Patents
Literature
509results about How to "Address risk" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
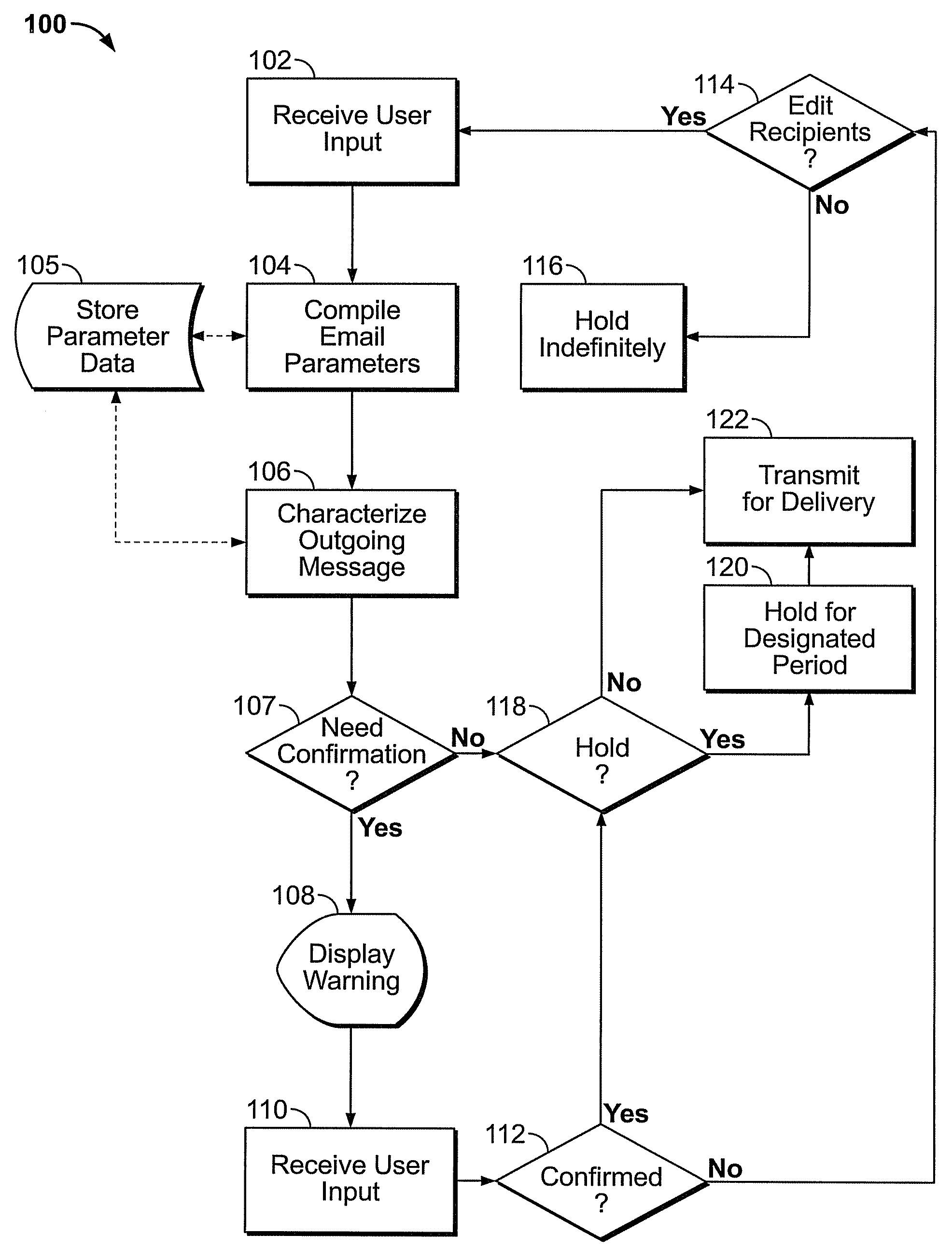
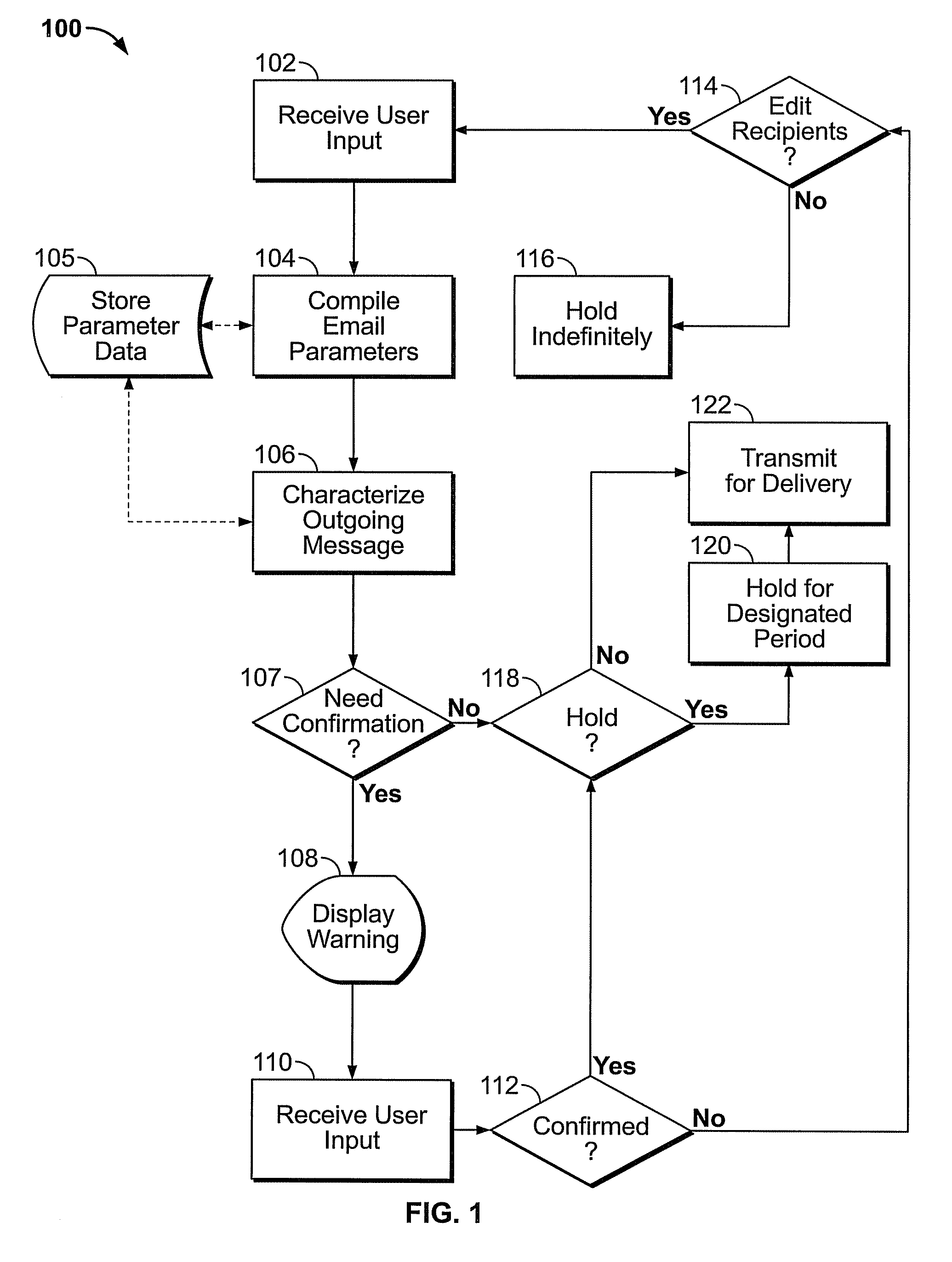
Erroneous addressing prevention for electronic messaging
ActiveUS20090210504A1Reducing addressing riskPrevent erroneous communicationMultiple digital computer combinationsData switching networksSubject matterClient-side
An electronic mail client includes features for preventing addressing errors in electronic messaging such as those caused by predictive text features. A messaging client tracks addressing parameters including the length of time since each previous addressee has been messaged, the quantity of times selected addressees have been co-addressees on messages, if any, whether the addressees are designated as sensitive and whether the messages contain sensitive subject matter. If a high risk of addressing error is determined, the client delays transmission of the message to permit the user to review the message recipient addresses and correct any erroneous addressees.
Owner:SHUSTER GARY STEPHEN
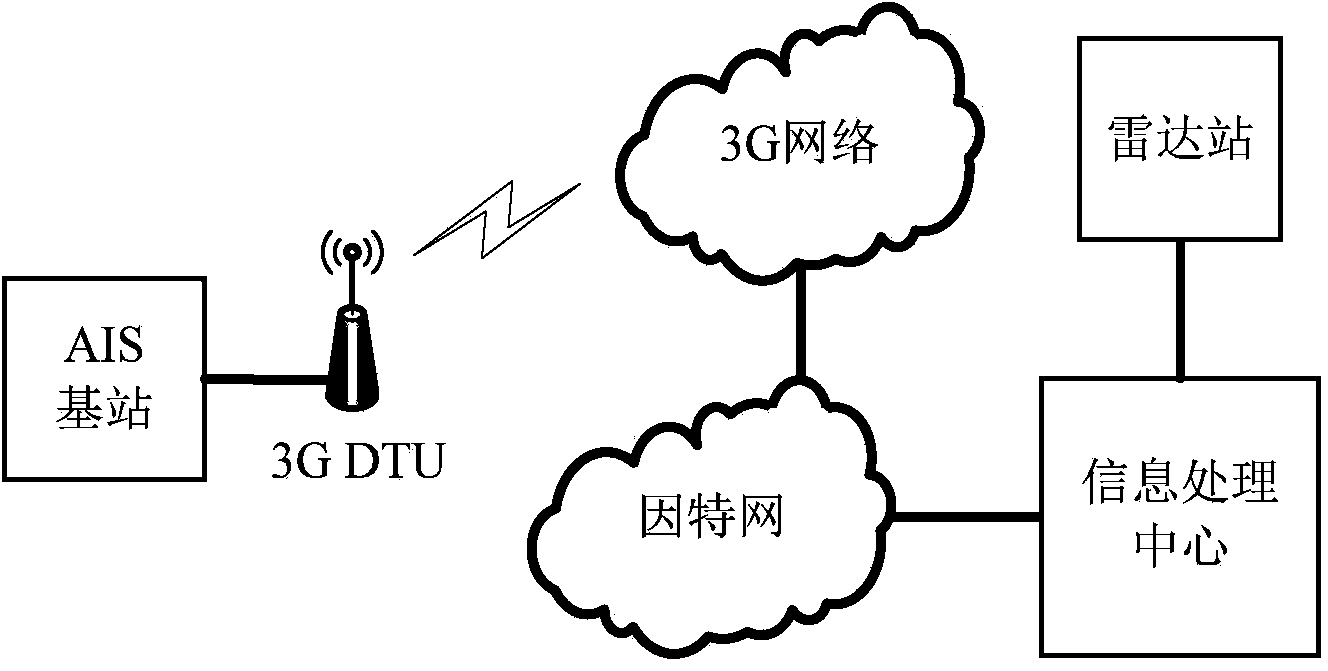
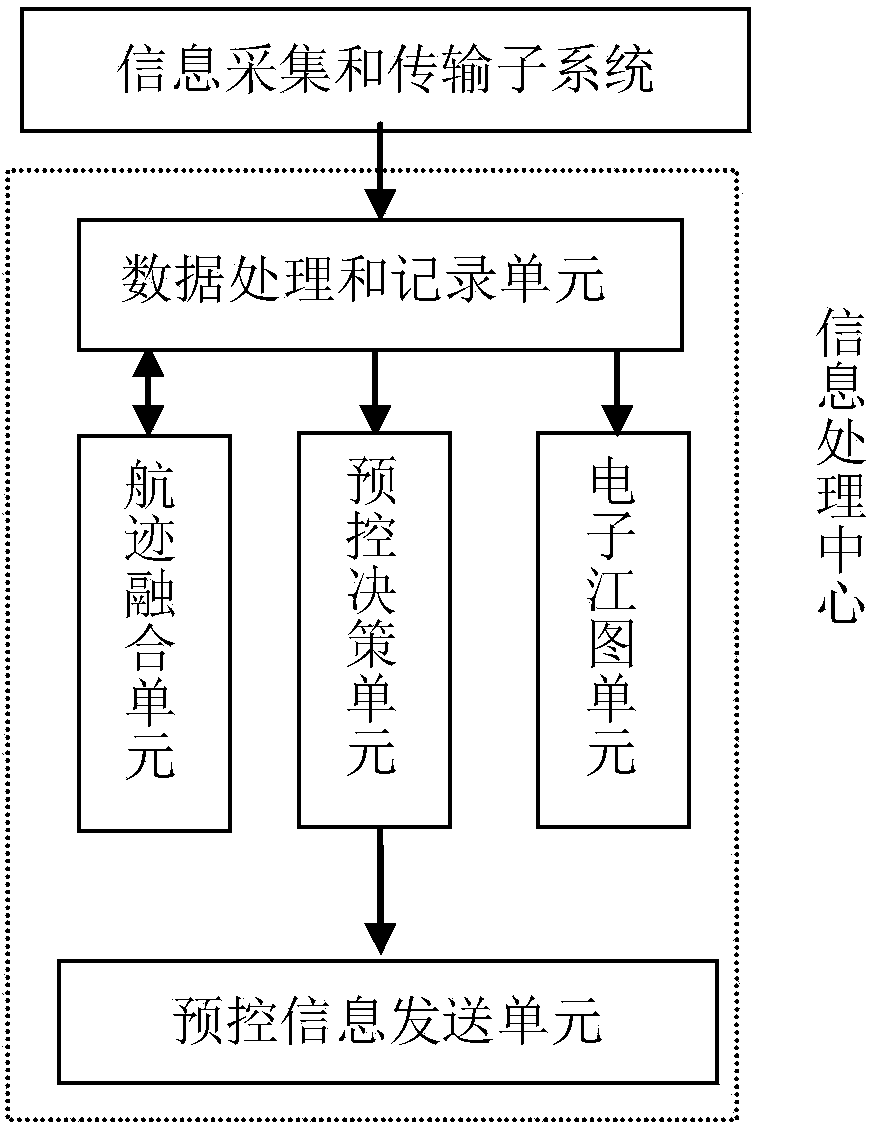
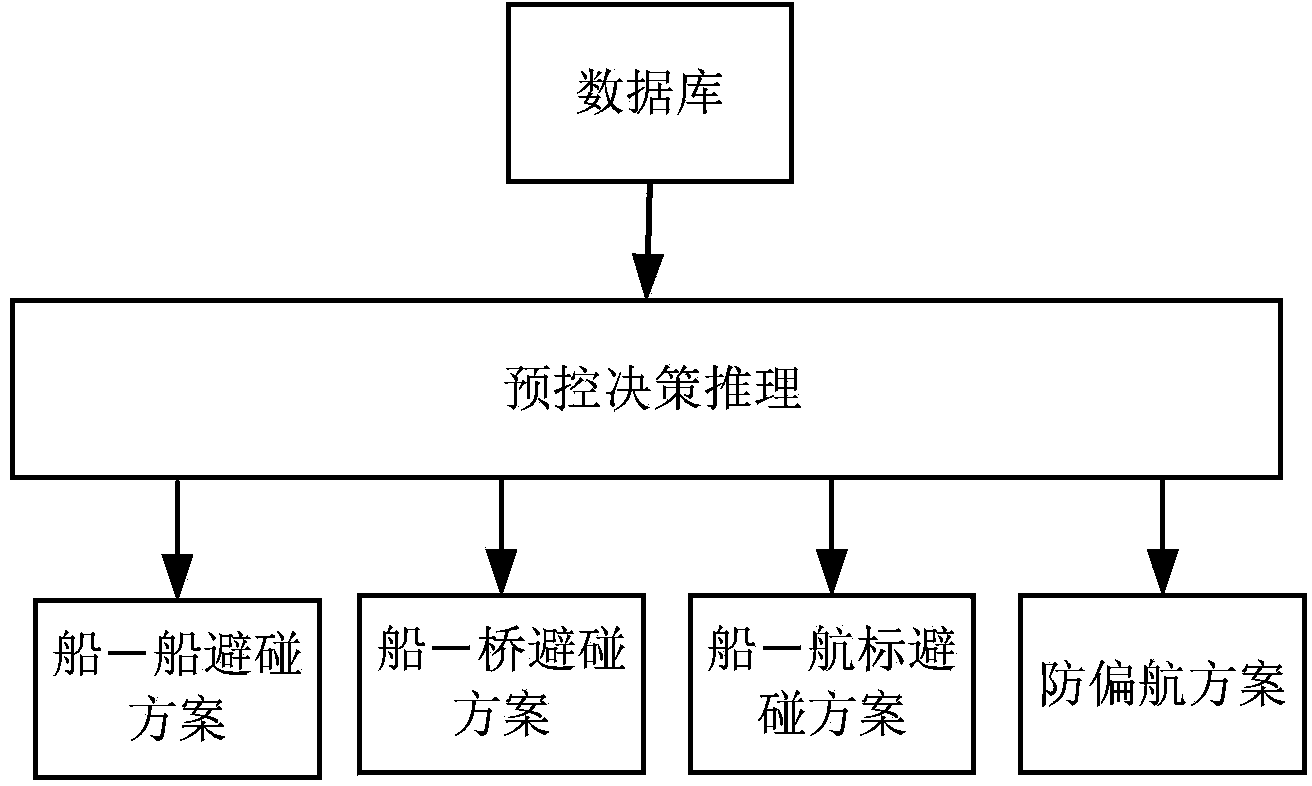
Inland river bridge area ship safe navigation precontrol system
InactiveCN103714718AAddress riskReduce work intensityMarine craft traffic controlInformation processingRadar
The invention relates to an inland river bridge area ship safe navigation precontrol system which comprises a radar station, an information processing center and an AIS base station. The radar station and the AIS base station are respectively in communication connection with the information processing center. The information processing center comprises a data processing and recording unit, a track fusion unit, an electronic river map unit, a precontrol decision-making unit and a precontrol information sending unit, wherein the data processing and recording unit obtains data from the radar station or / and the AIS base station and processes and records the data, the track fusion unit carries out fusion on the obtained radar or / and AIS data to obtain ship tracks, the precontrol decision-making unit carries out prediction according to the data processed and recorded by the data processing and recording unit and judges whether alarm instructions are sent out or not, and the precontrol information sending unit controls the AIS base station to send out alarms according to the instructions sent out by the precontrol decision-making unit. According to real-time traffic situations, the inland river bridge area ship safe navigation precontrol system can automatically identify navigation risks of the ships, automatically carry out early warning on the ships, guide the ships to pass through a bridge area safely, and reduce accident risks.
