Patents
Literature
538 results about "Network service provider" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
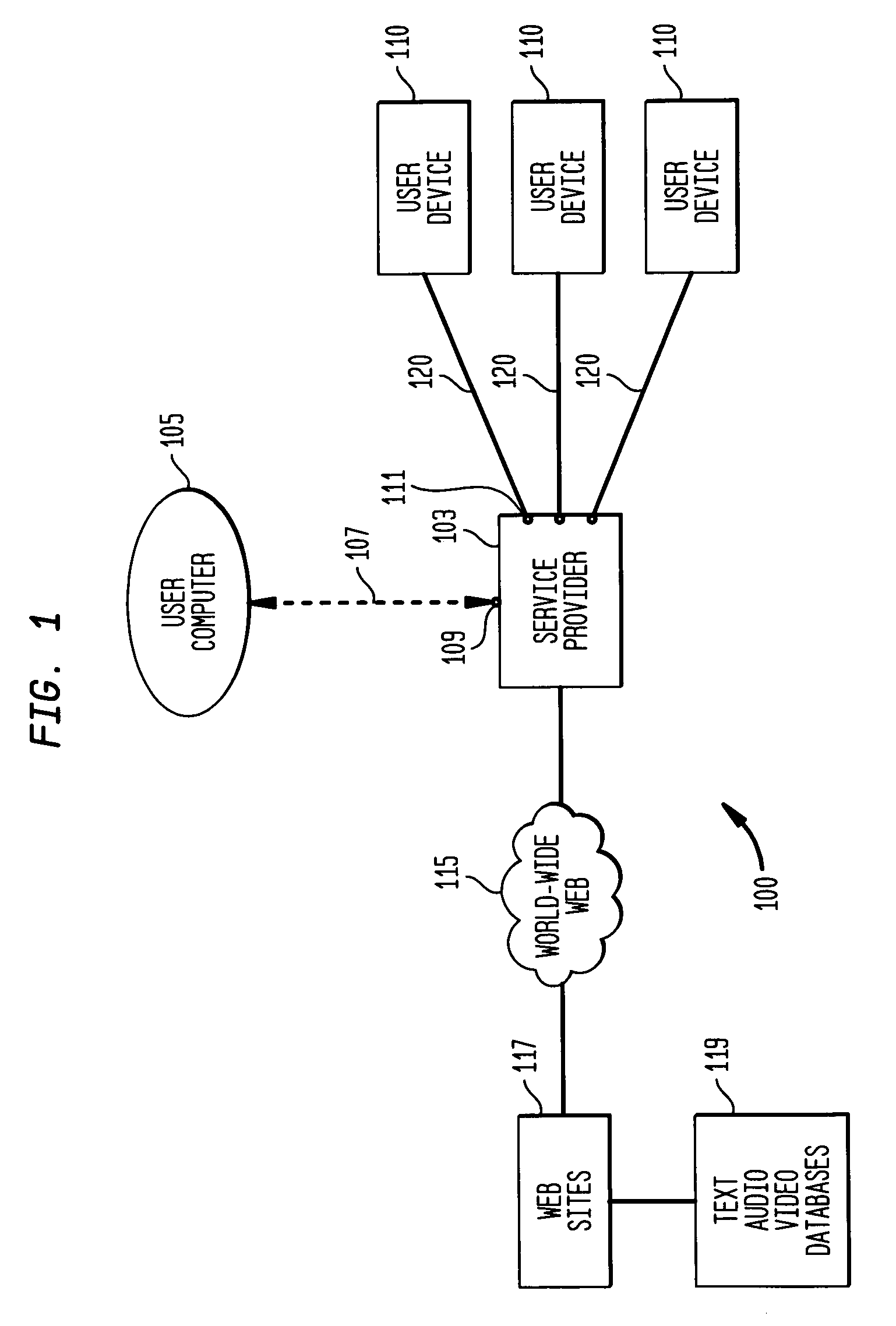
A network service provider (NSP) is a business or organization that sells bandwidth or network access by providing direct Internet backbone access to internet service providers and usually access to its network access points (NAPs). For such a reason, network service providers are sometimes referred to as backbone providers or internet providers.
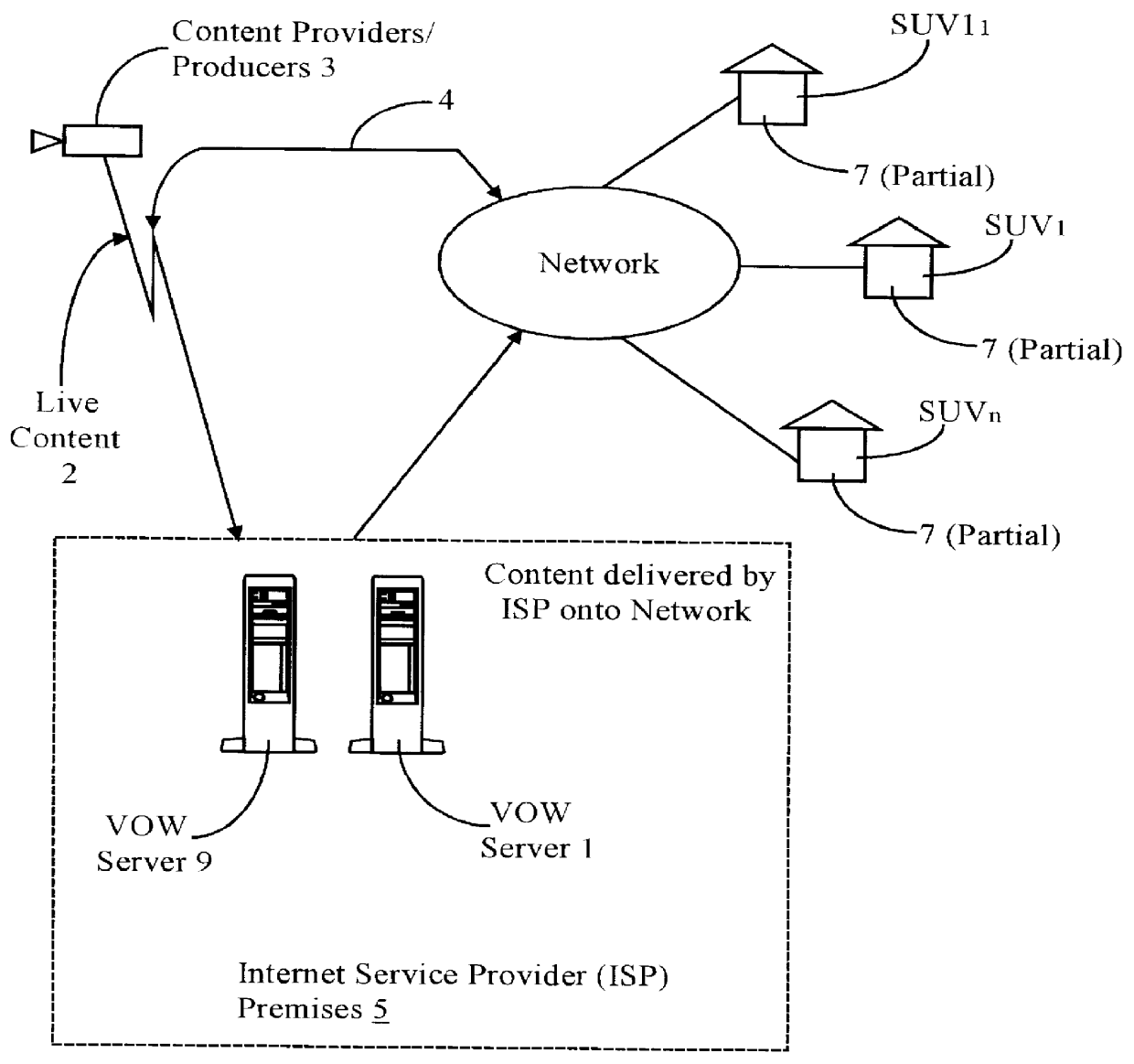
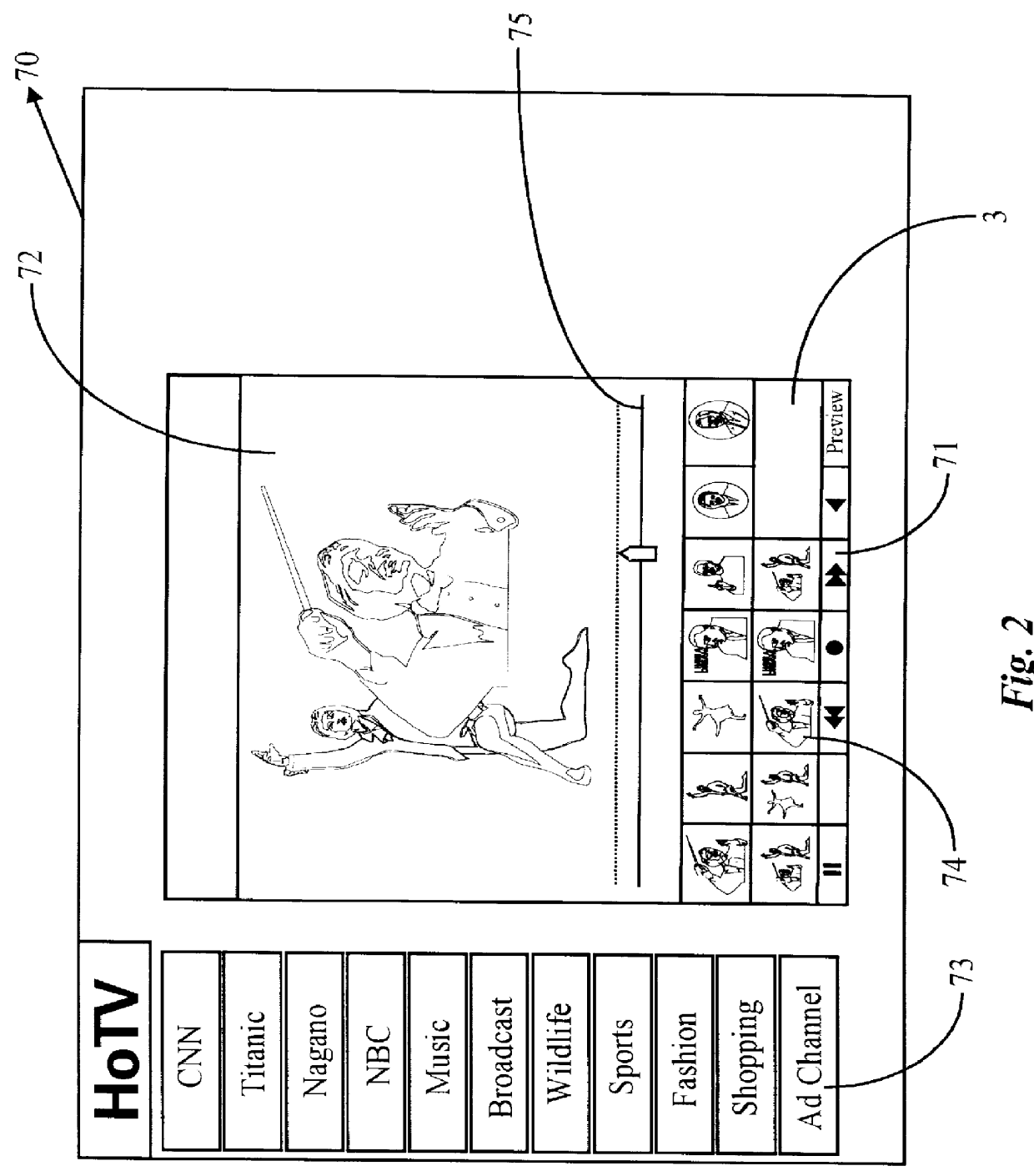
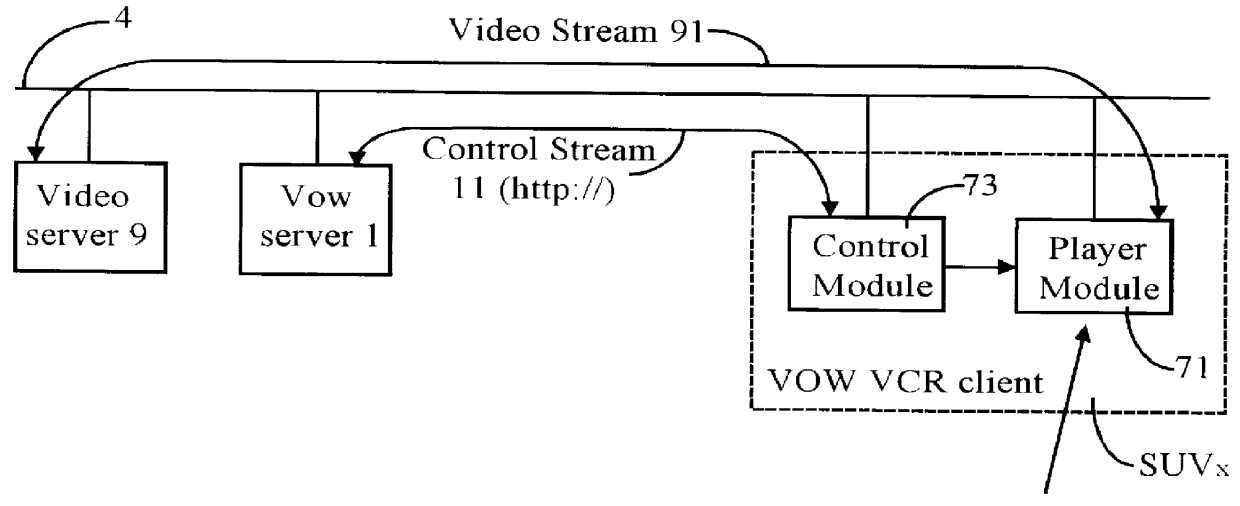
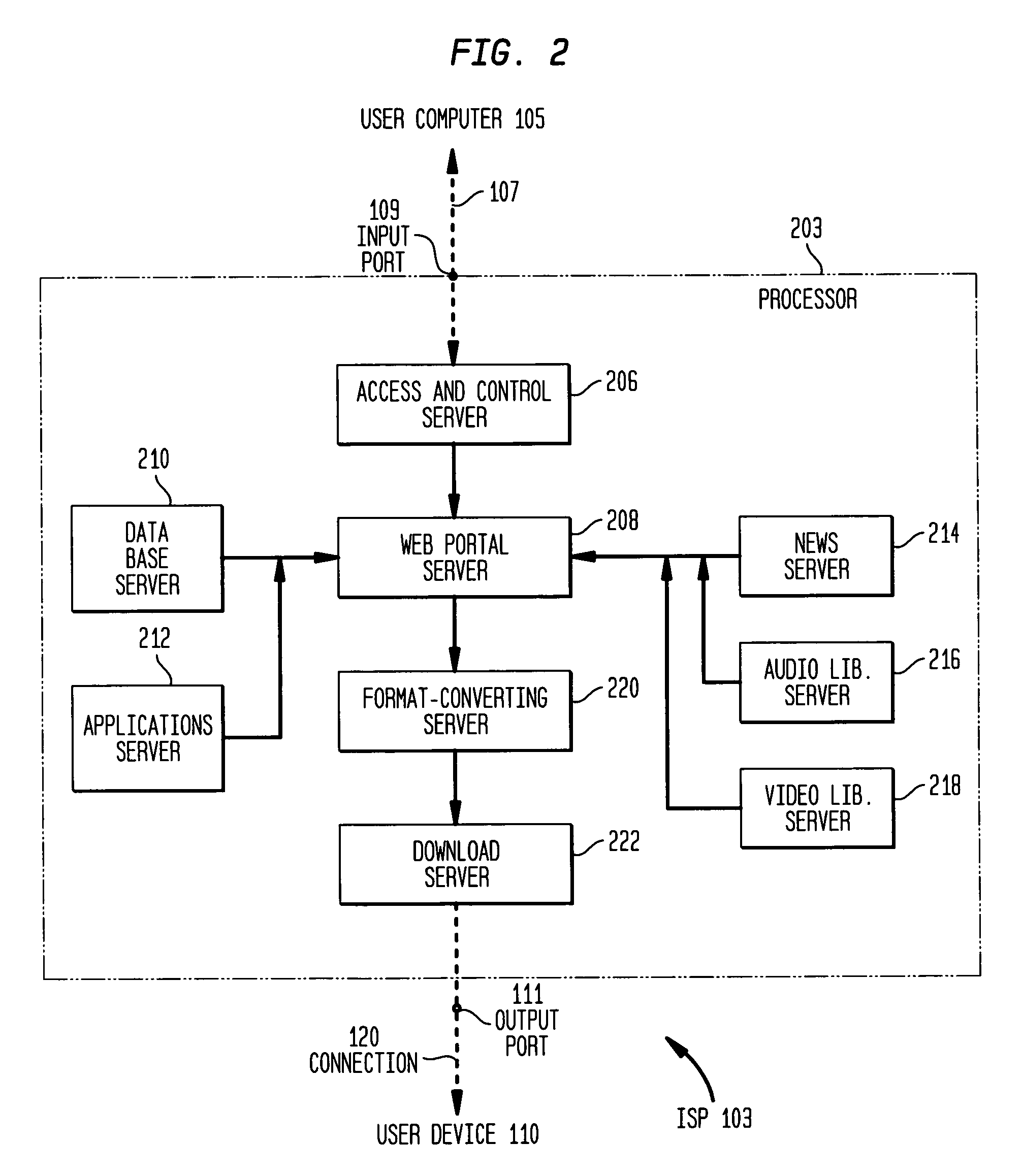
Real-time receipt, decompression and play of compressed streaming video/hypervideo; with thumbnail display of past scenes and with replay, hyperlinking and/or recording permissively intiated retrospectively
InactiveUS6154771AEfficient multicastingEasy to seeTelevision system detailsDigital data information retrievalFull customSoftware system
Streaming compressed digital hypervideo received upon a digital communications network is decoded (decompressed) and played in a client-computer-based "video on web VCR" software system. Scene changes, if not previously marked upstream, are automatically detected, and typically twenty-one past scenes are displayed as thumbnail images. Hyperlinks within the main video scene, and / or any thumbnail image, show as hotspots, with text annotations typically appearing upon a cursor "mouse over". All hyperlinks-as are provided and inserted by, inter alia, the upstream network service provider (the "ISP")-may be, and preferably are, full-custom dynamically-resolved to each subscriber / user / viewer ("SUV") upon volitional "click throughs" by the SUV, including retrospectively on past hypervideo scenes as appear within the thumbnail images. Hyperlinking permits (i) retrieving information and commercials, including streaming video / hypervideo, from any of local storage, a network (or Internet) service provider ("ISP"), a network content provider, and / or an advertiser network site, (ii) entering a contest of skill or a lottery of chance, (iii) gambling, (iv) buying (and less often, selling), (v) responding to a survey, and expressing an opinion, and / or (vi) sounding an alert.
Owner:TATA AMERICA INT
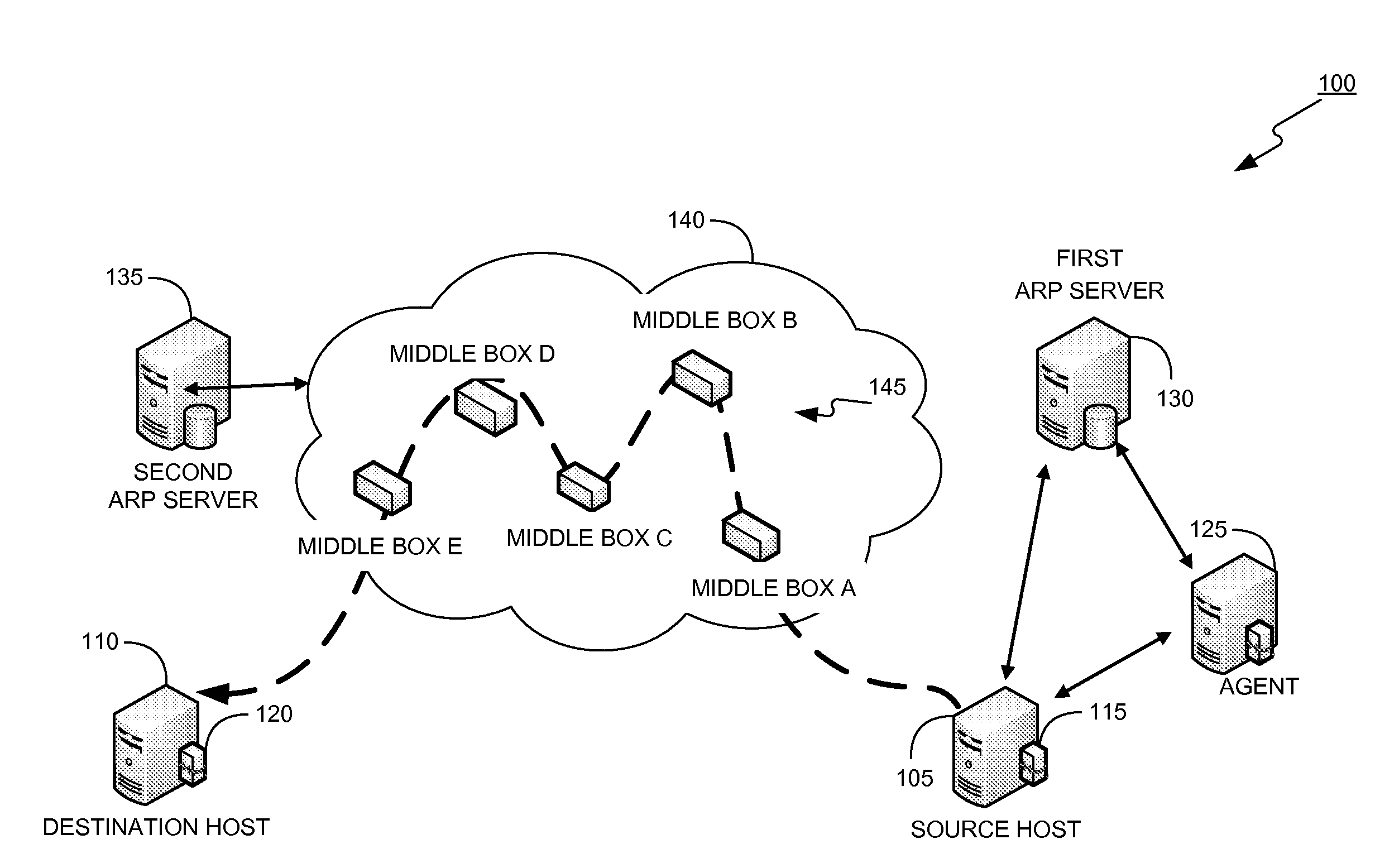
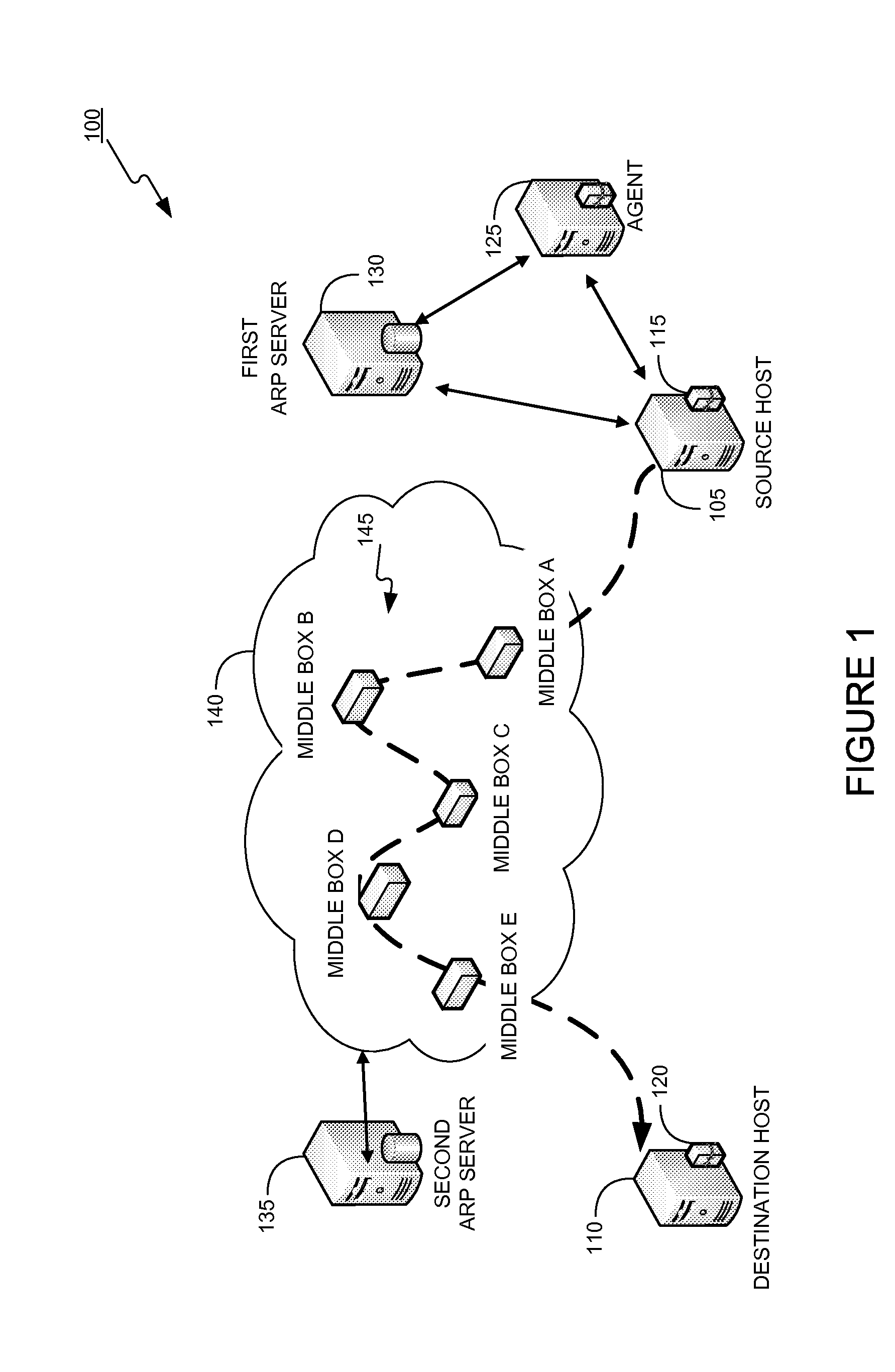
Dynamically provisioning middleboxes
Hybrid security architecture (HSA) provides a platform for middlebox traversal in the network. The HSA decouples the middlebox control from network forwarding. More specifically, such embodiments may receive a data packet having a packet header including an Ethernet header identifying source and destination addresses in the network. A traffic type of the data packet is determined. Then, layer-2 forwarding information, which encodes a set of non-forwarding network service provider middleboxes in the network to be traversed by the data packet, is determined based on the traffic type. The layer-2 forwarding information is inserted into the Ethernet header and the data packet is forwarded into the network. The data packet will then traverse, according to the layer-2 forwarding information, a sequence of the middleboxes in the network, wherein at least one non-forwarding network service will be provided by each of the middleboxes to the data packet in a sequence.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
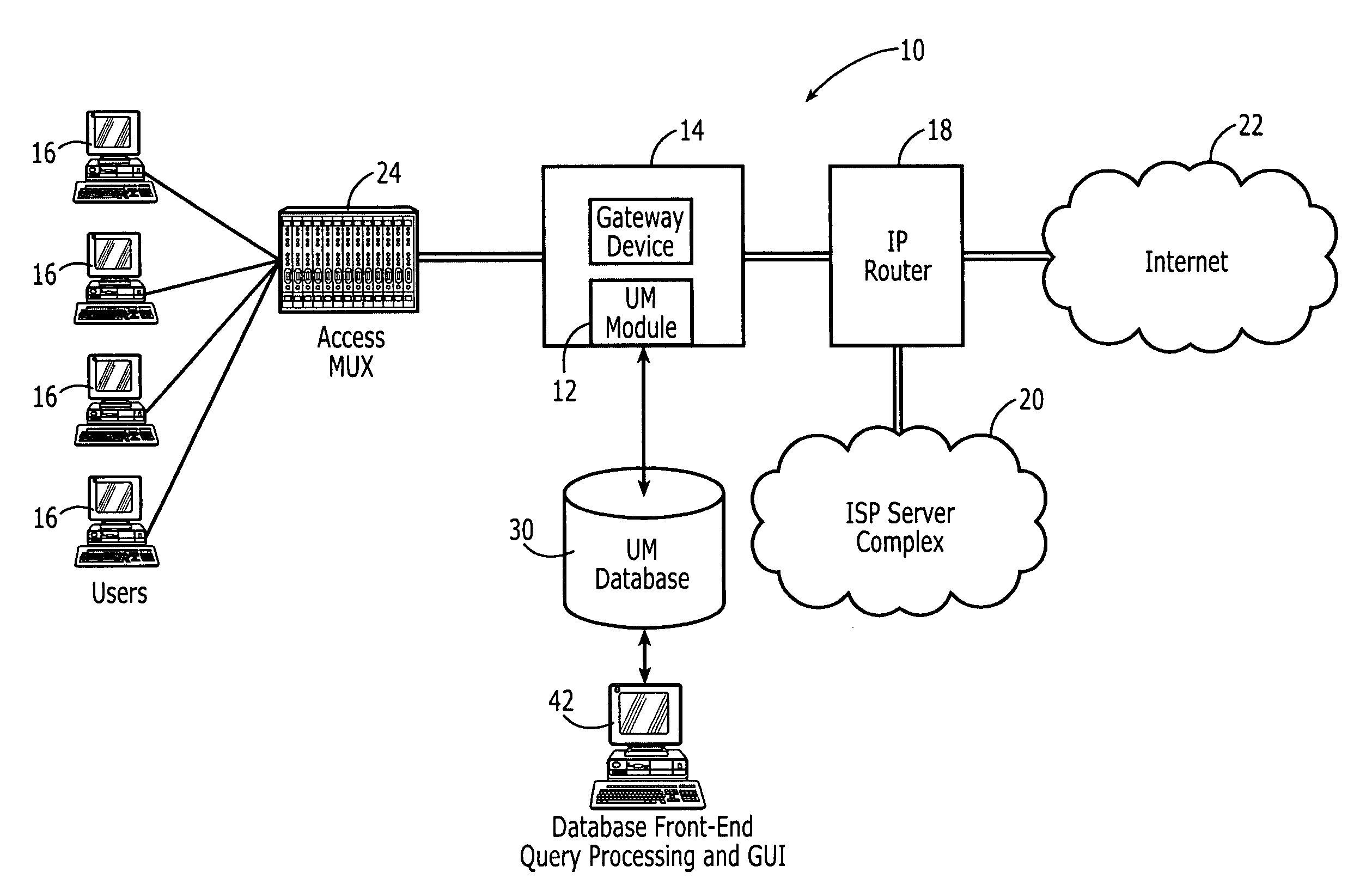
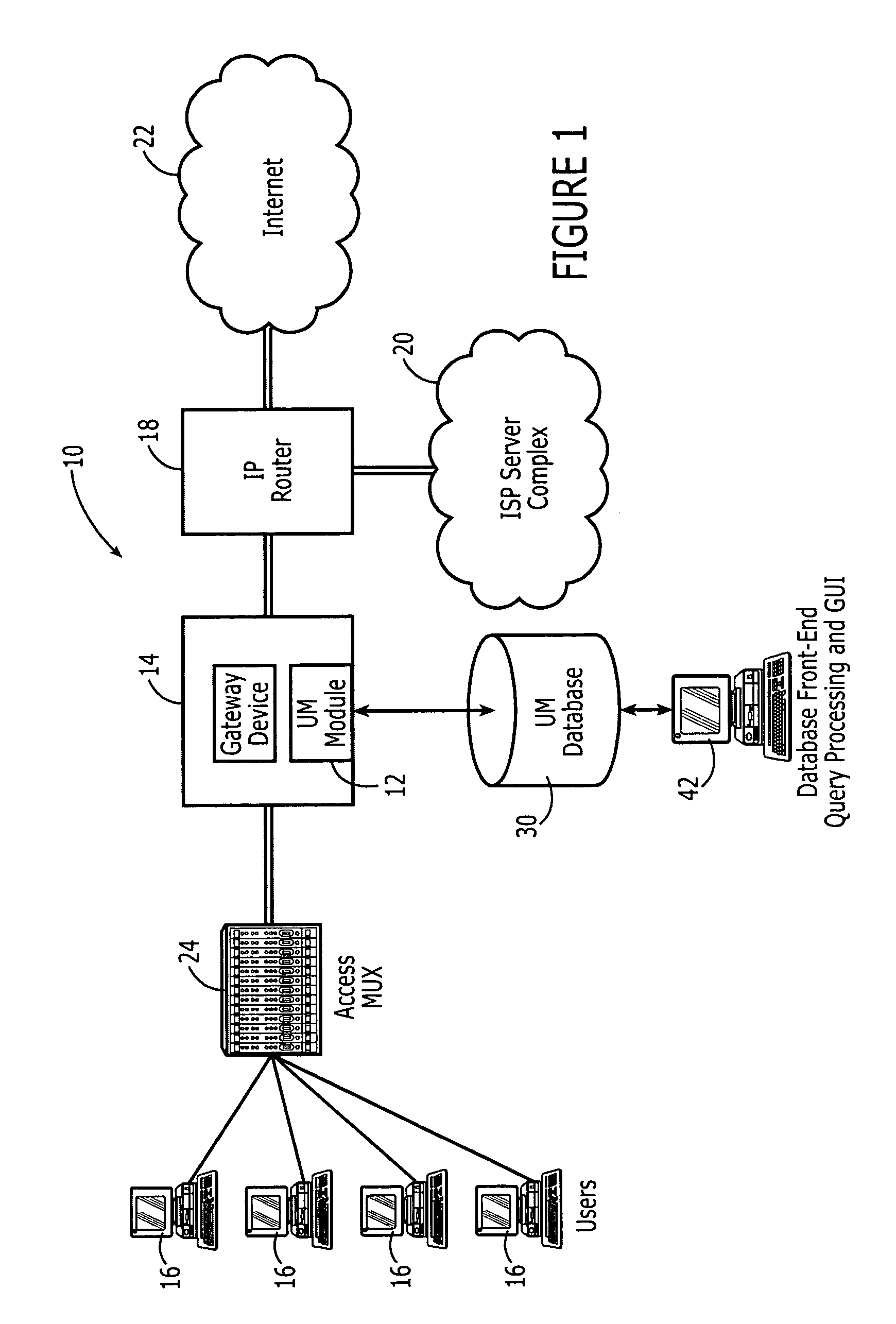
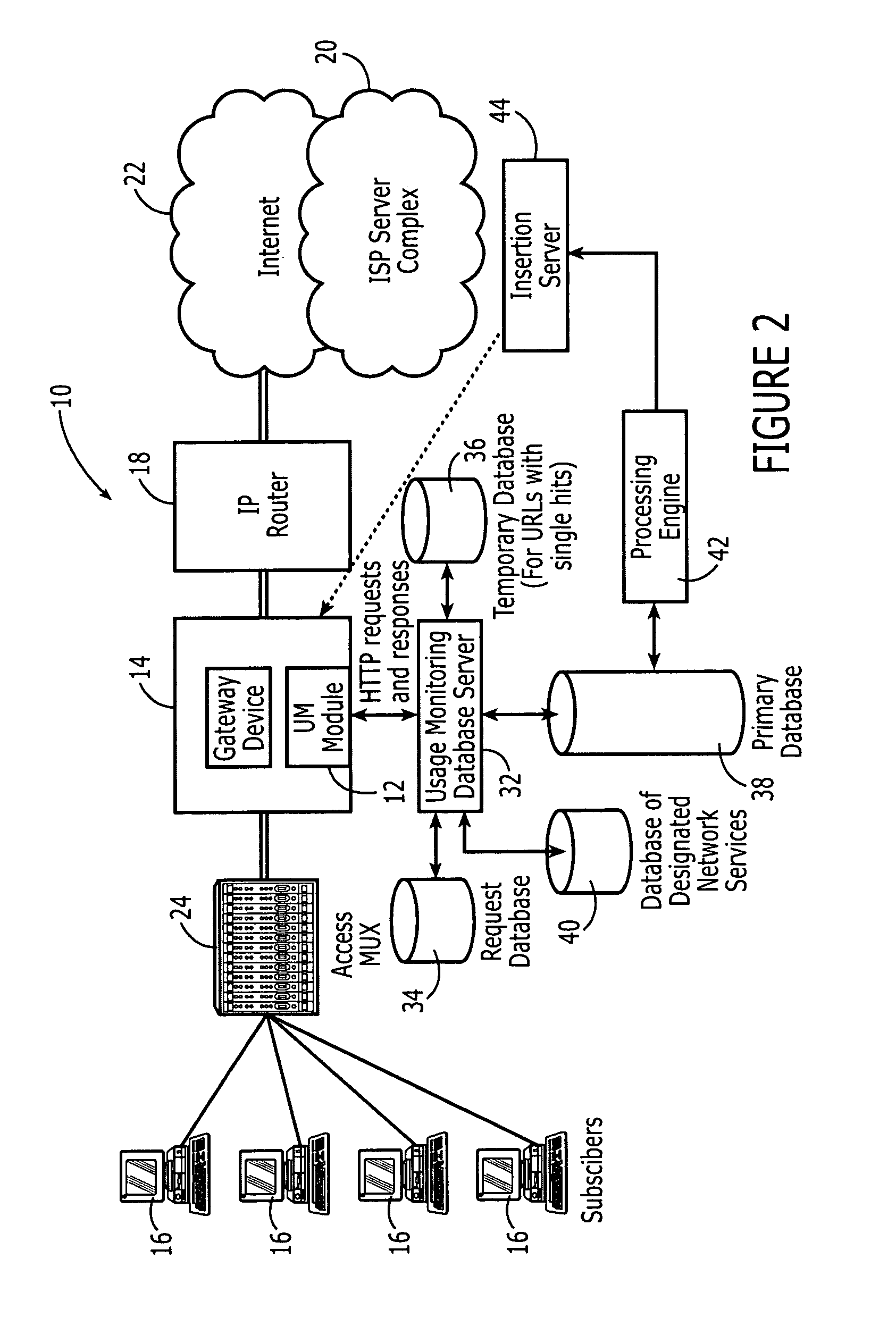
Network usage monitoring device and associated method
InactiveUS7020082B2Information can be usedIncrease valueError preventionFrequency-division multiplex detailsTraffic capacityNetwork interface device
A network usage monitoring module is provided for monitoring network usage at a network access point, i.e. network traffic aggregation point, typically at a gateway device or a similar network interface device. As such, the network usage monitoring module can monitor the usage of a number of network users who are attempting to access various network services provided via the gateway device. Thus, the usage information collected by the usage monitoring module is considerably more robust than that offered by conventional monitoring techniques. As such, the information is considerably more valuable to network service providers, network users, network beneficiaries and the like. In addition, the usage monitoring method and apparatus offers a number of particular features to improve the monitoring process as well as the value of the usage information that is collected.
