A binary program vulnerability mining method and system
A binary program and vulnerability mining technology, which is used in instrumentation, computing, electrical digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
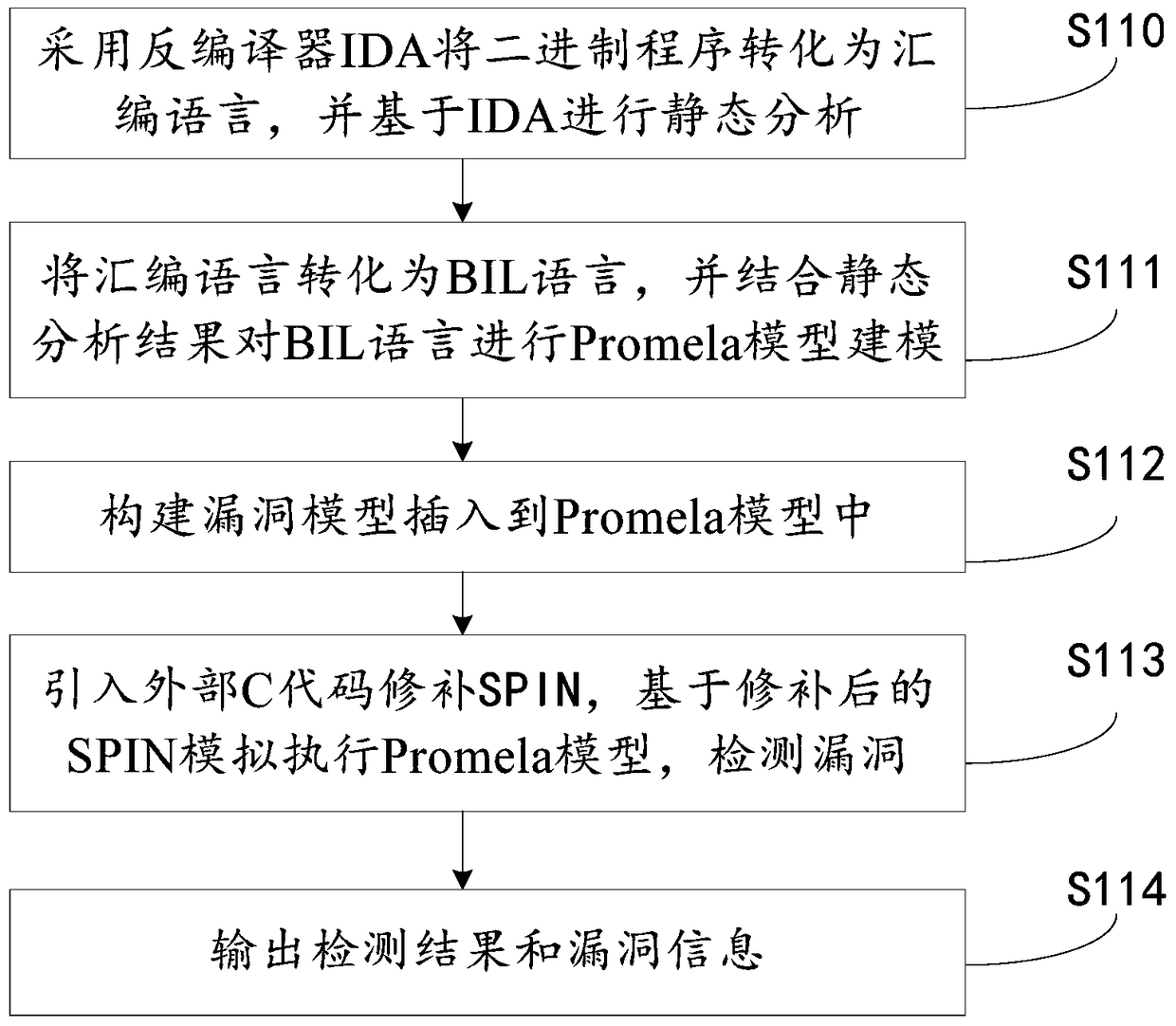
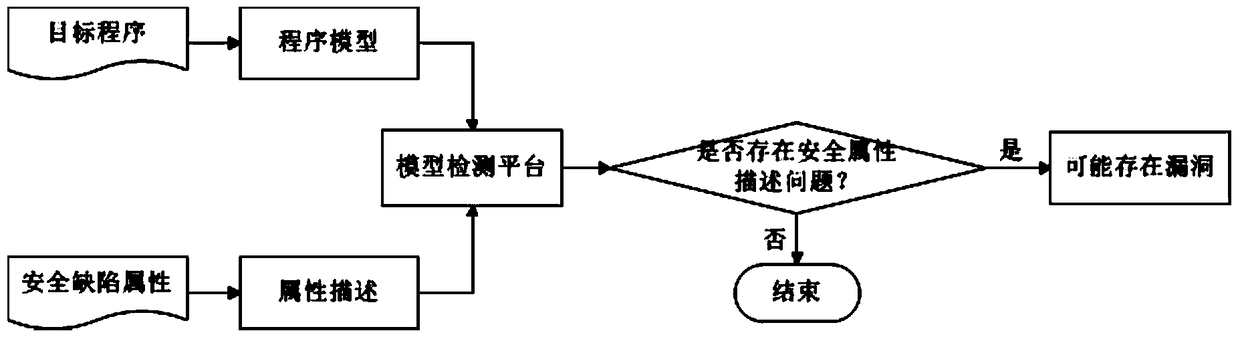
[0069] The embodiment of the present invention provides a binary program vulnerability mining method and system. see figure 1 As shown, the method includes the steps of:
[0070] Step S110, using the decompiler IDA to convert the binary program into assembly language, and performing static analysis on the assembly language level based on IDA to obtain a function flow diagram;
[0071] Step S111, converting assembly language into BIL language through the intermediate language platform BAP, and performing Promela model modeling on BIL language in combination with the analysis results of static analysis;
[0072] Step S112, building a vulnerability model and inserting it into the Promela model;
[0073] Step S113, introducing external C code to patch SPIN, and executing the Promela model based on the patched SPIN simulation to detect vulnerabilities;
[0074] Step S114, outputting detection results and vulnerability information.
[0075] The embodiment of the present inventio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com