Owner:WUHAN UNIV OF TECH
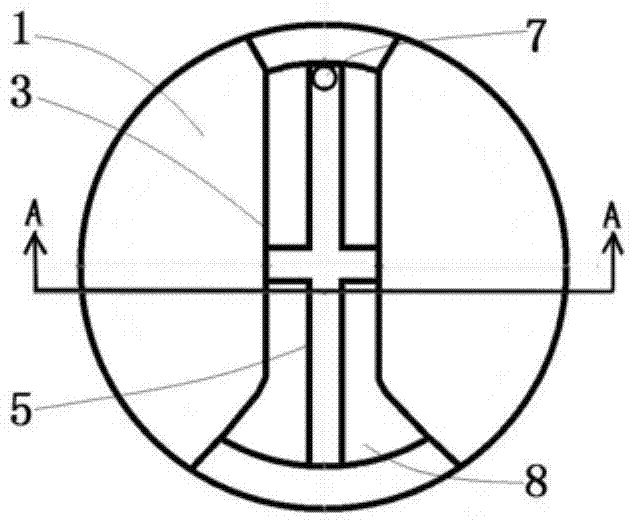
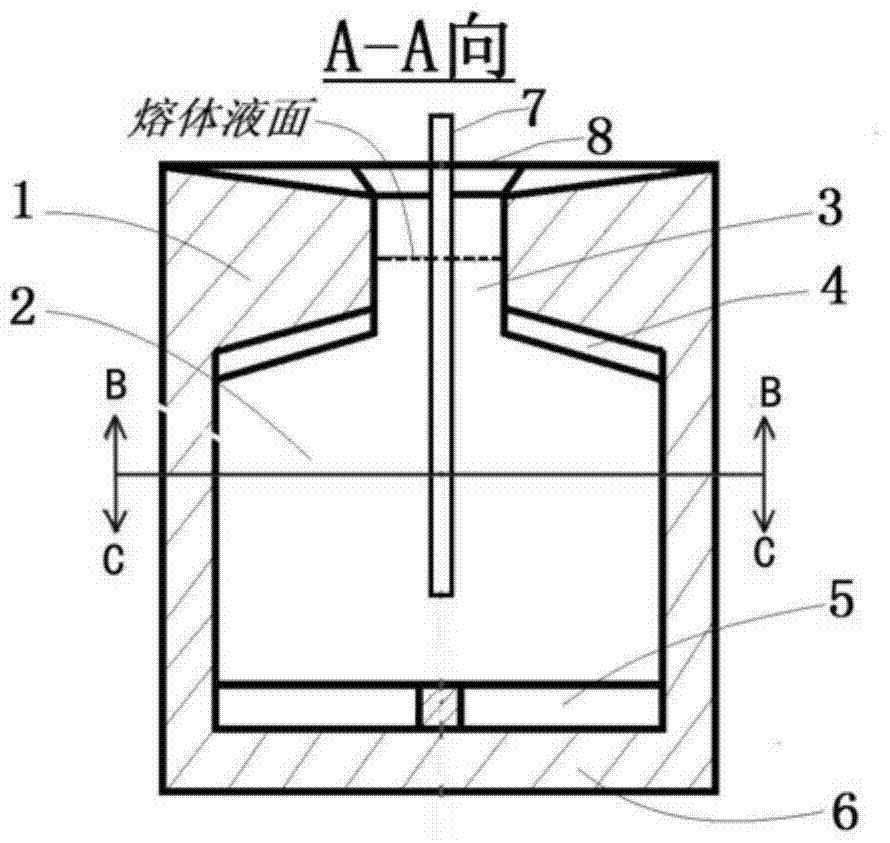
Stirring chamber for stirring molten metal and using method thereof
The invention discloses a stirring cavity used for stirring metal melt and a use method thereof, which belong to the field of material processing apparatuses for metallurgy, casting, chemical engineering and the like. The stirring cavity structurally consists of a melt container, a stirring cavity body, an upper stop opening, an upper blocking flange, a lower blocking flange, a lower bottom, a temperature sensor and a liquid taking / pouring port. According to the stirring cavity, the melt liquid level inside the stirring cavity is narrowed, so the stirring effect is effectively stopped from transferring to the liquid level, and the problems of melt oxidation and entrapped air risk are solved. The stirring cavity can be applied to various metal melt stirring and casting occasions; when the stirring cavity is used for batch-type casting such as pressure casting, the stirring cavity is adopted as the internal cavity structure of a pouring ladle; when the stirring cavity is used for continuous casting, the stirring cavity is adopted as the internal cavity structure of a melt hot top and can be directly connected with a continuous casting crystallizer; and full automation is realized in the whole process of melt stirring, chemical refining and casting in a pressure casting site.
Owner:GRIMAT ENG INST CO LTD
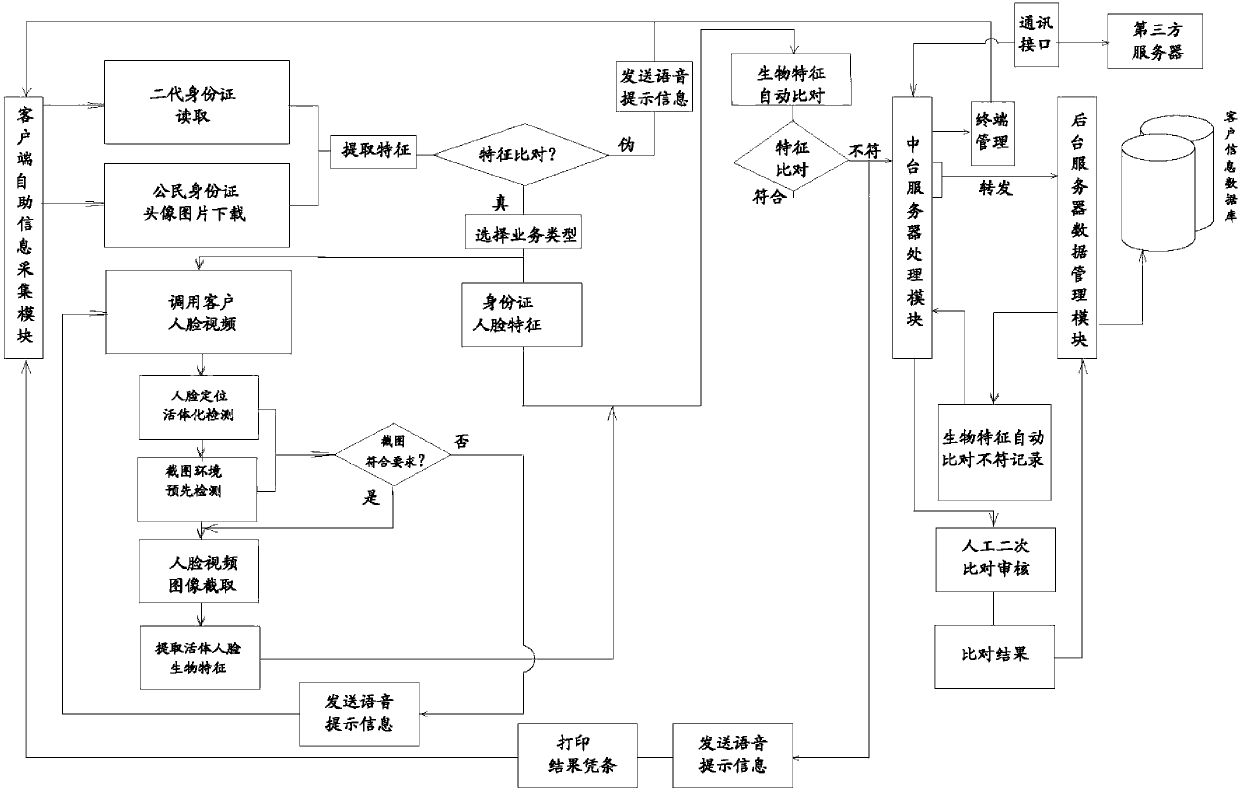
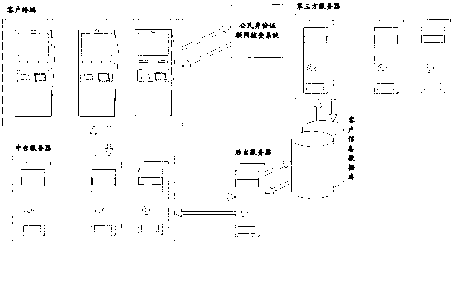
Identity verification system based on face recognition
InactiveCN102800017AGuaranteed identityPrevent cheatingFinanceCharacter and pattern recognitionE communicationCard reader
The invention discloses a network device based on a customer identity verification system, which aims to solve the problem that the cases resulting from name borrow and false name happen occasionally due to the shortcomings existing in the process of manually verifying the customer identity in the current financial industry. A customer terminal consists of a group of self-service information acquisition and real-time comparison terminals which perform real-time comparison on the information acquired by a camera and a second-generation identity card reader and directly transmit the acquired information and the comparison result to a background server or forward through a middleground server; and a third-party server reads the required information and comparison result directly from the background server database through a communication interface or through the middleground server. Through the invention, the identification accuracy of the customer identity is high, and the cases resulting from name borrow and false name in the banking business are greatly reduced. In combination with the characteristics of the bank, the information can be acquired in a self-service manner and automatically identified and compared to avoid human risk in the banking business, thereby laying a firm foundation for the sustainable development of the bank.
Owner:高艳玲
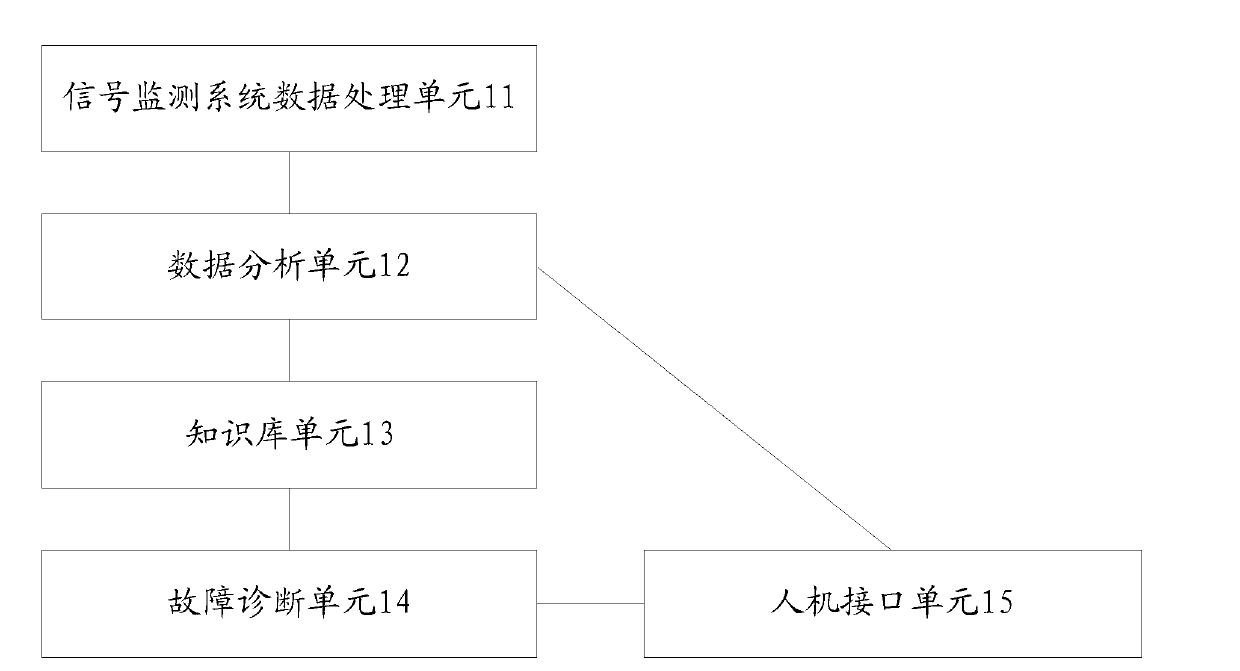
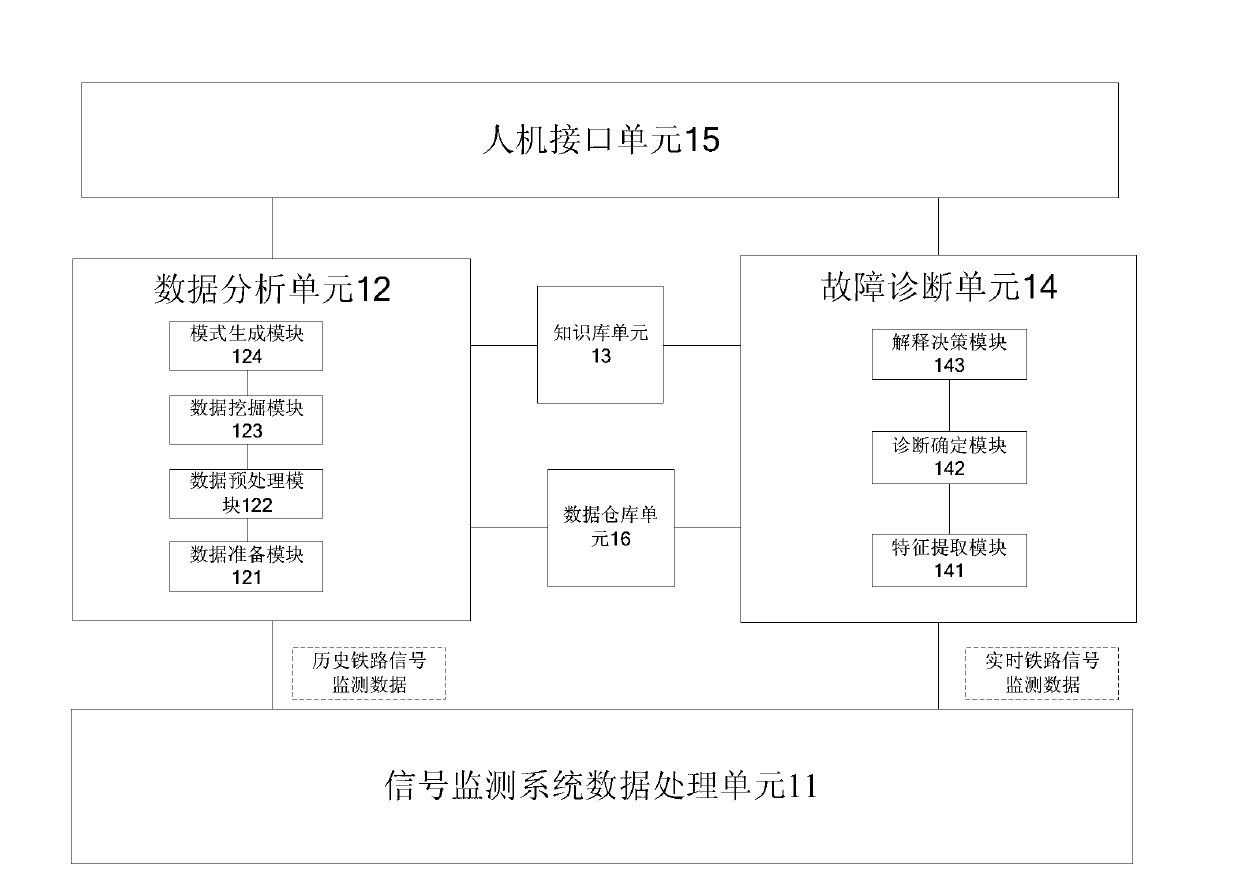
Mining analyzing and fault diagnosis system of rail transit monitoring data
ActiveCN103345207AReduce operational riskSolve the workloadProgramme total factory controlTechnical standardRailway signal
The invention discloses a mining analyzing and fault diagnosis system of rail transit monitoring data, and relates to the technical field of railway signals. The system comprises a signal monitoring system data processing unit, a data analyzing unit, a knowledge base unit and a fault diagnosis unit, wherein the signal monitoring system data processing unit is used for acquiring history railway signal monitoring data and real-time railway signal monitoring data from an on-site centralized signaling monitoring (CSM) device in each electric service workshop or work area. The data analyzing unit is used for analyzing the history railway signal monitoring data acquired by the signal monitoring system data processing unit, and generating fault diagnosis rules. The knowledge base unit is used for storing judging standards, and storing the fault diagnosis rules of the data analyzing unit, wherein the judging standards are formulated according to the work principle of each railway signal device and national and industry standards and specifications in the railway signal field and are used for fault diagnosis. The fault diagnosis unit is used for generating fault diagnosis results according to the fault diagnosis rules and the judging standards as for the real-time railway signal monitoring data acquired by the signal monitoring system data processing unit.
