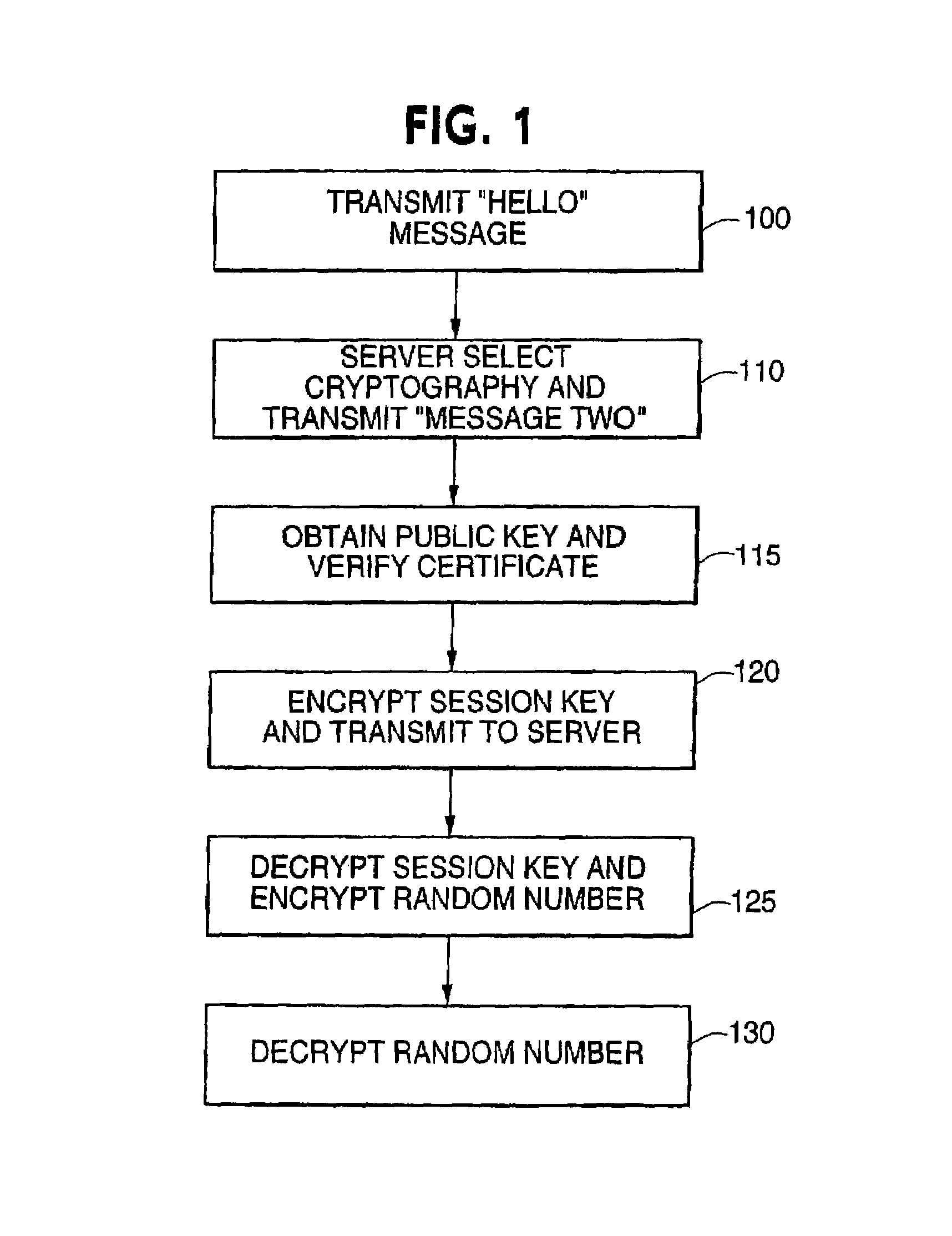
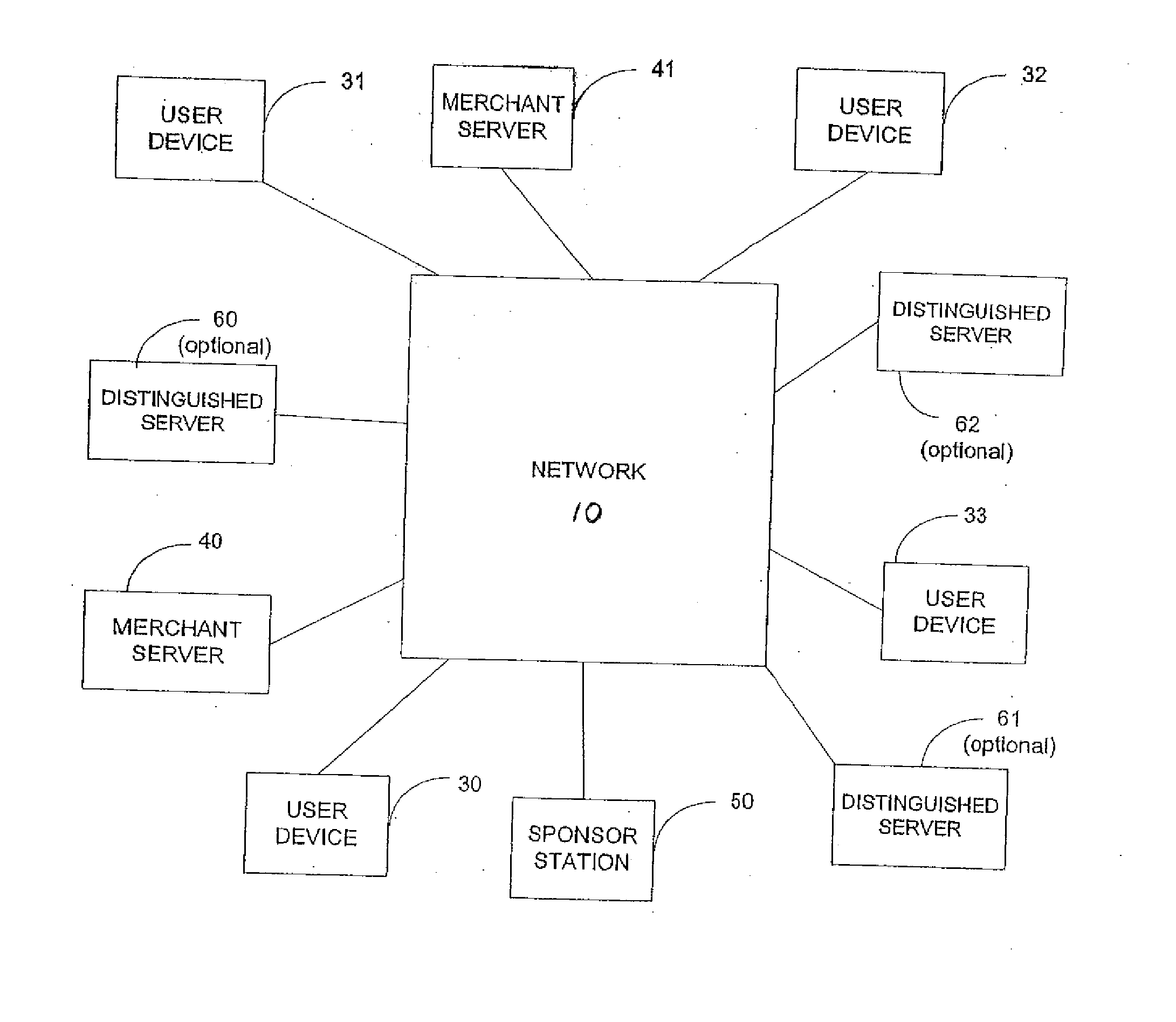
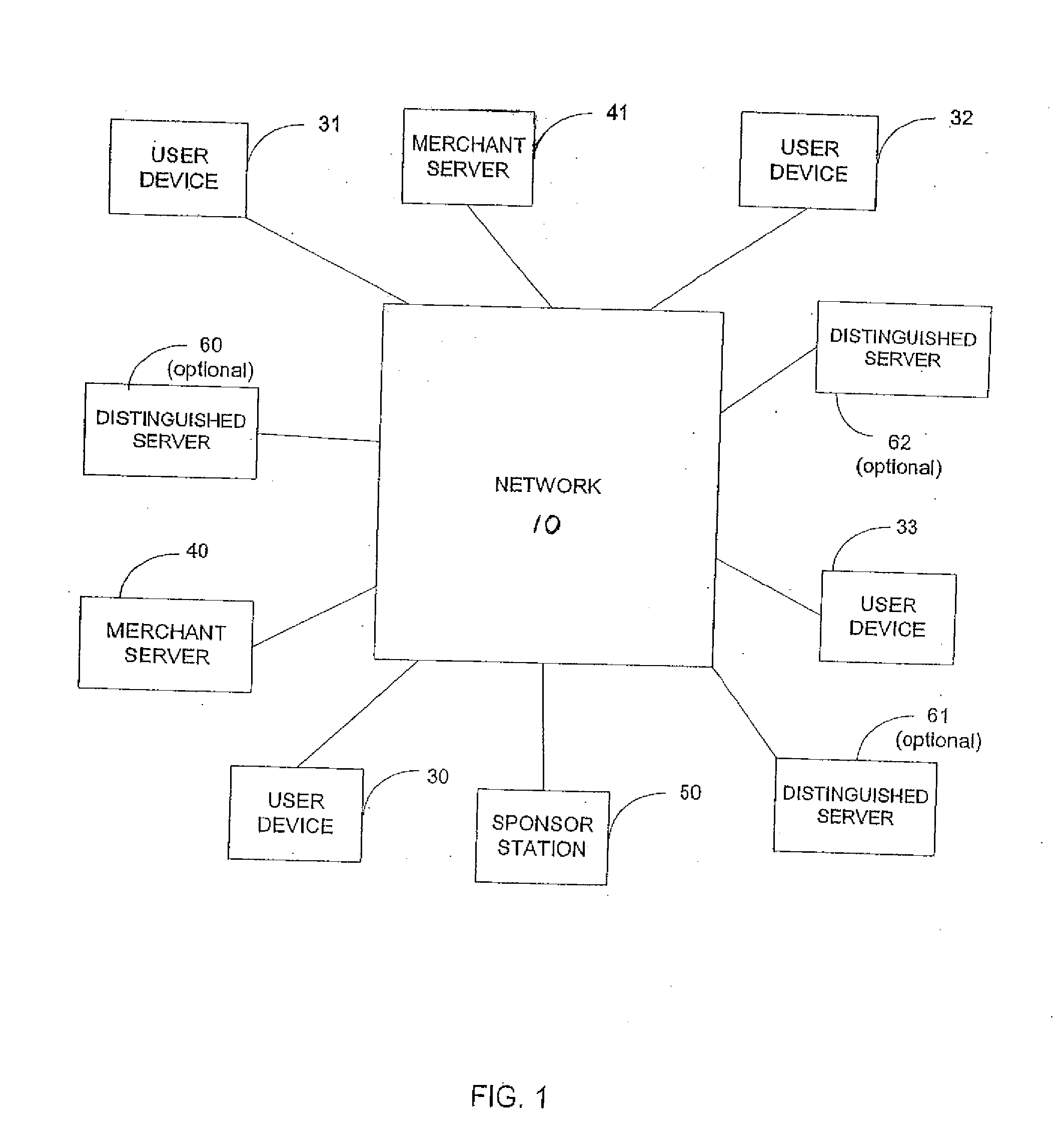
Patents
Literature
328 results about "Cryptographic key generation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
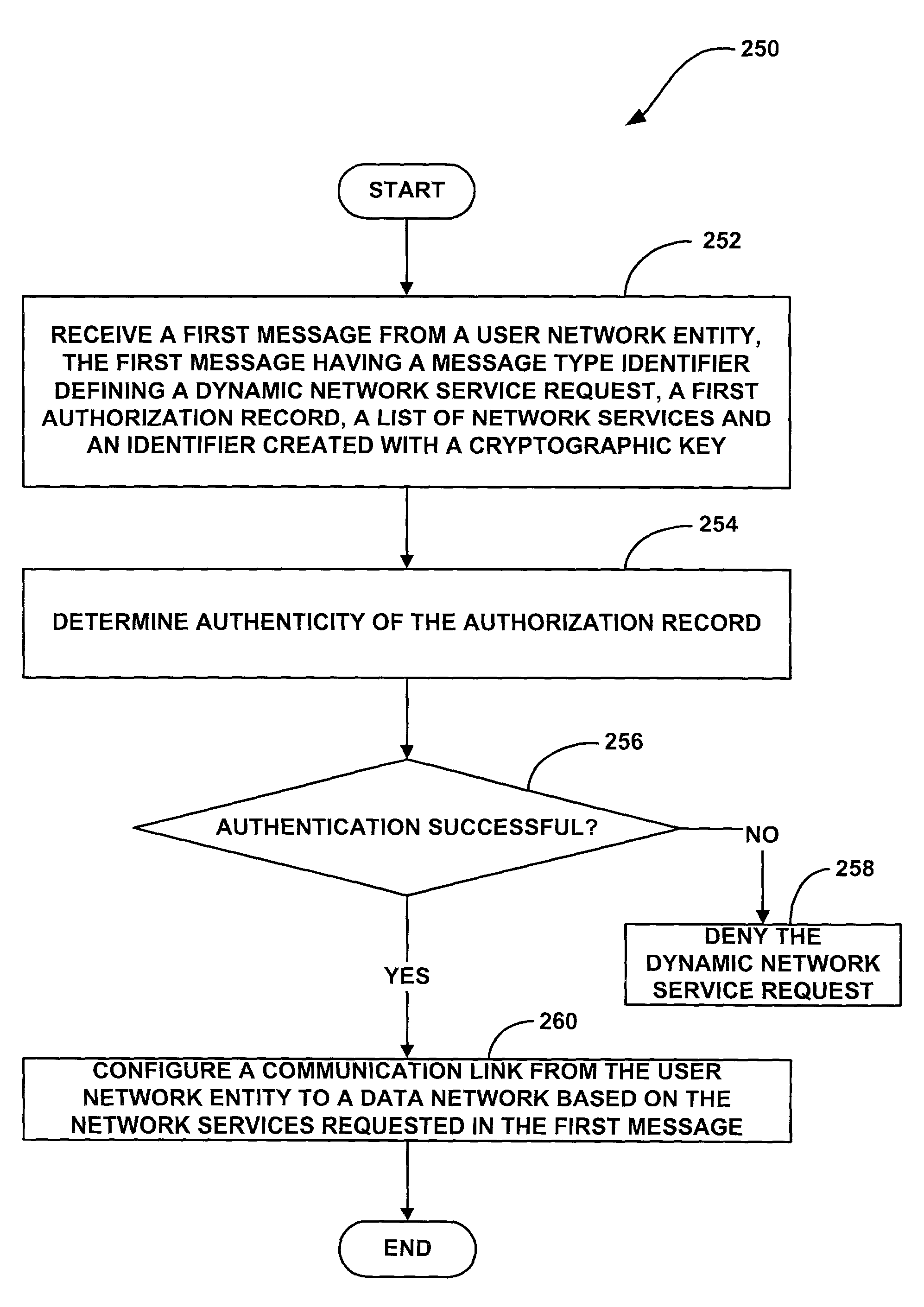
System and method for providing distributed and dynamic network services for remote access server users
InactiveUS7073055B1Overcome problemsDigital data processing detailsMultiple digital computer combinationsCryptographic key generationDigital signature
A system and methods for providing distributed and dynamic network services to remote access users. One of the methods includes providing a first certificate for requesting dynamic network services by a user network entity, and at least one second certificate for requesting static network services by the user network entity. According to one method, a user of the user network entity may generate a first message to request dynamic network services from a network service provider entity. For example, the first message may include the first certificate, a digital signature generated with a private encryption key associated with the first certificate and list of network service that the user wishes to set up dynamically. In one embodiment, when the network service provider entity receives the first message, the network service provider entity verifies the authenticity of the first certificate and, if the first certificate is authentic, the network service provider entity configures a network connection between the user network entity and a data network based on the network services requested by the user in the first message.
Owner:VALTRUS INNOVATIONS LTD
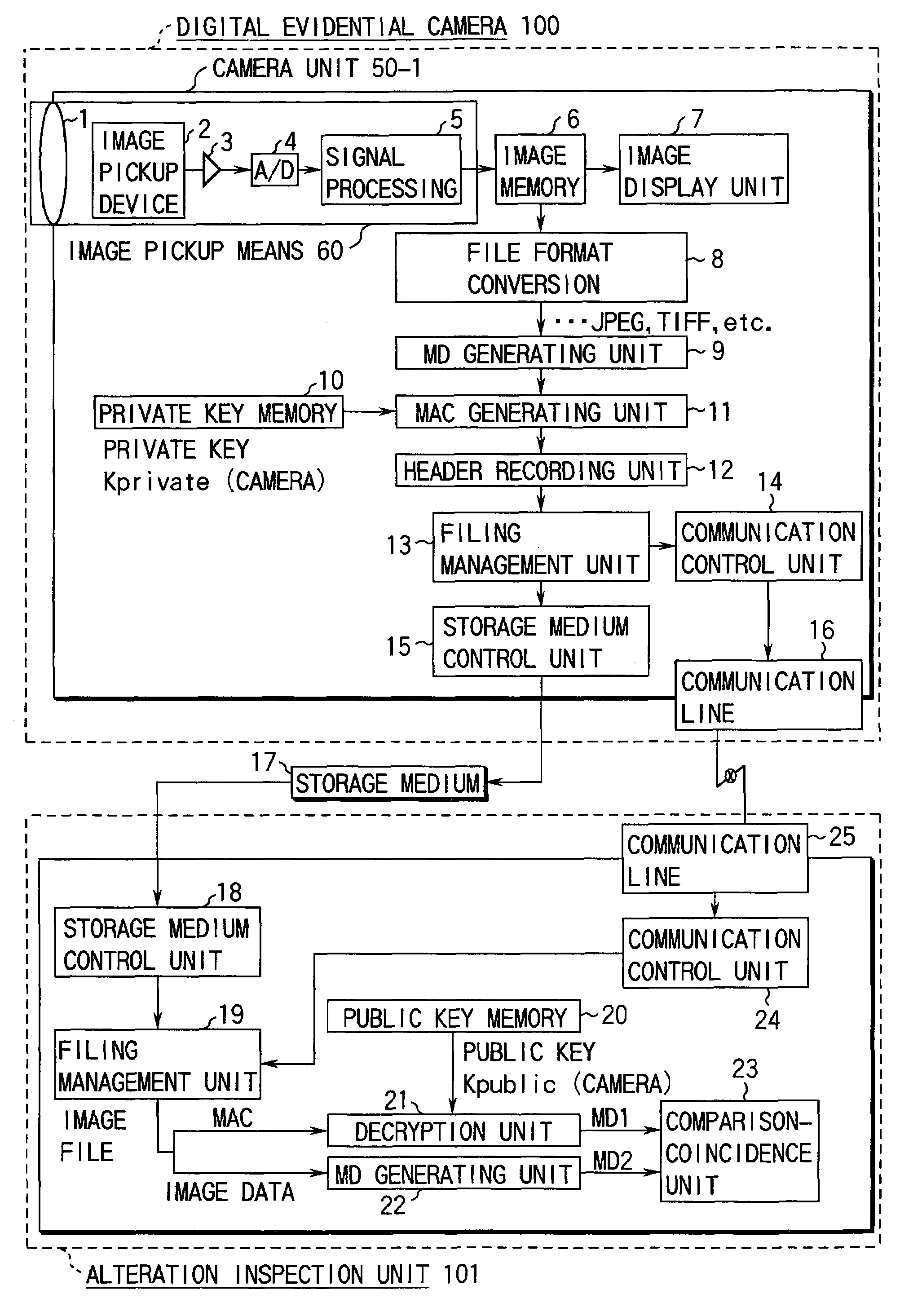
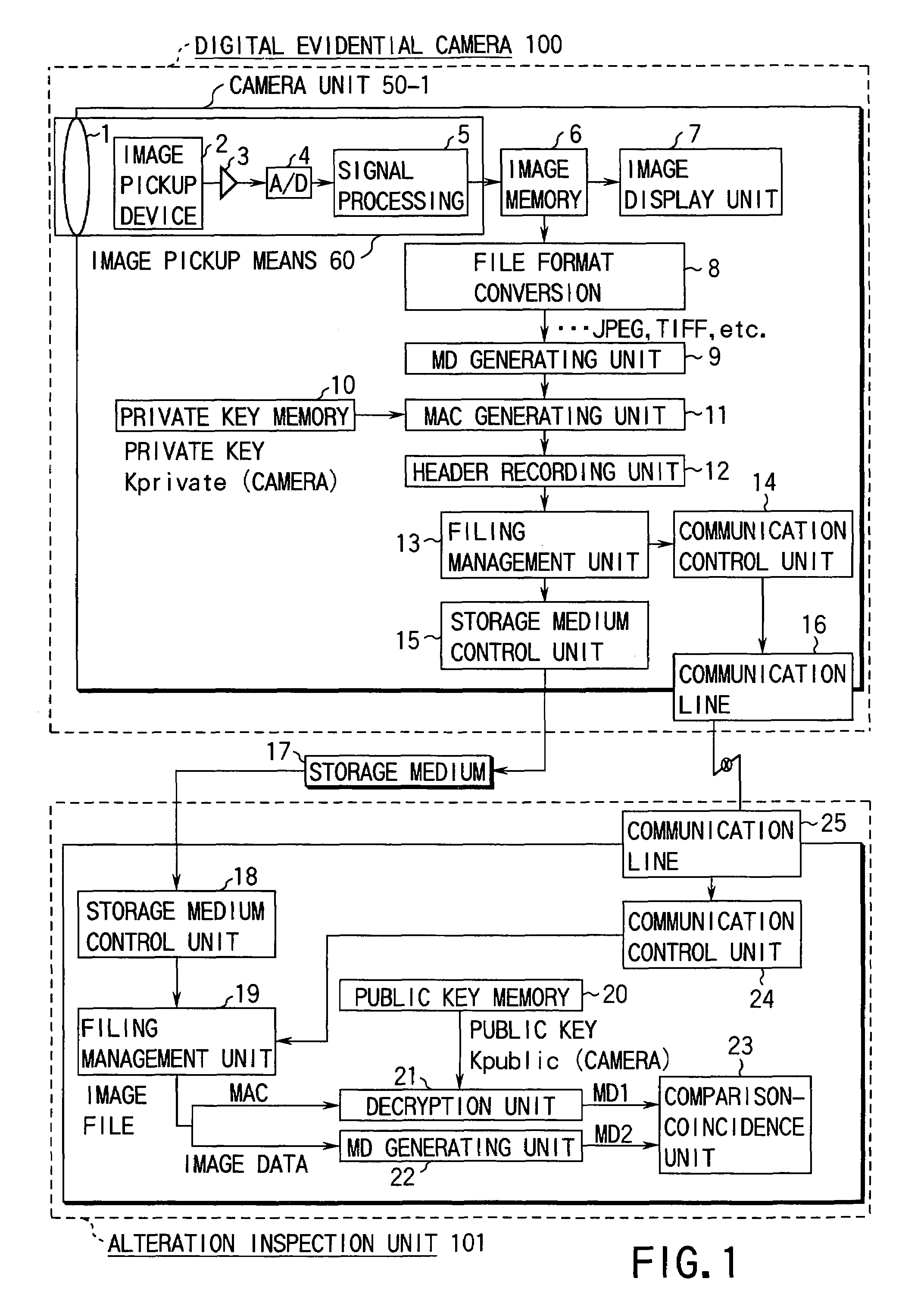
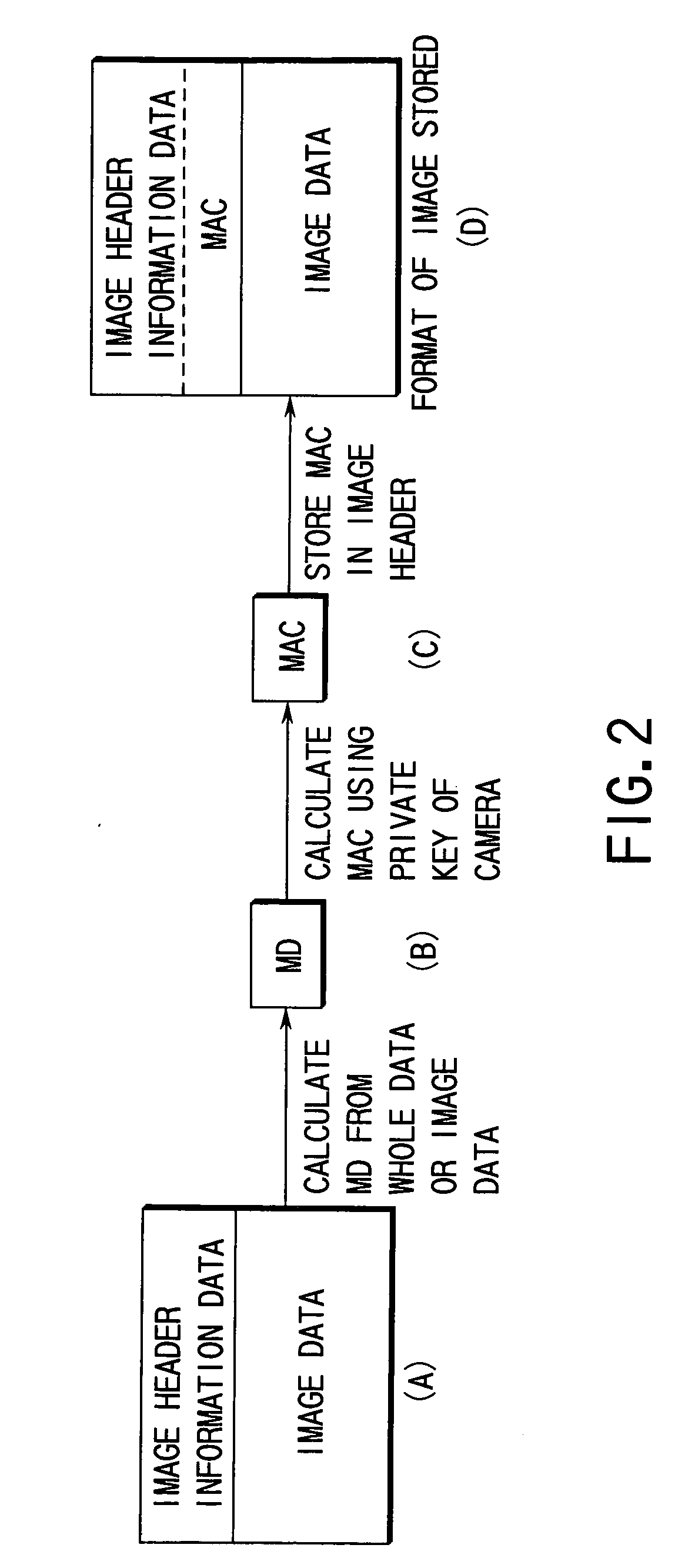
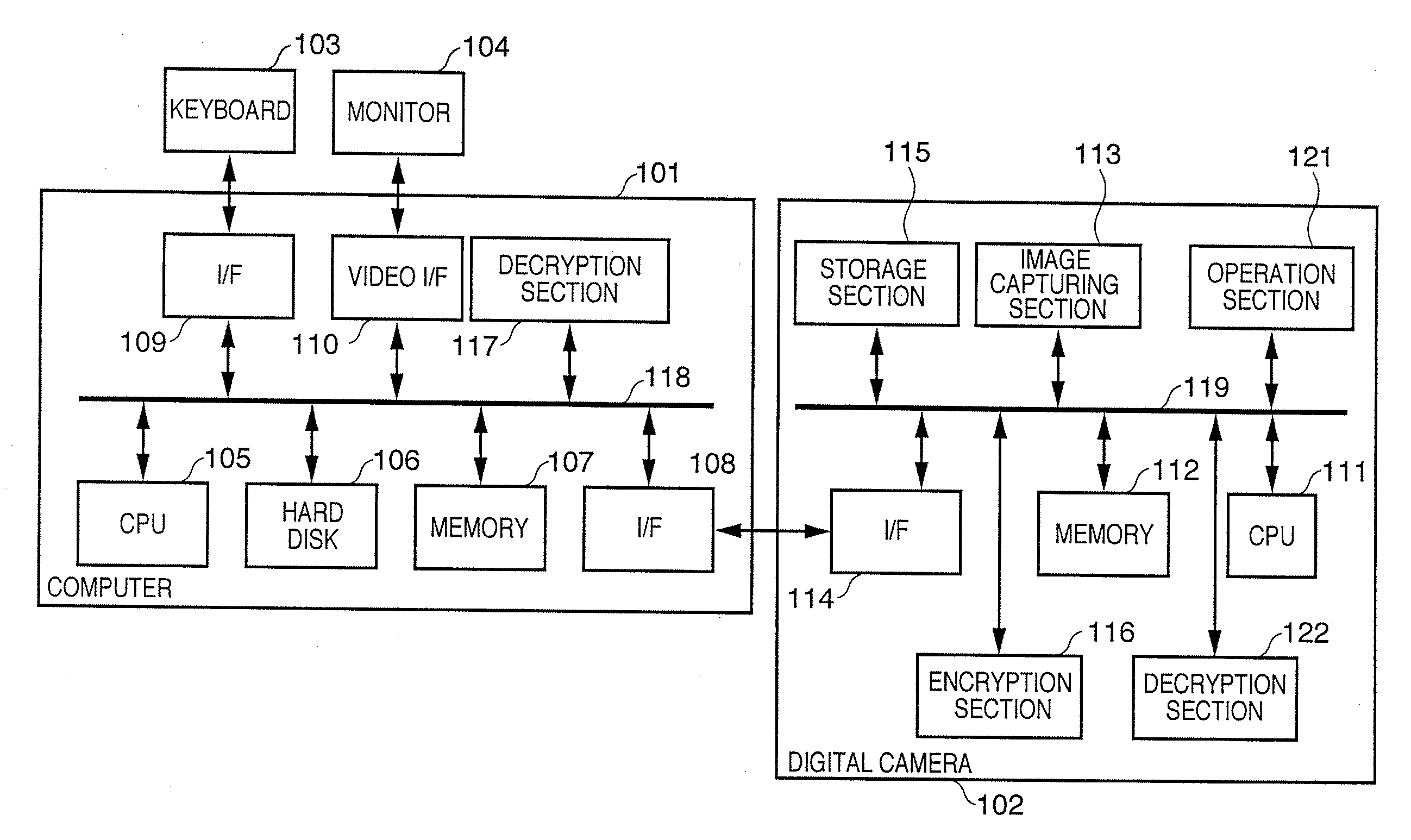
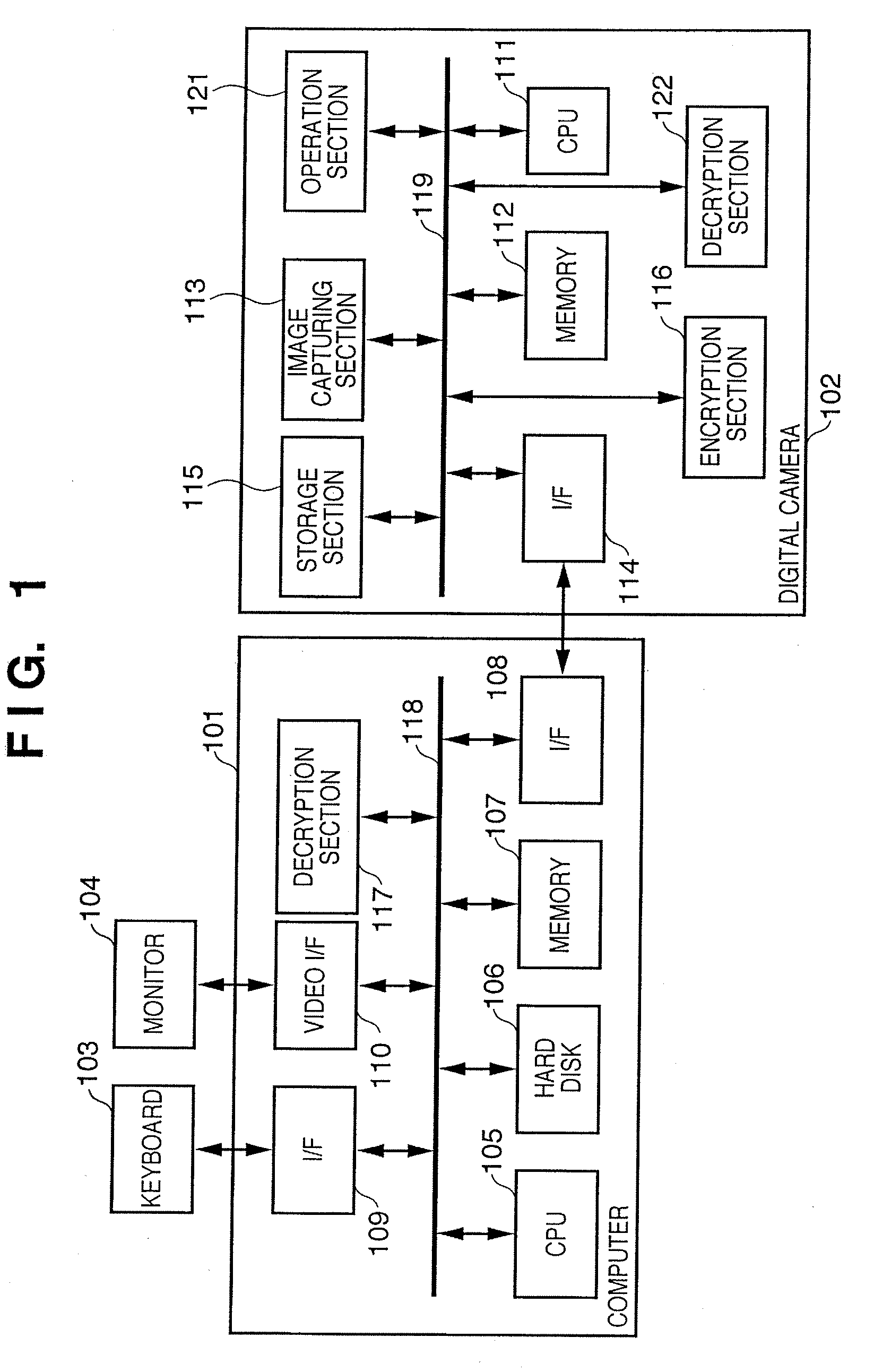
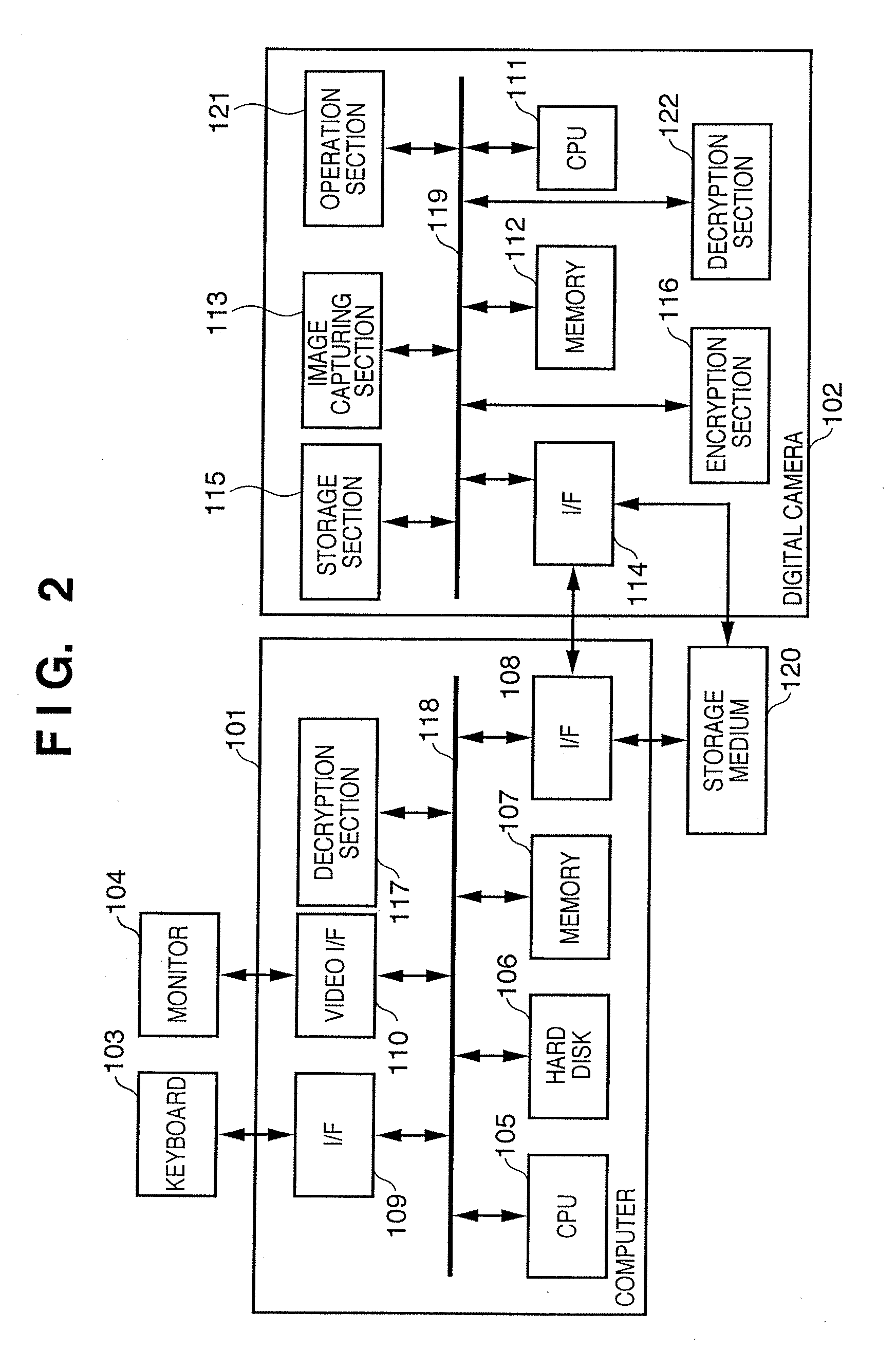
Digital evidential camera system for generating alteration detection data using built-in encryption key
InactiveUS6968058B1Television system detailsPublic key for secure communicationCryptographic key generationImaging data
A digital evidential camera system is for detecting the alteration of image data obtained by photographing an object. The system comprises the camera and an alteration detection unit. The camera includes an image pickup unit for picking up an image of the object and an encryption processing unit for generating the alteration detection data using an encryption key built therein from the image data obtained by the image pickup unit. The alteration detection unit decrypts the alteration detection data using a decryption key corresponding to the encryption key, and detects whether the image data is altered based on the result of decryption.
