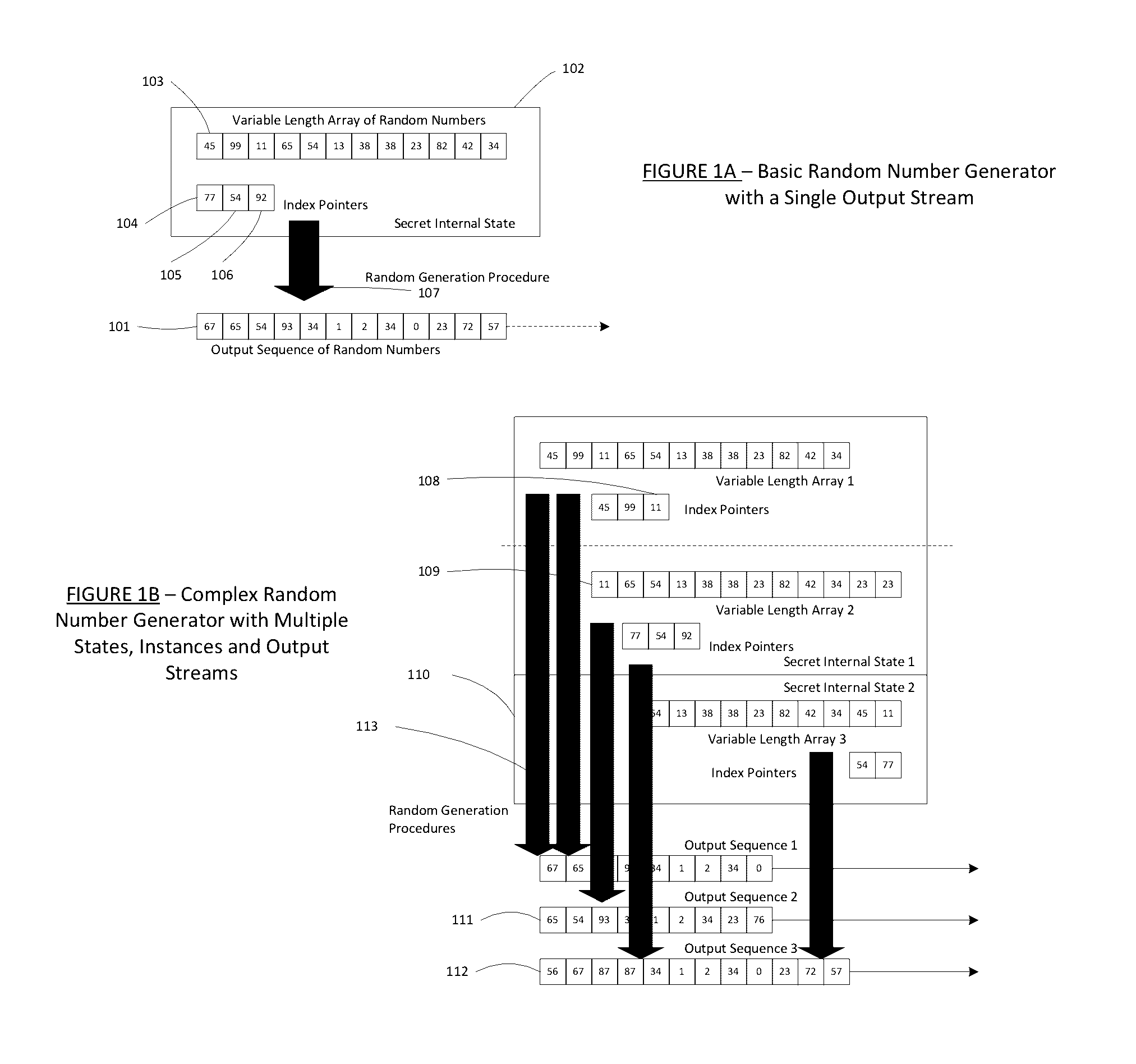
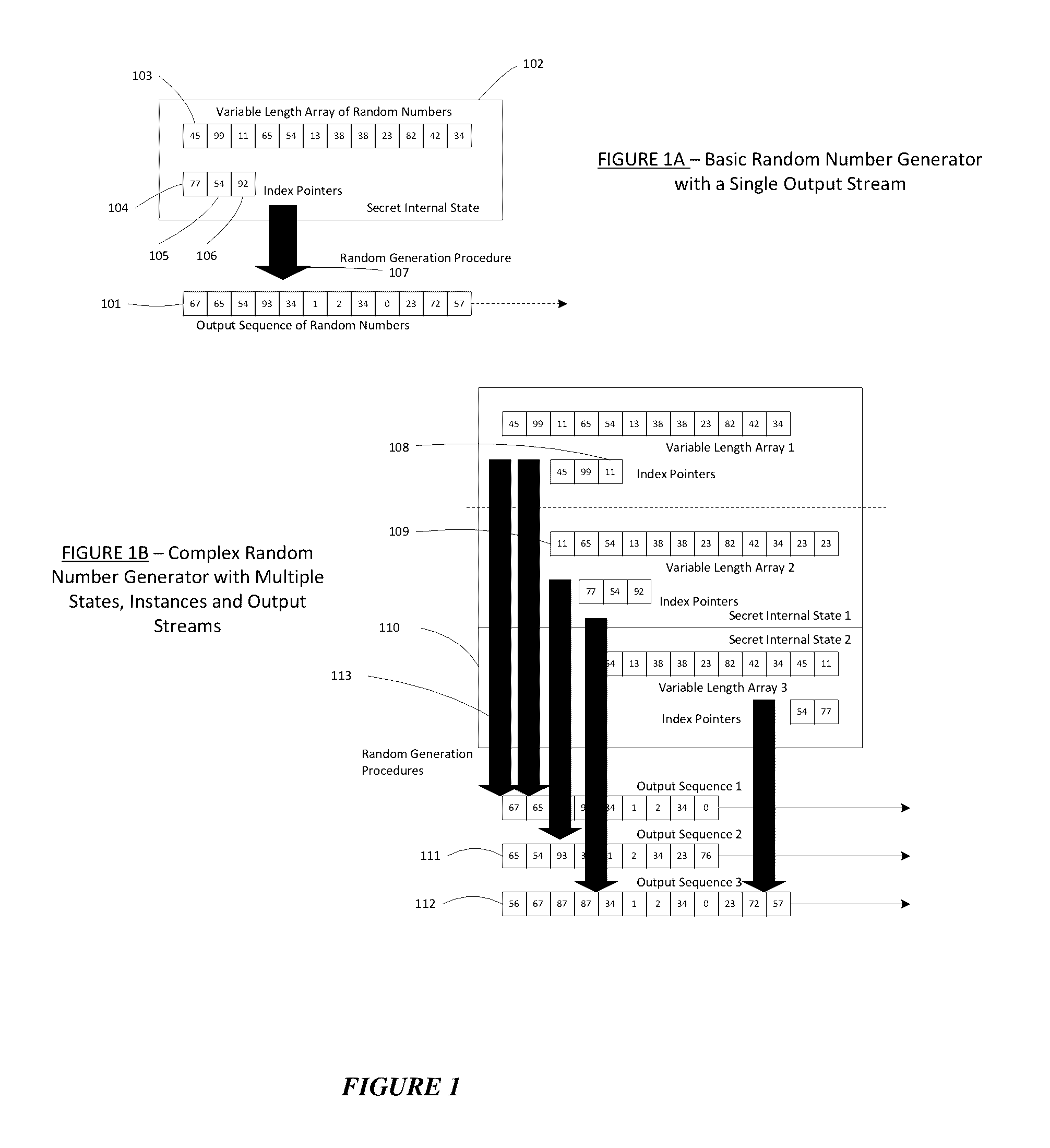
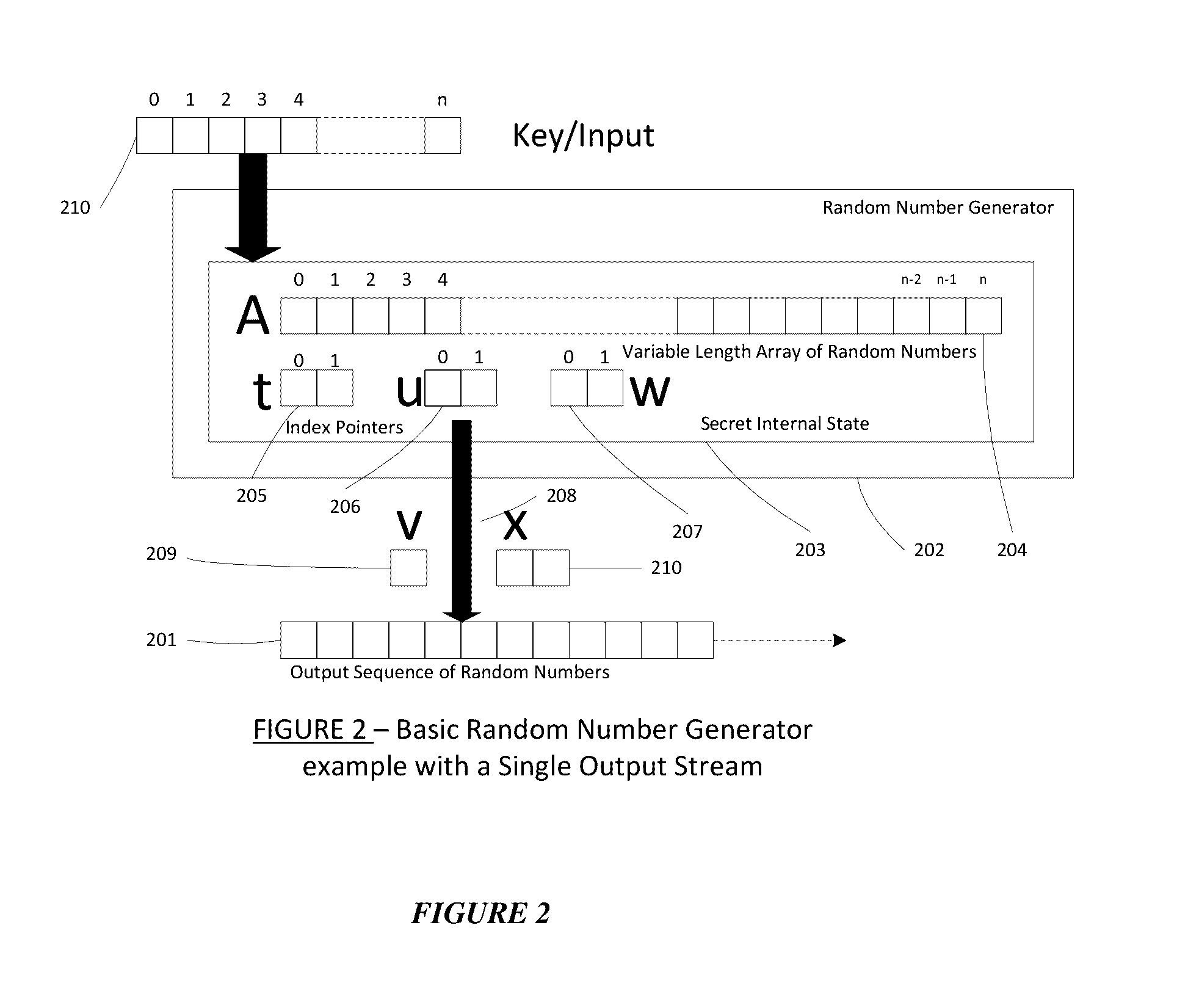
Patents
Literature