Owner:BEIJING TAILEDE INFORMATION TECH
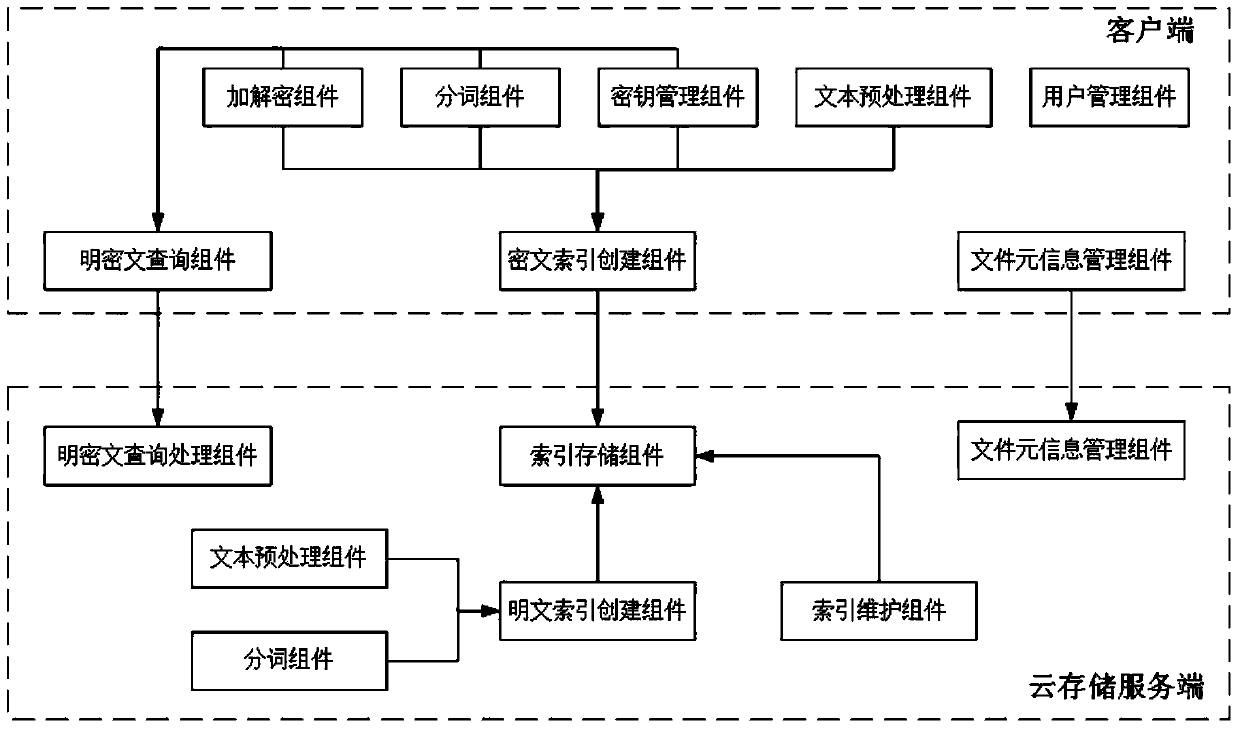
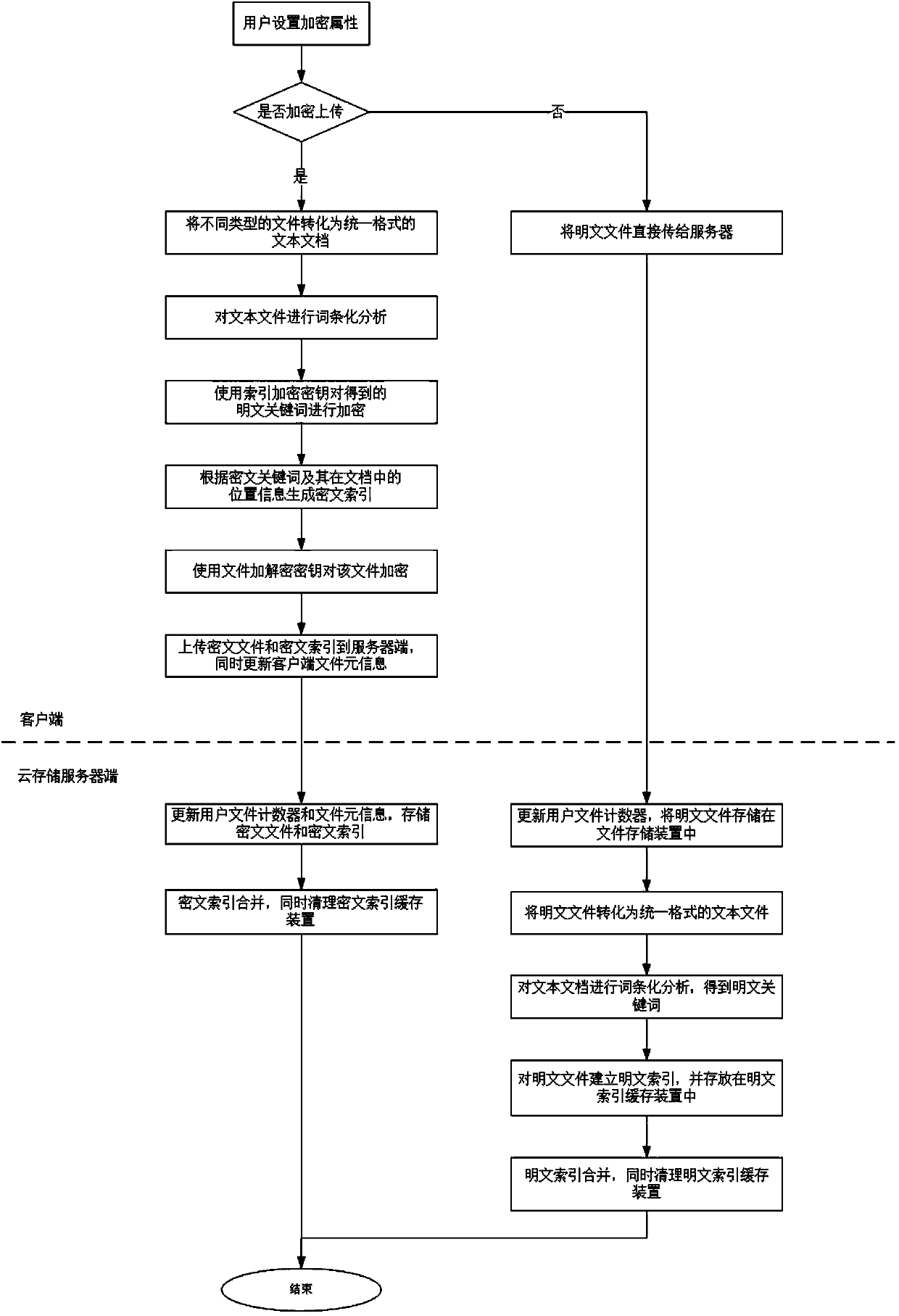
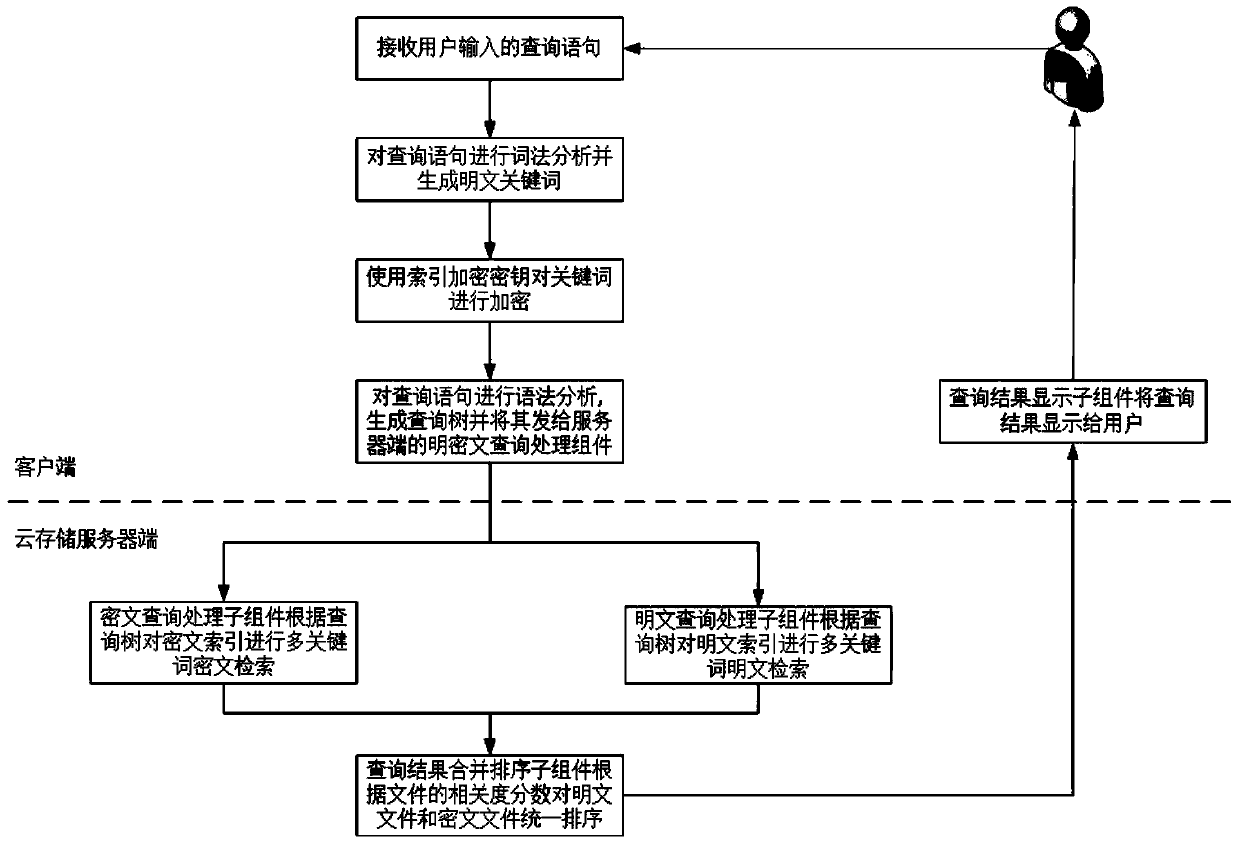
Multi-keyword plaintext and ciphertext retrieving method and device oriented to cloud storage
InactiveCN103593476AFix bugsAddress riskKey distribution for secure communicationComputer security arrangementsPlaintextComputer hardware
The invention relates to a multi-keyword plaintext and ciphertext retrieving method and device oriented to cloud storage and relates to the field of information safety. The method includes the following steps that firstly, a client terminal performs lexical analysis according to inquiry statements and generates plaintext keywords; secondly, a corresponding user index encryption key is obtained according to a main key bound with the identity of a user, and the plaintext keywords are encrypted with the encryption algorithm of the index encryption key, and ciphertext keywords are generated; thirdly, multi-keyword ciphertext retrieving is performed on a ciphertext index in a cloud storage server according to an inquire tree generated by the client terminal, and retrieved data element information and retrieved relevancy scores undergo inquiry result merging and sequencing; fifthly, inquiry result merging and sequencing are performed in the cloud storage server with the same method; sixthly, a unified sequence result is sent to the client terminal, and an inquiry result is displayed to the user. According to the multi-keyword plaintext and ciphertext retrieving method and device oriented to the cloud storage, a key management scheme which is higher in safety degree is provided, plaintext and ciphertext united retrieving can be supported and multi-keyword retrieving can be provided.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
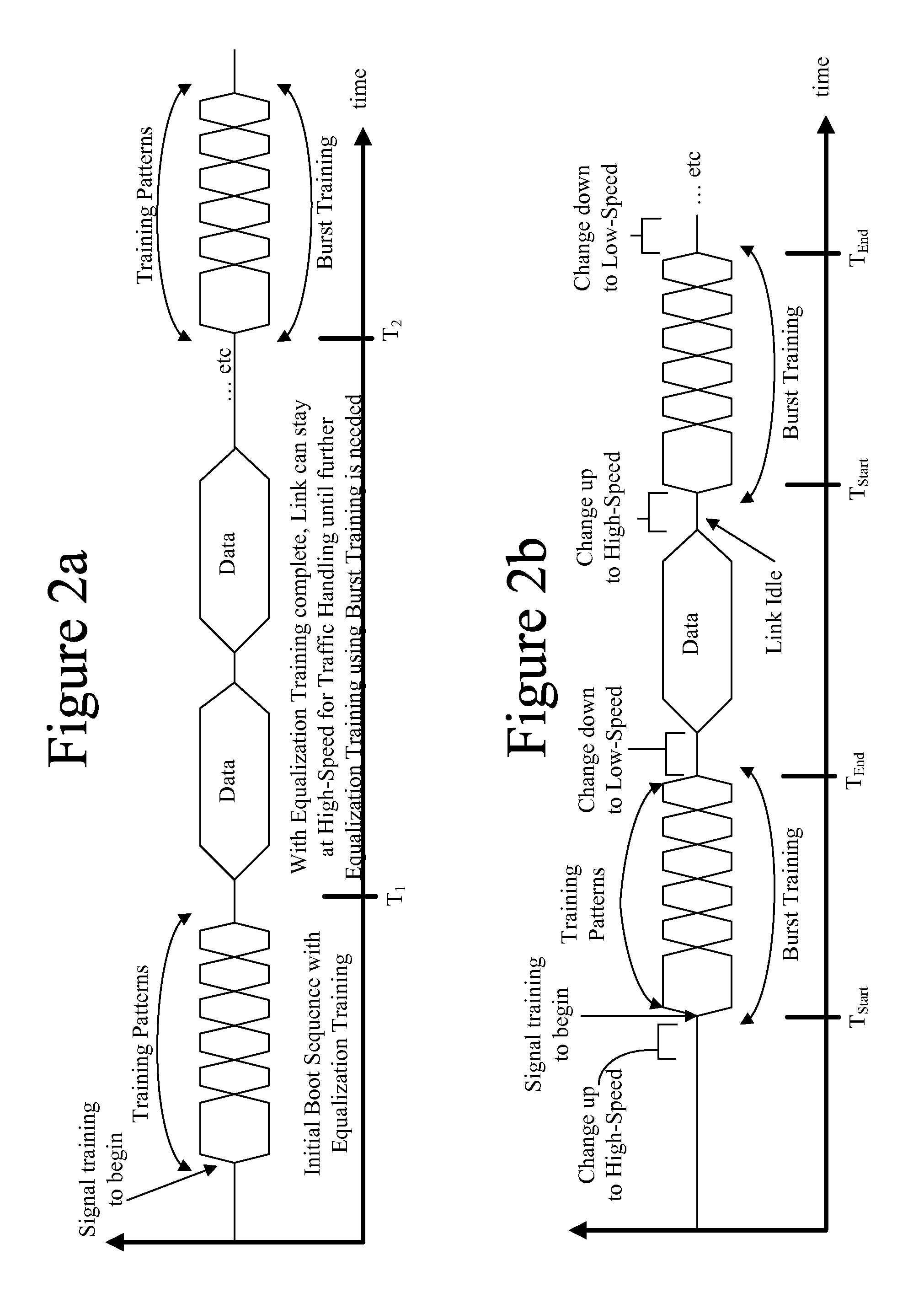
Method and apparatus for interleaving bursts of high-speed serial interconnect link training with bus data transactions
ActiveUS20130067127A1Optimal link speedAddress riskElectric digital data processingTelecommunicationsTelecommunications link
Owner:NVIDIA CORP
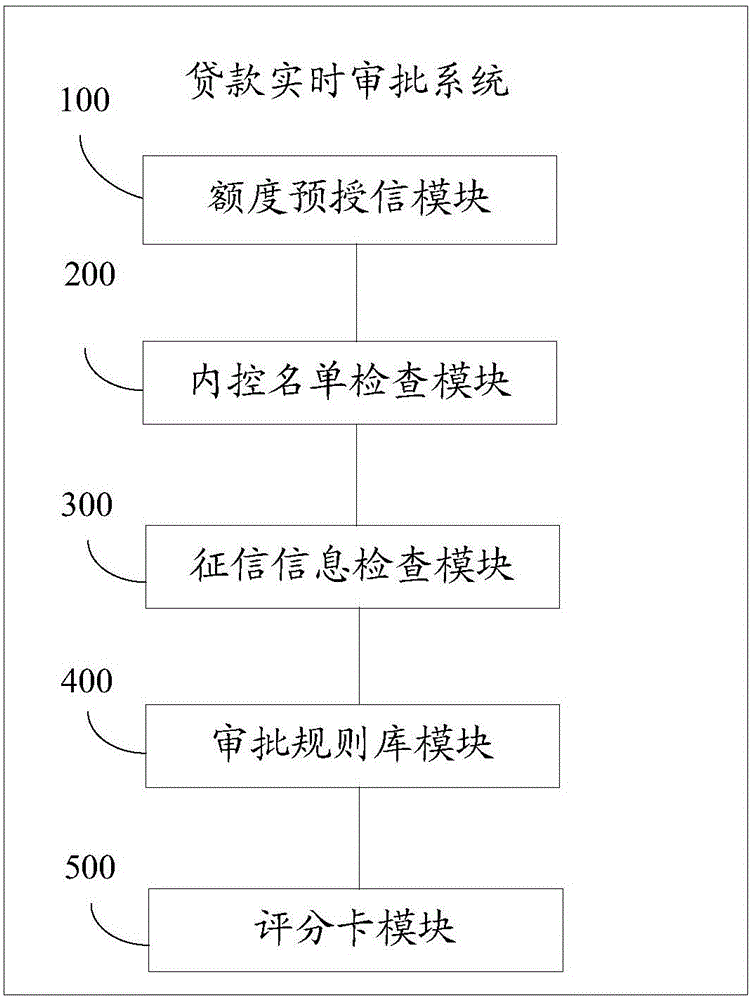
System and method for real-time loan approval
The invention discloses a system and a method for real-time loan approval. The system comprises a limit pre-credit module, an internal control list check module, a credit information check module, an approval rule base module and a score card module, wherein the limit pre-credit module is used for carrying out limit pre-credit processing on a customer according to contribution degree information of the customer in order to obtain integrated credit limit information of the customer; the internal control list check module is used for checking whether the customer is in an internal control list through matching information of three elements of identity of the customer; the credit information check module is used for judging whether loan is rejected according to a self-defined loan rejection rule; the approval rule base module is used for obtaining an initial neural network according to rule information in the initial rule base and predefined codes of training data and automatically judging whether the loan is rejected; and the score card module is used for obtaining a customer score and a load approval suggestion result according to customer application data, credit information of the People's Bank of China, a credit card score and a predefined calculation and classification rule. According to the system and the method, the effects of reducing the loan approval risk and improving the loan approval efficiency are realized.
Owner:CHINA CONSTRUCTION BANK
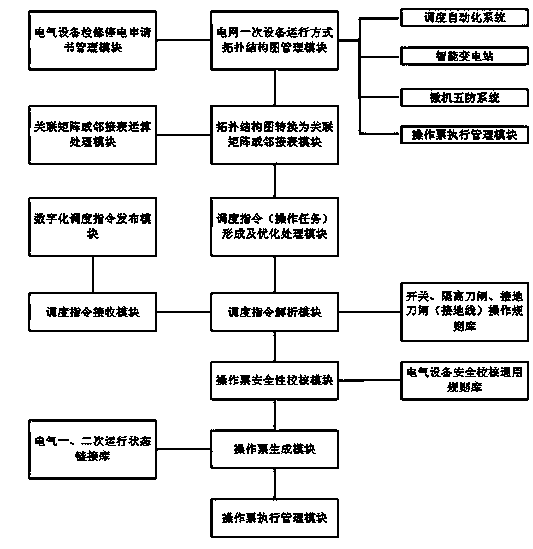
Power grid switching operation ticket automatic generating system and method
InactiveCN103679350ASolve manual analysis operation tasksSolving unoptimizedResourcesInformation technology support systemSystems designScheduling instructions
The invention provides a power grid switching operation ticket automatic generating system and method based on 'scheduling instruction parsing modes' and aims to solve the problems that the operation tasks of the existing scheduling instructions are manually parsed by operators, filling in switching operation tickets by the aid of a five-prevention system is time consuming, and operation ticket filling in errors are possible. The invention provides a method and a system for automatically generating a scheduling instruction ticket and aims to solve the problems that in large complex operations, scheduling operations are not optimized, switching operations have many procedures and are time consuming, and power grid transition operations and switching operations are high in risk.
Owner:SICHUAN LANXUNBAOER ELECTRONICS TECH +1
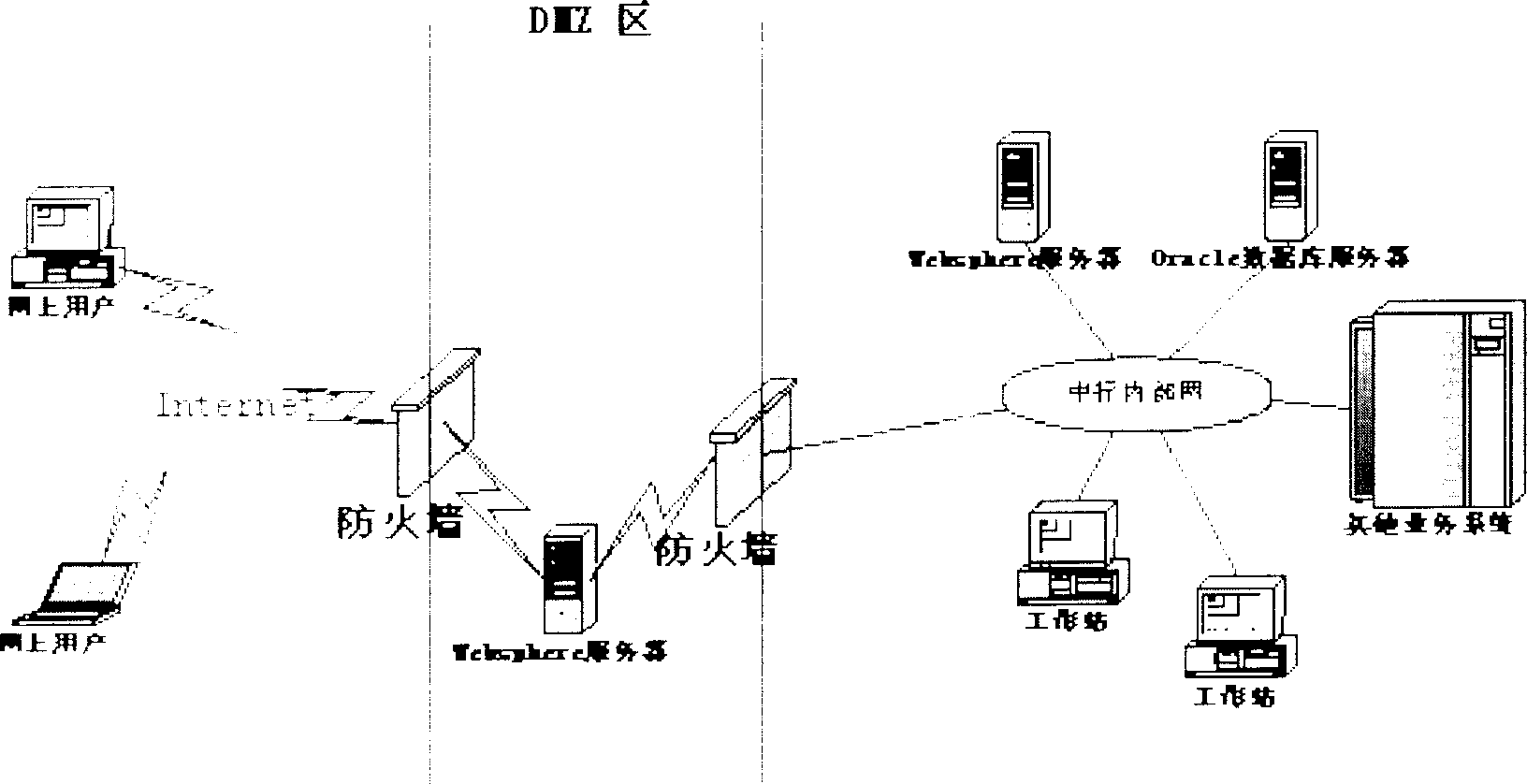
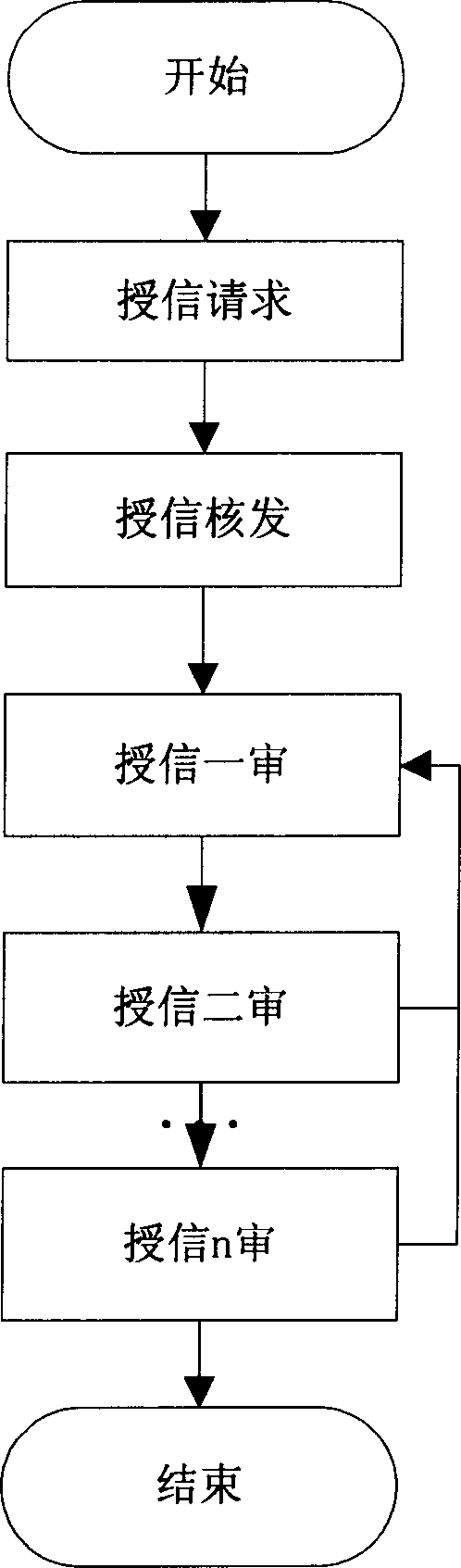
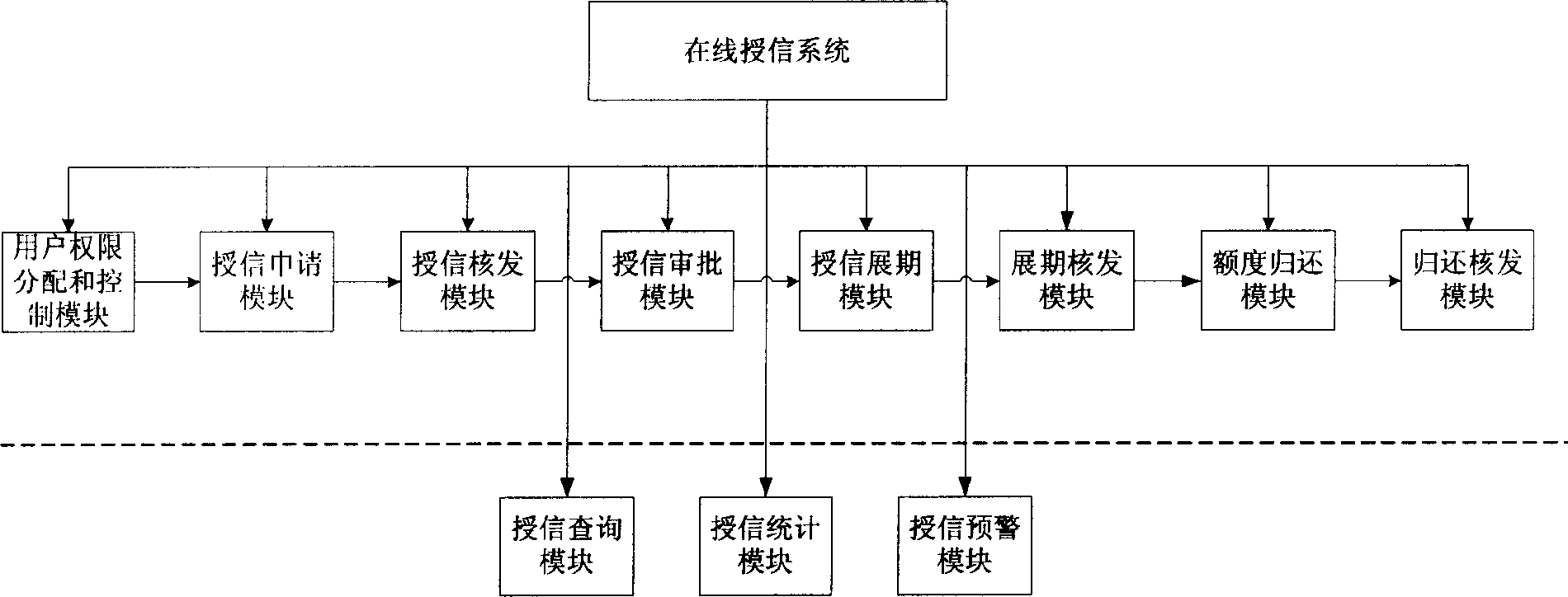
System and method for online user authorization for banks
A system of granting credit to the client on line by financial enterprise comprises user power distribution and control module, credit application module, credit checking and issuing module, credit approval module, credit extending module, extension period approval module, ceiling return module, return back checking and issuing module, credit inquiry module, credit statistic analysing module and credit prewarning module. The system can be used as control system of credit approval operation within financial enterprises.