Owner:NOMADIX INC
Updating routing information based on client location
ActiveUS20100125675A1Digital computer detailsLocation information based serviceIp addressClient-side
A system, method, and computer-readable medium for updating request routing information associated with client location information are provided. A content delivery network service provider receives a DNS query from a client computing device. The DNS query corresponds to a resource identifier for requested content from the client computing device. The content delivery network service provider obtains a query IP address corresponding to the client computing device. Based on routing information associated with the query IP address, the content delivery network service provider routes the DNS query. The process further includes monitoring performance data associated with the transmission of the requested resource and updating routing information associated with the query IP address based on the performance data for use in processing subsequent requests form the client computing device.
Owner:AMAZON TECH INC
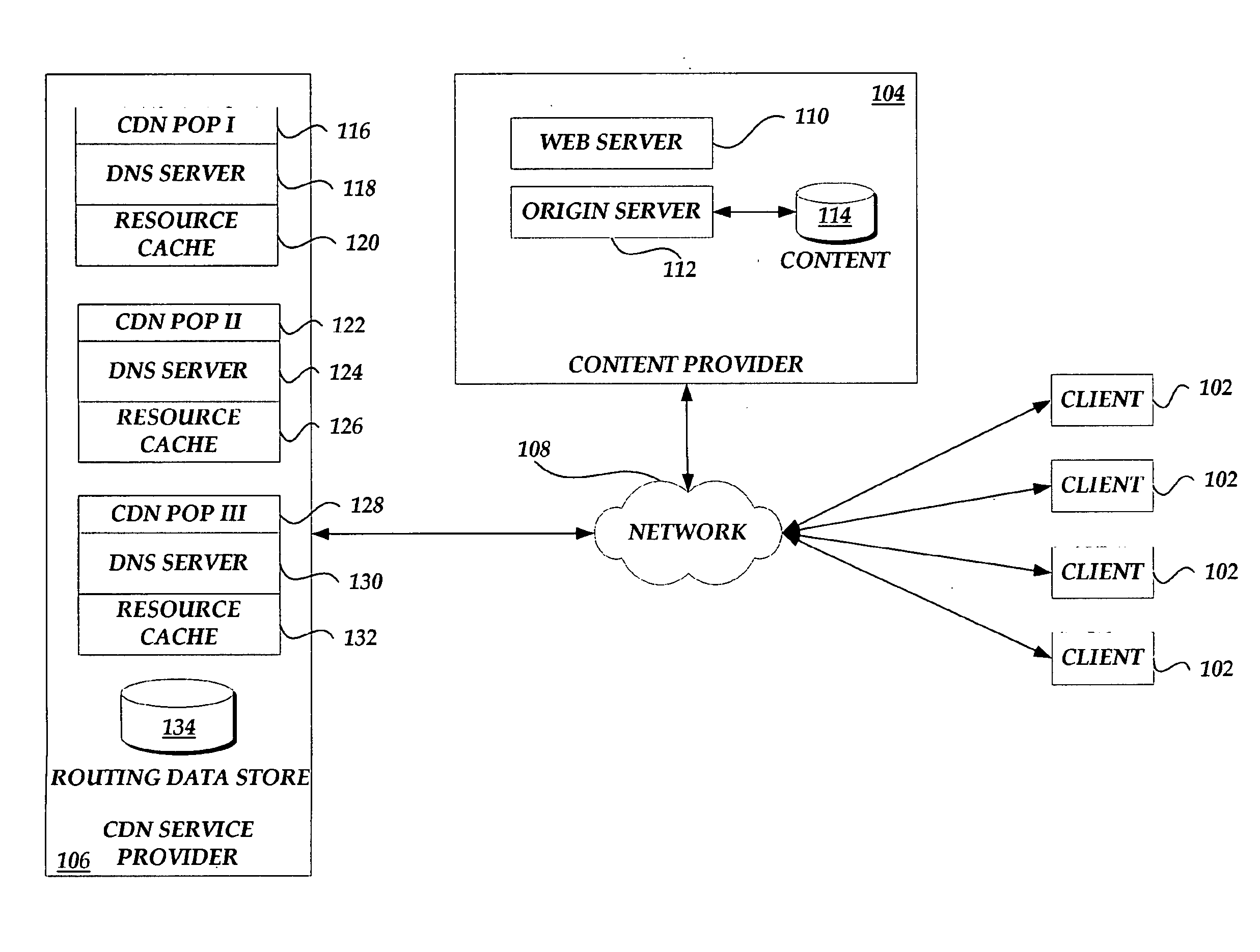
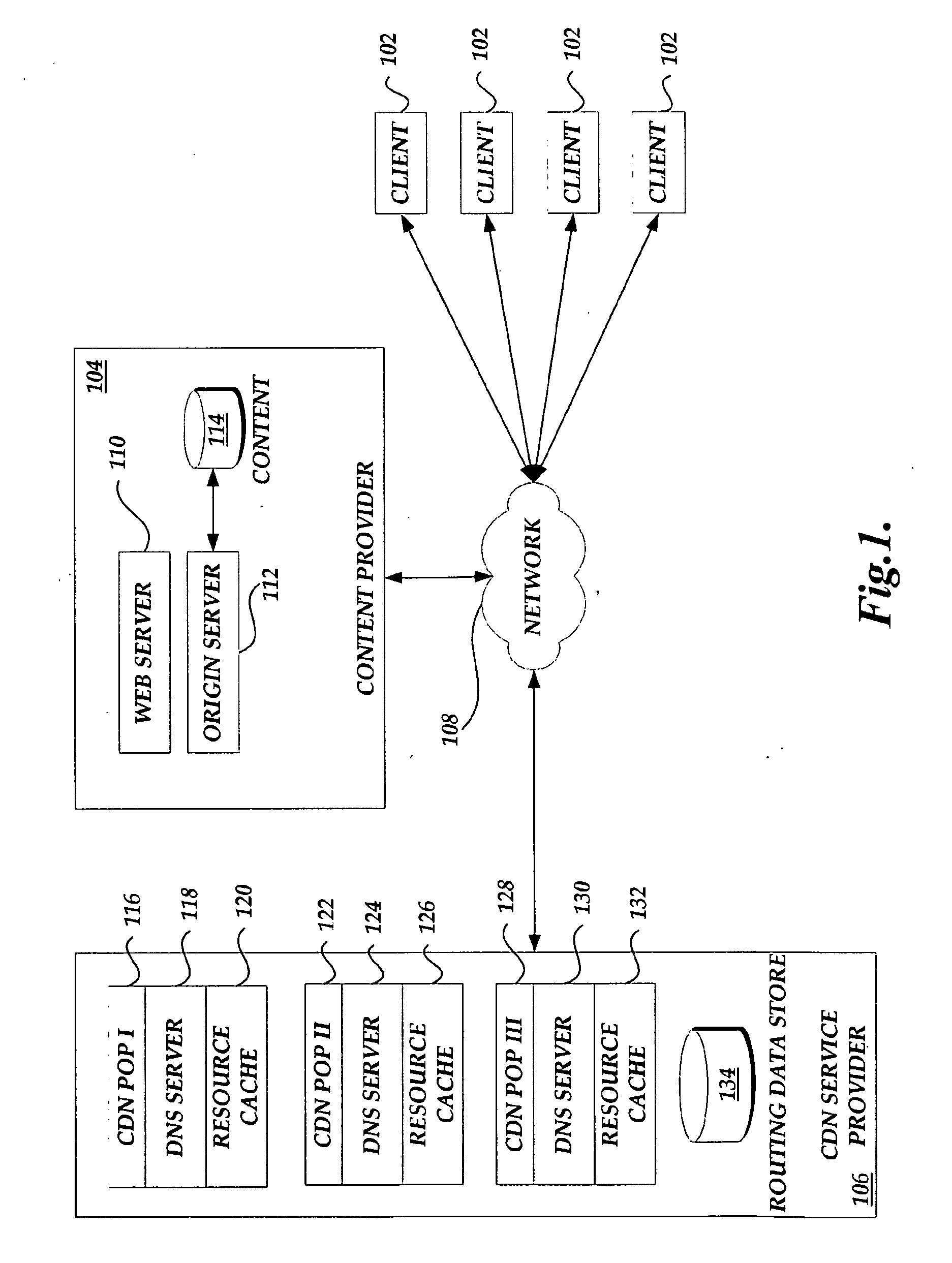
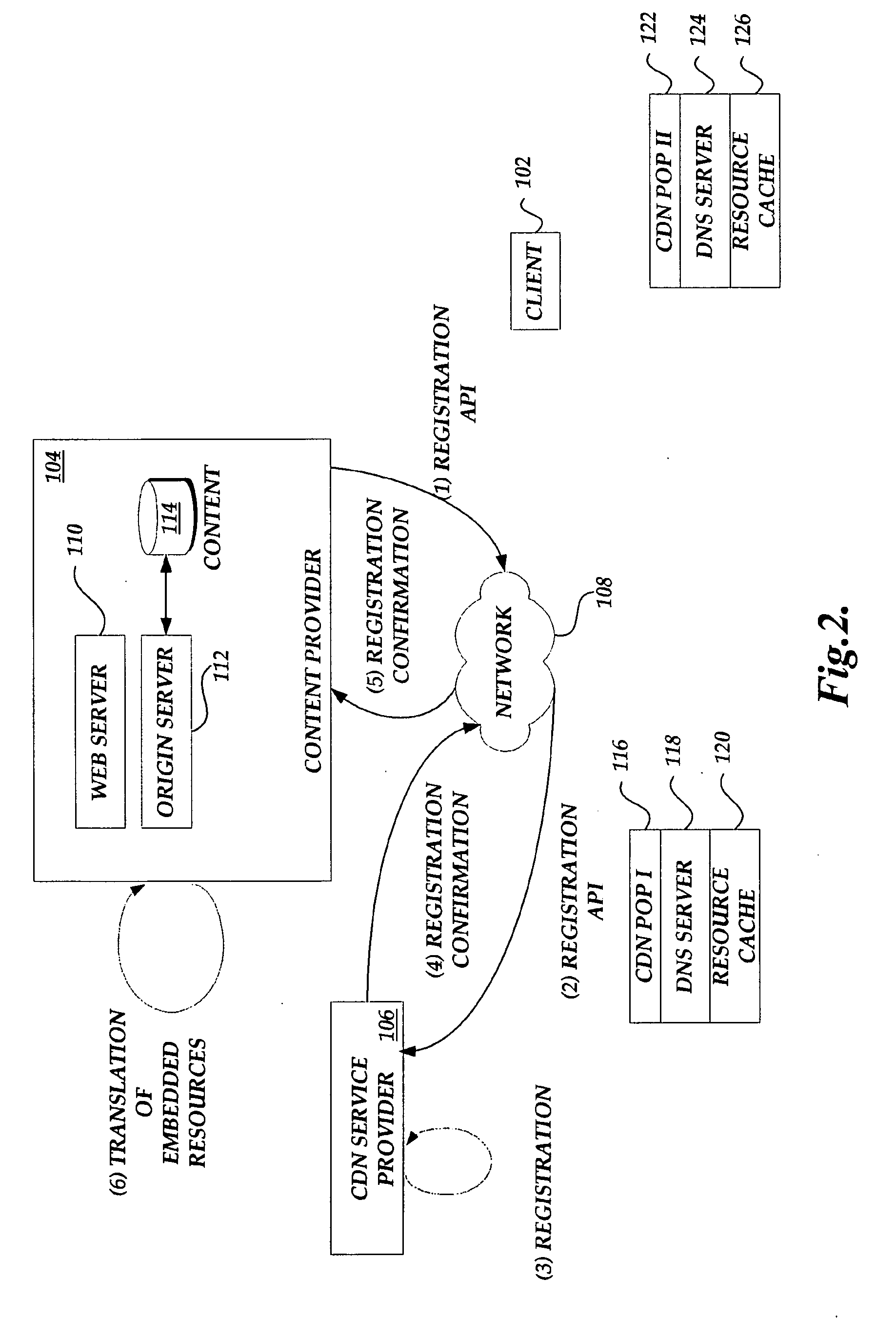
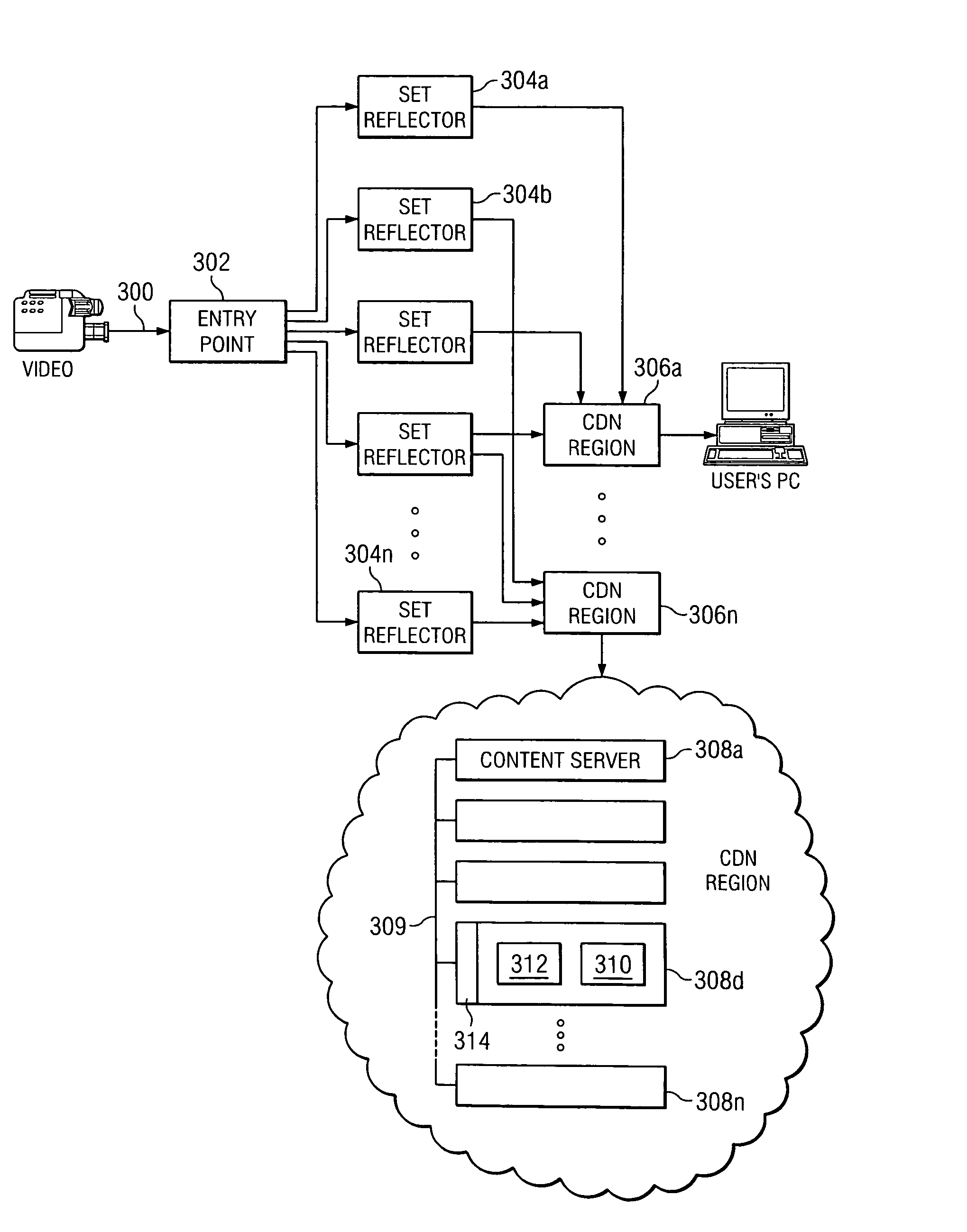
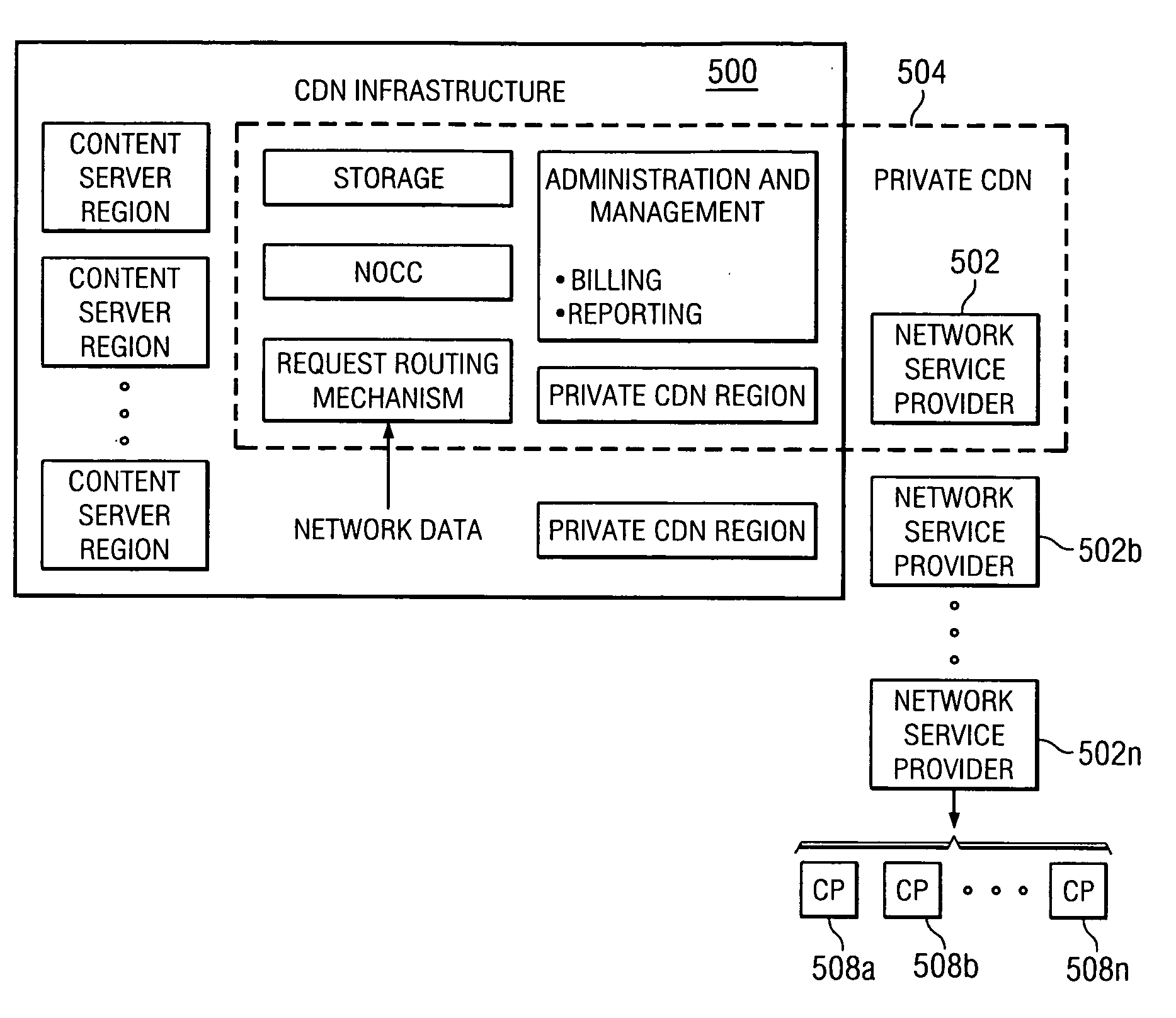
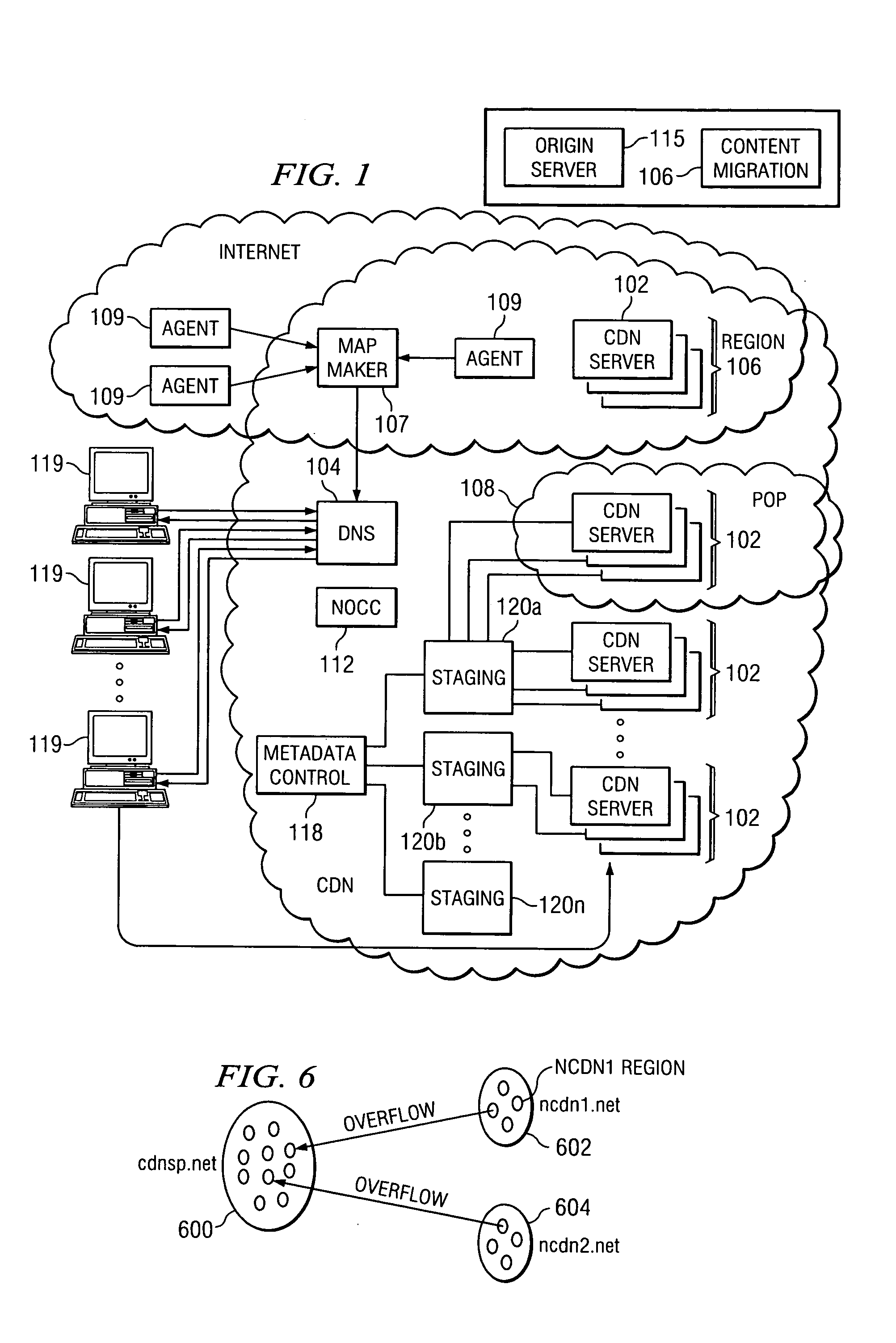
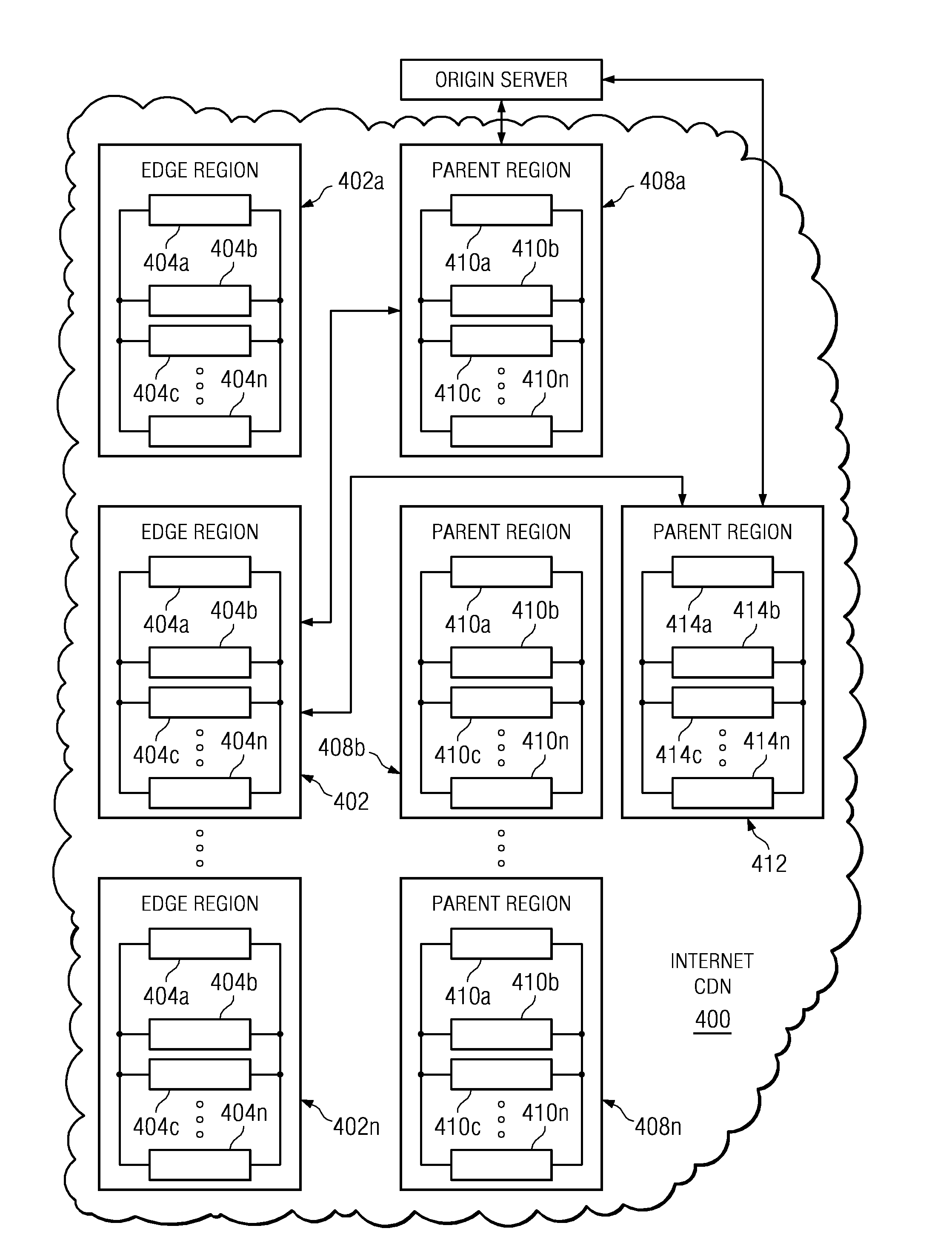
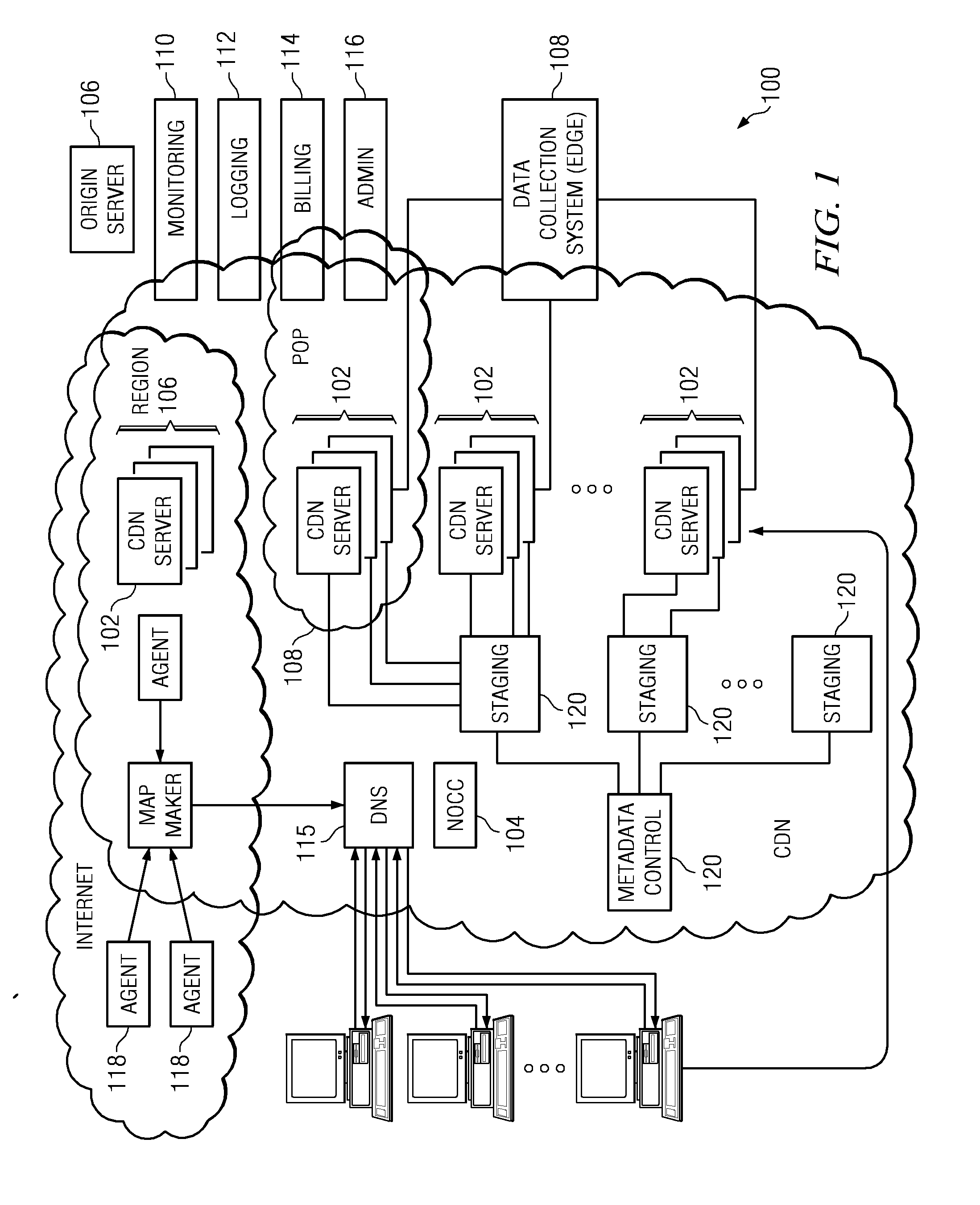
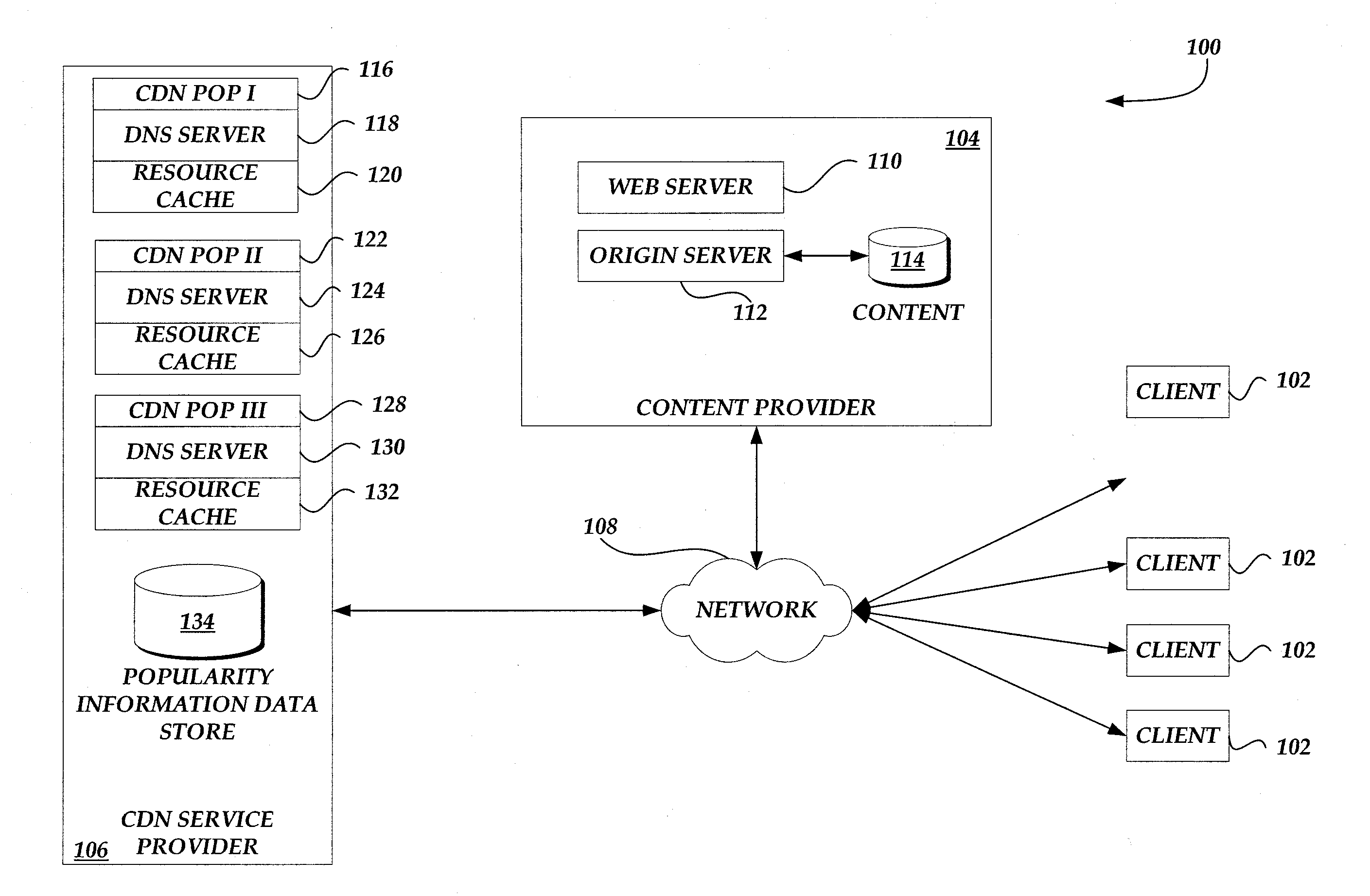
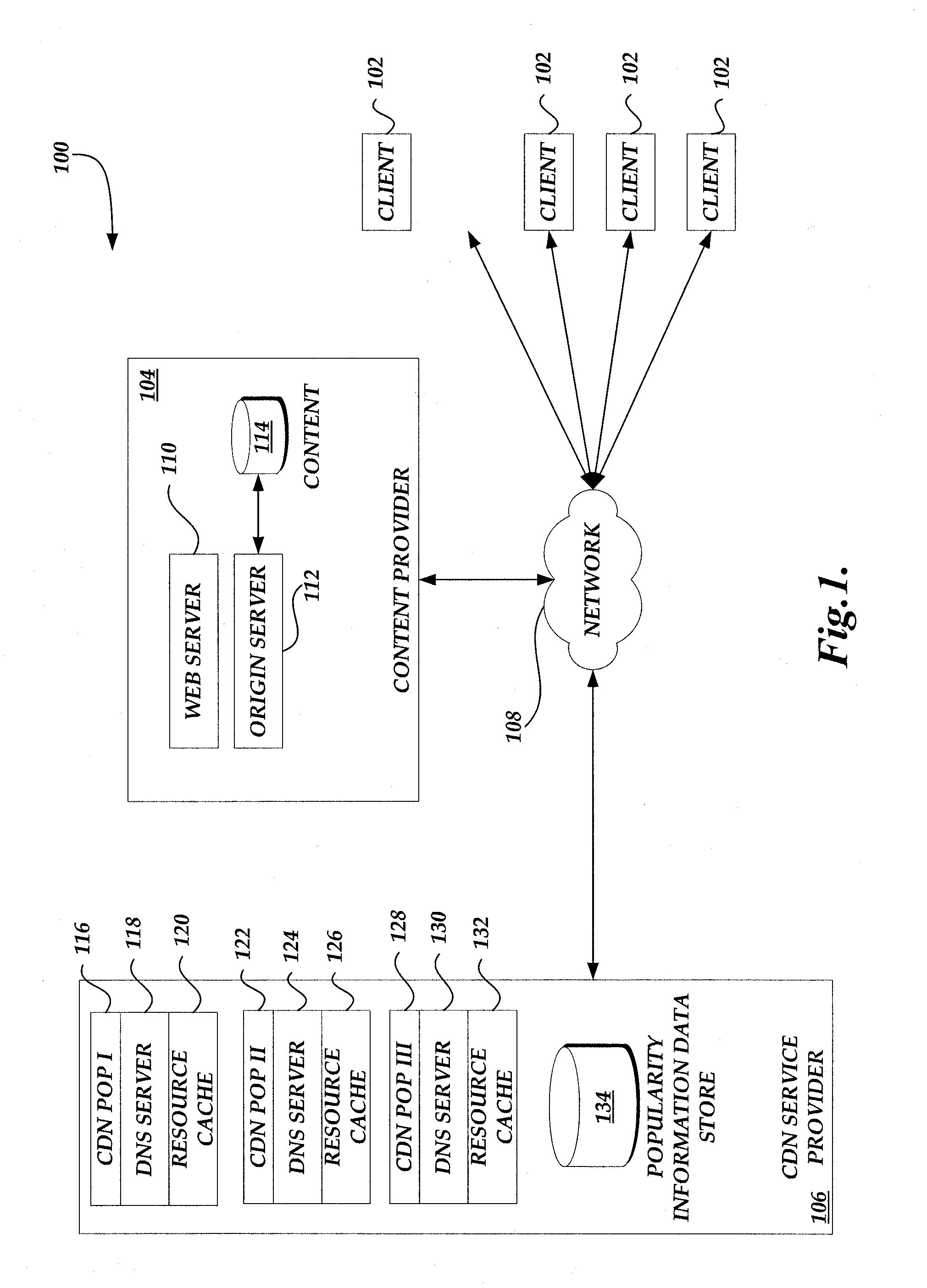
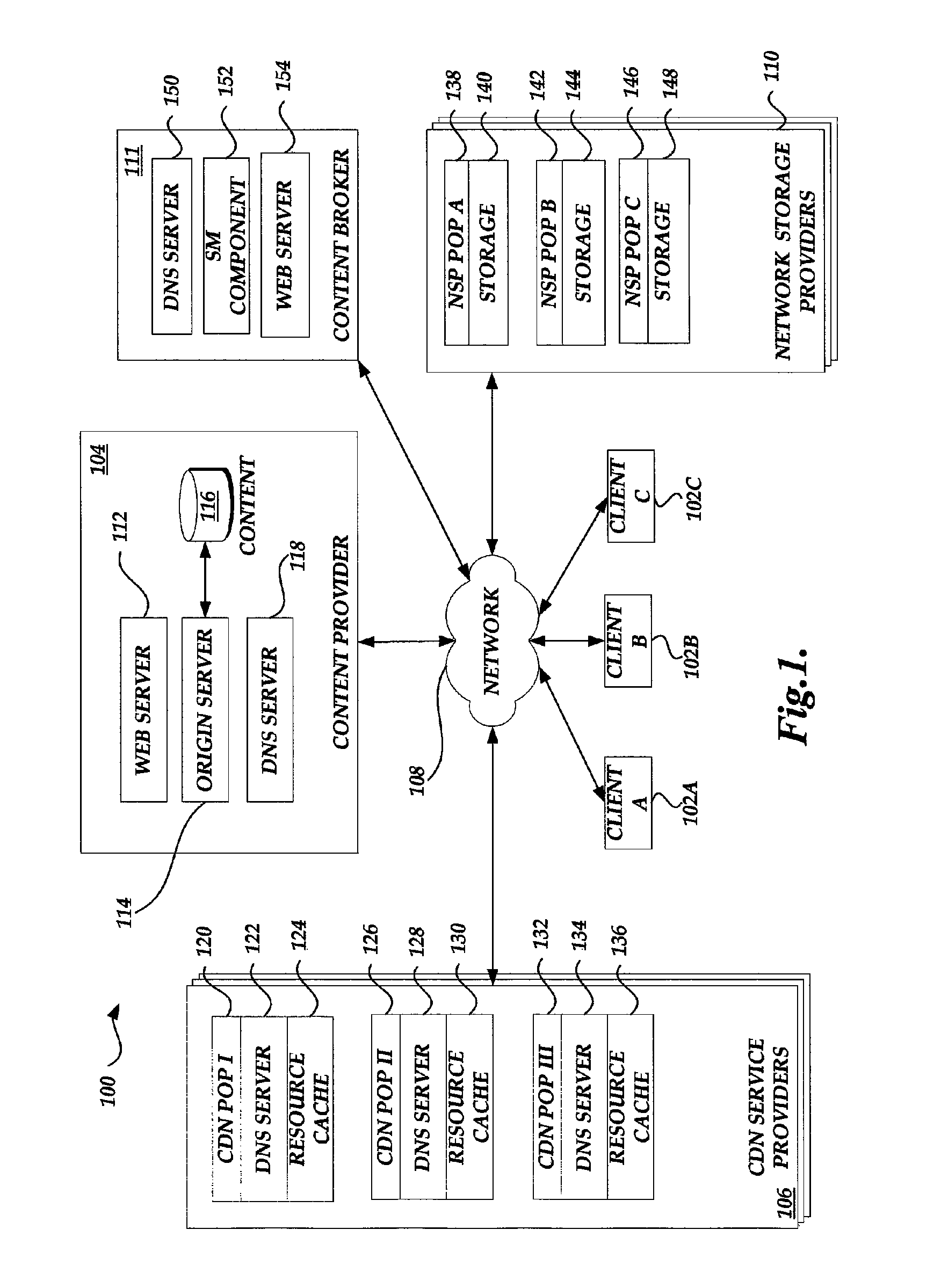
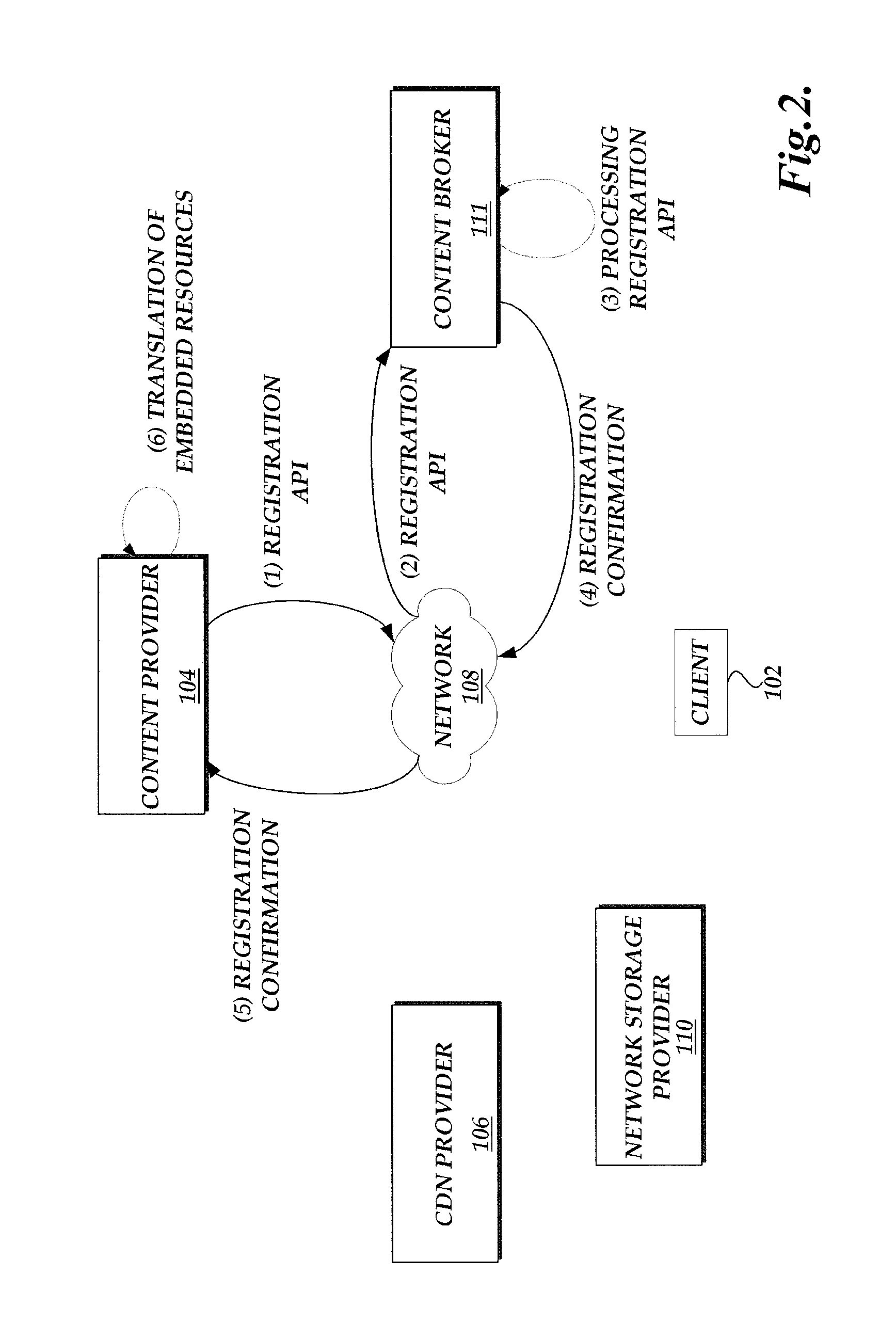
Content delivery network service provider (CDNSP)-managed content delivery network (CDN) for network service provider (NSP)
InactiveUS20070168517A1FinanceData switching by path configurationSchema for Object-Oriented XMLDistributed computing
A CDN service provider shares its CDN infrastructure with a network to enable a network service provider (NSP) to offer a private-labeled network content delivery network (NCDN or “private CDN”) to participating content providers. The CDNSP preferably provides the hardware, software and services required to build, deploy, operate and