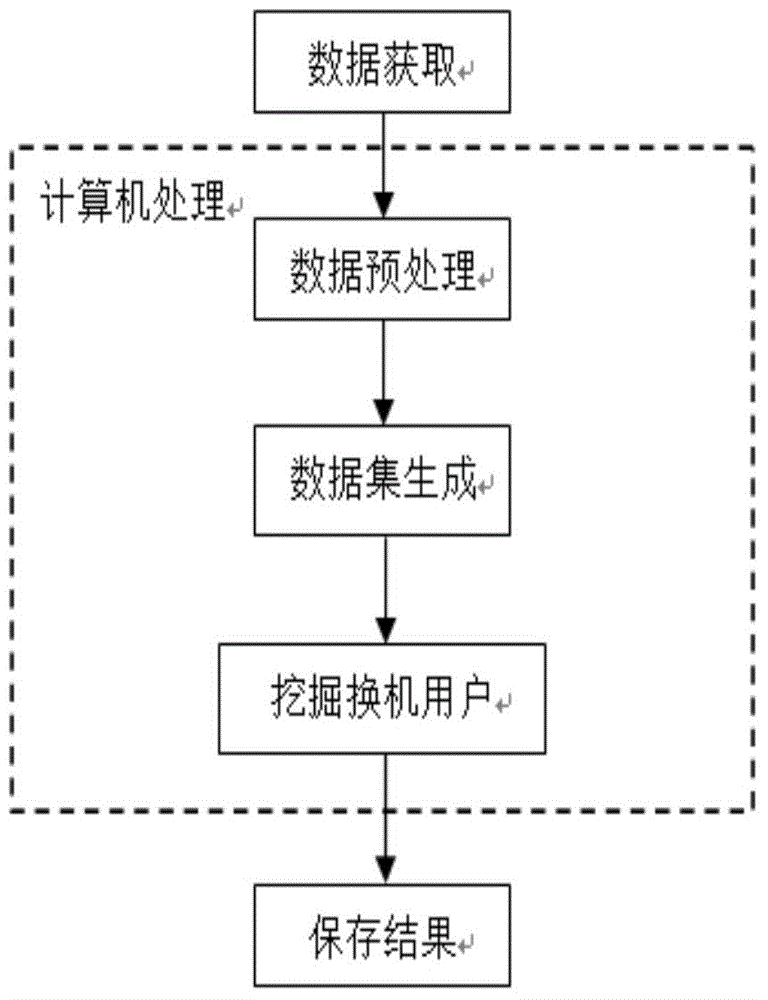
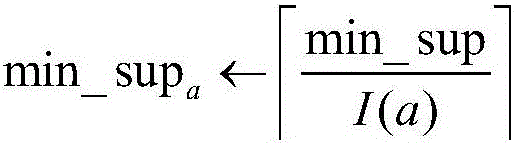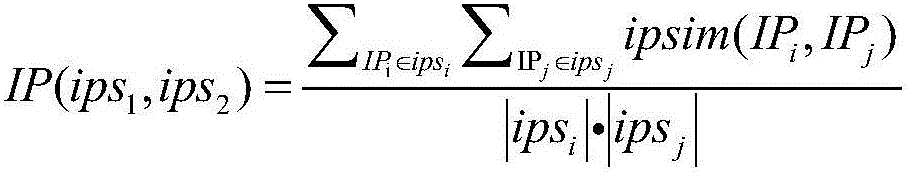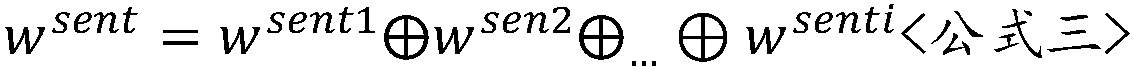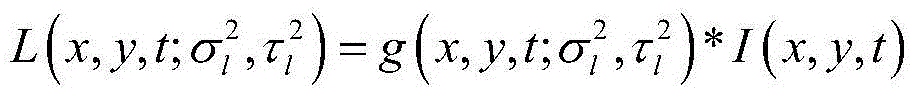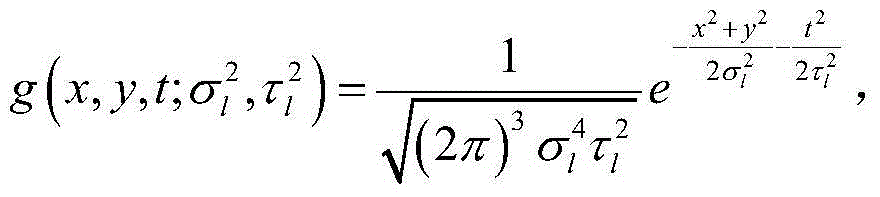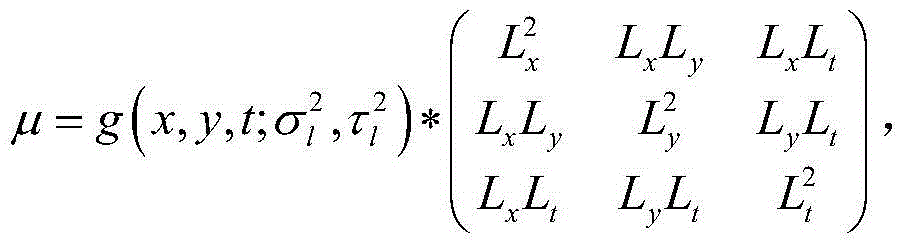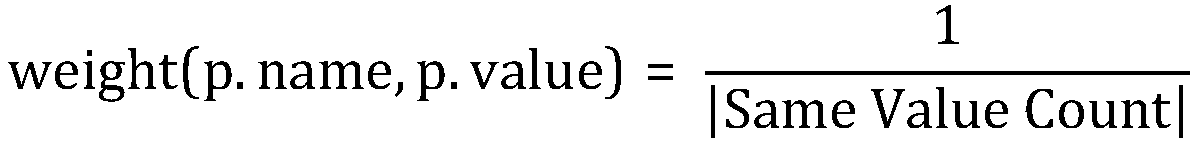Patents
Literature
297results about How to "Excavate accurately" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
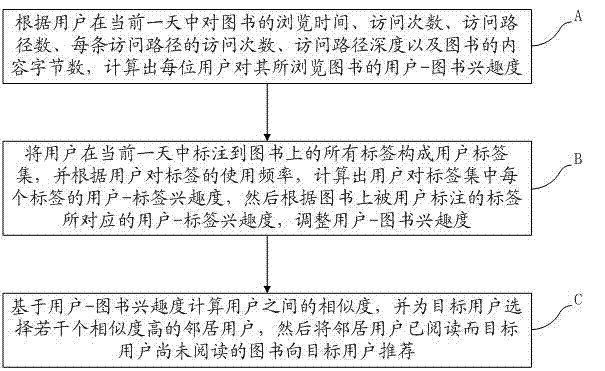
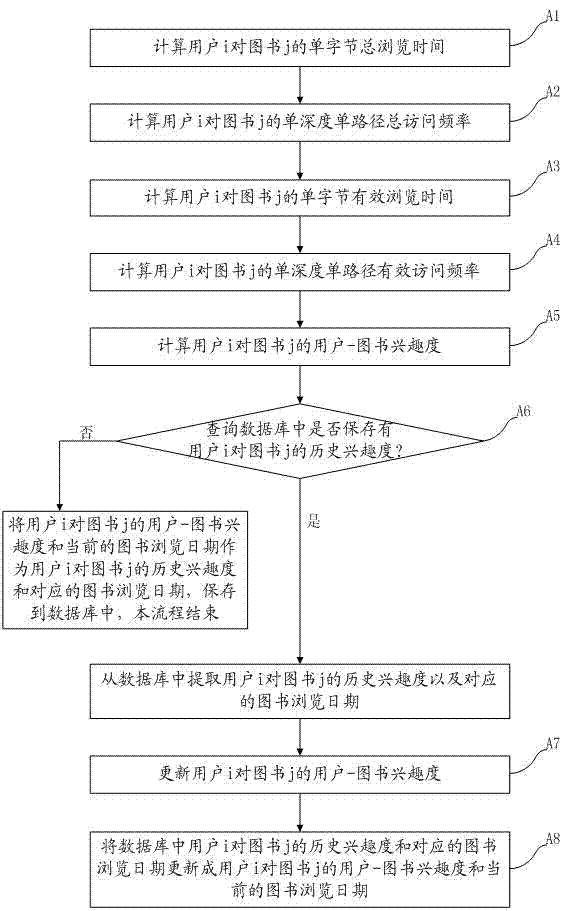
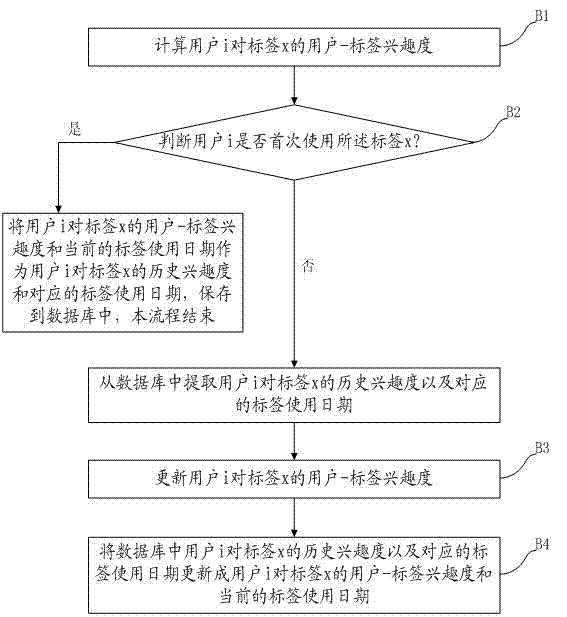
Book recommendation method based on user actions
ActiveCN102929959AAccurate book recommendation serviceExcavate accuratelySpecial data processing applicationsAccess timeE-commerce
The invention discloses a book recommendation method based on user actions. The book recommendation method comprises the following steps of: calculating user-to-book interestingness of each user to browsed books according to book browsing time, access times, the number of access paths, access times of each access path, the depth of each access path and the number of content bytes of the books of each user in a present day; and calculating the similarity among the users on the basis of the user-to-book interestingness, selecting a plurality of neighbor users with high similarity for a target user, and recommending the books which are read by the neighbor users but not read by the target user to the target user. The book recommendation method belongs to the technical field of e-commerce information retrieval and treatment based on a mobile internet, and can be used for exploring the preferences of the users according to the book browsing actions of the users so as to provide relatively accurate book recommendation service to the users.
Owner:EB INFORMATION TECH
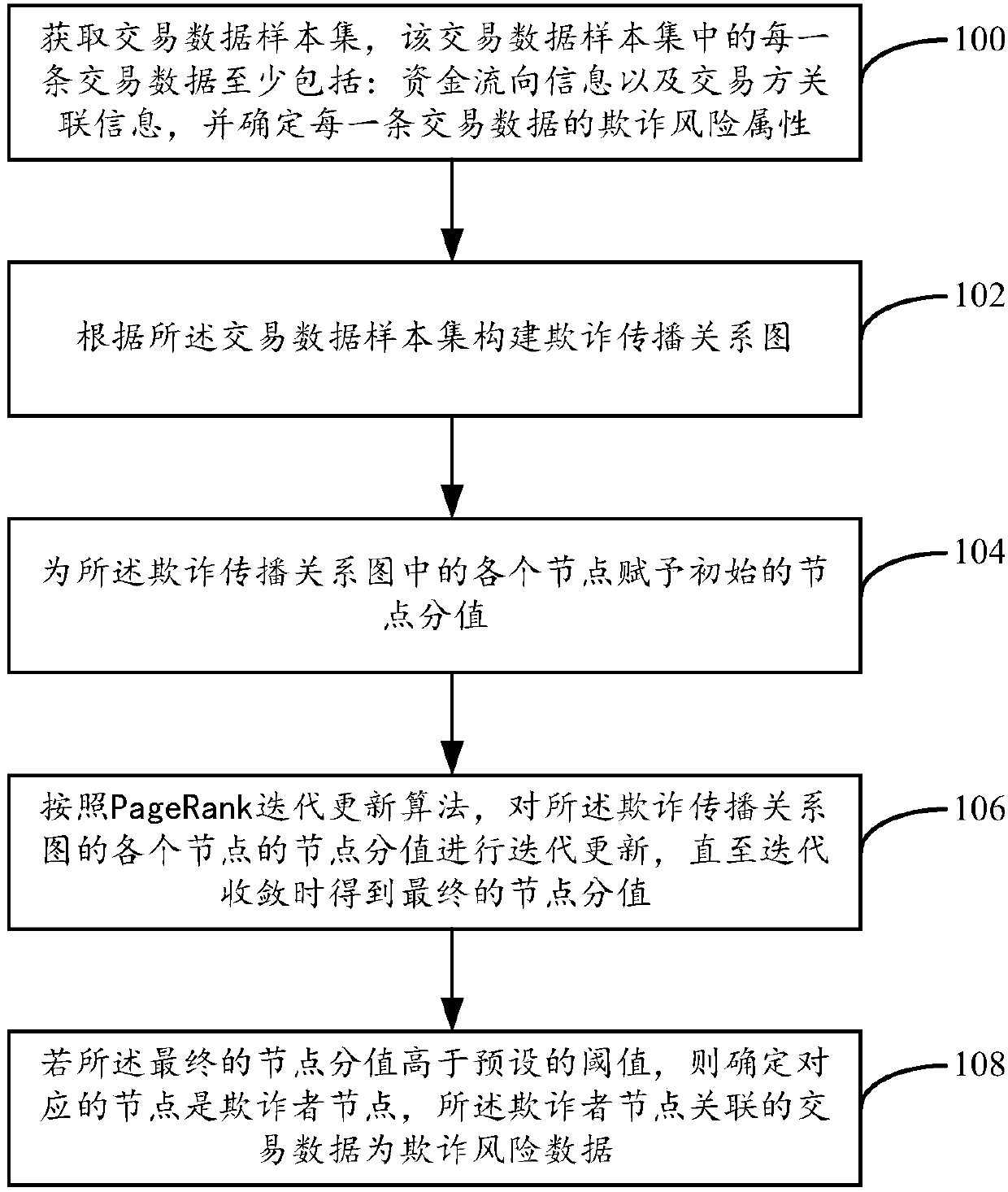
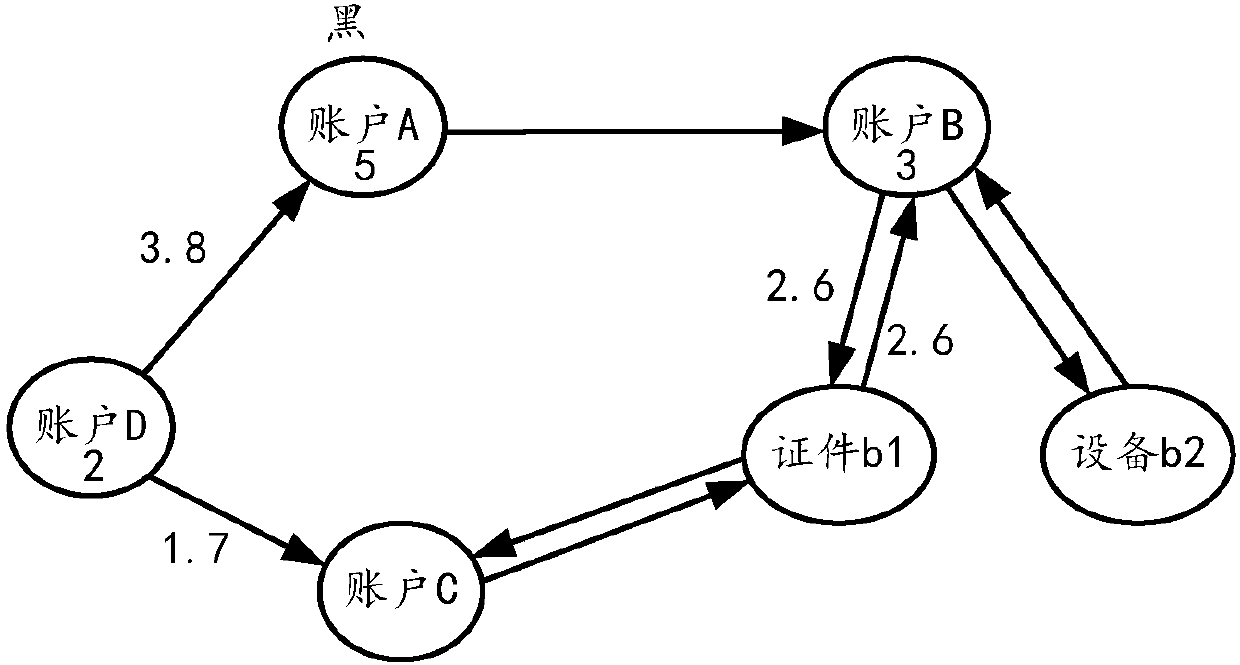
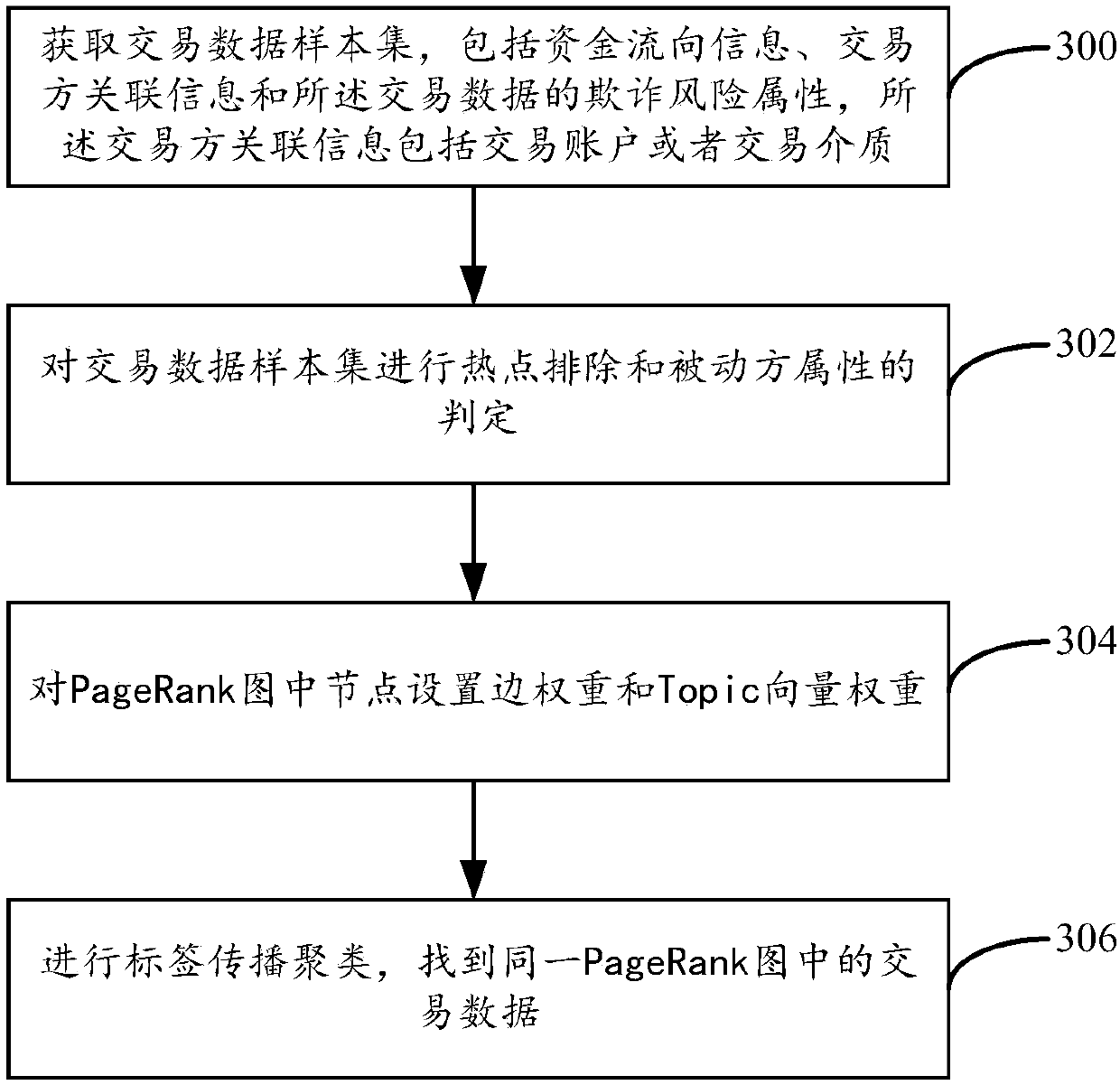
Fraud recognition method and fraud recognition device
ActiveCN107730262AFast convergenceExcavate accuratelyProtocol authorisationPagerank algorithmCounterparty
The embodiment of the invention provides a fraud recognition method and a fraud recognition device. The method comprises steps: a transaction data sample set is acquired, wherein each piece of transaction data in the sample set at least comprises fund flow information, transaction party correlation information and transaction data fraud risk attributes; a fraud spreading relation graph is built according to the sample set, wherein each node in the fraud spreading relation graph is built according to the transaction party correlation information, and the directed edge between the nodes is builtaccording to the fund flow information and the transaction party correlation information; an initial node value is assigned to each node in the fraud spreading relation graph; according to a PageRankiterative updating algorithm, the node value of each node is subjected to iterative updating until iterative convergence to obtain a final node value; and if the final node value is higher than a preset threshold, the corresponding node is determined to be a fraud person node, and the transaction data correlated to the fraud person node are fraud risk data.
