Patents
Literature
88 results about "Mobile authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
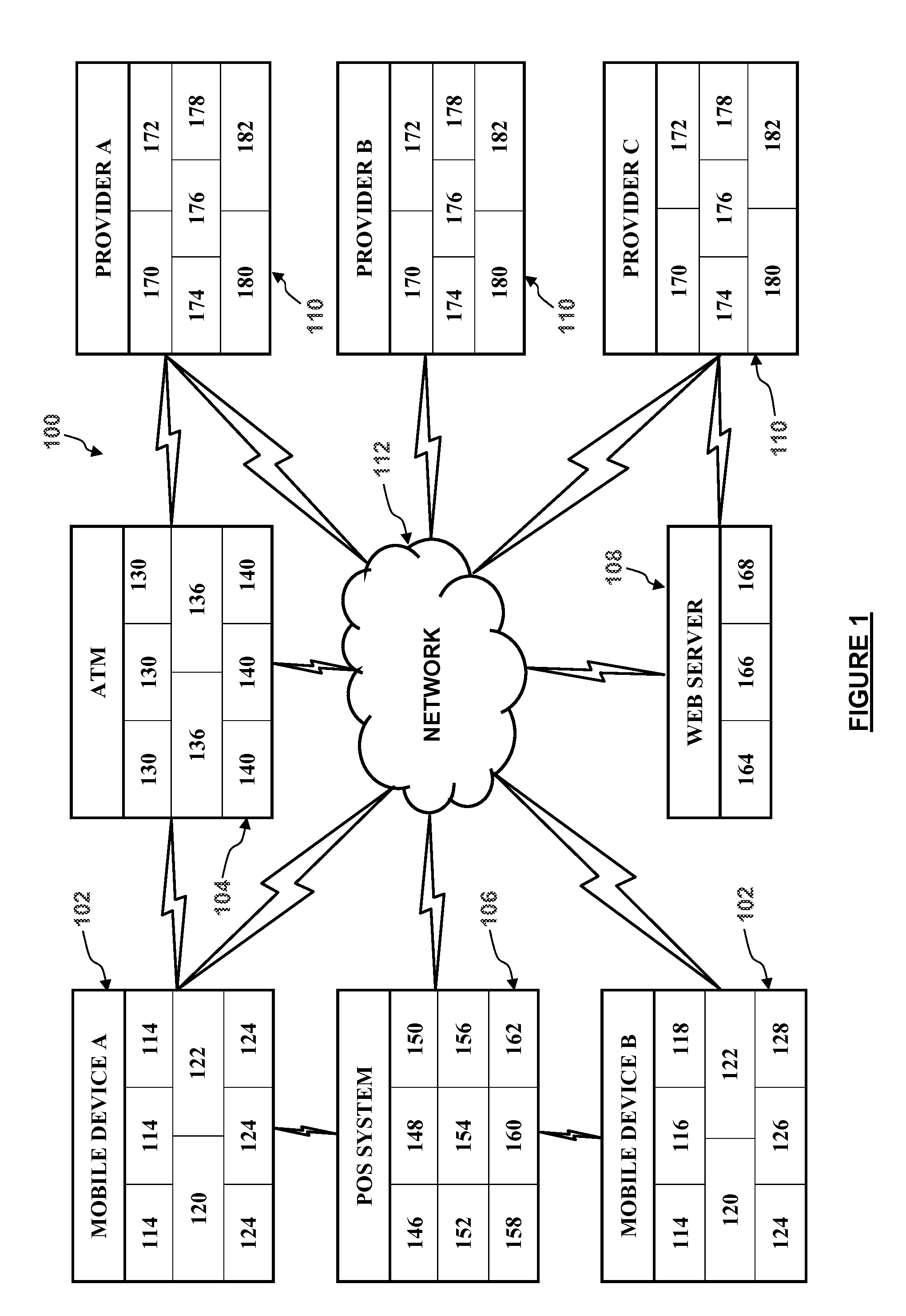
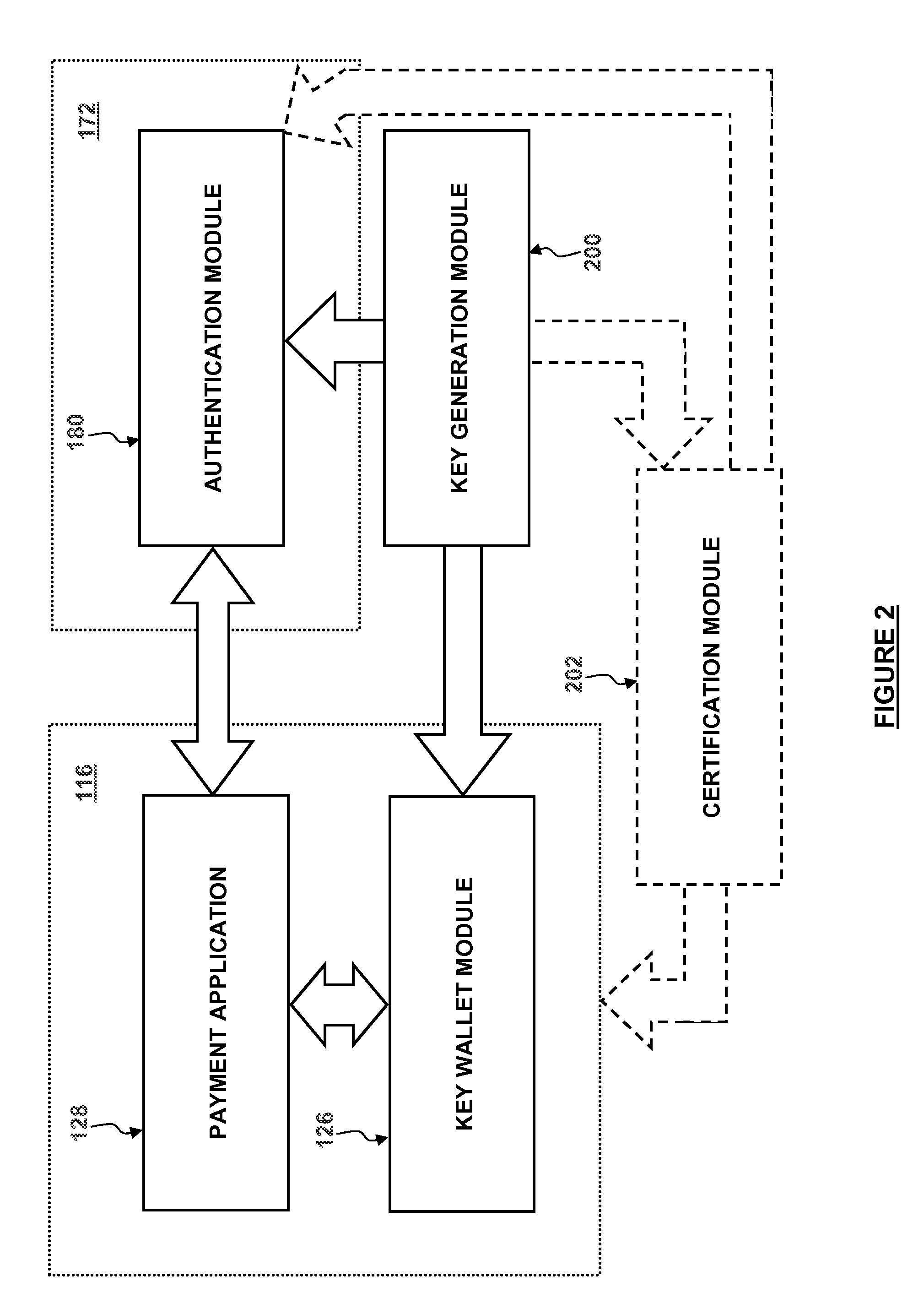
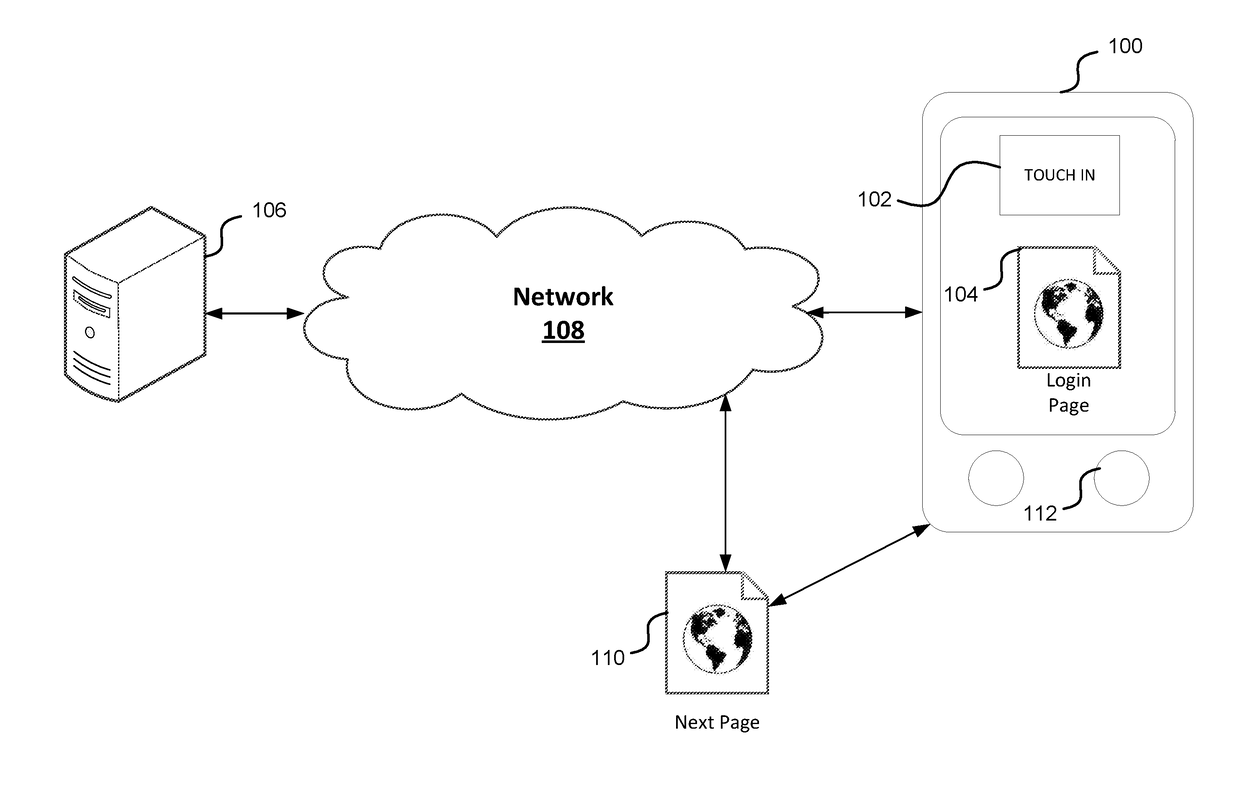
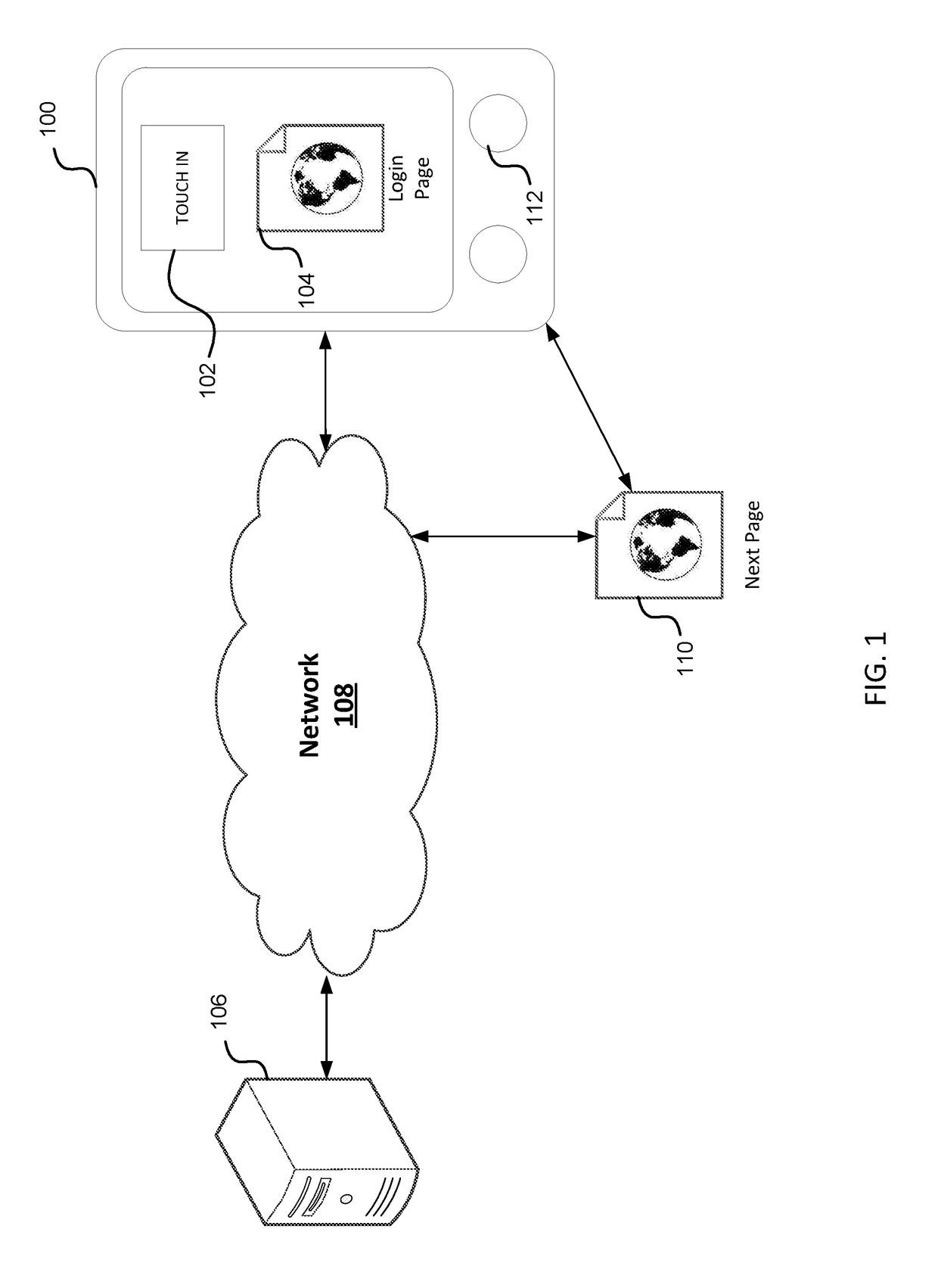
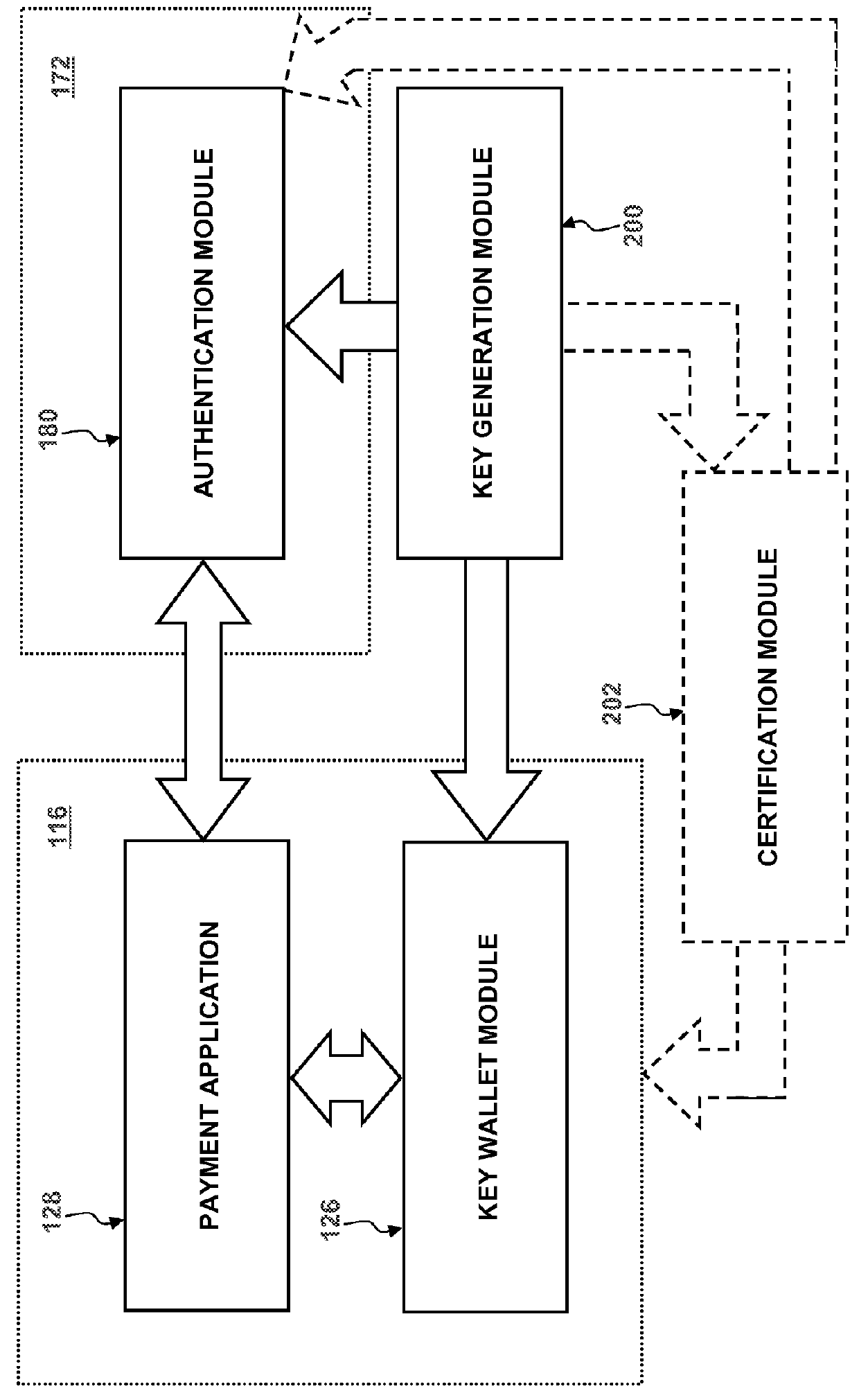
User-convenient authentication method and apparatus using a mobile authentication application
ActiveUS20140040628A1Authentication process can be made convenientCost-effectiveDigital data authenticationCoding/ciphering apparatusUser authenticationApplication software
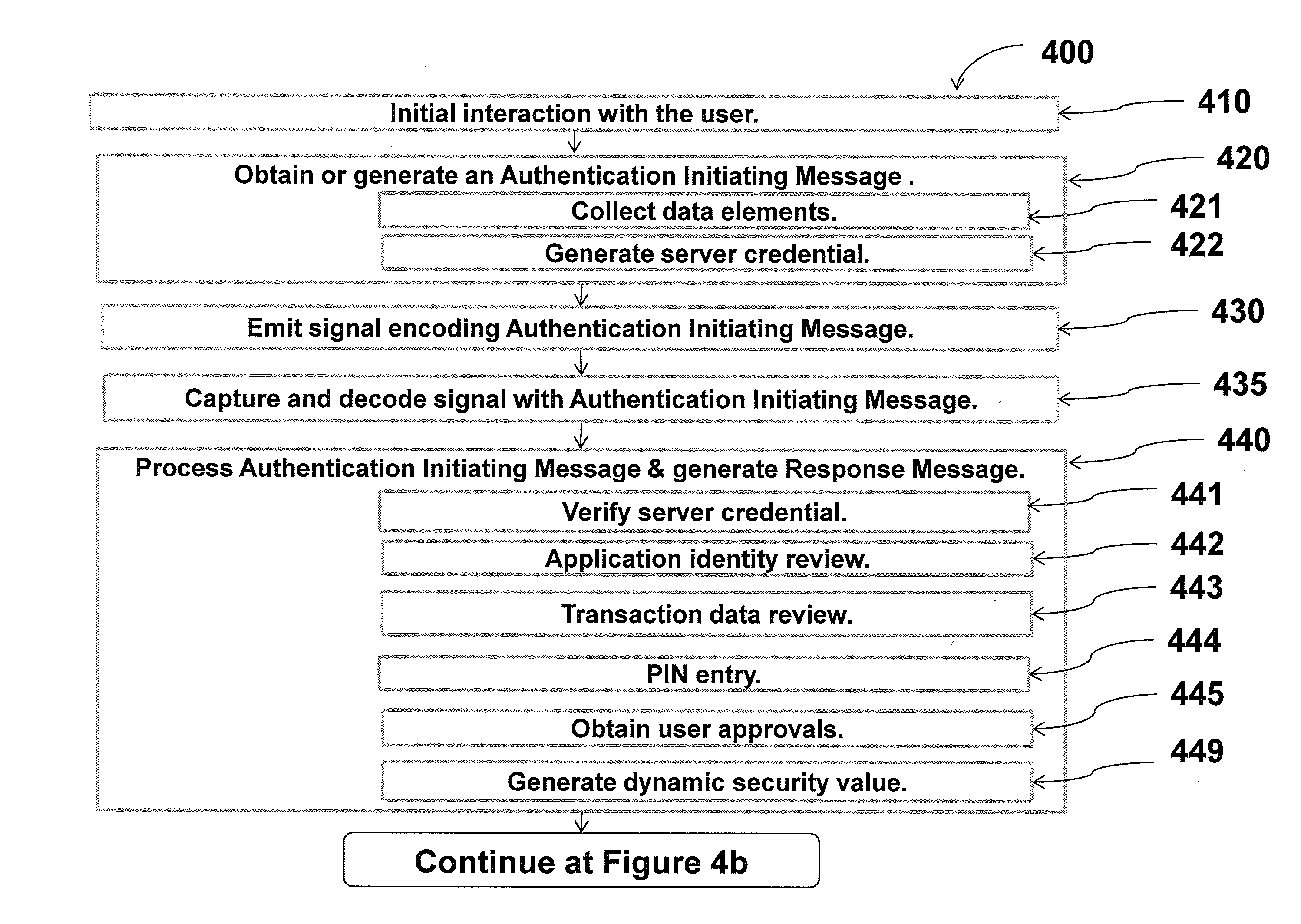
Methods, apparatus, and systems for securing application interactions are disclosed. Application interactions may be secured by, at a user authentication device, capturing a signal emitted by an access device encoded with an authentication initiating message including an application identifier, decoding the signal and obtaining the authentication initiating message, retrieving the application identifier, presenting a human interpretable representation of the application identity to the user, obtaining user approval to generate a response message available to a verification server, generating a dynamic security value using a cryptographic algorithm that is cryptographically linked to the application identity, and generating a response message including the generated dynamic security value; making the response message available to a verification server; and, at the verification server, receiving the response message, verifying the response message including verifying the validity of the dynamic security value, and communicating the result of the verification of the response message to the application.
Owner:ONESPAN NORTH AMERICA INC
Secure and convenient mobile authentication techniques
ActiveUS20140040147A1User identity/authority verificationDigital data authenticationTrusted ComputingMobile authentication
Security and convenience are provided by a system, apparatus, method, and computer program product that stores two or more encryption keys that correspond to two or more levels of authentication. The encryption keys may be encrypted and decrypted utilizing an endorsement key and trusted computing techniques. Or the encryption keys may be stored in a secure manner utilizing key protection techniques, such as cryptographic camouflaging. A first encryption key is recovered automatically for the first level of authentication. And input is requested to recover the second encryption key for the second level of authentication.
