Patents
Literature
377results about How to "Avoid performance bottlenecks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
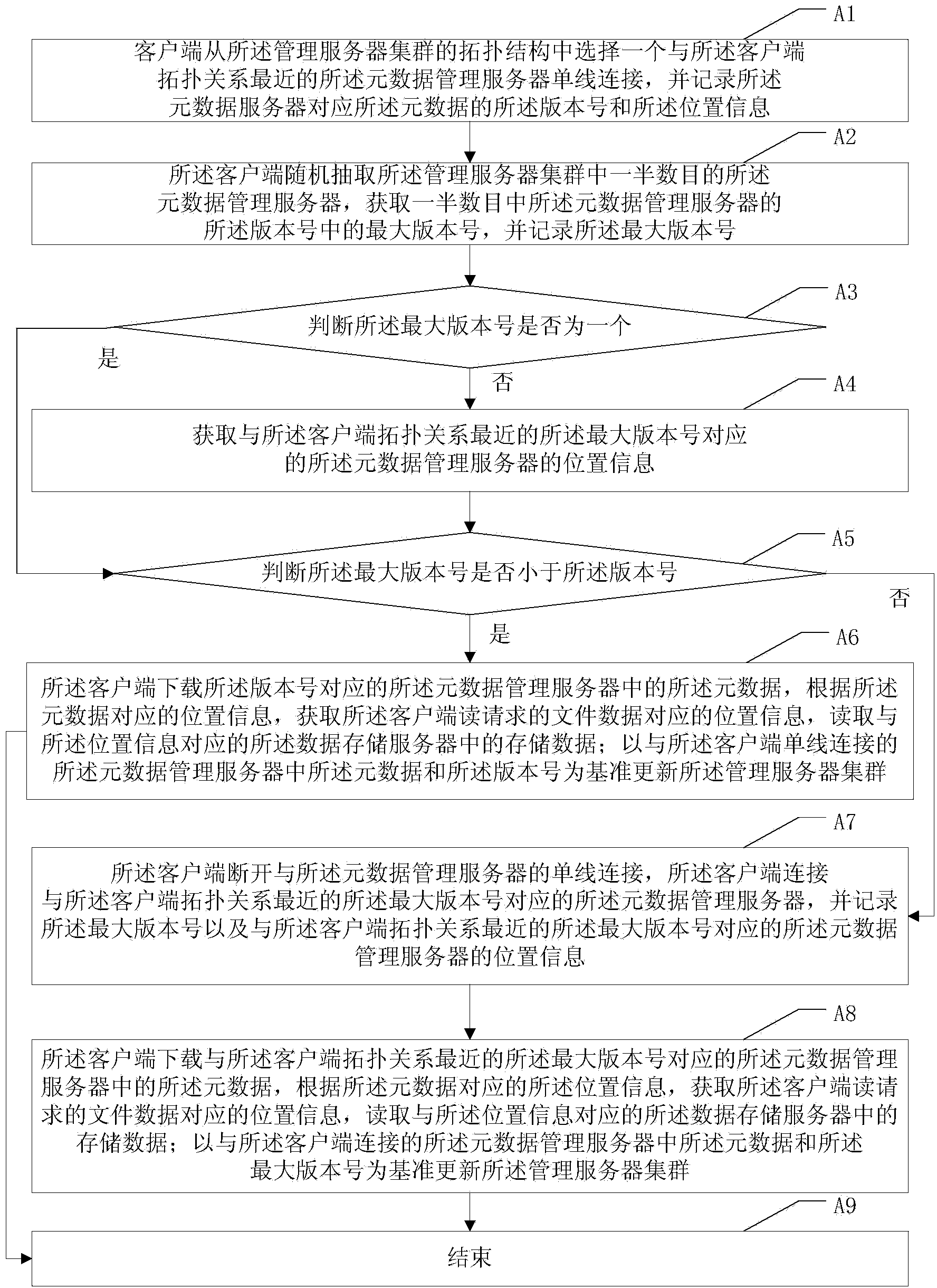
Distributed file system metadata management method facing to high-performance calculation
ActiveCN103150394AInhibit migrationLoad balancingTransmissionSpecial data processing applicationsDistributed File SystemMetadata management
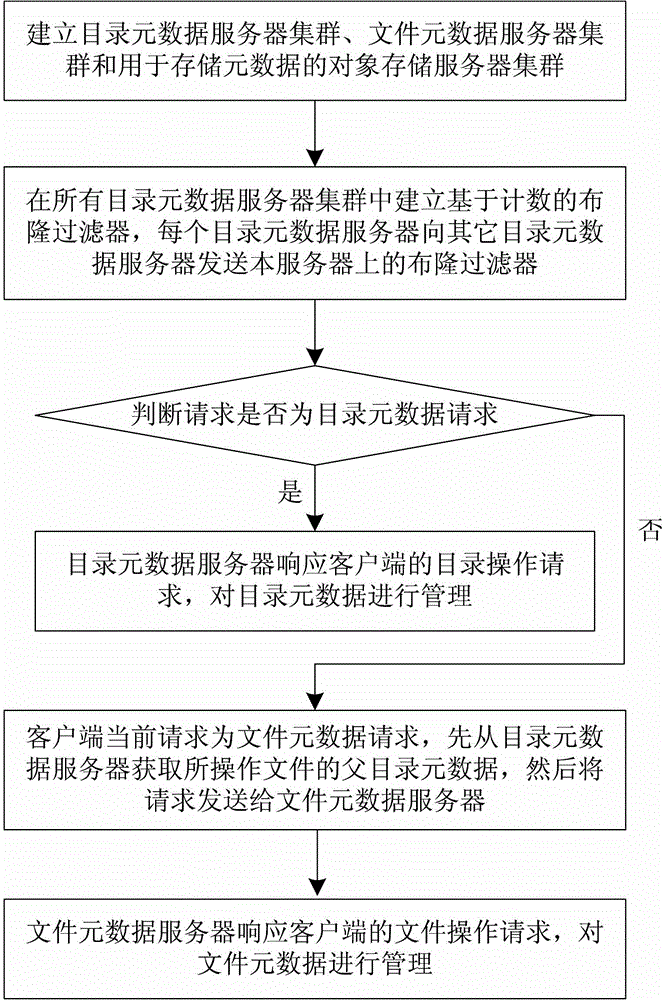
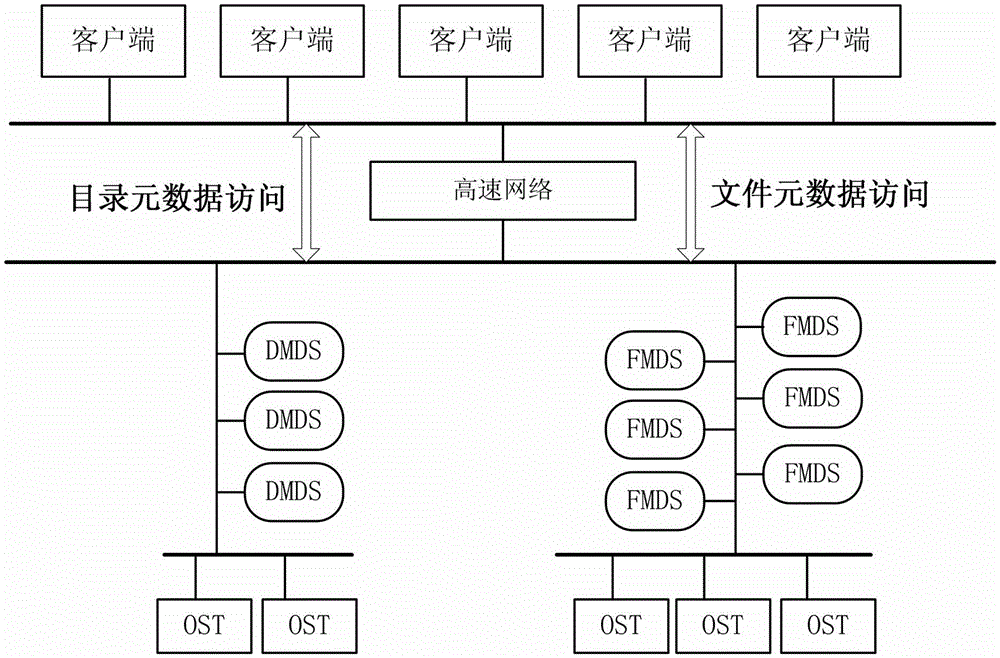
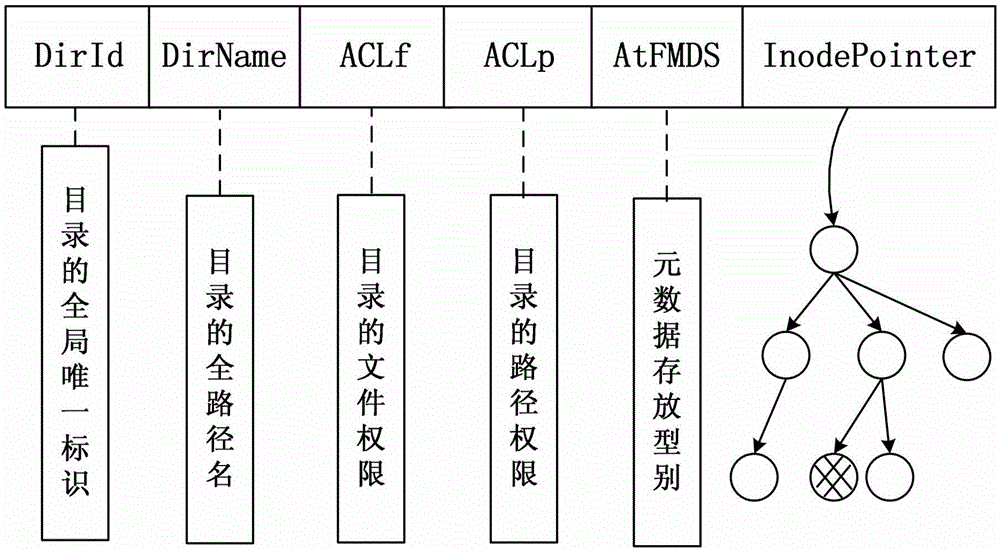
The invention discloses a distributed file system metadata management method facing to high-performance calculation. The method comprises the following steps of: 1) establishing a catalogue metadata server cluster, a file metadata server cluster and an object storage server cluster; 2) establishing a global counting-based bloom filter in the catalogue metadata server cluster; 3) when the operation request of a client side arrives, skipping to execute step 4) or 5); 4) enabling the catalogue metadata server cluster to respond to the catalogue operation request of the client side to manage the catalogue metadata; and 5) enabling the file metadata server cluster to respond to the file operation request of the client side to manage the file metadata data. According to the distributed file system metadata management method disclosed by the invention, the metadata transferring problem brought by catalogue renaming can be effectively solved, and the distributed file system metadata management method has the advantages of high storage performance, small maintenance expenditure, high load, no bottleneck, good expansibility and balanced load.
Owner:NAT UNIV OF DEFENSE TECH
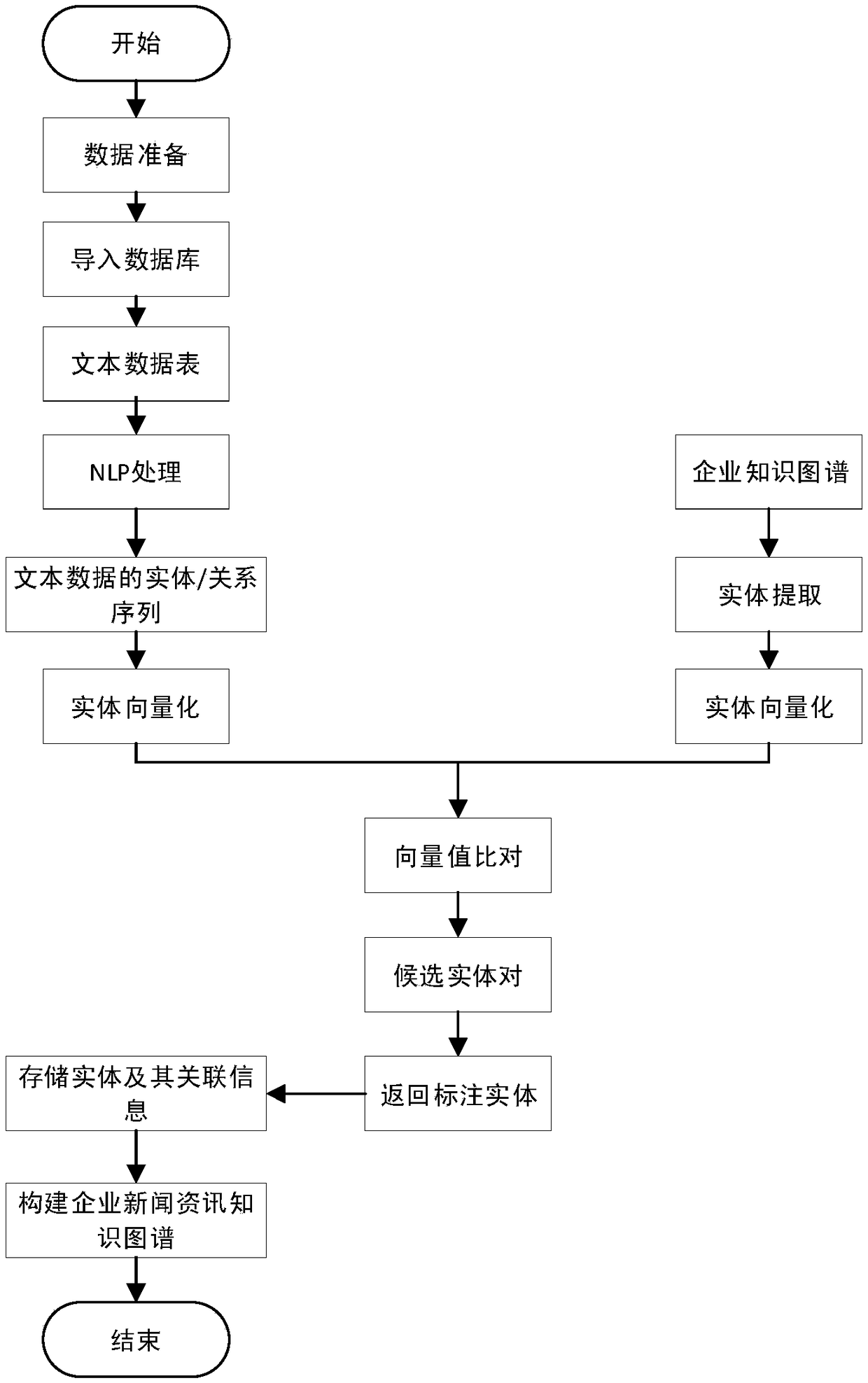
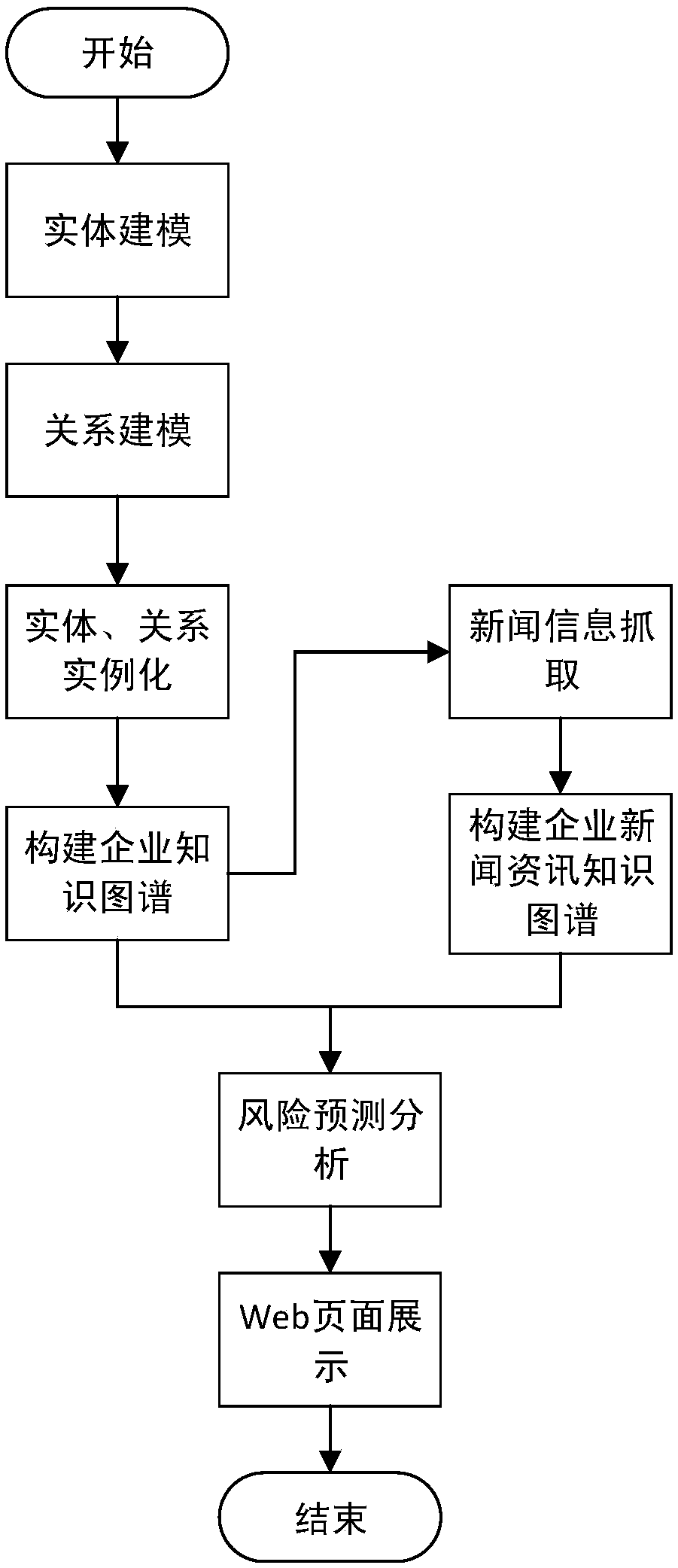
Knowledge graph-based enterprise risk prediction method and system
InactiveCN108596439ARealize knowledge extractionImplement storageResourcesSpecial data processing applicationsDatasourceKnowledge extraction
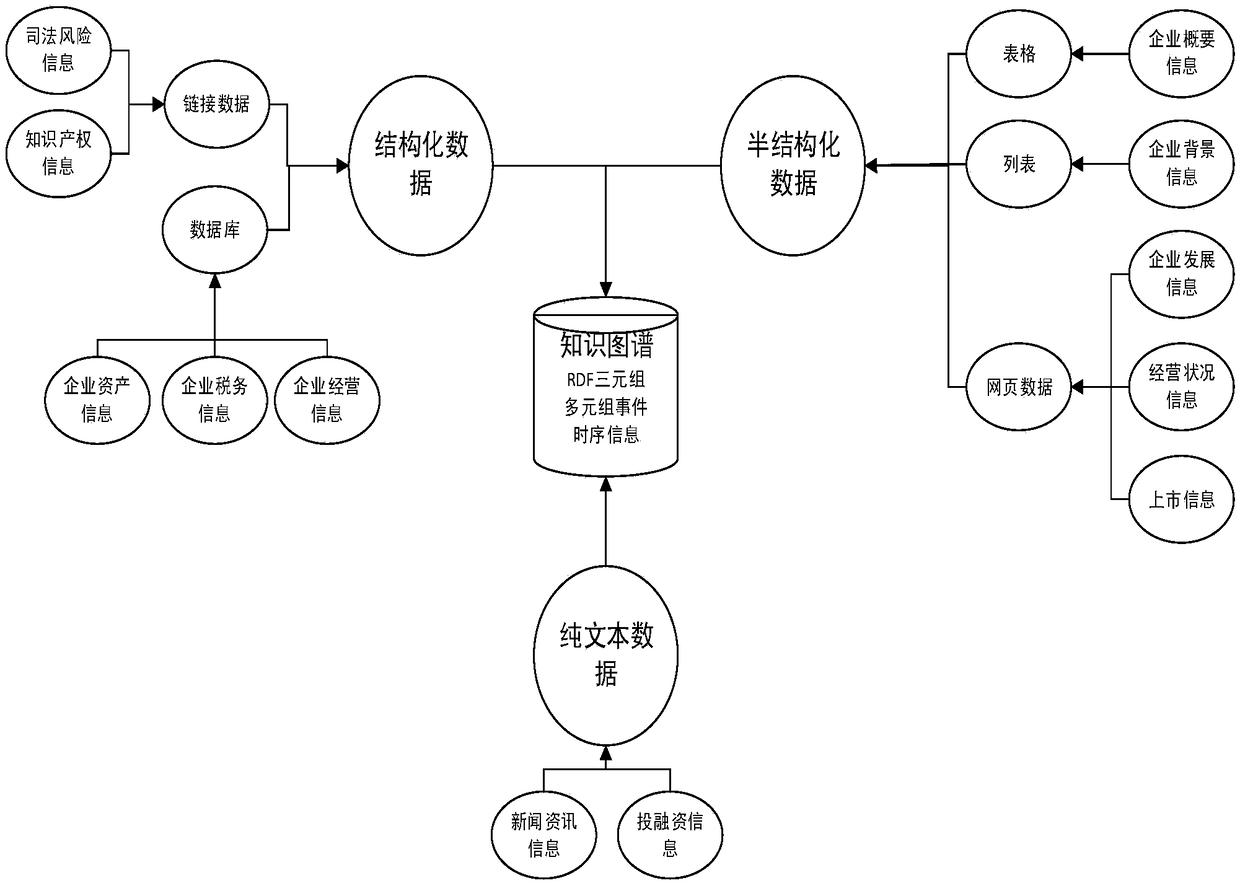
The invention discloses a knowledge graph-based enterprise risk prediction method and system. The method comprises the steps of 1) constructing entities of an enterprise knowledge graph, establishingrelationships between the entities, and extracting knowledge from set data sources to form the enterprise knowledge graph; 2) capturing news information of enterprises and related entities, processingthe captured news information based on the enterprise knowledge graph, marking relationships between the related entities and events, and storing marked information in a structured knowledge base toform an enterprise news information knowledge graph; and 3) performing enterprise risk prediction based on the enterprise knowledge graph and the enterprise news information knowledge graph. The blankof an existing knowledge graph in the field of enterprise risk analysis is filled; and the constructed enterprise knowledge graph and enterprise news information knowledge graph have relatively highpracticality.
Owner:BEIJING ZTE DIGITAL TECH
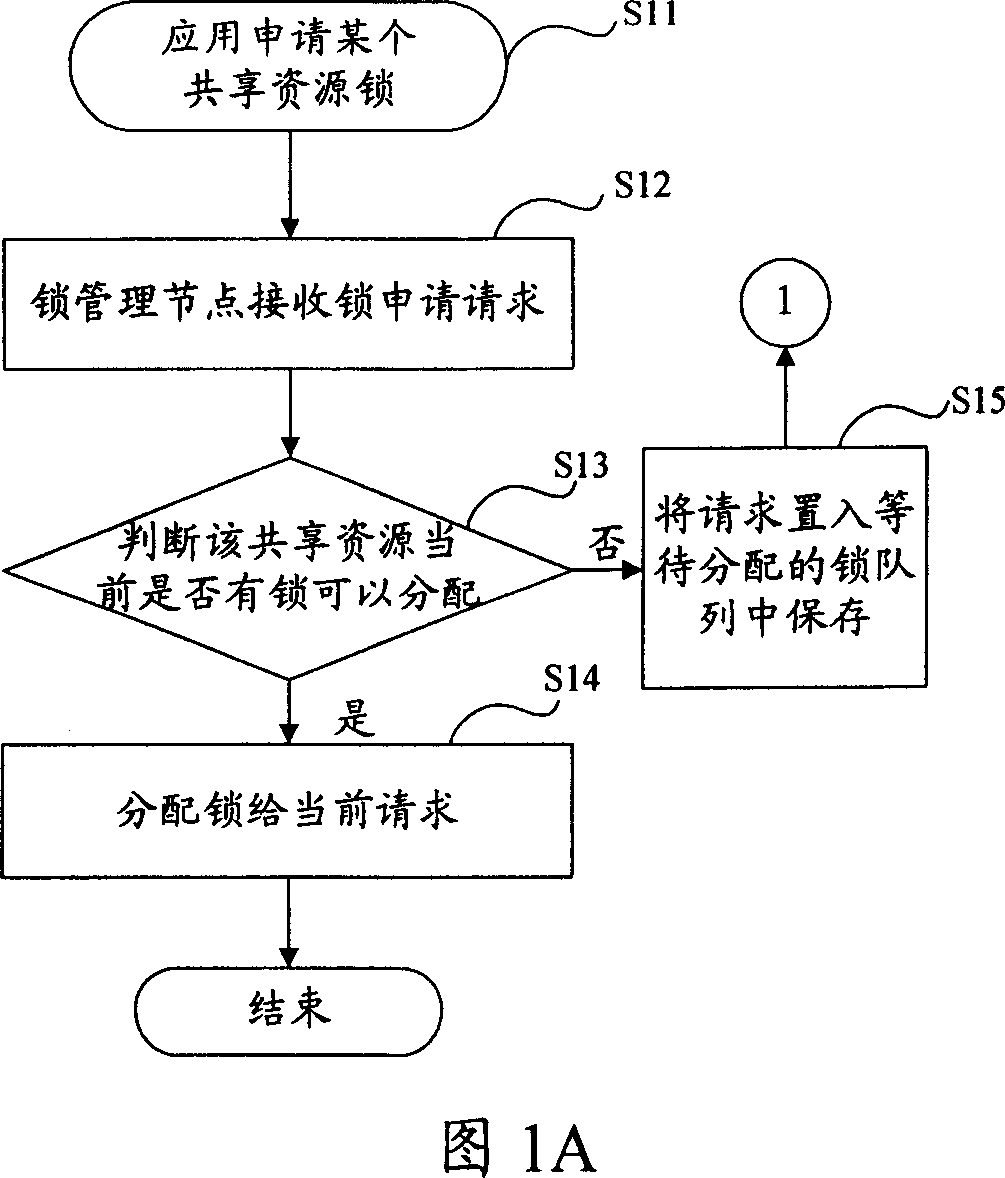
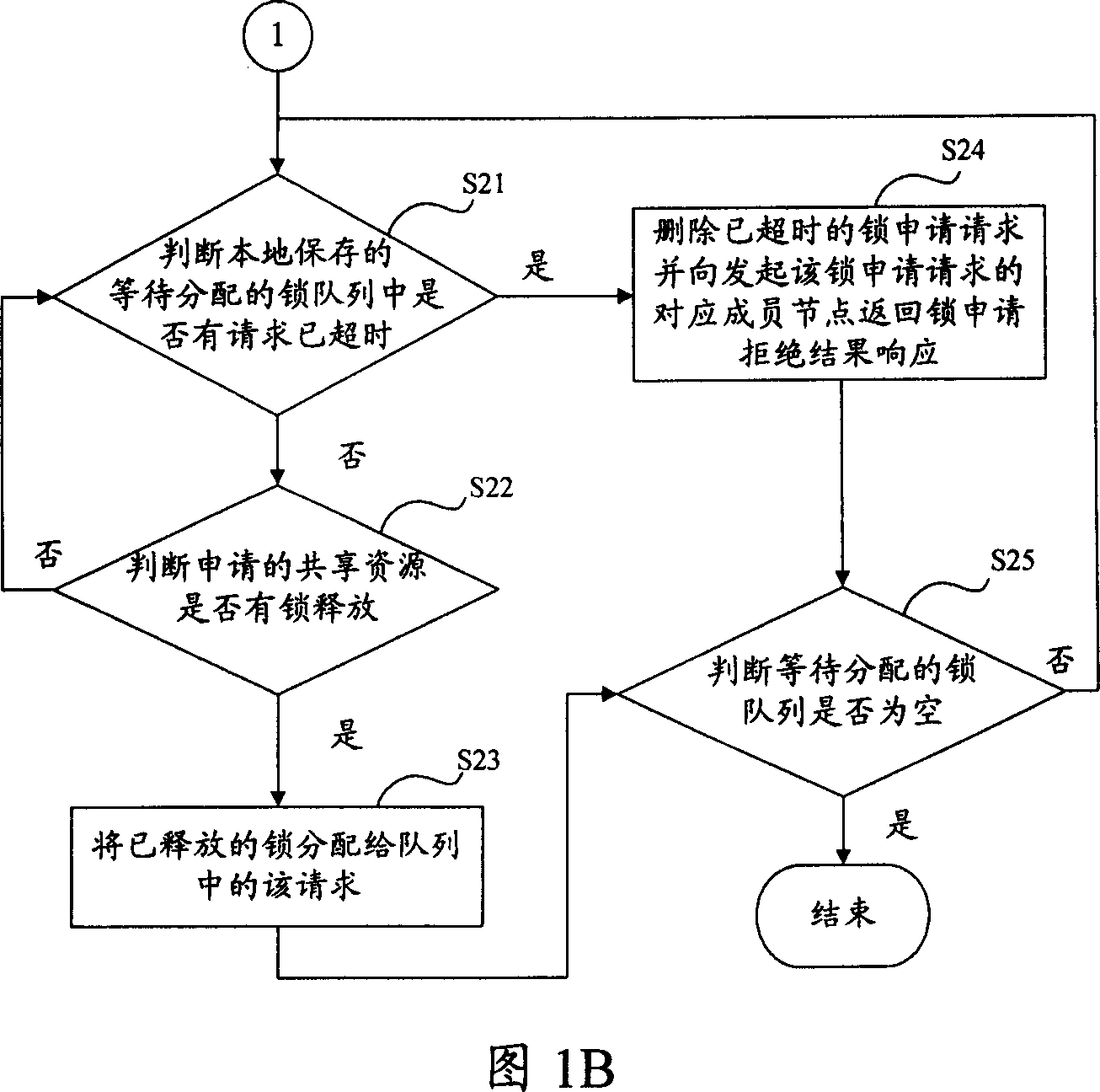
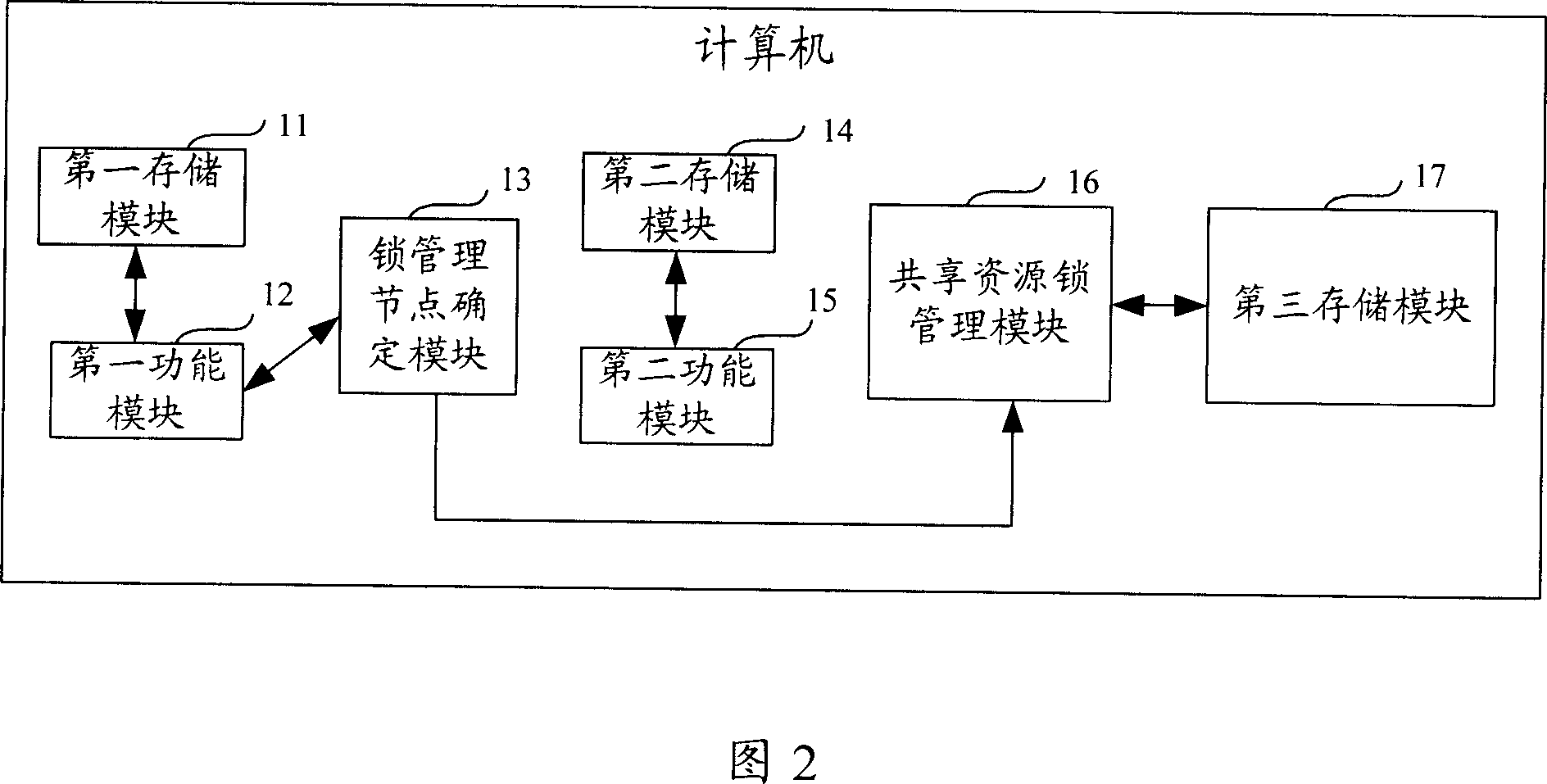
Method for distributing shared resource lock in computer cluster system and cluster system
ActiveCN1945539AAvoid performance bottlenecksTo achieve load balancingMultiprogramming arrangementsExtensibilityComputer cluster
This invention publishes a locked distribution method of shared resources in a type of computer integration system including: making more than one node of system members as locking management node of all the shared resources in the system, meanwhile each shared resource matches a locking management node; when one apply asks for applicant or release shored resources lock, and send applicant to the corresponding locking management node of this shored resources, the corresponding locking management node will finish the distribution and release of lock's applicant. This invention also publishes the corresponding structure of computer integration system. The invention can be used for realizing high usable locking service in the integration, and it has a high expansibility and realizes a balance of load.