Owner:BANK OF CHINA
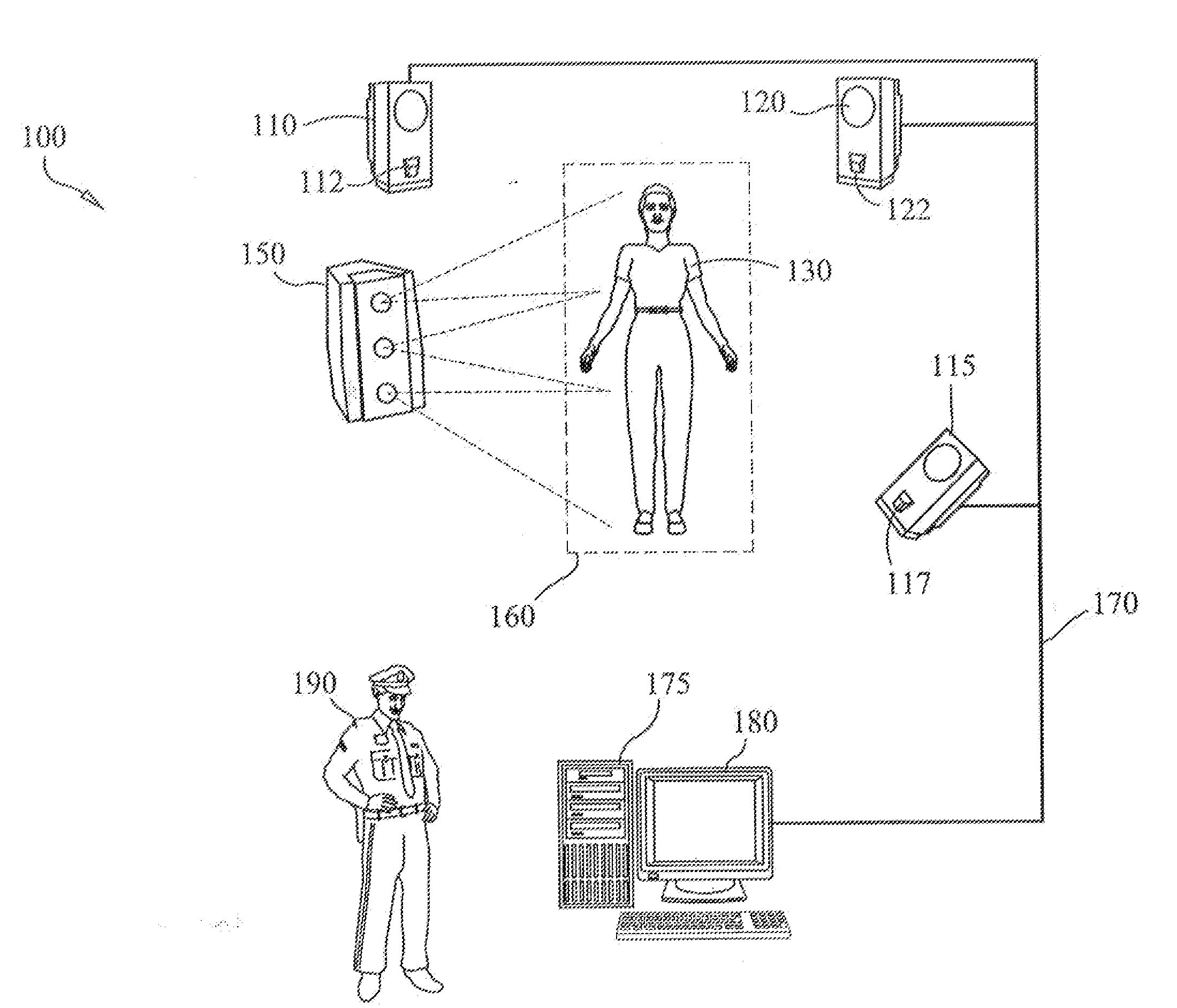
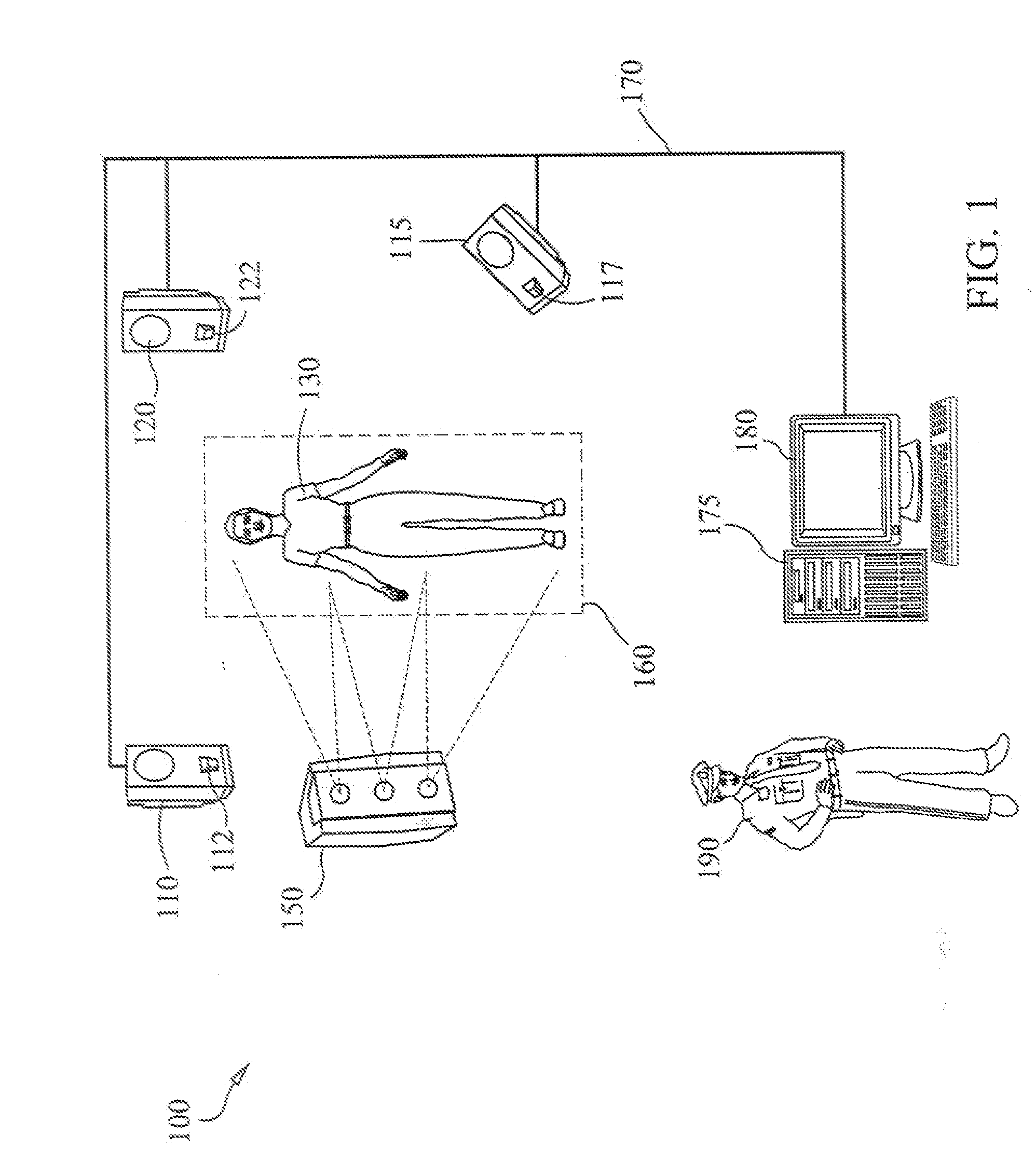
Multiple camera imaging method and system for detecting concealed objects
InactiveUS20090041293A1Successfully performedNon invasiveTelevision system detailsCharacter and pattern recognitionMillimetre waveOptical contrast
The present invention is an imaging system for detecting concealed objects on an individual. The imaging system includes an imaging zone that is illuminated with millimeter wave energy. A plurality of millimeter wave cameras are focused to fully surround the imaging zone and have the ability to detect millimeter wave frequencies reflected from the imaging zone. As an individual passes through the imaging zone the plurality of millimeter wave cameras detect concealed objects by identifying differences in the millimeter wave energy reflected by the individual's body and a concealed object. A composite image is generated by a central processing unit and displayed on a monitor showing the concealed object on the individual through optical contrast.
Owner:MICROSEMI
Insurance fraud detection method and system
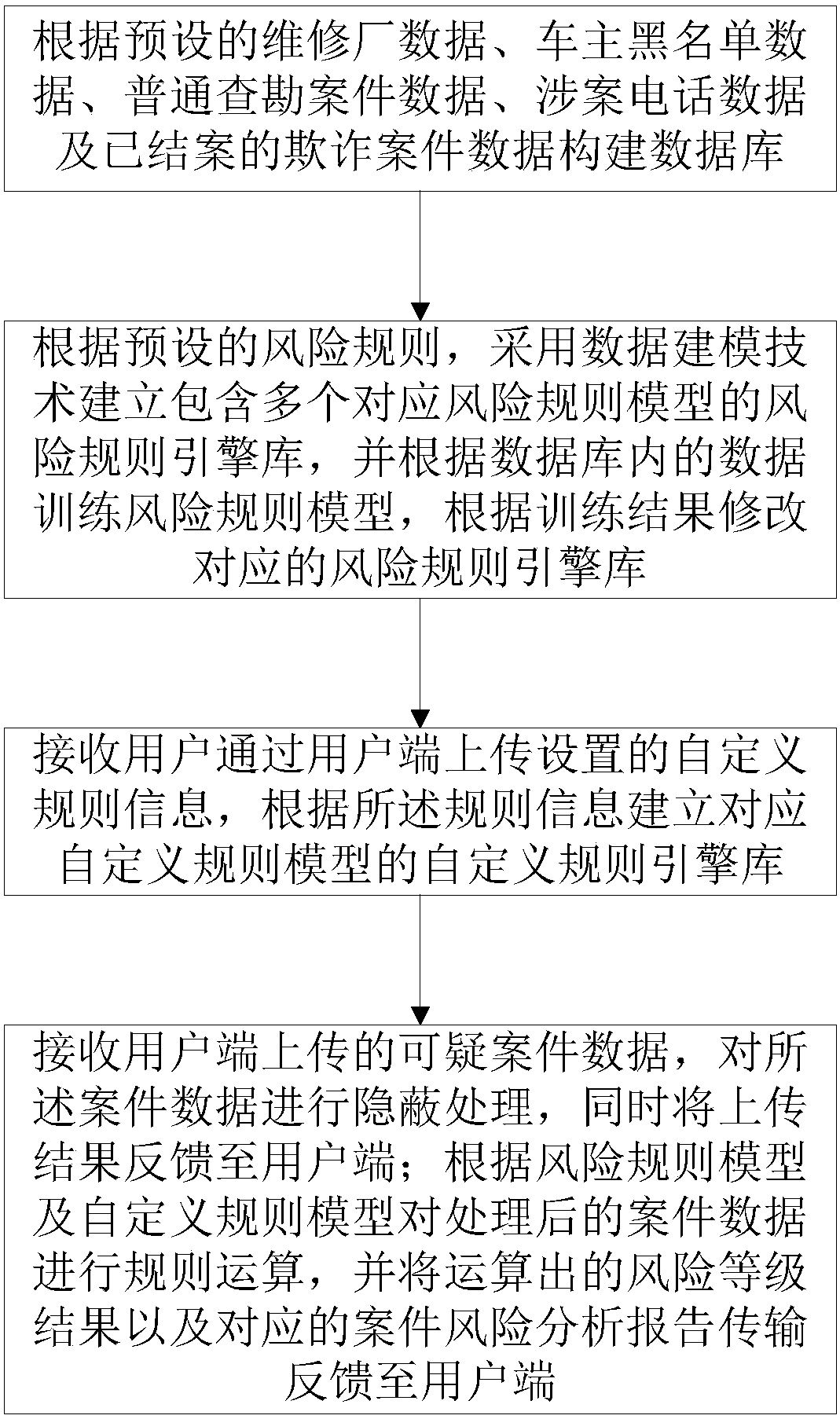
InactiveCN107657047ASolve the inability to effectively respond to the claims marketSolve the adjustmentFinanceOffice automationRisk levelRisk profiling
The embodiment of the invention discloses an insurance fraud detection method and system. The detection method comprises the following steps: constructing a database according to preset data; establishing a corresponding risk rule engine base according to the preset risk rule and the database; receiving self-defined rule information set by a user, establishing a corresponding self-defined rule engine base; receiving suspicious case data uploaded by the user, and performing hiding processing on the case data, and feedbacking an uploading result to the user; performing rule operation on the processed case data, and feedbacking the operated risk level result and the corresponding case risk analysis report to the user. Through the detection method disclosed by the embodiment of the invention,the corresponding case data is operated by constructing the risk rule engine base and the self-defined rule engine base so as to obtain the risk level result and the risk analysis report of the case,the problems of high auto insurance claim settlement risk, high anti-fraud cost and low efficiency are solved, and then a technical effect of replacing the artificial investigation with the bit data distributed computing analysis is achieved.
Owner:民太安财产保险公估股份有限公司
Fully-automatic single blanking mechanical arm
ActiveCN104070558AGet rid of influenceSolve labor intensityMetal working apparatusPunch pressInstability
The invention provides a fully-automatic single blanking mechanical arm. A loading plate device, a loading arm device, a blanking device, a horizontal conveying device, an unloading arm device, an upper partition paper device and a finish product collecting device are mounted on an existing punch press to form an excellent structural design, so that the fully-automatic single blanking mechanical arm can complete operations of loading, conveying, blanking, movement and the like of FPC (flexible printed circuit) boards; the cooperation of all the parts enables the fully-automatic single blanking mechanical arm to meet the requirements of single production, so that the problems existing in the signal production such as high labor intensity, high work-related injury risk, low production efficiency, large worker quantity and personnel instability can be solved.
