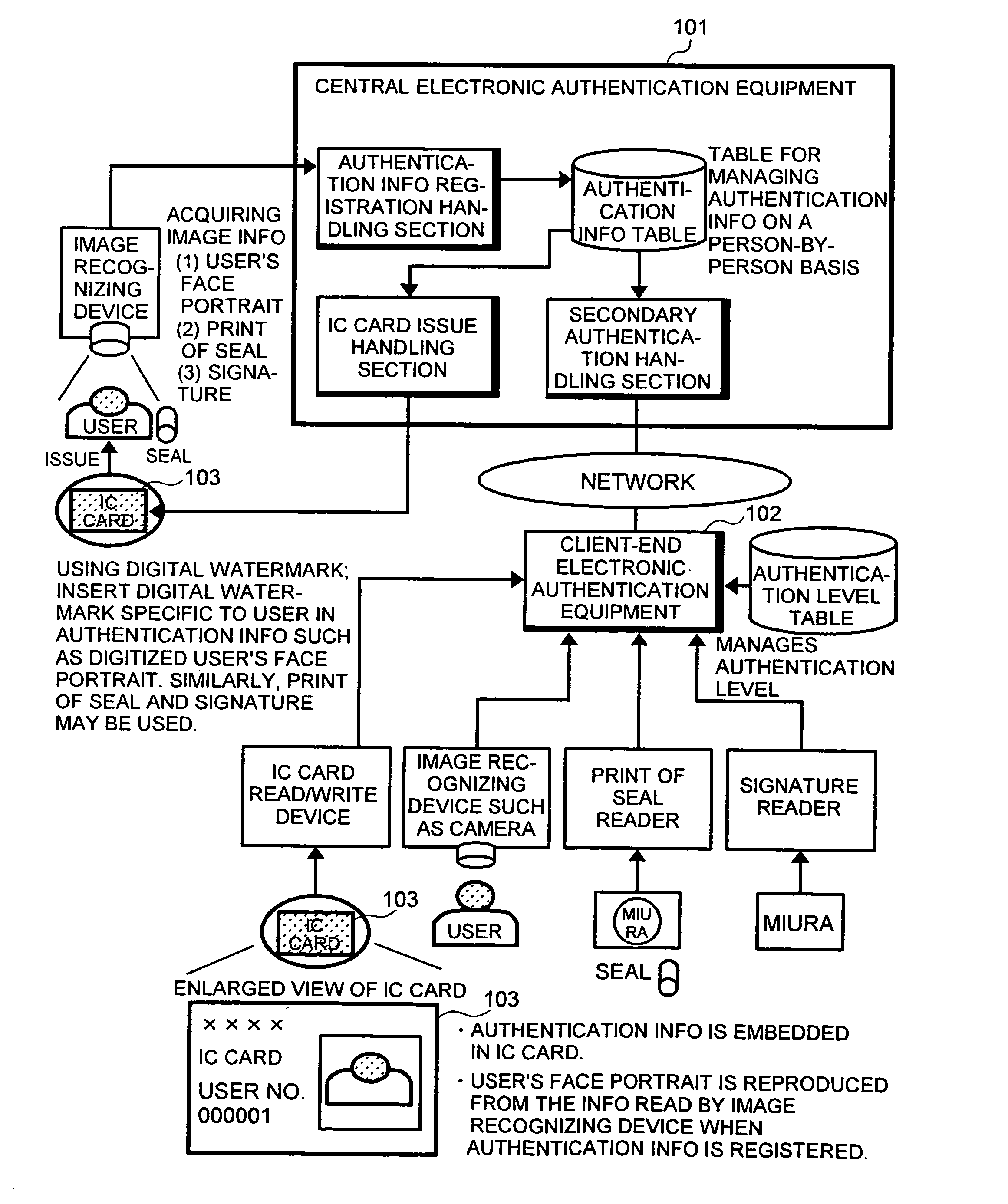
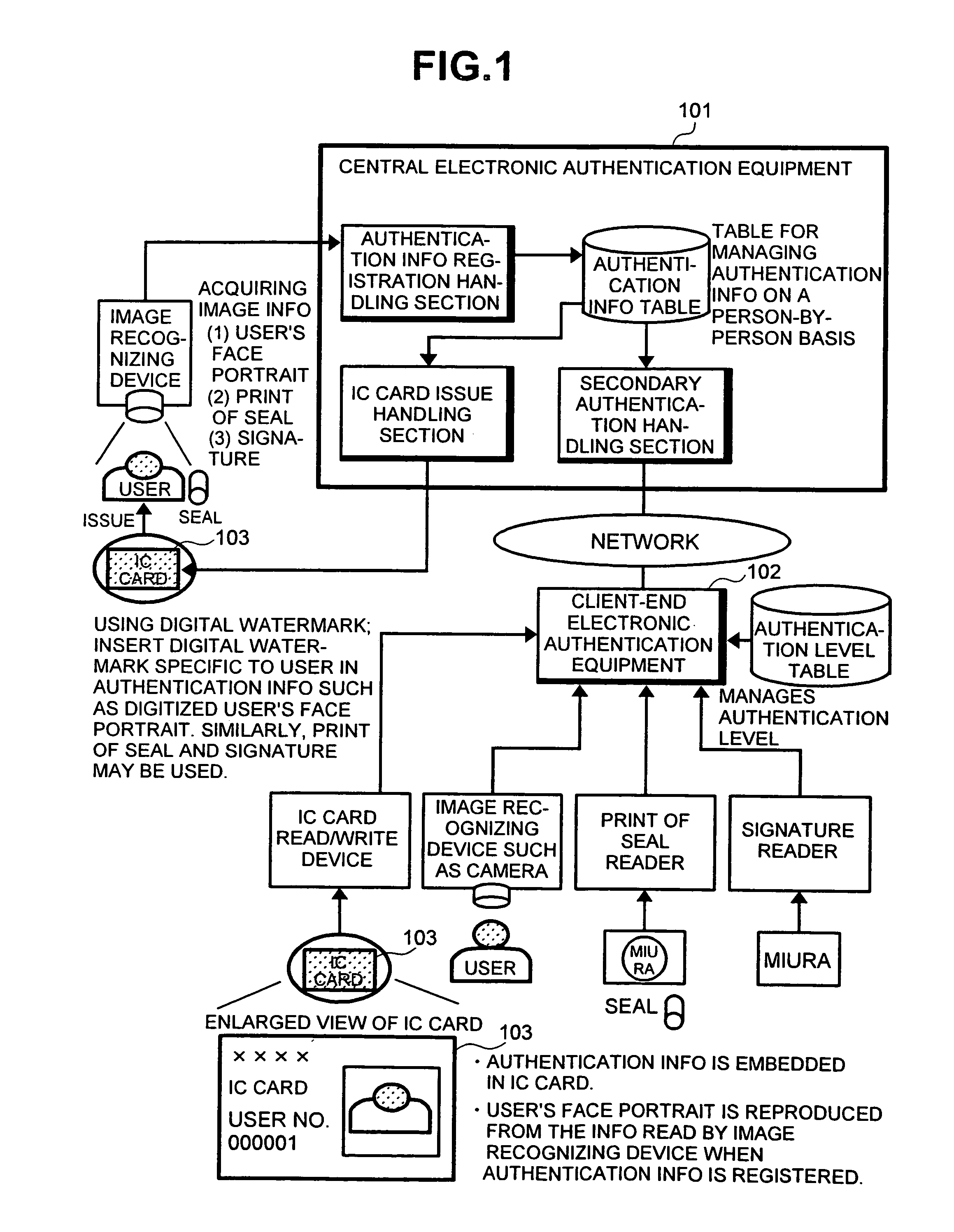
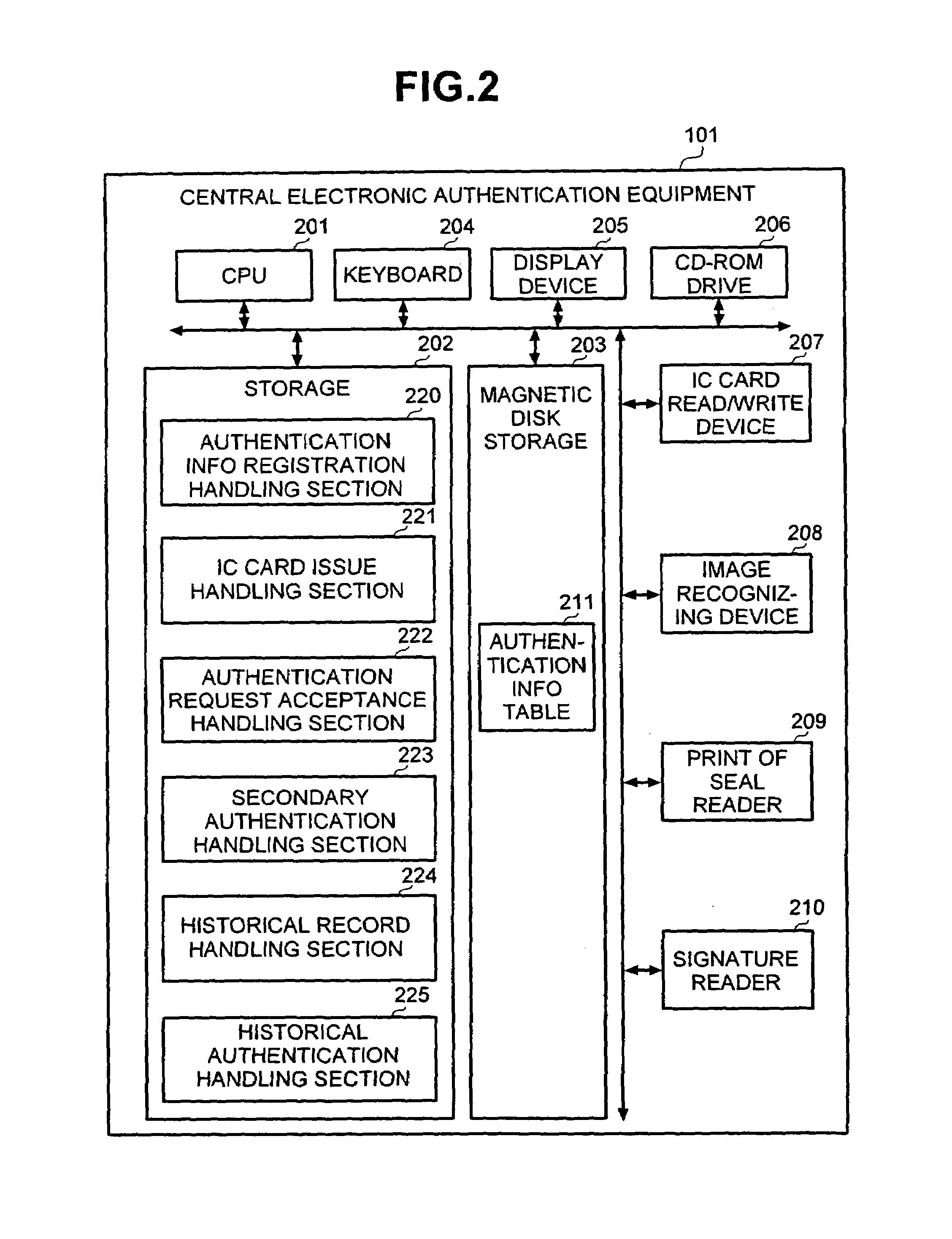
Patents
Literature
151 results about "Electronic authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
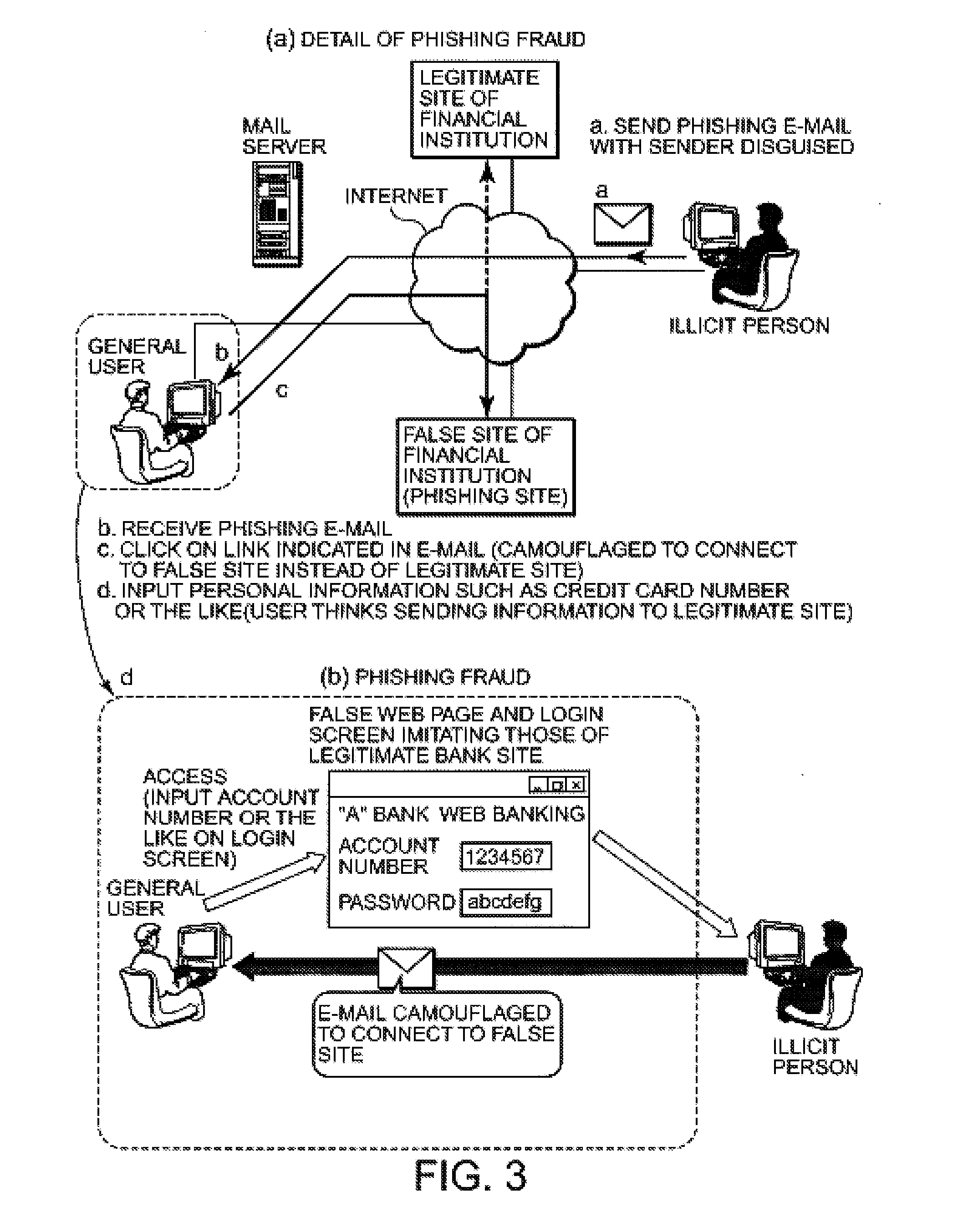
Electronic authentication is the process of establishing confidence in user identities electronically presented to an information system. Digital authentication or e-authentication may be used synonymously when referring to the authentication process that confirms or certifies a person's identity and works. When used in conjunction with an electronic signature, it can provide evidence whether data received has been tampered with after being signed by its original sender. In a time where fraud and identity theft has become rampant, electronic authentication can be a more secure method of verifying that a person is who they say they are when performing transactions online.
System and method for user enrollment in a secure biometric verification system
ActiveUS9721078B2User identity/authority verificationDigital data authenticationBiometric dataVerification system
Owner:ALCLEAR LLC
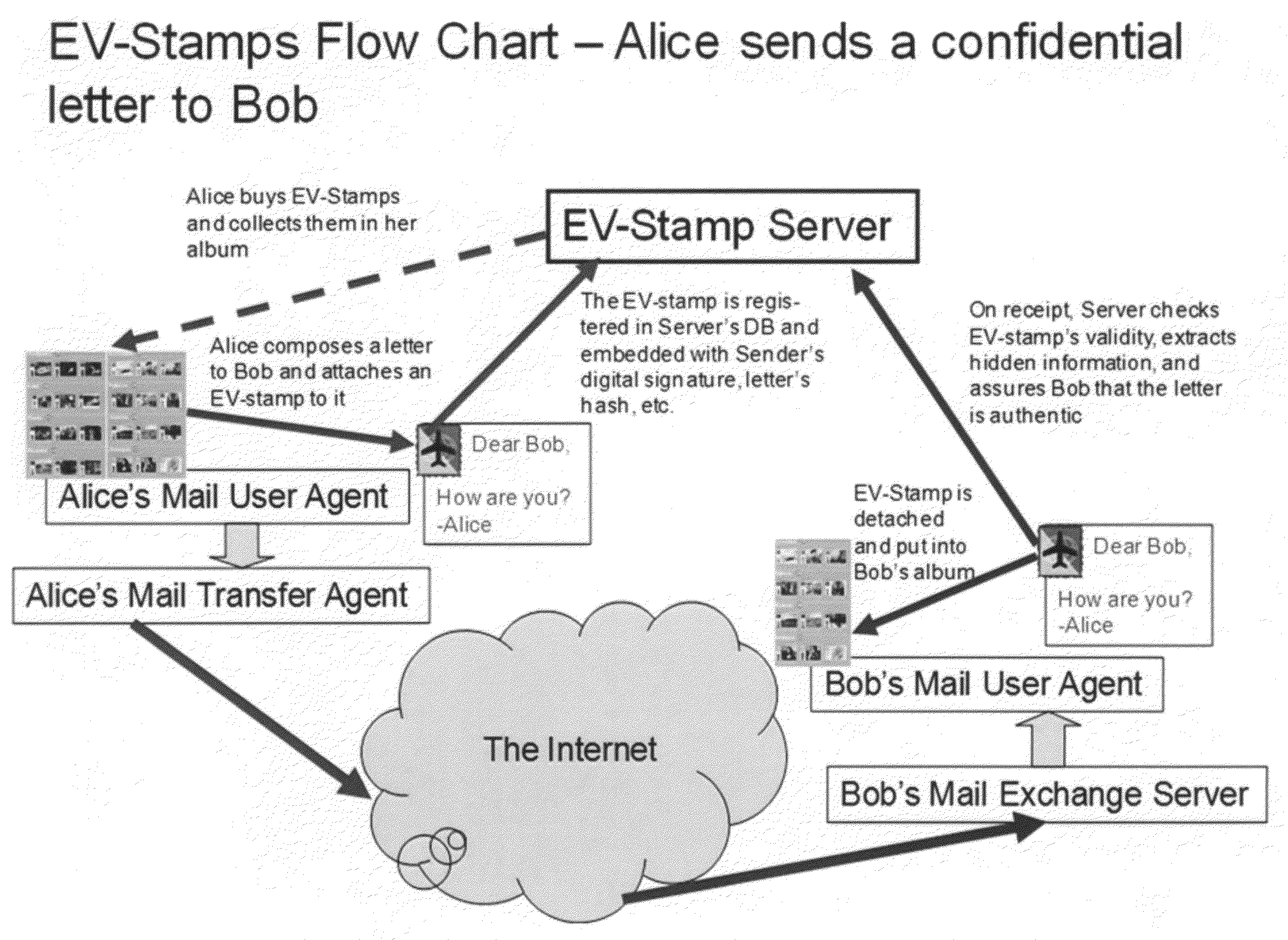
Electronic certification, identification and communication utilizing encrypted graphical images
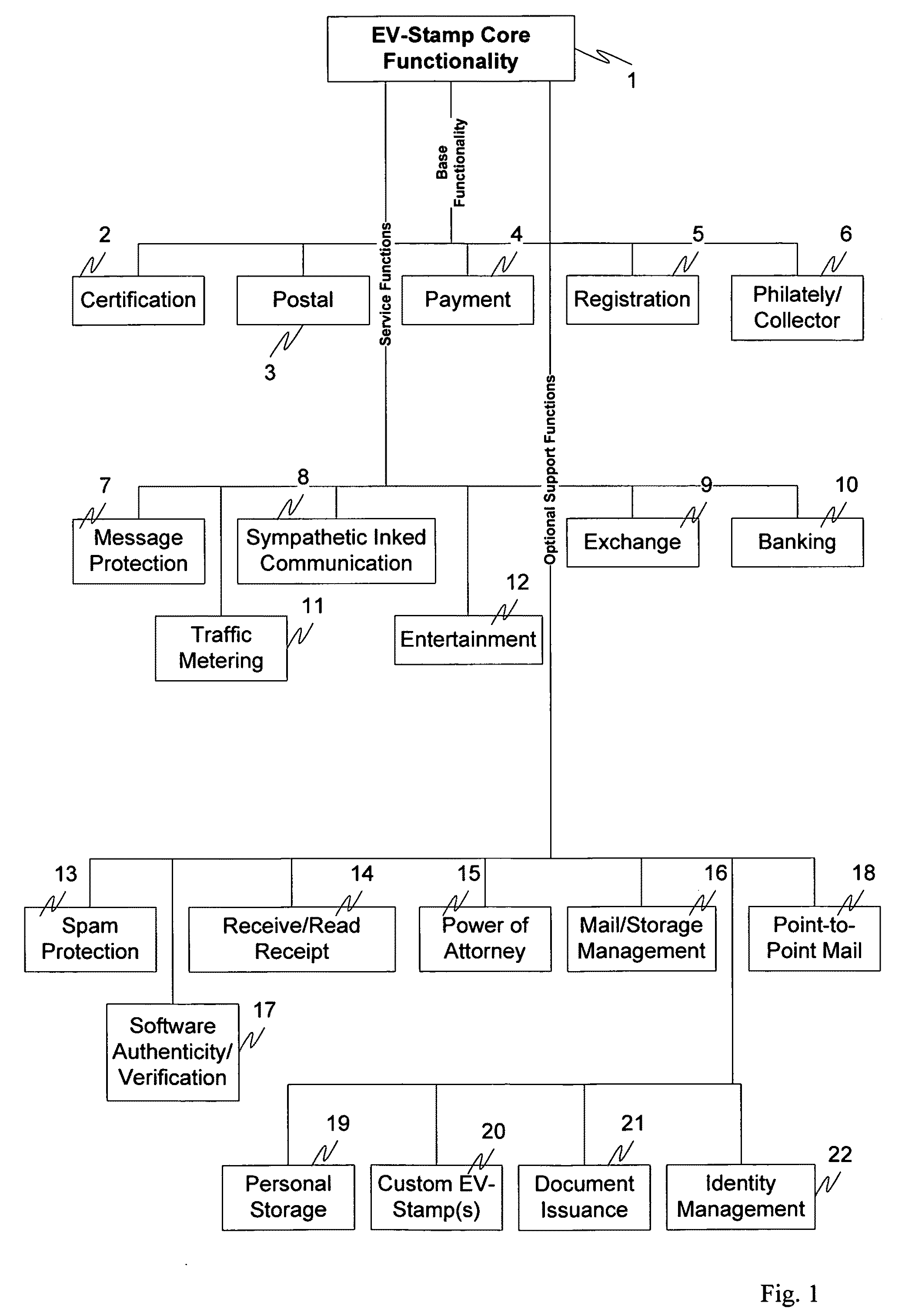
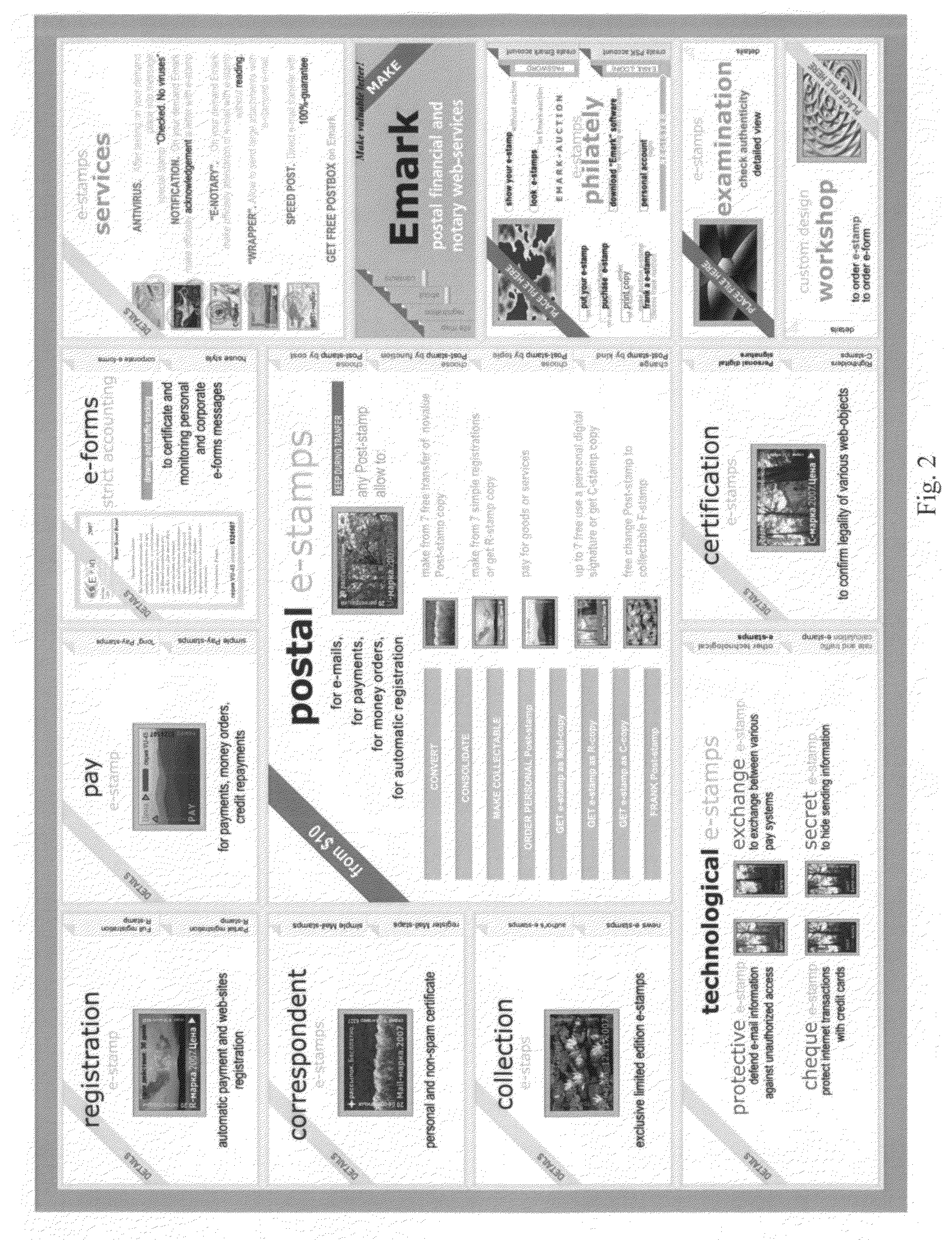
A system and method for electronic certification, identification and communication. According to an exemplary implementation, these processes are performed by using an electronic graphic image with encrypted information concerning the certified object. The object is accompanied with an application specific image hereafter called Electronic Virtual Stamp (EV-Stamp) having embedded and encrypted control information (keys and electronic signatures, identifiers of senders and receivers, date and other transaction related information) as well as any message to be passed. Each transaction of the EV-Stamp is monitored by a specialized Web server that maintains the records of all issued electronic stamps, all subscribed users, all involved financial transactions, and all registered assets. It is also possible to use any other graphical images to reflect on various possible applications such as exchange of the EV-Stamp for a good / service.
