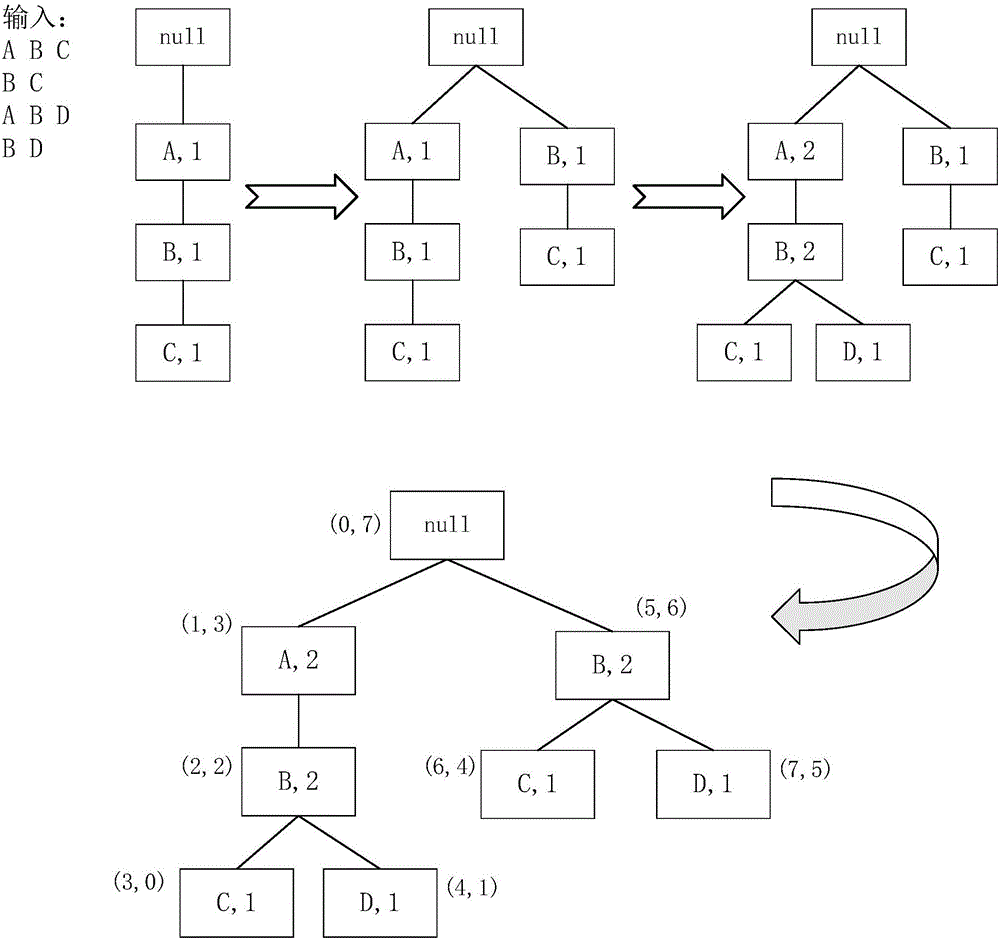
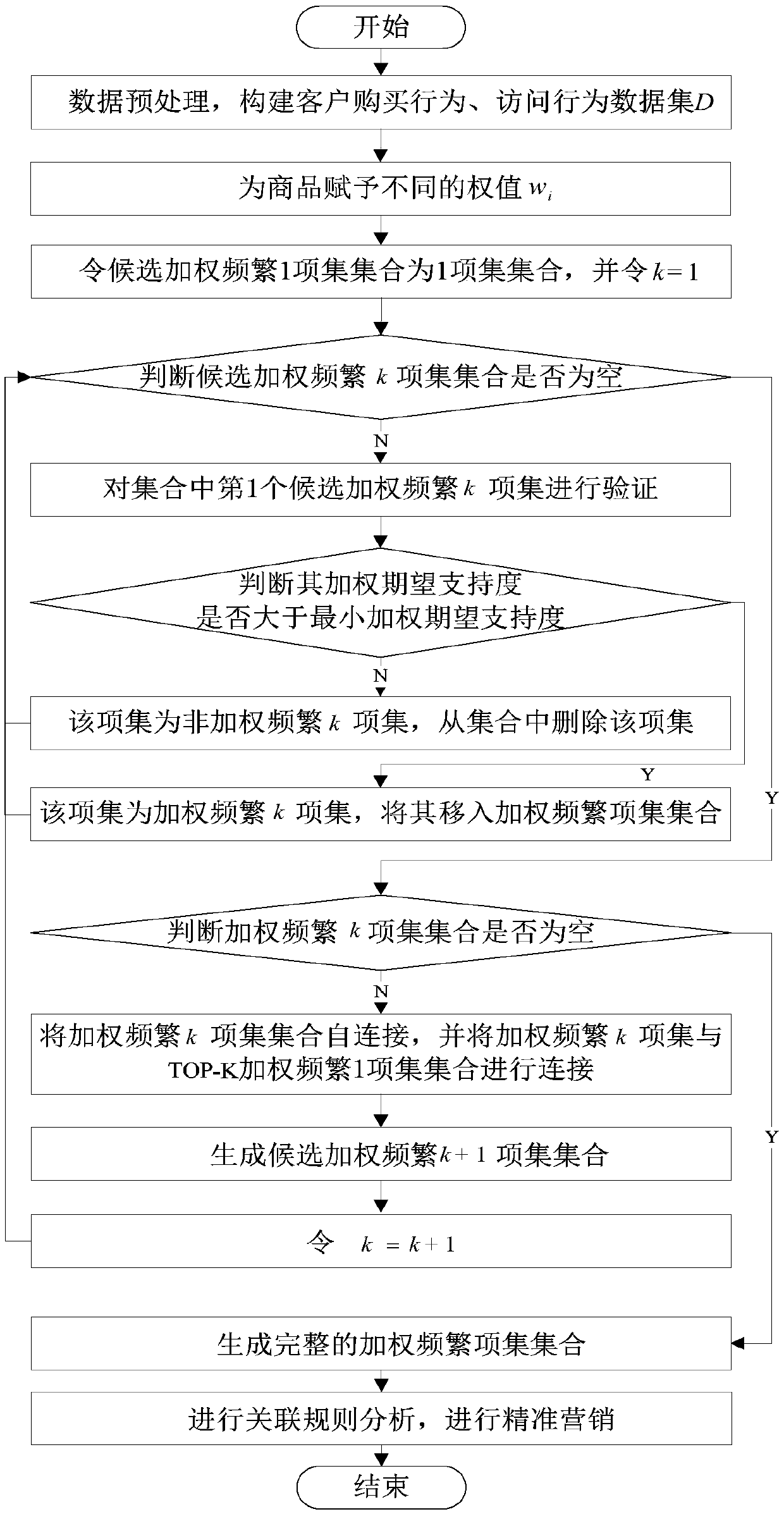
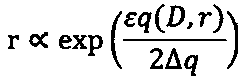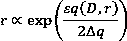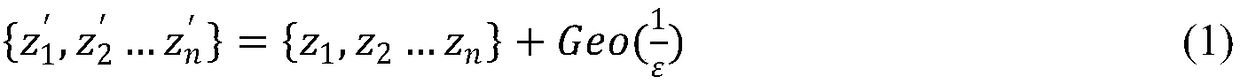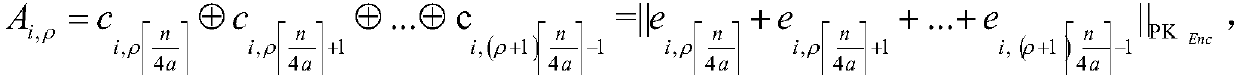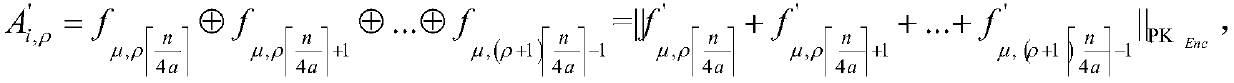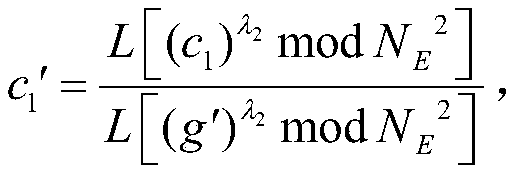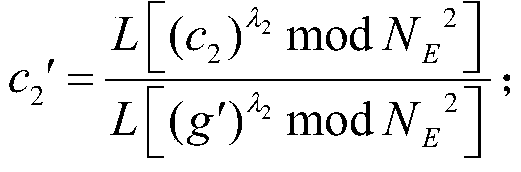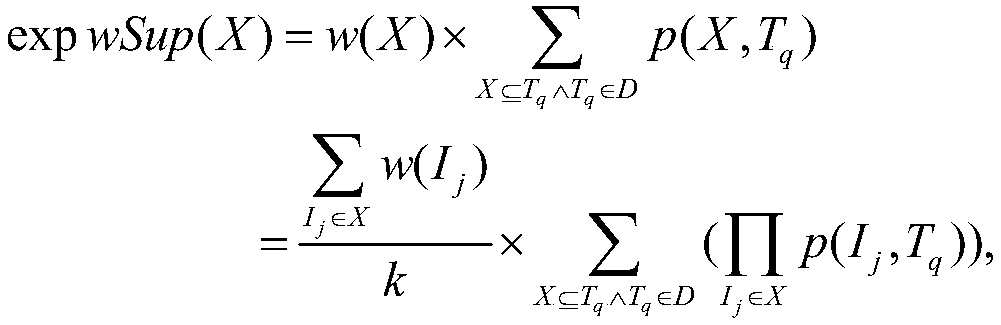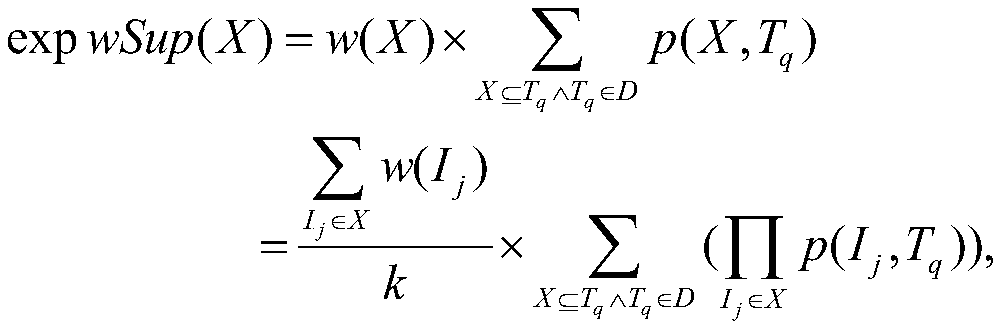Patents
Literature
81 results about "Item set mining" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
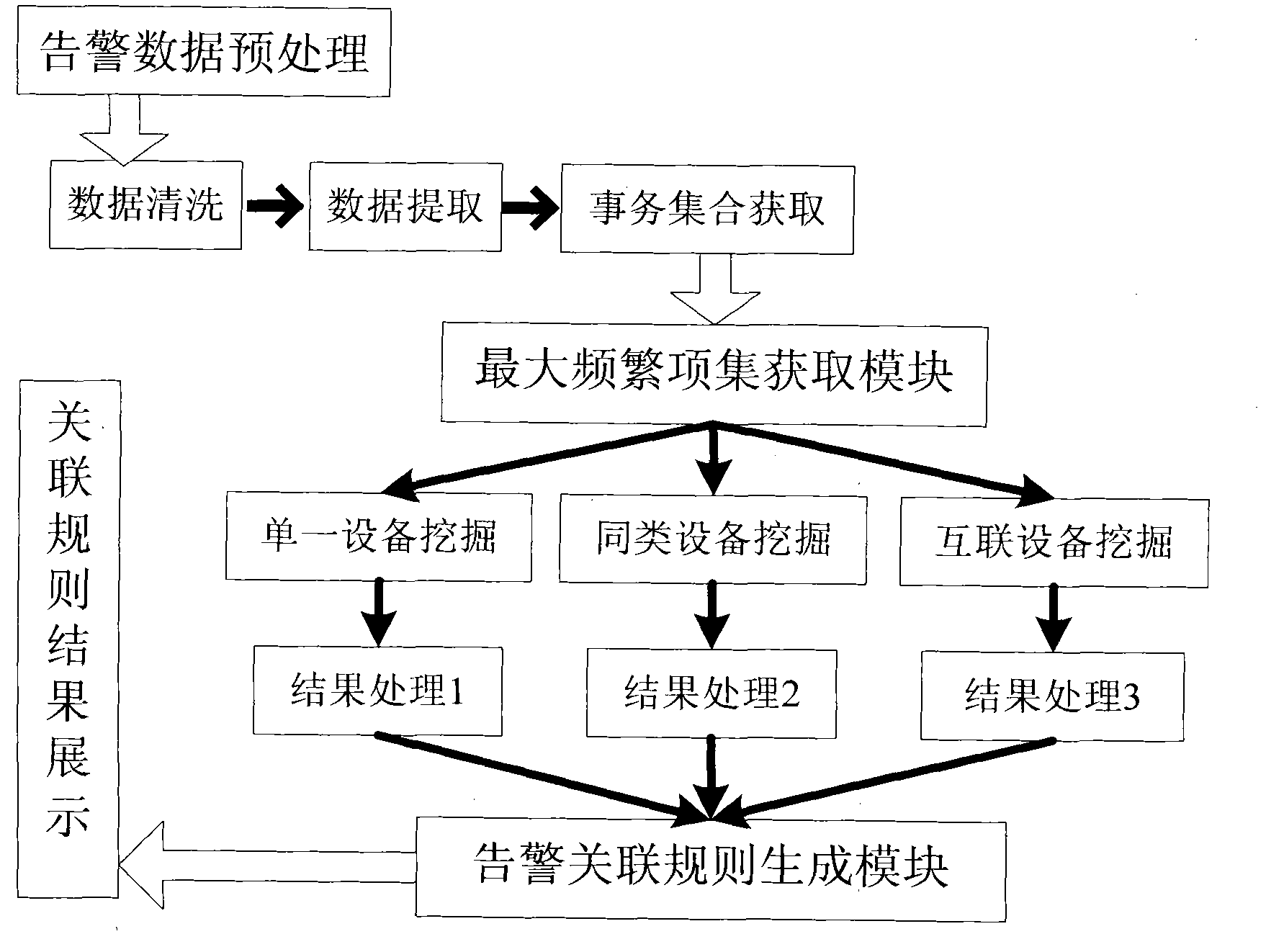
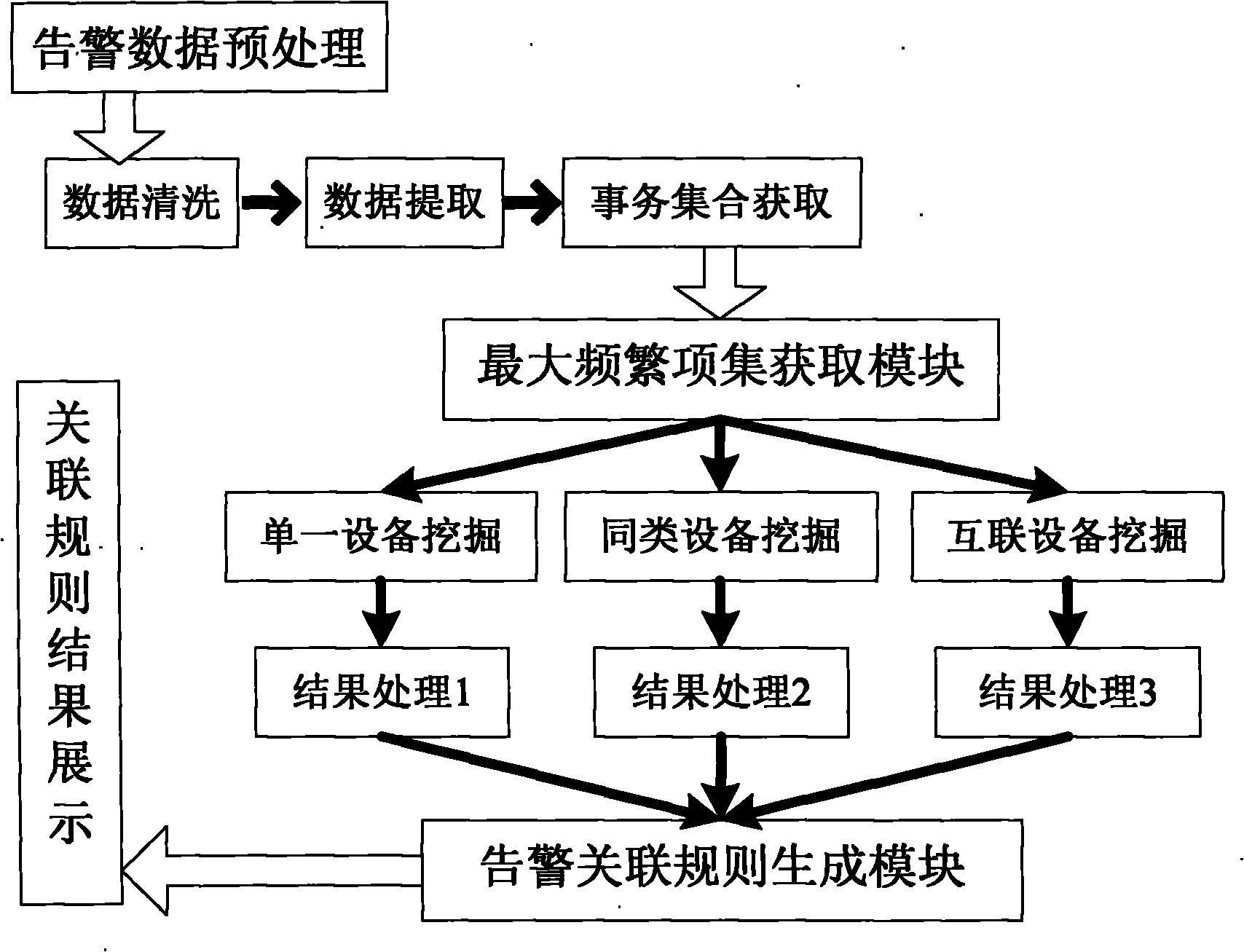
Mining method for communication alarm association rule based on maximal frequent item set
InactiveCN102111296AAccurate identificationImprove accuracyData switching networksSpecial data processing applicationsUser inputRule mining
The invention provides a method for building an alarm association rule mining system based on a maximal frequent item set DM (Data Mining) and the realization of that. Three different mining ways for single equipment, cognate equipment and linked equipment are designed aiming to different types of equipment in a communication network, and according to the mining range, the DM range can be positioned at specific city level or communication equipment manufacturer level; after the mining way is confirmed, the alarm association time window, the sliding step, etc are selected to acquire an alarm affair set assembly; and alarm association result mining is performed by utilizing the maximal frequent item set mining algorism after a user inputs the minimum support, and mining result treatment and display are performed according to different mining ways. Through the mentioned steps, the alarm association rule needed by the user can be found out from plenty of alarm data. The method has broad application prospect and favorable utility value.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
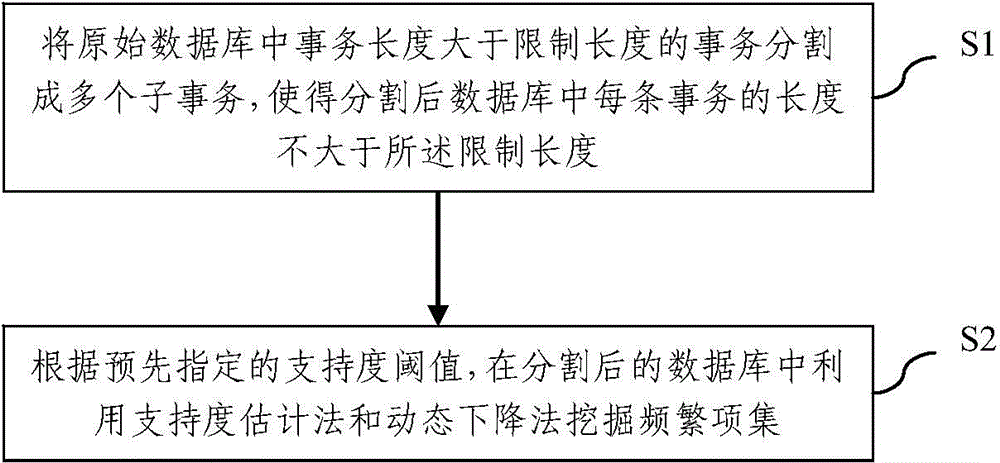
Frequent item set mining method
InactiveCN105740245AImprove digging efficiencyImprove resultsSpecial data processing applicationsEstimation methodsOriginal data
The invention relates to the technical field of data mining and data privacy, and discloses a frequent item set mining method. The frequent item set mining method comprises the following steps: S1: segmenting a transaction of which the transaction length is greater than a restriction length in an original database into a plurality of sub-transactions, and causing the length of each transaction in the segmented database to be smaller than or equal to the restriction length; and S2: according to a support degree threshold value which is appointed in advance, utilizing a support degree estimation method and a dynamic descent method to mine the frequent item set in the segmented database. The frequent item set mining method can provide higher mining efficiency and mining result availability while differential privacy protection is met.