Owner:SHENZHEN MAKEN M & E
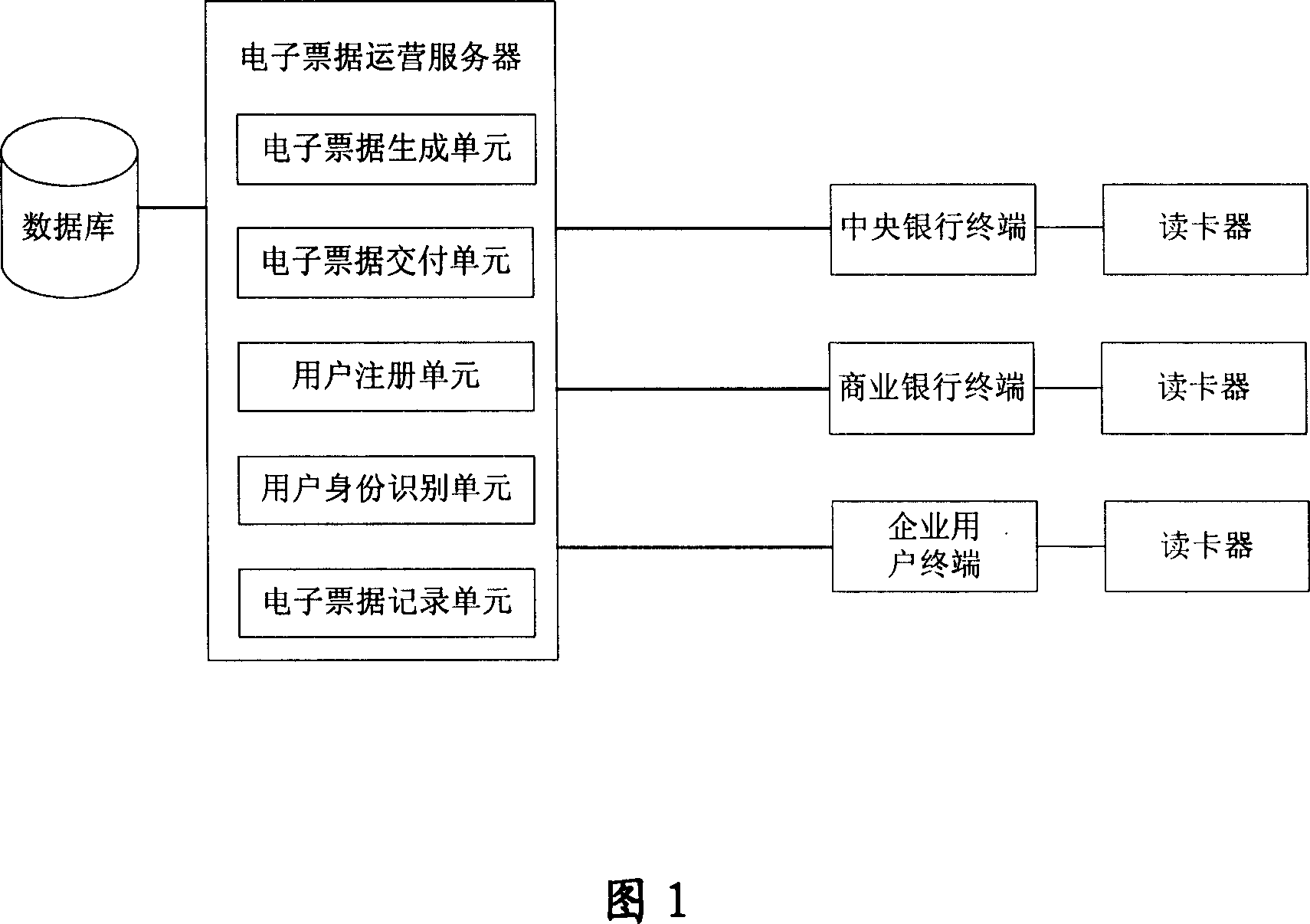
Electronic invoice system based on blockchain and realization method
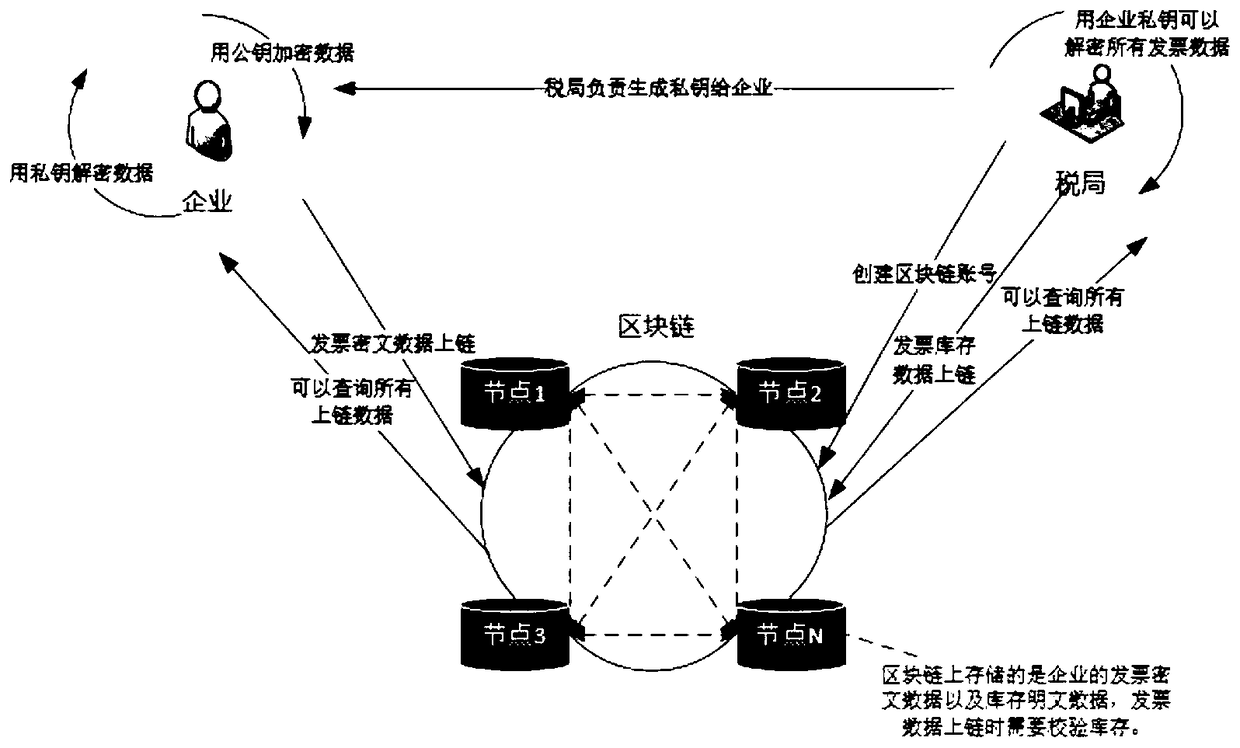
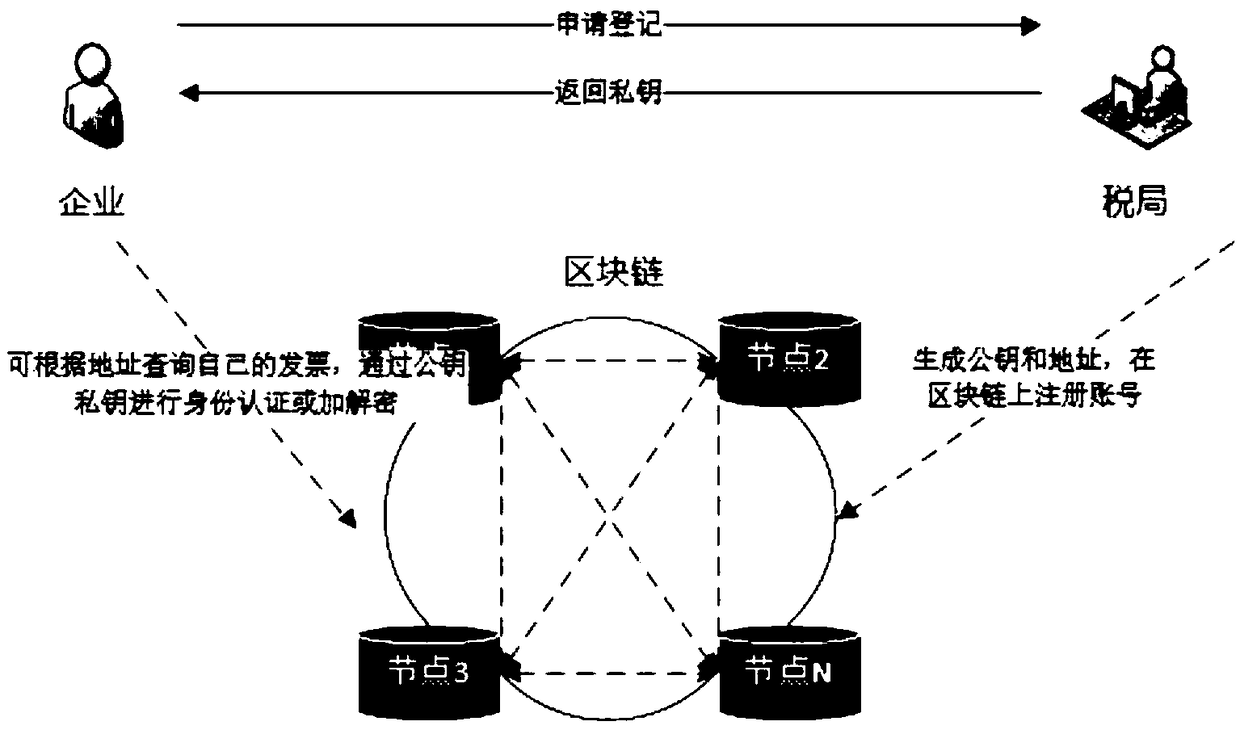
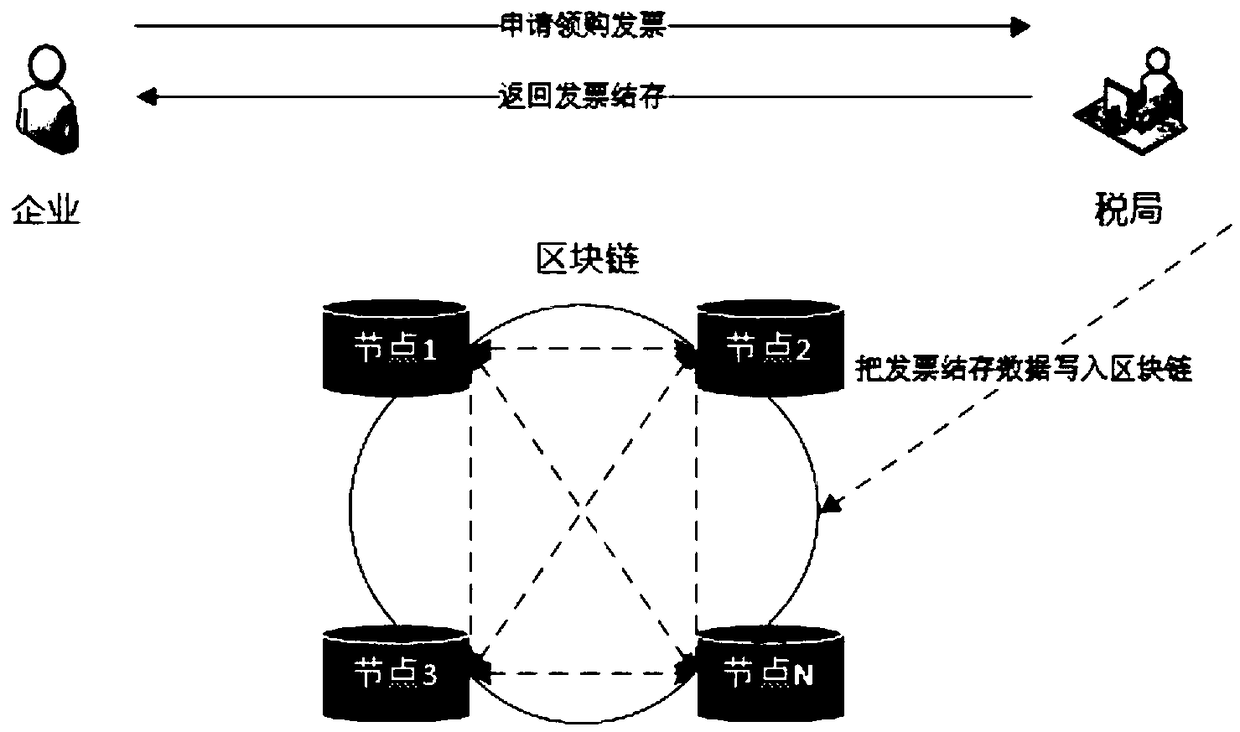
ActiveCN108830600AEffective interconnectionEffective decentralizationBilling/invoicingProtocol authorisationUser needsInvoice
The invention provides an electronic invoice system based on a blockchain and a realization method. The method includes steps: (S1), application registration: a tax bureau terminal generates a privatekey on a blockchain system according to a requirement of a taxpayer and generates a public key and an address through the generated private key; (S2), return of the private key: the taxpayer can inquire his own invoice according to the address generated by the tax bureau terminal and perform identity authentication or decryption through the public key and the private key; (S3), invoice purchase:the tax bureau terminal writes an invoice balance of the taxpayer into the blockchain system and returns the invoice balance to a taxpayer terminal; (S4), invoice issuing: the taxpayer terminal inputsinvoice data, encrypts the input data and then uploads the encrypted data to the blockchain system; and (S5), invoice inquiry: invoice information is inquired according to the address and the privatekey of the taxpayer terminal. The system and the method are advantageous in that the degree of mutual trust is high, data cannot be tampered, the data traceability is realized, interconnection and intercommunication are achieved, and distributed storage and decentralization can be realized.
Owner:FORESEE TECH
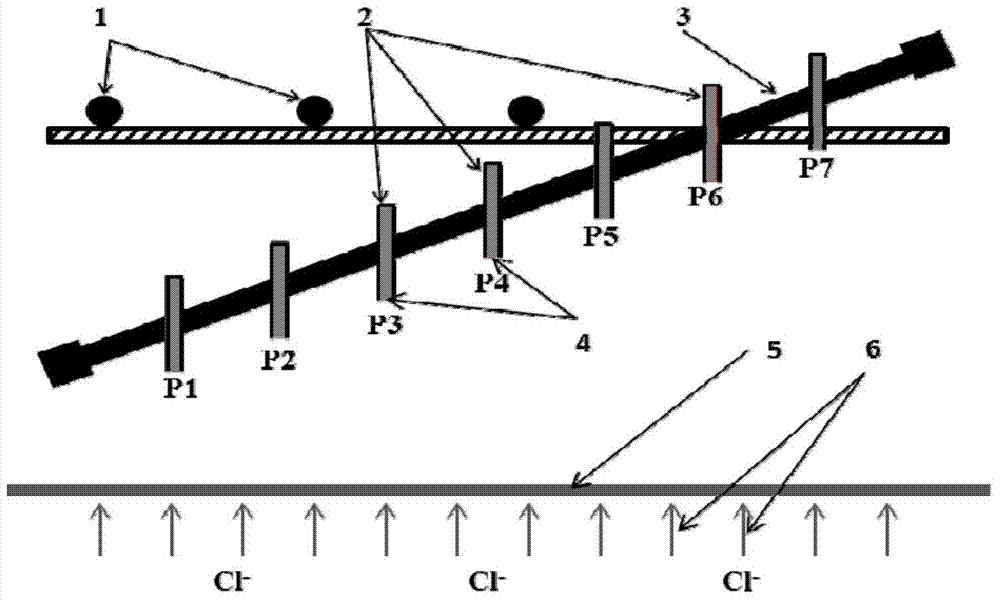
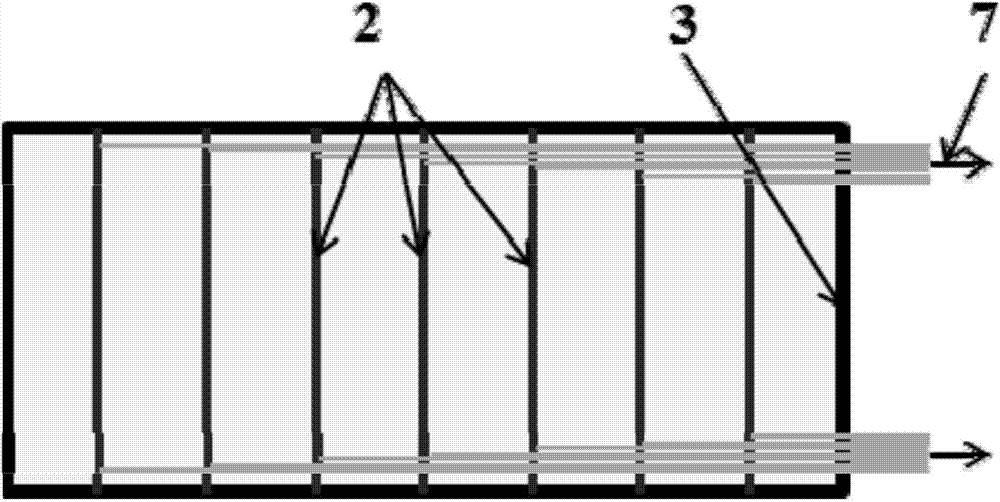
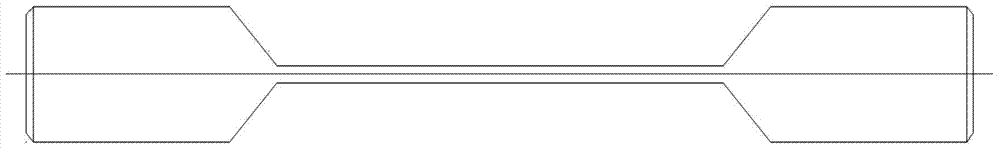
Method of monitoring rusting risk of reinforcement in concrete in situ
InactiveCN104729982ASimple and reliable designImprove monitoring efficiencyWeather/light/corrosion resistanceStress concentrationPre stress
The invention relates to a method of monitoring rusting risk of reinforcement in concrete in situ. The method includes the steps of 1, according to the principle of plane state of stress and stress concentration, applying prestress to rusting monitoring sensing units to enable them to be in a plane state of stress; 2, packaging three sides of each rusting monitoring sensing unit, and reserving one side as a rusting monitoring side; 3, distributing the rusting monitoring sensing units at equal intervals within a rectangular steel frame, before concreting, distributing the rectangular steel frame and the outer surface of concrete at a certain angle in an area to be subjected to reinforcement rusting monitoring, allowing the rusting monitoring sides to face a protective layer, and performing rusting monitoring through continuous strain measurement of different sectional heights of sheets. The method has the advantages that monitoring chloride threshold concentration fronts at different depths is achieved, initial rusting time of the reinforcement is predicted, results are updated according to monitoring data, the rusting monitoring sensing units as deep as the reinforcement allow the final initial rusting time, rusting rate and rusting degree of the reinforcement to be directly monitored.
Owner:UNIV OF SCI & TECH BEIJING +1
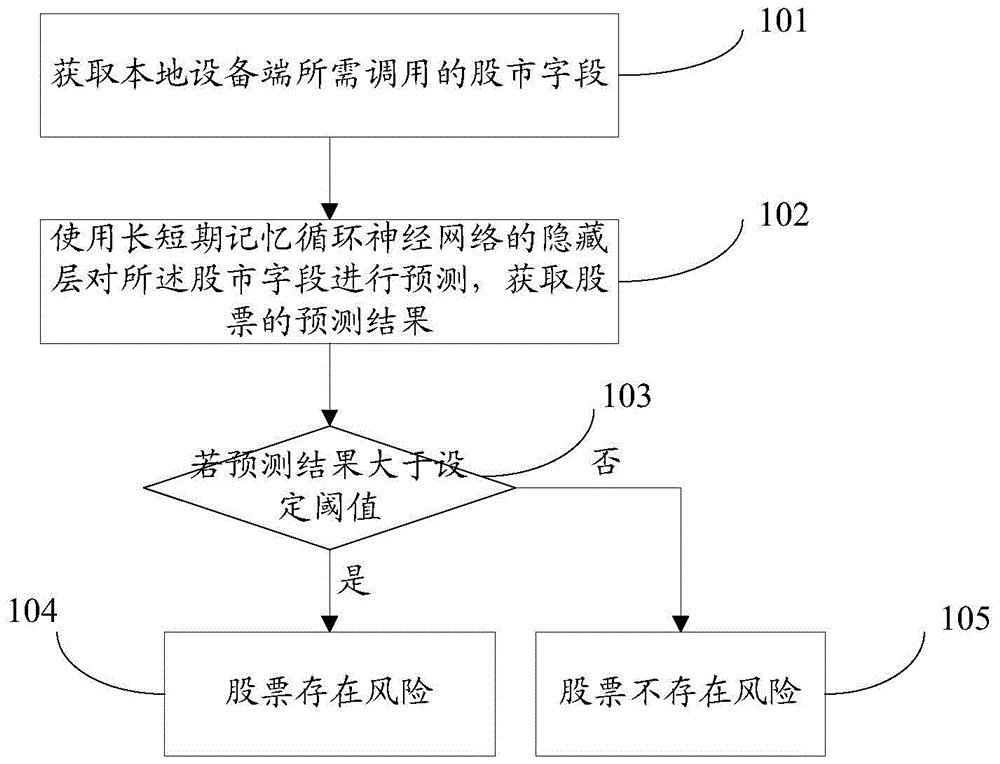
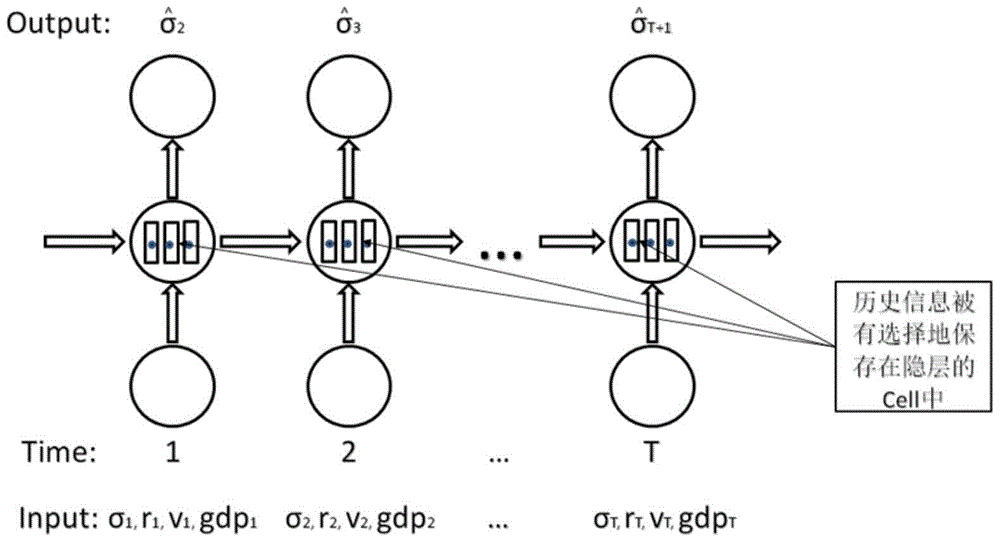
Stock risk prediction method and apparatus
The application provides a stock risk prediction method and an apparatus. The method includes the following steps: acquiring stock fields required by a local device terminal to be invoked; based on a hidden layer in the long and short term memory circulation neural network, predicting the stock fields to obtain a prediction result of the stock. The prediction result includes a prediction value of a fluctuation ratio of a stock market on a trading day. The long and short term memory circulation neural network also includes an input layer and an output layer. If the prediction result is greater than a determined threshold value, there are risks in the stock. According to the invention, the method and apparatus address the problem of high risks caused by inaccurate stock prediction by using the ARCH model or the GARCH model.
