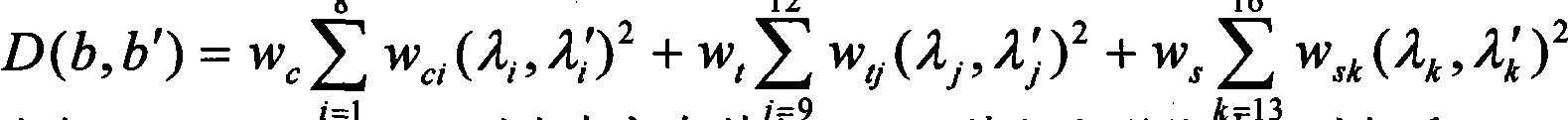Patents
Literature
2054results about How to "Improve retrieval efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for processing unmanned aerial vehicle polling image
ActiveCN103941746AEasy to handleRapid positioningPosition/course control in three dimensionsInformatizationImaging processing
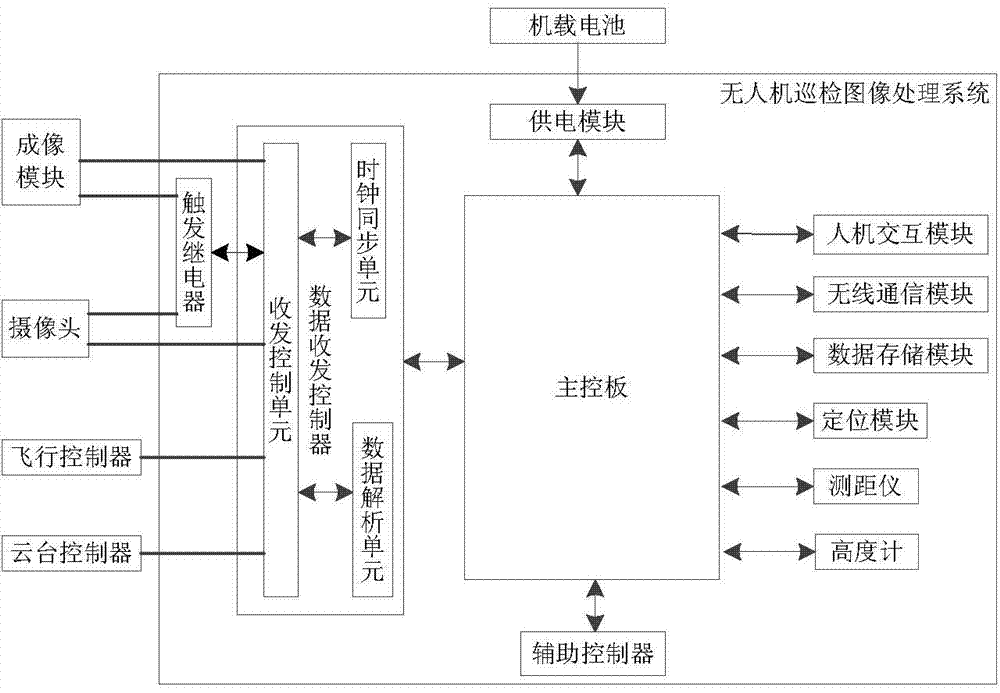
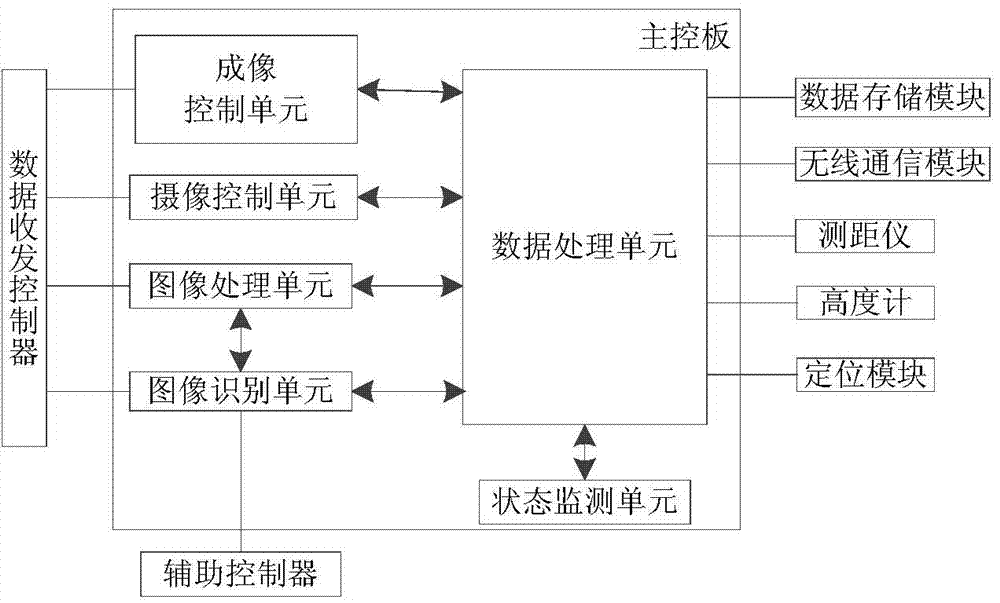
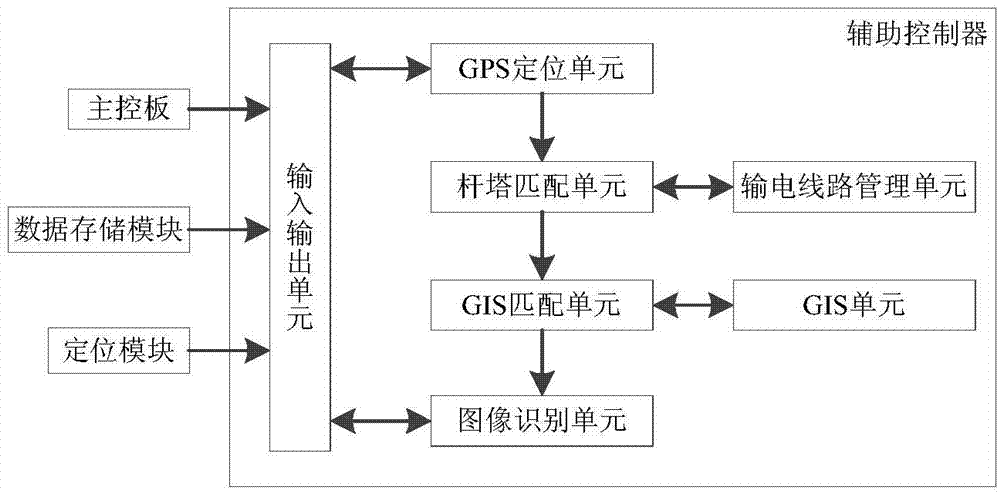
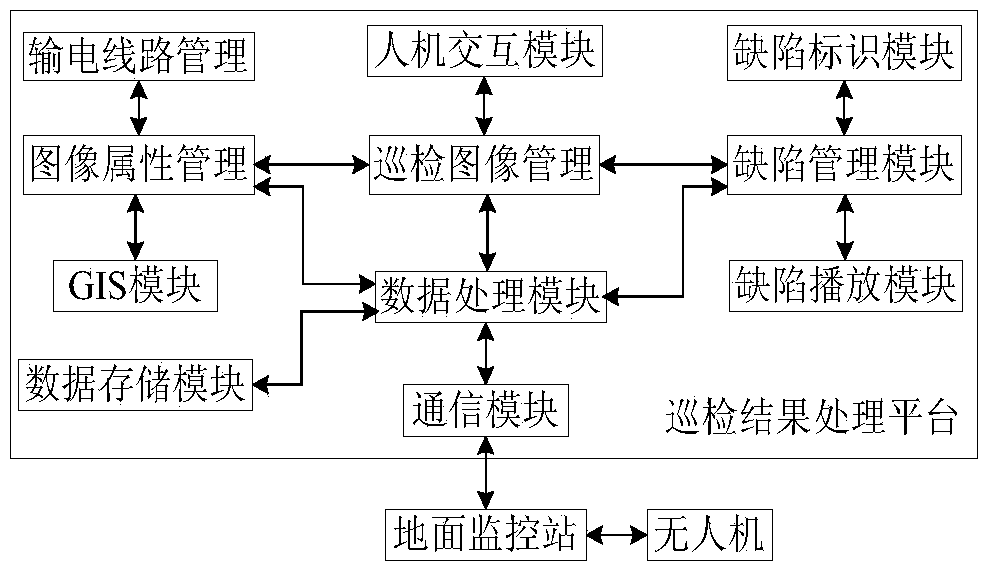
The invention discloses a system and method for processing an unmanned aerial vehicle polling image. The system comprises an unmanned aerial vehicle polling image processing system body which comprises a human-computer interaction module. After the human-computer interaction module obtains a user instruction, a main control panel analyzes the user instruction and transmits the analyzed instruction to a data receiving and transmitting controller, the data receiving and transmitting controller sends a parameter configuration instruction to corresponding peripheral equipment according to the instruction and transmits an instruction execution result back to the main control panel, and the main control panel processes the execution result of the parameter configuration instruction and then sends processed information to the human-computer interaction module so that the information can be displayed to a user. The main control panel is respectively communicated with a secondary controller, a power supply module, a wireless communication module, a data storage module, a locating module, a distance measuring meter and a height gauge. The system and the method improve the automation degree and the informationization degree of polling image processing, improve the efficiency of searching for and processing the polling result, and lower the cost of processing the polling result.
Owner:STATE GRID INTELLIGENCE TECH CO LTD
Intelligent inspection system and inspection method for electric transmission line by unmanned aerial vehicle
ActiveCN103824340AReduce idle rateImplement configurationRegistering/indicating working of machinesMonitoring systemUncrewed vehicle
The invention discloses an intelligent inspection system and an inspection method for an electric transmission line by an unmanned aerial vehicle. The intelligent inspection system comprises an inspection mission planning system, a dispatching system, a monitoring system, an inspection result processing platform and mobile branch stations, wherein the inspection mission planning system communicates with the inspection result processing platform and the dispatching system respectively; the inspection result processing platform and the dispatching system communicates with the monitoring system respectively; the monitoring system is connected and communicate with the mobile branch stations. The inspection method has the benefits that factors of the inspection unmanned aerial vehicle, inspection equipment, an inspector, and the like accessing the dispatching platform through a dispatching terminal can be dispatched effectively to realize equipped configuration of unmanned aerial vehicle inspection resource; the usage rates of personnel and equipment can be improved; the no-load rate and vacancy rate of the inspection equipment are reduced; through centralized monitoring of condition information inspected by the unmanned aerial vehicle, unmanned aerial vehicle inspection dispatching personnel can master unmanned aerial vehicle inspection in the large effectively; the service life of the unmanned aerial vehicle is prolonged.
Owner:STATE GRID INTELLIGENCE TECH CO LTD
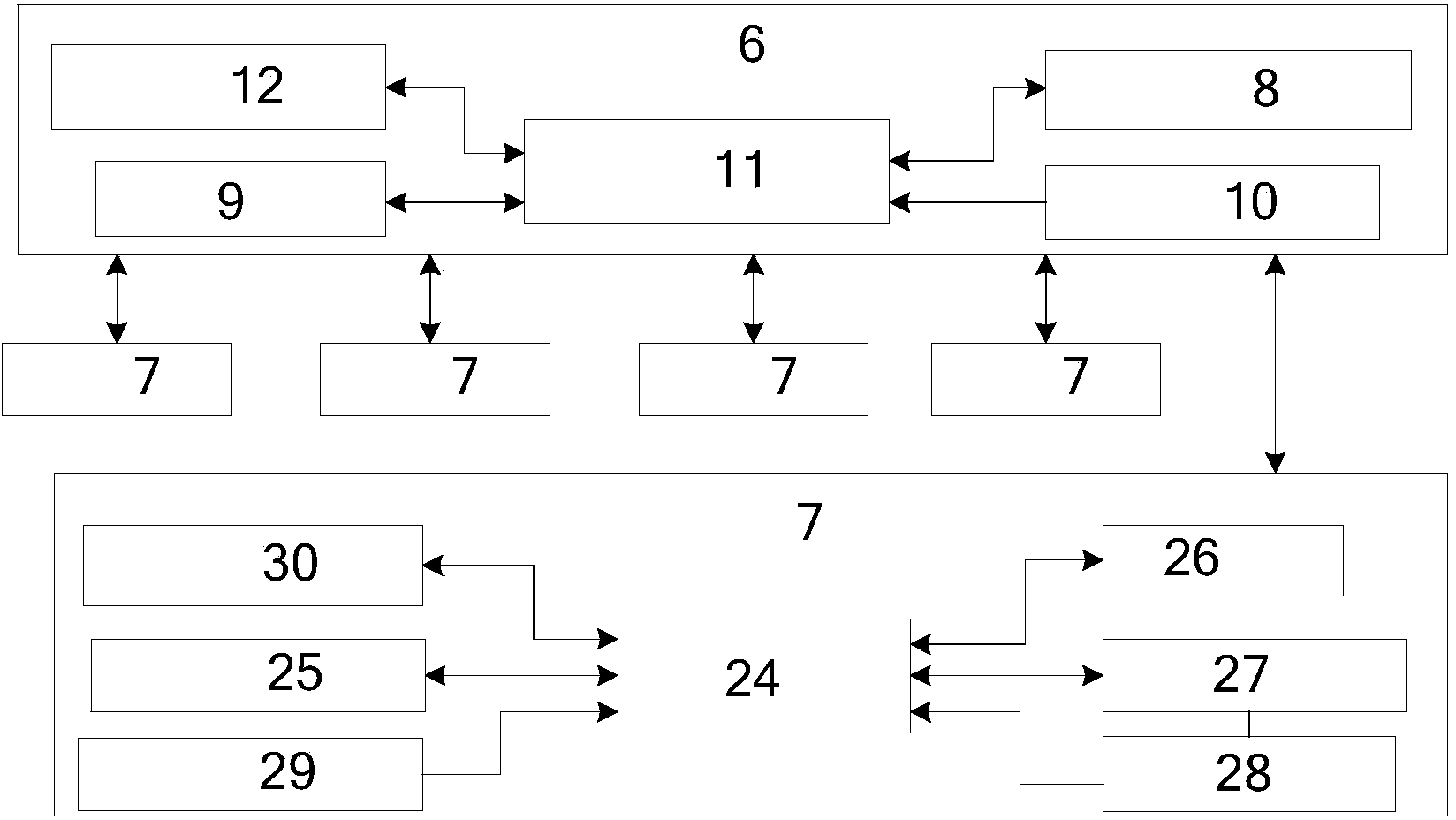
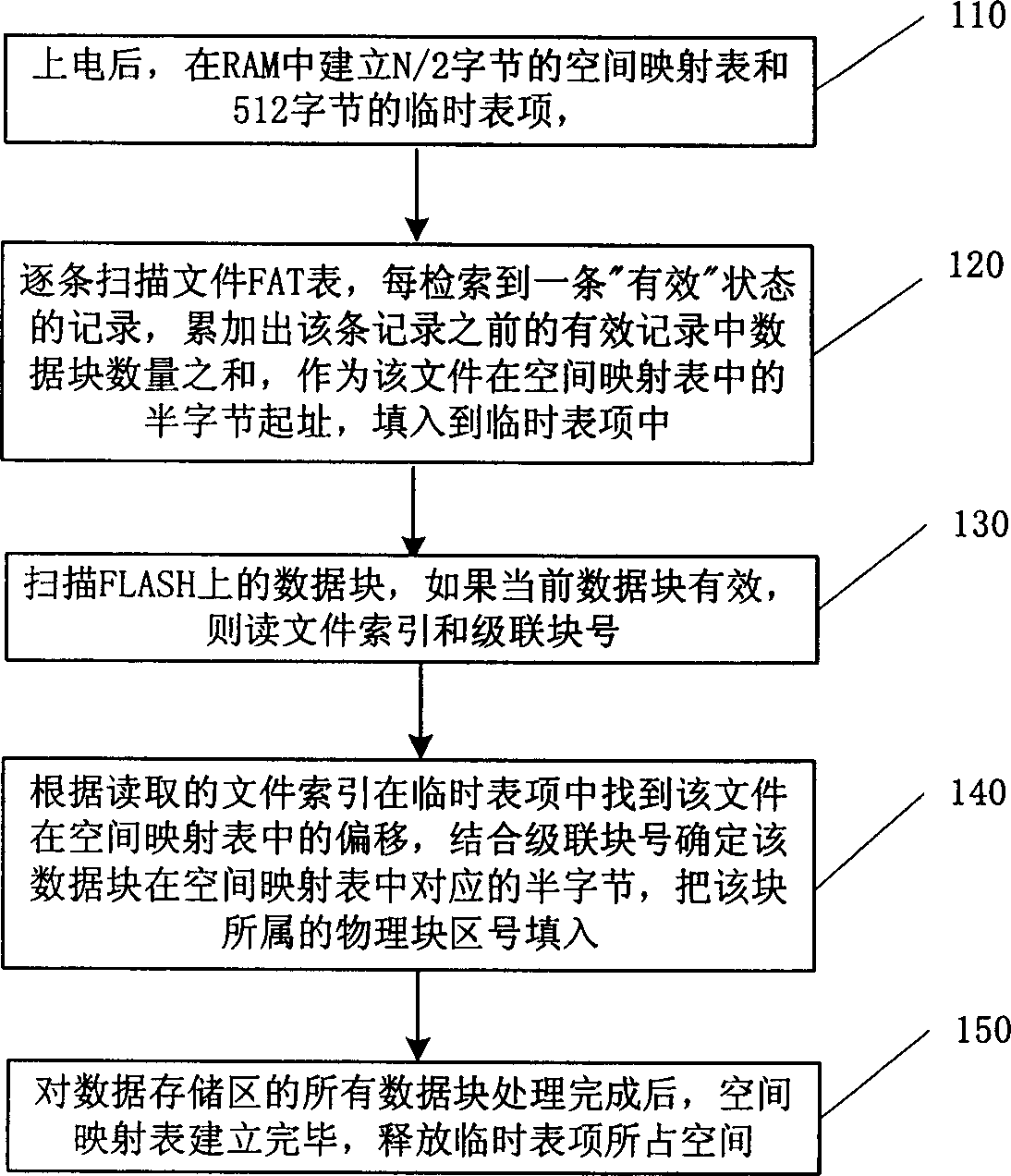
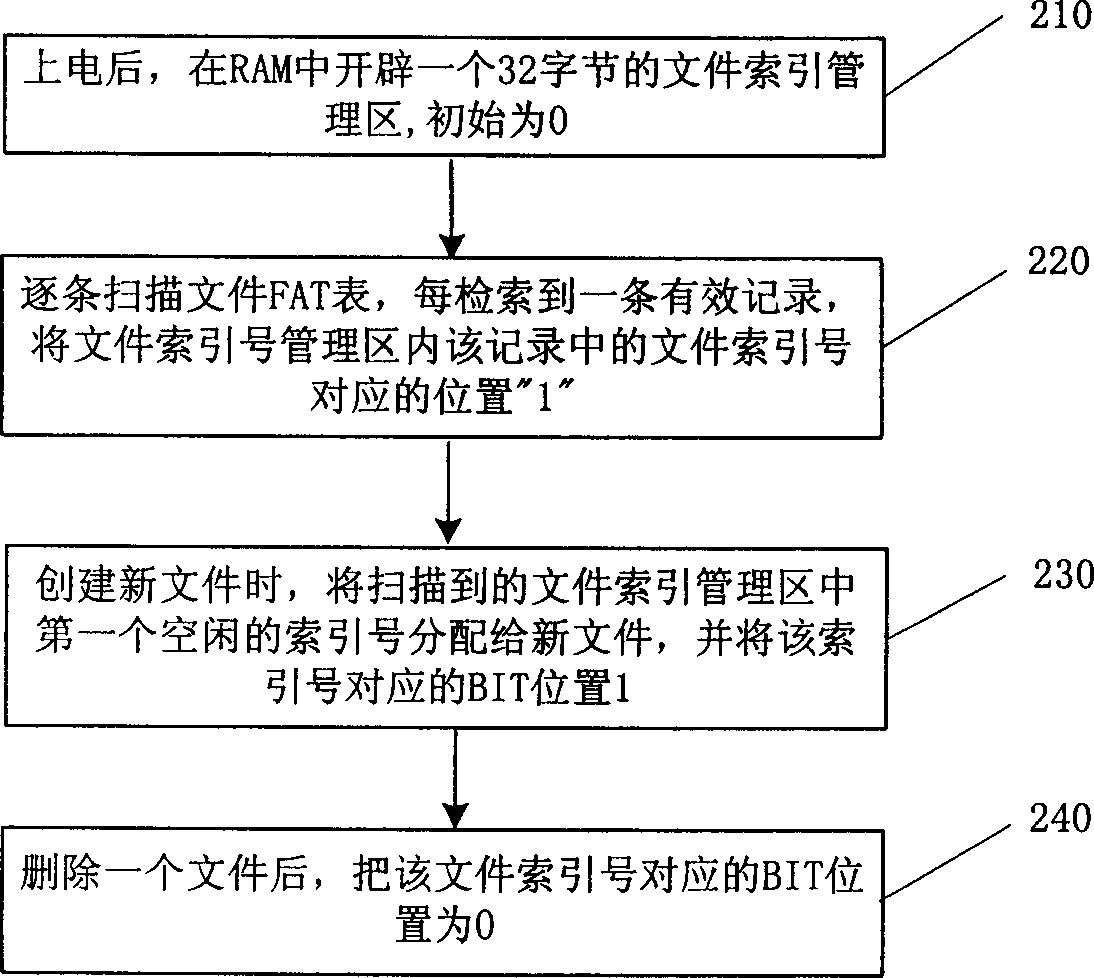
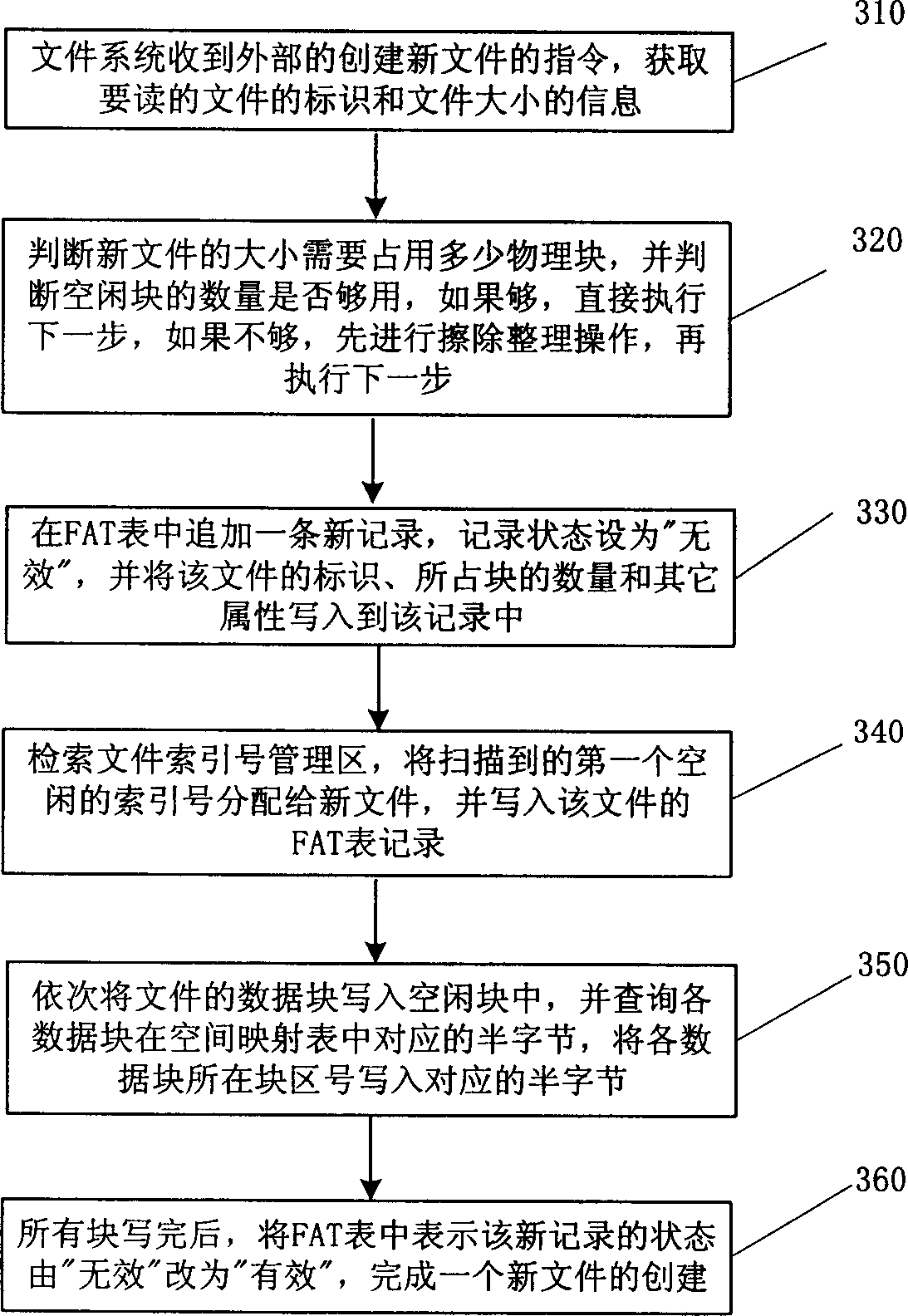
A flash memory file system management method
ActiveCN1632765AImprove retrieval efficiencyEnsure safetyRead-only memoriesMemory systemsFlash file systemFile system
This invention discloses a flash file system management method, which comprises the following steps: to divide the flash memory into FAT area and data memory area; to establish the space mapping form and to write the data block of each file into the block; to write the new file ID, block number, file researching number into the record; then to orderly write each data block into the spare block and to write each data block number into relative positions of the space mapping form; only to operate the file data memory area when updating file data; to identify the place of the data to be read when reading the data for searching the data block.