Owner:BEIJING UNIV OF POSTS & TELECOMM
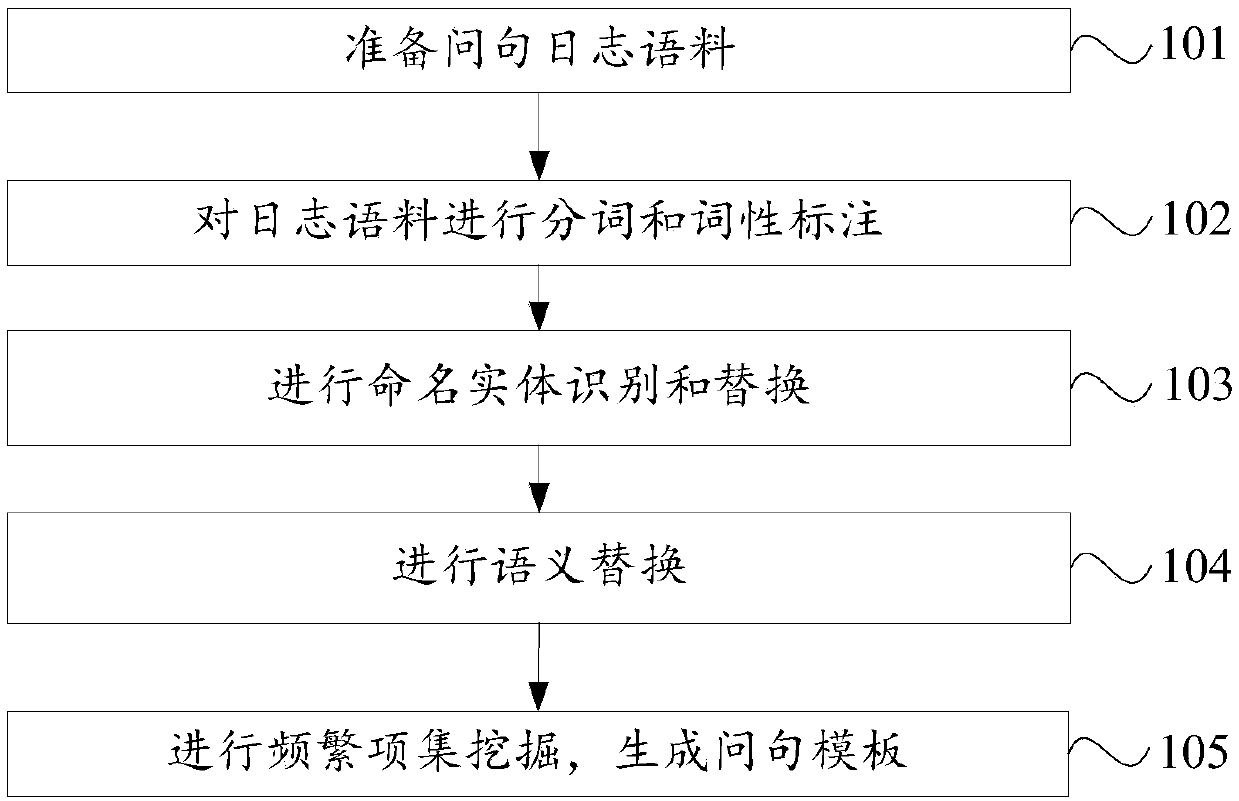
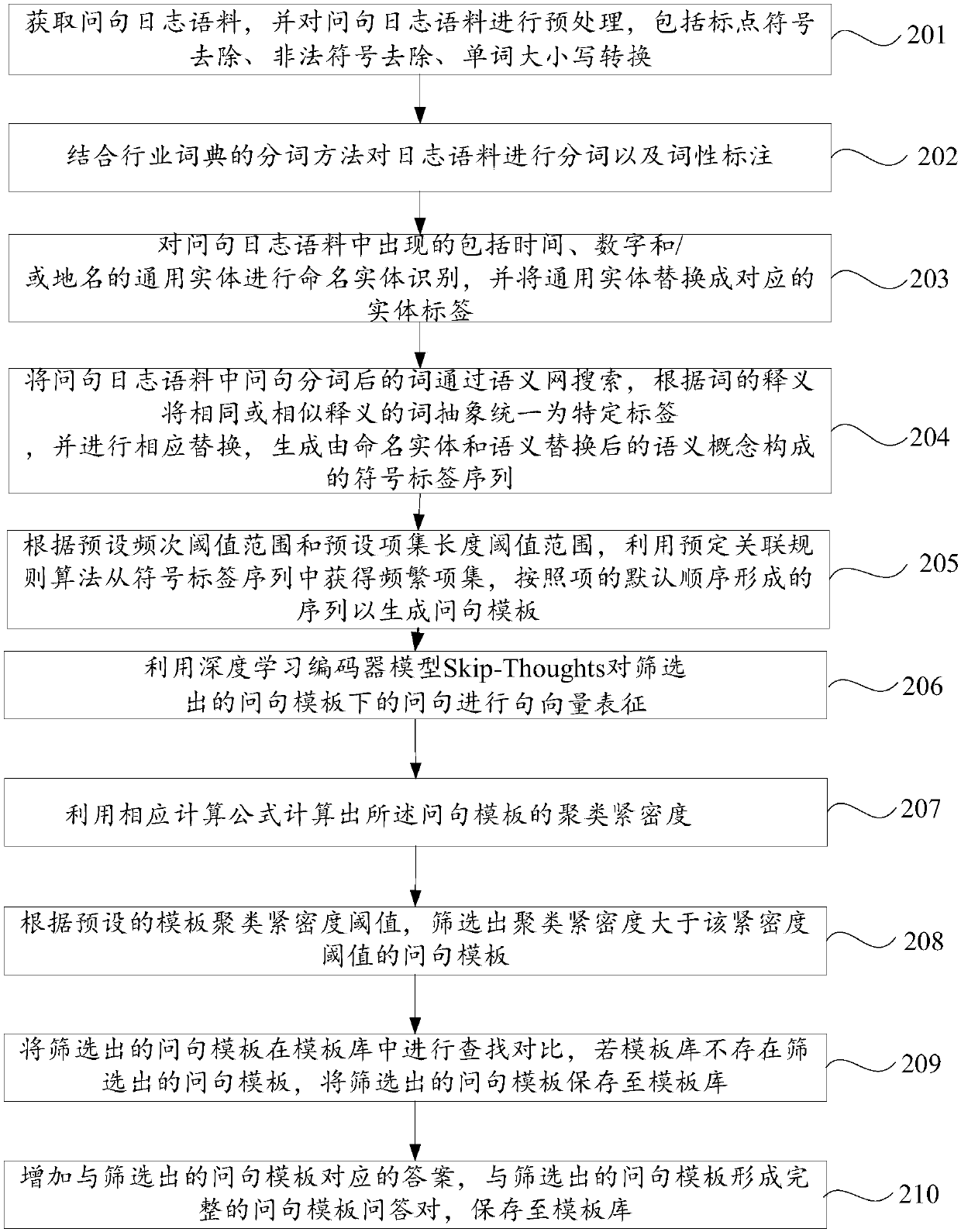
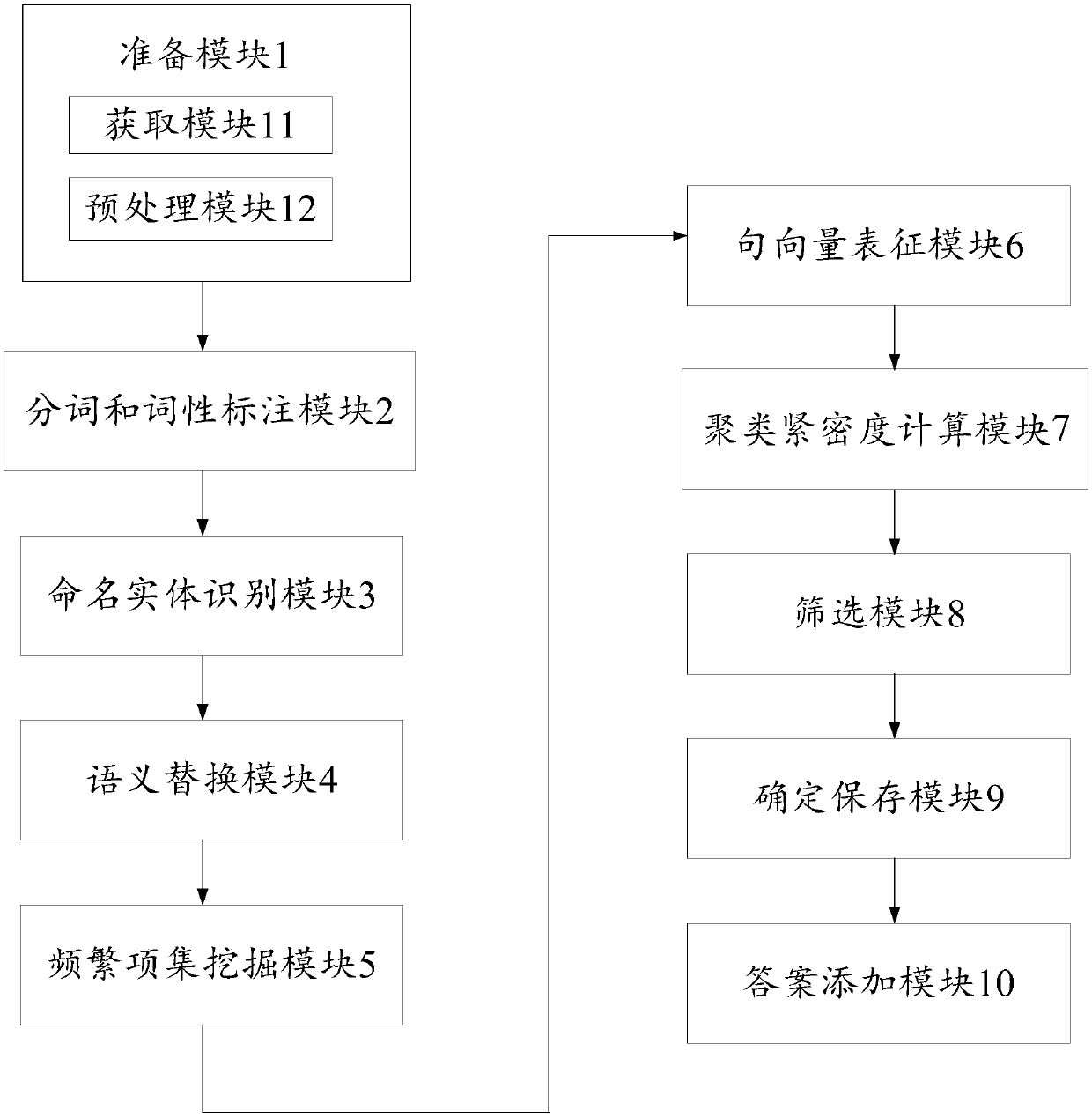
Question sentence template automatic generation method and apparatus
ActiveCN108038234AImprove generalization abilityImprove production efficiencySpecial data processing applicationsText database clustering/classificationNamed-entity recognitionQuestions and answers
The invention discloses a question sentence template automatic generation method and apparatus, and belongs to the technical field of intelligent question and answer. The method comprises the steps ofpreparing question sentence log corpora; performing word segmentation and part-of-speech tagging on the log corpora; performing named entity identification and replacement; performing semantic replacement; and performing frequent item set mining, and generating a question sentence template. According to the method and the apparatus, the question sentence template generation efficiency is improved; a large amount of labor resources are saved; the generated question sentence template can be assessed; a question sentence template library is autonomously and continuously expanded; and the qualityof a knowledge base of an intelligent question and answer system is improved.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
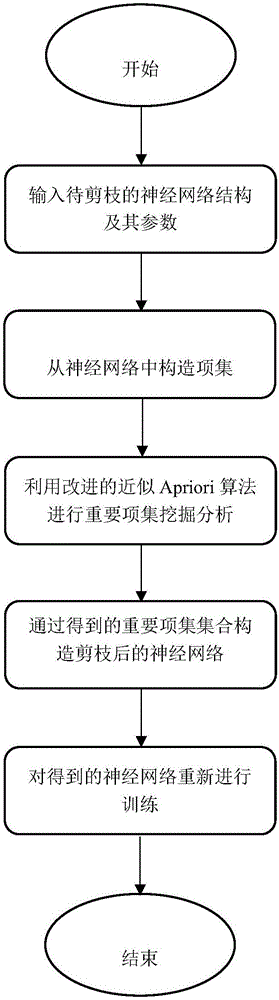
Computer neural network modified according to pruning method
InactiveCN106779075AAchieve the purpose of pruningStrong sparsityNeural learning methodsAlgorithmItem set mining
The invention discloses a computer neural network modified according to a pruning method. The method includes: as for a pre-trained neural network, constructing a plurality of item sets from network parameters, adopting an improved similar Apriori algorithm for frequency item set mining according to significances of the item sets to obtain a set of important item sets, and constructing a pruned neutral network according to the obtained item sets, and finally re-training the pruned neural network to obtain a final result.
Owner:NANJING UNIV
Denormalization strategy selection method based on frequent item set mining algorithm
ActiveCN103823823AAvoid performance bottlenecksLighten the build burdenRelational databasesSpecial data processing applicationsData setItem set mining
The invention discloses a denormalization strategy selection method based on the frequent item set mining algorithm and particularly relates to a denormalization strategy selection method for mass data sets based on the frequent item set mining algorithm. The frequent pattern mining method is applied to guiding database denormalization for the first time; based on the frequent pattern mining algorithm of a concise tree, a brand-new process of establishing the concise tree and a correct counting method, serving for database denormalization selection, are provided. The denormalization strategy selection method based on the frequent item set mining algorithm has the advantages that through the frequent item set mining algorithm of association rules, important association or relation of item sets in mass data is discovered to guide DBA and the like to select and build denormalization strategies of databases, and the problem of performance bottleneck caused by mass table joins in the mass data is solved.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
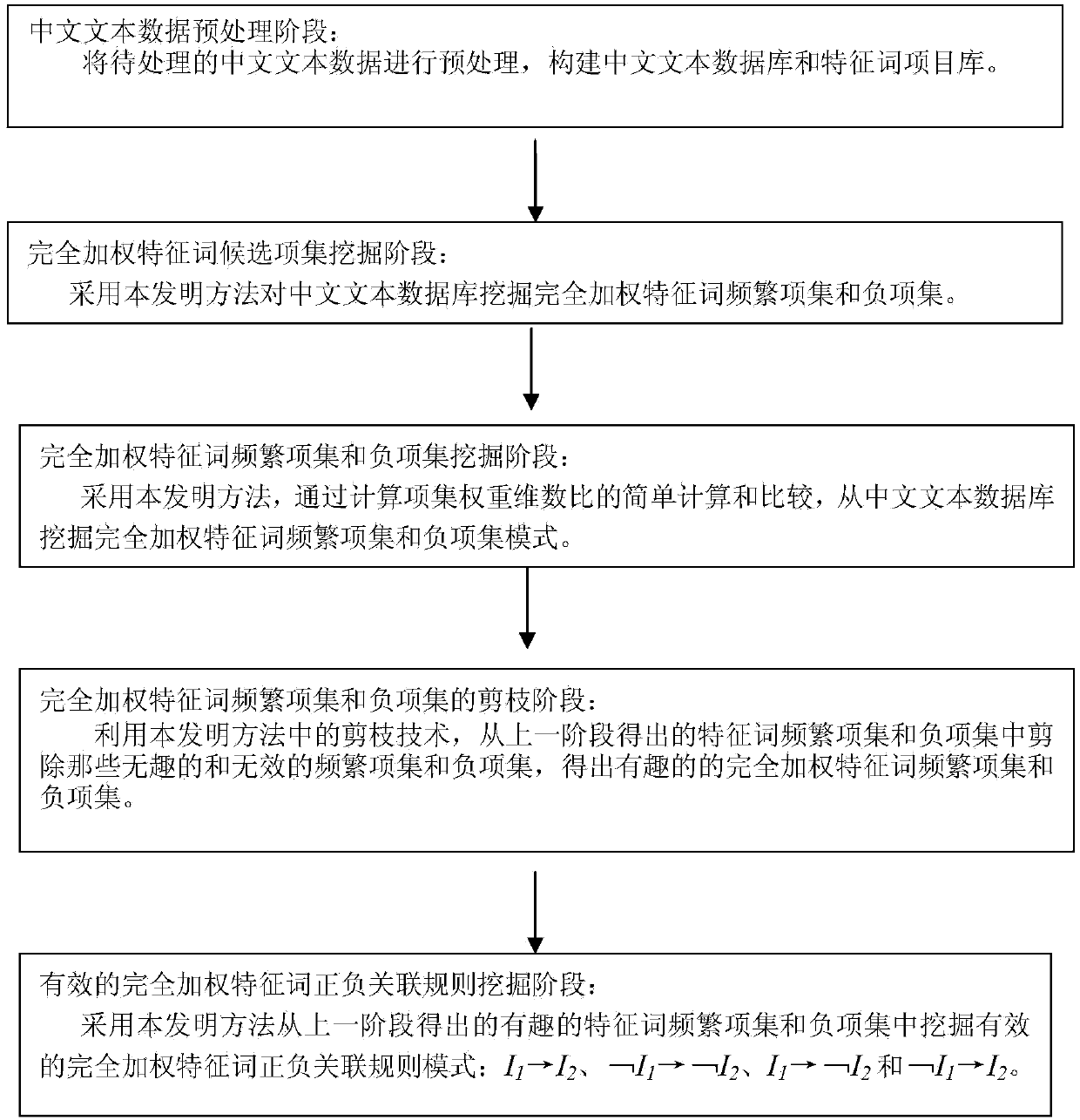
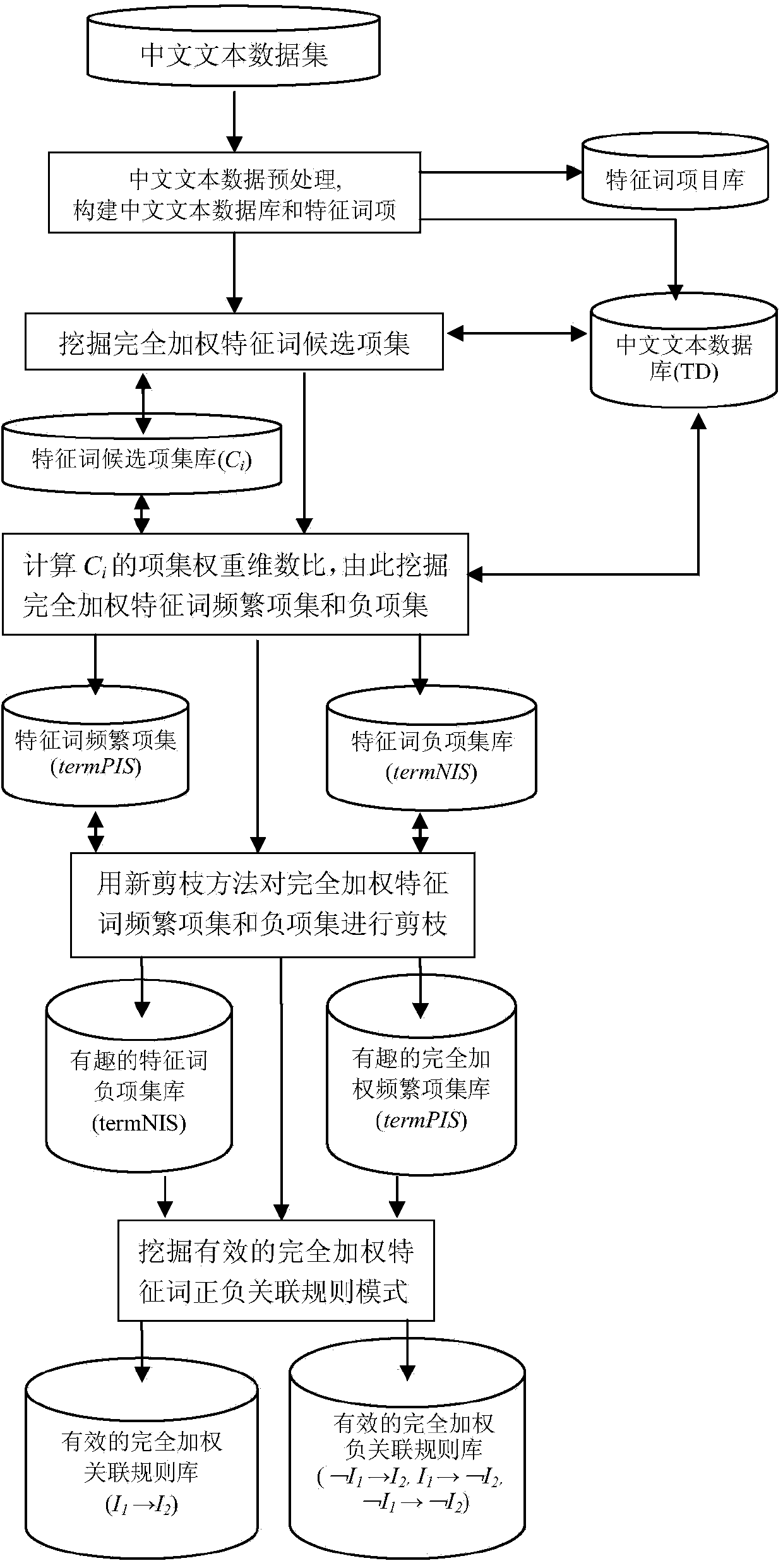
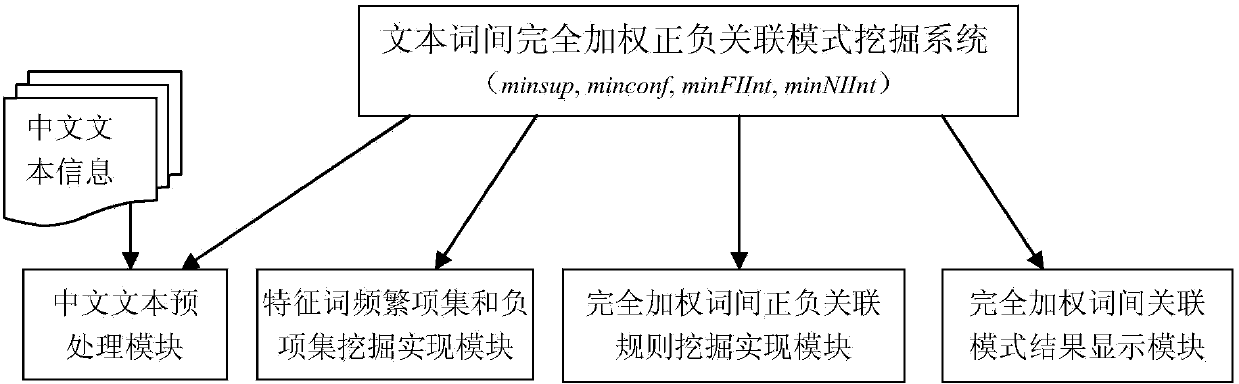
Method of item-all-weighted positive or negative association model mining between text terms and mining system applied to method
InactiveCN103955542AAvoid defectsAvoid it happening againSpecial data processing applicationsText databaseAssociation model
The invention discloses a method of item-all-weighted positive or negative association model mining between text terms and a mining system applied to the method. The method comprises the following steps of preprocessing by using a Chinese text preprocessing module to establish a text database and a feature word item library; mining item-all-weighted feature word candidate item sets from the text database by utilizing a feature word frequent item set and negative item set mining implementation module, calculating a weight dimension ratio, and cutting out uninteresting item sets by adopting a multi-interestingness threshold value pruning strategy to obtain an interesting item-all-weighted feature work frequent item set and negative item set model; mining an effective item-all-weighted positive or negative association rule model from frequent item sets and negative item sets by utilizing an item-all-weighted positive or negative association rule mining implementation module between terms, and outputting the mined positive or negative association rule model to a user by utilizing an item-all-weighted association model result display module between terms. By applying the method and the system, unnecessary frequent item sets, negative item sets and association rule models can be greatly reduced, Chinese feature word association rule mining efficiency is improved and a high-quality association model between Chinese terms is obtained.