Owner:HUAWEI TECH CO LTD +1
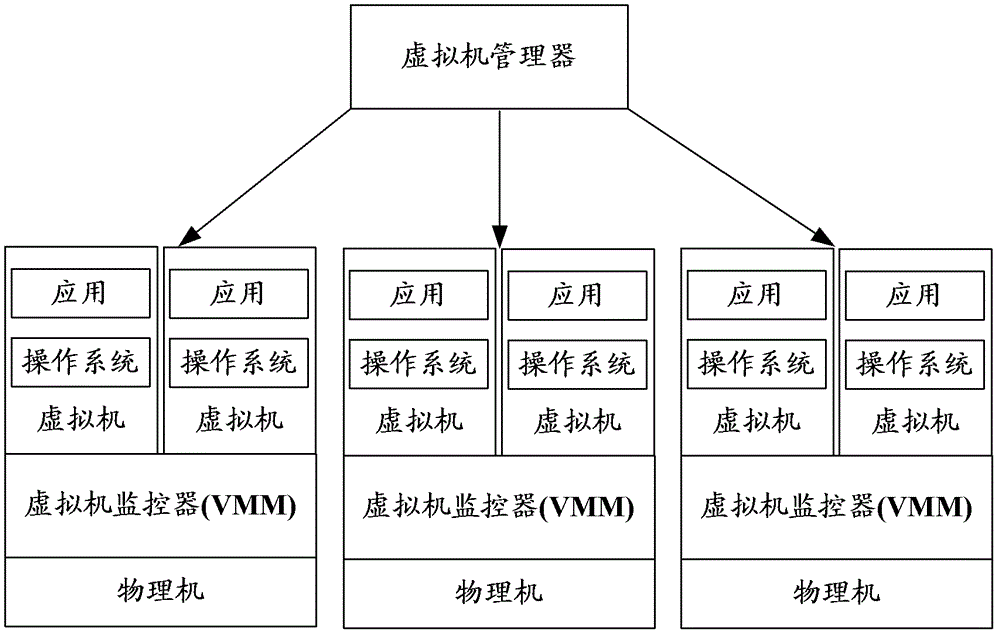
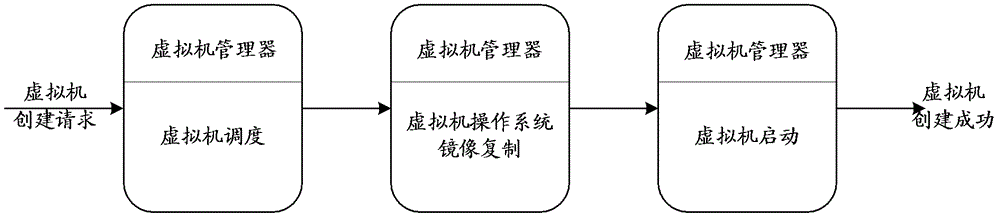
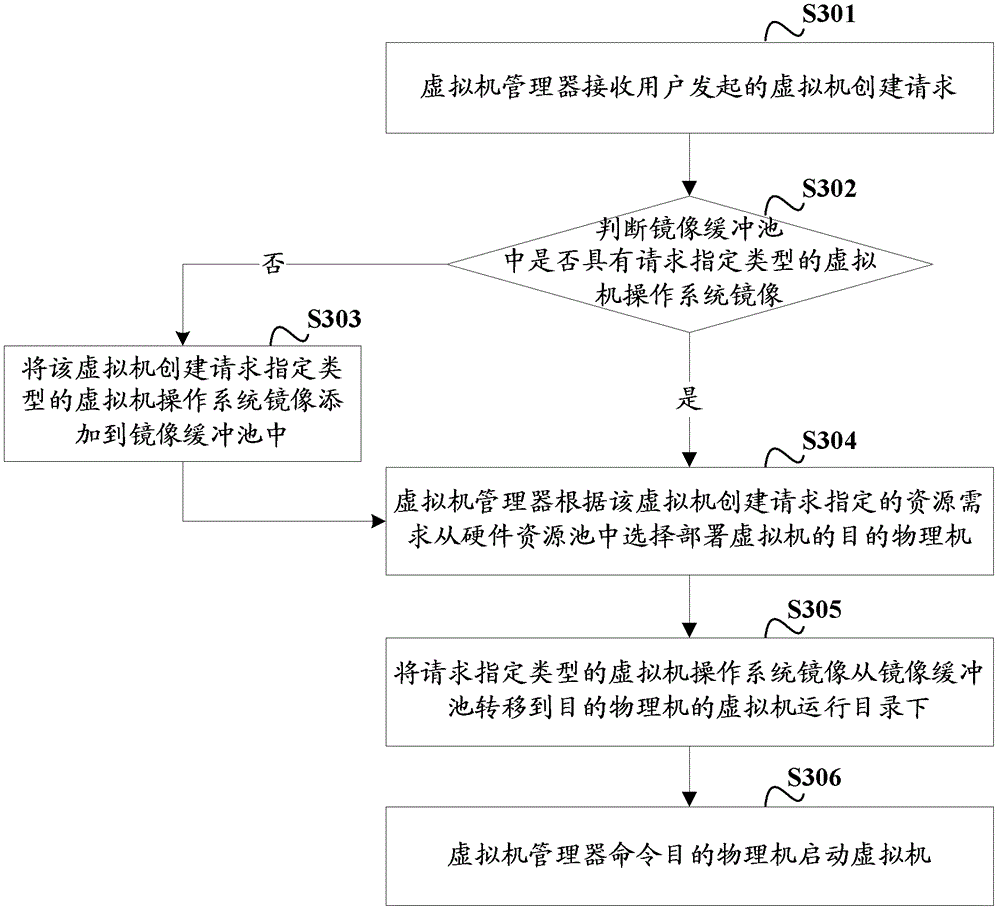
Creation method of virtual machine, management system of virtual machine and related equipment thereof
ActiveCN103067425AAvoid performance bottlenecksShorten the timeTransmissionResource poolImage storage
The invention discloses a creation method of a virtual machine, a management system of the virtual machine and related equipment of the management system. The creation method of the virtual machine, the management system of the virtual machine and related equipment thereof are used for improving performance of the network and an image storage server, and shortening the consumed time to create the virtual machine. The creation method of the virtual machine includes that receiving creation request initiated by a user, confirming a specified type of the virtual machine operating system image requested by the virtual machine creation in an image buffer pool, selecting an objective physical machine to deploy the virtual machine in a hardware resource pool composed of a large number of physical machines according to the creation request of the virtual machine for specified resource requirements, wherein the image buffer pool is built in hardware resources and composed of all physical machines for catching various types of virtual machine operating system images; transferring the specified type of the virtual machine operating system image requested by the virtual machine creation in the image buffer pool to virtual machine running directories of the physical machines; and ordering the physical machine to start the virtual machine.
Owner:CHINA MOBILE COMM GRP CO LTD
User access method and device based on SSL (Secure Socket Layer) VPN (Virtual Private Network) gateway cluster
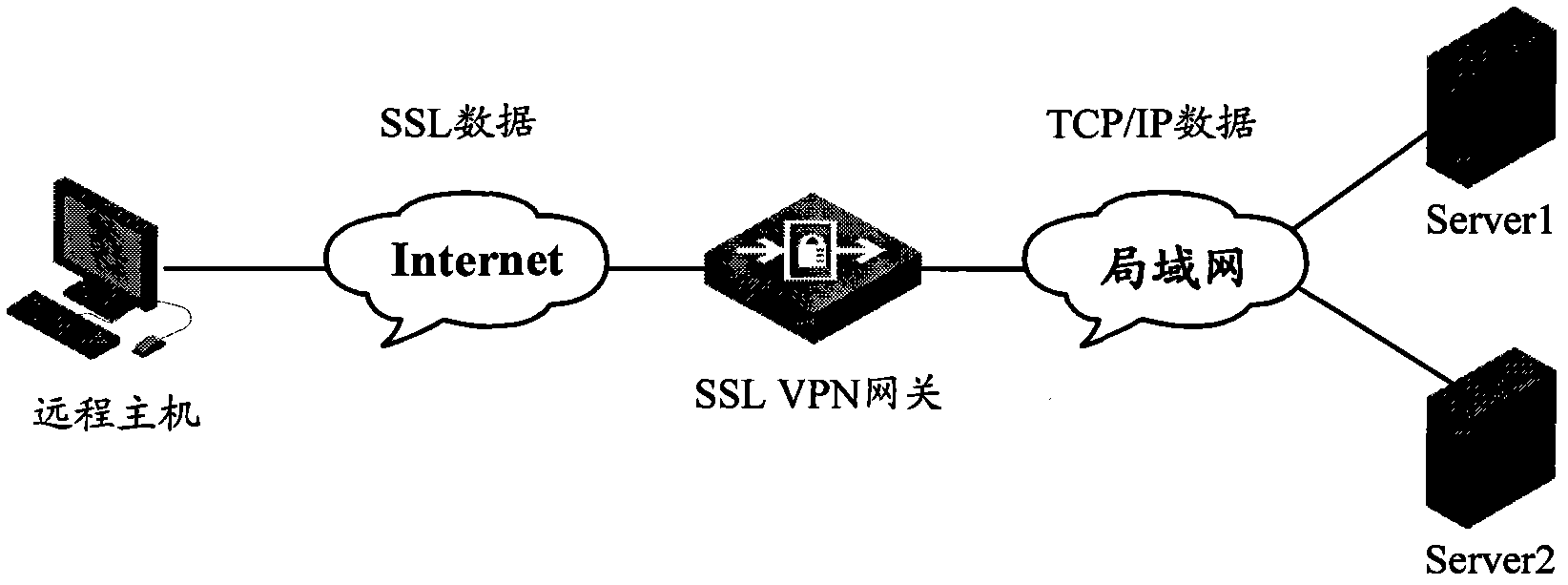
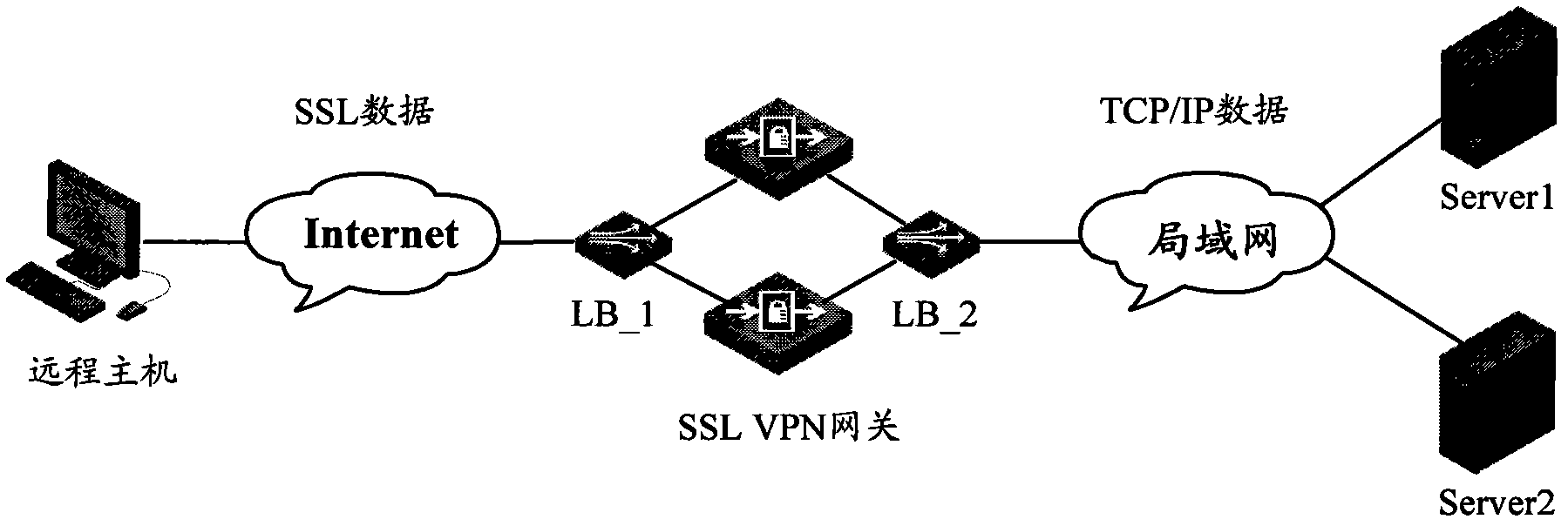
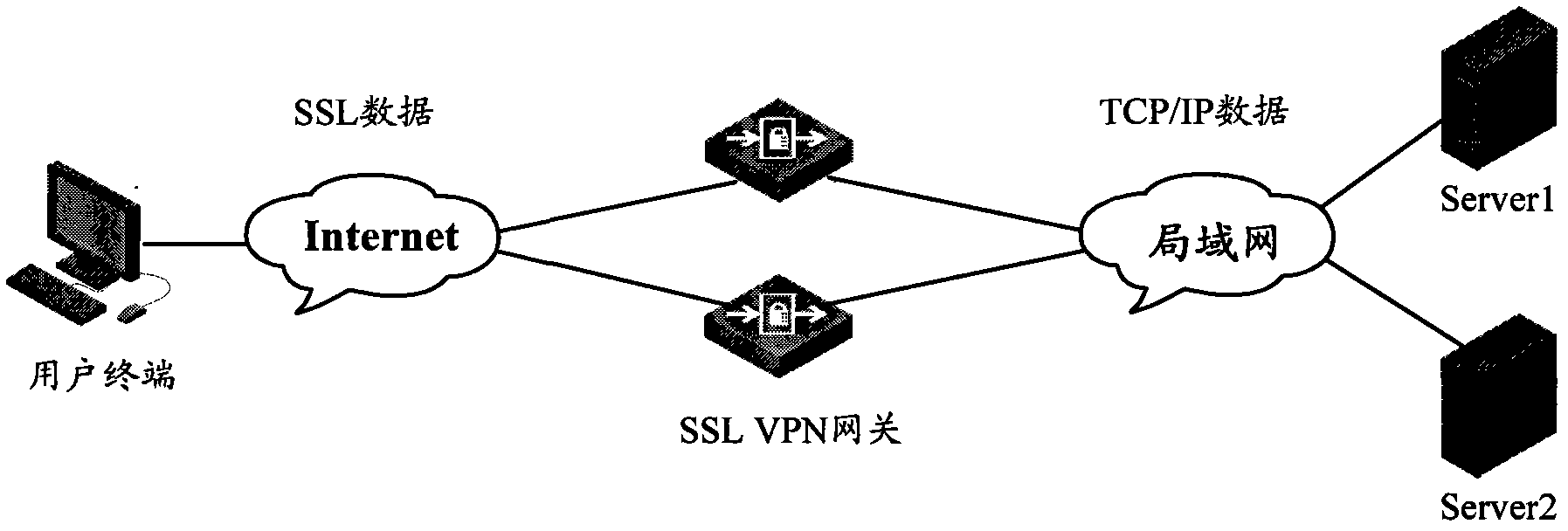
ActiveCN102223365ALow costAvoid performance bottlenecksNetwork connectionsAccess methodPrivate network
The invention discloses a user access method and a device based on an SSL (Secure Socket Layer) VPN (Virtual Private Network) gateway cluster. The gateways in the SSL VPN gateway cluster use a VRRP (Virtual Router Redundancy Protocol), and are configured with cluster neighbor table entries which contain the current states of neighbor gateways and current user connecting number. The method comprises the following steps that the gateways maintain the cluster neighbor table entries through a cluster neighbor probe process which is periodically executed; and when the master gateway receives an SSL access request transmitted to the SSL VPN gateway cluster VRRP backup tram address by a user terminal, and judges that no gateway processing source IP (Internet Protocol) address is the access request of the source IP address of the SSL access request, according to the current states of the neighbor gateways and the current user connecting number in the cluster neighbor table entries, as well as the current user connecting number of the master gateway, the gateway which has minimum load and can be accessible is selected, and the user terminal is redirected to the neighbor gateway. The invention can realize SSL VPN gateway cluster load balancing and improves the property of a system.
Owner:XINHUASAN INFORMATION TECH CO LTD
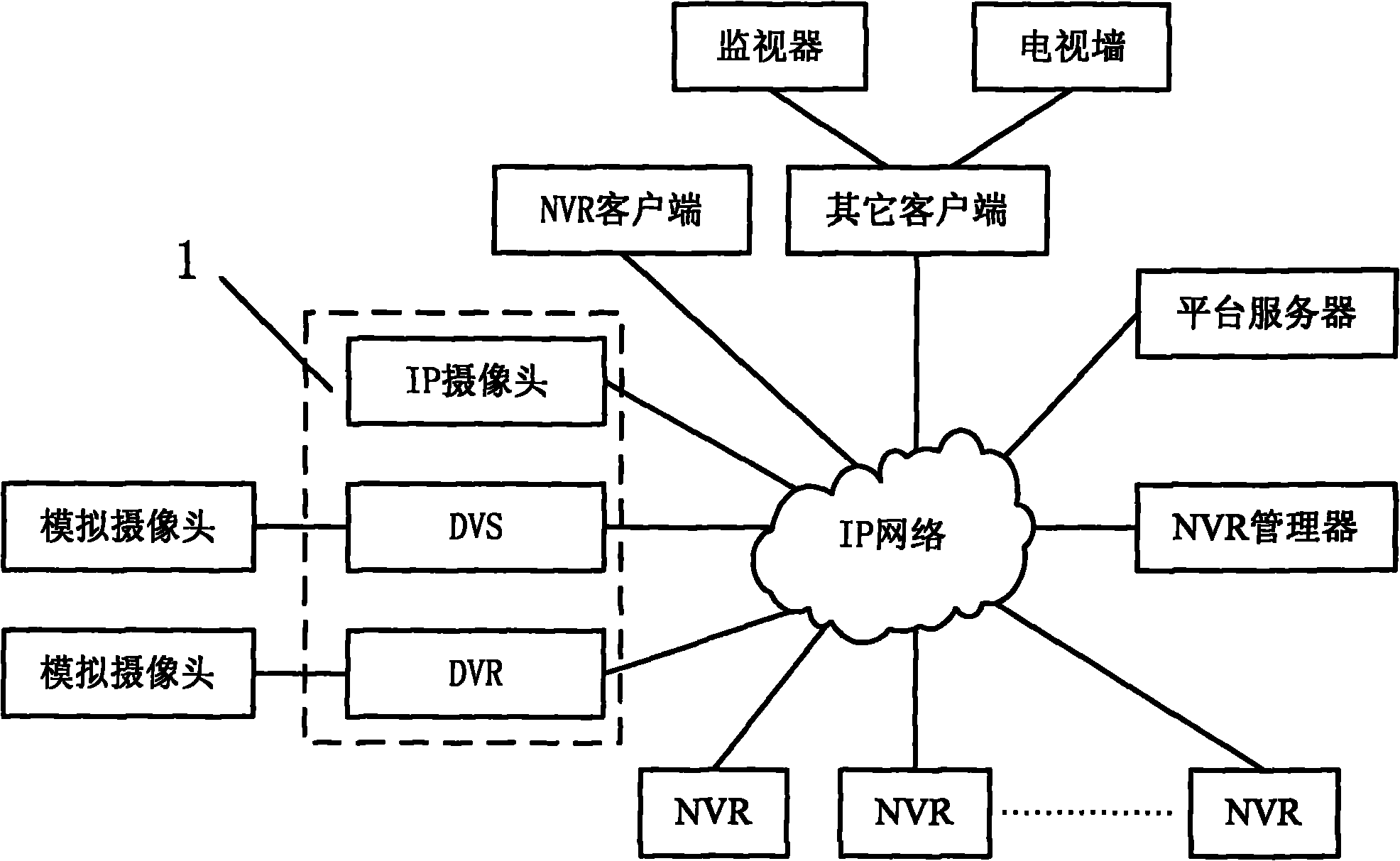
Network video recorder cluster video monitoring system and method
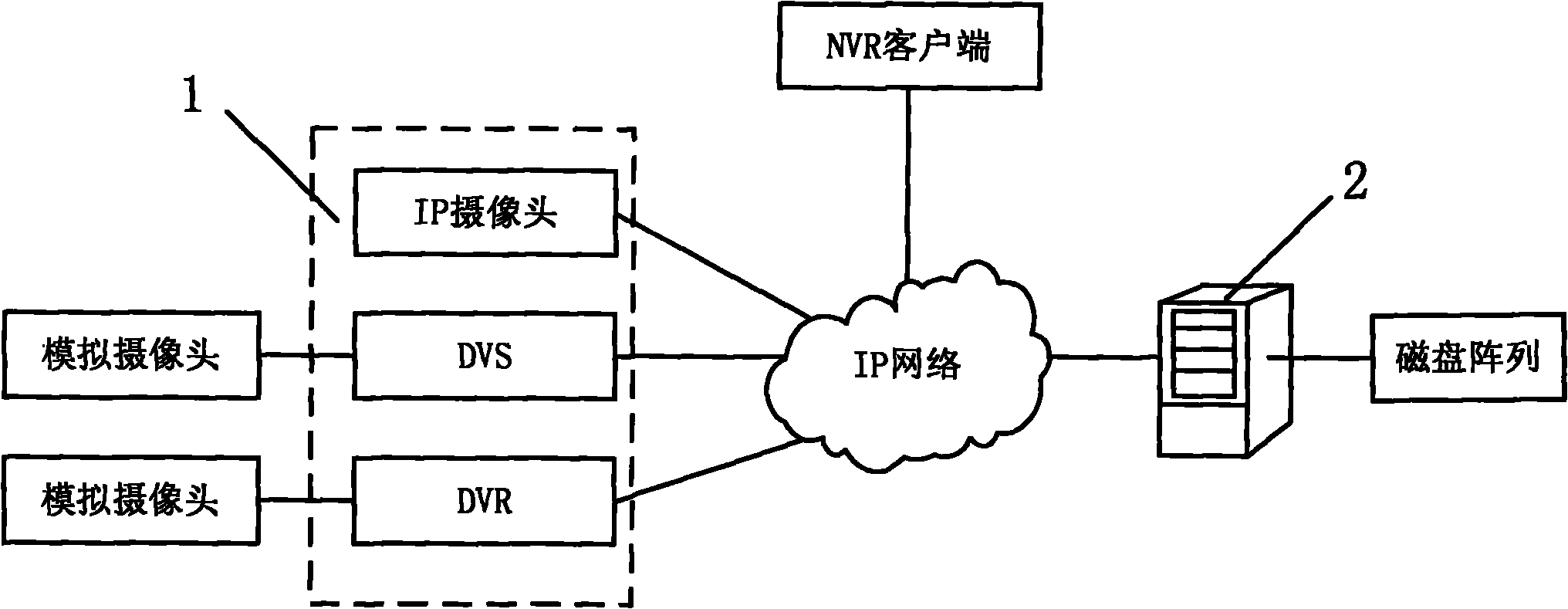
ActiveCN101877783ALow costMapping implementationClosed circuit television systemsData switching networksVideo monitoringVideo storage
The invention relates to a network video recorder cluster video monitoring system and a method. The system comprises a network encoder, a plurality of network video recorders (NVR) and an NVR manager, wherein the network encoder, the NVR manager and each NVR are all connected with an IP network; each NVR supports a network storage protocol that the network encoder can directly access to audio / video data thereon so as to directly store the audio / vide data output by the network encoder in an encoding manner in the NVR; the NVR manager is composed of a mapping module and a monitoring module, the mapping module is stored with the mapping relationship between the network encoder and each NVR, and the monitoring module monitors and manages the audio-video data received by each NVR; and each NVR receives the audio-video data encoded by the network encoder by the IP network under the control of the NVR manager, records, responses to access requests from a client side or the network encoder, and queries or replays or stores the recording data. The system can manage the NVR in a cluster manner, solves the problems of performance and storage bottlenecks simultaneously and improves the whole system performance.
