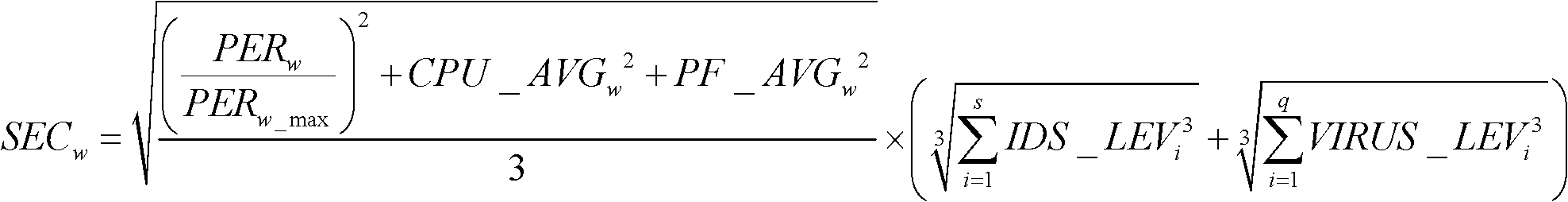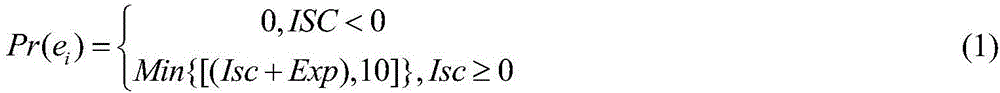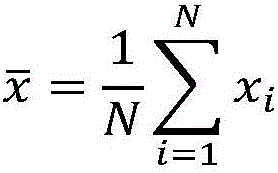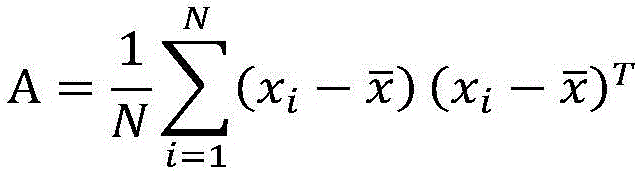Patents
Literature
278 results about "Network security management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
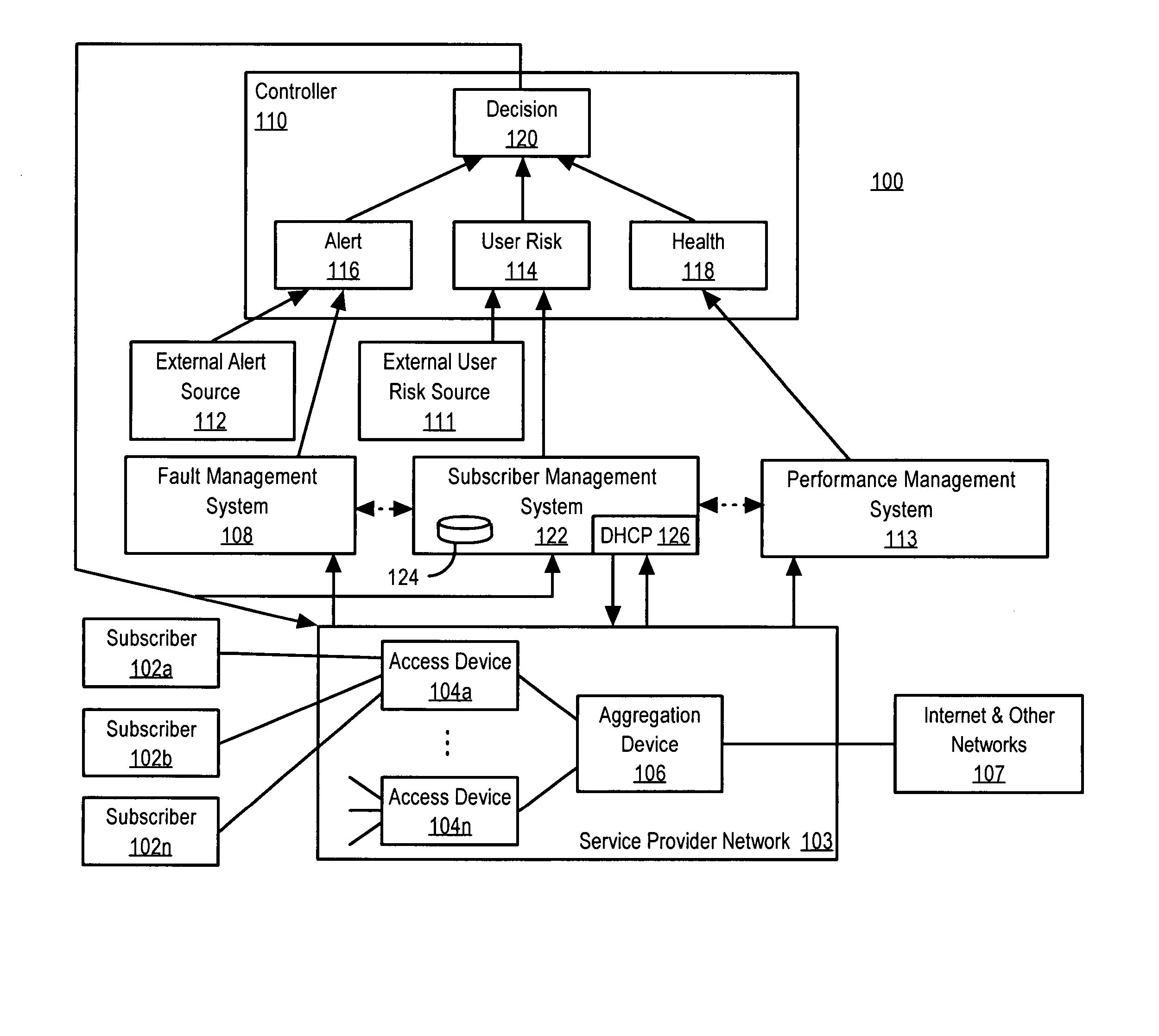
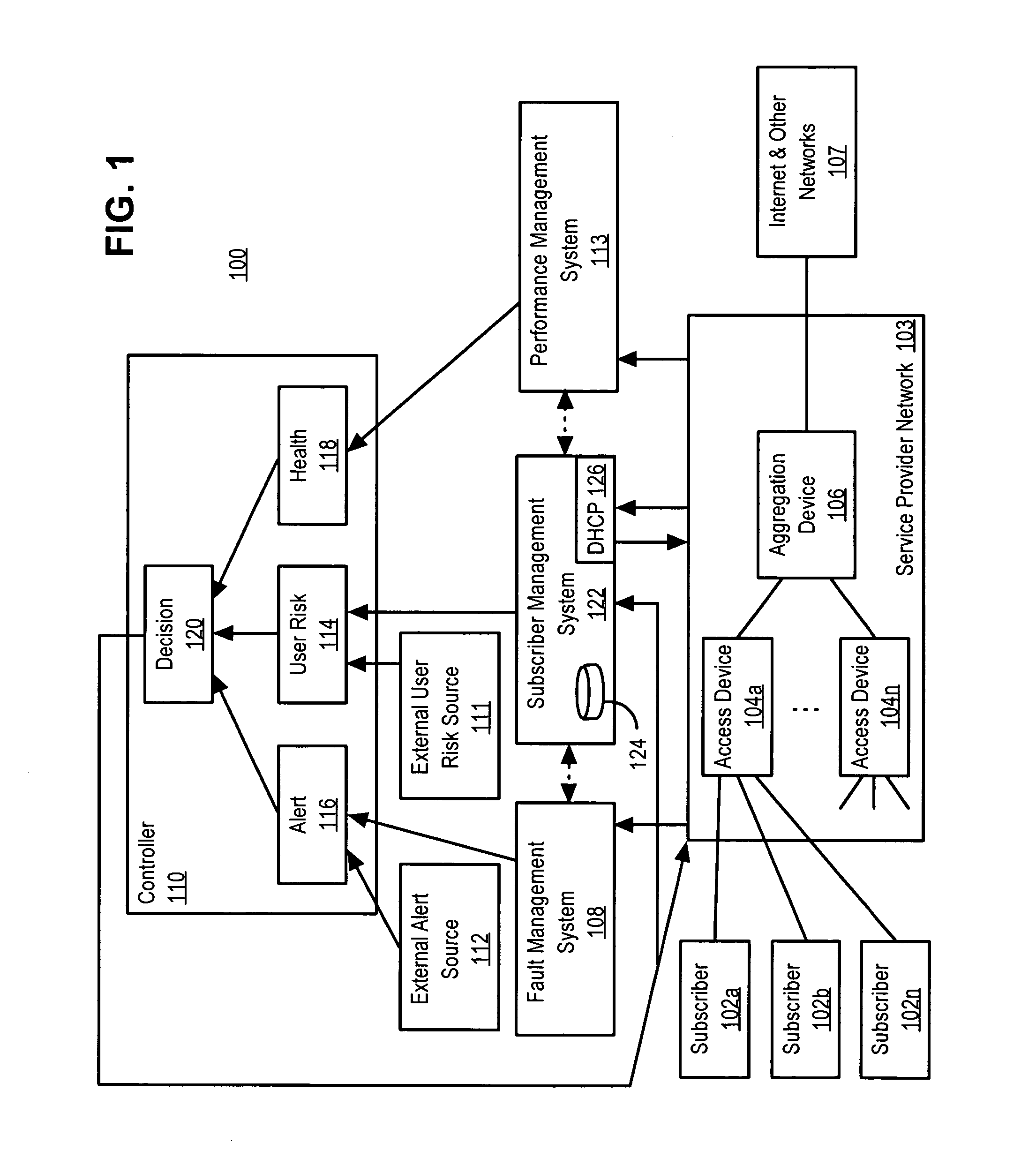
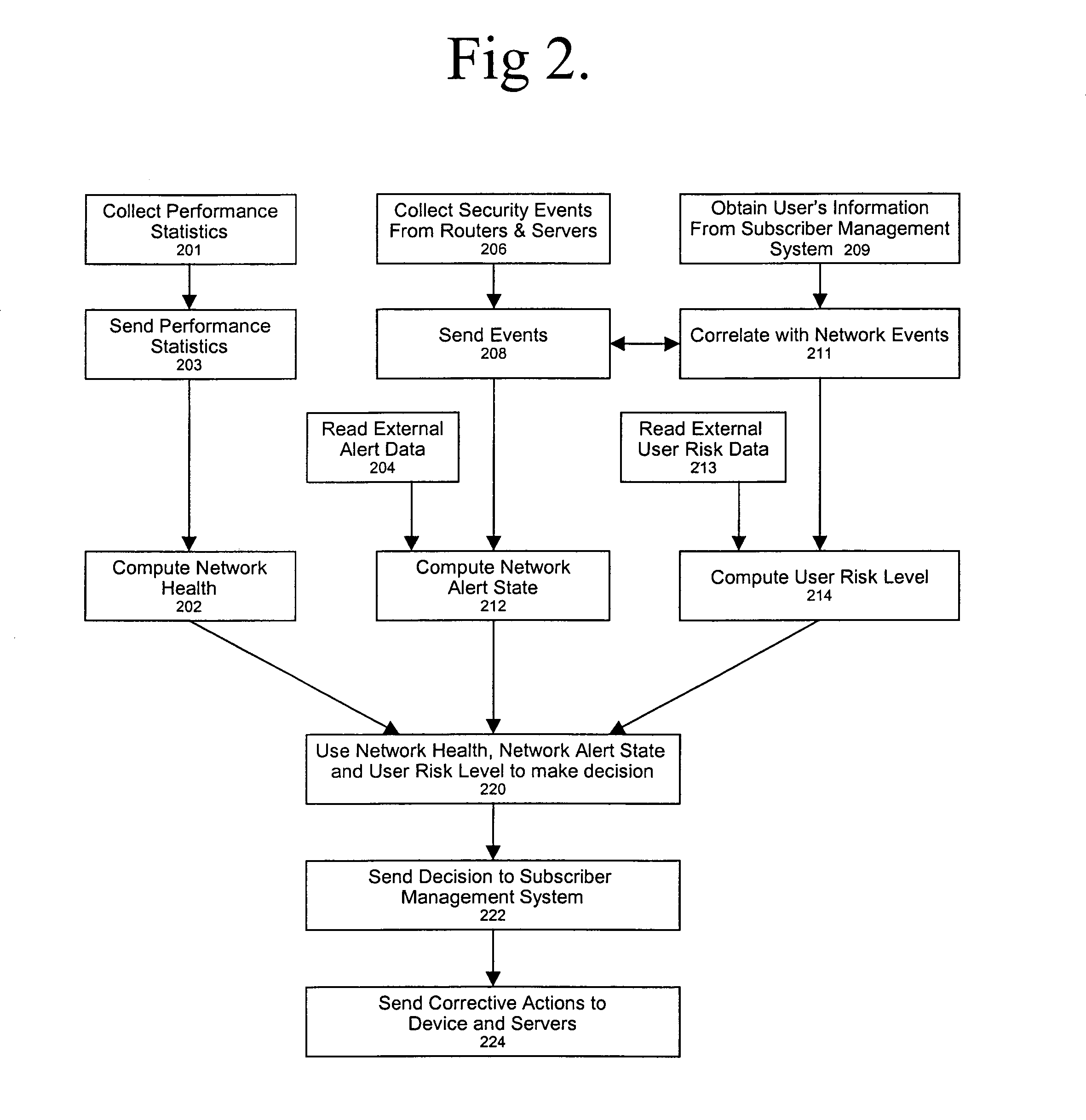
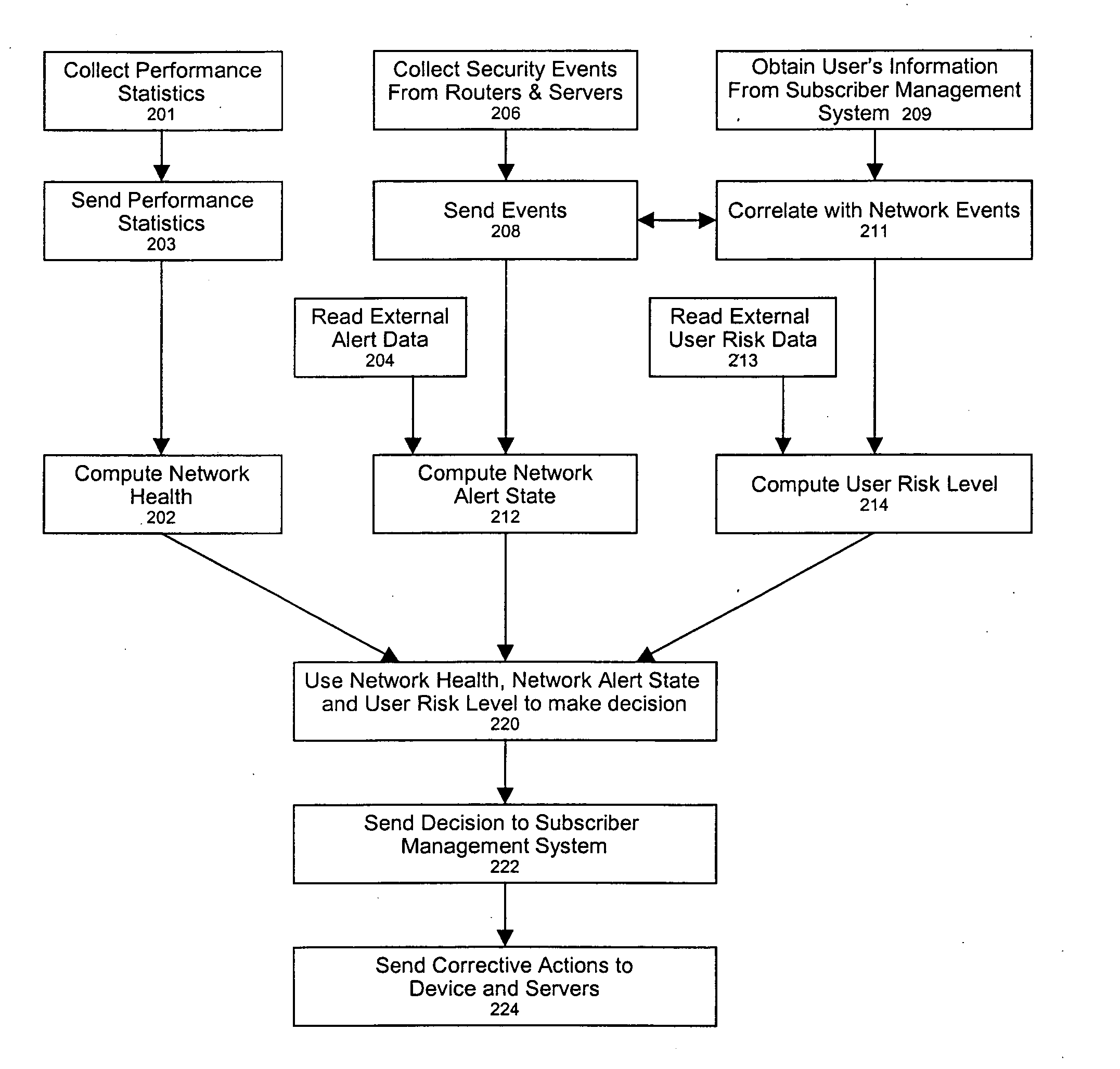
Network security management includes various rules and procedures adopted by network administrators to ensure that unauthorized users do not obtain access. Security involves a host of policies that limit access. The process makes the network secure and protects and manages network operations.
Policy-based network security management
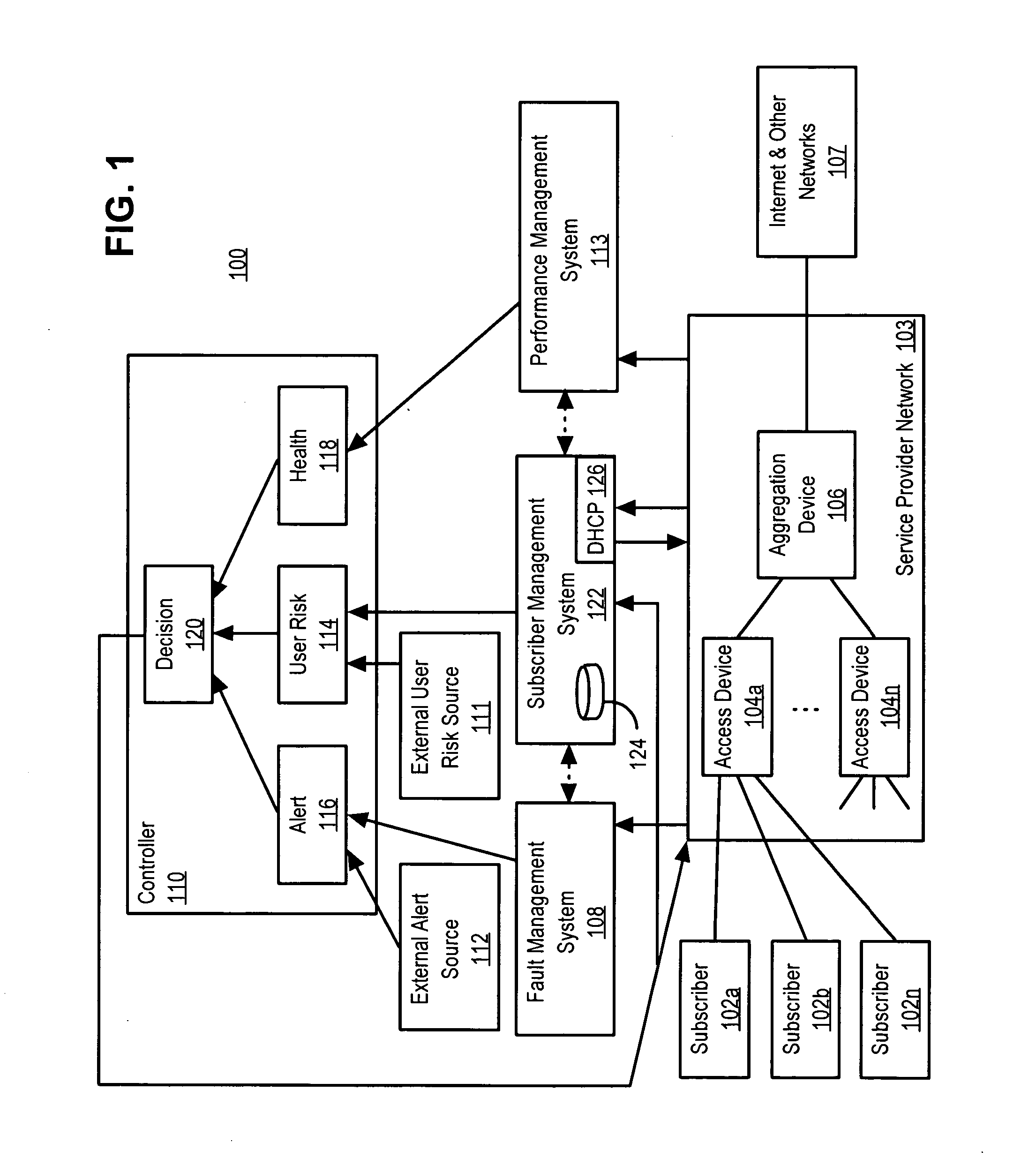
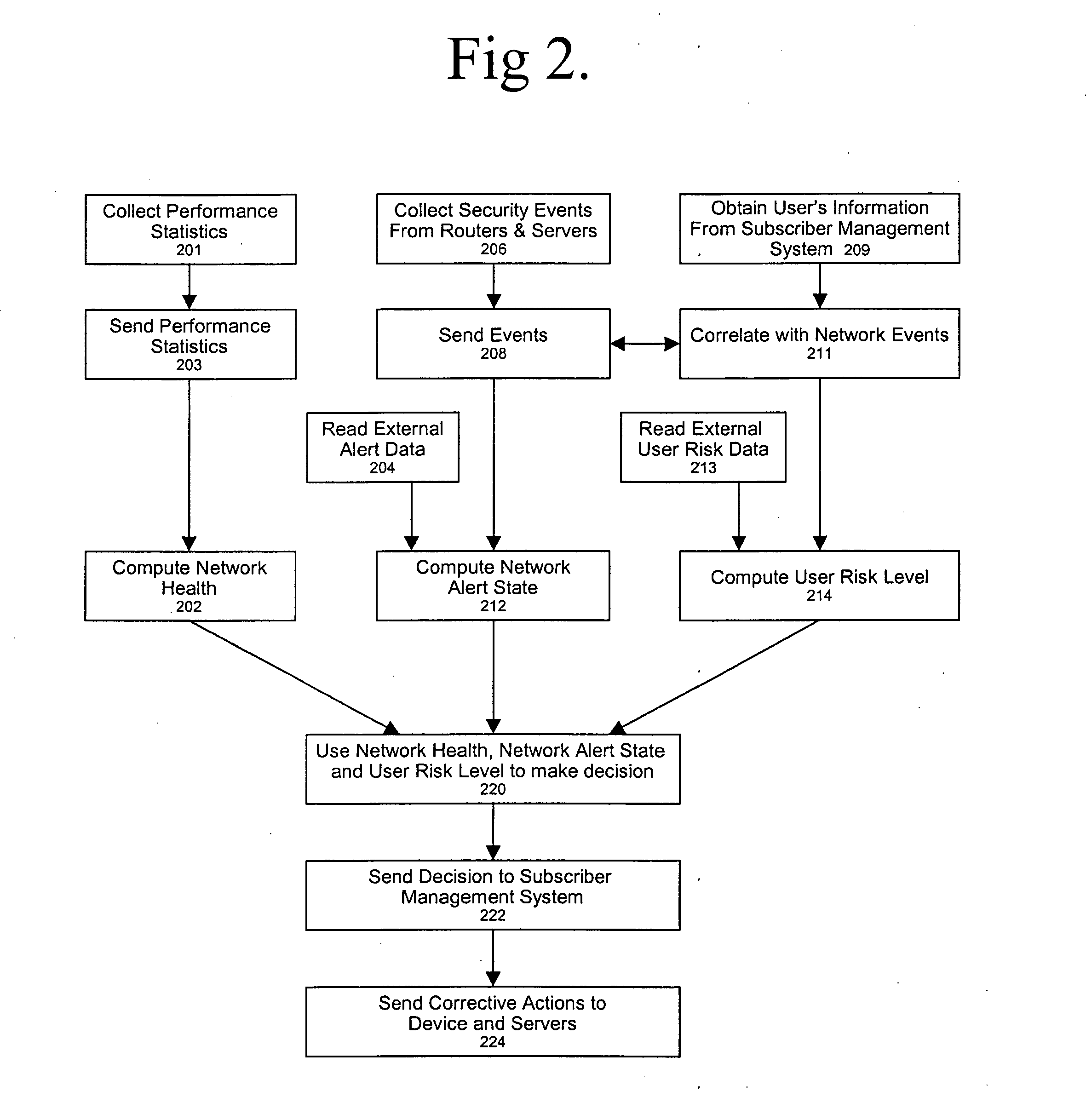
ActiveUS7237267B2Memory loss protectionError detection/correctionNetwork resource managementCourse of action
A policy-based network security management system is disclosed. In one embodiment, the system comprises a security management controller comprising one or more processors; a computer-readable medium carrying one or more sequences of instructions for policy-based network security management, wherein execution of the one or more sequences of instructions by the one or more processors causes the one or more processors to perform the steps of receiving a set of data regarding a user of a computer network; automatically deciding on a course of action based on the set of data, wherein the course of action may be adverse to the user although the set of data is insufficient to establish whether the user is performing a malicious action; and sending signals to one or more network elements in the computer network to implement the decision.
Owner:CISCO TECH INC
Policy-based network security management
ActiveUS20050086502A1Potential economic damageReduce riskMemory loss protectionUser identity/authority verificationCourse of actionSecurity management
A policy-based network security management system is disclosed. In one embodiment, the system comprises a security management controller comprising one or more processors; a computer-readable medium carrying one or more sequences of instructions for policy-based network security management, wherein execution of the one or more sequences of instructions by the one or more processors causes the one or more processors to perform the steps of receiving a set of data regarding a user of a computer network; automatically deciding on a course of action based on the set of data, wherein the course of action may be adverse to the user although the set of data is insufficient to establish whether the user is performing a malicious action; and sending signals to one or more network elements in the computer network to implement the decision.
