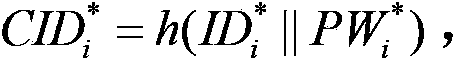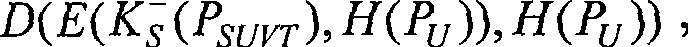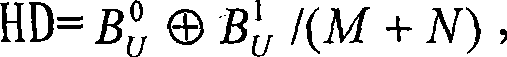Patents
Literature
38 results about "Biometric encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
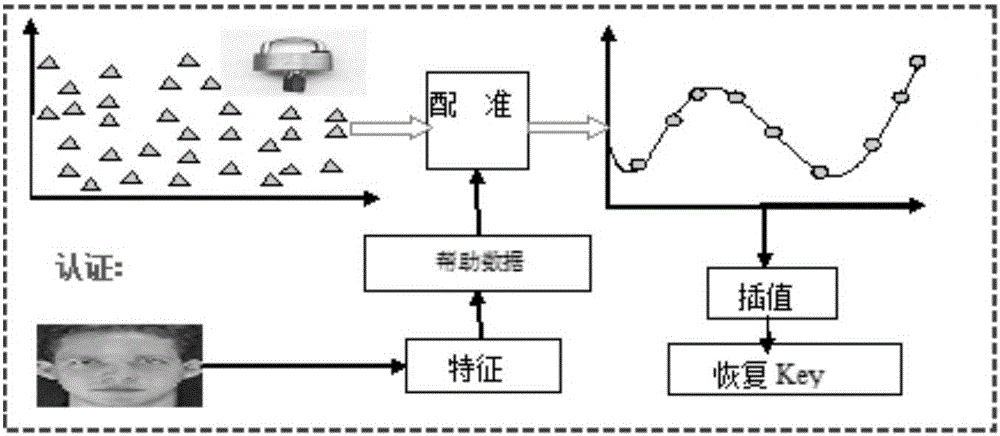
Biometric Encryption (BE) is a group of emerging technologies that securely bind a digital key to a biometric or generate a digital key from the biometric, so that no biometric image or template is stored.
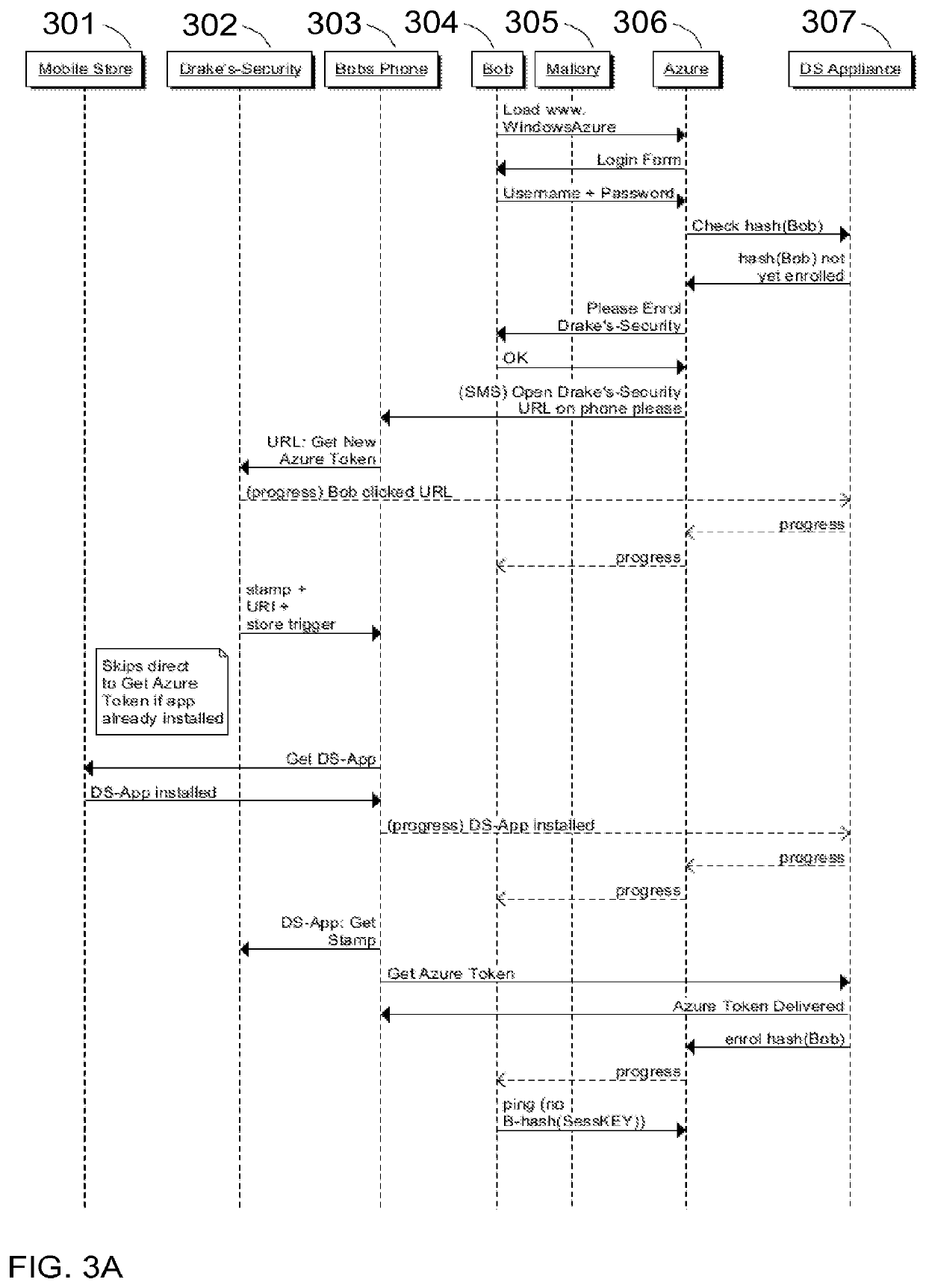
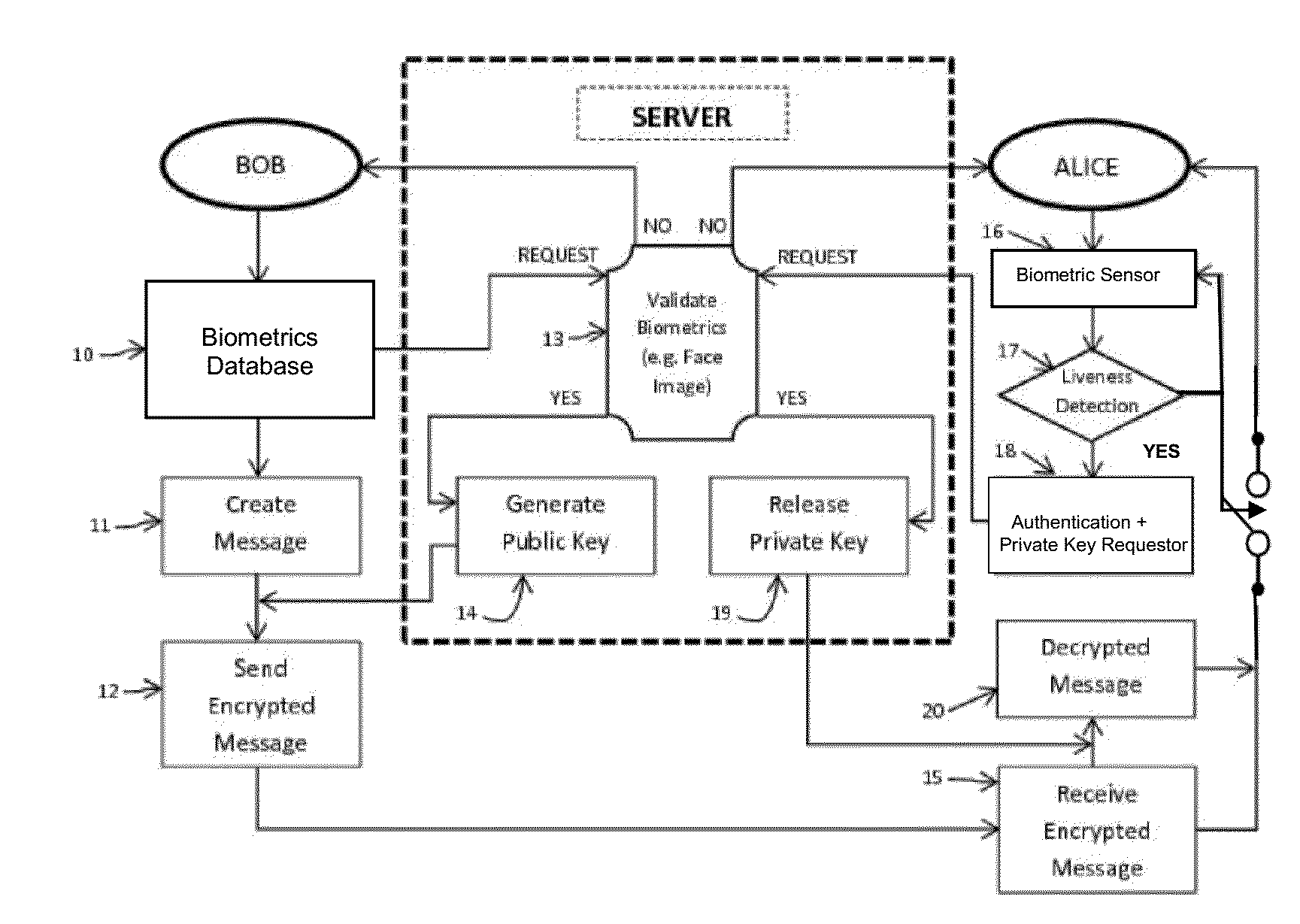
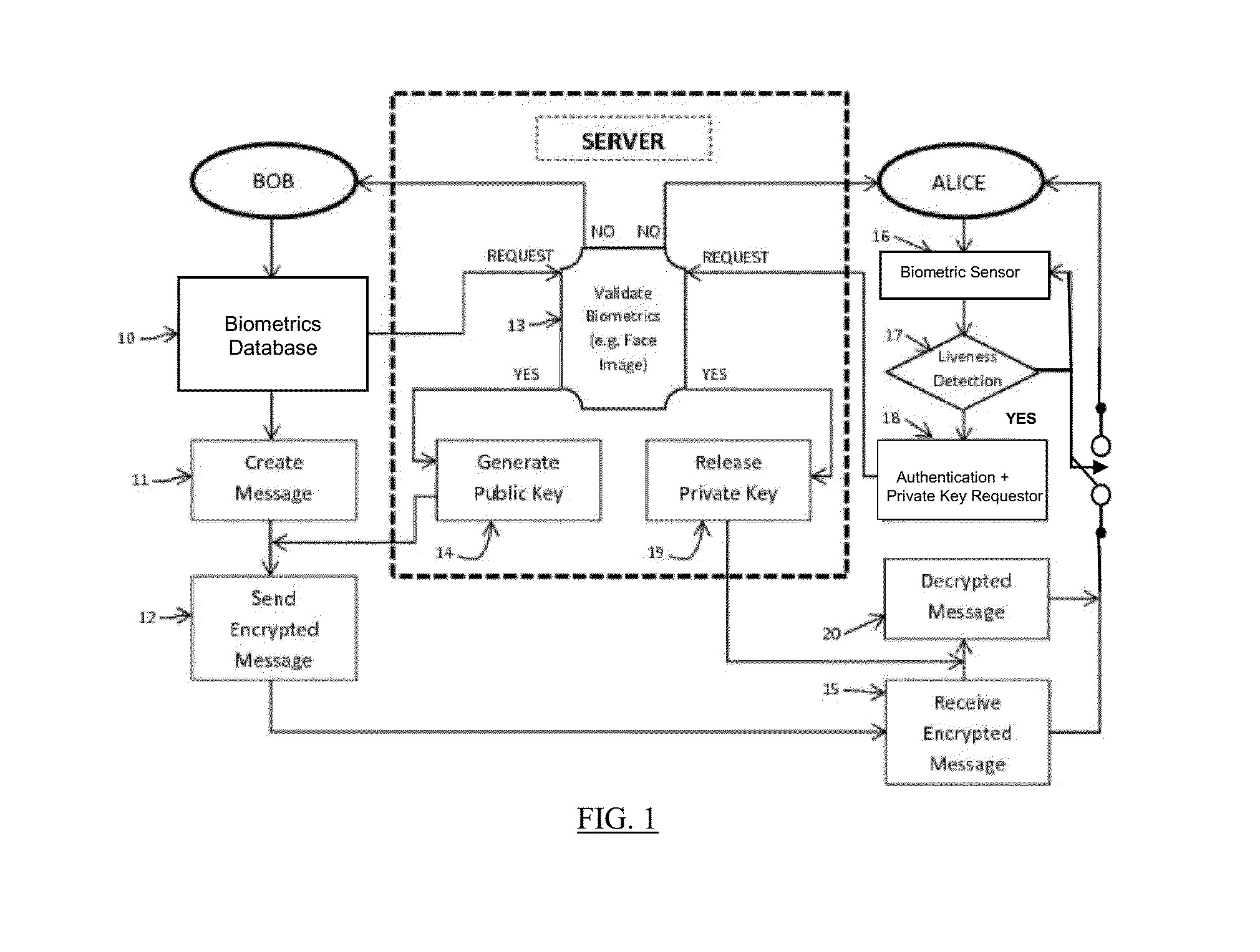
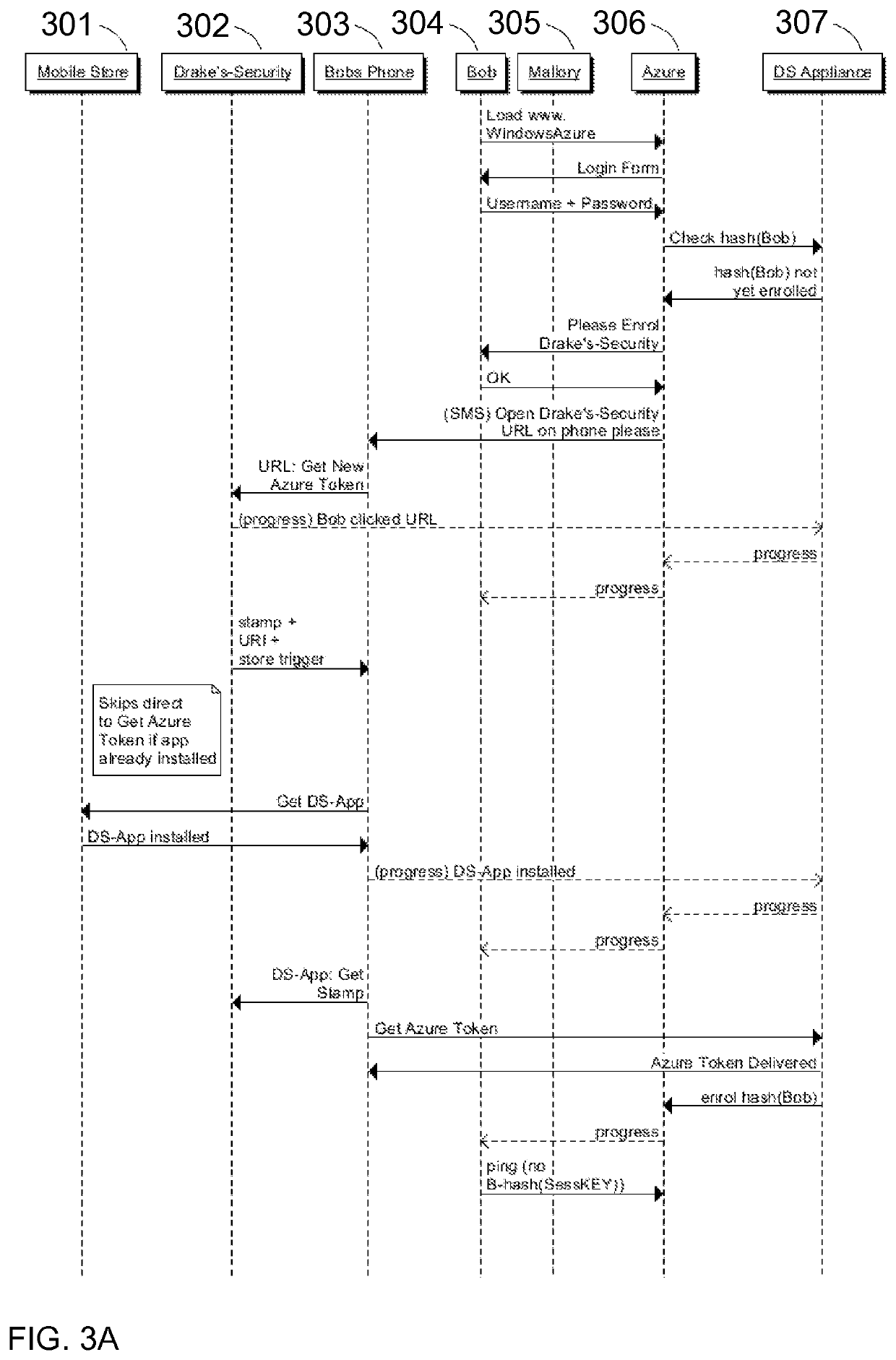
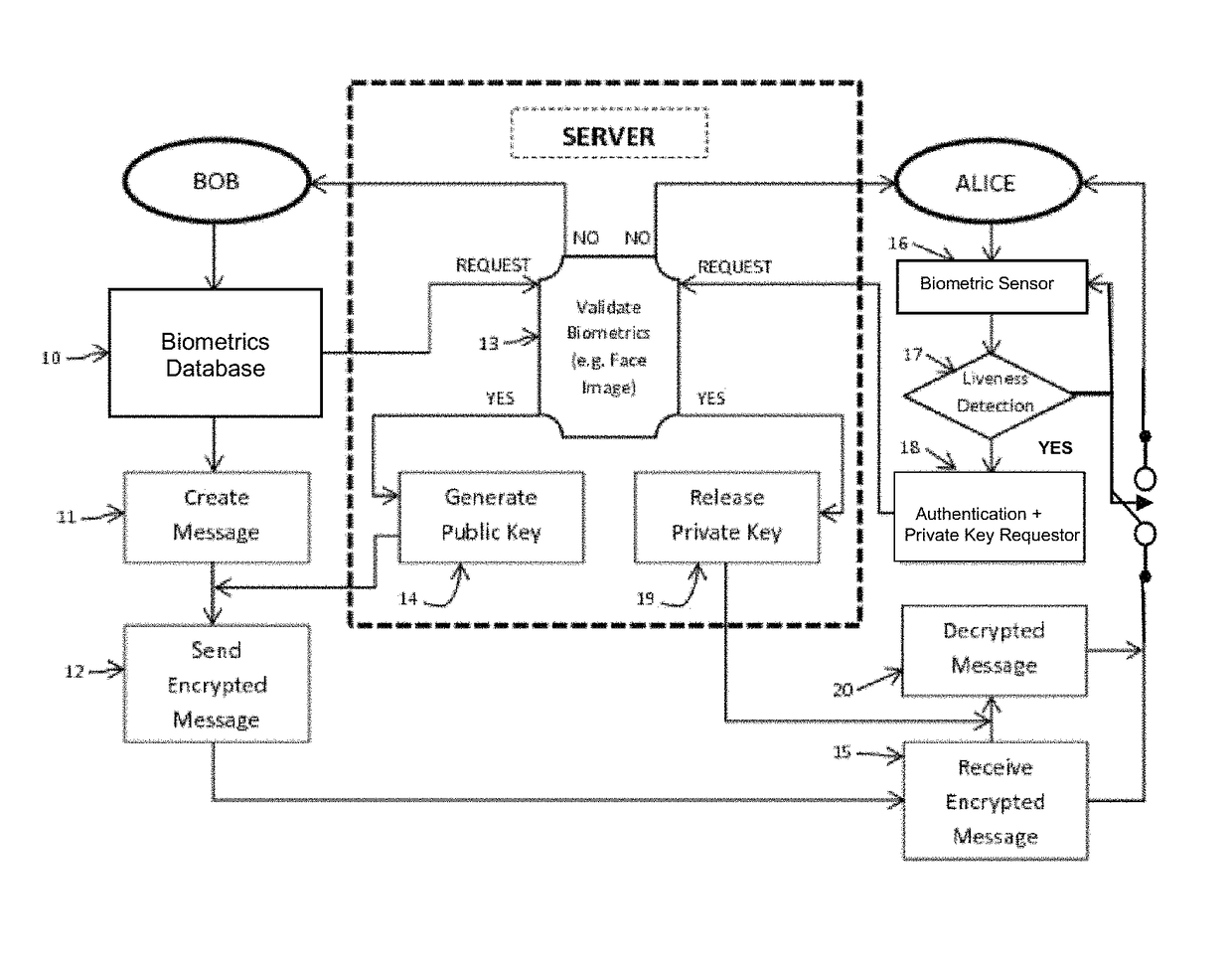
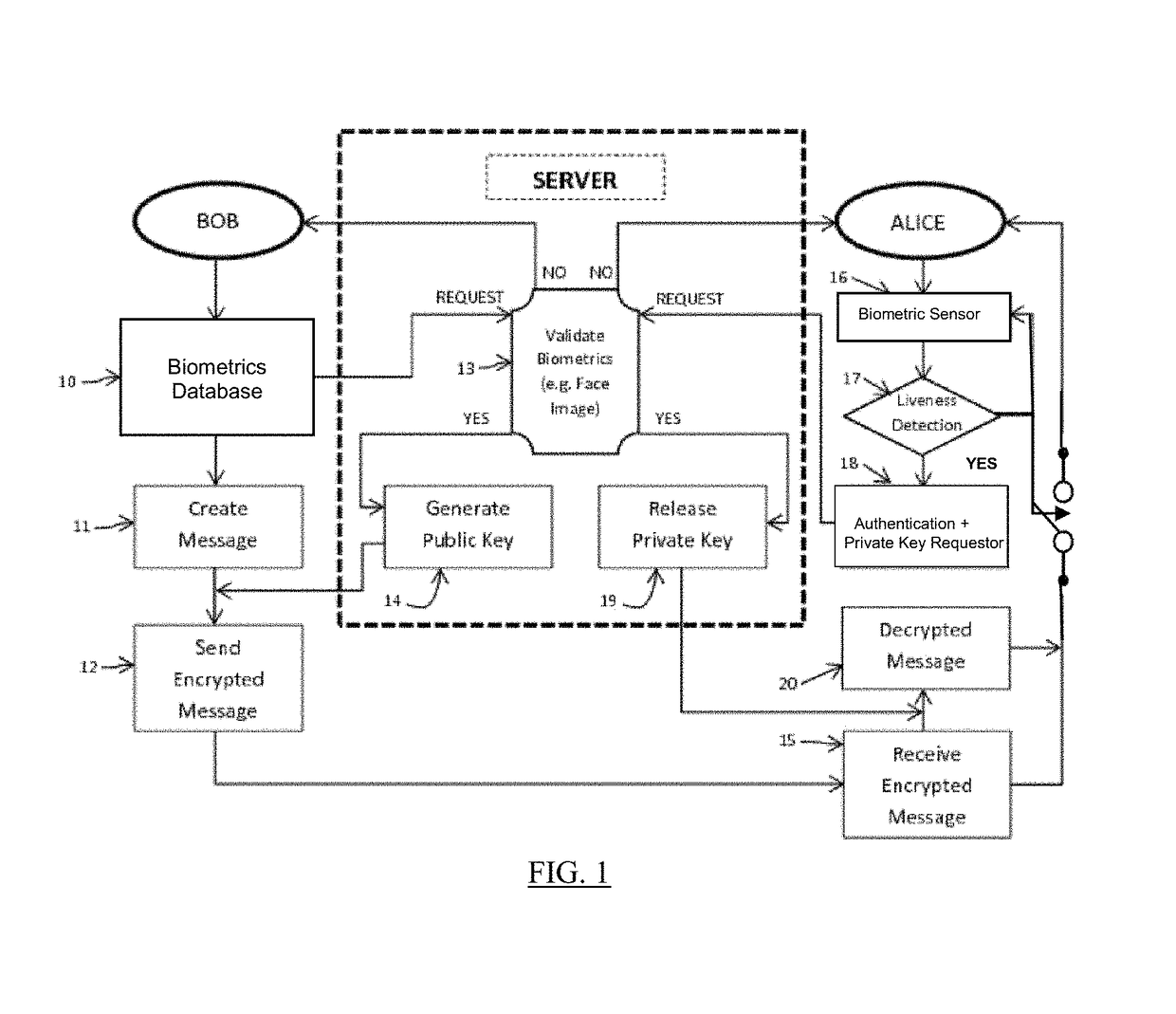
Mutual authentication security system with detection and mitigation of active man-in-the-middle browser attacks, phishing, and malware and other security improvements.