Owner:HANGZHOU HIKVISION DIGITAL TECH +1
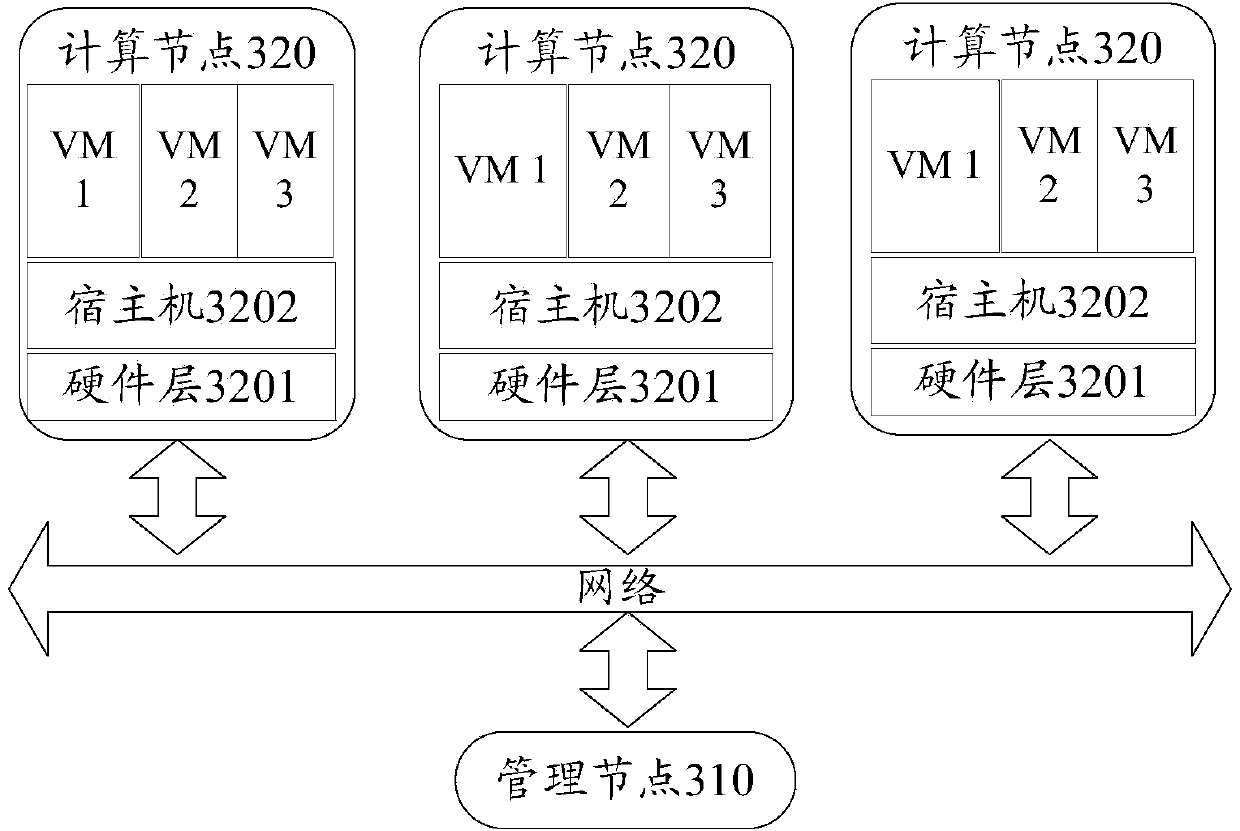
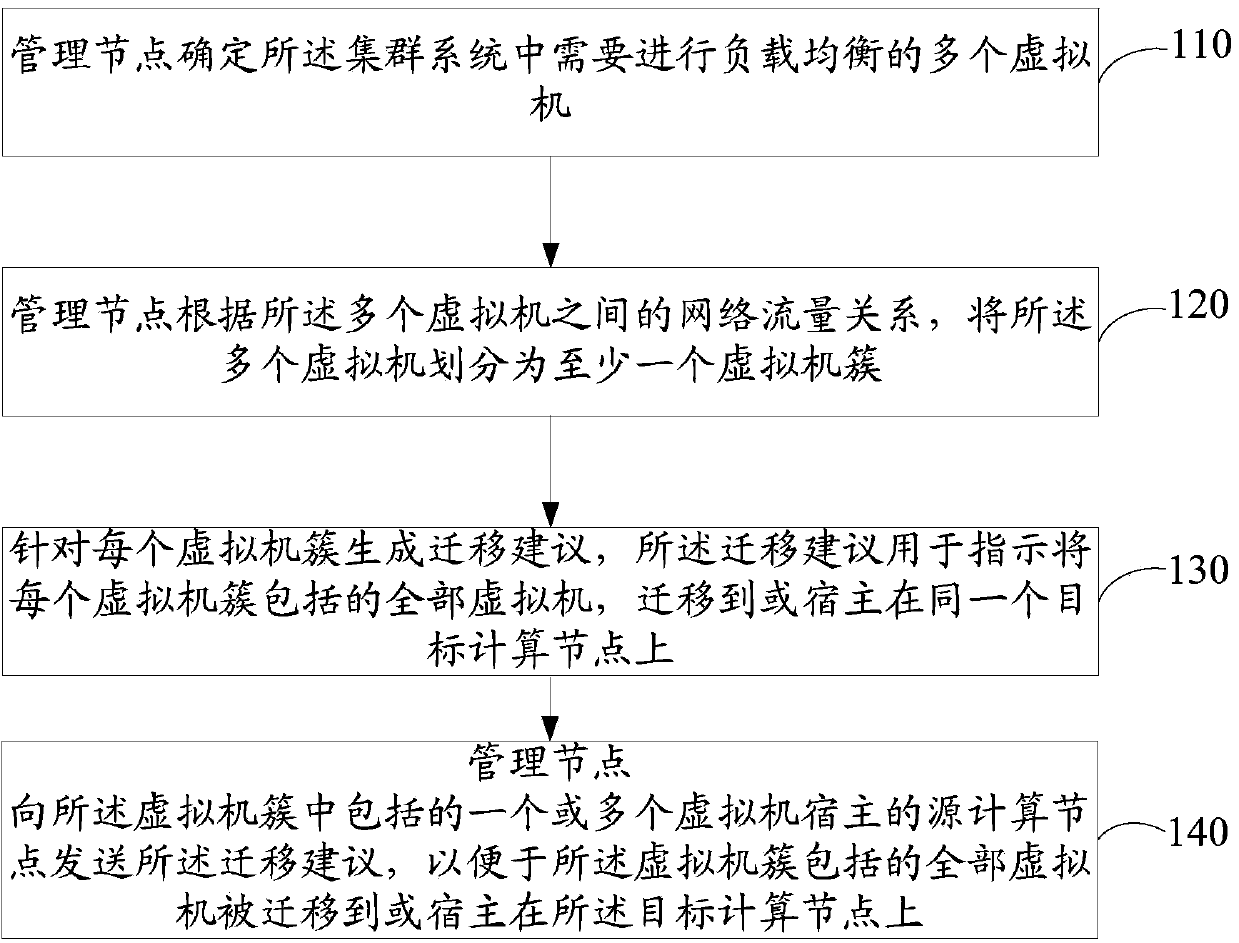
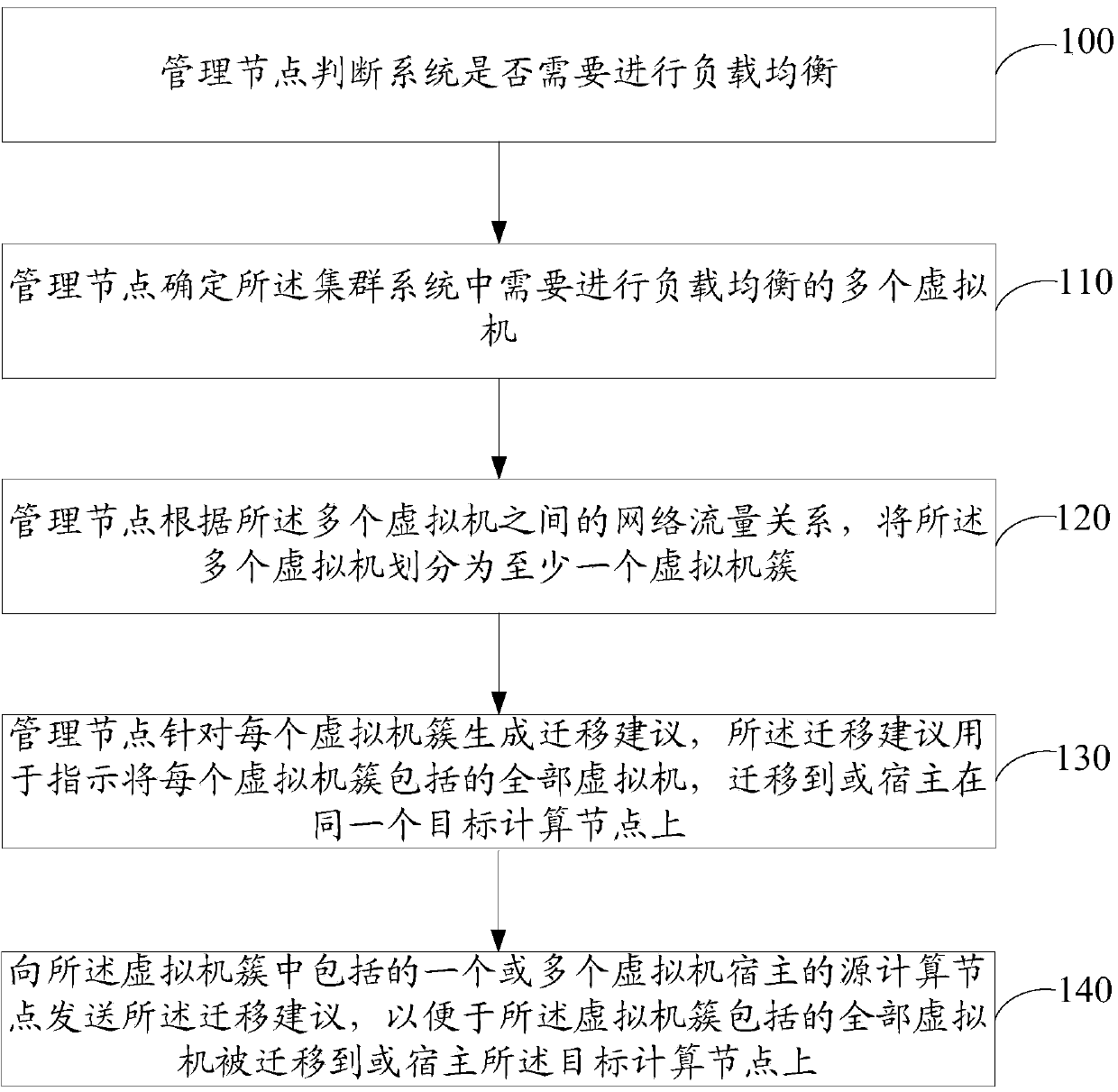
Load balancing method of virtual machines, related equipment and trunking system
InactiveCN104184813AImprove network performanceReduce loadResource allocationTransmissionCluster systemsTrunking
The invention discloses a load balancing method of virtual machines, related equipment and a trunking system. The network performance of the trunking system can be improved after load balancing. According to certain feasible execution modes, the method includes the steps that a management node determines a plurality of virtual machines in which load balancing is needed in the trunking system; according to the network flow relation among the virtual machines, the virtual machines are integrated into at least one virtual machine cluster, so that the network flow between each virtual machine and at least one other virtual machine in the same virtual machine cluster is larger than or equal to a network flow threshold value, and the network flow between each virtual machine and any other virtual machine in the different virtual machine cluster is smaller than the network flow threshold value; migration suggestions are generated, and the migration suggestions are used for instructing all the virtual machines included in each virtual machine cluster to be migrated or hosted to the same target computational node; the migration suggestions are sent to source computational nodes hosted by one or more virtual machines included in each virtual machine cluster.
Owner:HANGZHOU HUAWEI DIGITAL TECH
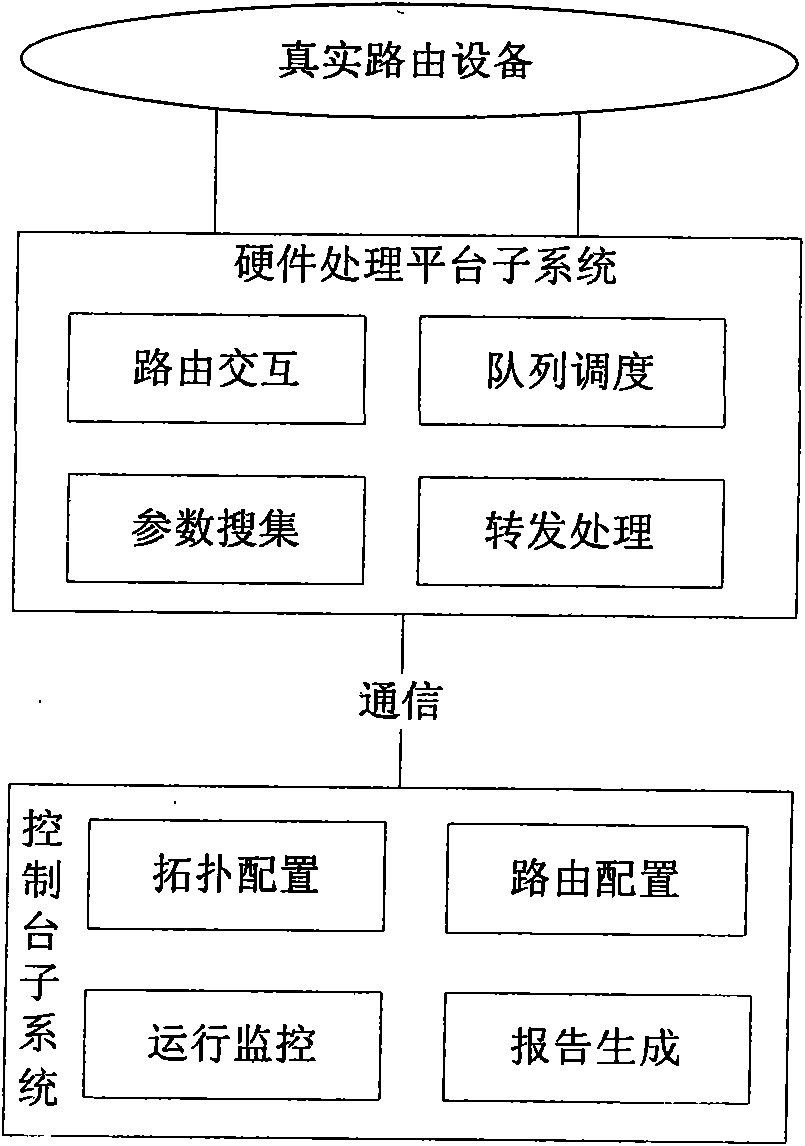
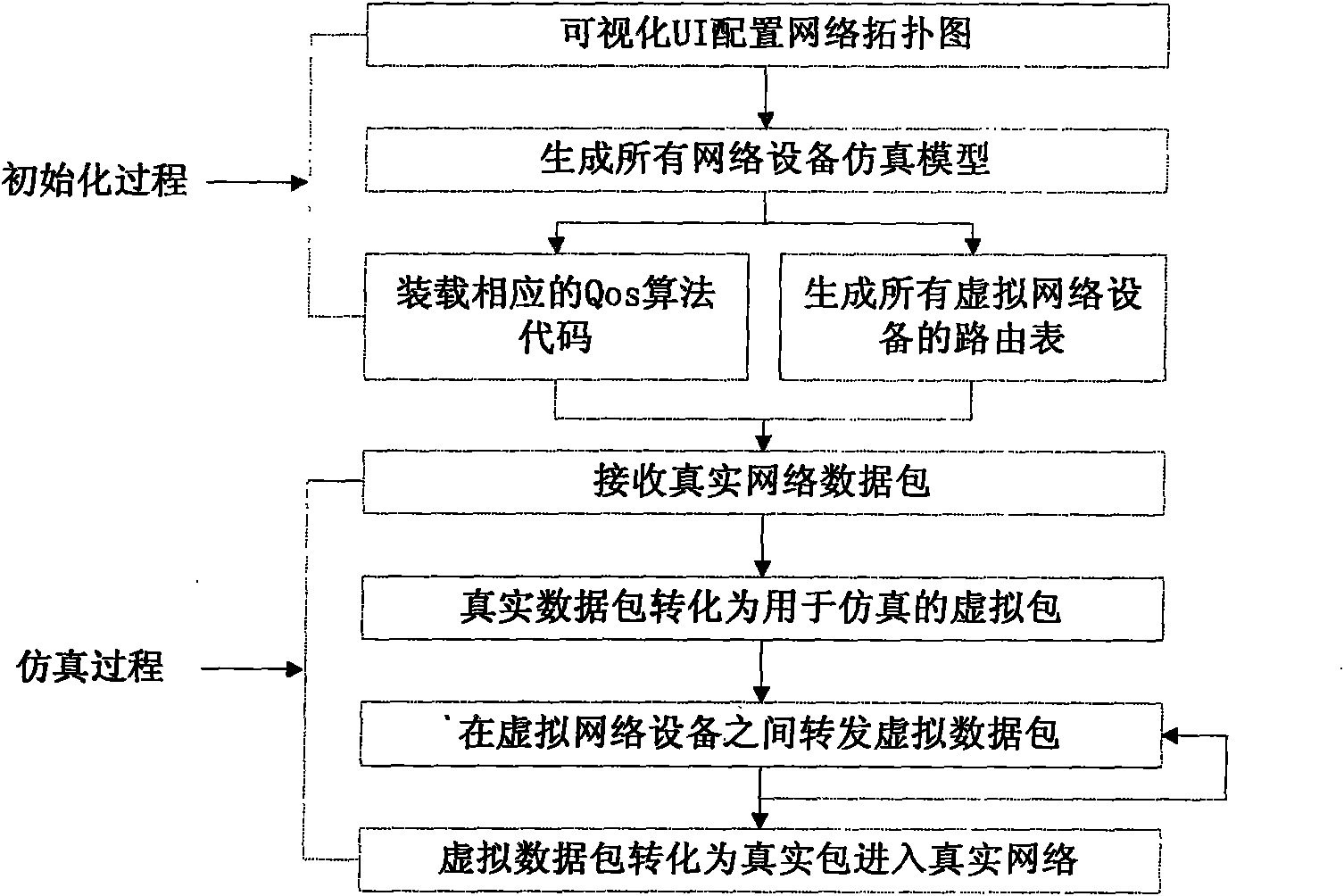
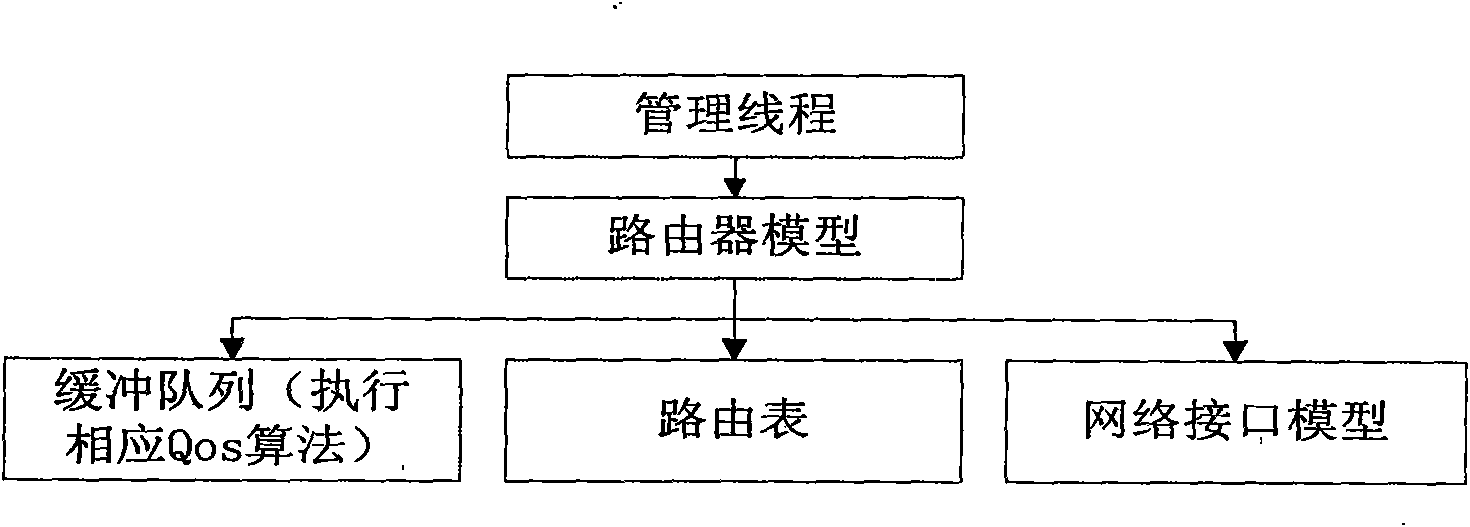
Large-scale network routing simulation method based on hardware
InactiveCN101567818AEasy to handleAvoid performance bottlenecksData switching networksRouting tablePrivate network
The present invention discloses a large-scale routing simulation method based on the hardware, and provides a large-scale routing simulation technique which is realized with a high-performance special network processing specialized platform. The initialization process of simulation is generated sequentially by three steps of: simulation of the network performance, loading of the corresponding QoS algorithm code and the virtual routing table. The simulation process comprises the following steps: firstly, receiving the real network data packages; then, converting the real network data packages to the virtual packages used for simulation; transmitting the virtual data packages between the virtual network devices; and converting the data packages to real data packages for entering the real network. The large-scale network routing simulation method based on hardware according to the invention has the advantages of high processing performance, providing of reliable virtual-real converting interface, strong extendibility, reduced cost, reinforced convenience and reinforced operability.
Owner:中国人民解放军总参谋部第五十四研究所 +2
Load balancing method in server cluster, as well as node server and cluster
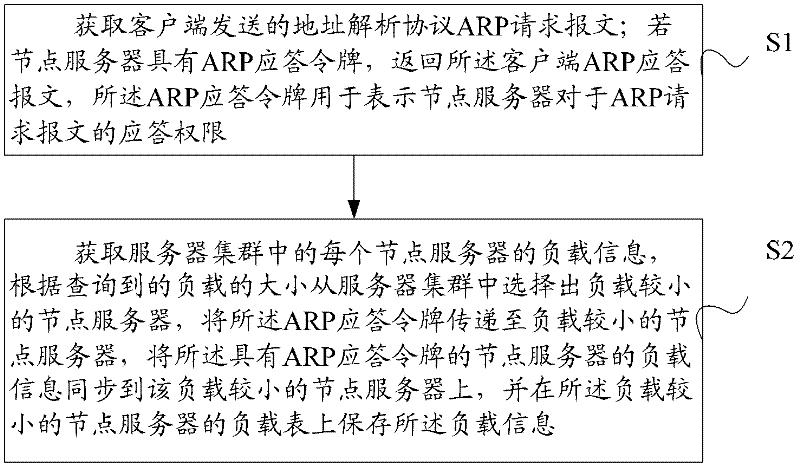
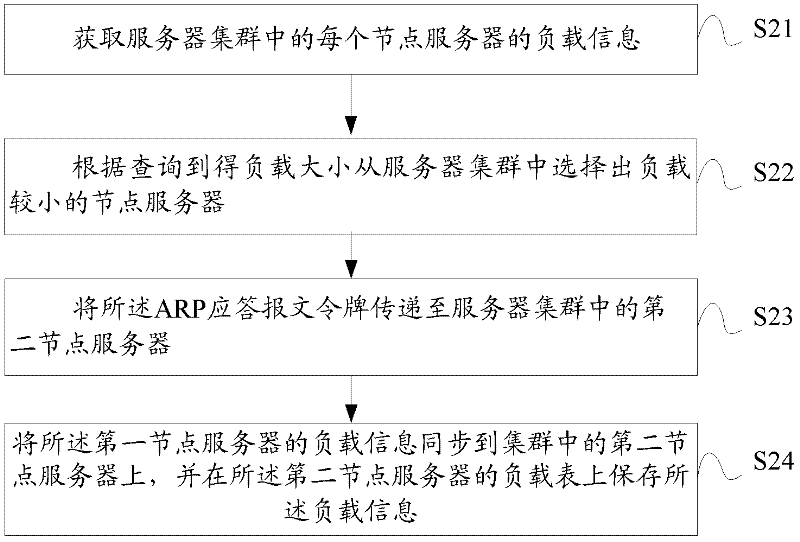
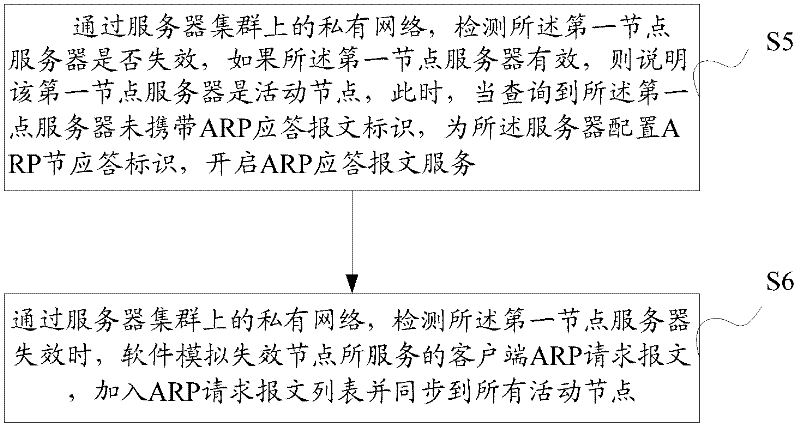
ActiveCN102447624AImprove network bandwidth utilization efficiencyFlexible Load SharingData switching networksAddress Resolution ProtocolName server
The embodiment of the invention discloses a load balancing method in server cluster comprising the following steps: acquiring an address resolution protocol ARP request message sent from a client; if a node server has an ARP response token, returning the client ARP response message, wherein the ARP response token is used for representing the response authority of the node server to the ARP request message; acquiring the load information of each node server in the server cluster, selecting the node server with small load from the server cluster according to the acquired load condition, transmitting the ARP response token to the node server with small load, synchronizing the load information of the node server with the ARP response token to the node server with small load and storing the load information on the load table of the node server with small load. The node server in the embodiment of the invention can flexibly distribute the load according to its own network adapter configuration condition and load condition to improve the server network bandwidth utilization rate, especially to fully utilize all server network adapters and to avoid the performance bottleneck caused by excessive reliance on the load balancing equipment when the server configures multiple network adapters.
