Trusted network identity management and verification system and method
A network identity and verification system technology, applied in user identity/authority verification, transmission systems, electrical components, etc., can solve the problem of not providing data content, data being easily hijacked or tampered with, and inability to determine message tampering and whether the source is correct, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] In order to make the above objects, features and advantages of the present invention more obvious and understandable, the present invention will be further described below through specific embodiments and accompanying drawings.
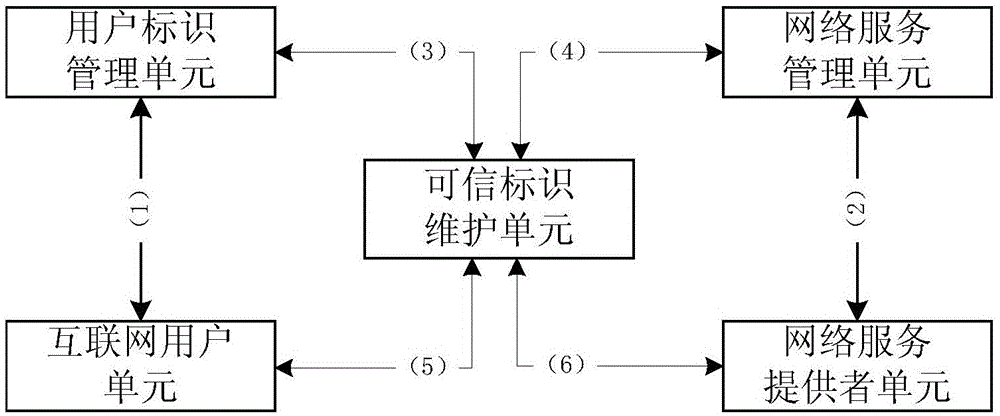
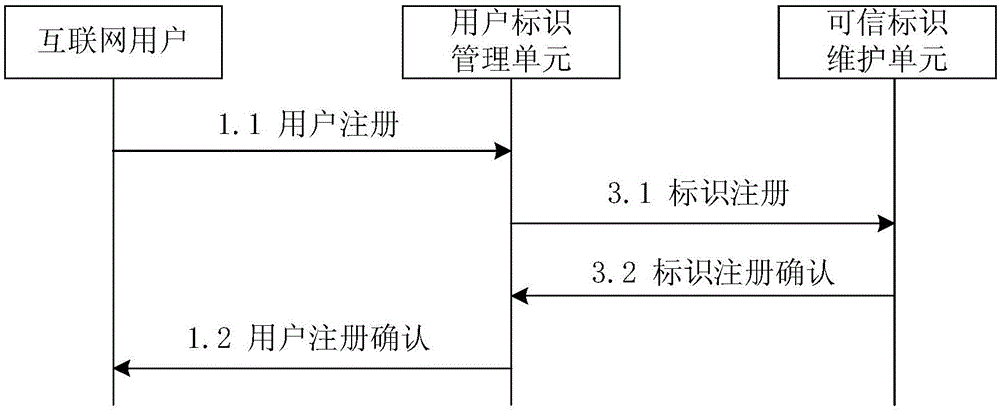
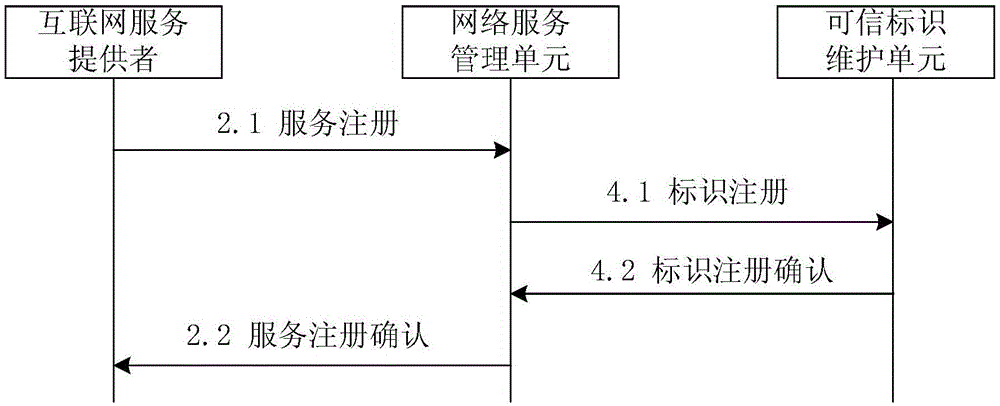
[0038] The present invention specifically includes five functional roles: an organization that manages user identity information, an organization that manages Internet service providers, an organization that maintains trusted identification information for users and services, Internet users, and network service providers. The above five functional roles can be realized by specific hardware devices or software modules, which can be called user identity management unit / device / module, network service management unit / device / module, trusted identity maintenance unit / device / module, Internet user unit / device / module and network service provider unit / device / module. The name "unit" is used below, such as figure 1 shown.
[0039] The user identification...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com