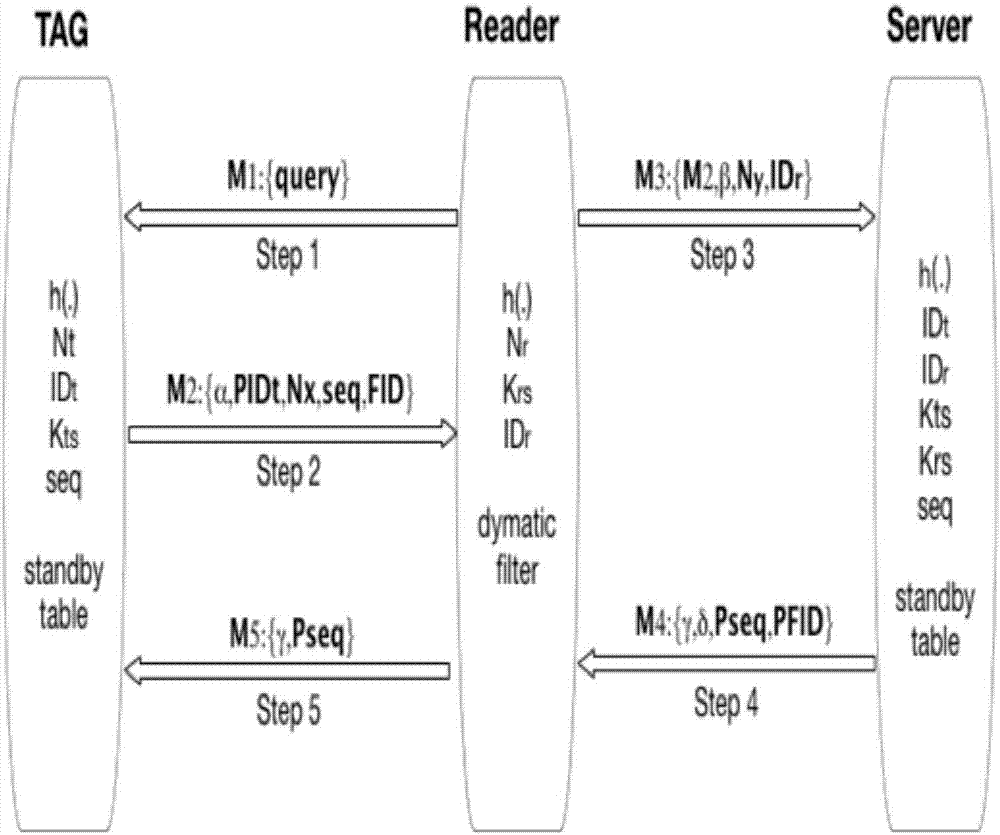
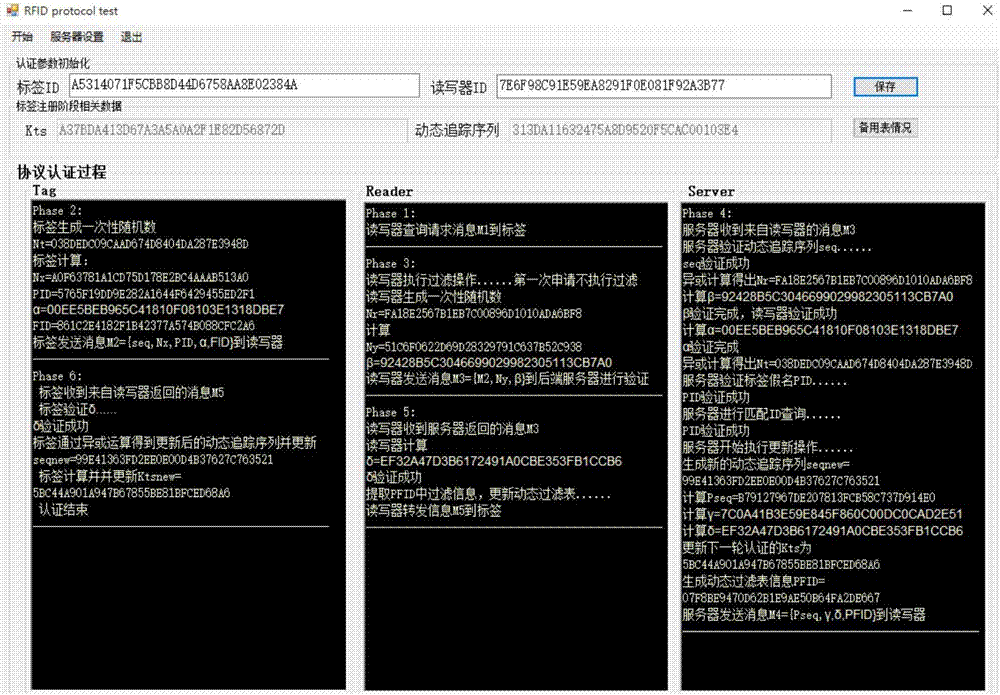
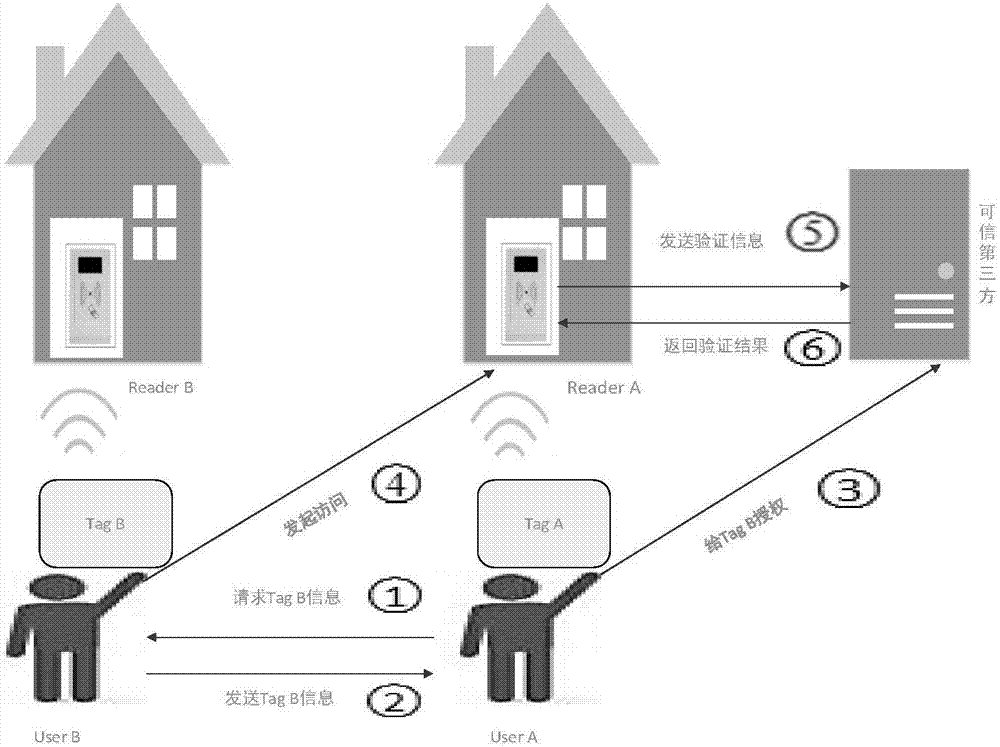
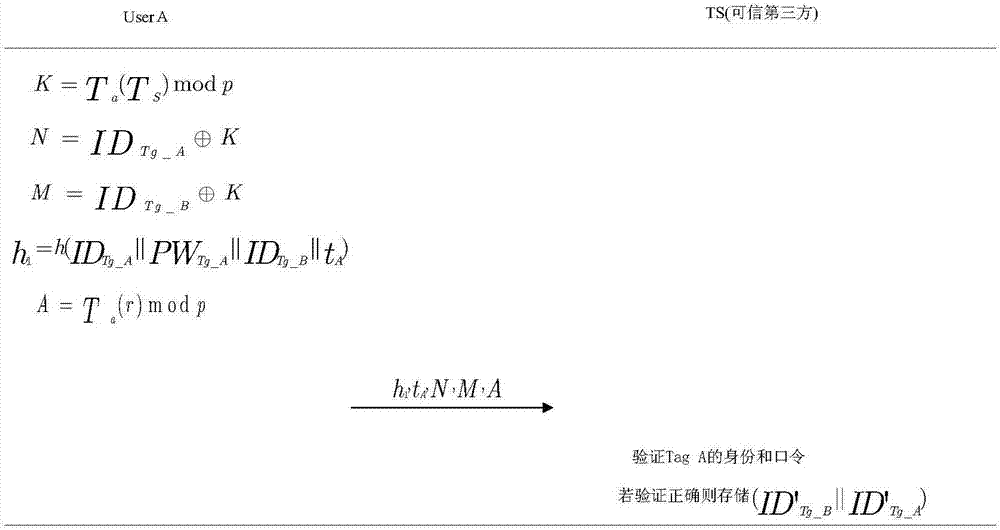
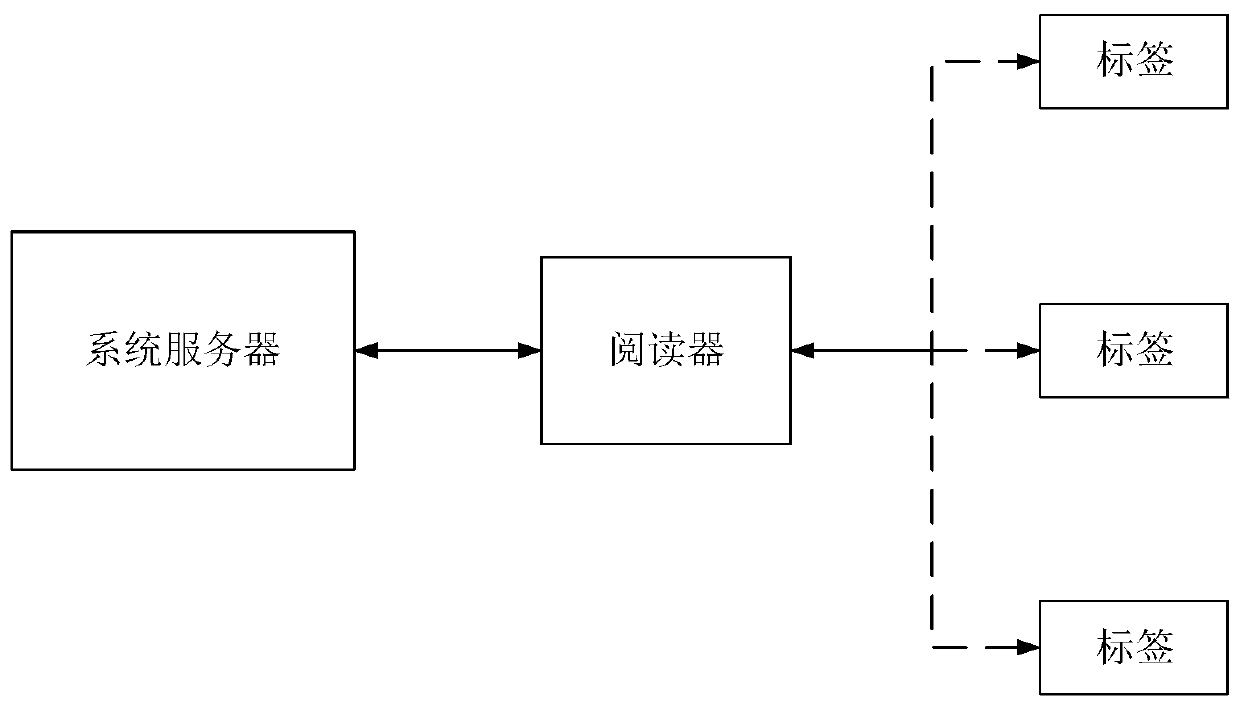
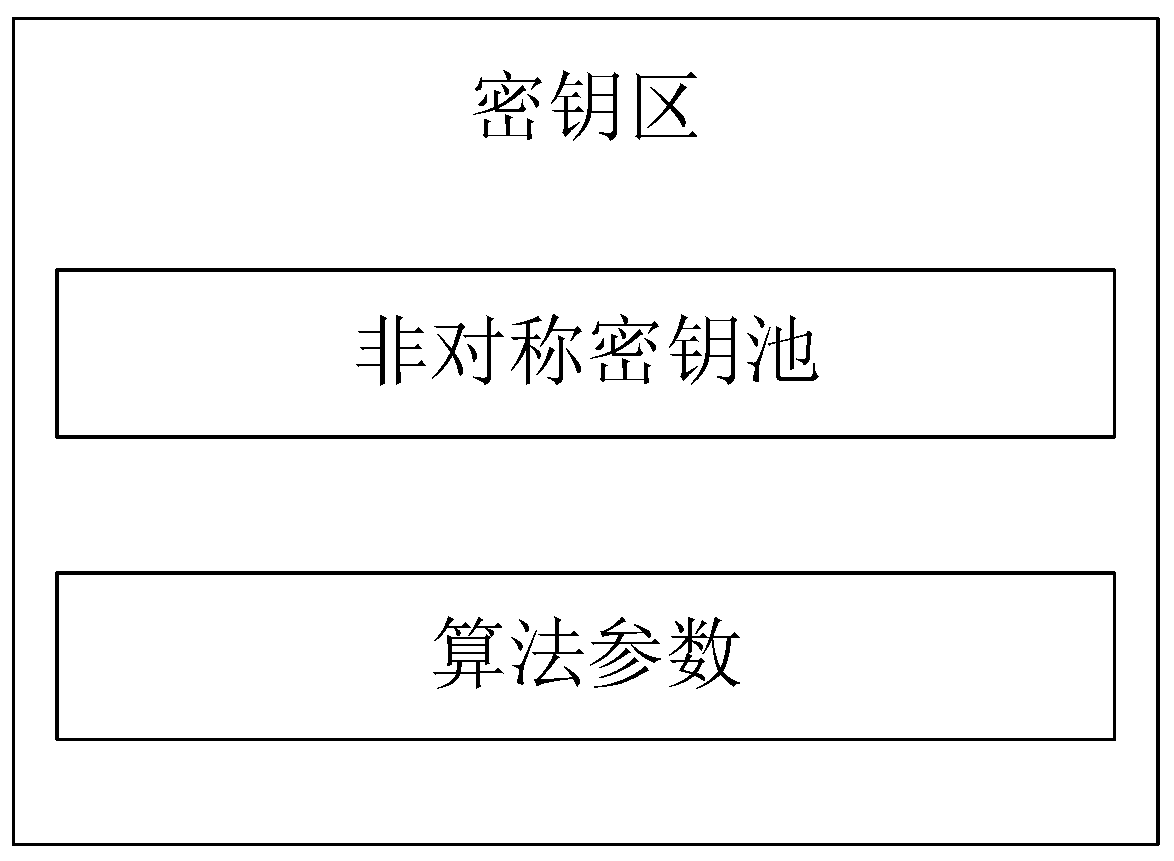
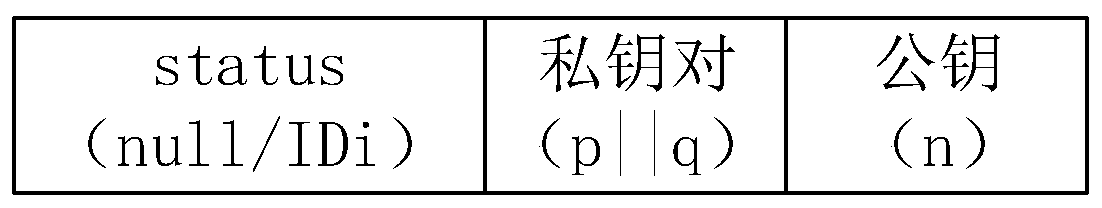
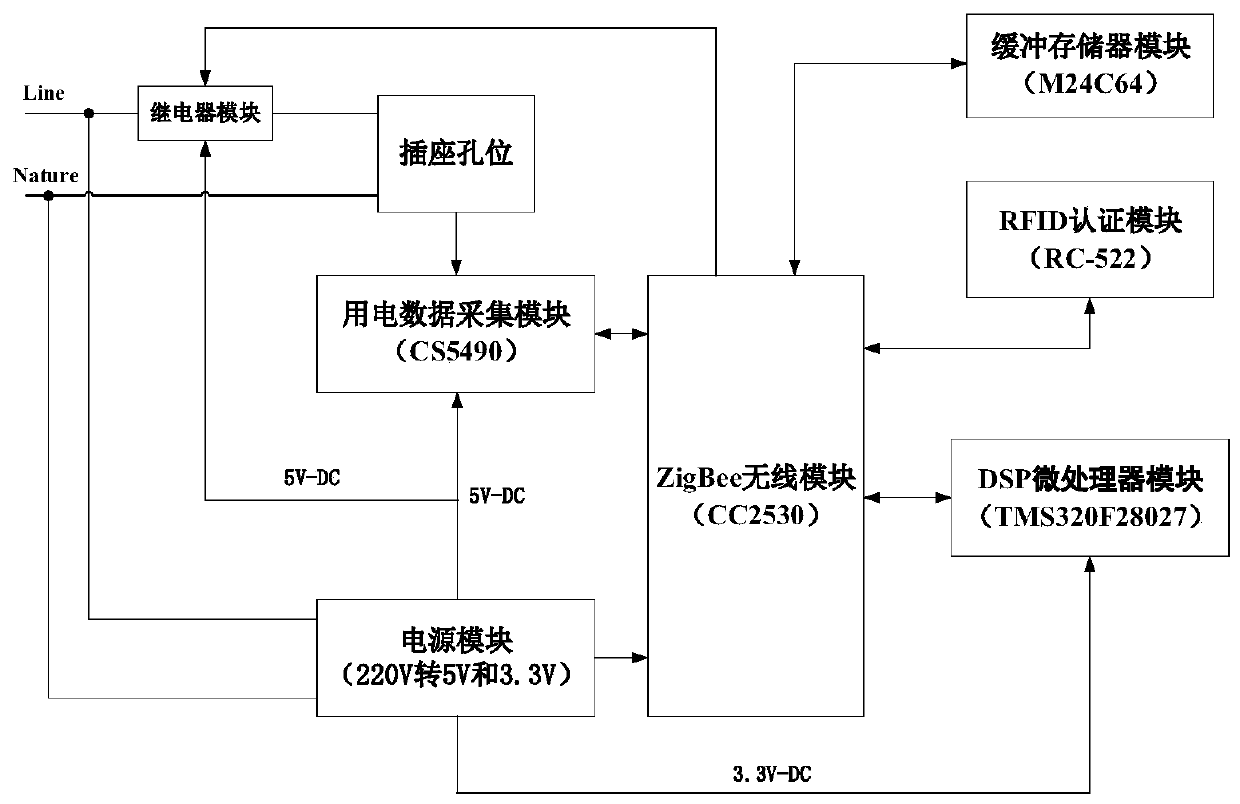
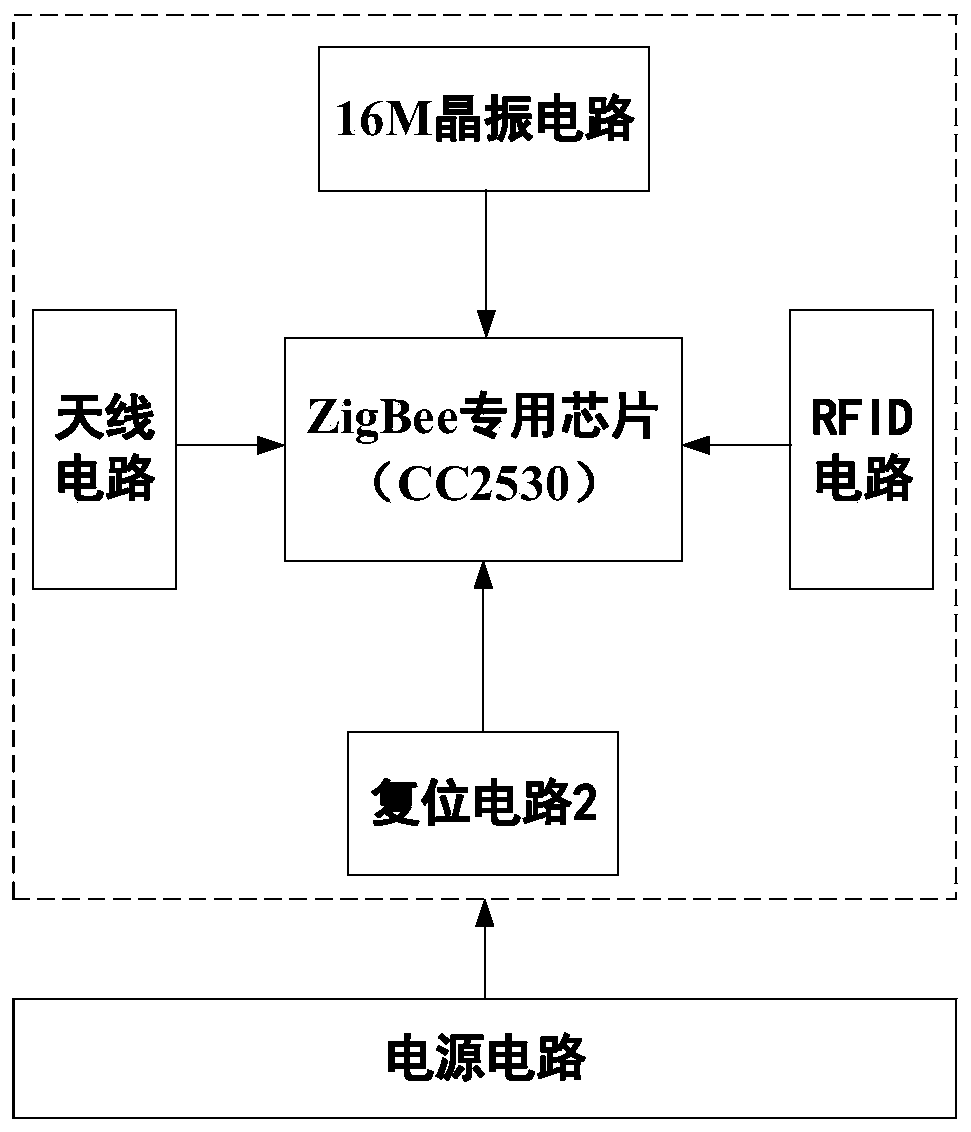
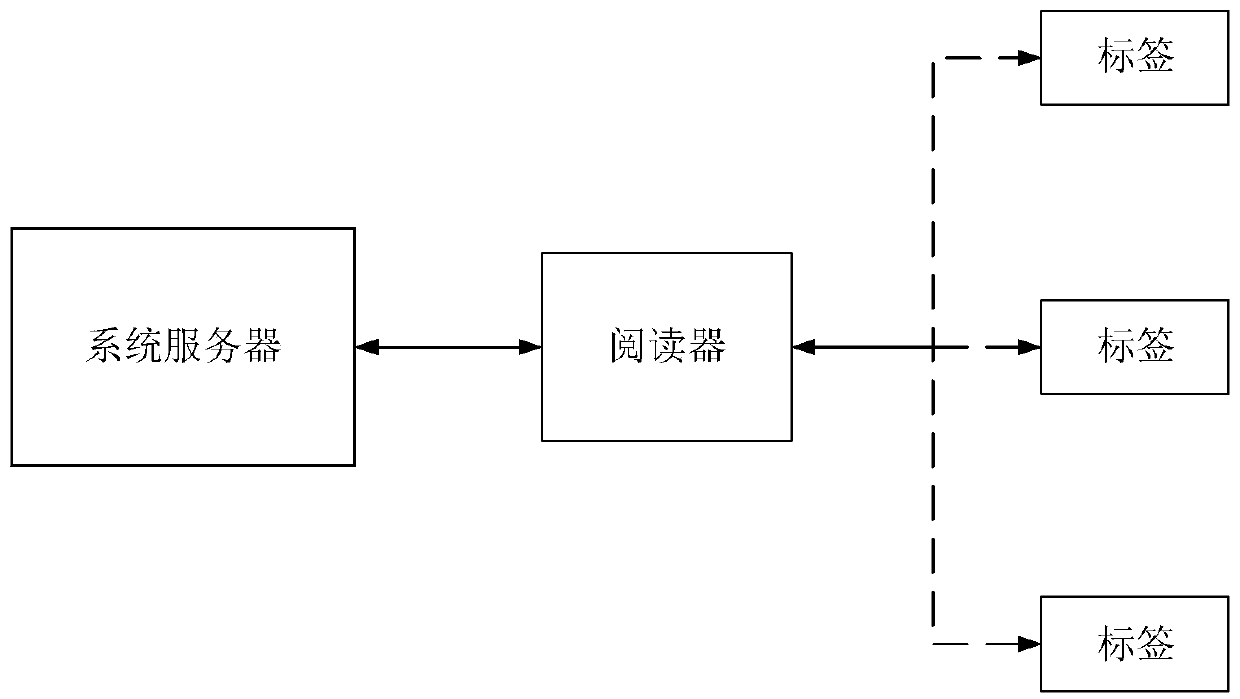
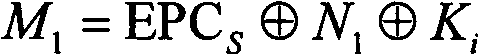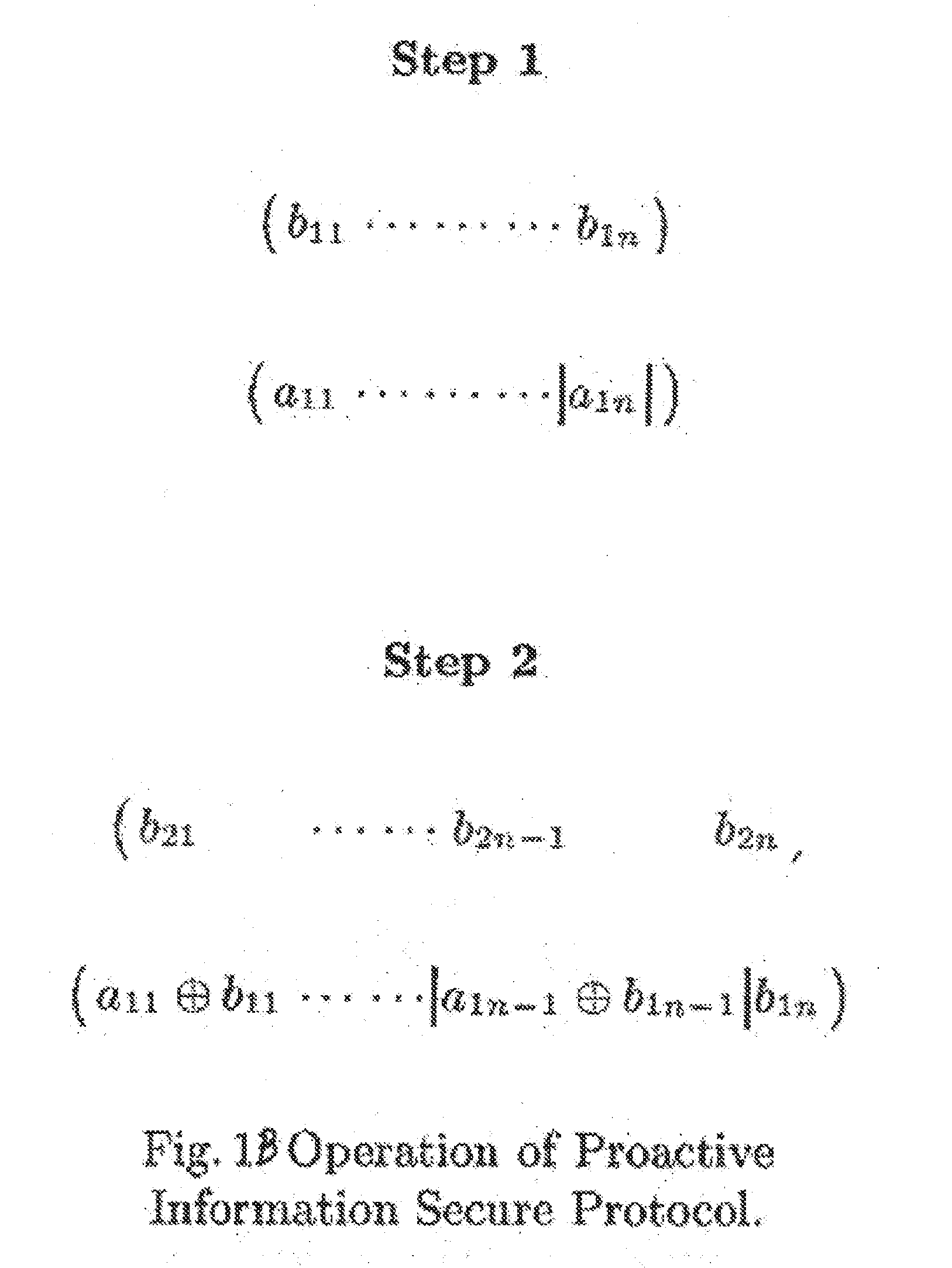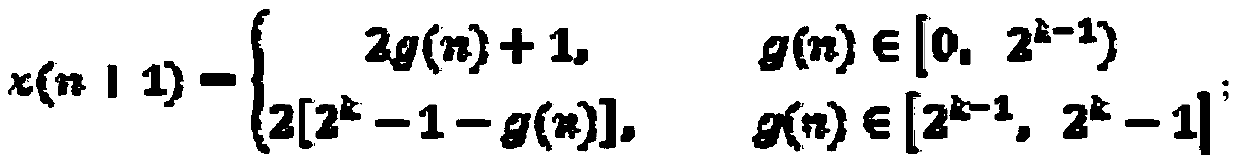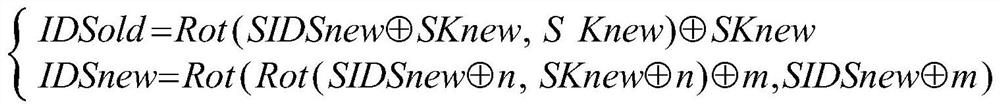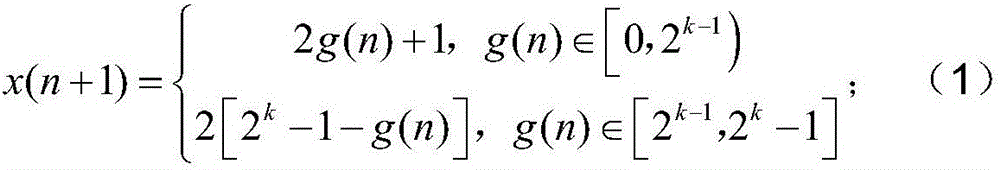Patents
Literature
71 results about "Rfid authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
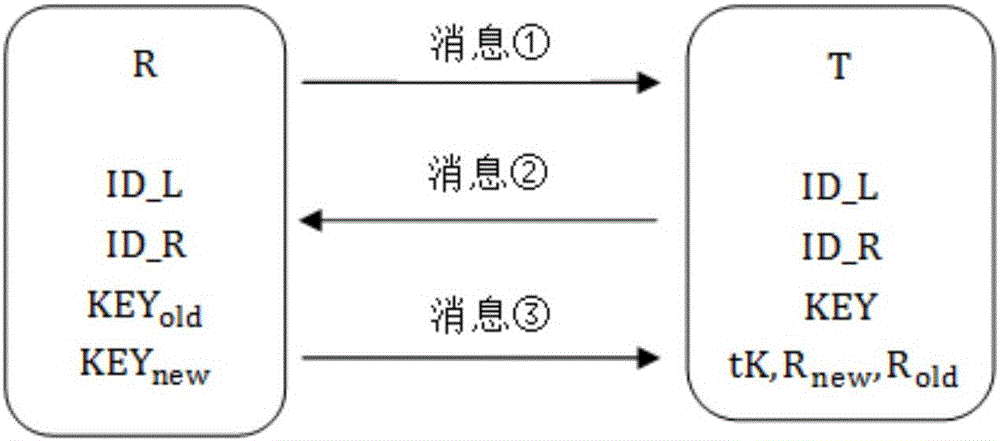
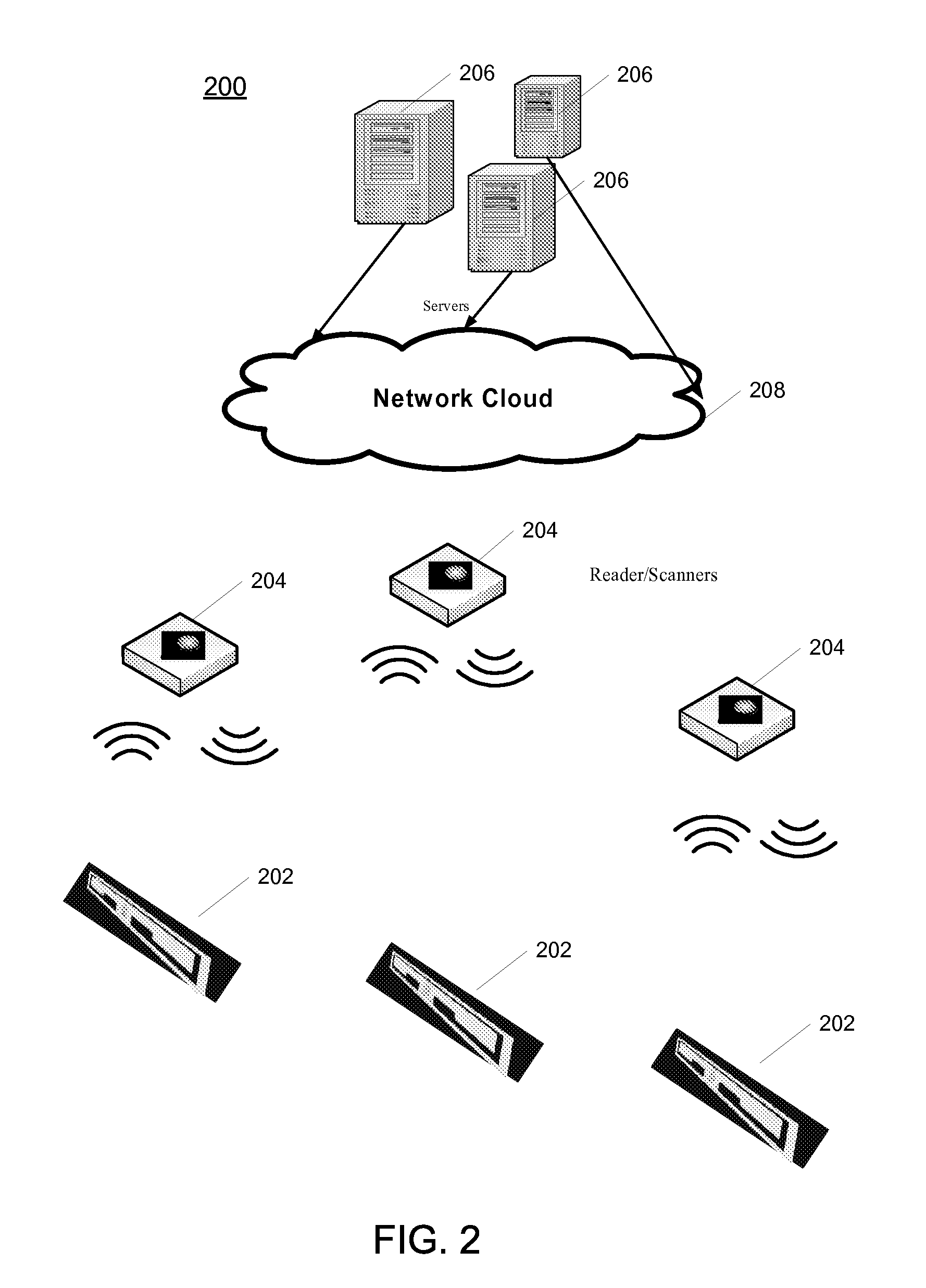
RFID Authentication. Radio-frequency identification (RFID) utilizes radio waves to communicate a unique identifier between a tag embedded in an RFID card and an RFID reader to verify a user’s identity and grant access.
User-friendly multifactor mobile authentication
ActiveUS20080289030A1Prevent unauthorized accessEliminate needDigital data processing detailsMultiple digital computer combinationsComputer hardwareRfid authentication
