Method for establishing vulnerability model based on chemical abstract machine
A construction method and vulnerability technology, which is applied in the field of vulnerability model construction based on chemical abstract machines, can solve the problems of difficult vulnerability causes and no vulnerability cause models, etc., and achieve the effect of improving effectiveness and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be further described below in conjunction with the accompanying drawings and examples. It should be noted that the described examples are only intended to facilitate the understanding of the present invention, and have no limiting effect on it.
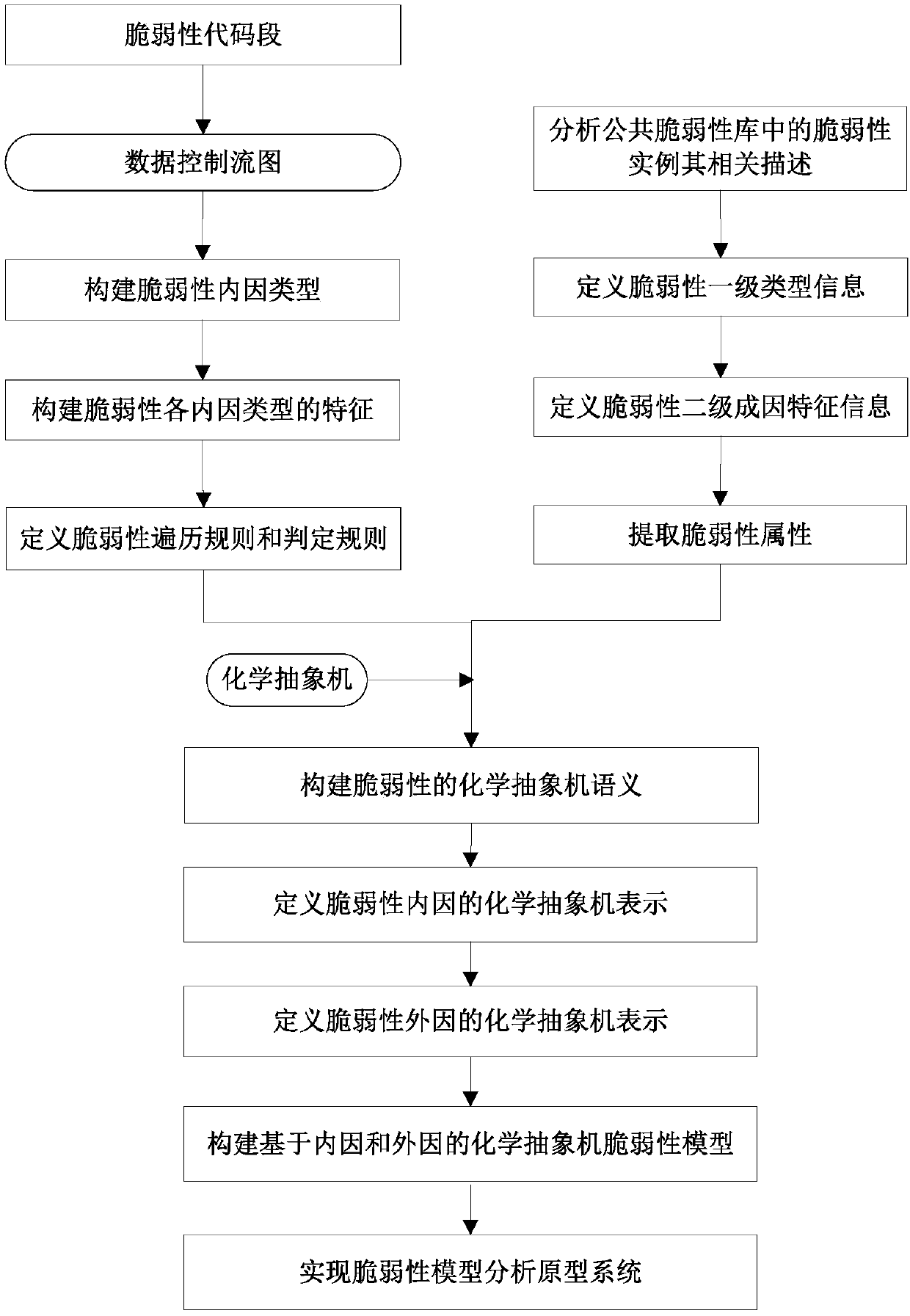
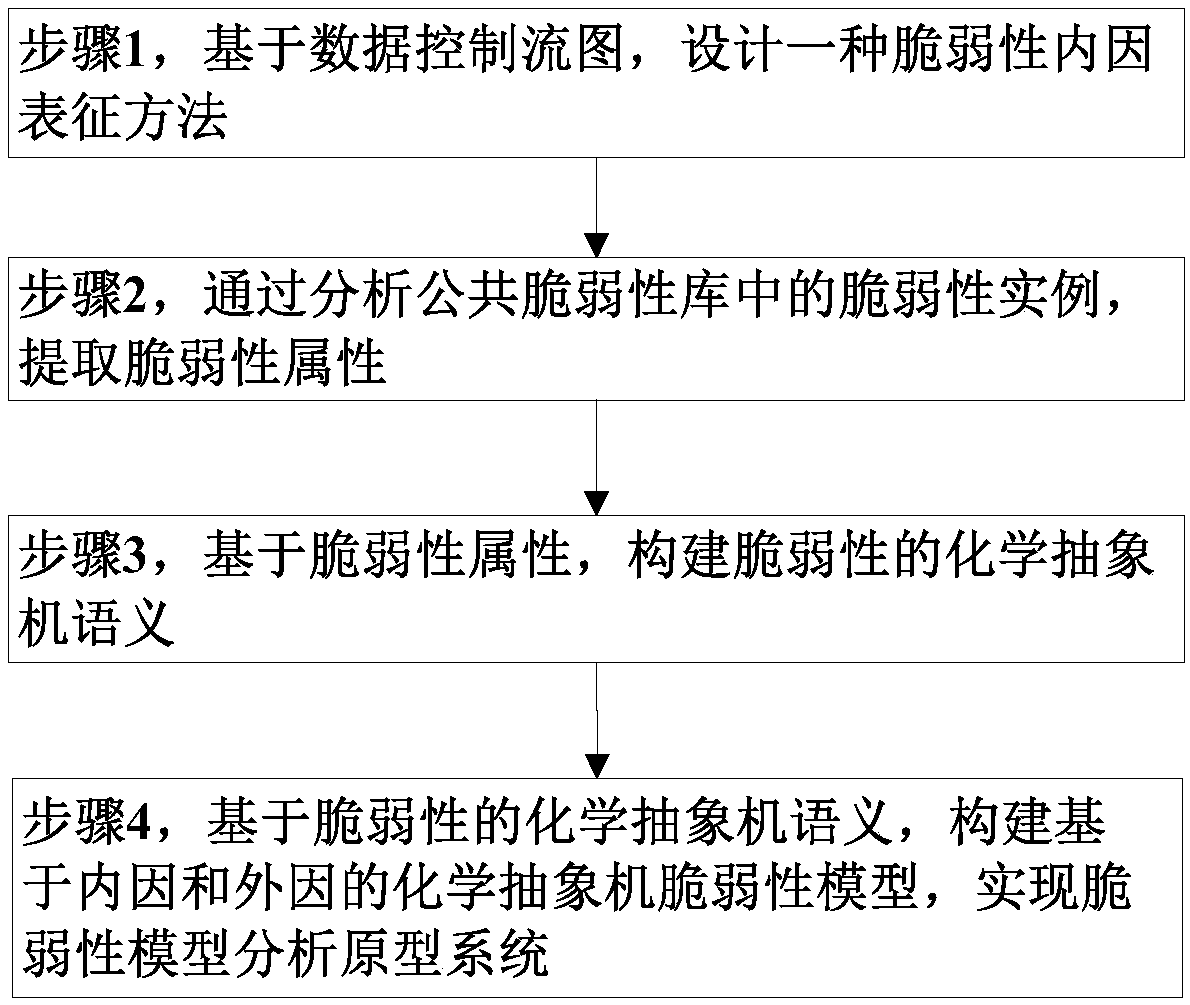
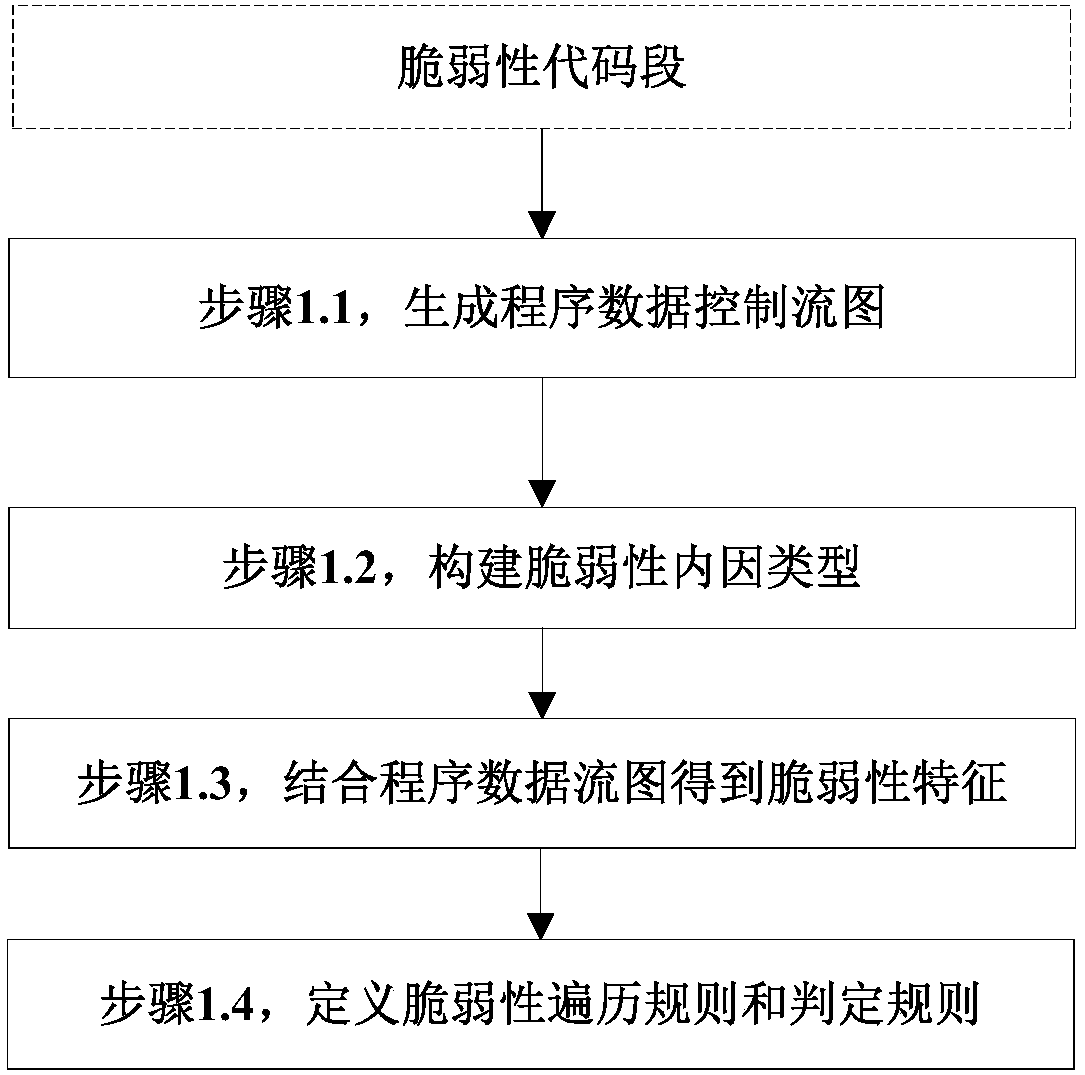
[0057] The invention provides a method for constructing a vulnerability model based on a chemical abstract machine for the purpose of studying the nature of the vulnerability. The present invention firstly designs a vulnerability internal cause characterization method, then extracts vulnerability attributes, and finally constructs a vulnerability model based on a chemical abstract machine, which has important guiding significance for studying the cause of vulnerability.
[0058] First, several concepts involved in the definition of the present invention are defined as follows.
[0059] Definition 1 Data control flow graph FG: FG=(T, E, λ, μ), where T represents the node on the data control flow graph,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com