Patents
Literature
815results about How to "Avoid risk of leakage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
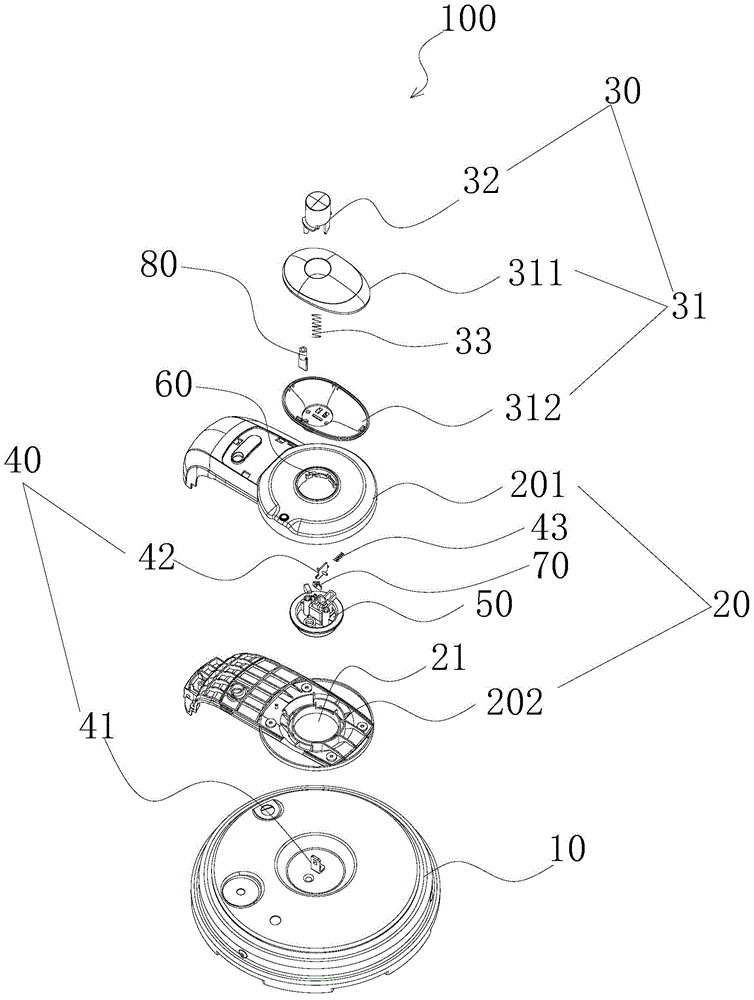
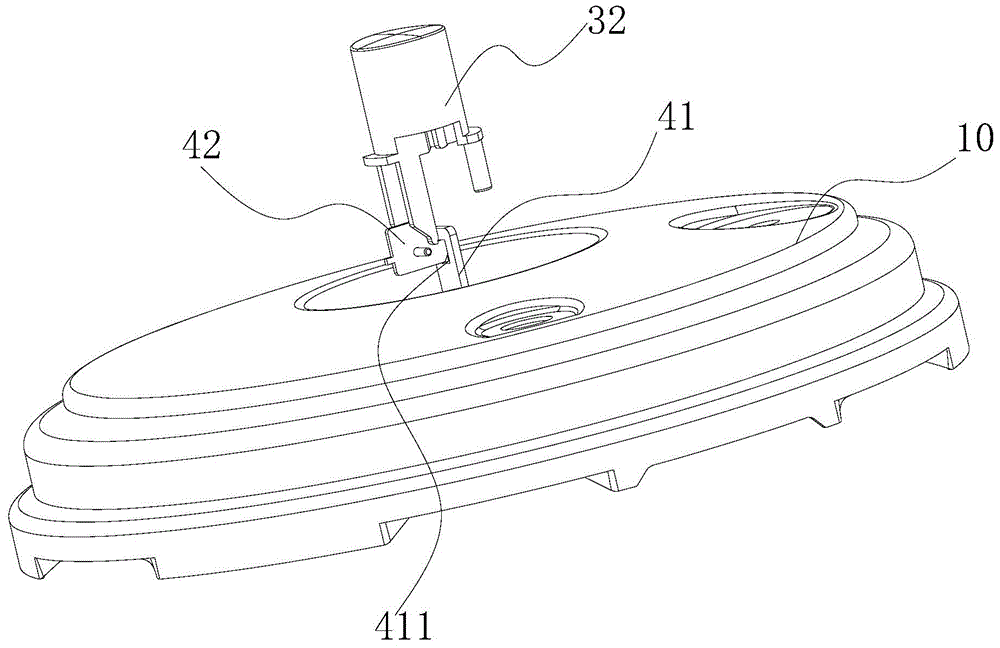
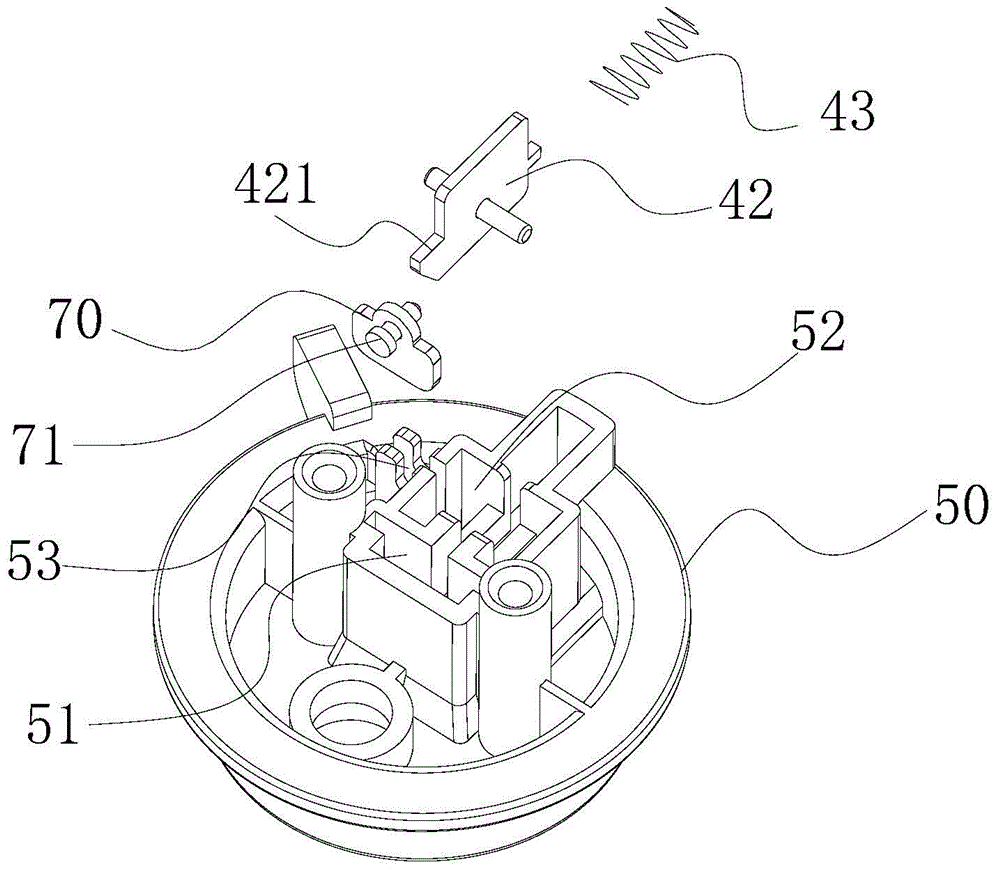
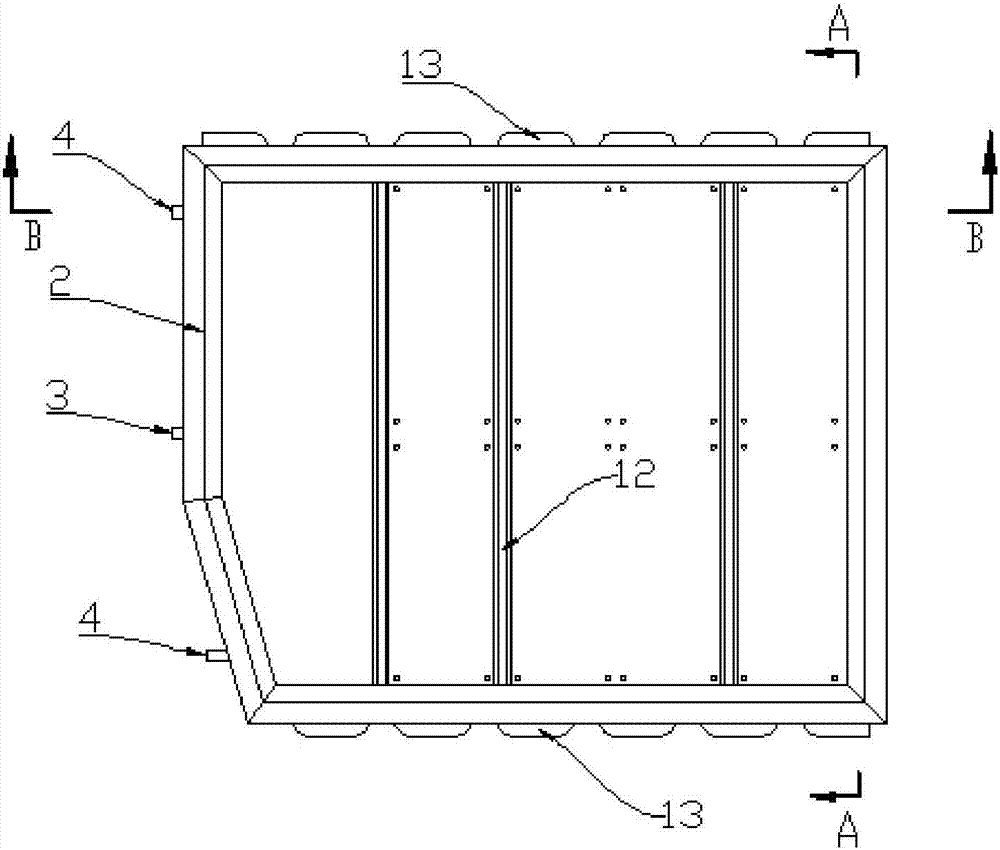
Pressure cooker
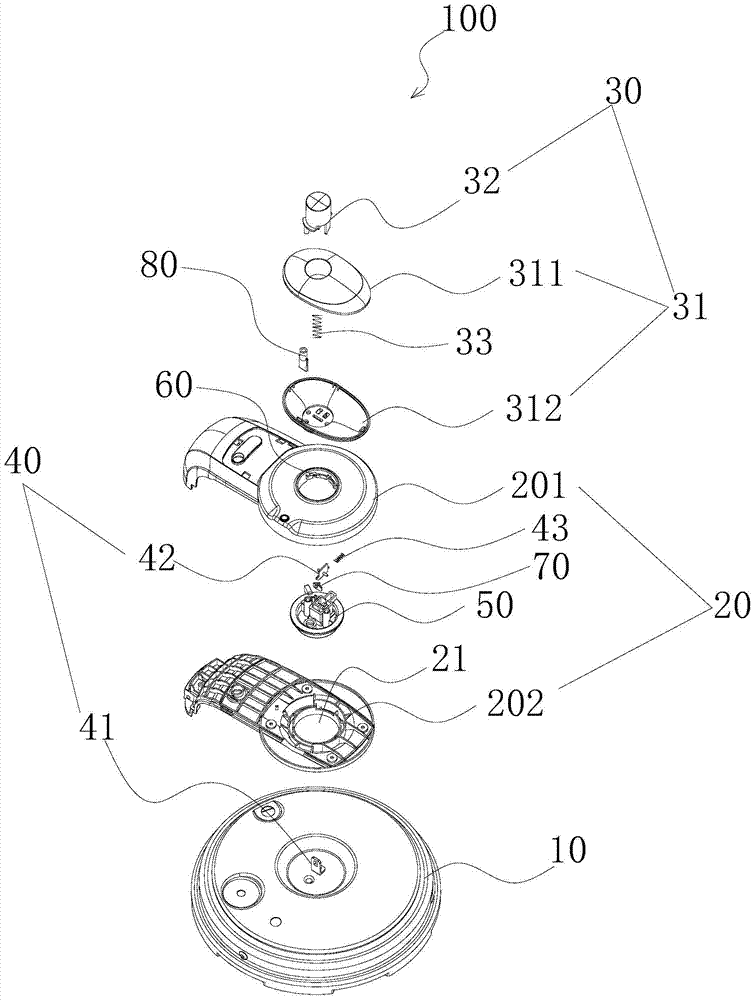
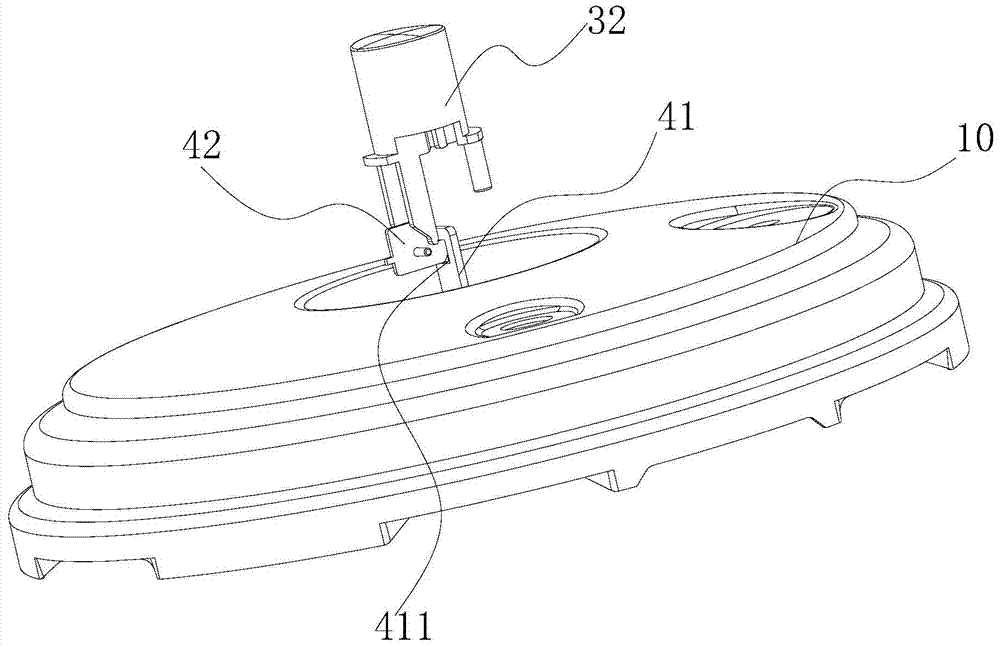
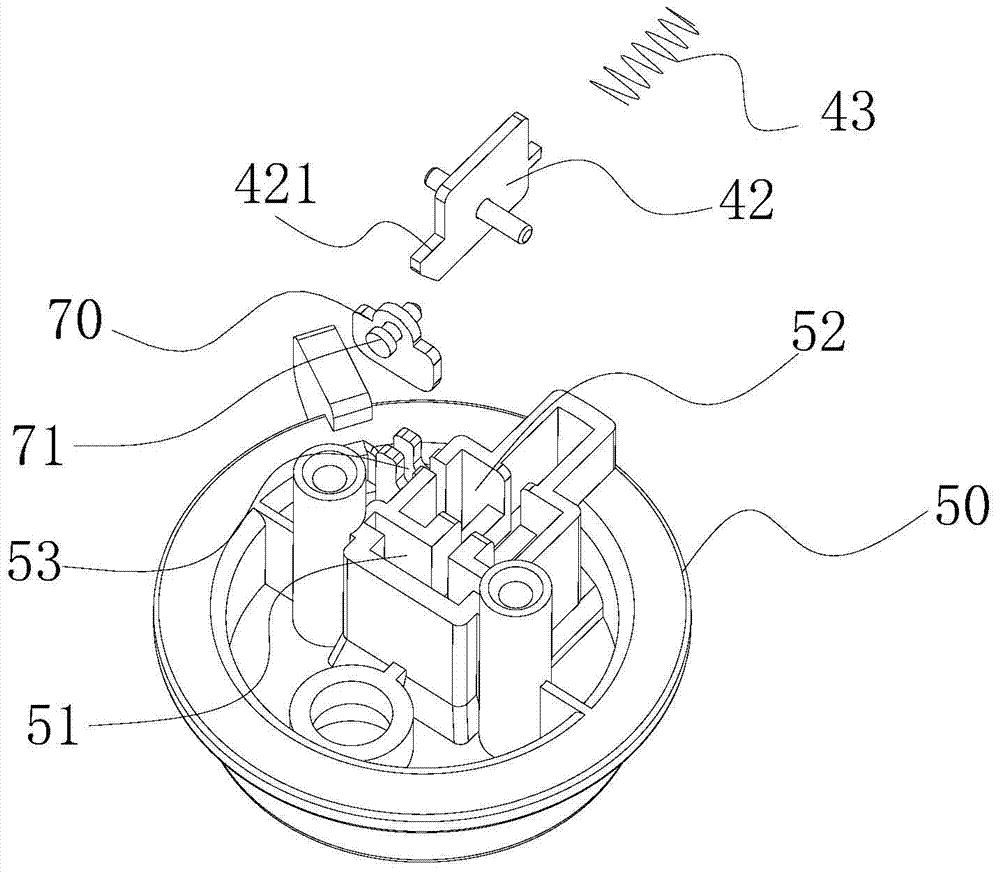
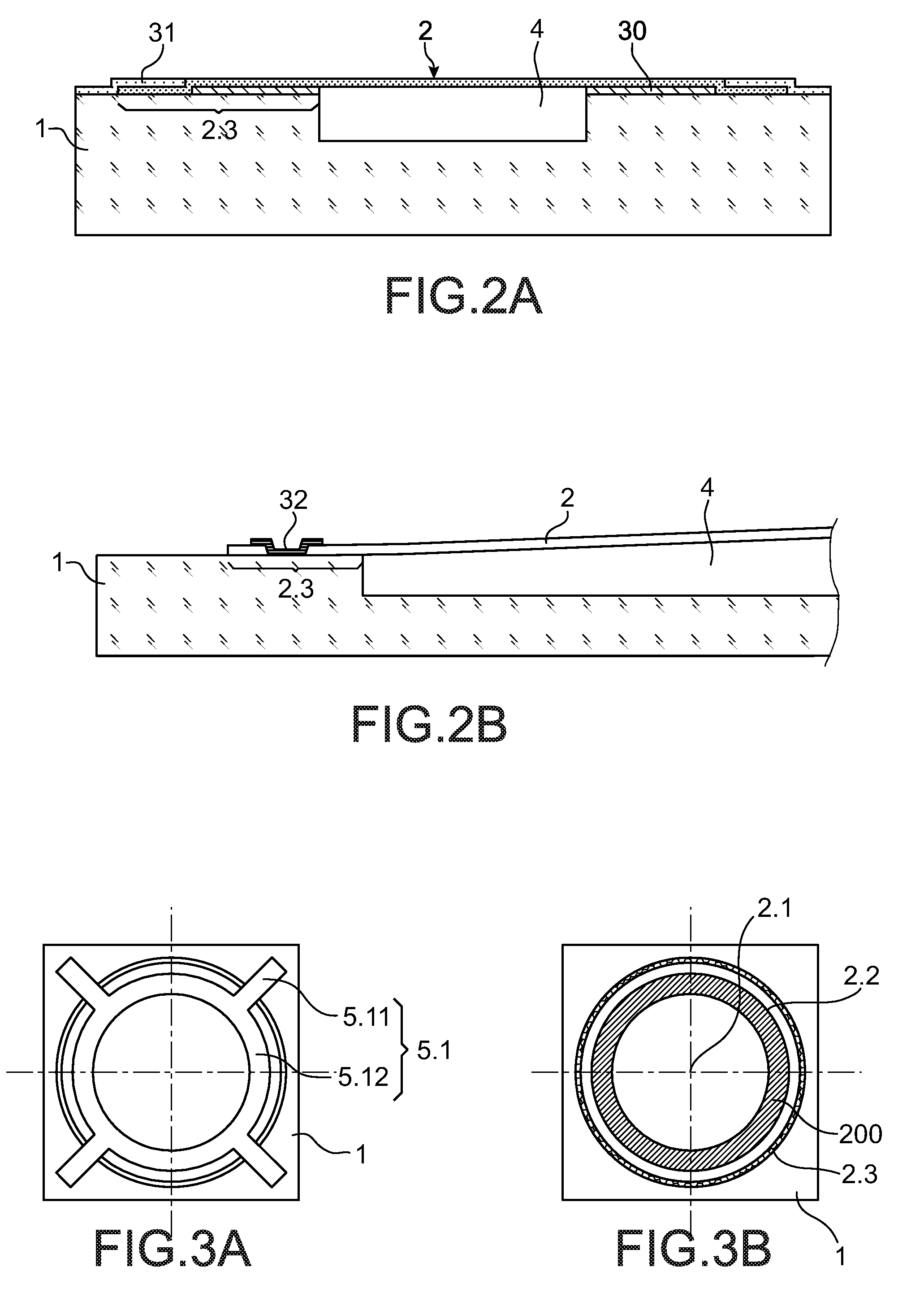
ActiveCN105212693AImprove the safety of useEasy to assemble and disassemblePressure-cookersEngineeringPressure cooking
The invention discloses a pressure cooker which comprises a cooker body, a lid integrated component, a lid assembly and a first locking component. The lid integrated component is pivotally connected onto the cooker body, the lid assembly is rotatably arranged on the lid integrated component along the peripheral direction of the cooker body and comprises a lid, a trigger assembly and a buckle device, the lid is connected with the lid integrated component by the buckle device, the trigger assembly is connected with the buckle device and is structured in such a manner that the buckle device can be released when the trigger assembly is triggered, and accordingly the lid can be separated from the lid integrated component; the first locking component is arranged on the lid integrated component, the buckle device can be driven by the trigger assembly to rotate between a first location and a second location relative to the lid integrated component, the trigger assembly can be triggered when the buckle device is positioned at the first location so as to relieve the buckle device, and the lid assembly and the lid integrated component cannot be detached when the buckle device is positioned at the second location. The pressure cooker in an embodiment of the invention has the advantage that the service safety of the pressure cooker can be improved.
Owner:谛卓(北京)咨询顾问有限公司
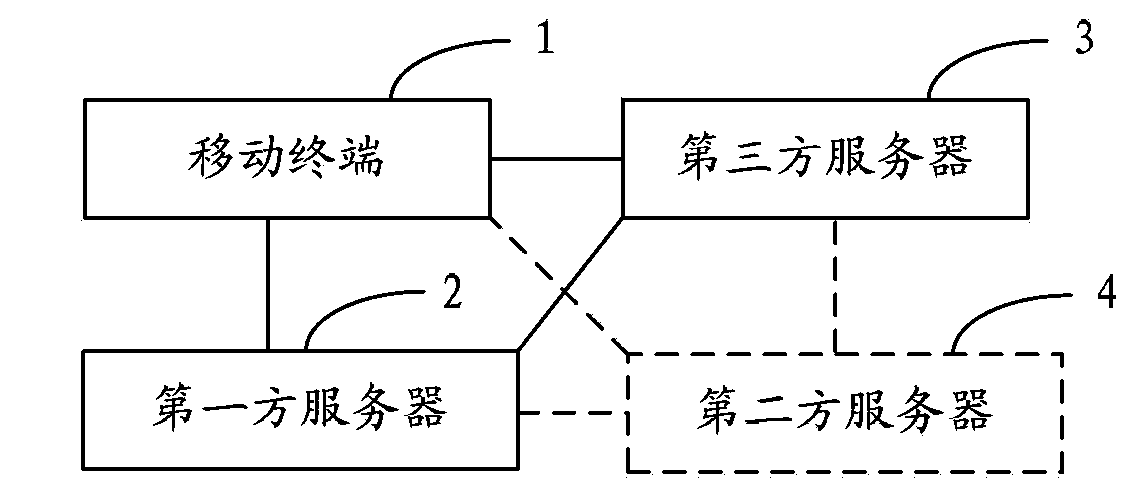
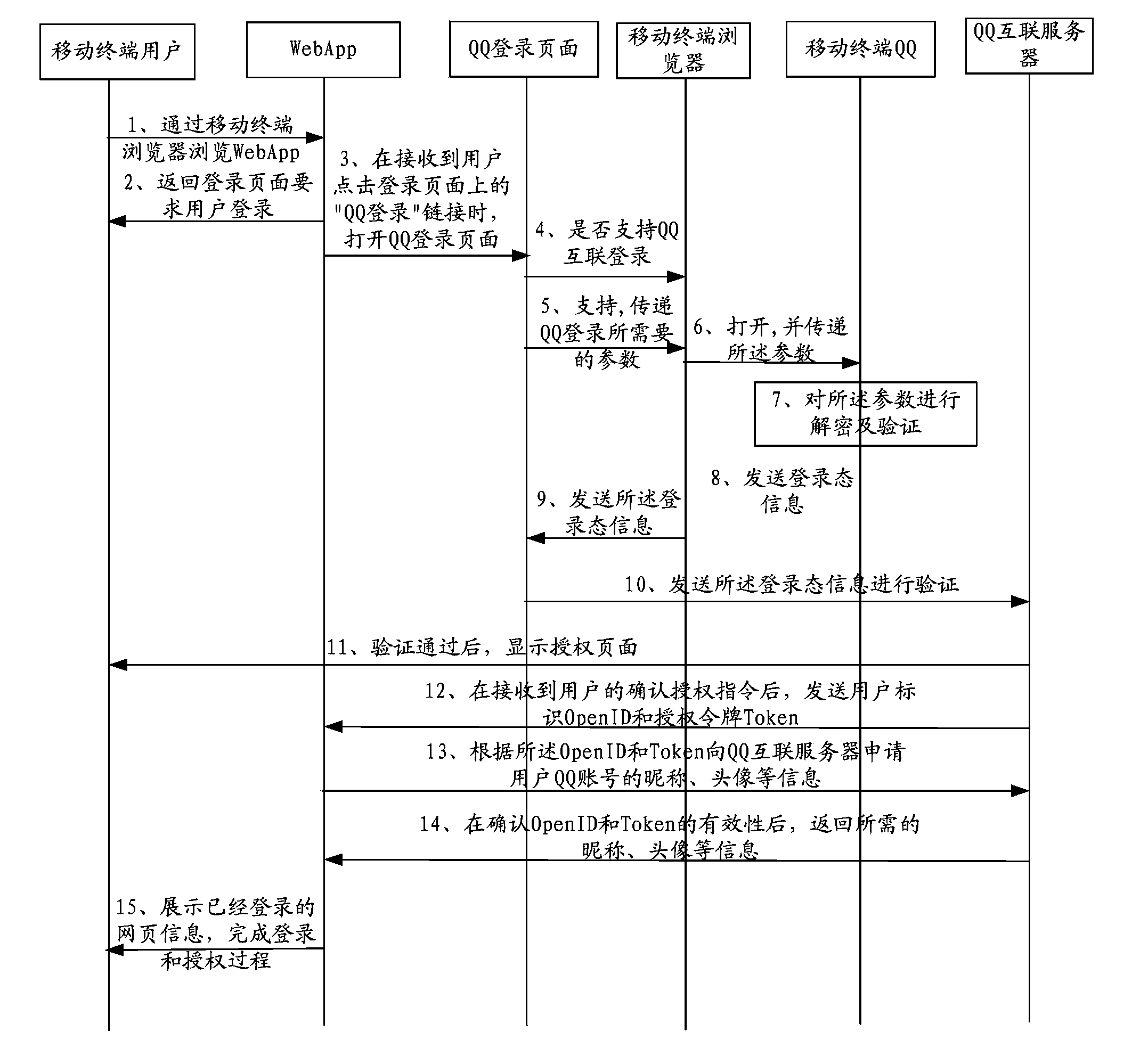
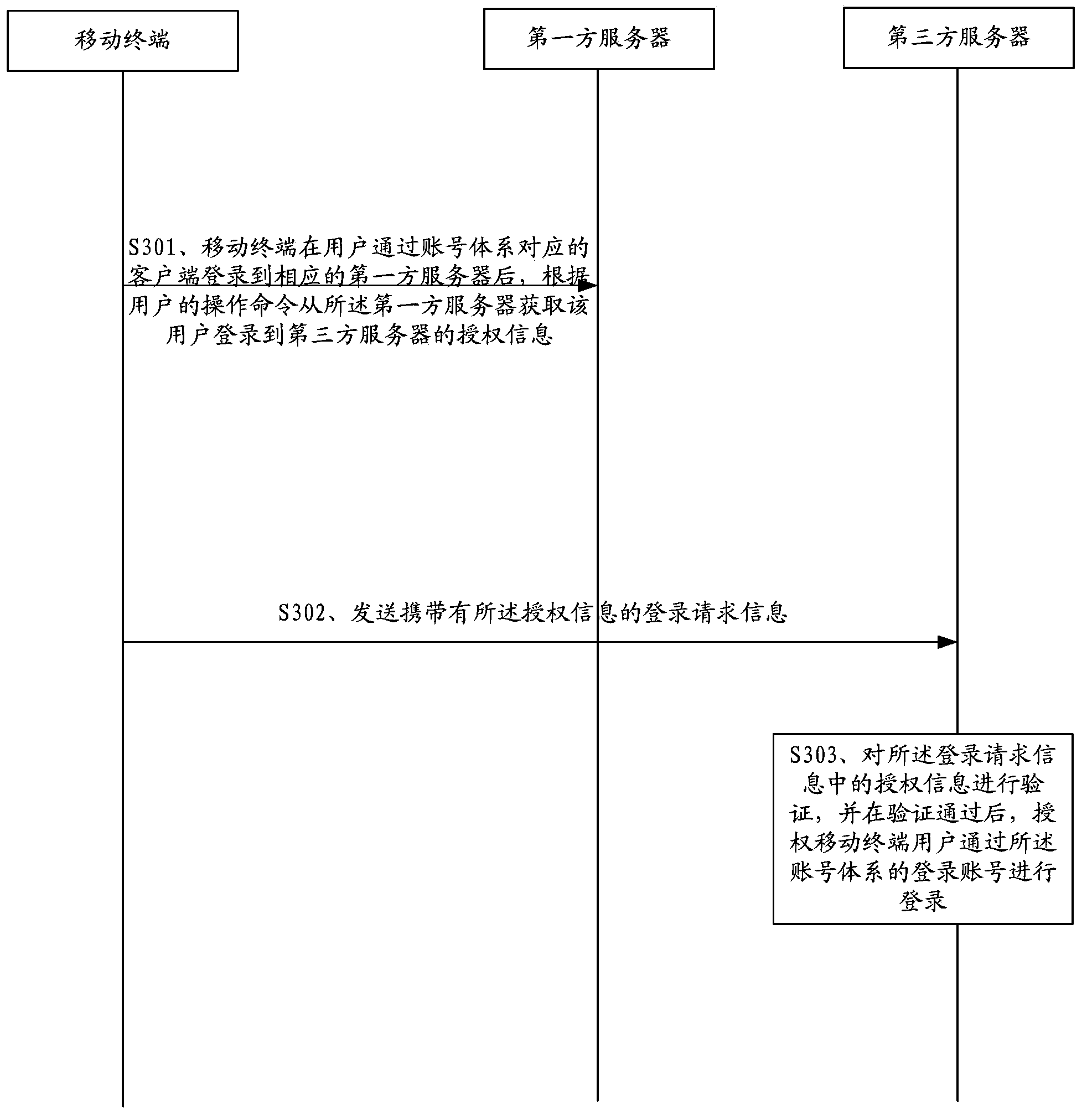
Method and system for controlling access of mobile terminal to third party server
ActiveCN104348777AEasy to operateImprove access efficiencyDigital data authenticationTransmissionThird partyInternet privacy
The present disclosure includes an exemplary method for controlling access to a third-party server by a mobile terminal. The method comprises : acquiring, at the mobile terminal from a first-party server, login authorization information using which a user of the mobile terminal has logged in the first-party server through a client-side application corresponding to the first-party server, wherein the login authorization information includes a logged-in account; transmitting, to the third-party server, a login request,wherein the login request includes the login authorization information that is to be verified; and receiving authorization for the user to log in the third-party server using the logged-in account included in the verified login authorization information.