Owner:CHENGDU HUAWEI TECH
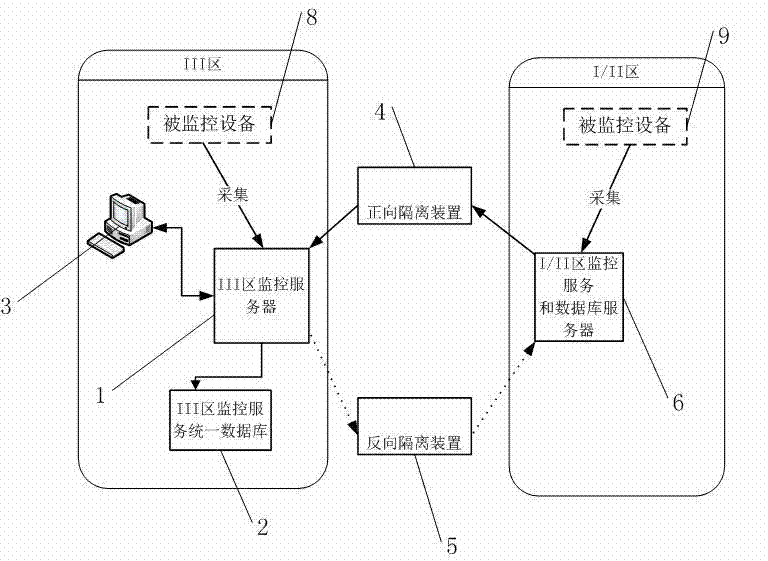
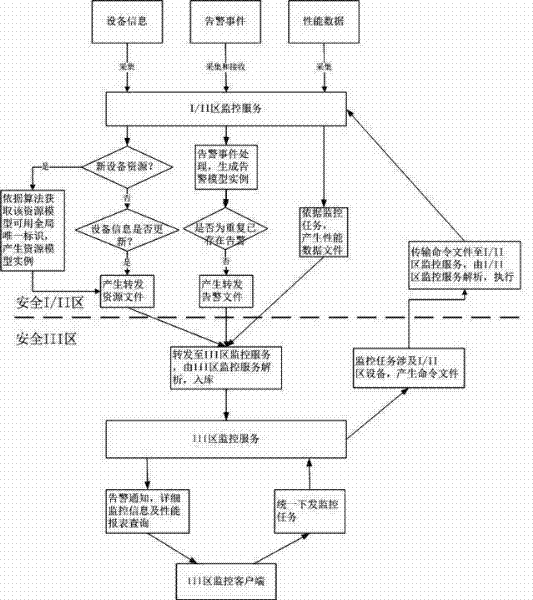
Safe region-crossing equipment uniform monitoring method based on independent monitoring services, and monitoring system for the same
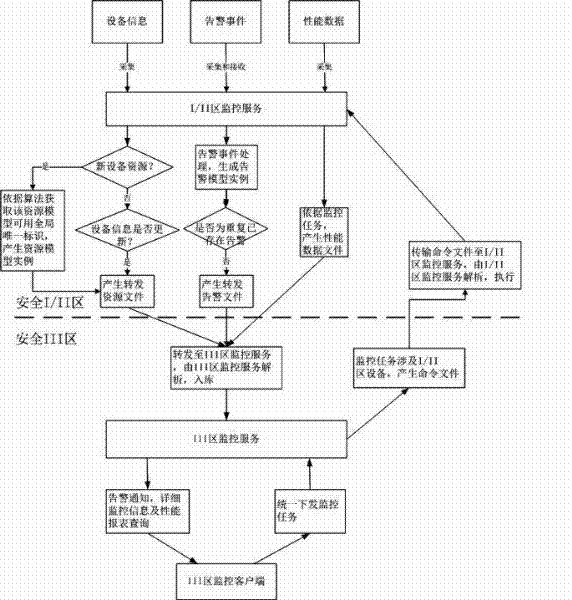
ActiveCN102521781AImprove data transfer efficiencyEfficient implementationData processing applicationsIntegrated monitoringMonitoring system
The invention discloses a safe region-crossing equipment uniform monitoring method based on independent monitoring services, and a monitoring system for the same, which are used for safe region-crossing equipment comprehensive monitoring of a power dispatching automation system. The monitoring services are independently arranged and run in different safe regions, a global unique production mechanism of the instance identifiers of resource, warning and performance models is used, timely collection of the safe region-crossing equipment resource, warning and performance information in a safe III region monitoring service is realized, and a III region monitoring client monitors and manages the equipment uniformly. With the method, the independently arranged monitoring services have basic capabilities in resource model management, equipment warning basic analysis and management, and performance data processing, thus, data redundant transmission through a physical isolation device is reduced, some of the pressure on the III region uniform monitoring service is shared, and finally, the safe region-crossing equipment uniform monitoring is finished.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD SHAOXING POWER SUPPLY CO +2
Service configuration switching method, device and system
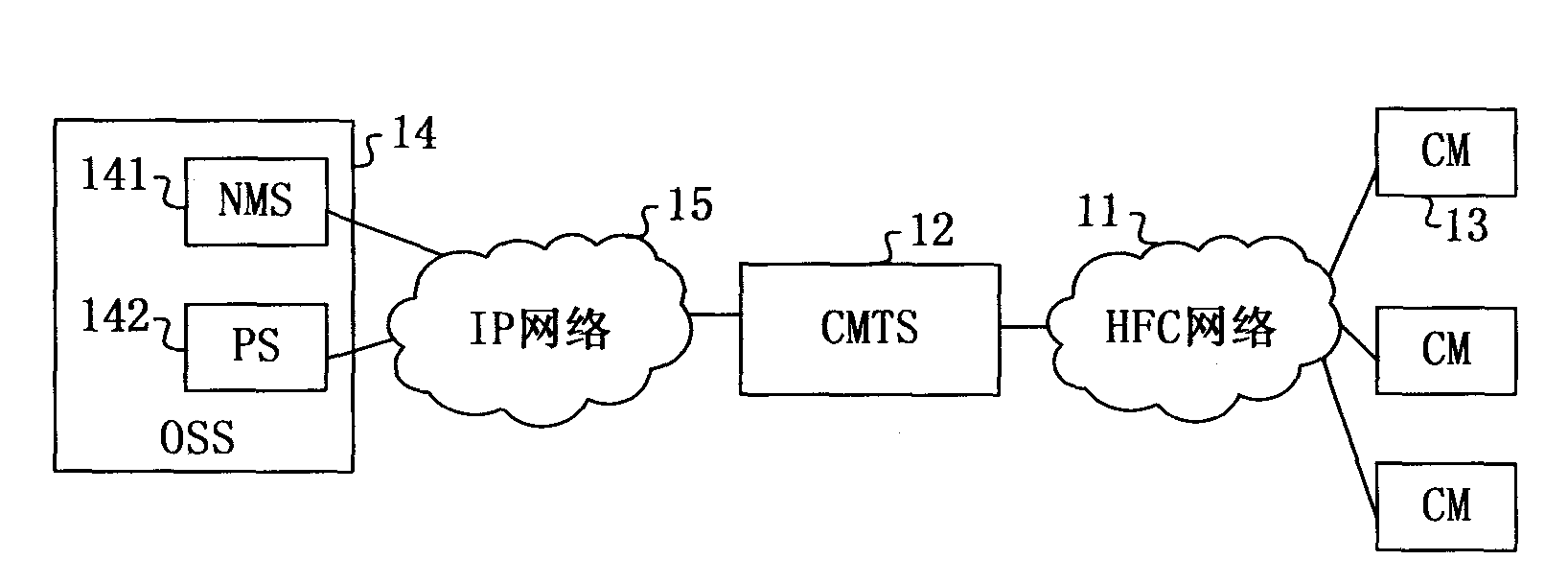
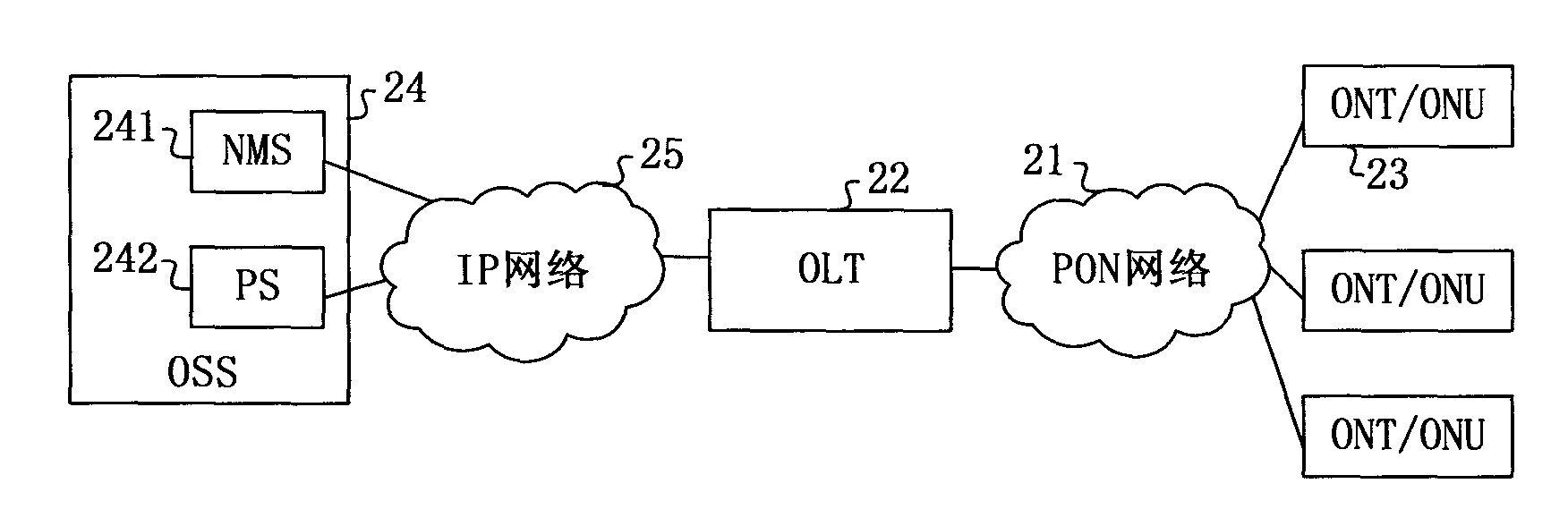
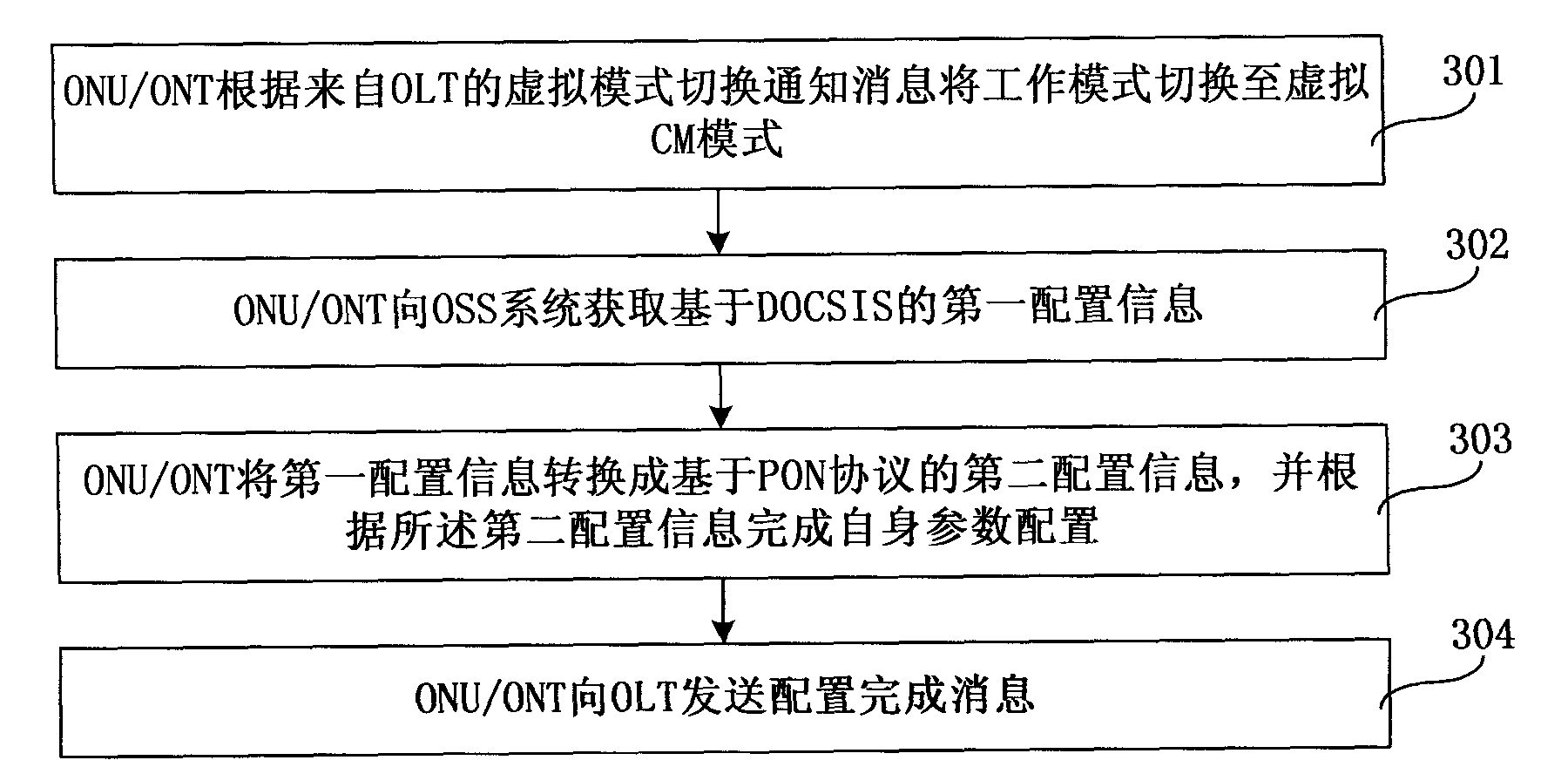
ActiveCN102082684ASolve performance bottlenecksImprove service delivery efficiencyMultiplex system selection arrangementsData switching networksDOCSISPons
The embodiment of the invention relates to a service configuration switching method, device and system. The method comprises the following steps: switching the operating mode into a virtual CM mode based on a virtual mode switching notification message from an OLT (optical line terminal); acquiring the first configuration information based on the DOCSIS (data over cable system interface specification) from an OSS (operation support system); converting the first configuration information into the second configuration information based on the PON (passive optical network) protocol, and performing self parameter configuration based on the second configuration information; and sending the second configuration information to the OLT after configuration. The service configuration switching method, device and system provided by the embodiment of the invention can solve the performance bottleneck of the OLT in the prior art, and improve service dispensing efficiency.
Owner:HUAWEI TECH CO LTD
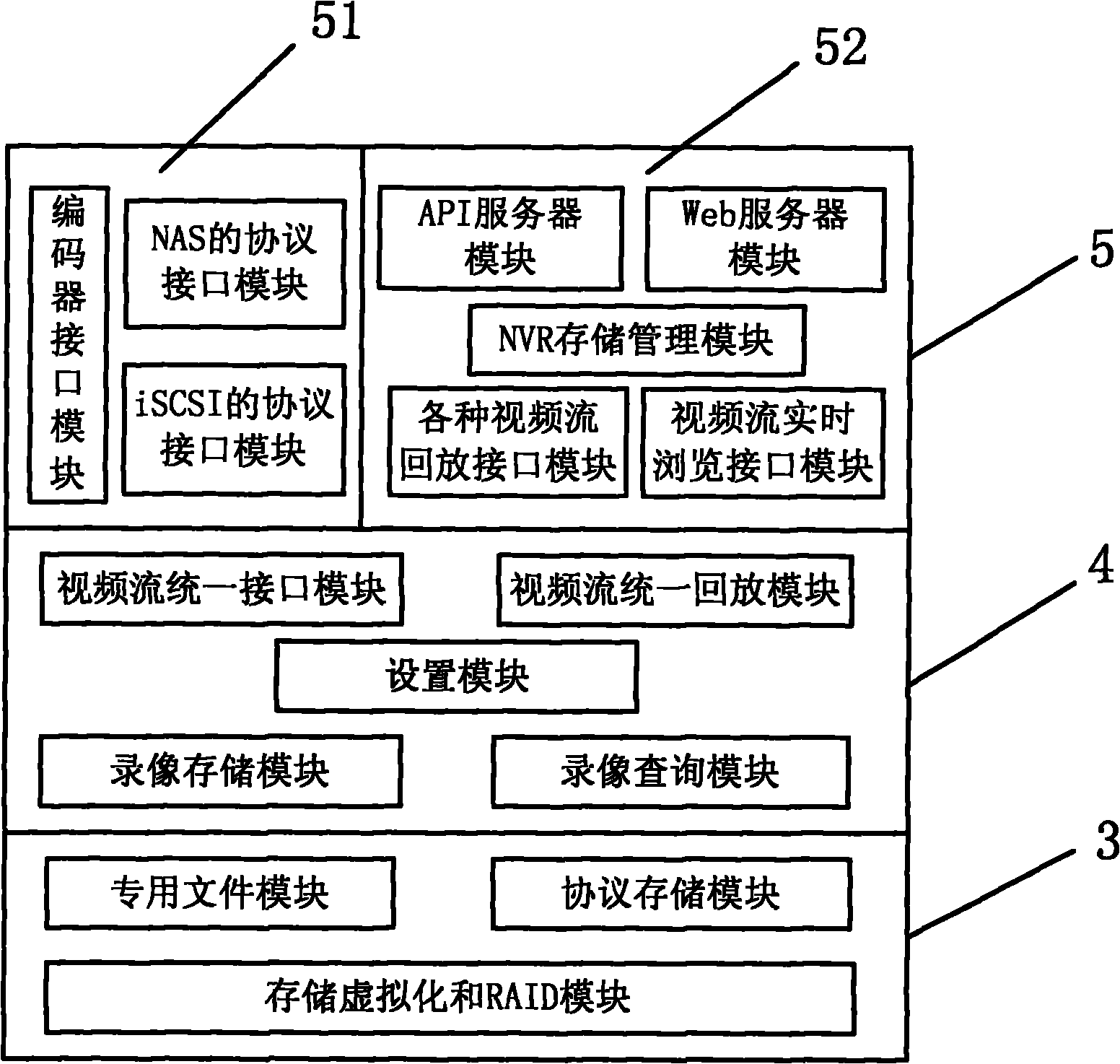
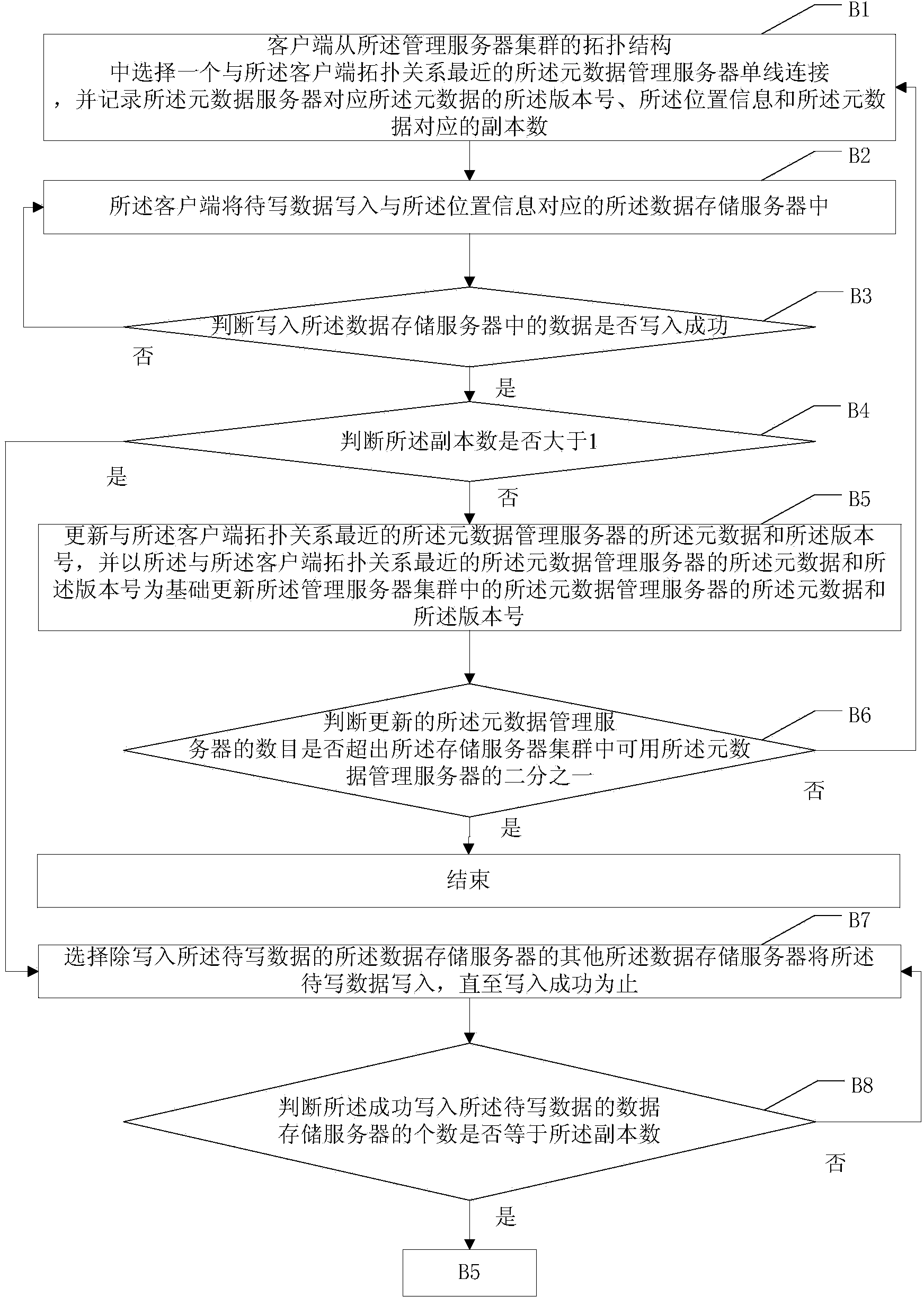
Distributed safety memory system
InactiveCN101316273AImprove securityAvoid performance bottlenecksTransmissionUser PrivilegeDistributed security
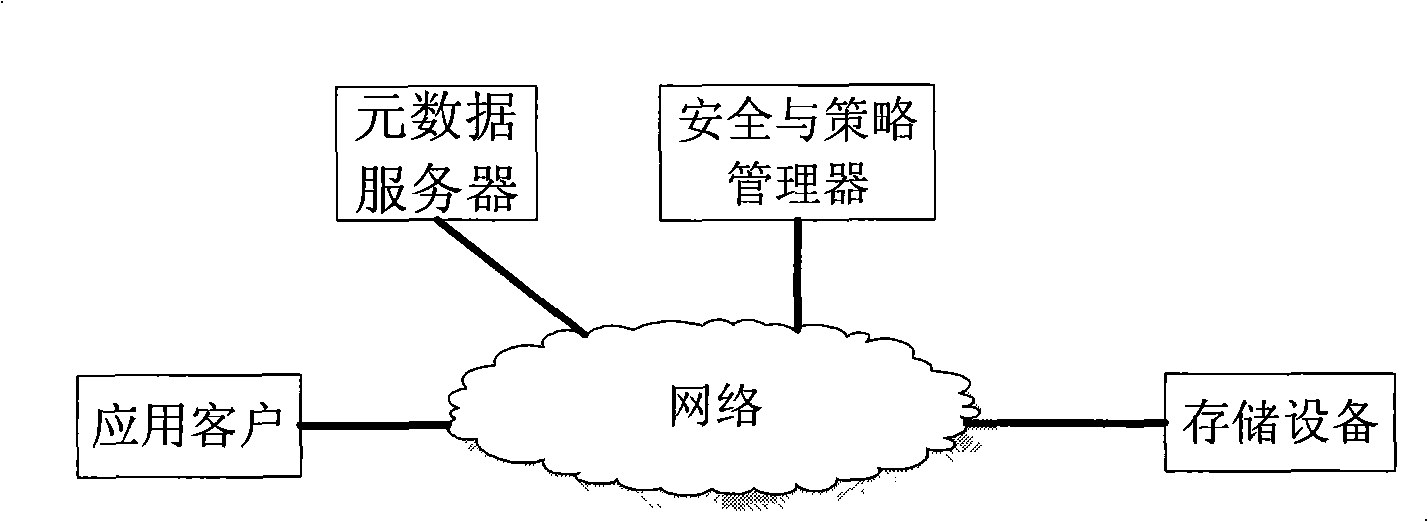
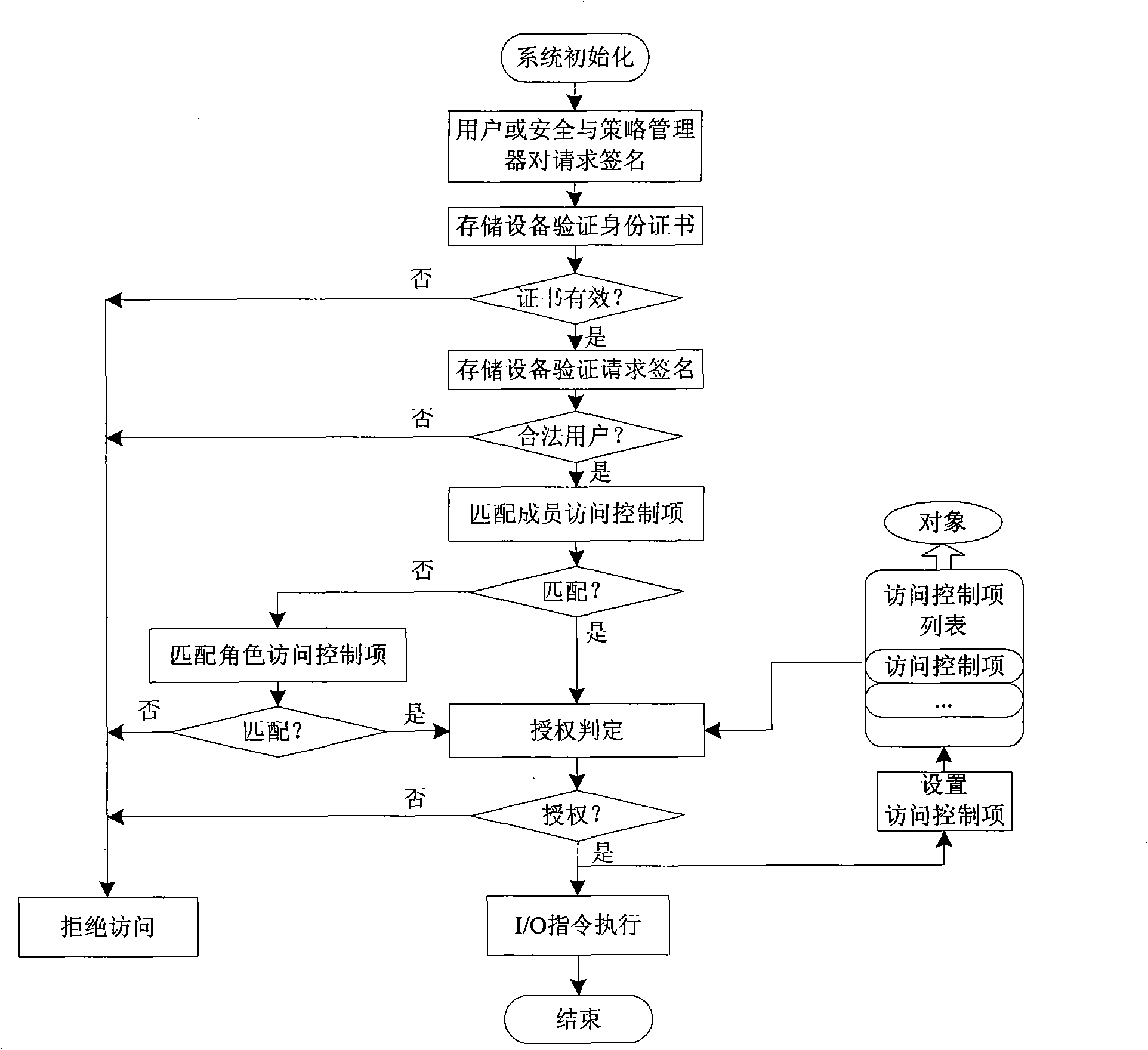
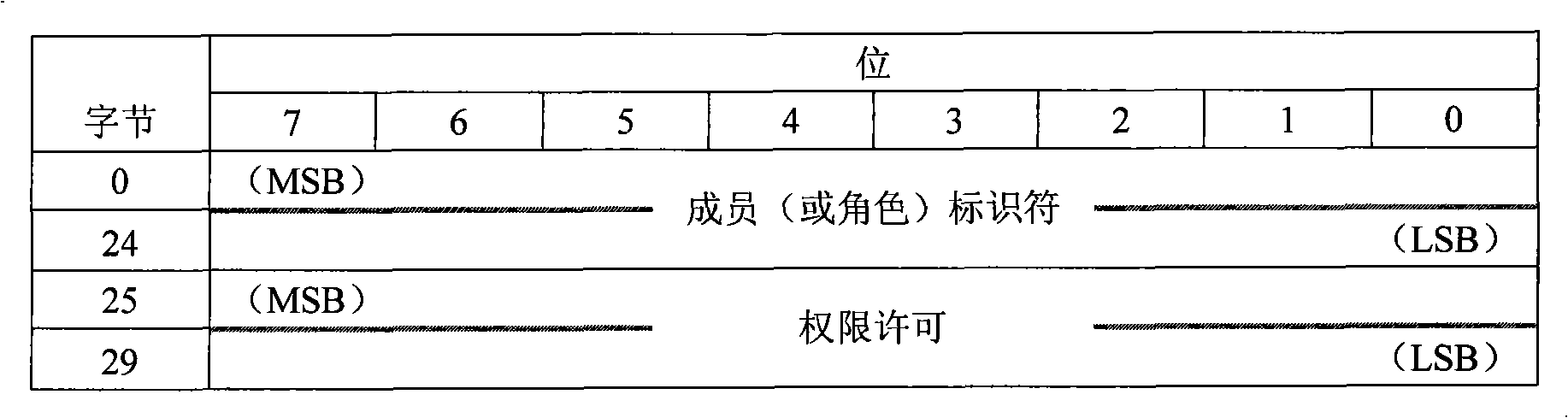
The invention discloses a distributed security storage system, pertains to the technical filed of computer storage and aims at overcoming the problems of the heavy burden of a security manager and complex user authority management in the current security storage system based on a certificate. The storage system of the invention consists of an application client connected to a network, a storage device, a security and strategy manager and a metadata server; the security and strategy manager stores and manages the access control entry, access control strategy and rule of the whole system and carries out access strategy control and authority control over the storage device according to the access control entry, access control strategy and rule of the whole system, including the changes of the priority and inheritance rules of the access control entry and adding and deletion of the access control entry. The storage system of the invention distributes centralized authorization to storage nodes, avoids the performance bottle neck of the security manager, solves the problem of the complex user authority management, combines identification management and access control, eliminates access control redundancy and security holes and is applicable to establishing a large-scale security storage system with high performance.
Owner:HUAZHONG UNIV OF SCI & TECH
Distributed storage method and distributed storage system
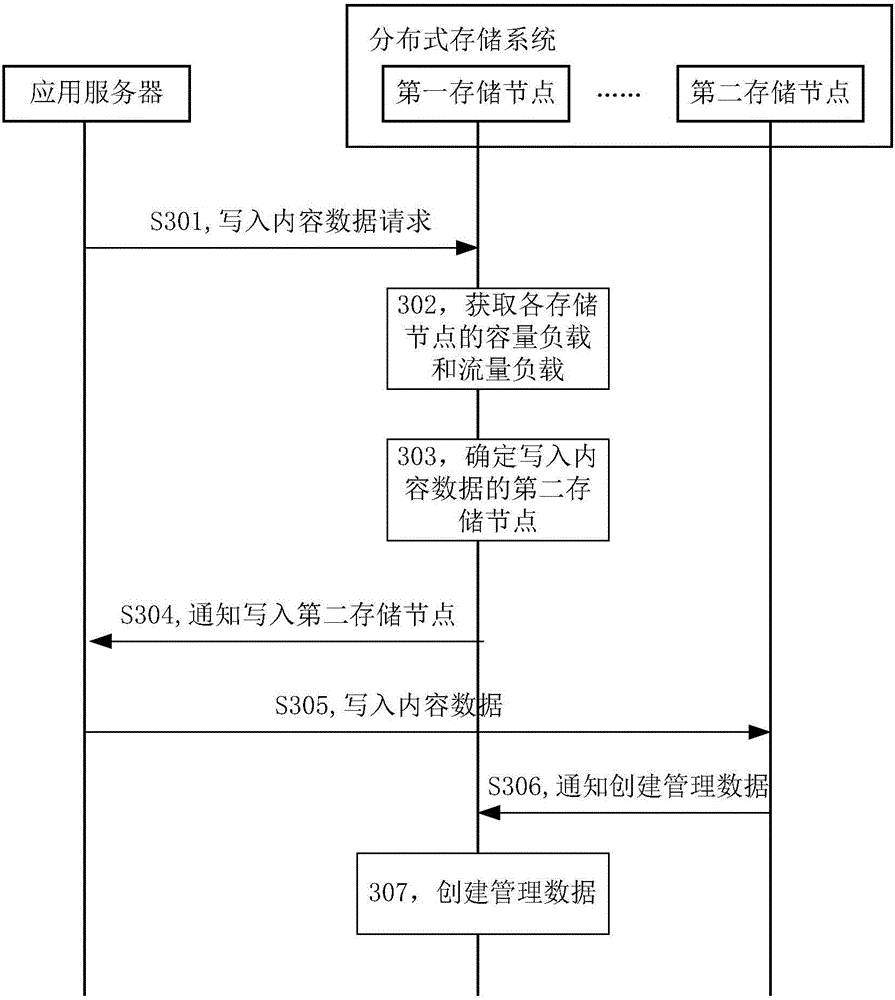
InactiveCN106161610AShorten delivery timeSolve wasteData switching networksSpecial data processing applicationsApplication serverDistributed computing
The invention discloses a distributed storage method. According to the distributed storage method, after a first storage node of a distributed storage system receives a content data writing request from an application server, the first storage node determines a second storage node for writing content data according to capacity loads and flow loads of storage nodes in the distributed storage system, notifies the application server of writing the content data into the determined second storage node and creates management data of the content data locally, wherein storage positions, namely storage nodes, of the content data are recorded in the management data. Since content data are distributed on the basis that the capacity conditions and the flow conditions of the storage nodes are taken into full consideration, the problem of resource waste caused by adoption of a unified algorithm for content data distribution is avoided.