Owner:GUANGXI UNIVERSITY OF FINANCE AND ECONOMICS
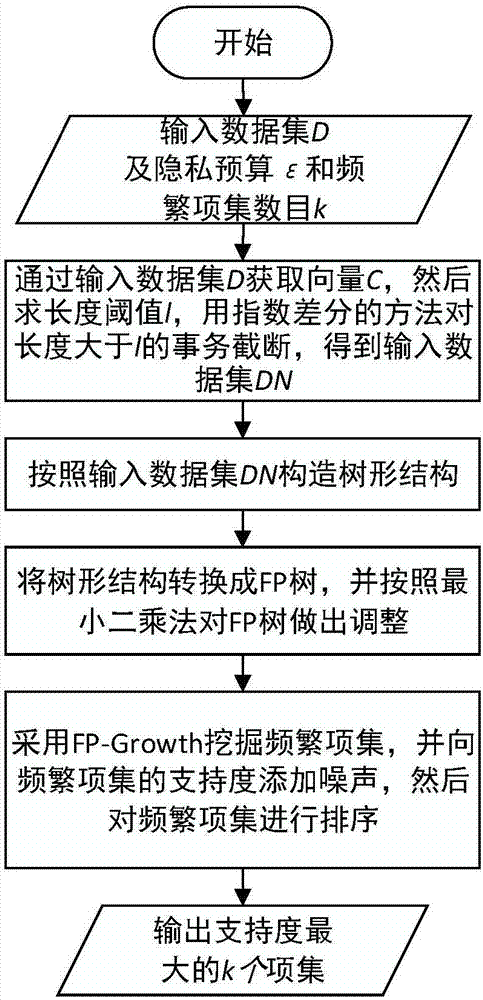
Frequent item set mining method and system supporting differential privacy
InactiveCN107092837AFix technical inefficienciesImprove digging efficiencyDigital data protectionData setData privacy protection
The invention discloses a frequent item set mining method and system supporting differential privacy, and belongs to the field of computer data privacy protection and data mining. The method comprises the steps of processing an original data set by adopting a transaction truncation method, and avoiding privacy leakage in the truncation process by using an exponential difference mechanism-based method; then constructing a tree structure, wherein each node corresponds to an item of a transaction, frequent information on the transaction is stored in a node corresponding to the last item of the transaction, and the support degree of each node is initialized by using Laplace noise to avoid the privacy leakage in the tree construction process; and converting the constructed tree into an FP tree, so that a frequent item set can be mined by using an FP-Growth method. According to the method and the system, the released frequent item set can meet security demands of the differential privacy; compared with an original frequent item set, the released frequent item set has relatively high similarity with the original frequent item set and relatively high data availability; and compared with a conventional algorithm, higher efficiency is achieved.
Owner:HUAZHONG UNIV OF SCI & TECH
Recommendation method in combination with frequent item set and deep learning under big data environment
InactiveCN105183841AEfficient Frequent Itemset MiningSolve Computational BottlenecksWeb data indexingSpecial data processing applicationsNerve networkComputational model
The invention discloses a recommendation method in combination with a frequent item set and deep learning under a big data environment. The recommendation method includes the following steps that behavior records of a user are collected, and a MapReduce parallel computation model is used for mining the frequent item set from the behavior records; a deep learning network is established, and the frequent item set is used for training the network; when recommendation is needed for the user, the behavior records of the user are collected as input, the established deep learning network is used for computation, and items are selected to be recommended to the user, wherein results of the items are larger than a threshold value. Based on the MapReduce parallel computation model, frequent item set mining can be efficiently performed inside a distributed system, with the frequent item set being a sample, the deep learning network is established, trained and used for recommendation, and compared with the mode that the frequent item set and a traditional neural network are directly utilized, recommendation can be performed for the user more accurately.
Owner:NANJING YOUZU INFORMATION TECH CO LTD
Abnormal group identification method and device
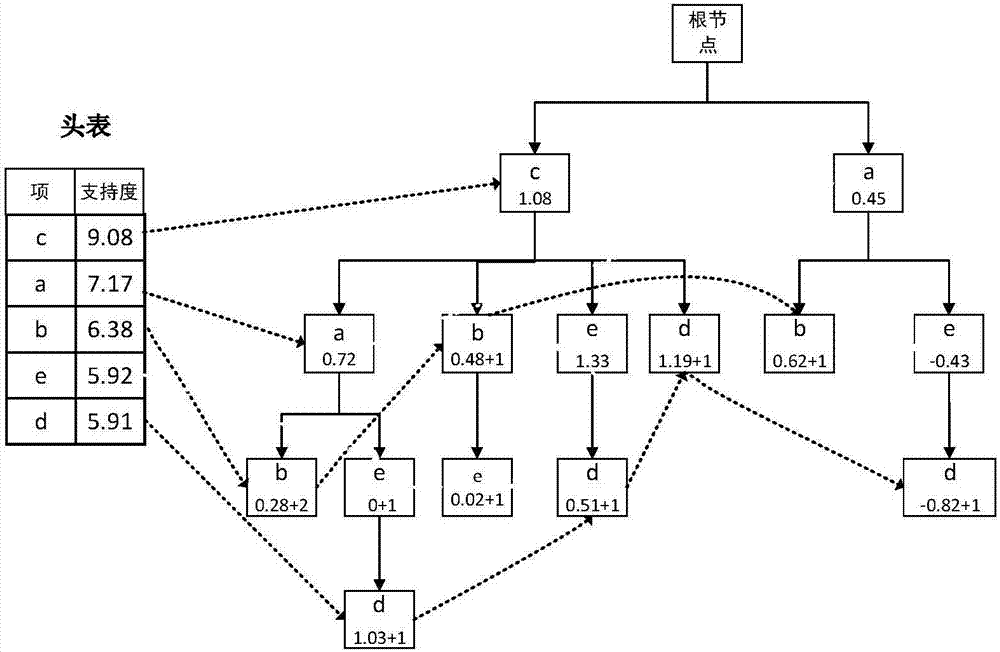
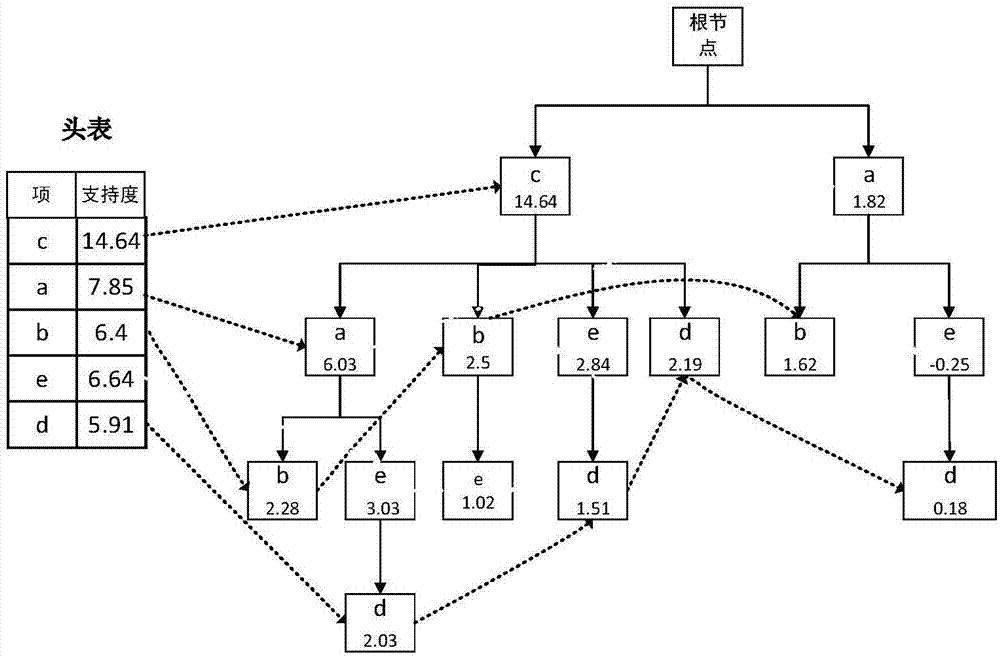
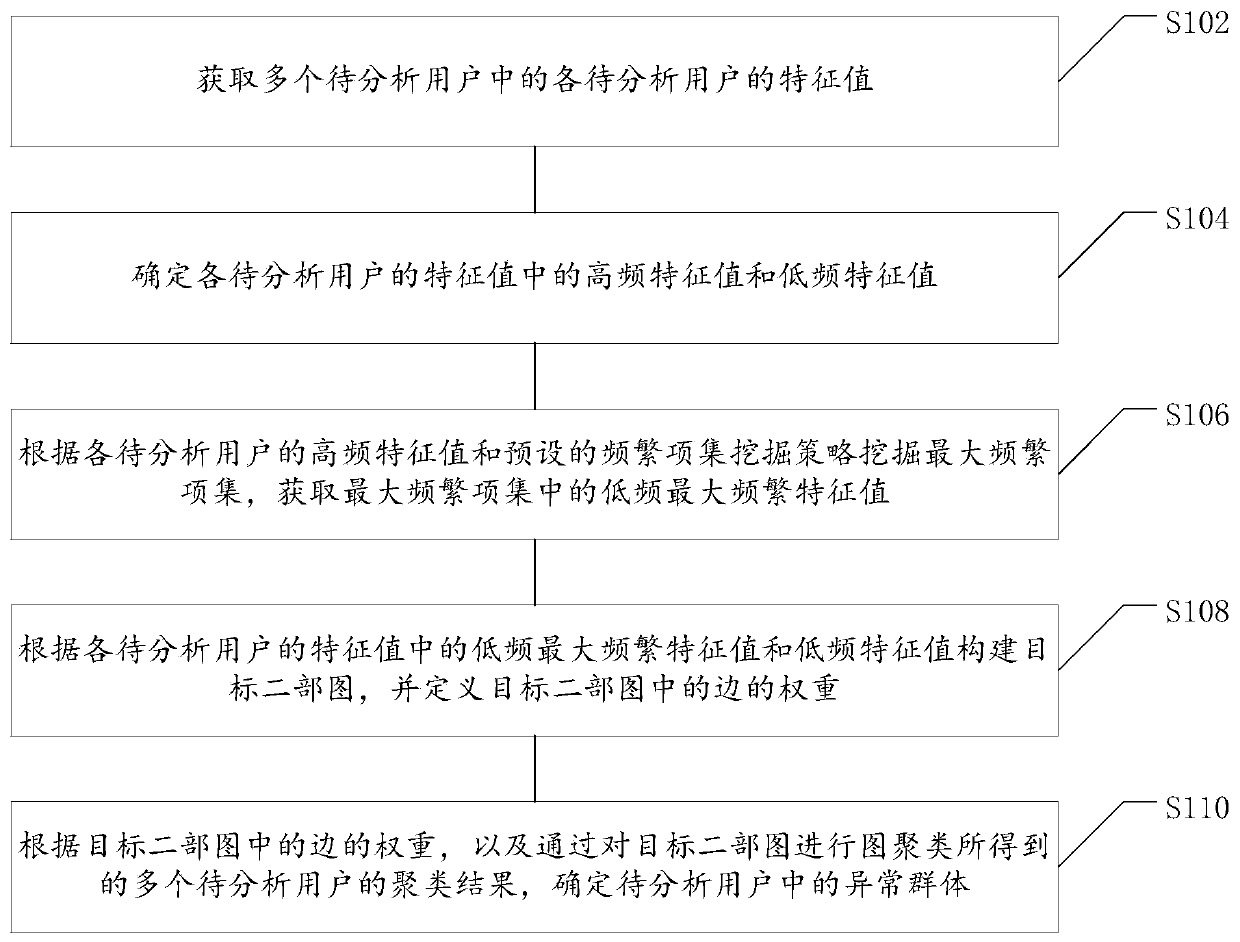
ActiveCN109948641AAccurate identificationSimple stepsCharacter and pattern recognitionEnergy efficient computingItem set miningData mining
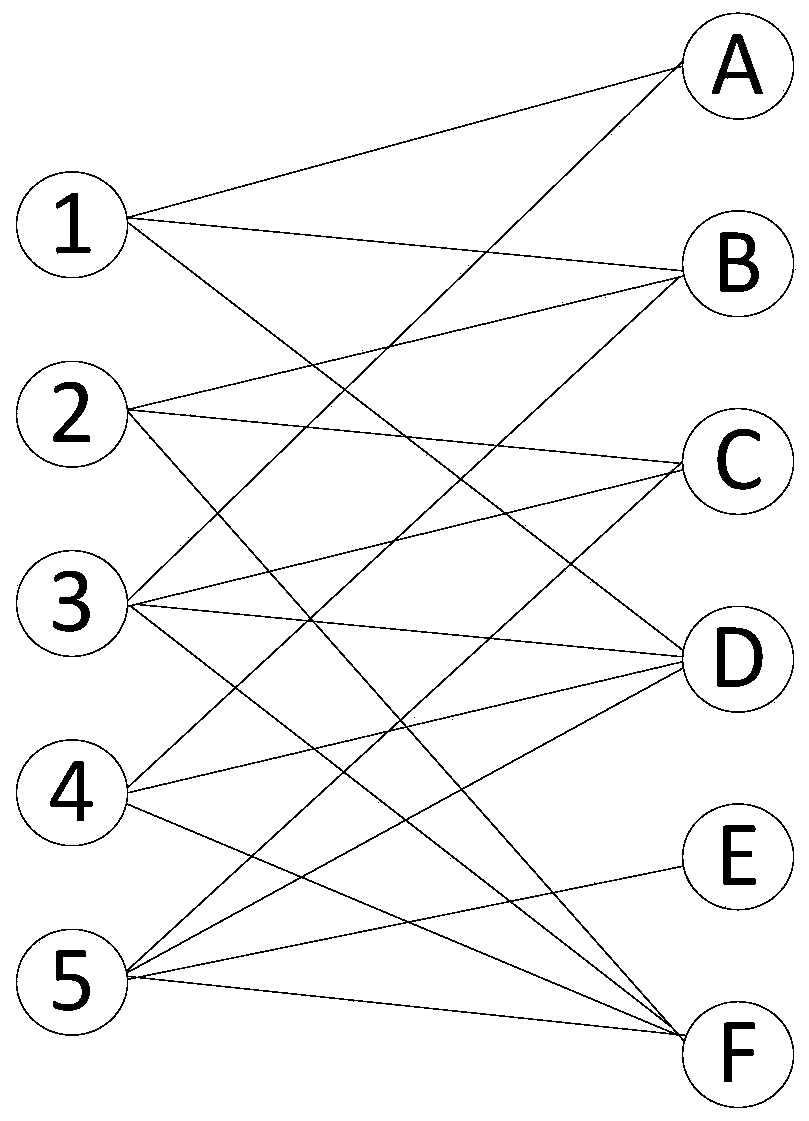
The embodiment of the invention provides an abnormal group identification method and device. The method comprises the steps of obtaining a feature value of each user to be analyzed in a plurality of users to be analyzed; Determining a high-frequency characteristic value and a low-frequency characteristic value in the characteristic values of the users to be analyzed; Mining a maximum frequent itemset according to the high-frequency characteristic value of each to-be-analyzed user and a preset frequent item set mining strategy, and obtaining a low-frequency maximum frequent characteristic value in the maximum frequent item set; Constructing a target bipartite graph according to the low-frequency maximum frequent characteristic value and the low-frequency characteristic value in the characteristic values of the users to be analyzed, and defining the weight of an edge in the target bipartite graph; And determining an abnormal group in the to-be-analyzed user according to the weight of the edge in the target bipartite graph and a clustering result of a plurality of to-be-analyzed users obtained by performing graph clustering on the target bipartite graph. According to the embodiment of the invention, the accuracy of abnormal group recognition is improved, and the steps are simple and easy to execute.