Owner:TENCENT TECH (SHENZHEN) CO LTD
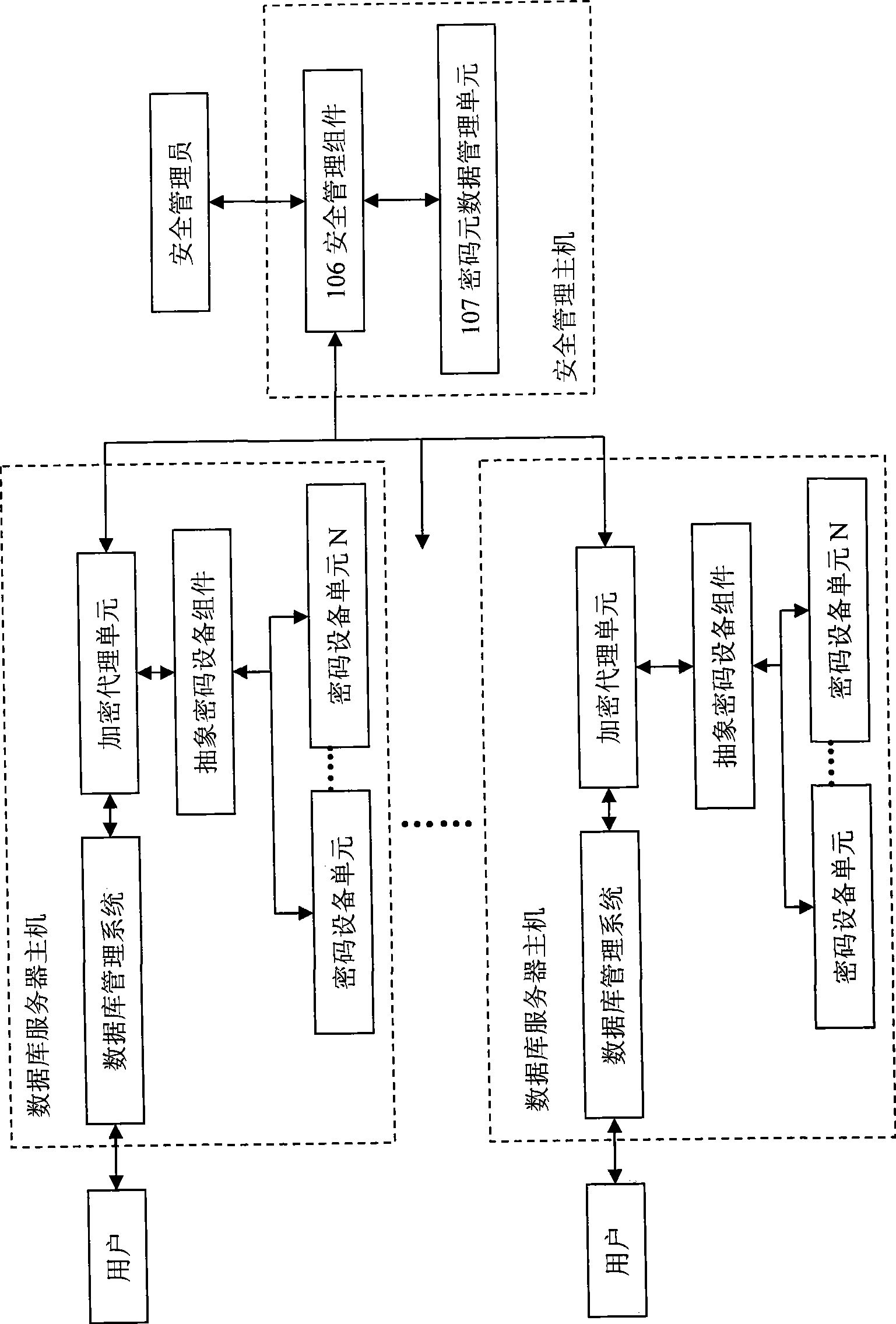
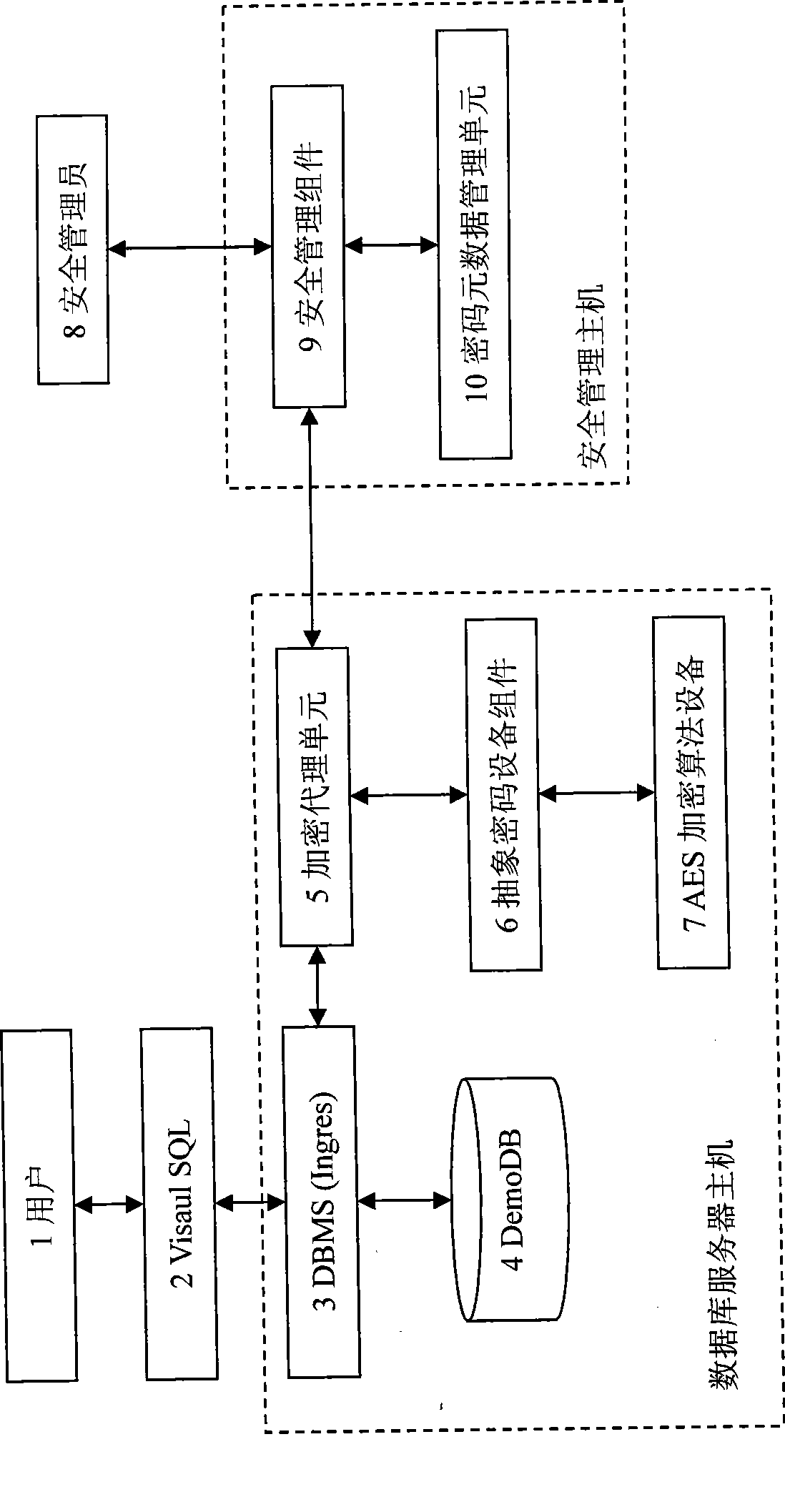
Database information encryption method and system
InactiveCN101504706AWith transparencyAvoid risk of leakageDigital data protectionDatasheetDatabase server
The invention discloses a database information encryption method and a database information encryption system using the same, which belong to the technical field of information security. The method comprises the following steps of: encrypting a sensitive field in a datasheet through a cryptoequipment unit, and creating a homonymous view which points to the encrypted datasheet for the sensitive field; maintaining the use permission of a user to a key, and encrypting the used cryptoequipment unit, an encryption mode and the key; allowing a user with the permission to successfully read and modify encryption information; and for a user without the permission, using a random key for error decryption when the encryption information is read, and returning key acquisition failure information when the encryption information is modified. The system comprises a security management host and one or more database server hosts, and is provided with an abstract cryptoequipment module for providing a uniform encryption and decryption interface and calling one or more different cryptoequipment units to realize the encryption and decryption. The database information encryption method and the database information encryption system can be used for the encryption of database information.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
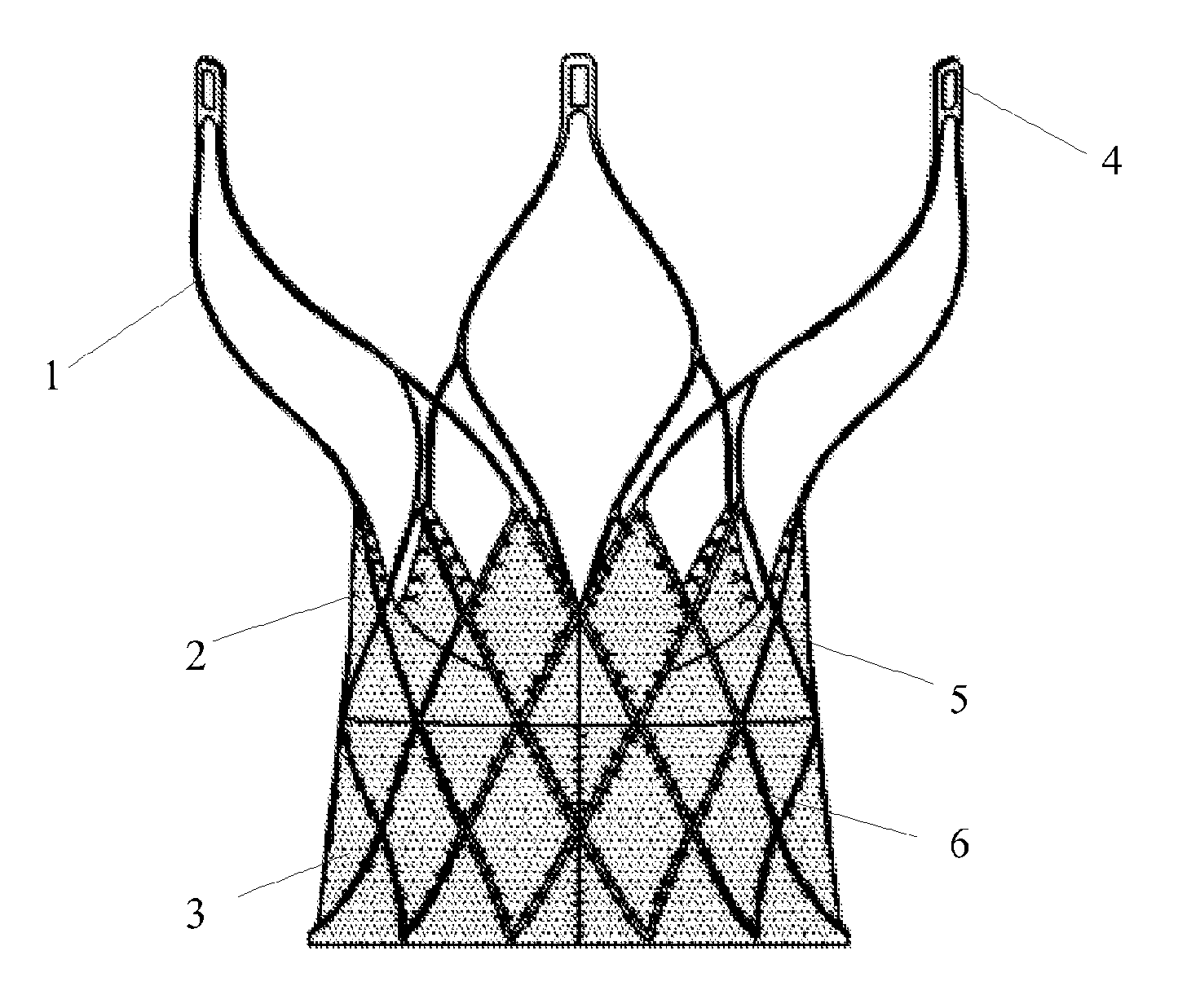
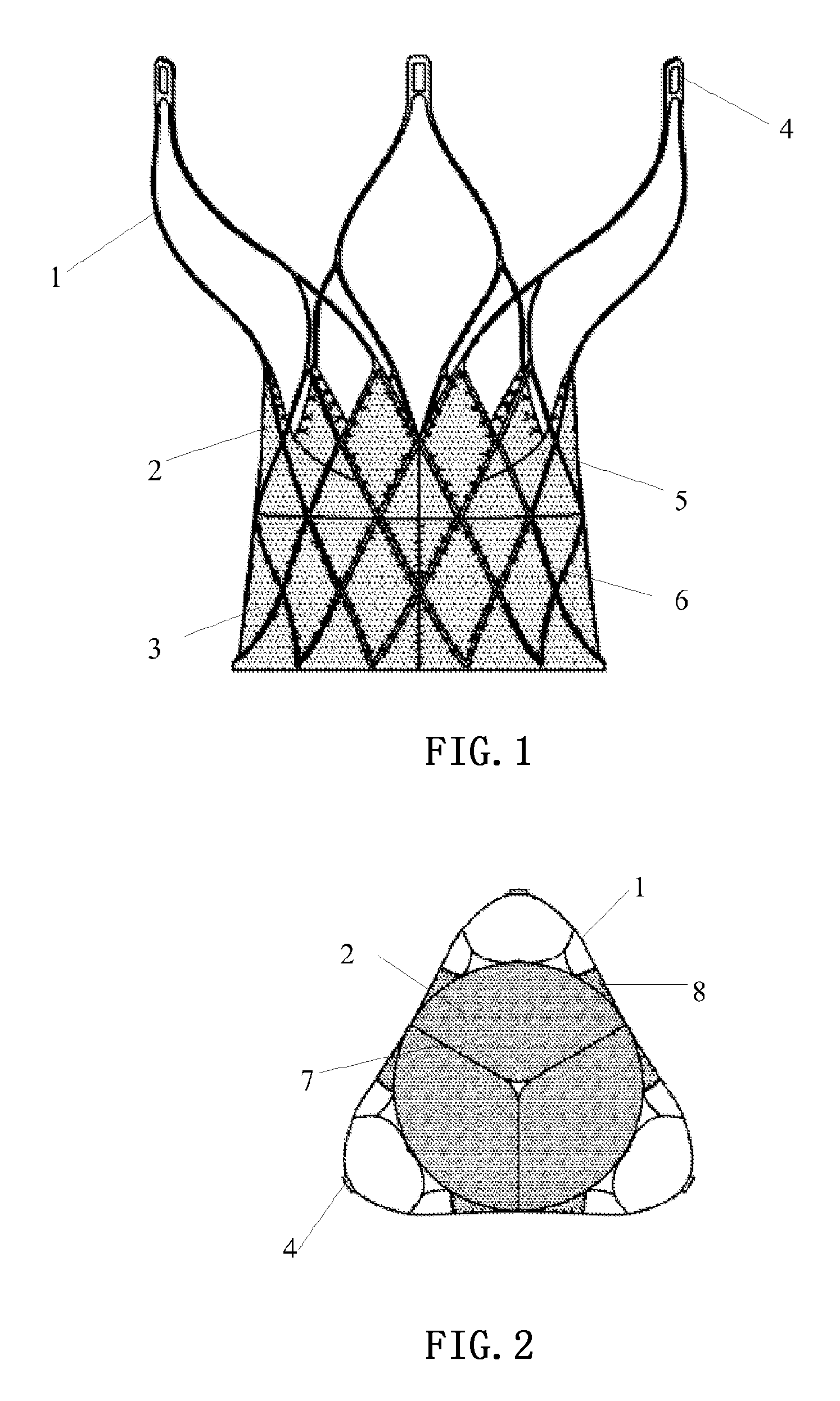
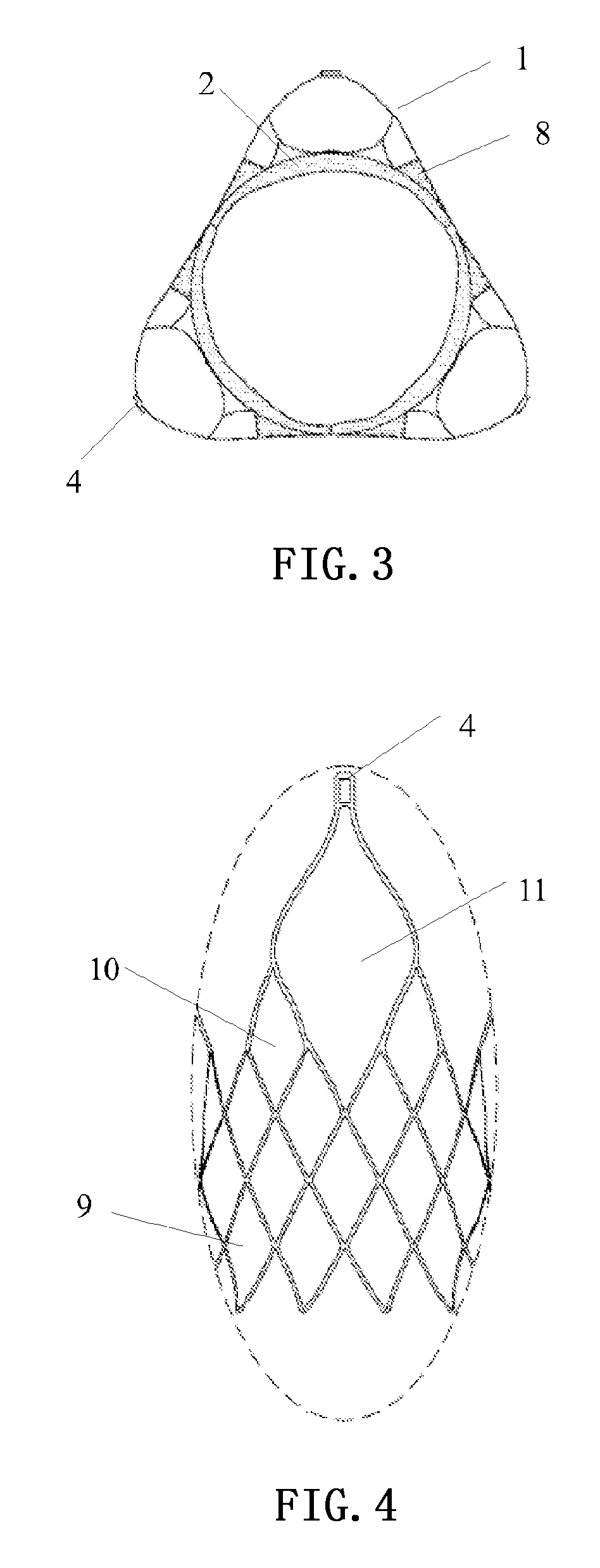
Invasive cardiac valve
ActiveUS20120316642A1Prevent cardiac valve displacementEfficiently attachedStentsHeart valvesCoronary arteriesInsertion stent
An invasive cardiac valve comprises a tubular stent (1) and a valve (2). One end of the tubular stent (1) is of a frusto-conical structure, the other end is wide open, and the diameter of the open end is greater than the diameter of the frusto-conical end. The valve (2) is attached to the frusto-conical end of the tubular stent (1); and a delivery and retrieval hole (4) of the cardiac valve is provided at the top of the open end of the tubular stent (1). Because the diameter of the open end is greater than the diameter of the frusto-conical end, the cardiac valve can be effectively fixed in a position of aortic annulus to prevent the cardiac valve displacement caused by the impact of the blood flow. Because the valve (2) is attached to the frusto-conical end of the tubular stent (1), the valve (2) can totally avoid the left and right coronary ostia and does not affect the haemodynamics of the coronary artery. Because a delivery and retrieval hole (4) of the cardiac valve is provided at the top of the open end of the tubular stent (1), the cardiac valve can be retrieved and reset at any time by handle control if it is found to be placed in an improper position during the release process.
Owner:SHANGHAI MICROPORT CARDIOFLOW MEDTECH CO LTD
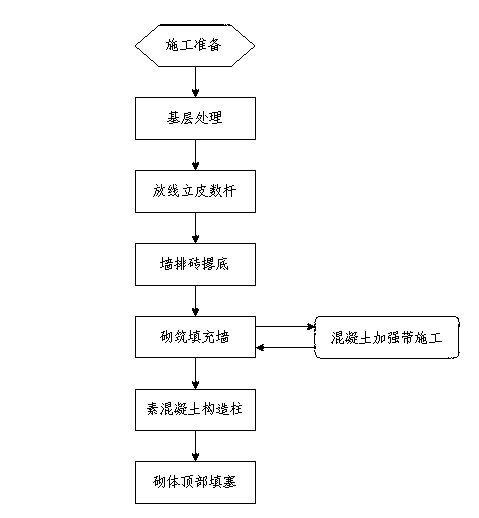
Construction method for preventing and treating cracks between concrete structure and filler wall
The invention discloses a construction method for preventing and treating cracks between a concrete structure and a filler wall. The construction method particularly comprises the following operation steps of step one, preparing construction; step two, treating a basic layer; step three, conducting paying off wire and setting up height pole; step four, conducting brick laying and putting down the bottom row of bricks; step five, masoning the filler wall; step six, constructing plain concrete constructional columns; step seven, filling the top of masonry. The construction method for preventing and treating the cracks between the concrete structure and the filler wall has the advantages of being wide in application range, and applicable to masonry construction of the filler wall with hollow bricks, autoclaved aerated concrete blocks and the like of the industrial and civil construction concrete structure; when the method compared with traditional processes, being capable of saving cost due to the fact that the main difference in procedure is that the plain concrete constructional columns, concrete reinforcing bands, wall crown filled with hard concrete and other portions replace the masonry; fundamentally solving the problem that cracks of a plaster layer and a coating layer caused by the cracks of the contact surface of the concrete structure and the filler wall, improving a project impression level and project quality, eradicating leakage risks of outer wall surfaces, reducing reworking cost and maintenance cost, saving materials, reducing production of construction waste, lowering a complaint rate of users, and being capable of setting up a corporate image in society and considerable in social benefit.