Owner:HUAWEI TECH CO LTD
Distributed virtual firewall device and method
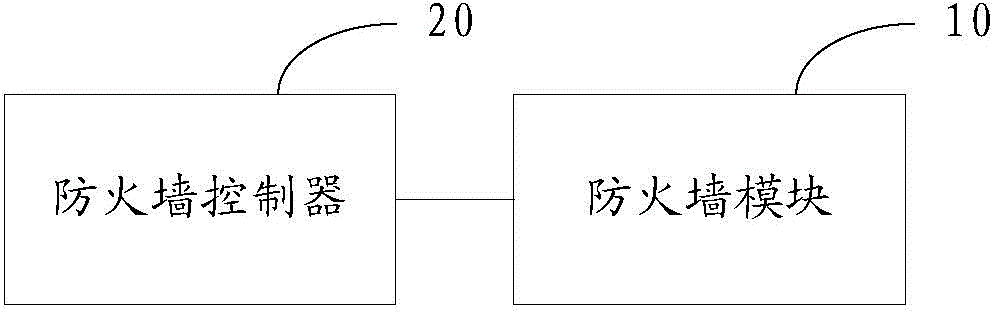
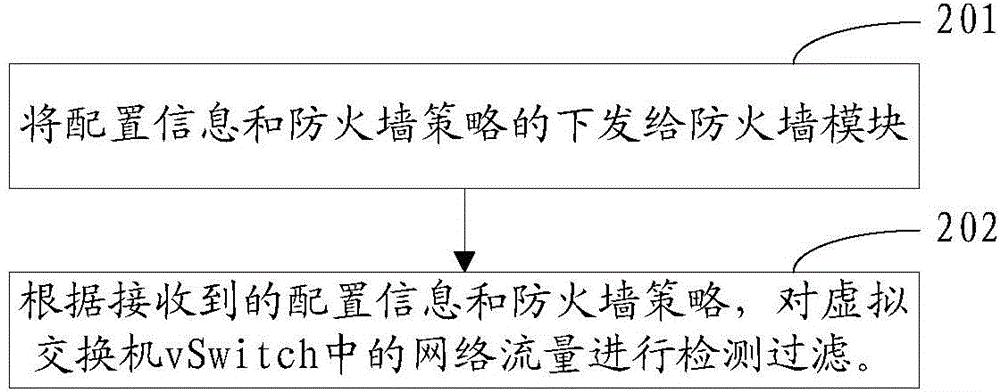
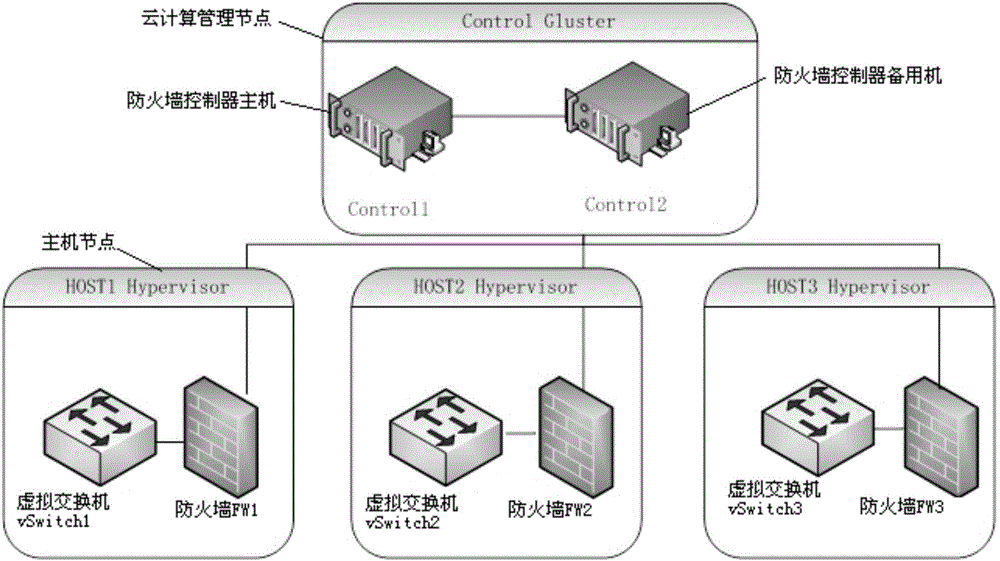
InactiveCN105141571ARapid detection filterAvoid performance bottlenecksSecuring communicationVirtual firewallVirtual switch
The invention provides a distributed virtual firewall device and a method. The device comprises a firewall controller and a firewall module, wherein the firewall controller is arranged on a cloud calculation management node and sends configuration information and firewall strategy information to the firewall module, the firewall module is arranged on a host node, and filtering detection on network flow in a virtual switch vSwitch is carried out according to the received configuration information and the firewall strategy information. Through the distributed virtual firewall device and the method, filtering detection on the network flow in the virtual switch vSwitch is carried out through the firewall module according to the received configuration information and the firewall strategy information, performance bottleneck in networking can be avoided, and the device further has advantages of abundant configuration strategy and flexible performance.
Owner:ZTE CORP
Network storage system
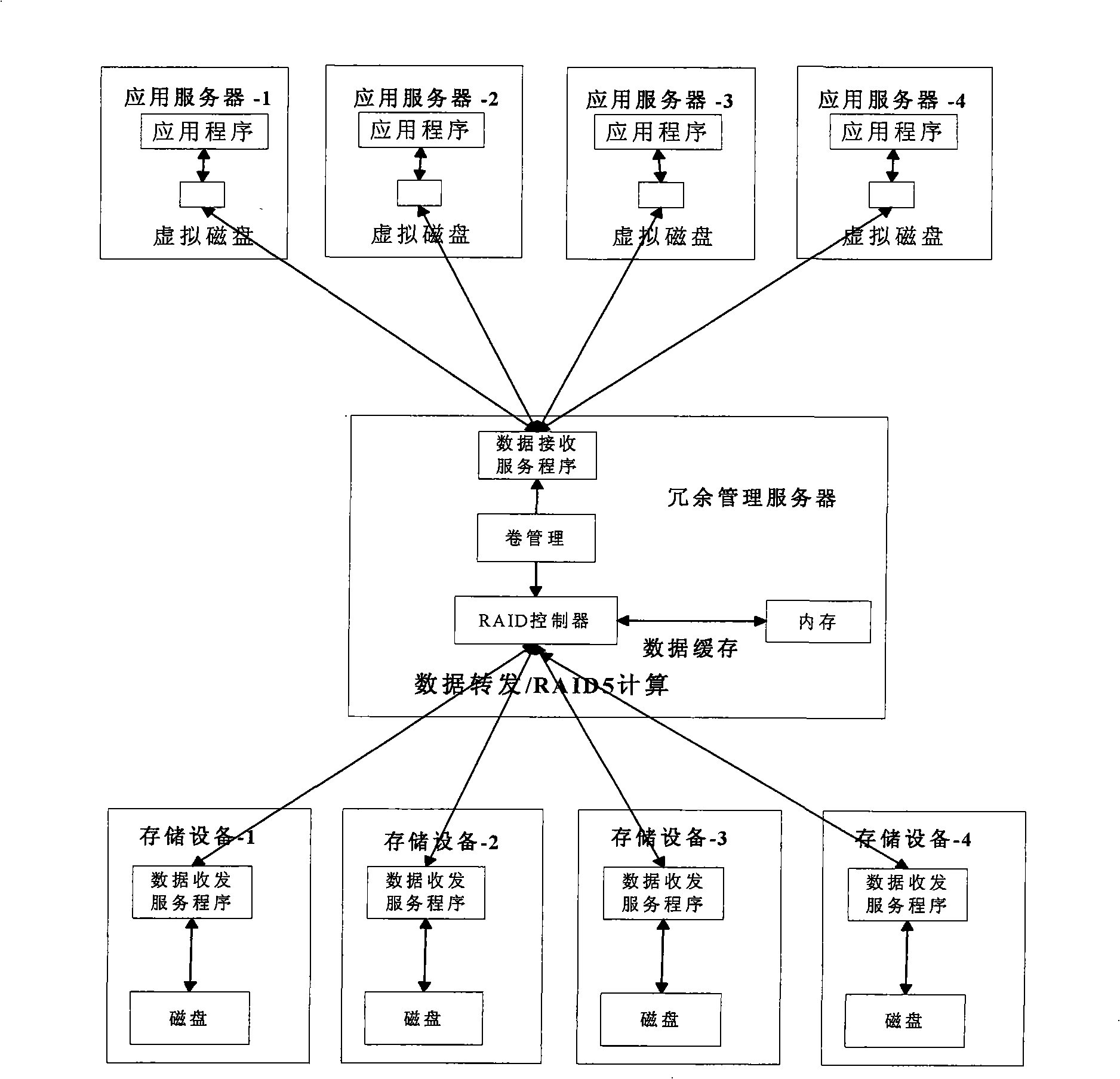
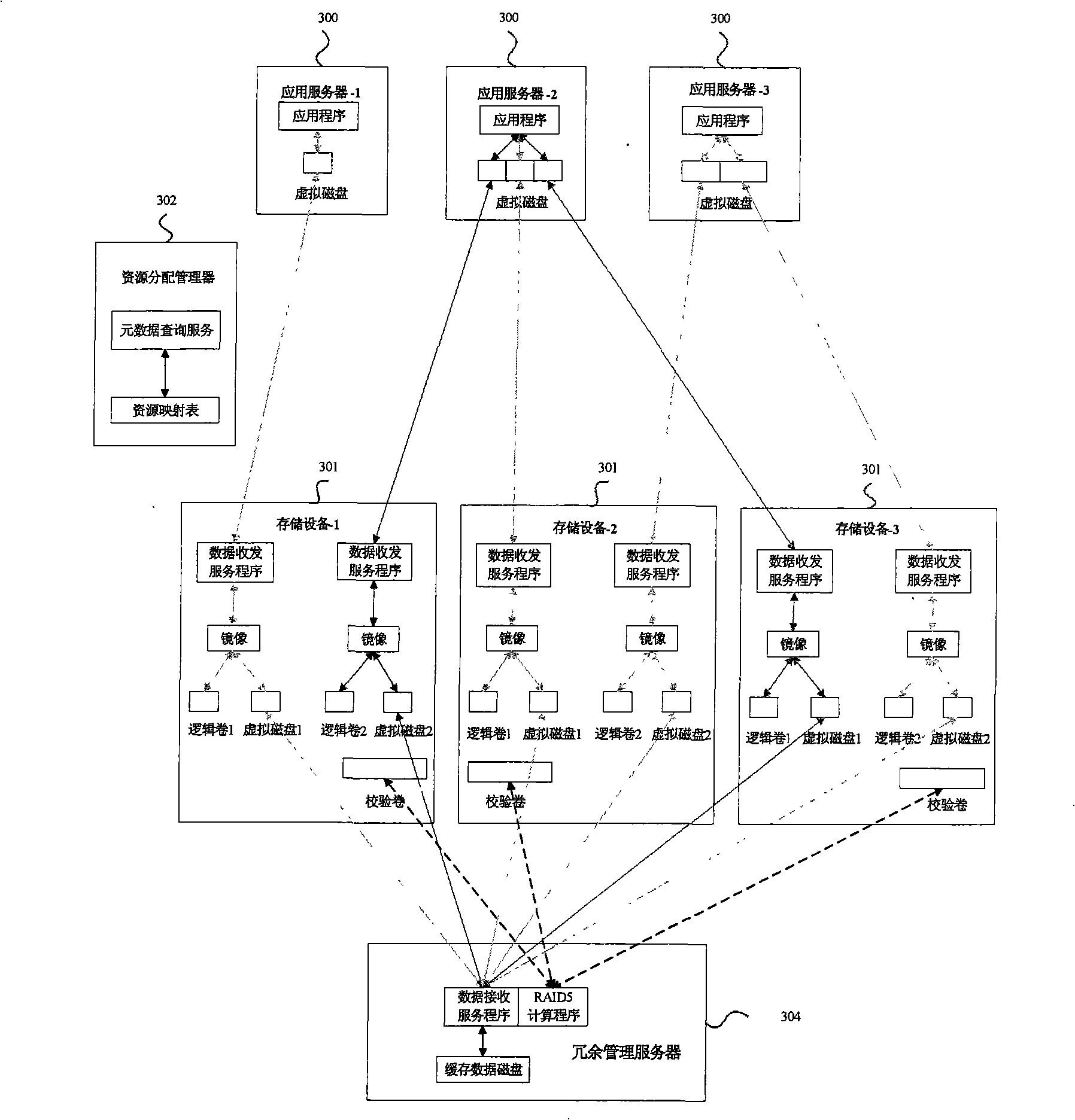
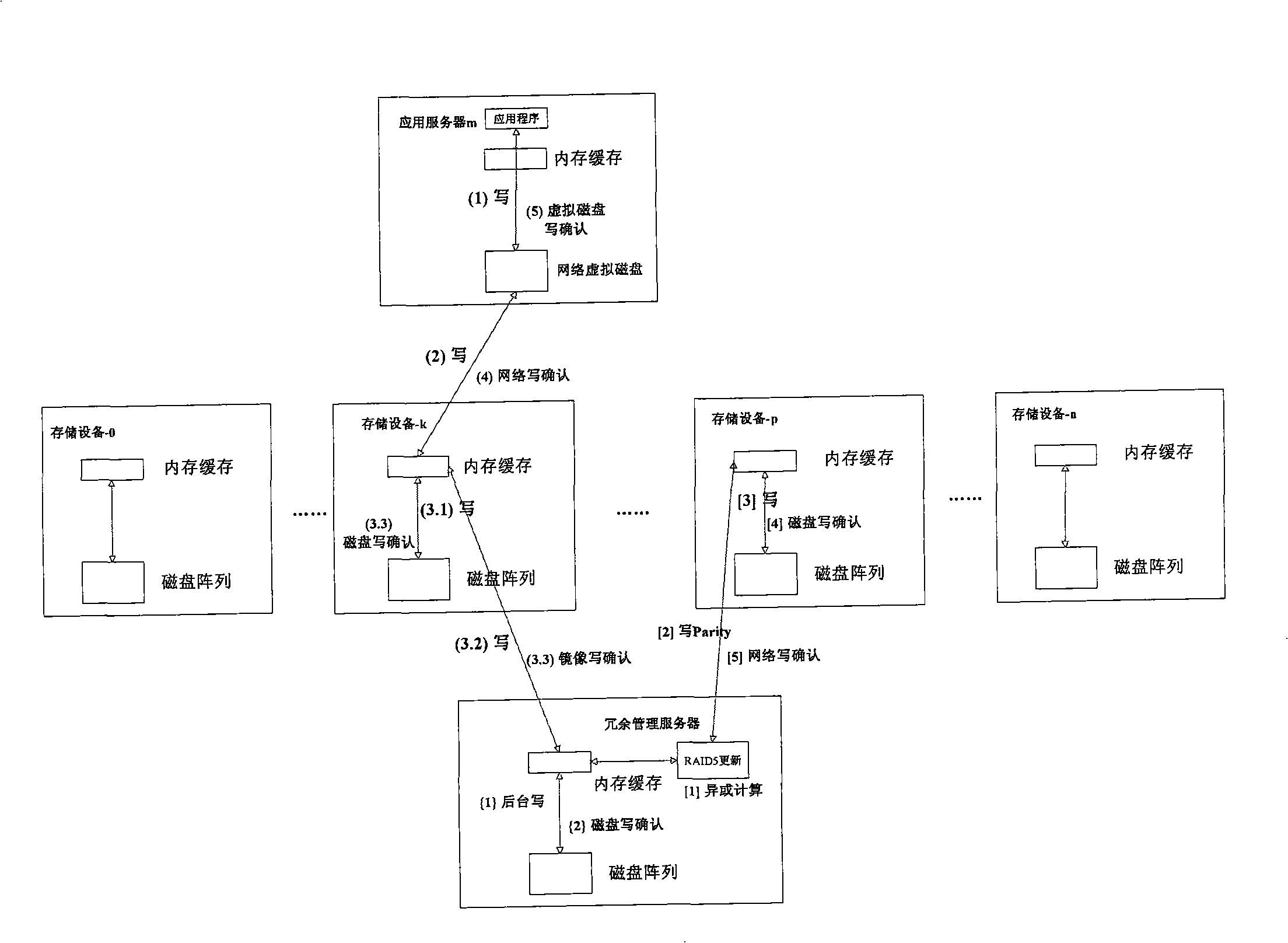
ActiveCN101291347AAvoid performance bottlenecksReduced write performance impactInput/output to record carriersTransmissionApplication serverStorage Resource Broker
The invention provides a network storage system which comprises an application server, data storage nodes, a resource allocation manager used to manage the address mapping relation of a storage resource, and redundancy management nodes used to manage the data redundancy relation among the data storage nodes, wherein, the application server directly accesses the data storage nodes, the redundancy management nodes are respectively connected to the rear end of each data storage node, and the redundancy management to the data storage nodes is realized by the redundancy management nodes. The system transfers the redundancy management nodes from the front end of a data channel to the rear end of storage equipment, which ensures that a reading / writing request on the application server can directly access the storage nodes and solves the performance bottleneck problem of control nodes of the front-end centralized redundancy management; and the redundancy management nodes perform the cache to data first and then compute redundancy data when a system is idle, which reduces the influence of the redundancy computation on the writing performance of the system.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method and device for configuring server cluster
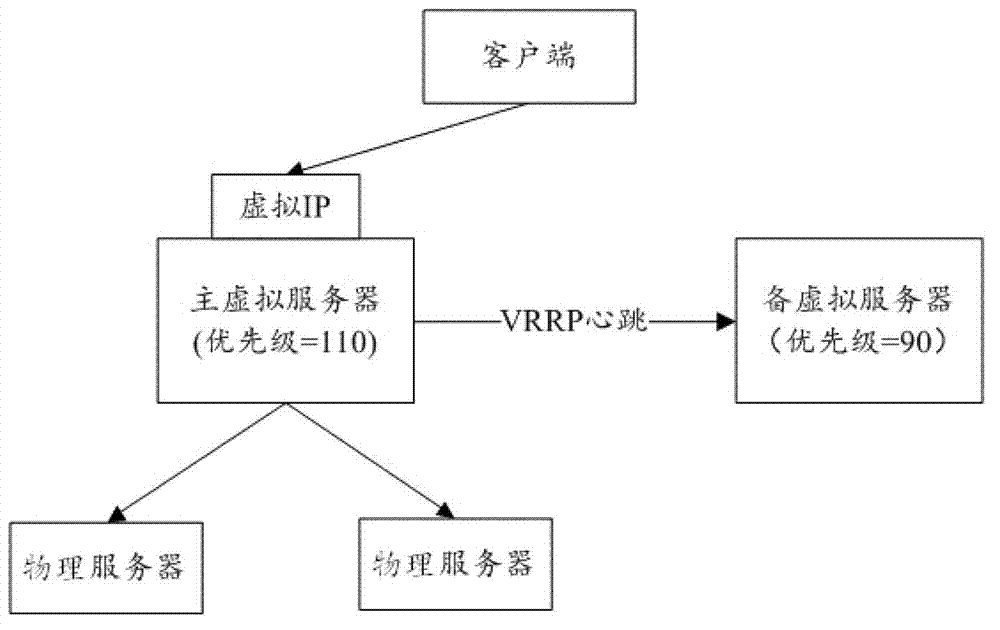
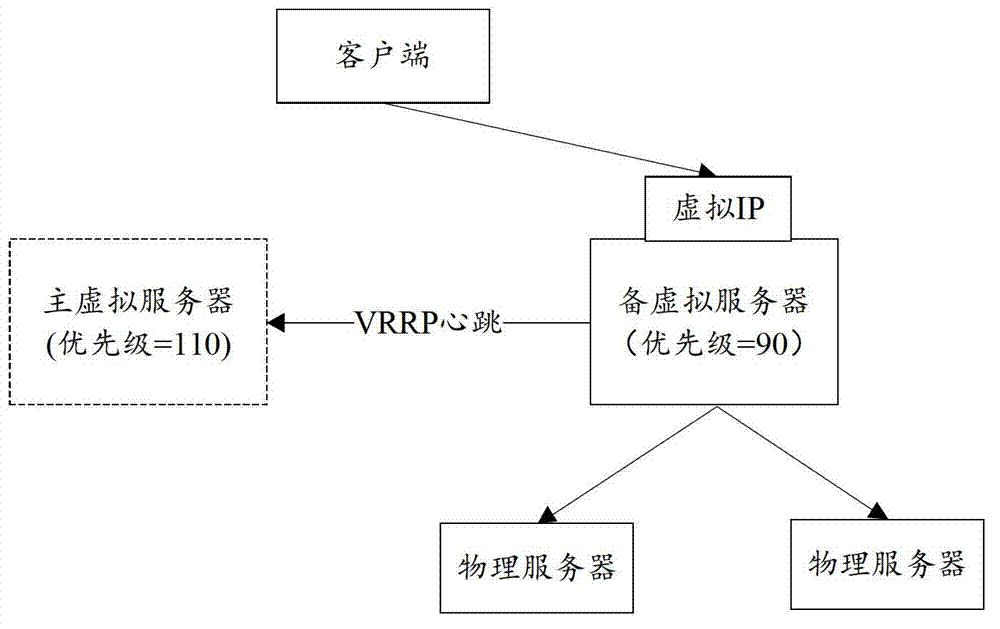
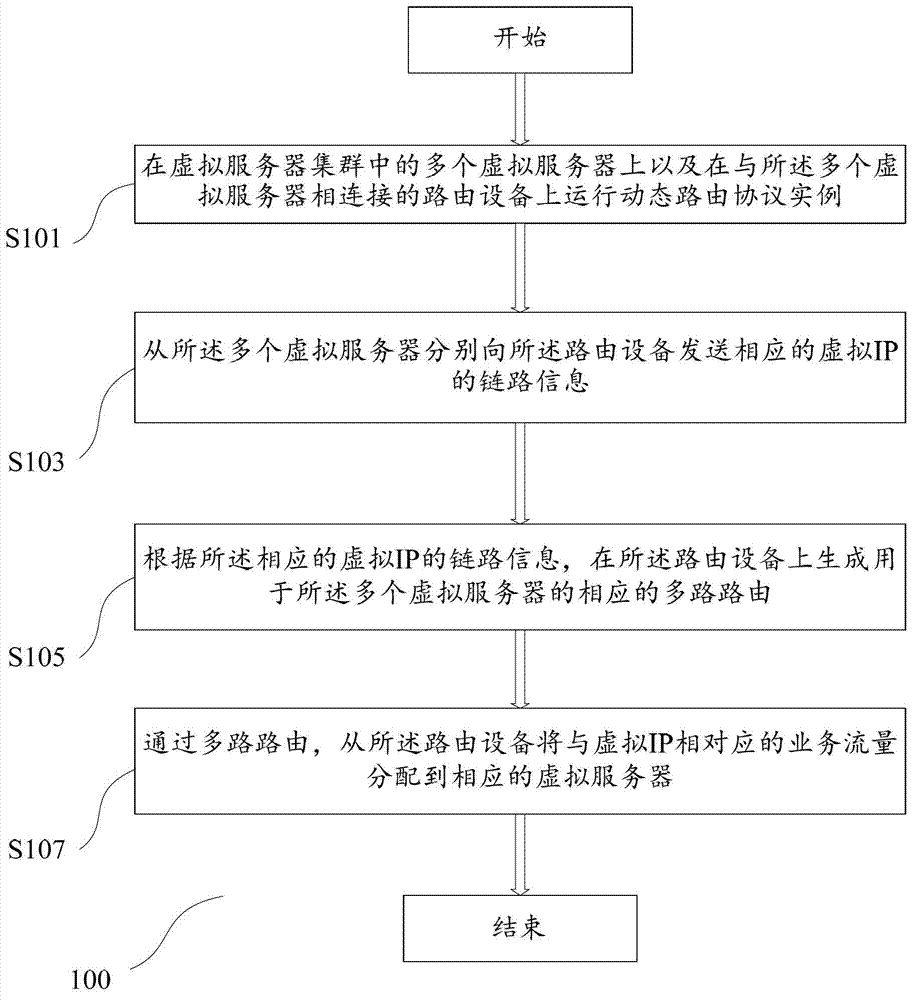
ActiveCN102821044ASolve performance bottlenecksEasy to expandNetworks interconnectionTraffic volumeTraffic capacity
The embodiment of the invention provides a method and a device for configuring a server cluster. The method comprises the following steps: running a dynamic routing protocol on a plurality of virtual servers in a virtual server cluster and a router connected with the plurality of virtual servers; sending link information of corresponding virtual IP (internet protocol) from the plurality of virtual servers to the router; generating a corresponding multi-path router for the plurality of virtual servers on the router according to the link information of the corresponding virtual IP; and distributing the traffic flows corresponding to the virtual IP from the router to the corresponding virtual servers through the multi-path router. According to the invention, the problem of performance bottleneck of the single virtual server can be solved, the virtual server cluster can be extended simply and conveniently, and the operation and maintenance cost is greatly reduced.