Owner:OLYMPUS CORP
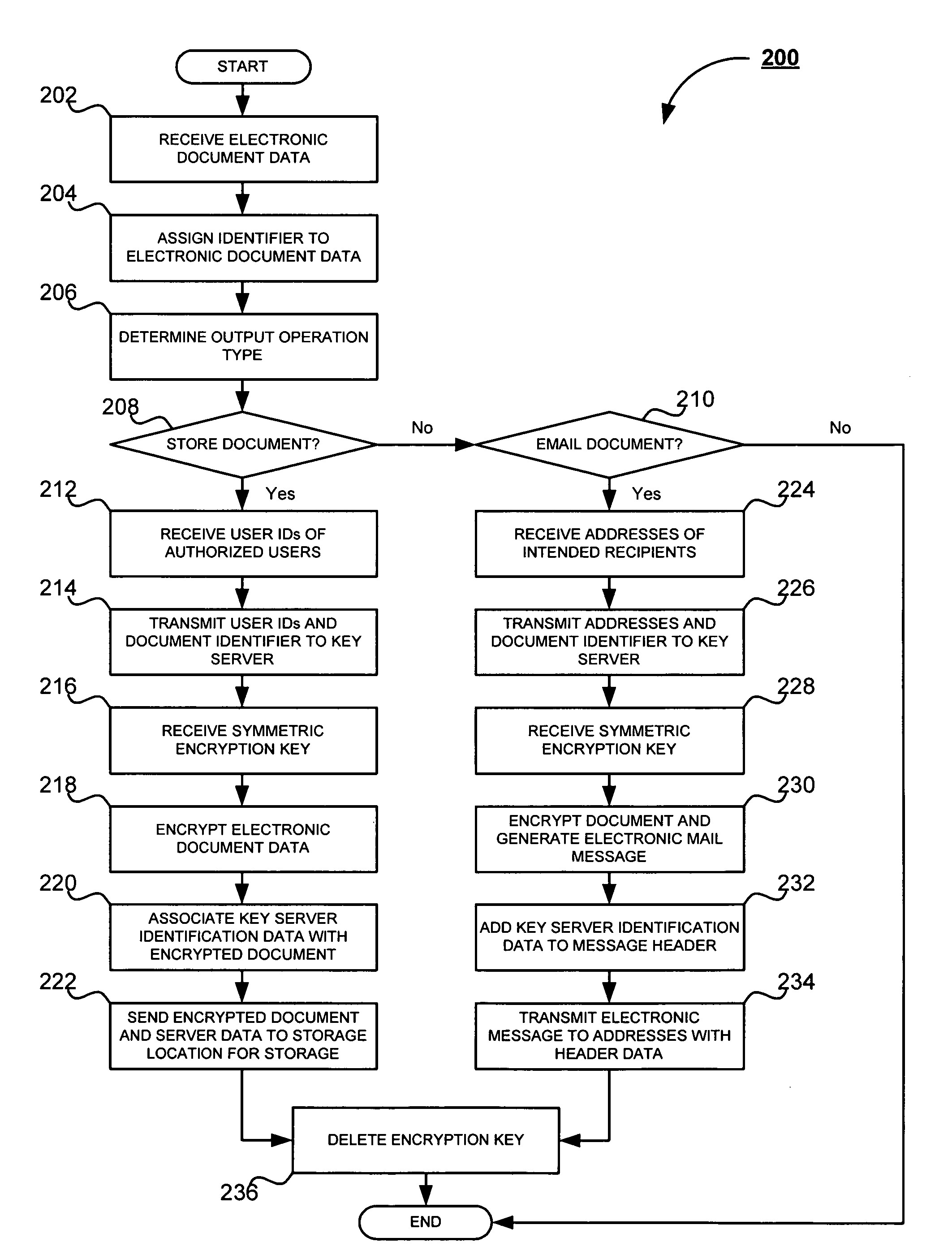
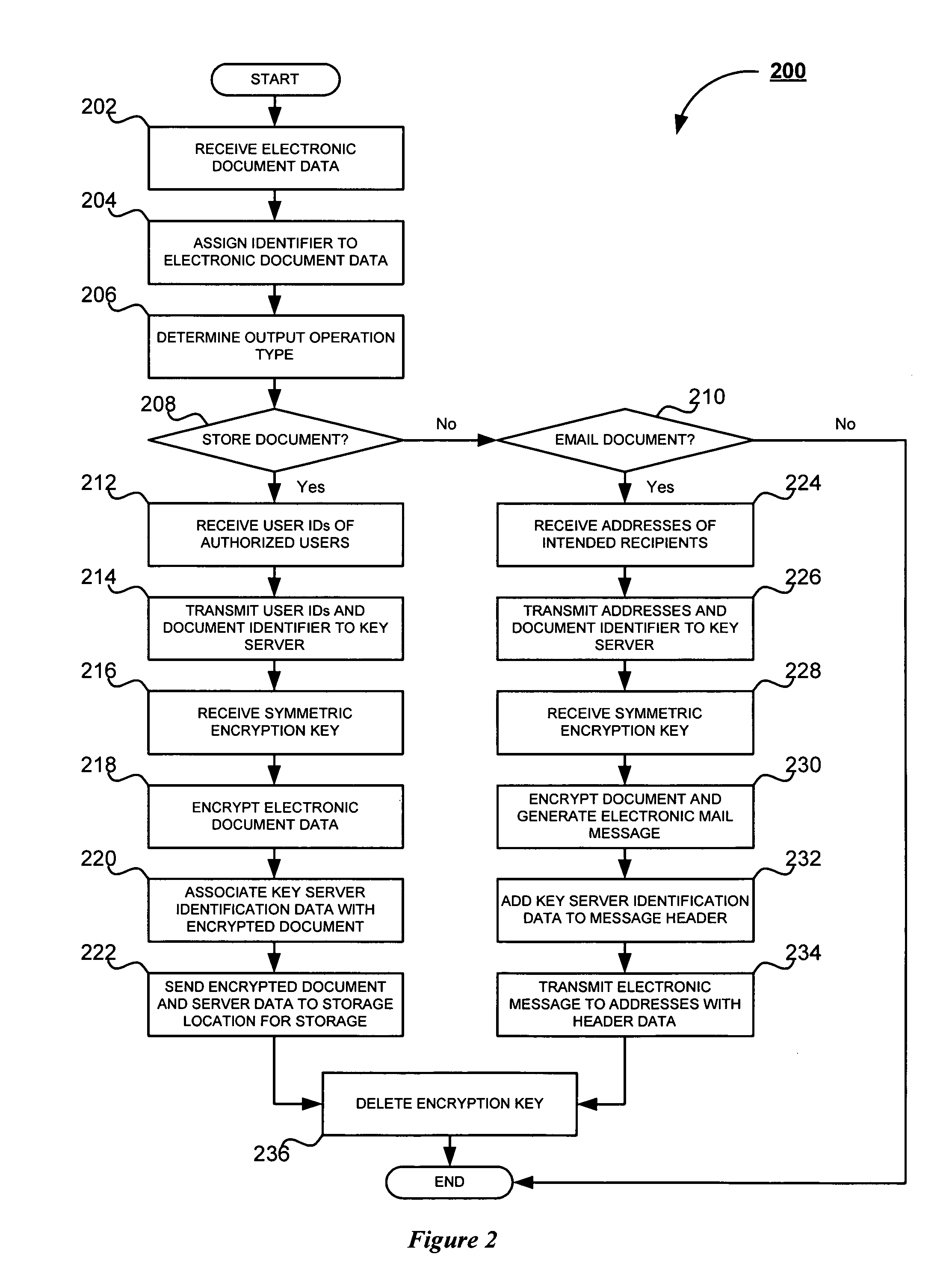
System and method for secure handling of scanned documents
InactiveUS20070283446A1Safe handlingMultiple keys/algorithms usageDigital data processing detailsCryptographic key generationElectronic document
A system and method for secure handling of scanned documents is provided. Electronic document data is received by a document processing device and assigned an identifier unique to the document. A user ID or electronic mail address is then received corresponding to the selected output operation. The user ID or address is then transmitted, along with the identifier, to an encryption key generator, which then generates a symmetric encryption key. The encryption key is then returned to the document processing device, whereupon the electronic document data is encrypted and the key is deleted by the document processing device. The encrypted document is then stored or transmitted via electronic mail, in accordance with the selected output operation. Decryption is thereafter accomplished using the document identifier, user ID or email address, and key generator identification data.
Owner:KK TOSHIBA +1
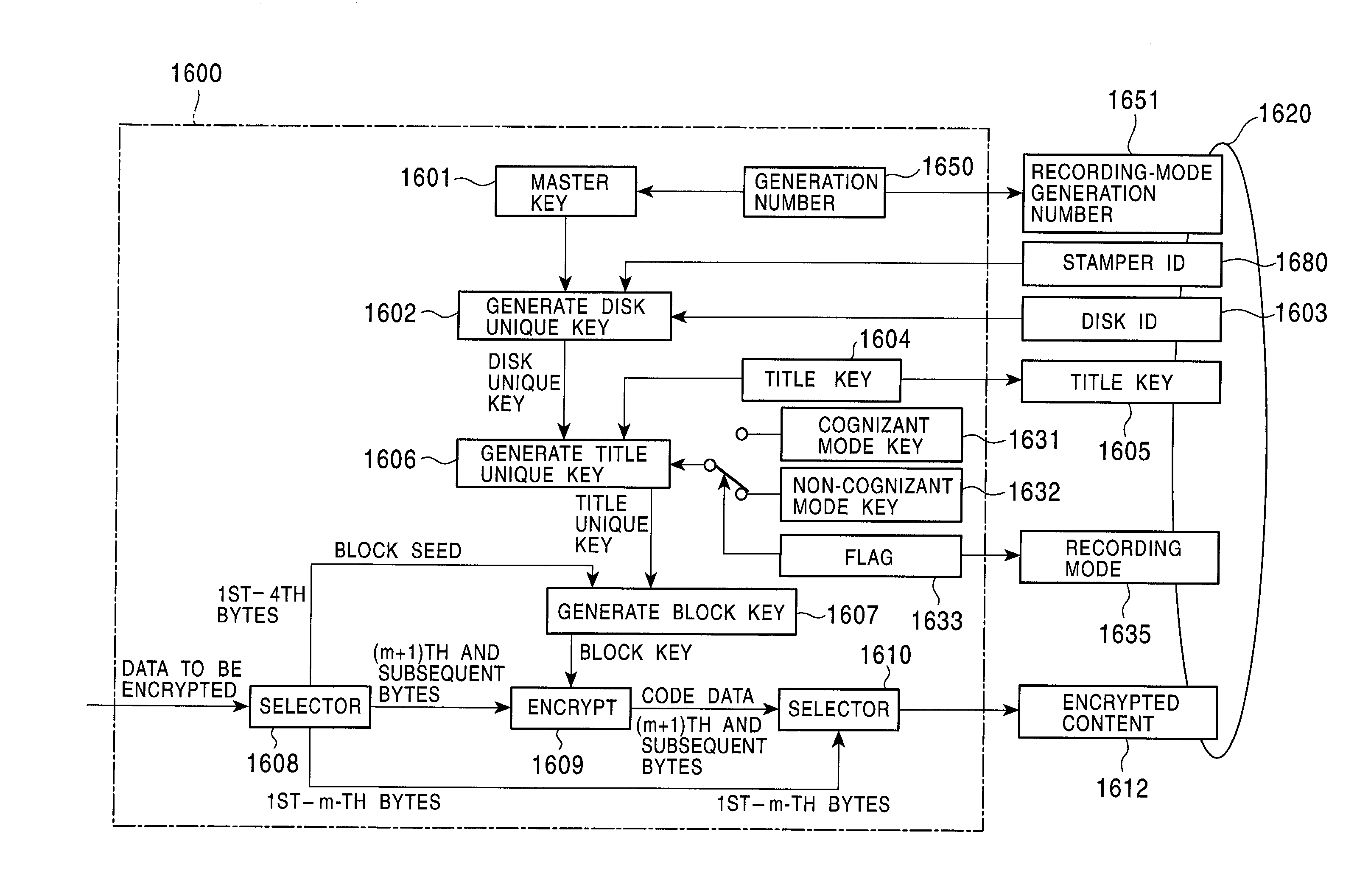
Method and apparatus for selectively executing information recording using a cognizant mode and a non-cognizant mode
InactiveUS7203968B2Reduce usagePreventing executionTelevision system detailsKey distribution for secure communicationCryptographic key generationPattern selection
When the recording mode of an information recording / playback device is a cognizant mode which analyzes embedded copy control information, the information recording / playback device performs content encryption using a content-encryption key generated by using a cognizant key as a content-encryption-key generating key in the cognizant mode. When the recording mode of the information recording / playback device is a non-cognizant mode which does not analyze the embedded copy control information, the information recording / playback device performs content encryption using a content-encryption key generated by using a cognizant key as a content-encryption-key generating key in the non-cognizant mode. By using these techniques, the above two recording modes are clearly distinguished and separately executed. This prevents an encryption mode indicator as copy control information and embedded copy control information from being mismatched.
Owner:SONY CORP
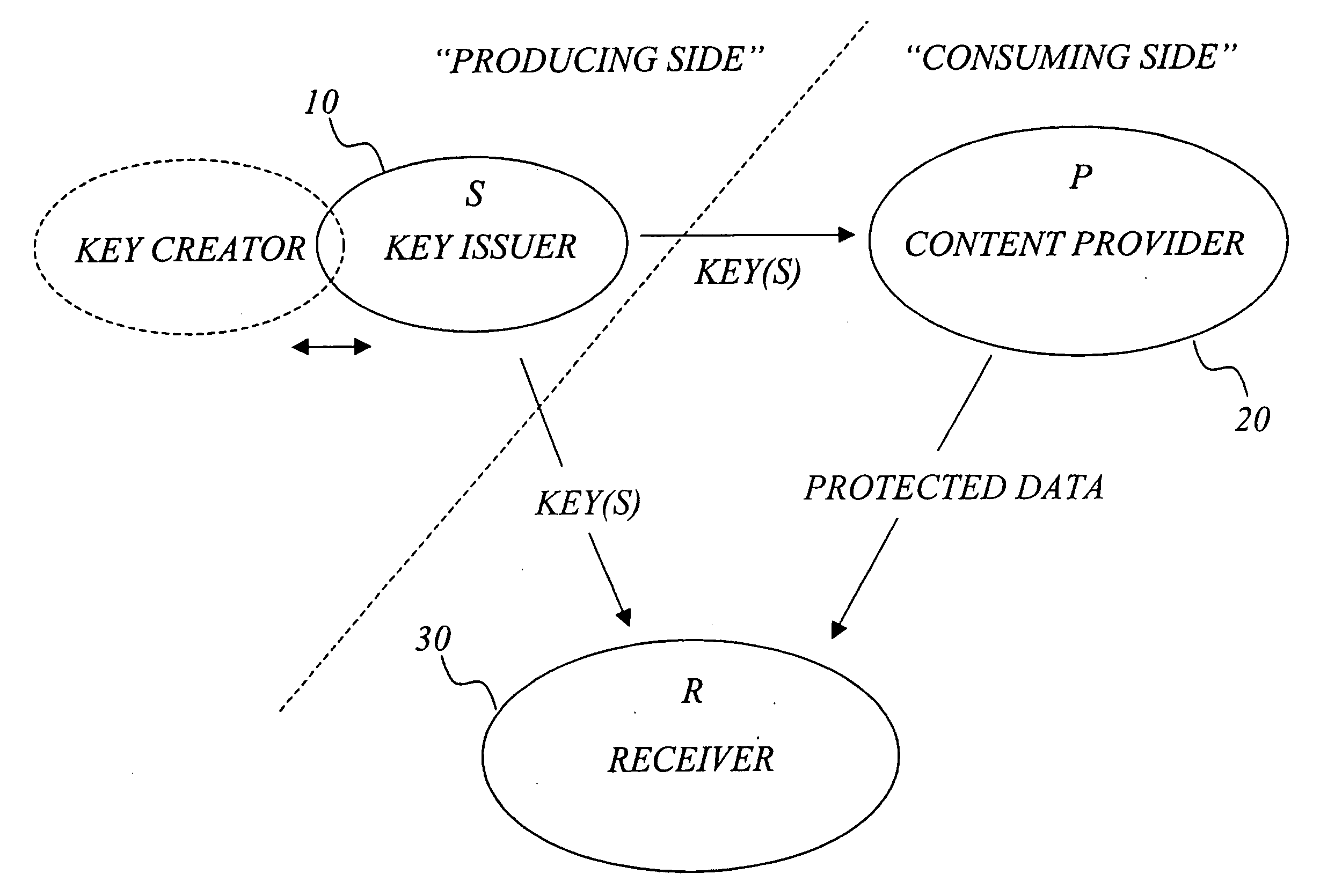
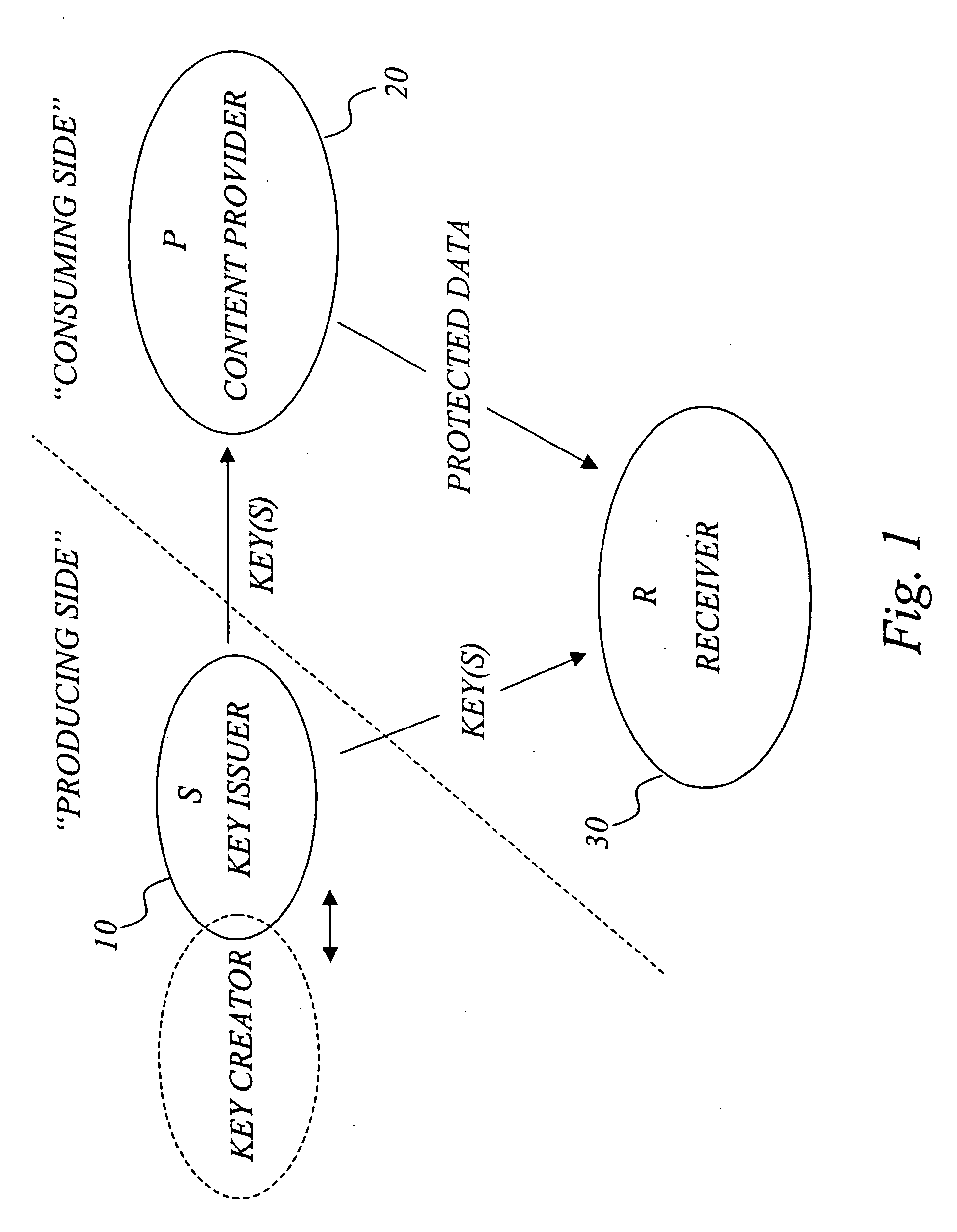
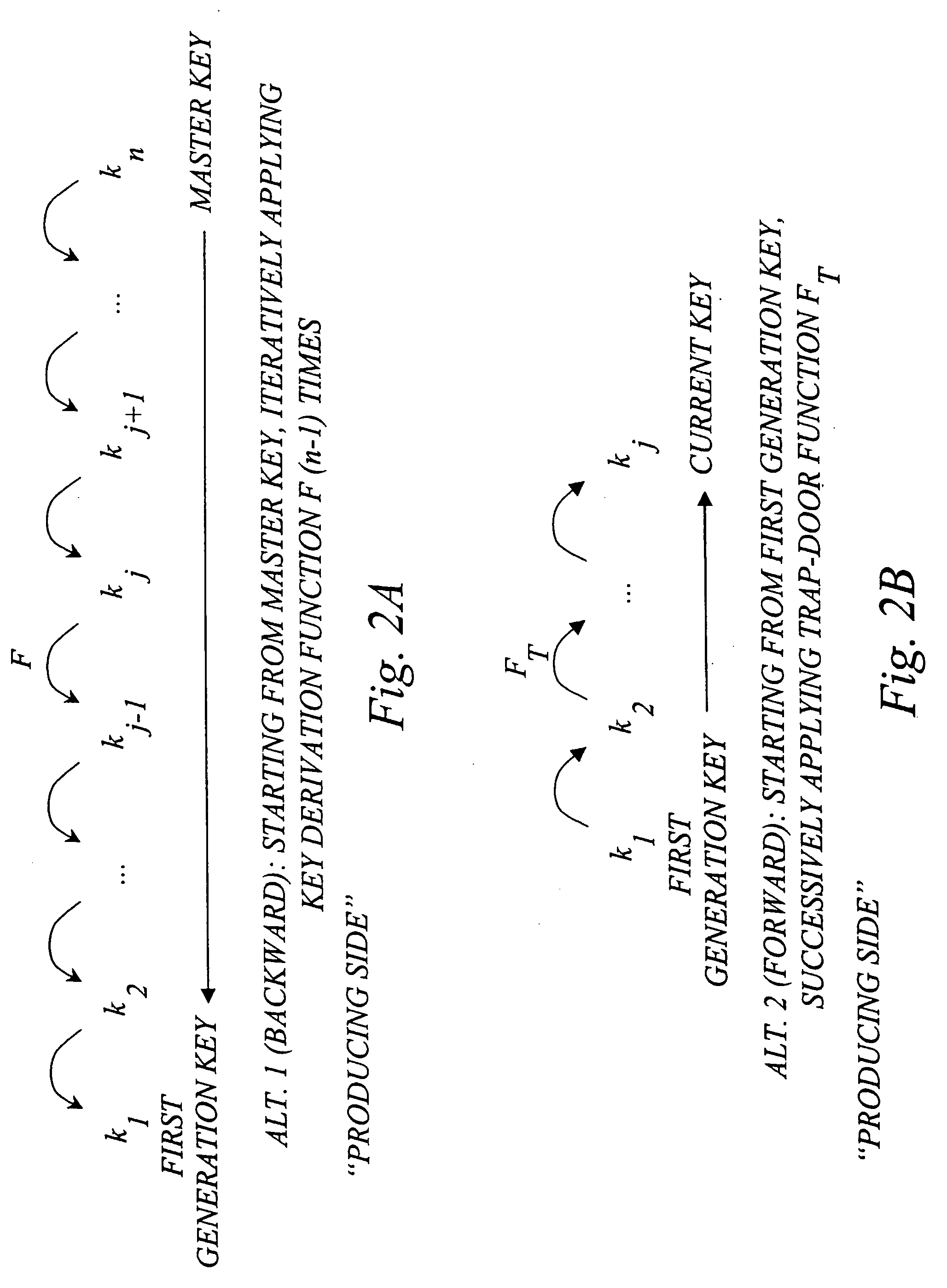
Efficient management of cryptographic key generations
InactiveUS20070127719A1Restricted accessEfficient storageKey distribution for secure communicationPublic key for secure communicationCryptographic key generationEarly generation
The invention generally relates to management of cryptographic key generations in an information environment comprising a key-producing side generating and distributing key information to a key-consuming side. A basic concept of the invention is to define, by means of a predetermined one-way key derivation function, a relationship between generations of keys such that earlier generations of keys efficiently may be derived from later ones but not the other way around. A basic idea according to the invention is therefore to replace, at key update, key information of an older key generation by the key information of the new key generation on the key-consuming side. Whenever necessary, the key-consuming side iteratively applies the predetermined one-way key derivation function to derive key information of at least one older key generation from the key information of the new key generation. In this way, storage requirements on the key-consuming side can be significantly reduced.