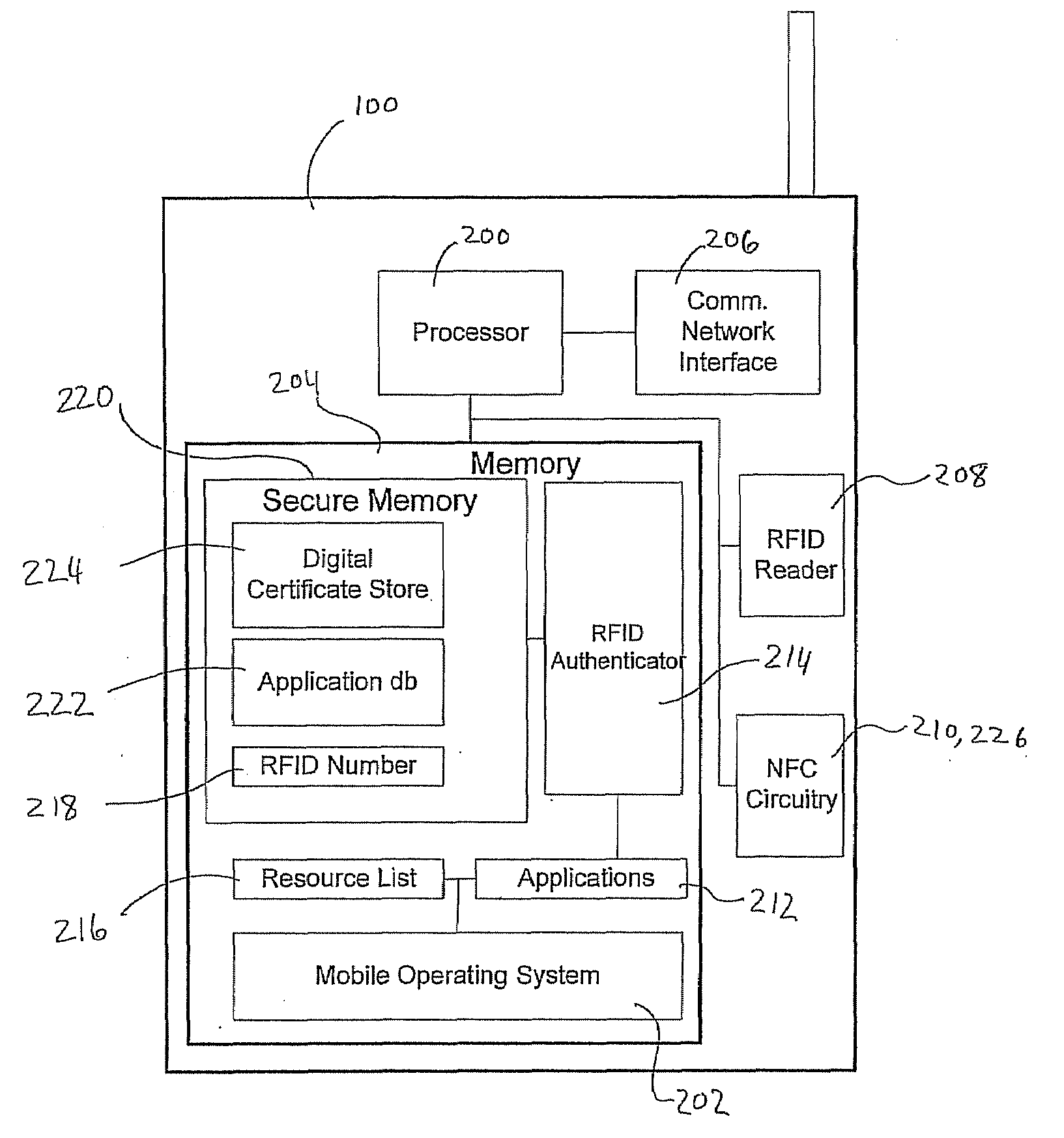
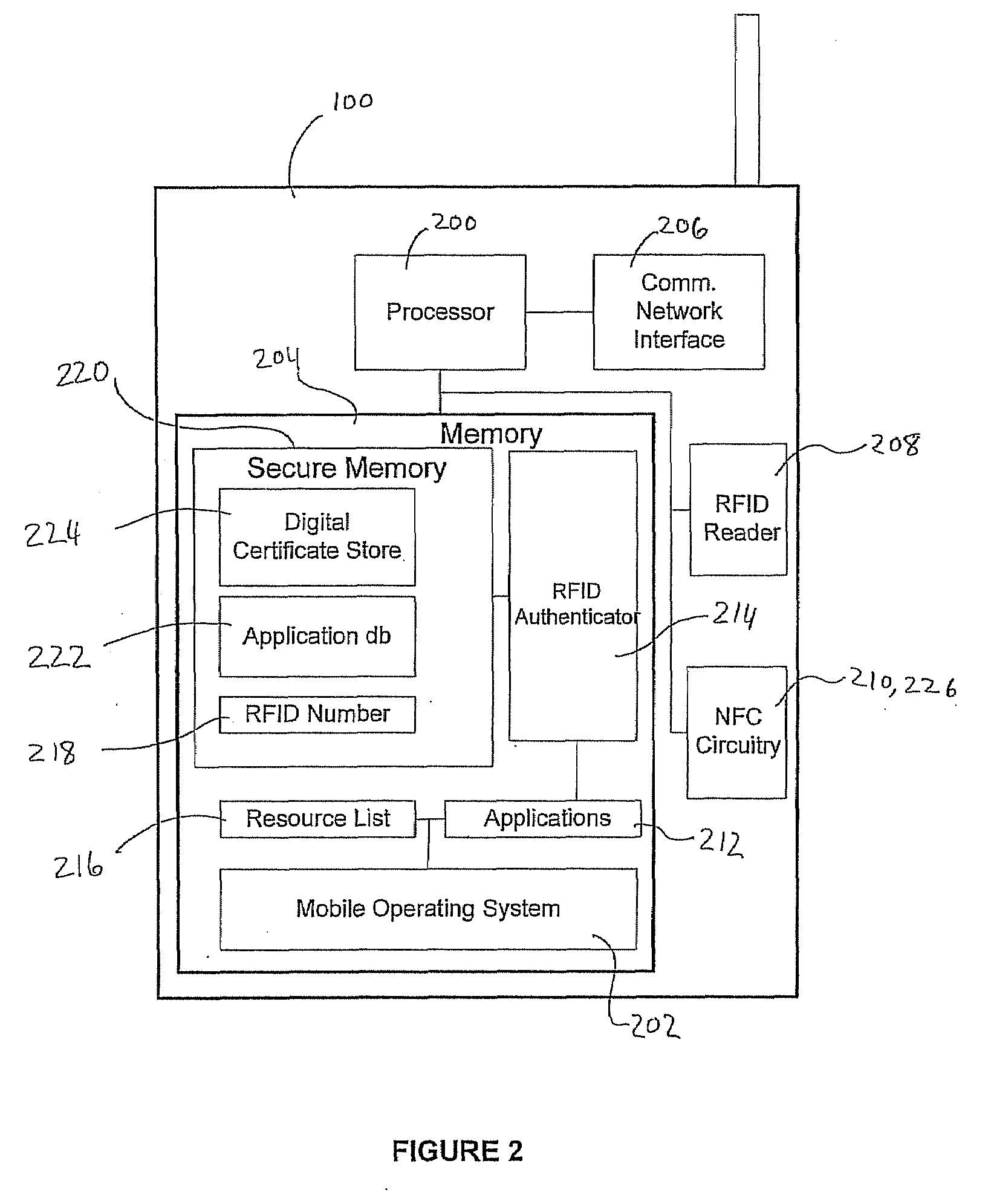
A system and method for performing multifactor mobile authentication are described whereby a mobile communications device includes a contactless reader for receiving and validating a unique identifier stored in an external authenticating module prior to granting access to locally stored electronic authenticating material required to access an external resource. In one embodiment, the mobile communications device is a mobile telephone having an RFID reader for receiving the unique identifier from an RFID tag incorporated into the external authenticating module. Preferably, the external authenticating module is associated with a user, such as by being part of the user's jewelry or clothing. The mobile authentication device includes an RFID authenticator module that detects external resource access requests and checks whether the requested resource is on a list of resources that require additional user authentication prior to granting access to locally stored authenticating material.
