Demand privacy protection method based on differential privacy and association rules
A privacy protection and differential privacy technology, applied in the field of computer information, can solve the problems of people's life impact, demand privacy leakage, and inability of attackers to distinguish target users, and achieve the effect of protecting the privacy of query content, protecting demand privacy, and ensuring service quality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
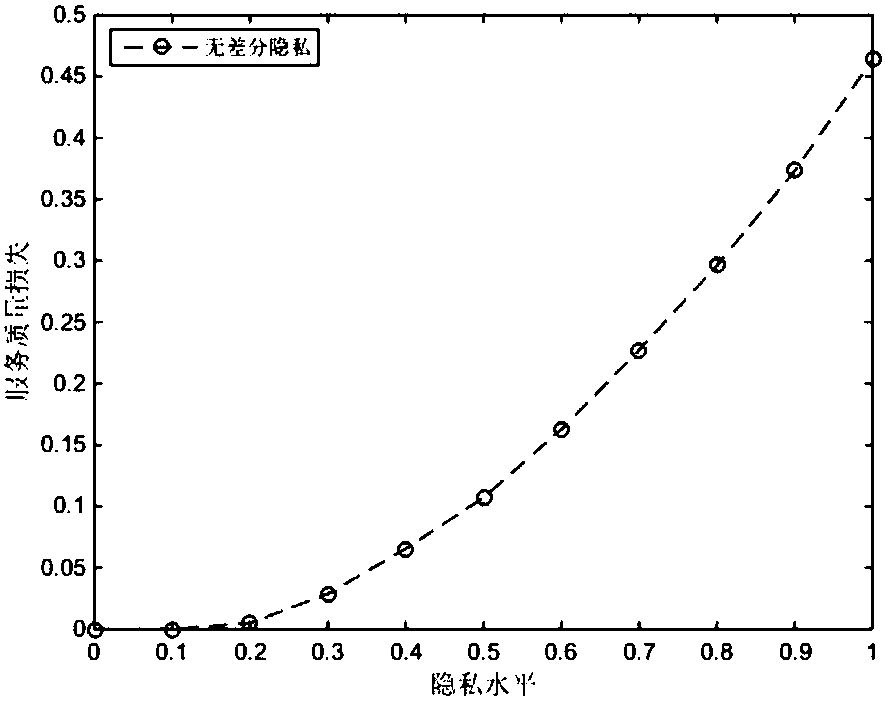
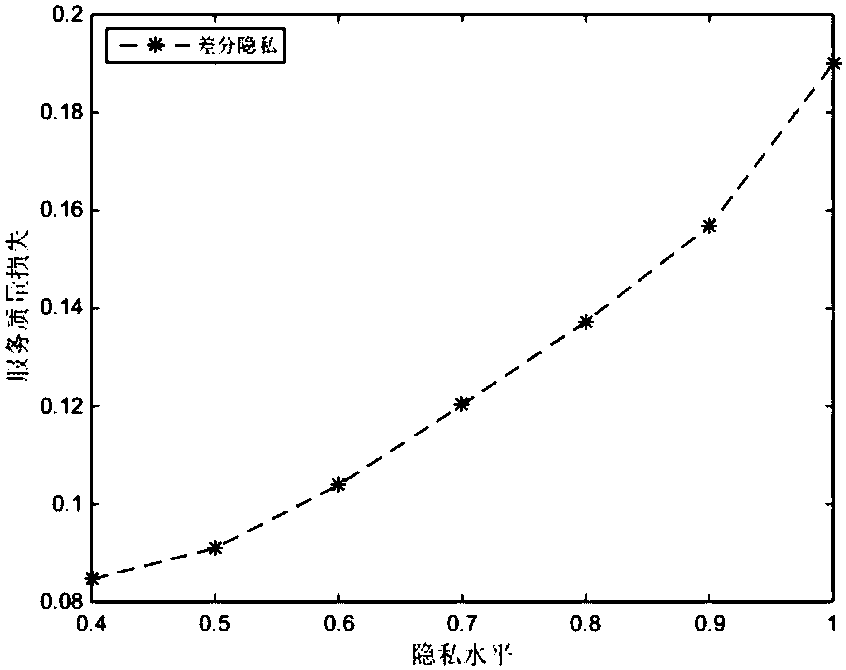
[0044] The system framework of the present invention is as figure 1 As shown, it is divided into three parts: users, protection systems and service providers. Among them, the user sends a request to the service provider for querying content. Protection system, the content sent by the user can be converted into other related things through the privacy protection system designed by the present invention. The service provider provides corresponding services for the content converted by the user, and returns to the privacy protection system. The privacy protection system screens out some reasonable services to the user, and completes the user's query content request. The main technologies adopted by the privacy protection system designed by the present invention are association rules and differential privacy.
[0045] Association rules reflect t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com