Patents
Literature
238 results about "Course of action" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
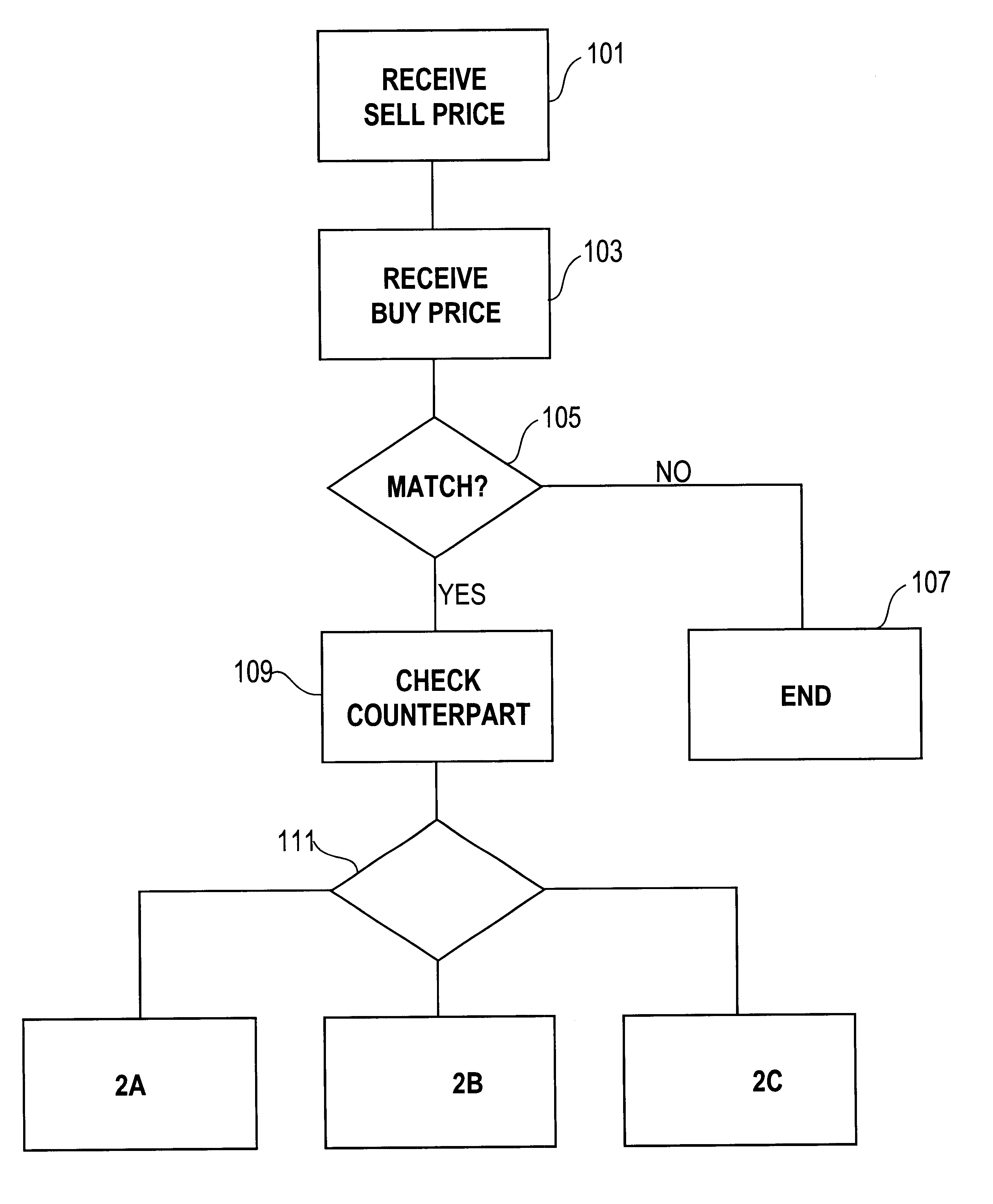
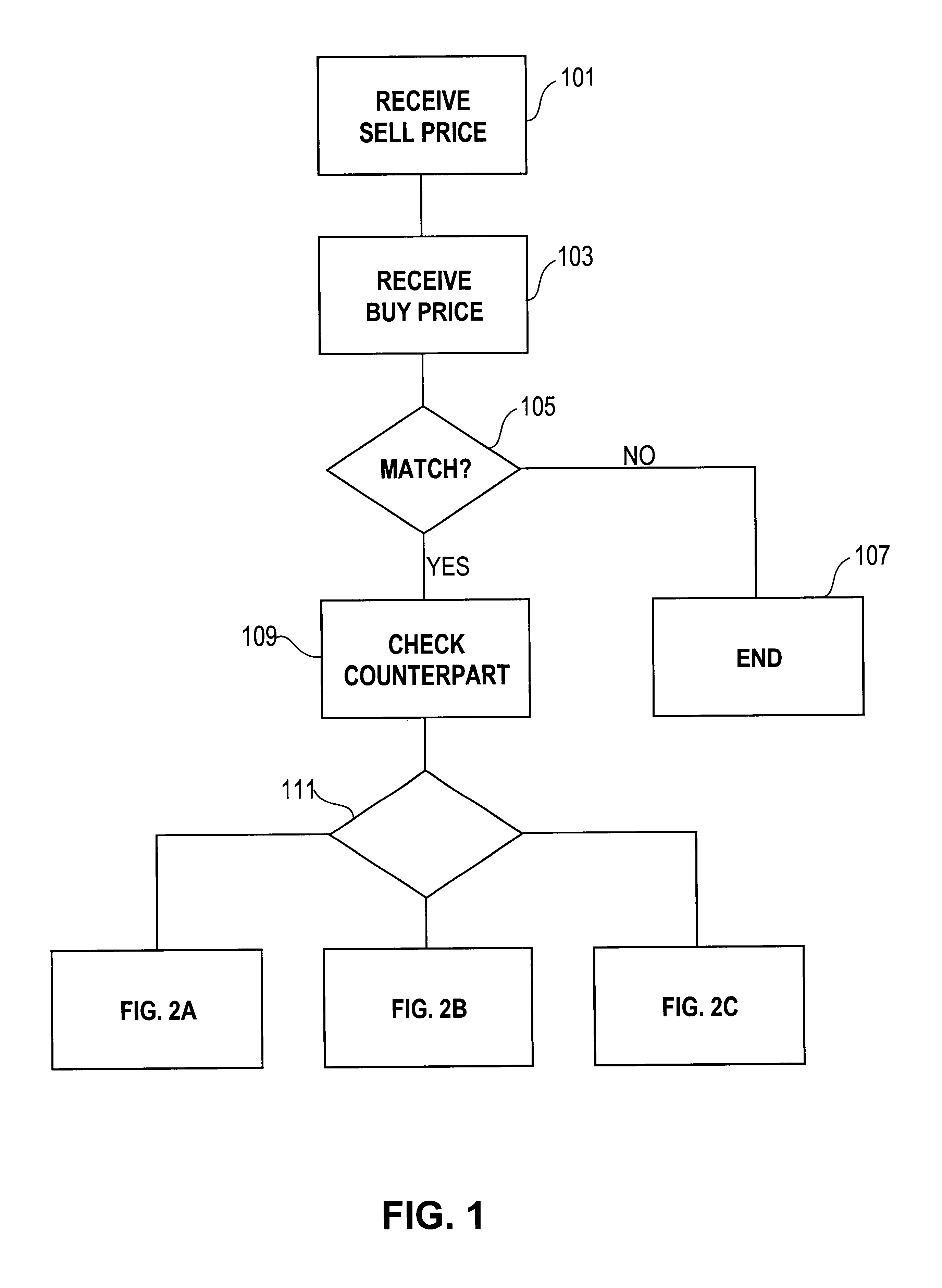
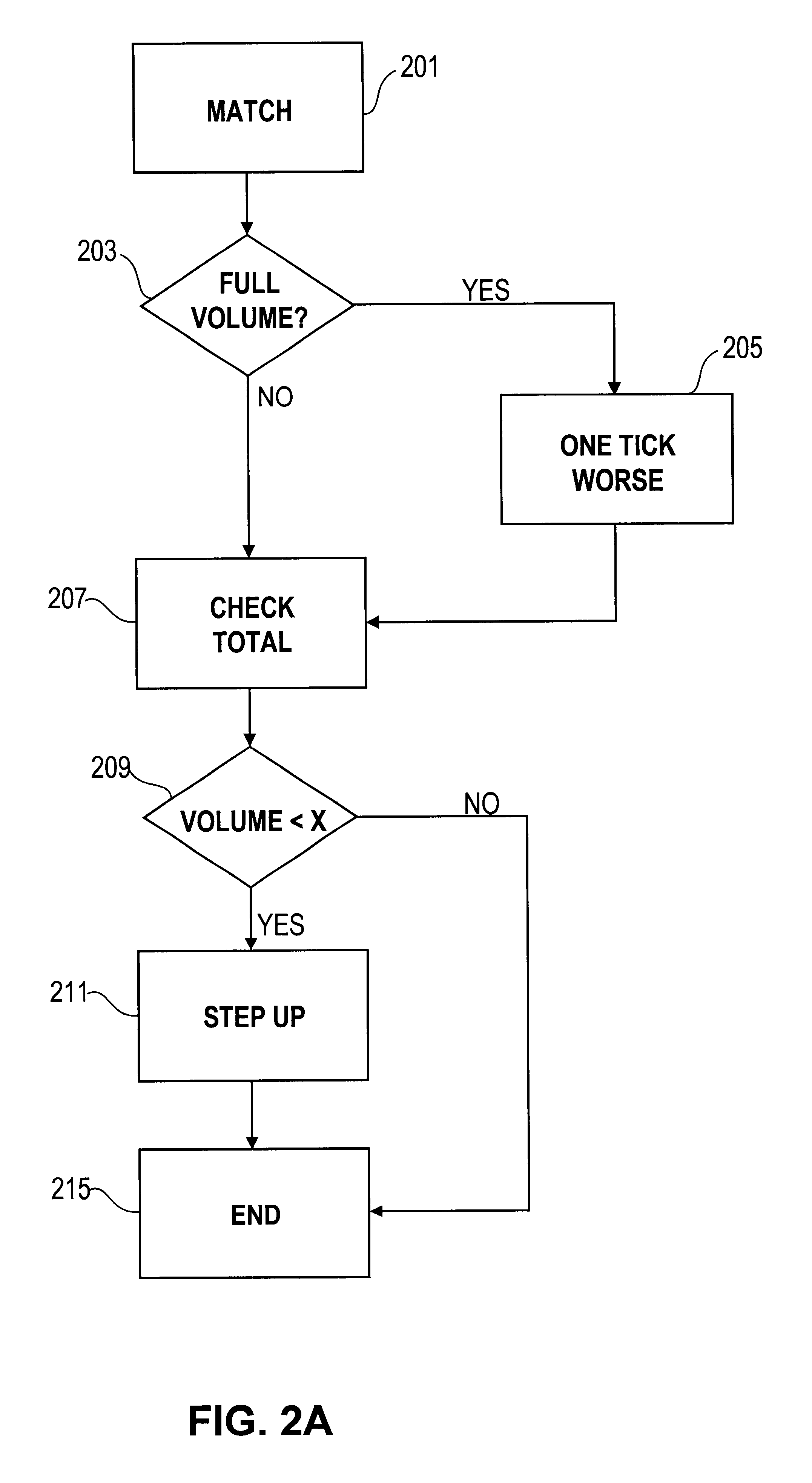
Automated exchange for matching bids between a party and a counterparty based on a relationship between the counterparty and the exchange
InactiveUS6405180B2Tight spreadReduced volume (risk)Special service provision for substationFinanceOrder formCourse of action
In an automated exchange system means are provided by means of which a market maker can enter a course of action in advance, so that the volume in the orderbook is continuously updated, and where the updating is performed differently with respect to different counter parts. Also, quotes that may result in a trade between Market Makers are hidden for some time before being matched, thus giving the Market Makers a chance to back off. The system employs a function that supports that Market Makers through pre-defined parameters will have new orders generated by the system and that a market maker can act differently with respect to different counterparts. The parameters specify if a Market Maker should add extra volume on an existing price or generate a new order at a worse price. In order to make it possible for market makers to have a very tight spread without forcing them to take larger risks, additional logic is used when matching orders. The algorithm used for this purpose protects the market makers in certain situations and gives market makers the possibility to have a tight spread without taking a large risk. The algorithm also supports that the market makers can take the risk to quote large volumes.
Owner:ISE LLC
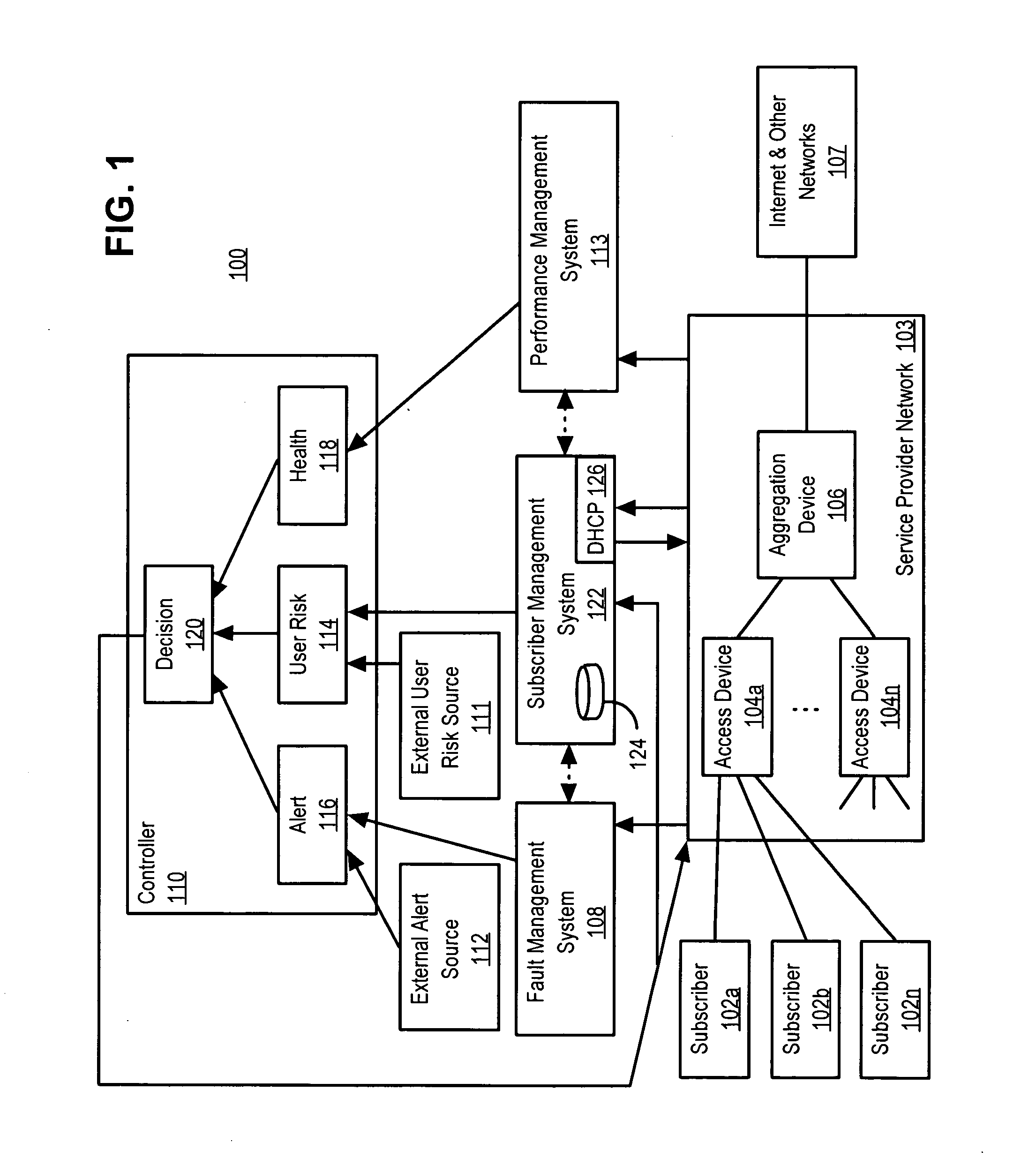
Policy-based network security management
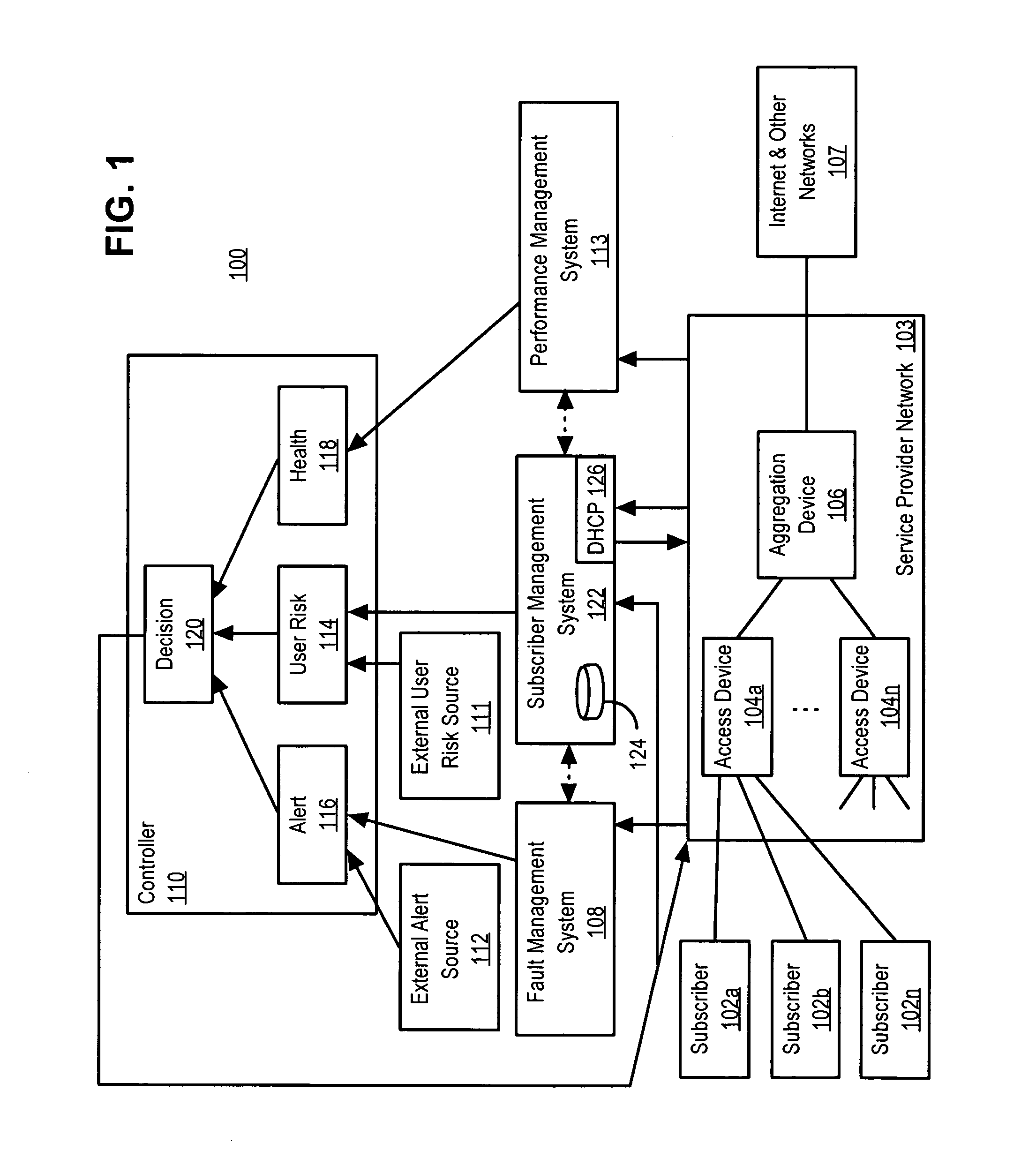
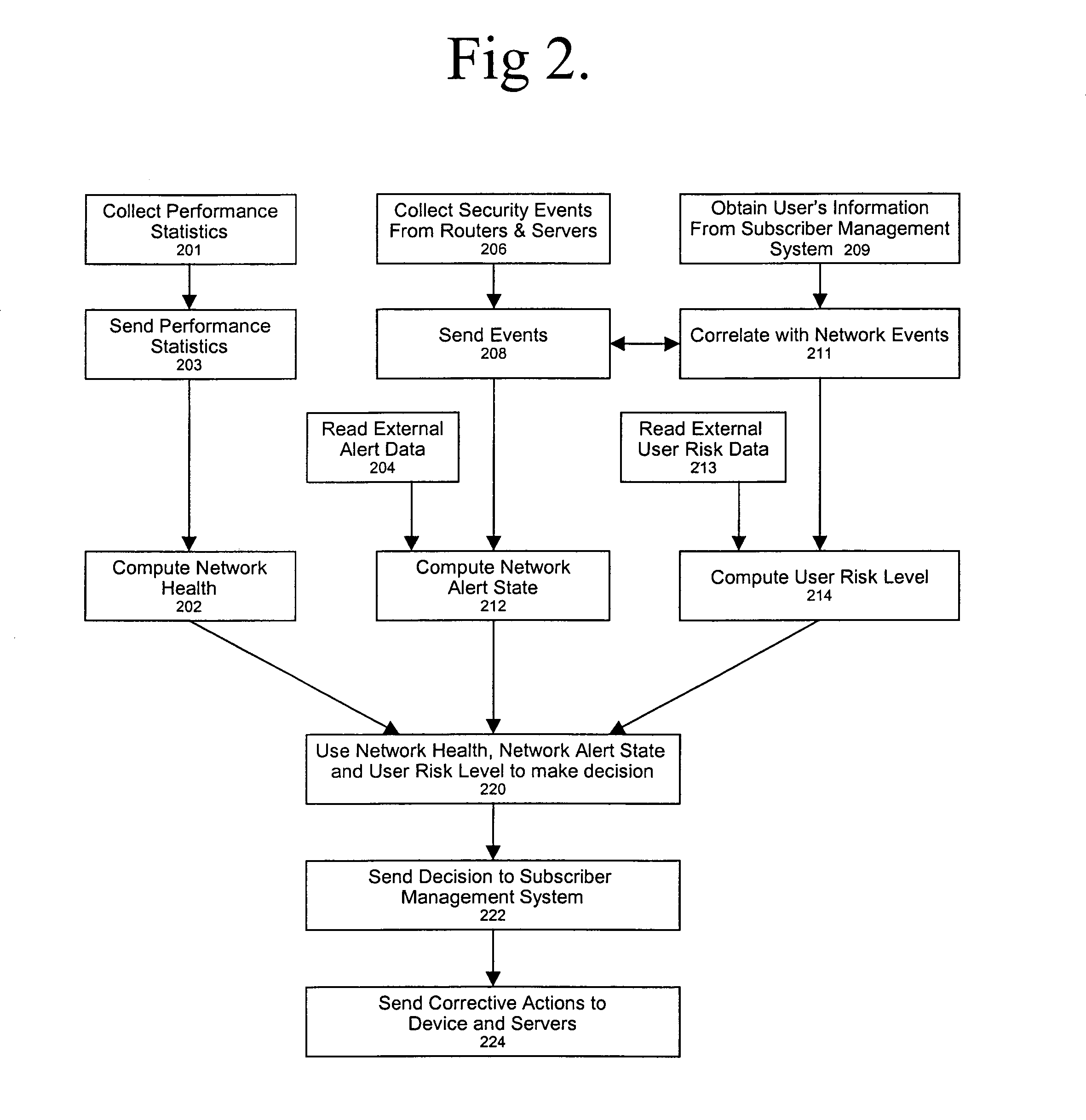
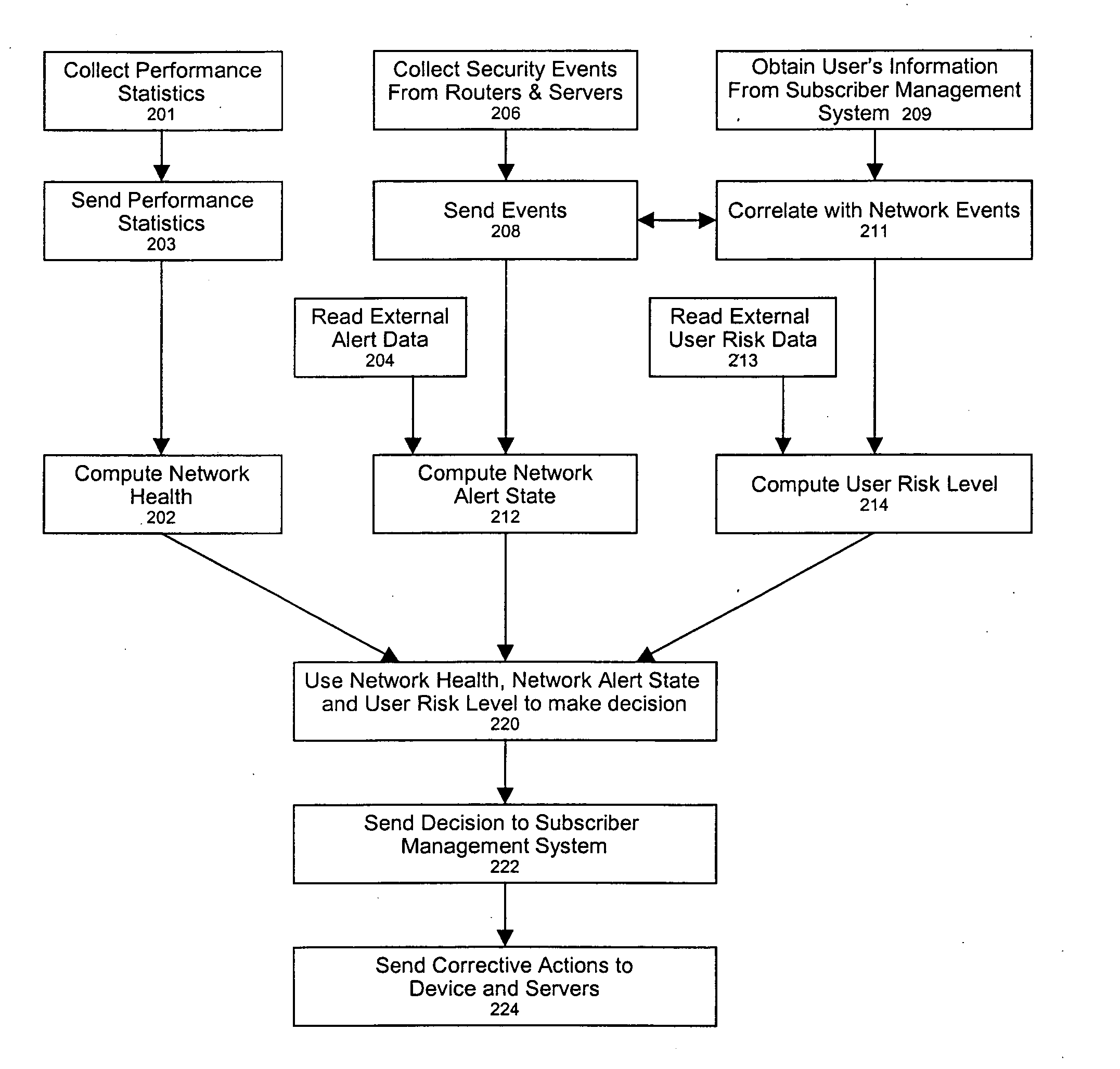
ActiveUS7237267B2Memory loss protectionError detection/correctionNetwork resource managementCourse of action
A policy-based network security management system is disclosed. In one embodiment, the system comprises a security management controller comprising one or more processors; a computer-readable medium carrying one or more sequences of instructions for policy-based network security management, wherein execution of the one or more sequences of instructions by the one or more processors causes the one or more processors to perform the steps of receiving a set of data regarding a user of a computer network; automatically deciding on a course of action based on the set of data, wherein the course of action may be adverse to the user although the set of data is insufficient to establish whether the user is performing a malicious action; and sending signals to one or more network elements in the computer network to implement the decision.