Owner:EMC CORP +1
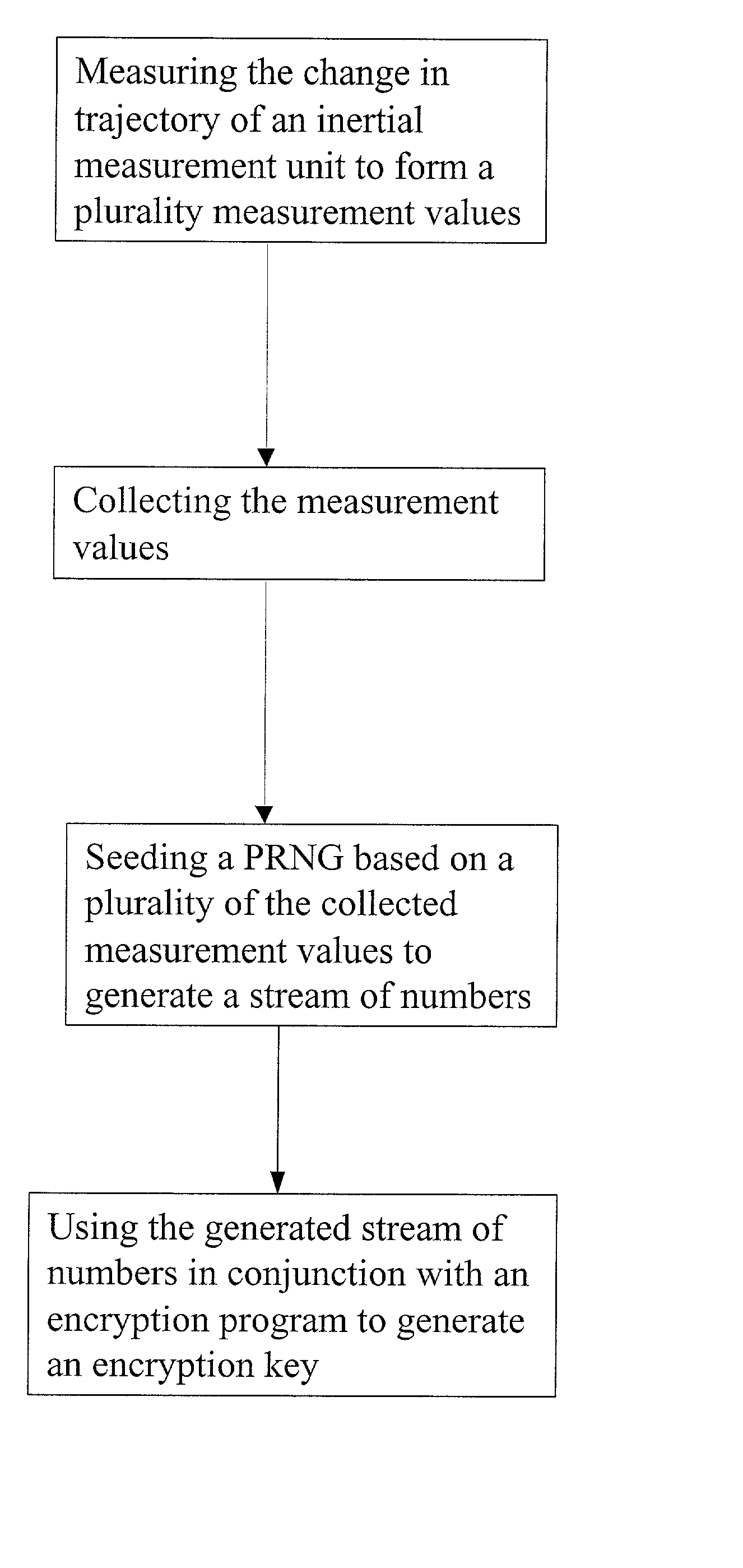
Entropy sources for encryption key generation
InactiveUS20020131592A1Maintain securityNecessary computer processing powerMechanically effected encryptionSecret communicationCryptographic key generationNumber generator
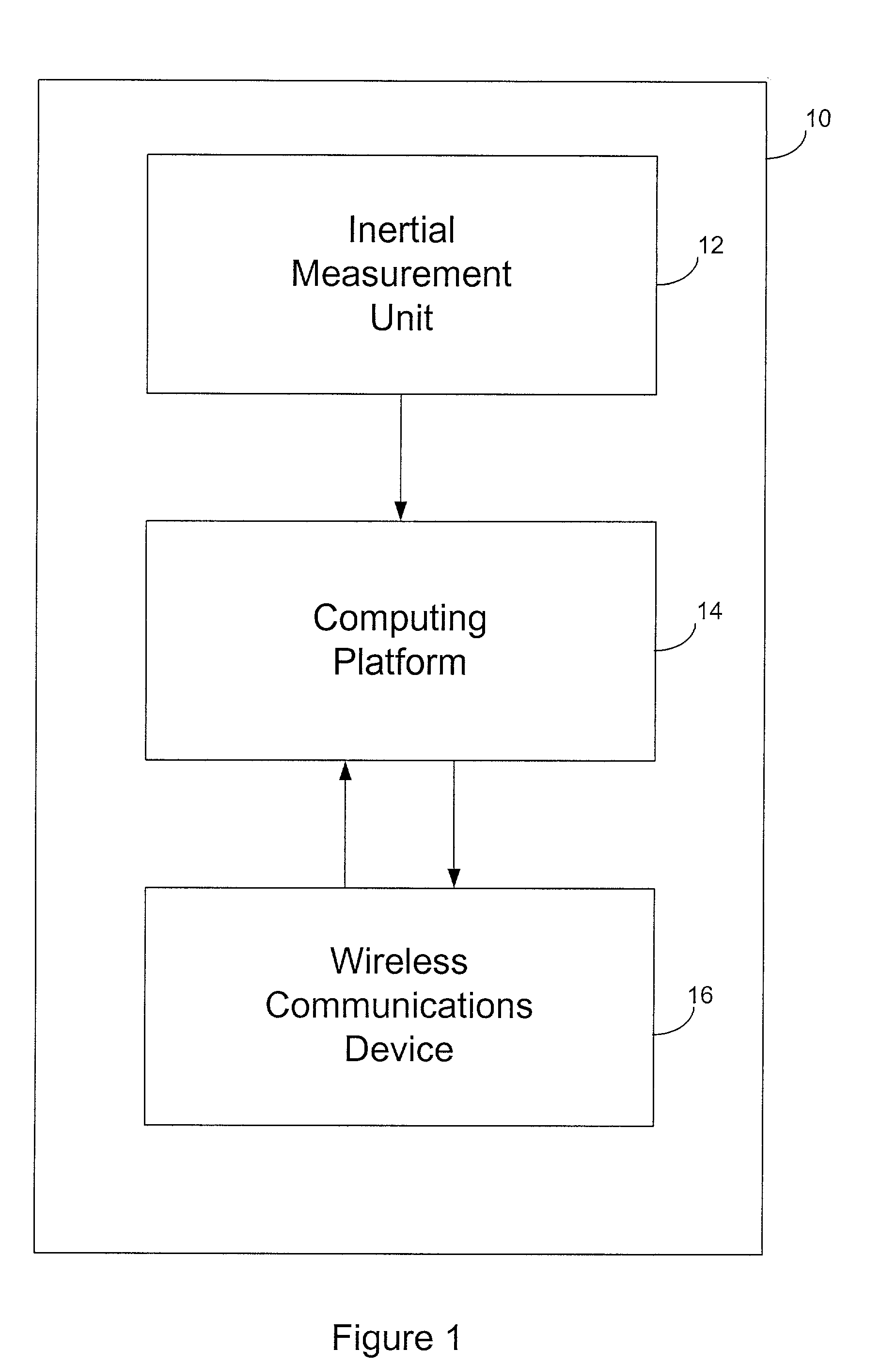
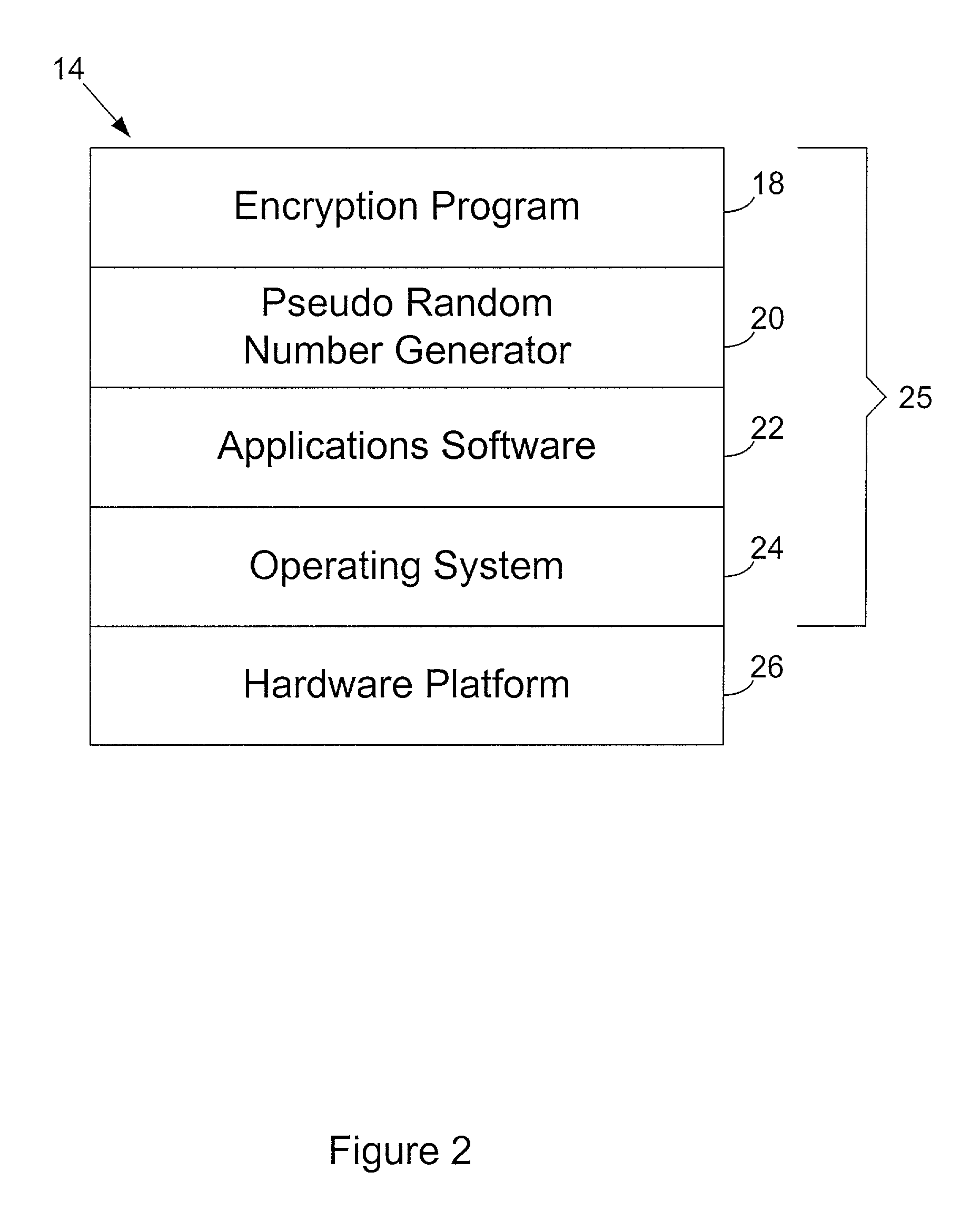
Inertial measurement units are subject to drift and noise characteristics that are normally distributed. While that drift and noise is problematic for inertial navigation, it is ideal for encryption key generation. The measurement values from an inertial measurement unit are random on several levels and can be used to effectively seed a pseudo random number generator for encryption key generation.
Owner:AIRBIQUITY INC
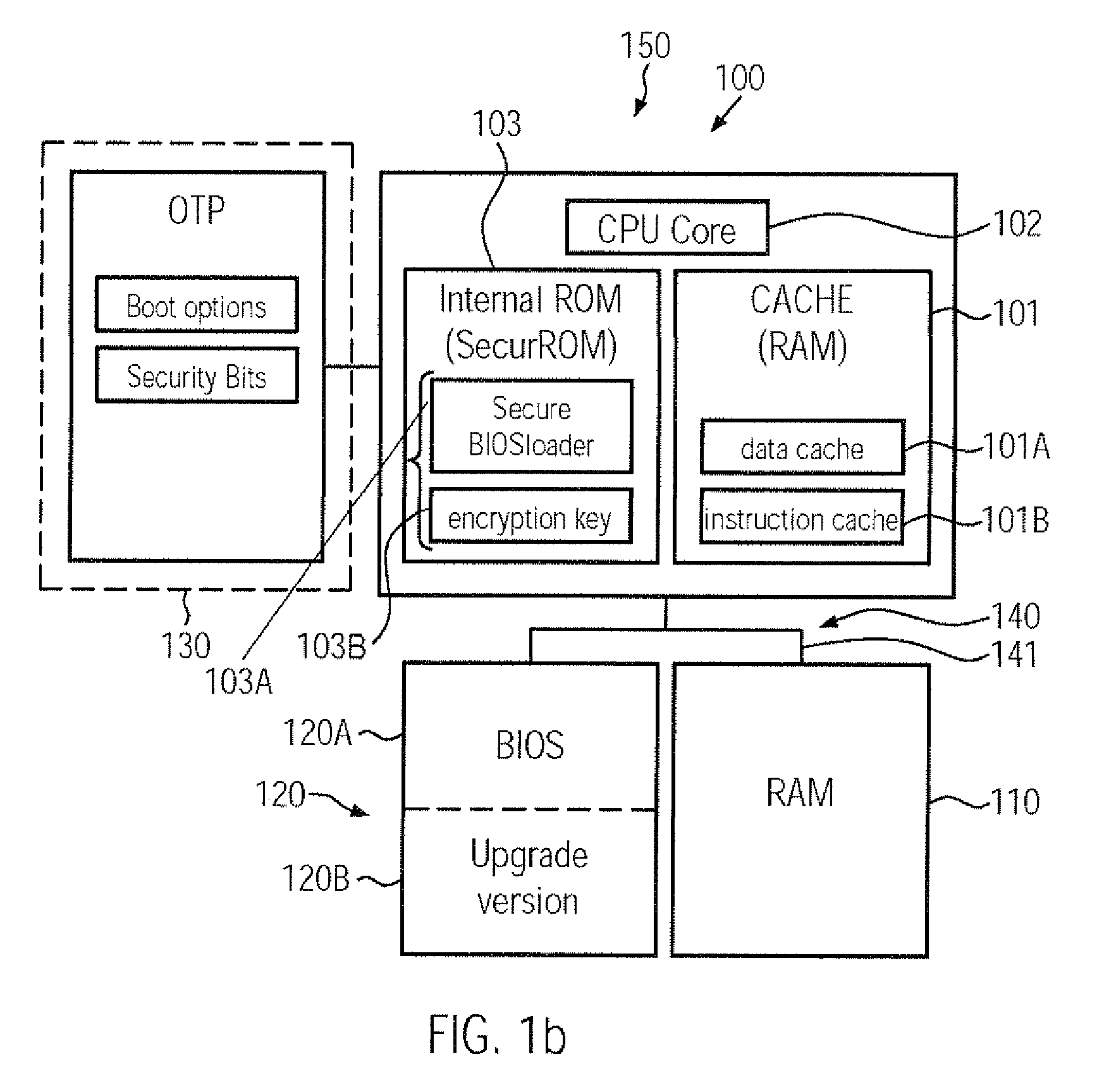
Computer system comprising a secure boot mechanism on the basis of symmetric key encryption
ActiveUS20090276617A1Improve integrityHigh protection levelUser identity/authority verificationDigital computer detailsCryptographic key generationComputerized system
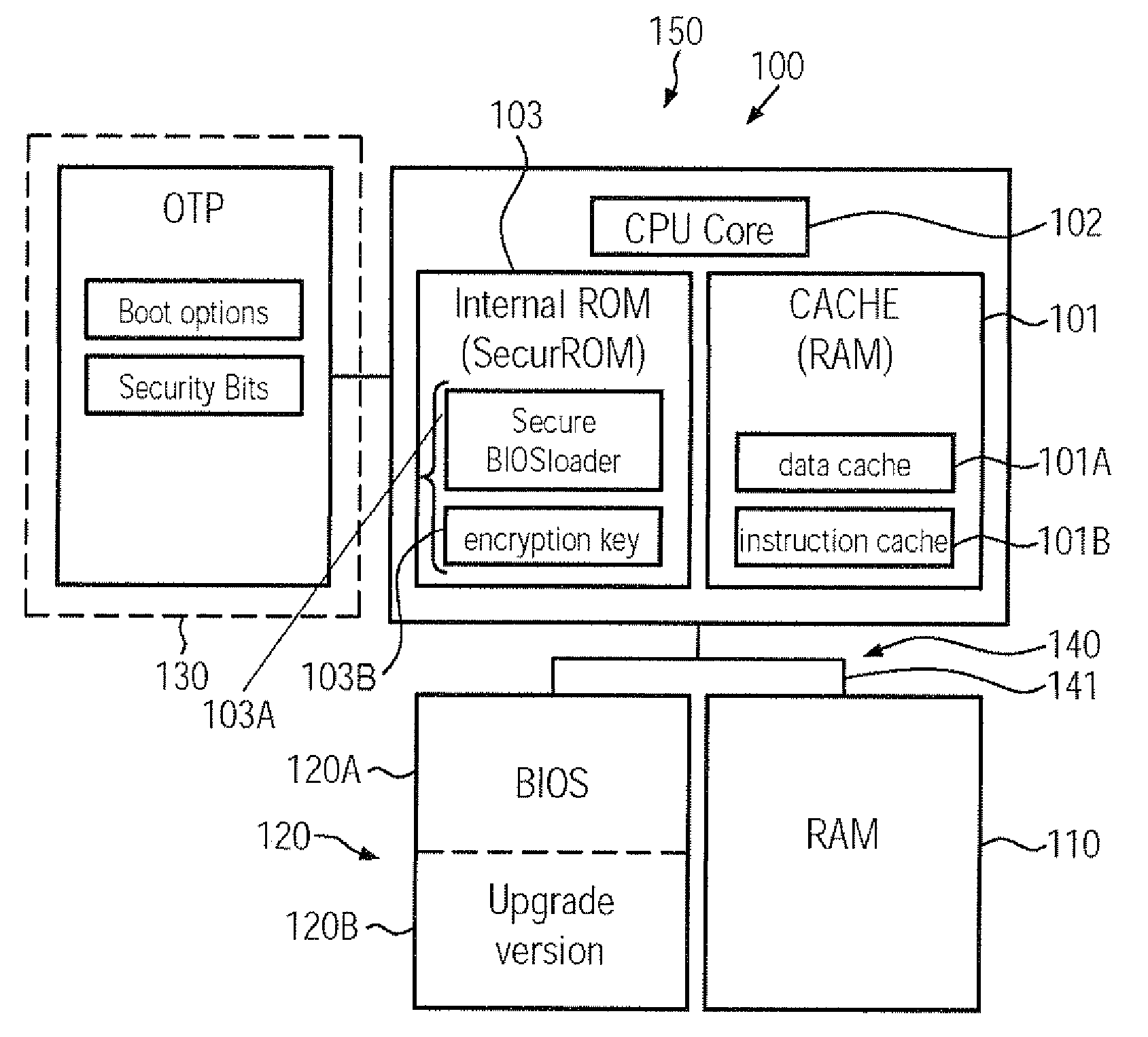
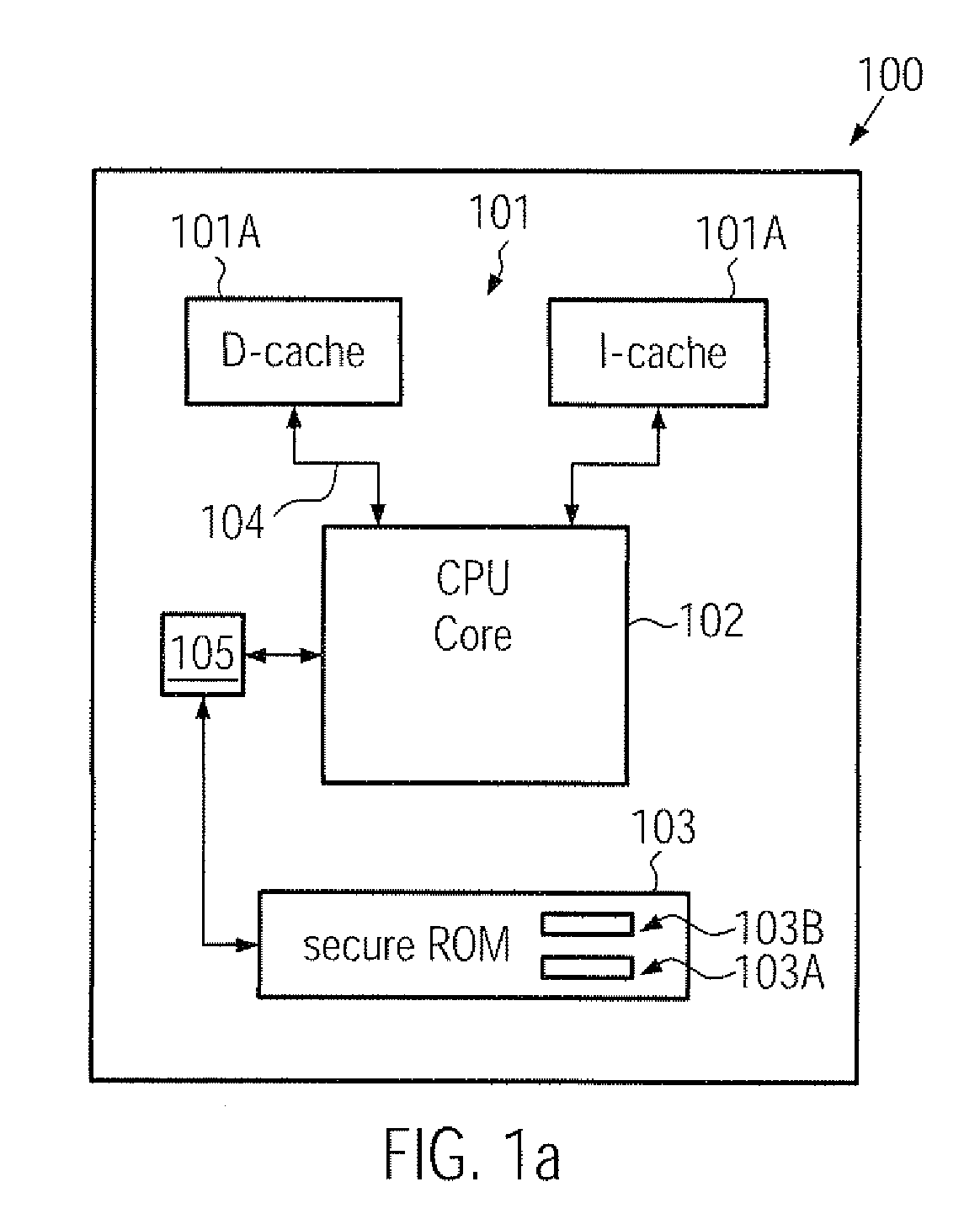
A CPU, a computer system and a secure boot mechanism are provided in which a symmetric encryption key may be incorporated into a non-volatile memory area of the CPU core, thereby substantially avoiding any tampering of the encryption key by external sources. Moreover, pre-boot information may be internally stored in the CPU and may be retrieved upon a reset or power-on event in order to verify a signed boot information on the basis of the internal symmetric encryption key. Furthermore, the BIOS information may be efficiently updated by generating a signature using the internal encryption key.
Owner:MEDIATEK INC
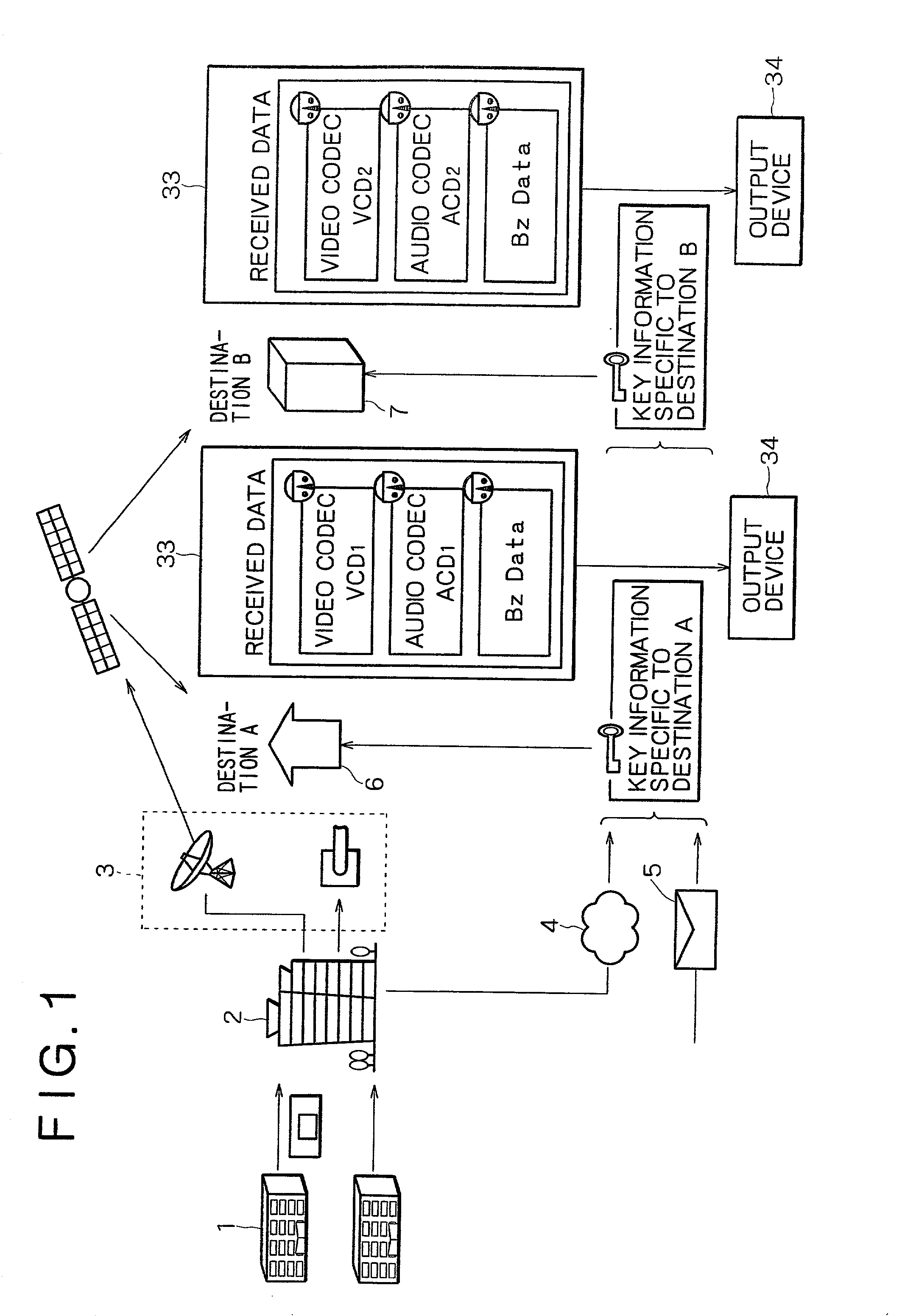
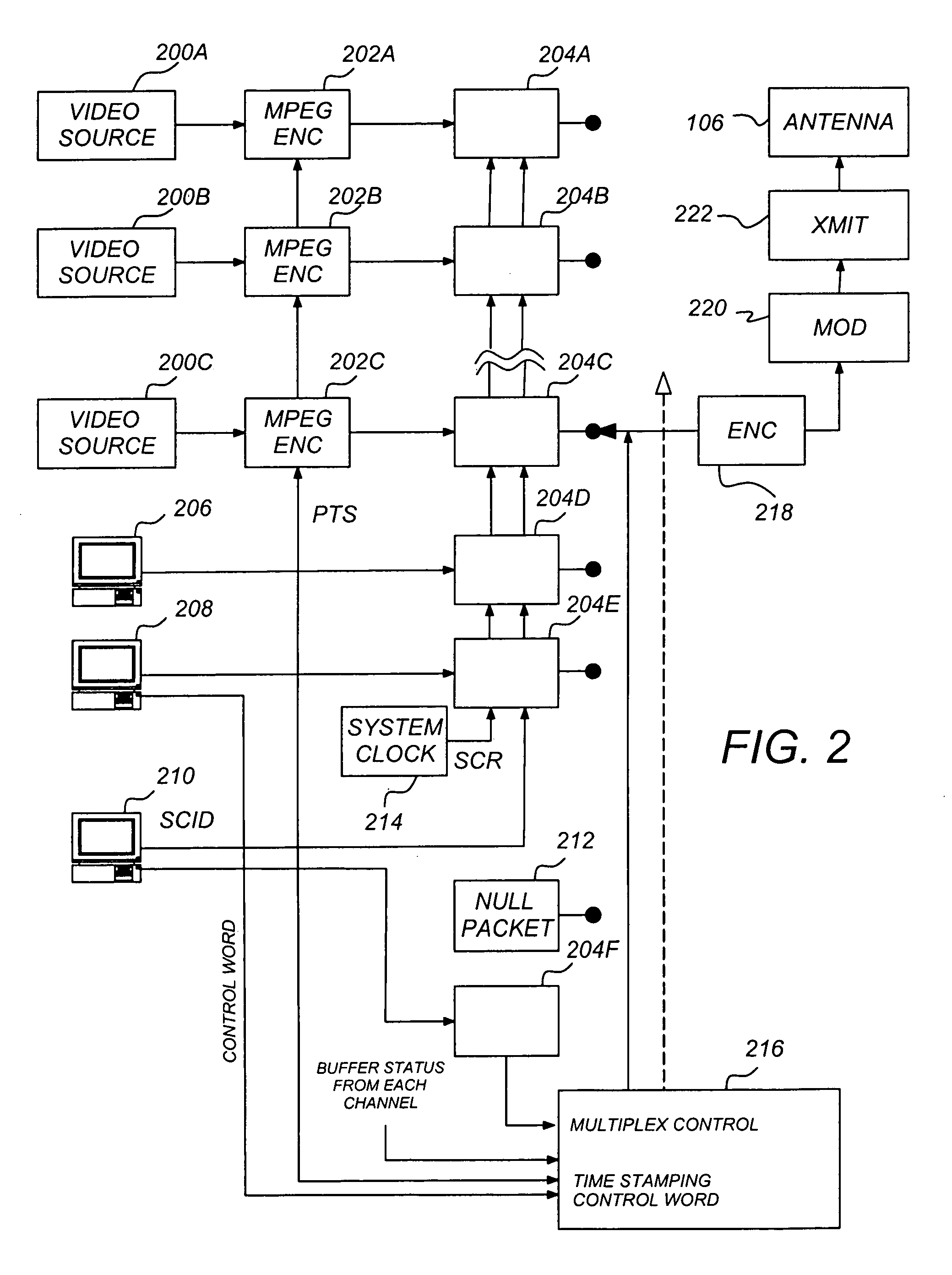
Data delivery method and data delivery system
InactiveUS20020106086A1EffectiveEasy to findTelevision system detailsKey distribution for secure communicationDigital dataCryptographic key generation
A data delivery system highly resistant to misappropriation of data. A plurality of pieces of key information are generated on the basis of an encryption key specific to each digital data item to be delivered. The multiple pieces of key information are delivered over routes which differ from the routes used to deliver the digital data and which further differ from each other. Physically different media or transmission over a network at different times are used to transmit the different sets of key information separately.