Owner:ADVANCED NEW TECH CO LTD
Differential privacy protection method based on Location BasedService
InactiveCN108563962AReduce Privacy Protection BudgetEasy to publishDigital data protectionSpecial data processing applicationsQuality of serviceData set
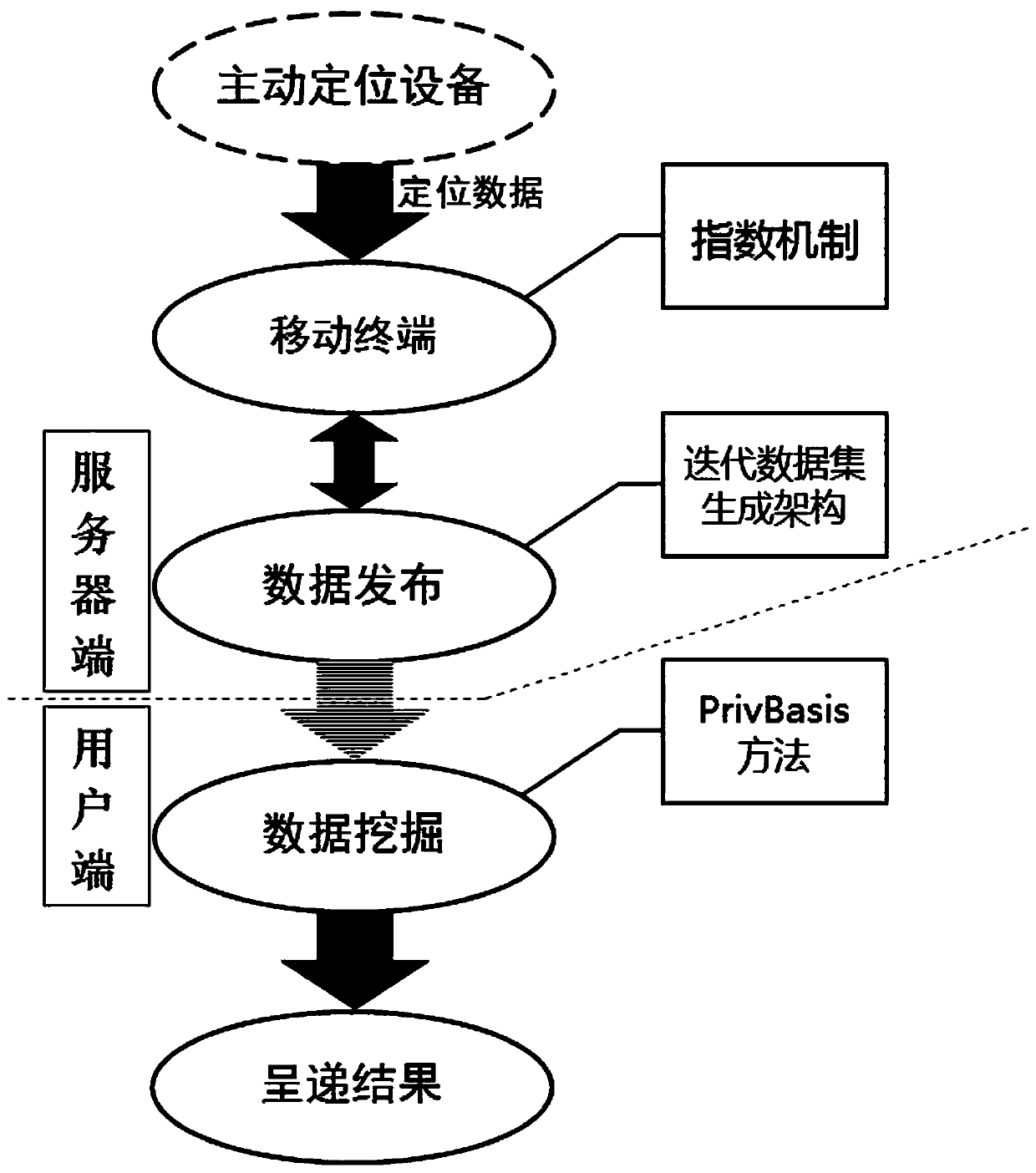
The invention relates to a privacy protection method based on the Location Based Service, which utilizes the differential privacy protection to protect various privacy information in the LBS data to the maximum extent without addingexcessive 'noise'and affecting the quality of service. Compared to traditional privacy protection, differential privacy protection can resist various forms of attacks with the attacker's greatest background knowledge. The method achieves the maximum benefit of privacy protection by virtue of this great advantage of differential privacy protection. In this method, anexponential mechanism is used on the coding mechanism to convert the coordinates of the three-dimensional space into an entity object; an interactive publishing mechanism is used for data publishing;an IDC Framework is used to reduce the costly privacy protection budget, thereby reducing the total amount of 'noise'; in the aspect of data mining in the query end, a frequent item set mining methodsuitable for the 3Ddata sets-PrivBasis is adopted, which can realize the differential privacy protection under the the premise of ensuring the computing performance.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Multi-computing framework processing system applied in big data and association rule mining method thereof
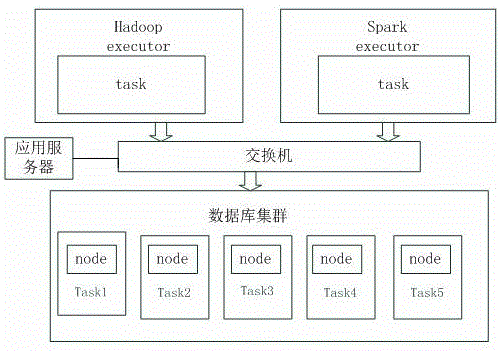
The invention discloses a multi-computing framework processing system applied in big data and an association rule mining method thereof. The system comprises a distributed computer cluster, a mapreduce system framework and a spark system framework sharing the distributed computer cluster. The computer cluster comprises a database cluster forming transactional databases, a switch, an application server, a Hadoop cluster, and a Spark cluster. Clusters are used to distribute computational tasks. Using advantages of multi-node parallel computation and distributed storage, multi-computing framework and the association rule mining algorithm are combined, transaction cluster division and a pruning strategy are combined, and data handling capacity is reduced, so processing efficiency is effectively improved. Through directly scanning value, a conditional pattern base is solved. The system has large improvement on aspect of overcoming limitation of shared memory, so computing resources are distributed in a balanced manner. The method effectively solves a problem that a conventional item-set mining algorithm is inadequate in computation and storage capability.
Owner:CHENGDU UNIV OF INFORMATION TECH
E-commerce platform individual recommendation method based on weighted frequent item set mining algorithm
InactiveCN108346085AImprove digging efficiencyBuying/selling/leasing transactionsSpecial data processing applicationsPersonalizationData set
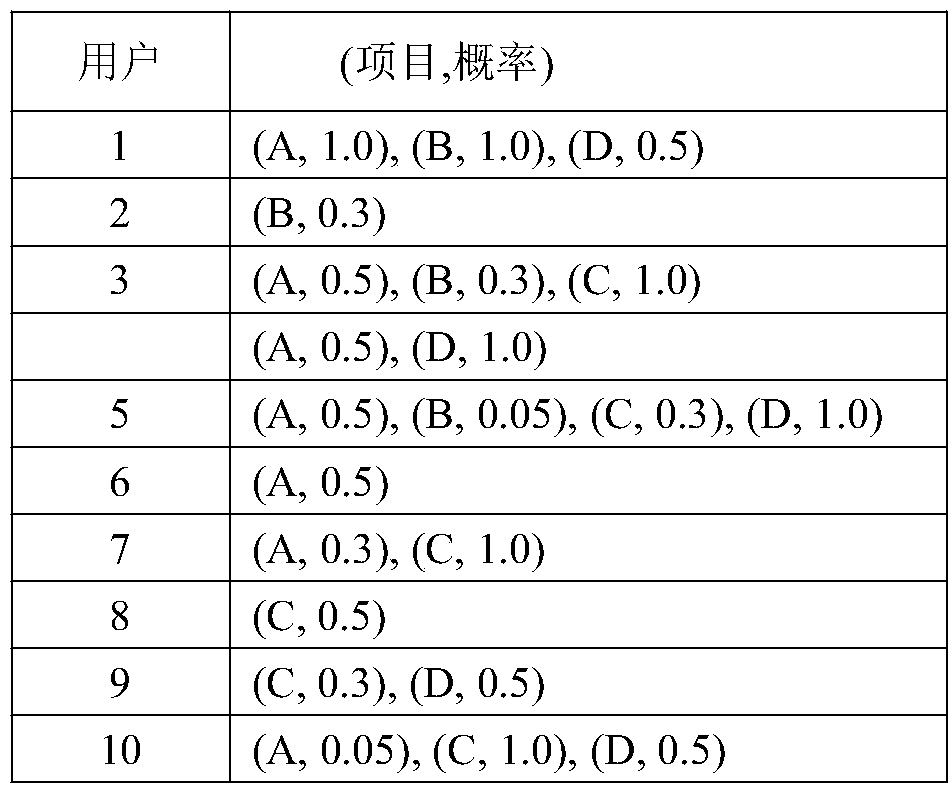
The invention discloses an e-commerce platform individual recommendation method based on a weighted frequent item set mining algorithm. The method, for the browse behaviors of an e-commerce platform user, assigns different probability values to different items according to behaviors of click browsing, collecting, adding to shopping cart and purchasing so as to reflect the user's preference for different items, and in combination with the income of different items (ie, commodities), mines the weighted frequent item set in an e-commerce platform user browse data set to achieve effective individual recommendation. The invention provides a weight decision downward closure feature and a weighted frequent subset existence characteristic for the e-commerce platform user browse data set weighted frequent item set mining, and provides a uncertain data frequent item set mining algorithm based on weight decision downward closure feature according to the above two characteristics, and takes account of the user's preference for different items and the benefits that the items bring to a merchant, and improves the mining efficiency.
Owner:NANJING UNIV OF POSTS & TELECOMM
Uncertain data model oriented utility item set mining method
InactiveCN105608182AReduce consumptionReduce running timeSpecial data processing applicationsResource consumptionItem set mining
The invention relates to an uncertain data model oriented utility item set mining method. The method comprises the steps of S1, verifying transaction weighting utility and expected support degree of each item set and forming a total candidate set by taking item sets passing the verification as candidate sets; and S2, verifying the utility of each item set in the total candidate set through an uncertain data model to obtain an uncertainty based high-utility item set, wherein the transaction weighting utility is equal to the sum of transaction utilities of all transactions containing the item sets in the uncertain data model, the item sets forming the total candidate set include a k-item set verified through the step S1, k is 1-n, n is an item number of the transaction with the most items in the uncertain data model, and when k is greater than 1, the k-item set is obtained by using a k-1-item set in the total candidate set as a subset and performing verification through the step S1. According to the method, an optimization method is added in an existing mining method, so that the technical effects of reducing resource consumption and shortening running time are achieved.
Owner:YILAN YUNLIAN TECH CO LTD
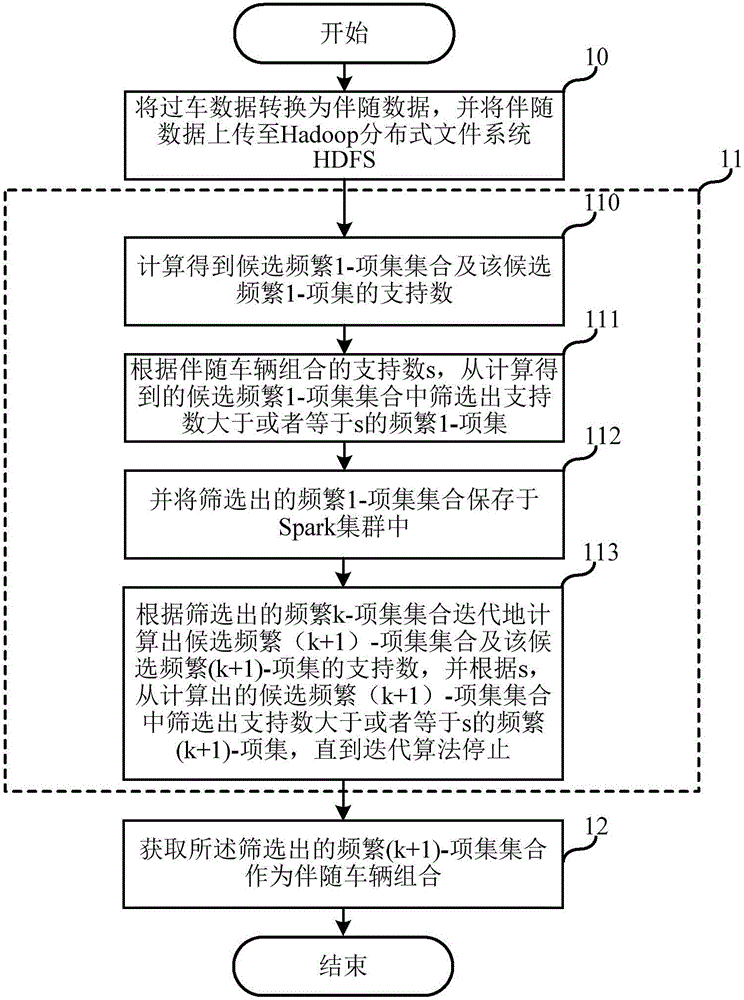
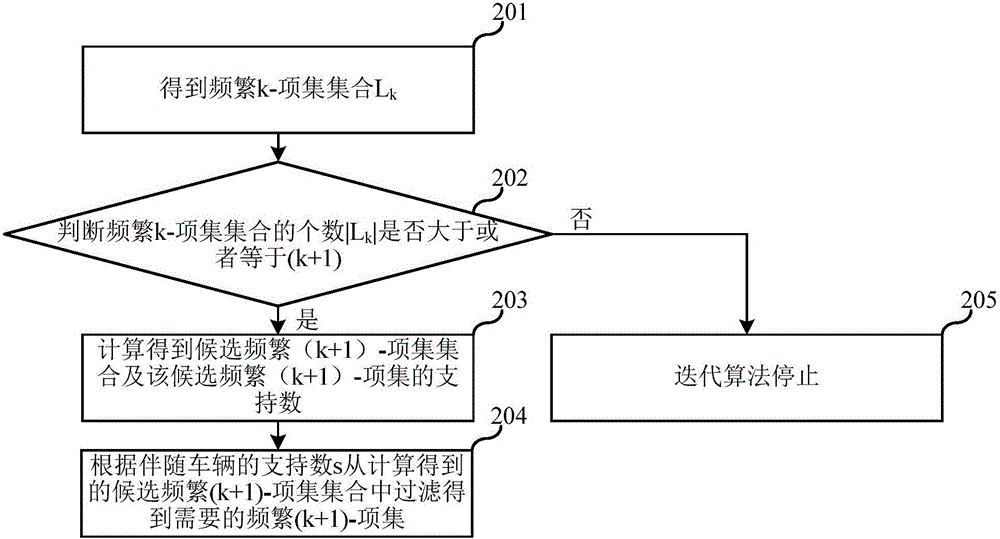
Large-scale vehicle-passing data oriented accompanying vehicle identification method
InactiveCN106021412AReduce in quantityImprove digging efficiencySpecial data processing applicationsItem set miningComputer science
The invention relates to the technical field of data mining, and discloses a large-scale vehicle-passing data oriented accompanying vehicle identification method. The large-scale vehicle-passing data oriented accompanying vehicle identification method comprises the steps of converting the vehicle-passing data into accompanying data and uploading the accompanying data to HDFS; and mining the accompanying data by using a Spark based matrix pruning parallel frequent item set mining algorithm to obtain an accompanying vehicle set. Compared with the prior art, the large-scale vehicle-passing data oriented accompanying vehicle identification method improves the identification efficiency of an accompanying vehicle and can reduce the identification cost of the accompanying vehicle.
Owner:上海市计算技术研究所有限公司
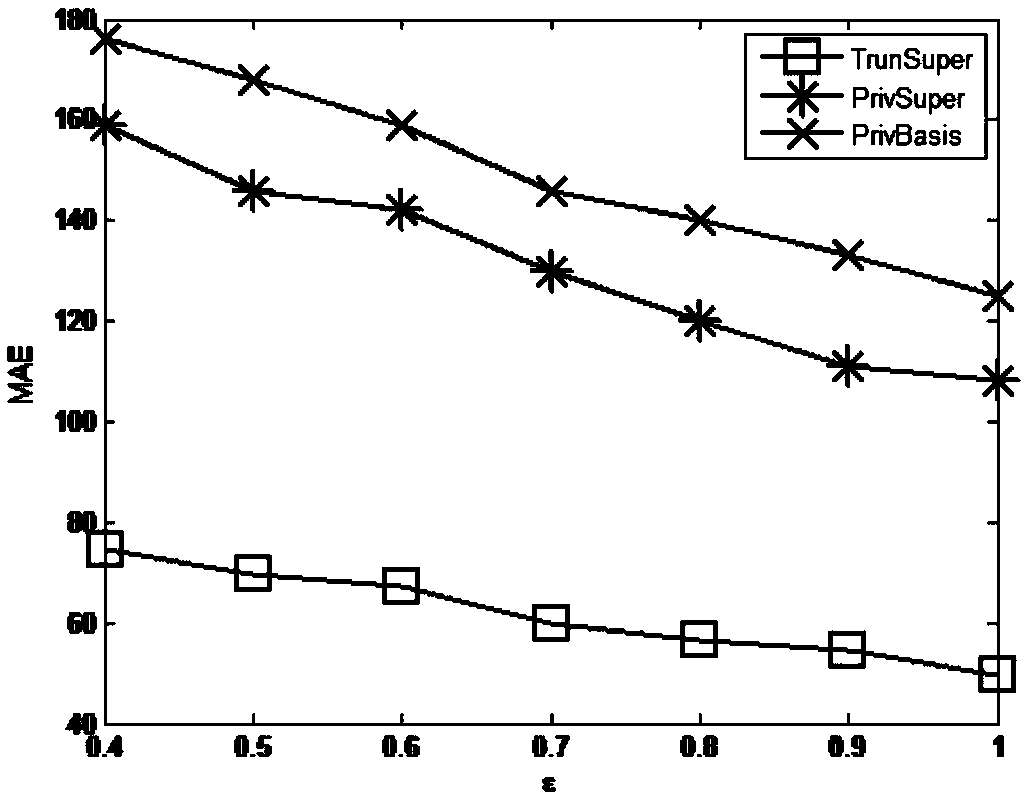
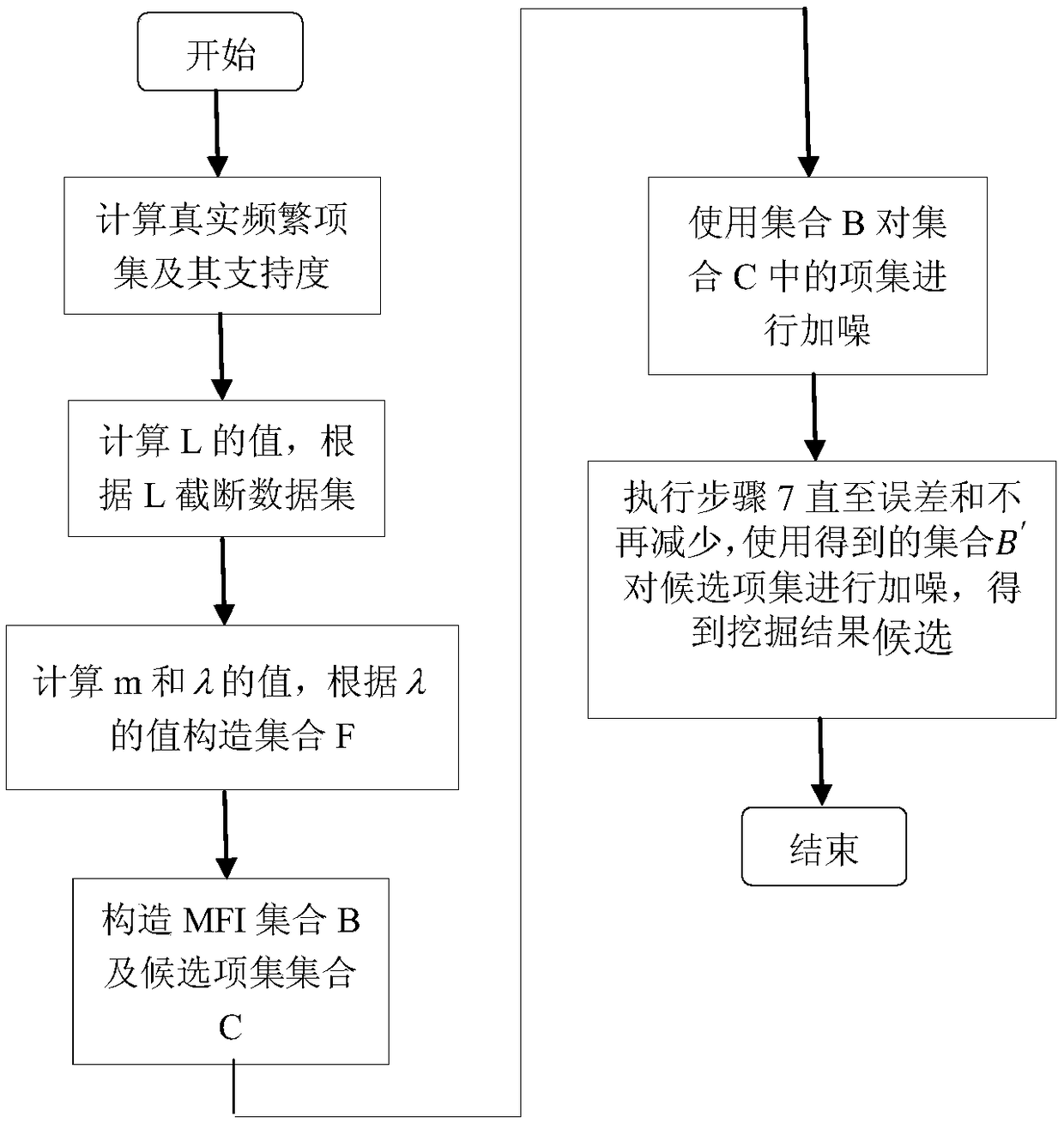
A frequent item set mining method for differential privacy protection
ActiveCN109409128AReduce support errorReduce dimensionalityDigital data protectionData setDifferential privacy
The invention discloses a frequent item set mining method for differential privacy protection, which comprises the following steps of: calculating support degrees of all item sets, and selecting frequent item sets from the support degrees; counting the length of each transaction in the data set, calculating a truncation length L and truncating the data set; calculating the upper limit m of the number of items contained in the frequent item set and the number of frequent items, and constructing a set F consisting of the frequent items according to the value; constructing a maximum frequent itemset MFI set B and a candidate item set C; adding noise to the item set in the set C by using the set B; calculating the support degree of each candidate item set by using the initial MFI set B, and then calculating the sum E of errors with the real support degree; Searching B, B in B, replacing B with B, and updating values of the error and E; and stopping iteration and outputting a result when the sum of the errors is no longer reduced. According to the method, personal privacy leakage caused by frequent item set release can be well prevented, and meanwhile, the availability of a mining result is effectively improved through data set truncation operation.
