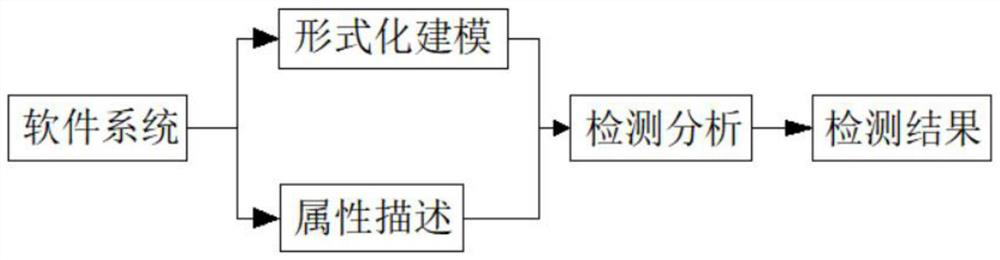
Patents
Literature
46 results about "Vulnerability model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Vulnerability-Stress Model (aka Stress-Vulnerability Model) The vulnerability-stress model (also known as stress-vulnerability model) is an examination of what causes psychiatric illness and what makes some people more vulnerable to psychiatric illnesses than others.
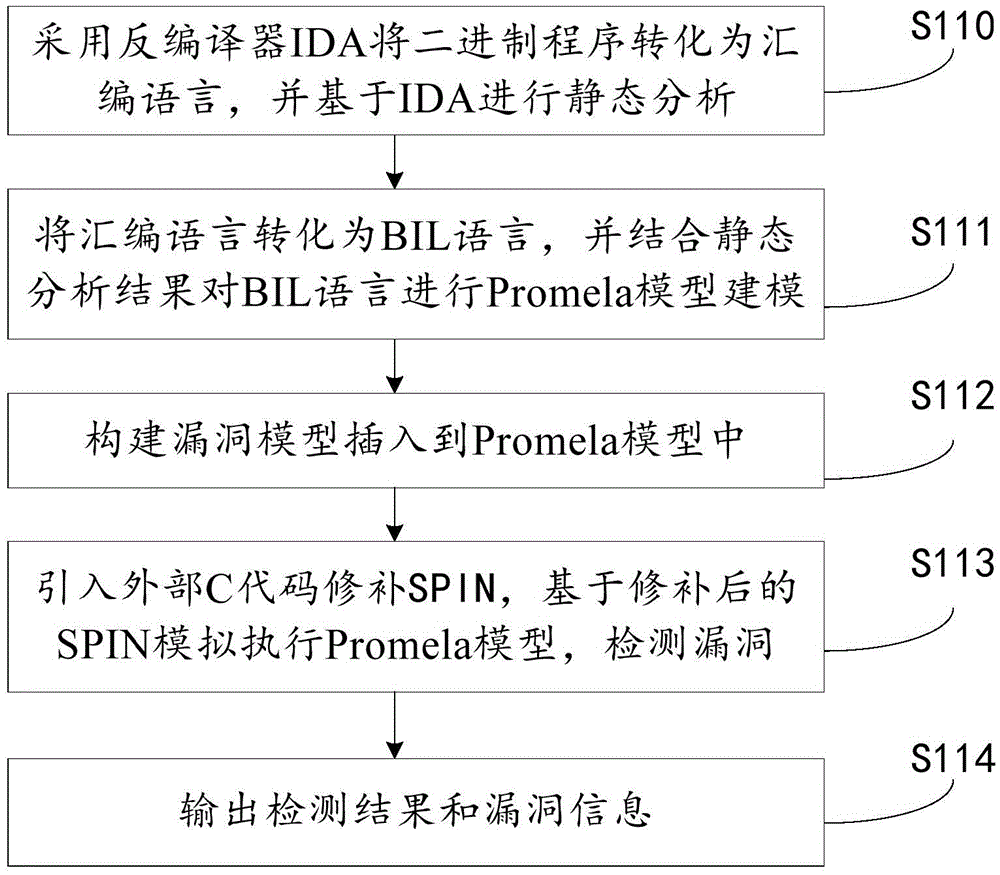
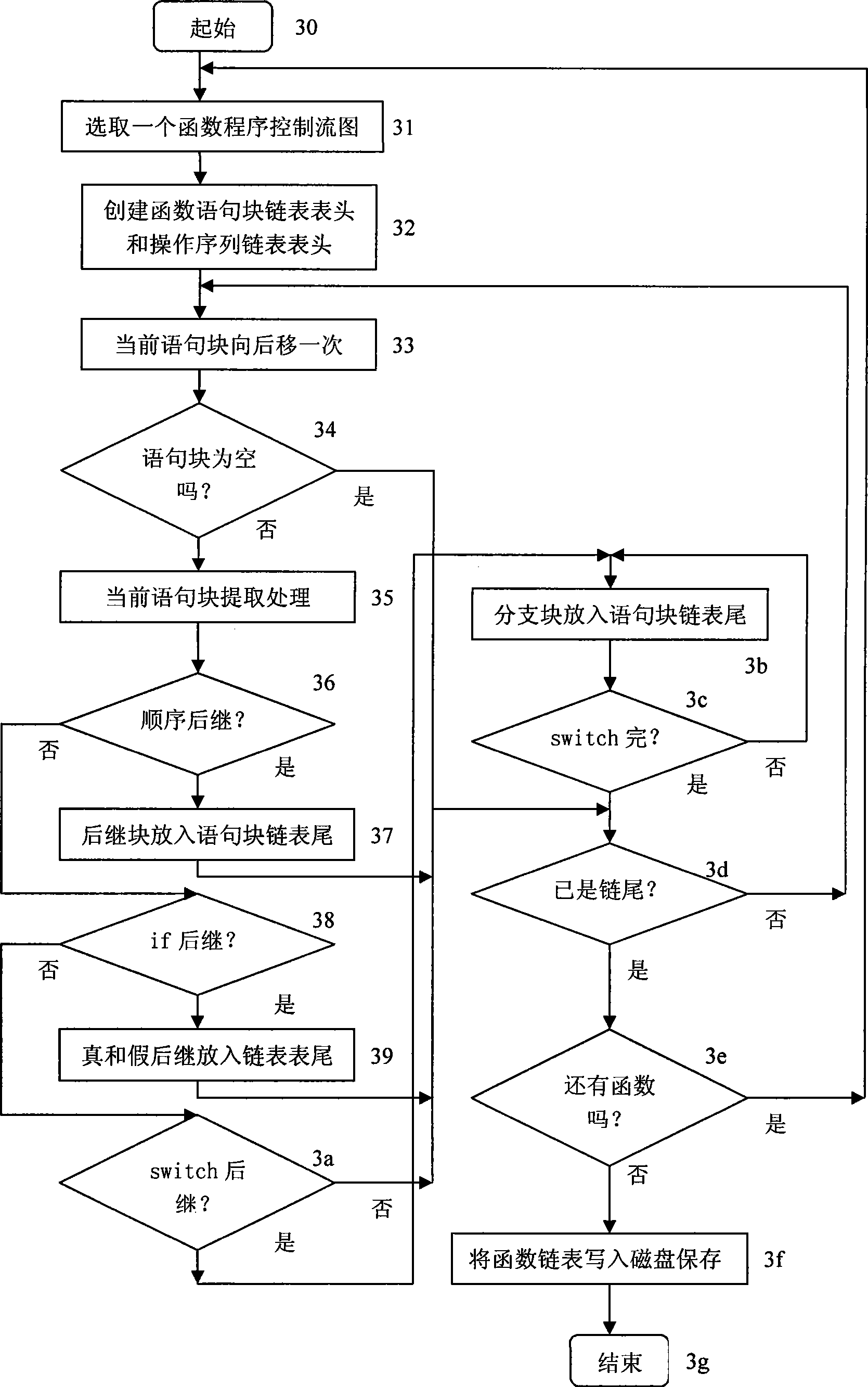
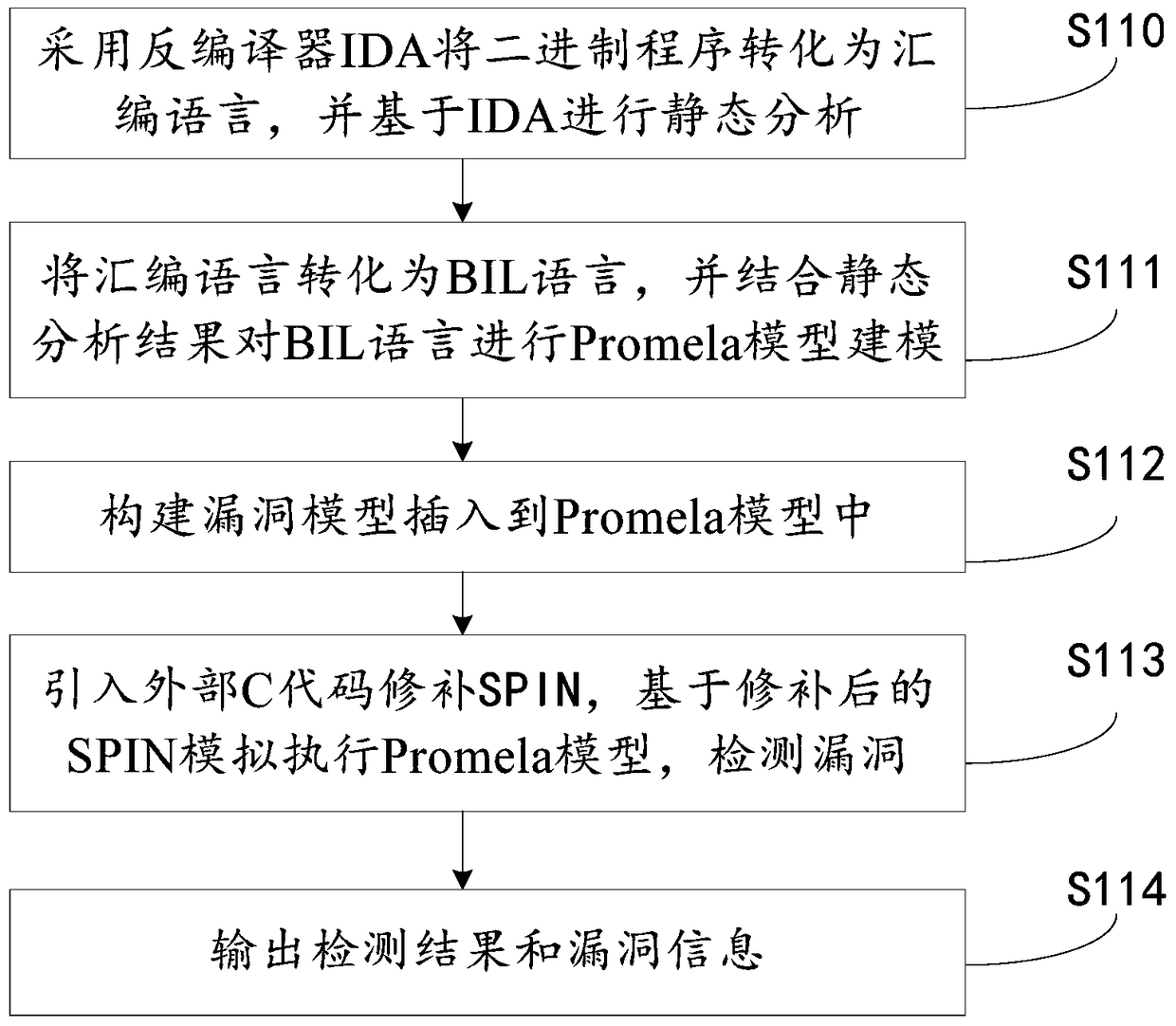
Binary program vulnerability discovery method and system
ActiveCN105678169AExcavate accuratelyAccurate locationPlatform integrity maintainanceCode conversionAssembly language
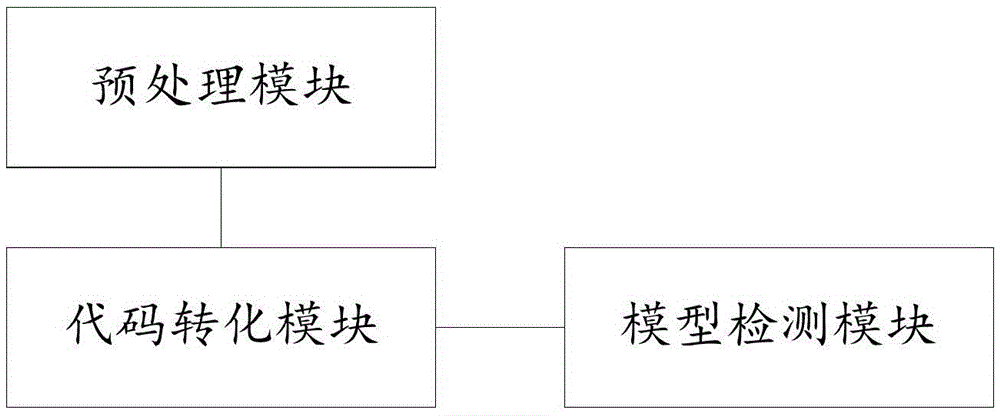
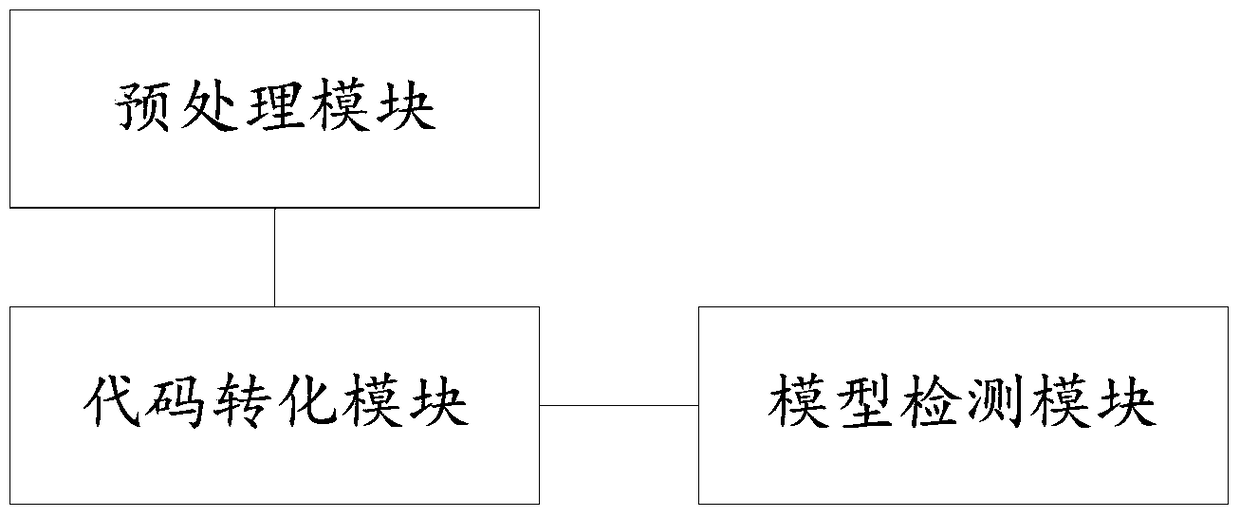
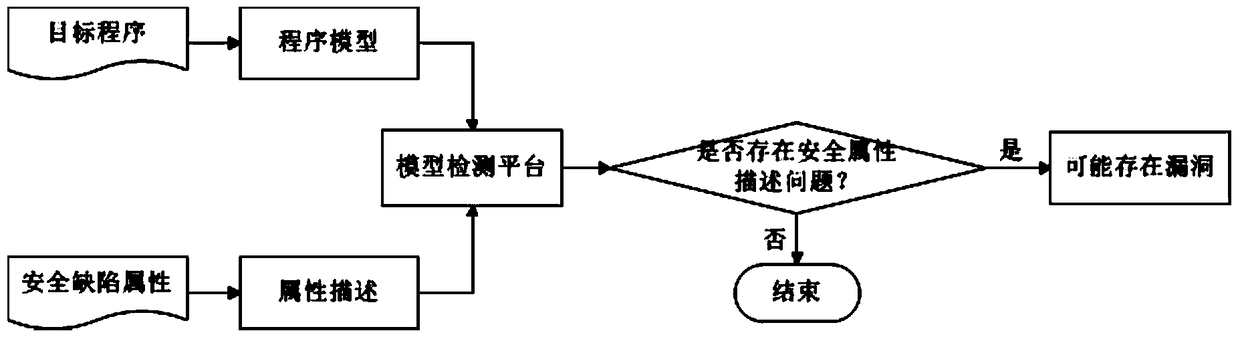
The invention provides a binary program vulnerability discovery method. The binary program vulnerability discovery method comprises steps of converting a target binary program into an assembly language, and carrying out static analysis to the assembly language; carrying out Promela model modeling to an intermediate language by combining the analysis result of the static analysis; establishing a vulnerability model and inserting the vulnerability model into the Promela model; introducing an external C code, simulating and executing the Promela model based on an SPIN, and detecting the vulnerability. The invention also provides a binary program vulnerability discovery system comprising a preprocessor module, a code conversion module and a model detection module. With respect to the binary program vulnerability discovery method and system, the intermediate language BIL is introduced to serve as a conversion bridge through which the binary program is converted into the Promela model, automatic modeling of the binary program is achieved, the embedded C function of the SPIN is employed to achieve simulation and execution, and the external C code is introduced to correct the defect of model detection. Experimental results show that the binary program vulnerability discovery method can effectively detect memory destructive vulnerabilities of binary programs.
Owner:XIAN HUMEN NETWORK TECH CO LTD
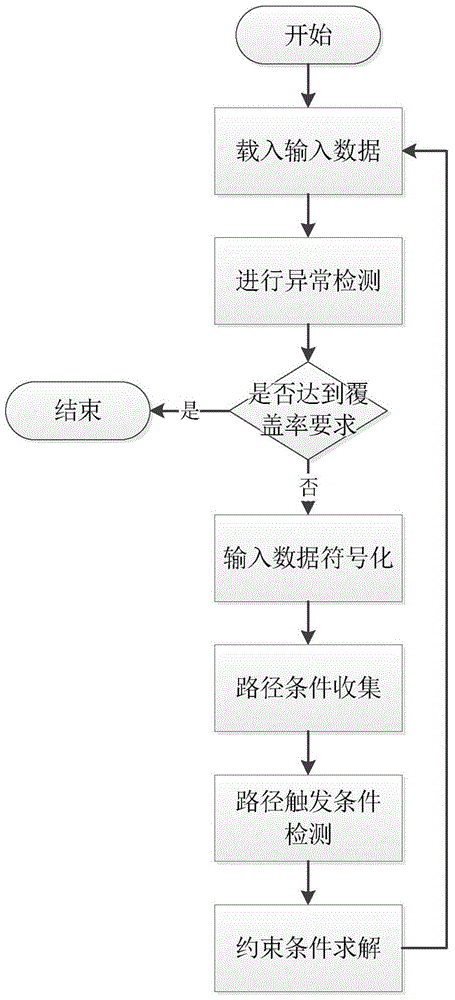
Software security detection method based on combination of vulnerability model and symbolic execution
InactiveCN105740149AEfficient security vulnerability type detectionHigh efficiency in triggering vulnerabilitiesSoftware testing/debuggingTest inputDeep level
The invention relates to a software security detection method based on combination of a vulnerability model and symbolic execution. The method comprises following steps of symbolizing input test data interacted by a program and an external environment; determining symbolic variables in a symbolic execution process; starting symbolic execution and actual execution; collecting path constraint conditions in the symbolic execution process; obtaining corresponding relationship information of the input data and a program operation path; according to the path constraint conditions, checking whether there is a code region possibly triggering a vulnerability or not; calculating a constraint condition capable of driving the program to be guided to the code region; according to the vulnerability ode, calculating a constraint condition possibly triggering the vulnerability; invoking an STP constraint solver to calculate the path constraint condition possibly triggering the vulnerability, thus obtaining input data possibly triggering the vulnerability; and loading the new input data in a to-be-tested program, thus carrying out a new round of test. According to the method, the program path through risk code region can be analyzed deeply; relatively accurate test input data is generated; the program vulnerability detection is triggered; and the software security is improved.
Owner:THE PLA INFORMATION ENG UNIV
Binary vulnerability detection method and system based on executable program and storage medium
PendingCN111475820AImprove accuracyRaise the level of presentationSemantic analysisPlatform integrity maintainanceData setEngineering
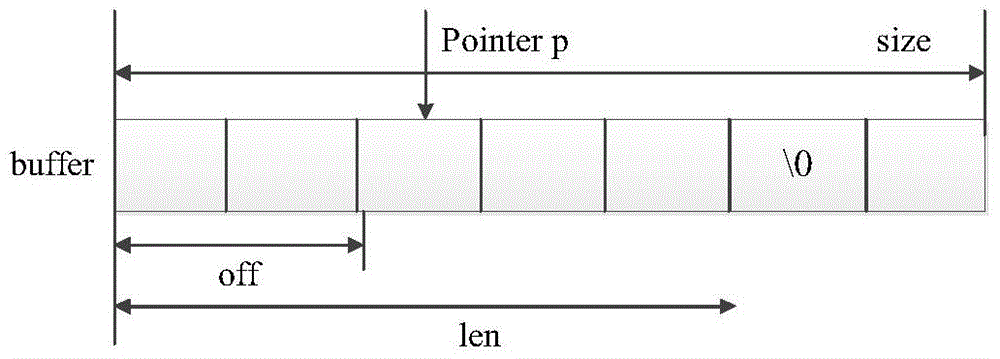
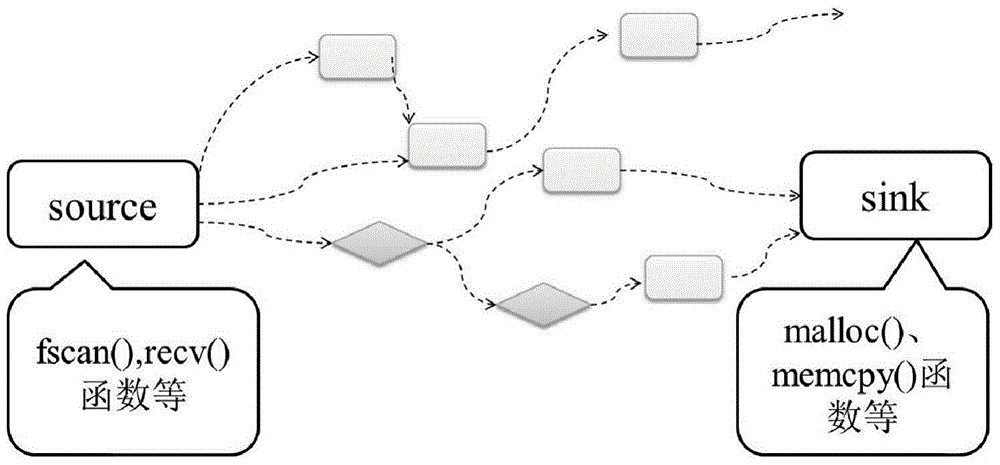
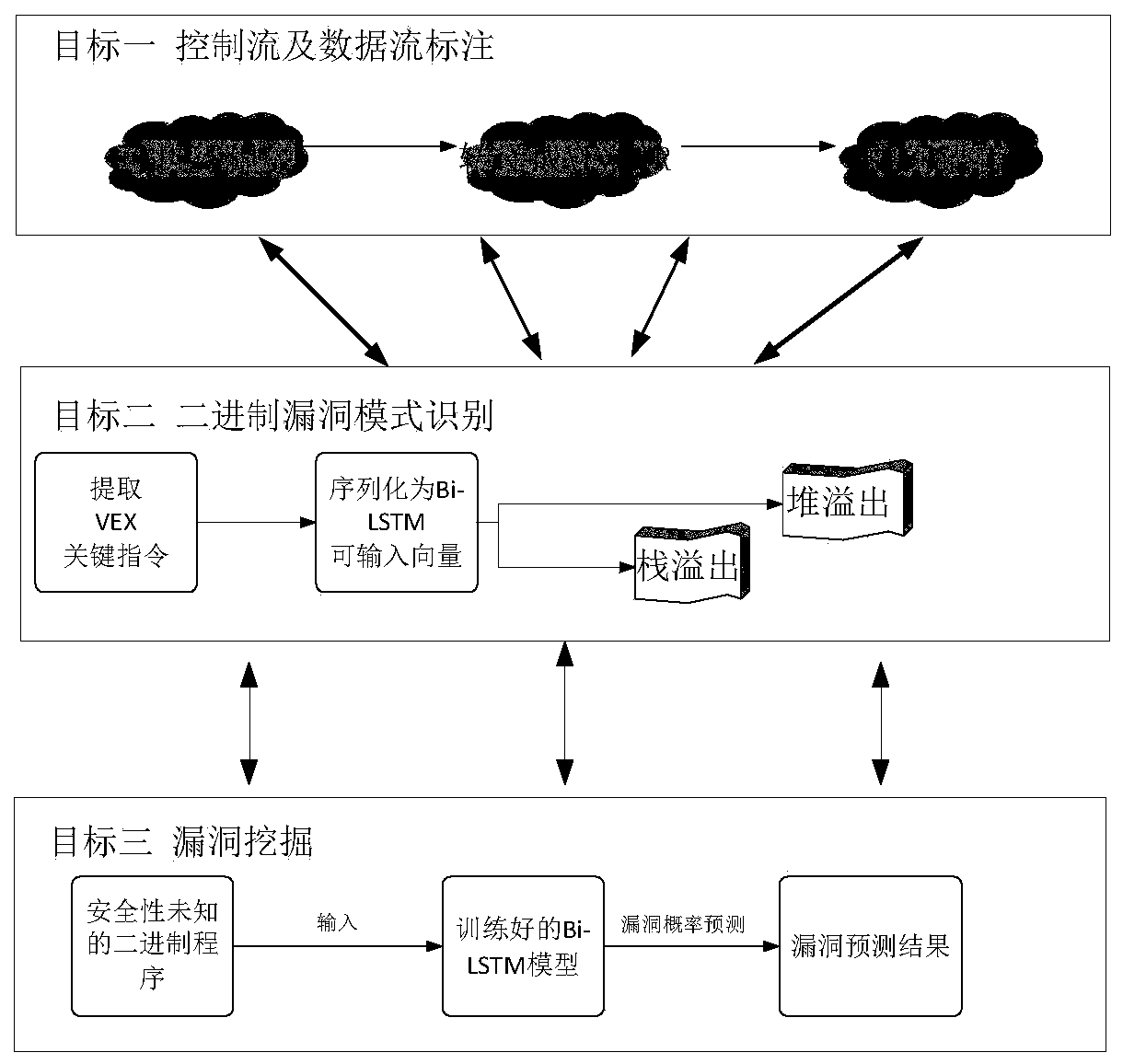
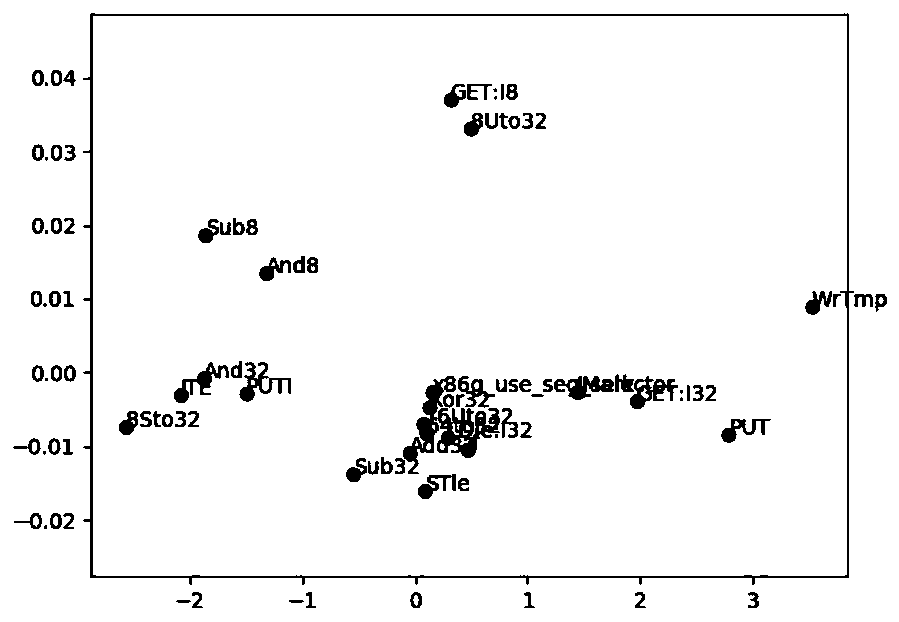
The invention discloses a binary vulnerability detection method and system based on an executable program and a storage medium. The method comprises the following steps: collecting an executable program with a known vulnerability, employing an angr framework supporting a VEX intermediate language to traverse the execution flow of the executable program, and translating the executable program intoa VEX text; cutting the VEX text into a plurality of text fragments, extracting keywords of the text fragments, and serializing all the text fragments; converting the keywords of the serialized text fragment into a text vector with context semantics by using Word2Vec; and converting the text vector into a digital vector, storing a file as input of a Bi-LSTM network model, respectively setting a training data set and a verification data set to train and verify the Bi-LSTM network model, and returning error rates and related record dictionaries on the training set and the verification set. According to the method, the intermediate language VEX IR is introduced into vulnerability detection, so that the execution flow of the program is recovered to a certain extent, and understanding of logicsemantics and context information of the program and establishment of a corresponding vulnerability model by a subsequent algorithm are facilitated .