ActiveUS20170346851A1Multiple keys/algorithms usagePublic key for secure communicationWeb sitePhishing
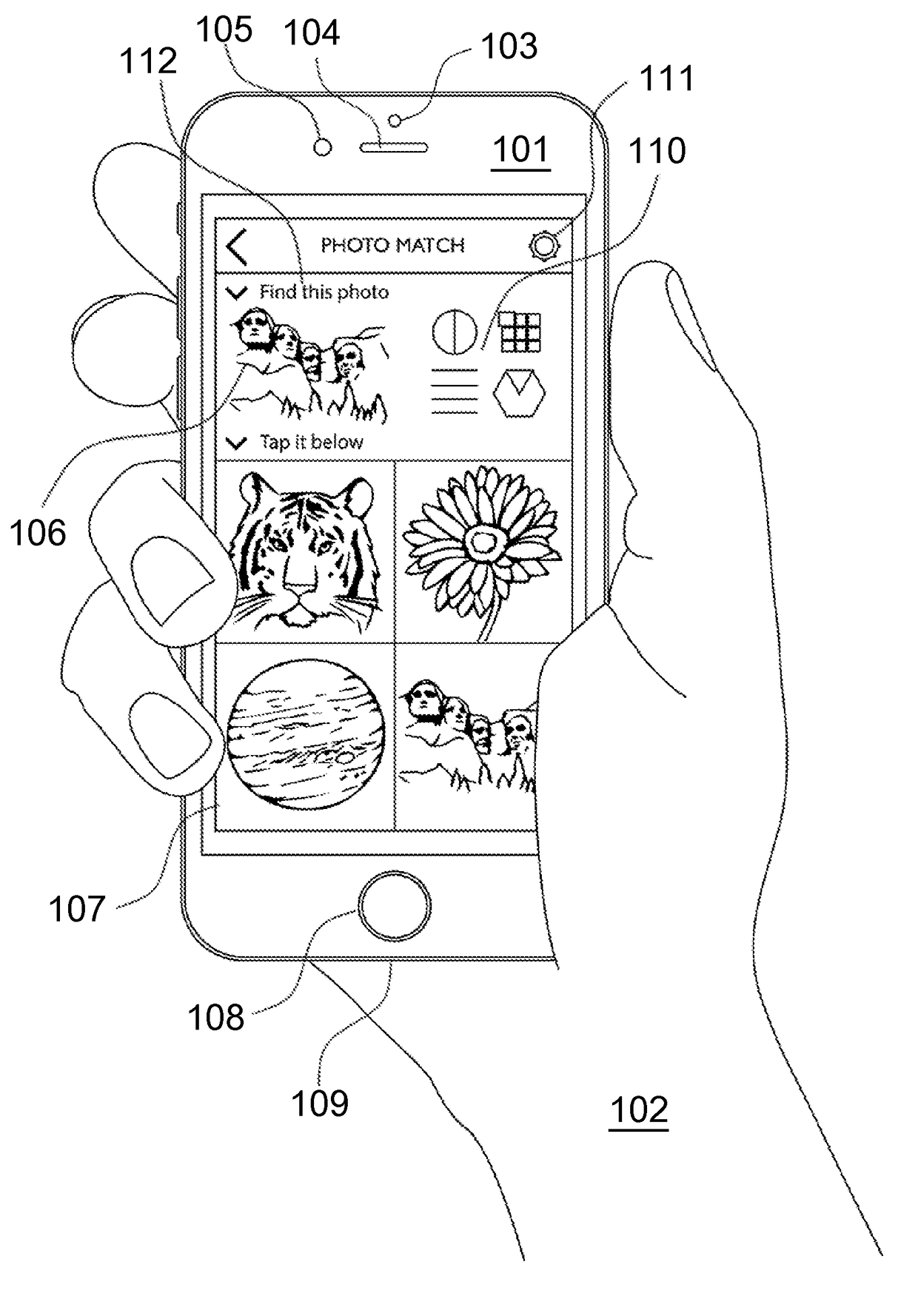
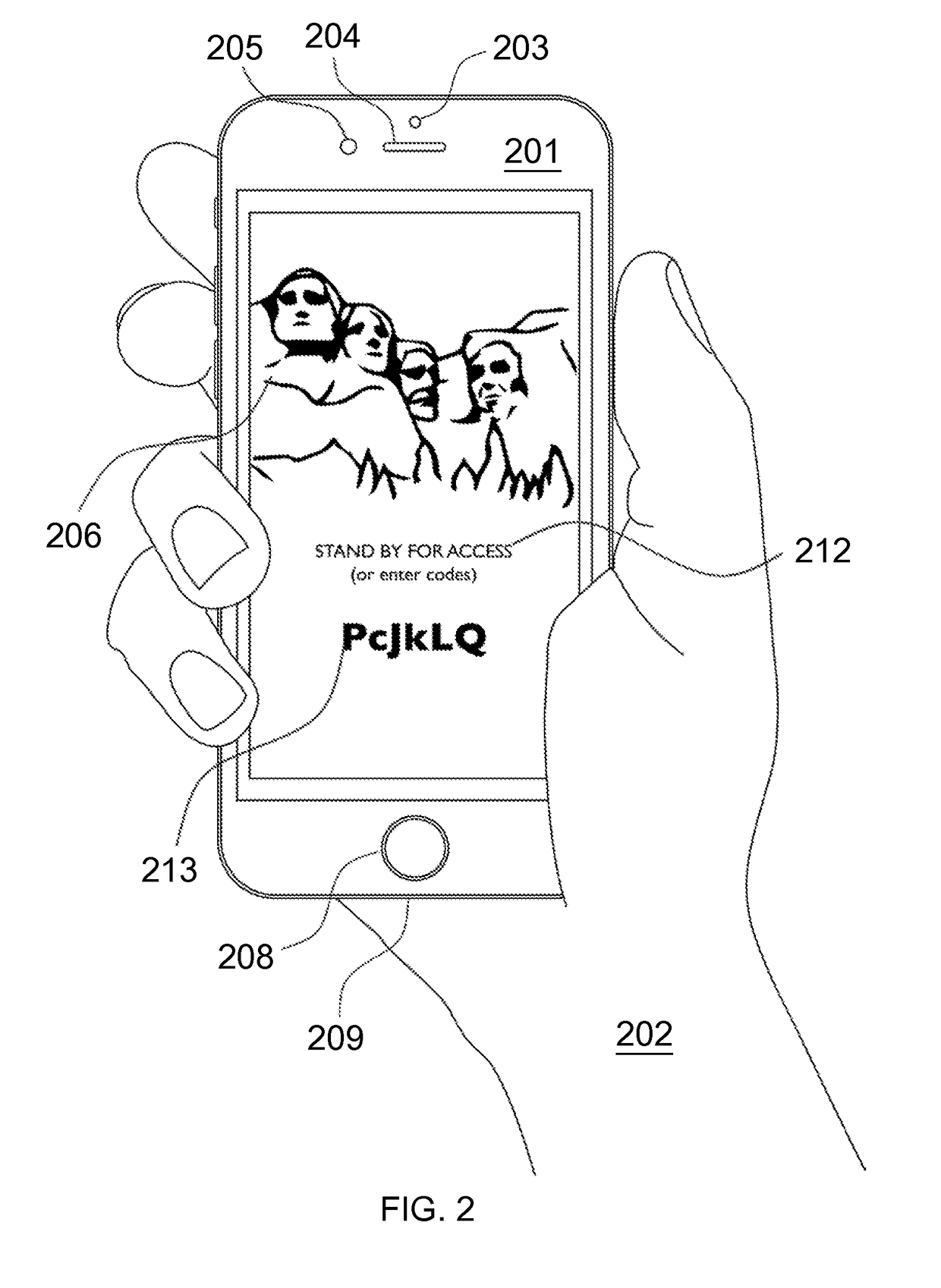
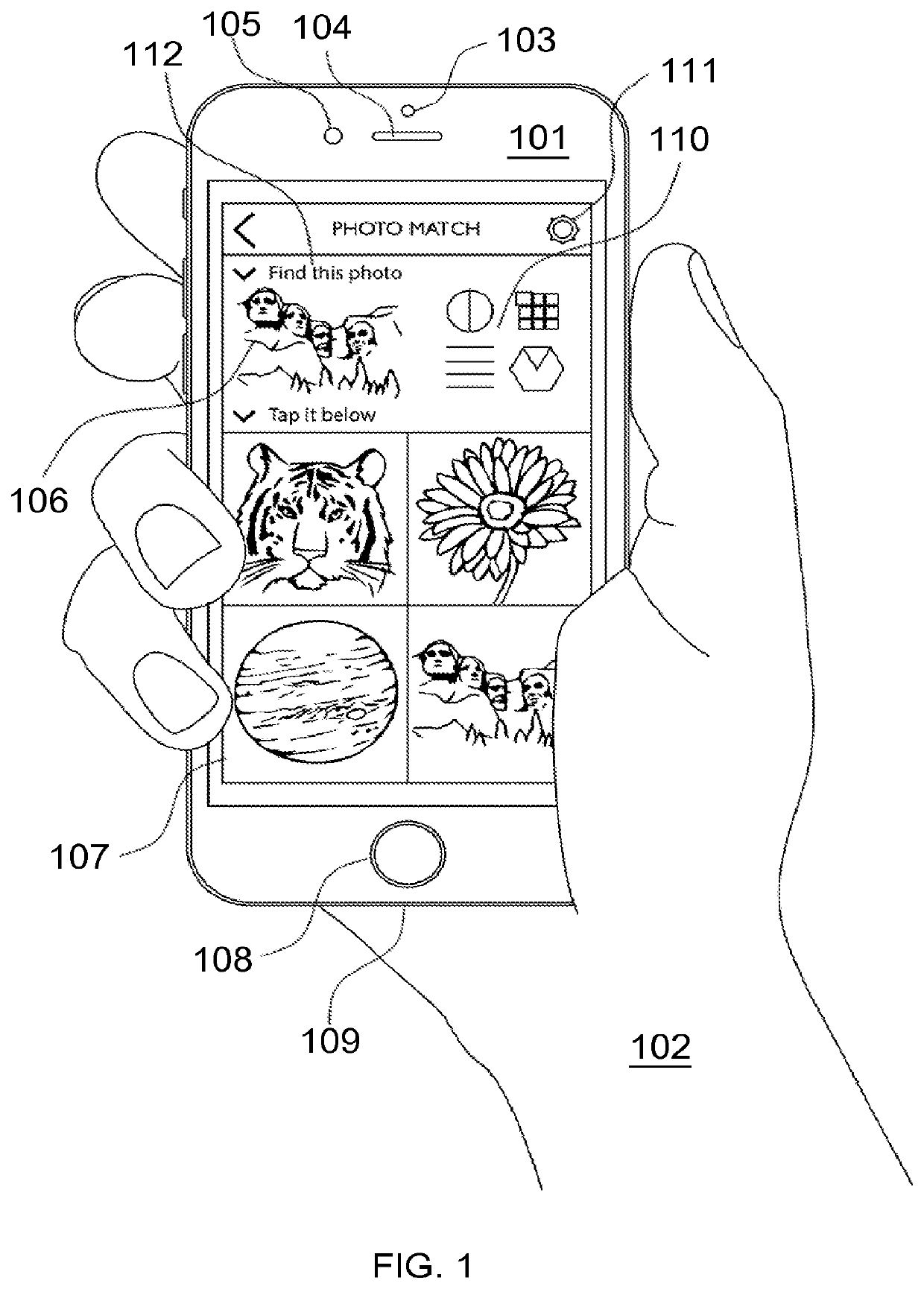
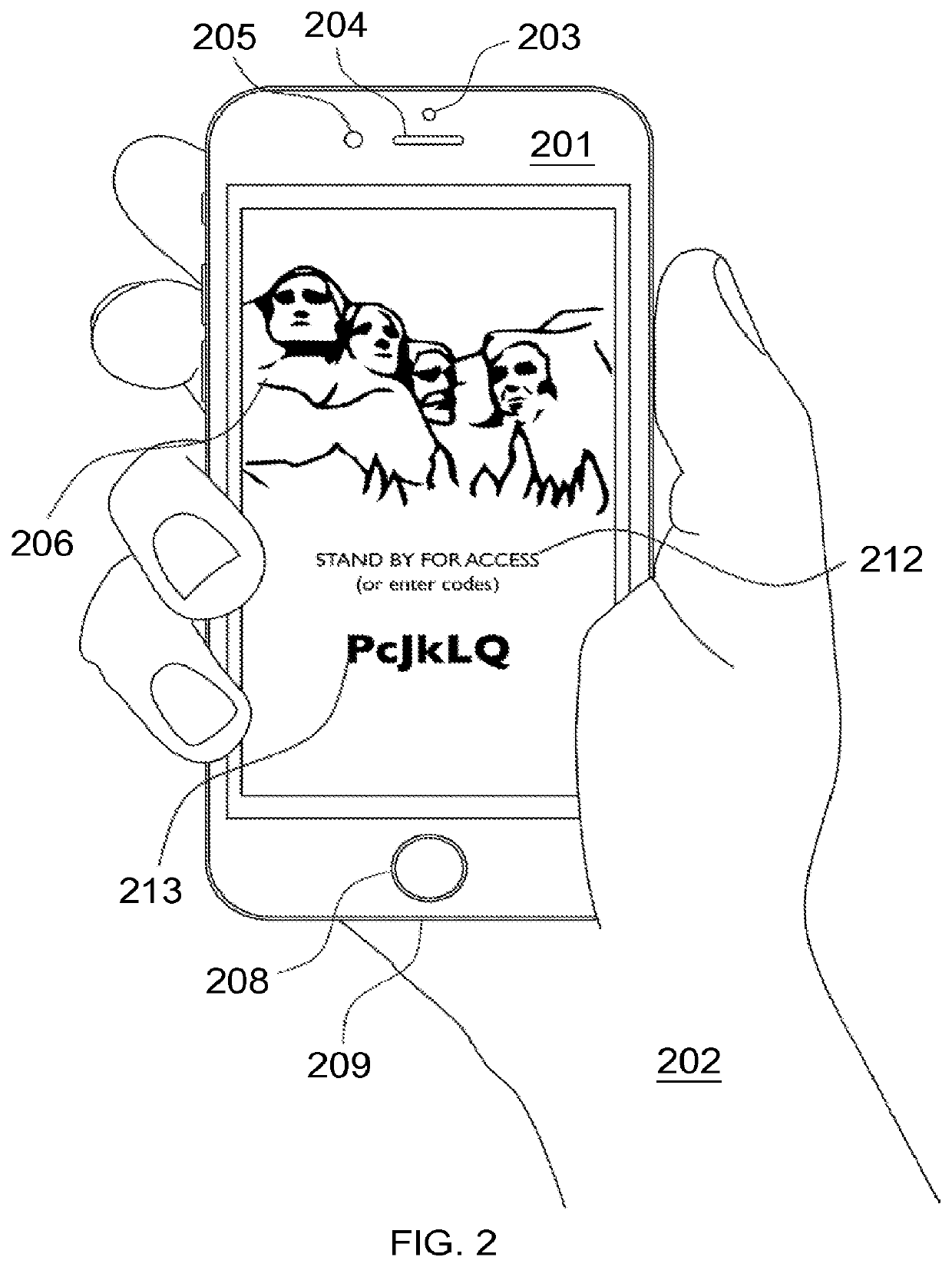
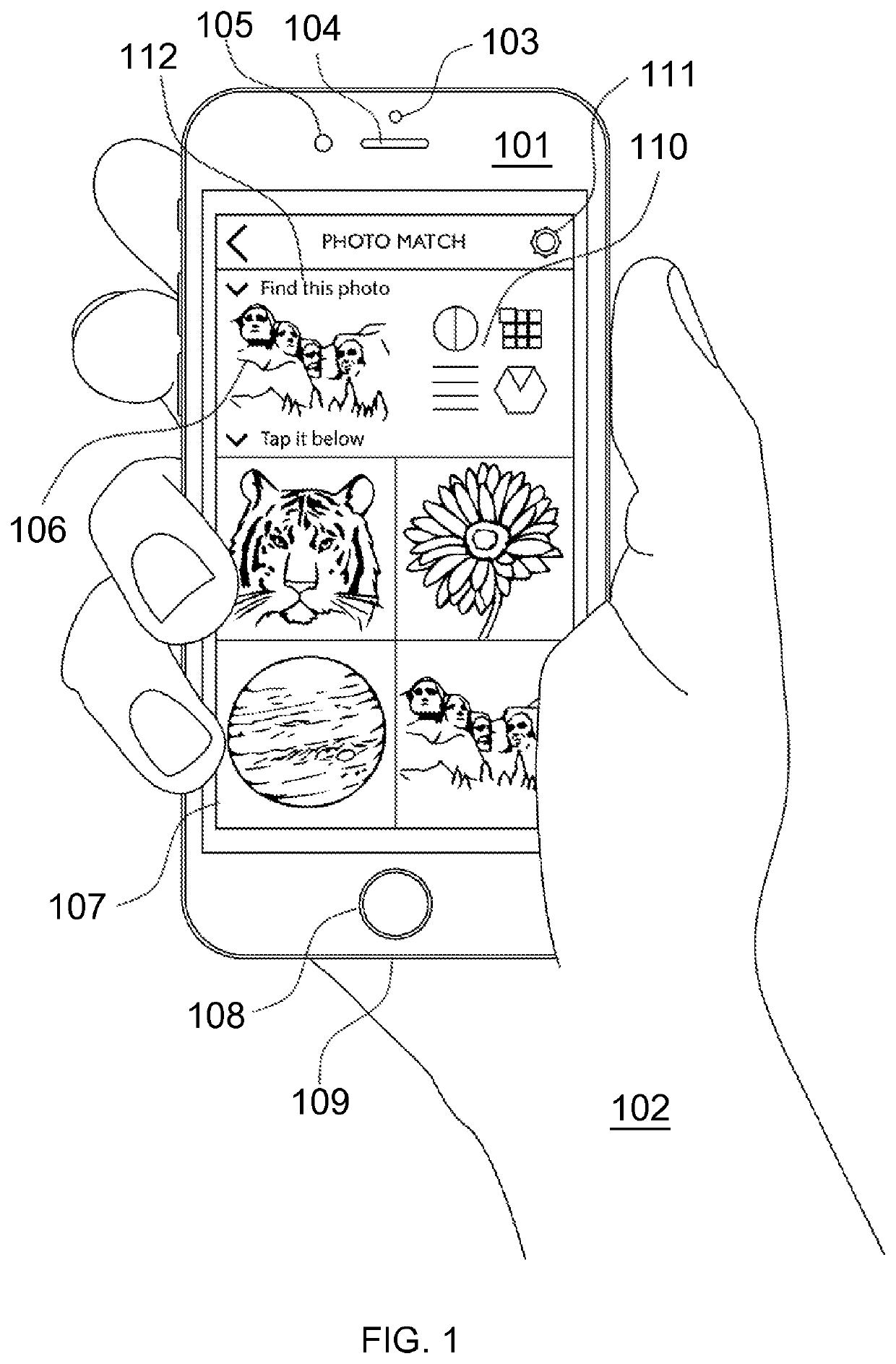
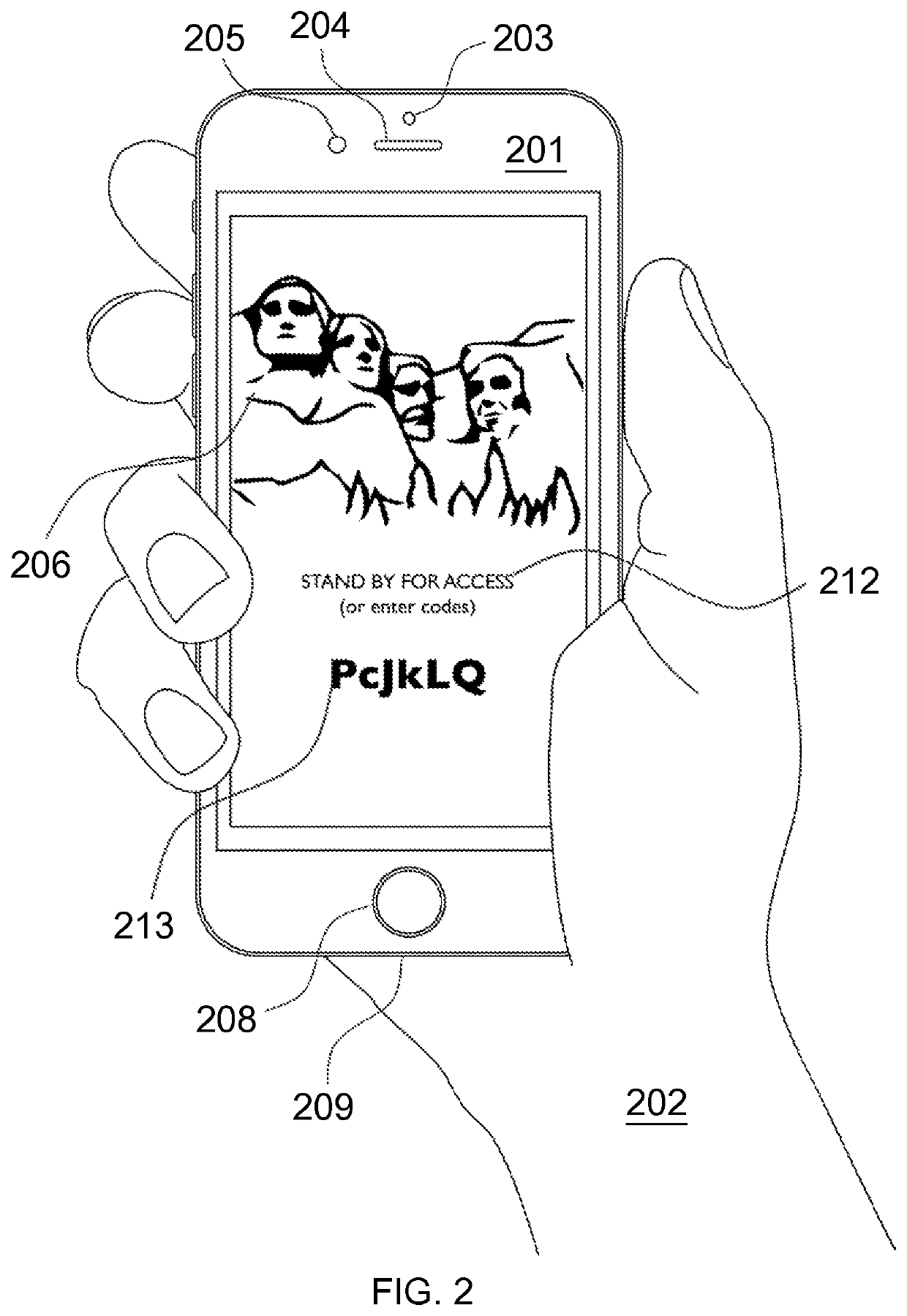
A strong, unified and comprehensive new computer security and authentication solution is disclosed. It is ideal for everyday users, and invents faster and easier enrollments, faster usage, easier usage, numerous aspects of stronger security including token based rapid mutual-authentication with protection against phishing, MitM, malware and user carelessness, secure resilience against token loss or theft, continuing protection in harsh situations, non-repudiation benefits, biometric encryption, code self-defenses, improved deployment, lower costs, new revenue opportunities, and more. One aspect's flow, visually-enforced mutual-authentication is: customer visits protected web site's login page, gets identified via Cookies, site displays one random photograph on said page, triggers customer's smartphone to automatically show a grid of random photos, one of which matches the login page photo, and customer taps it to login. Disclosed techniques teach how to block fraudulent sites and activity by preventing these producing any matching photo the customer can tap.
Owner:DRAKE CHRISTOPHER NATHAN TYRWHITT
Identity authentication method based on biological feature encryption and homomorphic algorithm
InactiveCN102664885AImprove privacyAvoid crackingUser identity/authority verificationTimestampAlgorithm
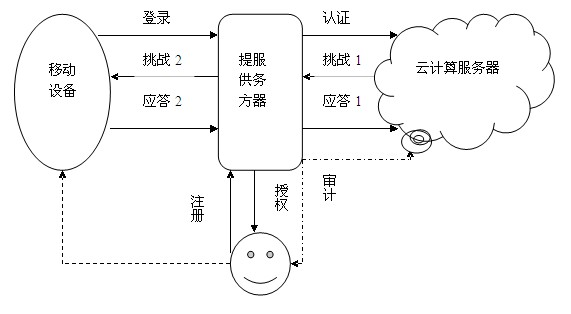
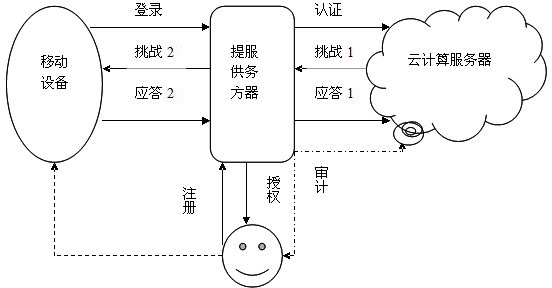
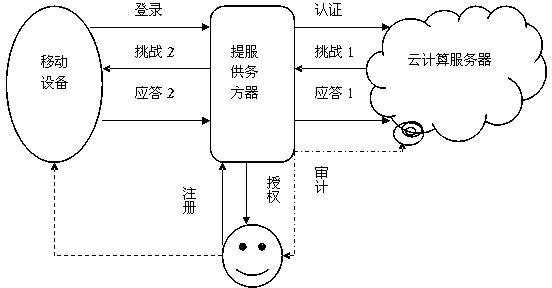
The invention discloses an identity authentication method based on biological feature encryption and a homomorphic algorithm. The method is quicker than a normal password method by using biological features of users as passwords to log in a system through a mobile device, using an encrypted biological template is safer, and privacy of the users can be guaranteed as information is transmitted in a ciphertext form. By adding factors such as timestamps, tri-party authentication among the users, a provider server and a cloud computing server is realized, and reliability among the three parties is enhanced. Legal users can be prevented from using resources in the cloud computing environment illegally to better manage the resources by means of user authentication operation according to attribution predicate encryption and real-time updating of permission information. Operation without encryption can be realized by the aid of the homomorphic algorithm, same effects as decrypting before operation can be achieved, time and space expenses can be saved, system efficiency is greatly improved, and the identity authentication method has high safety and efficiency.