Owner:SONY CORP
Method for transferring encrypted data and information processing system
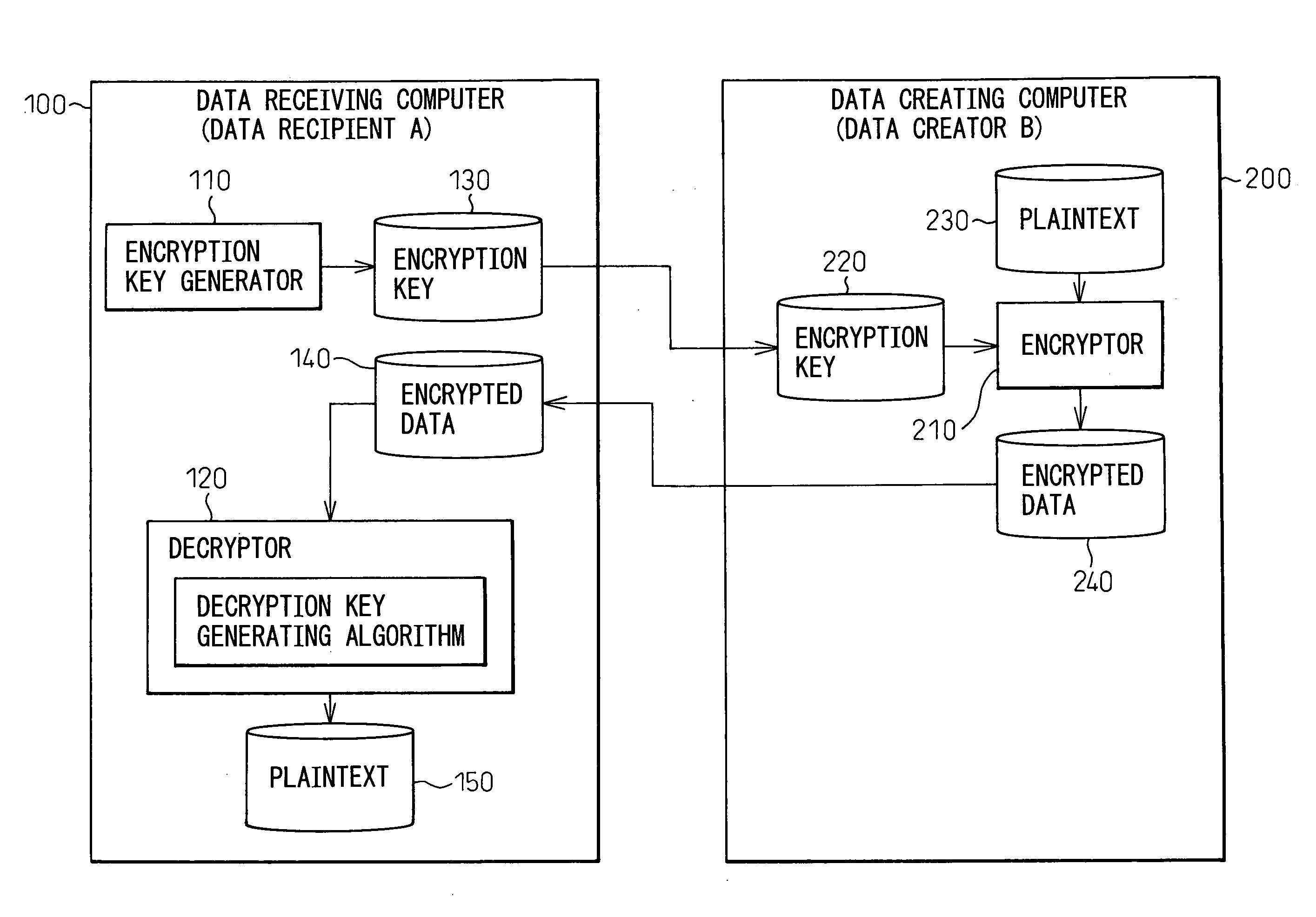
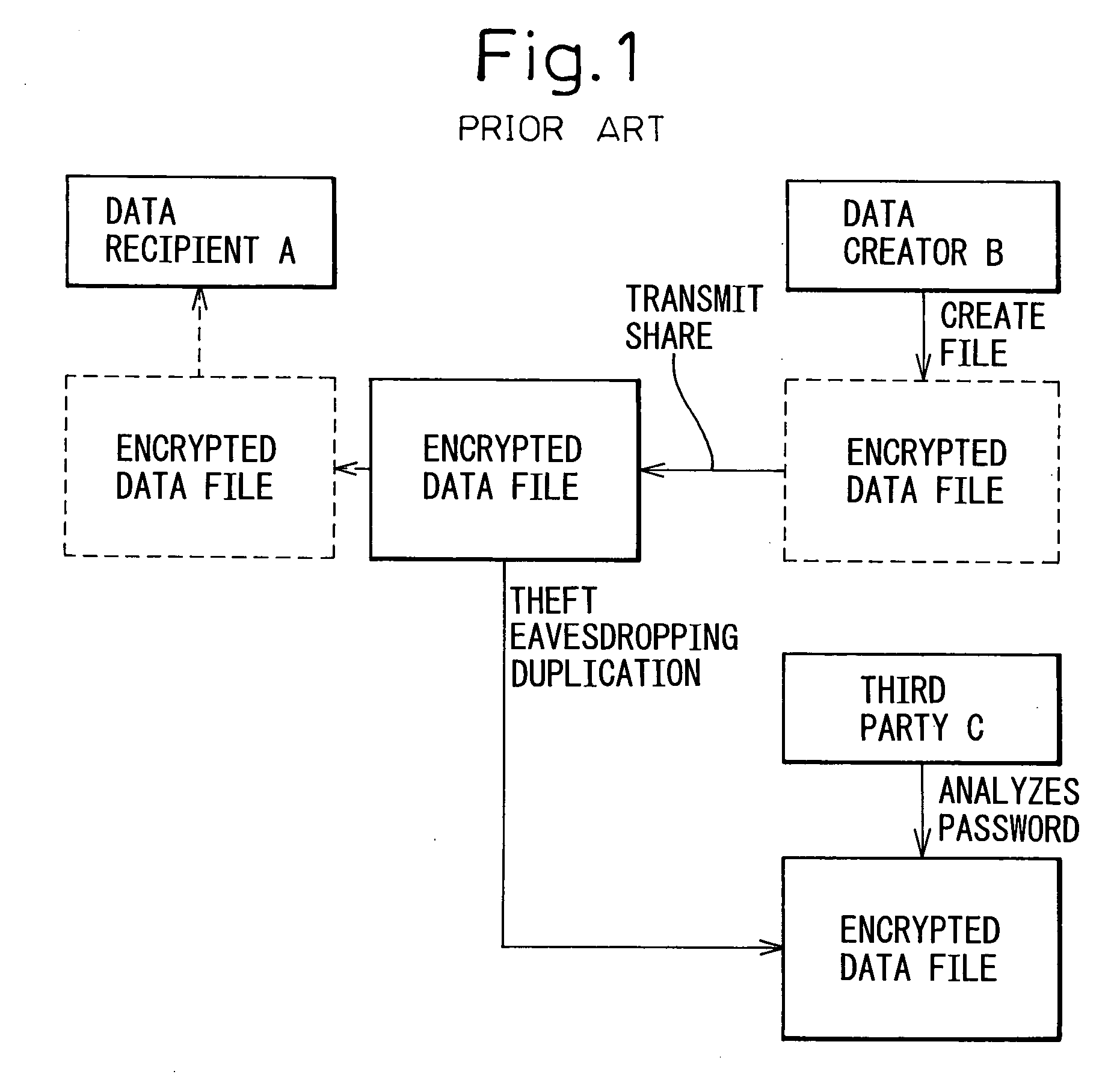
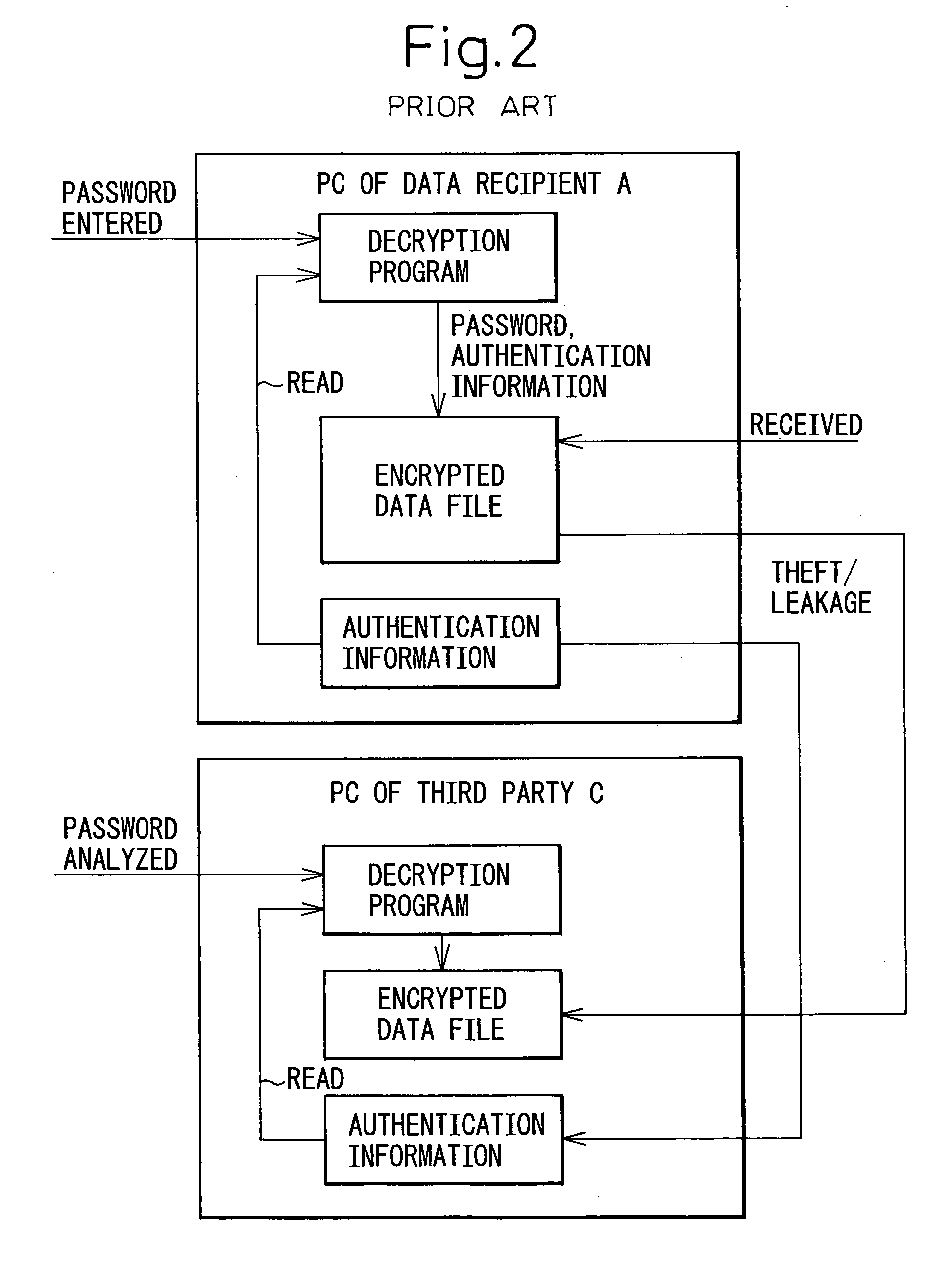
InactiveUS20070005974A1Improve securityUser identity/authority verificationUnauthorized memory use protectionInformation processingCryptographic key generation
A method for transferring encrypted data and an information processing system for implementing the method, wherein provisions are made to enhance the security of the encrypted data by allowing only the intended data recipient to handle the decryption key when transferring the encrypted data. In a computer network over which encrypted data is transferred between a data creating computer and a data receiving computer, the data creating computer includes an encryptor which encrypts plaintext data into encrypted data by using en encryption key transferred from the data receiving computer, and which transmits the encrypted data to the data receiving computer, and the data receiving computer includes an encryption key generator which generates the encryption key and transmits it to the data creating computer, and a decryptor which holds therein decryption key information corresponding to the encryption key in a form that cannot be copied, and which generates the decryption key based on the decryption key information and, using the decryption key, decrypts the encrypted data transferred from the data creating computer.
Owner:FUJITSU LTD
Cryptographic communications using in situ generated cryptographic keys for conditional access
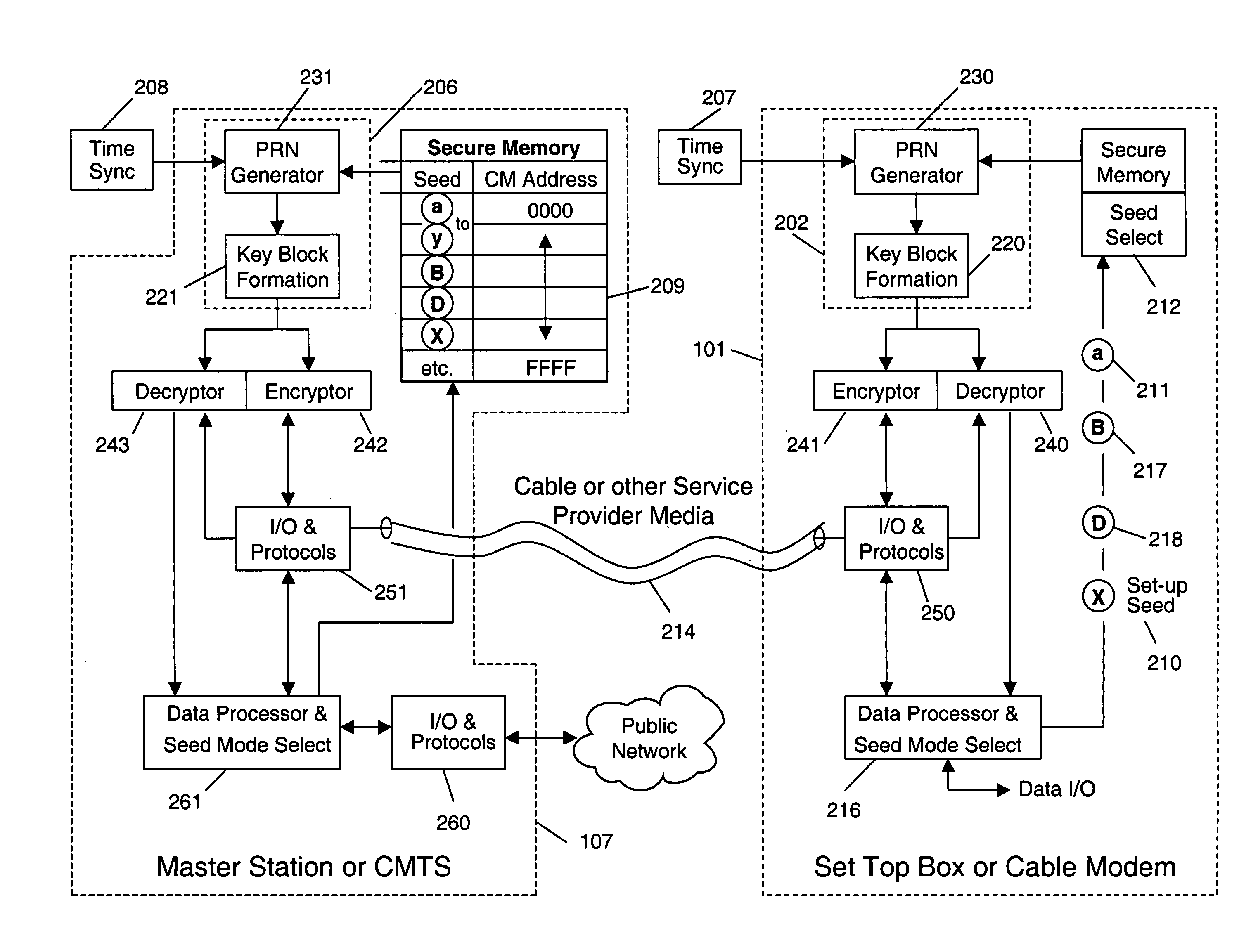
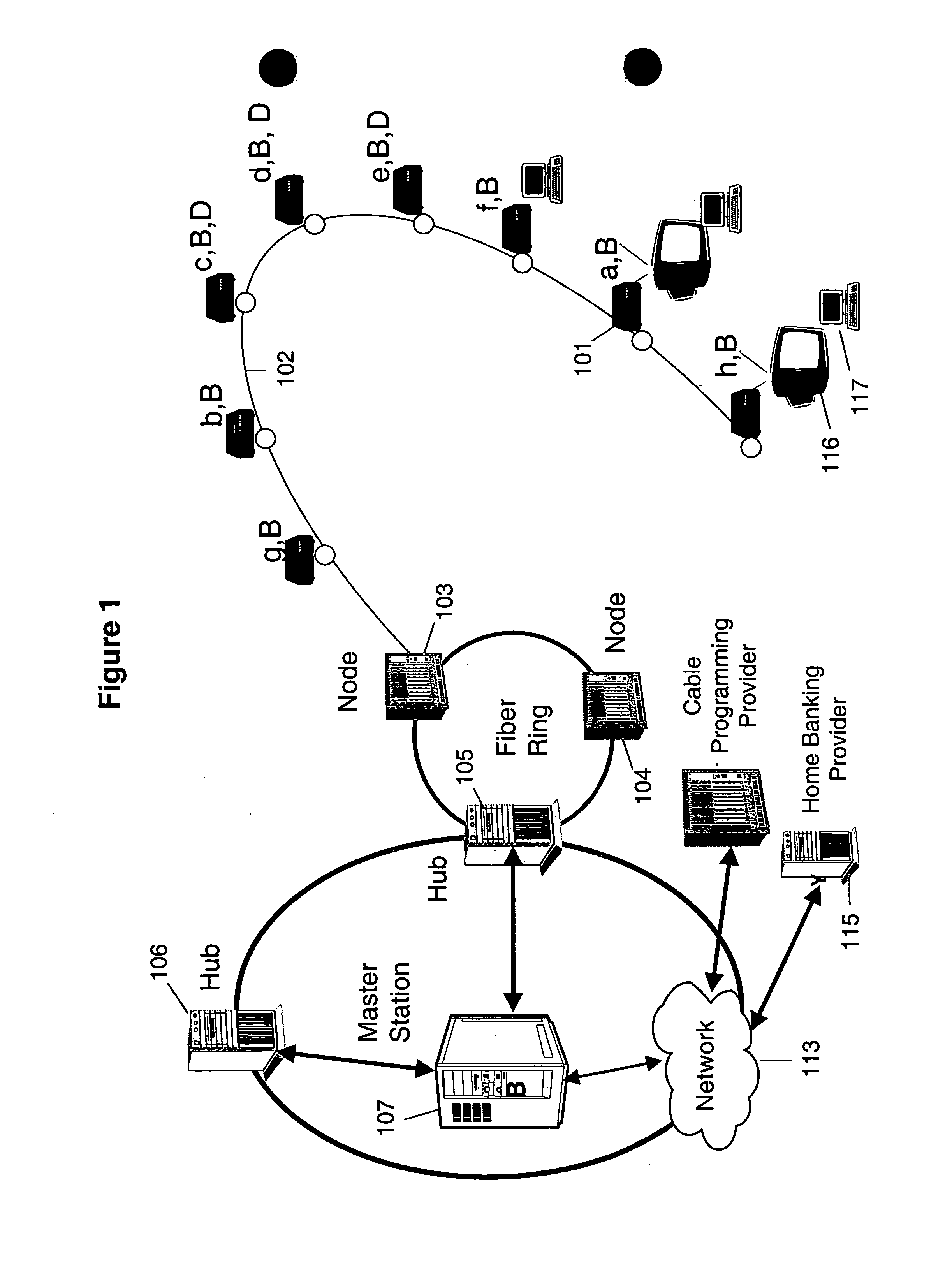
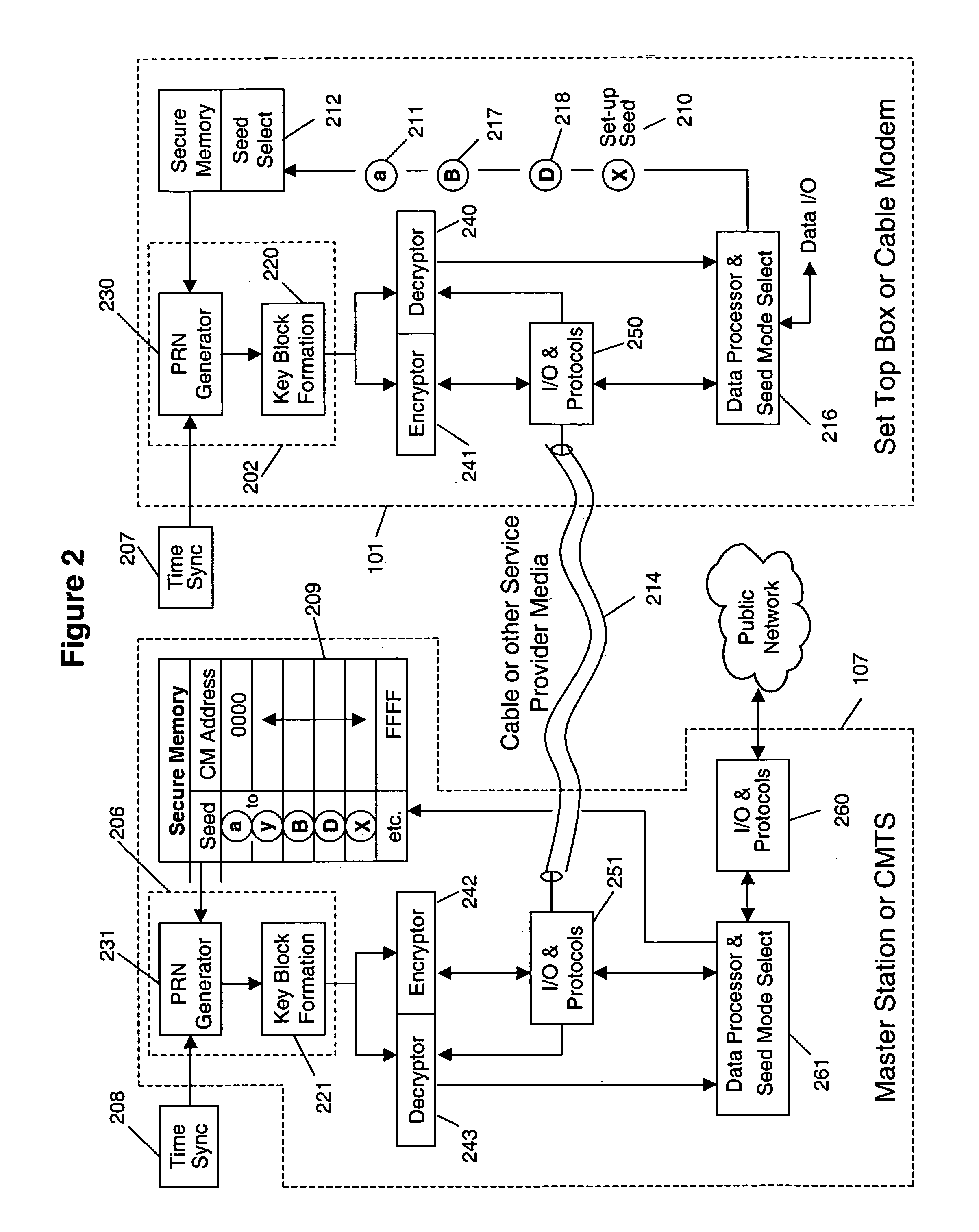
InactiveUS7149308B1Improve securityFacilitate communicationKey distribution for secure communicationComputer security arrangementsCryptographic key generationCommunication interface
A system and method for cryptographic communication among multiple users and a central service provider using in situ generated cryptographic keys. Each user communicates with the central service provider preferably using a user communication interface that includes an in situ key generator, which, after initialization with the user's own individual seed value, generates a unique cryptographic key. By distributing different user individual seeds unique to each user, each user's in situ key generator generates a unique set of keys. The central service provider also possesses an in situ key generator, and also preferably possesses a copy of all the individual seeds assigned to authorized users. The central service provider preferably communicates in a secure encrypted fashion with each user using cryptographic keys generated from that user's individual seed. Distribution of additional seed values common to more than one user, via encrypted communication using said unique individual cryptographic key generations, then permit secure conditional access to said users via signal encryption using key generations resulting from a seed value common to the intended group of users.
Owner:STEALTHKEY
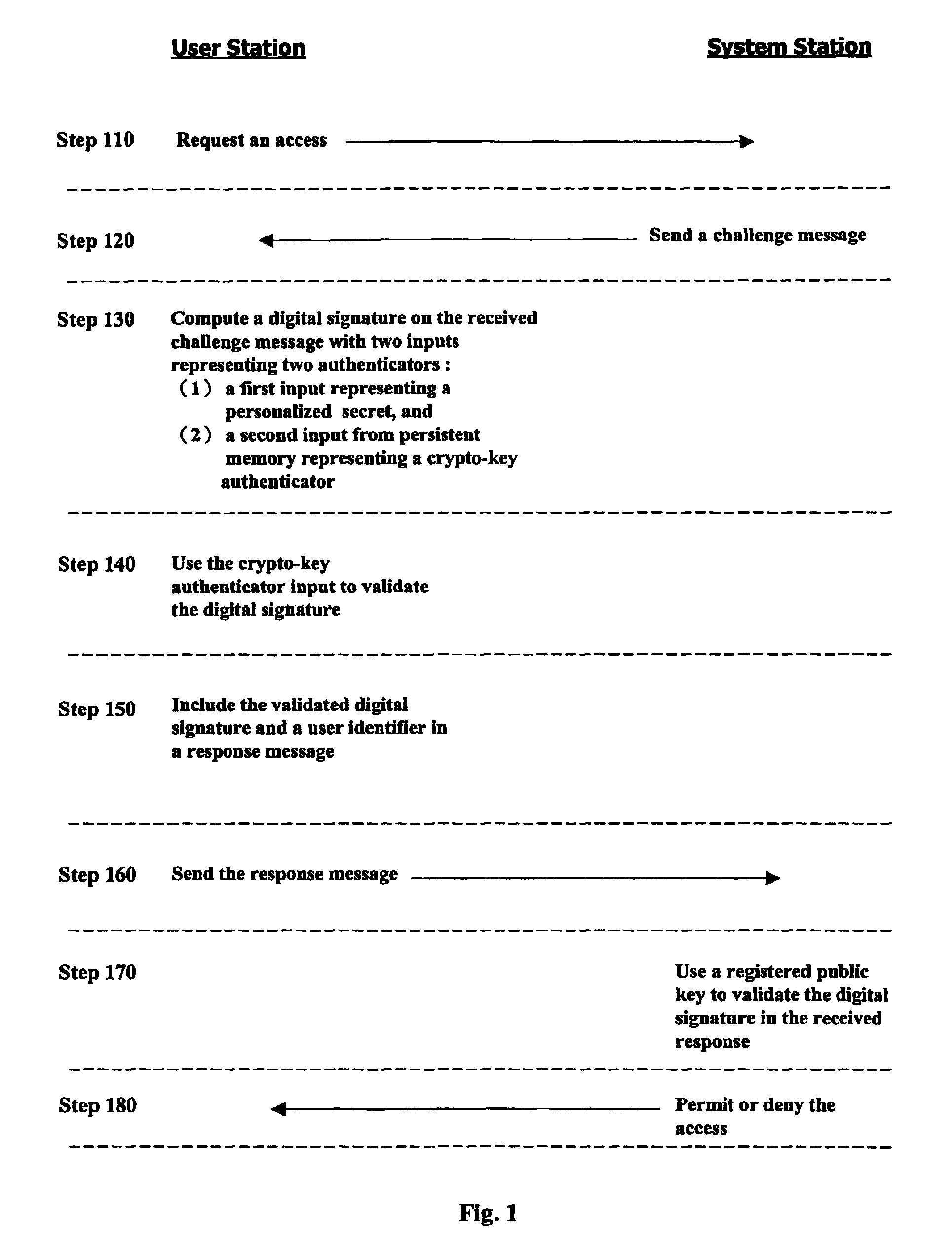
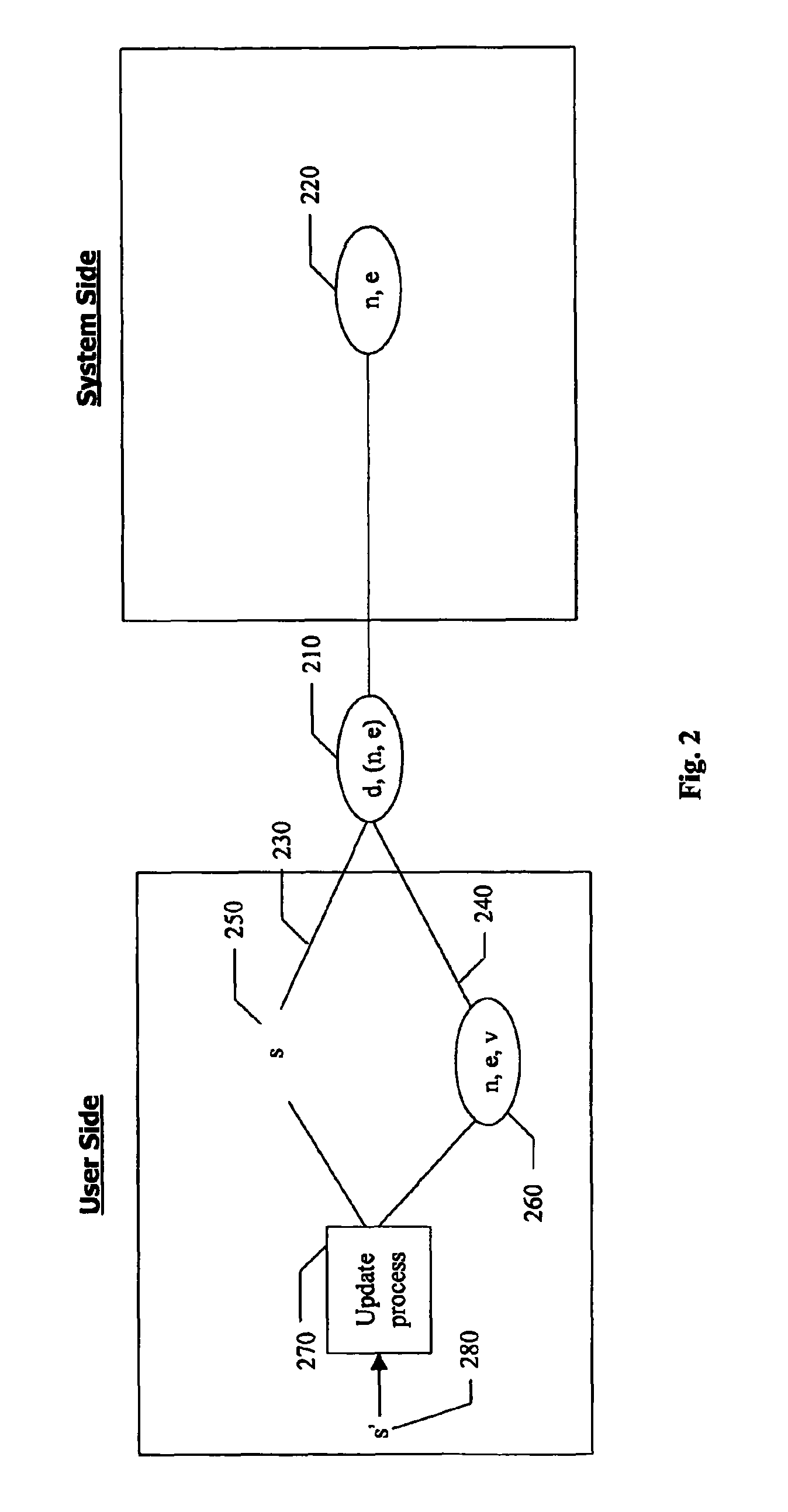
User authentication based on asymmetric cryptography utilizing RSA with personalized secret
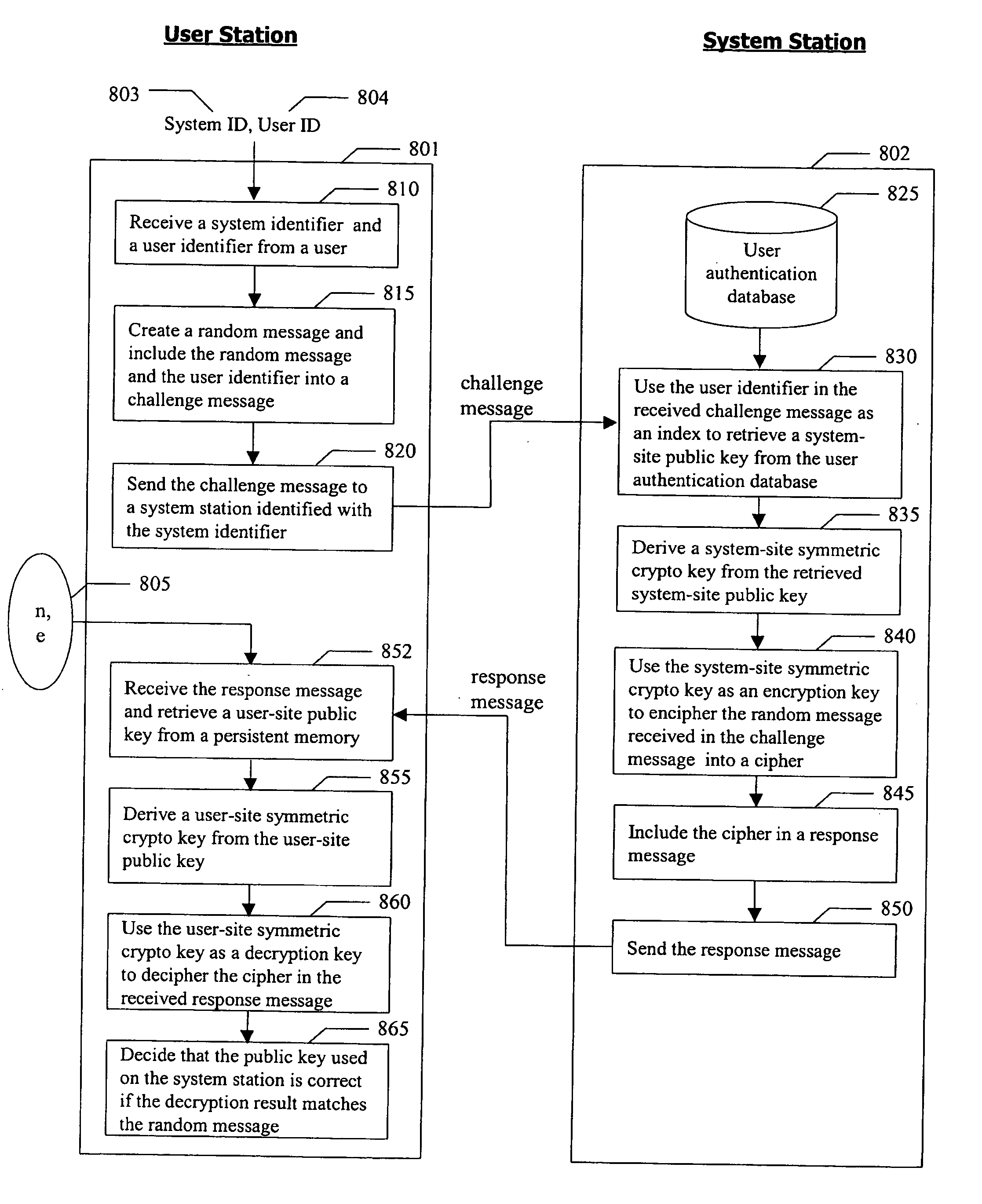
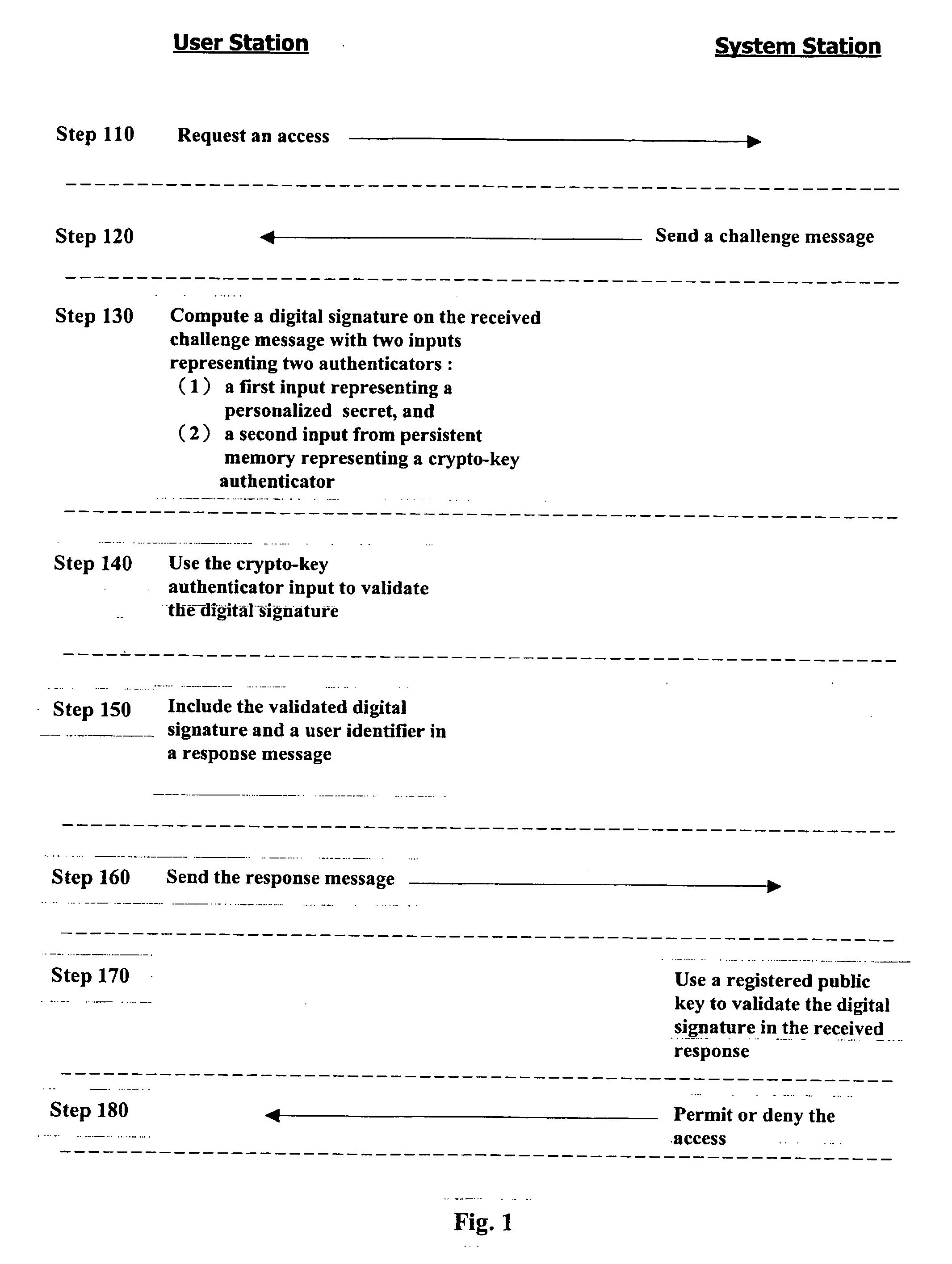
InactiveUS20070081667A1Ensure integrityDigital data processing detailsPublic key for secure communicationPersonalizationCryptographic key generation
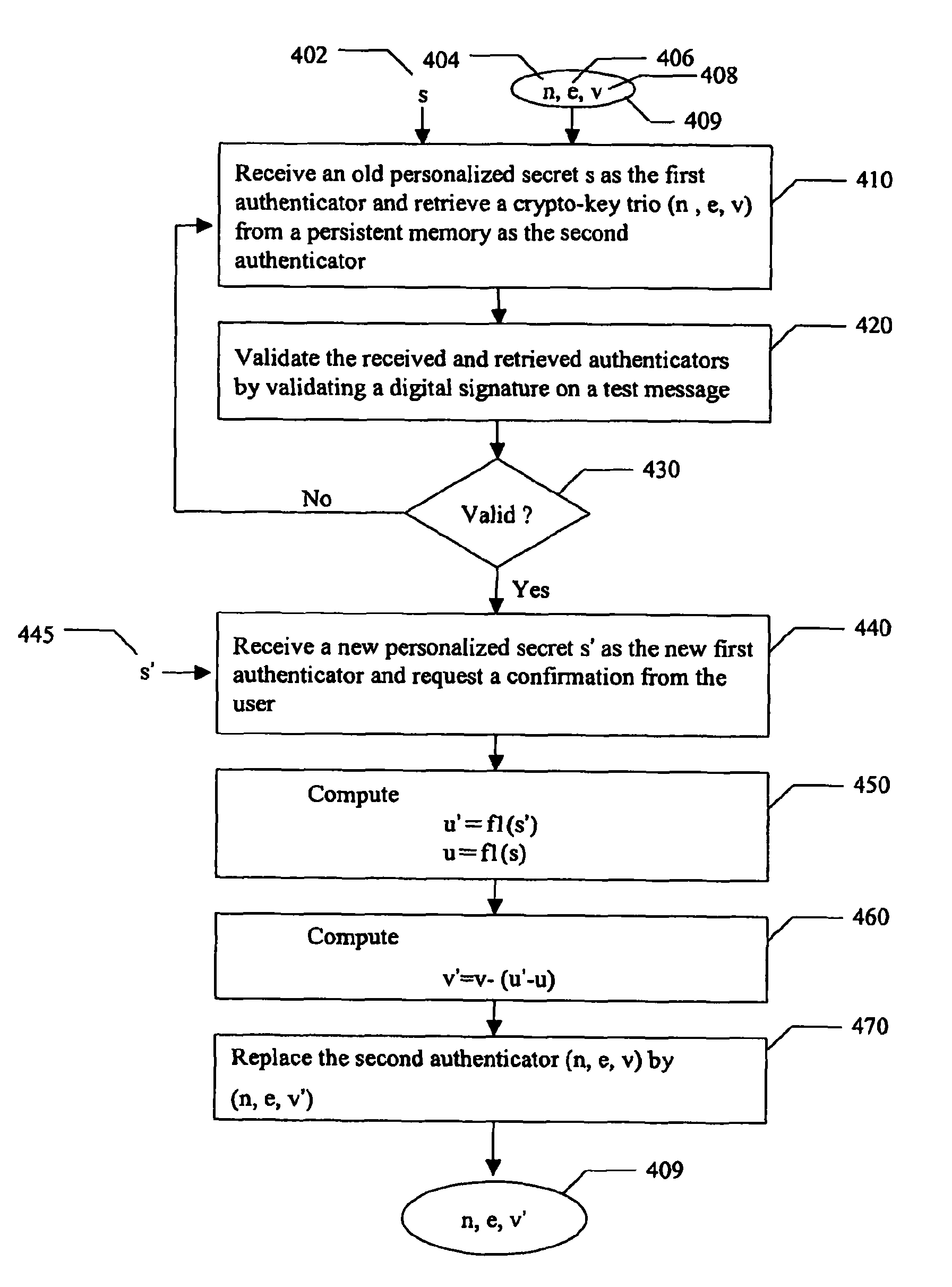
A method for authenticating a user to a computer system is disclosed, comprising using a first input and a second input in producing a digital signature in response to a challenge. The digital signature is valid when the first input matches a personalized secret and the second input matches a trio comprising a public modulus, a public exponent, and a private-key-dependent exponent. Selection of the personalized secret is discretionary and changeable. A crypto-key generation process uses the personalized secret and two primes as input to produce the trio. The public modulus and public exponent of the trio form a public key used in digital signature validation. Also disclosed is a business method that replaces the conventional public-key certificate with an agreement on the user's public key.