Owner:CISCO TECH INC
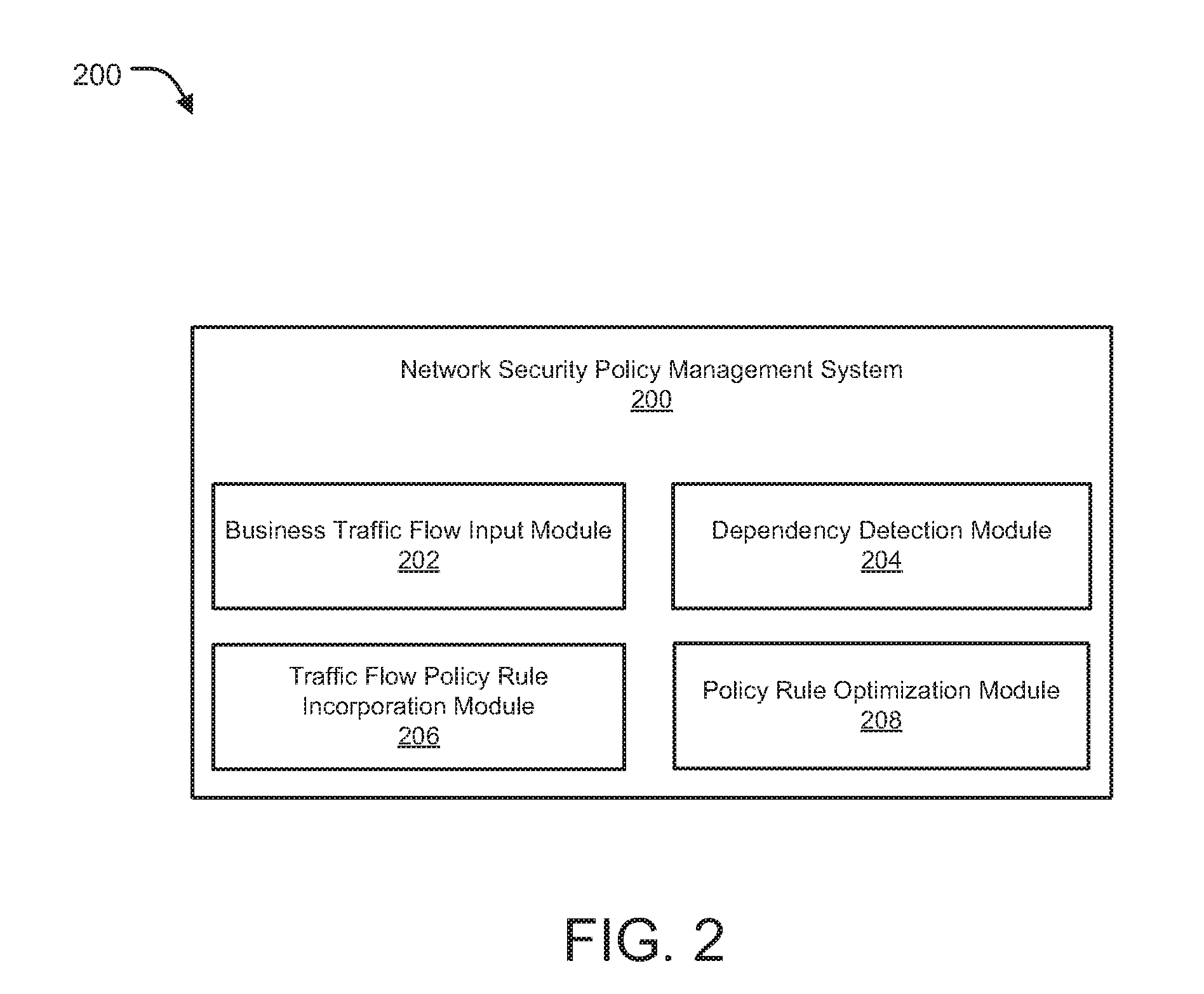
Dynamically optimized security policy management
ActiveUS20160191466A1TransmissionSpecial data processing applicationsTraffic characteristicPriority setting
Methods and systems for dynamically optimized rule-based security policy management are provided. A request is received by a network security management device to add a new traffic flow policy rule to multiple existing policy rules managed by the network security management device. Dependencies of the new traffic flow policy rule on the existing policy rules are automatically determined. An updated set of policy rules is formed by incorporating the new traffic flow policy rule within the existing policy rules based on the dependencies. The updated set of policy rules is then optimized by grouping, reordering and / or deleting a sub-set of policy rules of the updated set of policy rules based on one or more of weights assigned to particular types of traffic, preference settings, priority settings, network traffic characteristics and usage statistics for each policy rule of the updated set of policy rules.
Owner:FORTINET
Method and system for cyber security management of industrial control systems
ActiveUS20110039237A1Low chanceFull accessMemory loss protectionError detection/correctionCommand and controlData acquisition
A method and system for cyber security management of Supervisory Control And Data Acquisition (SCADA) systems is provided to enhance situational awareness and cyber security management for industrial control systems. A centralized System Security Manager (SSM) is integrated into a SCADA to collect security related data for the industrial control system and an integrated command and control user interface displays security related data, a system security level, and interfaces with a user to allows for changing of system security settings for the industrial control system based on the security related data collected and manages changes in operational state of the SCADA based on the security level to restrict use of system interfaces and system accesses.
Owner:SIEMENS AG
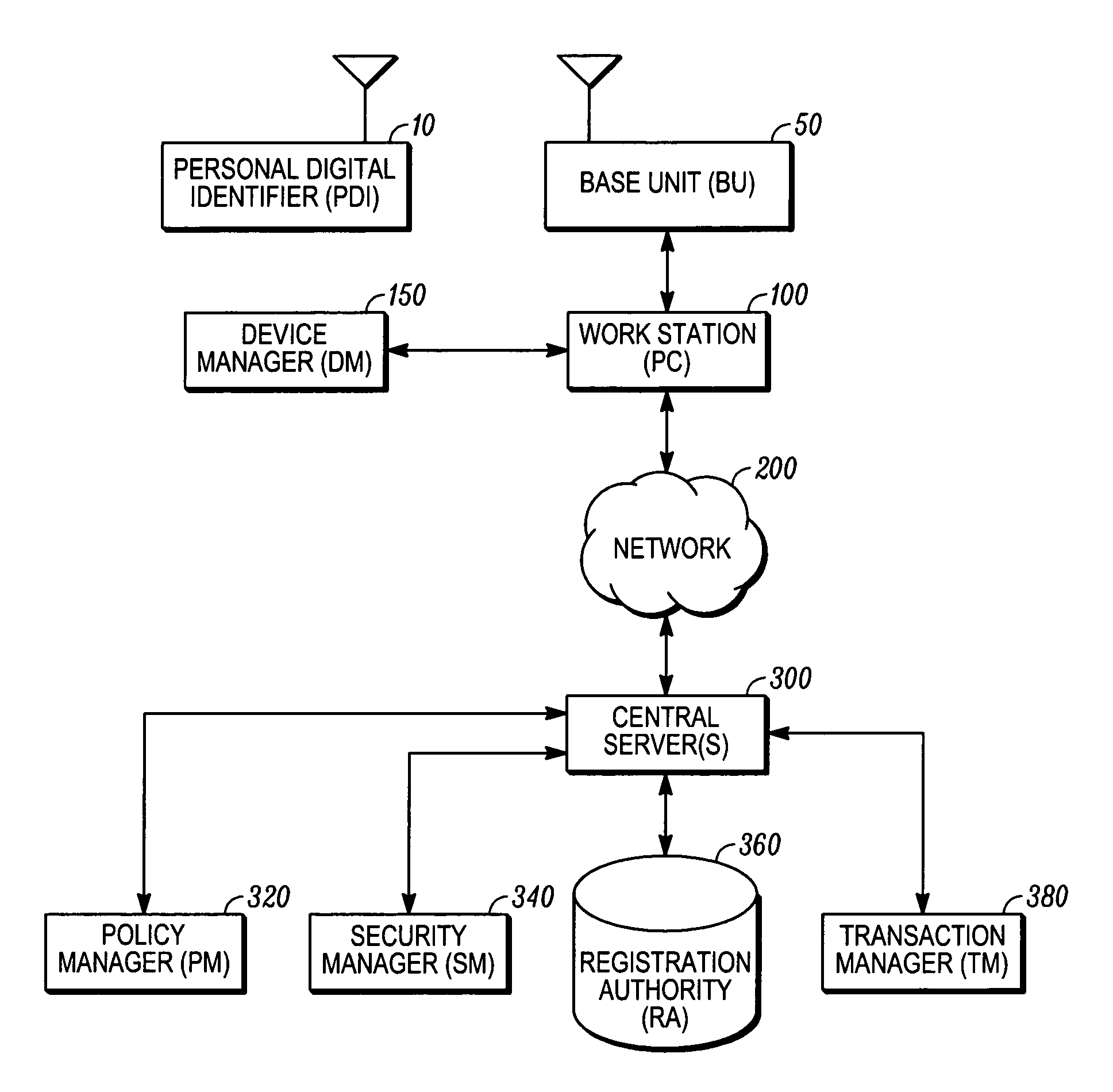
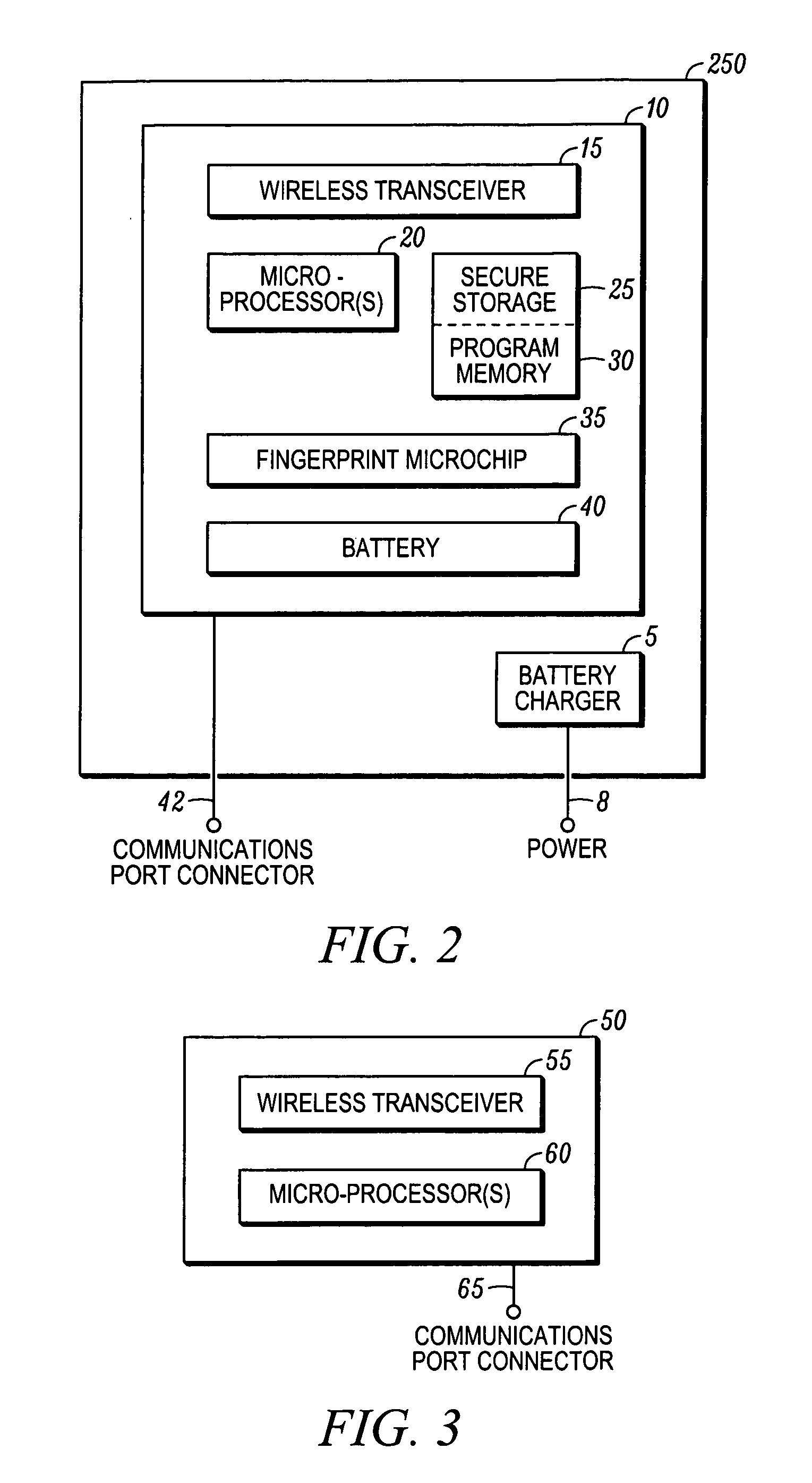
Method and system for securing a computer network and personal identification device used therein for controlling access to network components
InactiveUS7310734B2Real-time authenticationDigital data processing detailsUser identity/authority verificationDigital signatureIdentification device
An improved computer network security system and a personal identifier device used for controlling network with real time authentication of both a person's identity and presence at a computer workstation is provided. A new user is registered to a portable personal digital identifier device and, within the portable personal digital identifier device, an input biometric of the user is received and a master template is derived therefrom and securely maintained in storage. A private key and public key encryption system is utilized to authenticate a user registered to the portable personal digital identifier device. The personal digital identifier device verifies the origin of a digitally signed challenge message from the network security manager component. A digitally and biometrically signed challenge response message is produced and transmitted by the personal digital identifier device in response to the verified challenge message.
Owner:3M INNOVATIVE PROPERTIES CO
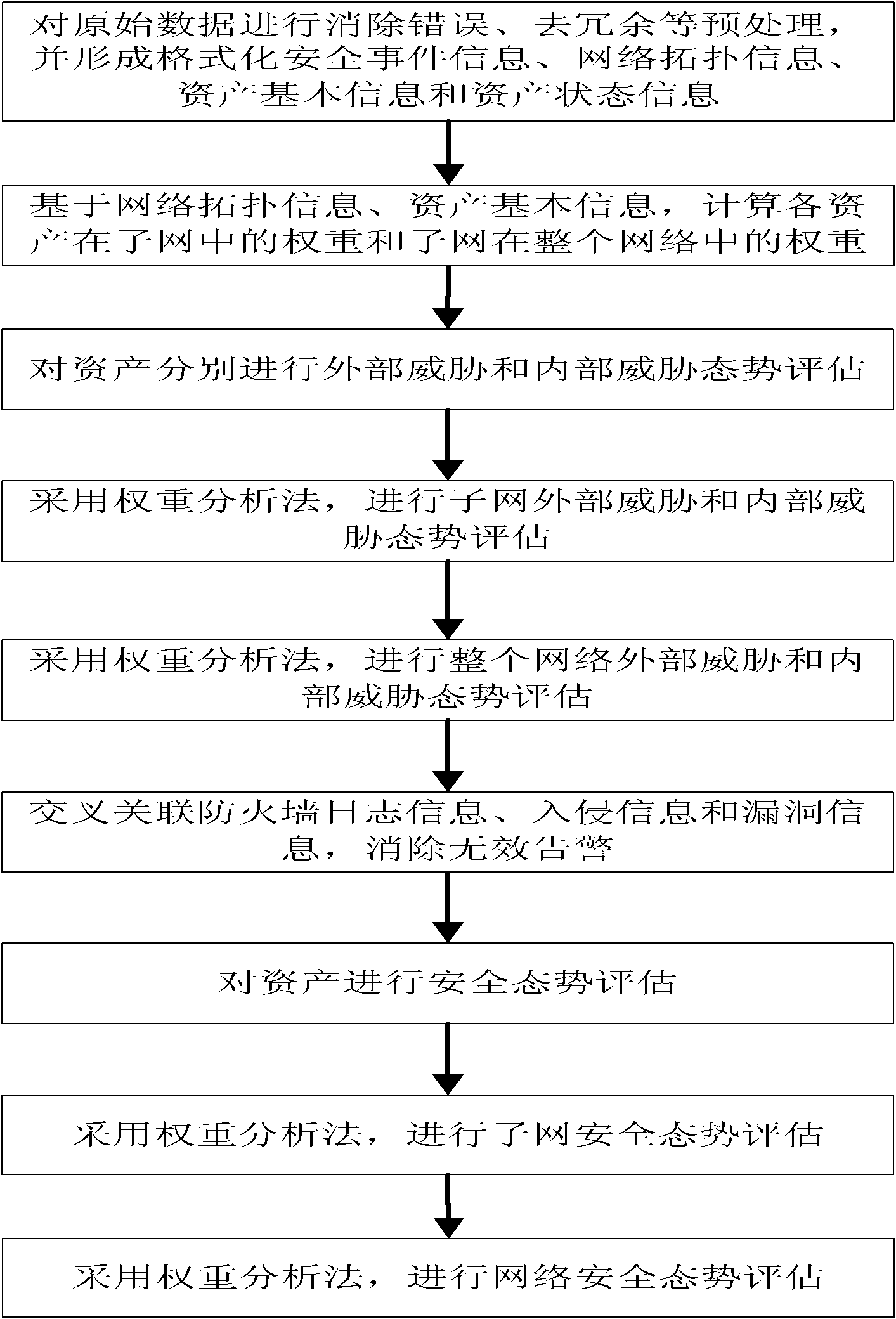
Network security situation evaluation method
ActiveCN102624696AComprehensive evaluation resultsThe assessment results are accurateTransmissionOriginal dataData source
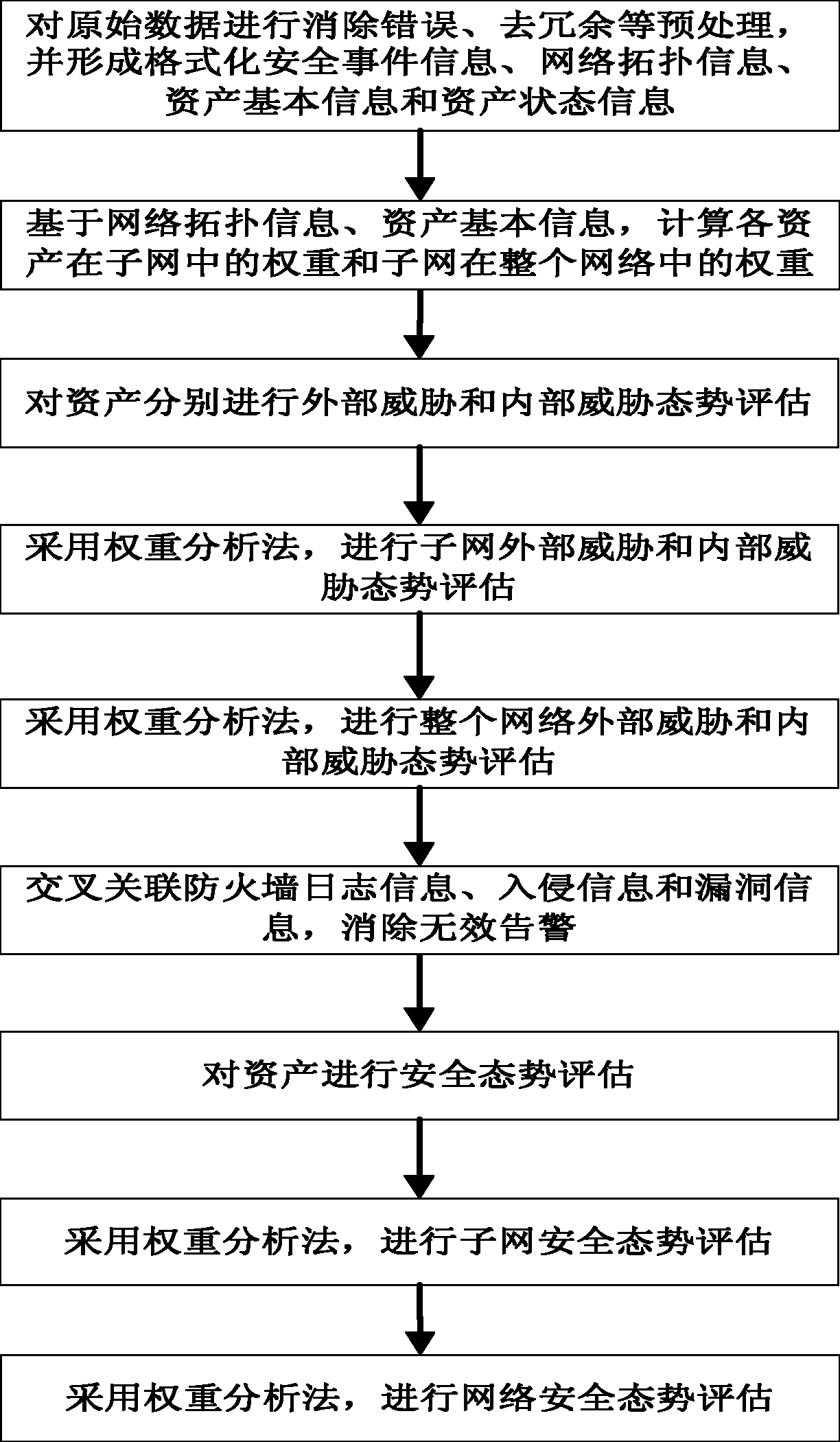
The invention provides a network security situation evaluation method, which comprises the steps as follows: raw data are preprocessed, and the weight of each asset in a subnet and the weight of each subnet in the whole network are calculated; each asset is subject to external threat situation evaluation; each asset is subject to internal threat situation evaluation; by adopting a weight analysis method, each subnet is subject to external threat situation evaluation and internal threat situation evaluation; the network is subject to external threat situation evaluation and internal threat situation evaluation; firewall log information, intrusion information and vulnerability information are correlated in a crossed manner, so as to eliminate ineffective alarms; the security situation of each asset is comprehensively evaluated; the security situation of each subnet is comprehensively evaluated; and by adopting the weight analysis method, the security situation of the network is comprehensively evaluated. By adopting the network security situation evaluation method, the problem of single data source in the prior art is solved, a network security situation evaluation result is enabled to be more comprehensive and more accurate; the overall condition of the network security is truly reflected; and the evaluation result is intuitive and practical and can be directly used for guiding the command and the decision of network security management.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
Electric power system interior APT attack detection and pre-warning system based on network architecture
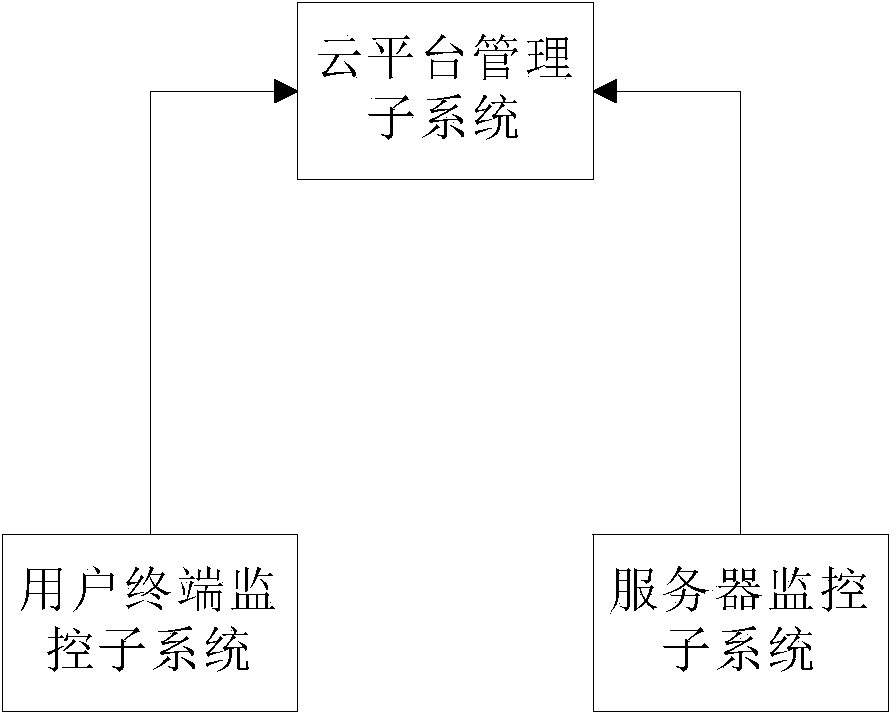
The invention provides an electric power system interior APT attack detection and pre-warning system based on network architecture. The system comprises a user terminal monitoring sub-system, a server monitoring sub-system and a cloud platform management sub-system. According to the characteristic that APT attacks are all pervasive, the APT attack detection and pre-warning system containing a user terminal and a system server is designed. The detection and pre-warning system has the common network security management function, meanwhile conducts analysis of exceptions on logs and events, and excavates and repairs loopholes of the system, after a network system is suffered from the APT attacks, data of attacked equipment can be quickly restored, and the system assists security managers in reversely tracking an attack source.
