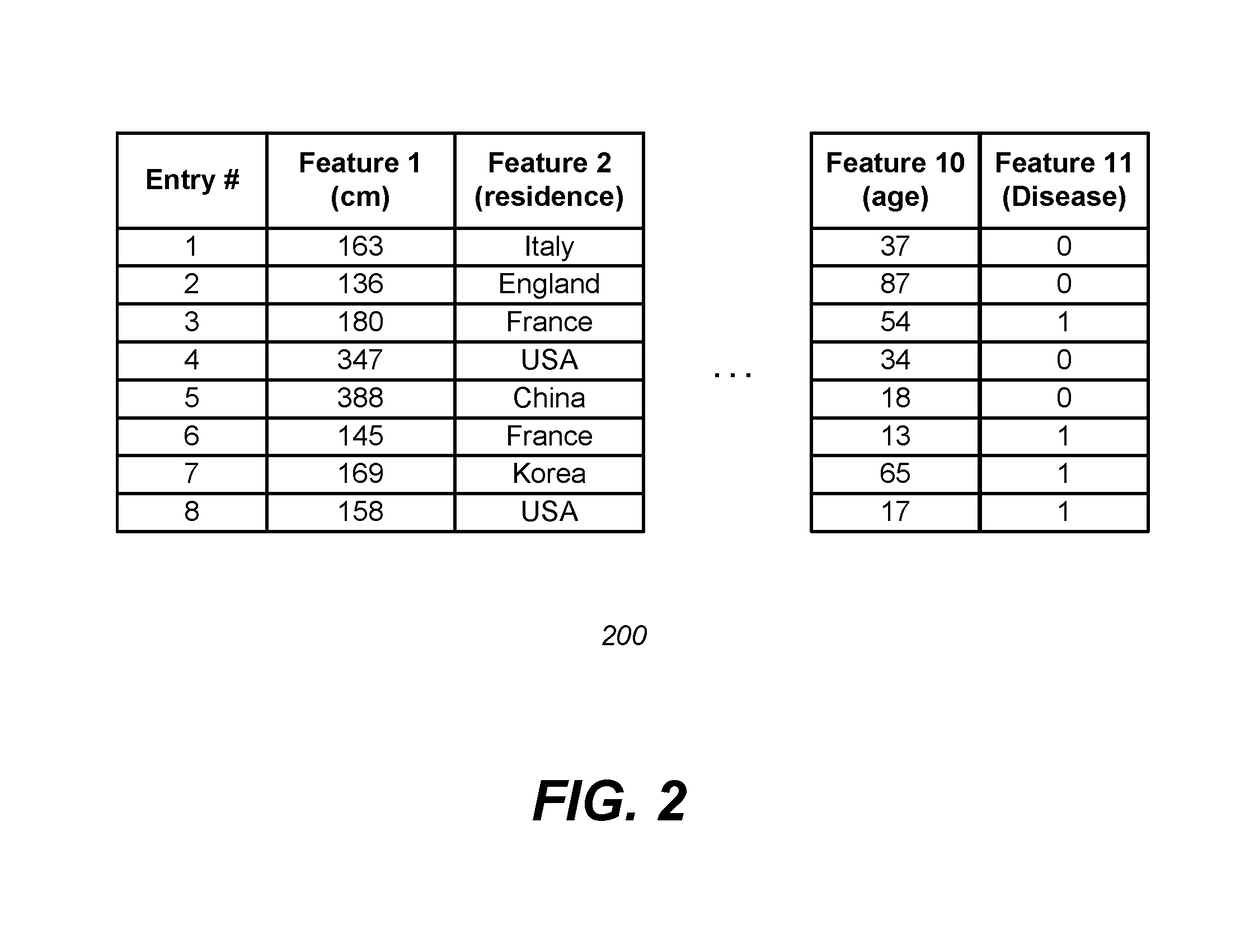
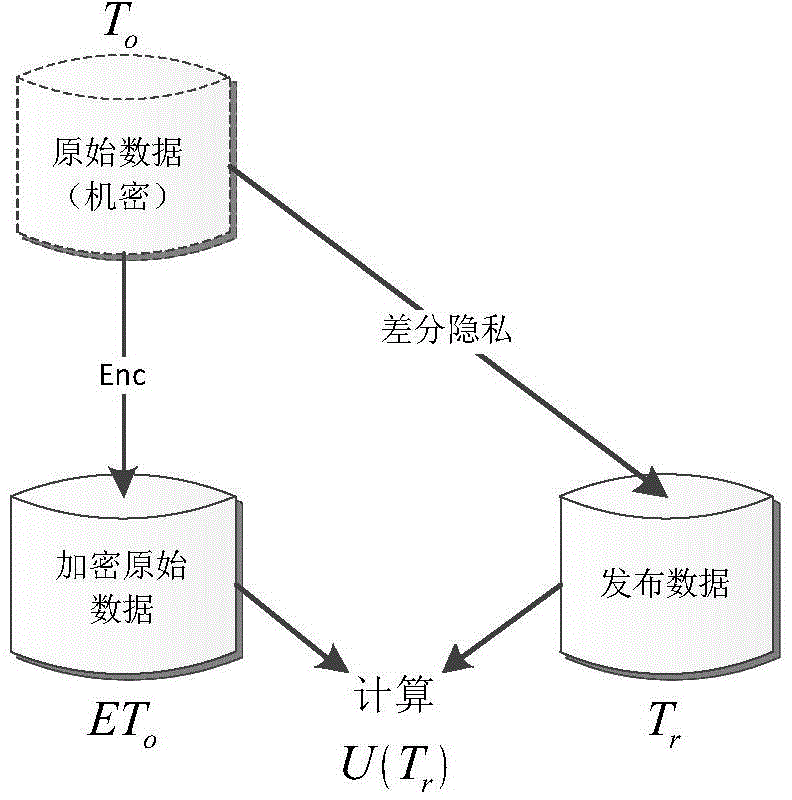
Differential privacy is a system for publicly sharing information about a dataset by describing the patterns of groups within the dataset while withholding information about individuals in the dataset. Another way to describe differential privacy is as a constraint on the algorithms used to publish aggregate information about a statistical database which limits the disclosure of private information of records whose information is in the database. For example, differentially private algorithms are used by some government agencies to publish demographic information or other statistical aggregates while ensuring confidentiality of survey responses, and by companies to collect information about user behavior while controlling what is visible even to internal analysts.
A combined deep learning training method based on a privacy protection technology
ActiveCN109684855AAvoid gettingSafe and efficient deep learning training methodDigital data protectionCommunication with homomorphic encryptionPattern recognitionData set
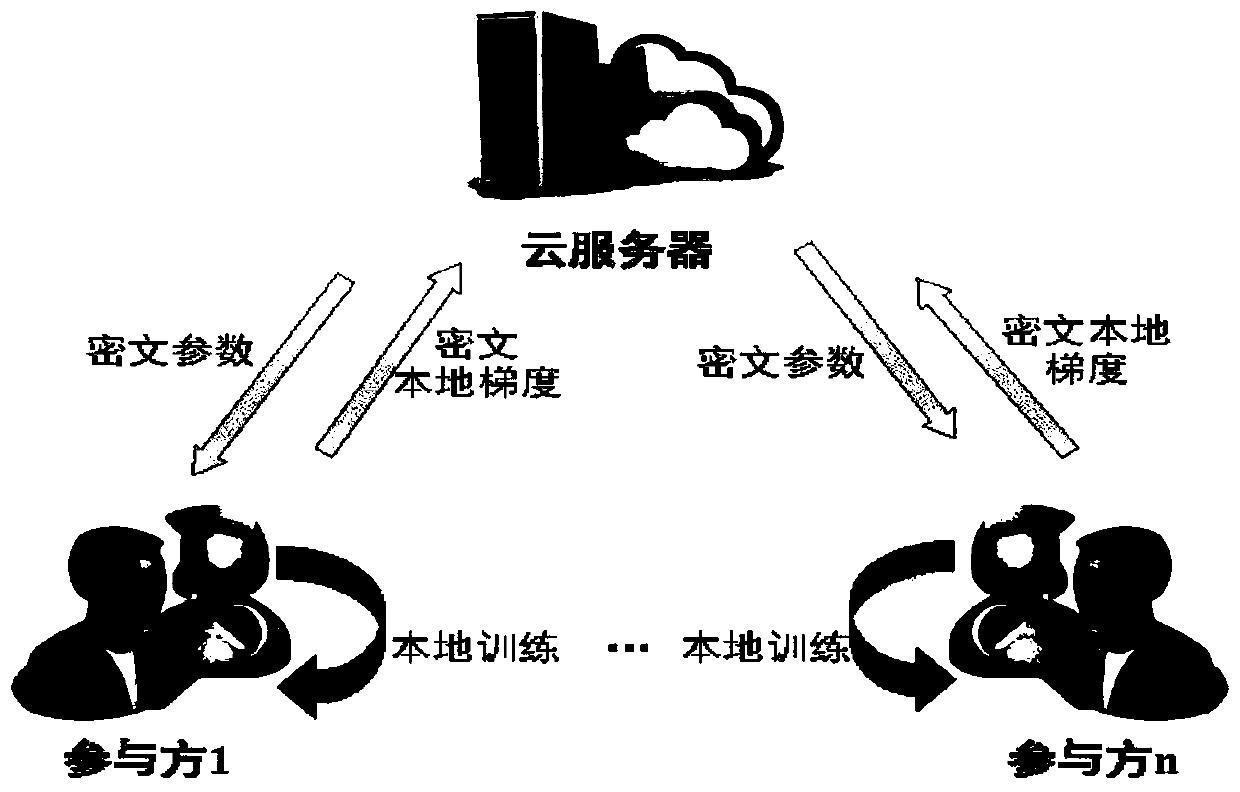
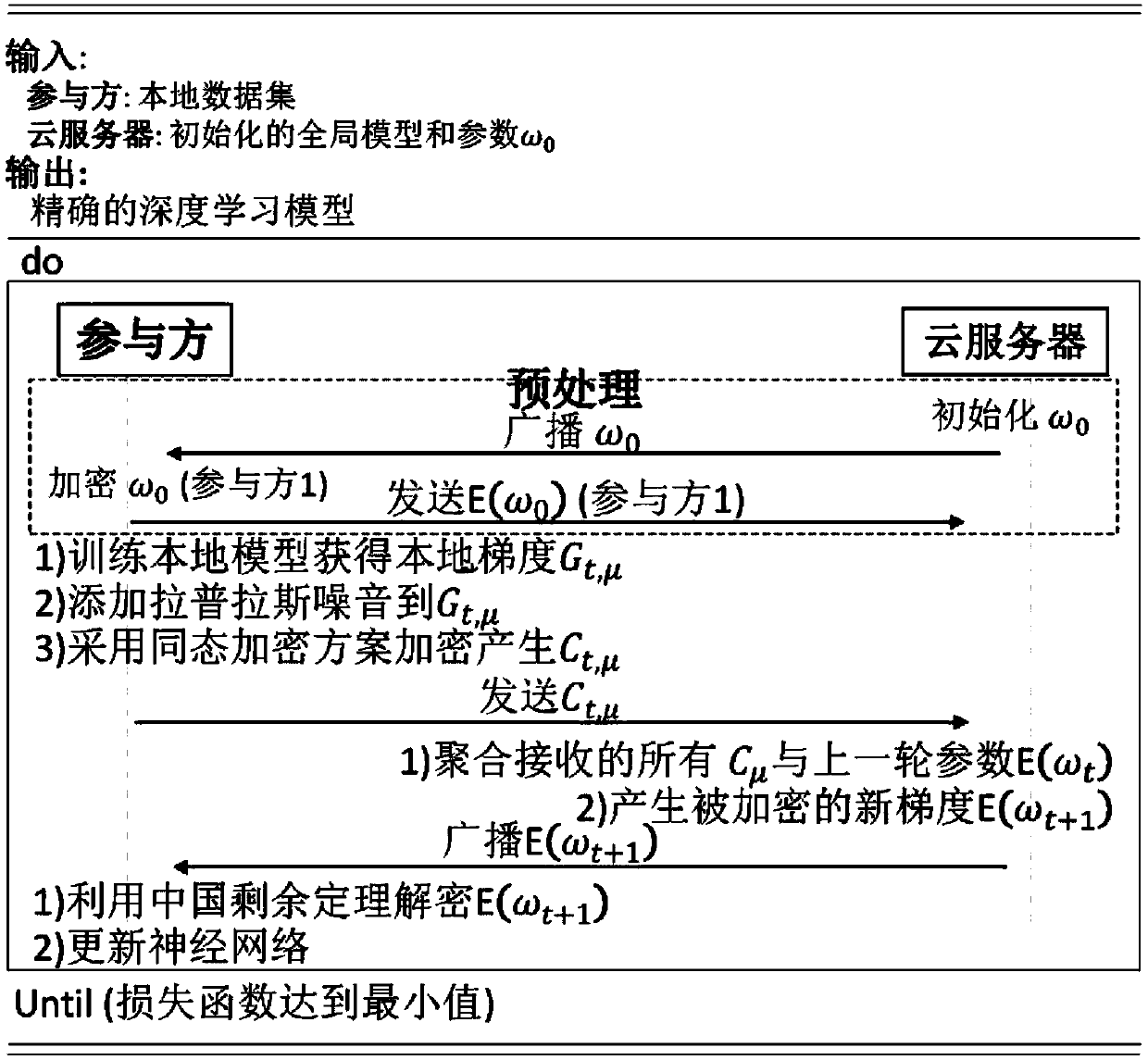
The invention belongs to the technical field of artificial intelligence, and relates to a combined deep learning training method based on a privacy protection technology. The efficient combined deep learning training method based on the privacy protection technology is achieved. In the invention, each participant first trains a local model on a private data set to obtain a local gradient, then performs Laplace noise disturbance on the local gradient, encrypts the local gradient and sends the encrypted local gradient to a cloud server; The cloud server performs aggregation operation on all thereceived local gradients and the ciphertext parameters of the last round, and broadcasts the generated ciphertext parameters; And finally, the participant decrypts the received ciphertext parameters and updates the local model so as to carry out subsequent training. According to the method, a homomorphic encryption scheme and a differential privacy technology are combined, a safe and efficient deep learning training method is provided, the accuracy of a training model is guaranteed, and meanwhile a server is prevented from inferring model parameters, training data privacy and internal attacksto obtain private information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
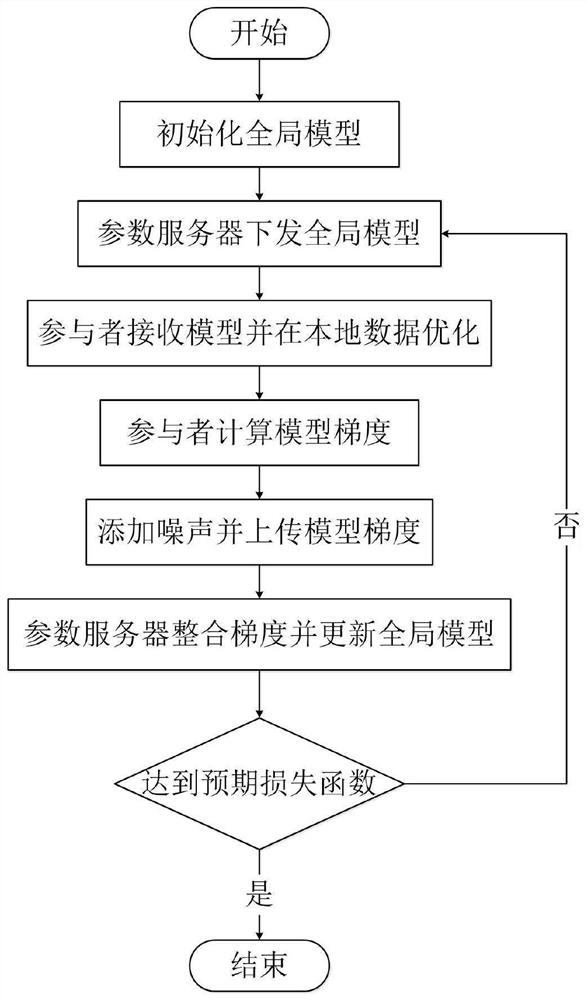
Federated learning information processing method and system, storage medium, program and terminal
ActiveCN111611610ARealize identity anonymityGuaranteed separation effectDigital data protectionNeural architecturesInformation processingData privacy protection
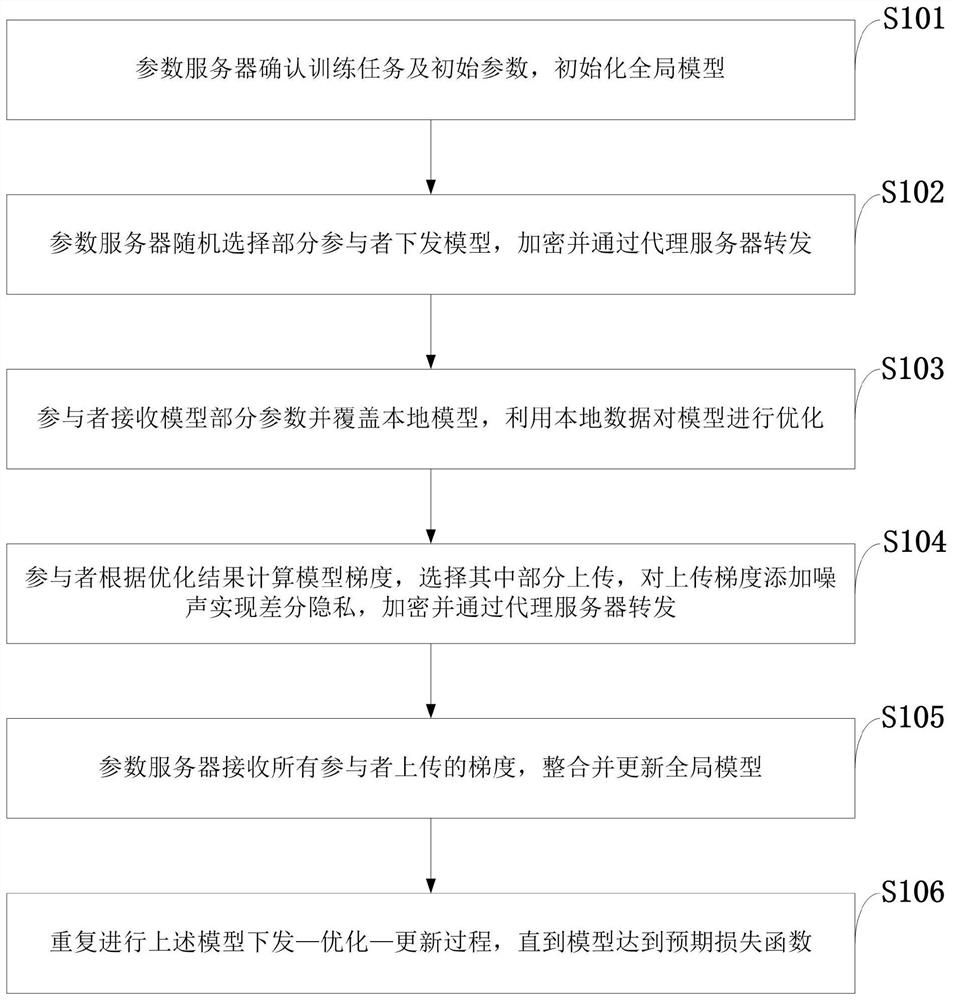
The invention belongs to the technical field of wireless communication networks, and discloses a federated learning information processing method and system, a storage medium, a program, and a terminal. A parameter serve confirms a training task and an initial parameter and initialize a global model. The parameter server randomly selects part of participants to issue model parameters, encrypts themodel parameters and forwards the model parameters through the proxy server; the participants receive part of parameters of the model and cover the local model, and the model is optimized by using local data; the participant calculates a model gradient according to an optimization result, selects a part of the model gradient for uploading, adds noise to the uploading gradient to realize differential privacy, encrypts the uploading gradient and forwards the uploading gradient through the proxy server; the parameter server receives the gradients of all participants, and integrates and updates the global model; and the issuing-training-updating process of the model is repeated until an expected loss function is achieved. According to the invention, data privacy protection is realized; the communication overhead of a parameter server is reduced, and anonymity of participants is realized.
