Safety assessment method and safety assessment equipment
A technology for evaluating equipment and safety, applied in the field of safety, it can solve the problems of relying on human evaluation, high requirements for human resources, and the inability of evaluation resources to meet evaluation needs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
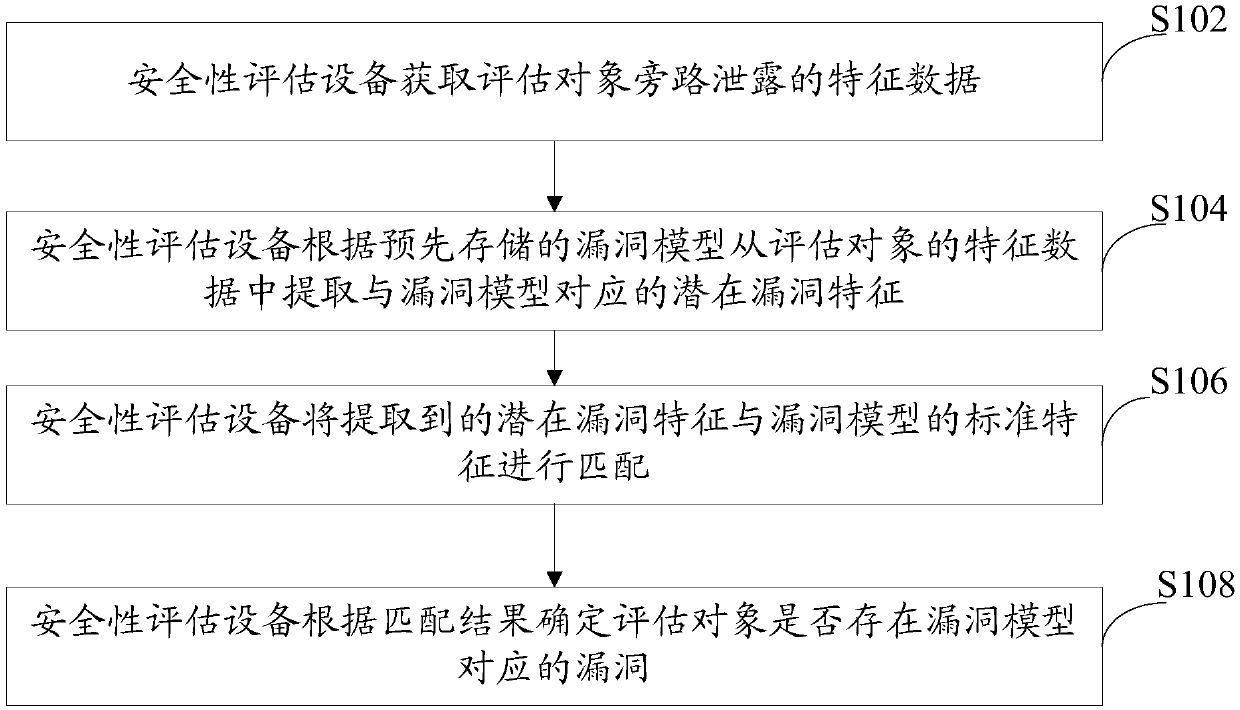
[0048] In order to solve the problem that the security assessment scheme in the prior art relies on a large amount of manpower input, resulting in the assessment resources being unable to meet the existing assessment requirements and restricting the improvement of industrial efficiency, this embodiment provides a security assessment method, see figure 1 Flowchart showing the safety assessment method:
[0049] S102: The security evaluation device acquires characteristic data of bypass leakage of an evaluation object.
[0050] The evaluation object refers to the object whose security needs to be evaluated, especially the object used for encryption. It can be hardware, such as a mobile phone, a security chip, etc., or program code. Taking encrypted electronic equipment in hardware devices as an example, it will generate bypass leakage information during operation, such as time consumption, power consumption or electromagnetic radiation, and these bypass leakage information may ...
