AADL-based system vulnerability model design method
A vulnerability and model technology, applied in the field of embedded software security modeling, can solve problems such as increasing software modeling capabilities and not being able to describe access control relationships
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] Now in conjunction with embodiment, accompanying drawing, the present invention will be further described:
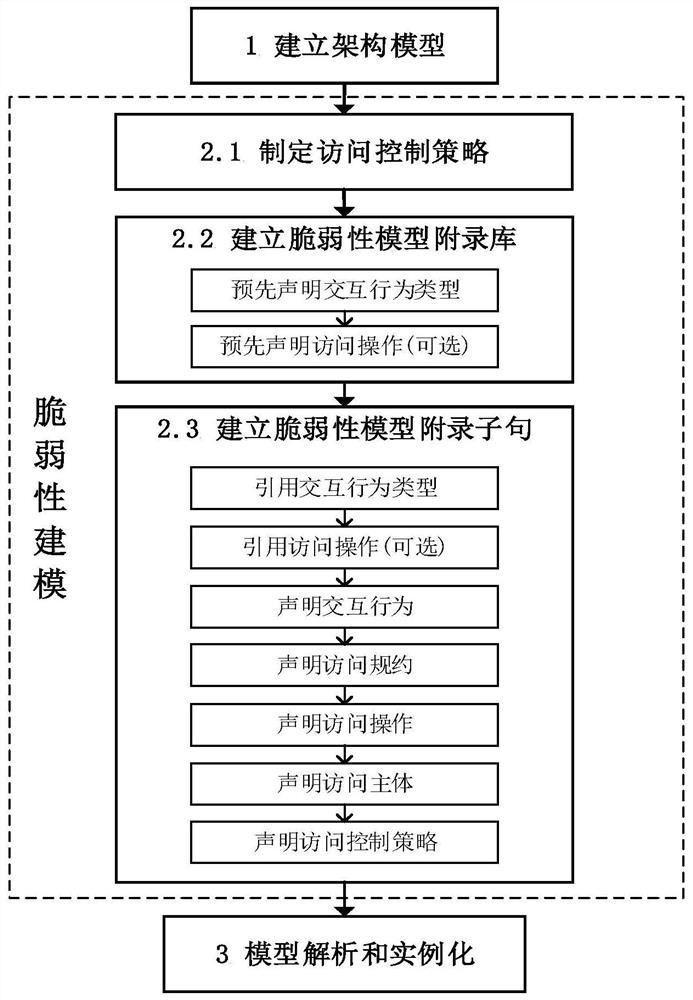
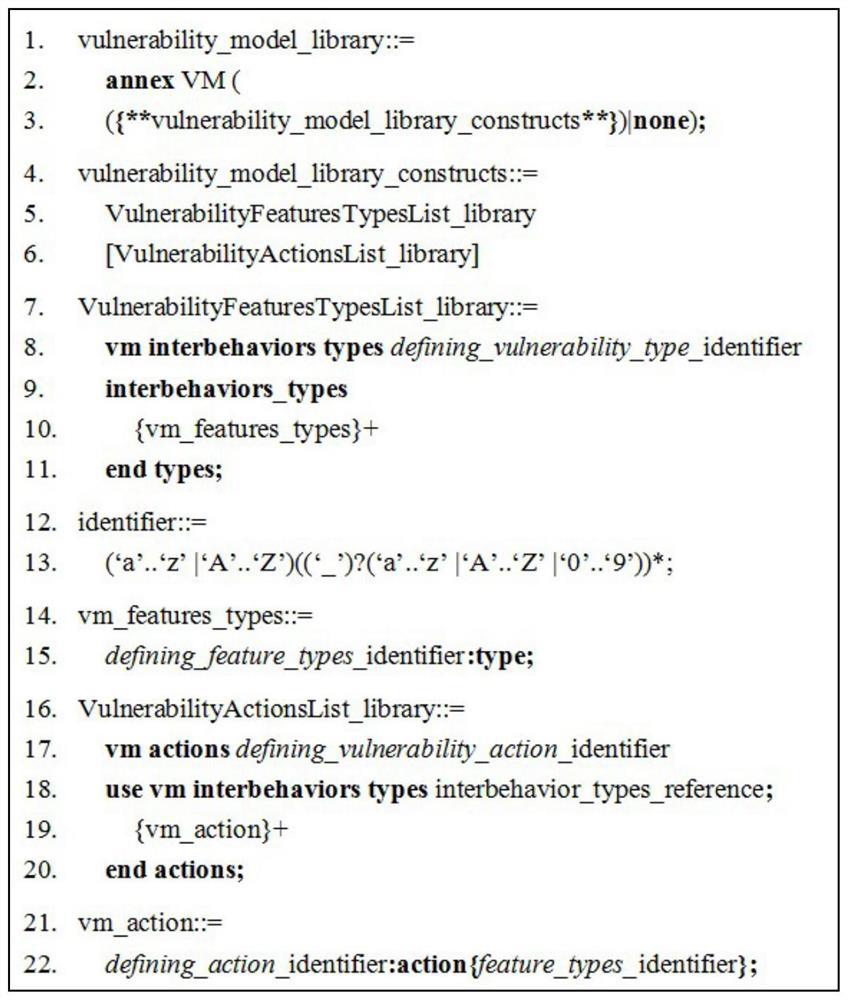
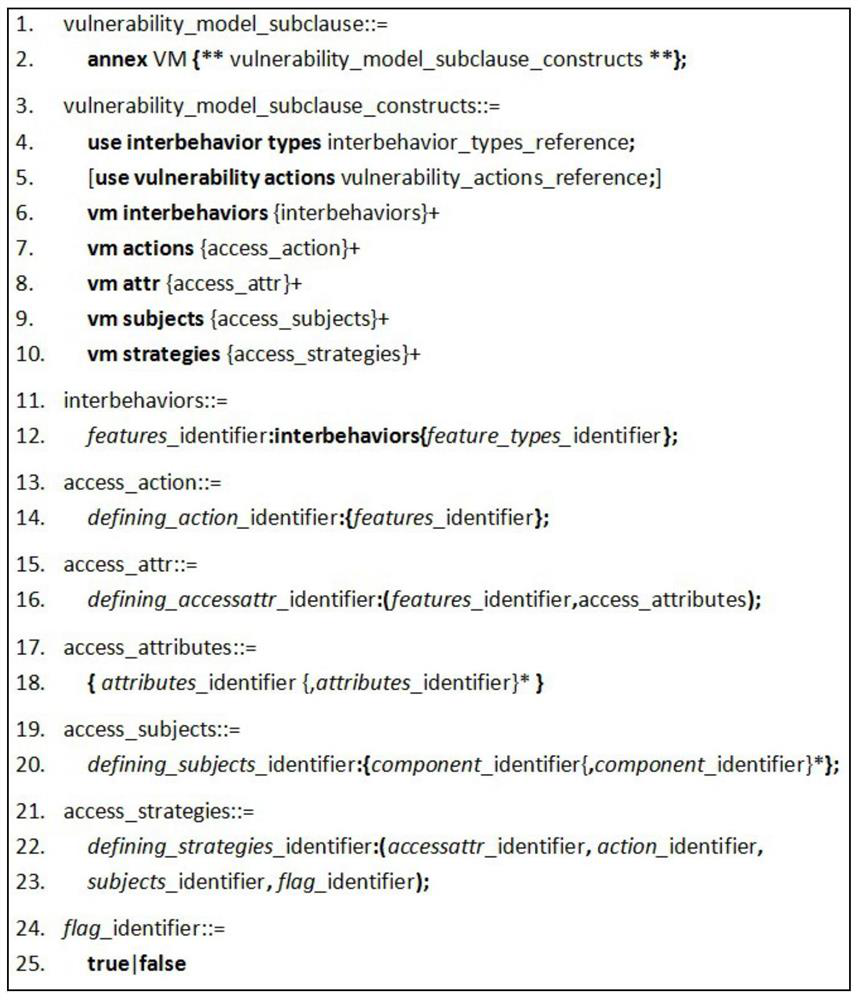
[0045] refer to Figure 1-7 , in combination with specific examples, the specific steps of the system vulnerability model design method based on AADL proposed by the present invention are as follows:
[0046] Step 1. Establish a system architecture model. Design the system architecture model according to the design requirements of the system, including component names, component features, component attributes and component connections.
[0047] Component names refer to the names of specific system components, process components, and thread components in the system architecture model;
[0048] Component characteristics means the characteristics in the component type declaration;
[0049] Component attributes refer to the attributes of specific system components, process components, and thread components in the system architecture model;
[0050] Component conn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com