Owner:张皓天
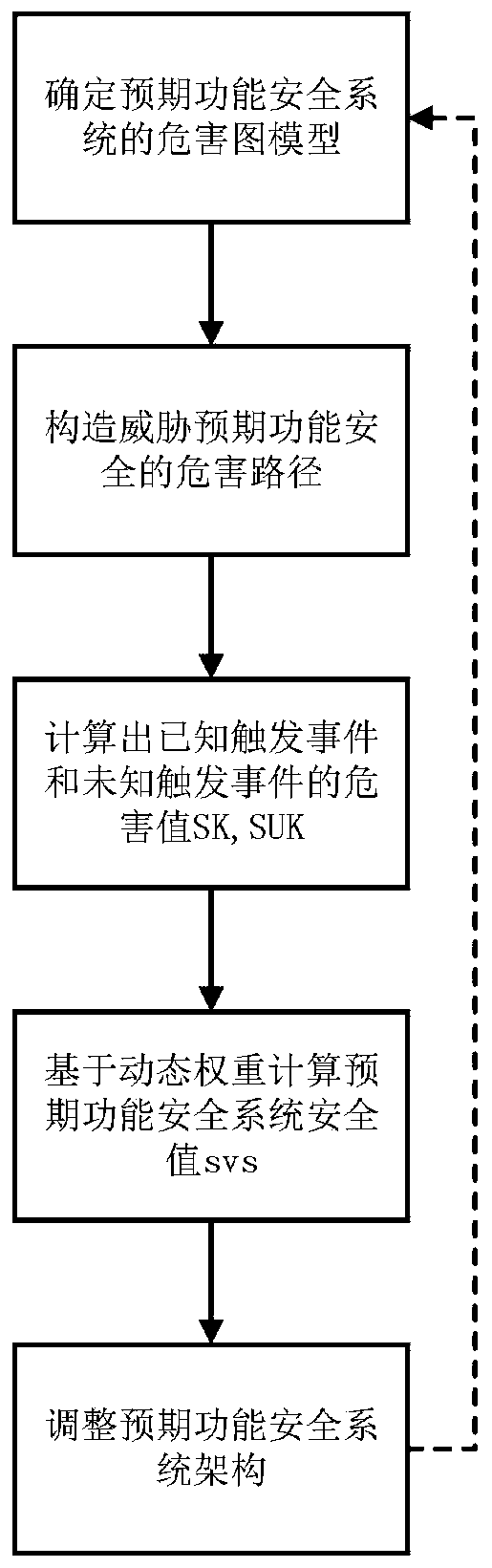
Automatic driving expected function safety hazard assessment method based on zero-day loopholes
PendingCN110930005AImprove hazard detection rateImprove securityDesign optimisation/simulationResourcesInformation securitySecurity system
The invention provides an automatic driving expected function safety hazard assessment method based on zero-day loopholes, which comprises the following four steps of: 1, determining a zero-day vulnerability hazard map model of an expected function safety system; 2, simplifying a zero-day vulnerability model of the expected function security system, and constructing a hazard path threatening the expected function security; 3, respectively calculating hazard values SK and SUK of a known trigger event and an unknown trigger event through a calculation program based on the hazard path; and 4, calculating an expected function safety system safety value svs based on the dynamic weight scheme. Hazard assessment of expected function safety and zero-day vulnerability safety assessment are combined, a solution for improving the expected function safety is invented based on an information safety solution, and the expected function safety hazard detection rate of an advanced driving assistance system and an automatic driving system is improved.
Owner:EAST CHINA NORMAL UNIV +1
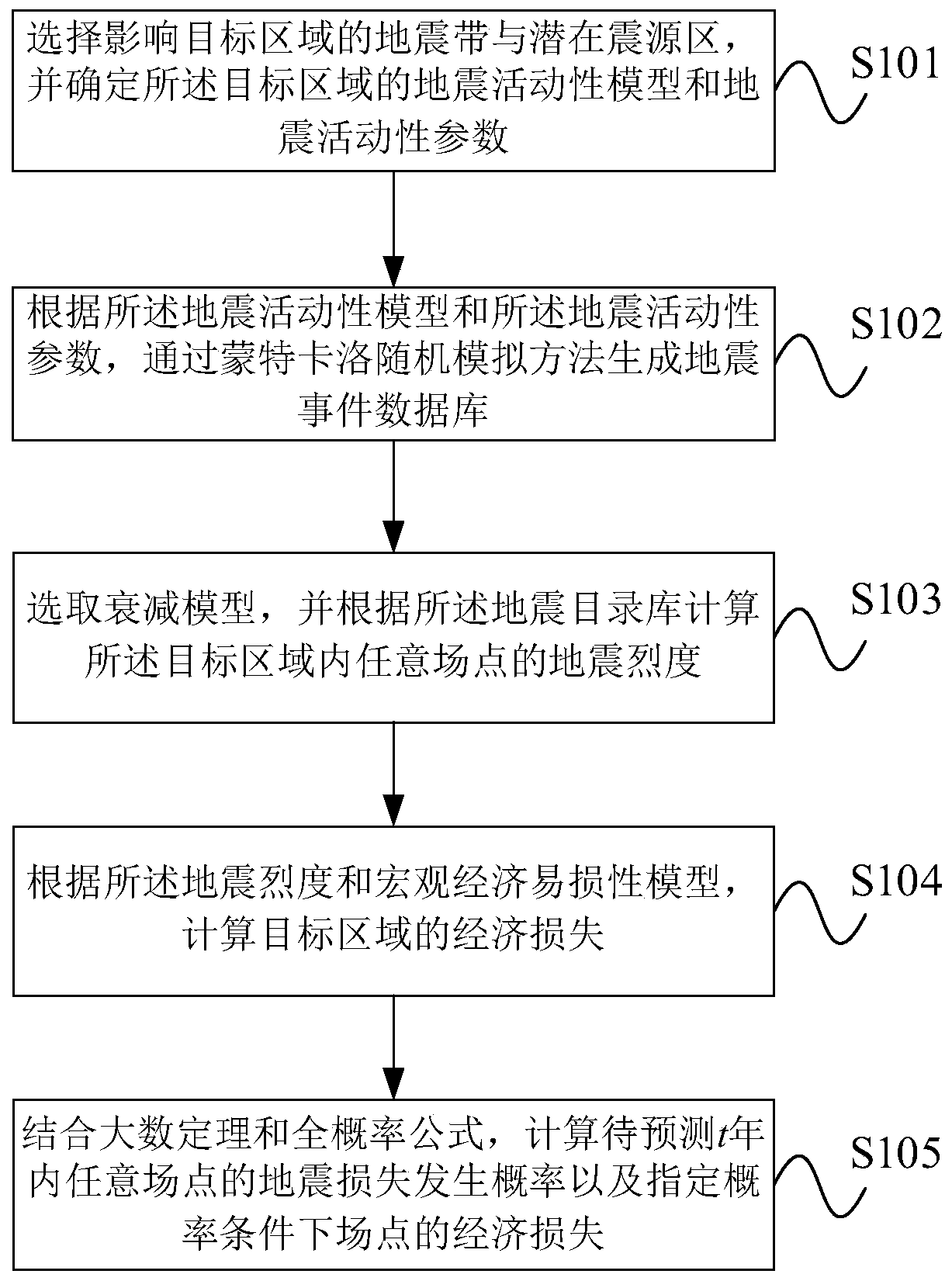
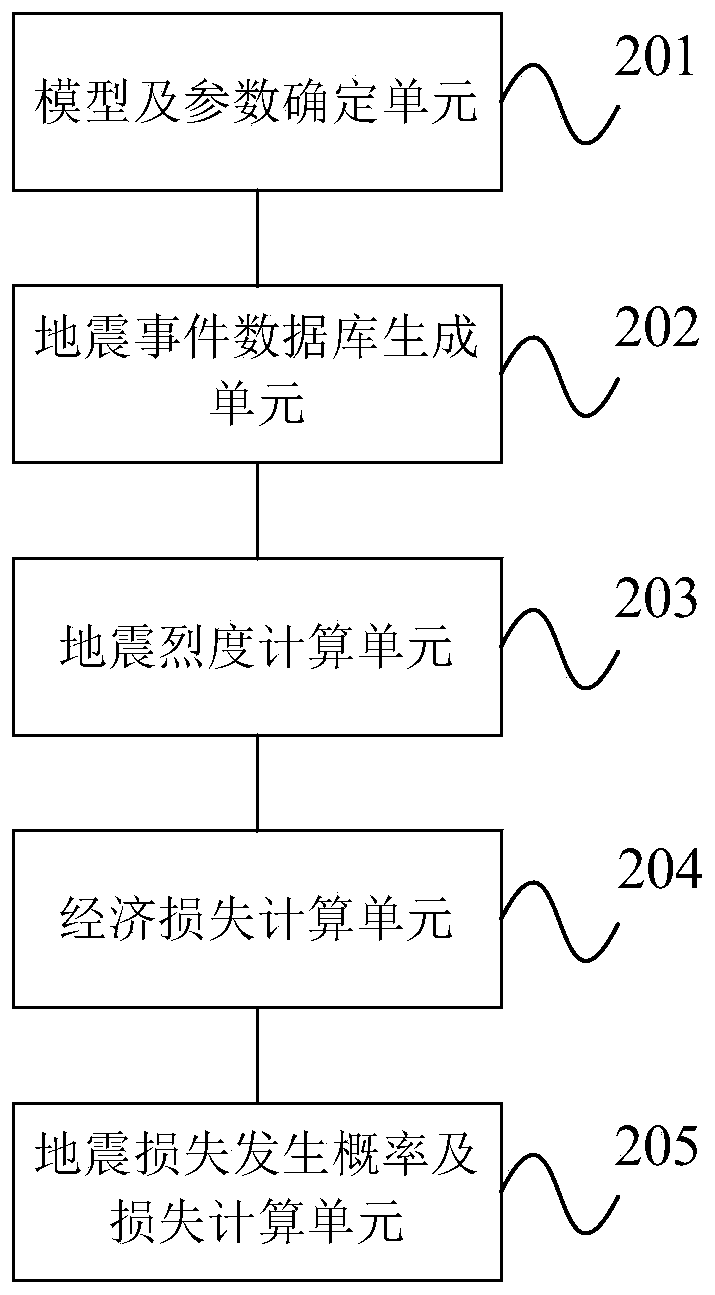
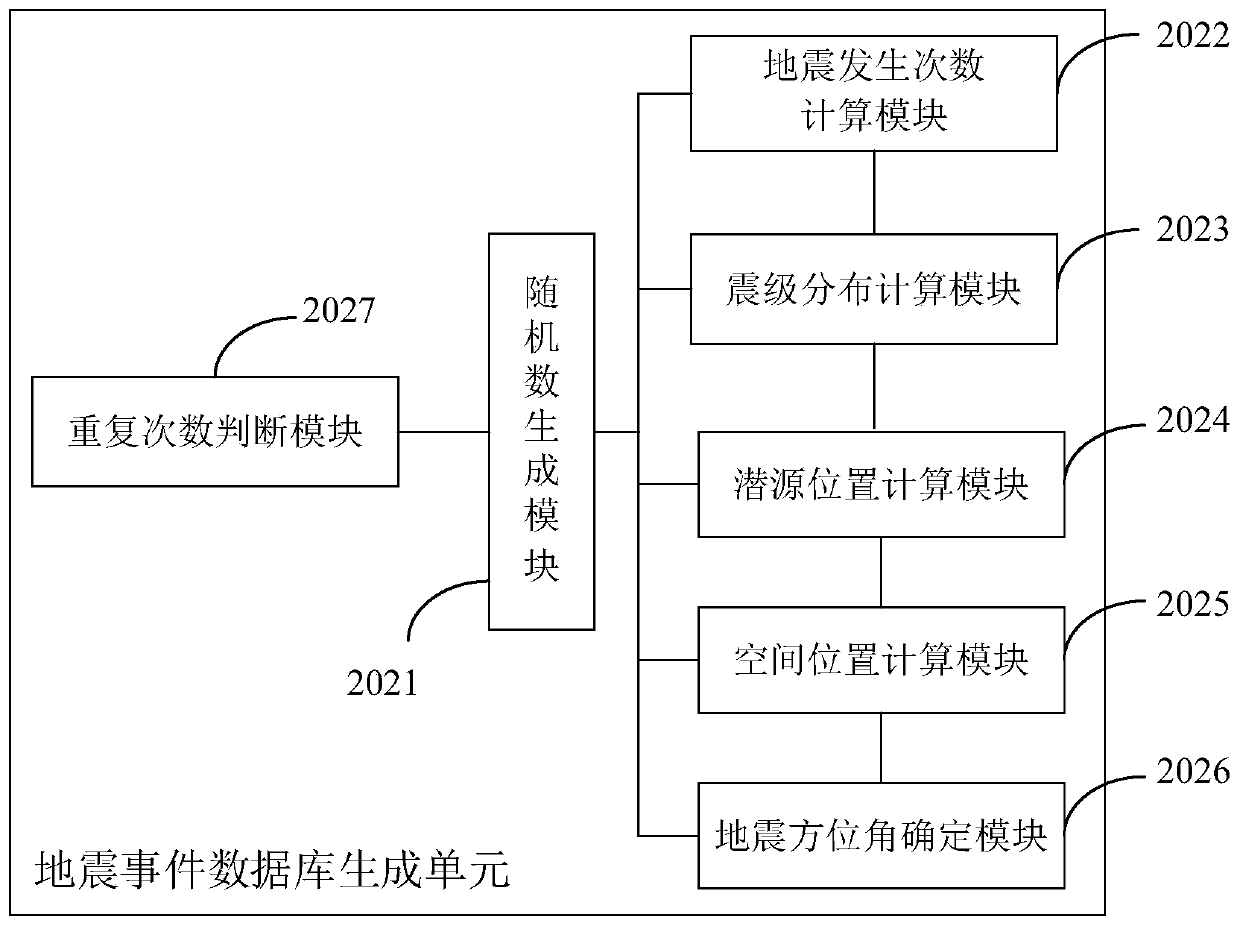
Probabilistic earthquake economic loss calculation method and system
PendingCN110046454AEarthquake Risk MitigationDesign optimisation/simulationResourcesEarthquake intensityLaw of total probability
The invention provides a probabilistic earthquake economic loss calculation method and system. The method comprises the following steps: selecting a seismic zone and a potential seismic source regioninfluencing a target region, and determining a seismic activity model and seismic activity parameters; generating a seismic event database through a Monte Carlo random simulation method; selecting anattenuation model, and calculating the seismic intensity of any field point in the target area according to the seismic directory library; calculating the economic loss of the target area according tothe seismic intensity and the macroeconomic vulnerability model; and calculating the earthquake loss occurrence probability of any field point in t years and the economic loss of the field point under the specified probability condition in combination with a large number theorem and a full probability formula. The system comprises a model and parameter determination unit, an earthquake event database generation unit, an earthquake intensity calculation unit, an economic loss calculation unit and an earthquake loss occurrence probability and loss calculation unit. The method considers that thefield points may suffer from the same intensity influence for many times, and provides technical support for earthquake loss prediction.
Owner:INST OF GEOLOGY CHINA EARTHQUAKE ADMINISTRATION
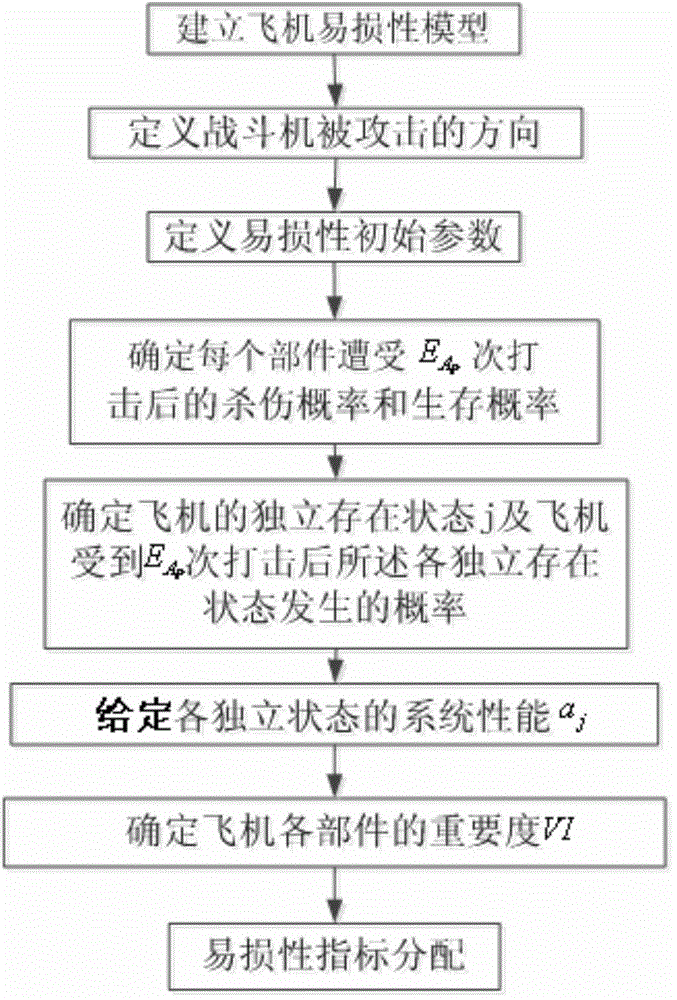
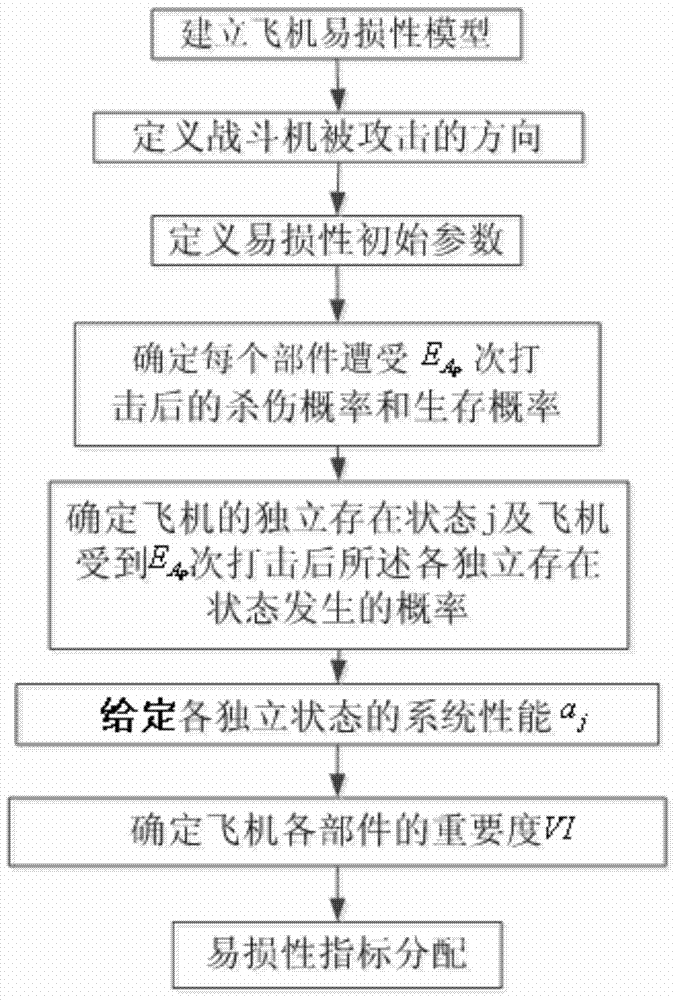
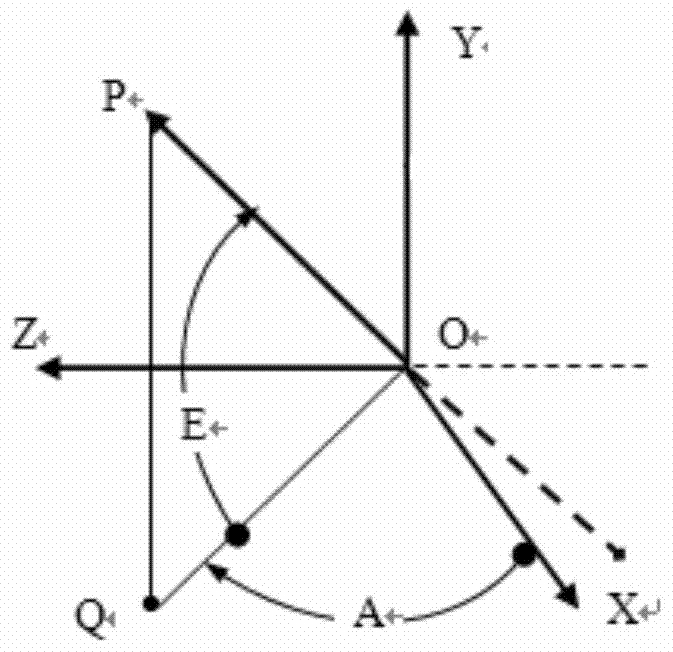
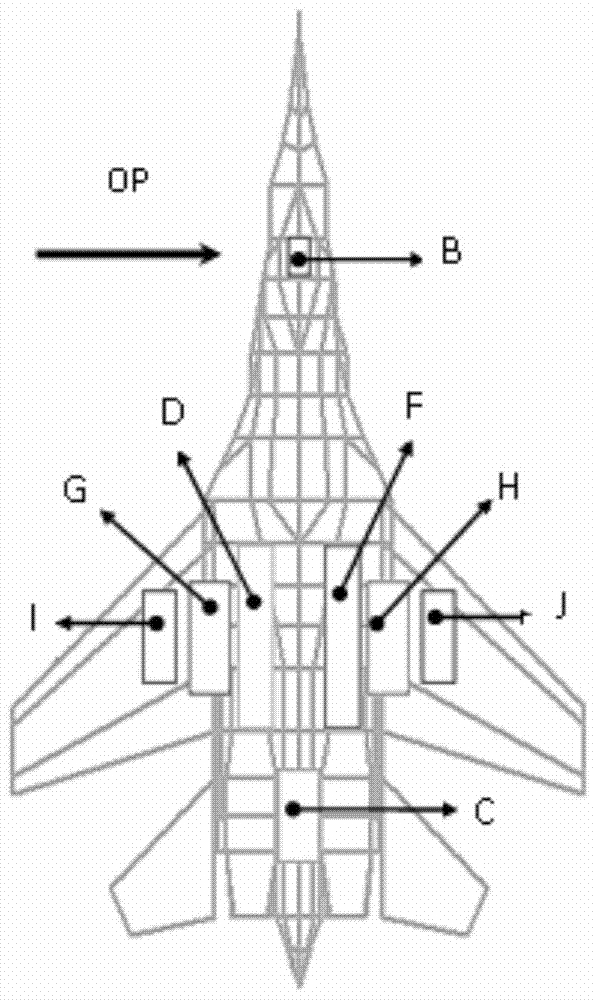
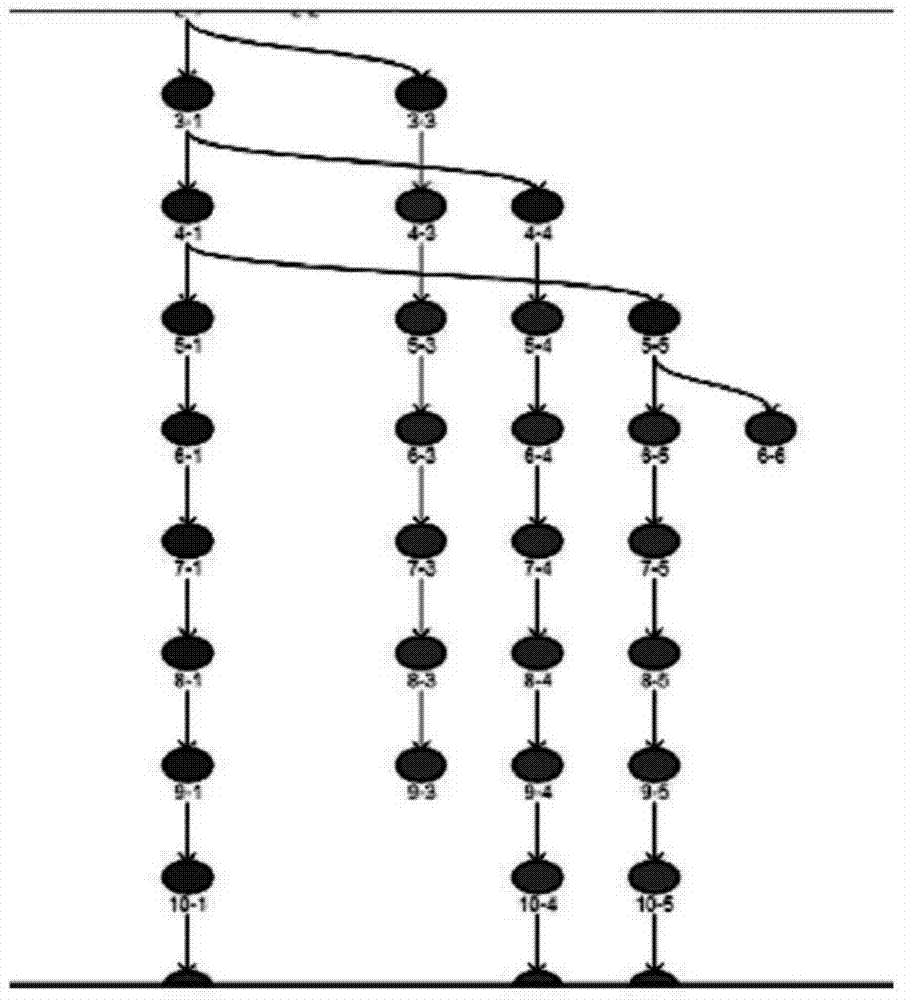
Method for distributing vulnerability index of combat aircraft system
ActiveCN104820778AImprove survivabilityReduce vulnerabilitySpecial data processing applicationsSurvivabilitySurvival probability
A method for distributing a vulnerability index of a combat aircraft system, comprising the steps as follows: determining a vulnerability initial parameter under a condition that menace and attack are determined through establishing a certain type fighter vulnerability model, then determining the times of the attack suffered by an aircraft, and the killing probability and the survival probability of each attacked component, determining the self-existent state of the aircraft and attacked probability of each state, substituting the obtained data into computational formulas of a comprehensive importance degree and a Griffith importance degree to obtain the comprehensive importance degree and the Griffith importance degree computational of each component, finally distributing the vulnerability of the whole aircraft by using a vulnerability index distribution method to obtain the vulnerability of each component. The method of the invention can be used for reducing the vulnerability of the component with large vulnerability after obtaining the vulnerability distributed to each component to reduce the vulnerability, thereby increasing the aircraft survivability.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
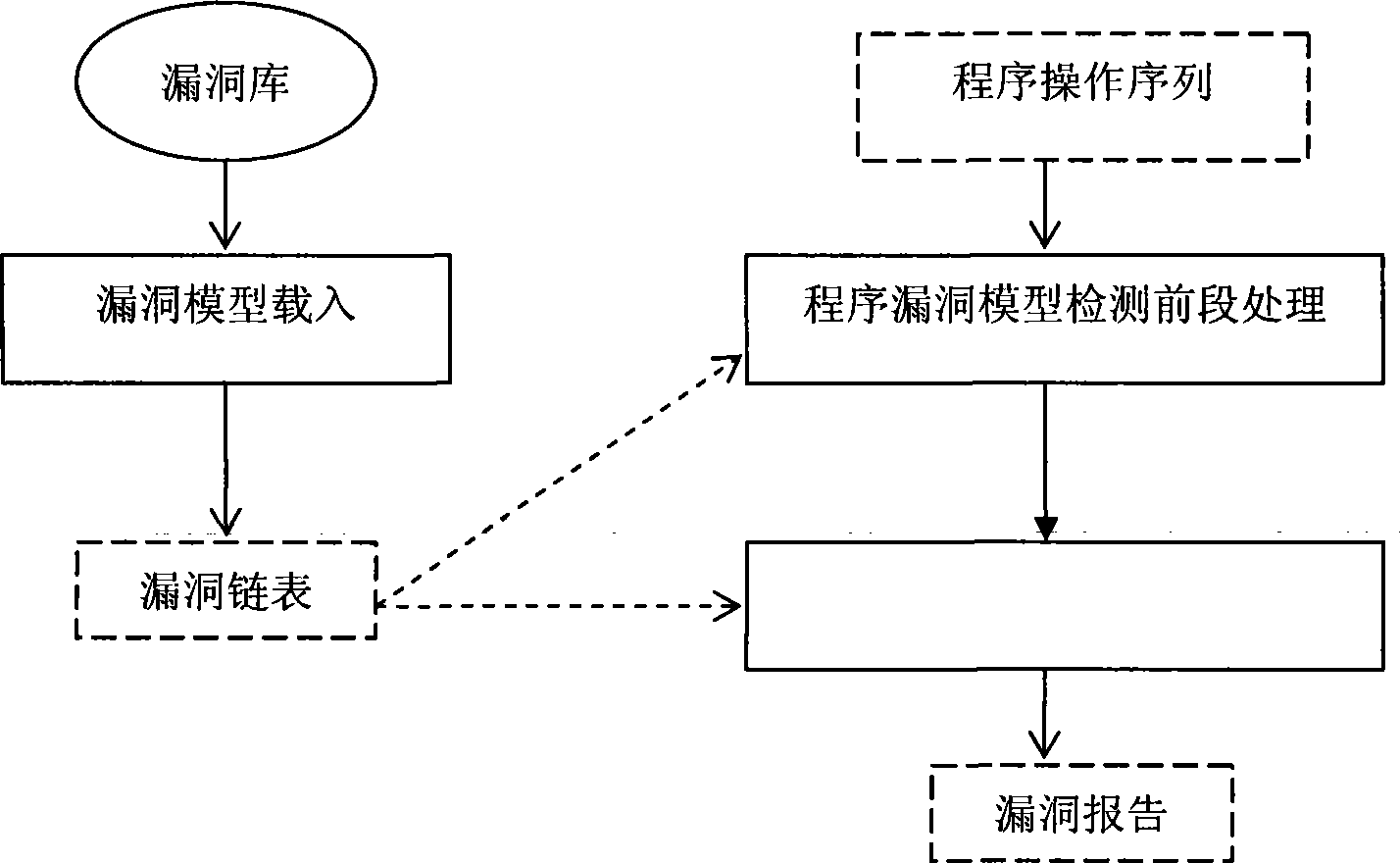
Program operation characteristic extracting method for detecting vulnerability model
InactiveCN101388055AJudgment of existenceAvoid duplication of workPlatform integrity maintainanceFeature extractionProcedural approach
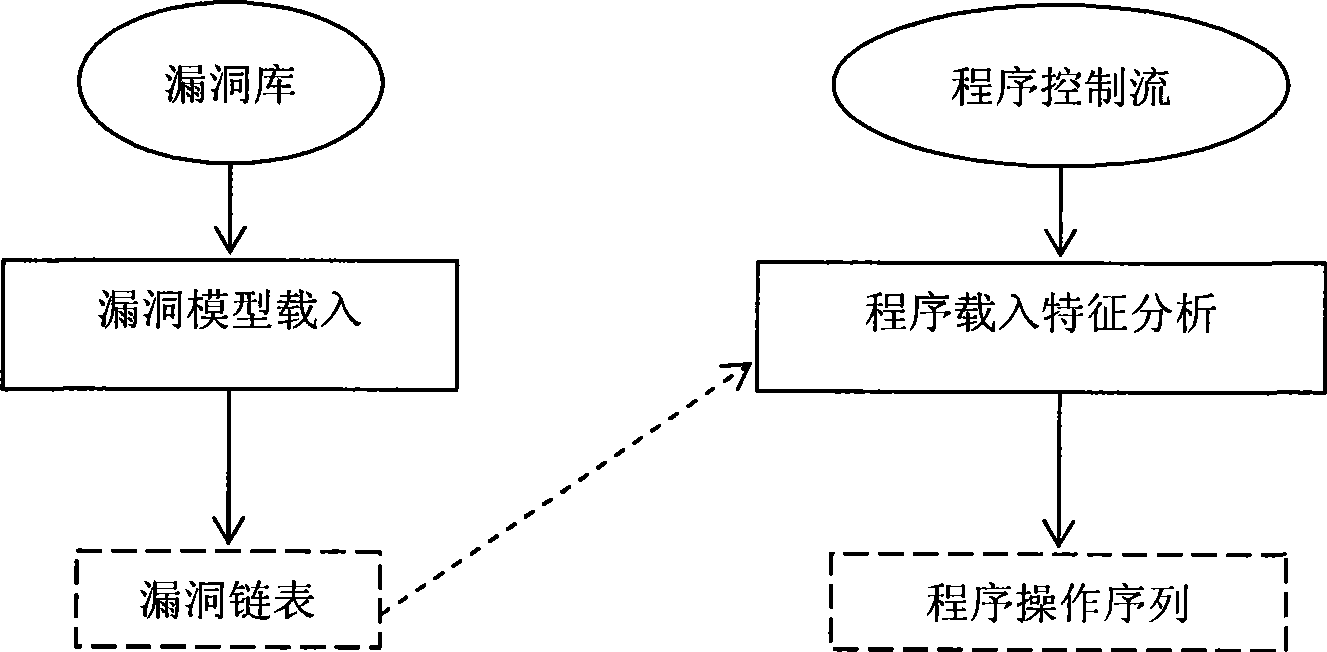
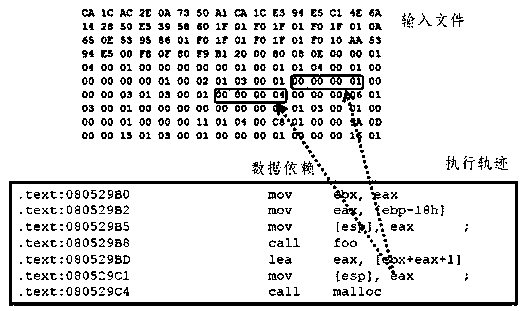
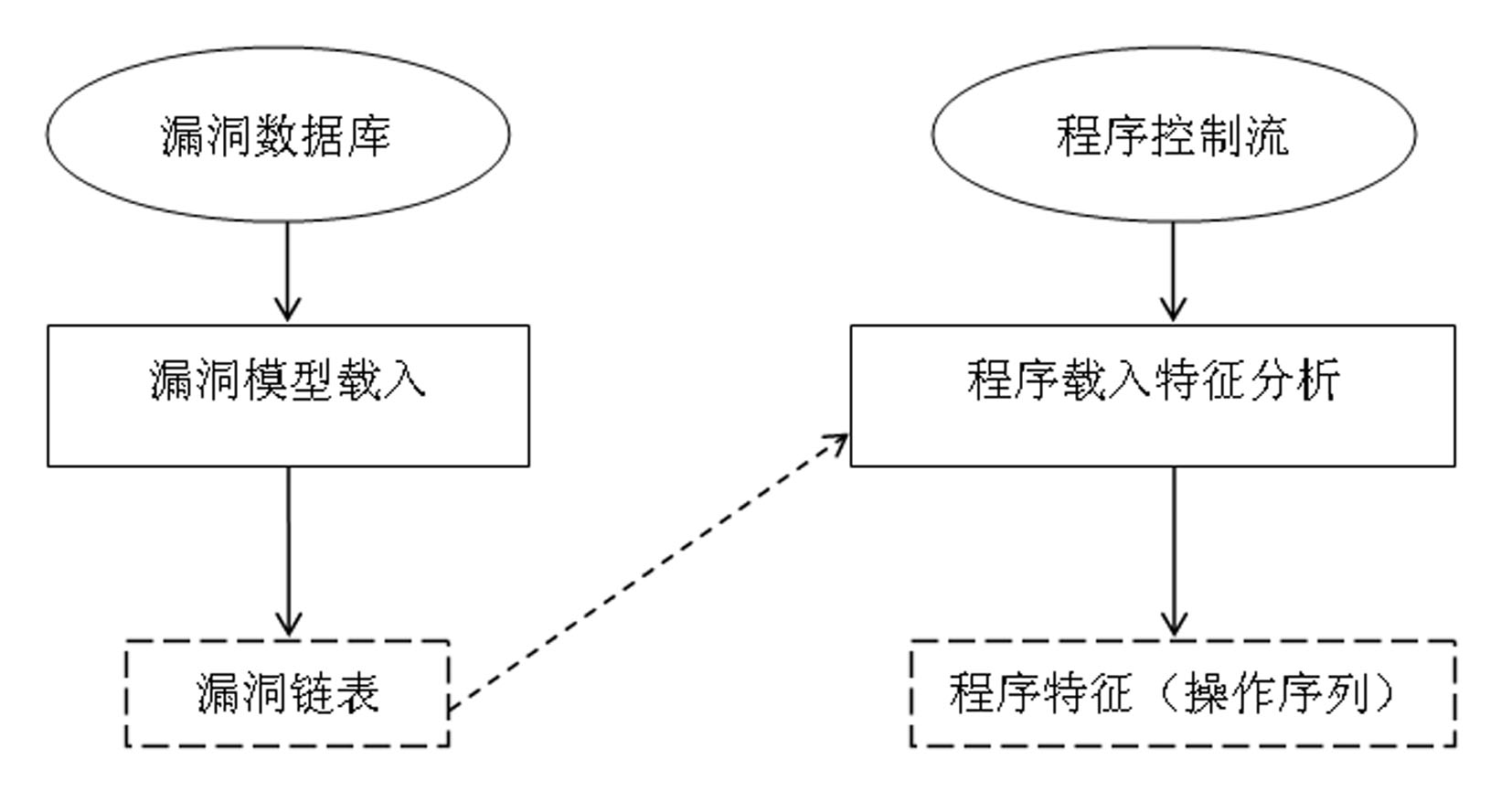