Owner:U S CELLULAR
System and method for secure asset management
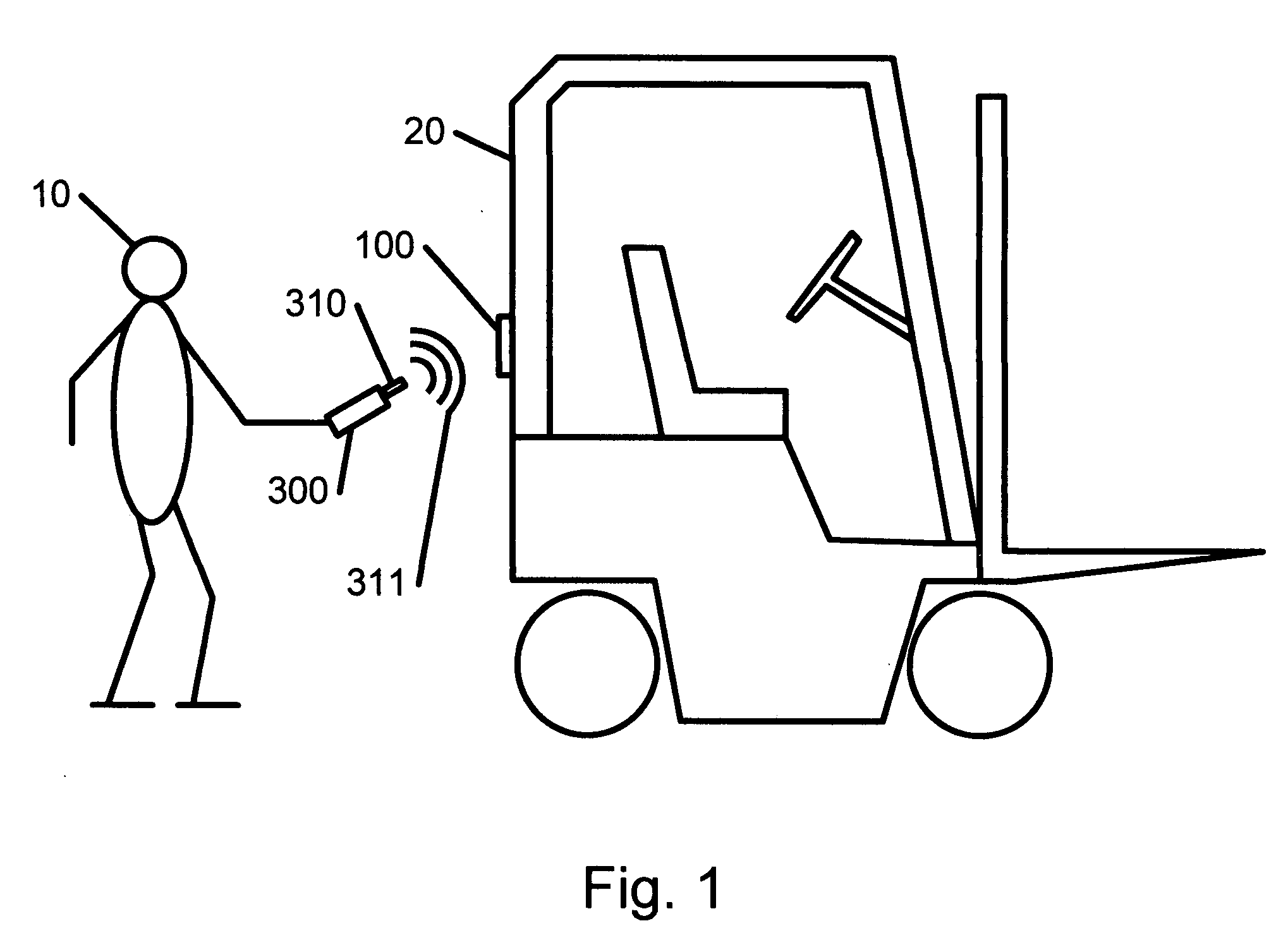
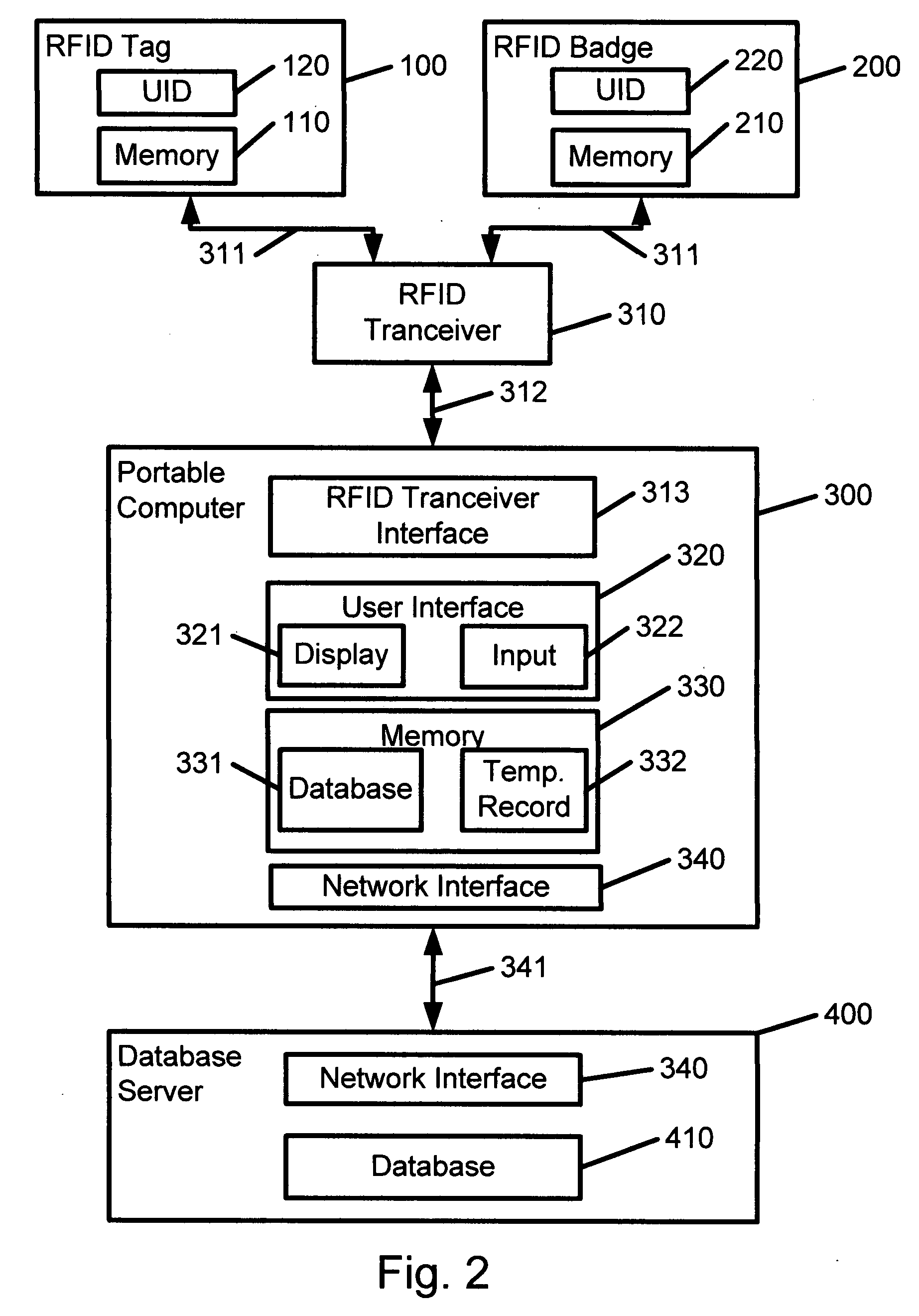
InactiveUS20080177665A1User identity/authority verificationComputer security arrangementsTransceiverRfid authentication
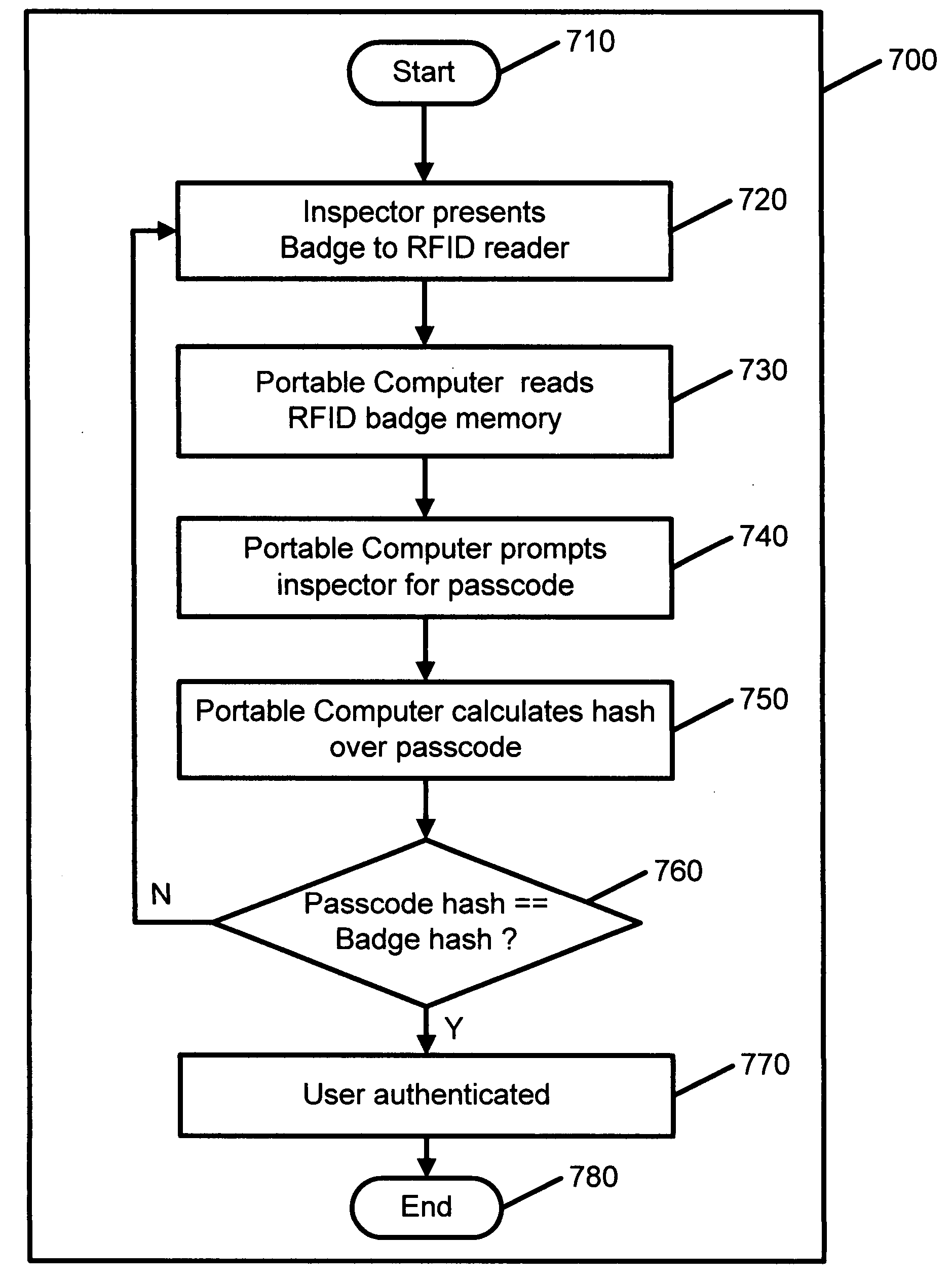
A system and method of secure asset management comprising an RFID tag attached to an asset, a portable computing device equipped with an RFID transceiver, an inspector RFID authentication badge, and a central database server. The RFID tag includes historical management records of the asset and a cryptographic hash calculated over relevant information to ensure security and authenticity thereof. The portable computing device can read from and write to the RFID tag and read from the RFID authentication badge. Management tasks to be performed by the inspector are determined by the portable computing device based on the authorization level of the inspector read from the RFID authentication badge and the asset information read from the RFID tag. Upon completion of asset management, historical management records are generated by the portable computing device and securely written to the RFID tag by including a cryptographic hash calculated over the relevant information. Historical management records may also include an identifier of the inspector, a timestamp of when the historical management record was generated, and error correction or detection data. Such historical management records may be synchronized with a central database server at a later time.
Owner:NOORDAM PIETER
RF transaction authentication using a random number
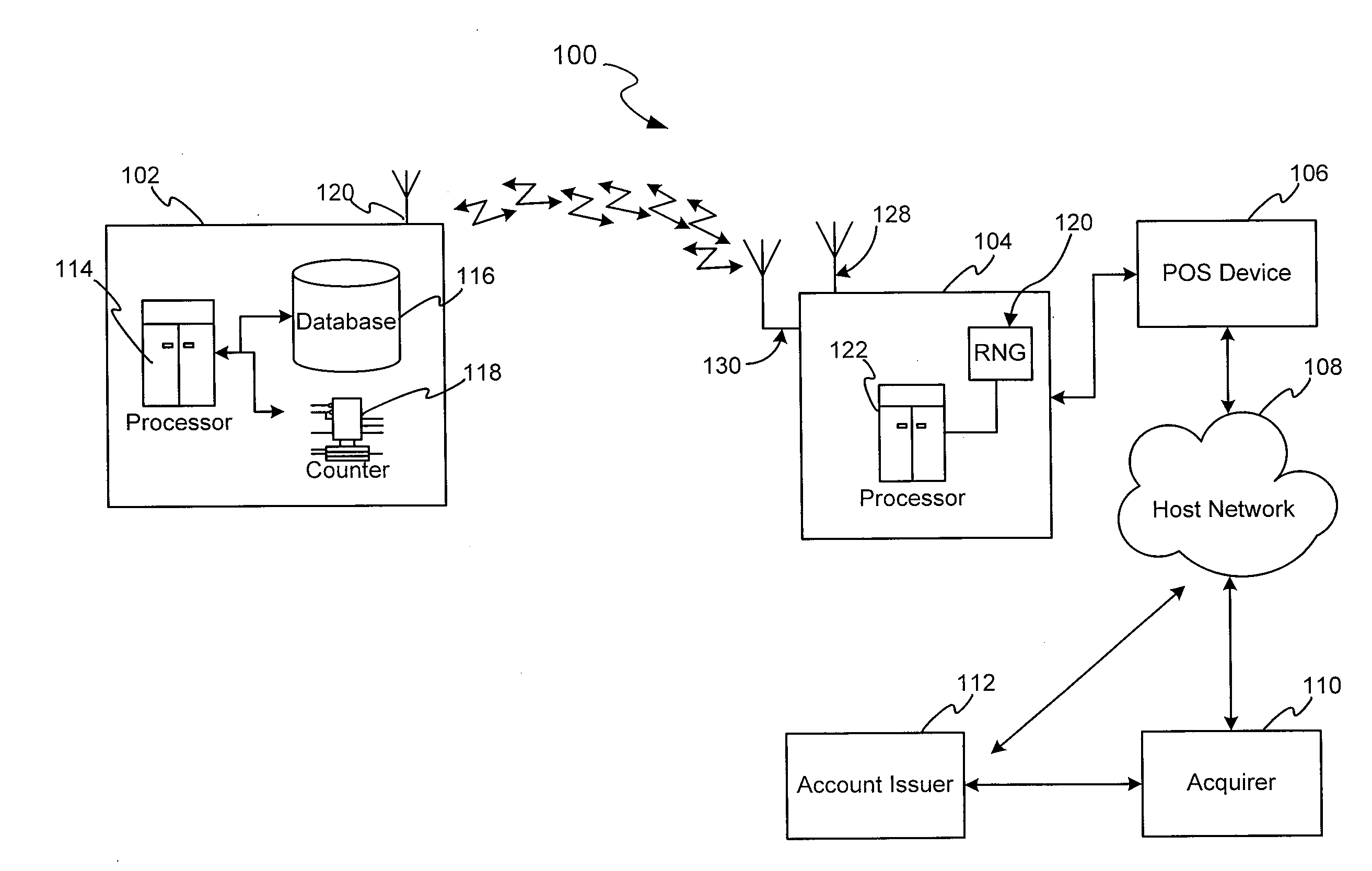
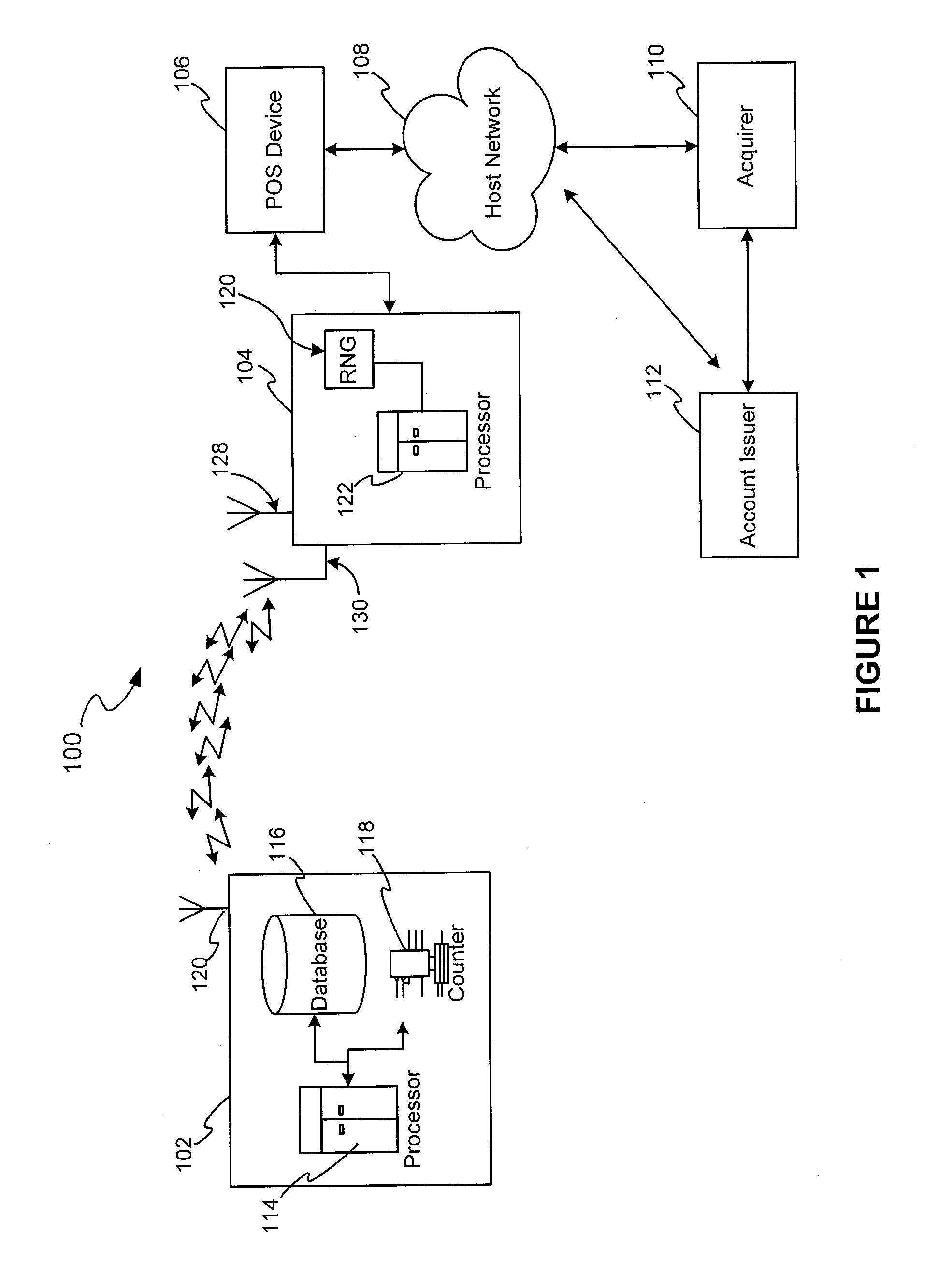
ActiveUS20090044012A1Acutation objectsEncryption apparatus with shift registers/memoriesComputer hardwareRfid authentication
A system and method for securing Radio Frequency Identification (RFID) transactions is provided. An exemplary method includes using a random number in an authentication tag and authorizing an RF transaction in response to verifying the authentication tag. The method may also involve variously validating an RFID device authentication tag and an RFID reader authentication tag. Additionally, a system and method is disclosed for verifying an RFID transaction device and RFID reader operable with an RF transaction system. The method involves presenting an RFID device to an RFID reader, receiving a random number, creating an RFID transaction device authentication tag using the random number and a counter value, providing the RFID transaction device authentication tag to an RFID reader, creating an RFID reader authentication tag using the counter, random number, and RFID authentication tag, and providing the RFID reader authentication tag and RFID transaction device authentication tag for authentication.