Owner:TSINGHUA UNIV
Method for authenticating validity of self-contained software of equipment system
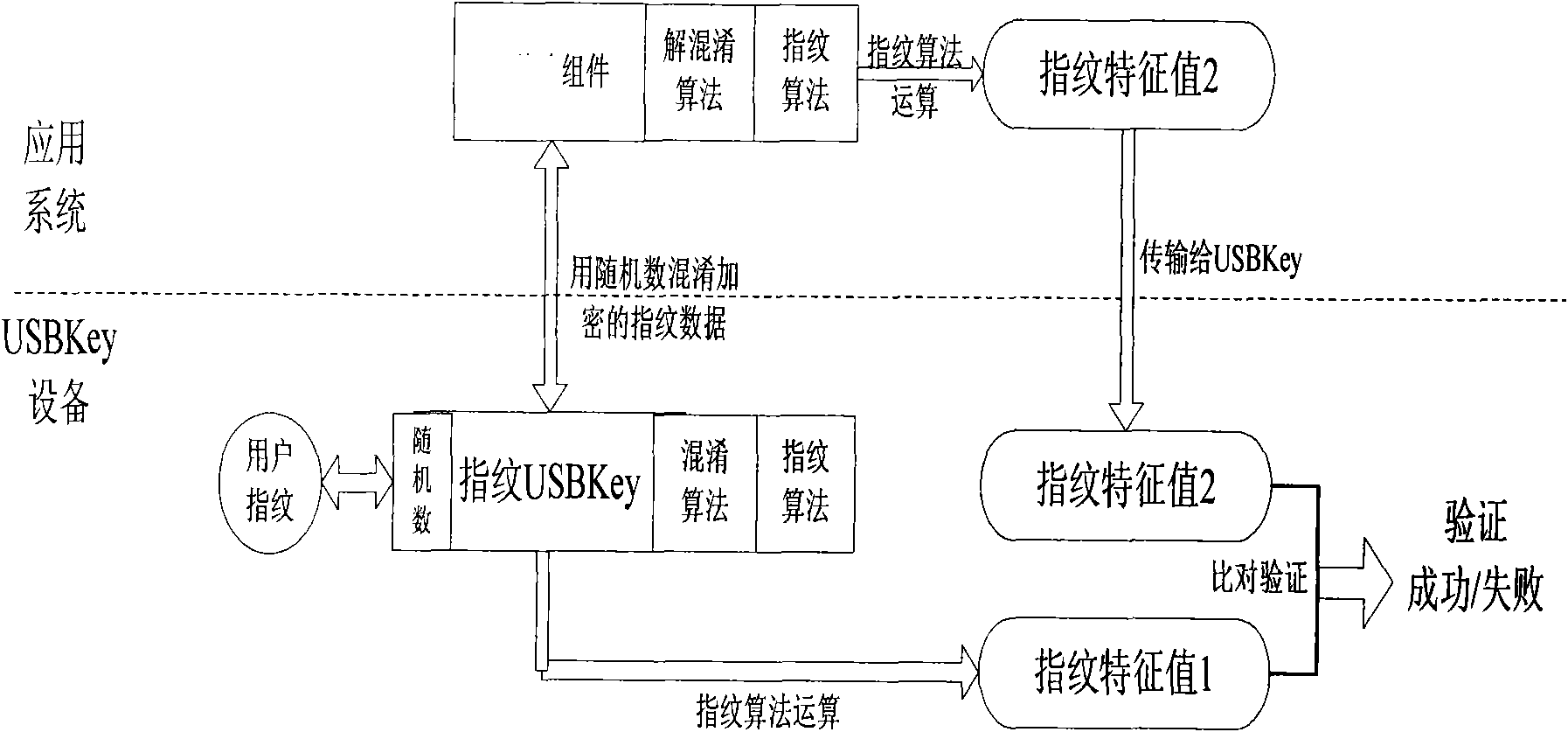
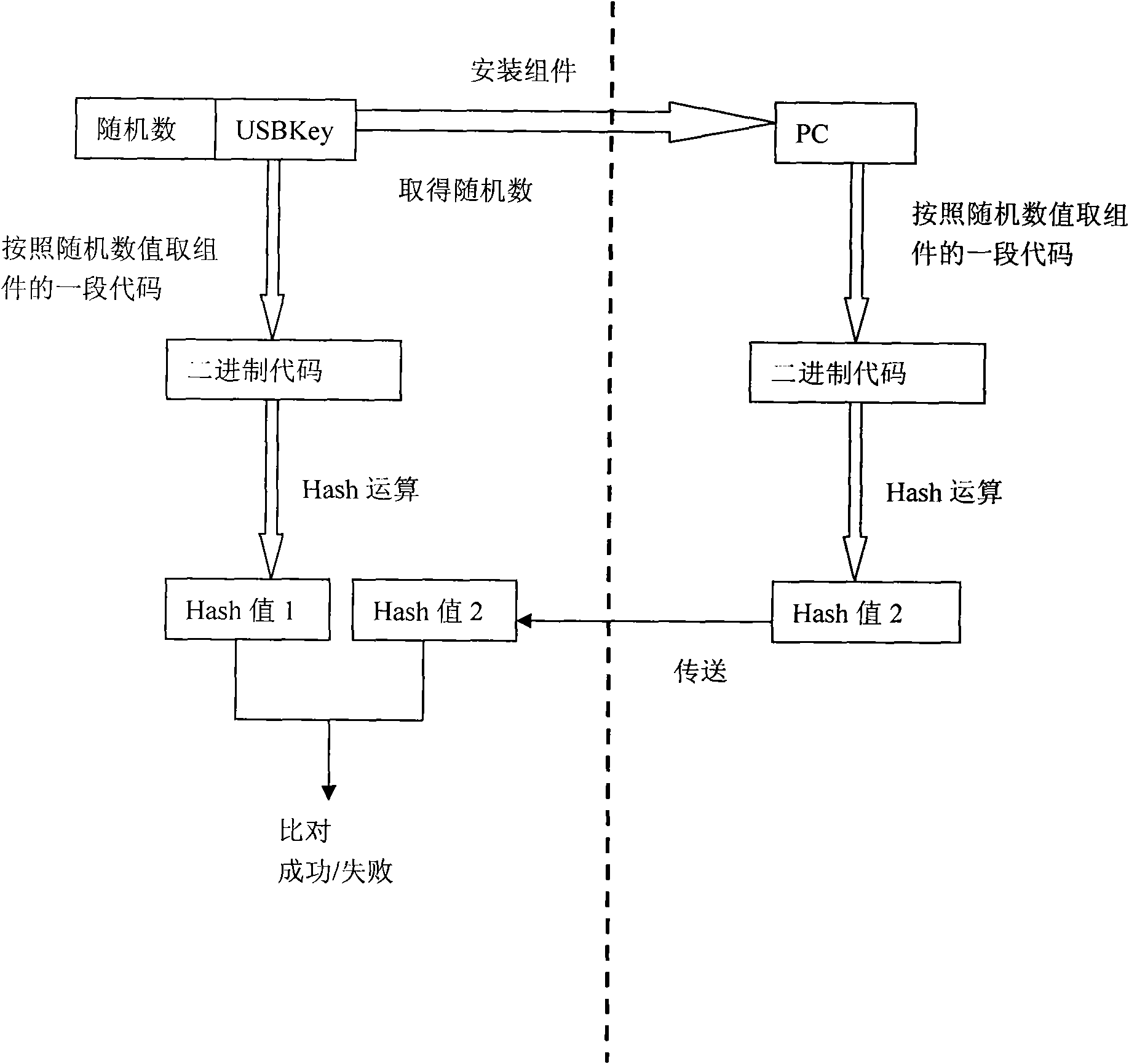
InactiveCN101661599AAddress riskStop stealingDigital data authenticationCommerceFingerprintSoftware system
The invention discloses a method for authenticating the validity of self-contained software of an equipment system; fingerprinting and a confusion key shared by system software and equipment are mounted into an operating system simultaneously; and when a user inputs information to confirm a trade, a USBKey obtains the fingerprint data of the user, generates a random number, uses the fingerprintingto encrypt the fingerprint data and the random number, and transmits to the system software. The system software obtains the fingerprint data after using a confusion arithmetic to decrypt, uses the fingerprinting to calculate the fingerprint characteristics of the user, and compares the fingerprint characteristics with the fingerprint characteristics obtained through USBKey calculation. If the comparison results are same, then authentication on the validity of the system software is passed and the trade is confirmed. Based on the thought of 'reliable equipment', the method for authenticatingthe validity of the self-contained software of the equipment system implements bidirectional authentication between important components and the system equipment in the software system; and the systemequipment can not work normally after the validity of the software system is confirmed to stop 'trojan' programs to fake as legal programs to visit equipment or steal and alter the input data of theuser.
Owner:ZHEJIANG WELLCOM TECH
Secure and reliable network access method for hardware device
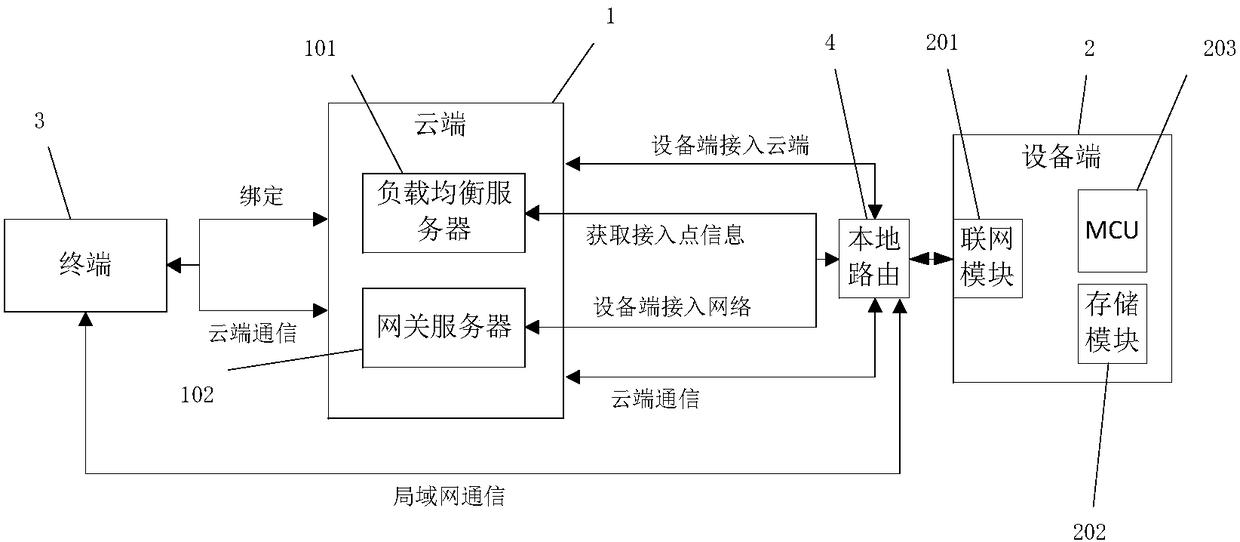
ActiveCN108933757AReduce overheadAddress riskEncryption apparatus with shift registers/memoriesCommunications securityAccess method
The invention discloses a secure and reliable network access method for a hardware device. The method includes the following steps: a device end networking module and a cloud end are connected to a network after being subjected to encryption two-way authentication; a dynamic encryption secret key is obtained for data communication security device binding, and uplink and downlink communication canbe realized. The method disclosed in the invention helps solve a problem of security risks such as device camouflage, cloud end DNS hijacking and the like in network accessing processes, security of an Internet of Things communication protocol and validity authentication of the device and the cloud end can be ensured, and reliable data transmission capacity can be provided for cloud end communication and local area network communication. The method is suitable for a WIFI module, a wired module, a GPRS module, a Linux system-based device, an Android system-based device, networking devices basedon Windows systems, and the like.
Owner:北京君泊网络科技有限责任公司
Electric tickets method and system based on network
A paying method of electronic bill based on network includes storing multiple bill for payment purpose and user data of these electronic bills; generating electronic bills corresponding to stored bills for payment purpose; forming said electronic bill by a mount of money, bill period, signature person and bill right transfer information being used as unique information to be logged in by user; logging in bill right transfer information by paying party and making said transfer information be corresponded to user data on electronic bill of paid party.
Owner:重庆浩泽网络技术有限公司
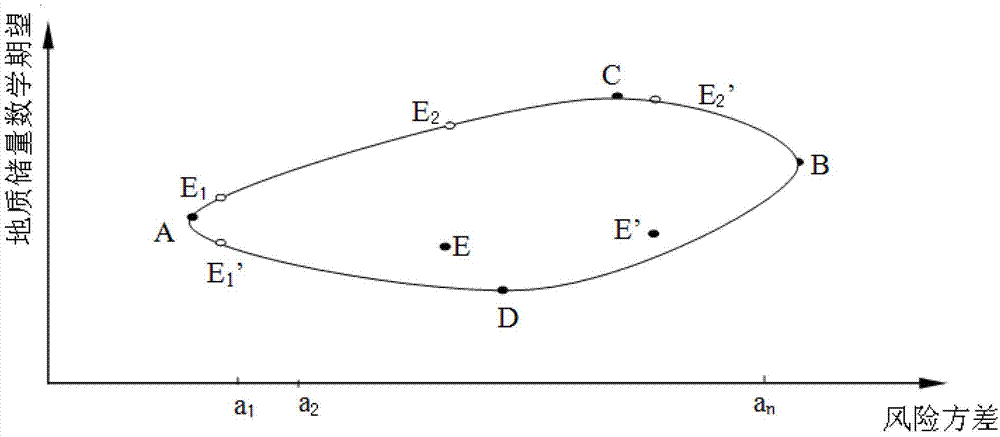
Oil and gas trap combination exploration optimization method
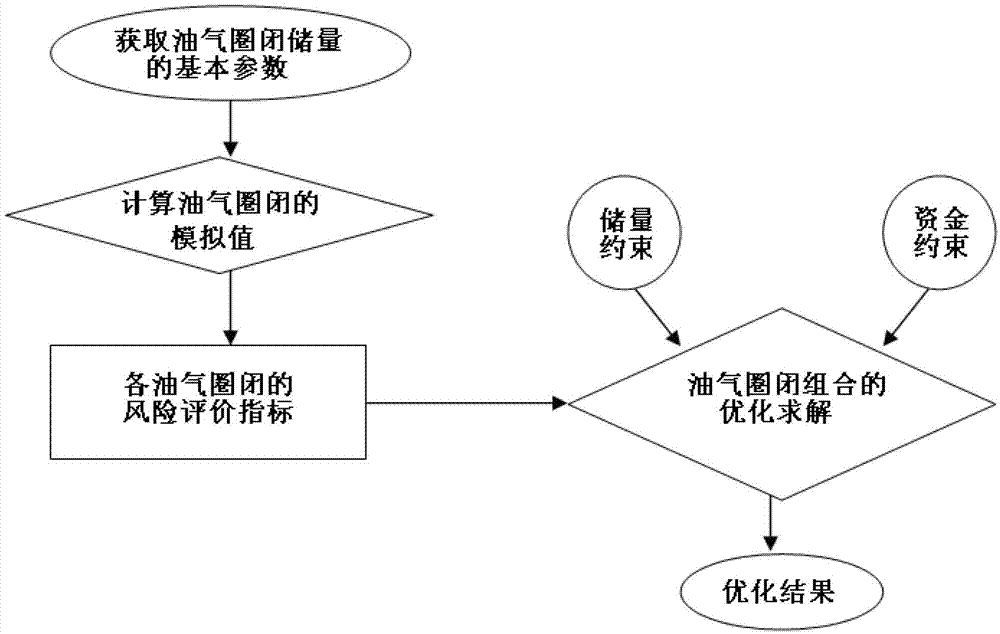
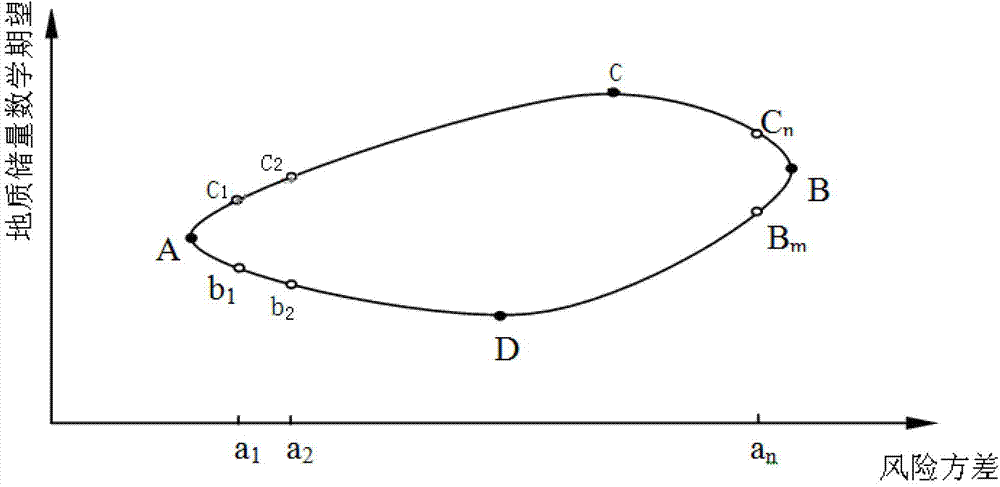
The invention relates to an oil and gas trap combination exploration optimization method. According to the optimization method, an optimization theory in operational research is used; on the basis that reasonable geological reserve calculation and strict risk analysis are carried out on a trap combination, an oil and gas trap linear programming model is established; under the conditions of capital constraint and a determined risk scope, the maximum geological reserve of the oil and gas trap combination is acquired; or under the conditions of capital constraint and a determined geological reserve condition, the minimum risk variance of the oil and gas trap combination is acquired; and balance between risk and return of the whole oil and gas trap combination exploration is realized. Practical application shows that the method has the advantages of reliable effect and strong operability, can provide a scientific basis for the decision of oil and gas trap exploration, and has strong practicality.