A method of program feature extraction for detecting software vulnerability models comprises steps of 1) loading a vulnerability model from a database to a memory, using the vulnerability model as a reference when analyzing the program and creating a data structure of the vulnerability model, 2) loading a program and a feature analysis extracting process, abstracting software codes compiled via a gcc, and extracting required operations according to the operating information related to the vulnerability model to obtain a sequence of program feature, namely a program feature sequence for detecting the vulnerability model. The loading process of the vulnerability model includes: the vulnerability model is composed of state nodes of the vulnerability state and the set of directed edges. The process of loading the program and extracting features includes extracting information related to the vulnerability state in a program control flow chart, and then organizing the information in terms of functions. The process of extracting the operating sequence related to the vulnerability model includes that each function program feature corresponds to one operation sequence linked list, and the operating sequence linked lists are organized in terms of functions, wherein the node of the operating sequence linked list is an operation or function related to the vulnerability state.
Owner:NANJING UNIV
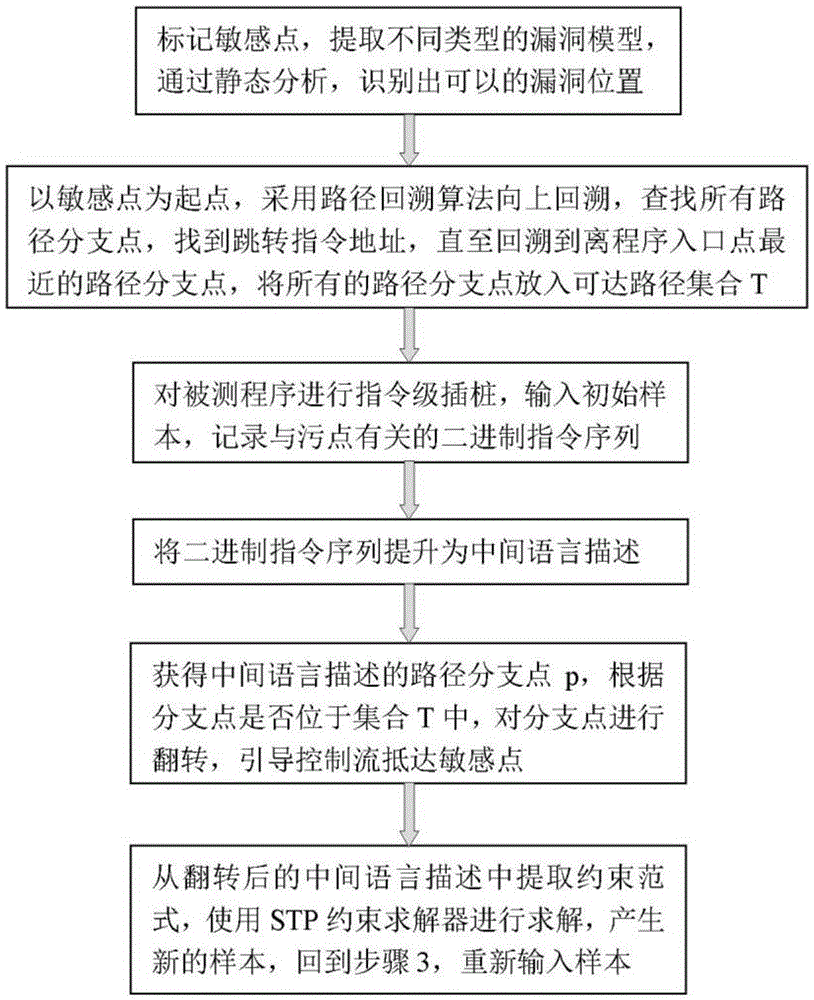
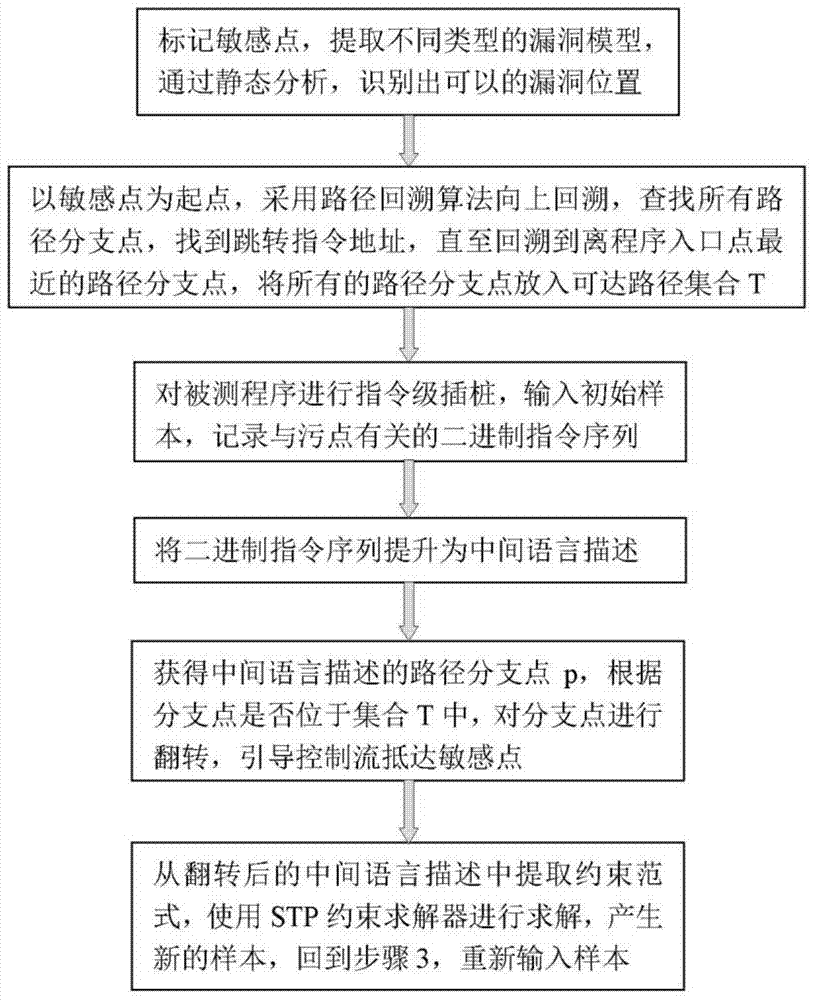
Sensitive point approximation method based on intelligent route guidance
InactiveCN105487983AAlleviate the problem of explosionReduce in quantitySoftware maintainance/managementSoftware testing/debuggingControl flowEntry point
The invention relates to a sensitive point approximation method based on intelligent route guidance. The method comprises the steps that vulnerability models of different types are extracted, and the position of a sensitive point is recognized through static analysis; upward backtracking is performed by taking the sensitive point as a starting point and adopting a route backtracking algorithm to look up all route branch points and is performed until the route branch point which is nearest away from a program entry point is found; instruction level instrumentation is performed on a tested program, an original sample is input, and a binary instruction sequence related to dirty points is recorded; the binary instruction sequence is lifted into intermediate language description; route branch points of the intermediate language description are acquired and turned according to whether the branch points are located in a set, and control flow is guided to reach the sensitive point; a constraint normal form is extracted from turned intermediate language description, solving is performed with an STP constraint solver, a new sample is generated, and returning is performed to re-input the sample. According to the method, the control flow is guided to reach the sensitive point position through the sensitive point, the problem of route explosion is effectively solved, and the vulnerability mining efficiency is improved.
Owner:ZHENGZHOU ENBEI NETWORK TECH CO LTD
Software fuzzy test method
ActiveCN110196815ASmall scaleImproving Vulnerability Analysis EffectivenessSoftware testing/debuggingMulti dimensionalReliability engineering
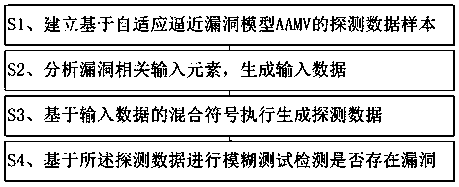
The invention provides a software fuzzy test method, which comprises the following steps of: extracting and establishing a detection data sample based on an adaptive approximation vulnerability model(AAMV) based on historical data, test cases and log information acquired in a software test stage; dynamically analyzing vulnerability-related input elements in the detection data sample based on thefine-grained stain, and generating input data based on the detection data sample; and generating high coverage probe data based on mixed symbols of the input data. An adaptive approximation vulnerability model AAMV based on a tree structure is provided, detection data generation is guided, and the software vulnerability analysis effect is improved. Fine-grained stain analysis is carried out to find out fragile point related input elements, and variation space of the input elements is reduced. The code coverage rate of the fuzzy test technology is improved. According to the multi-dimensional detection data generation technology based on the OMMutator operator, the detection data scale is greatly reduced under the condition that the hit rates of fragile points are the same.
Owner:NAT UNIV OF DEFENSE TECH
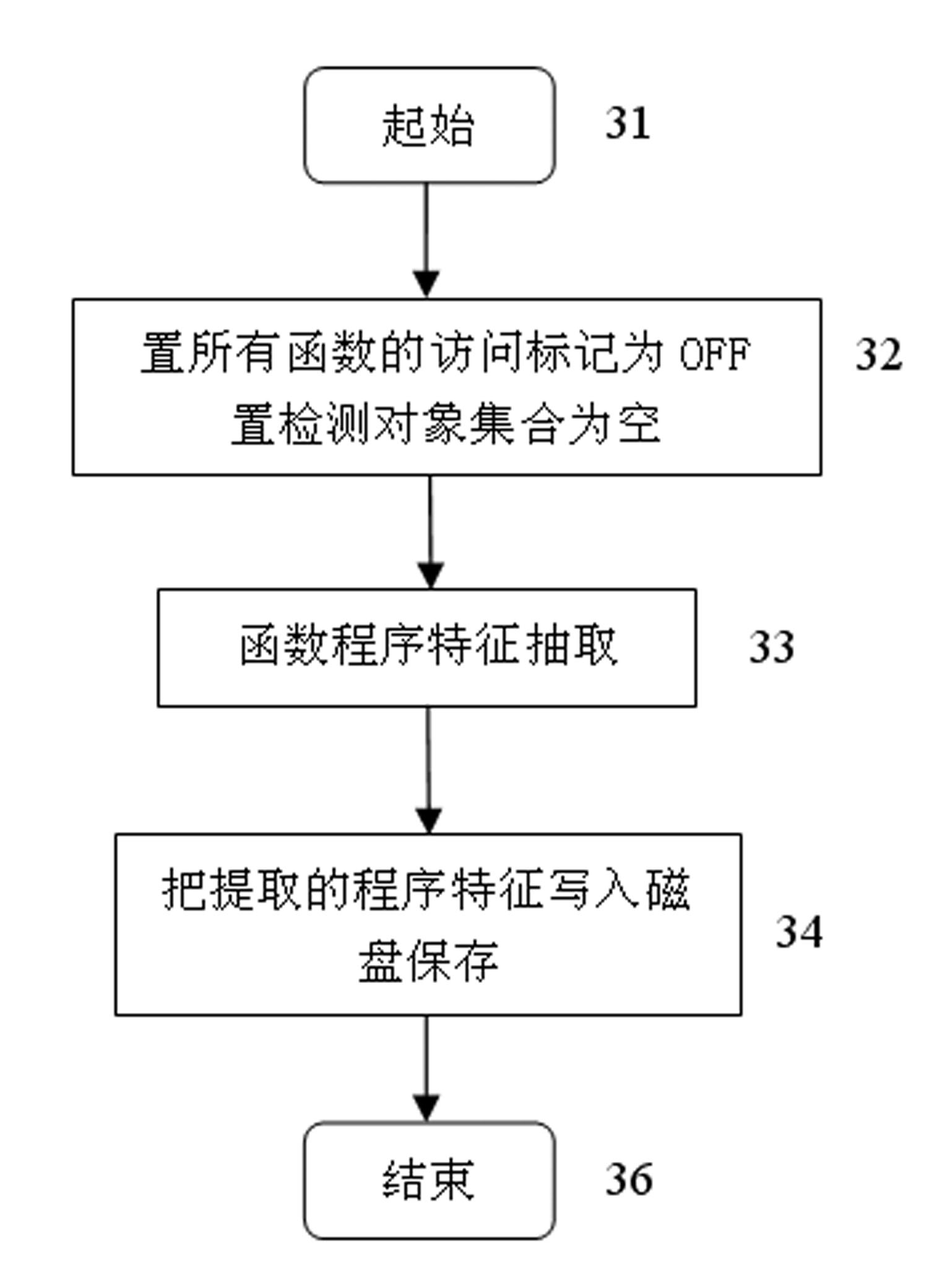
Detected object program feature extraction method for vulnerability detection
InactiveCN101937395AJudgment of existenceOvercoming duplication of workSoftware testing/debuggingFeature extractionTheoretical computer science
The invention relates to a detected object program feature extraction method for vulnerability detection, which comprises the following steps of: 1) loading vulnerability, namely establishing a data structure of a vulnerability model consisting of a set of states of a vulnerability state machine and a set of operation of the vulnerability state machine, wherein the states represent the state of the state machine and each state has state number, type and feature attributes; and 2) loading a program and analyzing and extracting features, namely carrying out abstraction on a software code which is subjected to gcc compilation, constructing a program feature sequence for detection of the vulnerability model based on a detected object, extracting program feature information related to the vulnerability state from a program control flow graph, organizing the program feature information by taking a function as a unit and organizing each function into a plurality of operation sequence link list indexed by the detected object. The method solves the problems of a great amount of repeated work, influence on detection speed and inaccurate parameter analysis of the conventional software vulnerability detection method so as to judge whether the vulnerability model exists in the code or not.