manage the CDN for the NCDN customer. Thus, the NCDN customer has access to and can make available to participating content providers one or more of the content delivery services (e.g., HTTP delivery, streaming media delivery, application delivery, and the like) available from the global CDN without having to provide the large capital investment, R&D expense and labor necessary to successfully deploy and operate the network itself. Rather, the global CDN service provider simply operates the private CDN for the network as a managed service.
Owner:AKAMAI TECH INC
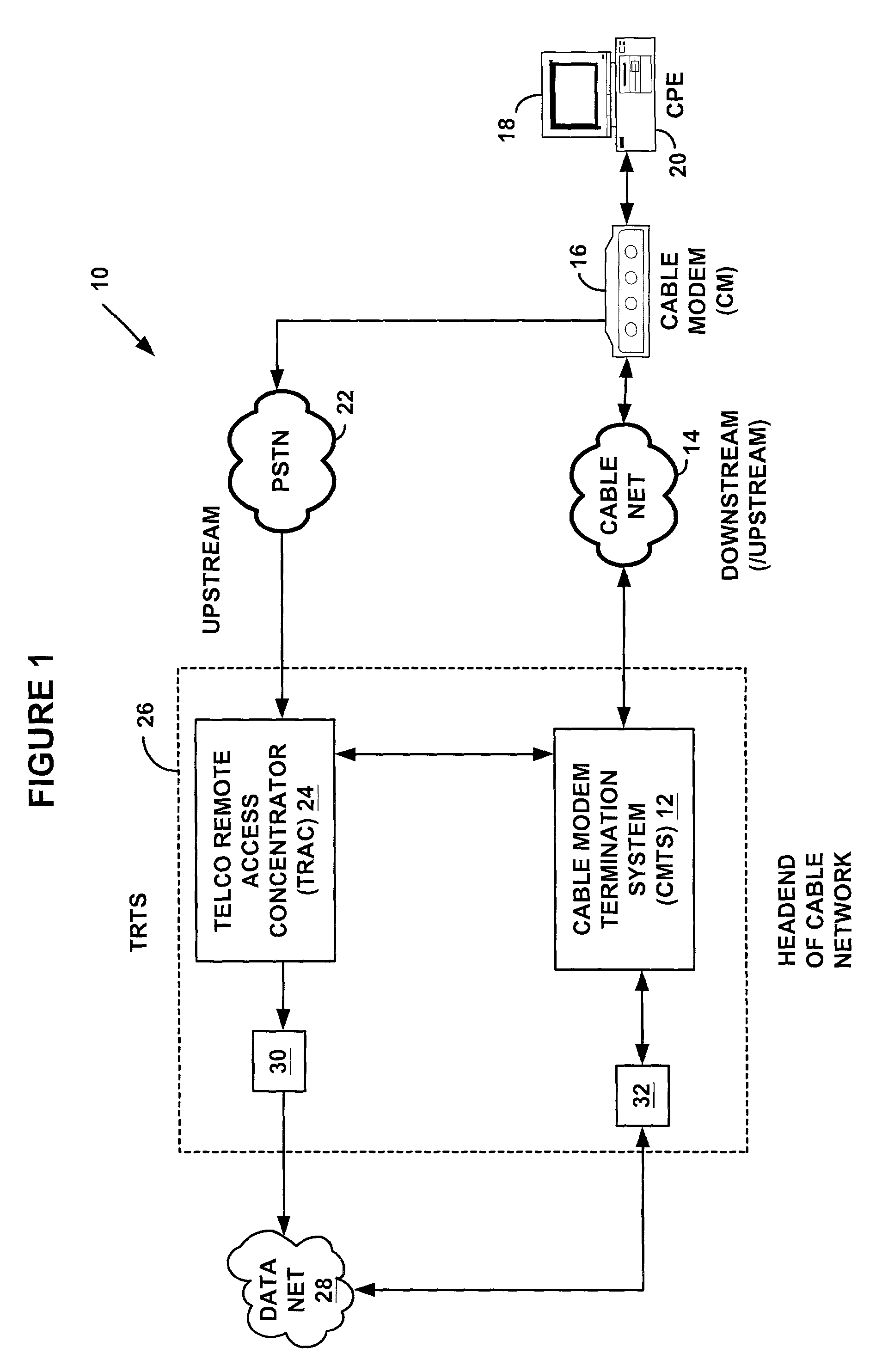
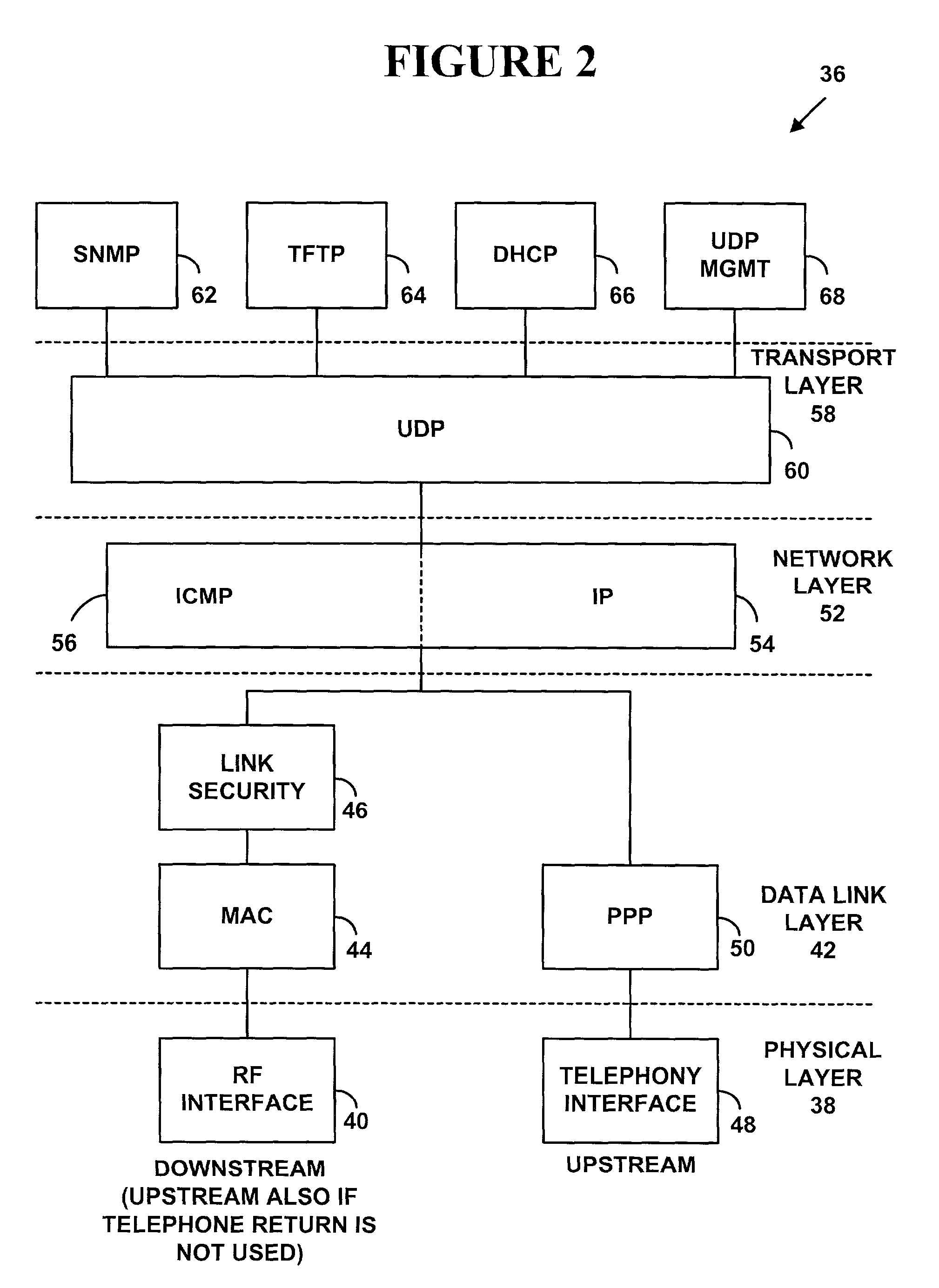
Method for service provisioning a broadband modem
A method for automatically provisioning a broadband communication service to a subscriber having a broadband modem. The method includes the step of transmitting a service request from the broadband modem to a central office, which is associated with a network service provider. The network is configured for service in response to the service request. The method further includes automatically configuring the broadband modem by transmitting a configuration signal from the central office to the subscriber. The configuration signal may be transmitted to the broadband modem over a POTS subchannel. Alternatively, the configuration signal may be transmitted to the broadband modem over a subchannel in a broadband service, such as a DMT subchannel for ADSL service.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
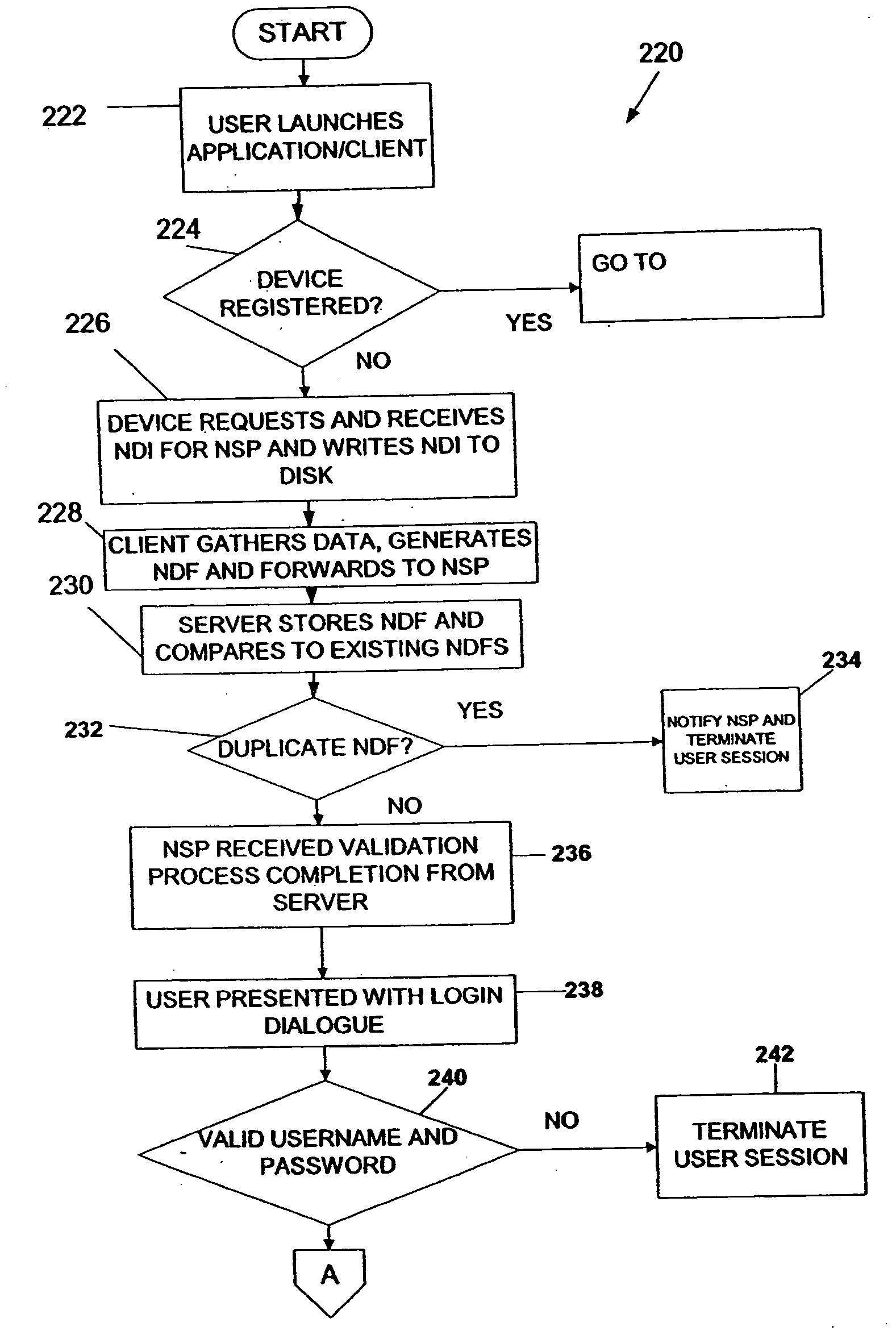
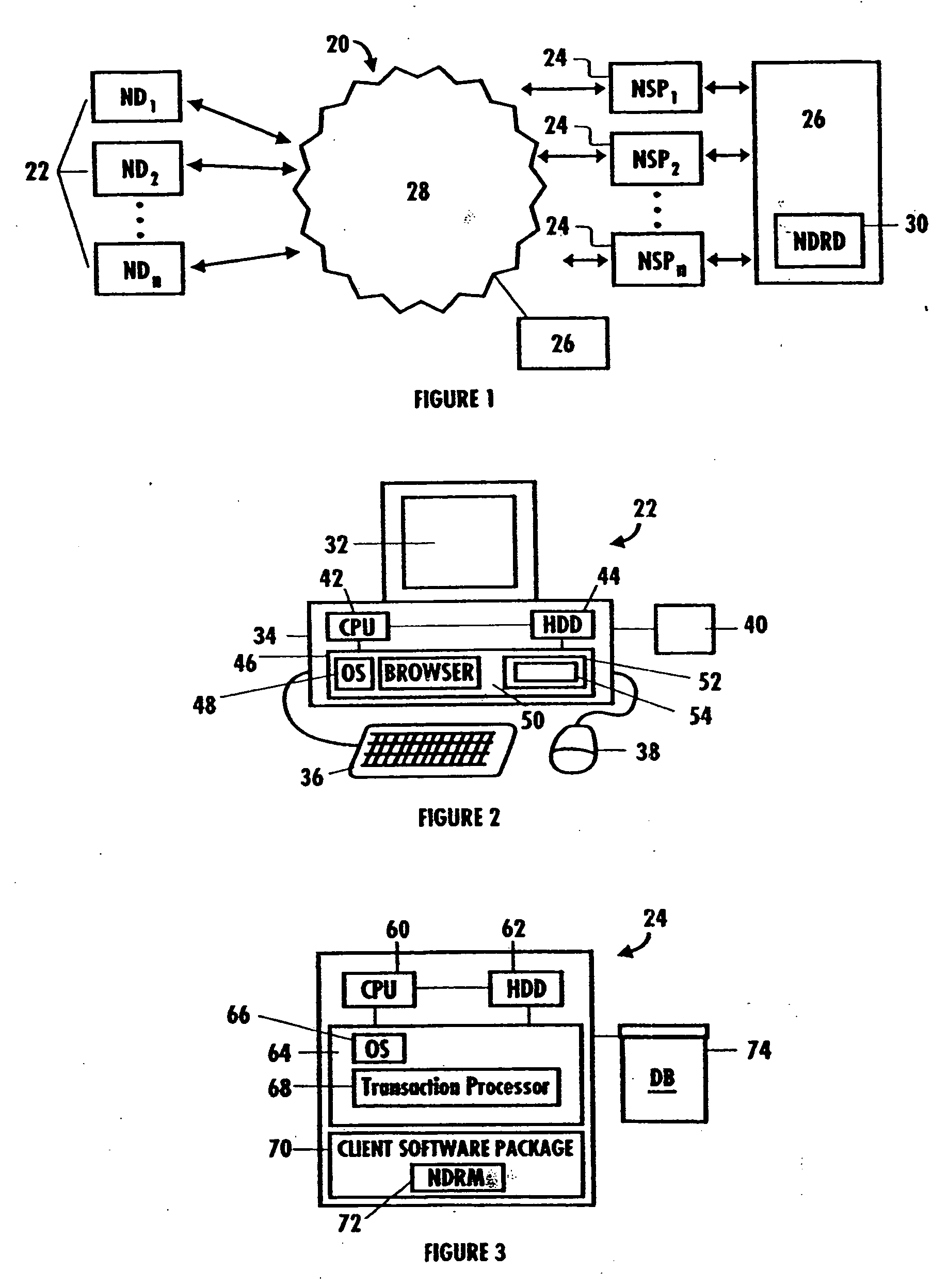
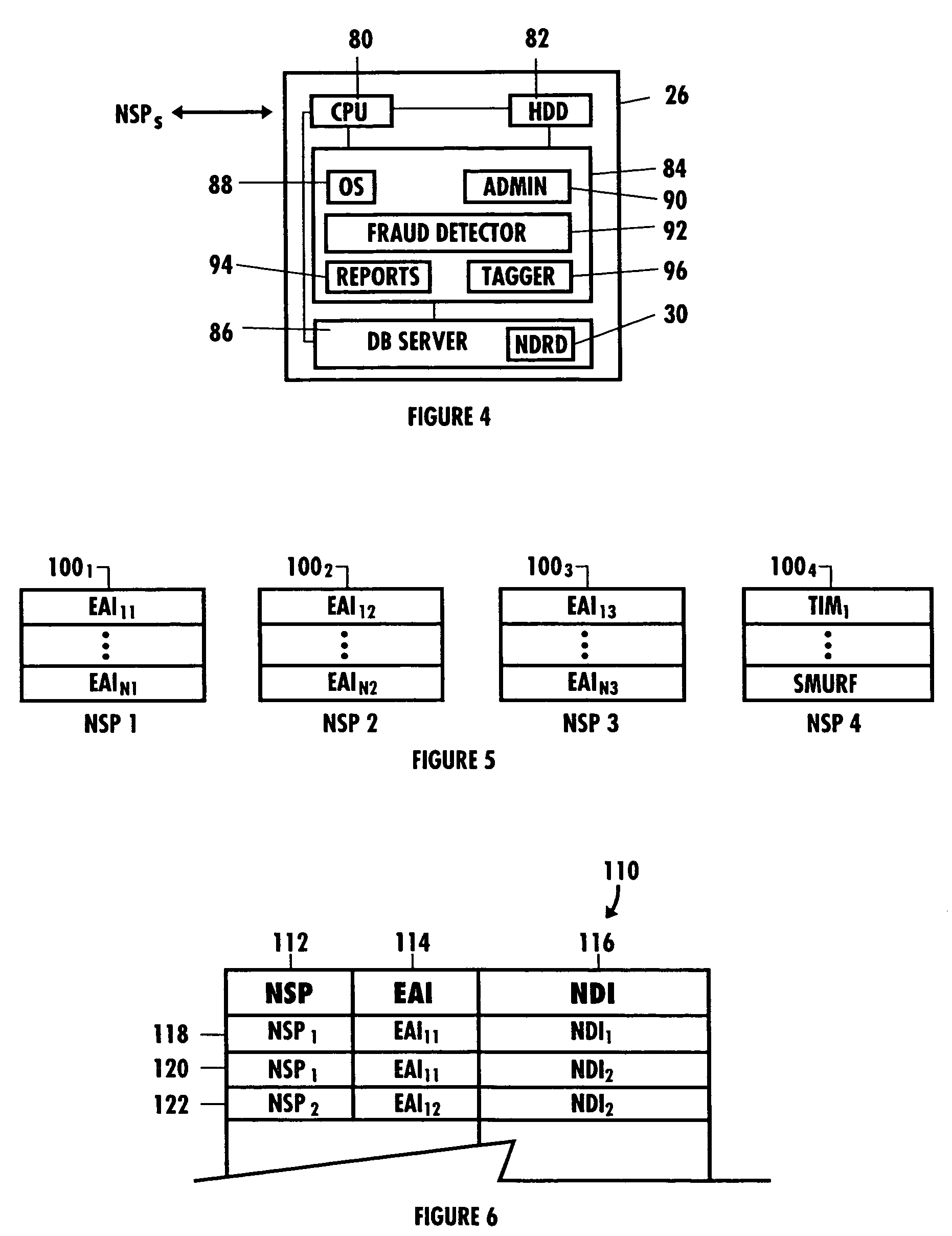
Network security and fraud detection system and method
ActiveUS20050278542A1Avoid connectionAccess is deniedUser identity/authority verificationComputer security arrangementsNetwork serviceEnd user
A system and method to detect and prevent fraud in a system is provided. The system may uniquely identify physical devices connecting to a network, register unique devices, track end-user logins, associate end-user accounts with specific devices, and share information with multiple network service providers is described.