Owner:LIBERTY PEAK VENTURES LLC
RFID (radio frequency identification device) authentication method and system based on PUFs (physical unclonable functions)
ActiveCN103391199ADefense against replay attacksResist impersonation attacksUser identity/authority verificationCo-operative working arrangementsRfid authenticationResource consumption
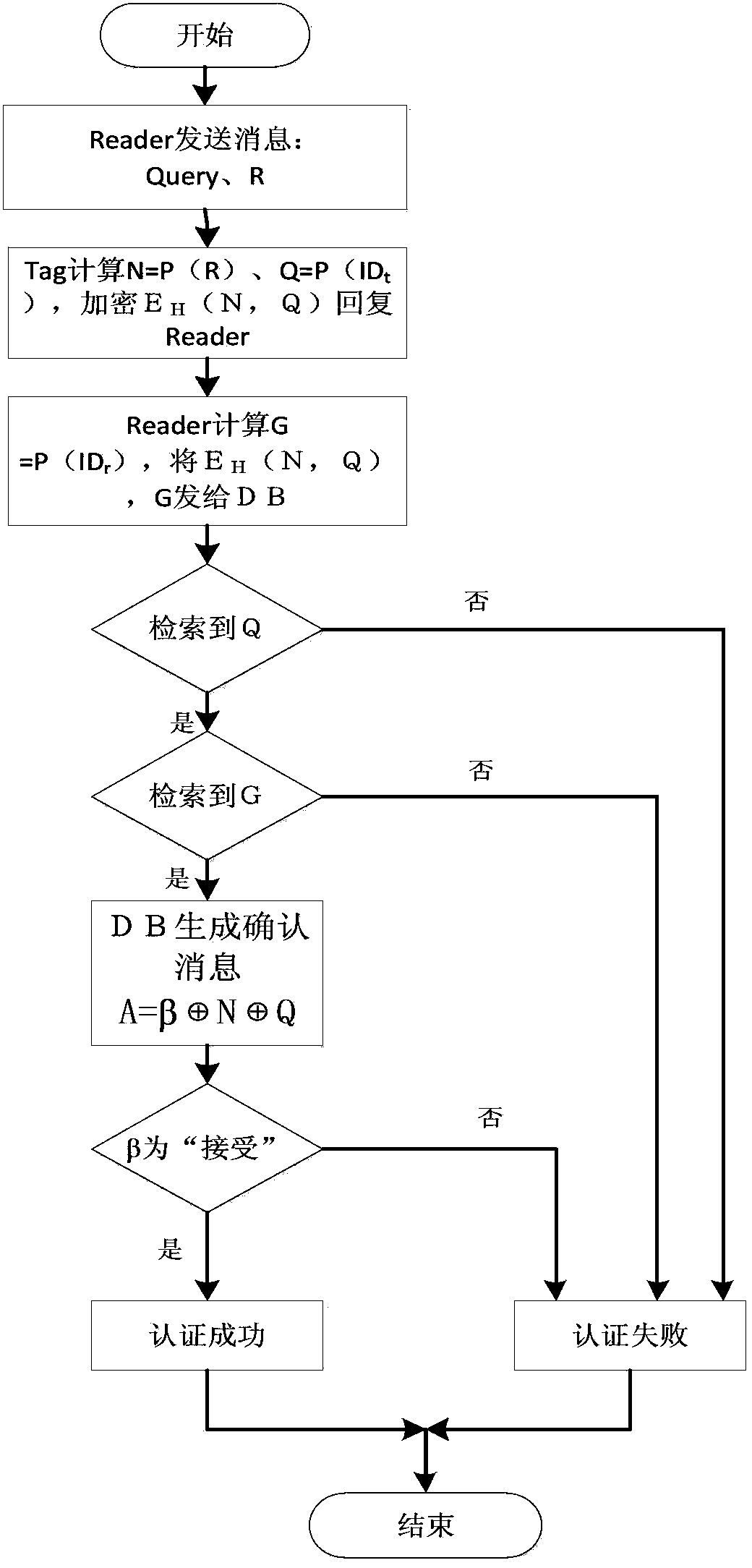
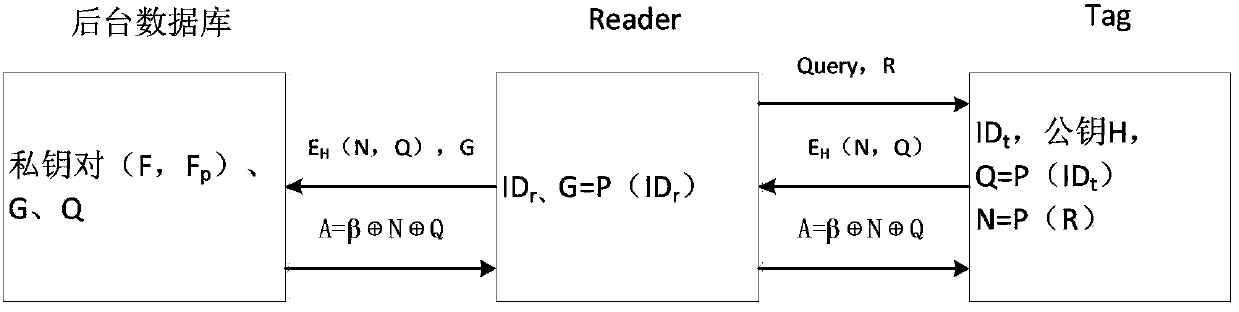
The invention discloses an RFID authentication method and system based on PUFs. The system comprises a backend database, a reader and a tag, wherein communication between the backend database and the reader can be realized by using a conventional network security technology, so that the communication between the backend database and the reader is safe; however, the communication between the reader and the tag is not realized through the conventional network security technology, so that the communication is not safe. The RFID authentication method has the advantages of high safety and authentication efficiency, little in resource consumption and the like, can resist typical attack techniques such as replay attacks, counterfeit attacks, track attacks, physical attacks and the like, has forward safety and backward safety, and realizes bidirectional authentication between the reader and the tag. A public key encryption method is used, so that the RFID authentication method has higher safety.
Owner:NANJING UNIV OF POSTS & TELECOMM
RFID security authentication method based on EPC C-1G-2 standard
InactiveCN102497264AGuarantee forward securityReduce storage requirementsKey distribution for secure communicationUser identity/authority verificationRfid authenticationLow-performance equipment
The invention discloses a RFID (Radio Frequency Identification) security authentication method based on an EPC (Electronic Product Code) C-1G-2 standard. The method is used for solving the technical problem of poor security of the existing RFID security authentication method based on the EPC C-1G-2 standard. A technical scheme is that a tag and a reader use cyclic redundancy check codes (CRC), a pseudo random number generator (PRNG) and bitwise exclusive OR operations, so that known security holes of the existing RFID authentication scheme are solved, tag tracking attacks are resisted effectively, and tag forward security is ensured. Moreover, the method meets the EPC C-1G-2 standard of the low-cost RFID tag, reduces demands on storage and calculation of the tag and can be well suitable for the requirement on application of low-performance equipment.
Owner:XIDIAN UNIV +1
Method, apparatus and product for RFID authentication
InactiveUS20090225985A1Reduce in quantityIncrease resistanceKey distribution for secure communicationDigital data processing detailsRfid authenticationAdversary
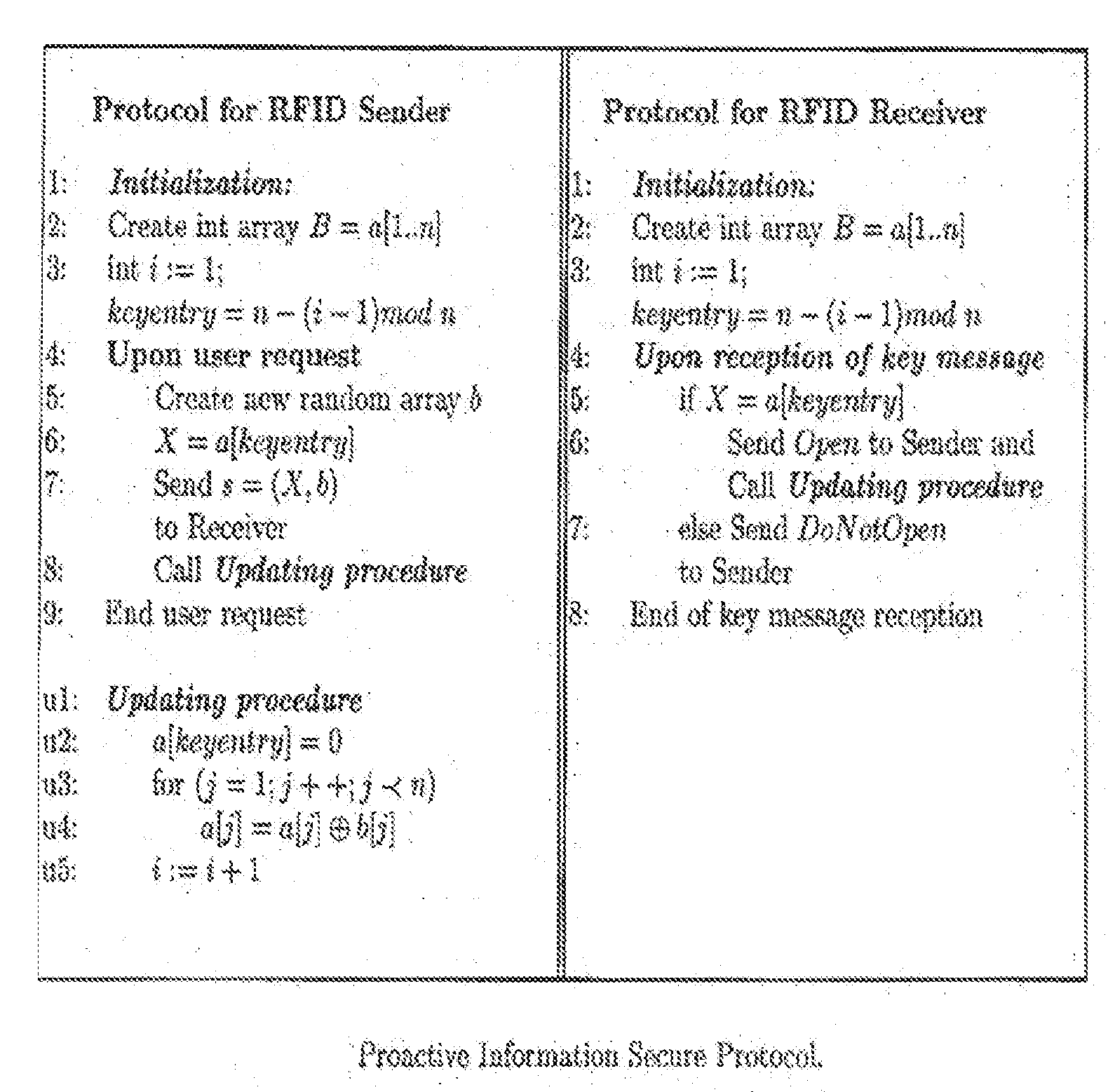
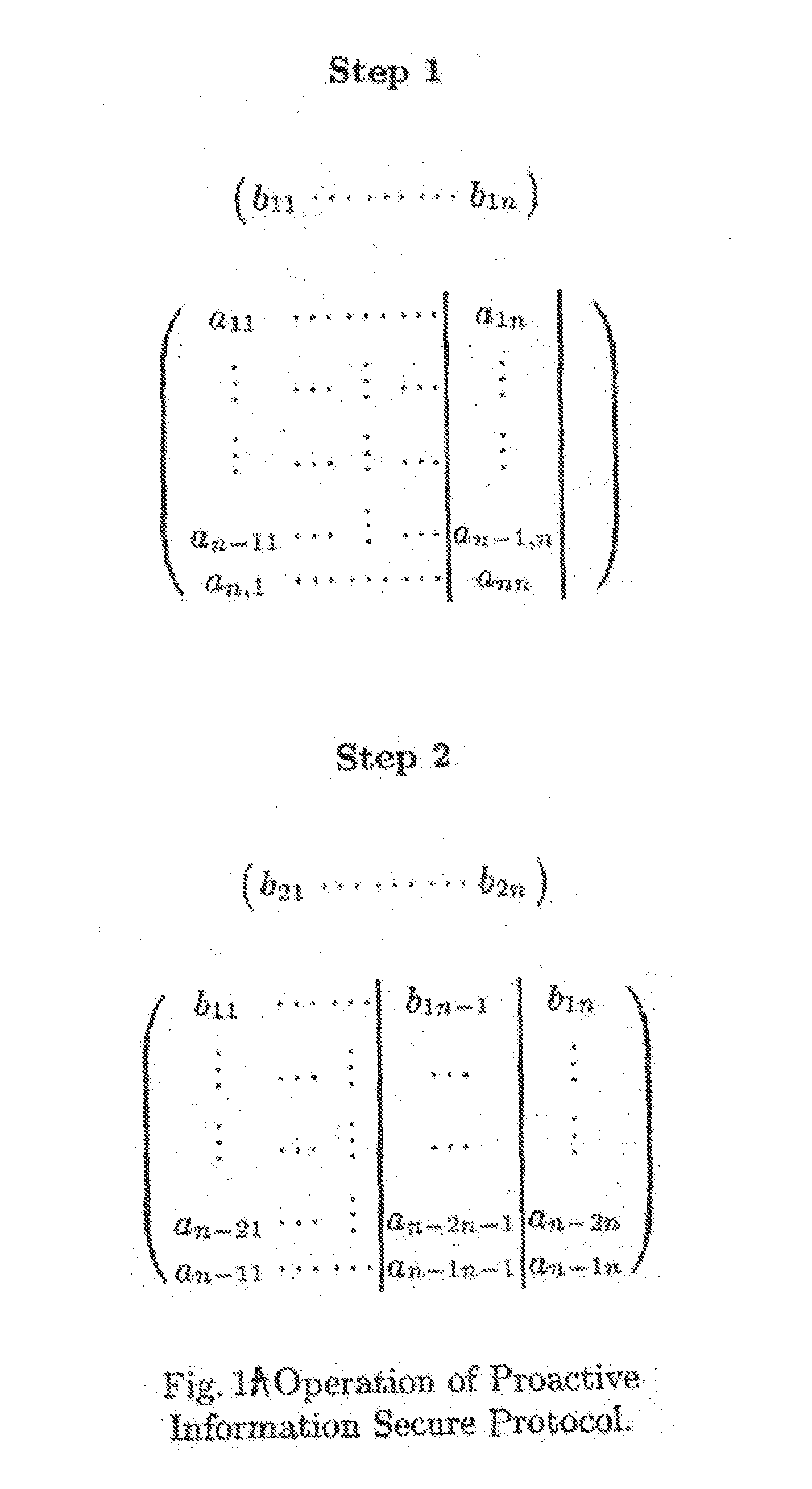
A method and apparatus for repeated communication sessions between a sender (e.g., RFID tag) and a receiver (RFID reader) that employs a proactive information security scheme is based on the assumption that the information exchanged during at least one of every n successive communication sessions is not exposed to an adversary. The sender and the receiver maintain a vector of n entries that is repeatedly refreshed by pairwise XORING entries, with a new vector of n entries that is randomly chosen by the sender and sent to the receiver as a part of each communication session. Also, a computational secure scheme based on the information secure scheme is employed to ensure that even in the case that the adversary listens to all the information exchanges, the communication between the sender and the receiver is secure. In particular, the scheme can be used in the domain of remote controls (e.g., for cars).