Owner:DATANG MICROELECTRONICS TECH CO LTD
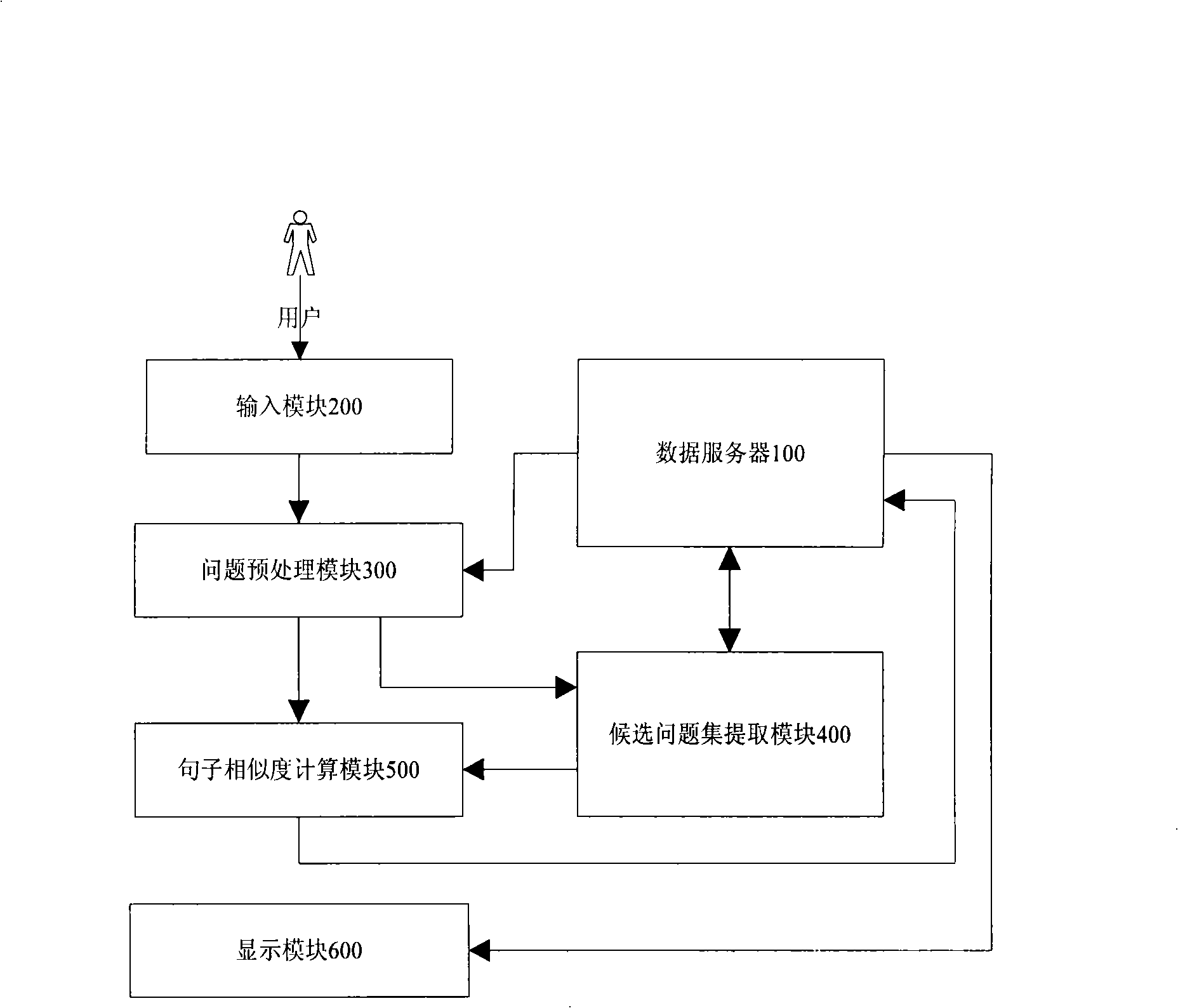
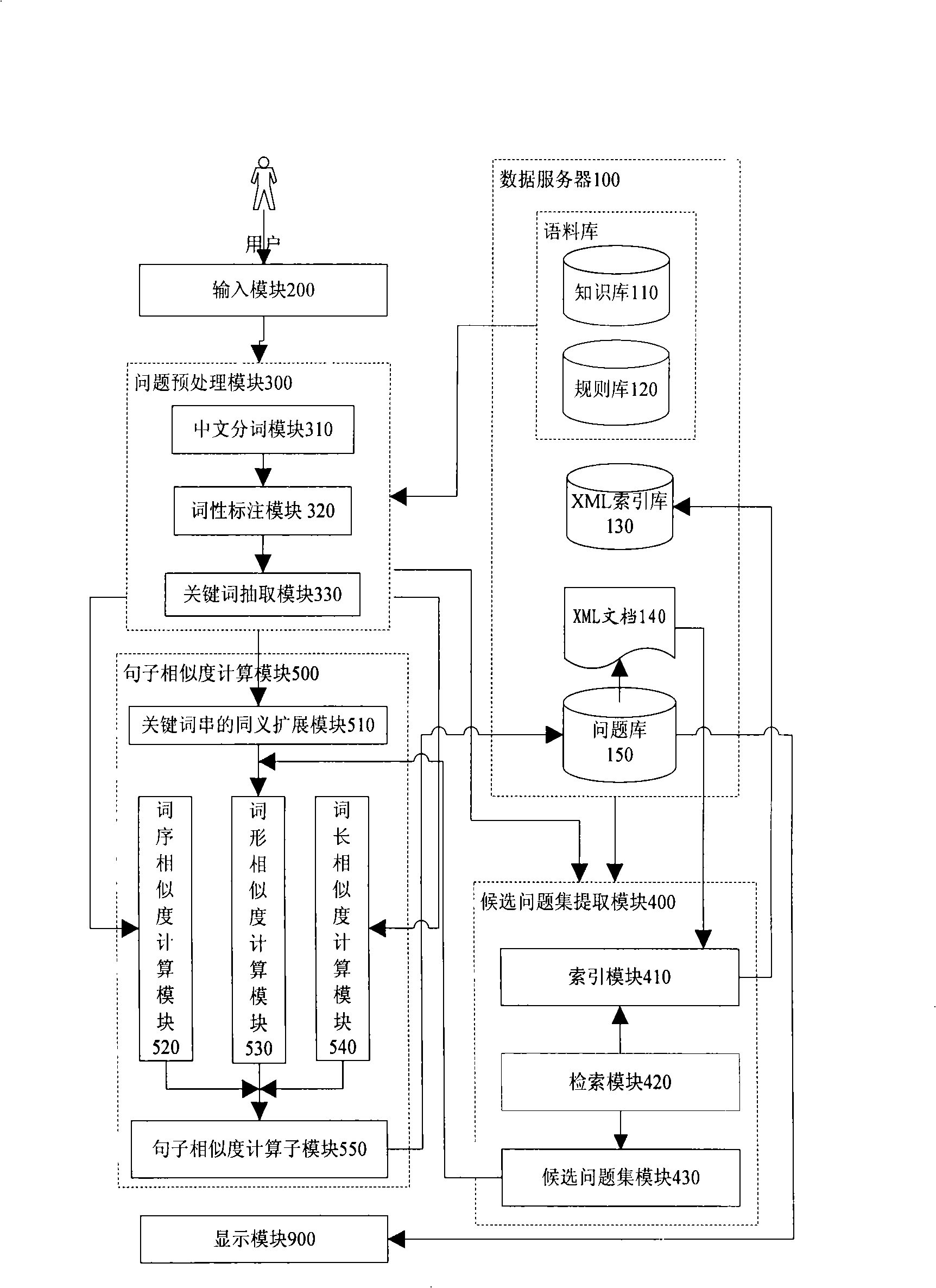
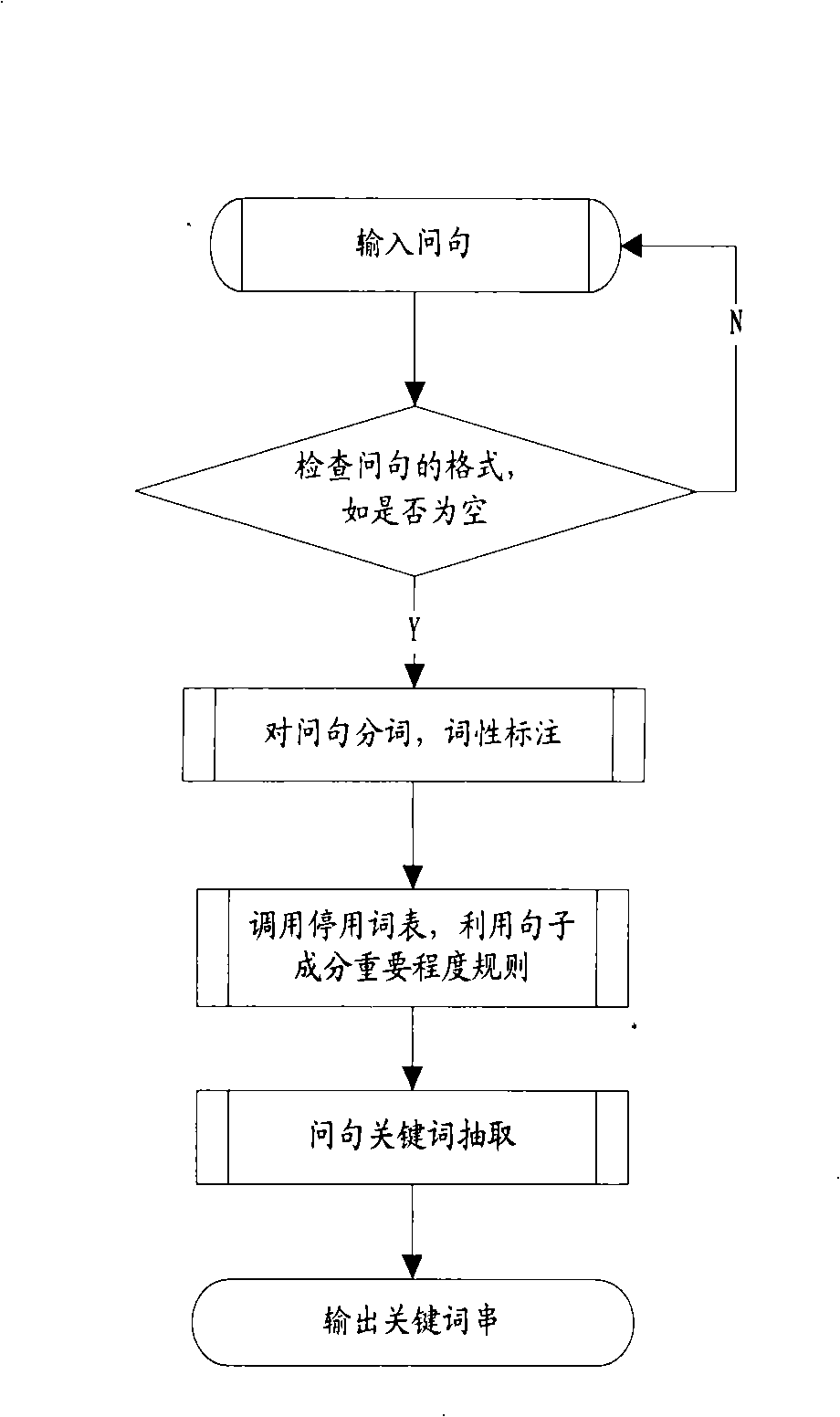
Intelligent Chinese request-answering system based on concept
InactiveCN101286161AImprove precisionImprove recallSpecial data processing applicationsUser inputQuestions and answers
The invention discloses a Chinese question answering system based on concept, which mainly comprises a data server, a question pre-treatment module, a candidate question set extracting module and a question sentence similarity calculation module. The invention aims at providing a question answering system which is based on concept, can carry out synonym expansion of keywords which are processed by question sentences which are input by the user, understand question sentences better, carry out searching and improve the recall ratio of the question answering system. Furthermore, the system has a Chinese sentence similarity calculation method based on concept from three aspects: word form, word order and word length, and improves searching precision ratio. Meanwhile, the system adopts a high-efficiency retrieval technology to realize rapid extraction of candidate question set, calculates question sentence similarity, sorts question set quickly and returns the sorted questions and answers to the user. The question answering system of the invention gives more precise understanding in concept to the question sentences input by the user and searches the accurate answers. Experiments show that the question answering system of the invention achieves high recall ratio and precision ratio.
Owner:HUAZHONG UNIV OF SCI & TECH
Patrolling result data processing system and method used for unmanned aerial vehicle patrolling
ActiveCN103886189AEasy to manageGuaranteed validitySpecial data processing applicationsData processing systemUncrewed vehicle
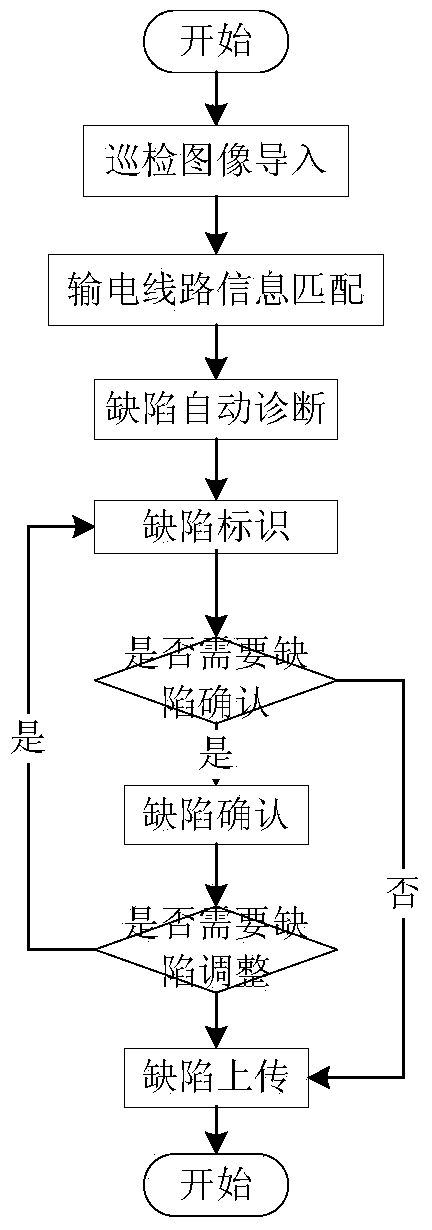
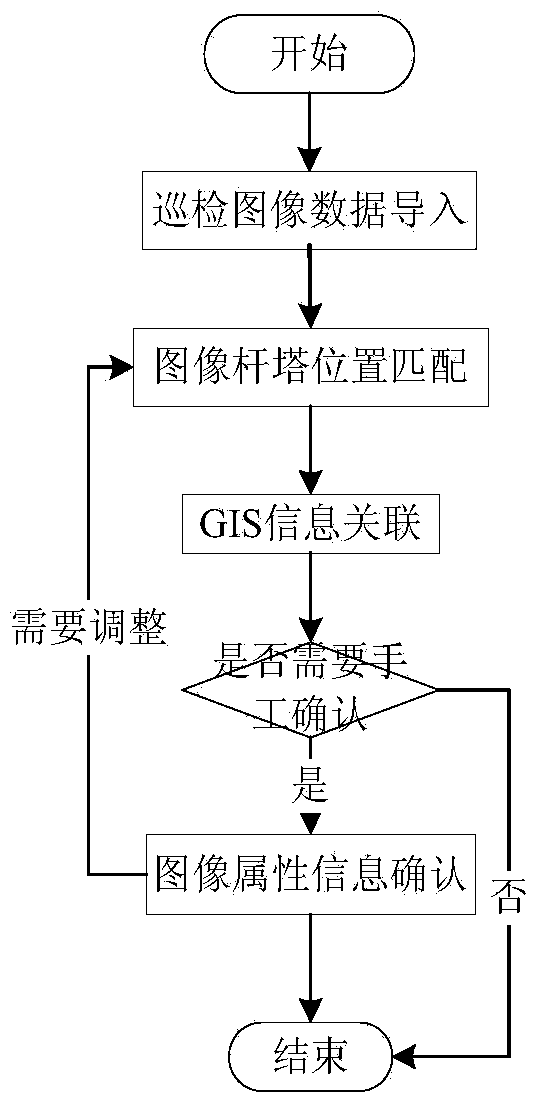
The invention discloses a patrolling result data processing system and method used for unmanned aerial vehicle patrolling. The system comprises an unmanned aerial vehicle, a plurality of ground monitoring stations and a patrolling result processing platform, wherein the unmanned aerial vehicle is used for patrolling a power transmission line, shooting image information of the power transmission line and transmitting the image information to the ground monitoring stations; the ground monitoring stations are used for communicating with the unmanned aerial vehicle, reading flight state data and patrolling result data of the unmanned aerial vehicle and sending the collected information to the patrolling result processing platform; the patrolling result processing platform is used for reading the flight state information and the patrolling result data of the unmanned aerial vehicle from the ground monitoring stations, and carrying out defect diagnosis on the patrolling result data and carrying out CRUD and playing management on defects diagnosed through defect diagnosis. Image defect identification information and image files are stored separately, corresponding defect information is associated with images during defect displaying, and positions, annotation or instructions and the like of the defects of the power transmission line in a patrolled image are displayed, so that efficient and quick processing of the patrolling result data of the unmanned aerial vehicle is achieved.
Owner:STATE GRID INTELLIGENCE TECH CO LTD
System and method for intelligent library management
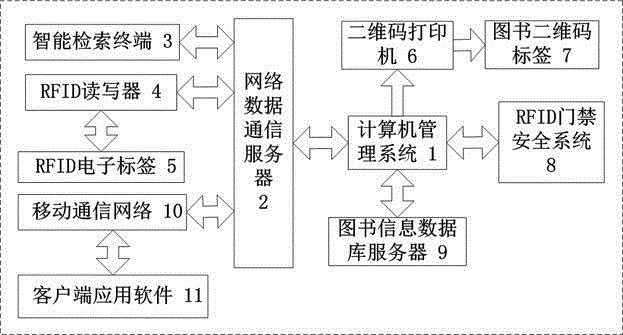
Provided are a system and a method for intelligent library management. The system is characterized in that the intelligent library management system comprises a computer management system, a network data communication server, an intelligent retrieval terminal, an RFID reader-writer, RFID electronic labels, a two-dimensional code printer, book two-dimensional code labels, an RFID entrance guard safety system, a book information database server, a mobile communication network, and client application software. The system and the method for intelligent library management realize accurate monitoring of books in any positions of a stack room, improve book retrieval efficiency, and monitor books in the stack room in real time. Readers borrow books, and return books in a self-service manner, and make the books in order on shelves. The system and the method provide convenience for readers and book managers to rapidly and accurately find books and positions thereof, thereby preventing false shelf of books and shelf disorder, and simplifying operation of the book managers.
Owner:UNIV OF JINAN
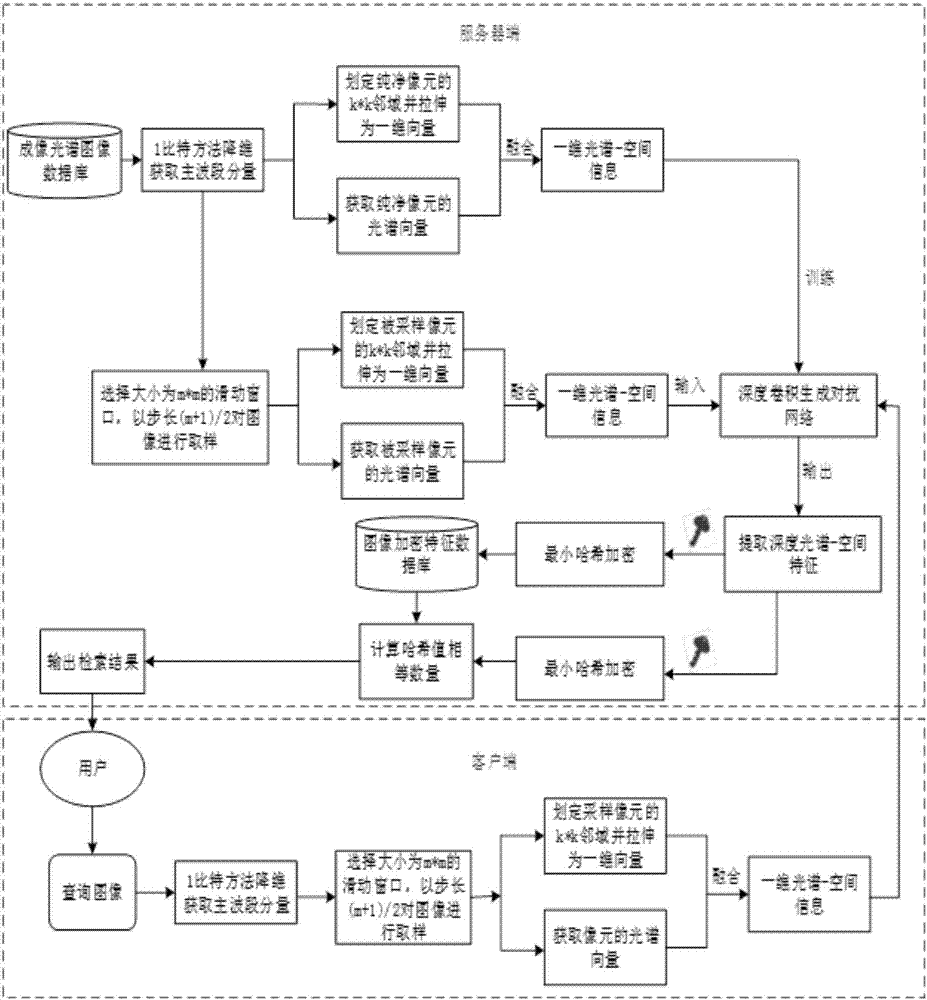
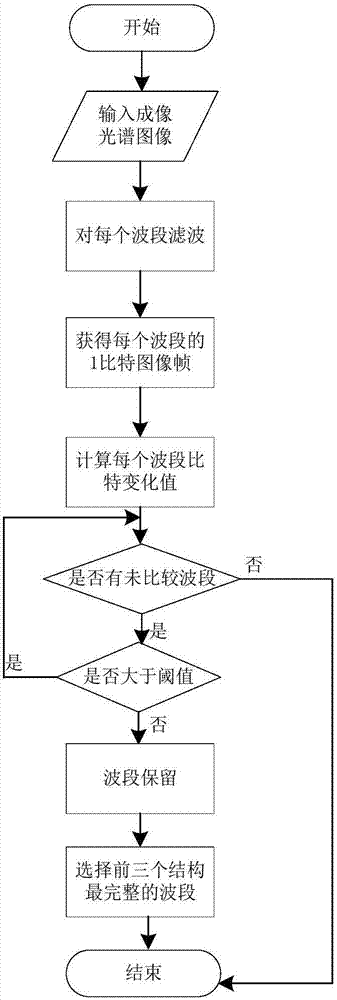
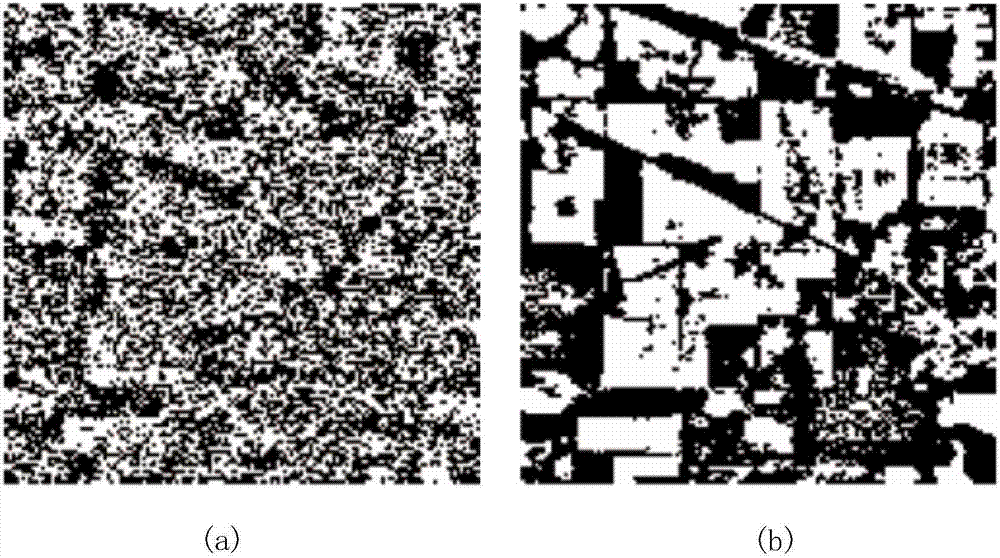
DCGAN-based spectral imagery secure retrieval method
ActiveCN106997380AImprove precisionImprove retrieval efficiencyDigital data protectionImage data processing detailsGenerative adversarial networkImage retrieval
The invention discloses a DCGAN (Deep Convolutional Generative Adversarial Network)-based spectral imagery secure retrieval method, and belongs to the field of spectral imageries. According to the method, the features of a spectral imagery are highly expressed by utilizing a DCGAN; and a new encrypted domain spectral imagery secure retrieval method is proposed. Firstly the deep spectral-spatial features of the spectral imagery are jointly extracted by utilizing the DCGAN, and the contents of the spectral imagery are accurately represented; in order to ensure the security in a remote sensing image retrieval process, the deep features are encrypted by adopting a Min-Hash method based on a criterion that the similarity of the encrypted features is unchanged, thereby protecting the deep features; and finally under the non-decryption condition, Jaccard similarity distance measurement is performed on image features directly by comparing the number of same Min-Hash values, and images similar to a query image are returned. Therefore, the information security is ensured while the retrieval is realized.