Owner:BEIJING QIHOO TECH CO LTD
Novel metadata server cluster and metadata management method based on reconciliation statement
InactiveCN101957861AAvoid performance bottlenecksIncrease flexibilitySpecial data processing applicationsMetadata managementEngineering
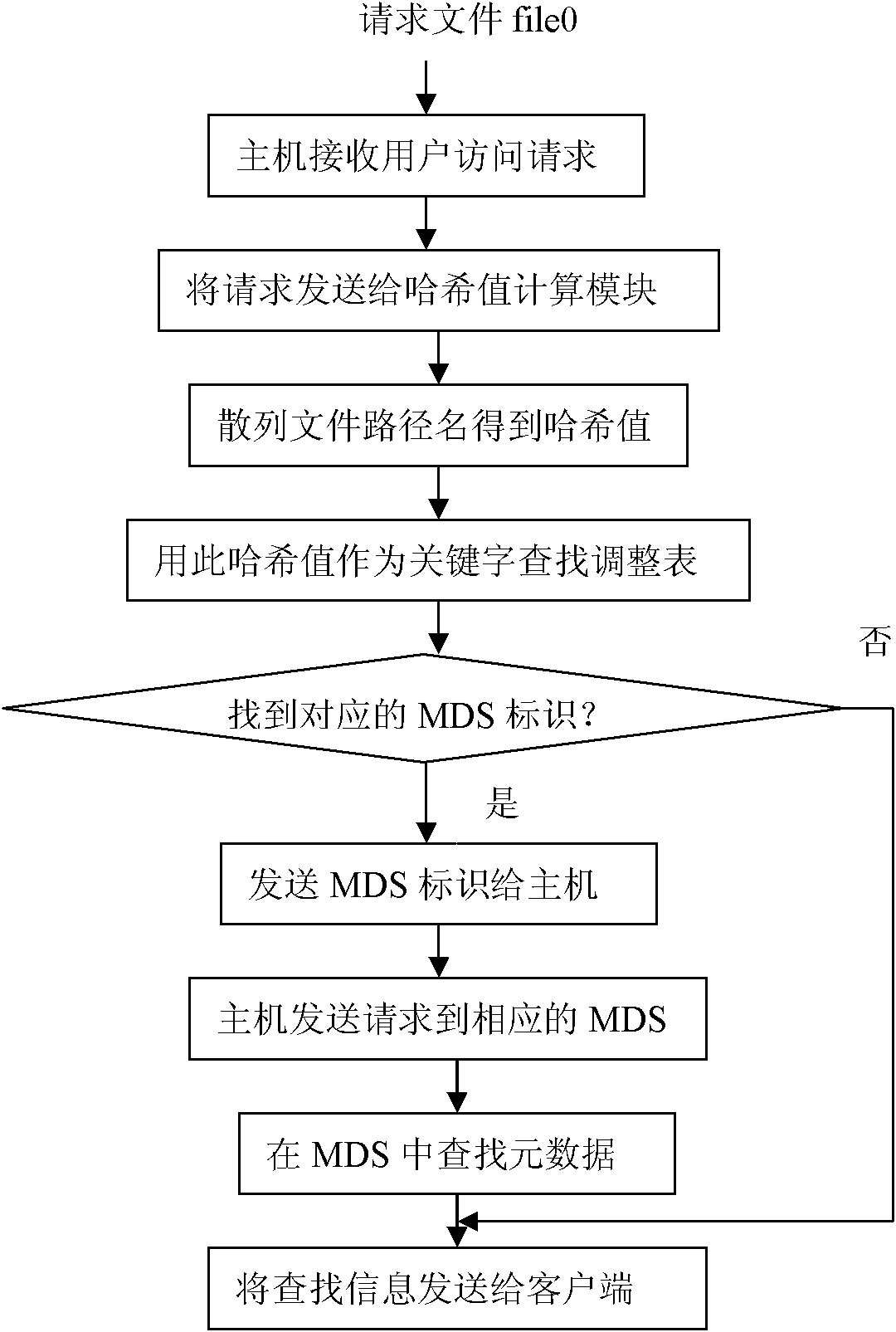
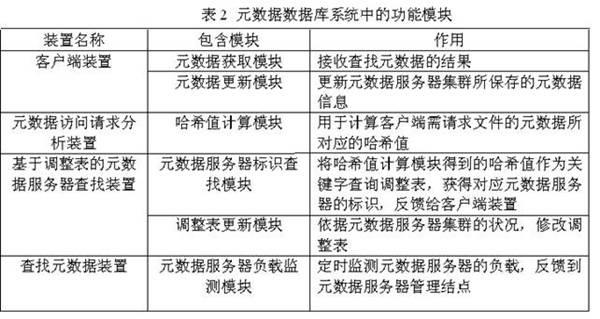
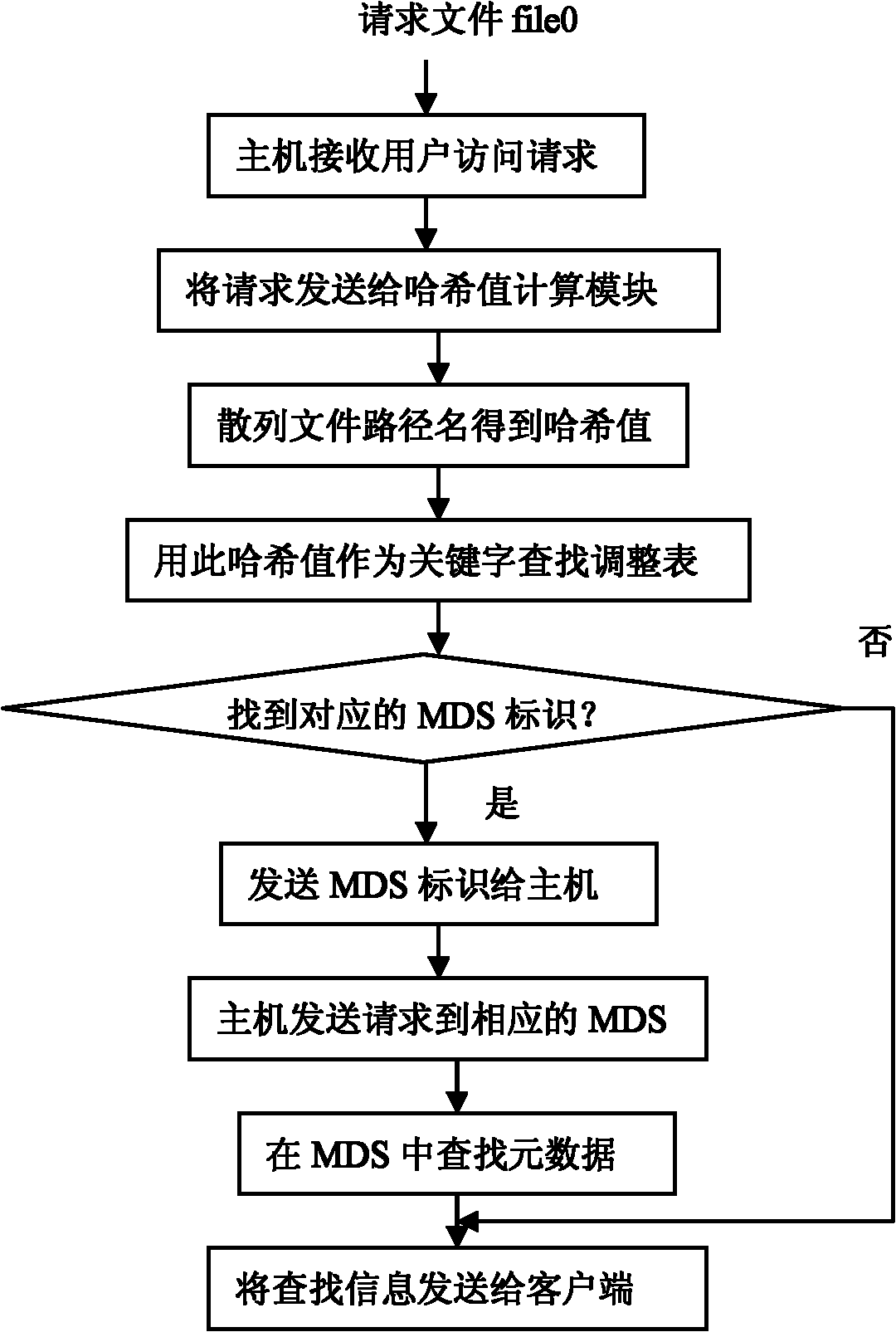
The invention discloses a metadata management method based on a reconciliation statement, which comprises the following steps: managing the metadata by a metadata server cluster, and after calculating Hash value by using document route, obtaining the corresponding metadata server identification by searching the reconciliation statement. The invention gives out the reconciliation statement regulation strategy under a plurality of typical situations, the novel metadata server cluster structure and introduces the flow of main functional modules. The invention can rapidly eliminate a hot spot metadata server in the metadata server cluster aiming at problems of the metadata management, is convenient for the system adjustment after adding and deleting the metadata server, reduces pay expenses of the time and space required for the metadata management, and improves flexibility of metadata management.
Owner:JIANGSU UNIV
Log data processing method and system
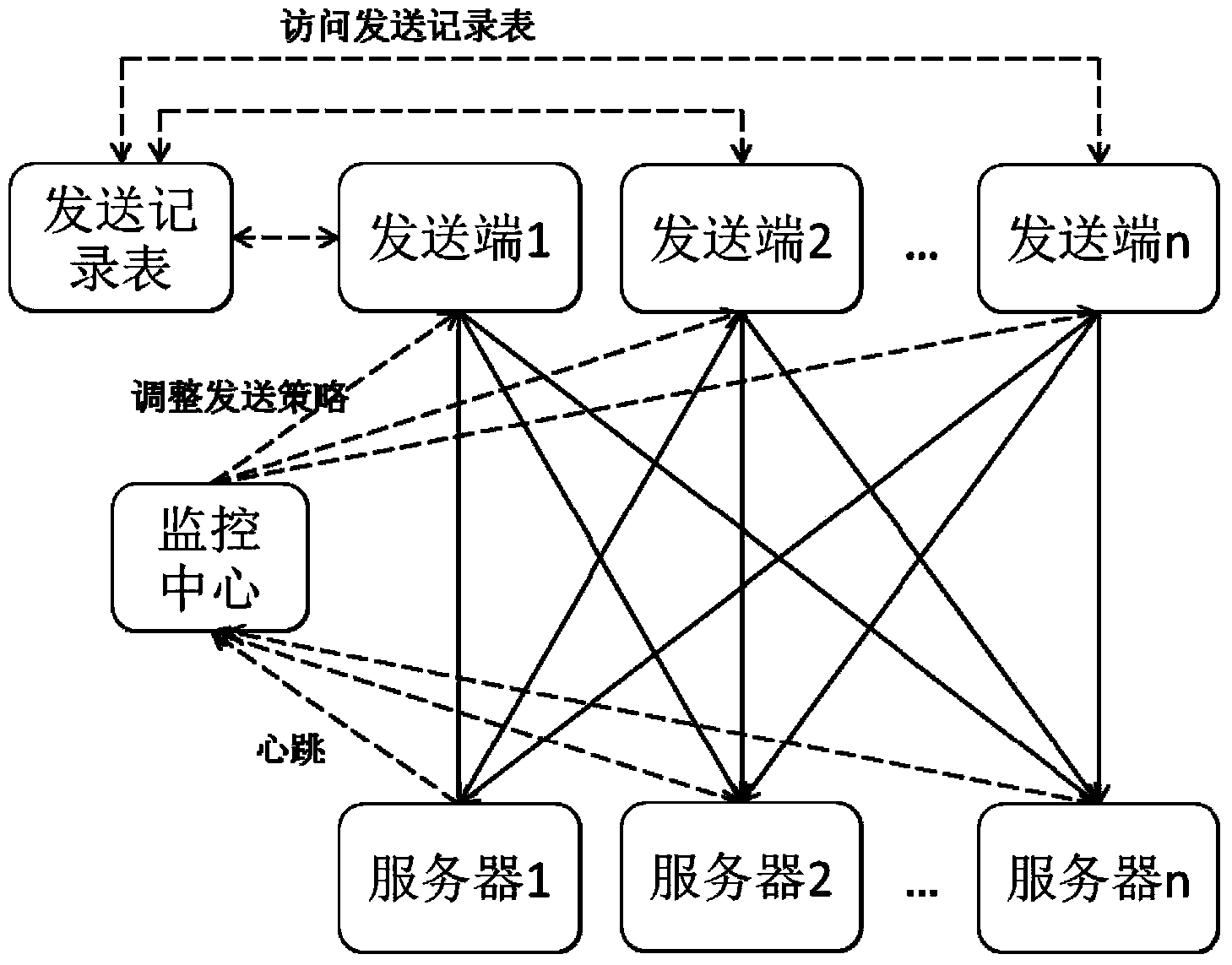
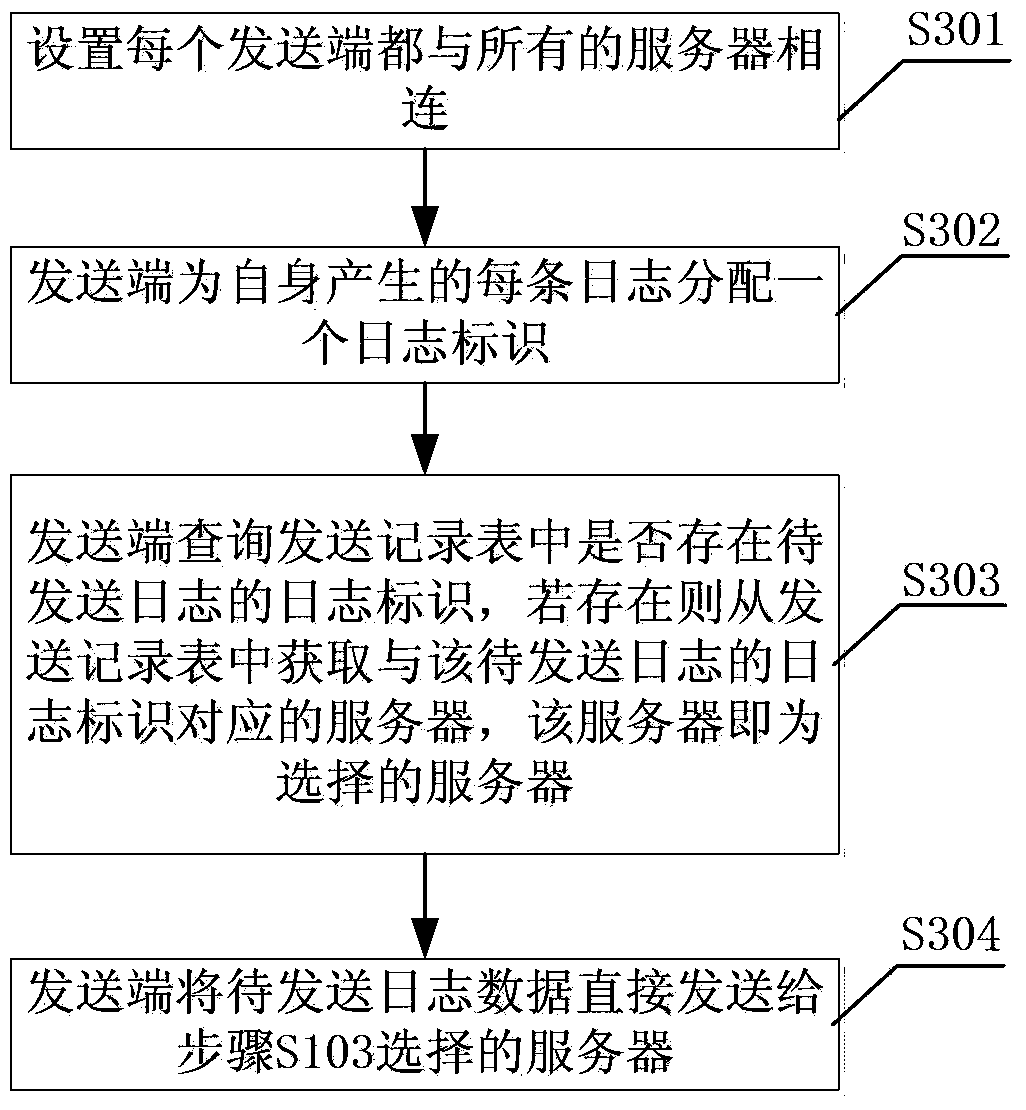
ActiveCN103401937AAvoid performance bottlenecksImprove scalabilityTransmissionUser identifierReal-time computing
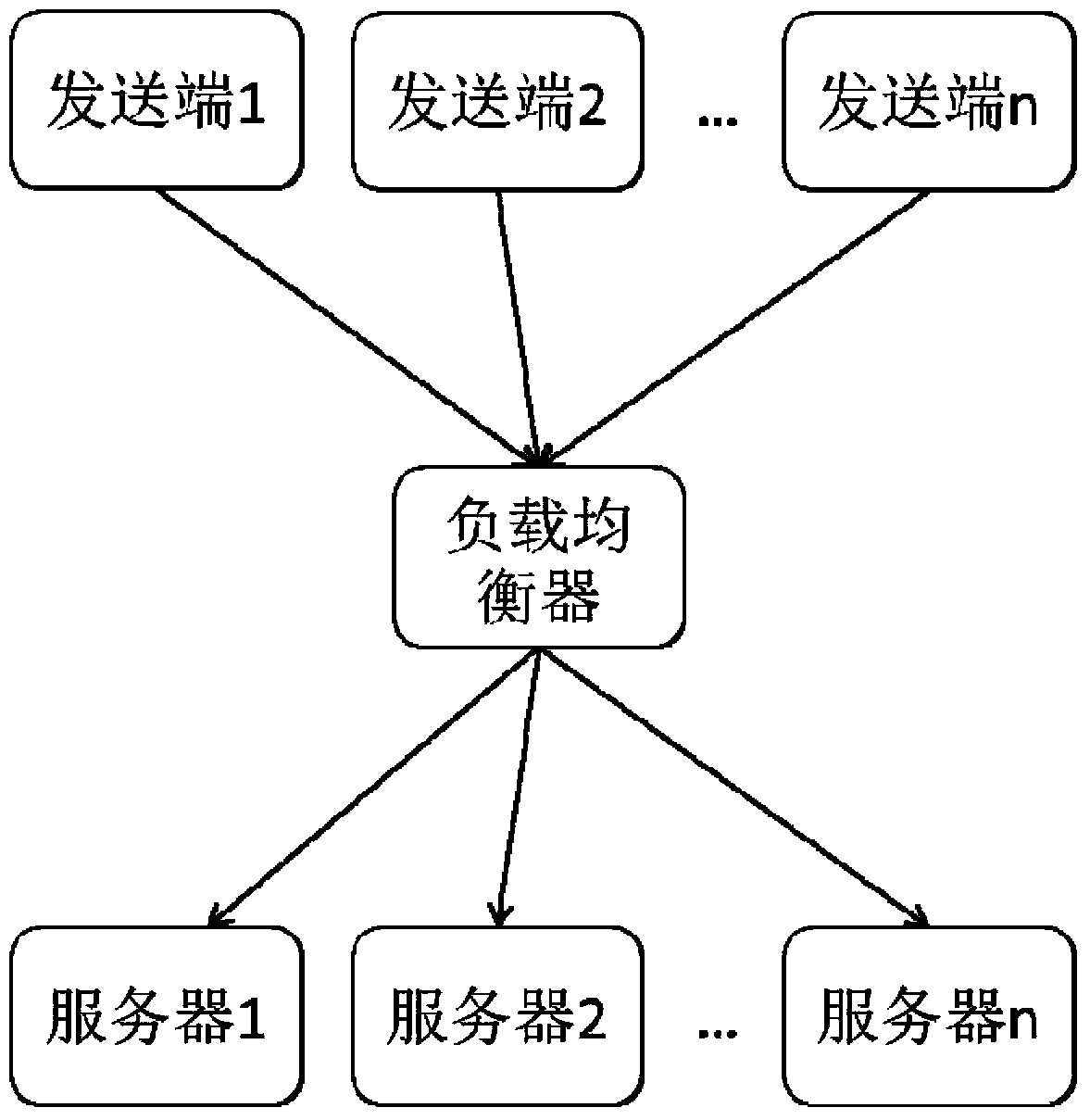
The invention relates to a log data processing method and system, wherein the log data processing method comprises the following steps: 1, each sending end is set to be connected with all servers; 2, the sending ends distribute a log identifier to each log self-generated; 3, the sending ends inquire whether the log identifier of the log to be sent in a sending record table or not, if so, the sending ends obtain a server identifier corresponding to the log identifier of the log to be sent from the sending record table, wherein the server corresponding to the server identifier is the selected server; and 4, the sending ends directly send the log data to be sent to the selected server. The method and system provided by the invention prevent a load balancer from becoming performance bottleneck, so that the system applying the log data processing method has good expandability, and better adapts the characteristics of large input data size and small output data size in log analysis.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Method and system for implementing database clustering function
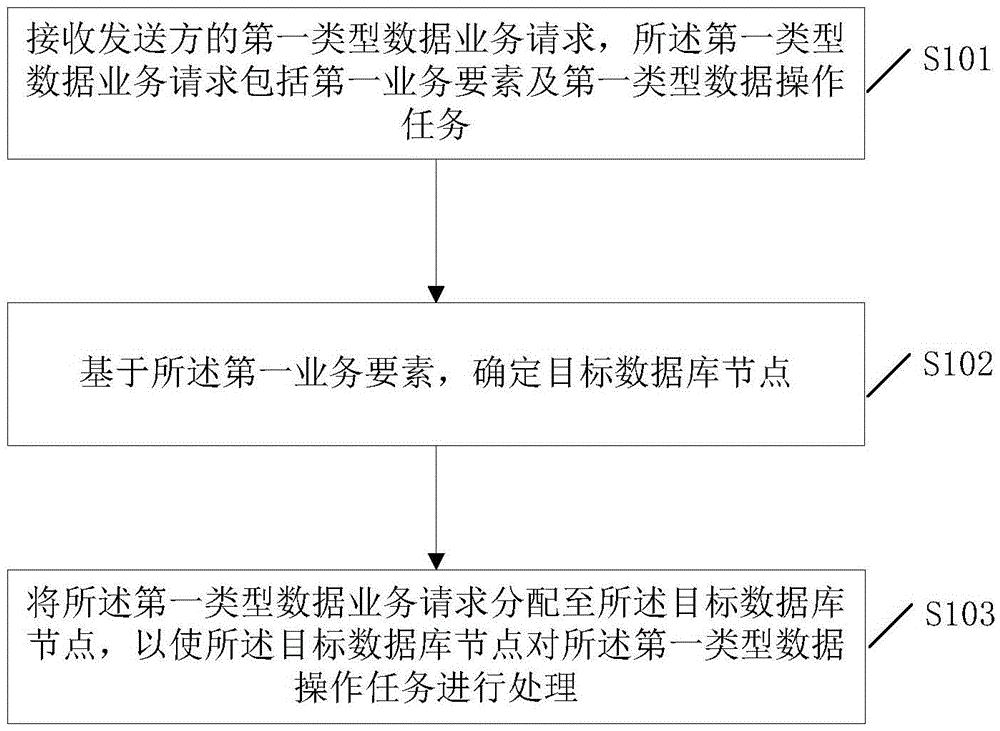
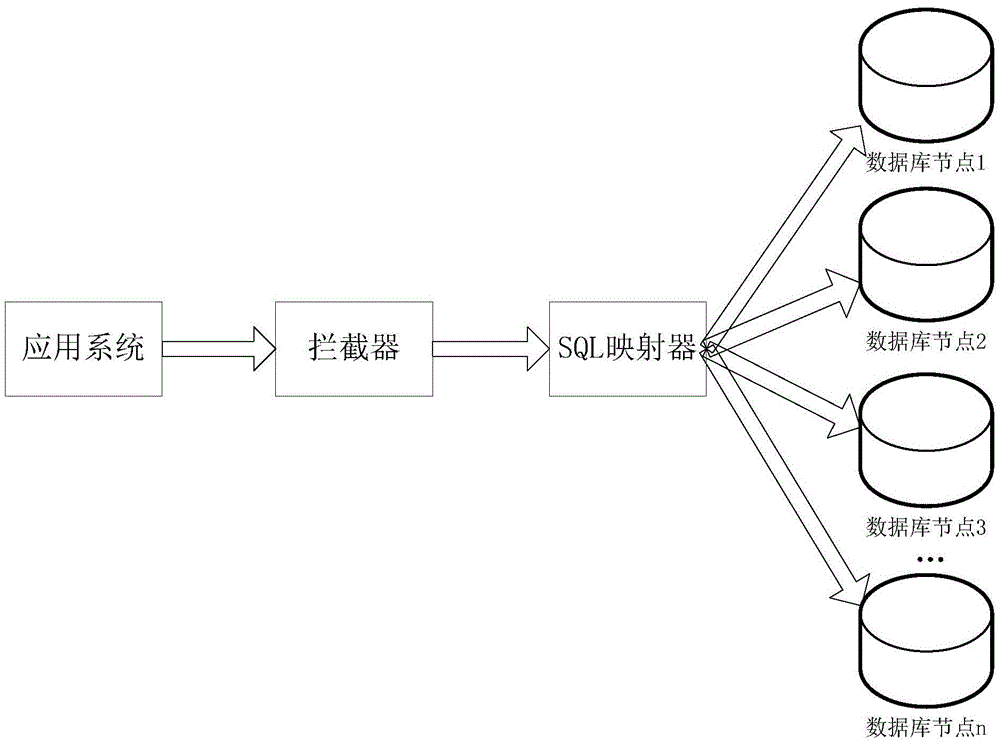
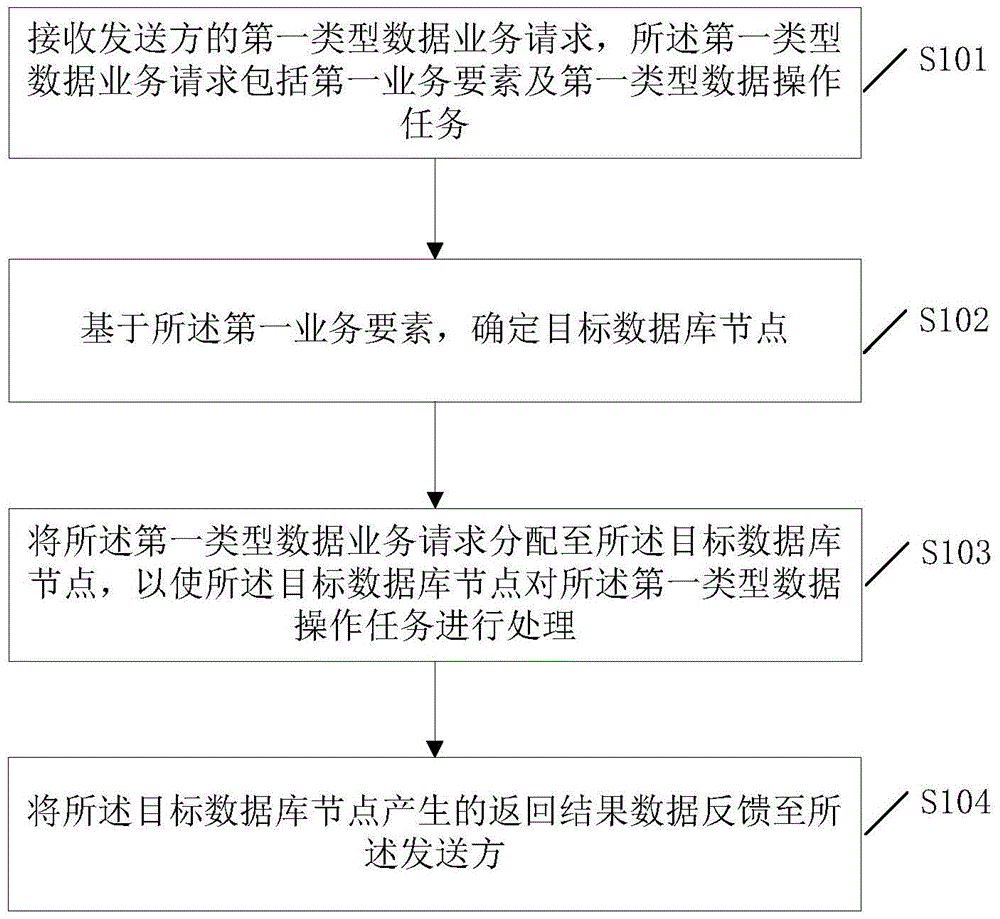
ActiveCN105631028AImplement database extensionsSolve performance bottlenecksDatabase distribution/replicationSpecial data processing applicationsData miningDatabase clustering
The invention discloses a method and system for implementing a database clustering function. According to the method and system, an existing database system only comprising a single database node is expanded into a database cluster comprising multiple database nodes, different kinds of first-type data are stored in the nodes of the database cluster respectively, on this basis, when a first-type data service request of a sender is received, a matched target database node is assigned for the request based on service elements included in the request, and then the request is distributed to the assigned target database node to be processed. Thus, different kinds of data are stored in different nodes of the database cluster, the database clustering function is achieved through effective service routing, database expansion can be effectively achieved based on the function, and therefore the problem of performance bottleneck brought by a single database is solved.