Owner:ASTAKHOV PAVEL
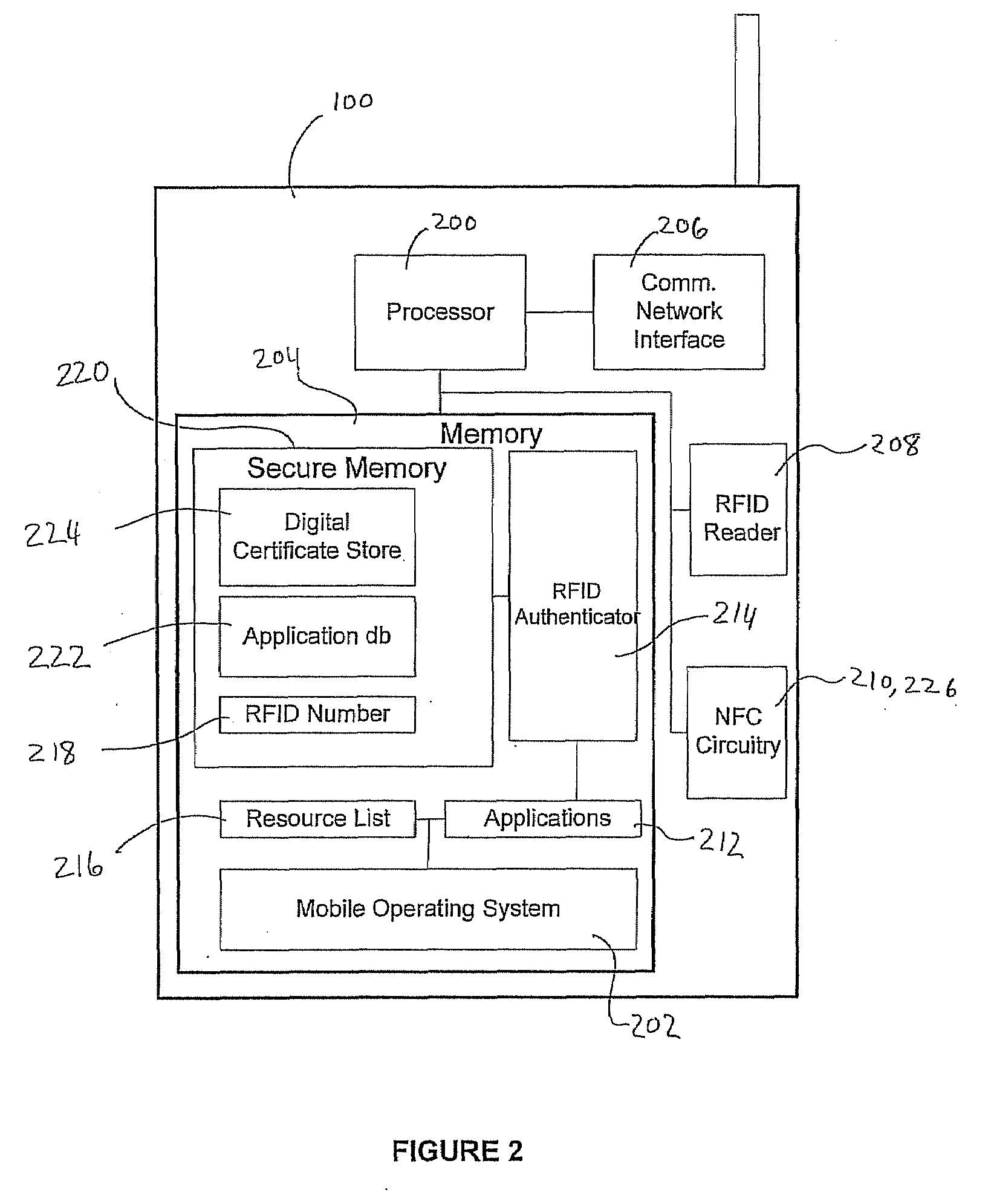
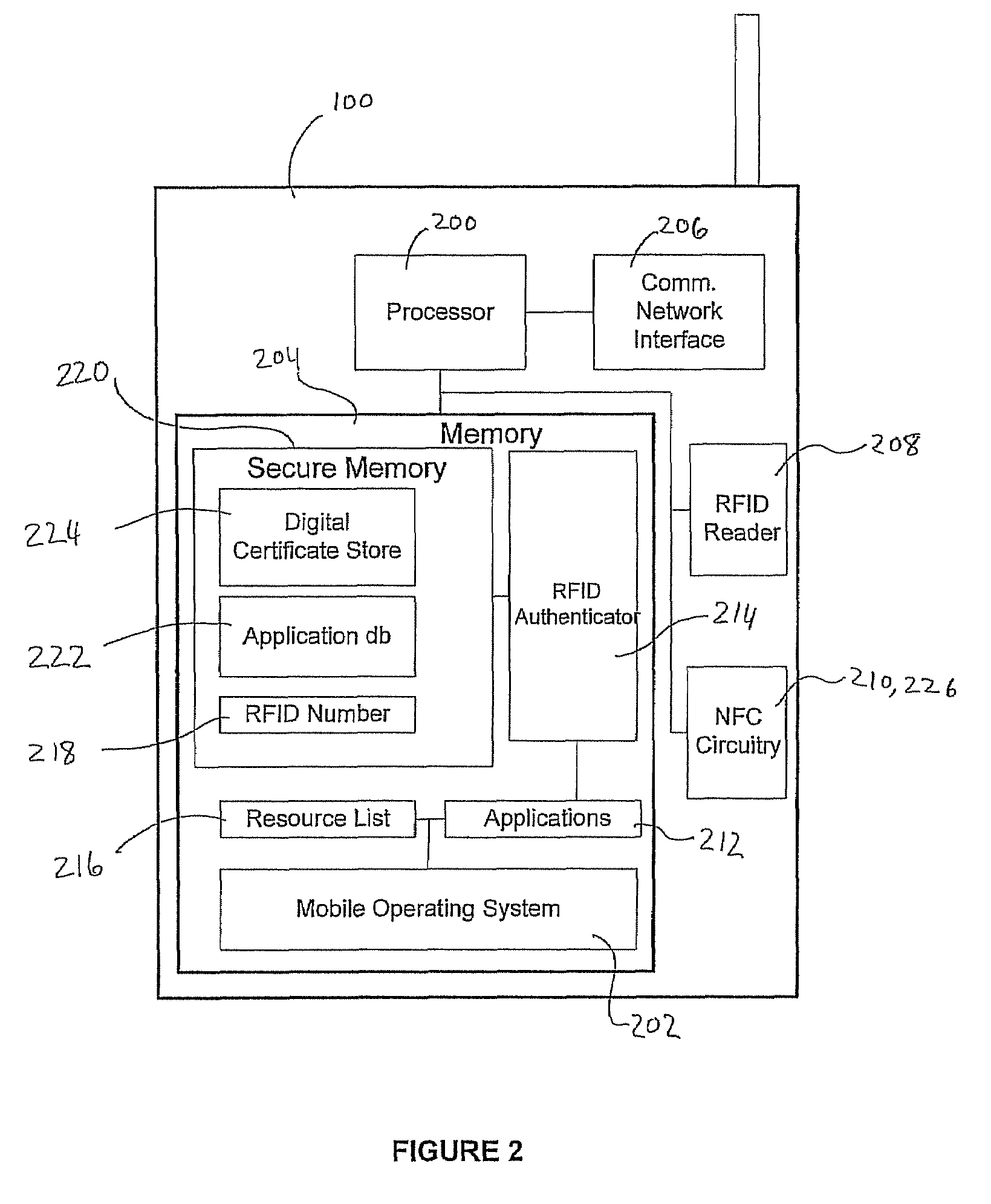
User-friendly multifactor mobile authentication
ActiveUS20080289030A1Prevent unauthorized accessEliminate needDigital data processing detailsMultiple digital computer combinationsComputer hardwareRfid authentication
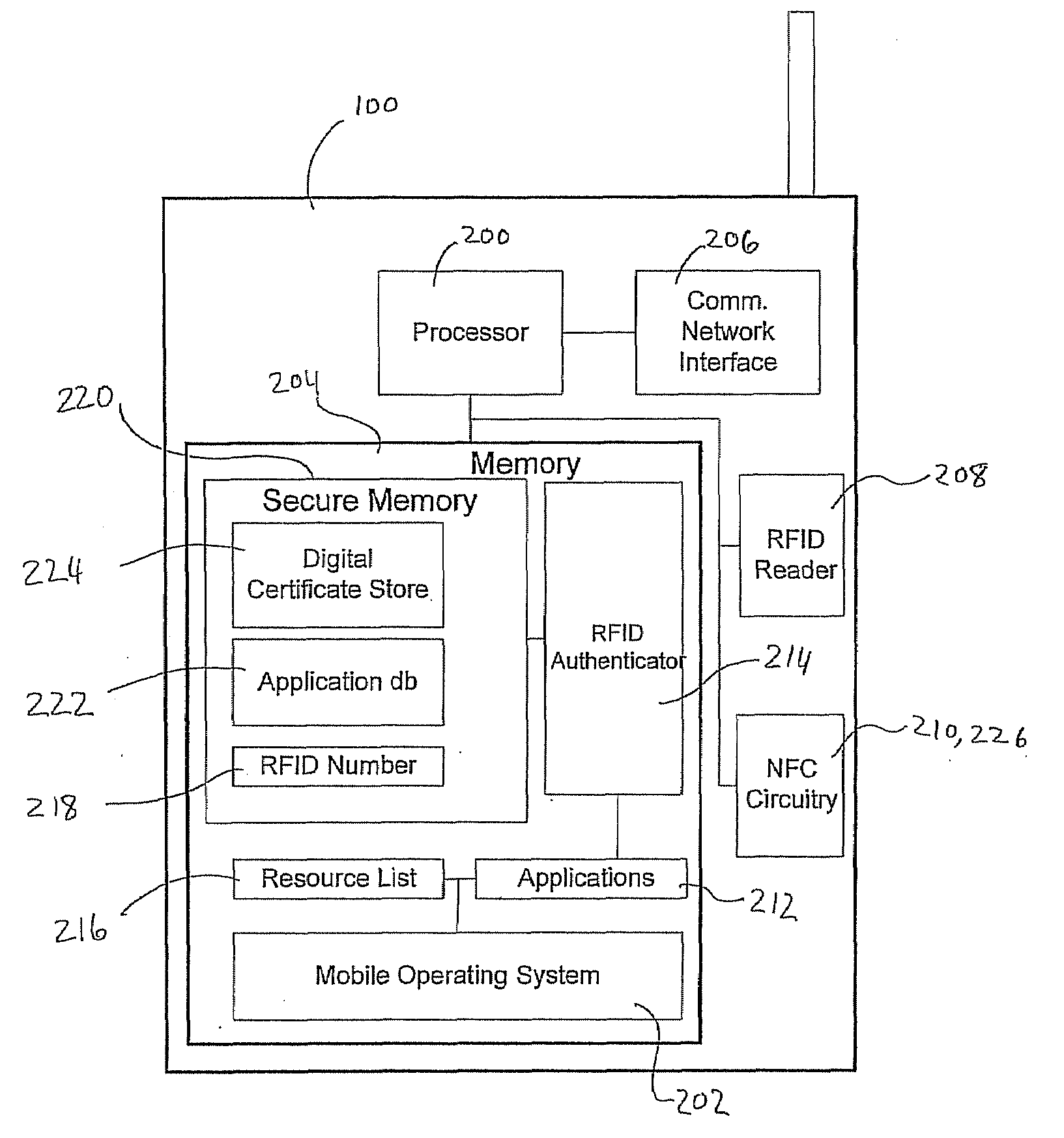
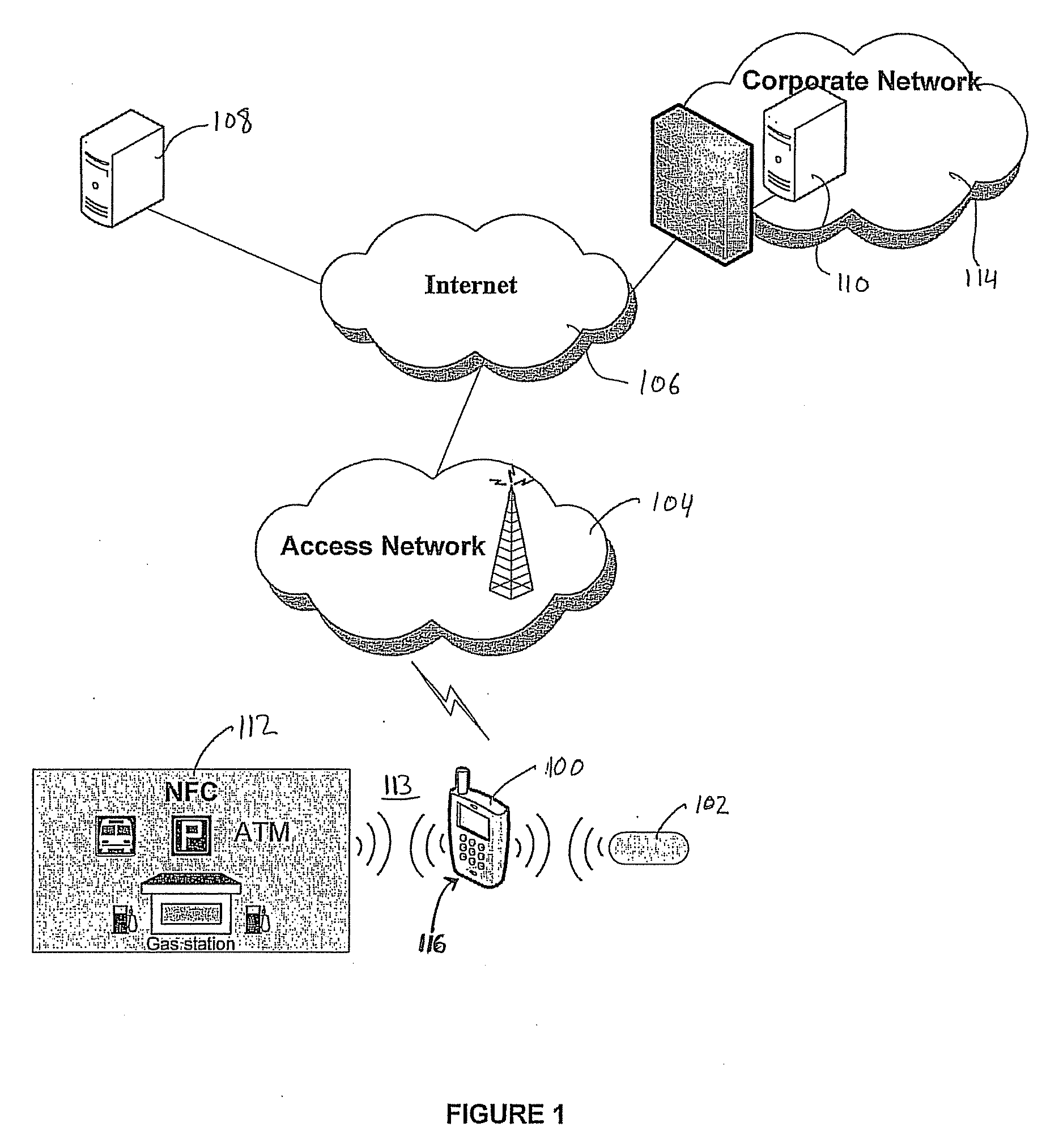
A system and method for performing multifactor mobile authentication are described whereby a mobile communications device includes a contactless reader for receiving and validating a unique identifier stored in an external authenticating module prior to granting access to locally stored electronic authenticating material required to access an external resource. In one embodiment, the mobile communications device is a mobile telephone having an RFID reader for receiving the unique identifier from an RFID tag incorporated into the external authenticating module. Preferably, the external authenticating module is associated with a user, such as by being part of the user's jewelry or clothing. The mobile authentication device includes an RFID authenticator module that detects external resource access requests and checks whether the requested resource is on a list of resources that require additional user authentication prior to granting access to locally stored authenticating material.
Owner:U S CELLULAR
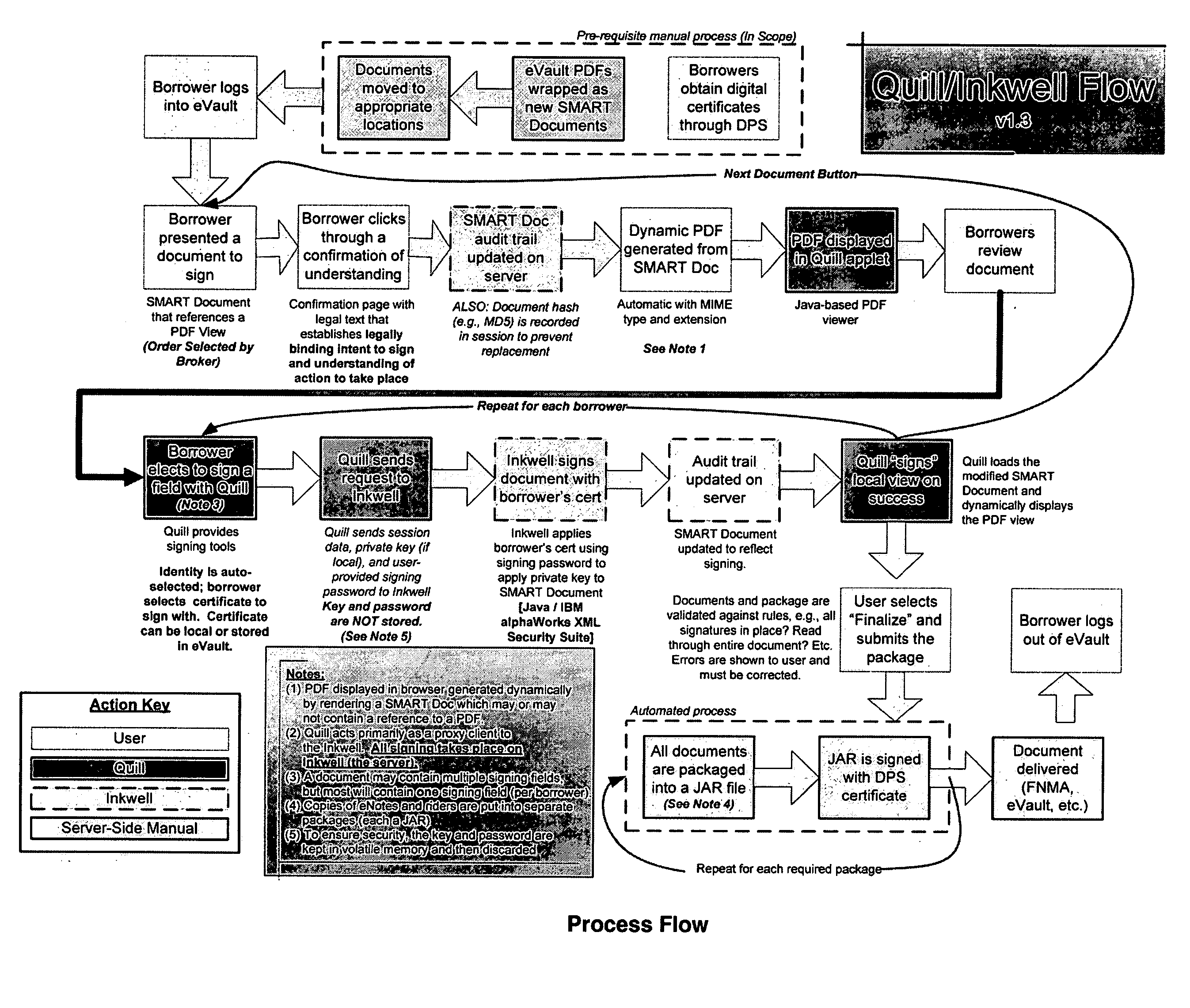
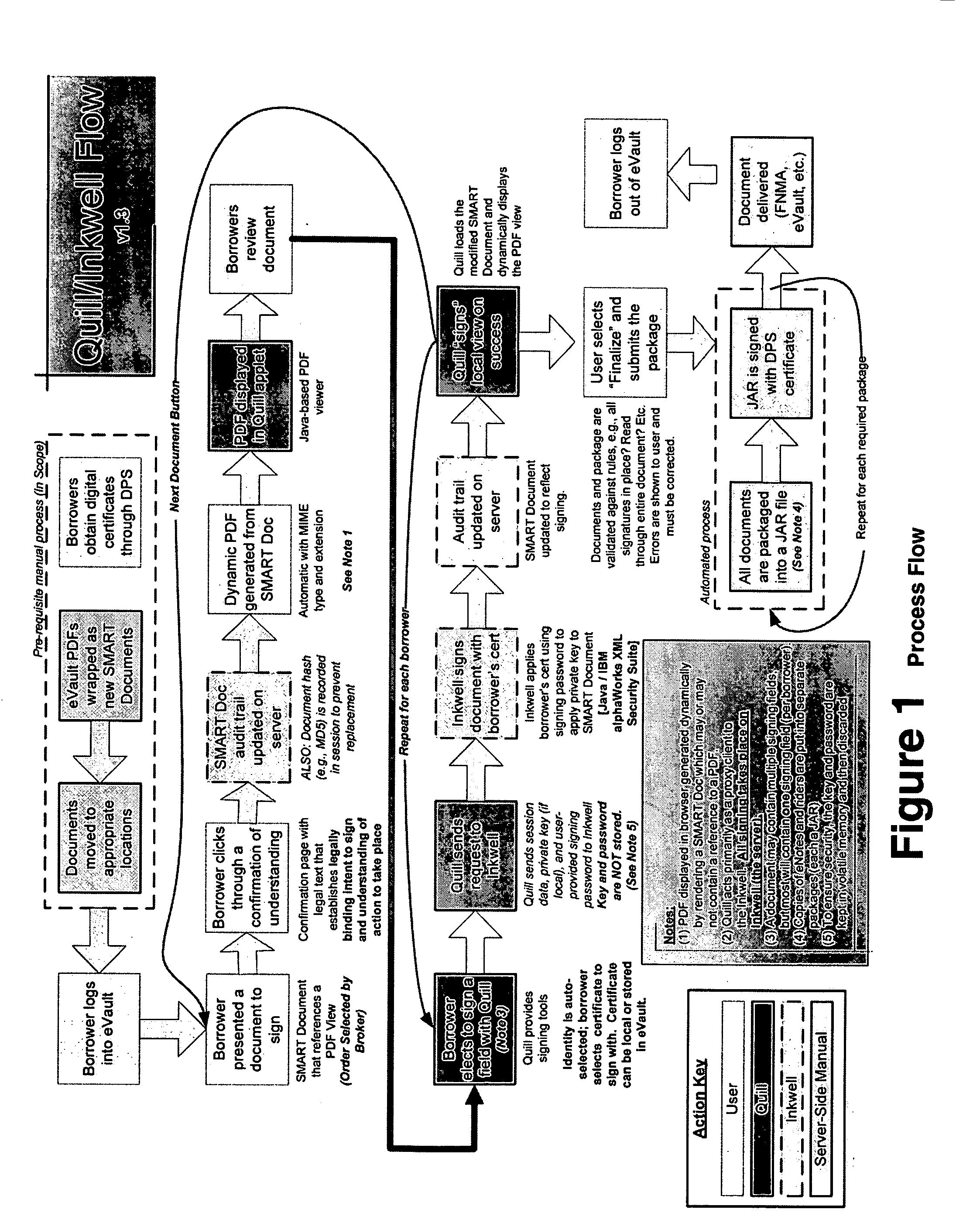
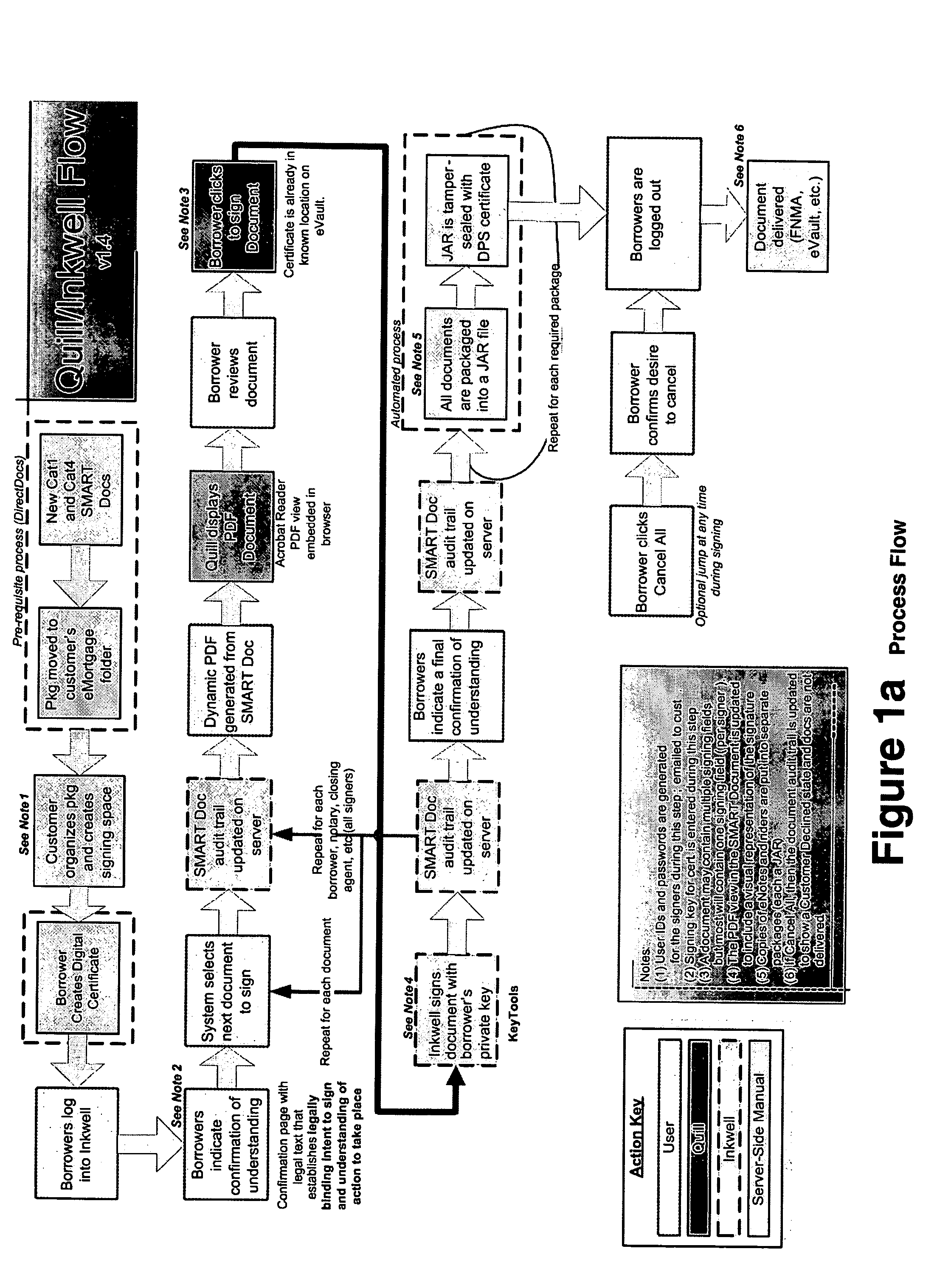
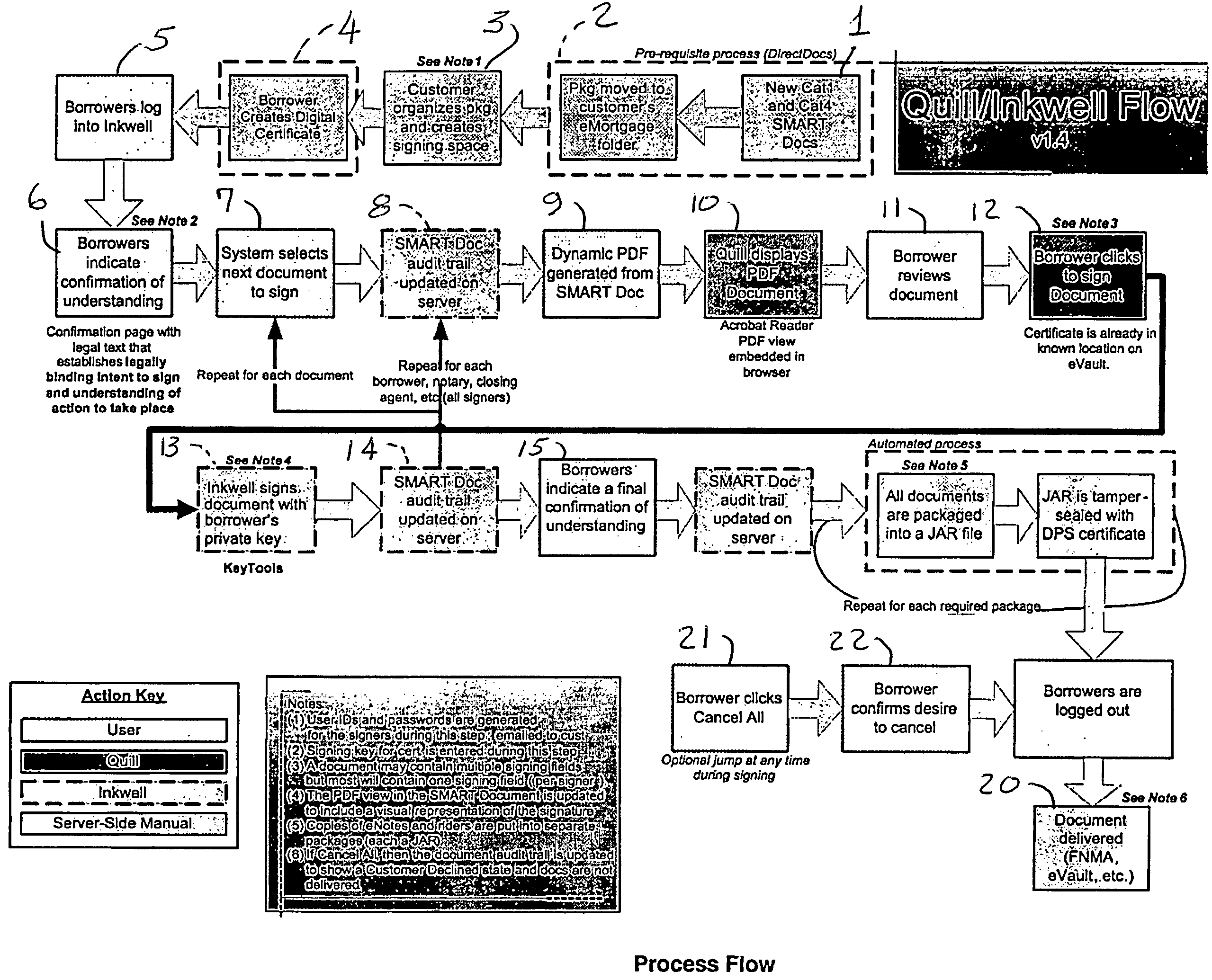
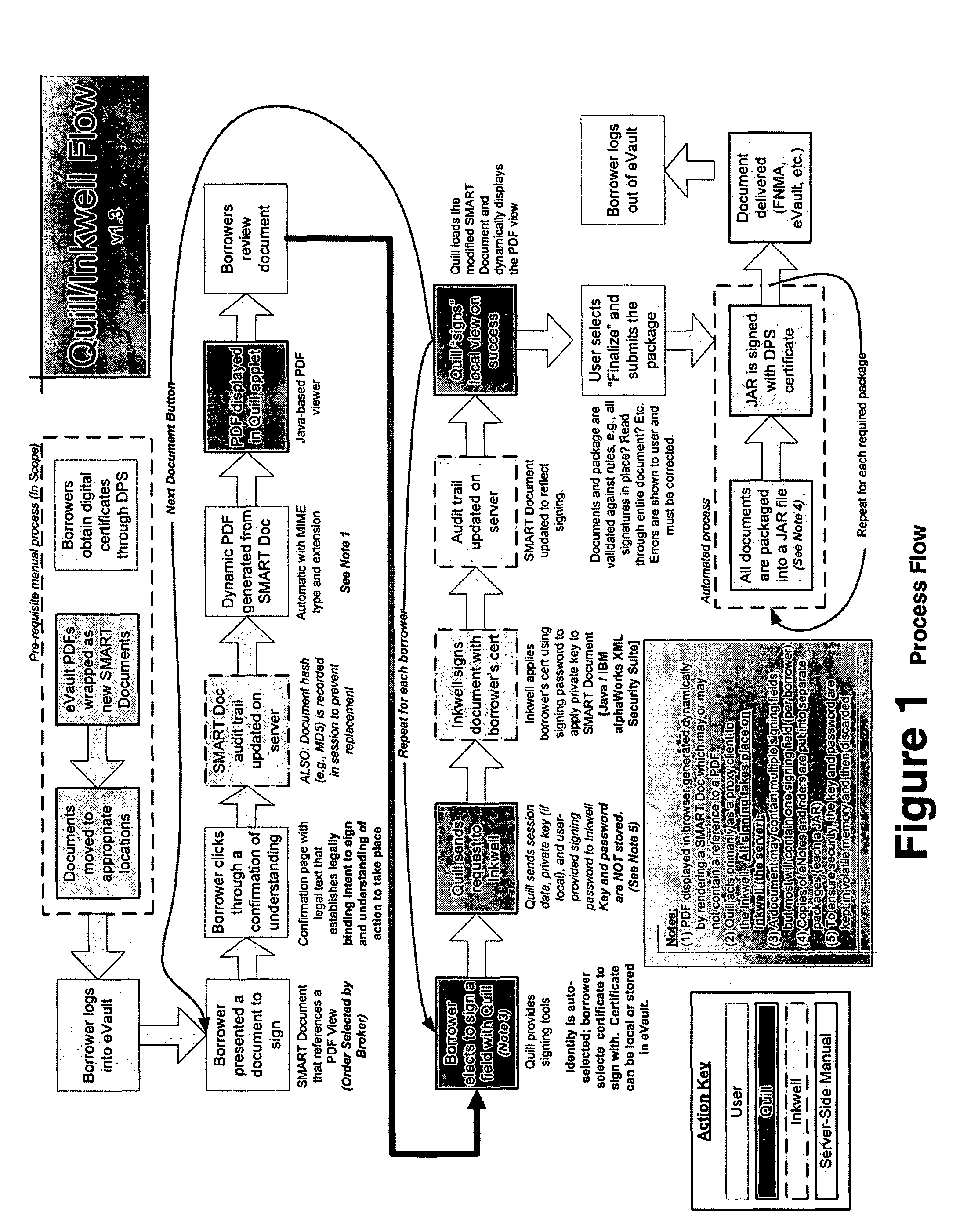
Paperless process for mortgage closings and other applications
ActiveUS20050177389A1Facilitates digital signingKey distribution for secure communicationFinanceElectronic documentPaper document
According to the present invention, there is provided an electronic document processing system and method including an electronic document generation mechanism, an encrypted digital certificate generator, a tool for coordinating the processing of electronic documents, a packaging mechanism for finalizing and authenticating electronic documents, a tracking log for recording relevant electronic document information, and a transferring protocol for transferring the ownership of electronic documents. The present invention also provides an electronic authentication system including an electronic document authentication watermark seal or signature line for confirming a document's signing within the view. Preferably, the present invention is directed towards a system, software program, and method for generating electronic documents, coordinating the signing of said electronic documents, digitally authenticating and certifying said electronic documents, and organizing said electronic documents for retrieval and transfer in the mortgage closing / financial services field.