Owner:南京邦普信息科技有限公司
Revocable biometrics with robust distance metrics
ActiveUS7773784B2Computer security arrangementsBiometric pattern recognitionBiometric encryptionPattern recognition
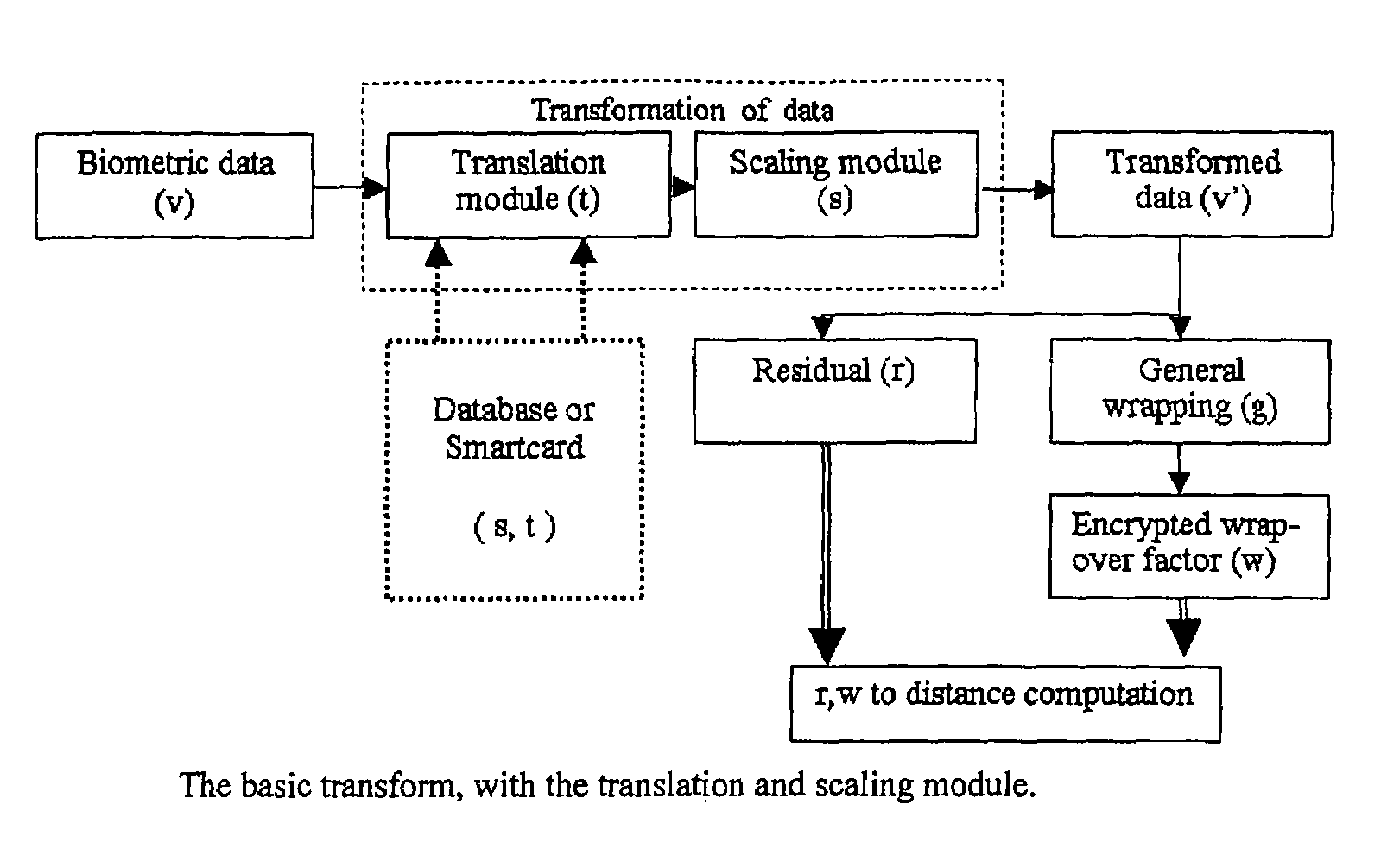
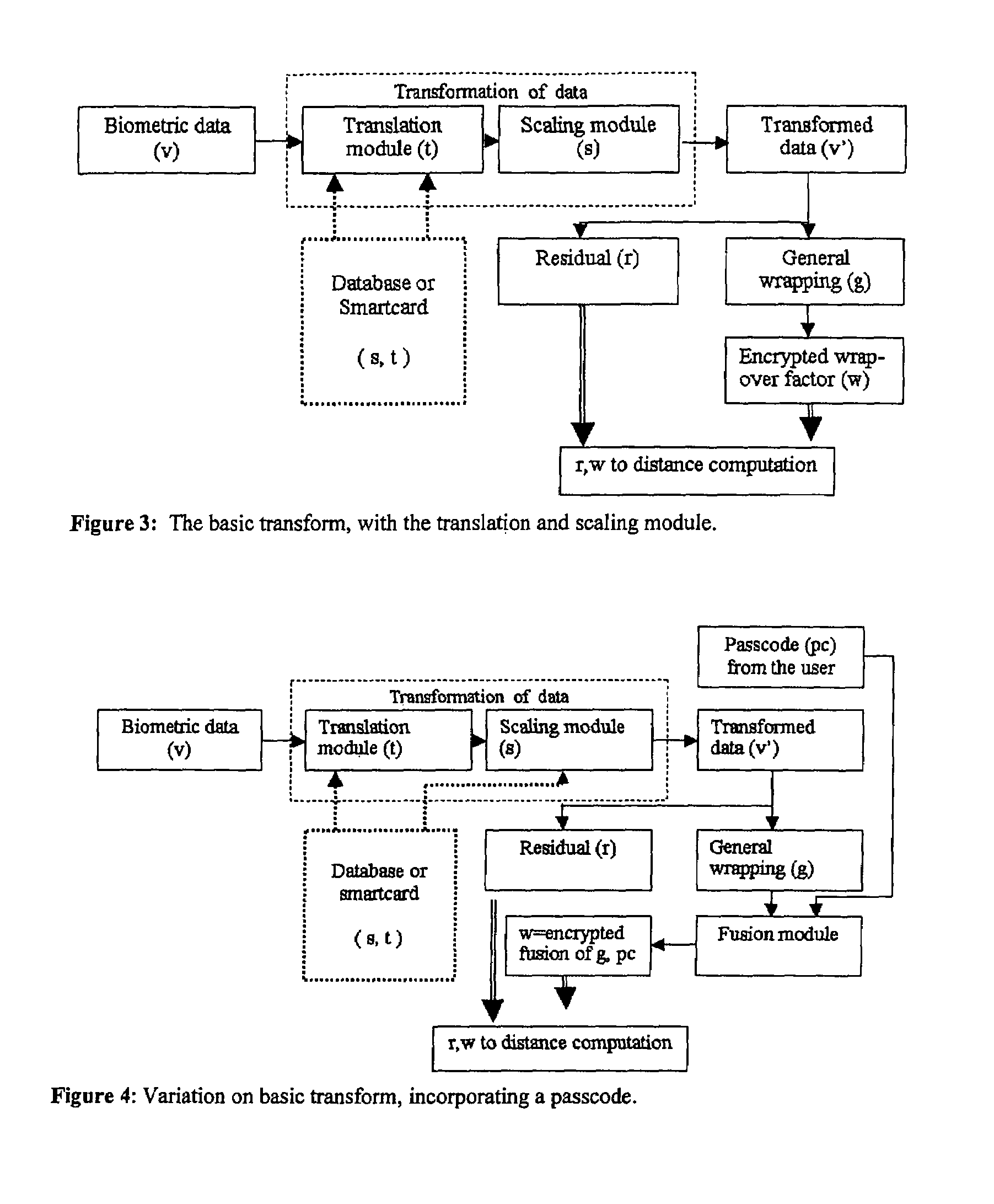
Techniques, systems and methods relating to cryptographically secure revocable biometric signatures and identification computed with robust distance metrics are described. Various biometric cryptographically secure revocable transformation approaches are described that support a robust pseudo-distance computation in encoded form, thereby supporting confidence in verification, and which can provide for verification without identification.
Owner:HID GLOBAL CORP
Bio-metric encryption key generator
InactiveUS20070239994A1User identity/authority verificationUnauthorized memory use protectionComputer hardwareCryptographic key generation
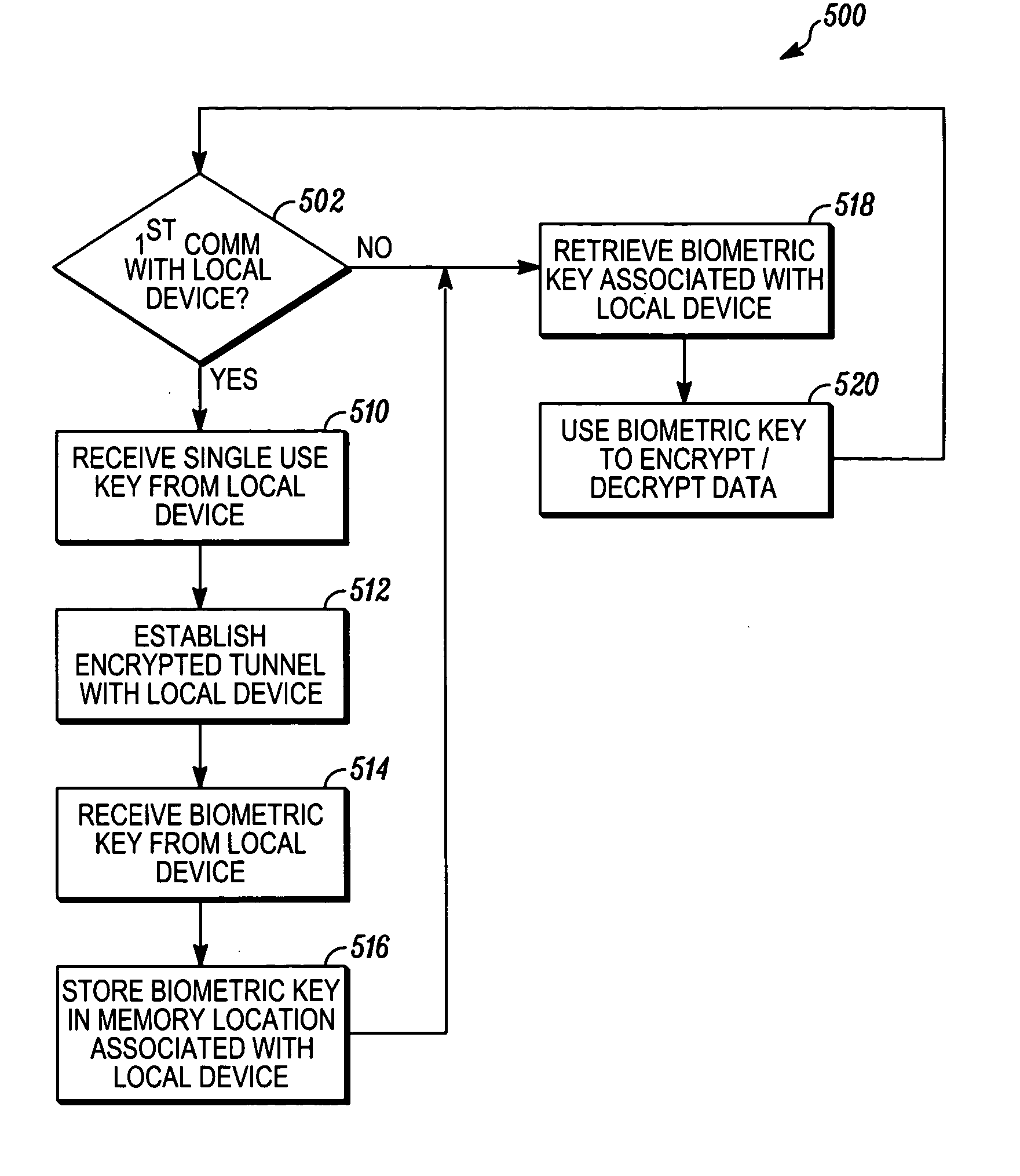
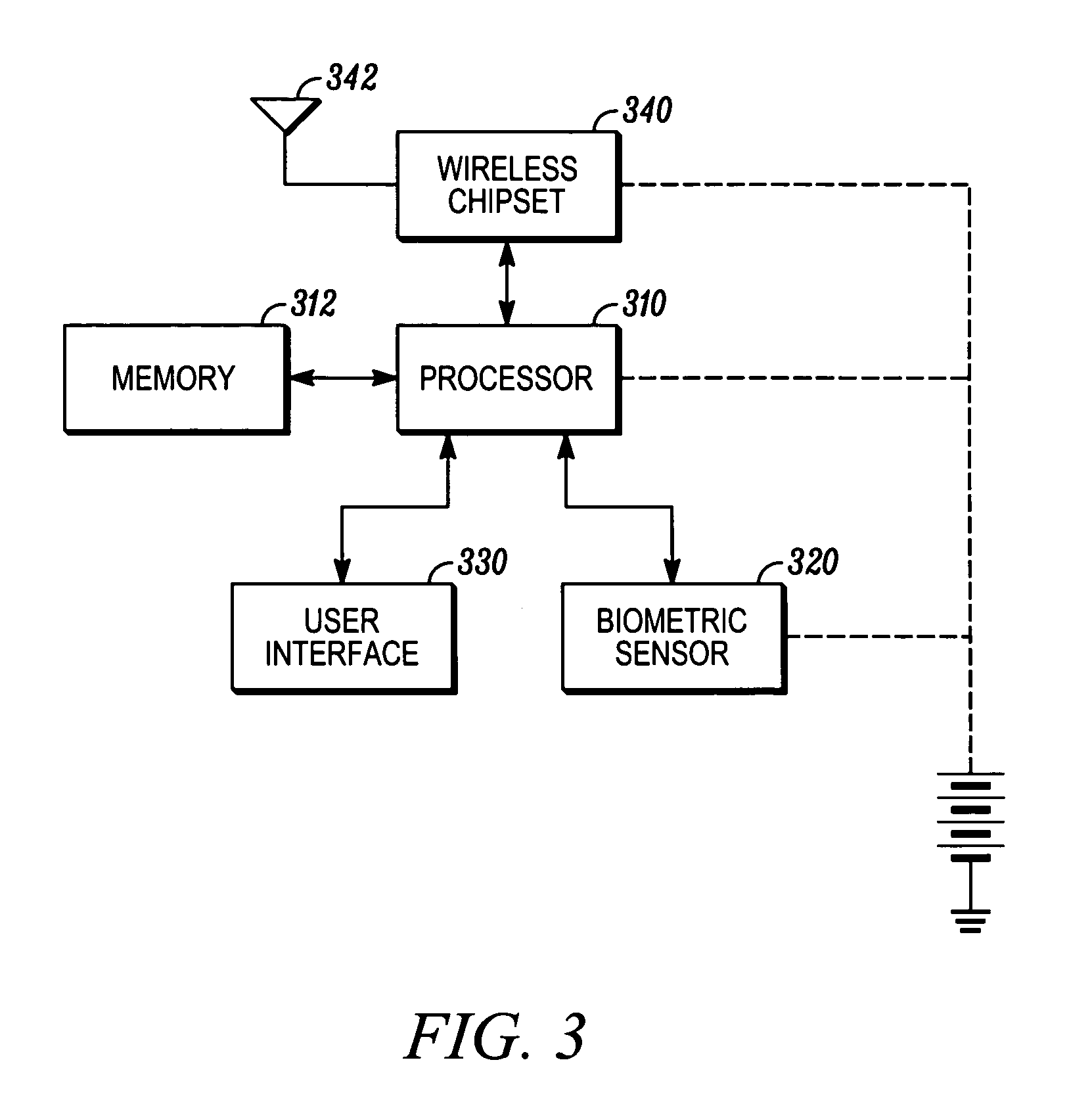
In a method of facilitating an encrypted communication for use in communication between a local device, operated by a user, and a remote device, a data representation of a biometric feature of the user is received from a biometric input interface. The data representation is transformed into a biometric encryption key using a predetermined set of rules. A device for communicating on a network includes a biometric input interface a processor, and a transceiver. The processor transforms a biometric data input from the biometric input interface into an encryption key and encrypts data for transmission onto the network using the encryption key, thereby generating encrypted data. The transceiver transmits the encrypted data to the network.
Owner:MOTOROLA INC
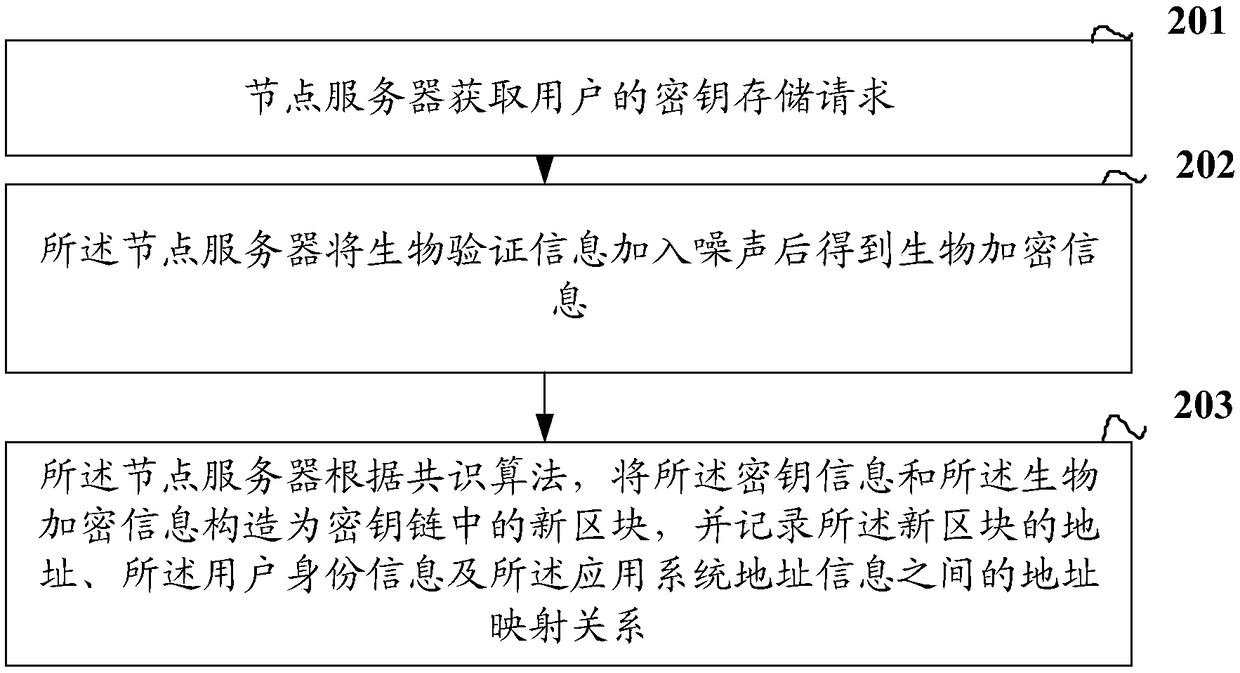
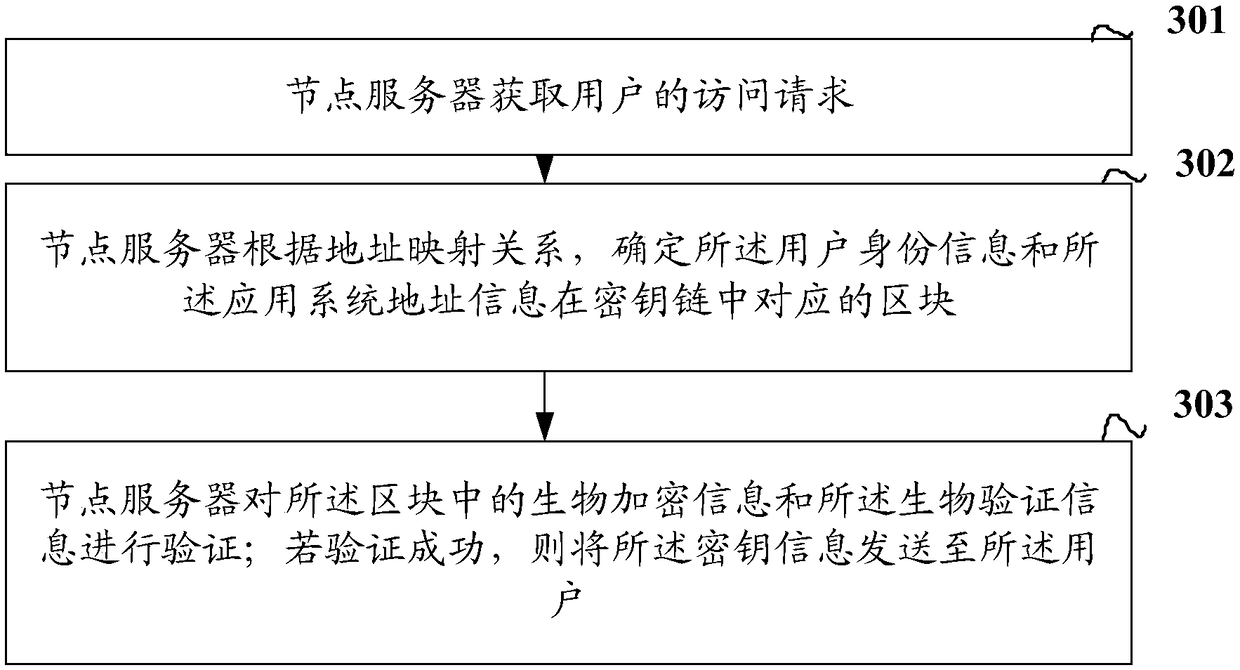
Key chain generation and verification method and device thereof
InactiveCN108959911ASolve the inconvenienceFix security issuesDigital data authenticationValidation methodsUser input
The invention discloses a key chain generation and verification method and a device thereof. The key chain generation comprises the following steps: a node server obtains a key storage request of a user, wherein the key storage request comprises user identity information, key information, application system address information and biological verification information, the key information is used for the user to log in the application system corresponding to the address information of the application system; the node server adds the biometric authentication information into the noise to obtain the biometric encrypted information; wherein the biometric encryption information is used for verifying the biometric authentication information input by the user before acquiring the key information;the node server constructs the key information and the bio-encryption information into a new block in a key chain according to a consensus algorithm, and records the address of the new block, and theaddress mapping relationship between the user identity information and the application system address information, wherein the key chain is used for storing key information of a user.