Owner:CA TECH INC
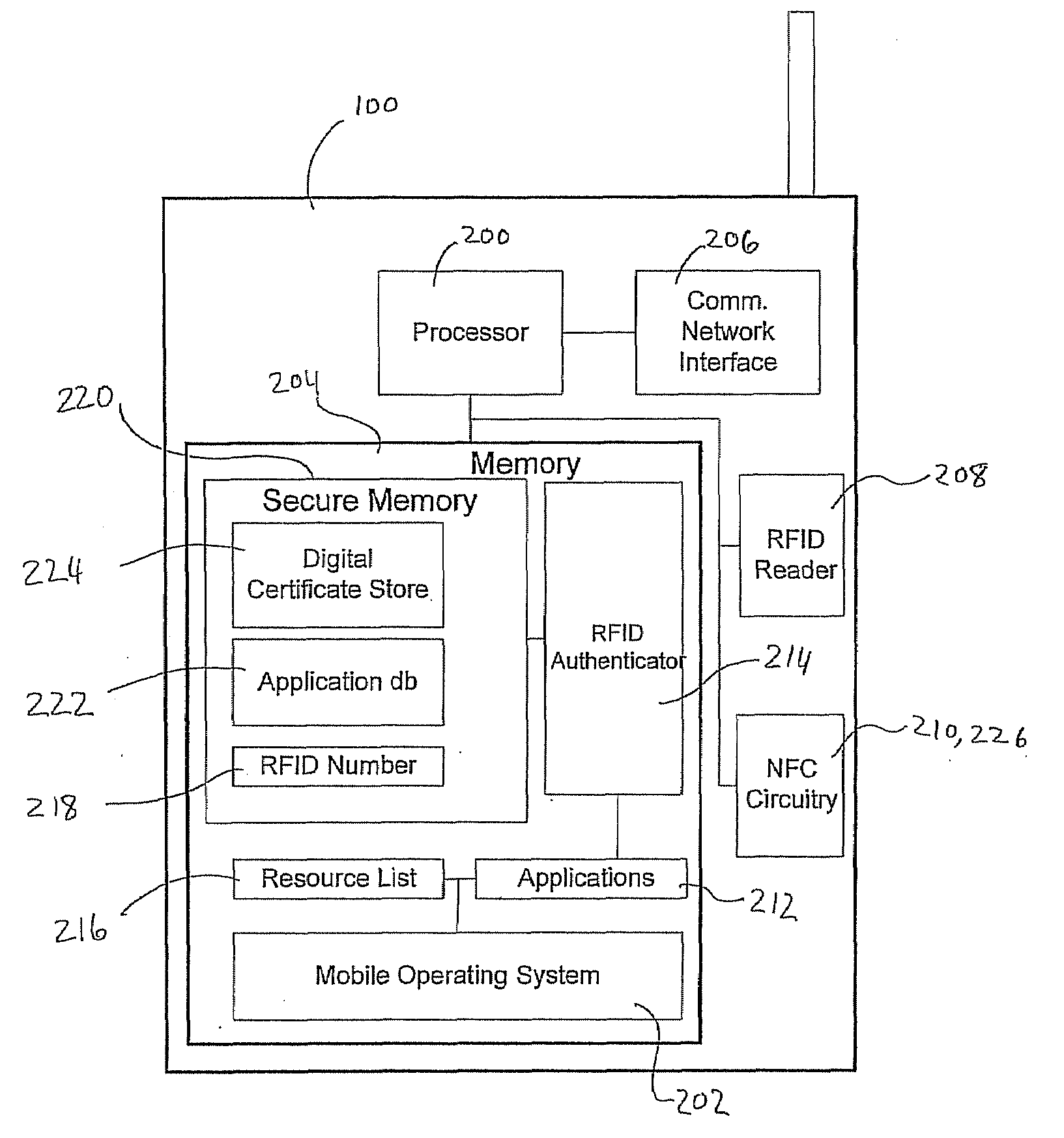
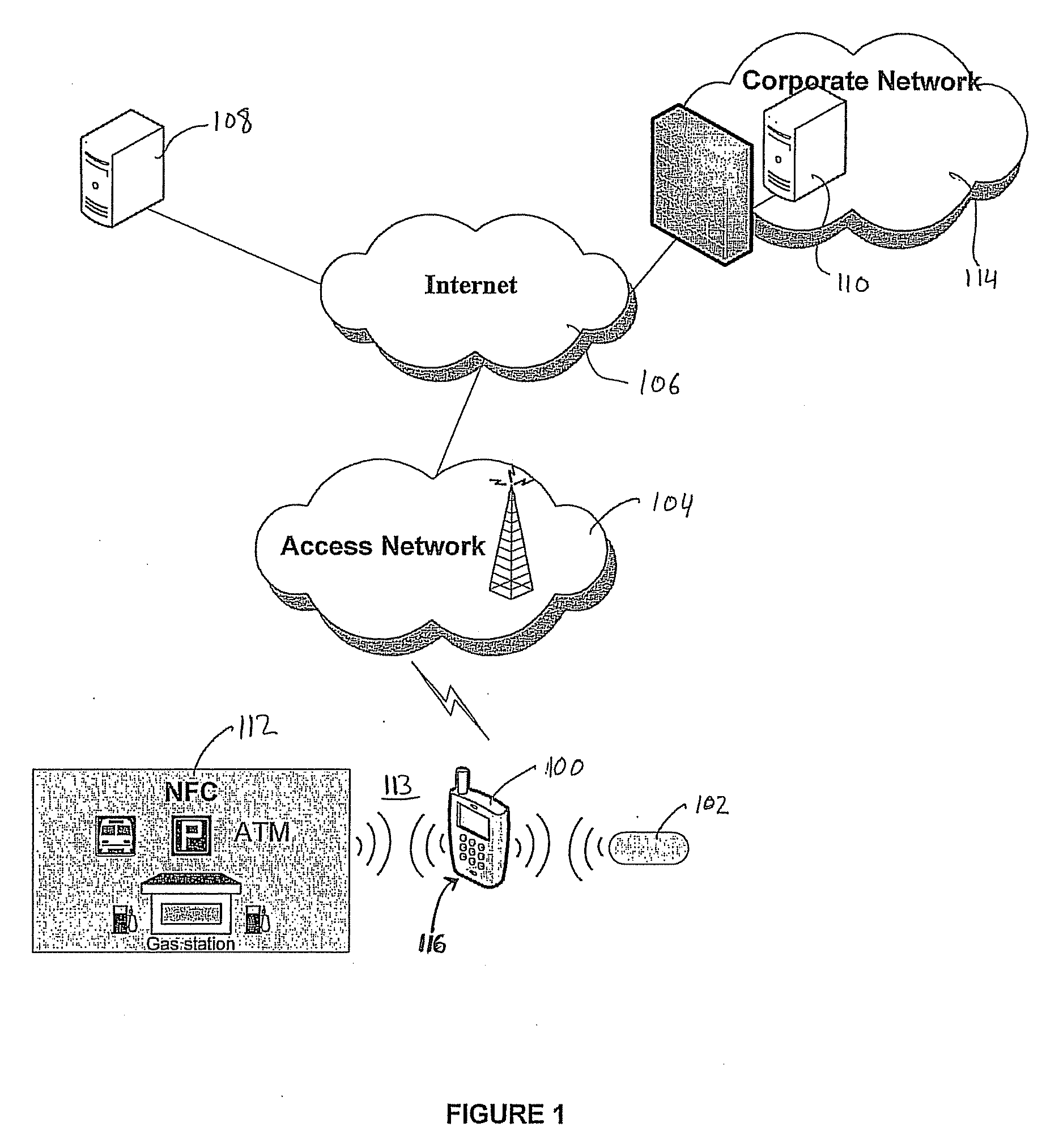
User-friendly multifactor mobile authentication
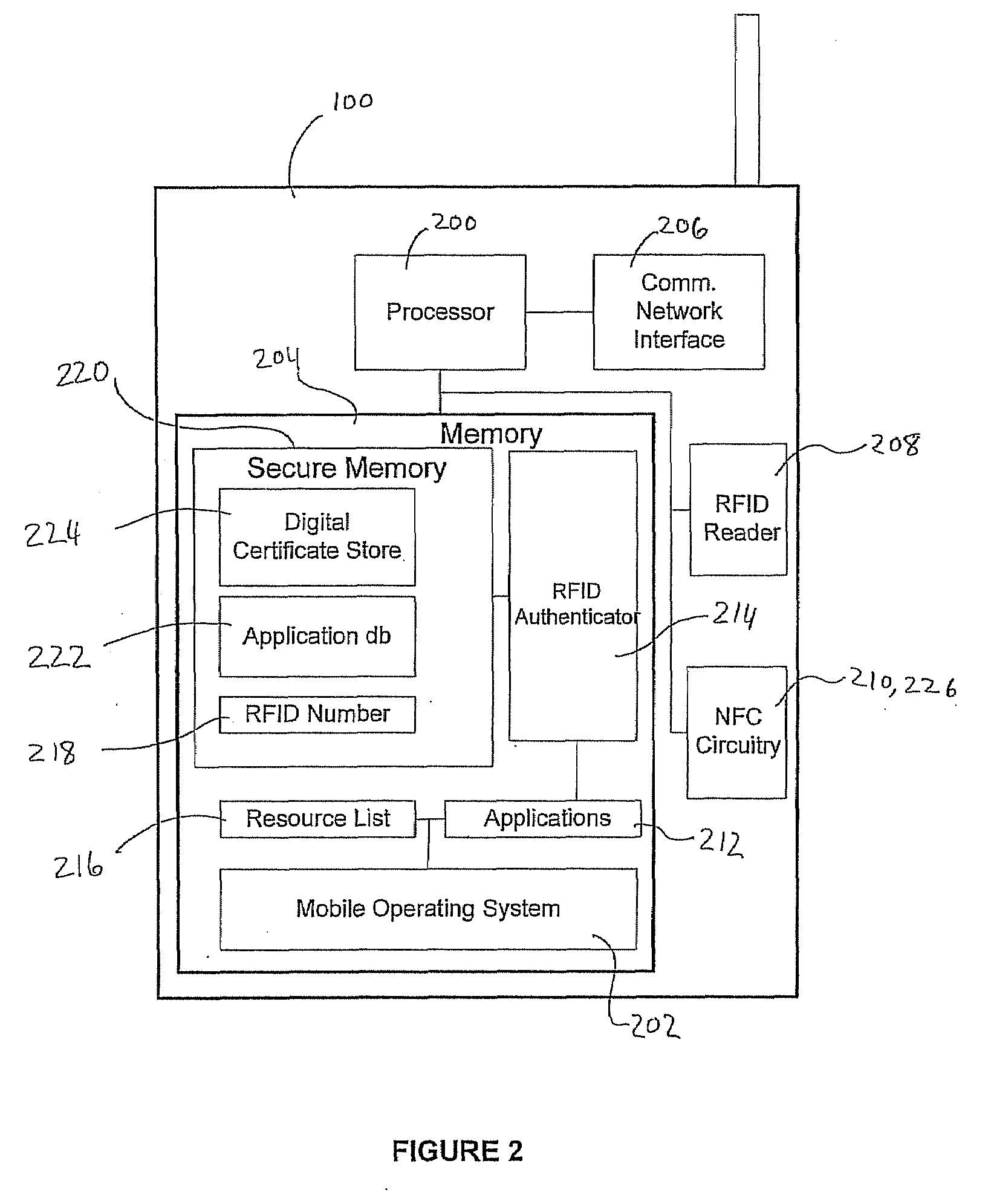
ActiveUS20080289030A1Prevent unauthorized accessEliminate needDigital data processing detailsMultiple digital computer combinationsComputer hardwareRfid authentication
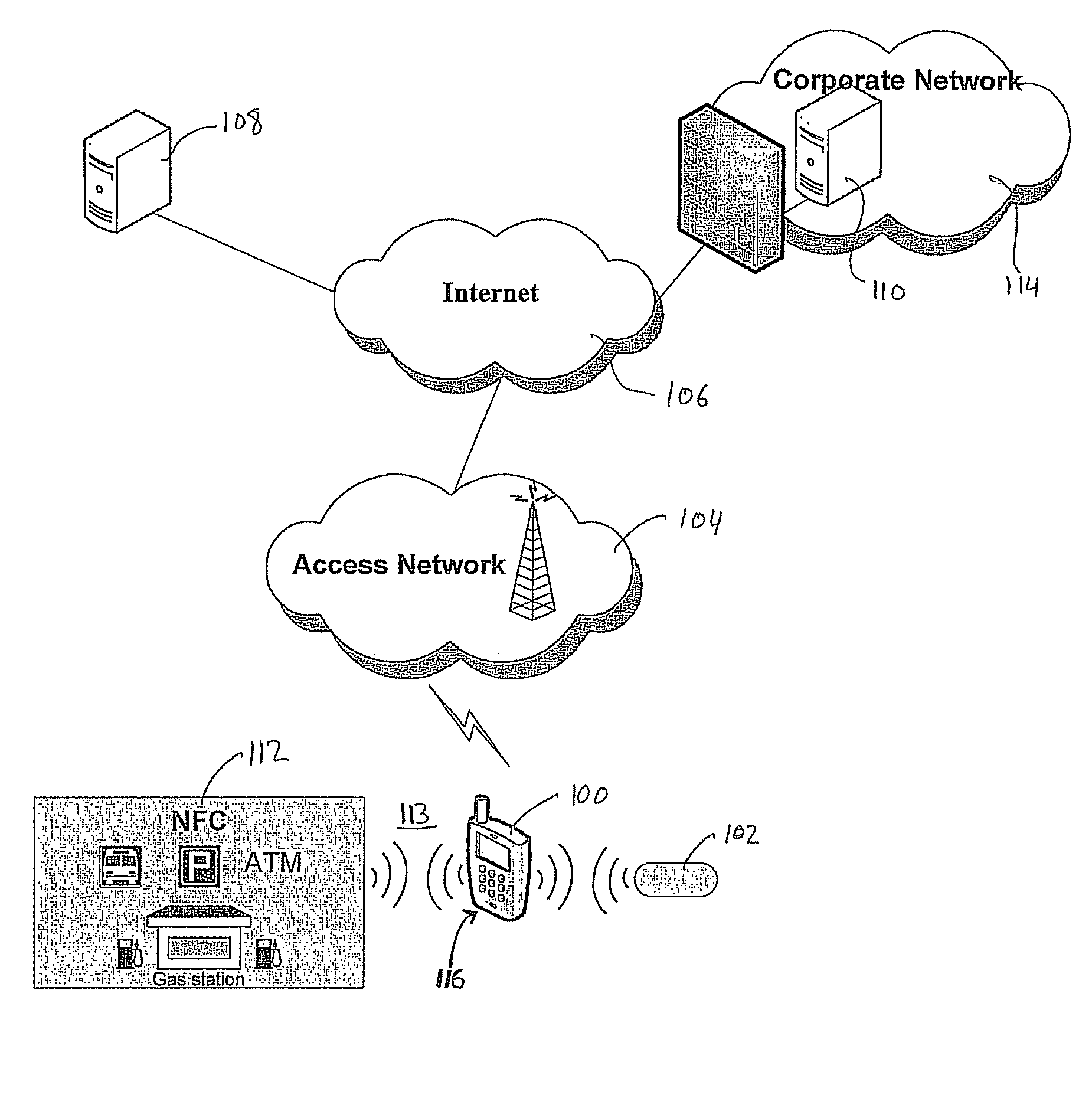
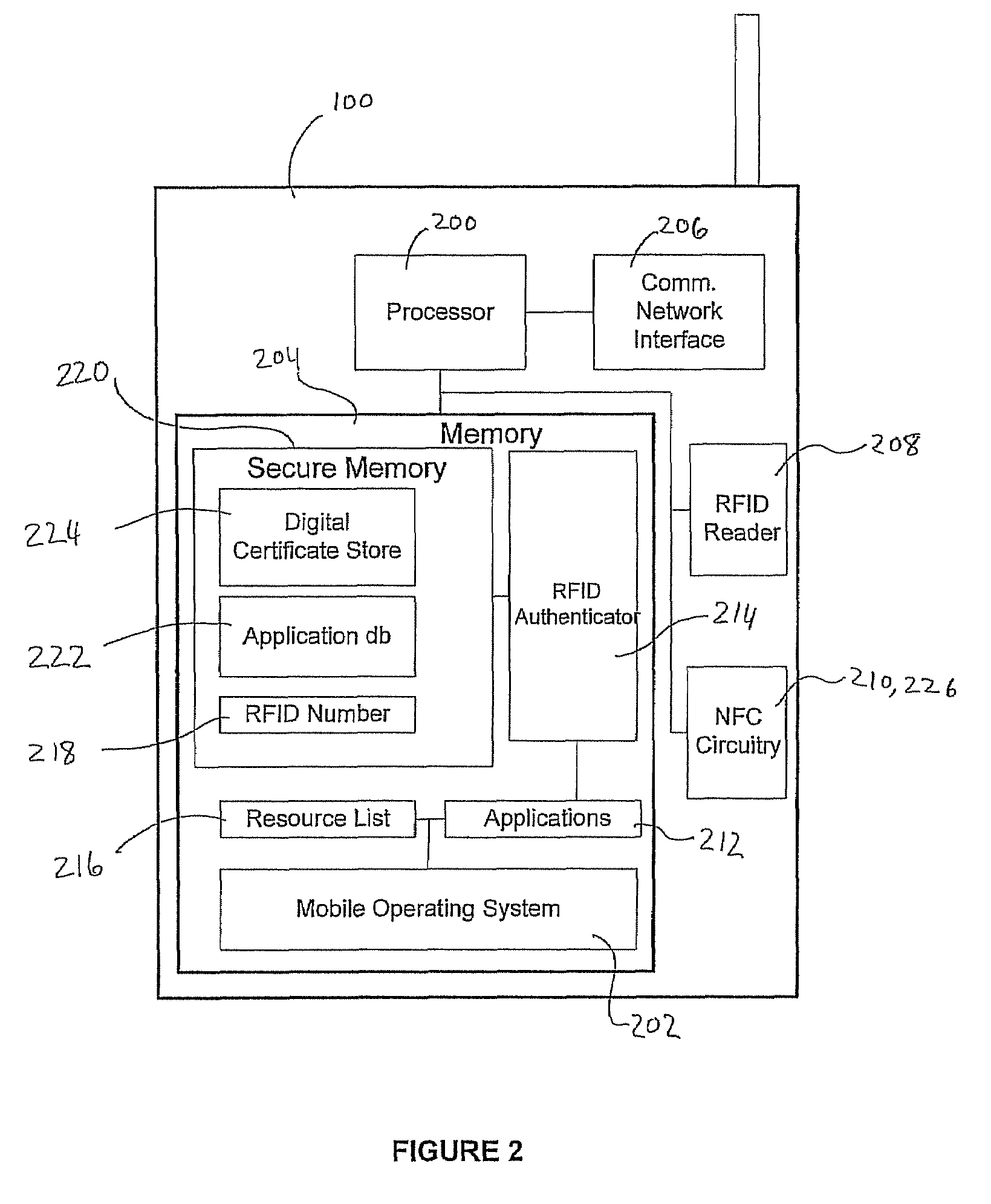
A system and method for performing multifactor mobile authentication are described whereby a mobile communications device includes a contactless reader for receiving and validating a unique identifier stored in an external authenticating module prior to granting access to locally stored electronic authenticating material required to access an external resource. In one embodiment, the mobile communications device is a mobile telephone having an RFID reader for receiving the unique identifier from an RFID tag incorporated into the external authenticating module. Preferably, the external authenticating module is associated with a user, such as by being part of the user's jewelry or clothing. The mobile authentication device includes an RFID authenticator module that detects external resource access requests and checks whether the requested resource is on a list of resources that require additional user authentication prior to granting access to locally stored authenticating material.
Owner:U S CELLULAR
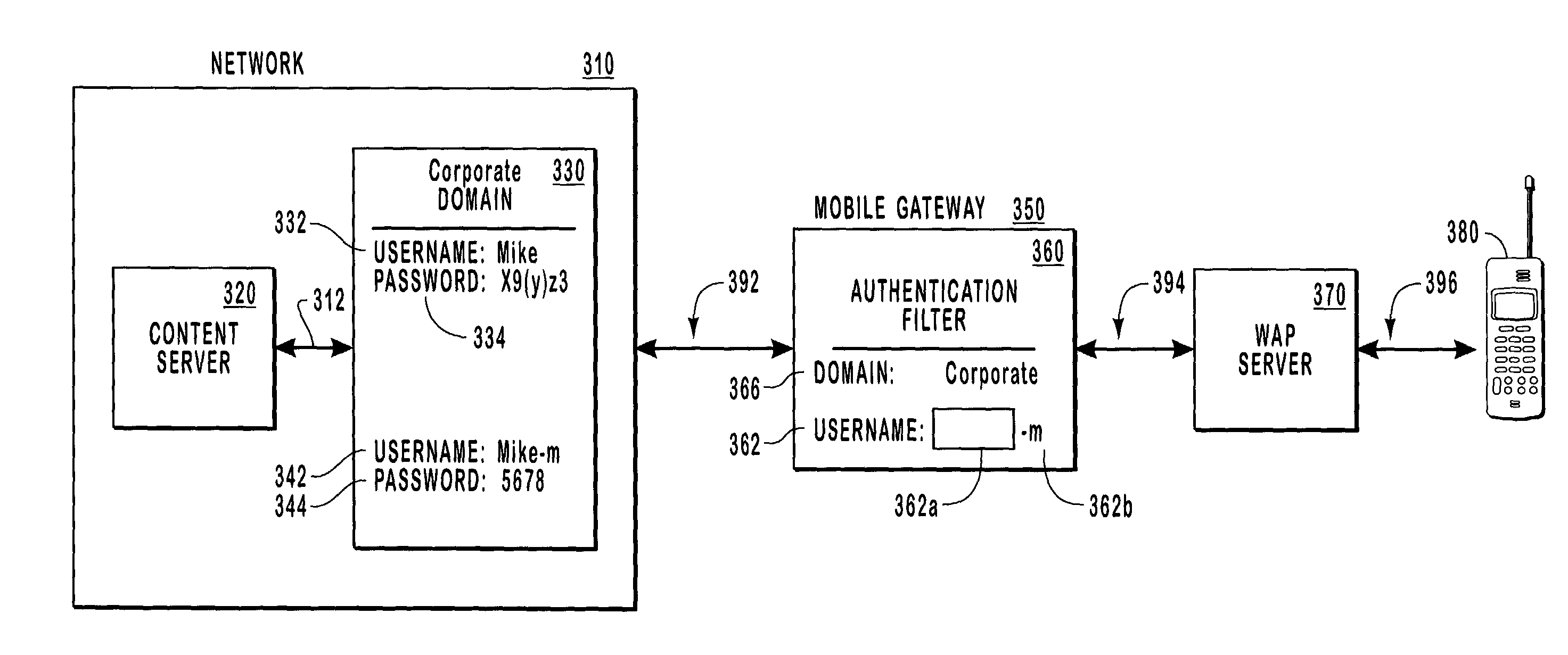
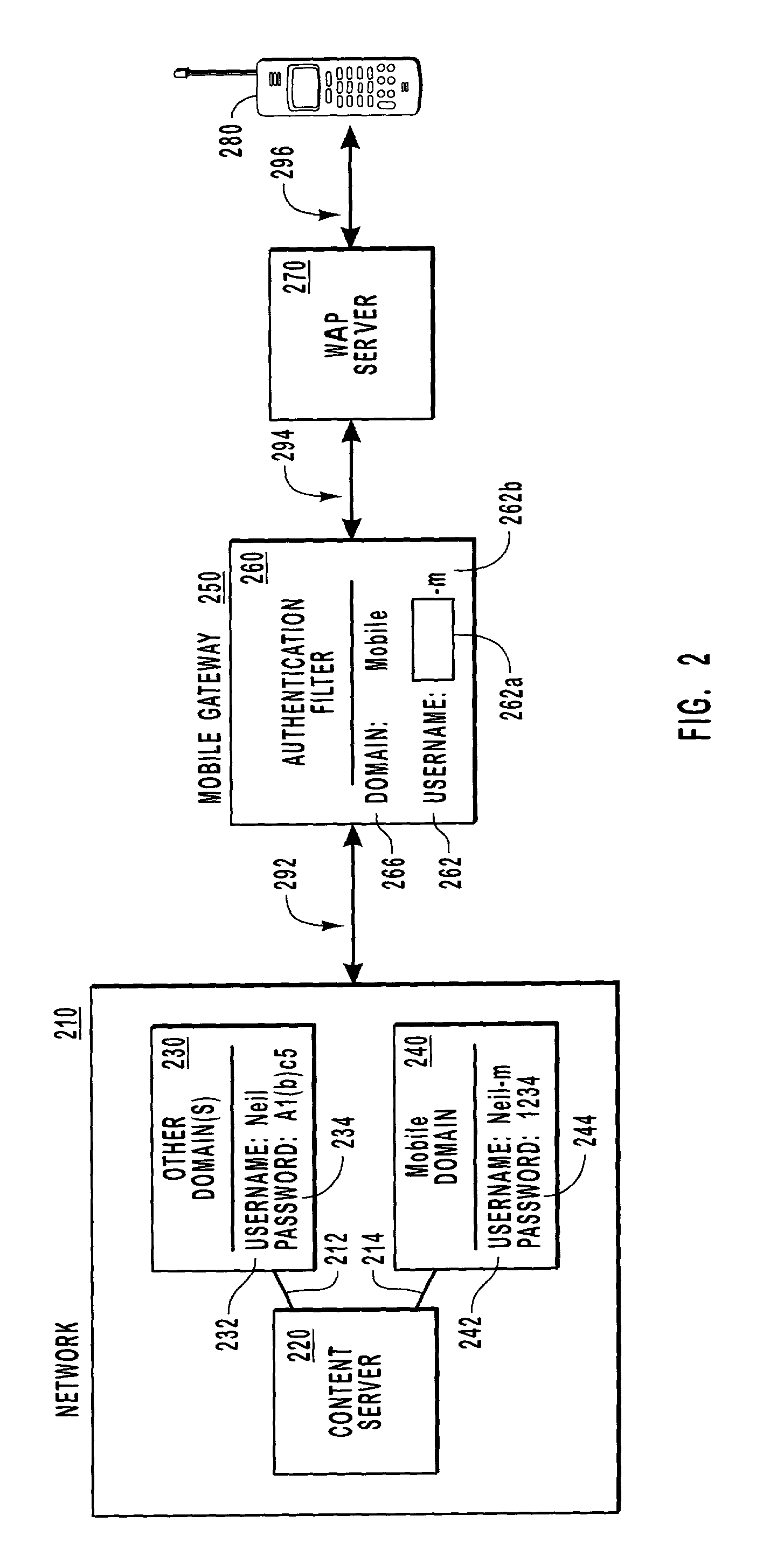
Credential authentication for mobile users
ActiveUS7047560B2Increased level of riskMinimal exposureDigital data processing detailsUser identity/authority verificationDomain nameTrust relationship
Methods, systems, and computer program products for authenticating a mobile client that may have an input system optimized for numeric input. A mobile gateway receives authentication credentials from a mobile client and uses an authentication filter to map the authentication credentials according to pre-established criteria. The authentication filter may change the domain name, the username, or both. Then, the mapped authentication credentials are sent to a network that includes the content server being accessed. Any access privileges granted to the mobile client are based on the mapped authentication credentials. The mobile gateway may be configured to accept connections only from known servers. Mobile authentication credentials may be maintained in one or more domains, possibly having a trust relationship, or may be stored in a separately administered credential database.
Owner:MICROSOFT TECH LICENSING LLC
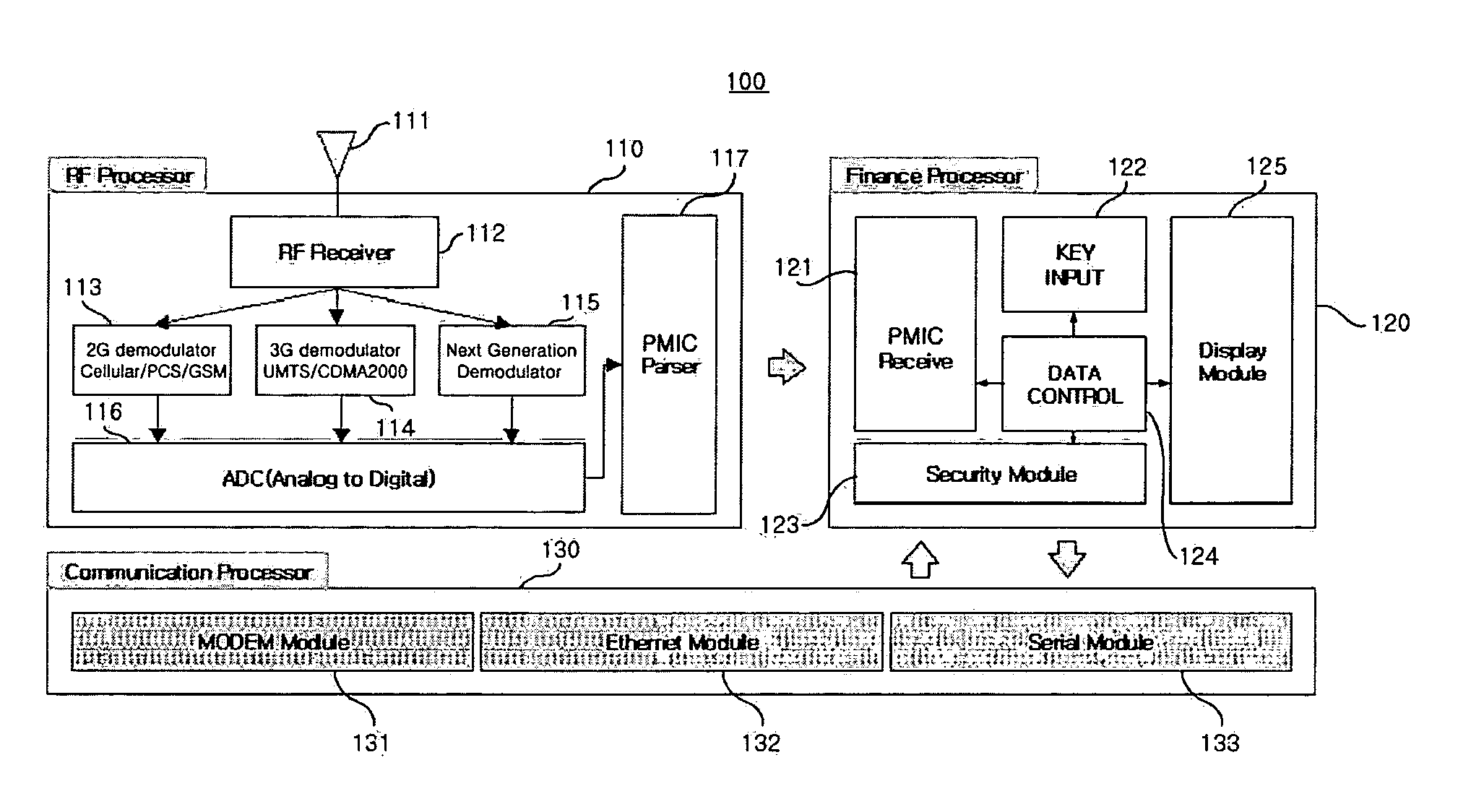
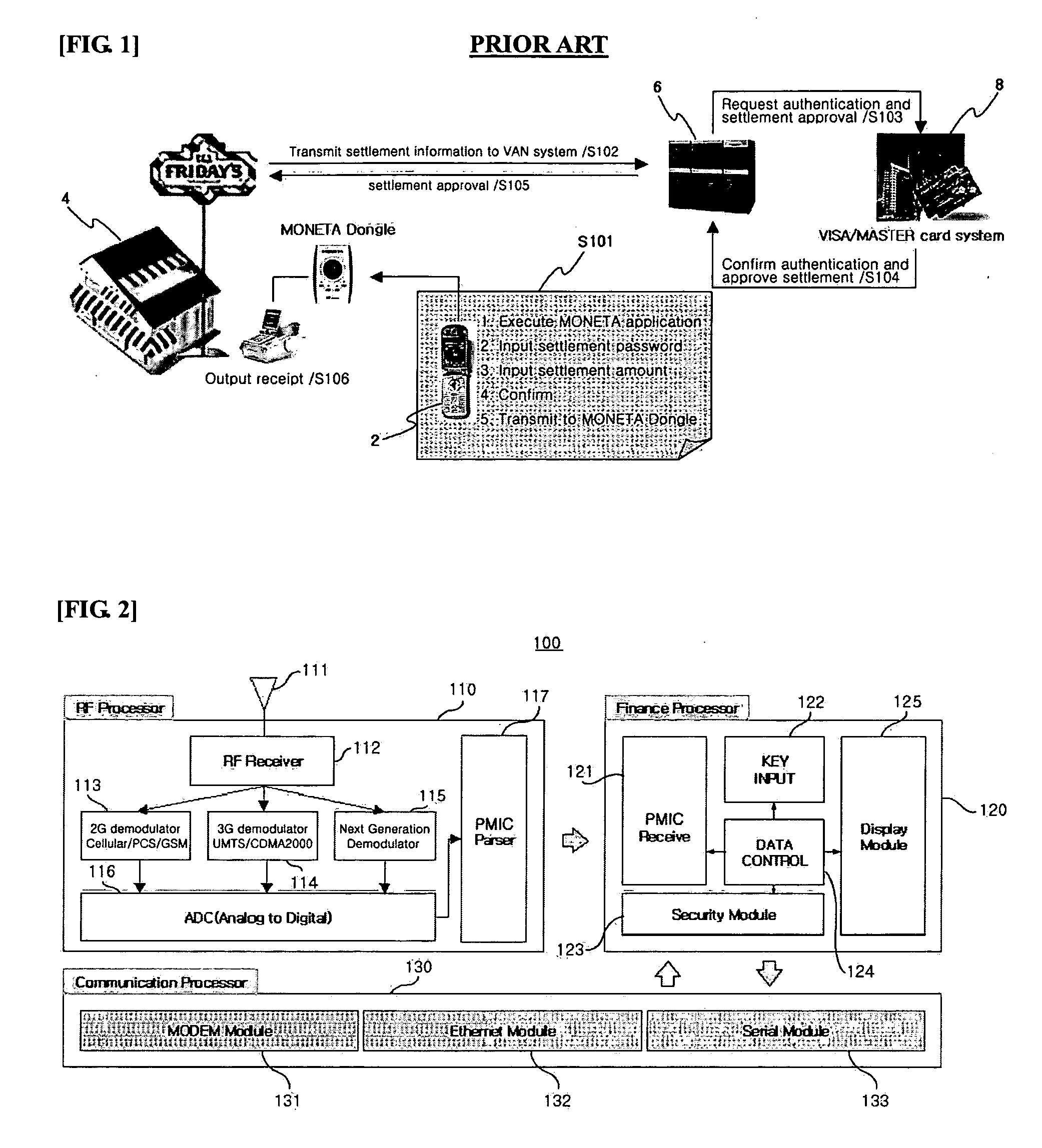
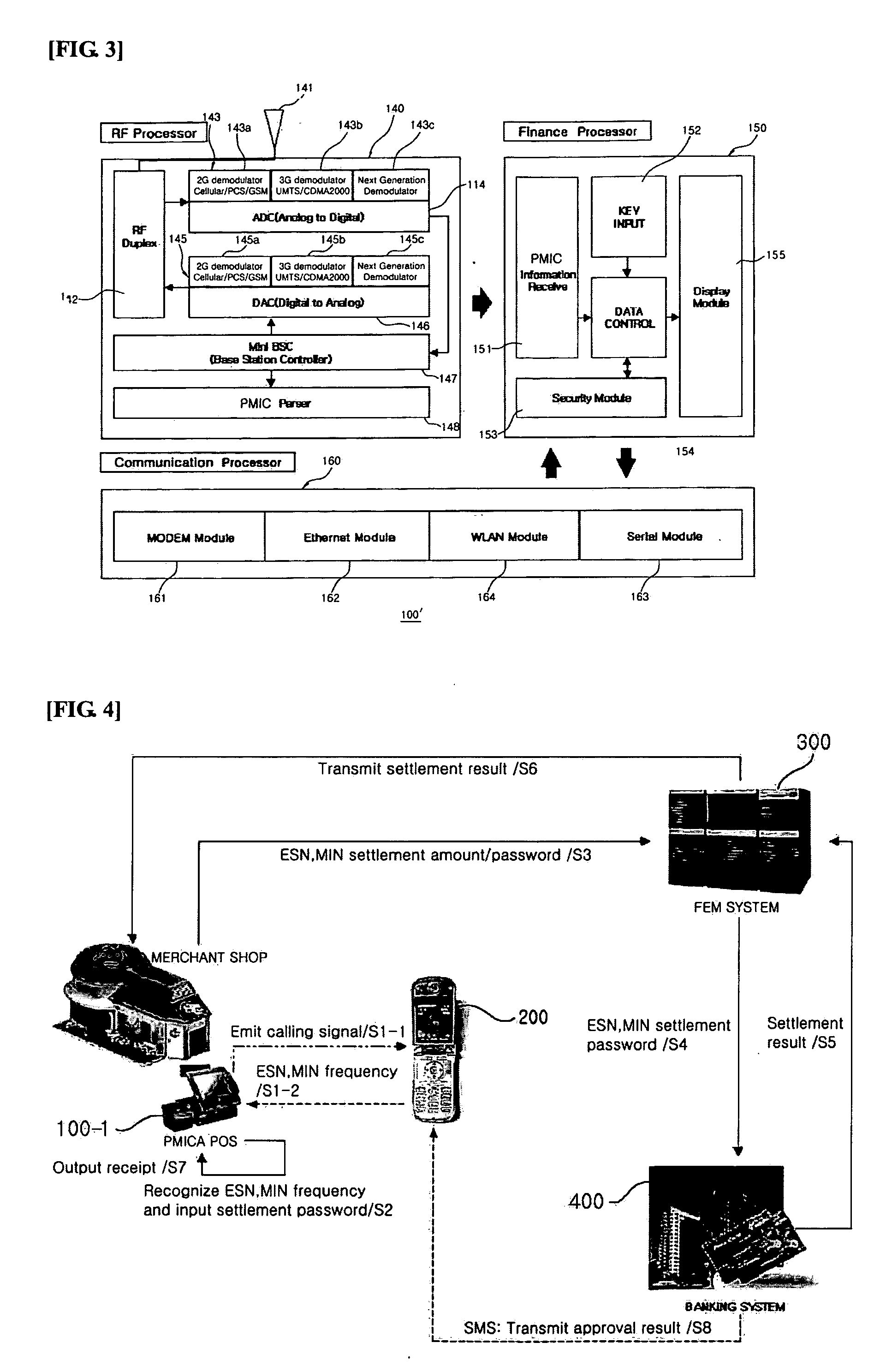
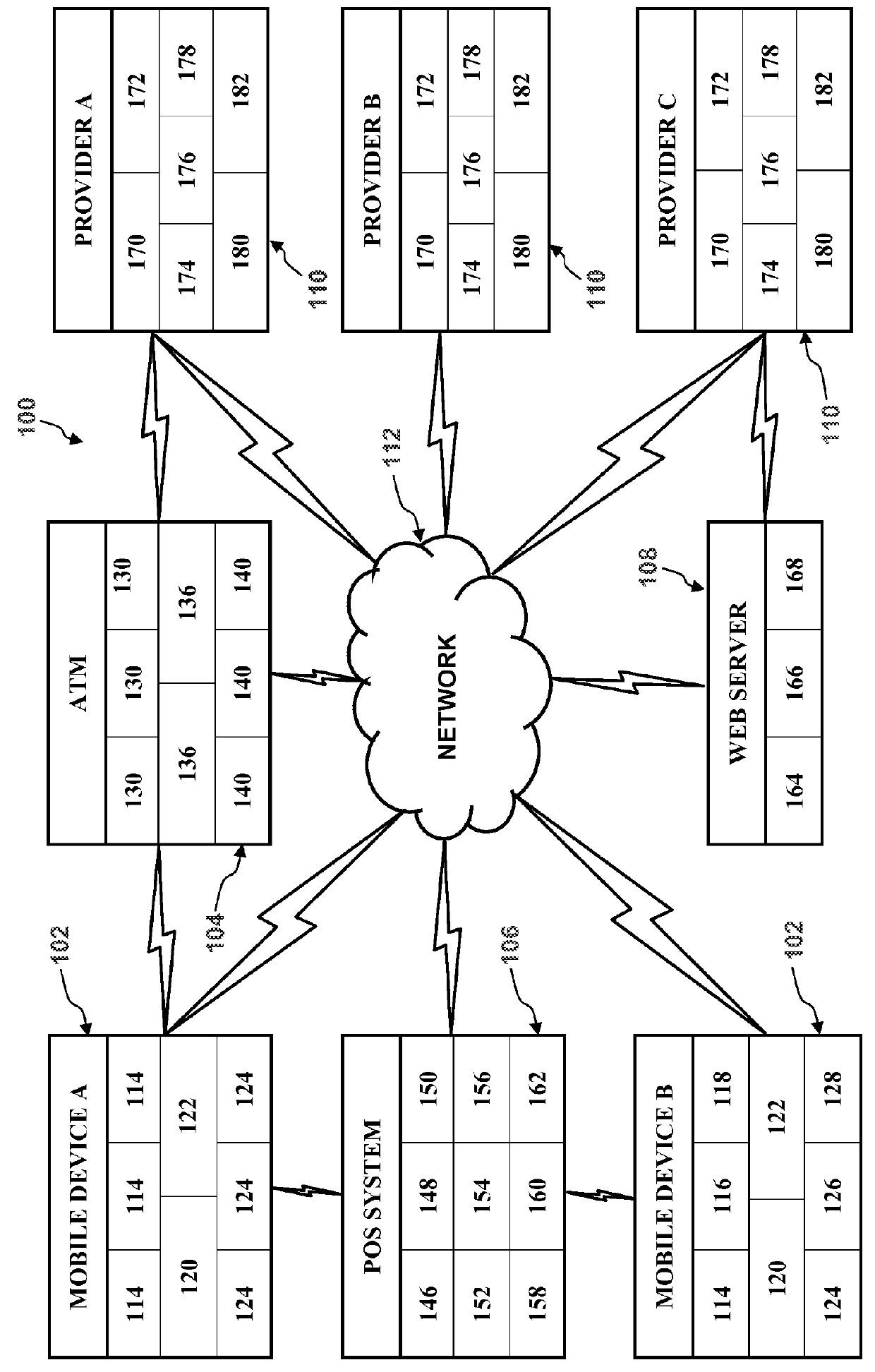
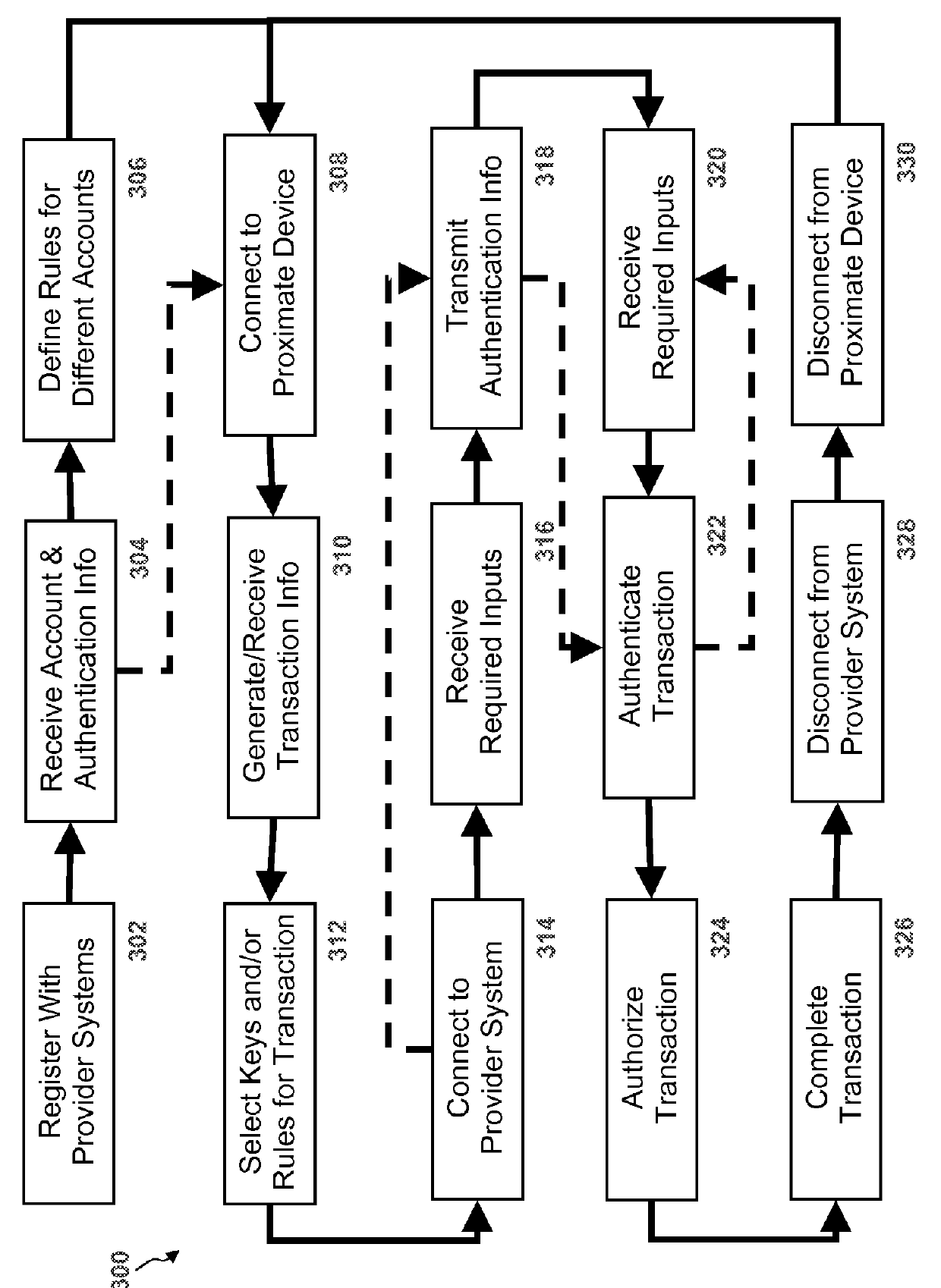
Mobile authentication/financial transaction system using a unique mobile identification code and method thereof
InactiveUS20050143051A1Telephonic communicationNetwork connectionsFinancial transactionIdentification device
The present invention discloses a mobile authentication / financial transaction system using a unique mobile identification code and method thereof, wherein mobile authentication and / or financial transaction are carried out without replacing a mobile communication terminal in such a way that various authentication and / or financial transaction are performed based on the unique mobile identification code received from a mobile communication terminal according to a standardized mobile communication protocol. A call information identification apparatus according to an aspect of the present invention includes a RF processing part for receiving a radio wave emitted from a mobile communication terminal to extract a unique mobile identification code loaded on the radio wave; a financial processing part for receiving the unique mobile identification code from the RF processing part to store the received the unique mobile identification code and a variety of financial transaction information necessary for authentication therein; and a communication processing part for receiving the unique mobile identification code or financial transaction information from the financial processing part to transmit the received unique mobile identification code or financial transaction information to an external system, and receiving information necessary for financial transaction from the external system.