Owner:CITRIN HLDG LLC
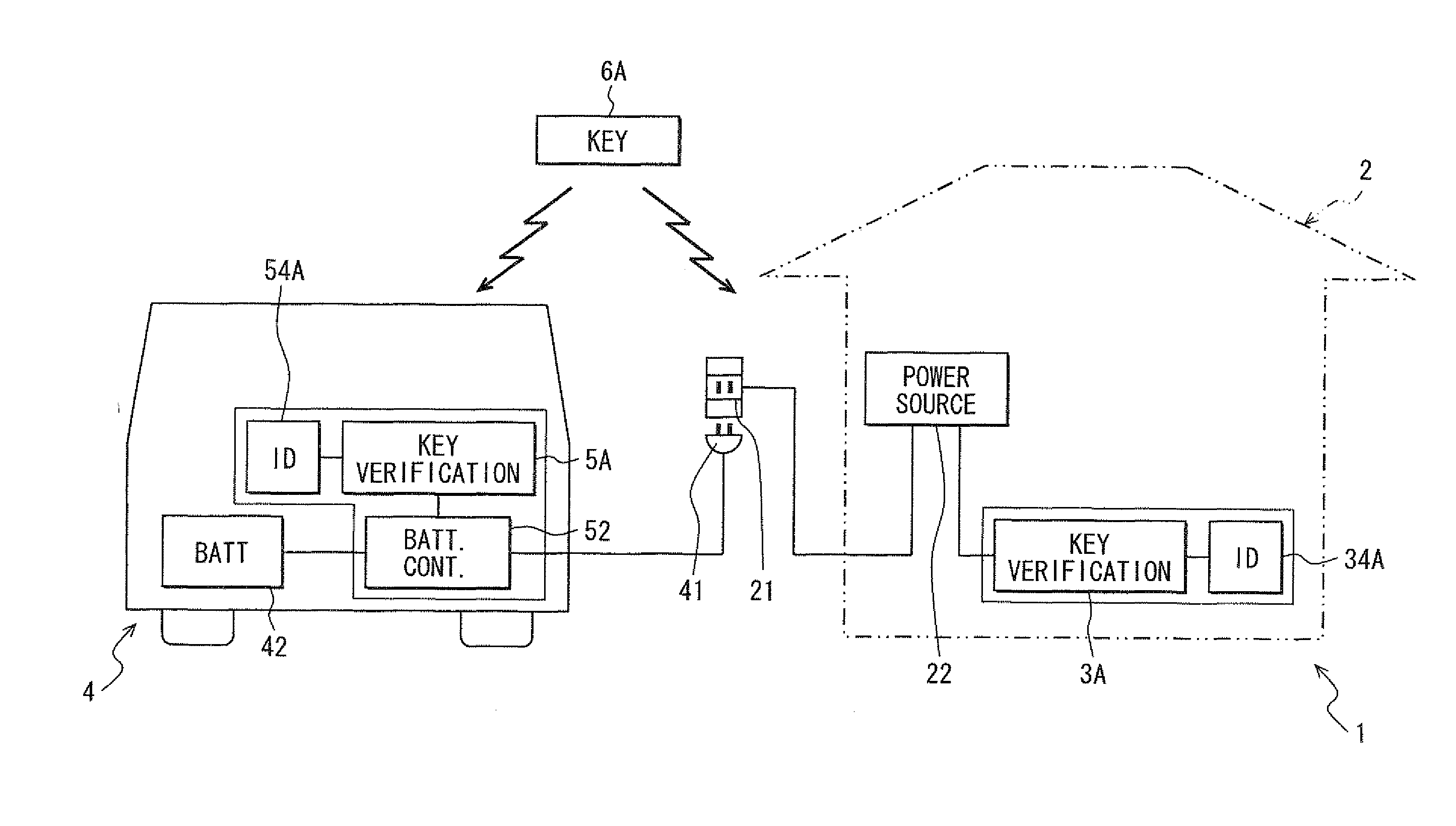
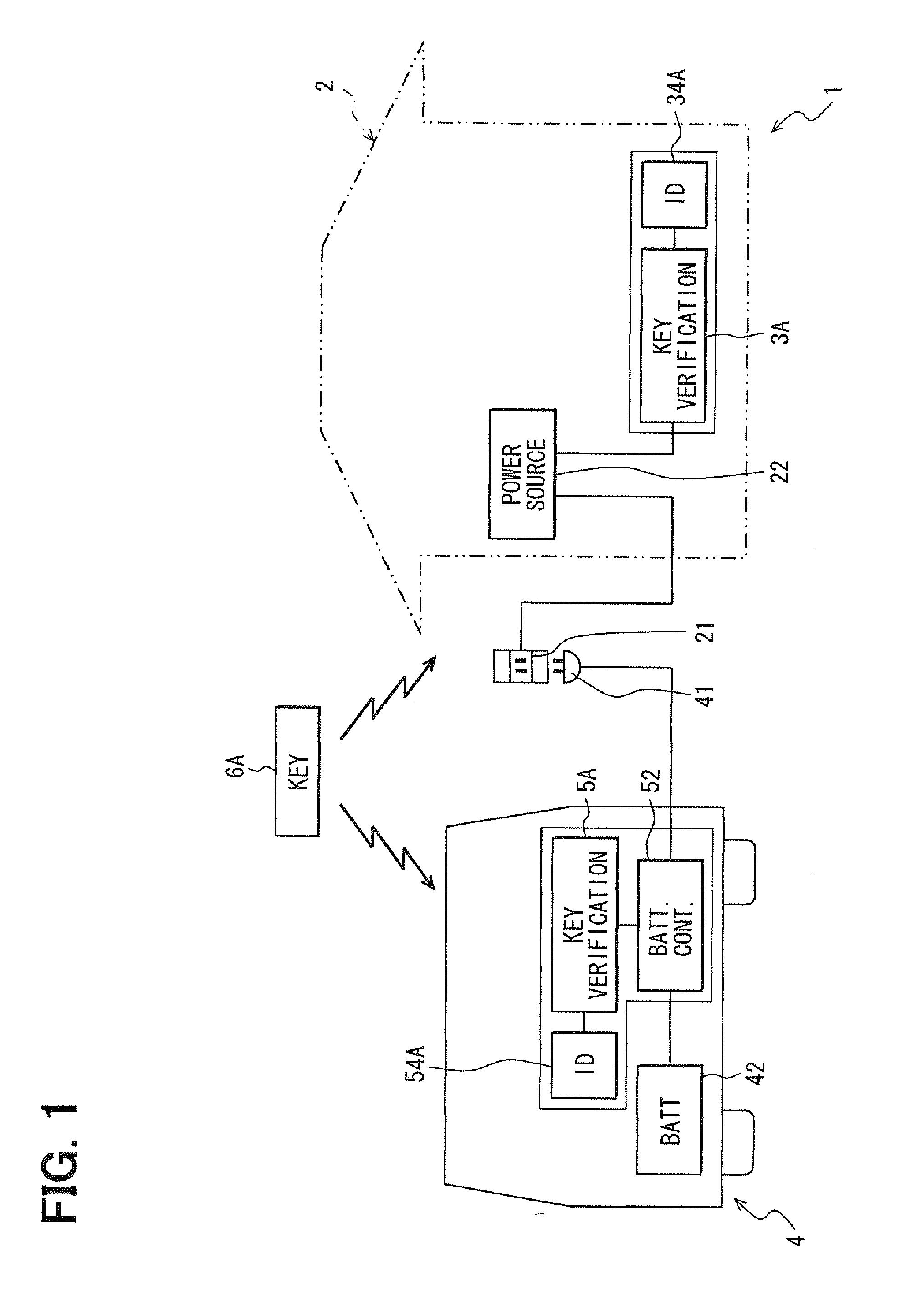
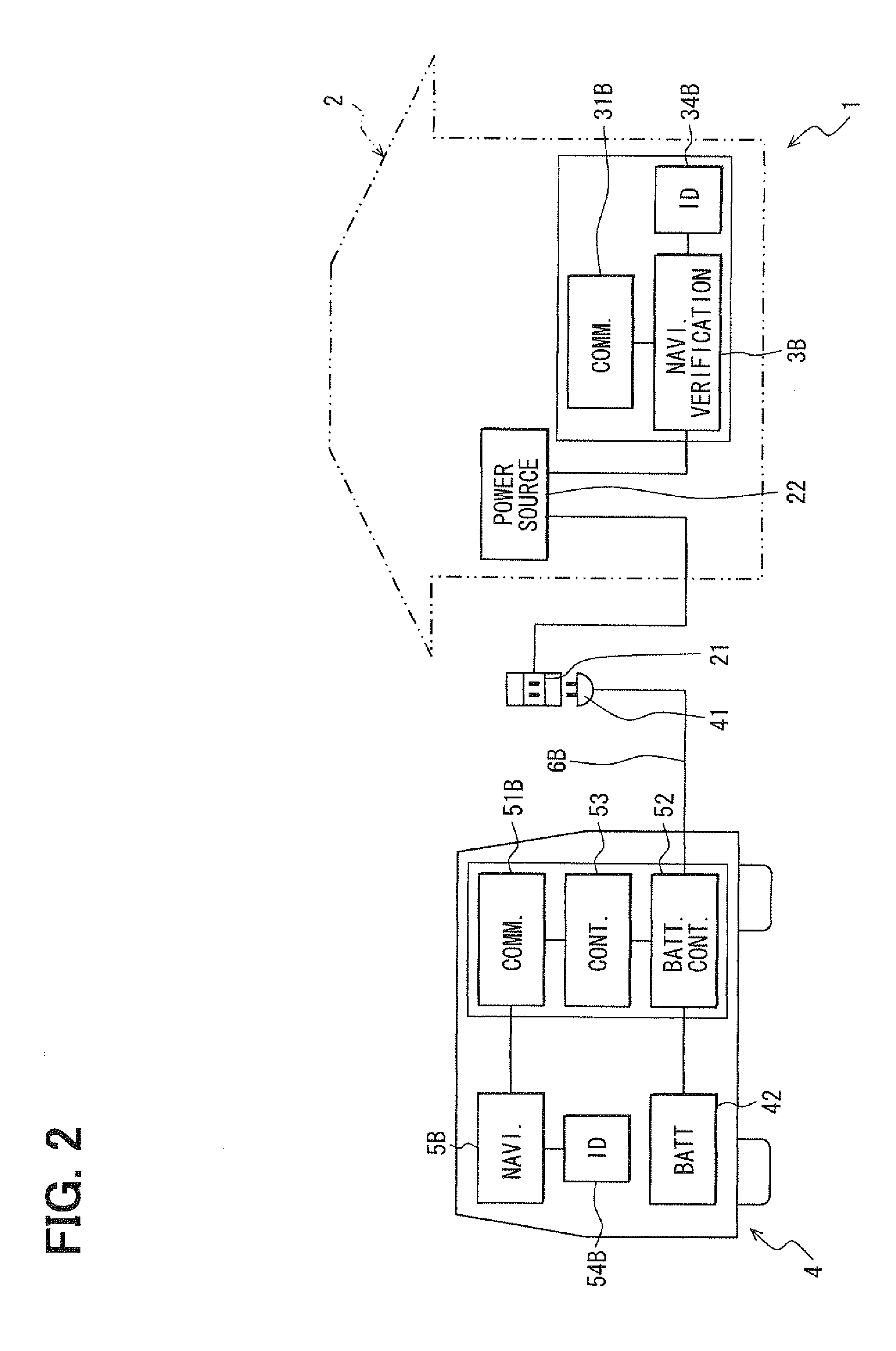
Management system for charging plug-in vehicle
InactiveUS20100194529A1Prevent electricity theftPrevent theftElectric signal transmission systemsMultiple keys/algorithms usageComputer moduleEngineering
A plug-in vehicle has a door lock system which uses an electronic certification key. The electronic certification key stores a certification code and has a wireless communication device to transmit the code. A management system for charging the plug-in vehicle has a wireless communication device which can receive the certification code from the key, and a key verification module which verifies whether a proper key exists at the charging station or not. If a proper key is detected, the system permits charging the plug-in vehicle from a power outlet. On the other hand, if a proper key is not detected, the system denies and prohibits charging the plug-in vehicle from the power outlet.
Owner:DENSO CORP
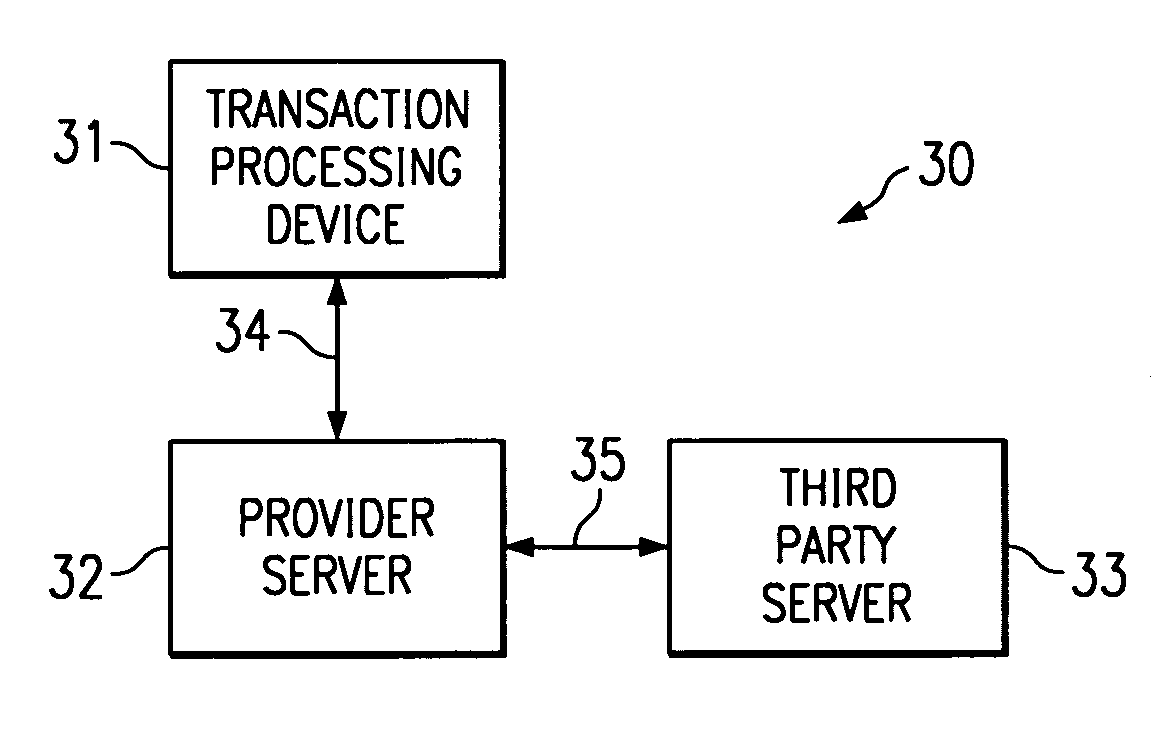
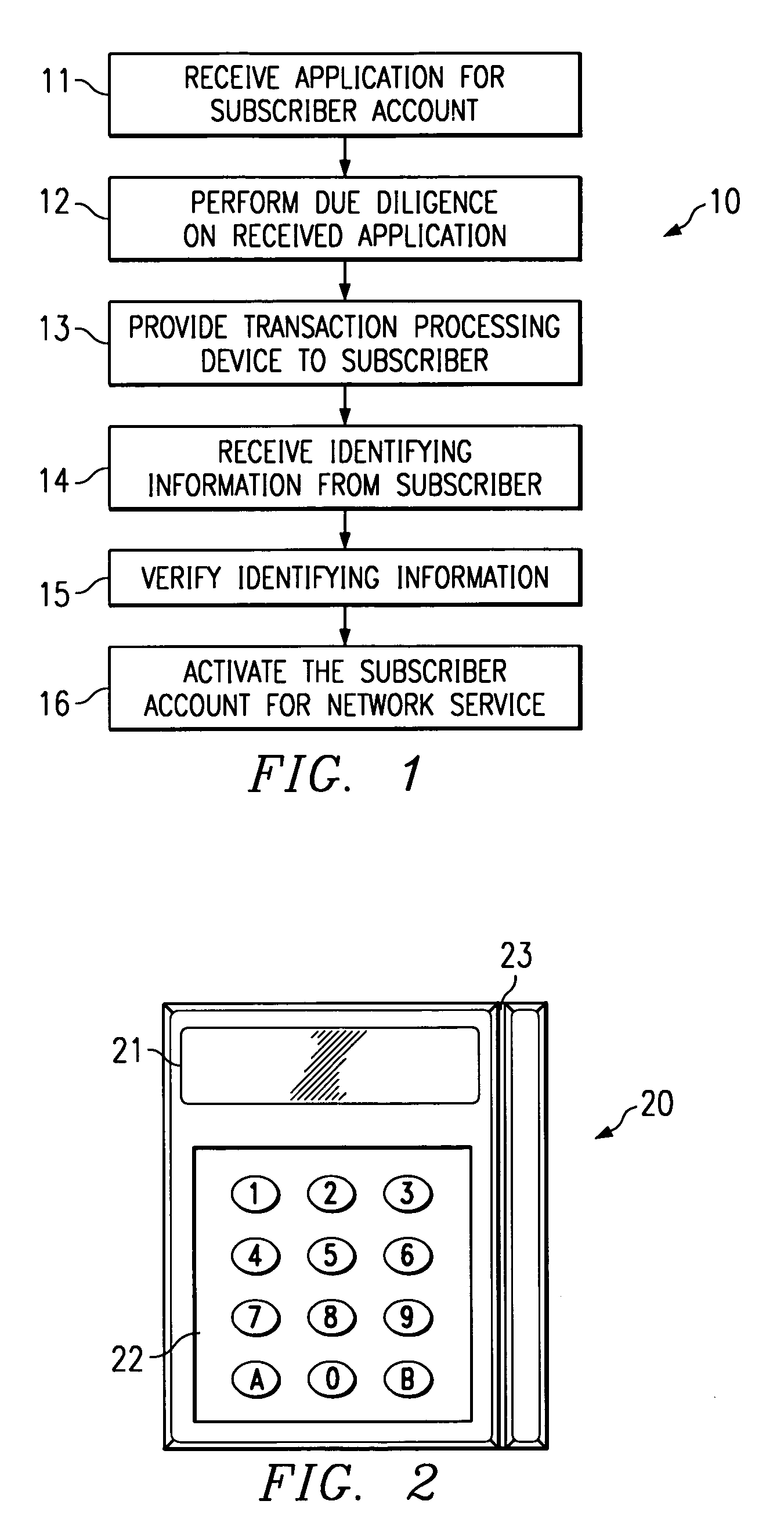
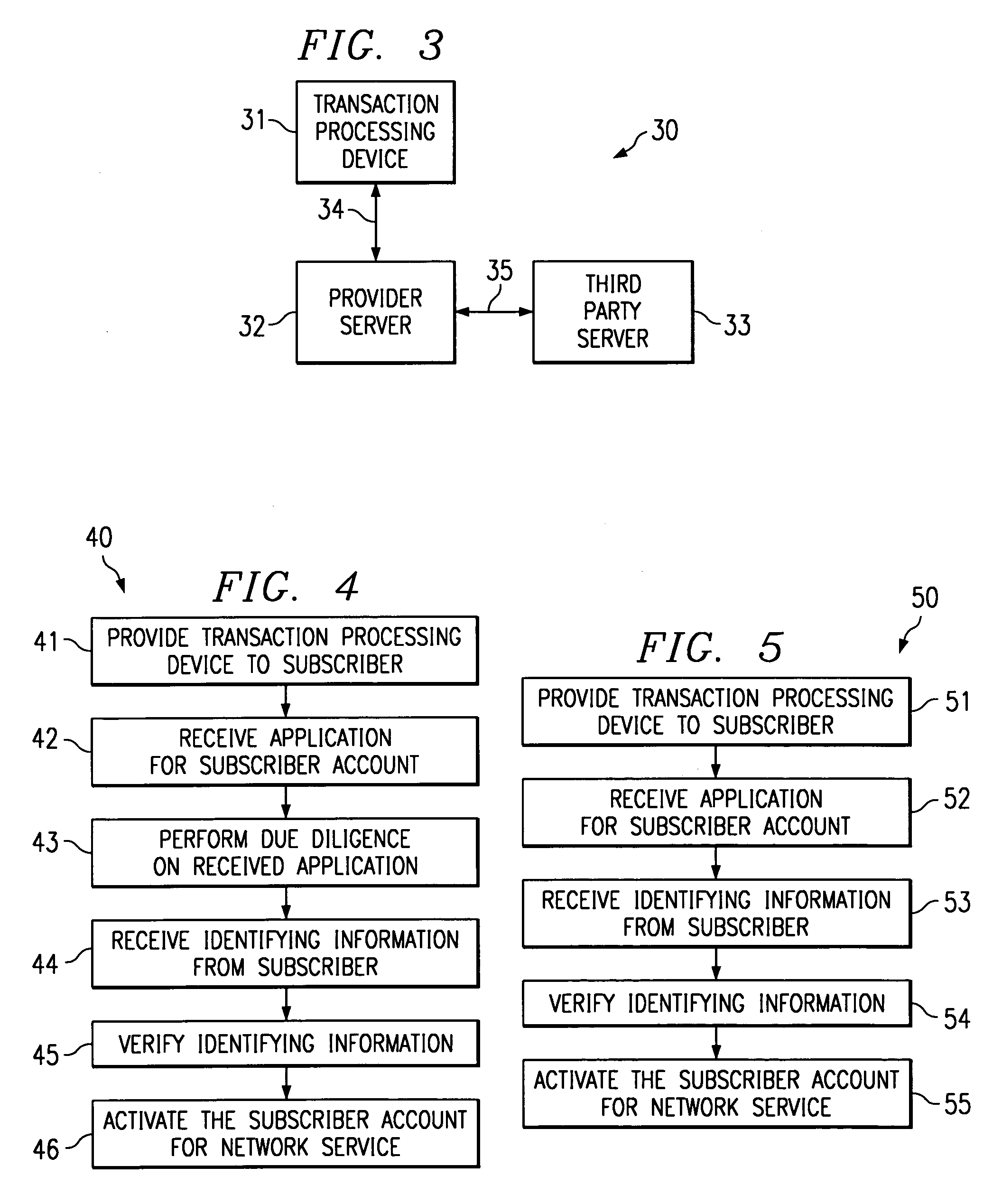
System and method for secure authentication of a subscriber of network services
InactiveUS6978380B1Credit registering devices actuationHand manipulated computer devicesSecure authenticationNetwork service
A system and method for electronically authenticating a subscriber account for a network service is disclosed. In the preferred embodiment, a subscriber account provider receives initial information from a subscriber. The received information is stored by the subscriber account provider. A transaction processing device is provided to the subscriber and the subscriber is electronically authenticated prior to enabling the subscriber account for performing the network service. In the preferred embodiment, the step of electronically authenticating the subscriber comprises receiving captured information from subscriber through said transaction processing device. After receiving the captured information the subscriber account provider utilizes the captured information to receive verifying information about the subscriber; and then compares the verifying information with the initial information to authenticate the subscriber.