Owner:ADVANCED NEW TECH CO LTD
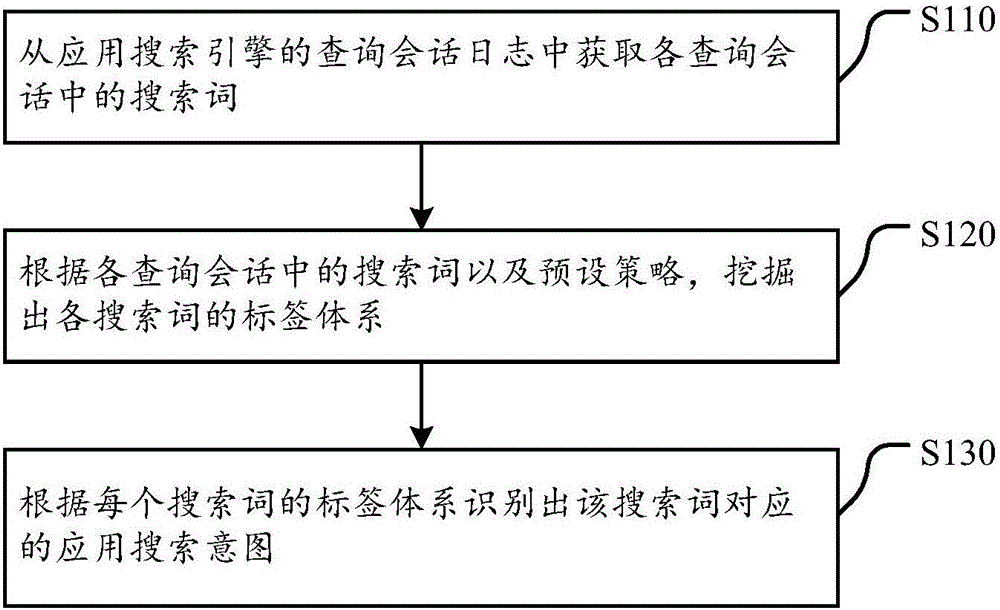
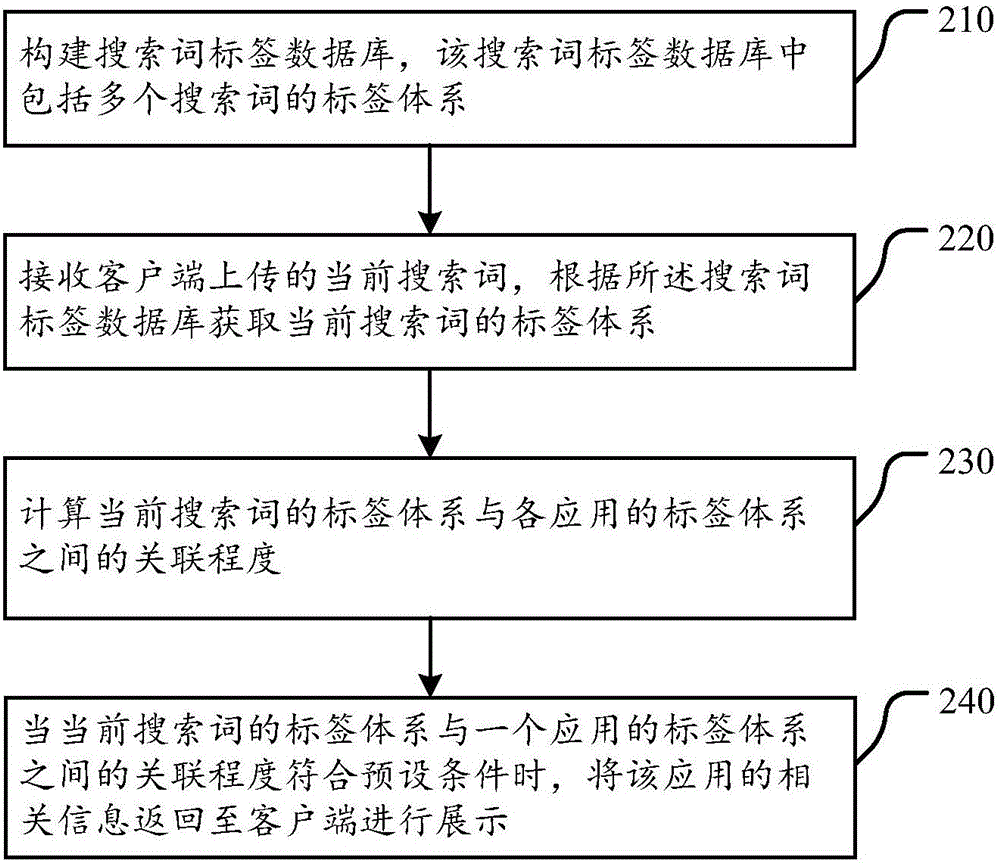
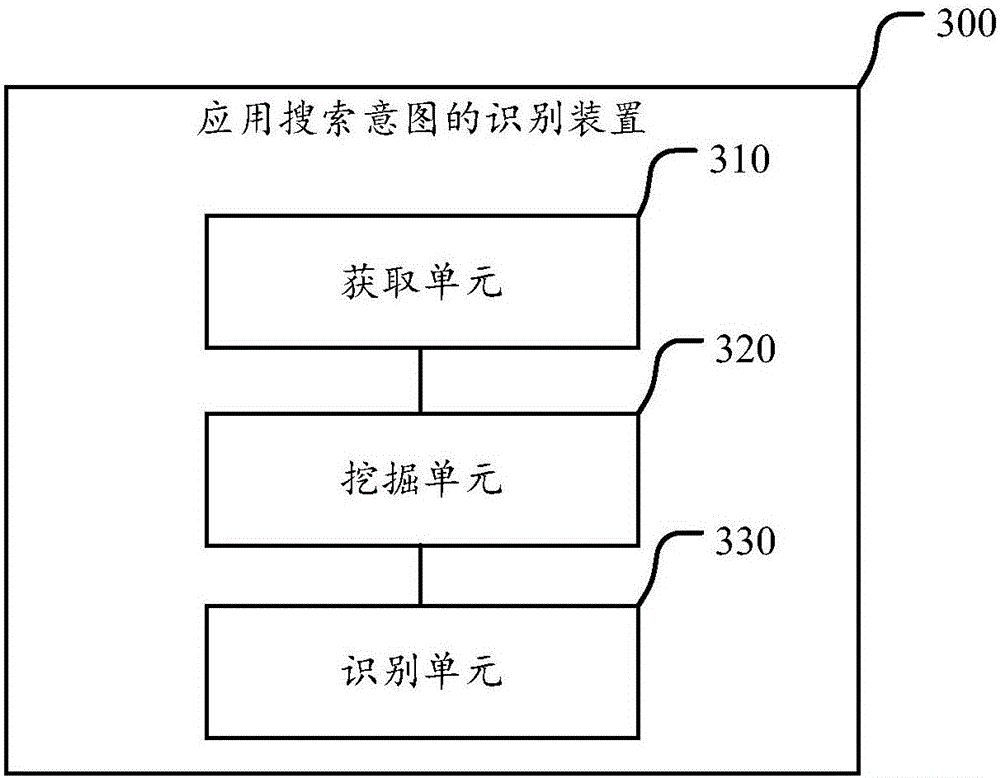
Recognition method and device for application search intentions and application search method and server
ActiveCN106649818ASolving the intent recognition problemExcavate accuratelyWeb data indexingSemantic analysisClassification methodsData mining
The invention discloses a recognition method and device for application search intentions and an application search method and server. The method includes the steps that search terms in query sessions are acquired from a query session log of an application search engine; label systems of the search terms are mined according to the search terms in the query sessions and preset strategies; the application search intentions corresponding to the search terms are recognized according to the label systems of the search terms. In the scheme, by proposing the label method of the recognition method for the user intentions corresponding to the app label systems, the fine-grained user query intentions are flexibly expressed. The label systems of the user intentions are constructed based on the unsupervised machine learning technology, a traditional user intention classification method is abandoned, an automatic user intention mining process is achieved, and a high-accuracy and high-recall-rate user intention label list can be generated; the user intentions and apps are mapped into the same label system, and thus a user can rapidly and accurately acquire apps meeting intentions when searching for apps.
Owner:BEIJING QIHOO TECH CO LTD
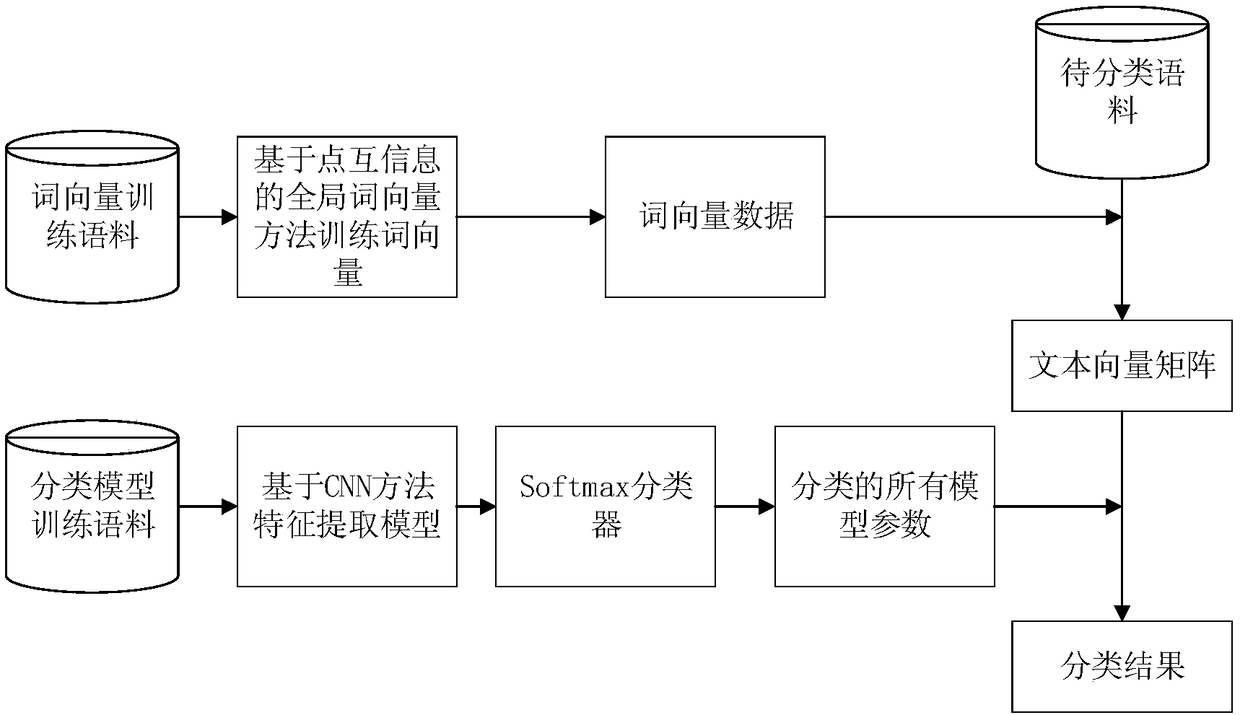
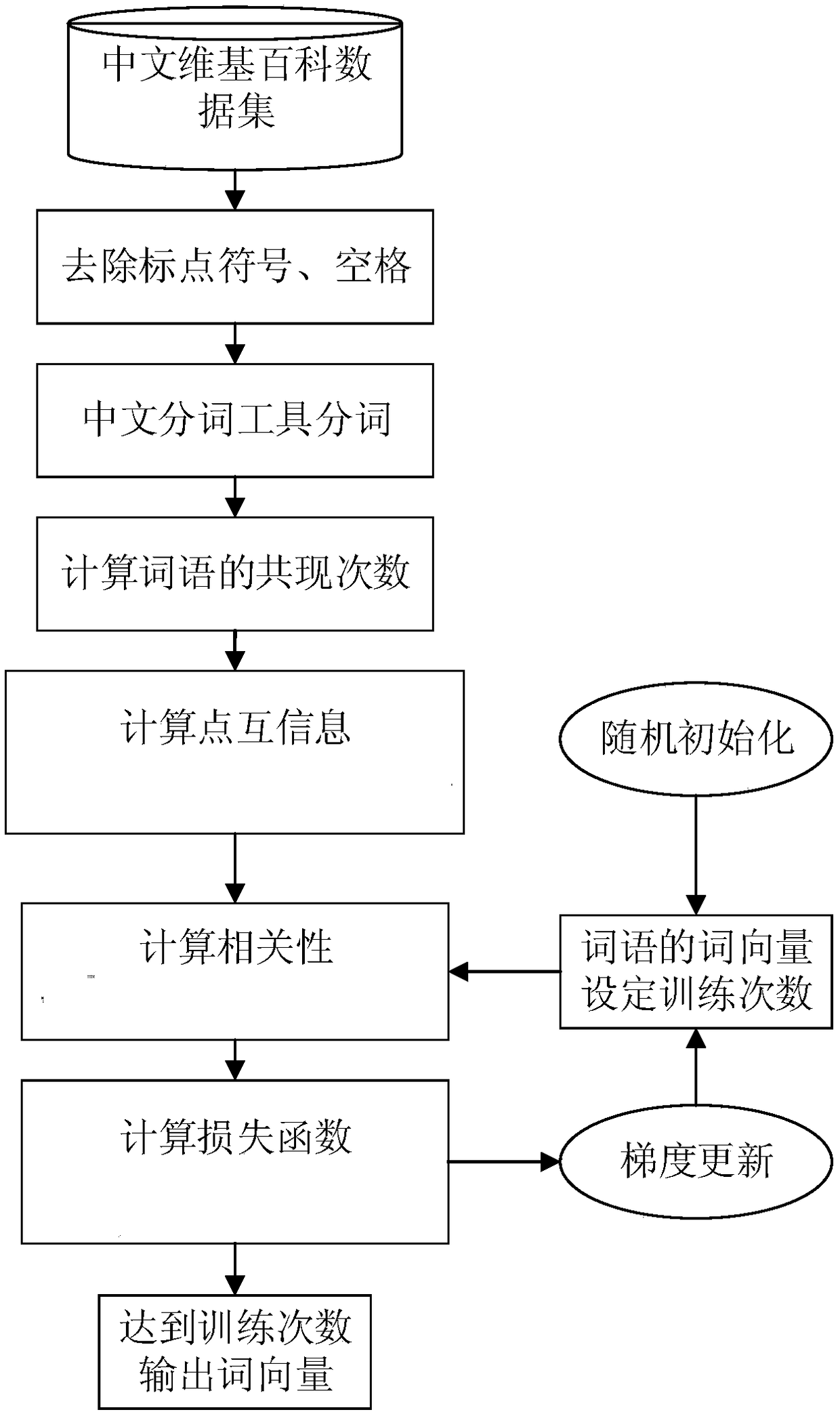
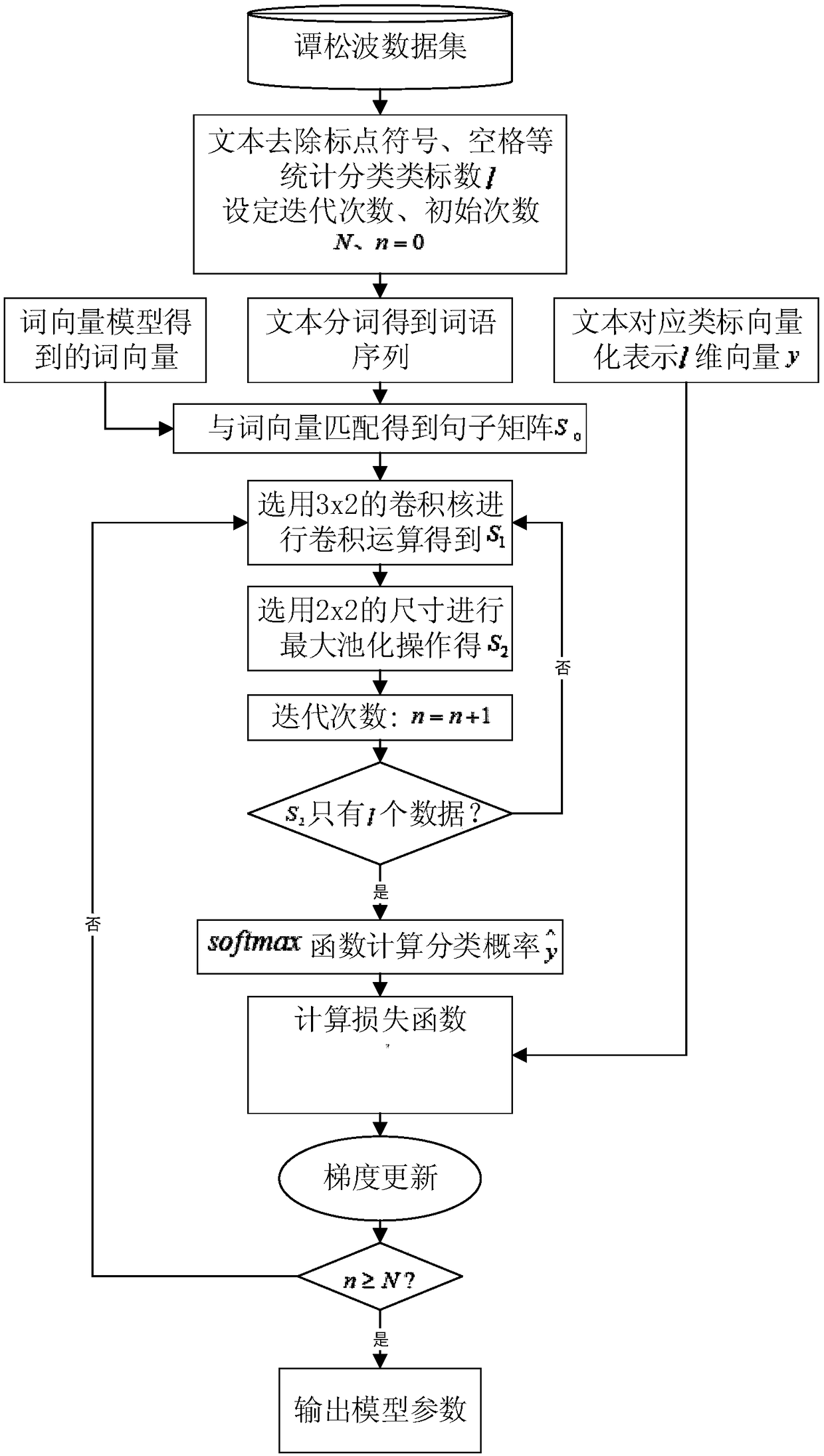
Word vector model based on point mutual information and text classification method based on CNN
ActiveCN109189925AImprove the objective functionExact objective functionCharacter and pattern recognitionNeural architecturesFeature extractionText categorization
The invention discloses a word vector model based on point mutual information and a text classification method based on CNN. The method comprises the following steps: (1) training a word vector modelthrough a global word vector method based on point mutual information; (2) determining a word vector matrix of the text according to the trained word vector model; (3) extracting features from word vector matrix by CNN and training classification model; (4) extracting input text features according to the trained word vector model and CNN feature extraction model; (5) according to the text featuresextracted from CNN feature extraction model, calculating the mapping distance between text and preset categories by softmax and the cross entropy method, wherein the nearest one is the correspondingcategory of text. This method overcomes the shortcomings of Glove word vector in the semantic capture and statistical co-occurrence matrix, reduces the training complexity of the model, can accuratelymine the text classification features, is suitable for text classification in various fields, and has great practical value.
Owner:NANJING SILICON INTELLIGENCE TECH CO LTD
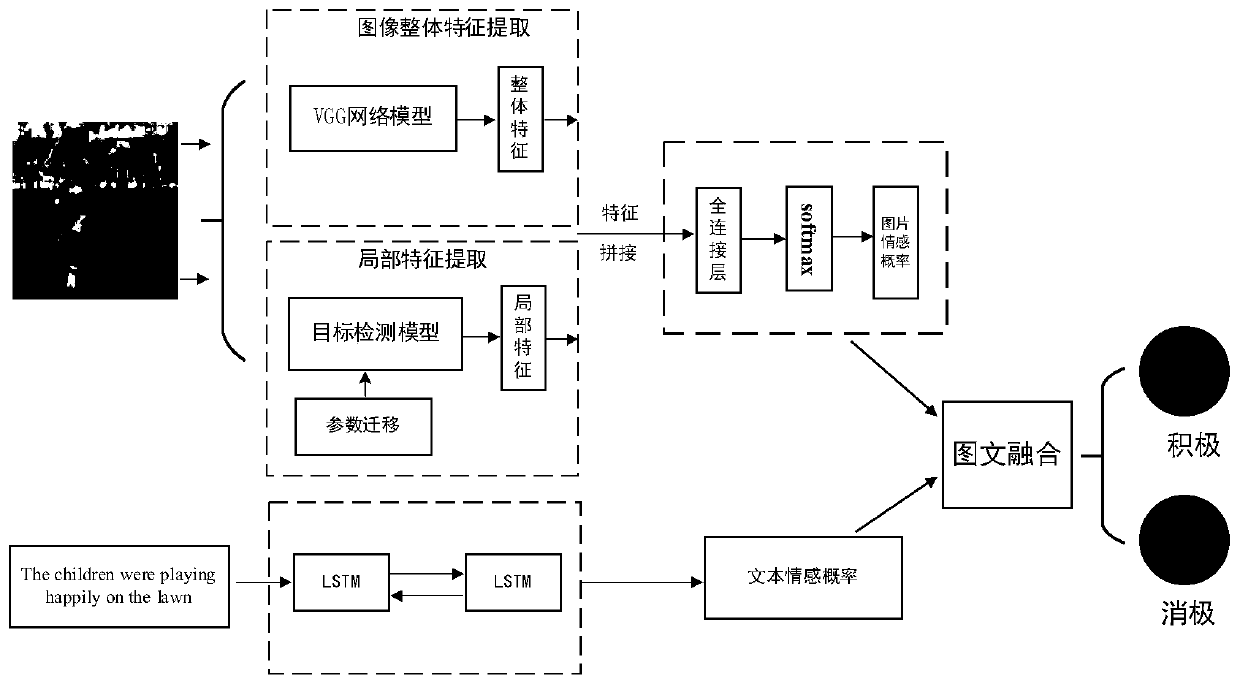
Global and local feature embedding and image-text fusion sentiment analysis method and system
ActiveCN110852368AEnhanced representationImprove accuracySemantic analysisCharacter and pattern recognitionSemantic contextConvolution
The invention discloses a global and local feature embedding and image-text fusion sentiment analysis method and system. The method comprises the following steps: firstly, extracting global features of an image by using a convolutional neural network, training a target detection model by using transfer learning, detecting and positioning a local region carrying emotion in the image, extracting local region features, and embedding the local region features into the global features to jointly train an image emotion classification model to obtain an emotion polarity probability of the image; expressing the text as a word vector containing rich semantic information, and inputting the word vector into a bidirectional LSTM capable of extracting text semantic context features to perform sentimentclassification to obtain the polarity probability of sentiment of the text; and finally, according to a later fusion formula, obtaining an emotion polarity probability after image and text fusion, and performing image-text emotion analysis. The method can effectively pay attention to the emotion information of the image-text, and improves the accuracy and robustness of image-text emotion classification through the extraction of global and local emotion features of the image and the fusion of text information.
Owner:NANJING UNIV OF POSTS & TELECOMM
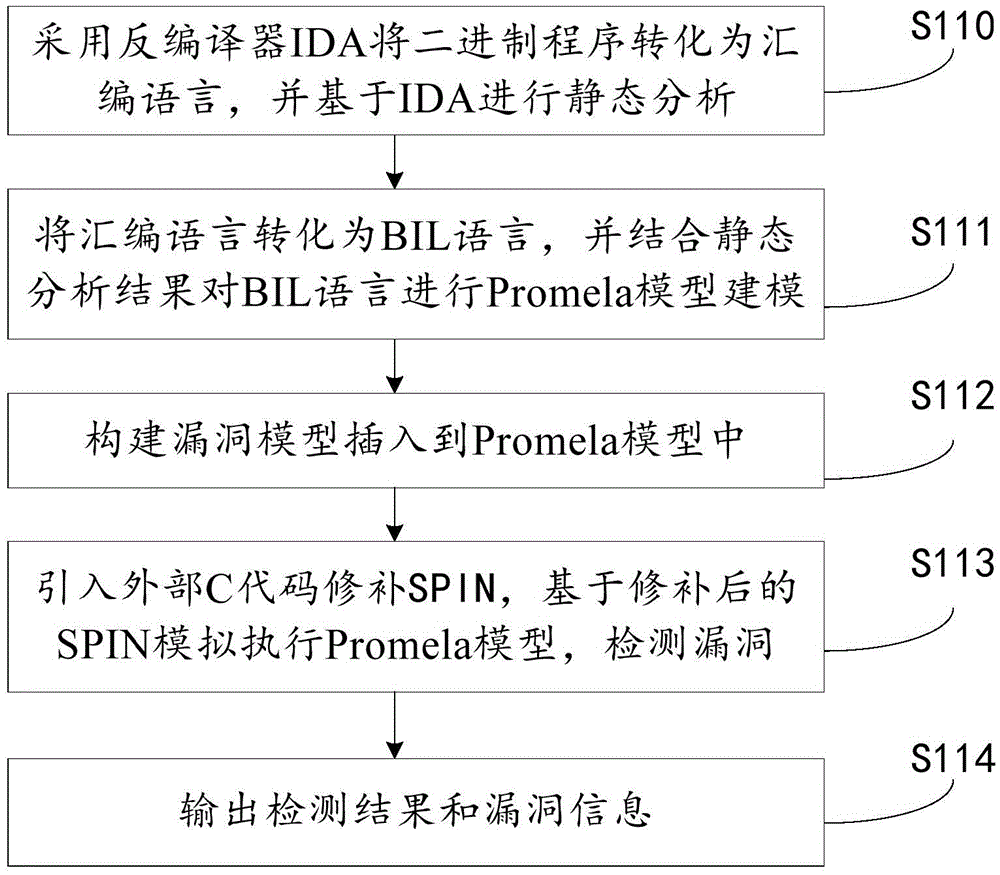
Binary program vulnerability discovery method and system
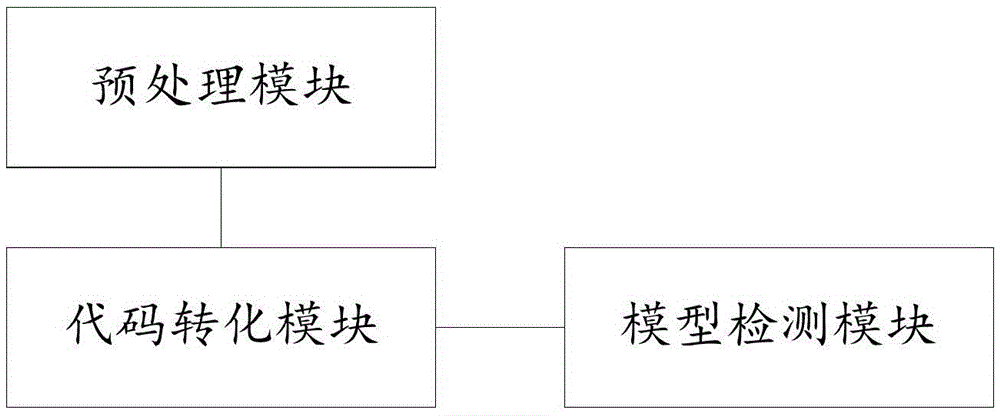
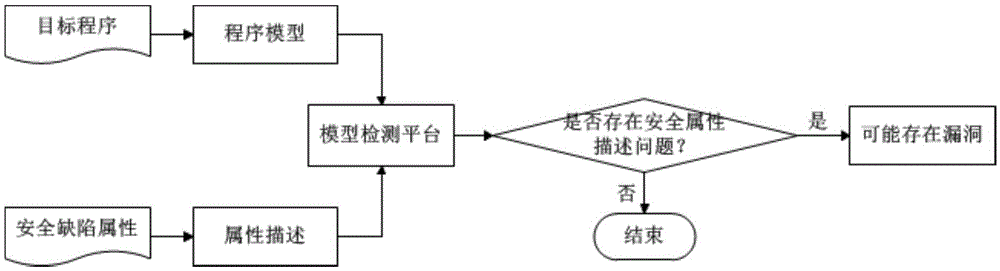
ActiveCN105678169AExcavate accuratelyAccurate locationPlatform integrity maintainanceCode conversionAssembly language
The invention provides a binary program vulnerability discovery method. The binary program vulnerability discovery method comprises steps of converting a target binary program into an assembly language, and carrying out static analysis to the assembly language; carrying out Promela model modeling to an intermediate language by combining the analysis result of the static analysis; establishing a vulnerability model and inserting the vulnerability model into the Promela model; introducing an external C code, simulating and executing the Promela model based on an SPIN, and detecting the vulnerability. The invention also provides a binary program vulnerability discovery system comprising a preprocessor module, a code conversion module and a model detection module. With respect to the binary program vulnerability discovery method and system, the intermediate language BIL is introduced to serve as a conversion bridge through which the binary program is converted into the Promela model, automatic modeling of the binary program is achieved, the embedded C function of the SPIN is employed to achieve simulation and execution, and the external C code is introduced to correct the defect of model detection. Experimental results show that the binary program vulnerability discovery method can effectively detect memory destructive vulnerabilities of binary programs.
