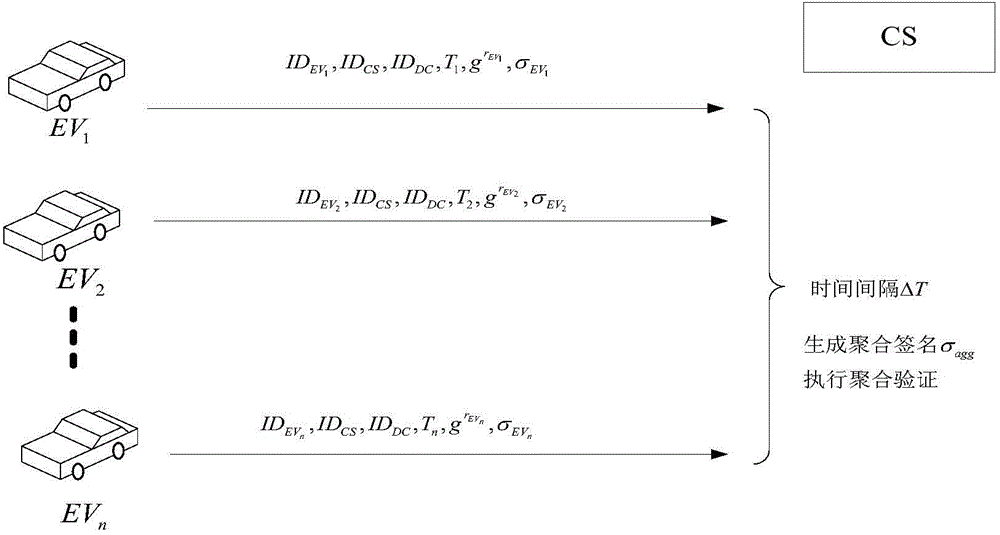Access authentication method of electric automobile
An electric vehicle and access authentication technology, which is applied to electrical components, transmission systems, etc., can solve problems such as inability to support efficient access authentication and high computing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
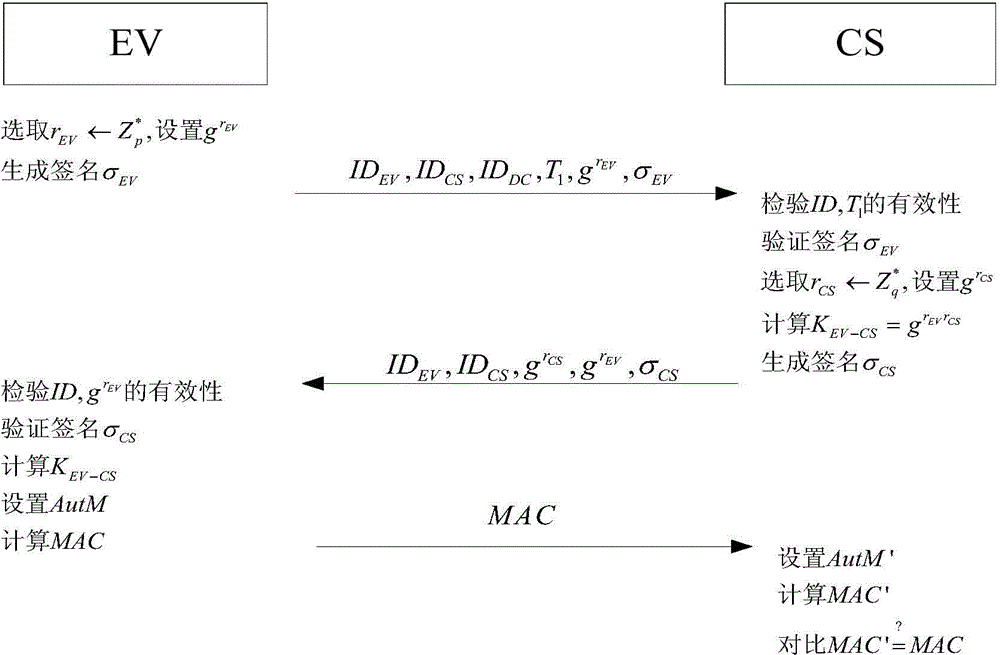
[0073] The invention of this example is an access authentication method for an electric vehicle, the method comprising the following steps:
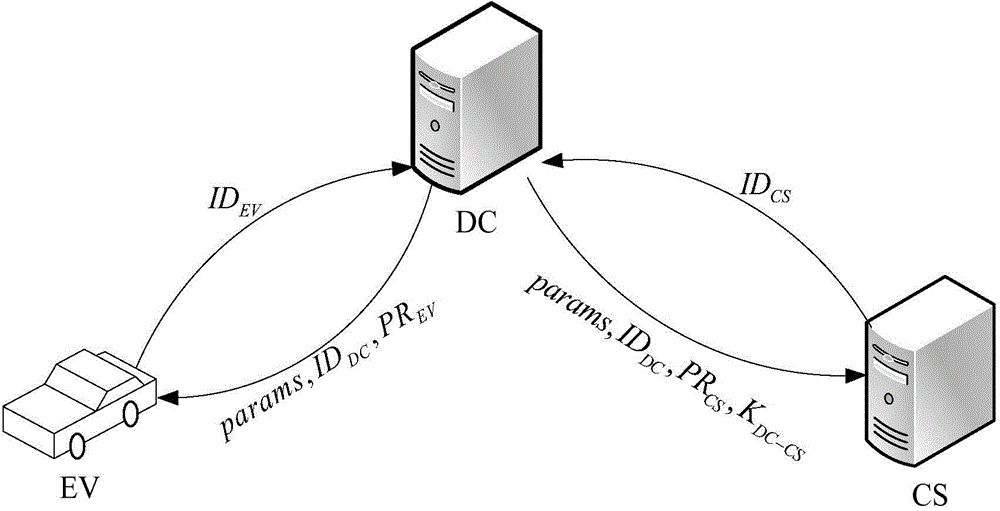
[0074] Given the initial registration process of electric vehicles (EV) and charging stations (CS) in the data center (DC), that is, system establishment, such as figure 1 Shown:
[0075] (1) DC is a trusted third party, which plays the role of private key generation center and runs identity aggregation signing
[0076] The initialization algorithm in the name is responsible for the management of the private key:
[0077] ·DC generates system parameters params and master secret key msk;
[0078] ·DC keeps msk secretly;
[0079] ·DC announces params, and its identity information ID DC bound.
[0080] (2) The EV needs to register with the data center initially, and the process is as follows:
[0081] EV submits its own identity information ID to DC EV ;
[0082] ·DC inspection ID EV The legitimacy of the DC runs the private key ge...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com