Owner:FINASTRA MERCHANT SERVICES INC
User-friendly multifactor mobile authentication
ActiveUS8646056B2Prevent unauthorized accessEliminate needDigital data processing detailsMultiple digital computer combinationsComputer hardwareUnique identifier
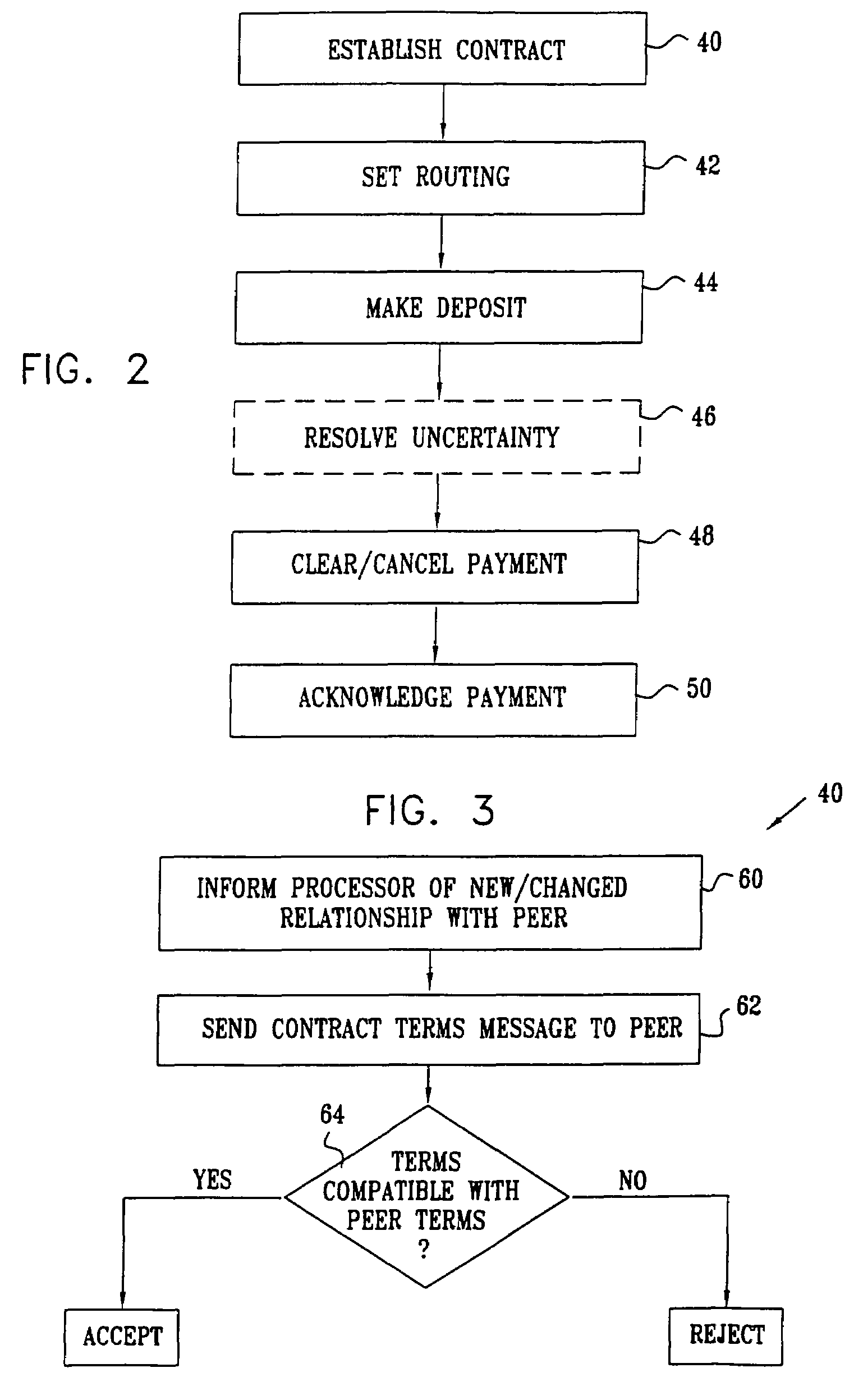
Owner:U S CELLULAR
System and method for user enrollment in a secure biometric verification system
ActiveUS20140289842A1Digital data processing detailsUnauthorized memory use protectionBiometric dataVerification system
A computer-implemented method and system for verifying the identity of a user in an identity authentication and biometric verification system which includes collecting information from the user regarding the user's identity, which is then electronically authenticated. Upon authentication, personal information regarding the verified identity of the user is retrieved from a source database which is used to verify the identity of the user, via user interaction. Upon successful verification and authentication, biometric data regarding the user is electronically collected.
Owner:ALCLEAR
Method and apparatus for providing electronic message authentication
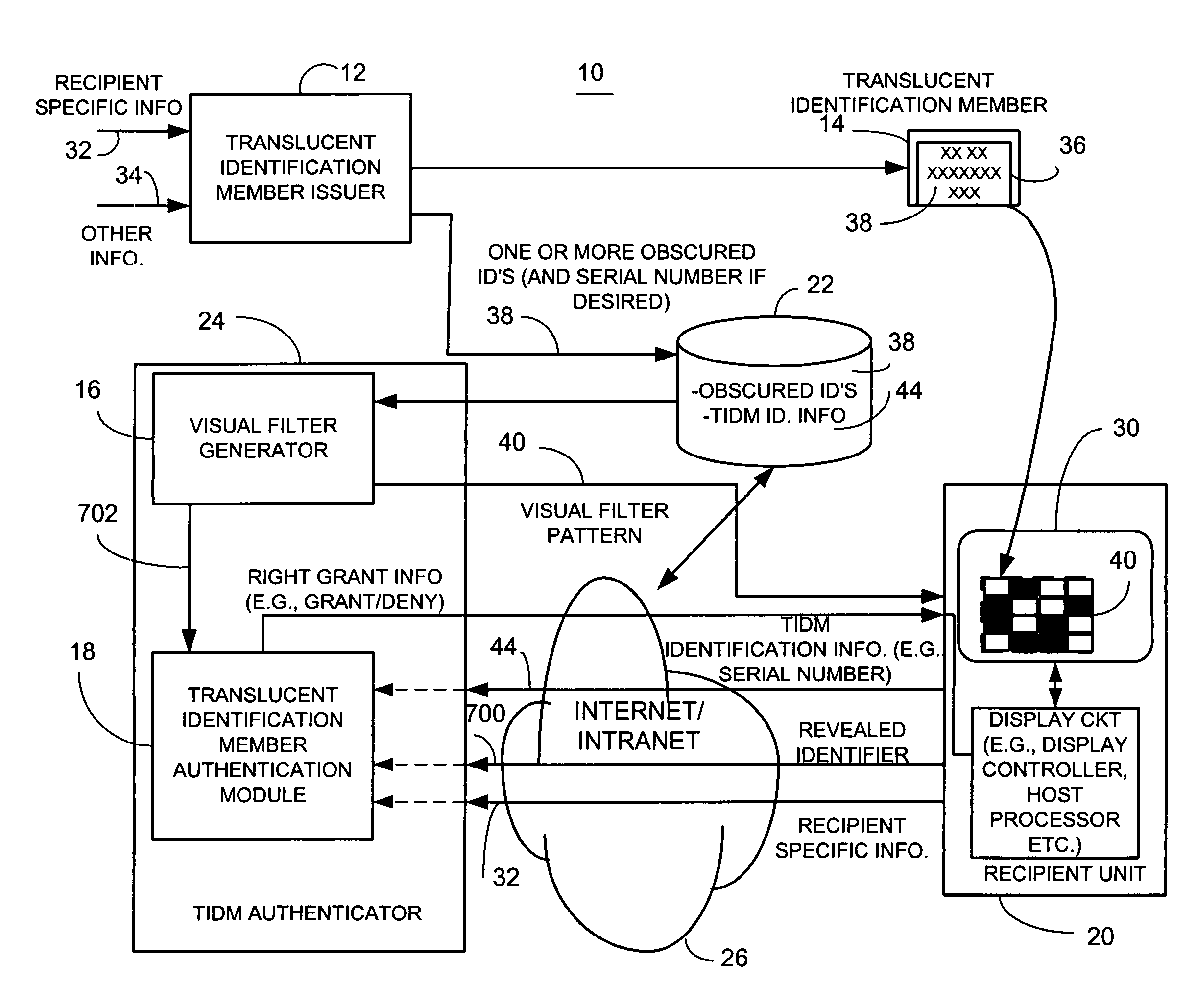
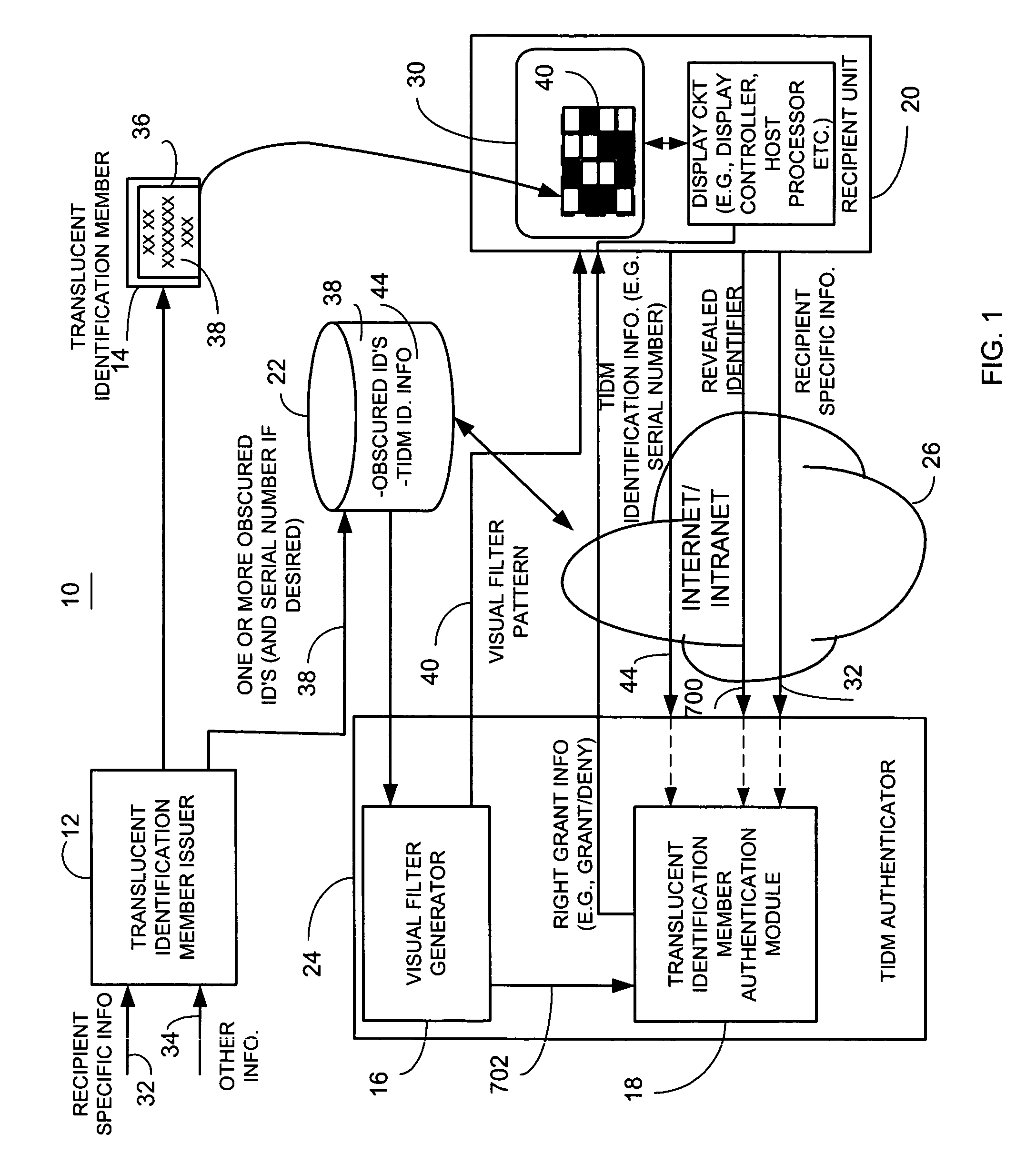
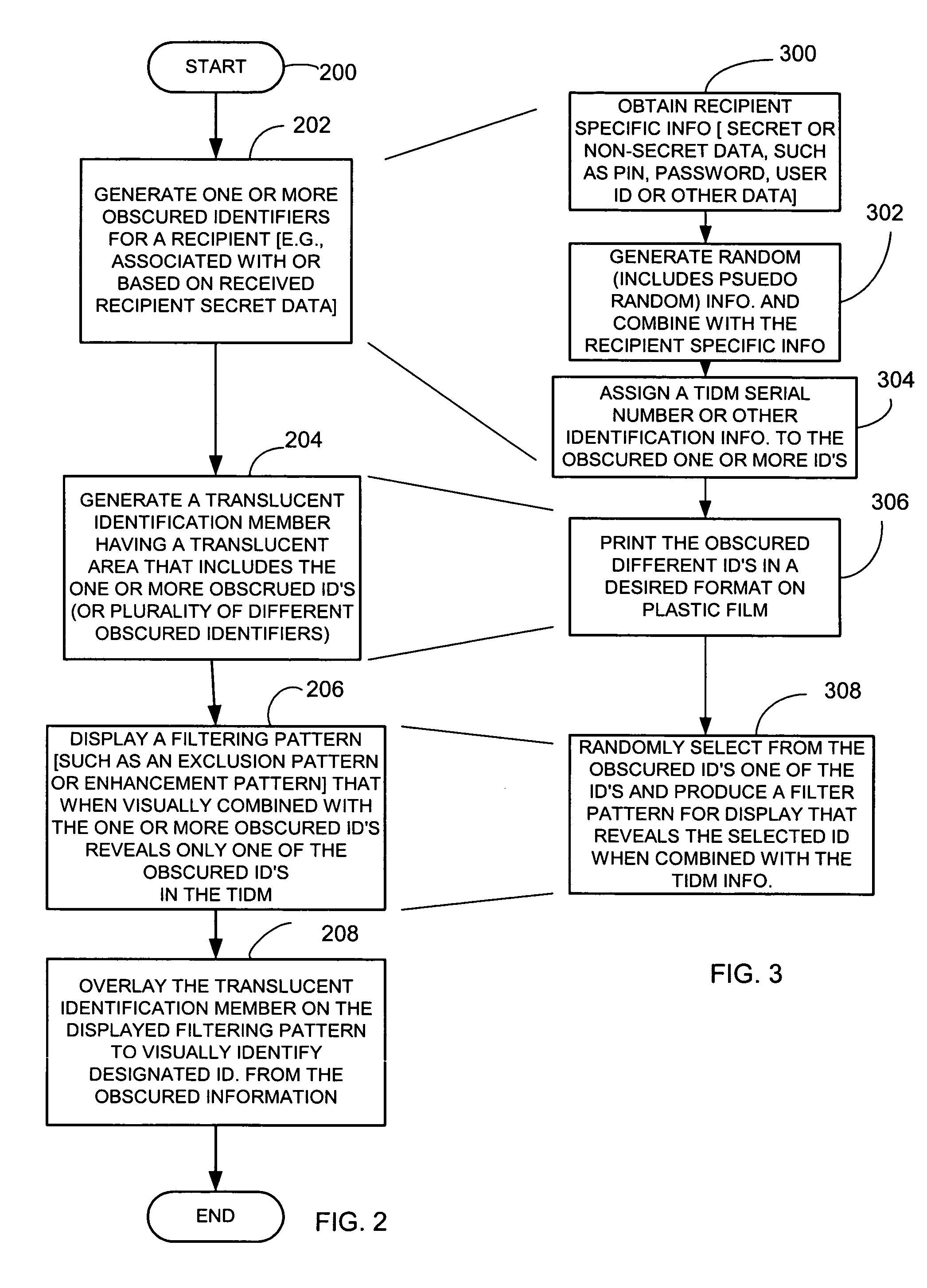
ActiveUS8060915B2Other printing matterData taking preventionInternet privacyAuthentication information
A method for providing electronic message authentication employs an article, such as a card, sticker, or any other suitable article, that includes sender authentication information and location information such as row and column headings. In one example, each recipient of interest is issued an article that embodies unique sender authentication information that is identifiable by corresponding location information such as column and row identifiers. In both an apparatus and method, when the sender of an electronic message wants to send a message to a recipient of interest, the sender sends the electronic message and both location information and corresponding desired sender authentication information located at the coordinate identified by the location coordinate information. If the sent desired sender authentication information matches authentication information found on the article, the sender of the message is trusted.
Owner:ENTRUST
Decentralized electronic certified payment
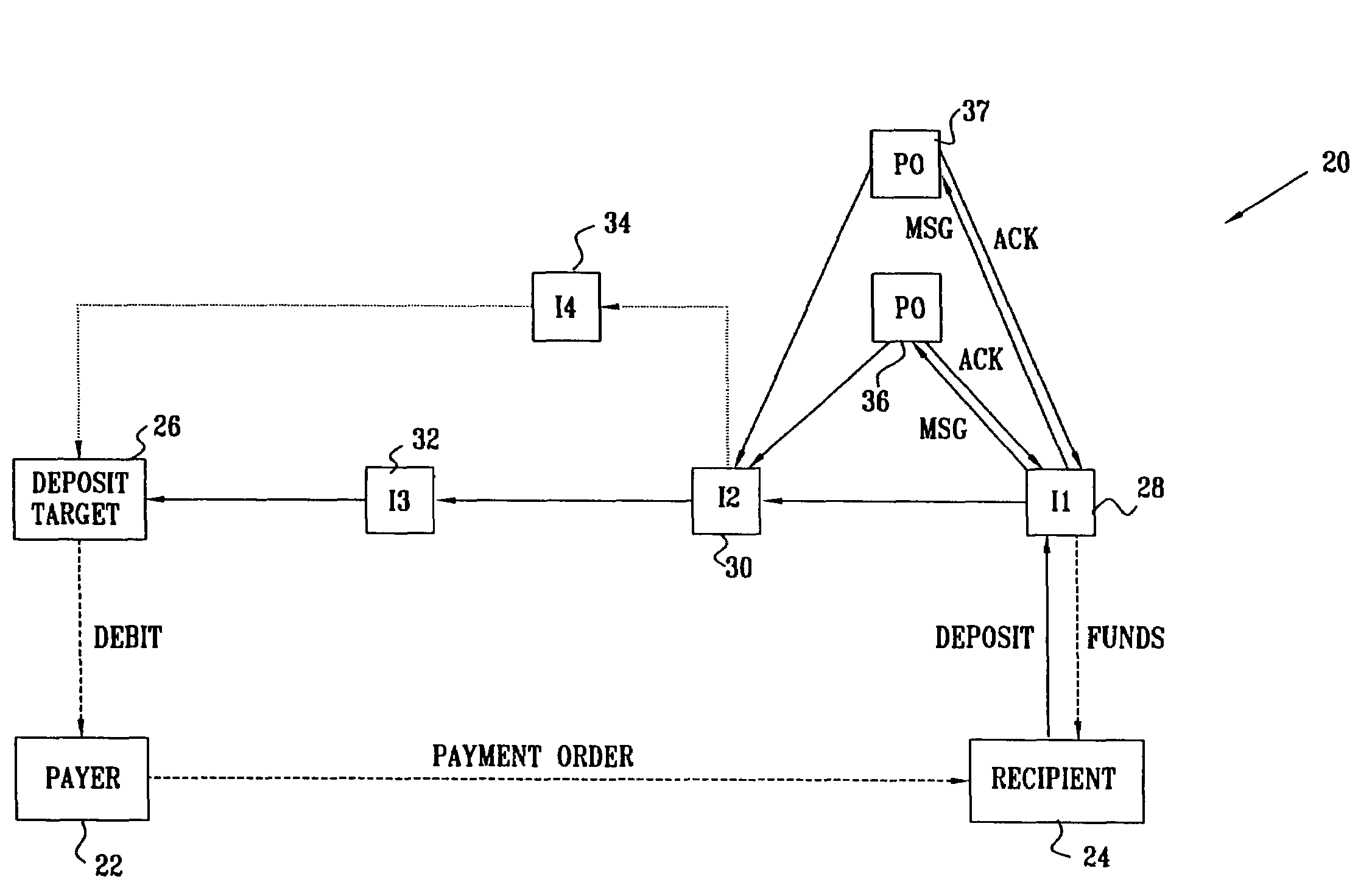
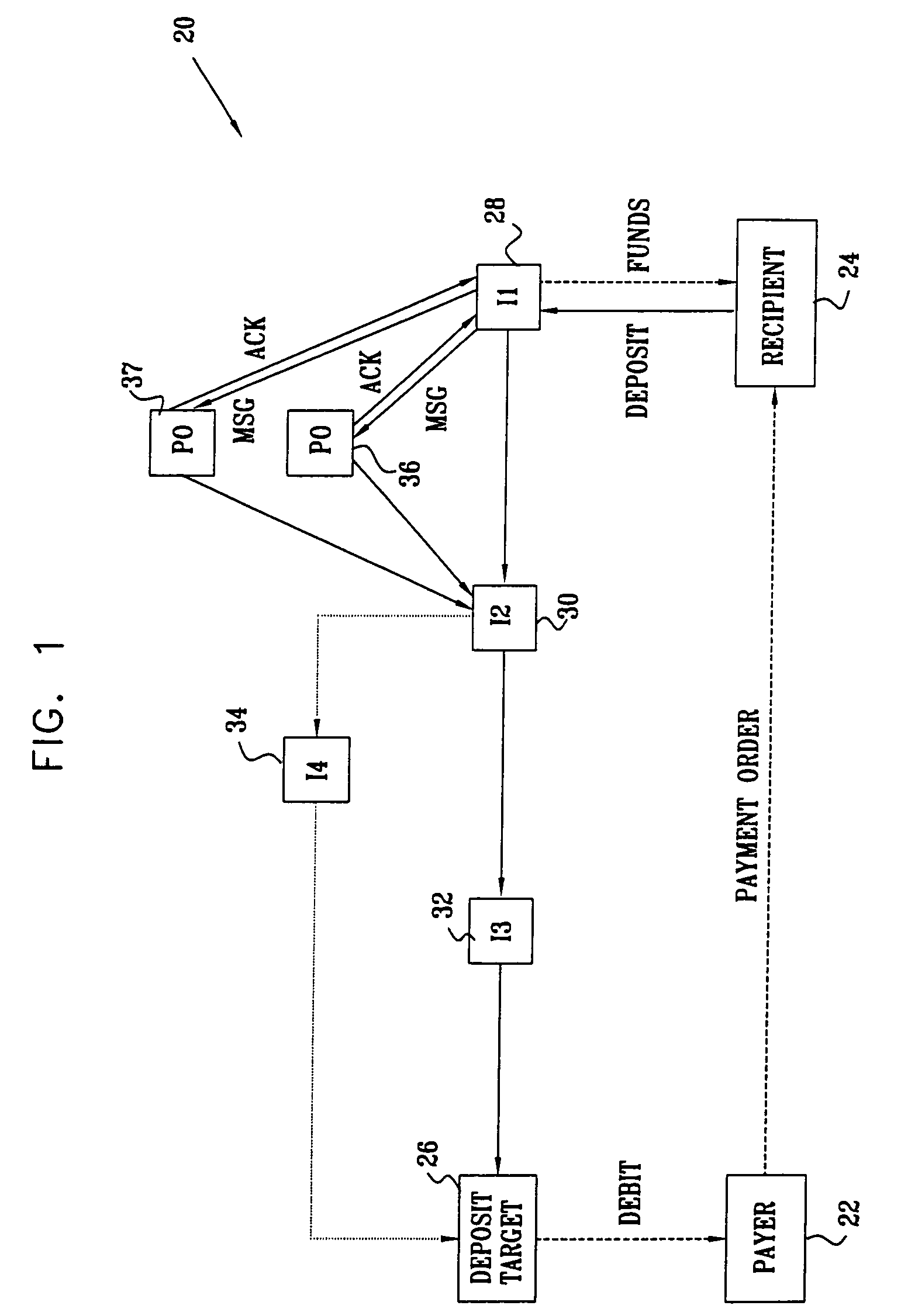
InactiveUS7546275B1Reduce overheadIncrease flexibilityFinanceComputer security arrangementsPaymentPayment order
A method for deposit of an electronic payment order by a first intermediary processor among a plurality of intermediary processors linked by a communication network. A routing message is received at the first intermediary processor, the message identifying one or more deposit target processors accessible through the network via the second intermediary processor and providing a respective secure identifier for each of the accessible deposit target processors. When the first intermediary processor receives the electronic payment order drawn on a specified one of the deposit target processors conveyed over the network from a depositing processor, it clears the payment order intermediary processor by checking the payment order against the secure identifier of the specified deposit target processor provided in the routing message. Responsive to clearing the order, the first intermediary processor transfers payment to the depositing processor, while conveying the payment order over the network to the specified deposit target.