Owner:XIAN HUMEN NETWORK TECH CO LTD
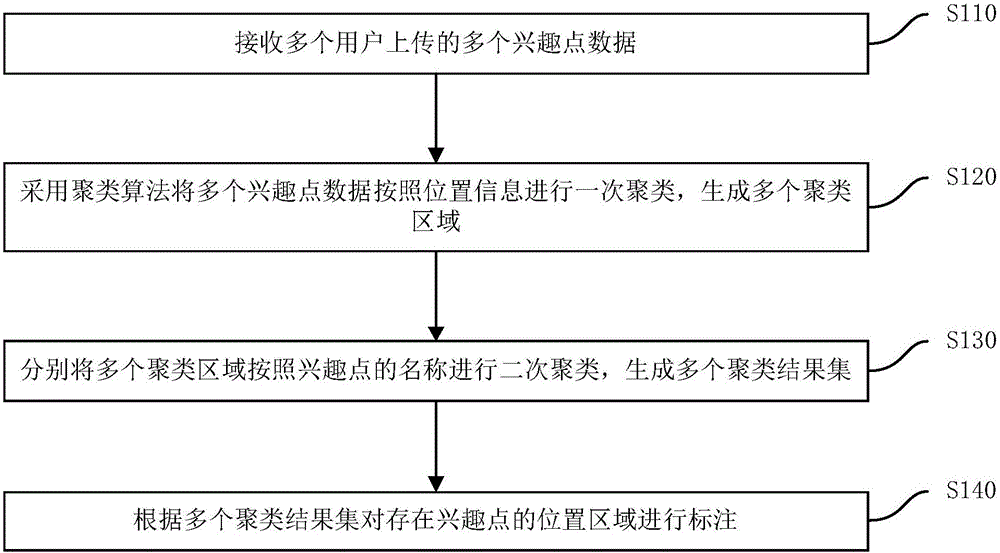
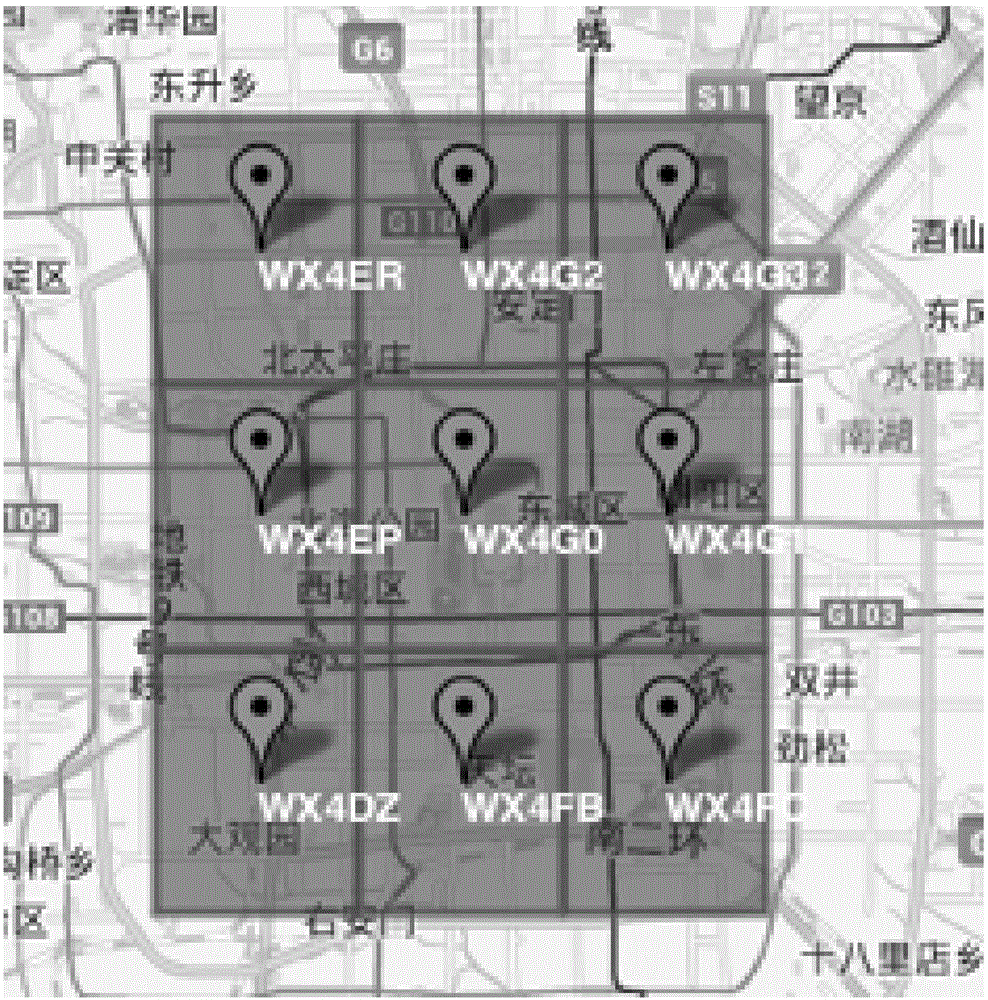
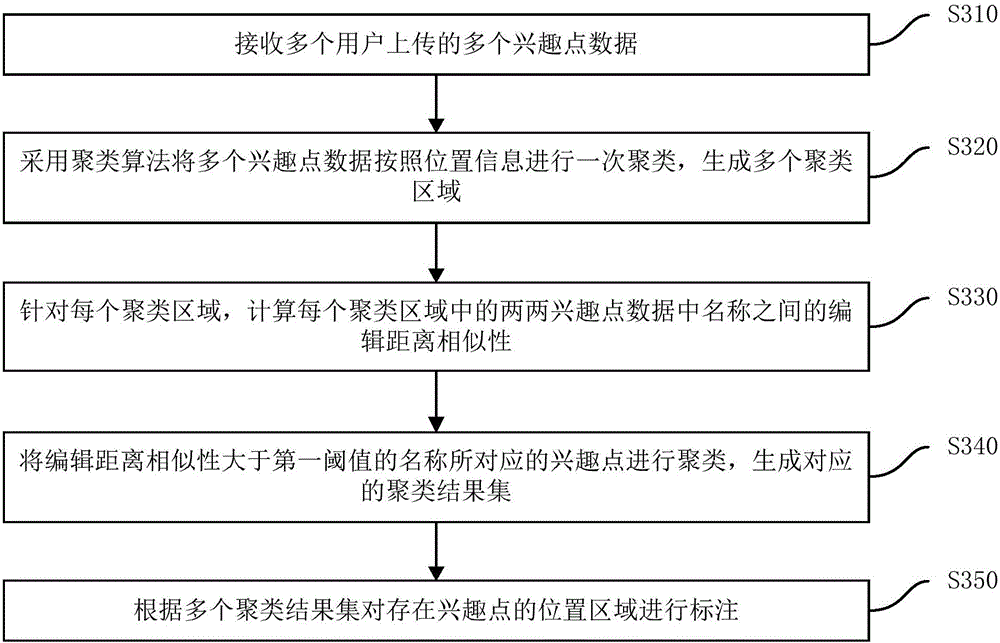
POI (Point Of Interest) labeling method and device
ActiveCN106528597AExcavate accuratelyFast updateGeographical information databasesSpecial data processing applicationsCluster algorithmMaterial resources
The invention discloses a POI (Point Of Interest) labeling method and device. The method comprises the steps of receiving multiple POI data uploaded by multiple users; carrying out primary clustering on the multiple POI data according to position information by employing a clustering algorithm to generate multiple clustering areas; carrying out secondary clustering on the multiple clustering areas respectively according to names of POIs to generate multiple clustering result sets; and labeling position areas in which the POIs exist according to the multiple clustering result sets. According to the method, by employing mass POI position and attribute information uploaded by the users, the POIs are dug out quickly and accurately, so the cost of manpower and material resources is saved, the POI update speed is improved, and the POI labeling efficiency is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
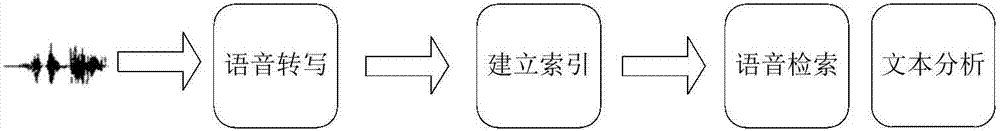
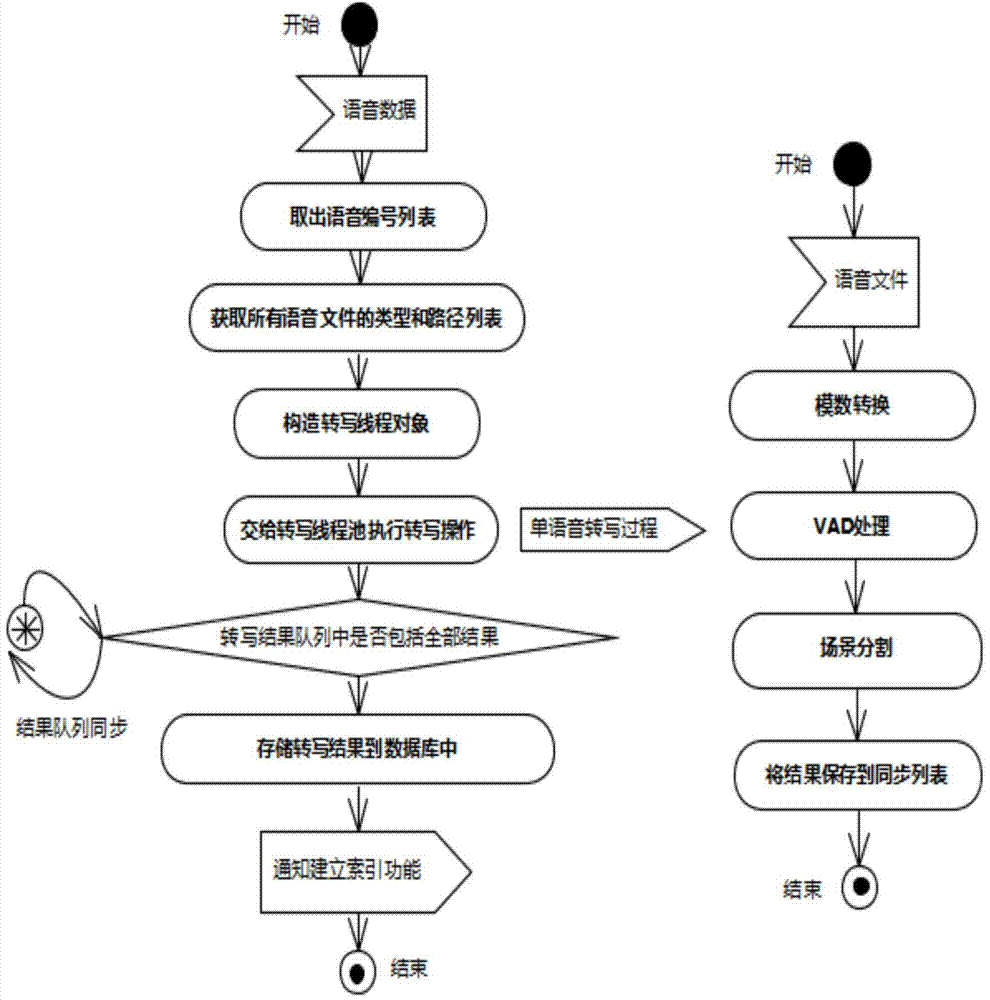
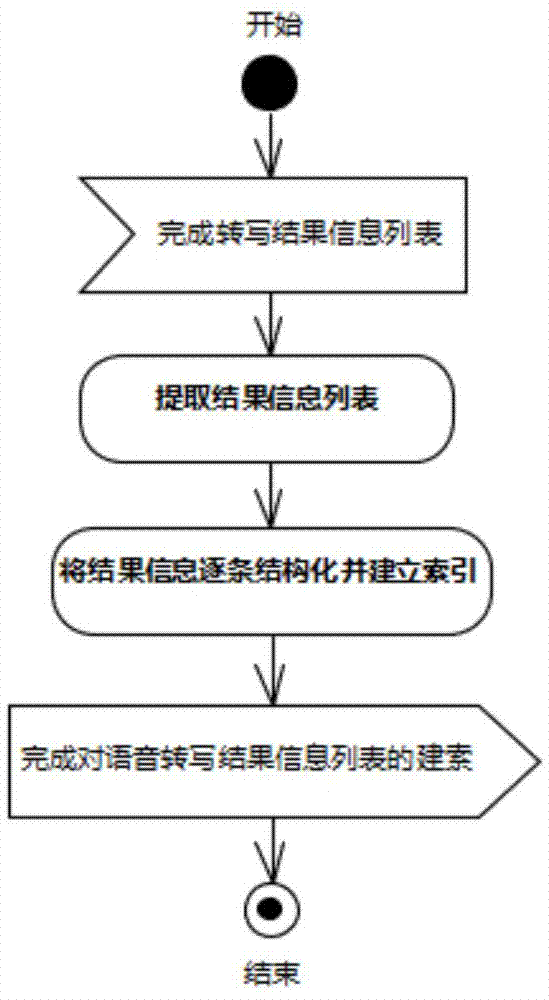
Service voice intelligent search and analysis system and method
InactiveCN103793515AImprove accuracyExcavate accuratelySpecial data processing applicationsMarket data gatheringKnowledge explorationTest analysis
A voice search and analysis system comprises a voice transcription module, an index establishing module, a voice search module and a test analysis module. Keywords contained in voice, positions where the keywords appear and other characteristic information are searched for. Analysis can be effectively performed on massive voice recording files and audio files through voice analysis, knowledge exploration in the voice and rapid search on the voice files are achieved, and the problems that voice data are difficult to search for and analyze are solved.
Owner:IFLYTEK CO LTD
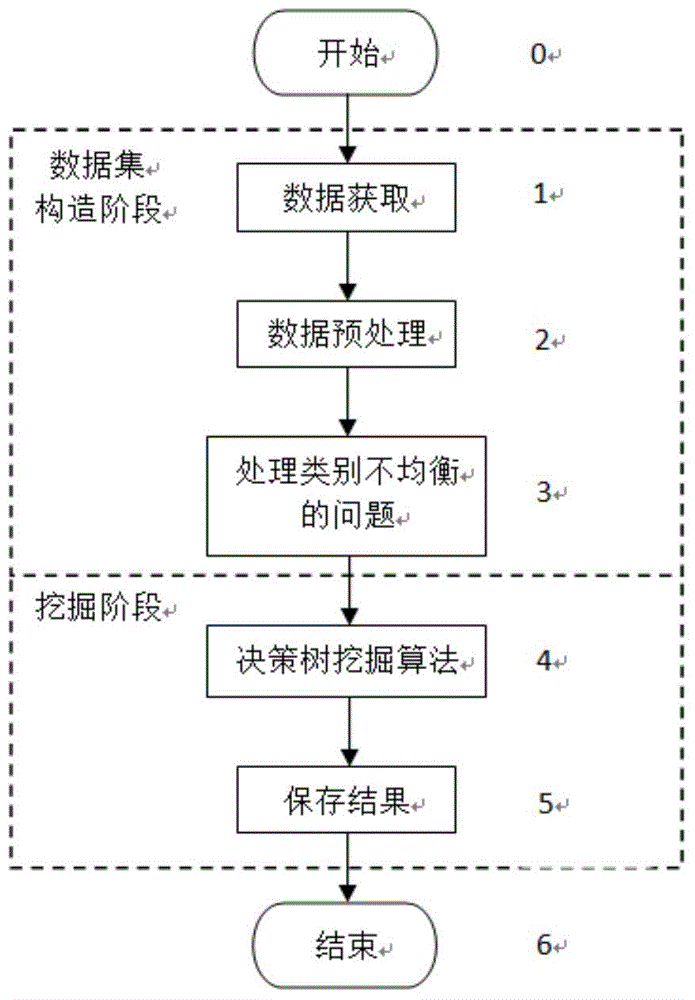
Data mining method for finding potential telecommunication users changing cell phones
ActiveCN104794195ABalanced uniformityEfficient miningSpecial data processing applicationsData dredgingData set
The invention provides a data mining method for finding potential telecommunication users changing cell phones. The data mining method comprises the following step of 1 the data set constructing stage and 2 the mining stage. The data set constructing stage comprises sub-steps of a, collecting consumption information of the users, historical information that the users change the cell phones, user information and terminal information; b, preprocessing data and generating data sets at the same time; c, processing the data sets in unbalanced categories and forming final training sets and prediction sets. The mining stage comprises the sub-steps of a, acquiring the data sets processed and generated in the step 1-c; b, finding the potential users changing the cell phones by implementing the decision tree algorithm; c, ending the stage. The potential users changing the cell phones are found in the telecommunication users based on the data mining technology. Compared with a traditional method, the data mining method is more accurate and efficient, and has the series of advantages of being easy to achieve, low in cost and the like.