Owner:CHANG GUNG UNIVERSITY
Method, system and device for enabling delegation of authority and access control methods based on delegated authority
ActiveUS20050058294A1Key distribution for secure communicationPublic key for secure communicationTrusted authorityCryptographic key generation
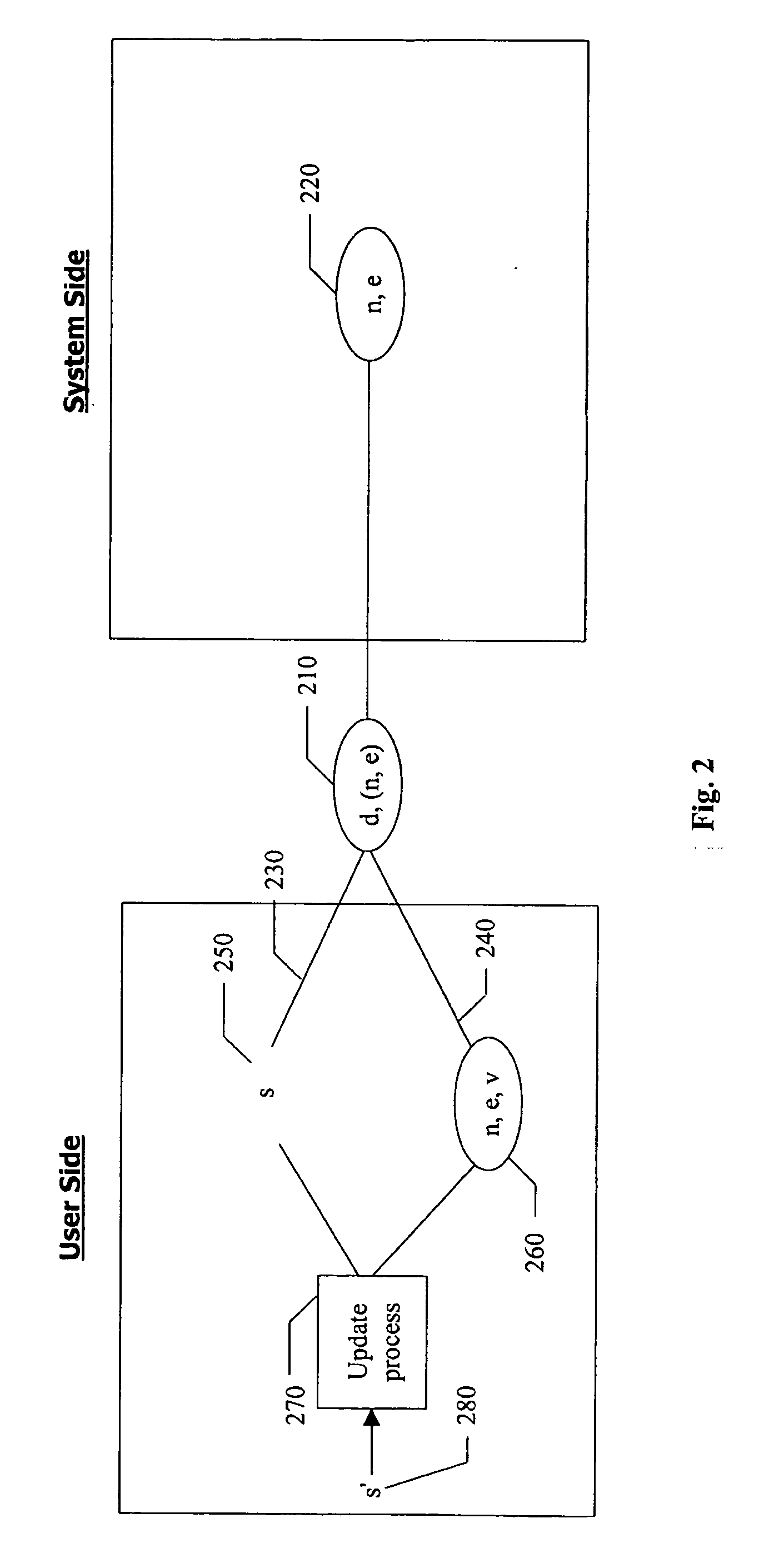
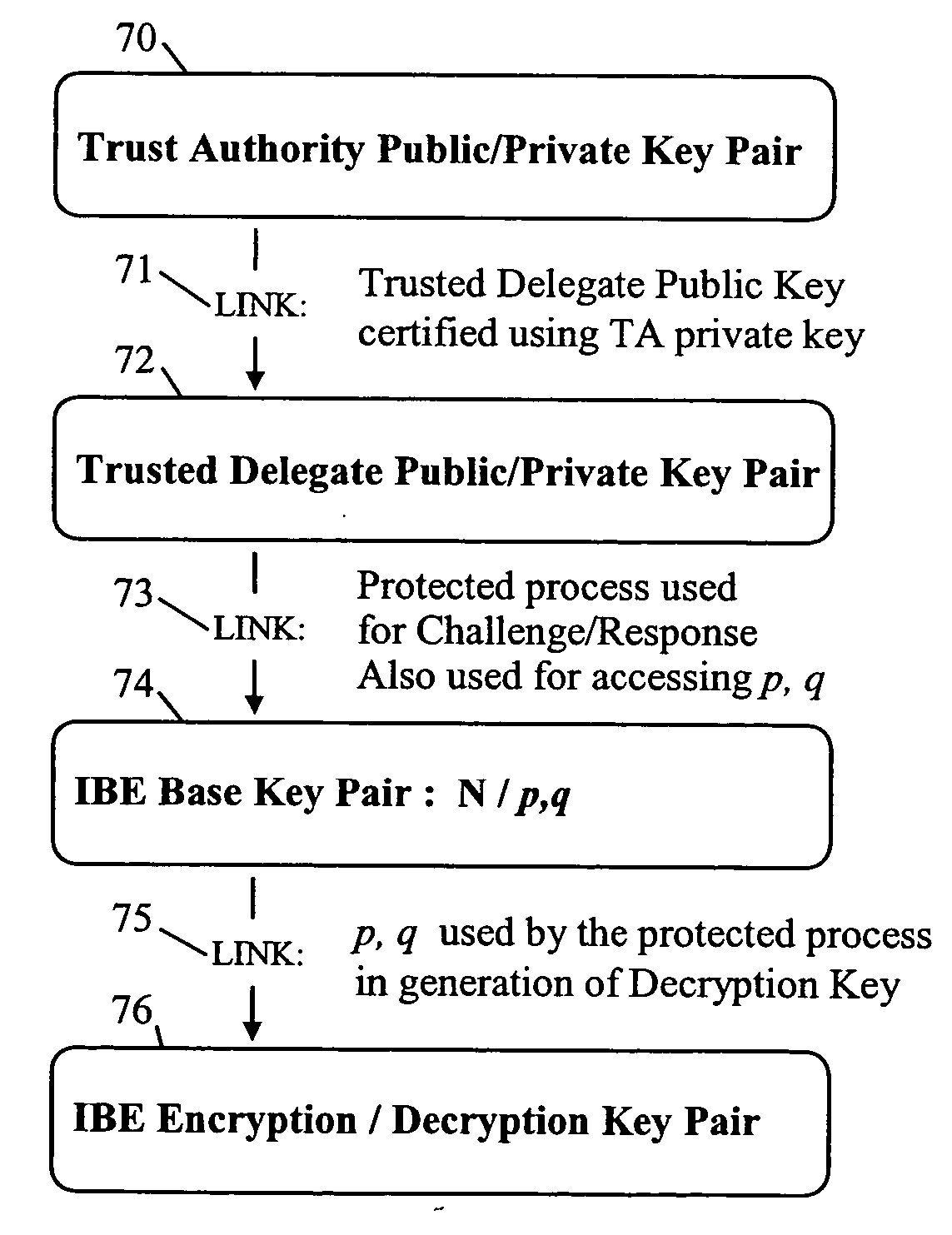
A trusted authority delegates authority to a device. This delegation of authority is effected by providing a yet-to-be completed chain of public / private cryptographic key pairs linked in a subversion-resistant manner. The chain terminates with a penultimate key pair formed by public / private data, and a link towards an end key pair to be formed by an encryption / decryption key pair of an Identifier-Based Encryption, IBE, scheme. The private data is securely stored in the device for access only by an authorized key-generation process that forms the link to the end key pair and is arranged to provide the IBE decryption key generated using the private data and encryption key. This key generation / provision is normally only effected if at least one condition, for example specified in the encryption key, is satisfied. Such a condition may be one tested against data provided by the trusted authority and stored in the device.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
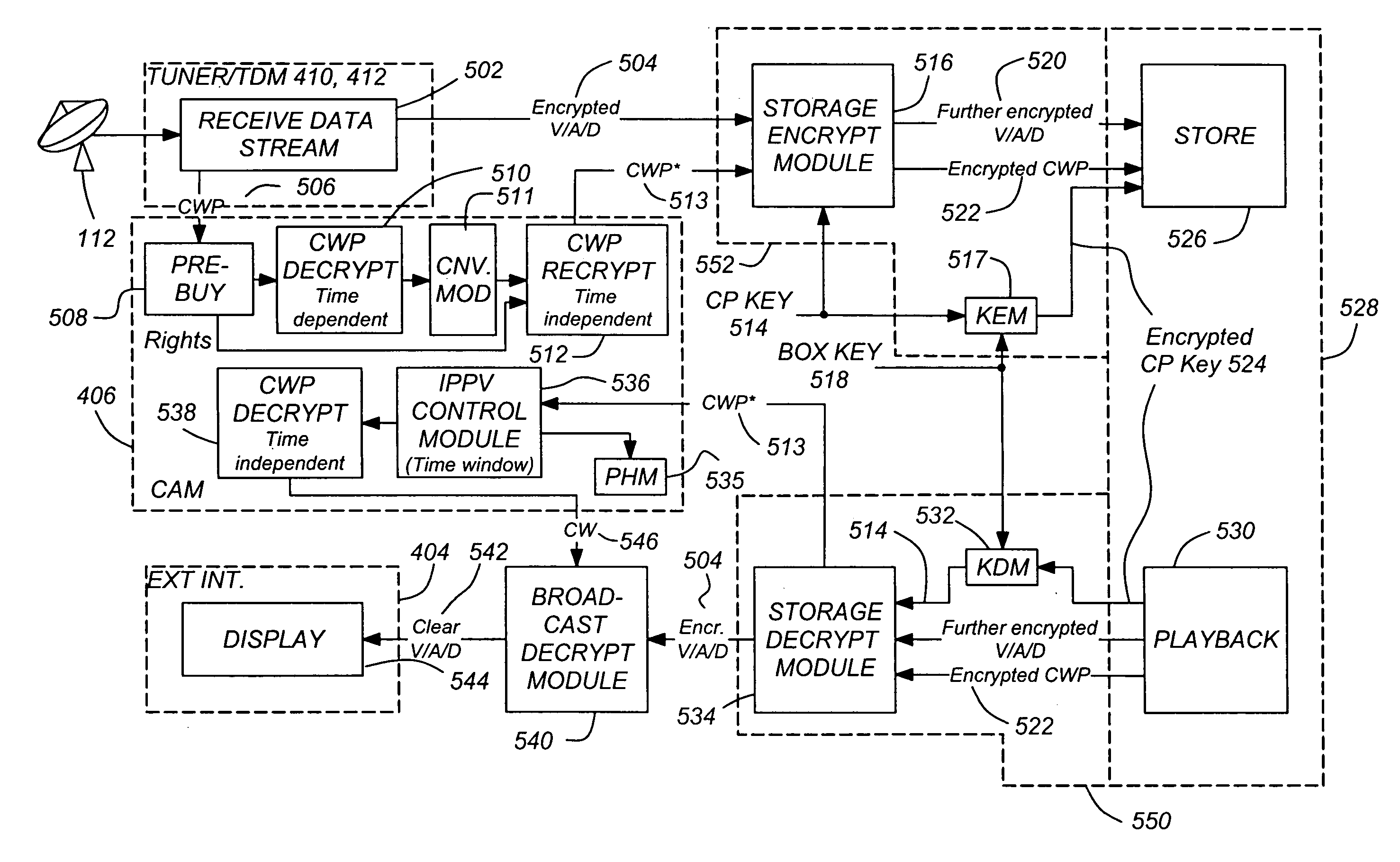
Super encrypted storage and retrieval of media programs with modified conditional access functionality
ActiveUS7203314B1Eliminate concernsTelevision system detailsSelective content distributionCryptographic key generationControl data
A method and apparatus for storing and retrieving program material for subsequent replay is disclosed. The apparatus comprises a conditional access module, for accepting encrypted access control information and the program material encrypted according to a first encryption key, the encrypted access control information including a first encryption key and temporally-variant control data; the conditional access module having a first decryptor module, for decrypting the encrypted access control information to produce the temporally variant control data; a conversion module for modifying the temporally-variant control data to produce temporally-invariant control data; a re-encryptor module, for re-encrypting the decrypted access control information; a second decryptor module for decrypting the re-encrypted access control information to produce the first encryption key; a copy protection encryption module, communicatively coupleable to the conditional access module and a media storage device, the copy protection encryption module for further encrypting the encrypted program material according to a second encryption key and for encrypting the second encryption key according to a third encryption key to produce a fourth encryption key; and a copy protection decryption module, communicatively coupleable to the conditional access module and the media storage device, the copy protection decryption module for decrypting the encrypted fourth encryption key to produce the second encryption key using the third encryption key.
Owner:HUGHES ELECTRONICS
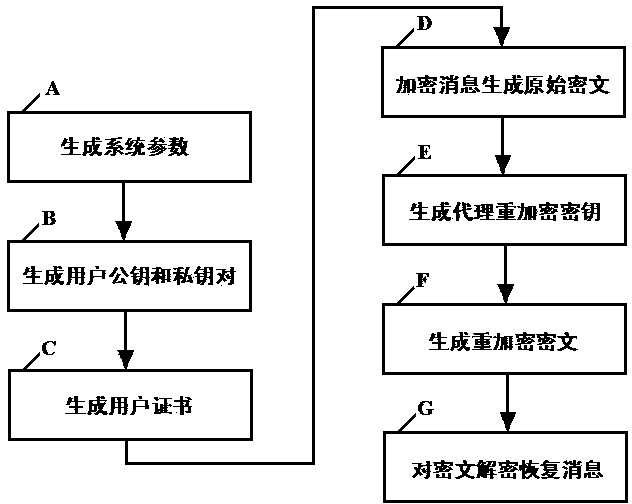
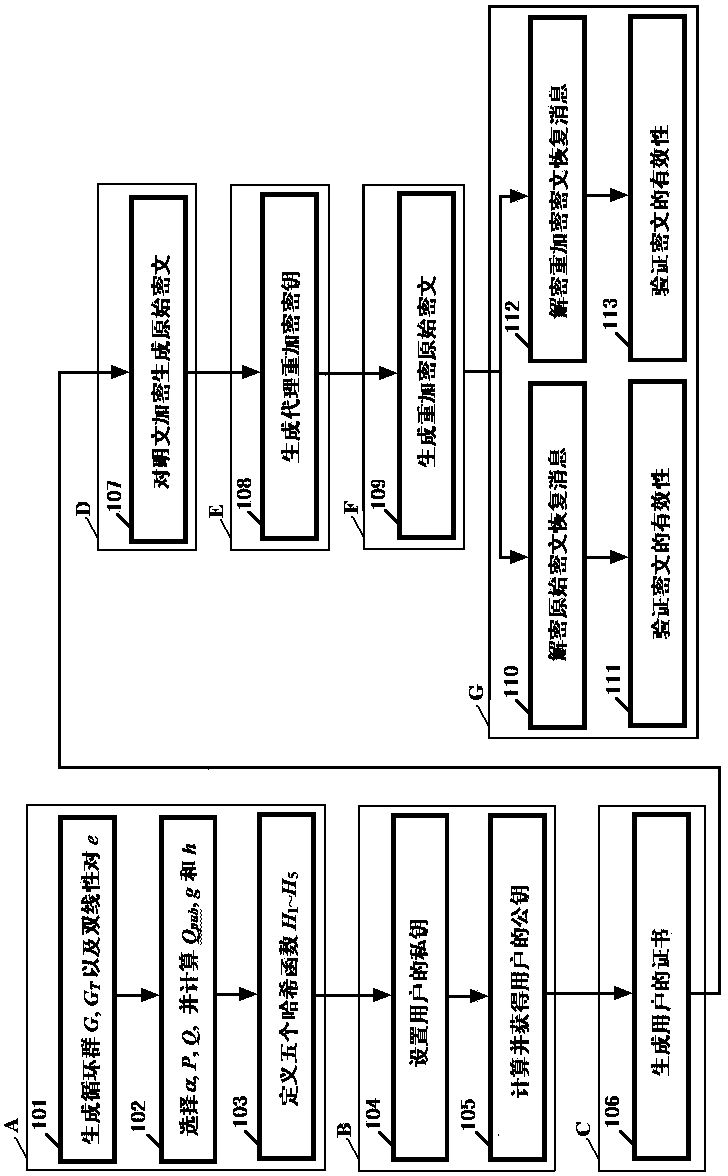
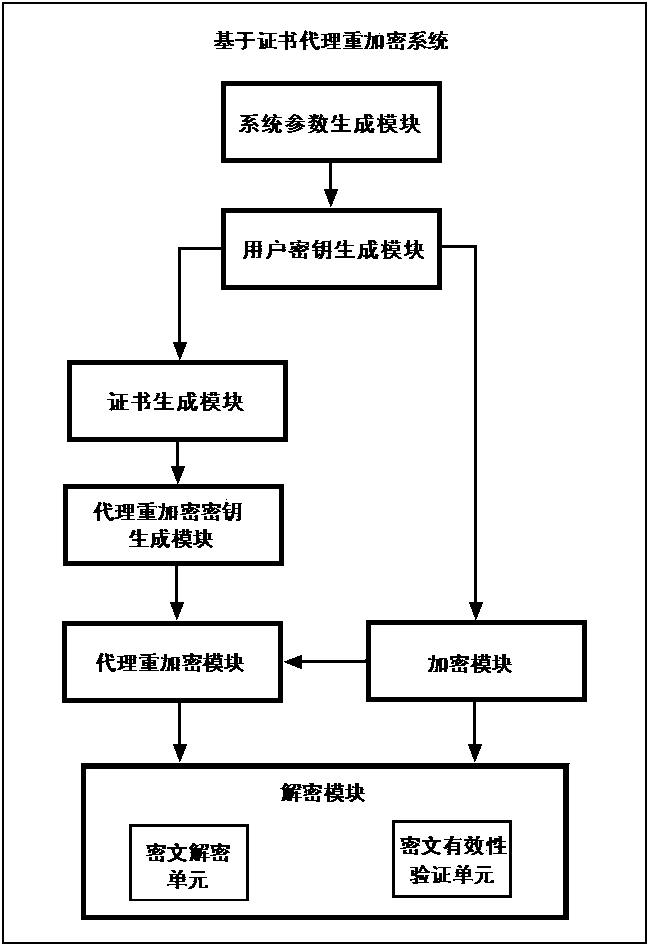
Certificate-based agent heavy encryption method and system
InactiveCN103647642AOvercome problemsSimplify the undo problemKey distribution for secure communicationPublic key for secure communicationCryptographic key generationPassword
The invention relates to the technical field of data encryption in information security, and discloses a certificate-based agent heavy encryption method and system, for solving the defect of a conventional agent heavy encryption method. The invention provides a certificate-based agent heavy encryption method by combining a certificate password system and agent heavy encryption. The method comprises the steps of generating system parameters, generating a user public key and private key pair, generating a user certificate, encrypting messages, generating agent heavy encryption secret key, agent heavy encrypting and message recovery. The invention also provides a certificate-based agent heavy encryption system. The system comprises a system parameter generation module, a user secret key generation module, a certificate generation module, an encryption module, an agent heavy encryption secret key generation module, an agent heavy encryption module and a decryption module. The technical scheme provided by the invention not only simplifies a certificate management process, but also eliminates the problems of secret key distribution and secret key hosting and facilitates application in open network environment.