Owner:CISCO TECH INC
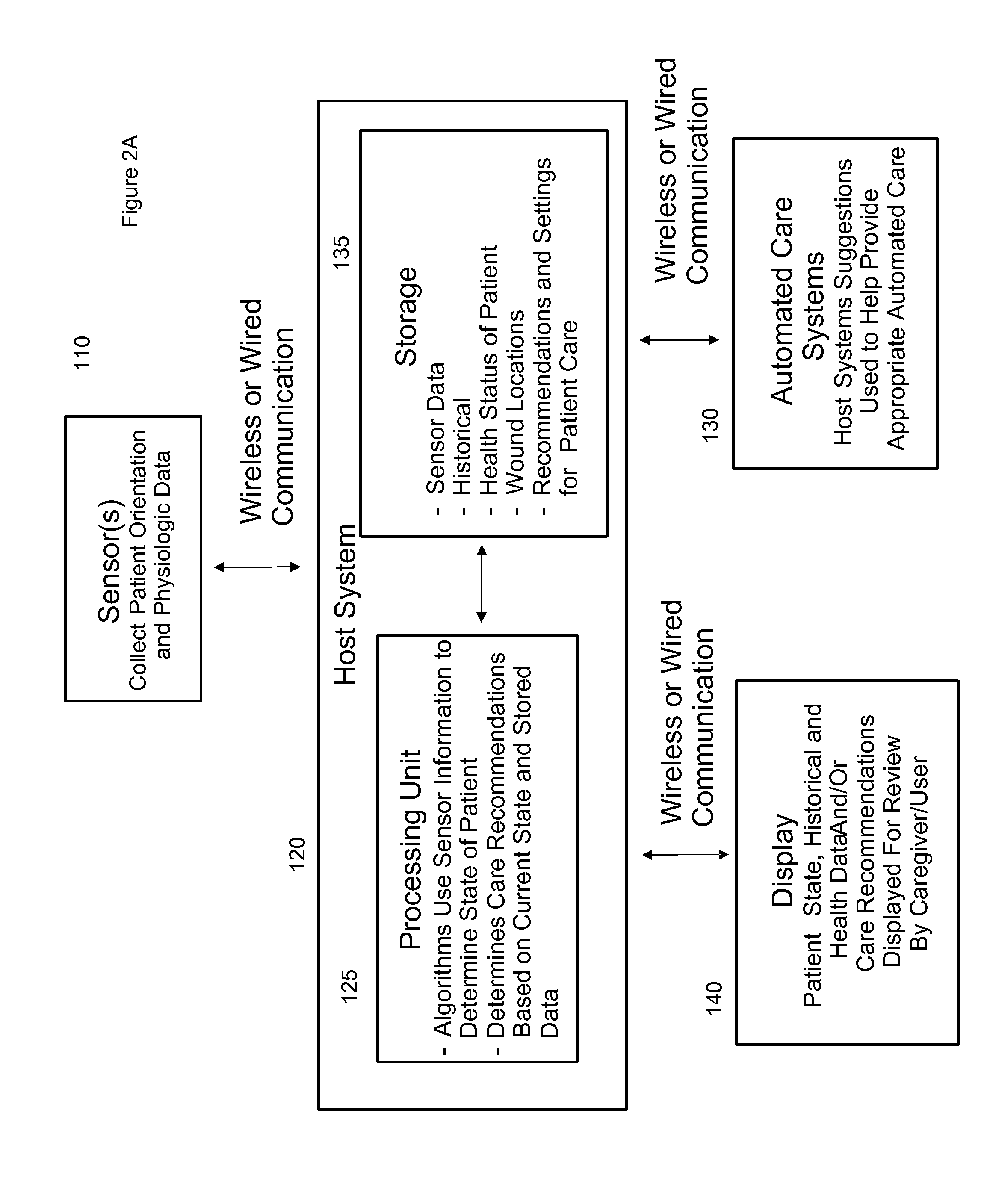
Systems, devices and methods for preventing, detecting and treating pressure-induced ischemia, pressure ulcers, and other conditions
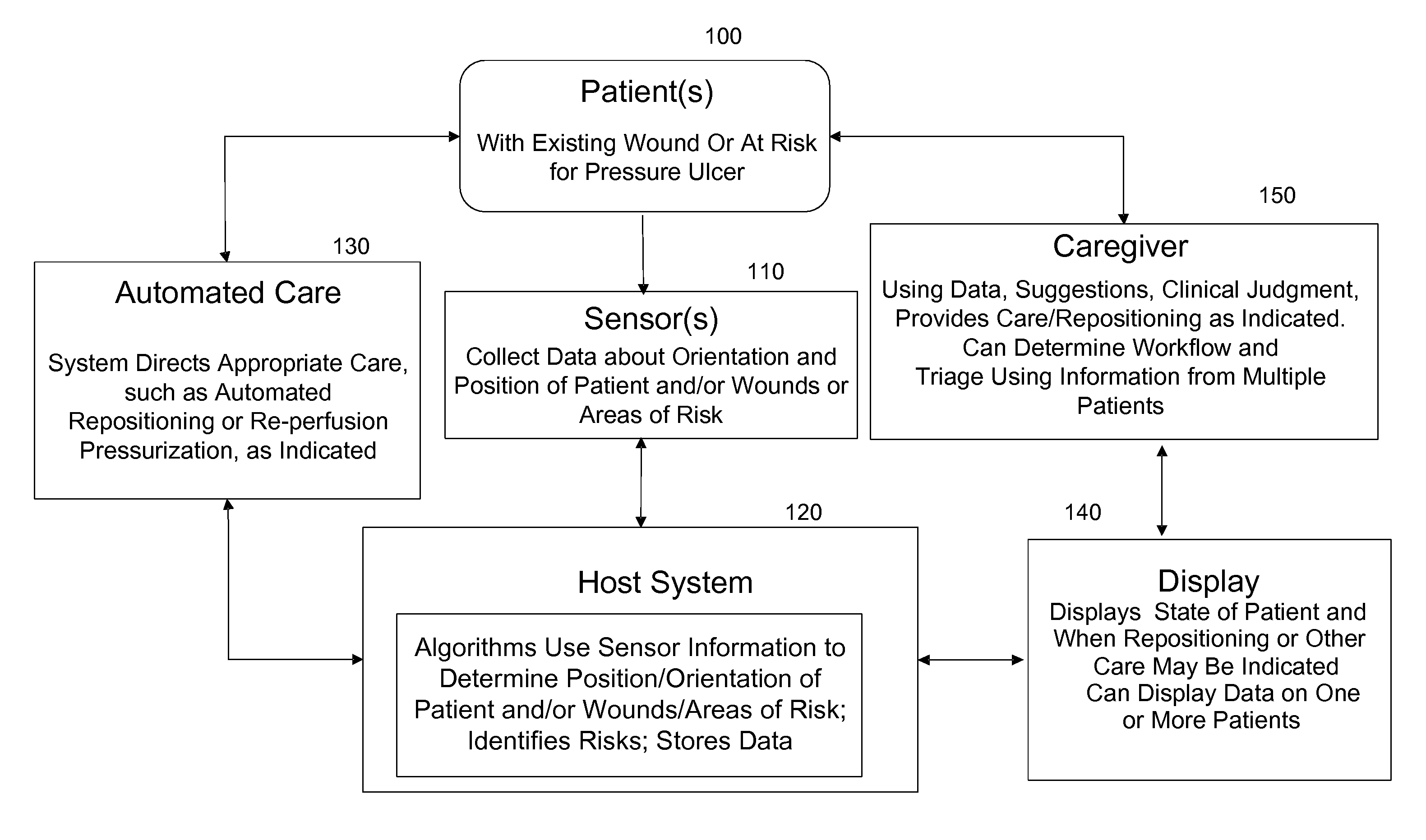
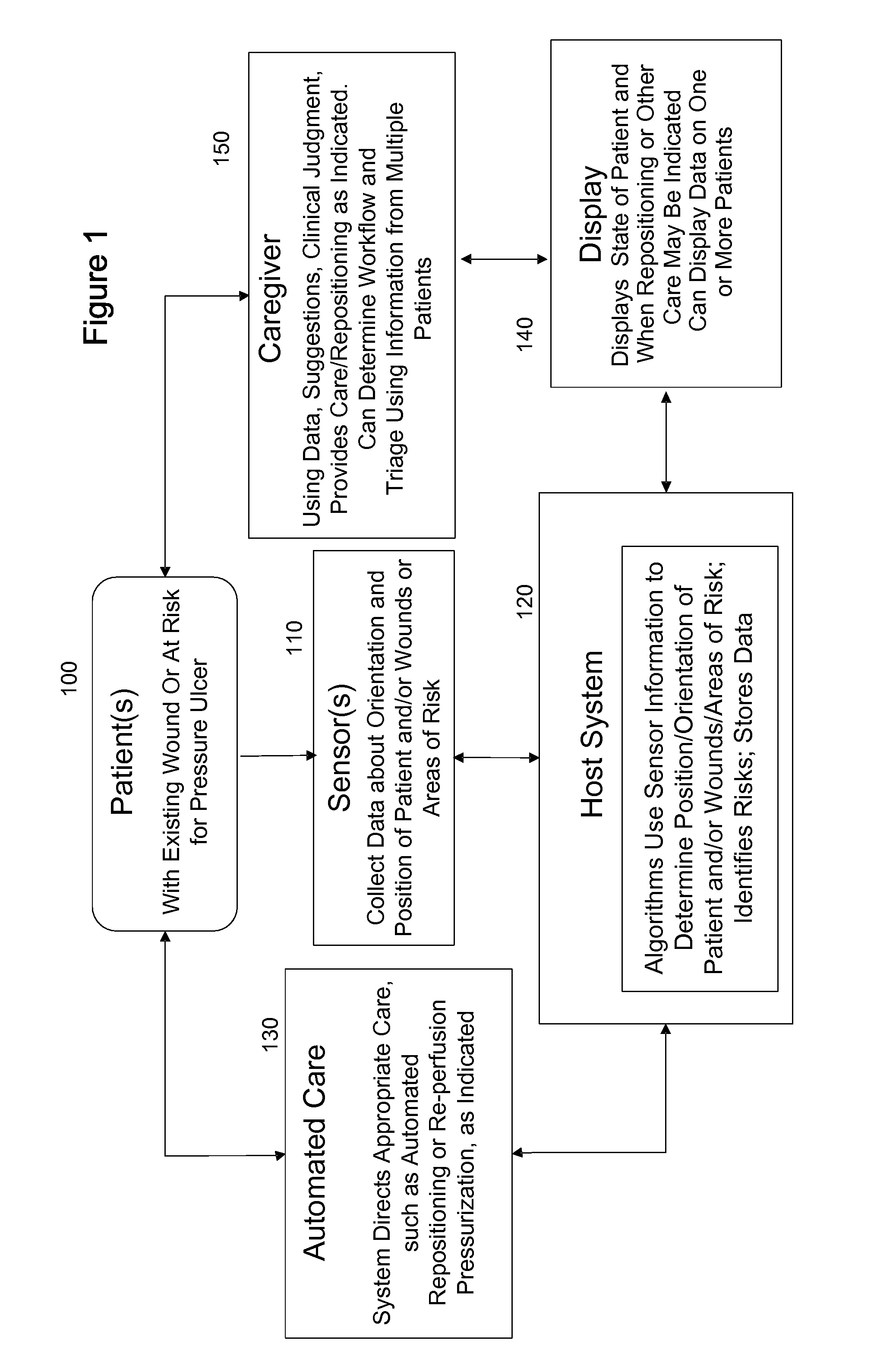
ActiveUS20110263950A1Minimize and eliminate physical contactPromote blood circulationMechanical/radiation/invasive therapiesOperating chairsAccelerometerPatient characteristics
A system for monitoring medical conditions including pressure ulcers, pressure-induced ischemia and related medical conditions comprises at least one sensor adapted to detect one or more patient characteristic including at least position, orientation, temperature, acceleration, moisture, resistance, stress, heart rate, respiration rate, and blood oxygenation, a host for processing the data received from the sensors together with historical patient data to develop an assessment of patient condition and suggested course of treatment. In some embodiments, the system can further include a support surface having one or more sensors incorporated therein either in addition to sensors affixed to the patient or as an alternative thereof. The support surface is, in some embodiments, capable of responding to commands from the host for assisting in implementing a course of action for patient treatment. The sensor can include bi-axial or tri-axial accelerometers, as well as resistive, inductive, capactive, magnetic and other sensing devices, depending on whether the sensor is located on the patient or the support surface, and for what purpose.
Owner:LEAF HEALTHCARE
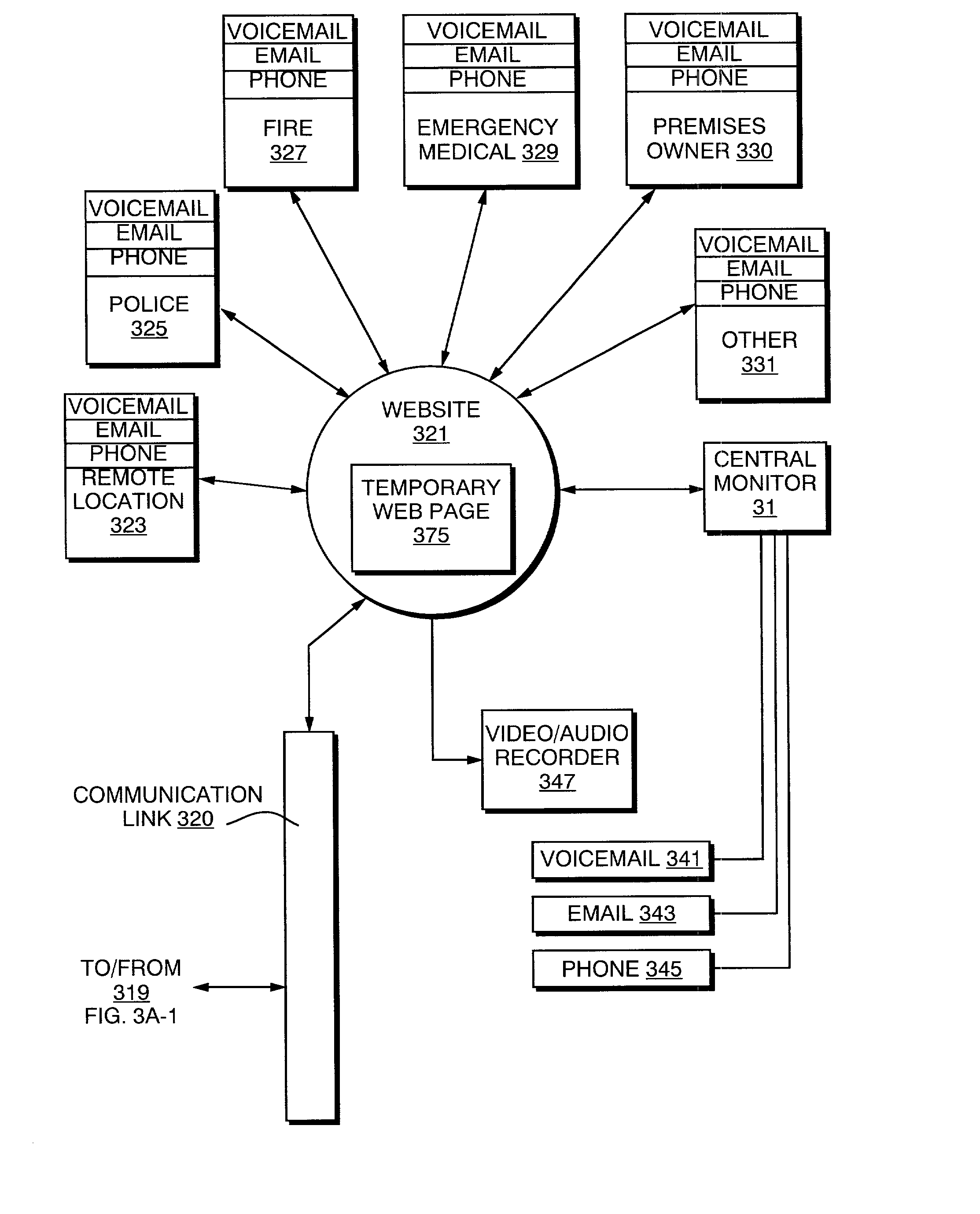
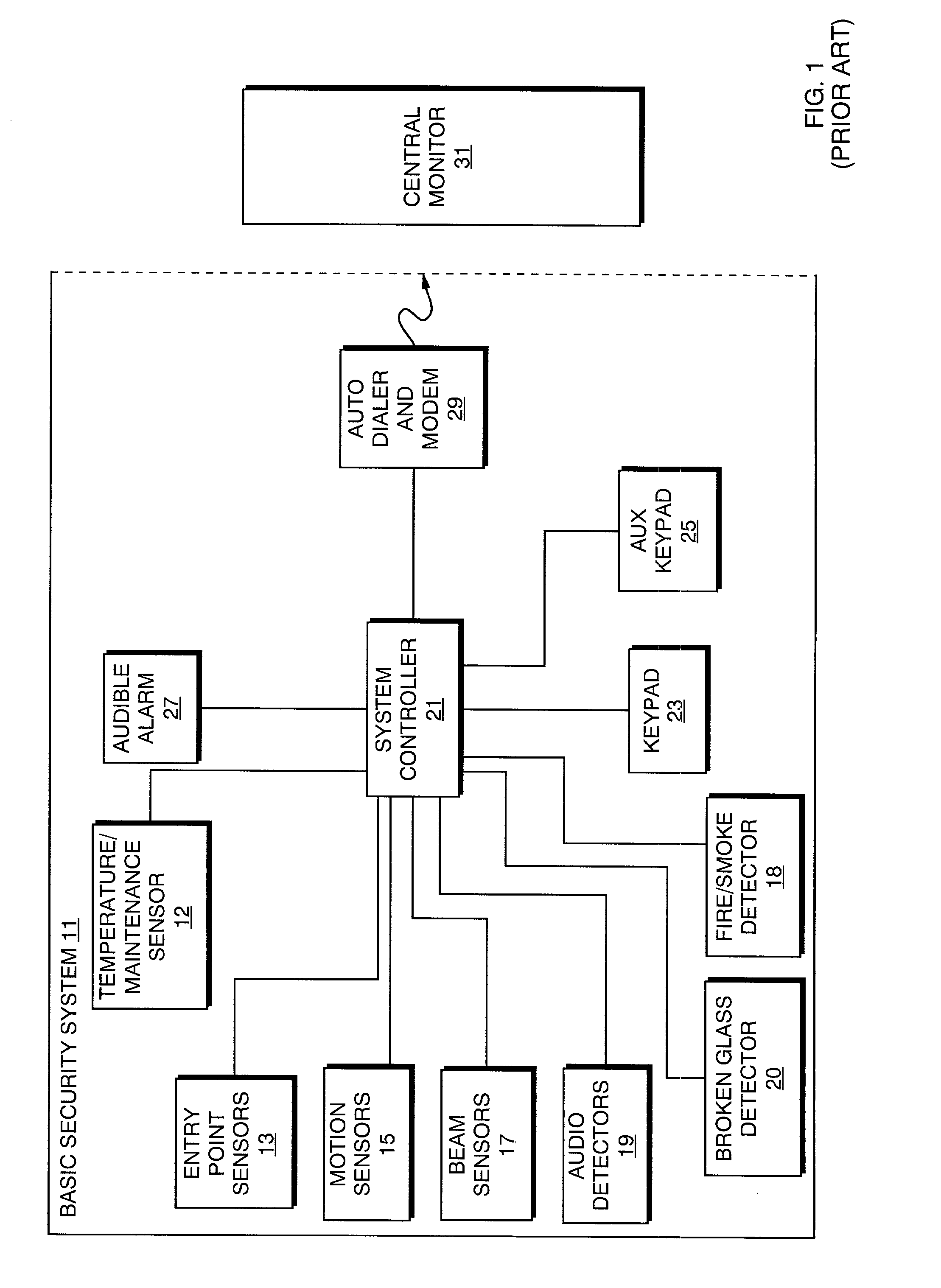
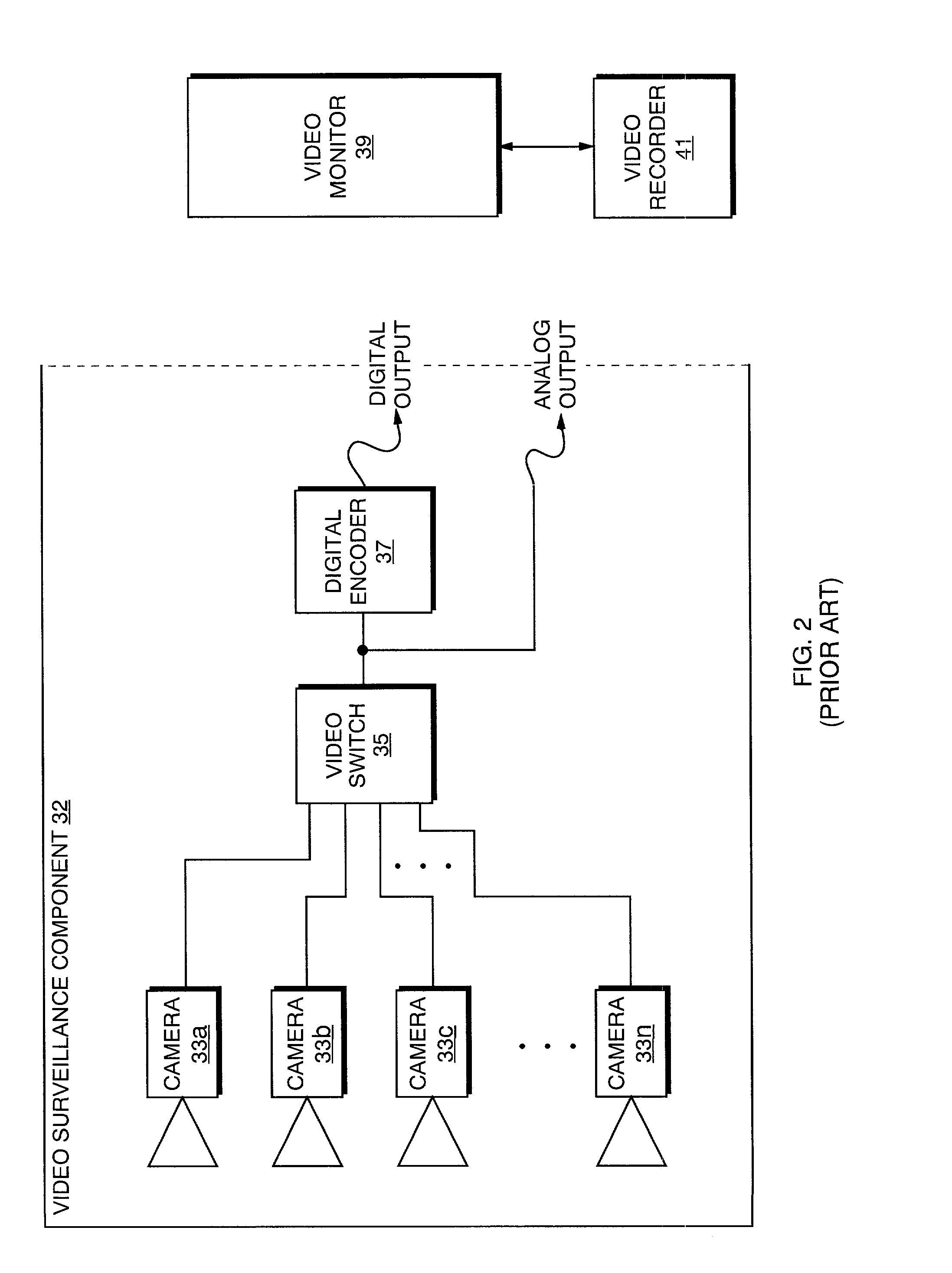
Internet based emergency communication system
InactiveUS20020005894A1Eliminating, or at least greatly reducing, false alarms and nuisance callsEliminates or reduces false alarmsColor television detailsClosed circuit television systemsCommunications systemCourse of action
Owner:CWITHIN +1
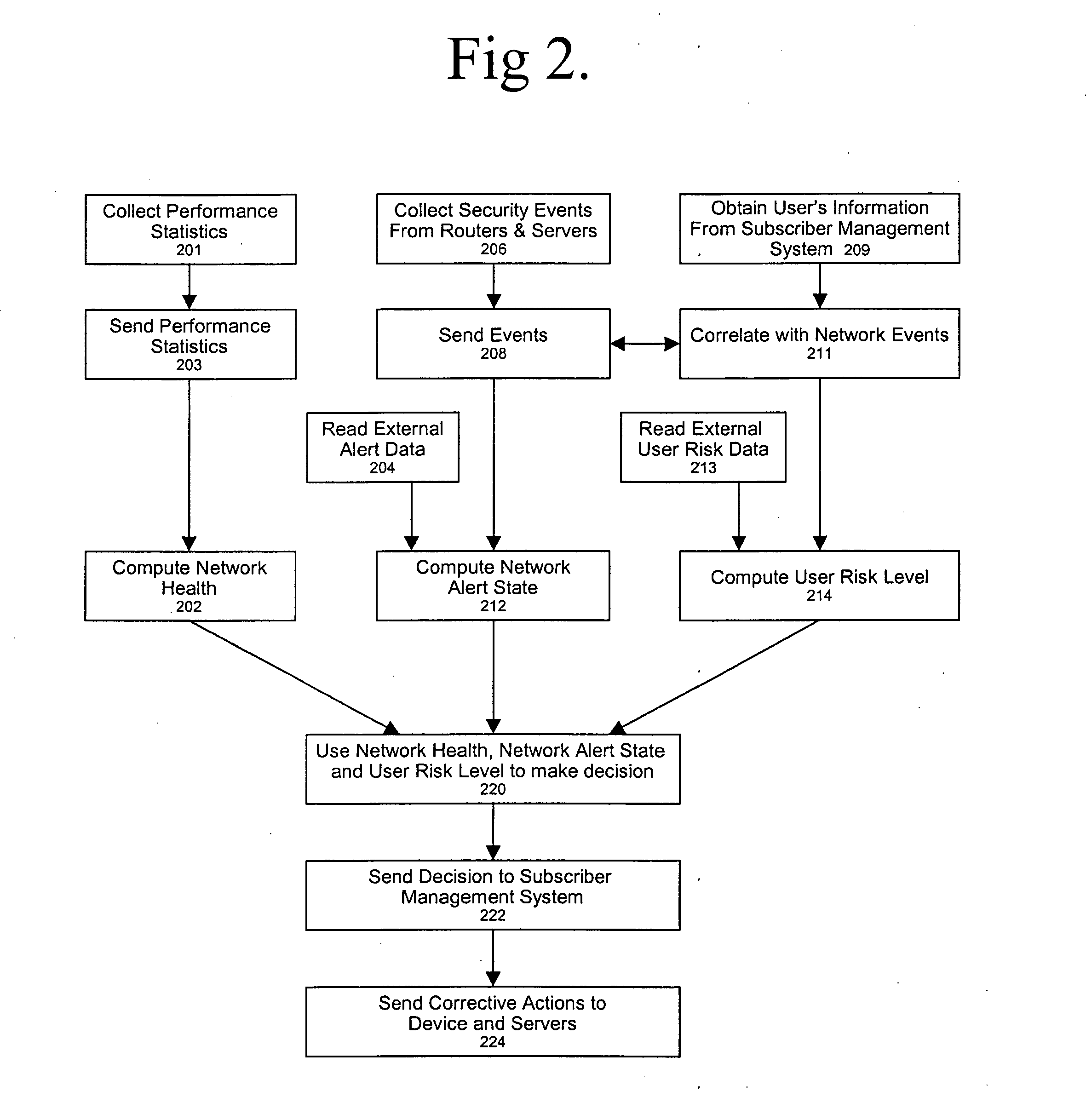
Policy-based network security management
ActiveUS20050086502A1Potential economic damageReduce riskMemory loss protectionUser identity/authority verificationCourse of actionSecurity management
A policy-based network security management system is disclosed. In one embodiment, the system comprises a security management controller comprising one or more processors; a computer-readable medium carrying one or more sequences of instructions for policy-based network security management, wherein execution of the one or more sequences of instructions by the one or more processors causes the one or more processors to perform the steps of receiving a set of data regarding a user of a computer network; automatically deciding on a course of action based on the set of data, wherein the course of action may be adverse to the user although the set of data is insufficient to establish whether the user is performing a malicious action; and sending signals to one or more network elements in the computer network to implement the decision.
Owner:CISCO TECH INC
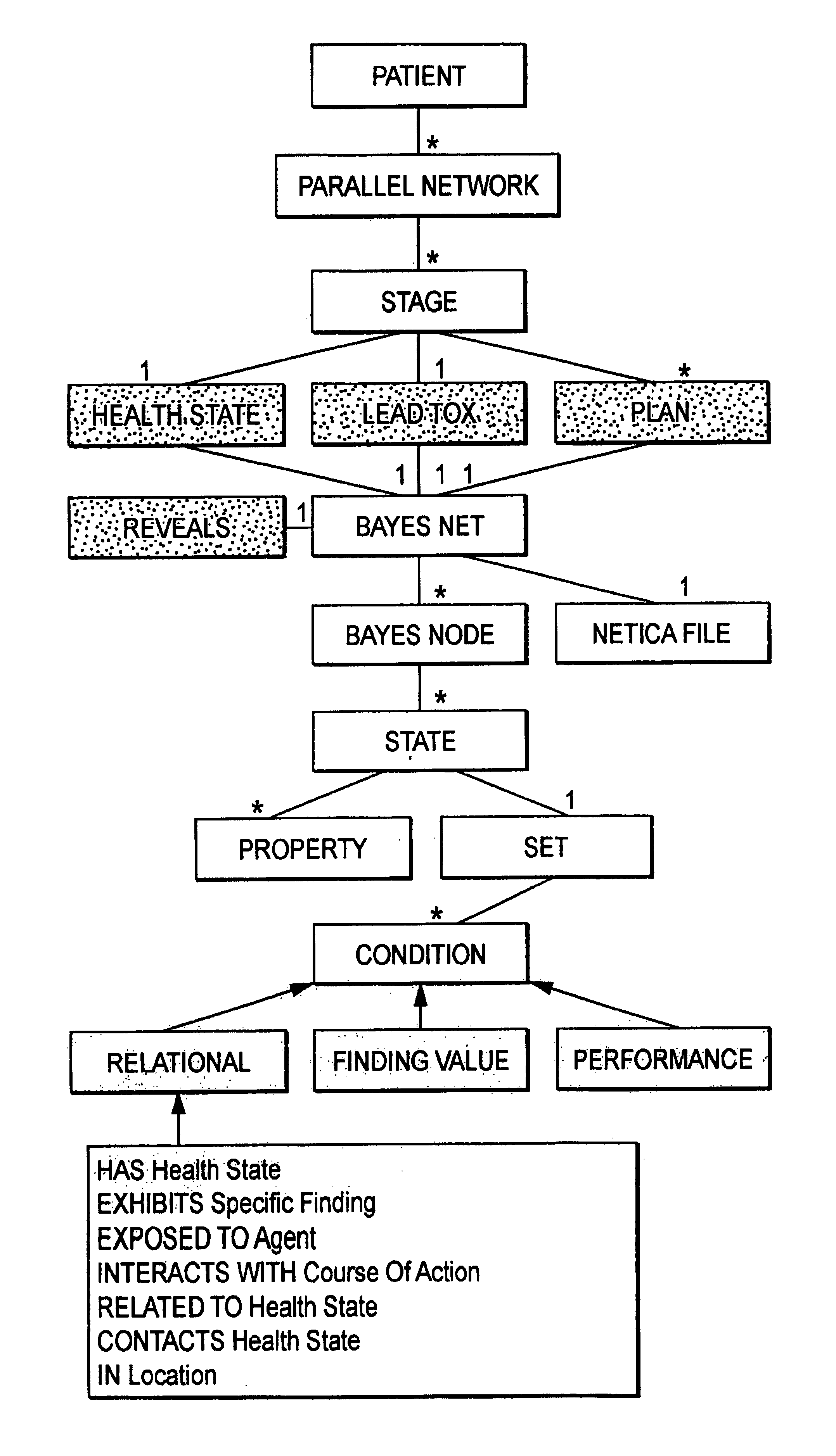
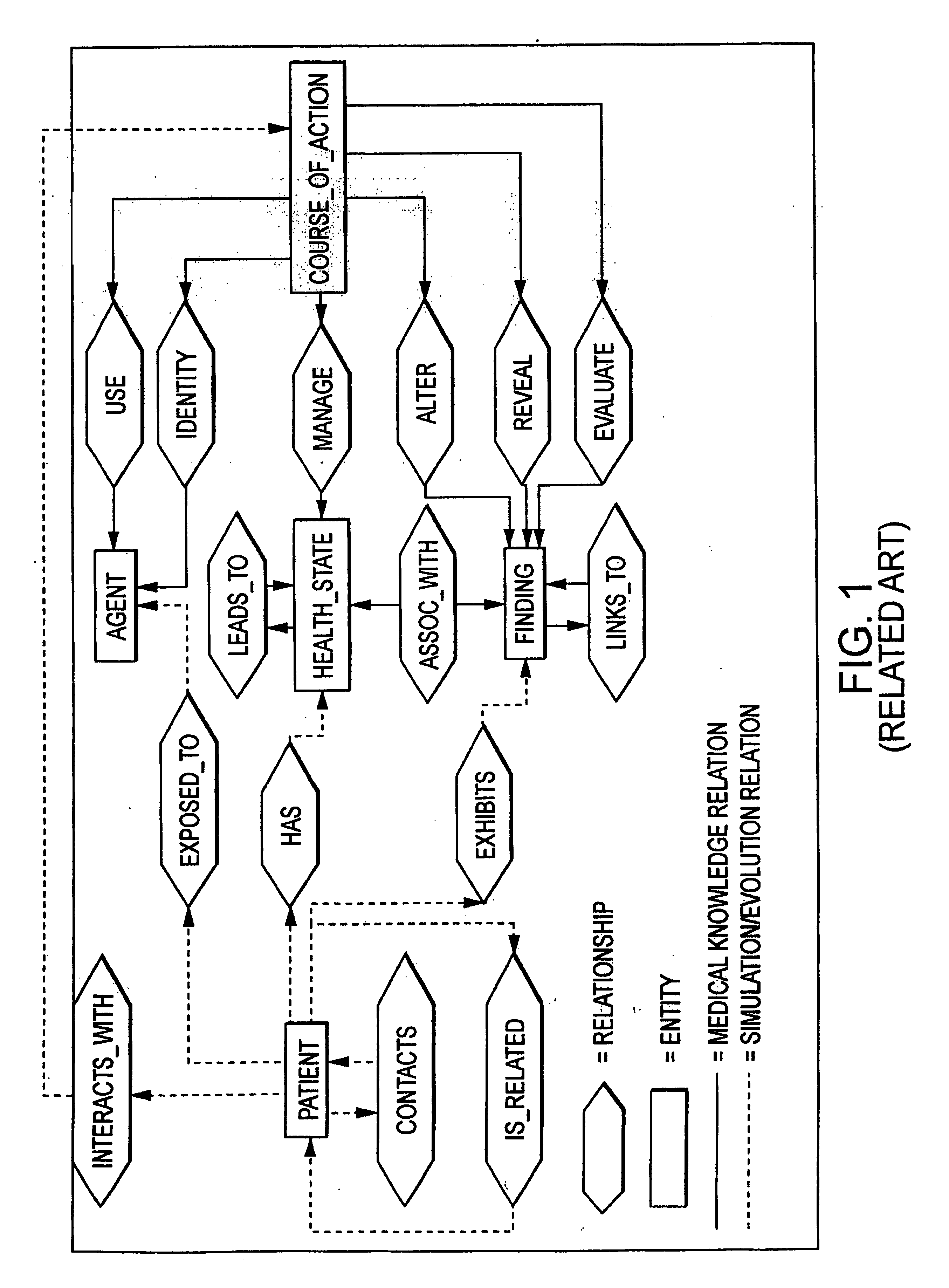
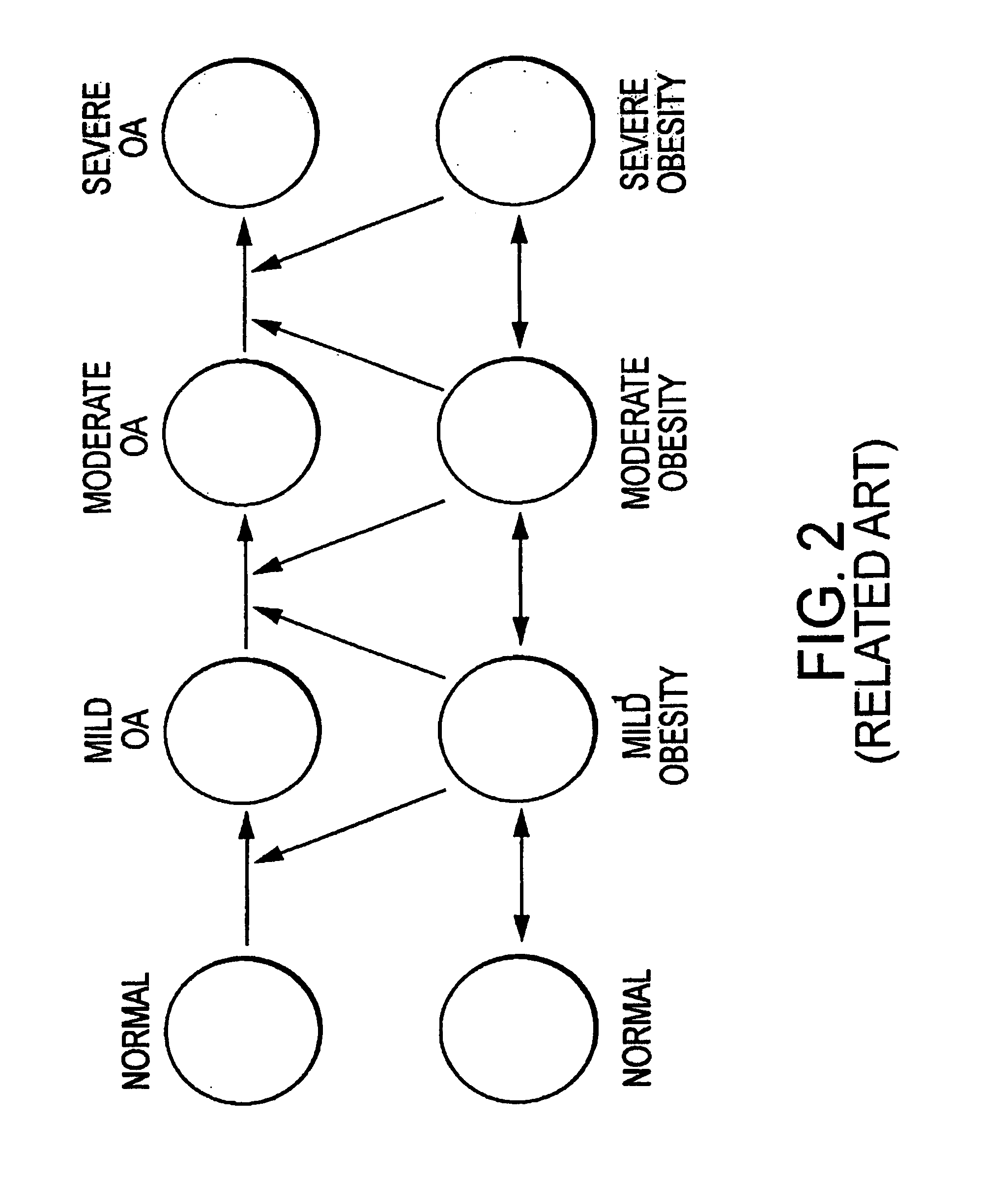
Computer architecture and process of patient generation, evolution, and simulation for computer based testing system using bayesian networks as a scripting language
InactiveUS7024399B2Economical and simpleReduce maintenance costsBiological neural network modelsComputer-assisted treatment prescription/deliveryScripting languageComputer access
A method and system for patient generation and evolution for a computer-based testing system and / or expert system. One or more belief networks, which describe parallel health state networks are accessed by a user or a computer. A knowledge base, at least in part, is scripted from the one or more belief networks by the computer. A model patient at least in part, is instantiated by the computer from the scripted knowledge base. Optionally, the model patient is evolved by the computer in accordance with the parallel health state networks and responsive to a received course of action.