Owner:NANJING UNIV
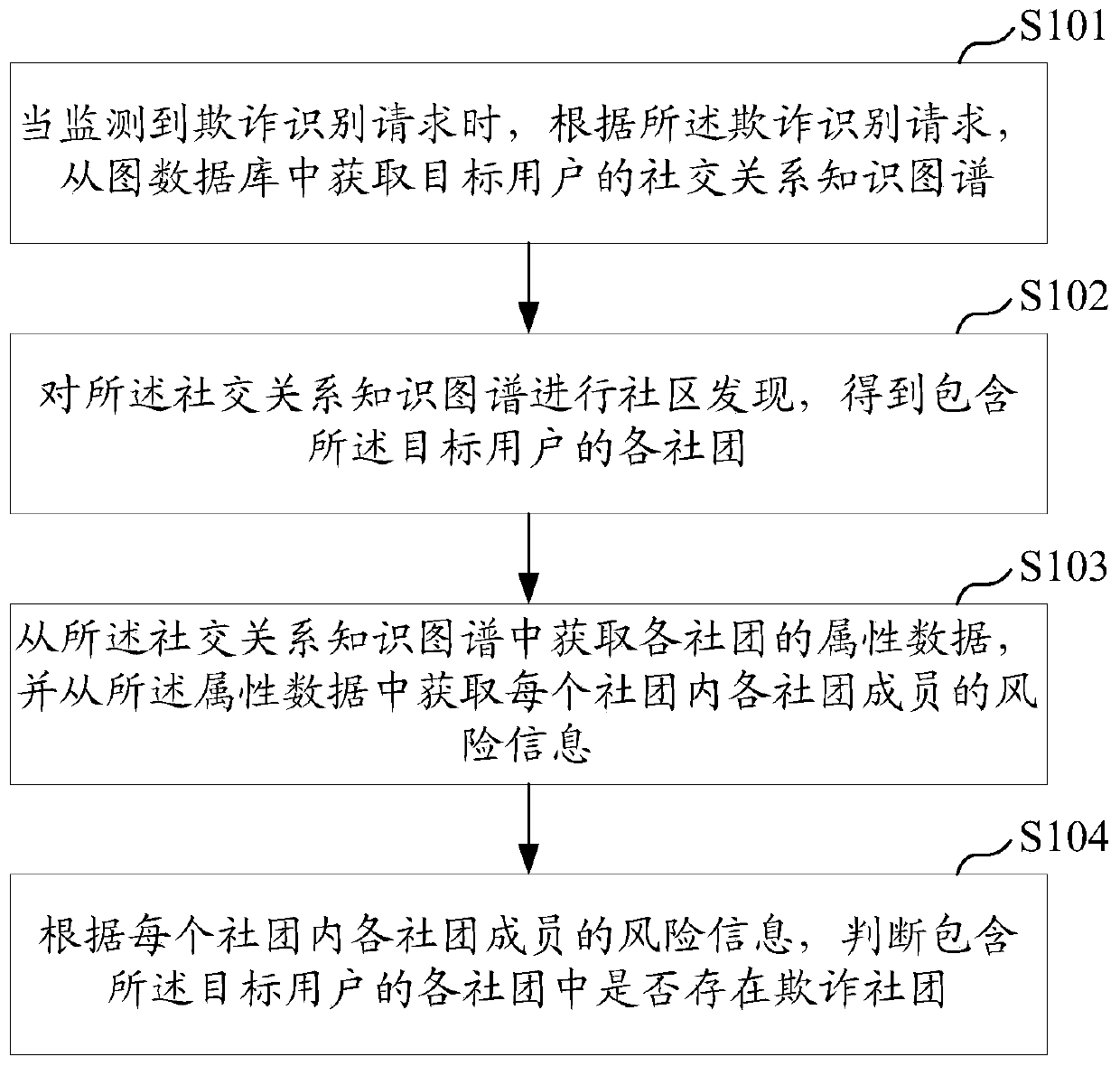
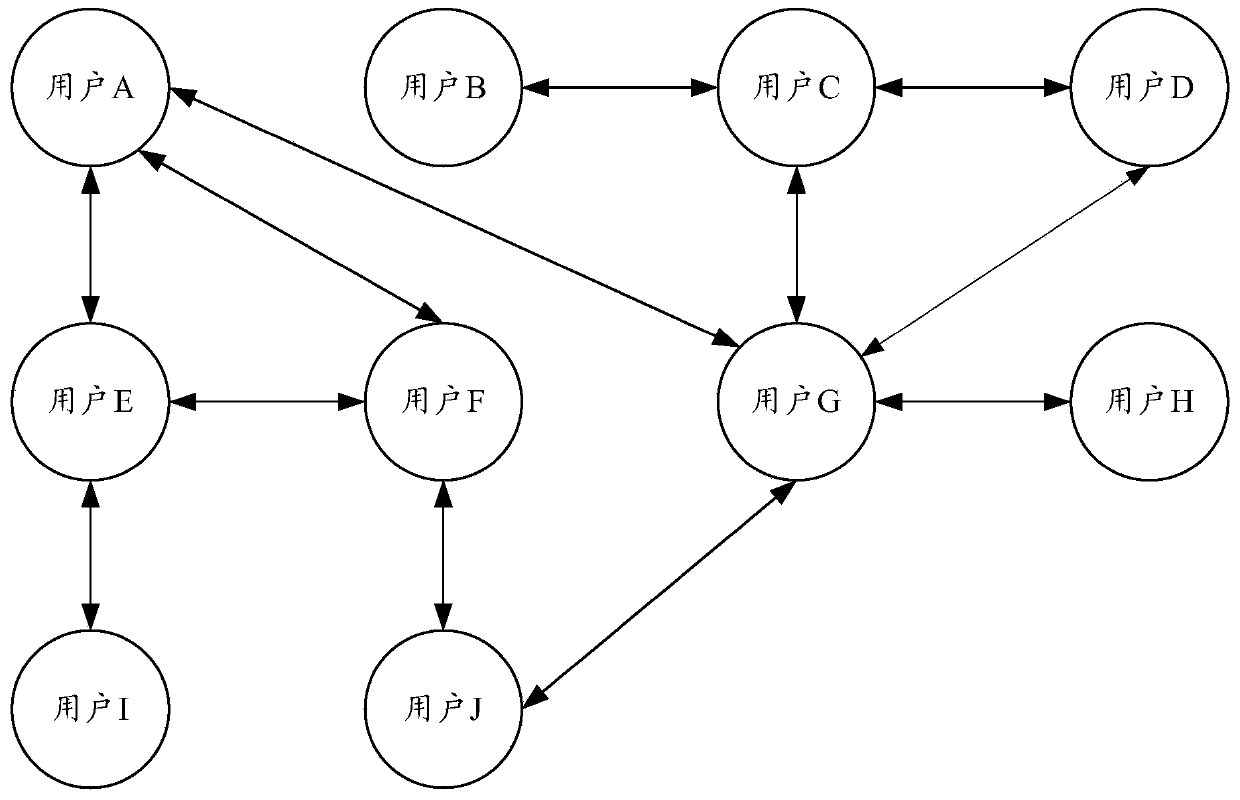
Fraud identification method and device, equipment and computer readable storage medium
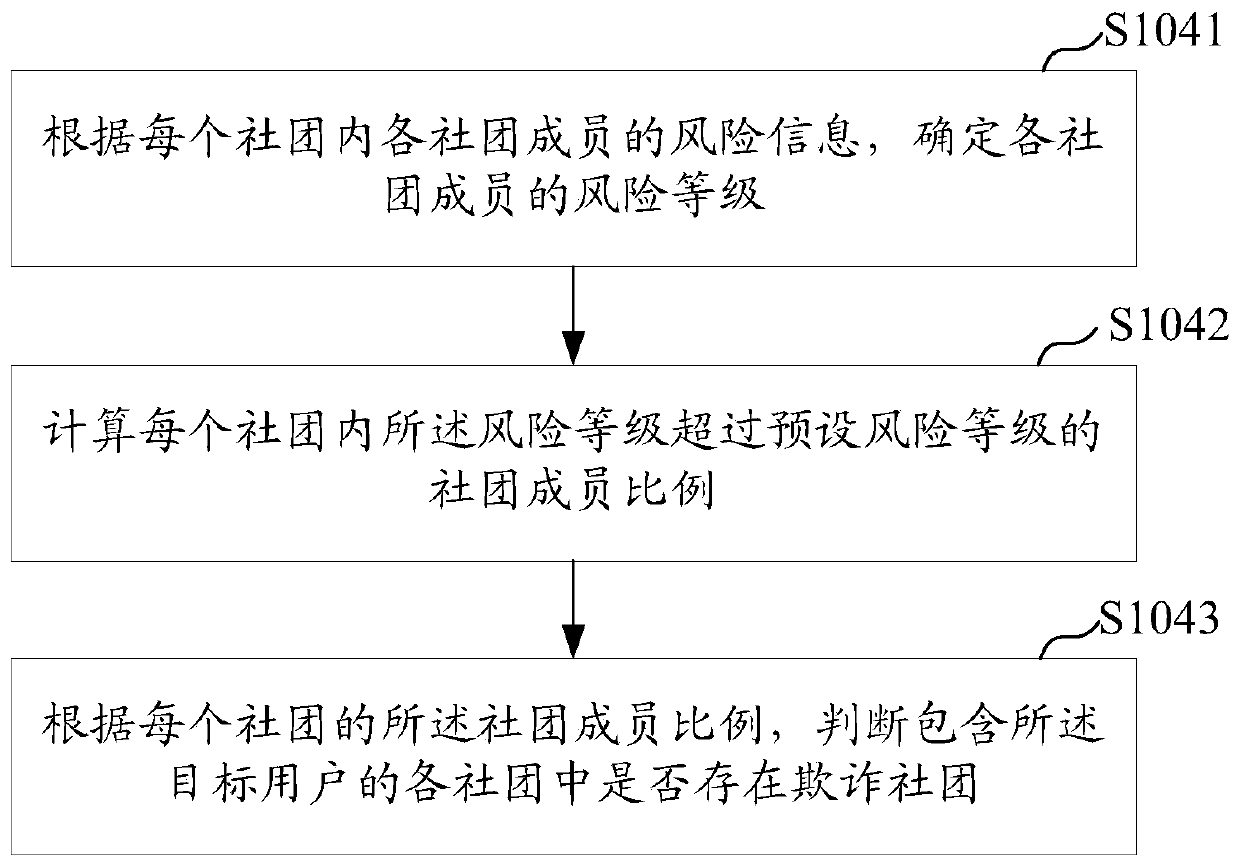
PendingCN110297912AImprove retrieval efficiencyImprove processing efficiencyFinanceSpecial data processing applicationsKnowledge graphData mining
The invention provides a fraud identification method and device, equipment and a computer readable storage medium. The fraud identification method comprises the steps: obtaining a social relation knowledge graph of a target user from a graph database according to a fraud identification request when the fraud identification request is monitored; performing community discovery on the social relationknowledge graph to obtain each community containing the target user; obtaining attribute data of each community from the social relation knowledge graph, and obtaining risk information of each community member in each community from the attribute data; and according to the risk information of each community member in each community, judging whether a fraudulent community exists in each communitycontaining the target user or not. According to the fraud identification method, the fraud community can be quickly and accurately mined through the knowledge graph, and the financial fraud recognition efficiency and accuracy are greatly improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
A specific target emotion analysis method based on a multi-channel model
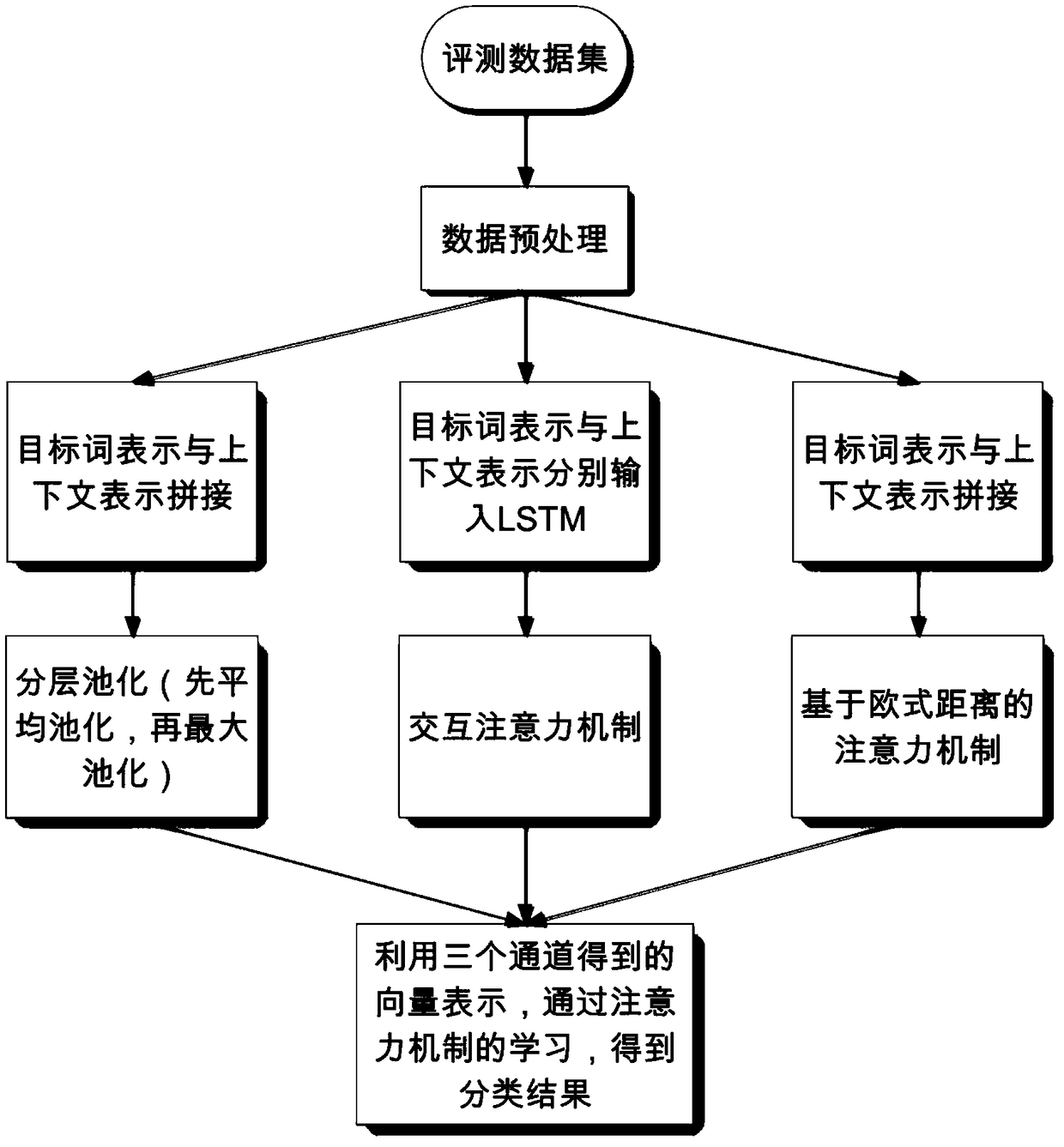
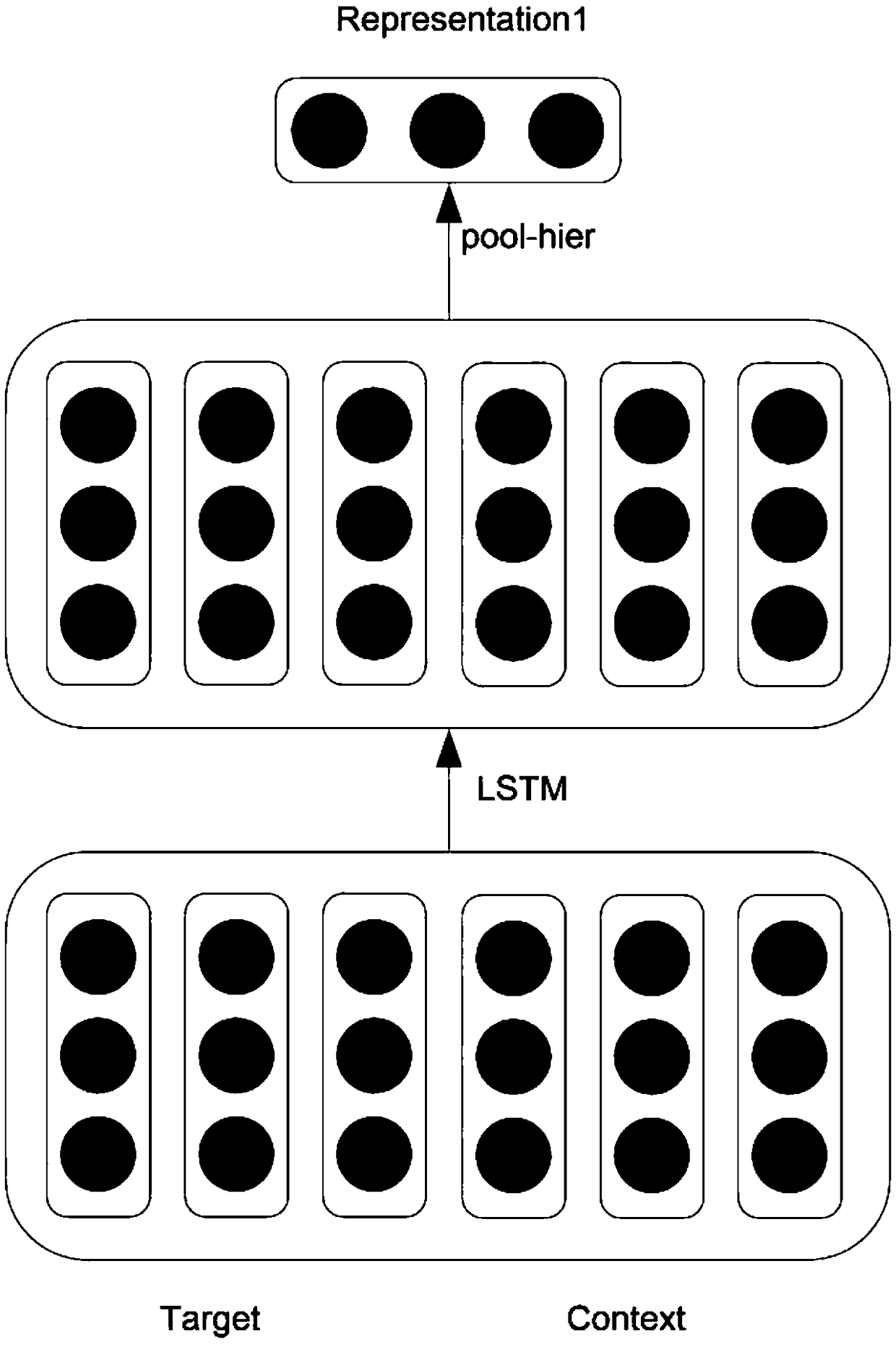
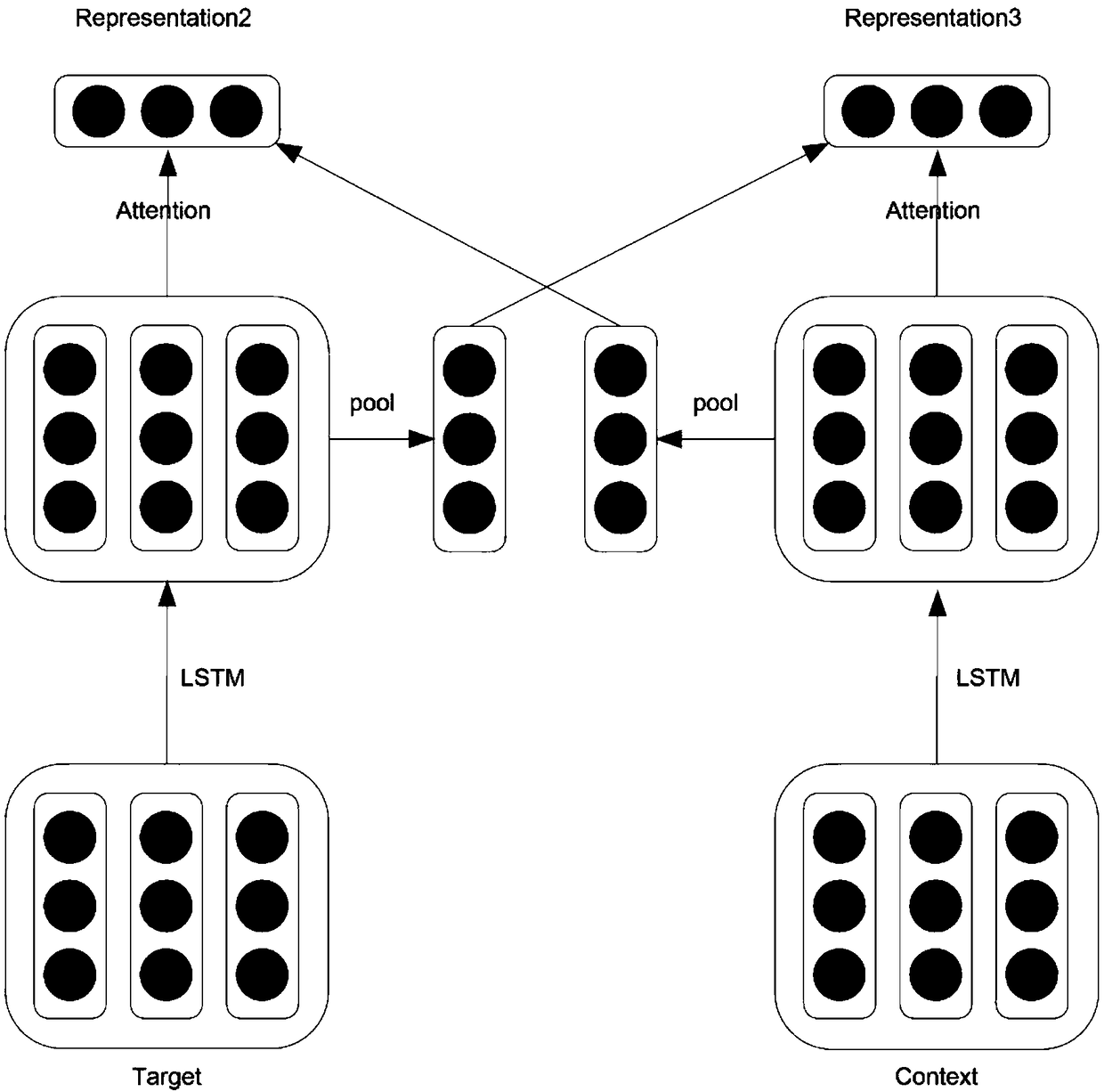
ActiveCN109408823AUnderstand opinionHigh practical valueMarket predictionsSemantic analysisData setFeature extraction
The invention discloses a specific target emotion analysis method based on a multi-channel model. According to the specific target emotion analysis method, target words and contexts are fully utilized, the method is provided with three channels, and expression of the target words and the contexts is obtained through a hierarchical pooling mechanism, an interaction attention mechanism and an attention mechanism based on the Euclidean distance. Through the three channels, the target words and the context can learn the expression helpful for sentiment classification; the technical scheme is as follows: (1) inputting a SemEval2014 data set, preprocessing the data set and dividing the data set into a training set and a test set; (2) inputting the preprocessed data into three channels respectively, and performing feature extraction to obtain vectors r1, r2, r3, r4 and r5; (3) obtaining a classification result through learning of an attention mechanism by utilizing vectors r1, r2, r3, r4 andr5; (4) carrying out sentiment classification on a specific target of each comment text in the test set by using the trained model, and comparing the sentiment classification with a label of the testset to calculate the classification accuracy; the invention belongs to the fields of natural language processing technology and sentiment calculation.