Owner:PAYPAL INC
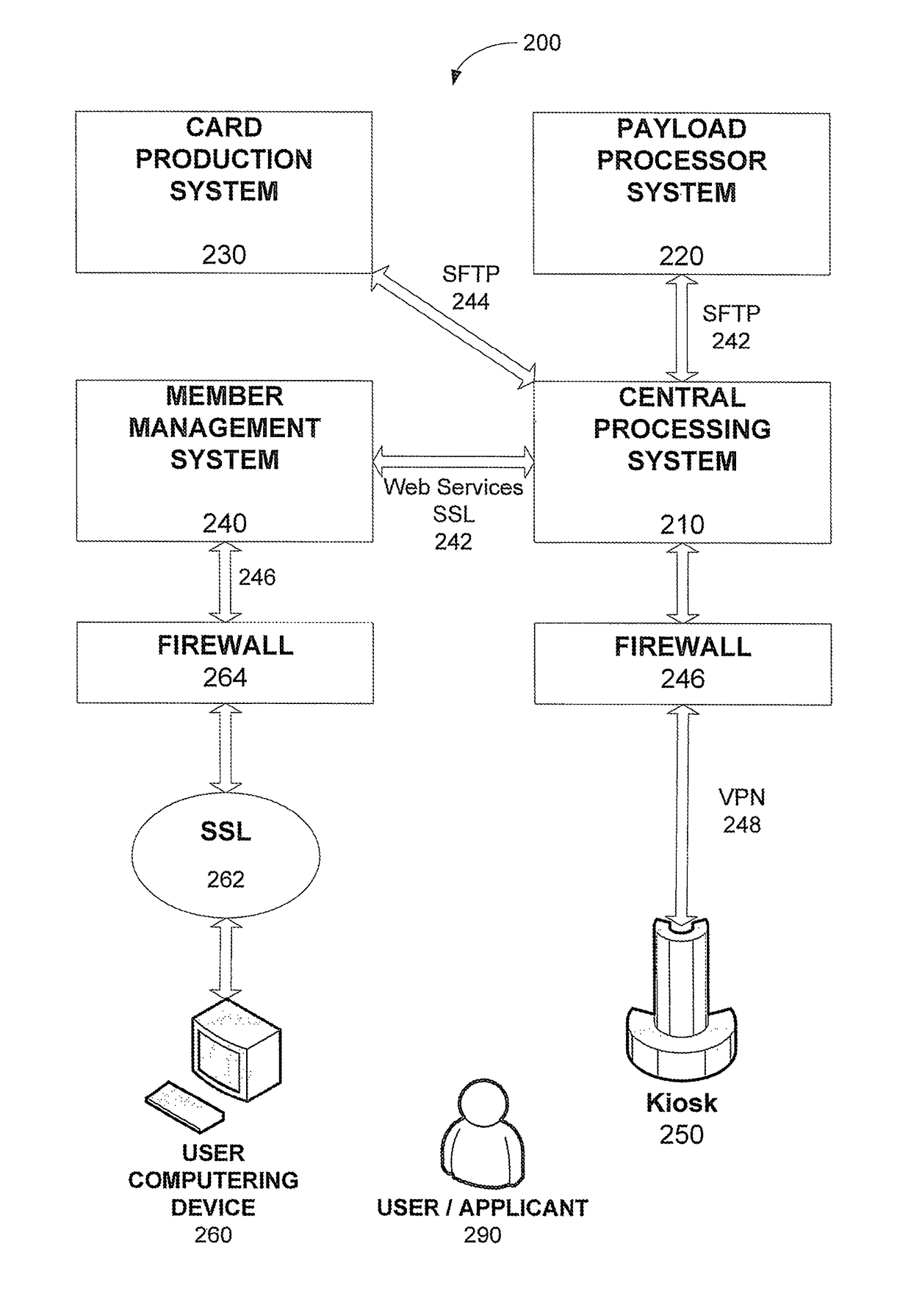
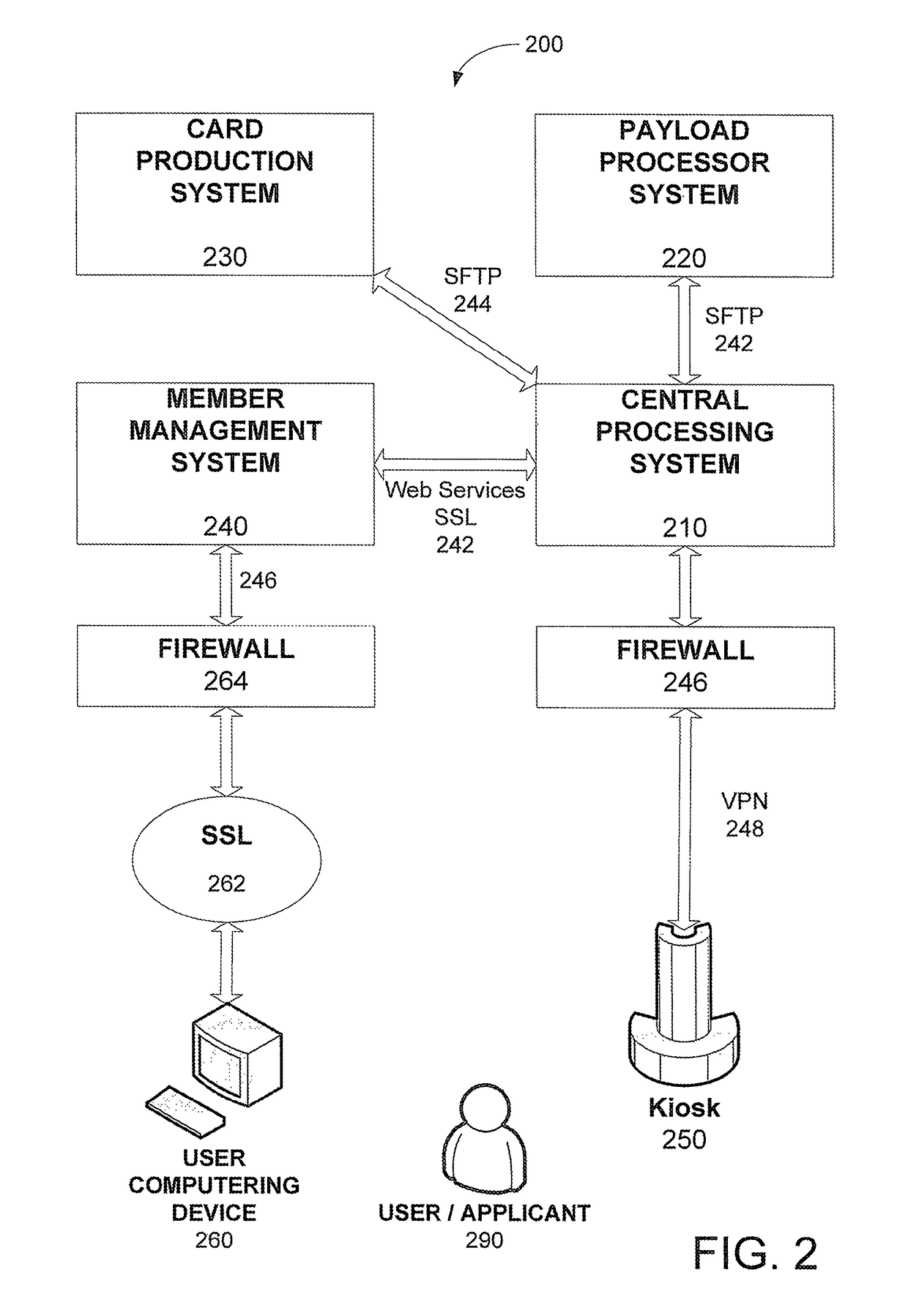
Electronic certification and authentication system
The invention is an automated system that works in the data center of certification offices connected to the internet which enables a member of the any of the certification offices to certify his document electronically from a distance using a computer connected to the internet, digital pad, an electronic pen and a printer.
Owner:HOUSE OF DEV
Motorcycle
ActiveUS20070285272A1Guaranteed to workSimple working processElectric signal transmission systemsAnti-theft cycle devicesModularityEngineering
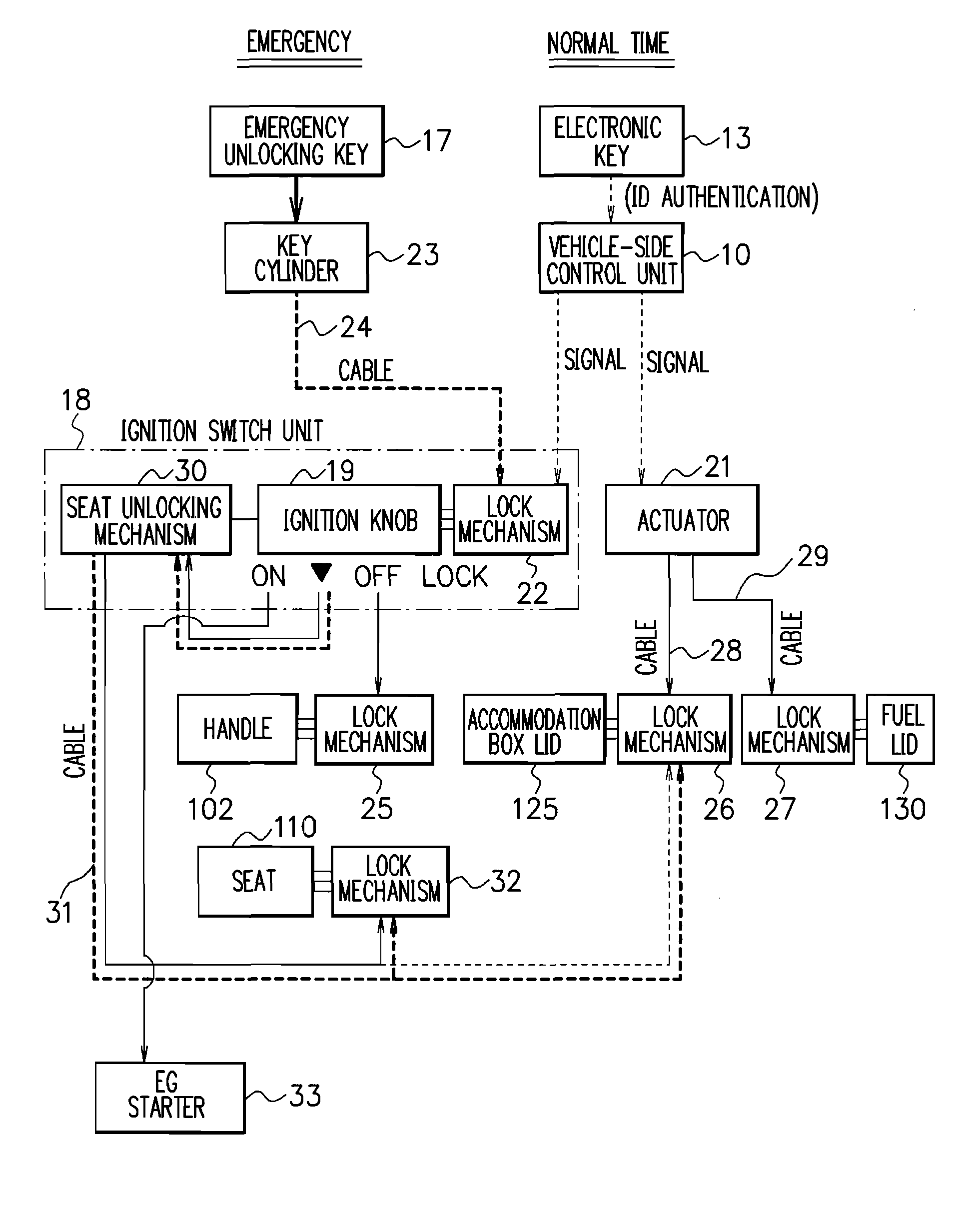
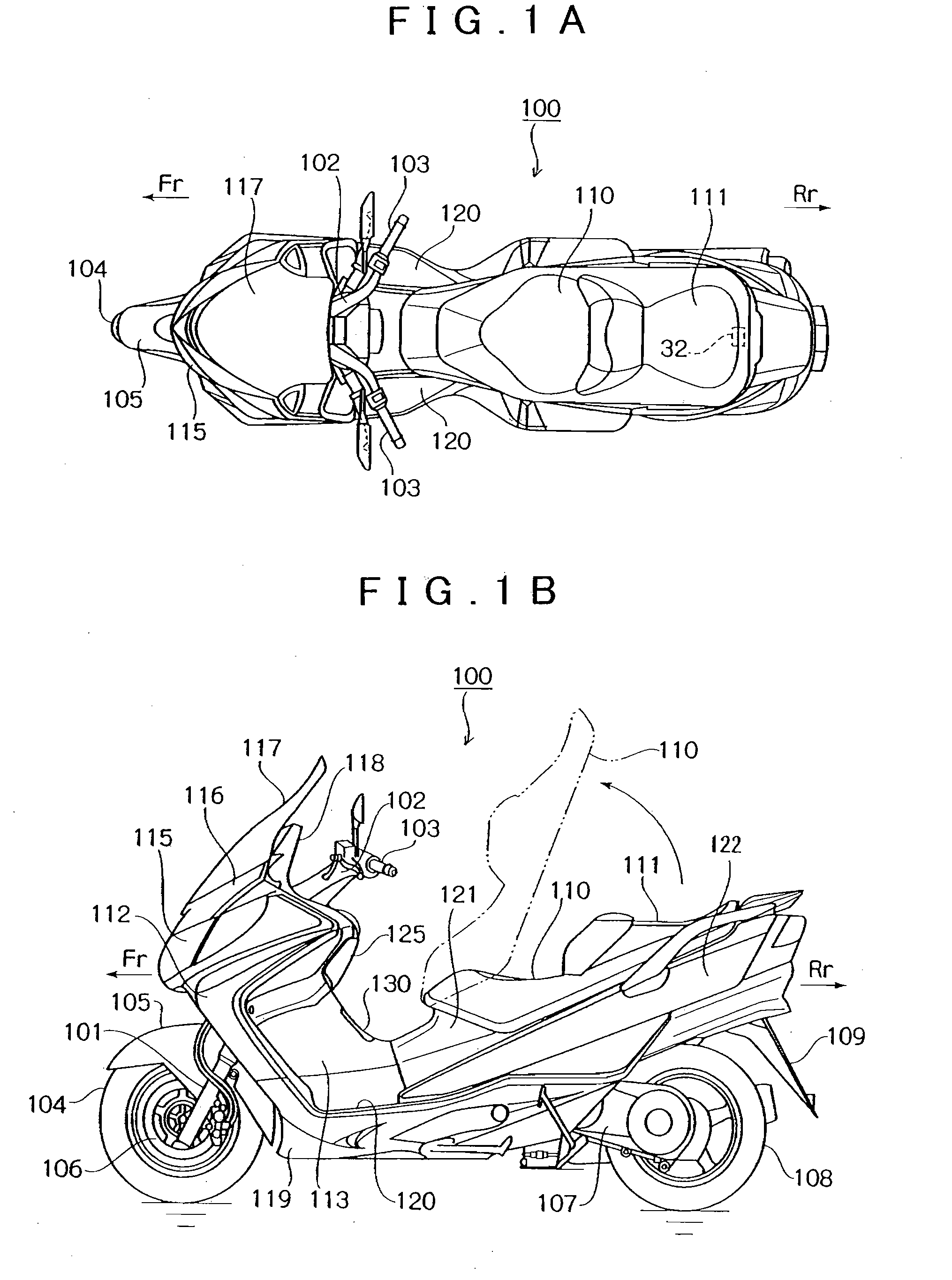
An electronic authentication system includes a vehicle-side control unit that judges whether ID information of an electronic key is identical to vehicle-side ID information, an ignition switch unit that permits engine starting operation and handle unlocking operation on the basis of the identity of the ID information of the electronic key to the vehicle-side ID information, and an actuator that unlocks an opening and closing lid such as a accommodation box lid. These component members are attached and fixed to a leg shield (an inner leg shield) and modularized. These members are preassembled into the inner leg shield and modularized like this, whereby the assembling work into the vehicle becomes very easy and it is possible to make the assembling work efficient to a great extent.
Owner:SUZUKI MOTOR CORP
Device, system, and method for mobile convergence payment
InactiveCN104881779AOpen online and offline paymentRealize the transaction closed loopDigital data authenticationProtocol authorisationPayment transactionClosed loop
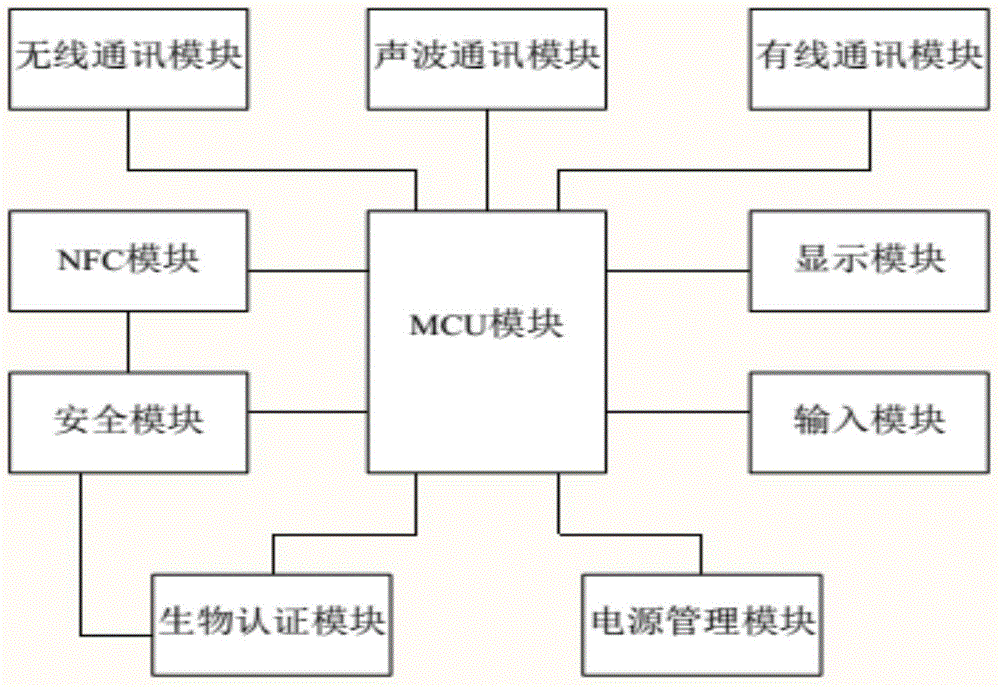
The invention relates to a device, a system, and a method for mobile convergence payment. The device comprises a MCU module, a safety module, a communication module, an NFC module, an input module, a display module, and a power management module. The safety module, the communication module, the NFC module, the input module, the display module, and the power management module are connected with the MCU module. The NFC module is connected with the safety module. The communication module at least comprises two kinds of communication channels. The device is provided with a plurality of safety submodules, and can effectively protect user transaction safety through implementing a safety payment transaction method, an electronic authentication method, and a plurality of safety data transmission methods. The device, the system, and the method are suitable to be used for online banking service, mobile banking service, industry IC card recharging service, IC card card-present payment service, and near-field payment service, and other applications. The device can be used offline, and can also be used online, and effectively gets through online and offline payment, realizes transaction closed loop. The device, the system, and the method can be used for various kinds of payment application scenarios.
Owner:HENGBAO
Method and system for electronic authentification
InactiveUS6952775B1Prevent cheatingFinanceDigital data processing detailsComputer hardwareUser input
An electronic authentication method for identifying a user who is going to use a recording medium into which the information for making use of any kind of computerized service has been stored, comprising a step to carry out authentication by comparing the authentication information input by the user who is going to use the recording medium into which the information for making use of any kind of computerized service has been stored with the authentication information recorded on the recording medium and a step to carry out authentication by comparing the authentication information input by the user or the authentication information recorded on the recording medium with the registered authentication information existing in the hub of the networking to provide the service.
Owner:HITACHI LTD
Data security system with encryption
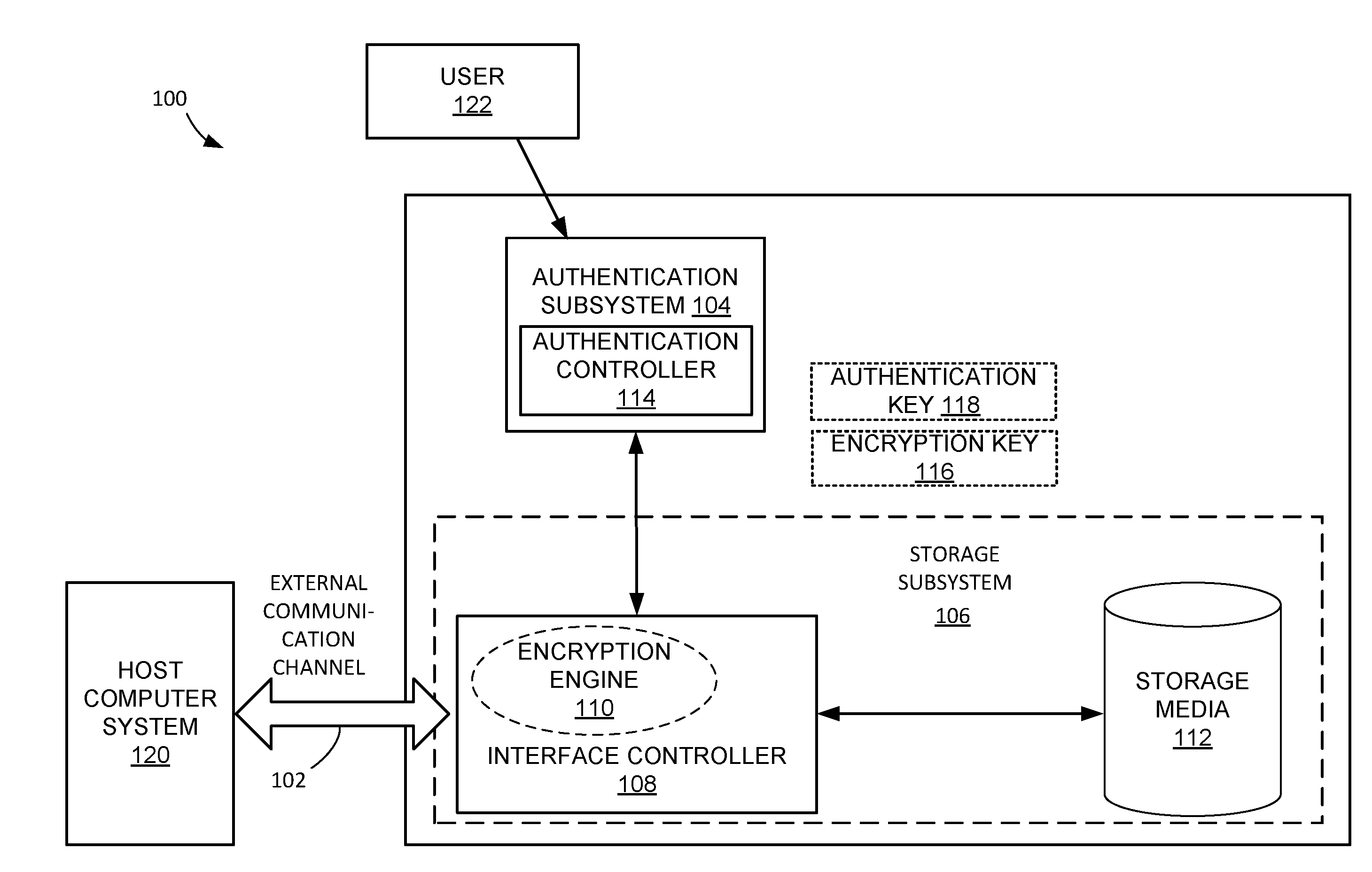
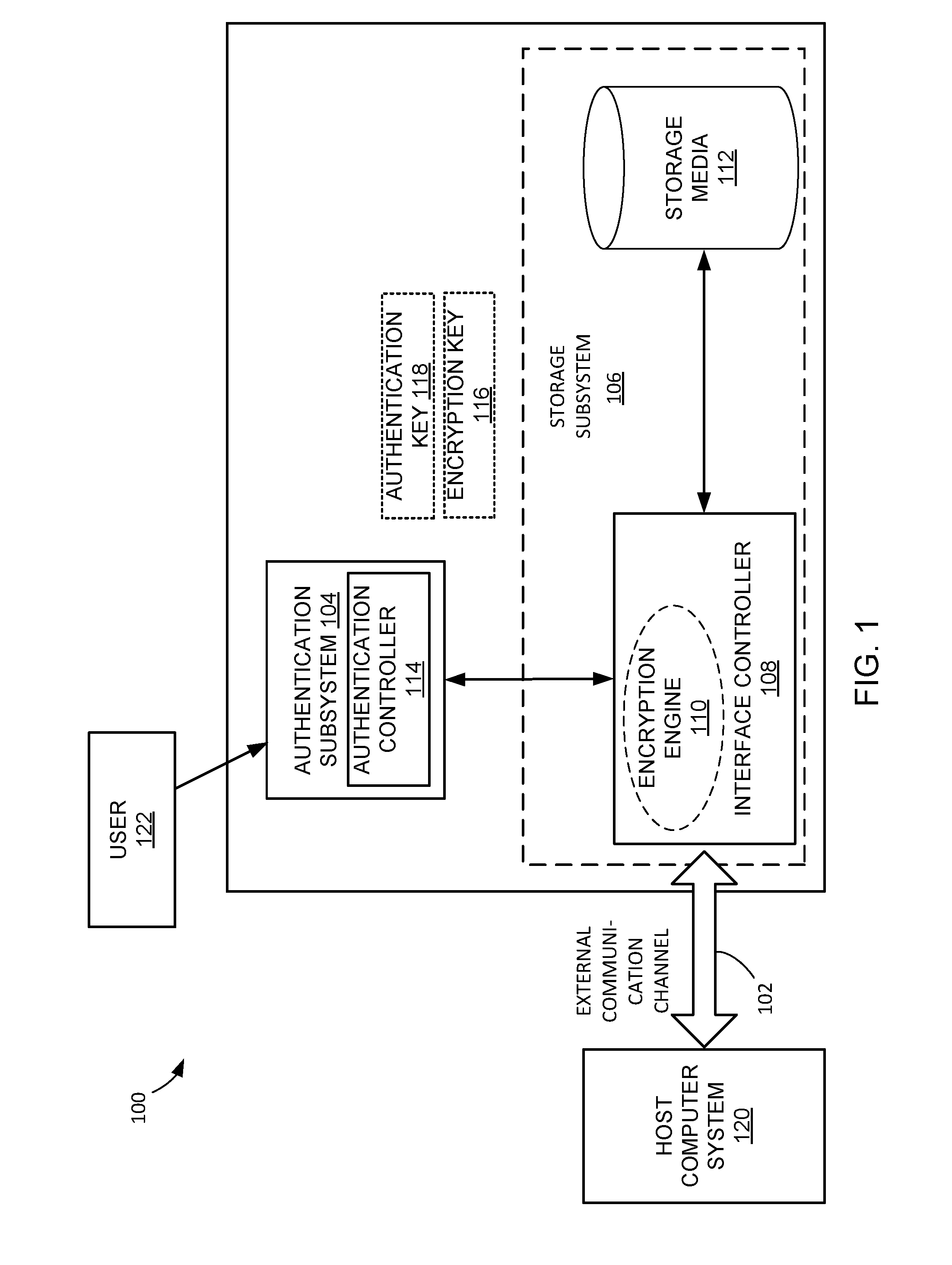
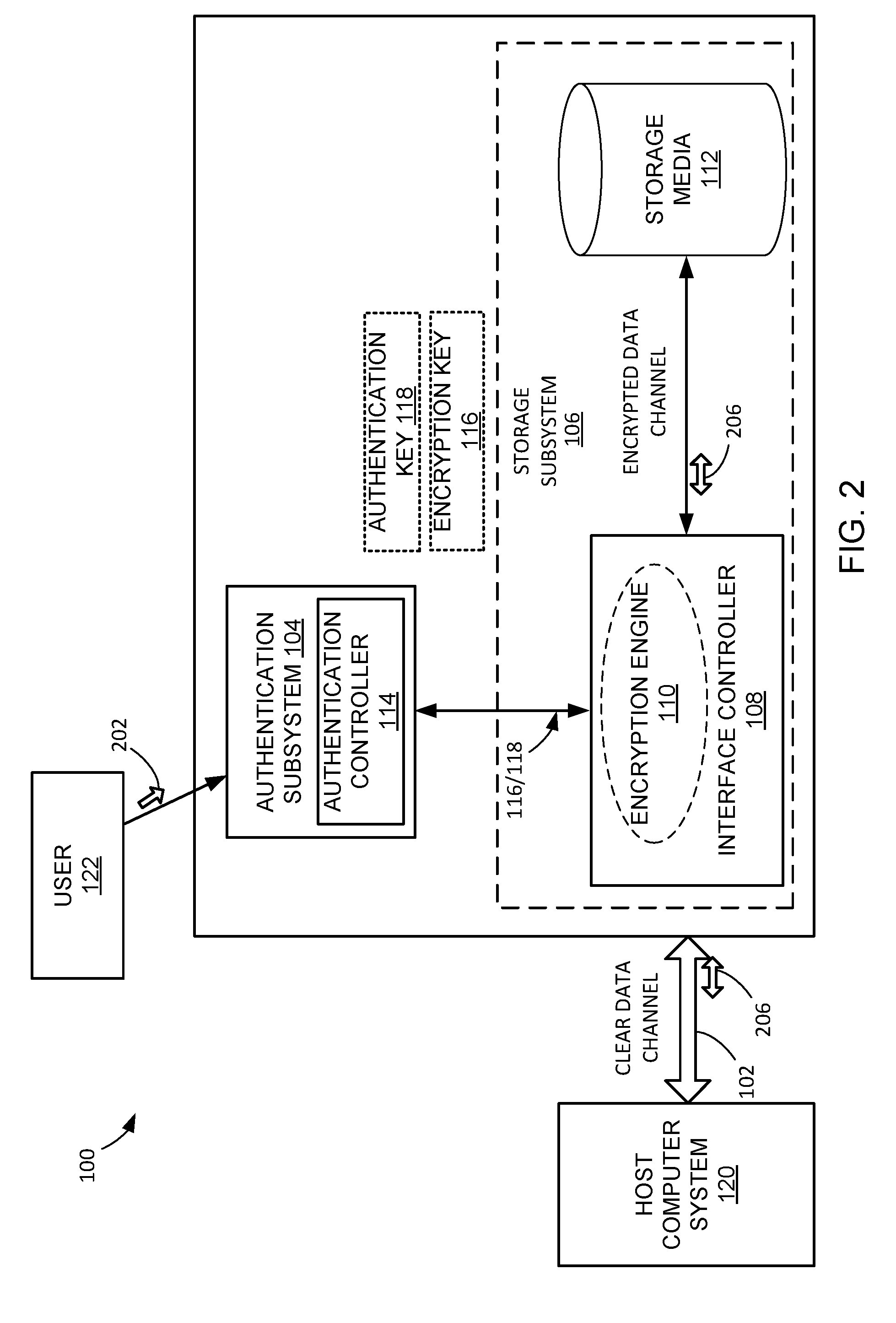
ActiveUS20160119339A1User identity/authority verificationInternal/peripheral component protectionComputerized systemEncryption
A data security system, and method of operation thereof, is provided that includes: an electronic authentication subsystem for verifying a user identification against an authentication key and for employing the authentication key for retrieving an encryption key, the authentication key only accessible from inside the electronic authentication subsystem, and the user identification supplied from outside the data security system to a receiver within the electronic authentication subsystem; and a storage subsystem employing the encryption key for allowing unencrypted communication through the storage subsystem between a host computer system and a storage media.