492 results about "Pseudorandom number generator" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A pseudorandom number generator (PRNG), also known as a deterministic random bit generator (DRBG), is an algorithm for generating a sequence of numbers whose properties approximate the properties of sequences of random numbers. The PRNG-generated sequence is not truly random, because it is completely determined by an initial value, called the PRNG's seed (which may include truly random values). Although sequences that are closer to truly random can be generated using hardware random number generators, pseudorandom number generators are important in practice for their speed in number generation and their reproducibility.
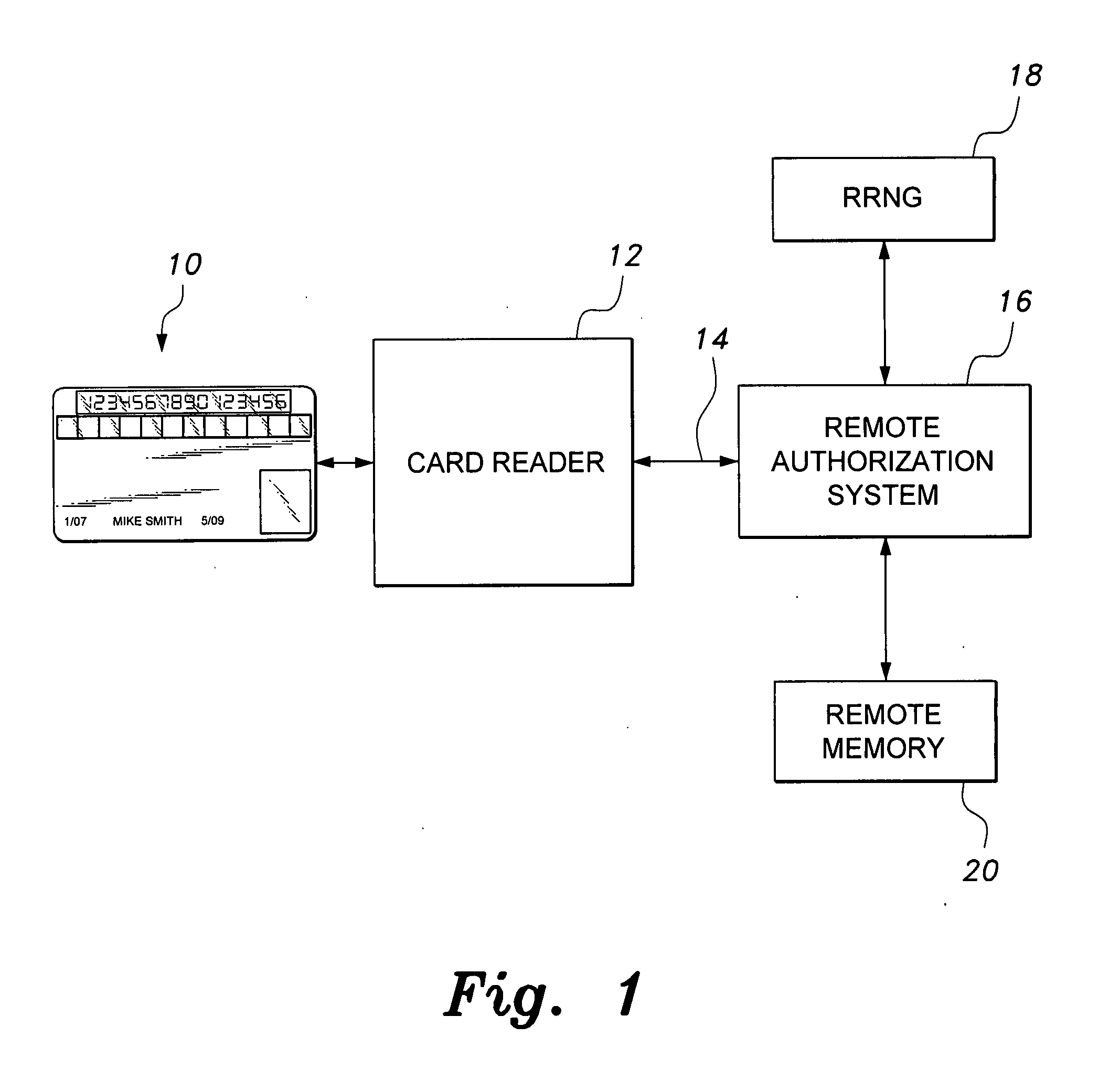
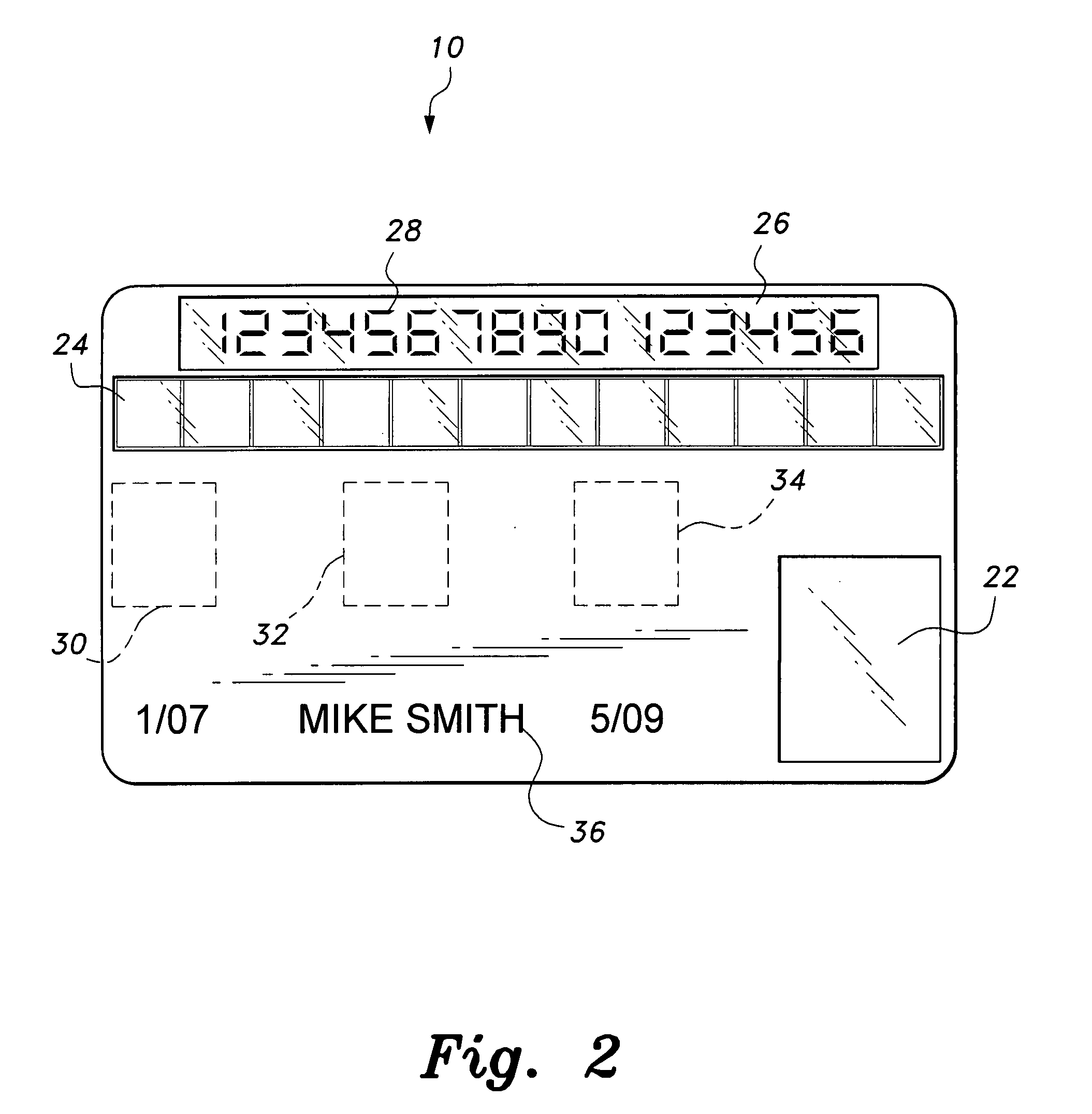
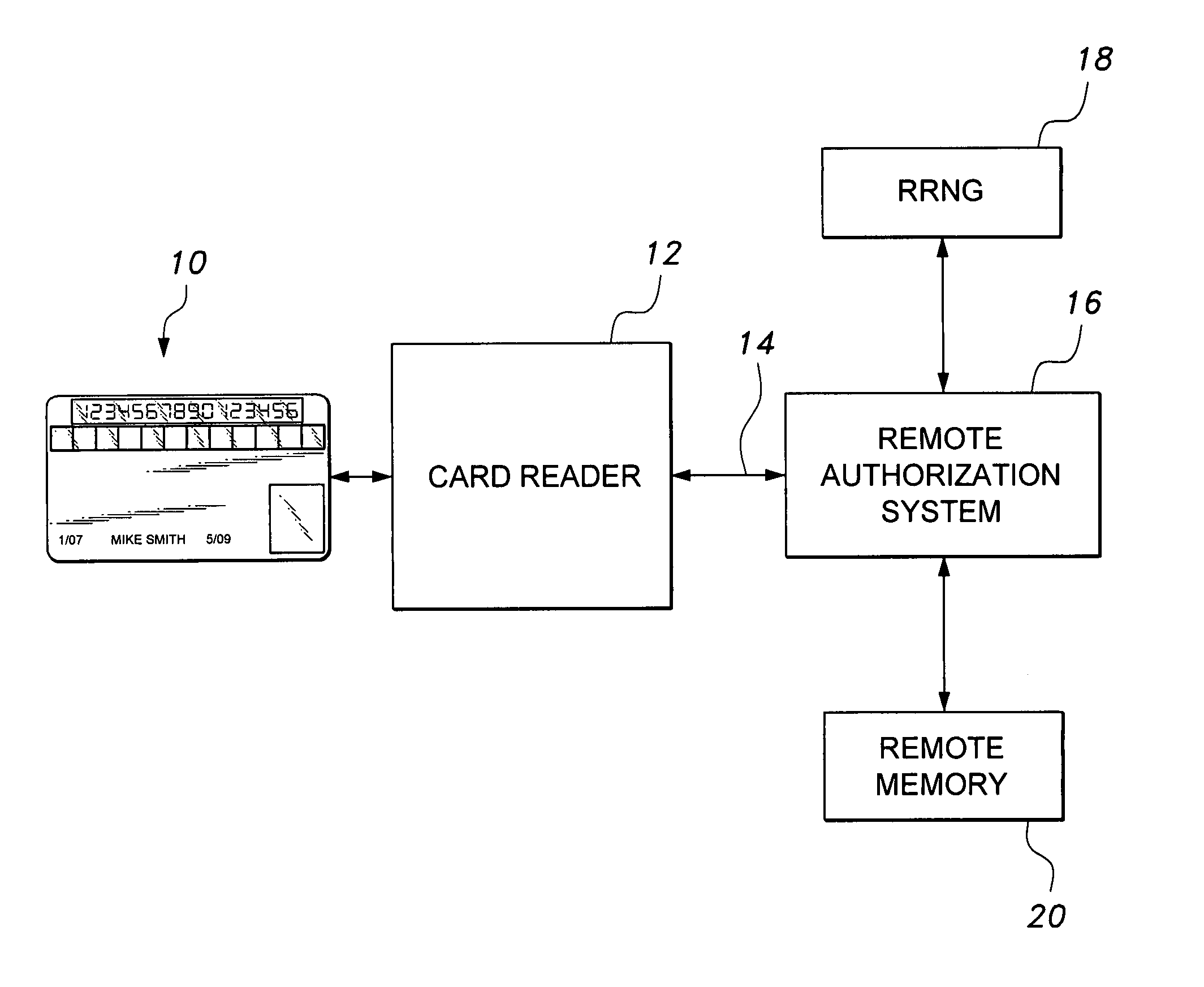
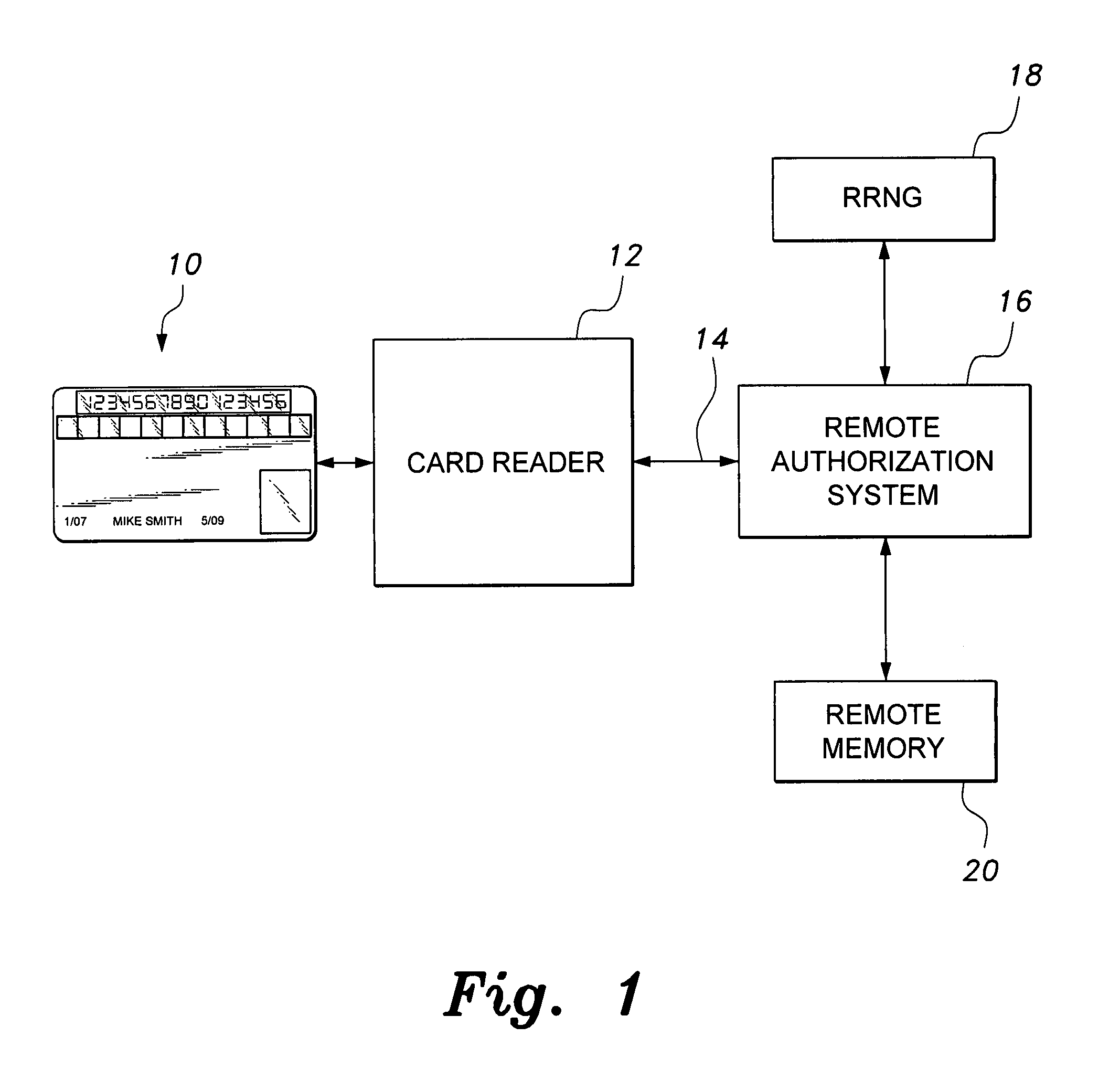