Owner:XIDIAN UNIV
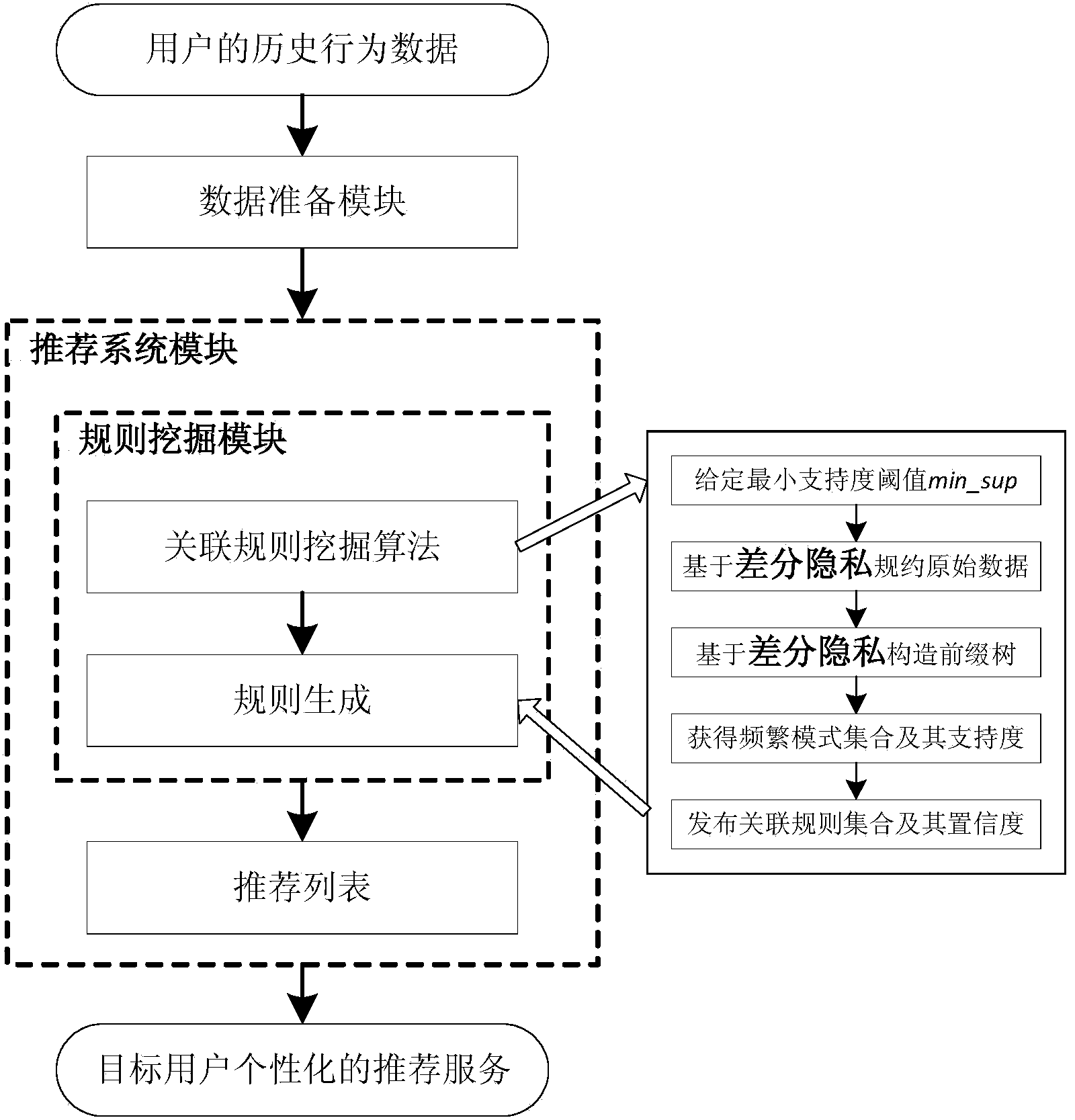
Individuality recommendation method and system protecting user privacy on basis of association rules
ActiveCN104050267ASolve protection problemsSolve the contradiction between improving the performance of personalized recommendation systemSpecial data processing applicationsPersonalizationOriginal data
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
High-efficiency difference disturbance location privacy protection system and method
ActiveCN104394509AGenerate efficientlyGuaranteed correctnessTransmissionLocation information based serviceK-anonymitySide information
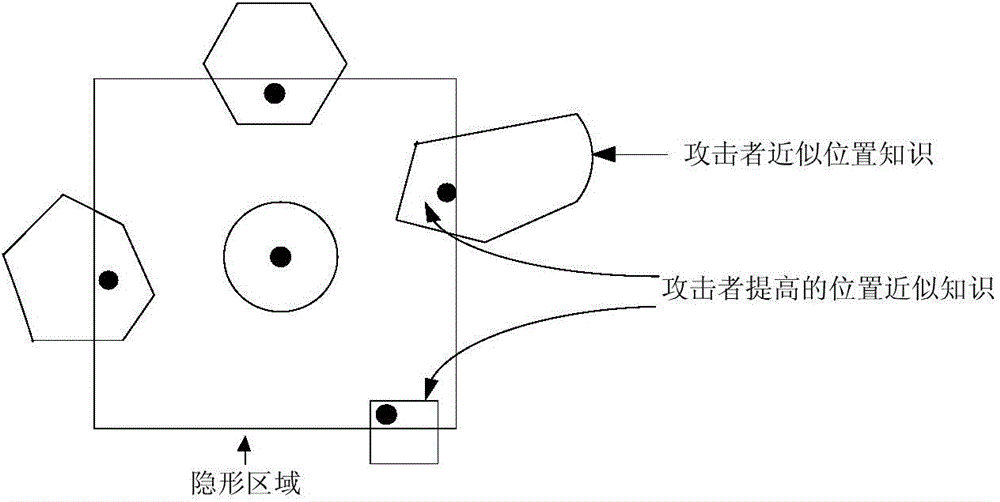
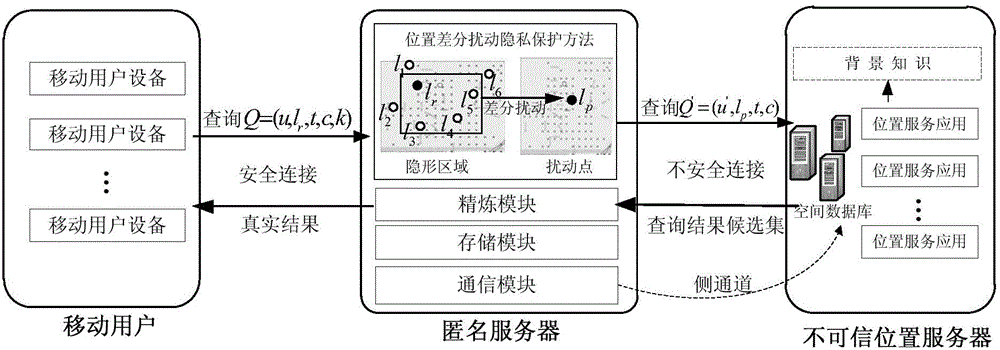
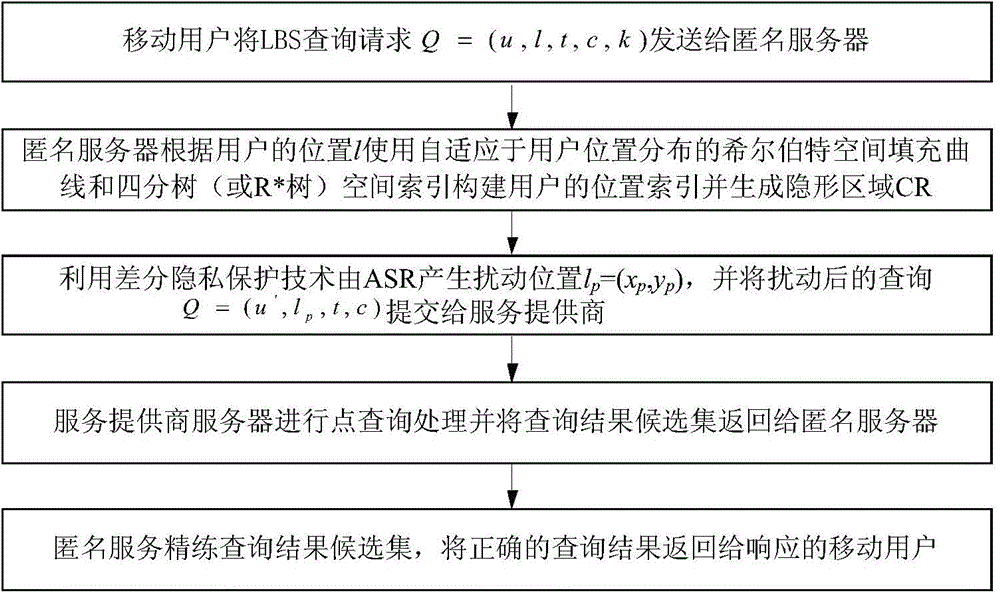
The invention discloses a high-efficiency difference disturbance location privacy protection system and a method, considering that the attacker has the challenge to the location privacy protection method based on the location disturbance and fuzzy technology about the background knowledge of the user side information, the difference privacy protection technology is guided to the location fuzzy privacy protection method, the Hilbert space filling curve capable of self-adaption transition on the user location according to the distributed change features in the geographic space of the mobile user and the current fashionable quadtree or R tree spatial index are used for forming the location index for all mobile users in the geographic space, and the K anonymity contact area satisfying the principle of reciprocity is effectively generated. Then, the difference privacy protection technology is used for generating the location disturbance point reasonable near user real location of k location points of the contact area as the query location of LBS user for requesting service from the LBS service provider, the problems and deficiencies of the existing method can be overcome.
Owner:XI AN JIAOTONG UNIV
Data sharing method, computer equipment applying same and readable storage medium
ActiveCN111931242AAddress privacy breachesSafe and reliableEnsemble learningDigital data protectionData informationSoftware engineering
The invention discloses a data sharing method, computer equipment applying the same and a readable storage medium, and belongs to the technical field of data information security. According to the method, a blockchain technology and a federated learning technology are combined, a data security sharing model based on the blockchain and federated learning is constructed, and a data sharing basic process is designed; a working node selection algorithm based on a block chain and node working quality is designed by taking reliable federated learning as a target; a consensus method of a block chainis modified, an excitation mechanism consensus algorithm based on model training quality is designed, and the purposes of encouraging excellent work nodes to work, simplifying the consensus process and reducing the consensus cost are achieved. The differential privacy algorithm suitable for federated learning is selected by taking balance data security and model practicability as targets. According to the invention, the problem of privacy leakage in a data sharing process can be solved; the blockchain technology is combined into data sharing, so that the security and credibility of data are guaranteed; meanwhile, the efficiency of federated learning tasks is improved.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
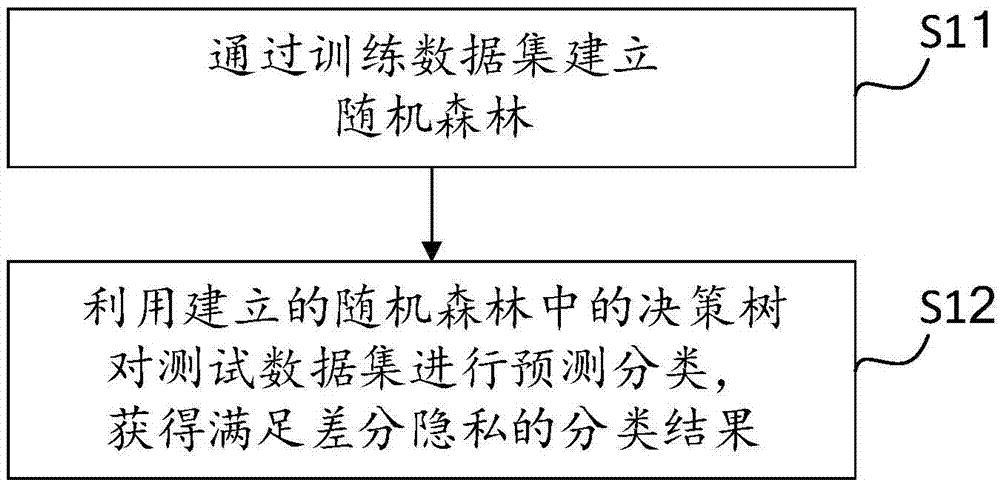
Data prediction classification method and device
InactiveCN105447525AAchieve high accuracy predictive classificationFast trainingCharacter and pattern recognitionData setClassification methods
The invention discloses a data prediction classification method and device relating to the data process technique field, solving the problem in the prior art that classification result itself and classification count value are possible to leak the private information of a user. The method comprises: building a random forest namely multiple decision trees through a training dataset; carrying out prediction classification to a test dataset by the decision trees in the random forest, and obtaining the classification result satisfying differential privacy. The invention can realize high accuracy prediction classification of the high-dimension large-scale data.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
User privacy protection method in personalized information retrieval
ActiveCN103279499AGuaranteed privacy and securityDoes not affect calculation resultsDigital data protectionSpecial data processing applicationsStatistical databasePersonalized search