Embodiment 2
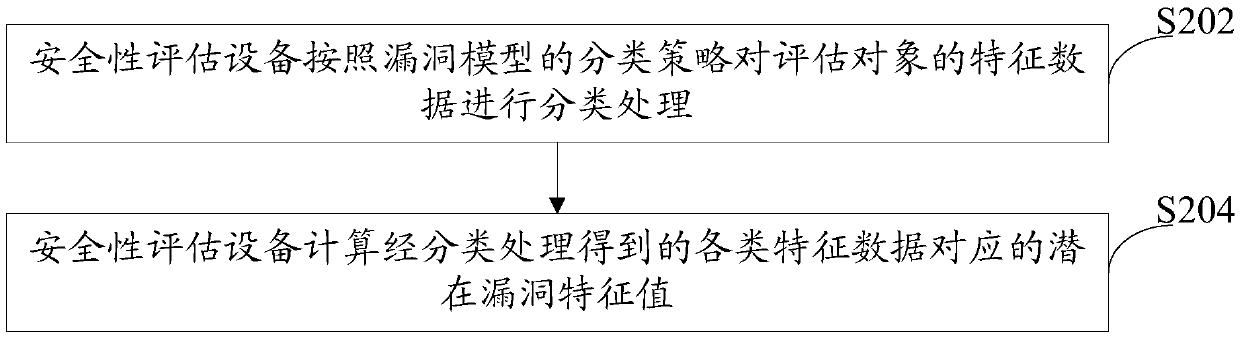
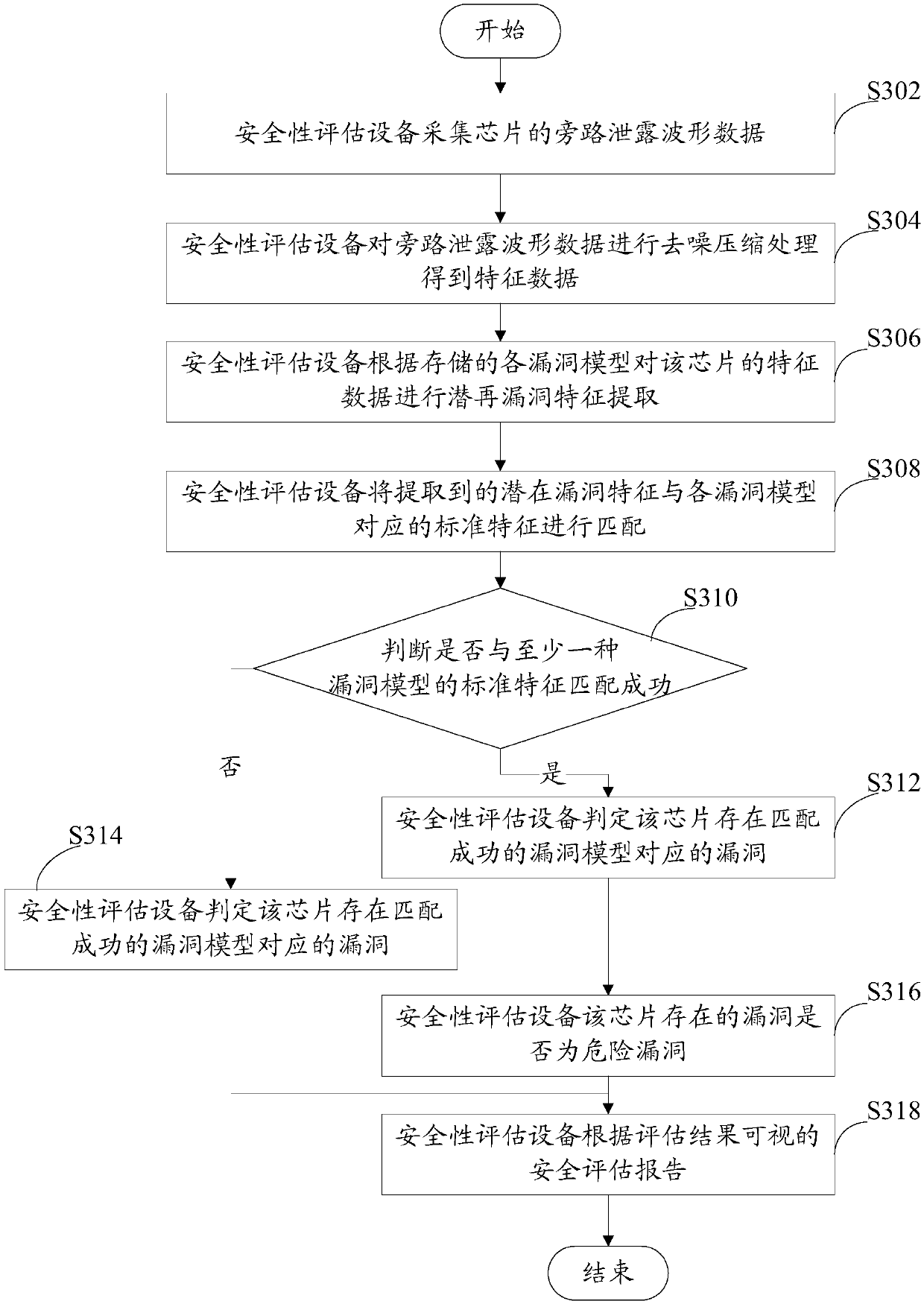
[0069] This embodiment will continue to introduce the security evaluation method provided by the present invention on the basis of the first embodiment. It is assumed that the evaluation object in this embodiment is a chip, and the evaluation personnel define various vulnerabilities that may appear in the chip based on experience. Corresponding vulnerability model. The vulnerability model can be stored in the memory of the security assessment device, or in other storage devices other than the security assessment device. The main security assessment device can obtain the corresponding vulnerability model data when evaluating the chip. , see below image 3 Flowchart of the safety assessment method shown:
[0070] S302: The safety evaluation device collects the bypass leakage waveform data of the chip.
[0071] First, the safety assessment equipment uses radio frequency acquisition equipment to collect the electromagnetic radiation of the target chip, and after frequency mixing...
Embodiment 3
[0101] This embodiment provides a security evaluation device, please refer to Figure 5 :
[0102] The security assessment device 50 includes a data acquisition module 502 , a feature extraction module 504 , a feature matching module 506 and a vulnerability judgment module 508 . Wherein the data acquisition module 502 is used to obtain the feature data of the evaluation object bypass leakage; the feature extraction module 504 is used to extract the potential vulnerability features corresponding to the vulnerability model from the feature data of the evaluation object according to the pre-stored vulnerability model; the feature matching module 506 It is used to match the extracted potential vulnerability features with the standard features of the vulnerability model; and the vulnerability judgment module 508 is used to determine whether the evaluation object has a vulnerability corresponding to the vulnerability model according to the matching result.
[0103] For the specific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com