Owner:AMERICAN BOARD OF FAMILY MEDICINE
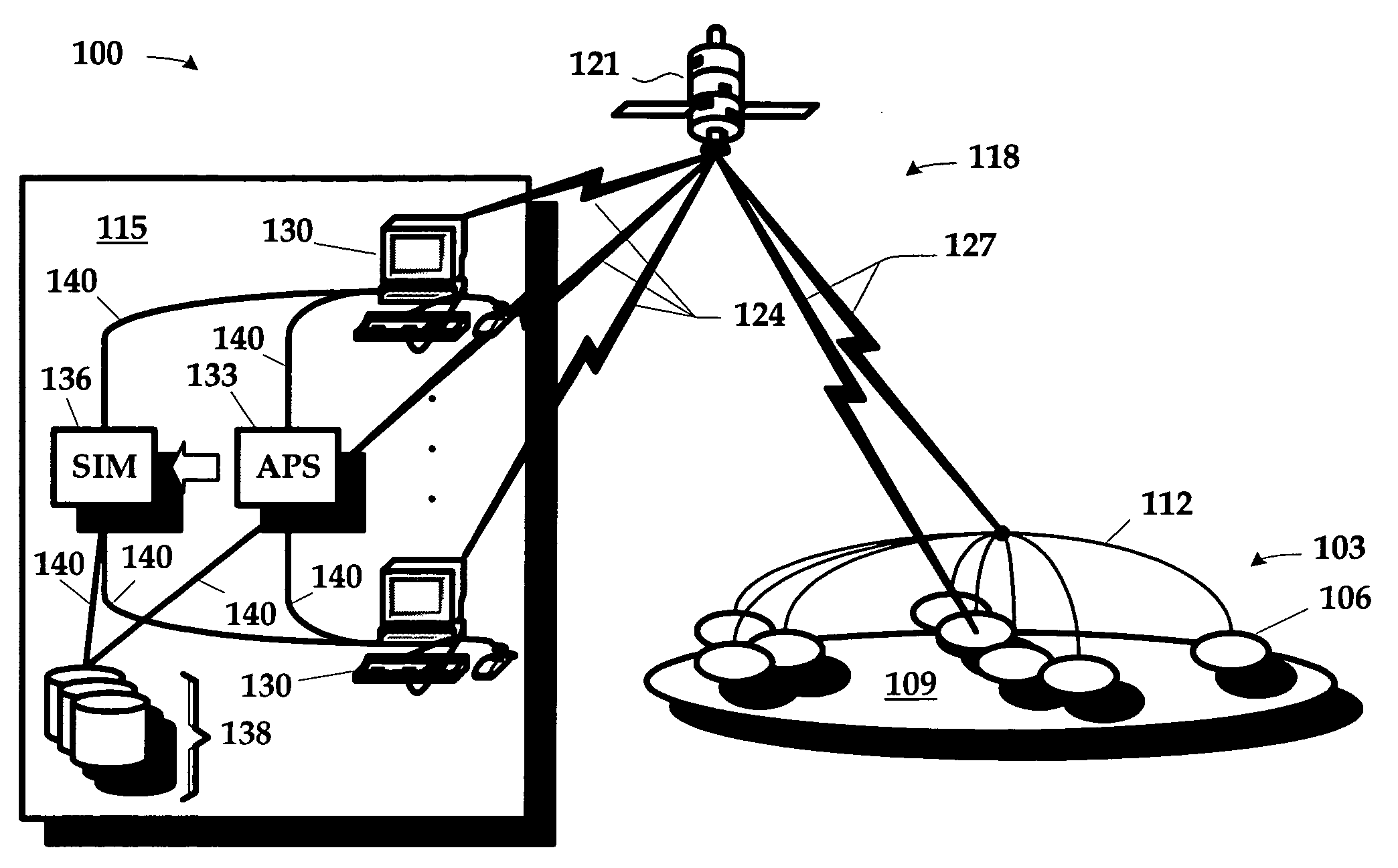
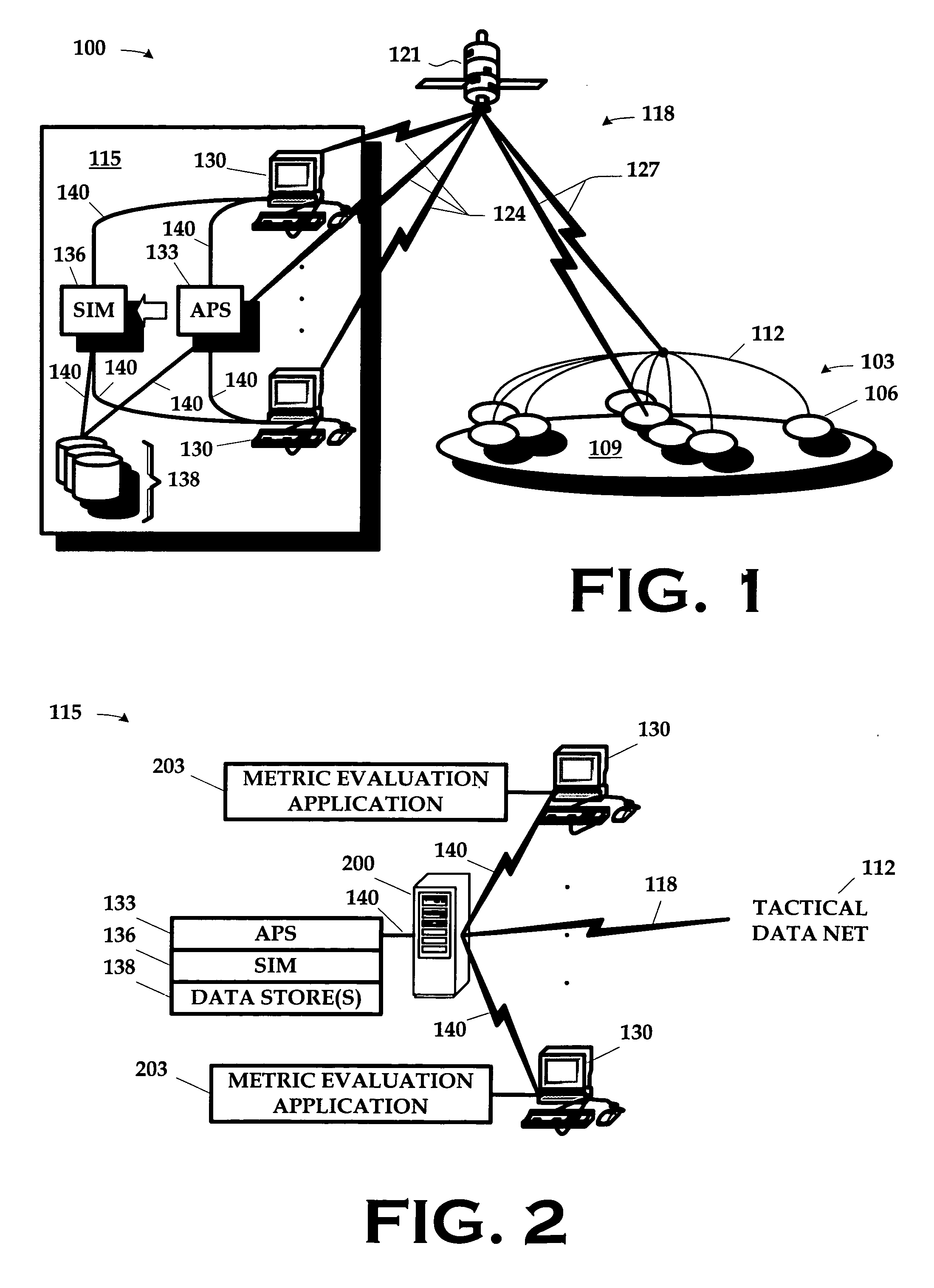
Method and apparatus for management for use in fleet service and logistics
InactiveUS20060190280A1Digital computer detailsMultiprogramming arrangementsLogistics managementCourse of action
An apparatus and a method for managing a fleet of assets and their associated logistics are disclosed. The apparatus includes an Autonomic Product Support (“APS”) system, a simulator, and fleet data including logistical data. A user can interact with the fleet data to make management decisions both in maintenance and operations through the APS system, including simulations on the simulator of what-if scenarios to determine preferred courses of action.
Owner:LOCKHEED MARTIN CORP
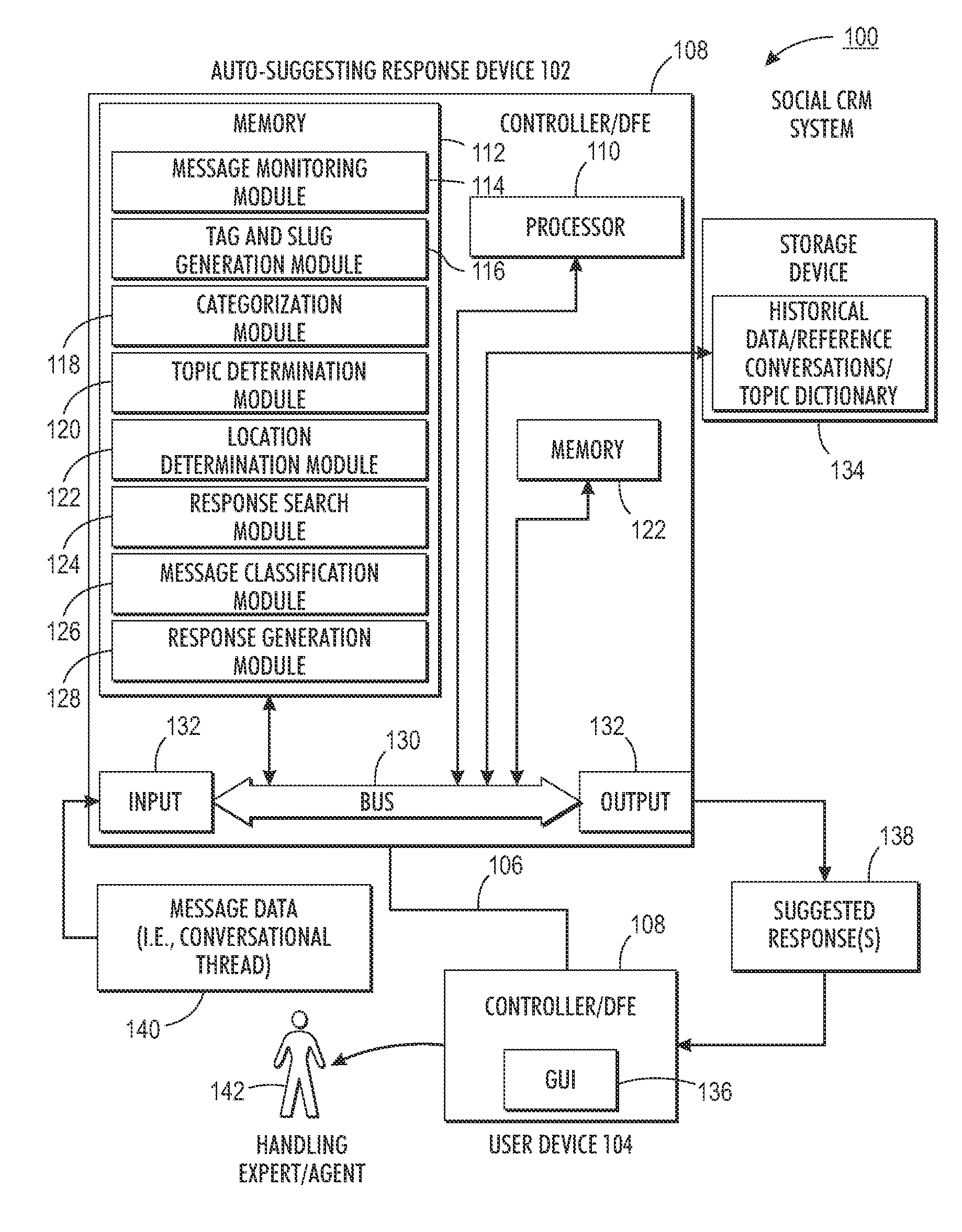
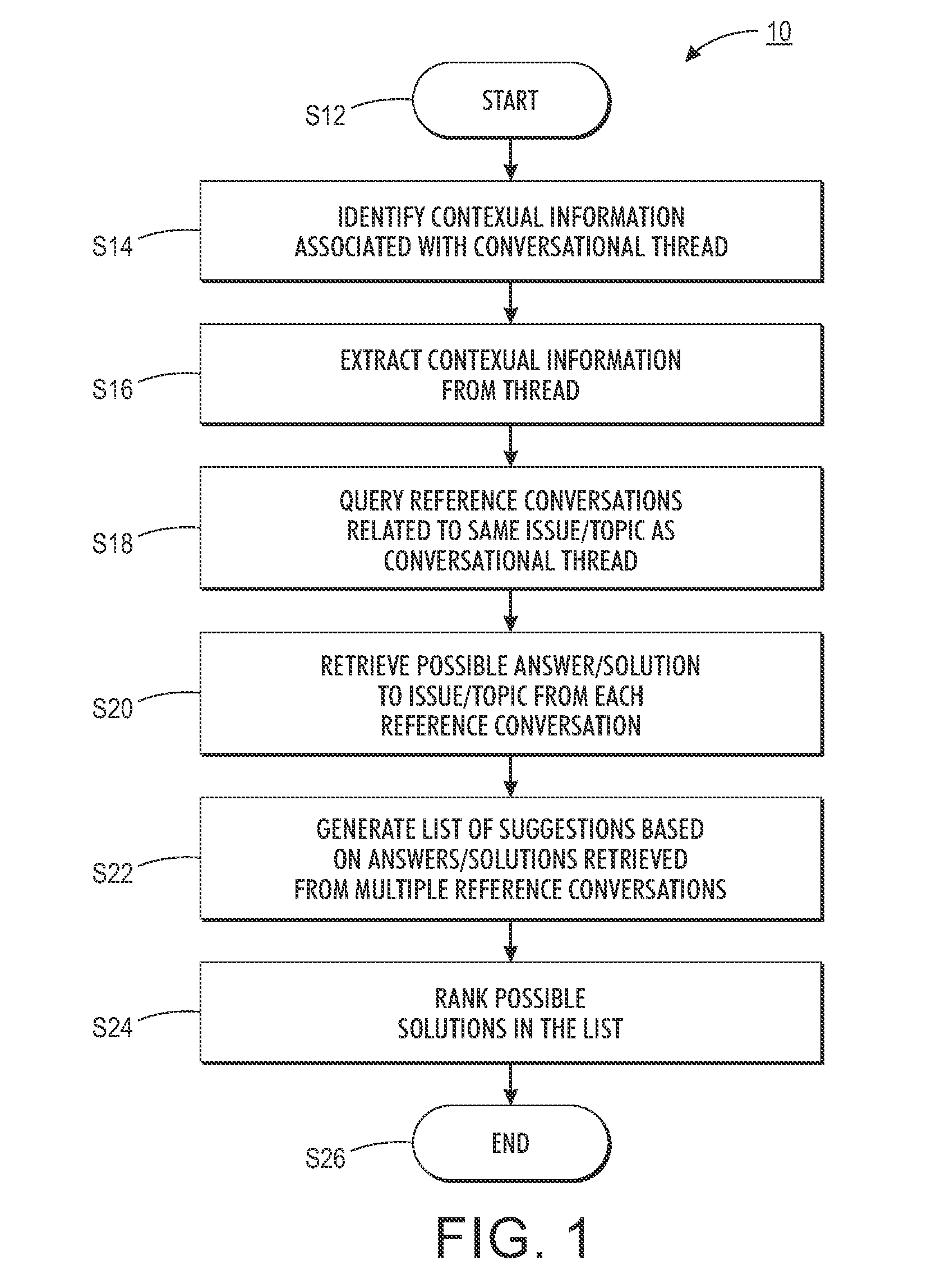
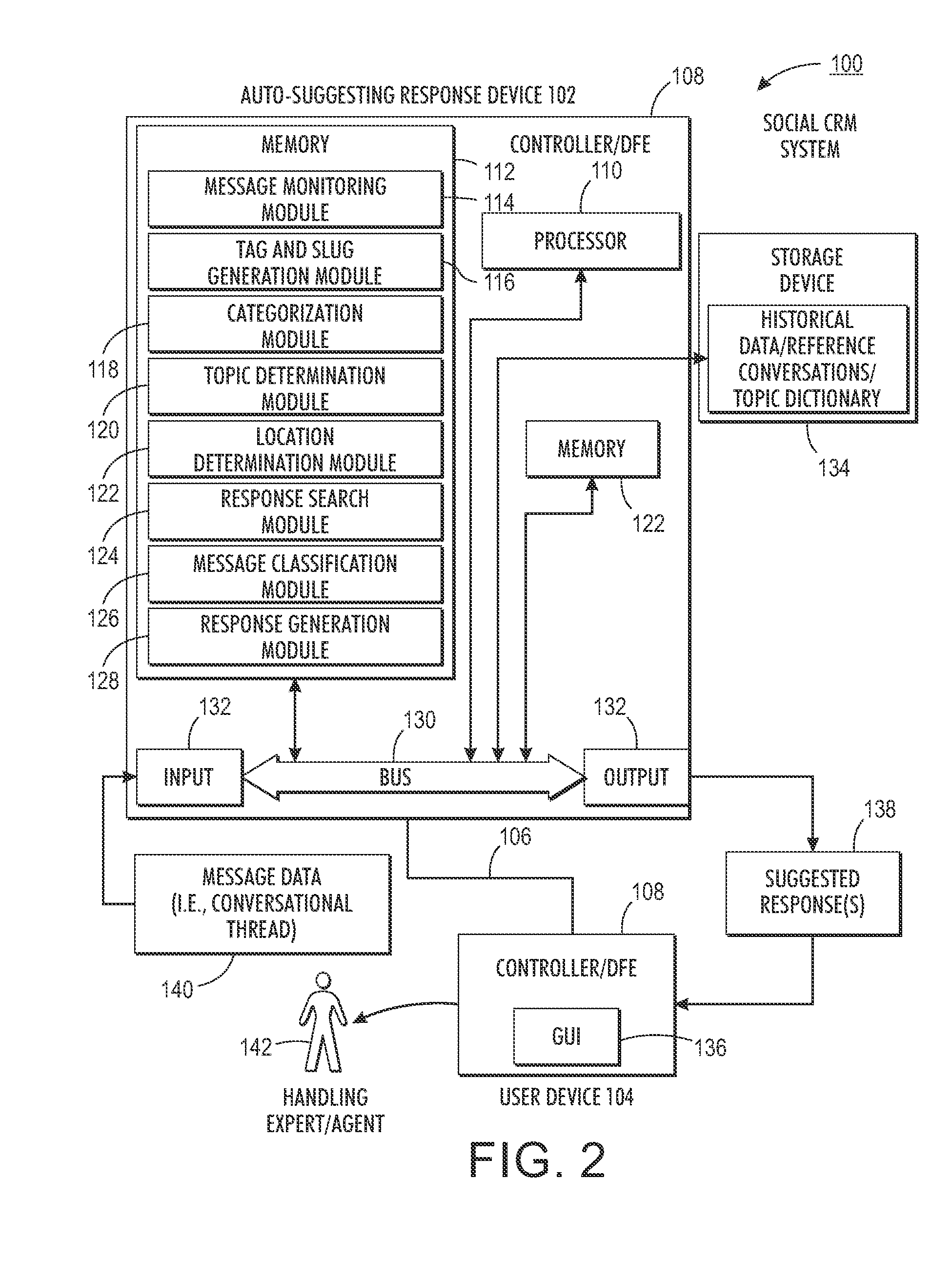
System and method for auto-suggesting responses based on social conversational contents in customer care services
A first embodiment of the disclosure relates to a method for responding to a message posted in a social media stream. The method includes monitoring a social media site for at least one message including select subject matter. In response to identifying a message, the method includes collecting a series of exchanges that form a conversational thread including the message. The method includes determining at least one content attribute of the message. The method includes classifying the message using at least one key attribute. The method includes searching a database for a reference message using a combination of the at least one content and key attributes. The method includes determining a previous outcome of a reference thread including the reference message. The method includes using the previous outcome for determining a course of action.
Owner:CONDUENT BUSINESS SERVICES LLC
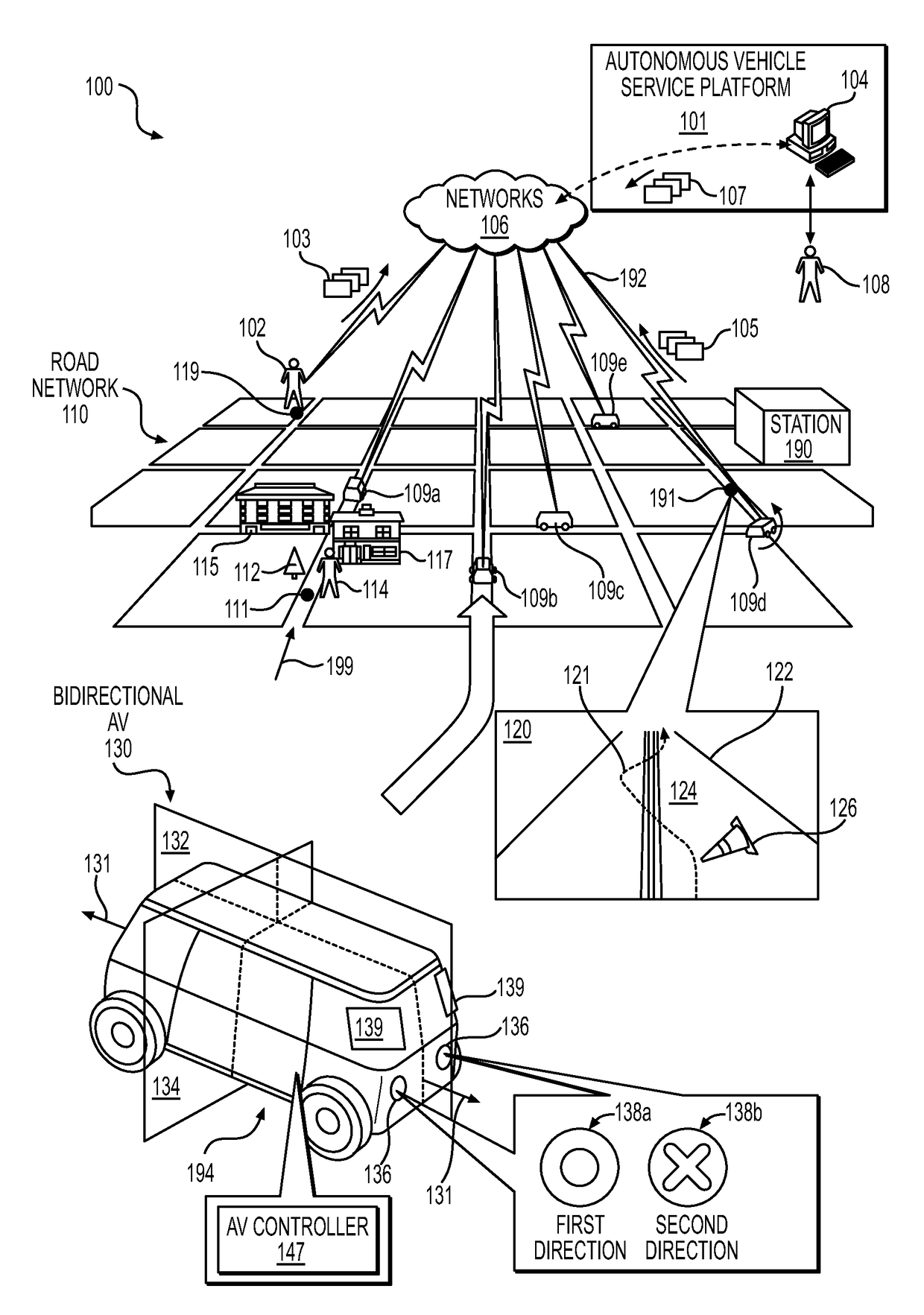
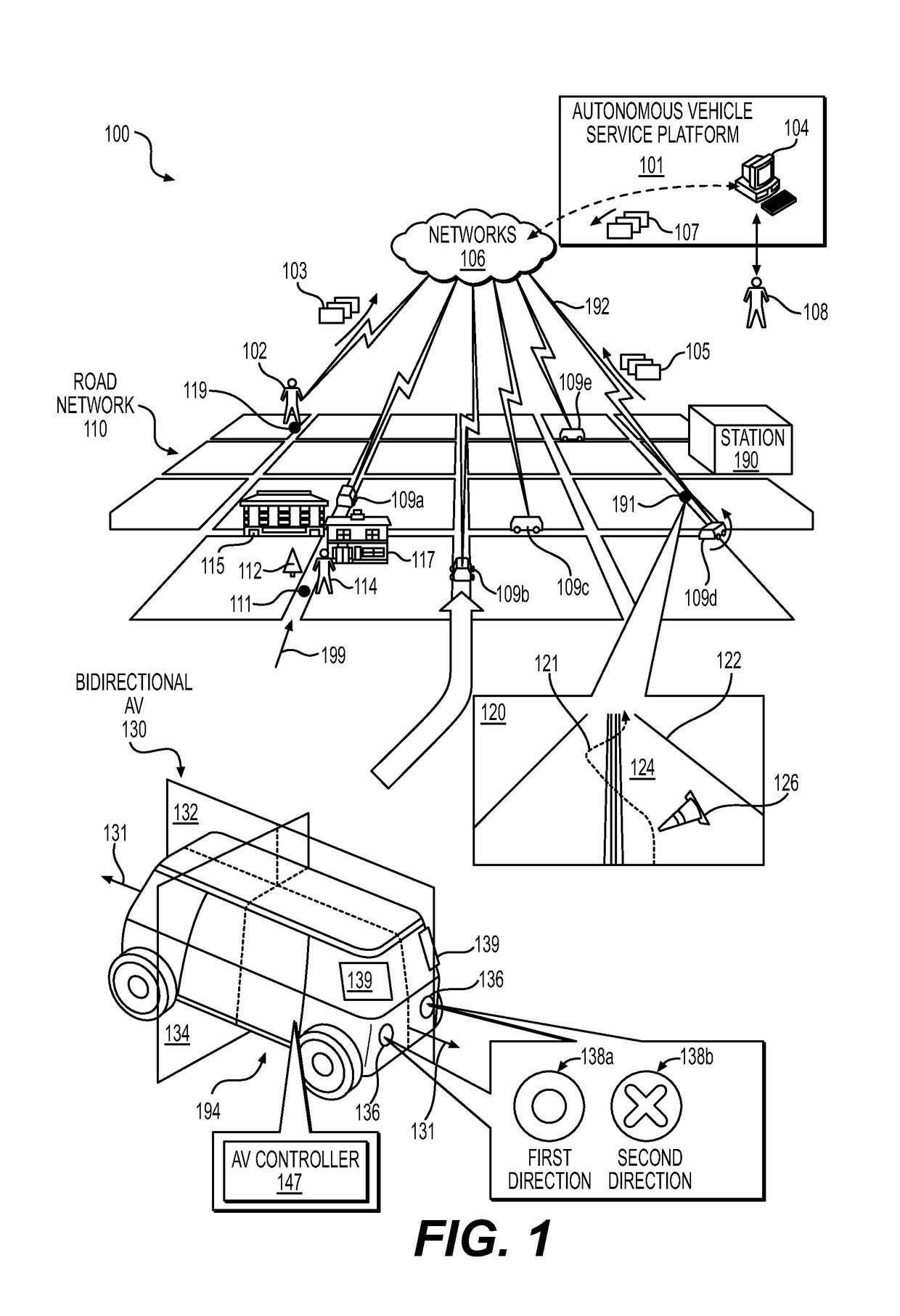
Teleoperation system and method for trajectory modification of autonomous vehicles
ActiveUS20180136651A1Autonomous decision making processDrawing from basic elementsOperational systemTelecommunications link
Various embodiments relate generally to autonomous vehicles and associated mechanical, electrical and electronic hardware, computer software and systems, and wired and wireless network communications to provide an autonomous vehicle fleet as a service. More specifically, systems, devices, and methods are configured to initiate modification of trajectories to influence navigation of autonomous vehicles. In particular, a method may include receiving a teleoperation message via a communication link from an autonomous vehicle, detecting data from the teleoperation message specifying an event associated with the autonomous vehicle, identifying one or more courses of action to perform responsive to detecting the data specifying the event, and generating visualization data to present information associated with the event to a display of a teleoperator computing device.
Owner:ZOOX INC
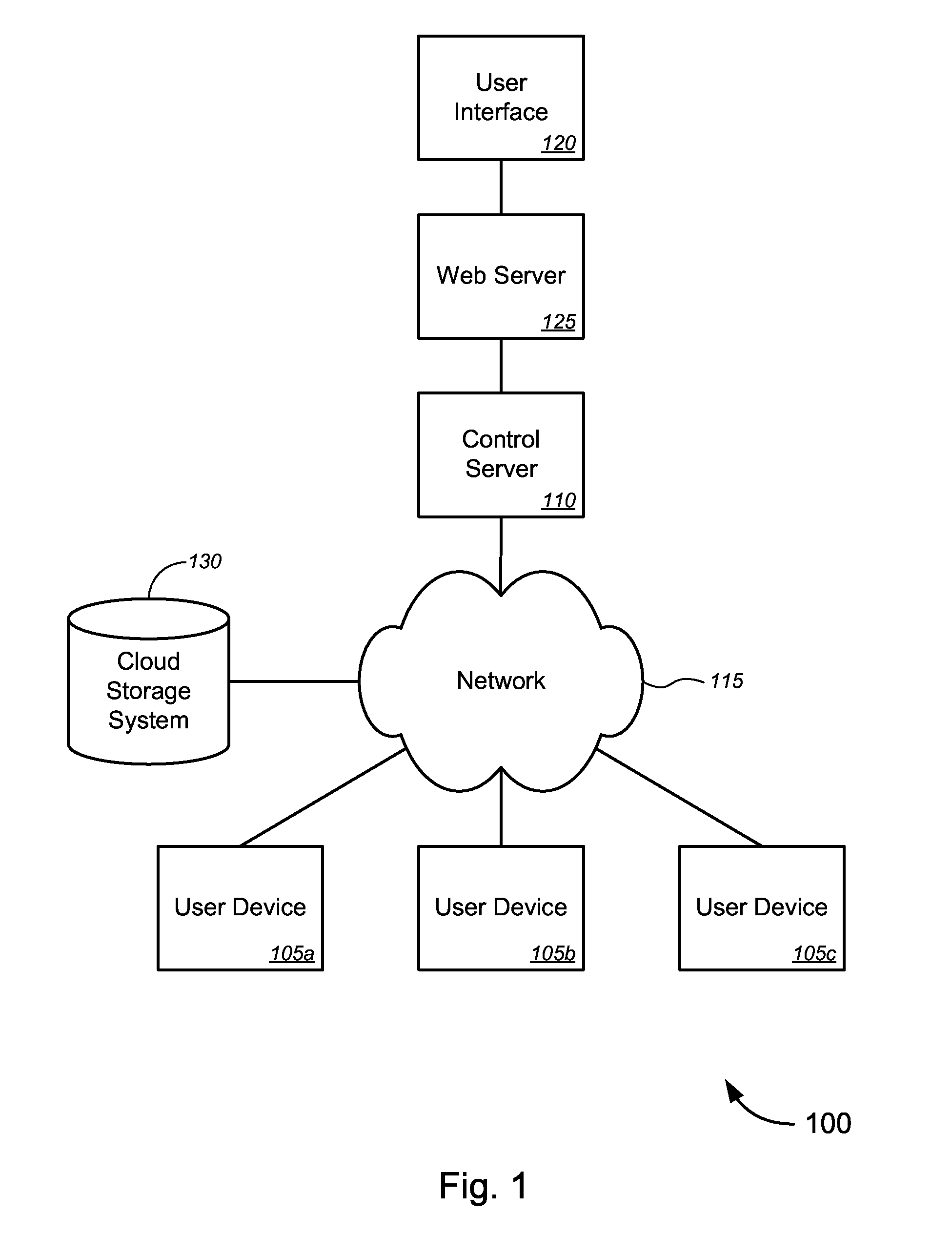
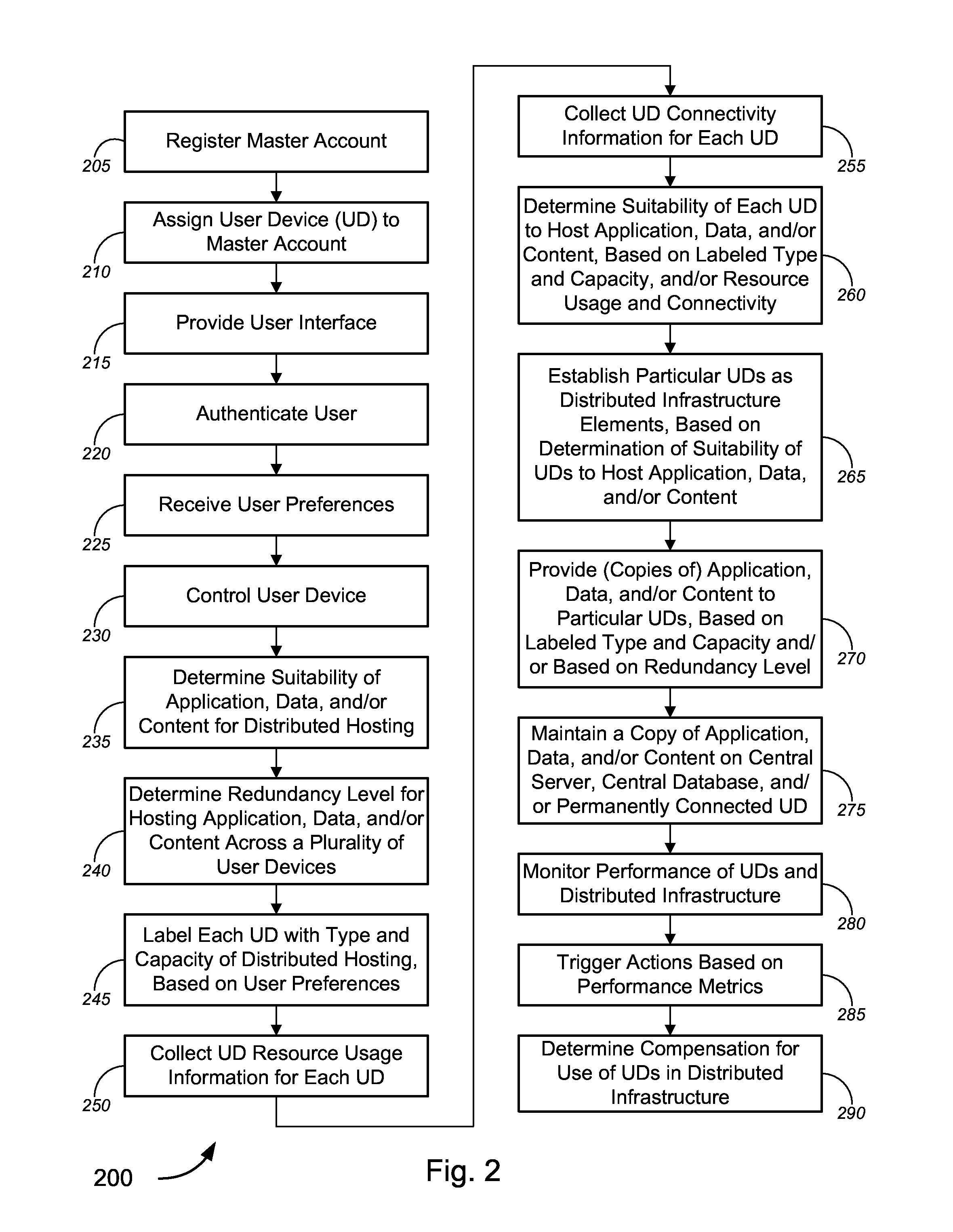
Distributed infrastructure
InactiveUS8914837B2Ease in allocationEase in configurationTelevision system detailsColor television detailsUser deviceCourse of action
Novel tools and techniques for implementing distributed infrastructure are provided. In some techniques, a plurality of user devices, each at a customer premises, can provide video calling services over a network. In some embodiments, each of one or more user devices might be established as a distributed infrastructure element for cloud computing, cloud-based application hosting, and / or cloud-based data storage. One or more software applications, customer data, and / or media content (collectively, “hosted content”) might be provided to the one or more user devices for hosting thereon. Resource usage information and / or network connectivity information might be collected for each user device, and suitability of a user device to host the hosted content might be determined based at least in part on the collected resource usage information and / or network connectivity information. One or more courses of action may be determined, and invoked, based on performance metrics of the user devices.
