Sensitive point approximation method based on intelligent route guidance
A technology of path guidance and sensitive points, applied in error detection/correction, instrumentation, software maintenance/management, etc., can solve problems such as increasing technical complexity, huge symbolic expressions, and complex path conditions, and alleviate the problem of path explosion , strong purpose, and the effect of reducing the false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
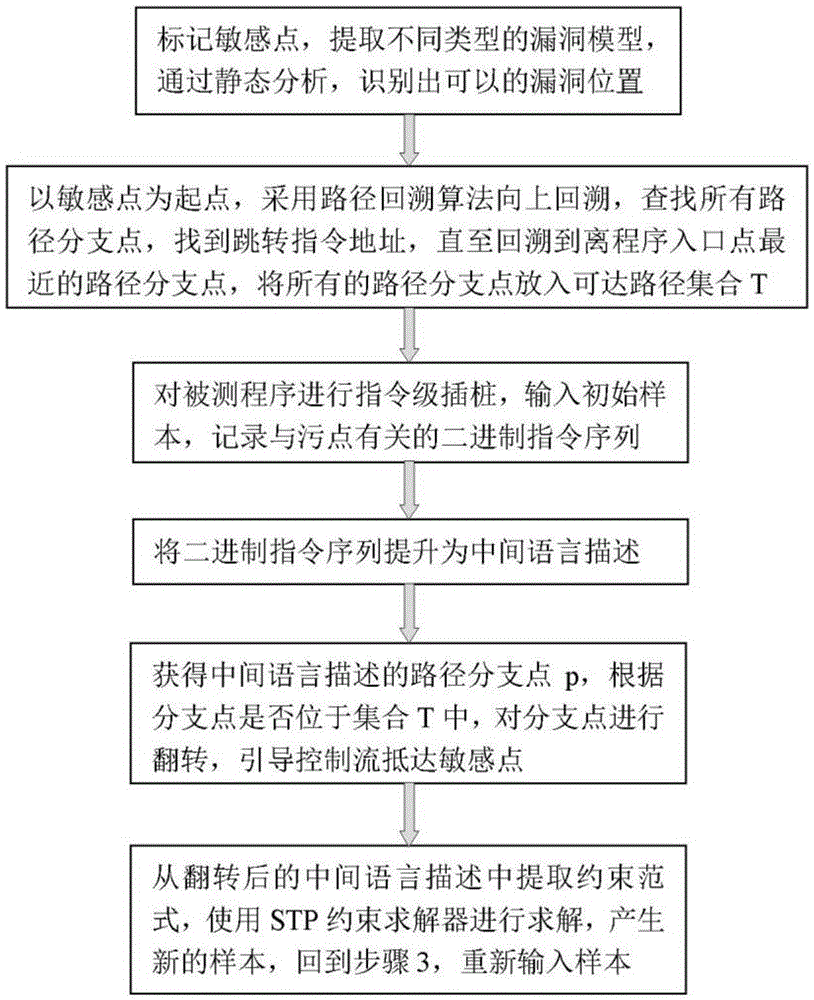
[0041] Embodiment one, see figure 2 As shown in , a method of approaching sensitive points based on intelligent path guidance includes the following steps:
[0042] Step 1. Mark sensitive points, extract different types of vulnerability models, identify suspicious vulnerability locations through static analysis, and mark them as sensitive points;
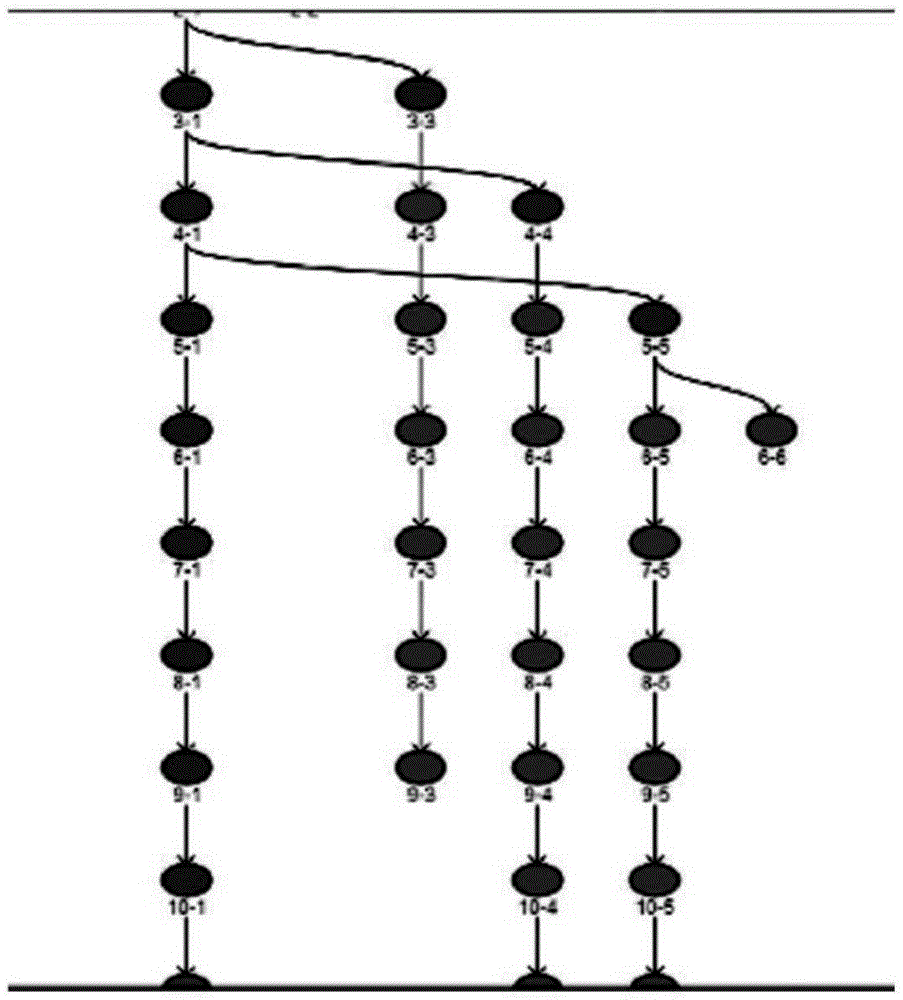
[0043] Step 2. Take the sensitive point as the starting point, use the path backtracking algorithm to backtrack upwards, find all the path branch points, find the address of the jump instruction, and trace back to the path branch point closest to the program entry point, and put all the path branch points into the available The set of reaching paths T=(t 1 ,t 2 ...t m );