Owner:WELGATE
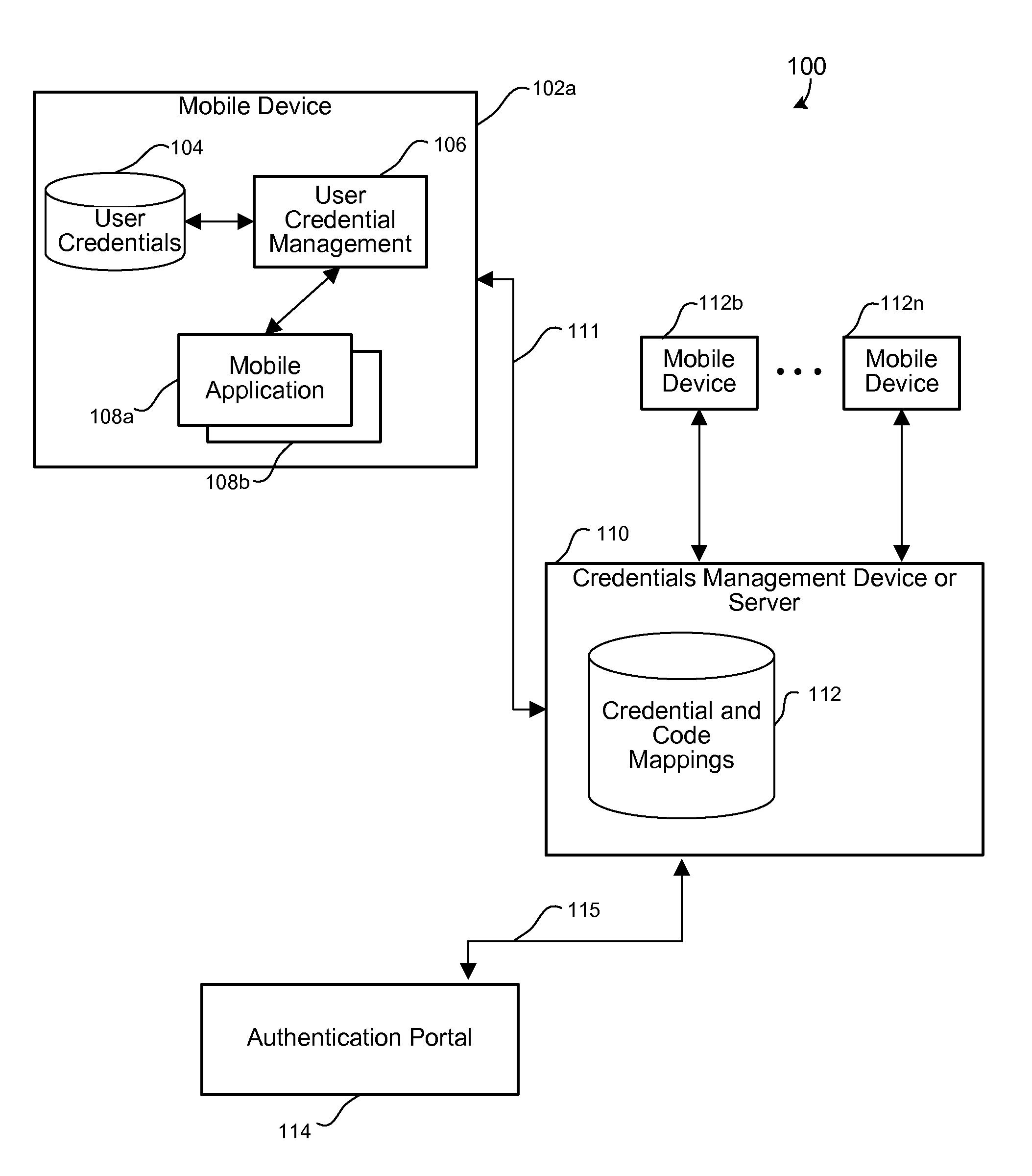
Mobile authentication framework
ActiveUS20090113527A1Digital data processing detailsMultiple digital computer combinationsWeb serviceMobile authentication
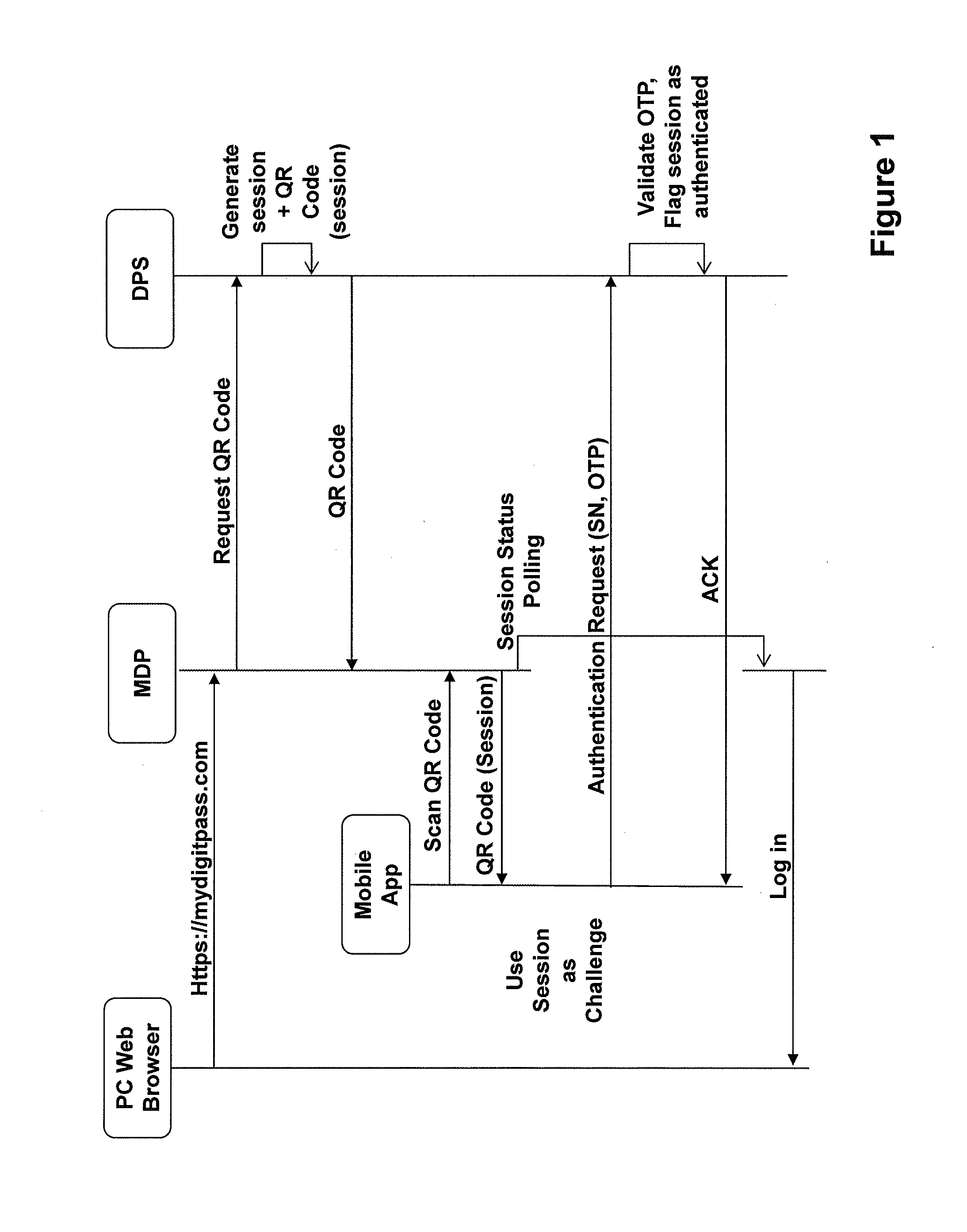
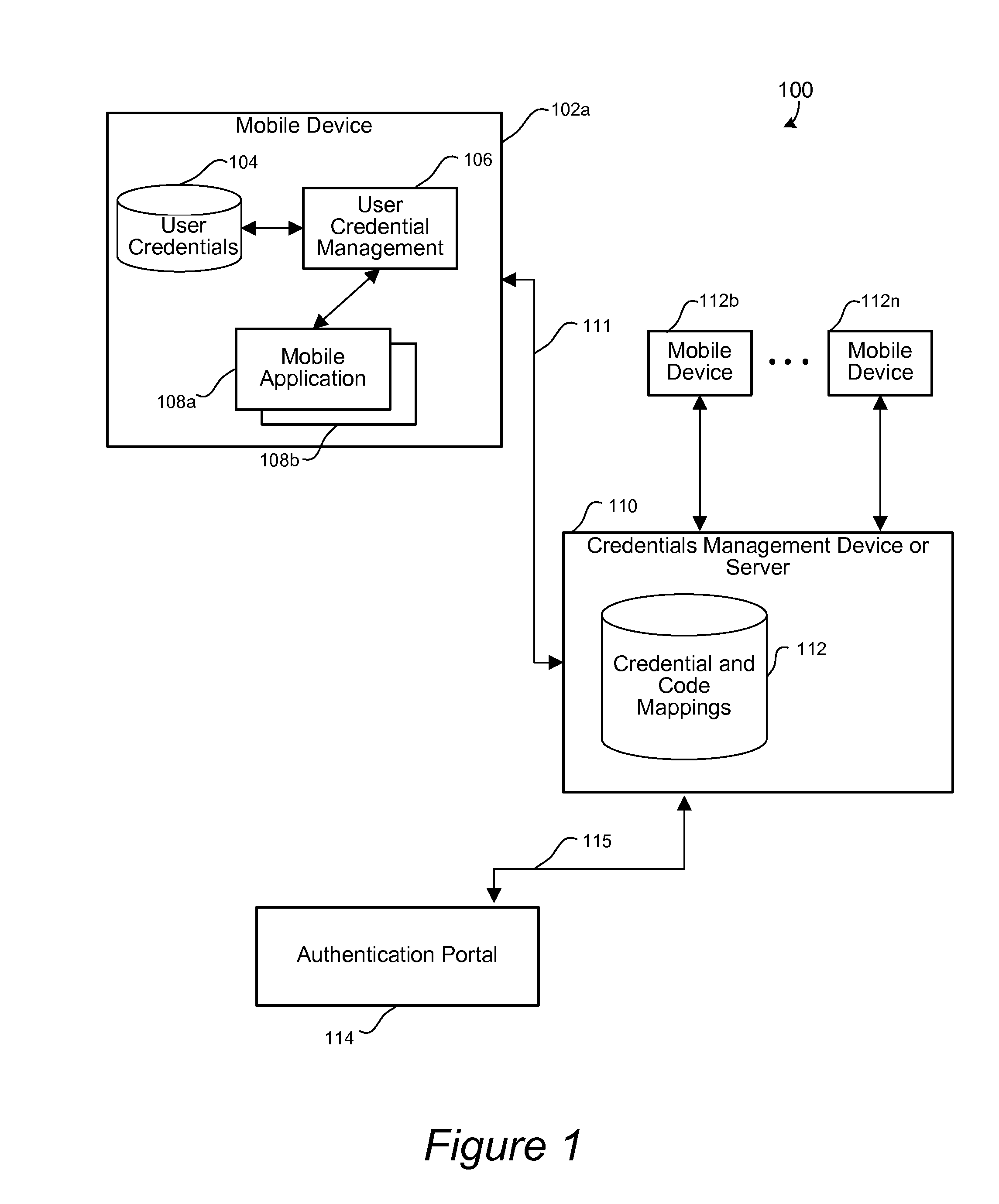
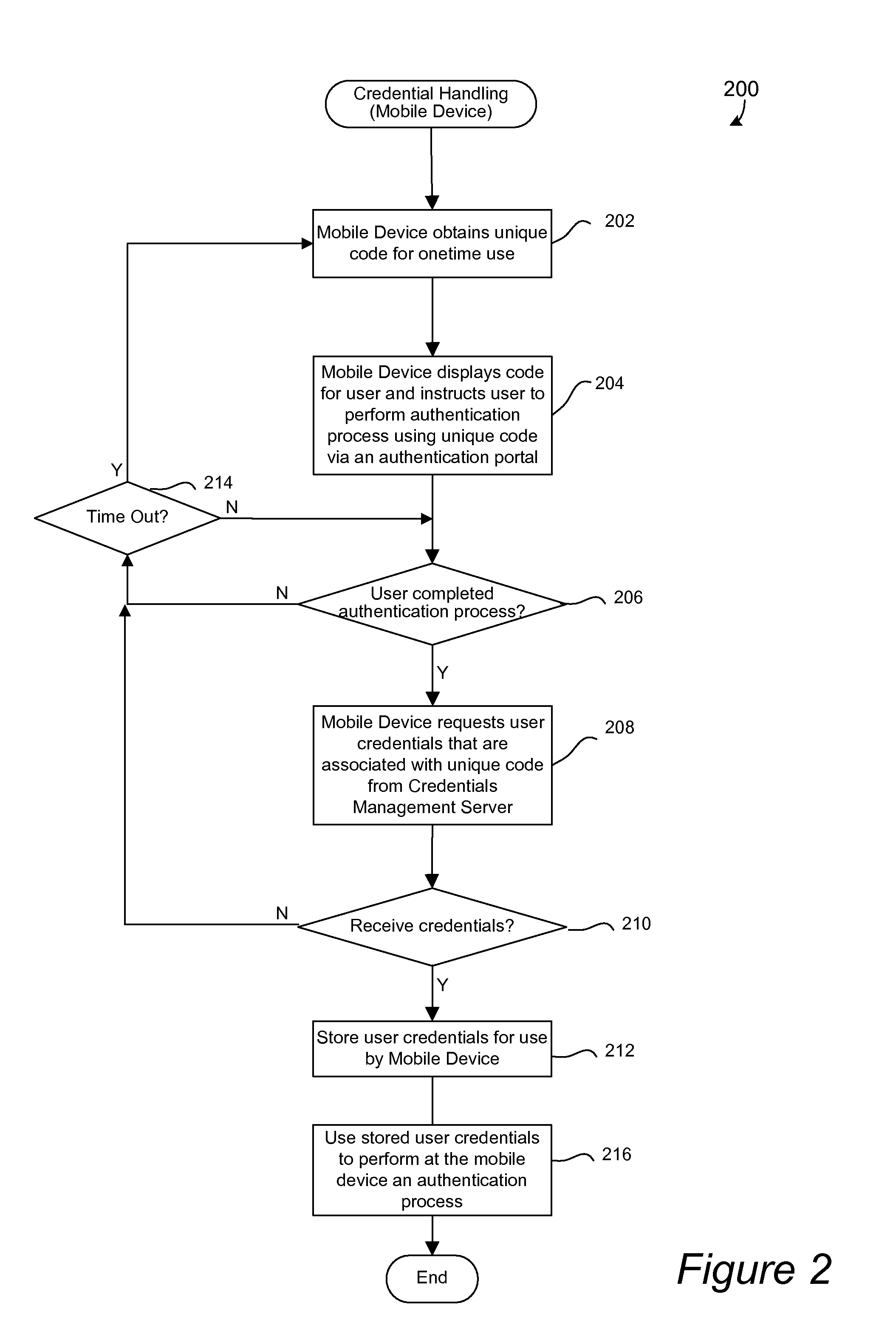
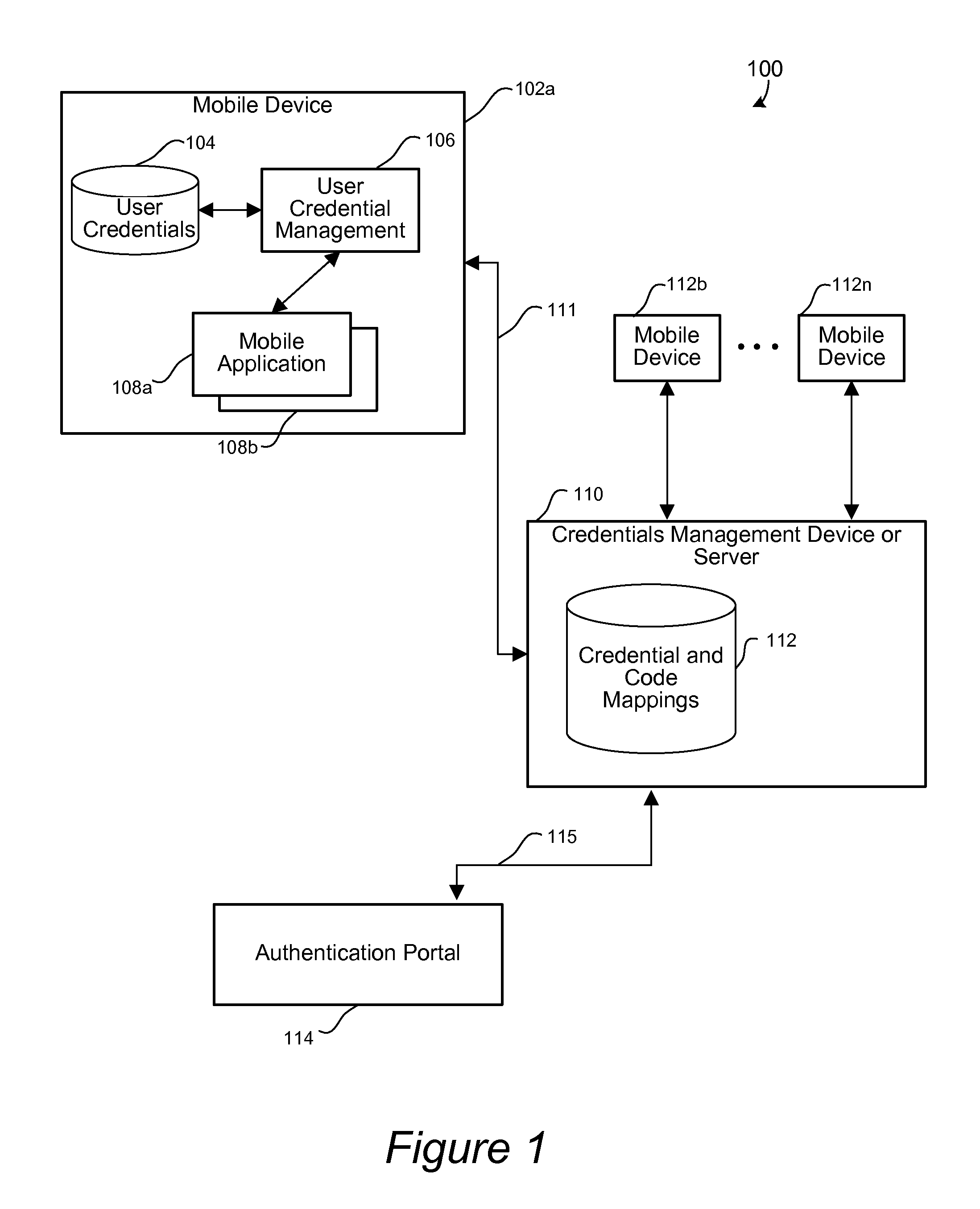
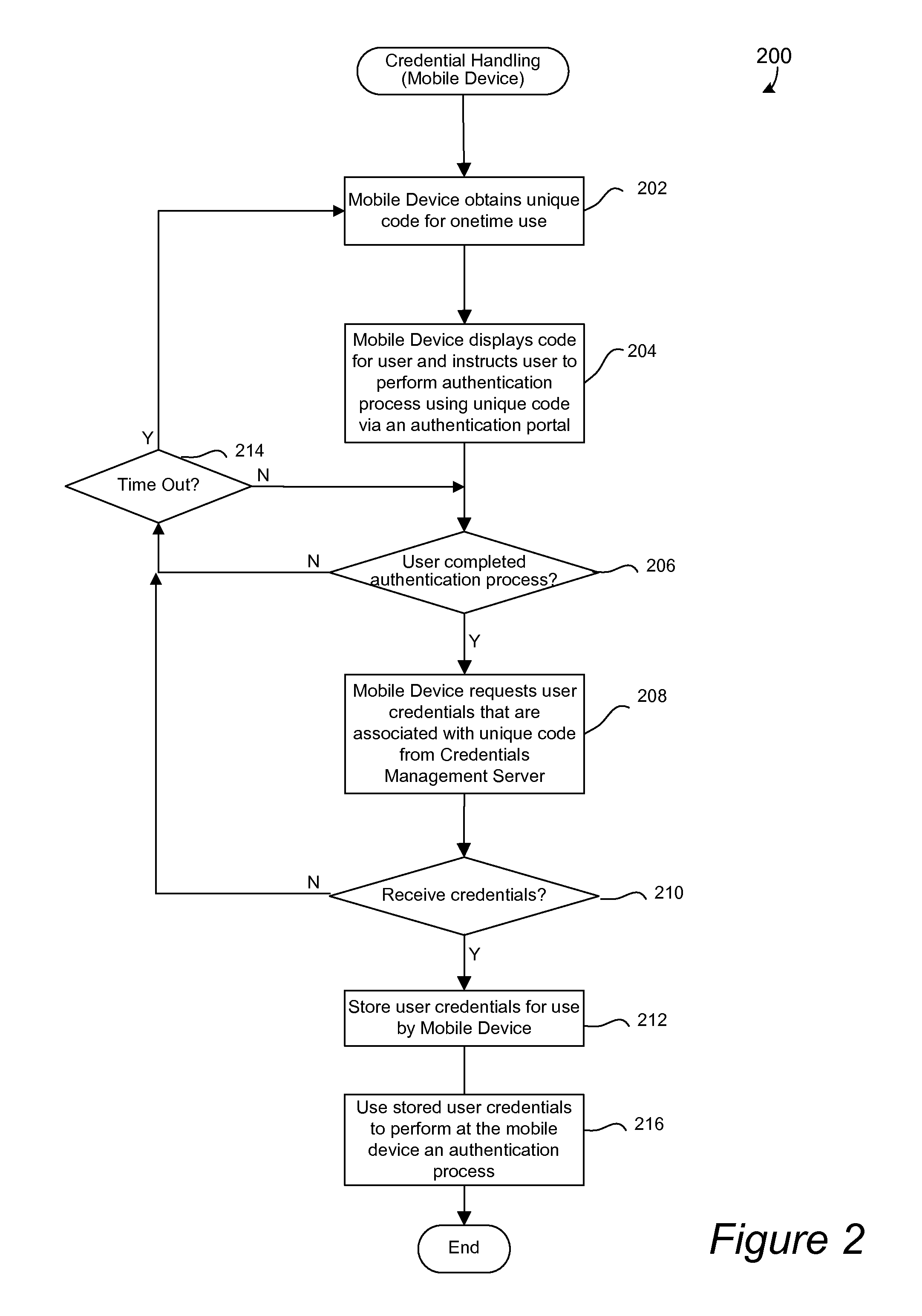
Disclosed are apparatus and methods for associating a mobile device with a web service or a user account. A unique code is displayed on the mobile device. The unique code is associated with a user account or web service to be utilized with the mobile device. Instructions for a user to enter the unique code in an authentication process via an authentication portal of a management device are also displayed. After it is determined that a user has performed the authentication process, any user identification, which has been associated with the unique code, is then obtained from the management device. The obtained user identification is then stored for use by the mobile device. After user identification has been obtained and stored, the stored user identification is used for the mobile device to participate in an authentication process for authorizing the mobile device to utilize a web service or user account associated with the user identification. The authentication process is participated in by the mobile device without requiring input from the user during such authentication process.