Owner:数安信(北京)科技有限公司
High speed filtering and stream dividing method for keeping connection features
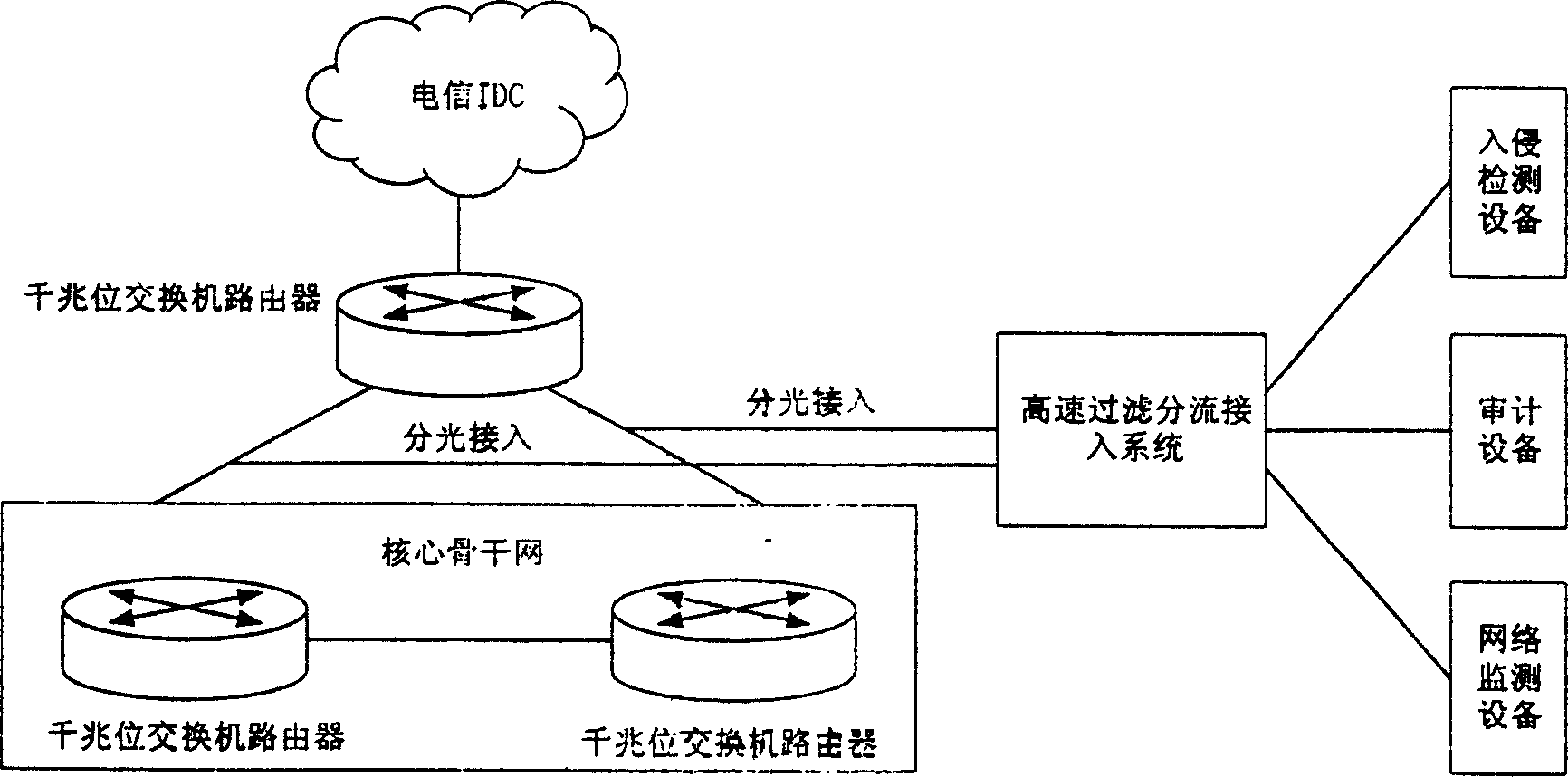
InactiveCN1564547AReduce processing burdenGuaranteed wire-speed processing requirementsData switching networksTraffic capacityData stream
First, the invention sets up output port grouping rule and filtering tapping rule. Then, data filtering tapping process is carried out. IP data packets are picked up from original data packets received from network based on protocol analysis. Based on filtering tapping rule, data relevant to following processes are partitioned to group of each output port. Hash operation is carried out for address of data packet and port information in partitioned each group. Modular operation is carried our between the said Hash value and total number of port. The result is number of output port for the corresponding data packet in the group the data packet belongs to. Under high-speed backbone network, the invention meets need for clustering process and forwarding at high speed for mass data stream.
Owner:上海光华如新信息科技股份有限公司
Multi-user supported searchable encryption system and method
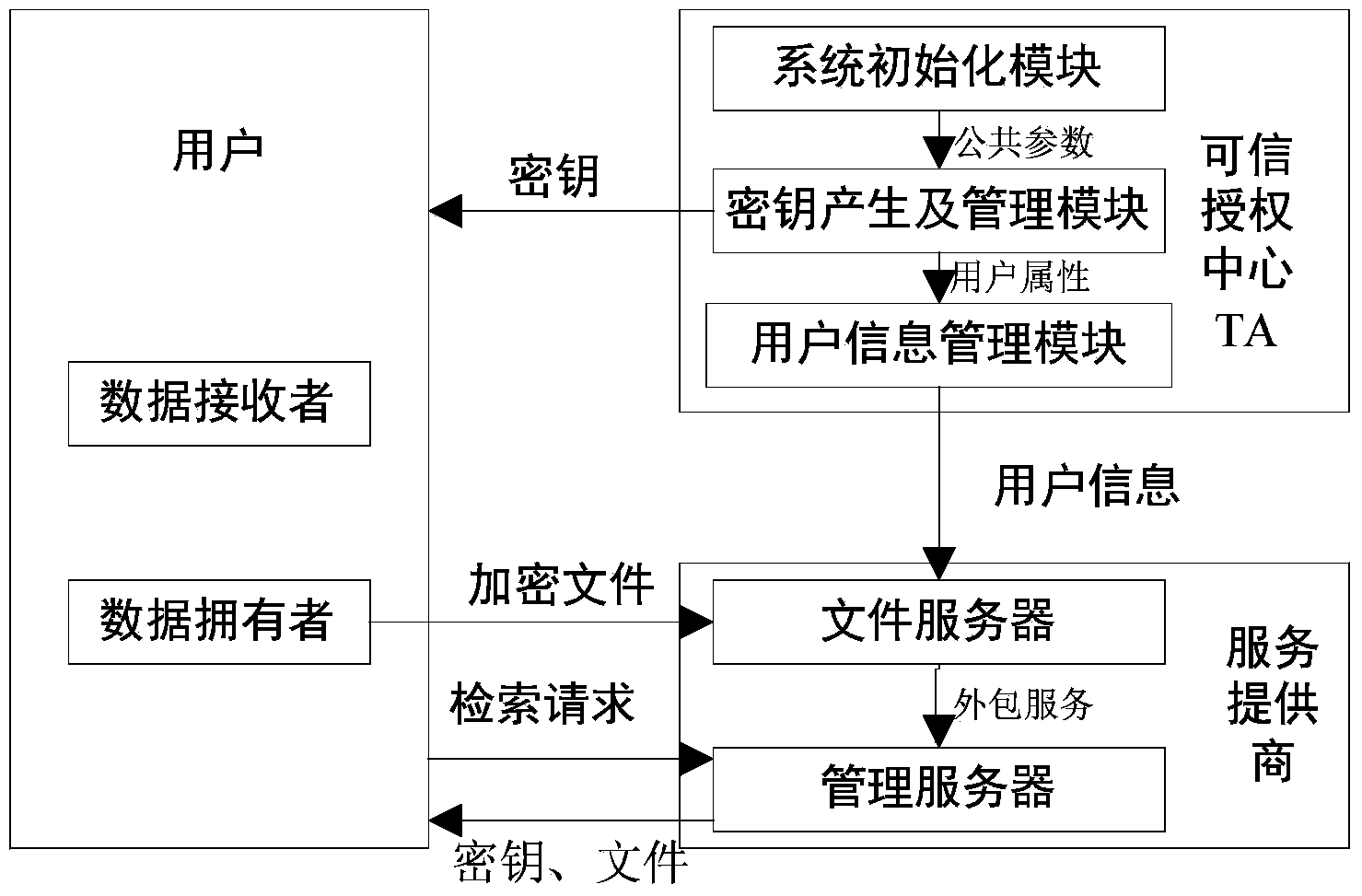
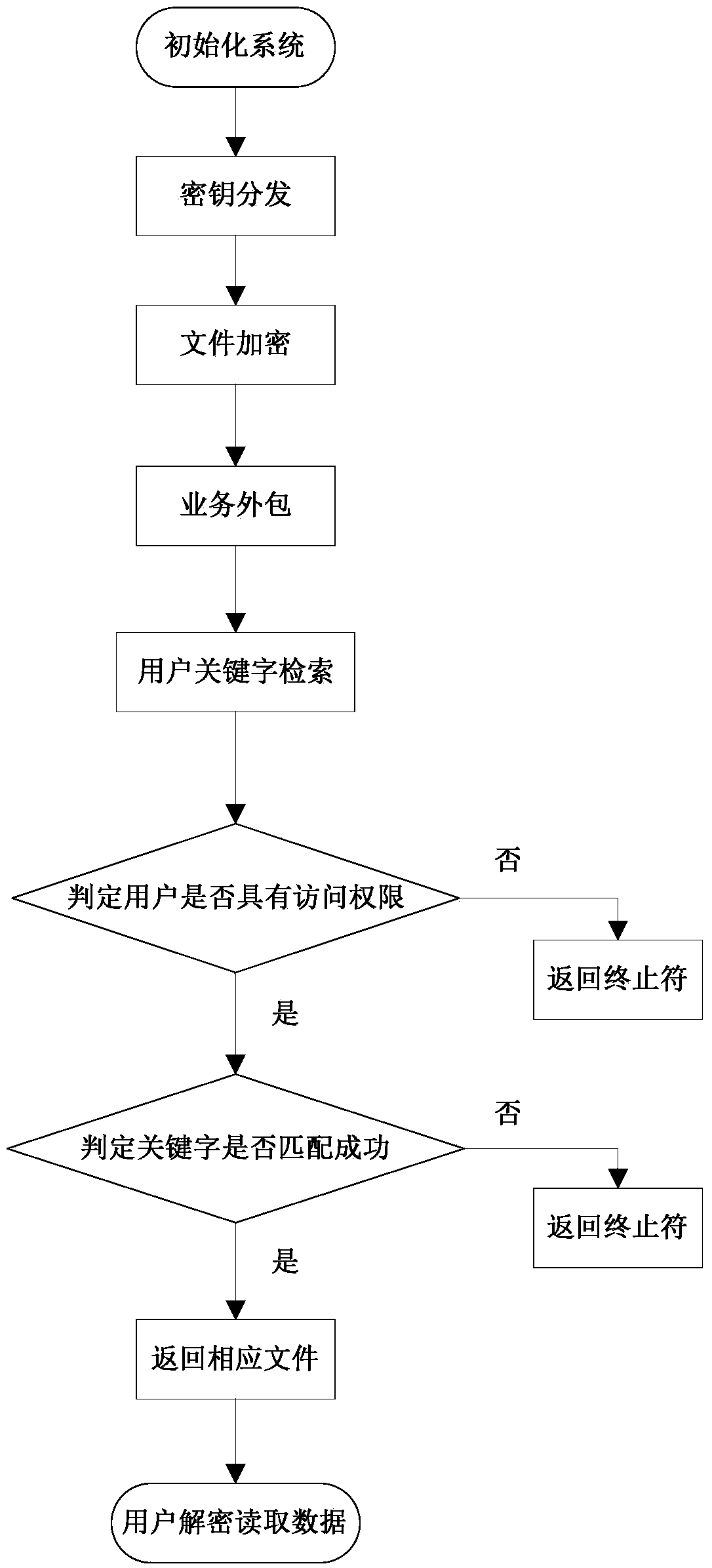
InactiveCN103731432AMeet the actual application needsImprove securityKey distribution for secure communicationSpecial data processing applicationsData providerService provision
The invention discloses a multi-user supported searchable encryption system and method and accordingly the problem that specific encrypted files cannot be searched accurately in the prior art is mainly solved. The multi-user supported searchable encryption system comprises a credible authorization center TA, service providers and users; the credible authorization center TA is formed by a system initialization module, a secret key generation and management module and a user information management module; the service providers comprise a file server and a management server; the users comprise data providers and data receivers. The multi-user supported searchable encryption method comprises the steps of system initialization, secret key distribution, file encryption, business outsourcing, file retrieval, user decryption and user logout and adding. According to the multi-user supported searchable encryption system and method, the file retrieval time of the users is shortened due to the establishment of a key word index on files, the storage and computational overhead of the users is reduced due to the accurate file retrieval, the file retrieval is accurate, meanwhile the forward and backward security of the files is ensured, and meanwhile the multi-user simultaneous decryption is supported.
Owner:西安电子科技大学昆山创新研究院 +1
Image search method based on target area matching
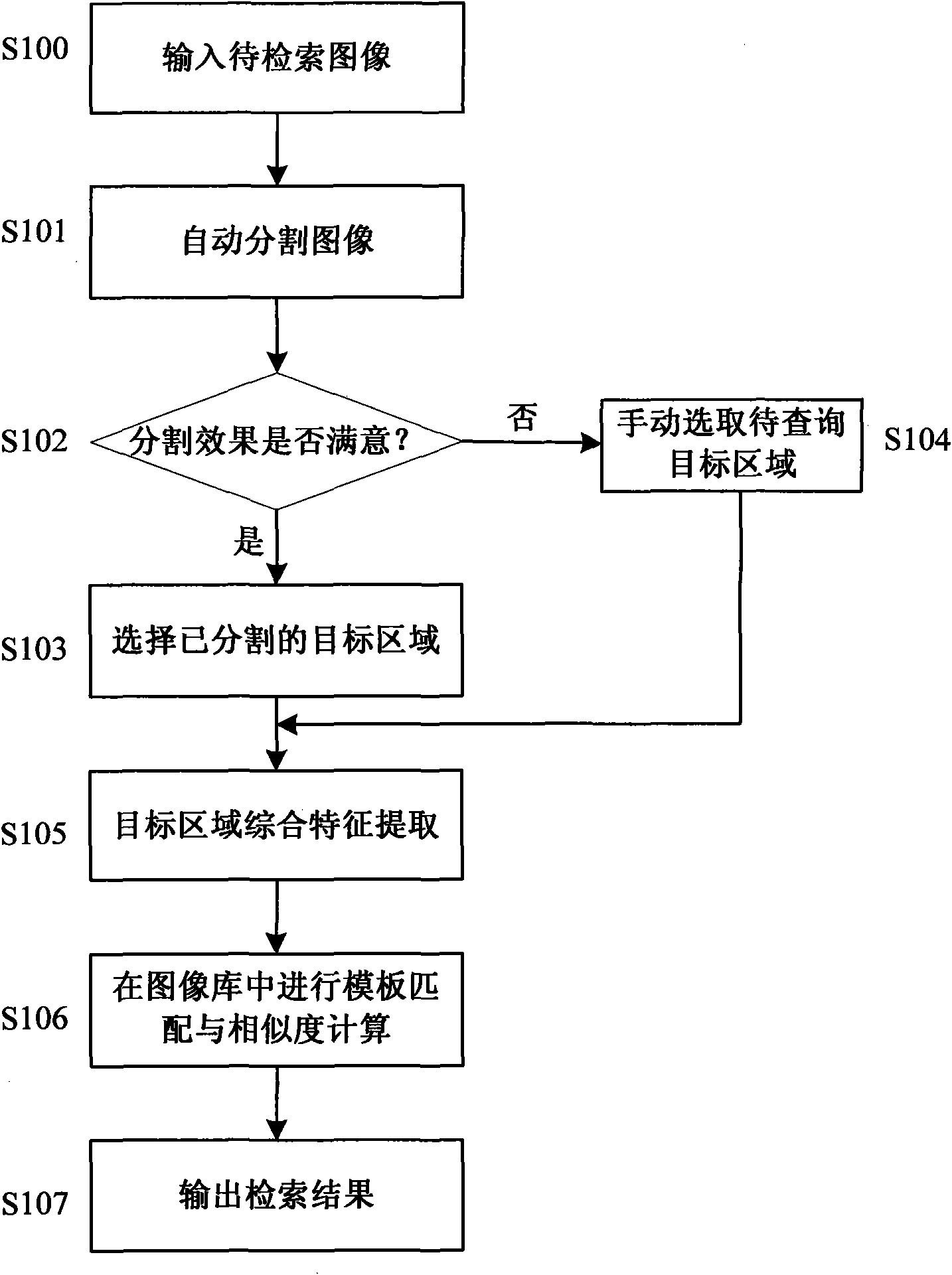
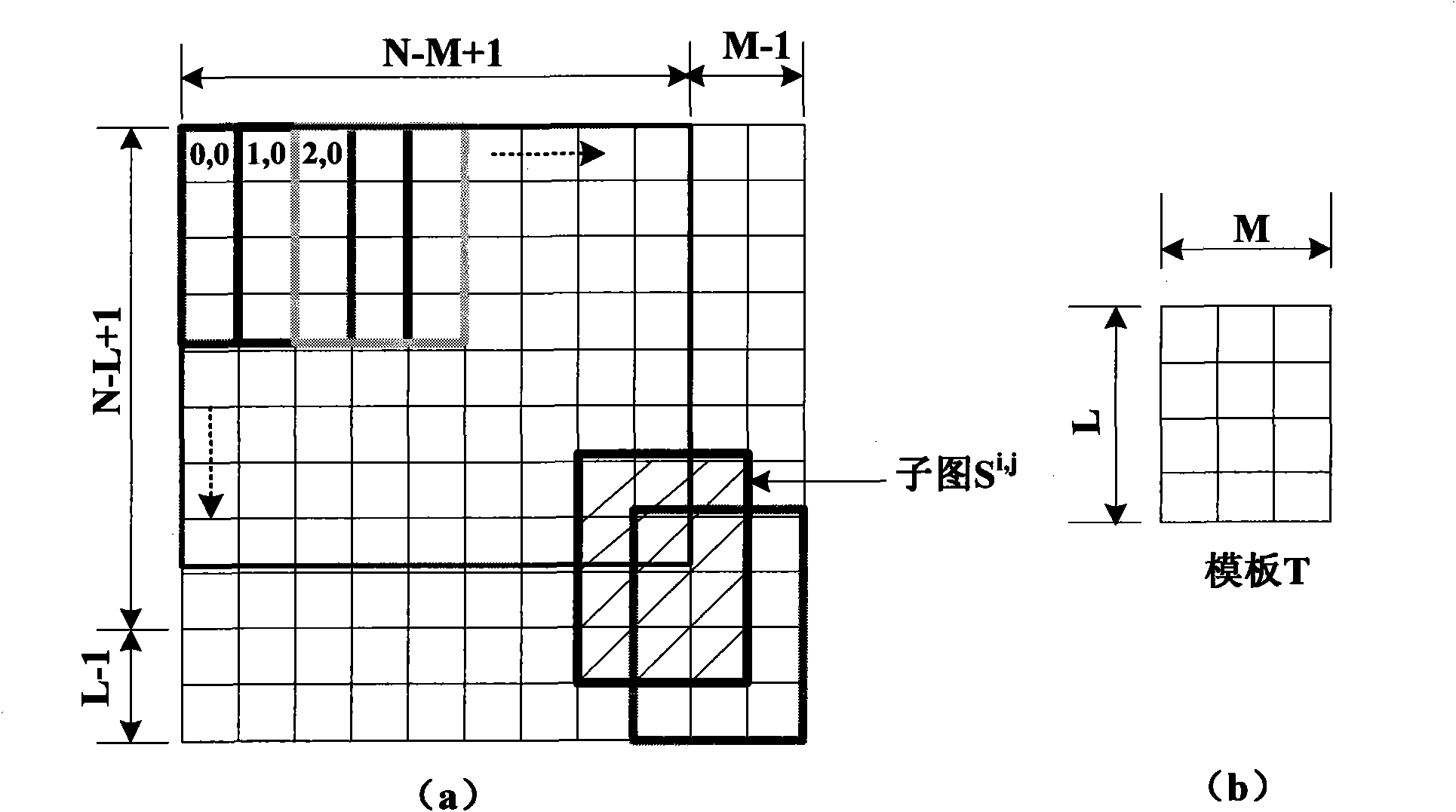
InactiveCN101639858AOvercome the defect of not being able to compare the similarity of images at the object levelImprove precisionImage analysisSpecial data processing applicationsTemplate matchingEdge detection
The invention discloses an image search method based on target area matching, which comprises the following steps: a, selecting an image to be searched, and utilizing an edge detection algorithm to automatically partition the image to be searched; b, judging the partitioning effect, confirming a searched target area if a user satisfies the target area which is automatically partitioned, and selecting a target area that the user is interested in as a searched target from images that are not partitioned by self if the user does not satisfy the target area which is automatically partitioned; c, extracting characteristic values of the target area; d, taking the target area confirmed by the user as a template, using a template matching mode to carrying out template matching and similarity calculation in an image library, taking the searched image as a target when the similarity reaches a preset threshold value, or carrying out the template matching and the similarity calculation continuously until the image is covered completely; and e, sequentially displaying the searched result according to the similarity after the images in a database are searched according to requirements.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD
