RFID entrusted authentication method for smart home
An authentication method and smart home technology, applied in encryption devices with shift registers/memory, inductive record carriers, transmission systems, etc., can solve problems such as potential safety hazards, high risks, and threats to residents' property safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
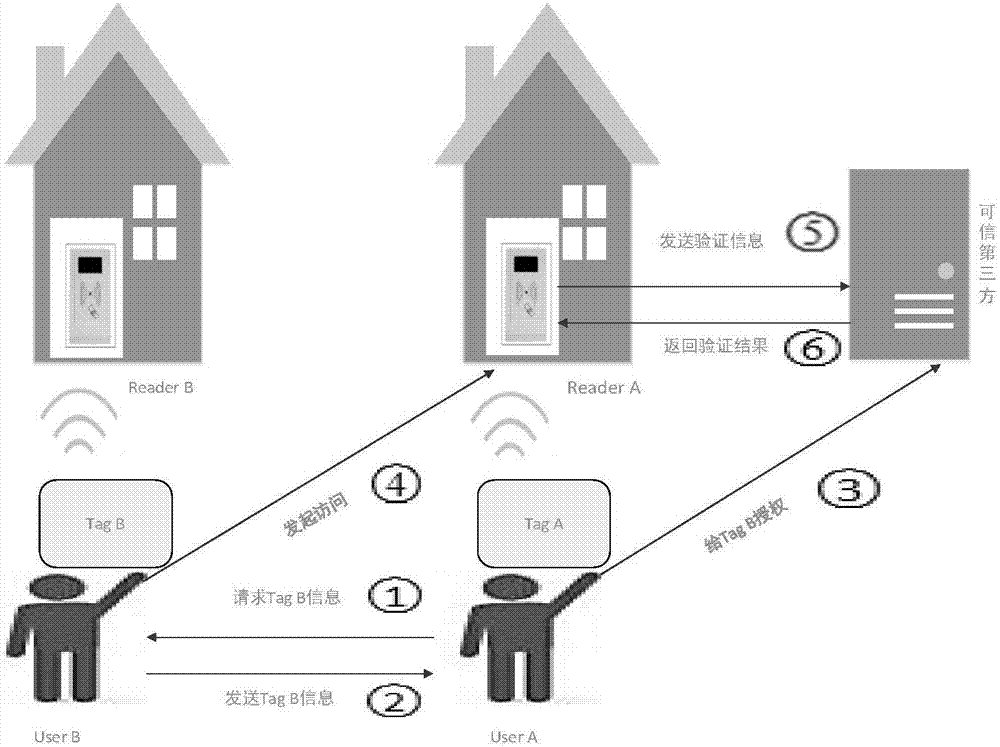
[0021] The technical scheme that the present invention solves the problems of the technologies described above is: with reference to Figure 1-Figure 3 said,
[0022] (1) Ordinary authentication. This authentication process corresponds to the authentication process performed by the user according to his own Tag and his own Reader. The specific steps are as follows:
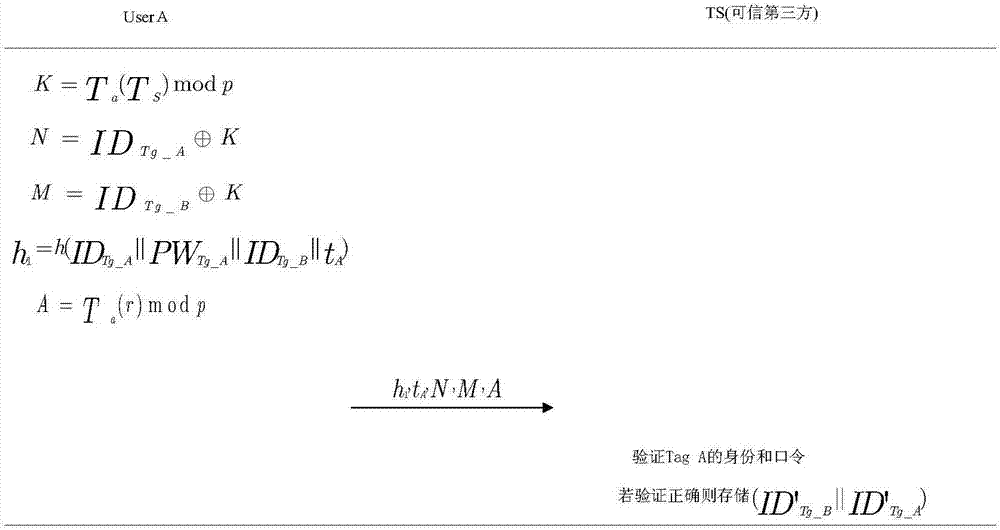
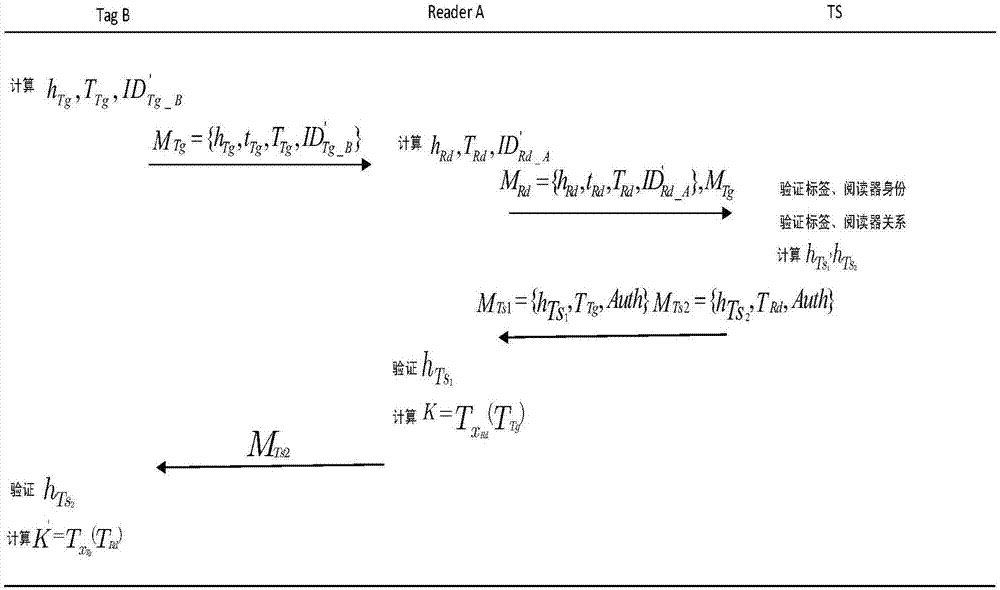
[0023] A) Tag Tag-A generates a random number x Tg then calculate h Tg =h(ID Tg_A ||PW Tg_A ||t Tg ||T Tg ), where r, TS=(Ts(r)modp), p is the public key of the trusted third party, s is the private key of the trusted third party, ID Tg is the name of the tag Tag-A, PW Tg is the shared password between Tag-A and the trusted third ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com