Owner:CHINA AEROSPACE CONSTR GROUP +1
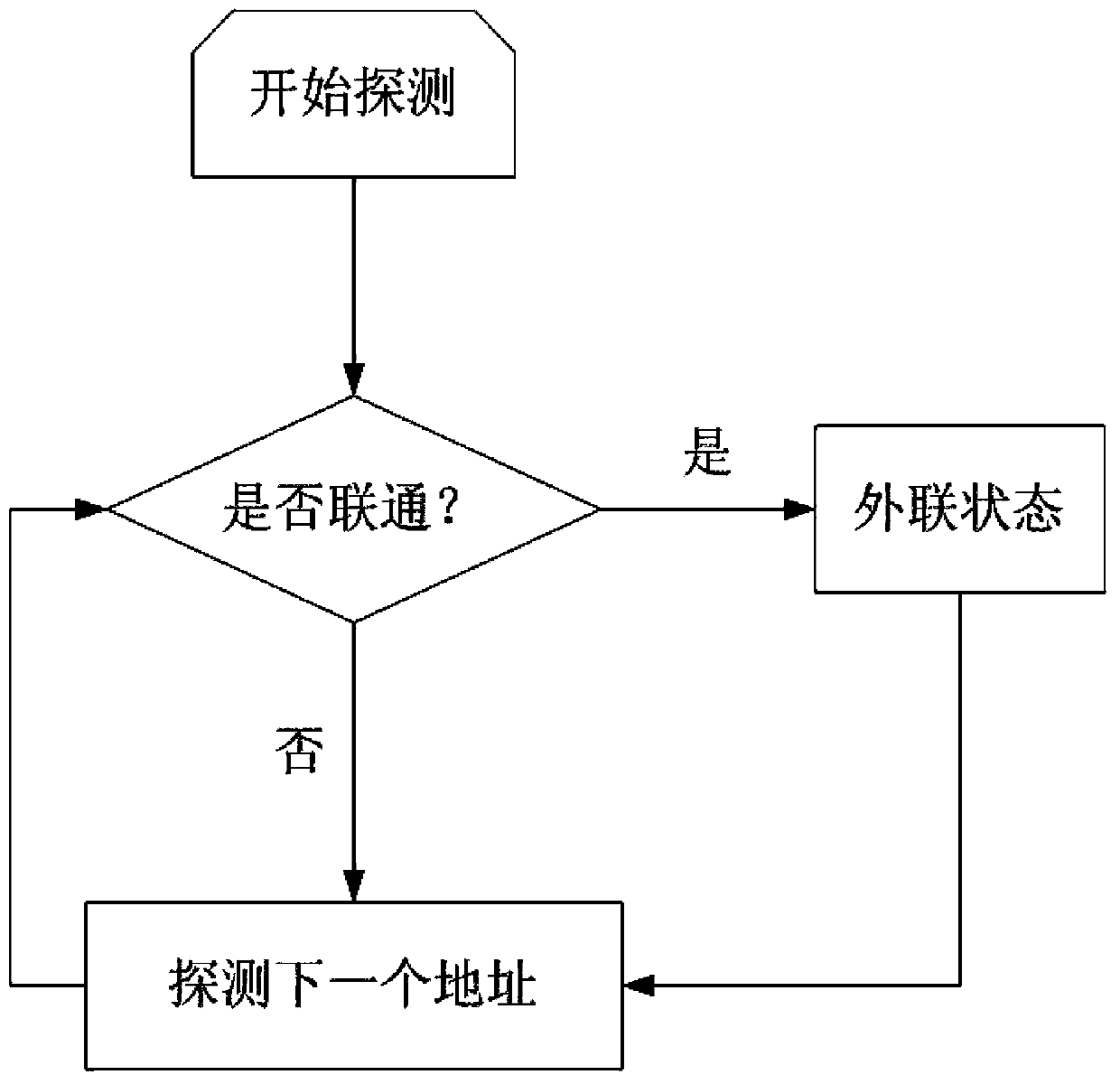
Alarm and blocking method for illegal external connections
ActiveCN103391216AEasy to deployHas practical valueData switching networksNetwork packetBlock method
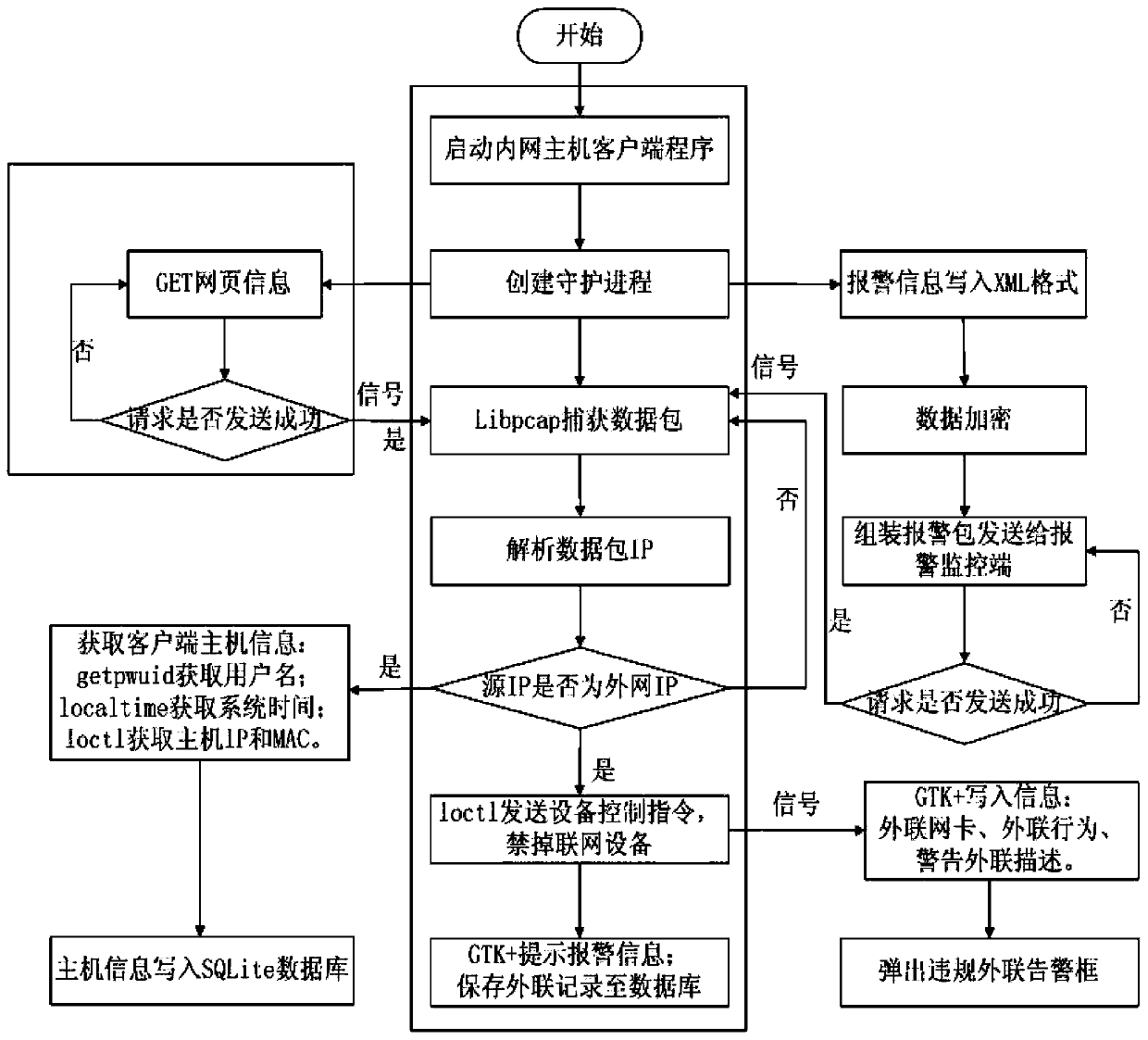
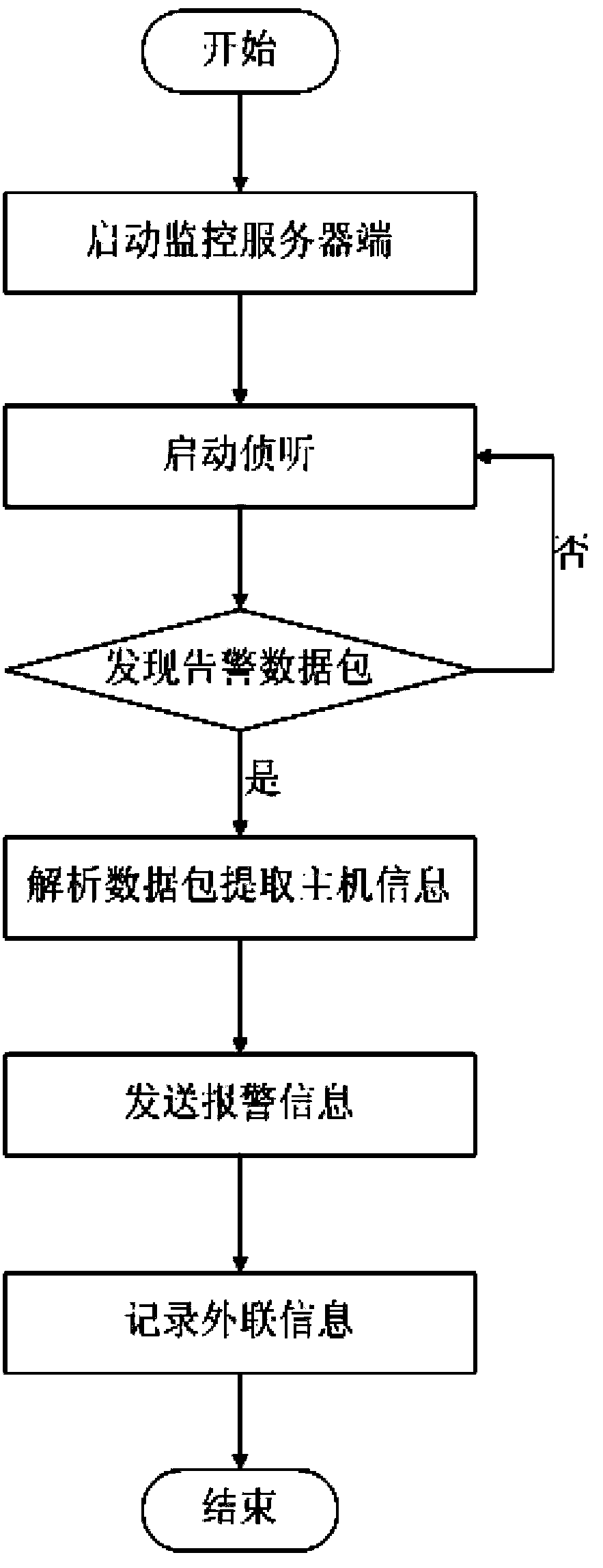
The invention relates to an alarm and blocking method for illegal external connections. The alarm and blocking method comprises that 1), an intranet host client monitors networking behaviors of intranet computers in real time according to a plurality of external connection modes; 2), the intranet host client initiatively sends an encrypted alarm data packet to an external connection alarm monitoring terminal by using a Libnet function library to detect whether the intranet computers have external connection behaviors and gives an alarm for illegal external connection behaviors; 3), the intranet host client performs bottom layer packet capture on alarmed intranet hosts to obtain all data packets passing through network cards of the hosts to judge the illegal external connection behaviors; 4), blocking the network cards of the hosts having the illegal external connection behaviors through judgment. The alarm and blocking method is high in timeliness and good in monitoring performance in the aspect of illegal external connection monitoring. By means of the alarm and blocking method, the safety and the transmission efficiency of the alarm data packets in systems are improved, leaking risks caused by stealing of alarm information are effectively avoided, meanwhile, the safety of software is improved, and the software has anti-shielding and anti-unloading capacities.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
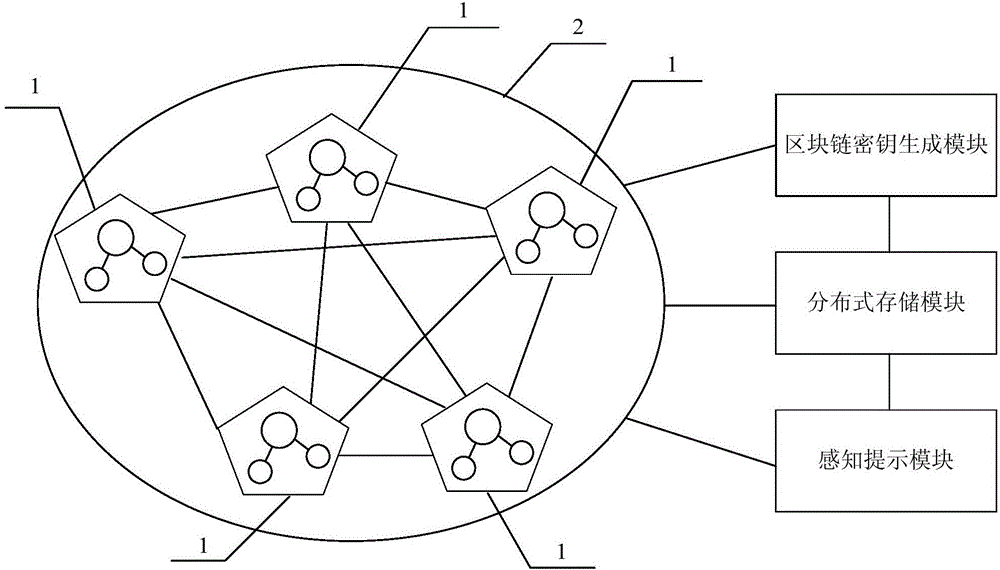
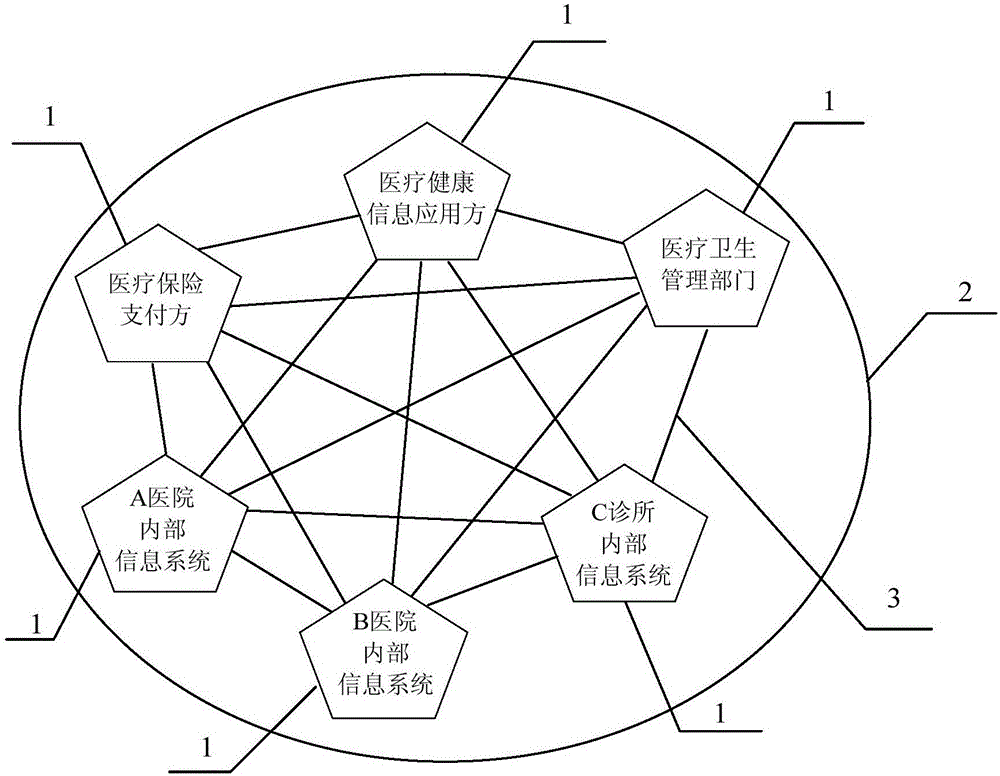
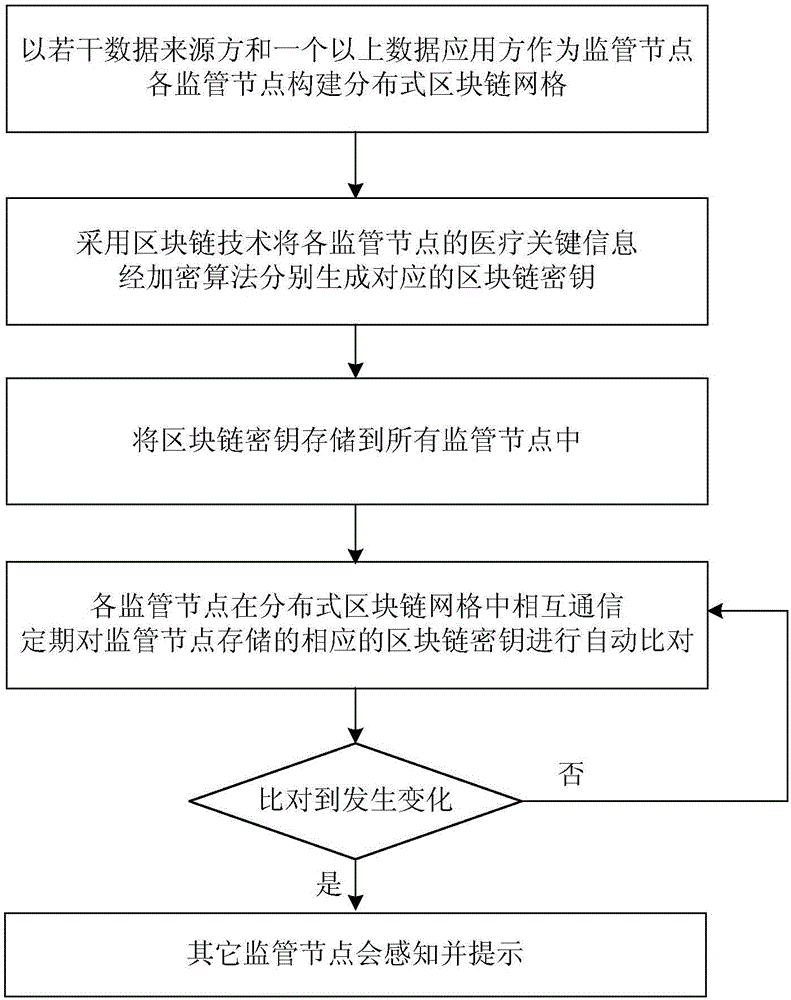
Hospital information supervision platform and method
PendingCN106777923AImplement encryptionImplement storageData processing applicationsHealthcare resources and facilitiesData sourceComputer module
The invention provides a hospital information supervision platform and method. The hospital information supervision platform comprises a distributed block chain network constructed by adopting a plurality of data source parties and one or more data application parties as supervision nodes and further comprises a block chain key generation module, a distributed storage module and a sensing prompting module. The block chain key generation module adopts the block chain technology for enabling medical key information of the supervision nodes in the distributed block chain network to generate corresponding block chain keys through an encryption algorithm; the distributed storage module stores the block chain keys into all the supervision nodes of the distributed block chain network; the supervision nodes are communicated in the distributed block chain network; if medical key information of any supervision node is modified, the corresponding block chain key changes, and the other supervision nodes can sense the changes and give a prompt. The platform achieves multi-point self-supervision and intelligent prompting, the medical key information safety management cost is lowered, and the medical key information of a hospital can be prevented from being modified improperly.
Owner:谭小刚
pressure cooker
ActiveCN105212693BImprove the safety of useEasy to assemble and disassemblePressure-cookersStructural engineeringPressure cooking
The invention discloses a pressure cooker, which comprises: a pot body; a pot cover connecting piece, which is pivotally connected to the pot body; a pot cover assembly, which is rotatable along the circumferential direction of the pot body The pot cover assembly includes a pot cover, a touch assembly and a buckle device, the pot cover and the pot cover joint piece are connected by a buckle device, and the touch assembly is connected with the buckle device and is configured to When it is touched, the buckle device is released to disengage the pot cover and the pot cover connector; The body member rotates between the first position and the second position. When the buckle device is in the first position, the touch assembly can be touched to release the buckle device. When the buckle device is in the second position, the pot cover assembly and the pot cover conjoined piece Not removable. According to the pressure cooker of the embodiment of the present invention, the use safety of the pressure cooker is improved.
Owner:谛卓(北京)咨询顾问有限公司
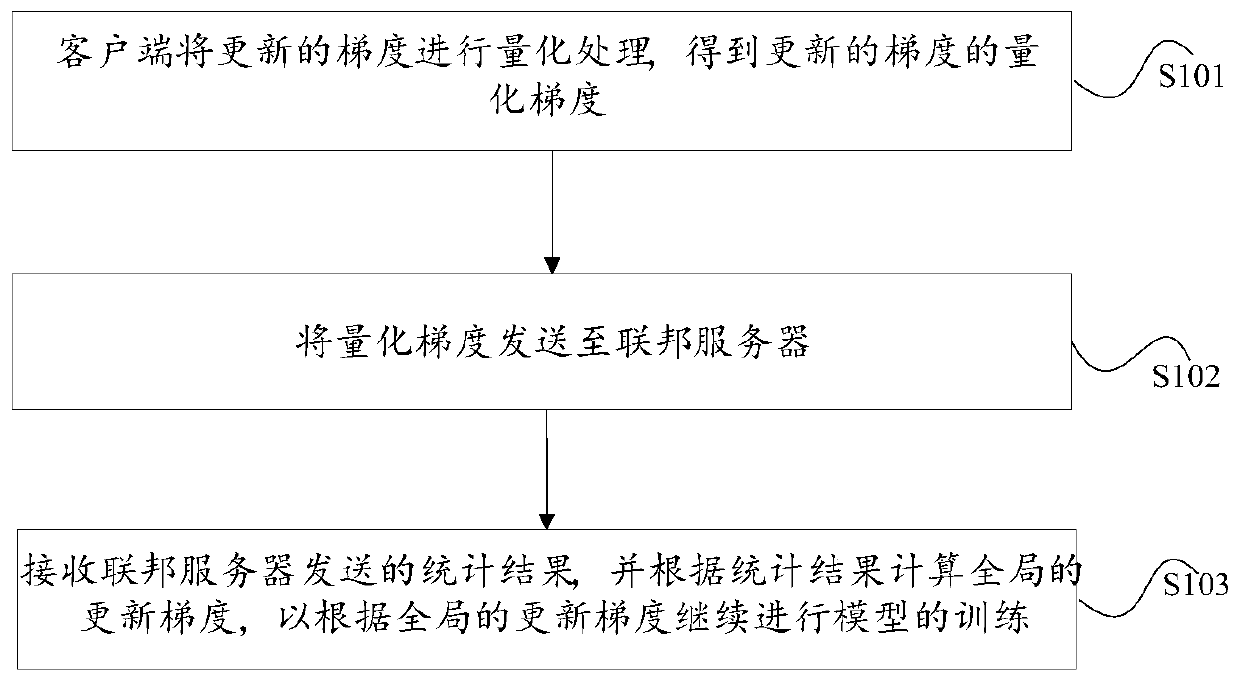
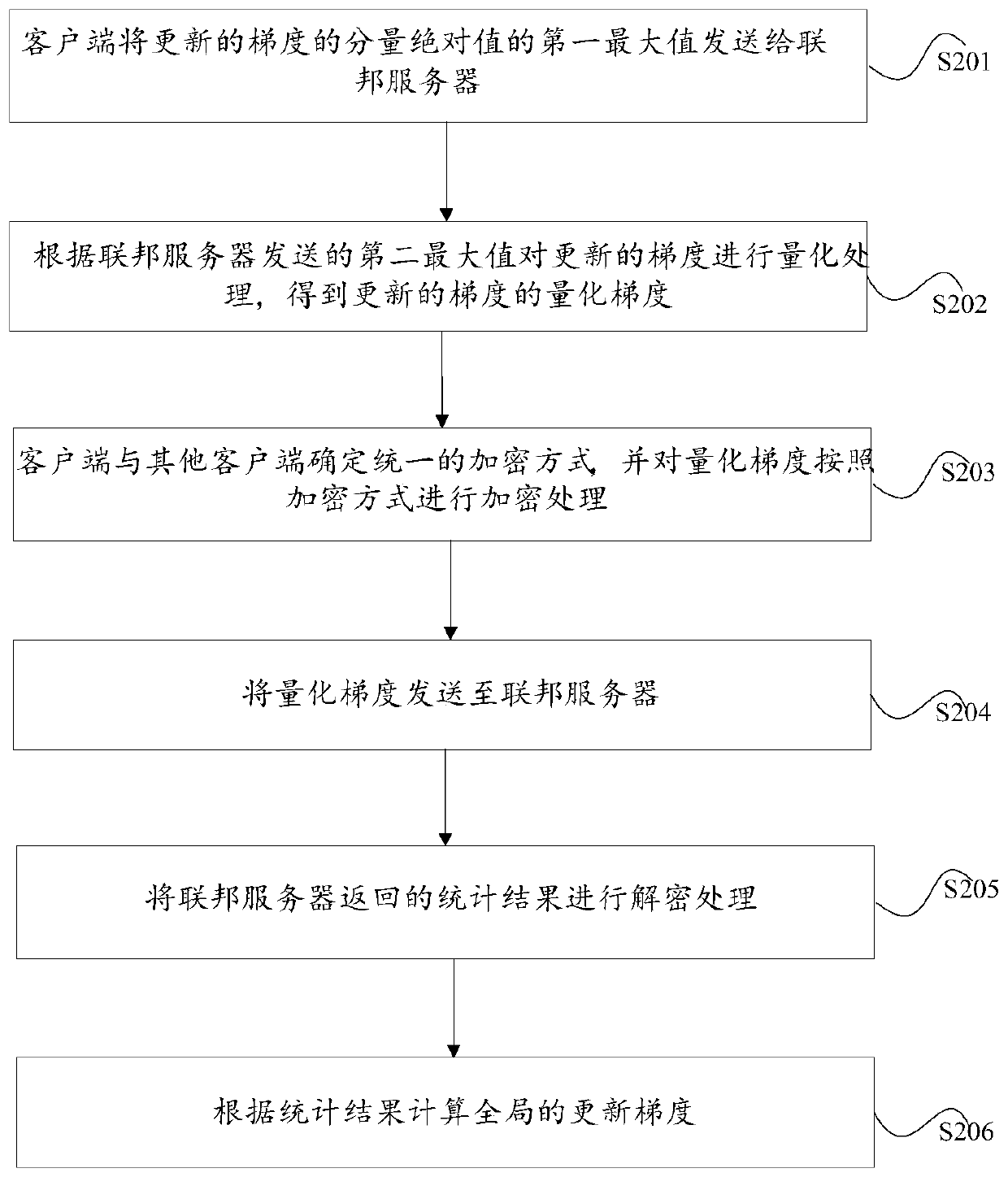
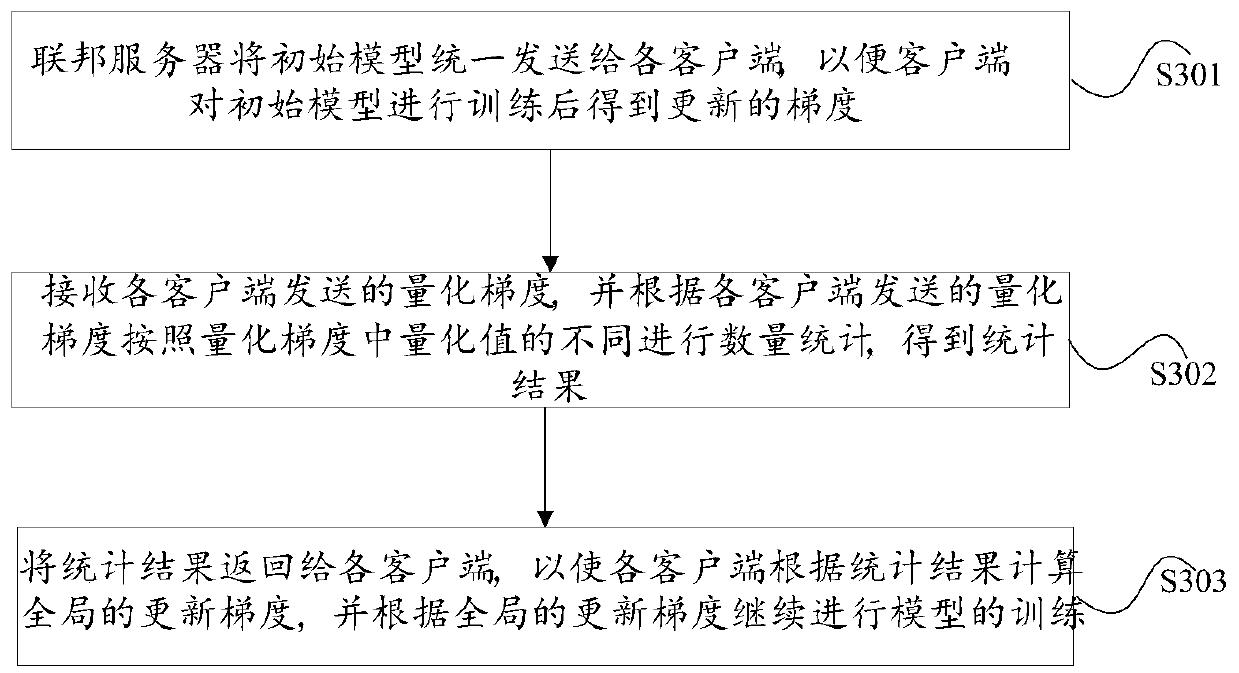
Federated learning method, device and system based on gradient compression
The invention discloses a federated learning method, device and system based on gradient compression. A federated server sends initial models to clients in a unified mode; the initial model is trainedby the client to obtain an updated gradient, the updated gradient is quantized to obtain a quantized gradient of the updated gradient, and the quantized gradient of the updated gradient is sent to afederated server; the federated server performs quantity statistics according to different quantized values in the quantized gradients based on all the quantized gradients corresponding to each clientto obtain a statistical result, and returns the statistical result to each client; and the client receives the statistical result sent by the federated server and calculates a global updated gradientaccording to the statistical result so as to continue model training according to the global updated gradient. The objective is to solve the problems of high network transmission overhead and unsafedata in an existing federated learning system.