Owner:DOLEV SHLOMI +2
Radio frequency recognizing privacy authentication method for dynamic cryptographic key update based on rarefaction tree
InactiveCN101256615AReduce overheadReduce storage overheadDigital data authenticationSensing record carriersRfid authenticationSystem maintenance
The invention relates to a radio frequency identification technology and discloses a method for privacy authentication of radio frequency identification based on dynamic key update of sparse tree, which comprises the following steps that: system initialization step, a read-write machine generates the key of each label stored by the sparse key tree; label identification step, the read-write machine sends an authentication request to the label, the label computes and sends the authentication information to the read-write machine, and the read-write machine identifies the label after receiving the authentication information; key updating step, after the label identification is finished, the read-write machine updates the key tree and sends the synchronous updating authentication information to the label which updates the stored keys; system maintenance step, once the label joins in or level RFID system, the read-write machine maintains the system sparse key tress. The invention is able to efficiently resist various passive and active attacks at present, and in contrast with the RFID authentication method based on the balance tree structure, greatly reduces the storage expense at the label end.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
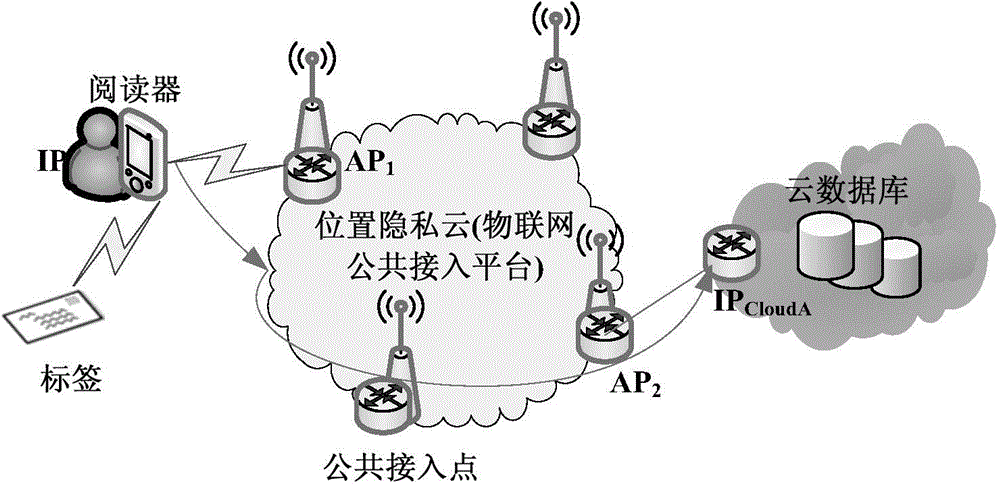
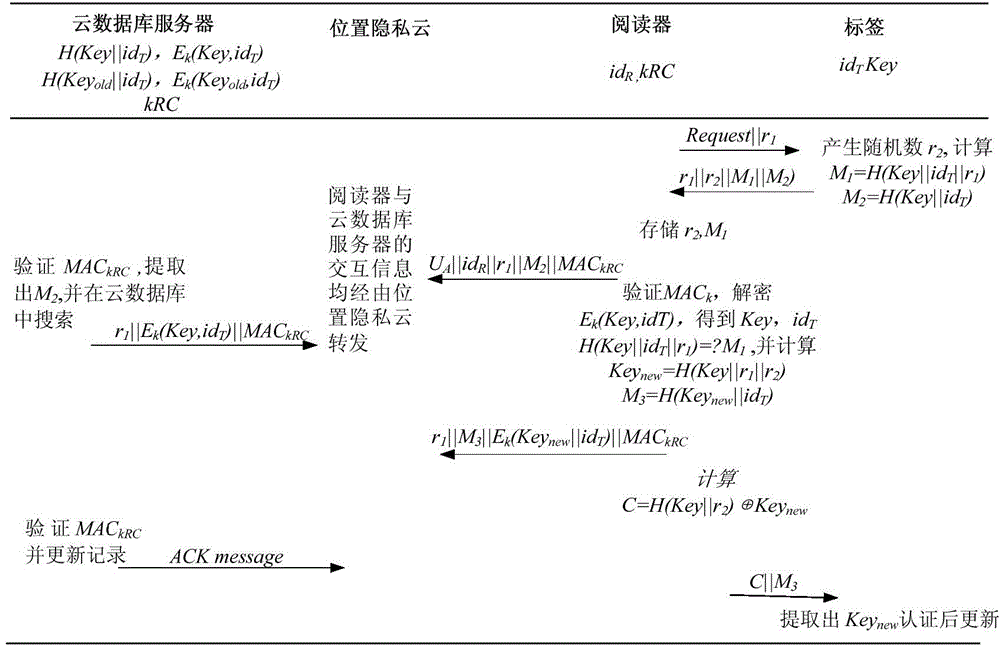
RFID authentication system and authentication method based on position privacy cloud
ActiveCN104683109AImplement two-way authenticationImprove retrieval efficiencyUser identity/authority verificationComputation complexityRfid authentication
The invention discloses an RFID authentication system and an authentication method based on position privacy cloud, and aims to solve the problems that the position privacy of a reader is revealed, and the tag calculation complexity degree is too high. The authentication method mainly comprises the following steps: transmitting an authentication request to a tag through the reader; responding to the request of the reader through the tag; forwarding the response of the tag to a cloud database server to check and match through the reader through position privacy cloud; feeding back succeeded matching to the reader through the cloud database server; decrypting messages through the reader, completing authentication on the tag, and calculating records required to be updated; after the cloud database server is updated, transmitting verification information to the reader; transmitting privacy values to the tag through the reader in an encryption manner; verifying through the tag, completing authentication on the reader, and updating the privacy value. Due to adoption of the position privacy cloud, the position privacy of the reader is effectively protected, the privacy security problem in the radio frequency recognition and authentication process is successfully solved, the application requirements of RFID are met, and the RFID authentication system and the authentication method are wide in application prospect.
Owner:XIDIAN UNIV
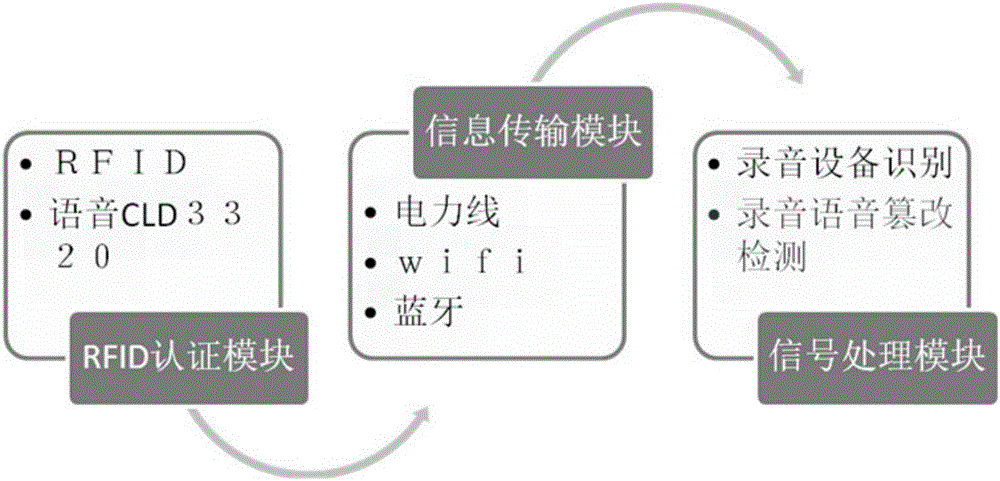
Audio tampering detection device based on time-frequency domain joint features
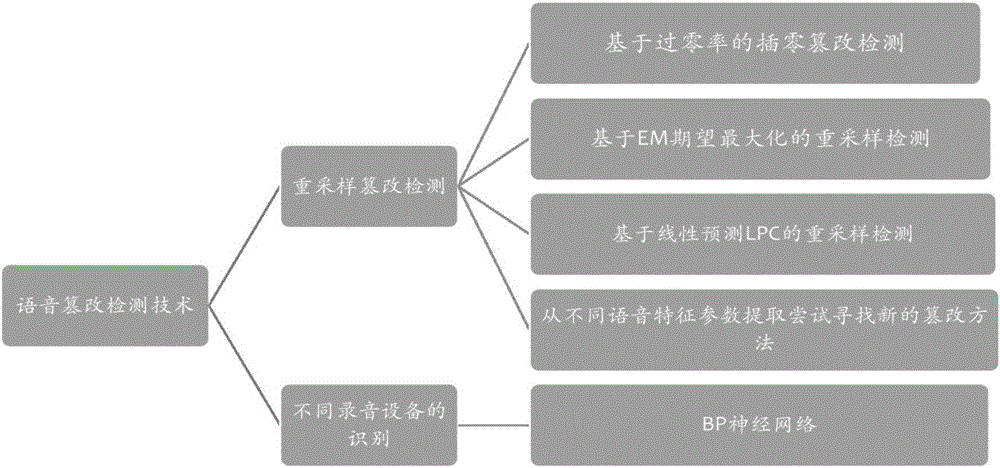
InactiveCN105023581AReal-time storageReduce the "fault" feelingSpeech analysisComputer hardwareMulti band
The invention discloses an audio tampering detection device based on time-frequency domain joint features. The device includes an RFID authentication module mainly used for identity authentication; a signal transmission module mainly used for communication with the RFID authentication module and a signal processing module; a signal processing module used for recording device recognition and voice tempering detection on received voice information, wherein voice tempering detection is mainly realized through a tempering detection algorithm of zero insertion for zero crossing rate, EM (Expectation Maximization) algorithm-based resampling voice tempering detection and LPC model-based initiative forensicvoice tempering detection; and recording device recognition is realized through BP neural network-based multimedia mobile equipment audio tempering recognition and detection. The device provided by the invention can store frequency spectruminformation in real time and has distinctive advantages in aspects of interference rejection, multi-band frequency and precision. The device provided by the invention has high economical efficiency, reliability and practical applicability.
Owner:NANJING INST OF TECH
Radio frequency identification (RFID) authentication apparatus having authentication function and method thereof
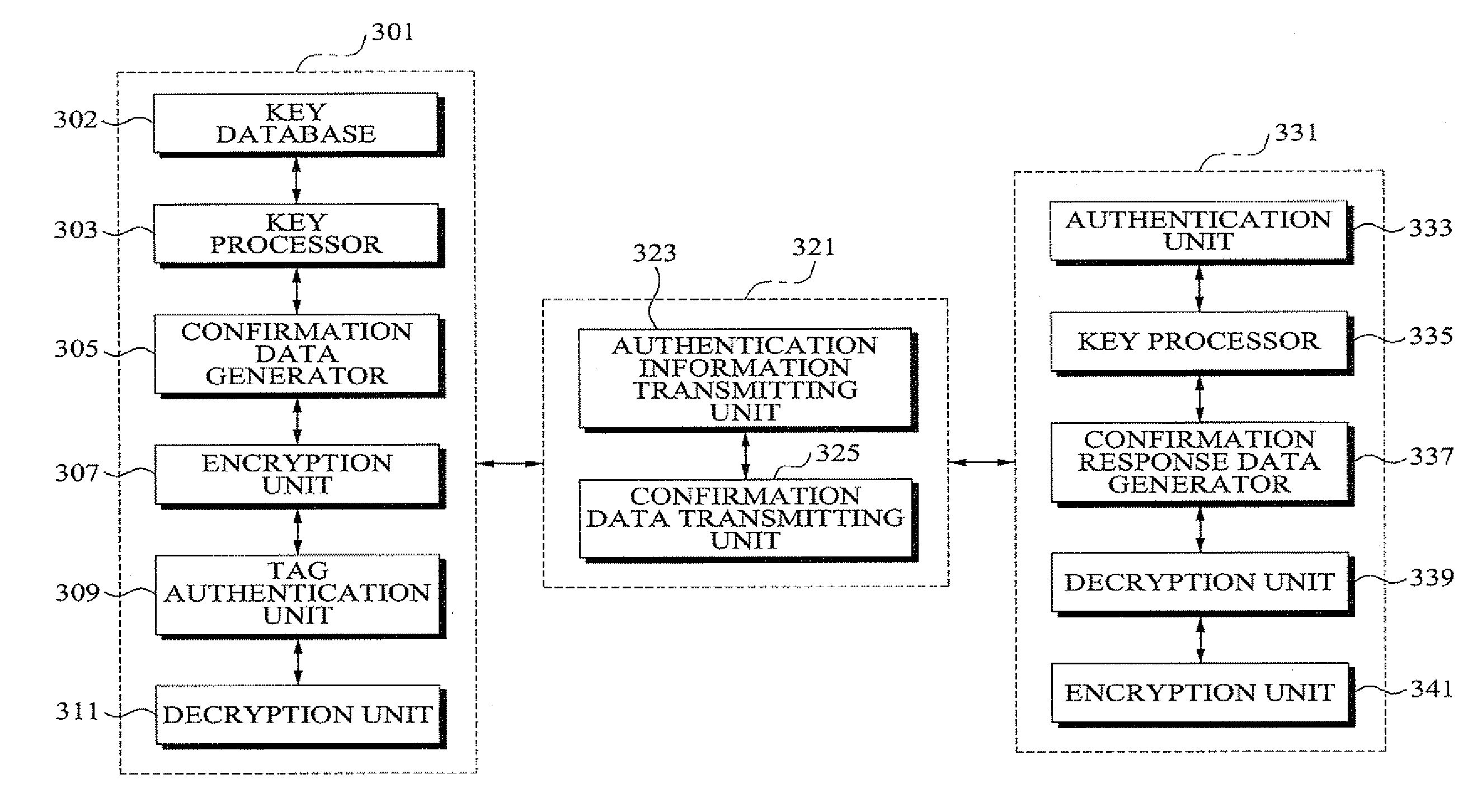
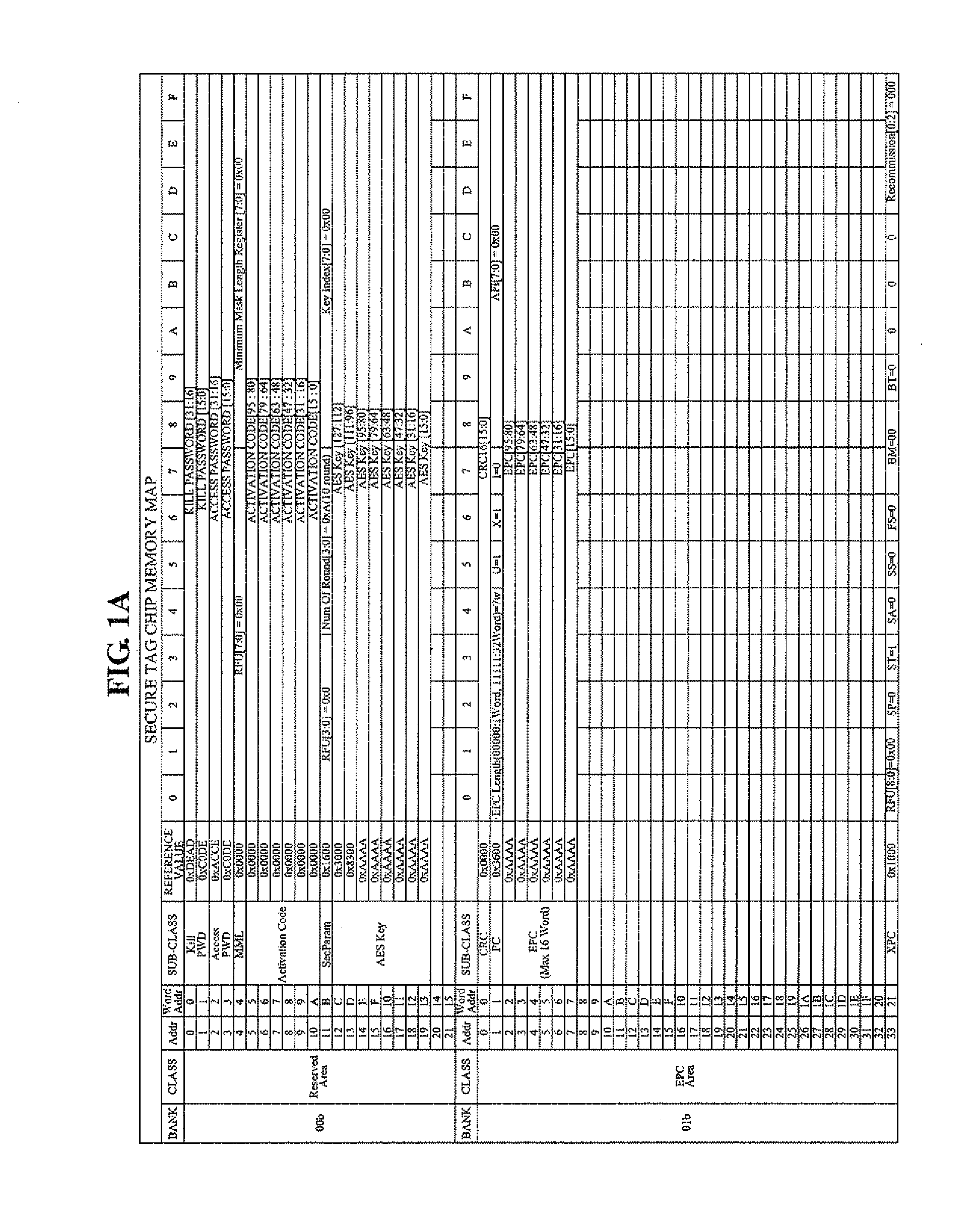
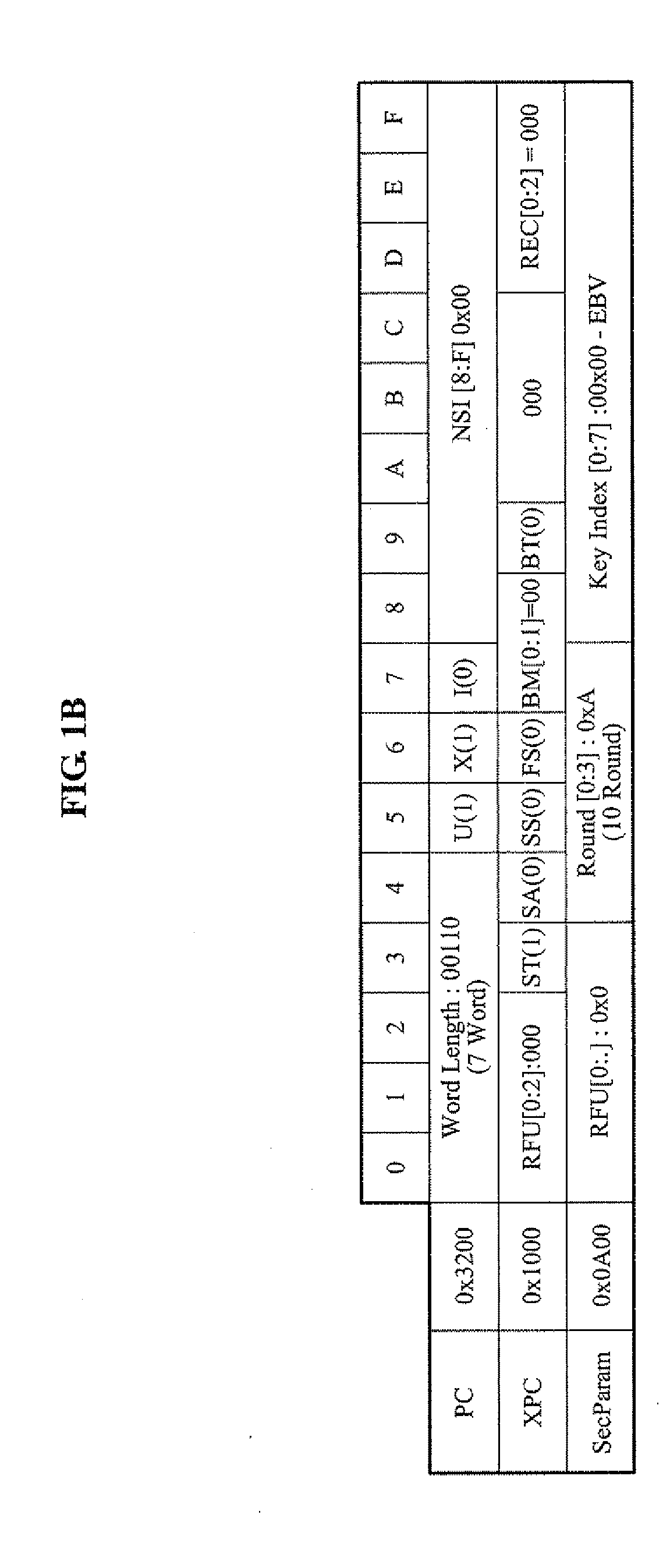
InactiveUS20100014673A1Verify authenticityProgramme controlElectric signal transmission systemsRfid authenticationAuthentication information
Disclosed are an RFID authentication apparatus having an authentication function and a method thereof. An RFID authentication method includes determining, by an authentication reader, an AES key using authentication information received from an authentication tag, generating an output key, encrypting a predetermined length of confirmation data by using the output key, transmitting the encrypted confirmation data to the authentication tag, receiving encrypted confirm response data corresponding to the confirmation data from the authentication tag to decrypt the encrypted confirm response data, and comparing the predetermined length of the confirmation data with the decrypted confirm response data to verify authenticity of the authentication tag.