Owner:IOVATION
System and method for providing service or adding benefit to social networks
InactiveUS20100145771A1Increase adoptionEfficient and cost-effective administrationDrawing from basic elementsOffice automationGraphicsRanking
A system and method for enhancing the revenue and / or efficiency of a network service is disclosed. The system constructs a graph of a social network in which users are capable of two-way communication with other users, the network service provider, or other entities such as advertisers. Using such methods as social VIP ranking, the system is capable of performing a variety of analyses, the results of which provide the network service provider insights on how to best perform such tasks as monitoring and enhancing campaign effectiveness, identify fraud, optimize resource allocation and ensure the quality of network management.
Owner:MARA ISON CONNECTIVE +1
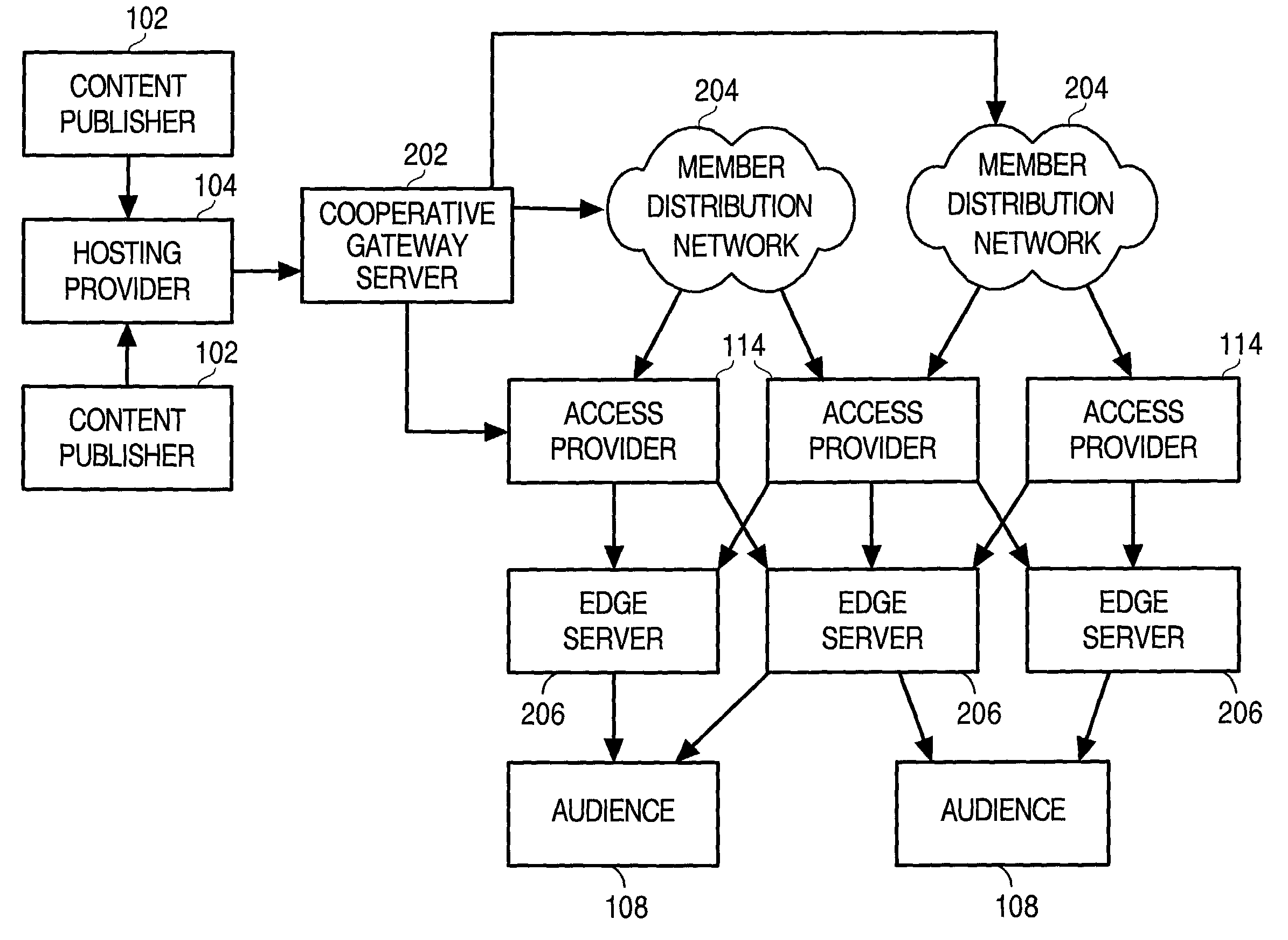
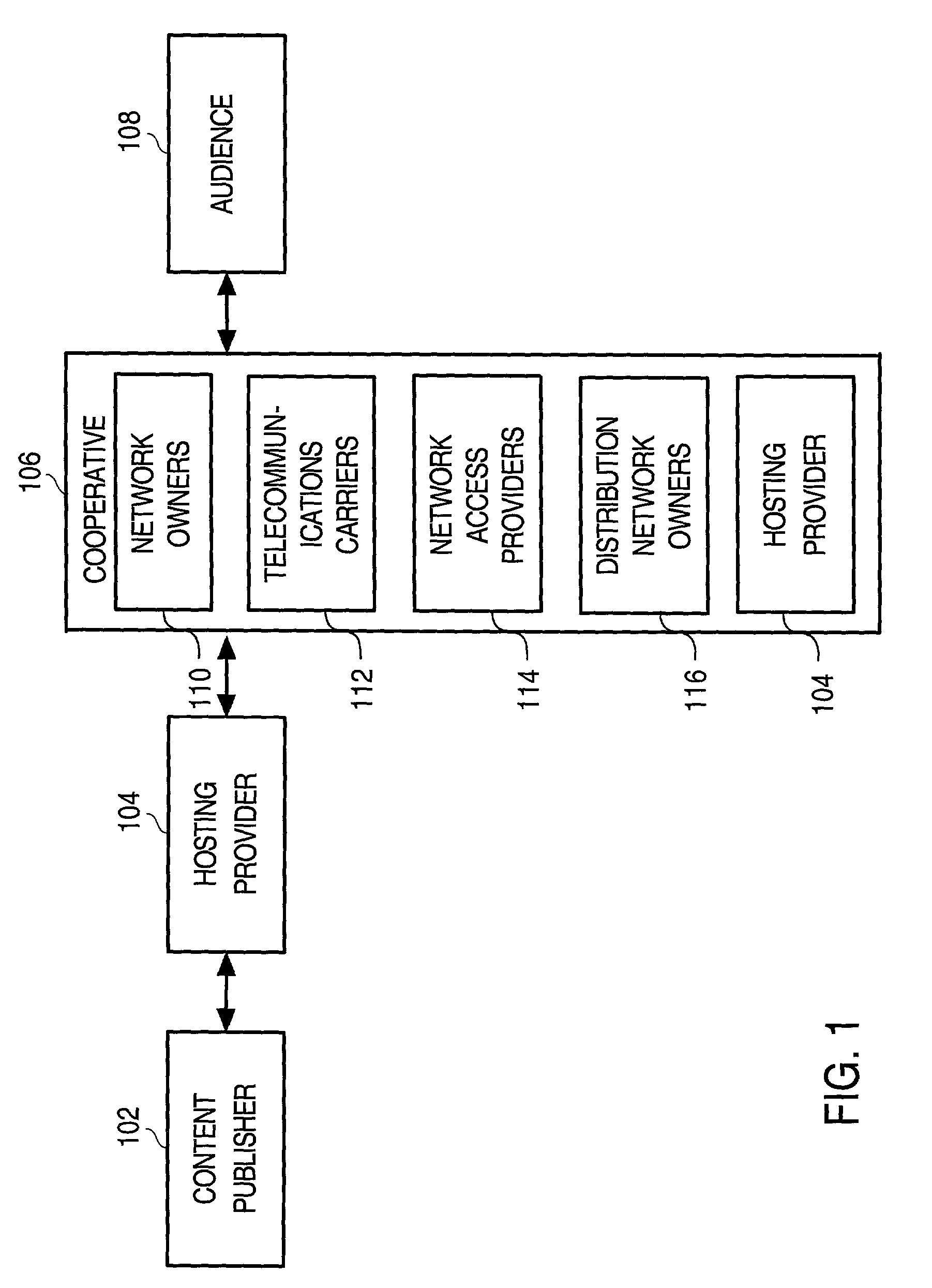
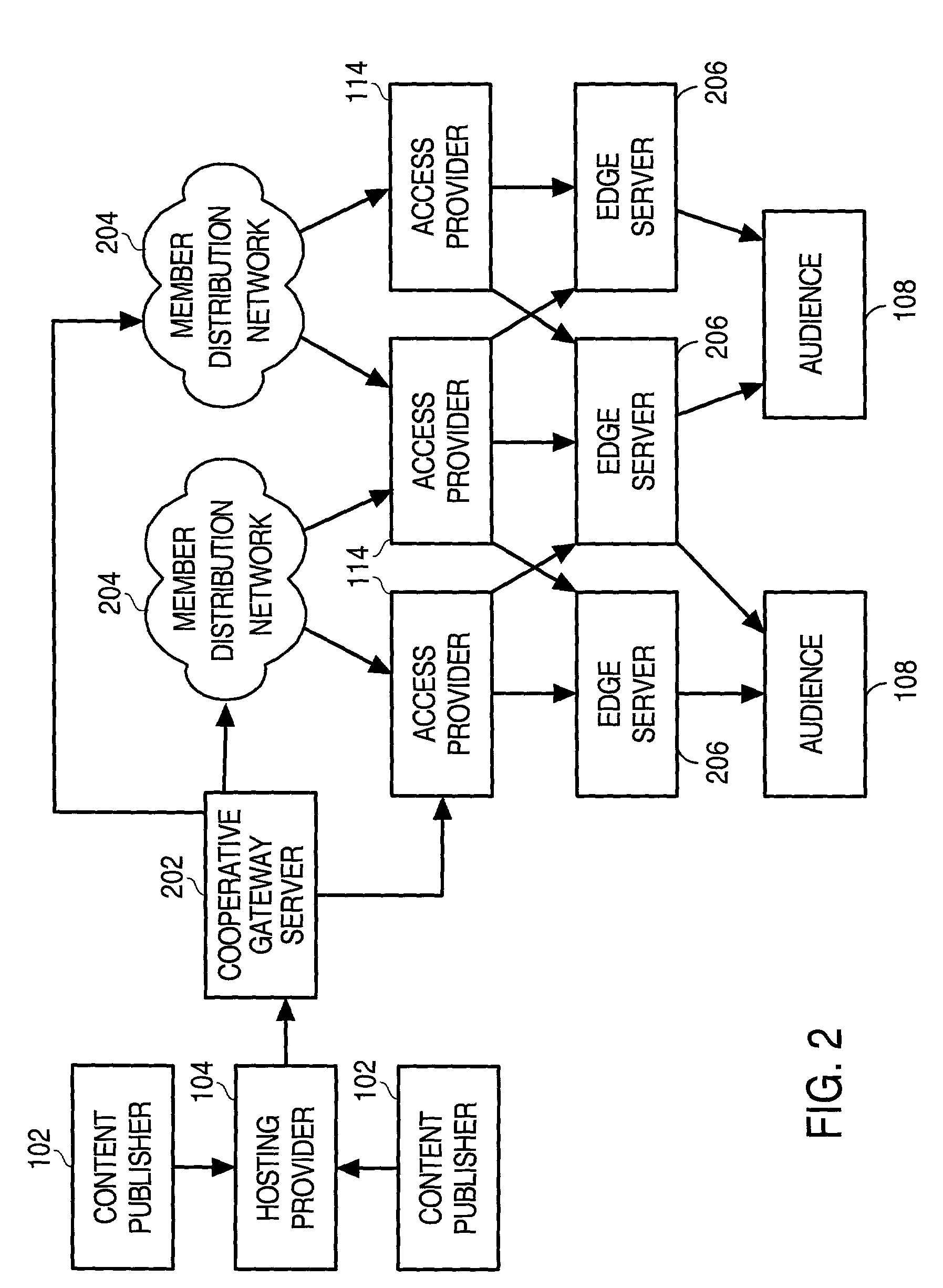
Cooperative management of distributed network caches
InactiveUS7117262B2Multiple digital computer combinationsSecuring communicationInternet contentControl signal
The techniques described employ a cooperative organization of network service providers to provide improved distributed network services. The network service providers that are constituent to the cooperative organization represent various perspectives within the overall Internet content distribution network, and may include network owners, telecommunications carriers, network access providers, hosting providers and distribution network owners, the latter being an entity that caches content at a plurality of locations distributed on the network. Aspects include managing content caches by receiving control signals specifying actions related to cached content that is distributed on a network, such as the Internet, and forwarding the control signals through to the caching locations to implement the actions represented by the control signals, thus providing content publishers the capability of refreshing their content regardless of where it is cached. Aspects include managing content caches by receiving activity records that contain statistics related to requests for cached content, segregating the statistics according to which content publisher provides the content associated with the statistics, and providing to each content publisher statistics corresponding to content provided by that content publisher, thus allowing them to monitor requests for their content regardless of where it may be cached on the network.
Owner:R2 SOLUTIONS
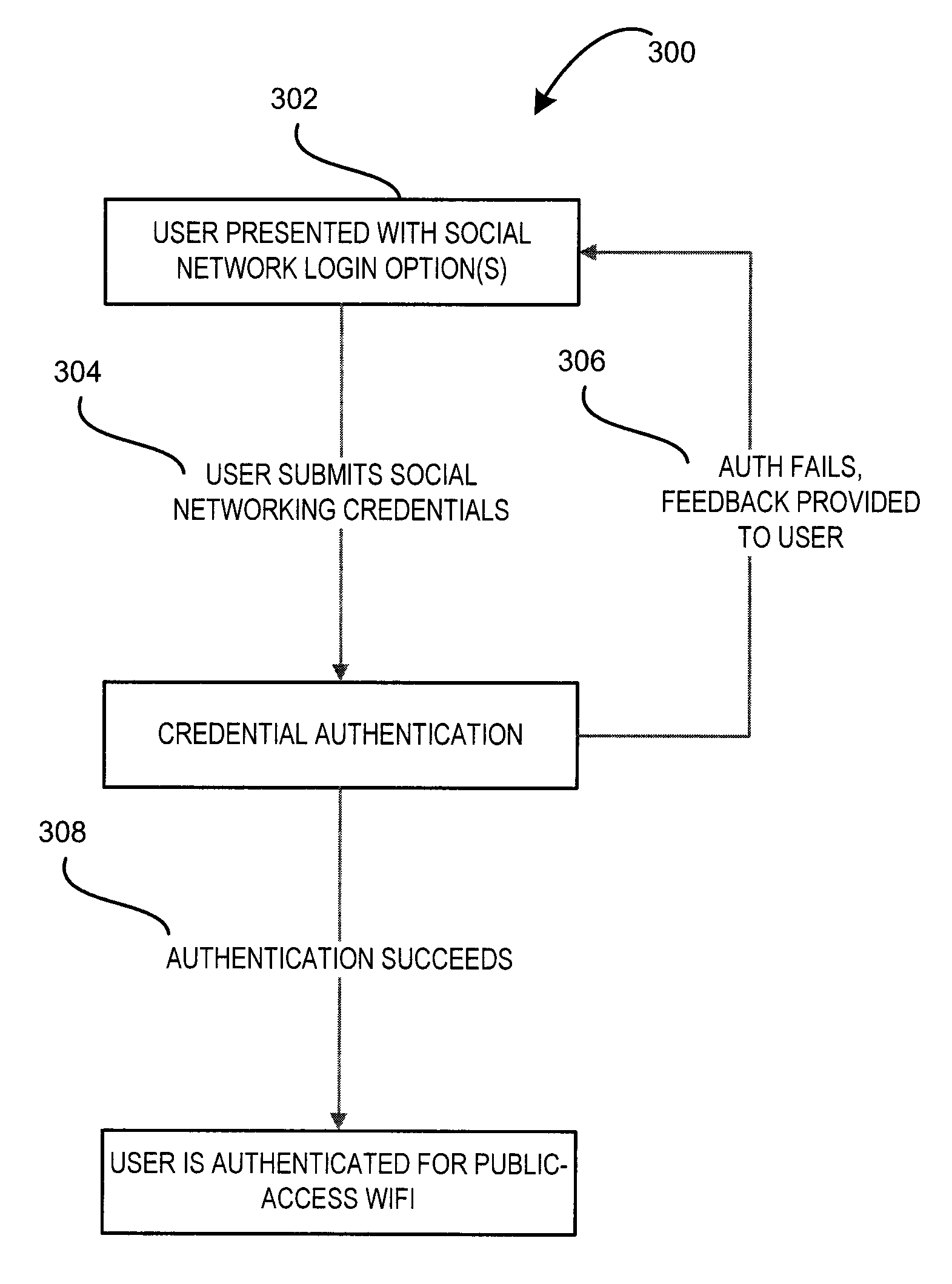
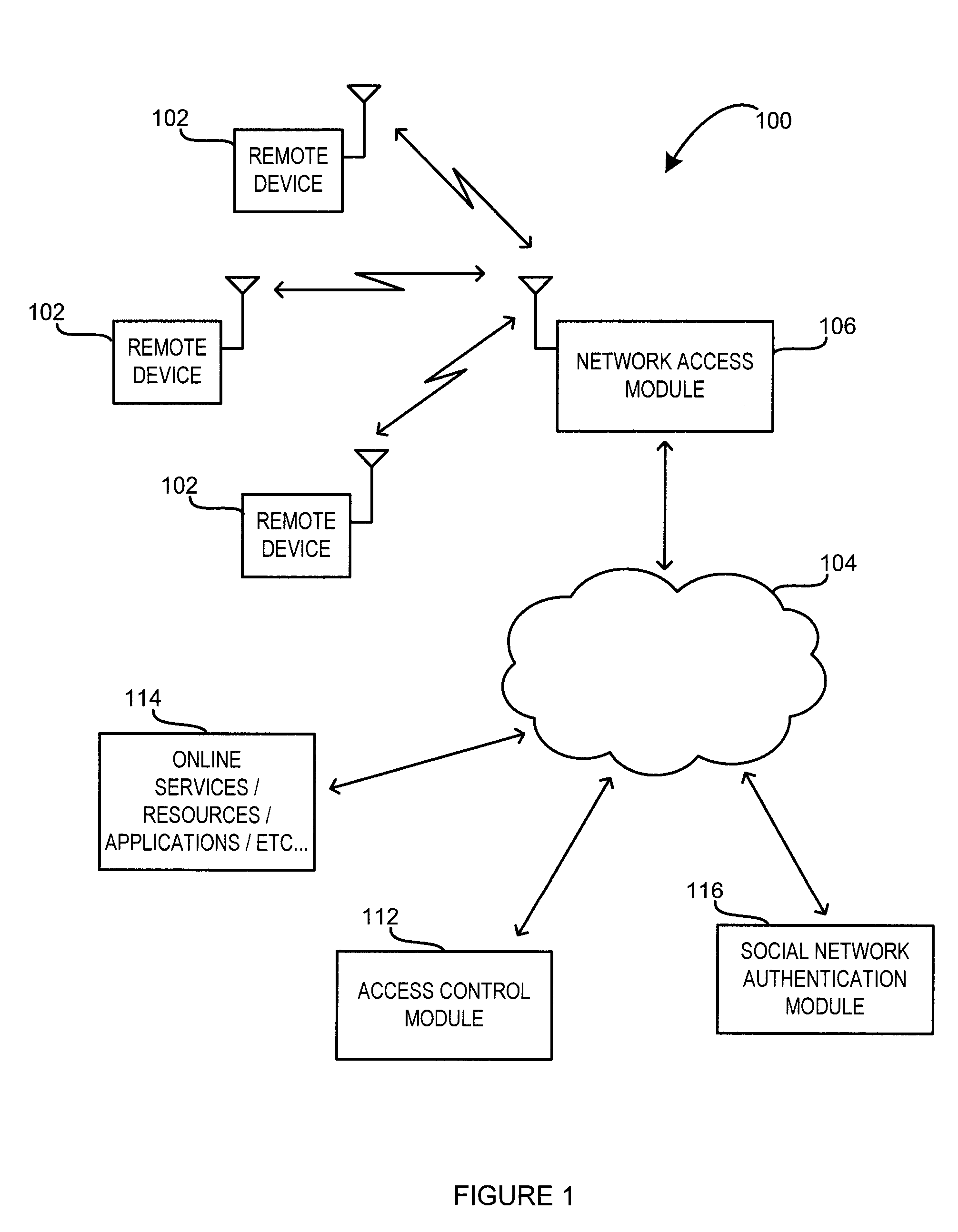
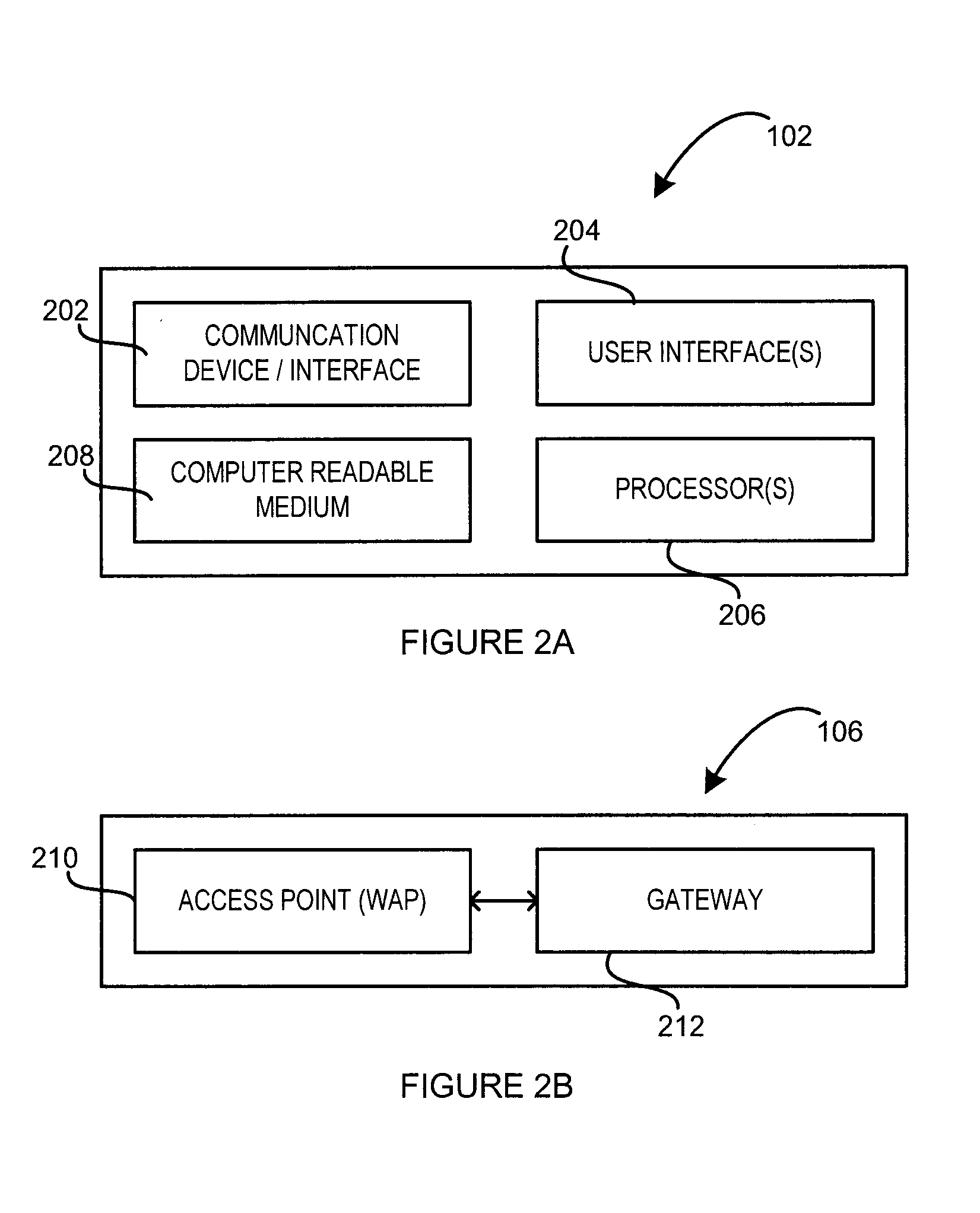
Hotspot network access system and method
ActiveUS20120192258A1Digital data processing detailsUser identity/authority verificationThird partyWireless transmission
A system and method are disclosed for providing wireless network access to a user of a remote device at a hotspot. In general, wireless communication is established by the system with the remote device to enable wireless transmission therefrom of social networking credentials associated with a social network profile maintained by a third party social network service provider. Using these credentials, the user is authenticated with the third party social network service provider, and, upon authentication, is provided wireless access to the network.
Owner:DATAVALET TECH
Network security and fraud detection system and method
ActiveUS7272728B2Avoid connectionAccess is deniedUser identity/authority verificationUnauthorized memory use protectionNetwork security policyNetwork service
A system and method to detect and prevent fraud in a system is provided. The system may uniquely identify physical devices connecting to a network, register unique devices, track end-user logins, associate end-user accounts with specific devices, and share information with multiple network service providers is described.