The invention discloses a user privacy protection method in personalized information retrieval. The user privacy protection method in personalized information retrieval is a user interest model anonymization method based on difference privacy and aims to remove contradiction between user privacy protection and improvement of personalized information retrieval performance. The user privacy protection method in personalized information retrieval aims to conduct anonymization after identifiers of a user interest model are concealed, and namely after the identifiers (including the ID, the name, the ID number, the SSN and the like of a user) are eliminated, related technologies of the difference privacy are mainly used for anonymizing standard identifiers of the user interest model. Namely, generalization is conducted on the standard identifiers of the user, Laplace noise is added so as to enable difference privacy protection requirements to be met, the inquiry precision of a statistical database is maximized, and the probability of identification of an entity and attributes is minimized. The user privacy protection method in personalized information retrieval can be widely applied to service systems, such as a personalized retrieval service system and a personalized recommendation service system. The invention belongs to the technical field of information and computers.
Owner:BEIJING INFORMATION SCI & TECH UNIV
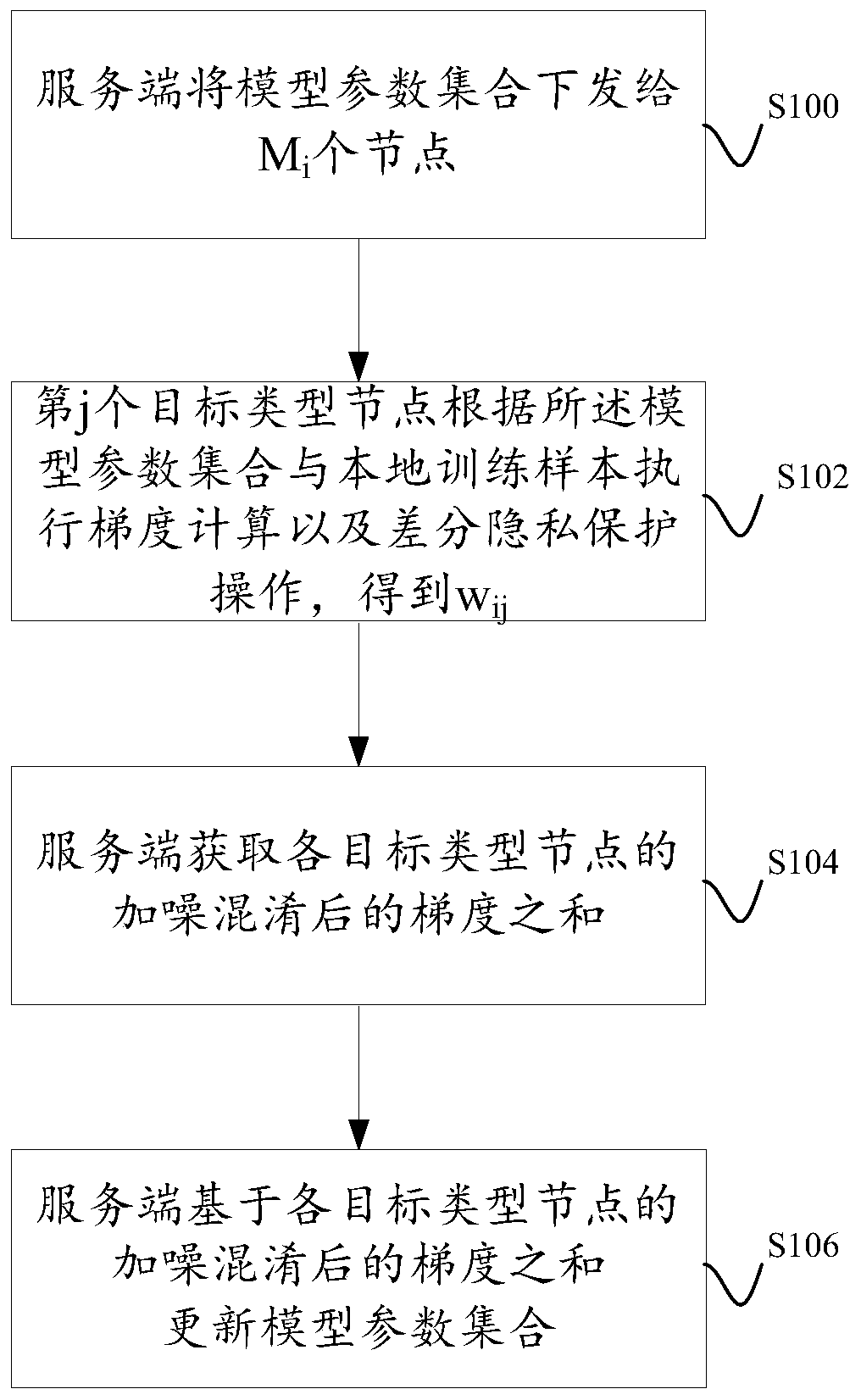
Model training method based on federated learning
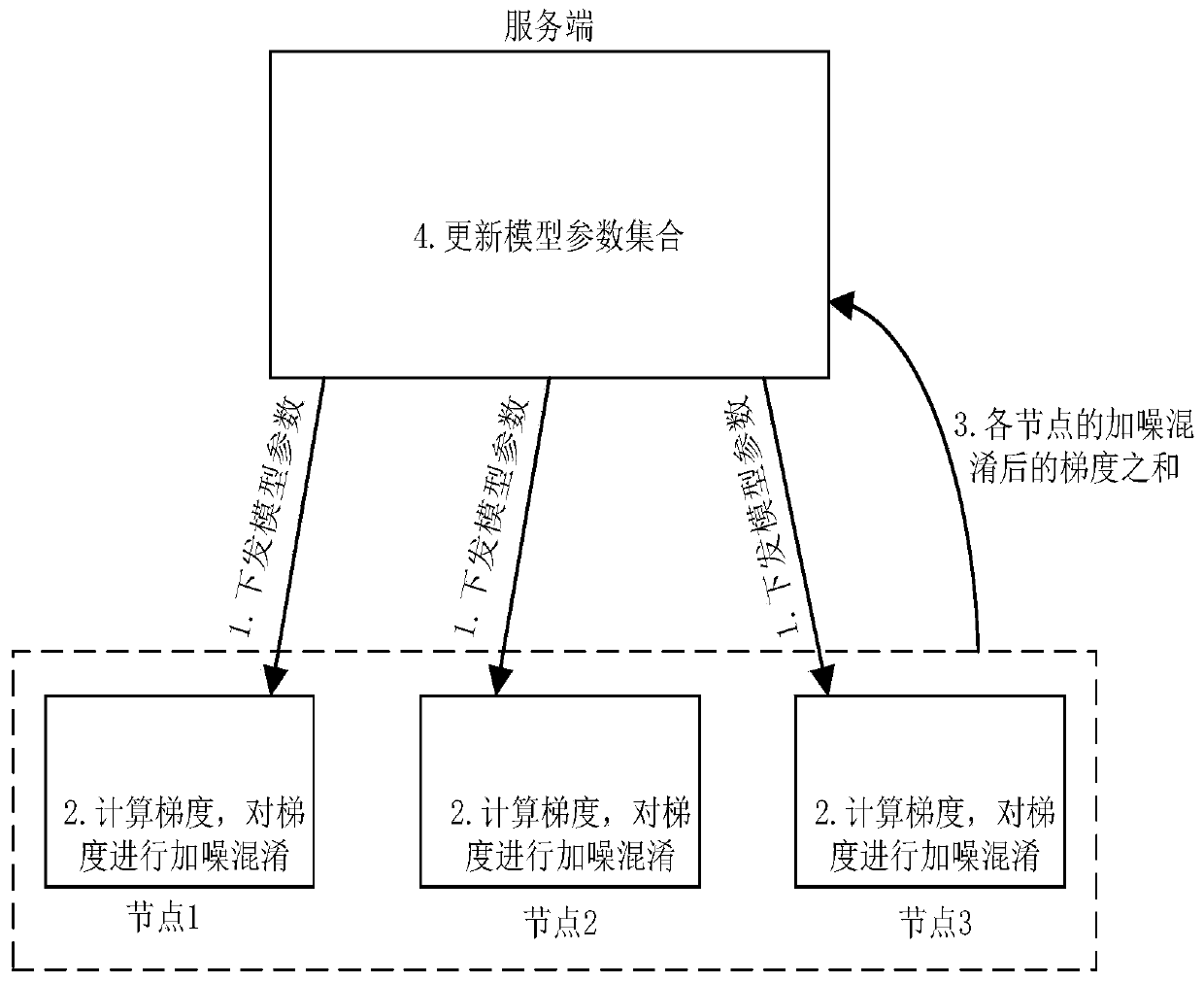
ActiveCN111046433AAchieving Noise and ObfuscationExamples cannot be limitedDigital data protectionMachine learningDifferential privacyEngineering
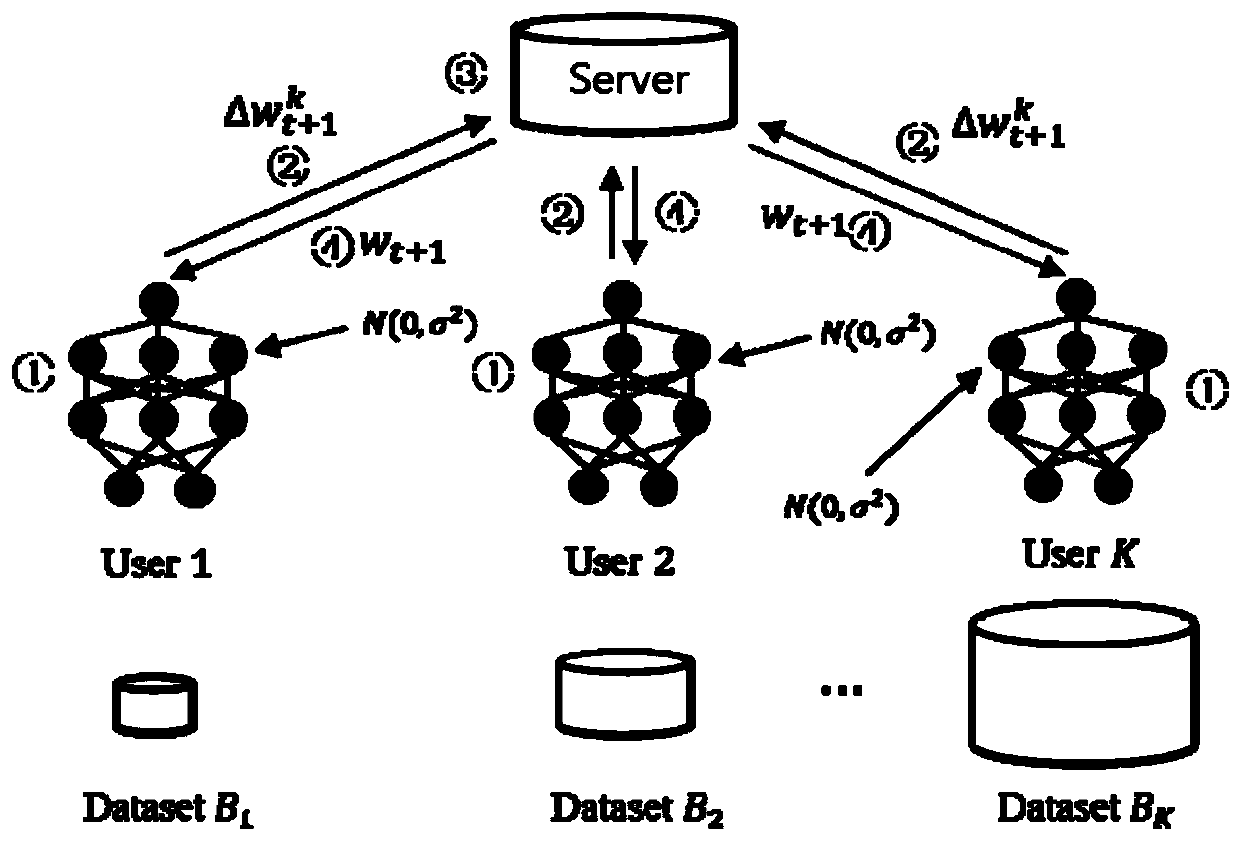
The invention discloses a model training method based on federated learning. In one training iteration, the nodes can achieve noise adding and confusion of the gradient through differential privacy protection operation, and the server can obtain the sum of the gradients after noise adding and confusion to update model parameters.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
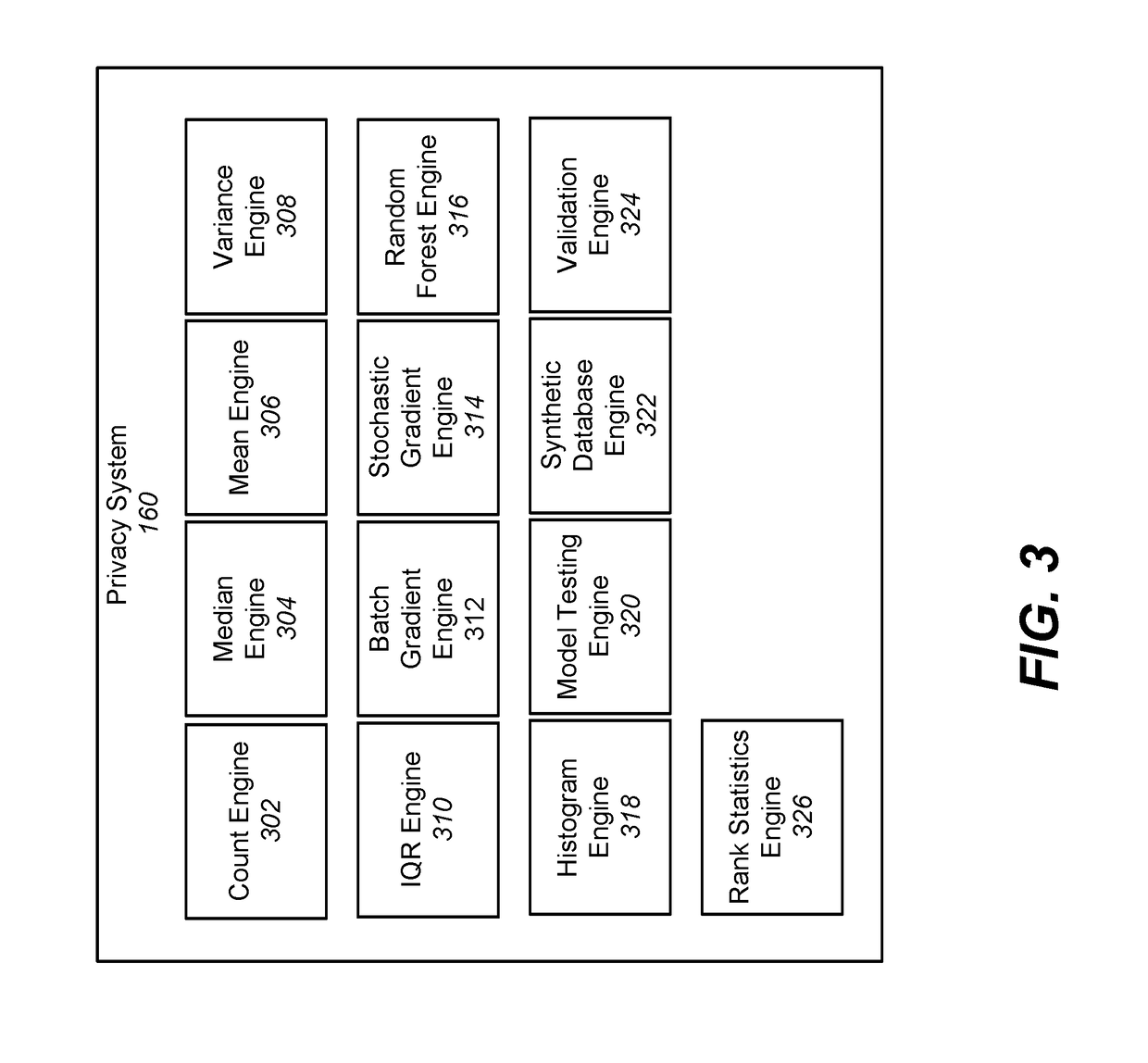
Differentially private database queries involving rank statistics
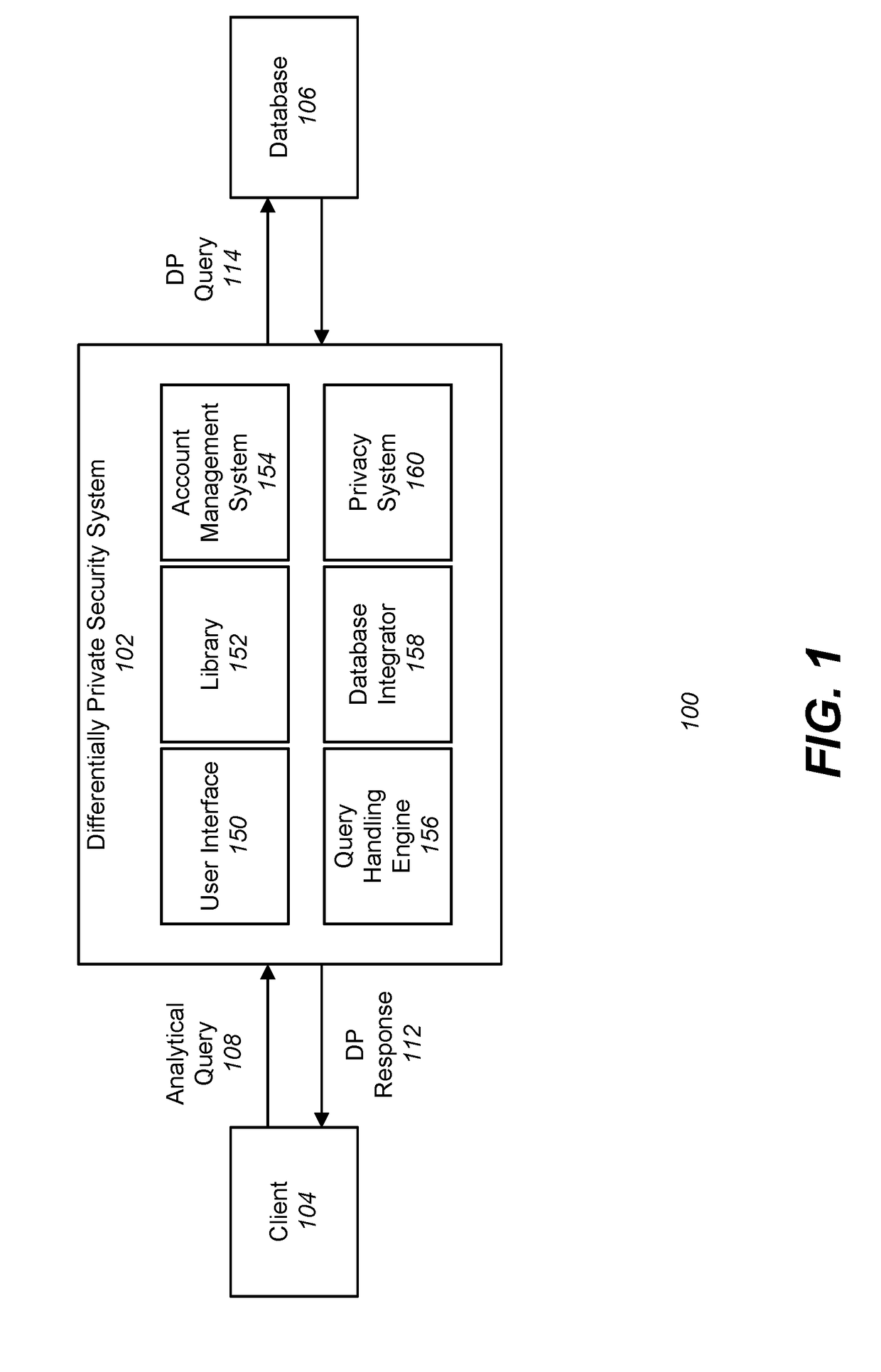
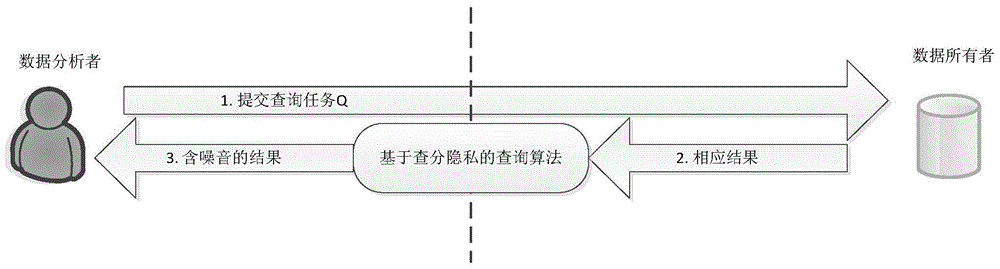
ActiveUS20180349384A1Digital data information retrievalDigital data protectionDifferential privacyClient-side
A differentially private security system is communicatively coupled to a database. The differentially private security system receives a request from a client device to perform a query of the database and identifies a level of differential privacy corresponding to the request. The identified level of differential privacy includes privacy parameters (ε,δ) indicating the degree of information released about the database. The differentially private security system performs a differentially private query upon a set of data in the database such that the performance of the query produces a result that is (ε,δ)-differentially private.
Owner:SNOWFLAKE INC
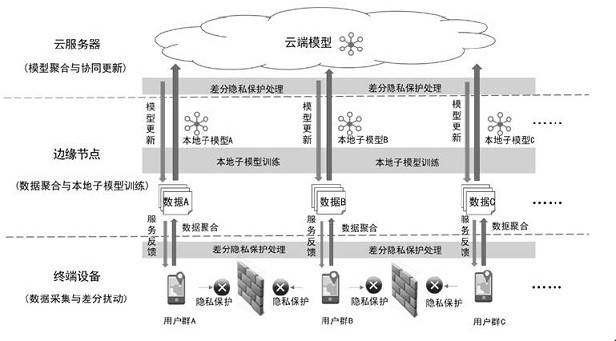
Edge computing-oriented federated learning indoor positioning privacy protection method
ActiveCN111866869AReal-time indoor positioning serviceSecure Indoor Positioning ServiceTransmissionSecurity arrangementEdge computingPrivacy protection
The invention provides an edge computing-oriented federated learning indoor positioning privacy protection method. The method is based on federated learning and differential privacy protection technologies. According to the method, credible federation training of an indoor positioning model is carried out in an edge computing environment; in the training process, all participating users do not share training data, distributed training and credible aggregation of the indoor positioning model are carried out only by sharing positioning model parameters, meanwhile, the model parameters are updated in an end-cloud cooperation iteration mode, so that the indoor positioning model is continuously optimized, and privacy protection and cooperative benefits of multi-user positioning model training are achieved. Experimental results show that compared with a traditional centralized model training method and a federated learning-based model training method, the method provided by the invention notonly can provide proven privacy protection, but also ensures the positioning effect of the model under the condition of increasing extremely little calculation overhead.
Owner:LANZHOU JIAOTONG UNIV
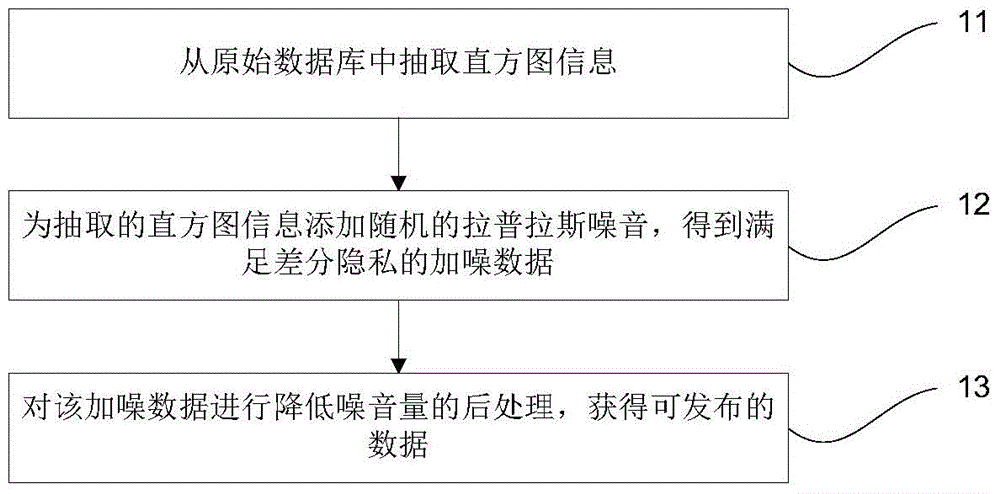
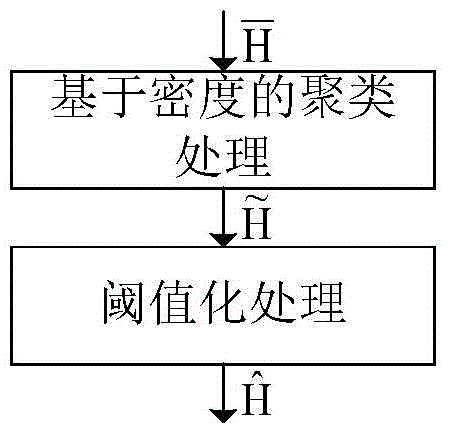
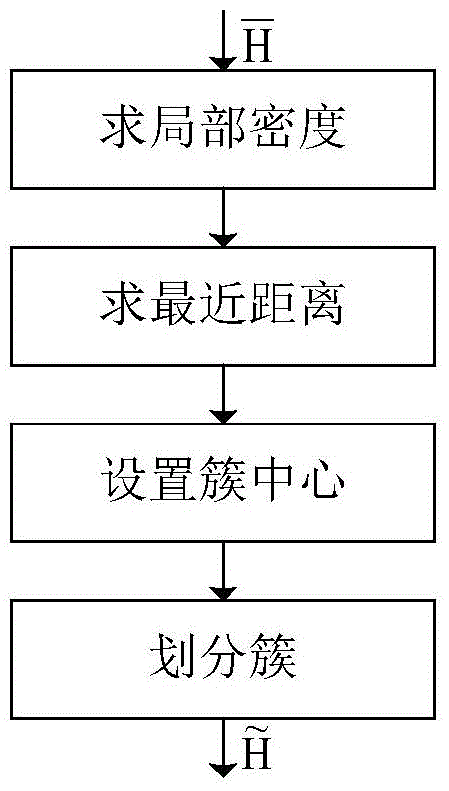
Histogram release method based on difference privacy
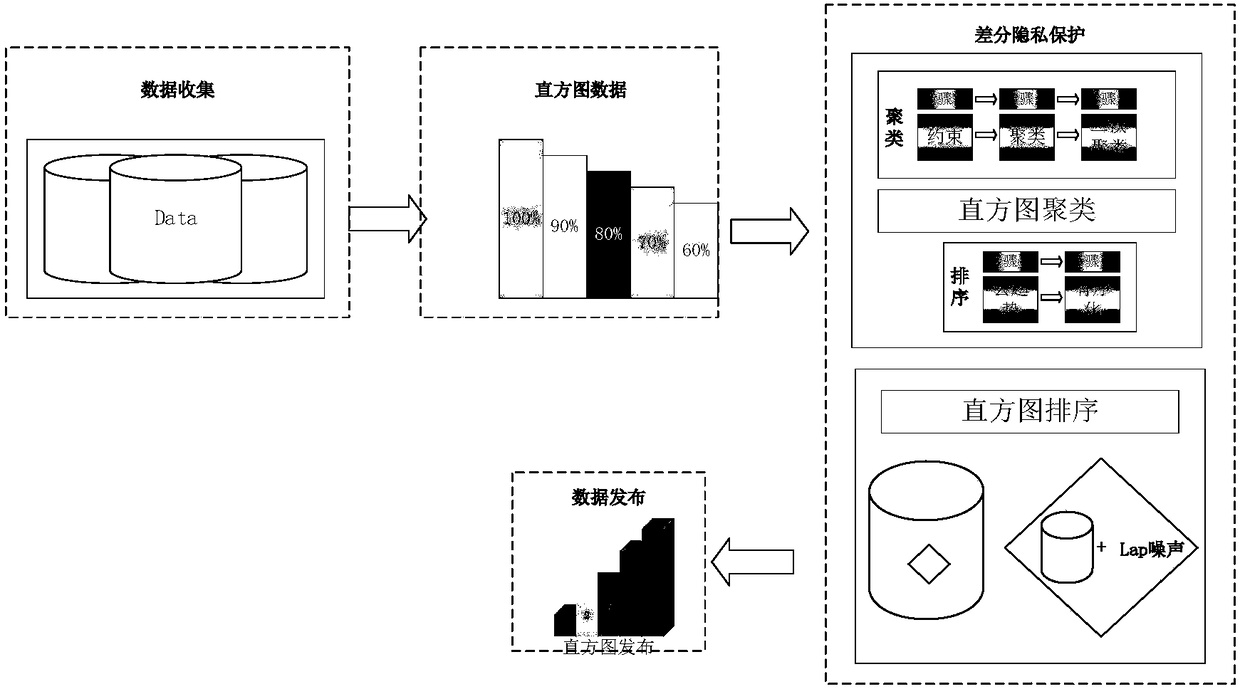
ActiveCN104809408AGuaranteed differential privacyGuarantee that data satisfies differential privacyDigital data protectionDifferential privacyNoise reduction
The invention discloses a histogram release method based on difference privacy. The method comprises the following steps: extracting histogram information from discontinuous regions in an original database; adding random Laplace noise the extracted histogram information to obtain noise-added data; performing noise reduction clustering and threshold processing on the noise-added data to obtain data which can be released. By adopting the method disclosed by the invention, the usefulness of released data is improved under the situation of ensuring the difference privacy.