Retrieval method and system for blockchain business information
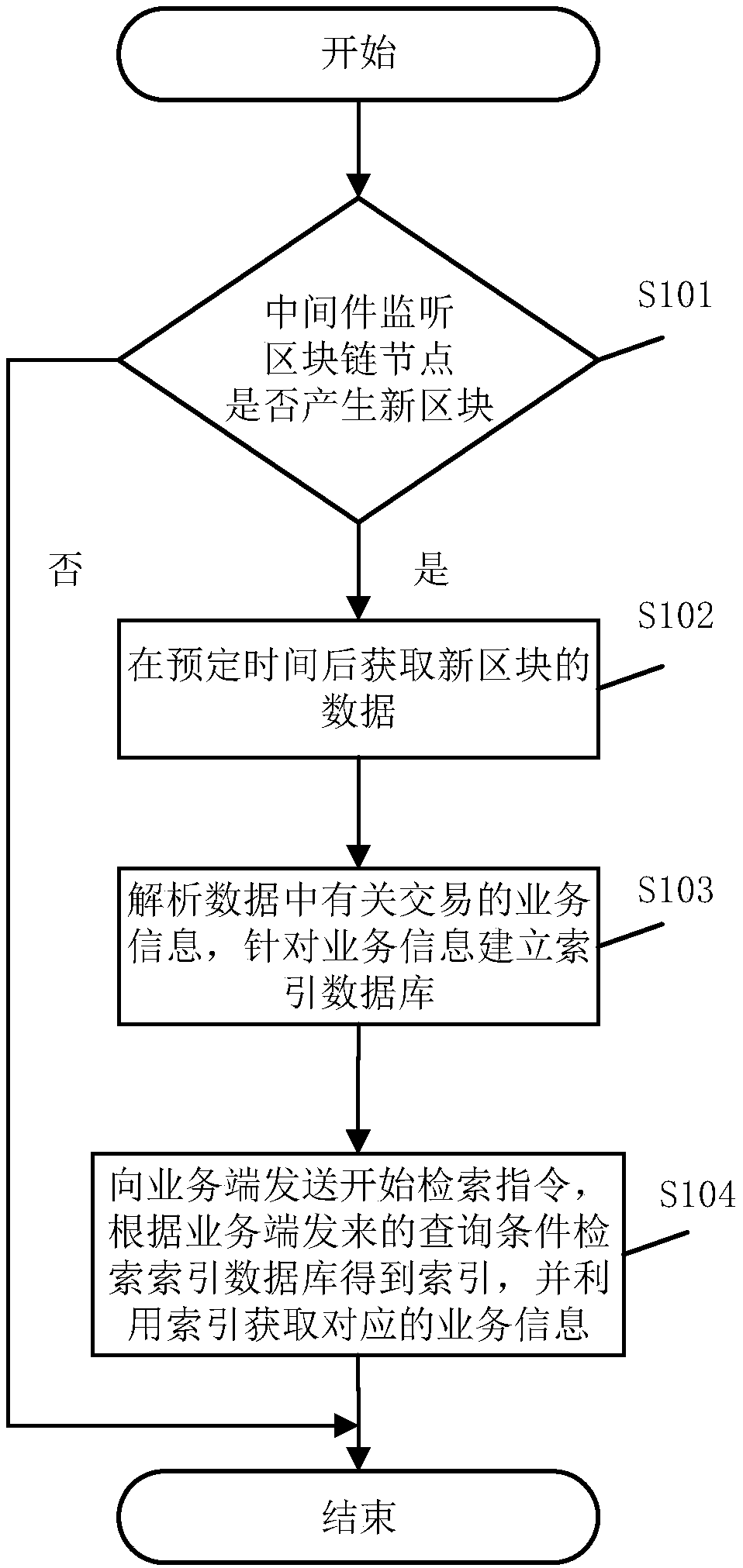
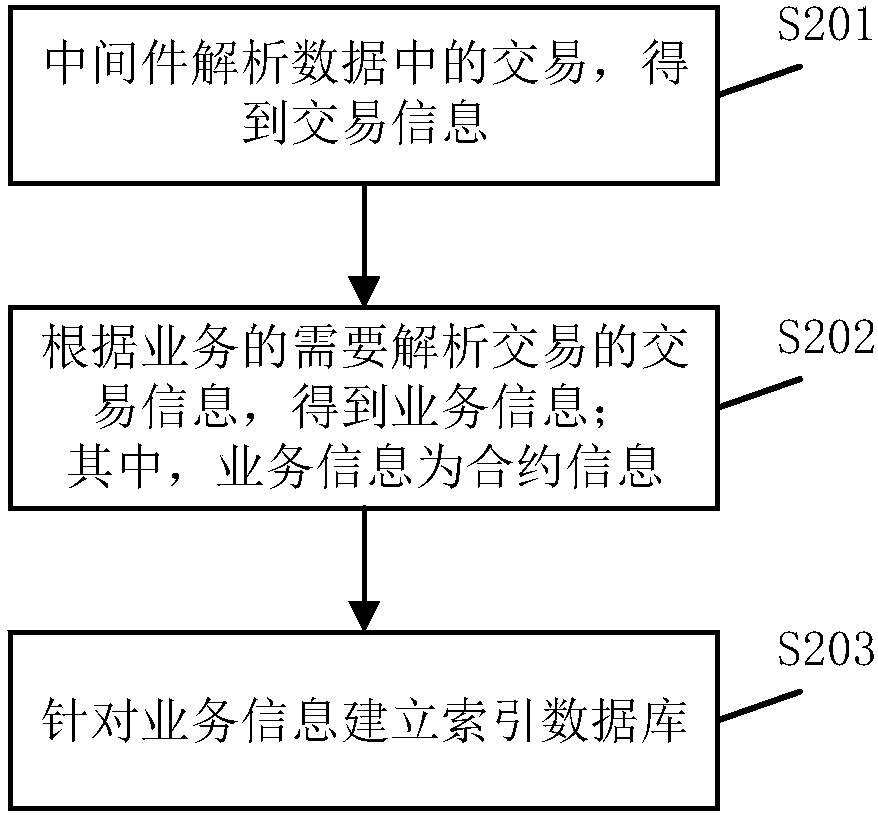
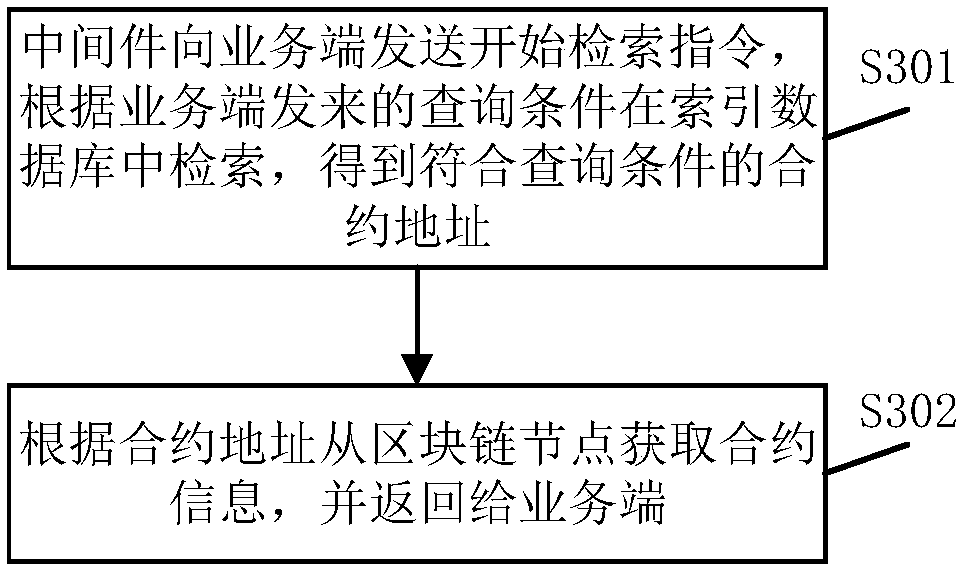
ActiveCN107943951AImprove retrieval efficiencySimple queryRelational databasesSpecial data processing applicationsMiddlewareBlockchain
The invention discloses a retrieval method for blockchain business information. The method comprises the following steps that: middleware monitors whether a blockchain node generates a new block or not, and the data of the new block is obtained after preset time if the blockchain node generates the new block; the business information of a related transaction in the data is analyzed, and an index database is established by aiming at business information; and according to a query condition sent from a business side, the index database is established to obtain an index, and the index is used forobtaining corresponding business information. According to a preset way, the data of the new block in the blockchain node is synchronized to obtain the index database related to the business, and thecorresponding business information is obtained according to the related index. The retrieval efficiency of blockchain business information is improved, meanwhile, the block contents of the blockchaindo not need to be re-arranged, and processing speed is quickened. The business information is taken as index contents so as to bring convenience for users to more visually inquire the business information. The invention also discloses a retrieval system for the blockchain business information, and the system has the above beneficial effects.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院
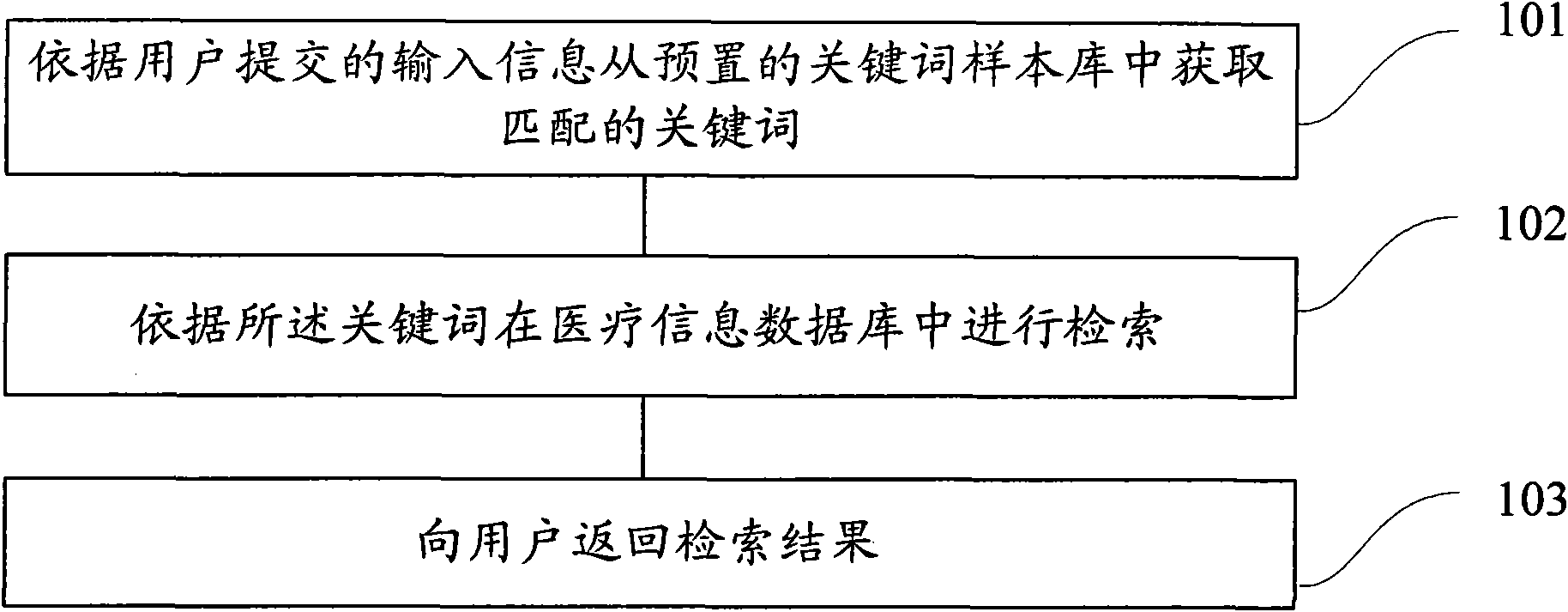
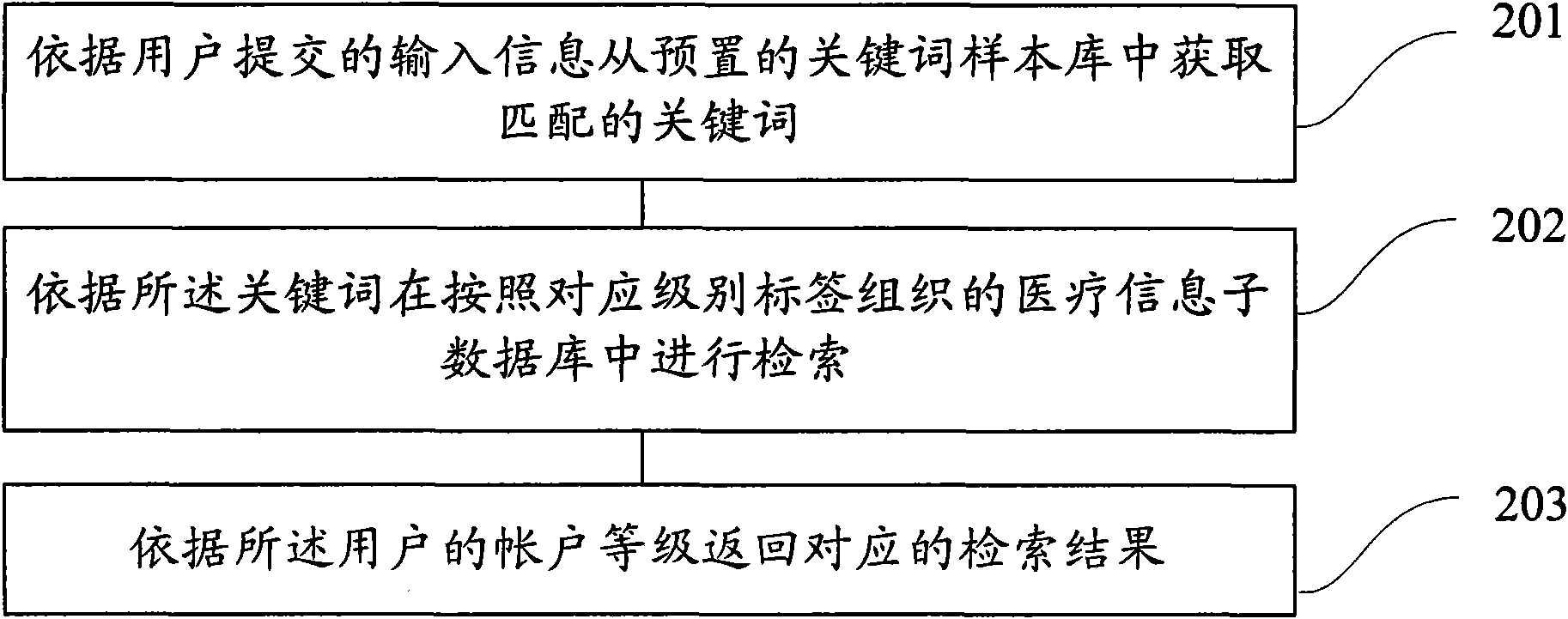
Method and system for retrieving medical information
InactiveCN102043812AImprove user experienceImprove retrieval efficiencySpecial data processing applicationsMedical treatmentData library
The invention provides a method for retrieving medical information, comprising the following steps of: obtaining matched keywords from a preset keyword sample bank according to input information committed by users; retrieving in a medical information database according to the keywords; and returning retrieving results to the users. With the method, the retrieved information can meet the real demands of the users to the maximum limit, that is to say, the validity of information retrieval is ensured.
Owner:PEKING UNIV
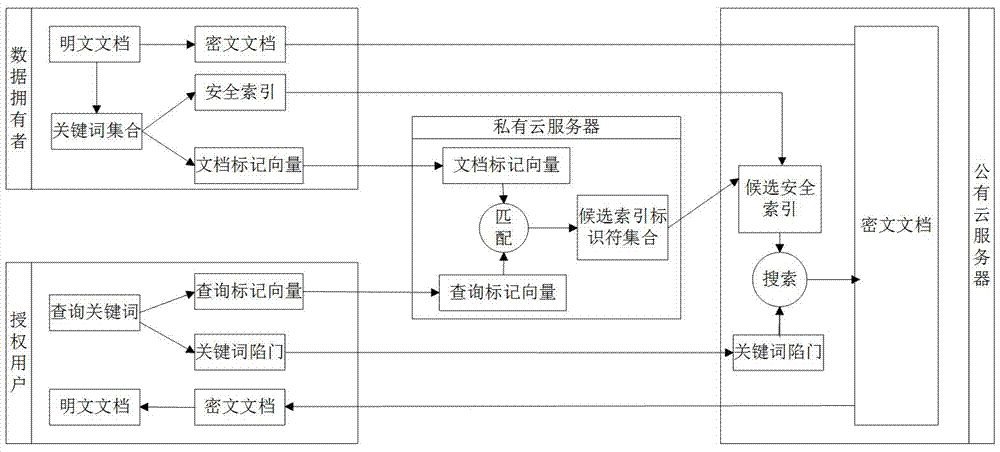
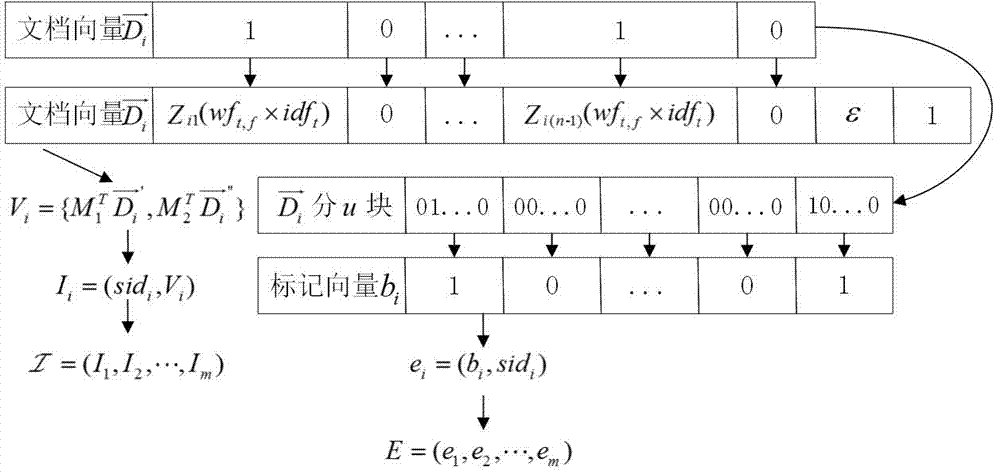
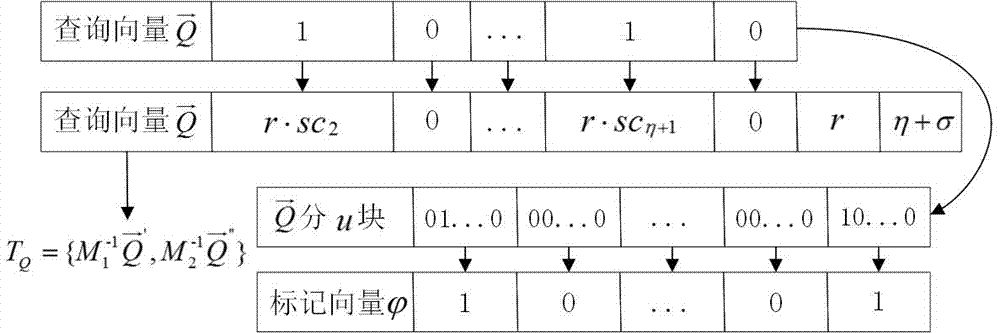
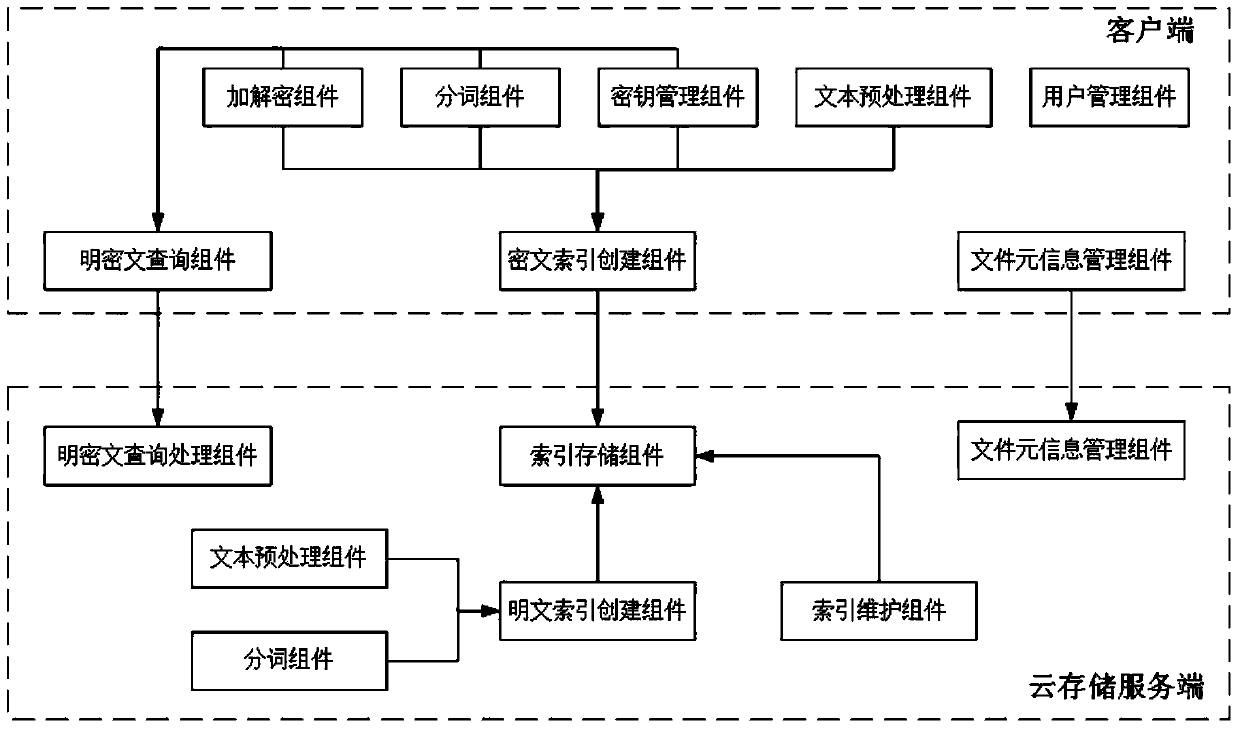
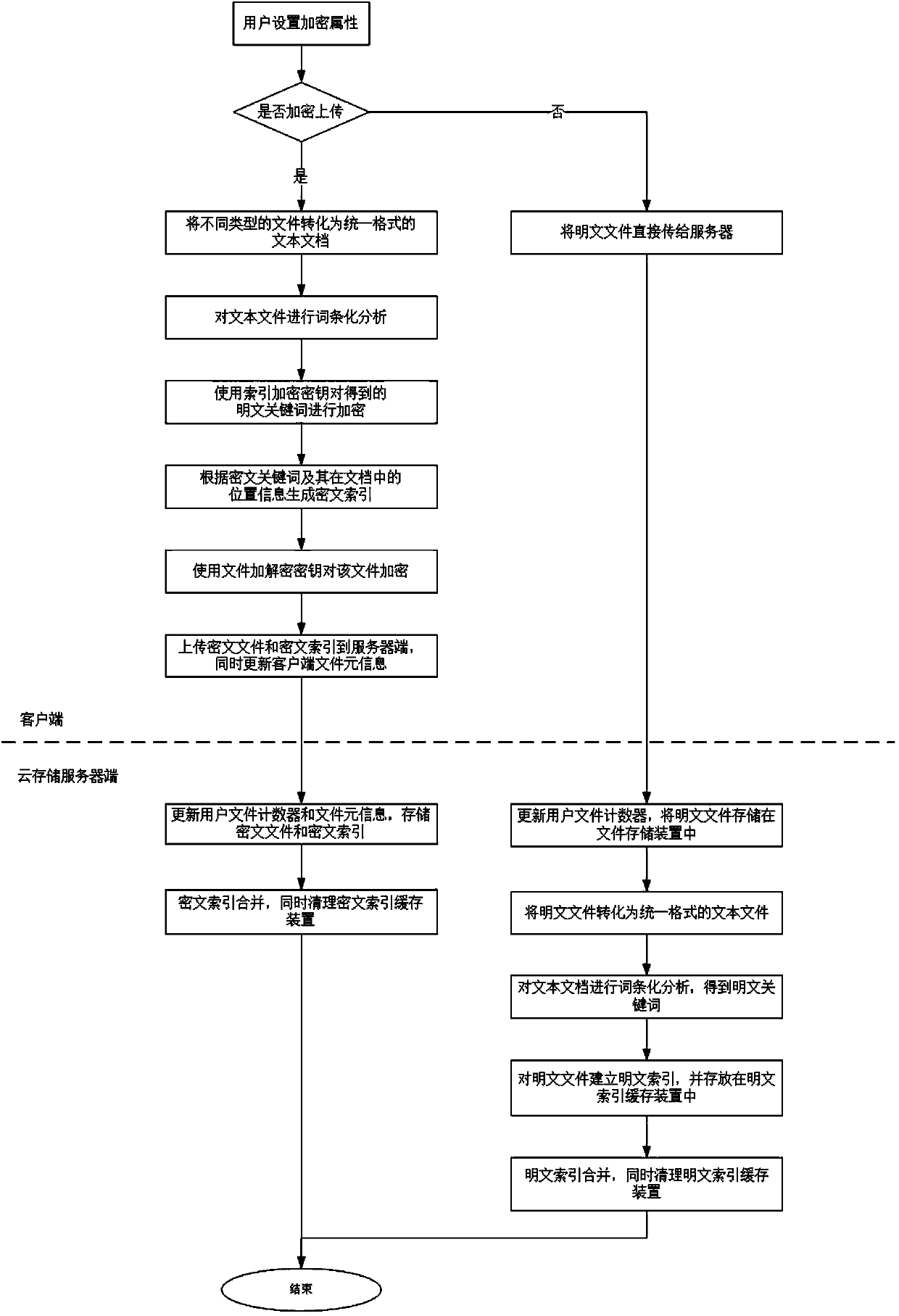
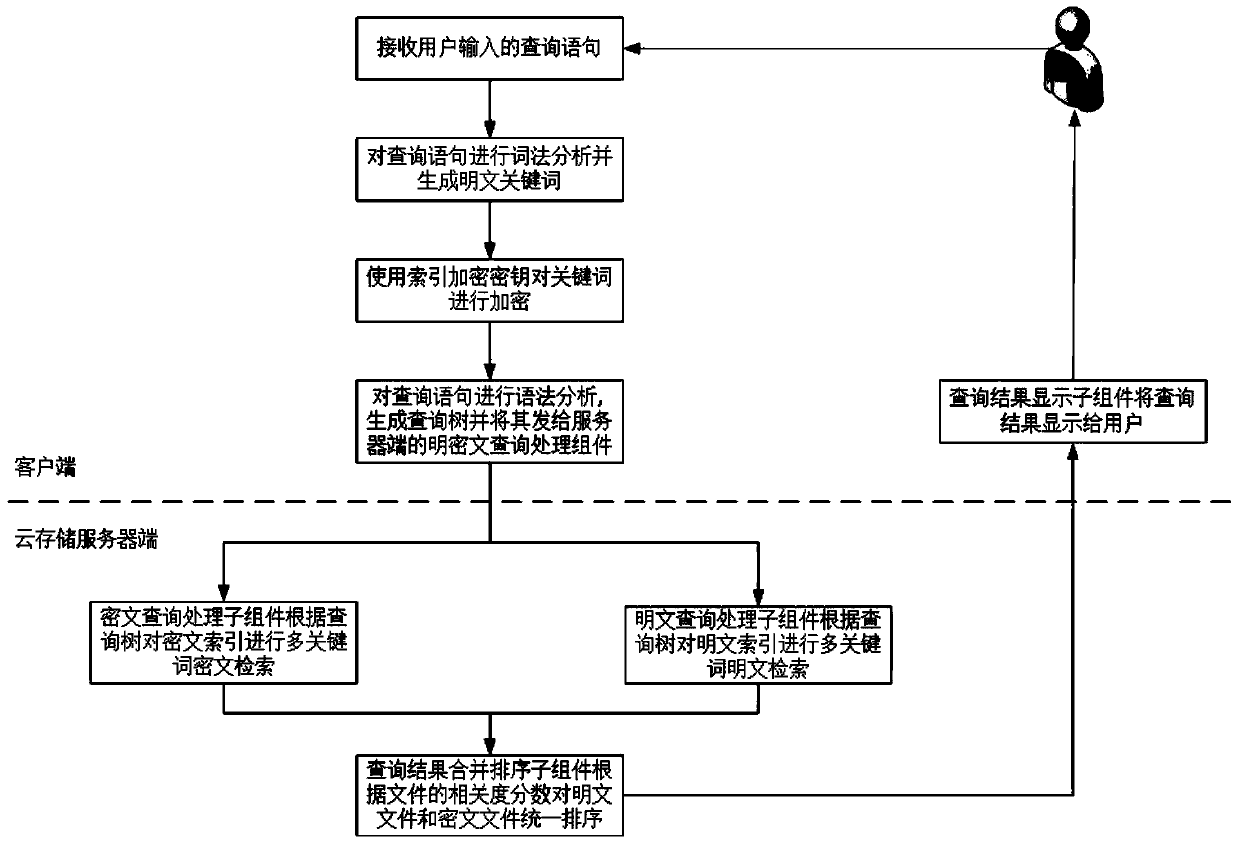
Ciphertext cloud-storage oriented document retrieval method and system
InactiveCN102024054AImprove securityEnsure safetyTransmissionSpecial data processing applicationsUser inputCiphertext
The invention discloses a ciphertext cloud-storage oriented document retrieval method and a ciphertext cloud-storage oriented document retrieval system, belonging to the technical field of information security. The method comprises the following steps: 1) a client generates an index key for a user by a master key imported by the user, and encrypts the index key by the master key, then stores the index key into a server; 2) after receiving the attribute metainformation of a document to be inquired input by a certain user, the client acquires a ciphertext of the index key from the server, then decrypts the ciphertext so as to obtain a decrypted index key; 3) the client encrypts the attribute metainformation of the document to be inquired by the decrypted index key, then sends the encrypted attribute metainformation to the server; and 4) the server carries out ciphertext retrieval on the index table according to the attribute metainformation, returning the retrieval records meeting the conditions to the client so as to obtain documents corresponding to the attribute metainformation. The system comprises a server and a plurality of clients, and the clients are respectively connected with the server through the Internet. The method and the system disclosed in the invention have the advantages that the security and retrieval efficiency of the ciphertext retrieval system are improved, and the expansibility is high.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Image inquiry method based on marking area