Owner:南京智慧橙网络科技有限公司
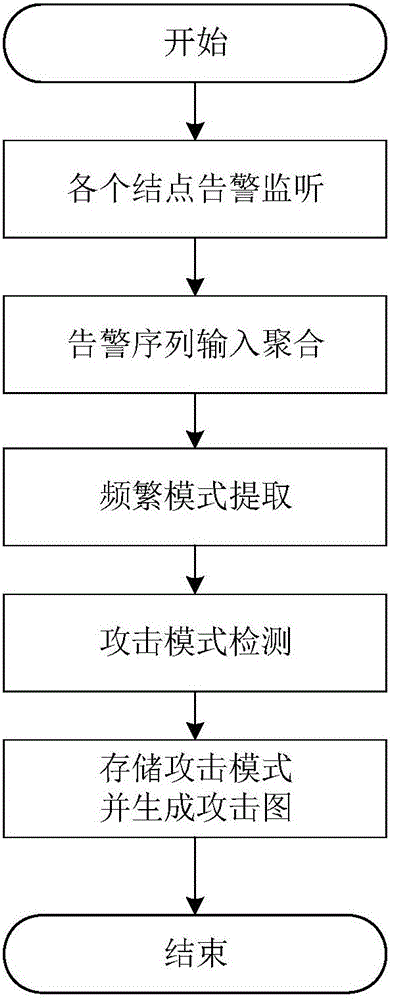
Attack mode detection method based on event slide window
ActiveCN106375339AGood lifting effectExcavate accuratelyPlatform integrity maintainanceTransmissionSlide windowSequence pattern
The invention relates to an attack mode detection method based on an event slide window. The method comprises the steps of S1, normalizing, integrating, compressing and preprocessing warning information, and aggregating the warning information with approximate attribute similarity into super warning; S2, carrying out protocol on frequent items, thereby obtaining frequent correlation sequence patterns according to a causal correlation matrix; S3, for the new frequent correlation sequence patterns at each time and warning pairs of the frequent correlation sequence patterns with different attributes, carrying out weight average on the participating attributes; and S4, generating an attack pattern graph consistent with invasion characteristics. According to the method, attack patterns existing in warning logs can be mined efficiently and accurately, new invasion access behaviors can be identified or intercepted rapidly, and the accuracy and speed of mining the attack patterns in the massive and seemingly meaningless warning logs can be greatly improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
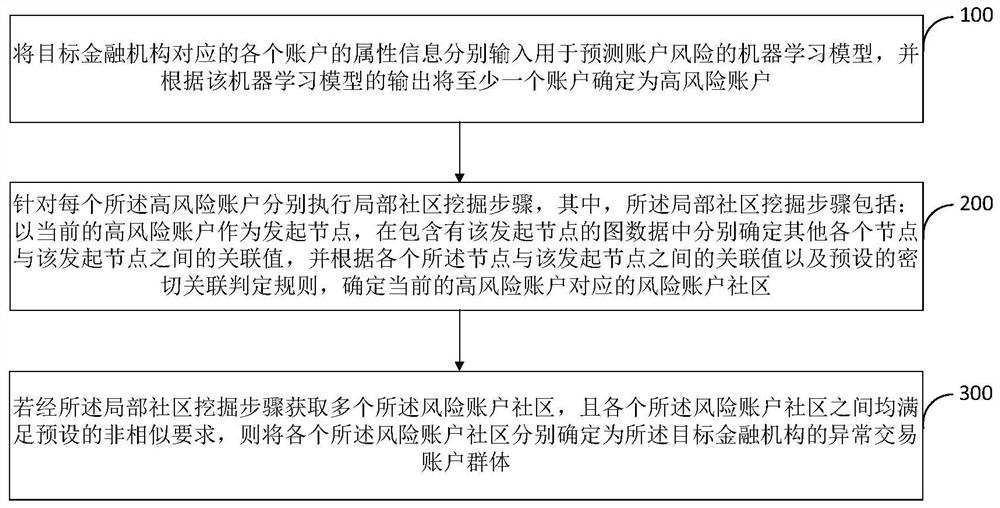
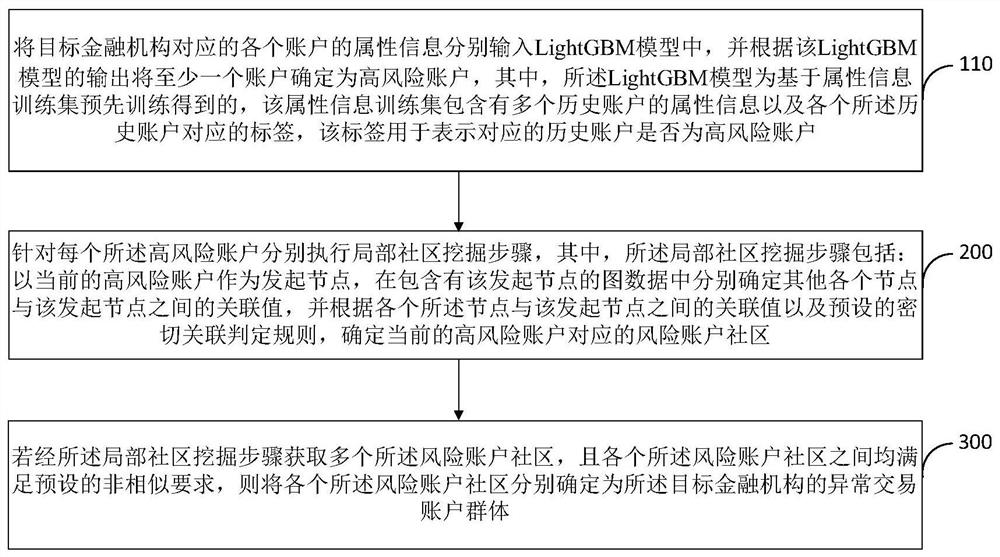
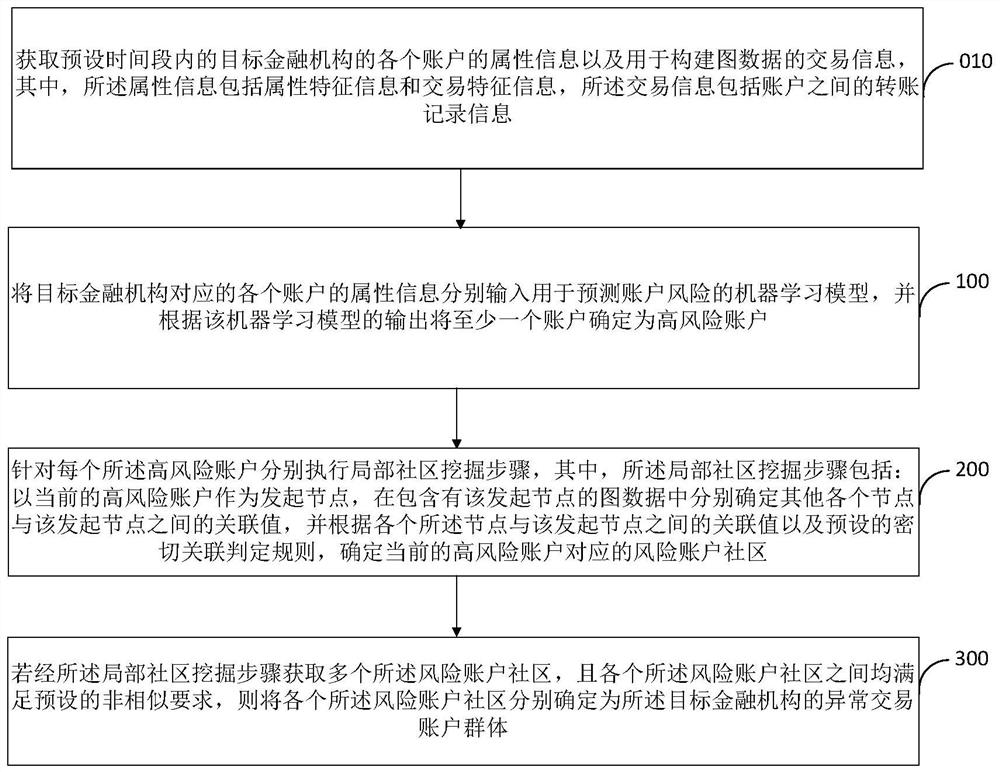
Abnormal transaction account group identification method and device
PendingCN111784502AImprove efficiencyImprove effectivenessFinanceEnsemble learningFinancial transactionData mining
The embodiment of the invention provides an abnormal transaction account group identification method and device. The method comprises the steps of respectively inputting the attribute information of each account into a machine learning model for predicting an account risk, and determining at least one account as a high-risk account; respectively executing a local community mining step for each high-risk account: taking the current high-risk account as an initiating node, respectively determining association values between other nodes and the initiating node in the graph data, and determining arisk account community corresponding to the high-risk account; and if a plurality of risk account communities are obtained and the risk account communities meet a preset non-similar requirement, determining each risk account community as an abnormal transaction account group of the target financial institution. According to the invention, the efficiency, reliability and accuracy of abnormal transaction account group identification can be effectively improved, and the operation safety and reliability of a financial institution obtaining an abnormal transaction account group through identification can be further improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
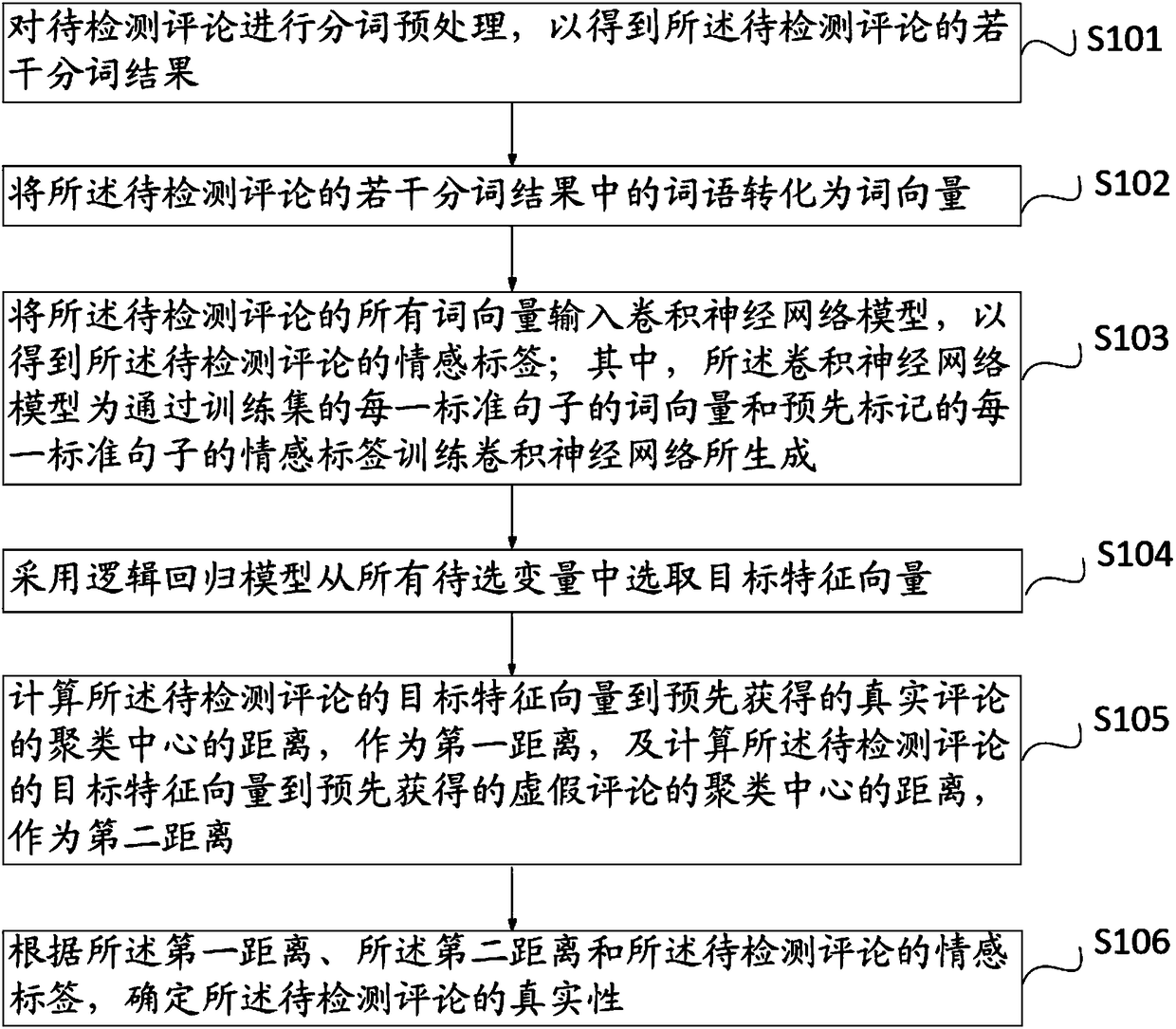
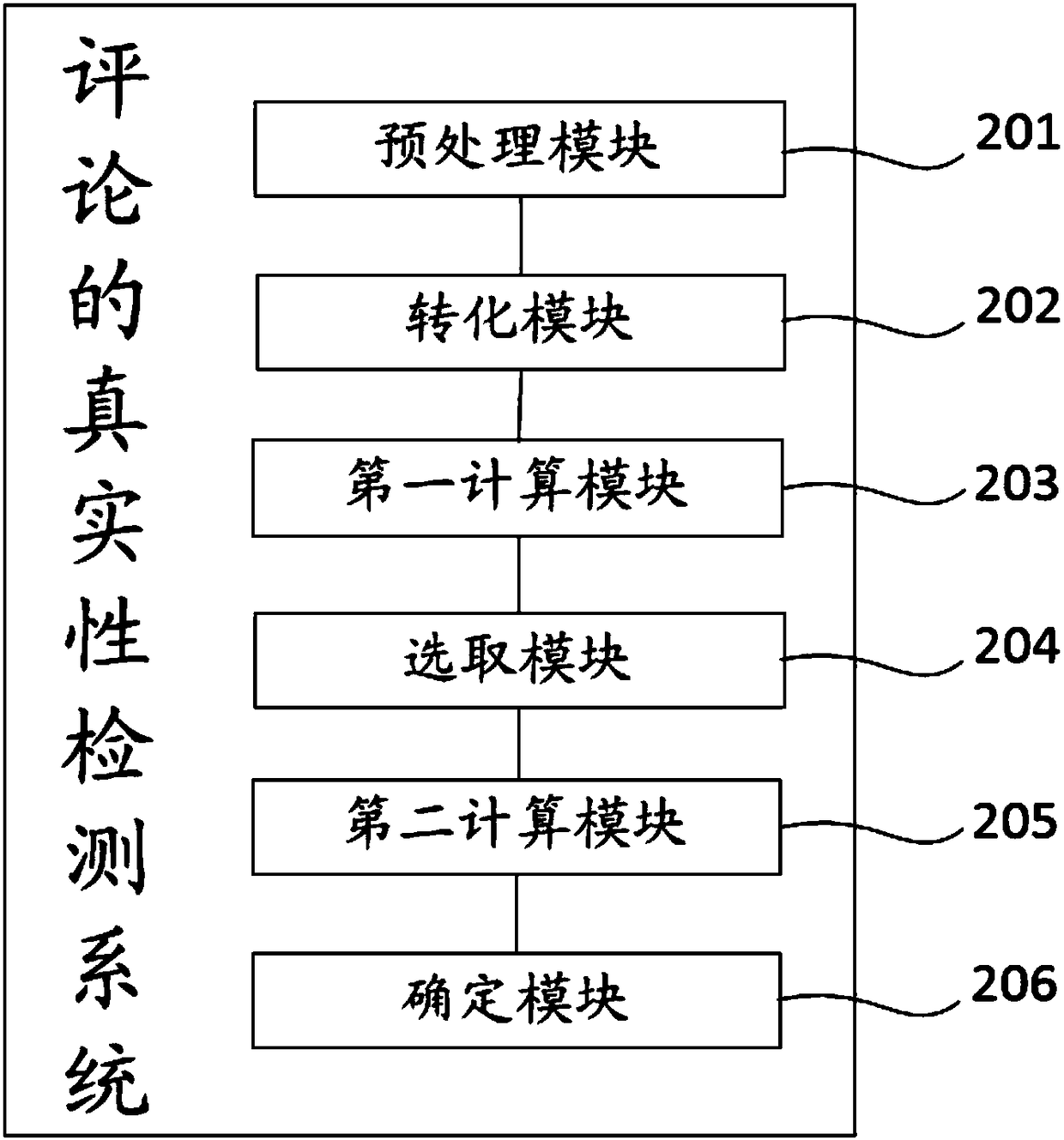
Comment authenticity detection method and system
ActiveCN108345587AExcavate accuratelyImprove accuracySemantic analysisSpecial data processing applicationsConvolutionConvolutional neural network
The invention discloses a comment authenticity detection method. The method comprises the steps of performing word segmentation preprocessing on a to-be-detected comment to obtain multiple word segmentation results; converting words in the word segmentation results into word vectors; calculating a sentiment label of the to-be-detected comment through a pre-built convolutional neural network model,wherein the convolutional neural network model is generated by training a convolutional neural network through word vectors and sentiment labels of standard sentences of a training set; selecting a target eigenvector from all to-be-selected variables by adopting a logic regression model; calculating a distance between the target eigenvector of the to-be-detected comment and a clustering center ofa real comment, and calculating a distance between the target eigenvector of the to-be-detected comment and a clustering center of a false comment; and according to the distances and the sentiment label of the to-be-detected comment, determining the authenticity of the to-be-detected comment. The accuracy of detecting the authenticity of the comment can be improved. Meanwhile, the invention furthermore provides a comment authenticity detection system.
Owner:GUANGZHOU UNIVERSITY +1
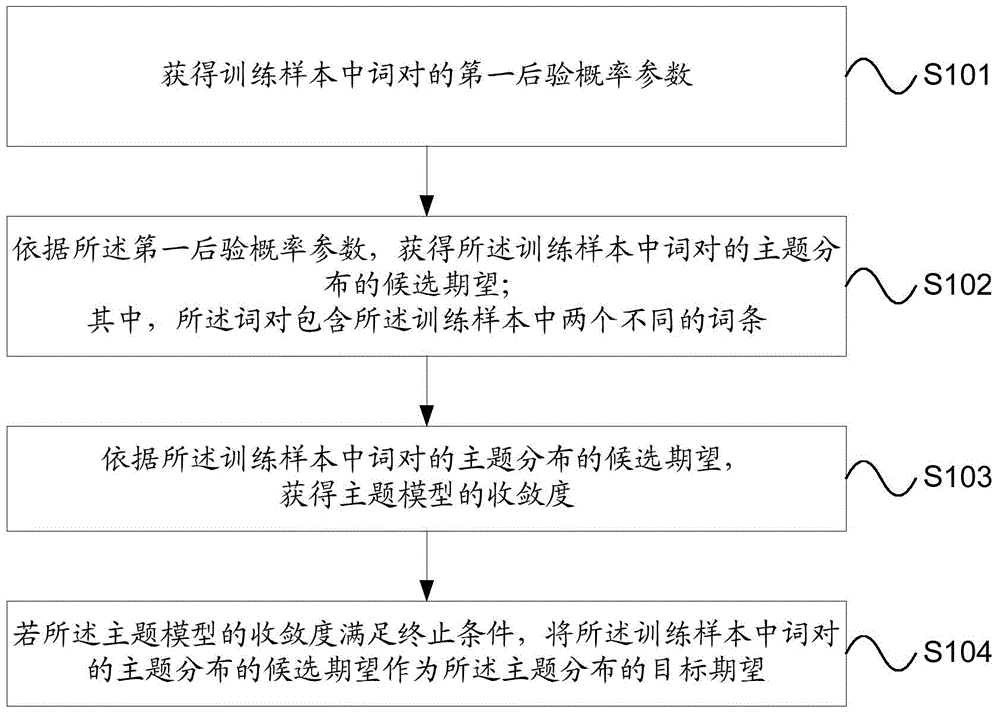
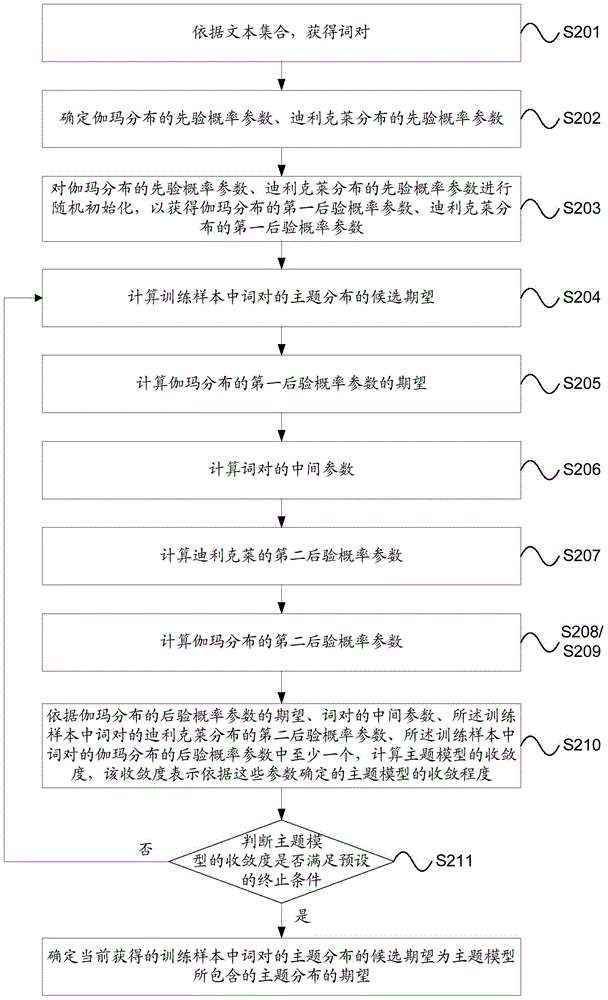
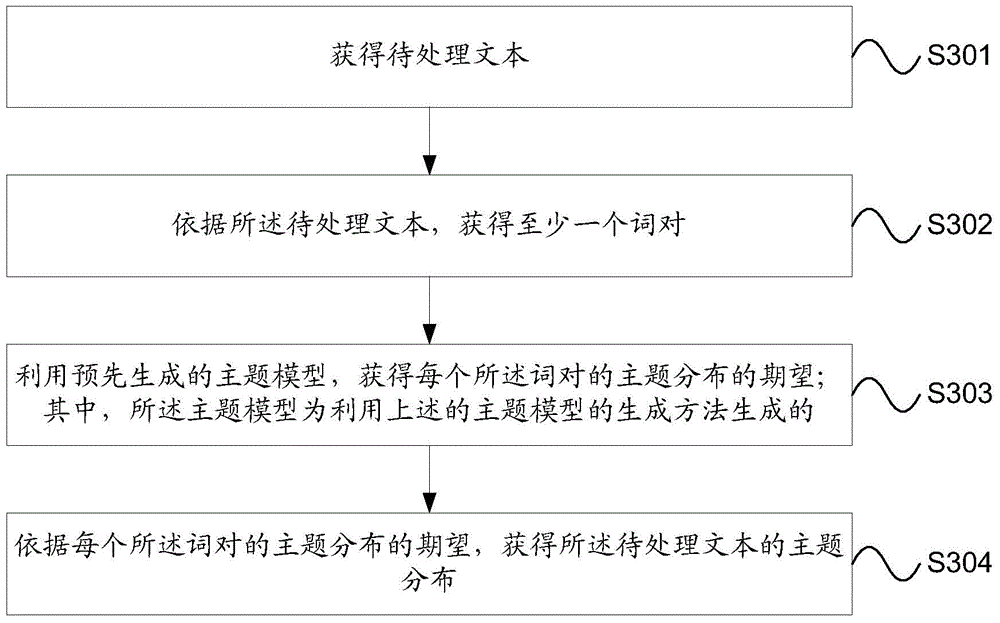
Generation method and device of topic model and acquisition method and device of topic distribution
ActiveCN104536979ASteady DiggingExcavate accuratelyDatabase distribution/replicationSpecial data processing applicationsAlgorithmProbit
The invention provides a generation method and a generation device of a topic model and an acquisition method and an acquisition device of topic distribution. On the one hand, a first posterior probability parameter of word pairs in a training sample is obtained, and therefore a candidate expectation of the topic distribution of the word pairs in the training sample is obtained according to the first posterior probability parameter, and on the other hand, a convergence degree of the topic model is obtained according to the candidate expectation of the topic distribution of the word pairs in the training sample, and then if the convergence degree of the topic model meets a terminal condition, the candidate expectation of the topic distribution of the word pairs in the training sample is used as a target expectation of the topic distribution. Each word pair comprises two different word entries in the training sample. Accordingly, the generation method and the generation device of the topic model and the acquisition method and the acquisition device of the topic distribution are used to solve the problems that a method of using a traditional topic model to obtain topic distribution of a text is low in accuracy and stability in the prior art.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Information mining method and device
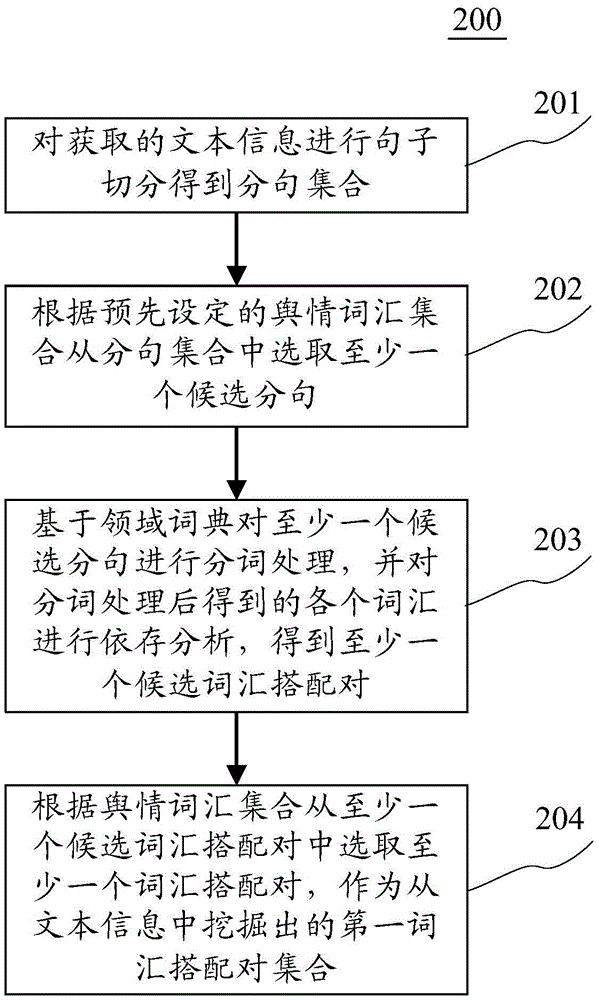
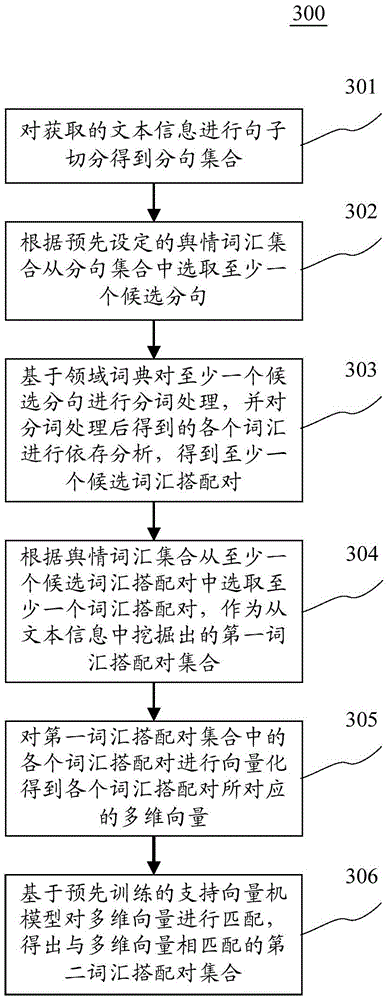
ActiveCN105574092AQuick digExcavate accuratelyNatural language data processingSpecial data processing applicationsCollocationSentence segmentation
The invention discloses an information mining method and device. A specific implementation way of the method comprises the following steps: carrying out sentence segmentation on obtained text information to obtain a sub-sentence set; selecting at least one candidate sub-sentence from the sub-sentence set according to the preset public opinion word set; carrying out word segmentation on the at least one candidate sub-sentence on the basis of a domain dictionary, carrying out dependency parsing on various words obtained after word segmentation to obtain at least one candidate word collocation pair; selecting at least one word collocation pair from the at least one candidate word collocation pair as a first word collocation pair set mined from the text information according to the public opinion word set. The implementation way achieves rapid and accurate information mining.