Owner:UNIV OF SCI & TECH OF CHINA
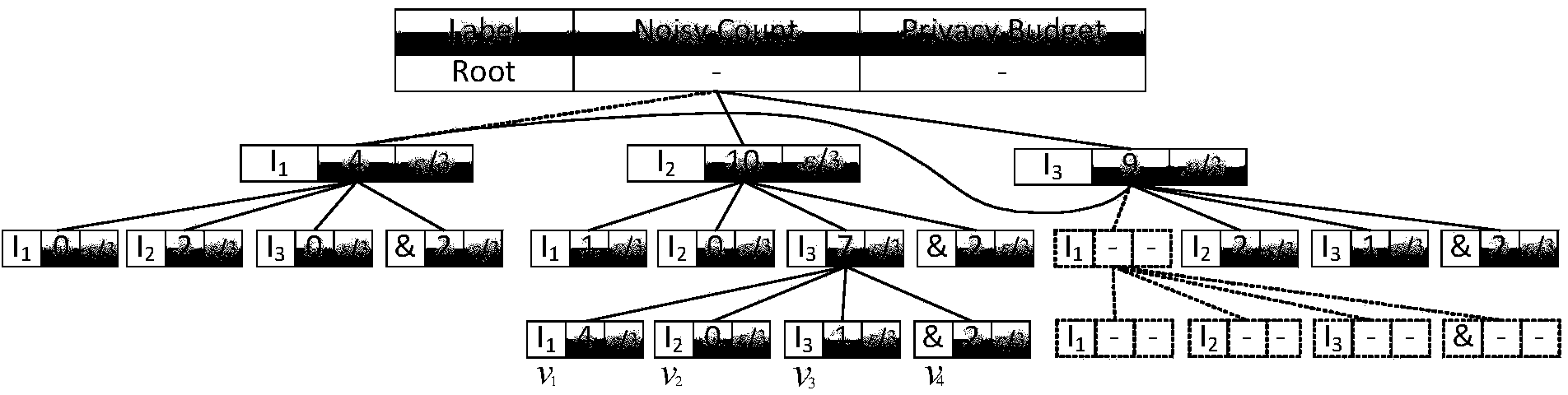
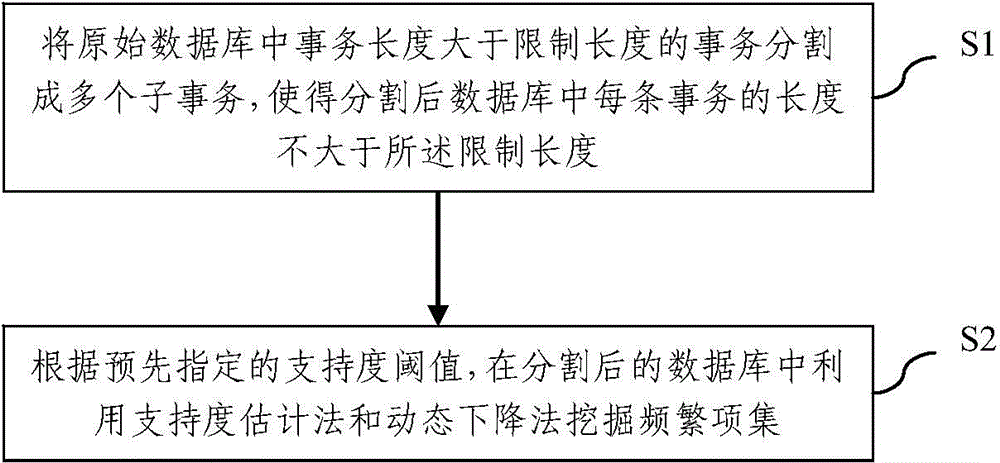
Frequent item set mining method
InactiveCN105740245AImprove digging efficiencyImprove resultsSpecial data processing applicationsEstimation methodsOriginal data
The invention relates to the technical field of data mining and data privacy, and discloses a frequent item set mining method. The frequent item set mining method comprises the following steps: S1: segmenting a transaction of which the transaction length is greater than a restriction length in an original database into a plurality of sub-transactions, and causing the length of each transaction in the segmented database to be smaller than or equal to the restriction length; and S2: according to a support degree threshold value which is appointed in advance, utilizing a support degree estimation method and a dynamic descent method to mine the frequent item set in the segmented database. The frequent item set mining method can provide higher mining efficiency and mining result availability while differential privacy protection is met.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Differential privacy for message text content mining
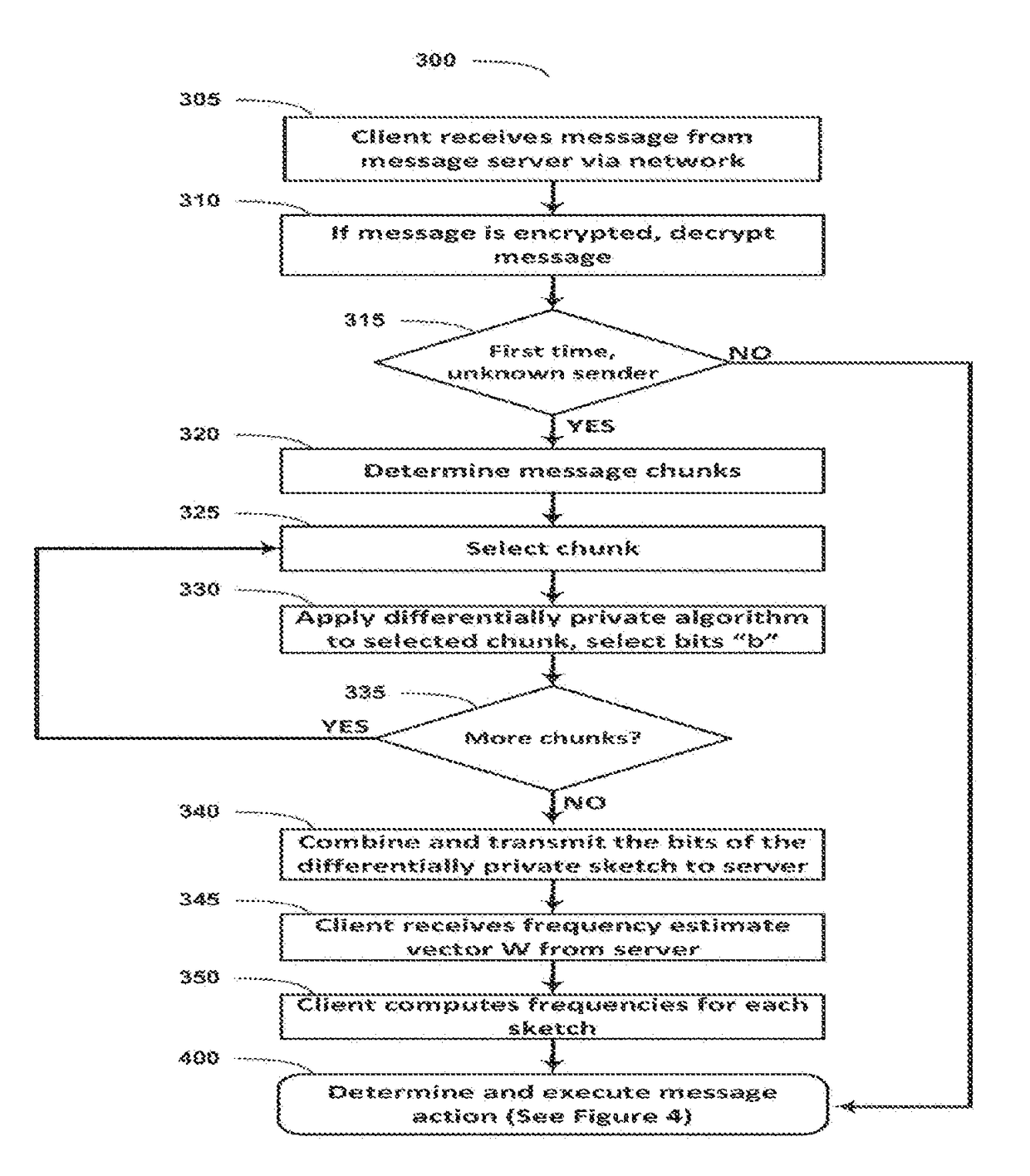
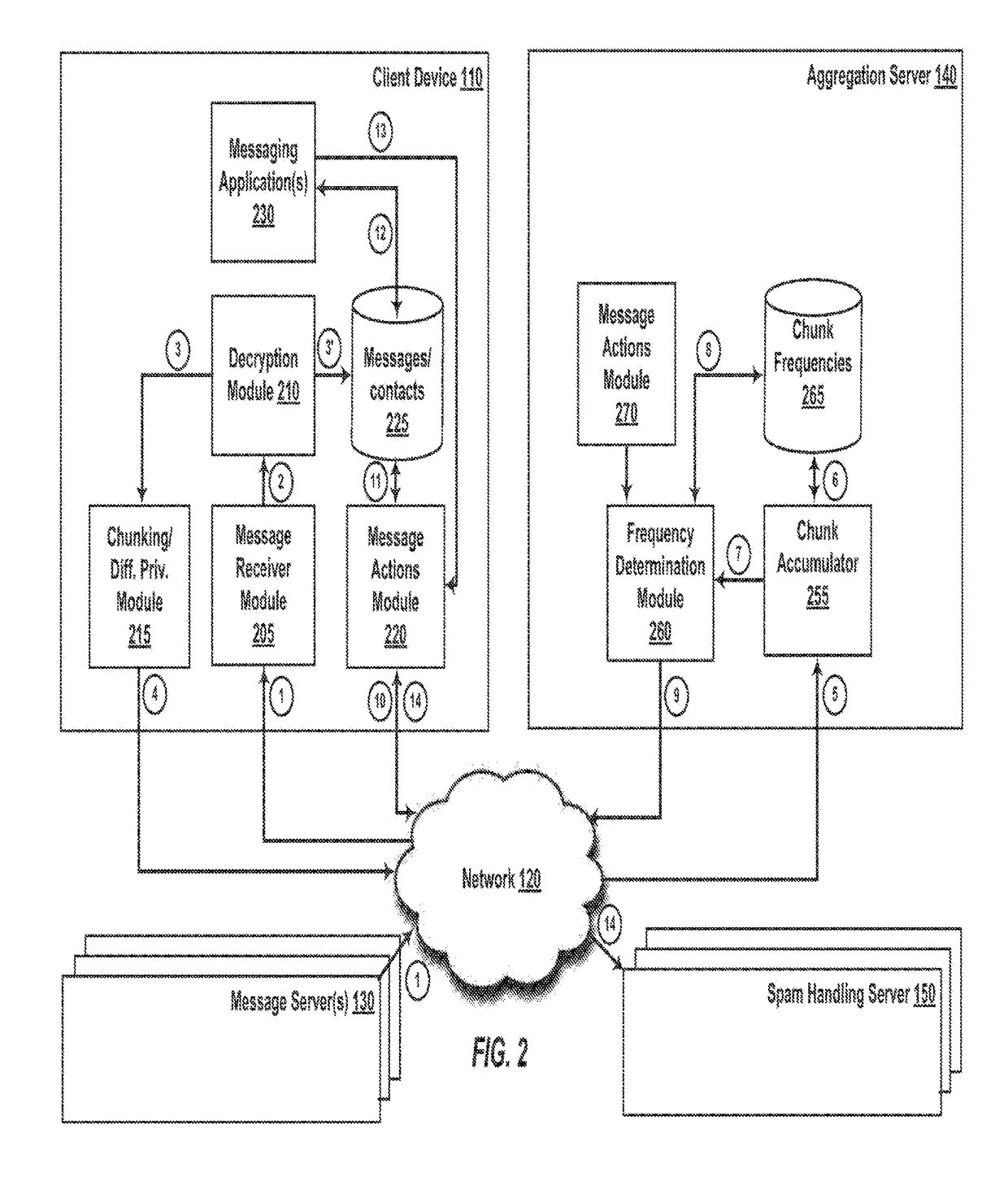
ActiveUS20180091466A1Computer security arrangementsNatural language data processingDifferential privacyClient-side
Systems and methods are disclosed for determining whether a message received by a client may be spam, in a computing environment that preserves privacy. The message may be encrypted. A client invokes the methods when a message is received from a sender that is not known to the client. A client can decrypt the message, break the message into chunks, and apply a differentially private algorithm to the set of chunks. The client transmits the differentially private message sketches to an aggregation server. The aggregation server receives a large collection of such message sketches for a large plurality of clients. The aggregation server returns aggregated message chunk (e.g. frequency) information to the client to assist the client in determining whether the message may be spam. The client can process the message based on the determination without disclosing the message content to the server.
Owner:APPLE INC
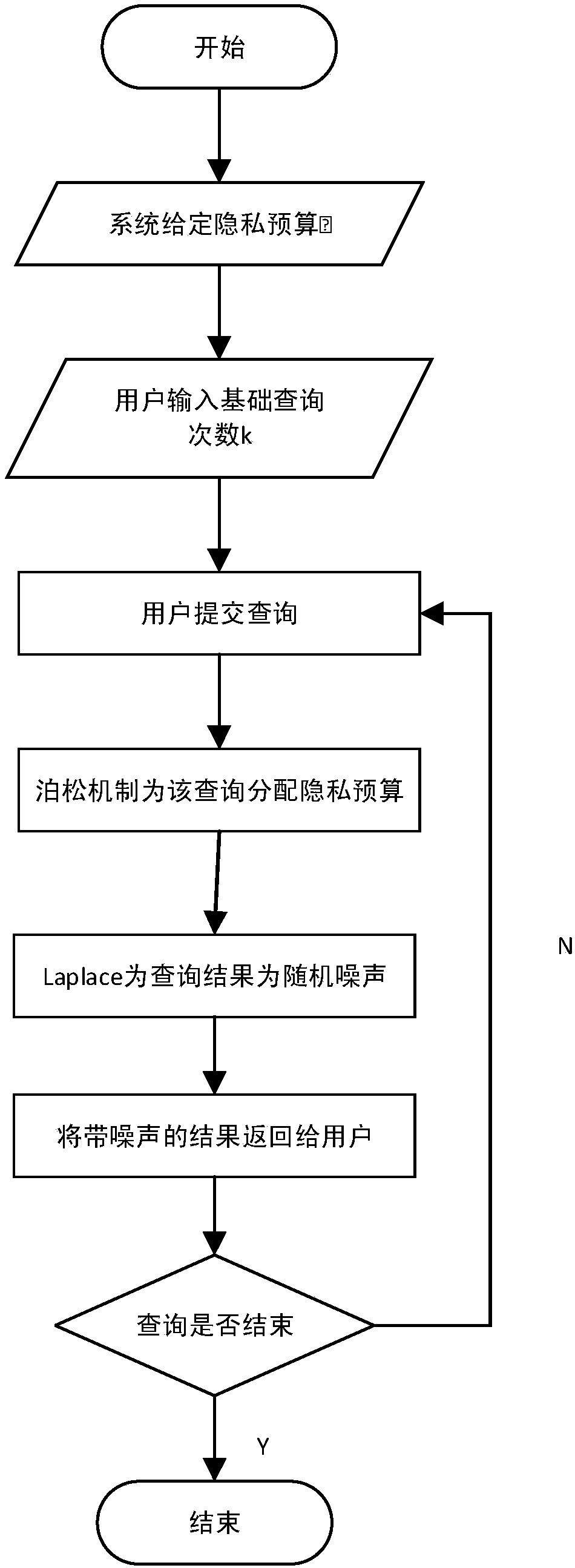
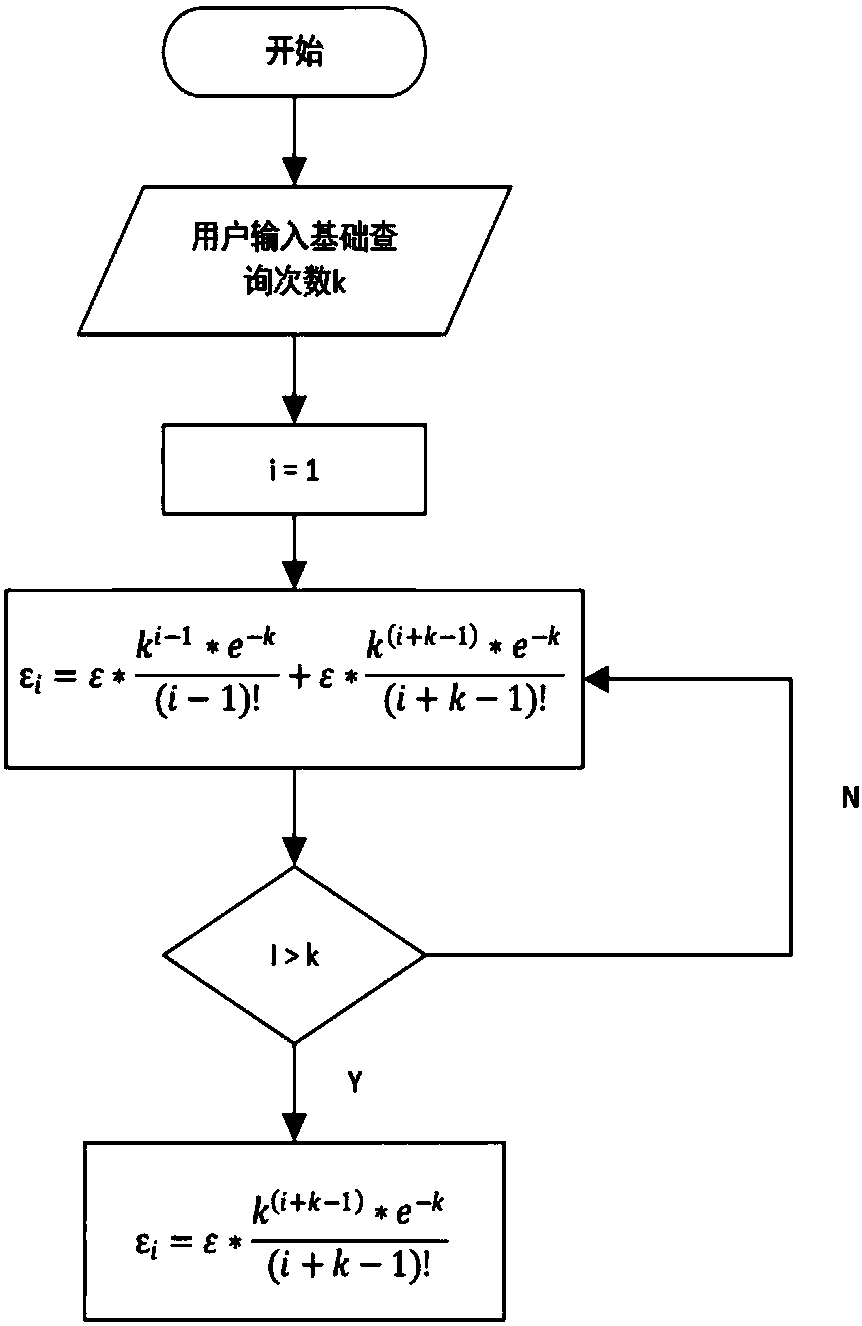
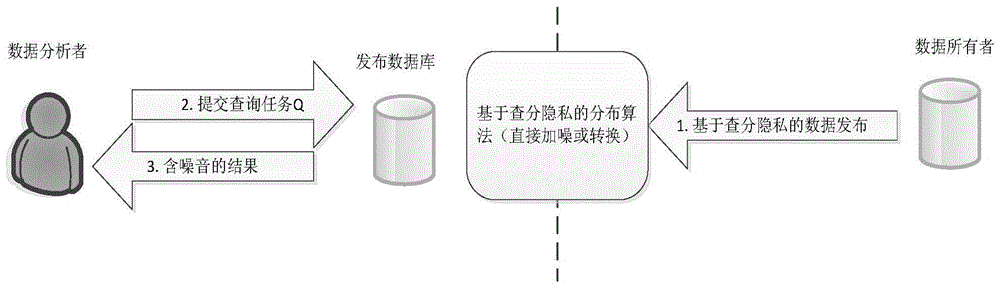
Privacy budget allocating and data publishing method and privacy budget allocating and data publishing system for protecting data query privacy
ActiveCN108537055APrivacy protectionGuaranteed availabilityDigital data protectionSpecial data processing applicationsAttackPrivacy protection
The invention discloses a privacy budget allocating and data publishing method for protecting the data query privacy. The privacy budget allocating and data publishing method includes steps of firstly, setting privacy budget parameters, to be more specific, giving privacy budgets of data by data administrators according to importance degrees of the data, denoting the privacy budgets of the data asepsilon, setting basic query frequencies of the data and denoting the basic query frequencies of the data as k; secondly, computing privacy budgets of each query; thirdly, acquiring the sensitivity delta f of the query according to the query f submitted by users, combining the sensitivity delta f with the privacy budget epsilon allocated to the query, and computing required-to-be-added noise forquery results by the aid of difference privacy protection algorithms so as to obtain query results with the noise; fourthly, returning the query results with the noise according to the query submittedby the users so as to protect the privacy of the data. The privacy budget allocating and data publishing method has the advantages that the privacy can be protected in data publishing procedures, accomplice attack can be resisted, the precision of first k times of query can be guaranteed, and the problem of excessively low data availability due to the fact that existing privacy budgets are infinitely allocated can be solved by the aid of the privacy budget allocating and data publishing method.