Owner:NANJING UNIV
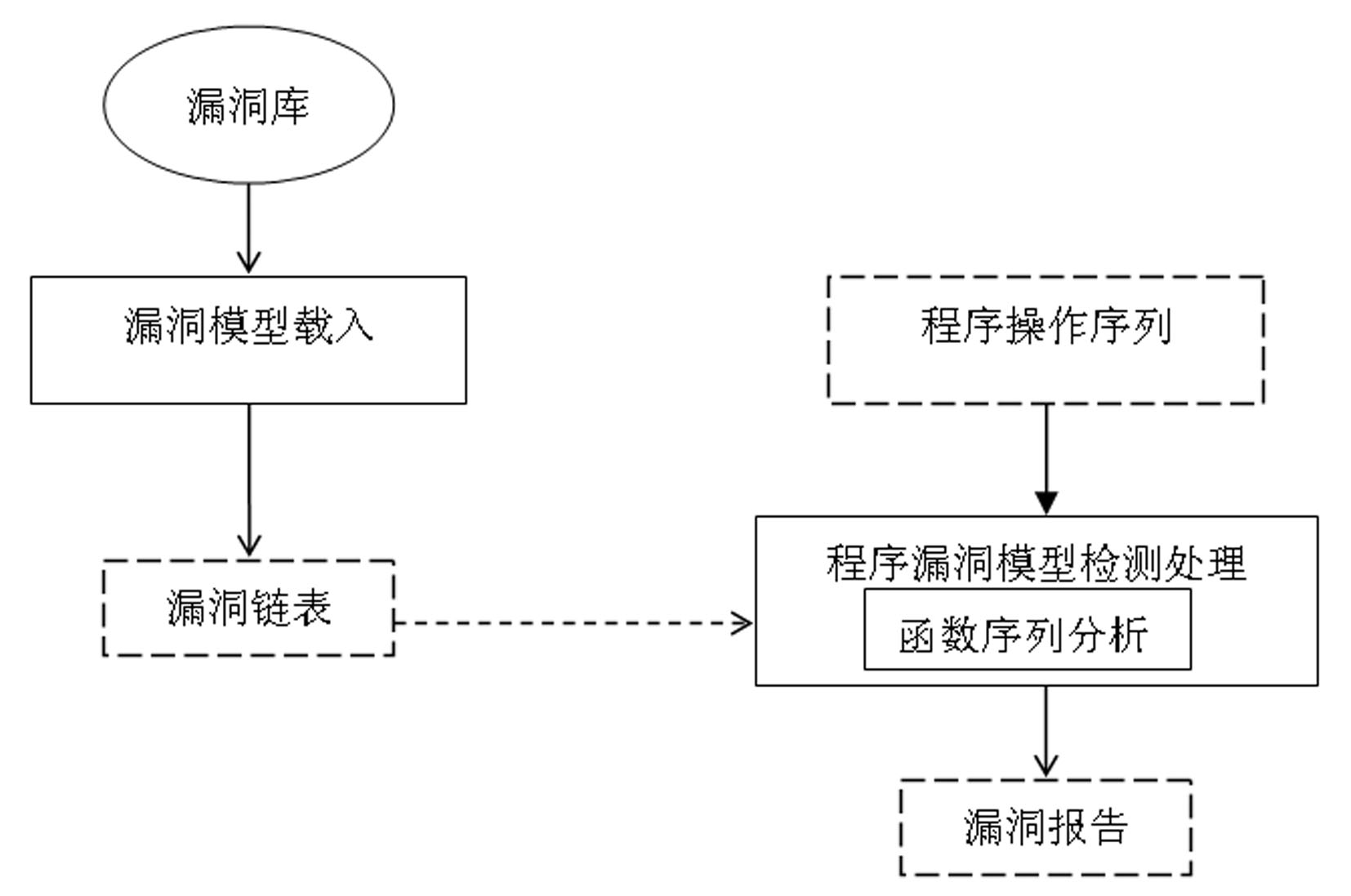
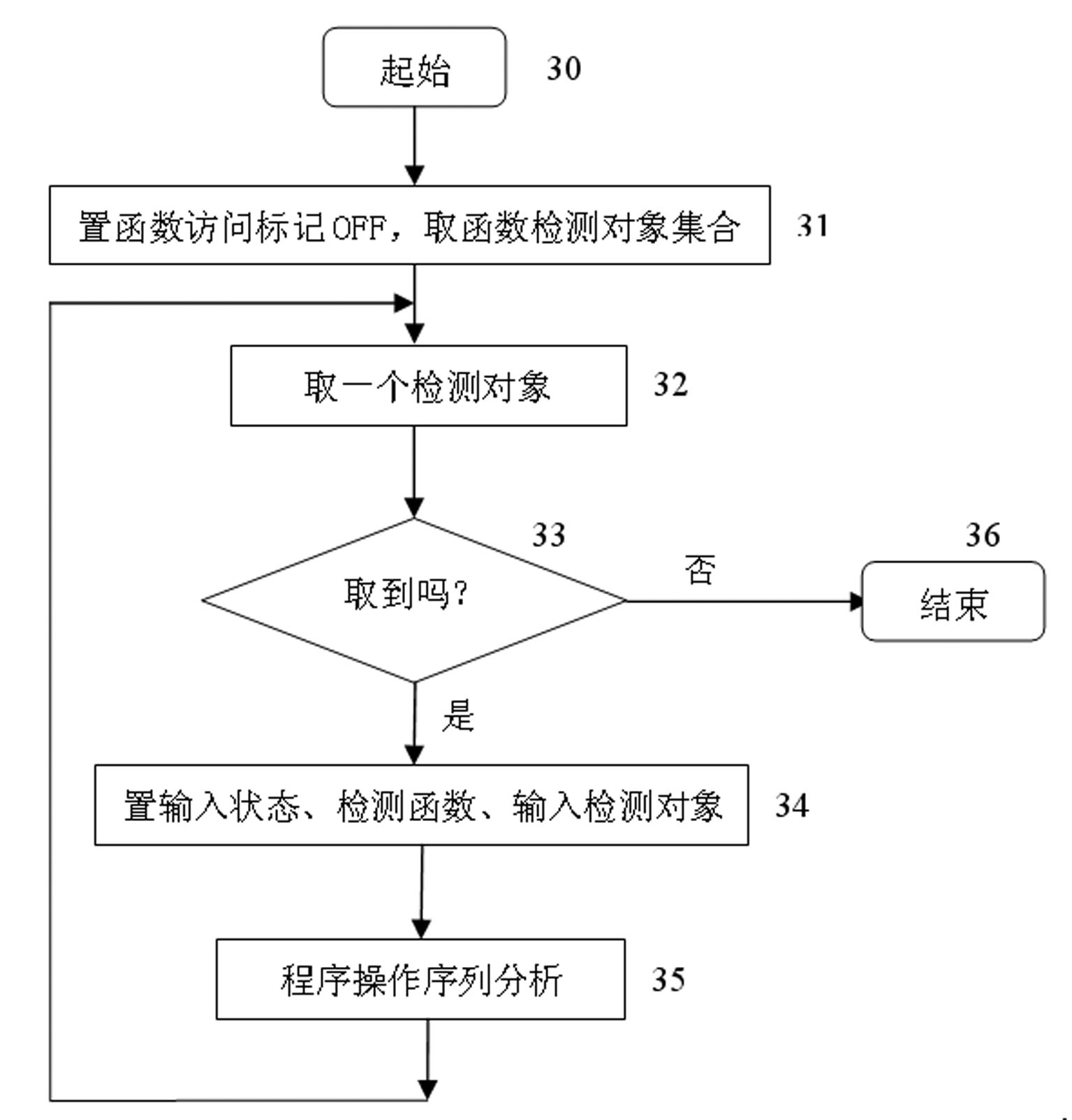
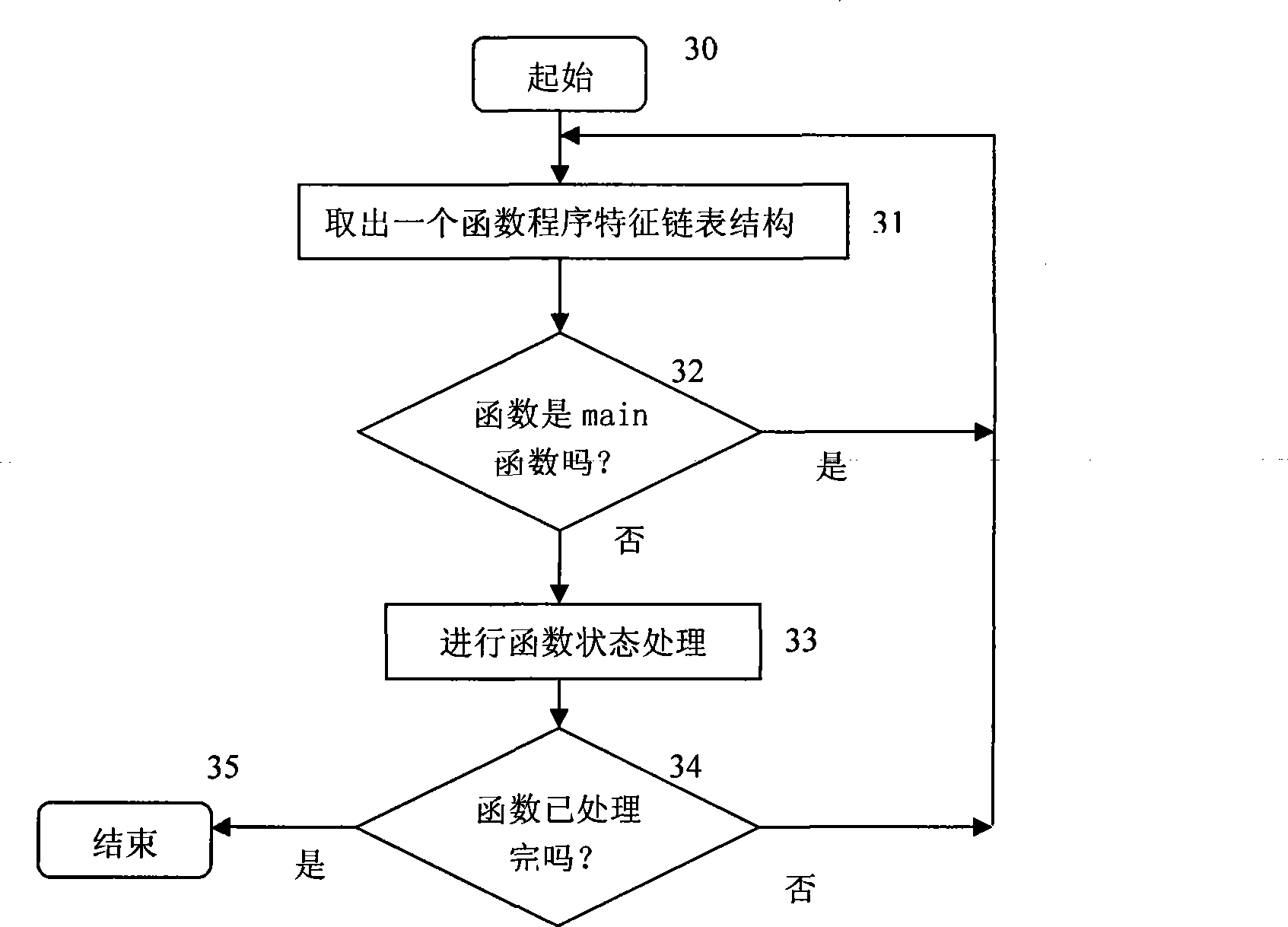
Detection object-based software vulnerability model detection method
InactiveCN101930401AGet over workOvercome speedSoftware testing/debuggingSequence analysisObject based
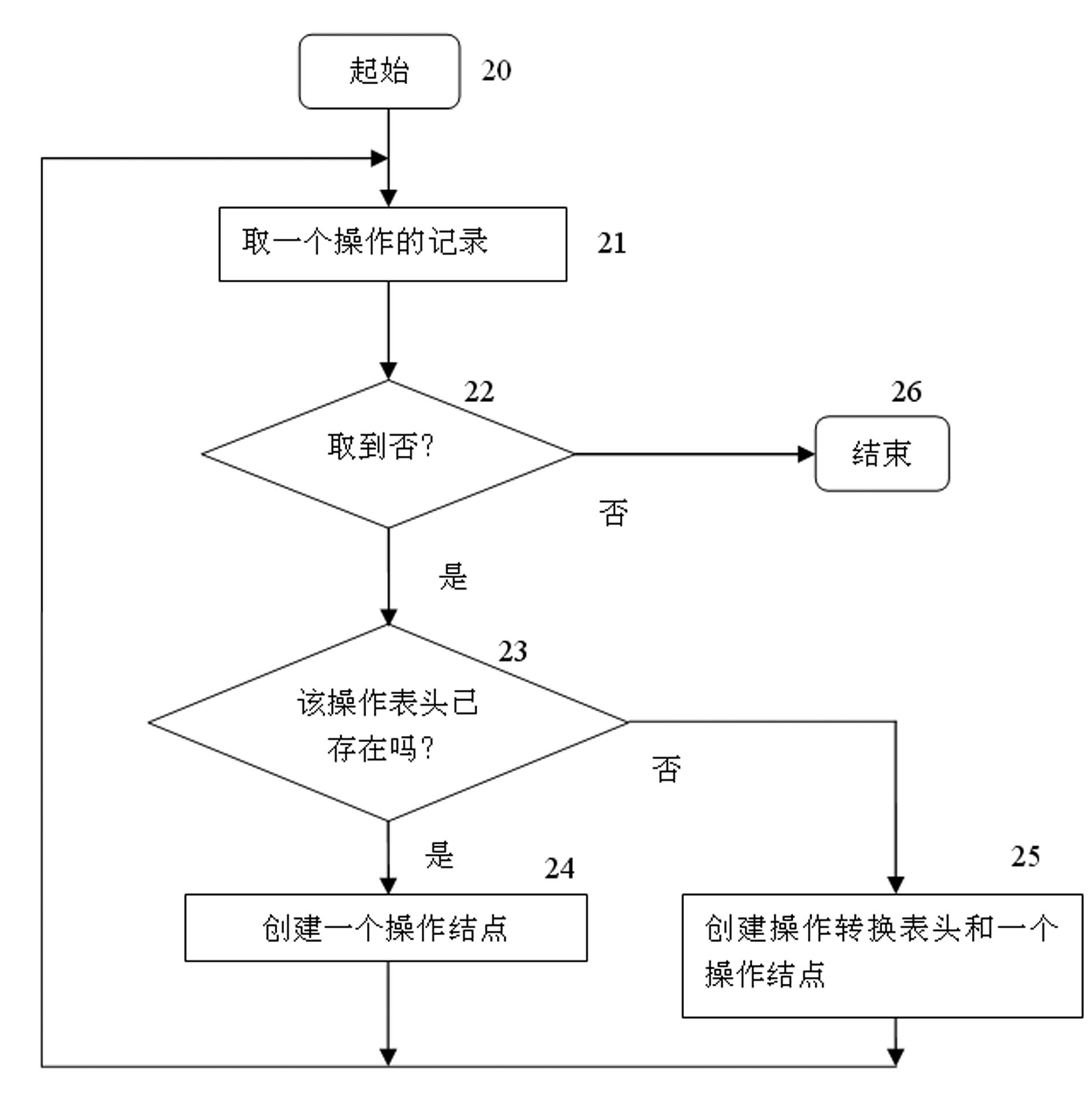
The invention discloses a detection object-based software vulnerability model detection method, which comprises the following steps: (1) flow of loading vulnerability in which a data structure of a vulnerability model is established, wherein the vulnerability model is composed of a state set and an operation set of a vulnerability state machine, and the state represents the state of the state machine; 2) flow of vulnerability model detection processing; 3) flow of analyzing function program operation sequence, namely a process of analyzing the function program sequence aiming at the detection object; and 4) process of operated state conversion processing in which the operated conversion state is calculated. The invention provides a vulnerability model-based software vulnerability model detection method. The software vulnerability-based state machine model is centered on a key detection object, which abstracts and models the software codes, performs vulnerability static detection only on the program operation sequence associated with the vulnerability state and judges the existence of the vulnerability model in the codes. The invention solves the problems that a lot of repeated work needs to be done, the detection speed is influenced and the accuracy is not high in the prior art.
Owner:NANJING UNIV
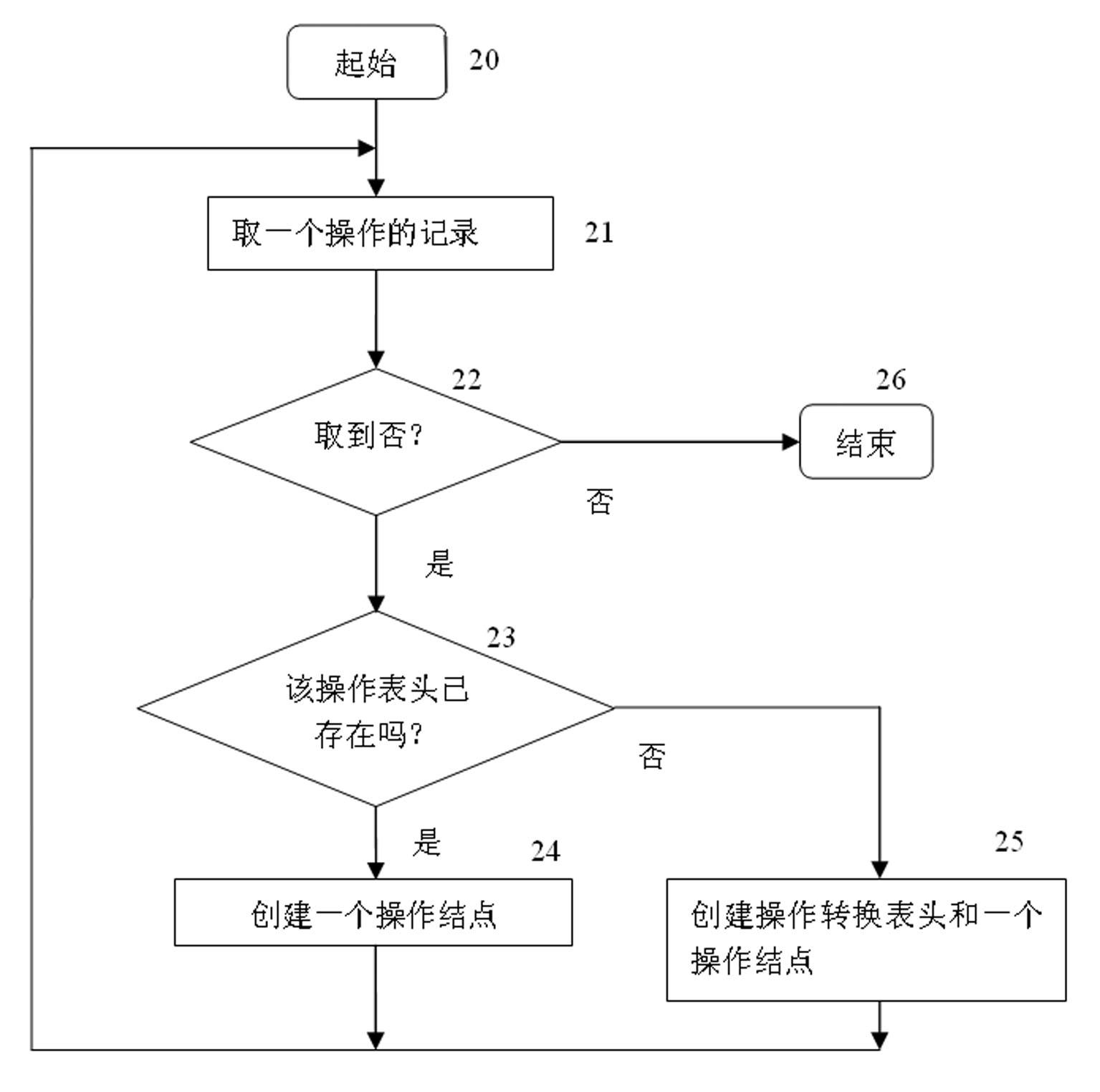
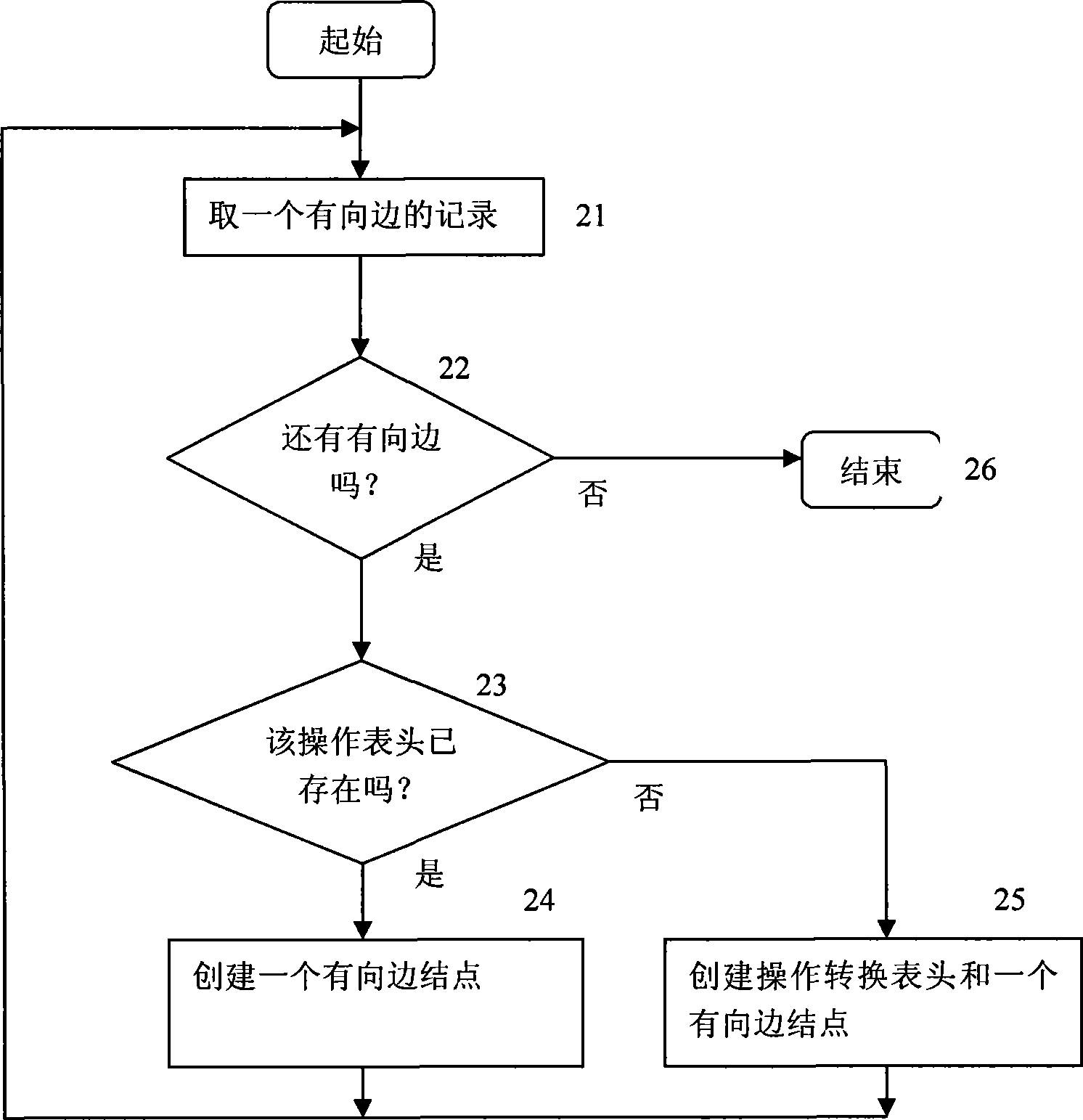
Method for detecting software loophole model based on loophole model
InactiveCN101373506AJudgment of existenceImprove reliabilityPlatform integrity maintainanceOperational transformationEdge type
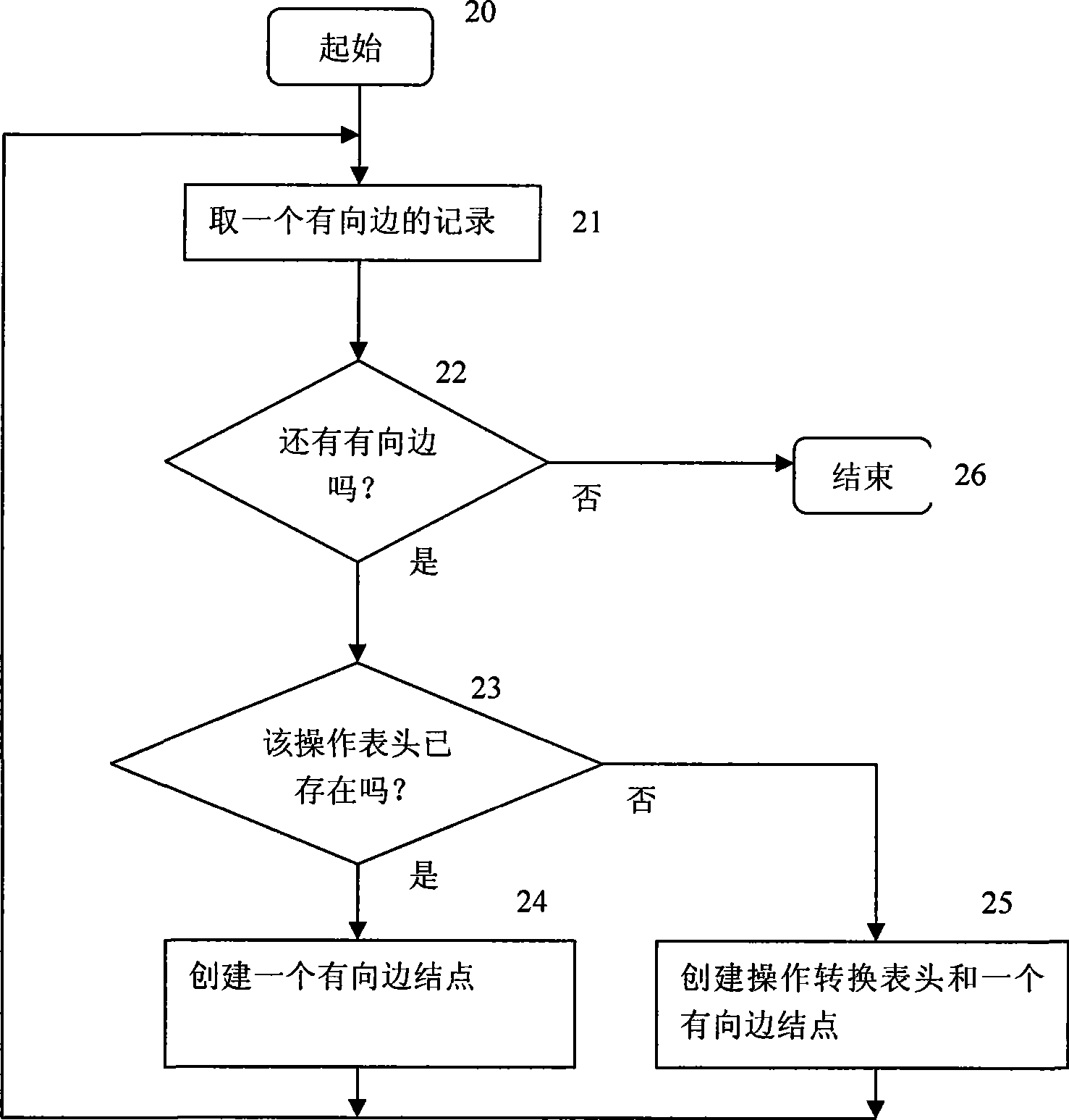
The invention provides a software vulnerability model test method based on vulnerability models. The method comprises the following steps: 1) the vulnerability models are loaded into a flow process from a database, that is, the vulnerability models are put into a memory, and data structures of the vulnerability models are established and used for reference during analyses of programs; 2) in the previous step for testing the models, models are tested according to relevant operations of vulnerability based on functions; and 3) in the final step for testing the models, the models are tested for principal functions, the states are tested and the existence of vulnerability is reported according to relevant operations of vulnerability and the model test results in the previous step. The vulnerability model load flow is as follows: the vulnerability models consist of vulnerability state nodes and gathers with directed edges; a flow for operating transition tables retrieved according to the directed edge types is established in a memory; irrelevant operations are filtered and removed through abstracting and processing programs in an abstract manner; the operation sequence flow relative to the vulnerability models is abstracted; and each function program feature corresponds to an operation sequence linked list.