Owner:SHANGHAI YOUYANG XINMEI INFORMATION TECH CO LTD
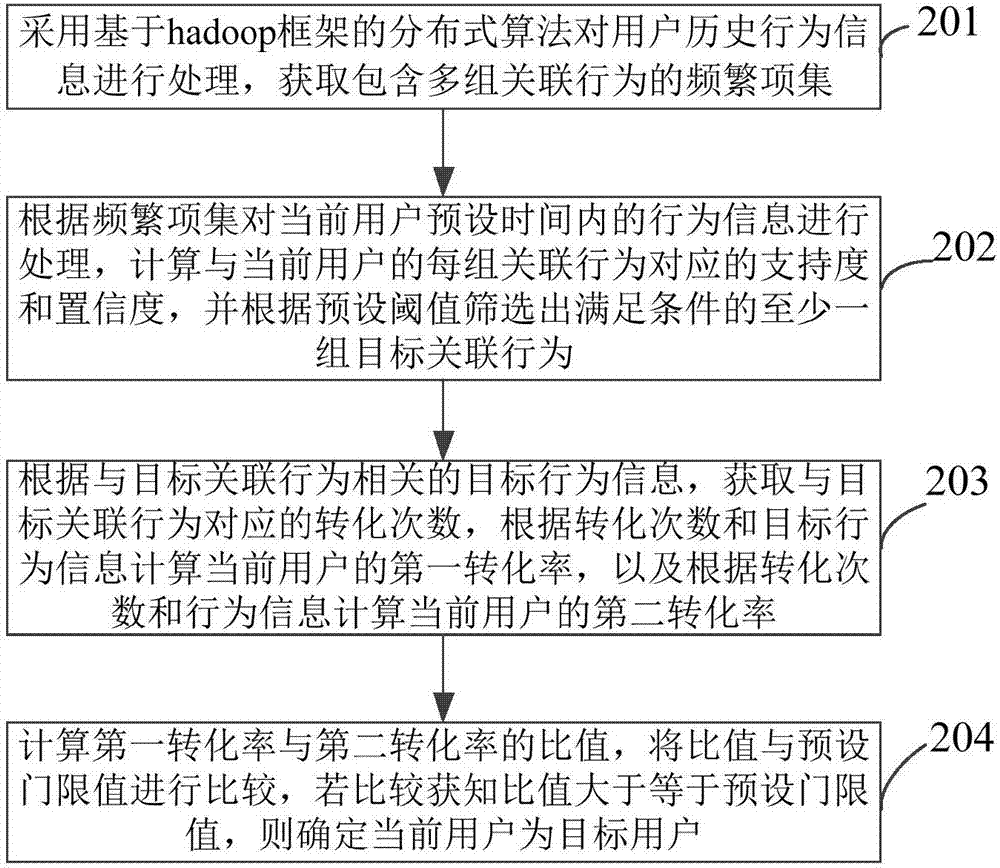
User mining method, apparatus and device
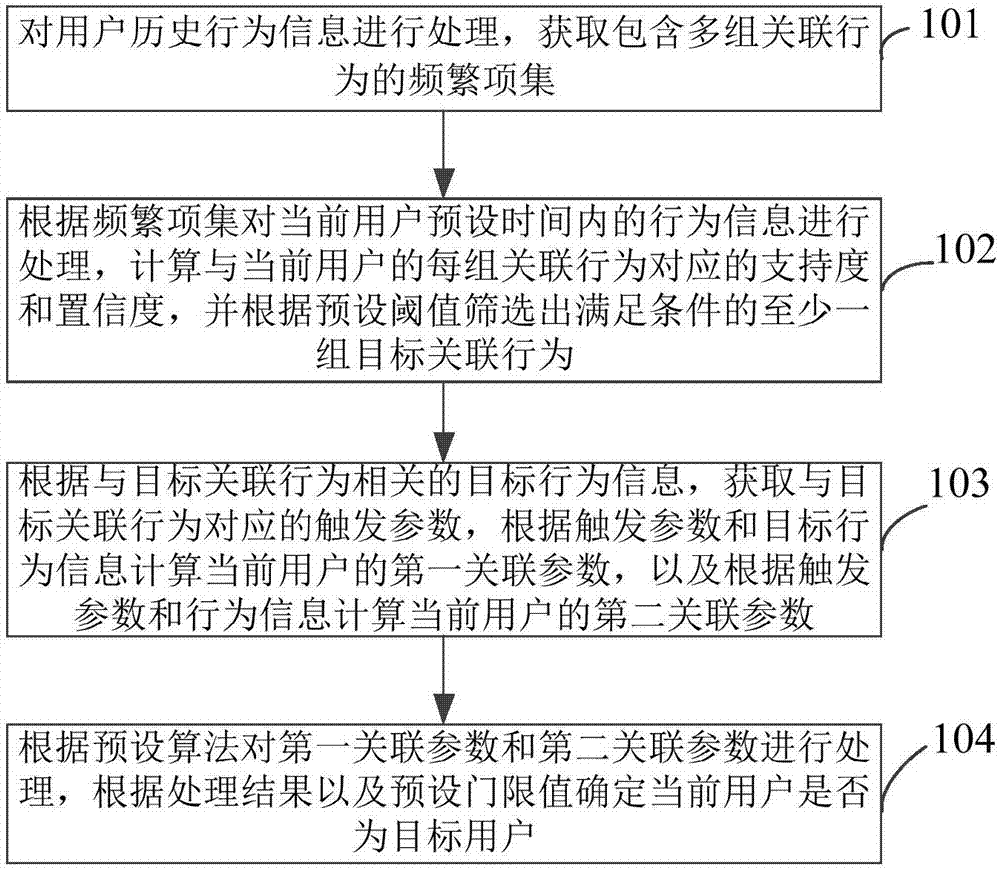
InactiveCN107392645AImprove the search experienceExcavate accuratelyMarket data gatheringProcess behaviorData mining
The invention provides a user mining method, apparatus and device. The method comprises the steps of processing historical behavior information of a user to obtain a frequent item set containing multiple groups of associated behaviors; processing behavior information in a preset time of the current user according to the frequent item set, calculating a support degree and a confidence degree corresponding to each group of the associated behaviors of the current user, and screening out at least one group of target associated behaviors meeting a condition according to a preset threshold; calculating first associated parameters and second associated parameters of the current user according to target behavior information related to the target associated behaviors and triggering parameters corresponding to the target behavior information; and processing the first associated parameters and the second associated parameters according to a preset algorithm to obtain a processing result, and determining whether the current user is a target user or not according to the processing result and a preset threshold. The target user can be accurately mined, and future possible behaviors of the user can be accurately predicted, so that commodities liked by the user are recommended, the search experience of the user is improved, and the conversion rate of a merchant is increased.
Owner:绿湾网络科技有限公司
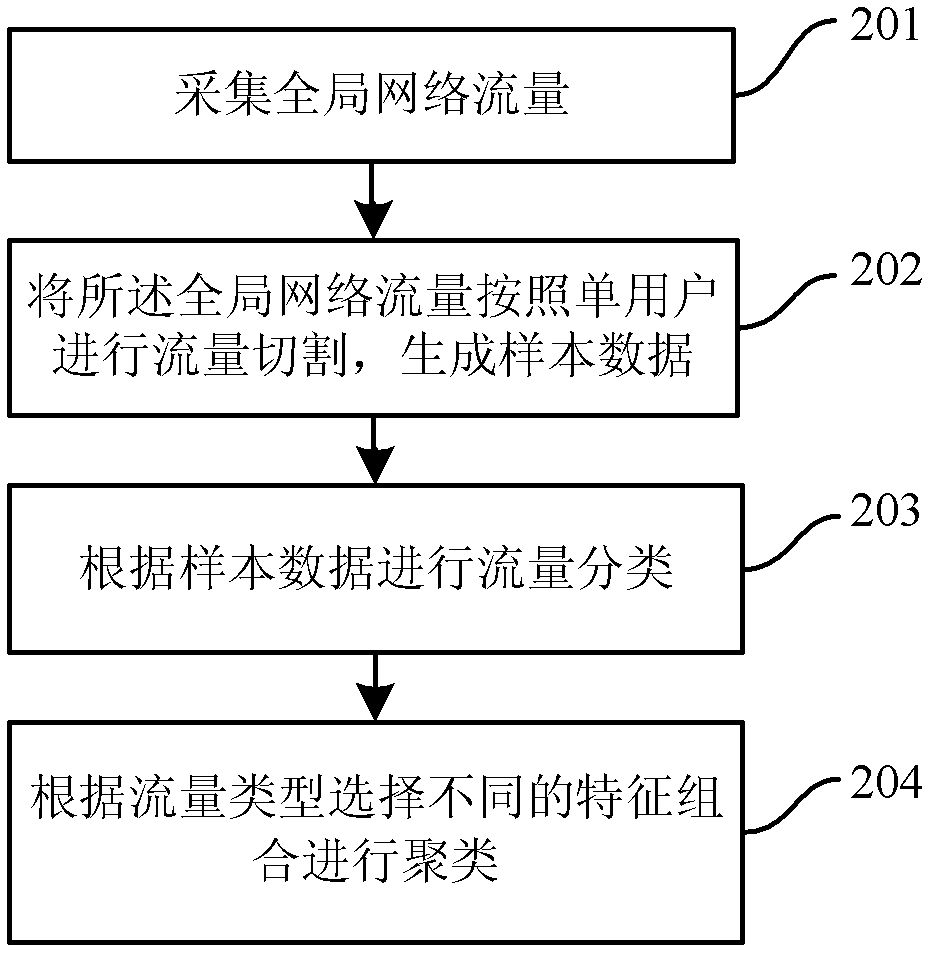
Method and device for network traffic clustering
ActiveCN102299863AImprove clustering accuracyImprove efficiencyData switching networksDistributed computingGenerating unit
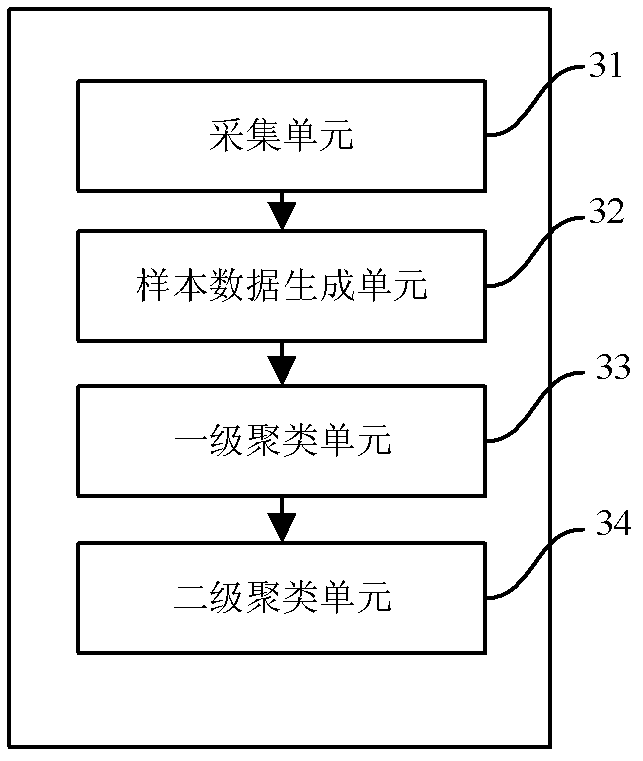
The invention discloses a method and equipment for clustering network flow. The method comprises the following steps of: acquiring global network flow; cutting the global network flow according to a single user to generate sample data; classifying network flow types of the flow according to the sample data; and selecting different characteristic combinations for clustering according to the flow types. The equipment comprises an acquiring unit, a sample data generating unit, a primary clustering unit and a secondary clustering unit. The method for clustering network flow has the advantages of high accuracy, high efficiency, wide flow identification range and capability of accurately mining application quantity in the network flow, and can be realized as network flow control equipment.
Owner:BEIJINGNETENTSEC
Excavating method of topic actions of man-machine interaction for video analysis
ActiveCN104700086AReliable captureExcavate accuratelyCharacter and pattern recognitionImaging processingBag-of-words model
The invention relates to an excavating method of topic actions of man-machine interaction for video analysis, and belongs to the field of an image processing technology. The method comprises the steps of extracting space-time interest points in a video, clustering characteristic descriptors by adopting a K-mean value method by virtue of an HOG (Histogram of Oriented Gradients) and an OFH (Optical Flow Histogram) to further form a bag of words model. A final characteristic matrix is obtained by using a vectoring method, the number of special topic actions can be obtained by a non-negative matrix factorization method with a bound term, and the topic actions are drawn on a whole time axis of a video sequence with different colors. Compared with general non-negative matrix factorization, the partition of the topic actions is more accurate by increasing an edge weight matrix, the bound term and the like. According to the method, based on the non-negative matrix factorization, a user can dig the information of topic actions in the video according to a subjective intention by deleting, adding and fusing algorithms, therefore the subjectivity and accuracy of the topic actions in the video analysis can be ensured.
Owner:TSINGHUA UNIV
A supply chain demand prediction method based on big data
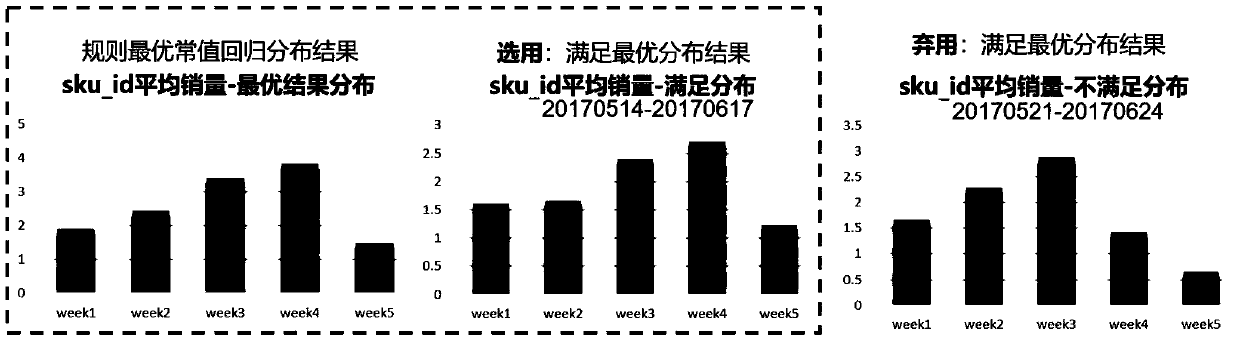
The invention belongs to the field of big data prediction, and particularly provides a supply chain demand prediction method based on big data. The method comprises the following steps of: fusing a rule model and an algorithm model, Different data partitions and feature projects are constructed by using historical sales data of commodities; and two algorithms of a tree model and a linear model areadopted to construct a model for prediction, so that the difference of the model is ensured, and finally, the rule model and the algorithm model with relatively high difference degree and accurate prediction effect are fused based on a tree structure to obtain a final future sales volume prediction result. According to the method, long-term commodity sales can be accurately predicted, a data basis is provided for the supply chain, and key technical support is provided for establishing a global supply chain scheme for an enterprise.
Owner:博拉网络股份有限公司
Hot content mining method and apparatus, computer device and storage medium
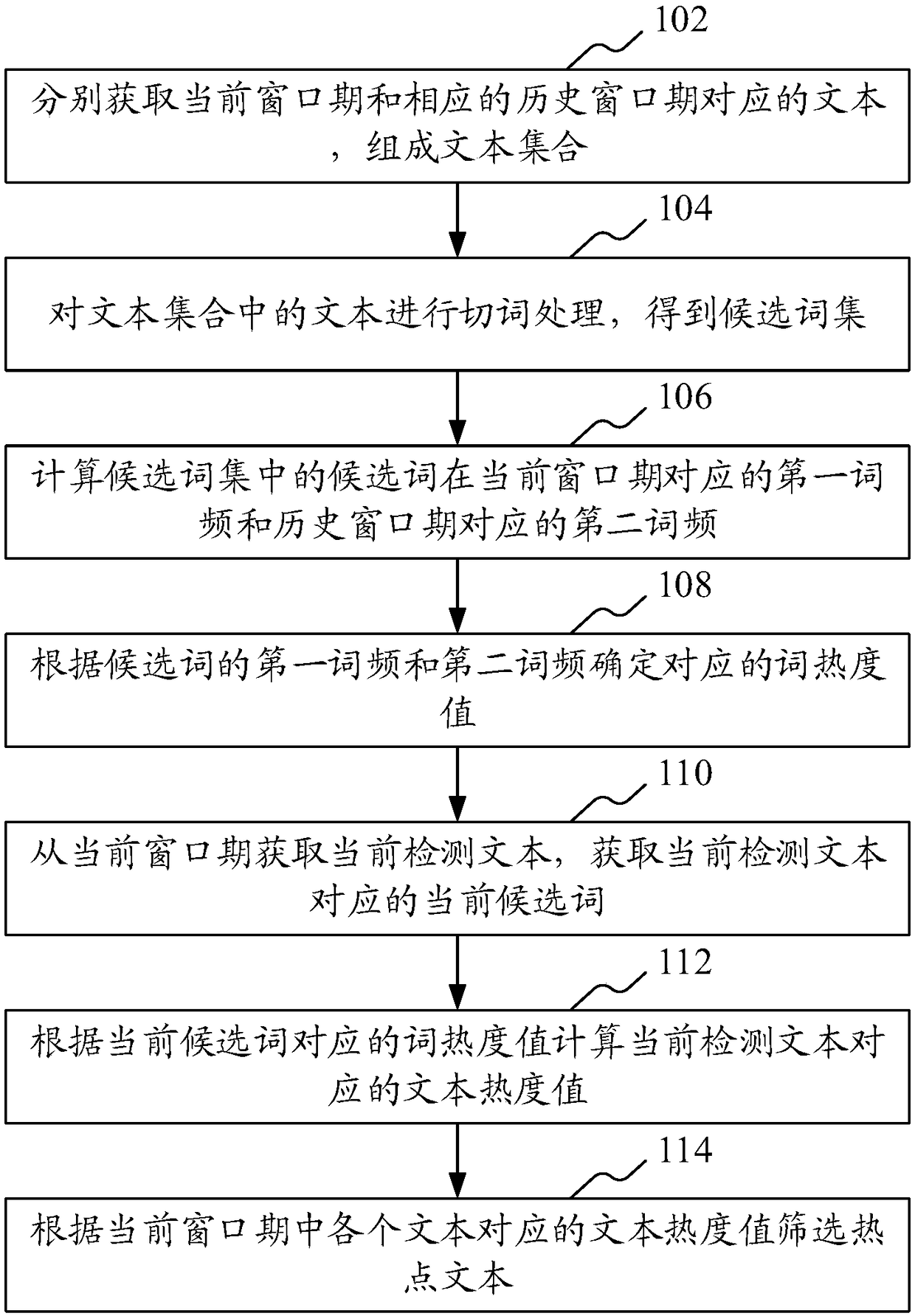
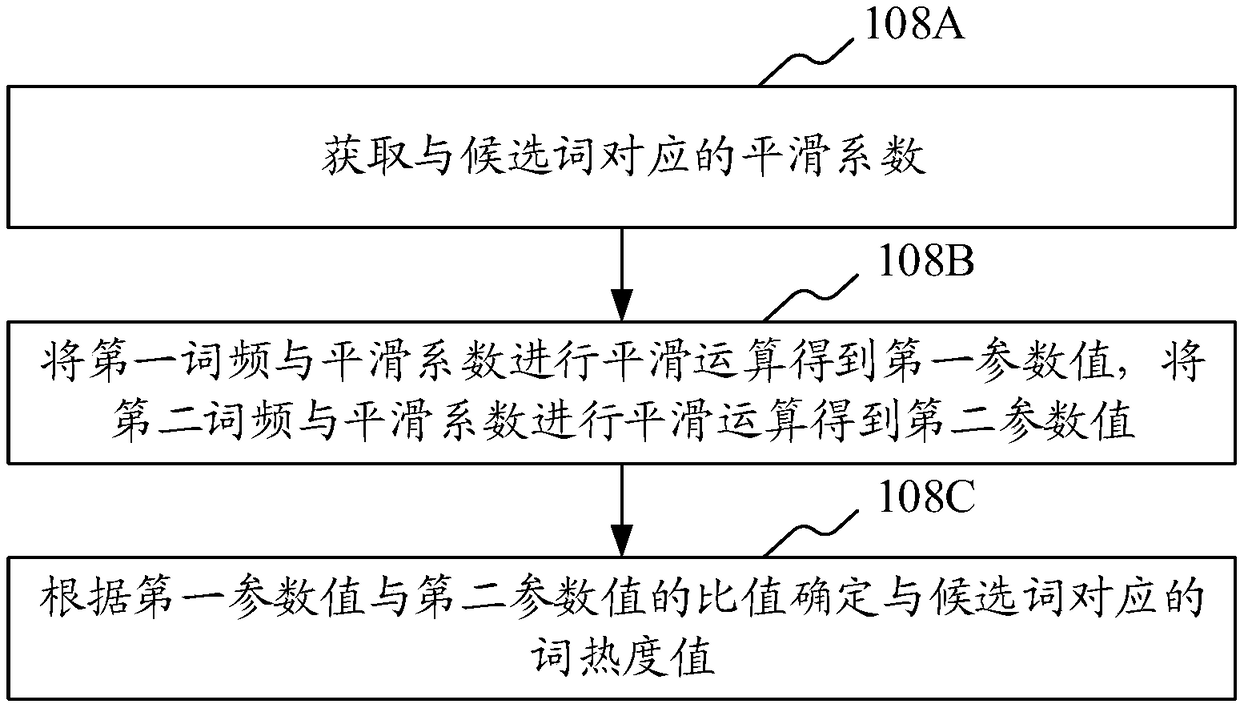
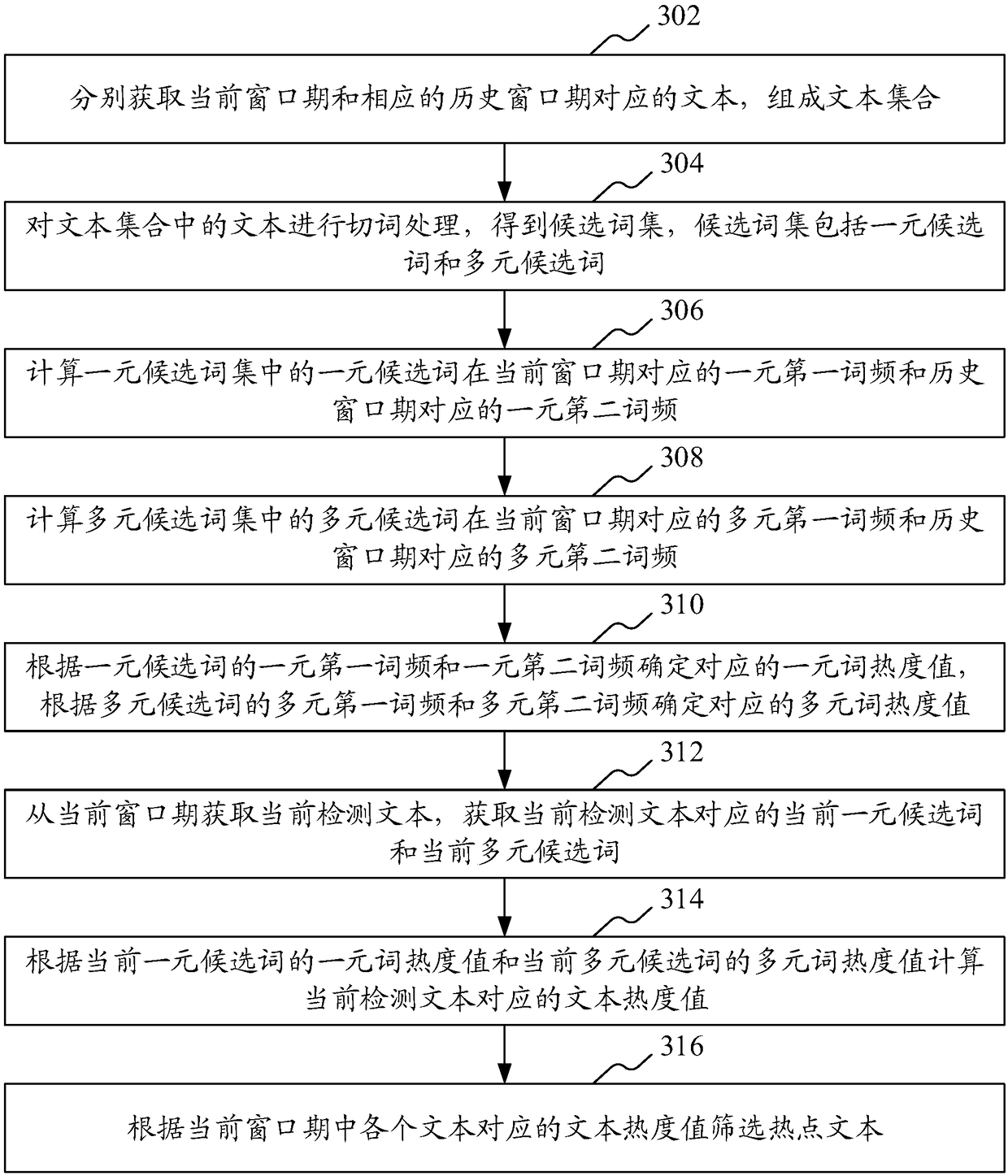
ActiveCN108304371AExcavate accuratelyNatural language data processingSpecial data processing applicationsInformation retrievalLexical frequency
The invention provides a hot content mining method. The method comprises the steps of obtaining texts corresponding to a current window period and a corresponding historical window period, thereby forming a text set; performing word segmentation processing on the texts in the text set to obtain candidate word sets; calculating corresponding first word frequencies and second word frequencies, in the current window period and the historical window period, of candidate words in the candidate word set; according to the first word frequencies and the second word frequencies of the candidate words,determining corresponding word popularity values; obtaining current detected texts from the current window period; obtaining current candidate words corresponding to the current detected texts; according to word popularity values corresponding to the current candidate words, calculating text popularity values corresponding to the current detected texts; and according to the text popularity valuescorresponding to the texts in the current window period, screening hot texts. According to the method, hot contents in the current window period can be mined more accurately. In addition, the invention provides a hot content mining apparatus, a computer device and a storage medium.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Recommendation method and device, terminal equipment and computer storage medium
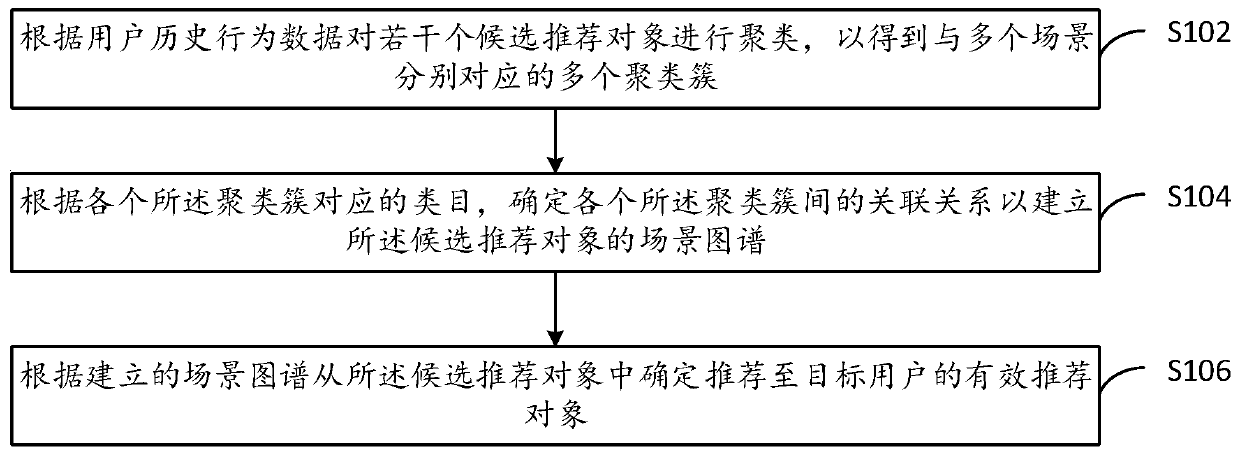
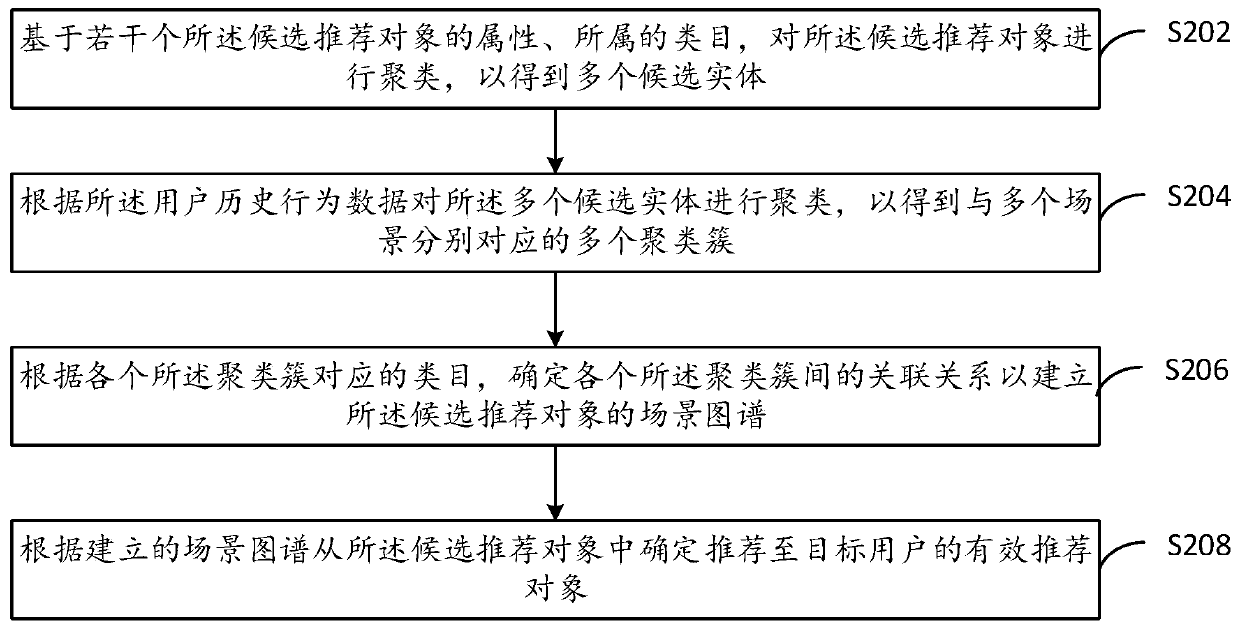
ActiveCN111523010AAccurately determineExcavate accuratelyBuying/selling/leasing transactionsOther databases clustering/classificationEngineeringScene graph
An embodiment of the invention provides a recommendation method, a recommendation device, terminal equipment and a computer storage medium. The recommendation method comprises the steps of: clusteringa plurality of candidate recommendation objects according to historical behavior data of a user to obtain a plurality of clustering clusters corresponding to a plurality of scenes; according to the category corresponding to each clustering cluster, determining an association relationship among the clustering clusters to establish a scene map of the candidate recommendation object; and determiningan effective recommendation object recommended to a target user from the candidate recommendation objects according to the established scene map. According to the recommendation method and the recommendation device provided by the embodiment of the invention, less manual intervention is required when a knowledge graph is established, and the production efficiency is improved.