Owner:NANJING UNIV OF POSTS & TELECOMM
Privacy protection frequent item set mining method for large-scale shopping mall transaction record
ActiveCN108900493AReduce the numberSmall amount of calculationKey distribution for secure communicationPublic key for secure communicationCiphertextPrivacy protection
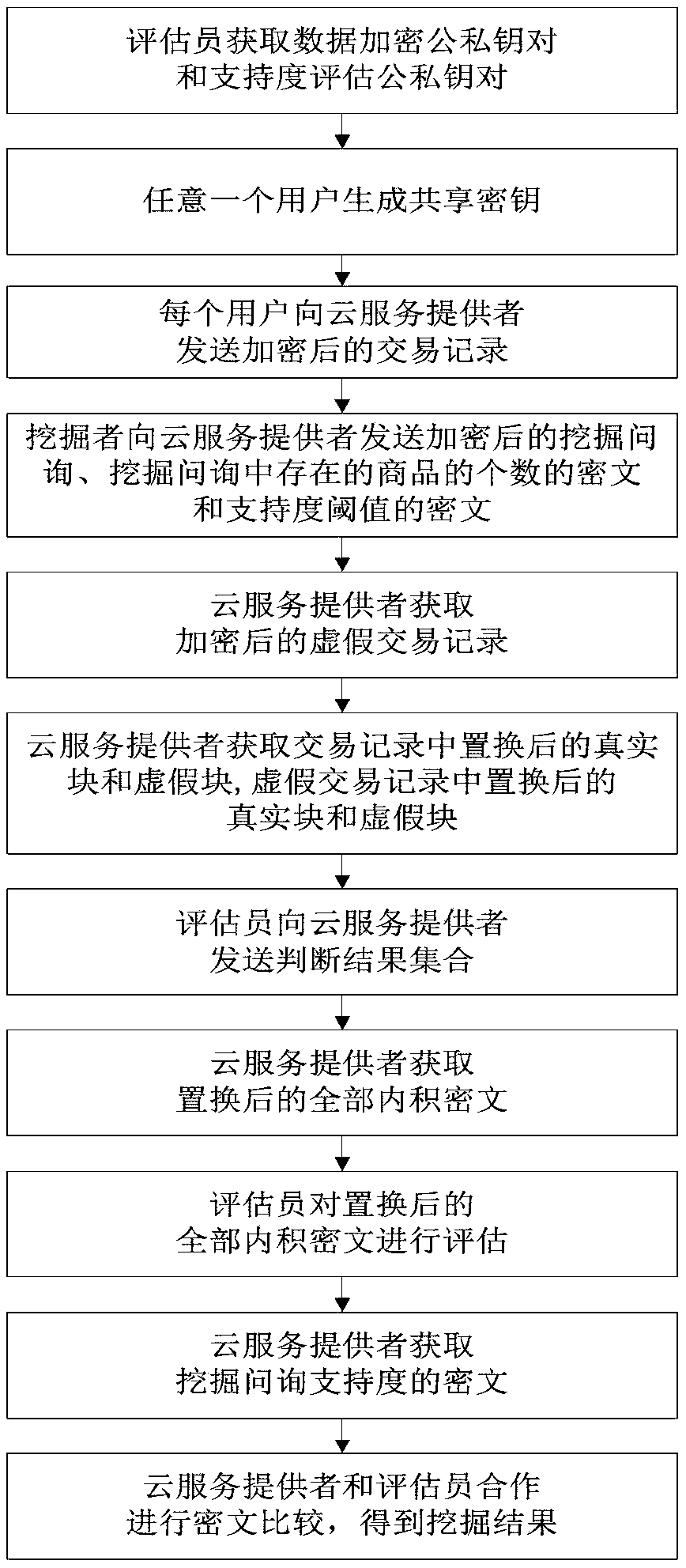
The invention provides a privacy protection frequent item set mining method for a large-scale shopping mall transaction record, so as to solve the technical problem of a large amount of calculation during a frequent item set mining process under a high privacy protection level existing in the prior art. The method comprises steps: an evaluator acquires a public-private key pair, and any user generates a shared key; each user sends an encrypted transaction record to a cloud service provider, and a miner sends an encrypted mining query, a ciphertext with a goods number existing in the mining query and a support threshold ciphertext to the cloud service provider; and the cloud service provider acquires an encrypted false transaction record; and the cloud service and the evaluator interact tojudge whether the mining query is a frequent item set. The mining frequency is high.
Owner:XIDIAN UNIV
Multidimensional analysis visual representation method of centralized monitoring mass data of transformer substation
InactiveCN104182904ARealize visualizationEasy to controlData processing applicationsSpecial data processing applicationsTransformerPower grid
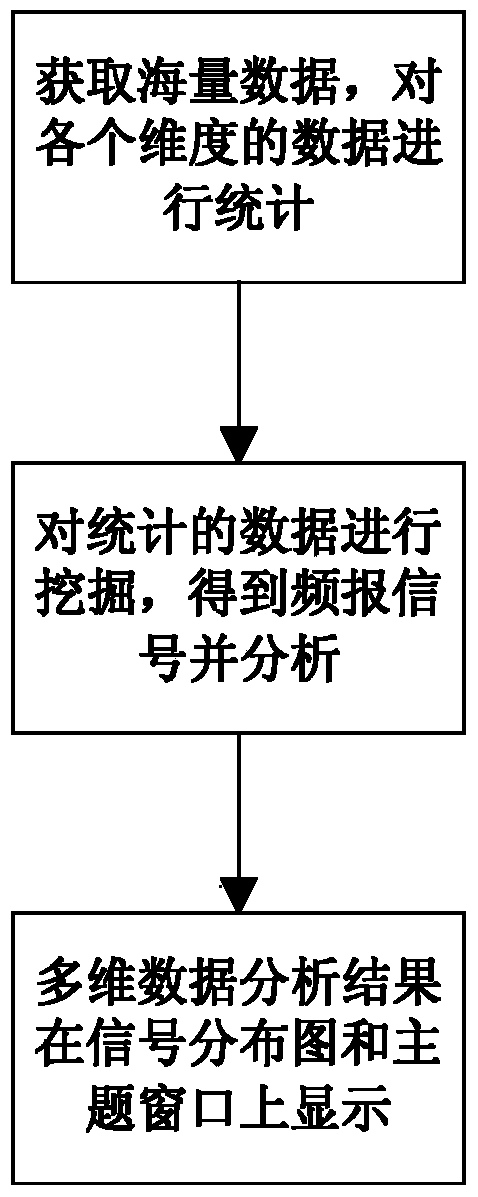
The invention discloses a multidimensional analysis visual representation method of the centralized monitoring mass data of a transformer substation. The multidimensional analysis visual representation method comprises the following steps: S1) obtaining the mass warning data of the transformation substation, carrying out each-dimensionality analysis statistical processing to the mass warning data, carrying out frequent item set mining to an analysis statistical result to obtain a frequent item set, i.e. equipment closely related to a frequency reporting signal; and S2) paying attention to the equipment which satisfies frequent item set conditions, and carrying out visual representation on a signal distribution diagram and a theme window. The invention can help a dispatcher to macroscopically master the general operation situation of a whole power grid, discloses possibly potential problems and weak links, and points out the potential risks of the power grid from multiple angles, such as single types, frequent warning, equipment types, power plant and power station gathering so as to alleviate monitoring pressure and improve the control ability of the dispatcher to the whole power grid.
Owner:STATE GRID CORP OF CHINA +3
Data flow maximal frequent item set mining method based on ordered composite tree structure
InactiveCN104850577AIncrease digging speedReduce consumptionSpecial data processing applicationsData streamSlide window
The invention discloses a data flow maximal frequent item set mining method based on an ordered composite tree structure. The data flow maximal frequent item set mining method is suitable for the fields of financial data time sequence mining, commercial data flow association analysis and the like. The invention is specific to the defects of low execution efficiency, excessive memory consumption and the like in an existing maximal frequent item set mining method. Data flow is processed with a sliding window; the sliding window is partitioned into a plurality of basic units; data flow fragment information is updated and acquired; and the fragment information is scanned once to obtain frequent item sets, and the frequent item sets are stored in a frequent item set list. According to the method, an ordered FP-tree is constructed, the structure of the tree is adjusted dynamically along with the insertion of the item sets, adjacent nodes with equal support degrees in a same branch are combined, and an ordered composite FP-tree is generated by means of compression. Through adoption of the method, maximal frequent item set mining can be performed efficiently and rapidly on data flow. The method has a high application value.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
On-line classroom discussion short text real-time grouping method and system based on text clustering
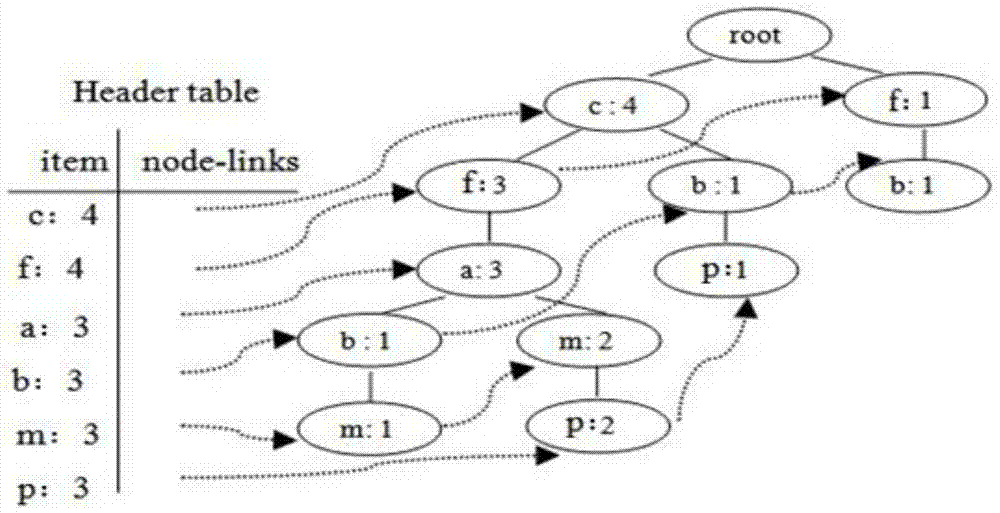
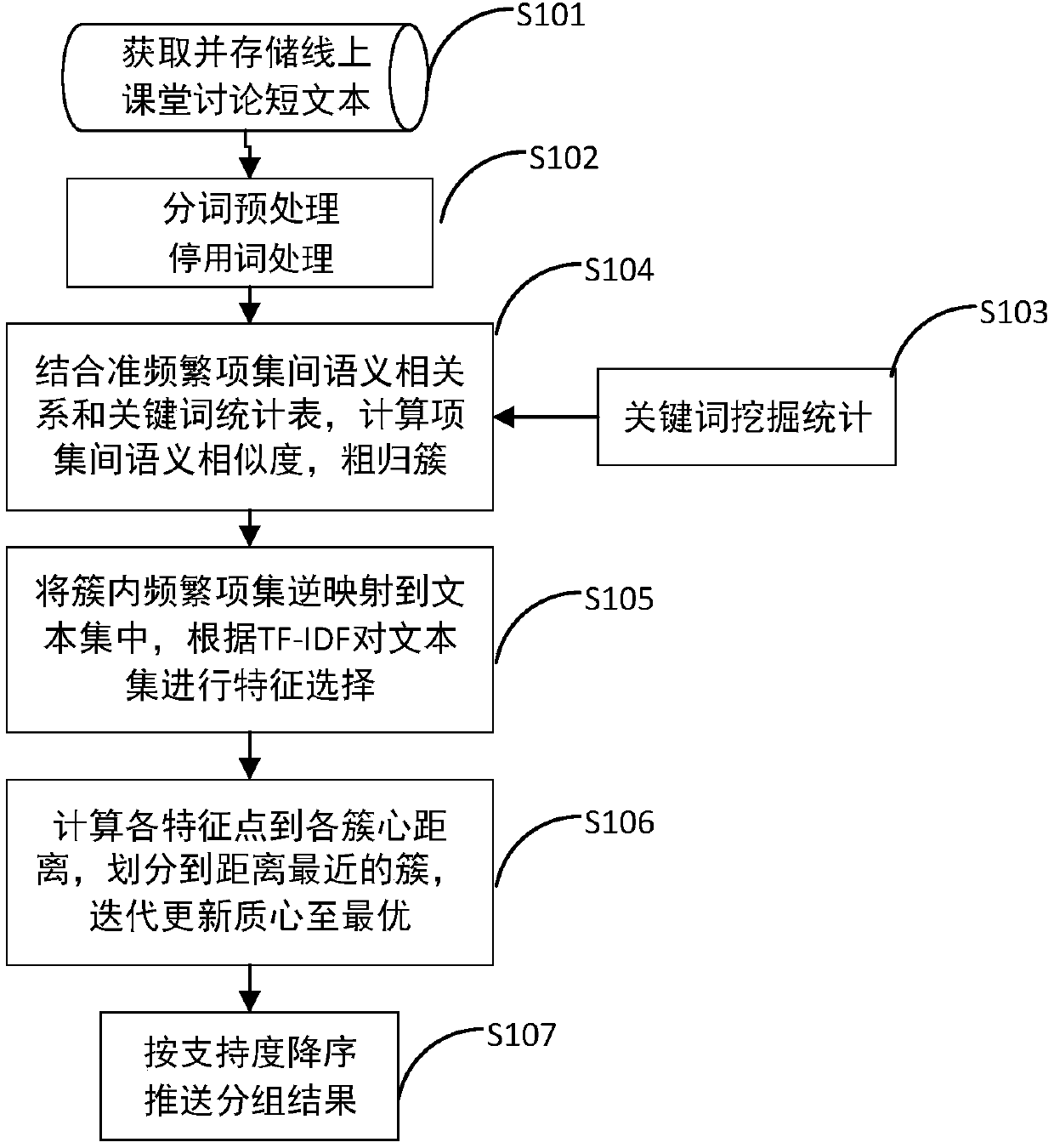
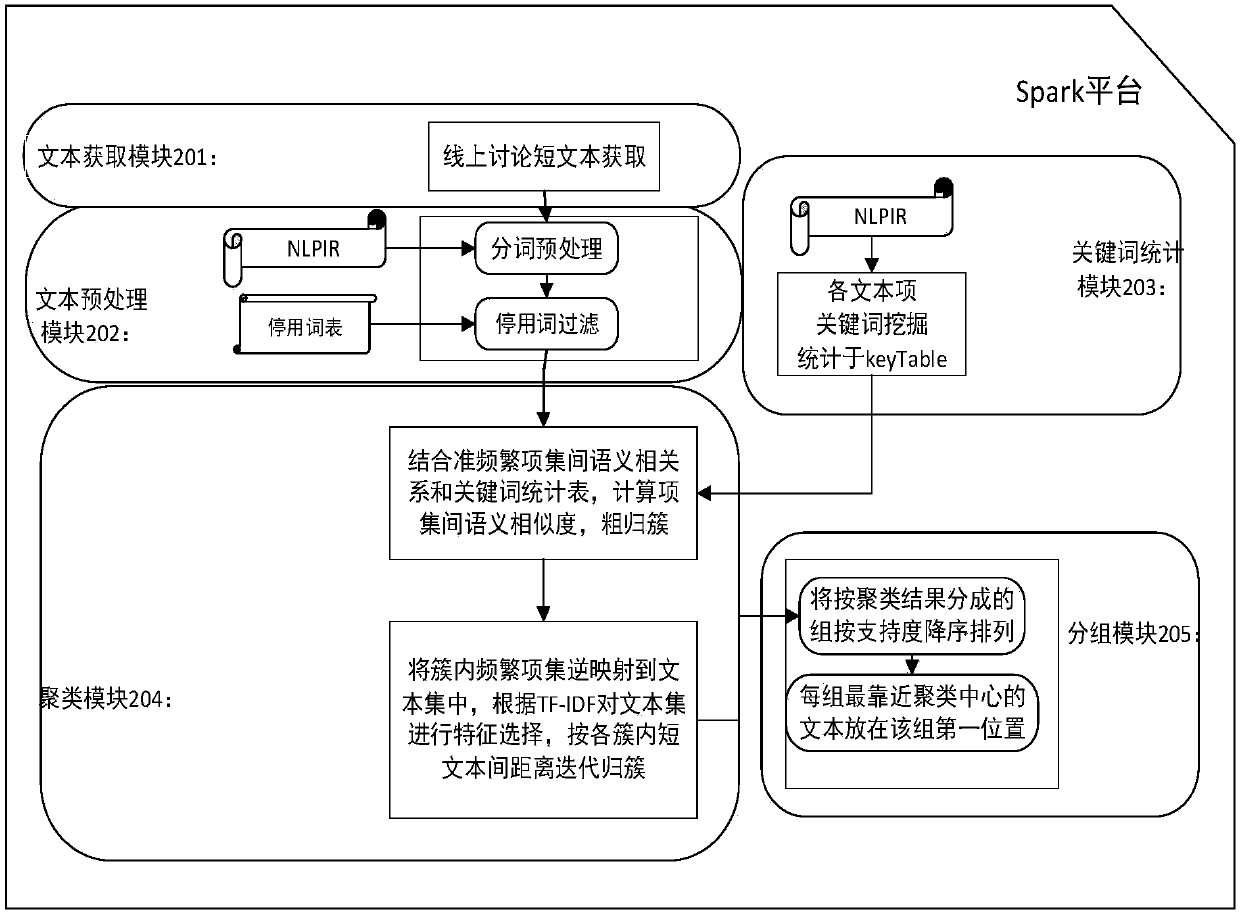
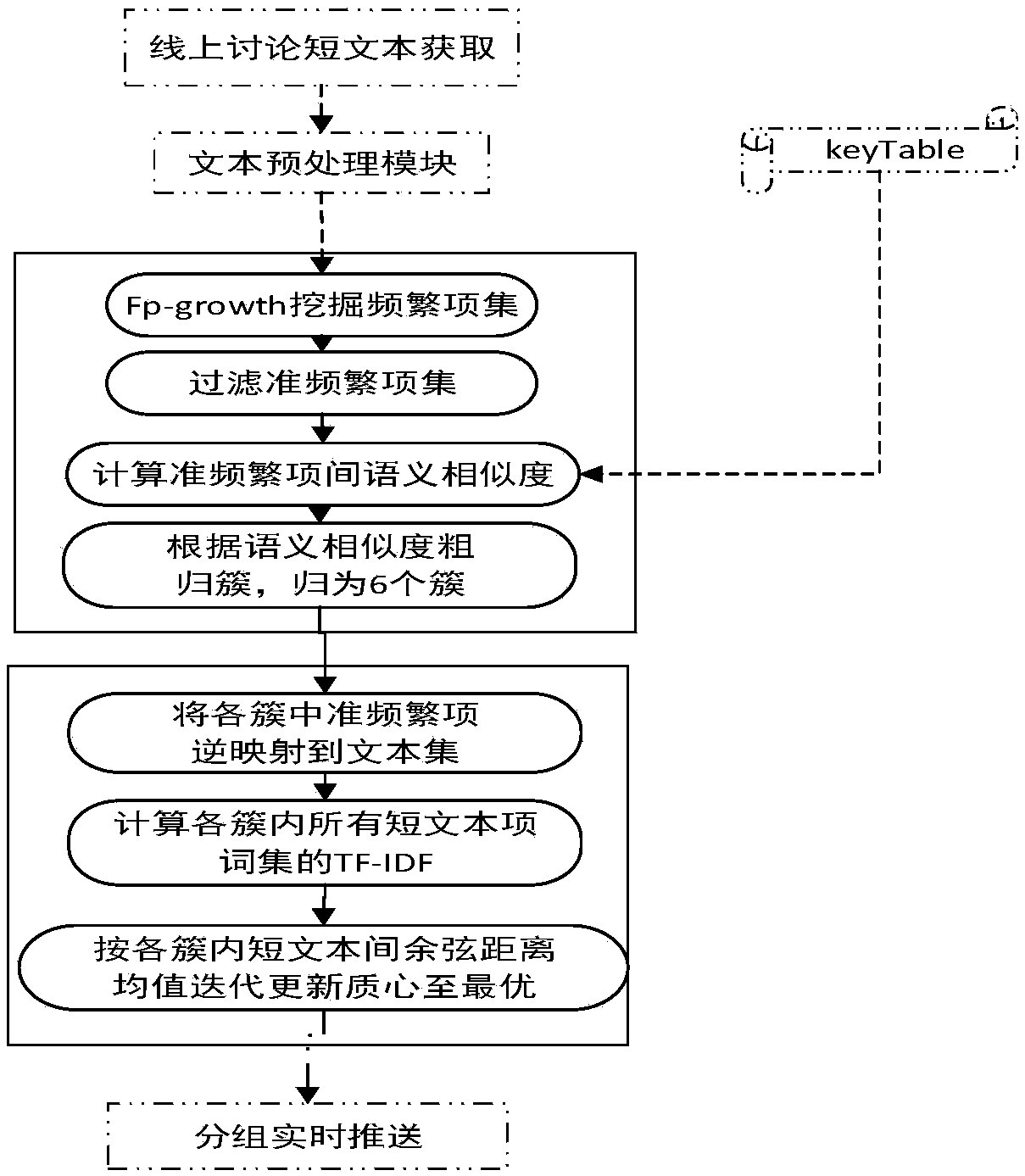
ActiveCN107862070AGuaranteed immediacyOvercoming the problem of low contribution valueNatural language data processingSpecial data processing applicationsGroup methodItem set mining
The invention discloses an on-line classroom discussion short text real-time grouping method and system based on text clustering. The method comprises the steps of conducting word-splitting preprocessing and stop-word preprocessing on text data; obtaining all text item keywords, counting all the text item keywords and storing the text item keywords into a keyword table keyTable; conducting frequent item set mining on a preprocessed text set, filtering all sub-item quasi-frequent item sets and conducting coarse cluster classification in combination with a keyword table definition quasi-frequentitem set similarity calculation rule; mapping points, the closest to the cluster center, of all clusters to the text set, calculating TF-IDF values of text word sets in all the clusters and iteratingthe center of mass to be optimal according to the distance; pushing the obtained K clusters in real time in group. Through the combination of the keyword table definition quasi-frequent item set similarity calculation rule, the clustering accuracy of an on-line discussion short text is effectively improved; through a quasi-frequent item set filtering strategy, the clustering efficiency is effectively improved, and a clustering method is accelerated; the text information content discussed on an on-line classroom is automatically classified into multiple themes, and the text content is groupedaccording to the themes.