InactiveCN101211356AConform to visual perceptionSimple calculationCharacter and pattern recognitionSpecial data processing applicationsPattern recognitionImage segmentation
The invention discloses an image inquiry method based on significant areas and includes the following steps: (1) performing grid partition for an image; (2) carrying out fuzzy clustering for the grids, so as to divide the image into a plurality of concerned areas; (3) Calculate the significance based on the concerned areas; (4) sorting all the grid points according to the significance, so as to gain the significant areas; (5) launching image inquiry. The invention has the advantages of simplified calculation, more complying with visual sense, improving searching efficiency and accuracy.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
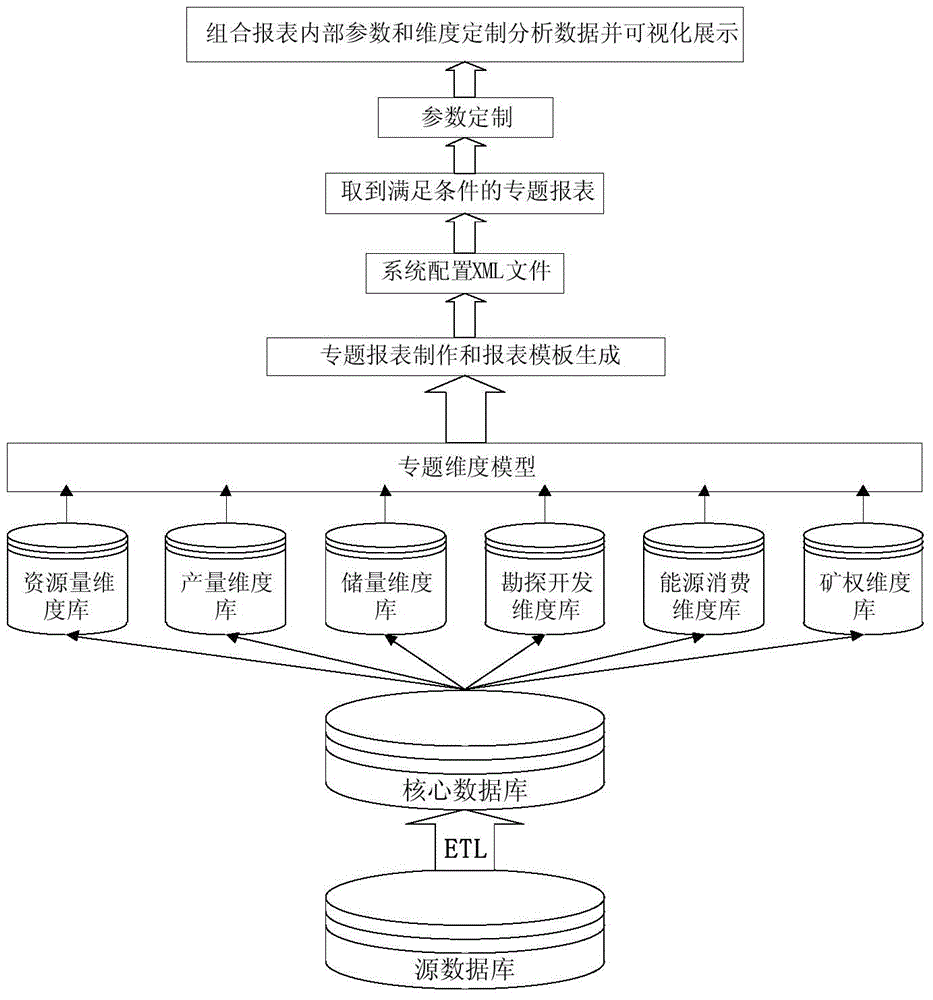
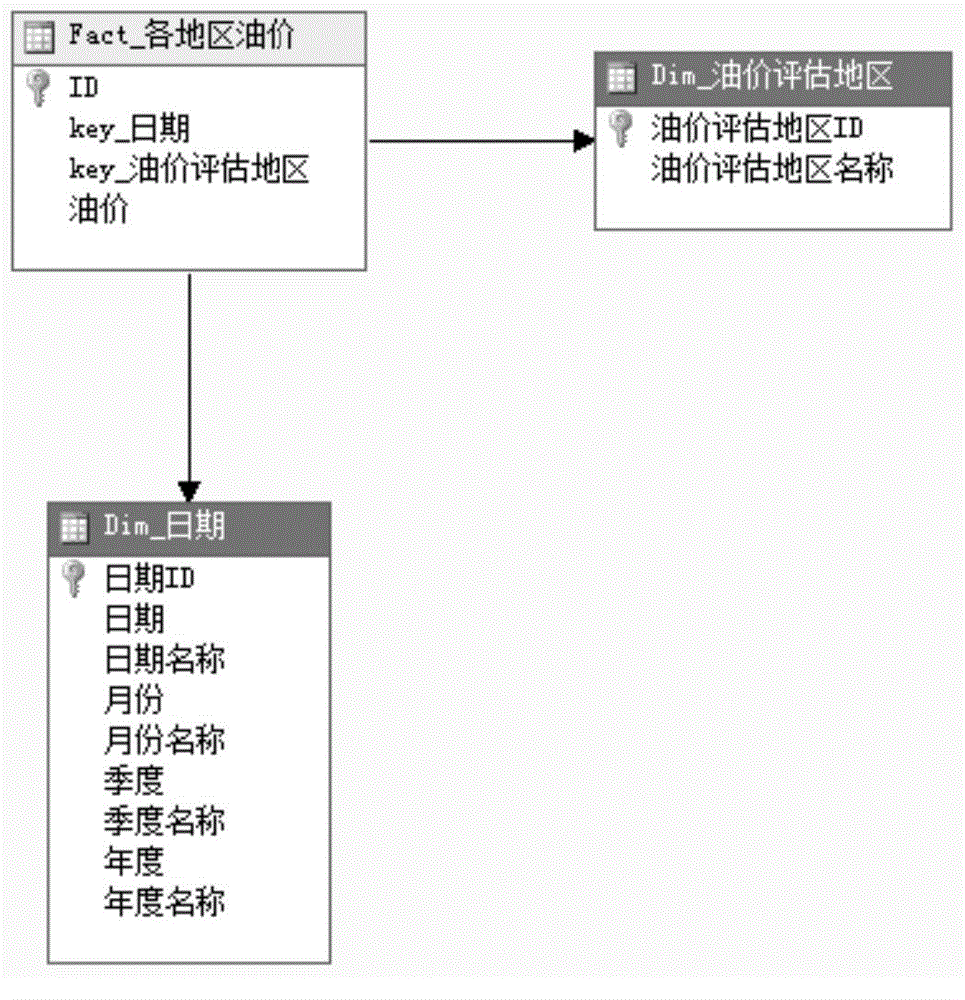
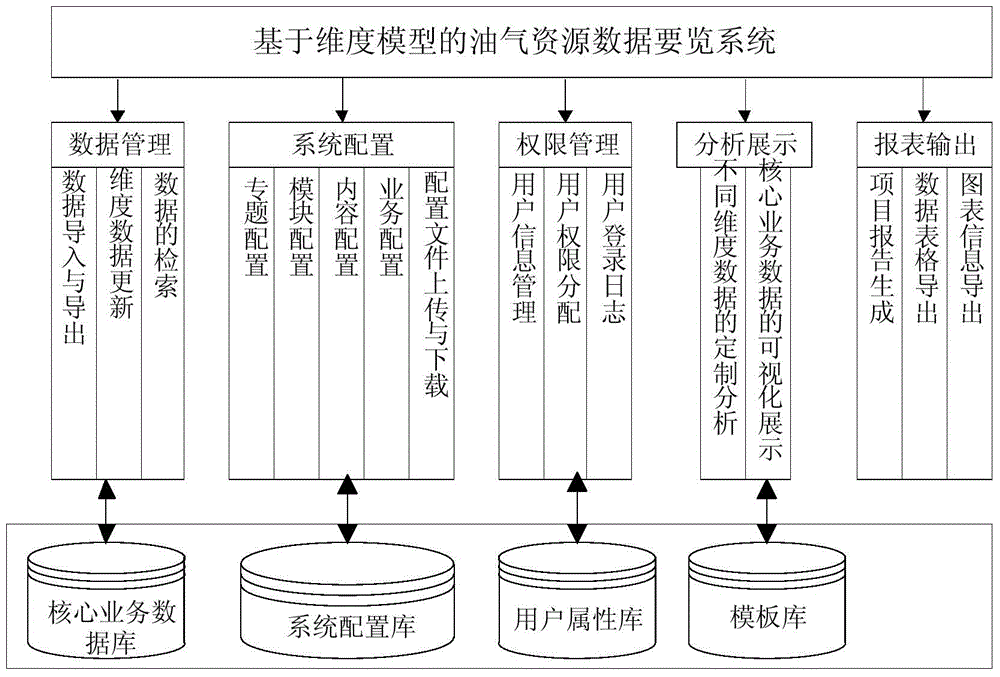
Multidimensional model based oil and gas resource data key system implementation method and system
InactiveCN103984755AImprove processing efficiencyRich display formData processing applicationsSpecial data processing applicationsGraphicsLatitude
The invention discloses a multidimensional model based oil and gas resource data key system implementation method and system. According to the multidimensional model based oil and gas resource data key system implementation system, sorting, cleaning, classification and systematization are performed on source data of oil and gas resources, cleaning, transformation and integration are performed based on an ETL (Extract-Transform-Load) framework, the source data are loaded into a data warehouse or a market to form a core database, and the data processing efficiency is improved and data mining is performed through establishment of a multidimensional model. According to the multidimensional model based oil and gas resource data key system implementation method, different latitudes of the data can be flexibly combined, the custom analysis on core data such as the oil price, the yield, reserves, the quantity of the resources, import and export and the mining right is achieved, integrated management and visual display of statements, graphics, texts and maps are supported, interfaces and function modules of the system are based on a configuration scheme, and accordingly the configuration is flexible, the extension can be performed, the use is easy, the display form of the data is enriched, and the retrieval efficiency is improved.
Owner:CHINA UNIV OF GEOSCIENCES (BEIJING)
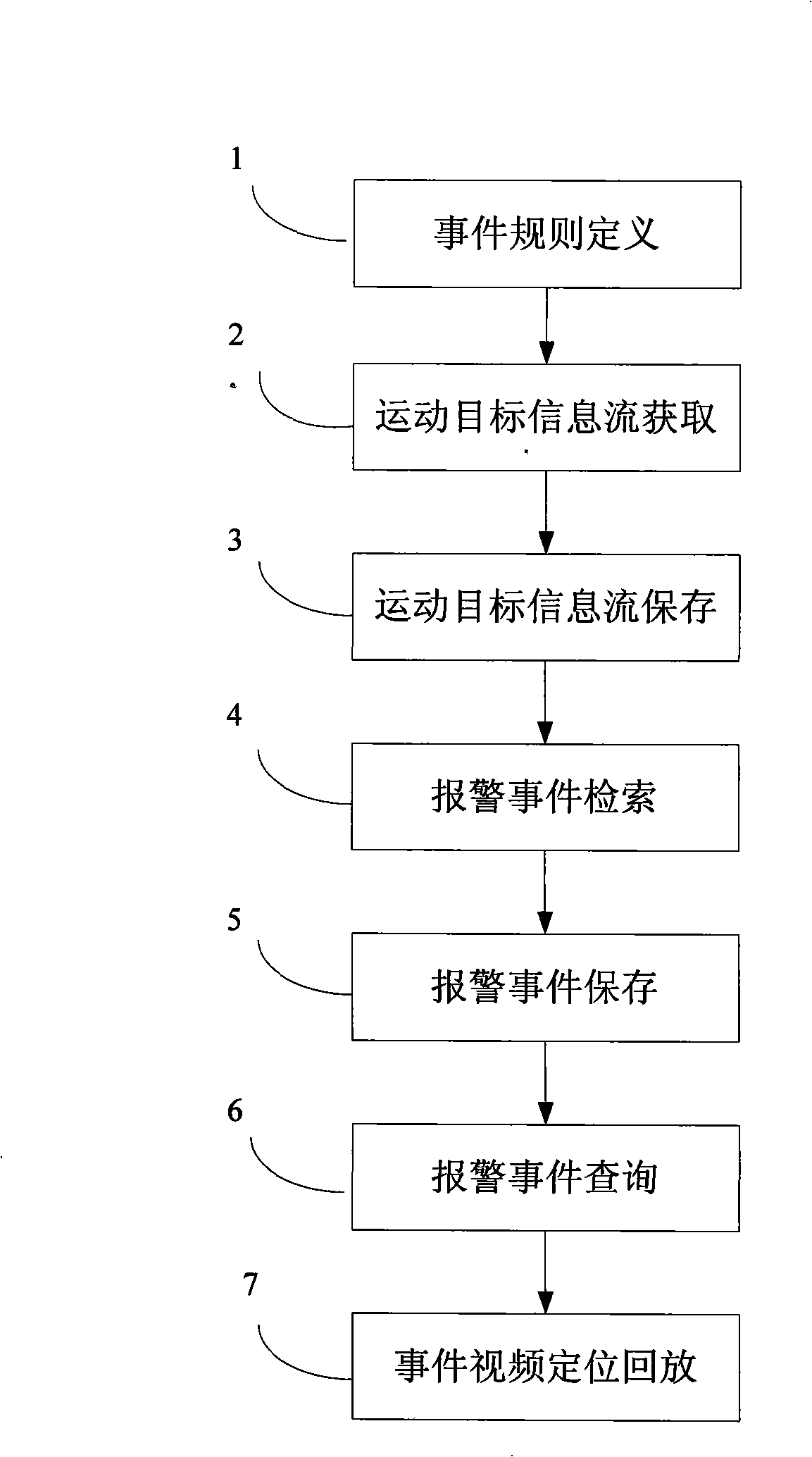
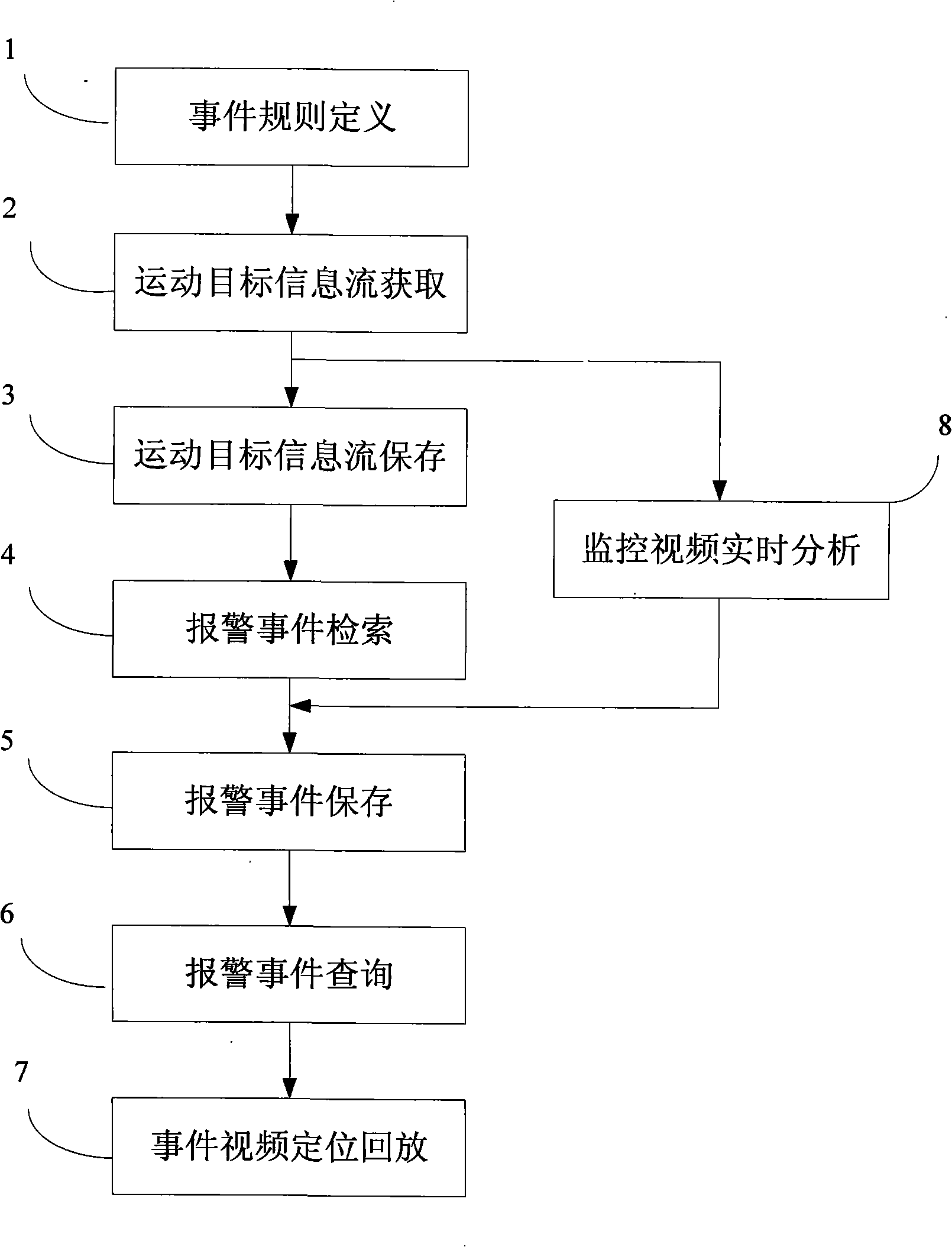
Method and system for researching intelligent video monitoring case
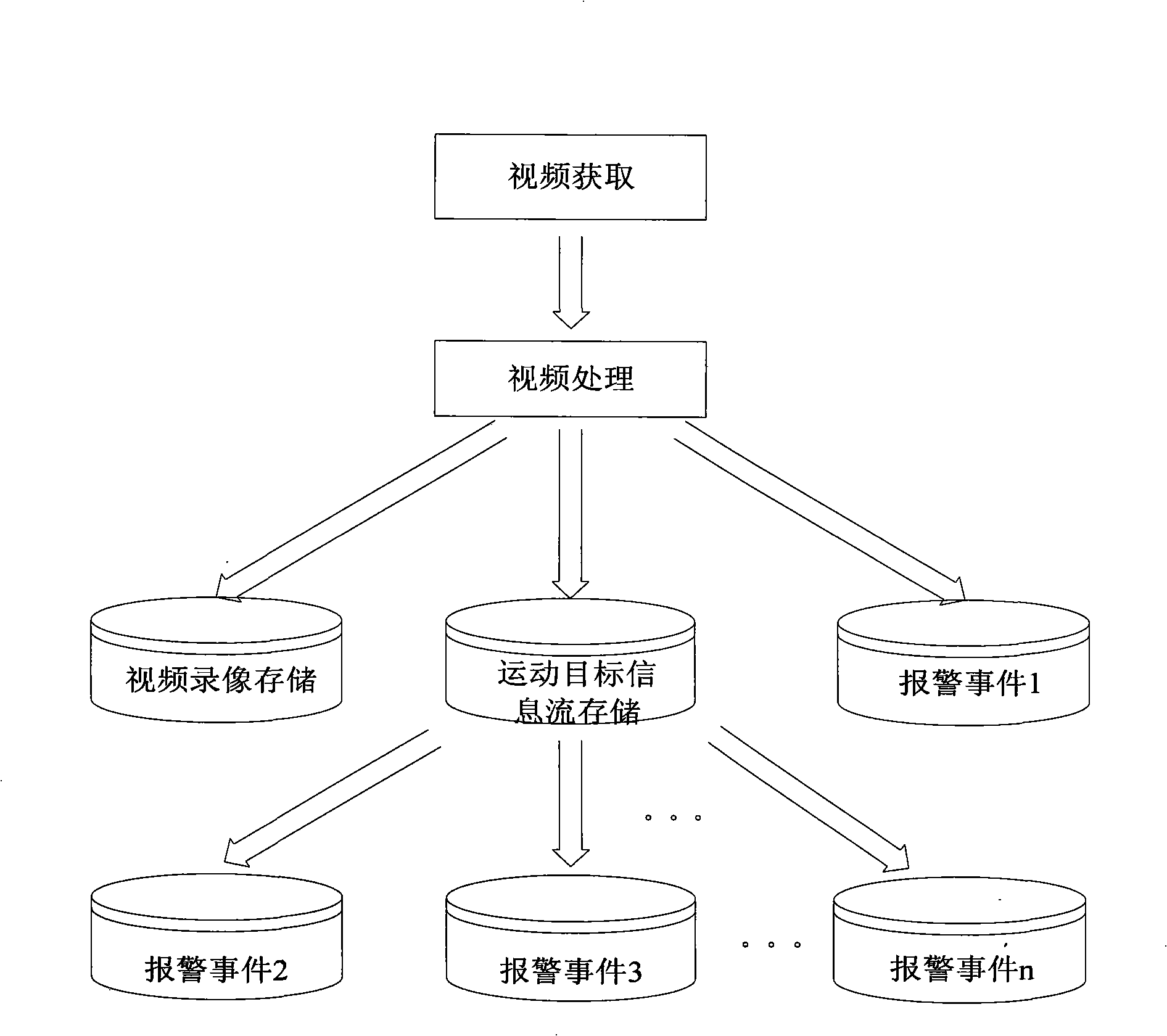
InactiveCN101281593AImprove retrieval efficiencyReduce data volumeImage analysisCharacter and pattern recognitionVideo monitoringPattern recognition
The invention discloses a intelligent video monitor search method, including the steps: collecting the video frame, extracting the moving target information flow, storing the corresponding moving target information flow of the video frame; searching the stored moving target information flow, judging the detected object whether matching with the defined affair rule, if so, determining the corresponding occurrence of the affair rule. Furthermore, the invention includes the step of inquiring the stored affair and the step of playing back the corresponding video frame based on the affair selection. The invention discloses an intelligent video monitor affair search system for executing the method. Due to the target information data flow smaller than the video data flow, hence the invention has faster searching speed, higher searching effectiveness, higher data transmission, lower cost compared with the prior scheme.