Owner:STATE GRID CHONGQING ELECTRIC POWER CO ELECTRIC POWER RES INST +1
Enterprise desktop security management and compliance verification system and method
InactiveUS8499330B1Improve developmentEasy to implementDigital data processing detailsAnalogue secracy/subscription systemsEnterprise security managementNetwork security policy
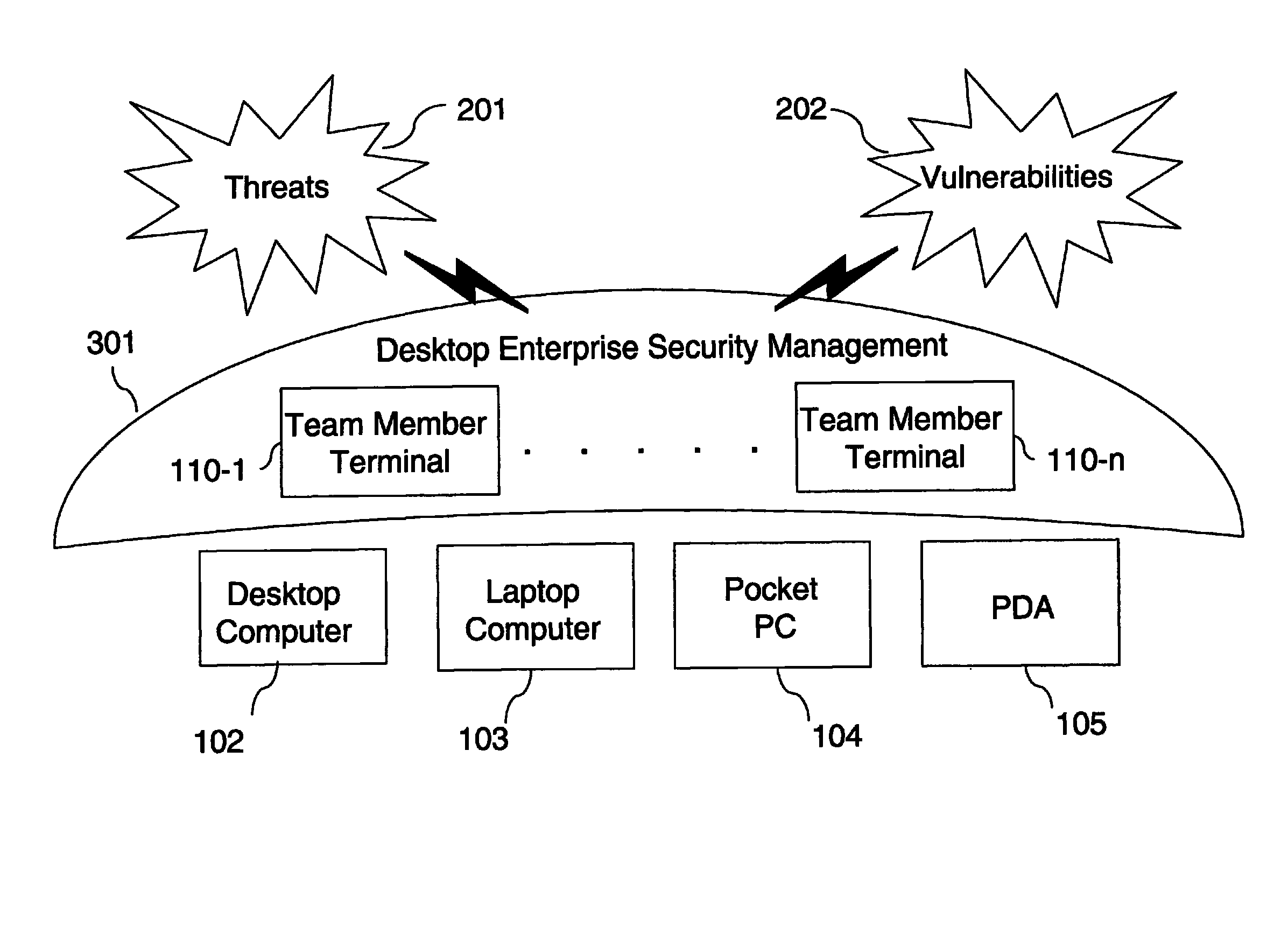
A method for desktop enterprise security management that addresses the multiple network and desktop security needs of an enterprise, facilitates the development, implementation, and enforcement of the enterprise's desktop security policies and procedures, and provides for review and revision of those policies and procedures. The method is based on a four-stage approach to desktop network security management. The first stage lays the foundation for the enterprise's network security policy. The second stage validates users and desktop devices according to the enterprise's desktop security policies, gathers data, and provides feedback to users regarding their compliance with the enterprise's desktop security policies. The third stage enforces the enterprise's desktop security policies by blocking access by desktop devices and / or users that do not comply with the enterprise's desktop security policies. The fourth stage includes periodic review of the enterprise's needs so that new desktop security support teams can be identified and the enterprise's desktop security policies implemented with the new teams.
Owner:AT&T INTPROP I L P
System and method for managing security of general network
InactiveCN101582883AImprove general performanceIncrease opennessData switching networksDistributed securityProtection system
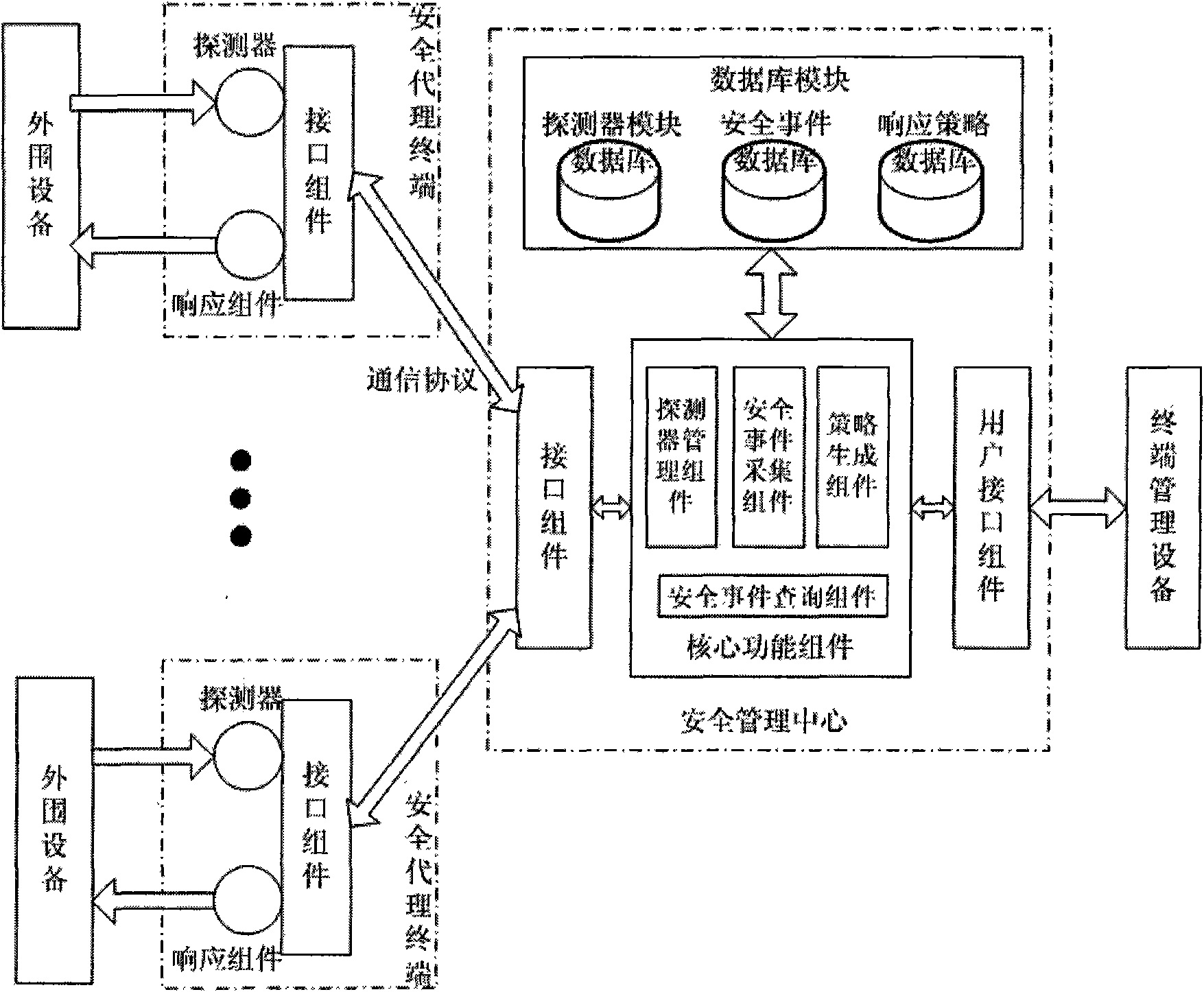
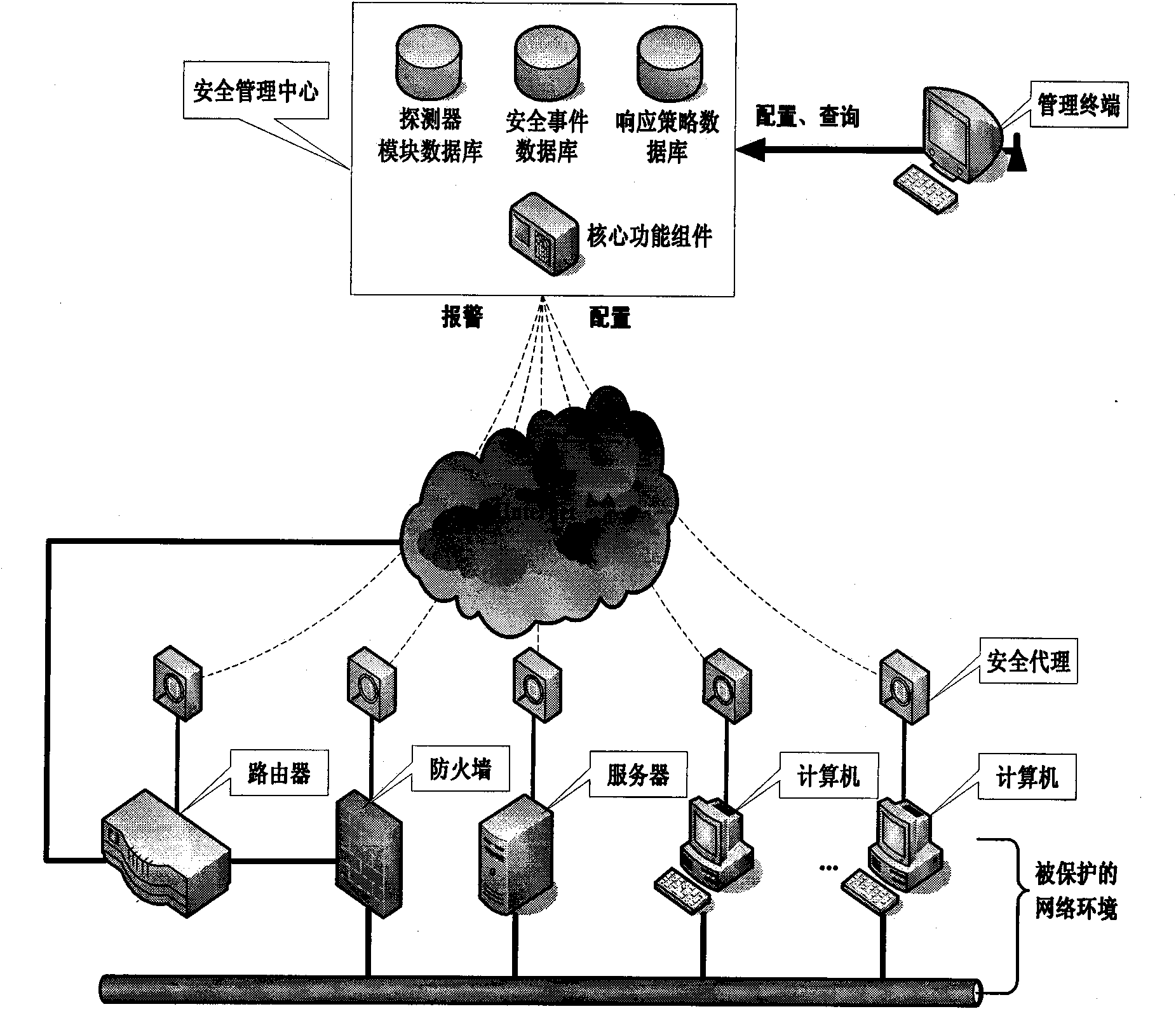
The invention discloses a system and a method for managing security of a general network, and mainly overcomes the defects of poor openness and expansibility and weak functional completeness existing in the prior network security management system. The system mainly comprises peripheral equipment, a security agent terminal, a security management center and terminal management equipment, wherein the security management center applies security technology of network access control, intrusion detection, virus detection and vulnerability management to the security agent terminal through an interface component, a data base module and a user interface component; and under the unified management and control, all security technology is mutually complemented and matched to detect and control network behaviors, so that a distributed security protection system structure in which security strategies are under central management and the security detection is separately distributed is formed. The system and the method have the advantages of flexible configuration, easy expansion, good openness, support of the different level management, and suitability for the security management and protection of the computer network in governments, colleges and universities, and large- and medium-sized enterprises.
Owner:XIDIAN UNIV
Automated generation of access control rules for use in a distributed network management system that uses a label-based policy model
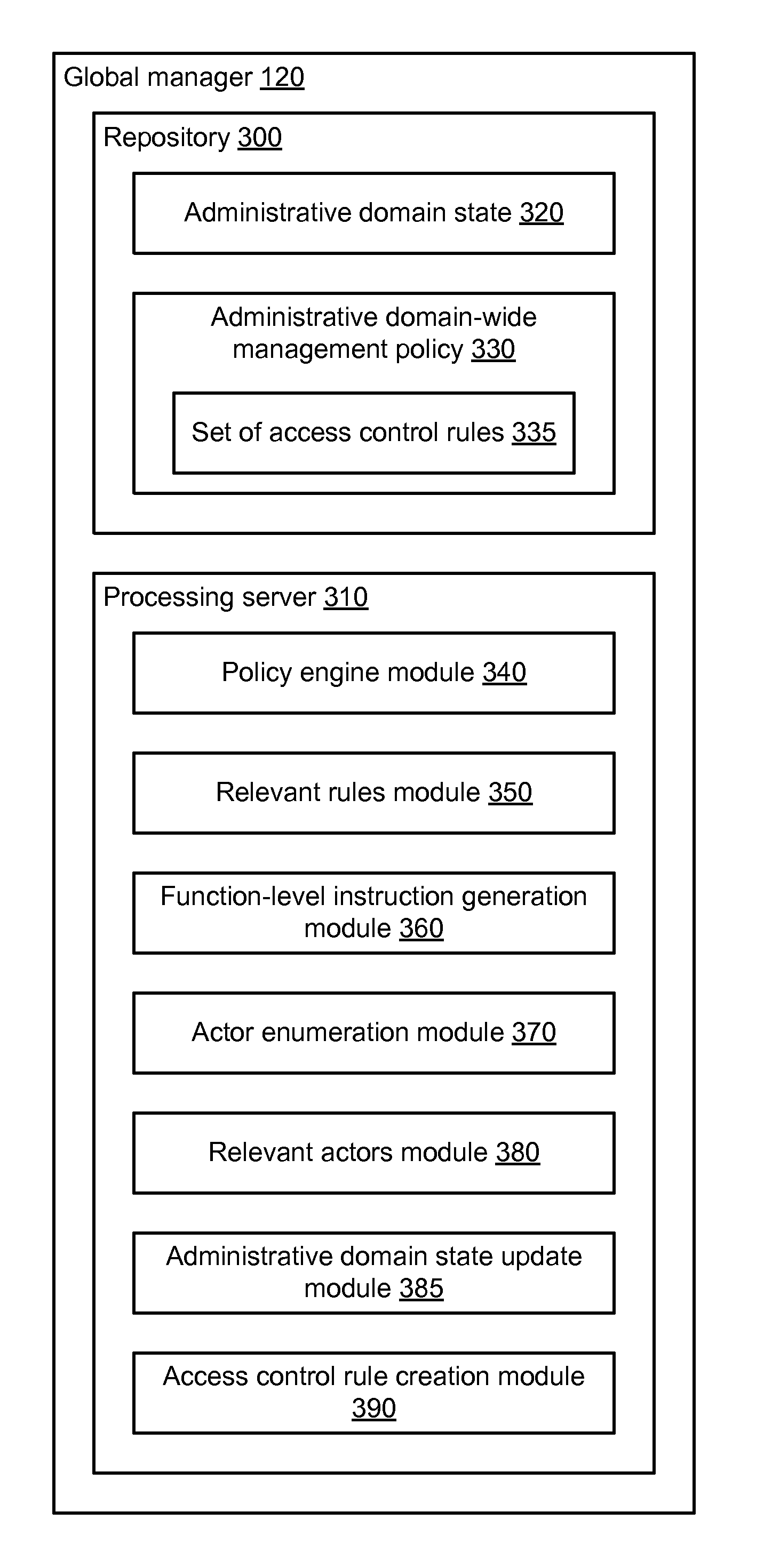
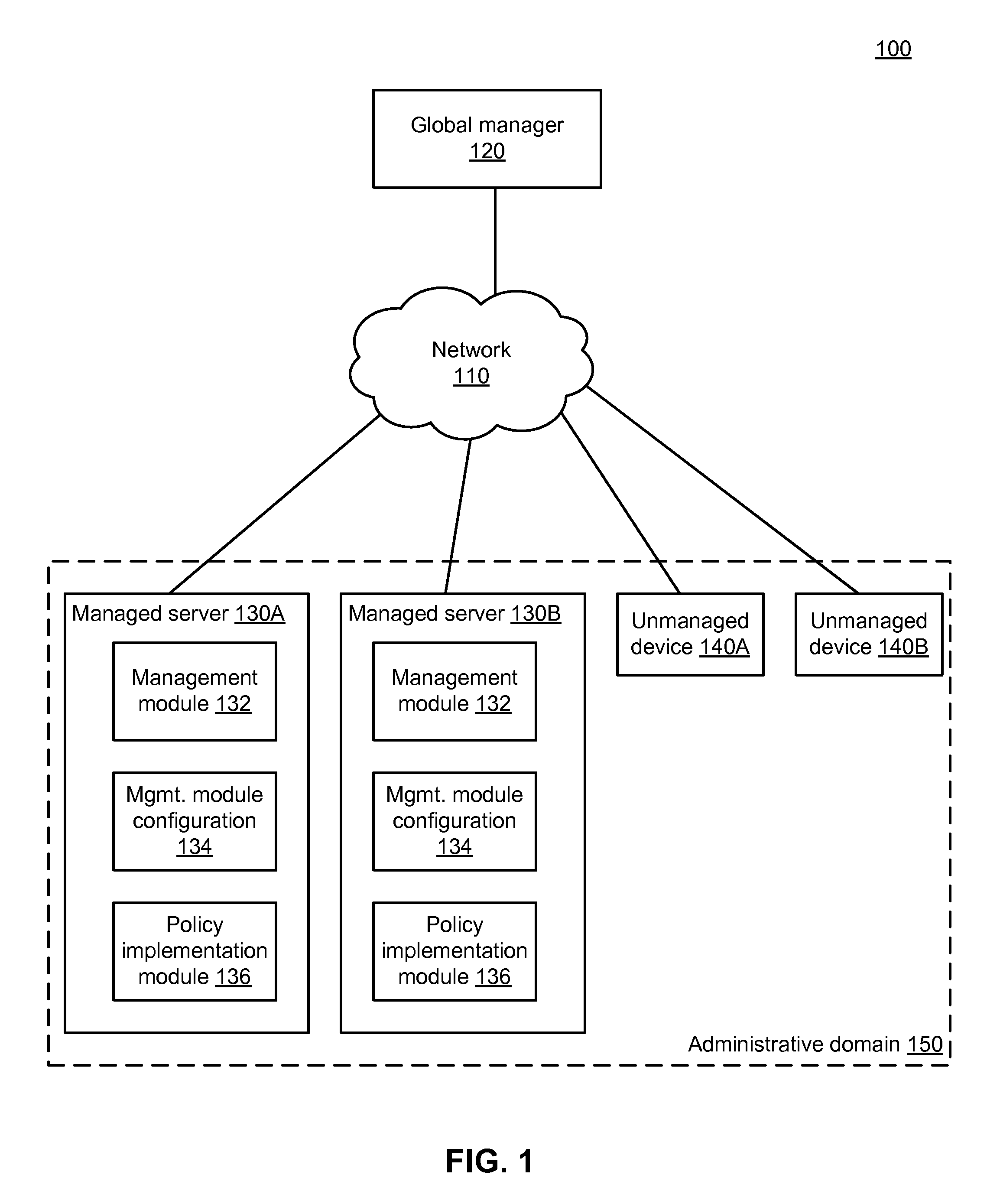
ActiveUS20150128211A1TransmissionSpecial data processing applicationsAdministrative domainNetwork management
An access control rule authorizing communication between a plurality of managed servers within an administrative domain is determined. Communication information describing past communication between the plurality of managed servers is obtained. A subset of managed servers from the plurality of managed servers is identified by grouping the plurality of managed servers based on the obtained communication information. A group-level label set is determined to associate with the subset of managed servers. Role labels are determined for managed servers in the subset of managed servers. A managed server is associated with one role label. Based on the group-level label set and the role labels, an access control rule is generated authorizing communication between a first managed server of the subset of managed servers and a second managed server. The access control rule is stored as part of an administrative domain-wide management policy.
Owner:ILLUMIO
Method and system for cyber security management of industrial control systems
ActiveUS8595831B2Low chanceFull accessMemory loss protectionError detection/correctionCommand and controlData acquisition
A method and system for cyber security management of Supervisory Control And Data Acquisition (SCADA) systems is provided to enhance situational awareness and cyber security management for industrial control systems. A centralized System Security Manager (SSM) is integrated into a SCADA to collect security related data for the industrial control system and an integrated command and control user interface displays security related data, a system security level, and interfaces with a user to allows for changing of system security settings for the industrial control system based on the security related data collected and manages changes in operational state of the SCADA based on the security level to restrict use of system interfaces and system accesses.
Owner:SIEMENS AG
Method and system for achieving right management in network management
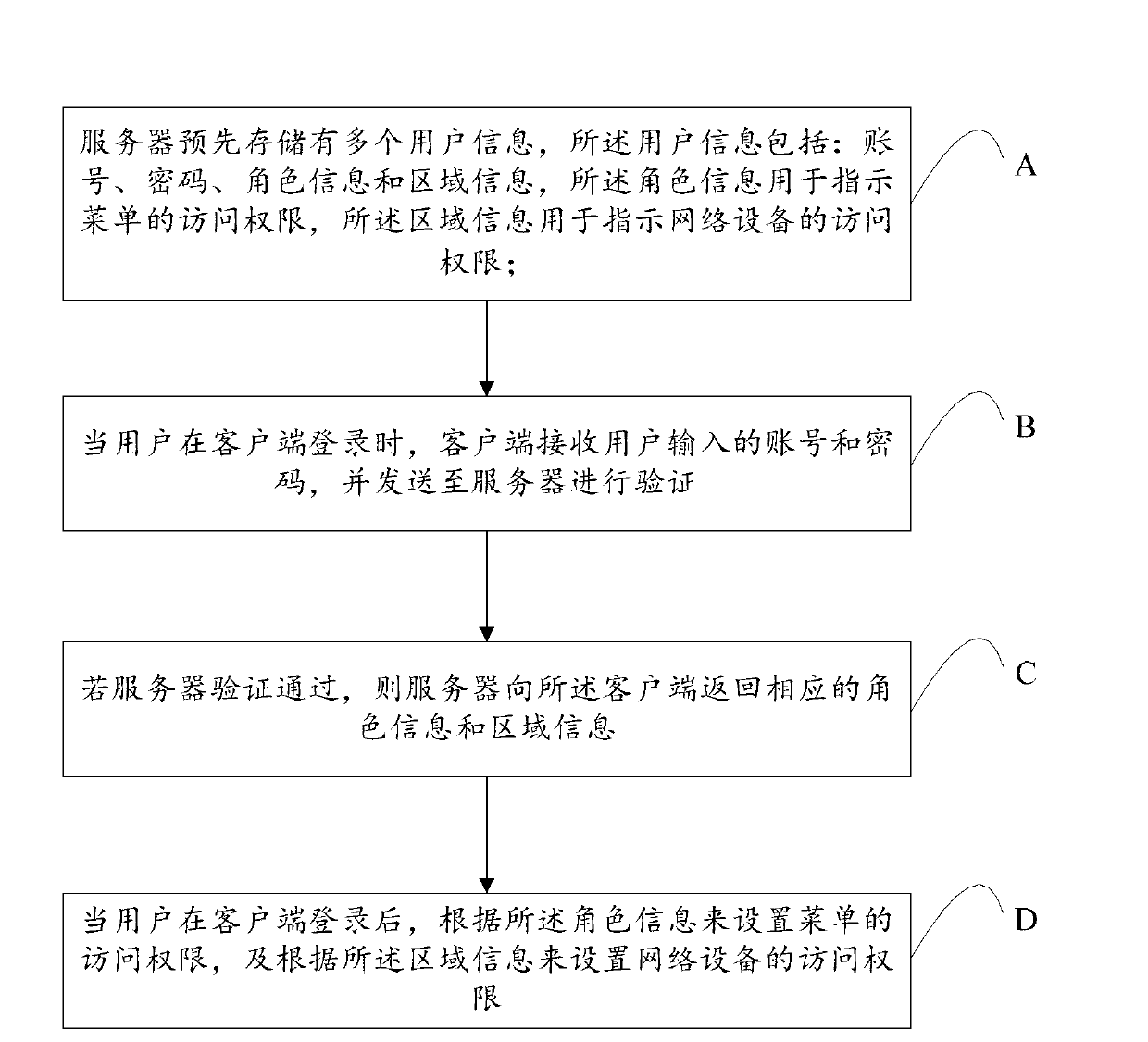
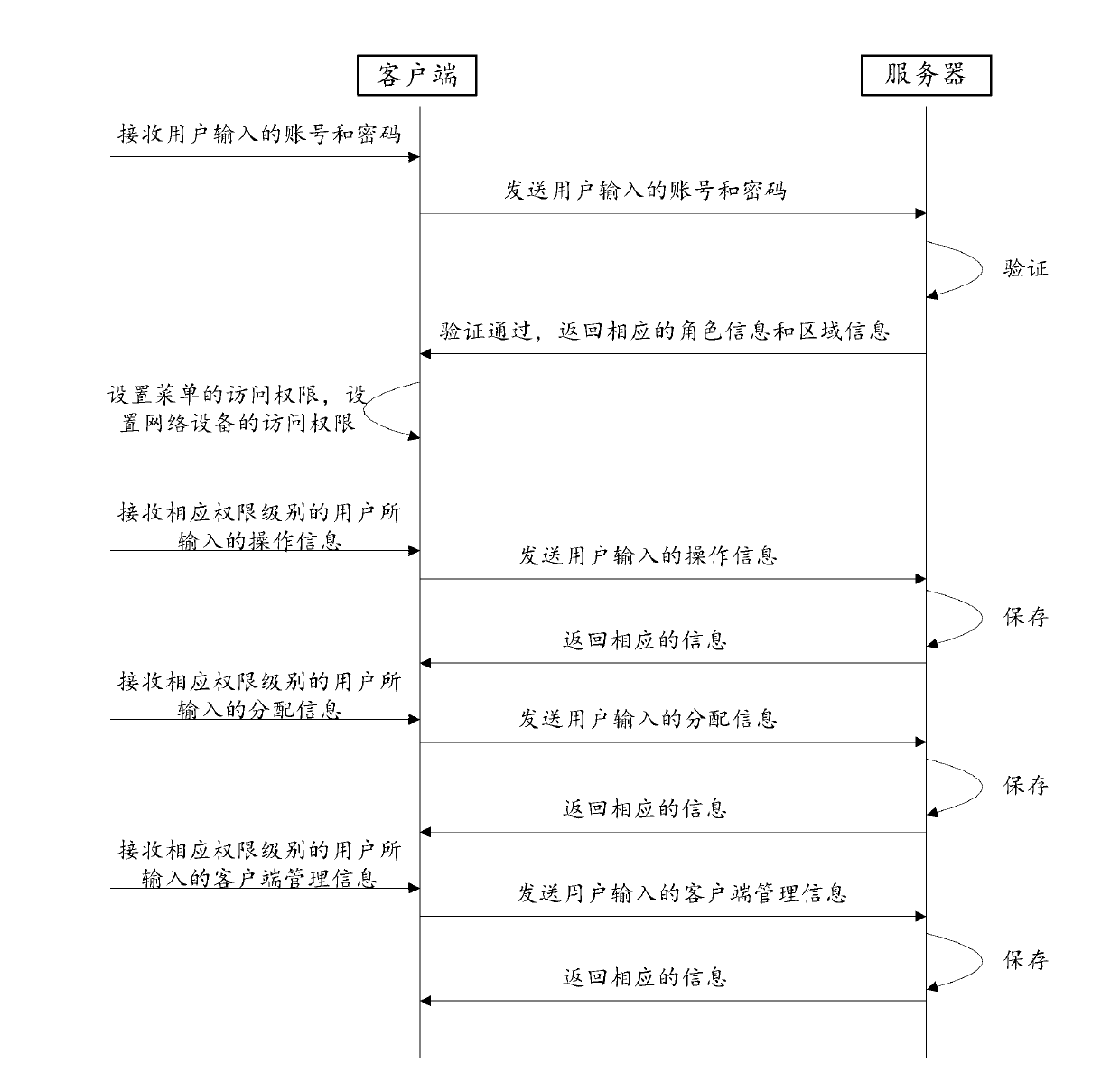
InactiveCN103001803AAvoid duplicationAvoid the problem of ultra vires managementData switching networksUser inputPassword
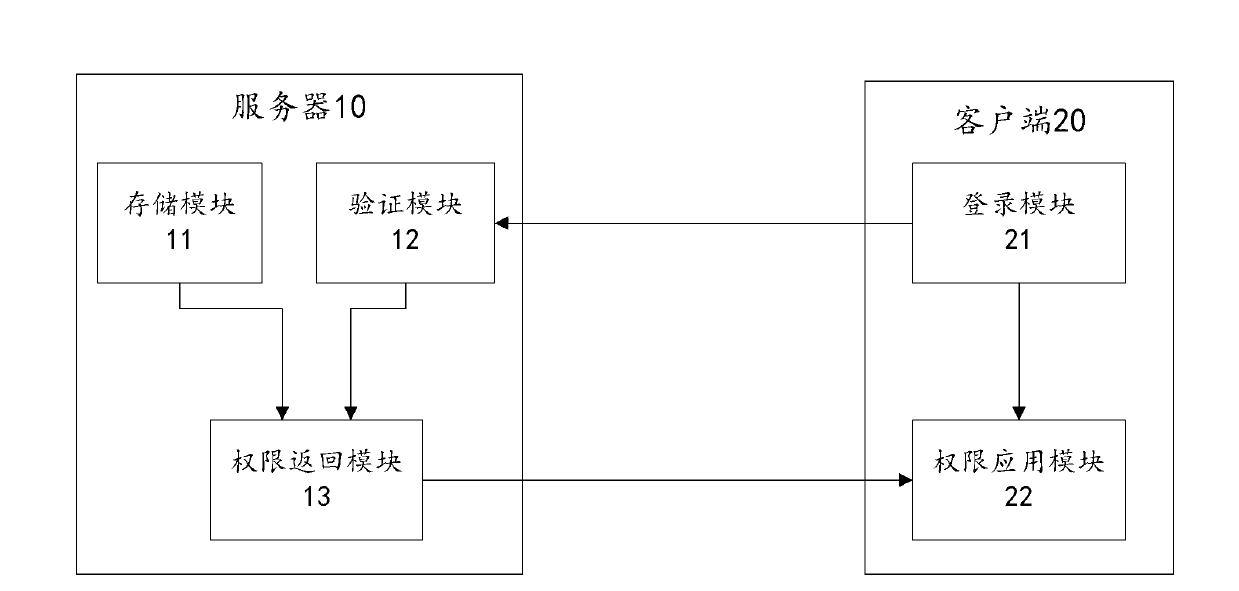
The invention discloses a method and a system for achieving right management in network management. The method includes that a server stores a plurality of pieces of user information including an account number, a password, role information and zone information, wherein the role information is used for indicating access rights of a menu and the zone information is used for indicating access rights of network equipment; a client receives and sends the account number and the password which are input by a user to the server for verification when the user logs in at the client; if the verification by the server is passed, the server returns the corresponding role information and the zone information to the client; and after the user logs in at the client, access rights of menus are set according to the role information and access rights of the network equipment are set according to the zone information. According to the method and the system, not only the problems of management repetition and management in excess of rights are solved, but also security guarantee is provided for maintenance of the network equipment, and safety of network management is safeguarded.