Owner:AGRICULTURAL BANK OF CHINA +1
Linkable distributed network intrusion detection method based on behavior description
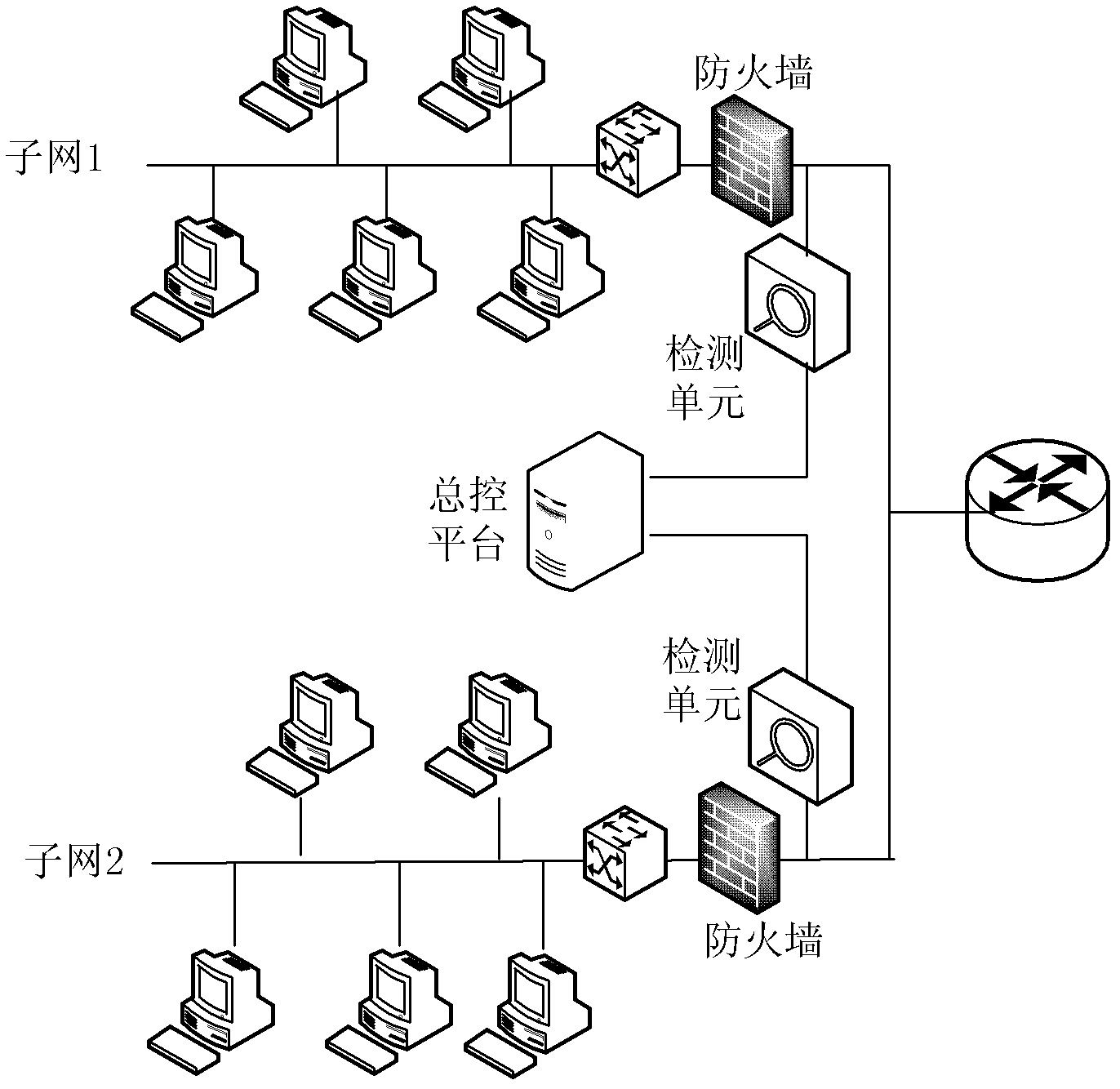
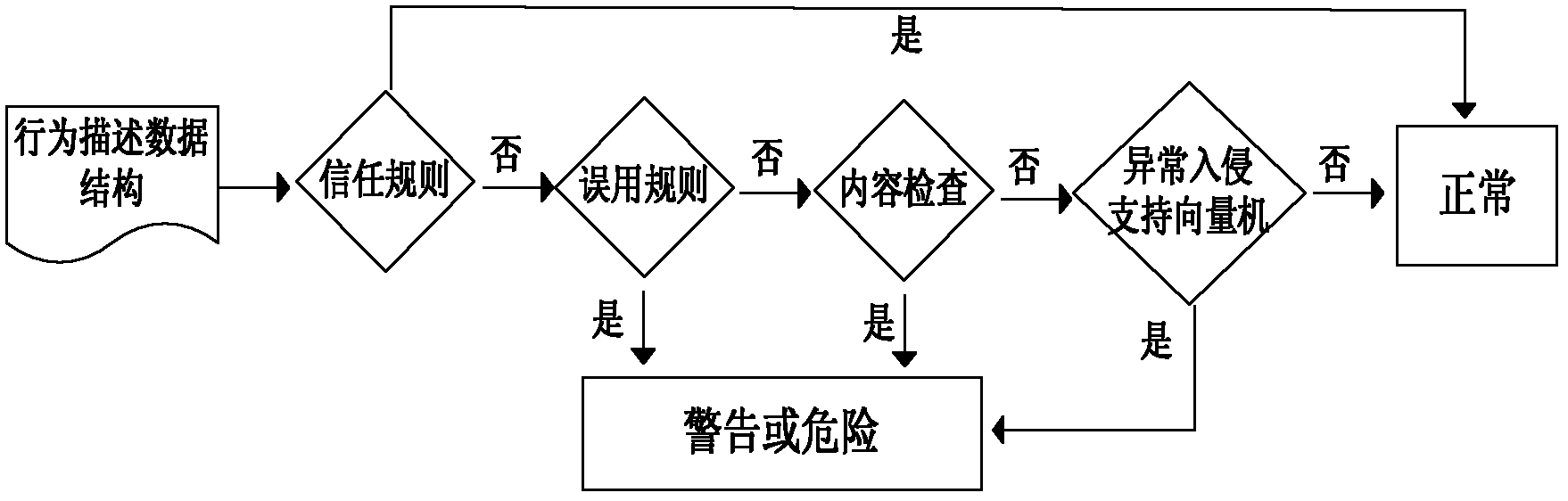
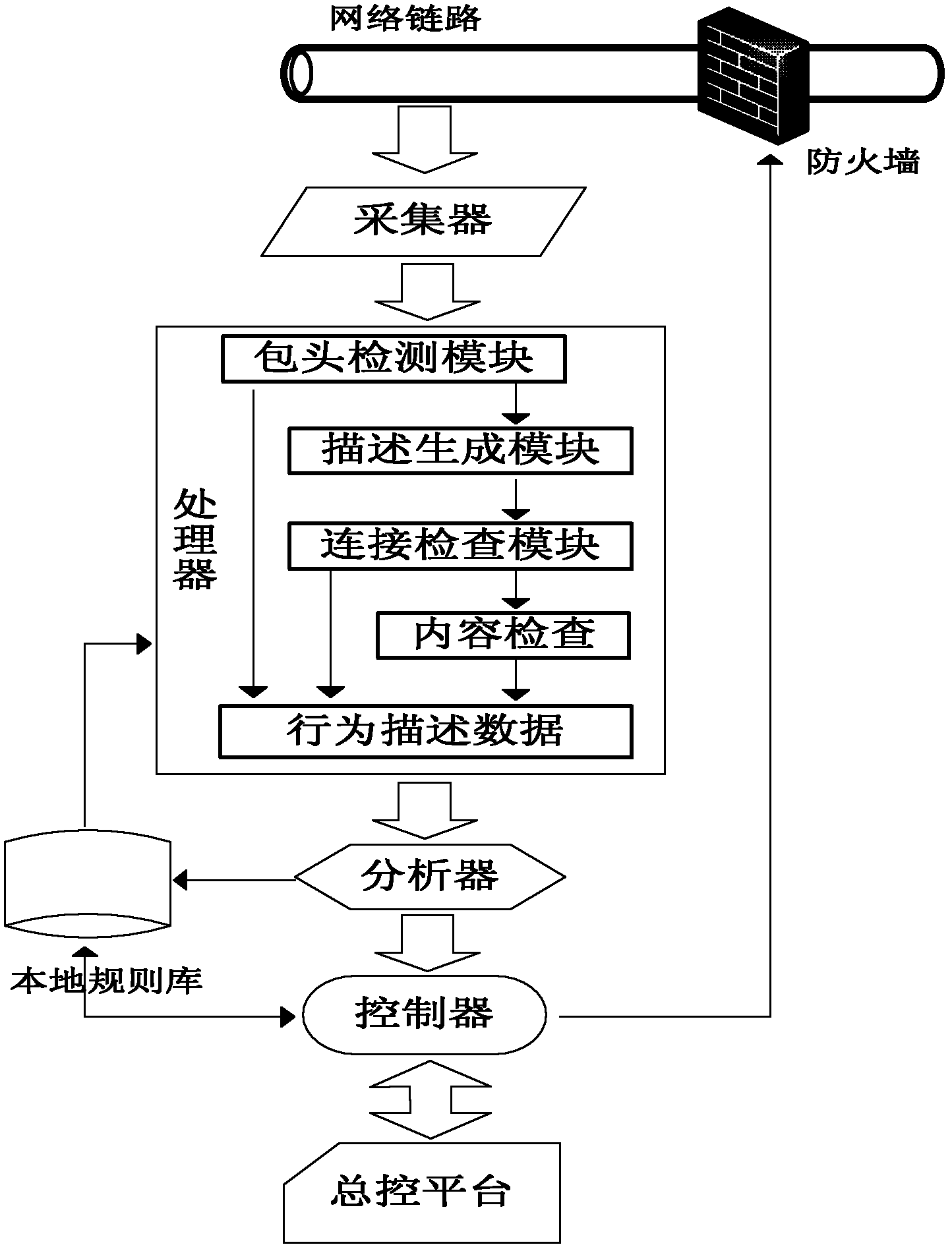
InactiveCN102594620AImprove detection efficiencyImprove global managementData switching networksUnit operationTraffic volume
The invention discloses a linkable distributed network intrusion detection method based on behavior description, which achieves the real-time detection of abnormal flow in a network and timely makes a response by applying methods of the network behavior description and the feature extraction in a distributed detection system and linking with a fire wall, particularly comprising the steps of (a), a detection unit operation process and (b), a master control platform operation process: applying a detection strategy based on the behavior description on distributed detection units to effectively organize the distributed detection units to be an efficient organic whole, thus avoiding the low efficiency and the dispersibility of the existing system scheme, wherein the aim is to solve the low efficiency of the abnormal flow detection on a large network in the practical application and improve the whole detection ability and the protection effect of the detection system for the network.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method, application and system for managing server cluster
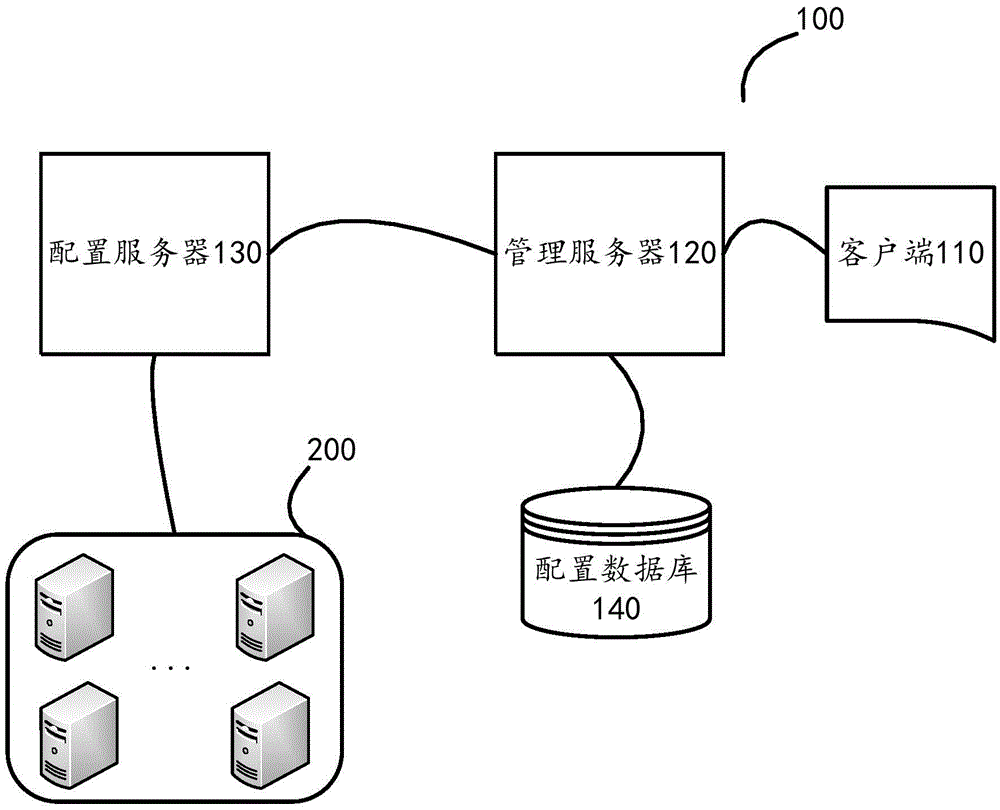
ActiveCN105610987ARealize centralized automation managementAvoid modificationTransmissionApplication serverConfiguration item
The invention discloses a method, application and system for managing a server cluster. The method for managing configuration data of the server cluster is applicable to be executed in a management server. The server cluster comprises a plurality of application servers. The method comprises the following steps: receiving first configuration information from a client, wherein the first configuration information comprises an identification of a corresponding configuration item and configuration data of the configuration item; and synchronizing the received first configuration information to a configuration server, so as to facilitate the configuration server to inform one or multiple of the plurality of application servers monitoring the configuration item to acquire the first configuration information.
Owner:CHEZHI HULIAN BEIJING SCI & TECH CO LTD
Cache data updating method and device
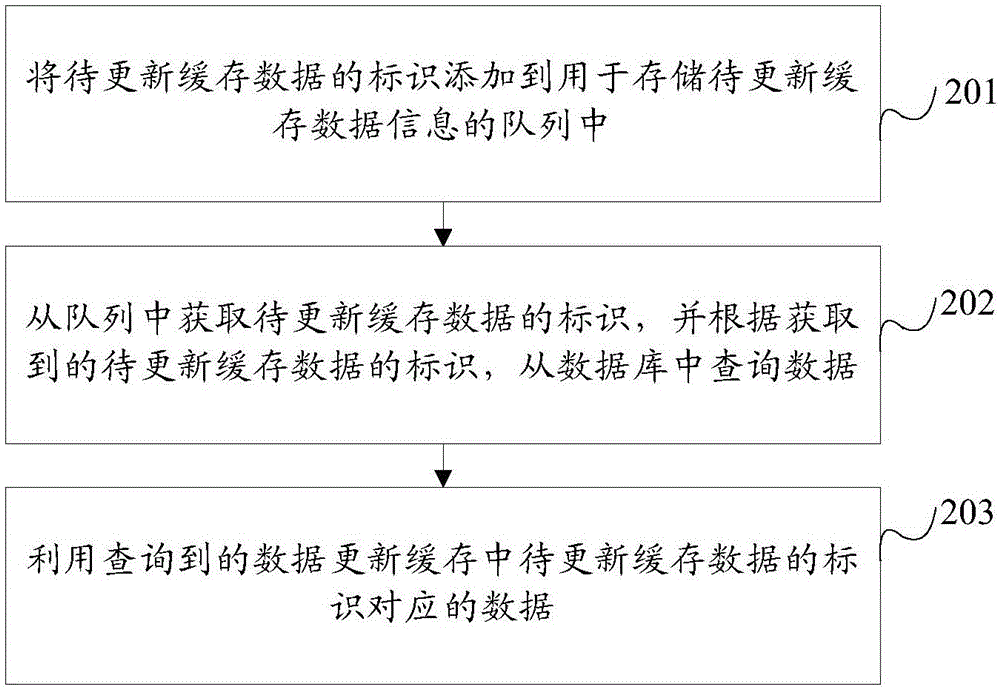
InactiveCN106815329ASmall amount of calculationImprove securityDatabase updatingInterprogram communicationParallel computingData messages
The embodiment of the invention provides a cache data updating method. The cache data updating method includes: adding an identification of cache data to be updated to a queue for storing information of the cache data to be updated; acquiring the identification of the cache data to be updated from the queue, and querying data from a database according to the acquired identification of the cache data to be updated; using the acquired data to update data, corresponding to the identification of the cache data to be updated, in a cache. The cache data updating method can timely update data in the cache, can reduce the calculation load, and can improve the security of the database. In addition, the embodiment of the invention provides a cache data updating device.
Owner:ALIBABA (CHINA) CO LTD
Query method based on big data
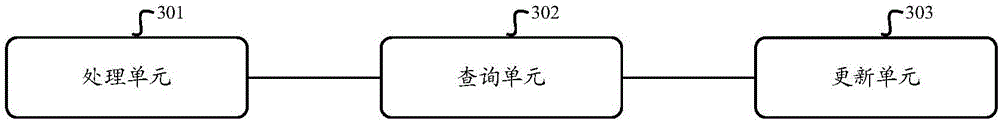
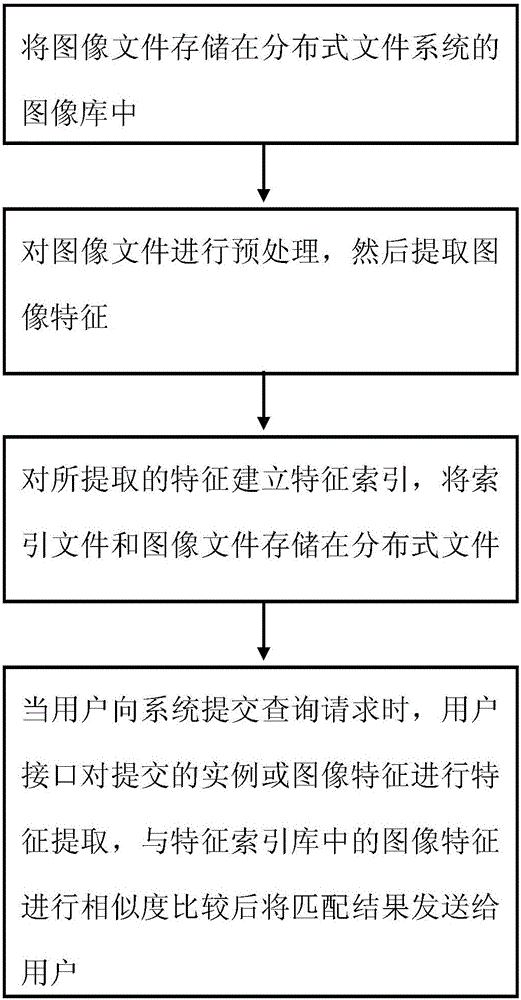
InactiveCN105160039AOptimize storageSearch process optimizationSpecial data processing applicationsDistributed File SystemIndexed file
The invention provides a query method based on big data. The method comprises the following steps: storing an image file into an image library of a distributed file system; preprocessing the image file, and extracting an image characteristic; establishing a characteristic index for the extracted characteristic, and storing an index file and the image file into a distributed file database; and when a user submits a query request to a system, a user interface carries out characteristic extraction on submitted living examples or the image characteristic, carries out similarity comparison with the image characteristic in a characteristic index database and then sends a matching result to the user. The invention provides the query method based on the big data, a storage and retrieval process of the image data is optimized through the distributed system, retrieval efficiency is improved, and performance bottlenecks are overcome.
Owner:SICHUAN XIECHUANG INFORMATION TECH SERVICE
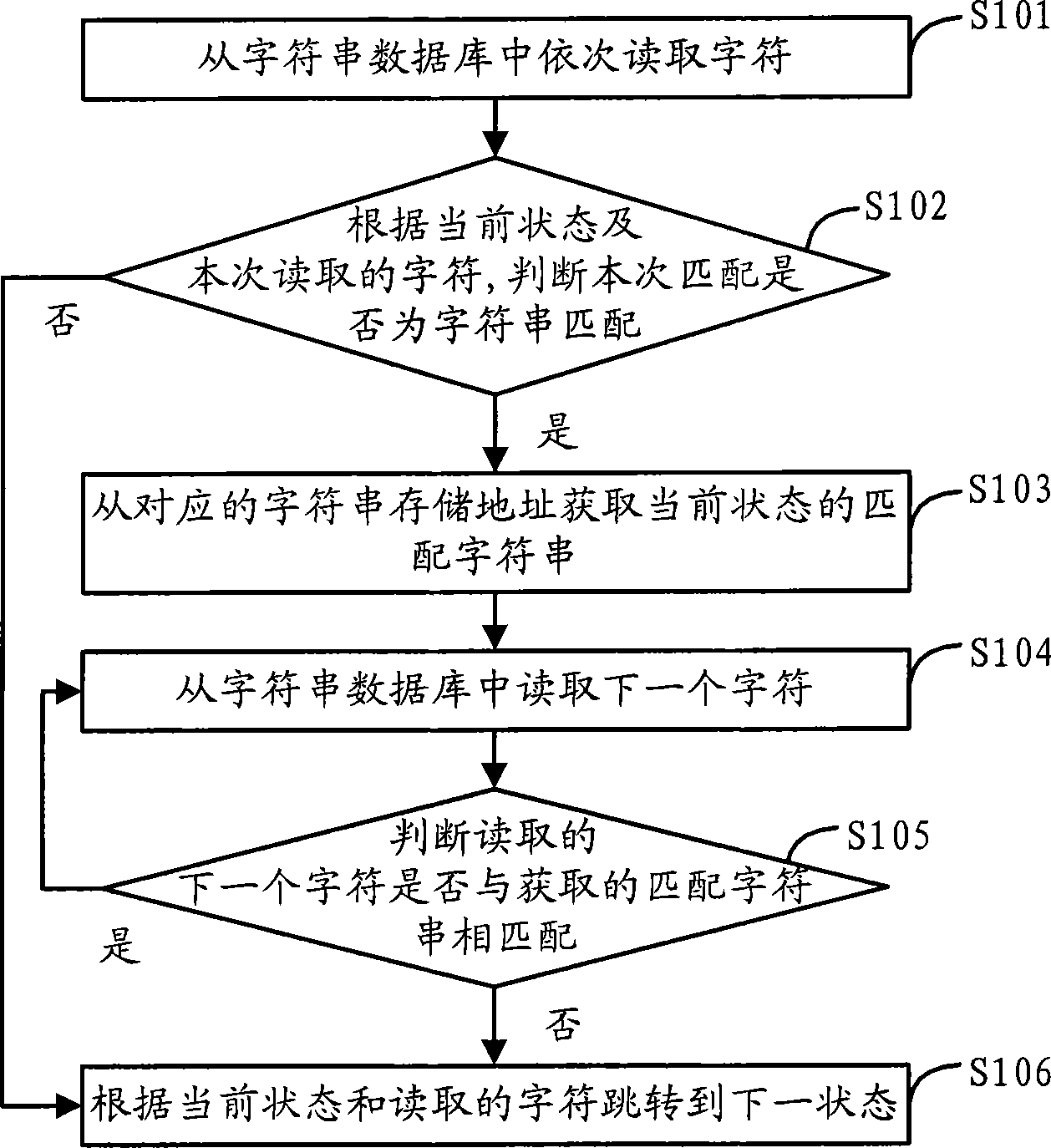
Character string matching method based on finite state automation and content filtering equipment
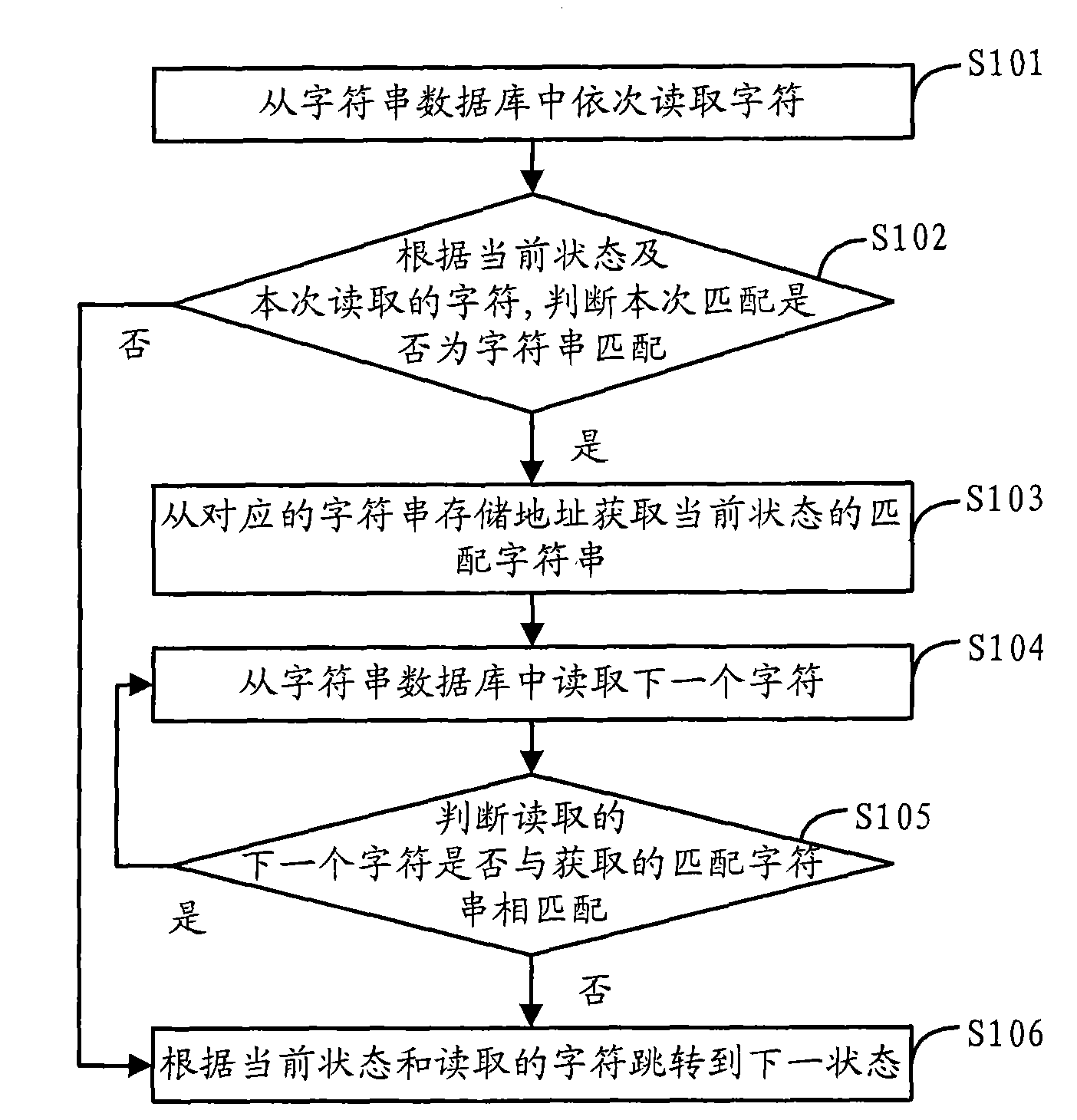
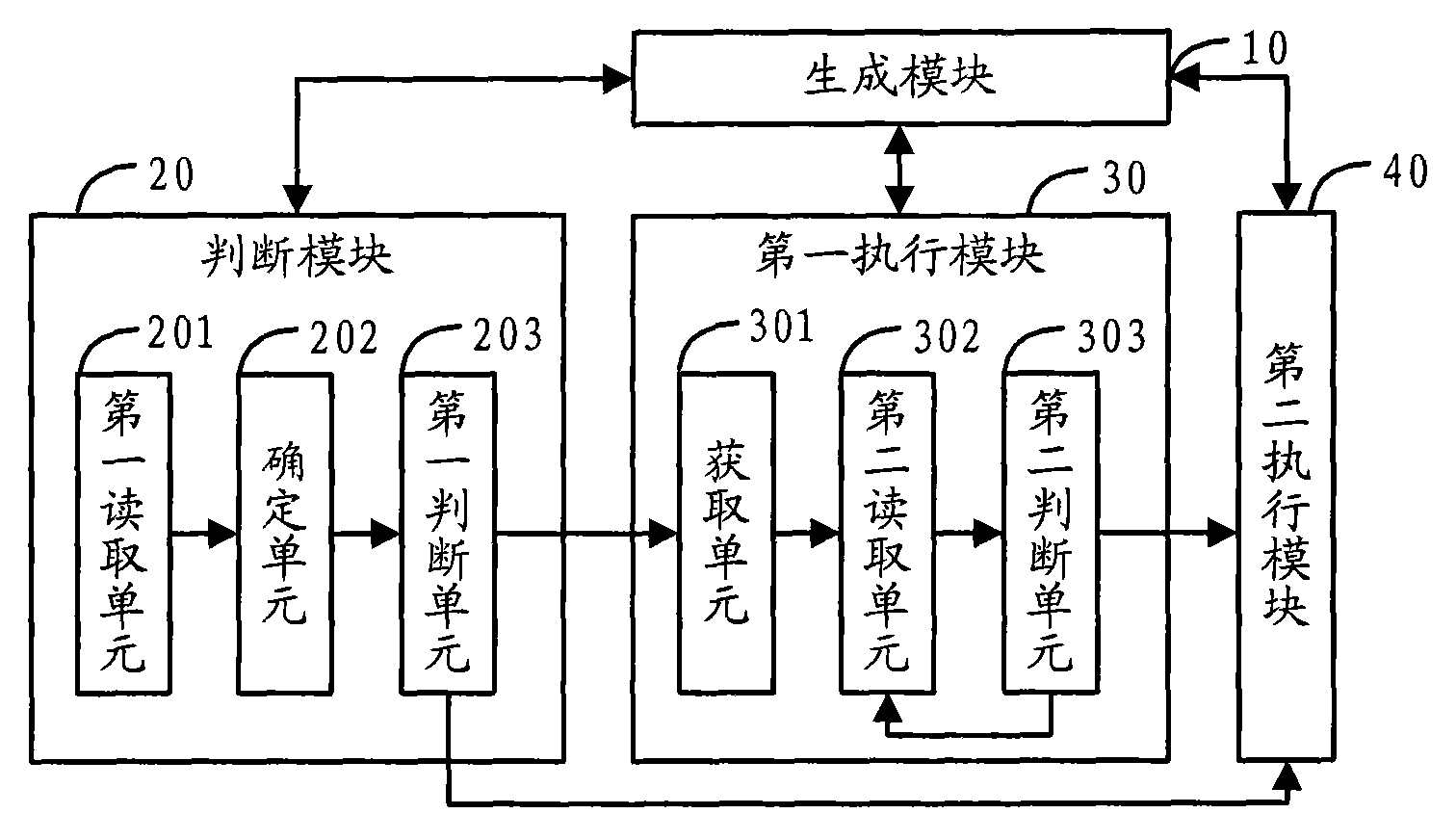
InactiveCN101876986AReduce the number of accesses to main memorySolve system performance bottlenecksSpecial data processing applicationsFinite stateString database
The invention discloses a character string matching method based on a finite state automation and content filtering equipment. The character string matching method comprises the step of combining two sequence-associated states meeting the set conditions in a DFA (Deterministic Finite Automaton) to obtain a combined DFA; the corresponding matching process of character strings comprises the following steps of: sequentially reading characters from a character string database and judging whether the matching is character string matching according to the current state and the read characters; if not, skipping to the next state according to the current state and the read characters; if so, acquiring a matched character string of the current state from the corresponding storage address of the character string, reading next character and judging whether to be matched with next character matched with the character string or not; during matching, continuously reading next character and skipping to the next state until the character strings are successfully matched; and if not, skipping to the next state according to the current state and the read characters. By using the method, the times for accessing a memory during the matching of the character strings can be reduced and the speed and the efficiency for the matching of the character strings can be improved.