Owner:ELECTRONICS & TELECOMM RES INST
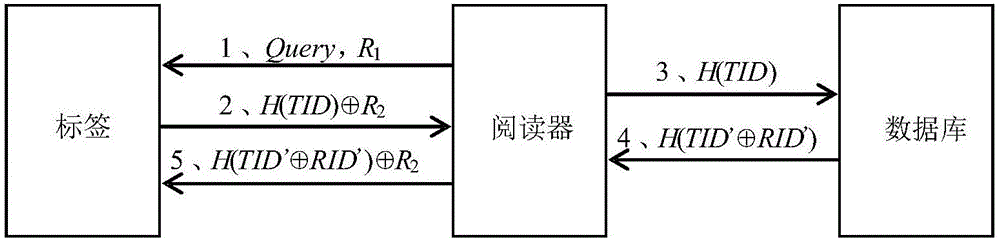
Hash function construction method applicable to RFID authentication system
InactiveCN105391544AEncryption apparatus with shift registers/memoriesArray data structureHash function
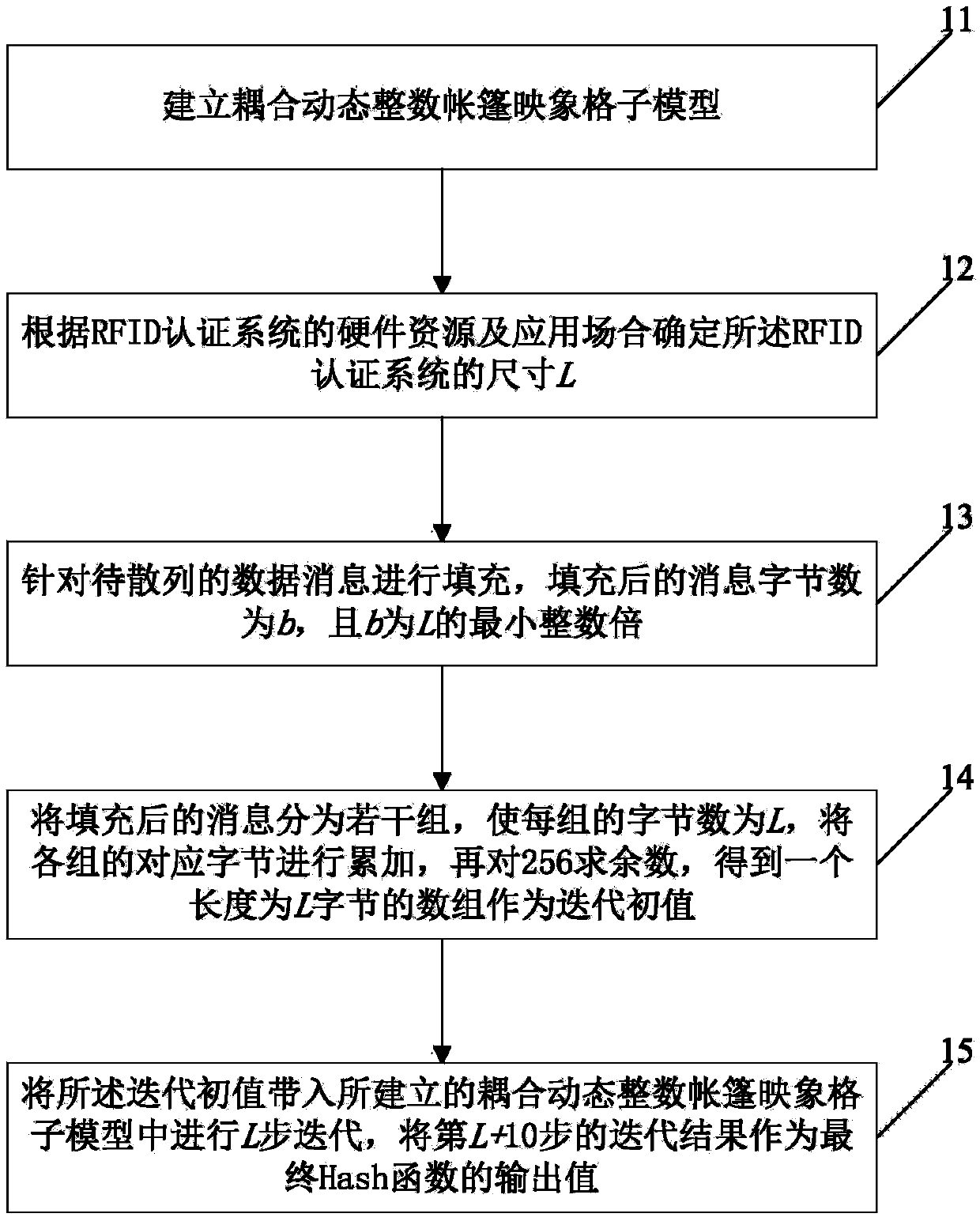
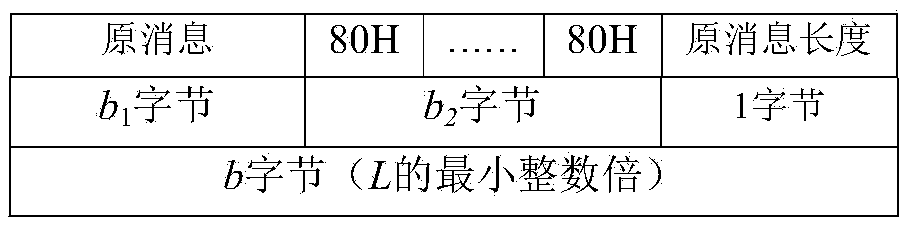
The invention discloses a Hash function construction method applicable to an RFID authentication system. The method comprises the steps of: establishing a coupled dynamic integer tent map lattice model; determining the size L of the RFID authentication system according to hardware resources and application occasions of the RFID authentication system; carrying out filling on data messages to be hashed, wherein the byte number of the messages after the filling is b, and b is a minimum integral multiple of L; dividing the messages after the filling into a plurality of groups, enabling the byte number of each group to be L, accumulating corresponding bytes of all the groups, then obtaining a remainder with regard to 256, obtaining an array whose byte length is L, and using the array as an iteration initial value; and taking the iteration initial value into the established coupled dynamic integer tent map lattice model for L steps of iteration, and using the iteration result of an L+10 step as an output value of a final Hash function. According to the invention, hashed values different in byte length can be obtained with the change of lattice number, and the hashed value of any byte length can be output.
Owner:BEIJING INSTITUTE OF PETROCHEMICAL TECHNOLOGY
Highly anonymous RFID authentication protocol based on Hash function and dynamic shared key
ActiveCN107147498AReduce loadEnhanced authenticationKey distribution for secure communicationMultiple keys/algorithms usageHash functionRfid authentication
The invention discloses an encryption method of information transmission in an RFID authentication process. A label can be in communication connection with a reader-writer, and the encryption method comprises the following steps: after the label receives an inquiry instruction of the reader-writer, generating a first random number, and performing xor operation on the first random number and a public key to obtain a first output; providing a label identifier, the first random number and a dynamic sequence value for a one-way Hash function as inputs so as to generate a second output; providing the second output, the public key, the first output and a reader-writer identifier for the one-way Hash function as inputs so as to generate a third output; providing the reader-writer identifier, the label identifier and the public key for the one-way Hash function so as to generate a filtering identifier; and sending a first message to the reader-writer by the label, wherein the first message comprises the second output, the third output, the filtering identifier and the dynamic sequence value. The invention further discloses a highly anonymous RFID authentication protocol based on a Hash function and a dynamic shared key.
Owner:JILIN UNIV
RFID entrusted authentication method for smart home
ActiveCN107423647AReduce overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareRfid authentication
The invention claims the protection for a RFID entrusted authentication method for smart home, and relates to the field of smart home. A RFID-based access control system is widely applied to resolutions for smart home. Current access control verification plans fail to be entrusted to scenarios, such as when a user travels or is on business trip and can not entrust other to enter his / her home to complete certain tasks. The invention provides a RFID entrusted authentication plan which can be authorized on the user's own to address the problem. According to the invention, firstly, a general RFID authentication protocol is designed and is applied to general authentication scenarios in smart home; and on the basis of the general RFID authentication protocol, for matters entrusted, an entrusted authentication protocol is provided. The technical solution is designed based on Chebyshev chaotic map, such that the user can remote complete matters entrusted.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Elliptic curve radio frequency identification authentication method based on resource-constrained tag
ActiveCN108520189AMeet low cost requirementsOvercome spaceKey distribution for secure communicationPublic key for secure communicationComputer hardwareCommunications security
The invention discloses an elliptic curve radio frequency identification authentication method based on a resource-constrained tag in order to mainly solve problems of constrained storage resources oftags, power consumption restriction and constraint of the calculating capability of the conventional radio frequency identification RFID authentication. The realization steps of the method include: (1) initializing protocol parameters; (2) authenticating a reader by an electronic tag; (3) updating the protocol parameters; and (4) authenticating the electronic tag by the reader. According to the method, compared with the prior art, mutual authentication between the electronic tag and the reader is realized, the calculating amount and occupied resources of the electronic tag are effectively reduced, the communication safety is guaranteed, and the method can be better applicable to a radio frequency identification RFID authentication system of the resource-constrained tag.
Owner:XIDIAN UNIV
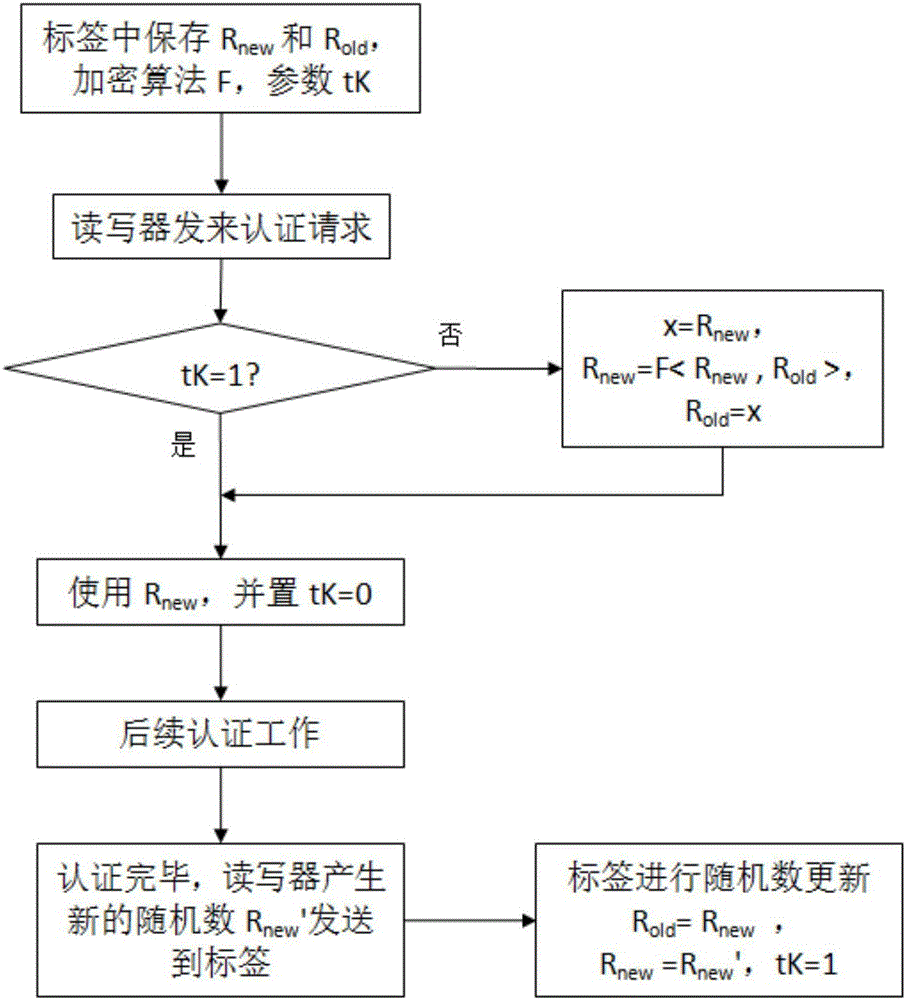
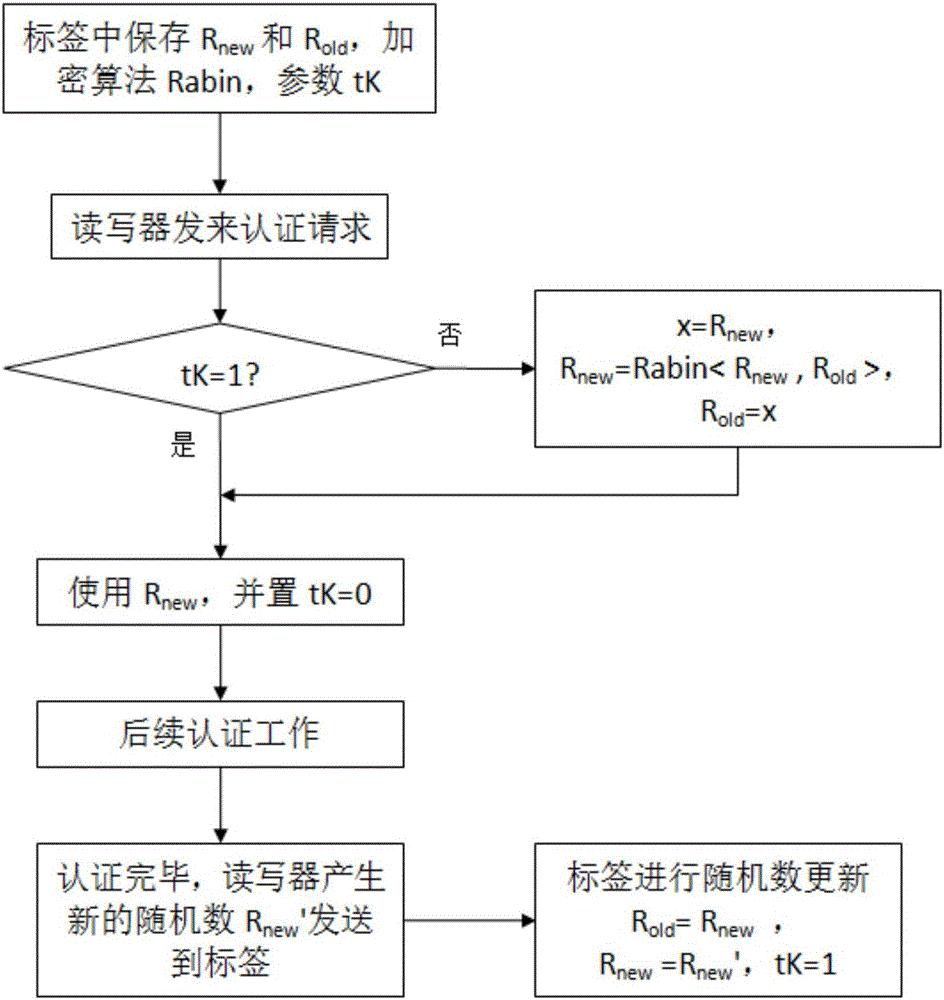
Secure RFID tag random number automatic updating method
InactiveCN106203579AReduce design costSimplify complexityRandom number generatorsRecord carriers used with machinesComputer hardwareRfid authentication
An RFID authentication method has the capacity of resisting tracking attack, the capacity is not only realized by simple secret key updating, a random number requires to be generated in a tag, and the random number is added to computing of authentication process transmission information. A generator of the random number brings increasing of the design complexity and cost of the tag so that the design of a random number automatic updating method has important research significance and use value. The invention provides a secure RFID tag random number automatic updating method. The conventional random number generator is replaced, and the random number is added to computing of the authentication process transmission information so that the RFID tag is ensured to have different feedback information in each time of authentication, and thus the effect of preventing tag tracking can be realized. The random number automatic updating method is based on the original encryption algorithm in the tag, such as HASH, MIXBITS and Rabin, etc. According to the method, the problem of high manufacturing cost of the tag of the present RFID system can be solved, and the security and the authentication efficiency of RFID authentication can be enhanced.