Owner:TONGDUN HLDG CO LTD
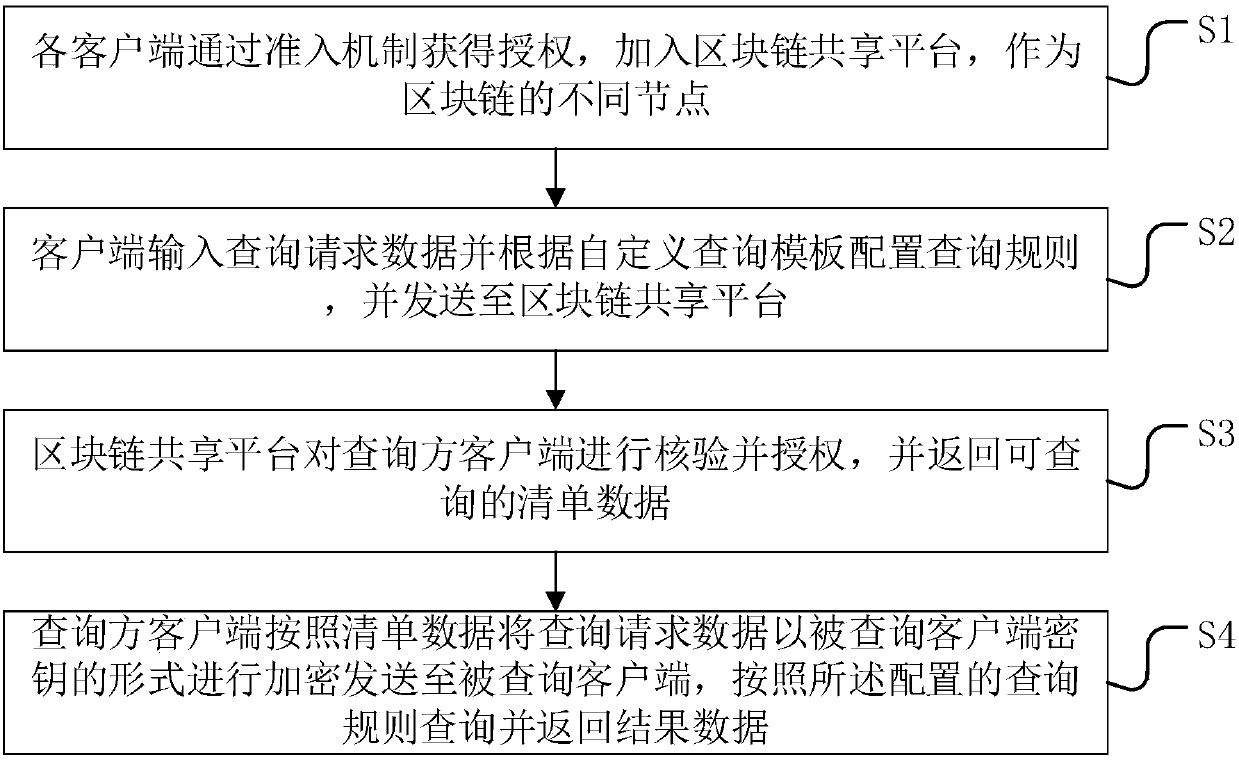
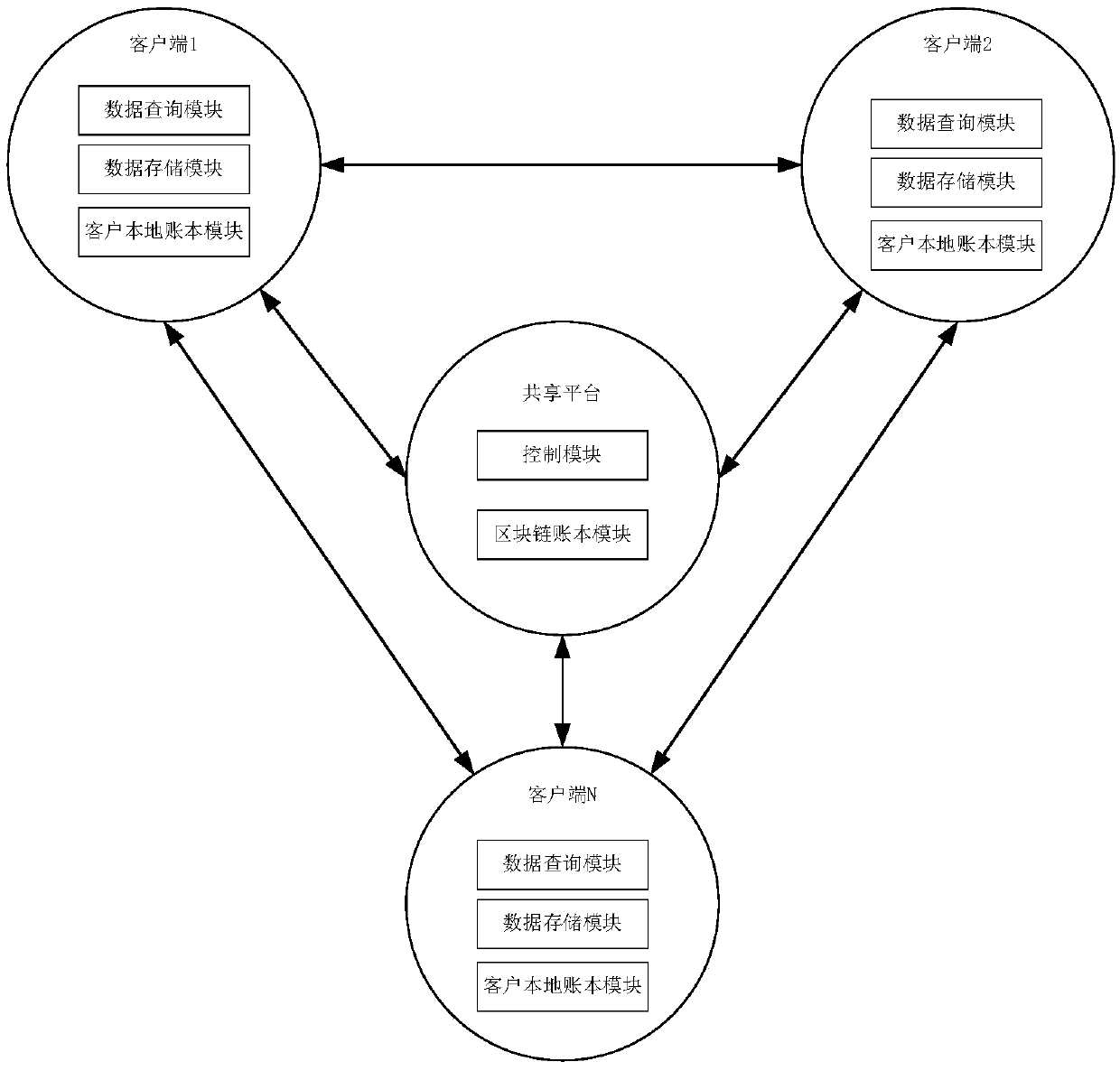
Financial institution user data sharing method and system based on a block chain technology
The invention provides a financial institution user data sharing method and system based on a block chain technology, and the method comprises the steps: S1, enabling each client to obtain authorization through an admission mechanism, and adding the authorization into a block chain sharing platform to serve as different nodes of a block chain; S2, enabling the client to input query request data and configures a query rule according to a user-defined query template; S3, enabling the block chain sharing platform to verify and authorize the query party client, and return inquirable list data; AndS4, enabling the query party client to encrypt the query request data in the form of a queried client key according to the list data, and querie and return result data according to the configured query rule. According to the method, financial platform user data sharing is achieved, desensitization, encryption and other technologies are adopted for multiple protection, original data cannot be checked, and the safety and integrity of the data cannot be affected; Based on the blockchain technology, a distributed transaction account book is co-built, and query information is accurately recorded and cannot be tampered.
Owner:青岛中瑞云数科技有限公司
Mobile payment system and method based on bank virtual card number
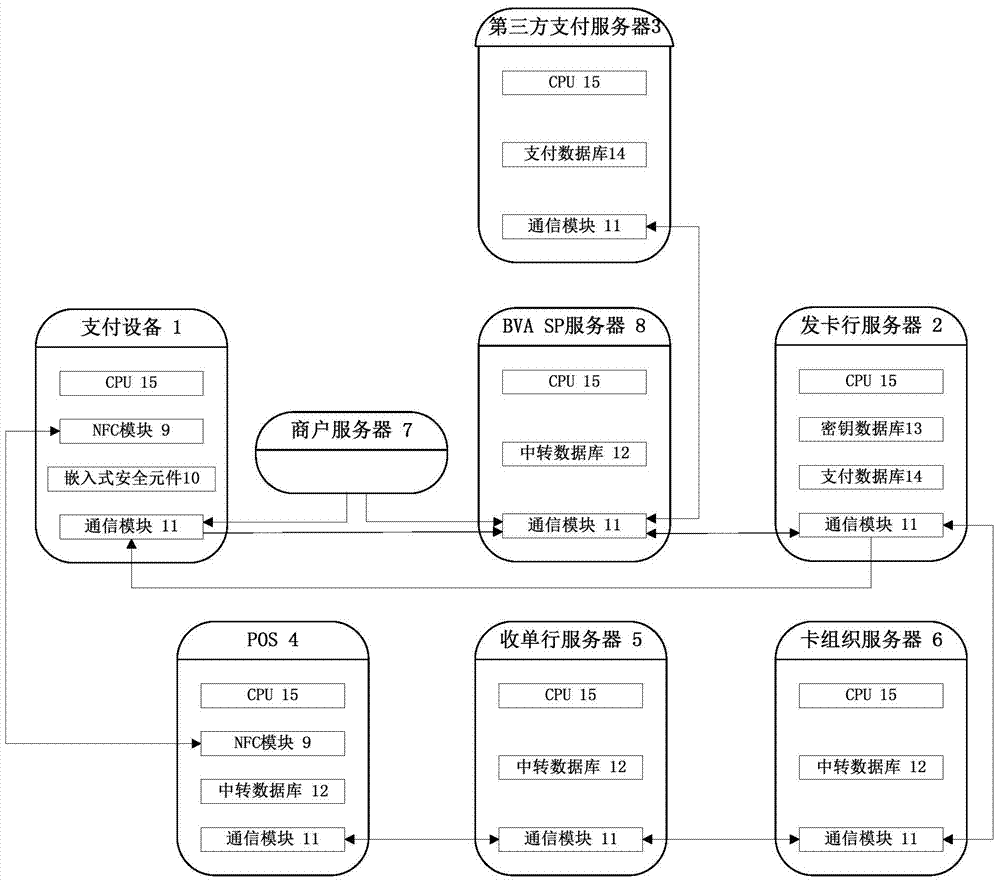
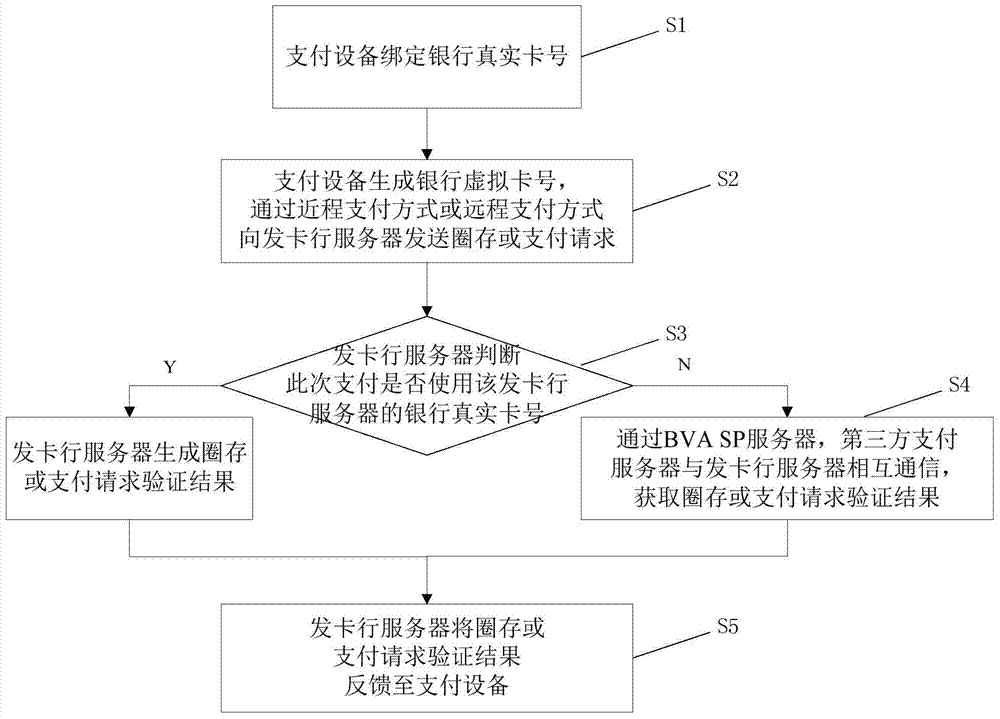
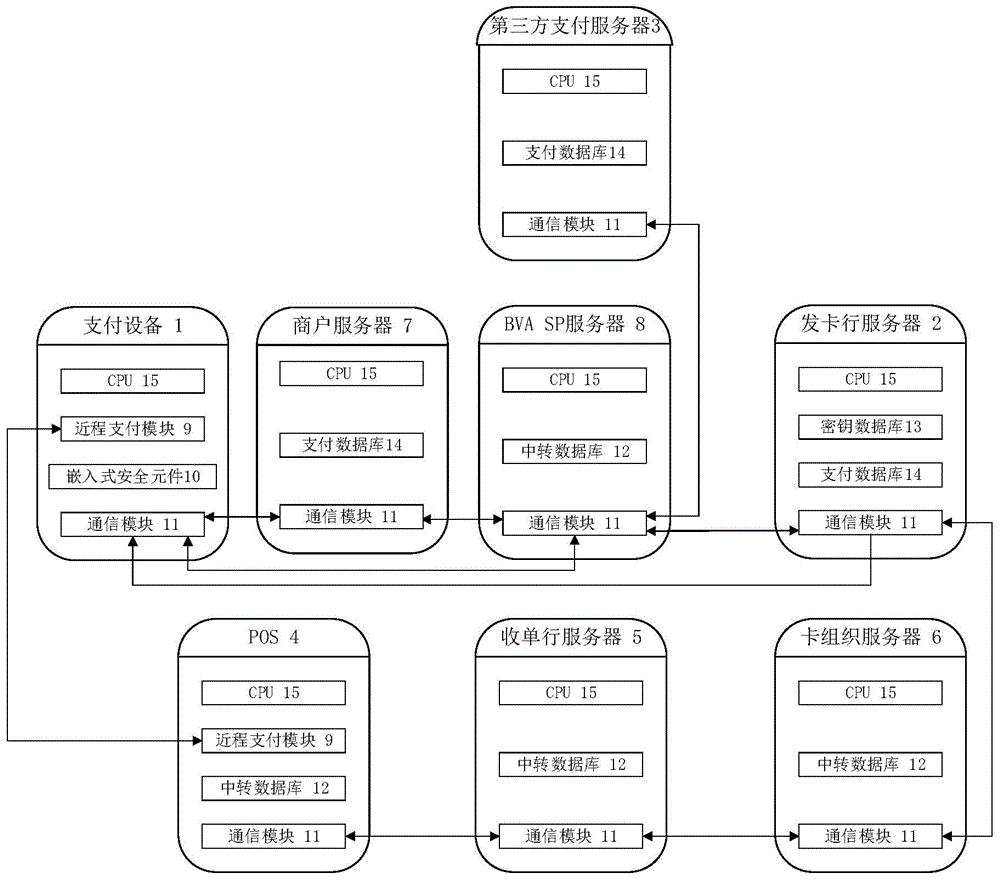
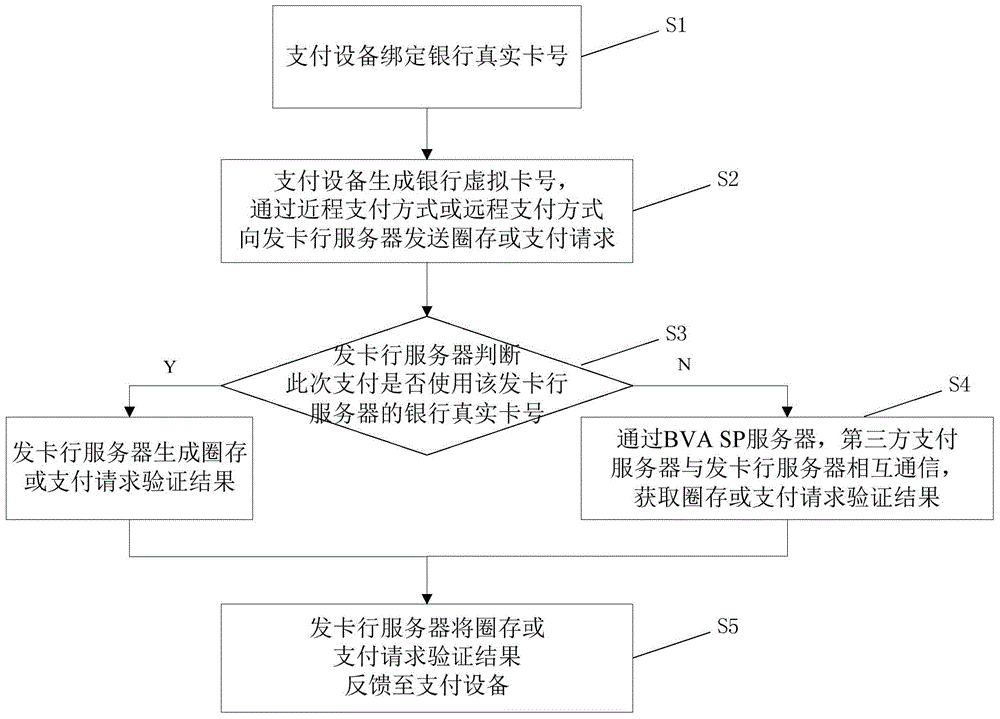
InactiveCN104504565AAvoid risk of leakageImprove securityPayment protocolsPoint-of-sale network systemsIssuing bankThird party
The invention relates to a mobile payment system based on a bank virtual card number. The mobile payment system based on the bank virtual card number comprises a payment device, a card issuing bank server, a third party payment server, a POS (machine point of sale machine), an acquiring bank server, a card organization server, a commercial tenant server and a BVA SP server, wherein the payment device generates the bank virtual card number used as a primary account number of a payment request or a transfer request, a payment request is sent to the card issuing bank server through transfer transmission of the POS, the acquiring bank server and the card organization server or a transfer request is sent to the card issuing bank server through transfer transmission of the BVA SP server, the card issuing bank server completes transfer or payment, and when the payment device uses a third party payment server for the payment, the card issuing bank server is communicated with the third party payment server through the transfer transmission of the BVA SP server, and completes the payment or the transfer after the payment request or the transfer request is verified. Compared with the prior art, the mobile payment system based on the bank virtual card number has the advantages of improving mobile payment safety, being strong in compatibility, facilitating operation of a user and the like.
Owner:SHANGHAI HAUKIT INFORMATION TECH CO LTD
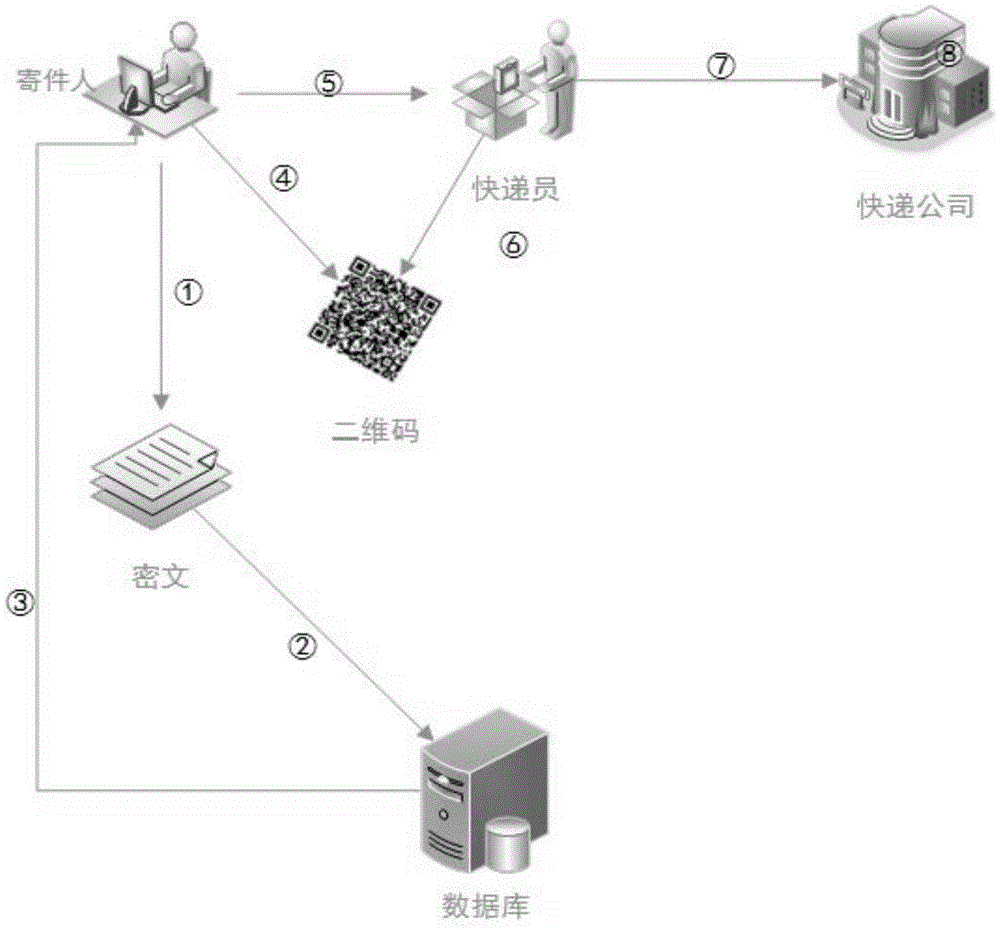
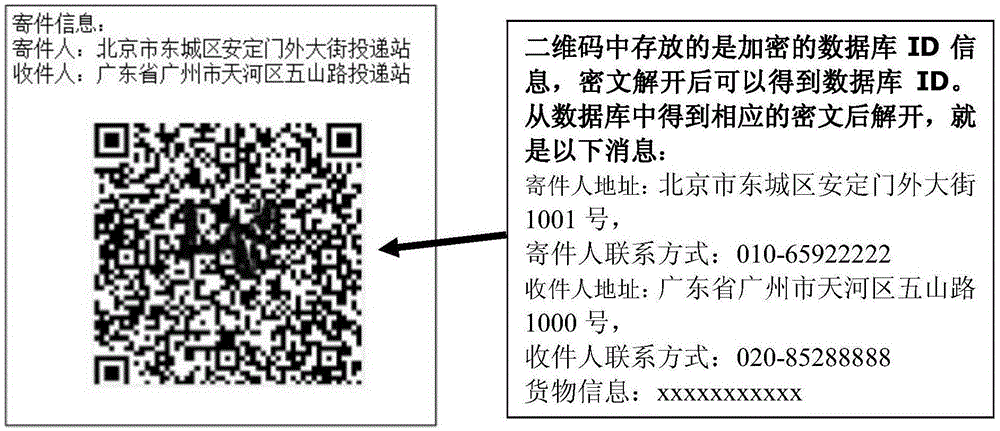
Anonymous express information security system based on two-dimension code
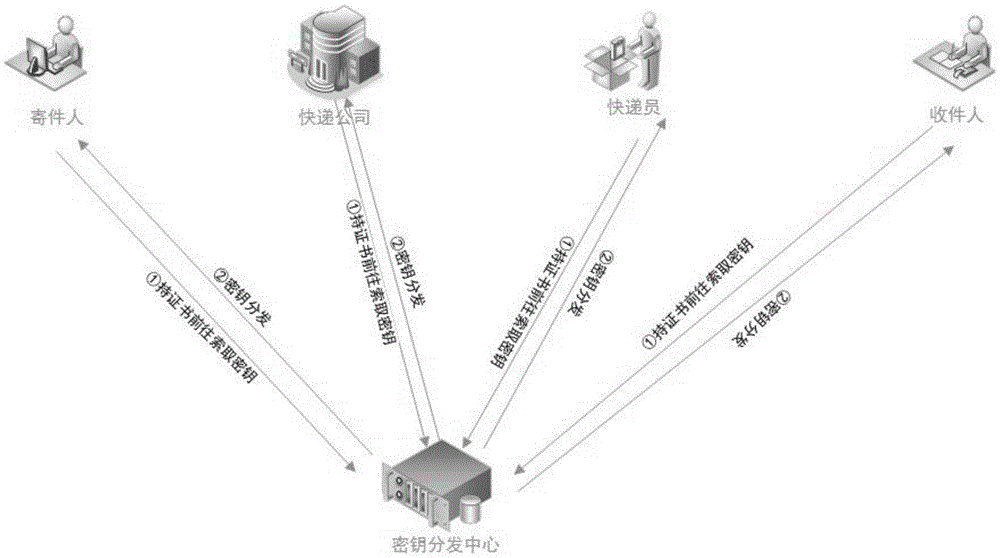
InactiveCN105574692AEnsure safetyGuaranteed confidentialityLogisticsAttribute-based encryptionManagement system
The invention discloses an anonymous express information security system based on a two-dimension code. The system comprises a key management subsystem and an express information management subsystem; the key management subsystem is used for distributing and managing the subsystems of system participants and is constructed by using an attribute based encryption technique; the express information management subsystem mainly comprises five entities of a sender, a receiver, a deliverer, a package and a database; the sender sends the package to the receiver through the deliverer; the tag on the package is used for identifying partial public information of the sender and the receiver; and the database is used for recording related package and the secret information of the sender and the receiver. According to the system of the invention, the information leakage problem possibly generated in the goods delivery process is taken into full consideration; all secret information not just the list number is hidden; the information security is ensured greatly; and the information leakage risk is avoided.
