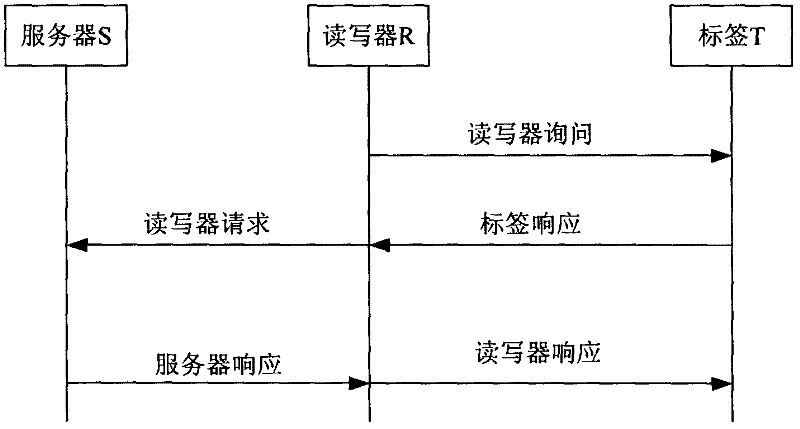
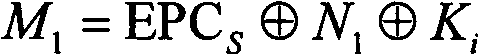RFID security authentication method based on EPC C-1G-2 standard
An EPCC-1G-2, security authentication technology, applied to key distribution, can solve problems such as poor security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Explanation of terms: EPC C-1G-2: Electronic Product Code class-1generation-2, the second generation standard of electronic product code class 1;
[0029] EPC: tag identifier;
[0030] EPC S : Tag identification code, a 16-bit character string generated by bitwise XOR of 96 bits of the tag identifier EPC divided into six 16-bit blocks;
[0031] N: the maximum number of tags in the RFID system;
[0032] i: positive integer (1≤i≤N);
[0033] l: data length value, usually set to the length of the tag identifier;
[0034] N 1 : a random number with a length of l bits;
[0035] N 2 : a random number with a length of l bits;
[0036] K i : the shared secret stored in the tag;
[0037] C i : The tag index number stored in the tag, used to find the corresponding record of the tag in the database;
[0038] new : The subscript new indicates the current value;
[0039] old : The subscript old indicates the previous value;
[0040] K inew : the current shared secret s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com