Owner:NANJING UNIV
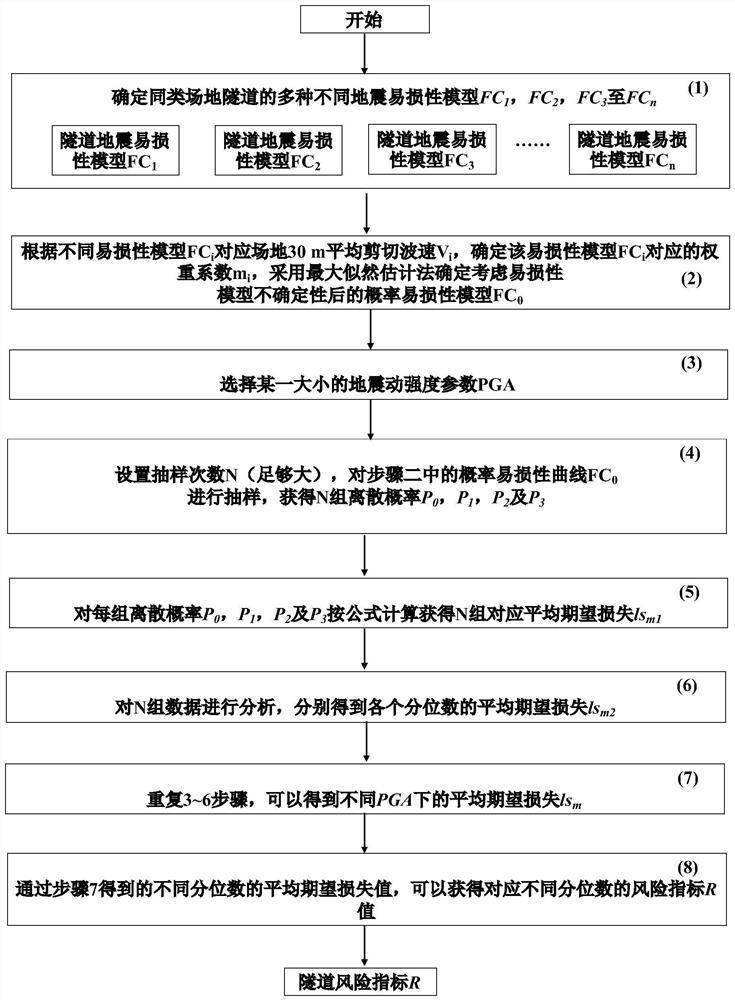
Shield tunnel risk assessment method considering uncertainty of earthquake vulnerability model
ActiveCN112541666AEfficiently assess uncertaintyThe calculation result is accurateResourcesComplex mathematical operationsStructural engineeringShield tunneling
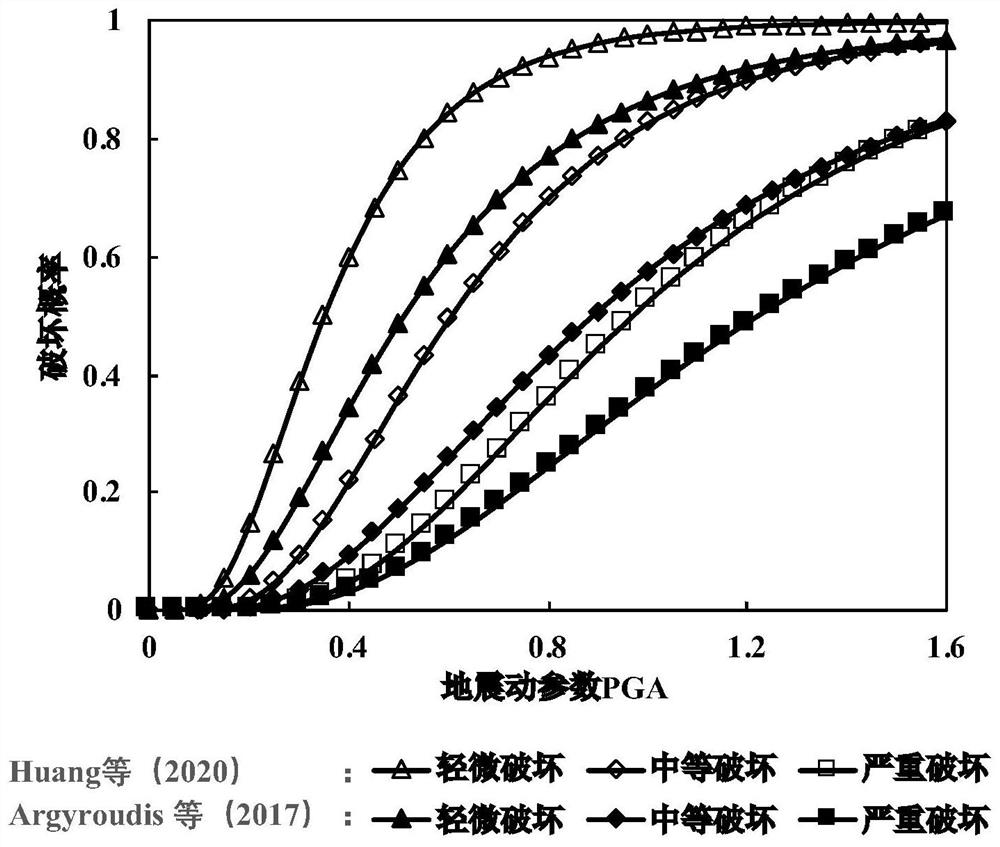
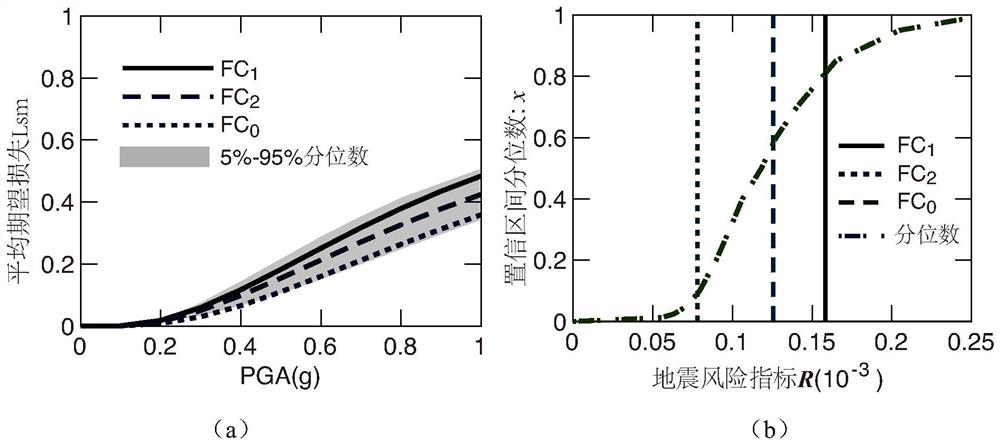
The invention relates to the field of tunnel risks, and provides a shield tunnel risk assessment method considering uncertainty of an earthquake vulnerability model. The method comprises the followingsteps: (1) determining various earthquake vulnerability models FC1, FC2 to FCn of tunnels in the same type; (2) establishing a vulnerability model FC0 considering uncertainty; (3) selecting a certainearthquake intensity PGA; (4) setting a sampling frequency N, and sampling the vulnerability model FC0 in the step (2) to obtain N groups of discrete probabilities P0, P1, P2 and P3 of different damage states; (5) obtaining N groups of average expected losses lsm1 according to the step (4); (6) calculating the average expected loss lsm2 of each quantile; (7) repeating the steps (3)-(6) to obtainthe average expected loss lsm of different PGAs; and (8) obtaining a risk index R value based on the result of the step (7). The scheme provided by the invention has the beneficial effects that errorscaused by a single model can be reduced, different vulnerability curve models are comprehensively considered, and the tunnel earthquake risk is analyzed more reasonably.
Owner:TONGJI UNIV
Cyberspace security system for complex systems
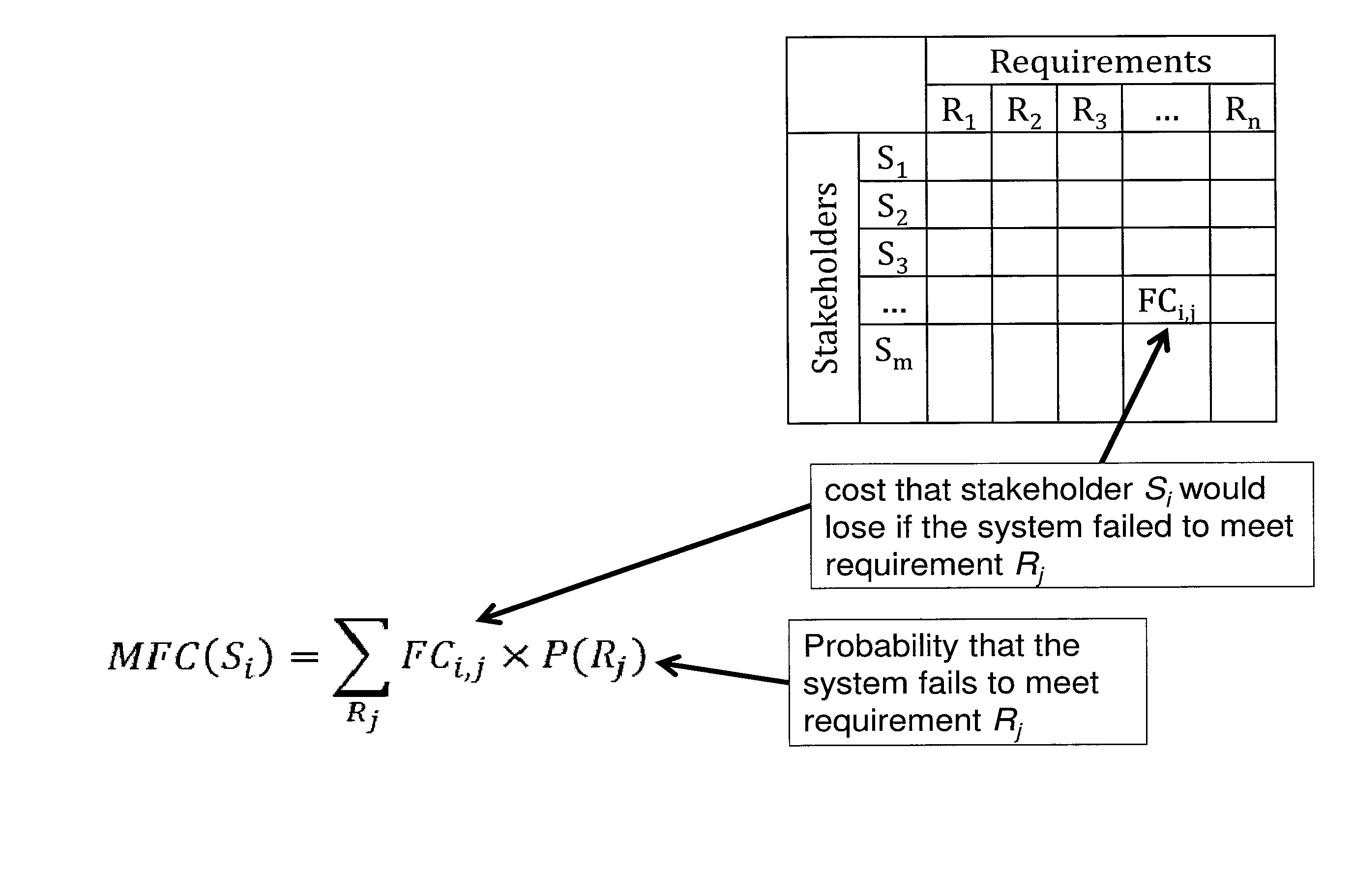
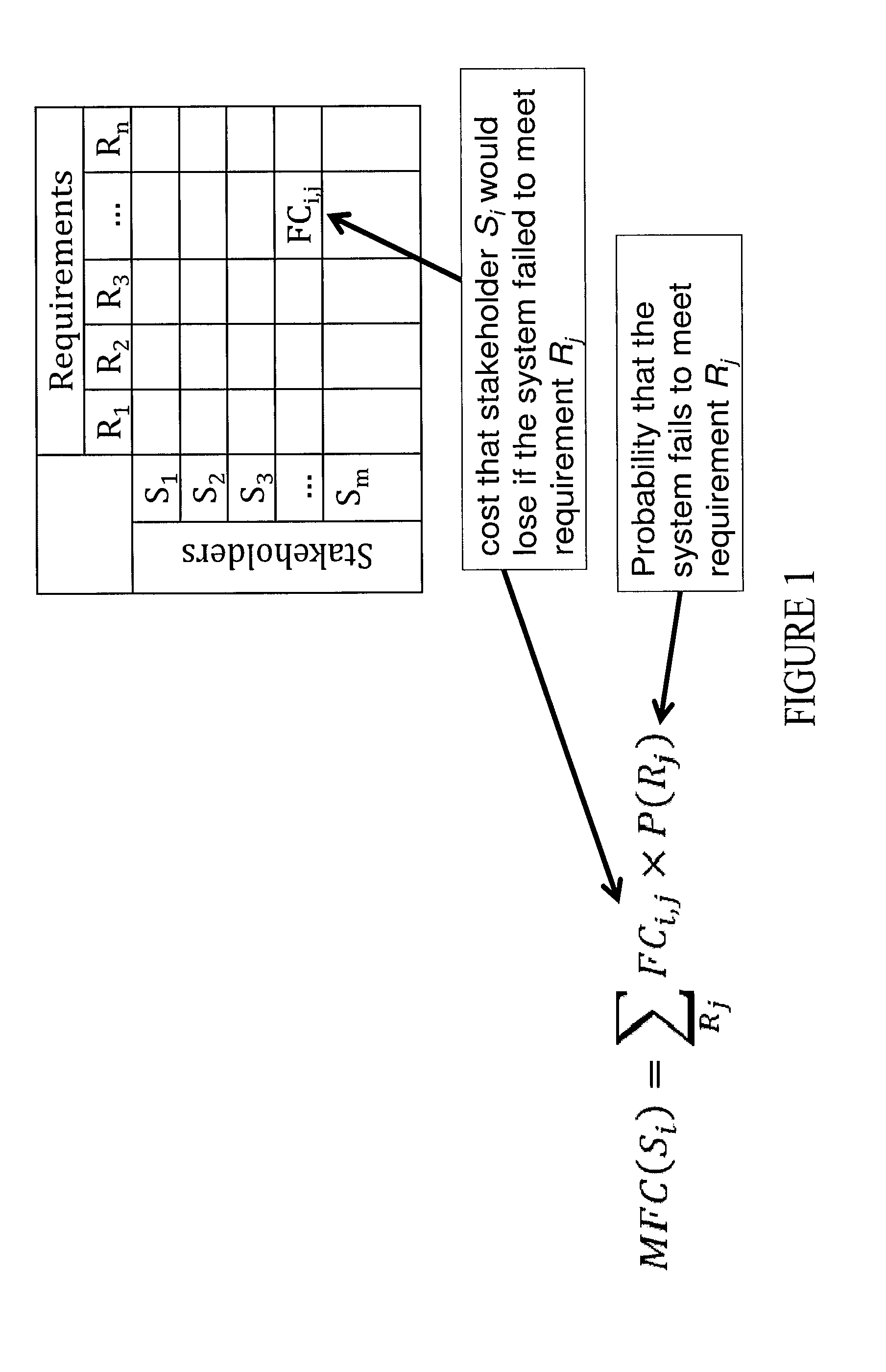
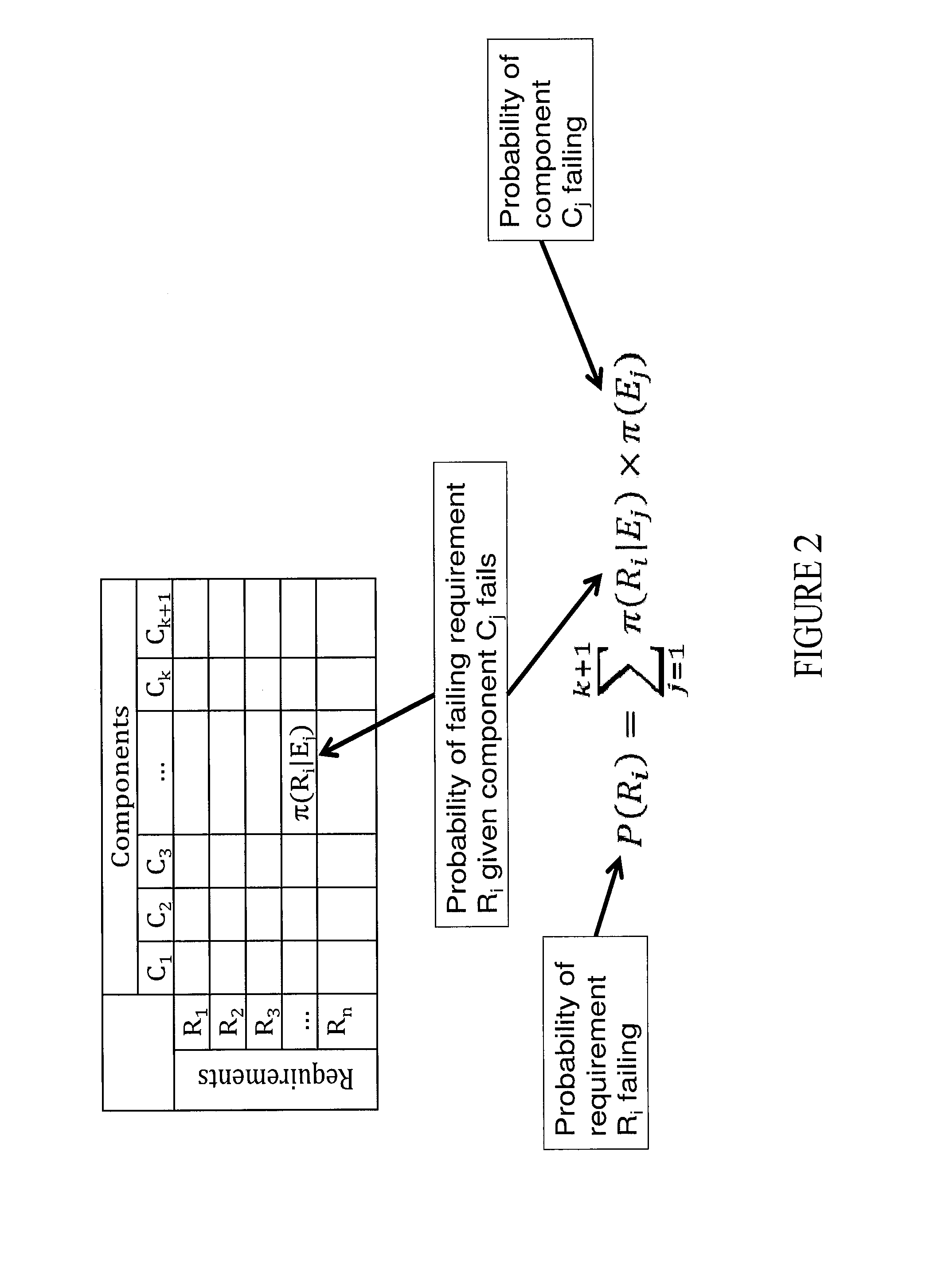
A computer implemented method monetizes the security of a cyber-system in terms of losses each stakeholder may expect to lose if a security break down occurs. A non-transitory media stores instructions for generating a stake structure that includes costs that each stakeholder of a system would lose if the system failed to meet security requirements and generating a requirement structure that includes probabilities of failing requirements when computer components fails. The system generates a vulnerability model that includes probabilities of a component failing given threats materializing and generates a perpetrator model that includes probabilities of threats materializing. The system generates a dot product of the stakes structure, the requirement structure, the vulnerability model and the perpetrator model. The system can further be used to compare, contrast and evaluate alternative courses of actions best suited for the stakeholders and their requirements.