Owner:卫安保安服务(上海)有限公司
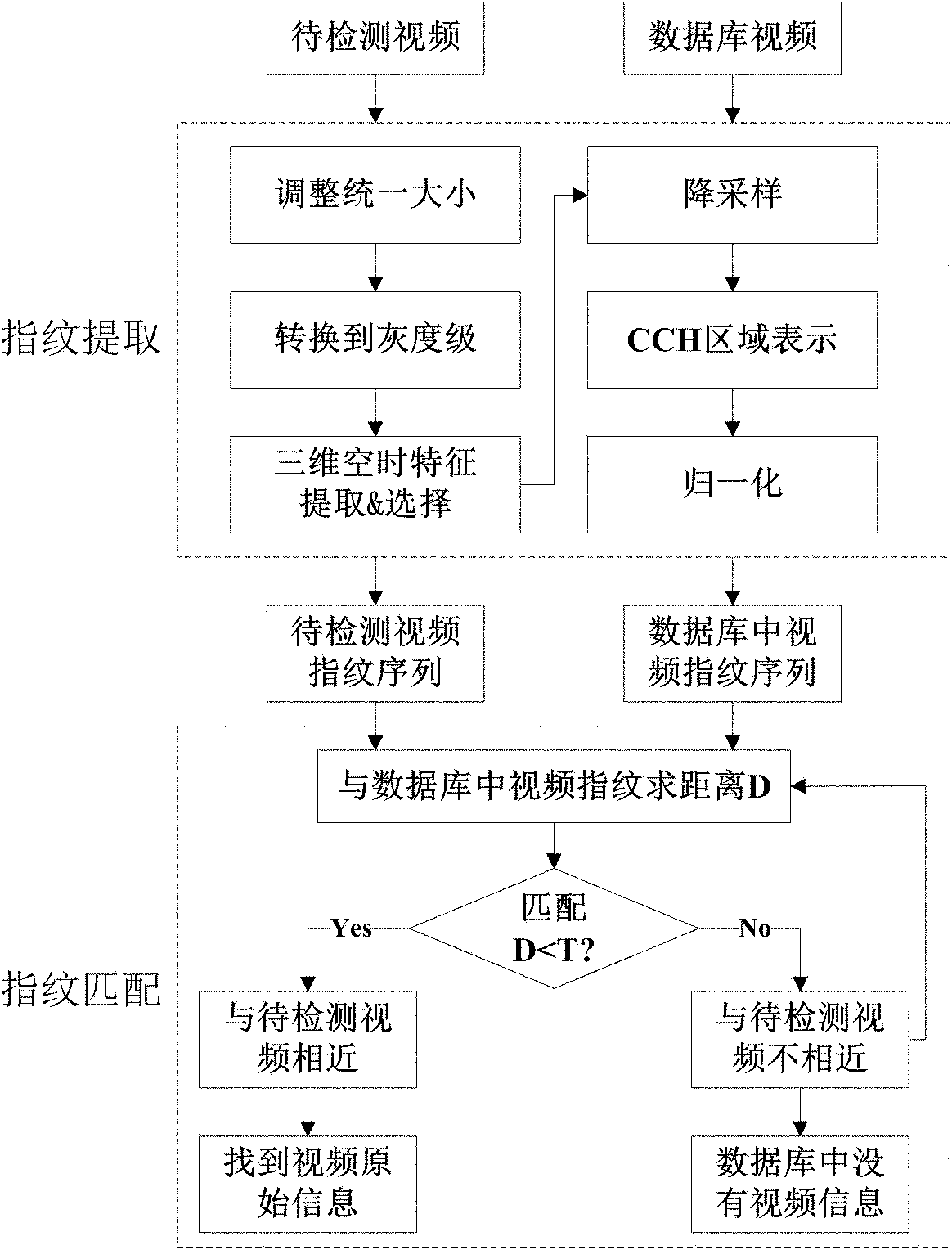
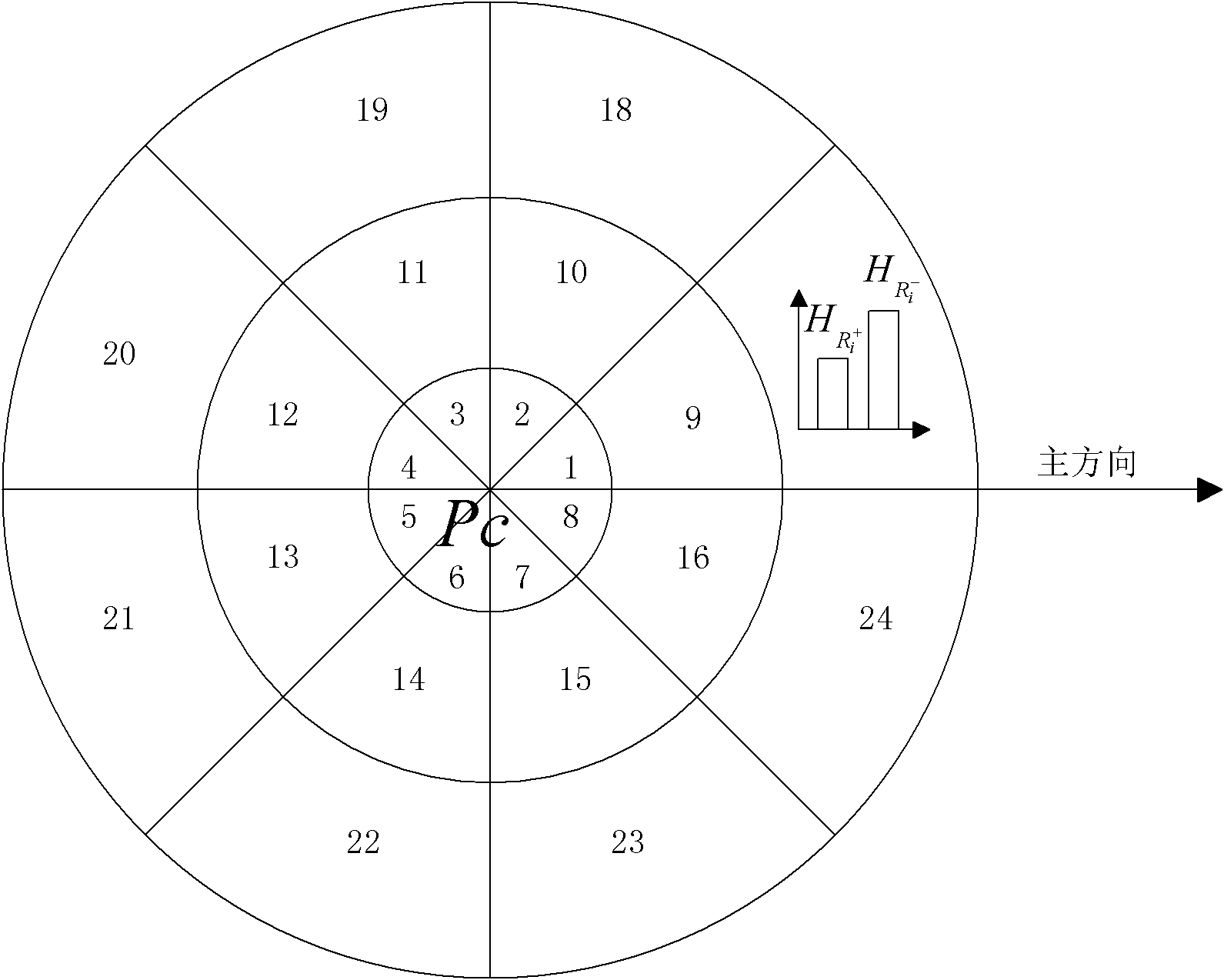
Robust video fingerprint method based on three-dimensional space-time characteristics
InactiveCN102176208ARobustResistance to size changesCharacter and pattern recognitionSpecial data processing applicationsThree-dimensional spaceCharacteristic strength
The invention discloses a robust video fingerprint extraction method based on three-dimensional space-time characteristics, which mainly overcomes the deficiency in utilization of video characteristics in the time direction in the traditional method. The robust video fingerprint extraction method is characterized in that the three-dimensional space-time characteristics are introduced in fingerprint extraction, namely, three-dimensional space-time characteristic points in the successive frames of a video to be detected are extracted firstly, and the most stable characteristic area in each frame is obtained through selection of the characteristic strength and characteristic scale; then the characteristic area is obtained through down sampling; finally, a contrast histogram is used for representing the area and normalized into a vector-form fingerprint sequence of the video to be detected; and the fingerprint sequence of the video to be detected and a candidate fingerprint sequence in a database are subjected to distance matching so as to obtain a candidate video relevant to the video to be detected. The robust video fingerprint extraction method disclosed by the invention reflects the space characteristic and the time characteristic at the same time, has extremely good robustness and can be used for video content authentication and near video detection.
Owner:XIDIAN UNIV
Index establishing and searching methods, devices and systems for audio-video file
InactiveCN102650993AImprove retrieval efficiencyIncrease success rateSpecial data processing applicationsBroadcastingContent management
The embodiment of the invention discloses index establishing and searching methods, devices and systems for an audio-video file, which relate to the field of audio and video technology and can improve the searching efficiency and success rate of the audio-video file. The index establishing method comprises the following steps of: extracting key information from the audio-video file, and storing incidence relation among the key information, the audio-video file and a storing position of the audio-video file as an index record. The index searching method comprises the following steps of: searching identification of a target audio-video file, which is matched with key information to be searched from the index record; obtaining the target audio-video file from a storing address relevant to the identification of the target audio-video file; and positioning a position of the key information to be searched in the target audio-video file. The index establishing and searching methods, devices and systems for the audio-video file provided by the embodiment of the invention are mainly applied to the technical field of broadcast television content management. Particularly, when a mass of the audio-video files are searched, the searching efficiency and success rate can be improved.
Owner:PEKING UNIV FOUNDER GRP CO LTD +2
Extendible repeated data detection method
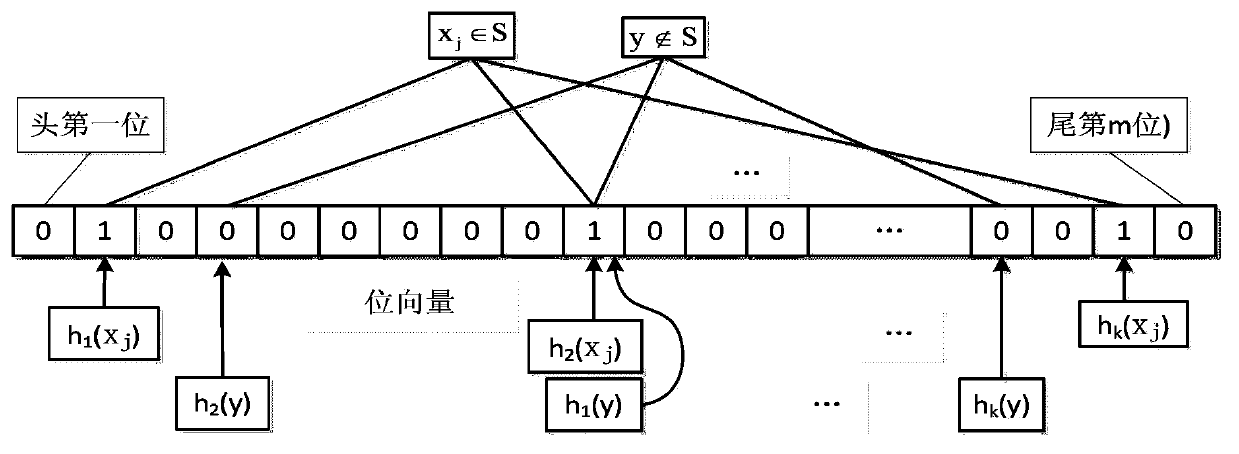
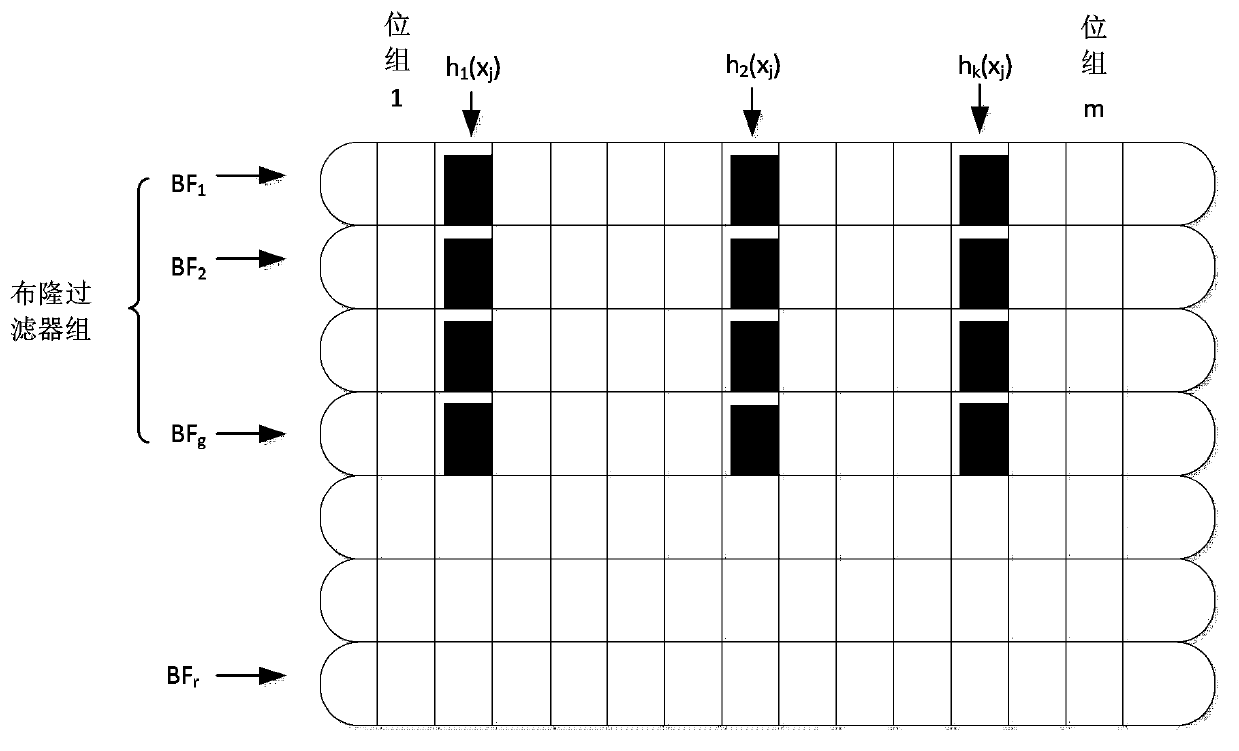
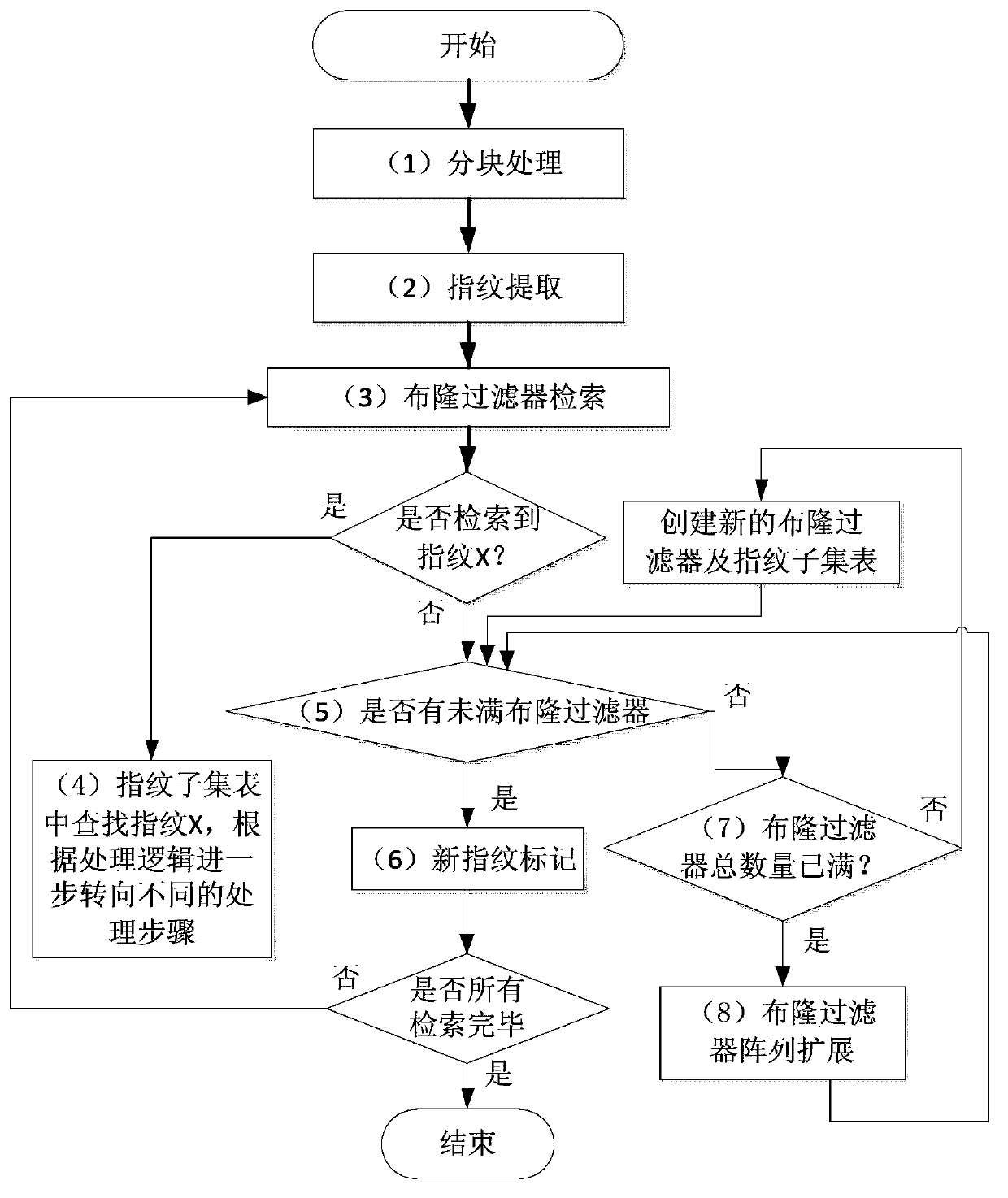
ActiveCN103970744ARapid positioningRealize detectionSpecial data processing applicationsInput/output processes for data processingBloom filterComputer science
The invention discloses an extendible repeated data detection method, belongs to the technical field of computer storage, and solves the problem that in the existing repeated data detecting method, the storage capacity cannot be efficiently extended, so as to meet the requirements of the current situation that the storage demand increases and repeatedly deleted systems need upgrading and updating. The extendible repeated data detection method comprises the following steps: partitioning processing, fingerprint extraction, retrieving of Bloom filters, retrieving of fingerprint subset table, judgment of unfulfilled Bloom filters, new fingerprint marking, judgment of Bloom filter quantity, and extending of Bloom filter array. In the invention, the Bloom filter array is used to retrieve the fingerprint data, so as to quickly locate the retrieval range, improve the retrieval efficiency and realize detection on the repeated data; the extendible repeated data detection method is high in expansibility and querying performance, can support element location and control the misjudgment rate, and further can effectively reduce the memory overhead. The Bloom filter array is composed of a series of isomorphic Bloom filters, so that once the misjudgment rate epsilon' and the pre-established retrieving fingerprint total quantity nmax are provided, the quantity of the required Bloom filters and the number of the hush functions can be worked out.
Owner:HUAZHONG UNIV OF SCI & TECH
Image retrieval, image information acquisition and image identification methods and apparatuses, and image identification system
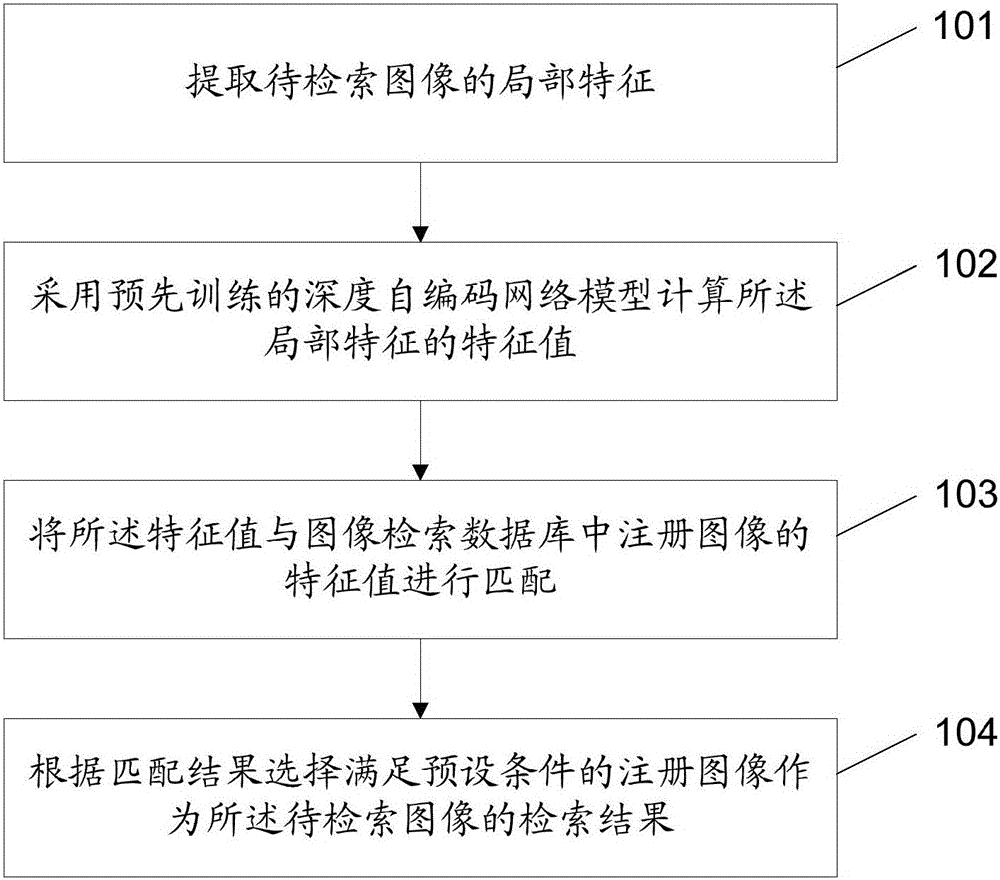
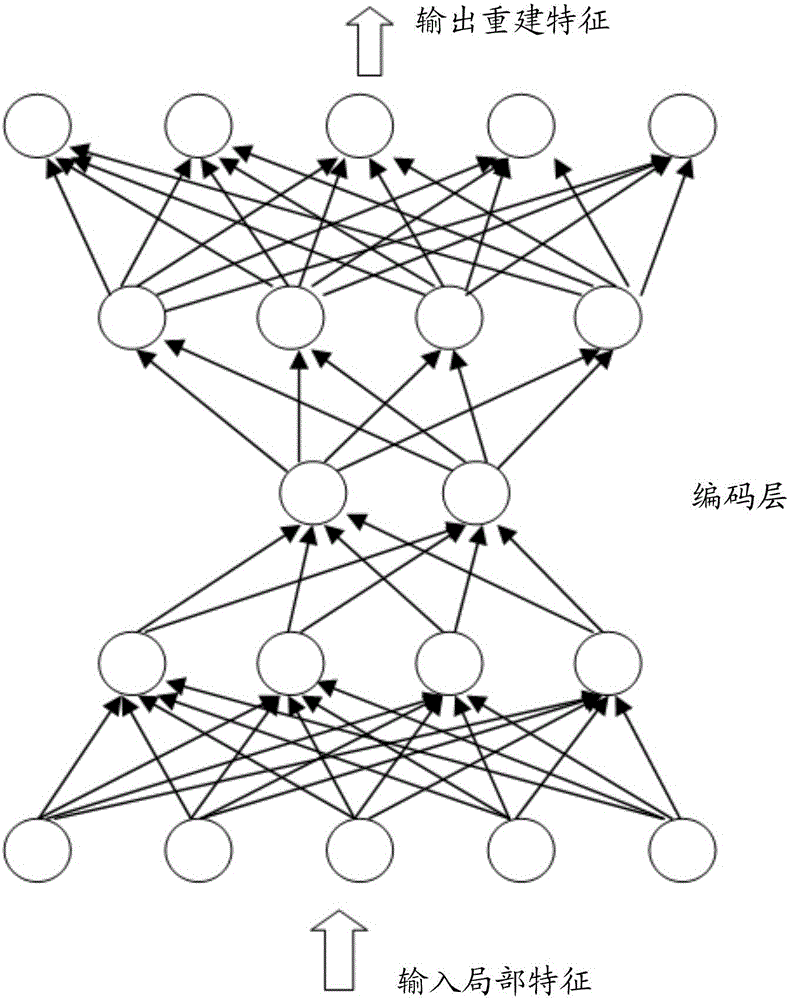
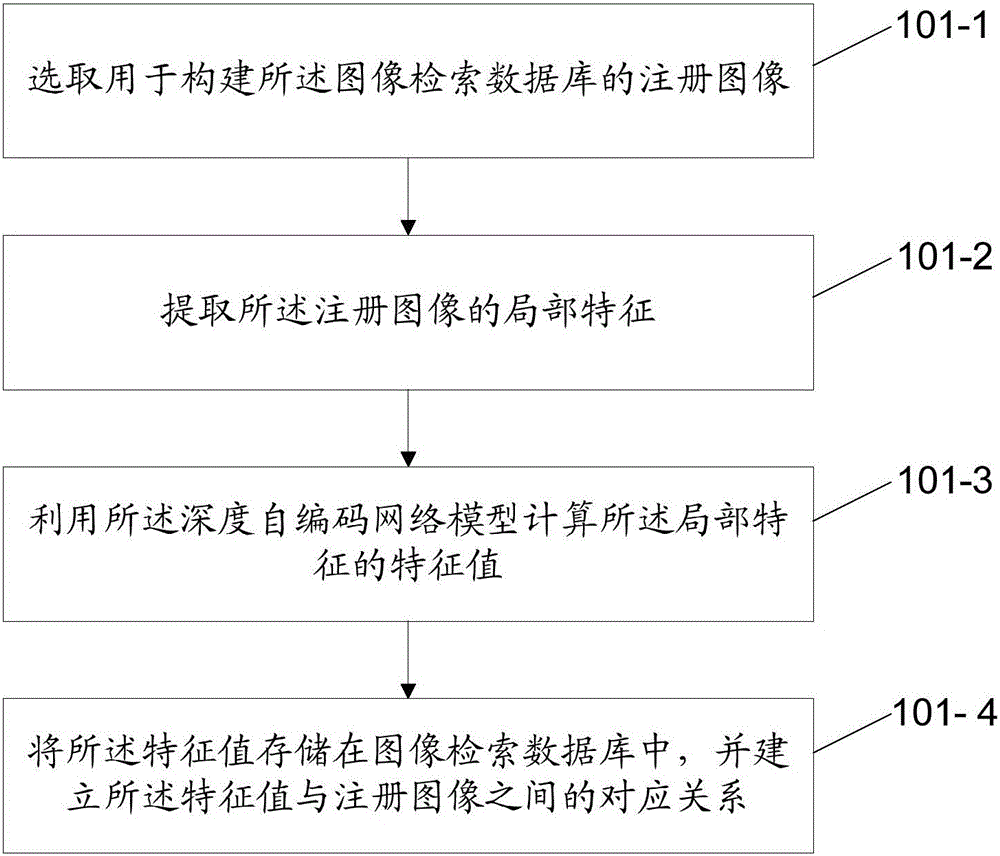
ActiveCN106445939AHigh precisionKeep distanceStill image data retrievalSpecial data processing applicationsFiltrationImage retrieval
The invention discloses an image retrieval method and apparatus, an image information acquisition method and apparatus, an image identification method and apparatus, an image identification system, a method and apparatus used for calculating an image feature value, and an electronic device. The image retrieval method comprises the steps of extracting a local feature of a to-be-retrieved image; calculating a feature value of the local feature by adopting a pre-trained depth autoencoder network model; performing matching on the feature value and feature values of registered images in an image retrieval database; and selecting a registered image, which meets a preset condition, as a retrieval result of the to-be-retrieved image according to a matching result. By adopting the method, a depth autoencoder network can effectively keep distance information and a distinguishing capability between the feature values in a process of performing compressed representation on the local feature, so that the image retrieval precision can be effectively improved, the workload of rearrangement and filtration can be reduced, and the retrieval efficiency can be enhanced.