Owner:PHICOMM (SHANGHAI) CO LTD
Associated equipment and method for internal network security management
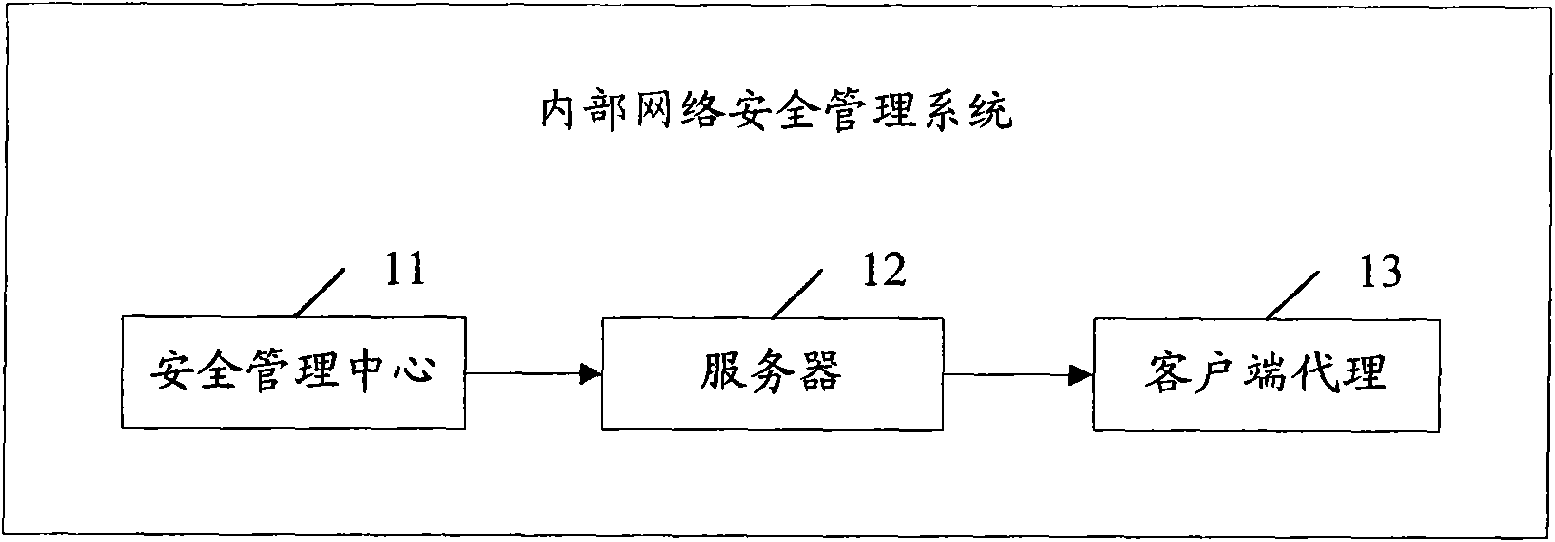
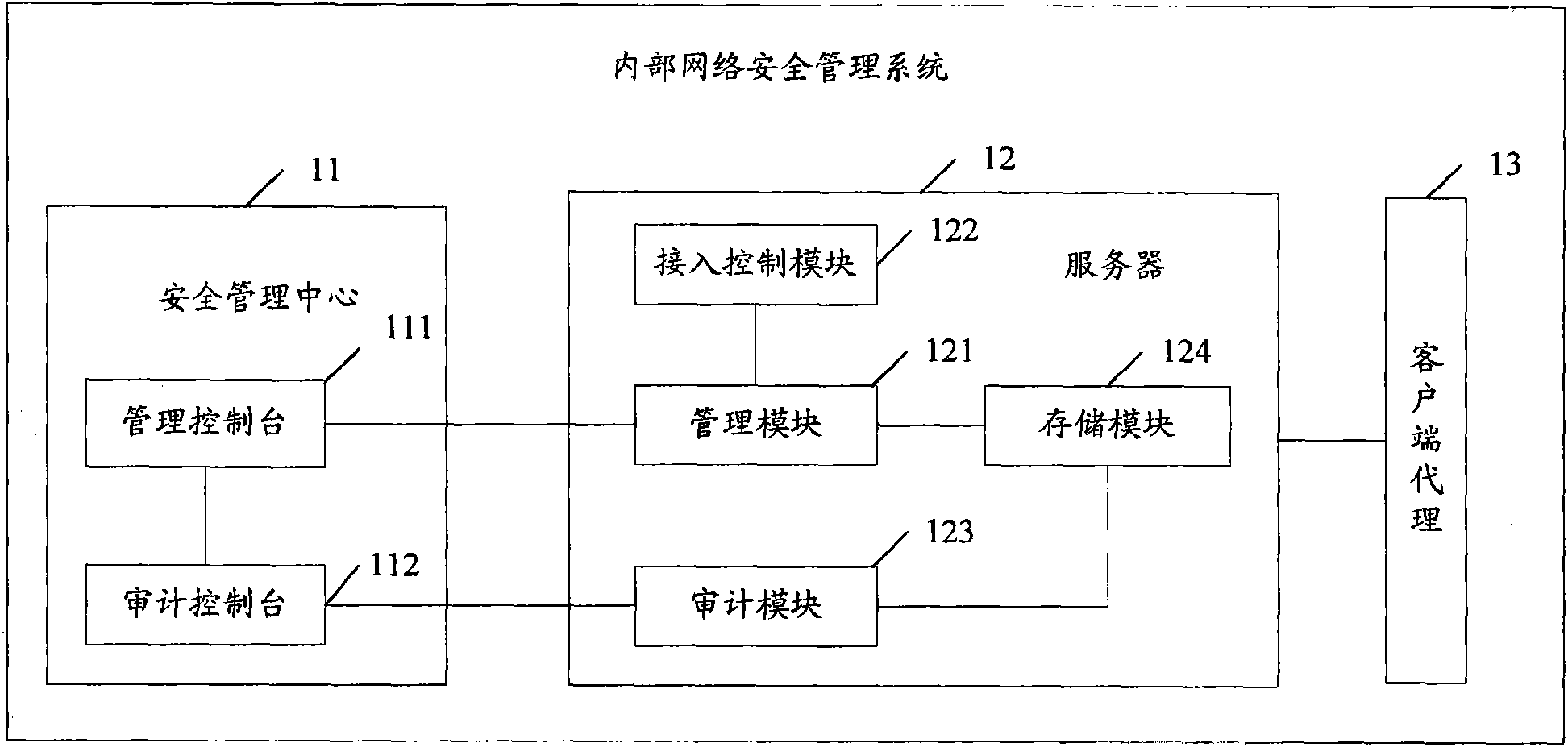
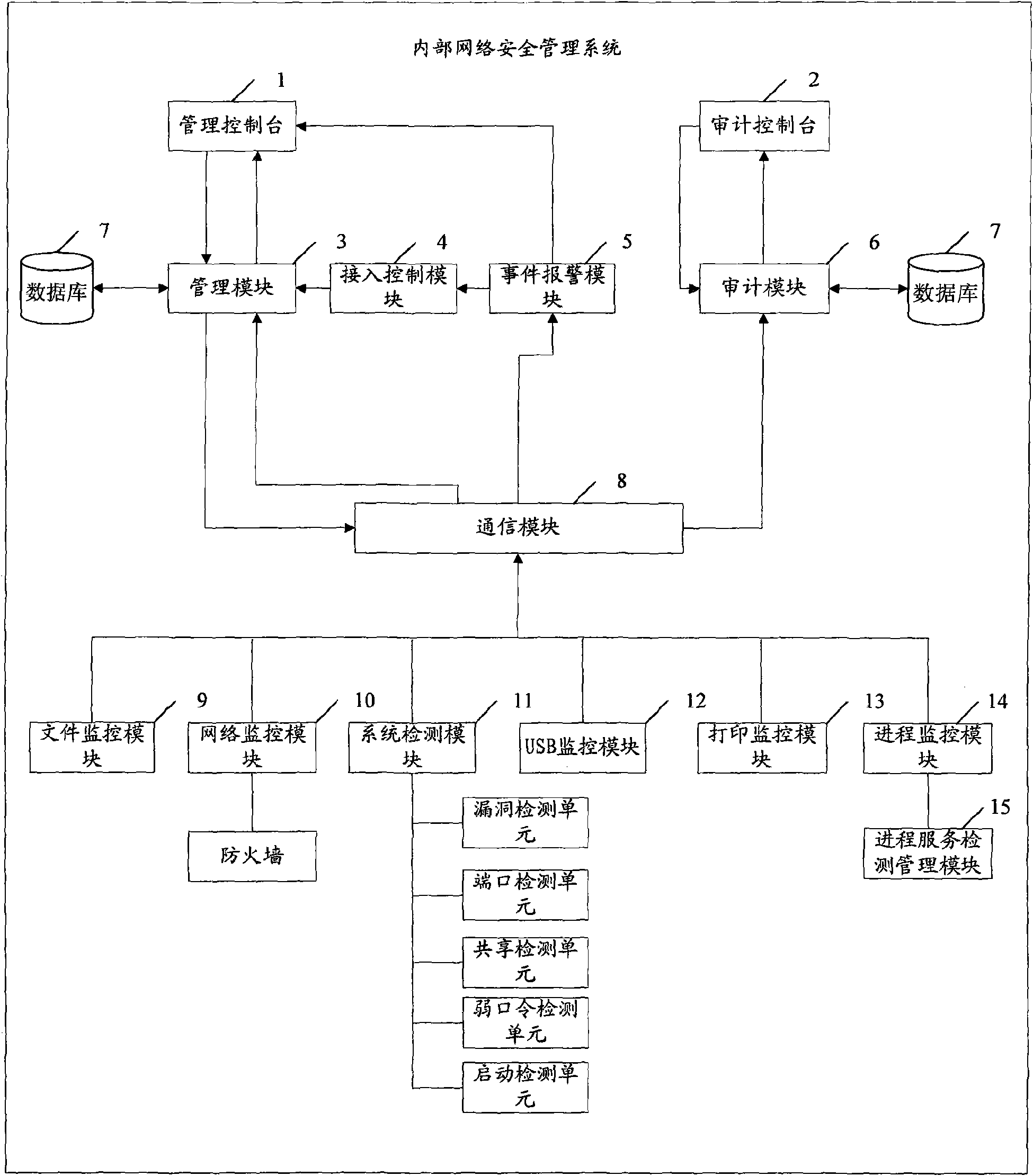
InactiveCN101588360AIntegrity guaranteedAvoid abuseData switching by path configurationTerminal equipmentNetwork isolation
The invention provides associated equipment and method for internal network security management, wherein, through generating and maintaining a security management strategy and an audit strategy; the invention ensures that all the terminals accessible to internal network submit to the strategies; with respect to an piece of equipment unqualified to the strategies, the system processes the equipment as follows: providing a network isolation and locking device, and sending an warning, with the purpose of ensuring that the equipment does not bring the whole network with bad influence on the security and management. The invention not only implements an active defense mechanism of the system, but also effectively prevents some malicious acts of validated user, such as misapplication of network resource, information theft, and active attack by means of internal computers.
Owner:SHENZHEN CITY ANLUODACHENG TECH
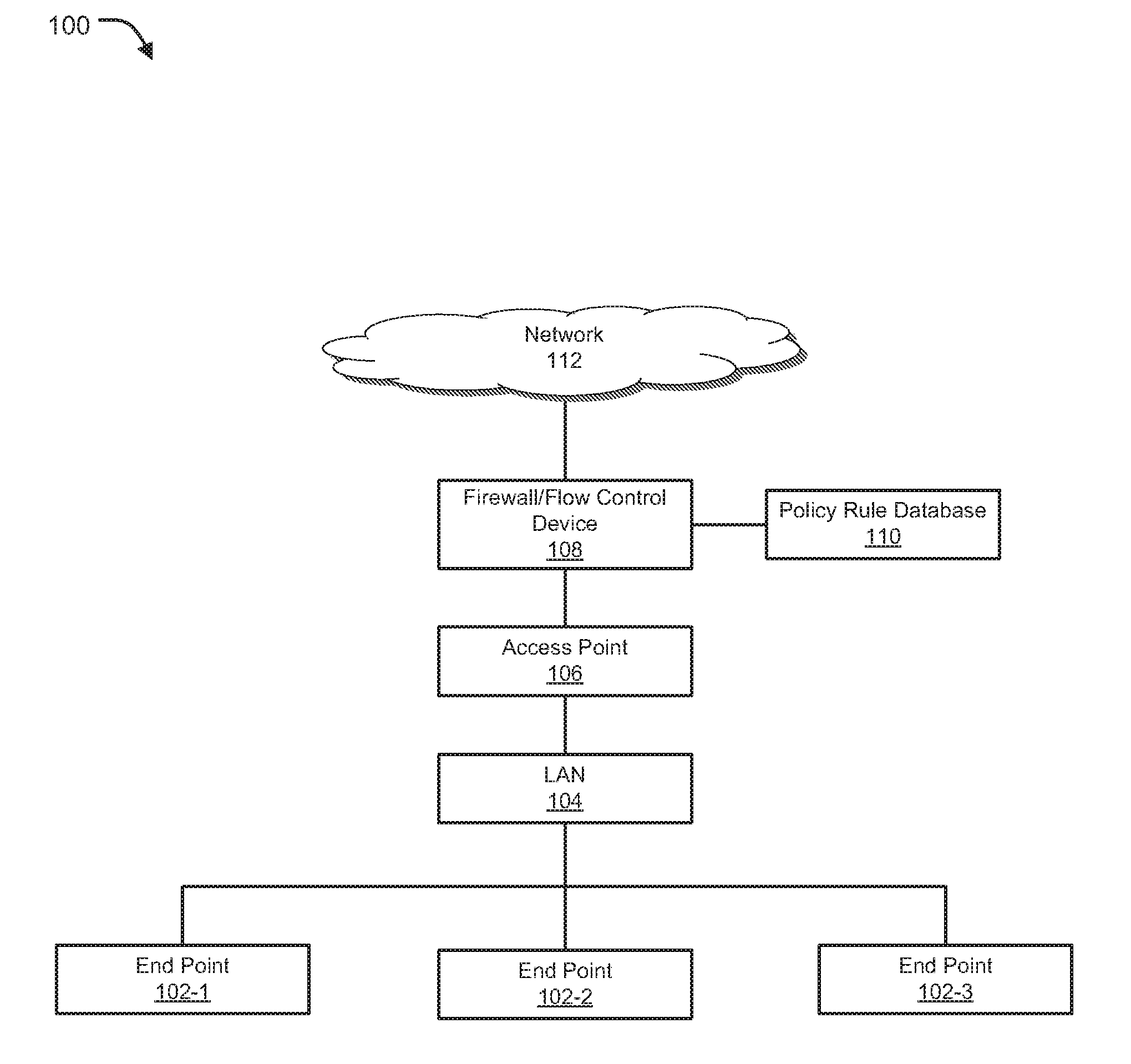
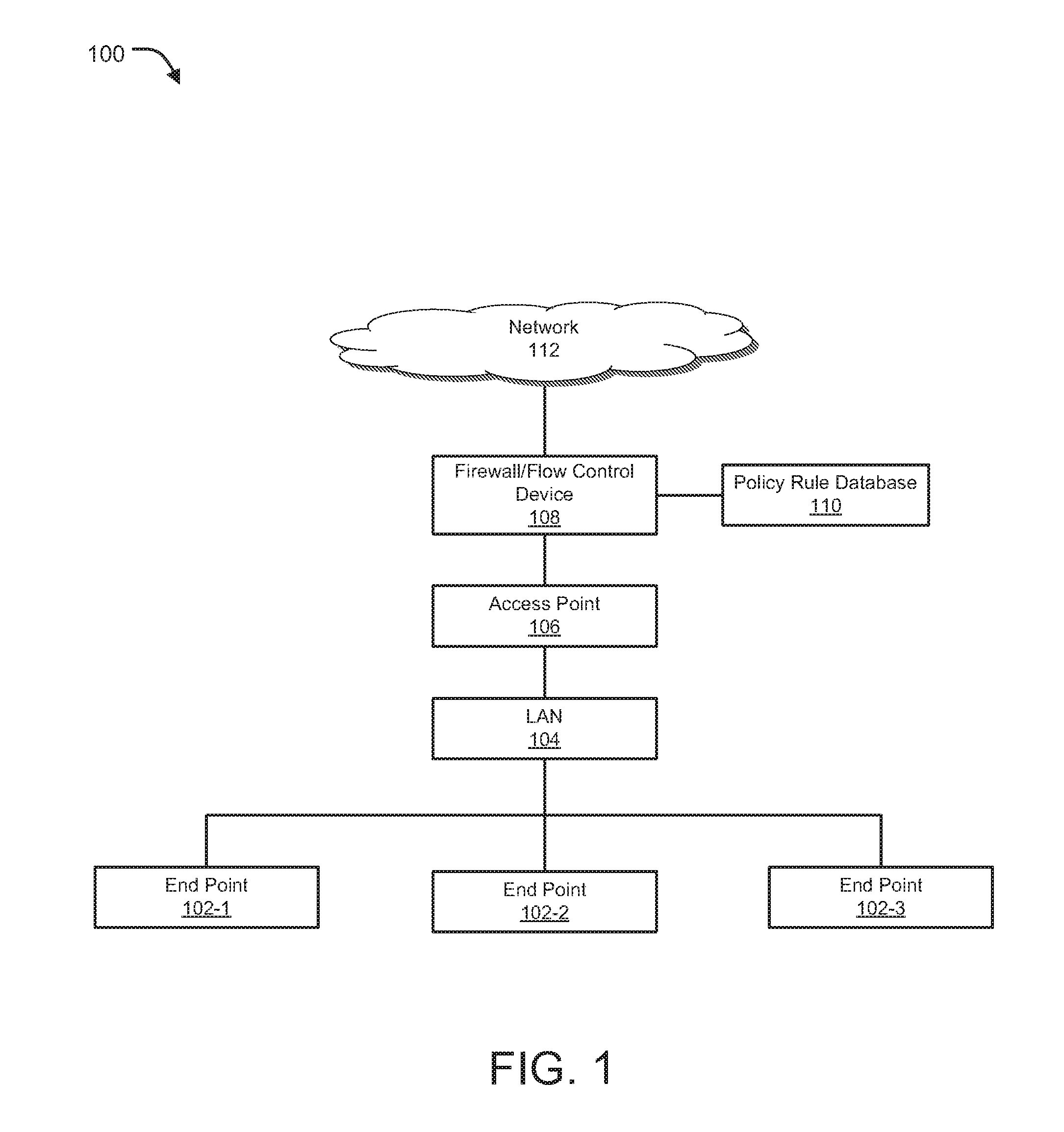
Secure access control system and method for network terminal nodes
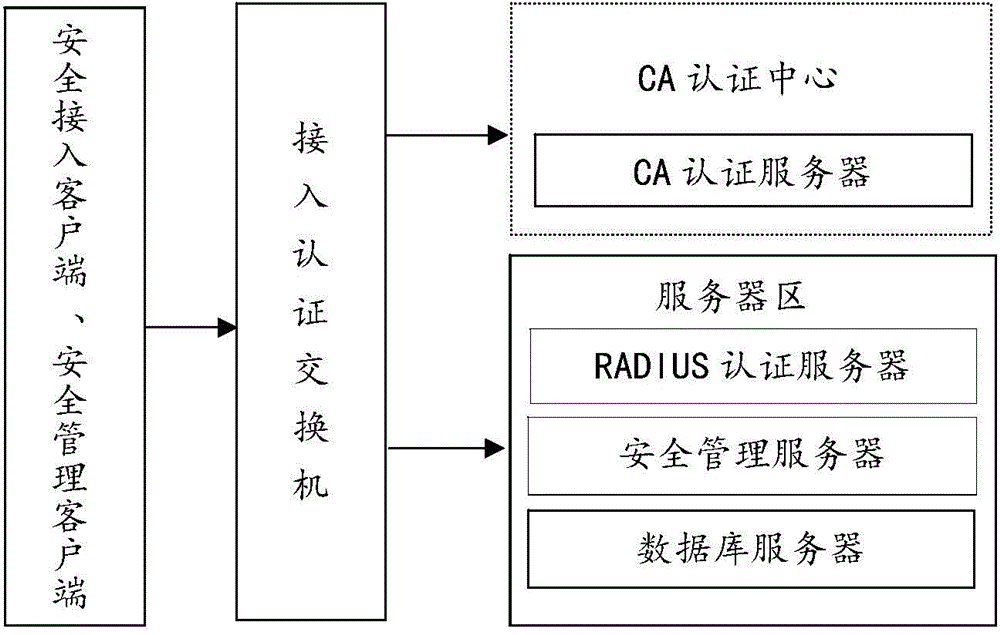
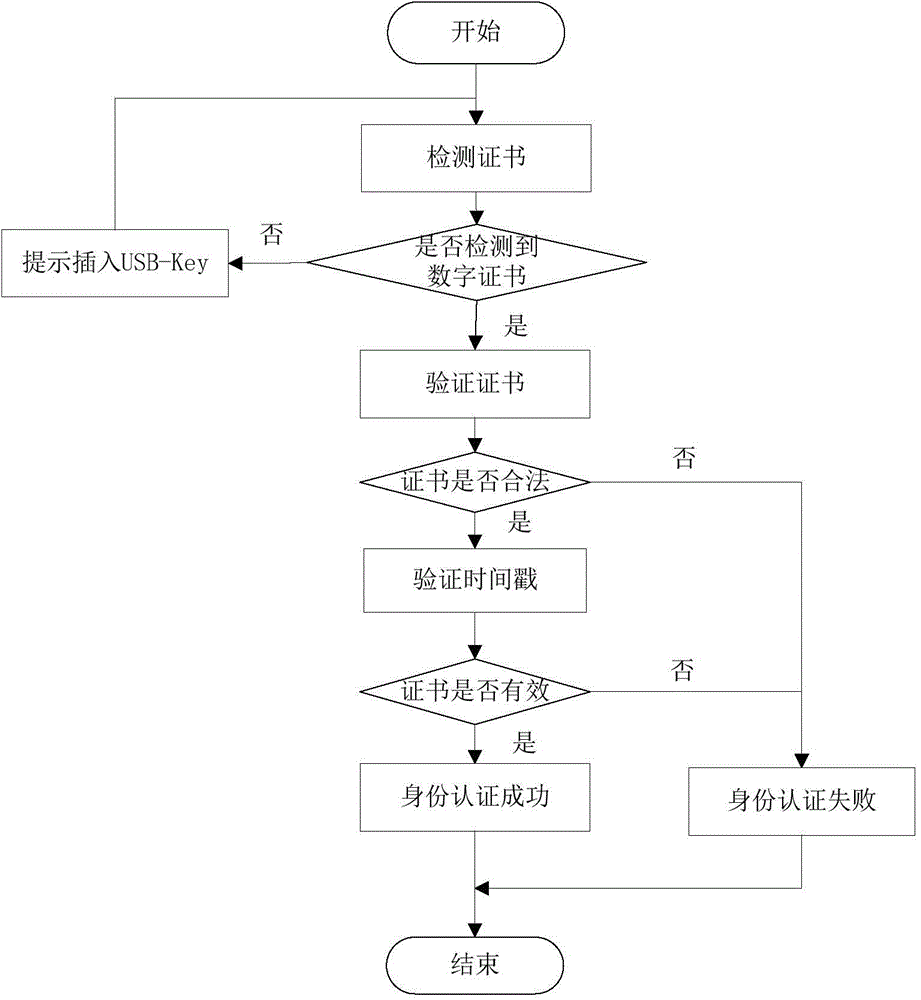
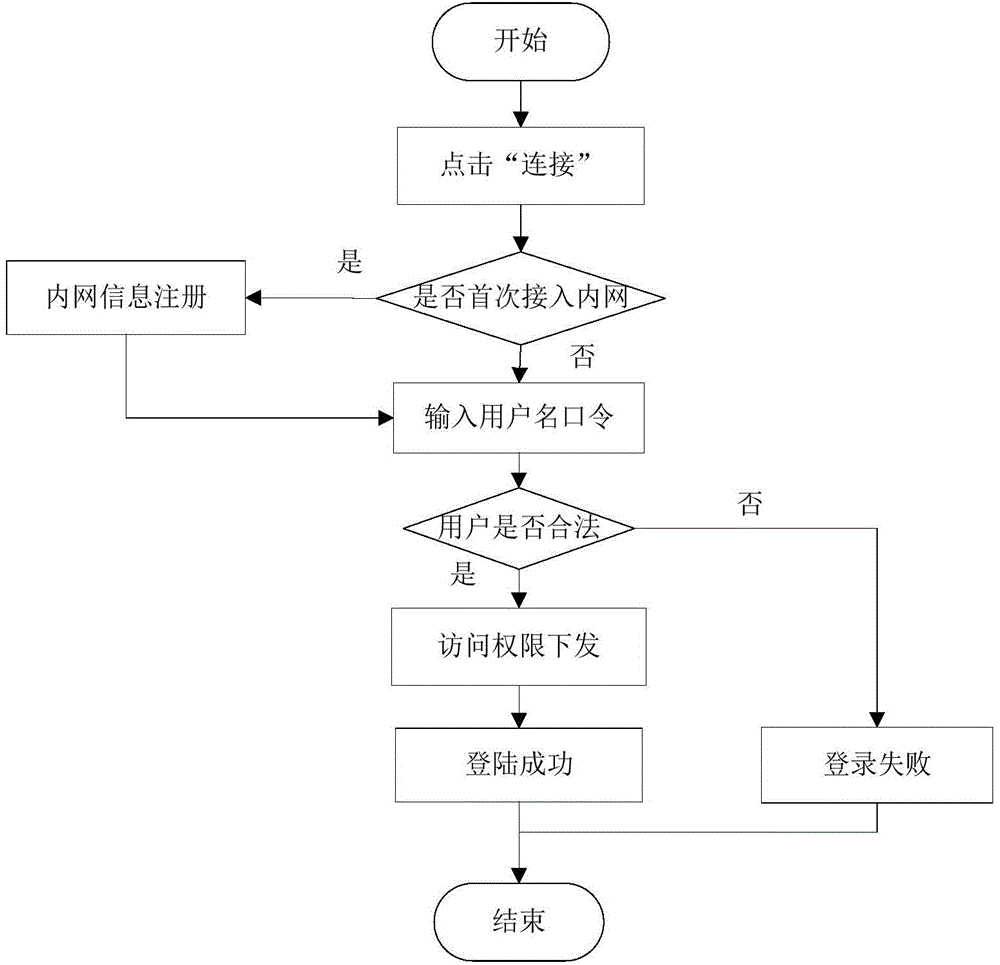
InactiveCN104796261AReal-time monitoring of identity informationReal-time monitoring of the access verification processUser identity/authority verificationNetwork terminationPrivate network
The invention discloses a secure access control system and method for network terminal nodes. A C / S (client / server) architecture is provided between a secure access client and a CA (certificate authority) authentication server, and another C / S architecture is provided between the secure access client and an RADIUS (remote authentication dial-in user service) authentication server; the two C / S architectures are used for user identity authentication and terminal access authentication, respectively. A B / S (browser / server) architecture is provided between a security management client and a security management server and is used mainly for registering and checking user information, setting network access group permissions and controlling and monitoring secure access in real time. The secure access control system and method has the advantages that the access terminals can be subjected to trusted identity authentication, trusted access authentication, terminal proxy authentication, network access permission control and network access state real-time monitoring; a trusted terminal access control system based on identity authentication is achieved and is stable and reliable and is high in authentication efficiency, violations such as NAT (network address translation) and proxy services can be detected and warned accurately, network states of terminal users are monitored and controlled through a web management interface, and the needs of private networks for safety management can be fully met.