Owner:CLEVX
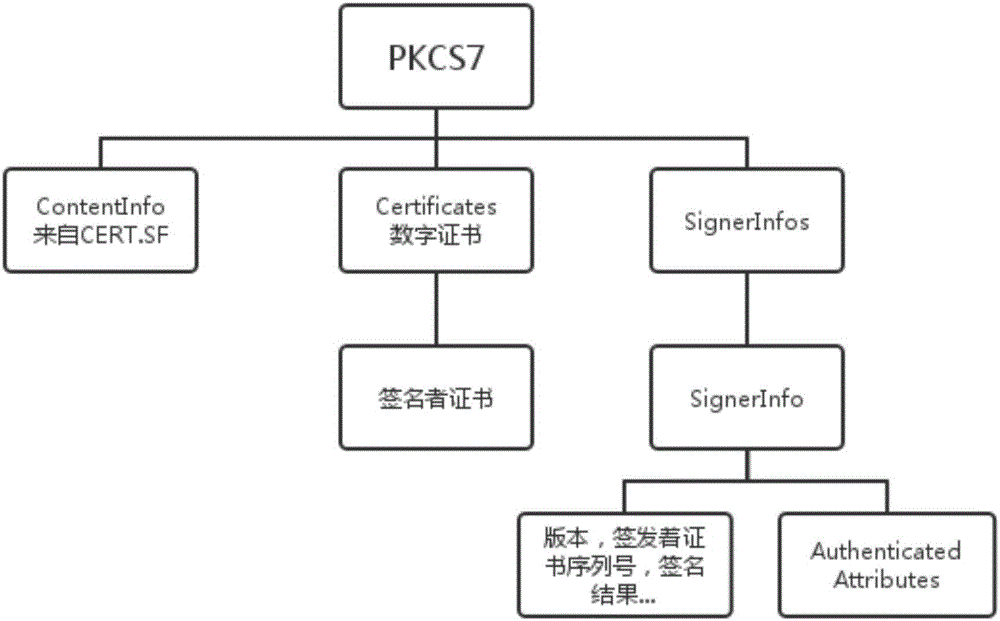
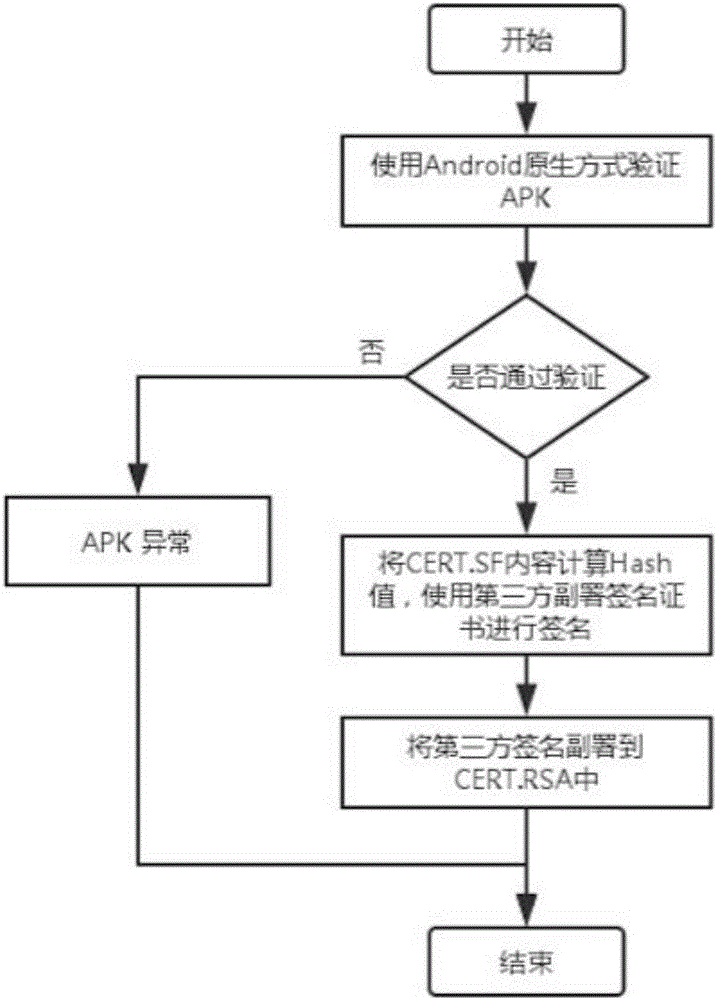
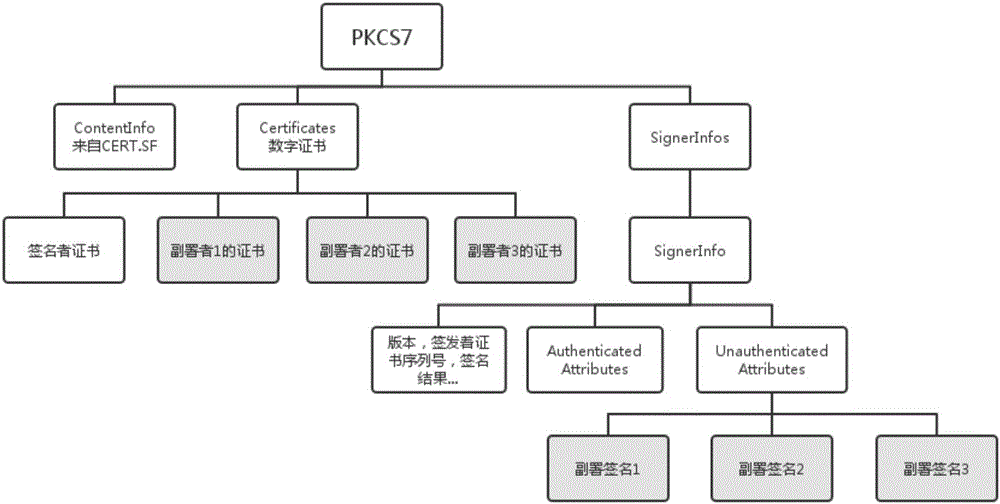
Android APK countersignature verification method
The invention proposes an Android APK countersignature verification method. The method comprises the following steps of 1, a developer writes a signature of CERT.SF into a CERT.RSA or CERT.DSA file by using an original private key; 2, a third party applies for a digital certificate from a credible electronic authentication service mechanism, performs countersignature on CERT.SF by using the digital certificate, and adds countersignature information into the CERT.RSA or CERT.DSA file, wherein countersignatures contain signature time; and 3, a native Android system performs verification on an APK, verifies the APK according to a native signature verification method of Android and does not verify the countersignature information; and if the APK is installed through system application software of the third party and native APK signature verification is passed, the countersignatures are further verified in sequence, and if all verifications are passed, APK installation is allowed, otherwise, the APK installation is refused. According to the method, the APK can be countersigned with a plurality of signatures on the premise of not destroying an existing signature verification mechanism of Android and an Android file structure, and any countersignature can be traced; and therefore, the method has a huge value in actual application.
Owner:江苏先安科技有限公司
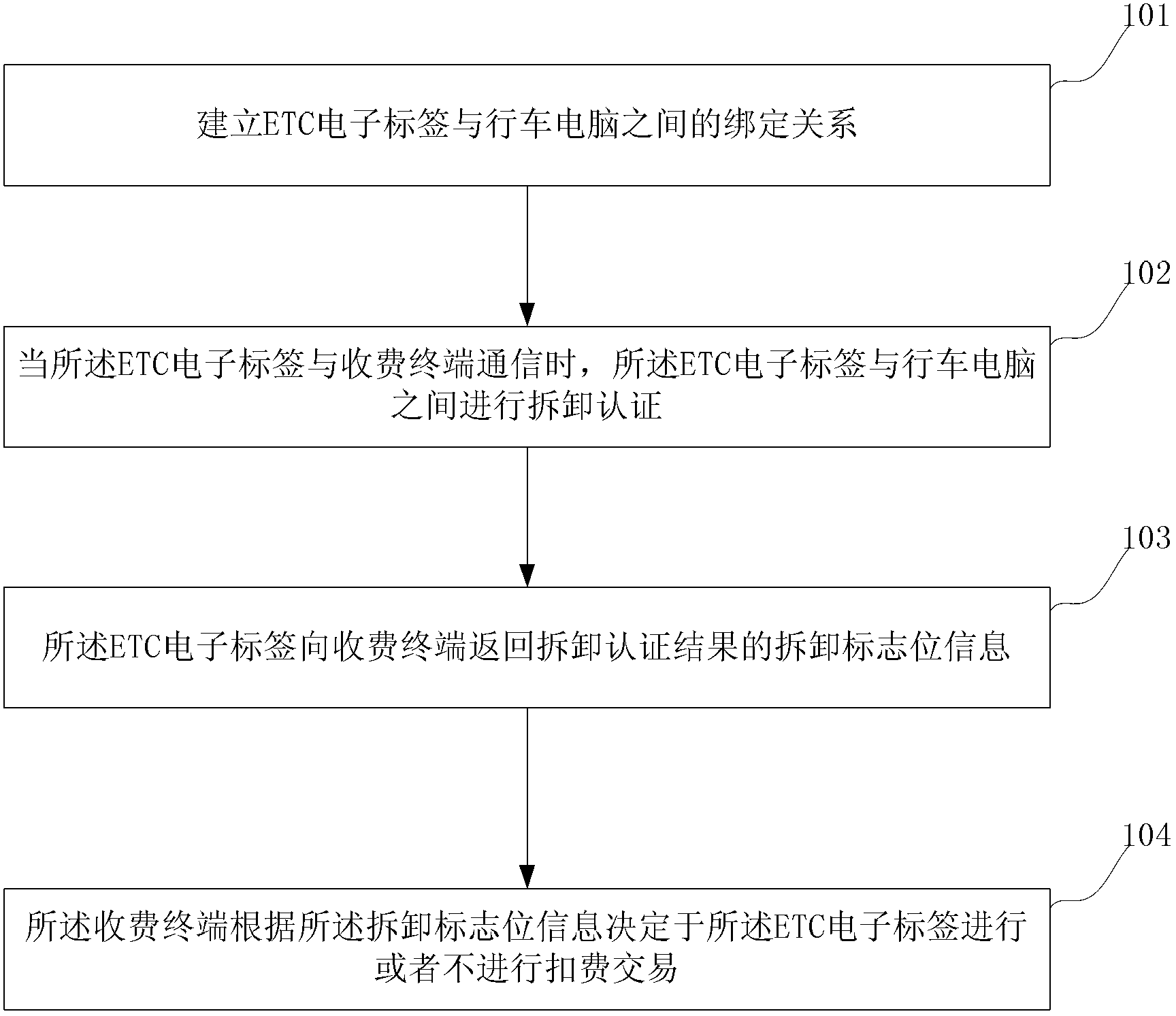
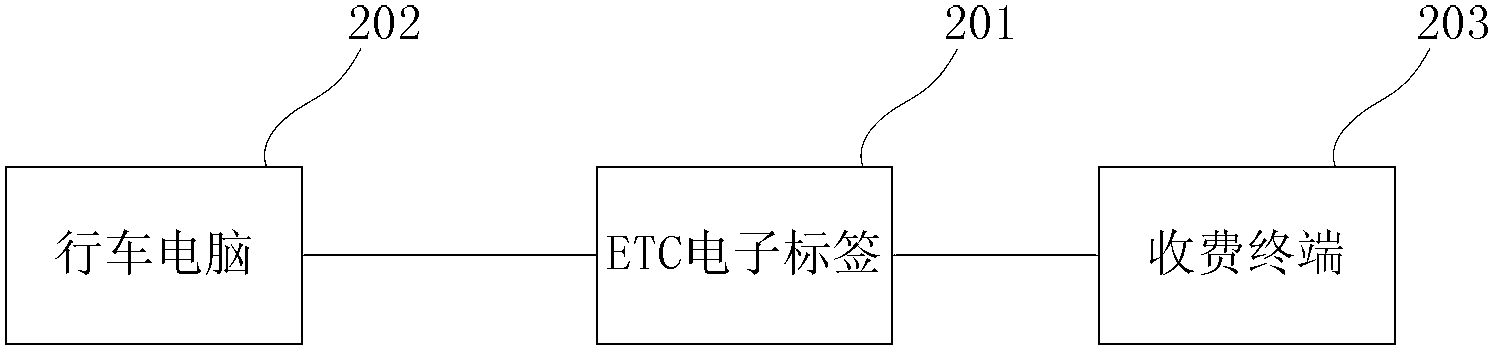
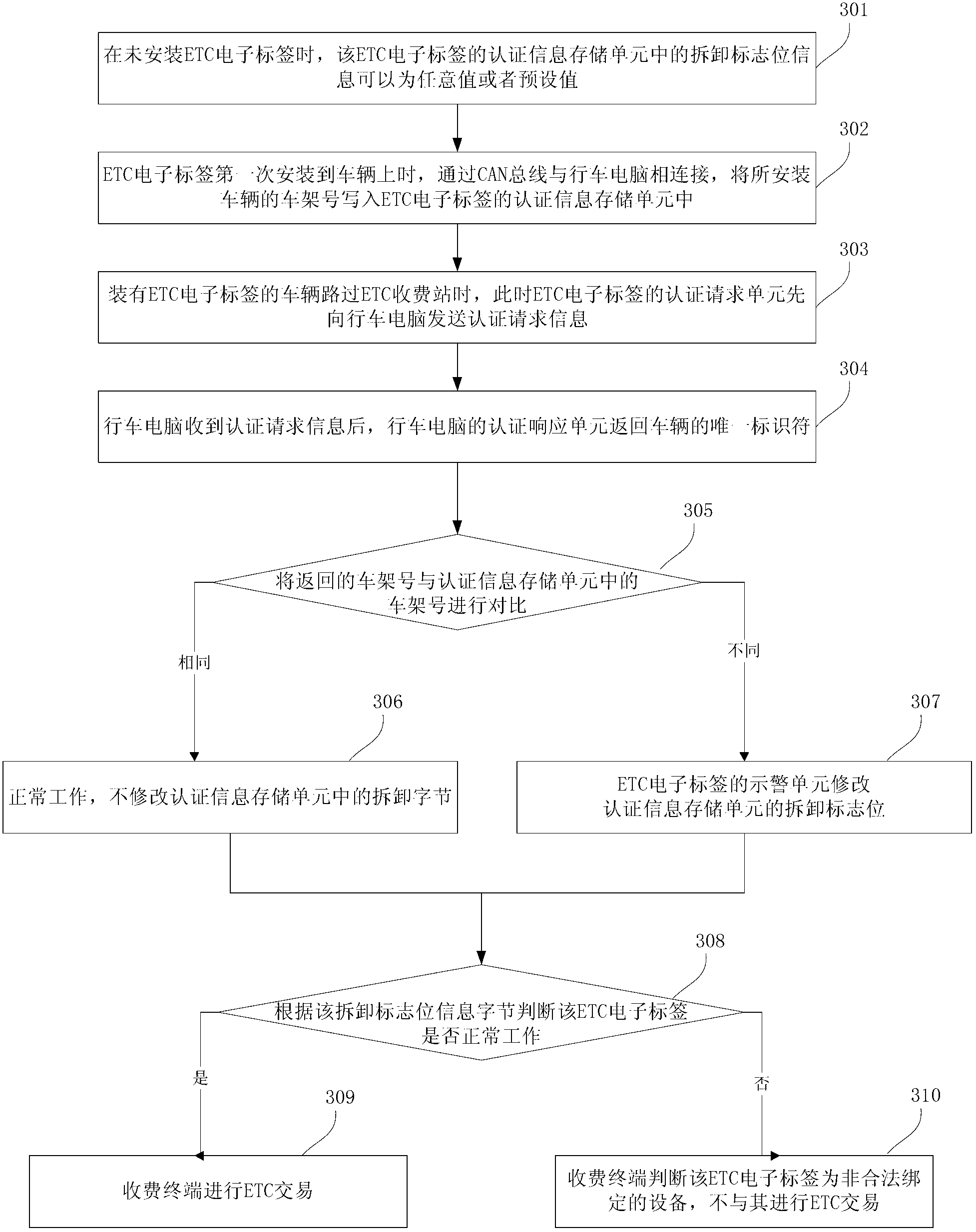
Electronic disassembling preventing method and electronic disassembling preventing system for electronic toll collection (ETC) electronic tags
InactiveCN102800133APlay the role of certificationTicket-issuing apparatusEngineeringElectronic toll collection
The invention relates to the field of electronic toll collection (ETC) electronic tags, in particular to an electronic disassembling preventing method and an electronic disassembling preventing system for ETC electronic tags. Disassembling prevention and thievery prevention are realized by binding the ETC electronic tags and trip computers of a vehicle one by one in an electronic authentication manner. The electronic disassembling preventing method comprises the following steps of: building a binding relation between the ETC electronic tags and the trip computers; performing disassembling information authentication between the ETC electronic tags and the trip computers when the ETC electronic tags are communicated with a charge terminal; returning a disassembling information authentication result, namely disassembling zone bit information, to the charge terminal by the ETC electronic tags; and judging whether the charge terminal transacts with the ETC electronic tags or not according to the disassembling zone bit information. According to an embodiment of the invention, the trip computers can be used for performing disassembling prevention and thievery prevention authentication on the ETC electronic tags, so that an accurate authentication effect can be achieved, and shortcomings of a mechanical disassembling preventing device are avoided.
Owner:北京速通科技有限公司
Authentication system by fingerprint
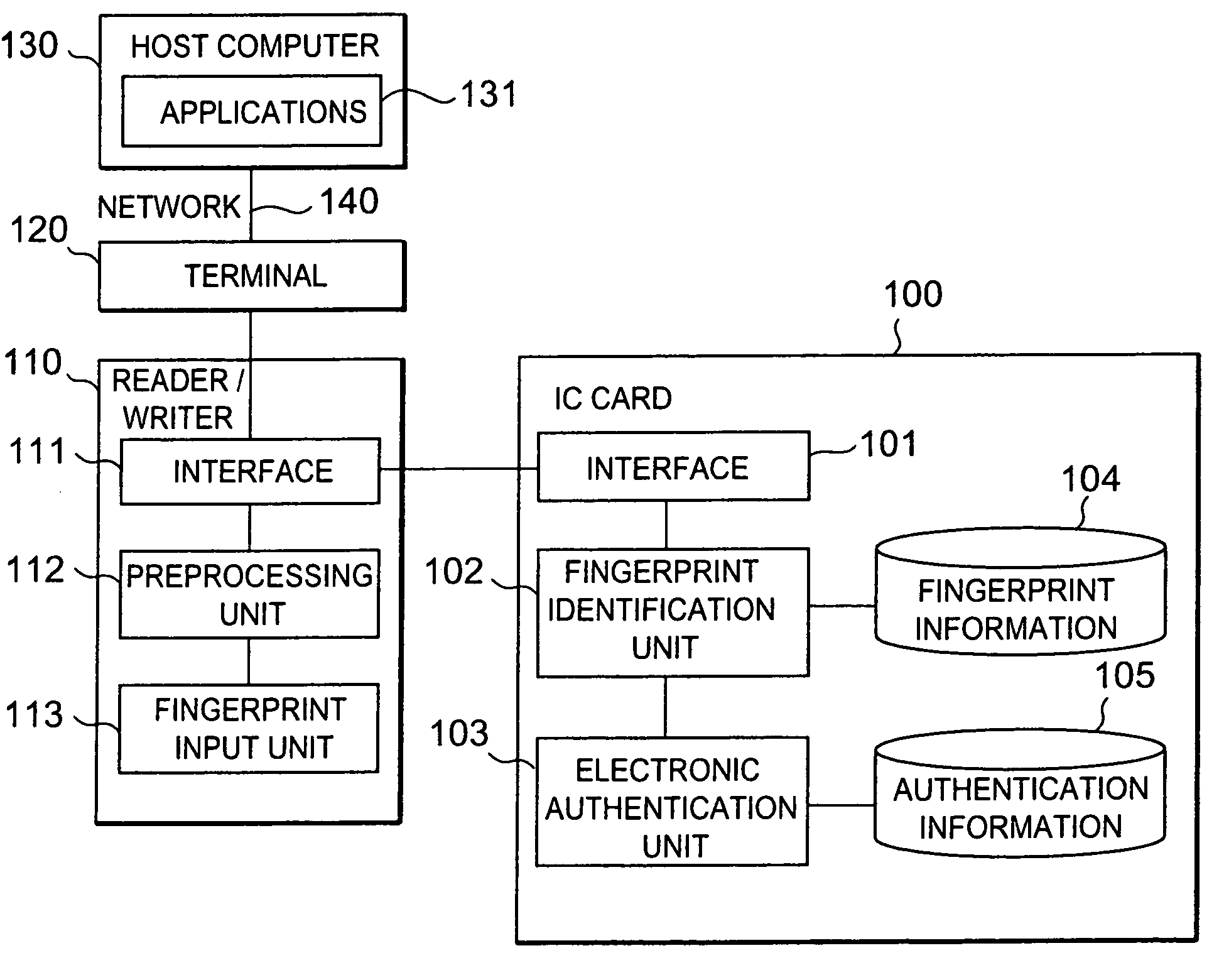
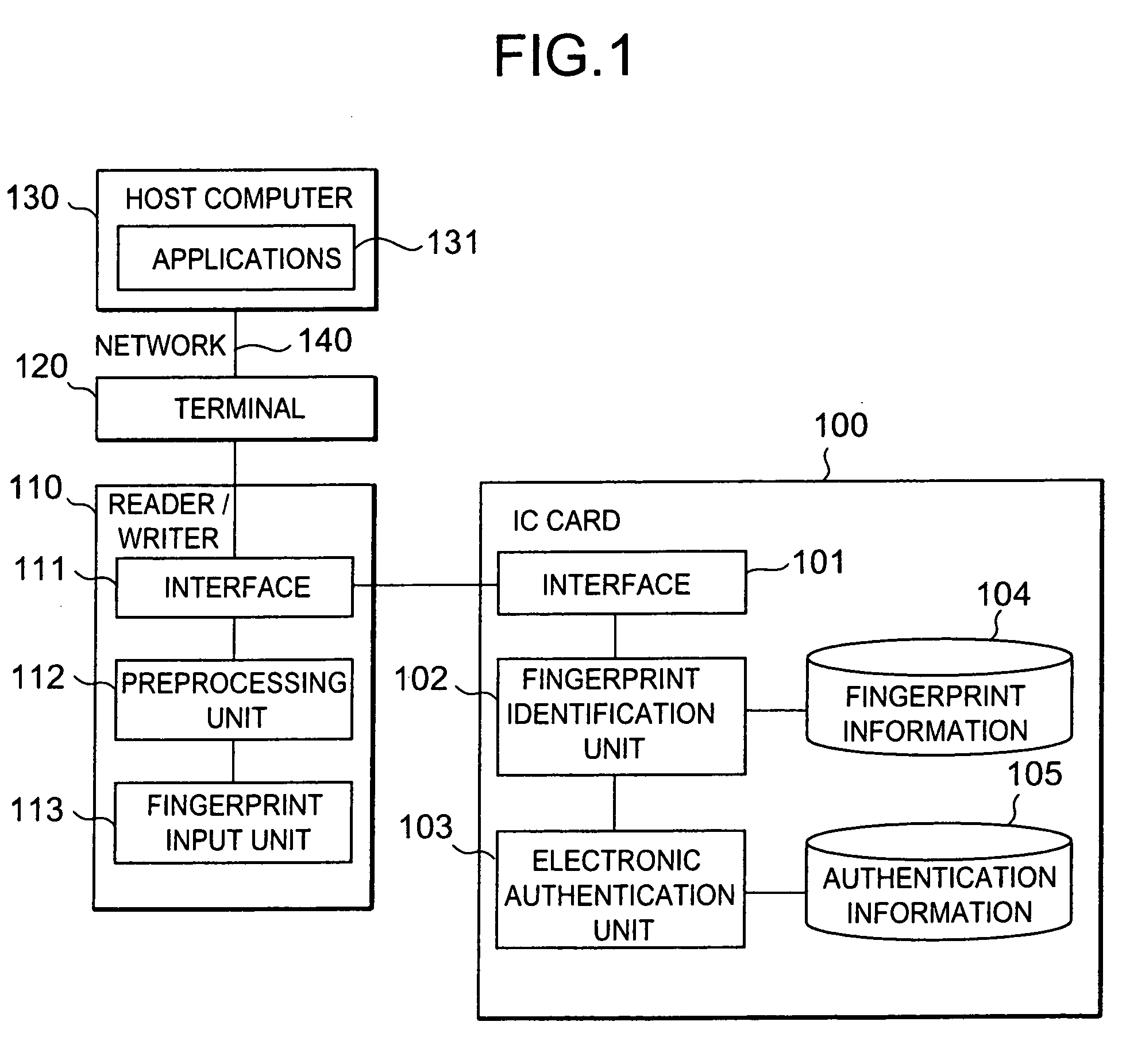
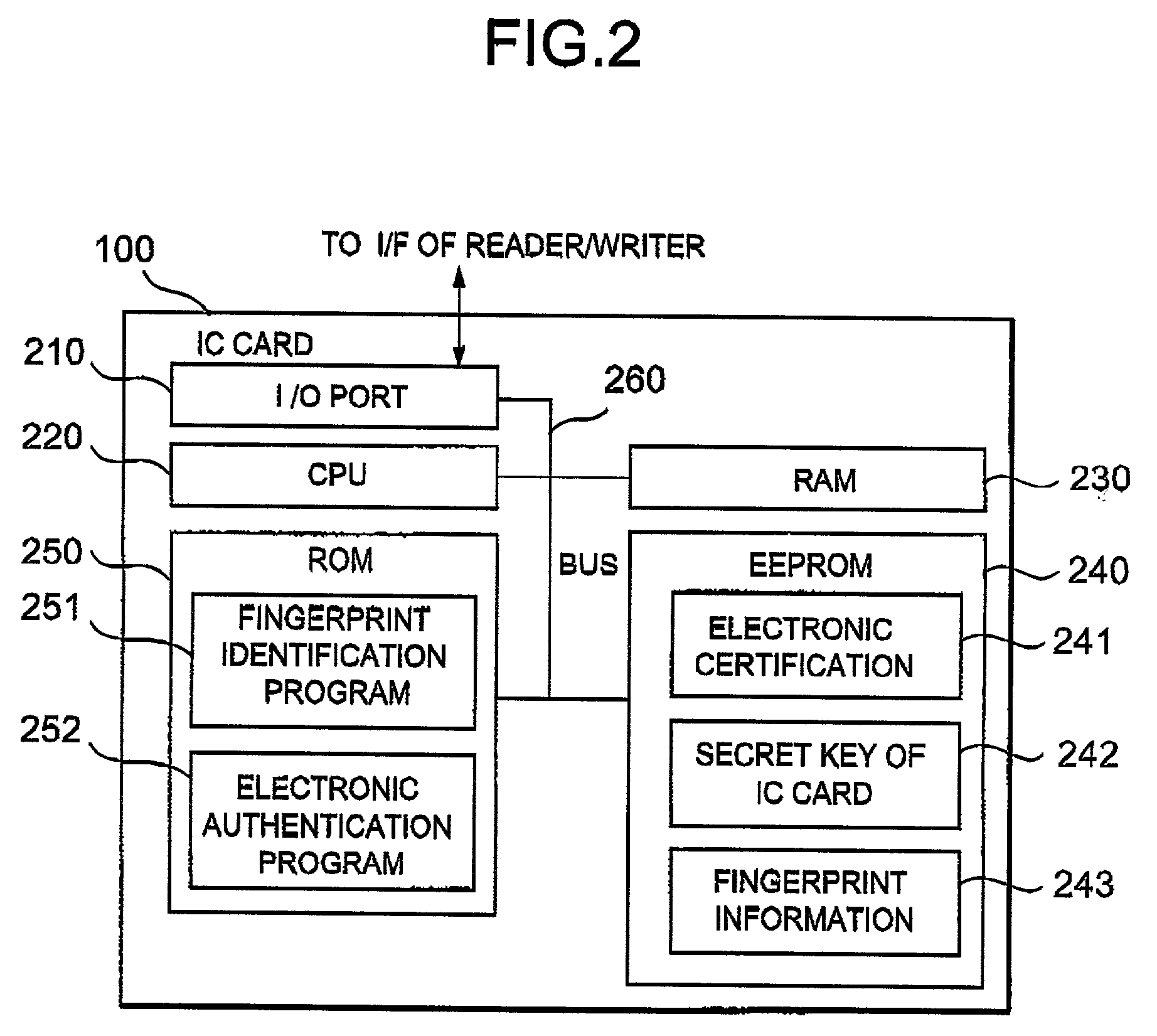
InactiveUS7162058B2Improve security levelLow costImage analysisUser identity/authority verificationComputer hardwareTamper resistance
A fingerprint identification system comprising: an IC card having a tamper-resistance; and a reader / writer having a tamper-resistance for reading / writing information from / into the IC card. In the reader / writer, a fingerprint image, as read by a fingerprint input unit, is preprocessed in a preprocessing unit, and extracted intermediate information is transmitted to the IC card. This IC card compares the intermediate information with the fingerprint information, and makes authentication information usable for an electronic authentication upon matching. By this electronic authentication with applications, the fingerprint identification system, which has a high level of safety and can reduce the cost is provided.