Owner:SOUTH CHINA UNIV OF TECH
Stochastic distributed data stream frequent item set mining system and method thereof
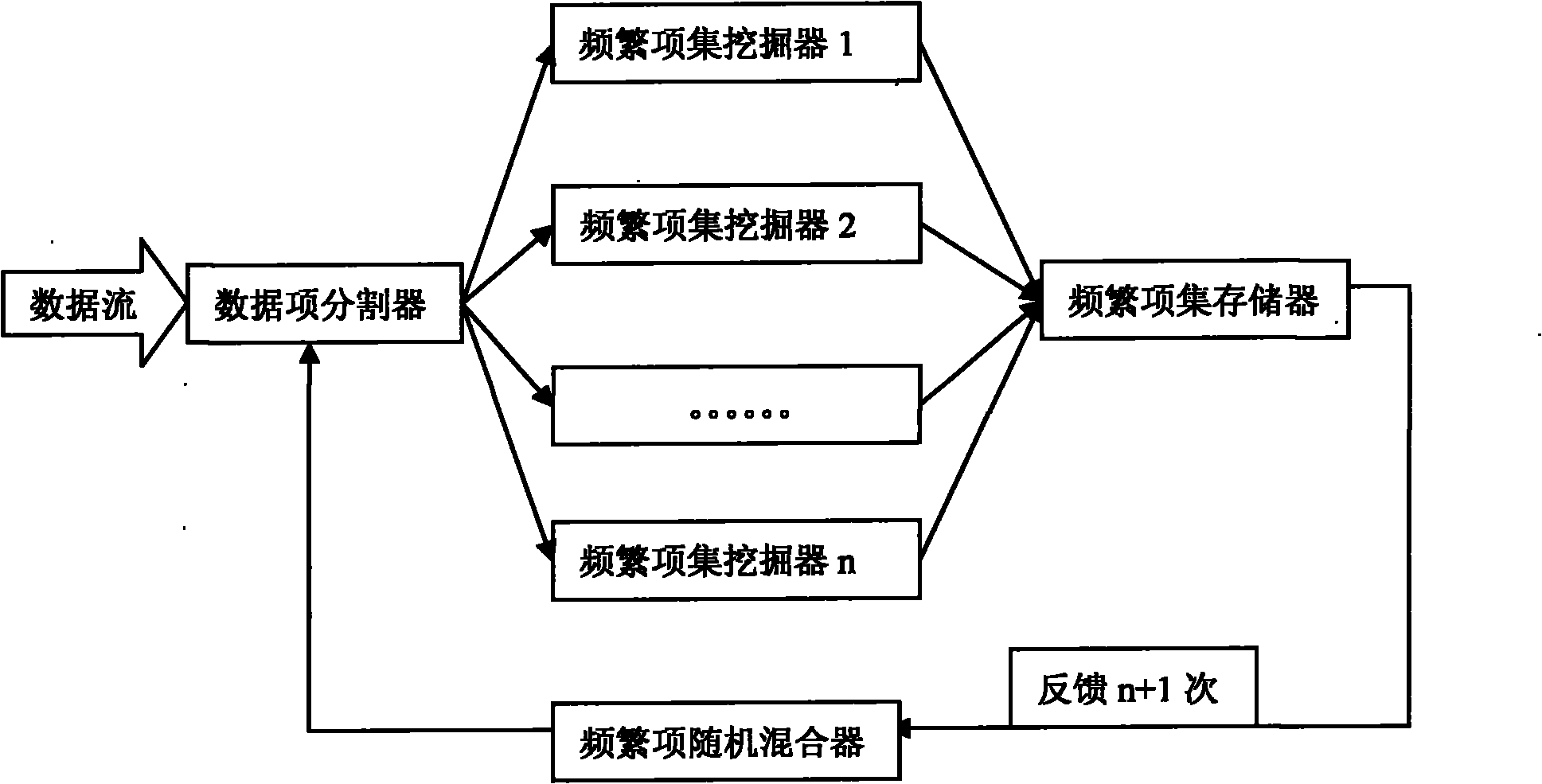
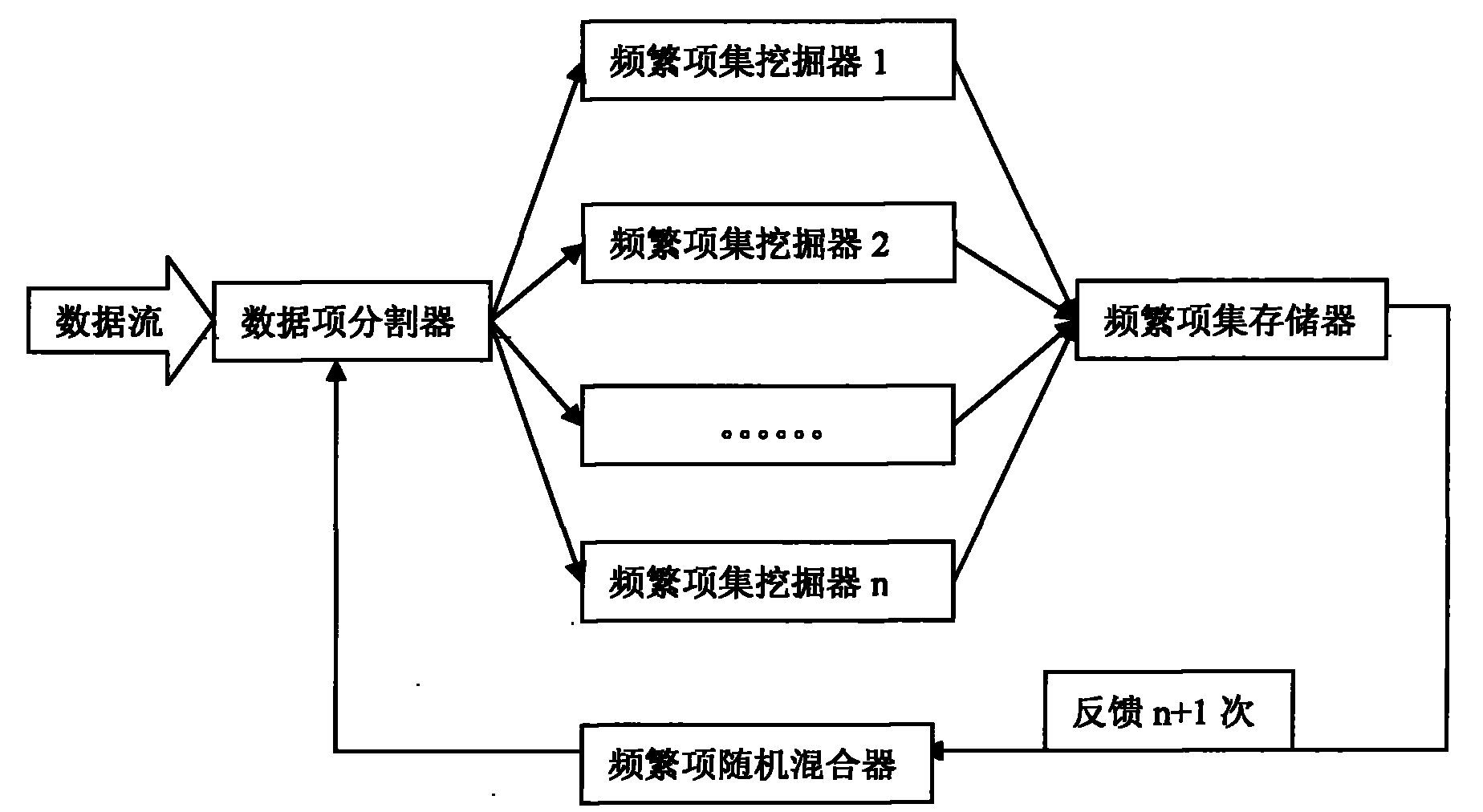
InactiveCN101887450AHigh precisionImprove operational efficiencySpecial data processing applicationsData stream miningData stream
The invention discloses a stochastic distributed data stream frequent item set mining system. In the system, a new distributed data stream mining mode for frequent item transactions is adopted, a stochastic frequent item mixer is introduced to improve the accuracy of mining, new transactions, when accumulated to the same number as basic windows, in a data steam are send to n frequent item set mining devices by a data item dividing method according to the different items in the transactions respectively, transaction numbers to which different data items belong are attached to the different data items, and in the frequent item set mining devices, frequent item sets are mined by running and operating different frequent item transactions and the mined frequent item sets are stored in a frequent item set storage. Finally, the data items are fed back to data item dividers through the stochastic frequent item mixer for deep mining. Compared with other methods, the method has the advantages of small memory storage space, high response speed and the like. Meanwhile, the coverage of mode mining can be ensured by increasing the number of the frequent item set mining devices or feedback times.
Owner:NORTHEAST DIANLI UNIVERSITY
Data processing method based on frequent item set mining
InactiveCN105159952AEasy accessFrequent itemset avoidanceSpecial data processing applicationsShopping basketItem set mining
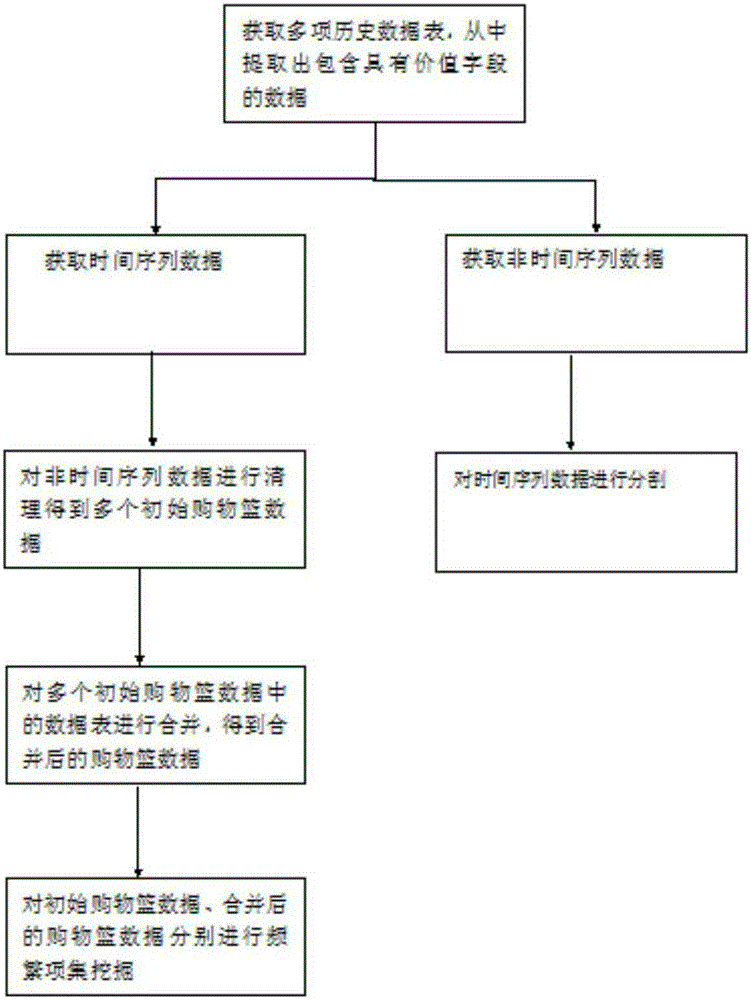
The present invention provides a data processing method based on frequent item set mining, which comprises the following steps of: acquiring a plurality of items of historical data tables and extracting data tables with value fields; acquiring time sequence data tables and non-time sequence data tables from the data tables with the value fields; carrying out segmentation on the time sequence data tables and carrying out cleaning on the non-time sequence data tables to obtain initial shopping basket data; merging a plurality of data tables in the initial shopping basket data to obtain merged shopping basket data; and respectively carrying out frequent item set mining on the initial shopping basket data and the merged shopping basket data to obtain a frequent item result with a designated support degree. According to the data processing method based on frequent item set mining, historical data is subjected to frequent item set mining to obtain the frequent item set support degree of each historical data table, frequent data in a random dimension can be inquired and the data processing method is convenient for an analyst to acquire the data; and meanwhile, the time sequence data is segmented, which is convenient for the analyst to inquire related data according to a time tag.
Owner:ANHUI XINHUABO INFORMATION TECH
Frequent item set mining method based on cloud outsourcing transaction data
ActiveCN110120873AImprove securityOvercome the disadvantage of agnostic originKey distribution for secure communicationUser identity/authority verificationUser verificationCiphertext
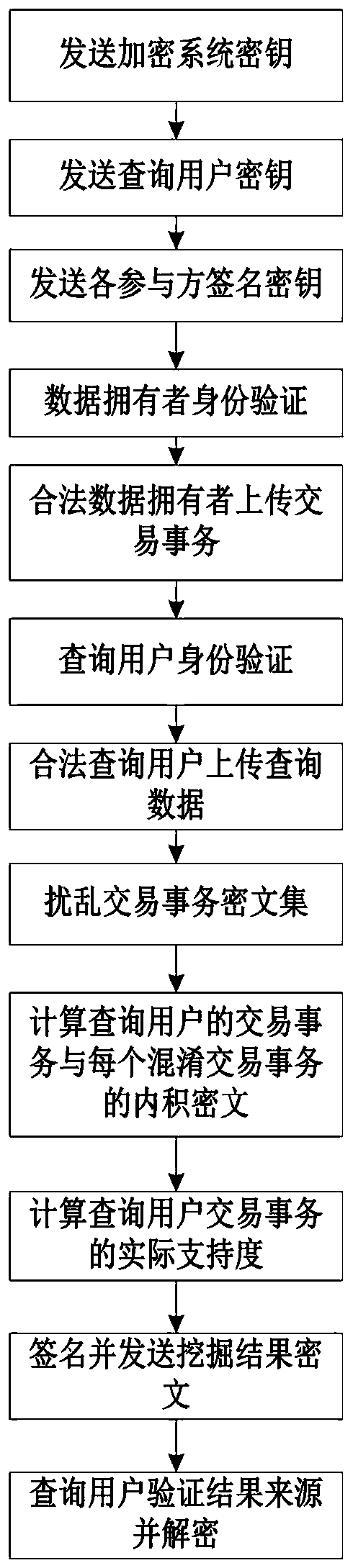
The invention discloses a frequent item set mining method based on cloud outsourcing transaction data. The method comprises the following steps: sending an encryption system key; sending a query userkey; sending the signature key of each participant; verifying the identity of the data owner; enabling the legal data owner to upload a transaction transaction; inquiring user identity verification; enabling the legal query user to upload query data; disturbing the transaction ciphertext set; calculating the inner product ciphertext of the transaction affair of the query user and each confused transaction; calculating the actual support degree of the transaction affair of the query user; signing and sending a mining result ciphertext; and inquiring a user verification result source and performing decrypting. A digital signature technology is used for verifying the user identity, the cloud server decryption capability is weakened based on a homomorphic encryption algorithm, the privacy of user outsourcing data and the privacy of a mining result are protected, and the safety and reliability of cloud outsourcing data mining are improved.
