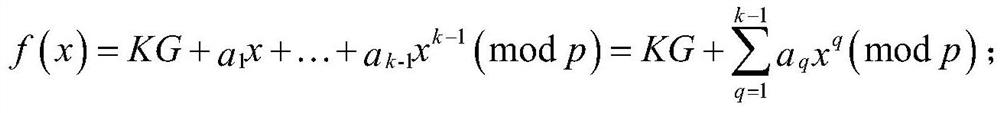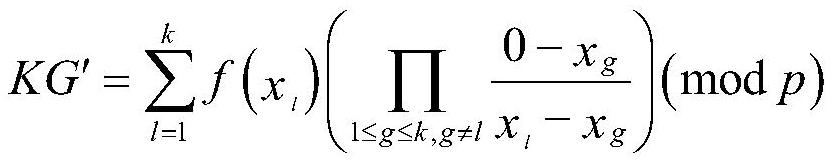Authentication method for multi-owner RFID tags
A technology of RFID tags and authentication methods, applied in the field of authentication for multi-owner RFID tags, can solve problems such as reducing information interaction, and achieve the effects of reducing information interaction, simplifying protocols, and improving computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
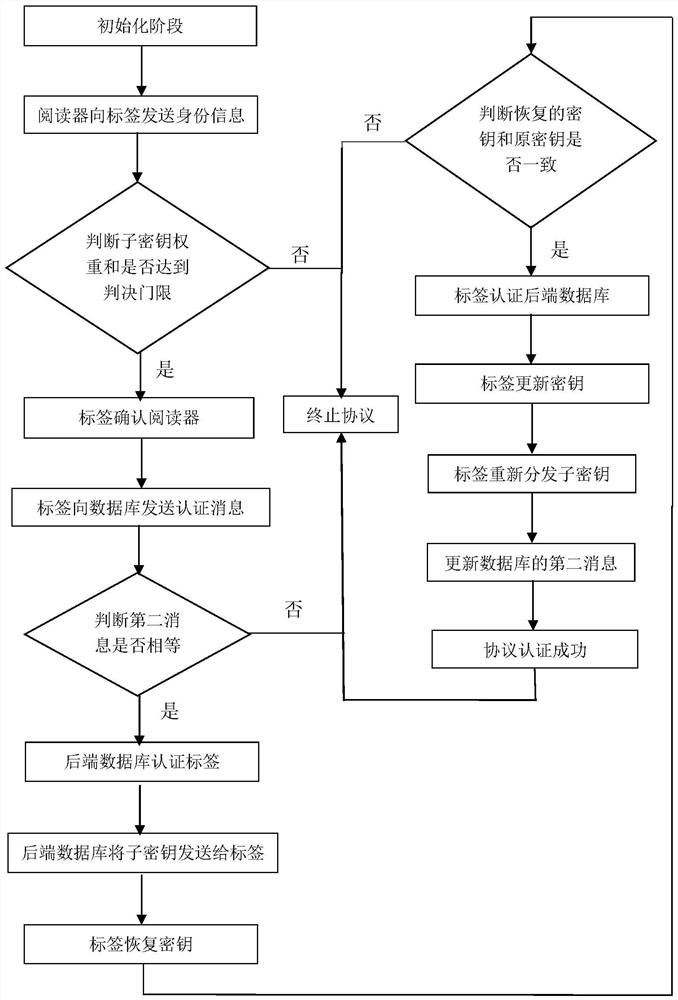
[0051] Below with reference to accompanying drawing, the present invention is described in detail:
[0052] refer to figure 1 , the authentication method for multi-owner RFID tags provided by the present invention, the specific implementation steps are as follows:
[0053] Step 1, initialization phase.
[0054](1a) Set the identity of the tag to TID, and set the identity of each reader to RID i , set the tag key to KG, and set the shared secret key between each reader and tag Set the sum of key weights to w.
[0055] (1b) Store the key and tag set in (1a), and the relevant information that comes with the reader:
[0056] Concatenate the tag's identity TID and the tag key KG, encrypt it using a hash operation, and record it as the original second message M' 2 , stored in the backend database BD;
[0057] Each reader's identity RID i And the corresponding subkey is stored in the backend database BD;
[0058] Each reader identity RID i , the shared key between each read...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com