Owner:CHINA PETROLEUM & CHEM CORP +1
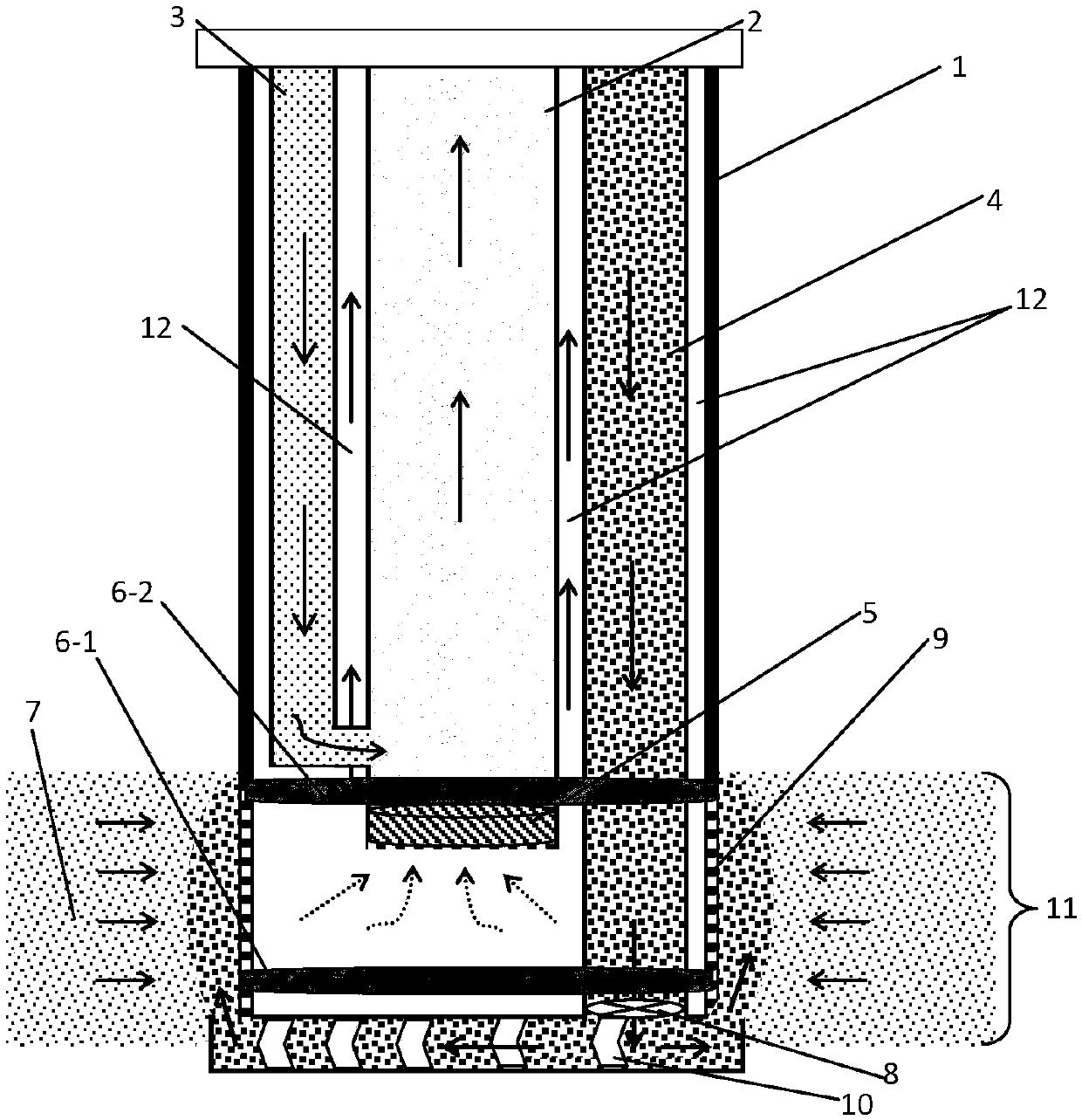
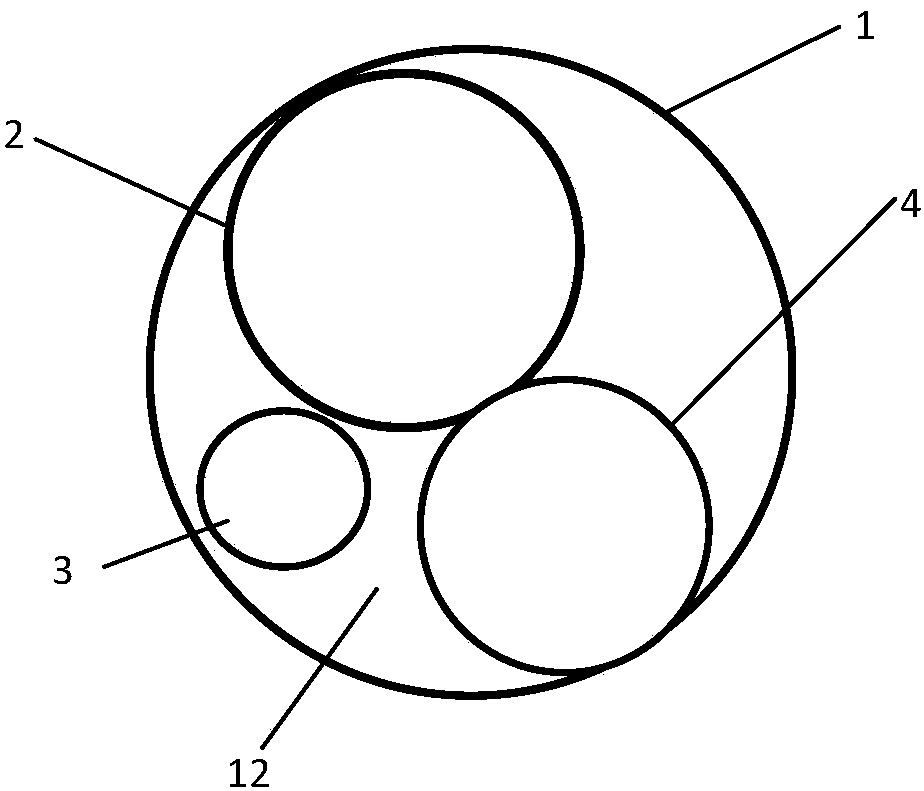
Marine gas hydrate and mortar replacement exploitation method and device
ActiveCN107676058APrevent large area deficitGuaranteed stabilityConstructionsFluid removalProduction tubingCoarse particle
The invention discloses a marine gas hydrate and mortar replacement exploitation method and device. According to the exploitation method, the sand blocking accuracy of a mechanical screen pipe is properly lowered to enable stratum mud and sand fine particles to flow into a shaft production pipe column and be discharged under the controllable condition, in the meantime, coarse-particle mortar is injected into a hydrate reservoir continuously, and through matching of a hydrate reservoir sand outlet management technology and mortar injection technology, replacement of the coarse-particle mortar and the stratum fine particles as well as the coarse-particle mortar and a hydrate space is achieved. The exploitation device comprises a production sleeve pipe, a production oil pipe, a shaft water injection pipe and a mortar back-injection pipe, the lower end of the production sleeve pipe is connected with the mechanical screen pipe, and the upper end and the lower end in the mechanical screen pipe are further provided with an upper mechanical packer and a lower mechanical packer correspondingly. The inlet end of the production oil pipe is provided with a gas separating device, and the position, above the upper mechanical packer, of the shaft water injection pipe communicates with the production oil pipe. The mortar back-injection pipe penetrates through the upper mechanical packer and the lower mechanical packer, extends to the bottom border of the production layer section of the hydrate reservoir and is connected with a gravel filling tool. Through the method and the device, the purpose of continuous and efficient production is achieved.
Owner:QINGDAO INST OF MARINE GEOLOGY
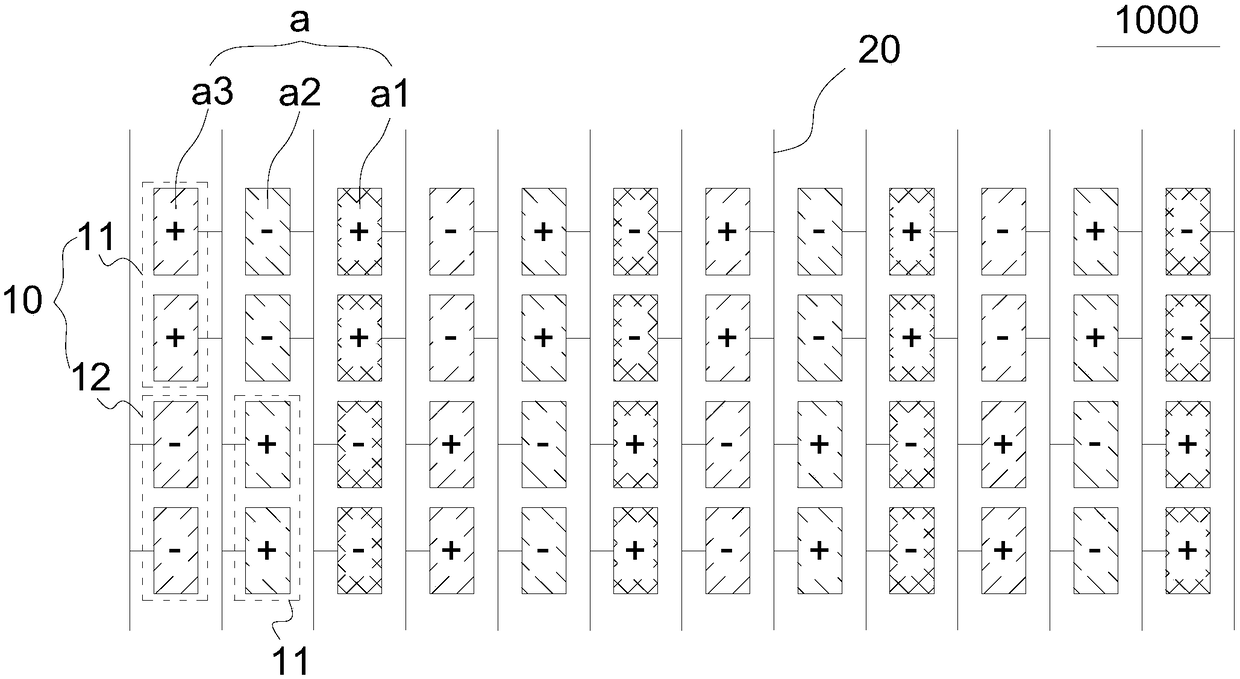
Pixel structure and liquid crystal display panel
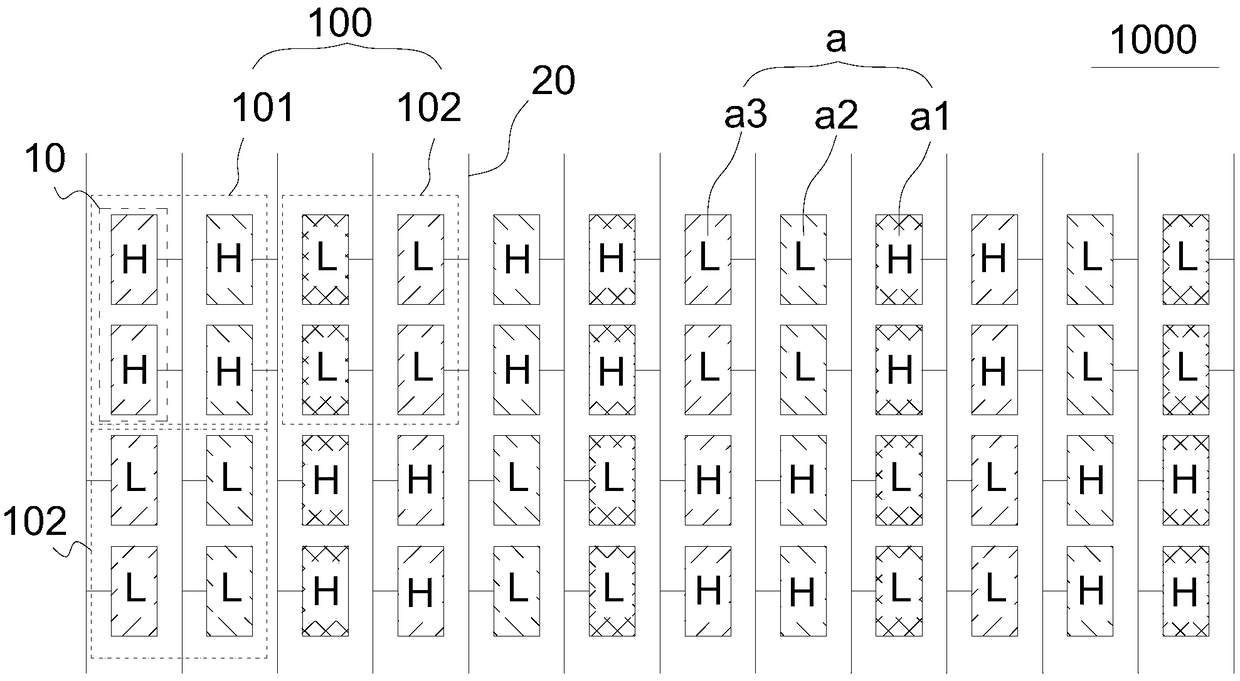
InactiveCN109272951AAddress riskSolve the technical problem of low viewing angle of chromaticityStatic indicating devicesLiquid-crystal displayData lines
The invention provides a pixel structure and a liquid crystal display panel. The pixel structure comprises a plurality of flip units arranged in an array. When the same frame is displayed, the polarities of two adjacent flip units are opposite in the column entry. In the row item, the polarities of the two adjacent flip cells are opposite; the flipping unit includes at least two sub-pixels of thesame color, and the polarities of the sub-pixels of the same flipping unit are the same; the pixel structure comprises a plurality of data lines, wherein the data lines and the column item flipping units are alternately arranged; In two adjacent columns of flip cells, flip cells of the same polarity connect data lines between two adjacent columns of flip cells. The present application avoids tampering and reduces power consumption of a driver chip by a column flipping mode of flipping units connected to the same data line.
Owner:TCL CHINA STAR OPTOELECTRONICS TECH CO LTD
New energy relay protection intelligent checking and early warning system based on OCR technology
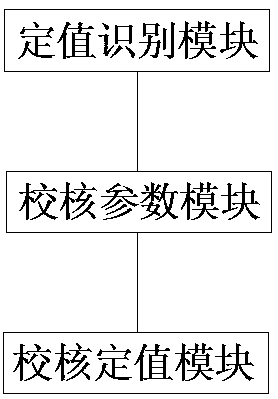
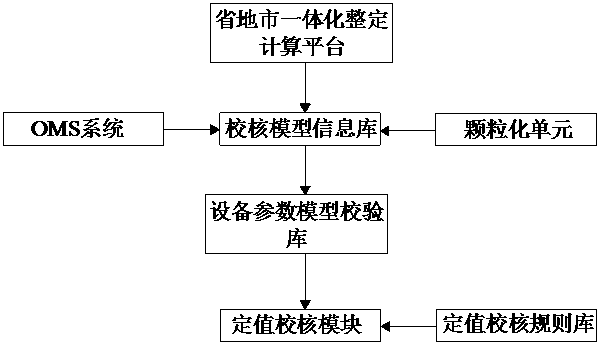
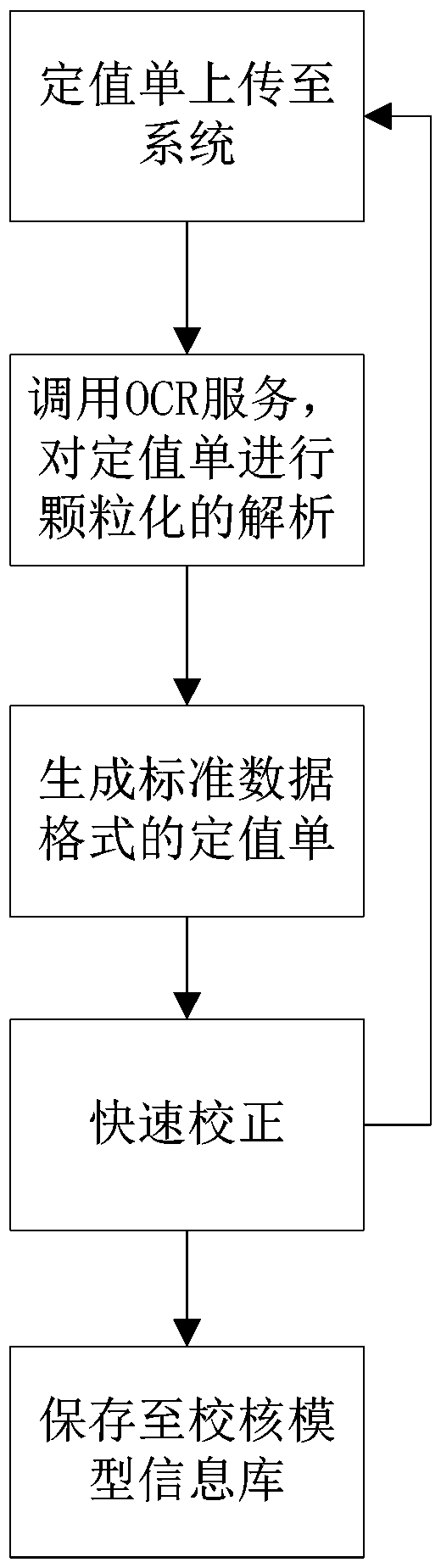
ActiveCN110854807AAvoid imperfectionAvoid inaccuraciesData processing applicationsEmergency protection data processing meansEarly warning systemStation
The invention provides a new energy relay protection intelligent checking and early warning system based on the OCR technology. The system comprises a constant value identification module, a parameterchecking module and a constant value checking module which are connected in sequence, wherein the constant value identification module is used for carrying out information acquisition of a relay protection constant value list based on the OCR technology to obtain a constant value list in a standard data format, the parameter checking module is used for collecting and checking each parameter and constructing an anti-error mechanism, and the constant value checking module is used for performing checking and early warning of the constant value outputted by the constant value identification module. The system is advantaged in that granular information collection of the relay protection constant value list is performed based on the OCR technology, accuracy of the constant value is controlled from a source of the device, problems existing in relay protection constant value setting in a station are solved, by setting intelligent checking, an early warning function is realized, the safety risk of the relay protection setting value is reduced, efficient and safe network access operation of new energy is powerfully guaranteed, and problems in network-related setting value checking in the prior art are solved.
Owner:STATE GRID HEBEI ELECTRIC POWER RES INST +1
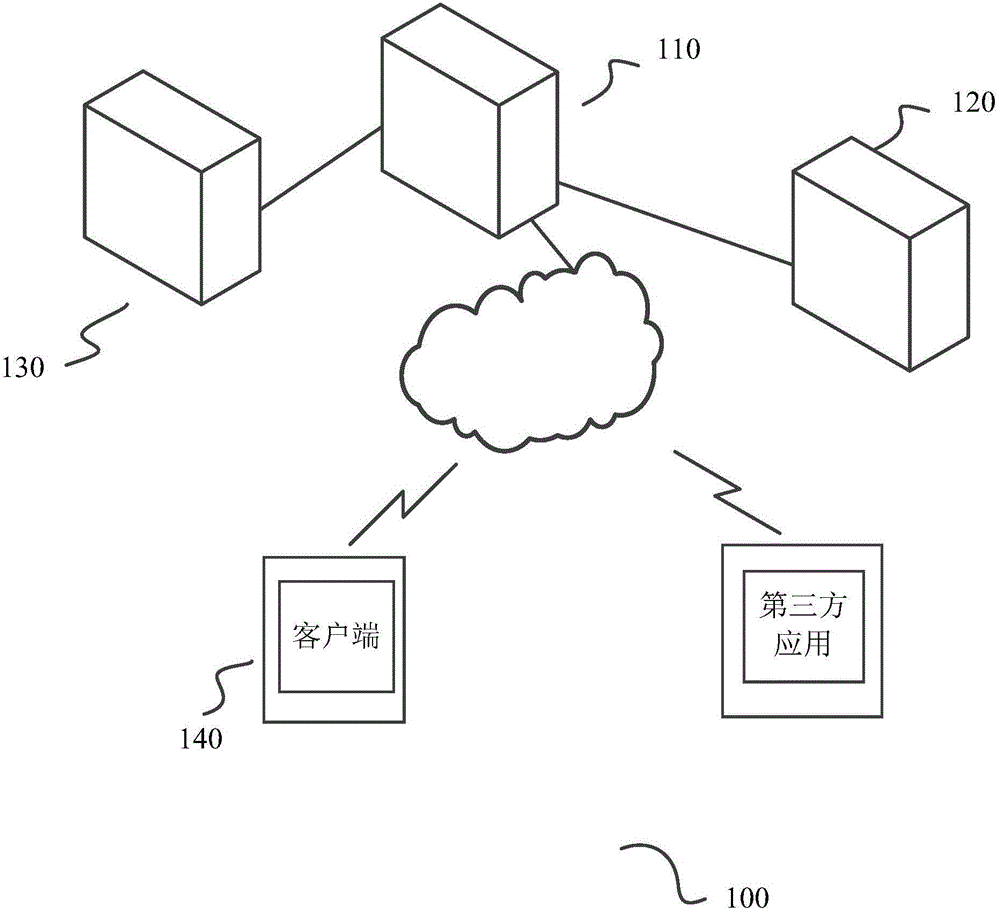
Two dimension code registration method, server and system
ActiveCN104901970AQuick authentication loginSecurity authentication loginDigital data authenticationTransmissionThird partyClient-side
The invention discloses a two dimension code registration method executed in a first server; the method comprises the following steps: receiving a first request coming from a third party application and requesting a two dimension code; creating an event mark related to the first request; relating the event mark with first information generating the two dimension code; returning the event mark and a two dimension code address of the two dimension code to the third party application for displaying the two dimension code, and generating a second request comprising the event mark and sending the second request to the first server; receiving second information comprising first information and generated after a client side scanning the two dimension code, and relating the event mark, related with the first information in the second information, with a user mark; responding to the second request from the third party application, sending the user mark, related to the event mark, in the second request to the third party application, so the third party application can register a third party account corresponding to the user mark. The invention also provides a two dimension code registration system and the first server.