Owner:IOVATION
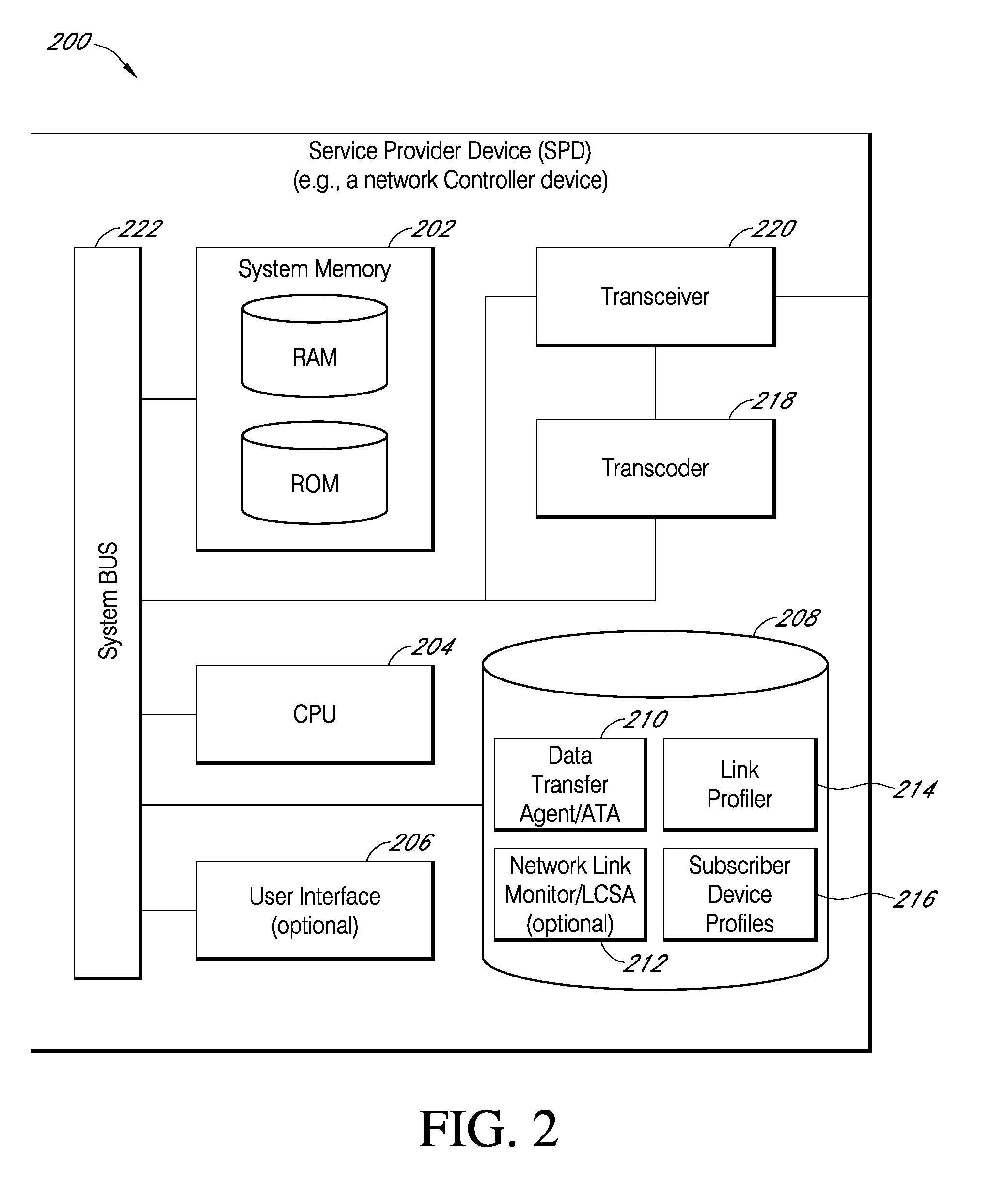
Systems and methods for enhanced data delivery based on real time analysis of network communications quality and traffic
ActiveUS8019886B2Network traffic/resource managementInformation formatDigital dataReal time analysis
A system for improving digital data content delivery based on real time analysis of one or more network communications states. The networked computing system may include a network service provider device, a user equipment, a network link monitor, a data transfer agent, and a data communications network facilitating data communications amongst all devices of the networked computing system. The networked computing system may be configured to: detect at least one network communications metric, determine a network communications state associated with diminished communications throughput based on the detected at least one network communications metric, and then select an optimal rate for a data content transfer based on the determined network communications state. The network communications state may relate to either a state of network congestion or a state of reduced regional radio communications quality.
Owner:OPANGA NETWORKS
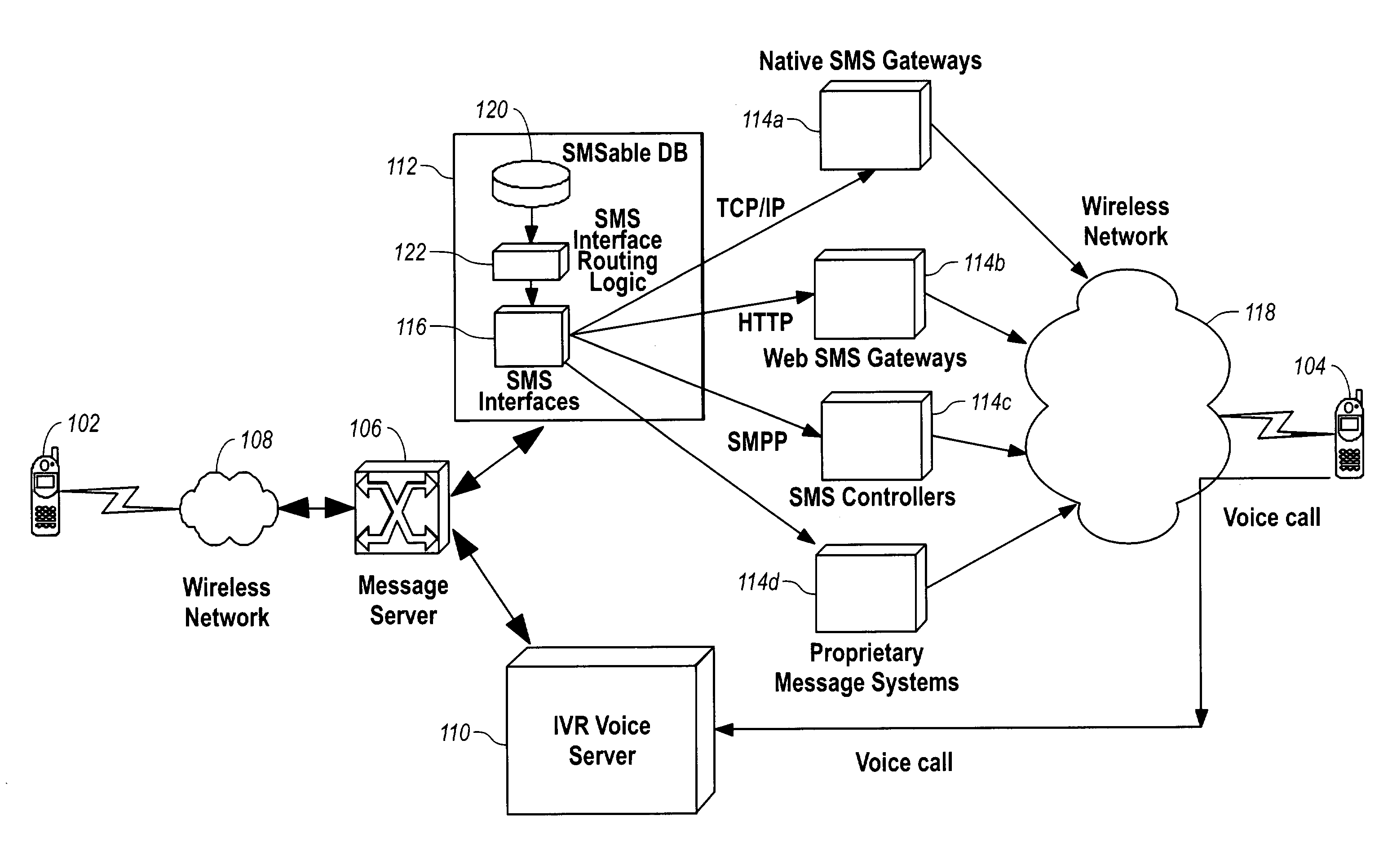
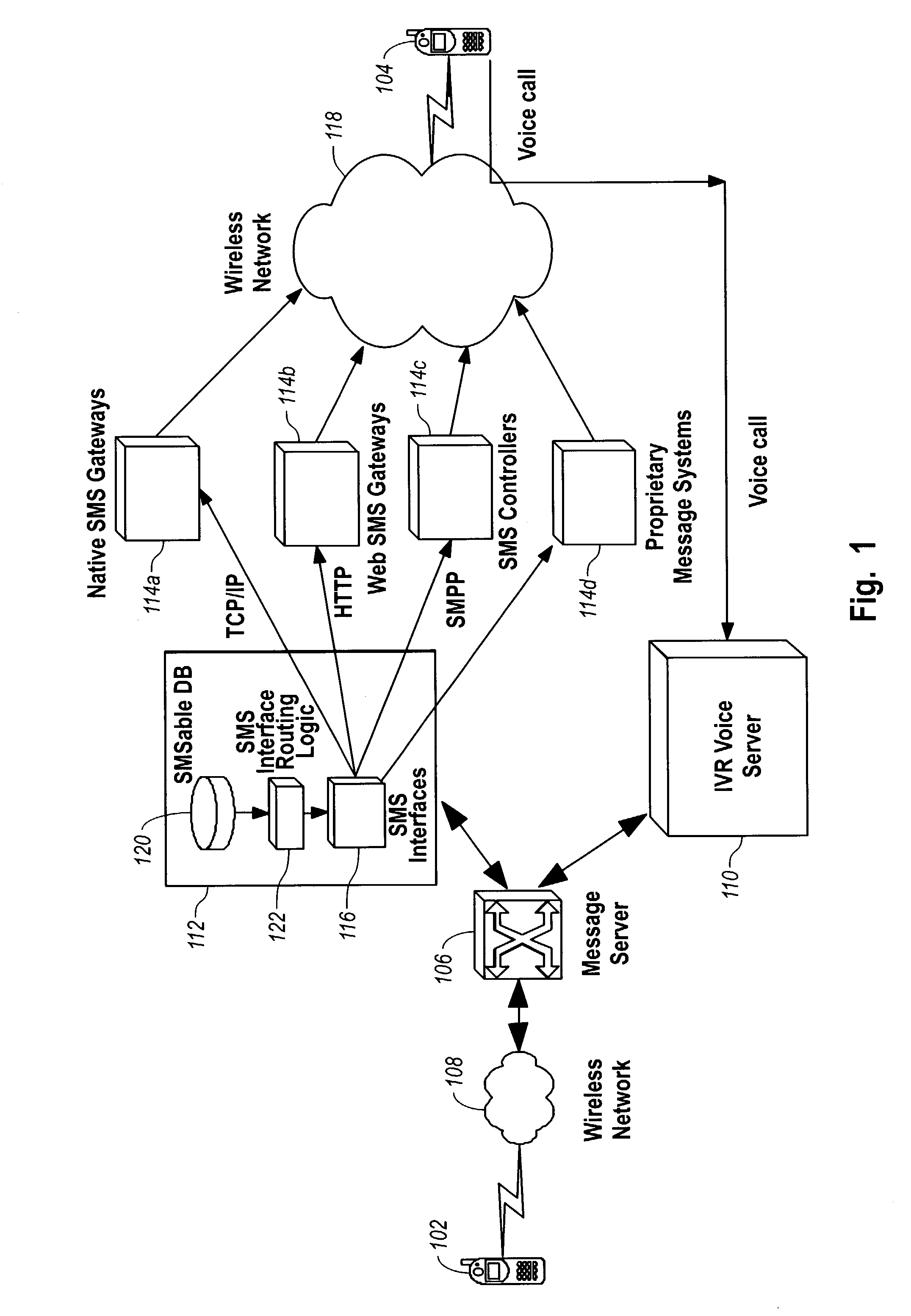
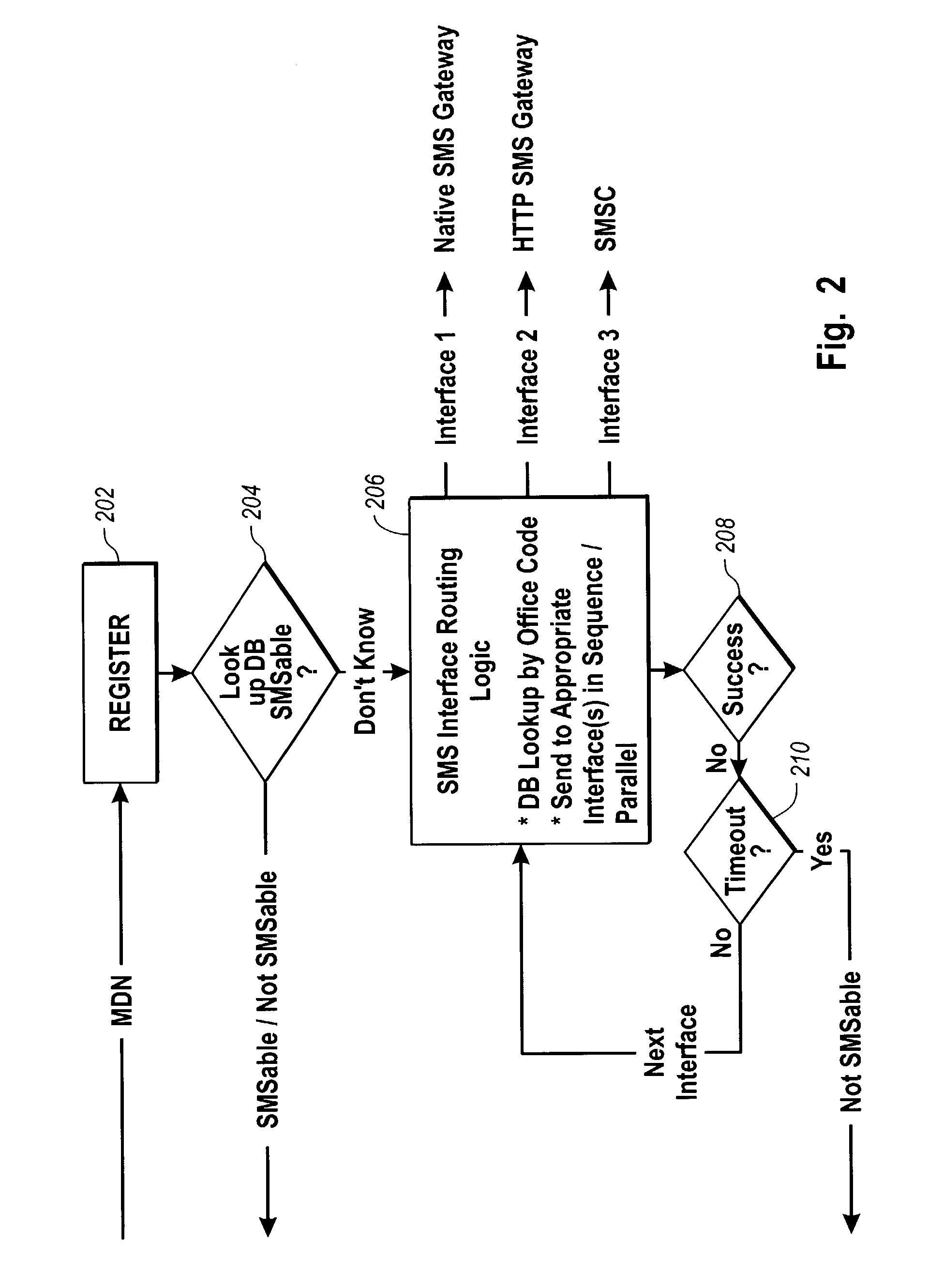
Delivery of an instant voice message in a wireless network using the SMS protocol
ActiveUS7013155B1Easy to recordTransmission easilyAutomatic call-answering/message-recording/conversation-recordingRadio/inductive link selection arrangementsPasswordNetwork service
A sender can create and send a message that can be delivered to recipients with SMS-enabled wireless stations regardless of the other communication capabilities of the wireless stations and the network or network service providers of the recipients. The sender creates a voice message and sends the message to a message server, which stores the message in an interactive voice response (IVR) system. An SMS notification is sent to the recipient and includes instructions for accessing the voice message from the IVR system. The recipient views the SMS notification and accesses the IVR system. After entering a password or otherwise authenticating the recipient or the recipient wireless station, the recipient retrieves the message from the IVR system. If it is not known whether the recipient has an SMS-enabled wireless station, the message server initiates attempts to send SMS notifications using multiple SMS message generation mechanisms.
Owner:SMITH MICRO SOFTWARE INC
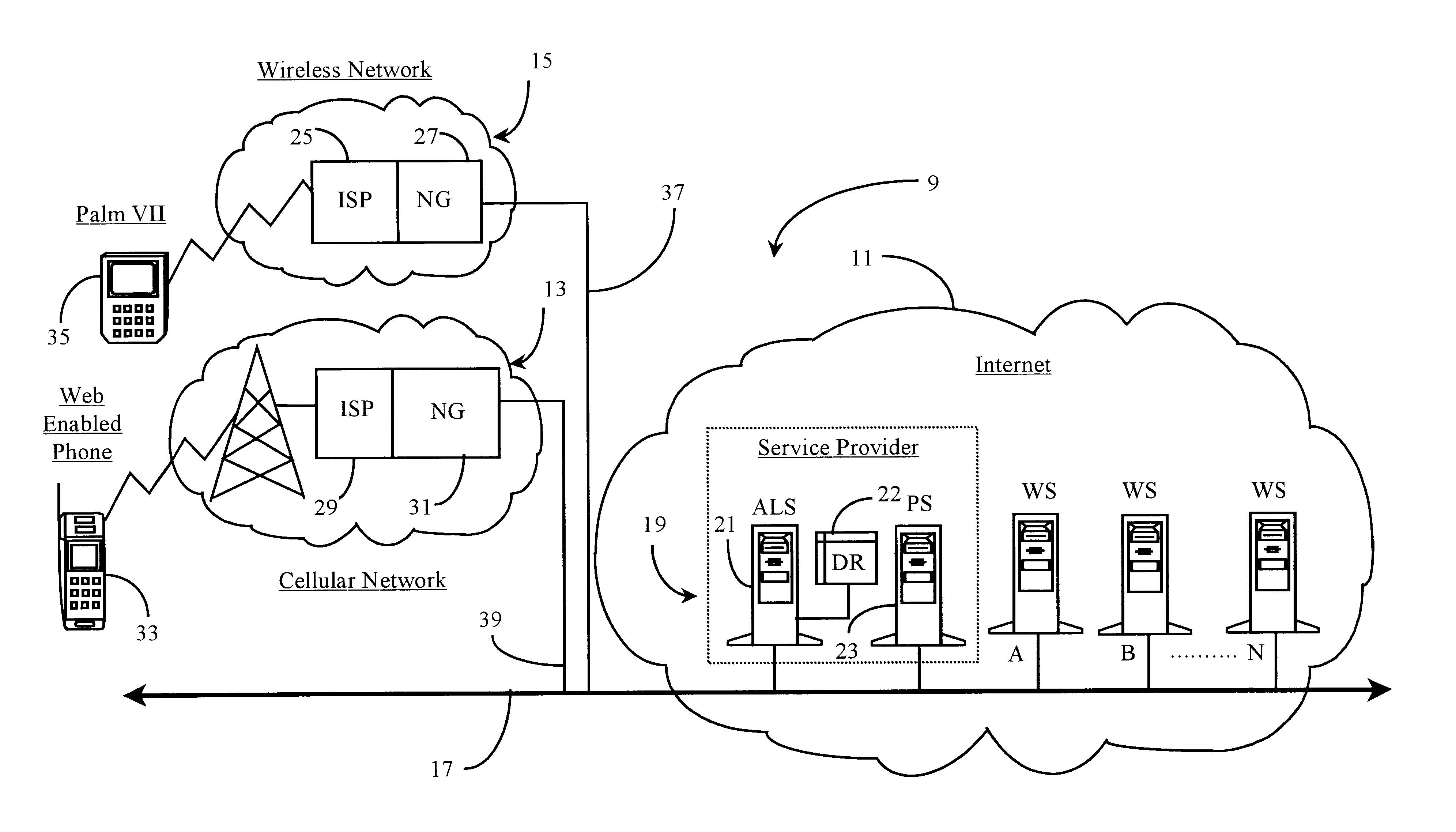
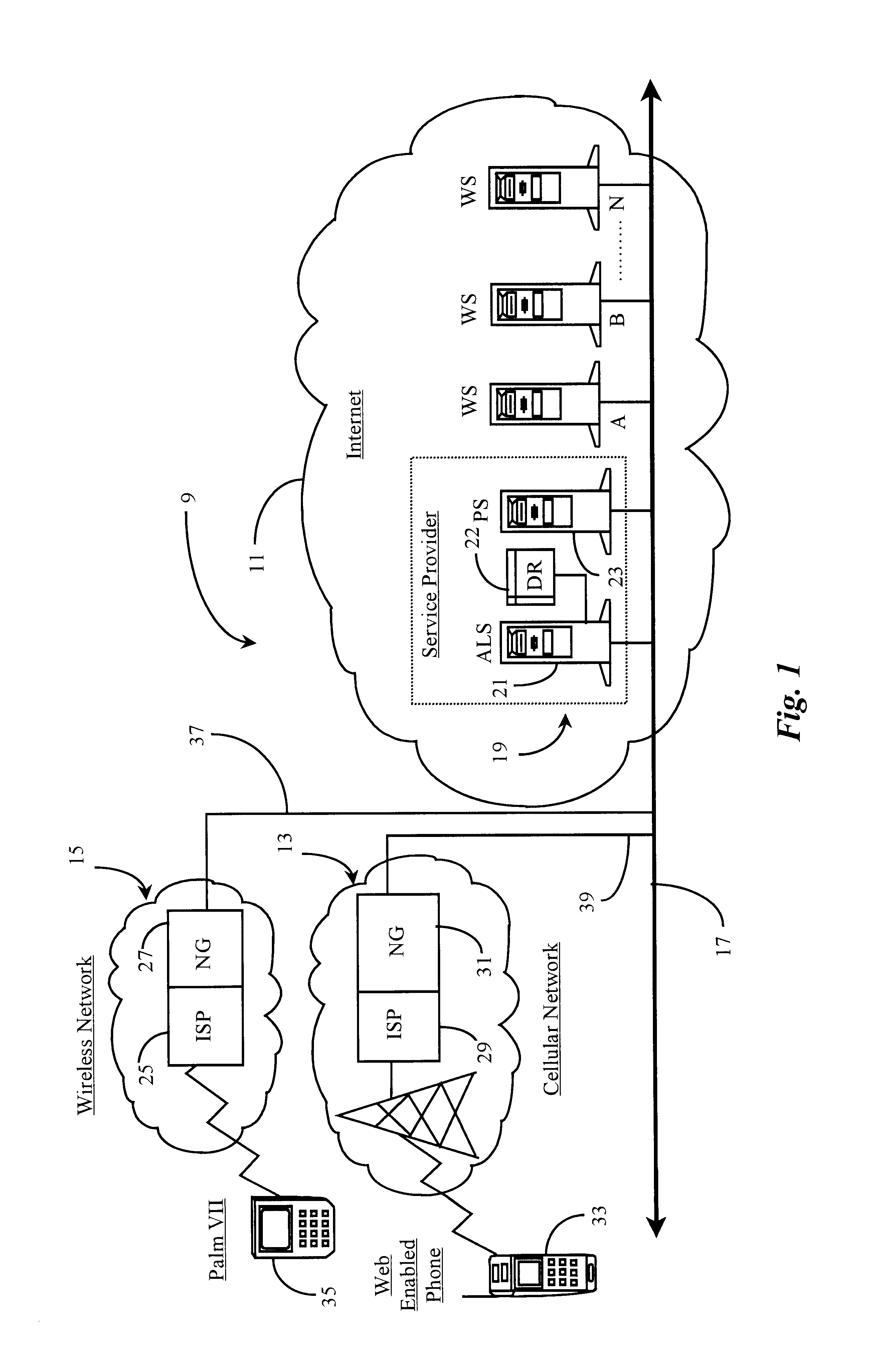
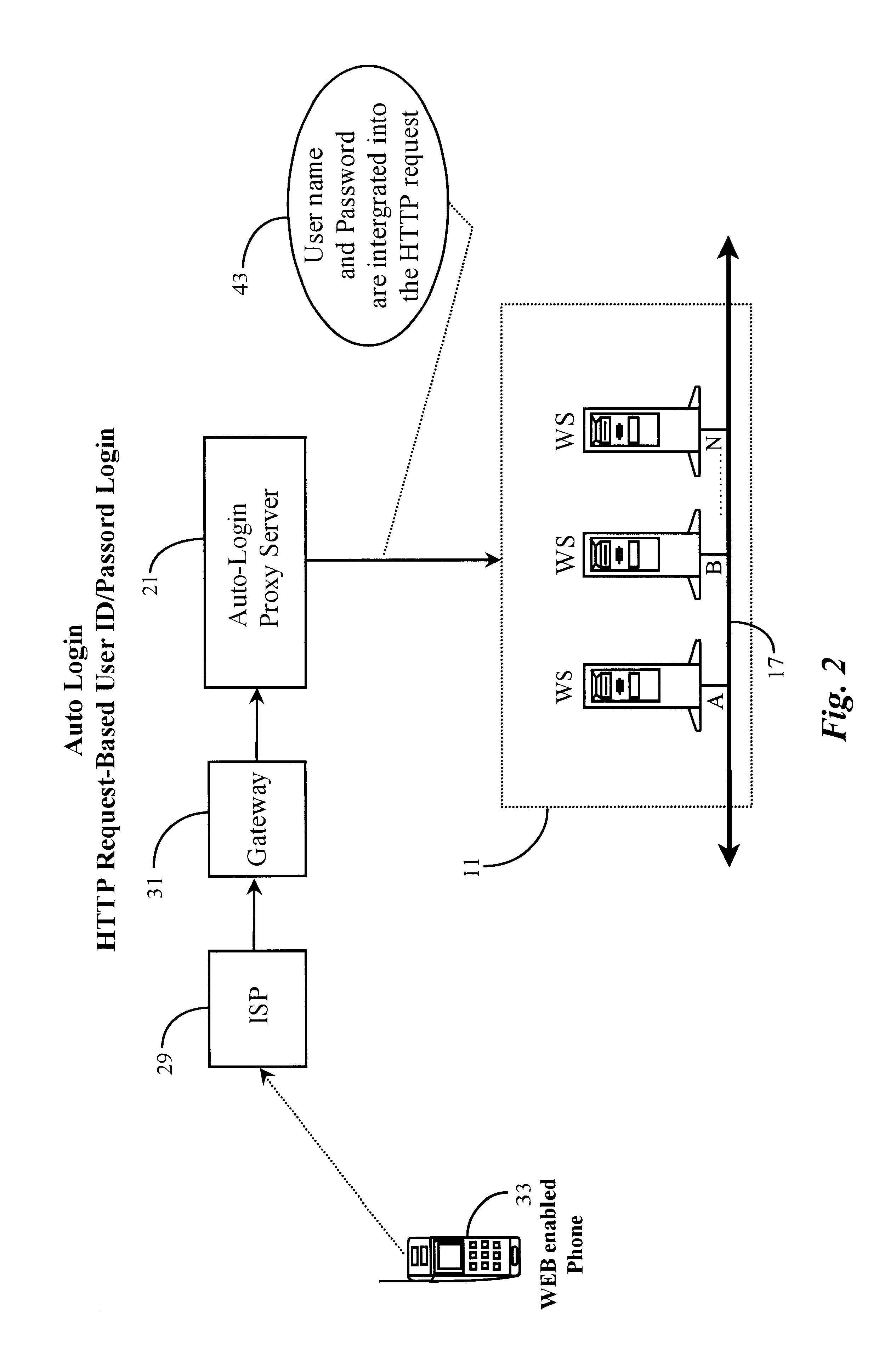
Method and apparatus enabling automatic login for wireless internet-capable devices
ActiveUS6865680B1More frustratingUnauthorized memory use protectionHardware monitoringHyperlinkNetwork connection
A network-based system for providing automatic login to a network-connected data source on behalf of a network-connected user accessing the system through a wireless communication appliance is provided. The system comprises, a wireless communication appliance, the appliance having network capability and an interactive user interface, the appliance operated for the purpose of accessing the network-connected data source, a network service-provider for providing access to the network; a network gateway for managing communication between the appliance and network-connected data source, a network-connected server node for performing proxy navigation and automated login services for the network-connected user, a data repository accessible to the network-connected server node, the data repository for holding data about the network-connected user and, a network-connected data source, the data source accessible to the network-connected server node. In preferred embodiments, a user operating the appliance while connected to the network invokes a hyperlink displayed in the user interface, the hyperlink containing a browser instruction for contacting the network-connected server node, the server node directing automated navigation to and login to the data source defined by the hyperlink, the login is accomplished through automated insertion of user data retrieved from the data repository into the appropriate fields of a login request.