Owner:UNION MOBILE PAY
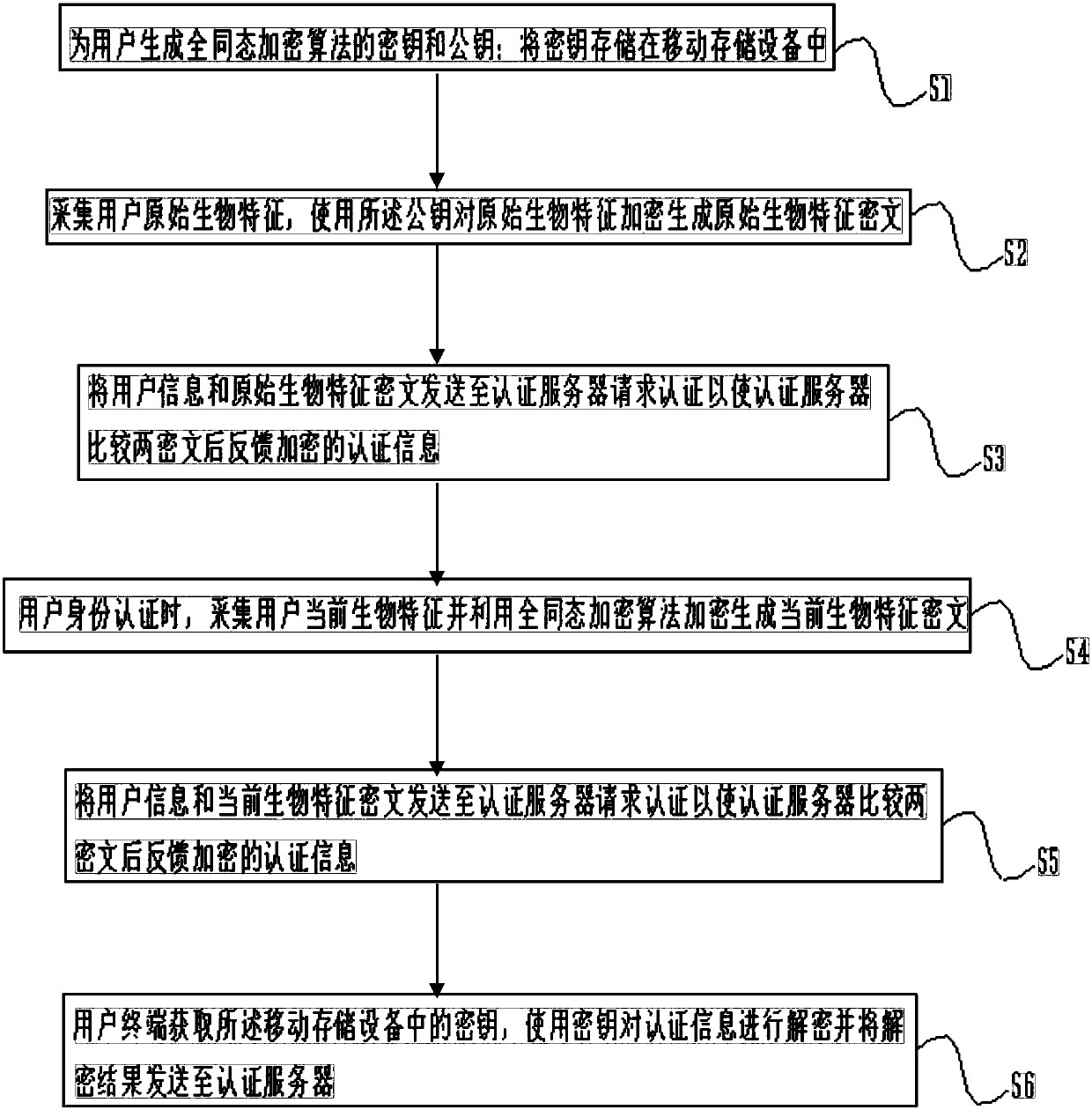
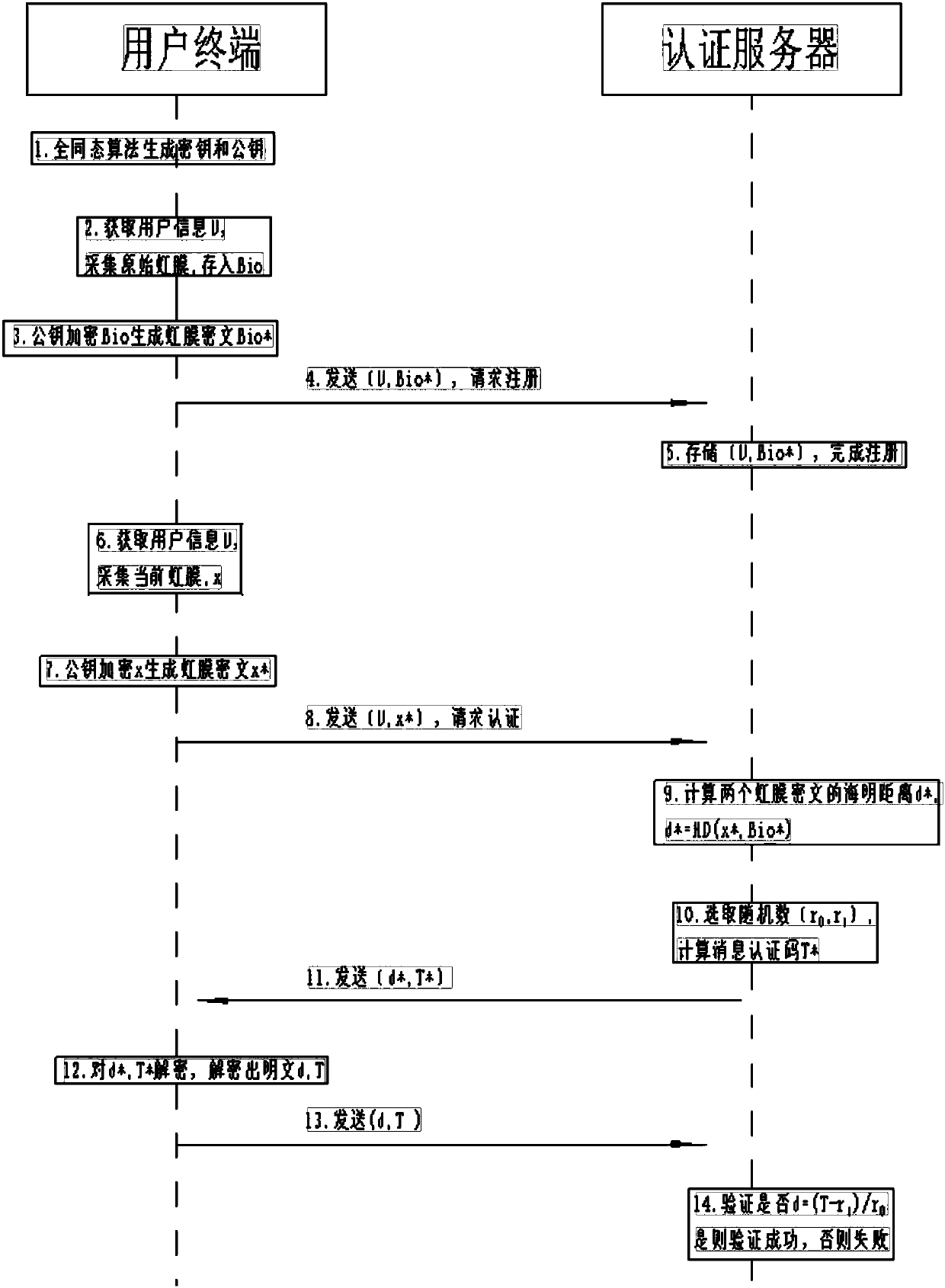
Authentication method based on homomorphic encryption, user equipment and authentication server
ActiveCN107819587AAvoid risk of leakageWill not be exposedKey distribution for secure communicationUser identity/authority verificationHomomorphic encryptionBiometric encryption
The invention discloses an authentication method based on homomorphic encryption. The authentication method comprises the following steps: generating a secret key and a public key of a homomorphic encryption algorithm for a user; storing the secret key in mobile storage equipment; collecting original biological features of the user, encrypting the original biological features by using the public key to generate the original biological feature ciphertext; and sending the original biological feature ciphertext to store in an authentication server, thereby accomplishing the registration; collecting the current biological features of the user, and encrypting the current biological features by using the homomorphic encryption algorithm to generate the current biological feature ciphertext; sending the current biological feature ciphertext to the authentication server, requesting the authentication under the ciphertext state, and acquiring the secret key in the mobile storage equipment, decrypting the authentication information by using the secret key and sending the decryption result to the authentication server. Through the adoption of the method disclosed by the invention, the biological features are authenticated under the ciphertext state, the strong safety guarantee is provided, and the biological feature information leakage of the user is avoided.
Owner:陈智罡
Encrypting method base on biology characteristic information
InactiveCN101350724AThere is no key leakage problemPrevent decryption of informationUser identity/authority verificationCharacter and pattern recognitionPlaintextPassword
The present invention relates to an encryption method based on biometric information. The encryption method provides a dual-factor encryption method based on the biometric information and the secret key, and a single-factor encryption method based on the biometric information. And the encryption method can be used in the fields of network and information security, bio-certification, biometric encryption, and so on. The dual-factor encryption and decryption of the information by the user both require the biometric information and the secure secret key or password which is automatically selected; if either of the biometric information and the secure secret key is not correct, the correct plaintext information can not be decrypted. The single-factor encryption and decryption of the information by the user only requires the biometric information. The encryption method can prevent the non-intended message recipient from decrypting the information; the attacker who obtains the decryption key of the other people can not complete the correct decryption process; the decryption process and the physical identity verification are completed simultaneously; the legitimacy of the identity of the decrypting person is verified; and the system has higher security.
Owner:XIDIAN UNIV
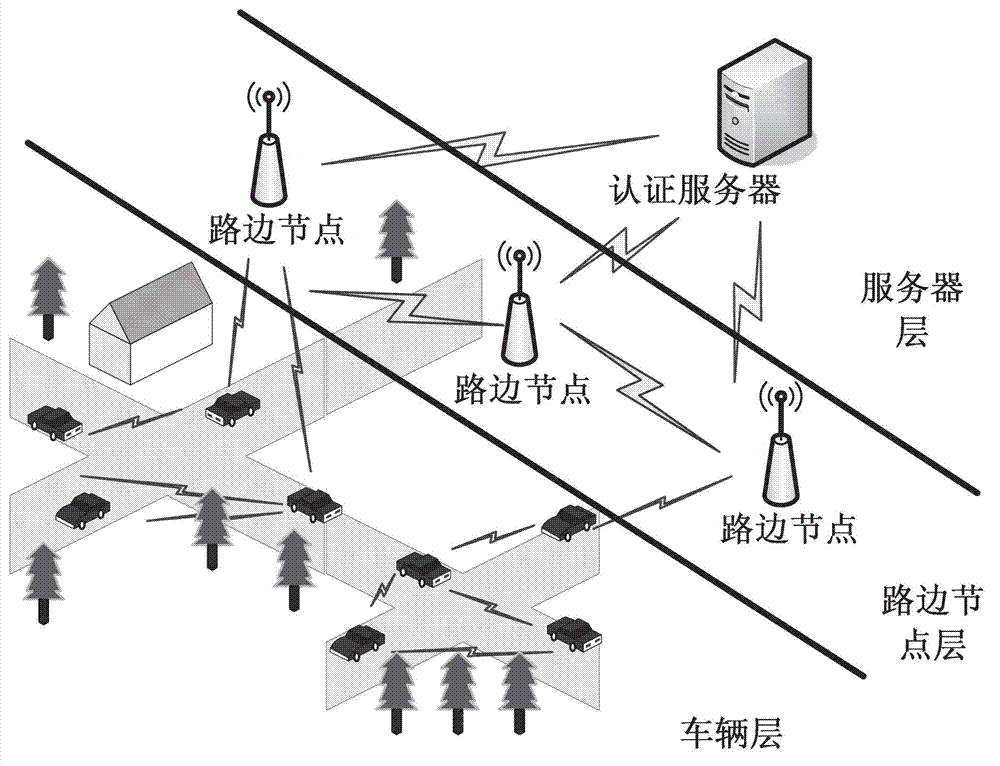
Anonymous authentication scheme under vehicular ad hoc network based on biometric encryption technology
InactiveCN102904896AProtect biological privacyProtect real identityParticular environment based servicesUser identity/authority verificationCiphertextAnonymous authentication
The invention discloses an anonymous authentication scheme under a vehicular ad hoc network based on a biometric encryption technology, belonging to the technical field of information security, and particularly relating to a biometric encryption algorithm and an MAC (Media Access Control) address hiding technology. The anonymous authentication scheme is characterized in that the biometric encryption technology is used for organically combining a biological template of a user with a secret key to generate a biological ciphertext; the biological ciphertext hides biological characteristics and information of the secret key, and is used for representing a unique identity of one user; the generation of the biological ciphertext is unidirectional, and the biological information and the encrypted secret key are mutually independent; and a new MAC address is generated while the users negotiate a session key, thus the subsequent anonymous communication is realized. The anonymous authentication scheme has the advantages and the beneficial effects that the biometric encryption technology solves the problem of leakage of the biological template, the unidirectional generation of the ciphertext ensures that an attacker can not crack the biological information through the secret key; and the MAC address hiding technology can protect the real identifies of the users, thus the anonymous communication is realized, and the higher service quality is ensured by easily updated characteristics.
Owner:DALIAN UNIV OF TECH
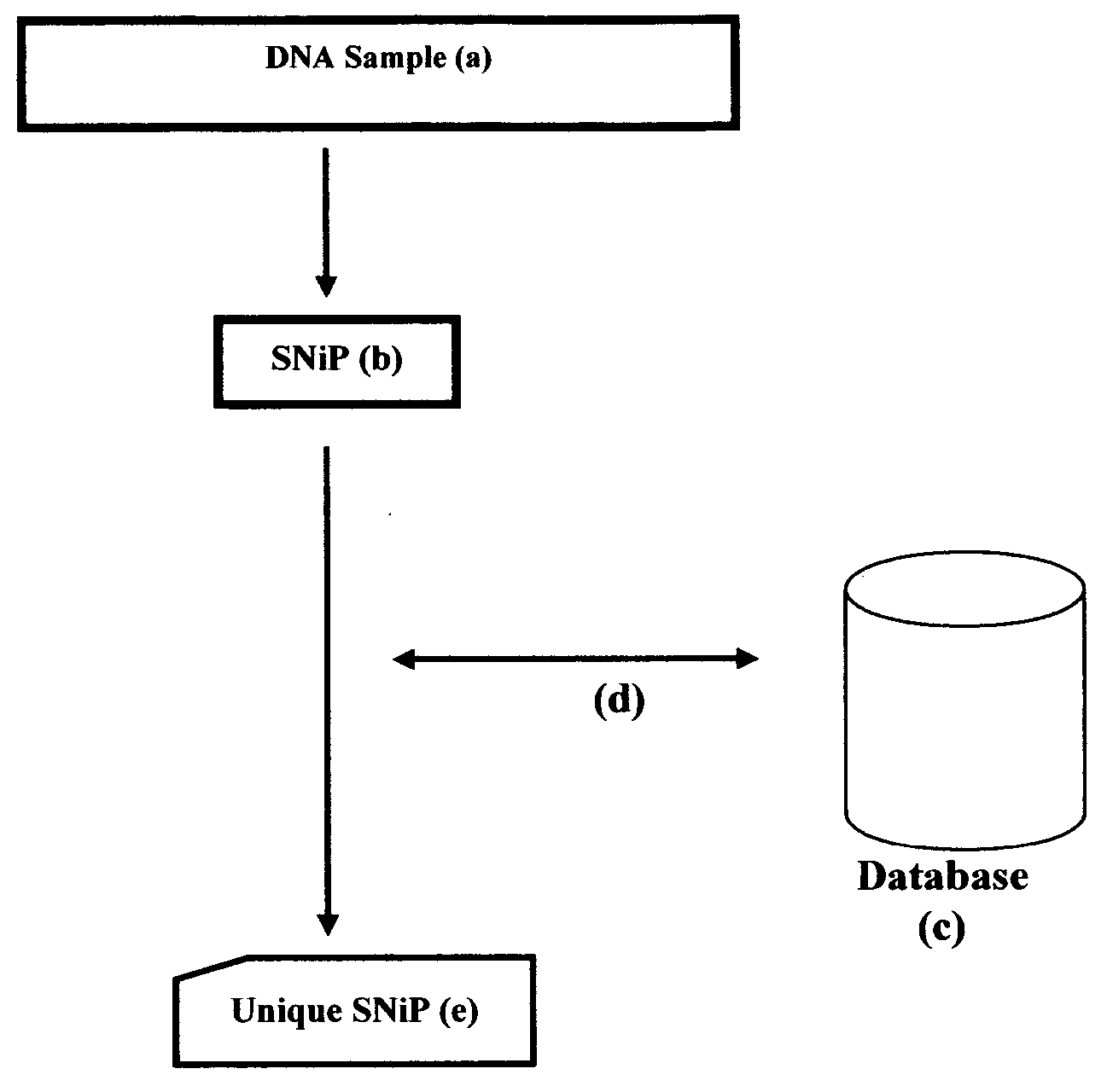
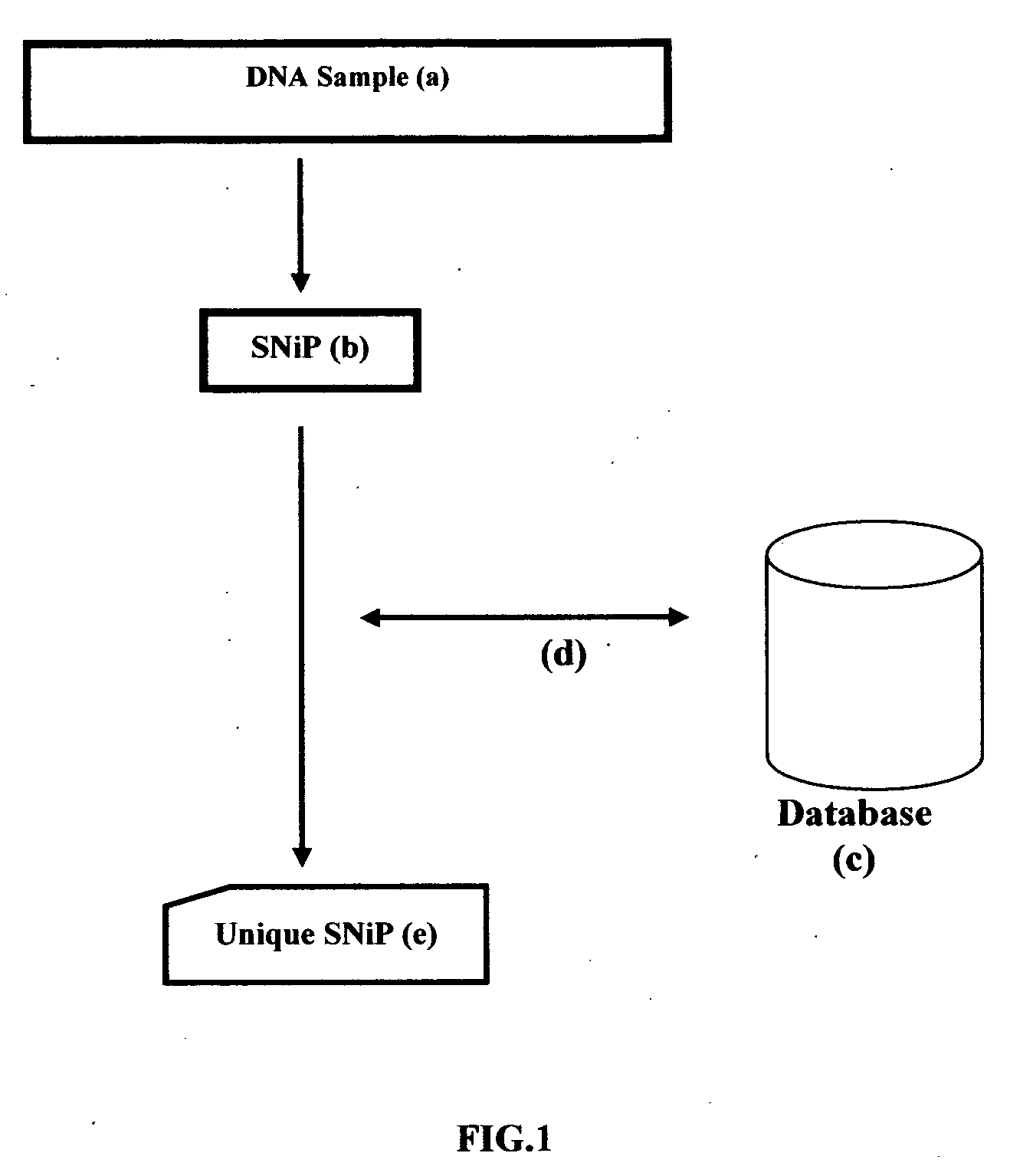
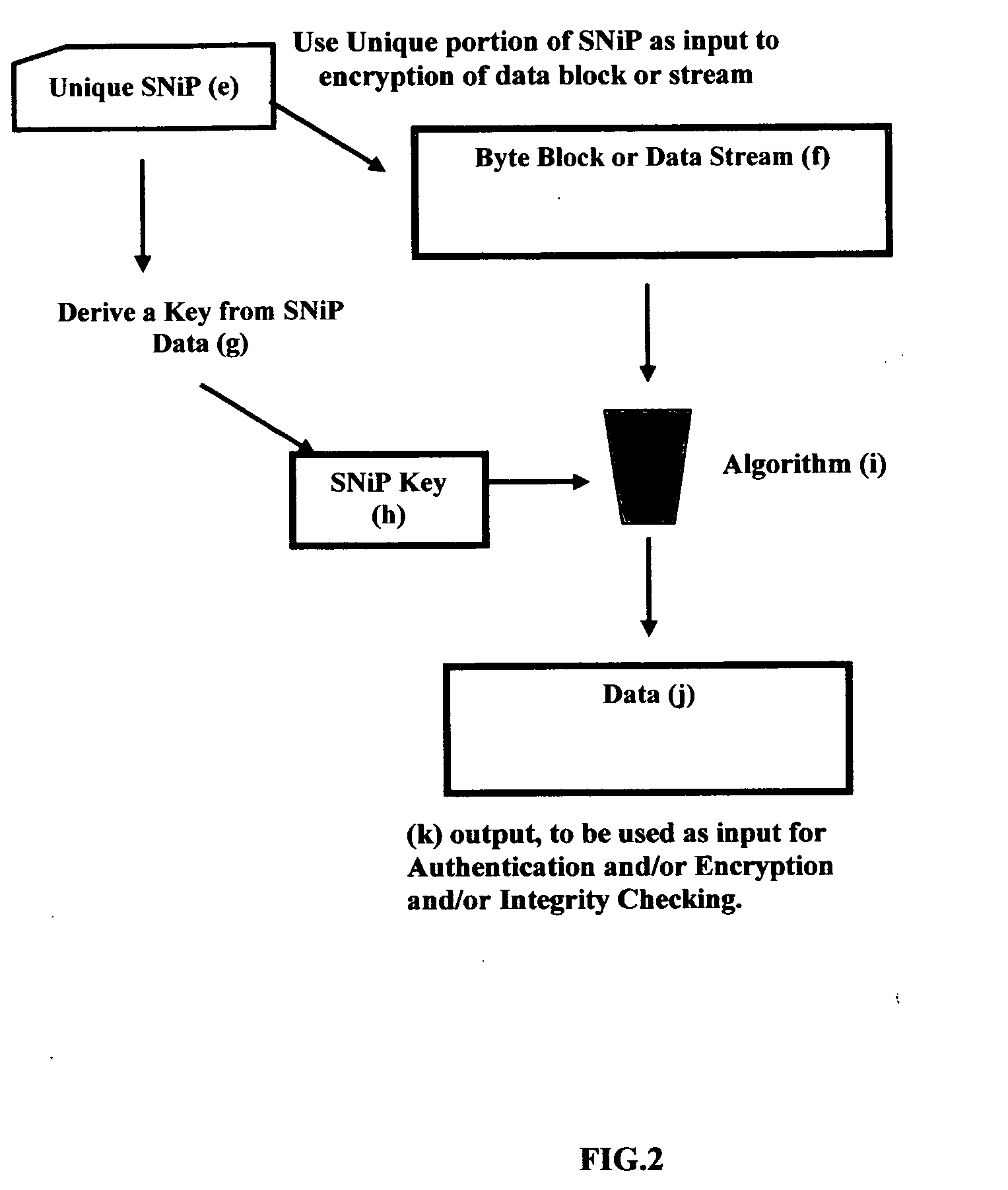
Unique SNiP for use in secure data networking and identity management
InactiveUS20070118885A1Digital data processing detailsUser identity/authority verificationData packData stream
A Process, Method of extracting the unique SNiP portion of DNA then using that unique SNiP to formulate a unique SNiP key and / or unique SNiP data, and using that key and / or data as input into Cryptography Systems, Data Encryption / Decryption, Data Transmission Model, then converting that binary data to a Network address for use in Identity Management, Biometric Encryption, Data Network Security, Digital Certificates, Wired and / or Wireless Data Communications and Identification, Authentication, Authorization, Accounting, Auditing, Encryption, Integrity Checking, IPv4, IPv6, Ethernet, Wired and Wireless data transmission, RFID, RFID location tracking, GPS location and tracking systems, National and / or Global Identification of organisms especially human, living or non-living, mobile or stationary, Ethernet, Identity Based Networking, Identity Tracking, Government National Id, x.400, x.500, x.509, Directory Services, LDAP, Database(s), AAA, TACACS+, Data Storage, Storage Area Networking, conversions and translations between directory services; DNA to provide encryption for data, and tie ownership of that secure data, packets and data streams to an individual human, non-human, living or non-living, mobile or stationary.