Owner:NANJING UNIV OF POSTS & TELECOMM
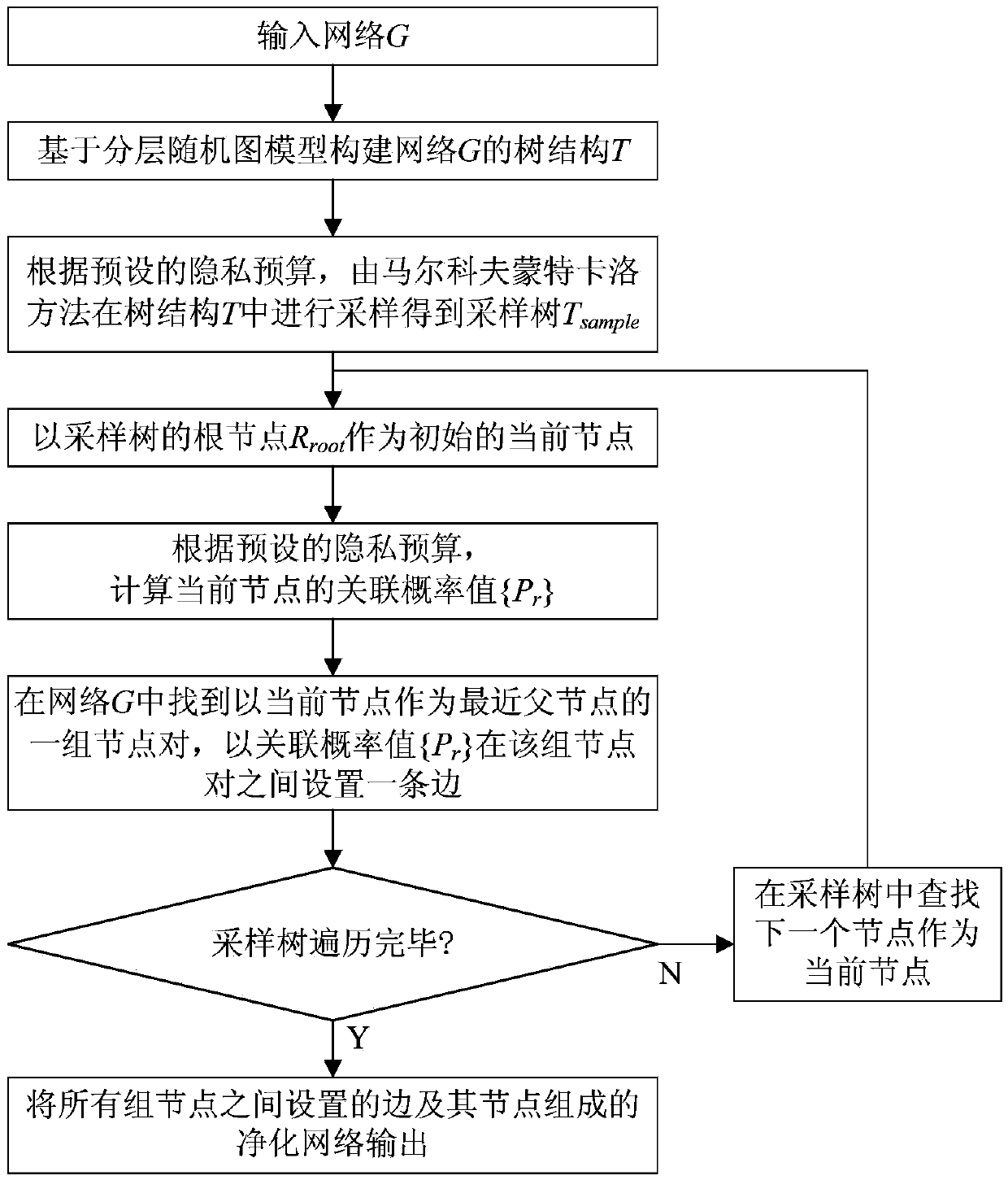
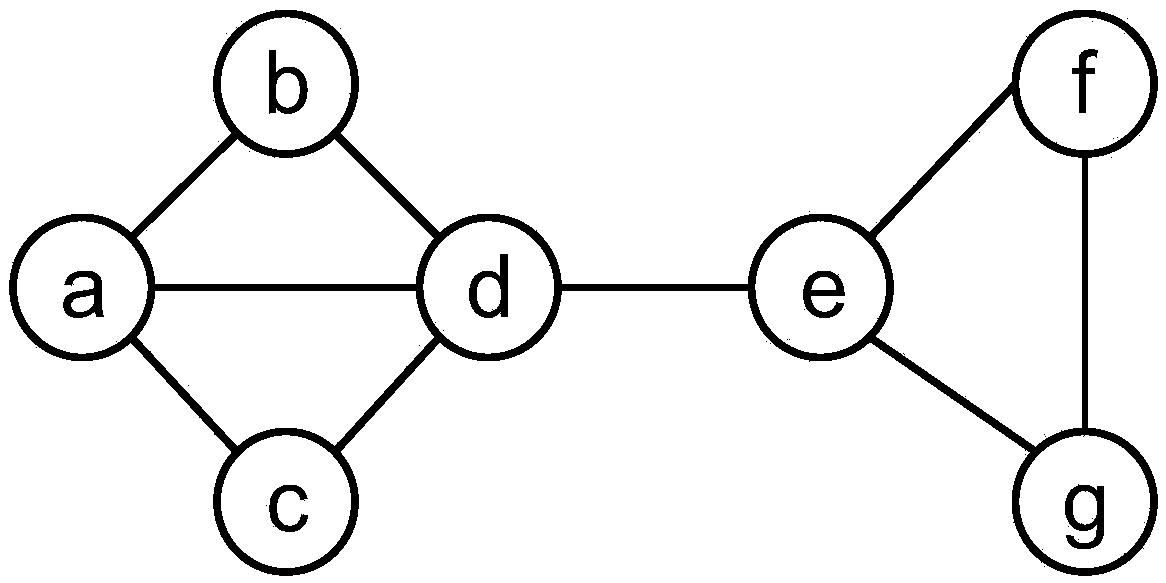
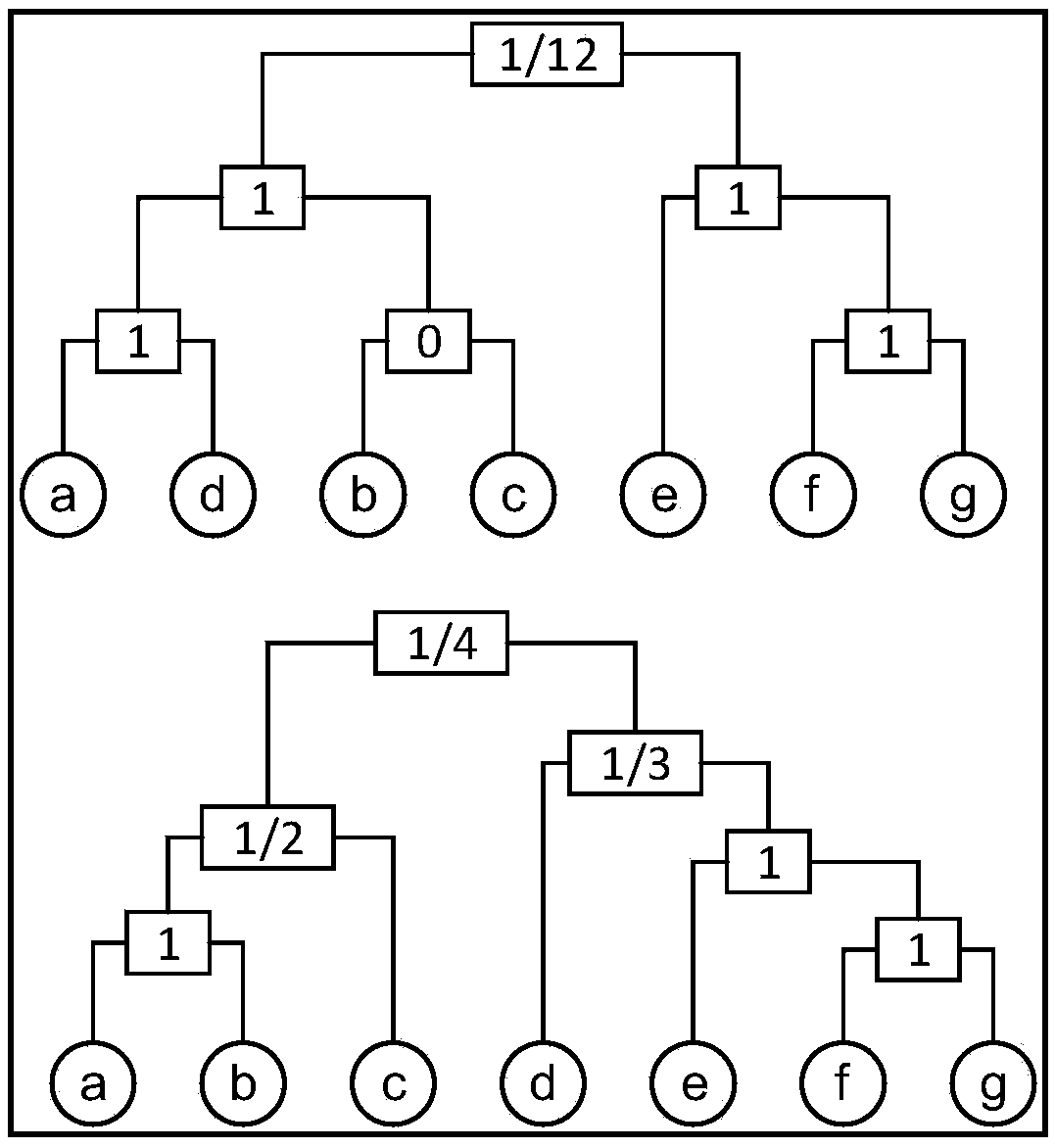
Differential privacy protection method for online social network based on stratified random graph
InactiveCN105376243ASolve the problem of privacy protectionGuaranteed availabilityTransmissionNODALRelationship - Father
The invention discloses a differential privacy protection method for an online social network based on a stratified random graph. The differential privacy protection method comprises the following steps: inputting a network; constructing a tree structure of the network based on a stratified random graph model; sampling in the network through a Markov chain Monte Carlo method according to a preset privacy budget so as to obtain a sampled tree; taking the root node of the sampled tree as an initial current node; calculating an associated probability value of the current node according to the preset privacy budget; finding out a set of node pairs by taking the current node as the nearest father node in the network, and setting an edge among the set of node pairs according to the associated probability value; judging whether traversal of the sampled tree is completed or not, and if not, continuously traversing the next node in the sampled tree; and otherwise, outputting a purified network composed of edges arranged among all the sets of nodes and nodes thereof. According to the invention, the privacy protection problem of sensitive structural data information in the social network can be solved; differential privacy protection requirements can be satisfied; and simultaneously, the good data availability is kept.
Owner:NAT UNIV OF DEFENSE TECH
Availability computing method of data published based on differential privacy
ActiveCN104135362AShow securityShow correctnessSpecial data processing applicationsSecuring communicationData setPassword
The invention discloses an availability computing method of data published based on differential privacy and aims at collection data and relational data to respectively provide a DiffPart-based data availability computing method capable of protecting privacy and a DiffGen-based data availability computing method capable of protecting privacy, availability is defined, availability functions for measuring information losses of two methods are respectively given, some encrypted auxiliary data sets are published through a publisher, the auxiliary data sets are encrypted by a password system constructed on Z*n, the auxiliary data sets are verified in sequence to check whether data of the publisher are included in the auxiliary data sets correctly, and availability of the finally published data set is figured up by utilizing the auxiliary data sets. An experiment shows that the scheme has higher efficiency, and is mainly influenced by the number of data providers and the data scale.
Owner:NANJING UNIV
Federated learning method and device based on differential privacy and storage medium
ActiveCN111091199AHigh precisionGuarantee privacy and securityMachine learningDifferential privacyEngineering
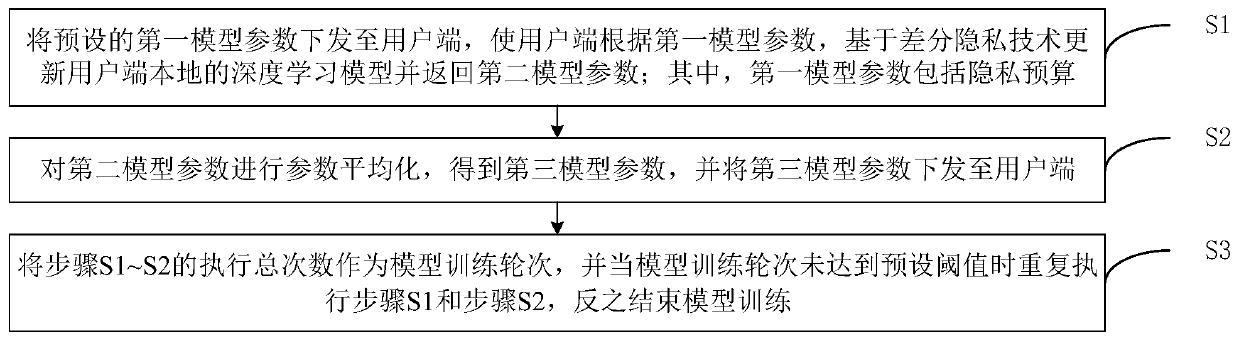
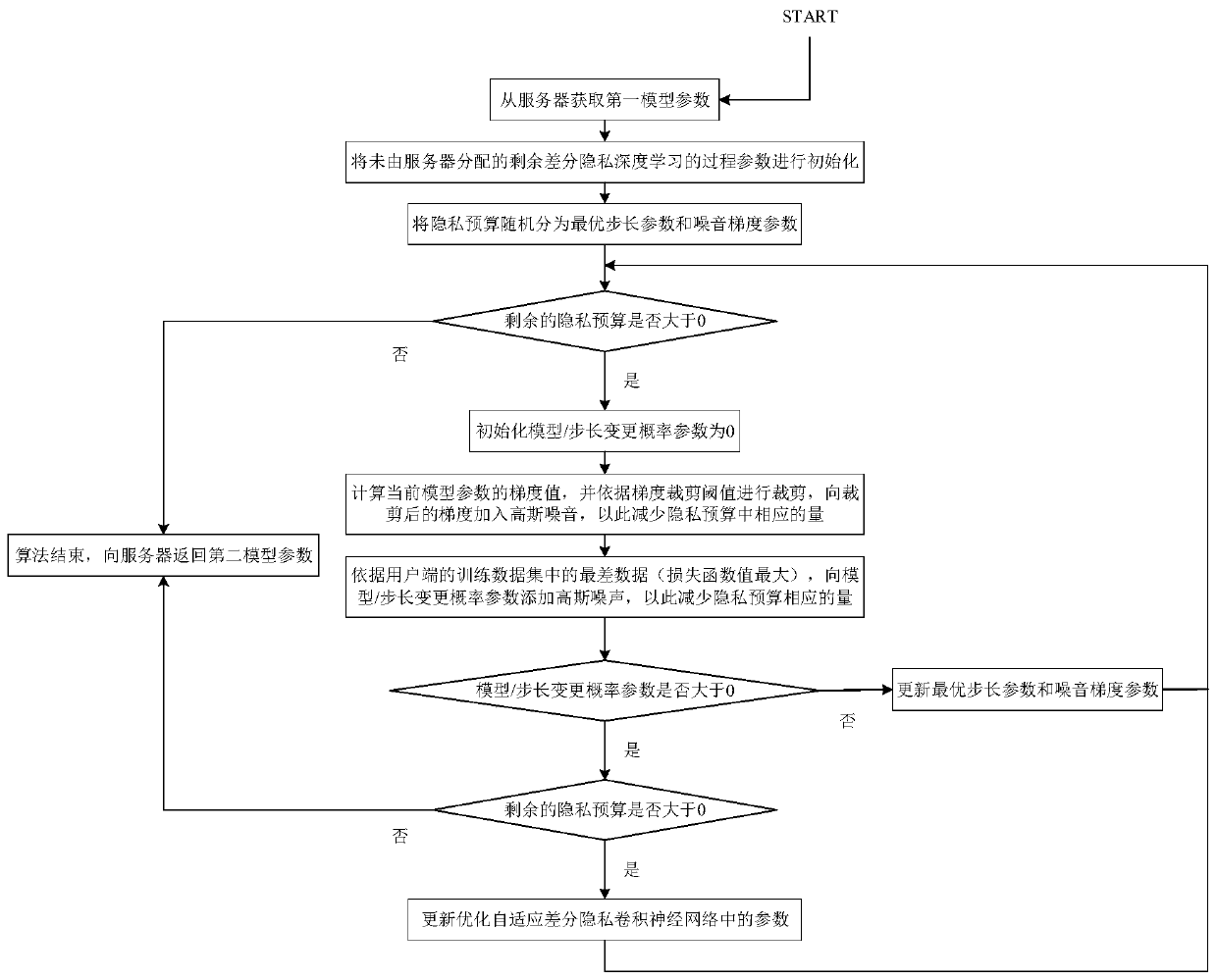
The invention discloses a federated learning method and device based on differential privacy and a storage medium. The method comprises the steps that S1, a preset first model parameter is issued to auser side, so that the user side updates a local deep learning model of the user side based on a differential privacy technology according to the first model parameter and returns a second model parameter; wherein the first model parameter comprises a privacy budget; S2, performing parameter equalization on the second model parameter to obtain a third model parameter, and issuing the third modelparameter to the user side; and S3, taking the total execution times of the steps S1 to S2 as a model training round, and repeatedly executing the steps S1 and S2 when the model training round does not reach a preset threshold, otherwise, ending the model training. According to the invention, the data privacy safety can be ensured, and the accuracy of the training model is improved.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
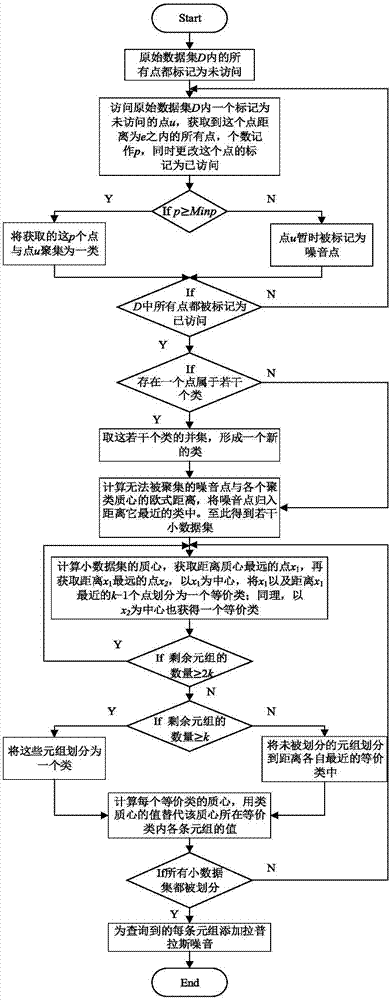
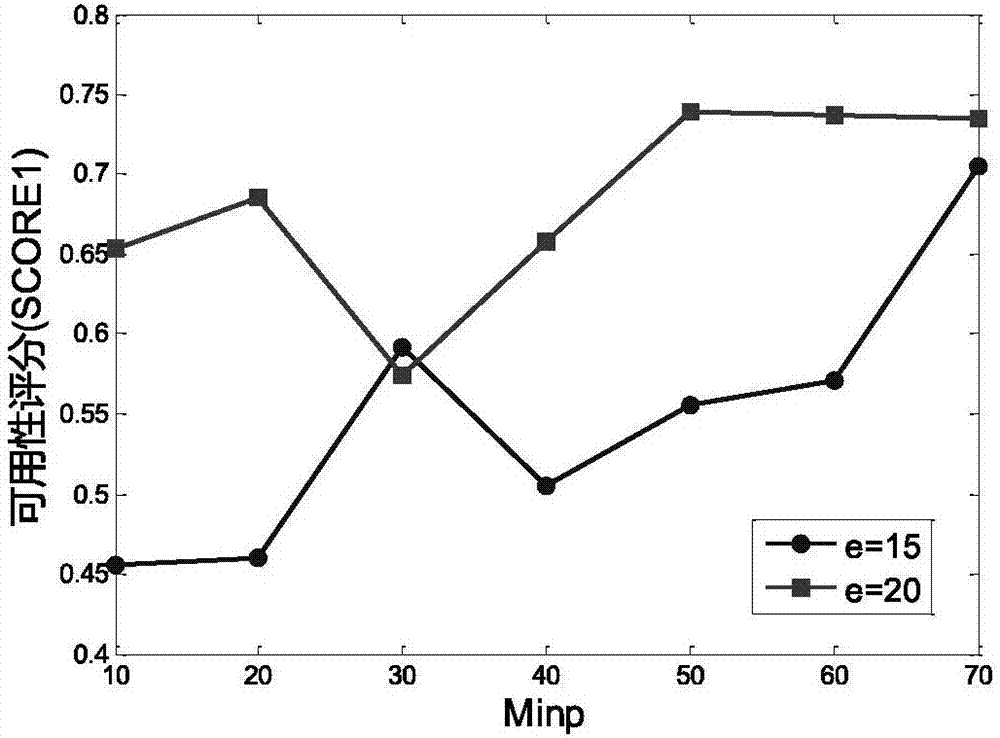
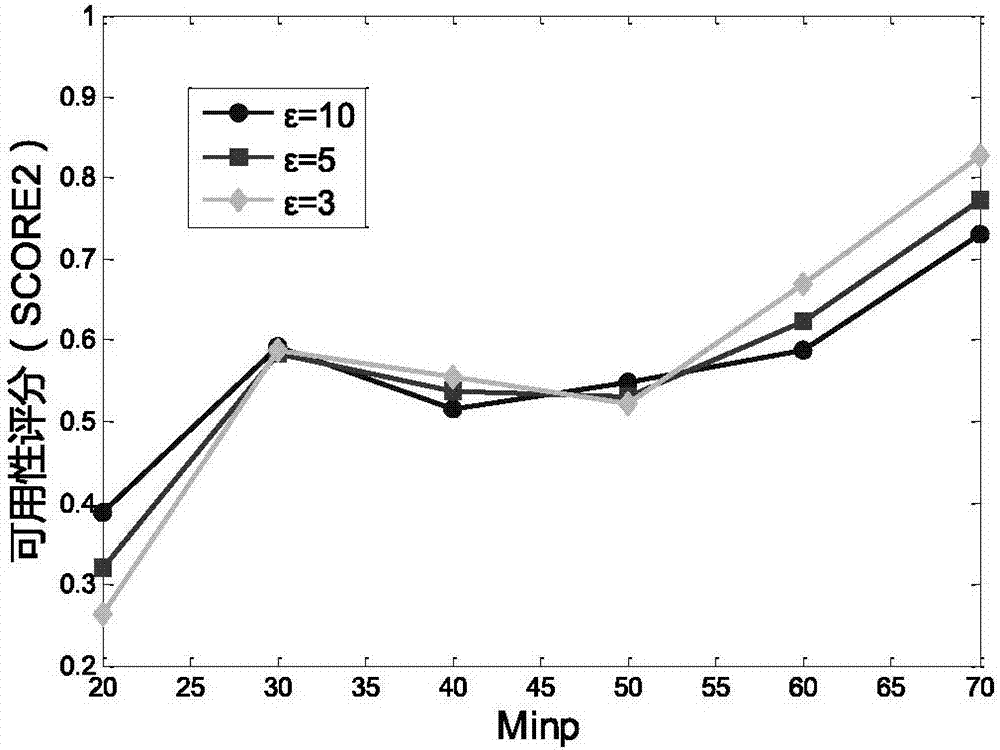
Differential privacy protection method based on microaggregation anonymity
The invention discloses a differential privacy protection method based on microaggregation anonymity and relates to the technical field of data anonymization and differential privacy protection. According to the invention, an original data set is classified according to density through a DBSCAN cluster function and abnormal points and noisy points are classified into closest classes; the cluster is classified for a second time by means of the MDAV function and anonymization is performed the equivalent class record number is controlled between k and 2k-1; finally, by means of the differential privacy protection technology, adding Laplace noise to each data record. Experiments show that, compared with existing methods, the DCMVDP method has less information loss and higher data availability under the premise of ensuring privacy data.