Owner:BISCOTTI
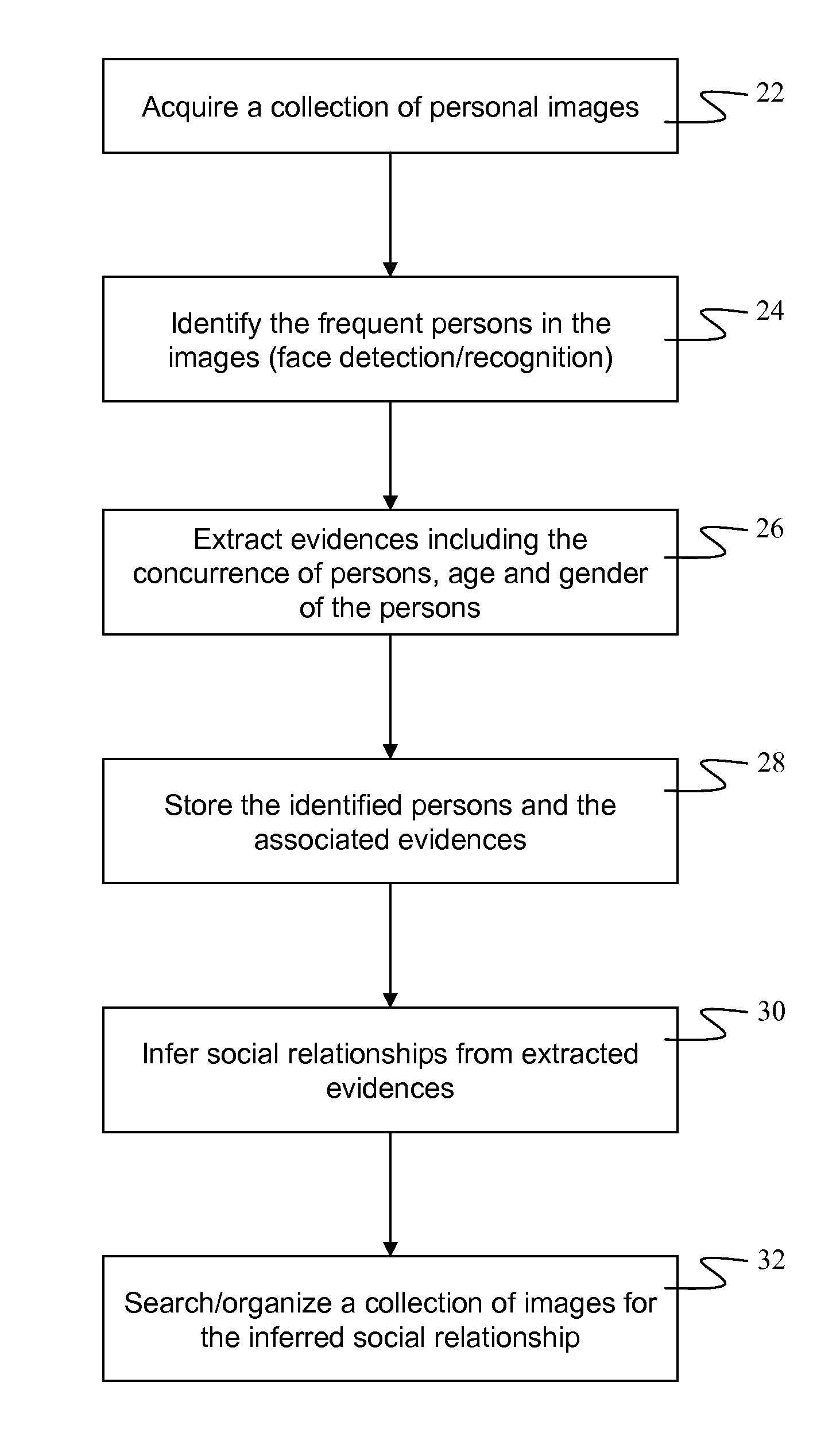
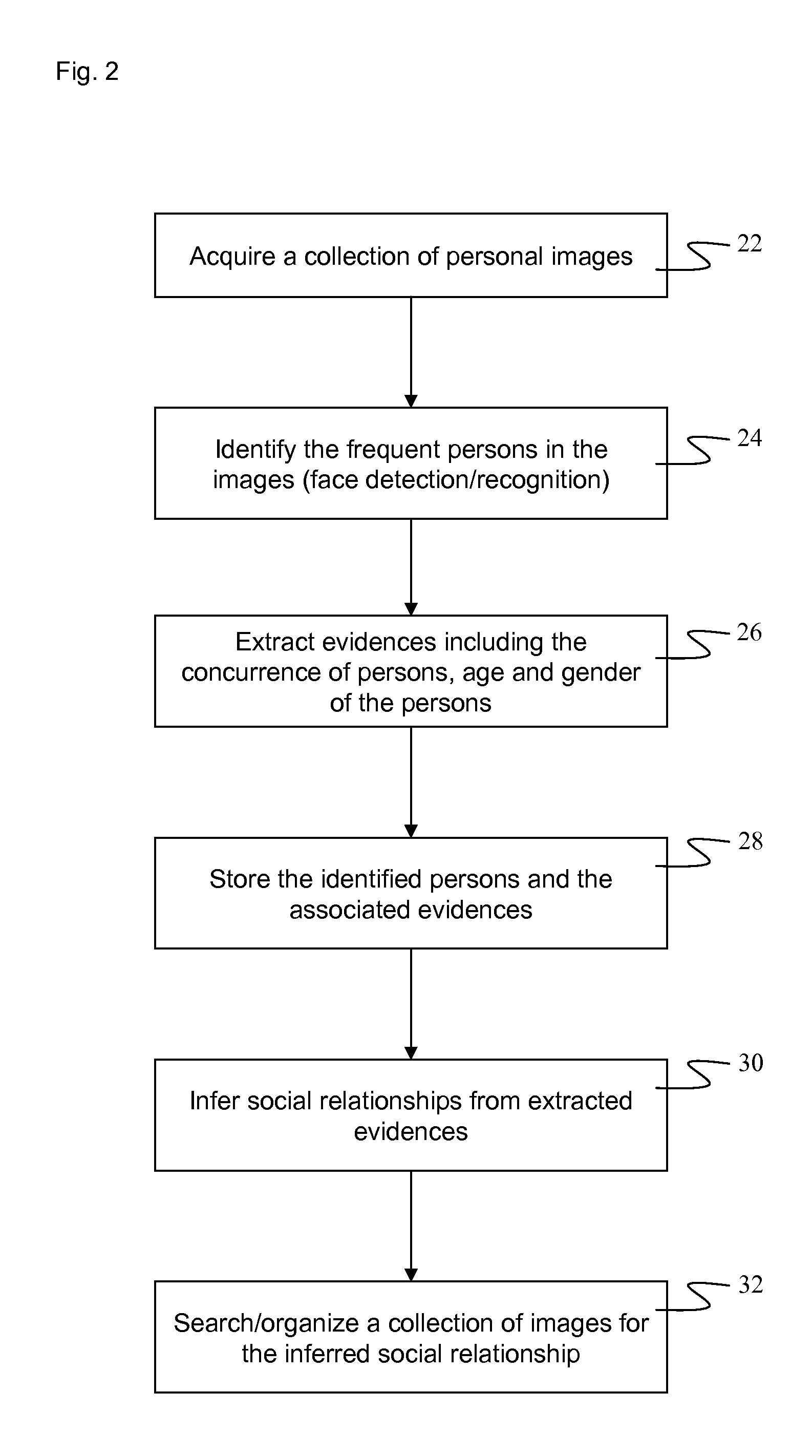
Action suggestions based on inferred social relationships
A method of categorizing a social relationship between individuals in a collection of images to suggest a possible course of action, includes searching the collection to identify individuals and determining their genders and their age ranges; using the gender, and age ranges of the identifies individuals to infer at least one social relationship between them; and using at least one inferred social relationship to suggest a possible course of action.
Owner:INTELLECTUAL VENTURES FUND 83 LLC
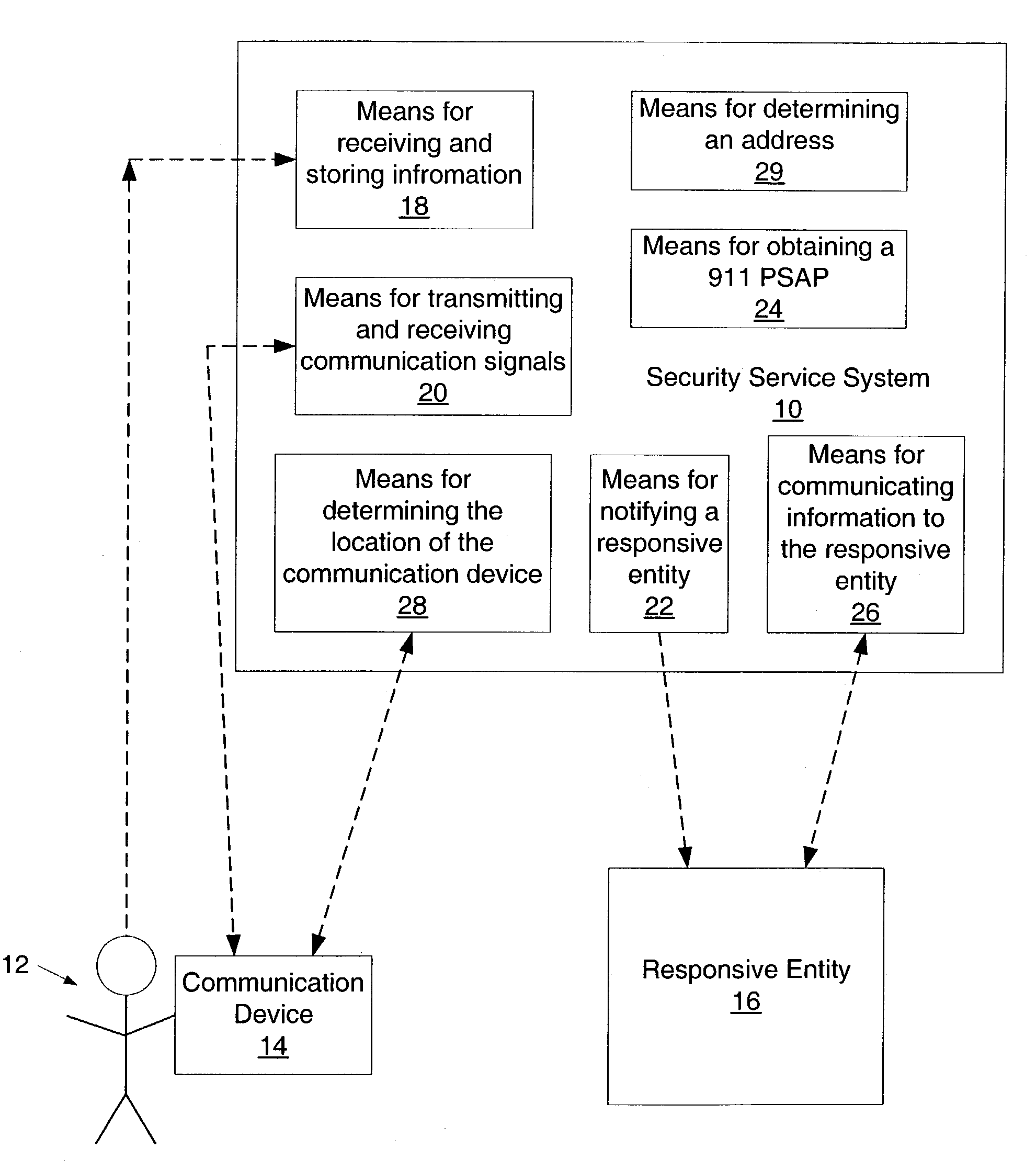
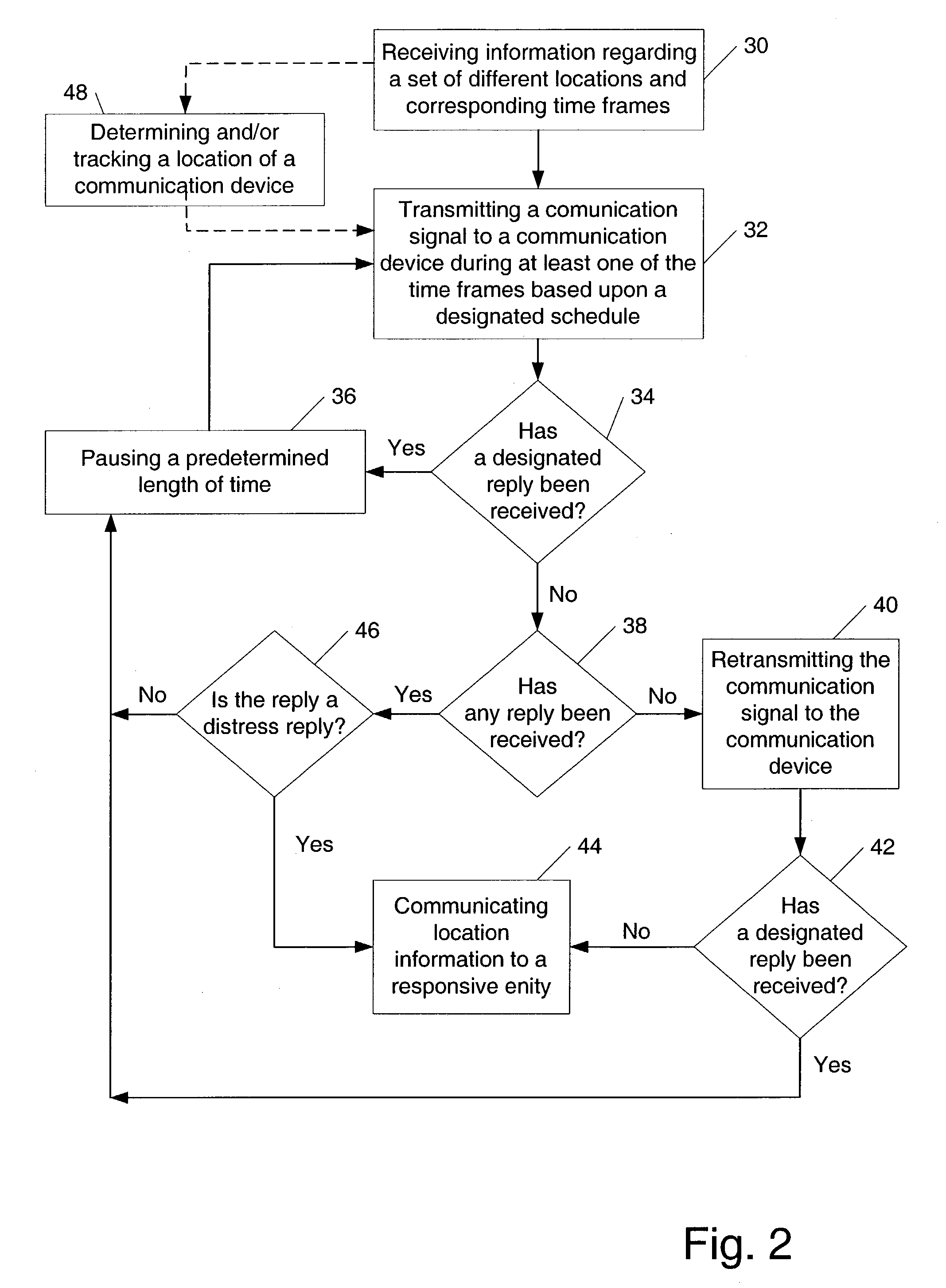
Portable personal security system
A system which is adapted to provide a personal security system to a mobile individual is presented. In addition, a method for providing a security system to a mobile individual is presented as well as a method of using such a security system. In general, the method of providing a personal security system to a mobile individual using the system described herein may include receiving information regarding a set of different locations and corresponding time frames. In addition, the method may include transmitting a communication signal to a communication device during at least one of the time frames based upon a designated schedule. Subsequently, the method may include determining a subsequent course of action based upon whether a designated reply has been received in response to the transmitted communication. In some cases, the method may include notifying a responsive entity of location information upon failing to receive the designated reply.
Owner:RESOURCE CONSORTIUM LTD LLC +1
Electrical anomaly detection method and system
InactiveUS20110153236A1Current/voltage measurementDigital computer detailsElectricityElectrical conductor
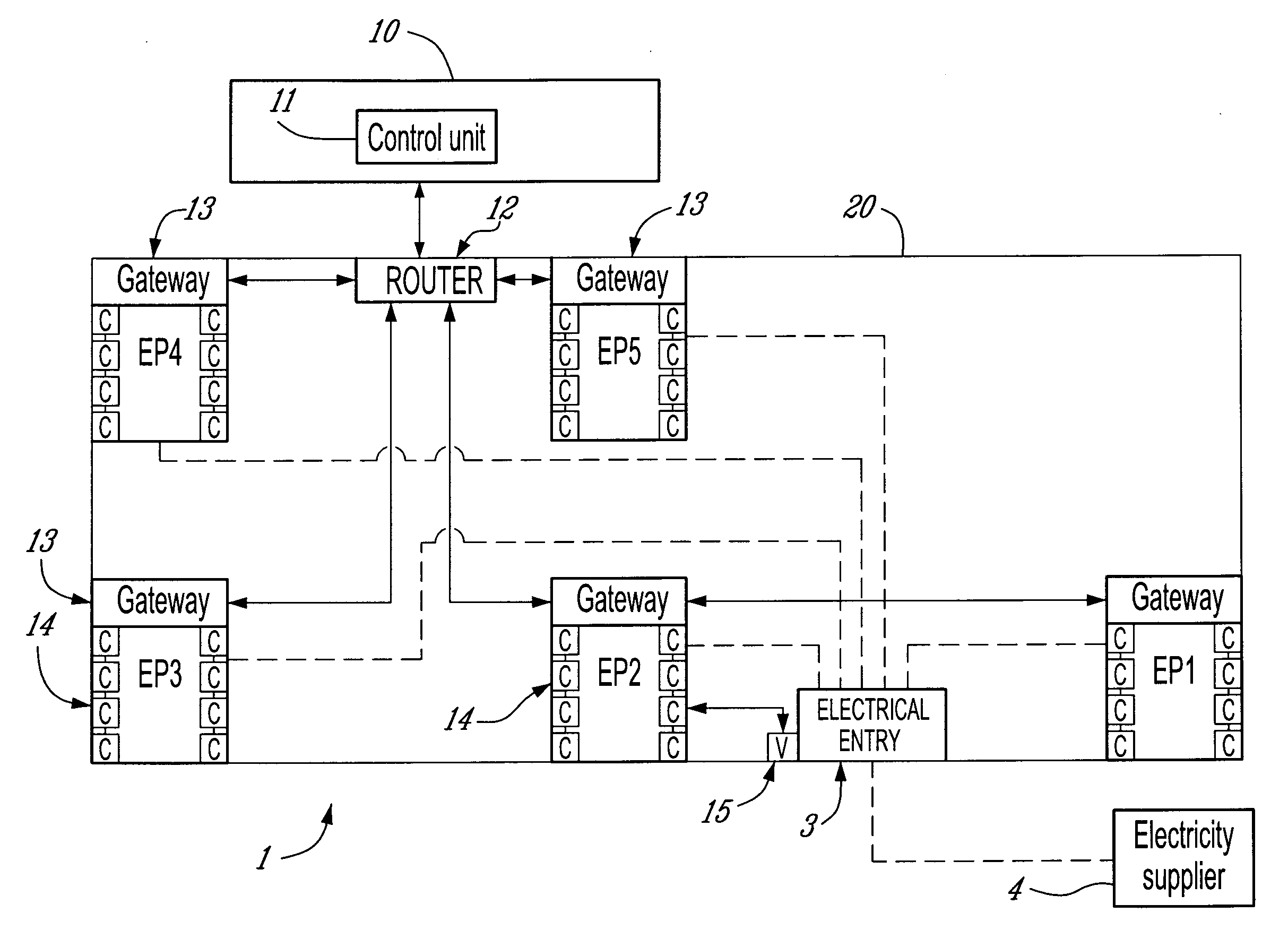
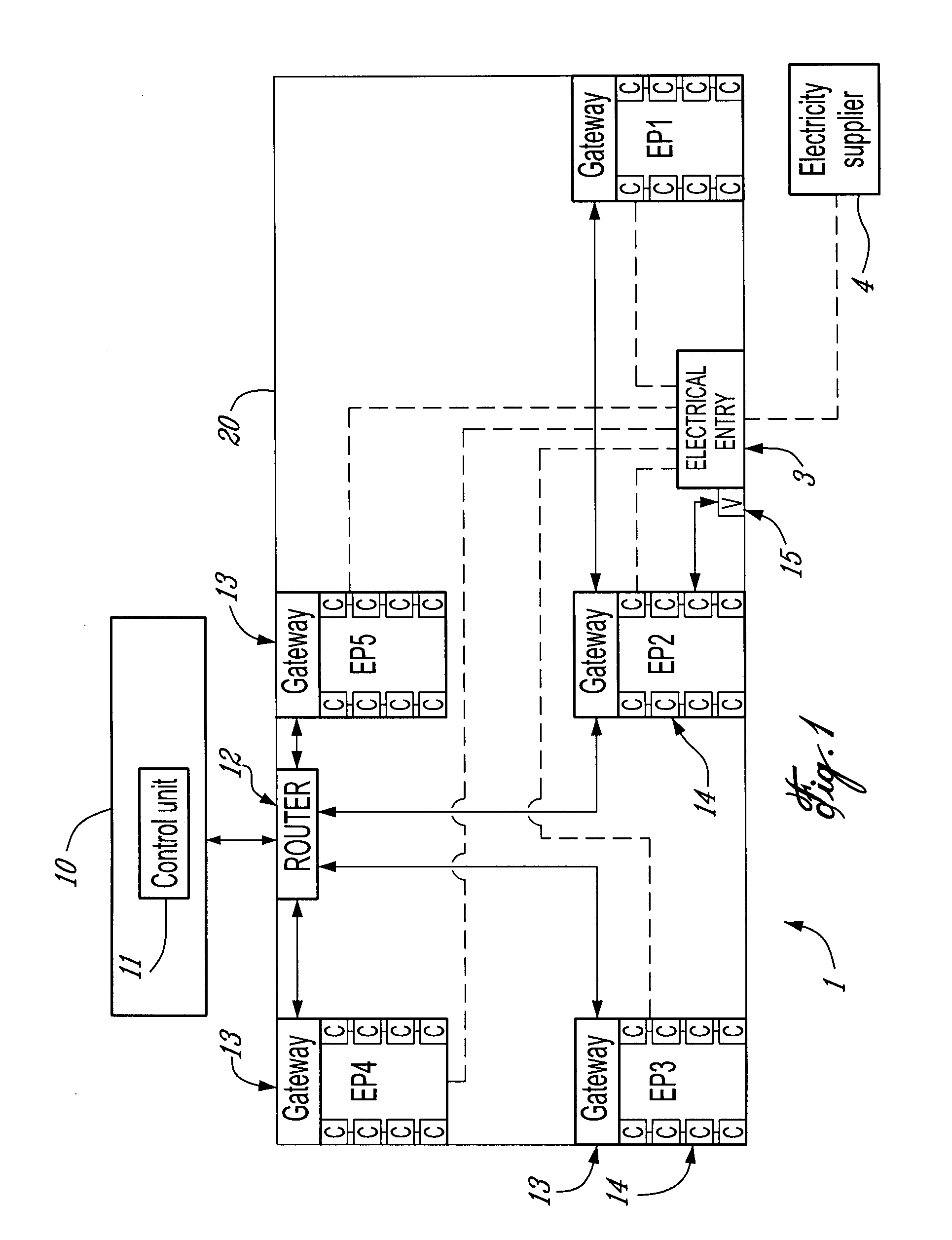
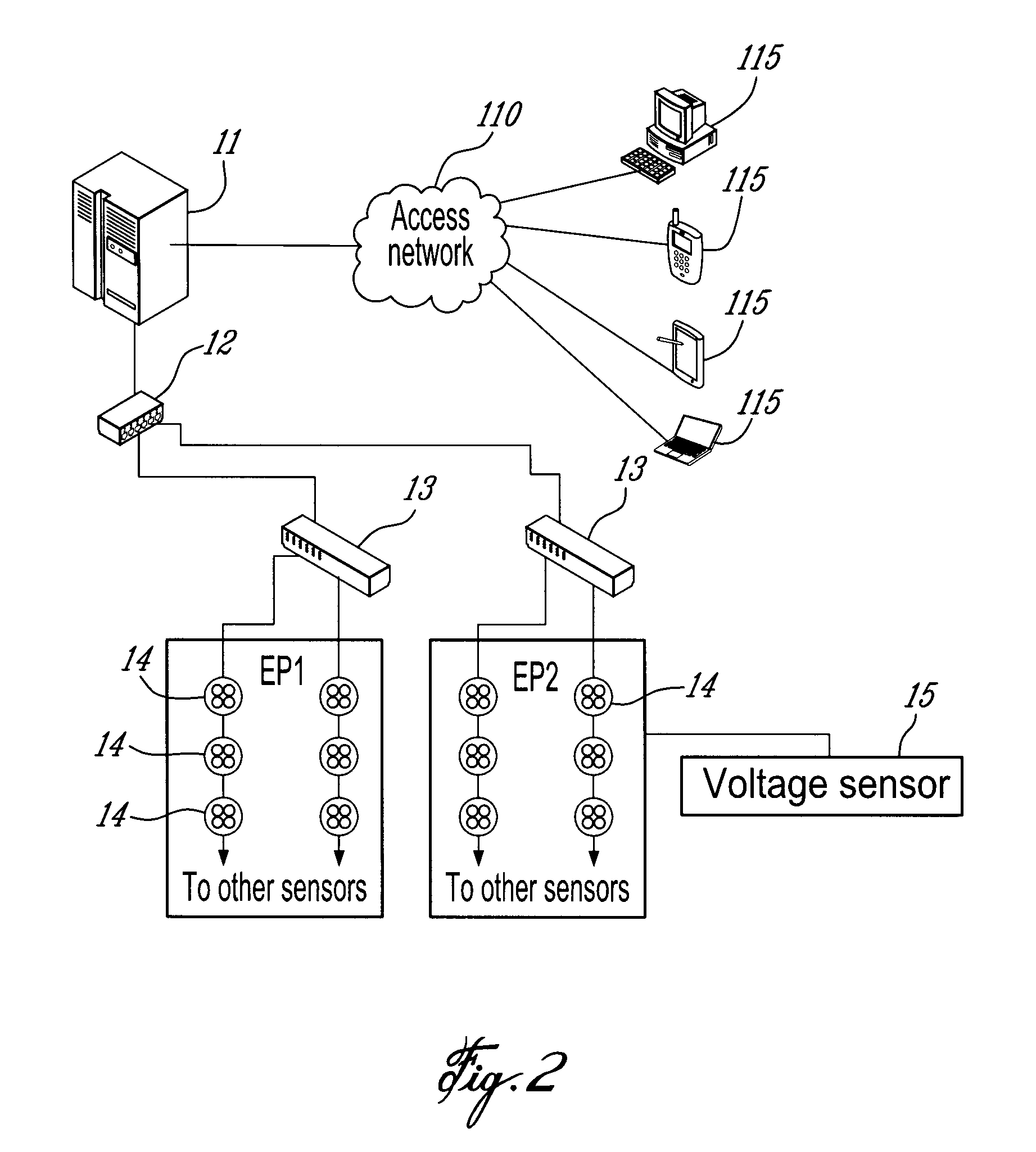
There are provided a method and a system for real time monitoring of a powered on electrical network in a facility in order to detect an electrical anomaly while the electrical network is in use. The system comprises a sensor data receiver for receiving real time sensor data including at least one measured value measured in real time by at least one sensor installed on a conductor of the electrical network in the facility while the electrical network is in use; an anomaly detector for retrieving an anomaly detection rule from an anomaly detection rule database, the rule having an identification of a required input, a formula, and a threshold reference value, for a detection of an anomaly; receiving the real time sensor data from the sensor data receiver and extracting at least one relevant measured value from the at least one measured value using the identification of the required input; comparing the at least one relevant measured value to the threshold reference value according to the formula to determine one of a presence and an absence of the anomaly in the real time sensor data; an event generator controlled by the processor for retrieving and providing anomaly monitoring data if the anomaly is determined to be present by the processor, the anomaly monitoring data including an indication of a monitoring course of action to be carried out to address the anomaly determined to be present.
Owner:CORP NUVOLT INC
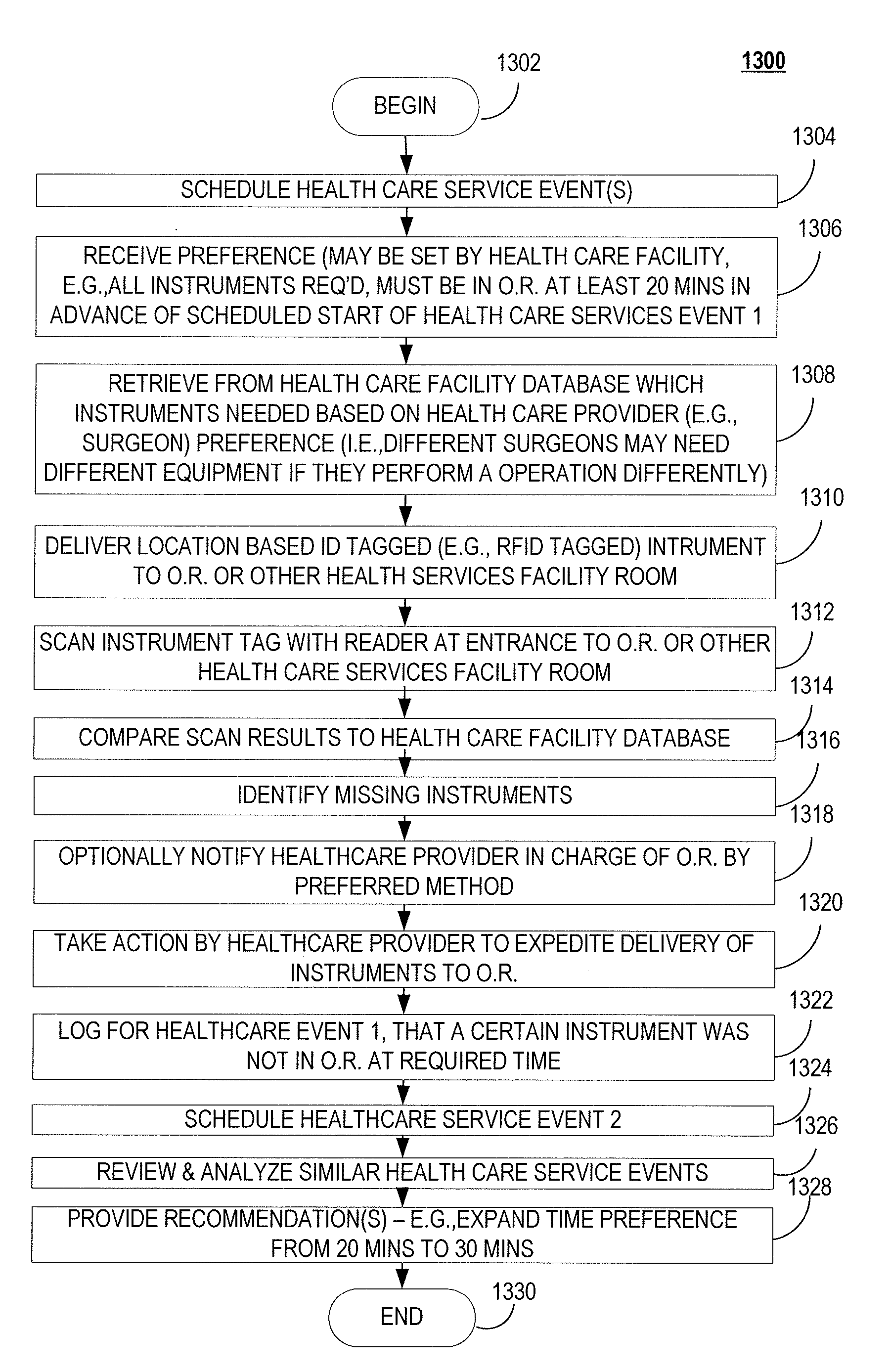
System, method and computer program product for providing health care services performance analytics
InactiveUS20090099862A1Maximize useContinually improvingData processing applicationsTherapiesCourse of actionCausality
A system, method and computer program product for improving the delivery of healthcare services may include, e.g., but not limited to, in an exemplary embodiment, a) capturing data associated with at least one health care services event, wherein said data comprises at least one aspect of said at least one health care services event; b) categorizing, into at least one category, said at least one aspect of said at least one health care services event; c) analyzing said data associated with said categorized health care services event comprising: i) determining a correlation between said at least one aspect of said data to said at least one category, and ii) determining any cause and effect relationship between said at least one aspect and said at least one category; and d) recommending at least one course of action based on said at least one aspect having said correlation and said cause and effect relationship to said at least one category, is disclosed.