Owner:SOUTH CHINA AGRI UNIV
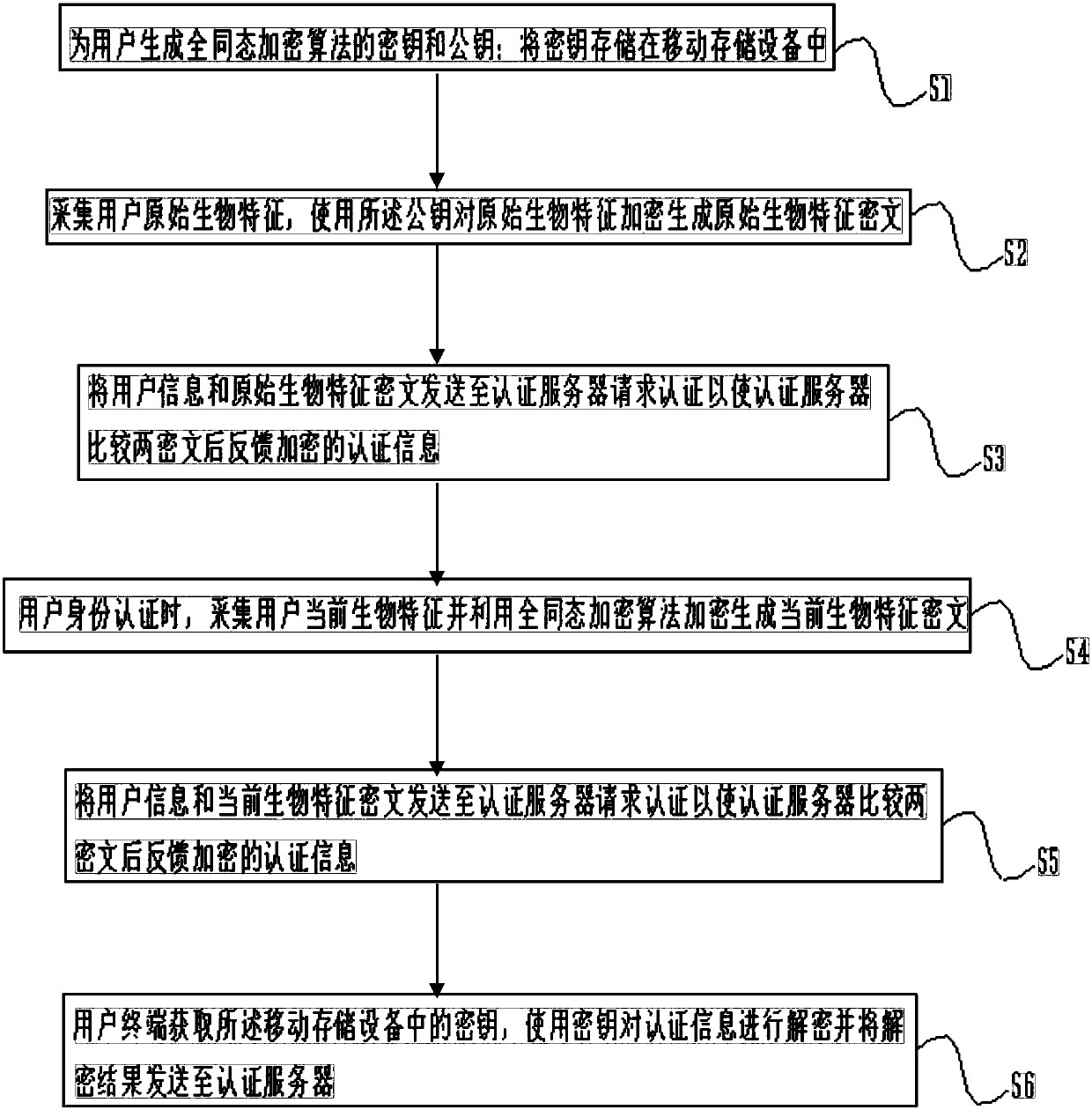
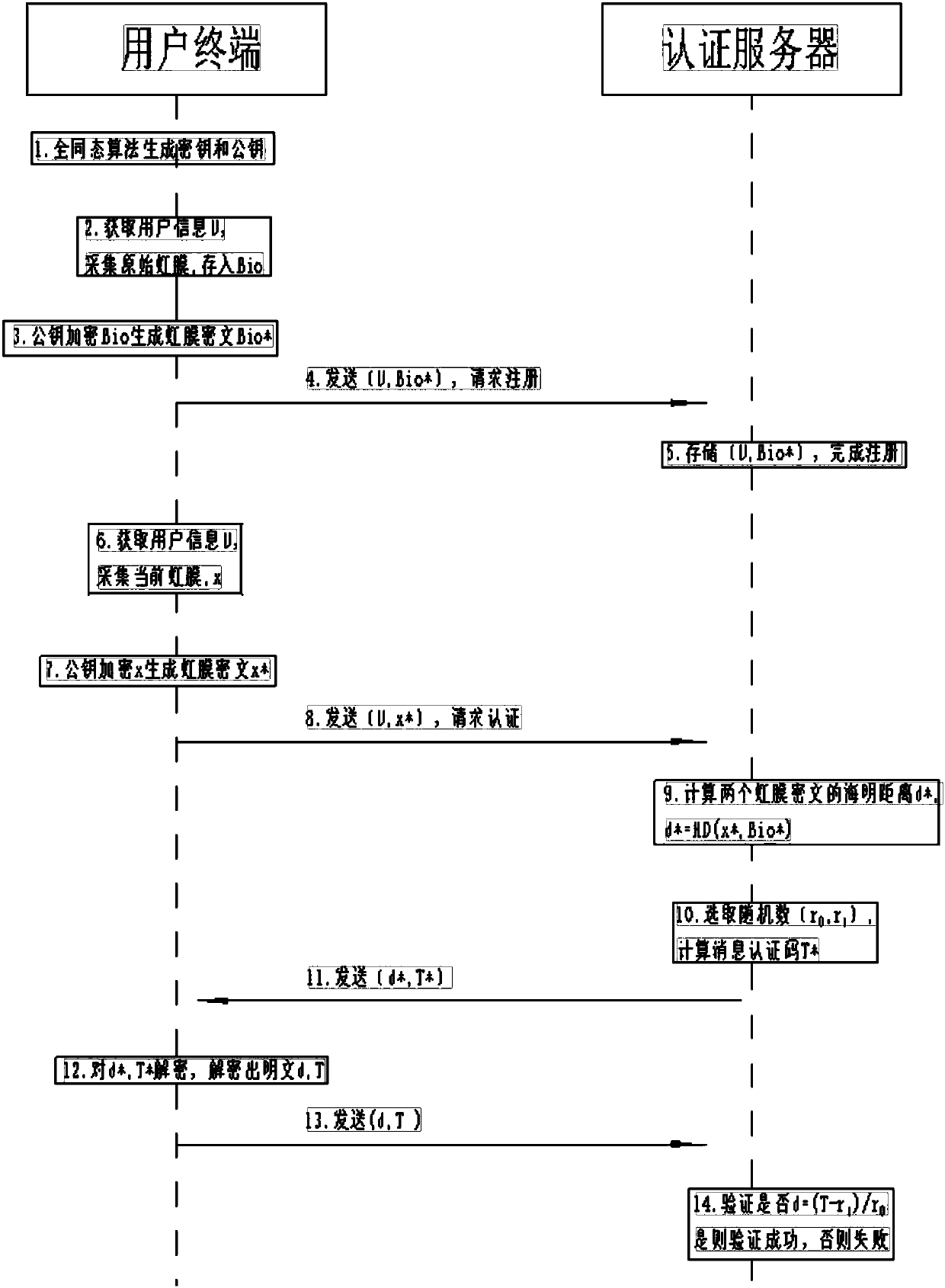
Authentication method based on homomorphic encryption, user equipment and authentication server
ActiveCN107819587AAvoid risk of leakageWill not be exposedKey distribution for secure communicationUser identity/authority verificationHomomorphic encryptionBiometric encryption
The invention discloses an authentication method based on homomorphic encryption. The authentication method comprises the following steps: generating a secret key and a public key of a homomorphic encryption algorithm for a user; storing the secret key in mobile storage equipment; collecting original biological features of the user, encrypting the original biological features by using the public key to generate the original biological feature ciphertext; and sending the original biological feature ciphertext to store in an authentication server, thereby accomplishing the registration; collecting the current biological features of the user, and encrypting the current biological features by using the homomorphic encryption algorithm to generate the current biological feature ciphertext; sending the current biological feature ciphertext to the authentication server, requesting the authentication under the ciphertext state, and acquiring the secret key in the mobile storage equipment, decrypting the authentication information by using the secret key and sending the decryption result to the authentication server. Through the adoption of the method disclosed by the invention, the biological features are authenticated under the ciphertext state, the strong safety guarantee is provided, and the biological feature information leakage of the user is avoided.
Owner:陈智罡
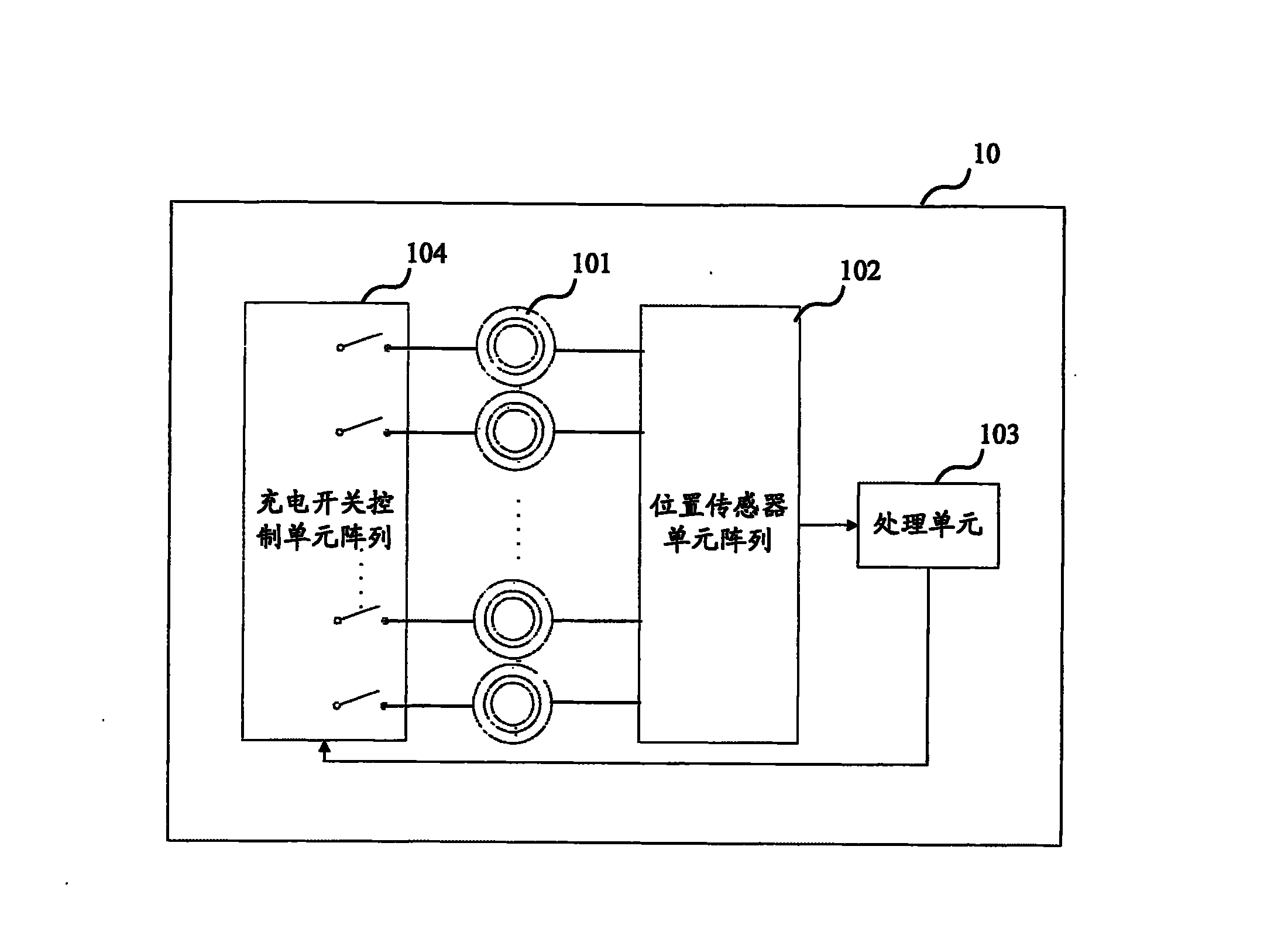
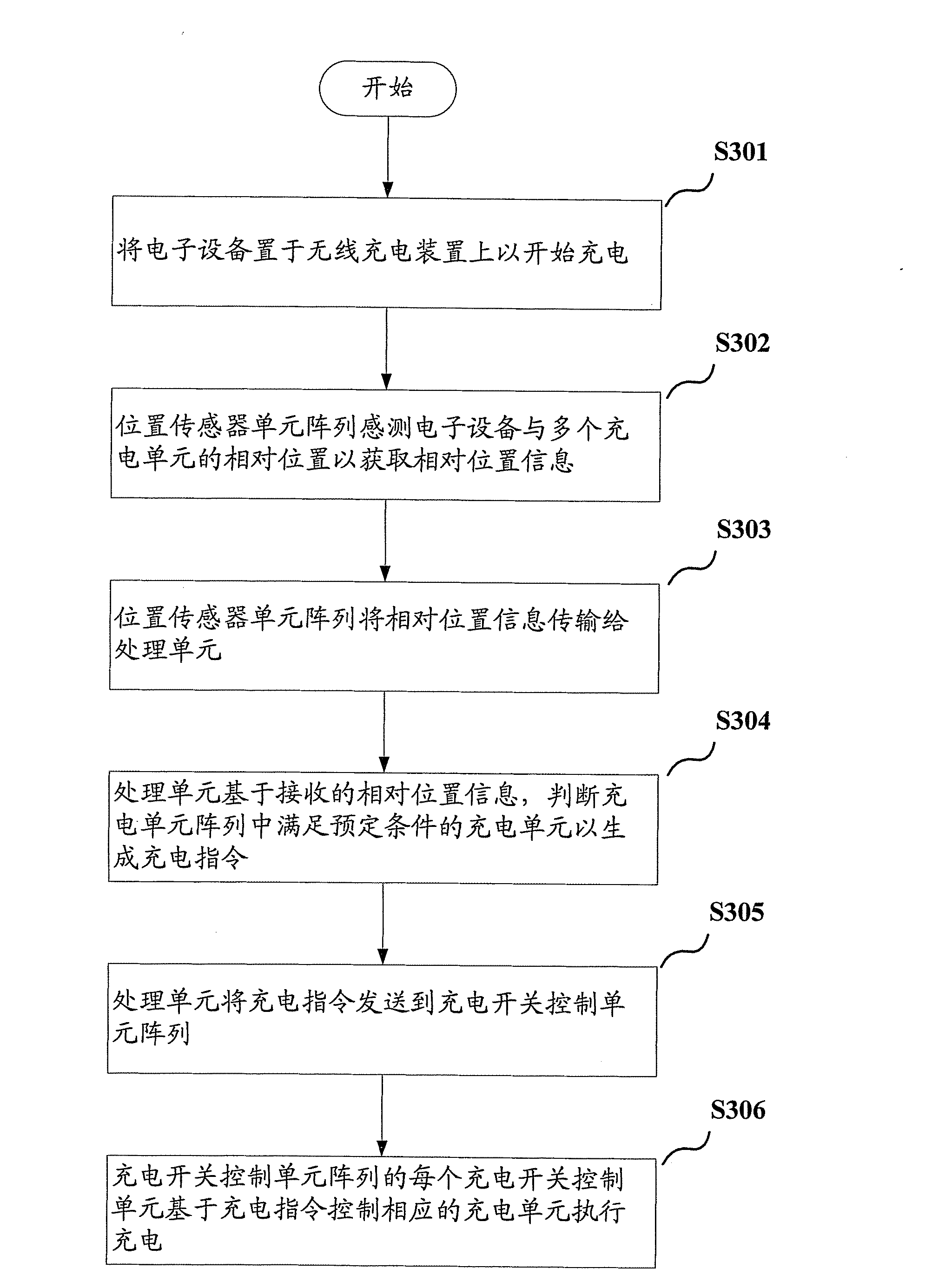
Wireless charging control method and wireless charging device
ActiveCN103259297AImprove versatilityImprove usabilityBatteries circuit arrangementsElectromagnetic wave systemCharging orderCharge control
The invention discloses a wireless charging control method and a wireless charging device which adopts the wireless charging control method. The wireless charging device comprises a processing unit, an array of a plurality of charging units and an array of a plurality of positioning sensor units which correspond to the charging units. The method comprises the following steps: the array of the positioning sensor units detects the relative position of electronic equipment and the charging units to acquire relative position information and sends the relative position information to the processing unit; the processing unit judges charging units which meet predetermined conditions in the array of the charging units based on the received relative position information to generate a charging order and transmits the charging order to the charging units which meet the predetermined conditions; the charging units which meet the predetermined conditions charge the electronic equipment according to the charging order.
Owner:LENOVO (BEIJING) CO LTD
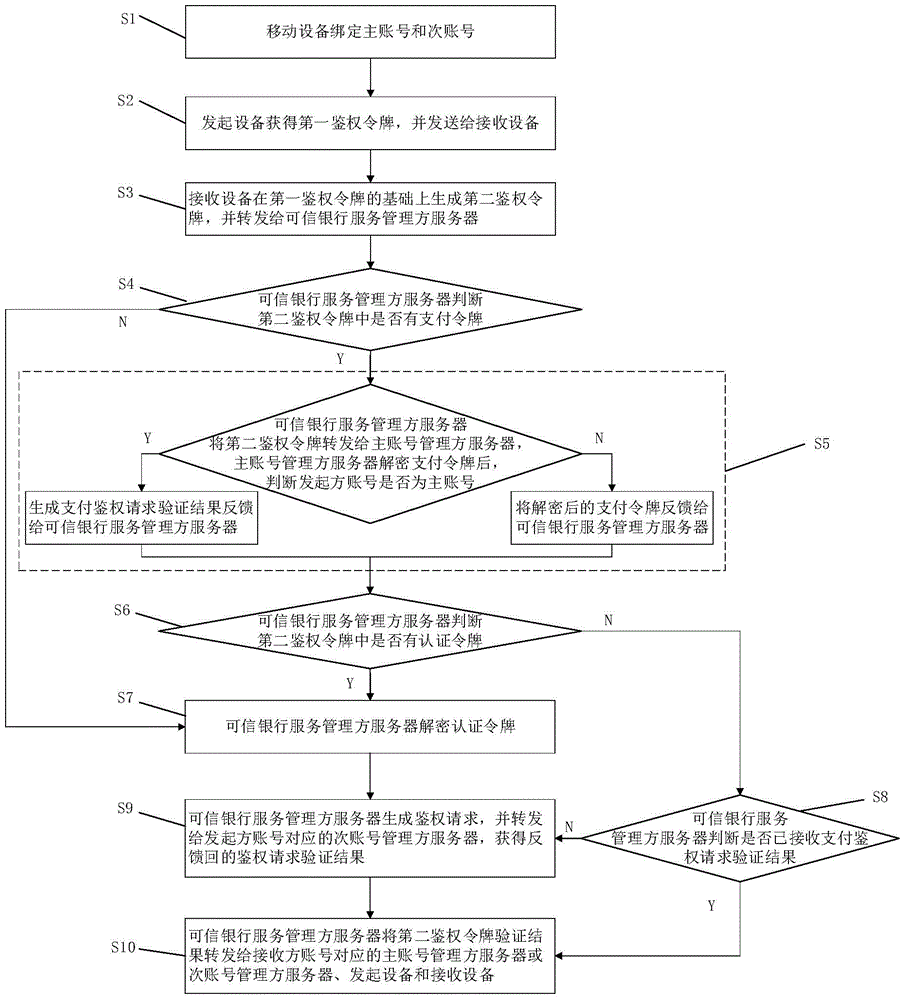
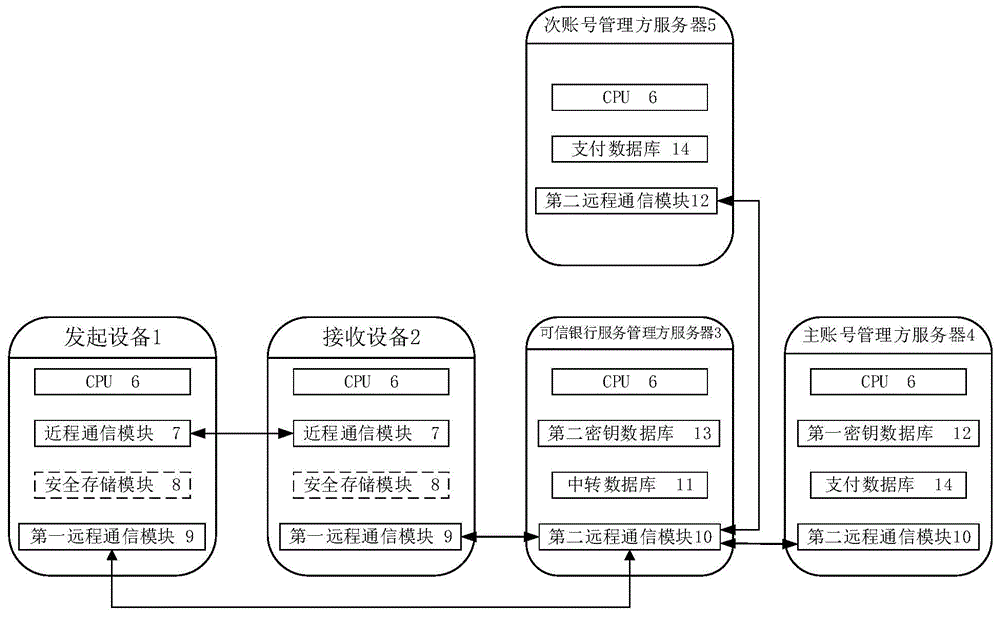
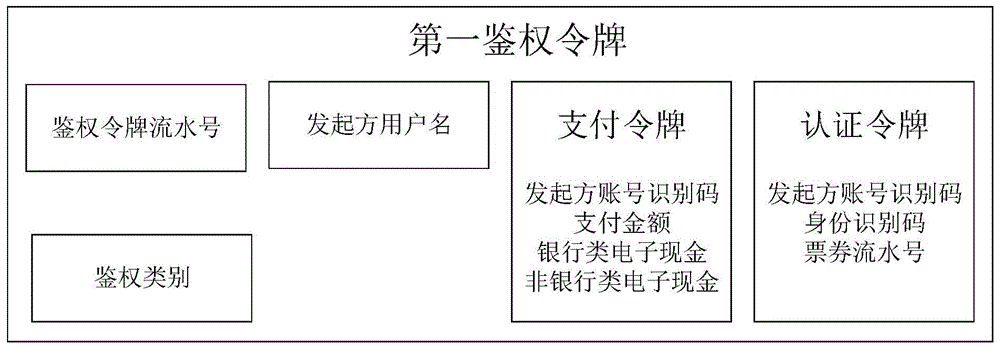
Authentication method and authentication system among mobile devices
ActiveCN104951937AAvoid risk of leakageImprove securityPayment protocolsAuthentication serverMobile authentication
The invention relates to an authentication method and an authentication system among mobile devices. The authentication method includes that after selecting an initiator account number, an initiating device obtains a first authentication token for mobile payment, identity authentication and ticket verification through an encryption method and sends the first authentication token to a receiving device; after selecting a receiver account number, the receiving device encrypts to generate a second authentication token on the basis of the first authentication token and forwards the second authentication token to a credible bank service manager server; the credible bank service manager server is communicated with a corresponding primary account number manager server or a secondary account number manager server according to content of the second authentication token to obtain a fed back authentication request verification result, generates a second authentication token verification result and forwards the second authentication token verification result to the initiating device, the receiving device and the primary account number manager server or the secondary account number manager server corresponding to the receiver account number. Compared with the prior art, the authentication method and the authentication system have the advantages that mobile authentication safety is enhanced, mobile authentication compatibility is increased, user experience is improved and the like.
Owner:上海太炎信息科技有限公司
Cold and hot integrated box body structure
ActiveCN106935756AEliminate the assembly processCompact structureSecondary cellsCell component detailsLiquid cooling systemEngineering
The invention provides a cold and hot integrated box body structure comprising a main body of a box body with an upper opening, wherein the main body of the box body comprises a bottom plate and a side plate, the bottom plate and the side plate are used for constituting an accommodation cavity for accommodating a battery, a liquid cooling system and a heating system are alternately distributed in the bottom plate, at least one fluid inlet and at least one fluid outlet communicated with the liquid cooling system are formed in the side plate, the liquid cooling system is cooling fluid flow channels distributed in the bottom plate in a snake shape, the heating system comprises a first hollow cavity arranged between cooling fluid flow channels and a heating device padded in the first hollow cavity, and a flow channel bridge used for changing the flow direction of the fluid is arranged at the reserving site of the cooling fluid flow channel. According to the box body structure provided by the invention, the liquid cooling system, the heating system and a heat insulation system are highly integrated with the section bar box body, thereby improving the weight energy density ratio and the volume energy density ratio of the battery and reducing and even eliminating the fluid leakage risk of the cooling fluid.
