Optimal protection policy analysis system and method based on improved ant colony algorithm
A technology of protection strategy and ant colony algorithm, which is applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of complex multi-step, huge cost, and difficulty for protection personnel to determine the attacker's attack path and target node, etc., to achieve The effect of reducing cybersecurity risk
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but is not limited thereto.
[0072] The present invention involves knowledge related to graph theory and Bayesian belief network, and explains the relevant content:
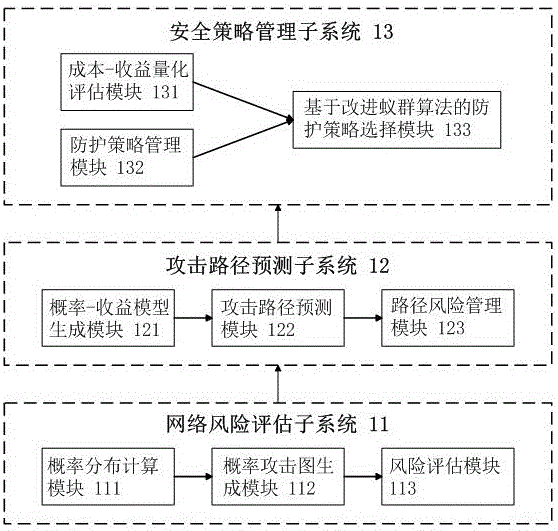
[0073] The probabilistic attack graph includes 7 kinds of influencing factors, including attribute node set S, atomic attack node set A, directed edge set E of the attack graph, relationship set ε between a node and its parent node set, conditional probability distribution T, and protection strategy set M , The cost set C of the defense strategy.
[0074] The probabilistic attack graph is a directed acyclic graph, expressed as BPAG=(S, A, E, ε, T, M, C).
[0075] The attribute node set S uses Bernoulli random variables to represent the resources and permissions owned by the intruder during the intrusion process, and the value space is {0, 1}. Attribute nodes are divide...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com