Owner:HEURISTIC ANALYTICS
Diet and exercise planning and motivation including apparel purchases based on future appearance
InactiveUS7328119B1Good choiceIncrease successPhysical therapies and activitiesGymnastic exercisingCourse of actionEngineering
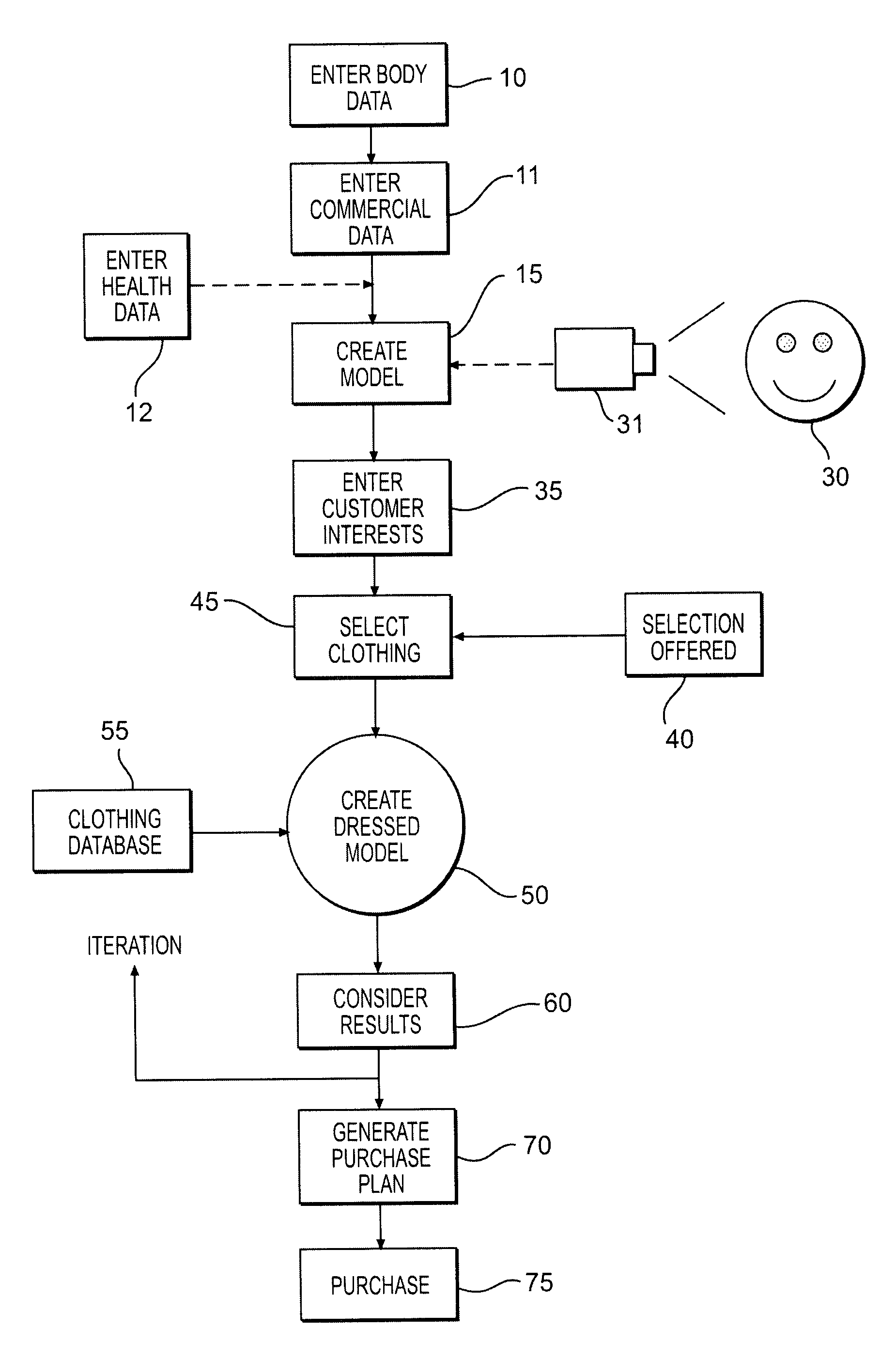
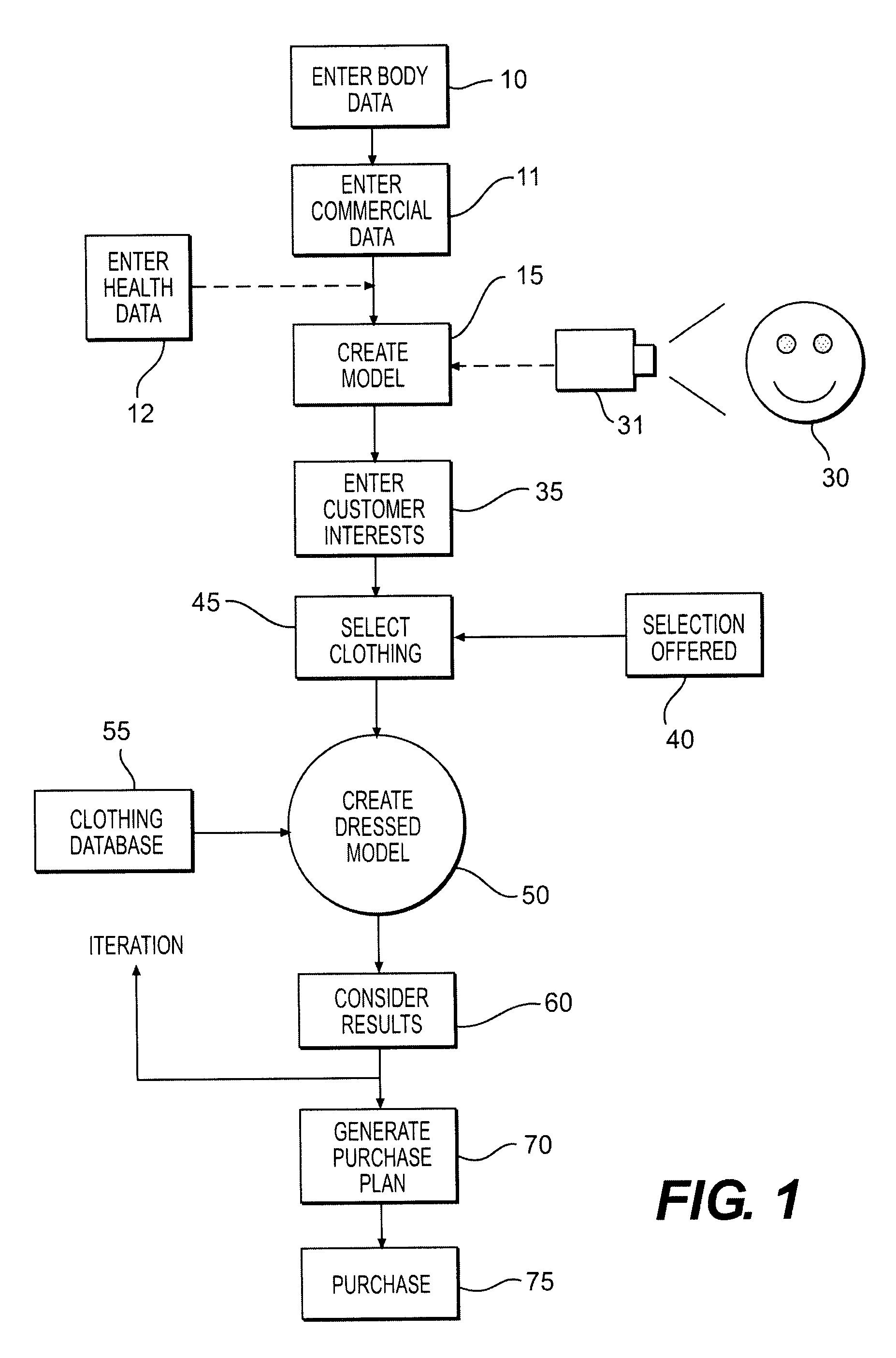
The disclosed invention relates to methods for assisting and motivating persons with respect to various dietary and exercise regimens they might undertake, providing an interactive, iterative, “what-if” type of procedure where someone can see their predicted appearance in the future, also in clothes of their choice, and balance this with realistic expectations of what they may be able to achieve in terms of modification of their physical shape as a result of a planned course of action. This in turn leads to new methods of purchasing and manufacturing apparel and dietary or exercise related items in the present and future. A unique life size display screen, a “digital mirror” so to speak, with optional touch capabilities is also disclosed for input to, and display of, the computer aided models used, as well as inputs from a persons body sensed by TV cameras. The invention also has potential application to for diagnosis and / or treatment of certain mental and other disorders, and in other situations where a form of companionship may be provided the user.
Owner:PRYOR TIMOTHY R +1
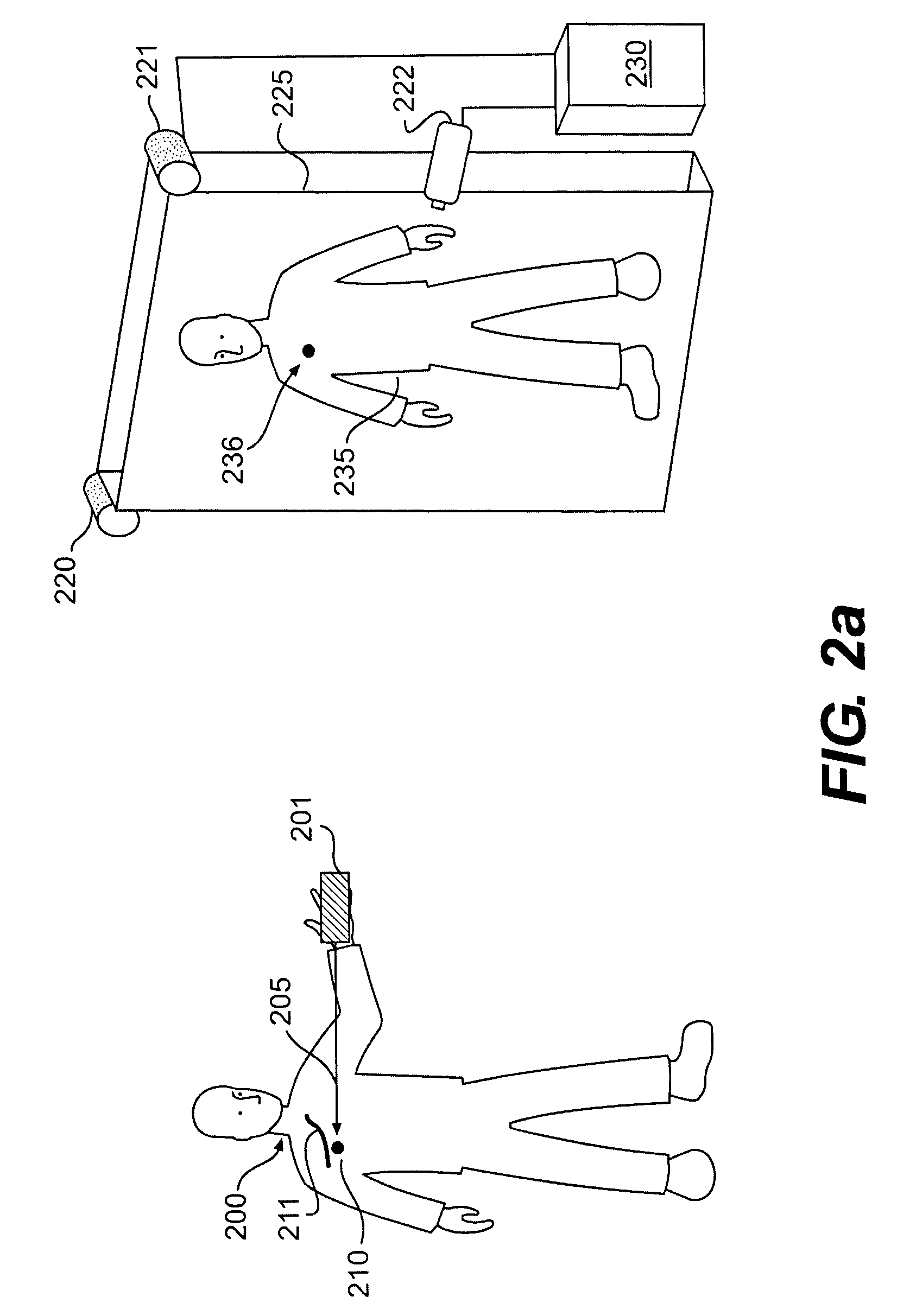
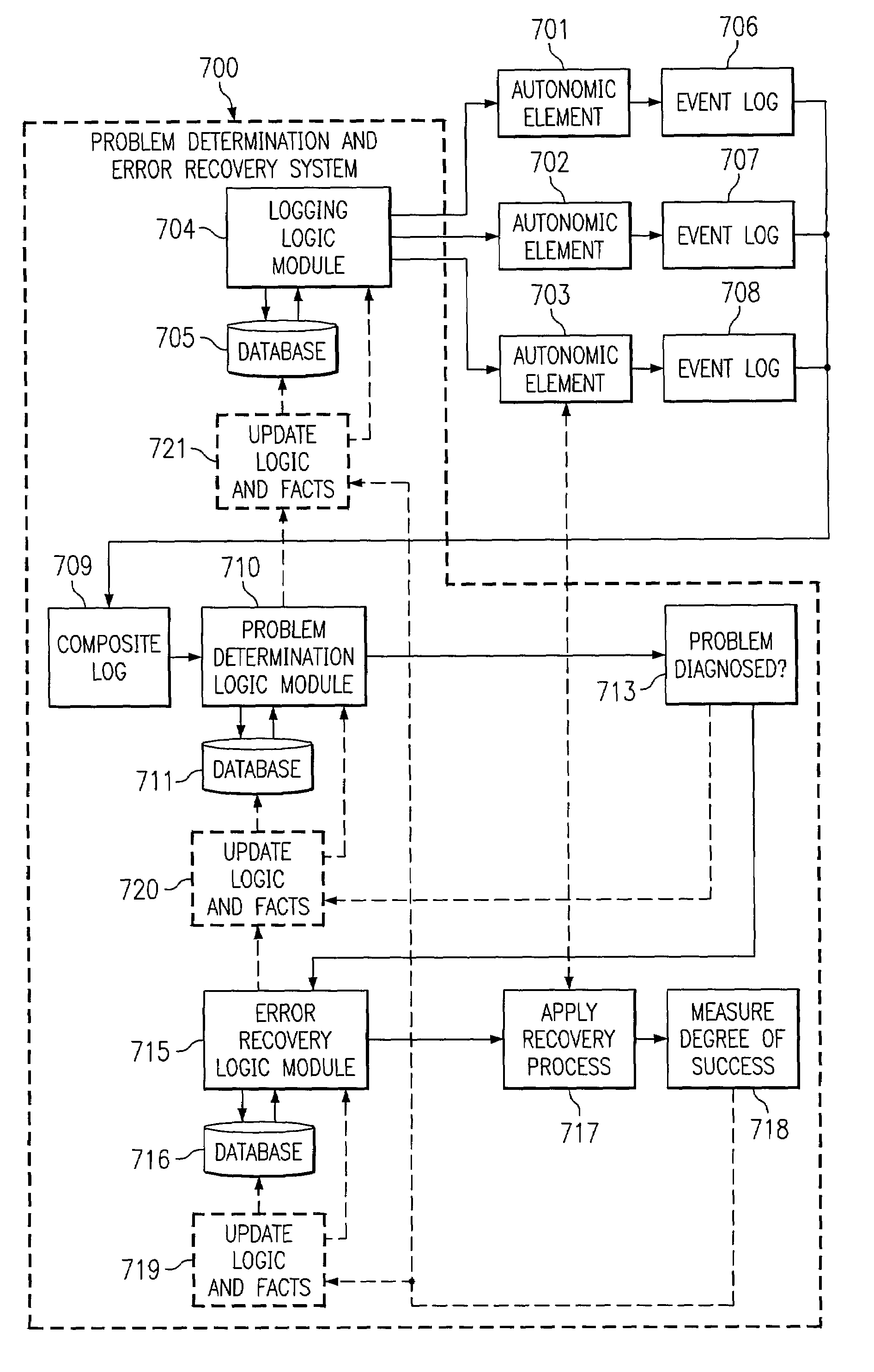
Adaptive problem determination and recovery in a computer system
InactiveUS7194445B2Reliability increasing modificationsError preventionSoftware engineeringSystem configuration
A method, computer program product, and data processing system for recognizing, tracing, diagnosing, and repairing problems in an autonomic computing system is disclosed. Rules and courses of actions to follow in logging data, in diagnosing faults (or threats of faults), and in treating faults (or threats of faults) are formulated using an adaptive inference and action system. The adaptive inference and action system includes techniques for conflict resolution that generate, prioritize, modify, and remove rules based on environment-specific information, accumulated time-sensitive data, actions taken, and the effectiveness of those actions. Thus, the present invention enables a dynamic, autonomic computing system to formulate its own strategy for self-administration, even in the face of changes in the configuration of the system.
Owner:LENOVO PC INT
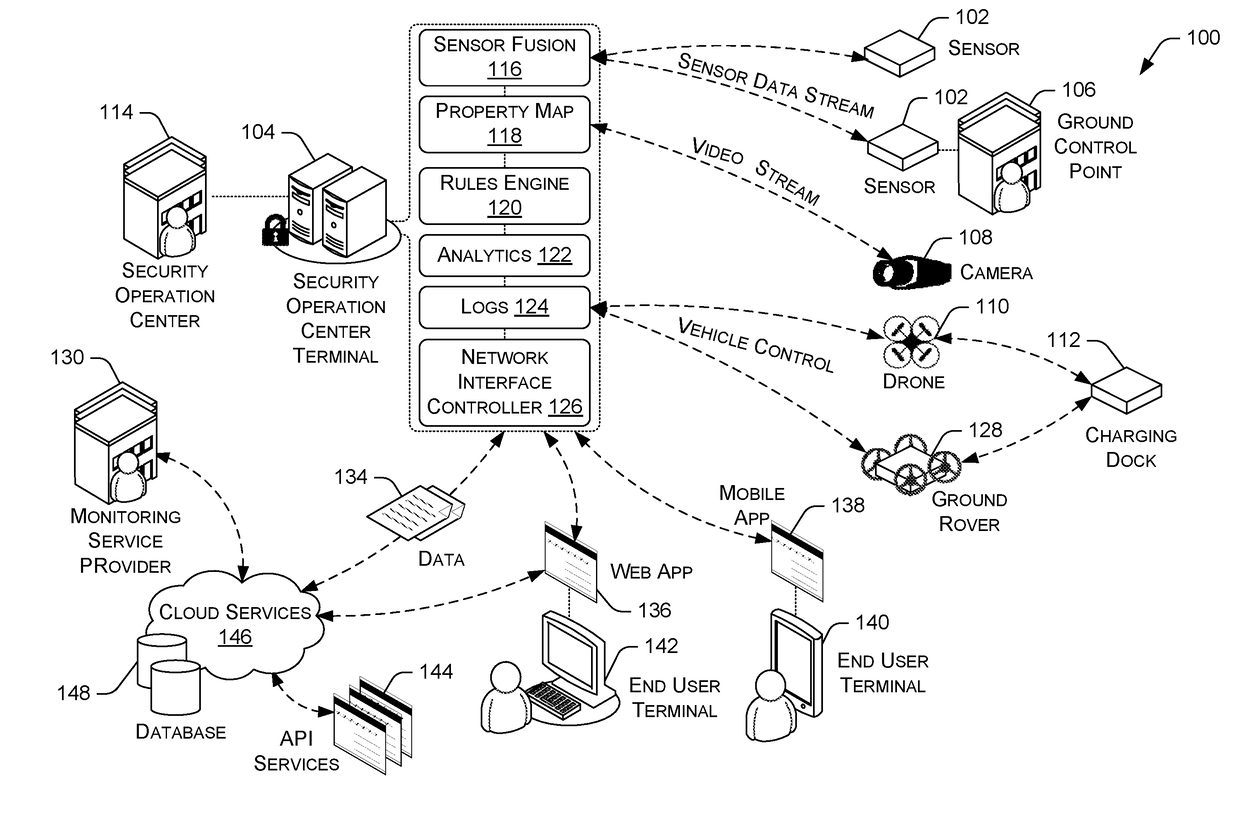
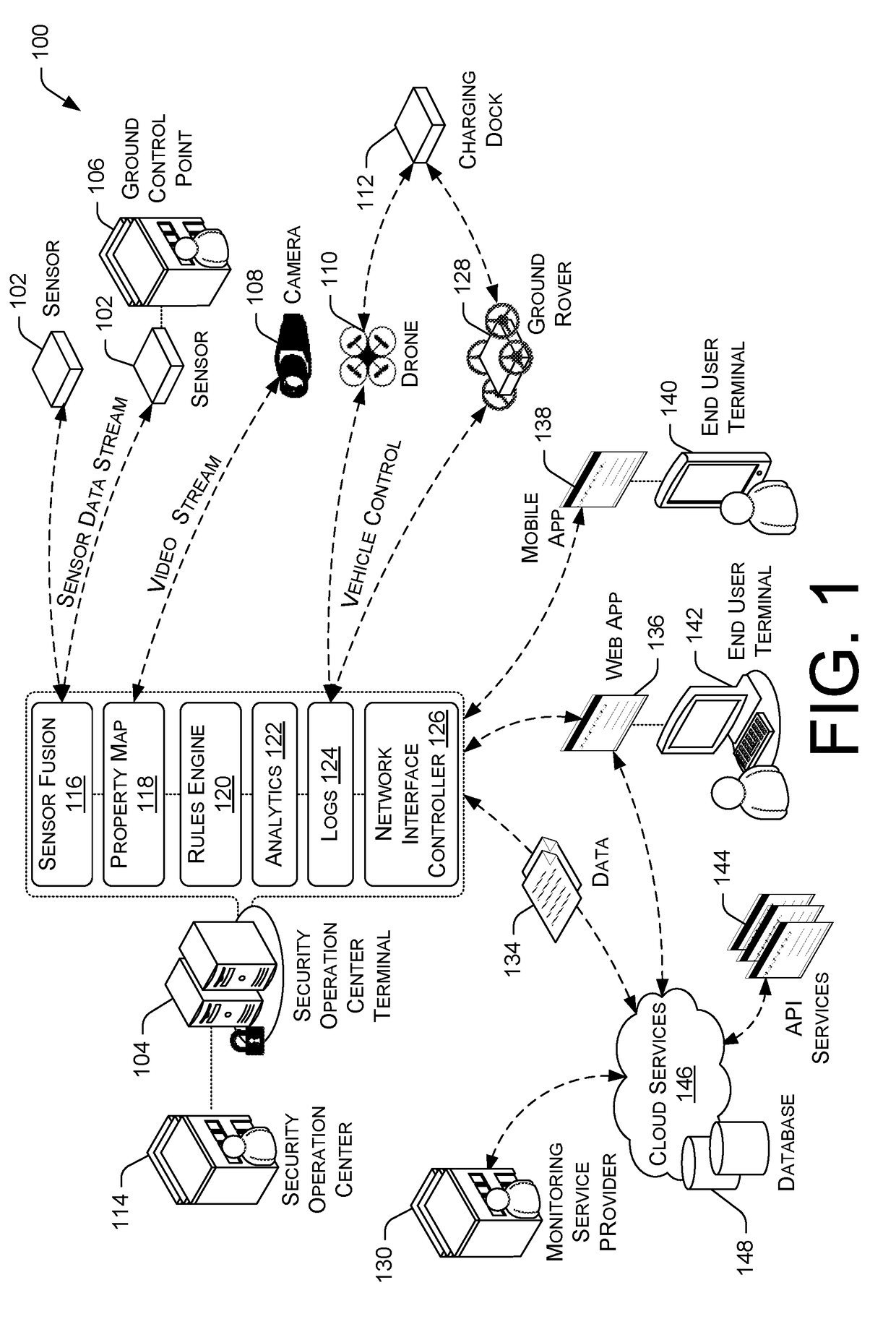
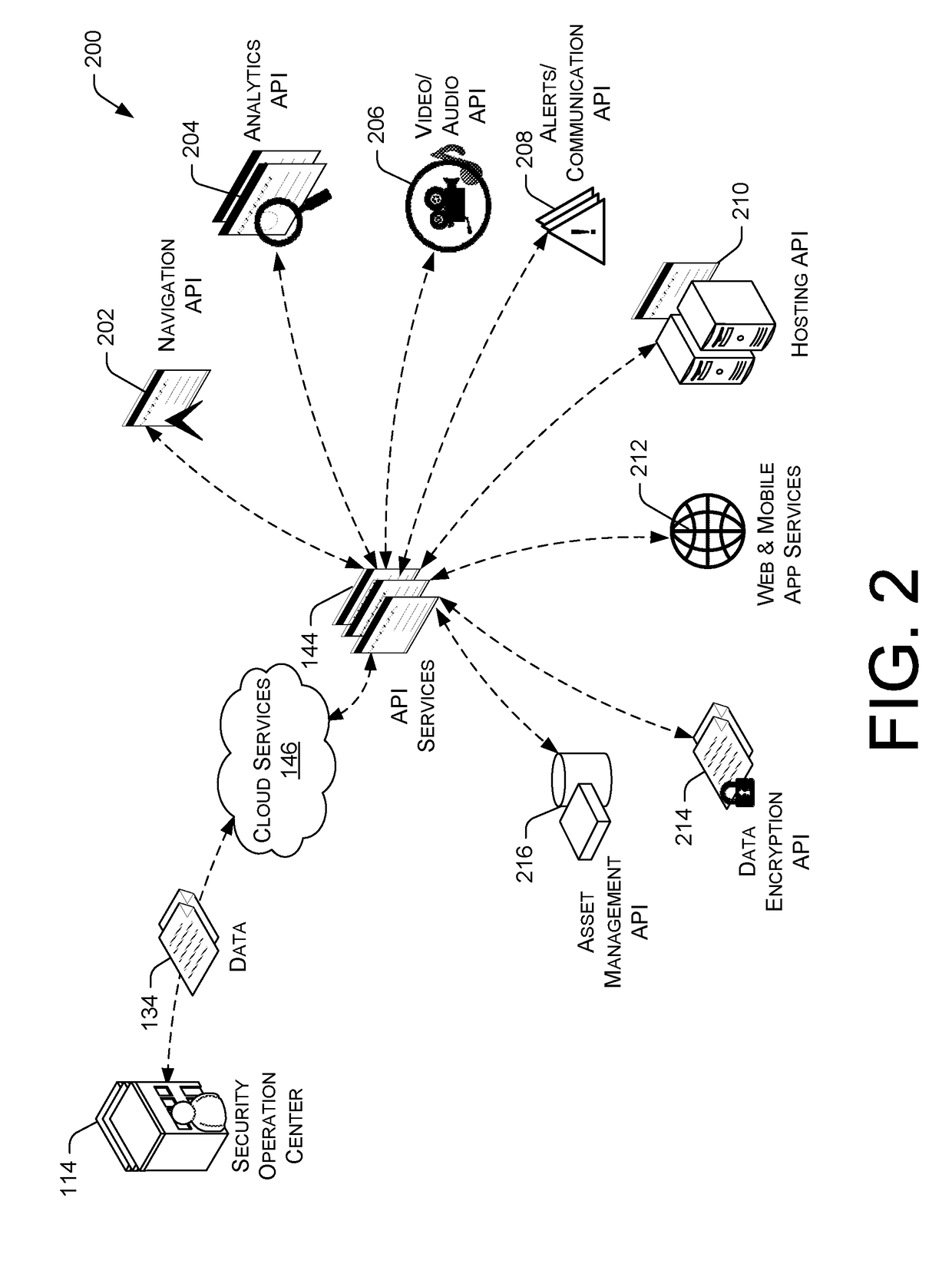
Total Property Intelligence System
ActiveUS20180211115A1Multiple keys/algorithms usagePublic key for secure communicationPhysical securityApplication software
A total property security system may be implemented to conduct security and surveillance operations. The system includes security operations centers that are connected to one or more sensors and vehicles for collecting and transmitting surveillance data to a database hosted on cloud services. The collected surveillance data is analyzed in order to automatically deploy security measures and / or recommend courses of action using a rules engine that can be configured to client-specific or user-specific security needs. The cloud services can provide a set of application program interface services that can act on the surveillance operations center. Sensor fusion data and other surveillance data can be also transmitted to vetted monitoring service providers on a subscription basis to provide physical security services to the area within the property perimeter. During the subscription period, the selected monitoring service providers can obtain time-based encryption token for accessing surveillance data.
Owner:KLEIN MATIAS
Identification assessment and response to environmental conditions while in an automobile
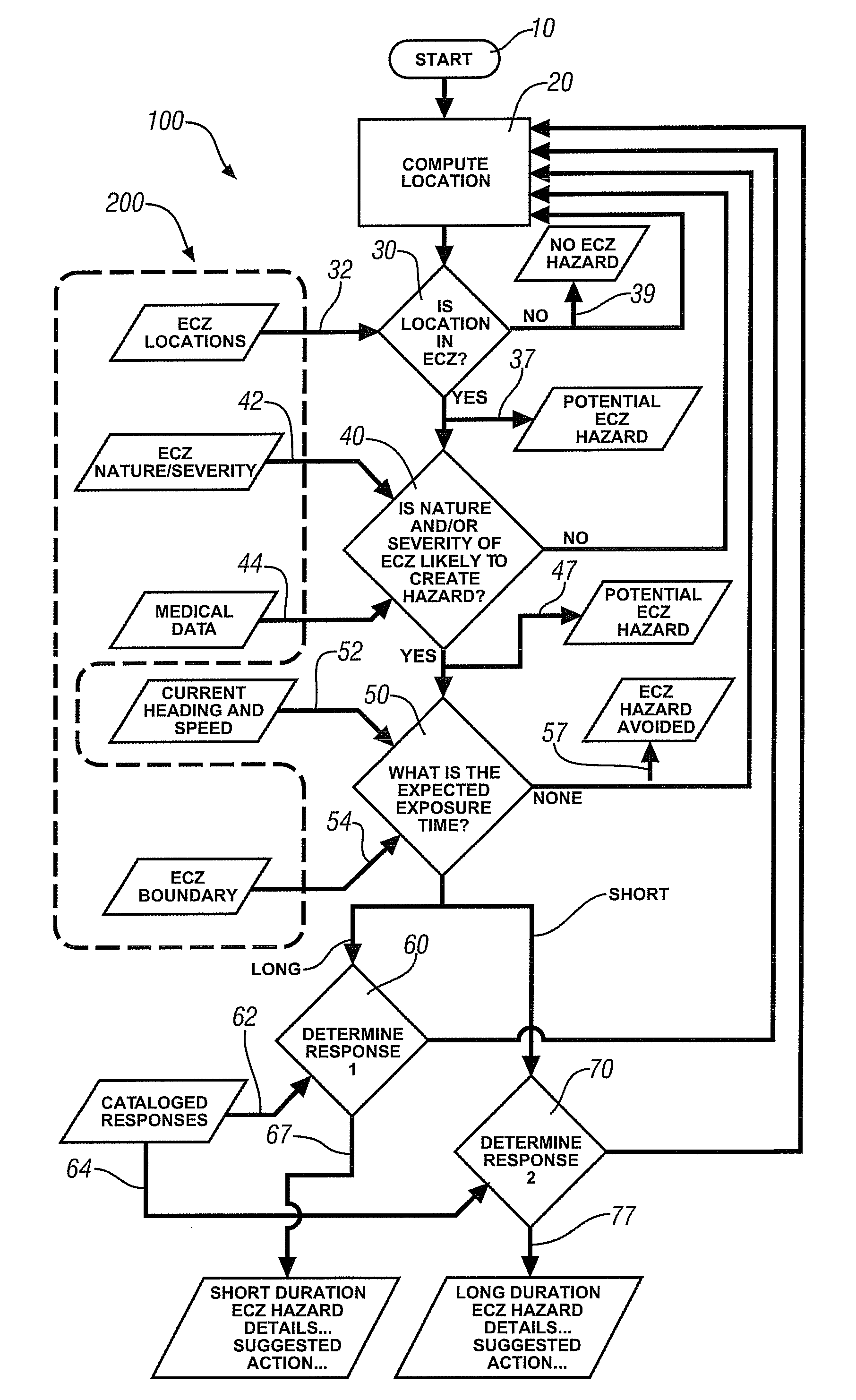
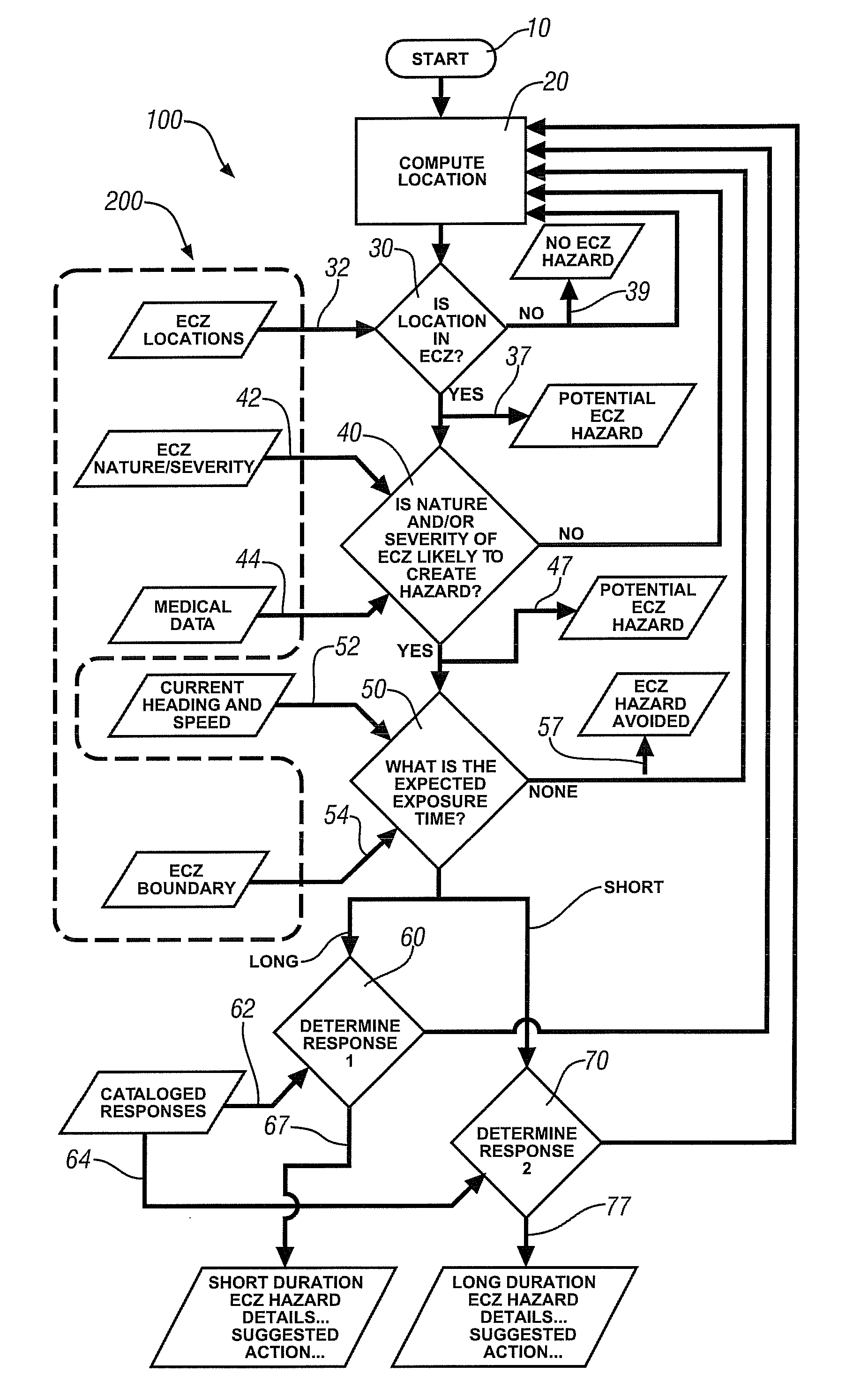
ActiveUS20110084824A1Suppress notificationVehicle heating/cooling devicesOptical signallingEngineeringCourse of action
A method is disclosed for estimating the exposure of vehicle occupants to environmental conditions capable of inducing a least discomfort. The occupants are alerted to their proximity to a zone where environmentally-challenging conditions exist and, in a first embodiment, the details of the environmental condition and the estimated duration of any exposure is communicated to the occupants; in a second embodiment a suggested course of action by which the occupants may mitigate the effect of the environmental occurrence is communicated; and in a third embodiment the proposed course of action is automatically executed subject to override by the occupants.
