RFID authentication system and authentication method based on position privacy cloud
An authentication system and privacy cloud technology, applied in the RFID authentication system based on the location privacy cloud, mutual authentication between RFID tags and readers, can solve the problem of insufficient communication channel security, exposure of reader location privacy, and limited tag storage resources and other problems, to achieve the effect of solving the location privacy problem, high retrieval efficiency, and low label calculation complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
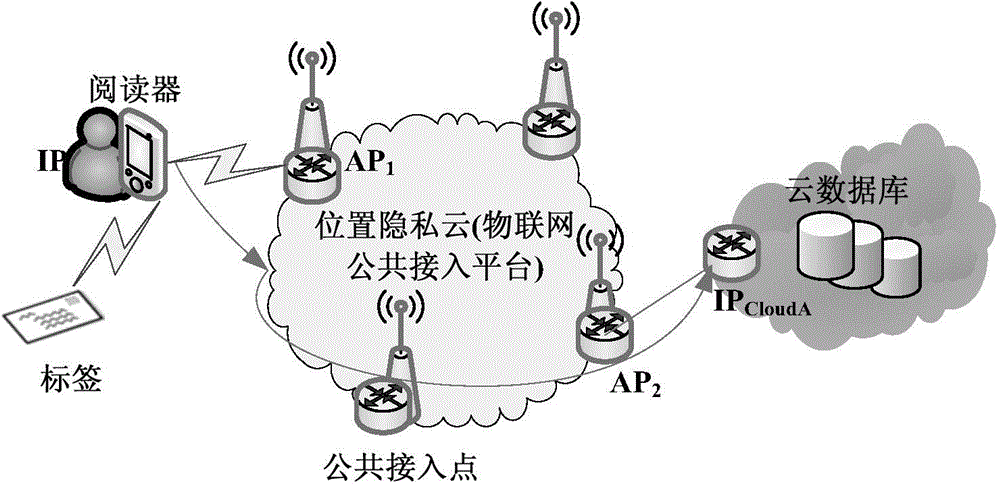
[0038] The present invention first proposes an RFID authentication system based on location privacy cloud.
[0039] see figure 1 , the RFID authentication system based on the location privacy cloud includes a radio frequency identification tag, a mobile reader and a cloud database server, and it is important that the present invention also includes a public access platform that can protect the location privacy of the mobile reader, that is, a location privacy cloud, and a location privacy cloud It is an IoT infrastructure maintained by a trusted third party or a trusted organization that provides privacy services, such as an IoT public access platform. It can provide readers with support for public services such as location privacy protection transmission and data information aggregation. The background server of the present invention is constituted by a cloud database server. The interactive information between the reader and the tag of the present invention is forwarded to...
Embodiment 2
[0046] The composition of the RFID authentication system based on the location privacy cloud is the same as that in Embodiment 1. There are independent public access points distributed in the location privacy cloud, and one of the public access points is called an edge access point, and the edge access point is connected to the cloud database. The server is directly connected, and the rest are ordinary access points, all of which are directly or indirectly connected to the edge access point. After the mobile reader moves to a certain place and registers with the public access point of the location privacy cloud, the information exchanged between the reader and the tag The public access point of the location privacy cloud is successively forwarded to the cloud database server, thereby protecting the location privacy of the mobile reader. When the mobile reader is directly registered to the edge access point, the information exchanged between the reader and the tag is directly fo...
Embodiment 3
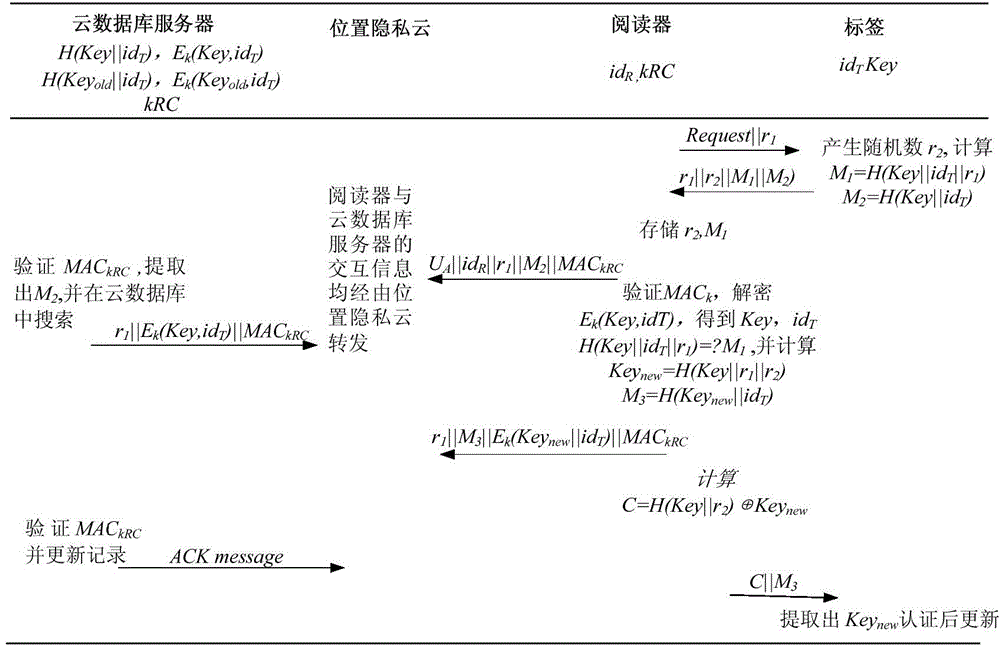
[0062] The present invention also proposes an RFID authentication method based on location privacy cloud. Based on the above system structure, it is the same as Embodiment 1-2. After system initialization, refer to figure 2 , the specific process of authentication is as follows:
[0063] Step (1) The reader sends an authentication request to the tag.
[0064] (1a) The mobile reader R uses the lightweight sequence cipher algorithm Grain v1 to generate a random number r 1 .
[0065] (1b) Send an authentication request Request||r to the tag T 1 .
[0066] Step (2) Tag's response to reader.
[0067] (2a) The tag uses the lightweight sequence cipher algorithm Grain v1 to generate another random number r 2 .
[0068] (2b) The tag uses the hash function SHA-3 standard algorithm to calculate M 1 =H(Key||id T ||r 1 ) and M 2 =H(Key||id T ).
[0069] (2c) send r 1 ||r 2 ||M 1 ||M 2 to the reader in response to it.
[0070] Step (3) The reader sends a request to the cloud...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com