Owner:TIANJIN ENERGIES
Membrane, especially for an optical device having a deformable membrane
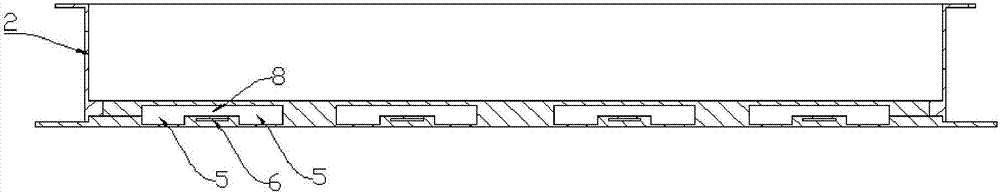
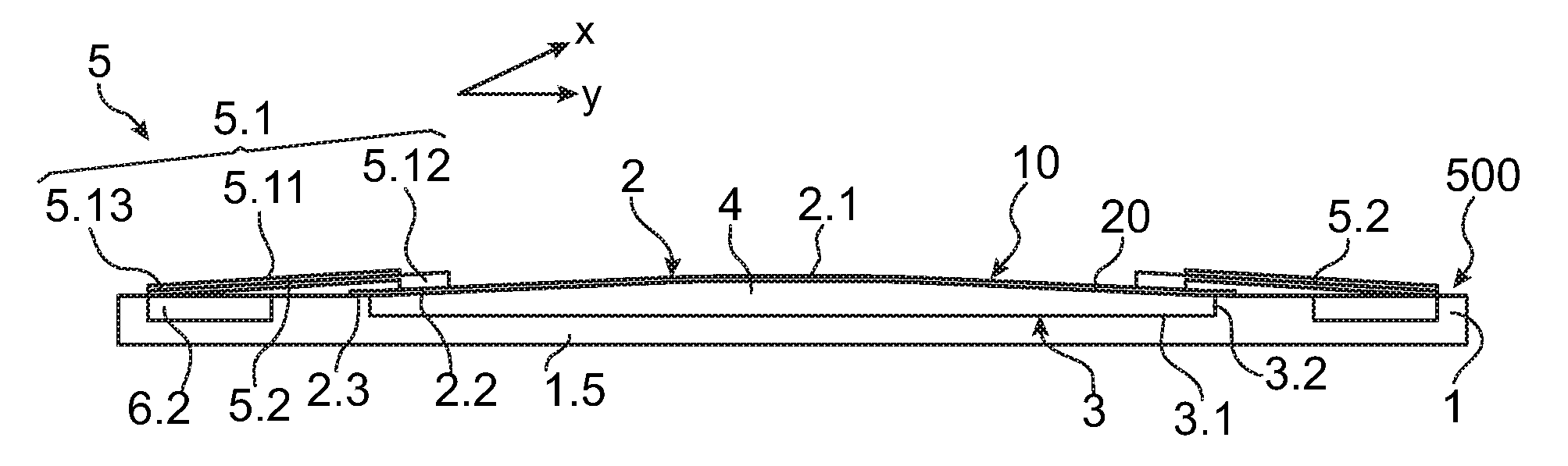
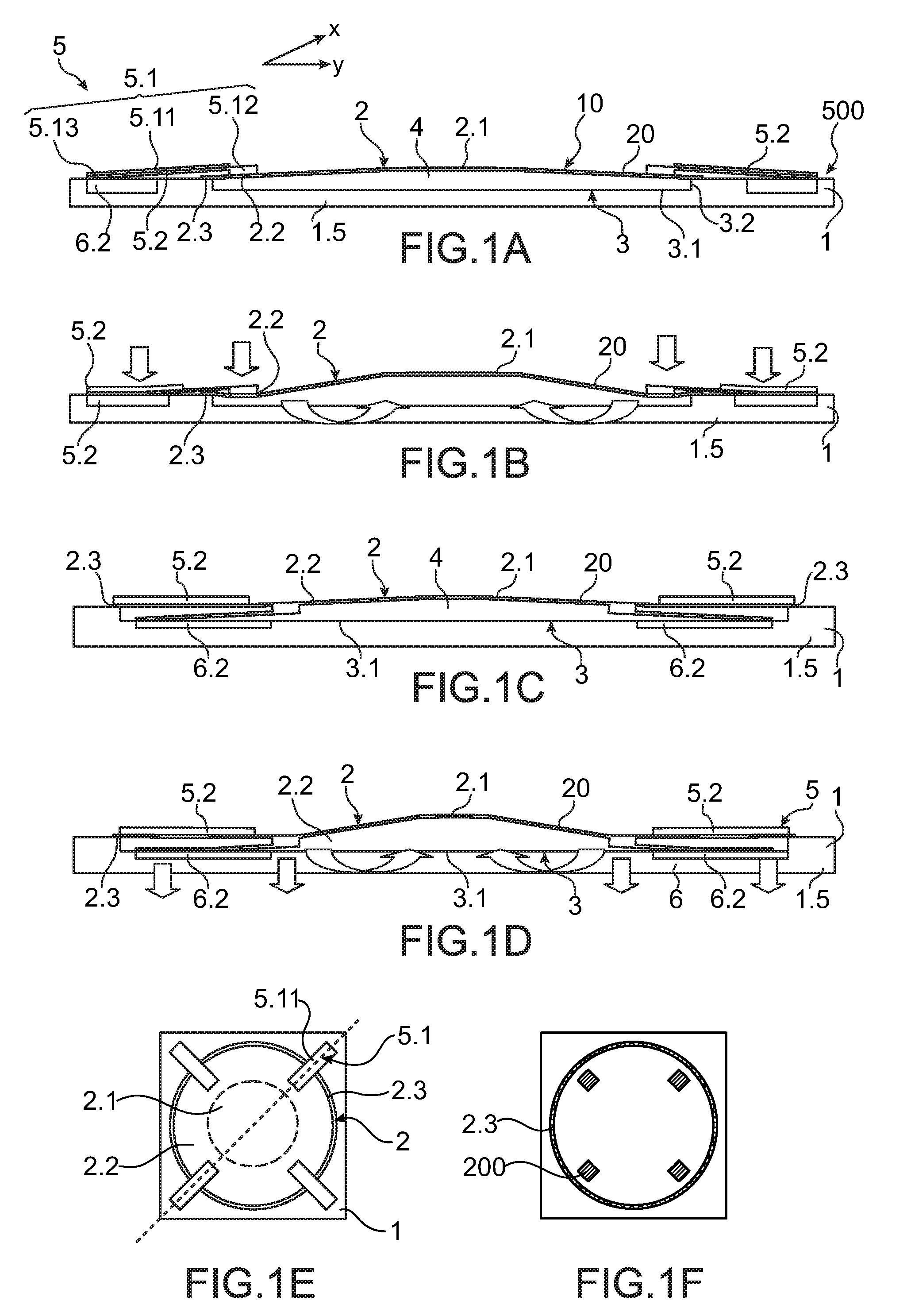
ActiveUS20110032624A1Adjust the radius of curvature of the membraneAvoid risk of leakageOptical articlesForming microstructural systemsEngineeringElectrode
An optical device having a deformable membrane comprising a flexible film having at least one peripheral anchoring zone, a central zone and an intermediate zone between the central zone and the anchoring zone. The membrane also includes one or more movable parts of electrostatic actuating means, each movable part being formed from a leg terminating on one side in a foot mechanically fastened to a film-fastening region located in the intermediate zone and terminating on the other side in a free end. The legs incorporate a movable electrode, the free end having to be attracted by a fixed electrode of the actuating means. The free end is placed facing the free end so as to deform at least the central zone of the membrane.
Owner:WEBSTER CAPITAL LLC
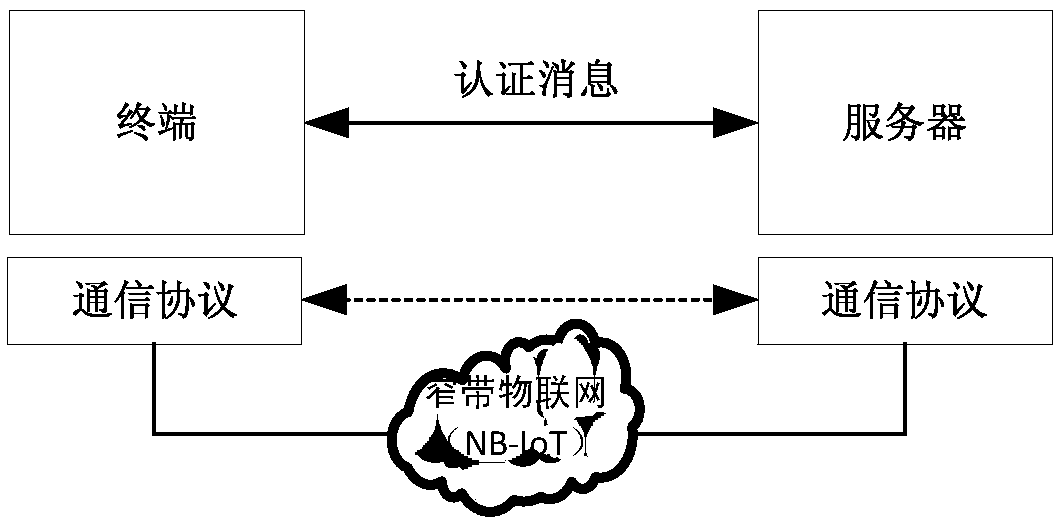
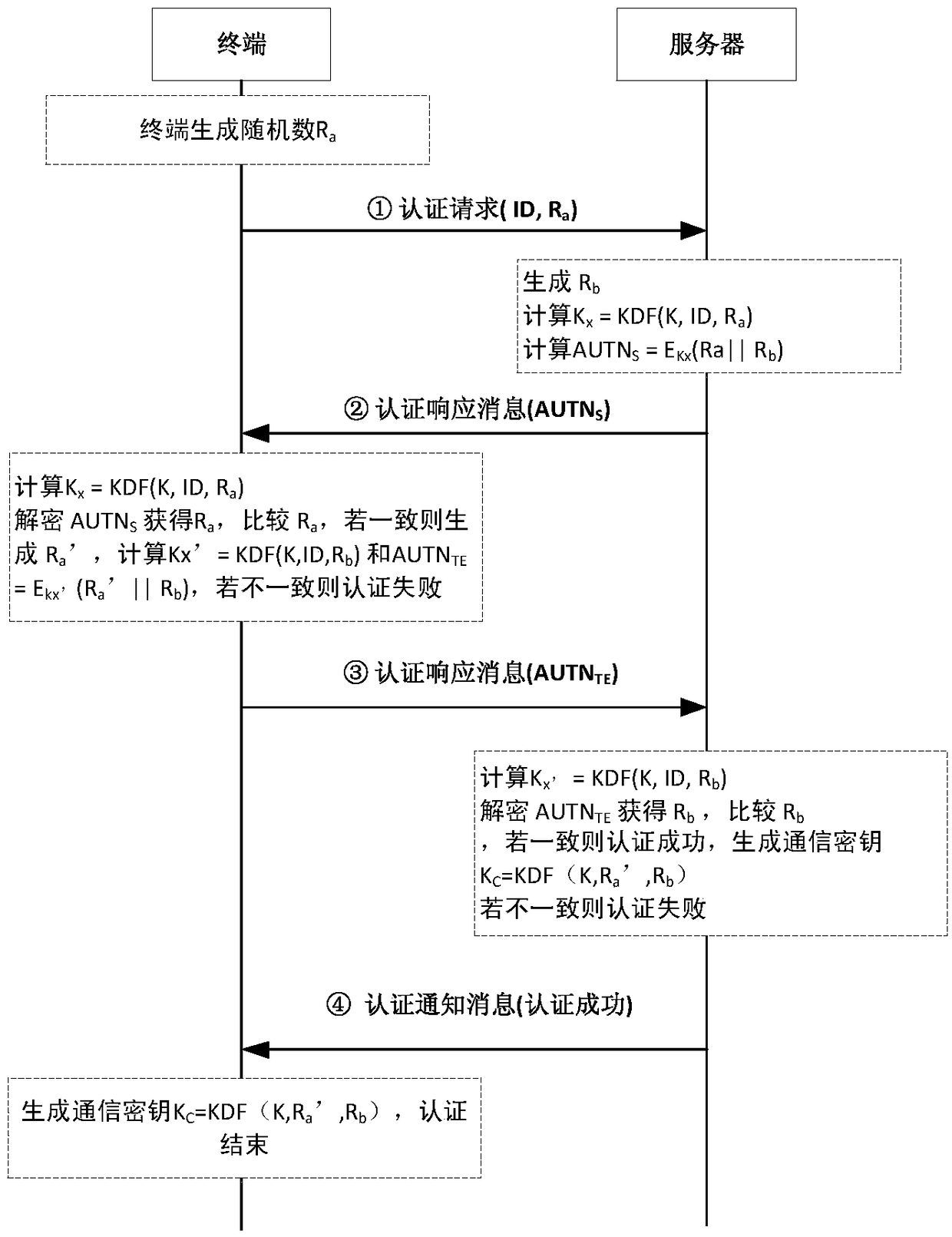
A lightweight secure authentication and key exchange method for narrowband Internet of things
ActiveCN108989318AAvoid risk of leakageReduce Interaction ComplexityTransmissionKey exchangeThe Internet
The invention discloses a lightweight security authentication and key exchange method for narrow-band internet of things. The communication main body comprises a terminal and a server. Before the communication is established, the root key is shared between the terminal and the server, and the two-way authentication is realized by adopting a challenge-response interaction mechanism based on a symmetric cryptosystem. The present invention mainly solves the problem of the two-way identity authentication and key exchange between the terminal and server in the Internet of Things application systembased on NB-IoT and other narrow-band Internet of Things connection technologies, can realize lightweight security authentication algorithm, protocol and key agreement mechanism, and meet the design requirements of low power consumption, low bandwidth consumption, low interaction frequency and high security.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
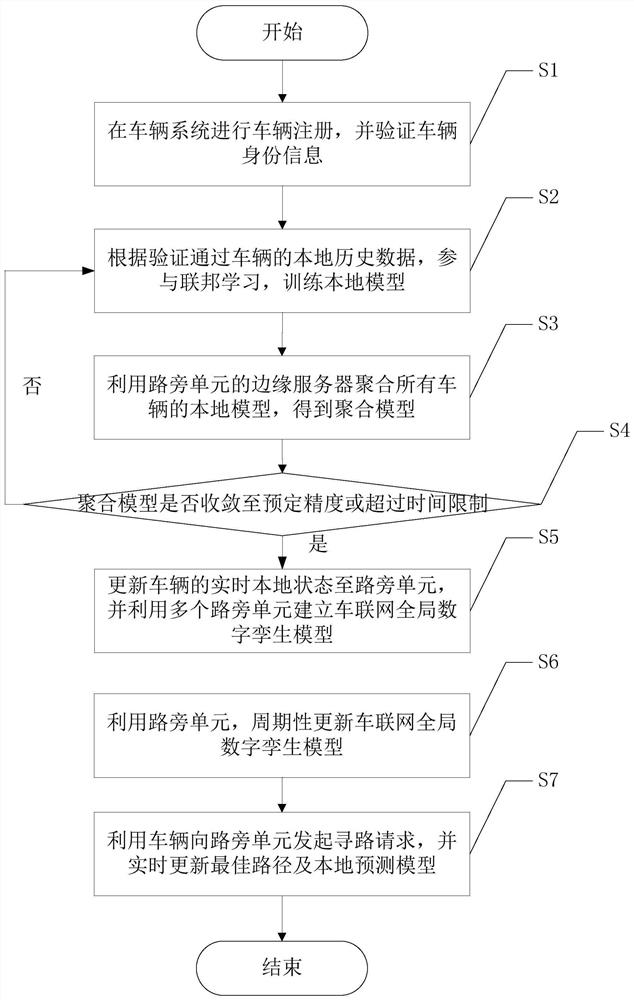
Intelligent traffic path planning method based on federated learning and digital twinning
ActiveCN112700639AReduce riskReduce latencyDetection of traffic movementParticular environment based servicesTraffic predictionSimulation
The invention discloses an intelligent traffic path planning method based on federated learning and digital twinning. The method comprises the following steps of: S1, carrying out vehicle registration in a vehicle system, and verifying the identity information of vehicles; S2, according to the local historical data of the vehicles, participating in federated learning, and training a local model; S3, aggregating the local models of all the vehicles to obtain an aggregation model; S4, judging whether the aggregation model converges to preset precision or exceeds a time limit or not, if yes, entering the step S5, and otherwise, returning to the step S2; S5, establishing an Internet-of-vehicles global digital twinning model; S6, periodically updating the Internet-of-vehicles global digital twinning model; and S7, initiating a path finding request to a roadside unit, and updating the optimal path and the local prediction model in real time. The planning method provided by the invention is applied to the field of Internet of vehicles, so as to solve the problems of low flow prediction and path planning accuracy, high time delay and privacy leakage risk in the current road traffic system.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
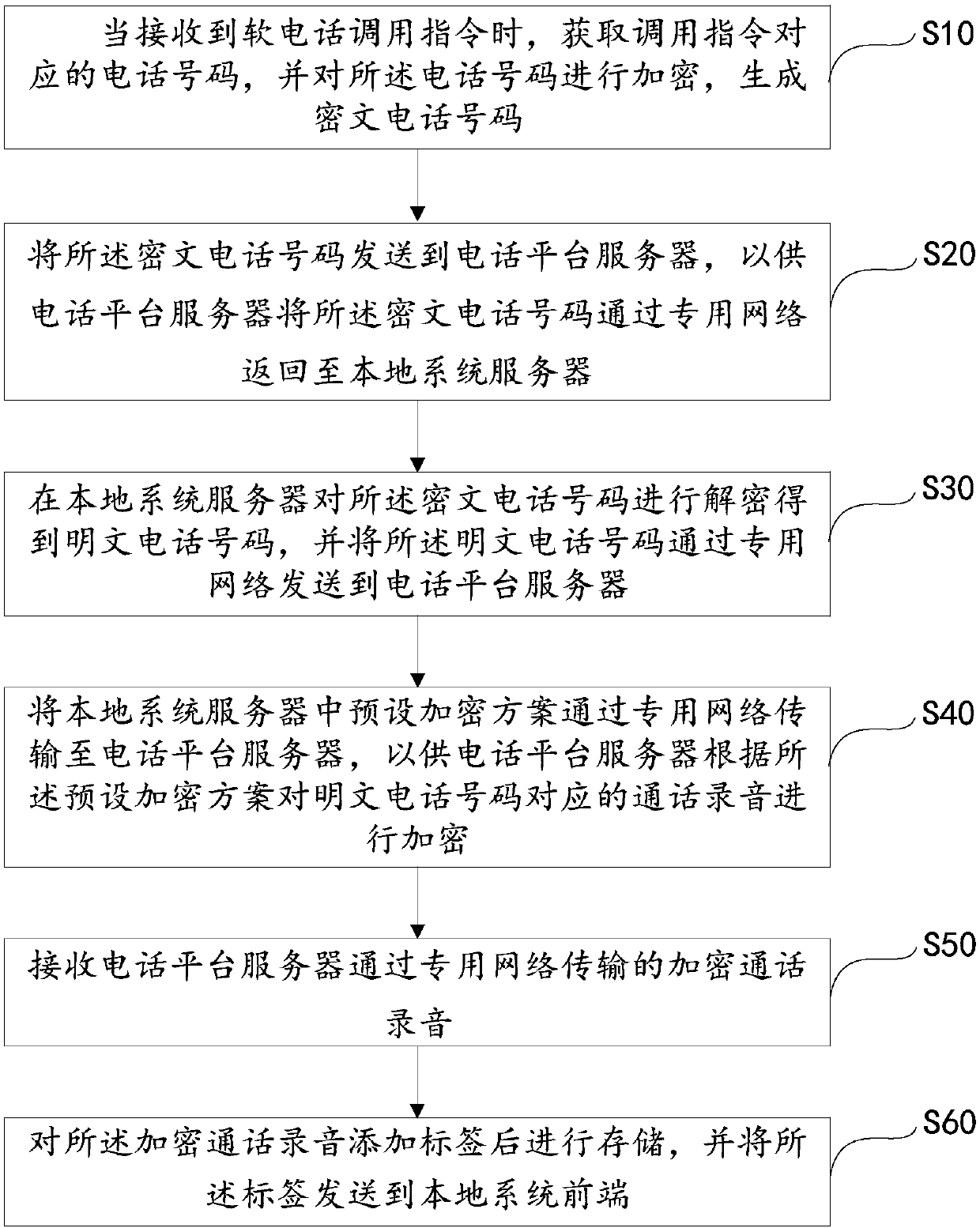
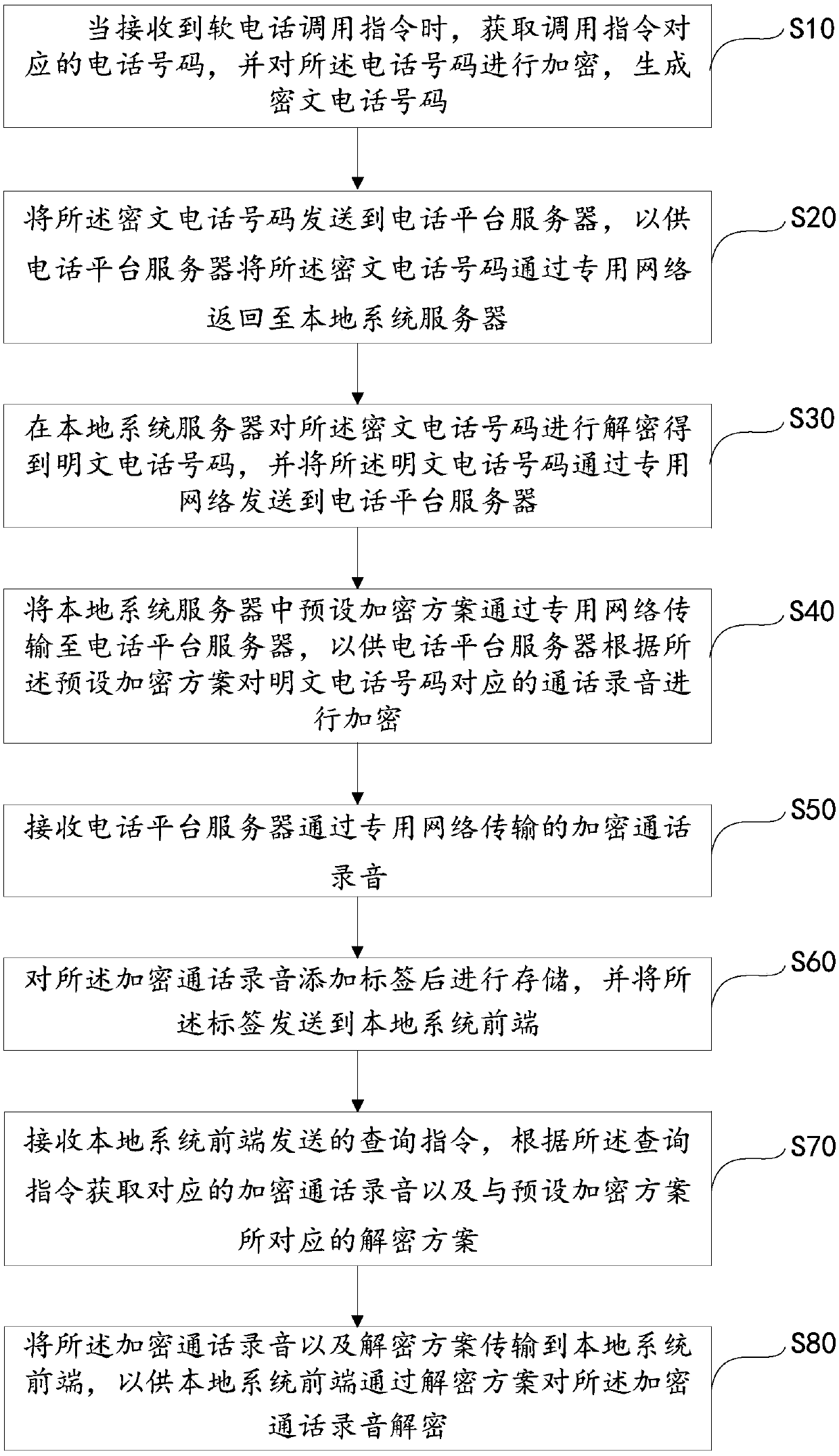
Softphone encryption and decryption method and device and computer readable storage medium
ActiveCN107682577AGood decryption securityEnsure safetyKey distribution for secure communicationInterconnection arrangementsPlaintextPrivate network
The invention discloses a softphone encryption and decryption method and device and a computer readable storage medium. The method comprises the steps of: when receiving a softphone calling instruction, acquiring a phone number corresponding to the calling instruction, and carrying out encryption on the phone number to generate a ciphertext phone number; sending the ciphertext phone number to a phone platform server, so that the phone platform server returns the ciphertext phone number to a local system server by a special network; and carrying out decryption on the ciphertext phone number bythe local system server to obtain a cleartext phone number, and sending the cleartext phone number to the phone platform server by the special network. According to the scheme, both phone number encryption and decryption for a softphone are carried out by the local system server, and a secret key does not need to be sent to the phone platform server, and thus, security is high, and the case that the secret key is intercepted in the transmitting process is avoided; and the decrypted phone number is sent to the phone platform server by the special network, so that the leakage risk is further avoided, and security of personal information of a client is ensured.
Owner:PING AN TECH (SHENZHEN) CO LTD
Collection method and device based on user data and storage medium
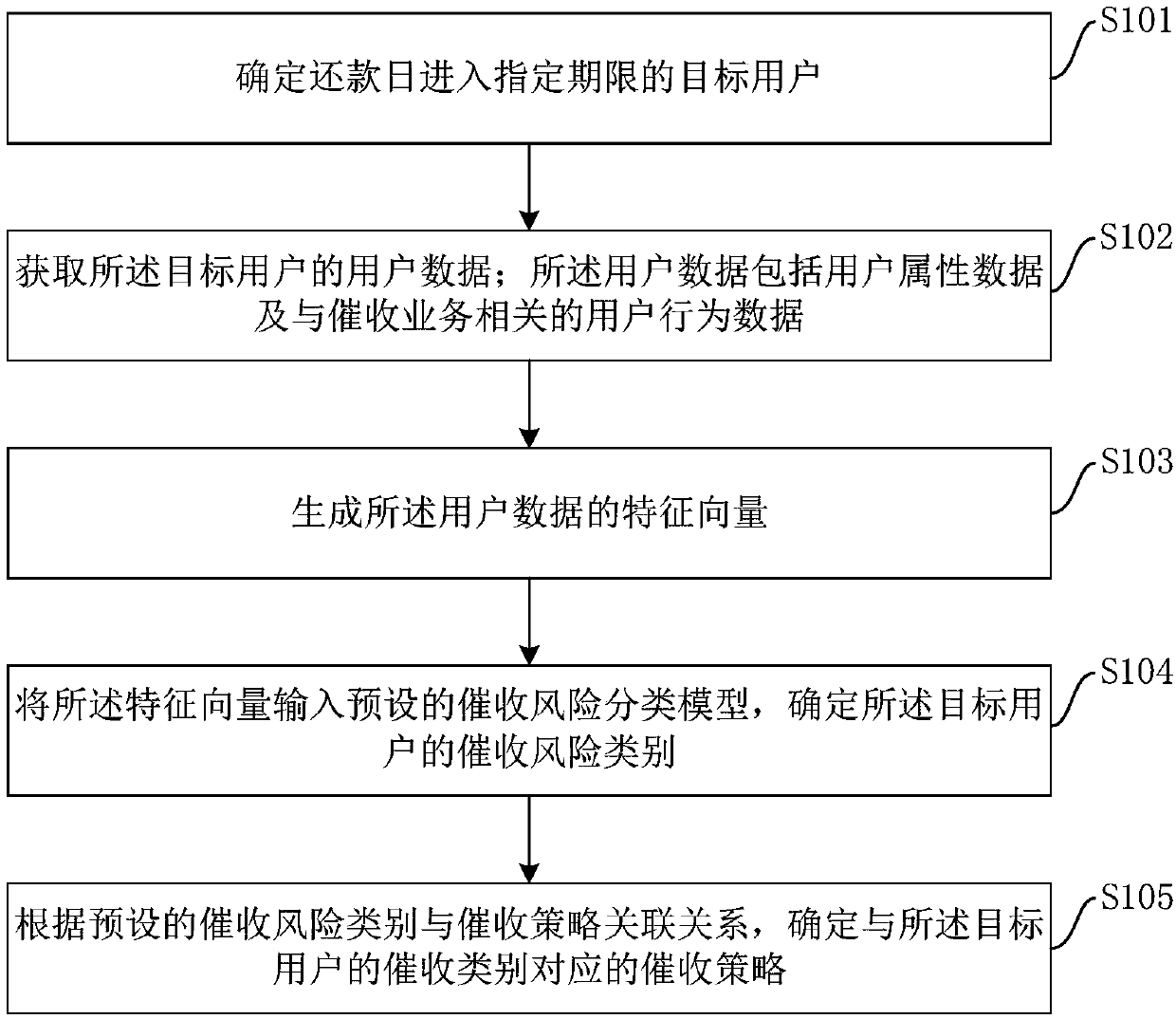
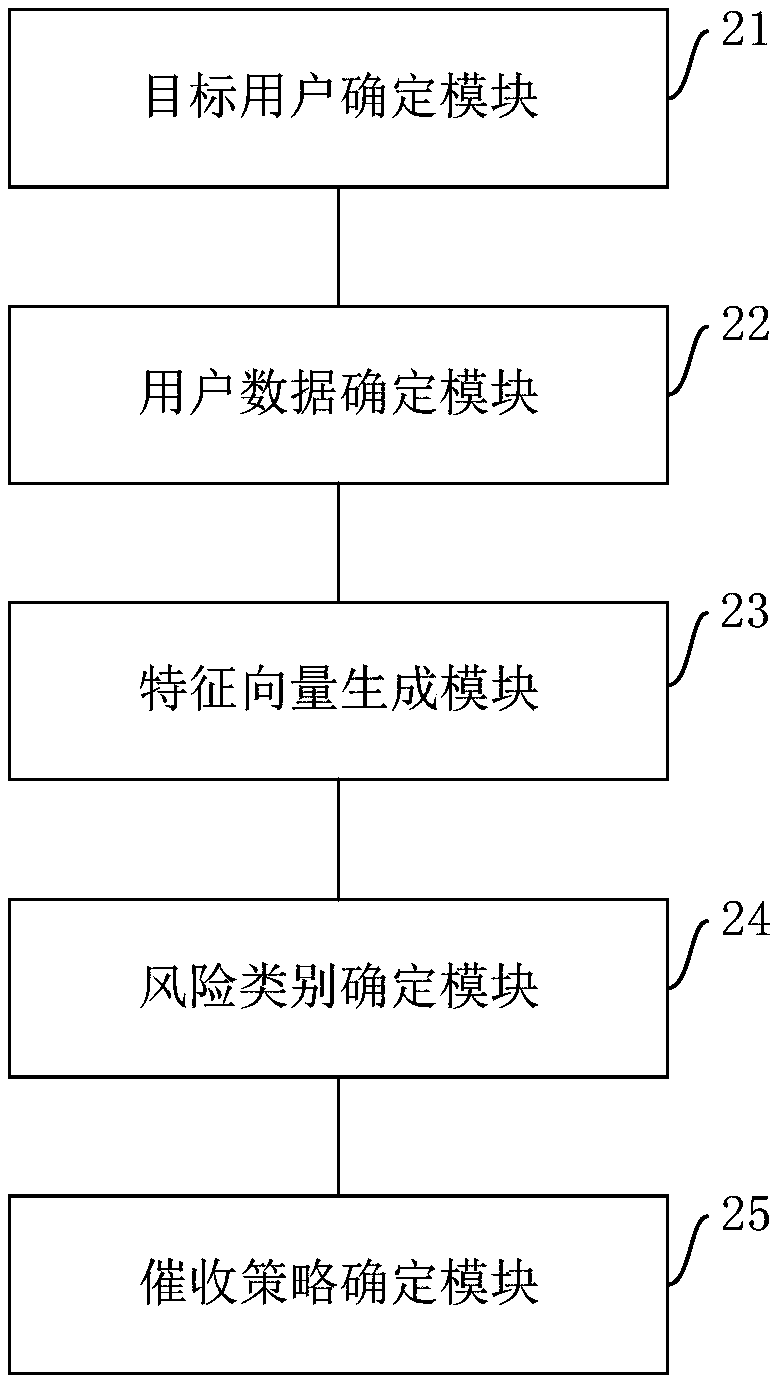
InactiveCN109559221AImprove collection success rateImprove collection efficiencyFinanceFeature vectorRisk classification
The embodiment of the invention provides a collection method and device based on user data and a storage medium. The method comprises the steps of determining a target user whose repayment day entersan appointed deadline; obtaining user data of the target user, wherein the user data comprises user attribute data and user behavior data related to the collection service; generating a feature vectorof the user data; Inputting the feature vector into a preset collection risk classification model, and determining a collection risk category of the target user; and determining a collection strategycorresponding to the collection category of the target user according to a preset corresponding relation between the collection risk category and the collection strategy. The embodiment of the invention can improve the collection success rate, and is high in efficiency and low in cost.