Owner:VERIZON PATENT & LICENSING INC
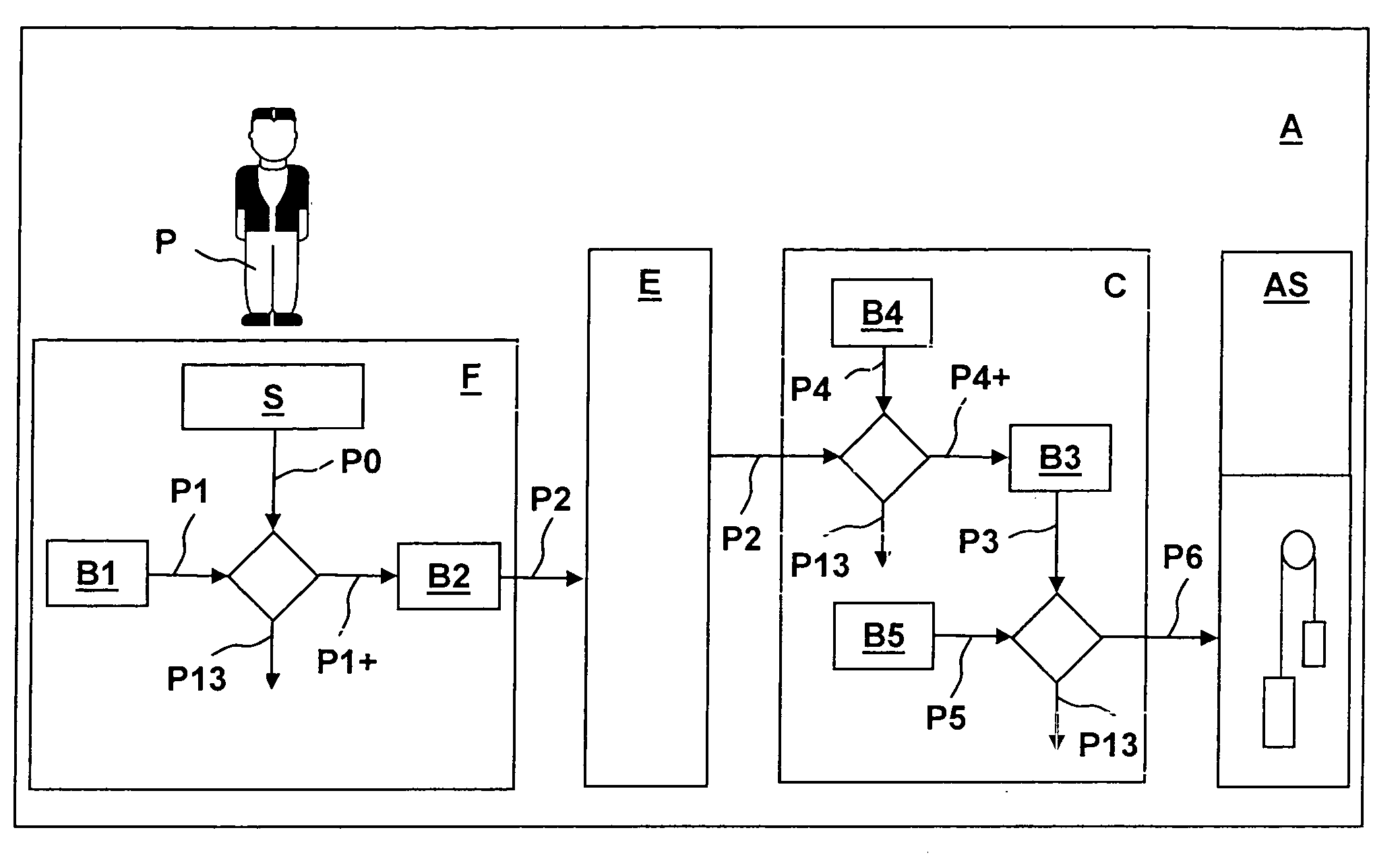
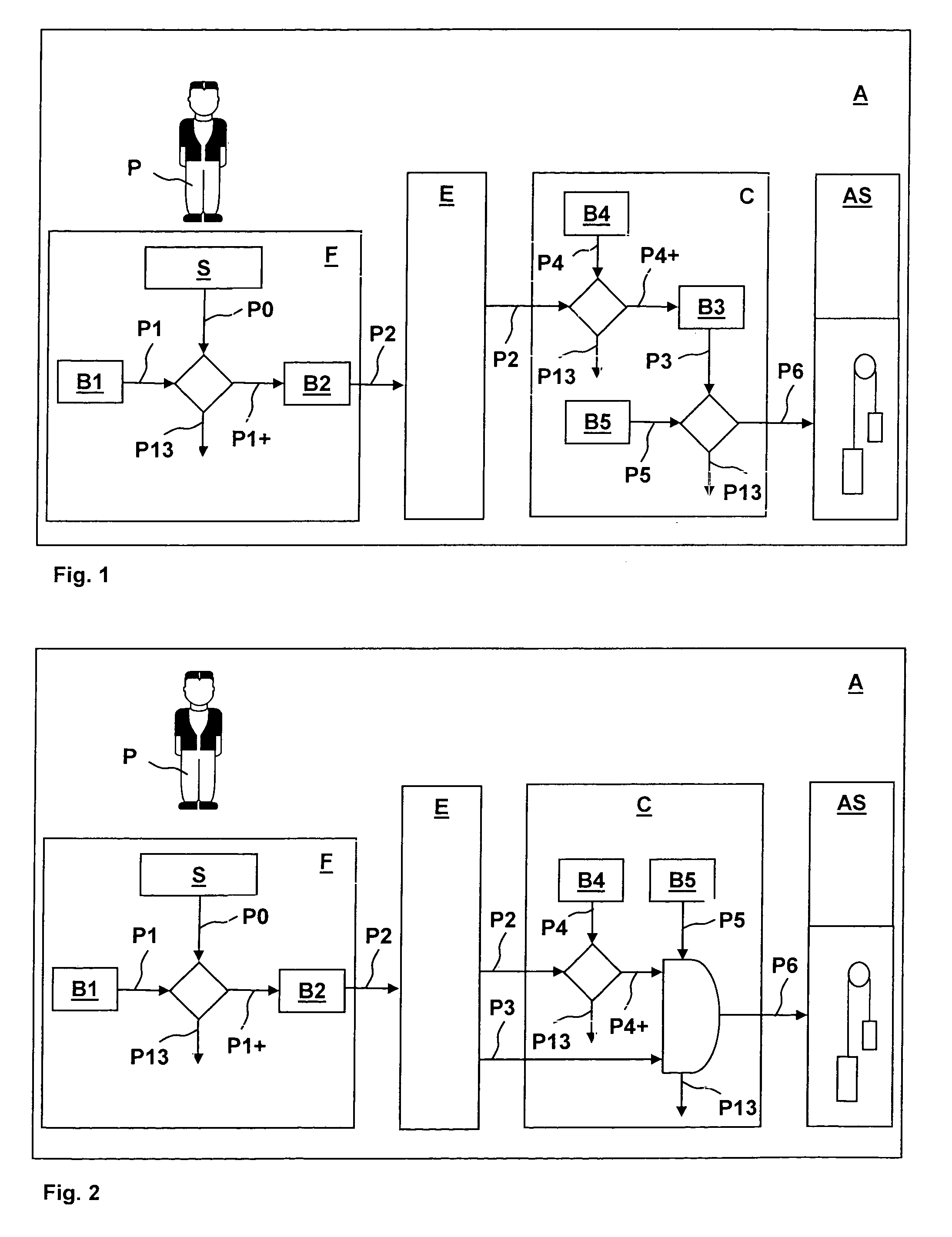
System for security checking or transport of persons by an elevator installation and a method for operating this system
ActiveUS20050138385A1Improve reliabilitySimple patternDigital data processing detailsComputer security arrangementsIdentification deviceMobile authentication
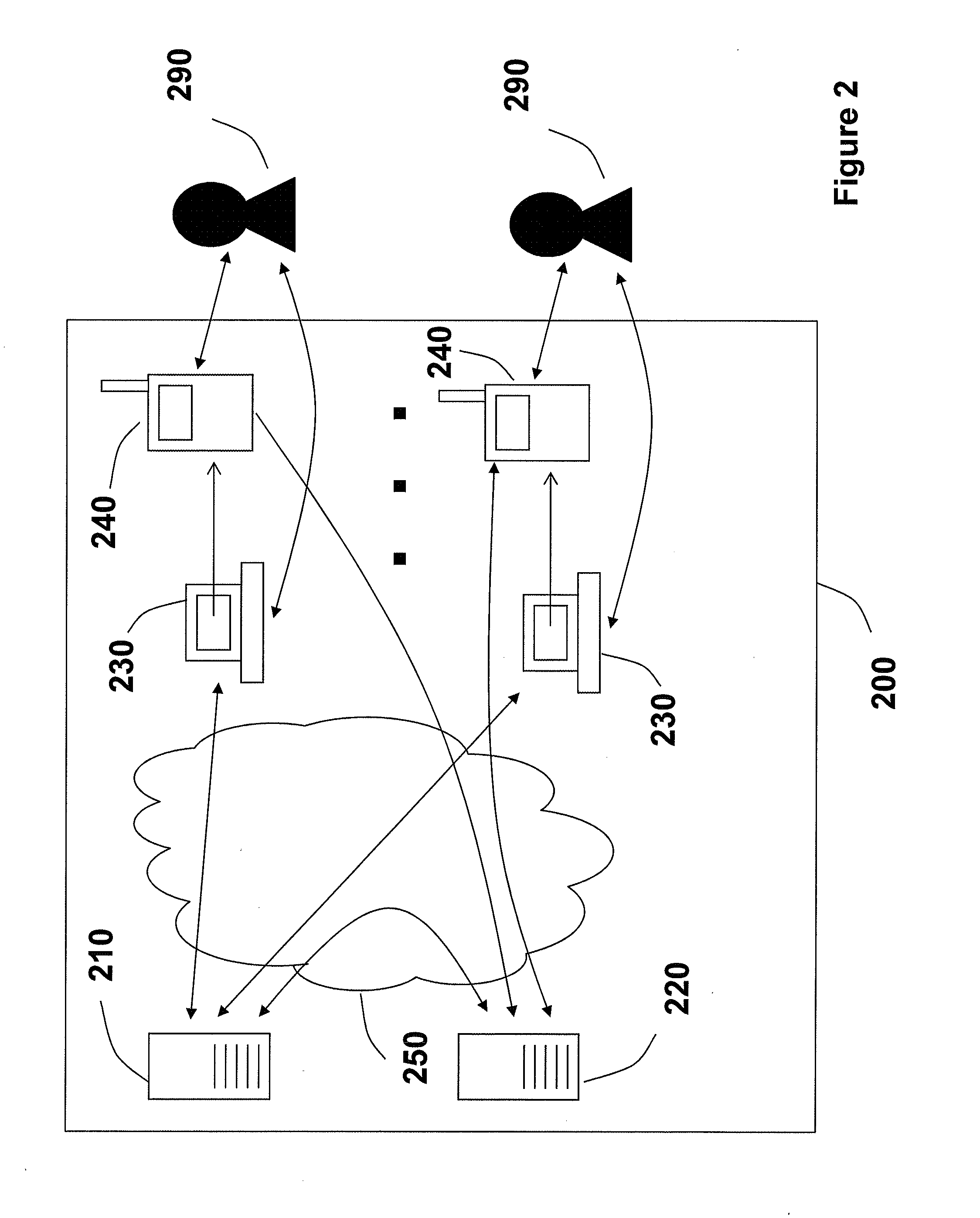
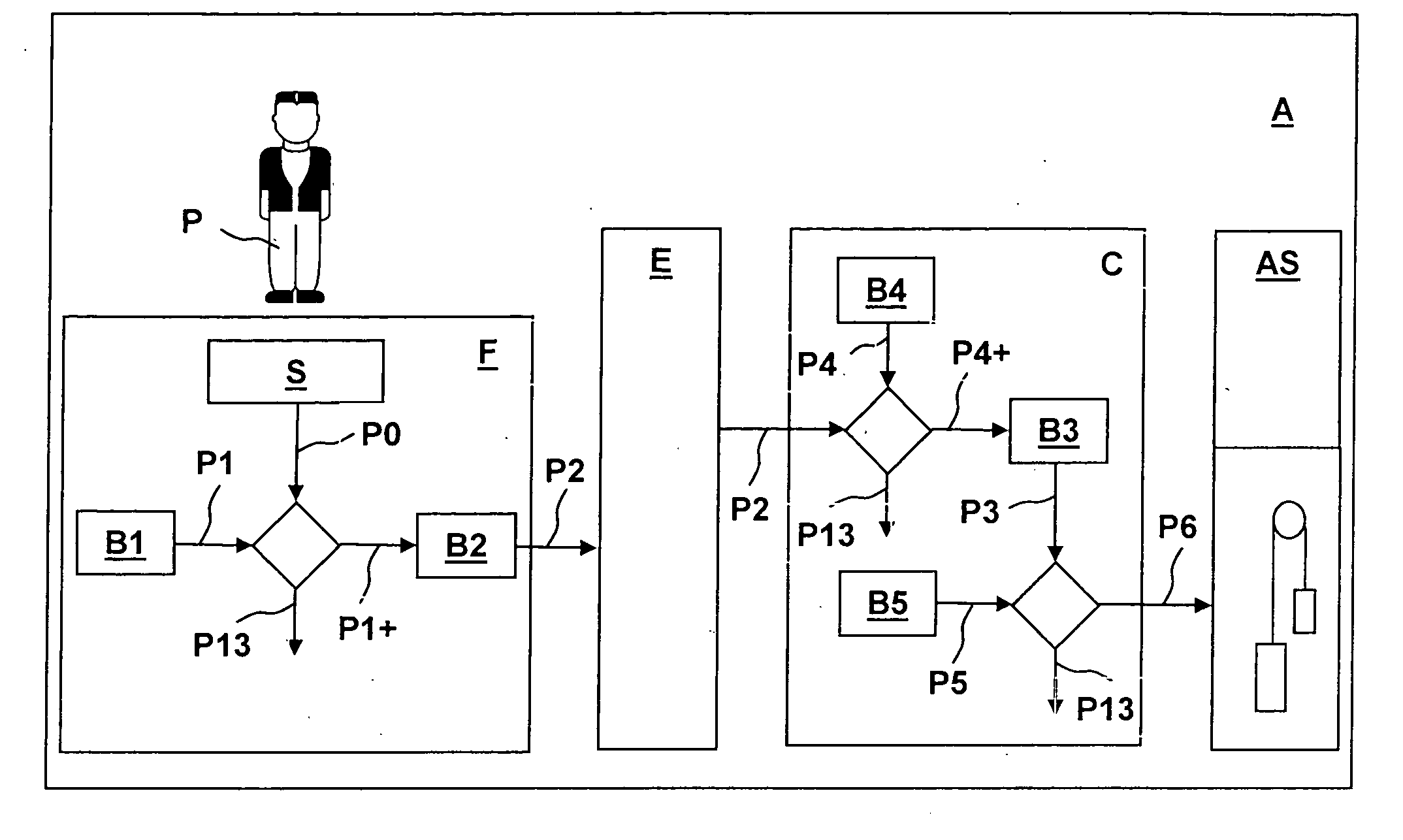
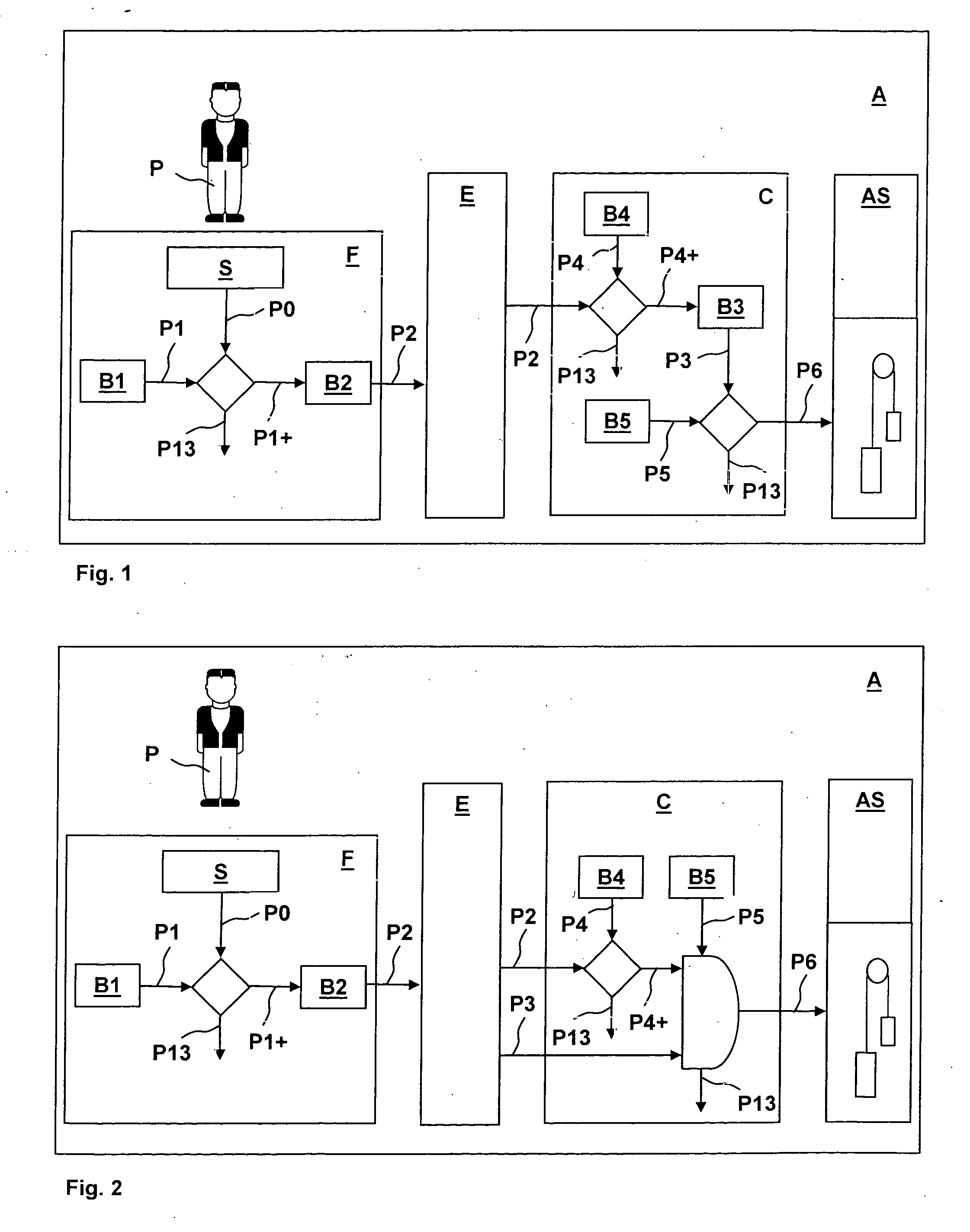
A system for security checking or transport of persons by an elevator installation and to a method of operating this system wherein in a person is authenticated by at least one authentication signal. At least one mobile authentication device carried by the person detects an authentication signal of the person and checks it with at least one person reference. In the case of correspondence of the authentication signal and the person reference, at least one identification code is provided. The identification code is detected by a stationary recognition device and assigned to a predefined travel destination or to an input travel destination input at the recognition device by the person.
Owner:INVENTIO AG
System for validating a biometric input
InactiveUS20170085563A1Improves website log in processStreamlined one-click purchasesAdvertisementsUser identity/authority verificationCommunication interfaceApplication software
A computing device for biometric authentication includes an input interface, a biometric input interface with a biometric sensor, a communications interface, a memory, and a processor. The processor navigates a browser to a website and receives an input associated with a biometric access icon associated with a secure webpage that is displayed on the website. The processor launches an interface of a mobile authentication application upon receiving the input. The interface includes an instruction to provide a biometric input. The processor receives the biometric input and compares the received input with a stored input. The stored input is stored on the memory. The processor authenticates a user of the computing device based on the comparison of the received input and the stored input, communicates an authentication confirmation to an entity associated with the secure webpage, and receives a uniform resource locator (URL) associated with the secure webpage.
Owner:FIRST DATA
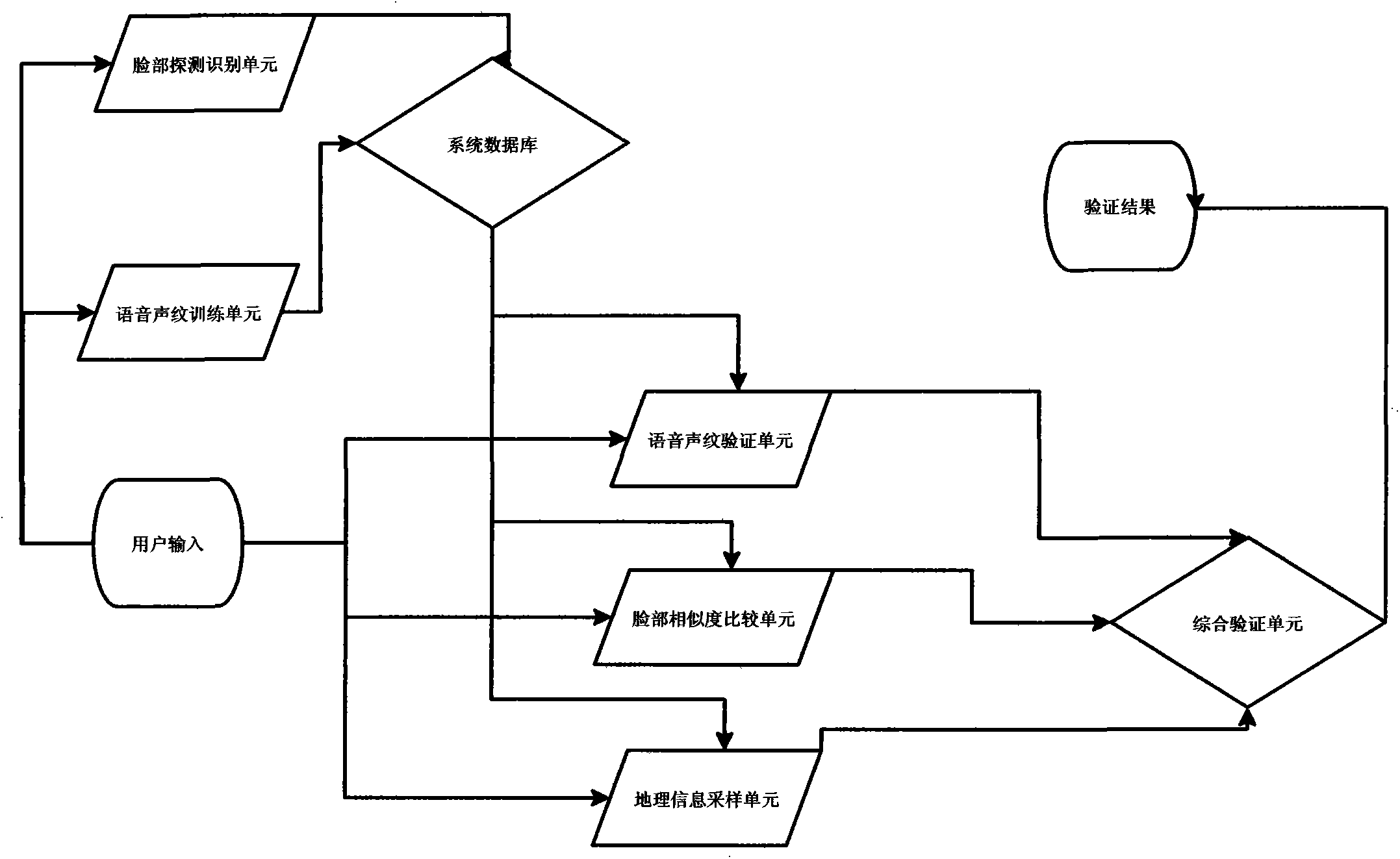
Mobile authentication system and method based on voiceprint recognition, face recognition and location service
The invention provides a mobile authentication system and a method, wherein a voice, imagine and the like multimode-based high precision combined authentication system and a location information-based signing system are combined in the mobile authentication system and the method. A voiceprint recognition, face recognition and location information combined dynamic verification mode is employed, so that the results of verification is more comprehensive and reliable. Hand-held equipment is employed, so that large-scaled group simultaneous verification is supported, and verification speed is increased greatly. The whole verification process is completed by servers automatically, and operation is quite convenient.
Owner:SHANGHAI JIAO TONG UNIV +1
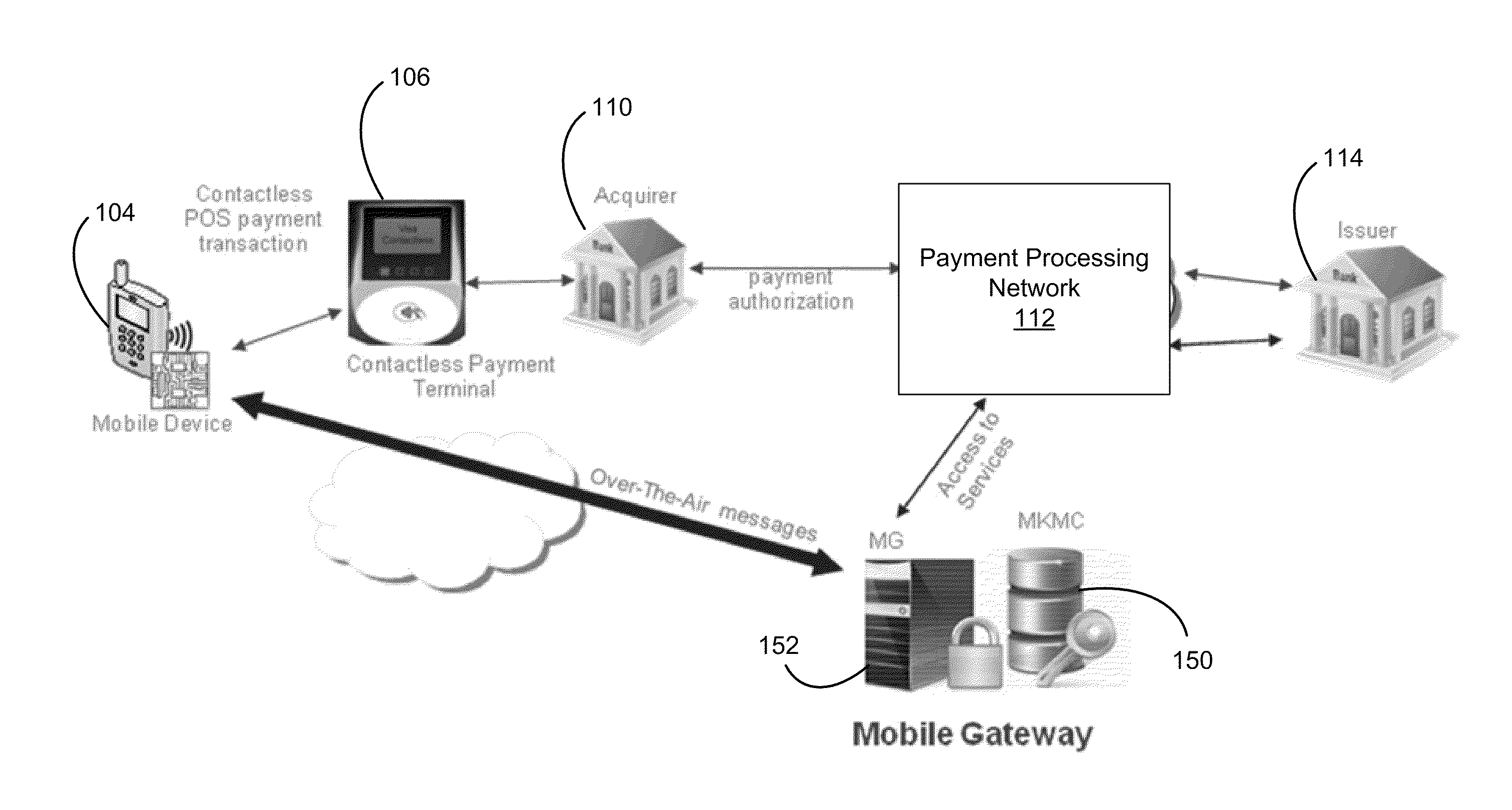
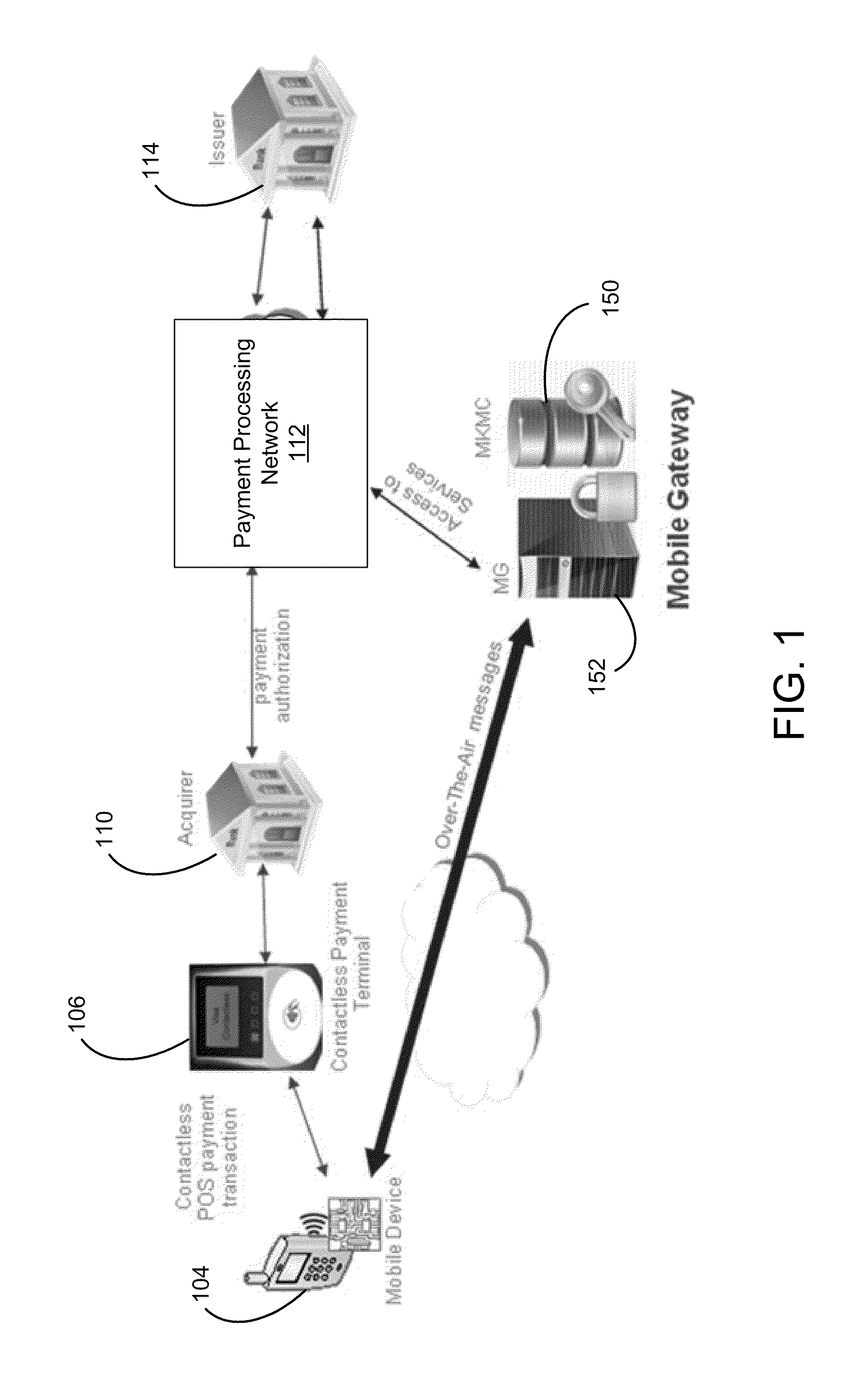
Mutual Mobile Authentication Using a Key Management Center
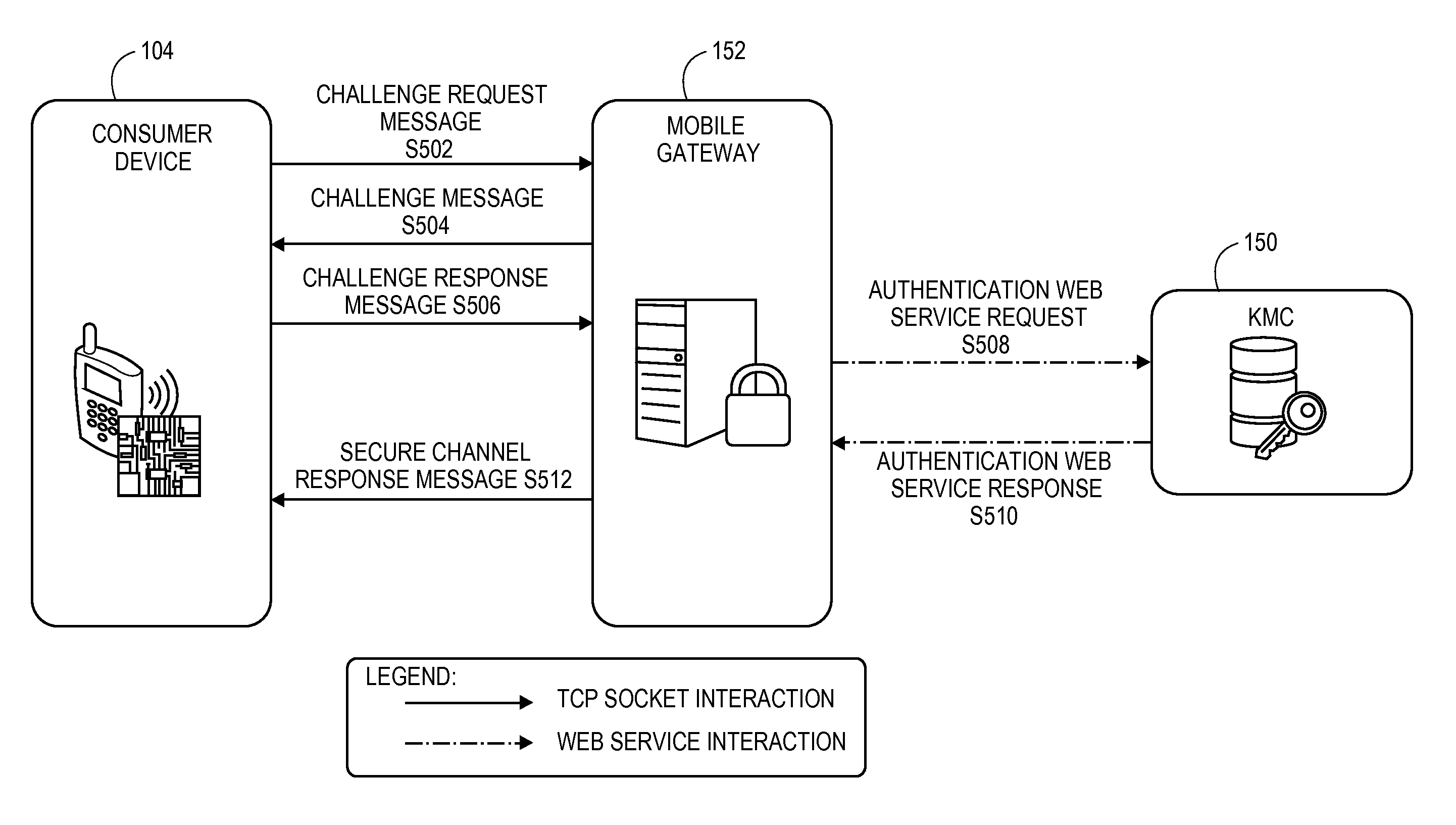
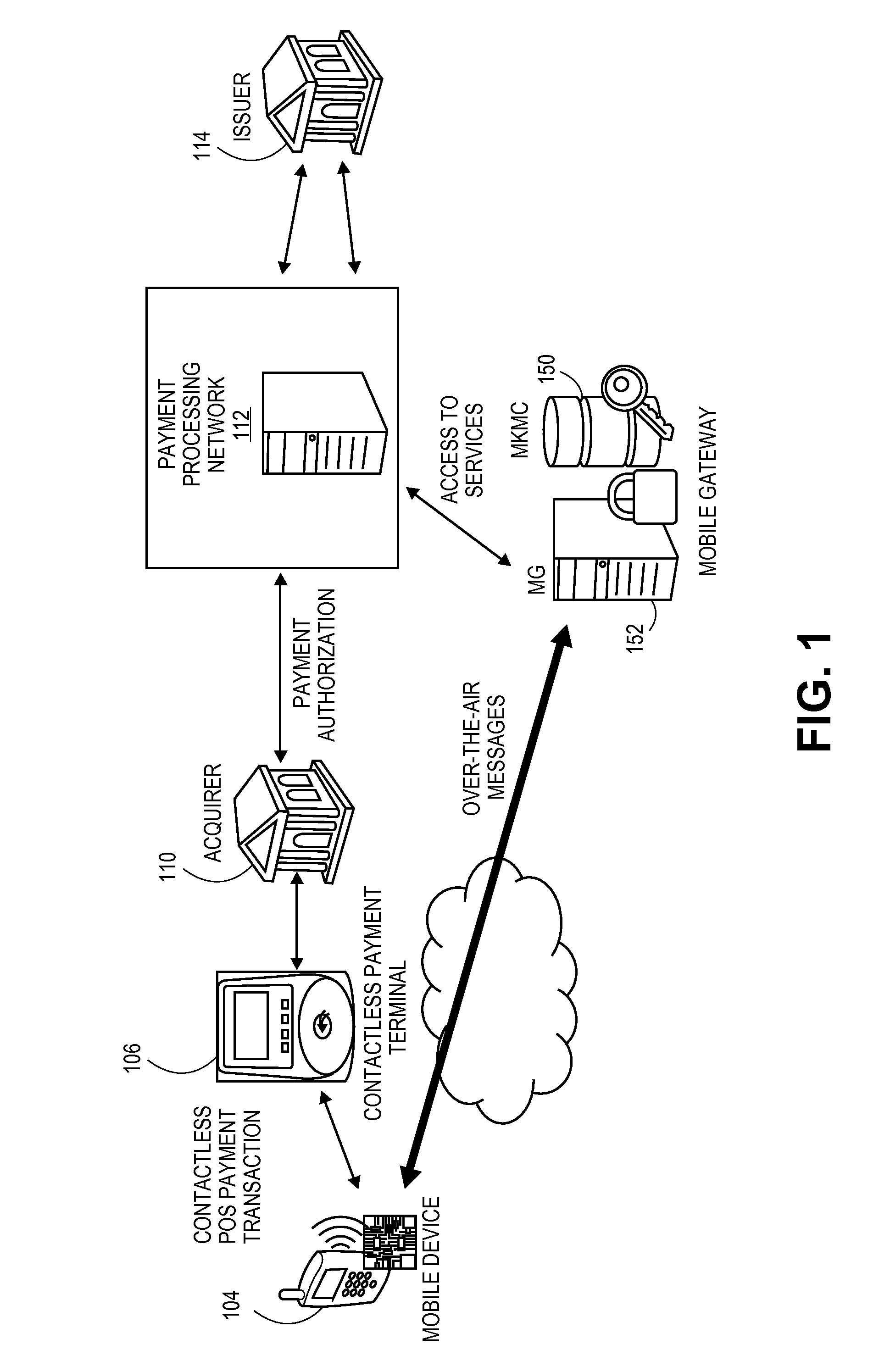
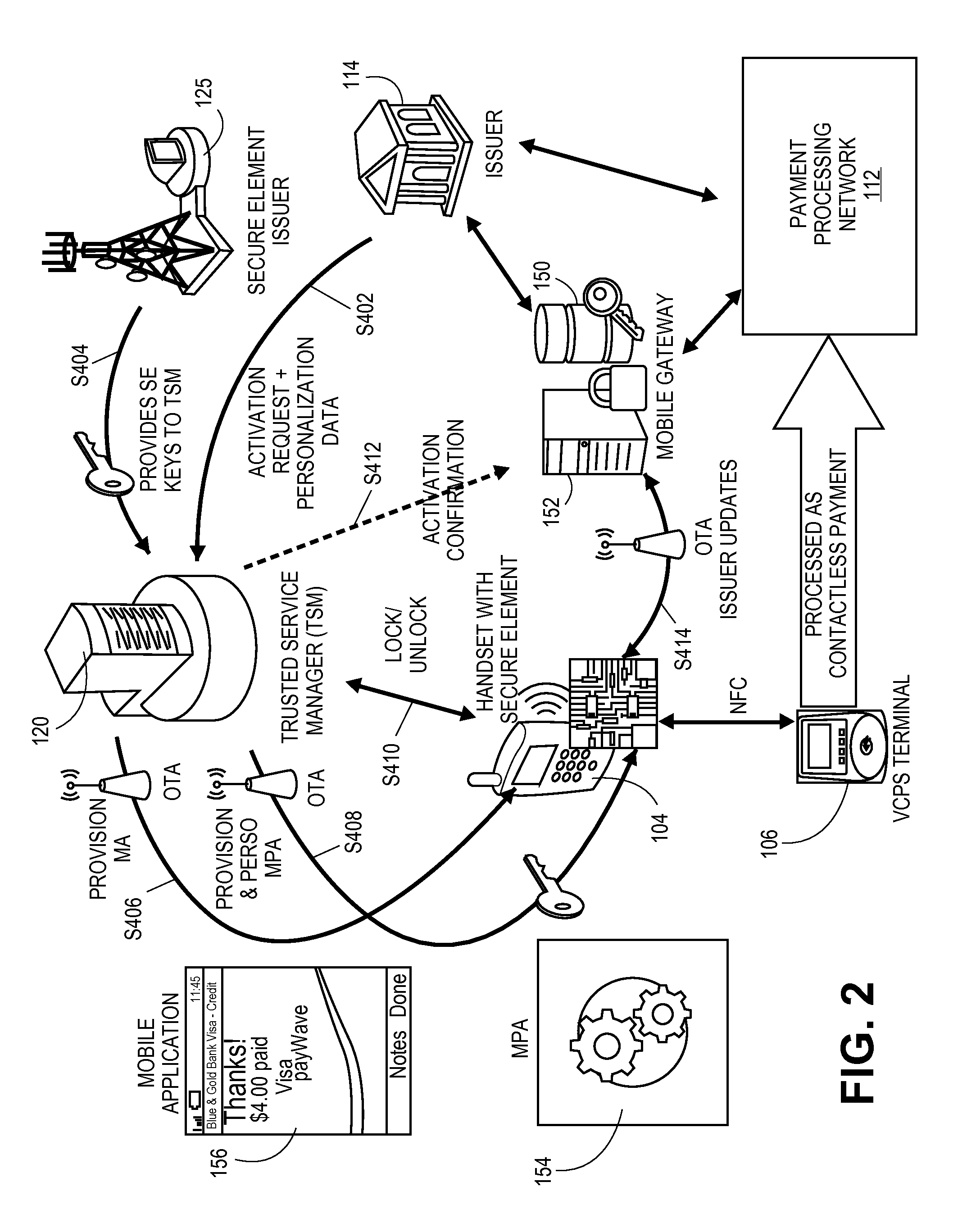
ActiveUS20110247063A1Improve information securityImprove securityKey distribution for secure communicationDigital data processing detailsSecure communicationMobile authentication
A system, method, and server computer configured to authenticate a consumer device. The consumer device is authenticated via a mobile gateway using challenge-response authentication. If the consumer device is successfully authenticated, a secure channel is established between the consumer device and a first entity. The secure channel allows for secure communication between the consumer device and the first entity.