Owner:HITACHI LTD
Electronic Certification and Authentication System
InactiveUS20060161779A1User identity/authority verificationPayment architectureDigital padData center
The invention is an automated system that works in the data center of certification offices connected to the internet which enables a member of the any of the certification offices to certify his document electronically from a distance using a computer connected to the internet, digital pad, an electronic pen and a printer.
Owner:HOUSE OF DEV
Systems and methods for real estate process management
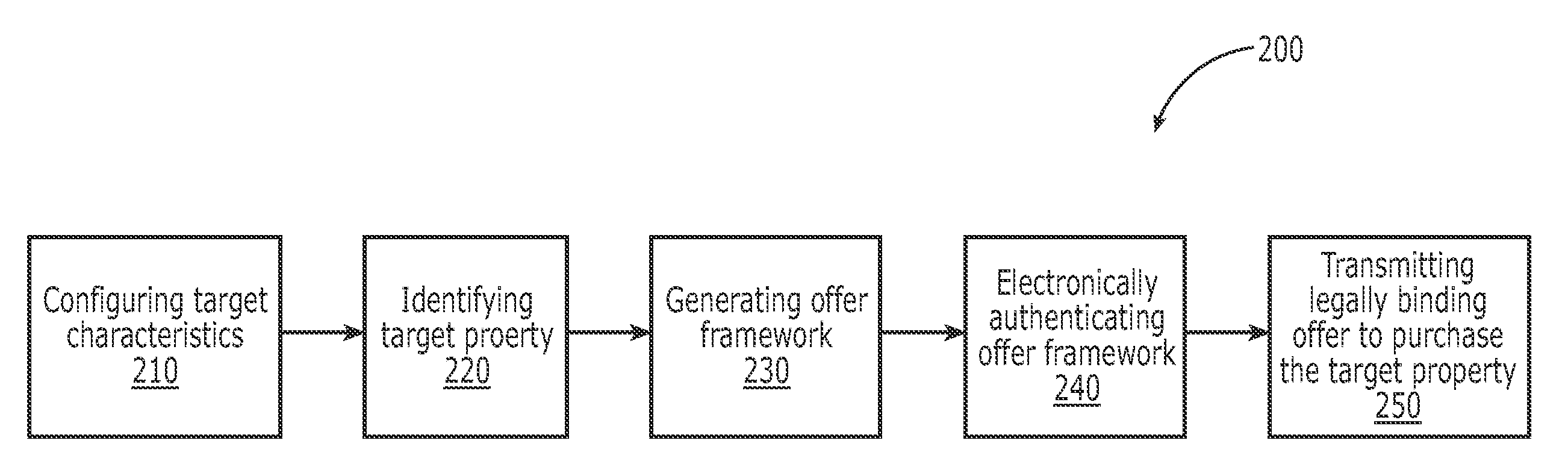
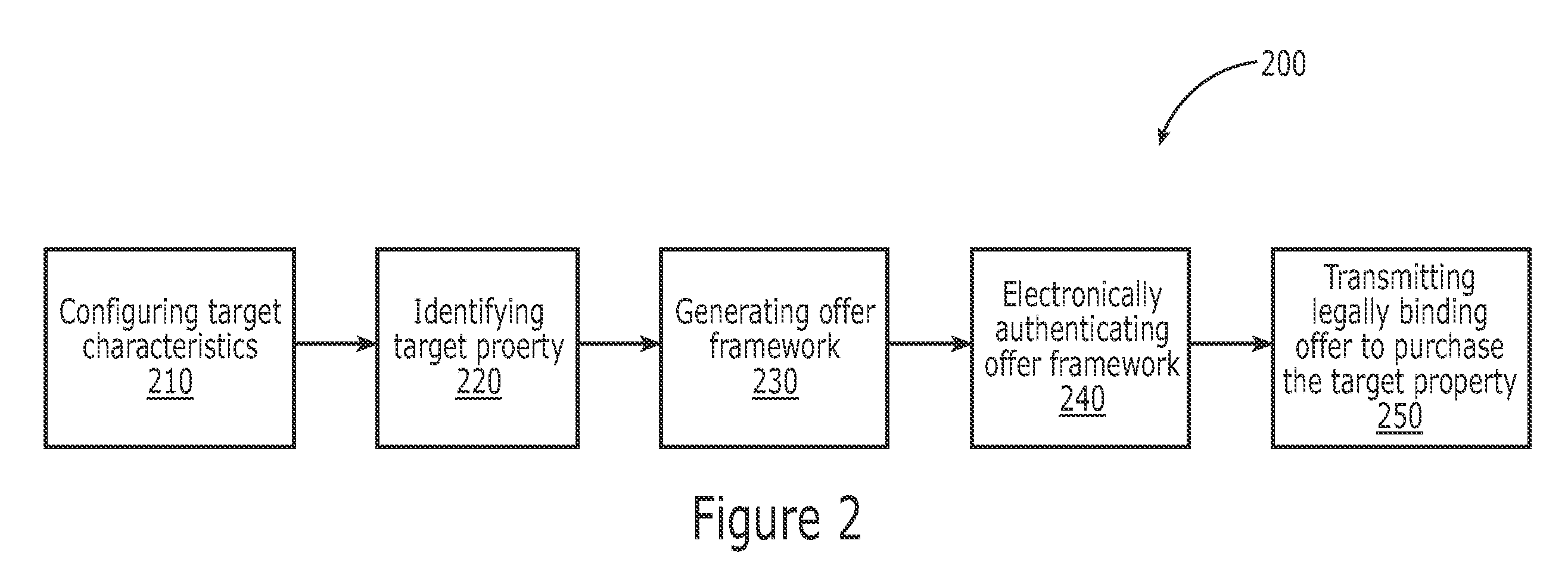
InactiveUS20070244798A1Facilitate paperless real estate acquisitionRaise the possibilityFinanceOffice automationData scienceElectronic authentication
The present invention relates to systems and methods that may be used to facilitate paperless real estate acquisition. One embodiment of the present invention relates to a paperless method of generating and submitting a legally binding real estate offer to purchase an electronically identified property. The method includes identifying a target property according to a correlation algorithm that utilizes a set of target characteristics specific to a buyer. An offer framework is prepared to purchase the target property including the target property location and offer price. The offer framework is electronically authenticated so as to form a legally binding offer to purchase the target property. The legally binding offer is transmitted to a correspondent for the property. A second embodiment of the present invention relates to an electronic offer generation system, including a property identification module, an offer generation module, and a communication module.
Owner:WEIDENBENNER JASON
Method and system for electronic authentication
A method and system for authenticating, in a host managing an electronic site and a site information table, user information inputted by a communication terminal communicably connected to the electronic site. The user information may comprise a dynamic password that corresponds to a static password and is contained in a local information table. Upon receiving user information transmitted by the communication terminal, the host authenticates the user information based on its site information table in order to allow for performing a transaction from the communication terminal. The host changes the user information to update the site information table during a transactable period after authenticating the user information and transmits the changed user information to the communication terminal in order to update the user information at the communication terminal. Upon receiving the changed user information from the host, the communication terminal updates the user information in its local information table accordingly.
Owner:IBM CORP
Issuing method of IC card internet terminal and management system
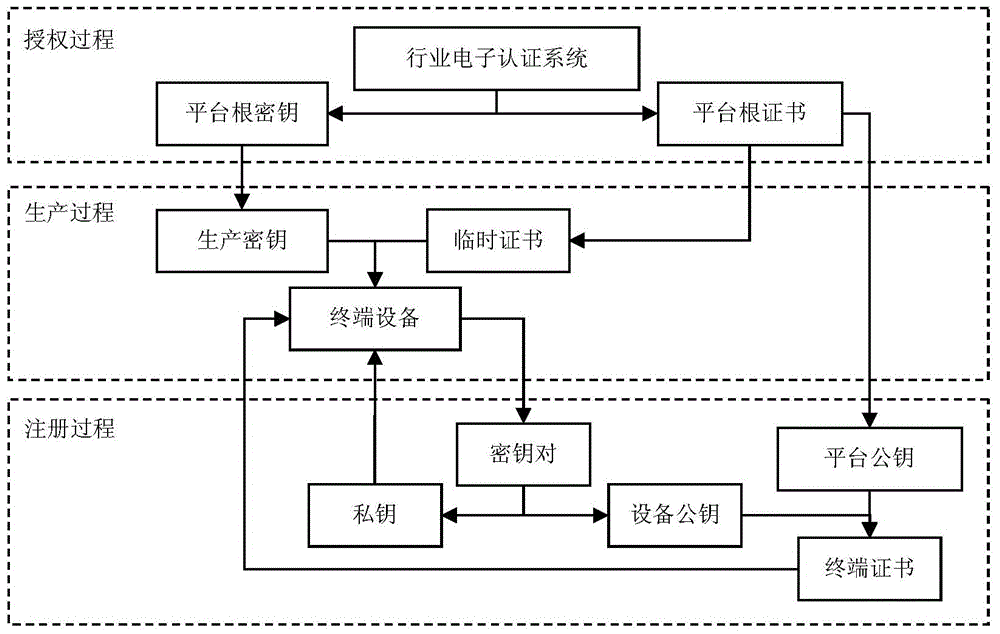
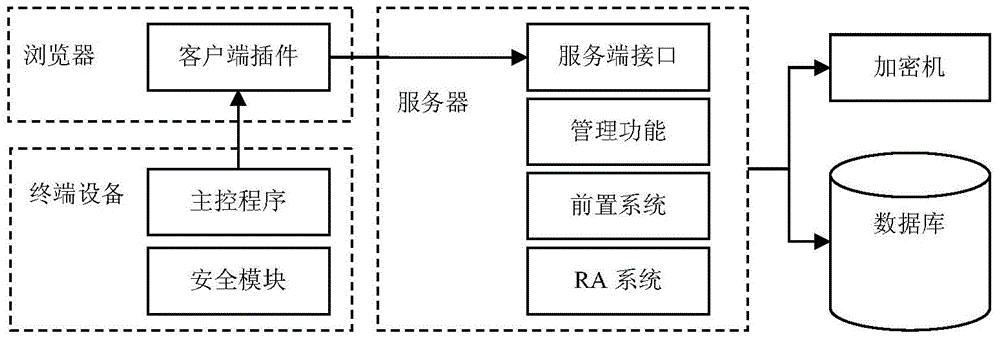
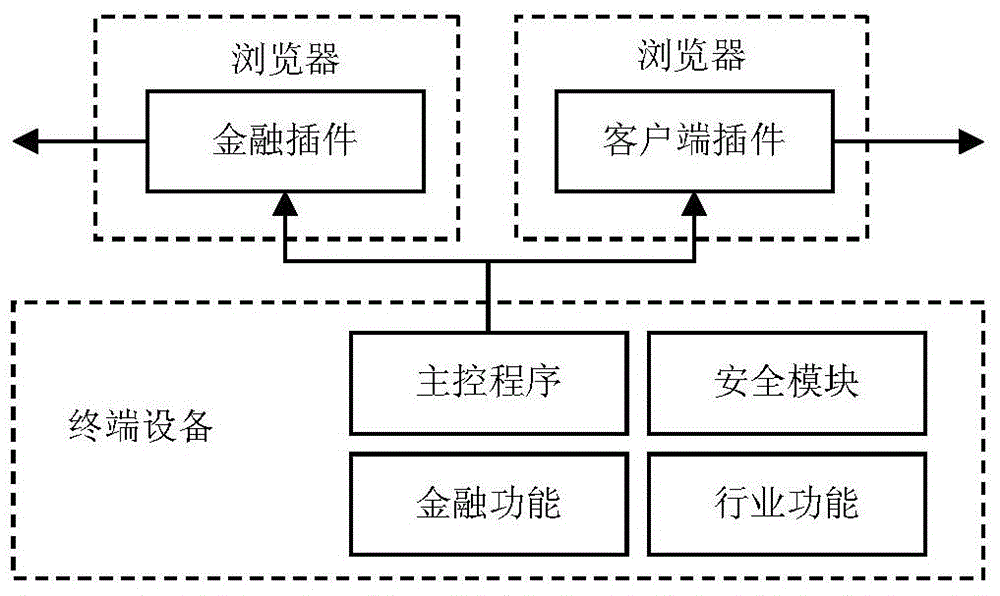
The invention discloses an issuing method of an IC card internet terminal. The method comprises following steps: A, an authorization process: applying a platform root key and a platform root certificate to an industrial electronic authentication system based on an Internet platform; B, a production process: producing a key and writing in a temporary certificate and initialization to terminal equipment; C, a login process: the management system of the IC card internet terminal is used for automatically starting the login process of the terminal equipment.The issuing method of the IC card internet terminal and the management system have following beneficial effects: by means of factorized configuration of industrial temporary certificates and on-line update of formal certificates, issuing regulation and industrial application support of the IC card internet terminal are achieved in support of hardware realization of domestic password algorithms; the working environment for a personal client is provided for application of industrial IC cards; security technology integration and issuing management difficulties of large-scale industrial application based on financial standard equipment are solved; and the issuing method of the IC card internet terminal and the management system help to fill the gap of management work.
Owner:GUANGDONG HUADA INTERNET CO LTD
System and Method for Electronic Certification and Authentification
InactiveUS20090031139A1User identity/authority verificationComputer security arrangementsElectronic documentSecure transmission
The invention relates to electronic document security systems and in particular to user authentication and to the certification and secure transfer of sensitive document information of various type, like whole documents, certificates, signatures, stamps, etc., especially by verifying its correctness and safety / immunity from fraud.
Owner:HOUSE OF DEV
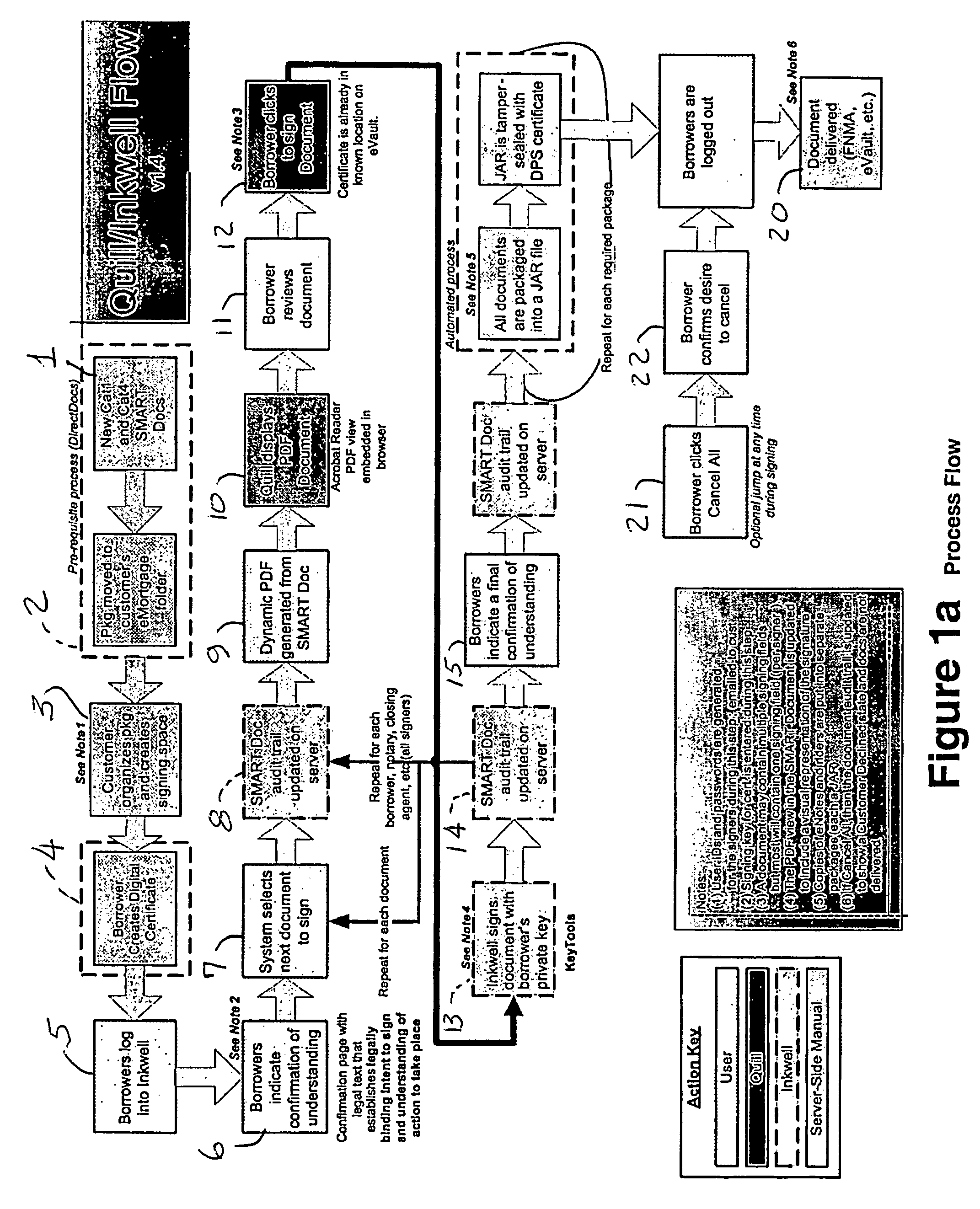
Paperless process for mortgage closings and other applications
According to the present invention, there is provided an electronic document processing system and method including an electronic document generation mechanism, an encrypted digital certificate generator, a tool for coordinating the processing of electronic documents, a packaging mechanism for finalizing and authenticating electronic documents, a tracking log for recording relevant electronic document information, and a transferring protocol for transferring the ownership of electronic documents. The present invention also provides an electronic authentication system including an electronic document authentication watermark seal or signature line for confirming a document's signing within the view. Preferably, the present invention is directed towards a system, software program, and method for generating electronic documents, coordinating the signing of said electronic documents, digitally authenticating and certifying said electronic documents, and organizing said electronic documents for retrieval and transfer in the mortgage closing / financial services field.
Owner:CITRIN HLDG LLC
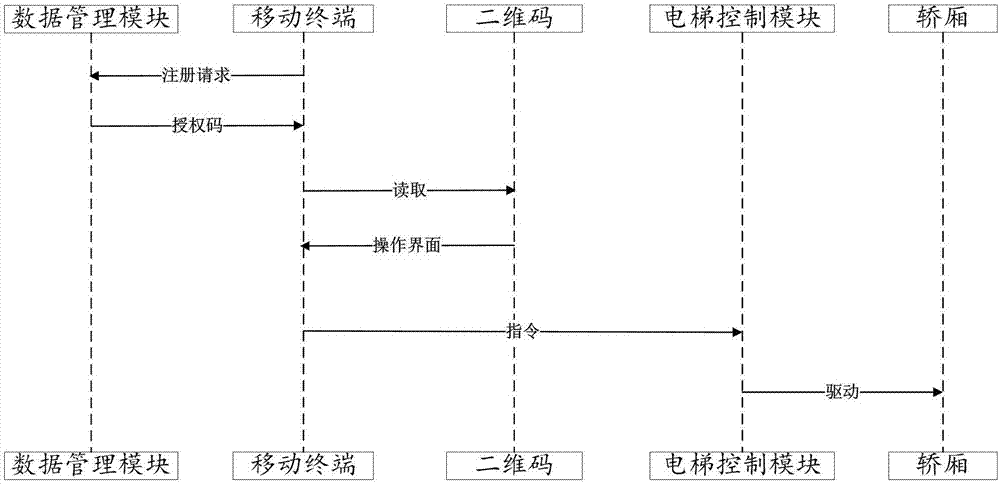
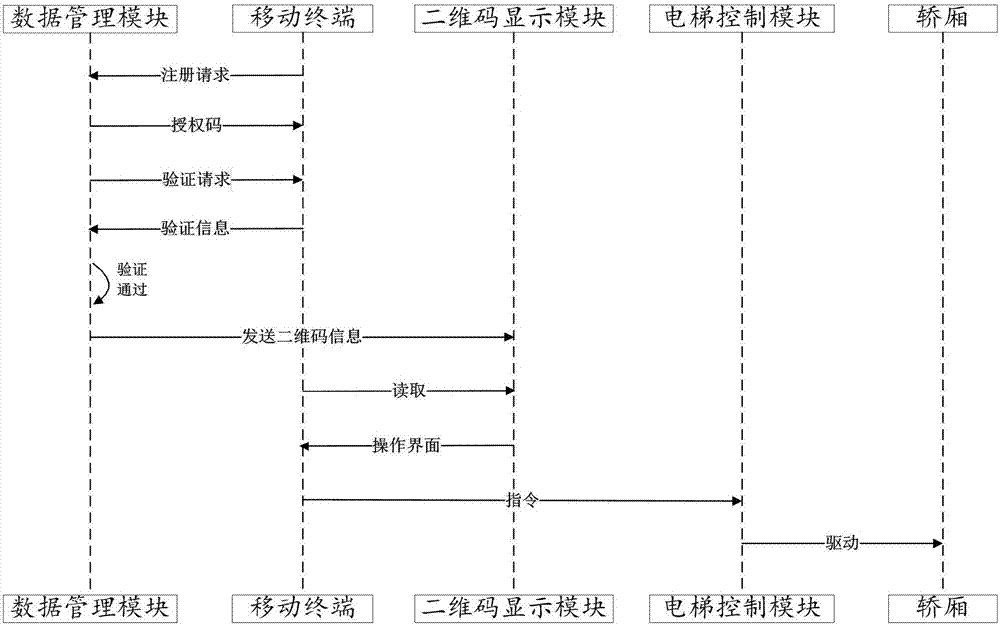
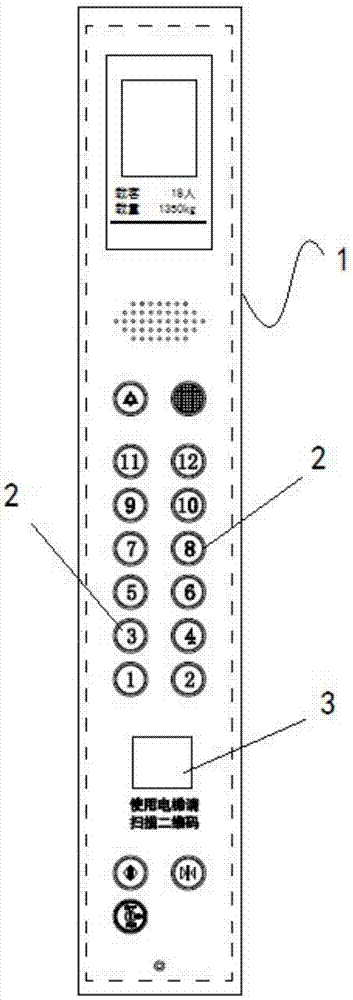
Elevator calling system and elevator calling method based on two-dimensional codes and elevator
PendingCN107572318AImplement rights managementReduce setup costsElevatorsGraphicsGraphical user interface
The invention discloses an elevator calling system and an elevator calling method based on two-dimensional codes and an elevator. The elevator calling system comprises an elevator control module, a mobile terminal and a data management module; the mobile terminal is provided with a camera; the mobile terminal sends registration requests to the data management module; the registration requests comprise user identity information; the data management module returns authorization codes to the mobile terminal according to the registration requests; based on the authorization codes, the mobile terminal can obtain elevator operation graph user interfaces through scanning the two-dimensional codes; the mobile terminal sends operation instructions to the elevator control module through the interfaces; and the elevator control module drives the elevator to act according to the operation instructions. The elevator calling system has no need to issue access cards to save the cost, manages the elevator use authority through an electronic authentication mode, realizes elevator calling through scanning the two-dimensional codes, and is convenient to operate.