Owner:BANK OF CHINA
Battery pack and battery case thereof
PendingCN108461685AImprove connection strengthReduce welding stressBattery isolationPropulsion by batteries/cellsElectrical batteryEngineering
The invention provides a battery pack and a battery case thereof. The battery case comprises a bottom plate, a plurality of first beams, a plurality of second beams, a plurality of corner connectors,aplurality of fixed beams, and a plurality of fixed beam connectors, wherein the first and second beams are fixed on the bottom plate to form an accommodating cavity, each first beam is provided witha first cavity, and each second beam is provided with a second cavity; each corner connector is provided with a first connecting portion and a second connecting portion, which form a first angle, thefirst connecting portion of each corner connector islocated in the first cavity of the corresponding first beam and fixedly connected to the first beam, the second connecting portion of each corner connector is located in the second cavity of the corresponding second beam and is fixedly connected to the second beam; the fixed beams are fixed on the bottom plate and are located in the accommodatingcavities., and two ends of each fixed beam are connected with the second beams, respectively; each of the fixed beam connectors is connected with a fixed beam and a second beam. The reliability of the battery case provided by the invention is improved.
Owner:AIWAYS AUTOMOBILE CO LTD
Cooling device of heat pipe fins for power battery system and mode selecting method
The invention relates to a cooling device of heat pipe fins for a power battery system and a mode selecting method. The cooling device of the heat pipe fins for the power battery system comprises a battery box, wherein a plurality of battery module groups are arranged in the battery box in parallel; each battery module group is provided with a heat pipe group in a matched manner; and two ends of each heat pipe group penetrate through the battery box and are connected with cooling fins. The mode selecting method comprises the following steps: establishing equivalent heat resistance models of the heat pipe groups and the cooling fins; establishing a concentrated parameterized ID heat transfer modules for a main heat transfer path after the equivalent heat resistance models are established; establishing a partial differential equation of a heat transfer process of each element; and after determining a convective heat transfer coefficient (h) required for the system, selecting a cooling scheme. The cooling device of the heat pipe fins for the power battery system has the advantages of high cooling efficiency, low complexity of the system and high safety; meanwhile, the expandability is high, the cooling mode can be randomly adjusted according to actual demands of products, and the degree of standardization is high; and IP67 design of the battery box is realized easily, space and cost are saved, and safety of the power battery system is improved.
Owner:杭州捷能科技有限公司
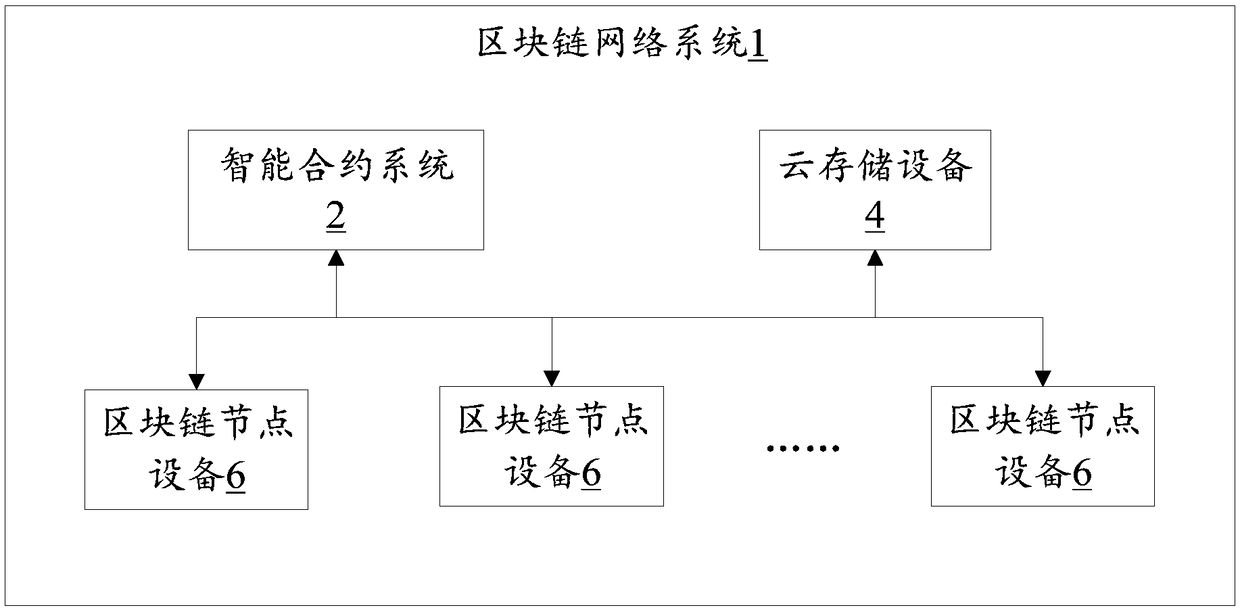
Cloud stored data encrypted transmission method, system, equipment and storage medium
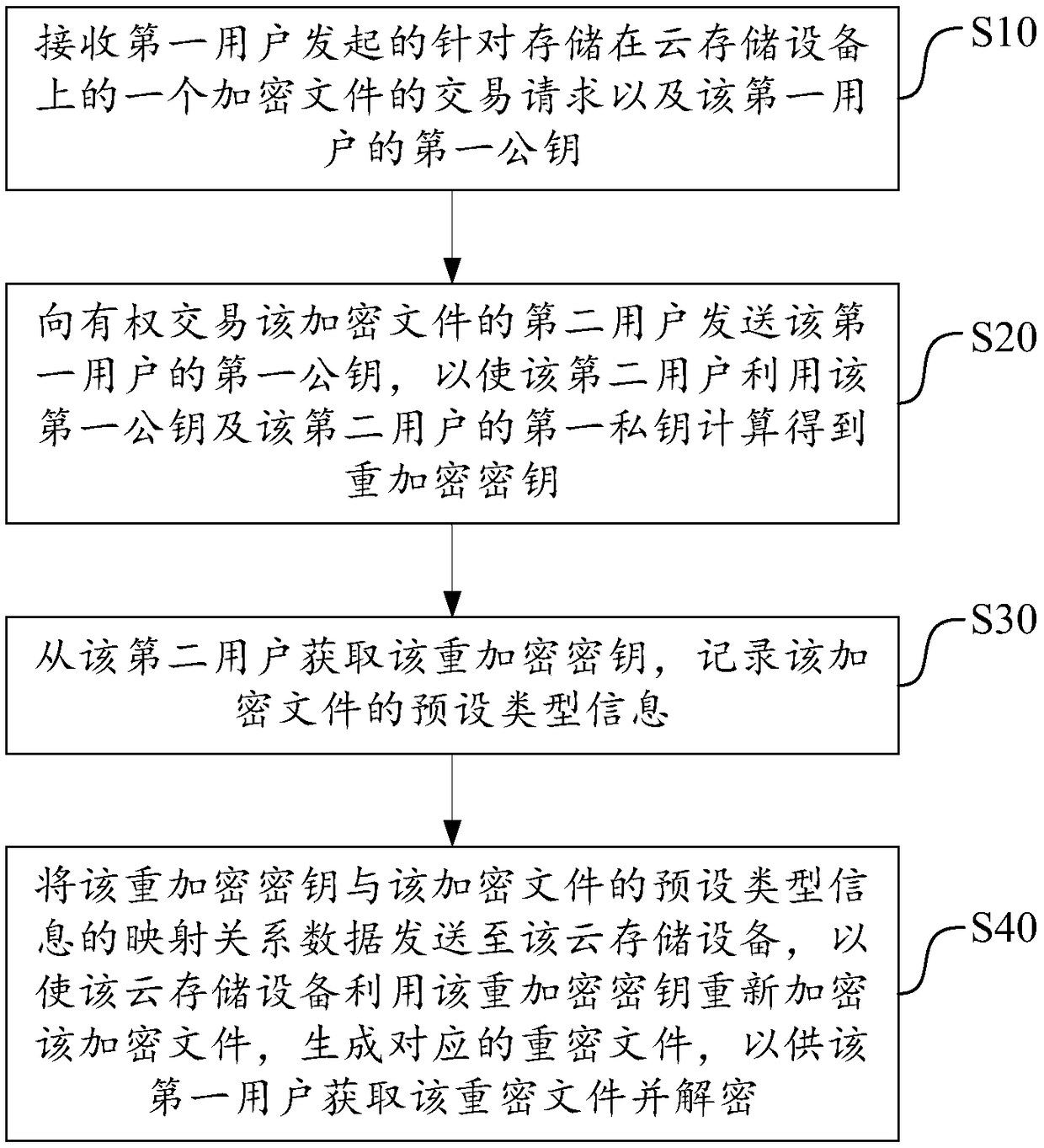
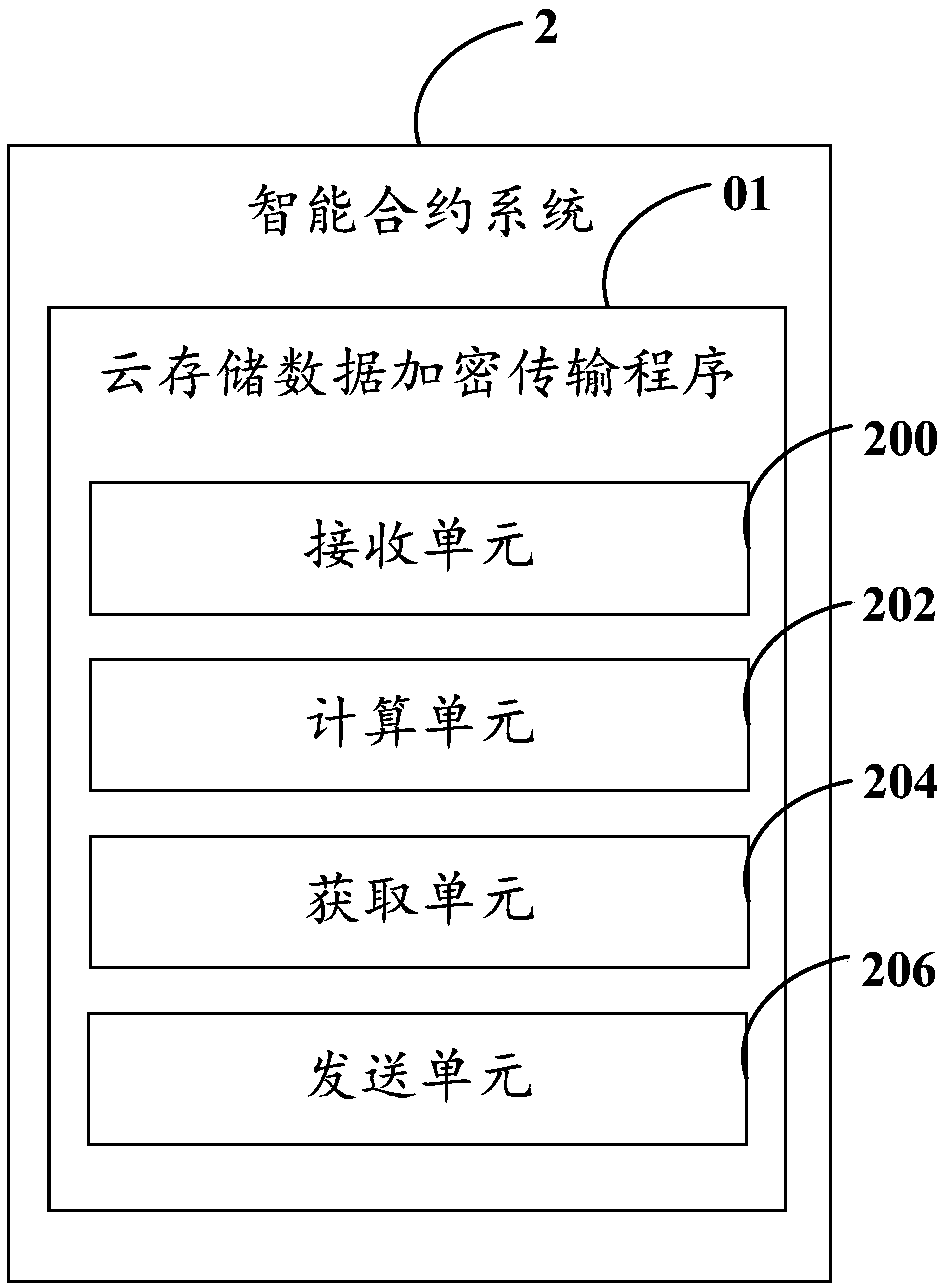
InactiveCN109361704AReduce risk of leakageAvoid risk of leakageTransmissionTransaction dataData file
The invention discloses a cloud stored data encrypted transmission method which comprises the steps of: receiving a transaction request which is initiated by a first user and aims at one encrypted file stored on cloud storage equipment and a public key of the first user; sending the public key of the first user to a second user, so that the second user utilizes the public key of the first user anda private key of the second user to calculate to obtain a re-encrypted key; acquiring the re-encrypted key from the second user, and recording preset type information of the encrypted file; and sending mapping relationship data between the re-encrypted key and the preset type information of the encrypted file to the cloud storage equipment, so that the cloud storage equipment utilizes the re-encrypted key to re-encrypt the encrypted file and generates a corresponding re-encrypted file for the first user to acquire the re-encrypted file and decrypt. The invention further discloses a smart contract system, cloud storage equipment and a storage medium. According to the invention, the risk of data leakage in the data file transaction process, which is caused by the mutual trust problem, can be effectively avoided.
Owner:SHENZHEN THUNDER NETWORK TECH +1
Bank virtual card number based mobile payment system and method
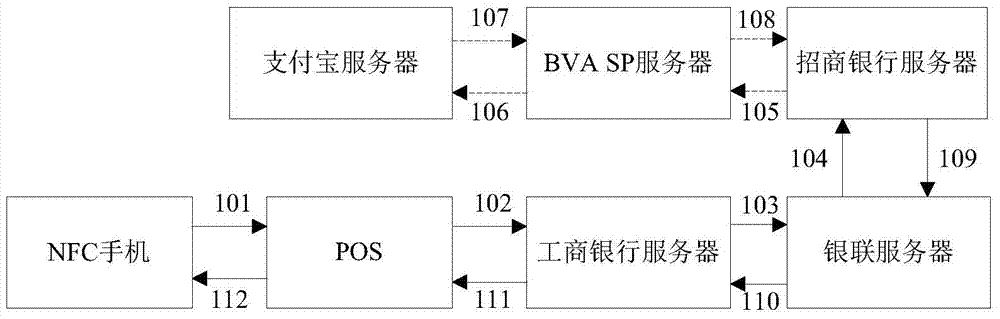
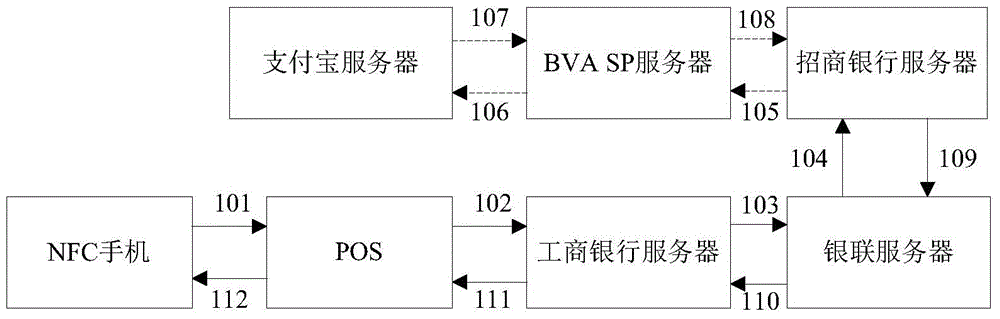
ActiveCN104700267AAvoid risk of leakageImprove securityPayment protocolsPoint-of-sale network systemsIssuing bankThird party
The invention relates to a bank virtual card number based mobile payment system and method. The system comprises a payment device, an issuing bank server, a third-party payment server, a POS, an acquiring bank server, a card organization server, a merchant server and a BVA SP server; the payment device is used for generating a bank virtual card number used as a main account of a payment requirement or a transfer request; the payment request is transferred and transmitted through the POS, the acquiring bank server and the card organization server, or the transfer request is sent to the issuing bank server through the BVA SP server; the issuing bank server can perform the payment or transfer; when the payment device pays or transfers through the third-party payment account, the issuing card server communicates with the third-party payment server through the BVA SP server, and then the payment or transfer can be done after verifying the payment request or the transfer request. Compared with the prior art, the system has the advantages of improving the mobile payment security, being high in compatibility, and facilitating a user to operate.
Owner:上海太炎信息科技有限公司
Beauty data storage system based on block chain
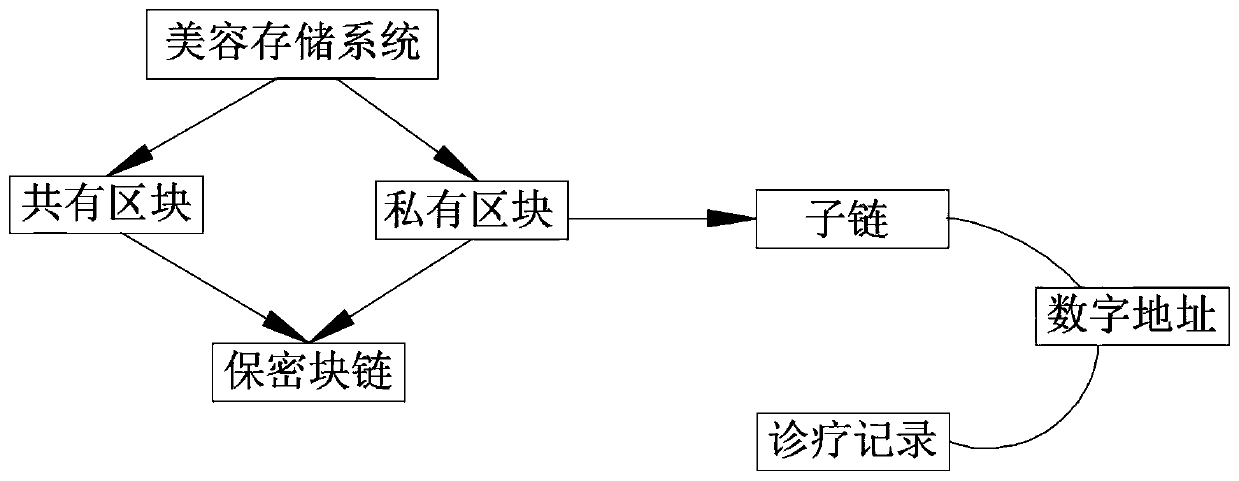
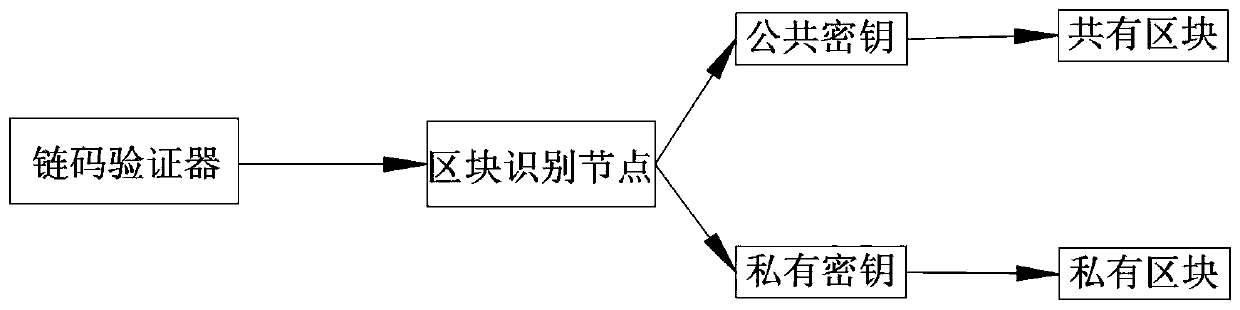
ActiveCN110929293AProtection securityOvercome leakageDigital data protectionPatient-specific dataData storage systemBlockchain
The invention provides a beauty data storage system based on a block chain. The beauty data storage system based on a block chain comprises a public block, a private block and a confidential block chain, wherein the public block is used for storing diagnosis and treatment operation and diagnosis and treatment information; the private block is configured to store a patient personal diagnosis and treatment record; the confidential block chain is configured to be used for verifying identities of the public block and the private block; and both the public block and the private block are connectedwith the secret chain. Personal information of a patient is stored by adopting a private block chain, so that the risk of leakage of traditional electronic archive information is overcome, and sensitive personal information of the patient is protected, and the worry that the patient worries about plastic surgery information leakage is solved.
Owner:FOSHAN UNIVERSITY
Passive outboard cooling system suitable for underwater platform
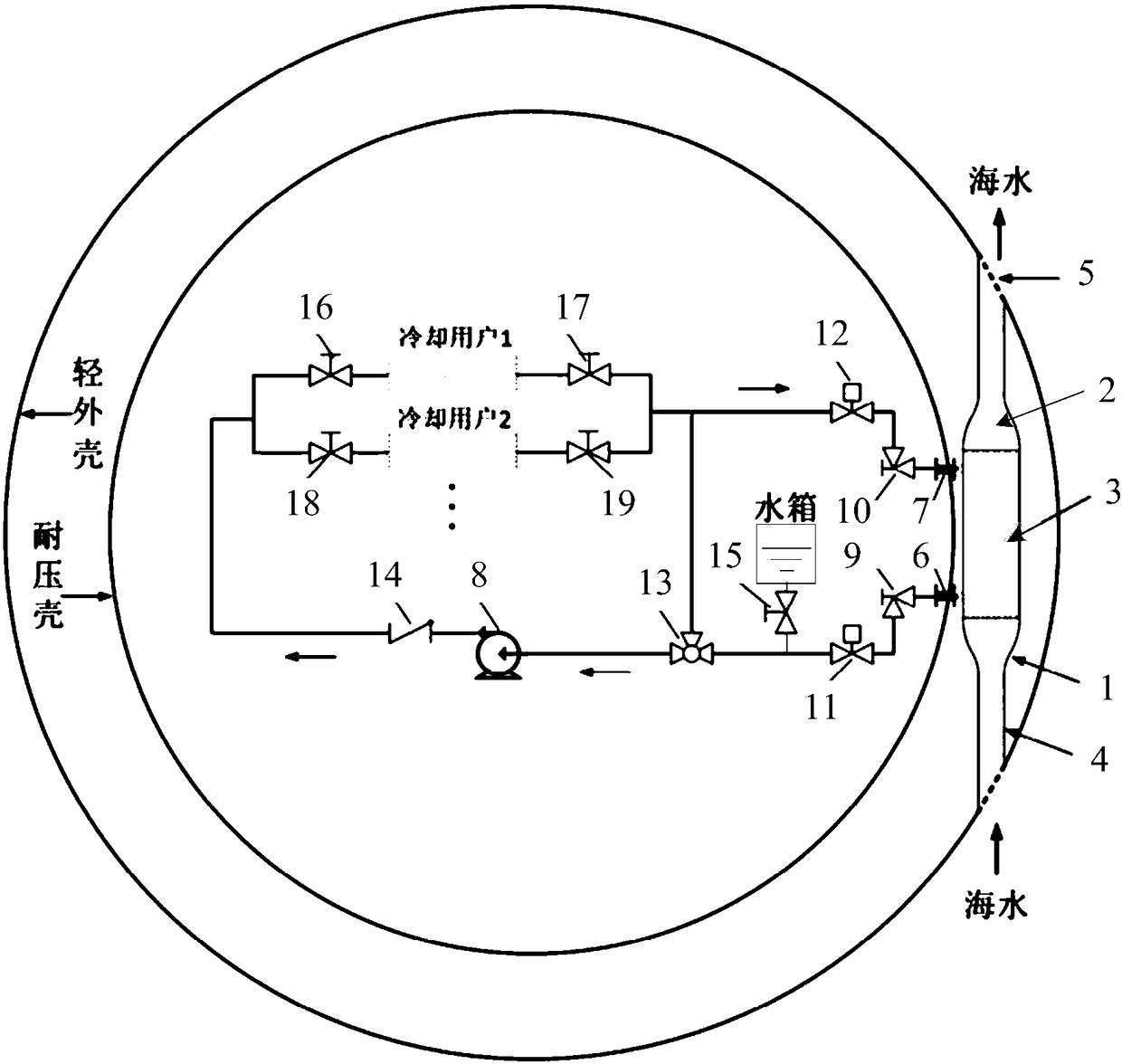
InactiveCN109000413AReduce occupancyAvoid risk of leakageLighting and heating apparatusCooling fluid circulationClosed loopEngineering
The invention discloses a passive outboard cooling system suitable for an underwater platform, and relates to the field of underwater platform cooling systems. The passive outboard cooling system suitable for the underwater platform comprises a passive heat exchanger and a fresh water circulating pipeline. The passive heat exchanger is arranged outside the board and vertically arranged in the region which is located between a pressure-resistant shell and a light shell. The fresh water circulating pipeline is arranged in a cabin. The passive heat exchanger comprises heat exchange tubes, a firstwater collecting chamber and a second water collecting chamber. The first water collecting chamber and the second water collecting chamber are connected with a water inlet and a water outlet formed in the light shell through connecting pipes correspondingly, and filtering screens are installed in the water inlet and the water outlet. A shell of the passive heat exchanger is connected with a firstcabin penetrating part and a second cabin penetrating part. The fresh water circulating pipeline is formed by a water tank, a fresh water pump, cooling users, valves and pipelines through connection.One end of the fresh water circulating pipeline is connected with the first cabin penetrating part, the other end of the fresh water circulating pipeline is connected with the second cabin penetrating part, and the fresh water circulating pipeline and the passive heat exchanger are combined to form a closed loop. The occupation of the space in the pressure-resistant cabin is reduced, the risk ofleakage of seawater pipelines is avoided, and the system energy consumption and the noise are reduced.