Owner:VISA INT SERVICE ASSOC
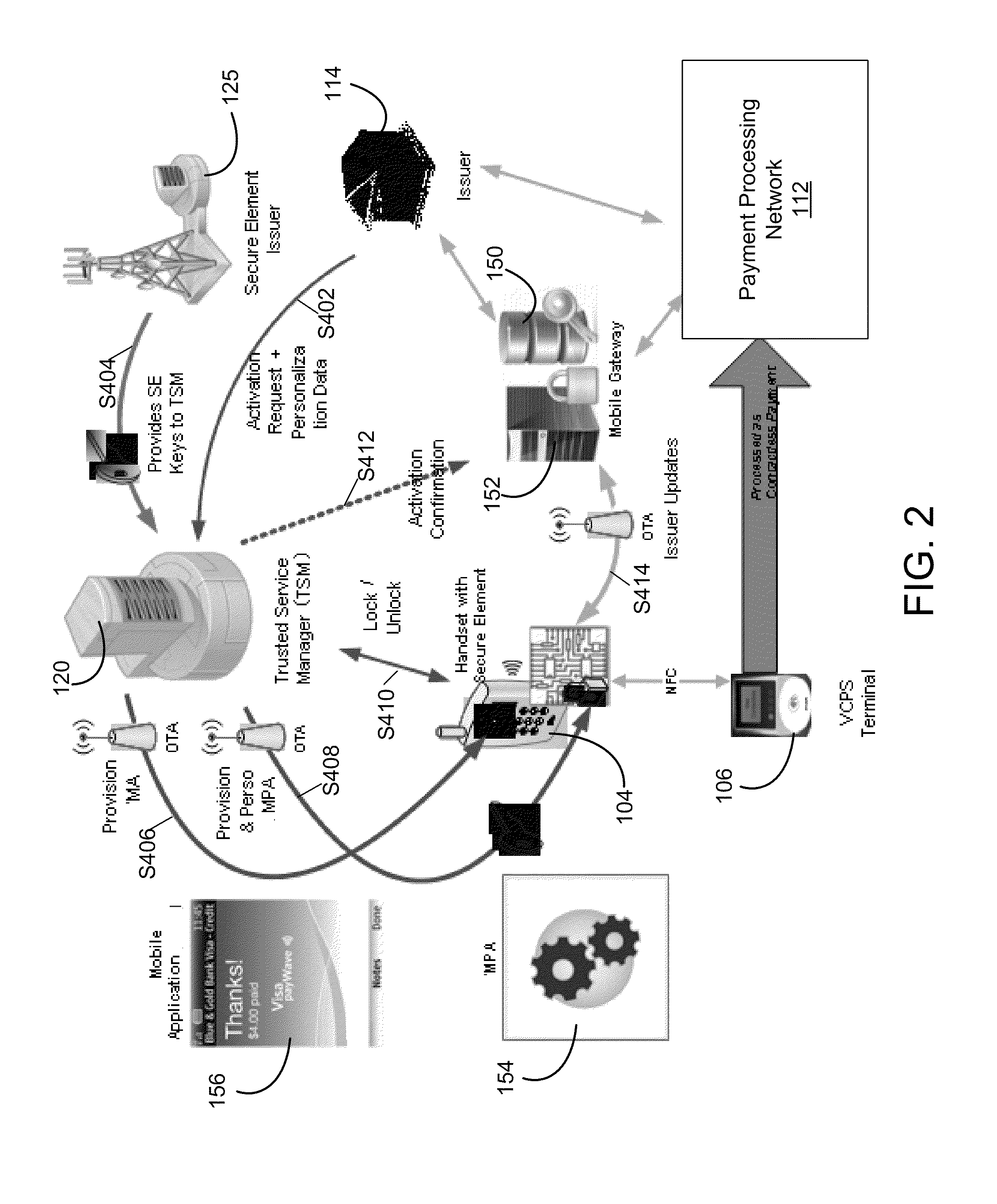
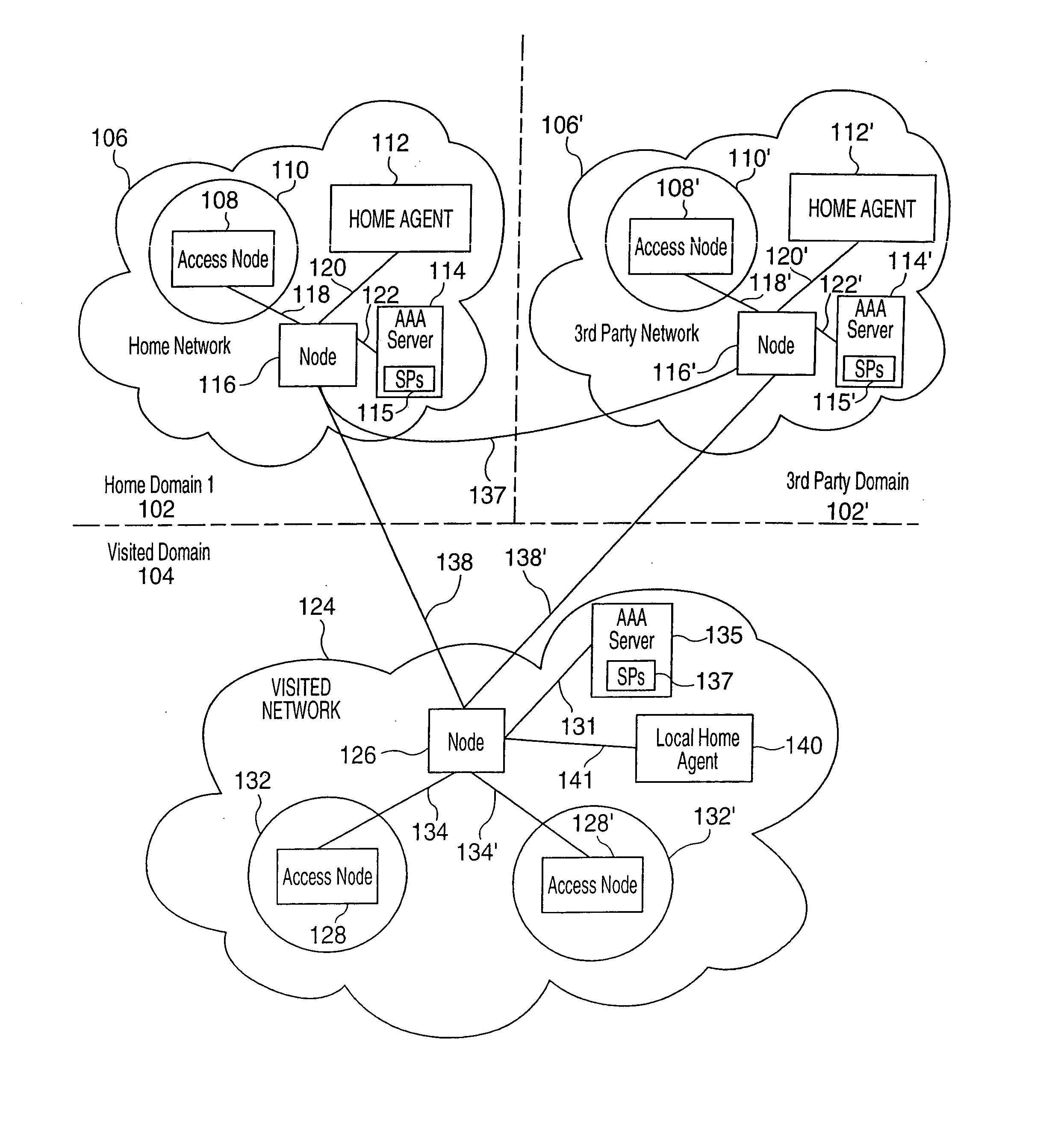
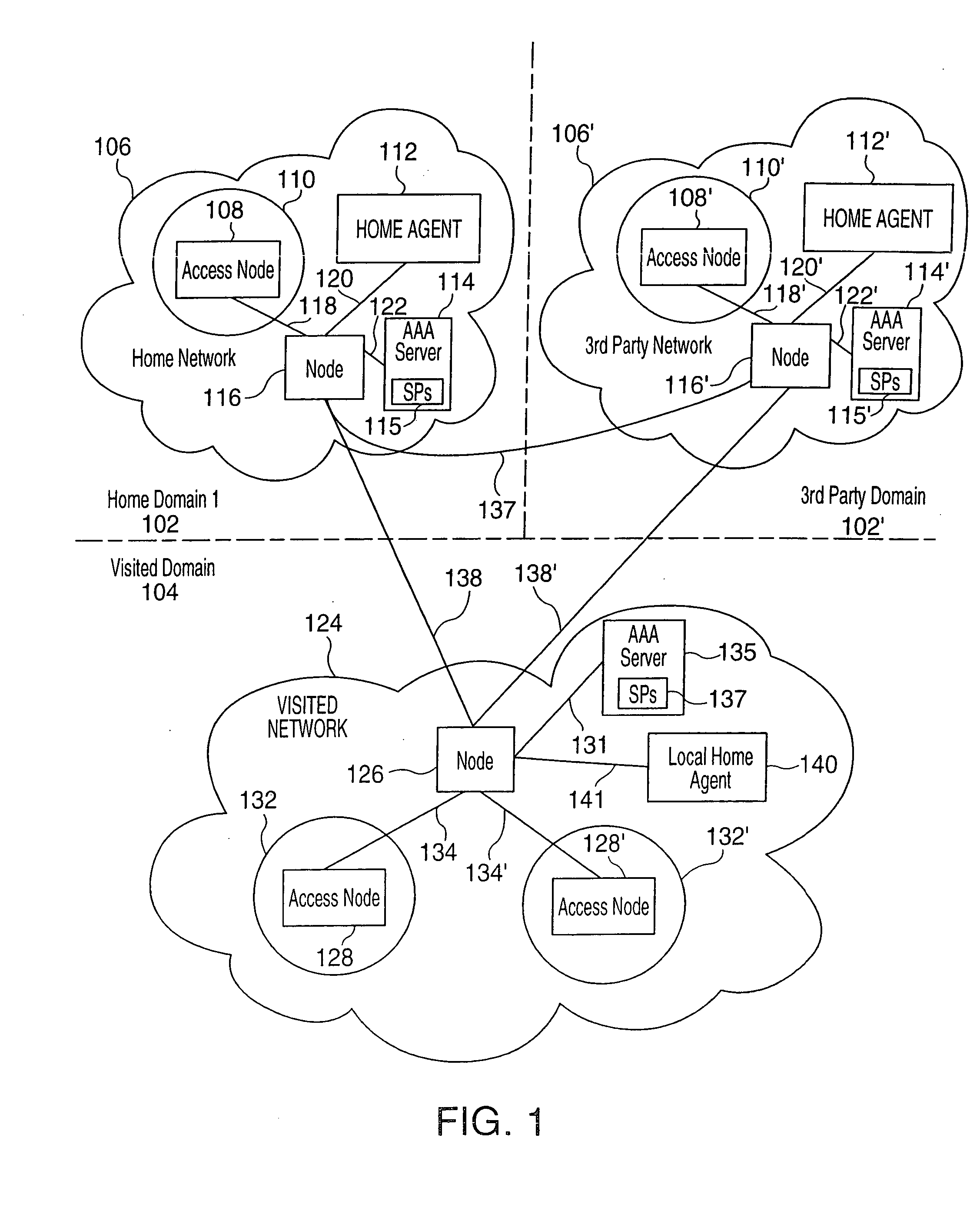
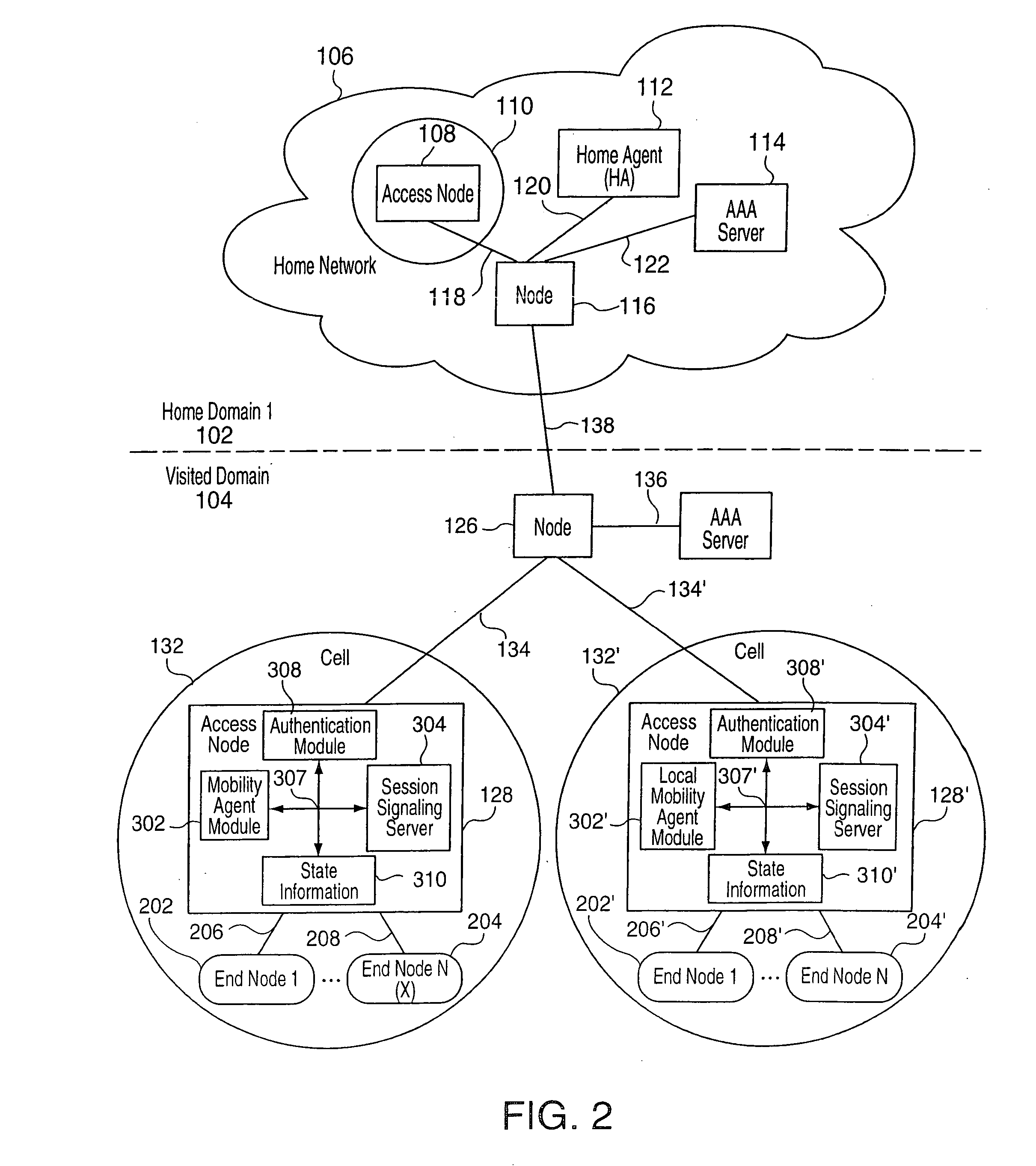
Method for extending mobile IP and AAA to enable integrated support for local access and roaming access connectivity
ActiveUS20050041650A1Reduce in quantityActive radio relay systemsUnauthorized memory use protectionPaper documentDocument preparation
This document describes a way to extend Mobile IP Authentication Authorization and Accounting (AAA) signaling to enable a node to request from a network operator combinations of home and local service capabilities (when roaming) in an efficient and scalable manner. It also enables the home and foreign service providers to constrain and account for actual services provided based on a combination of the foreign and home operator policy.
Owner:QUALCOMM INC
User-friendly multifactor mobile authentication
ActiveUS8646056B2Prevent unauthorized accessEliminate needDigital data processing detailsMultiple digital computer combinationsComputer hardwareUnique identifier
Owner:U S CELLULAR
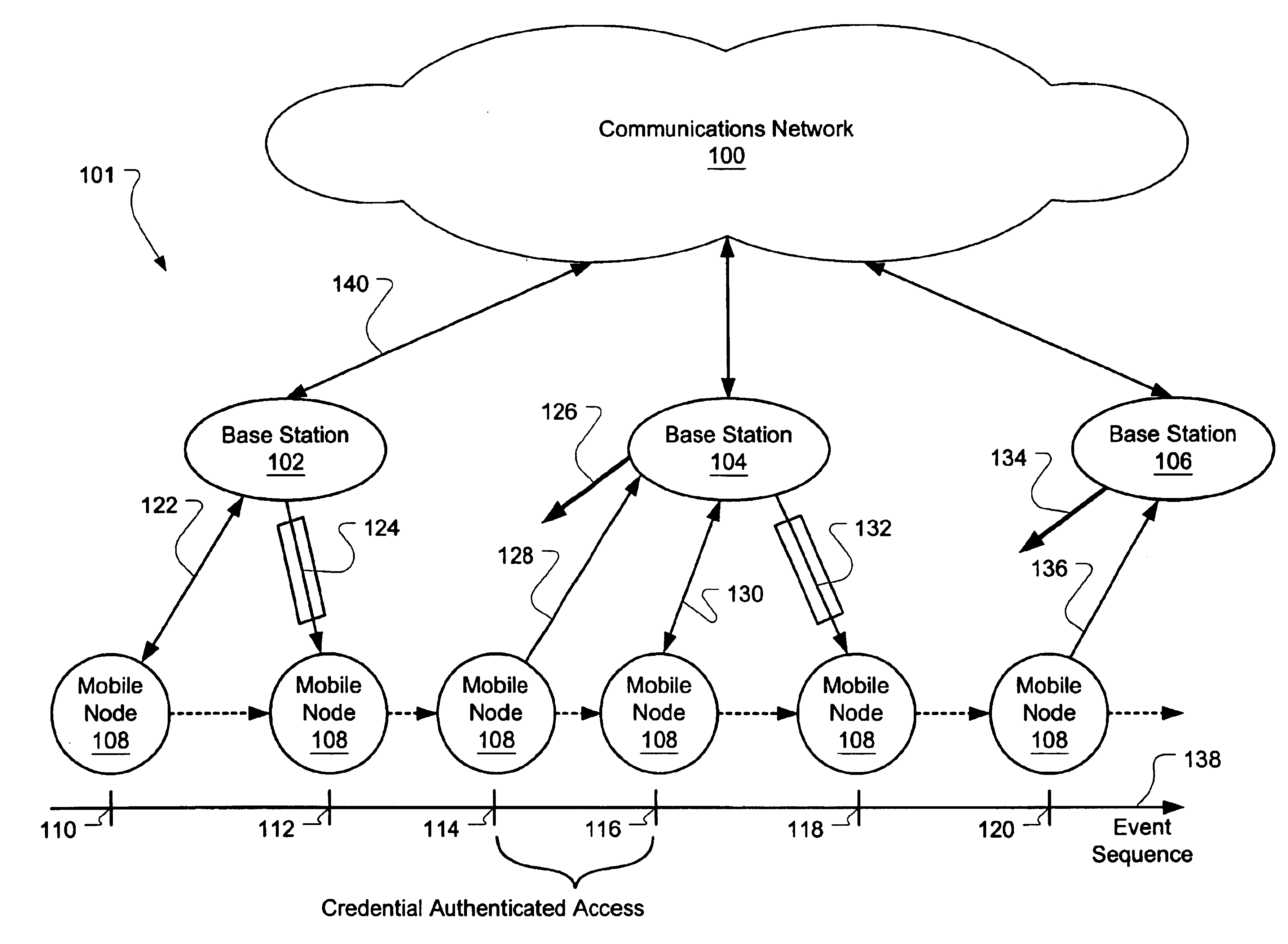
Mobile authentication system with reduced authentication delay
ActiveUS6947725B2Minimal service latencyReduce service latencyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile authenticationNetwork access point
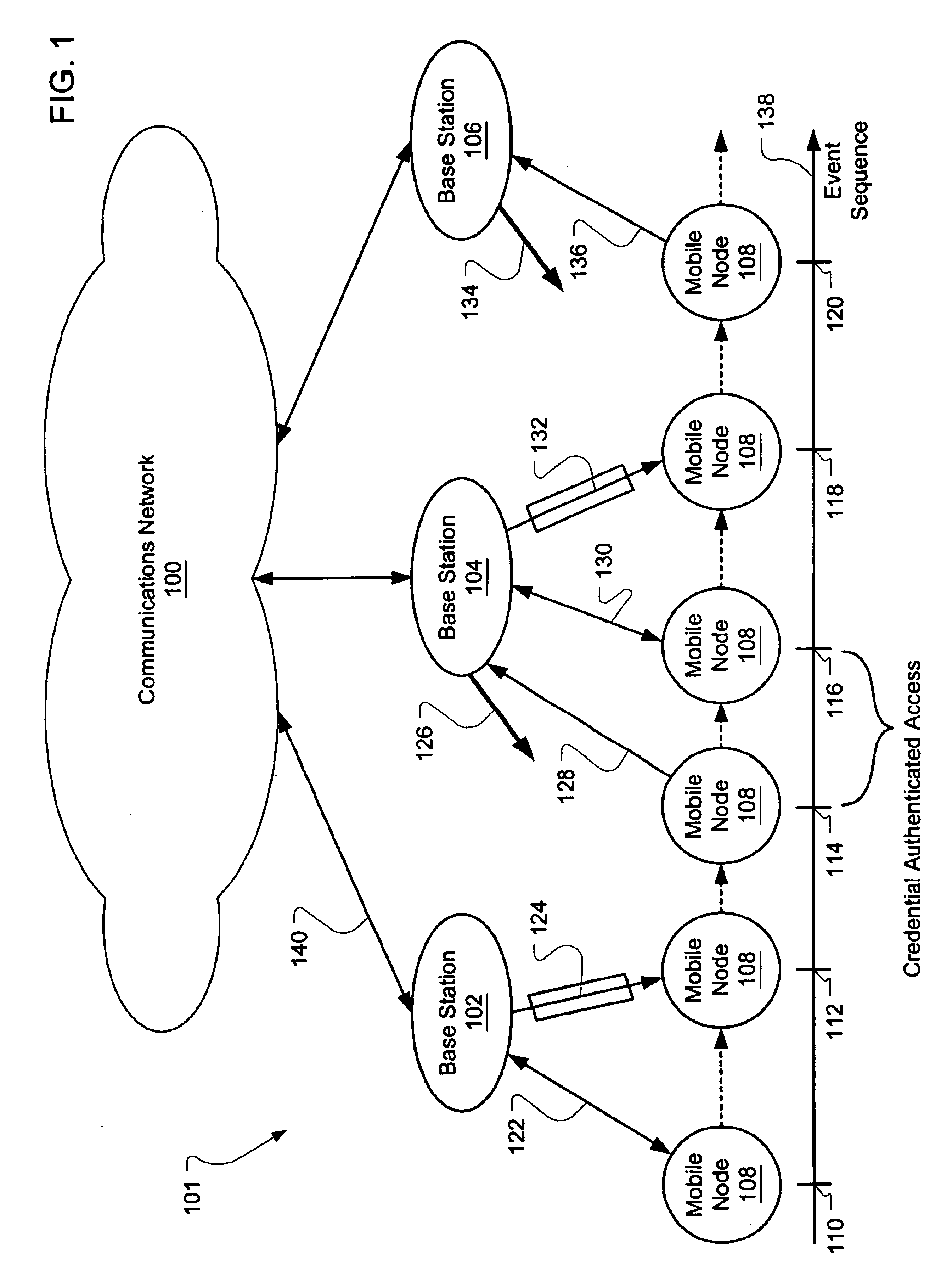
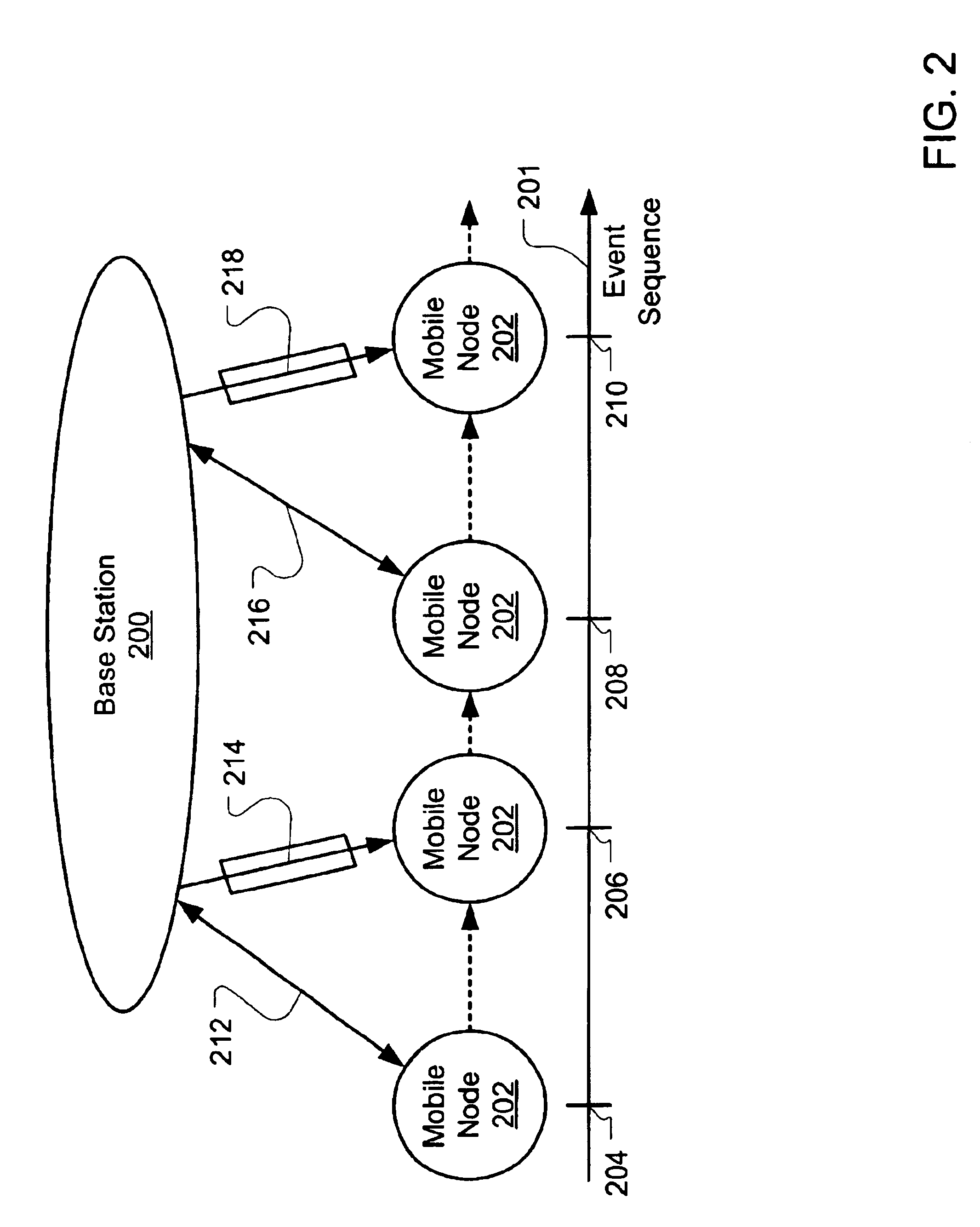
Many examples exist of a mobile node moving between the operational zones of multiple network access points or base stations. To minimize delay in re-authenticating with the network through a new base station, an additional form authenticated access mode called “credential authenticated” access is provided. The mobile unit is fully authenticated in the first base station (e.g., the user has logged in and paid for service). Thereafter, the first base unit transmits a “credential” to the mobile node that may be used by other base stations to establish trust with the mobile node prior to full re-authentication. Upon entering the operational zone of the second base station, the mobile node can transmit the credential to the second base station, which may accept the credential and allow access by the mobile node to the network through the second base station before full authentication has completed.