Owner:HOHAI UNIV
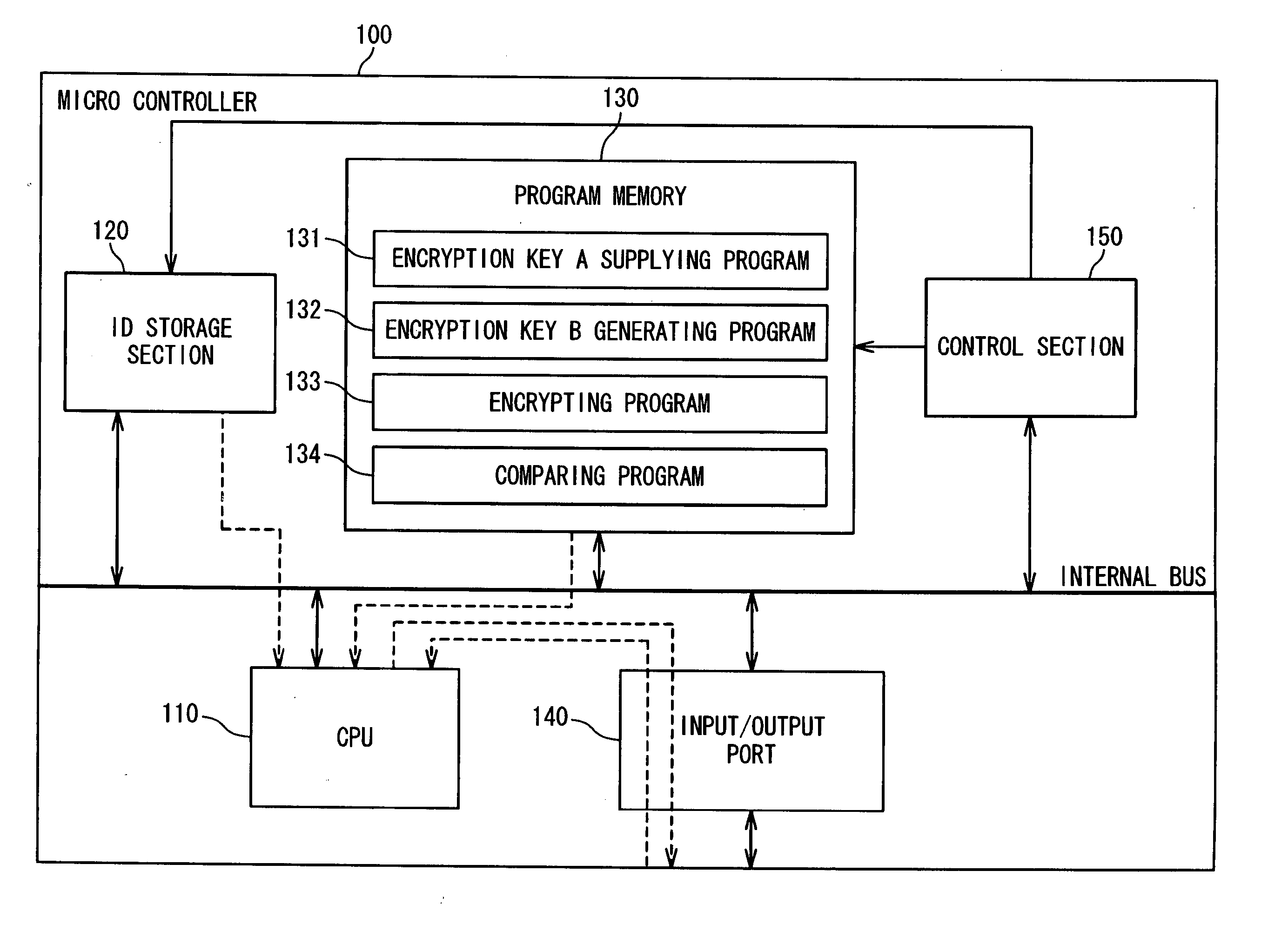
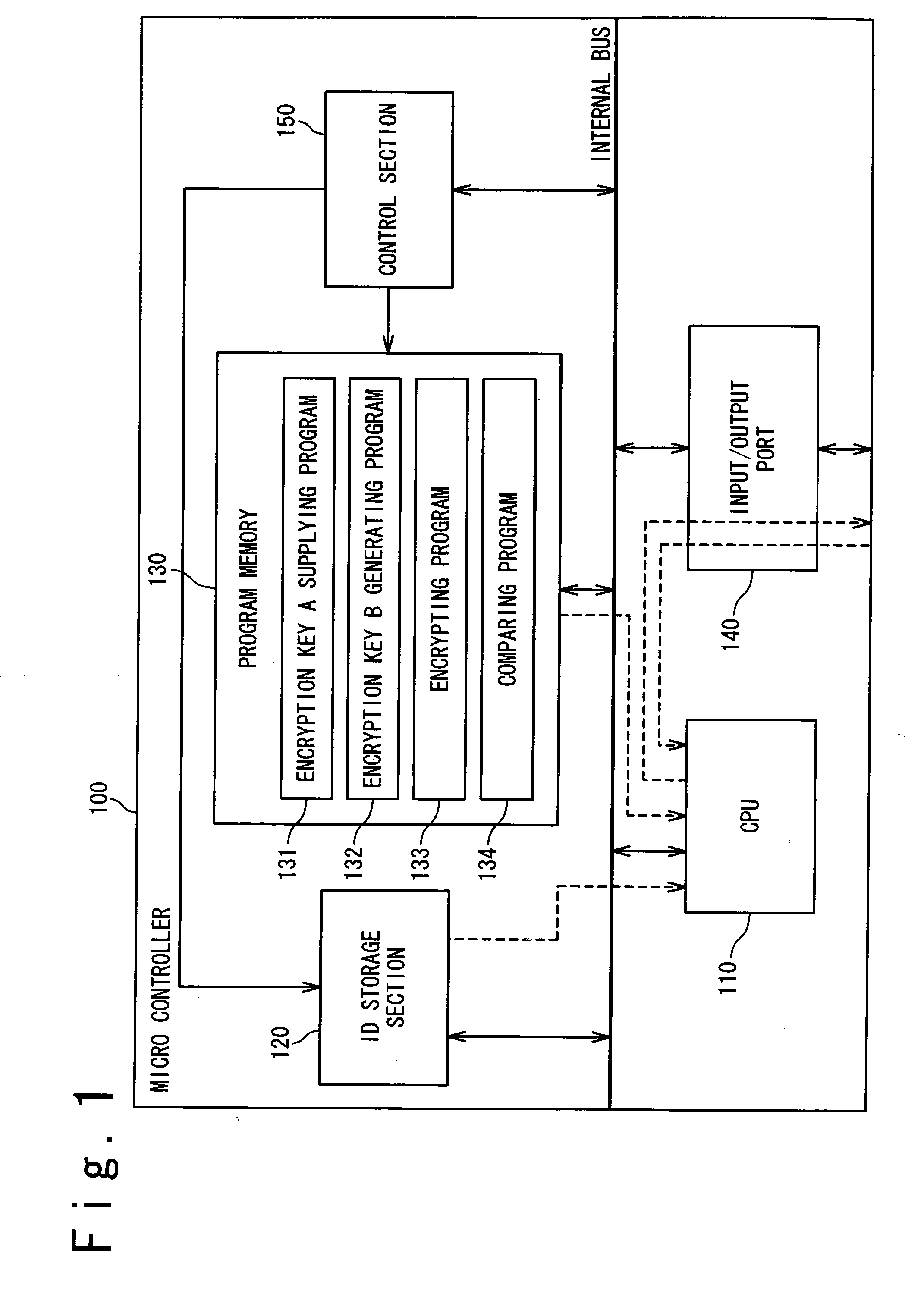
Microcontroller and authentication method between the controllers
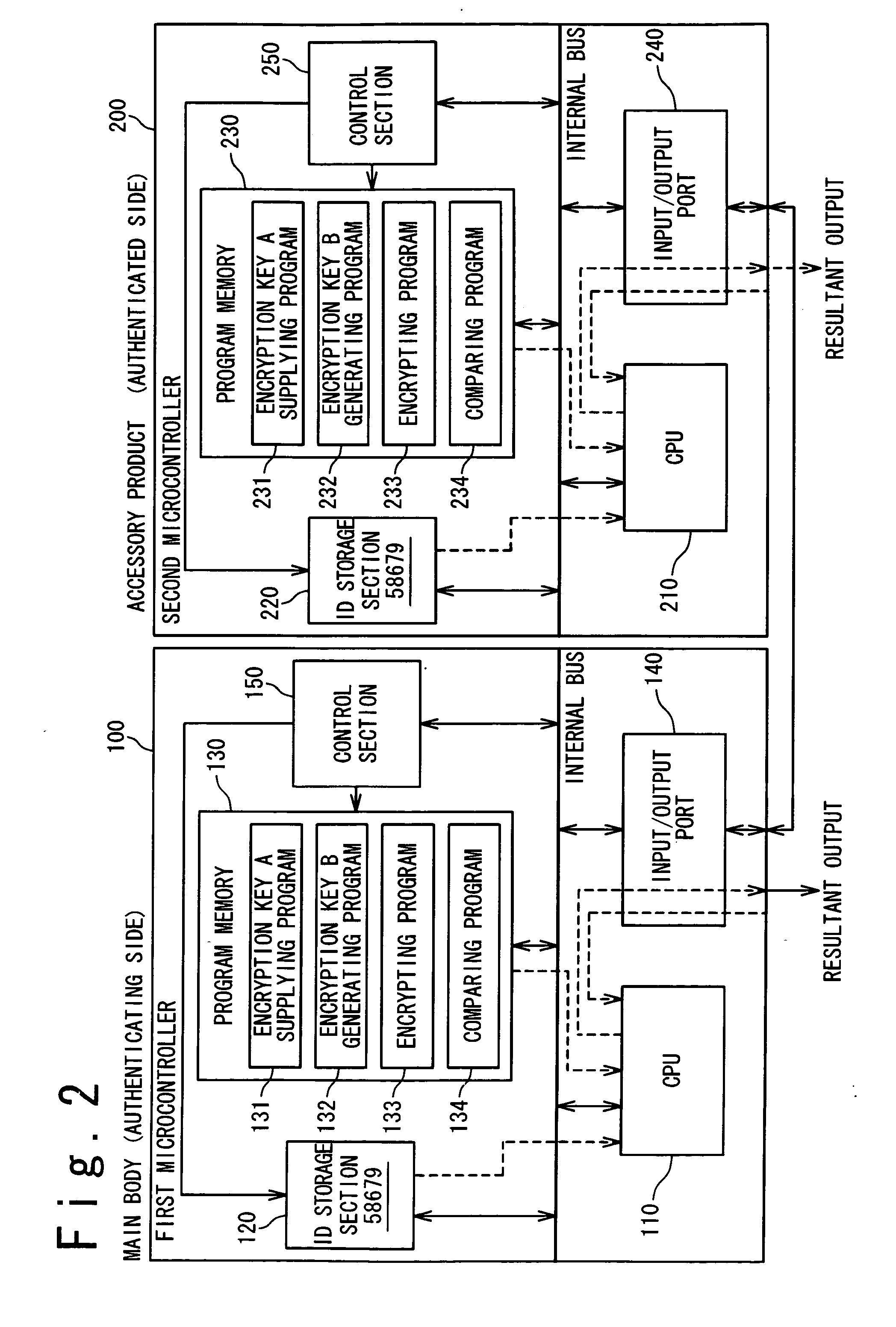
ActiveUS20070160204A1Unauthorized memory use protectionHardware monitoringCryptographic key generationMicrocontroller
A microcontroller includes a program memory configured to store a program group and a first encryption key; a CPU; and an identification (ID) storage section configured to store an identification data peculiar to a user of the microcontroller. The CPU executes the program group to generate a second encryption key based on the identification data and the first encryption key and to encrypt a random number with the second encryption key.
Owner:RENESAS ELECTRONICS CORP
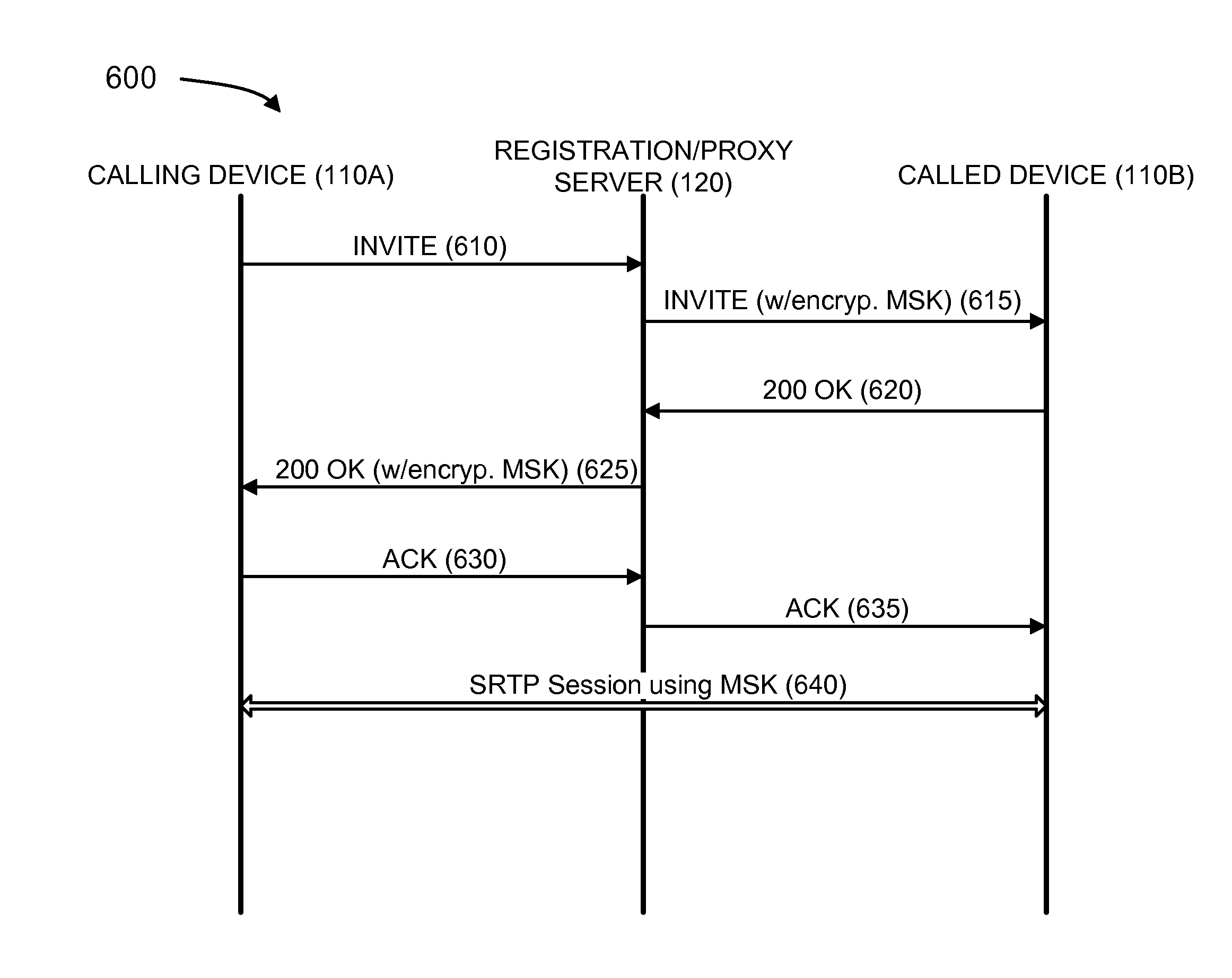
Secure communication session setup
A device receives an encrypted key generating value from a first device and decrypts the encrypted key generating value. A temporary session key associated with the first device is generated based on the key generating value. A secure session invitation message is received from the first device. A master session key is generated and encrypted using the temporary session key associated with the first device. The encrypted master session key is transmitted to the first device.
Owner:VERIZON PATENT & LICENSING INC
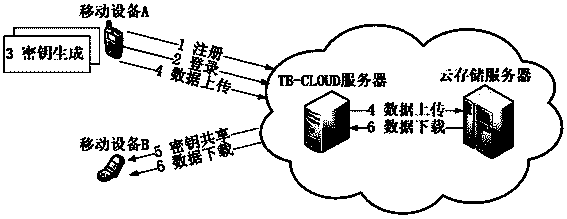
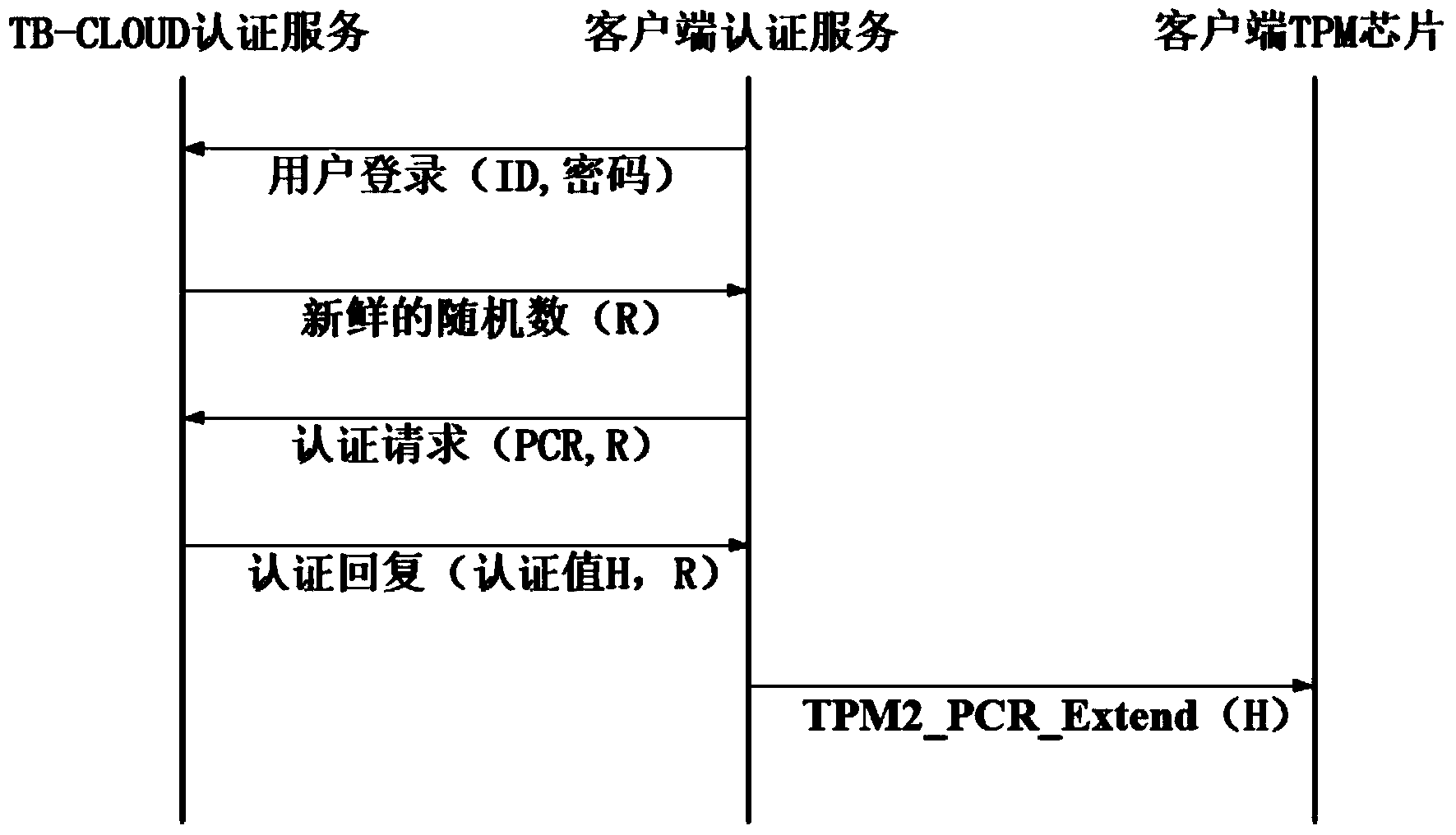
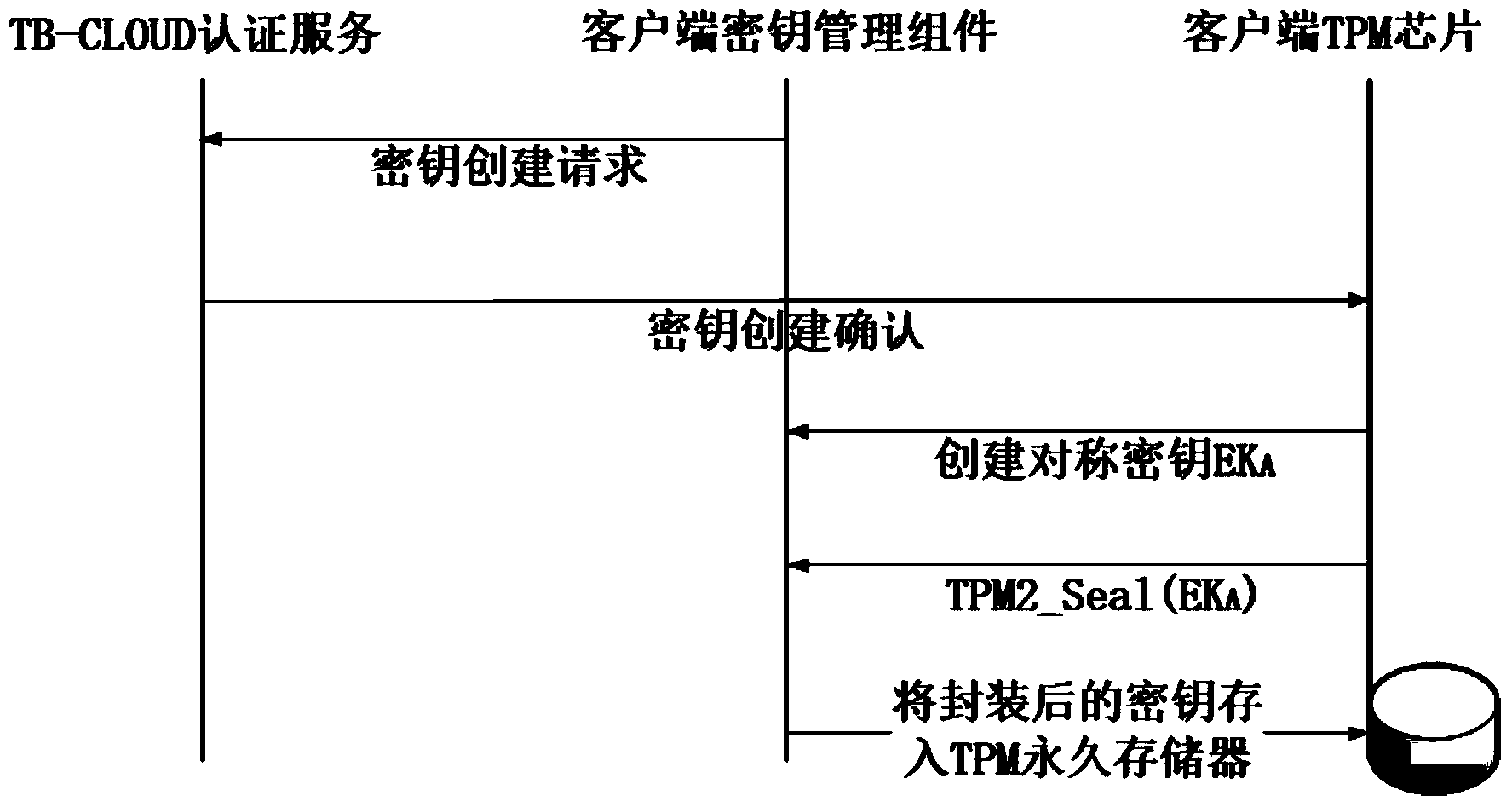
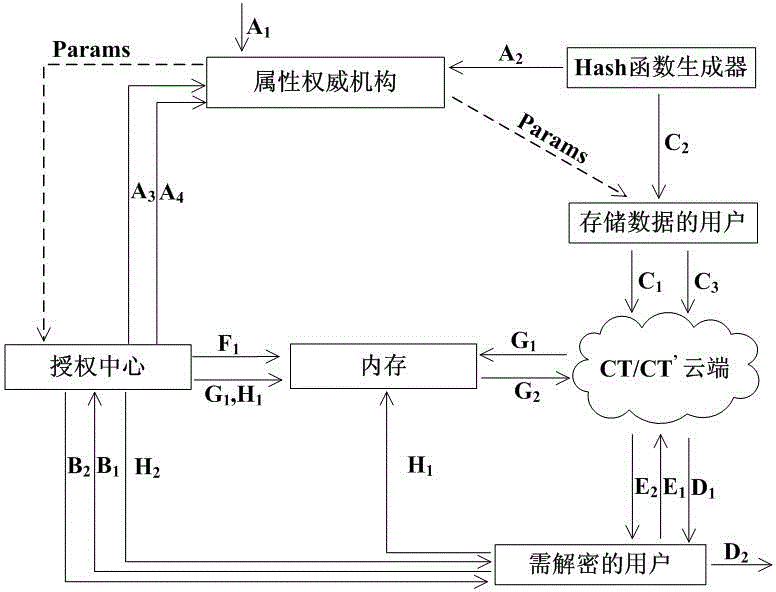
Credible data access control method applied to cloud storage of mobile devices
ActiveCN103763315AReduce the amount of data interactionConfidenceTransmissionCryptographic key generationKey size
The invention relates to a credible data access control method applied to cloud storage of mobile devices. The credible data access control method includes six steps including user registering, user login, secret key generation, data encryption uploading, data downloading and decryption in three stages. The first step is user registering, the second step is user login with an authentication process, the third step is encryption secret key generation, the fourth step is user data encryption uploading, the fifth step is secret key sharing among the multiple mobile devices, and the sixth step is data downloading and decryption. According to the credible data access control method, transmitting of a credible chain in the secret key exchanging process is guaranteed by a user through a mobile TPM chip, the length of a secret key is reduced through encryption based on a elliptic curve, it is guaranteed that the multiple mobile devices can safely share the secret key, compared with a traditional server terminal or client terminal data encryption method provided by a cloud storage service provider, the credible data access control method is safe, reliable, high in confidence degree and small in interaction data amount, and the good practical value and the wide application prospect are achieved in the technical field of cloud storage safety.
Owner:BEIHANG UNIV
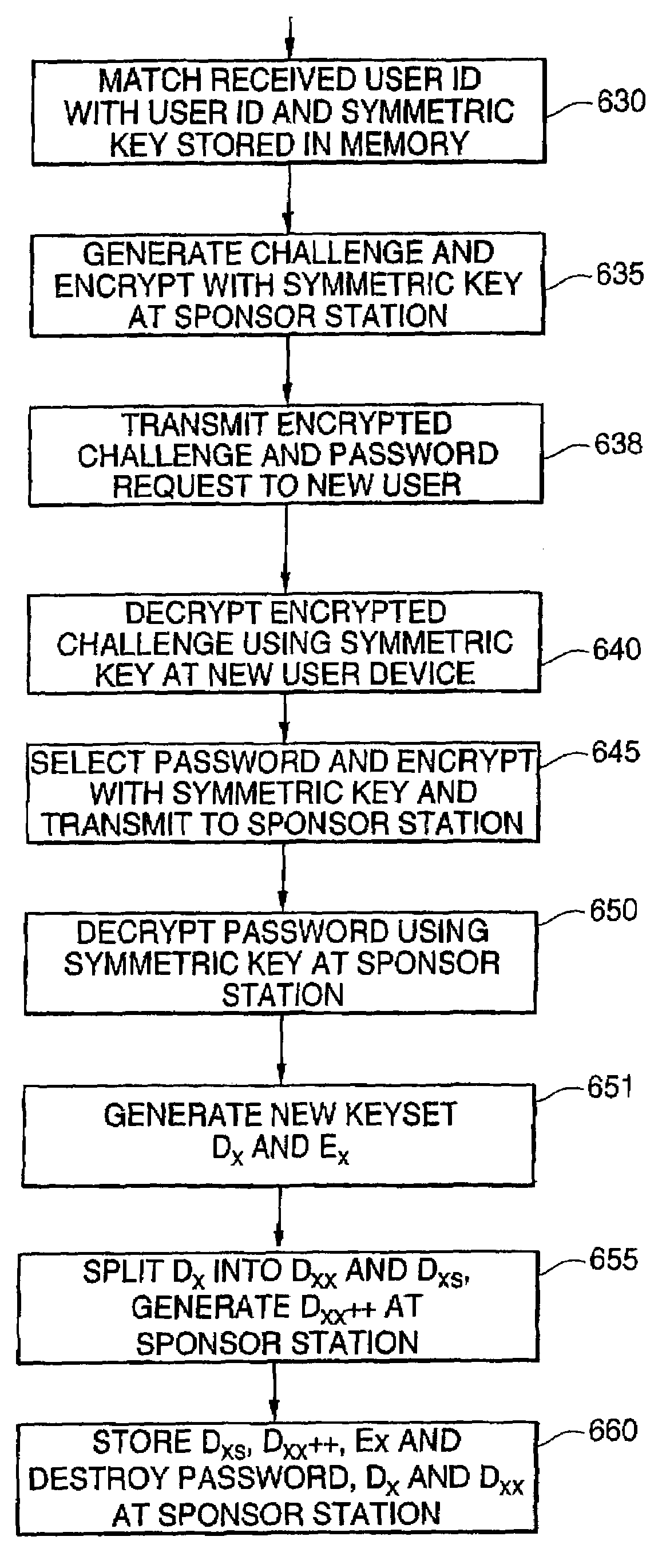
System and method for crypto-key generation and use in cryptosystem
InactiveUS6970562B2Improve security levelShort passwordKey distribution for secure communicationPublic key for secure communicationCryptographic key generationPassword
A first processor generates a private crypto-key and a public crypto-key. The first processor divides the private crypto-key into two portions, a first private key portion, based upon a user's password, and a second private key portion. The private crypto-key and the first private key portion are then destroyed. The remaining portion, second private key portion, and the public crypto-key are stored in a memory. A second processor generates the first private key portion based upon the user's password and responsive to receiving the user's password. The second processor then destroys the generated first private key portion with out storing the generated first private key portion.
Owner:VMWARE INC
Augmented single factor split key asymmetric cryptography-key generation and distributor
ActiveUS20070033392A1Key distribution for secure communicationPublic key for secure communicationKey generationCommon key
To establish credentials, a user network station transmits a first value. An authenticating entity network station generates a first key portion based on the transmitted first value and a second value unknown to the user, splits one of a private key and a public key of a user asymmetric crypto-key into the first key portion and a second key portion, stores the second key portion of the one key so as to be accessible only to the authenticating entity network device, generates a cookie including the second value, transmits the generated cookie to the user network station, and destroys the transmitted first value, the second value, the one key, and the first key portion of the one key. The first value represents a first and the second value included in the transmitted cookie represents a second user credential useable to authenticate the user.
Owner:VMWARE INC
Method of generating an encryption key without use of an input device, and apparatus therefor
InactiveUS20050063542A1Maintain securityKey distribution for secure communicationMultiple keys/algorithms usageCryptographic key generationWireless lan
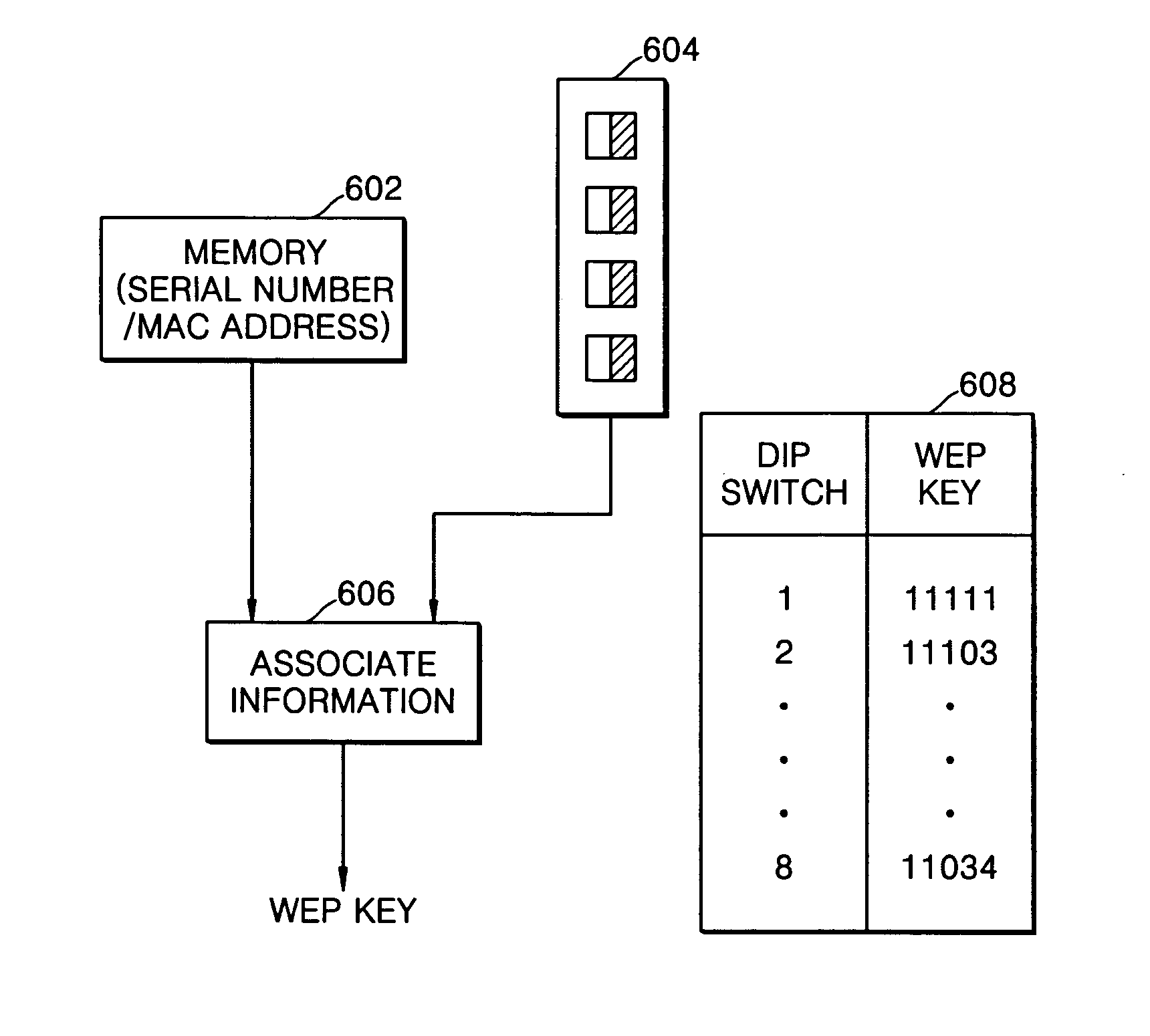
A method of generating an encryption key in a host system that transmits an encrypted signal. The encryption key generating method can be used in a host system that doesn't have an input device such as a keyboard or mouse. The encryption key generating method can be used in a network environment having a host system that can transmit an encrypted signal and a client system that can receive and accept the encrypted signal by using an encryption key determined in the host system. The method can include the acts of reading a pre-designated number of the host system, reading a current value of a dip switch installed in the host system, associating the pre-designated number with the current value, and generating an encryption key in a wireless LAN environment by using the associated value. Since the encryption key generating method generates an encryption key by using the pre-designated number of the host system which is unique to each system and not externally exposed, and also increases the number of possible encryption keys by using the dip switch, increased security can be achieved.