Owner:CHANGAN UNIV
Anti-replay-attack system for industrial wireless network
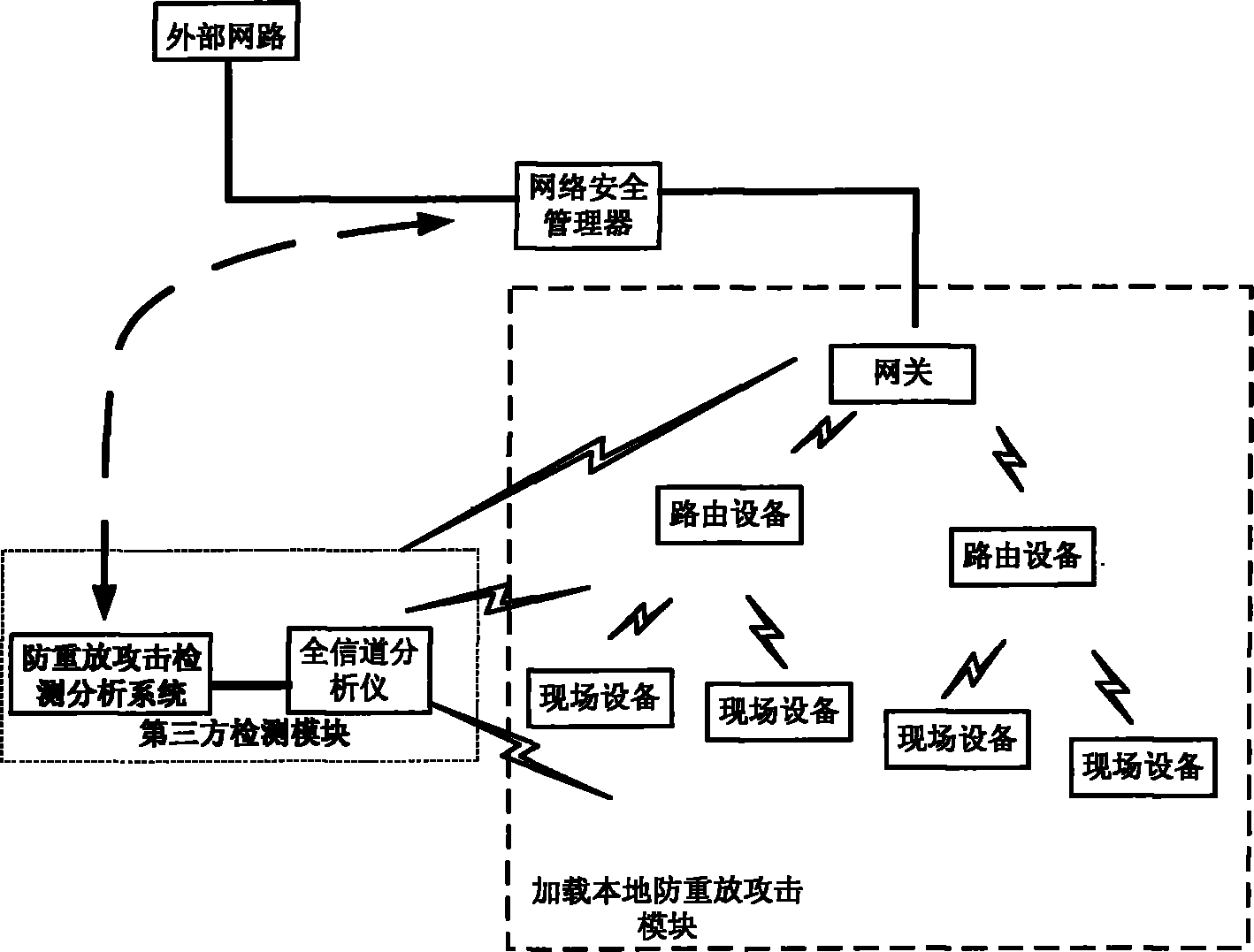
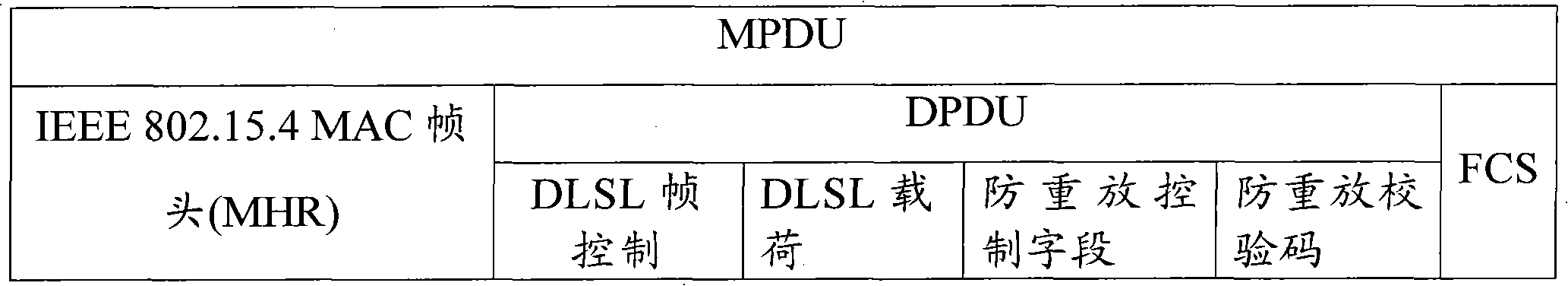
InactiveCN101800989AReduce consumptionAvoid consumptionNetwork traffic/resource managementSecurity arrangementThird partyResource consumption
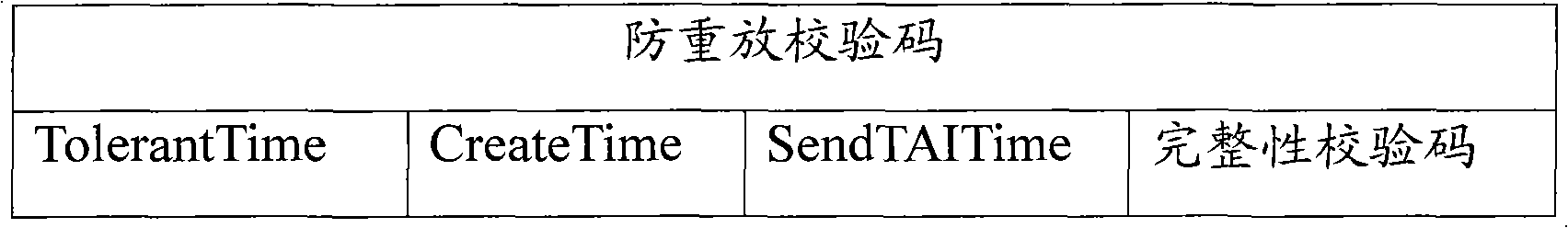
The invention provides an anti-replay-attack system for an industrial wireless network, which introduces a third-party detection mechanism in order to reduce system resource consumption. The industrial wireless network comprises a gateway, a router, field equipment and network security manager. The anti-replay-attack system for the industrial wireless network comprises a third-party detection module used for detecting whether intrusion data packets and replay attack data packets exist in the industrial wireless network or not and sending detection results to the network security manager, and the network security manager compares the system resource consumption caused by replay attacks with resource consumption brought by using an anti-replay-attack means to determine whether the anti-replay-attack means is used, thereby effectively preventing the anti-replay-attack means from bringing more system resource consumption than the replay attacks, and two time stamps of creation time and sending time are added in the data packet by a sender, so that the certainty and uniqueness of messages can be ensured; a receiver detection mechanism is adopted, and the data packets of the replay attacks are judged and discarded by a receiver so as to solve the problems of ID authentication and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
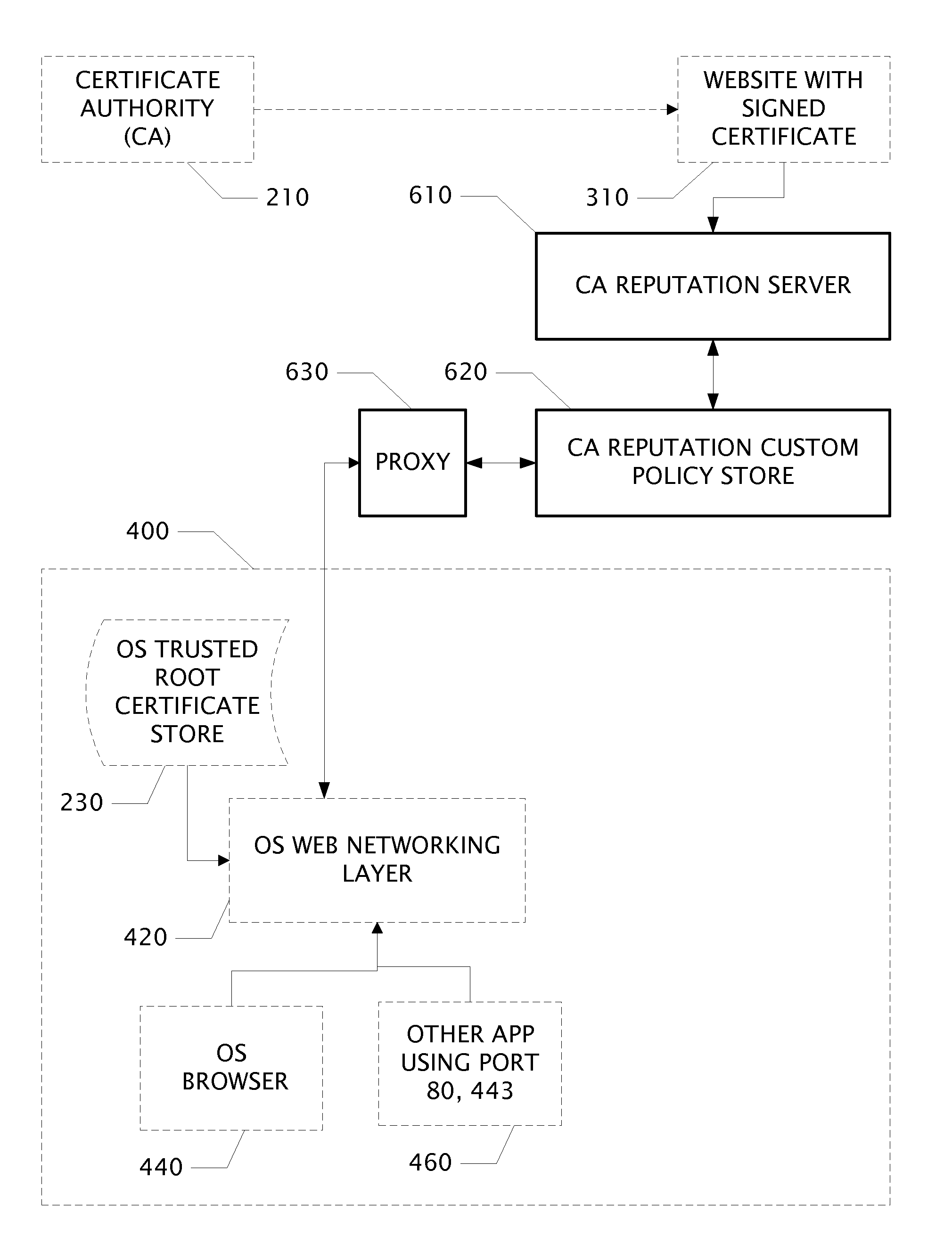
System and Web Security Agent Method for Certificate Authority Reputation Enforcement
InactiveUS20130061281A1Internal/peripheral component protectionDigital data authenticationThird partyRoot certificate
Owner:BARRACUDA NETWORKS
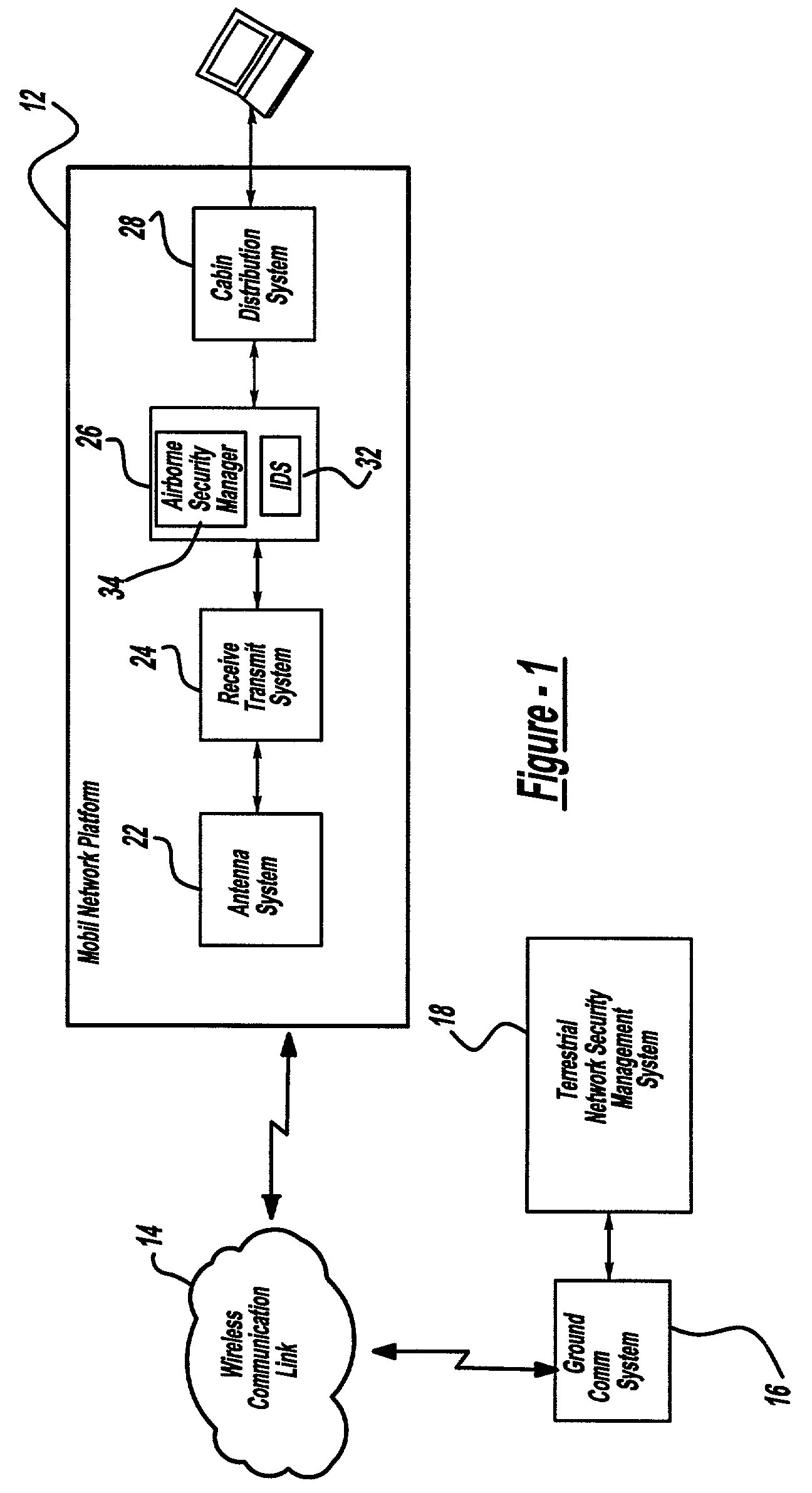
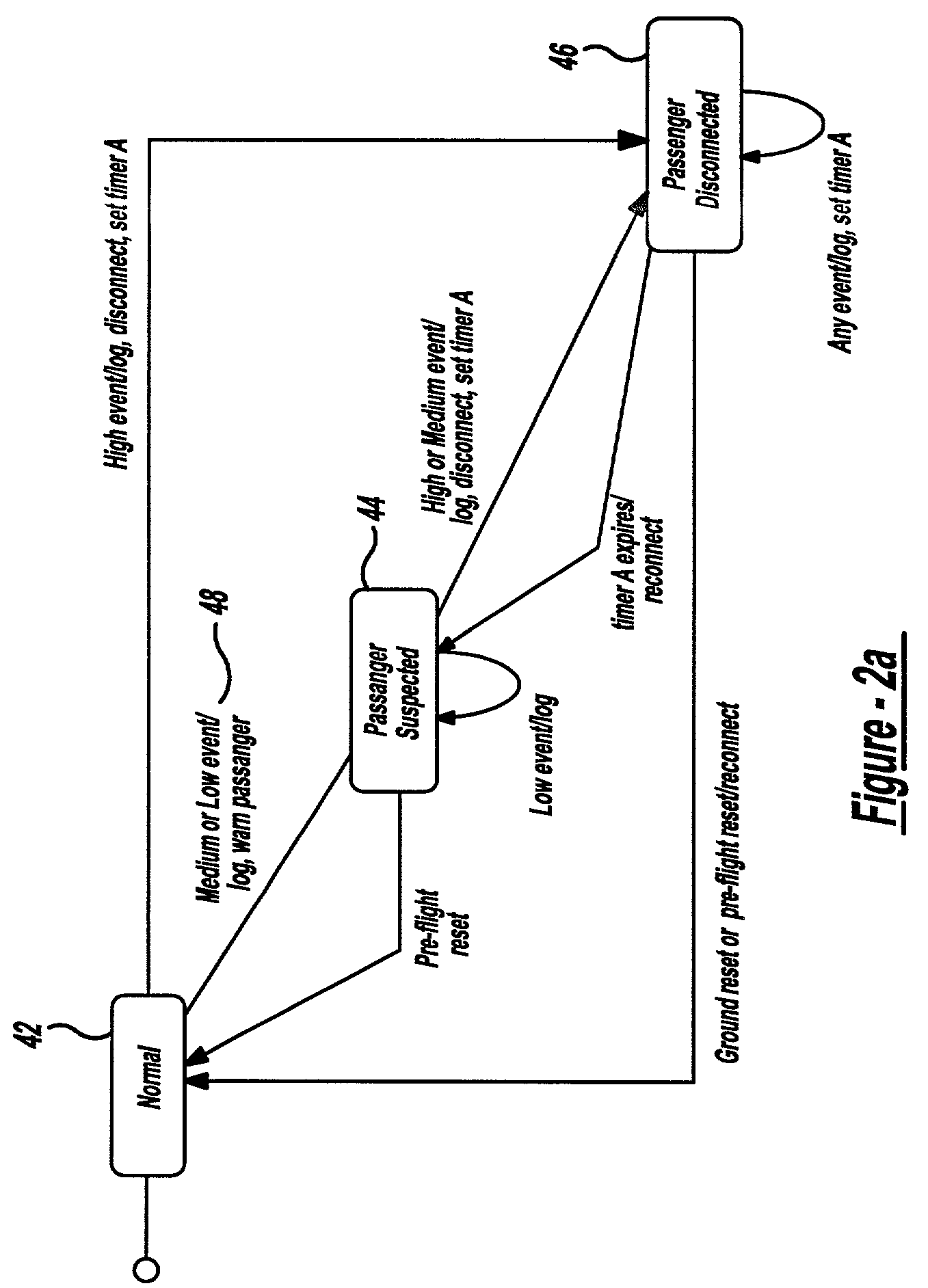
Airborne security manager
InactiveUS7715819B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunications linkSafety management systems
An airborne security management system is provided for monitoring security activities in a mobile network platform. This system includes a mobile network that is interconnected via an unreliable communication link to a terrestrial-based network security management system; an intrusion detection system connected to the mobile network and operable to detect a security intrusion event whose origination is associated with the mobile network; and a mobile security manager adapted to receive the security intrusion events from the intrusion detection system. The mobile security manager is operable to transmit a message indicative of the security intrusion event to the network security management system and to perform security response activities in response to security commands received from the network security management system. The mobile security manager is further operable to command security response activities on the mobile network platform, when the mobile network platform is not connected with network security management system.