Owner:YODLEE COM INC
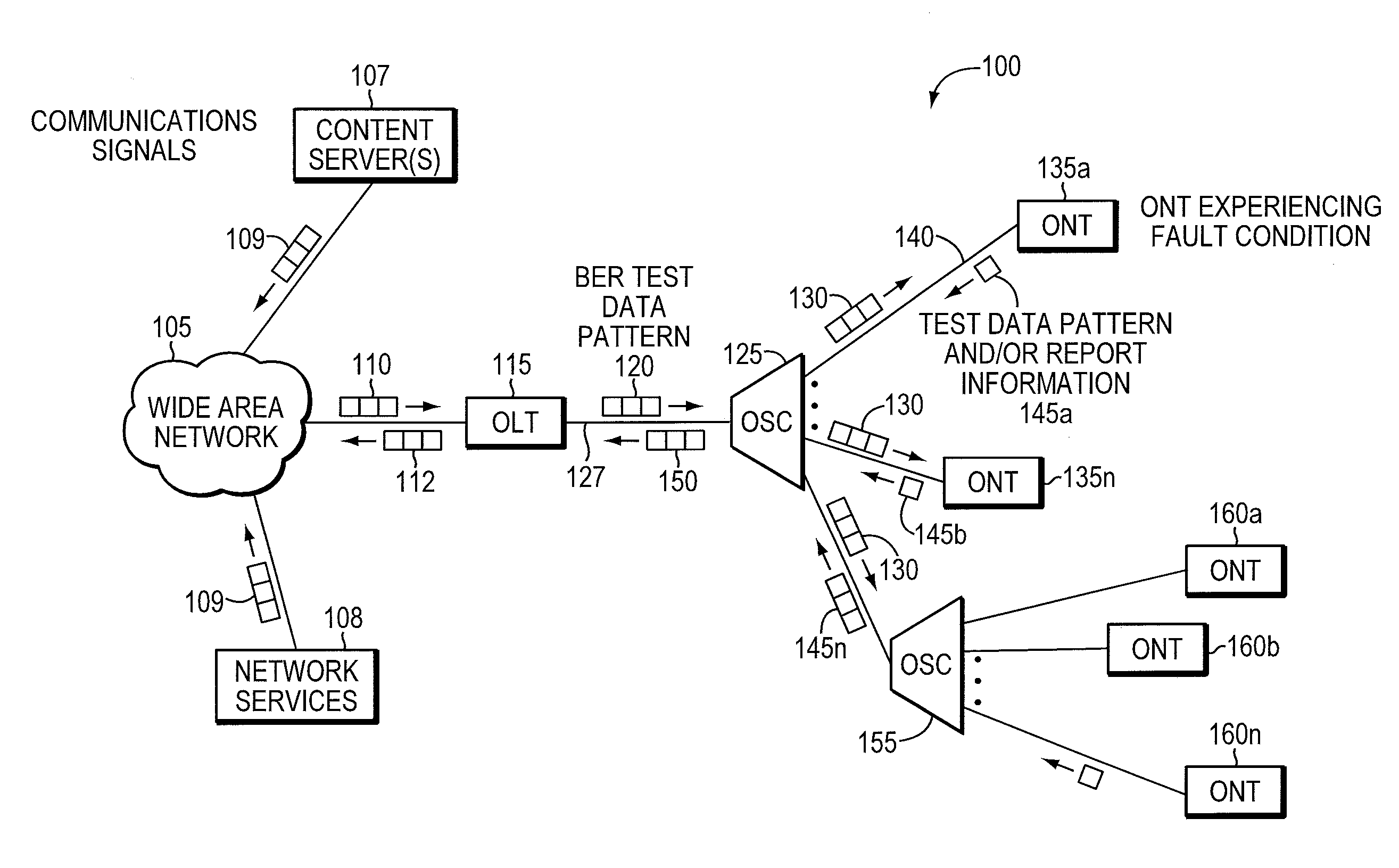
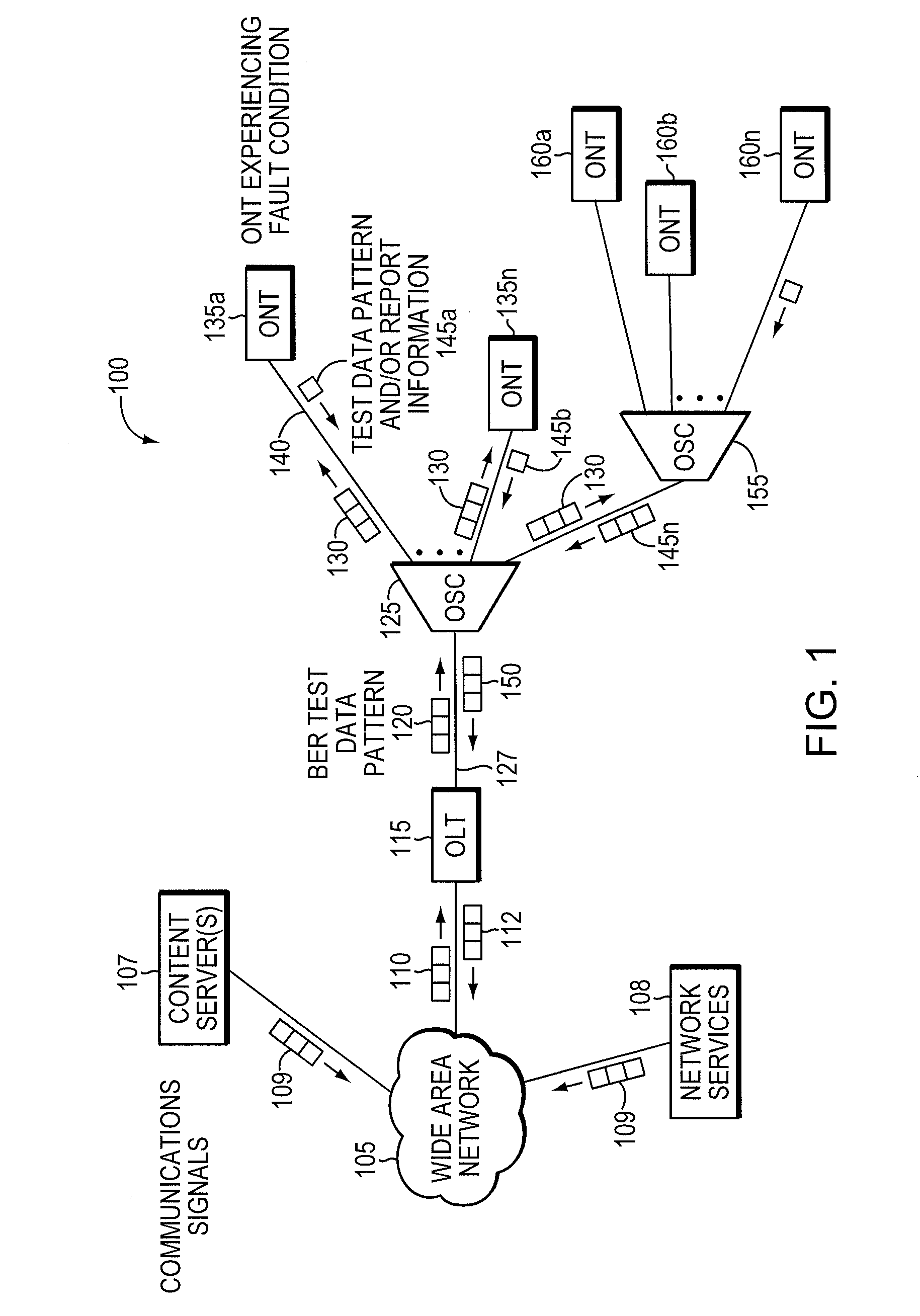
Method and apparatus for correcting faults in a passive optical network
ActiveUS8090258B2Transmission monitoringTransmission monitoring/testing/fault-measurement systemsSignal-to-noise ratio (imaging)Engineering
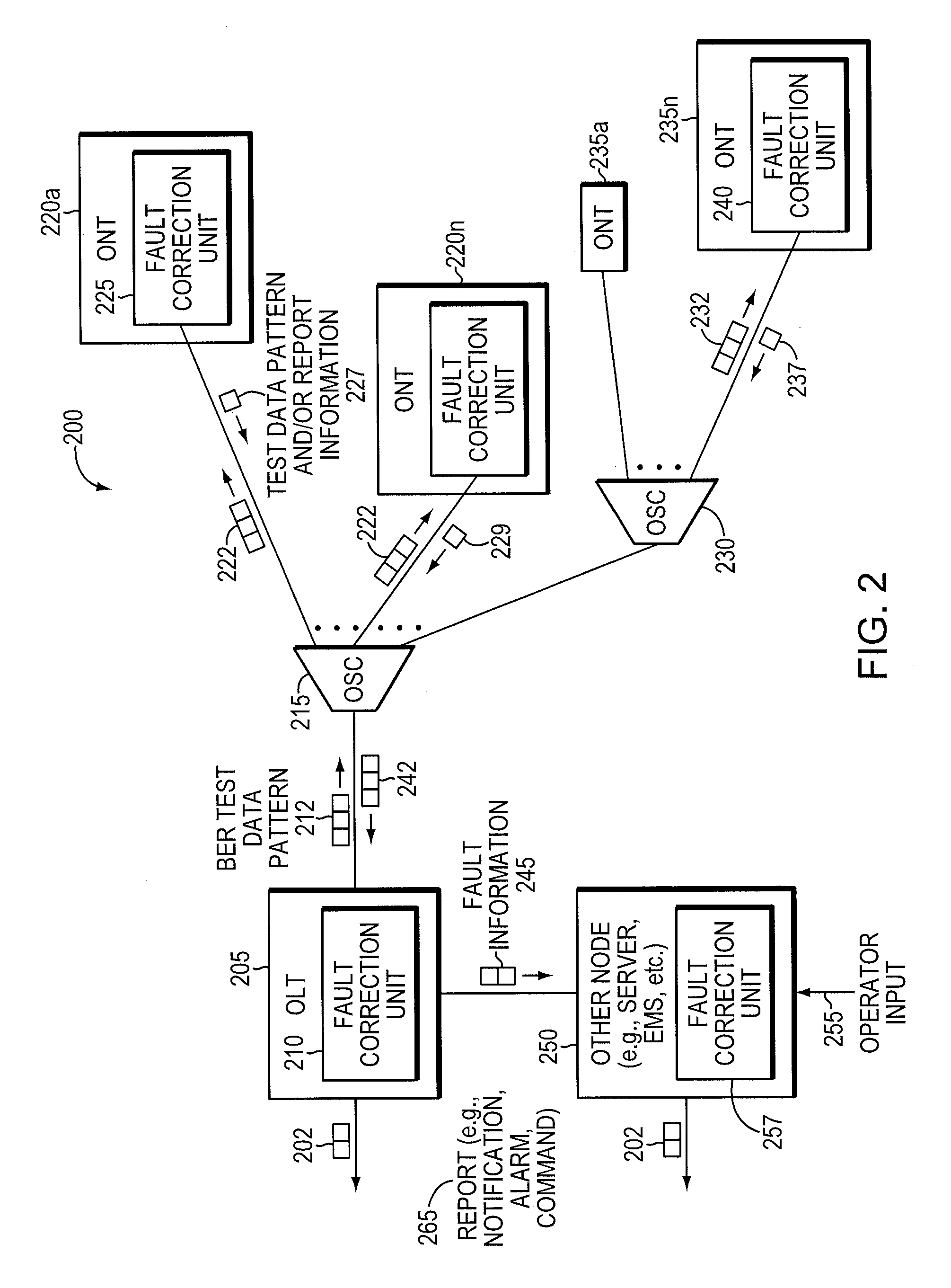
Component malfunctions in passive optical networks (PON) can increase bit error rates and decrease signal-to-noise ratio of communications signals. These faults may cause the receivers of the signals, either the optical line terminal (OLT) or optical network terminals (ONTs), to experience intermittent faults and / or may result in misinterpreted commands that disrupt other ONT's communication, resulting in a rogue ONT condition. Existing PON protocol detection methods may not detect these types of malfunctions. An embodiment of the present invention identifies faults in a PON by transmitting a test series of data patterns via an optical communications path from a first optical network node to a second optical network node. The test series is compared to an expected series of data patterns. An error rate may be calculated as a function of the differences between the test series and expected series. The error rate may be reported to identify faults in the PON. Through use of the embodiment, network faults can be identified and optionally automatically corrected, saving a network service provider from expending technician time and maintaining an operating state of the network.
Owner:TELLABS PETALUMA
Content delivery network service provider (CDNSP)-managed content delivery network (CDN) for network service provider (NSP)
ActiveUS7149797B1Large capital investmentSimple configurationFinanceMultiprogramming arrangementsComputer scienceWeb content
A CDN service provider shares its CDN infrastructure with a network to enable a network service provider (NSP) to offer a private-labeled network content delivery network (NCDN or “private CDN”) to participating content providers. The CDNSP preferably provides the hardware, software and services required to build, deploy, operate and manage the CDN for the NCDN customer. Thus, the NCDN customer has access to and can make available to participating content providers one or more of the content delivery services (e.g., HTTP delivery, streaming media delivery, application delivery, and the like) available from the global CDN without having to provide the large capital investment, R&D expense and labor necessary to successfully deploy and operate the network itself. Rather, the global CDN service provider simply operates the private CDN for the network as a managed service.
Owner:AKAMAI TECH INC
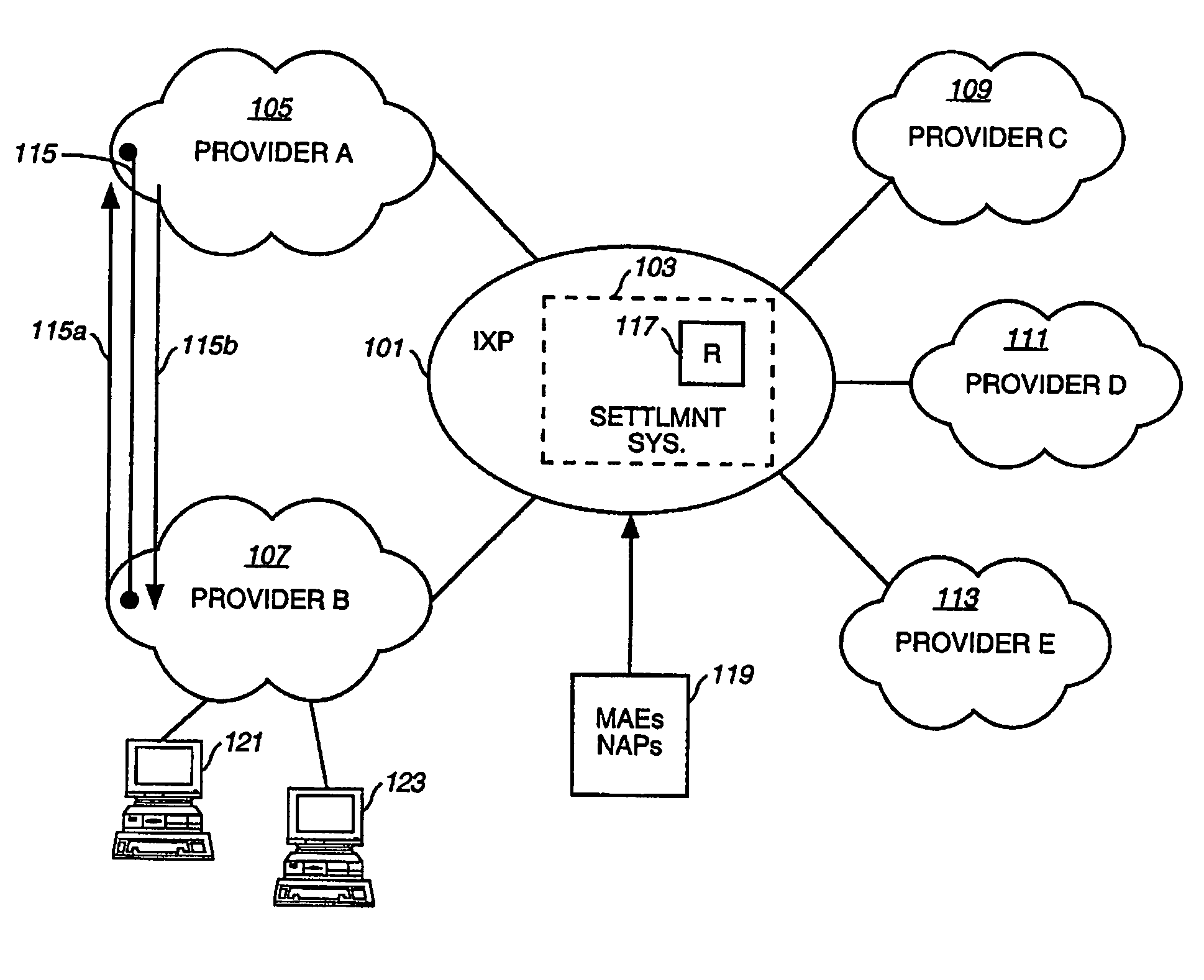
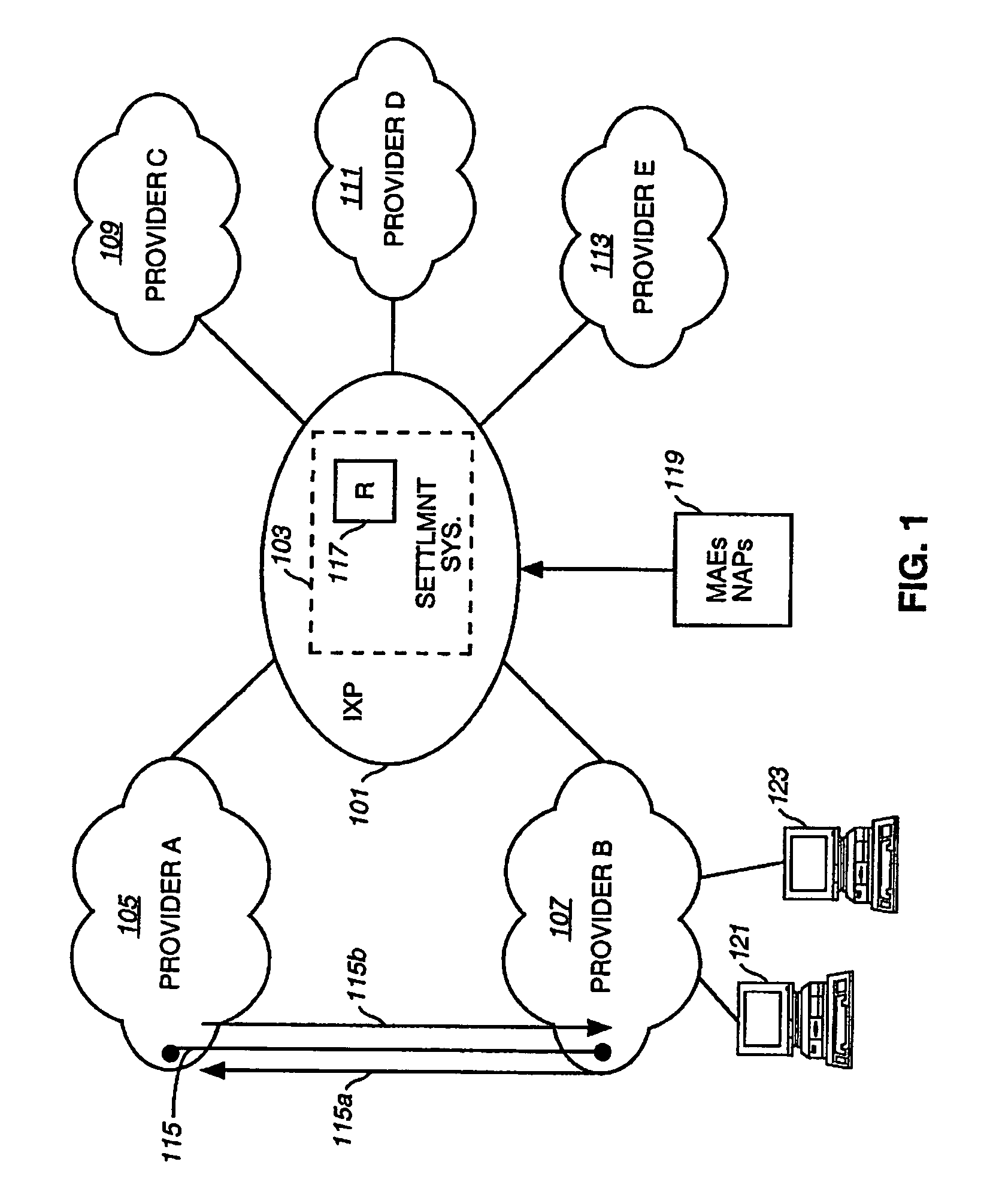
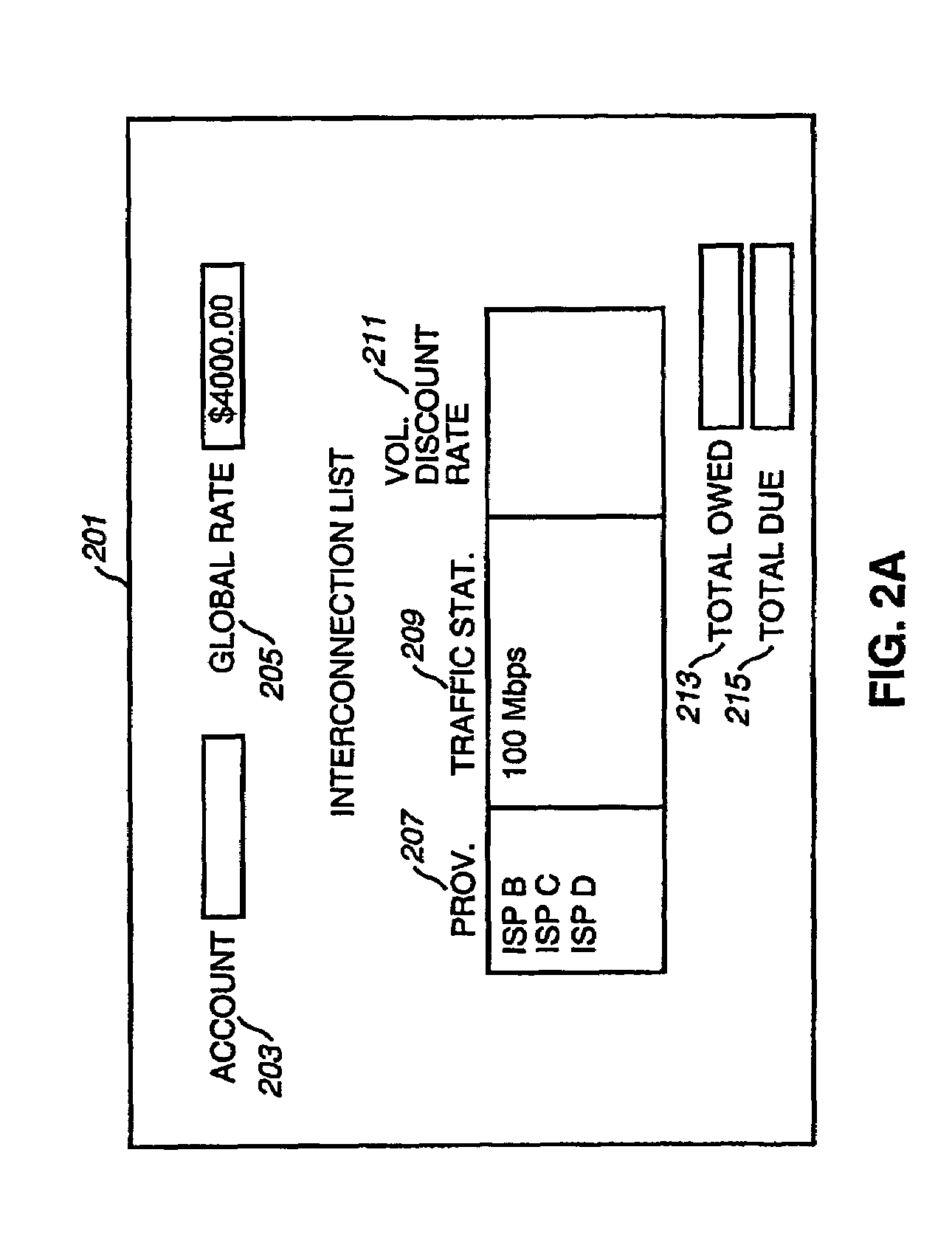
Method and system for providing settlement of interconnected packet-switched networks
InactiveUS6950407B1Interconnection arrangementsMetering/charging/biilling arrangementsTraffic capacityNetwork service
An approach for supporting settlement of network usage associated with multiple network service providers is disclosed. A settlement system includes a processor that determines a settlement agreement among the network service providers. The settlement agreement specifies rate information associated with traffic exchange among the corresponding networks of the network service providers. A traffic monitor measures source traffic statistics, which is stored in a settlement database. Additionally, the settlement database stores the settlement agreement. The processor computes settlement information based upon the stored traffic statistics; the settlement information includes usage cost differential information for reconciliation of network usage among the various networks.
Owner:VERIZON PATENT & LICENSING INC
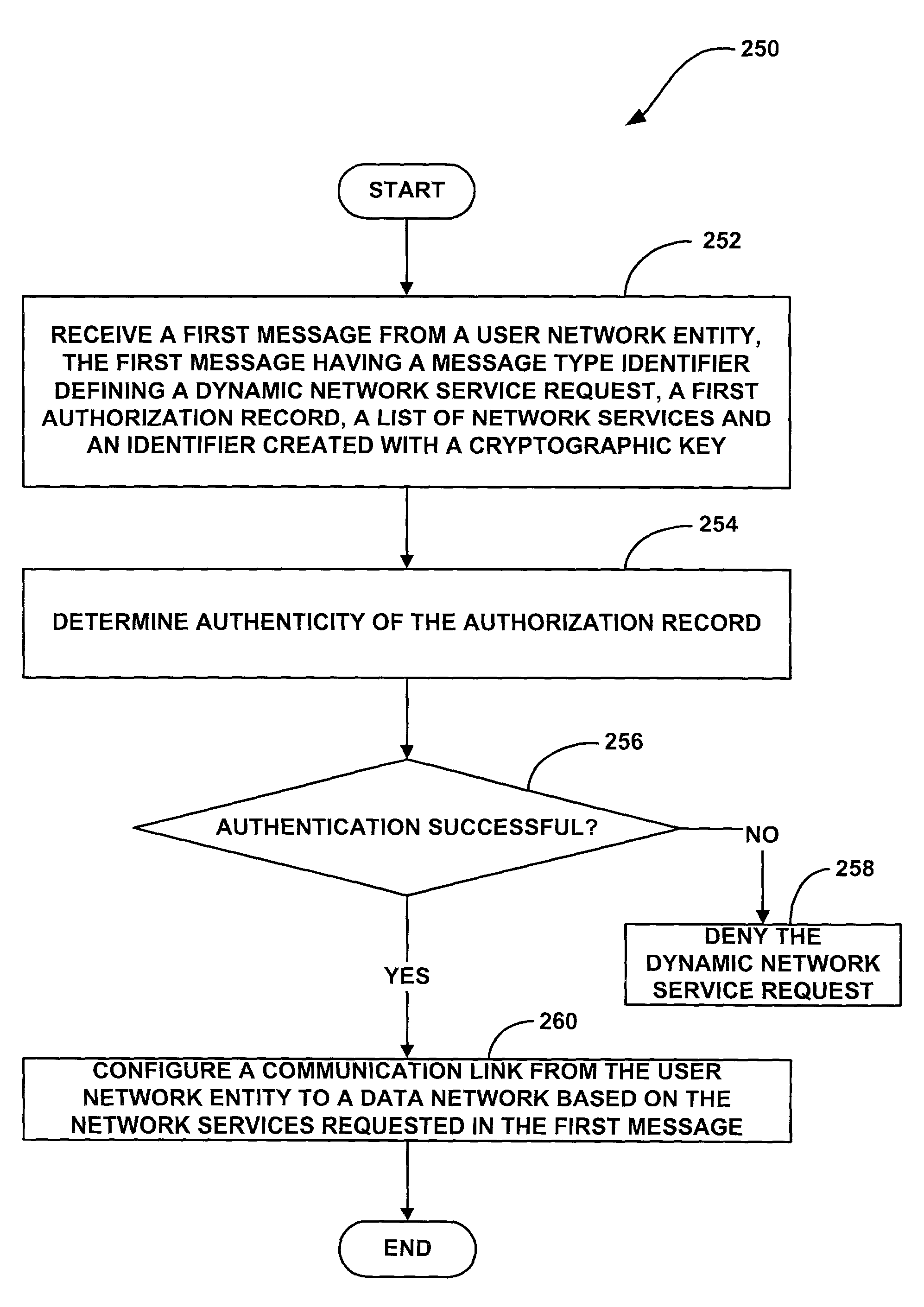
System and method for providing distributed and dynamic network services for remote access server users
InactiveUS7073055B1Overcome problemsDigital data processing detailsMultiple digital computer combinationsCryptographic key generationDigital signature
A system and methods for providing distributed and dynamic network services to remote access users. One of the methods includes providing a first certificate for requesting dynamic network services by a user network entity, and at least one second certificate for requesting static network services by the user network entity. According to one method, a user of the user network entity may generate a first message to request dynamic network services from a network service provider entity. For example, the first message may include the first certificate, a digital signature generated with a private encryption key associated with the first certificate and list of network service that the user wishes to set up dynamically. In one embodiment, when the network service provider entity receives the first message, the network service provider entity verifies the authenticity of the first certificate and, if the first certificate is authentic, the network service provider entity configures a network connection between the user network entity and a data network based on the network services requested by the user in the first message.
Owner:VALTRUS INNOVATIONS LTD
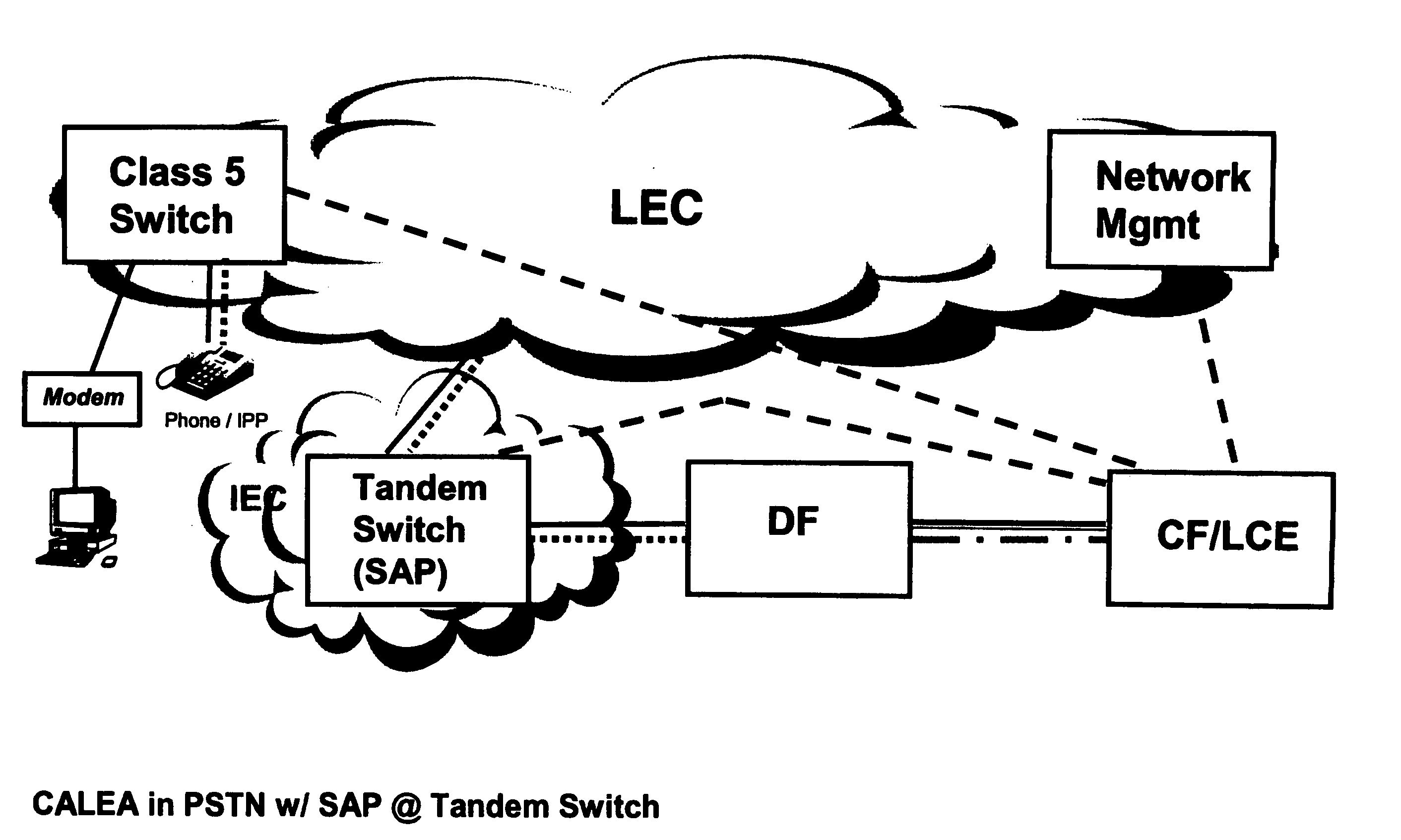
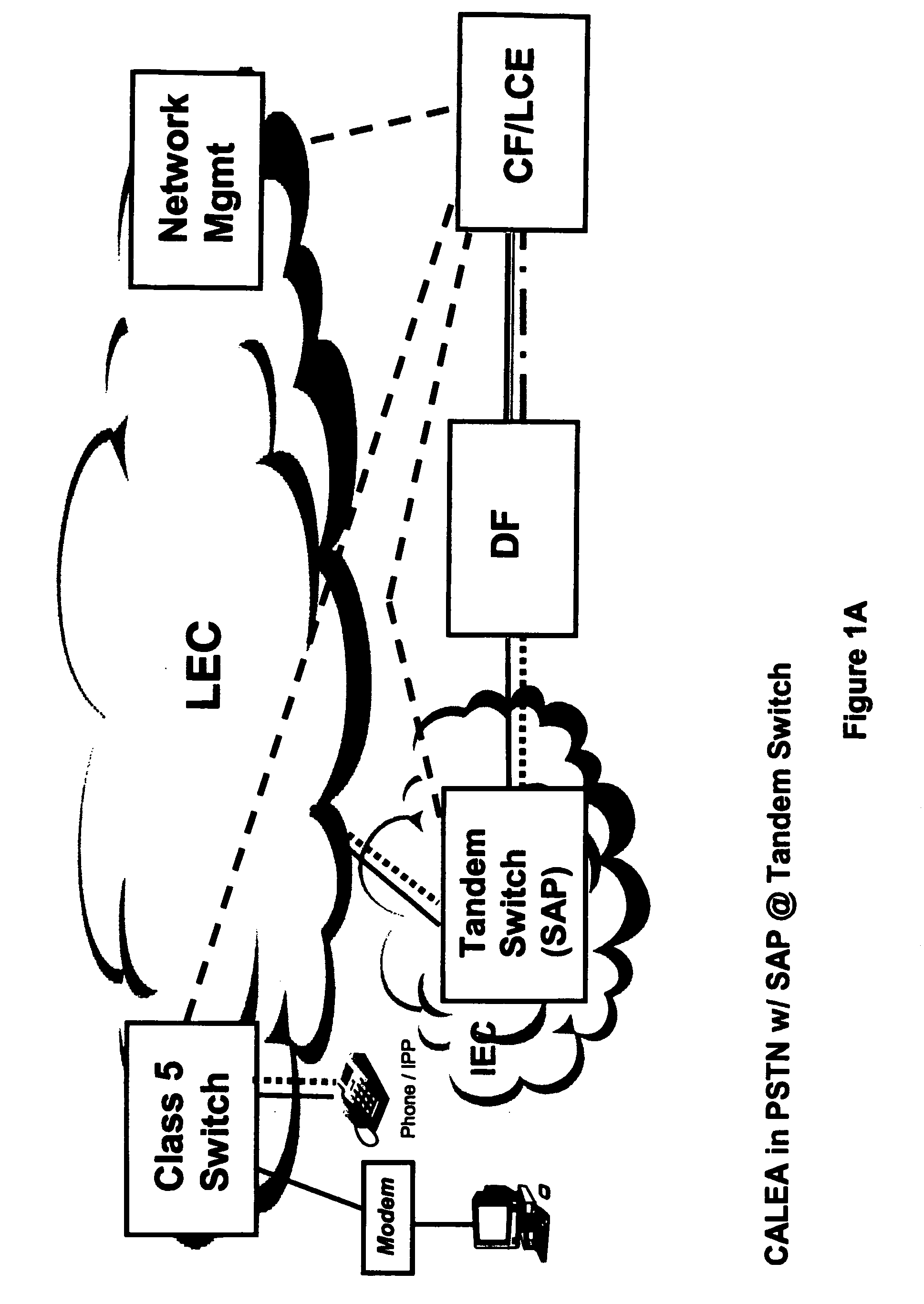
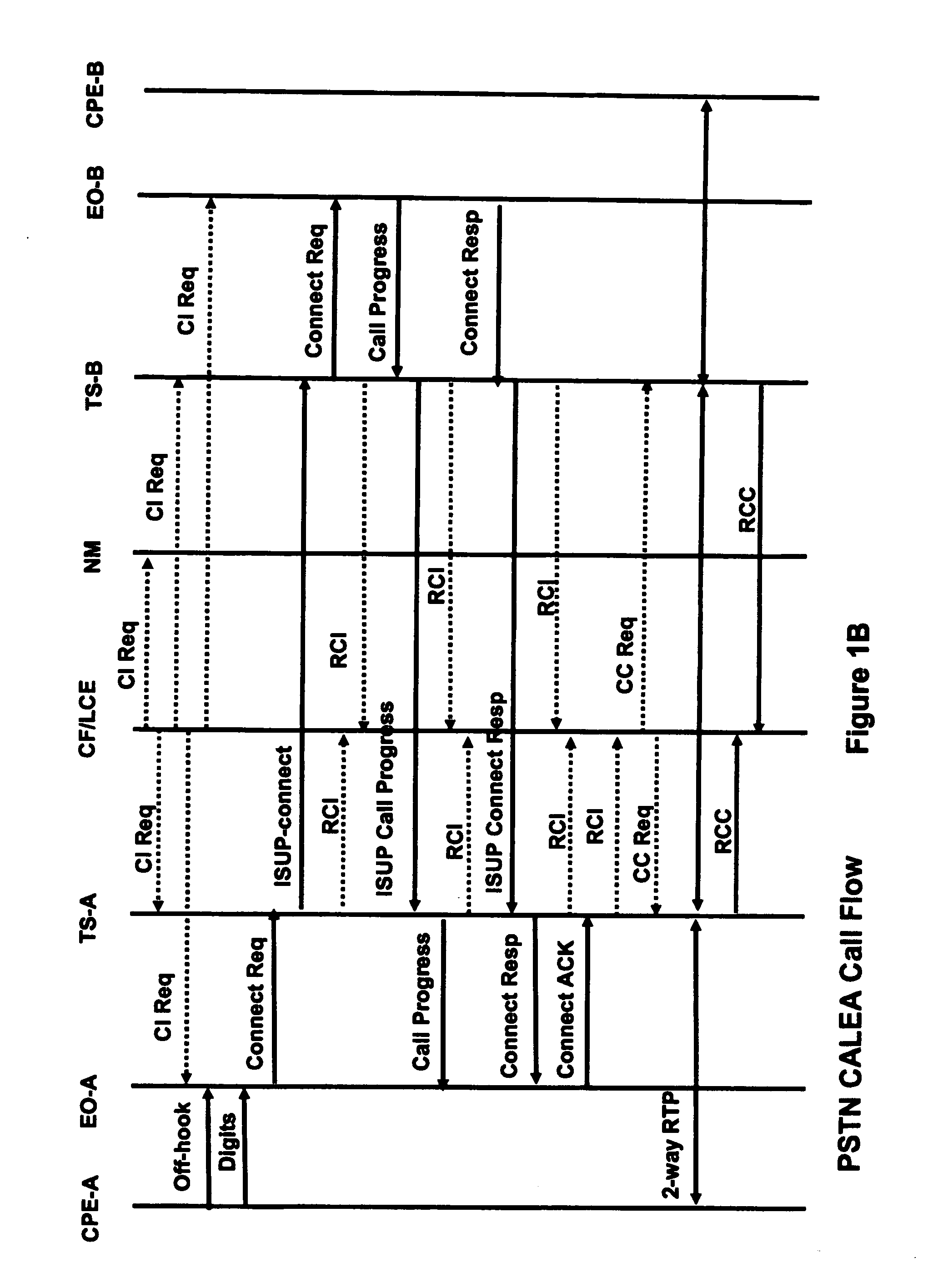
Surveillance implementation in managed VOP networks
A procedure for accomplishing surveillance within a managed VoP network when end-user encryption / decryption and NAT are in place. The procedure comprises first analyzing the network from call signaling and message standpoints, leading to the identification of suitable surveillance access points (SAPs) for packet interception. A Delivery Function (DF) facilitated by the network service provider provides the means to intercept (without alteration) and replicate packets transmitted across the SAPs. The packets are then transmitted via the DF for collection within a Collection Function (CF), which is managed by a Law Enforcement Agency (LEA), for analysis by the LEA. This analysis provides, among other benefits, the opportunity to decrypt the intercepted packets and to identify additional suitable SAPs. In demonstrating the procedure, several embodiments of network surveillance models are described. Each one identifies the location of SAPs for that model. In each model, different information is collected and different processes are followed.