Owner:ALIBABA GRP HLDG LTD
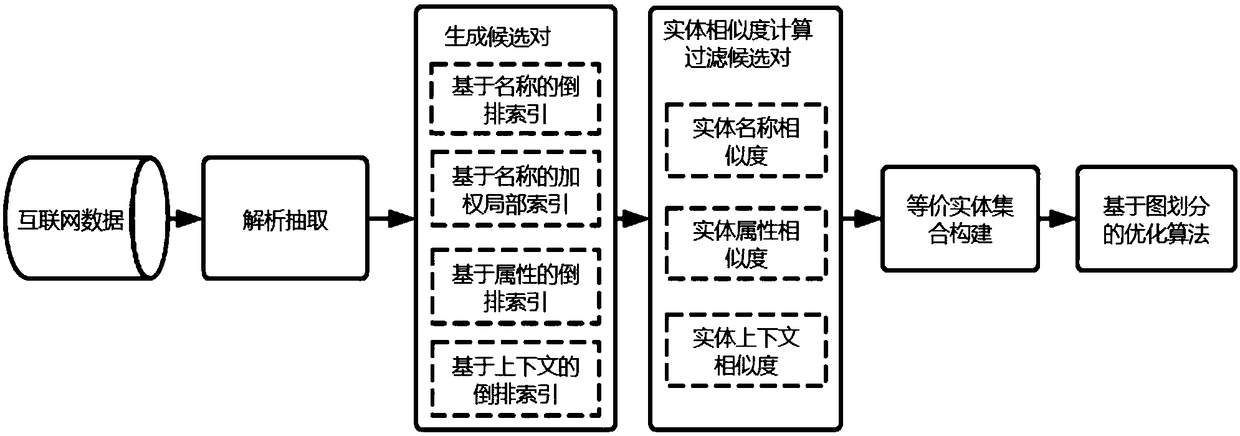
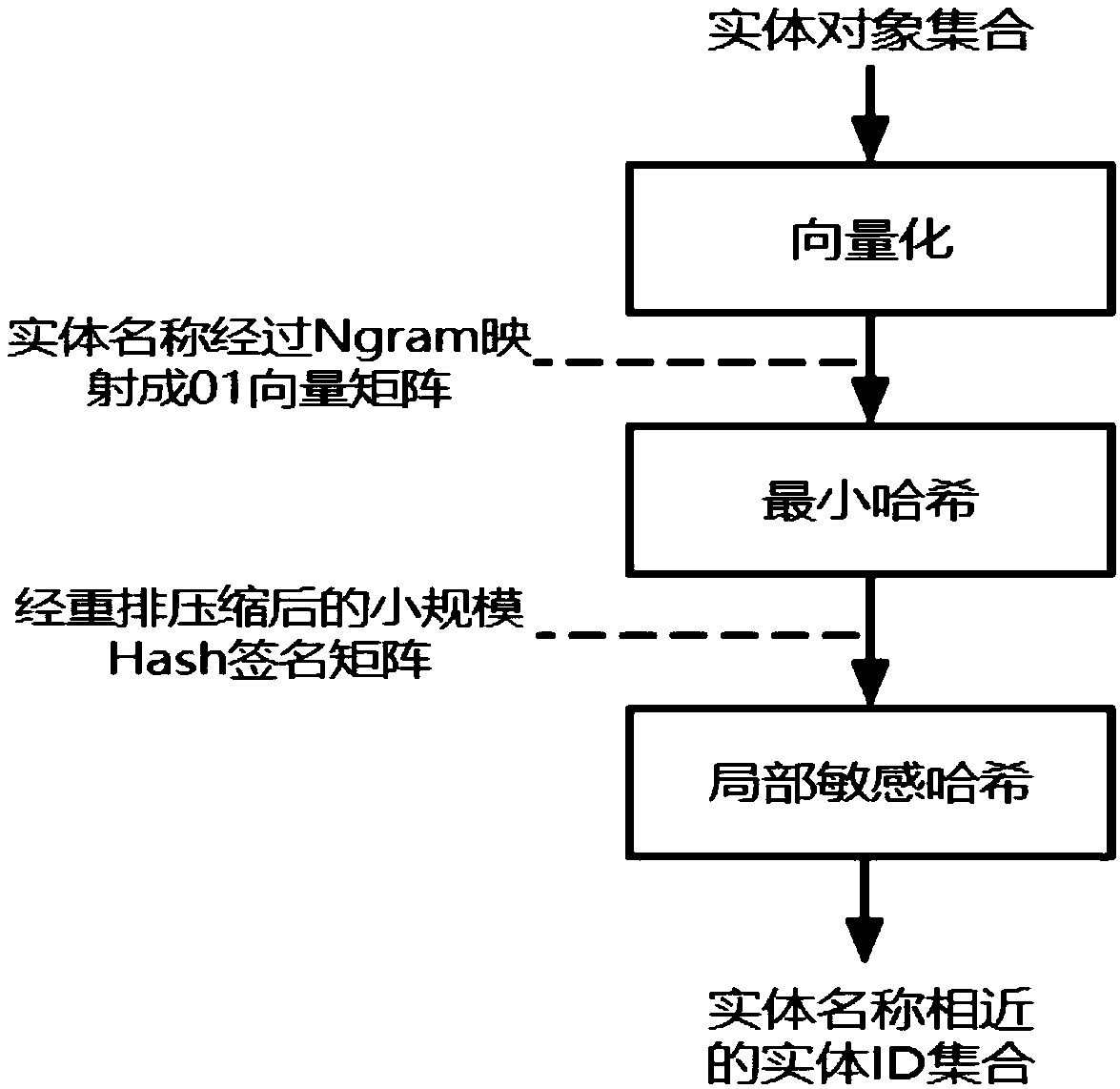
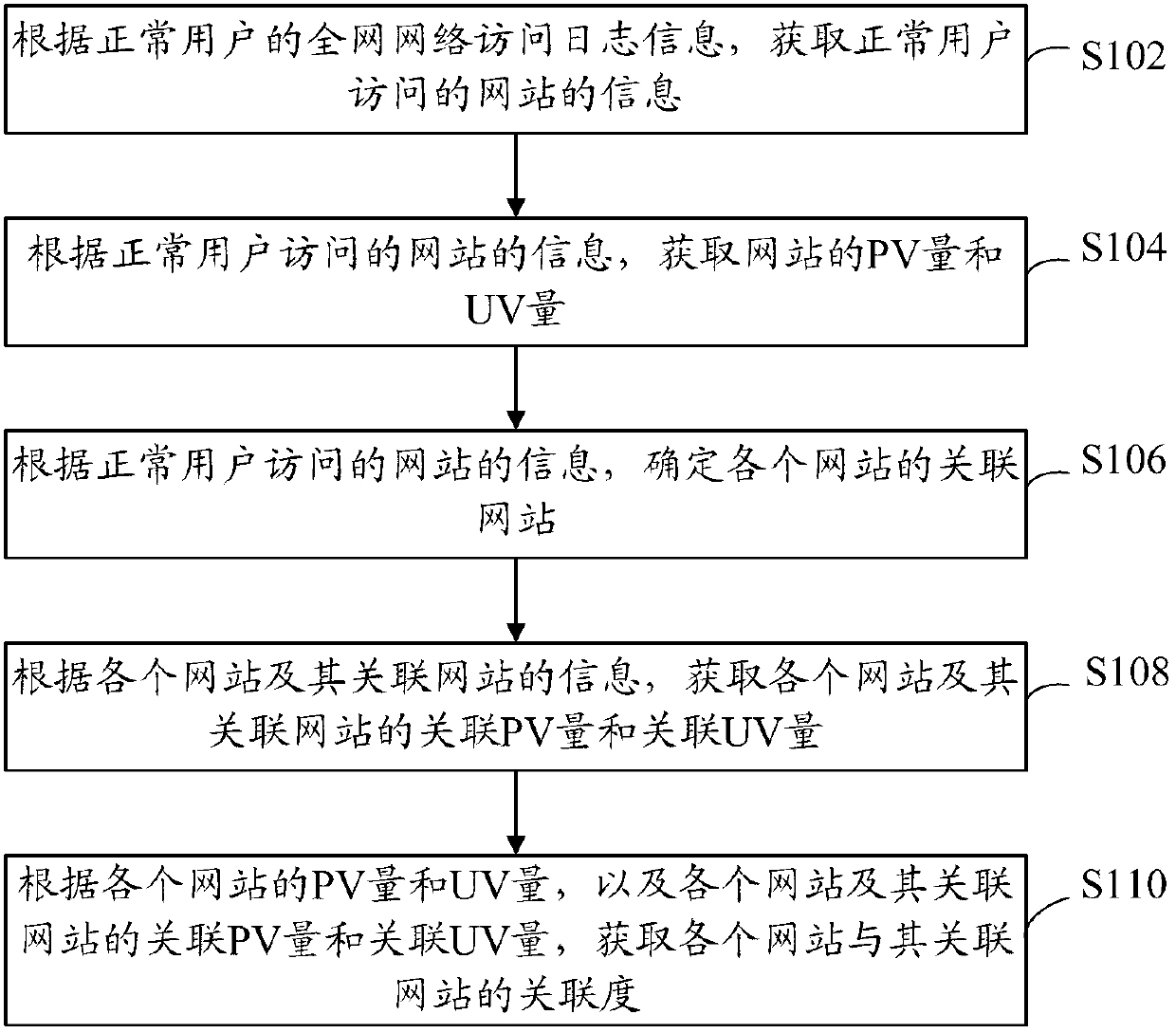
An optimization method of entity alignment based on graph partition
ActiveCN109359172AImprove accuracyQuality improvementWeb data retrievalText database indexingAlgorithmThe Internet
The invention discloses an optimization method of entity alignment based on graph partition . Candidate entity pairs are mined from all entities by composite index, and whether the candidate entity pairs are aligned or not is judged by entity similarity measurement method, and then an optimization algorithm based on graph partition is proposed to improve the accuracy of equivalent entity alignmentby utilizing the similarity relationship between entities. The method of the invention solves the entity alignment problem of the large-scale Internet data, and can accurately and completely mine theentity set equivalent to each other in the original data.
Owner:ZHEJIANG UNIV
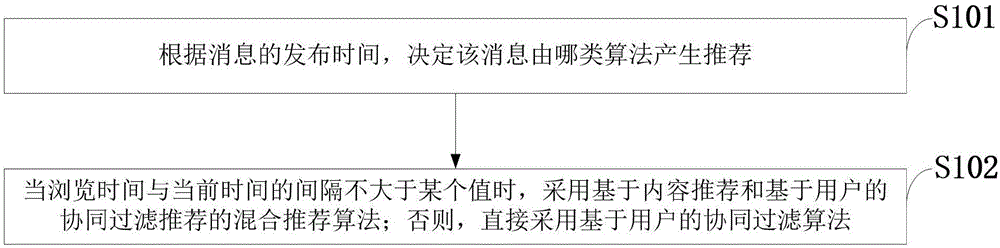
Recommendation method for personalized information
ActiveCN106682152AExcavate accuratelyAccurate descriptionSpecial data processing applicationsPersonalizationComputer science
The invention discloses a recommendation method for personalized information. The recommendation method for the personalized information comprises the steps of deciding what kind of algorithm should be adopted to generate a recommendation for the information according to the publishing time of the information; adopting a mixed recommendation algorithm of a recommendation based on content and a collaborative filtering recommendation based on a user when the interval between the browsing time and the current time is no bigger than a certain value; otherwise, directly adopting a collaborative filtering algorithm based on the user. According to the recommendation method for the personalized information, the characteristics of the information and the user can be accurately dug and described through the recommendation based on the content, and as for information, a special recommendation object, higher accuracy can be obtained through the recommendation based on the content; the information has timeliness and a hot property, the recommendation based on the content is free of a cold boot problem of new information and is free of influence of the hot degree of the information at the same time, and instead, the news content is directly dug; due to the fact that the interest of a user quickly changes along with the change of time, a more comprehensive recommendation result can be obtained by combining a result of the collaborative filtering recommendation based on the user.
Owner:XIDIAN UNIV
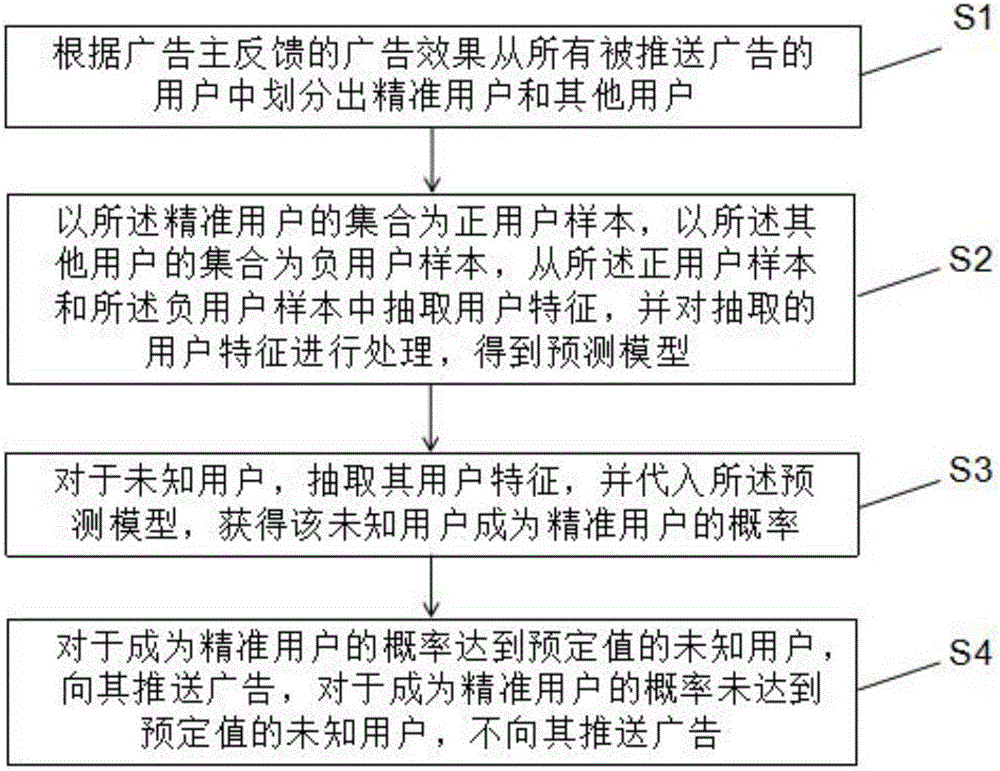
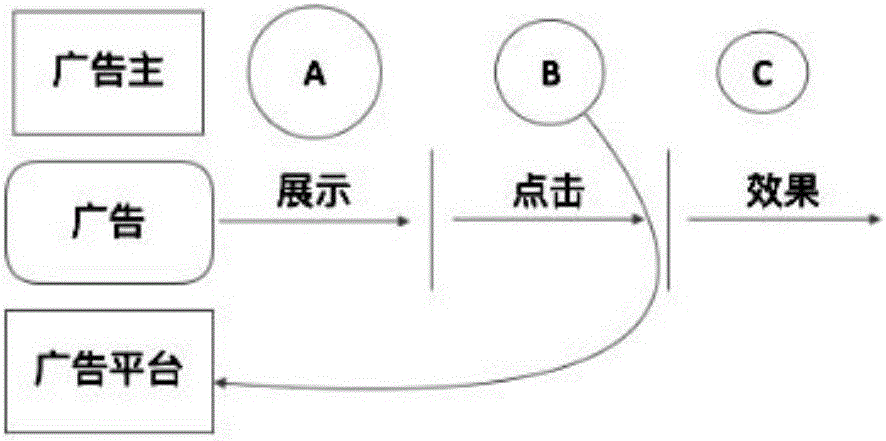
Advertisement promotion method combined with advertiser effect feedbacks
InactiveCN106022836AWith a clear purposeExcavate accuratelyMarketingComputer scienceCost performance
The invention discloses an advertisement promotion method combined with advertiser effect feedbacks. The method comprises: according to advertisement effect fed back by an advertiser, all users to whom an advertisement is pushed are divided into accurate users and other users; a set of the accurate users is taken as a positive user sample and a set of the other users is a negative user sample, user features are extracted from the positive user sample and the negative user sample, the extracted user features are processed, and a prediction model is obtained; for an unknown user, user features of the unknown user are extracted and applied to the prediction model, and the probability of the unknown user becoming an accurate user is obtained; the advertisement is pushed to the unknown user whose probability of becoming an accurate user reaches a preset value, and is not pushed to the unknown user whose probability of becoming an accurate user does not reach the preset value. The method can improve the cost-performance ratio of advertisement delivery and the promotion efficiency of the whole advertisement platform.
