Edge computing-oriented federated learning indoor positioning privacy protection method
A privacy protection and indoor positioning technology, applied in security devices, network planning, electrical components, etc., can solve the problems of difficulty in adapting to the exponential growth of terminal equipment data volume, privacy, confusing contributions, inapplicability, etc., and achieve accurate indoor positioning services. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention and its effects will be further described below in conjunction with the accompanying drawings.
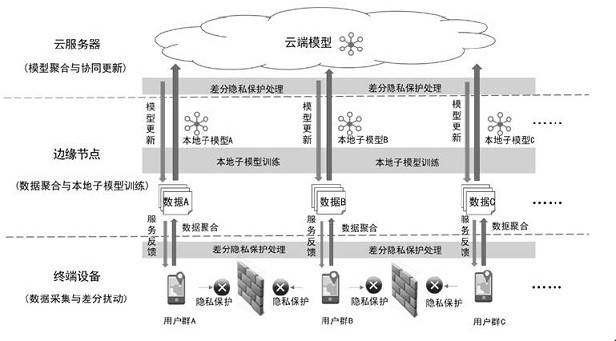
[0031] like figure 1 As shown, the system model of the present invention consists of three entities: terminal equipment, edge nodes and cloud servers. These systems are described as follows:
[0032] (1) Terminal device: The user's terminal device collects wireless signal strength RSSI data from multiple wireless sensor beacons in indoor areas (eg, shopping malls, underground parking lots, exhibition halls, etc.). In order to solve the problem of privacy leakage, the terminal device first independently performs privacy protection processing on the original RSSI data that satisfies differential privacy, and then sends the processed data to nearby edge nodes, where multi-user data aggregation is performed. End devices are considered trusted in this model.
[0033] (2) Edge nodes: Edge nodes are some intelligent gateways with data computing and storage ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com