Owner:SJEC CORP
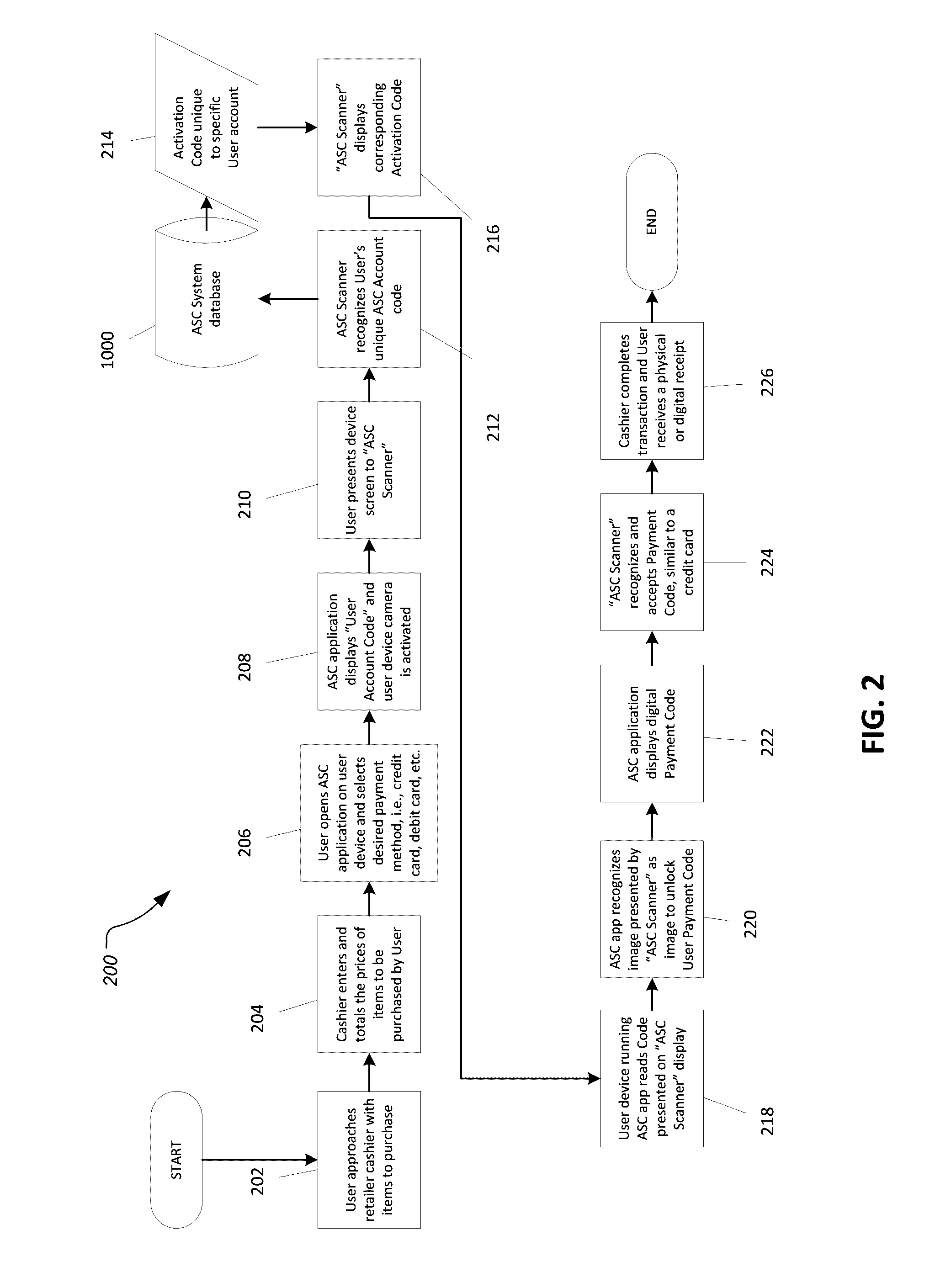
Authenticated scannable code system
A method of electronically authenticating an electronic ticket upon entry to a venue can include displaying a first scannable code on a display of a user device, placing the user device adjacent to a scannable code reader device, scanning the first scannable code of the user device with the scannable code reader device, generating a second scannable code and displaying the second scannable code on the scannable code reader device, scanning the second scannable code with a camera on the user device, generating a user ticket code on the display of the user device, and displaying the user ticket code on the user device to gain admittance into the venue.
Owner:WADLEY WILLIAM A
Systems and methods for trustworthy electronic authentication using a computing device
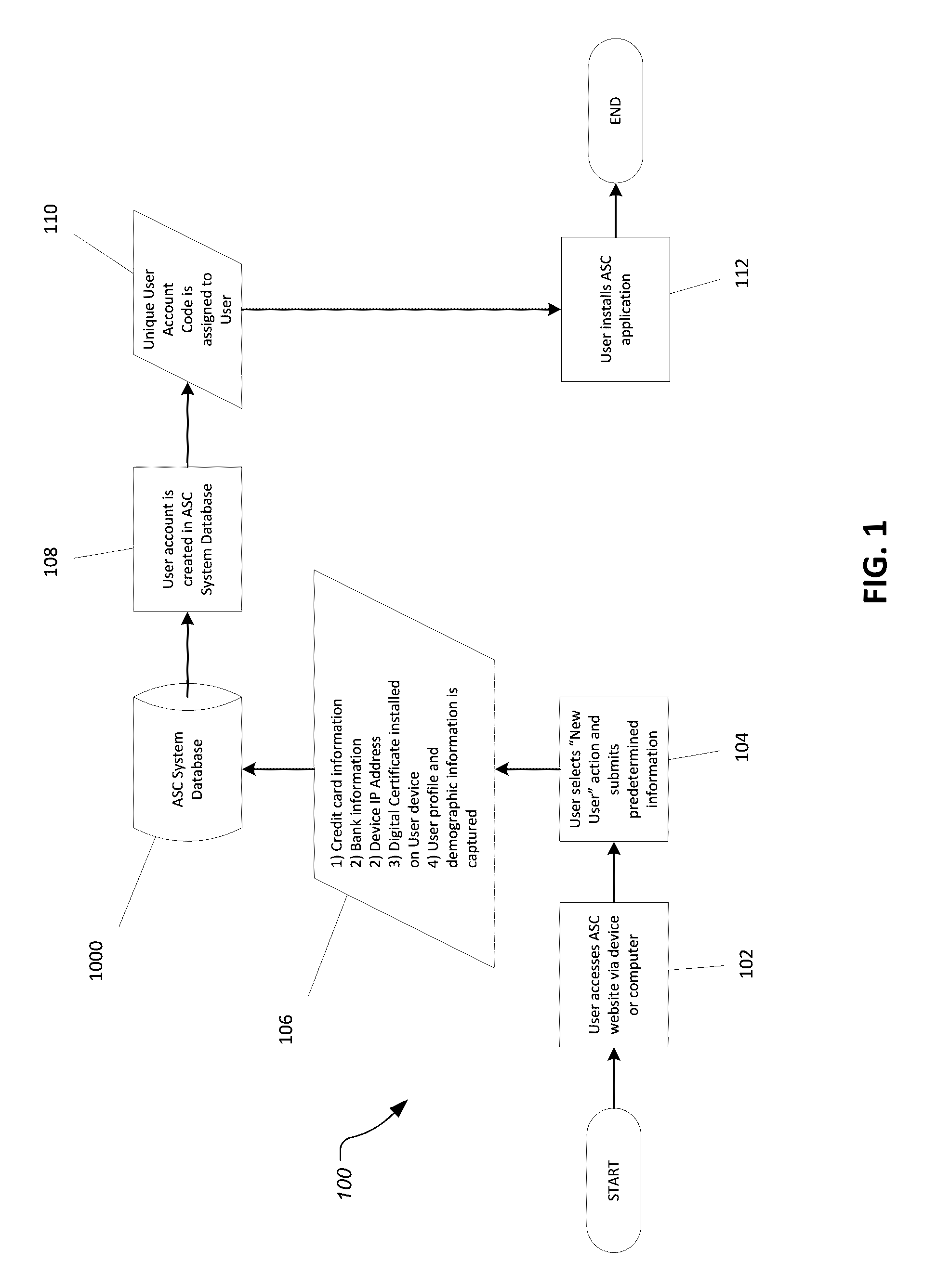
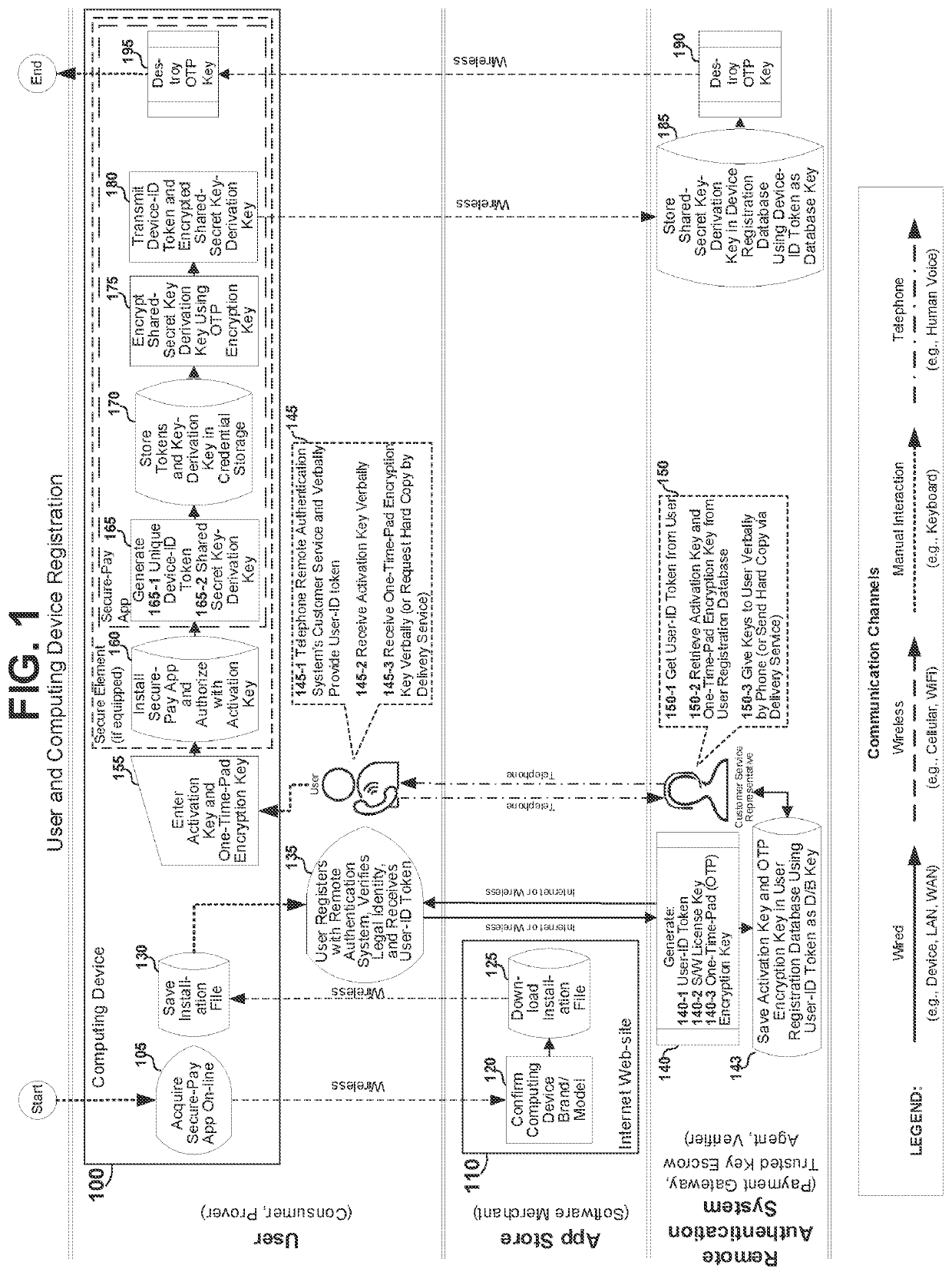
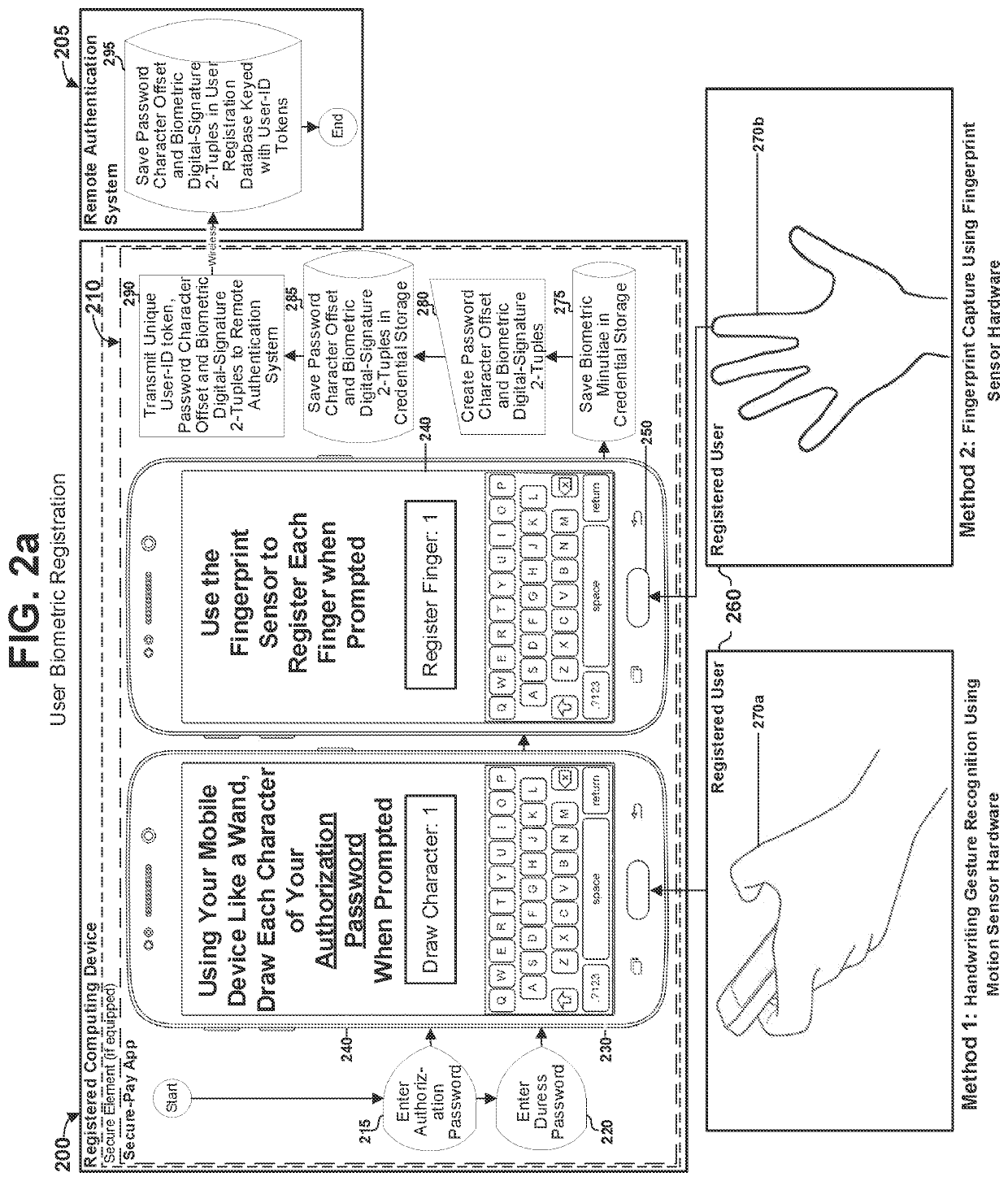
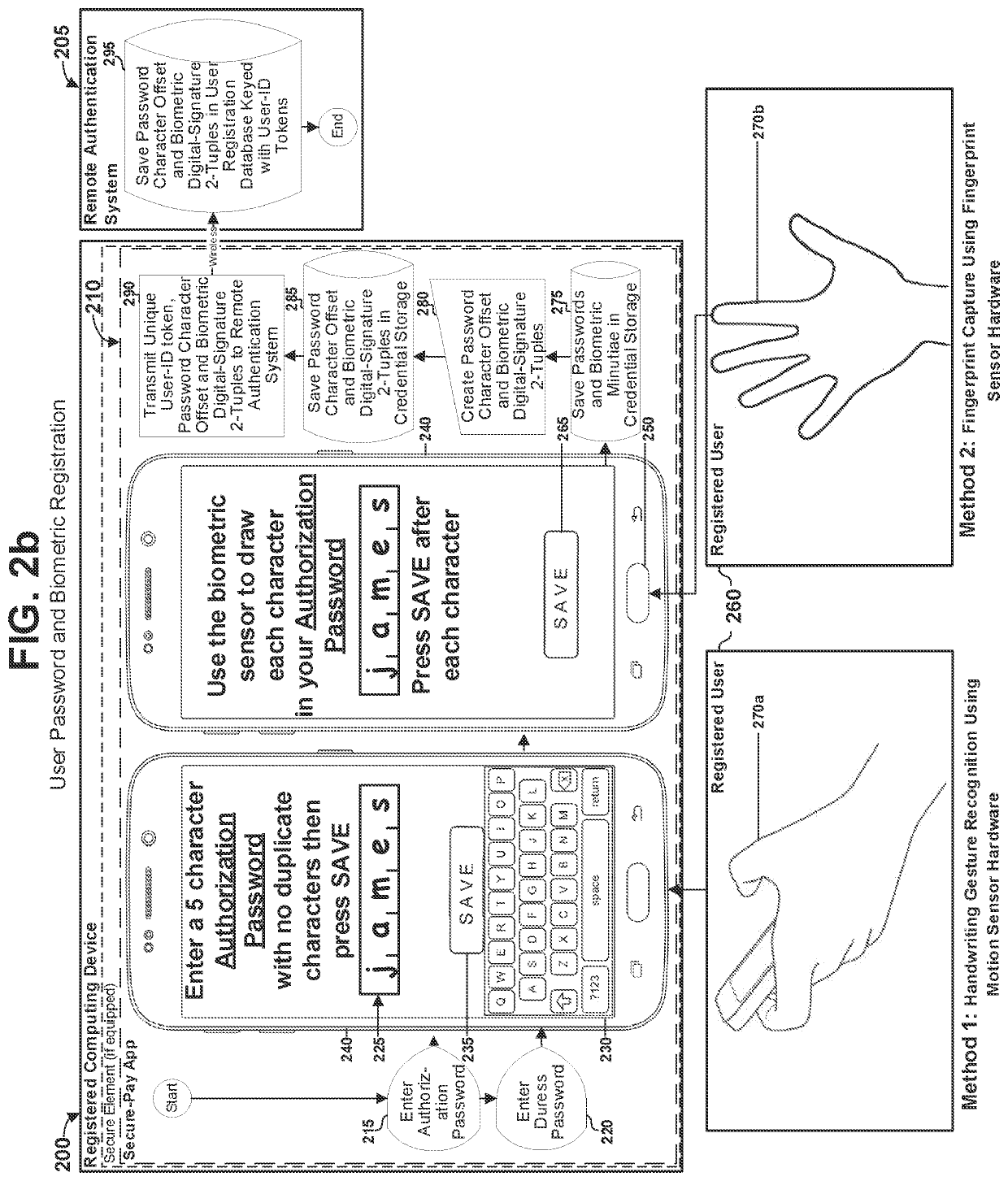
ActiveUS11405189B1Overcome disadvantagesIncreasing security strength and trustworthinessKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCryptographic key generationInternet privacy
A method, system, and digital recording medium provides for convenient and trustworthy user authentication with a computing device combining four authentication factors through use of a remote authentication system (RAS). An identity token (Device-ID) cryptographically bound to the user's computing device is generated as a first authentication factor. A password known only to the user is a second factor. Cryptographic signatures generated from the user's biometric minutiae is a third factor. A random challenge received from the RAS is a fourth factor. An encryption key-generation key is created cryptographically using the Device-ID and stored locally, which together with the user's cryptographic signatures are encrypted with a one-time-pad encryption key obtained from the RAS on a communication channel different from that used for other communication between the device and the RAS to provide perfect secrecy, then transmitted from the device to the RAS on a connection therebetween to register said shared-secrets.
Owner:BENNISON JAMES E
Electronic payment terminal capable of ensuring confidentiality and integrity of information transmission
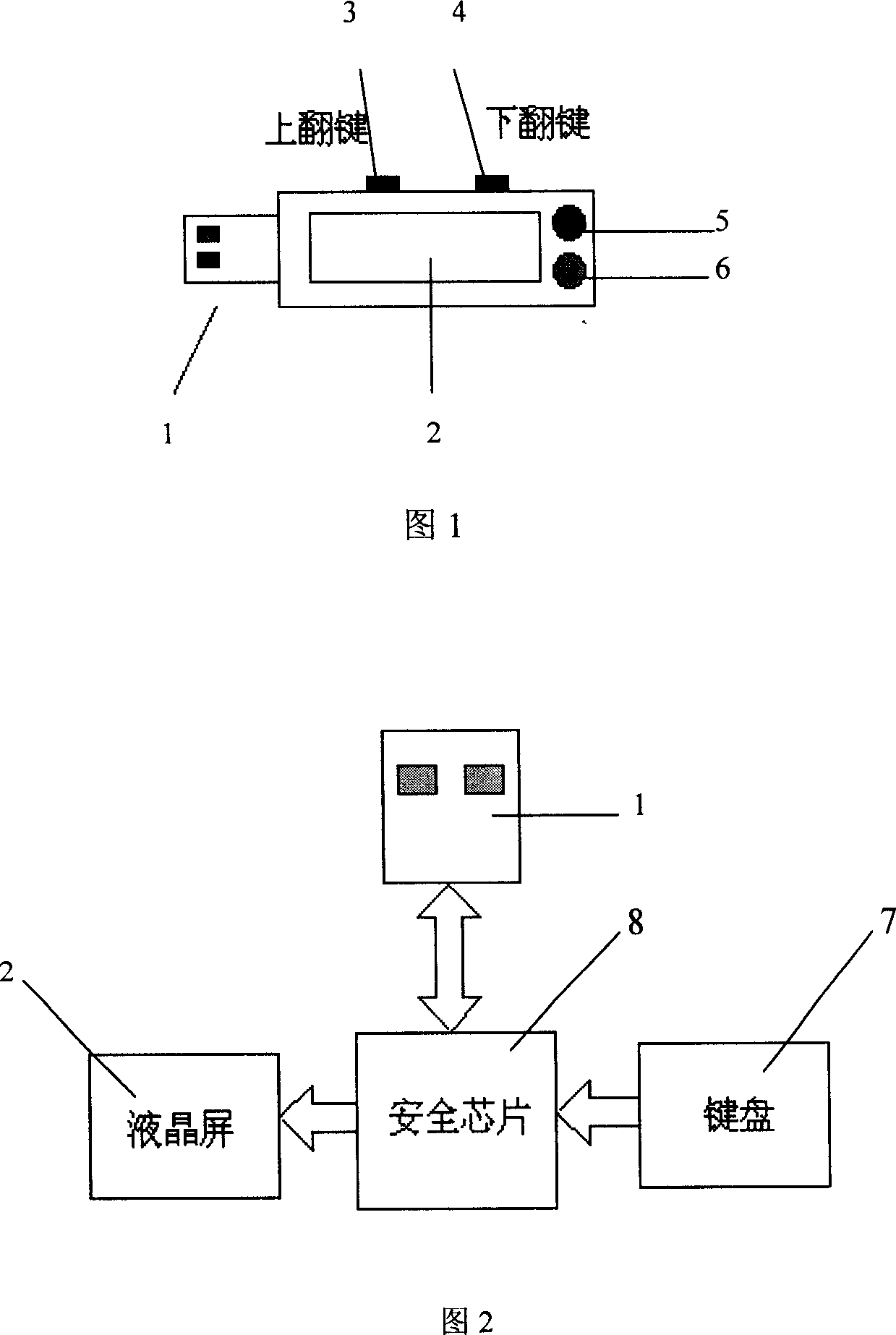
An electronic payment terminal being able to ensure information safety and completeness in transmission is prepared as controlling display screen and keyboard directly by safety chip, displaying all external I / O certification and transaction information on display screen on electronic certification and payment terminal, always using keyboard on electronic certification and payment terminal to confirm or to cancel transaction when transaction is confirmed or cancelled by user, transmitting confirmed or cancelled information after they are enciphered by safety chip.
Owner:上海麦柯信息技术有限公司
Measurement authentication method based on digital signature
InactiveCN101123502ASolving difficult-to-verifiable problemsReduce difficultyTariff metering apparatusUser identity/authority verificationData authenticityDigital signature
The present invention relates to a measuring value authentication method based on digital signatures, which utilizes a password algorithm with identification ability to digitally sign the measuring value of a measuring meter, such as an electricity meter, a water meter, a gas meter, a heat energy meter, etc., and a measuring value electronic authentication system consists of a coder and a decoder that are based on the password algorithm. The coder connected with the measuring meter reads a measuring value and then utilizes an encryption algorithm to realtimely convert the measuring value and the user identity information into a code, that is, a digital signature; whereas the decoder utilizes a decryption algorithm to revert the code back to the corresponding measuring value and the user identity information, that is, a verification digital signature. The basic operation of the measuring value electronic authentication is divided into two steps, the authentication registration and the authentication, wherein the authentication registration is a process in which a service provider registers the code generated by the coder, and the authentication is a process in which the service provider utilizes the decoder to revert the code obtained by the authentication registration back to the corresponding measuring value and the user identity information. Characterized in strong conditionality and simple operation, the present invention eliminates the defect that the authenticity of data is hard to be verified in manual metering.
Owner:ZHEJIANG UNIV
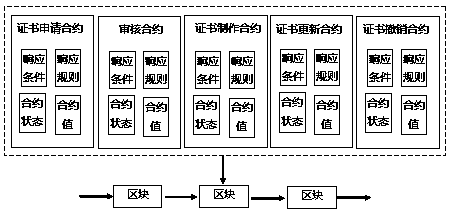
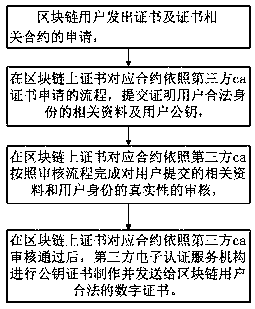
Digital certificate issuing method on block chain
InactiveCN107623572AIncrease credibilityReduce inconvenienceUser identity/authority verificationThird partyThe Internet
The invention discloses a digital certificate issuing method on a block chain and relates to the technical field of an Internet application. A certificate application contract, a check contract, a certificate production contract, a certificate updating contract and a contract revocation contract are established on the block chain according to certificate application, check, certification production, certificate updating and certificate revocation processes of a third party electronic authentication service mechanism; a public key digital certificate demand is provided for a block chain user; and block chain user anonymity system-to-real-name system conversion is realized. Compared with the prior art, the method has the advantages that a real-name system is carried out on the block chain user, the inconvenience and risk resulting from anonymity are reduced, and the credibility of the block chain is further improved.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com