Owner:TELOGY NETWORKS
Content delivery network (CDN) cold content handling
ActiveUS20120226649A1Multiple digital computer combinationsKnowledge representationDomain nameDomain Name System
A method of content delivery in a content delivery network (CDN), where the CDN is deployed, operated and managed by a content delivery network service provider (CDNSP). The CDN comprises a set of content servers and a domain name system (DNS). For a given content provider, a determination is first made whether the content provider has “cold content” delivery requirements by evaluating one or more factors that include: total content size, size of content objects expected to be served, uniqueness of content, total number of content objects, and a percentage of the total content size that is expected to account for a given percentage of traffic. Upon a determination that the content provider has cold content delivery requirements, a subset of the CDN content servers are configured to implement a set of one or handling rules for managing delivery of the cold content from the CDN content servers.
Owner:AKAMAI TECH INC
System and method for dynamic simultaneous connection to multiple service providers
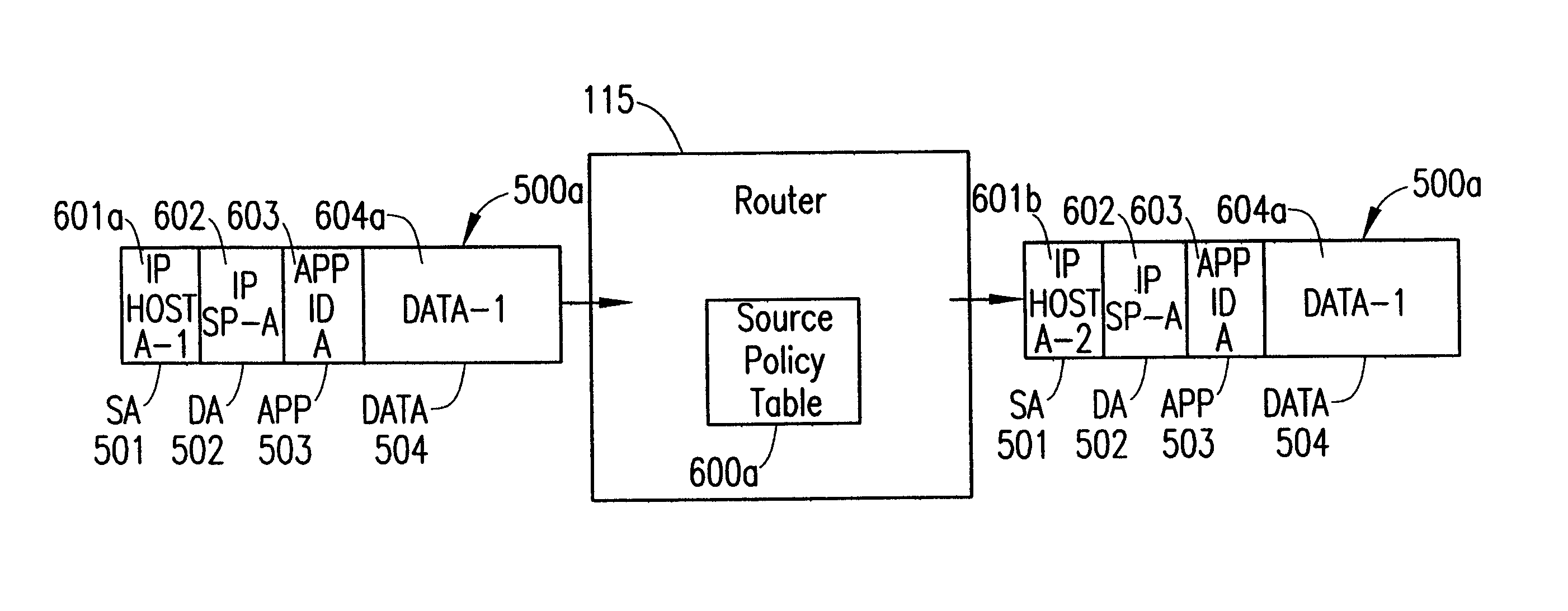
InactiveUS6801528B2Data switching by path configurationMultiple digital computer combinationsAccess networkNetwork address translation
A policy enables a subscriber to connect to multiple service providers simultaneously using a network address translation technique that translates an address identifying the subscriber and associated with a first service provider into an address identifying the subscriber and associated with a second service provider for a particular application. The subscriber registers with a single home service provider and connects to that single home service provider for a packet session. To connect to additional service providers that provide additional applications during the packet session, the NAT rule is downloaded from the home service provider to a router at the border between the subscriber and the access network of the home service provider. Each IP packet received at the router to or from the subscriber is filtered to determine the subscriber's address and an application identifier. Based on the combination of both the subscriber's address and the application identifier, the router translates the subscriber's address into a new address, using the NAT rule. The new address is used to connect the subscriber to an additional service provider for a particular application during the packet session with the home service provider.
Owner:ERICSSON INC
Personalized network-based services
A network-based service where different sets of customized information are delivered to a user at different times to different destinations (i.e., different user devices) selected by the user. More particularly, a user accesses a network-based server, generally owned by a network service provider and defines a user profile which specifies the information or other content to be made available. The user may request that the information be delivered later automatically or be made available on demand. The user has flexibility in requesting a particular format to receive the information on demand. In case of the later delivery, the user requests specified times in a form of a schedule and specified destinations (i.e., user devices) for the delivery of the information. The user also has flexibility in selecting the format for the delivery of information. Sometimes, the format is dictated by the selection of a user device, e.g., the selection of a radio implies audio format, and the selection of a television implies video format. However, some user devices are capable of receiving information in more than one format, e.g., a computer may have the capability to receive information in audio, video, or text format. Depending on the implementation, one or more customized sets of information are delivered to one or more user devices as a function of the specified format or the specified time or both.
Owner:SOUND VIEW INNOVATIONS
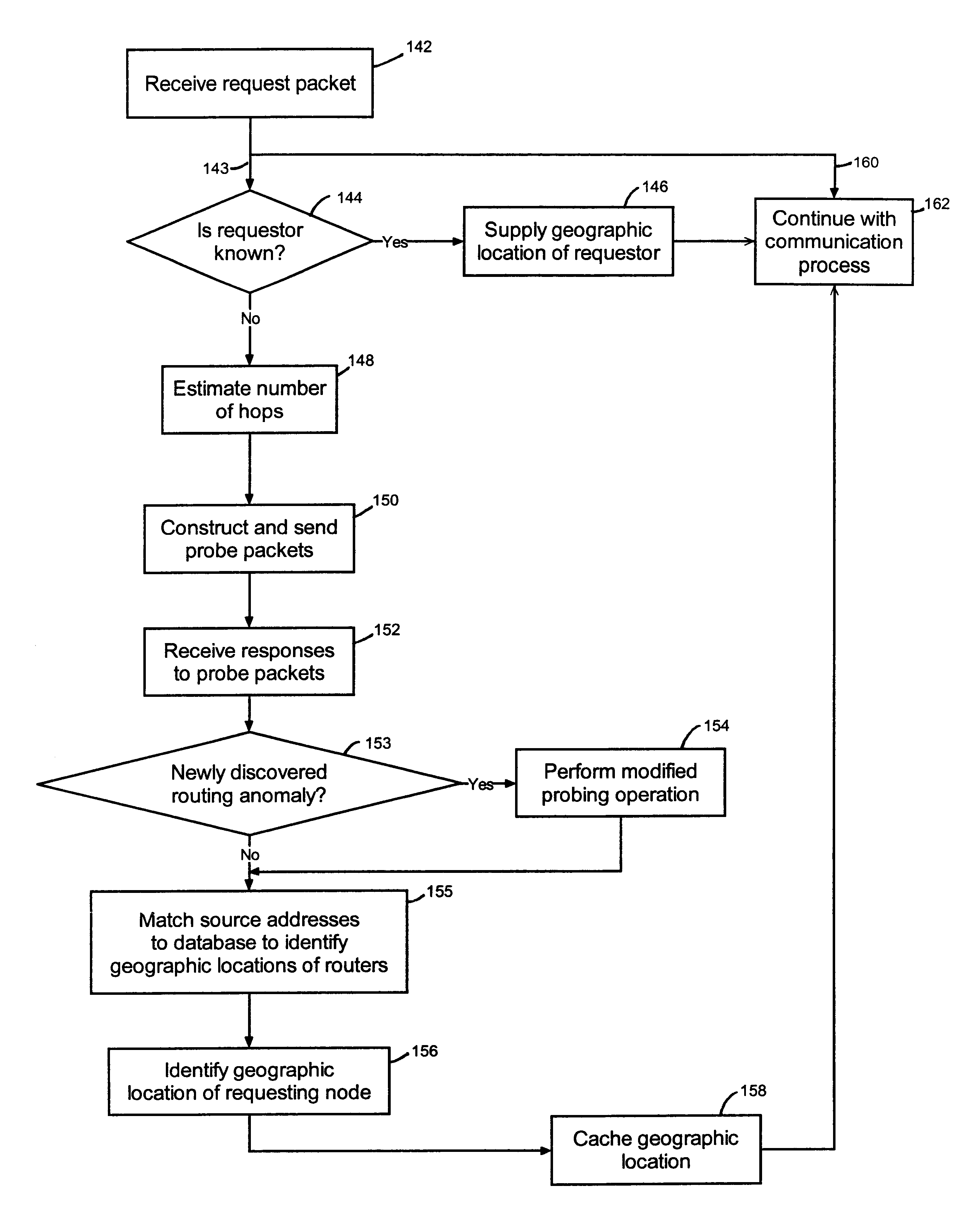
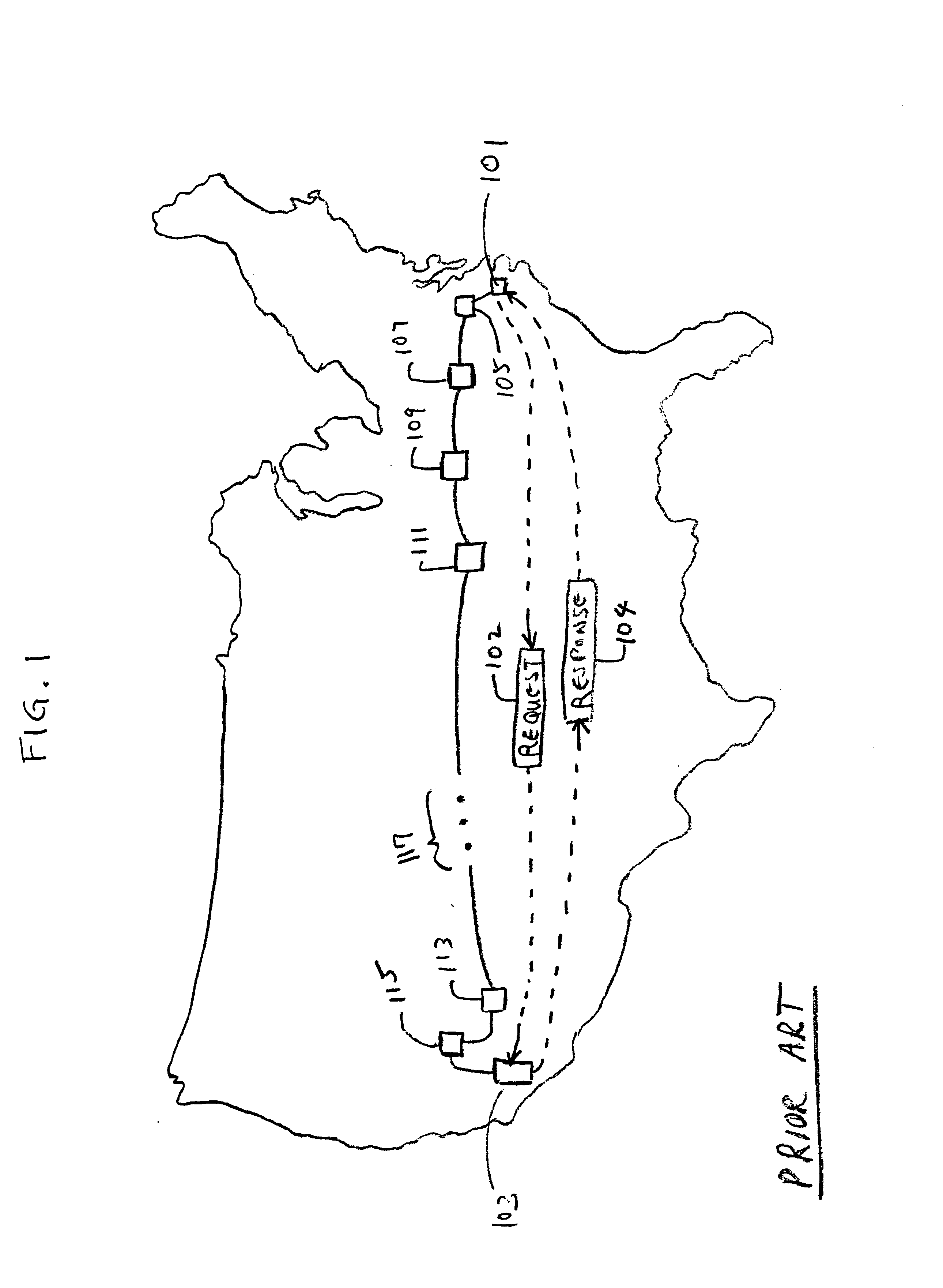
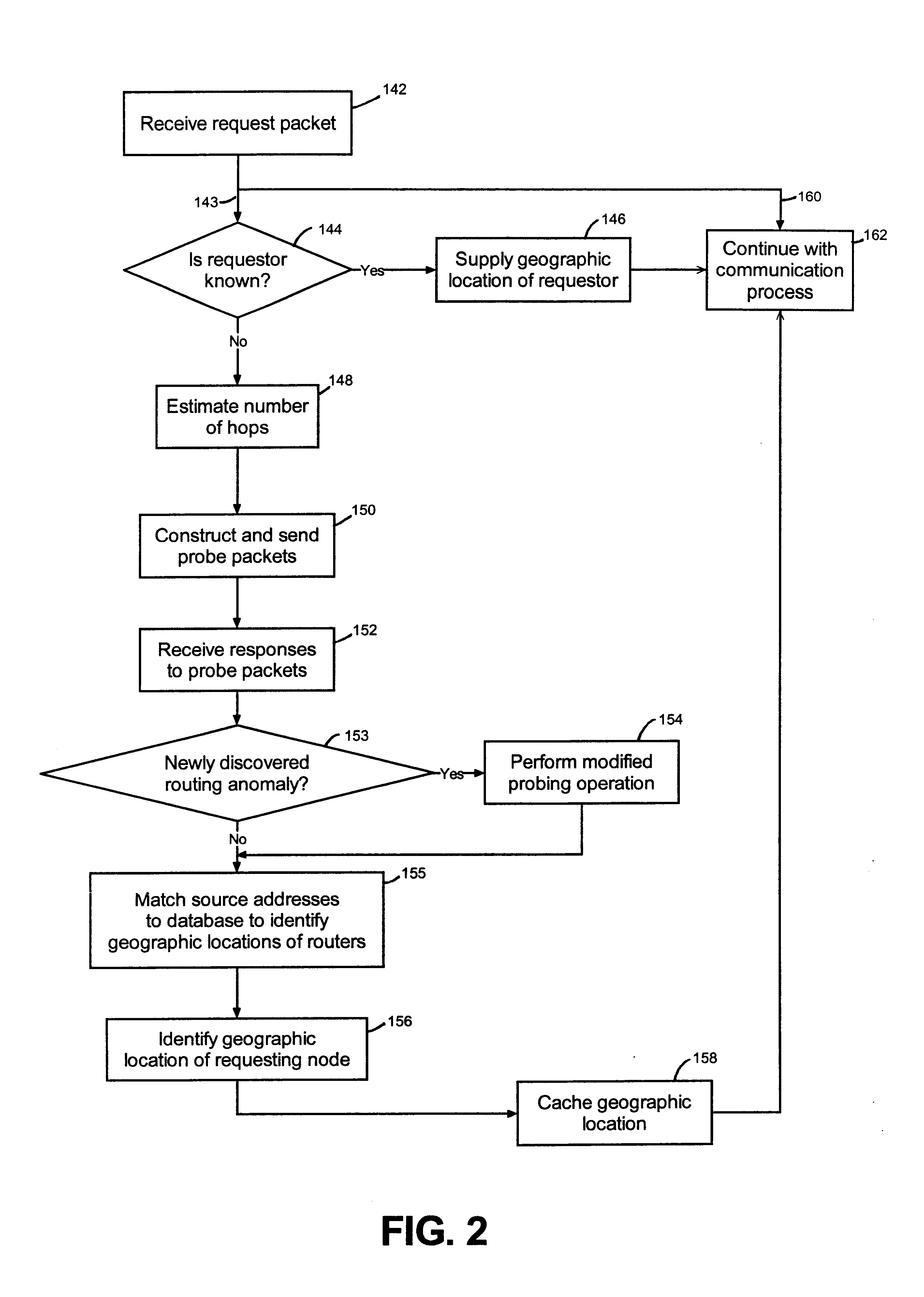
Creating a geographic database for network devices
InactiveUS6778524B1Error preventionFrequency-division multiplex detailsNetwork connectionGeolocation
A database is populated with geographic locations for network devices by providing a node on a network and making a connection into a network service provider (NSP) point of presence (POP) to obtain a connection to the network via the NSP. A message is then transmitted to the node over the network connection obtained from the NSP. The message is received at the node and a source network identifier is extracted from the message. The source network identifier is then associated with a known geographic location for the POP in a database. The foregoing steps are then repeated for multiple different POPs. Also, a database is populated with geographic locations for network devices by providing a node on a network and making a connection into a network service provider (NSP) point of presence (POP) to obtain a connection to the network via the NSP. A message is then transmitted to the node over the network connection obtained from the NSP. The message is received at the node and a source network identifier is extracted from the message. The route over the network between the node and the POP is then probed to obtain network identifiers for routers along the route. The foregoing steps are then repeated for multiple different POPs.
Owner:RESOURCE CONSORTIUM LTD LLC
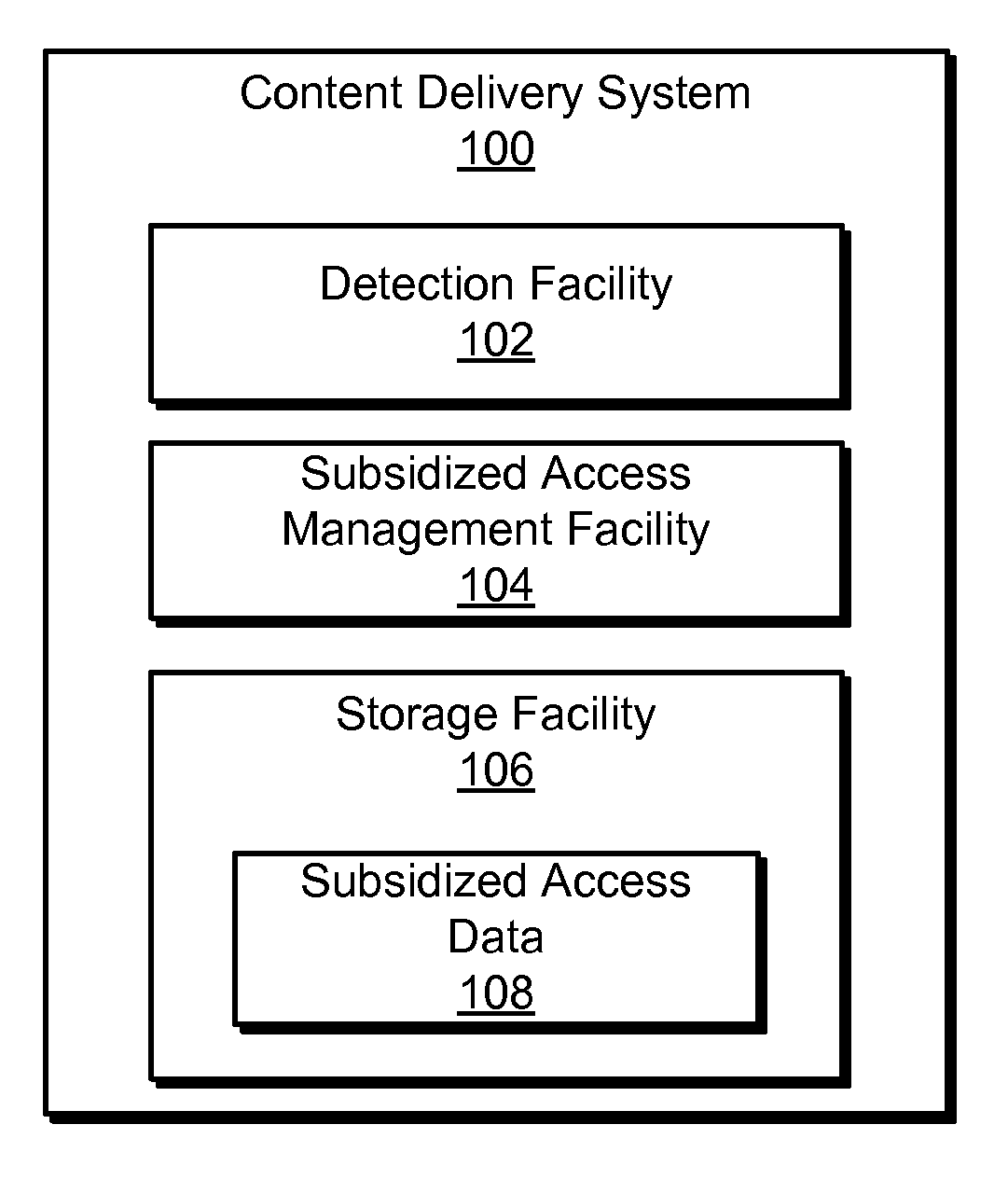
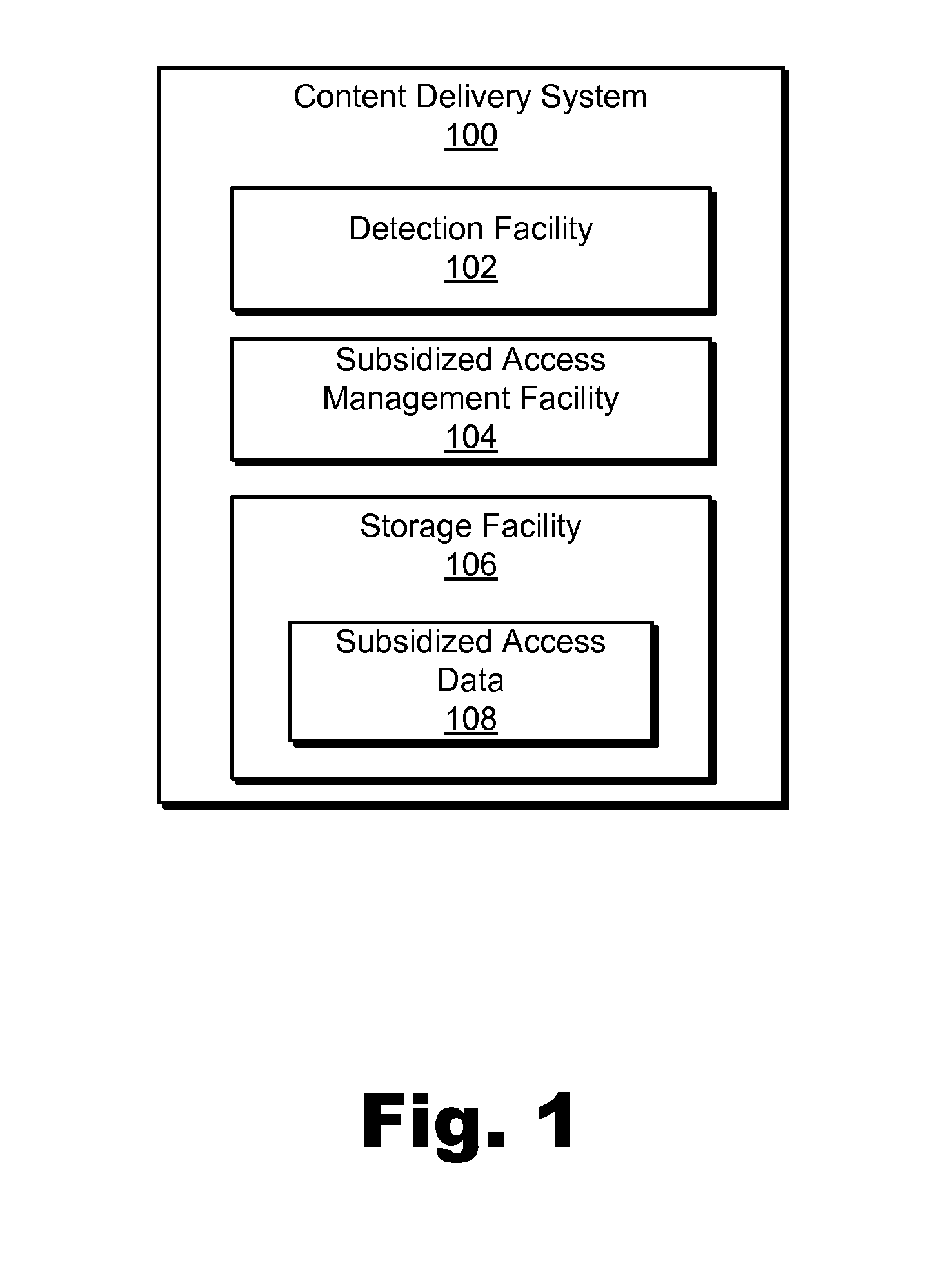
Methods and Systems for Providing Subsidized Access to Network Content
An exemplary method includes a content delivery system 1) detecting a request provided by an access device associated with a user to access network content by way of a network provided by a network service provider, the network content associated with a content provider and maintained by a content provider subsystem, 2) determining that a data usage charge for access by the user to the network content by way of the network is subsidized by the content provider in accordance with a subsidized access arrangement between the content provider and the network service provider, and 3) providing the user with subsidized access to the network content in accordance with a rule set associated with the subsidized access arrangement. Corresponding methods and systems are also disclosed.