Owner:GM GLOBAL TECH OPERATIONS LLC
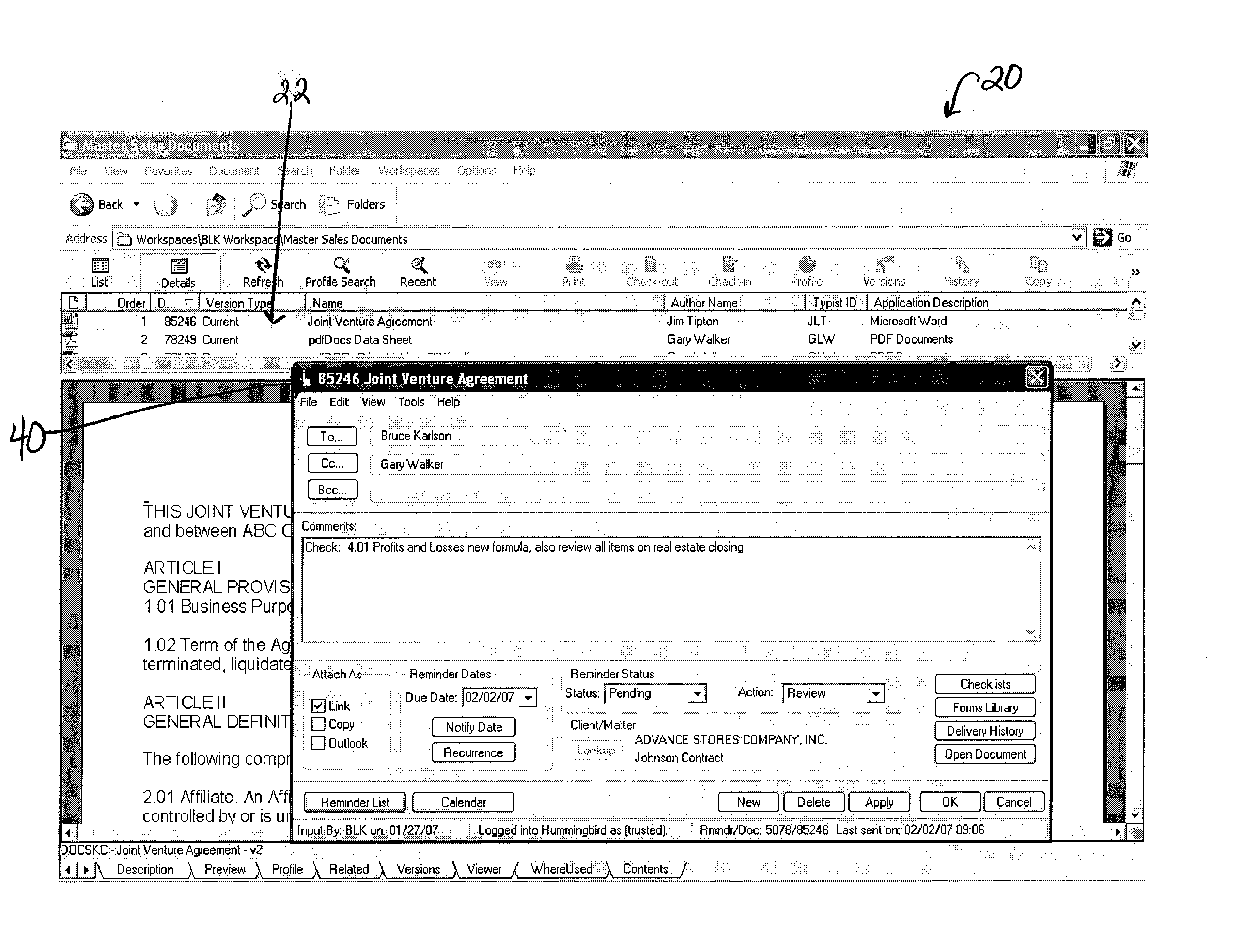
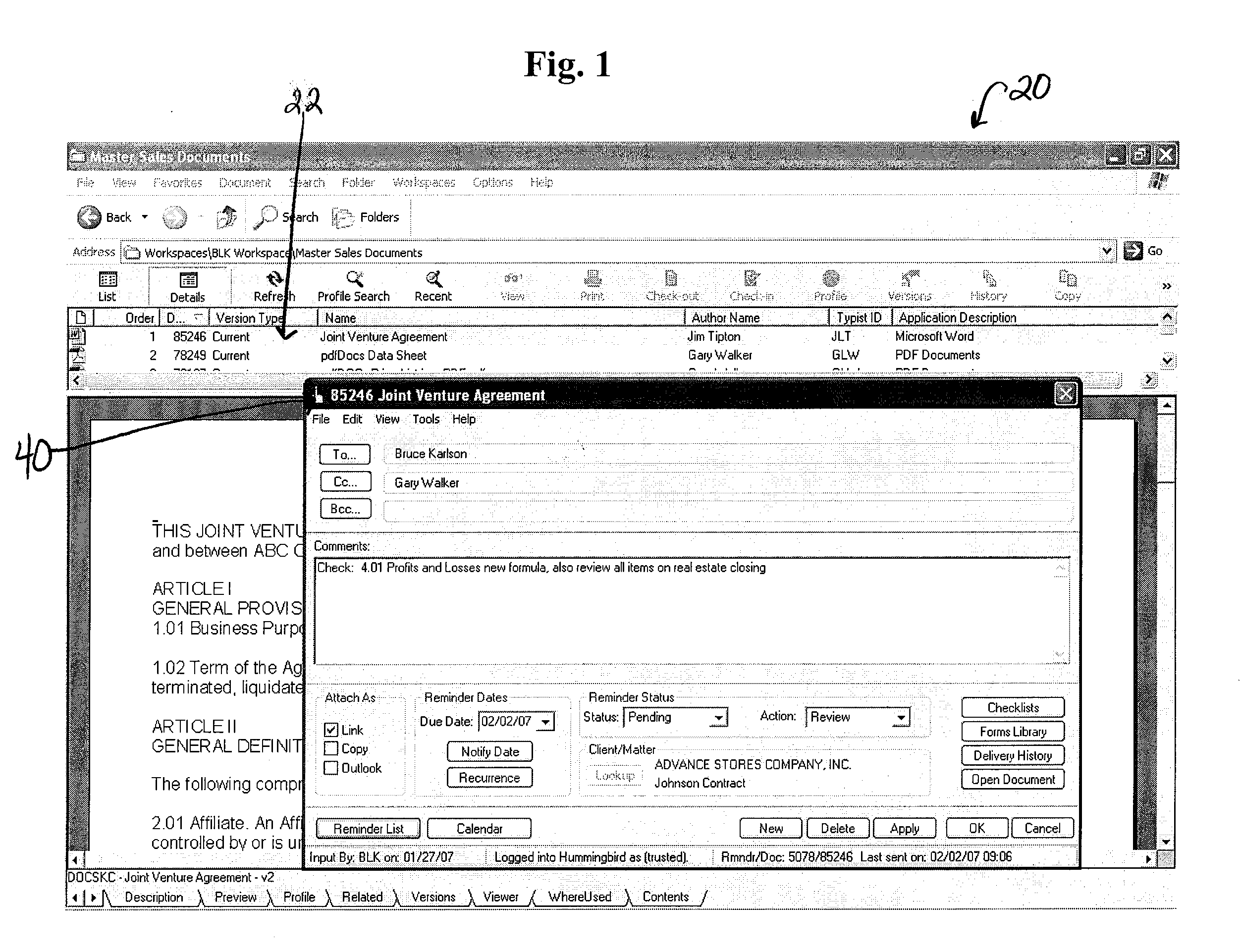
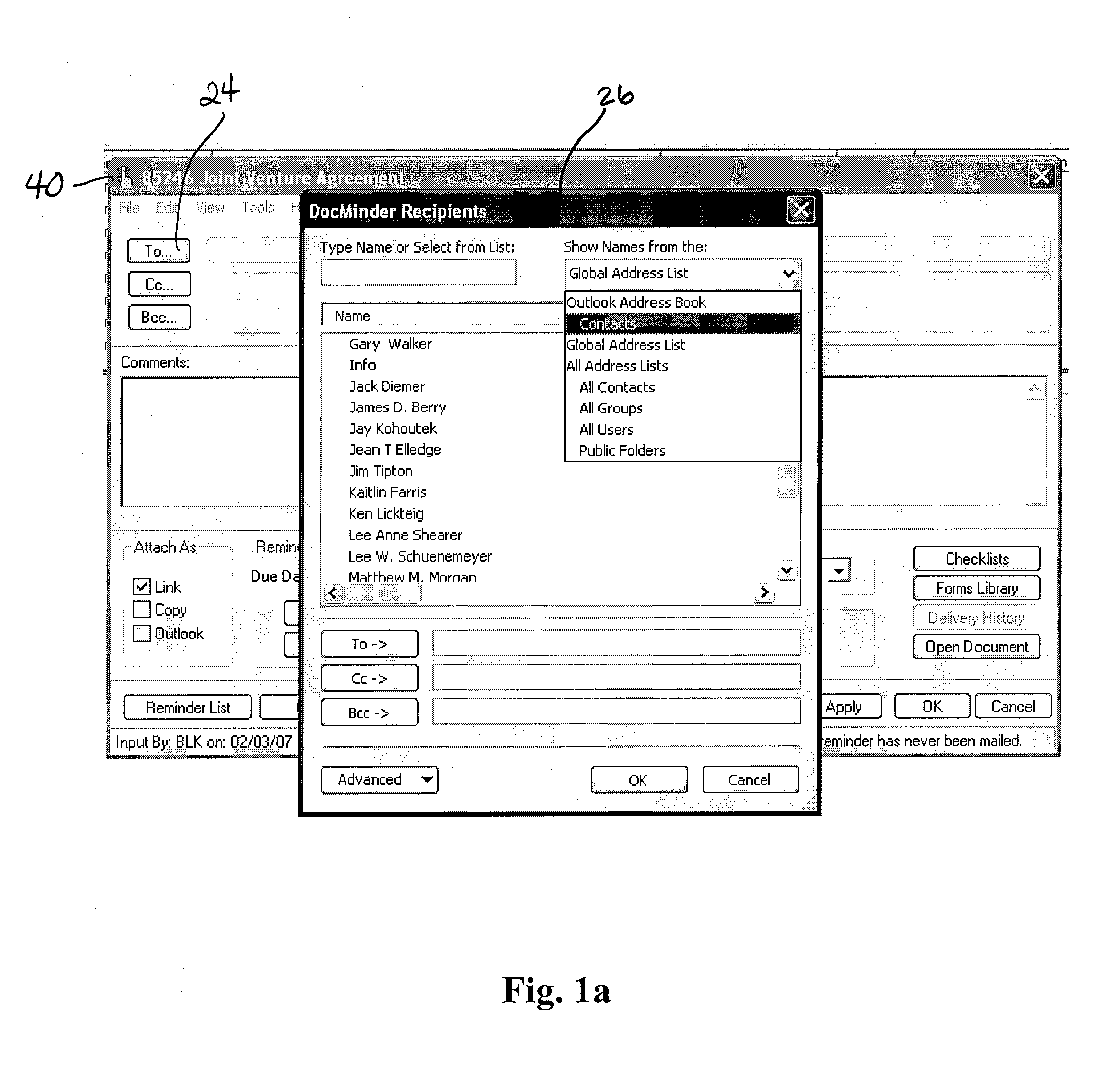
Document reminder system
ActiveUS20070192423A1Easy to useImprove usabilityMultiple digital computer combinationsSpecial data processing applicationsClassified informationCourse of action
A document reminder system is provided. The system provides a user-friendly interface to a user's existing document management, email, calendar and other systems in order to ensure that an appropriate user is notified when action should be taken on a specific document, and also provides notation to the user indicating the appropriate course of action to be taken. The system provides a calendaring feature where a supervisor or manager can determine the workload of a group of workers for an upcoming time period. The system provides an easily accessible and traceable database of information pertaining to a document, a client name, a client matter number, a document type, or other customizable fields in order for a user to search and sort the information for their own use.
Owner:DOCSOF
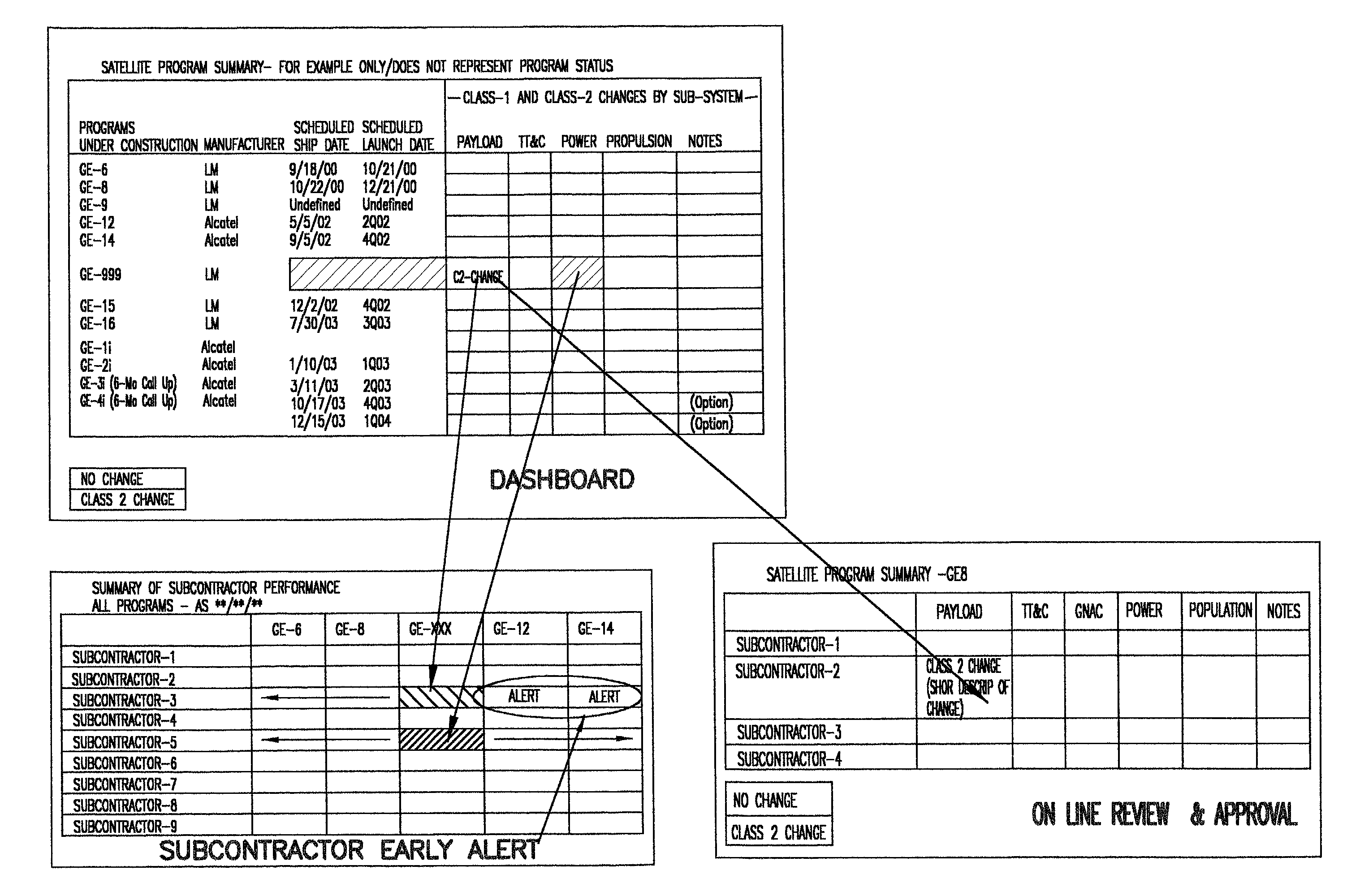
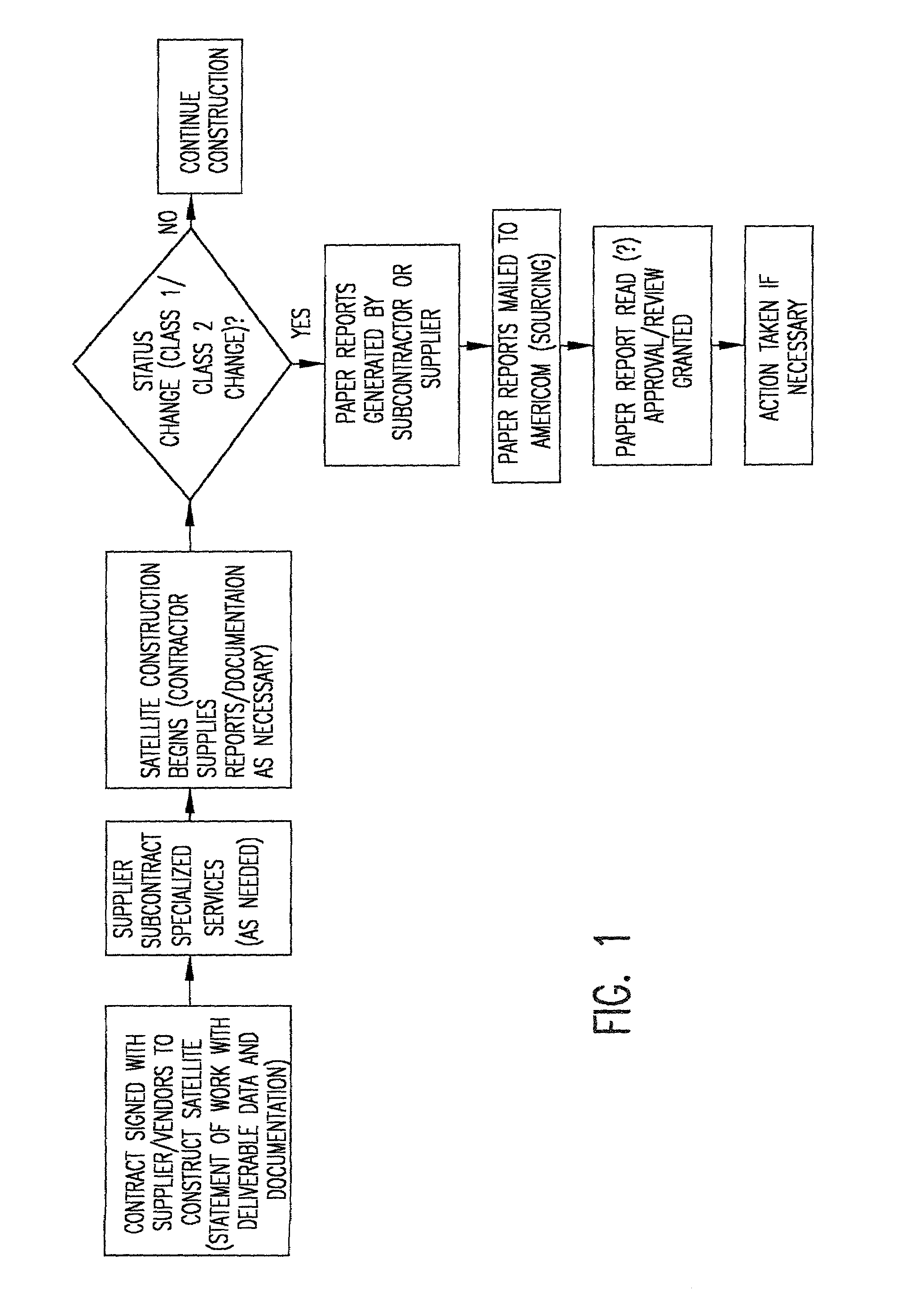
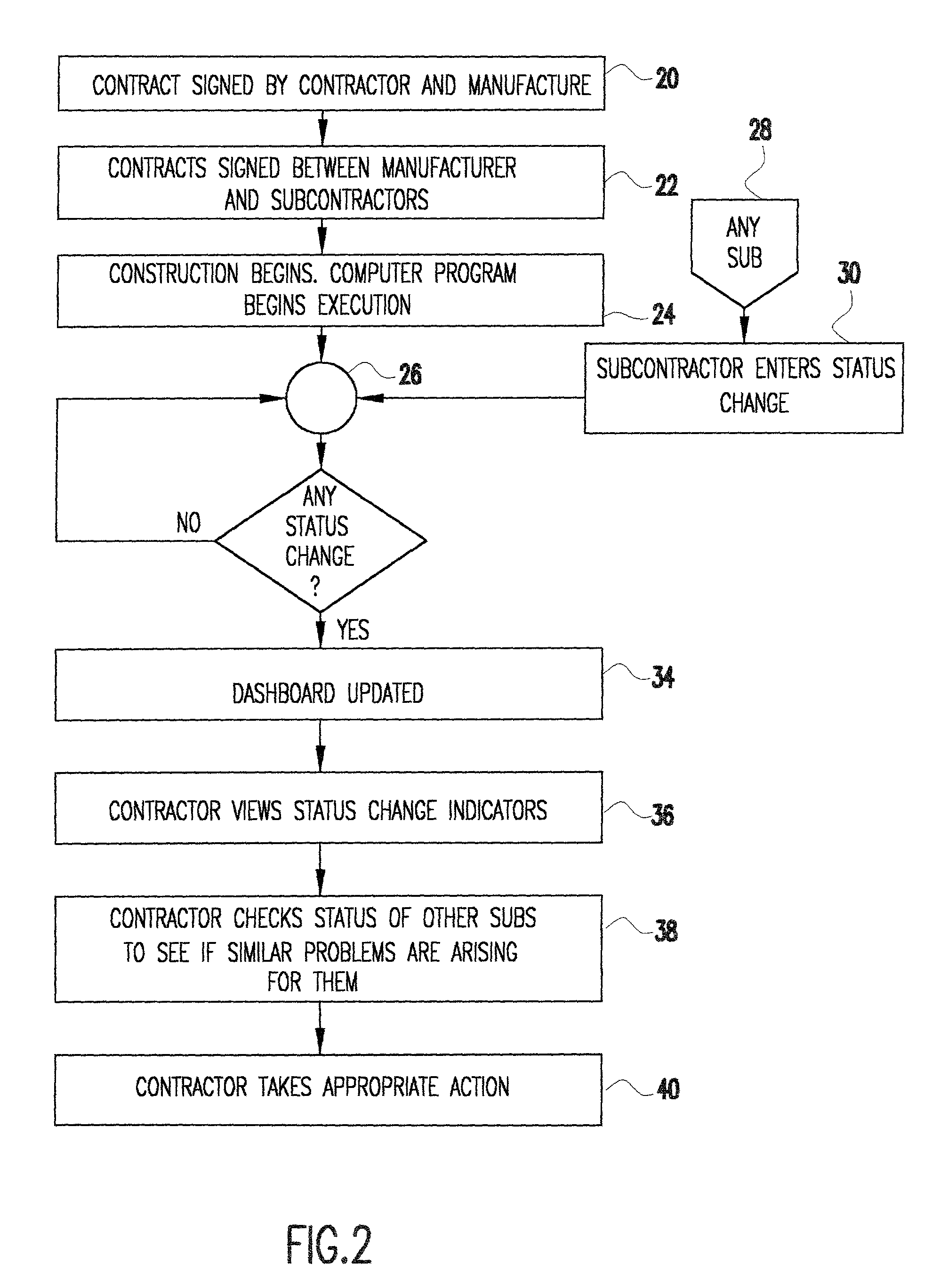
Project management for complex construction projects by monitoring subcontractors in real time
A method and system for managing complex construction projects by monitoring subcontractors in real time. Whenever a subcontractor realizes a need for a change in specification or anticipates any other reason that might delay completion of construction as scheduled, the subcontractor selects from a computerized menu the appropriate new status for the subcontractor's task and provides other information relevant to the changed situation. The status change is displayed on a display device, an electronic dashboard, so as to be easily noticed, the dashboard also providing one-click links to a display showing how widespread are the problems and a display for on-line review and approval of the status change by a manager or engineer in charge of the project, who notes the status change on the display and with whatever input may be provided by the other persons notified of the status change, decides the best course of action to keep the construction on schedule.
Owner:GEAMERICOM COMM
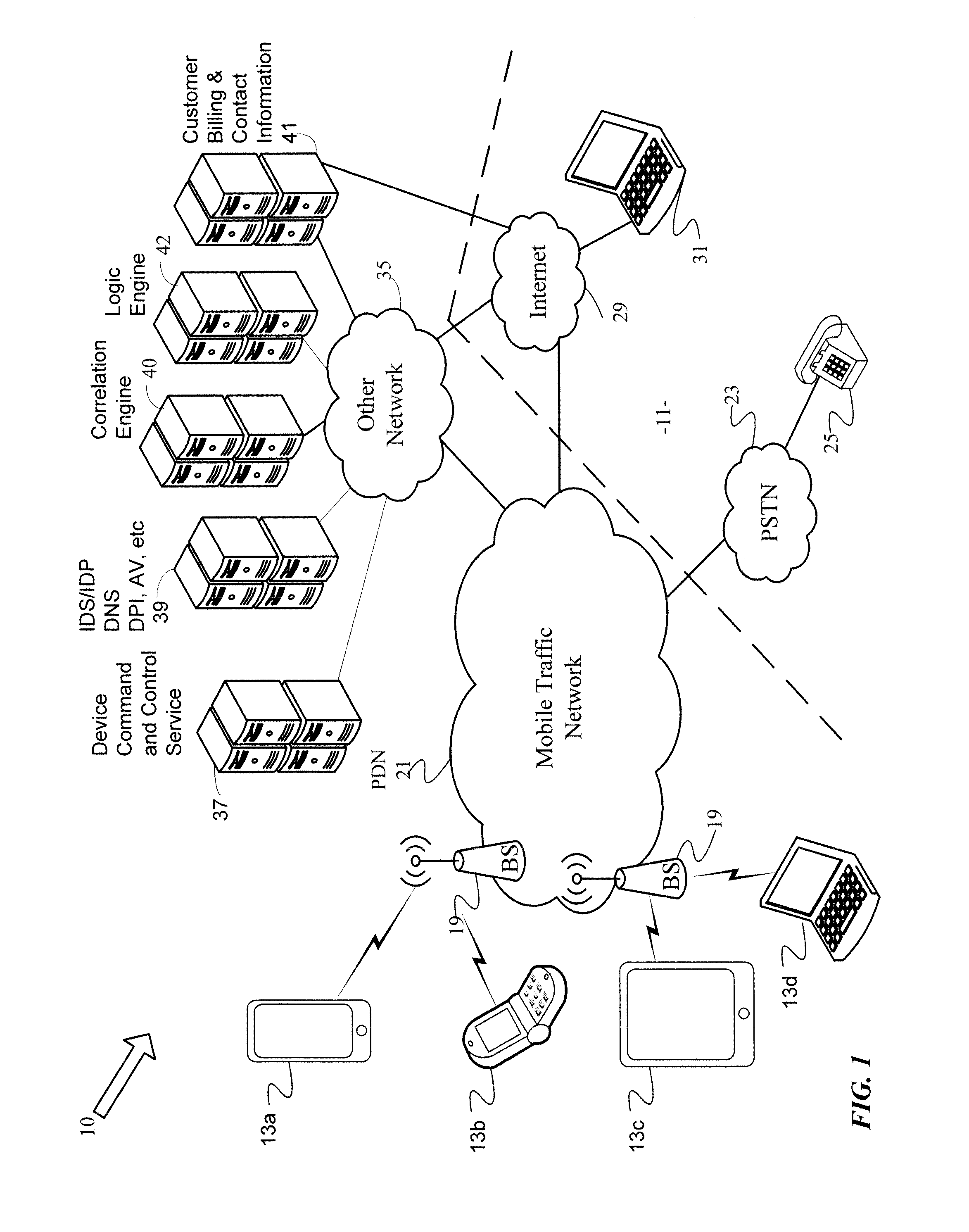
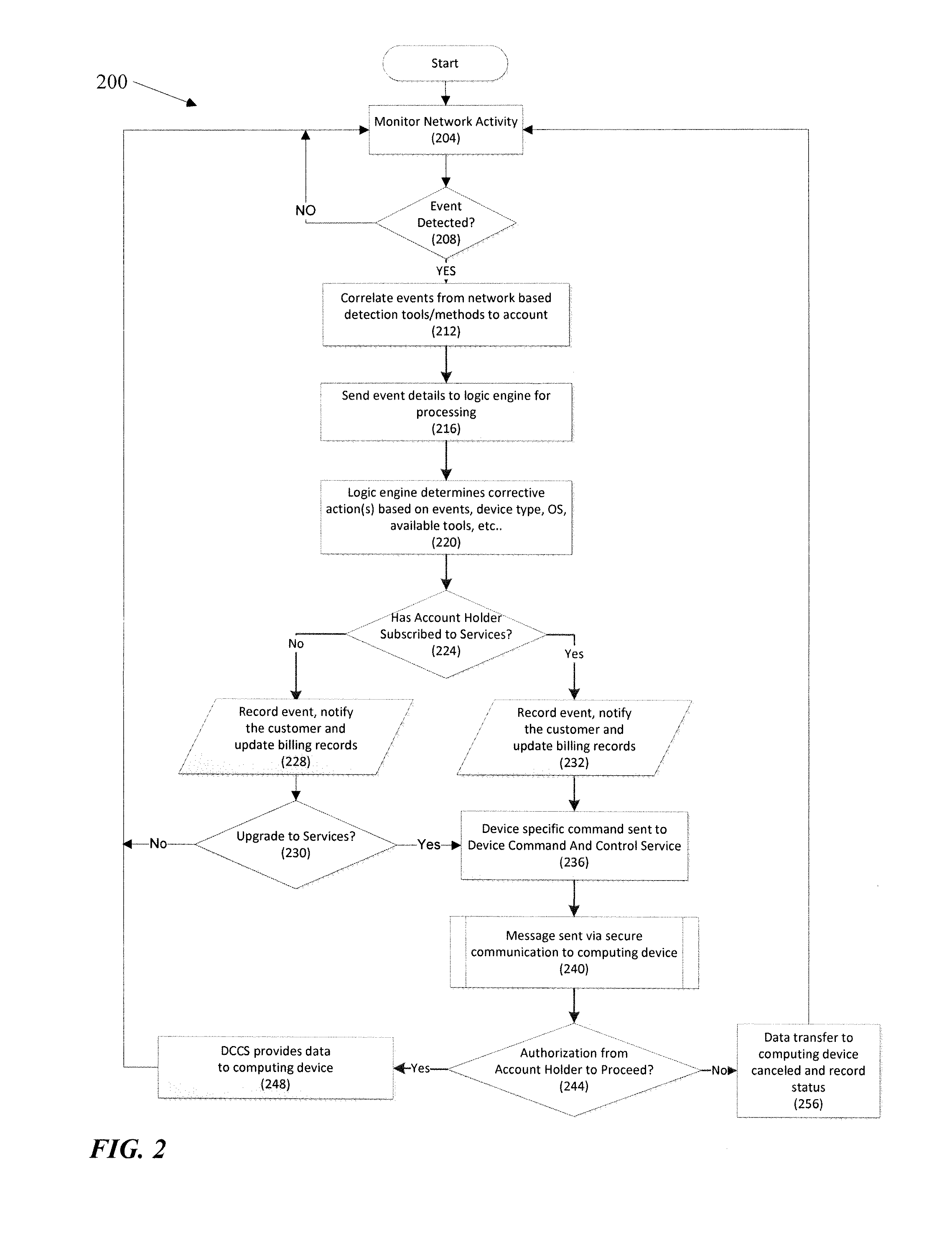
Network based device security and controls
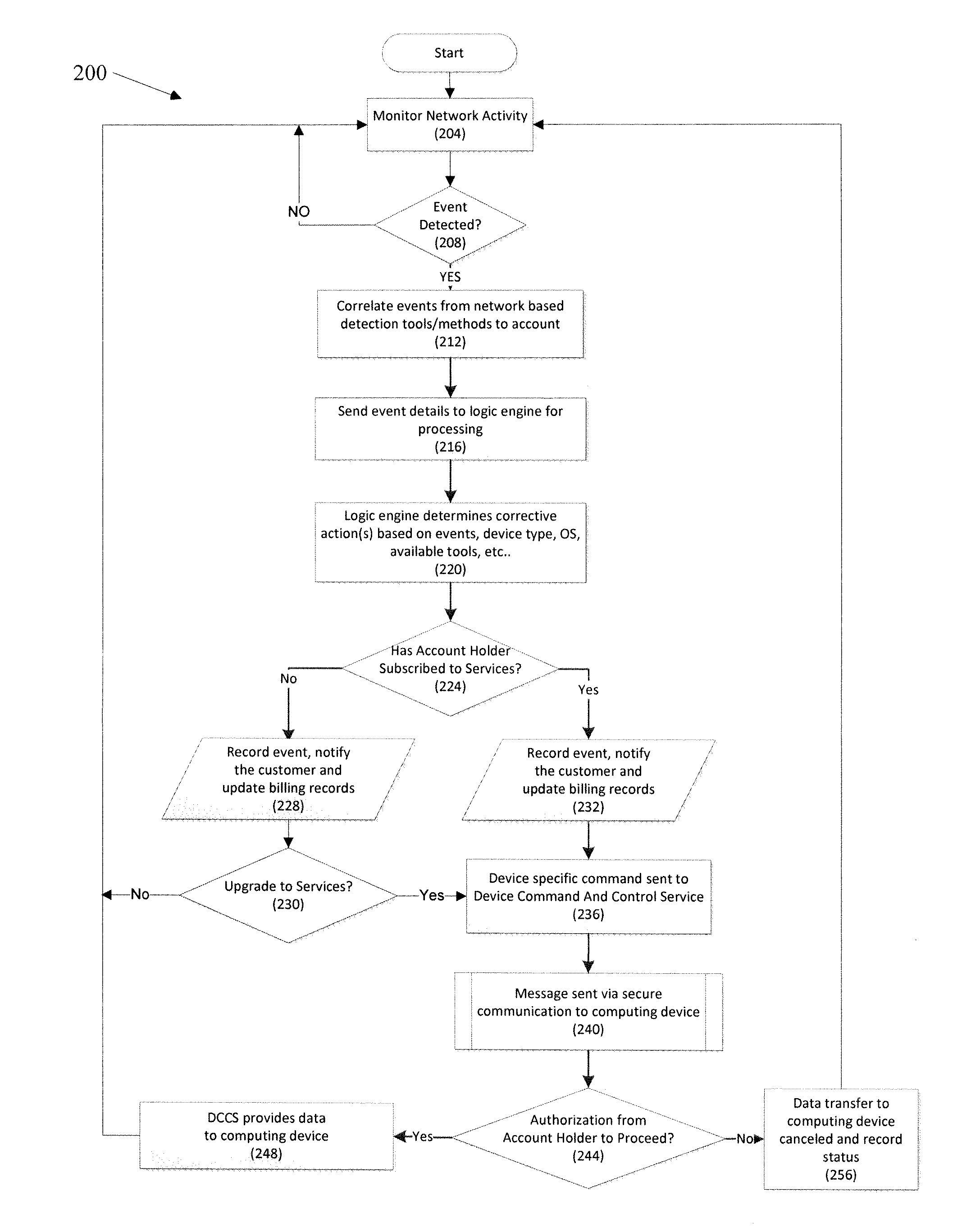
ActiveUS20130333032A1Memory loss protectionError detection/correctionOperational systemInternet traffic
Protection against security attacks involves monitoring network traffic for a computing device security attack and determining whether there is a security event, using one or more network based security tools. Next, it is determined whether an event pattern involving two or more security events meets a predetermined criteria. Upon determining that there is a security attack, corrective action is tailored, based on the type of the computing device, the operating system of the computing device, the type of security attack, and / or the available protection tools. A course of action is performed depending on whether an account of the computing device includes a security protection service. If there is a security protection service, a message is sent over a secure link to the computing device. This message includes the corrective action to cure the computing device from the security attack.