Owner:XIDIAN UNIV
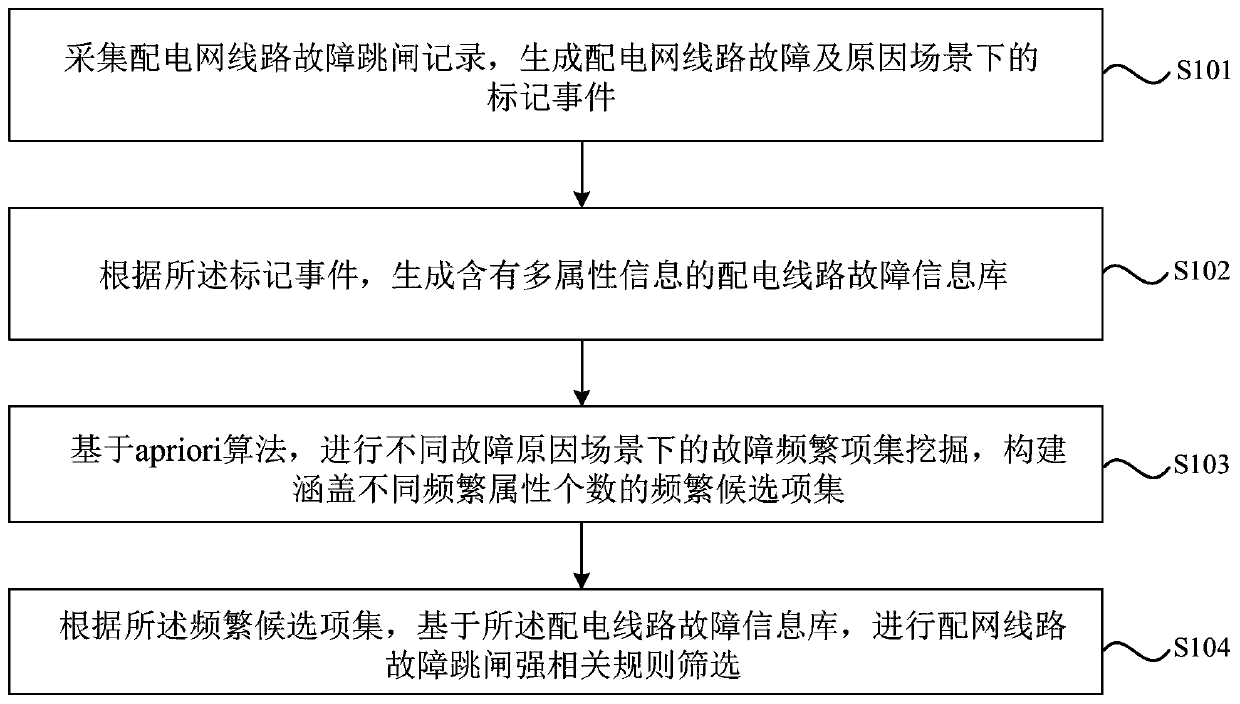
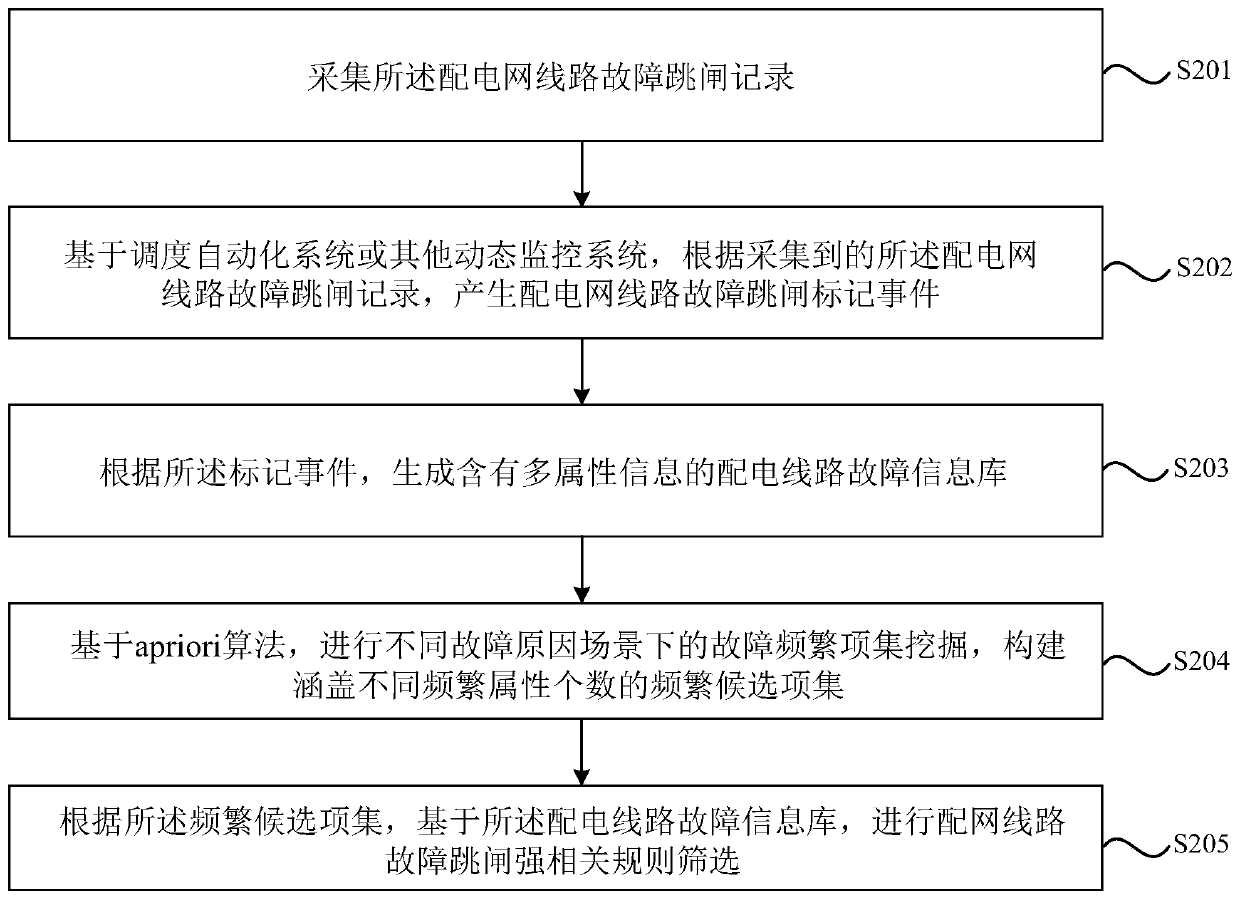
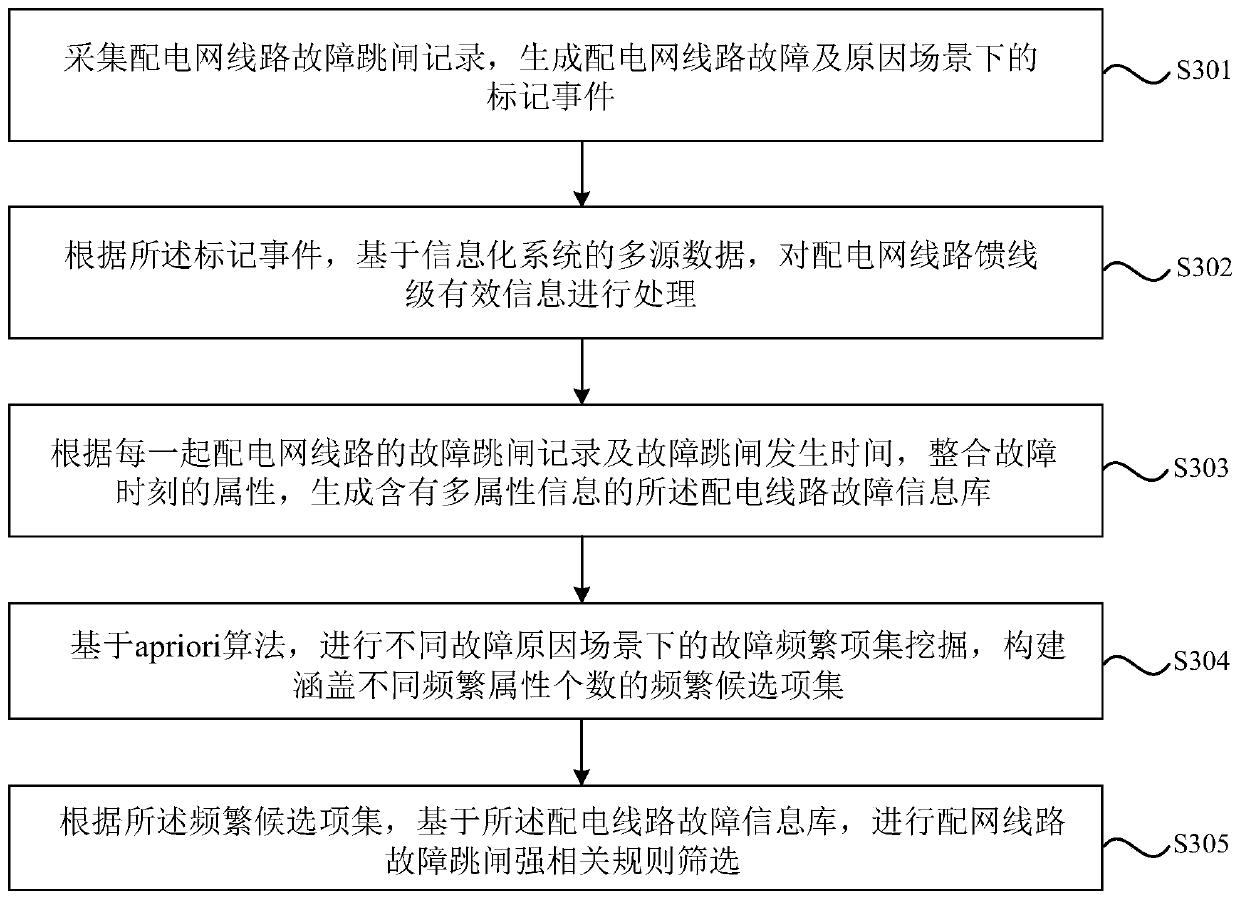
Power distribution network line fault rule mining method, system and medium of frequent item set
PendingCN110244184AReduce the scope of patrol operation and maintenanceImprove operational reliabilityFault locationInformation repositoryMultiple attribute
The embodiment of the invention discloses a power distribution network line fault rule mining method, system and medium of a frequent item set. The method comprises the following steps: collecting a power distribution network line fault tripping record, and generating a mark event under a power distribution line fault and reason scene; generating a power distribution network line information base containing multiple attribute information according to the mark event; based on an apriori algorithm, performing fault frequent item set mining under different fault reason scenes, and constructing the frequent item set covering different frequent attribute numbers; and performing power distribution line fault tripping strong-related rule screening based on the power distribution line fault information base according to the frequent candidate set. Through the technical scheme disclosed by the embodiment of the invention, the existing power distribution fault sample data is integrated with the frequent item set data mining method, thereby mining a fault association rule, reducing the power distribution network patrolling operation and maintenance range, and solving the problem that the patrolling and overhauling charge of the whole region line of the existing power distribution network and the equipment is huge.
Owner:JIANGSU ELECTRIC POWER CO +3
Mining method, device and system of frequent item set
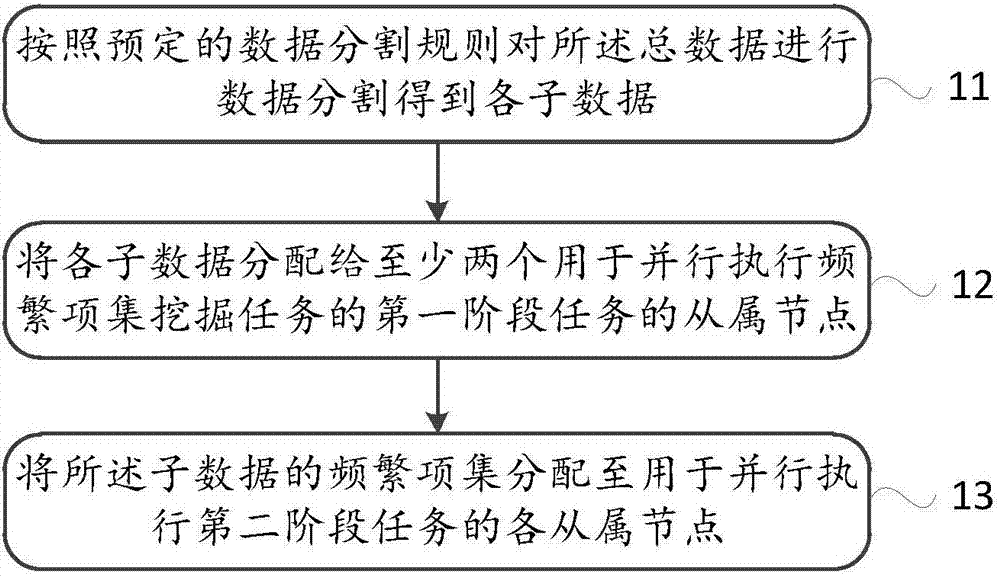
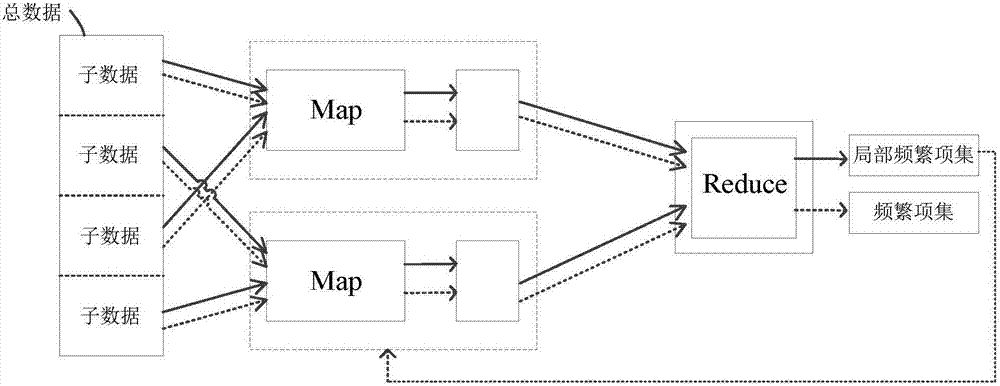
InactiveCN107291734AImprove digging efficiencySpecial data processing applicationsItem set miningBig data
The invention discloses a mining method of a frequent item set. The mining method is used for solving the problem in the prior art that a plenty of time is consumed by mining the frequent item set in big data. The mining method of the frequent item set comprises the steps of carrying out data segmentation for total data to obtain each sub-data after a main node receives a frequent item set mining task which is appointed by a client and aims at the total data; distributing each sub-data to at least two slave nodes which are used for performing a first-stage task in parallel, wherein the first-stage task specifically comprises the sub-step of carrying out frequent item set mining for the distributed sub-data by utilizing the frequent item set mining algorithm to obtain a local frequent item set; and by the main node, distributing the frequent item set to each slave node which is used for performing a second-stage task in parallel, wherein the second-stage task comprises the sub-step of obtaining the frequent item set of the total data by each slave node which is used for performing the second-stage task. The invention also discloses a mining device of the frequent item set and a mining system of the frequent item set.
Owner:ADVANCED NEW TECH CO LTD
Frequent item set mining method for game prop recommendation
InactiveCN106815302AReduce complexityReduce the number of merge comparisonsResource allocationSpecial data processing applicationsReducerItem set mining
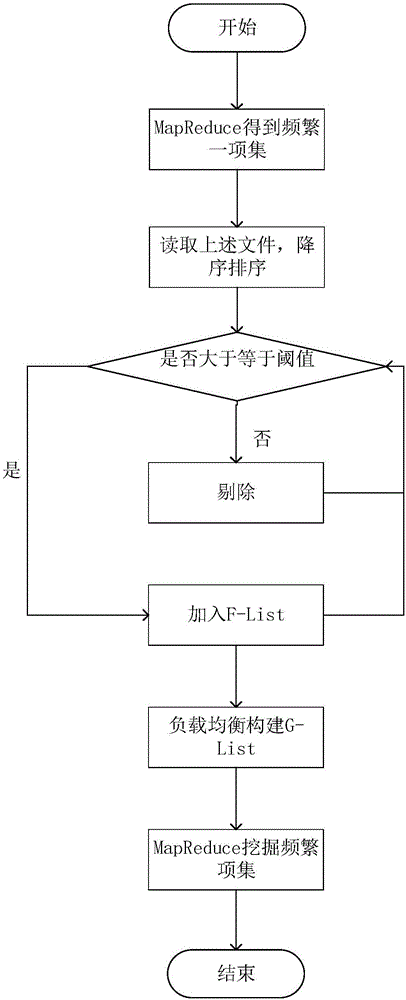
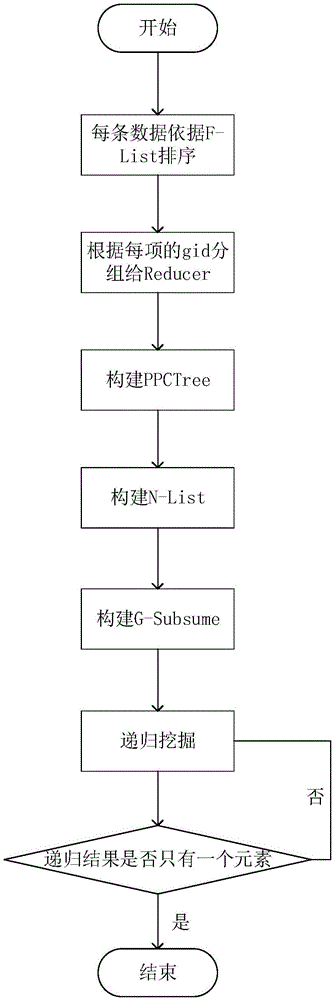
The invention discloses a frequent item set mining method for game prop recommendation and belongs to the technical field of data mining. The frequent item set mining method comprises the following steps: firstly, acquiring occurrence times of each item on MapReduce, performing sequencing and threshold screening to reject unqualified items and obtain F-List, dividing the F-List so as to obtain G-List, according to division of G-List, transmitting data to Mapper, performing Mapper processing, transmitting data to Reducer, and performing MapReduce mining on the Reducer; and for mining, firstly acquiring PPCTree on each Reducer, after PPCTree is obtained, acquiring L-List and G-Subsume of corresponding items on each Reducer, and finally performing recursion according to the N-List and the G-Subsume, thereby obtaining a final frequent item set. By adopting the frequent item set mining method, the data is reasonably divided according to load prediction, and thus load balance can be ensured; and as the recursion mining process is optimized, the dense data mining time can be greatly shortened.
Owner:HUAZHONG UNIV OF SCI & TECH
Weighted frequent item set mining algorithm for precision marketing
PendingCN109558435ANarrow down the search spaceReduce in quantityDigital data information retrievalSpecial data processing applicationsE-commercePrecision marketing
The invention provides a weighted frequent item set mining algorithm for precision marketing. According to the invention, firstly, aiming at the problem that a marketing strategy of a sales enterprisehas difficulty in finding a client and the problems of the high customer acquisition cost, the low operation efficiency and the like, the early purchase behaviors of customers and the access behaviors of the customers on an e-commerce platform are analyzed, and different purchase probability values are given to behaviors of purchasing commodities, clicking and browsing, collecting commodities, joining shopping carts and the like so as to reflect preference degrees of the users for different projects; secondly, by endowing the commodity with different weights according to the proportion of theprofit of the commodity to the profit of the enterprise, the importance degree of different commodities to the enterprise are reflected. According to the method, the time efficiency of the algorithmis improved, the frequent item set information with important significance to users can be quickly mined from massive uncertain data, and the accurate marketing is achieved.
Owner:NANJING UNIV OF POSTS & TELECOMM
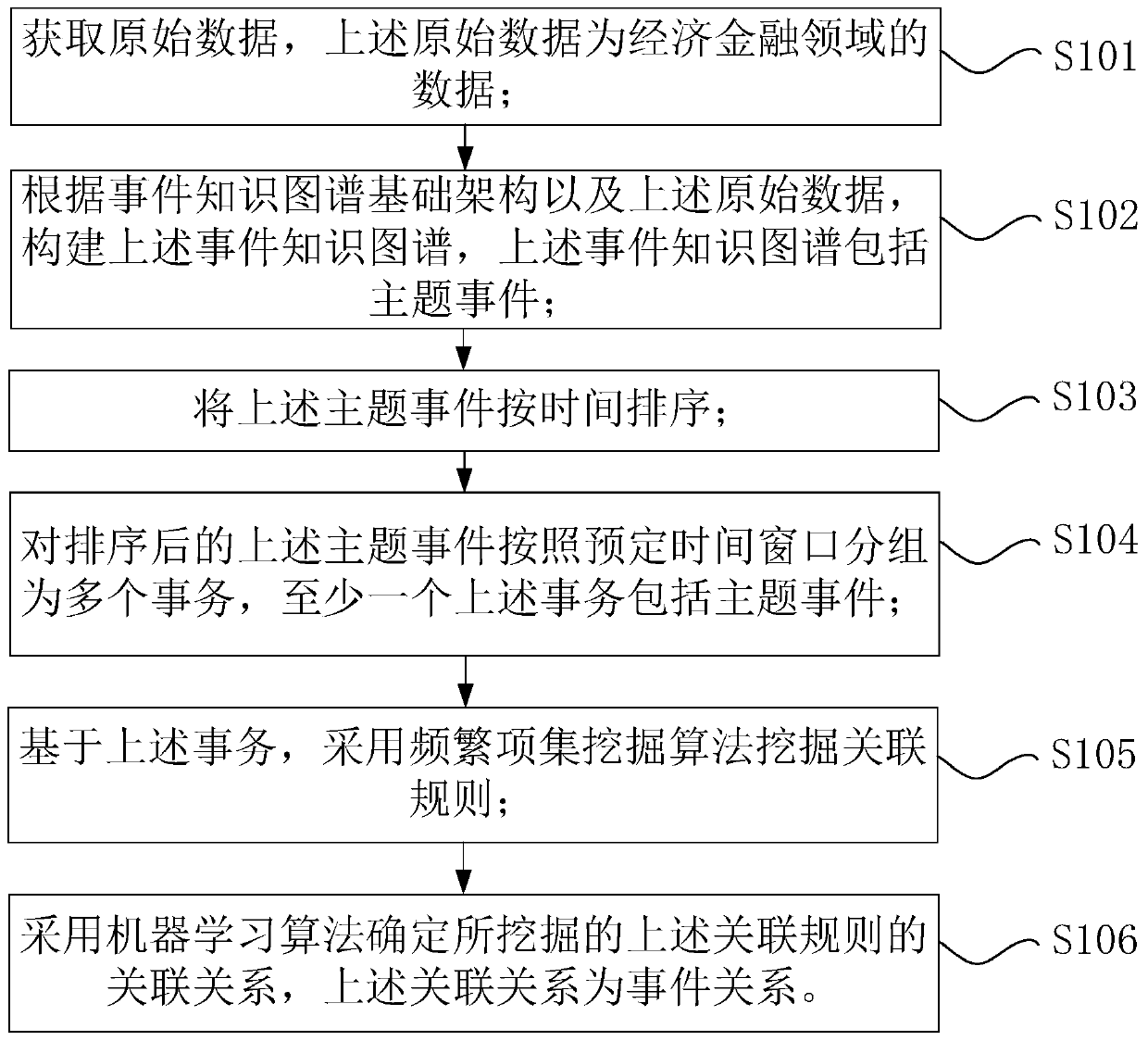
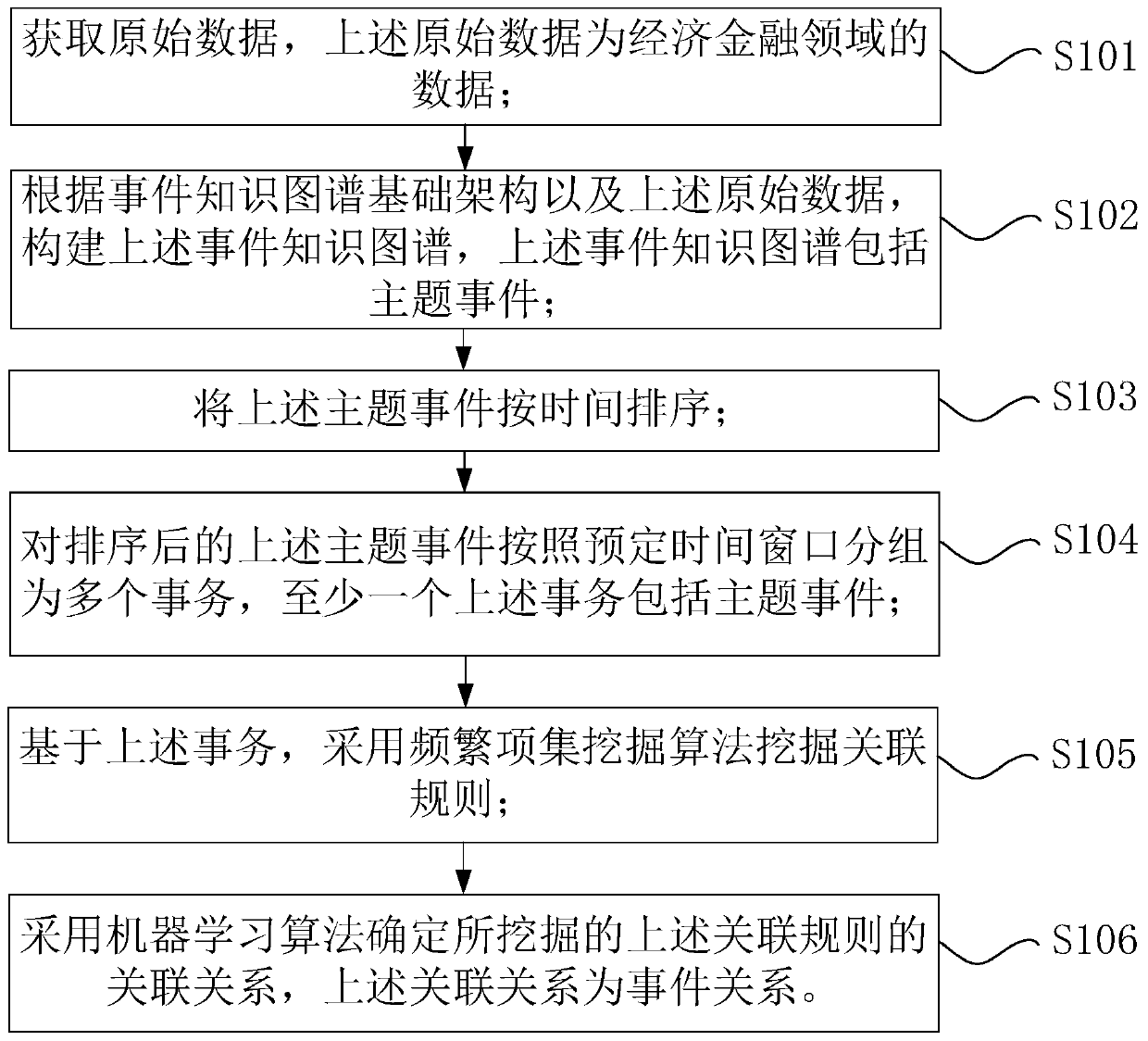
Method and device for automatically extracting relation between knowledge graph events in economic field
PendingCN111159428AQuick judgmentSpecial data processing applicationsSemantic tool creationOriginal dataTimsort
The invention provides a method and device for automatically extracting relation beteween knowledge graph events in an economic field , a storage medium and a processor. The method comprises the steps: obtaining original data, wherein the original data is data in the field of economy and finance; according to the event knowledge graph infrastructure and the original data, constructing an event knowledge graph, wherein the event knowledge graph comprises theme events; sorting the theme events according to time; grouping the sorted theme events into a plurality of transactions according to a preset time window, wherein at least one transaction comprises the theme events; based on the affairs, mining association rules by adopting a frequent item set mining algorithm; and determining an association relation of the mined association rules by adopting a machine learning algorithm, wherein the association relation is an event relation. According to the method, the association rules are minedthrough a frequent item set mining algorithm, then the association relation of the mined association rules is determined through a machine learning algorithm, and compared with a judgment method in the prior art, the method can achieve rapid judgment of the event relation.