Owner:GUANGDONG UNIV OF TECH
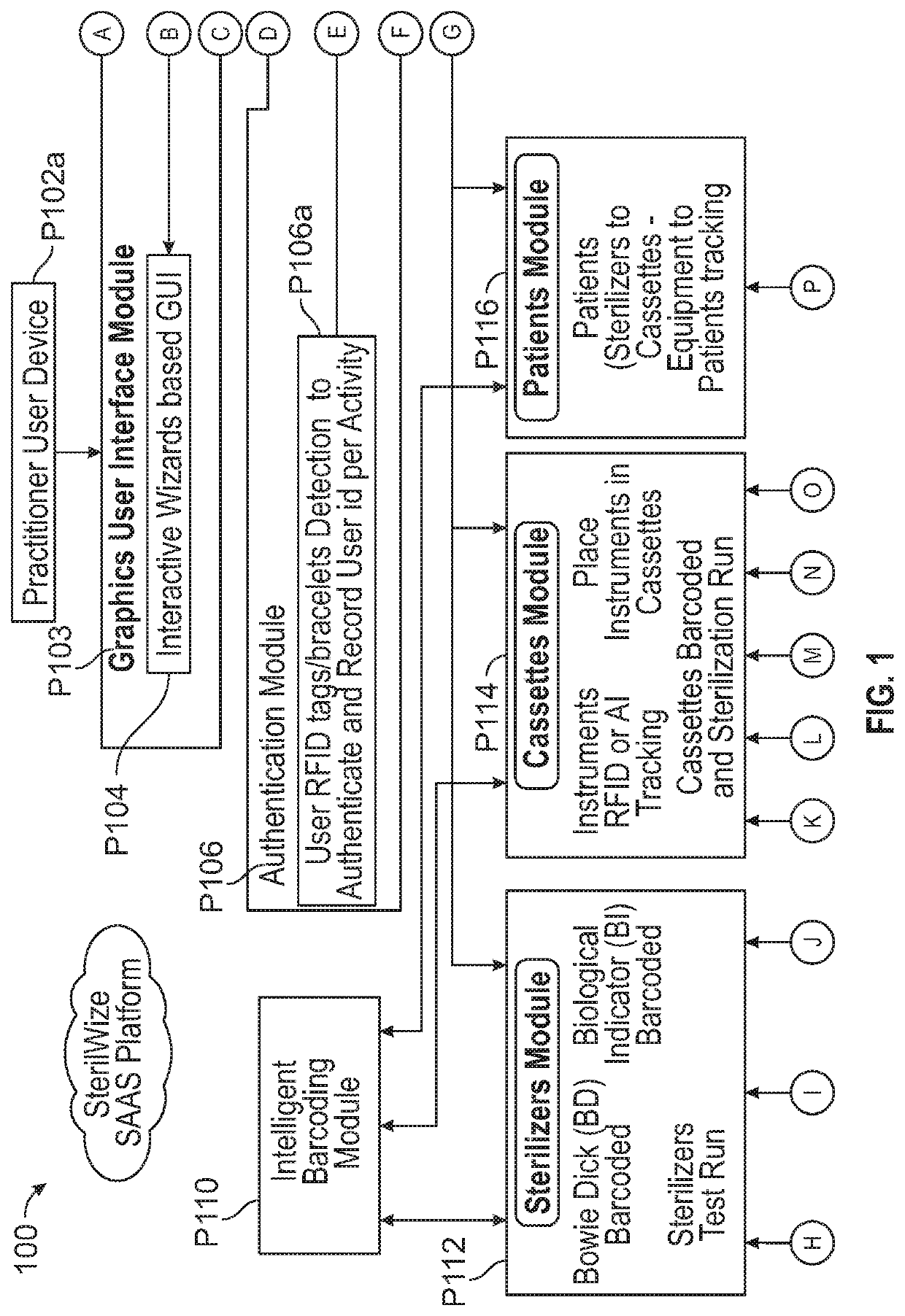
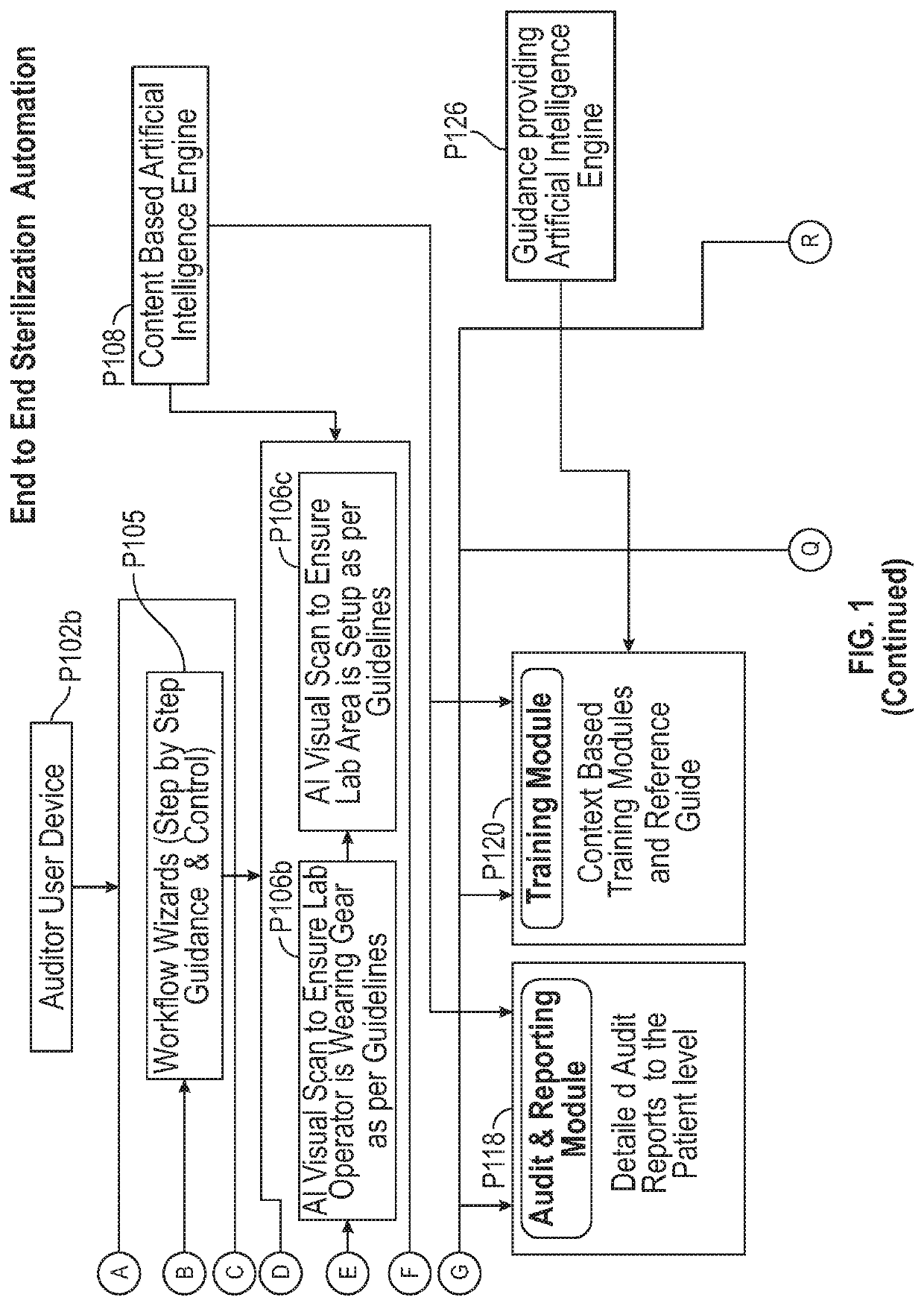
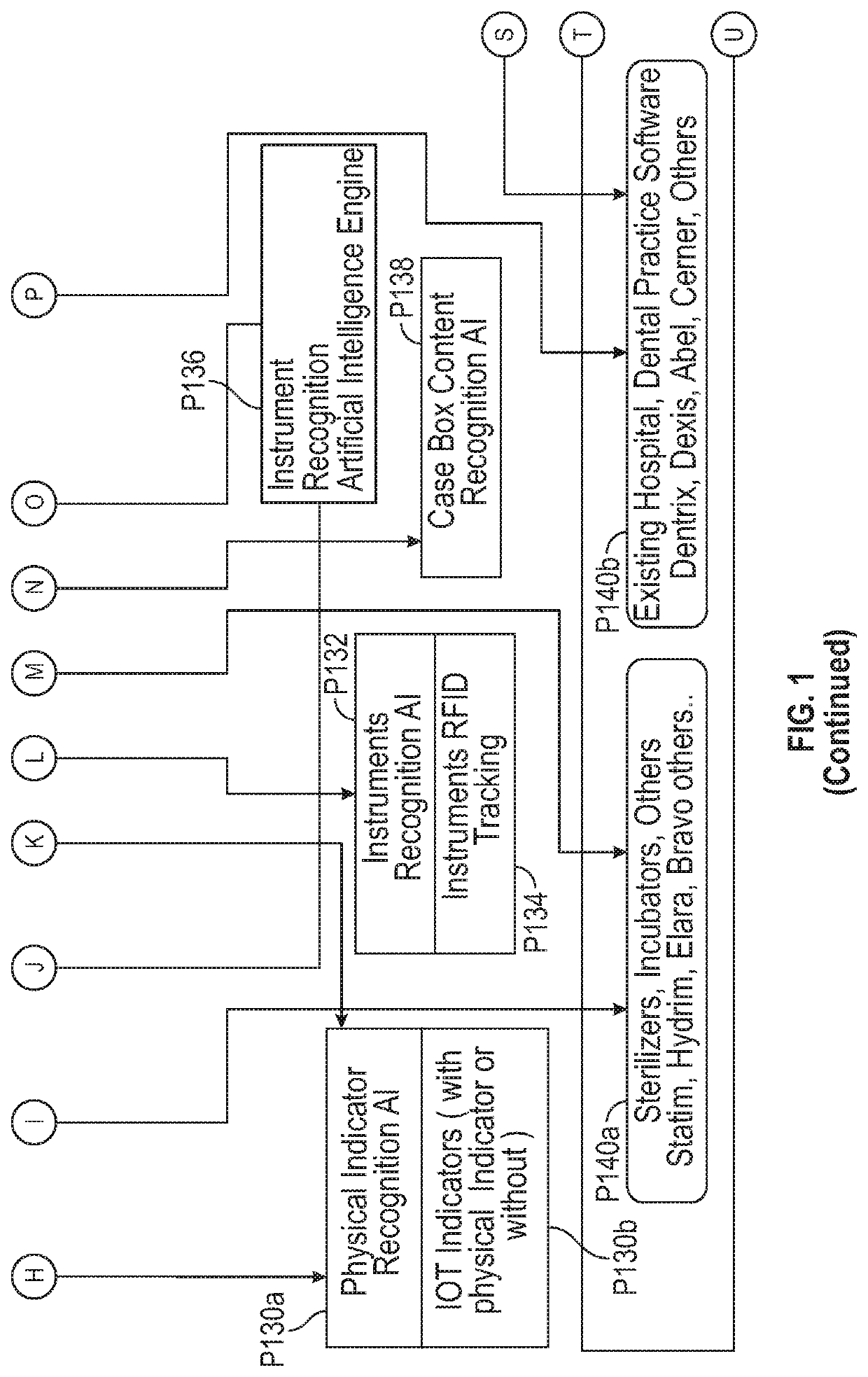
Automated sterilization system with artificial intelligence for processing surgical instruments and methods employed thereof
Exemplary embodiments of the present disclosure are directed towards an artificial intelligence sterilization system and a novel process of providing outsourced sterilization services for processing surgical instruments comprising of: a GUI module along with wizards representing an interactive user interactions to direct to the next action to be performed, authentication module comprising of RFID authentication / AI facilitated control of protective gear worn by the users as well as the workspace, sterilizer's module configured to automate, control and track sterilizer level operations; cassettes module configured to automate, control and track surgical lab instruments with RFID or AI tracking and place instruments in their respective cassettes; patient's module configured to deal with the surgical lab instruments to cassettes to equipment to patient tracking; audit and reporting module configured to deal with a detailed audit report; training module providing context based training modules and reference manuals, inventory module providing requirement based auto replenishments of the surgical lab instruments directed by artificial intelligence.
Owner:SINGH RAJ +1
Bicycle garage access system
The invention discloses a bicycle garage access system. The bicycle garage access system comprises a garage, a parking space circulation mechanism and an access control system. The parking space circulation mechanism comprises an annular guide rail, a base, a parking space telescopic platform and a bicycle fixing device. The parking space telescopic platform is provided with a sliding mechanism. The side wall of the garage is provided with an access door. A starting and stopping device is arranged in the position close to the access door. A pushing and pulling mechanism is arranged on the other side, corresponding to the access door, of the guide rail. The access control system comprises a control unit, an access request device and a parking detector. According to the bicycle garage access system, by adopting the parking space circulation mechanism, storage of a bicycle is more convenient, the access efficiency is improved, and the implementation cost is low; by adopting RFID verification for an access user, access for the bicycle of the user can be managed better; by placing the bicycle garage access system in a container, mobility of the garage is achieved, the cost can be reduced, and the access using rate of the garage is improved; and by arranging a rear panel and a concave pit on the bicycle fixing device, fixing is simple, convenient, stable and firm, and the fact that the bicycle is separated from the fixing device is prevented.
Owner:成都市五度空间立体车库科技有限公司
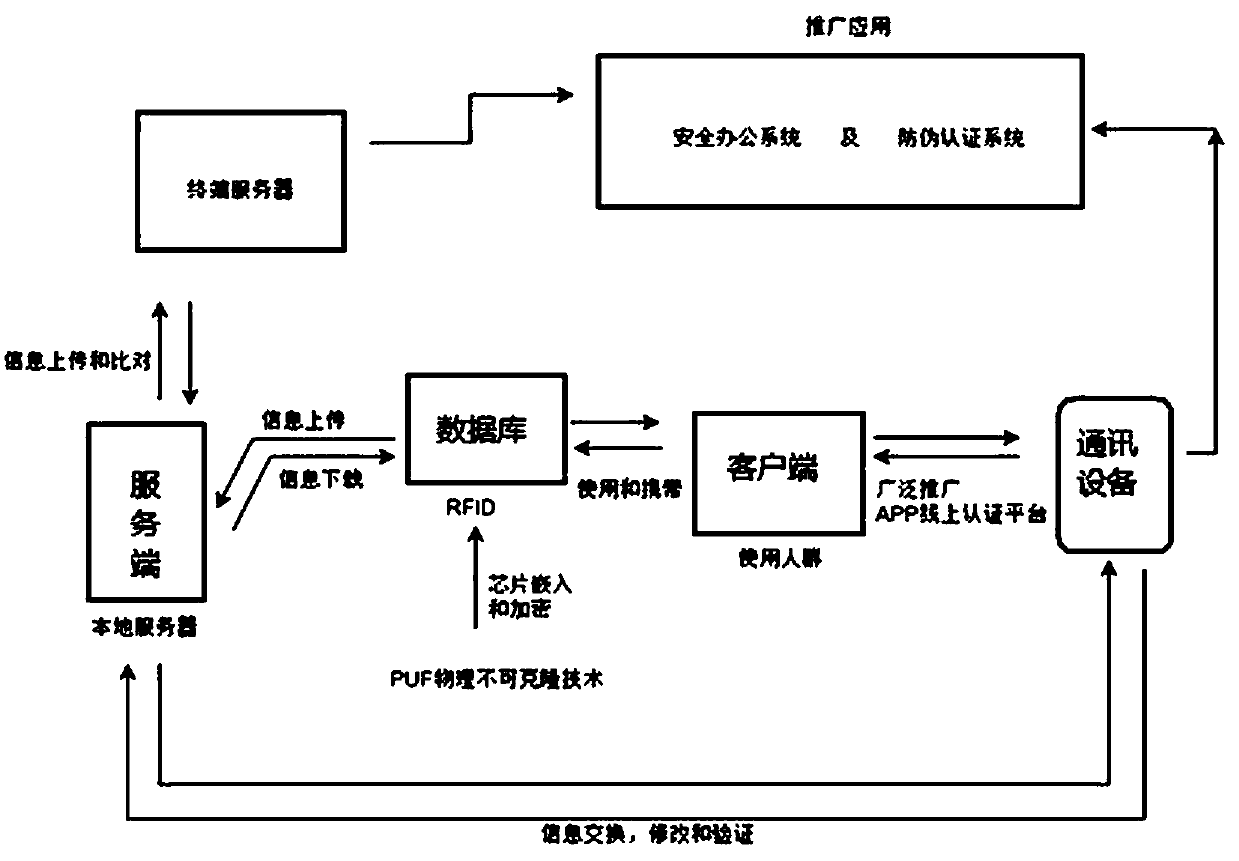
Highly encrypted RFID authentication system for chip fingerprints
PendingCN110276423ARobustNon-clonableCo-operative working arrangementsInternal/peripheral component protectionRfid authenticationTerminal server
The invention discloses a highly encrypted RFID authentication system for chip fingerprints. The highly encrypted RFID authentication system comprises a server, a terminal server, a popularization and application module, communication equipment, a client and a database, wherein the server is in control connection with the terminal server; the server is in control connection with the communication equipment and used for achieving information exchange, modification and verification; the server is in control connection with the database, the client and the communication equipment in sequence; and the server and the database are used for controlling information uploading and downloading. In this way, the highly encrypted RFID authentication system for chip fingerprints utilizes the internal physical structure of the physical entity to uniquely identify a single physical entity to realize an effective authentication thought, fully utilizes the RFID of the PUF (Physical Unclonable Function), and utilizes the characteristics of robustness, unclonability and unpredictability of the PUF at the same time, so that the highly encrypted RFID authentication system for the chip fingerprint is widely applied to the field of authentication.
Owner:苏州因缇格电子科技有限公司
RFID authentication method for elliptic hyperbola-based public key encryption mechanism
InactiveCN109687957AGuaranteed randomnessGuaranteed unpredictabilityKey distribution for secure communicationPublic key for secure communicationRfid authenticationData stream
The invention discloses an RFID authentication method for an elliptic hyperbola-based public key encryption mechanism. According to the method, key distribution is carried out by using an elliptic hyperbola DH theory, a generation system of fresh keys is constructed, communication data between encryption entities of the fresh keys is used for ensuring the randomness and unpredictability of a datastream, and a secure communication channel between a label and a reader is established; communication entities store a public key and private key pair generated by the elliptic hyperbola theory, and identity authentication between the entities is realized in a digital signature mode, so that the effectiveness of the authentication is ensured; and after the security authentication is realized, a session key used for encrypting the data is generated, so that sensitive data interaction between the entities is facilitated. Common security threats such as mutual authentication, anonymity, reliability, forward privacy, location privacy, man-in-the-middle attack, counterfeit attack and the like can be prevented, and a distribution function of the session key is provided, so that the security andprivacy of the channel between the label and the reader are ensured.
Owner:WUXI FANTAI TECH
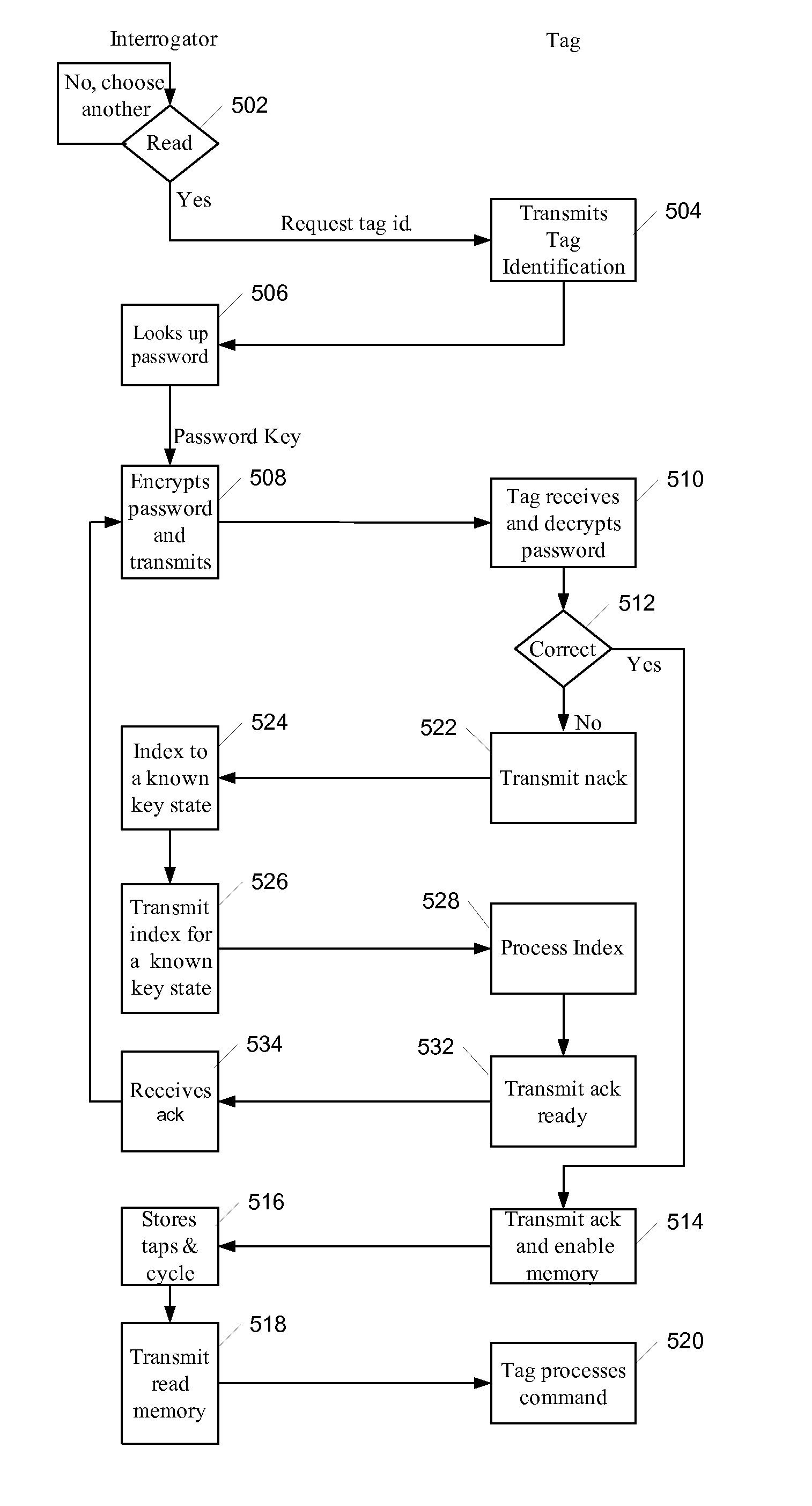
RFID authentication architecture and methods for RFID authentication
ActiveUS8681987B2Key distribution for secure communicationMultiple keys/algorithms usageRfid authenticationPassword
A method for mutual authentication in an RFID system comprising an RFID reader and an RFID tag, the method comprising requesting an identification from the tag, receiving the identification, using the received identification to select a password associated with the identification, generating a password key based on the selected password, encrypting the selected password using the password key, and transmitting the encrypted password to the tag.
Owner:SMART COSMOS SOLUTIONS INC
An RFID tag random number synchronous updating method
ActiveCN109766966AReduce overheadFast operation and high efficiencyKey distribution for secure communicationCo-operative working arrangementsComputer hardwareRfid authentication
The invention discloses an RFID (Radio Frequency Identification Device) tag random number synchronous updating method, which generally needs to keep the freshness of a message through a random numberin an authentication process of an RFID tag, so as to prevent tracking attack and desynchronization attack on the tag. Due to the computing power of the tag, a common random number generator is difficult to be used in the tag, so that the design of a simple random number updating method of the tag is of great significance. In the random number updating method provided by the invention, a method for generating a new random number by using a random number sent by a reader-writer at a tag end in combination with an encryption function of a tag and initializing a shared random number is provided.According to the method, the freshness of information fed back by the tag each time can be ensured, various attacks such as desynchronization attacks and the like for the RFID tag can be resisted, andthe safety in the RFID authentication process and the generation efficiency of a tag random number are improved.
Owner:GUANGDONG UNIV OF TECH
Authentication method for multi-owner RFID tags
ActiveCN111931533AReduce interactionProtocol is simpleKey distribution for secure communicationSensing by electromagnetic radiationRfid authenticationInternet privacy
The invention discloses an authentication method for a multi-owner lightweight RFID tag, and mainly solves the problems of information interaction and resource consumption in the process of authenticating ownership of the tag by multiple owners in radio frequency recognition RFID authentication. The scheme comprises the following steps: 1) initializing protocol parameters; 2) the reader sends identity information to the label; 3) the electronic tag authenticates the reader, and judges whether the sub-key weight contained in the reader reaches a threshold value or not; 4) the rear-end databasereceives the judgment information of the tag and compares the judgment information with self-stored information to authenticate the electronic tag; 5) the label recovers the secret key, compares the secret key and authenticates the back-end database; according to the key sharing method adopted by the invention, the key can be recovered when the weight of the received sub-key reaches a threshold value, so that the protocol is simplified, the information interaction is reduced, the communication safety is ensured, and the key sharing method can be better suitable for a multi-owner RFID authentication system.