Owner:CELLCO PARTNERSHIP INC +1
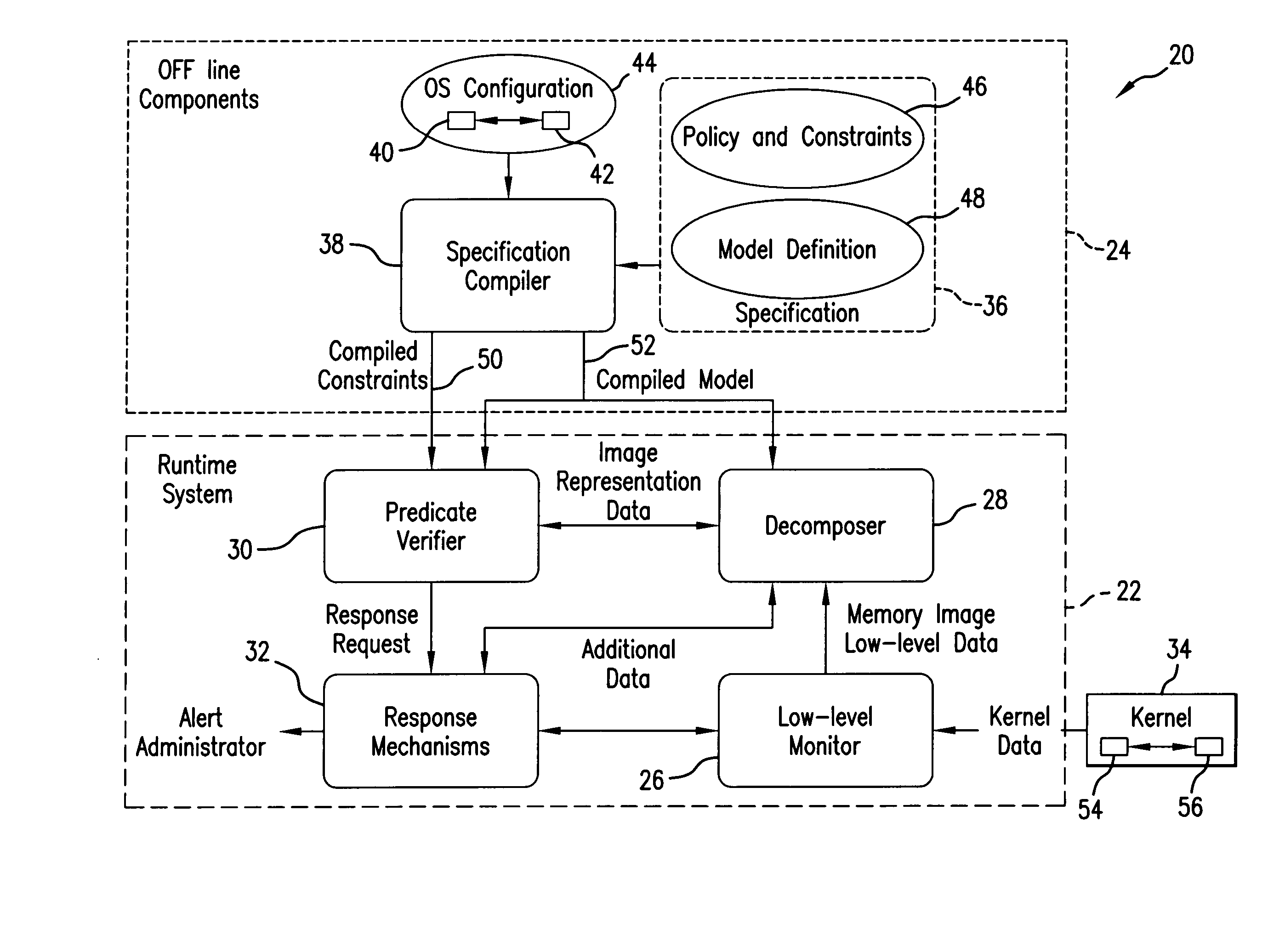
Method & system for monitoring integrity of running computer system
ActiveUS20070261120A1Digital data processing detailsAnalogue secracy/subscription systemsCourse of actionSystem monitor
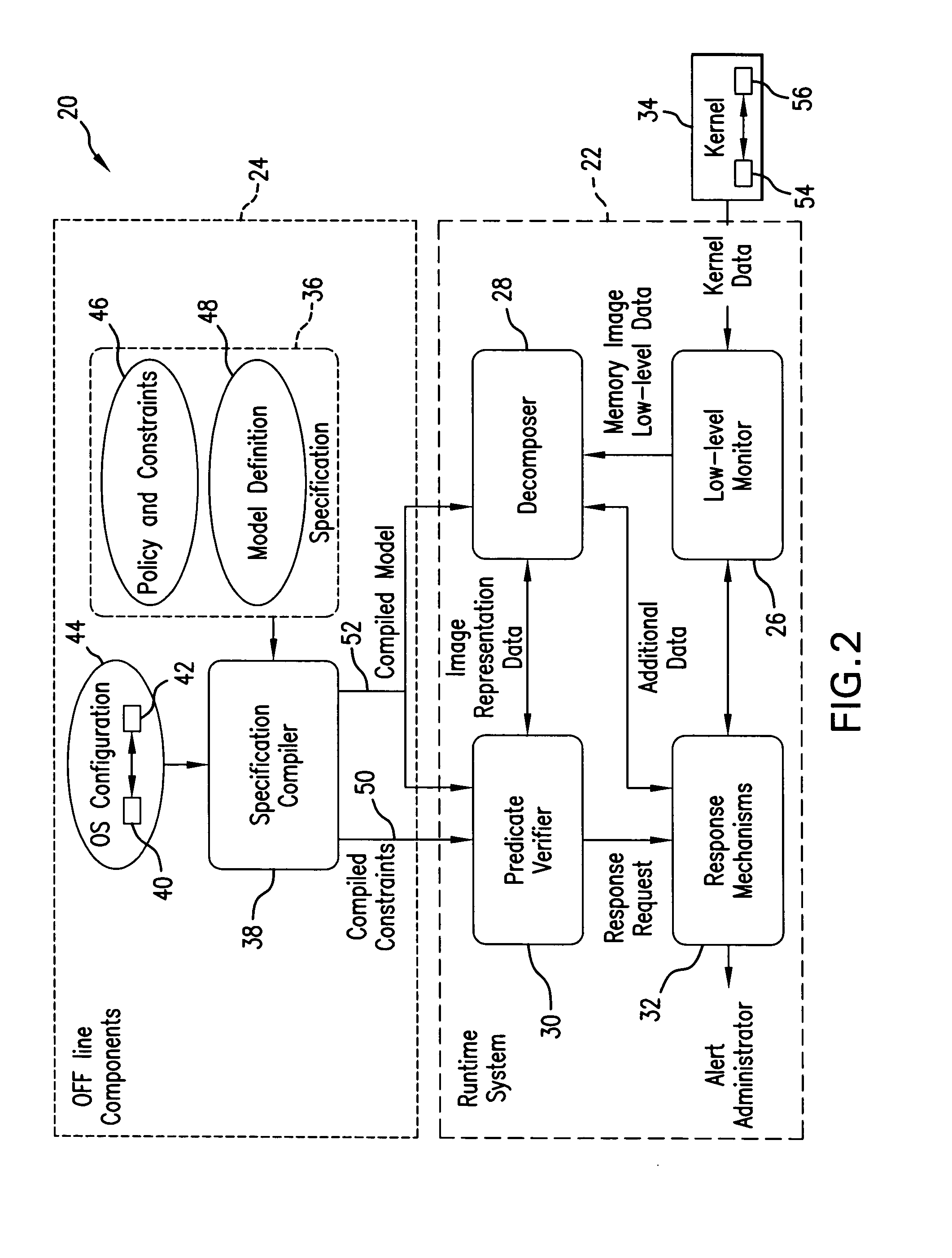
Monitoring integrity of a running computer system is based on creating a Test Model which includes predicates descriptive of invariant properties of security relevant objects and their attributes in the monitored structure known-to-be “healthy”, acquiring memory image of a portion of the running monitored structure, decomposing the acquired memory image to retrieve representation of the security relevant objects of interest, by implementing the attributes of the Test Model, and verifying, by implementing the predicates, whether the invariant properties defined in the Test Model remain unchanged for the running host system. If a discrepancy is detected, a signal indicative of a detected discrepancy is transmitted to a management entity for analysis and formulating a course of action.
Owner:MICROSOFT TECH LICENSING LLC
TLB operations based on shared bit
InactiveUS6839813B2Memory architecture accessing/allocationEnergy efficient ICTCoprocessorCourse of action
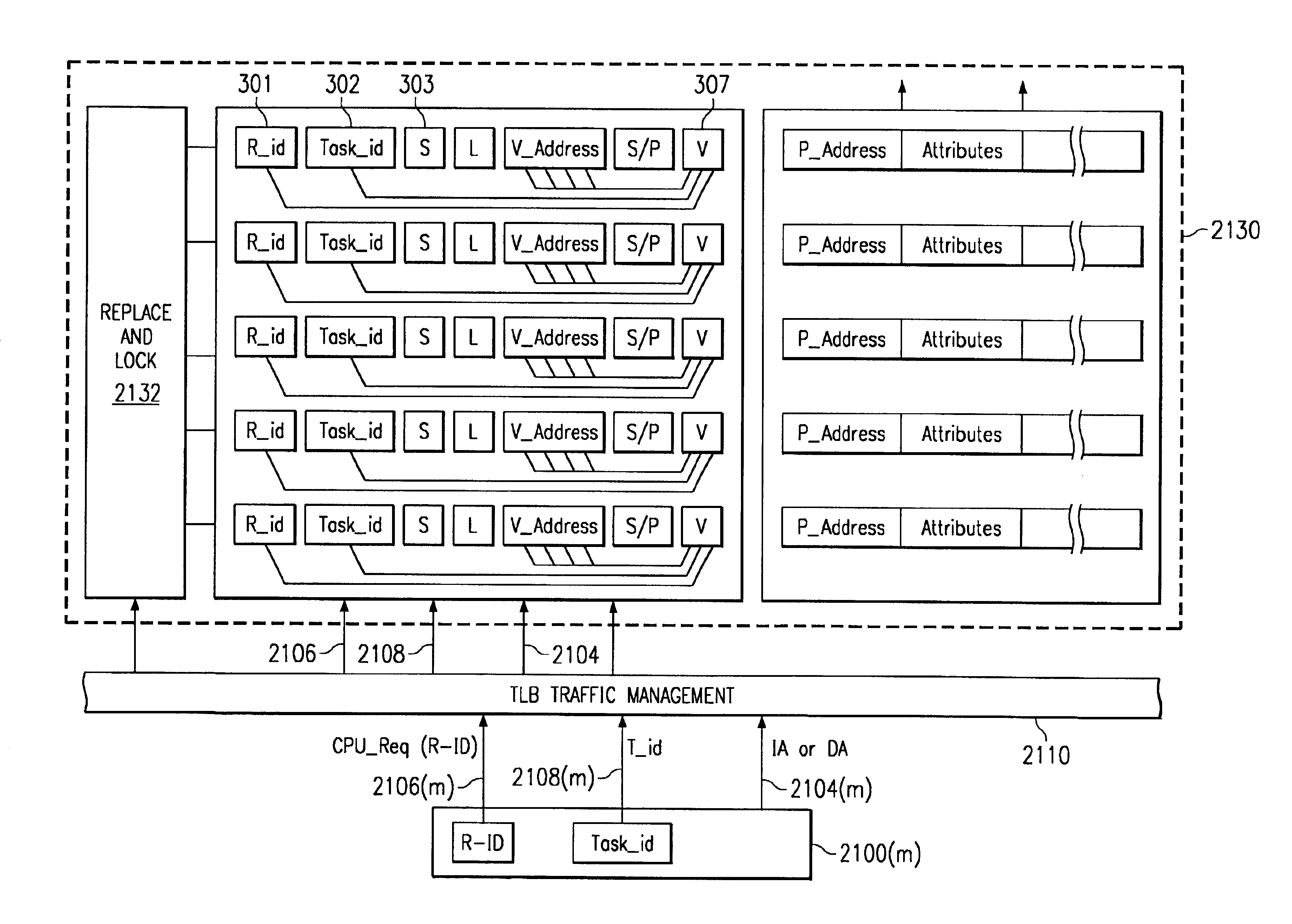
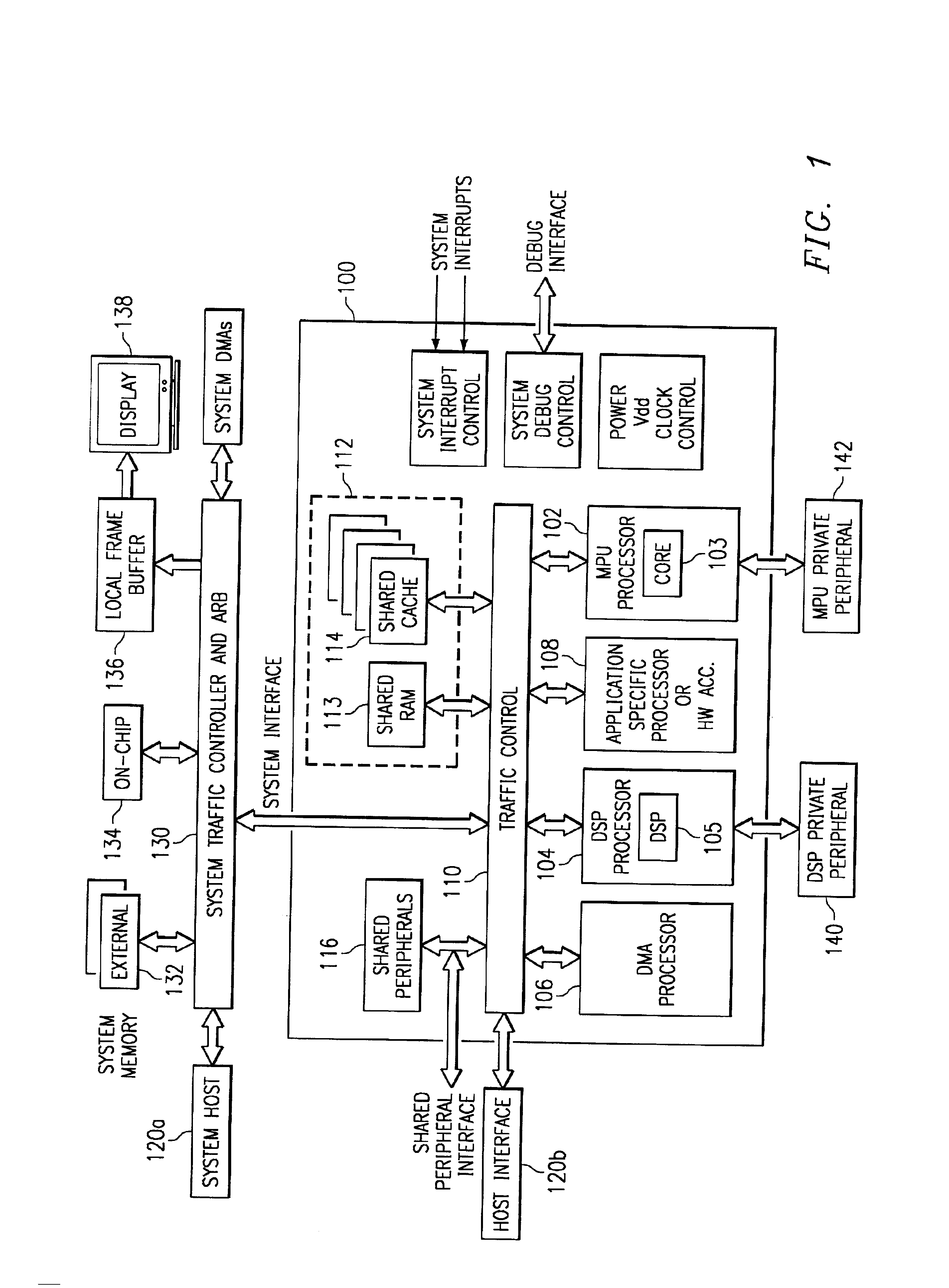
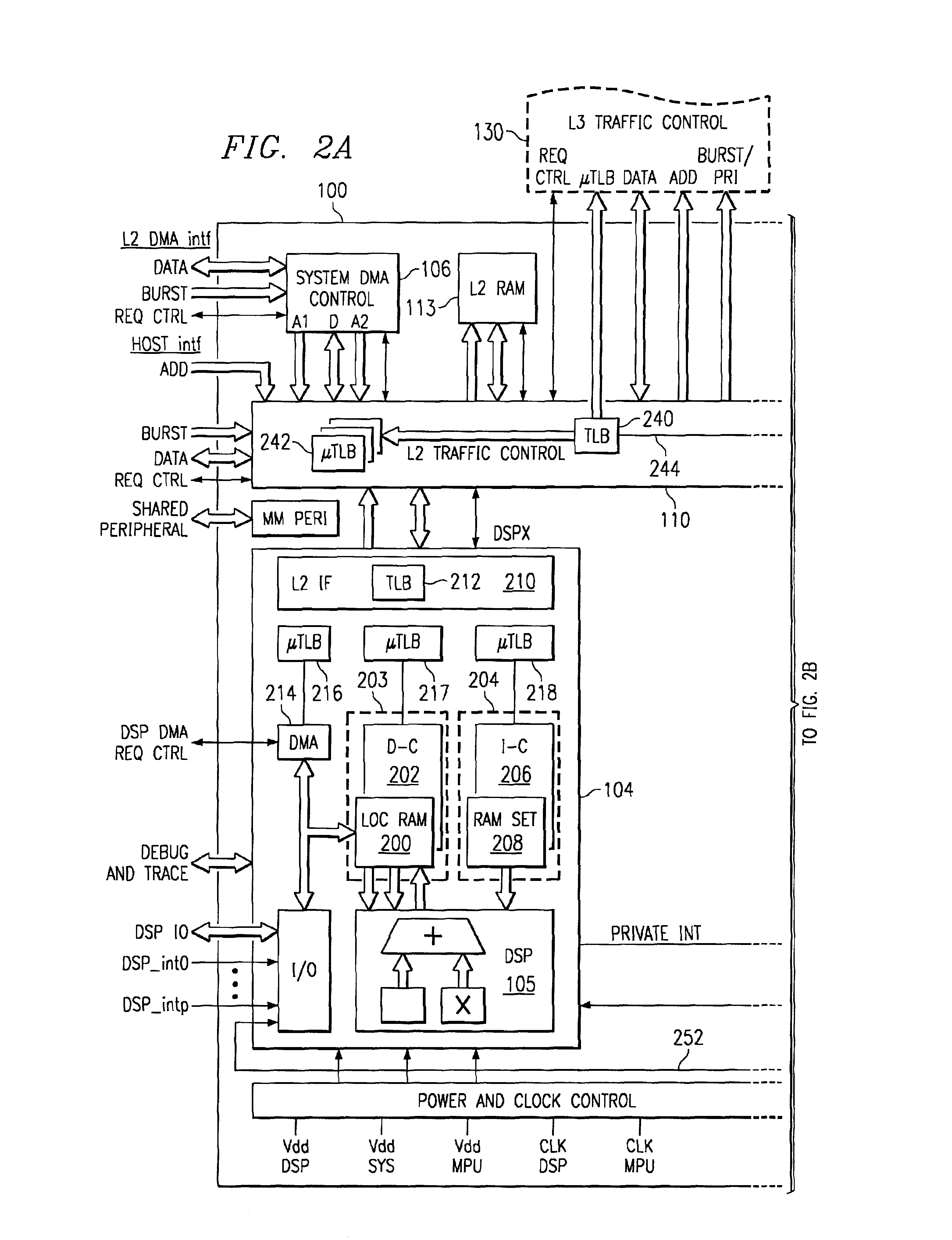
A digital system and method of operation is provided in which several processing resources (340) and processors (350) are connected to a shared translation lookaside buffer (TLB) (300, 310(n)) of a memory management unit (MMU) and thereby access memory and devices. These resources can be instruction processors, coprocessors, DMA devices, etc. Each entry location in the TLB is filled a during the normal course of action by a set of translated address entries (308, 309) along with qualifier fields (301, 302, 303) that are incorporated with each entry. Operations can be performed on the TLB that are qualified by the various qualifier fields. A command (360) is sent by an MMU manager to the control circuitry of the TLB (320) during the course of operation. Commands are sent as needed to flush (invalidate), lock or unlock selected entries within the TLB. Each entry in the TLB is accessed (362, 368) and the qualifier field specified by the operation command is evaluated (364). This can be task ID field 302, resource ID field 301, shared indicator 303, or combinations of these. Operation commands can also specify a selected virtual address entry (305). Each TLB entry is modified in response to the command (366) only if its qualifier field(s) match the qualifier(s) specified by the operation command.
Owner:TEXAS INSTR INC
System and method for emergency response
InactiveUS7343302B2Facilitate decision-makingImprove situational awarenessData processing applicationsAlarmsResource Management SystemCrowds
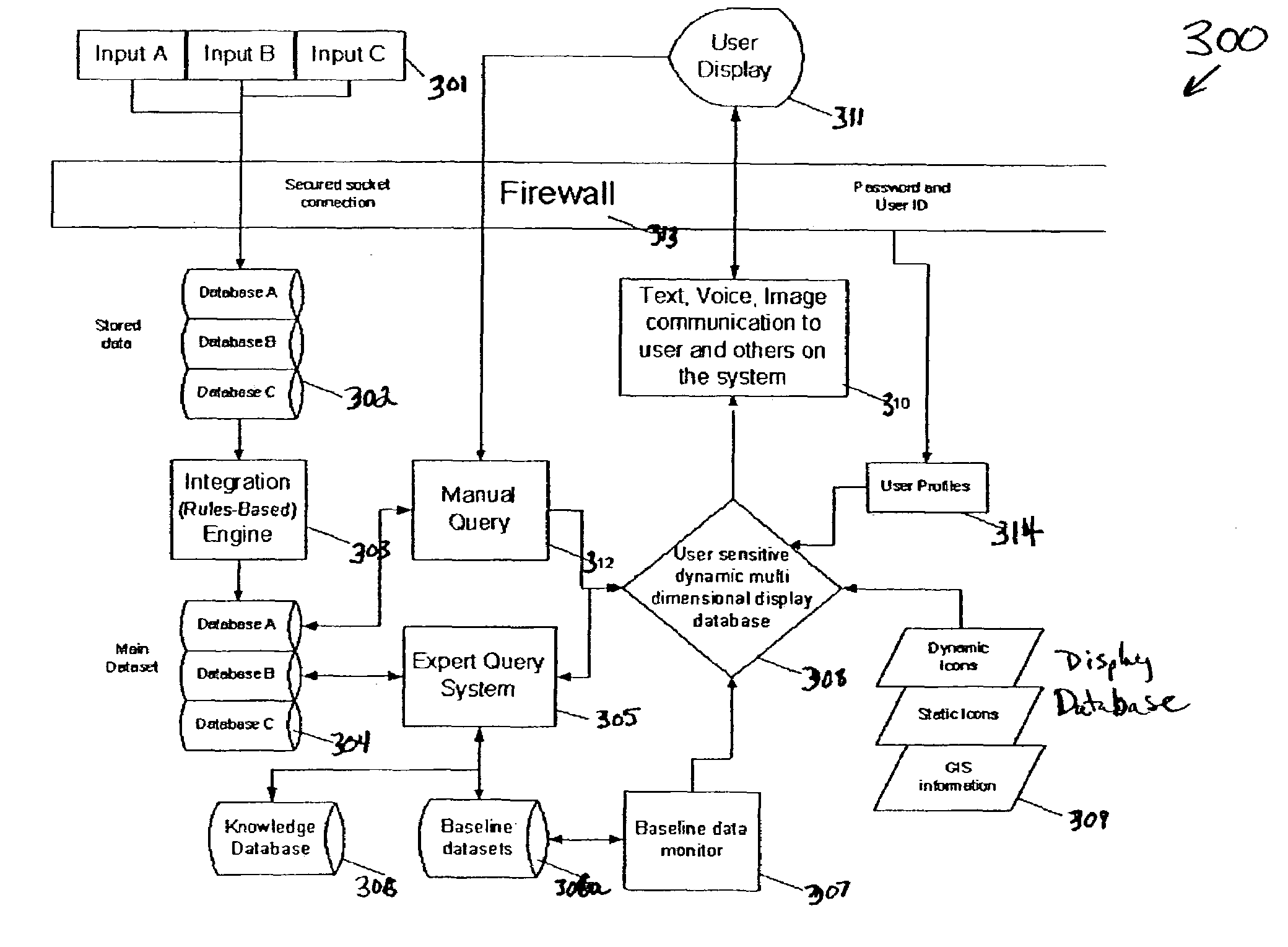
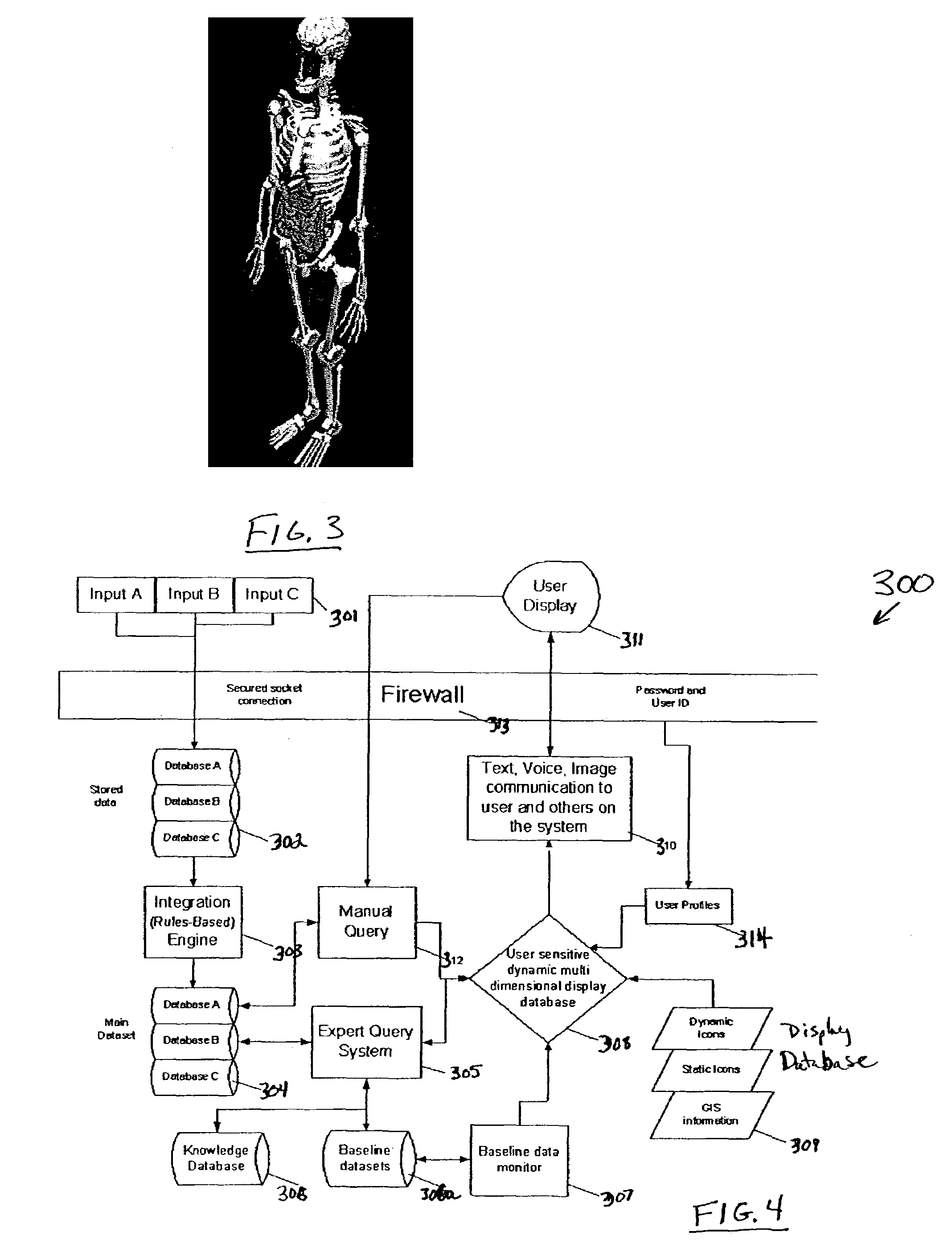
This application describes an information and resource management system for collecting data from diverse sources and organizing multiple types of data and information to facilitate dynamic multi-dimensional displays that will enhance cognition and situational awareness for diverse user communities. This system may facilitate collaborative cross-agency research and response to public health and safety issues. The system will generate more rapid awareness of potentially critical situations and promote greater awareness of the cost and benefits of alternative courses of action across diverse agencies and organizations serving common populations and communities. The invention includes customized geographically enabled data collection tools and techniques, dedicated databases and parsing schemes that feed into customized data visualization and simulation engines that drive the display of context sensitive interactive environments on a wide variety of computing platforms. The invention provides a novel approach to inter-disciplinary information integration processing, visualization, sharing and decision-making in the domain of public health and safety, disaster management and mitigation.