Owner:智慧神州(北京)科技有限公司
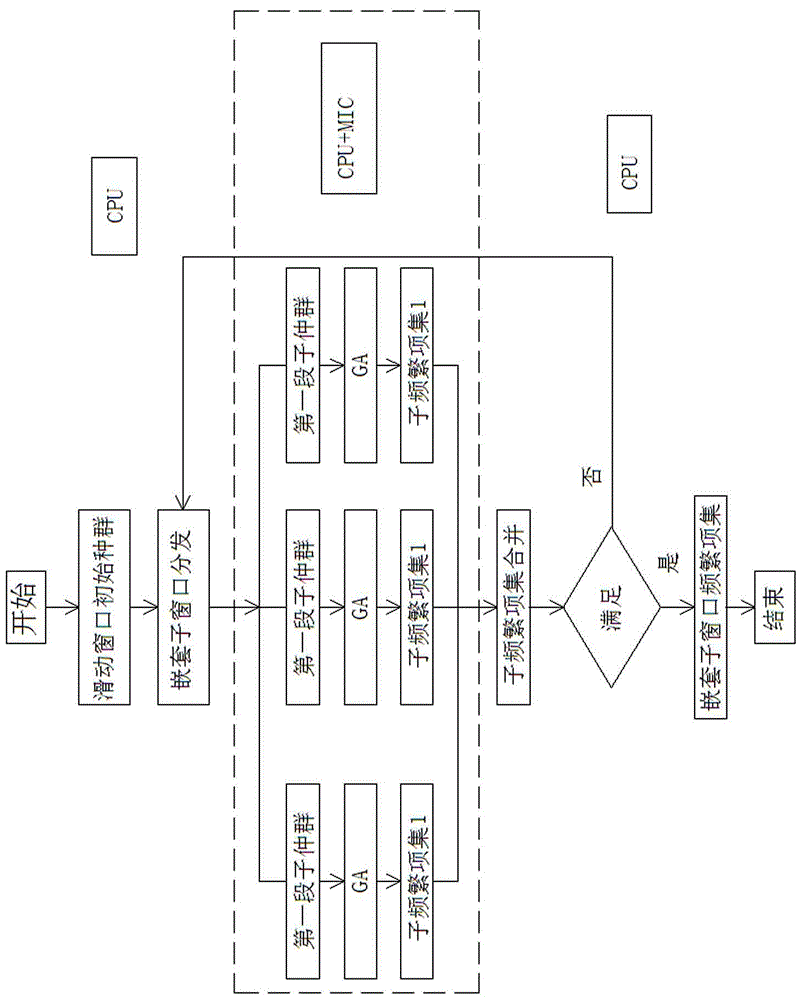
Recent data stream frequent item set mining method based on CPU+MIC (Central Processing Unit+ Many Integrated Core) cooperative computing
InactiveCN105740457AExcavate accuratelyReasonable designEnergy efficient computingSpecial data processing applicationsData streamElectric power
The invention discloses a recent data stream frequent item set mining method based on CPU+MIC (Central Processing Unit+ Many Integrated Core) cooperative computing. The method is implemented through a CPU and an MIC coprocessor. The method is based on the CPU+MIC cooperative computing. The method comprises the following steps: setting an initial population, wherein individuals in the population are a series of frequent item sets to be selected; implementing a searching process based on crossover, variation and selection operations of a genetic algorithm; and traversing multiple generations of processing to obtain final frequent item sets. Compared with the prior art, the recent data stream frequent item set mining method based on the CPU+MIC cooperative computing has the advantages of reasonable design, easiness and convenience in operation, high mining efficiency and the like. According to the method, data streams in a nested window are processed through the genetic algorithm based on the CPU+MIC cooperative computing, so that a frequent mode in the data streams in the nested window can be rapidly and accurately mined. The method can be applied to decision making in industries of water conservation runoff analysis, power load, financial information and the like.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
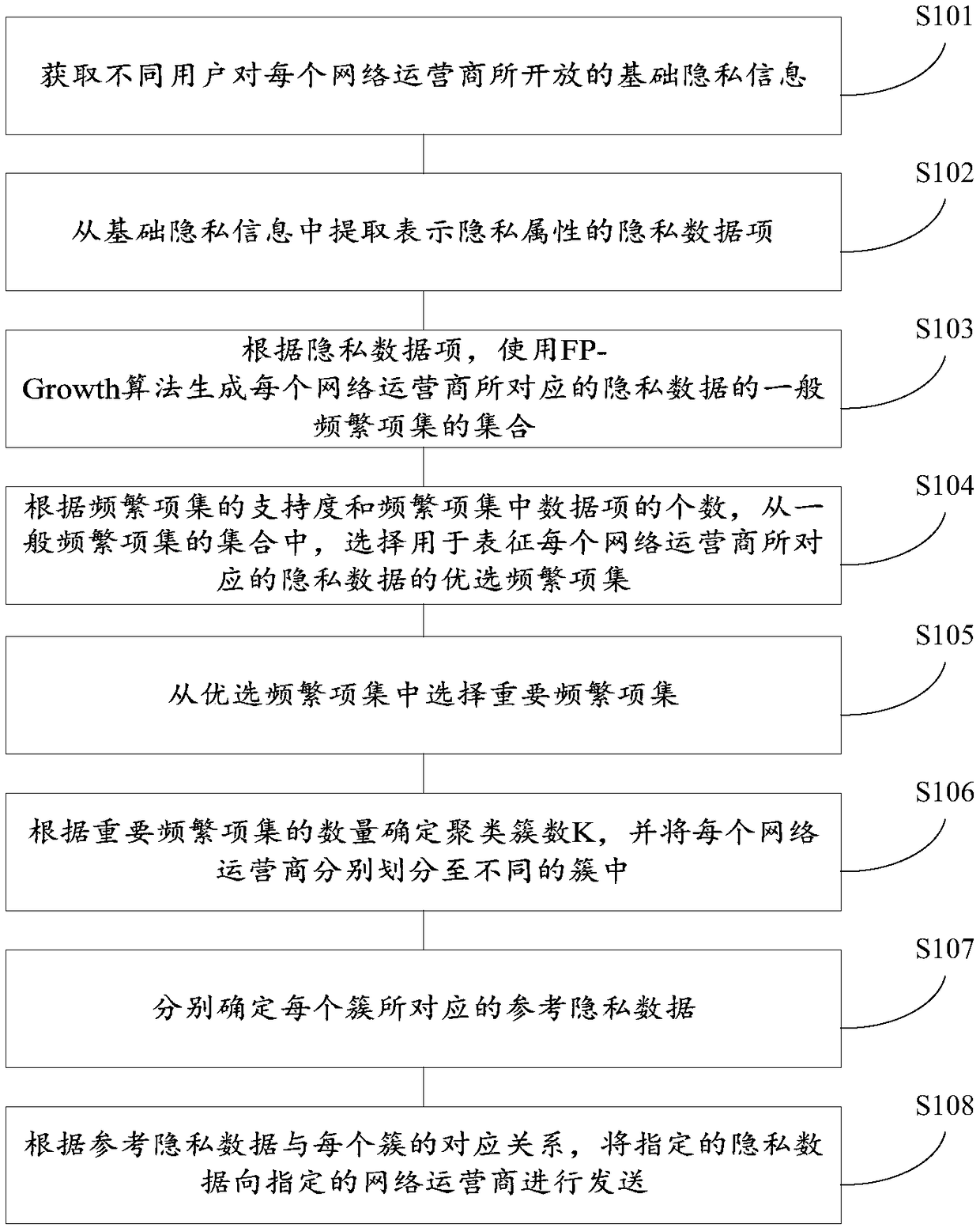
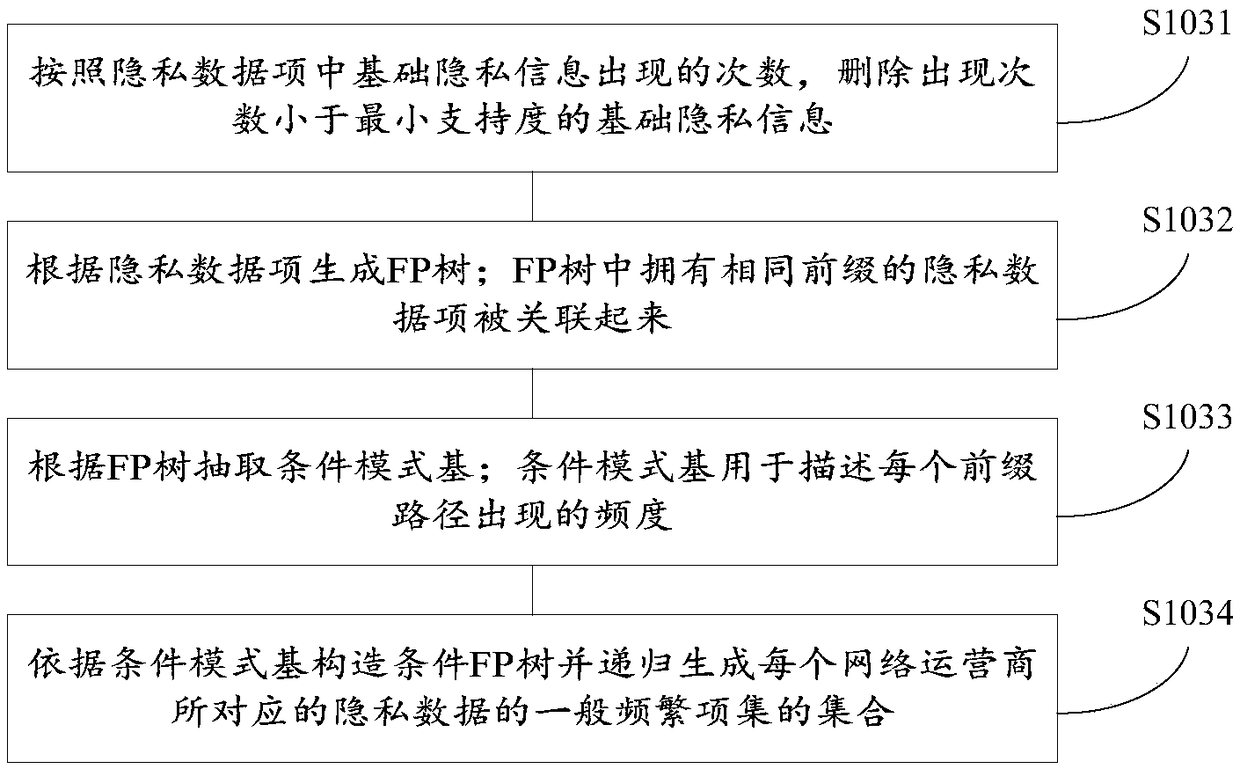
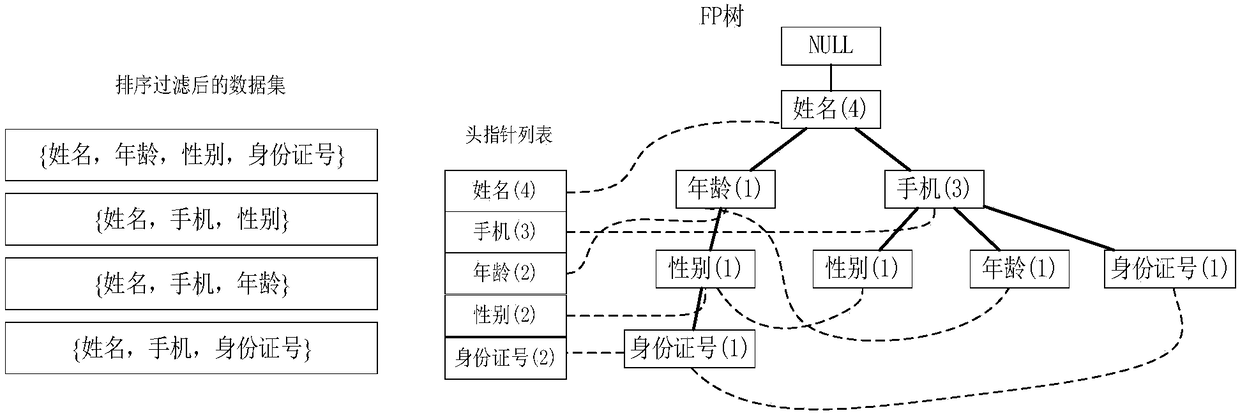
Private data supplying method and device
InactiveCN108830106ACharacter and pattern recognitionDigital data protectionCyber operationsPrivacy protection
The invention provides a private data supplying method and device, and relates to the field of privacy protection. The private data supplying method comprises the steps that firstly, private data (regarding different network operators, the opened private data of all users) of all the users is resumptively extracted, and private data items of the corresponding private data are generated; frequent item set mining is conducted on the private data items, and a frequent item set is utilized to represent the feature portion of the private data about one network operator; then the frequent item set is utilized to conduct clustering, and the network operators with similar private data are gathered as a cluster; finally, representative reference private data is extracted from the private data corresponding to each network operator cluster, taken as data capable of being directly acquired by the network operators, and sent to the designated network operators to complete uploading of the privatedata. The mode of uploading the private data can avoid the situation to a certain extent that the private data of the users is excessively disclosed.
Owner:CHINA ELECTRONICS CORP 6TH RES INST
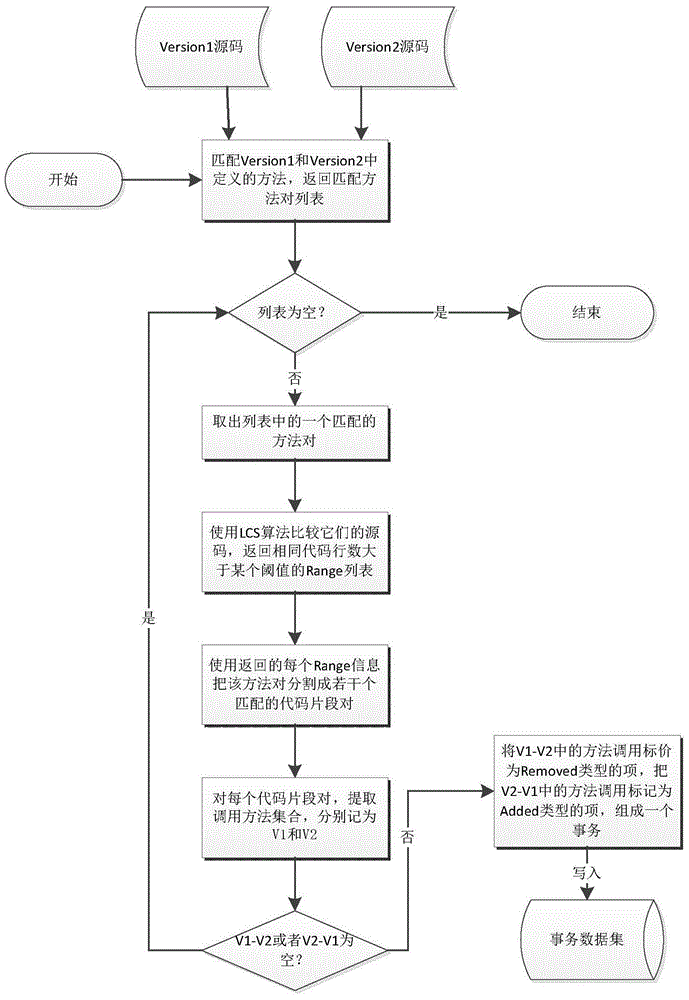
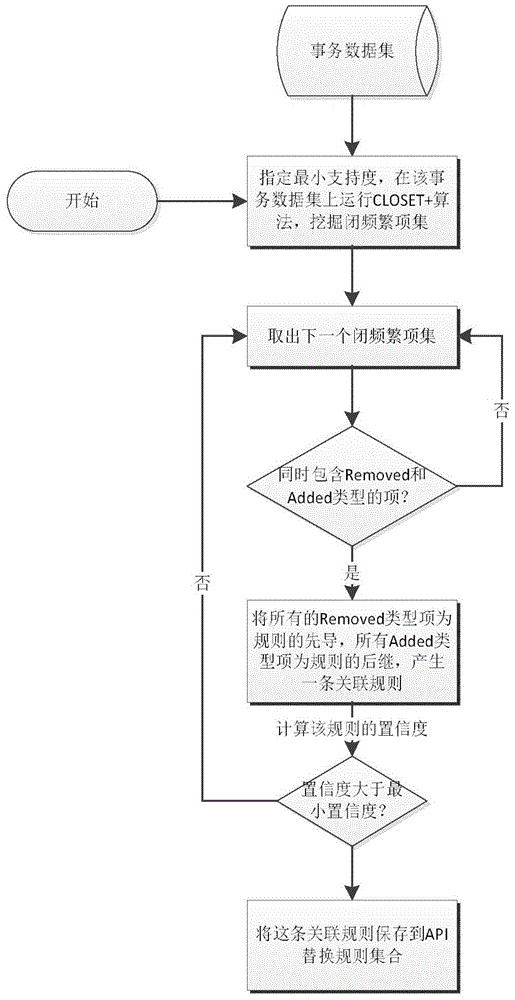
Fine-granularity method for generating API substitution rules based on frequent item set mining
ActiveCN104820587AReduce inaccuracyReduce false positive (False Positive) problemSpecific program execution arrangementsGranularityRule of replacement
The present invention discloses a fine-granularity method for generating API substitution rules based on frequent item set mining. The method is characterized by deducing the substitution rules of old and new versions of API in application by using a frequent item set mining algorithm according to the change of the dispatching of the earlier and latest versions of APIs in a class library. When services are extracted from each matched method pair, original codes of the matched method pair are compared by an LCS algorithm, a plurality of matched code segment pairs are generated by taking a point in which the number of same code lines is greater than the Range of the specified threshold as a division point, then the services are generated by change of the dispatching relation of each pair of code segments. Compared against the solution of generating the change of the dispatching relation by taking the method as a unit, the context information of the dispatching method is retained to a certain extent; the accuracy of the services is improved; according to the method, frequency item sets are generated by applying the frequent item set mining algorithm to the generated service sets, then association rules are generated, such that more various API substitution rules can be generated.
Owner:NANJING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com