Owner:CHINA SHIP SCIENTIFIC RESEARCH CENTER (THE 702 INSTITUTE OF CHINA SHIPBUILDING INDUSTRY CORPORATION)
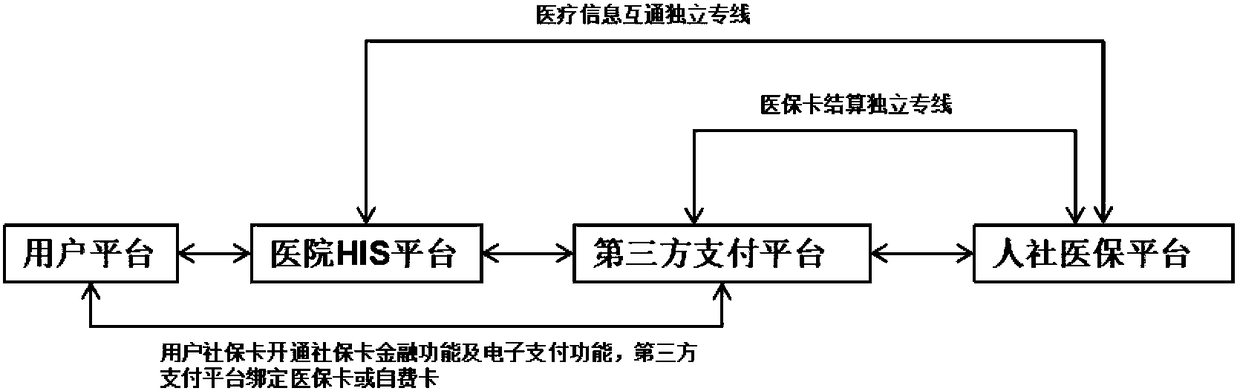
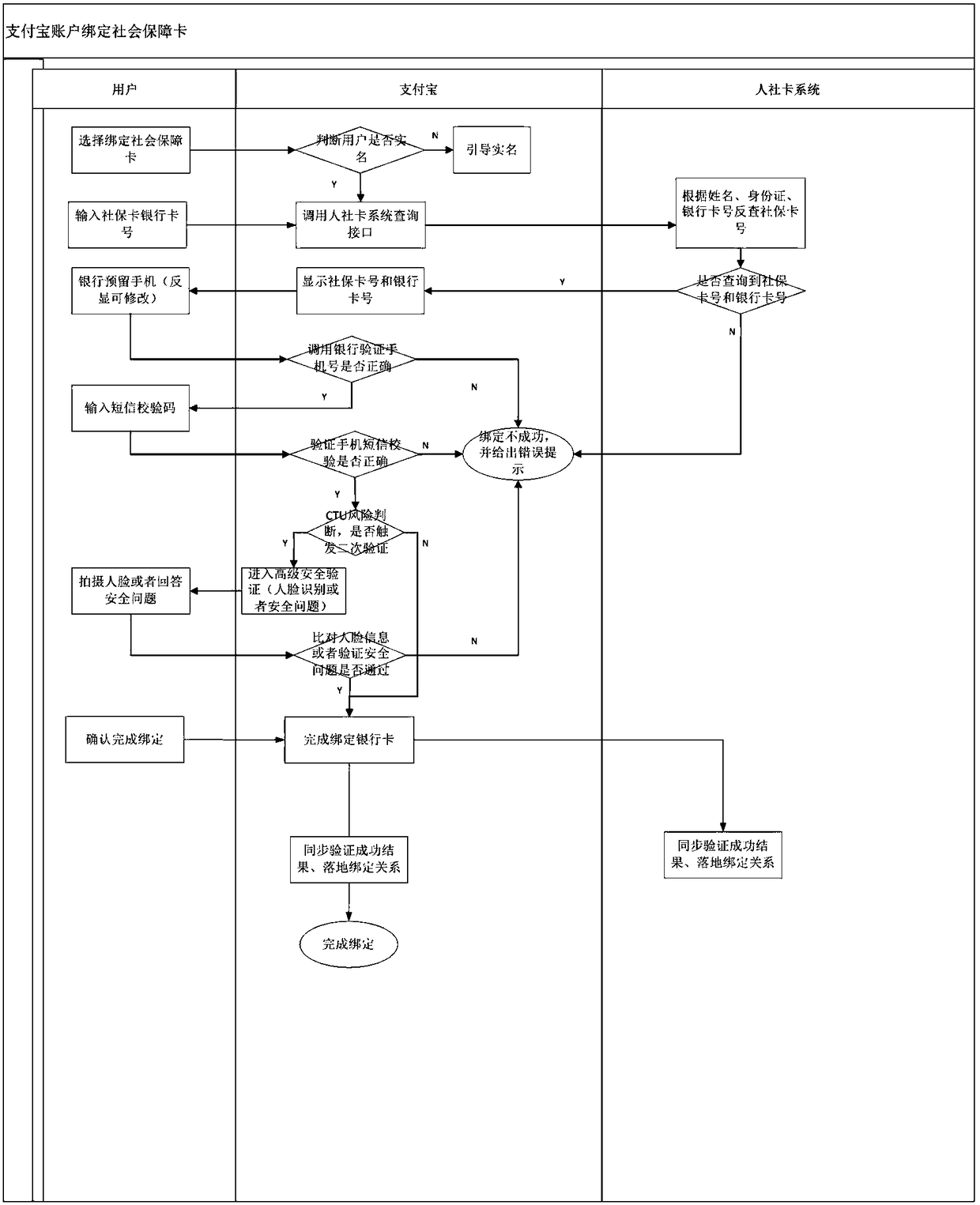
System with support of mobile payment of social security card
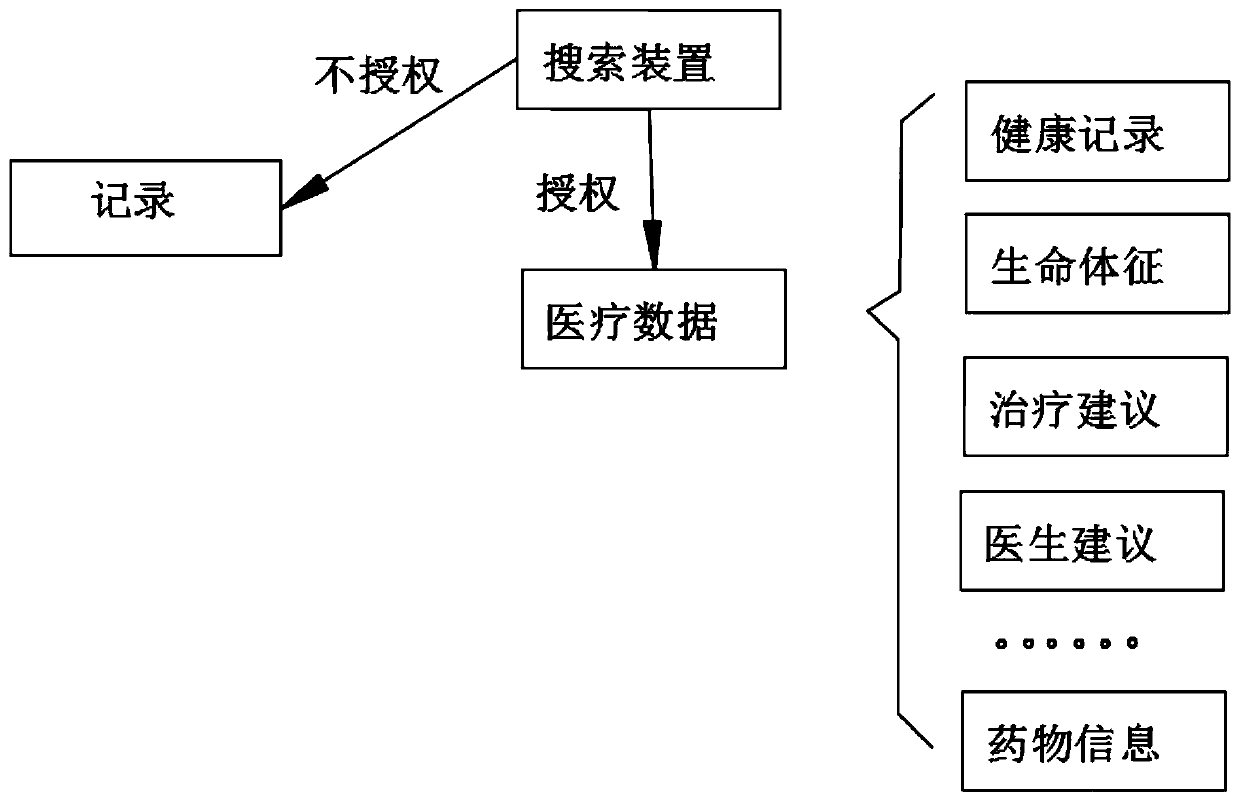
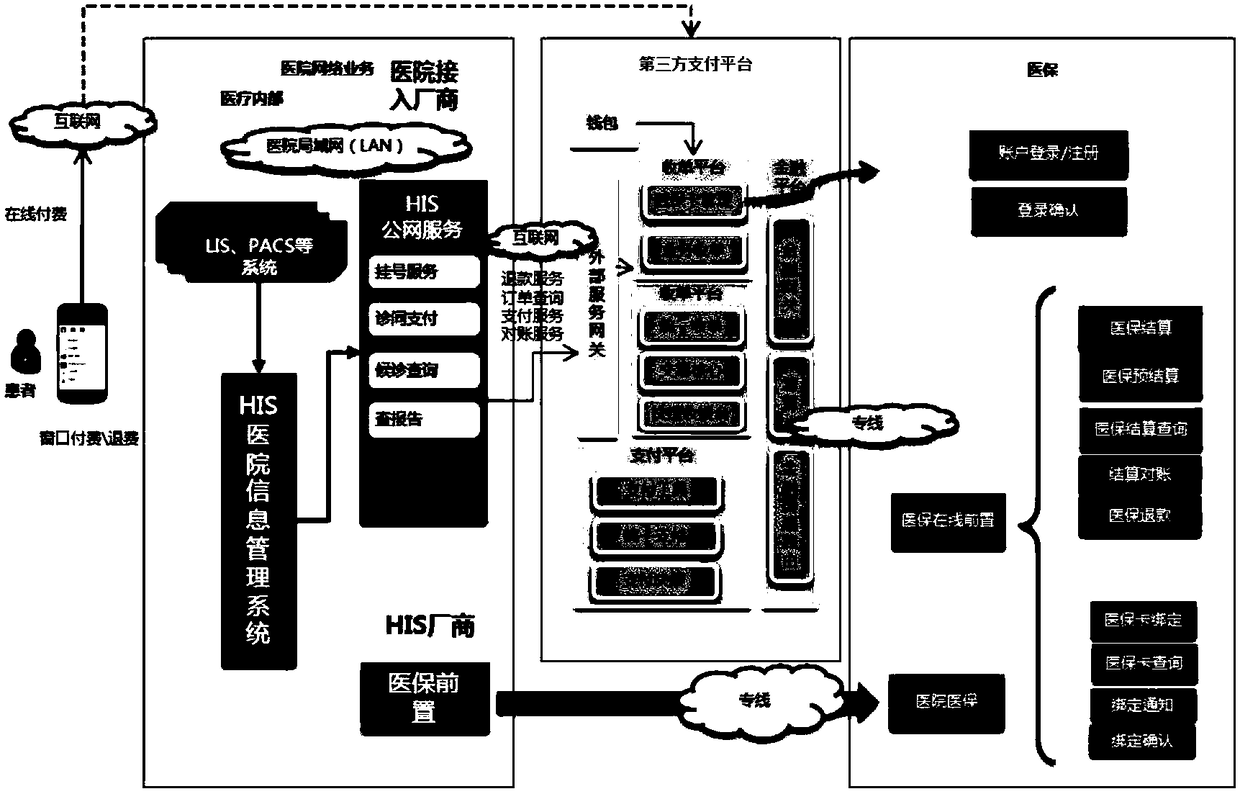
InactiveCN108766537AAvoid risk of leakageGuaranteed real-name authenticationFinanceDigital data protectionThird partyPayment transaction
The invention relates to a system with the support of the mobile payment of a social security card. The system comprises a hospital network service system, a third party payment platform and a medicalinsurance platform. The hospital network service system comprises an HIS hospital information management system and a mobile medical platform. The system can be conveniently and quickly connected tothe medical insurance of a mobile terminal, the real-time card-free settlement of medical insurance costs is achieved, and the payment of medical insurance reimbursable funds is not needed. At the same time, the development of a dedicated payment platform is not needed, the security of payment transactions can be ensured, the safety of each transaction is ensured to ensure the property security and information security of a user, and thus the user experience is improved at the greatest extent.
Owner:ZHENJIANG NO 1 PEOPLES HOSPITAL
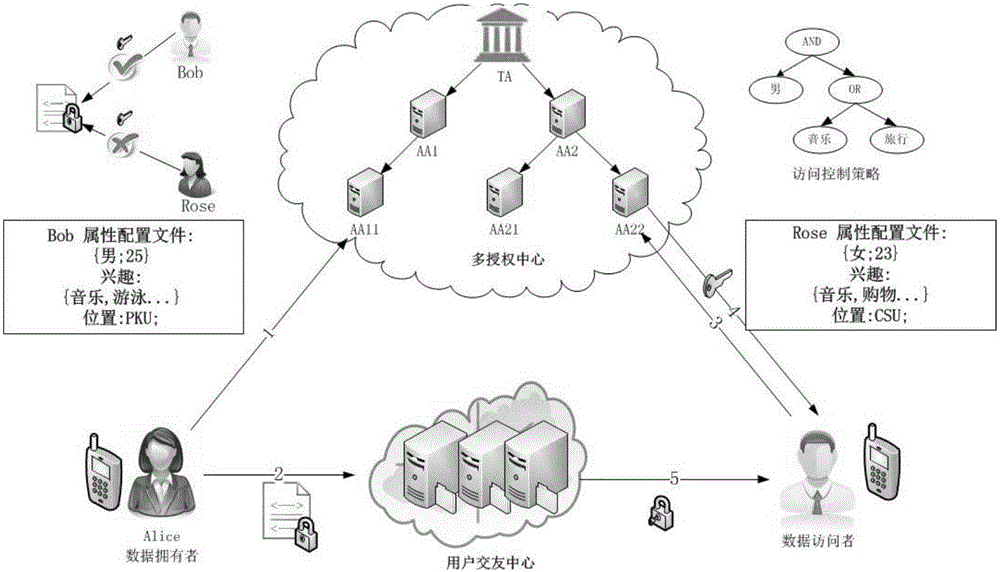
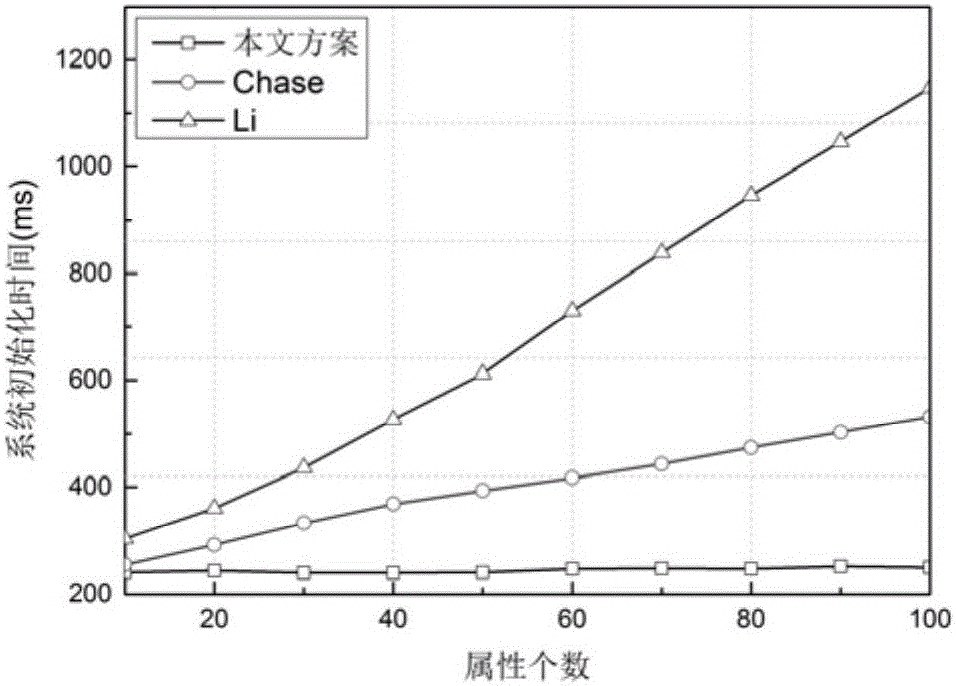
Social privacy protection method of multi-level attribute management center based on characteristic encryption
InactiveCN106022167ASolve performance bottlenecksSolve difficultyDigital data protectionTransmissionCiphertextPrivacy protection
The invention provides a social privacy protection method of a multi-level attribute management center based on characteristic encryption. A friend making sponsor uploads encrypted personal information files to a remote friend finder, and a certain kind of user-defined attribute characteristics and a friend making access control strategy are uploaded to the multi-level attribute management center; the multi-level attribute management center generates ciphertext according to the attribute characteristics and is associated with an access strategy tree corresponding to attributes; a friend making requester requests for checking friend making information of other users in the friend finder, when an attribute set of the friend making requester is matched with the access strategy tree of the friend making sponsor, the multi-level attribute management center sends a secrete key corresponding to the attribute of the friend making sponsor to the friend making requester, and the friend making requester decrypts data ciphertext of an information owner of the friend finder. The method solves the single-point fault and performance bottleneck problems of a single-authorization center, and also solves the problems that an intelligent terminal does not depend on an authorization center and accordingly monitoring difficulty is high and application scenes are limited.
Owner:HUNAN UNIV OF SCI & ENG
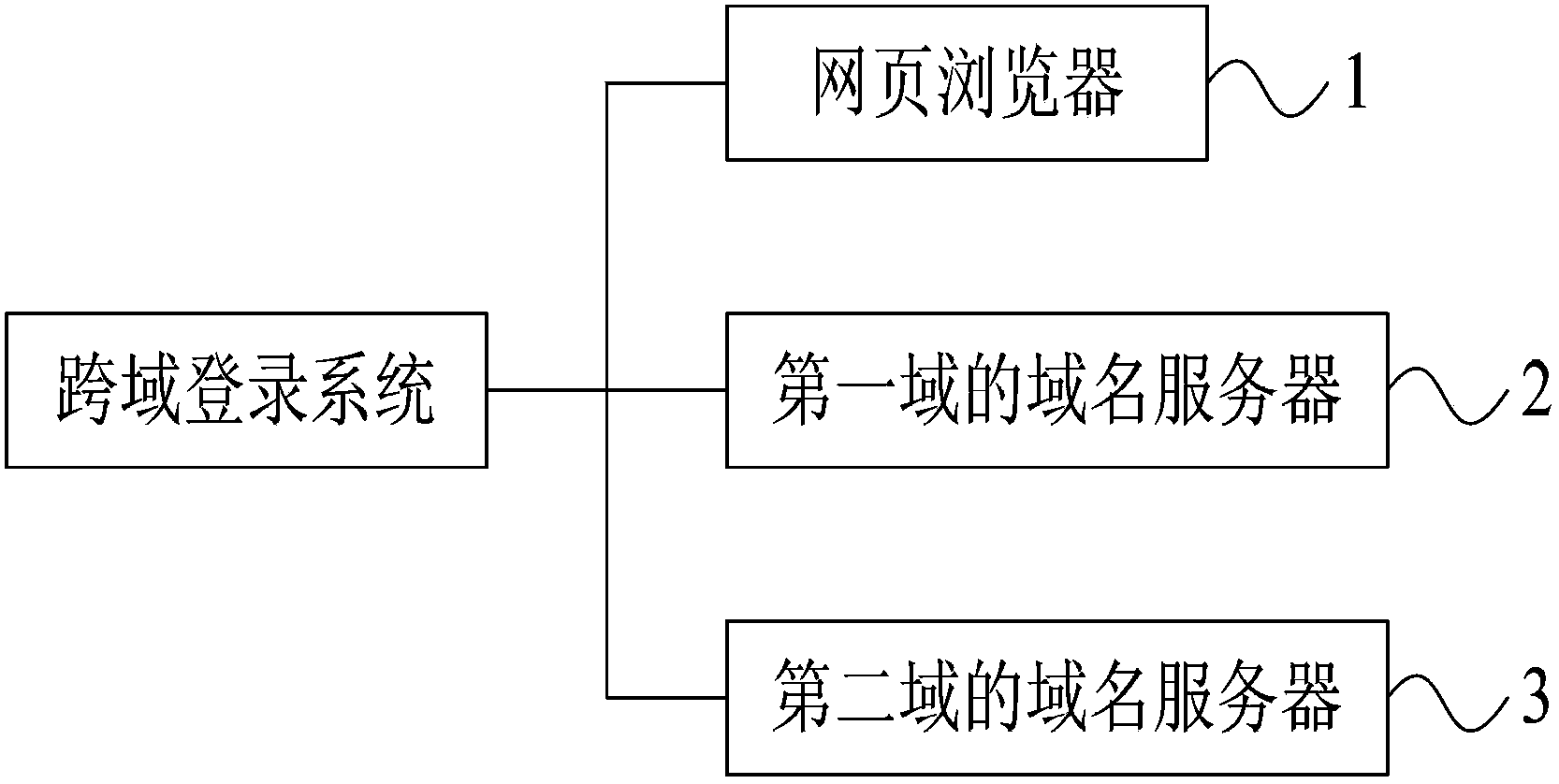
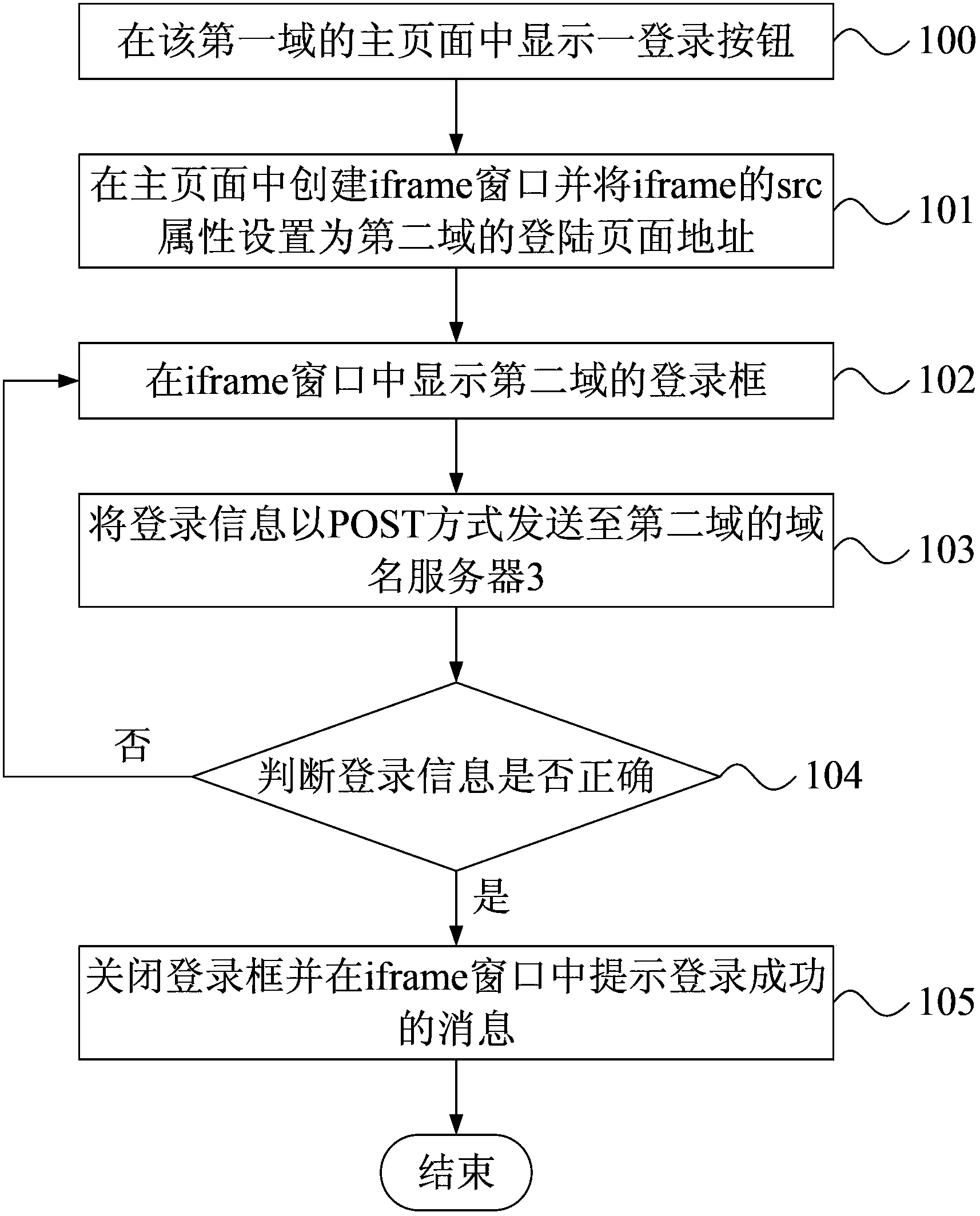
Cross domain login system and method
The invention discloses a cross domain login system and method. The method comprises the following steps that: S1, after an access request is received, a login button is displayed on a home page of a first domain; S2, after operation of clicking a button is received, an iframe window is create on the home page, and an SRC property is set to a login page address of a second domain; S3, a login box of the second domain is displayed, and the login box includes a form field and a confirm button; S4, after operation of clicking the confirm button is received, login information is sent to a domain name server of the second domain in a POST manner; S5, whether the login information is correct is judged, if the login information is correct, a step S6 is carried out, and if the login information is not correct, the step S3 is repeated; and S6, the login box is closes, and a message of successful login is displayed in the iframe window. In the invention, the POST manner can be used to transmit data and the iframe window is used to carry out the cross domain data exchange, so as to ensure the safety of the cross domain login.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com