Owner:JAIN AGRI SERVICES
Method and system for the dynamic customization of graphical user interface elements
A method and system for customizing graphical user interface elements displayed within a graphic interface of a data-processing system and for customizing graphical user interface elements, such as menus displayed within a graphic interface of a data-processing system. Each menu has a series of menu items, such that a selection of a particular item triggers a standard course of action associated with the menu item. The standard course of action can be initiated in response to a normal selection of a particular menu item. An alternative selection technique, recognizable by the data-processing system, is defined to support customization of the selected menu items associated with the selected menu. The alternative selection technique is utilized to initiate an alteration to a menu item selected by a user. The alternative selection technique can be initiated by a particular combination of keystrokes and / or user input derived from a pointing device. Utilization of the alternative selection technique enables a user to modify words, picture, location, or visibility associated with a selected menu choice, or other graphical user interface elements.
Owner:LENOVO (SINGAPORE) PTE LTD
Control system and device for patient assist
ActiveUS20150051519A1Avoid oscillationDampens actionDiagnosticsChiropractic devicesPhysical medicine and rehabilitationControl system
Systems and methods for use with haptic devices. A control system for haptic devices determines a first course of action based on a user's motion. Prior to implementing the first course of action, the control system determines if the first course of action would lead to instability in the haptic device which could cause an unsafe situation such as failure of its components. If the first course of action would lead to instability, the control device determines a second course of action that would not lead to instability and implements this second course of action. To assist in this second course of action and to prevent potential oscillation in the haptic device, the control system also selectively dampens a projected action of the haptic device. A haptic device using such a control system is also disclosed.
Owner:MORBI ALIASGAR +2
Methods and apparatus for facilitating a secure session between a processor and an external device
InactiveUS20060179324A1Verify integrityUnauthorized memory use protectionHardware monitoringOperational systemCourse of action
Methods and apparatus provide for verifying operating system software integrity prior to being executed by a processor, the processor including an associated local memory and capable of operative connection to a main memory such that data may be read from the main memory for use in the local memory; storing a status flag indicating whether the operating system software integrity is or is not satisfactory; and ensuring that the status flag indicates that the operating system software integrity is satisfactory before permitting the processor to continue in a course of action.
Owner:SONY COMPUTER ENTERTAINMENT INC
Subjective and statistical event tracking incident management system
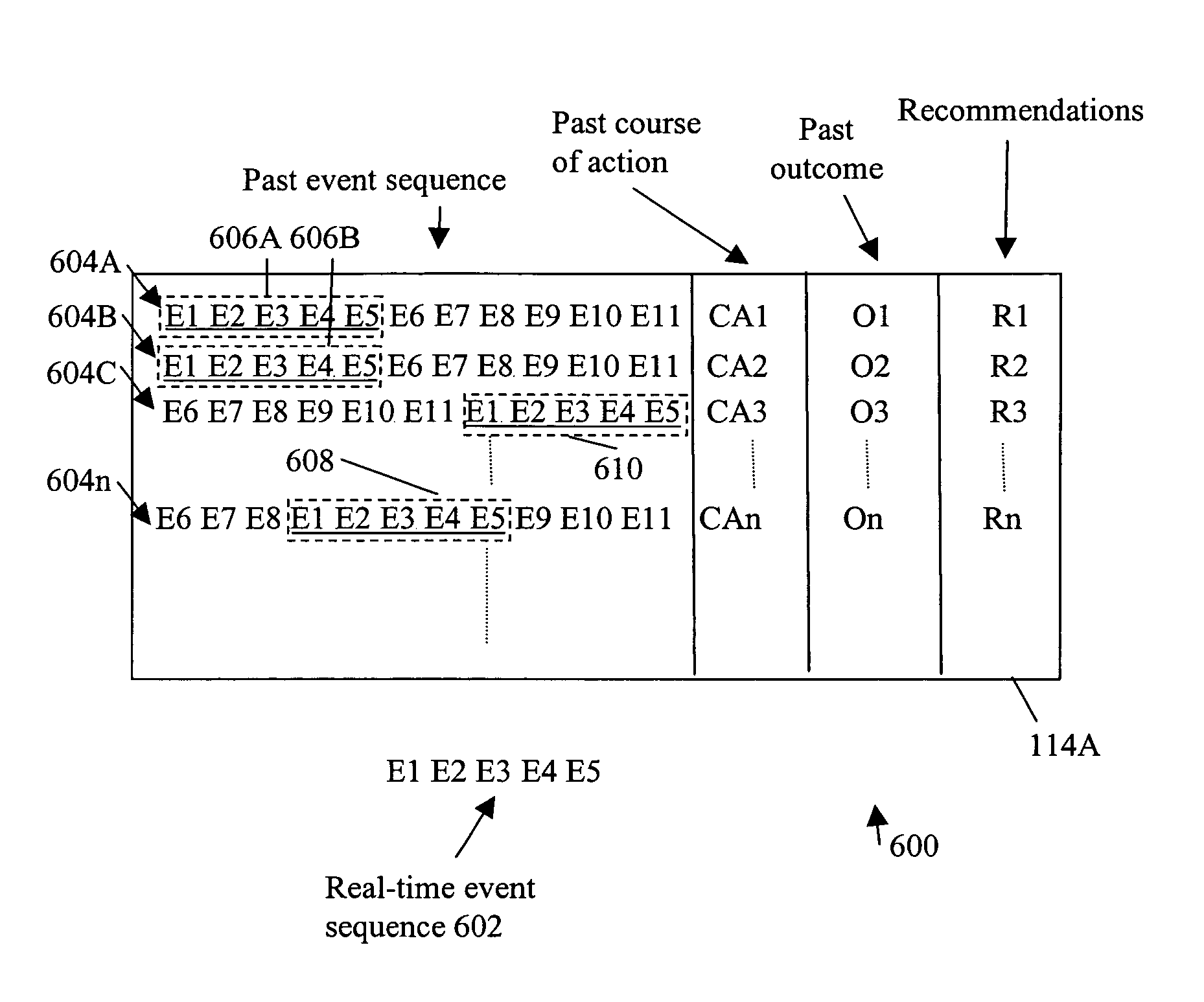
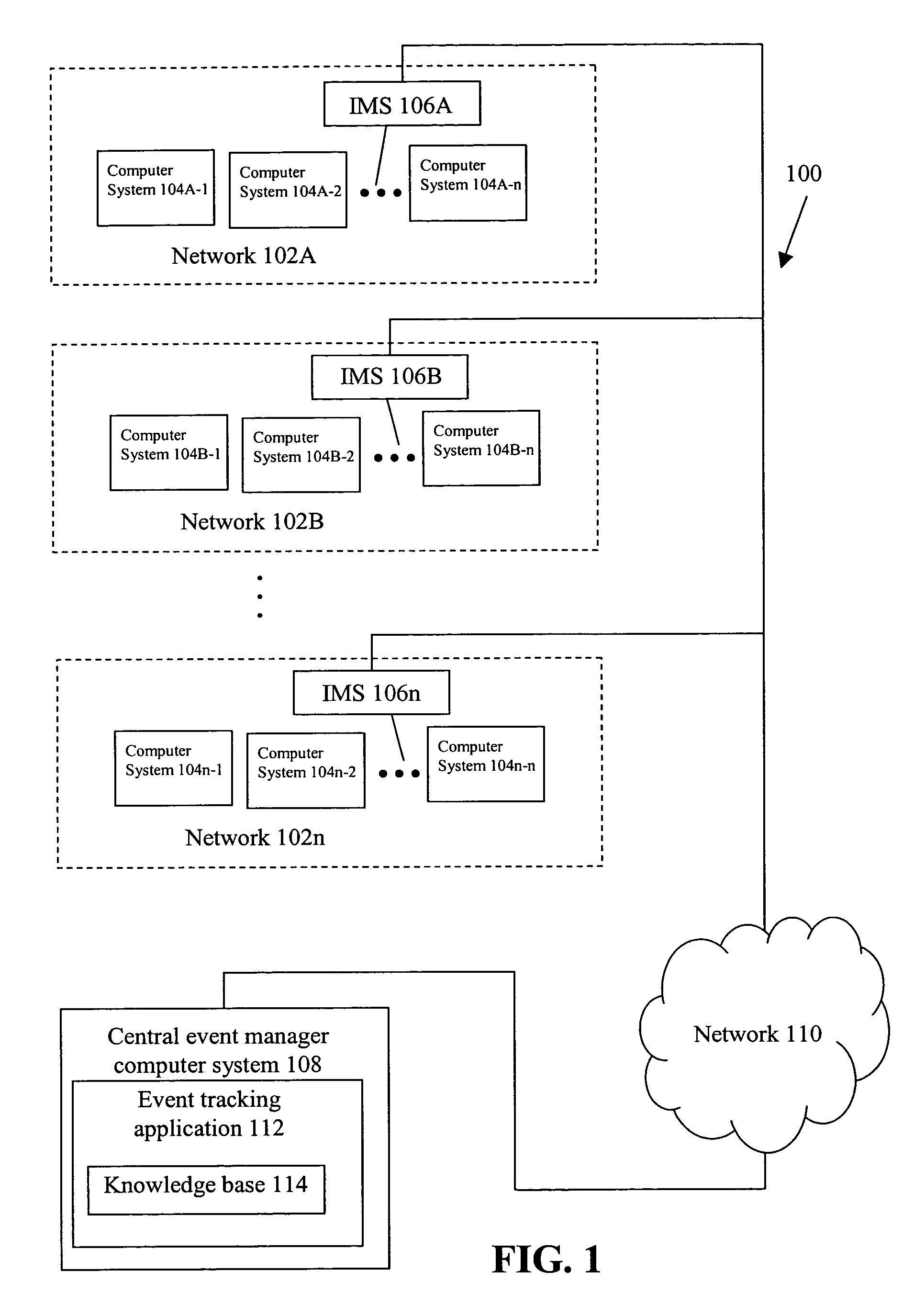
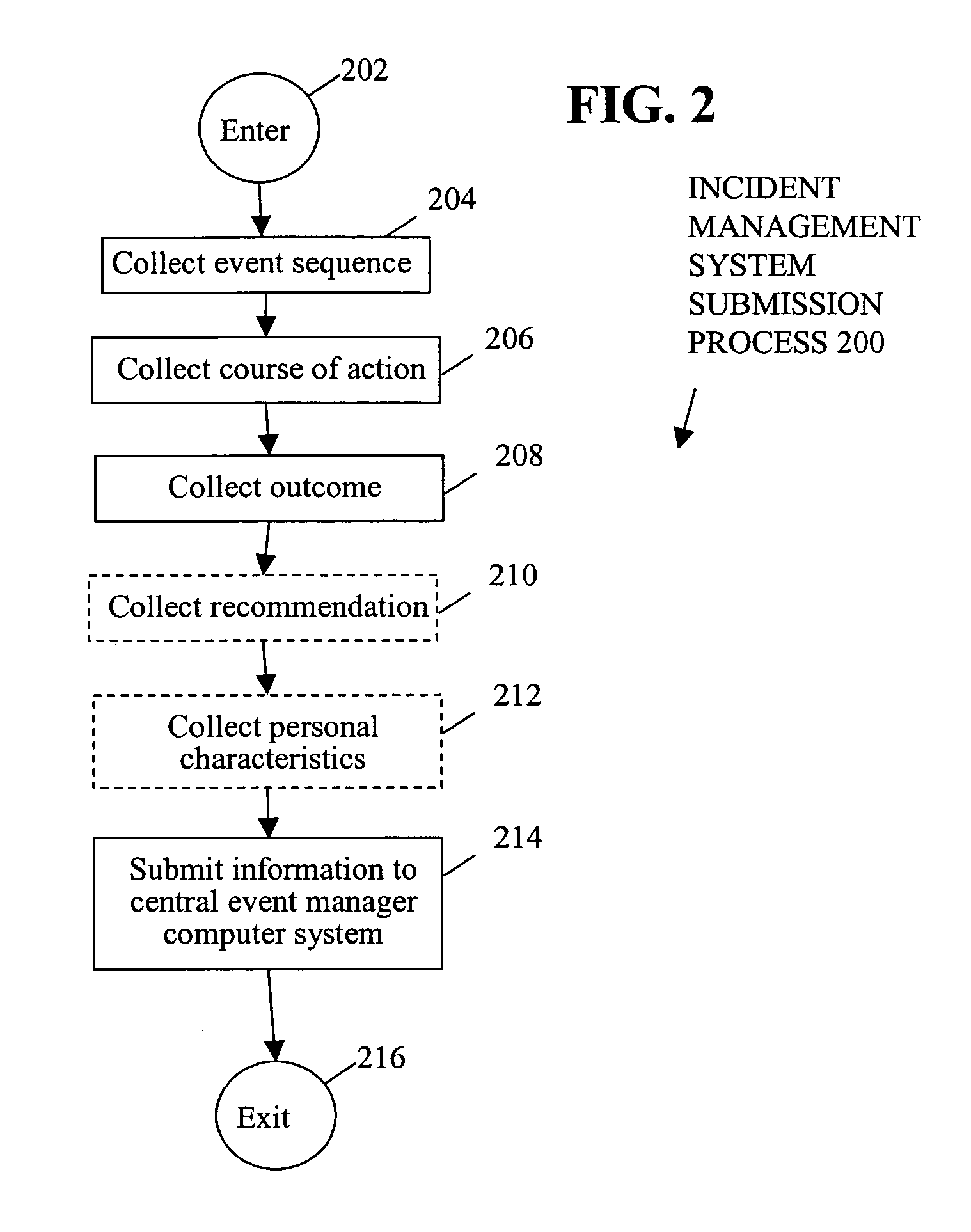
A method includes logging past event sequences in a knowledge base, receiving a real-time event sequence, comparing the real-time event sequence to the past event sequences to determine a predicted event sequence for the real-time event sequence, and providing the predicted event sequence, a suggested course of action with predicted outcome, and a recommendation of a user who previously encountered the event sequence. In the above manner, use of subjectively characterized and / or raw historic data to match real-time event sequences provides users with both subjective advice from those who had previously faced similar conditions as well as raw statistical predictions as to what is expected to come next. This allows the users to take a course of action that results in the most desirable outcome.
Owner:CA TECH INC
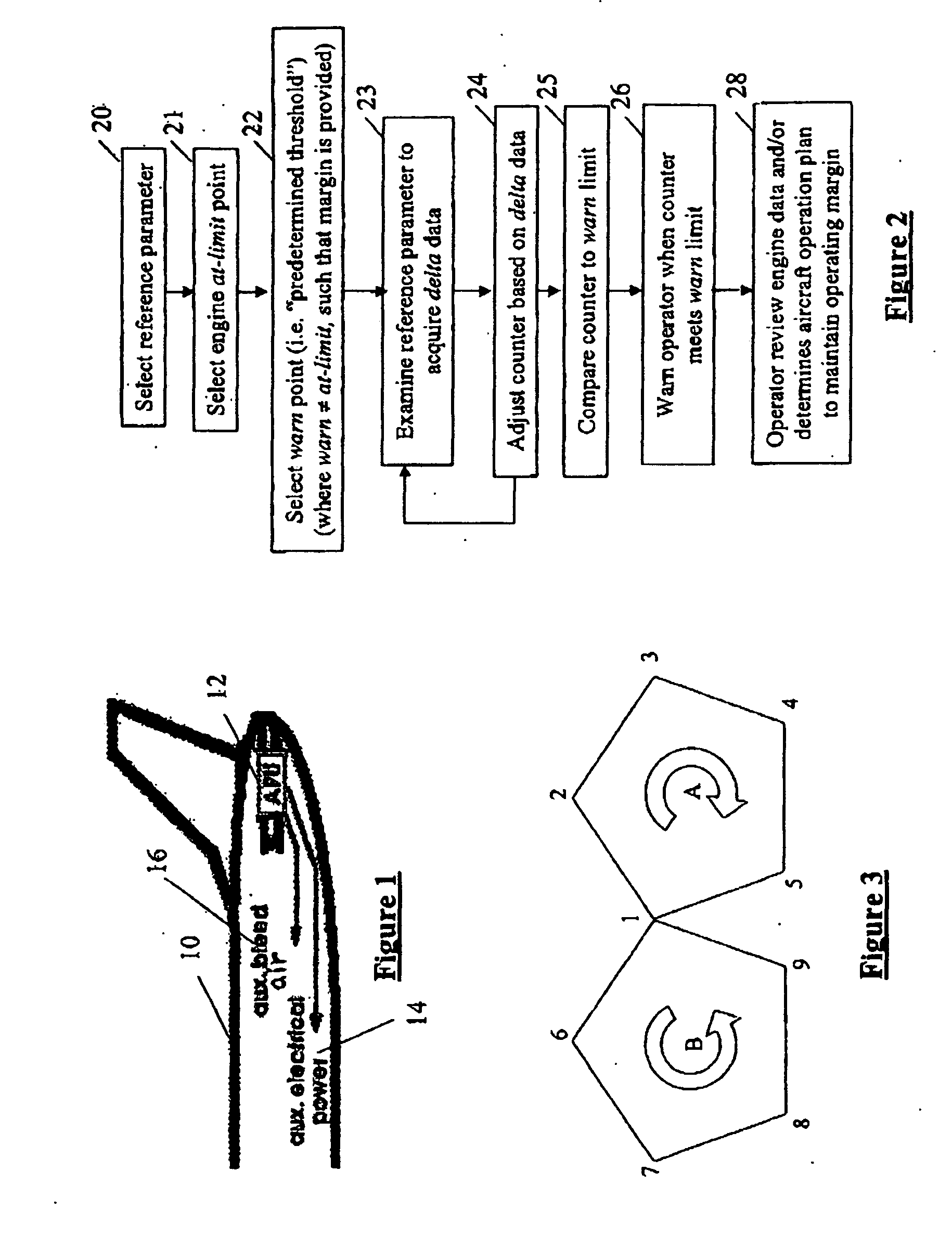
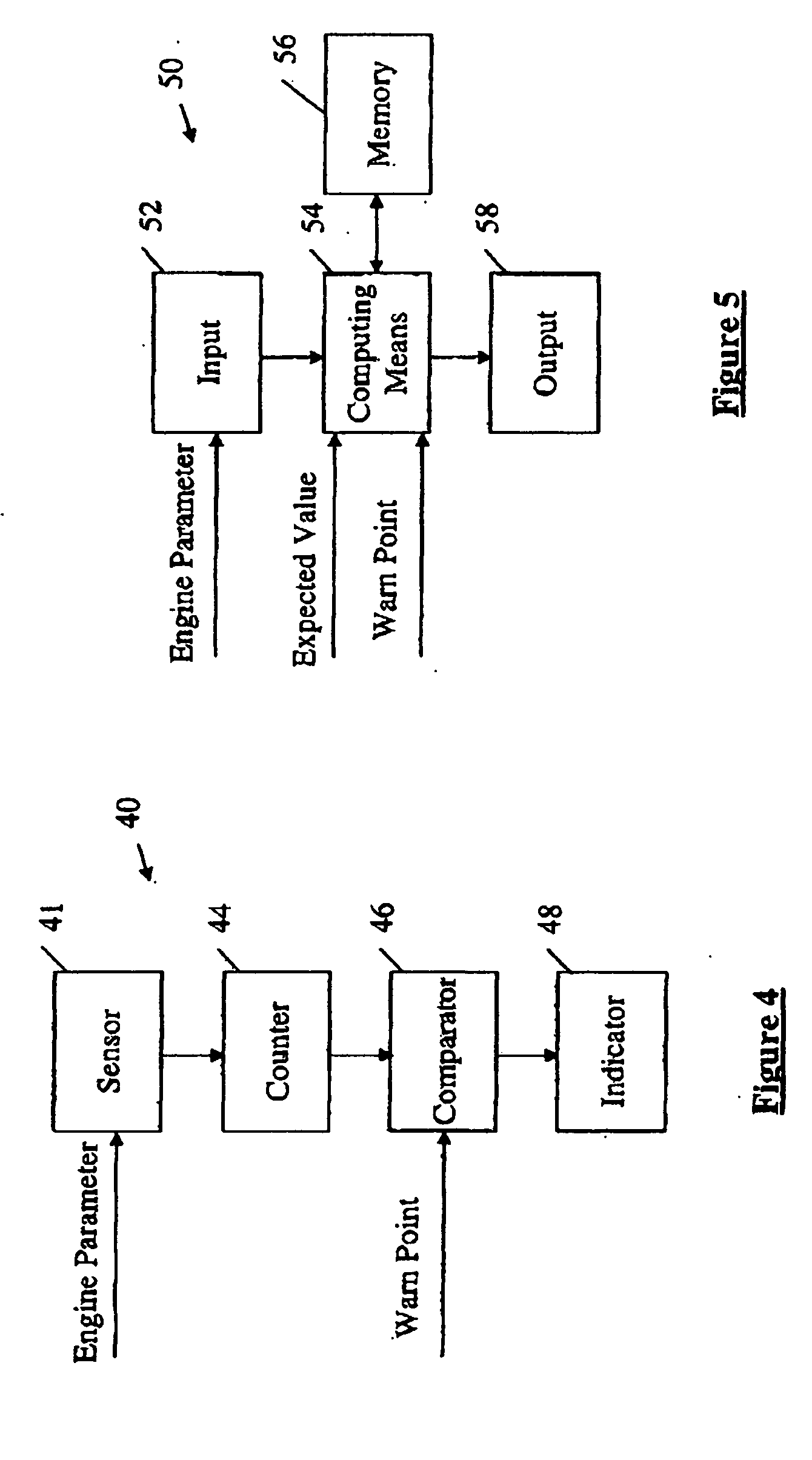
Method of monitoring gas turbine engine operation
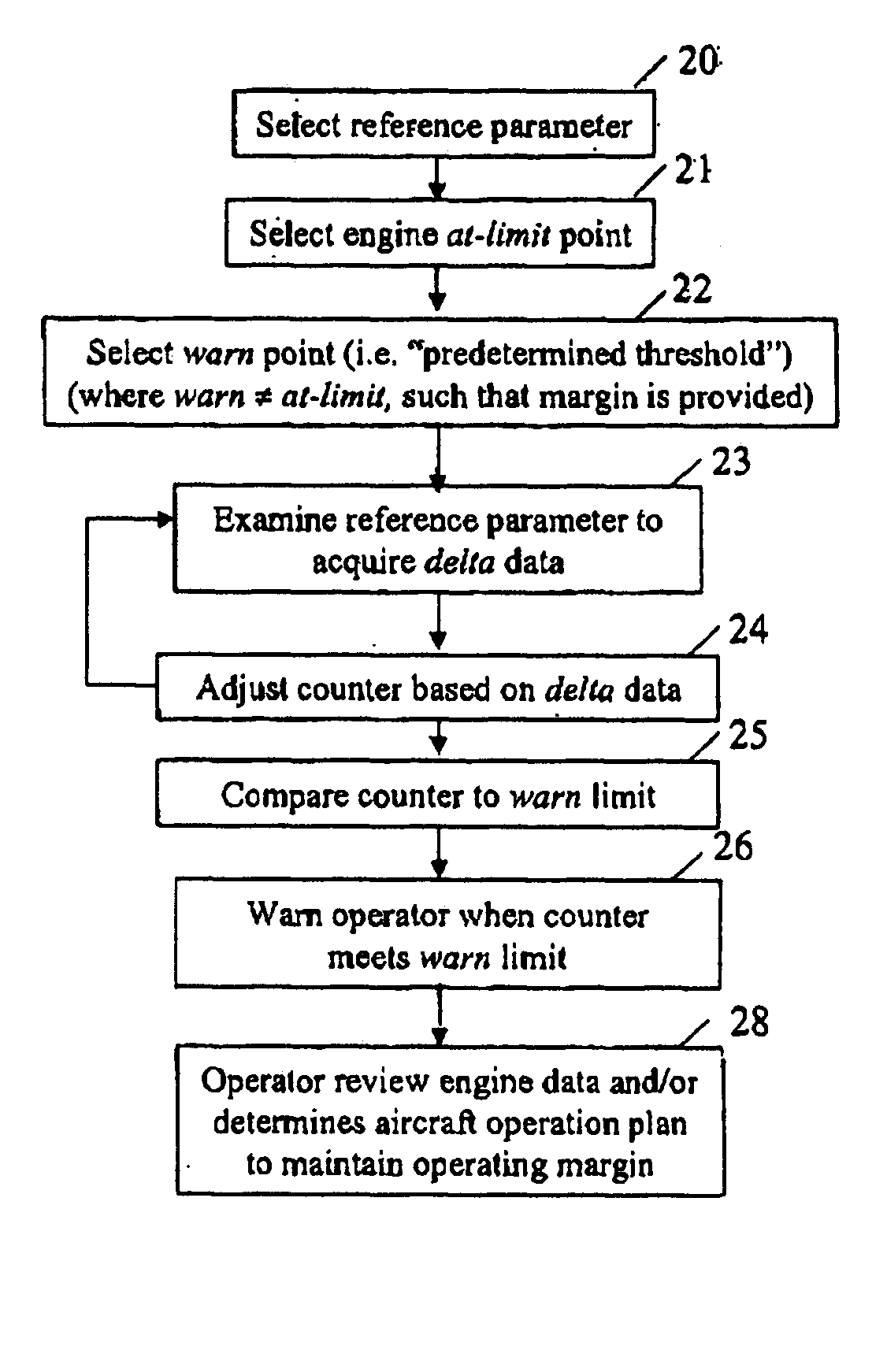
ActiveUS20050261820A1Easy to operateVehicle testingTurbine/propulsion fuel supply systemsEngineeringCourse of action
A system, method and apparatus for monitoring the performance of a gas turbine engine. A counter value Indicative of the comparison between the engine condition and the threshold condition is adjusted. The aircraft operator is warned of an impending maintenance condition based on the counter value and determines an appropriate course of action.
Owner:PRATT & WHITNEY CANADA CORP
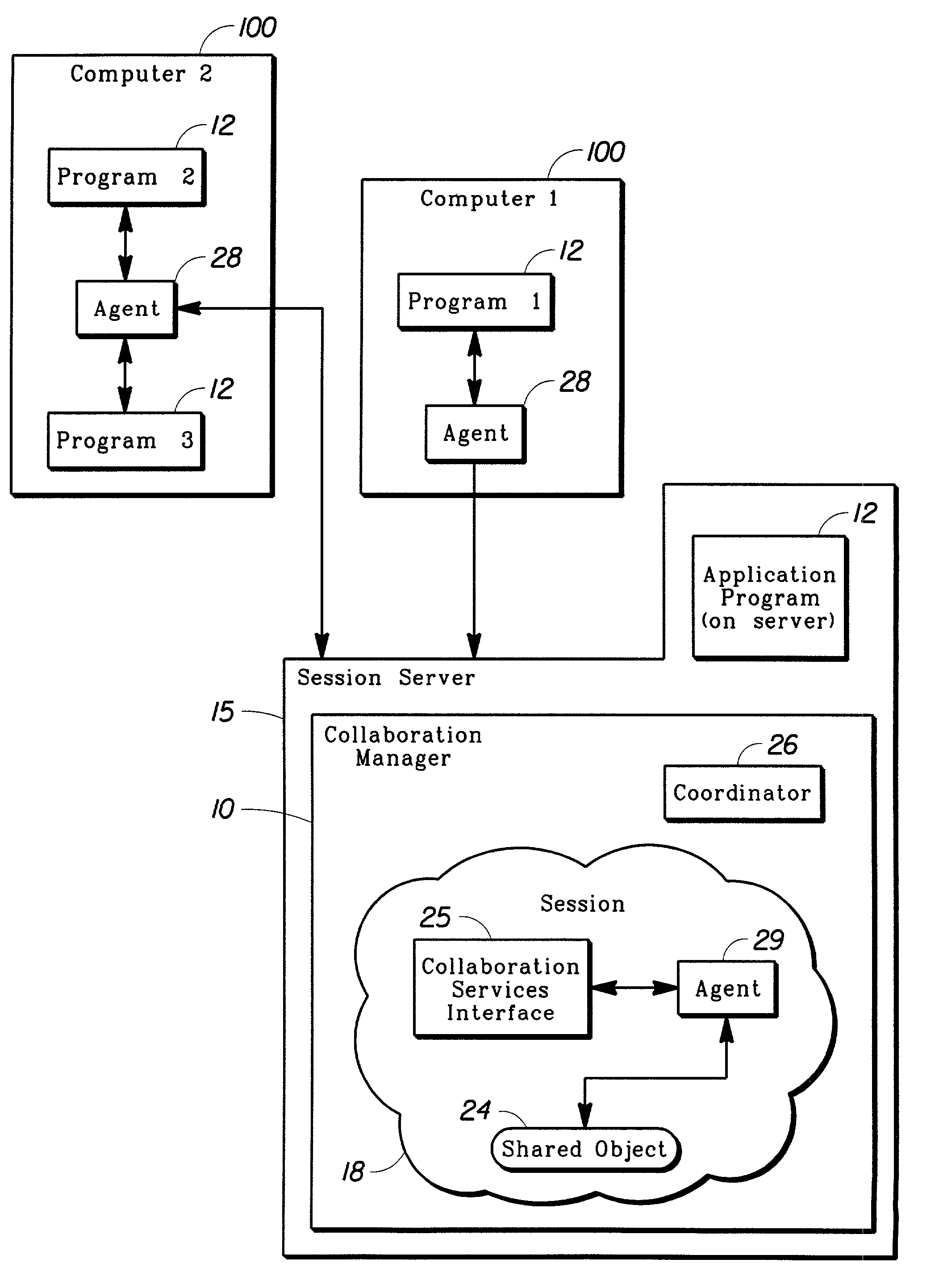
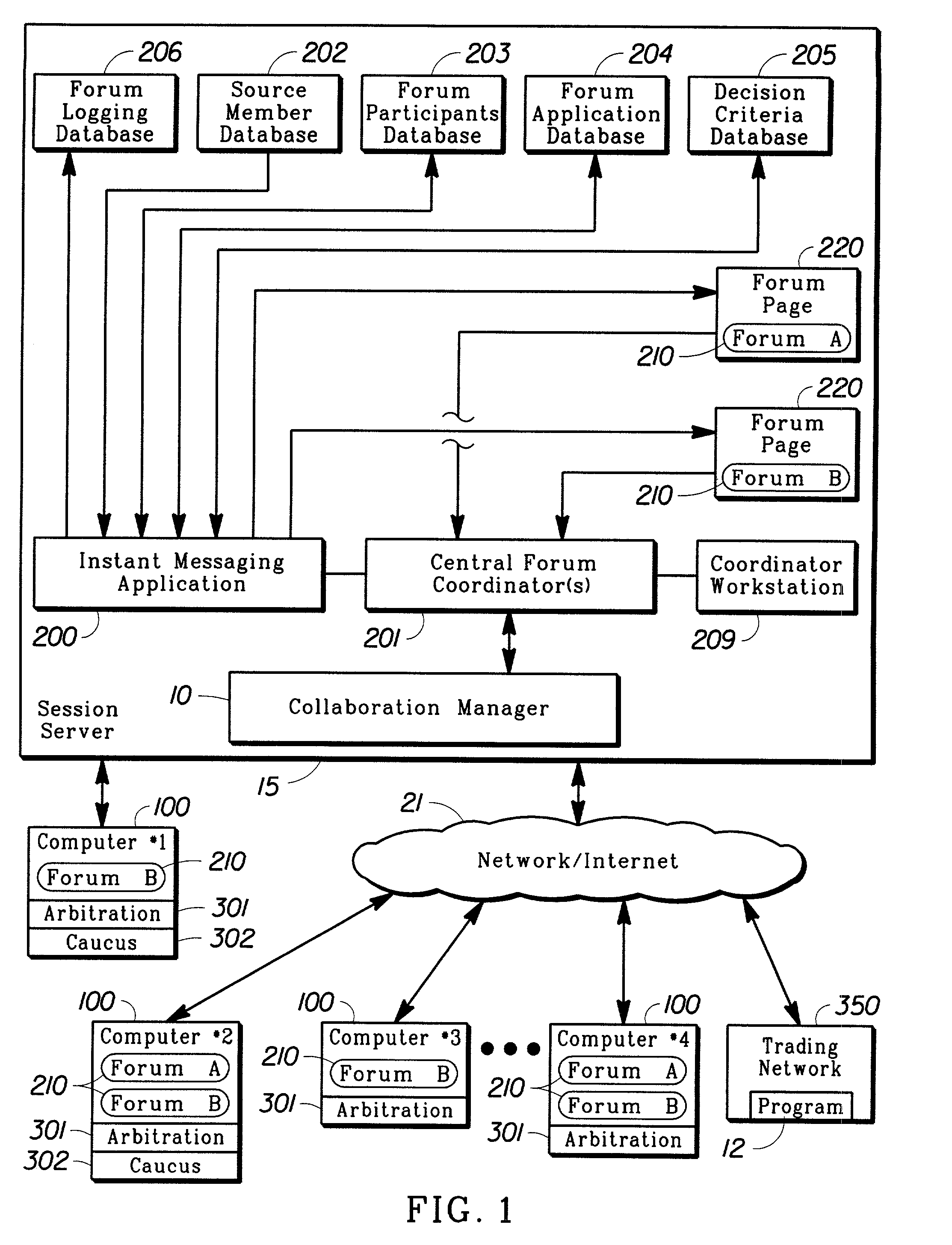
Method for collective decision-making
InactiveUS6980983B2Data processing applicationsDigital data processing detailsElectronic communicationCourse of action
A method and a computer program product for promoting collaborative, consensus-driven decisions from a plurality of decision-making entities using electronic communications in a real-time forum. The inventive instant messaging application can be used for registering participants, developing forum pages, communicating queries, receiving messages and tallying responses that can enable implementation of online trading transactions. The application module and support databases are maintained by one or more central coordinators that reside as software objects on a server. Setpoint values are used for measuring the extent to which the participants' cumulative response satisfies one or more decision parameters. Arbitration and intra-group caucussing can also be initiated as a means to promote consensus and arrive at a collective decision. The collective decision can be used to initiate a specific course of action that may involve further communications with one or more remote trading networks.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com