Owner:UT BATTELLE LLC
Rapid modeling method for armored vehicle target vulnerability model
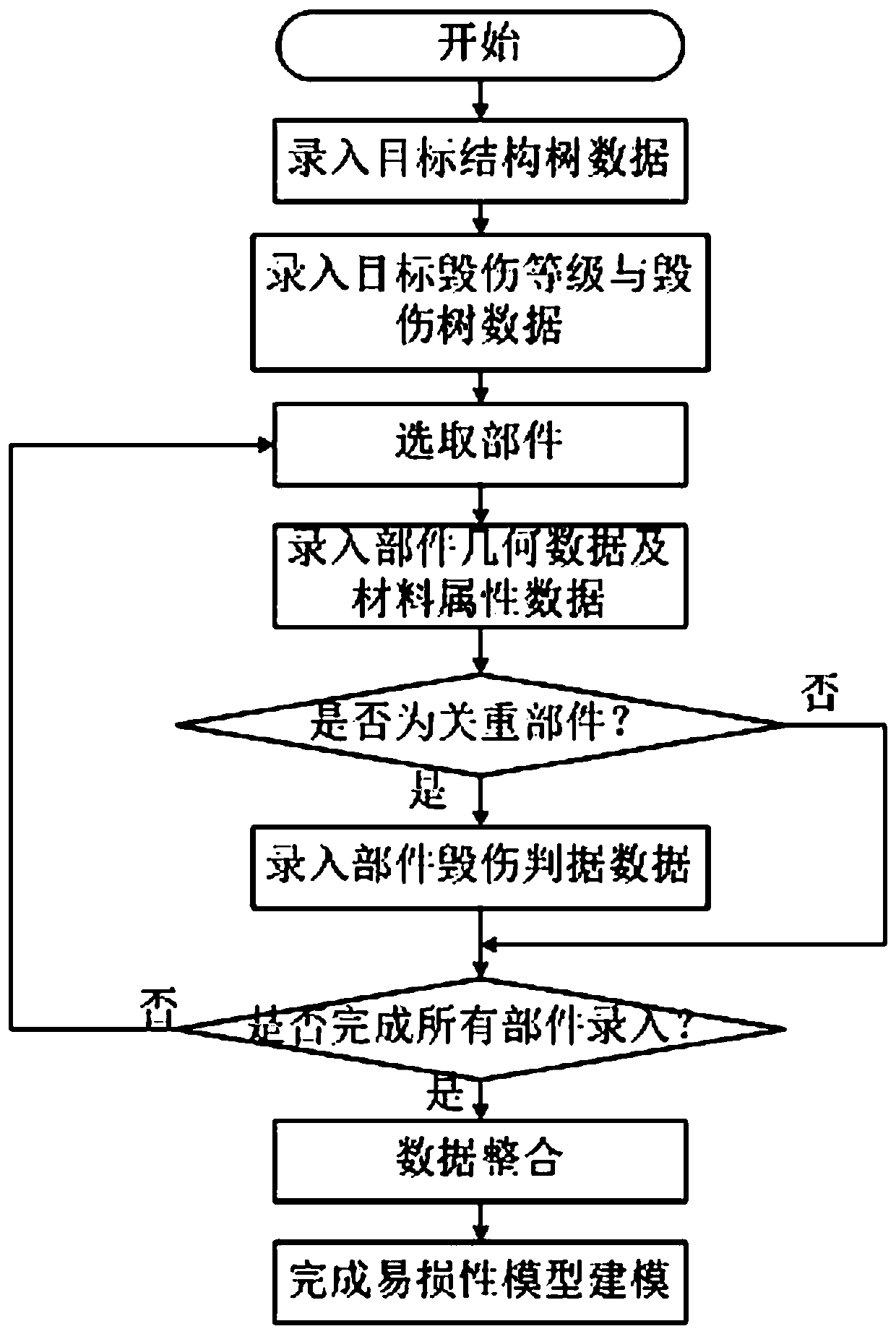
The invention discloses a rapid modeling method for an armored vehicle target vulnerability model. The method can provide basic data support for armored vehicle vulnerability analysis and damage evaluation. The method specifically comprises the following steps: 1, processing; the method is based on function and structure analysis of an armored vehicle target. Determining an equivalent geometry structure of the target component; rapid establishment of an equivalent three-dimensional structure model of each part of a target is realized in a parameterized equivalent geometry driving mode, and a target structure tree, a damage level damage tree, geometric data of the equivalent model of the parts, material characteristic data and damage criterion data are integrated in a database form to finish modeling of the target vulnerability model of the armored vehicle. According to the armored vehicle target vulnerability model building method provided by the invention, the armored vehicle target vulnerability model can be quickly built, the occupied resources are few, the use cost is low, the efficiency is high, the universality is achieved, and the method has positive significance for armoredvehicle target vulnerability analysis and damage evaluation calculation.
Owner:SHENYANG LIGONG UNIV
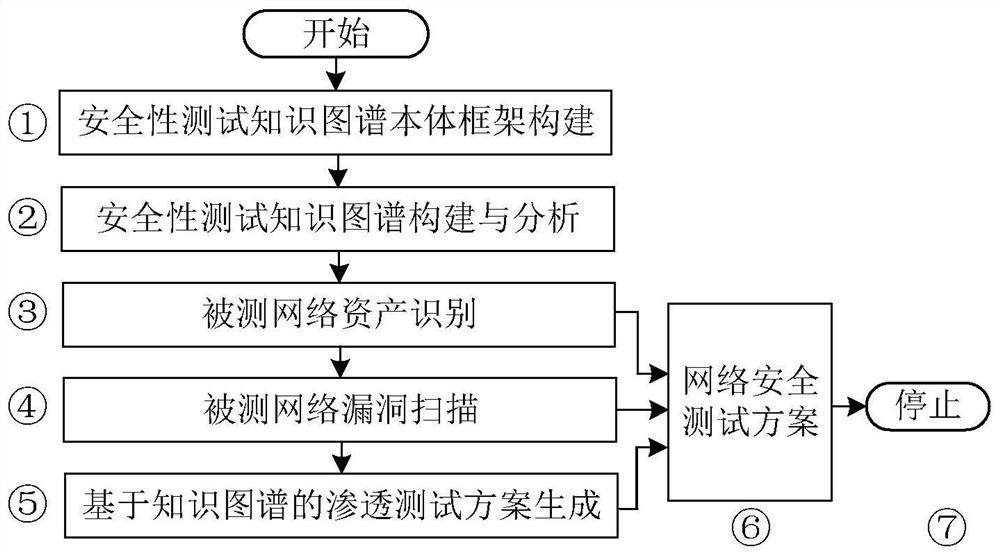
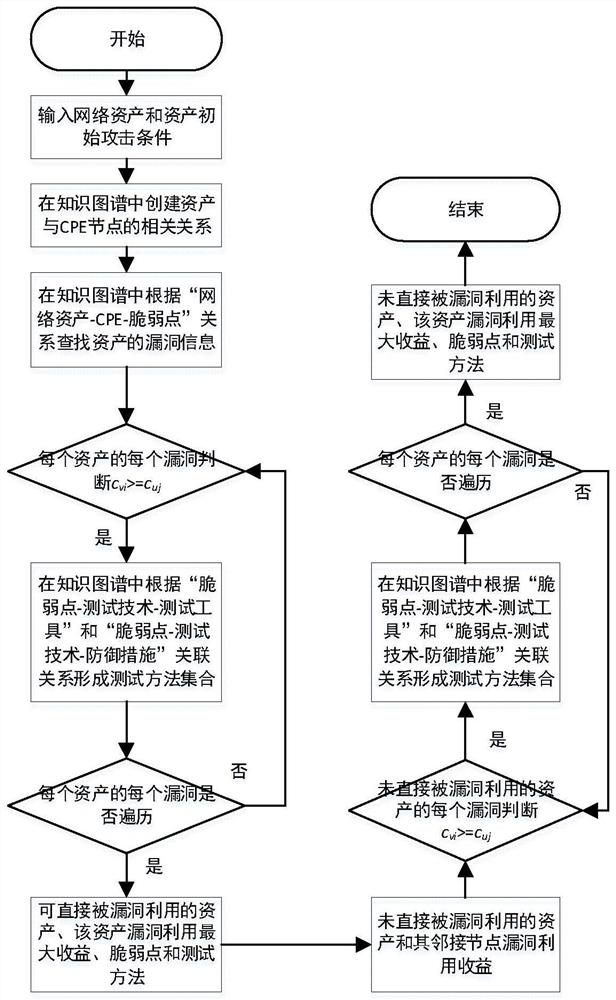
Network security test generation method based on knowledge graph
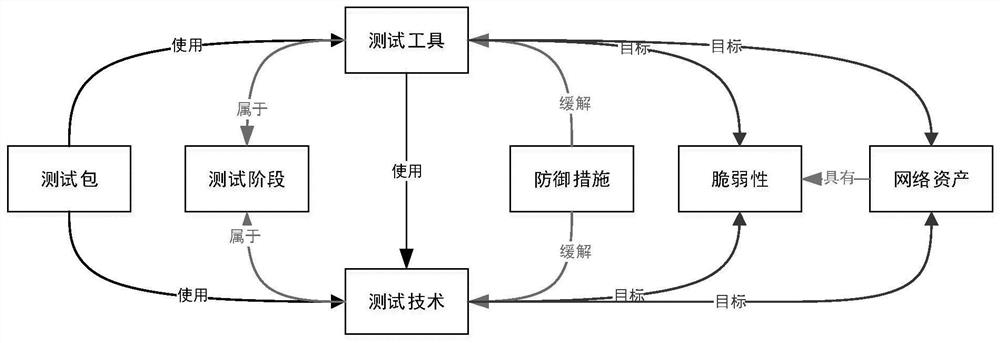
PendingCN114257420ARealize intelligent retrievalImplement automatic inferential associationWeb data indexingNatural language data processingAttackEngineering
The invention belongs to the technical field of network security testing, and discloses a knowledge graph-based network security testing generation method, which comprises the following steps of: firstly, designing a mutual association ontology framework of a security testing field asset model, a vulnerability model and an attack technology model; secondly, extracting network security historical data, and constructing a network security test knowledge graph by using a graph database; and finally, generating a network security test based on the knowledge graph. According to the method, the penetration test in the security test can be represented by the attack model, attack activities, vulnerabilities, attack stages and the like are associated, historical attack test data can be fully utilized, a security test scheme can be generated through intelligent recommendation, and intelligent retrieval and automatic reasoning association of knowledge are realized. And the integrity and the high efficiency of the network security test are greatly improved.
Owner:中国人民解放军63891部队
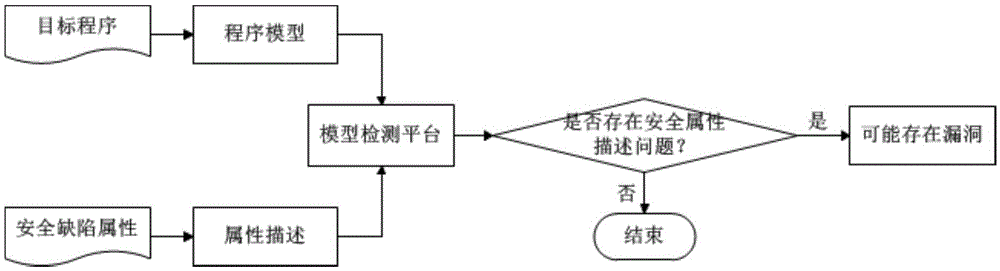
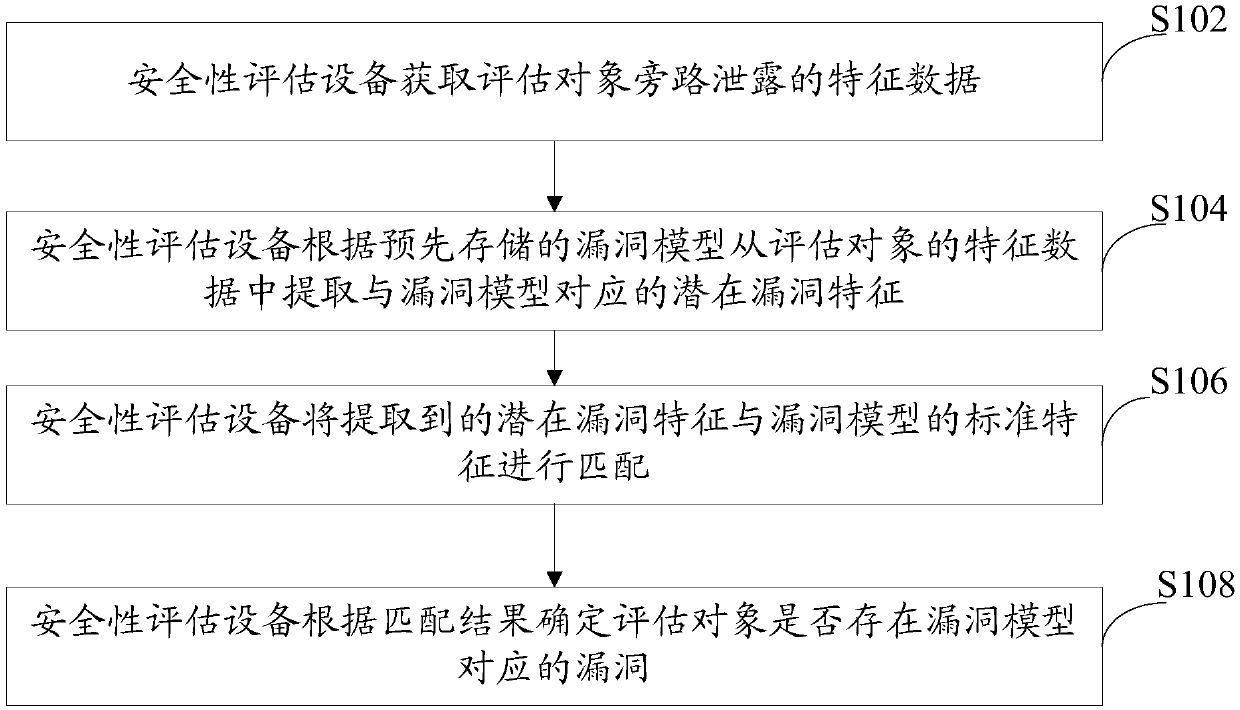
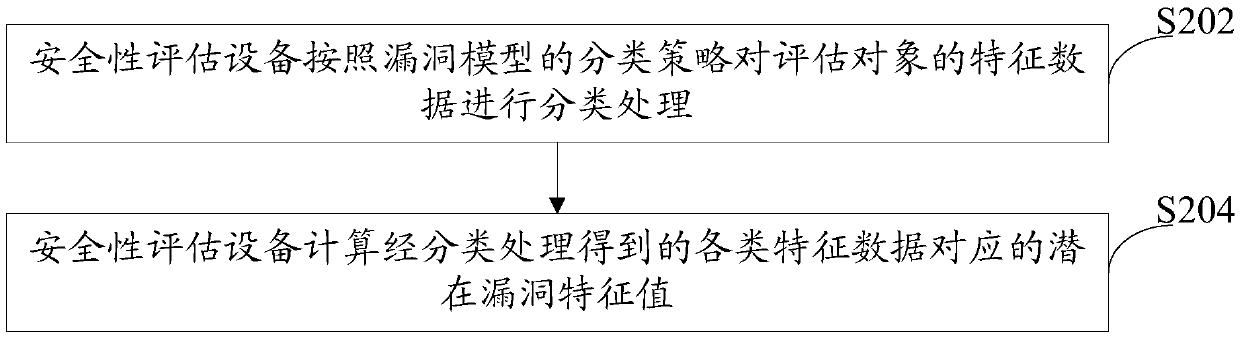
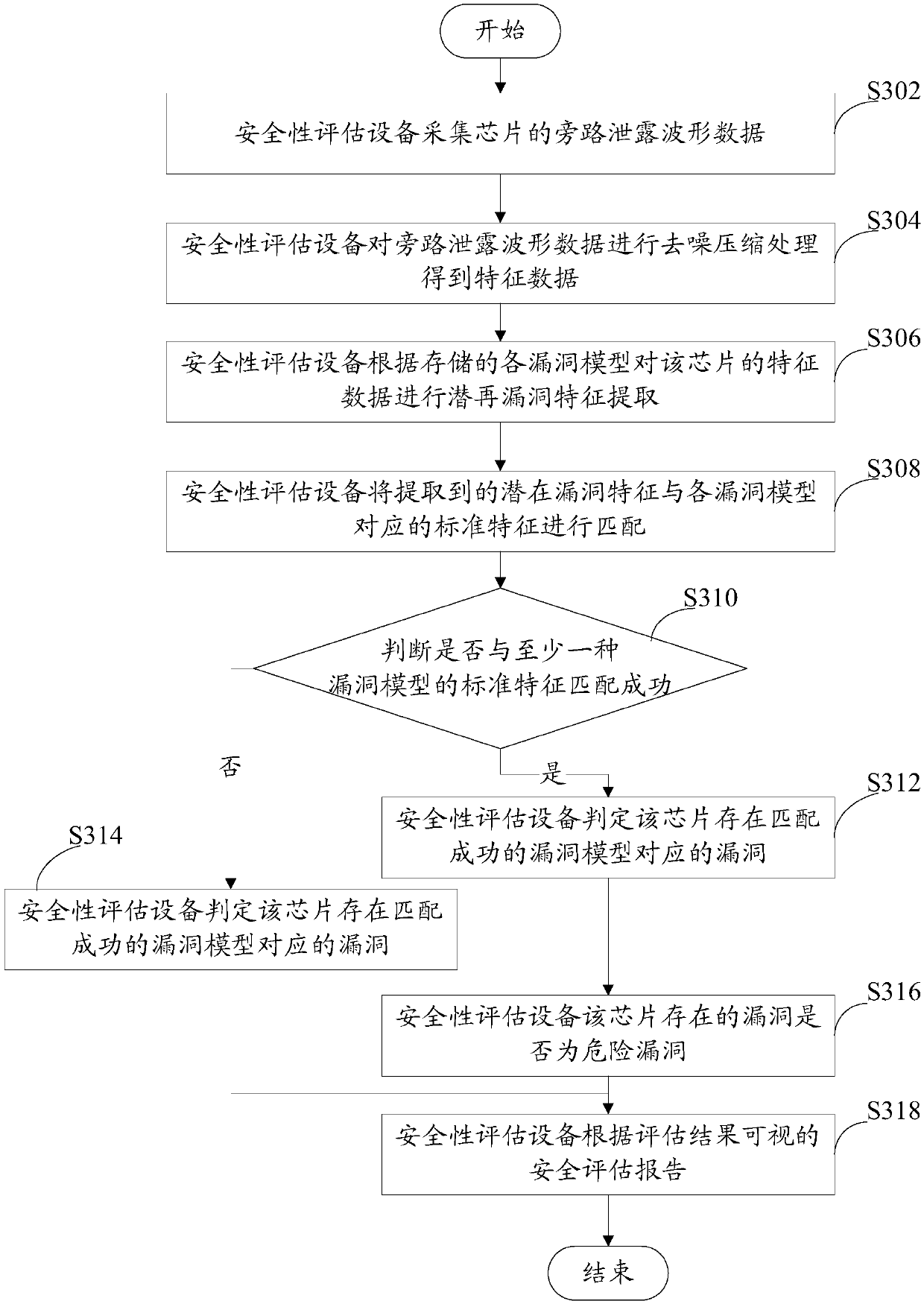
Safety assessment method and safety assessment equipment
The invention discloses a safety assessment method and safety assessment equipment, and the safety assessment equipment obtains a vulnerability model in advance through abstraction according to vulnerabilities possibly appearing in an assessment object, and stores the vulnerability model and standard features of the vulnerability model. During an evaluation phase, the safety assessment equipment acquires characteristic data of the assessment object, extracts potential vulnerability features corresponding to the vulnerability model from the feature data of the assessment object according to a preset vulnerability model of the assessment object, and matches the extracted potential vulnerability features with standard features of the vulnerability model to determine whether the assessment object has a leakage hidden danger corresponding to the vulnerability model or not according to a matching result. When the safety assessment is carried out on the assessment object, the safety assessment equipment can automatically carry out assessment work according to the preset vulnerability model and the standard characteristics corresponding to the vulnerability model without depending on manpower, so that the requirement of safety assessment on manpower resources is reduced, and the optimal configuration of the resources is favorably realized.
Owner:NATIONZ TECH INC
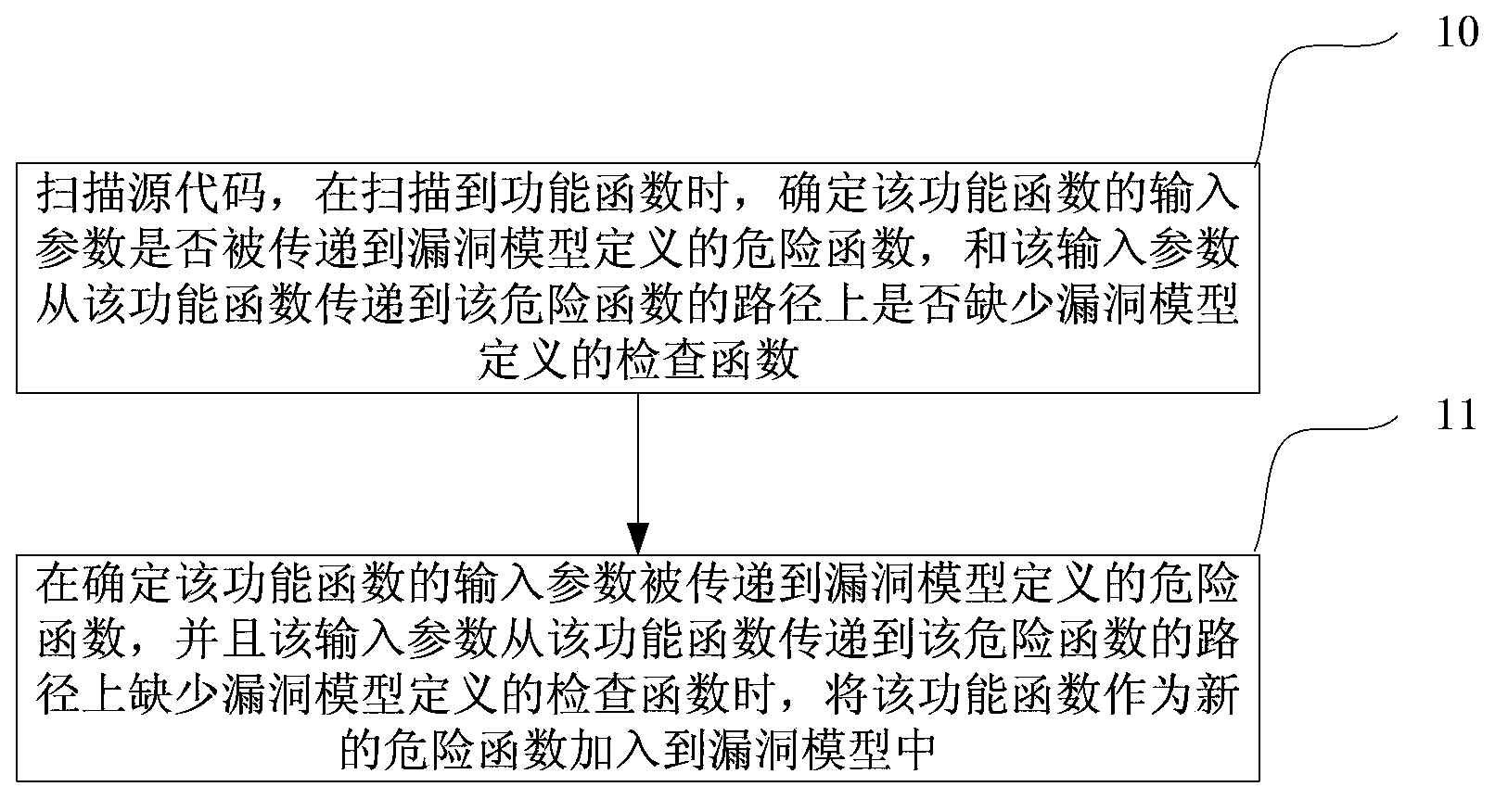
Program code verification method and device
ActiveCN103577758ARealize self-learning functionShorten the timePlatform integrity maintainancePerformance functionSource code
The invention discloses a program code verification method and device using a vulnerability model. The method includes: scanning a source code of a program; when a performance function is scanned, determining whether an input parameter of the performance function is transmitted or not to a dangerous function defined by the vulnerability model and whether a path where the input parameter is transmitted from the performance function to the dangerous function lacks or not a check function defined in the vulnerability model; if the input parameter of the performance function is transmitted to the dangerous function defined by the vulnerability model and the path where the input parameter is transmitted from the performance function to the dangerous function lacks the check function defined in the vulnerability model, adding the performance function as a new dangerous function into the vulnerability model, and determining a security vulnerability detected. The vulnerability model at least includes the dangerous function of the code scanned and definition information of the check function. Through the application of the method and device, code verification is more efficient and applicable.