Owner:XIDIAN UNIV
Bidirectional identity authentication method for ultra-lightweight RFID authentication protocol
ActiveCN111680531ALow costImprove securityDigital data authenticationRecord carriers used with machinesRfid authenticationAttack
The invention discloses a bidirectional identity authentication method for an ultra-lightweight RFID authentication protocol. The method is mainly characterized in that a back-end database server andan electronic tag respectively generate verification information by using exclusive-OR and cyclic shift operations, and mutual authentication is carried out between the electronic tag and a reader inthe ultra-light radio frequency identification RFID system. The method is specially designed for a resource-limited low-cost passive radio frequency identification (RFID) tag. The method is mainly characterized in that the method is safe and efficient, is easy to implement, can effectively resist common attacks in RFID authentication, such as a replay attack, a man-in-the-middle attack, a secret key leakage attack, a desynchronization attack and an anti-tracking attack, and is higher in safety.
Owner:XIDIAN UNIV
Anti-quantum computing RFID authentication method and system based on asymmetric key pool and secondary remainder
ActiveCN110620764AMake up for the lack of securityAvoid crackingKey distribution for secure communicationUser identity/authority verificationRfid authenticationQuantum computer
The invention relates to an anti-quantum computing RFID authentication method and system based on an asymmetric key pool and secondary remainder. The participants comprise an authentication party anda request party which interact in an RFID mode. Each participant is configured with a key fob; wherein an identity label, a true random number, a public key and a secret key pointer address of the requester are stored in a secret key card of the requester; wherein the key pointer address is used for extracting a corresponding asymmetric key unit from the asymmetric key pool, and by adopting the method, the storage cost in a key card of a requester can be reduced, and the safety in an authentication interaction process of the requester and the requester can be improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
RFID authentication method and RFID authentication system
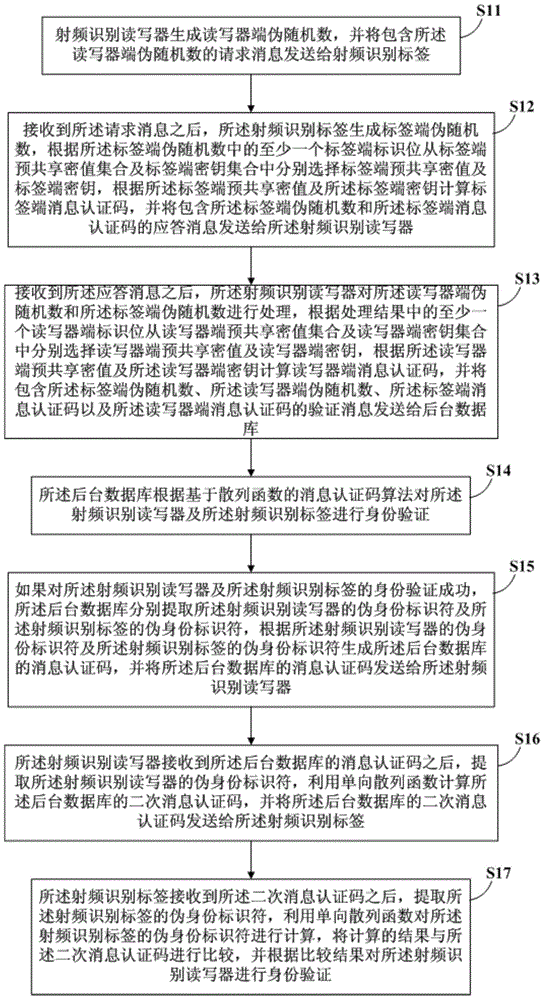
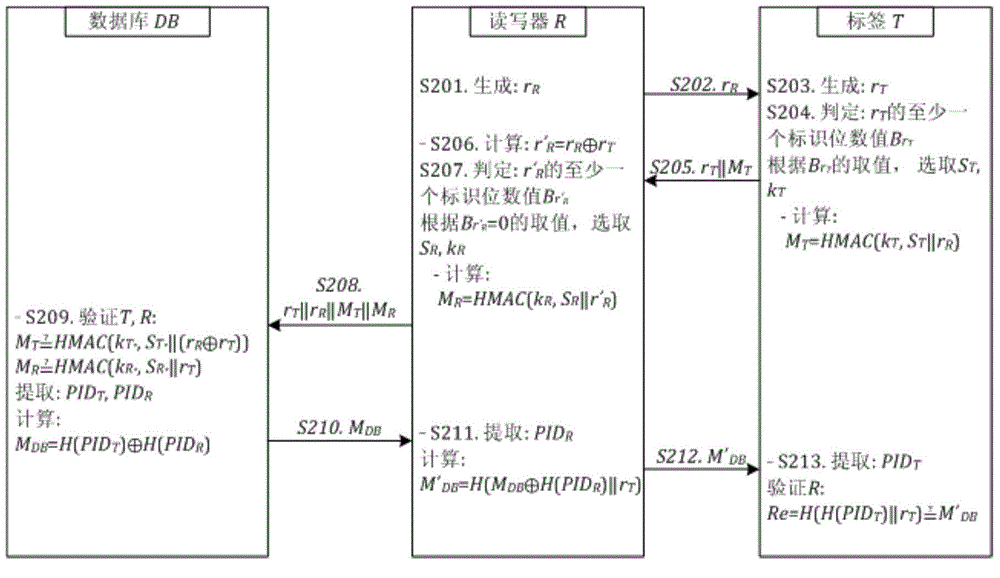
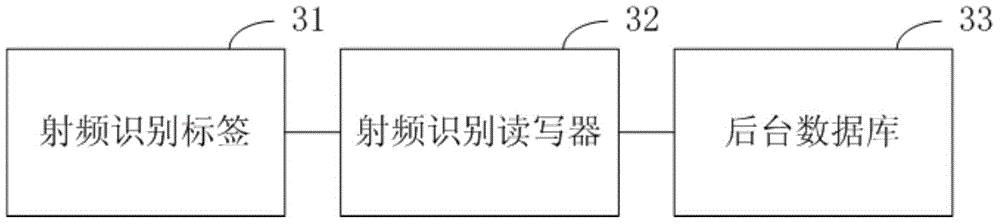
The embodiment of the invention discloses an RFID (Radio Frequency Identification) authentication method and an RFID authentication system. According to the method, at least one identification bit number in pseudo random numbers is used for realizing the dynamic selection of labels, a reader-writer pre-shared value and a reader-writer pre-shared key; and the randomness of a protocol conversation period is improved. By aiming at the speciality and the limitation of an RFID system label and a reader-writer air interface, the method introduces an Hash-based message authentication code and a one-way Hash function to realize the forward security of an interaction message; an authentication mechanism is used for realizing the identity authenticity verification of a label and a reader-writer; and the secure data transmission problem of an RFID system is effectively solved. The method is practical and novel; a lightweight cryptology operator is used for identity verification; the dynamic performance of conversation period interaction data is improved; and the method is applicable to an RFID application scene with limited system resources.
Owner:RUN TECH CO LTD BEIJING
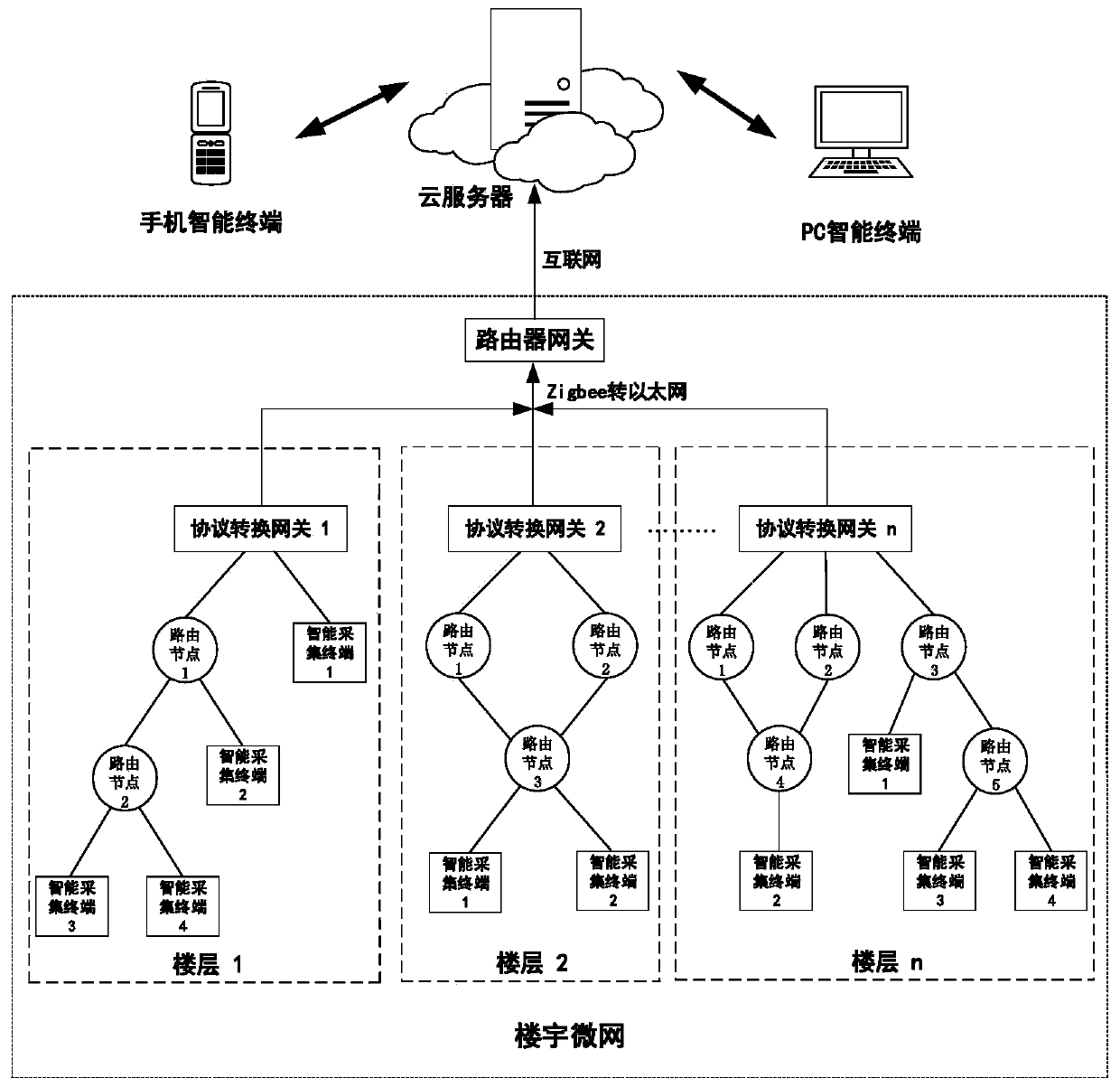
Building microgrid power consumption data security transmission technology based on RFID authentication and hybrid encryption
InactiveCN109982309AUser identity/authority verificationSecurity arrangementRfid authenticationMicrogrid
The invention relates to a technology for transmitting and visualizing building microgrid power consumption data, and provides a building microgrid power consumption data security transmission technology based on RFID legal authentication and hybrid encryption in order to prevent an information eavesdropper from eavesdropping, tampering and forwarding the building power consumption data. Transmission system hardware applying the technology is composed of an intelligent acquisition terminal, a routing node, a protocol conversion gateway and a cloud server. The intelligent acquisition terminal acquires related power utilization data and self-organizes the data to form a ZigBee wireless transmission network. the legality of each node in the ZigBee network is ensured by integrating the RFID technology and the hybrid encryption algorithm, and the security of power utilization data transmission is improved; the encrypted data is packaged into a data frame by a user-defined communication protocol; the encrypted data is transmitted to the protocol conversion gateway through the routing node to realize protocol conversion, finally, the data message is sent through the gateway and stored inthe database of the cloud server, and the client can visualize the power consumption data and remotely control the intelligent acquisition terminal, so that the safety and convenience of building microgrid power consumption data transmission are improved.
Owner:XIANGTAN UNIV
Anti-quantum computing RFID authentication method and system based on symmetric key pool and online and offline signatures
ActiveCN110650004AReduce the possibilityMake up for the lack of securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesRfid authenticationOnline and offline
The invention relates to an anti-quantum computing RFID authentication method and system based on a symmetric key pool and online and offline signatures. The parties comprise an authentication party and a request party which interact with each other in an RFID mode, wherein each party is configured with a key fob; algorithm parameters are stored in the key fob; an identity label and a public key of the request party, a private key corresponding to the public key, a temporary public key, a temporary private key corresponding to the temporary public key and a symmetric key unit are stored in a key fob of the request party; a symmetric key pair is stored in the symmetric key unit, and the symmetric key pair comprises a first symmetric key, a second symmetric key and a key pointer address; andthe key pointer address is used for extracting a related symmetric key unit from a symmetric key pool. By adopting the anti-quantum computing RFID authentication method, the storage cost in the key fob of the request party can be reduced, and the security in the authentication interaction process of the request party and the request party can be improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
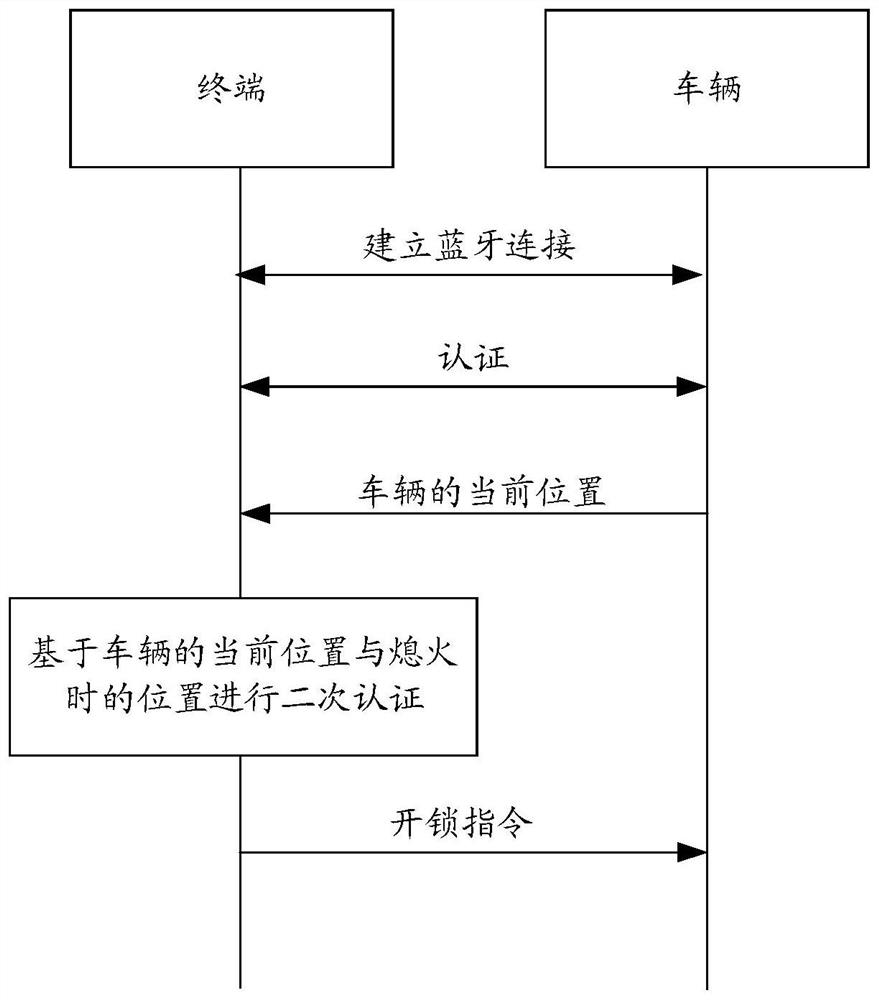
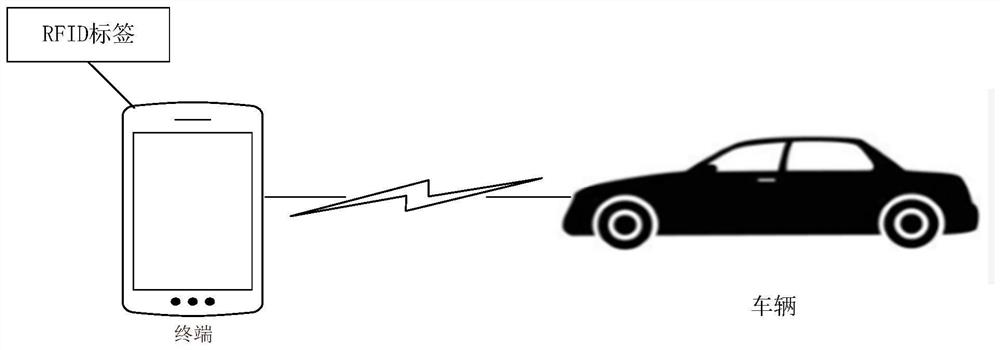
Verification method and device
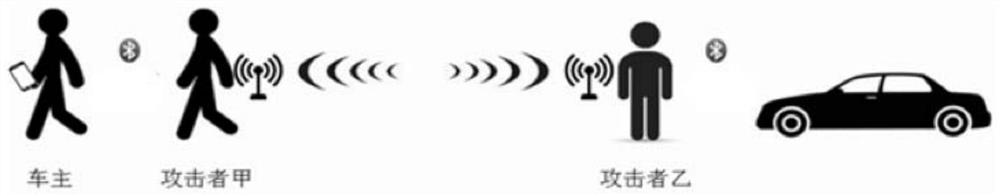
The embodiment of the invention provides a verification method and device, and the method comprises the steps: carrying out the Bluetooth authentication with a terminal based on Bluetooth authentication information; after the Bluetooth authentication with the terminal succeeds, acquiring RFID authentication information, wherein the RFID authentication information comprises tag information of an RFID tag and authorization information, and the authorization information is used for indicating an association relationship between the RFID tag and the terminal; and based on the RFID authentication information, executing RFID authentication, and after the RFID authentication succeeds, staying in a controllable state. According to the invention, relay attacks can be effectively prevented, and the security of the controlled equipment is improved.
Owner:PETAL CLOUD TECH CO LTD
Lightweight RFID authentication method based on integer chaos
ActiveCN106487495APrevent eavesdroppingPrevent replay attacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesRfid authenticationHash function
The invention discloses a lightweight RFID authentication method based on integer chaos. According to the invention, by use of pseudo random numbers, freshness of labels and communication contents of readers are ensured; and by use of the Hash function, confidentiality of the communication contents is ensured. Thus, common attack means such as counterfeiting attacking, replay attacking and eavesdropping can be resisted.
Owner:BEIJING INSTITUTE OF PETROCHEMICAL TECHNOLOGY
Anti-quantum computing RFID authentication method and system based on asymmetric key pool and IBS
ActiveCN110768782AEnsure safetySmall amount of calculationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesRfid authenticationInternet privacy
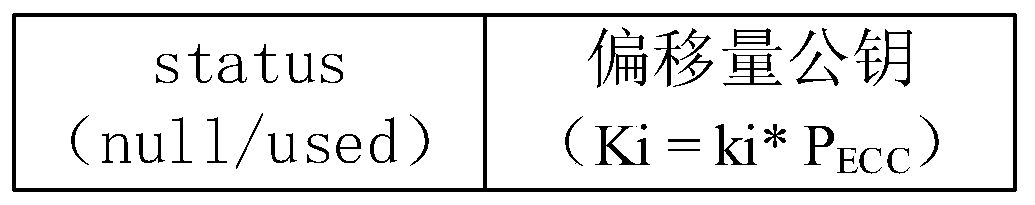
The invention relates to an anti-quantum computing RFID authentication method based on an asymmetric key pool and an IBS. The participants comprise an authentication party and a request party which interact in an RFID mode. Each participant is configured with a key fob; an authentication party public key, a pointer address, an IBS signature public and private key pair, an IBS signature random number, an IBS signature parameter and an identity parameter issued by the authentication party are stored in a key card of the request party, and the identity parameter comprises an identity number of the request party, the request party public and private key pair and an offset public key. By adopting the method, the storage cost in the key fob of the requester can be reduced, and the security in the authentication interaction process of the requester and the requester can be improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com