Owner:ELROD CRAIG THOMAS
Quick custom clearance method based on biological passport
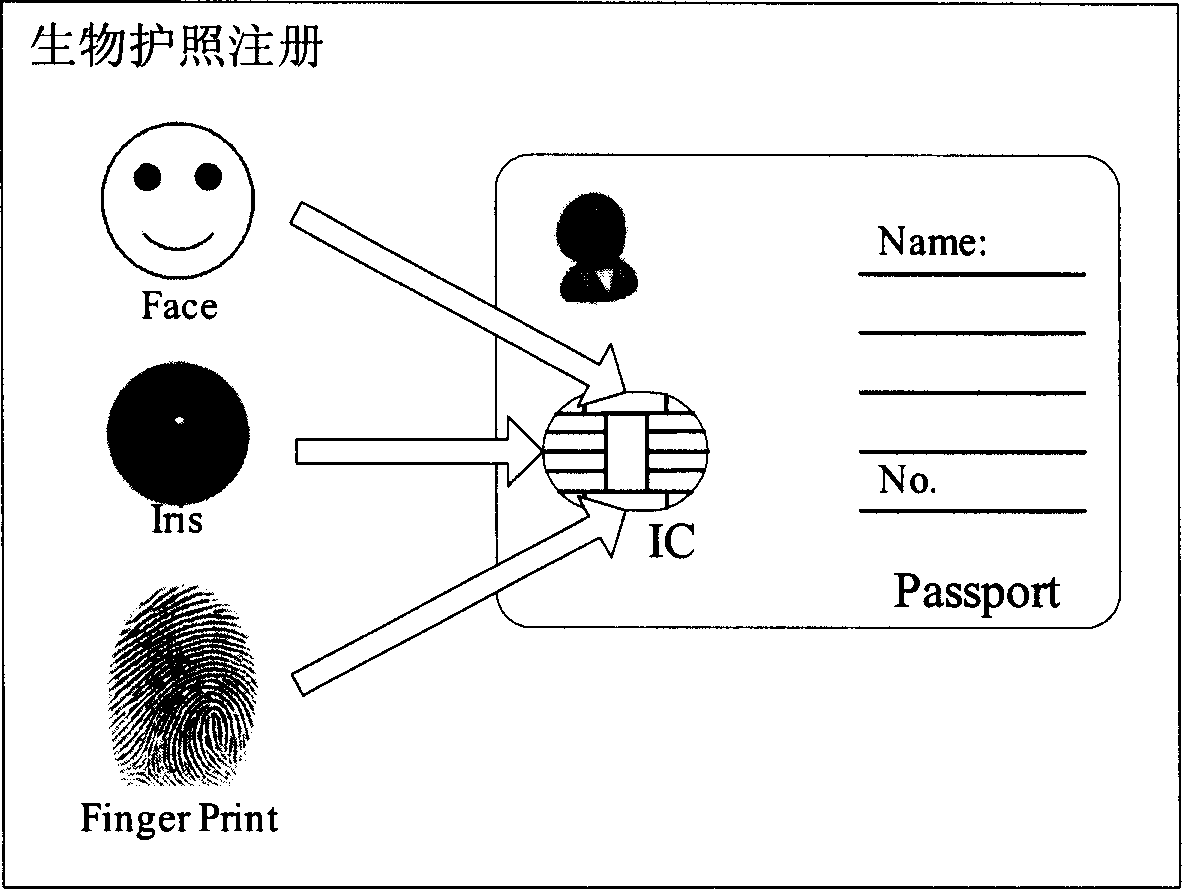
InactiveCN1801178AFast trackCharacter and pattern recognitionTicket punchesFace detectionBiometric data
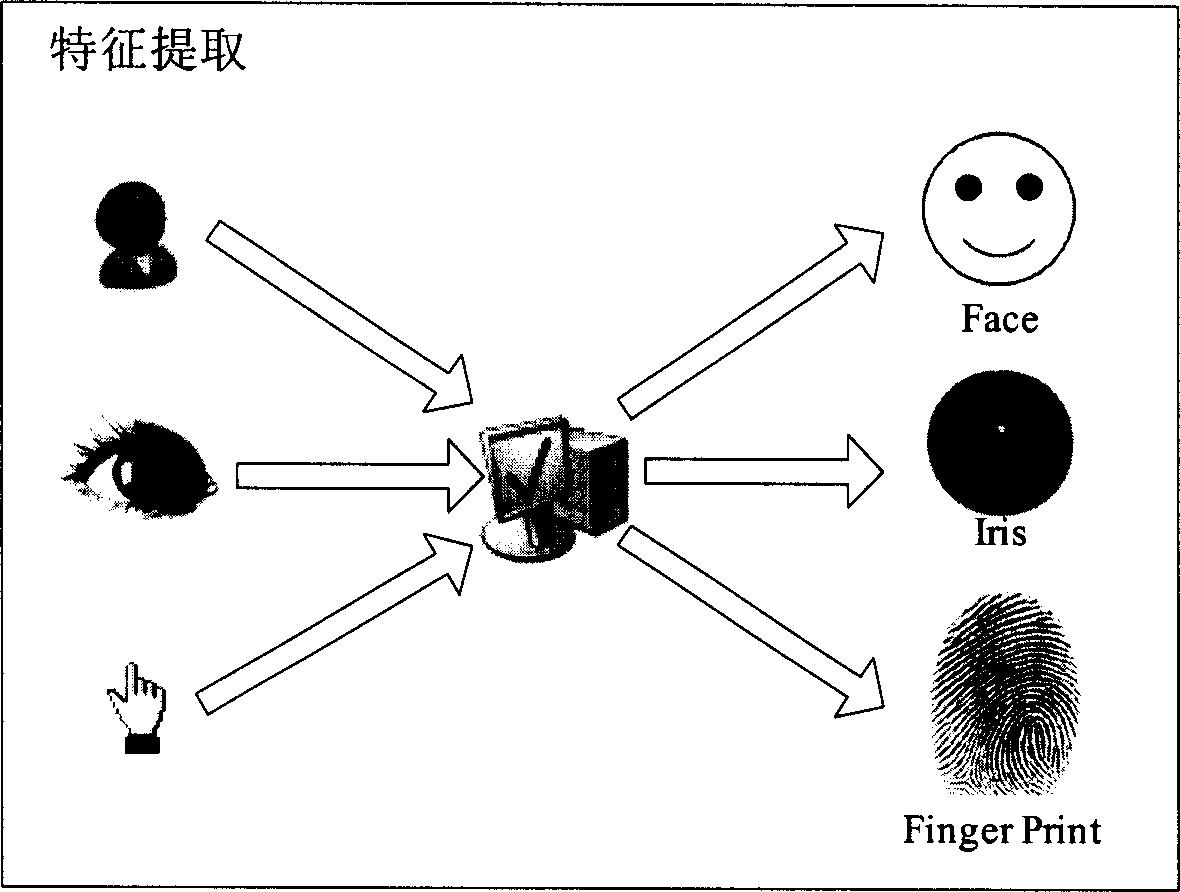
The invention discloses a rapid passing method based on biological passport within face detection and identification technique, iris extraction and identification technique, fingerprint collection and identification technique, ray disposal technique and coding technique in the pattern identification technique domain, which comprises the following steps: collecting the biological feature of biological passport holder within face, fingerprint and iris; storing the gathered image feature in the non-touchable large-capacity IC RF chip; reading the biological feature data through custom system; comparing the gathered feature with the present holder; permitting the passing if successful comparison; rejecting passing if fail comparison.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI +1
Mutual authentication security system with detection and mitigation of active man-in-the-middle browser attacks, phishing, and malware and other security improvements
InactiveUS20200404019A1Key distribution for secure communicationUser identity/authority verificationWeb siteAttack
Owner:DRAKE CHRISTOPHER NATHAN TYRWHITT
Mobile data communication using biometric encryption
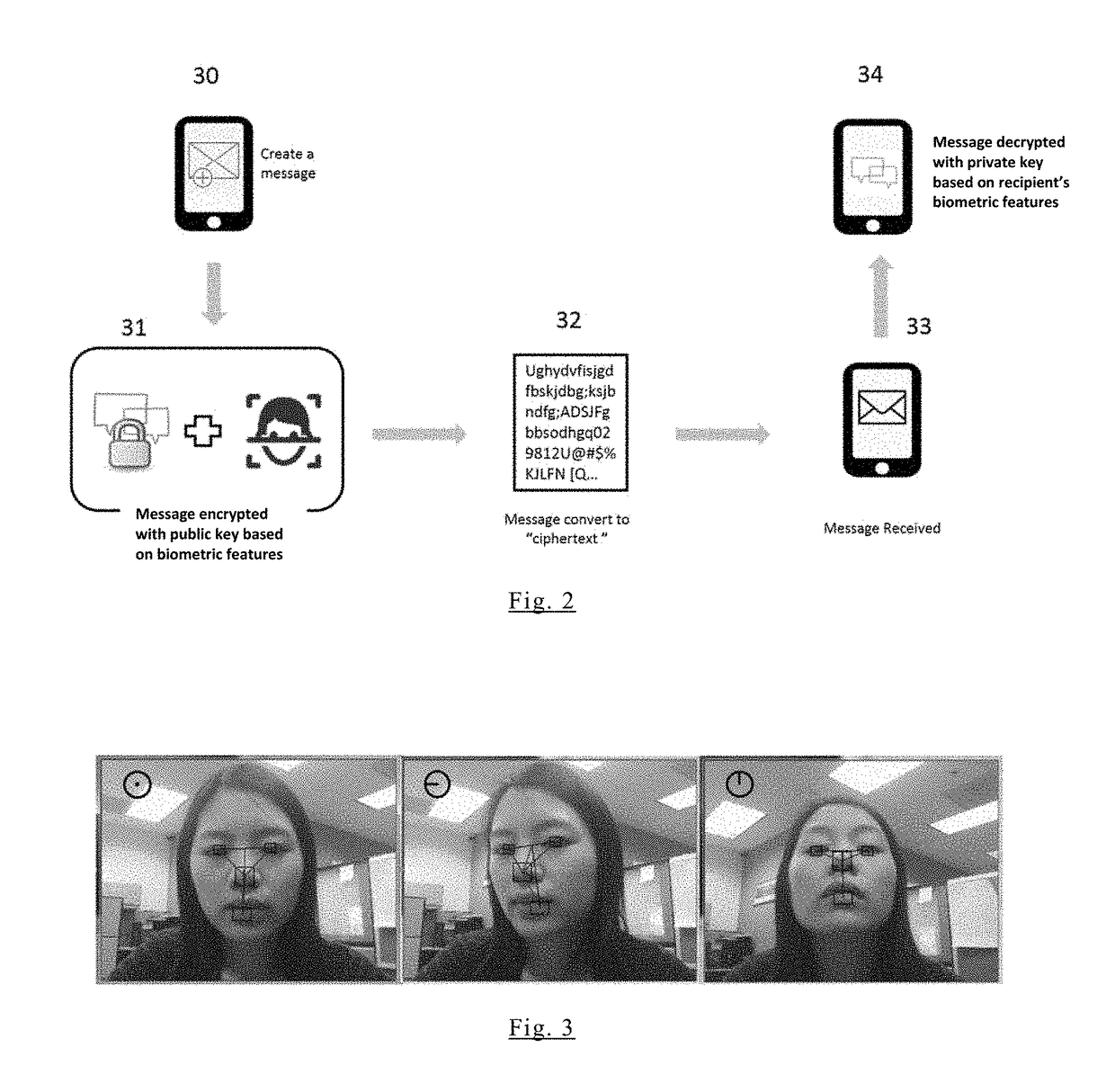
InactiveUS20160100314A1Improve robustnessProtect dataUser identity/authority verificationDigital data protectionMobile appsFeature vector
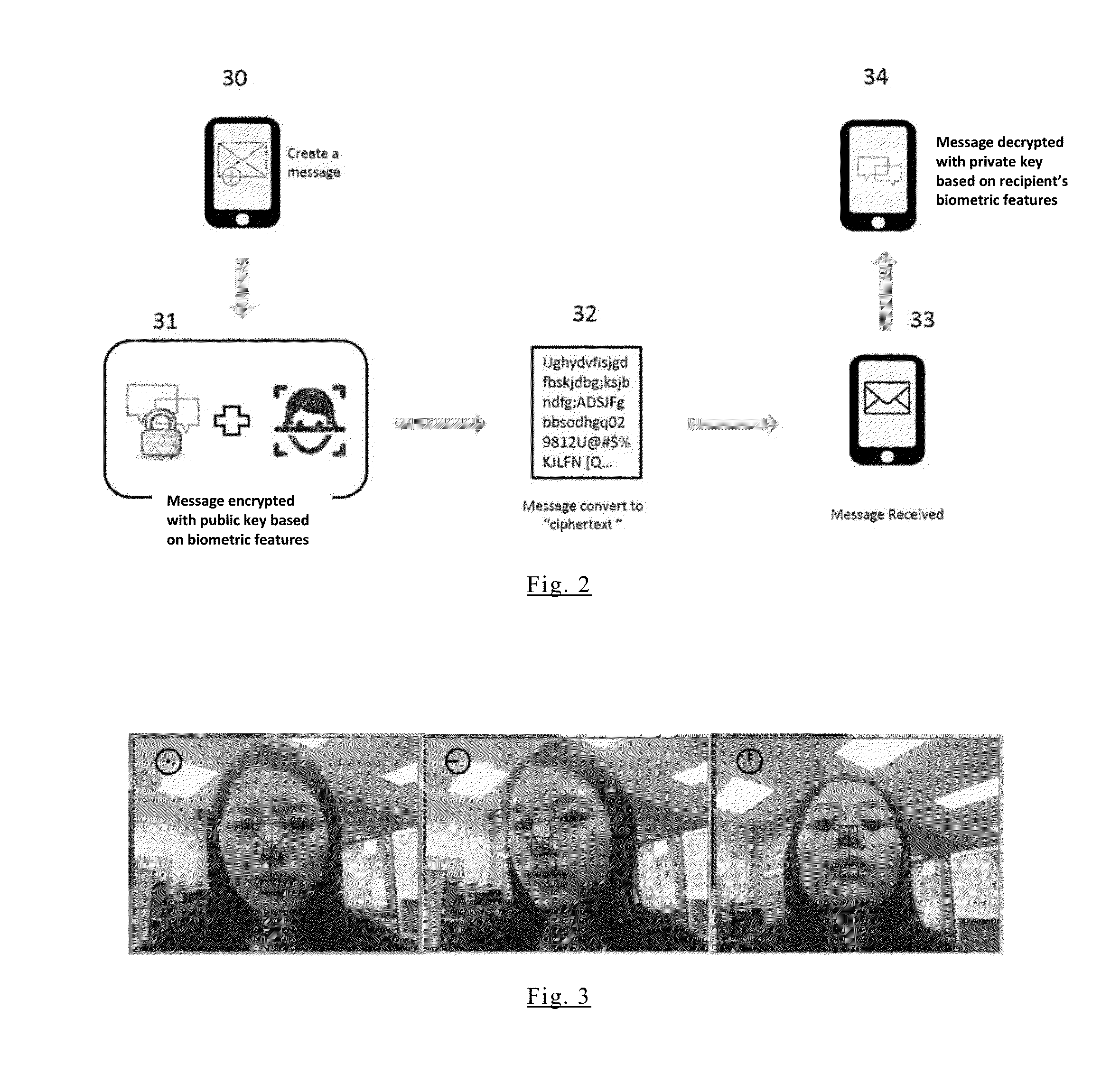
A mobile App using biometric encryption and decryption for privacy and security having both authentication and recognition functions. It utilizes the built-in camera of the mobile device to provide facial images for authentication purposes. It further includes a secured data communication system for conveniently sending and receiving data on the mobile devices. The secured data communication system also utilizes biometric encryption and decryption technology for granting permissions to access the data communication system. The biometric encryption is implemented by using a selective biometric feature and optimized biometric feature detection and tracking methods. Different biometric feature authentication methods are optimized for use on various mobile platforms, such as, Android, iOS, Windows and others. Data encryption and decryption are achieved by using selected biometric feature vectors as cryptographic keys. The biometric data encryption system further includes liveness detection module with anti-spoofing features to ensure the encryption and decryption processes only accept biometric features from a live person conveniently without the user's intervention. Alternative authentication method is provided if the biometric feature authentication module fails to recognize the valid user, or fails in the liveness detection module in order to maintain privacy and security of the data in the mobile device.
Owner:WASHINGTON SOFTWARE INC
Mutual authentication security system with detection and mitigation of active man-in-the-middle browser attacks, phishing, and malware and other security improvements
ActiveUS10574692B2Key distribution for secure communicationPublic key for secure communicationWeb siteAttack
Owner:DRAKE CHRISTOPHER NATHAN TYRWHITT
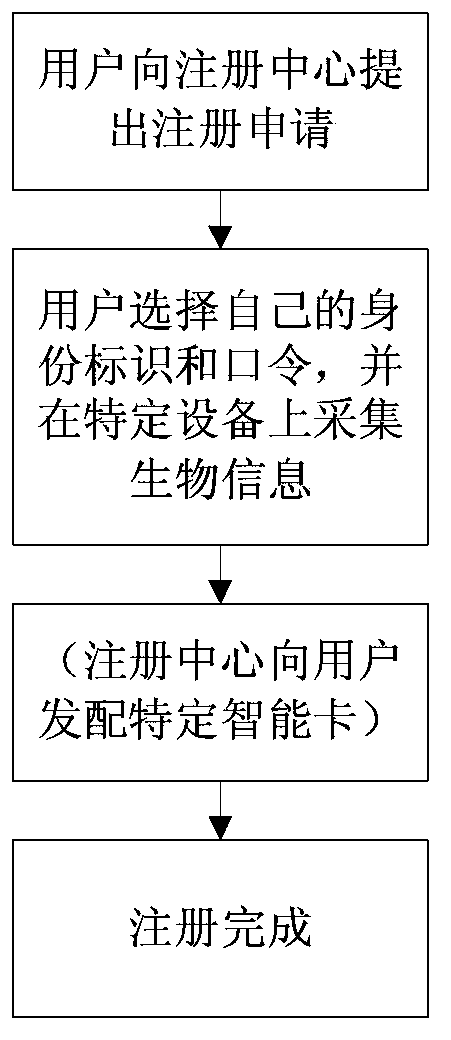
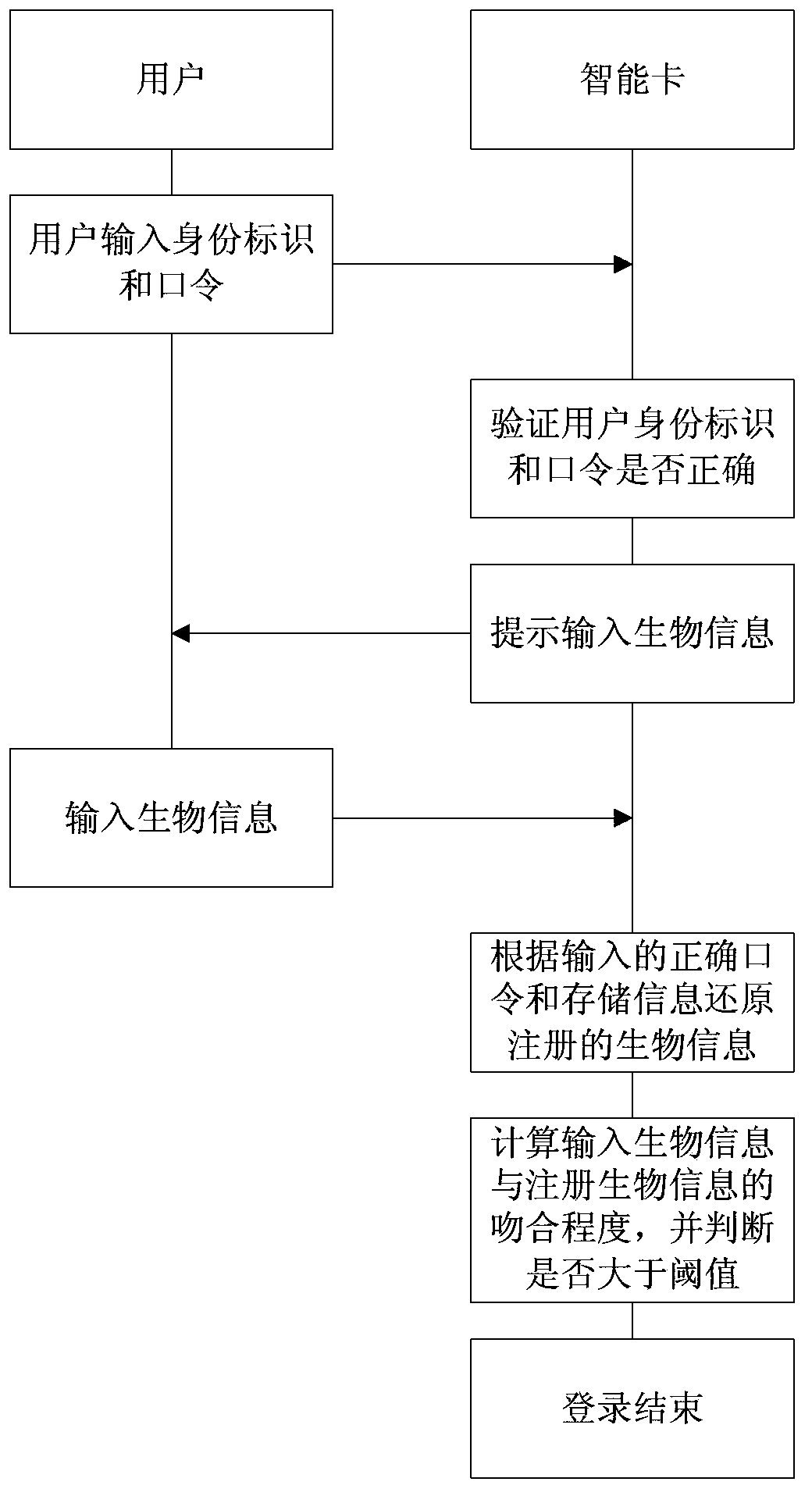
Smart card registration entry method based on password and biological characteristics
ActiveCN103368954AResistance to imitation attacksPlay a role in preventing repudiationTransmissionUser inputPassword
The invention discloses a smart card registration entry method based on a password and biological characteristics. The method comprises a registration step and an entry step, wherein the registration step further comprises the following steps of transmitting a user identity label, the password and the biological characteristics to a registration center, carrying out the encryption through the registration center to obtain a password encrypted value and a biological characteristic encrypted value, and storing the password encrypted value, the biological characteristic encrypted value and an encryption method to a smart card; and the entry step further comprises the following steps of utilizing the smart card to encrypt the identity information and password, inputted by a user through the same method to obtain password verification information, determining that the password is correct if the password verification information is identical to the password encrypted value, reading the biological characteristics to be verified and inputted by the user through the smart card, restoring the biological characteristics in registration according to the password and biological characteristic encrypted value, verifying the matching degree, and succeeding in entry if the matching degree is greater than a set threshold value. Due to the adoption of the smart card registration entry method, different known attacks can be more effectively resisted, and only the user can enter the system.