Owner:SIEMENS AG
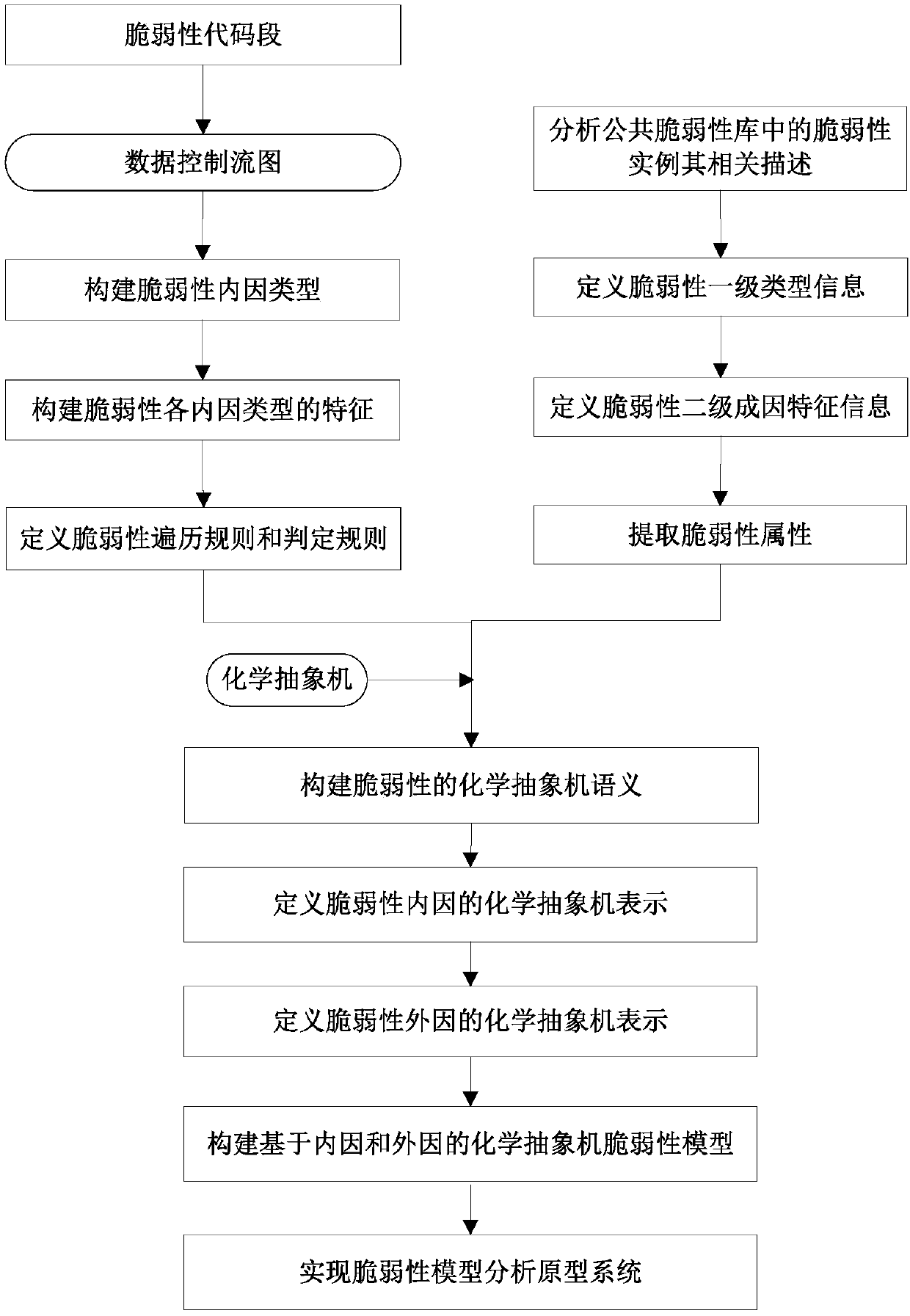
Method for establishing vulnerability model based on chemical abstract machine
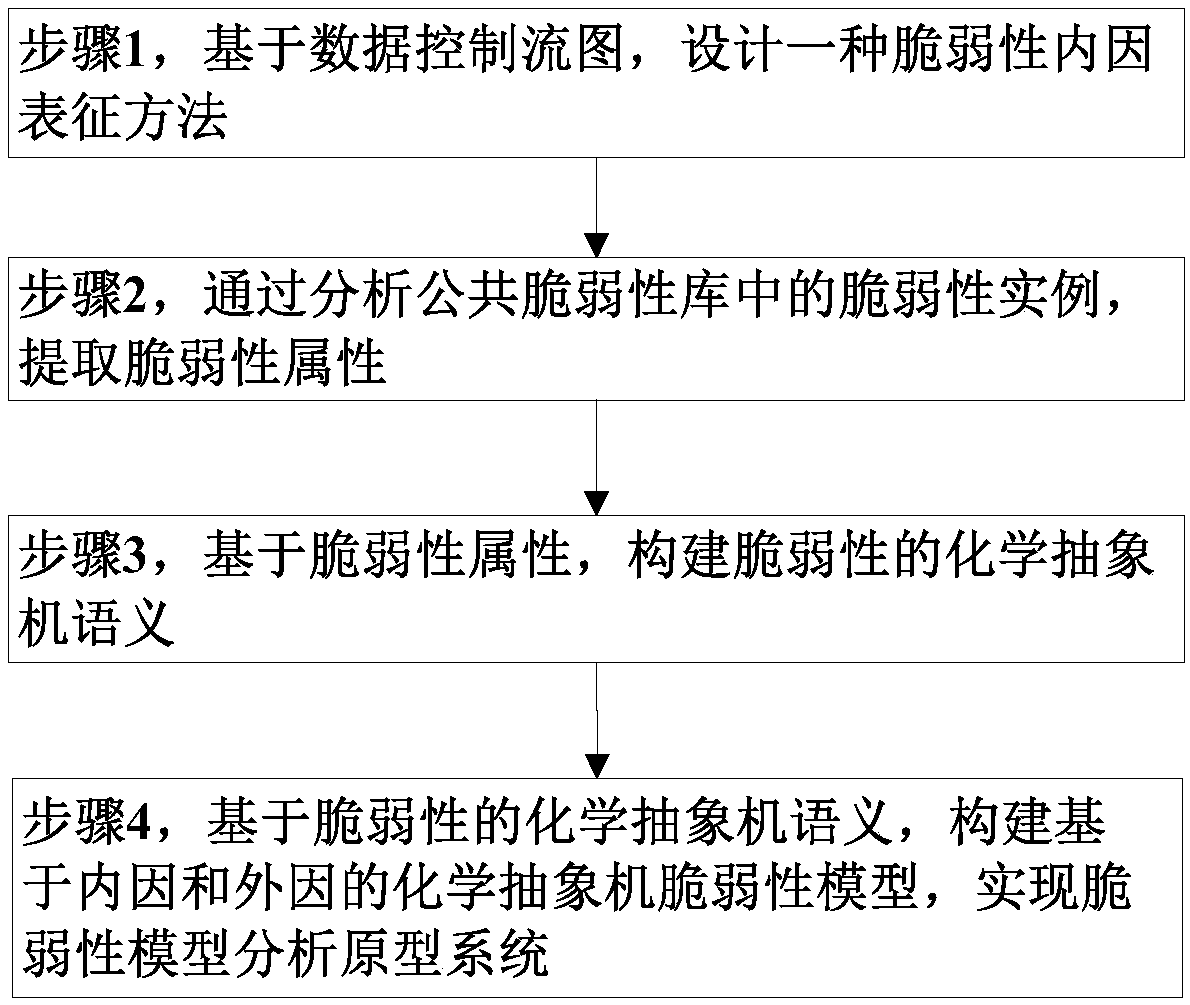
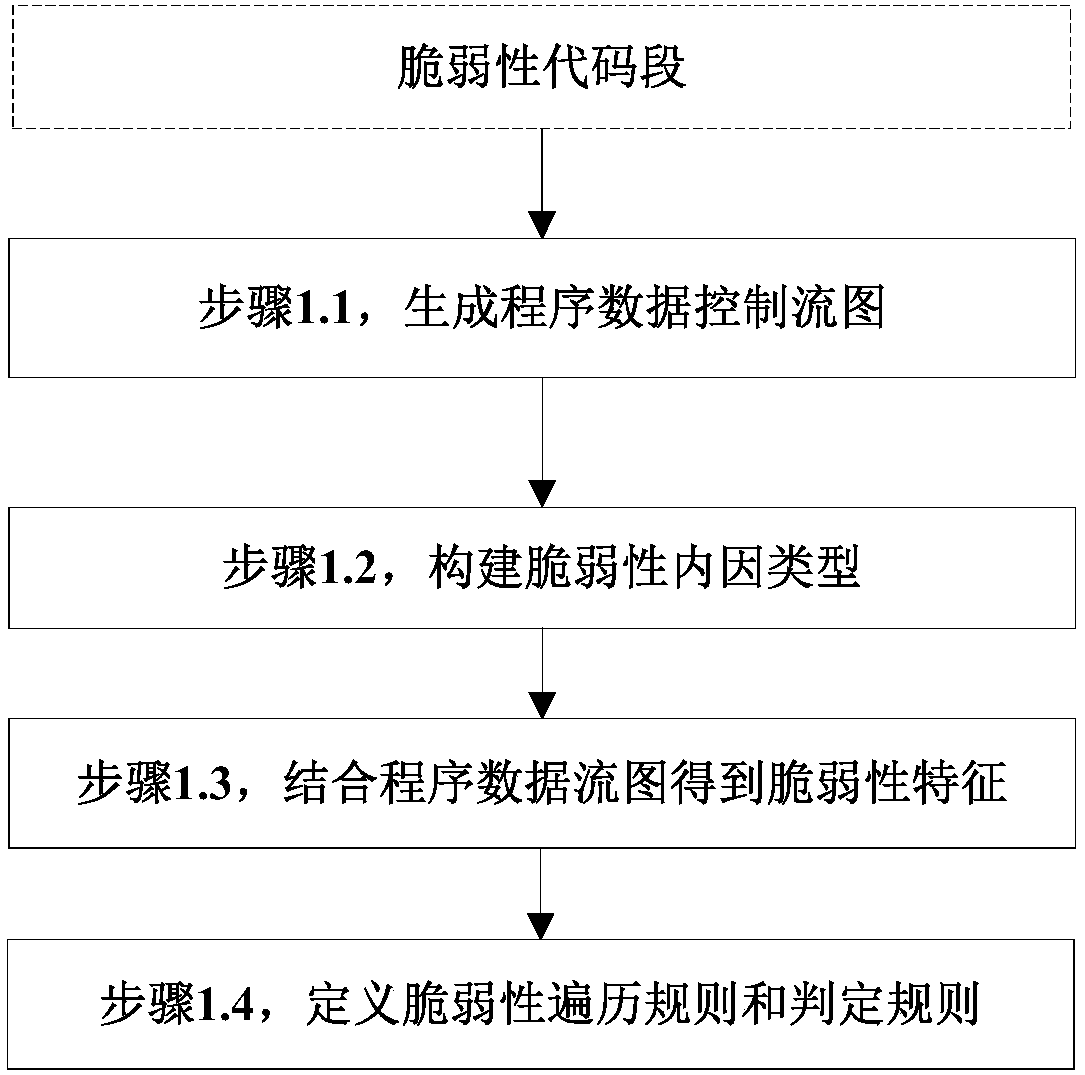
ActiveCN107392029AAchieve representationImplementation descriptionPlatform integrity maintainanceData controlSoftware brittleness
The invention discloses a method for establishing a vulnerability model based on a chemical abstract machine and belongs to the field of trusted computing. The method comprises the steps that 1, a vulnerability internal-cause characterization method is designed based on a data control flow diagram; 2, vulnerability attributes are extracted by analyzing vulnerability examples in a public vulnerability library, and expression and description of the types and causes of the vulnerability model are achieved; 3, chemical abstract machine semantics of the vulnerability are established based on the vulnerability attributes; 4, chemical abstract machine vulnerability models of an internal cause and an external cause are established based on the chemical abstract machine semantics of the vulnerability. In addition, a preliminary prototype system-vulnerability model analysis system is also achieved, the method is compared with other bug mining tools, and the effectiveness of the method is verified. The method can help to further deeply know the essence of the vulnerability, is conductive to the improvement of vulnerability acquaintance, and accordingly helps to reduce the losses brought by the vulnerability to national security, economic stability and social development.
Owner:中国人民解放军63928部队 +1
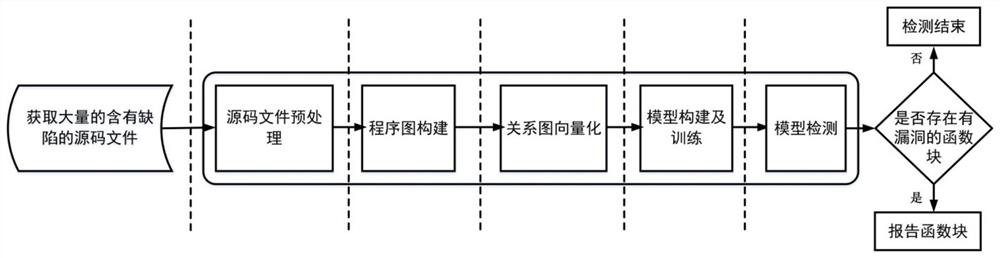
Multi-relational graph network-based vulnerability model construction method and detection method thereof
ActiveCN113158194AShorten the training periodSpread fastNatural language data processingPlatform integrity maintainanceAlgorithmTheoretical computer science
The invention discloses a multi-relational graph network-based vulnerability model construction method and a detection method thereof, and the method comprises the steps: collecting a source code program file, carrying out the preprocessing of the source code program file, obtaining a function block, and according to whether a function name corresponding to the function block contains a good and a bad, enabling a corresponding label to be a function block without a vulnerability and a function block with a vulnerability; processing the function blocks without the vulnerabilities and the function blocks with the vulnerabilities to obtain respective corresponding second abstract syntax trees; and performing first traversal on the second abstract syntax tree to obtain seven edge relationships. On the basis of extracting node information of the abstract syntax tree in the prior art, seven edge relationships are added, and the seven edge relationships can remarkably improve the accuracy rate in the aspect of vulnerability detection and reduce the missing report rate; when the GGNN vulnerability model is built, the GRU and the highway gate are fused to improve the propagation speed of the vector among different relational graphs, so that the model training period is shortened, and the technical problem that the detection effect of a vulnerability detection model is poor in the prior art is solved.
Owner:NORTHWEST UNIV(CN)
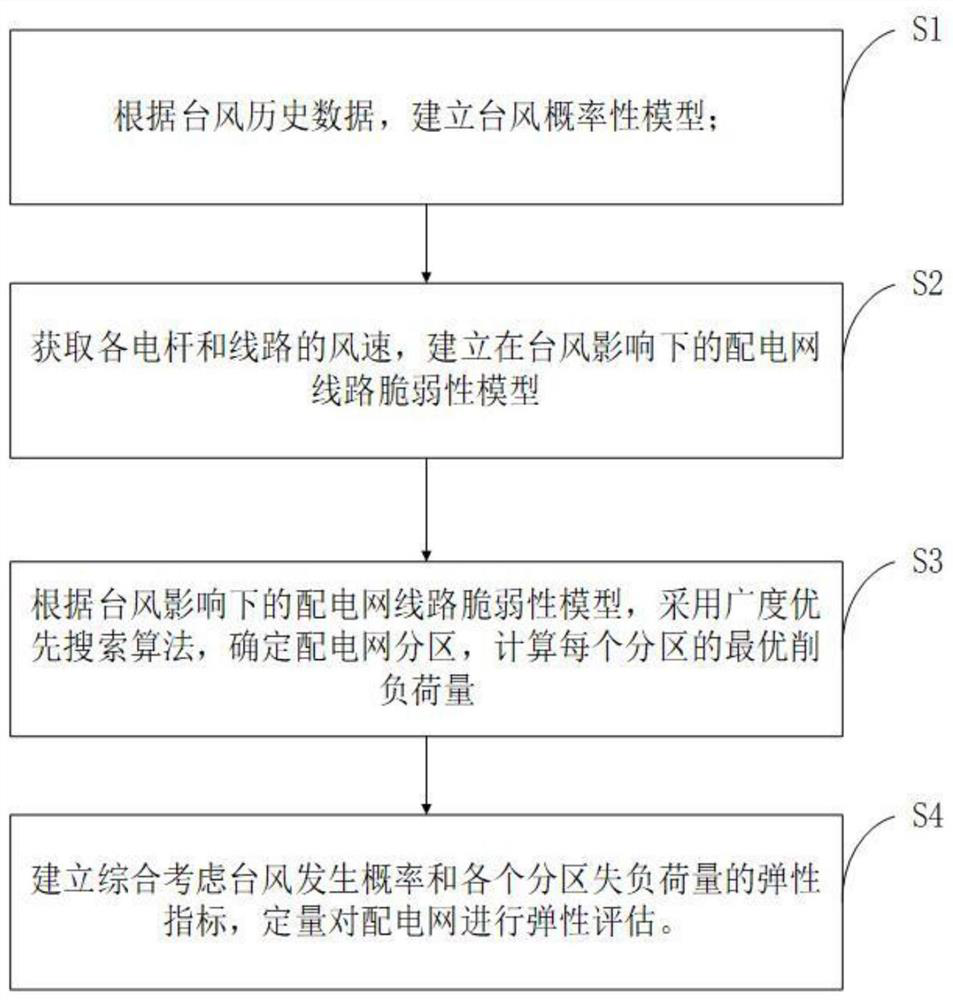
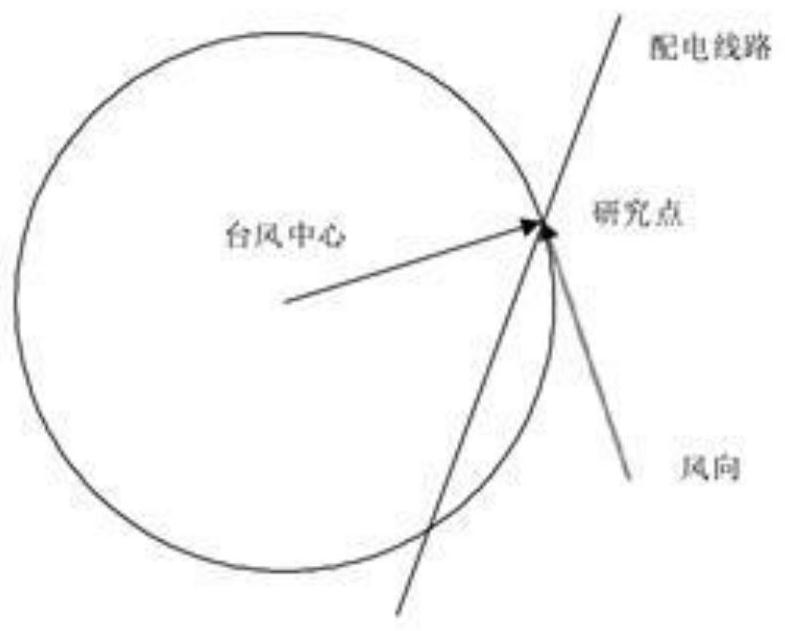
Power distribution network elasticity evaluation method under typhoon disaster
PendingCN114117730AAccurately account for the impact of resiliency assessmentsData processing applicationsDesign optimisation/simulationMicrogridElectric power system
The invention discloses a power distribution network elasticity evaluation method under typhoon disasters, and the method comprises the following steps: S1, considering a typhoon generation scene, and building a typhoon model according to the typhoon historical data; s2, considering time-space factors of typhoon, and establishing a vulnerability model of the typhoon to lines and towers of the power distribution network unit; s3, performing island division on the distribution network by adopting a breadth-first search algorithm, calculating a load loss amount of an island microgrid, and quantitatively performing elastic evaluation on the distribution network according to an elastic index; and S4, establishing an elastic index which comprehensively considers the typhoon occurrence probability and the load loss capacity of each partition, and quantitatively performing elastic evaluation on the power distribution network. According to the method provided by the scheme, the influence of each factor on the elastic evaluation of the distribution network can be accurately considered, and a quantitative reference basis is provided for later planning and scheduling of a power system.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD HANGZHOU POWER SUPPLY CO
Method and system for determining risk value of security incident
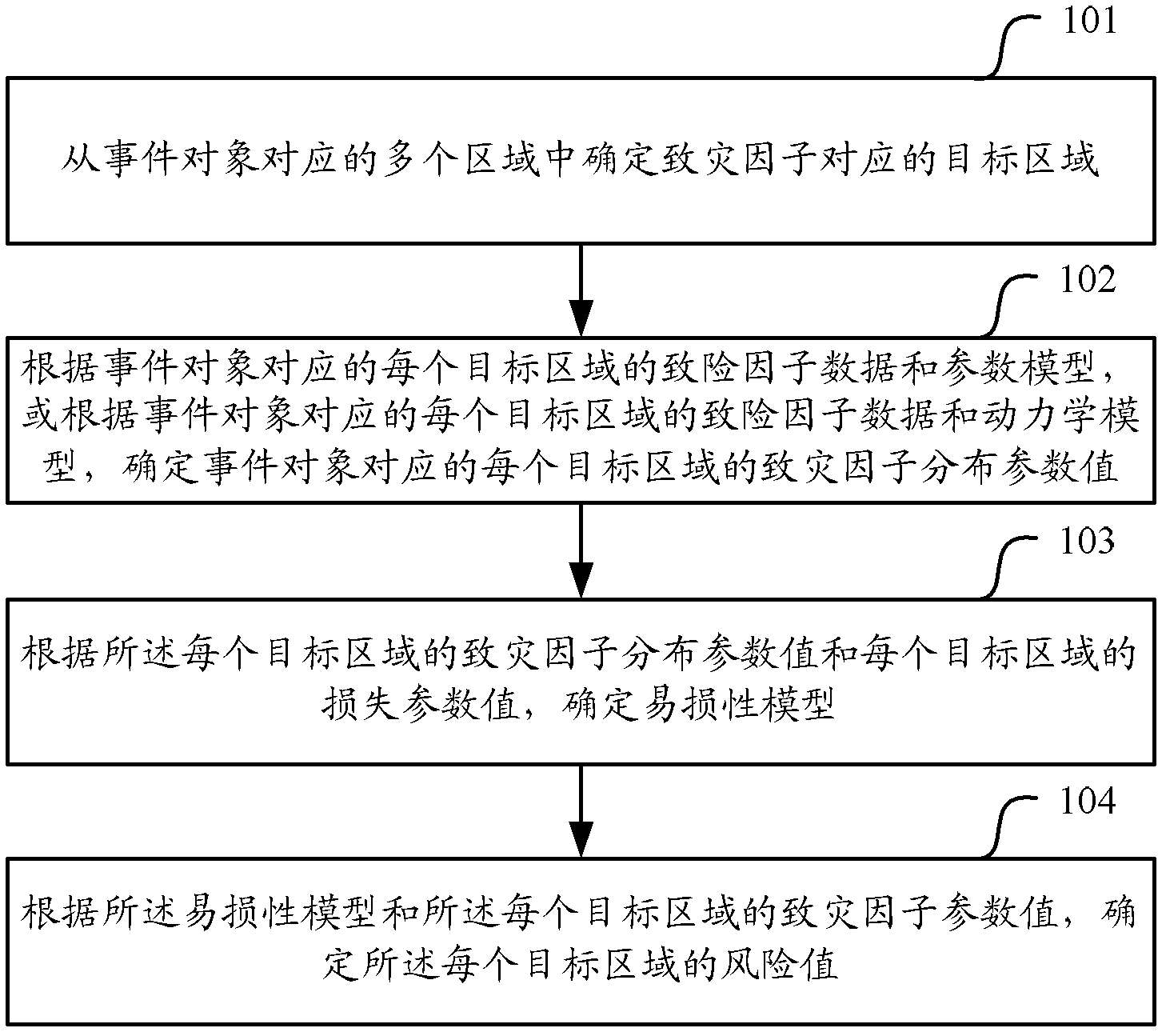
InactiveCN103186709AImprove basic securityReduce lossesSpecial data processing applicationsData miningEvent object
The embodiment of the invention relates to the technical field of computers and particularly relates to a method and a system for determining a risk value of a security incident. The method and the system are used for determining the risk value of the security incident, thereby controlling wideband network resources to improve basic guarantee. The method in the embodiment of the invention comprises the following steps: determining an object region corresponding to a risk factor from a plurality of regions corresponding to incident objects; determining a risk factor distribution parameter value of each object region corresponding to each incident object according to risk factor data of each object region corresponding to each incident object; determining a vulnerability model according to the risk factor distribution value of each object region and a loss parameter value of each object region; and determining a risk value of each object region according to the vulnerability model and the risk factor parameter value of each object region. Due to the adoption of the embodiment of the invention, the wideband network resources are controlled to improve the basic guarantee and the loss caused by the security incidents is possibly reduced to the maximum extent.