Owner:BANMA ZHIXING NETWORK HONGKONG CO LTD
Image target searching method and device
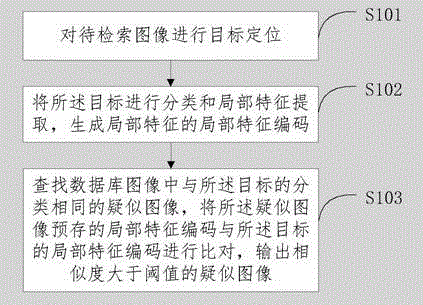
InactiveCN106354735AImprove retrieval accuracyImprove retrieval efficiencyRelational databasesStill image data indexingPattern recognitionComputer science
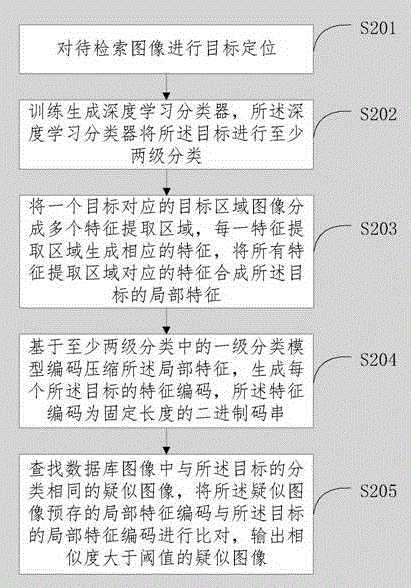
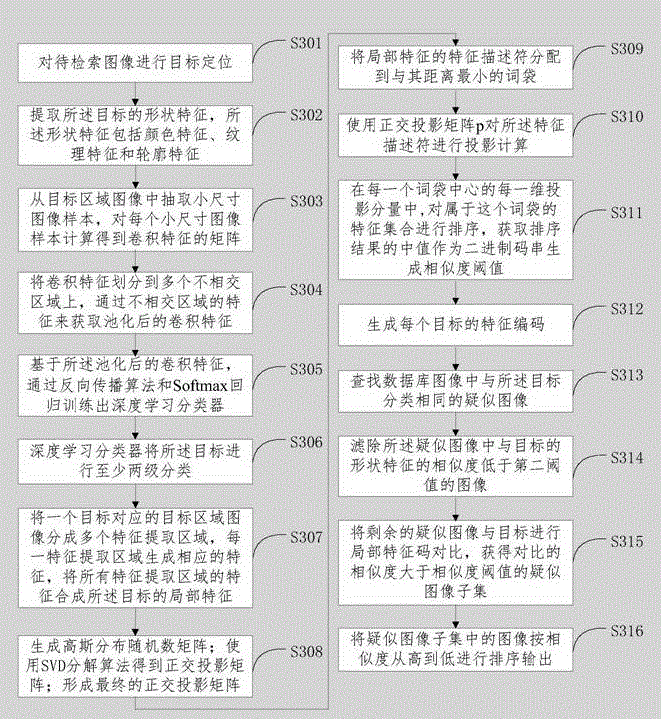
The invention discloses an image target searching method and device. The searching method includes: targeting and locating the to-be-searched image; classifying and extracting local features of the target, to generate the local feature codes for the local features; searching for similar images in the database that belong to the same class with the aforementioned target; comparing the saved local feature codes of the similar images with the codes of the target local features, then outputting similar images with similarity greater than the threshold. Through targeting and locating the to-be-searched image, classifying the target into at least two classes, and generating the local feature codes for the targets. When searching, search according to the search target classifications and order according to the similarities. Through target classifications, the searched target is matched using a model under the same target classification, thus increasing the search accuracy and efficiency.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Document similarity calculating method and similar document whole-network retrieval tracking method
InactiveCN106095737AAccurate processing of similarityAccurate analysis and statisticsSemantic analysisText database indexingCosine similarityTwo-vector
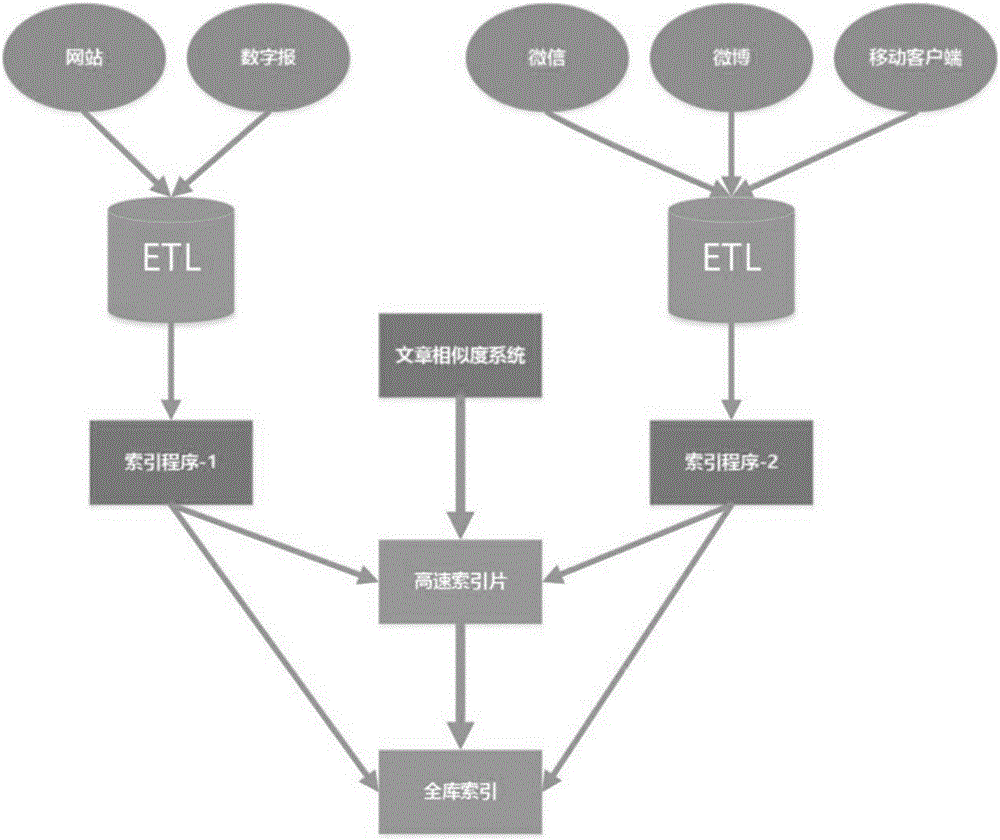
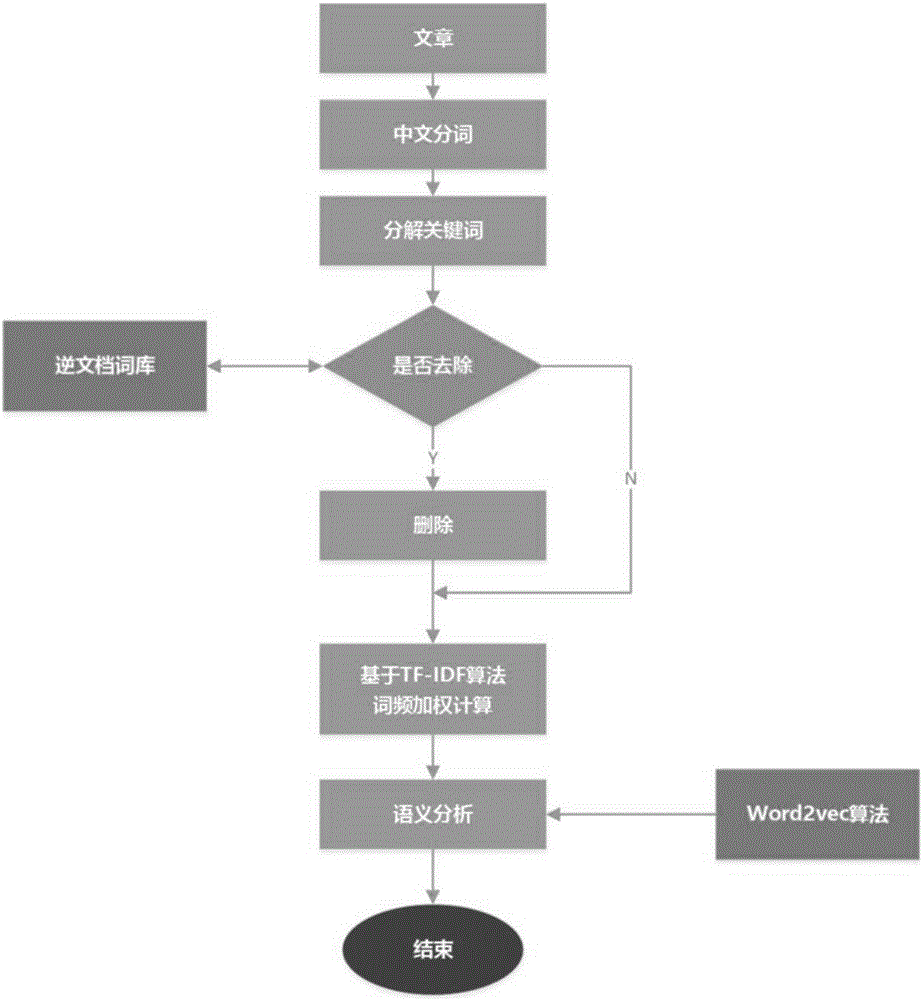
The invention relates to a document similarity calculating method and a similar document whole-network retrieval tracking method. The technical scheme is characterized in that the document similarity calculating method includes: S01, performing word segmentation on an original document and a target document to acquire respective word segmentation sets; S02, performing preprocessing and feature weighting: utilizing TF-IDF technology to calculate weight of each word segmentation, extracting core key words, utilizing Word2vec to dig correlation degree among different word segmentation in the documents, and performing semantic analysis on each document; S03, adopting a vector space model and a cosine similarity algorithm: utilizing a cosine value of an included angle of two vectors in vector space to evaluate similarity of the documents, wherein the cosine value is between 0 and 1, and the greater the cosine value is, the higher the similarity of the documents is. The document similarity calculating method and the similar document whole-network retrieval tracking method are suitable for news information redistribution tracking and transmissibility statistics.
Owner:HANGZHOU FANEWS TECH
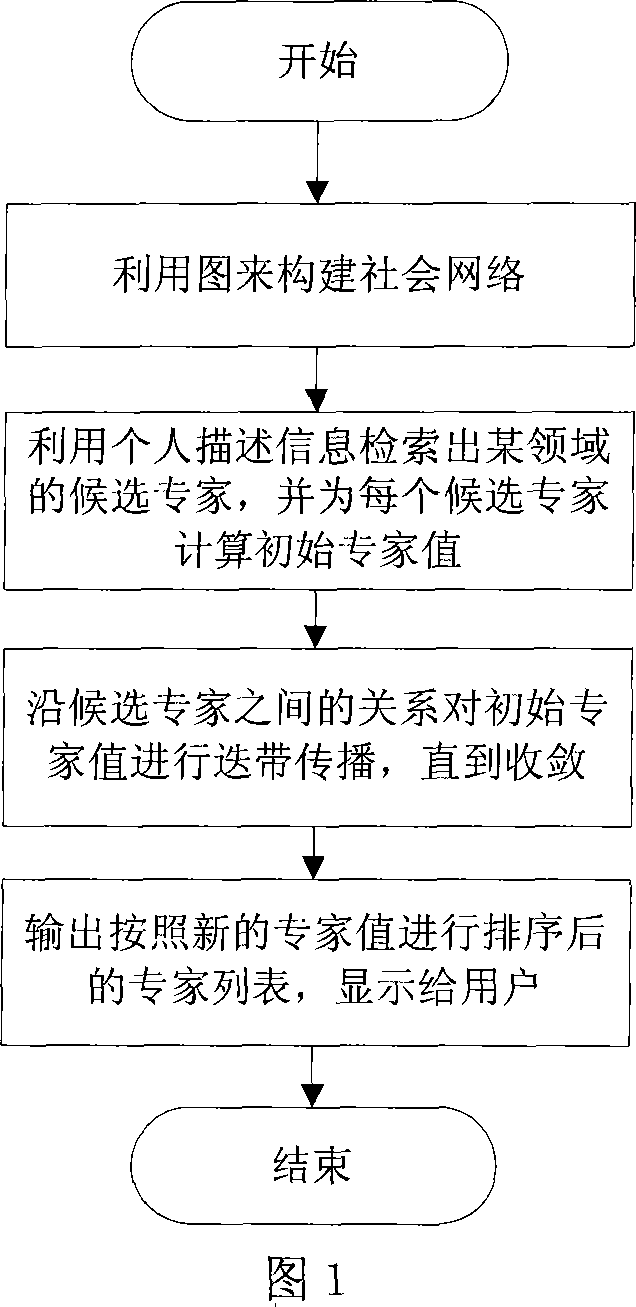
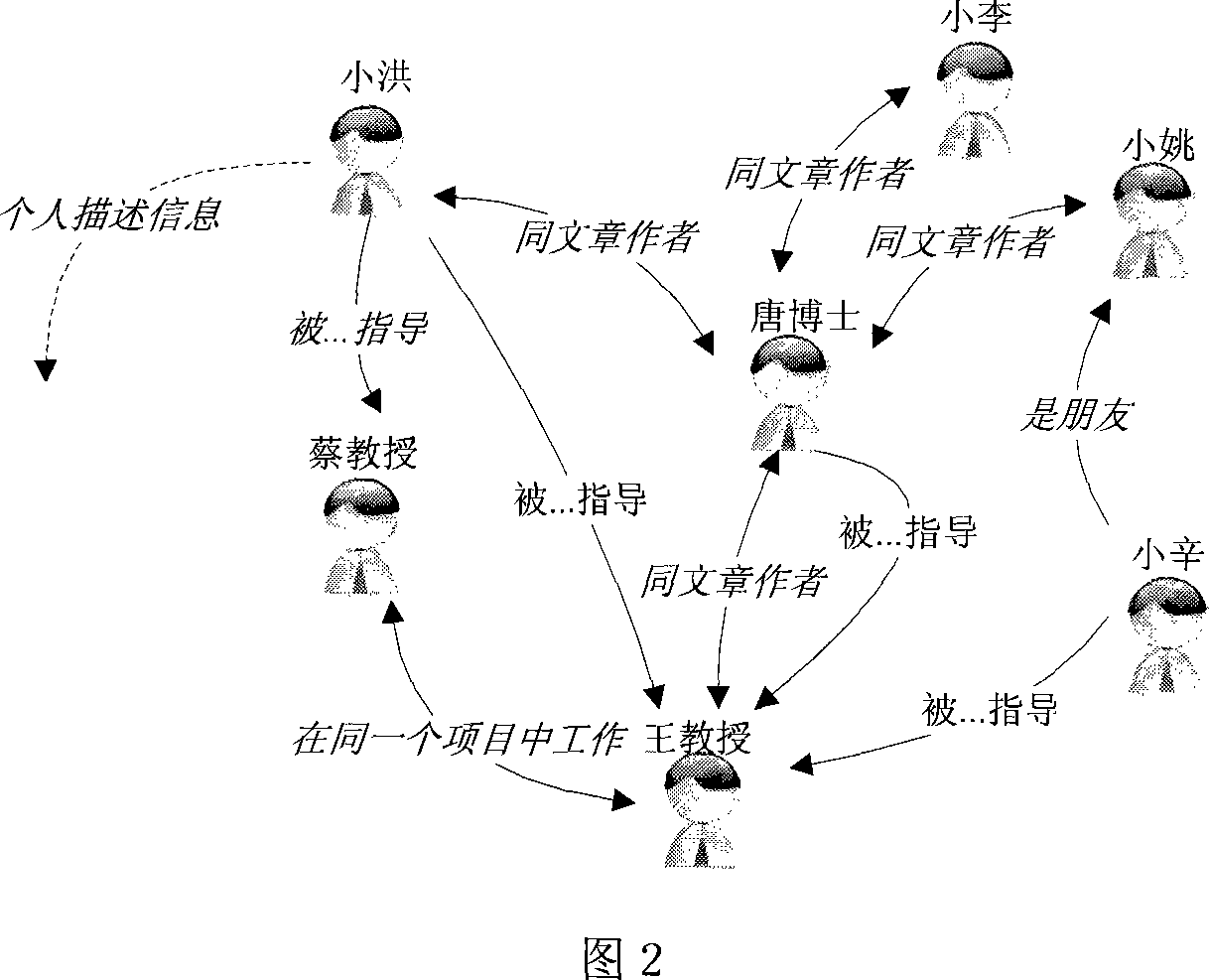
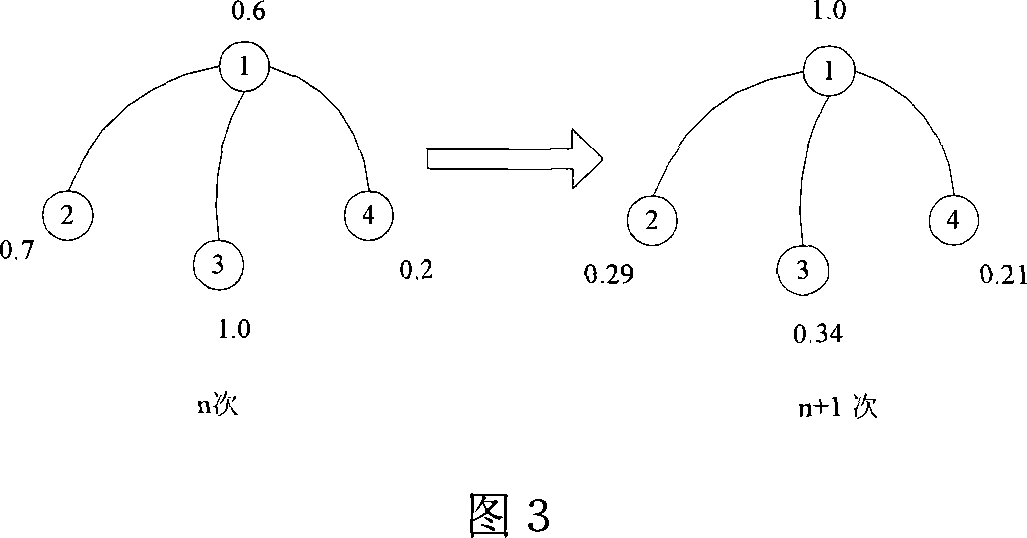
Method and system for processing social network expert information based on expert value progation algorithm
InactiveCN101075942AHuge usersImprove retrieval efficiencyData switching by path configurationStore-and-forward switching systemsWeb serviceSocial network
The method comprises: establishing a society relation network graph by using society relation network generation server; said graph is described by using personal description information, human relation, relation type and the mapping function between human relation and relation type; the expert value calculation server reads the information from the database server, and according to the weighting, analyzes the correlation between the key word, the person description information and the thesis information to get a initiative expert value; then according to the importance and osculation of human relation, constructs a propagator matrix; according to the initiative expert value and the propagator matrix, makes iteration to get the expert value of all experts; after normalization, arranging it in descending order; outputs it to the Web server to provide the option for user.
Owner:TSINGHUA UNIV
Quick multi-keyword semantic sorting search method for protecting data privacy in cloud computing
ActiveCN106951411AQuick filterShorten the timeSemantic analysisSpecial data processing applicationsComputational semanticsCiphertext
The invention relates to a quick multi-keyword semantic sorting search method for protecting data privacy in cloud computing. A domain weighted scoring concept is introduced in document scoring, and keywords in different domains such as a title, an abstract and the like are endowed with different weights to be distinguished; a retrieval keyword is subjected to semantic expansion, semantic similarity is calculated, a three-factor sorting method is designed by combining the semantic similarity, the domain weighted scoring and a correlation score, and a cloud server can perform accurate sorting on search results and return a sorting result to a search user; and for the defect of low query efficiency of a searchable encryption scheme, a vector block segmentation marking matching algorithm is designed, and a document vector created by a vector space model is subjected to block segmentation to generate a marking vector with a relatively small dimension number. According to the method, the query efficiency can be improved, the index creation time can be shortened, and semantic ciphertext keyword search is realized.
Owner:FUZHOU UNIV
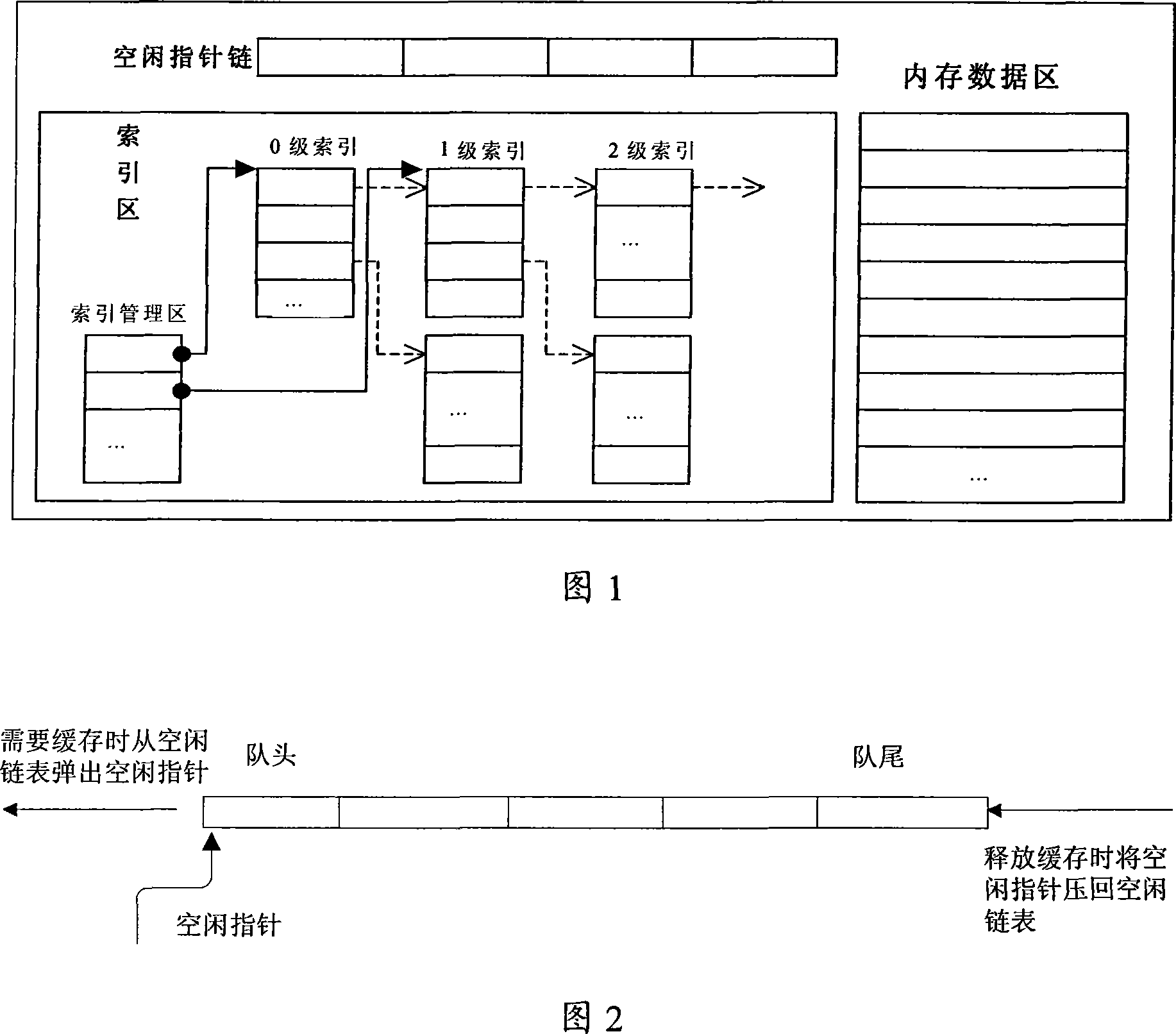
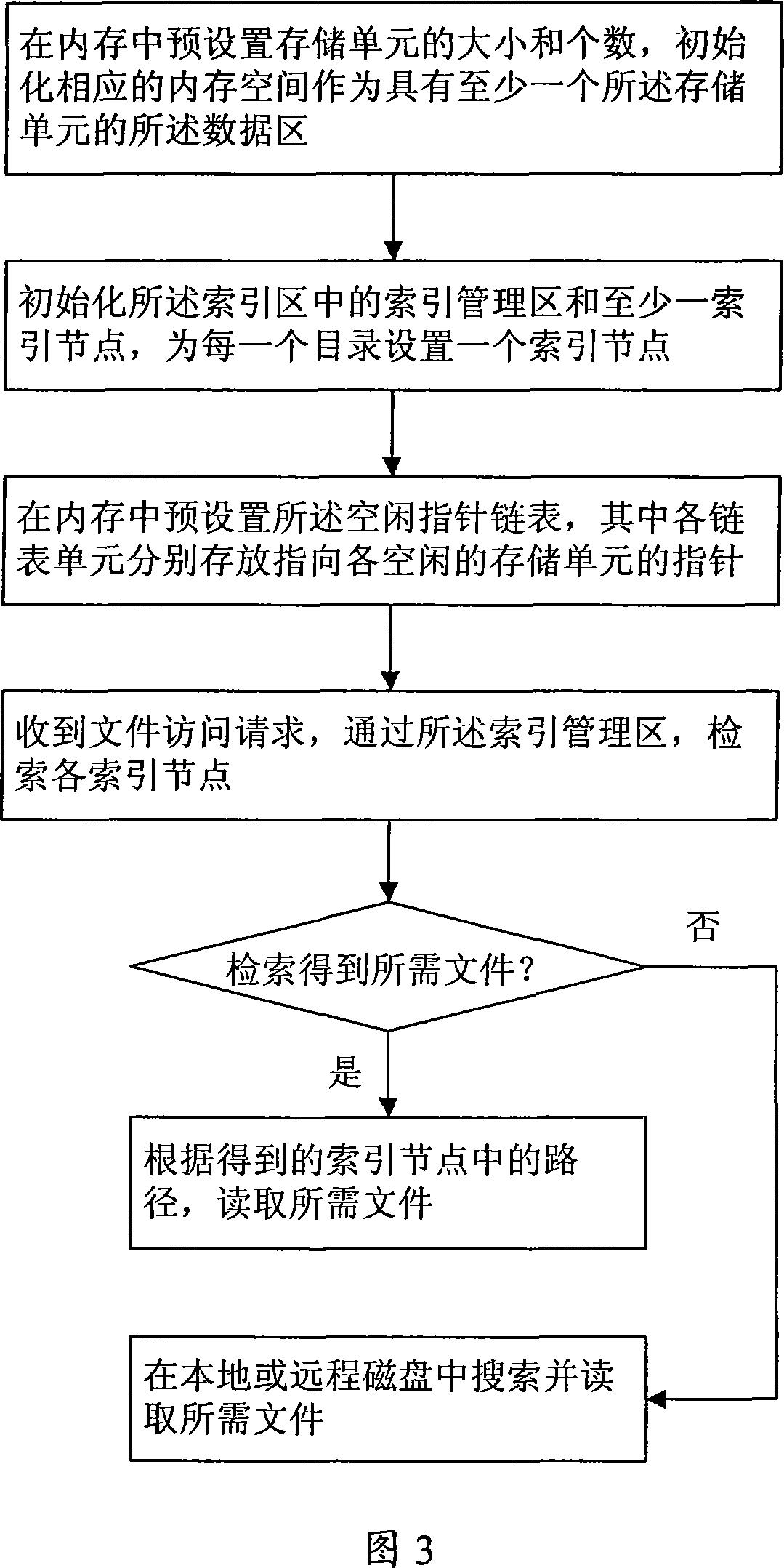
High speed cache system and method for implementing file access
ActiveCN101187901AImplement cachingImprove retrieval efficiencyMemory adressing/allocation/relocationSpecial data processing applicationsInodeComputer science
The invention discloses a high speed cache system for realizing file visit and a method, the system comprises an index area unit, a data area unit, and an idle pointer chained list unit, wherein the data area unit comprises continuous storing units with fixed sizes, the data area unit occupies continuous and corresponded inner memory spaces which are used as each storing unit according to size and number of the storing units which are preset, the storing units record information of files, the index area unit is provided with index managing area modules and at least one index node. Each catalog is provided with an index node which stores the absolute path which is corresponded with the catalogs and catalogs and information of files under the absolute path, and the index nodes adopt an object pointer to point ate each storing unit which records information of each file. The idle pointer chained list unit maintains an idle point chained list, and each chained list unit respectively stores pointer of each storing unit. The invention has the advantage of flexible and convenient application, and quickly realizes high-speed cache of data of local or remote magnetic disks, and improves index efficiency of files.