Owner:XUZHOU MEDICAL UNIV
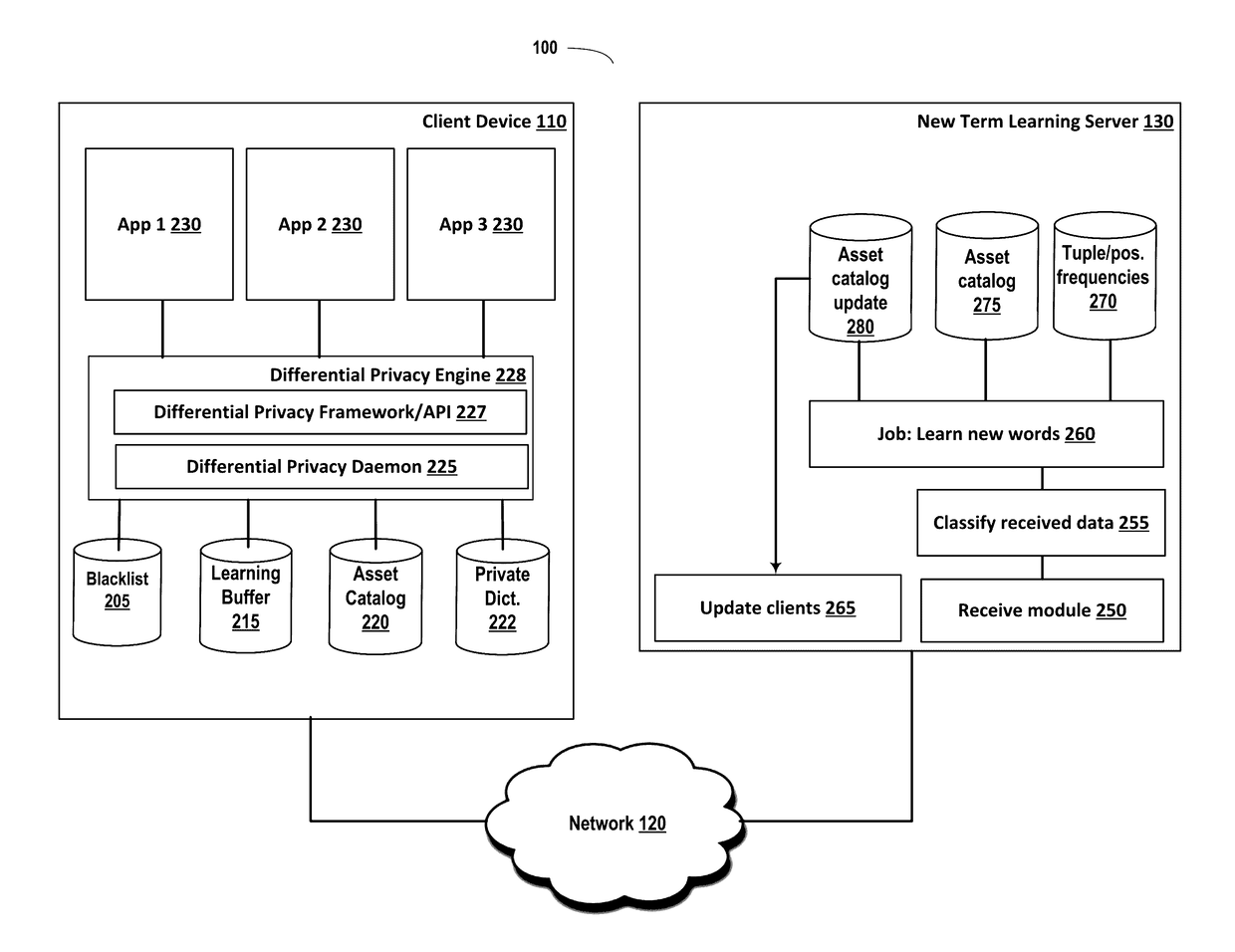
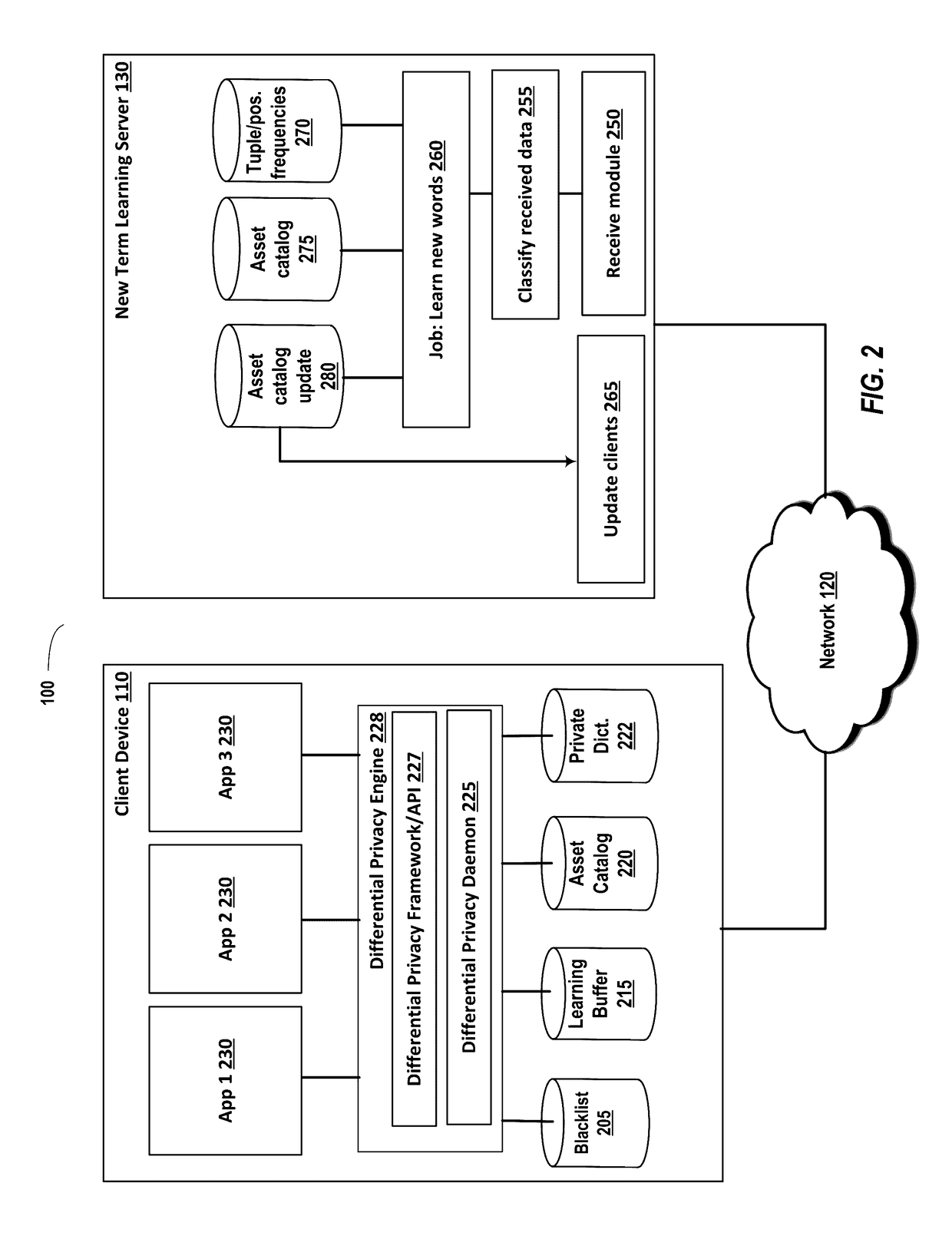
Learning new words
ActiveUS9594741B1Preserve the privacy budgetSufficient budgetDigital data processing detailsNatural language data processingInternet privacyDifferential privacy
Systems and methods are disclosed for a server learning new words generated by user client devices in a crowdsourced manner while maintaining local differential privacy of client devices. A client device can determine that a word typed on the client device is a new word that is not contained in a dictionary or asset catalog on the client device. New words can be grouped in classifications such as entertainment, health, finance, etc. A differential privacy system on the client device can comprise a privacy budget for each classification of new words. If there is privacy budget available for the classification, then one or more new terms in a classification can be sent to new term learning server, and the privacy budget for the classification reduced. The privacy budget can be periodically replenished.
Owner:APPLE INC
Smart power grid aggregation method and system for differential privacy security and fault tolerance
ActiveCN104579781AEfficient and flexible fault toleranceResistance to Differential Privacy AttacksPower network operation systems integrationCircuit arrangementsFault toleranceTelecommunications link
The invention discloses a smart power grid aggregation method and system for differential privacy security and fault tolerance. The method comprises the steps that a smart electric meter records and reports the electricity consumption of users in real time; a control center is responsible for collecting, processing and analyzing real-time electricity consumption data; a gateway is responsible for instruction delivery, data aggregation and security transmission between the control center and the users; a credible center is responsible for managing the whole system, and main function modules include a system initialization function module, a data aggregation request function module, a data aggregation request relay function module, a user data report function module, a security data aggregation function module and an aggregated data recovery module. According to the smart power grid aggregation method and system, the common fault tolerant function is supported, a difference privacy attack can be resisted, and the phenomenon that a hostile attacker exposes and obtains privacy information of the users by eavesdropping user communication links can be resisted; when some user data are not reported successfully, the electricity consumption of all the users with normal data reporting can still be aggregated; the smart power grid aggregation method and system have the high elastic expandability and can support efficient million-scale smart power grid electricity consumption data aggregation.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
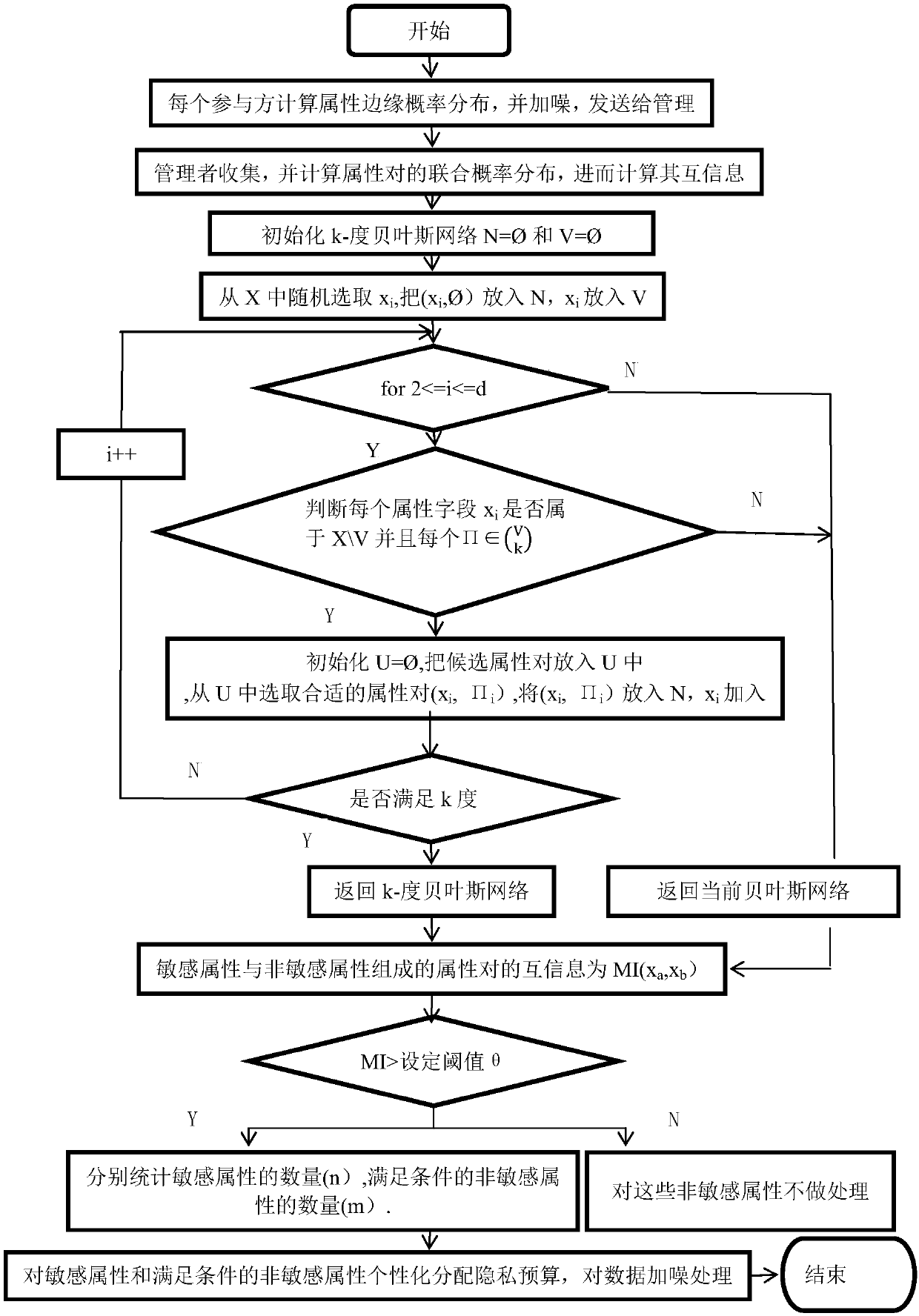
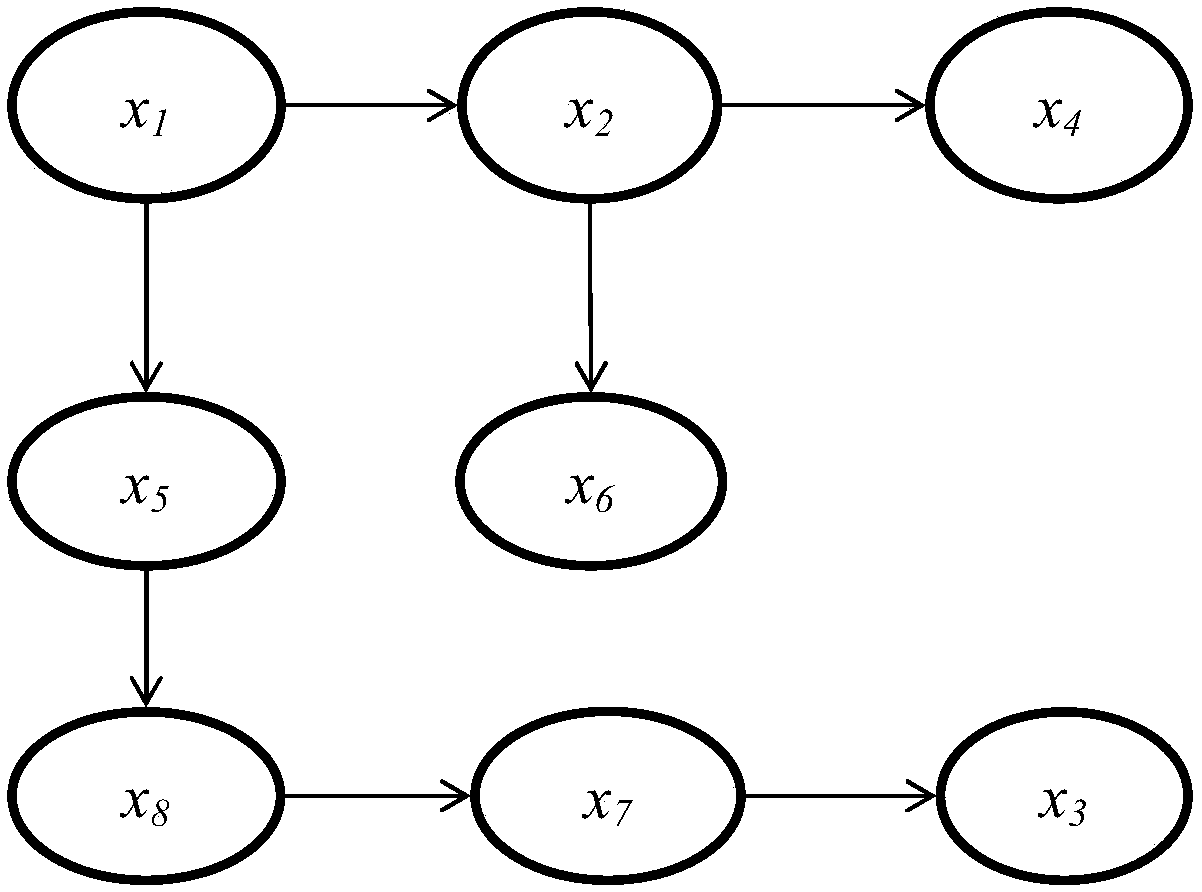
Individual differential privacy protection method for high-dimensional data publishing in distributed environment
ActiveCN107871087AMinor changesImprove utilizationDigital data protectionSpecial data processing applicationsPersonalizationPrivacy protection
The invention discloses an individual differential privacy protection method for high-dimensional data publishing in a distributed environment. According to the method, the correlation among properties is quantified through mutual information, and the mutual information of corresponding property pairs is calculated by use of a mutual information formula; an approximate k-degree Bayesian network isconstructed according to the mutual information, and the Bayesian network can well reflect dependency among the properties; privacy budgets are allocated individually according to the quantity of sensitive properties and the quantity of non-sensitive properties meeting conditions; all participants perform noise addition processing on data according to the allocated privacy budgets, and a random response mechanism is adopted to perform noise addition; and the data obtained after noise addition is sent to a manager, the manager gathers the data and synthesizes the data into an integrated dataset, and then the dataset is published to the outside. Through the method, when the data is published, a privacy requirement is guaranteed, a large amount of processing data is reduced, therefore, change of the data is lowered, the utility of the data is improved, and the method is beneficial for a data analyzer to perform relevant analysis.