Owner:FOUNDER BROADBAND NETWORK SERVICE
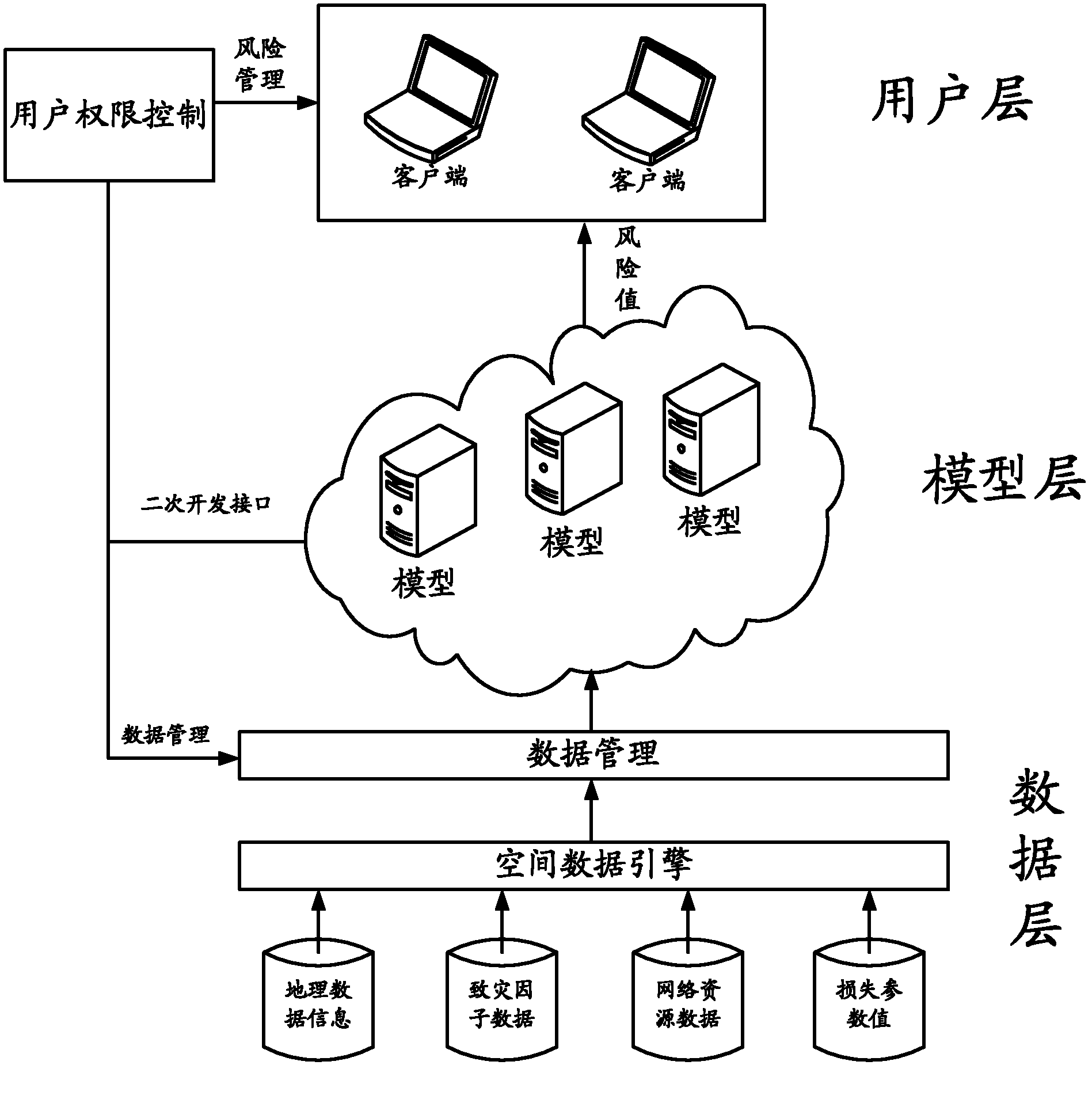
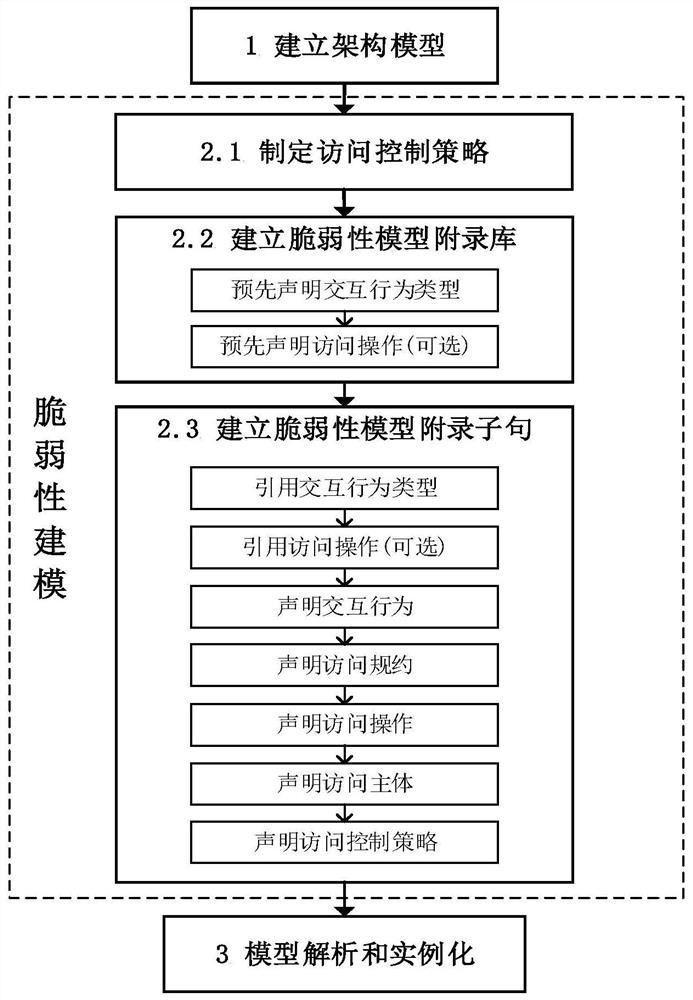
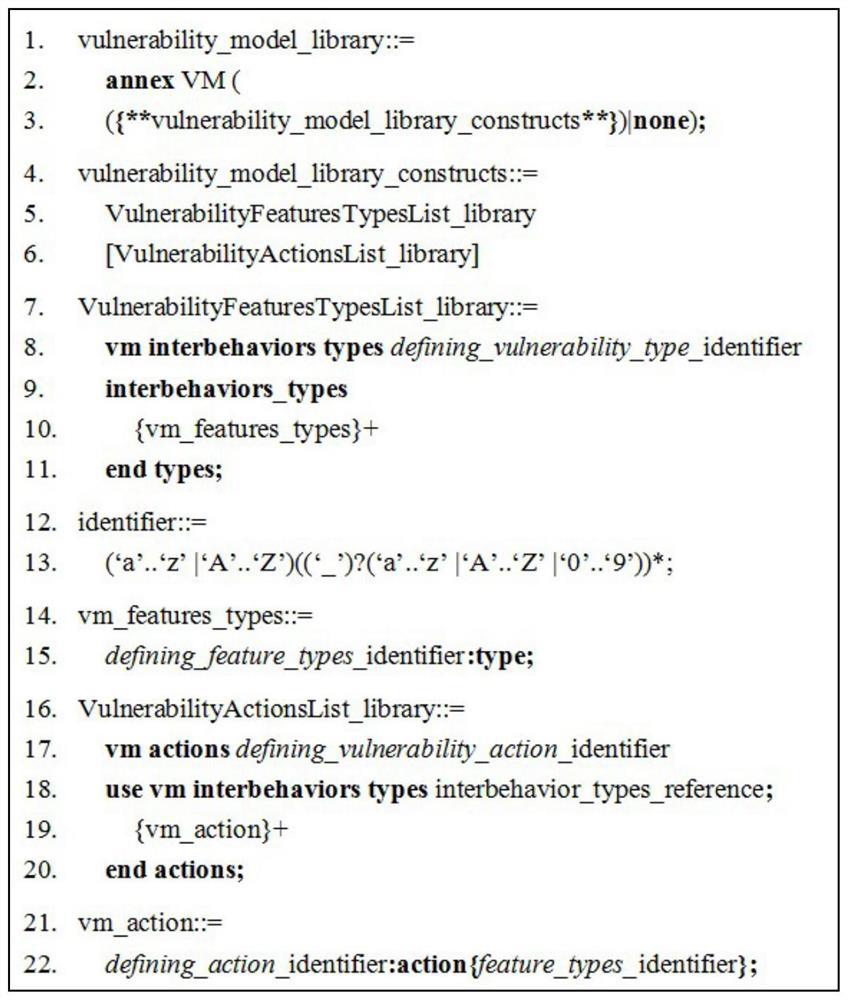
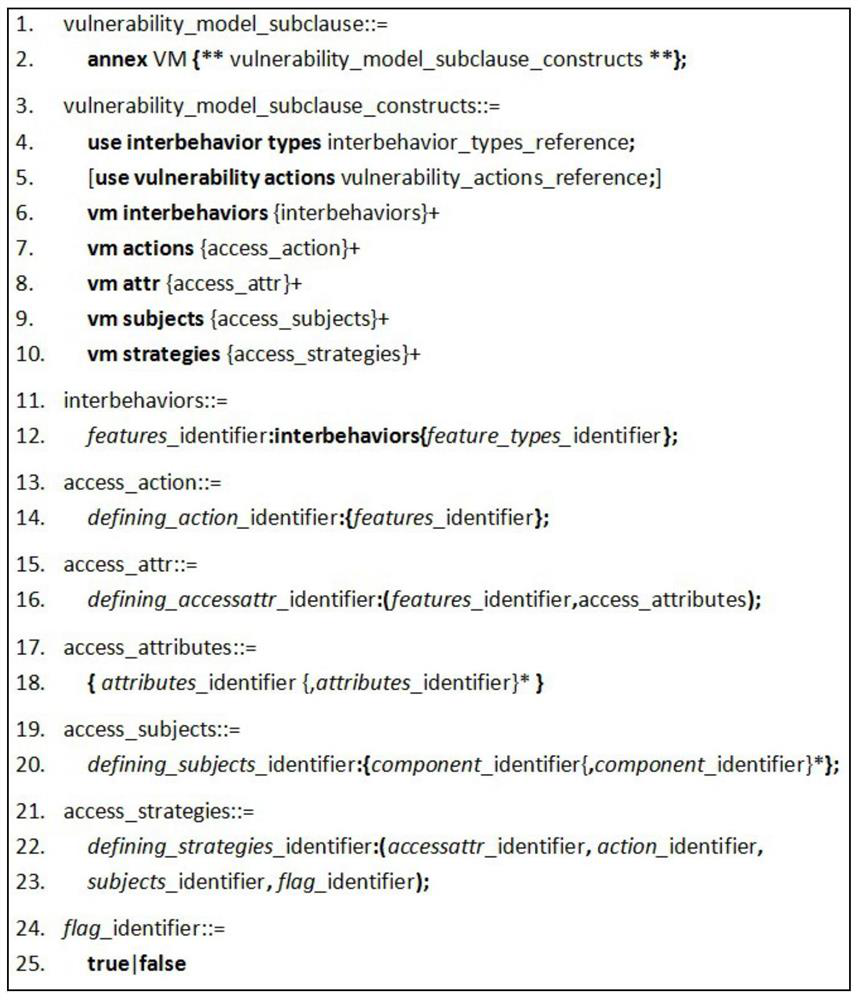
AADL-based system vulnerability model design method
PendingCN112764722AImprove the effect of the modelSimple designSoftware designRequirement analysisSystems designSoftware system
The invention relates to an AADL-based system vulnerability model design method, which establishes an access control strategy on the basis of a software architecture model, carries out system vulnerability modeling, and improves the modeling capability of the AADL. According to the method, in the form of AADL appendix extension, an AADL appendix sublanguage is provided to achieve vulnerability modeling. The method comprises the following steps: (1) establishing a system architecture model; (2) establishing a system vulnerability model, including designing an access control strategy and establishing a vulnerability model appendix library and vulnerability model appendix clauses; and (3) integrating the architecture model and the vulnerability model to obtain a system model containing the vulnerability model. According to the method, a system vulnerability model is established in the software design stage, an architecture model and access control are combined, the access control relation between software system components is described, a basis is provided for detecting vulnerability defects generated in the design stage, and optimization of the system design is facilitated.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Urban hydrologic station network layout method and system based on 3S technology
PendingCN114528672ALayout saves time and effortAccurately determineGeometric CADClimate change adaptationSensing dataData mining
The invention provides an urban hydrologic station network layout method and system based on a 3S technology. The method comprises the following steps: establishing an urban rainstorm high-risk model; establishing an urban flood risk model; establishing an urban disaster-bearing body vulnerability model; and establishing an urban hydrologic station network planning demand index model. Based on remote sensing data, land utilization type data, historical disaster situation data and a 3S technology, detailed analysis is performed from three aspects of urban rainstorm high-risk zoning, flood risk zoning and disaster-bearing body vulnerability, and then a hydrological station network layout demand index model is comprehensively considered from the perspective of data fusion to perform overall optimization layout of a hydrological station network. The specific layout position of the hydrologic station network can be accurately, rapidly and intelligently determined, compared with a traditional hydrologic station network layout method, much time and manpower needed by field investigation are saved, and the result is accurate and reliable.
Owner:NANJING AUTOMATION INST OF WATER CONSERVANCY & HYDROLOGY MINIST OF WATER RESOURCES
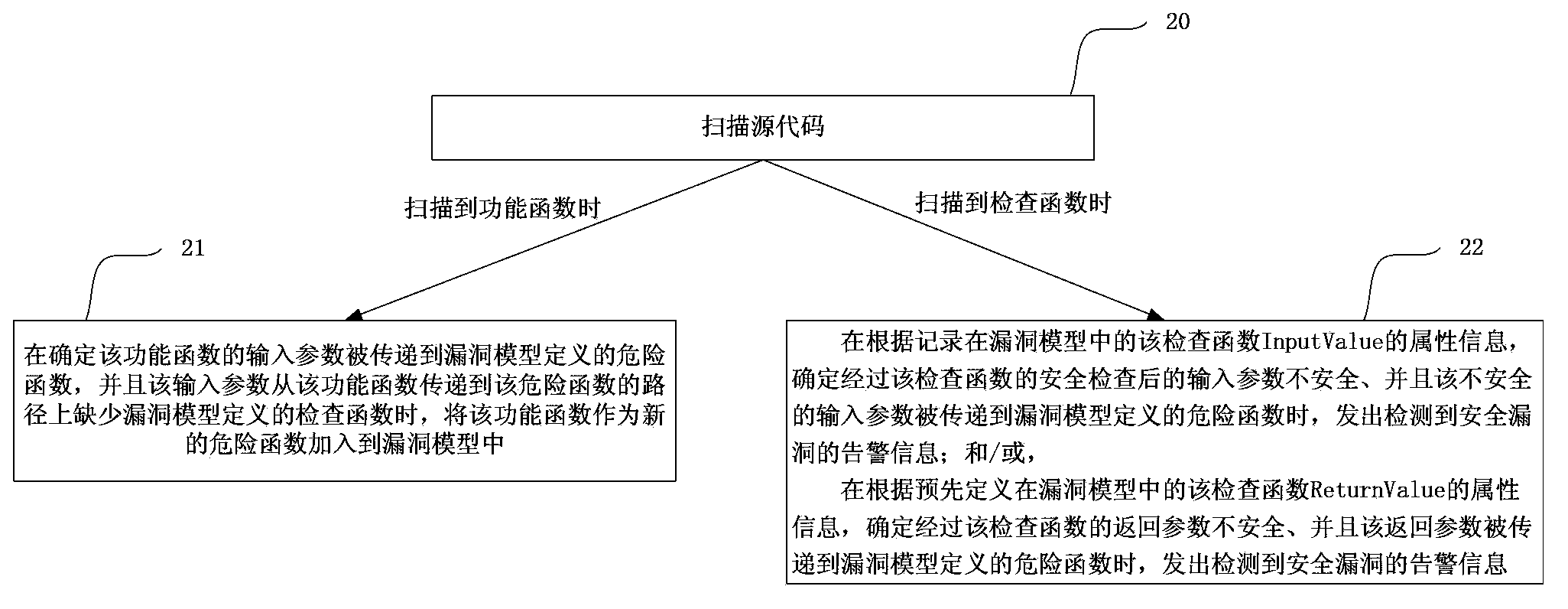
Software vulnerability model detection method based on vulnerability model
InactiveCN114726624APrivacy protectionAvoid destructionCharacter and pattern recognitionPlatform integrity maintainanceFeature setSoftware system
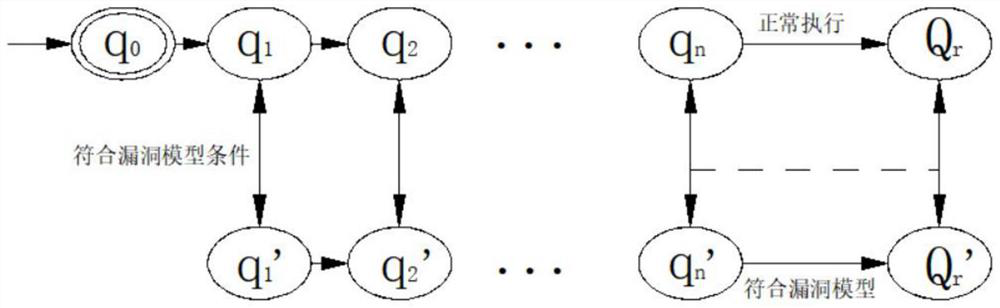
The invention discloses a software vulnerability model detection method based on a vulnerability model, which comprises the following steps of: performing state derivation on execution input, a software calling process and a function set of software so as to judge whether state transition exceeds a safe range or not; feature code scanning and specific function or specific process detection can be carried out on the public vulnerabilities to determine whether the software system has the vulnerabilities or not; for unknown vulnerabilities, whether a software system has vulnerabilities or not can not be obtained through direct detection generally, and due to the fact that the unknown vulnerabilities often cause the vulnerabilities for specific execution processes and / or specific input conditions of unsafe codes, the method solves the problem that the vulnerabilities cannot be generated in the process of system vulnerability detection and protection in Web application at present. In the prior art, the privacy of data information cannot be effectively protected, and an attacker can identify the information of the Web site accessed by the user according to the contour features of the Web information flow, so that the Web content of the user is leaked.
Owner:厦门农芯数字科技有限公司
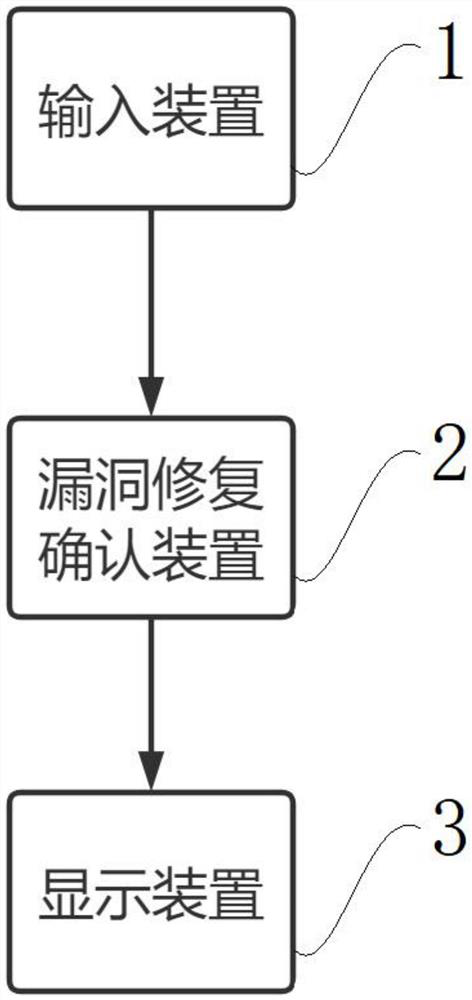
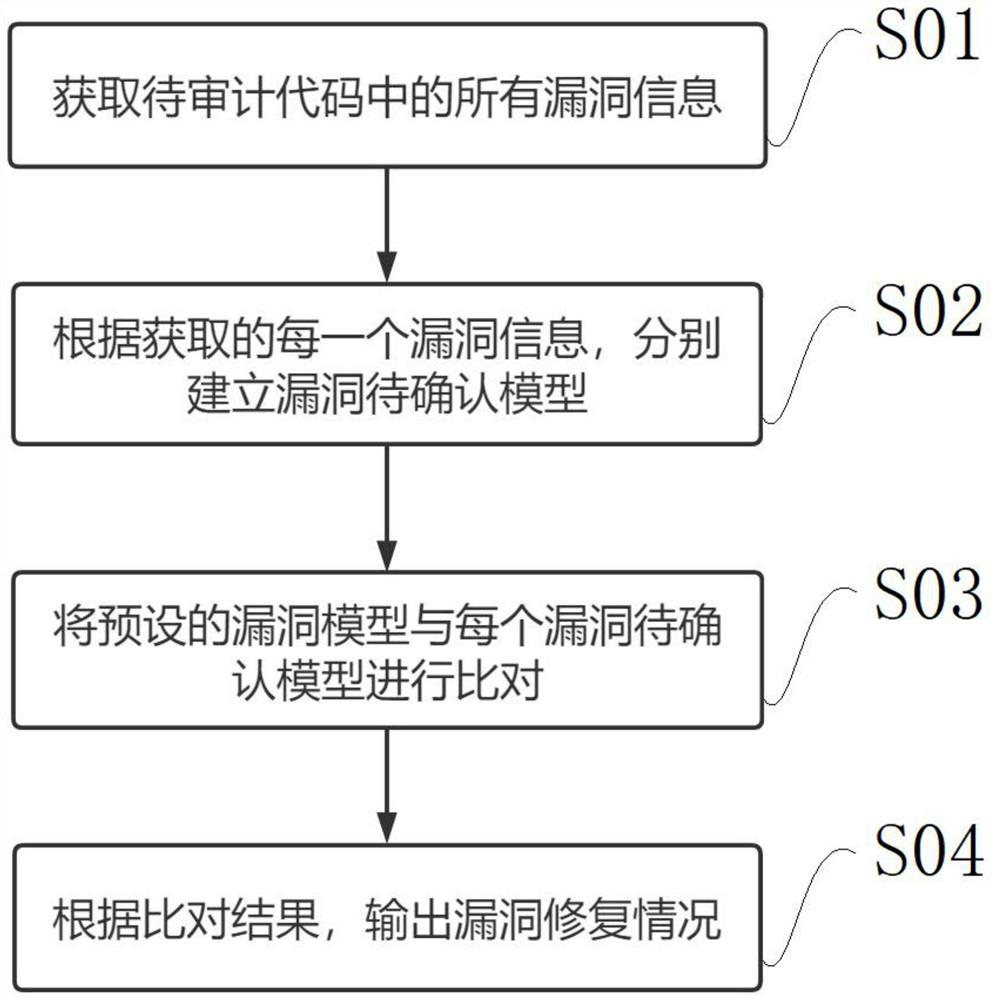
Vulnerability repair confirmation method and device, terminal and storage medium
PendingCN113886112AAudit went wellReliability/availability analysisNon-redundant fault processingComputer securityVulnerability model
The invention discloses a vulnerability repair confirmation method and device, a terminal and a storage medium, and relates to the field of code auditing, and the method comprises the steps: obtaining all vulnerability information in a to-be-audited code; according to each piece of acquired vulnerability information, establishing a vulnerability to-be-confirmed model; comparing a preset vulnerability model with each vulnerability to-be-confirmed model; and according to a comparison result, outputting a vulnerability repair condition. According to the method, the preset vulnerability model is compared with each vulnerability to-be-confirmed model obtained and established from the to-be-audited code one by one, and the vulnerability repair condition is output according to the comparison result, so that code auditing personnel can directly check the vulnerability repair condition, the repair condition of the vulnerability of the to-be-audited code can be intuitively known, and the code auditing can be smoothly carried out.
Owner:SECZONE TECH CO LTD
Allocation Method of Combat Aircraft System Vulnerability Index
ActiveCN104820778BImprove survivabilityReduce vulnerabilitySpecial data processing applicationsSurvivabilitySurvival probability
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Sensitive point approach method based on intelligent path guidance
InactiveCN105487983BAlleviate the problem of explosionReduce in quantitySoftware maintainance/managementSoftware testing/debuggingEntry pointIntermediate language
The invention relates to a sensitive point approximation method based on intelligent route guidance. The method comprises the steps that vulnerability models of different types are extracted, and the position of a sensitive point is recognized through static analysis; upward backtracking is performed by taking the sensitive point as a starting point and adopting a route backtracking algorithm to look up all route branch points and is performed until the route branch point which is nearest away from a program entry point is found; instruction level instrumentation is performed on a tested program, an original sample is input, and a binary instruction sequence related to dirty points is recorded; the binary instruction sequence is lifted into intermediate language description; route branch points of the intermediate language description are acquired and turned according to whether the branch points are located in a set, and control flow is guided to reach the sensitive point; a constraint normal form is extracted from turned intermediate language description, solving is performed with an STP constraint solver, a new sample is generated, and returning is performed to re-input the sample. According to the method, the control flow is guided to reach the sensitive point position through the sensitive point, the problem of route explosion is effectively solved, and the vulnerability mining efficiency is improved.
Owner:ZHENGZHOU ENBEI NETWORK TECH CO LTD
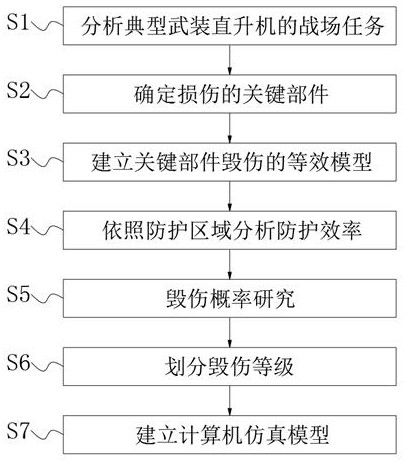
Method for constructing vulnerability model of typical armed helicopter
PendingCN112685843AEffective judgment basisThe theoretical basis is correctGeometric CADStructural engineeringVulnerability evaluation
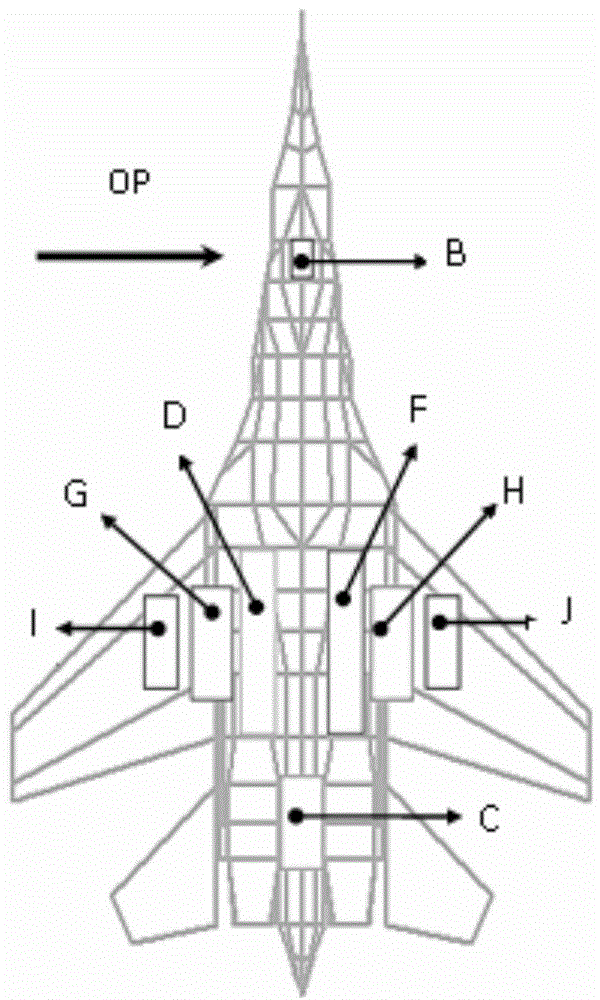
The invention discloses a construction method of a typical armed helicopter vulnerability model, key parts are damaged to cause key function failure of an armed helicopter, and the key parts comprise a detector cabin, a cockpit, an electronic equipment cabin, a generator, a transmission device, an oil tank, an engine, a tail beam and ammunition. If some of the key components above are damaged, armed helicopter will be correspondingly damaged in different degrees. The vulnerability of the armed helicopter can be analyzed in a contrastive manner according to the damage of the key parts by determining the vulnerable key parts of the armed helicopter in the actual construction model and establishing the equivalent model of the damage of the key parts; therefore, a more effective judgment basis can be provided when people analyze the vulnerability of the armed helicopter, and meanwhile, key components are used as vulnerability evaluation indexes, so that a more accurate theoretical basis is conveniently provided for the establishment of a subsequent computer simulation model.
Owner:中国人民解放军63863部队
A binary program vulnerability mining method and system
ActiveCN105678169BExcavate accuratelyAccurate locationPlatform integrity maintainanceCode conversionAssembly language
The invention provides a binary program vulnerability discovery method. The binary program vulnerability discovery method comprises steps of converting a target binary program into an assembly language, and carrying out static analysis to the assembly language; carrying out Promela model modeling to an intermediate language by combining the analysis result of the static analysis; establishing a vulnerability model and inserting the vulnerability model into the Promela model; introducing an external C code, simulating and executing the Promela model based on an SPIN, and detecting the vulnerability. The invention also provides a binary program vulnerability discovery system comprising a preprocessor module, a code conversion module and a model detection module. With respect to the binary program vulnerability discovery method and system, the intermediate language BIL is introduced to serve as a conversion bridge through which the binary program is converted into the Promela model, automatic modeling of the binary program is achieved, the embedded C function of the SPIN is employed to achieve simulation and execution, and the external C code is introduced to correct the defect of model detection. Experimental results show that the binary program vulnerability discovery method can effectively detect memory destructive vulnerabilities of binary programs.
Owner:XIAN HUMEN NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com