Owner:RUIJIE NETWORKS CO LTD
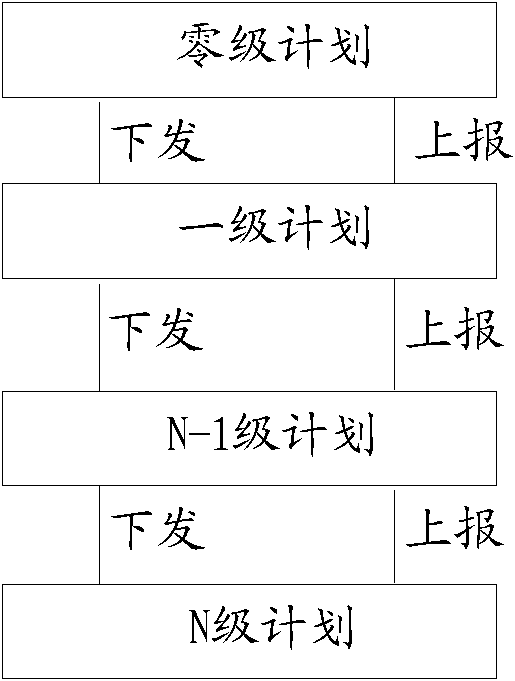
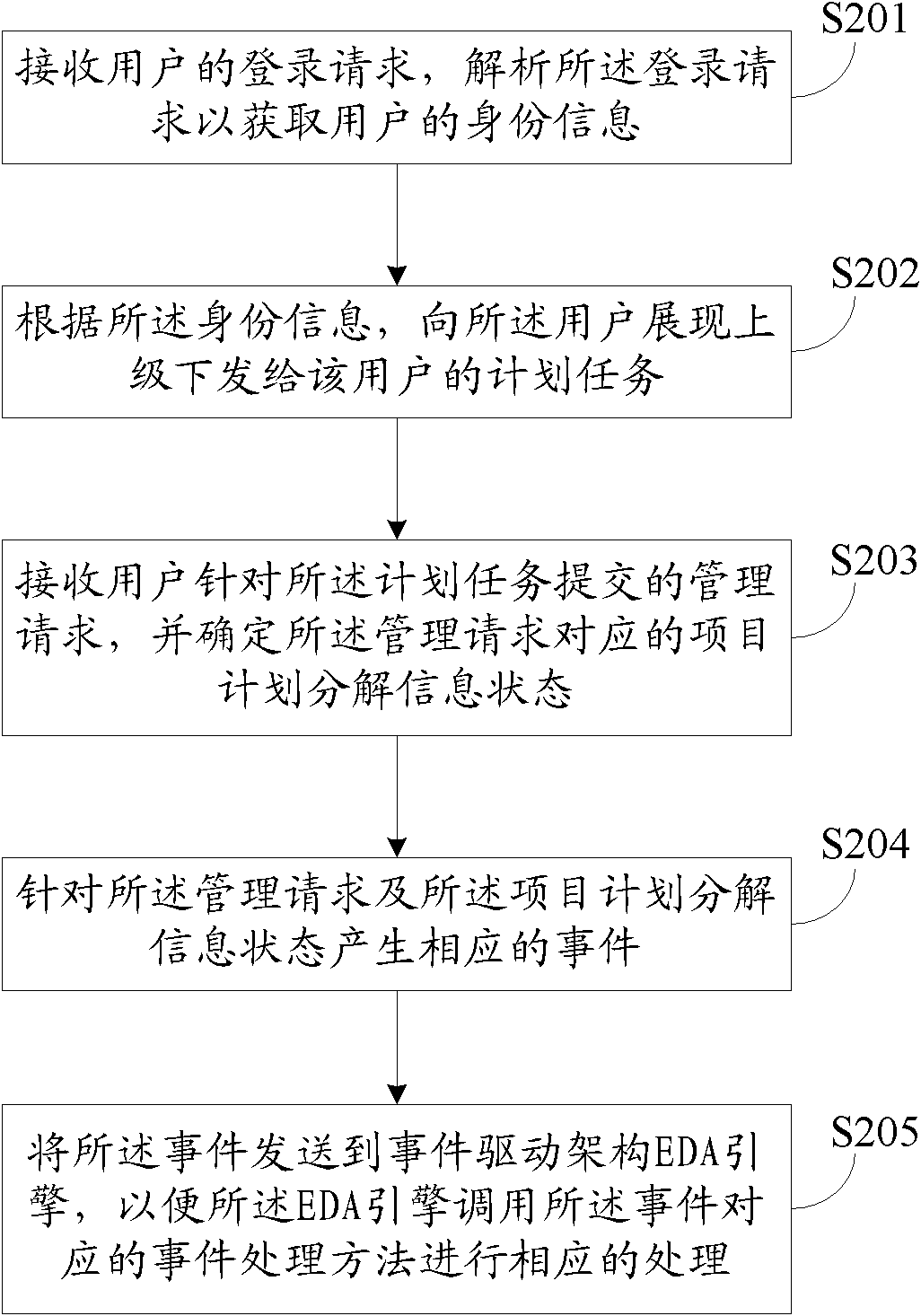
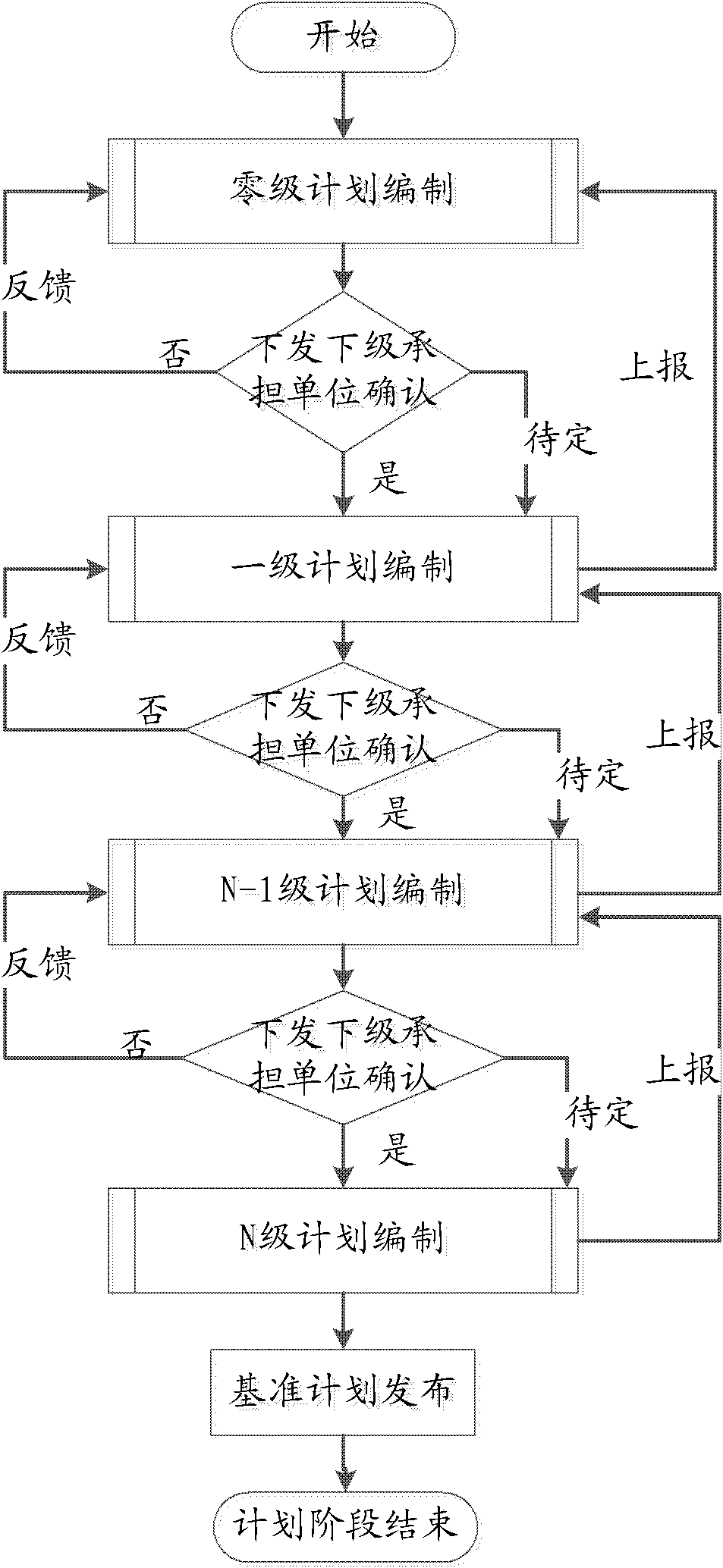
Method and system for processing project plans
The invention discloses a method and a system for processing project plans. The method of the invention comprises the following steps of: receiving a logging-on request of a user and analyzing the logging-on request for obtaining identity information of the user; presenting a plan task given by superior to the superior-appointed user according to the identity information; receiving a management request submitted by the user with regard to the plan task and determining the project plan decomposition information state corresponding to the management request; generating corresponding events according to the management request and the project plan decomposition information state; and sending the events to an EDA (Event Driven Architecture) engine so that the EDA engine calls an event processing method corresponding to the events to process the events. The method enables users to achieve more efficient work decomposition by means of computer system, thereby being suitable for the plan cooperation of large project having multiple layers and units.
Owner:泛太领时科技(北京)有限公司
Real-time data storage and reading method of relational database
InactiveCN102831245AImprove storage efficiencyImprove storage densitySpecial data processing applicationsReal-time dataExternal data
The invention discloses a real-time data storage and reading method of a relational database, and the method comprises the following steps of real-time data storage: receiving external data; searching a data cache block corresponding to the received data; utilizing the data recorded by the data cache block to judge whether the currently received data is required to record or not; writing the currently received data into the data cache block; judging whether the data cache block is filled or not; submitting the data in the data cache block to a database engine; and real-time data reading: transmitting a data inquiry request; searching a data cache block corresponding to the inquired data; judging whether the currently inquired data is completely filled in the data cache block; submitting an inquiry request to the database engine, and writing the data returned by the database engine into a temporary cache zone; restoring corresponding data; and merging the data in the data cache block and the data in the temporary cache zone, and returning the inquiry result. Due to the adoption of the method, the problems that the traditional relational database is slow in reading-writing speed and poor in access performance can be solved.
Owner:LUOYANG XIANGFEI ELECTRICAL & MECHANICAL TECH
Remote automatic upgrading method for digital monitoring equipment
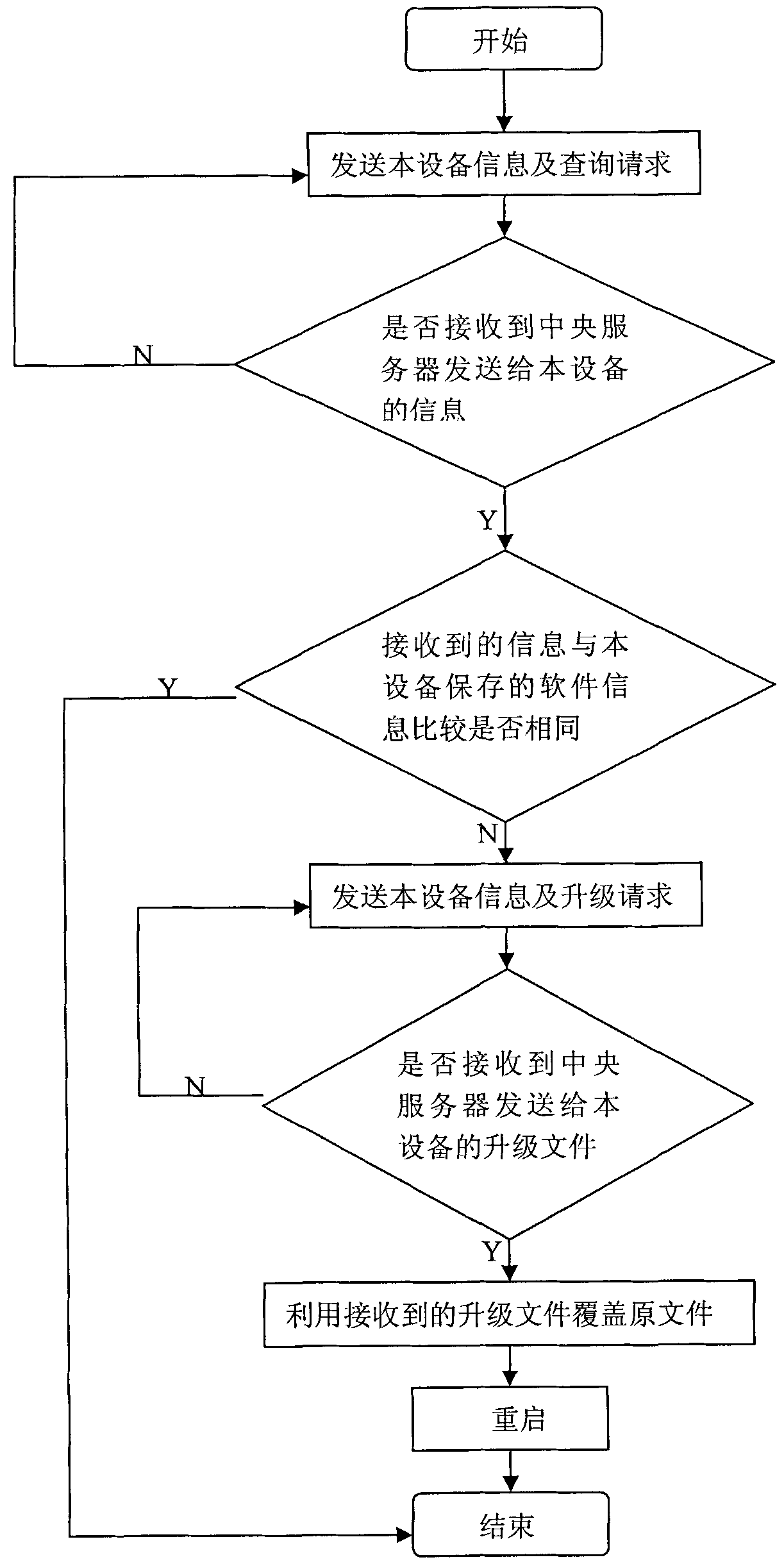
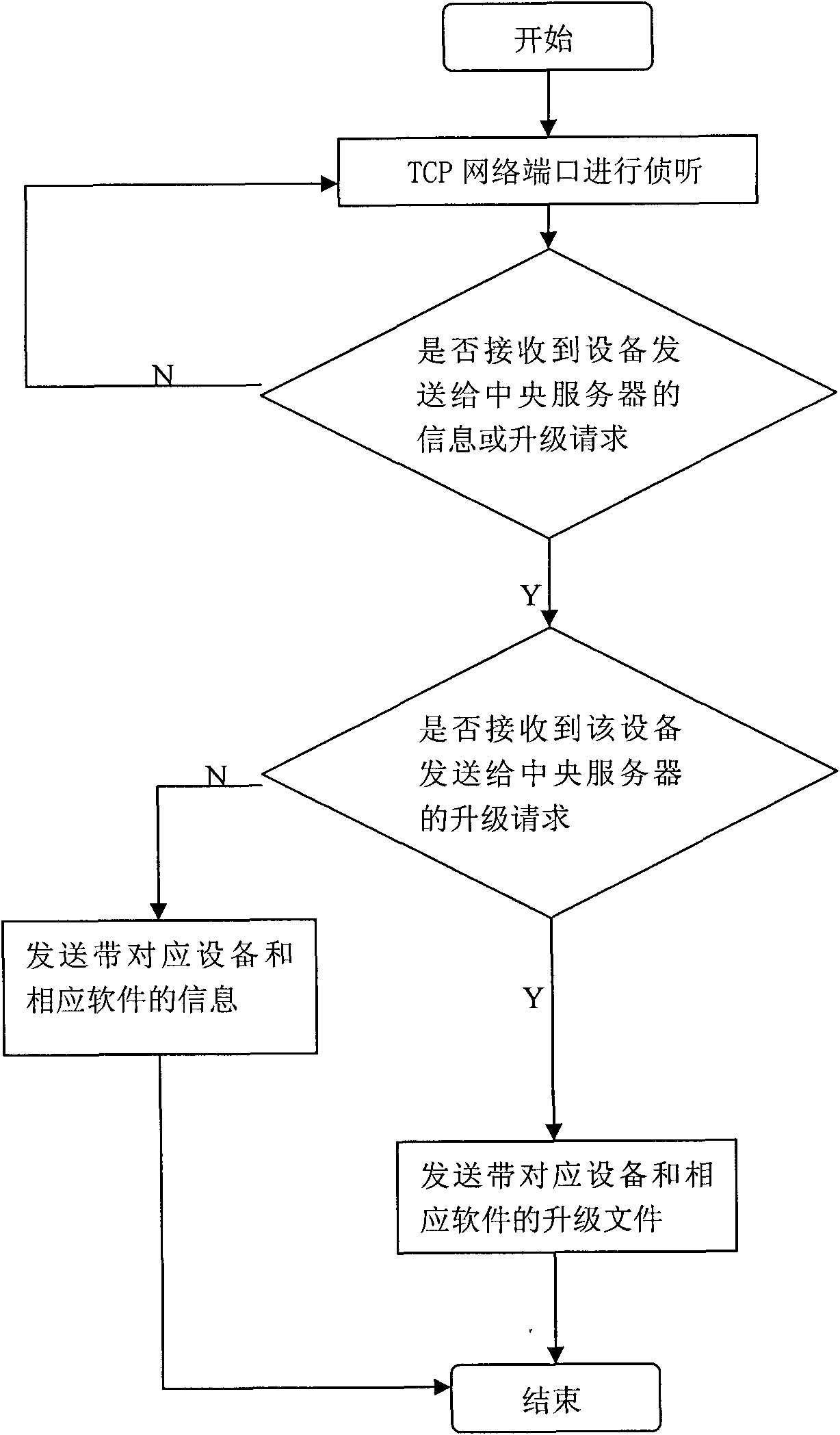
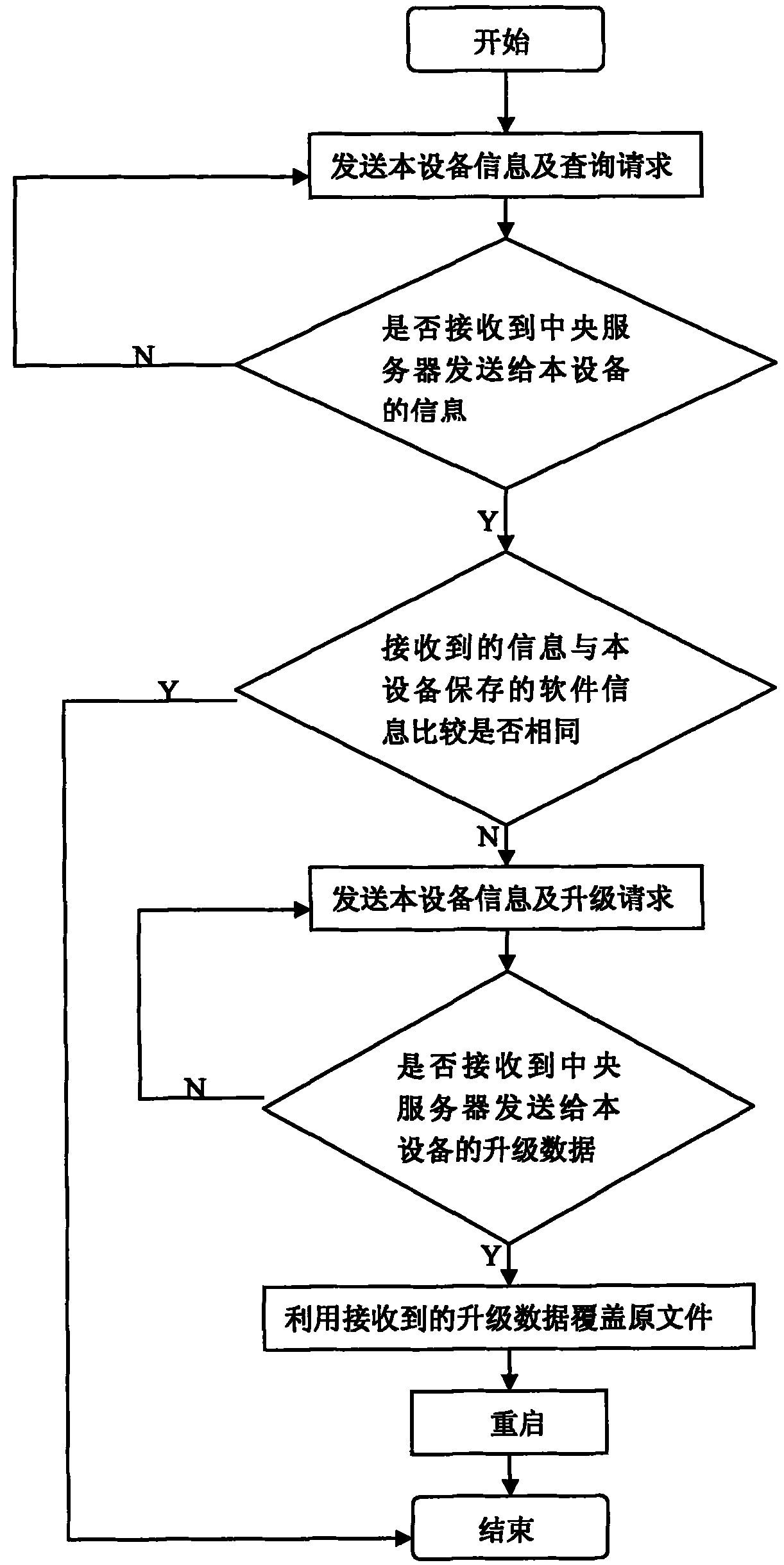
InactiveCN101841536AEasy to deployEasy maintenanceData switching networksComputer hardwareMonitor equipment
The invention discloses a remote automatic upgrading method for digital monitoring equipment. The method comprises the following two parts: the digital monitoring equipment upgrades a client program, and the central server upgrades a service program. The method comprises the following specific steps: after the monitoring equipment is started, transmitting an inquiry request to a central management server at regular intervals; when the port of the central server monitors that the monitoring equipment requires the inquiry request, upgrading the service program and transmitting the information of the corresponding software to the monitoring equipment; after the monitoring equipment receives the information, comparing the information with the locally stored information; and when the comparison result indicates that upgrading is allowable, requiring the central server to download a corresponding file, covering the file and rebooting the system. The invention has the advantages of simple layout and maintenance, high efficiency and flexibility, can use the mode of regular detection by using the digital monitoring equipment, and does not need too complicated manual intervention.
Owner:SHENZHEN INFINOVA
Search method based on big data
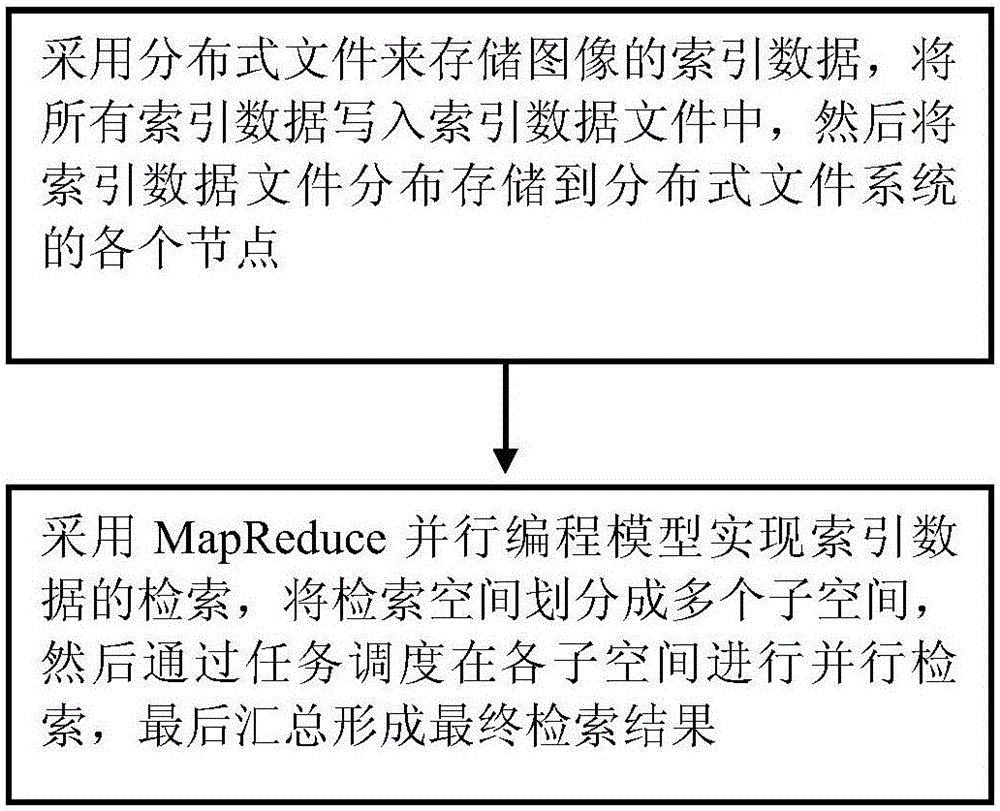
InactiveCN105117502AImprove retrieval efficiencyAvoid performance bottlenecksSpecial data processing applicationsDistributed File SystemParallel programming model
The invention provides a search method based on big data. The method comprises steps as follows: index data of images are stored by the aid of distributed files, all the index data are written into index data files, and then the index data files are distributed and stored in various nodes of a distributed file system; the index data are searched through a MapReduce parallel programming model, a search space is divided into multiple subspaces, then parallel searches are performed on the subspaces through task scheduling, and finally, a final search result is formed through summarizing. With the adoption of the search method based on the big data, processes for storing and searching the data of the images by the aid of the distributed system are optimized, the search efficiency is improved, and the performance bottleneck is overcome.
Owner:SICHUAN ZHONGKE TENGXIN TECH
Metadata cluster distribution storage system and storage data reading and writing method
ActiveCN104378423AAvoid performance bottlenecksAchieve consistencyTransmissionData fileStructure of Management Information
The invention discloses a metadata cluster distribution storage system and a storage data reading and writing method. The metadata cluster distribution storage system comprises a storage network platform and a management network platform, wherein the storage network platform is used for storing data and transmitting the data to a client, the management network platform is used for storing metadata and the information about the position where the data corresponding to the metadata are stored in a storage server cluster, the reading and writing request of the client is responded to according to a preset flow distribution strategy, the data file copy request in the storage network platform is controlled, and the management network platform is of a topological structure.
Owner:ISOFT INFRASTRUCTURE SOFTWARE
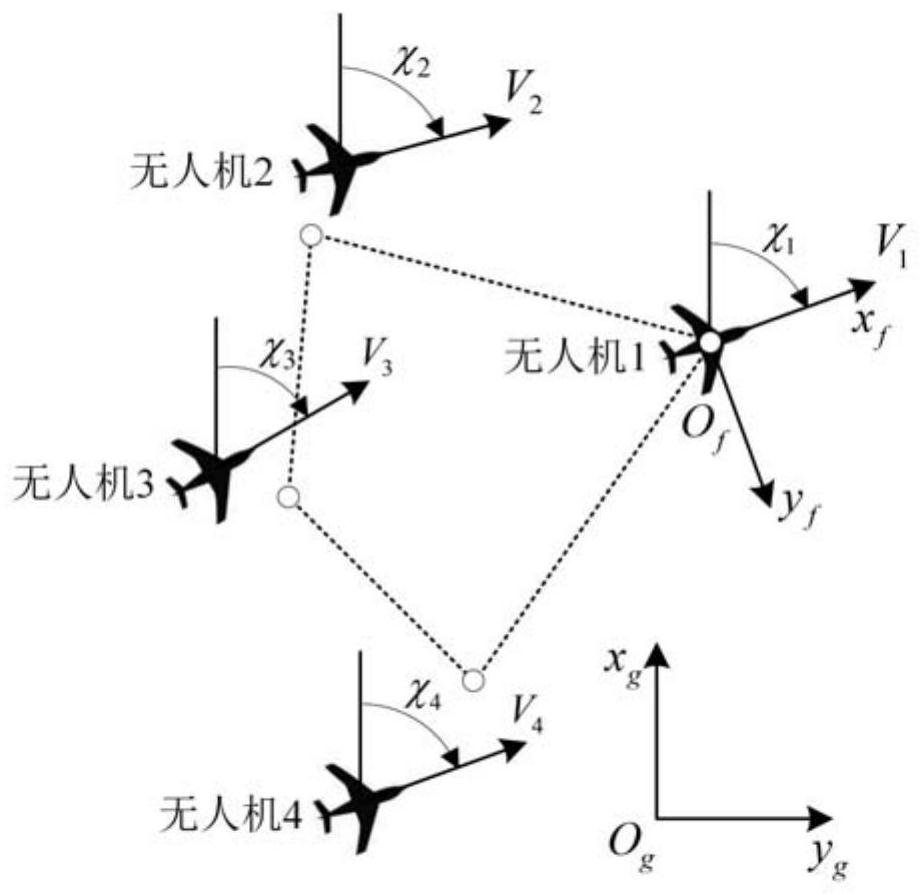
Multi-unmanned-aerial-vehicle formation consistency control method based on event-triggered communication
ActiveCN111638726AFlexible choice of topologyImprove scalabilityPosition/course control in three dimensionsCommunications systemInformation transmission
The invention discloses a multi-unmanned-aerial-vehicle formation consistency control method based on event-triggered communication. With the distributed control architecture, the control center in the centralized control architecture is removed, so that no phenomenon of formation failure due to the destruction of the central control node exists. Computing tasks of the UAV formation are controlled, the tasks are distributed from a control center to onboard computers of the member UAVs, thereby greatly improving the overall computing power of the formation and breaking through the performance bottleneck caused by the computing power; with introduction of an event trigger communication mechanism, the algorithm does not need to acquire cooperative state information in each control cycle continuous communication, and only intermittent communication needs to be carried out under a trigger communication condition. Compared with a consistency algorithm based on continuous communication, the algorithm has the advantages that the network information transmission quantity can be greatly reduced, the limited communication bandwidth is used for transmitting more task information, and the dependence on the performance of a communication system can be reduced The algorithm has certain tolerance to transient communication interruption or signal interference, and engineering implementation isfacilitated.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com