Owner:THE BOEING CO
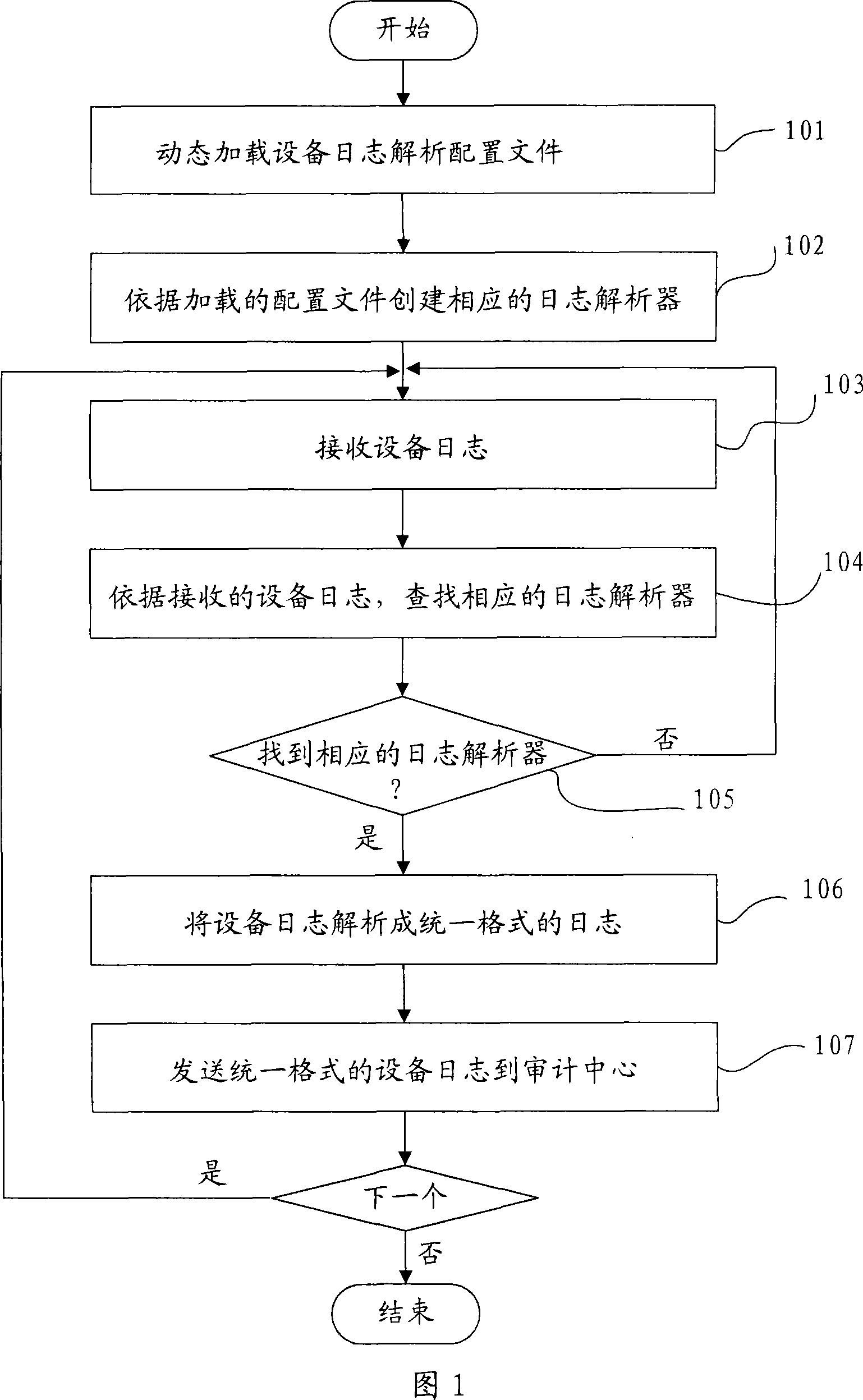
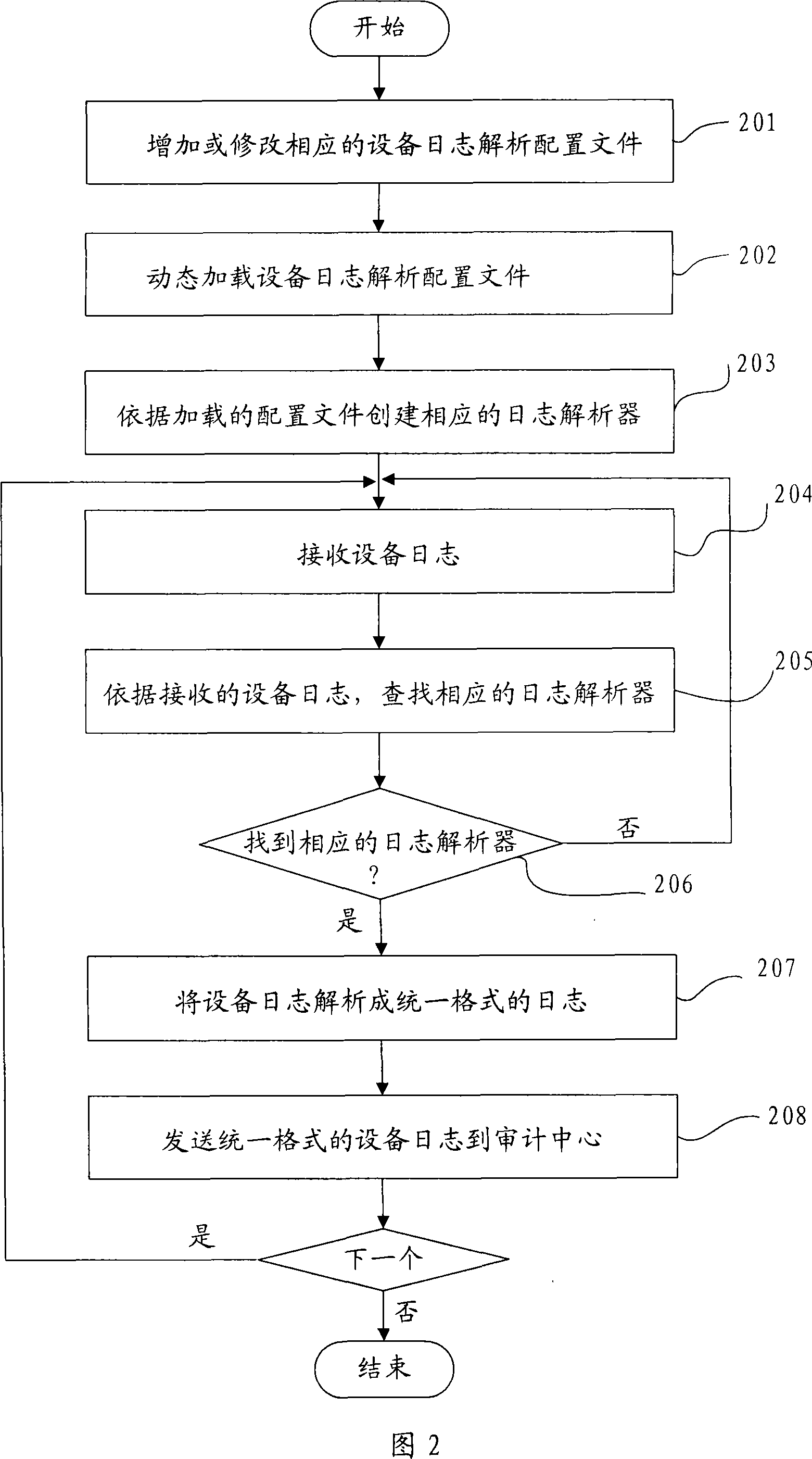
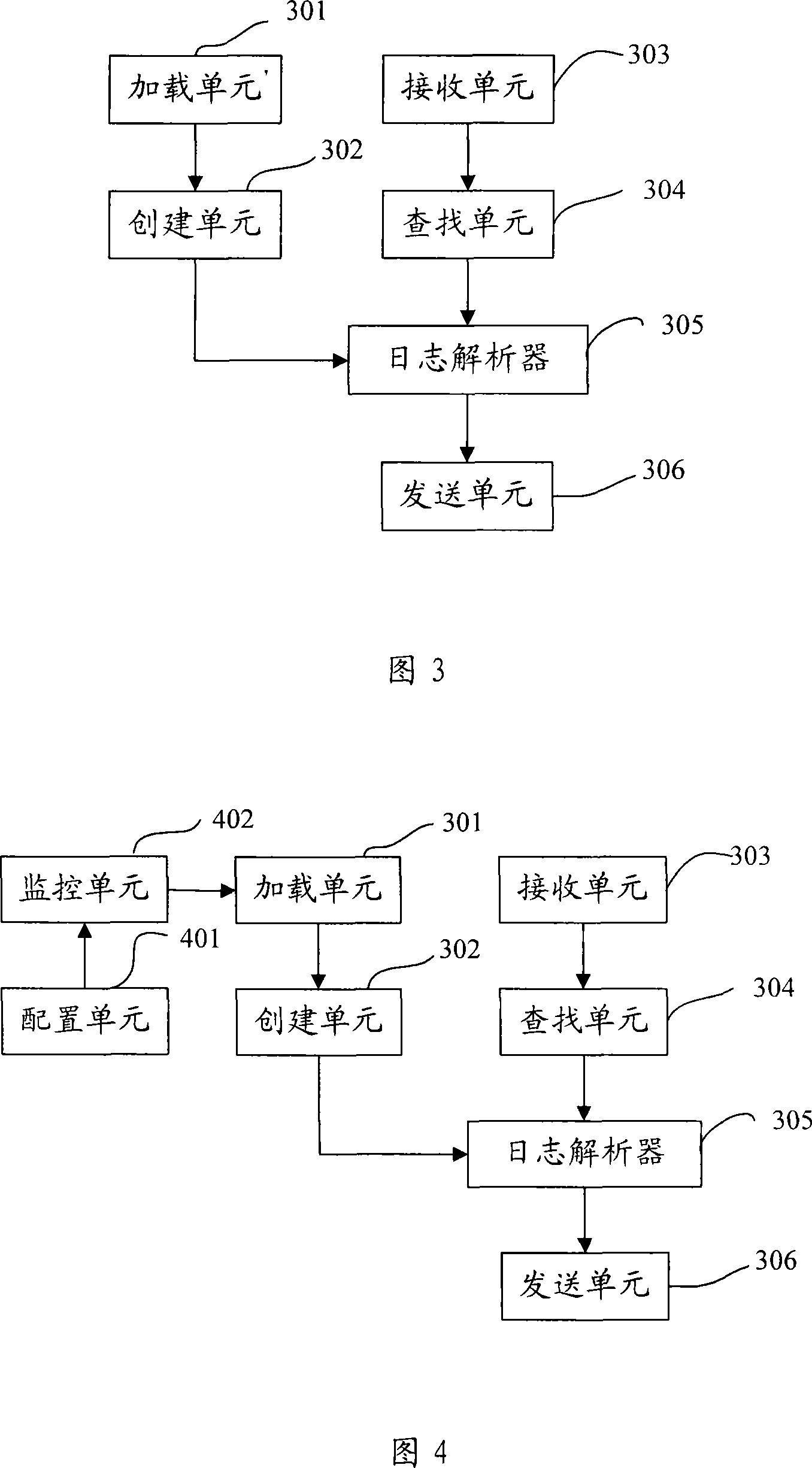
Method, device and system for real time parsing of device log
The embodiment of the invention discloses a realtime analysis method, a realtime analysis device and a realtime analysis system of an equipment journal, relating to the computer network safety management technology. The invention is invented to realize realtime receiving and analysis of the equipment journal without compiling an analysis code and restarting the system. The method comprises the following steps: dynamic loading of an equipment journal analysis configuration file is completed and a corresponding journal analyzer is created; a journal sent by equipment is received; a corresponding journal analyzer is searched; if a corresponding journal analyzer is searched, the received equipment journal is analyzed and the analysis result is sent to an audit center. The device comprises a loading unit, a creating unit, a receiving unit, a searching unit, a journal analyzer and a transmitting unit. The system comprises an equipment control desk, a journal collecting module and an audit center. When a new equipment type is added in the system, the embodiment of the invention can realize realtime receiving and analyzes the journal of the newly arranged equipment type without restarting the system and compiling an analysis code.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Security system of wireless industrial control network, and method for implementing security policy
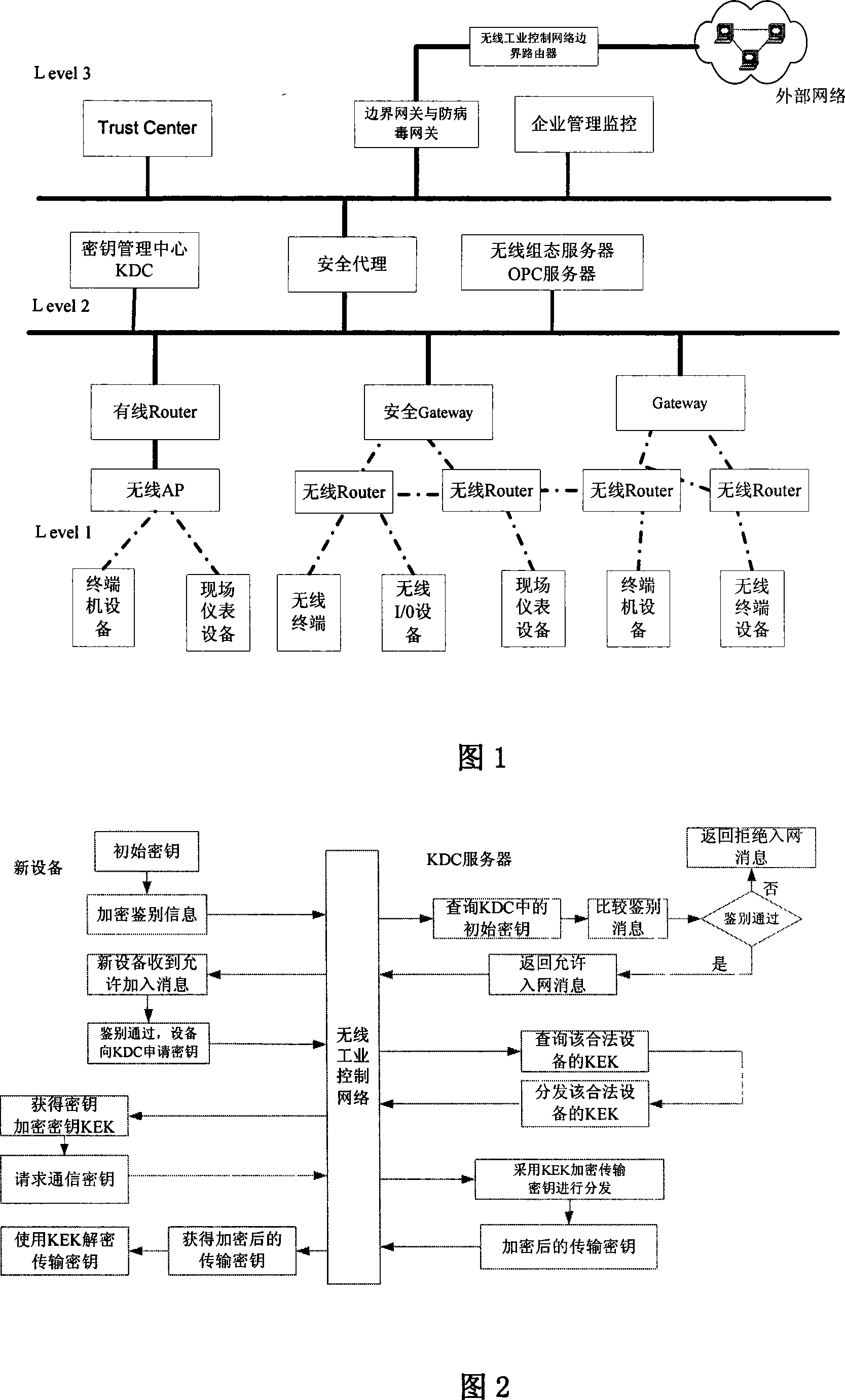
InactiveCN101094056AGuaranteed uptimeNormal production orderKey distribution for secure communicationData switching by path configurationInformation repositoryStructure of Management Information
The technical scheme of this invention is that dividing the wireless industry control net (WICN) into three net sections: a enterprise managing layer, a process controlling layer and field equipment layer. According to the hiberarchy of WICN, a WICN safety managing system is built. This system defines the built WICN into 4 safety levels. According to the access control list in the sever pool of the key administration center KDC, via the mechanism of key managing and the equipment verifying basis on KDC, the wireless safety gateway, the wireless net safety application managing entity and the wireless safety managing info database, different safety precautions are applied on the various layers and various safety levels of nets. This invention suits the industry field control to solve effectively the safety problems of resource and data comm. within the WICN and ensures the normal system running.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
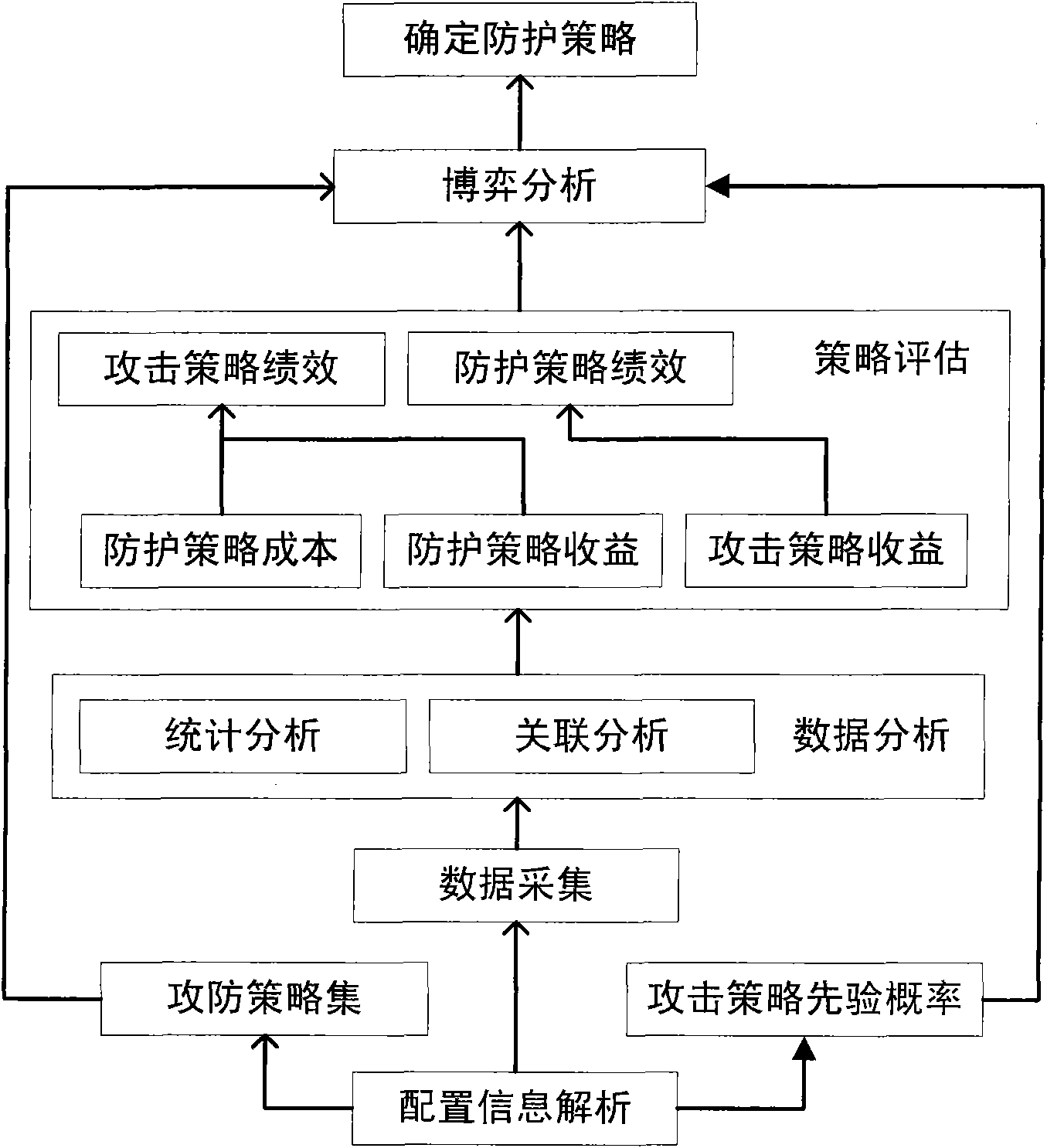
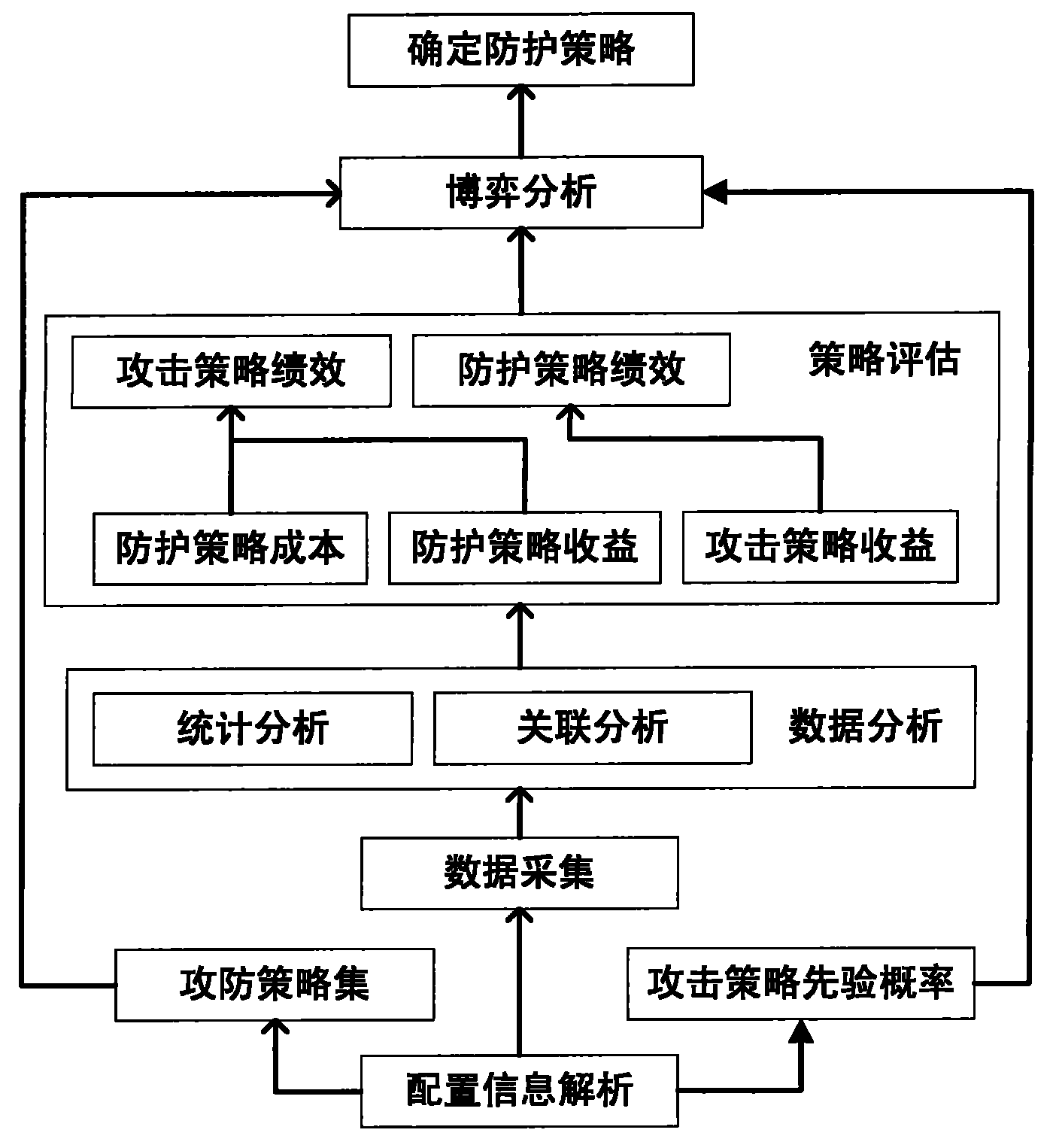
Method for selecting optimized protection strategy for network security
InactiveCN101820413AAccurate and effective strategic performanceData switching networksStatistical analysisAttack strategy
The invention discloses a method for selecting an optimized protection strategy for network security and belongs to the technical field of the network security. The method for selecting the optimized protection strategy for the network security comprises the following steps of: 1) analyzing user configuration information, and acquiring host information, link information, service information, protection system information, economic cost information and property importance information in the attack-defense process; 2) performing statistic analysis and association analysis on the acquired information, and outputting an analysis result; 3) calculating the protection strategy performance and attacking strategy performance according to the analysis result; 4) establishing a static Bayesian game model for the attacking party and the defending party according to the user configuration information and the calculated result in the step 3); and 5) calculating Bayesian Nash equilibrium according to the established static Bayesian game model, and determining the protection strategy during the Bayesian Nash equilibrium as the network security protection strategy. Compared with the prior art, the method for selecting the optimized protection strategy for the network security integrates various factors to provide the optimized protection strategy for a network security manager.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
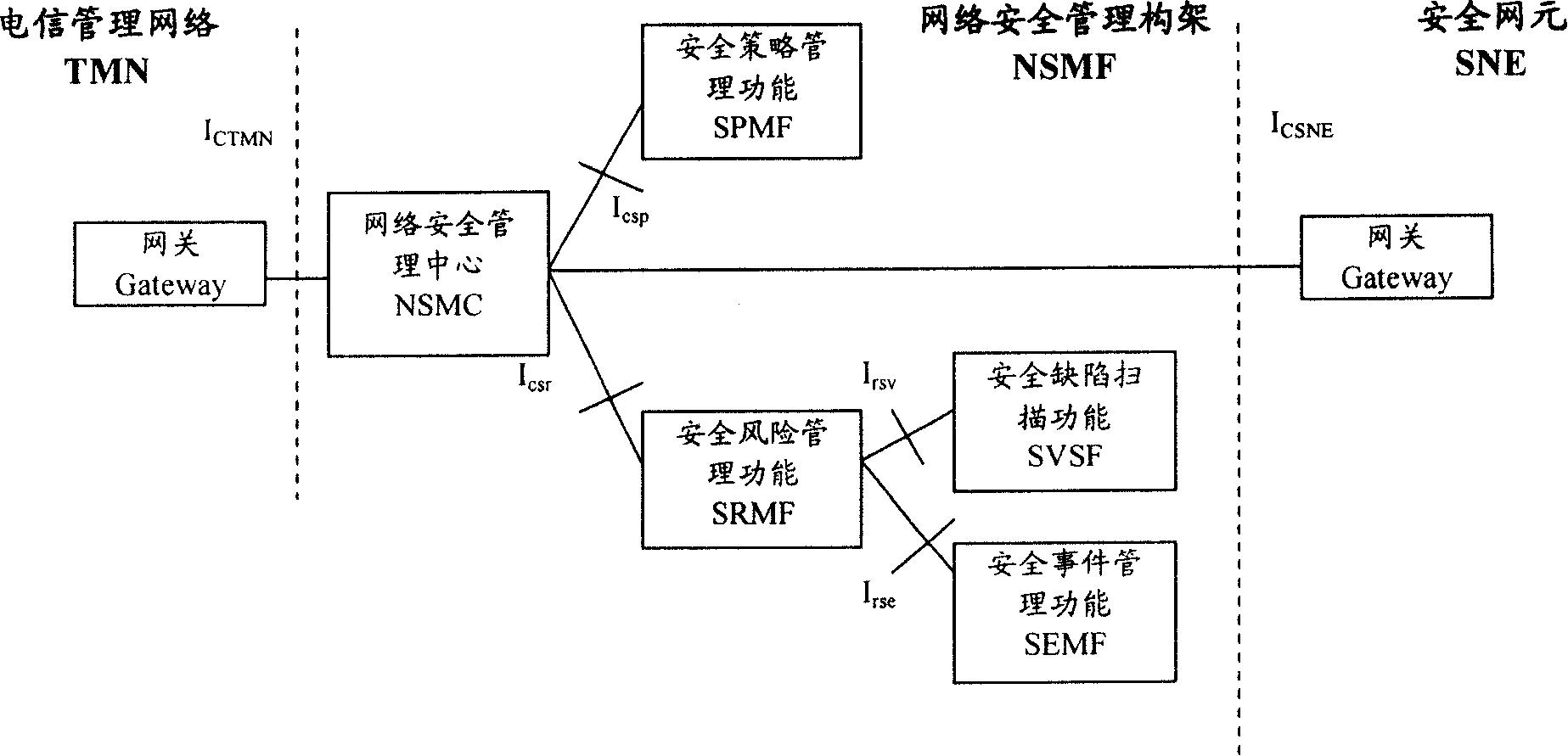
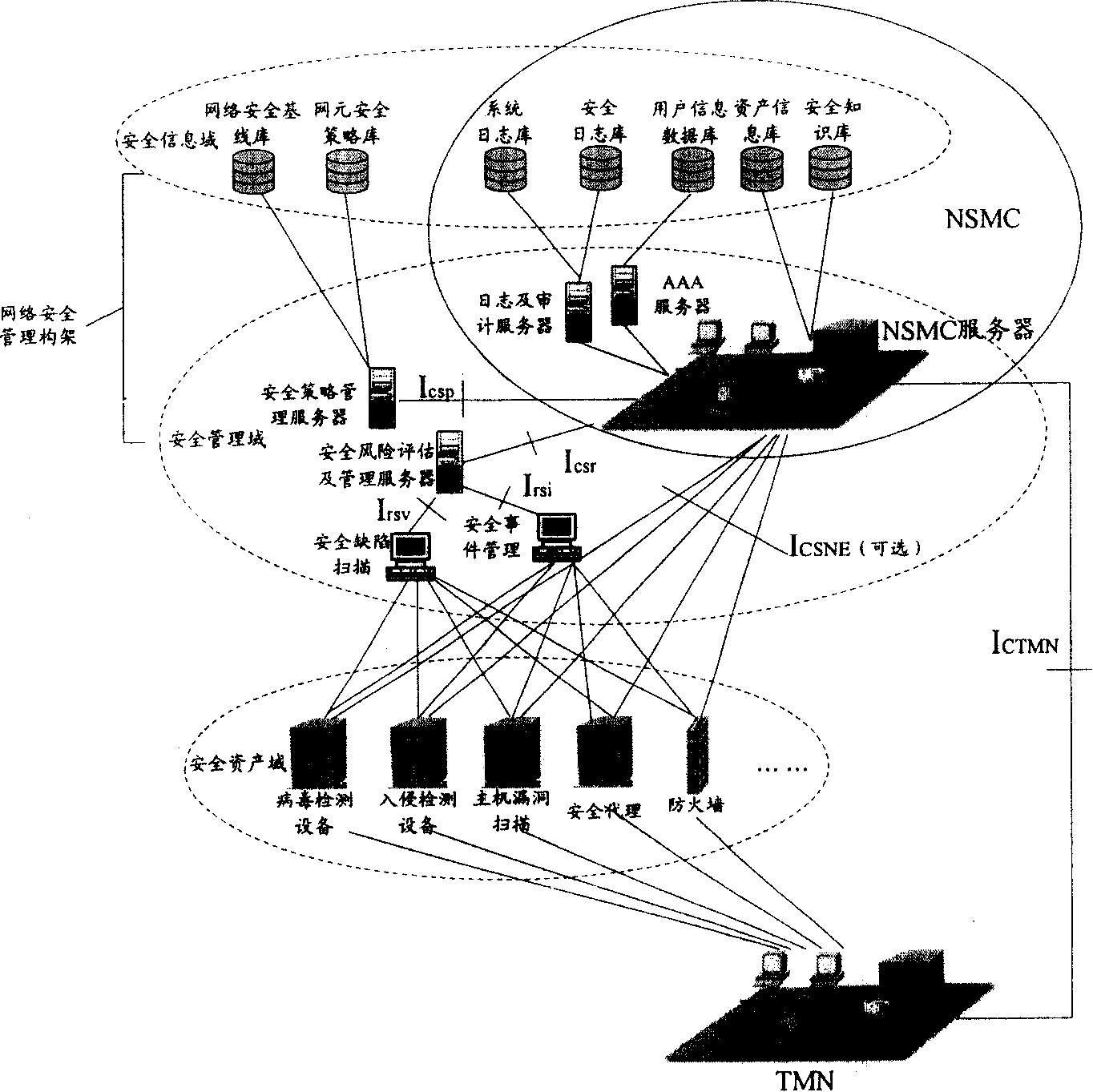
Network safety control construction
InactiveCN101174973ASecurity Management DynamicsData switching networksIT risk managementSafety control
The invention discloses a network safety management frame, which includes a network safety management center and a safety risk management system. The network safety management center controls the network safety management frame in a centralized way, analyzes the safety risk reports from the safety risk management system and finishes the safety configuration of network elements. The safety risk management system collects safe event information and safe defect information and analyzes to obtain the safety risk reports. The invention can provide a network information safe management method which centers on the safety risk management.