Owner:KONKA GROUP
Multi-keyword plaintext and ciphertext retrieving method and device oriented to cloud storage
InactiveCN103593476AFix bugsAddress riskKey distribution for secure communicationComputer security arrangementsPlaintextComputer hardware
The invention relates to a multi-keyword plaintext and ciphertext retrieving method and device oriented to cloud storage and relates to the field of information safety. The method includes the following steps that firstly, a client terminal performs lexical analysis according to inquiry statements and generates plaintext keywords; secondly, a corresponding user index encryption key is obtained according to a main key bound with the identity of a user, and the plaintext keywords are encrypted with the encryption algorithm of the index encryption key, and ciphertext keywords are generated; thirdly, multi-keyword ciphertext retrieving is performed on a ciphertext index in a cloud storage server according to an inquire tree generated by the client terminal, and retrieved data element information and retrieved relevancy scores undergo inquiry result merging and sequencing; fifthly, inquiry result merging and sequencing are performed in the cloud storage server with the same method; sixthly, a unified sequence result is sent to the client terminal, and an inquiry result is displayed to the user. According to the multi-keyword plaintext and ciphertext retrieving method and device oriented to the cloud storage, a key management scheme which is higher in safety degree is provided, plaintext and ciphertext united retrieving can be supported and multi-keyword retrieving can be provided.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Generation system and method for structured query sentence used for precise retrieval of natural language
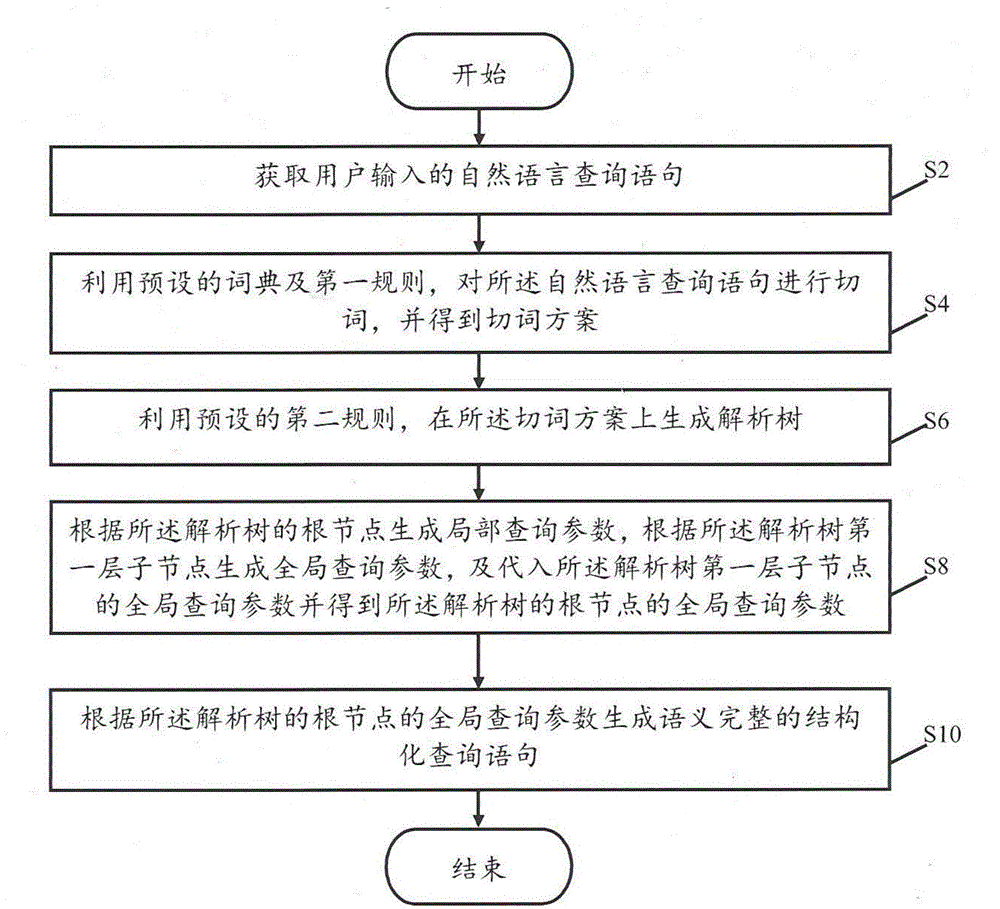
ActiveCN104657439AEasy inputHigh precisionSpecial data processing applicationsPhase retrievalHuman language
The invention discloses a generation method for a structured query sentence used for the precise retrieval of a natural language. The generation method comprises the following steps: obtaining a natural language query sentence; carrying out word segmentation on the natural language query sentence by a preset dictionary and a first rule to obtain a word segmentation scheme; generating an analytic tree on the word segmentation scheme by a preset second rule; according to the root node of the analytic tree, generating a local query parameter, and substituting the global query parameter of a first layer of subnodes of the analytic tree, and obtaining the global query parameter of the root node of the analytic tree; according to the global query parameter of the root node of the analytic tree, generating the structured query sentence. The invention also provides a generation system for the structured query sentence used for the precise retrieval of the natural language. According to the generation method and the generation system, the natural language query sentence can be automatically converted into the structured query sentence.
Owner:欧阳江
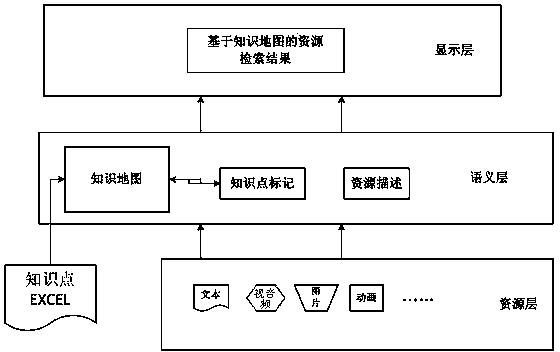
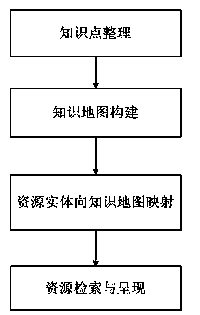
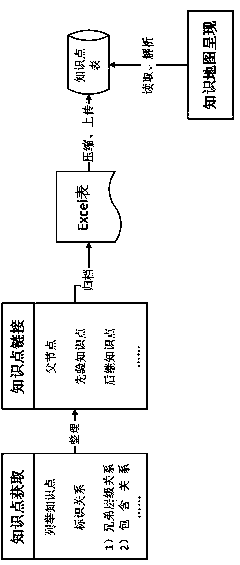
Knowledge map based resource retrieval method
ActiveCN103605706AIntuitive imageEasy to graspMaps/plans/chartsSpecial data processing applicationsLearning resourceData science
Owner:HUAZHONG NORMAL UNIV
Searchable encryption method supporting multiple users in cloud storage
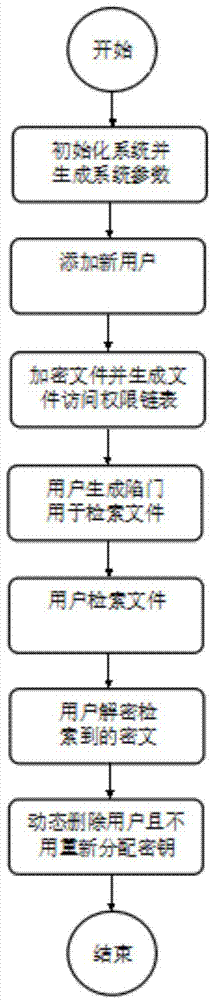
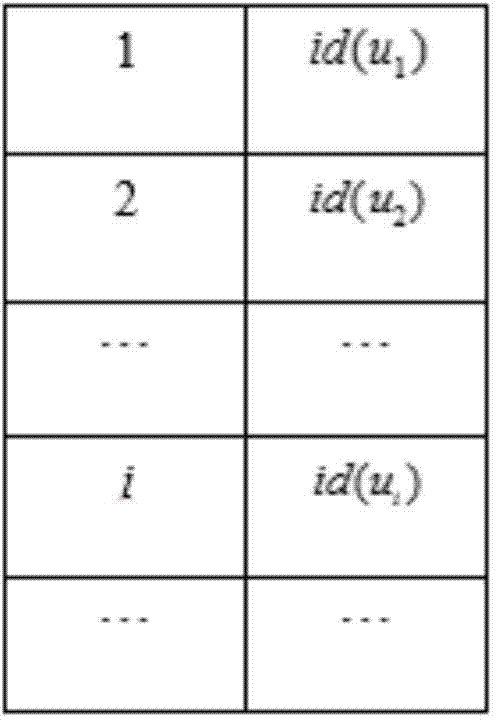
ActiveCN104780161AImplement direct retrievalAchieve deleteTransmissionSpecial data processing applicationsCiphertextDynamic management
The invention discloses a searchable encryption method supporting multiple users in cloud storage. The method comprises the following steps: encrypting and decrypting files through a symmetrical encryption algorithm; encrypting key words trough a symmetrical searchable encryption scheme and generating a trap door; solving the problems of dynamic management of authorized users and file access control in the traditional multiuser searchable encryption technology through a method of adding access rights to users. The method realizes direct retrieval of ciphertext, improves the efficiency and the security, improves the file retrieval efficiency, realizes the access right control of files, and realizes dynamic adding and deleting of users.
Owner:NANJING UNIV OF POSTS & TELECOMM
Target retrieval method based on group of randomized visual vocabularies and context semantic information
InactiveCN102693311AAddressing operational complexityReduce the semantic gapCharacter and pattern recognitionSpecial data processing applicationsImage databaseSimilarity measure
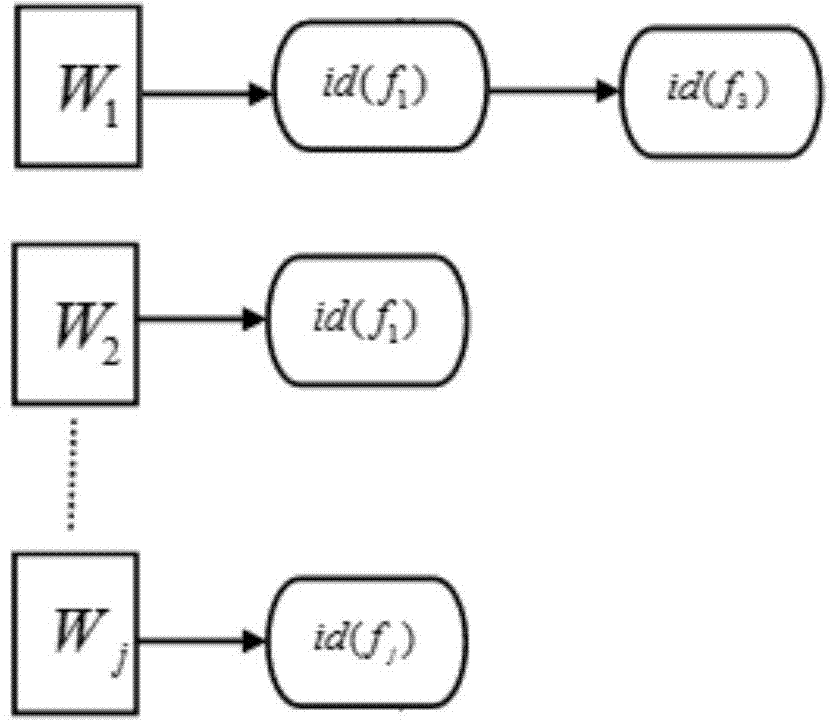
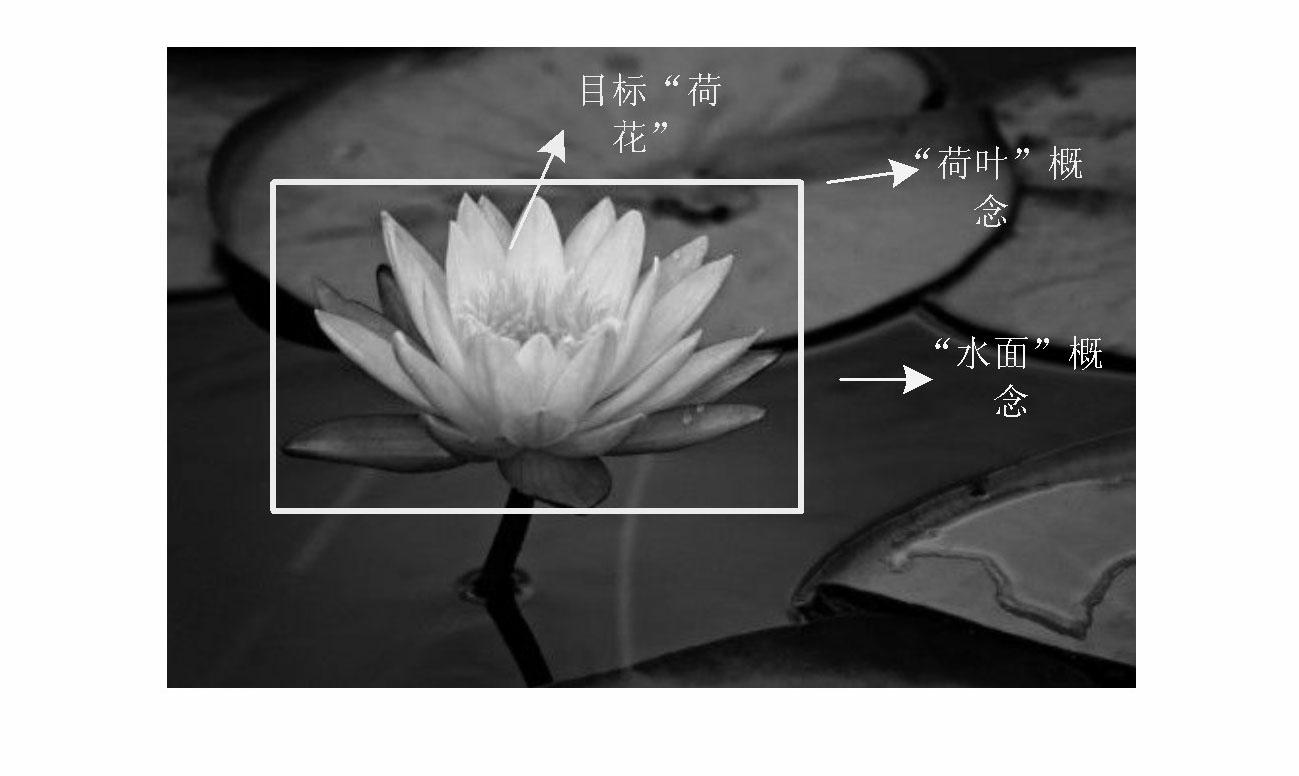
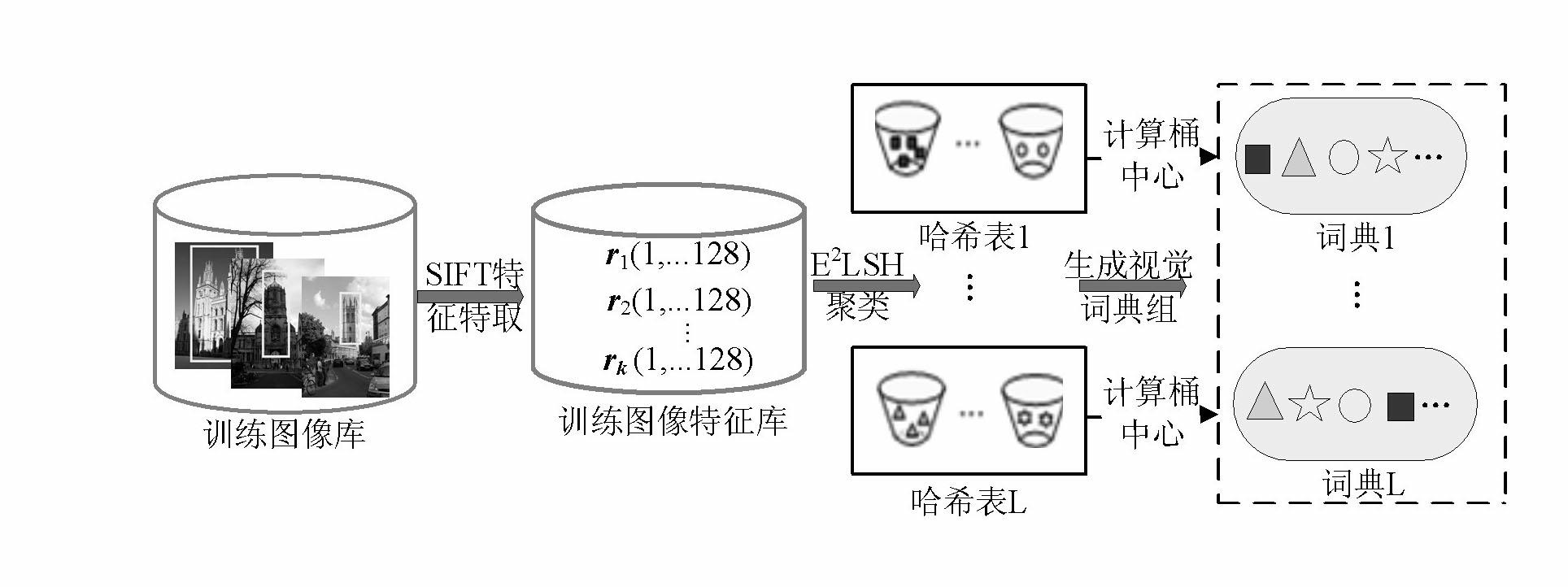
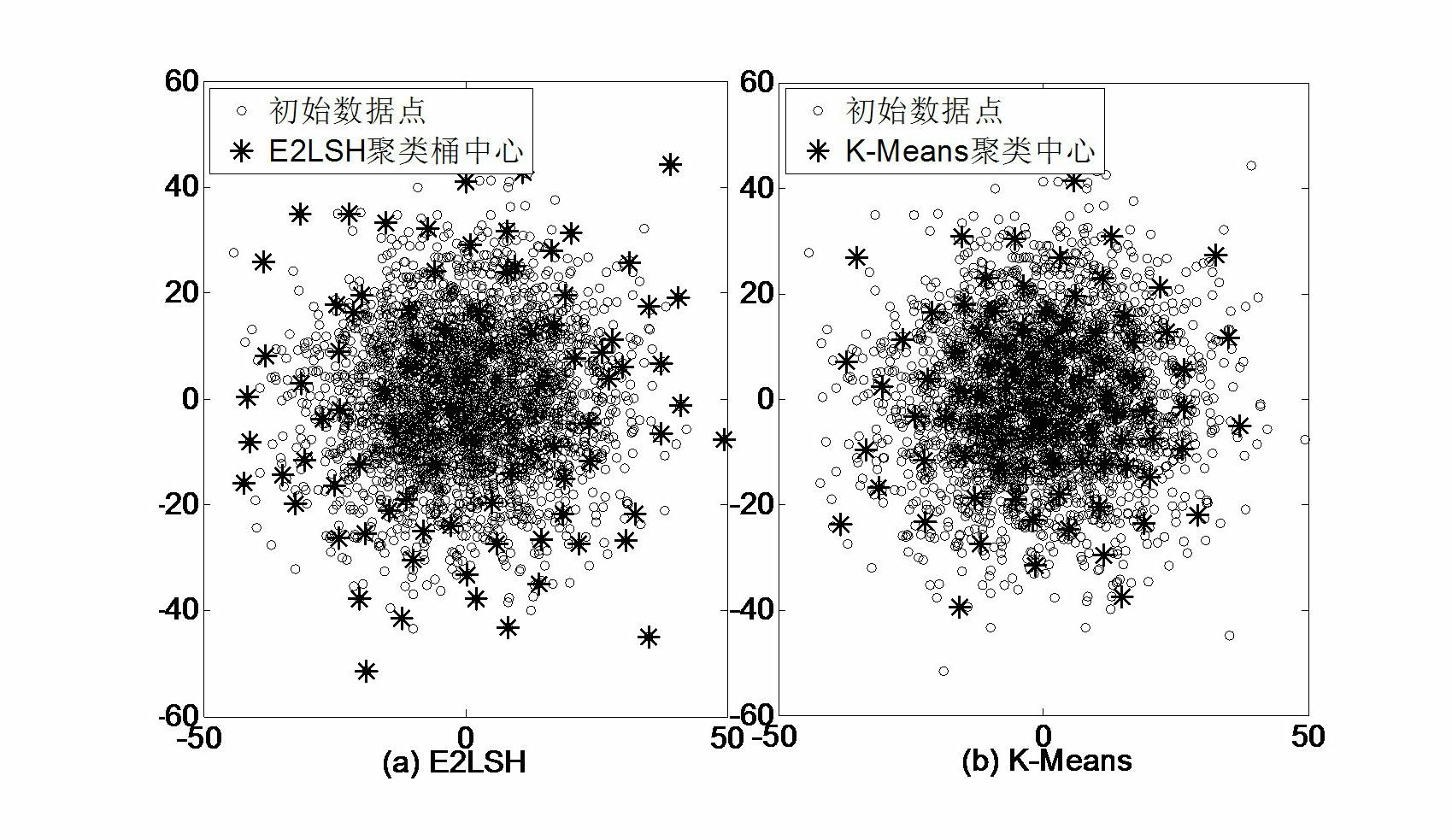
The invention relates to a target retrieval method based on a group of randomized visual vocabularies and context semantic information. The target retrieval method includes the following steps of clustering local features of a training image library by an exact Euclidean locality sensitive hash function to obtain a group of dynamically scalable randomized visual vocabularies; selecting an inquired image, bordering an target area with a rectangular frame, extracting SIFT (scale invariant feature transform) features of the inquired image and an image database, and subjecting the SIFT features to S<2>LSH (exact Euclidean locality sensitive hashing) mapping to realize the matching between feature points and the visual vocabularies; utilizing the inquired target area and definition of peripheral vision units to calculate a retrieval score of each visual vocabulary in the inquired image and construct an target model with target context semantic information on the basis of a linguistic model; storing a feature vector of the image library to be an index document, and measuring similarity of a linguistic model of the target and a linguistic model of any image in the image library by introducing a K-L divergence to the index document and obtaining a retrieval result.
Owner:THE PLA INFORMATION ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com