Owner:GUANGXI NORMAL UNIV
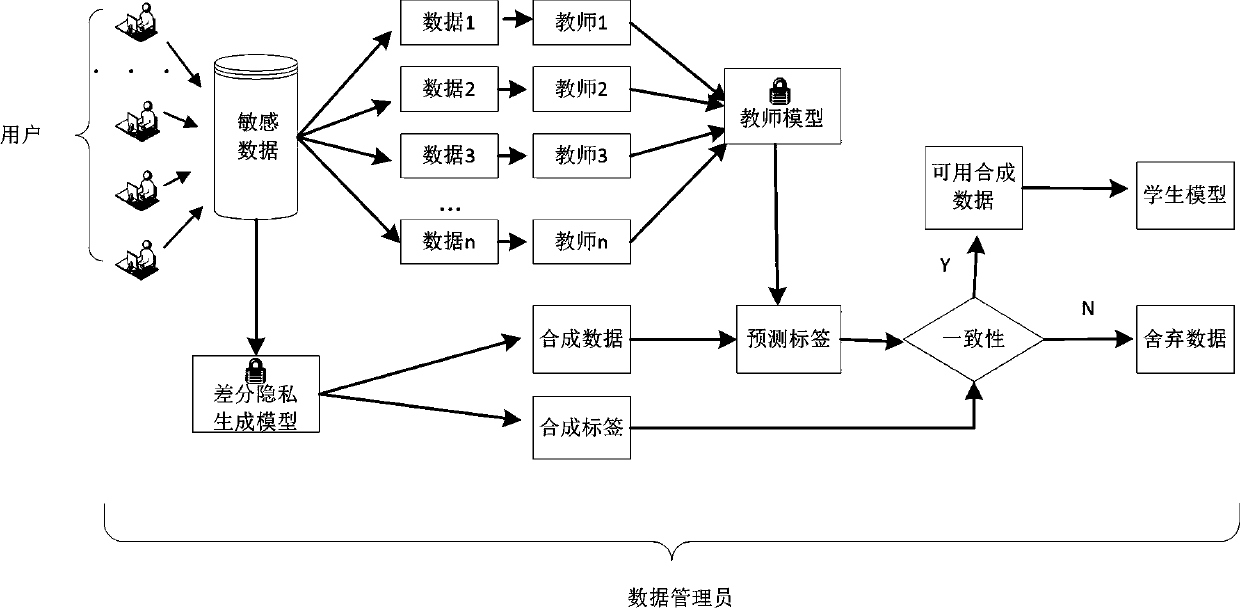
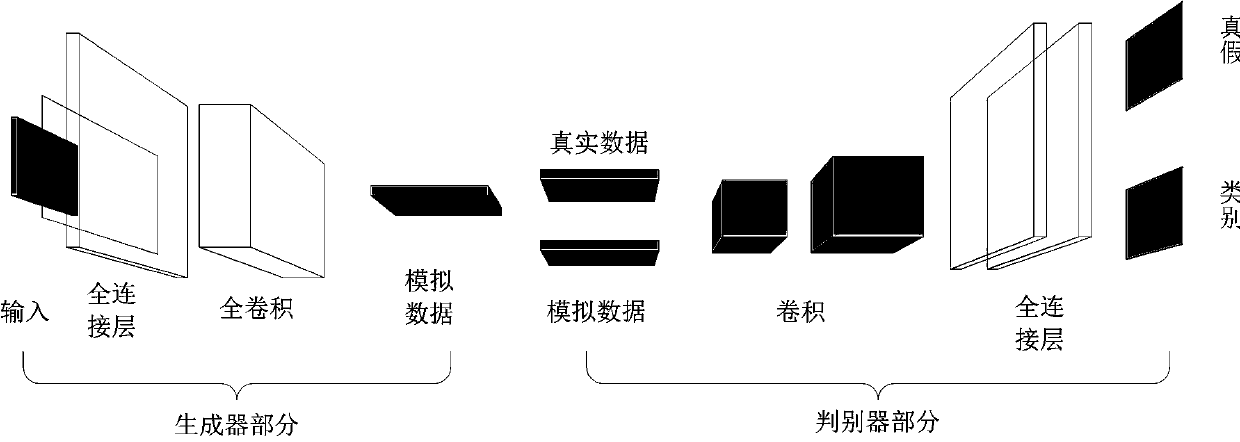
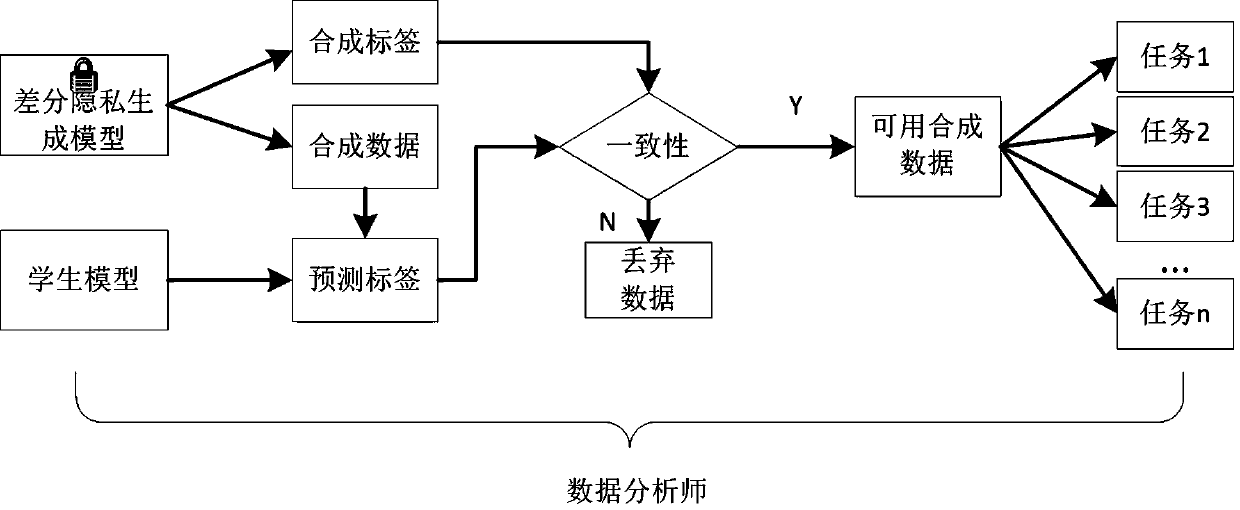
Form data privacy protection method fusing differential privacy GAN model and PATE model
ActiveCN109784091ARealize privacy protectionCharacter and pattern recognitionDigital data protectionData privacy protectionData set
The invention relates to a form data privacy protection method fusing a differential privacy GAN model and a PATE model. The method comprises the steps of 1, training a differential privacy generationmodel by using original table data; 2, training a teacher classifier under the differential privacy budget by using the original table data; Step 3, generating 'false' table data by using the generation model, predicting labels of the 'false' table data by using a teacher classifier, selecting data with consistent prediction labels and generated labels, defining an 'available' data set, and training a student classifier by using the 'available' data set; and step 4, releasing the generation model and the student classifier, synthesizing data by using the generation model, selecting the data by using the student model, and finishing a data analysis task. According to the method, privacy protection is carried out on the table data in the data release stage, a data analyst cannot restore original training data through a generation model and cannot speculate the original training data through a student model, protection on the original table data is achieved, and the requirement of the data analyst for the data is met.
Owner:FUZHOU UNIV
Federation prediction method based on federation learning
ActiveCN112364943AImprove performanceIncrease aggregation weightForecastingCharacter and pattern recognitionDifferential privacyNetwork model
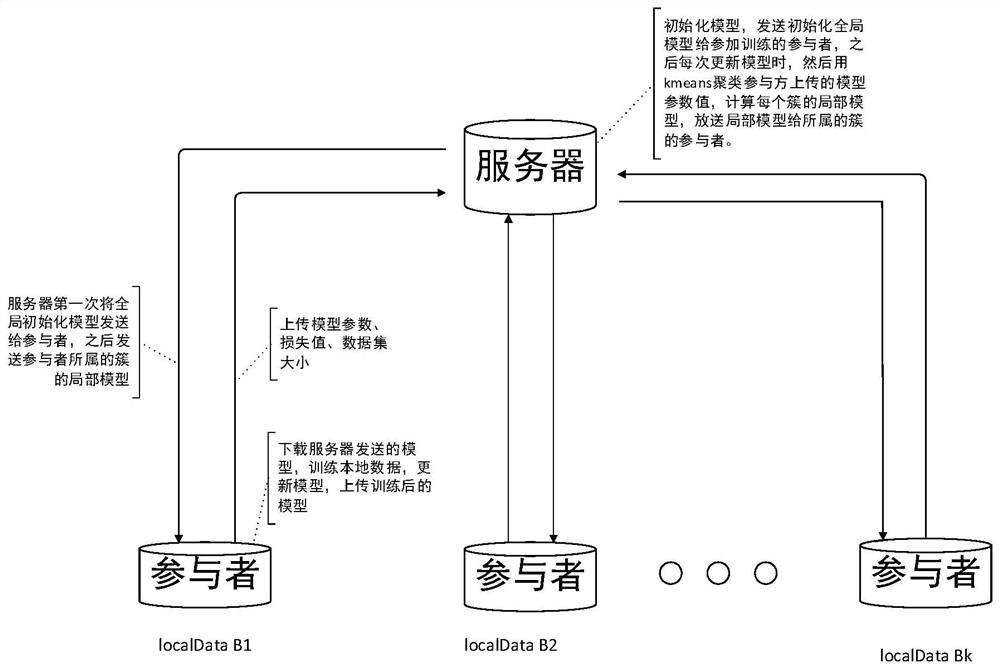
The invention discloses a federation prediction method based on federation learning, and the method enables the parameter change of a neural network model updated by a single participant to have onlydirection difference and no size difference through the unitization of a locally updated gradient vector, thereby protecting the data privacy, and avoiding the use of homomorphic and differential privacy or other encryption technologies. Under the condition of not losing data precision, the communication cost between the equipment and the server is greatly reduced. Besides, considering that the difference of data in a federated learning scene is large, the performance of a local participant can be improved by increasing the local information of the data, the uploaded neural network model parameters are clustered by utilizing a k-means algorithm to obtain similar neural network model parameters, the neural network model parameter aggregation weight is improved. The method is more suitable for the data scene of the participant.
Owner:GUANGXI NORMAL UNIV
Differential privacy data publishing method and system based on dependency removal
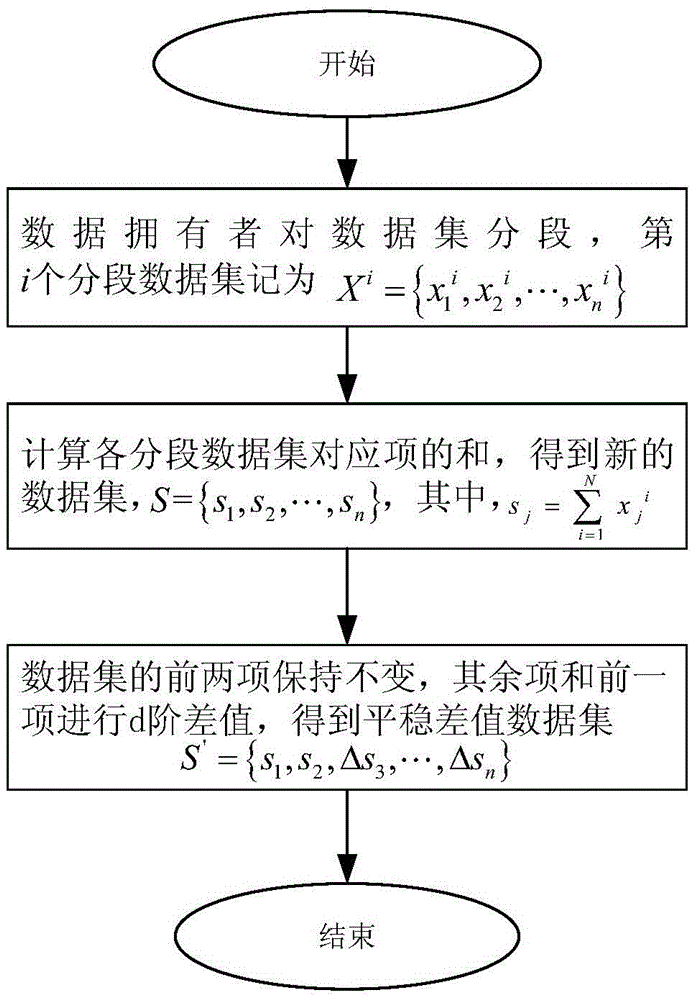
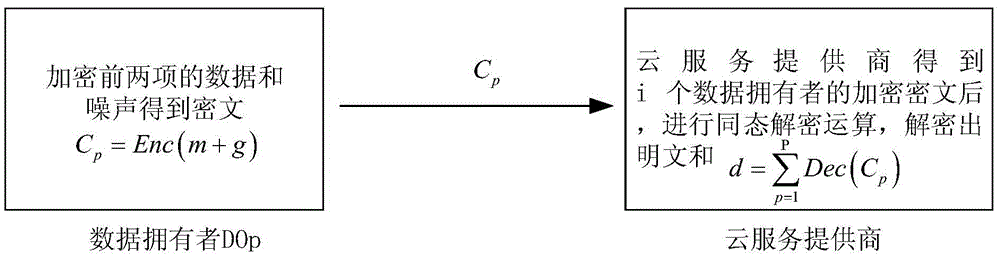
ActiveCN105608388AGuaranteed privacy and securityReduce computational complexityDigital data protectionTransmissionData setOriginal data
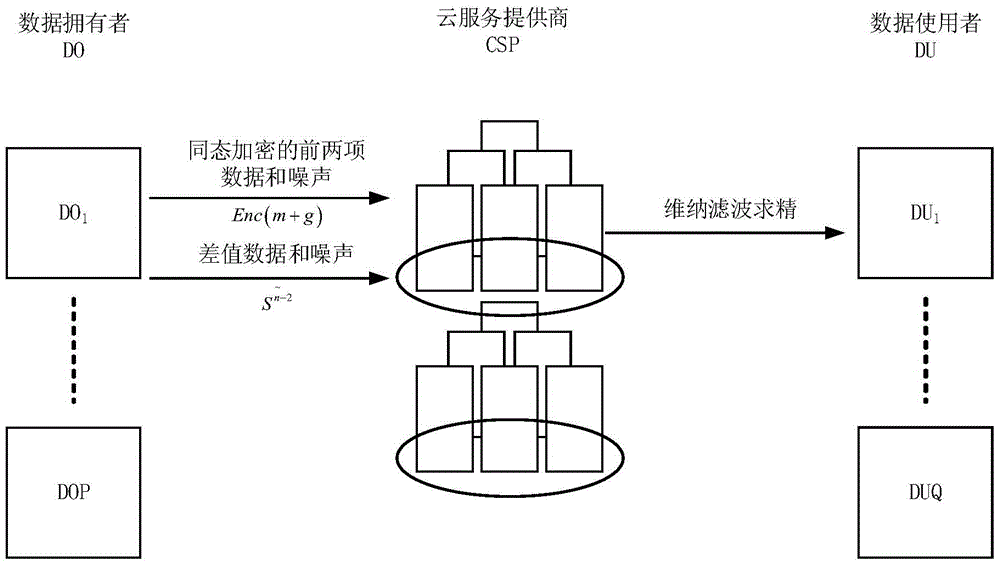
The invention discloses a differential privacy data publishing method and system based on dependency removal. Each data owner independently sections an own original data set and obtains a differential value data set, the first two items of the differential value data set are subjected to summation and noise adding, then, the obtained value is uploaded to a cloud service provider after the obtained value is subjected to homomorphic encryption, and the cloud service provider carries out homomorphic decryption operation; each data owner transforms the differential value data set item to obtain a transformation coefficient, and stable noise consisting of white noise which is mutually independent and complies with Gaussian distribution is added; the data owner carries out inverse wavelet transform to obtain a scrambled data set, and the data set is uploaded to the cloud service provider; and the cloud service provider utilizes Wiener filtering to carry out filtering, and the cloud service provider carries out inverse transformation on a refined data set and publishes the refined data set to the data item of a third-party data user when the data user requests the data set. The differential privacy data publishing method and system effectively reduces the data calculation amount and interaction amount and improves a resource use ratio and data availability.