Owner:SHANDONG UNIV OF SCI & TECH
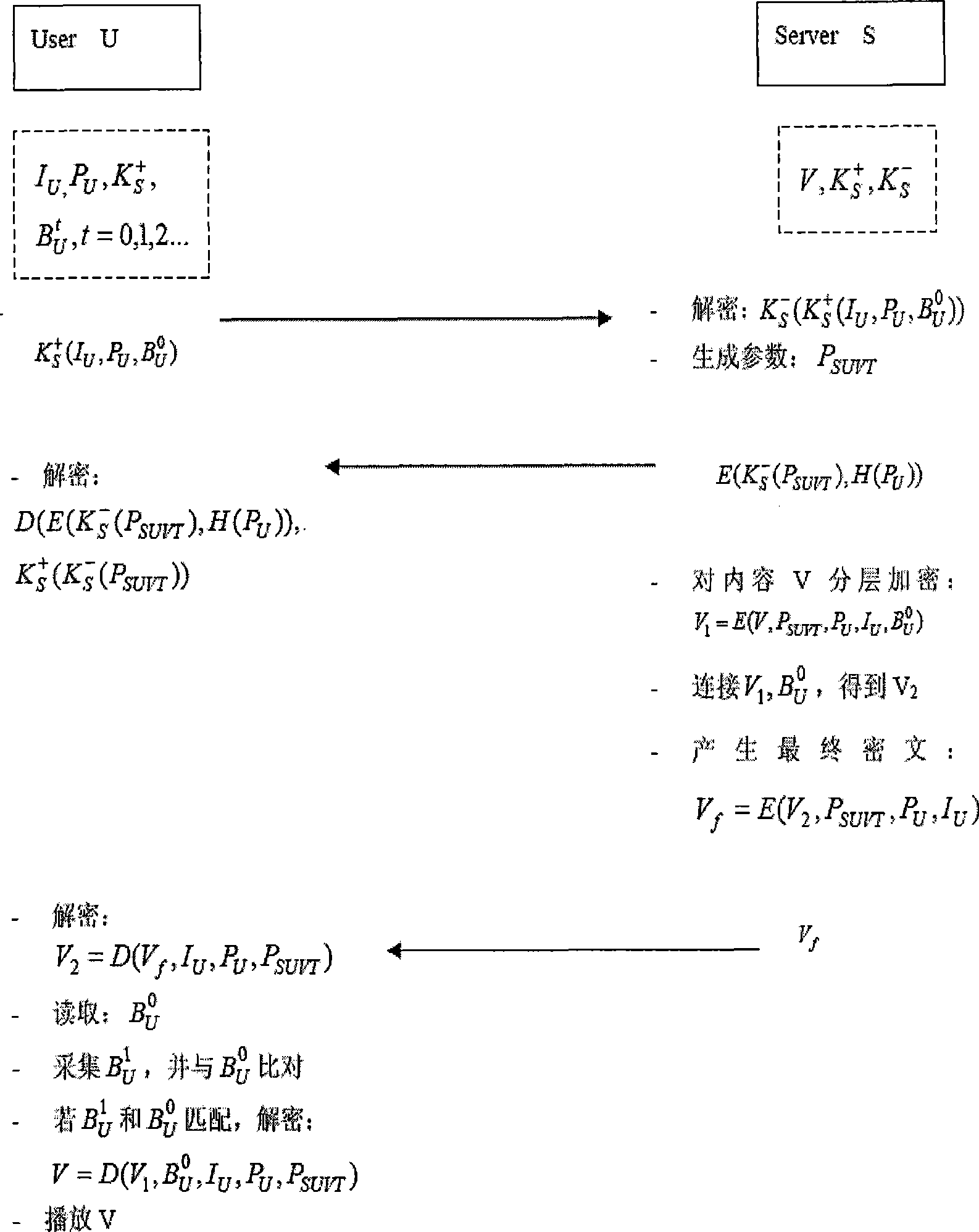
Digital content protection method ciphered by biological characteristic
InactiveCN101383701AWill not limit playbackNot easy to forgetKey distribution for secure communicationPublic key for secure communicationDigital contentNumber content
The invention relates to an encrypted digital content guard method adopting biological characteristic, which belongs to the technical field of information security. The invention adopts the guard proposal that biometrics characteristics of a user is used to encrypt digital multimedia content, the guard proposal is based on the biometrics data of the user and one layered encryption and decryption plan, uses the combination of a symmetric key system and an asymmetric system, and prevents the illegal sharing of the keys through using the biometrics data as the keys. The proposal includes two communication bodies, i.e. a multimedia server S and a user U, the U receives and broadcasts a multimedia file V stored in the S. When the communication starts, the user sends the self biometrics characteristics to the server, the server uses the biometrics characteristics to encrypt the multimedia content which is then sent to the user, when the biometrics characteristics of the user matches with encrypted keys, the multimedia content can be watched, thereby the guard of the multimedia content is realized.
Owner:BEIJING UNIV OF TECH
Biometric card with biometric authentication sensor
InactiveUS20180357644A1Reduce insecurityAvoid data lossMatching and classificationMultiple biometrics useSecurity solutionNanofiber
A biometric card includes sensors embedded in nanofiber substrate for detecting biometric contents. The sensor are configured for analyzing biological characteristics such as human characteristics for security and identification purposes. Embodiments provide means for identifying biological characteristics to detect from a database of fingerprints, a known criminal by matching fingerprint samples collected with prints in the criminal database. Embodiments provide a sweep-able biometric card embedded with biometric authentication sensor associated with biometric authentication sensing surface disposed in a reachable low-stress region. The reachable low-stress region has a dimension substantially smaller than the biometric card for biometric detections and applications for DNA fingerprinting. Embodiments provide a system for verifying and tracking identification information and for delivering security solutions that includes one of the following: a radio frequency (RF) identification device, an identification mechanism that includes a person, wearables, card, sticker, DNA fingerprinting and programmed phone number, and an RF reader.
Owner:TABE JOSEPH A
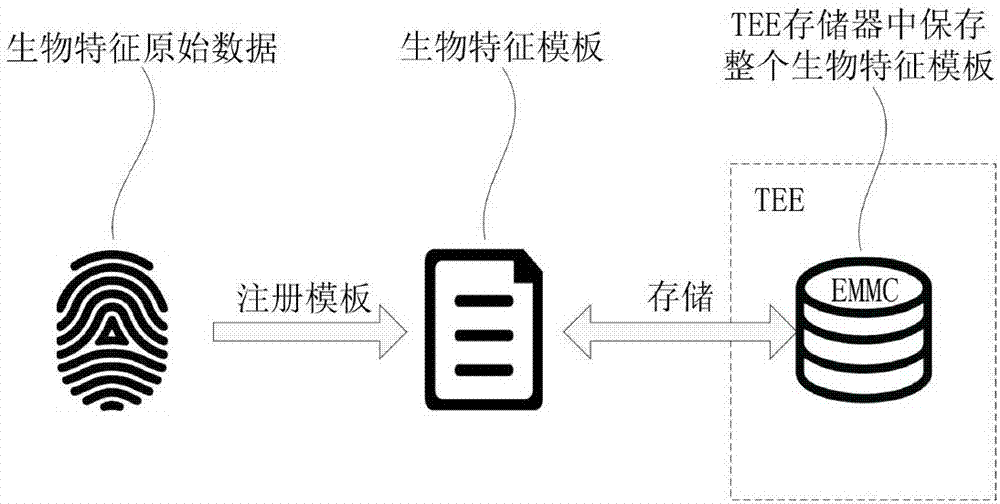
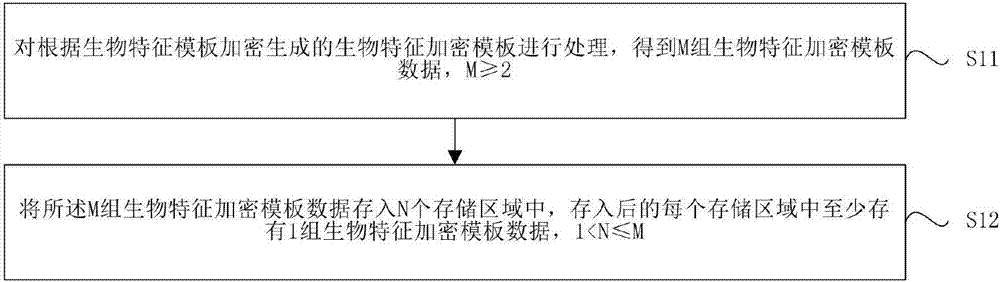
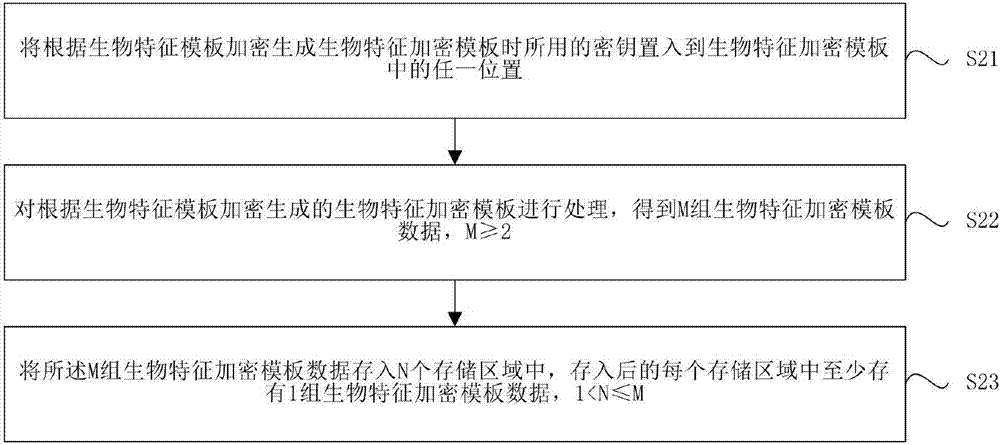
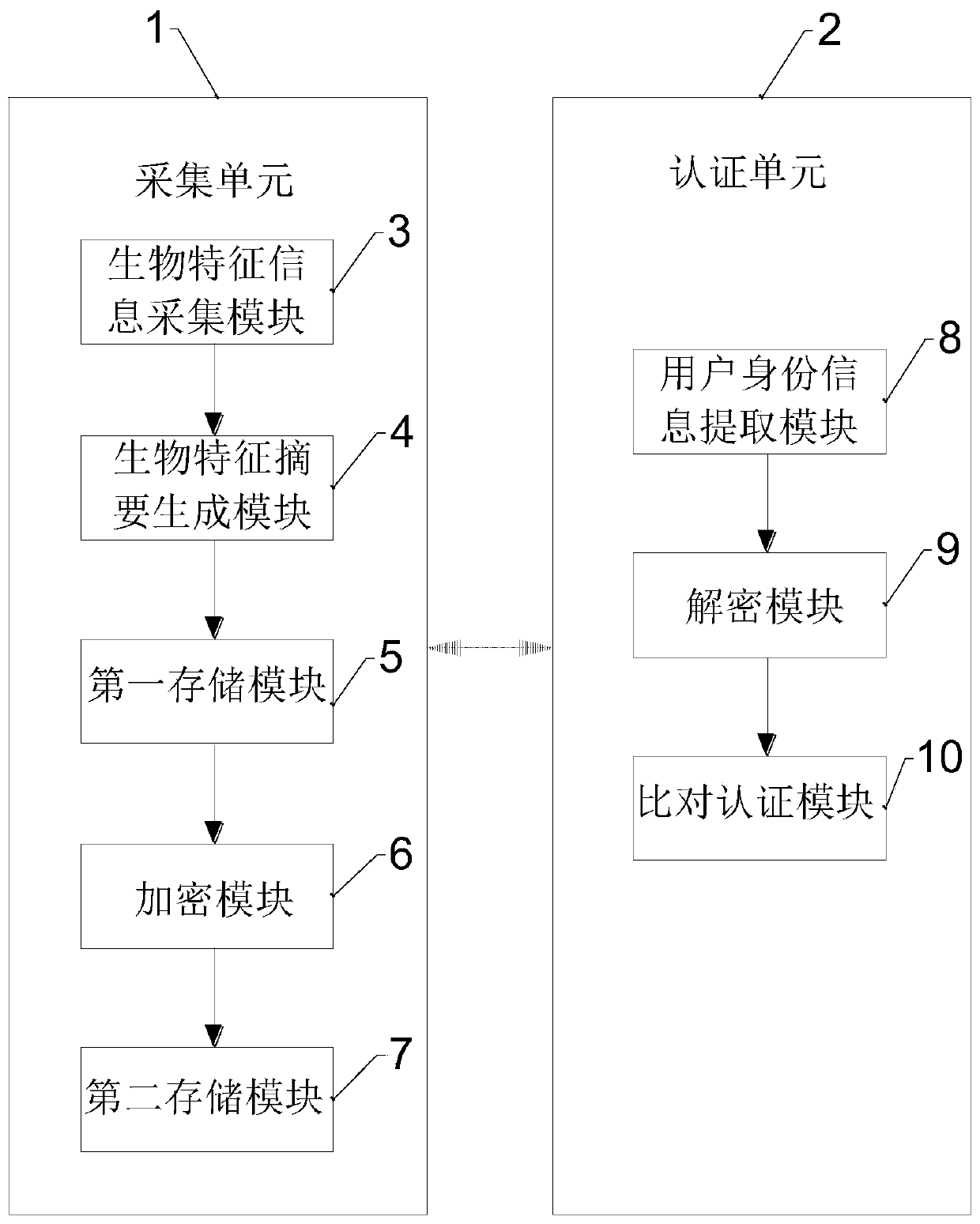
Biological feature template saving and verification method and biological feature identification device and terminal
ActiveCN107113170AReduce the probability of attackReduce leak rateKey distribution for secure communicationUser identity/authority verificationIdentification deviceBiometric encryption
The embodiments of the present invention provides a biological feature template saving and verification method and a biological feature identification device and terminal, and belongs to the biological identification technology field. The biological feature template saving method comprises the steps of processing a biological feature encryption template encrypted and generated according to a biological feature template to obtain M sets of biological feature encryption template data, wherein M >=2; storing the M sets of biological feature encryption template data in N storage areas, at least one set of biological feature encryption template data is saved in each storage area, wherein 1<N<=M. According to the embodiments of the present invention, the biological feature encryption template is processed into multiple sets of biological feature encryption template data, and then the biological feature encryption template data is saved in at least two storage areas dispersedly, so that the multiple sets of biological feature encryption template data is saved in the plurality of storage areas dispersedly, is not easy to leak overall, and accordingly the larger potential safety hazards brought by the prior art to the application of the biological feature template can be eliminated effectively.
Owner:SHENZHEN GOODIX TECH CO LTD
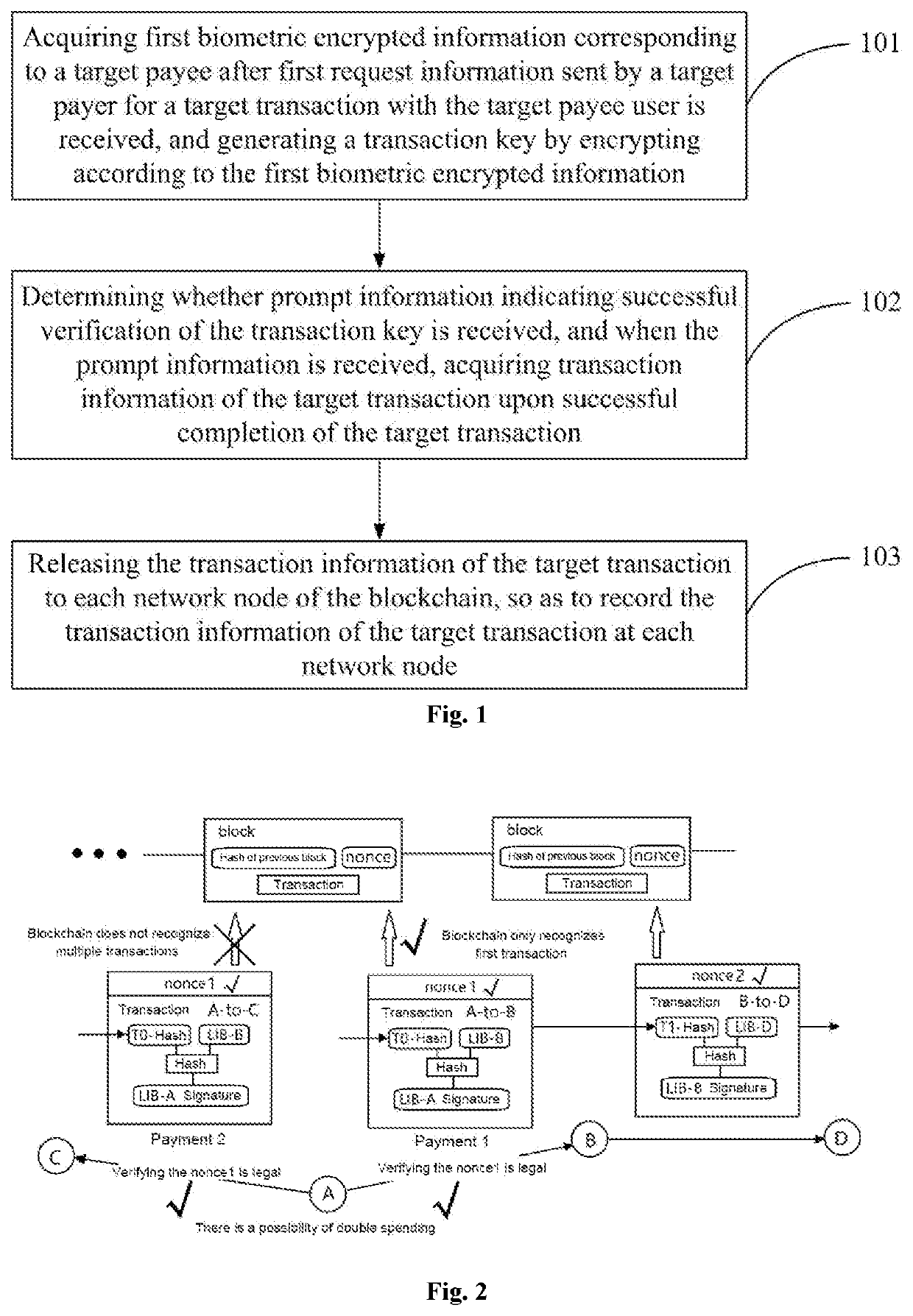
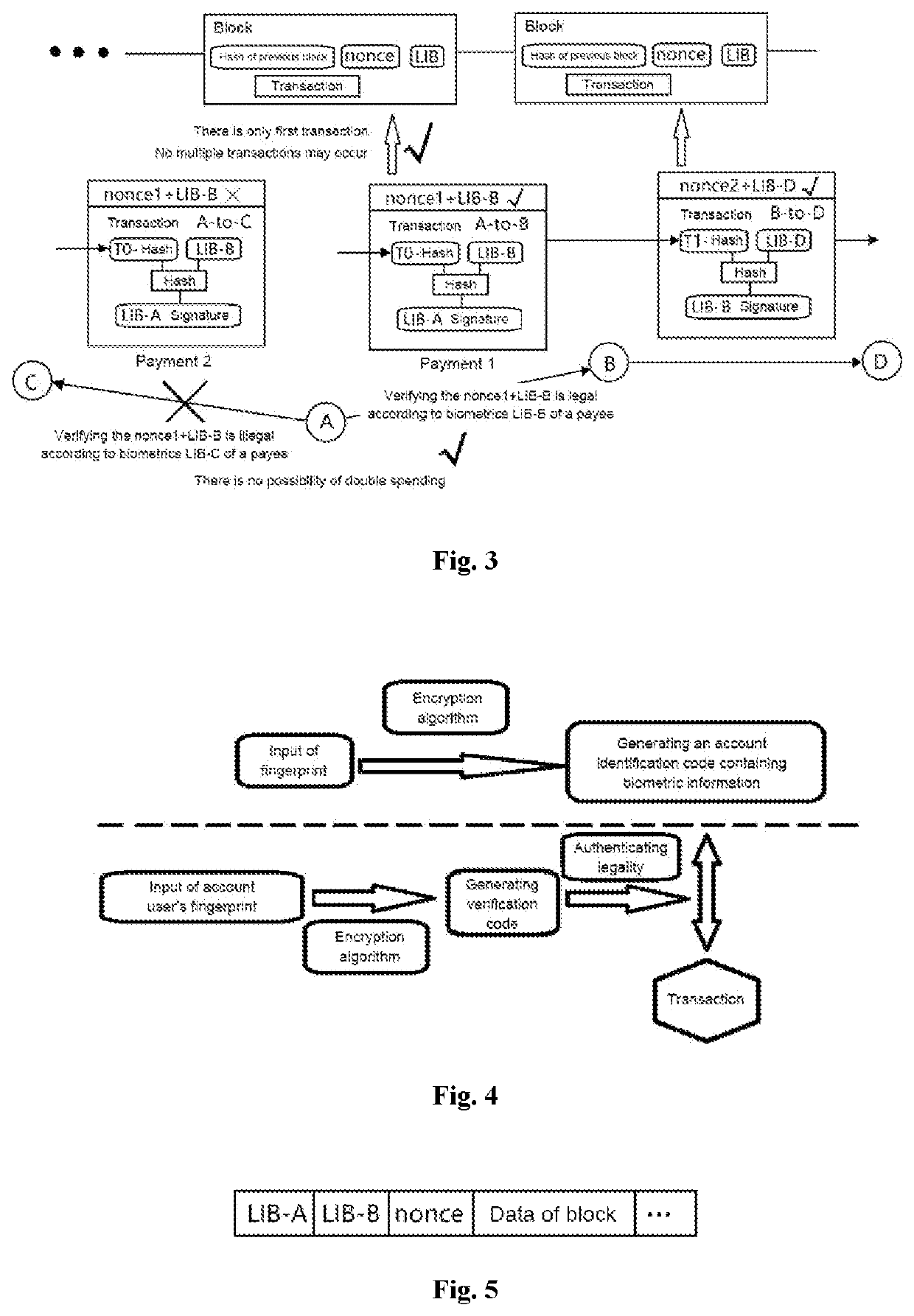
Blockchain secure transaction method and device based on biomarker authentication
InactiveUS20210279736A1Avoid problemsNone of methods is secureCryptography processingPayment circuitsInternet privacyS/KEY
The embodiments of the present application disclose blockchain secure transaction methods and devices based on biomarker authentication. When a digital transaction voucher for the transaction between the payer and the payee is generated, the legality of the transaction is verified, instead of only using nonce, using the transaction key generated according to the biometric encrypted information of the payee user as the digital transaction voucher of the transaction. It can be guaranteed that the transaction will only occur between the payer and the payee designated by the payer due to the uniqueness of the biometric encrypted information. By the methods above, the legal identity information of the payer and payee to the transaction is authenticated from the perspective of the underlying blockchain information encryption, thereby ensuring that a digital transaction voucher can only be used once in a transaction and avoiding the problem of double spending. In addition, the user's digital assets can be recovered by using the uniqueness of the biometric encrypted information for identity authentication when the user's key is lost or the account is embezzled.
Owner:TSINGHUA UNIV
Mobile data communication using biometric encryption
InactiveUS9888382B2Privacy protectionImprove securityKey distribution for secure communicationUser identity/authority verificationBiometric dataInternet privacy
A mobile App using biometric encryption and decryption for privacy and security having both authentication and recognition functions. It utilizes the built-in camera of the mobile device to provide facial images for authentication purposes. It further includes a secured data communication system for conveniently sending and receiving data on the mobile devices. The secured data communication system also utilizes biometric encryption and decryption technology for granting permissions to access the data communication system. The biometric encryption is implemented by using a selective biometric feature and optimized biometric feature detection and tracking methods. Different biometric feature authentication methods are optimized for use on various mobile platforms, such as, Android, iOS, Windows and others. Data encryption and decryption are achieved by using selected biometric feature vectors as cryptographic keys. The biometric data encryption system further includes liveness detection module with anti-spoofing features to ensure the encryption and decryption processes only accept biometric features from a live person conveniently without the user's intervention. Alternative authentication method is provided if the biometric feature authentication module fails to recognize the valid user, or fails in the liveness detection module in order to maintain privacy and security of the data in the mobile device.