Owner:HUAWEI TECH CO LTD
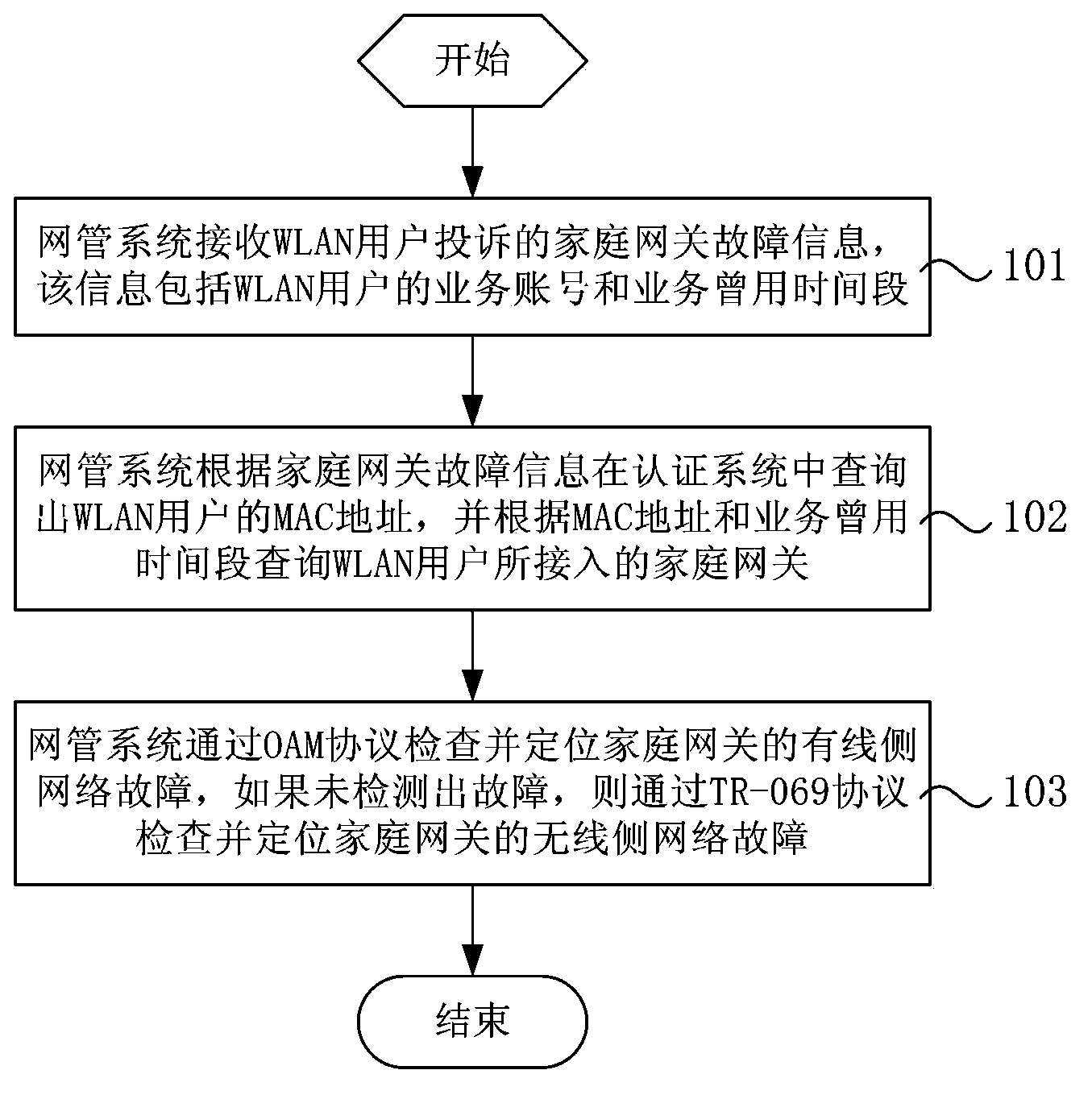
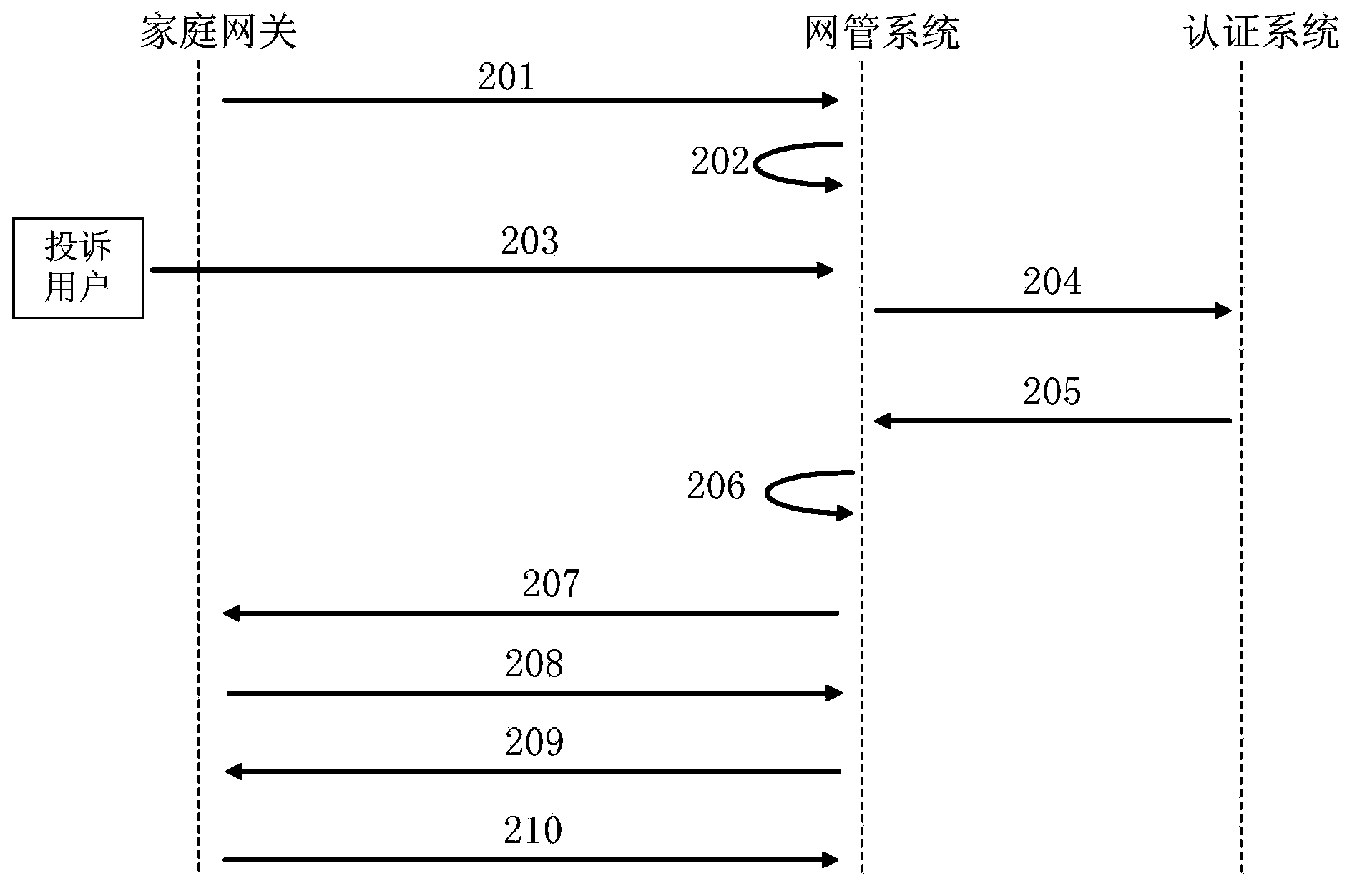
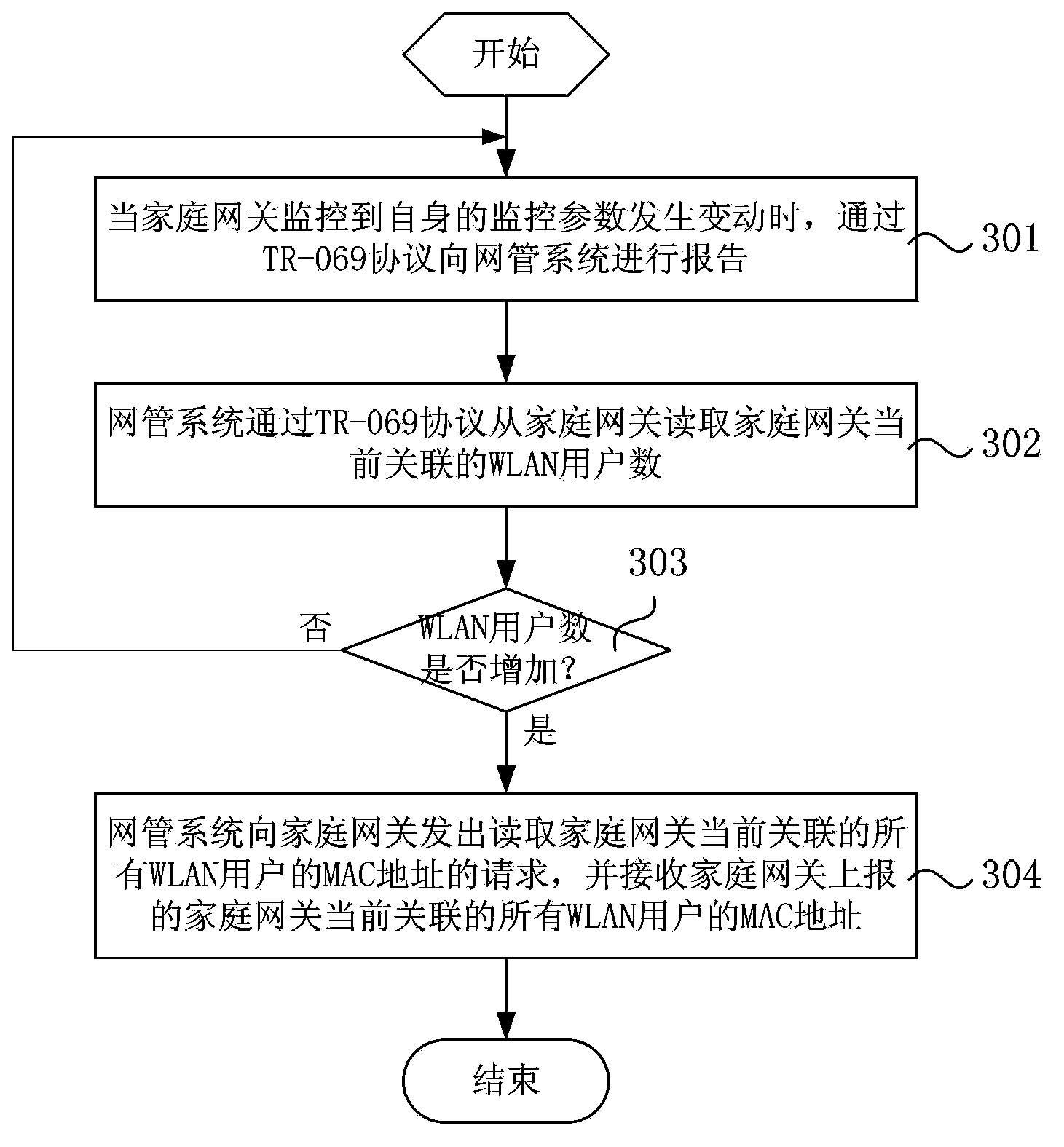
Home gateway WLAN (Wireless Local Area Network) network fault location method and network management system
ActiveCN103701625ASupport operation and maintenance workData switching by path configurationNetwork connectionsTR-069Network management
The invention relates to a home gateway WLAN network fault location method and a network management system. The location method comprises the following steps: the network management system receives home gateway fault information complained by a WLAN user; the network management system queries MAC (Media Access Control) address of the WLAN user from an authentication system according to the home gateway fault information, and further checks the home gateway accessed by the WLAN user; the system detects and locates the wired side network fault of the home gateway according to an OAM (Operation Administration and Maintenance) protocol; if the fault is not detected, the system detects and locates the wireless side network fault of the home gateway according to a TR-069 (Technical Report) protocol. The network management system can quickly locate the complained home gateway from the whole network according to the home gateway fault information complained by the WLAN user, comprehensively utilize multiple network detection skills to quickly and accurately detect and analyze the network fault type of the home gateway in a remote manner, and locate the fault reason, so as to allow telecom operators to effectively support running and maintenance of the home gateway WLAN network.
Owner:CHINA TELECOM CORP LTD
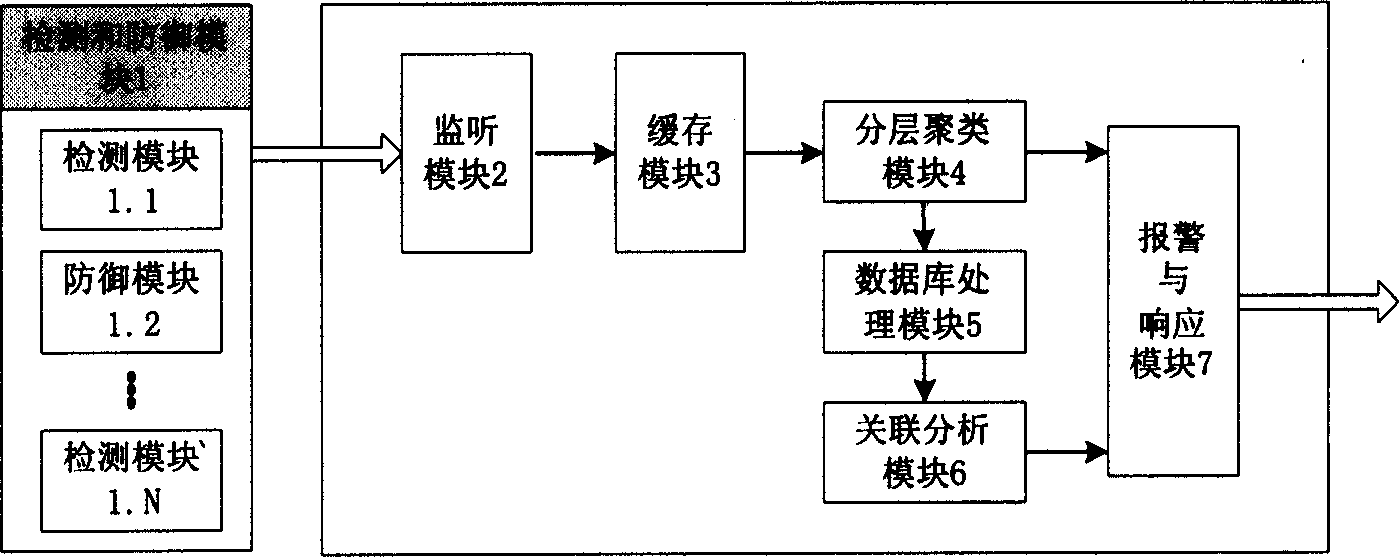
Network safety warning system based on cluster and relavance
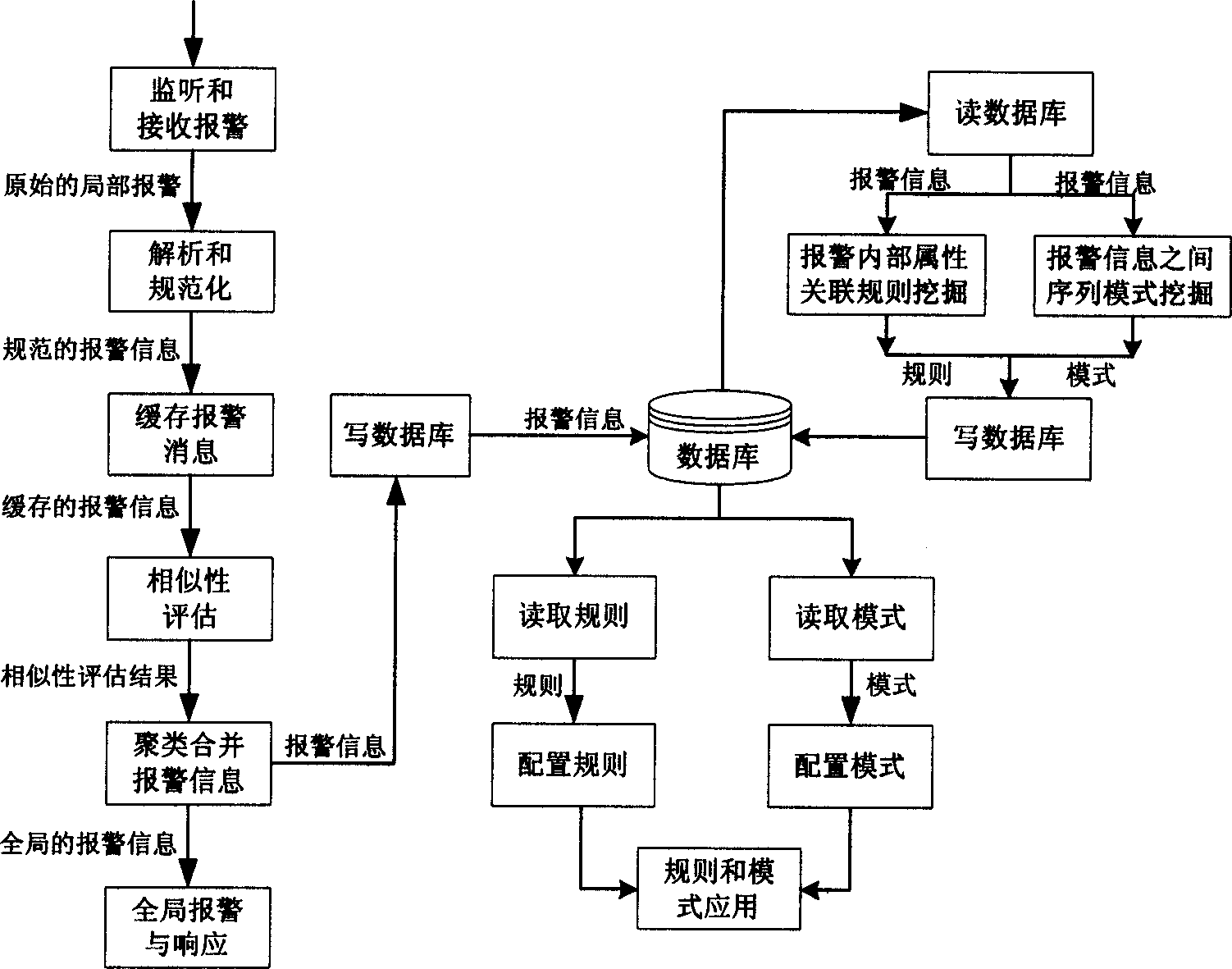
InactiveCN1588880AVersatileImprove performanceData switching networksSpecial data processing applicationsProcess moduleComputer module
This invention relates to an system based on alarming cluster and associated network safety including a monitor module, a buffer memory module, a hierachi clustering module, a database process module, an associated analysis module and an alarm and response module integrated on the upper control stand. The hierachi clustering module can reduce the same or similar redundant alarm information, so as to reduce its transmission volume or extra loads and reduce process burden of network managers who can be even more clear about the attack behavior and configurated safety strategy.