Owner:广州密码科技有限公司
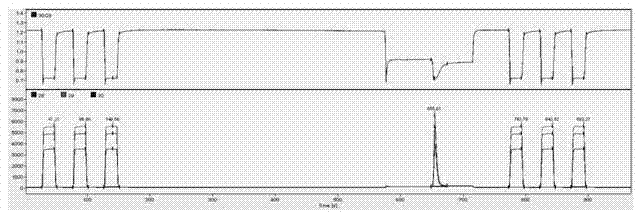
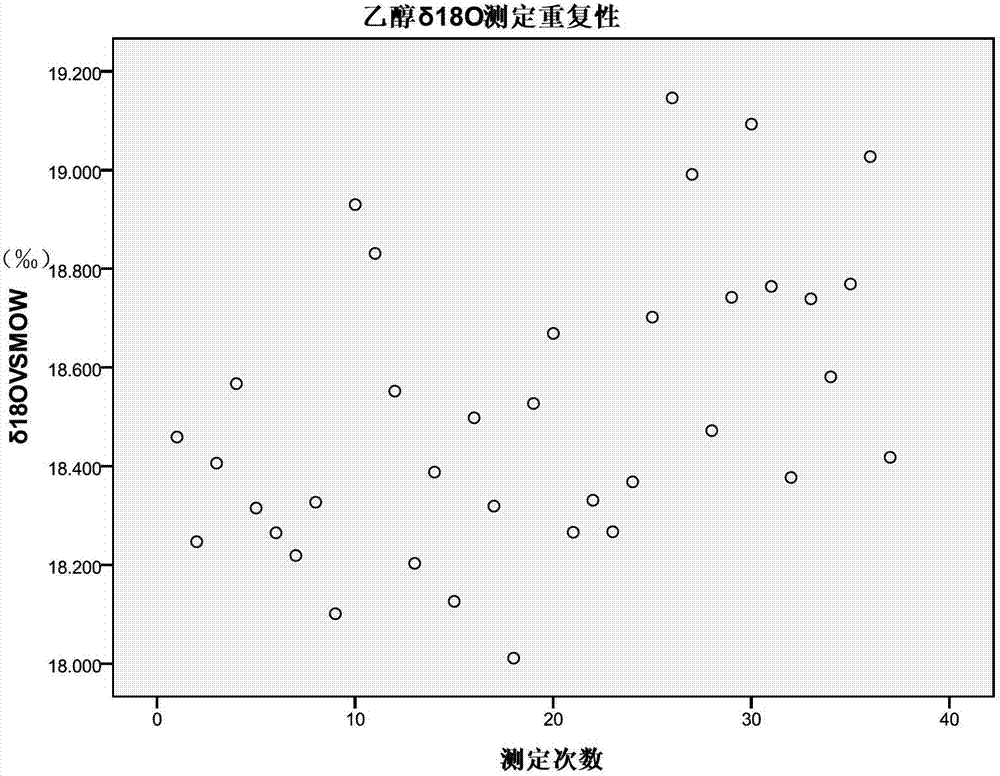
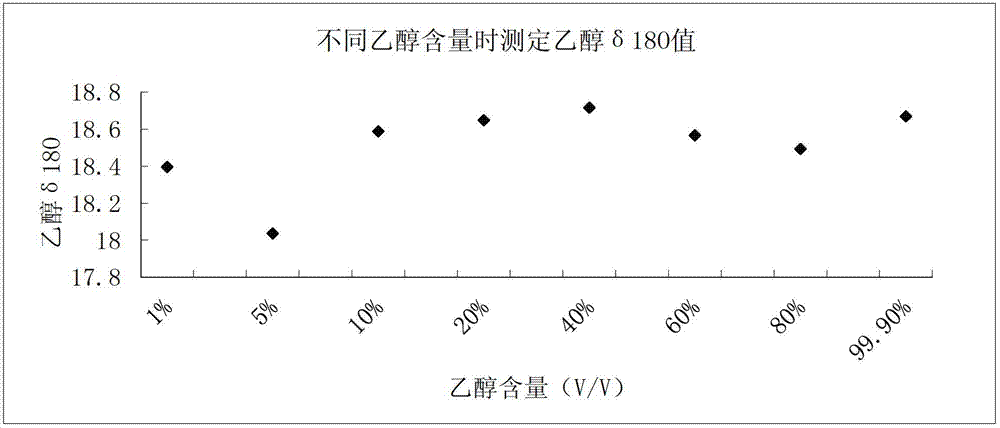
Rapid determination method for oxygen stable isotope of ethanol in alcoholic beverage
The invention relates to a rapid determination method for oxygen stable isotope of ethanol in an alcoholic beverage, and belongs to the technical field of stable isotope analysis. The method comprises the following steps: 1) using acetone to dilute an alcoholic beverage, and mixing for stand-by; 2) injecting a sample by a liquid injection needle, and using a GC with molecular sieve chromatographic capillary column to separate ethanol, acetone, water and other oxygen-containing compounds; 3) converting ethanol into CO with an on-line pyrolysis device; 4) determining delta 18O in CO produced by ethanol by CF-IRMS; and 5) based on a measured delta 18 O value of an isotopic reference material, correcting and calculating delta 18OVSMOW of the ethanol sample. The invention utilizes GC-TC-IRMS to realize rapid determination of oxygen stable isotope of ethanol in alcoholic beverage, and solves series of existing technical problems in pretreatment, such as ethanol purification before determination of oxygen stable isotope of alcohol in alcoholic beverage. The project can promote technological progress of ethanol oxygen isotope determination, and also provides technical methods for the future research on authentication and metabolic path of alcoholic beverage or biofuel.
Owner:CHINA NAT RES INST OF FOOD & FERMENTATION IND CO LTD
Vulcanization startup method of hydrocracking device
ActiveCN103059968APlay a supporting roleReduce energy consumptionTreatment with hydrotreatment processesVulcanizationBuffer tank
The invention discloses a vulcanization startup method of a hydrocracking device. The method comprises: injecting startup vulcanization oil and a vulcanizing agent into a refining reactor, and conducting vulcanization on a refining catalyst in a wet process; subjecting the refining reactor effluent to gas-liquid separation to obtain a hydrogen sulfide-containing gas, carrying out heat exchange on the gas, then passing it through a hydrocracking reactor, performing vulcanization on a cracking catalyst in a dry process, and cycling the obtained refined oil back into a startup oil buffer tank; and at the end of a low temperature vulcanization constant temperature section, supplementing a certain proportion of inferior diesel oil to the vulcanization startup oil, and making use of the temperature rise generated by heat release of an inferior diesel oil hydrogenation reaction to assist a heating furnace to perform temperature raising operations till the end of vulcanization. The method provided in the invention can produce a part of hydrofined products on the basis of guaranteeing the vulcanization effect, and also can reduce the heating furnace energy consumption and the vulcanizing agent dosage.
Owner:CHINA PETROLEUM & CHEM CORP +1
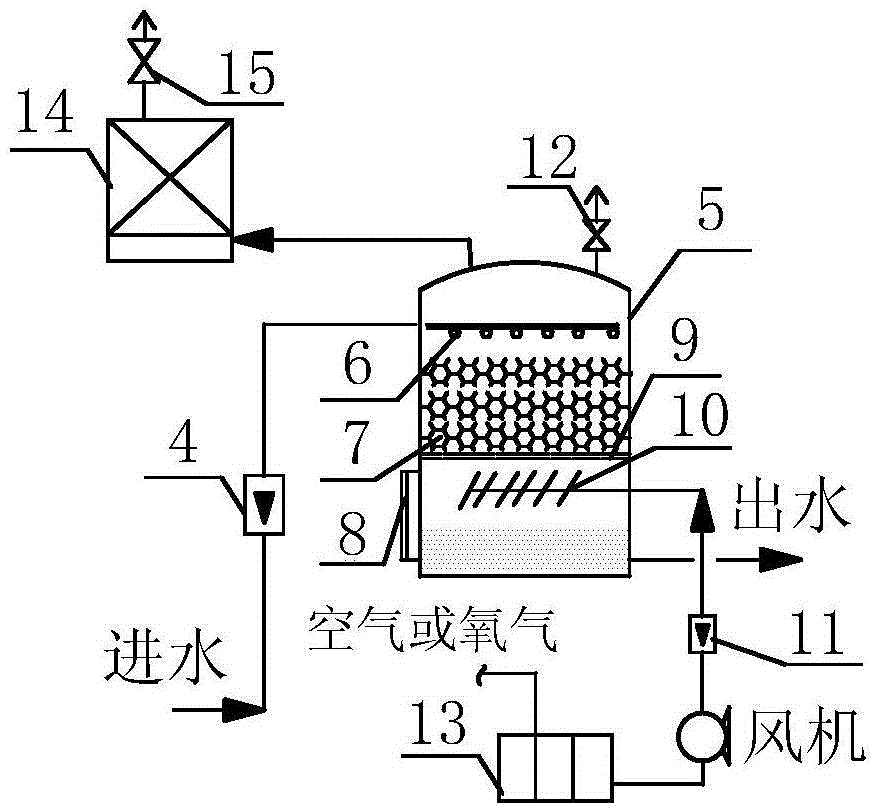
Technology and device for treating coking wastewater through ozone catalytic oxidation combined biofilter
ActiveCN104926034AReduce ozone concentrationImprove catalytic oxidation efficiencyMultistage water/sewage treatmentWater useCatalytic oxidation
The invention discloses a technology and device for treating coking wastewater through an ozone catalytic oxidation combined biofilter. The technology and device are reasonable in design, low in operation cost, solve the problem related to advanced treatment and recycling of coking wastewater, and have a high engineering application value; the technology and device eliminate the unsafe factors for operators and potential risks threatening the health in a heavily polluted environment with coking wastewater, and are simple to operate and low in operation cost; the effluent water quality meets different water use requirements.
Owner:武汉钢铁有限公司
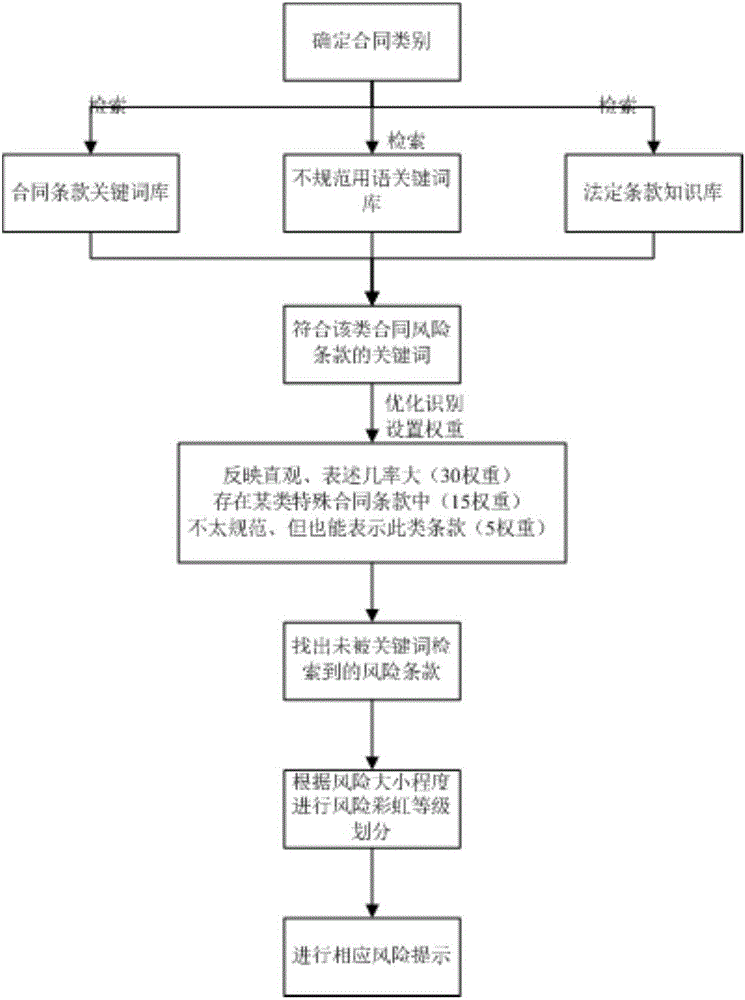
Method and system for identifying risk of contract terms
InactiveCN106844544AAddress neglected issuesAddress riskResourcesSpecial data processing applicationsCost (economic)Data science
The invention provides a method and system for identifying risk of contract terms. The method comprises the steps of determining the type of contract, and extracting the key words in each type of contract; optimizing and identifying the key words, and prompting risks. According to the method, by combining the methods such as the combination of key words, the adoption of parallel or exclusion method of and-or, and identification of the overall semantic, the existing terms in the contract are identified, risk terms and missing terms are excluded, and specific and professional suggestions are made; by the specific risk suggestions to the terms in the contract, the neglected problems or the encountered risks in the contract signing of both parties are effectively solved, the losses of time and economic costs caused by lack of legal knowledge are greatly reduced.
Owner:全民互联科技(天津)有限公司
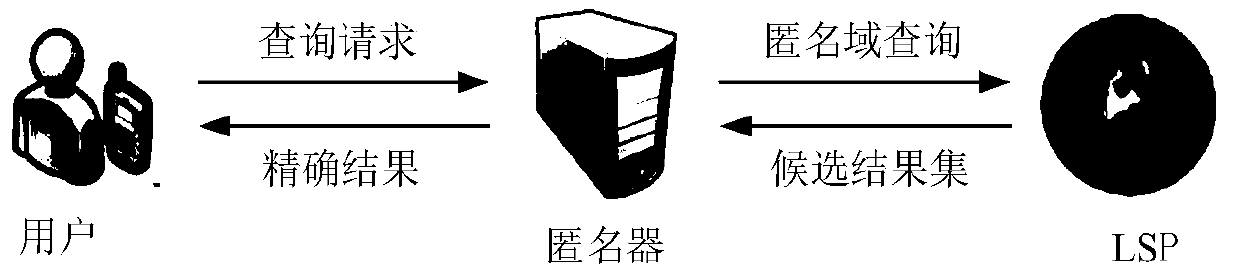
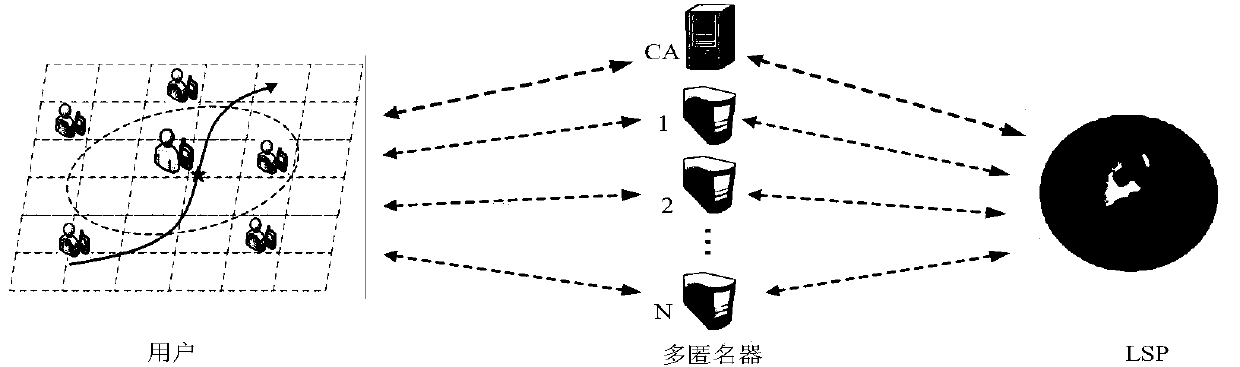
Anonymity based on multi-anonymizer (AMA) location service method
InactiveCN108632237AImprove privacy protectionResist Privacy AttacksKey distribution for secure communicationUser identity/authority verificationPrivacy protectionComputer terminal
The invention discloses an Anonymity Based on Multi-Anonymizer (AMA) location service method. The AMA location service method comprises the steps that: step 1, a mobile terminal conducts identity authentication in a CA to obtain a pseudonym, and user query content is divided into n pieces of sub-information by using a Shamir threshold scheme; step 2, the mobile terminal selects n different anonymizers to anonymize the user, and transmits the n pieces of sub-information to an LBS server by means of the anonymizers; step 3, the LBS server aggregates t pieces of information received from the n anonymizers at first, restores the user query content according to the Shamir threshold scheme, and then queries POIs contained in an anonymous region in an LBS database according to the query content;step 4, the LBS server randomly selects w different anonymizers to forward an encrypted candidate result set to the mobile terminal; step 5, and the mobile terminal obtains a precise query result through filtering and refinement. The AMA location service method strengthens the trajectory privacy protection of the user, and effectively solves the single point failure risk of a single anonymizer.
Owner:HUNAN UNIV OF SCI & TECH
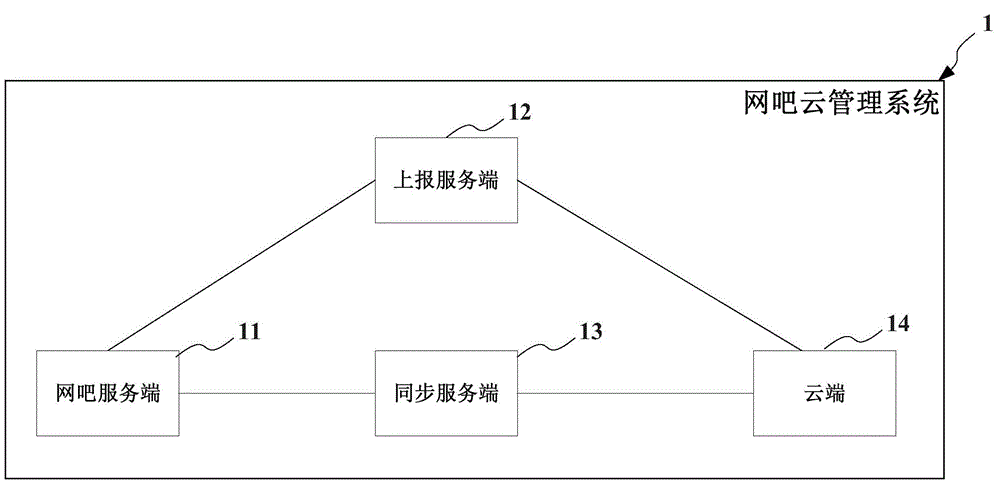
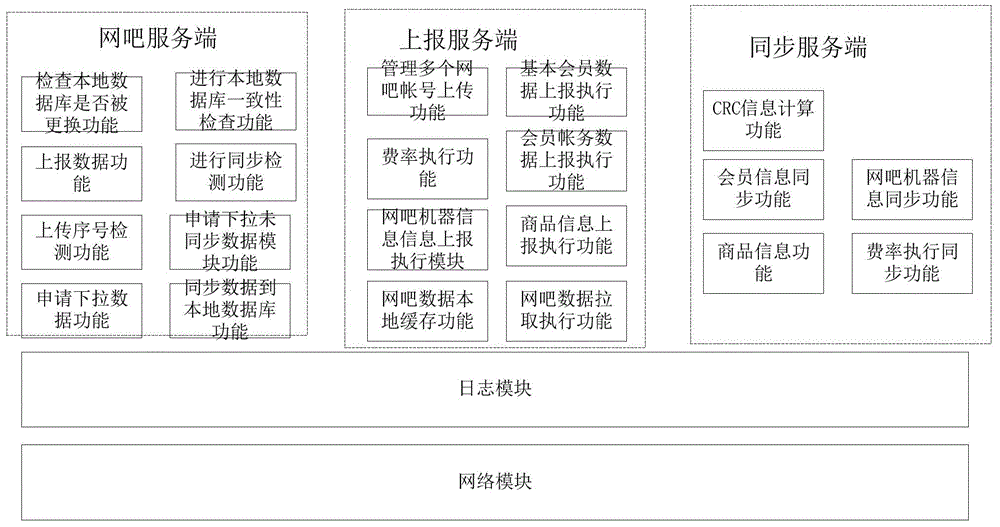
Internet bar cloud management system and applied Internet bar networking management method
InactiveCN105023103AIncrease attractivenessIncrease operating incomeResourcesTransmissionData synchronizationThe Internet
The invention provides an internet bar cloud management system and an applied internet bar networking management method. The system comprises one or more internet bar service ends, a report service end connected with the internet bar service ends, a synchronous service end connected with the internet bar service ends, and a cloud end connected with the report service end and the synchronous service end. The internet bar service ends report local business data to the cloud end, and the internet bar service ends can be synchronized with the local business data reported to the cloud end by means of the synchronous service end, so that data consistency is realized. The internet bar service ends can be managed only by the cloud end, and business development of the internet bar service ends in different internet bars can be performed by data synchronization through the cloud end, so that the development of internet bar business is substantially facilitated, and the commercial value is improved.
Owner:CHENGDU JISHENG TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com