Owner:MICROSOFT TECH LICENSING LLC
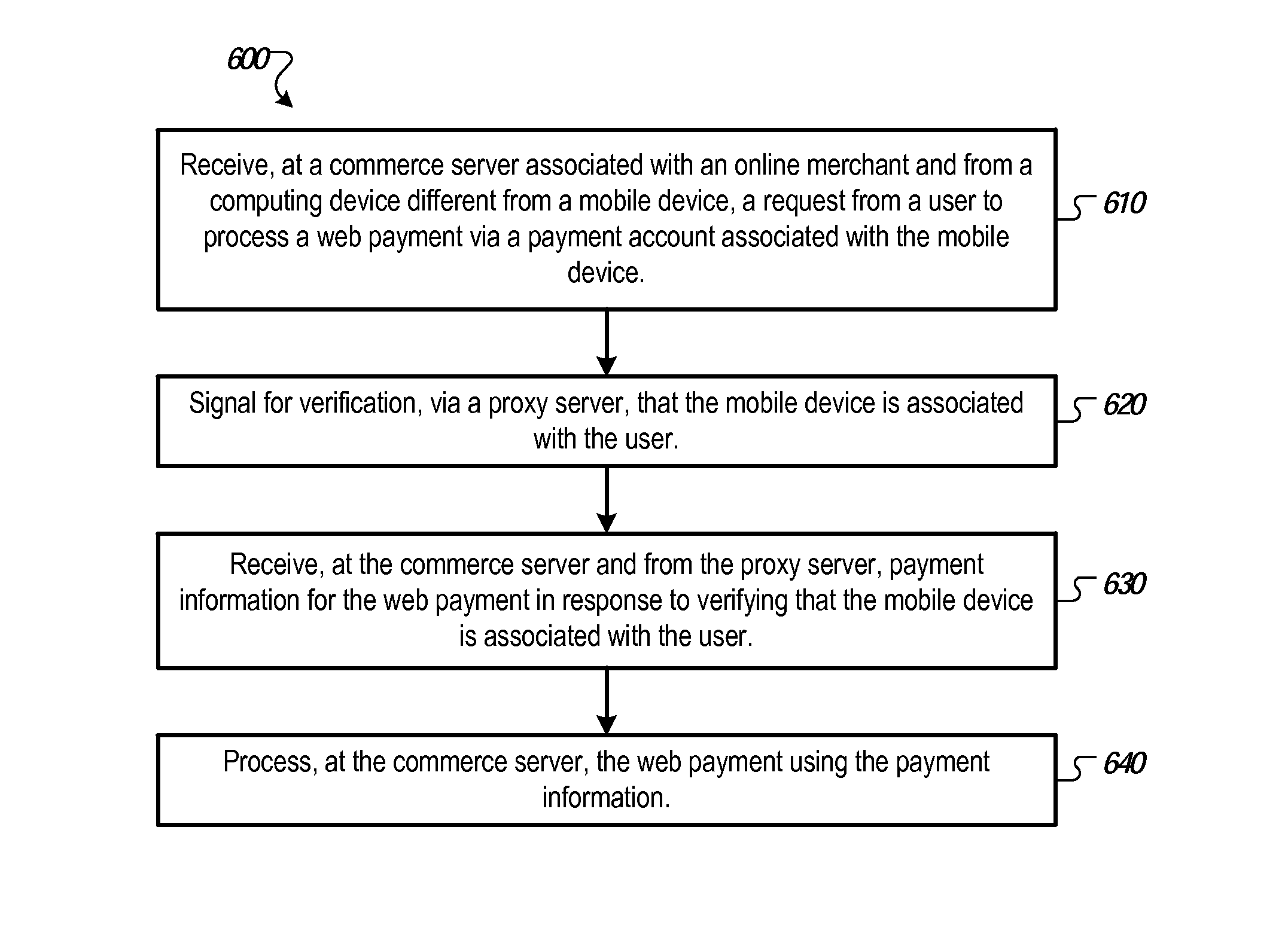
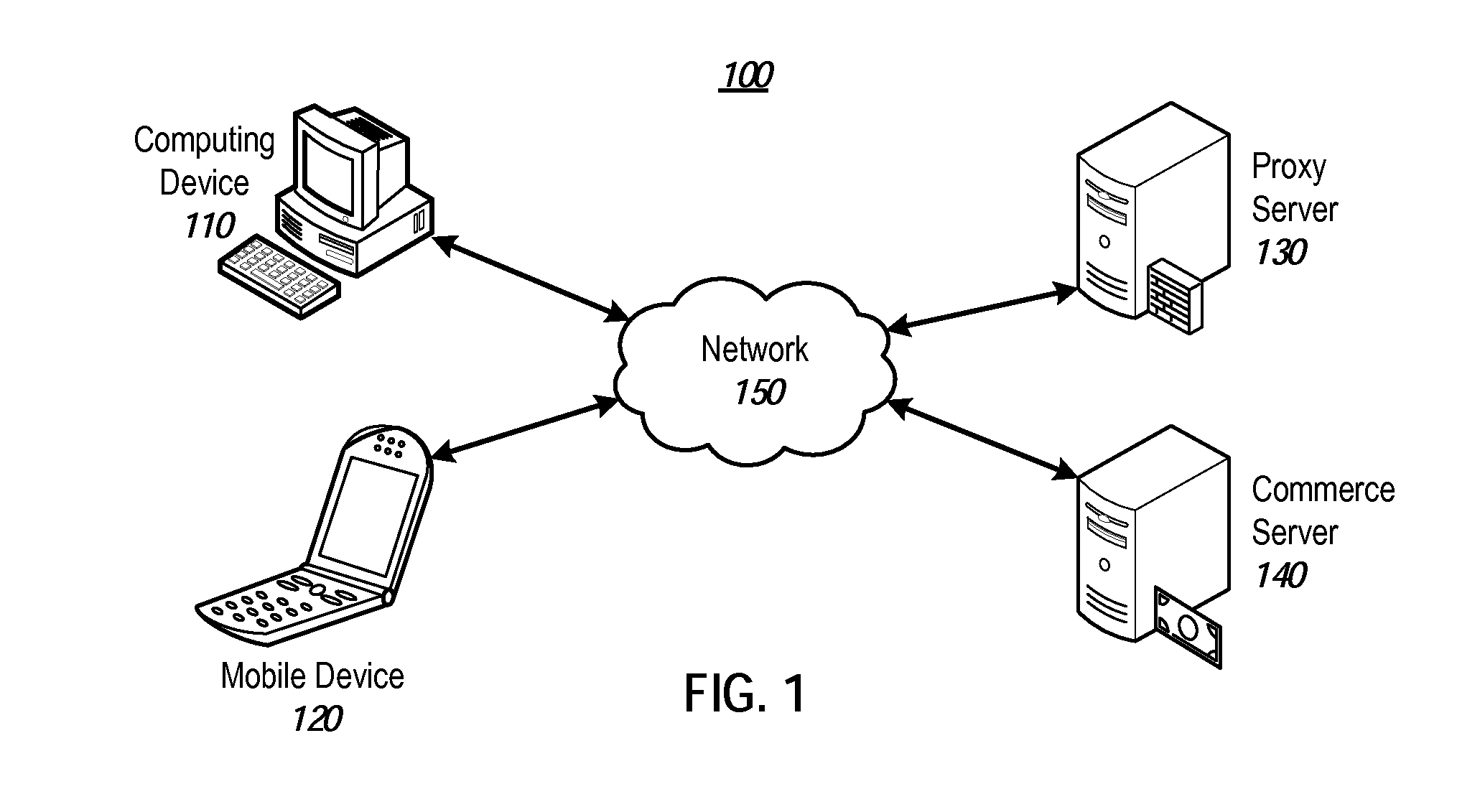
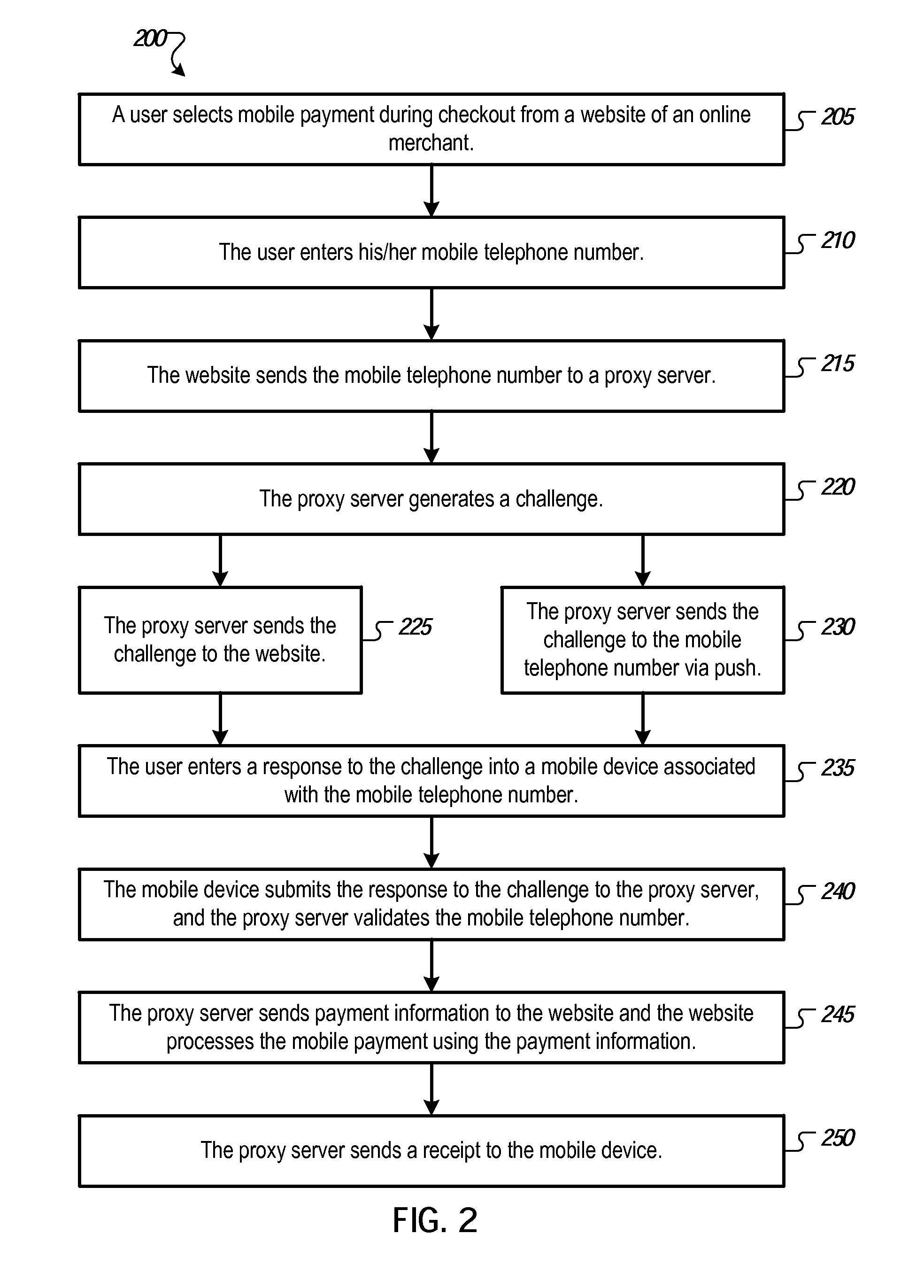
Mobile authentication for web payments using single sign on credentials
Owner:CELLCO PARTNERSHIP INC
Mutual mobile authentication using a key management center
ActiveUS8601266B2Improve securityKey distribution for secure communicationDigital data processing detailsSecure communicationMobile authentication
A system, method, and server computer configured to authenticate a consumer device. The consumer device is authenticated via a mobile gateway using challenge-response authentication. If the consumer device is successfully authenticated, a secure channel is established between the consumer device and a first entity. The secure channel allows for secure communication between the consumer device and the first entity.
Owner:VISA INT SERVICE ASSOC
Centralized authentication system
InactiveUS7454615B2Unauthorised/fraudulent call preventionDigital data processing detailsPersonalizationInternet content
Centralized authentication systems are provided. A representative system, among others, includes a mobile authentication registration system, a content provider and a wireless internet server. The mobile authentication registration system resides on a content provider which is coupled to the internet, and is operable to receive a single identification number and password from a user independent of a platform the user is associated with, and determine that the identification number and password combination provided by the user is associated with a registered user. The content provider provides personalized internet content to any of a plurality of registered users on a plurality of platforms. The wireless internet server receives a connection request from a wireless device, sends an authentication request to the mobile authentication registration system, and provides a personalized internet content from the content provider to said at least one wireless device. Methods and other systems for multiple access portals are also provided.
Owner:AT&T INTPROP I L P
Authentication method and authentication system among mobile devices
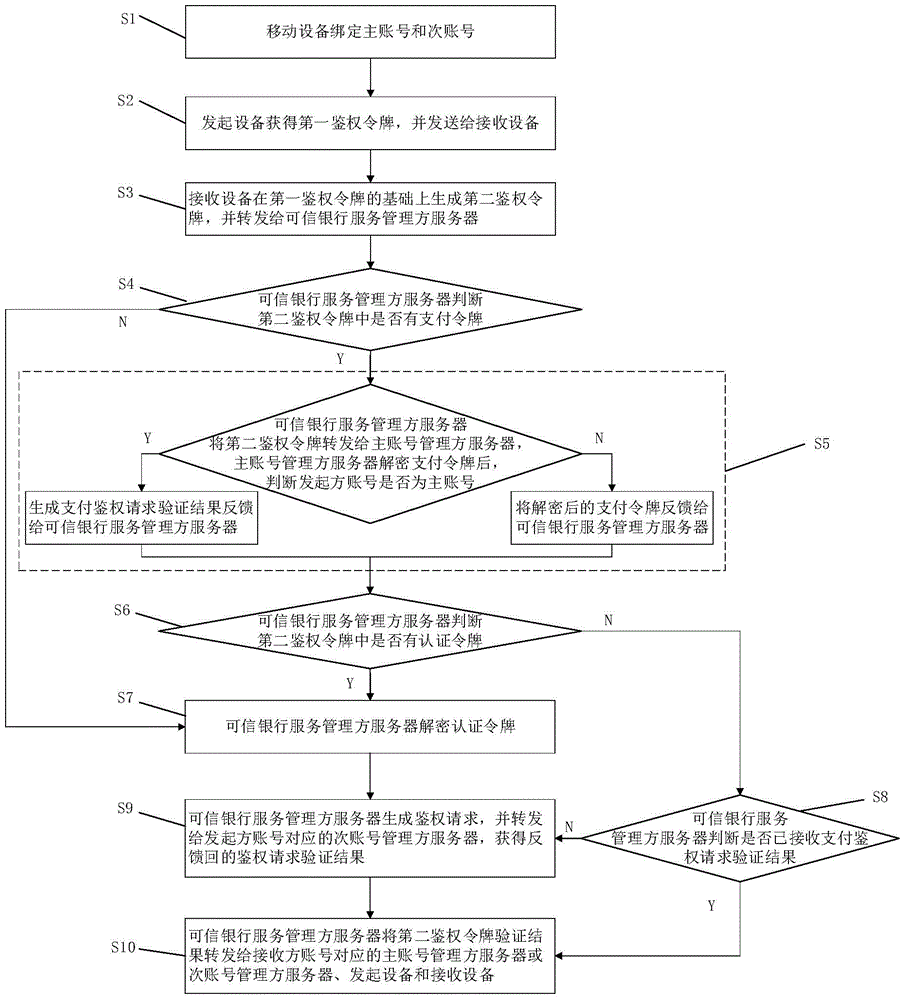
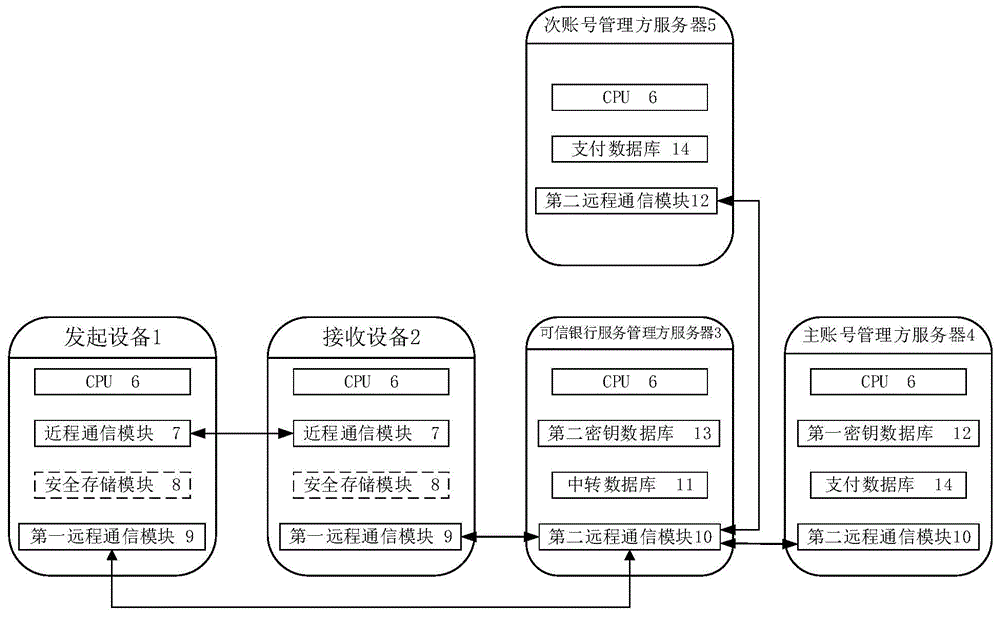
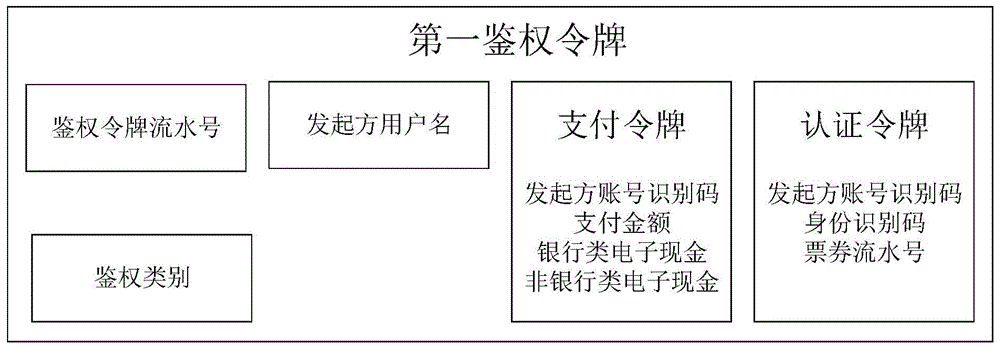
ActiveCN104951937AAvoid risk of leakageImprove securityPayment protocolsAuthentication serverMobile authentication
The invention relates to an authentication method and an authentication system among mobile devices. The authentication method includes that after selecting an initiator account number, an initiating device obtains a first authentication token for mobile payment, identity authentication and ticket verification through an encryption method and sends the first authentication token to a receiving device; after selecting a receiver account number, the receiving device encrypts to generate a second authentication token on the basis of the first authentication token and forwards the second authentication token to a credible bank service manager server; the credible bank service manager server is communicated with a corresponding primary account number manager server or a secondary account number manager server according to content of the second authentication token to obtain a fed back authentication request verification result, generates a second authentication token verification result and forwards the second authentication token verification result to the initiating device, the receiving device and the primary account number manager server or the secondary account number manager server corresponding to the receiver account number. Compared with the prior art, the authentication method and the authentication system have the advantages that mobile authentication safety is enhanced, mobile authentication compatibility is increased, user experience is improved and the like.
Owner:上海太炎信息科技有限公司
Trading method for implementing payment by transfer of accounts and cash withdrawing without card
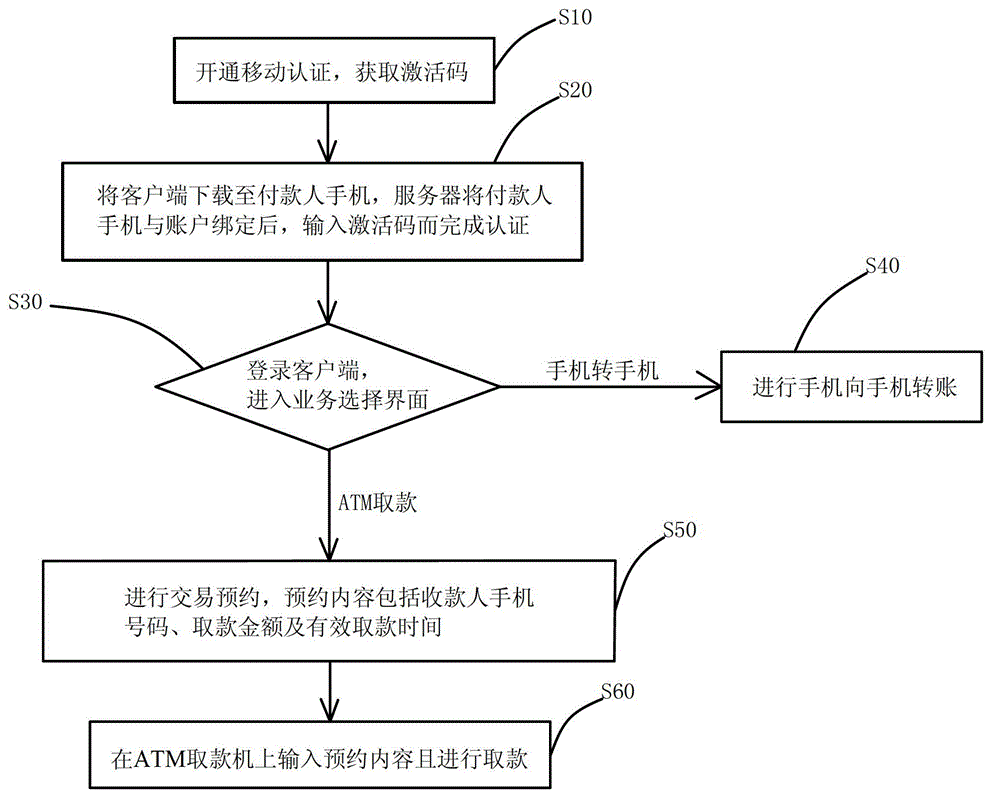
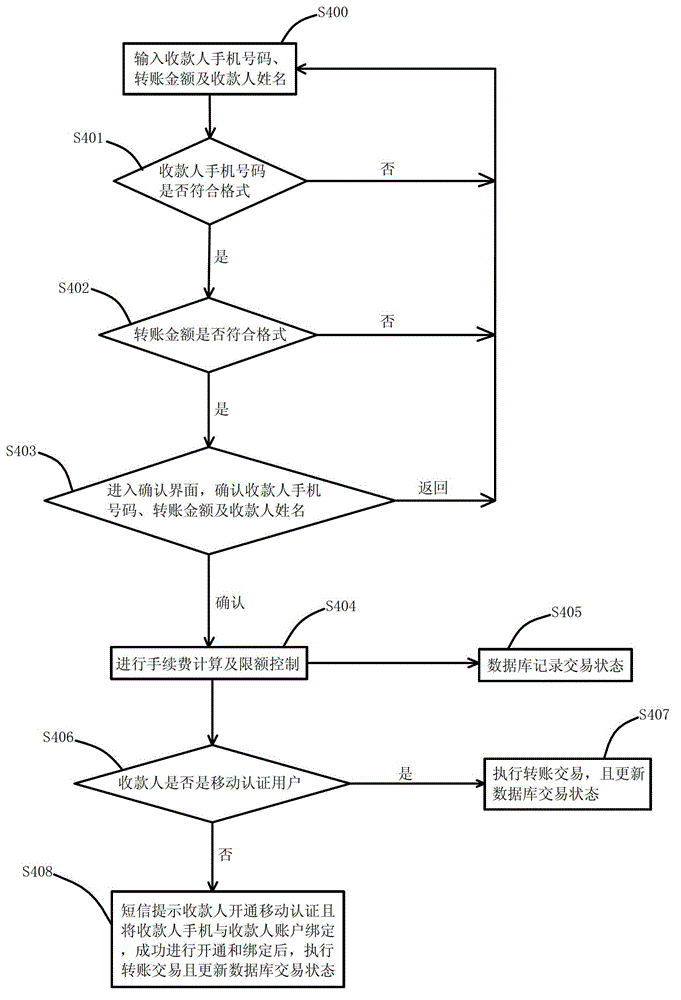
InactiveCN103150649APrevent leakageImprove portabilityComplete banking machinesPayment architecturePaymentMobile Telephone Number
The invention discloses a trading method for implementing payment by transfer of accounts and cash withdrawing without a card. The method comprises the following steps: S10, opening mobile authentication, and acquiring an activation code; S20, downloading a client side to a mobile phone of a payer, binding the mobile phone of the payer and an account, and inputting the activation code to finish authentication; S30, logging in the client side, entering a business selection interface, if a mobile phone to a mobile phone is selected, executing a step S40, and if the cash is withdrawn in an ATM (automatic teller machine), executing a step S50; S40, transferring accounts through the mobile phone to the mobile phone; S50, carrying out trading appointment, wherein the appointment contents comprise telephone numbers of payers, withdrawn amounts and effective withdrawing time; and S60, inputting appointment contents on the ATM and withdrawing the cash. The trading method for implementing the payment by the transfer of accounts and the cash withdrawing without the card has the advantages of being good in portability and good in practicability.