Owner:WASHINGTON SOFTWARE INC
Method and System to Electronically Identify and Verify an Individual Presenting Himself for Such Identification and Verification
InactiveUS20070253601A1User identity/authority verificationCharacter and pattern recognitionDatabase machineOn-the-fly encryption
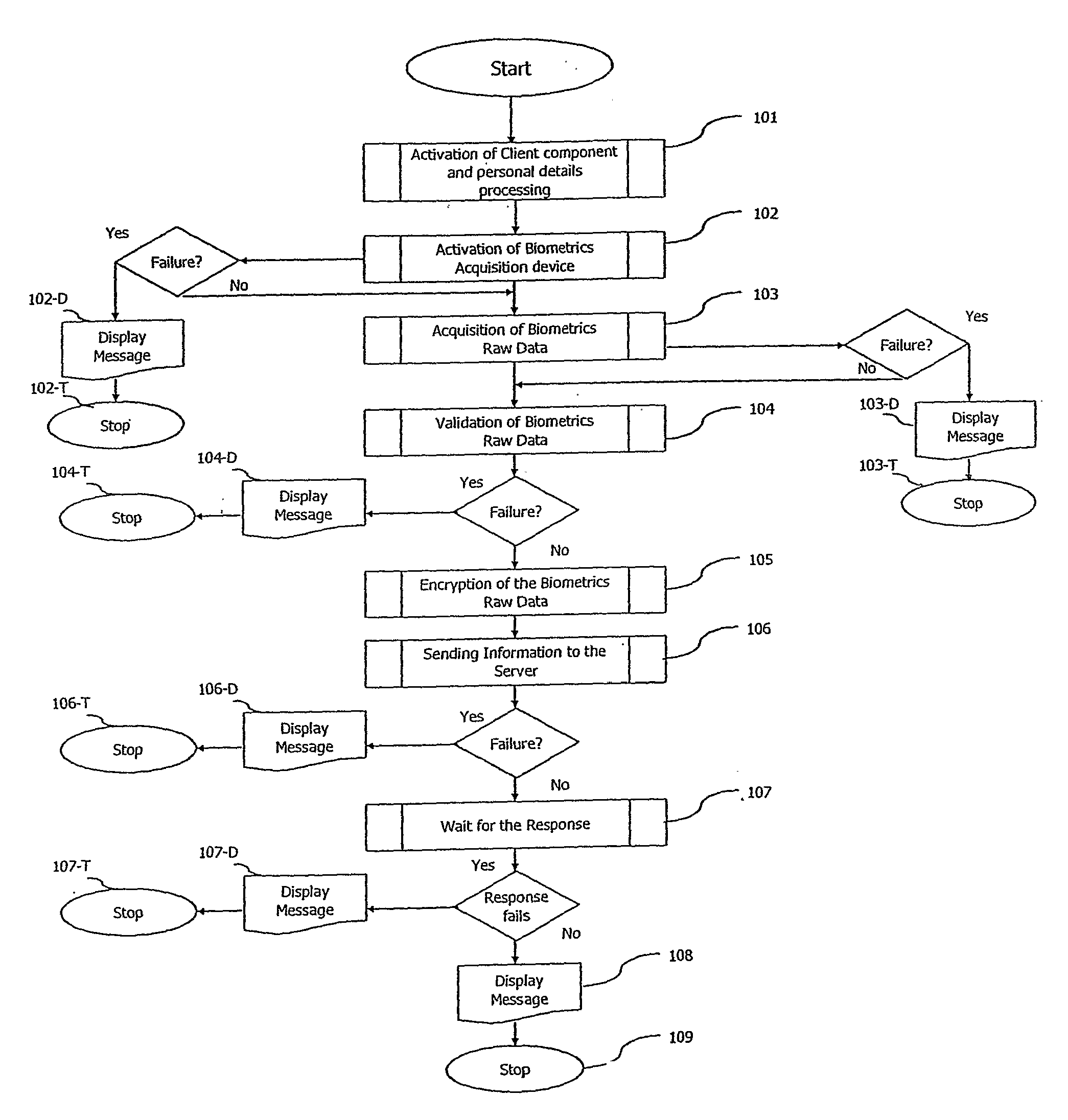
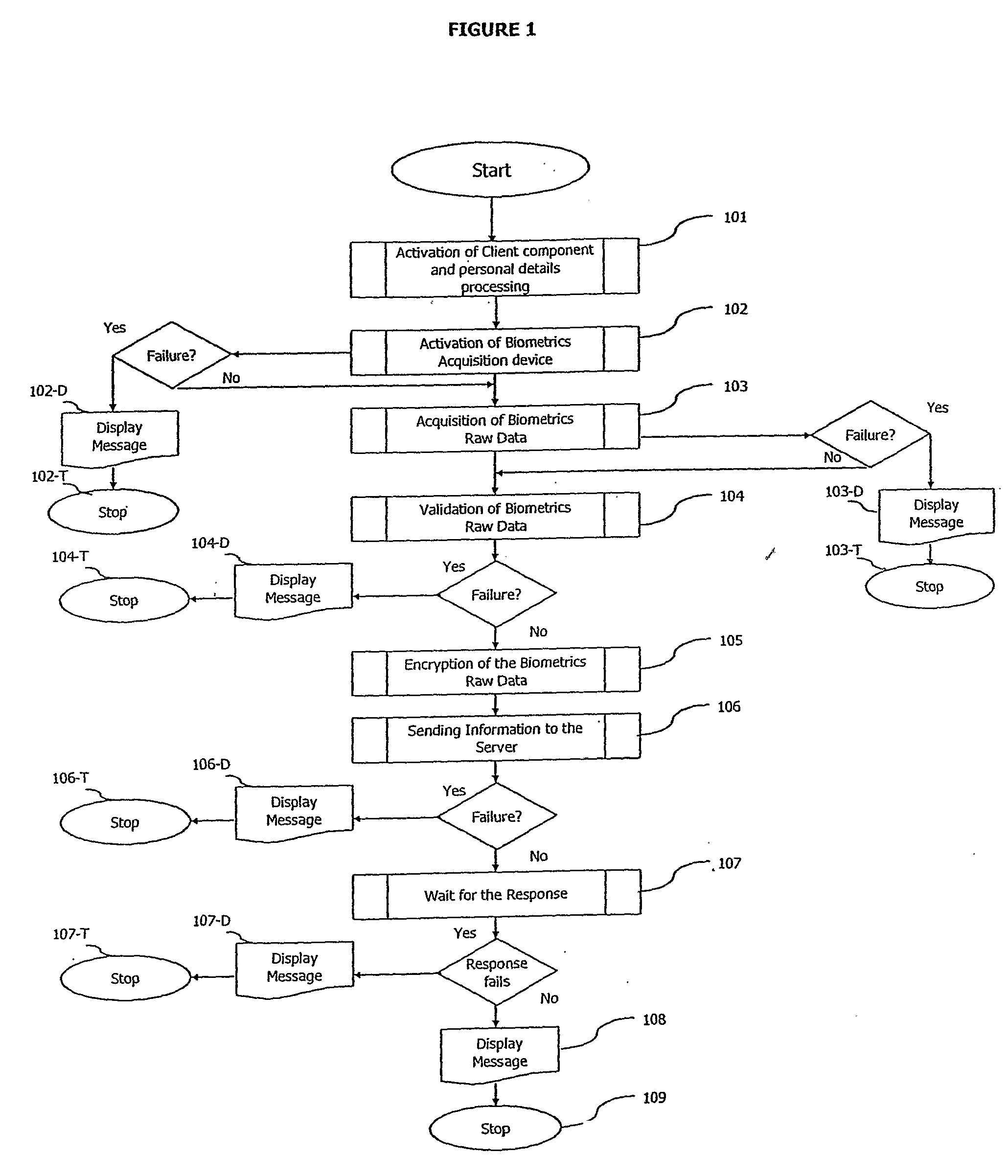
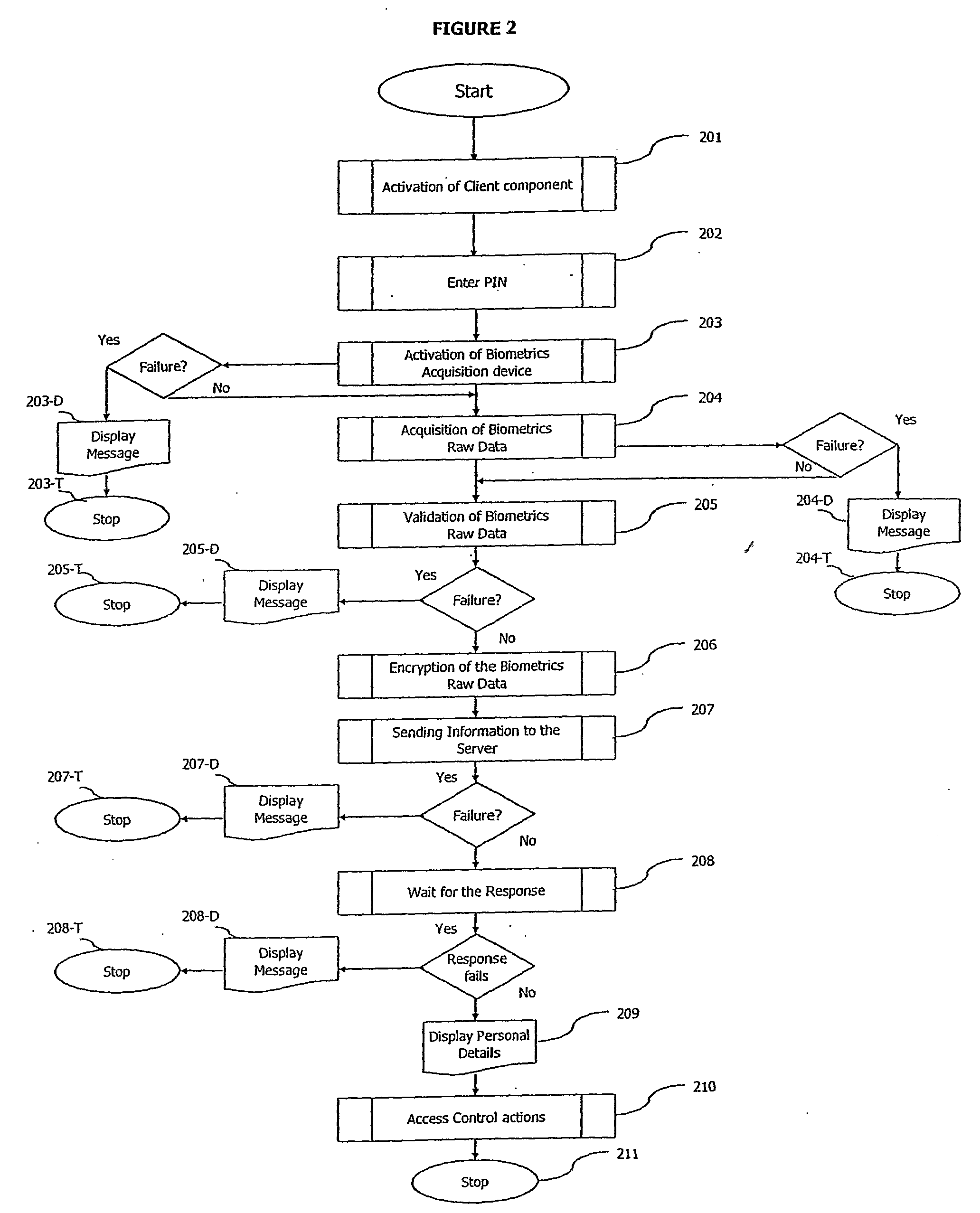
A method and a system of electronically identifying and verifying an individual utilising at least one biometric features of the individual is disclosed. The method includes the steps of activating an access apparatus with a means to capture at least one biometric feature of an individual in a secure manner using dynamic encryption, capturing the biometric feature of an individual wherein key features of biometric raw data are extracted, encrypting in a dynamic manner the biometric features, transmitting the encrypted data of the biometric feature to at least one server; and verifying the biometric features captured in the fruit step with a pre-stored biometric feature in the server. Wherein upon positive identification and verification of the individual access is given to an auxiliary means such as but not limited to access to secured doors, database, computer network and servers.
Owner:SURESHWARA
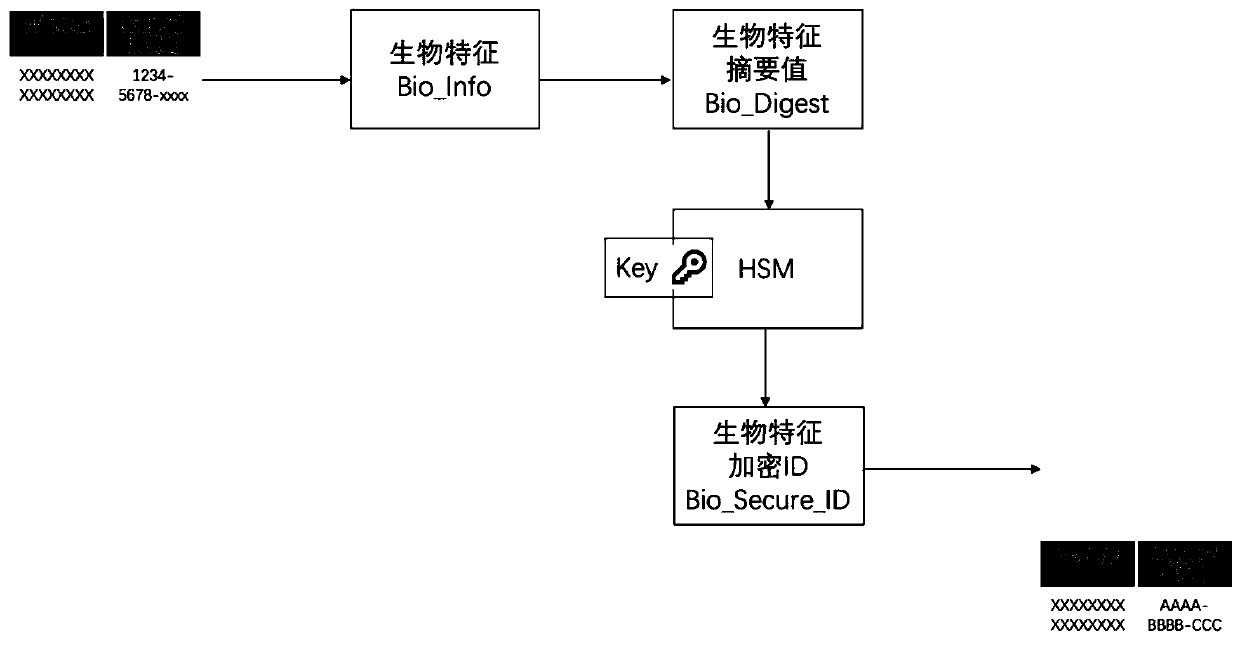
Biological characteristic information and identity information association method, system and device
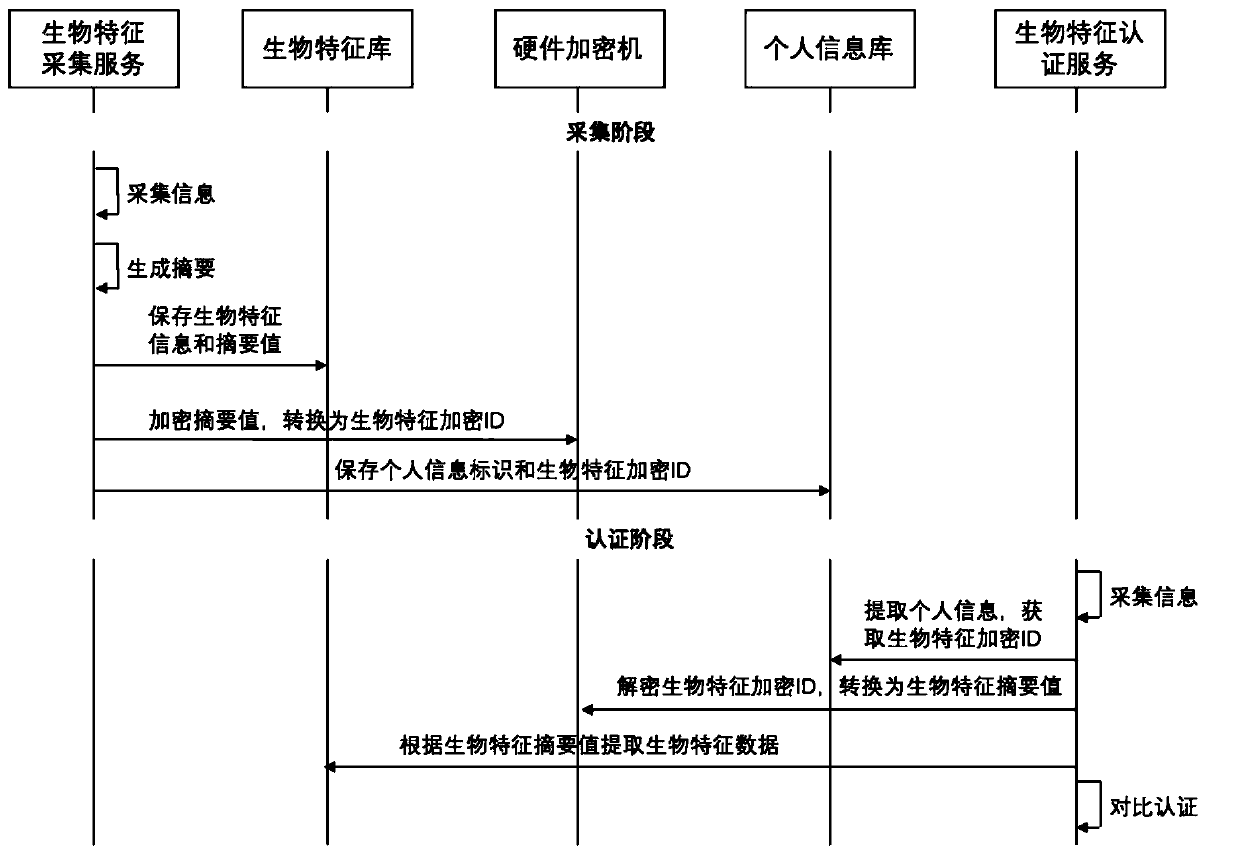
InactiveCN110287670AAvoid risk of leakageAvoid catastrophic effectsDigital data protectionDigital data authenticationComputer scienceSerial code
The invention discloses a biological characteristic information and identity information association method, system and device, and the method comprises the steps: in an acquisition stage, collecting the biological characteristic information of a user at a biological characteristic information side, and generating a biological characteristic abstract value according to the biological characteristic information; storing the biological characteristic information and the generated biological characteristic abstract value through a biological characteristic library; encrypting the biometric abstract value and converting the biometric abstract value into a biometric encryption serial number of a user identity information side; and storing the user identity information and the biological characteristic encryption serial number. In the authentication stage, user identity information is extracted, and a biological characteristic encryption serial number corresponding to the user identity information is obtained; decrypting the biological characteristic encryption serial number to obtain a biological characteristic abstract value; and retrieving the biological characteristic information according to the biological characteristic abstract value for comparison and authentication. According to the technical scheme, the biological characteristic information and the identity information are isolated, the abstract information is protected through encryption, catastrophic influence caused by library file leakage is avoided, and safety is high.
Owner:上海芯安能众微电子技术有限公司
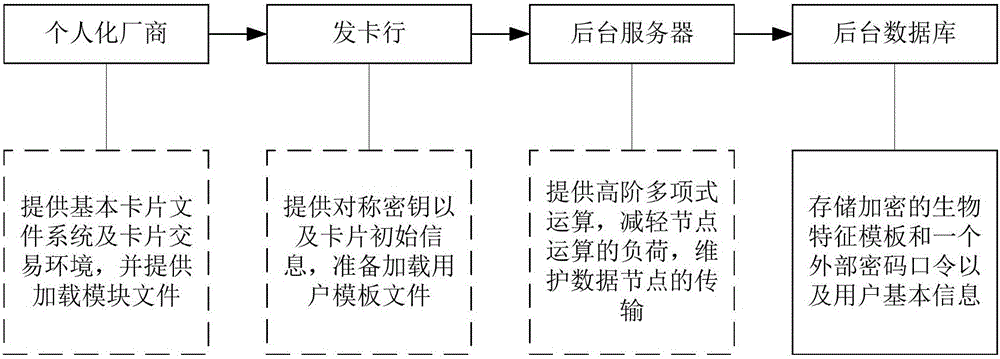
Method, device and system for PBOC transaction based on biometric encryption
InactiveCN106709716AResolve UncertaintyAddress decipherable flawsProtocol authorisationPasswordUser input
The invention relates to a method, a device and a system for PBOC transaction based on biometric encryption. The method comprises steps: biometrics of a user are acquired, and effective biometrics are extracted; based on a password inputted by the user, a private key of the user is generated; a fuzzy vault algorithm is adopted to combine the effective biometrics and the private key to generate a biometric template for marking the user identity information; the biometric template is stored to a backstage database, and is located to a financial IC card; and the biometric template in the financial IC card and the password inputted by the user are submitted to the backstage server for verification, and after the verification is passed, the financial IC card is allowed to perform PBOC transaction. The defect that when the financial IC card is adopted to perform PBOC transaction, an asymmetric algorithm is overly dependent and can be decoded can be solved, and the biometric encryption technology is introduced to solve the uncertainty generated as a process with many human factors exists in the PBOC transaction.
Owner:AEROSPACE INFORMATION
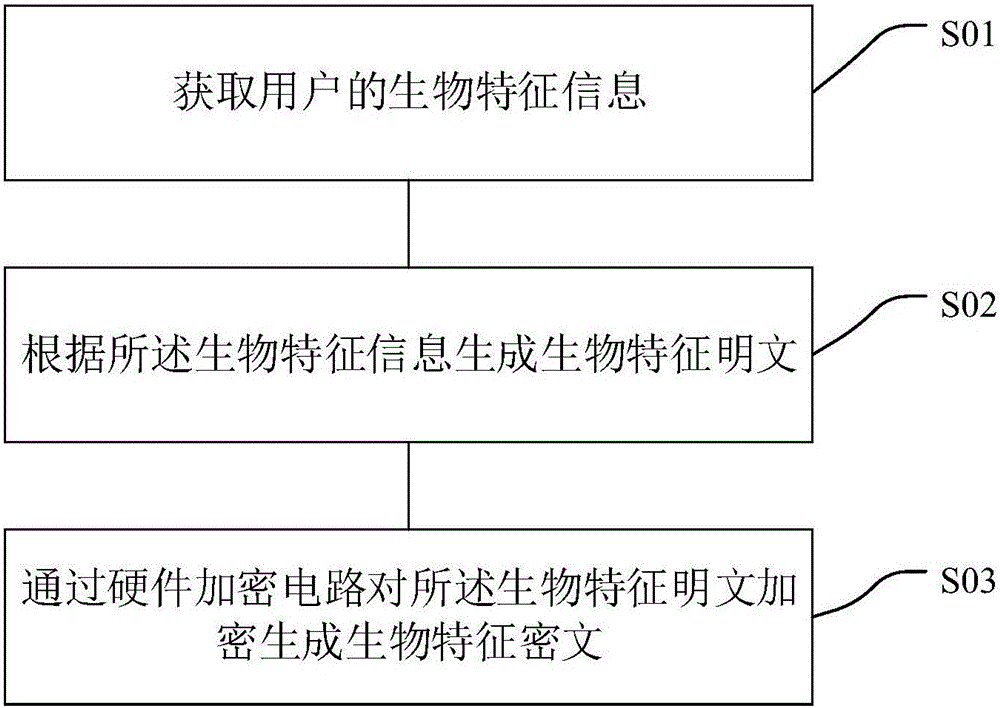
Biological characteristic encryption method and device
ActiveCN105978889AReduce dependenceImprove securityKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
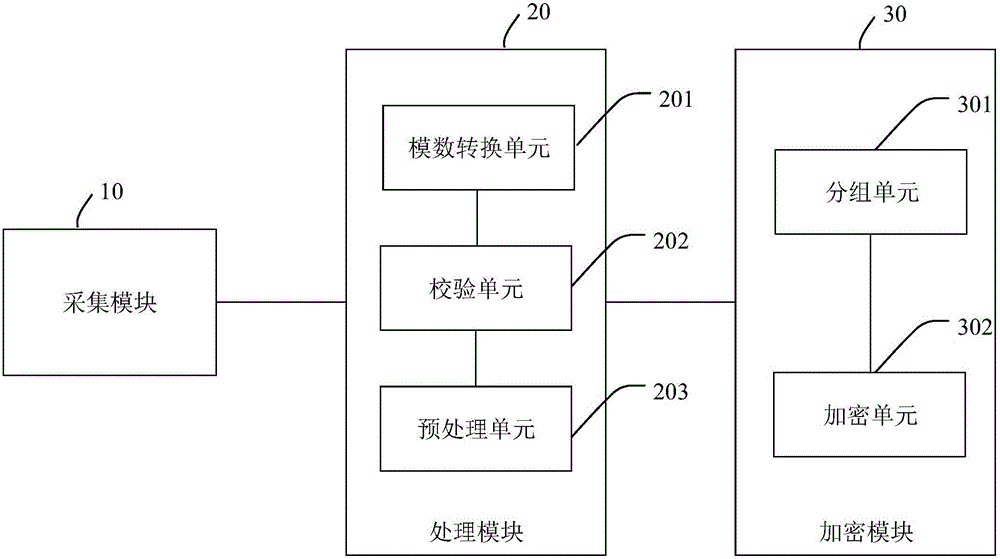
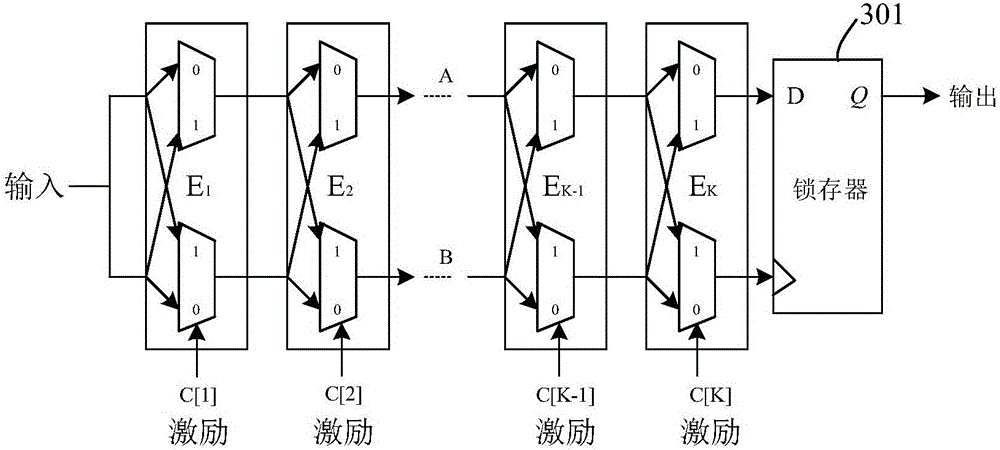
The invention discloses a biological characteristic encryption method. The method comprises the steps of obtaining biological characteristic information of a user; generating a biological characteristic plaintext according to the biological characteristic information; and generating a biological characteristic ciphertext through encryption of the biological characteristic plaintext in a hardware encryption mode. The invention also discloses a biological characteristic encryption device. The biological characteristic information of the user is encrypted through a hardware encryption circuit; the dependence of an algorithm on a processor is reduced; encryption is realized in a same chip; and the data transmission security and efficiency can be improved.