Owner:HUAZHONG UNIV OF SCI & TECH
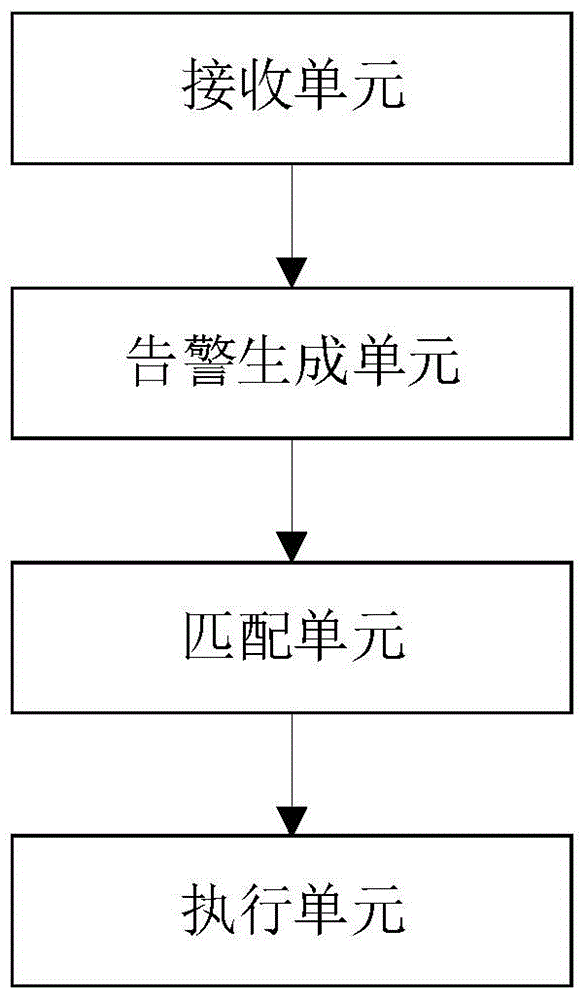
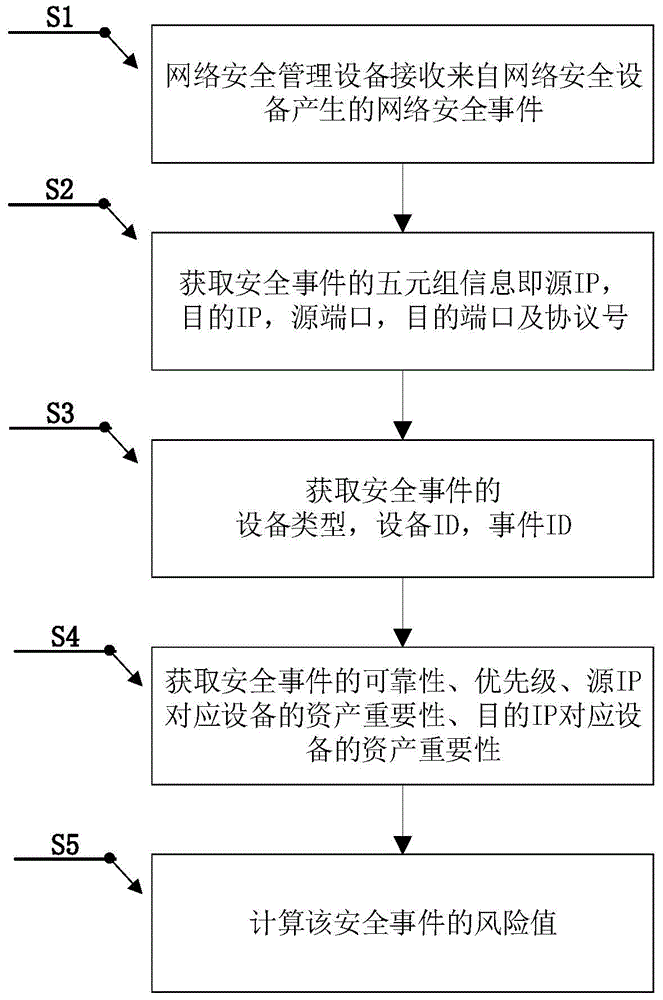
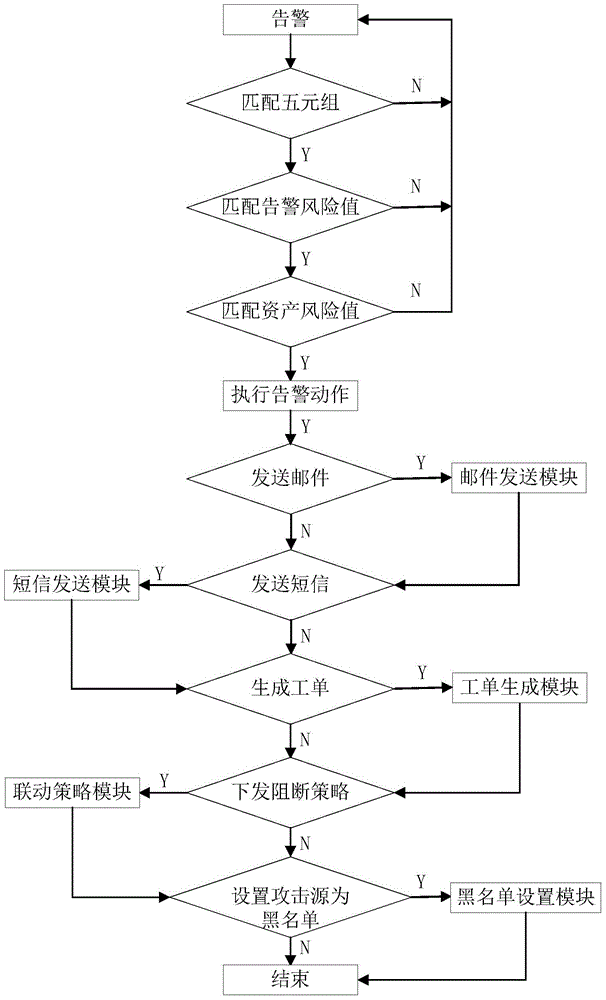
Device and method for network security management based on alarm strategy
The invention discloses a device and a method for network security management based on an alarm strategy. The device for network security management comprises a receiving unit, an alarm generation unit, a matching unit and an execution unit, wherein the receiving unit is used for receiving a security incident generated by the device for network security management; the alarm generation unit is used for generating an alarm based on the security incident with a greater risk value than a preset threshold; the matching unit is used for matching the alarm and an alarm strategy table to obtain an alarm strategy corresponding to the alarm; and the execution unit is used for executing the alarm according to the alarm strategy. According to the device and the method, the alarm information can be corrected and managed, controllability, real-time performance and flexibility of network security are improved, meanwhile, reliability for outputting the alarm information is guaranteed, and the security threat in the network is effectively blocked.
Owner:OPZOON TECH
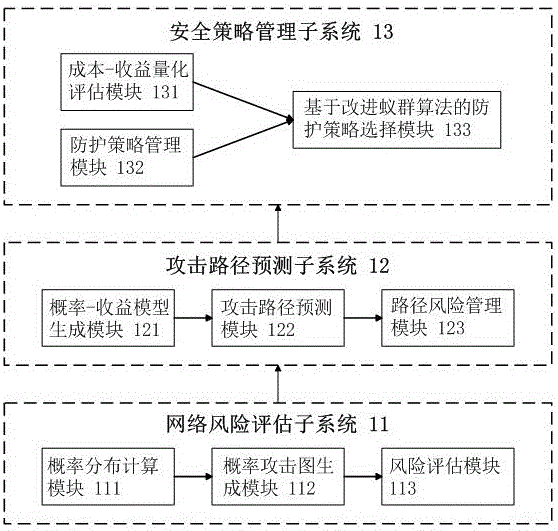
Optimal protection policy analysis system and method based on improved ant colony algorithm
InactiveCN107528850AReduce security risksMaximize utilizationData switching networksLimited resourcesSecurity policy management
The invention provides an optimal protection policy analysis system and method based on an improved ant colony algorithm. The system comprises a network risk assessment subsystem, an attack path prediction subsystem and a security policy management subsystem. The method comprises the following steps: 1) importing a Bayesian probabilistic model to describe the complex relationship between multiple steps of atomic attacks, and constructing an attack diagram by using the Bayesian belief network to evaluate a network security risk; 2) simulating a decision making process of an attacker in combination with the quantitative indexes of the protection cost and the gain, and predicting a possible attack path; and 3) using the improved ant colony algorithm capable of calculating the quasi-optimal solution within a polynomial time to solve the security policy selection problem on the attack path. By adoption of the optimal protection policy analysis system and method, a risk solution can be provided for a network security administrator in time, the attack path prediction and protection strategy selection problems in network security protection are solved, and the security of the whole network under the condition of limited protection resources is effectively protected.
Owner:NORTHWEST UNIV
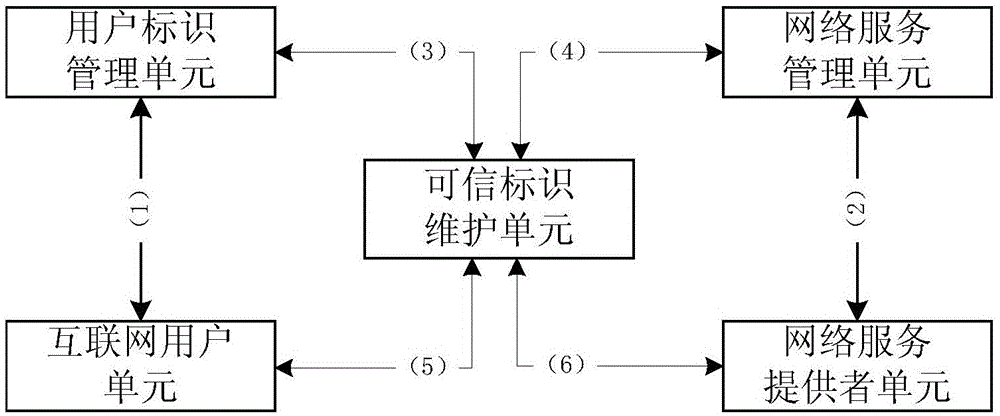
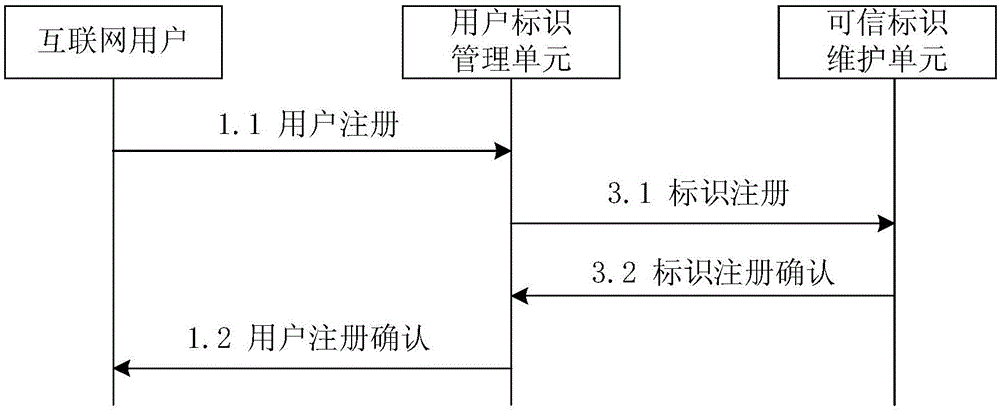
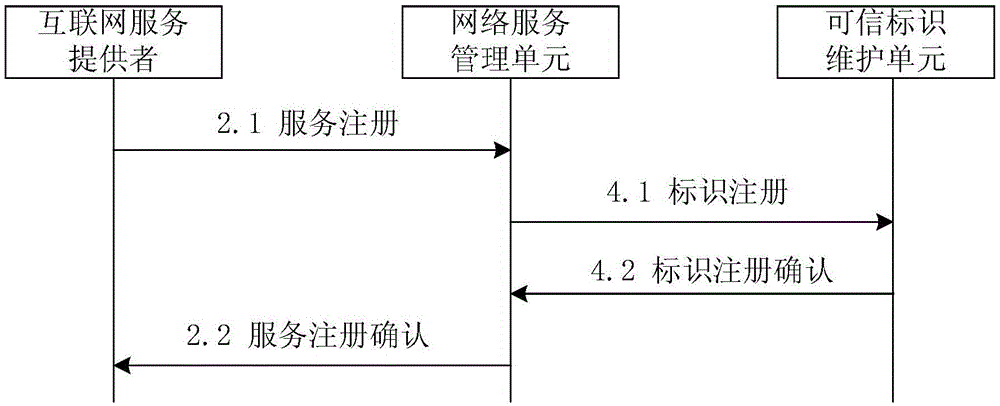
Trusted network identity management and verification system and method
The invention relates to a trusted network identity management and verification system and method. The method comprises the following steps that: a user identity management unit maintains network identity information of a user, binds a network identity of the user with public key information, and registers the bound network identity and public key information to a trusted identity maintenance unit; a network service management unit manages an Internet service, binds corresponding public key information with a domain name, and registers the bound public key information and domain name to the trusted identity maintenance unit; the trusted identity maintenance unit deploys a DNSSEC (Domain Name System Security Extensions) protocol, and maintains identity and public key binding information of the user and the Internet service; an Internet user unit saves and manages private key information of the Internet user unit, and acquires information of a trusted Internet service provider by inquiring the trusted identity maintenance unit; and an Internet service provider unit saves and manages private key information of the Internet service provider unit, and acquires user information by inquiring the trusted identity maintenance unit. Through adoption of the trusted network identity management and verification system and method, functions such as bidirectional identity authentication, key negotiation and secure communication between the service provider and an Internet user can be supported.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Network vulnerability evaluation method
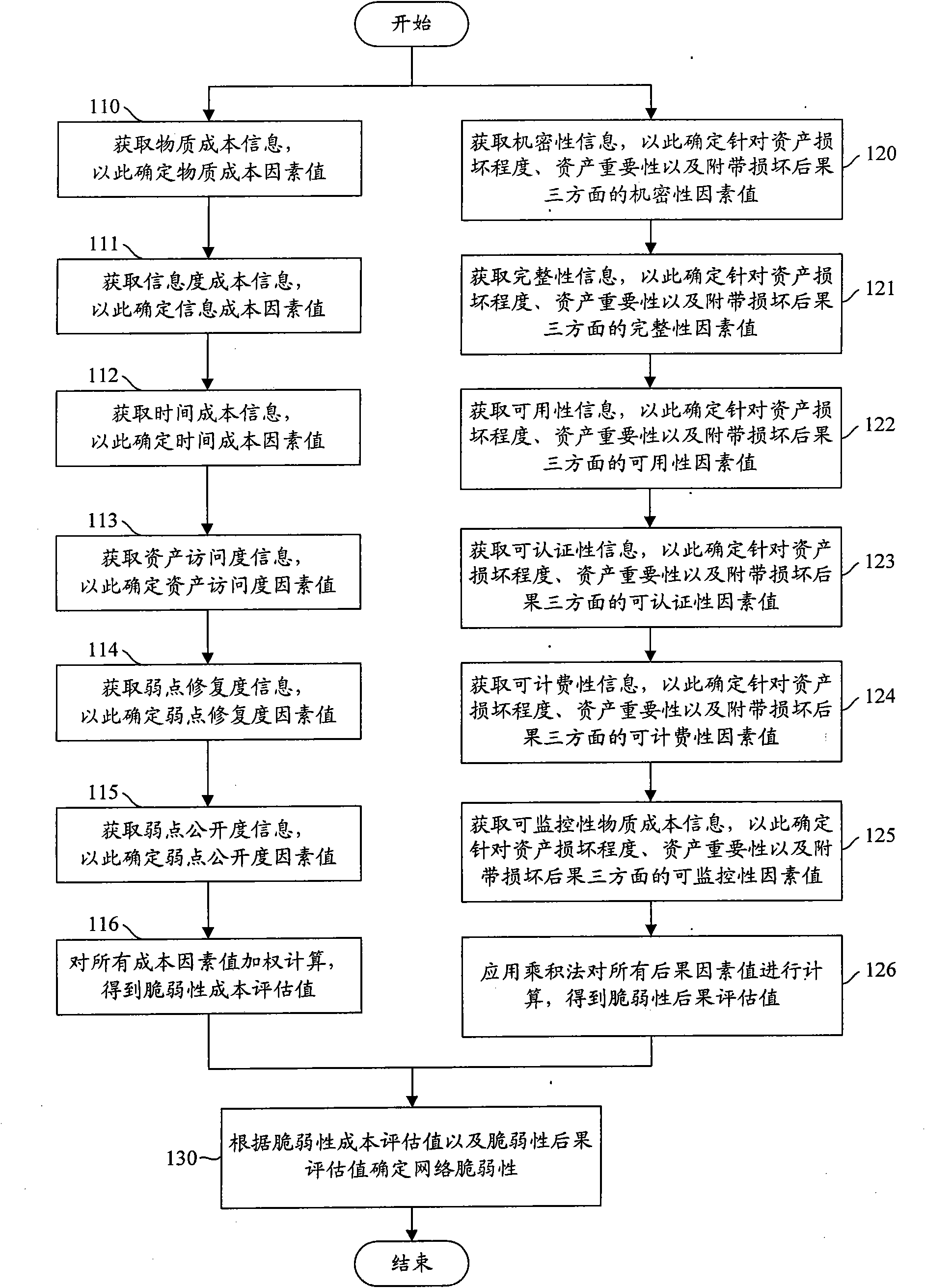
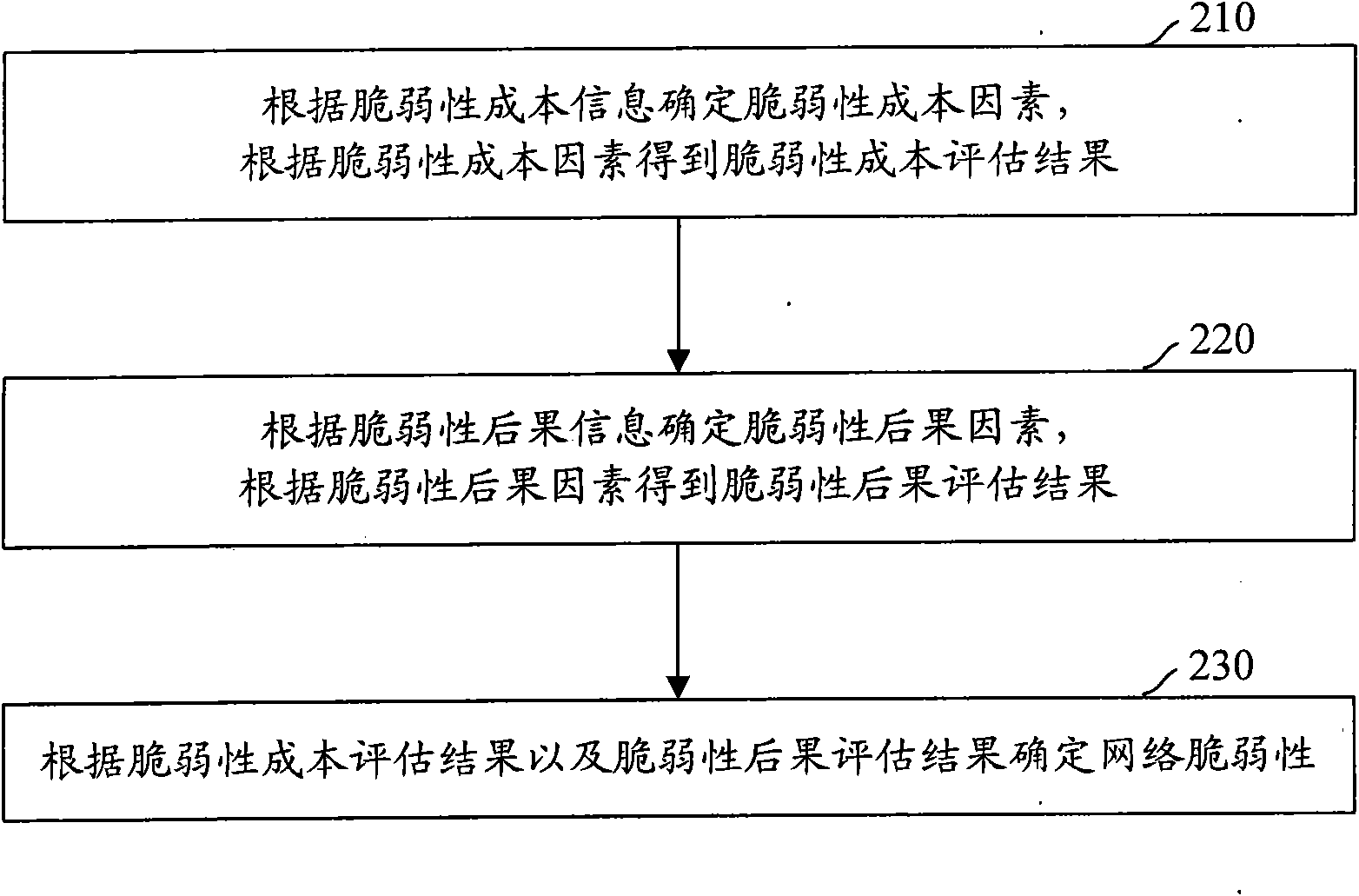
InactiveCN101964730AImprove accuracyAvoid bad consequencesData switching networksCost evaluationEvaluation result
The invention discloses a network vulnerability evaluation method. The method comprises the following steps of: determining vulnerability cost factors according to vulnerability cost information; obtaining a vulnerability evaluation result according to the evaluation cost factors; determining vulnerability consequence factors according to vulnerability consequence information; obtaining a vulnerability consequence evaluation result according to the vulnerability consequence factors; and determining network vulnerability according to the vulnerability cost evaluation result and the vulnerability consequence evaluation result. Therefore, the method of the invention takes the vulnerability cost factors and the vulnerability consequence factors into consideration comprehensively when evaluates the network vulnerability, and enriches and perfects the basis for network vulnerability evaluation in a targeted way, so that the accurate performance of the network vulnerability evaluation is improved obviously. Moreover, the obtained improved network vulnerability evaluation accuracy can provide important reference for network safety management, ensures that corresponding safety measures can be implemented more targeted in a planned manner based on the reference, and avoids a serious result caused by utilizing the network vulnerability.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Cloud computing information safe visualization system based on trusted computing
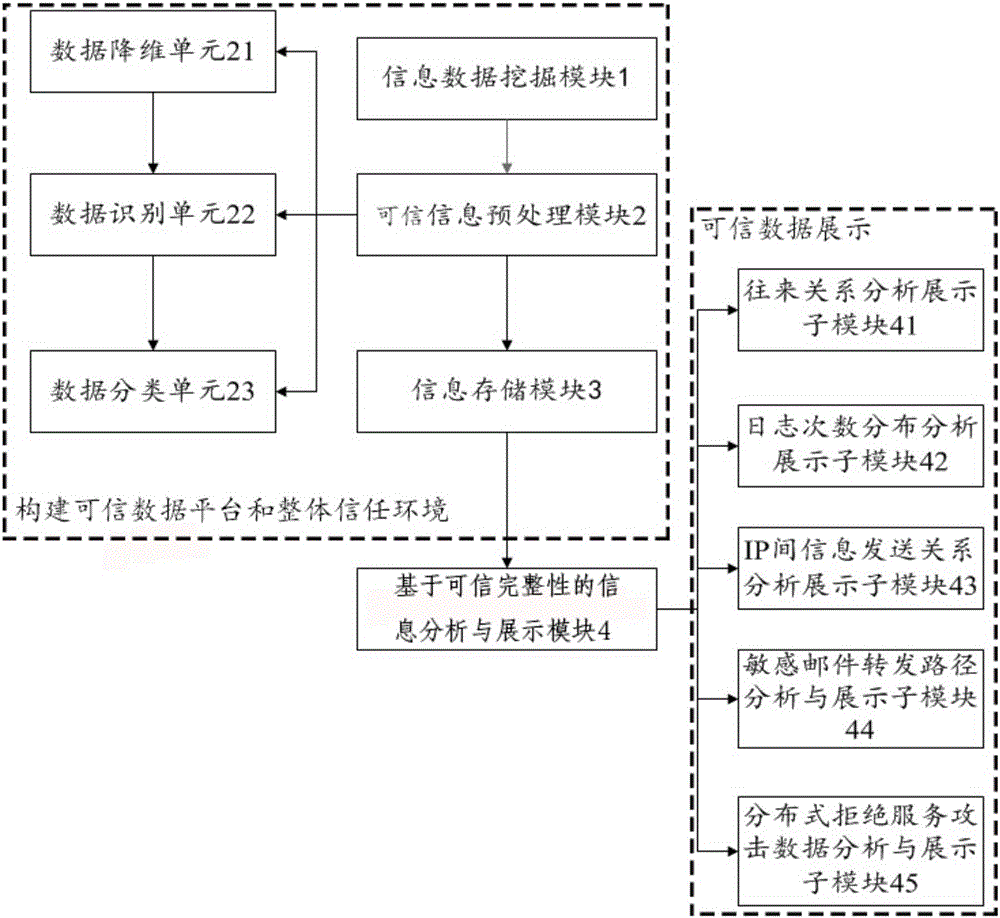
The invention provides a cloud computing information safe visualization system based on trusted computing. According to the visualization system, an integrated trust environment is established on the basis of function modules such as data mining, data identification and data dimension reduction, so that the information safe visualization system from data mining to data processing and storage, and to trusted data display is established. Starting from data mining and preprocessing modules, the data of a trusted data information analysis and display module is trusted. According to the system, through adoption of a brand new module combination and an innovative algorithm, the trust and safety of the network information are ensured; trusted quantification and visualization evaluation of the information safety are realized; and the convenience is provided for a manager in an aspect of network safety management.
Owner:GUANGXI POWER GRID CORP
Network security management and control system for accessing social video networks to video private network
InactiveCN106027358ARealize security management and controlSafe and reliable connectionClosed circuit television systemsNetworks interconnectionDigital videoData stream
The invention discloses a network security management and control system for accessing social video networks to a video private network. The network security management and control system comprises the video private network, multiple social video networks and multiple access equipment arranged among the video private network and the social video networks; and an integrated management platform is arranged on the video private network. According to the network security management and control system disclosed by the invention, security management and control of a network is realized through the access equipment and the integrated management platform; an illegal data flow and access of an illegal user are intercepted in a physical isolation manner from a bottom protocol level of a network data packet while real-time transmission requirements of digital video information are ensured; and thus, the access security from the social video networks to the video private network is ensured.
Owner:SHANGHAI HORIZON INFORMATION TECH
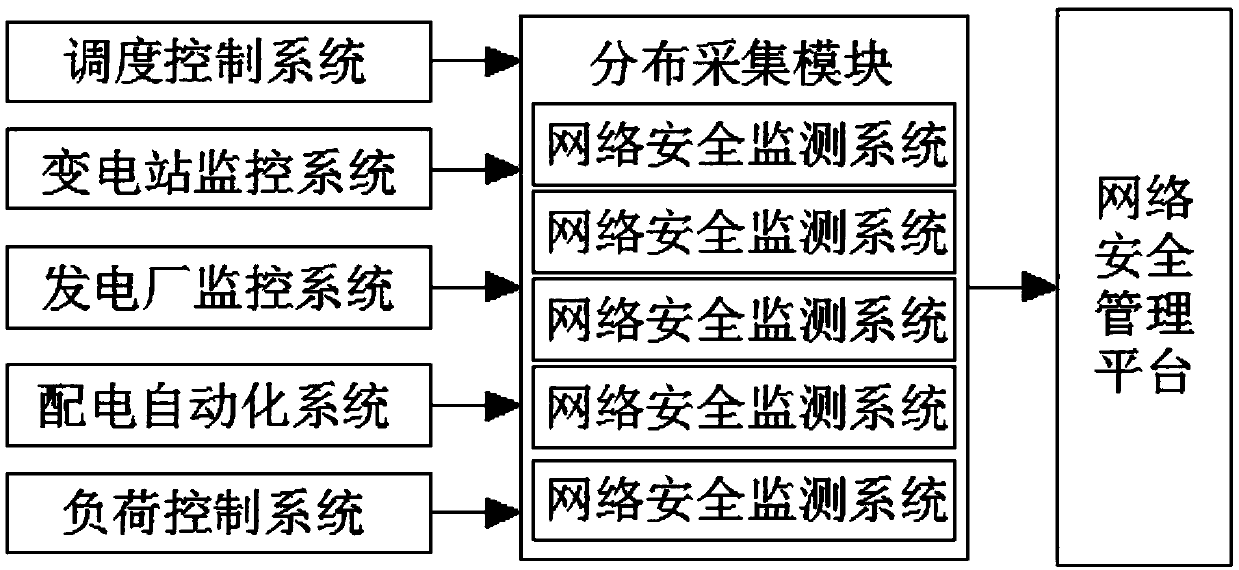
Network security monitoring system applied to power monitoring system
InactiveCN108683549AReal-time monitoringReal-time monitoring and effective managementCircuit arrangementsData switching networksEngineeringSingle point of failure
The invention discloses a network security monitoring system applied to a power monitoring system, and belongs to the technical field of network security monitoring systems. The network security monitoring system comprises a dispatch control system, a substation monitoring system, a power plant monitoring system, an automatic power distribution system and a load control system, output ends of thedispatch control system, the substation monitoring system, the power plant monitoring system, the automatic power distribution system and the load control system are electrically connected with an input end of a distributed collection module, the output end of the distributed collection module is electrically connected with the input end of a network security management platform, real-time monitoring and effective management of network space security are achieved through the independent collection of network security events of various monitoring points and the distributed processing of data, real-time monitoring and online management can be performed on the security risks and the security events of the power monitoring system to avoid the problem that the whole system cannot run due to a single point fault, the subsequent expansion and maintenance are facilitated, and the security coefficient is high.
Owner:HUBEI INFOTECH SYST TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com