Owner:PING AN BANK CO LTD
System and method for security authentication via mobile device
InactiveUS20150200936A1Improve user convenienceEnsure safetyUser identity/authority verificationSecurity arrangementSecurity authenticationMobile authentication
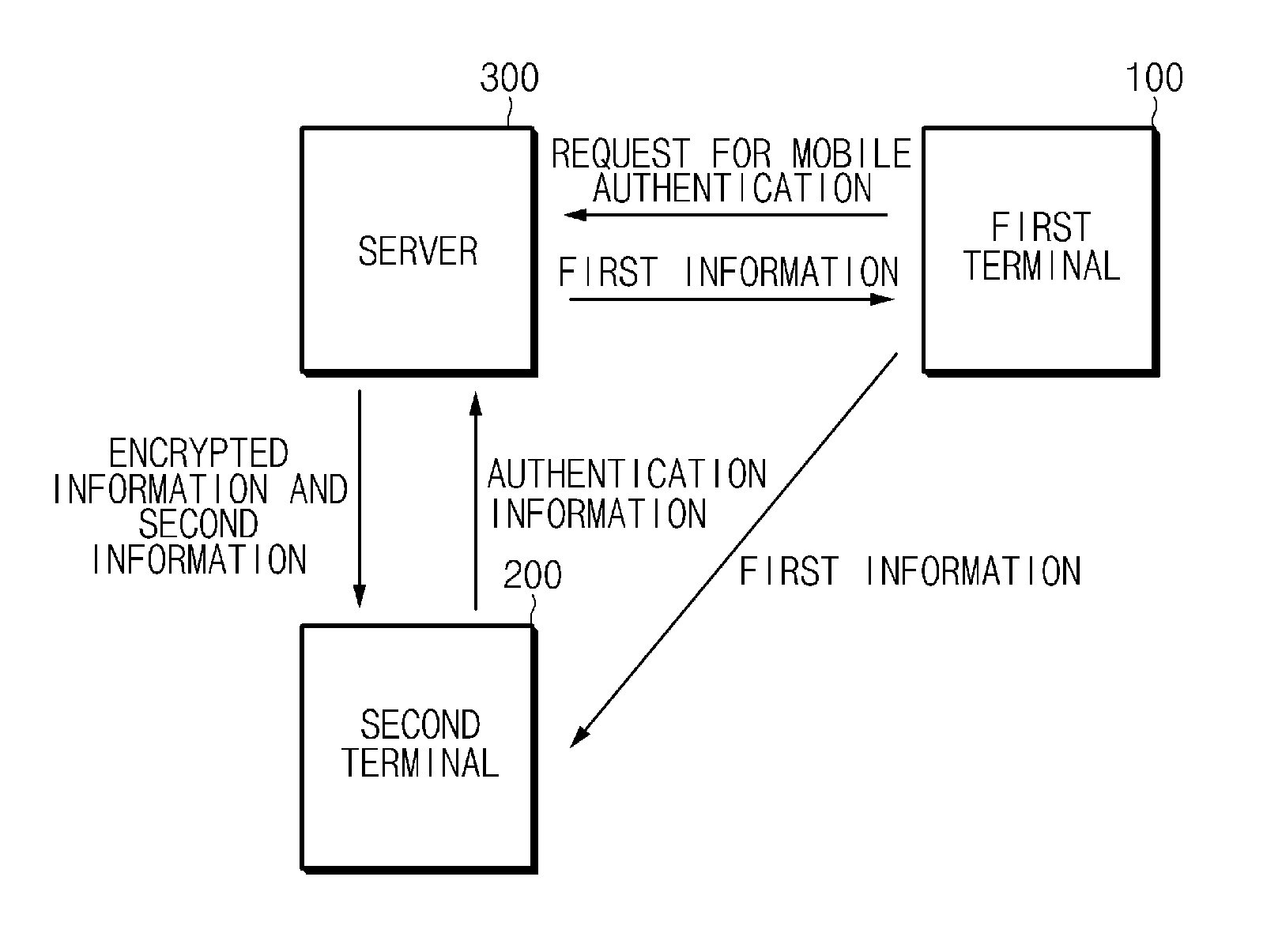
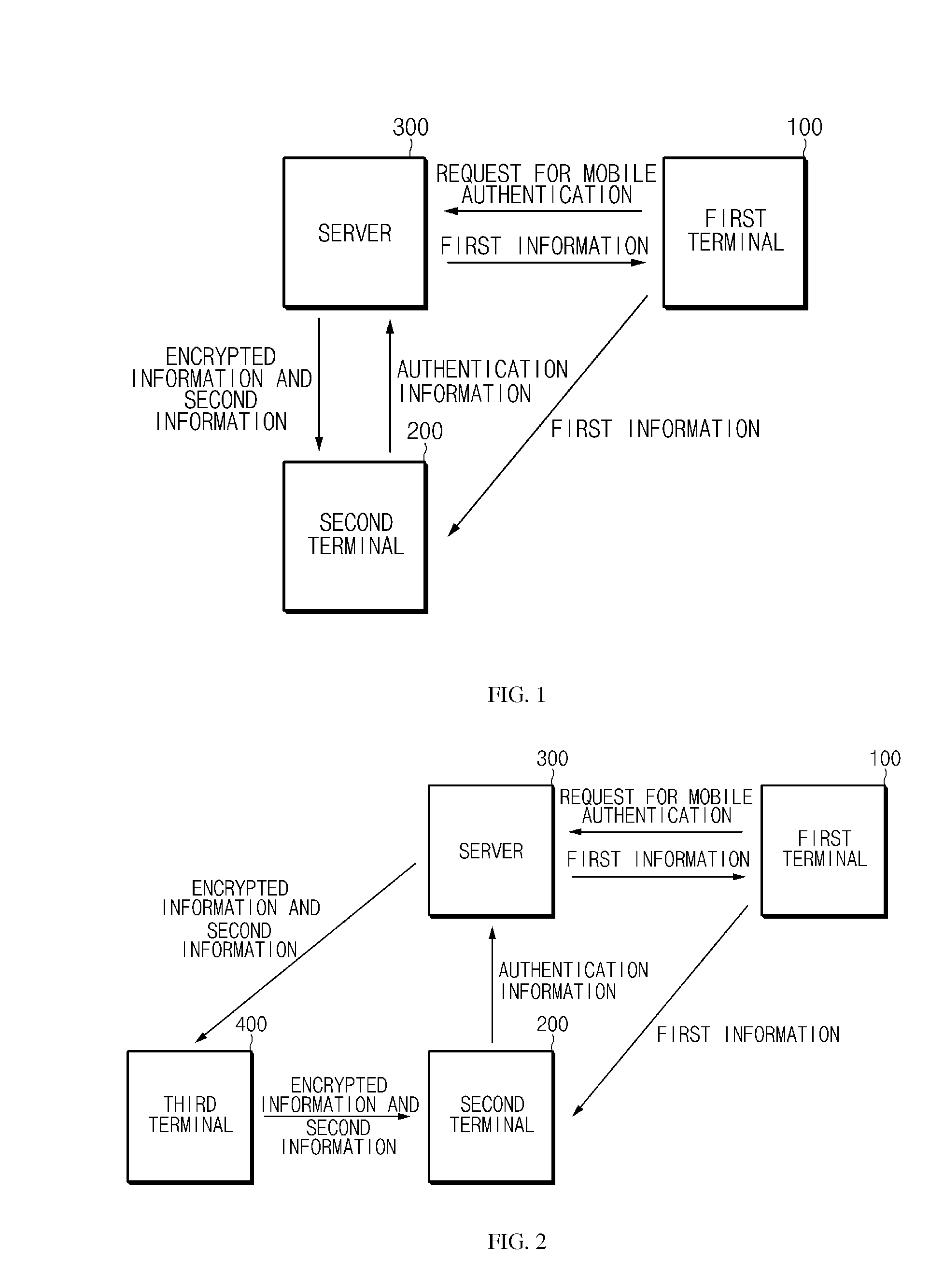
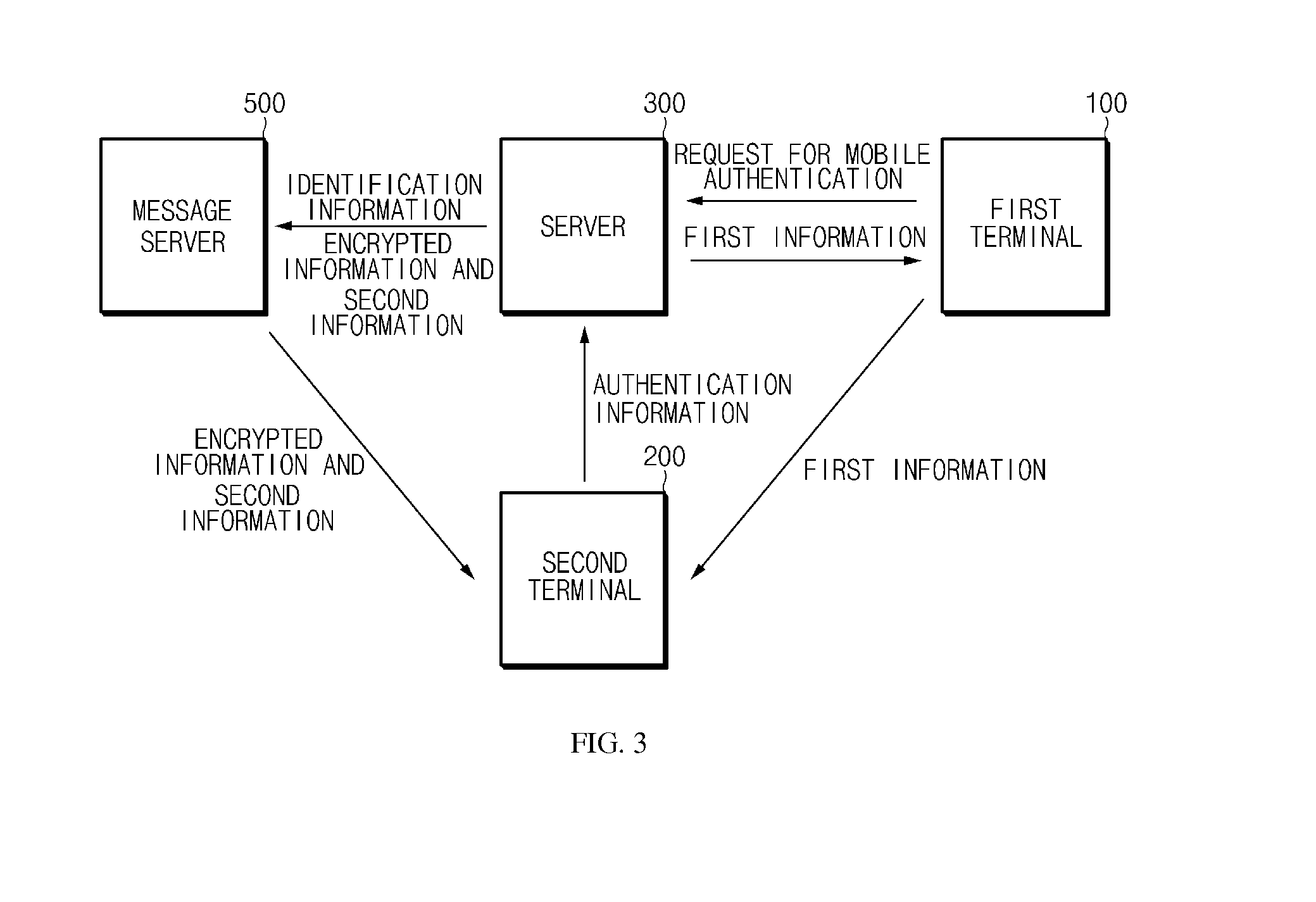
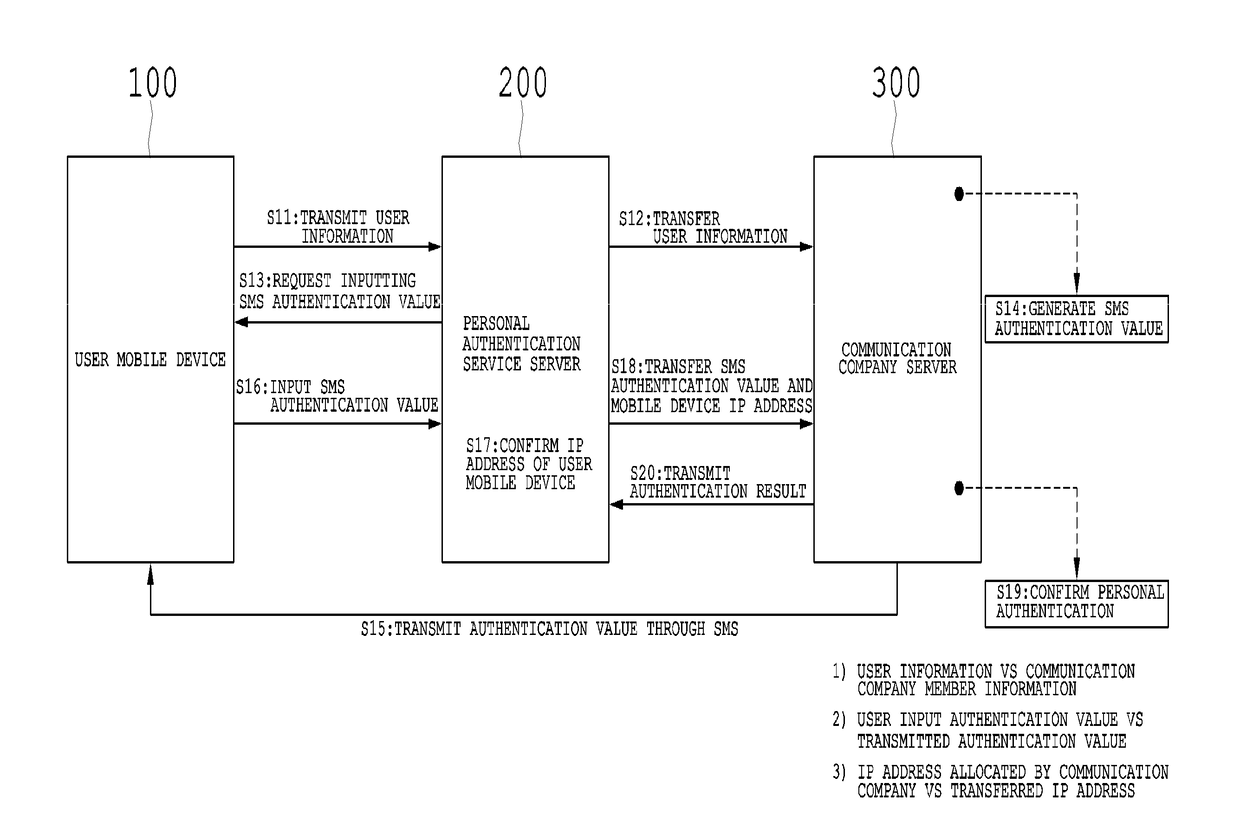
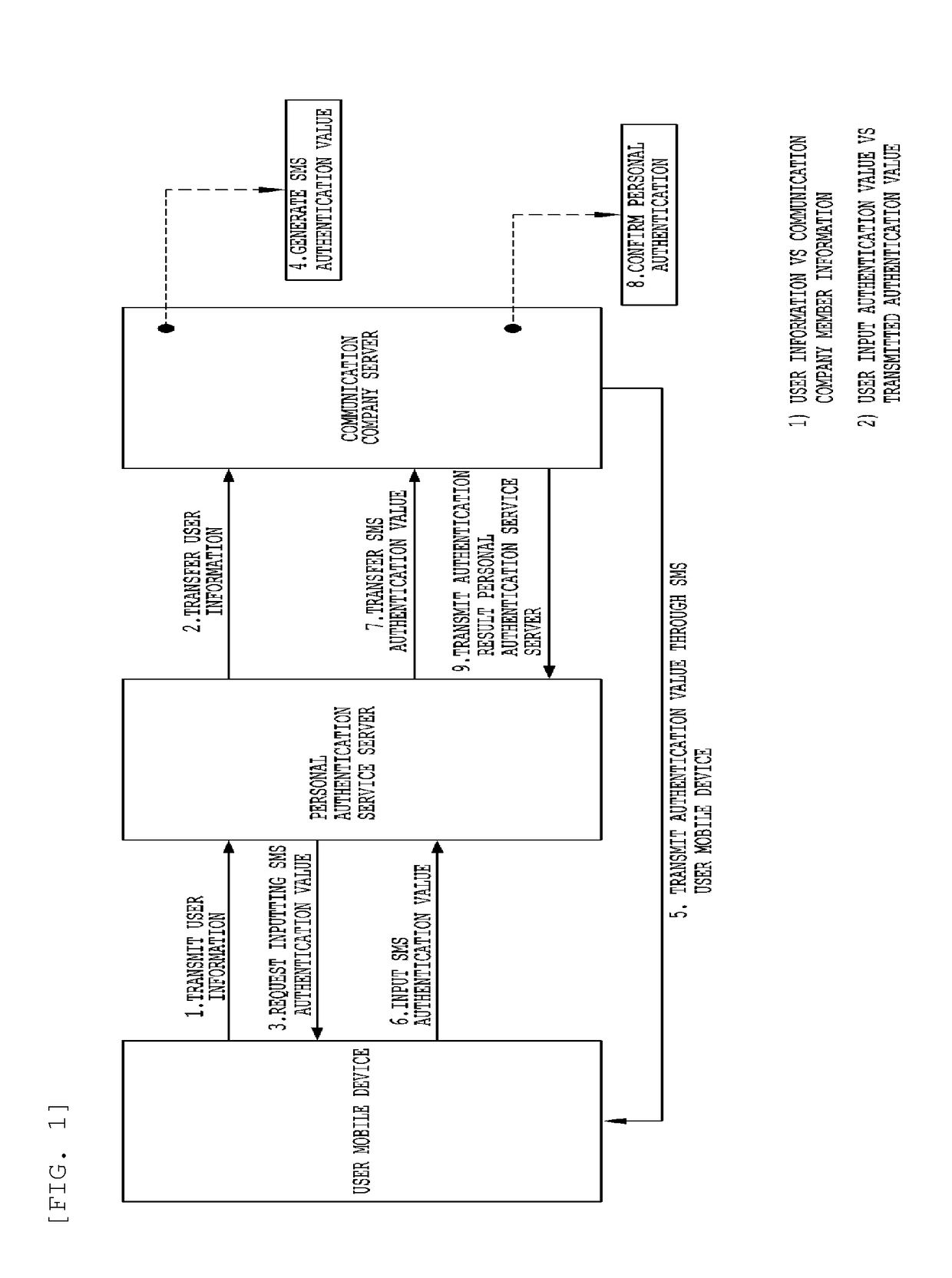
Disclosed are a system for security authentication via a mobile device, which includes: a first terminal of a user which requests mobile authentication; a server which generates authentication information and a key for encryption, encrypts the authentication information with the key, and divides the key into first information and second information to transmit the first information to the first terminal and transmit the second information and the encrypted information to a second terminal of the user; and the second terminal which acquires the first information from the first terminal, generates the key based on the first information and the second information, and acquires the authentication information by using the generated key.
Owner:ELECTRONICS & TELECOMM RES INST
Secure and convenient mobile authentication techniques
ActiveUS9361619B2Key distribution for secure communicationDigital data authenticationTrusted ComputingMobile authentication
Owner:CA TECH INC
Mobile authentication framework
ActiveUS20110265173A1Digital data processing detailsMultiple digital computer combinationsWeb serviceMobile authentication
Disclosed are apparatus and methods for associating a mobile device with a web service or a user account. A unique code is displayed on the mobile device. The unique code is associated with a user account or web service to be utilized with the mobile device. Instructions for a user to enter the unique code in an authentication process via an authentication portal of a management device are also displayed. After it is determined that a user has performed the authentication process, any user identification, which has been associated with the unique code, is then obtained from the management device. The obtained user identification is then stored for use by the mobile device. After user identification has been obtained and stored, the stored user identification is used for the mobile device to participate in an authentication process for authorizing the mobile device to utilize a web service or user account associated with the user identification. The authentication process is participated in by the mobile device without requiring input from the user during such authentication process.
Owner:VERIZON PATENT & LICENSING INC
Mobile authentication system based on intelligent mobile phone
InactiveCN101304569AStrong computing powerHigh speedUser identity/authority verificationRadio/inductive link selection arrangementsOperational systemMobile authentication
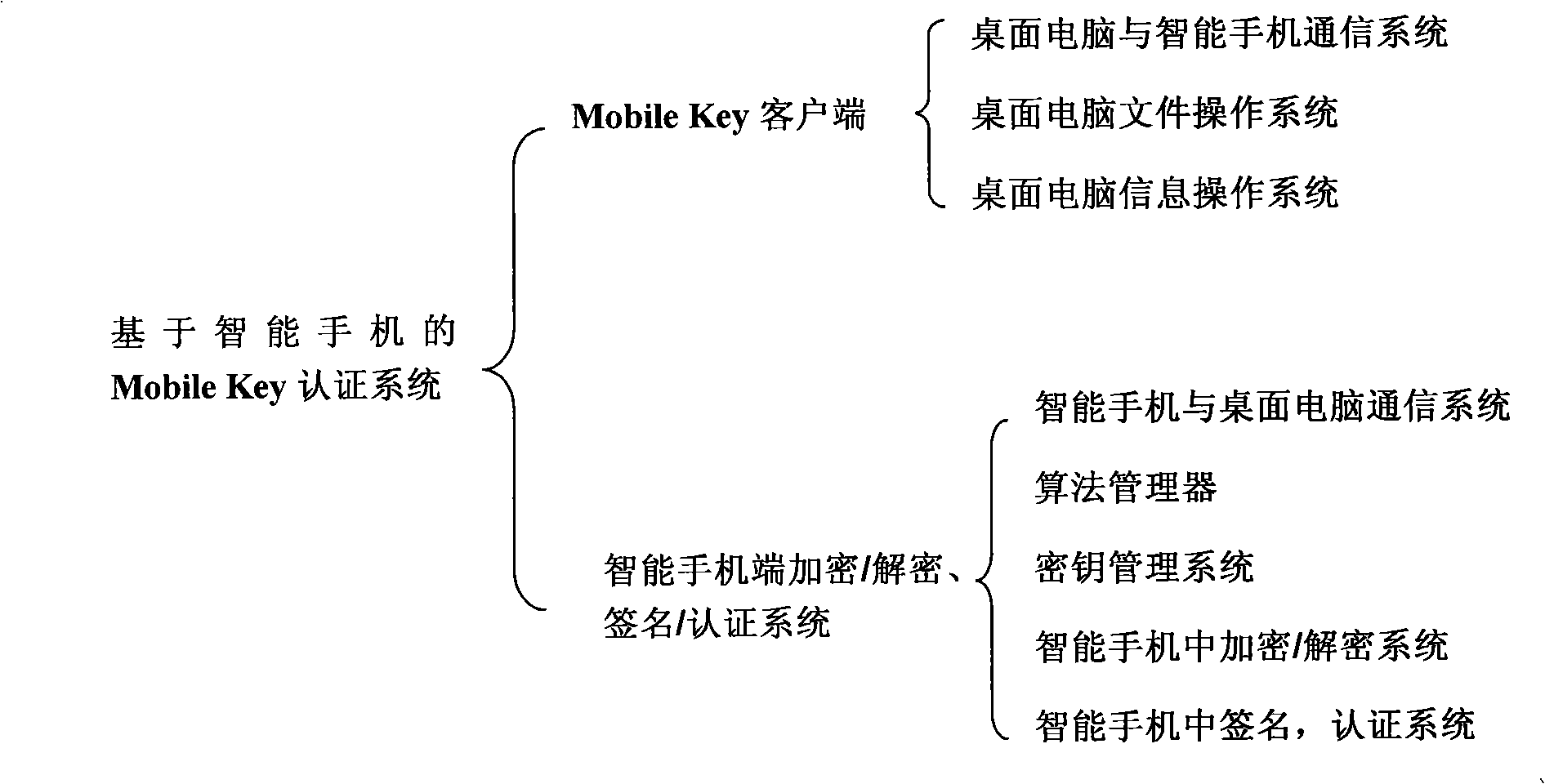
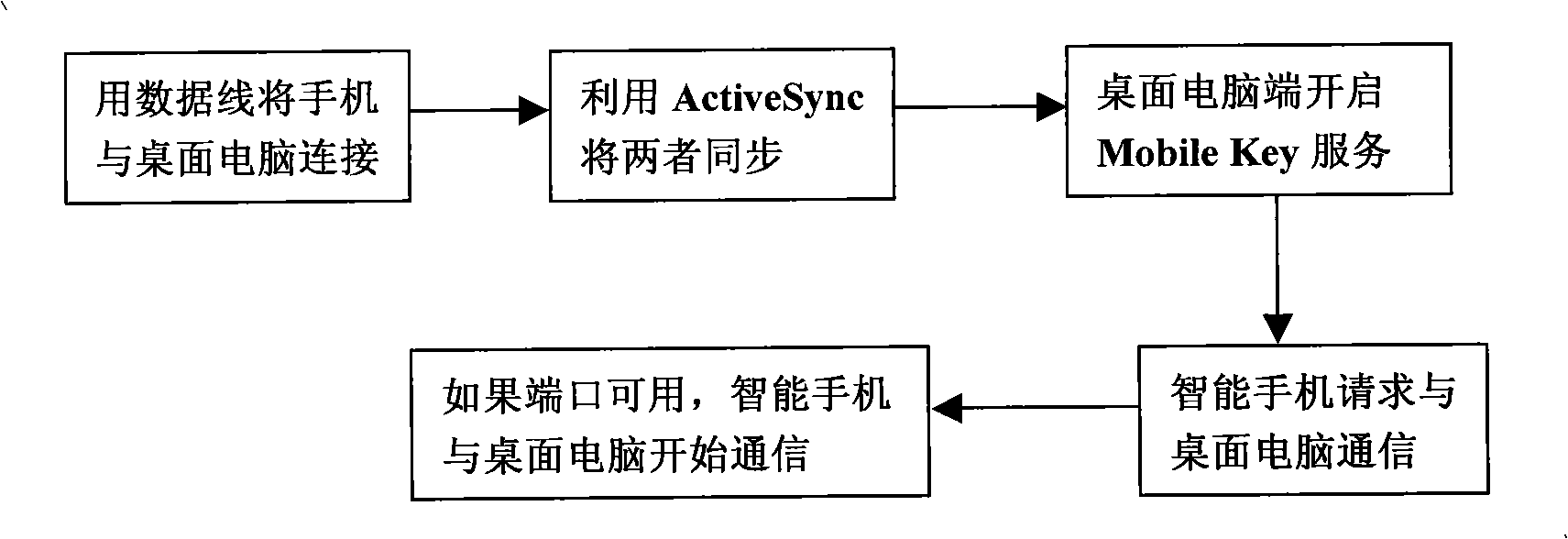
The invention discloses a system combined with smartphones of carrying out digital signature and certification, file encryption and decryption by utilizing mobile key technology, which saves user keys or certificates on the smartphones and also carries out the processes of signature / certification, encryption / decryption on the smartphones. The invention mainly uses a smartphone of Windows mobile operating system, a desktop computer software module and a smartphone software module. Firstly, a mobile key client is designed and realized on the desktop computer, including file encryption and decryption files, office signature, and certification Plug-ins. Then, a security system of mathematical manipulation of digital signature, certification, file encryption / decryption, etc. is designed and realized on the smartphone. Beside the inherent advantages of a USB key of convenient use, high security, etc., the invention also has multiple advantages that the USB Key does not have, such as, rapid arithmetic speed, long key support, supporting the processing of overlarge files, good sharing performance, high security and better expandability.
Owner:SUN YAT SEN UNIV
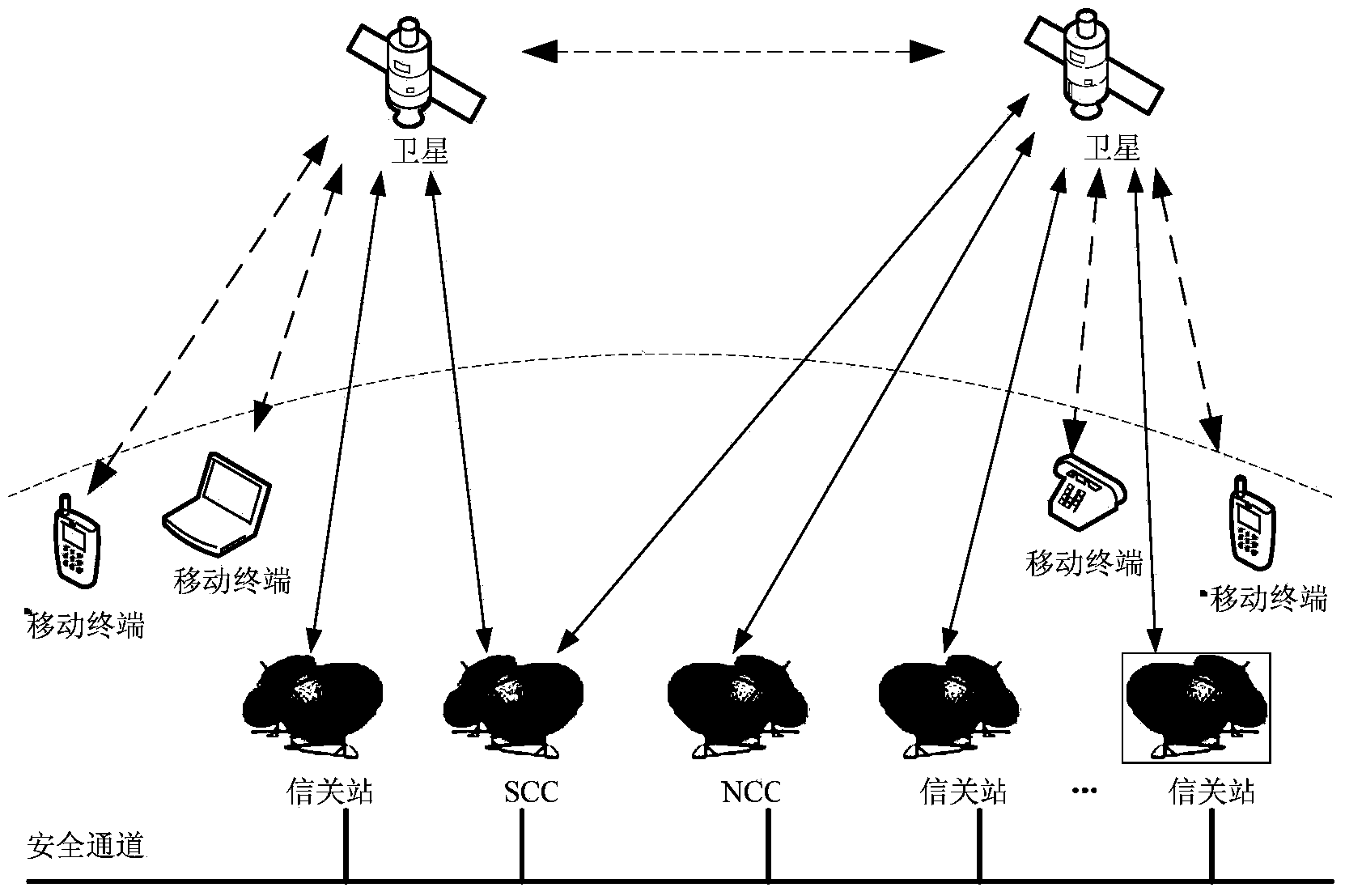
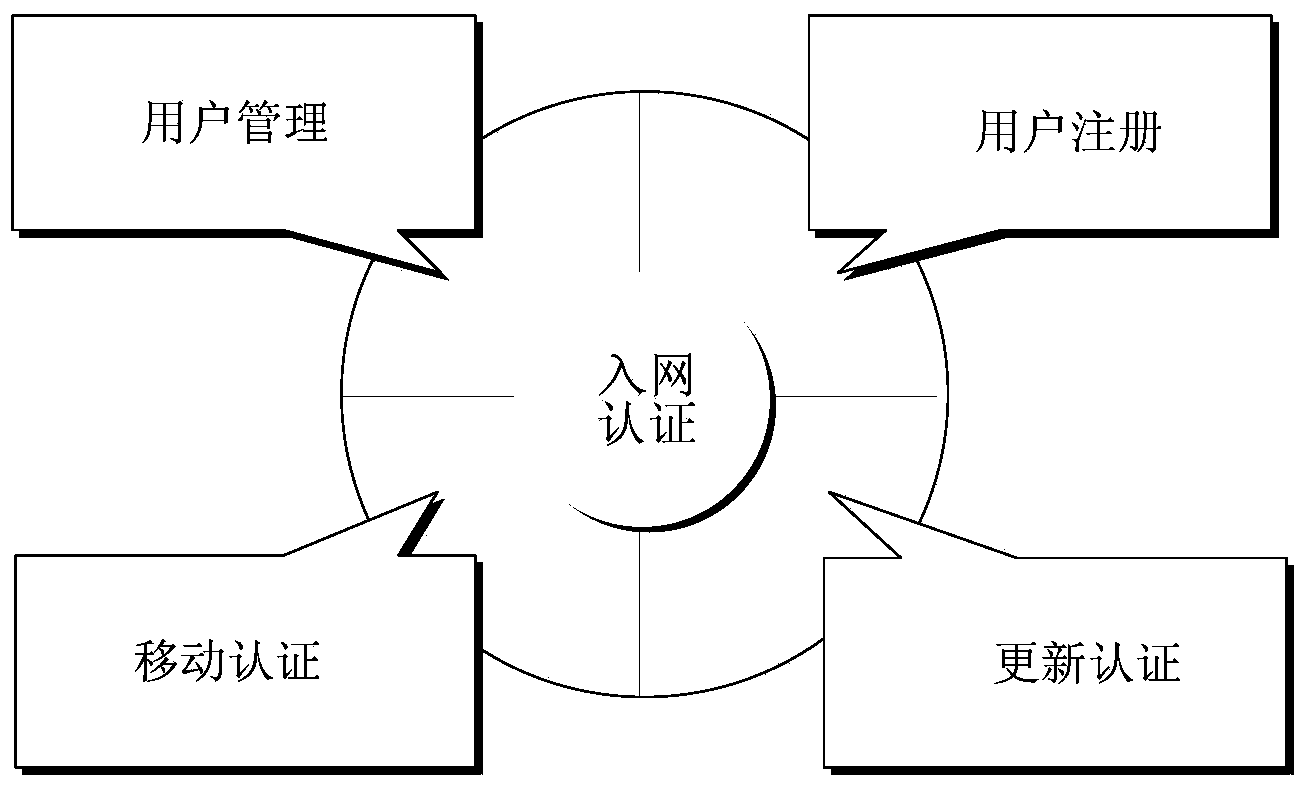
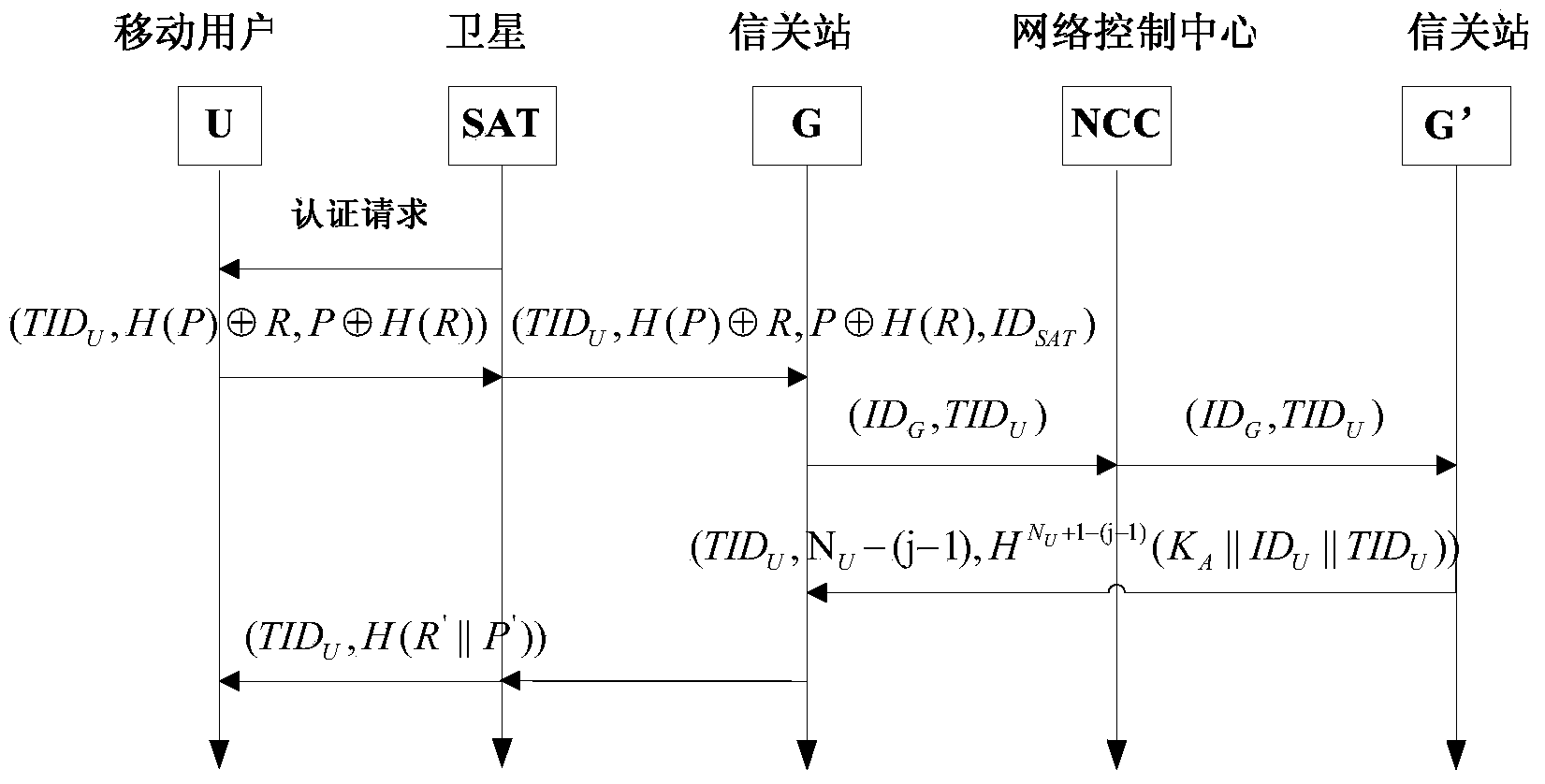
Network access authentication method applicable to satellite mobile communication network
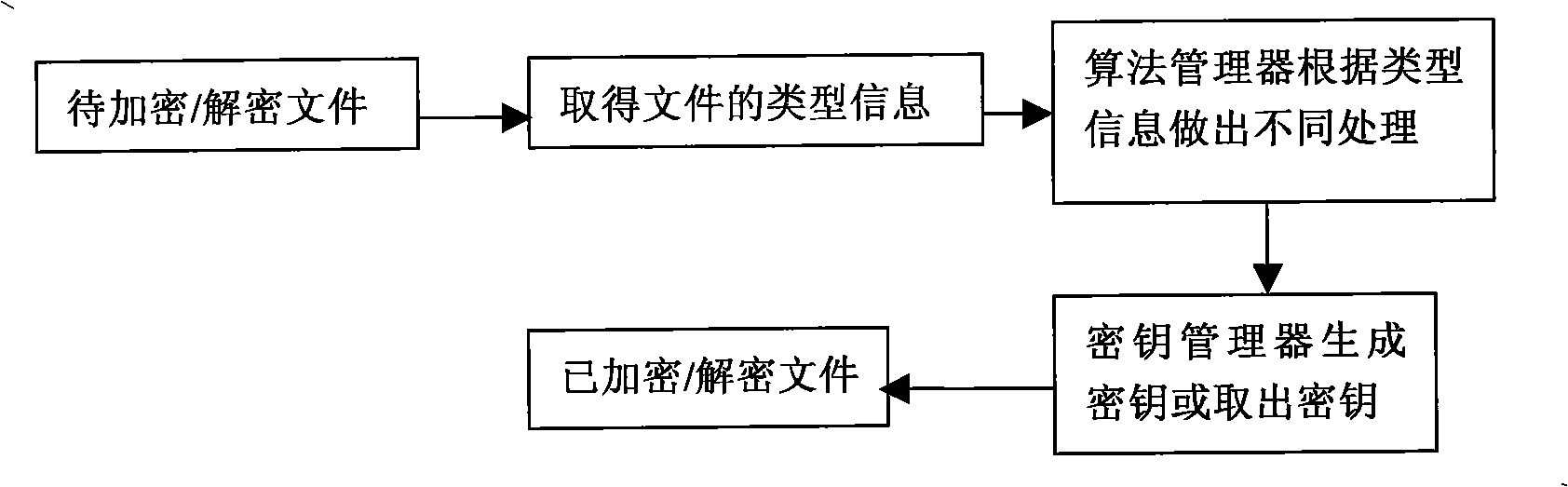
InactiveCN104038937AImprove securityReduce authentication computing loadSecurity arrangementNetwork controlMobile authentication
The invention relates to a network access authentication method applicable to a satellite mobile communication network. The network access authentication method comprises four steps of user registration, user management, mobile authentication and update of authentication; an effective network access authentication protocol is of great importance for the security of the satellite mobile communication network. The network access authentication method is characterized in that the authentication role of a gateway station is emphasized and the authentication calculation load of an NCC (Network Control Center) is reduced; common attacks such as masquerading, tampering and replay of any party can be resisted, and meanwhile, integrity protection on the transmitted data is realized, and therefore, the security of the satellite mobile communication network is greatly improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
System for security checking or transport of persons by an elevator installation and a method for operating this system
ActiveUS7620817B2Improve reliabilitySimple to useDigital data processing detailsComputer security arrangementsIdentification deviceSecurity check
A system for security checking or transport of persons by an elevator installation and to a method of operating this system wherein in a person is authenticated by at least one authentication signal. At least one mobile authentication device carried by the person detects an authentication signal of the person and checks it with at least one person reference. In the case of correspondence of the authentication signal and the person reference, at least one identification code is provided. The identification code is detected by a stationary recognition device and assigned to a predefined travel destination or to an input travel destination input at the recognition device by the person.