Owner:SHENZHEN ZHUIYI TECH CO LTD
Object recommendation method and device based on intelligence, and storage medium
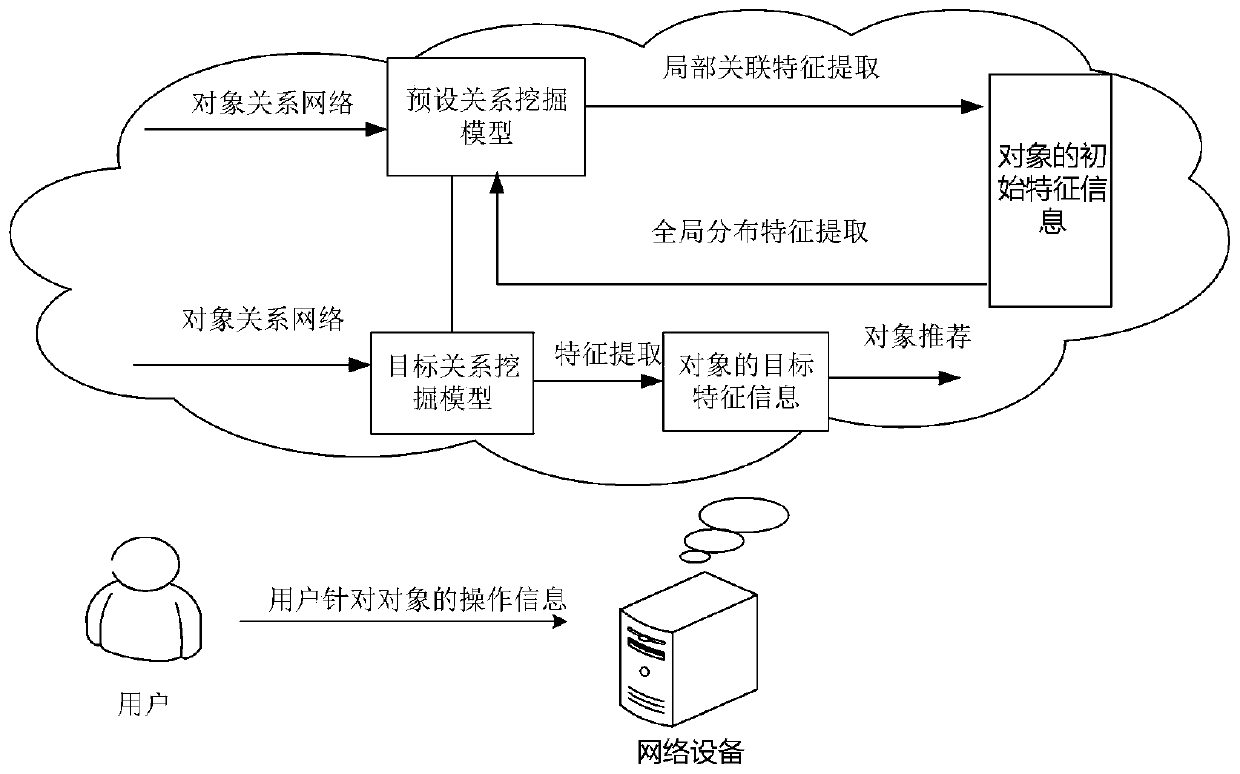
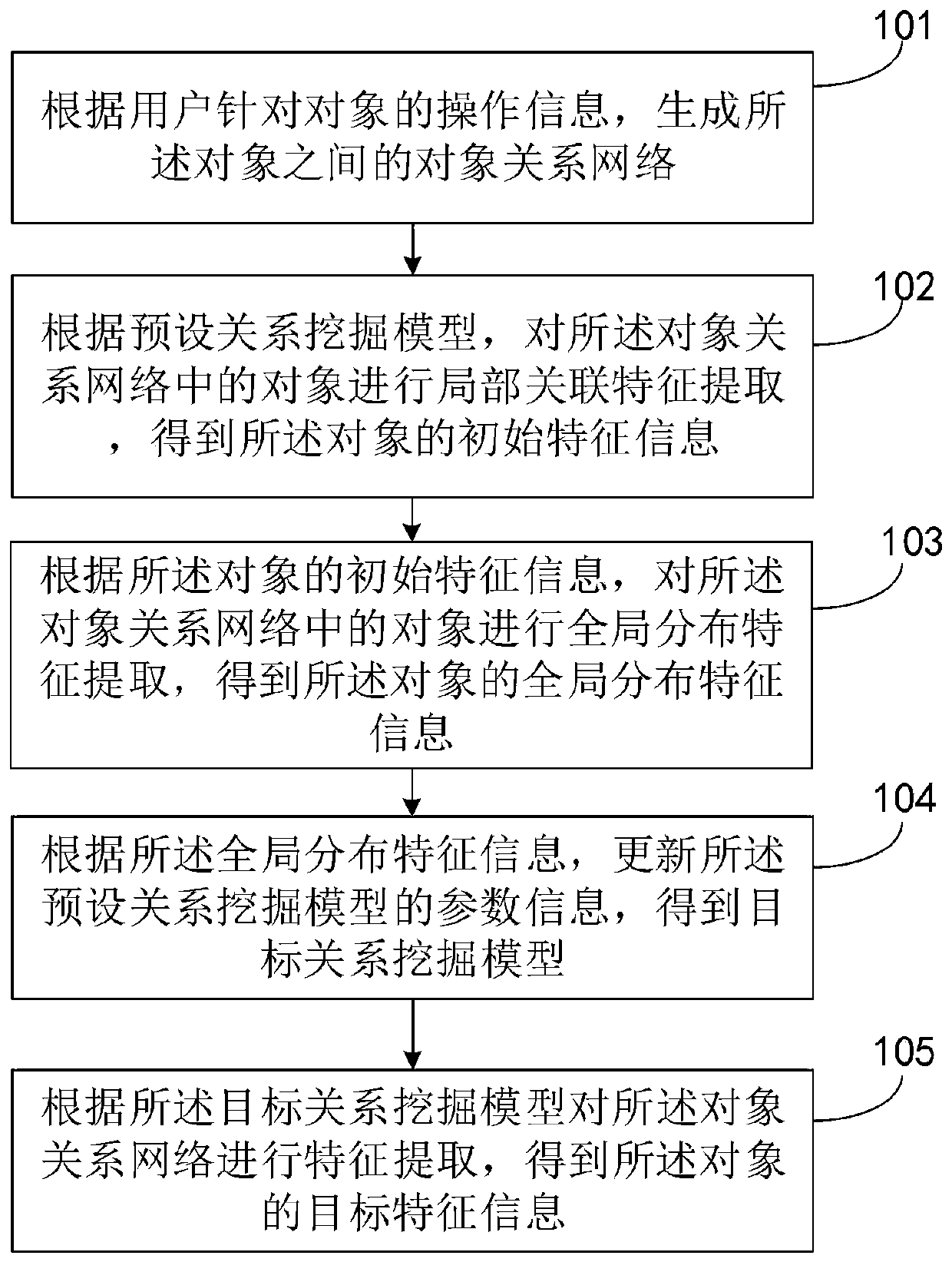
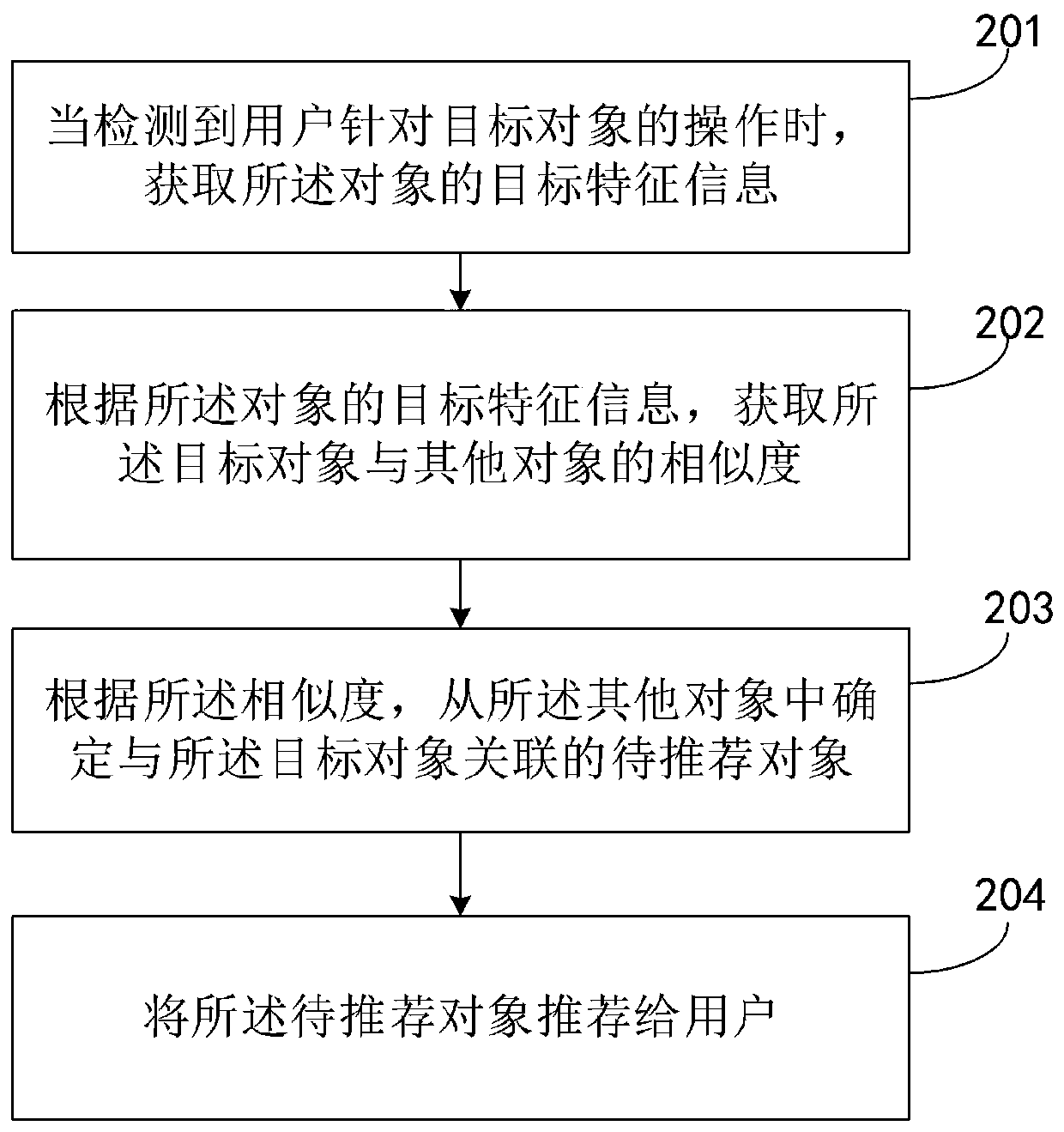
ActiveCN111382190AImprove noise immunityExcavate accuratelyDigital data information retrievalCharacter and pattern recognitionFeature extractionEngineering
An embodiment of the invention discloses an object recommendation method and an object recommendation device based on intelligence, and a storage medium. The object recommendation method comprises thesteps of: generating an object relationship network according to operation information of a user for an object; performing local association feature extraction on the object in the object relationship network to obtain initial feature information of the object according to a preset relationship mining model; performing global distribution feature extraction on the object in the object relationship network to obtain global distribution feature information of the object according to the initial feature information of the object; updating parameter information of the preset relationship mining model according to the global distribution feature information to obtain a target relationship mining model; performing feature extraction on the object relationship network according to the target relationship mining model to obtain target feature information of the object; and performing object recommendation according to the target feature information. According to the object recommendation method and the object recommendation device, the association relationship between the objects can be mined more comprehensively and accurately, so that the objects can be recommended to the user more accurately.
Owner:TENCENT TECH (SHENZHEN) CO LTD
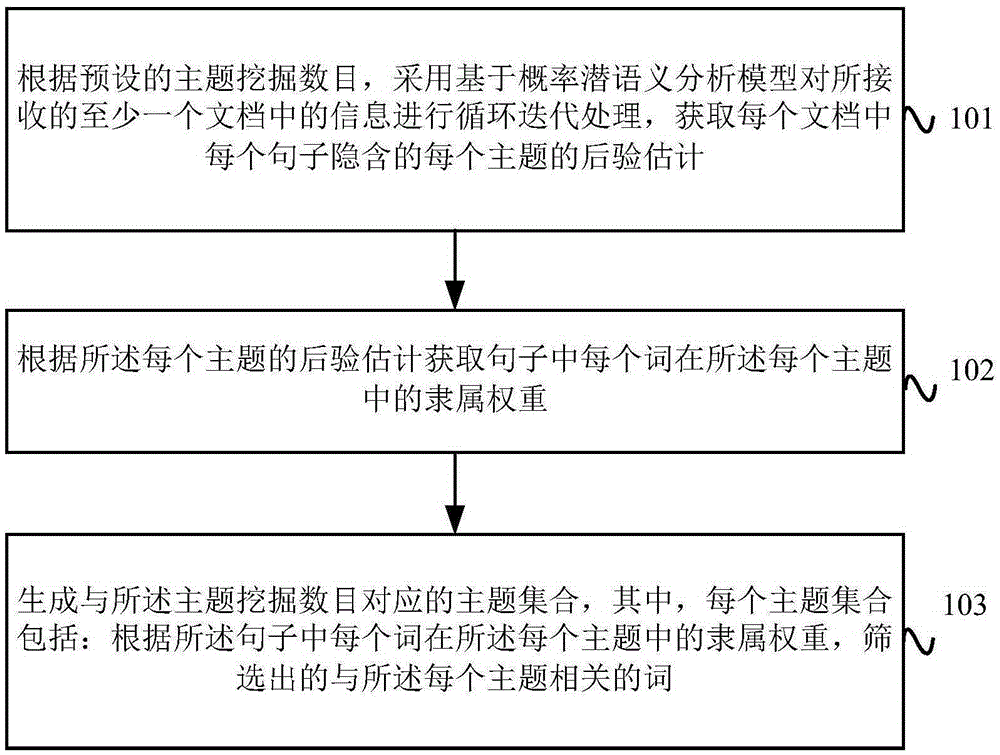
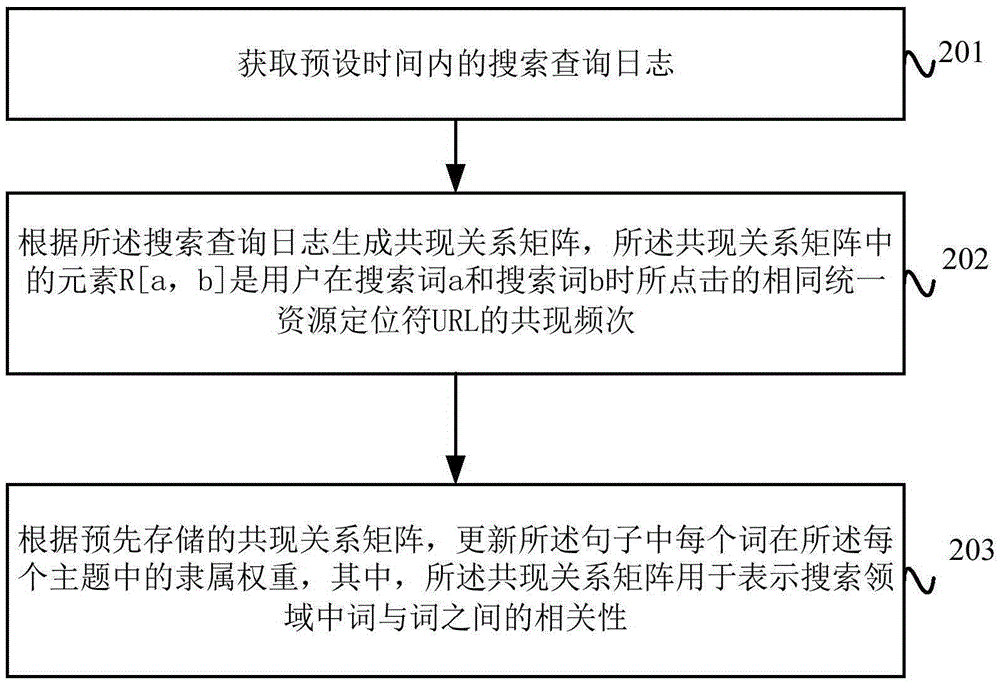
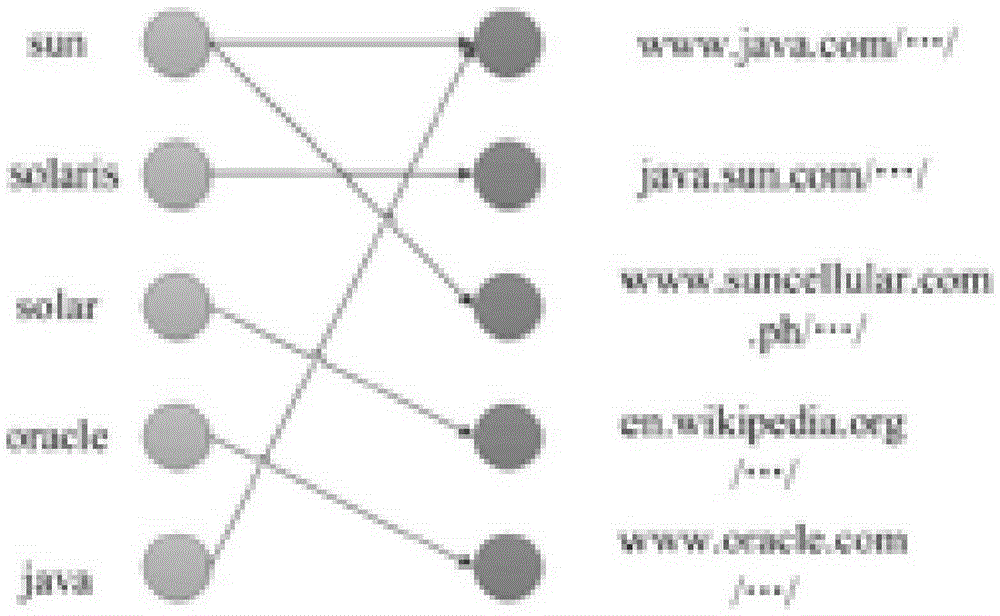
Document topic mining method and apparatus
ActiveCN105243083AExcavate accuratelyImprove relevanceNatural language data processingSpecial data processing applicationsTopic miningInformation retrieval
The present application proposes a document topic mining method and apparatus. The method comprises: according to a preset topic mining number, performing loop iteration processing on information in at least one received document based on a probabilistic latent semantic analysis model, and acquiring a posteriori estimate of each topic implied by each sentence in each document; according to the posteriori estimate of each topic, acquiring a membership weight of each word in each topic in each sentence; and generating a topic set corresponding to the topic mining number, wherein each topic set comprises a word related to each topic and screened out according to the membership weight of each word in each topic in the sentence. According to the document topic mining method and apparatus provided by the present application, the document topic is more comprehensively and accurately mined based on a PLSA (Probabilistic Latent Semantic Analysis) algorithm, and the correlation of document topic content is improved, thereby enabling a result of a search engine to be closer to semantic information of the document.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
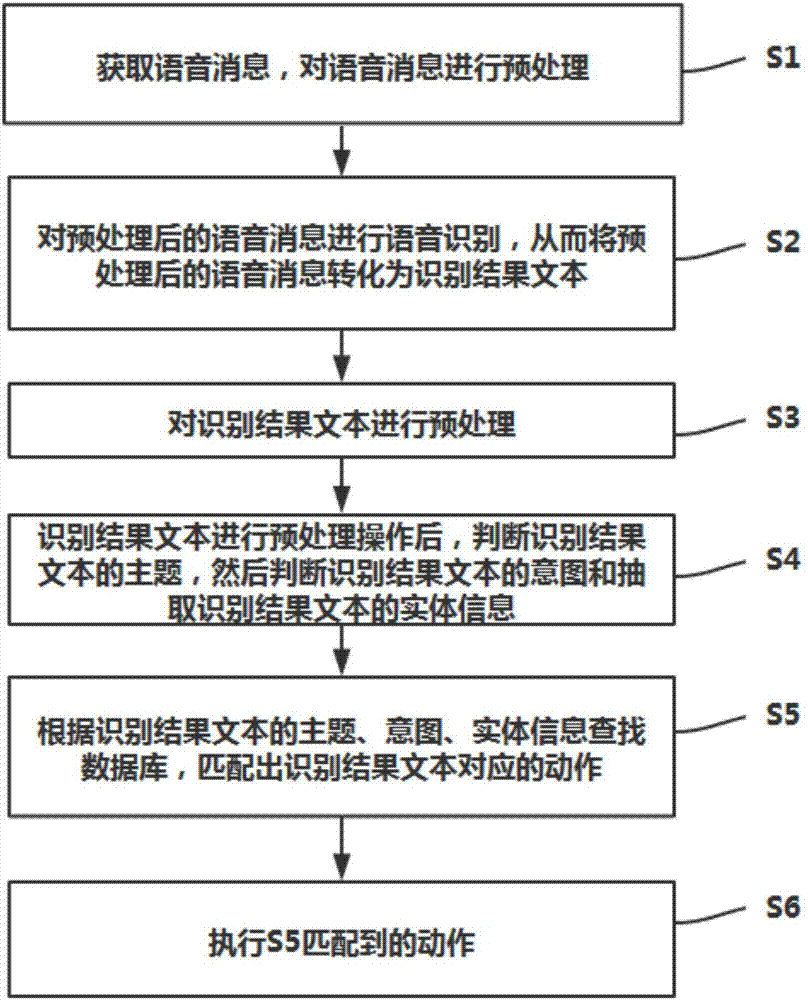
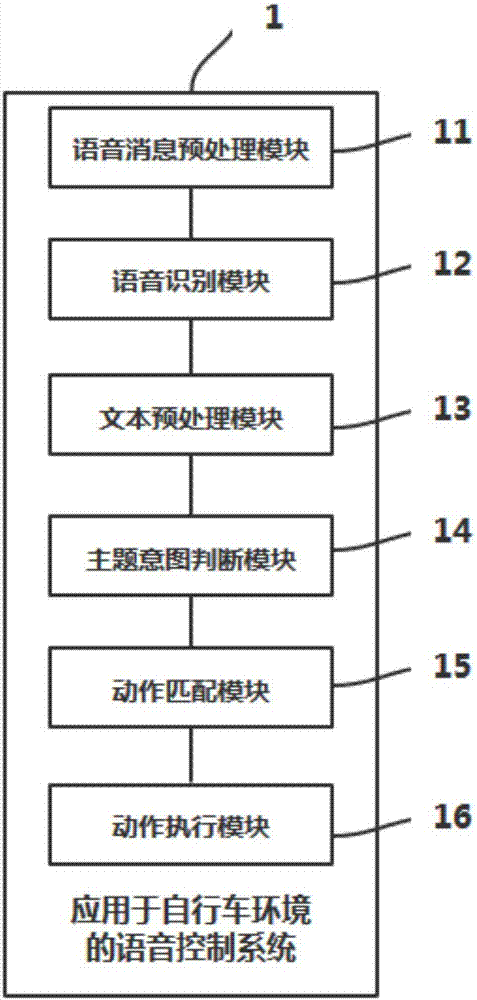
Voice control method and system applied to bicycle environment
ActiveCN107403619AExcavate accuratelyStrong voice recognition effectSemantic analysisBiological neural network modelsSpeech controlSpeech identification
The invention discloses a voice control method and system applied to a bicycle environment. The voice control method comprises the following steps: acquiring a voice message, and preprocessing the voice message; carrying out voice recognition on the voice message, so that the voice message is converted into a recognition result text; preprocessing the recognition result text; judging the subject of the recognition result text, and judging the intention of the recognition result text and extracting entity information; and searching a database according to the subject, the intention and the entity information of the recognition result text, carrying out matching, and executing the actions corresponding to the recognition result text. The method and the system have the beneficial effects that a mixed model of an artificial neural network model and a hidden markov model is used for carrying out voice recognition, and thus the voice recognition effect is good; the subject is judged first, then the situation that the intention belongs to which intention in the intention set corresponding to the subject is judged, so that the intention of a user can be accurately excavated; manual programming of features is not needed, the accuracy is high, the system expansibility / maintainability is strong, and the time consumption is little.
Owner:WUHAN TIPDM INTELLIGENT TECH
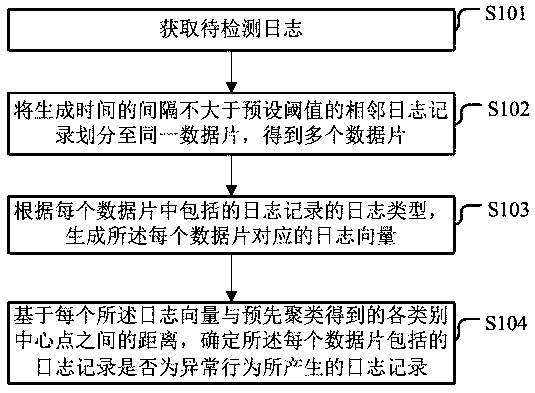
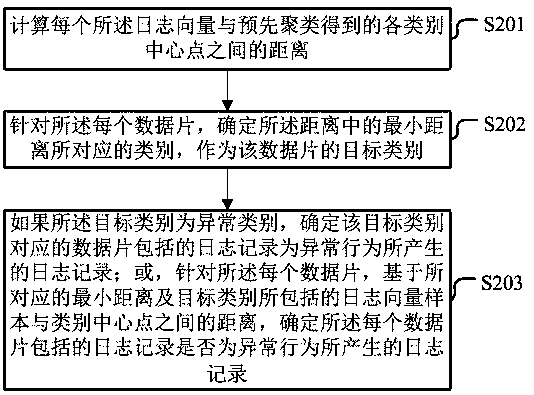
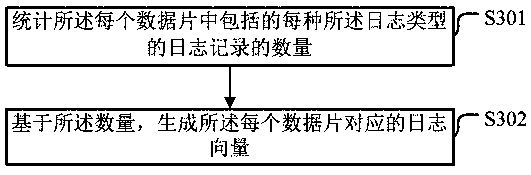
Abnormal behavior detection method and device, electronic equipment and storage medium
ActiveCN111538642AAccurately determineExcavate accuratelyHardware monitoringCharacter and pattern recognitionAlgorithmEngineering
Embodiments of the invention provide an abnormal behavior detection method and device, electronic equipment and a storage medium. The method comprises the steps of obtaining a to-be-detected log; dividing the adjacent log records of which the generation time intervals are not greater than a preset threshold value into the same data piece to obtain a plurality of data pieces; generating a log vector according to the log type of the log record included in each data piece; and based on the distance between each log vector and each category center point, determining whether the log record is a logrecord generated by an abnormal behavior, the category center point being a category center point obtained by clustering log vector samples corresponding to data slice samples obtained by dividing log samples obtained in advance. Due to the fact that when the data pieces are divided, the adjacent log records with the interval of the generation time not larger than the preset threshold value are divided into the same data piece, the log records generated by continuous physical behaviors cannot be divided into different data pieces, and the log records corresponding to abnormal behaviors can beaccurately determined.
Owner:HANGZHOU HIKVISION DIGITAL TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com