Owner:SAMSUNG ELECTRONICS CO LTD
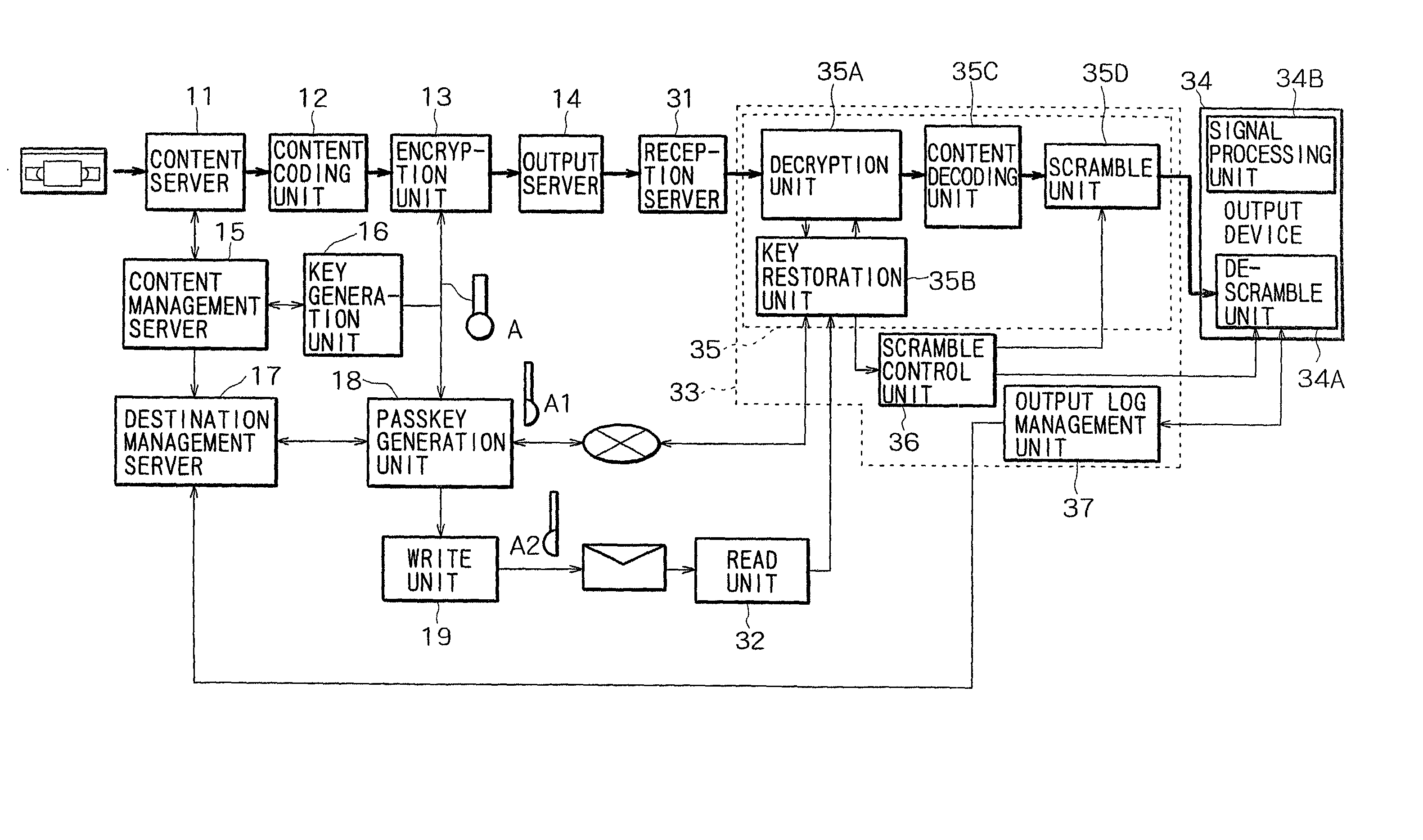
Data delivery method and data delivery system using sets of passkeys generated by dividing an encryption key
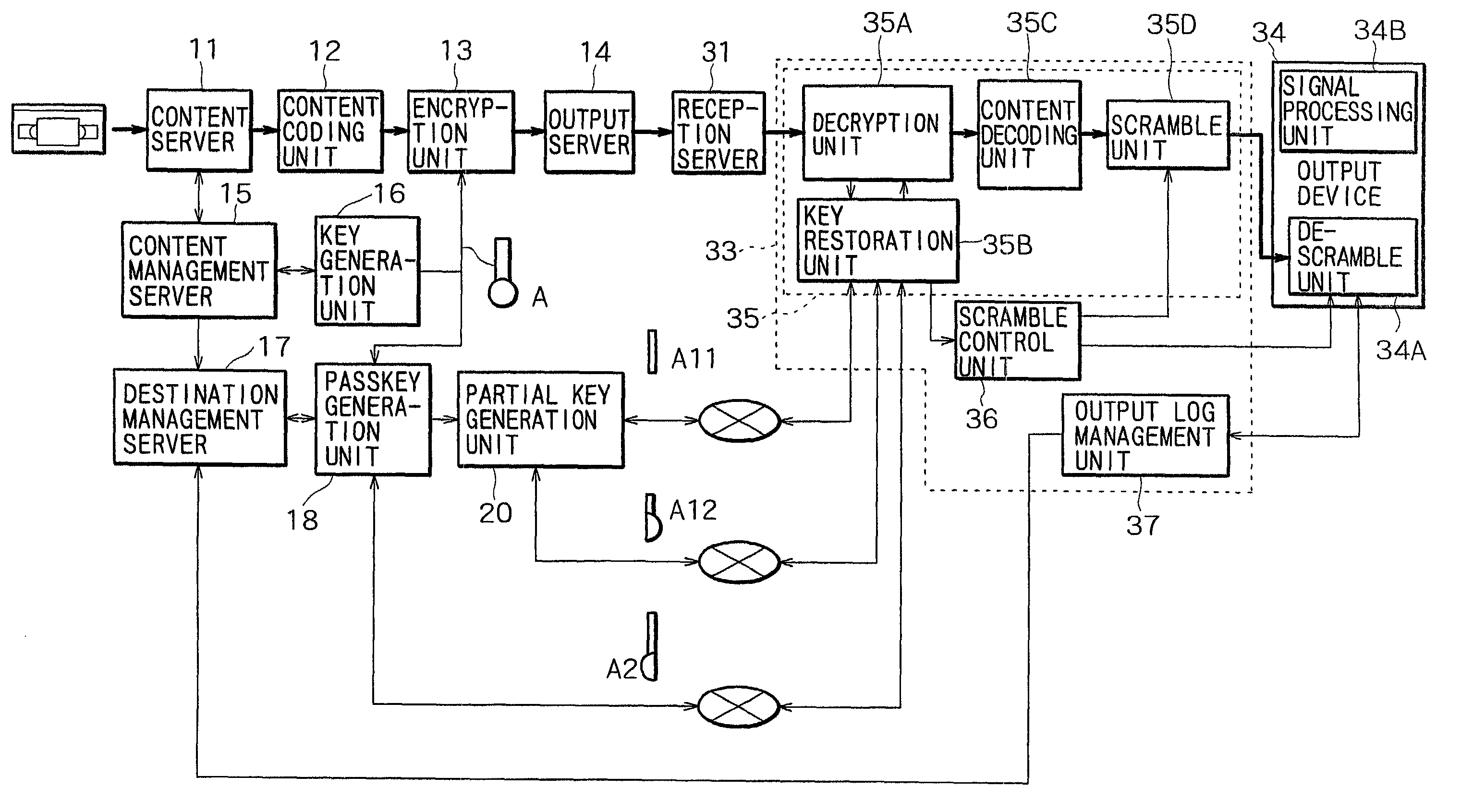
InactiveUS7421082B2Low costMinimize timeTelevision system detailsKey distribution for secure communicationDigital dataCryptographic key generation
A data delivery system providing multipoint delivery of encrypted digital data to specific destinations. A plurality of pieces of key information are generated on the basis of an encryption key specific to each digital data item to be delivered. The multiple pieces of key information are delivered over routes which differ from the routes used to deliver the digital data and which further differ from each other. Physically different media or transmission over a network at different times are used to separately transmit different sets of key information.
Owner:SONY CORP
Bio-metric encryption key generator
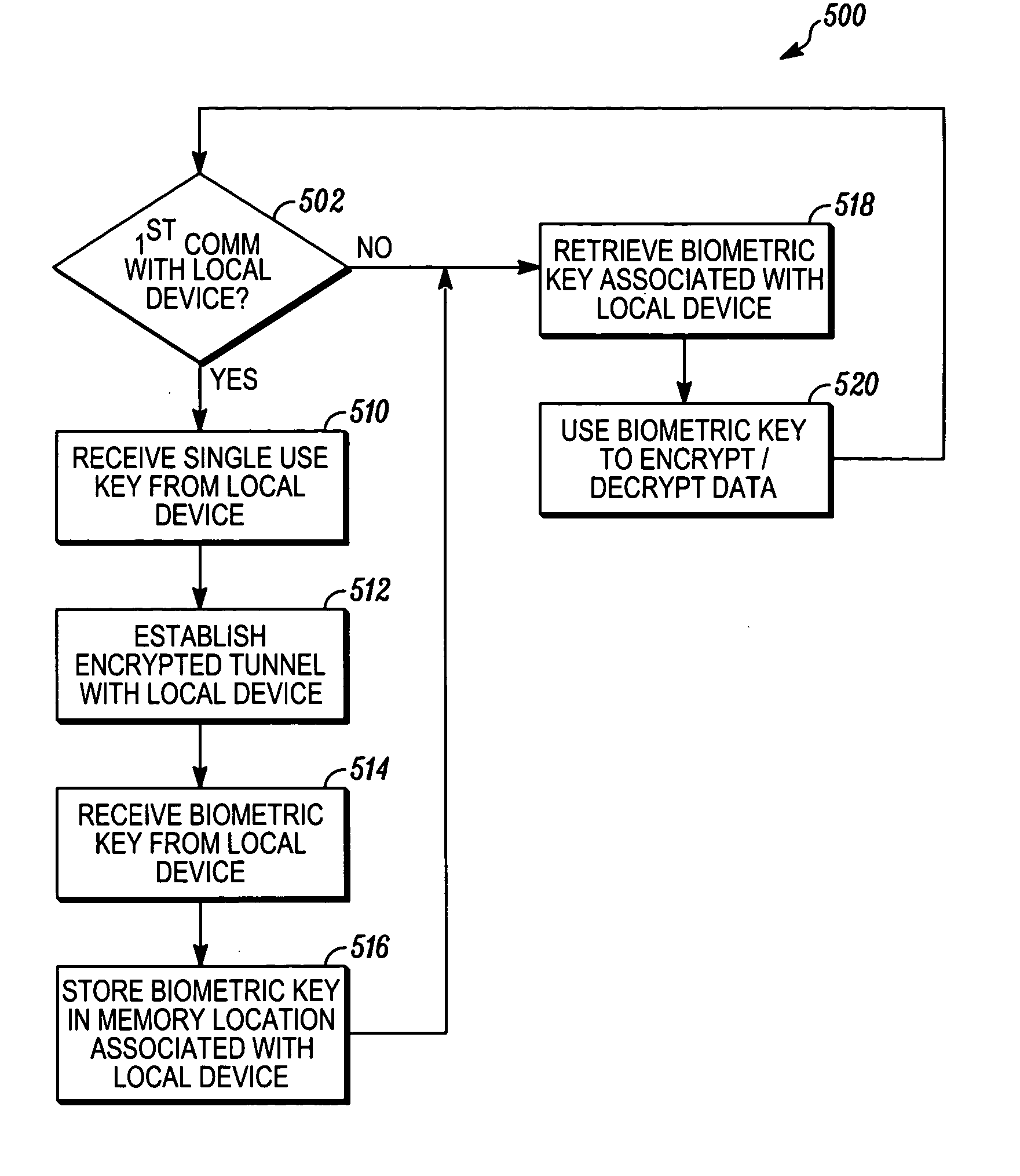
InactiveUS20070239994A1User identity/authority verificationUnauthorized memory use protectionComputer hardwareCryptographic key generation
In a method of facilitating an encrypted communication for use in communication between a local device, operated by a user, and a remote device, a data representation of a biometric feature of the user is received from a biometric input interface. The data representation is transformed into a biometric encryption key using a predetermined set of rules. A device for communicating on a network includes a biometric input interface a processor, and a transceiver. The processor transforms a biometric data input from the biometric input interface into an encryption key and encrypts data for transmission onto the network using the encryption key, thereby generating encrypted data. The transceiver transmits the encrypted data to the network.
Owner:MOTOROLA INC
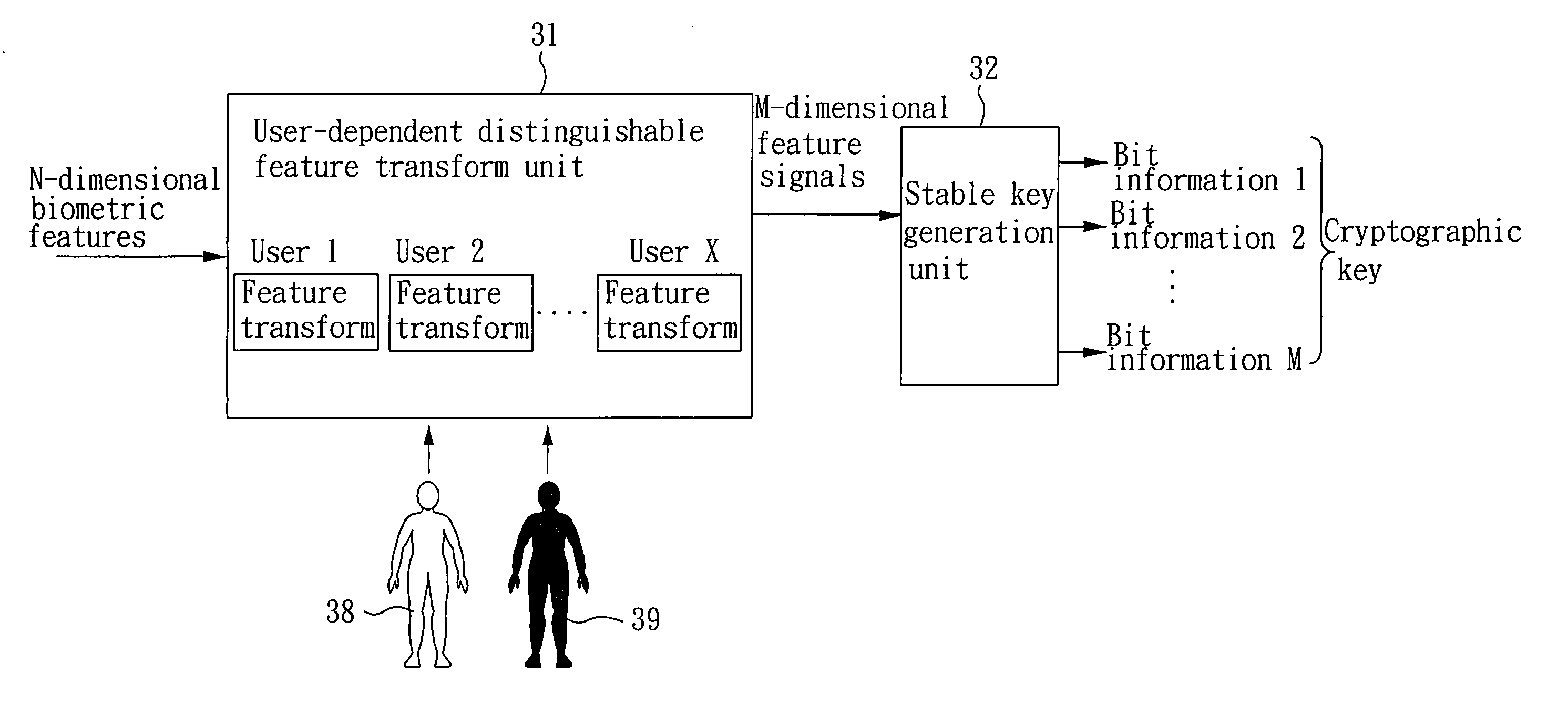
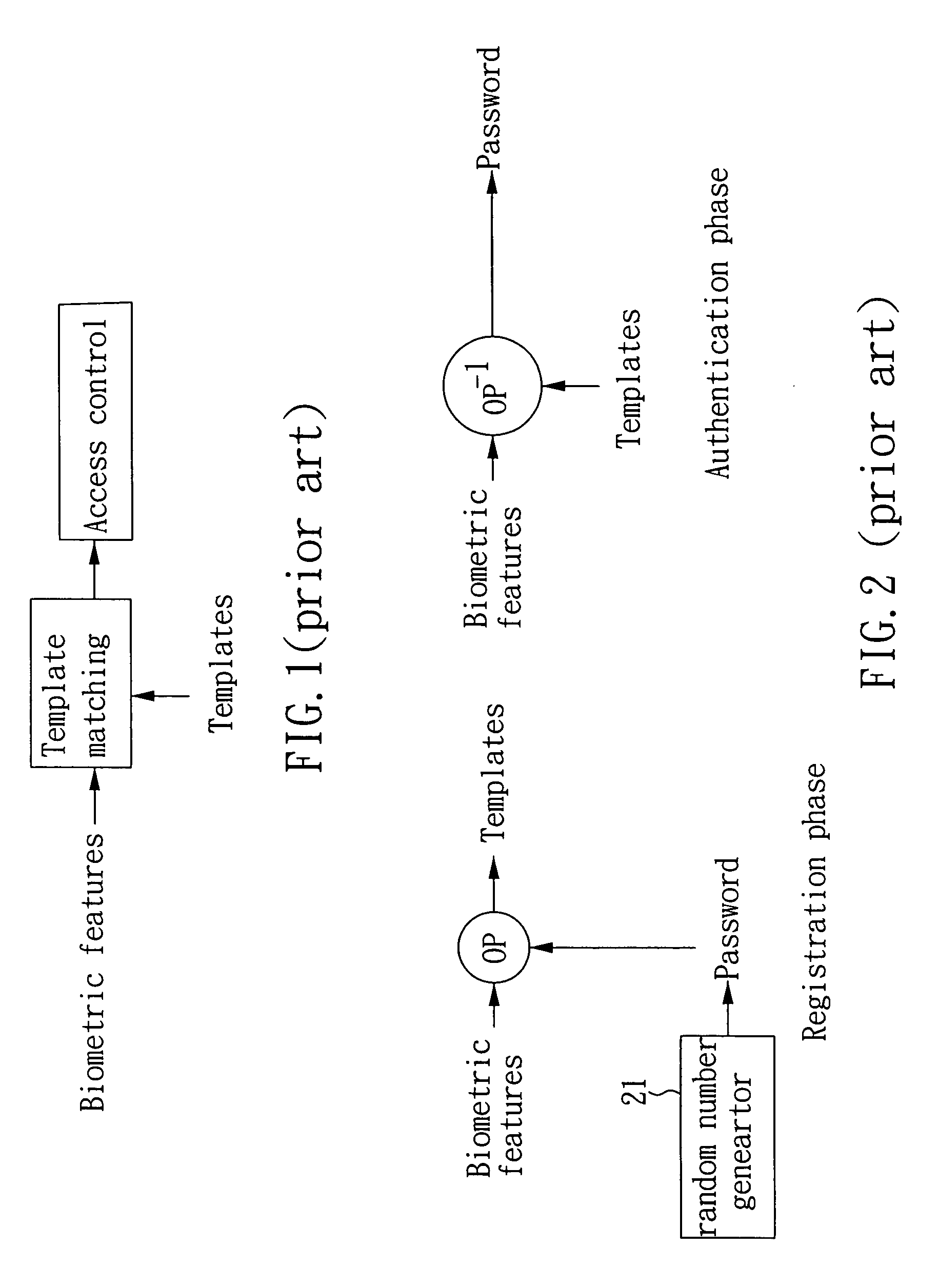
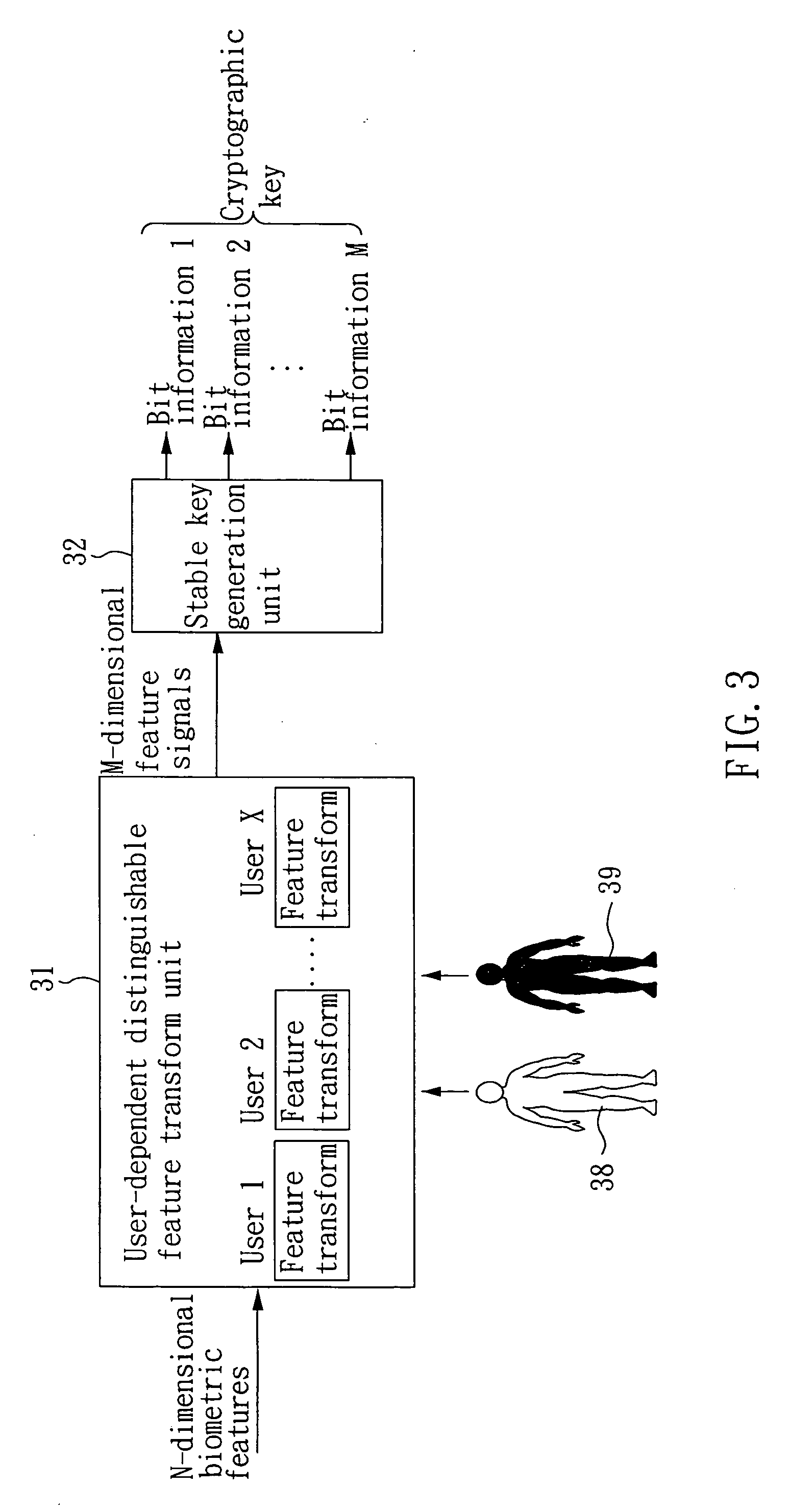
Biometrics-based cryptographic key generation system and method
ActiveUS20060083372A1Increasing length of keyExpand the key spaceComputer security arrangementsSpeech recognitionCryptographic key generationCharacteristic space
The present invention provides a biometrics-based cryptographic key generation system and method. A user-dependent distinguishable feature transform unit provides a feature transformation for each authentic user, which receives N-dimensional biometric features and performs a feature transformation to produce M-dimensional feature signals, such that the transformed feature signals of the authentic user are compact in the transformed feature space while those of other users presumed as imposters are either diverse or far away from those of the authentic user. A stable key generation unit receives the transformed feature signals to produce a cryptographic key based on bit information respectively provided by the M-dimensional feature signals, wherein the length of the bit information provided by the feature signal of each dimension is proportional to the degree of distinguishability in the dimension.
Owner:A10 NETWORKS
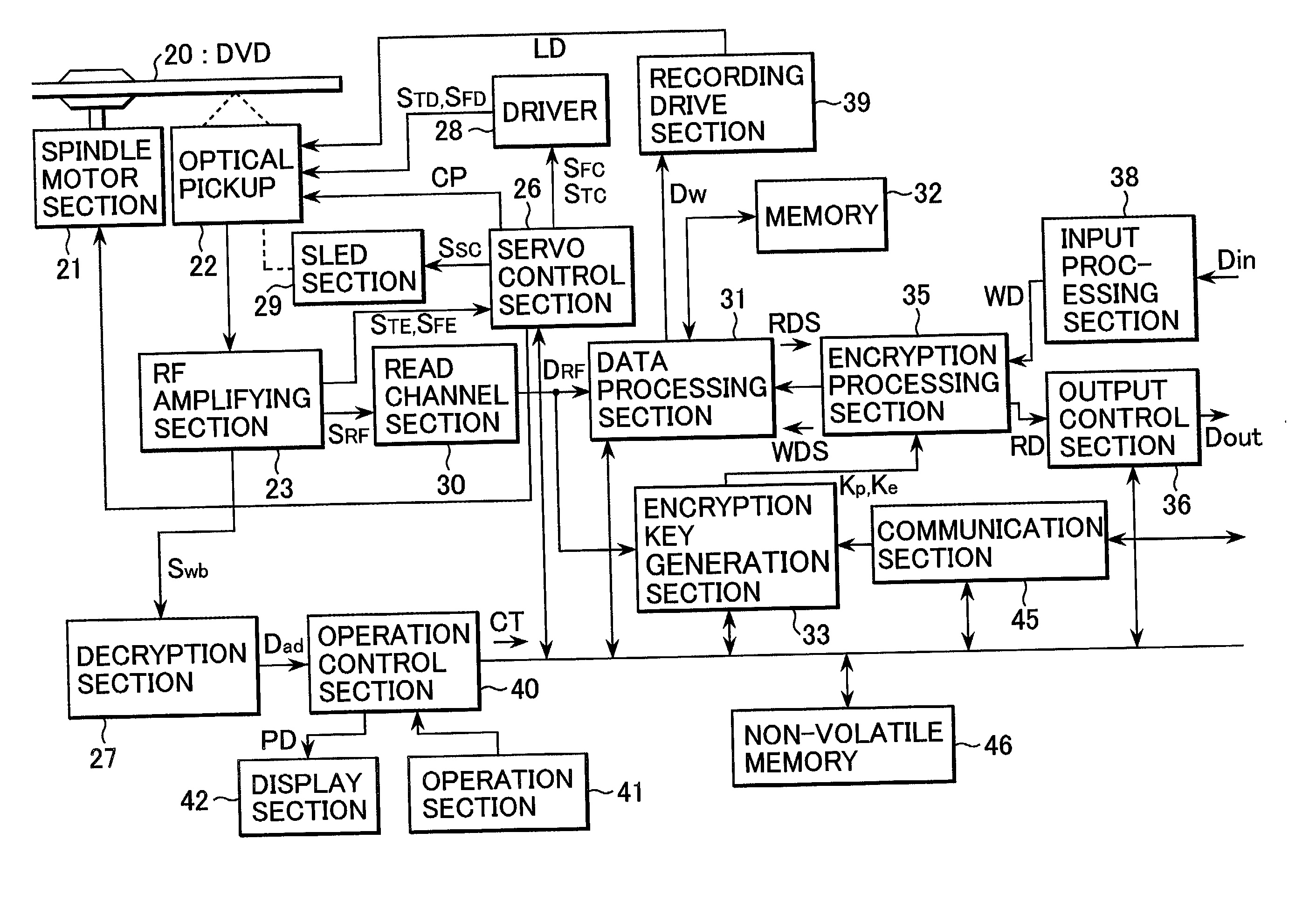
Signal recording medium, content signal generation apparatus, content signal reproduction method, and content signal reproduction apparatus
ActiveUS20020159594A1Controlled reproductionEasy to adaptTelevision system detailsMultiple keys/algorithms usageComputer hardwareCryptographic key generation
A content signal having a control signal added thereto indicating whether or not a playback restricting function for restricting reproduction is activated is recorded on a disk. When an encryption key generation section determines at the time of reproduction that the content signal has the control signal added thereto indicating that the playback restricting function is activated, it is determined whether or not a playback permission condition is satisfied. The playback permission condition is read from the disk, or acquired via a communication section if it is not stored on the disk. A correct encryption key Kp is supplied to an encryption processing section only when the playback permission condition is satisfied. The encryption processing section decrypts the encrypted content signal recorded on the disk with the encryption key Kp and the correctly decrypted content signal is outputted from an output control section.