Owner:VERIZON PATENT & LICENSING INC
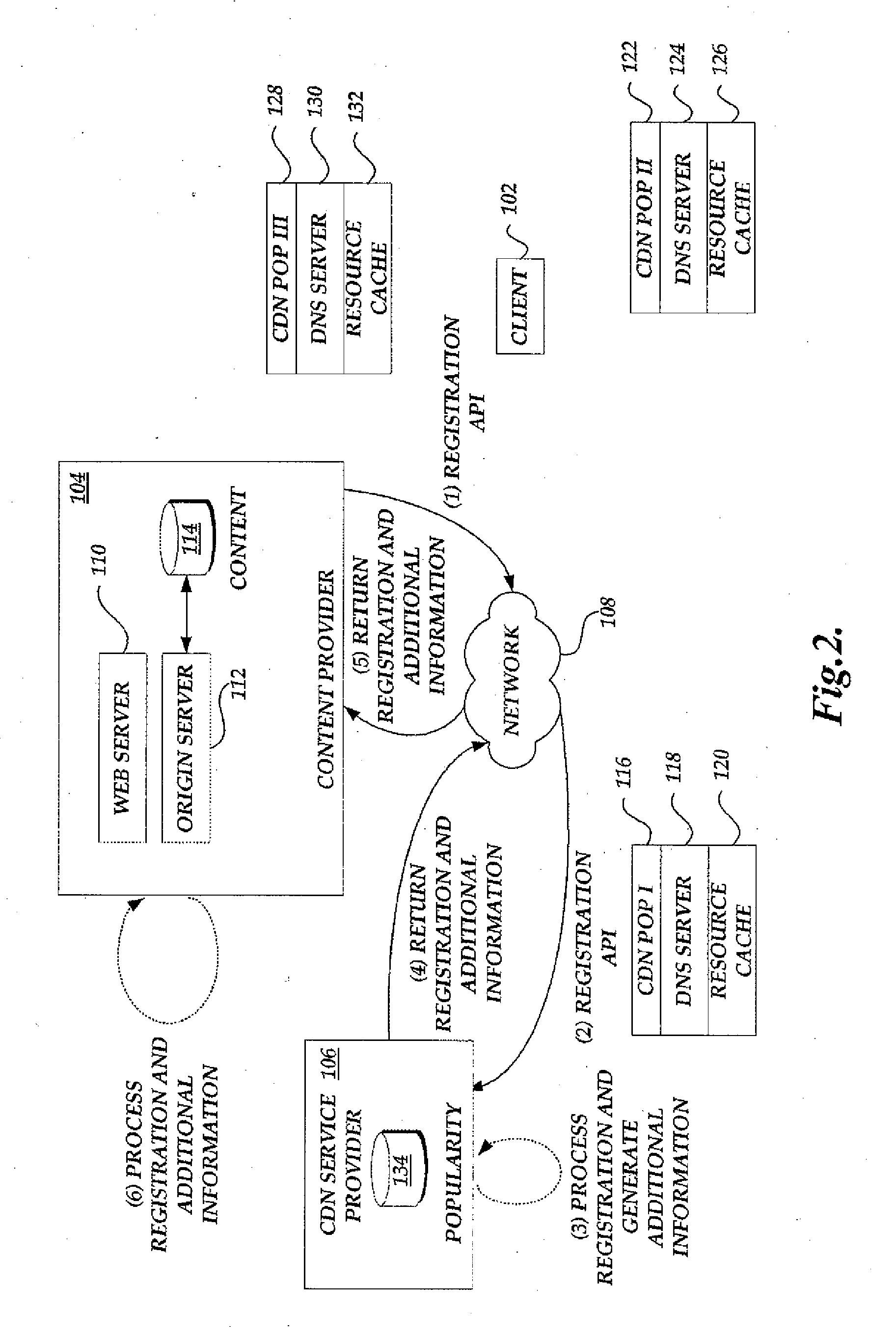
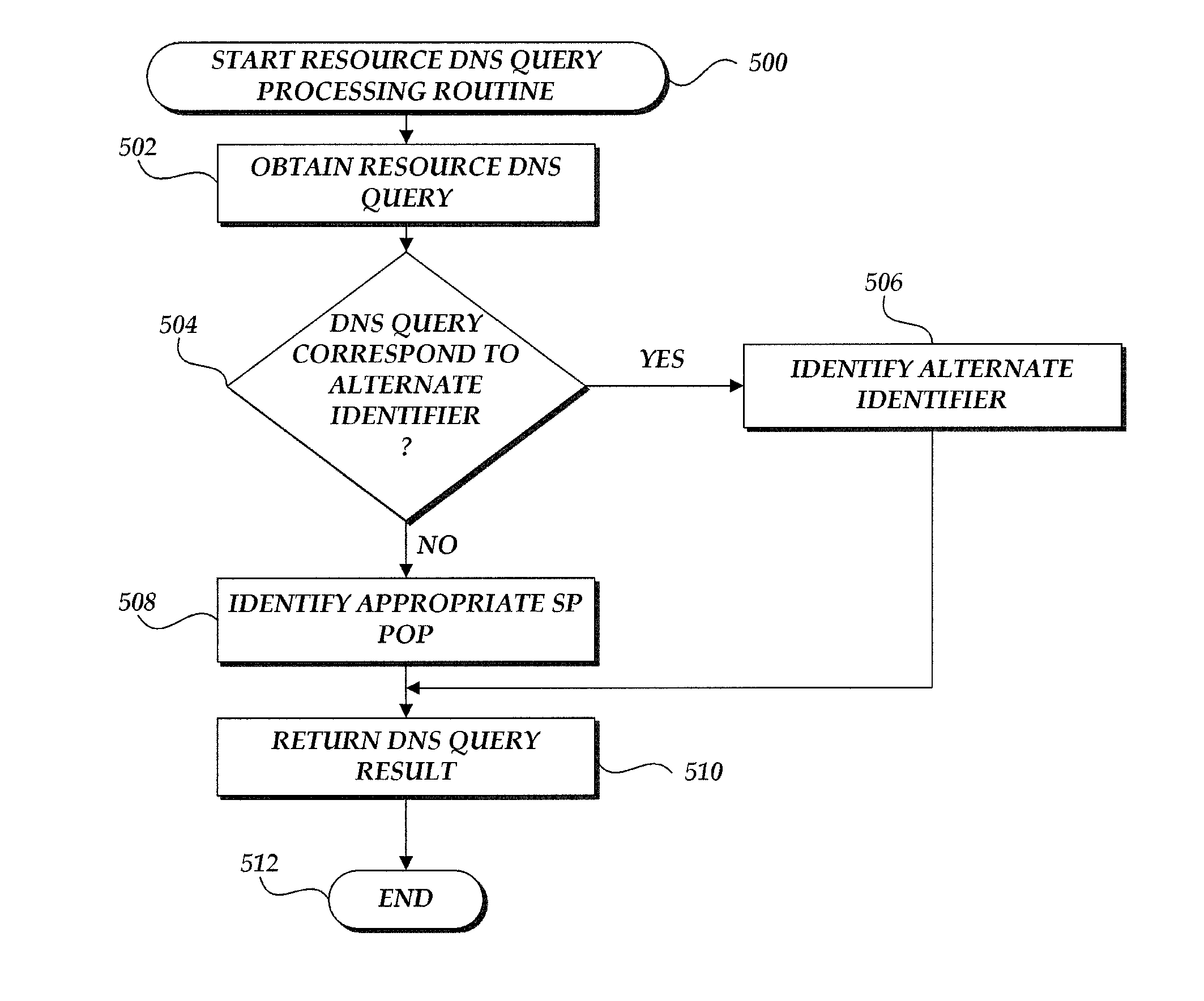
Translation of resource identifiers using popularity information upon client request
A system, method and computer-readable medium for request routing based on content popularity information are provided. A client computer transmits a request for content from a content provider. The content provider utilizes executable code, such as translation request code, for facilitating request routing utilizing popularity information. The translation request code, may direct a client computing device to request further translation request code and / or translation information. Thereafter, the client issues a DNS query with the translated information including popularity information. The content delivery network service provider can then either resolve the DNS query with an IP address of a cache component or transmit another alternative resource identifier that will resolve to the content delivery network service provider. The process can repeat until a DNS nameserver resolves a DNS query from the client computing device.
Owner:AMAZON TECH INC
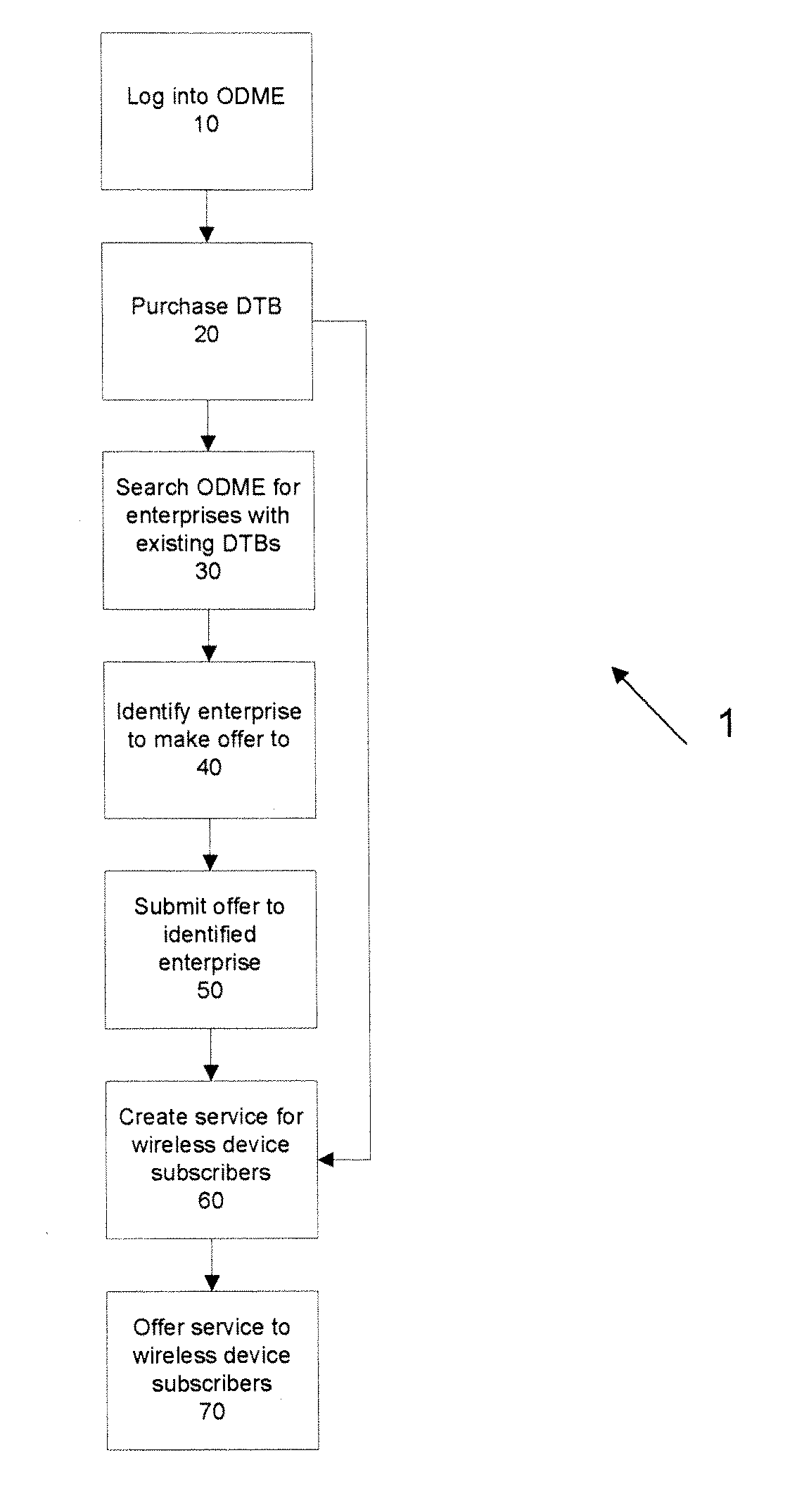
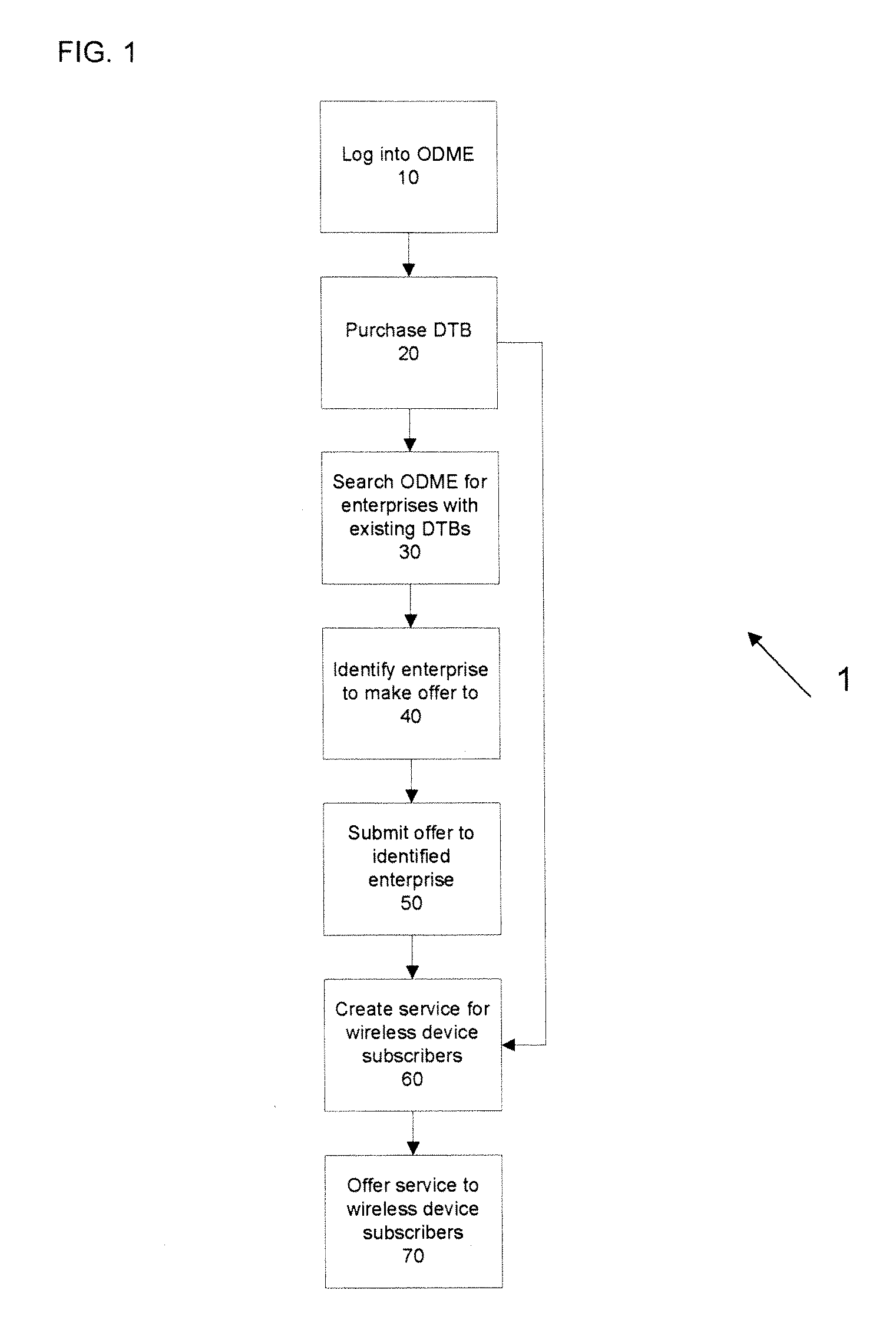
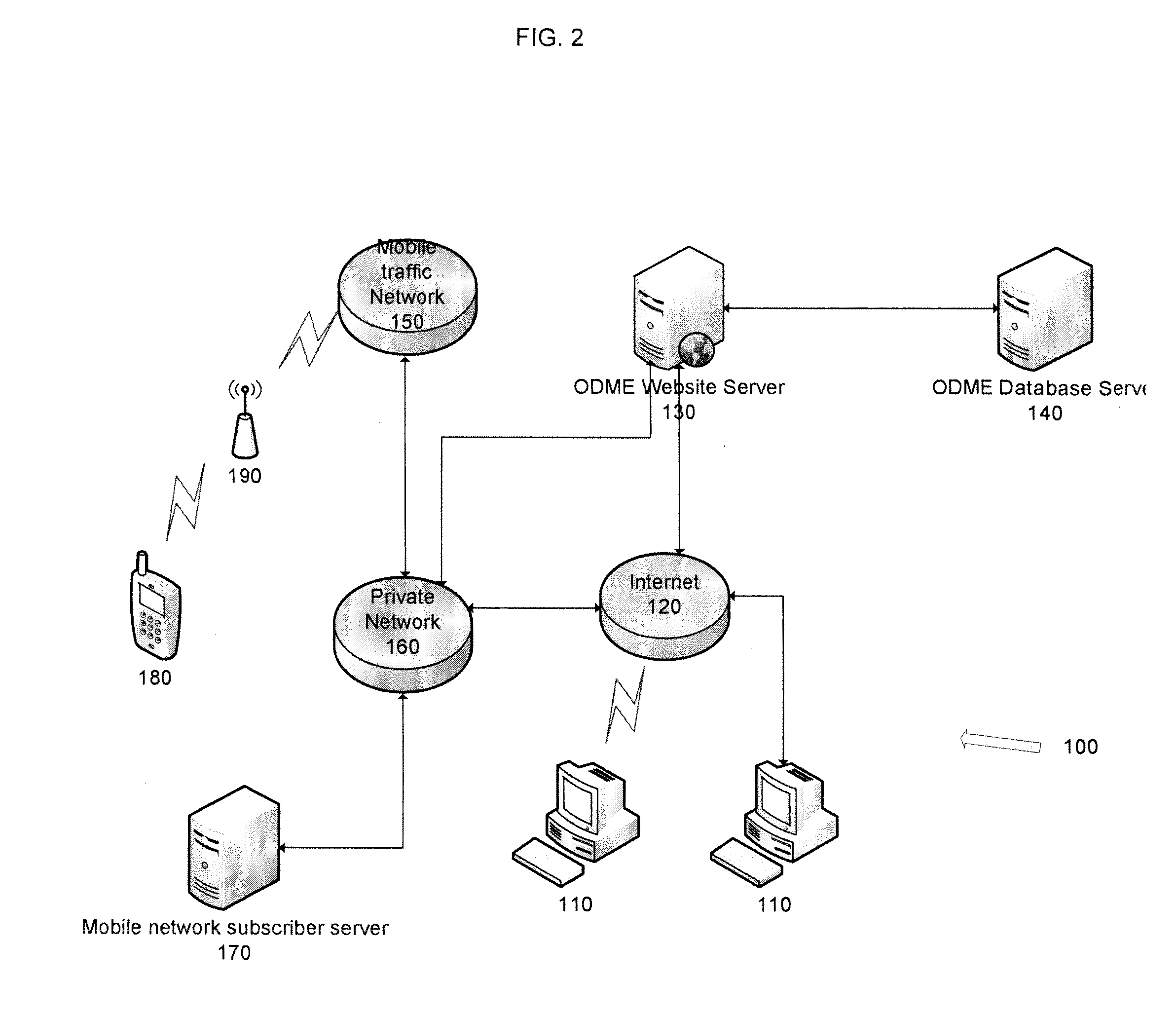
Alternative data plans
A method is presented that enables the creation of an alternative data plan by third party enterprises for mobile network end users. The method includes purchasing data transport bundles from one or more network service providers through an exchange, and either alone or with other enterprises, developing the alternative data plan for offer to end-users to consume data transport from the data transport bundle or bundles. The alternative data plan may be offered to the end user for free or the end user may be charged for use of the ADP based on the number of transactions, file type. The ADP may be billed to the user by the network provider or the ADP may be pre-purchased from the creator of the ADP.
Owner:CELLCO PARTNERSHIP INC
Managing content delivery network service providers by a content broker
InactiveUS8788671B2Computer security arrangementsMultiple digital computer combinationsClient-sideDistributed computing
A system, method, and computer readable medium for managing network storage provider and CDN service providers are provided. A content broker component obtains client computing device requests for content provided by a content provider. The content broker processes the client computing device requests and determines whether a subsequent request for the resource should be directed to a network storage provider or a CDN service provider as a function of the updated or processed by the content broker.
Owner:AMAZON TECH INC
System that provides early detection, alert, and response to electronic threats
InactiveUS20100031358A1Memory loss protectionDigital data processing detailsData streamProtection layer
The invention is a computer system that provides early detection alert and response to electronic threats (eThreats) in large wide area networks, e.g. the network of an Internet Services Provider or a Network Services Provider. The system of the invention accomplishes this by harnessing the processing power of dedicated hardware, software residing in specialized servers, distributed personal computers connected to the network, and the human brain to provide multi-layered early detection, alarm and response. The layers comprise: a Protection Layer, which detects and eliminates from the network data stream eThreats known to the system; a Detection Layer, which detects and creates signatures for new eThreats that are unknown to the system; an Expert Analysis Layer, which comprises a group of human experts who receive information from various components of the system and analyze the information to confirm the identity of new eThreats; and a Collaborative Detection & Protection Layer, which detects potential new eThreats by processing information received from various system agents and users. A Dynamic Sandbox Protection Layer associated with the distributed personal computers connected to the network. can optionally be part of the system of the invention.
Owner:DEUTSCHE TELEKOM AG
Apparatus for public access mobility LAN and method of operation thereof
ActiveUS7483411B2Key distribution for secure communicationAccounting/billing servicesAir interfaceThe Internet
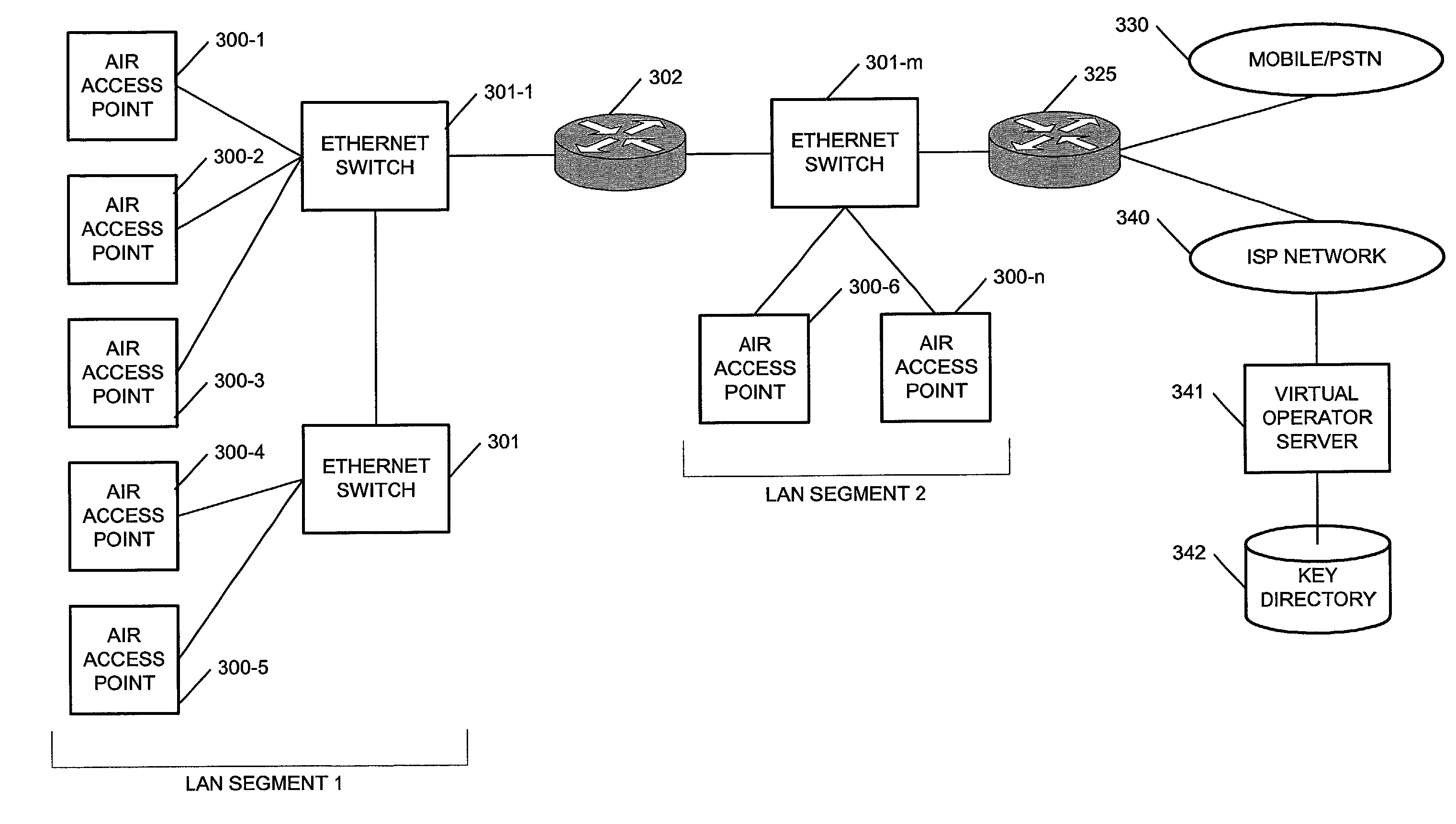
Public wireless communications will increasingly extend into wireless LAN (WLAN) environments in order to meet the ubiquitous access, high data rate, and local services demands of future Internet appliances. By relying on IP-level services mechanisms, the Public Access Mobility LAN (PAMLAN) can simultaneously support different air interfaces, franchises for multiple services providers, and a multi-segment LAN environment including handoffs. The PAMLAN supports virtual operator LANs representing different network services providers, authorization and accounting mechanism, support of multiple air interfaces, and local IP mobility. A router associated with each base station realizes this highly distributed IP networking environment, and a QoS-enabled switched Ethernet core supports virtual networks and QoS services.
Owner:NEC CORP
Anycast service registration, method and apparatus, switching equipment and systems
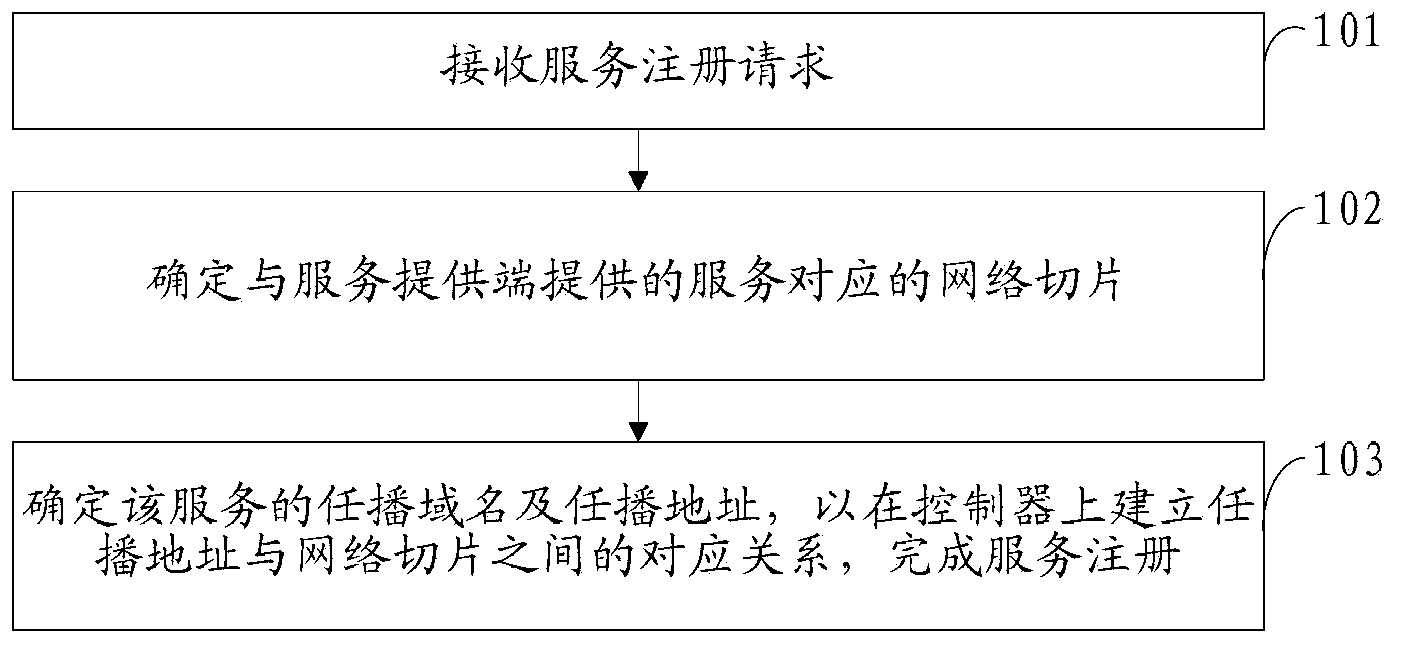
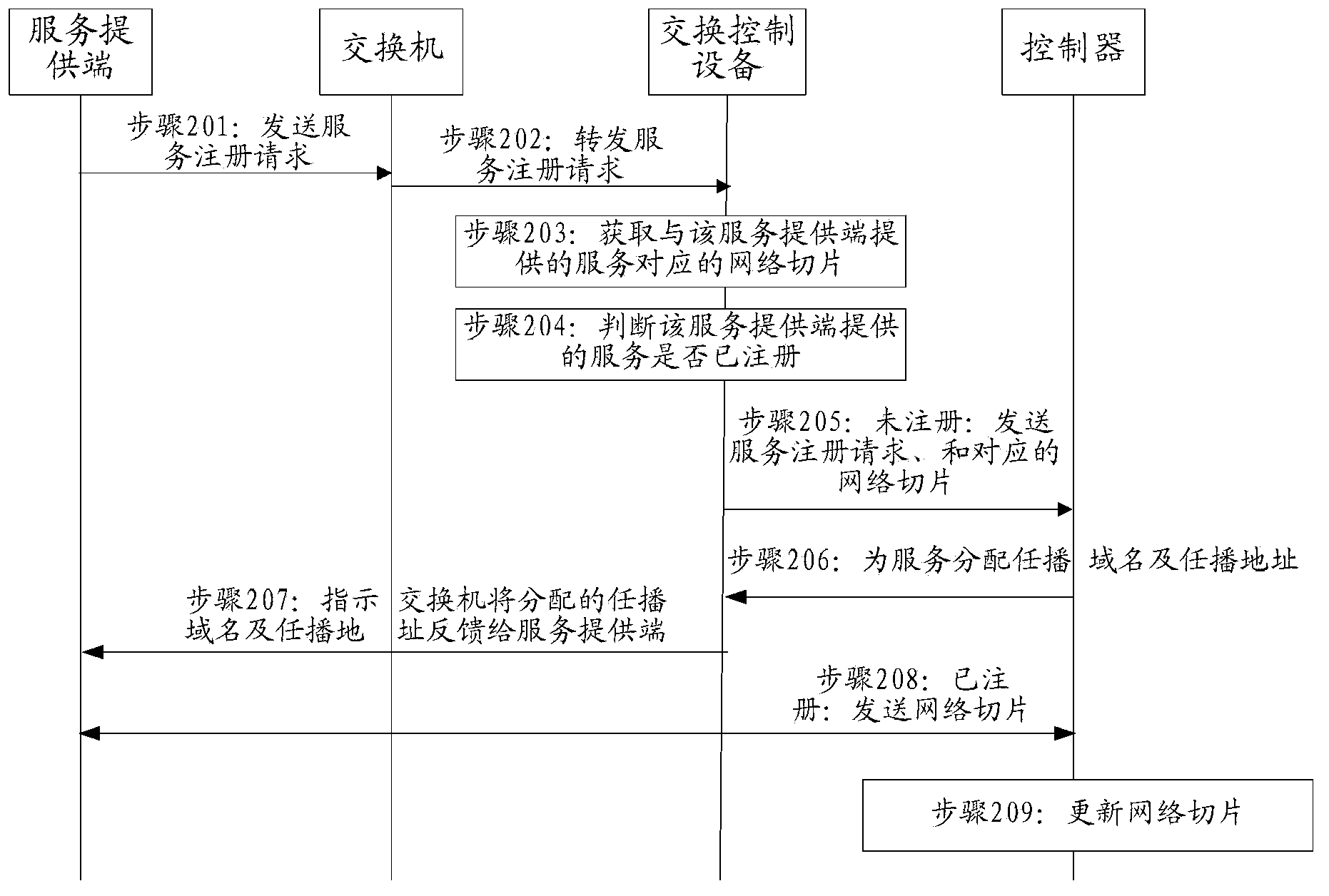
ActiveCN103650437AReduce application costReduced Node Capability RequirementsData switching networksDomain nameAnycast
Embodiment of the present invention provides a method according to any multicast service registration method and apparatus, and system for switching equipment, communications, involving registration method comprising: receiving a service registration request, the service name of the service registration request, the network including access requirements, and the service provider unicast address, the network access requirements for describing the services provided by the network server and the data transmission requirements; determining the service providing terminal sections provide a corresponding network, the network slice including the current network service provider for each switch to the side of the unicast address path, the path of the network to meet the access needs; determining anycast anycast address and the domain name services to establish that the controller said anycast addresses with the corresponding relationship between the network slicing complete service registration. The present invention can reduce costs anycast technology applications.
Owner:上海朋熙半导体有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com