Owner:WUHAN UNIV
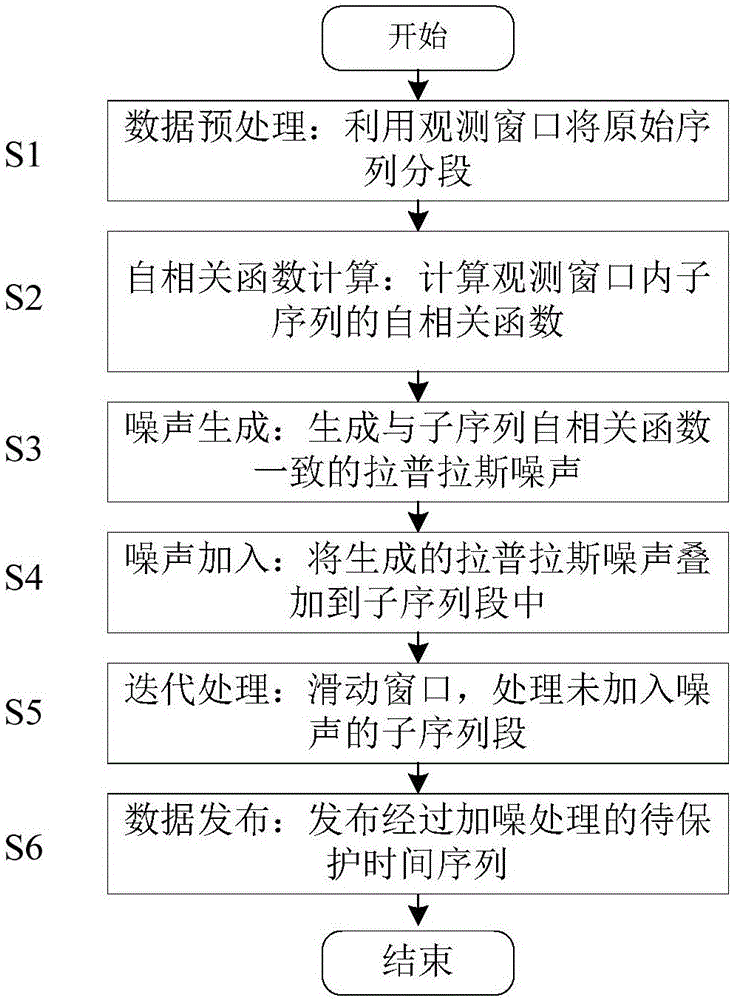
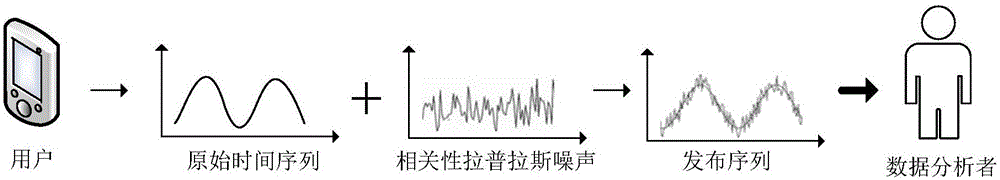
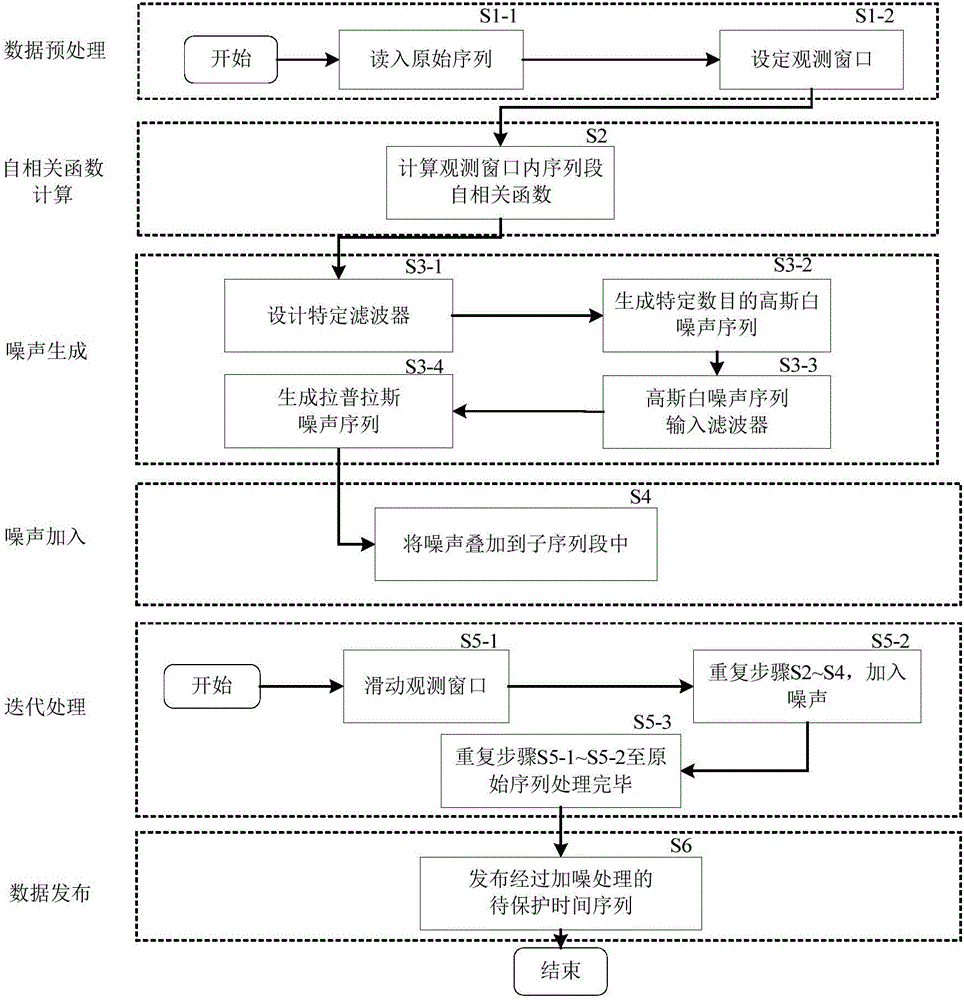
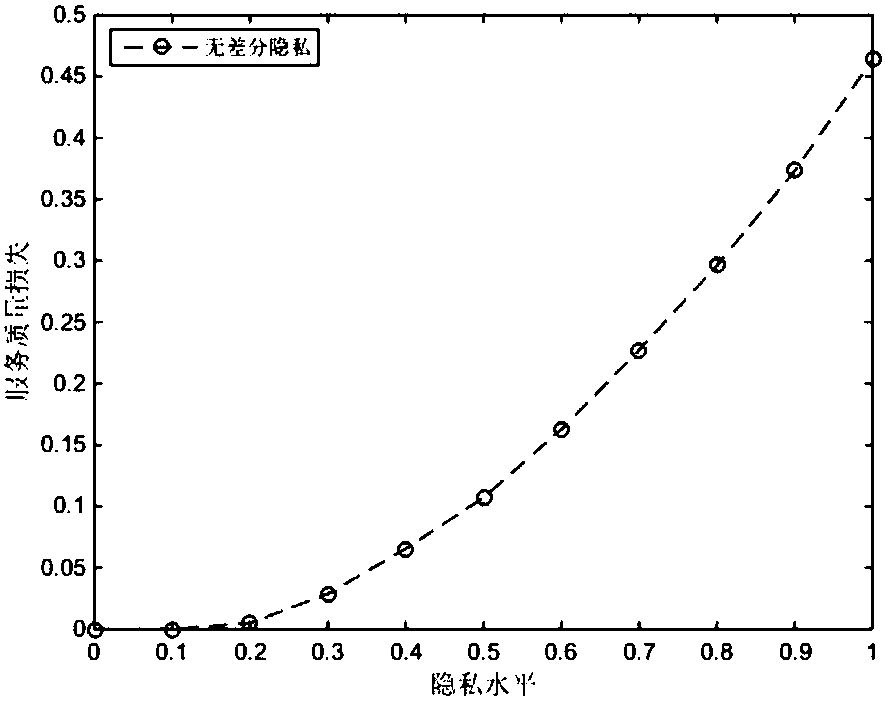
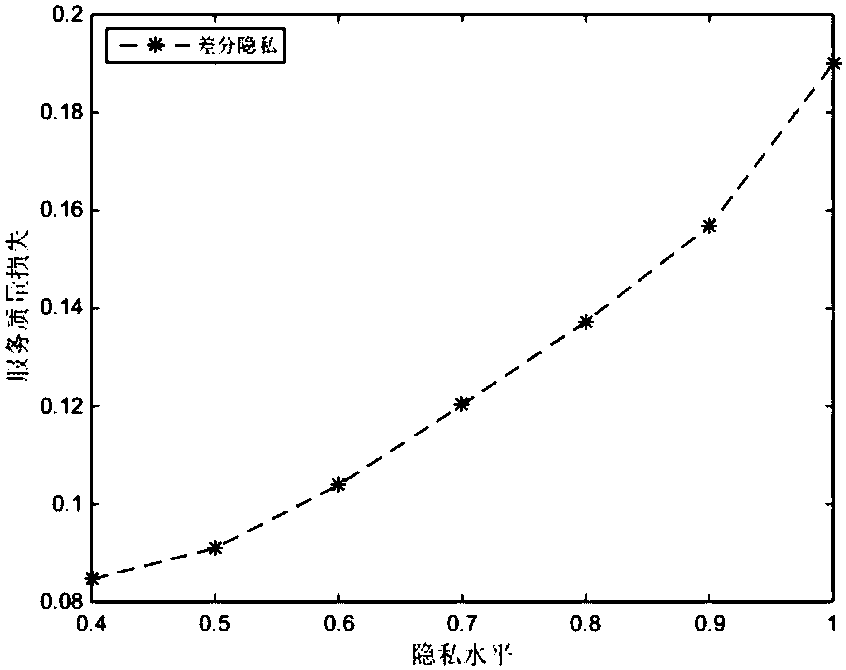
Correlation time series issuing method and system based on differential privacy
ActiveCN106407841APrevent Filtering AttacksEffective privacy protectionDigital data protectionSequence processingSlide window
Owner:WUHAN UNIV
Demand privacy protection method based on differential privacy and association rules
InactiveCN108520182APrivacy protectionProtect the privacy of your needsDigital data protectionDifferential privacyPrivacy protection
The invention provides a demand privacy protection method based on differential privacy and association rules. The method can effectively protect the privacy of the query content of a user in a socialnetwork, and Laplace noise (the differential privacy) is added to the confidence among required things, so that the privacy of the user is further protected. By adopting the privacy protection methodof the game, not only can the privacy required by the user be protected, but also the service quality of the user can be well guaranteed, and a privacy protection system can adaptively protect the privacy of the user. For the privacy preference of the user, the dynamic protection method is adopted to meet different privacy requirements of the user.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
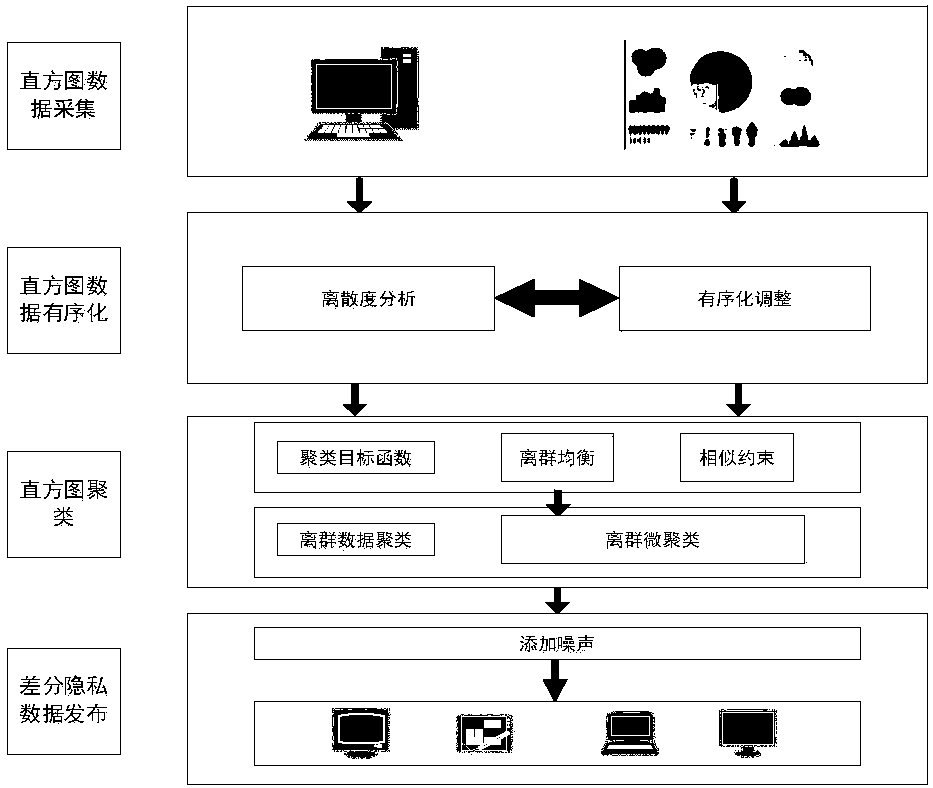
Detrended analysis differential privacy protection-based histogram data release method
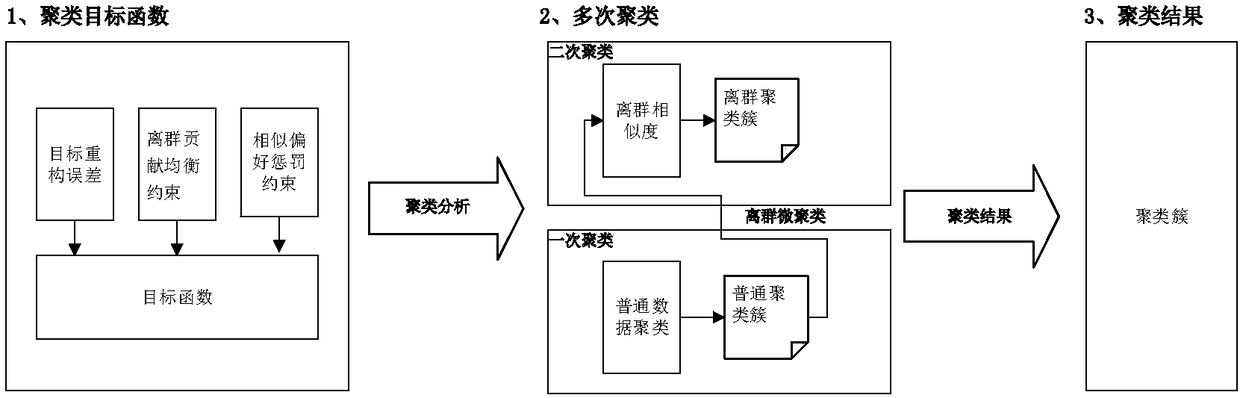
ActiveCN108446568ACutting stabilityOutlier reductionCharacter and pattern recognitionDigital data protectionPrivacy protectionDifferential privacy
The invention discloses a detrended analysis differential privacy protection-based histogram data release method. A method for judging a signal sequence trend is introduced in judgment of histogram anomaly distribution; a large amount of outliers cause relatively great fluctuation of data distribution, so that the stability is reduced; and from the perspective, a histogram bucket count distribution condition is regarded as continuous digital signals to perform data outlier processing. Meanwhile, for a clustering objective function causing the large amount of the outliers in a conventional method, outlier balance constraints and similar penalty constraints are added for balancing the influence of similar bucket and outlier bucket data on clustering, so that the occurrence of the outliers isreduced; and outlier data micro-clustering is performed based on outlier similarity for outlier data.
Owner:NORTHWEST UNIV
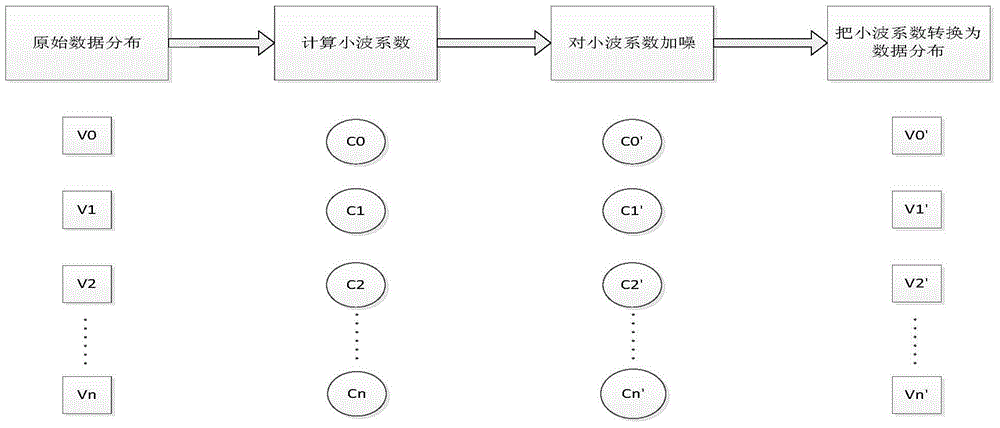
Differential private data publishing method based on wavelet transformation
ActiveCN104573560AImproved Noise EffectImprove classification accuracyDigital data protectionNODALData set
The invention discloses a differential private data publishing method based on wavelet transformation. The method is characterized in that the attribute values of an original data set are generalized the values of the topmost layer in a predefined generalization tree structure, and the subdivided values of the generalization tree structure from top to bottom are used to convert the generalized attribute values into subdivided attribute values; a known index noise adding method is used on a selection algorithm for selecting attributes to perform subdivision; a wavelet transformation noise adding method is introduced into the noise adding of leaf nodes, so that the noises of the newly published data set relative to the original data set is reduced to the greatest extent under the premise that differential privacy protection is satisfied. The method has the advantages that the wavelet transformation and an index mechanism are combined to perform noise adding in a synergy manner, noise accumulation during the noise adding process of an original data set is reduced effectively, the method conforms to the definition of differential privacy protection, cost of privacy protection is reduced, and the utilization rate of the data set after differential privacy protection.
Owner:SHANGHAI JIAO TONG UNIV
Service providing system and method based on deep learning
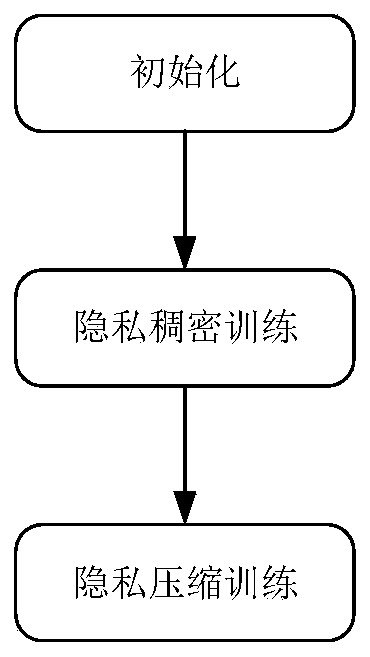
PendingCN110084365APrivacy protectionImprove service qualityNeural architecturesNeural learning methodsEdge serverData information
The invention belongs to the field of edge data information calculation, and discloses a service providing system and method based on deep learning, so as to protect privacy of training data and improve edge end service quality. In a cloud server side a compression deep learning model of privacy is generated by combining a differential privacy mechanism.A full-connection deep learning model with privacy protection is generated in privacy dense training to protect privacy of training data. In privacy compression training, a full-connection deep learning model with privacy protection is cut. A compression deep learning model with privacy protection is generated, and privacy of training data is protected. The size of the privacy compression model can be reduced to 1 / 9 of the size of the original model, so that the privacy compression model is very suitable for being embedded into an edge server, and edge service quality is improved by accessing the edge server by adjacent mobile equipment.
Owner:XIDIAN UNIV
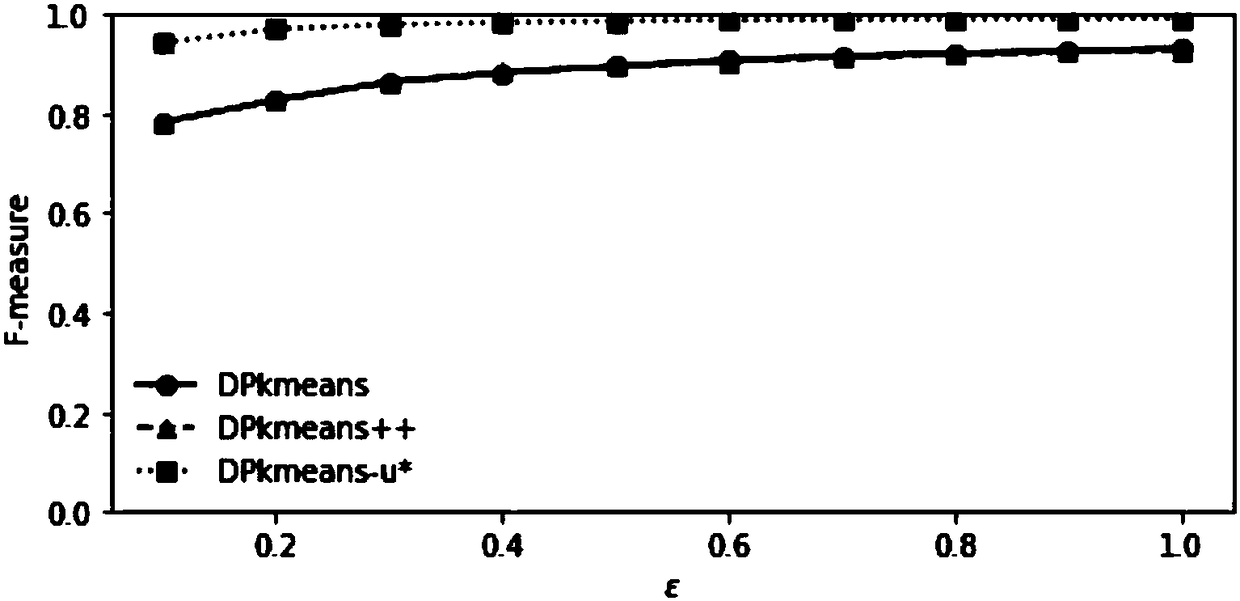
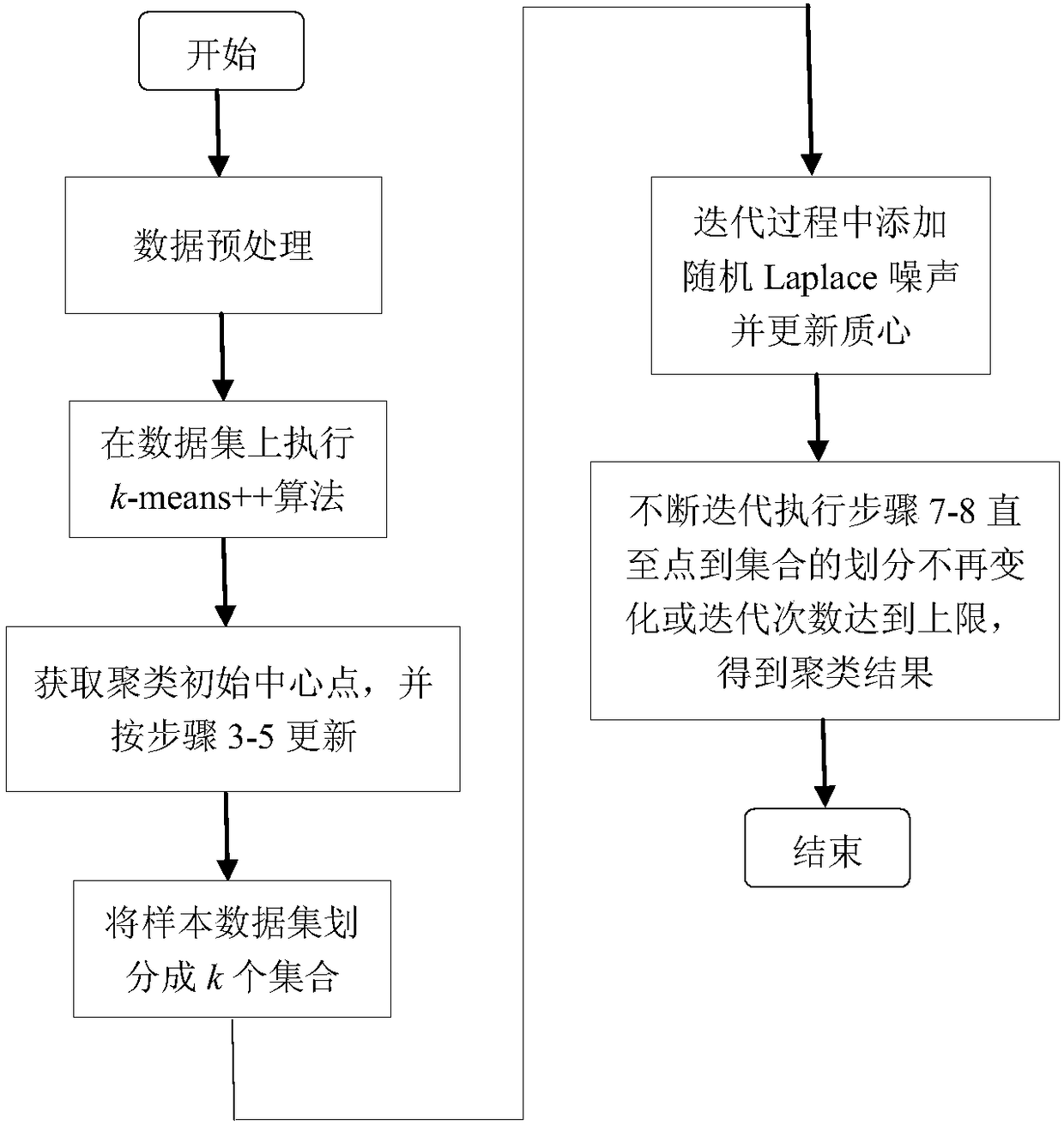
Differential privacy protection-oriented k-means clustering method adopting
ActiveCN108280491AImprove balanceImprove usabilityCharacter and pattern recognitionDigital data protectionData setPrivacy protection
The invention discloses a differential privacy protection-oriented k-means clustering method. The K-means clustering method comprises the following steps: performing data preprocessing; ensuring thatC indicates a clustered centered point set, and C indicates a sum of error square of a given data set and a cluster center C; judging the volume of C; performing cyclic execution until retry is greater than a maximum value retrymatx of given retry times, and then returning to the best central point Cbest; traversing each point of the data set X, classifying the points to the nearest central point;setting added random noises; renewedly calculating the sum of the data points of each cluster and the quantity of the points, and adding the noises and finally updating the quality center of the cluster; and repeatedly carrying out the steps until the sum of error square is converged or iteration times reach the upper limit. According to the differential privacy protection-oriented k-means clustering method disclosed by the invention, the appropriate random noises which are specially distributed are added in an iteration process of a k-means clustering algorithm, so that a clustering result is distorted to a certain extent, the aim of privacy protection is fulfilled, and meanwhile, the availability of data is ensured.
Owner:DONGGUAN MENGDA INDAL INVESTMENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com