Owner:SONY CORP
System for scrambling and methods for use therewith
ActiveUS20120033809A1Unauthorized memory use protectionHardware monitoringCryptographic key generationBlock code
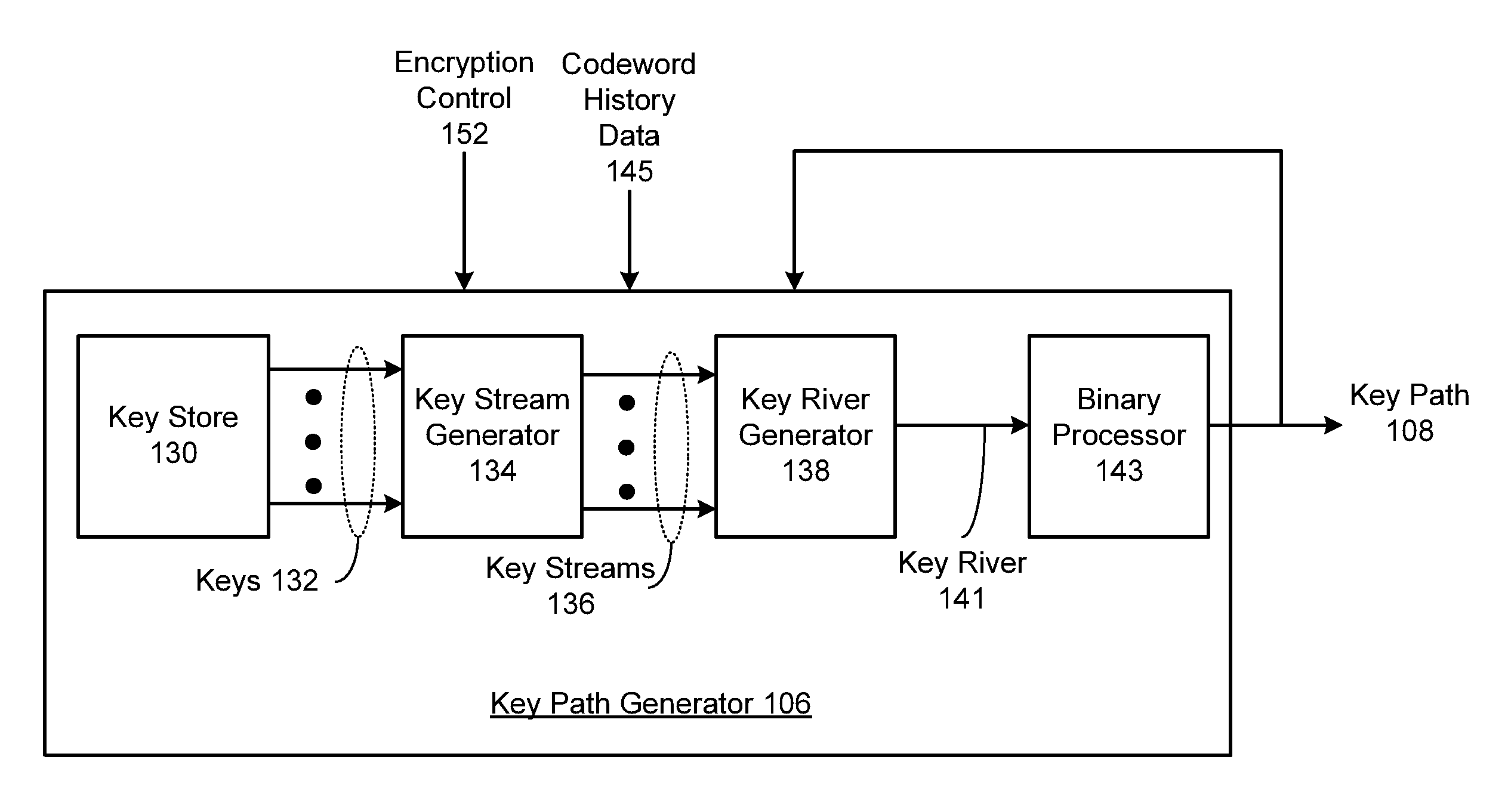
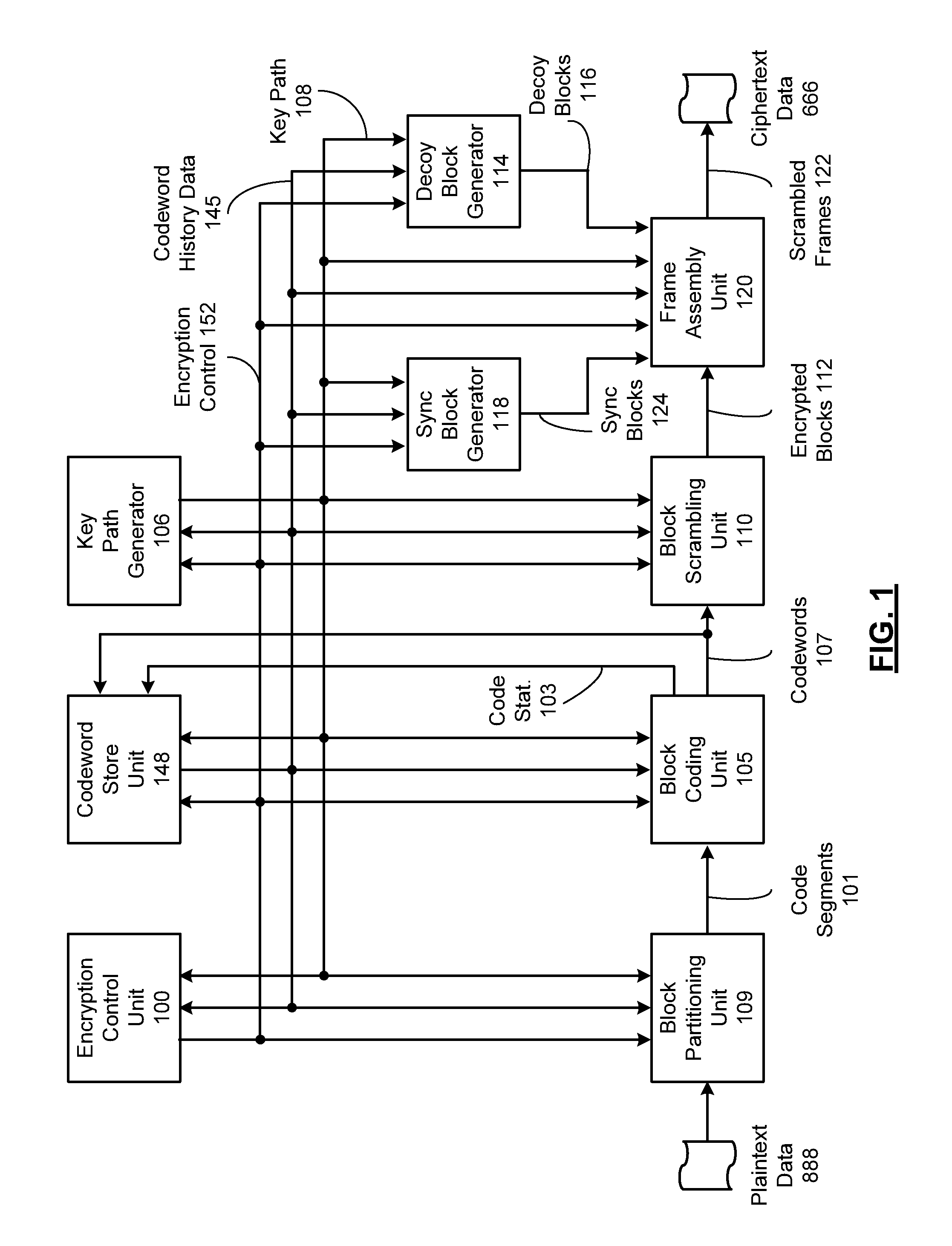
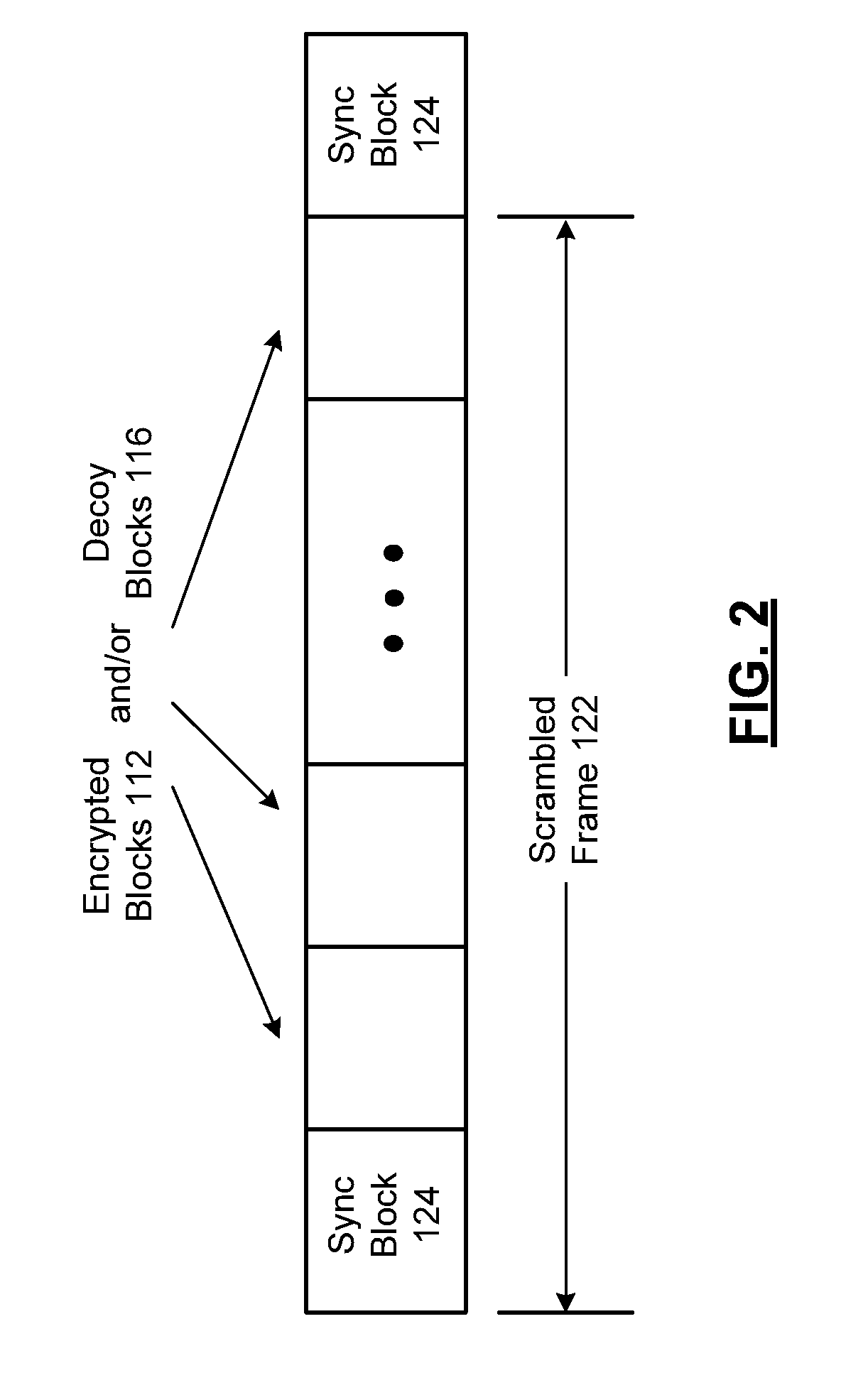
A system includes a key path generator that generates a key path based on a plurality of encryption keys. A block coding unit generates a plurality of codewords based on a plurality of data blocks. A block scrambling unit scrambles the plurality of codewords to generate a plurality of encrypted blocks by entropy processing, chaos processing and permutation processing each of the plurality of codewords, based on the plurality of encryption keys.
Owner:HUANG LAWRENCE P
User authentication based on asymmetric cryptography utilizing RSA with personalized secret
InactiveUS7958362B2Digital data processing detailsPublic key for secure communicationPersonalizationCryptographic key generation
A method for authenticating a user to a computer system is disclosed, comprising using a first input and a second input in producing a digital signature in response to a challenge. The digital signature is valid when the first input matches a personalized secret and the second input matches a trio comprising a public modulus, a public exponent, and a private-key-dependent exponent. Selection of the personalized secret is discretionary and changeable. A crypto-key generation process uses the personalized secret and two primes as input to produce the trio. The public modulus and public exponent of the trio form a public key used in digital signature validation. Also disclosed is a business method that replaces the conventional public-key certificate with an agreement on the user's public key.
Owner:CHANG GUNG UNIVERSITY
Information processing apparatus, data processing apparatus, and methods thereof
InactiveUS20080031446A1Television system detailsRecord information storageInformation processingData validation
An object of this invention is to protect the right of a content holder without any necessity of a special storage medium incorporating a copyright protecting mechanism when the content holder does not coincide with a content creator. Information for encryption key generation is input. An encryption key is generated from the information for encryption key generation. Encryption key verification data is acquired from a storage medium, and the validity of the generated encryption key is authenticated based on the verification data. Generated data is encrypted by using the encryption key whose validity is authenticated by the authentication. The encrypted data is stored in the storage medium.
Owner:CANON KK
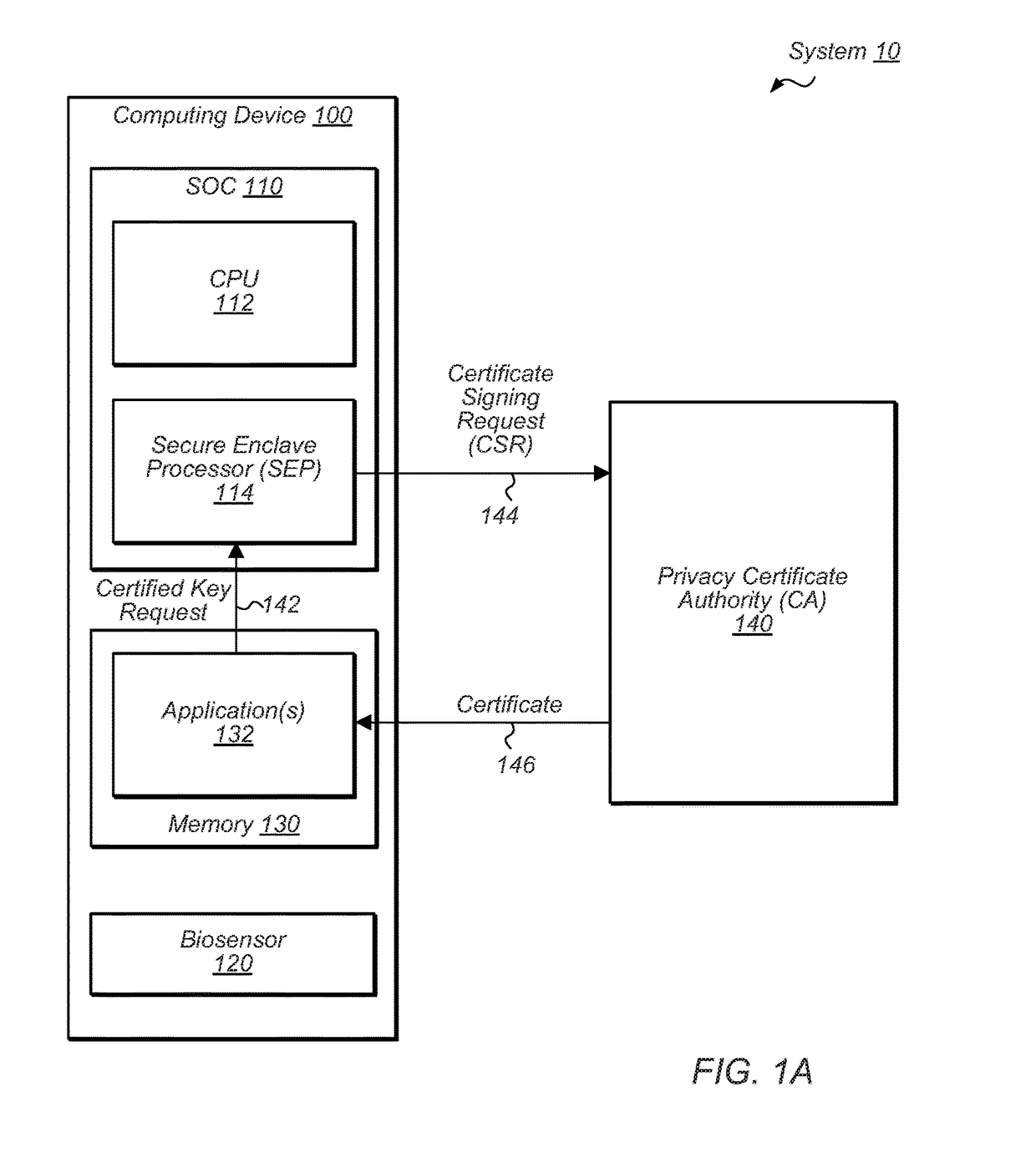
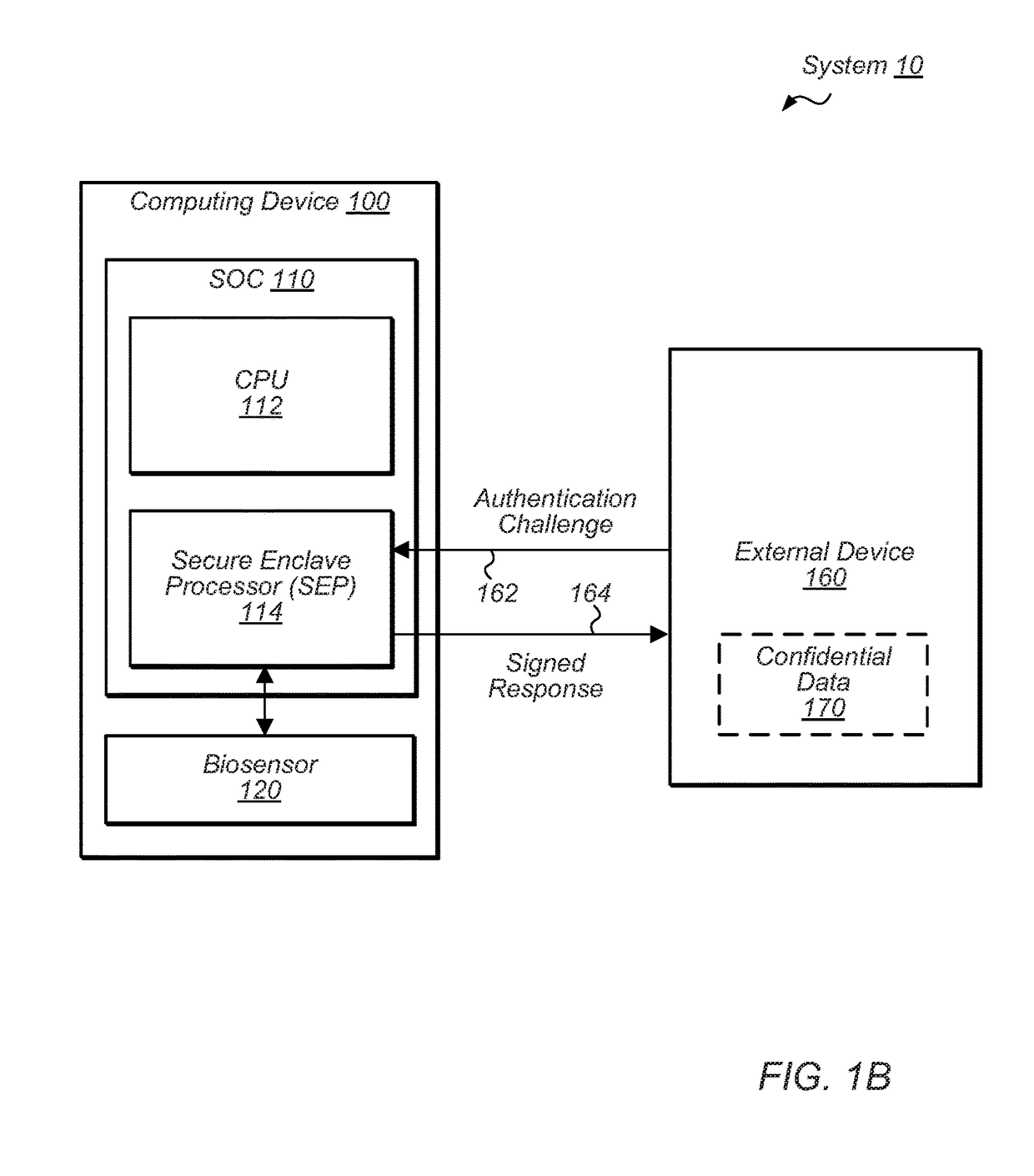
Secure circuit for encryption key generation
ActiveUS20170373843A1Easy to useKey distribution for secure communicationMultiple keys/algorithms usageCryptographic key generationCertificate signing request
Techniques are disclosed relating to relating to a public key infrastructure (PKI). In one embodiment, an integrated circuit is disclosed that includes at least one processor and a secure circuit isolated from access by the processor except through a mailbox mechanism. The secure circuit is configured to generate a key pair having a public key and a private key, and to issue, to a certificate authority (CA), a certificate signing request (CSR) for a certificate corresponding to the key pair. In some embodiments, the secure circuit may be configured to receive, via the mailbox mechanism, a first request from an application executing on the processor to issue a certificate to the application. The secure circuit may also be configured to perform, in response to a second request, a cryptographic operation using a public key circuit included in the secure circuit.
Owner:APPLE INC
Encryption method and system based on attributes
InactiveCN104363215APrivacy protectionReduce loadPublic key for secure communicationCryptographic key generationAttribute-based encryption
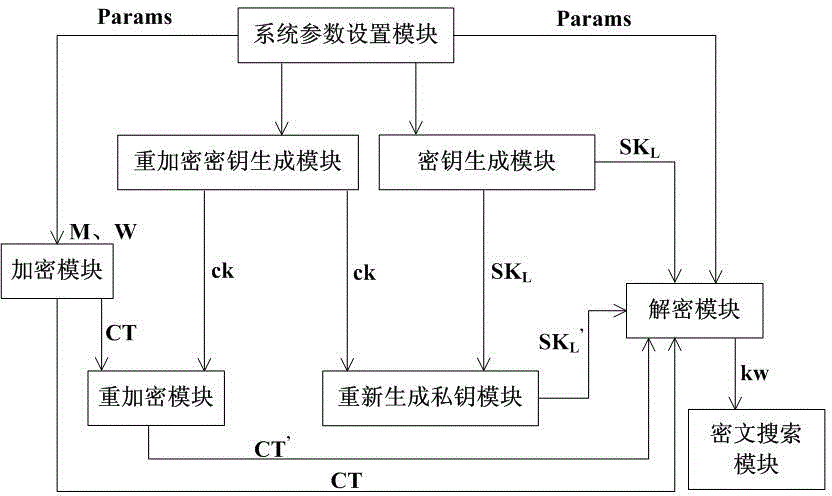
The invention discloses an encryption system based on attributes. The encryption system comprises a system parameter setting module, a key generation module, an encryption module, a decryption module, a cryptograph retrieval module, a re-encryption key generation module, a re-encryption module and a private key re-generation module, wherein the system parameter setting module is used for generating system public parameters, the key generation module is used for generating private keys of users for decrypting messages according to attribute sets of the users; the encryption module is used for encrypting the messages; the decryption module is used for decrypting the messages, the cryptograph retrieval module is used for retrieving the cryptographs; the re-encryption key generation module is used for generating re-encryption keys and updating the cryptographs and the private keys; the re-encryption module is used for re-encrypting the messages on the basis of the original cryptographs; the private key re-generation module is used for updating the private keys of the users. The invention further discloses an encryption method based on the attributes. By the encryption system and method based on the attributes, the problem of privacy protection during cloud computing can be solved, attribute withdrawal and safety retrieval of the cryptographs are supported, and the encryption system is high in flexibility.
Owner:HOHAI UNIV
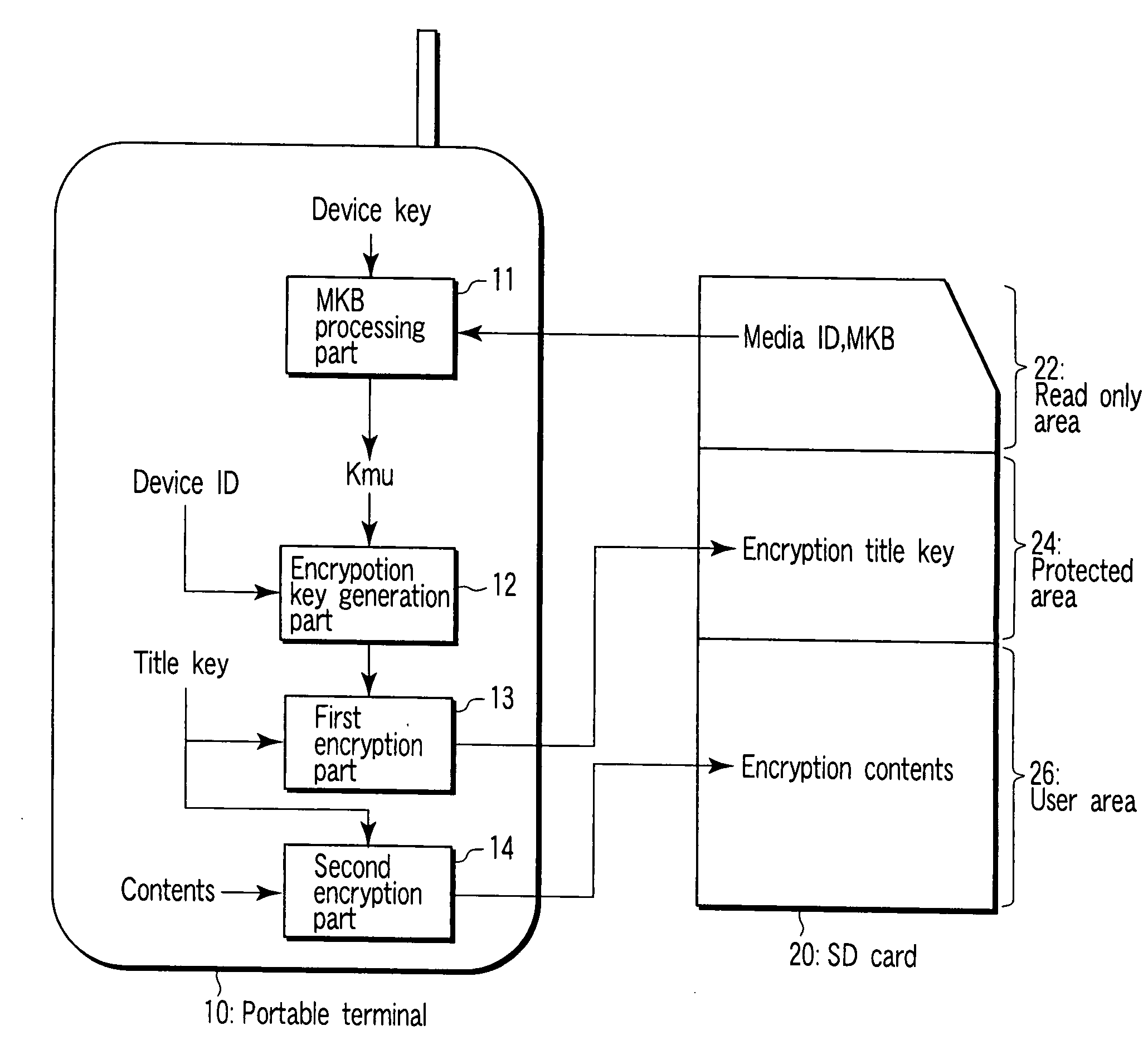
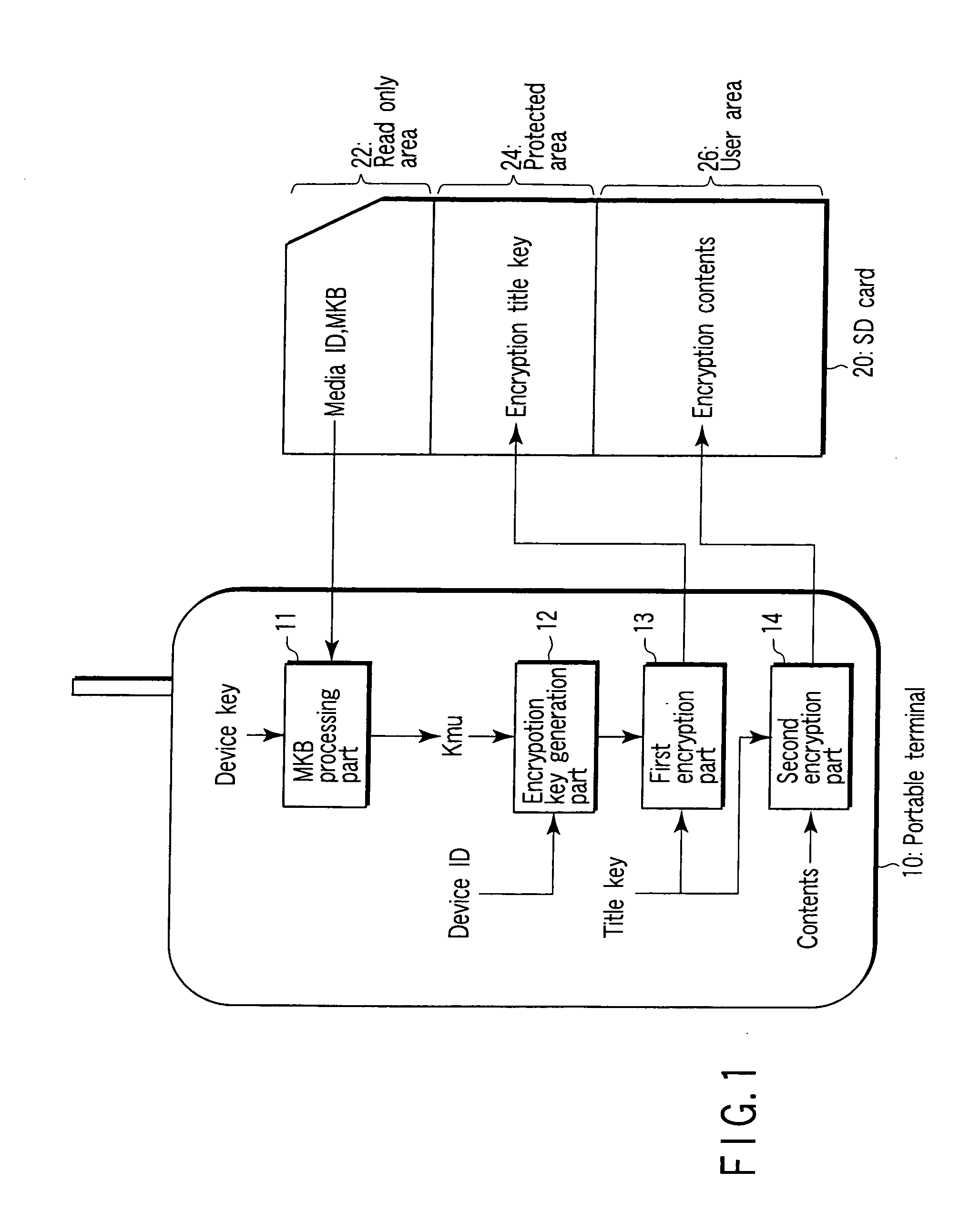
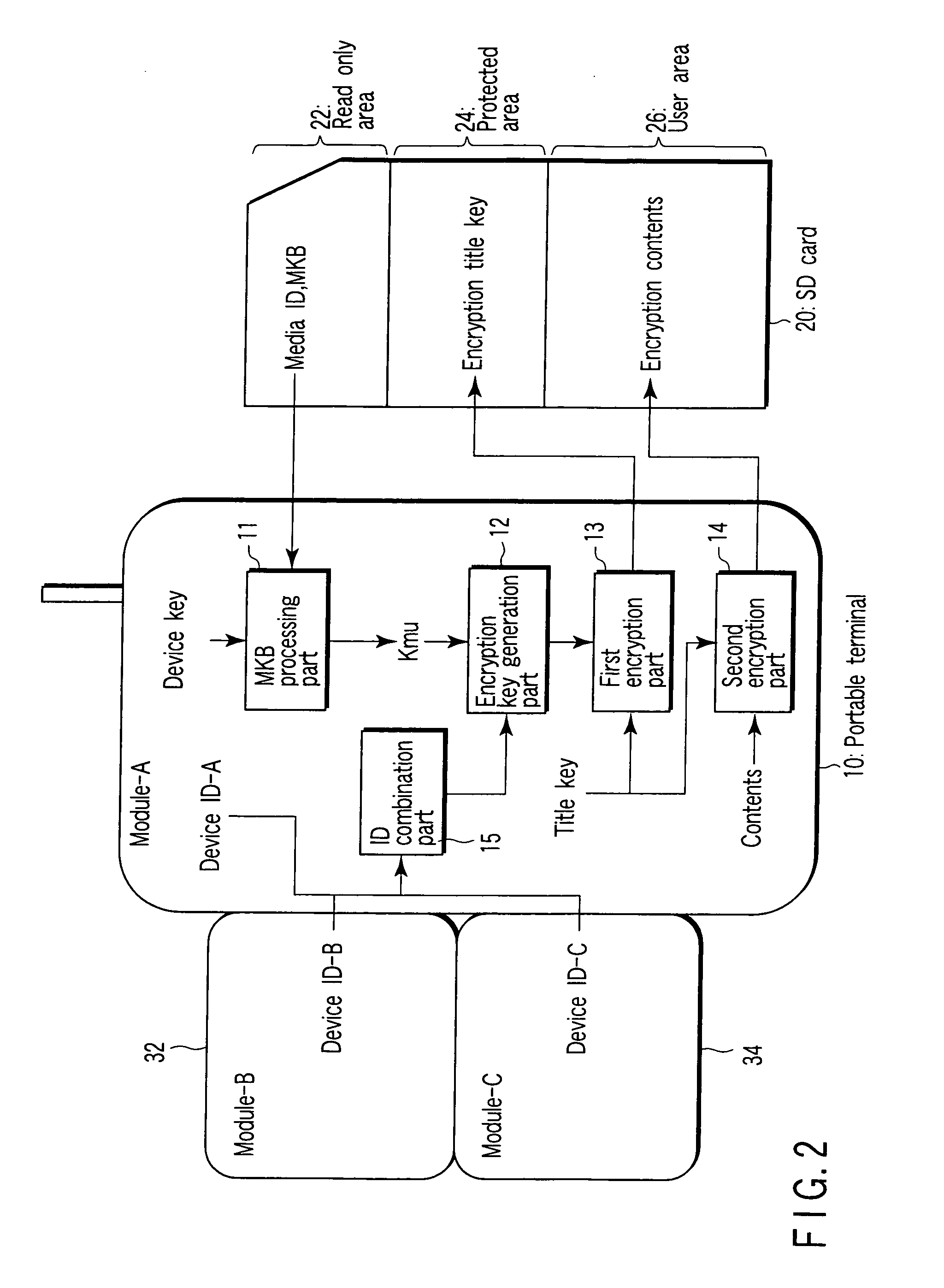
Portable terminal
InactiveUS20070214370A1Reducing risk of hackingReduce riskKey distribution for secure communicationDigital data processing detailsCryptographic key generationComputer module
A portable terminal capable of encrypting a content and connectable to a module and removable memory card which stores an encrypted content, comprising an ID combination part configured to generate a combination ID by combining a device ID of the portable terminal and a device ID of at least the one module, and an encryption key generation part configured to generate an encryption key by using the combination ID generated from the ID combination part.
Owner:KK TOSHIBA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com