Owner:CHIPONE TECH BEIJINGCO LTD
Bio-metric encryption key generator
InactiveCN101461171AKey distribution for secure communicationUser identity/authority verificationComputer hardwareCryptographic key generation
Owner:MOTOROLA INC
Security lock based on laser holography
InactiveCN109448185AImprove information securityIndividual entry/exit registersMemory chipLaser holography
The invention relates to a security lock based on laser holography, and relates to the technical field of optical image encryption. The security lock, which optically and holographically encrypts users' PIN codes by taking biological feature information as secret keys, is characterized in that the users' original PIN codes are converted into PIN images, biological feature encryption images generate biological feature encryption secret keys, encrypted holograms are generated by optical holographic encryption paths and are stored in optical holographic recording materials, and the optical holographic recording materials are embedded in front of an electronic chip of a smart card; users' biological feature decryption images generate biological feature decryption secret keys to pass through optical holographic decryption paths, correct PIN decryption images are output to acquire the correct PIN codes if the decryption secret keys are correct, and user information is output; a security lockis added at the front end of a memory chip, an optical encryption method is integrated on the basis of original digital encryption of the smart chip card, and accordingly, the information security ofthe smart card is improved.
Owner:SHANGHAI NORMAL UNIVERSITY
Identity authentication method based on biological feature encryption and homomorphic algorithm
InactiveCN102664885BImprove privacyAvoid crackingUser identity/authority verificationAlgorithmCiphertext
An identity authentication method based on biometric encryption and homomorphic algorithm, which uses the user's biometrics as a password to log in to the system through a mobile device, which is faster than the usual password method, and the use of encrypted biometric templates is more secure, while information is transmitted The process is transmitted in the form of ciphertext, which ensures the privacy of the user; factors such as time stamps are added to enable three-party authentication between the user and the provider server and cloud computing server, which enhances the credibility of the three parties; The user performs the authorization operation based on the predicate encryption of the attribute and updates the permission information in real time, which can prevent legitimate users from illegally using resources in the cloud computing environment and better manage resources. The homomorphic algorithm can be used to operate without decryption, just as the effect of decryption first and then operation is the same, which saves time and space overhead, greatly improves the efficiency of the system, and has high security and efficiency.
Owner:南京邦普信息科技有限公司
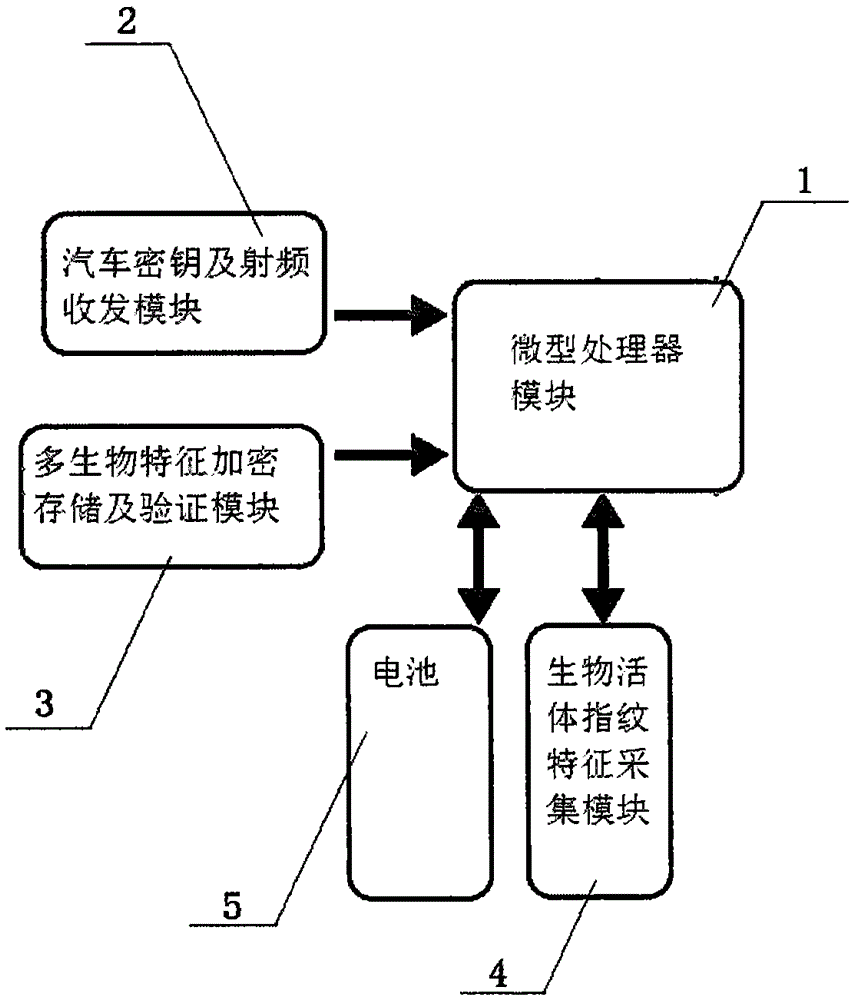
Biological characteristic circumstantial evidence-based high safety and loss resisting automobile remote control key
The invention relates to a biological characteristic circumstantial evidence-based high safety and loss resisting automobile remote control key. The number of cars increases fast in recent years, and vehicle safety problems, such as key loss, exist, so a biological characteristic circumstantial evidence-based high safety and loss resisting automobile remote control key is urgently needed. The key improves the safety without damaging user experiences. The key comprises a microprocessor module, a car secret key and radiofrequency transmit-receive module, a multi-biological characteristic encrypted storage and verification module, a biological in vivo fingerprint characteristic collecting module and a battery.
Owner:HUNAN UNIV OF HUMANITIES SCI & TECH +1
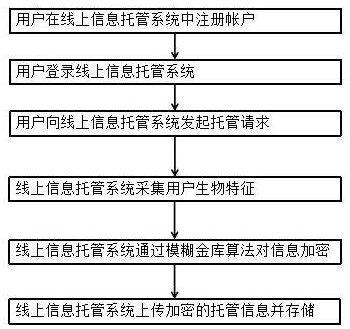
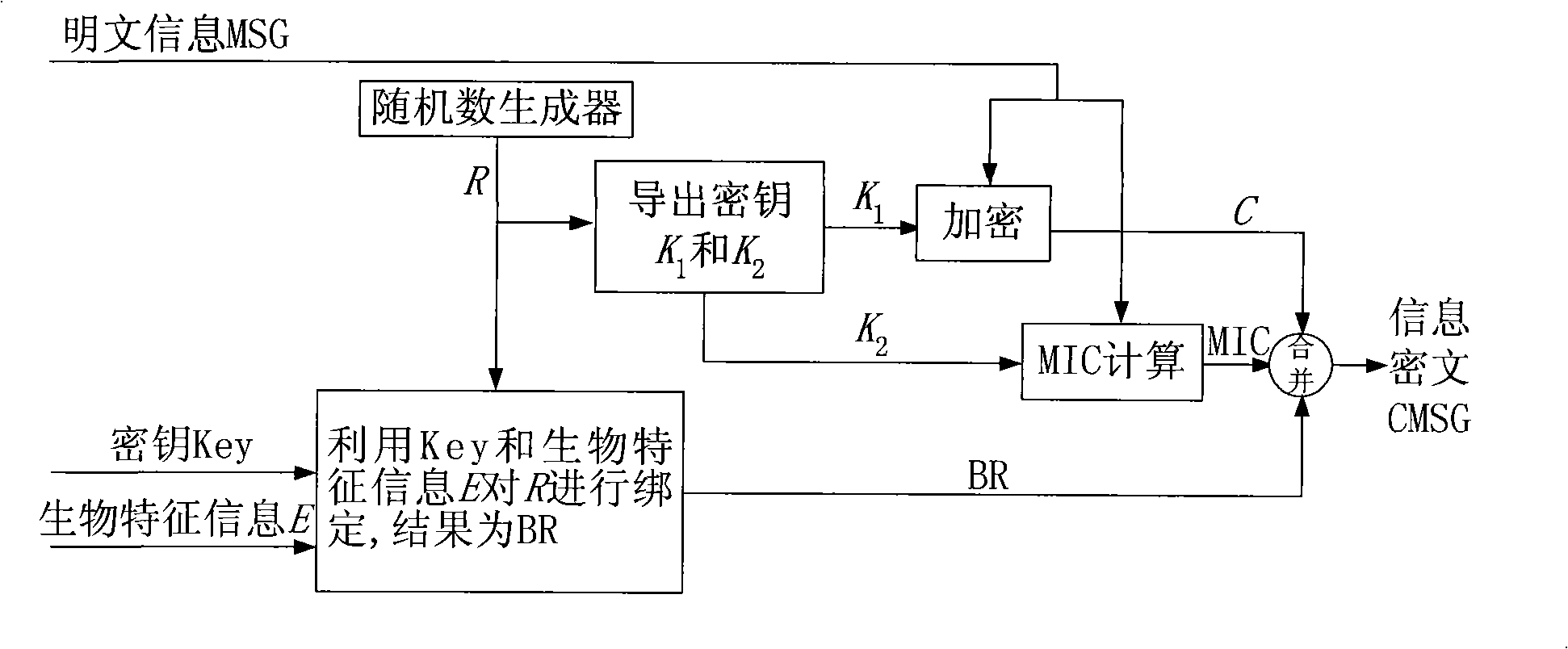
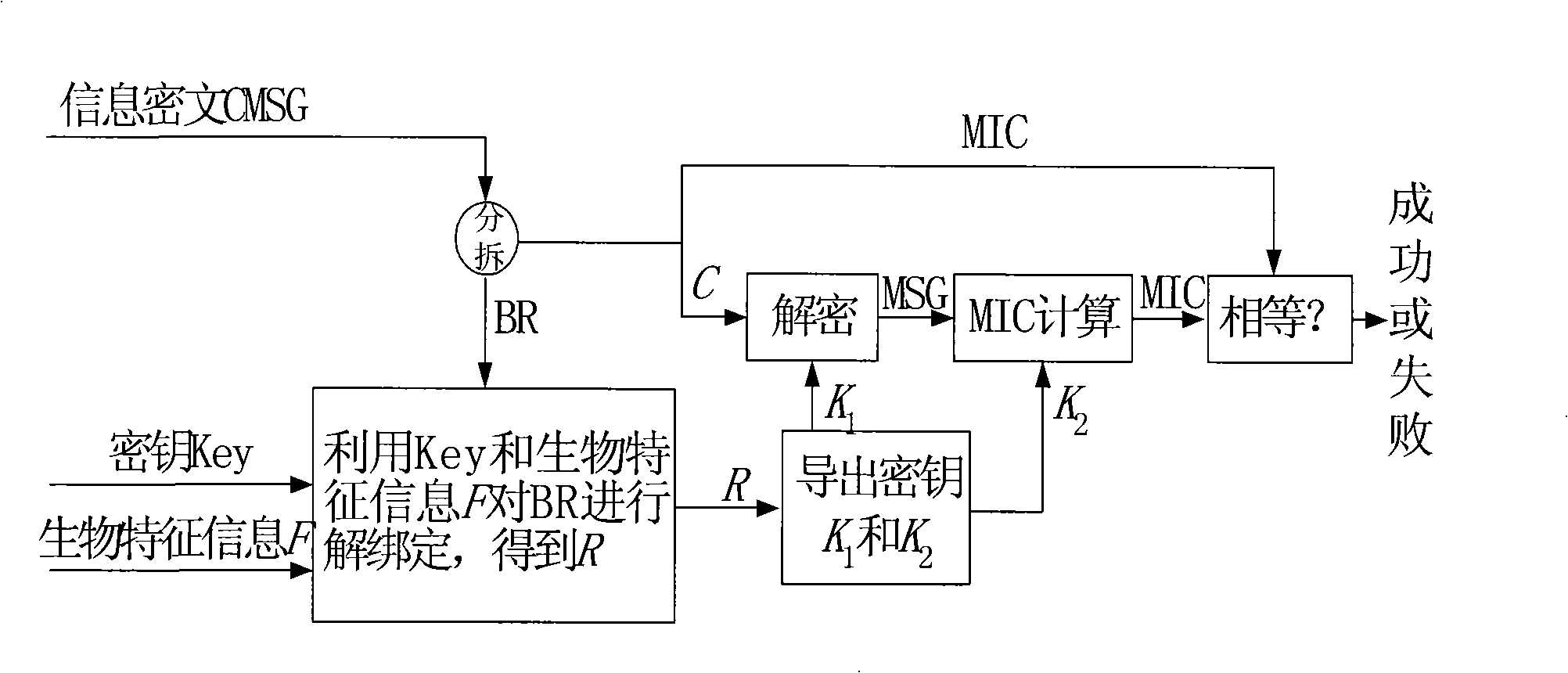
A method and system for online information trusteeship integrating biometric encryption technology
ActiveCN109039650BPrevent theftLarge capacityKey distribution for secure communicationUser identity/authority verificationSoftware systemEngineering
Owner:朱俊
Encrypting method base on biology characteristic information
InactiveCN101350724BWill not pose a safety hazardThere is no key leakage problemUser identity/authority verificationCharacter and pattern recognitionPlaintextPassword
Owner:XIDIAN UNIV
Key generation device, key utilization device, and key generation method
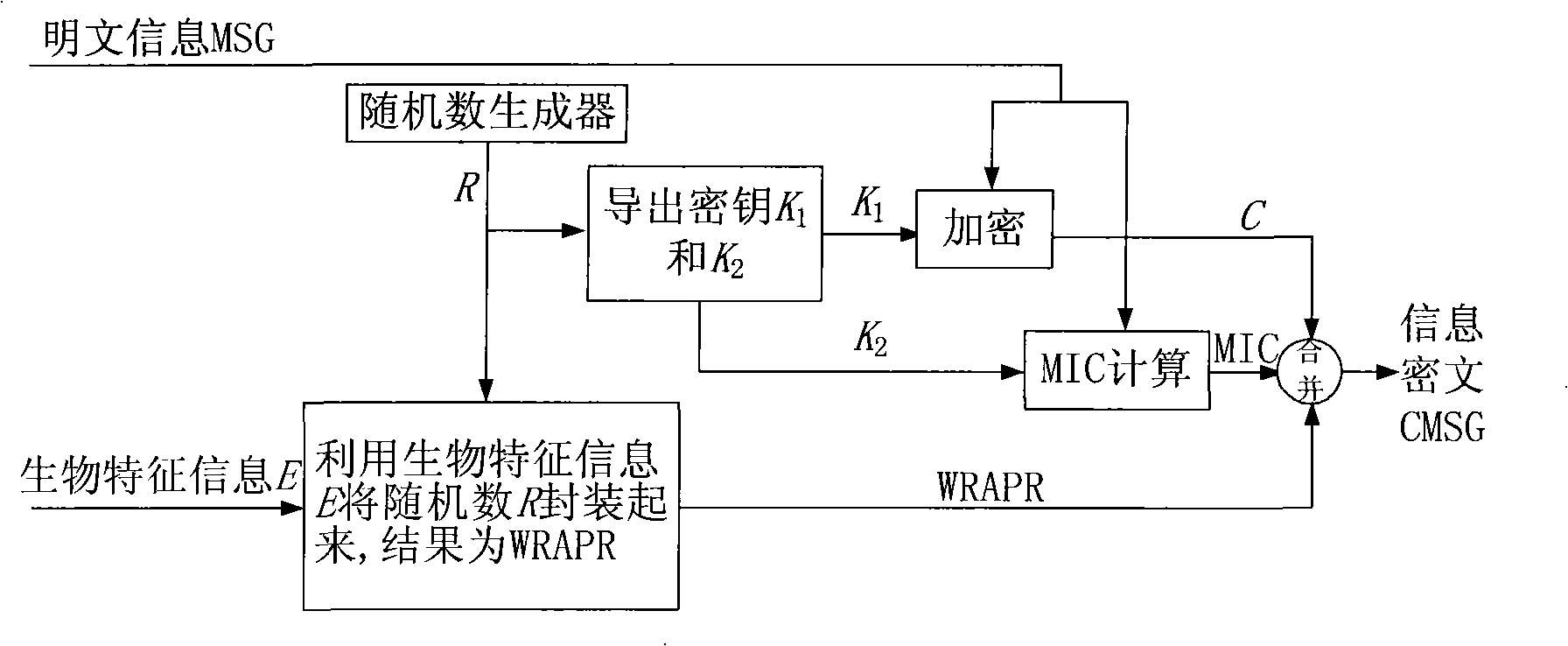
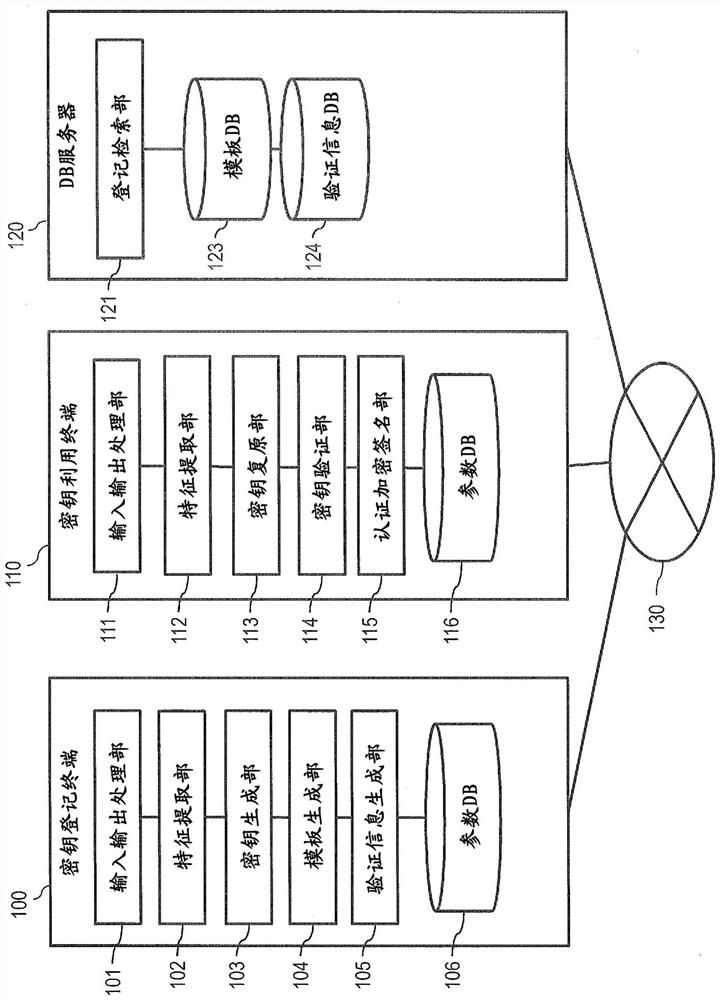
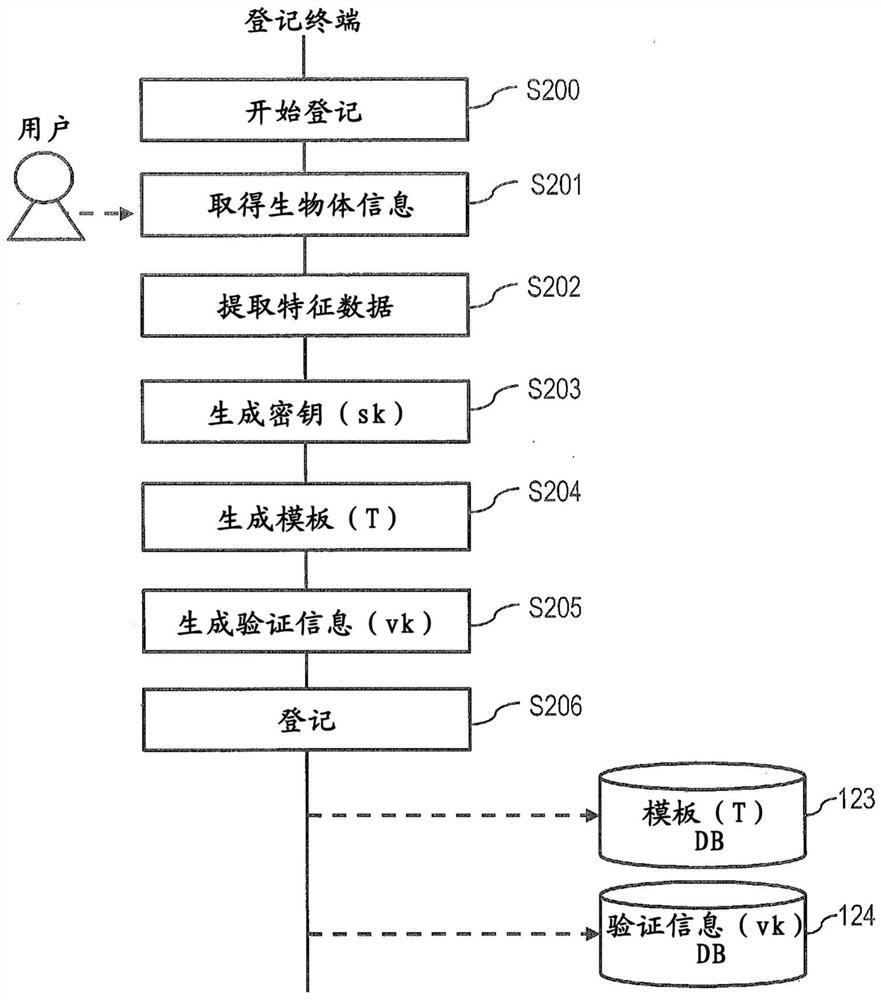
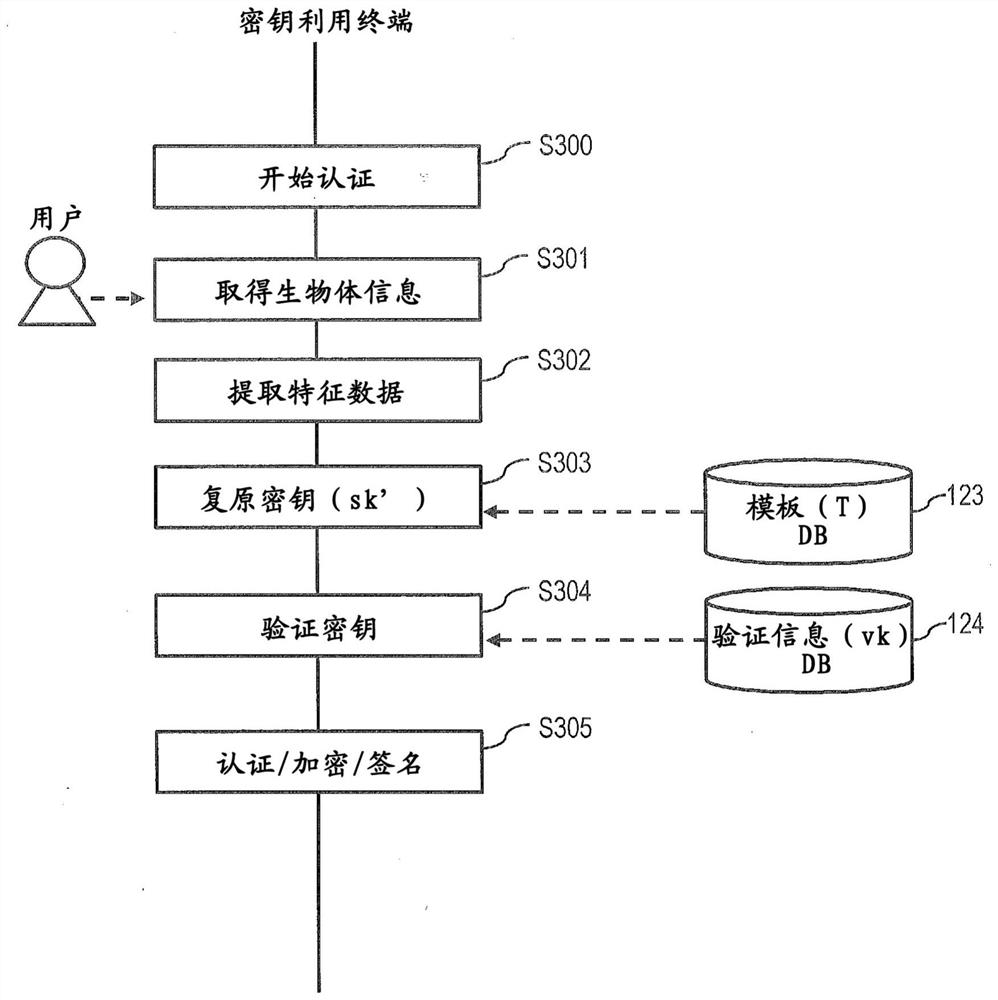
PendingCN114762287AAchieve high-precision authenticationClear structureKey distribution for secure communicationUser identity/authority verificationBiological bodyFeature vector
A key generation device is used for realizing high-precision authentication in biometric encryption and biometric signature based on a feature vector in a high-dimensional Euclidean space. The key generation device holds a first feature vector indicating a feature of the first biological information, and a parameter for determining a ball filling configuration having a density less than 1 and higher than a predetermined value, or a ball covering configuration having a density of 1 or more and lower than the predetermined value, and determines the ball filling configuration or the ball covering configuration on the basis of the parameter. A first point included in the determined ball filling configuration or ball covering configuration is selected, a predetermined first conversion is performed on the first point to generate a first key, and a template corresponding to the first biological information is generated on the basis of the first feature vector and the first point.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com