[0044] Step 3. Perform instruction-level instrumentation on the program under test, input the initial sample, and record the binary instruction sequence related to the taint;
[0045] Step 4. Promote the sequence of binary instructions to an intermediate lan...
Embodiment 2
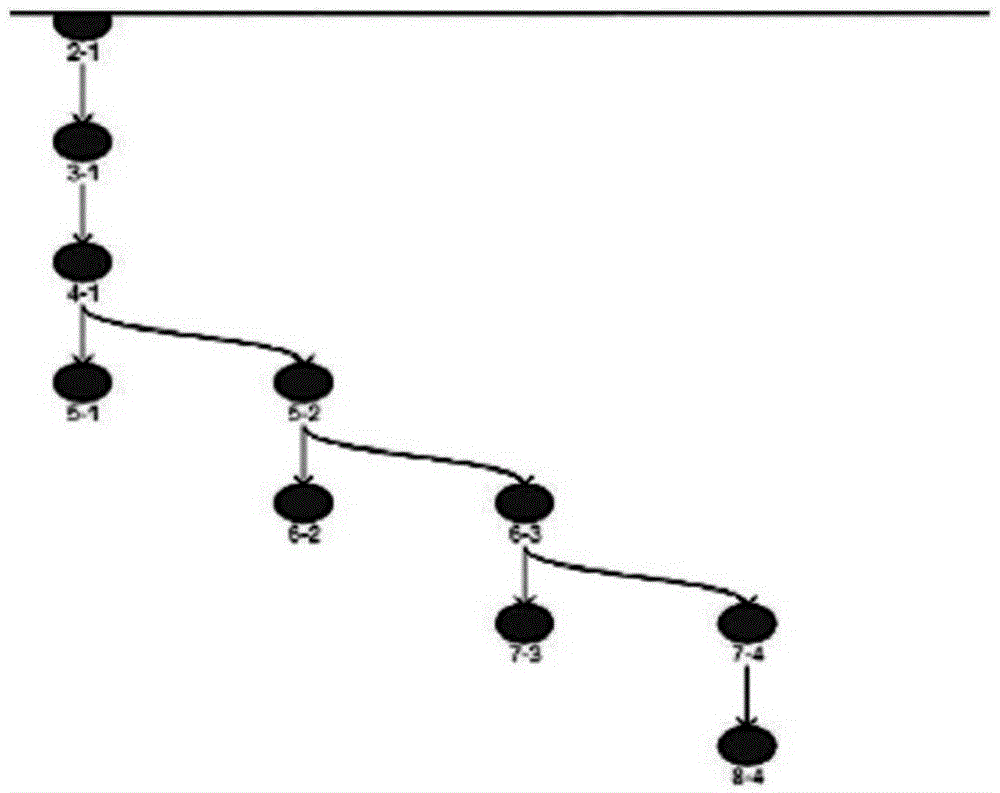
[0048] Embodiment two, see Figure 2~3 As shown, a method for approaching sensitive points based on intelligent path guidance, intelligently guides the path through the following steps, and finally reaches the sensitive point of buffer overflow, as follows:
[0049] Step 1. Mark sensitive points, extract different types of vulnerability models, identify suspicious vulnerability locations through static analysis, and mark them as sensitive points;
[0050] Step 2. Take the sensitive point as the starting point, use the path backtracking algorithm to backtrack upwards, find all the path branch points, find the address of the jump instruction, and trace back to the path branch point closest to the program entry point, and put all the path branch points into the available The set of reaching paths T=(t 1 ,t 2 ...t m ), which specifically include the following:
[0051] Step 2.1, record the position of the sensitive point as A, establish queues L1 and L2, and initialize them to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com