Owner:INVENTIO AG
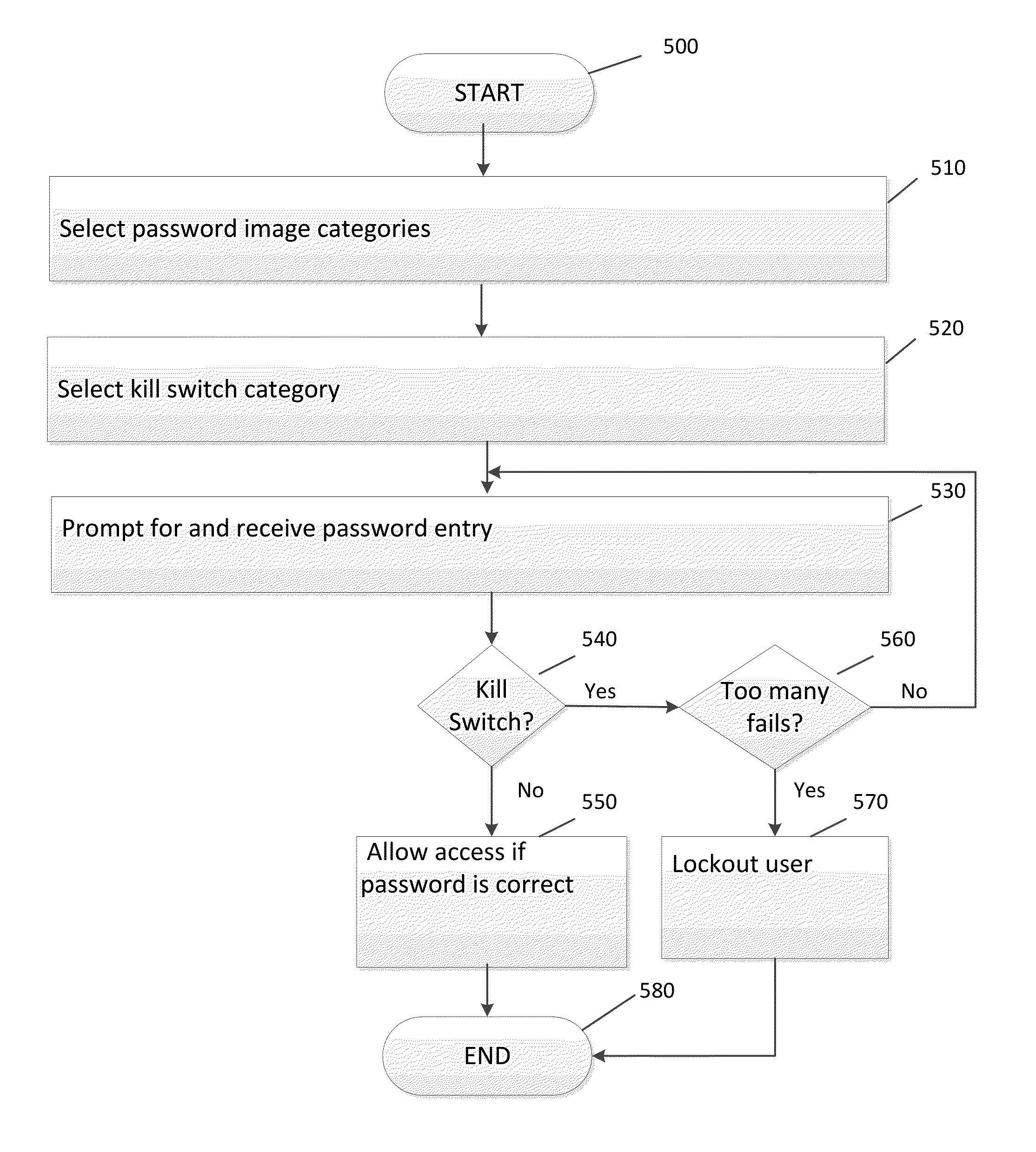
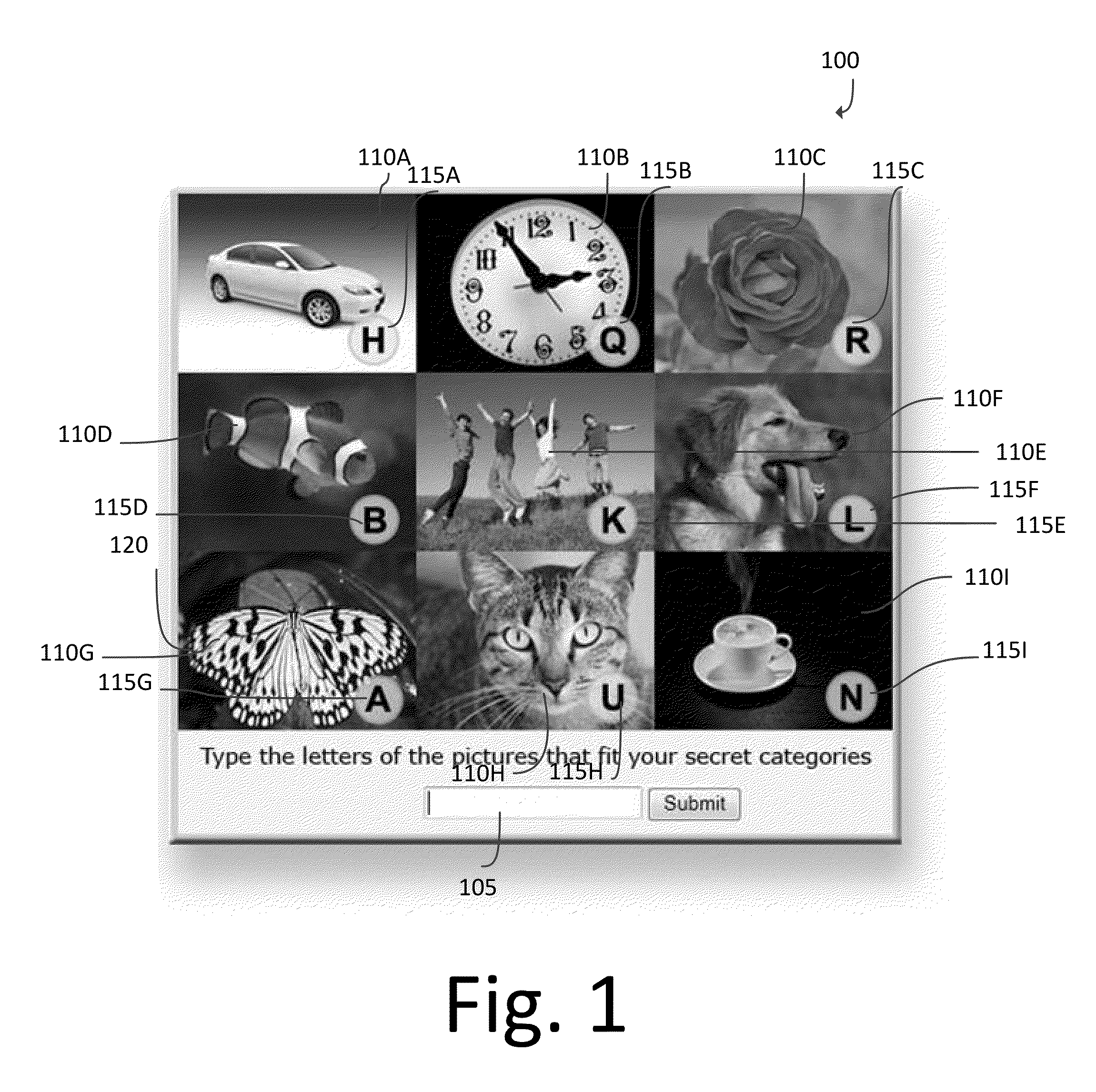
Kill switch security method and system
InactiveUS20130117813A1Improve securityReduce probabilityDigital data processing detailsUser identity/authority verificationWeb sitePassword
The present invention provides, in at least one embodiment, a system and method to bolster website and mobile authentication providing an additional security layer for access to password protected information. An authorized user is asked to select a kill switch, including one or more image categories or alphanumeric characters that the authorized user would never select while inputting their password. If the kill switch is entered once or too many times, as defined and specified ahead of time by a set of rules and conditions, during password entry, the kill switch kills the password entry operation. User input can be evaluated at the time of entry according to these rules by a rule processing decision engine. Killing the operation can include taking one or more actions, such as locking out the user, sending a notification of breach, and cataloging information about the source of the breach.
Owner:DEFENDERS OF THE AMERICAN DREAM LLC
Centralized authentication system
InactiveUS20090068987A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPersonalizationPassword
Centralized authentication systems are provided. A representative system, among others, includes an authentication registration system, a content provider and an internet server. The mobile authentication registration system resides on a content provider, and is operable to receive a single identification number and password from a user independent of a platform the user is associated with, and determine that the identification number and password combination provided by the user is associated with a registered user. The content provider provides personalized content to any of a plurality of registered users on a plurality of platforms. The server receives a connection request from a wireless device, sends an authentication request to the authentication registration system, and provides a personalized content from the content provider to said at least one device. Methods and other systems for multiple access portals are also provided.
Owner:AT&T INTPROP I L P
Method, Apparatus and Computer Program Product for Providing Key Management for a Mobile Authentication Architecture
InactiveUS20090232310A1Improve securityEncryption apparatus with shift registers/memoriesMultiple digital computer combinationsMobile authenticationComputer science
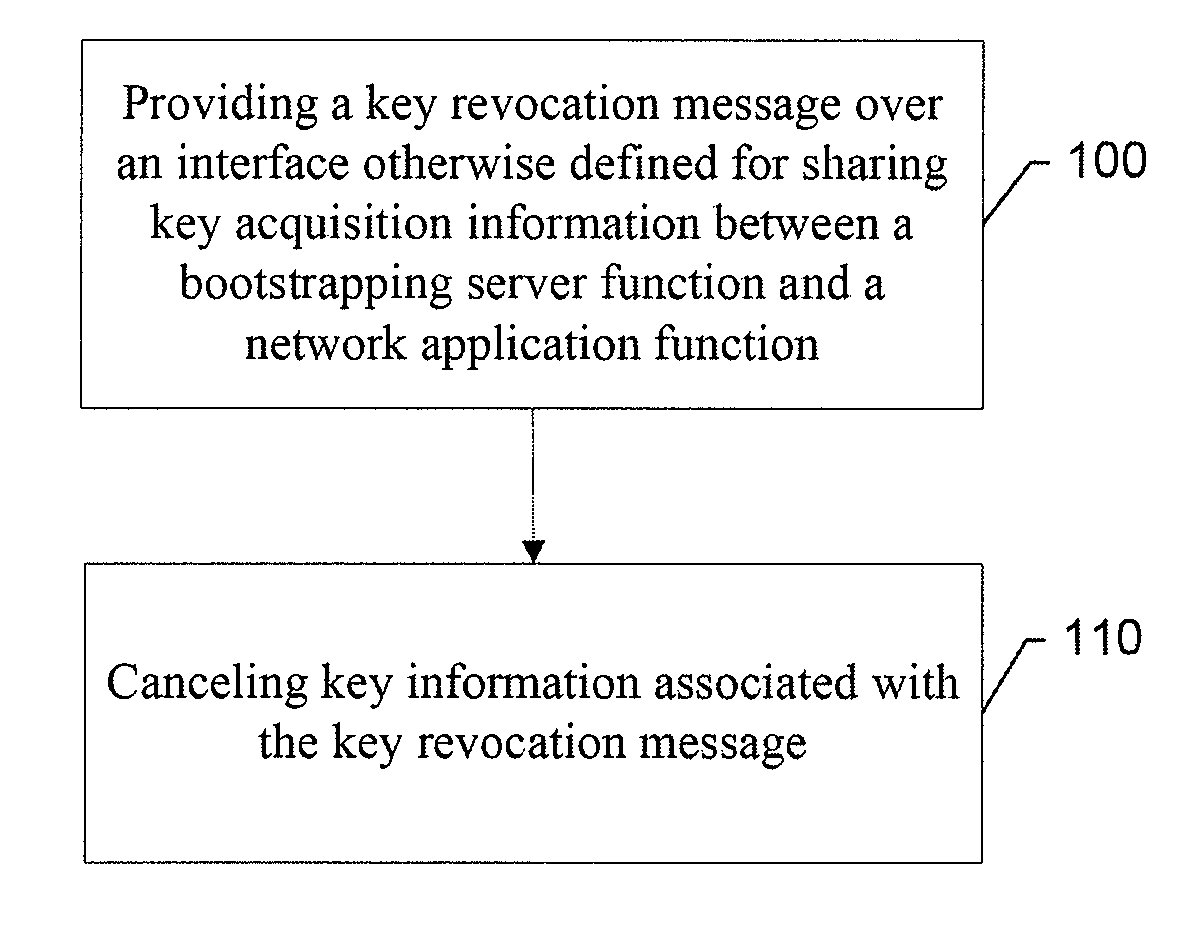
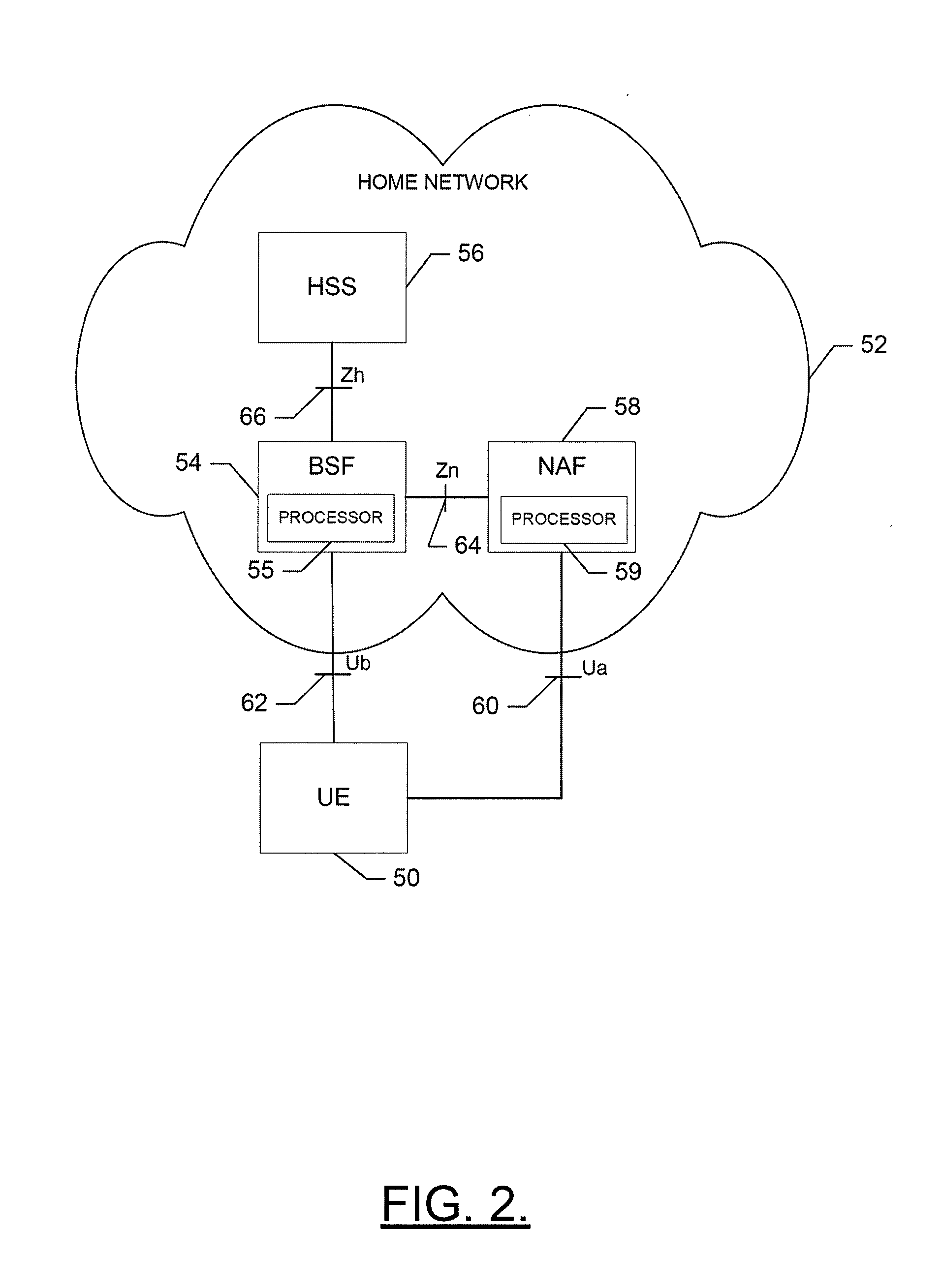
An apparatus for providing key management for a mobile authentication architecture may include a processor. The processor may be configured to provide a request for key revocation over an interface otherwise defined for sharing key acquisition information between a bootstrapping server function and a network application function, and cancel key information associated with the request for key revocation.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Handset sim card paster based mobile authentication method of banking businesses
InactiveCN101729537AEnsure safetyEnsure transaction securityUser identity/authority verificationMessaging/mailboxes/announcementsDigital signatureMobile authentication
The invention discloses a handset sim card paster based mobile authentication method of banking businesses. A paster which can store a user certificate and carry out digital signature is inserted into a handset sim card slot of a user; when the user initiates the fund change of a transaction account, a background transaction system sends transaction information to a mobile authentication gateway, and the mobile authentication gateway sends the transaction information to a handset of the user to request the digital signature; after a request is received by the paster and then displayed to the user, the user verifies the signature and then returns a signature result to the mobile authentication gateway and transmits the signature result to the background transaction system; and the background transaction system verifies the signature result and the content of the signature request and correspondingly operates the transaction account of the user after determining that the signature is effective. The mobile authentication method can request the digital signature of the user in time when user funds are changed, ensure the security of the user funds and provide the convenience when the user goes out and has non-repudiation property, thereby ensuring the transaction security of both parties.
Owner:CHINA ZHESHANG BANK
Method and device for identifying channel conflict
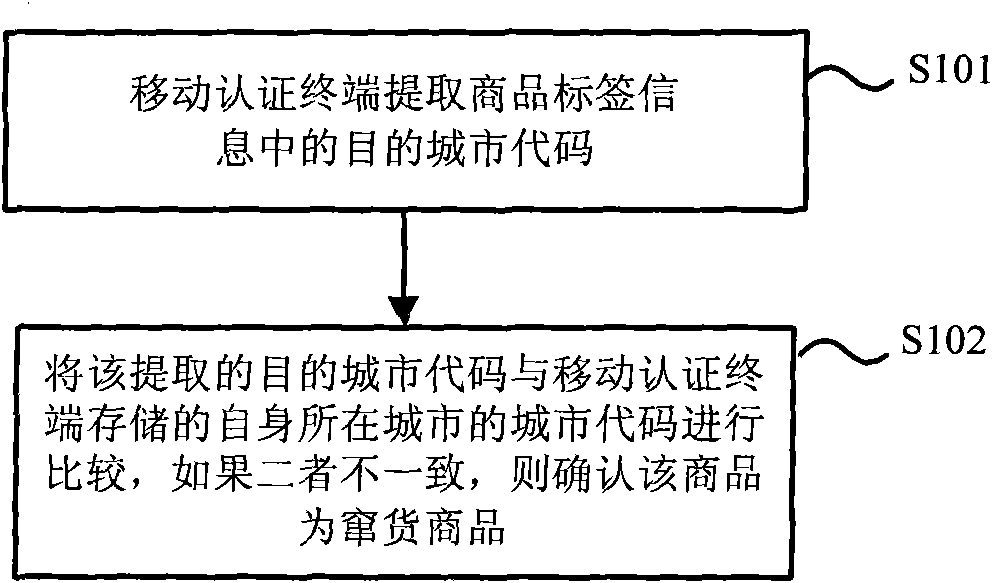
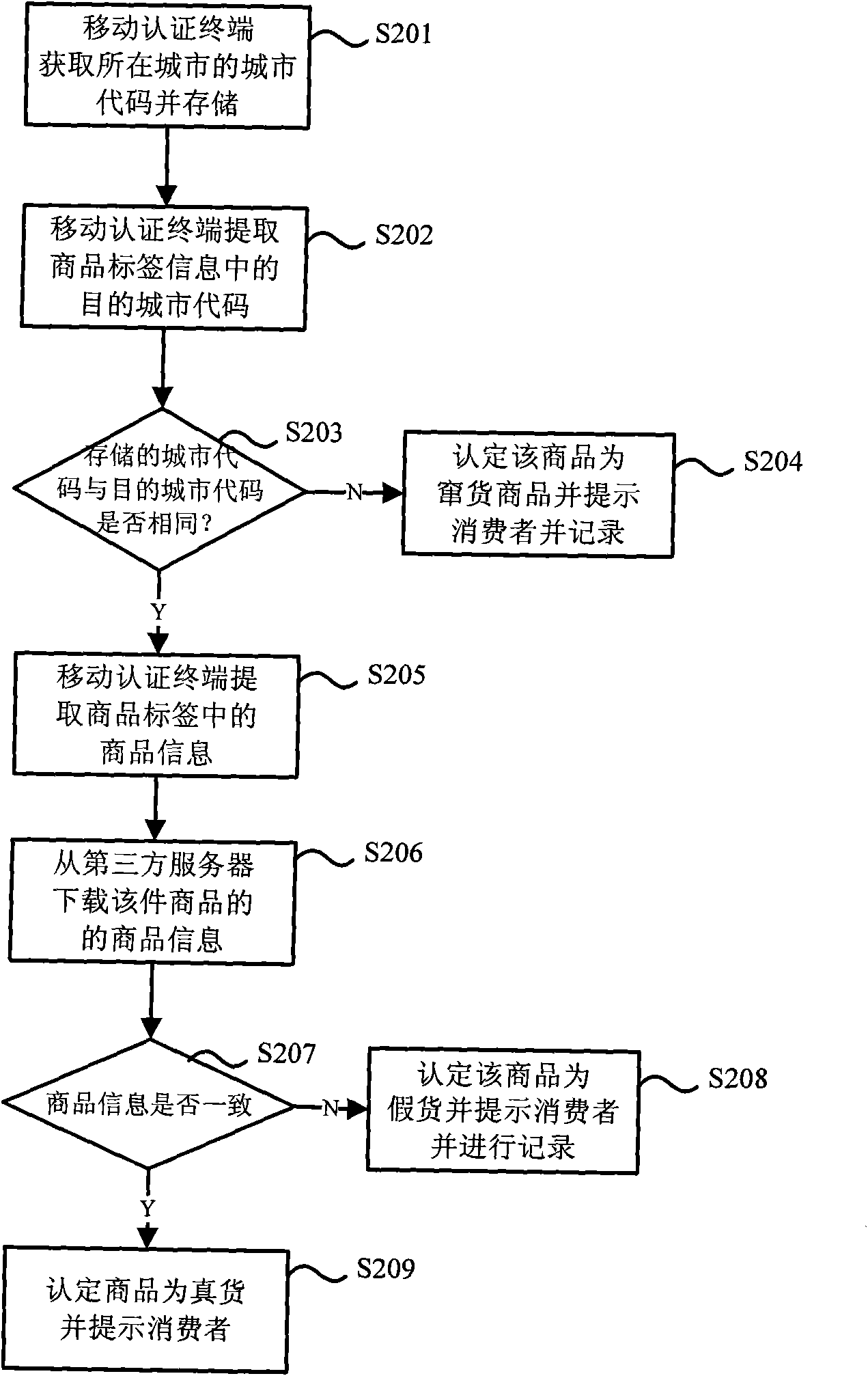
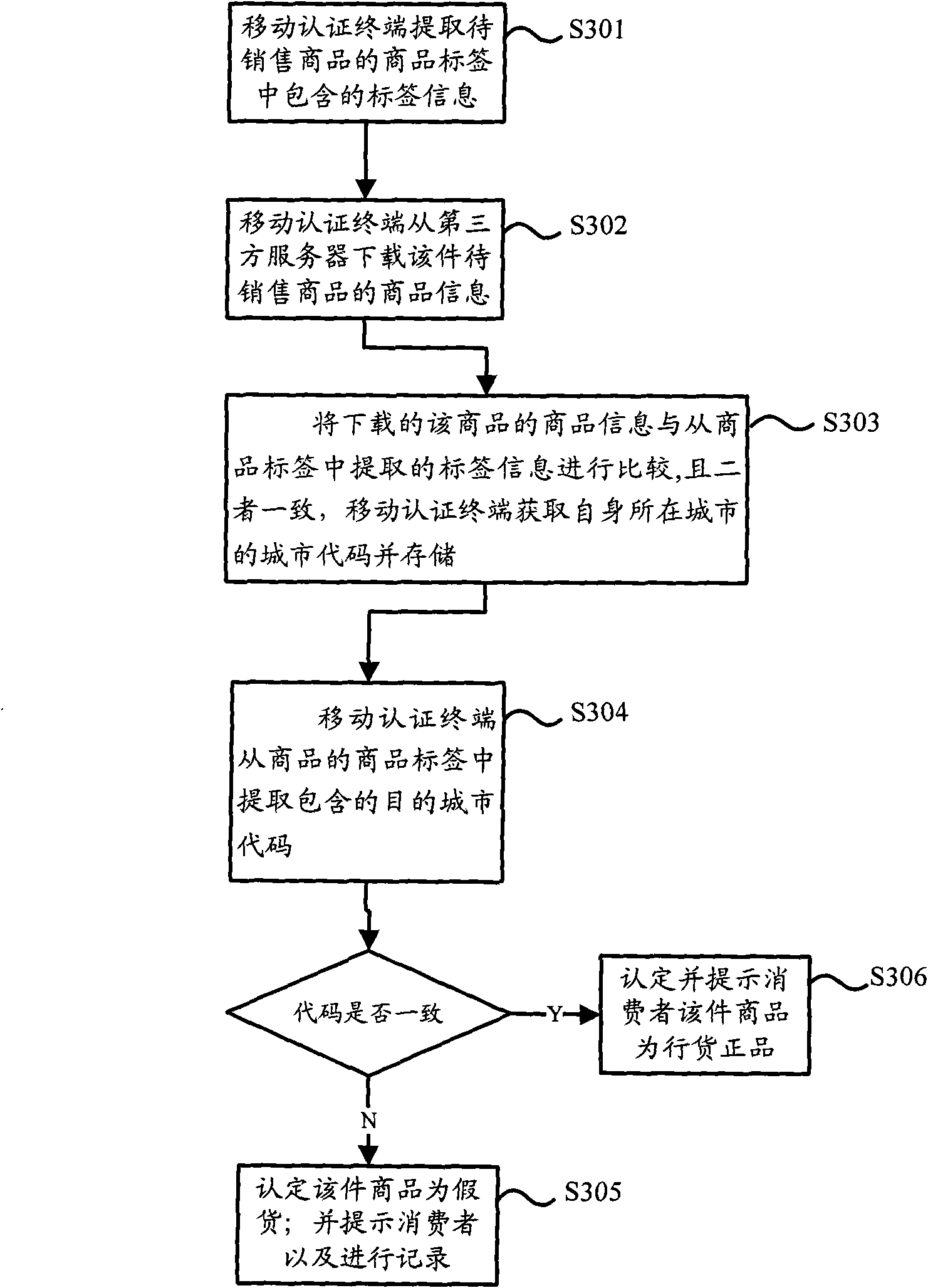
The invention discloses a method and a device for identifying channel conflict. The method for identifying the channel conflict comprises the following steps of: extracting destination city codes contained in label information of a commodity through a mobile authentication terminal; and when the extracted destination city codes are not consistent with the stored city codes by comparison, determining that the commodity is a channel conflict commodity. The method for identifying the channel conflict performs channel conflict authentication identification on each commodity in a sale link by using the mobile authentication terminal provided by a third party so as to effectively realize monitoring of the commodities entering the circulation domain and prevent the channel conflict selling behaviors of merchants of the circulation domain.
Owner:CHINA MOBILE COMM GRP CO LTD
Method and system for authentication
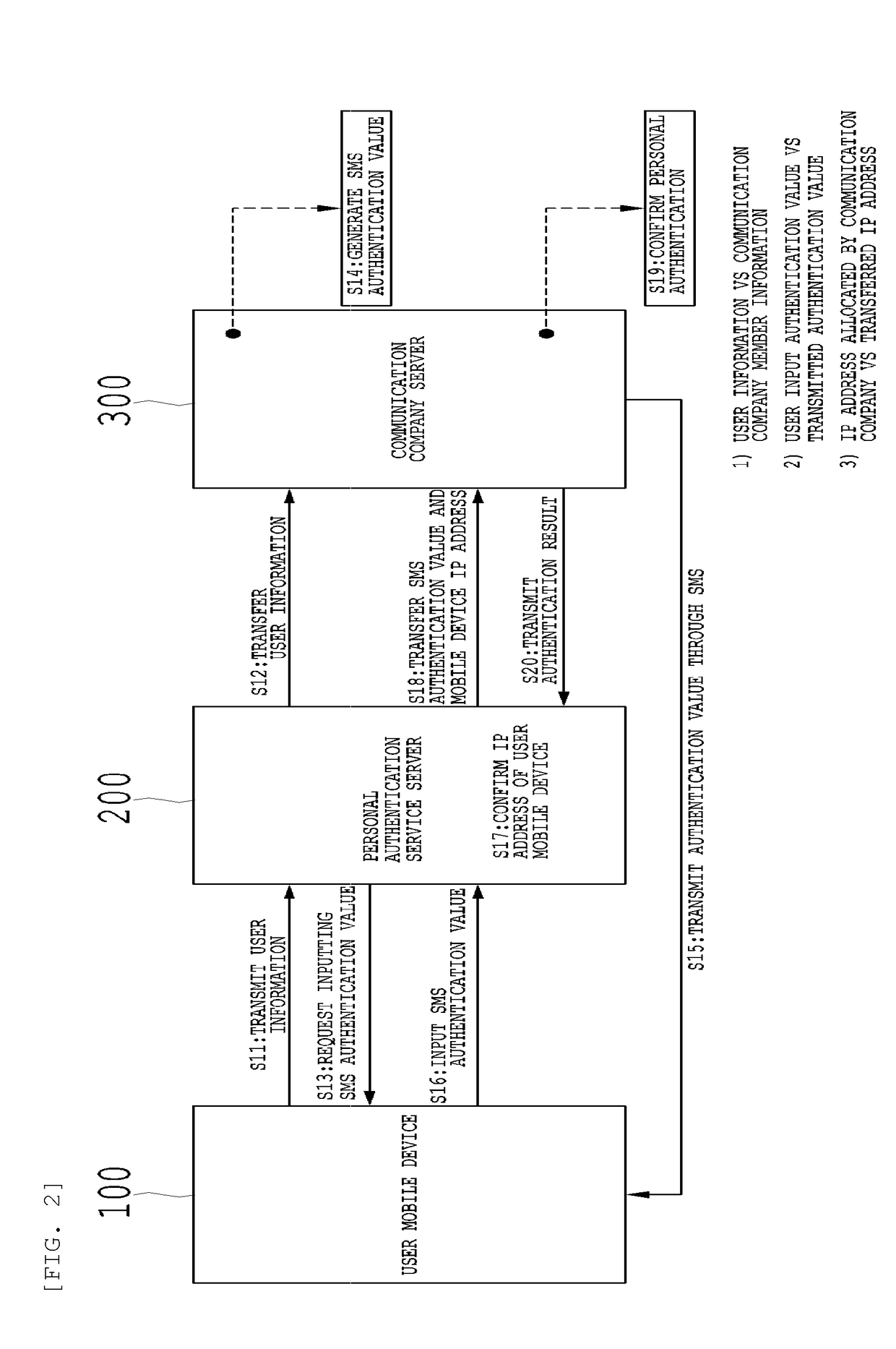
PendingUS20180219851A1Overcome limitationsSecure habitDigital data authenticationMessaging/mailboxes/announcementsPasswordMobile authentication
An authentication system performing user-centered authentication may include: an authentication service component acting as an authentication procedure of an online service server; and a mobile authentication agent component acting as the authentication procedure of an access terminal which accesses the online service server. Herein, the authentication service component may confirm a mobile authentication agent component corresponding to user information input from the access terminal as basic authentication information, transmit an authentication password value to each of the confirmed mobile authentication agent component and the online service server which the access terminal intends to access, and transmit an authentication success message to the online service server when a password verification value or an authentication agreement value corresponding to the authentication password value is received from the mobile authentication agent component.
Owner:ESTORM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com