Secure credit card
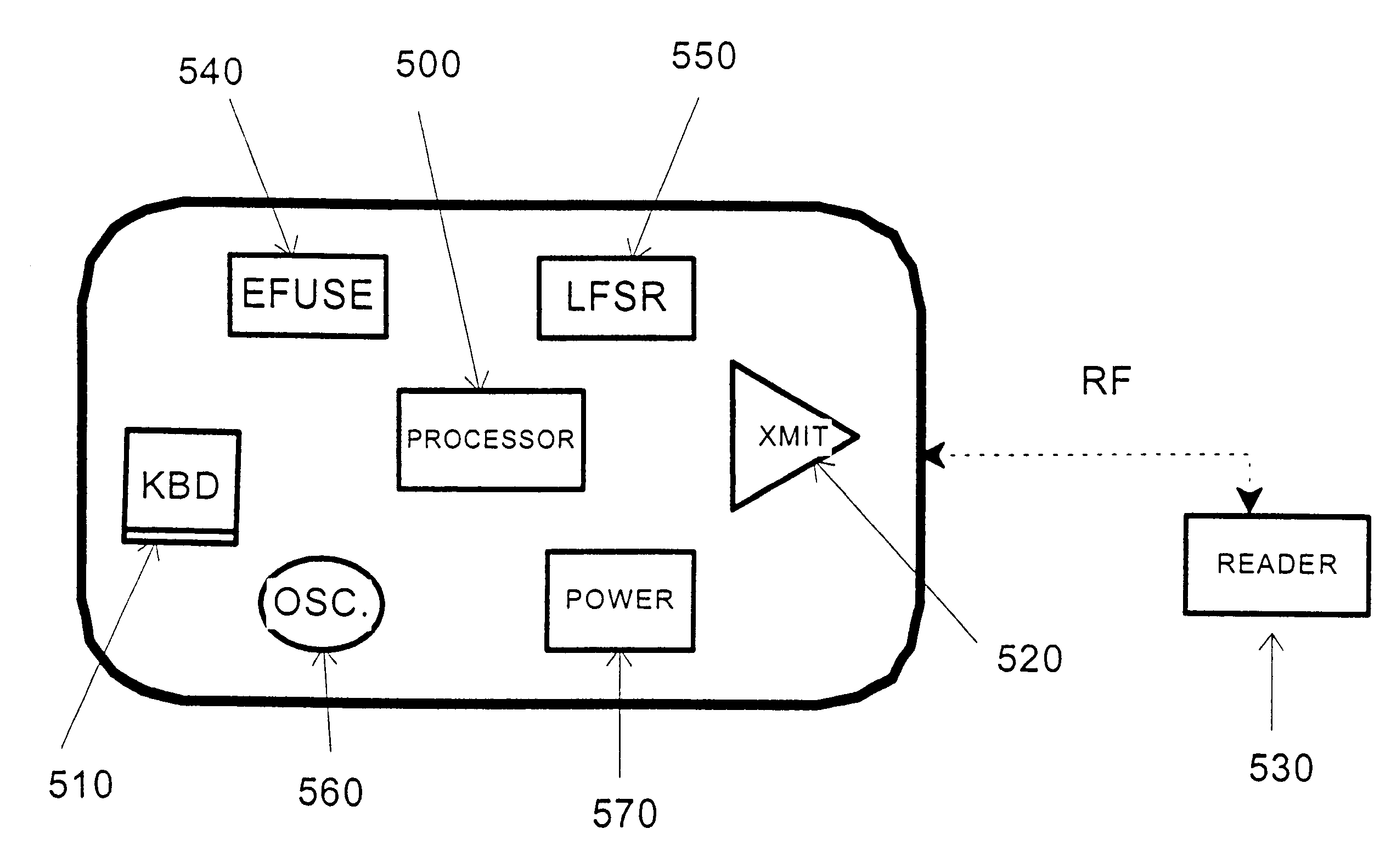
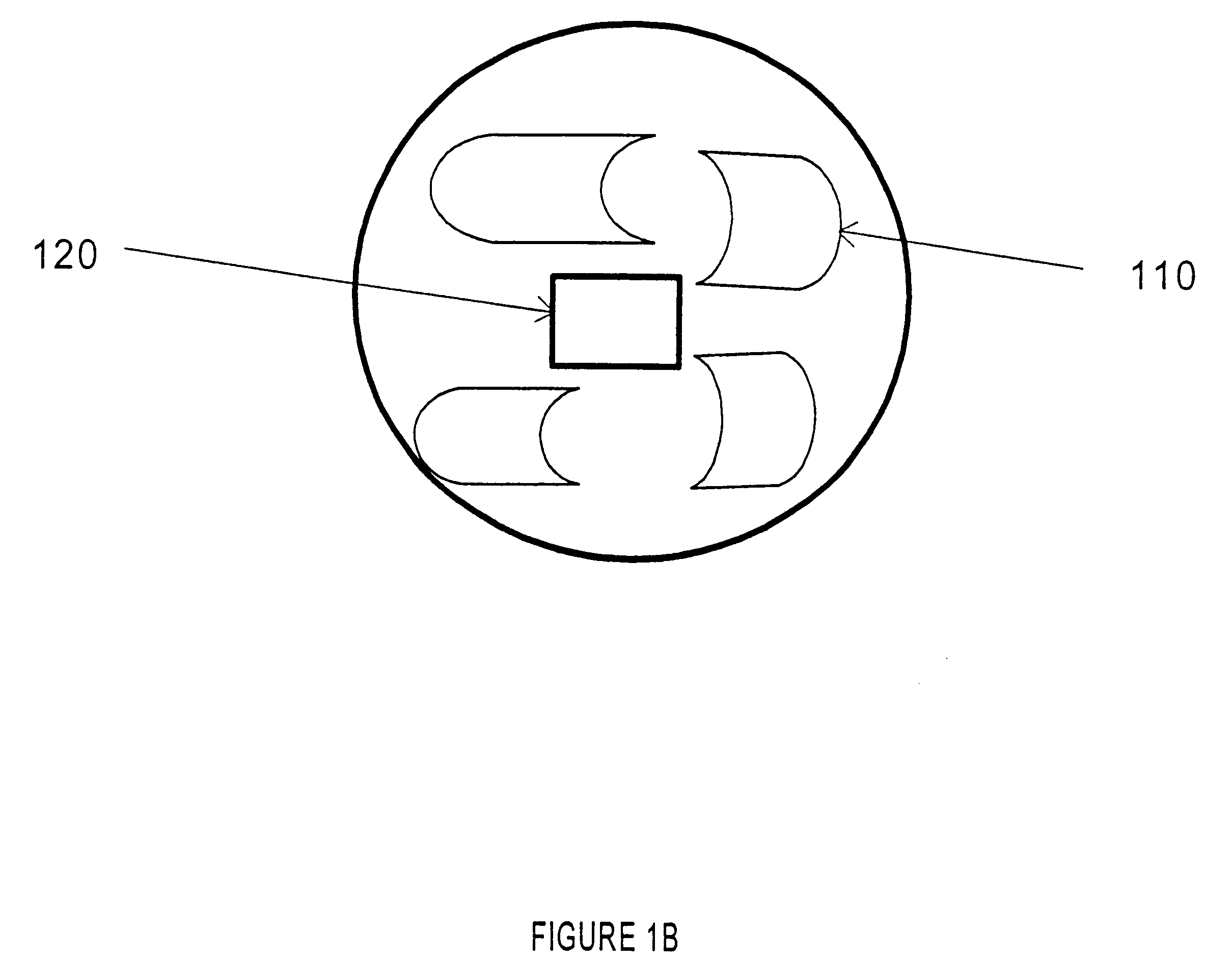
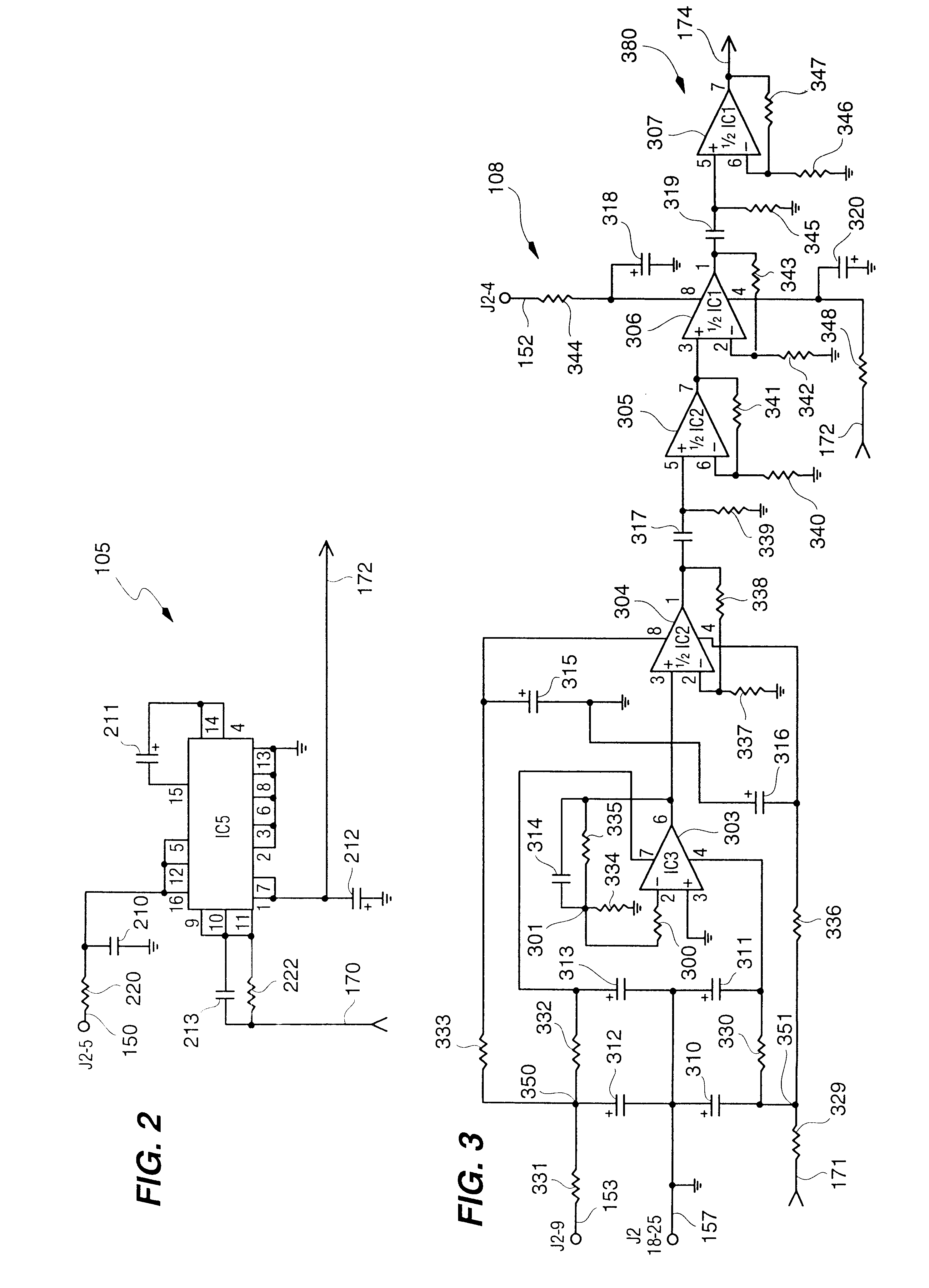
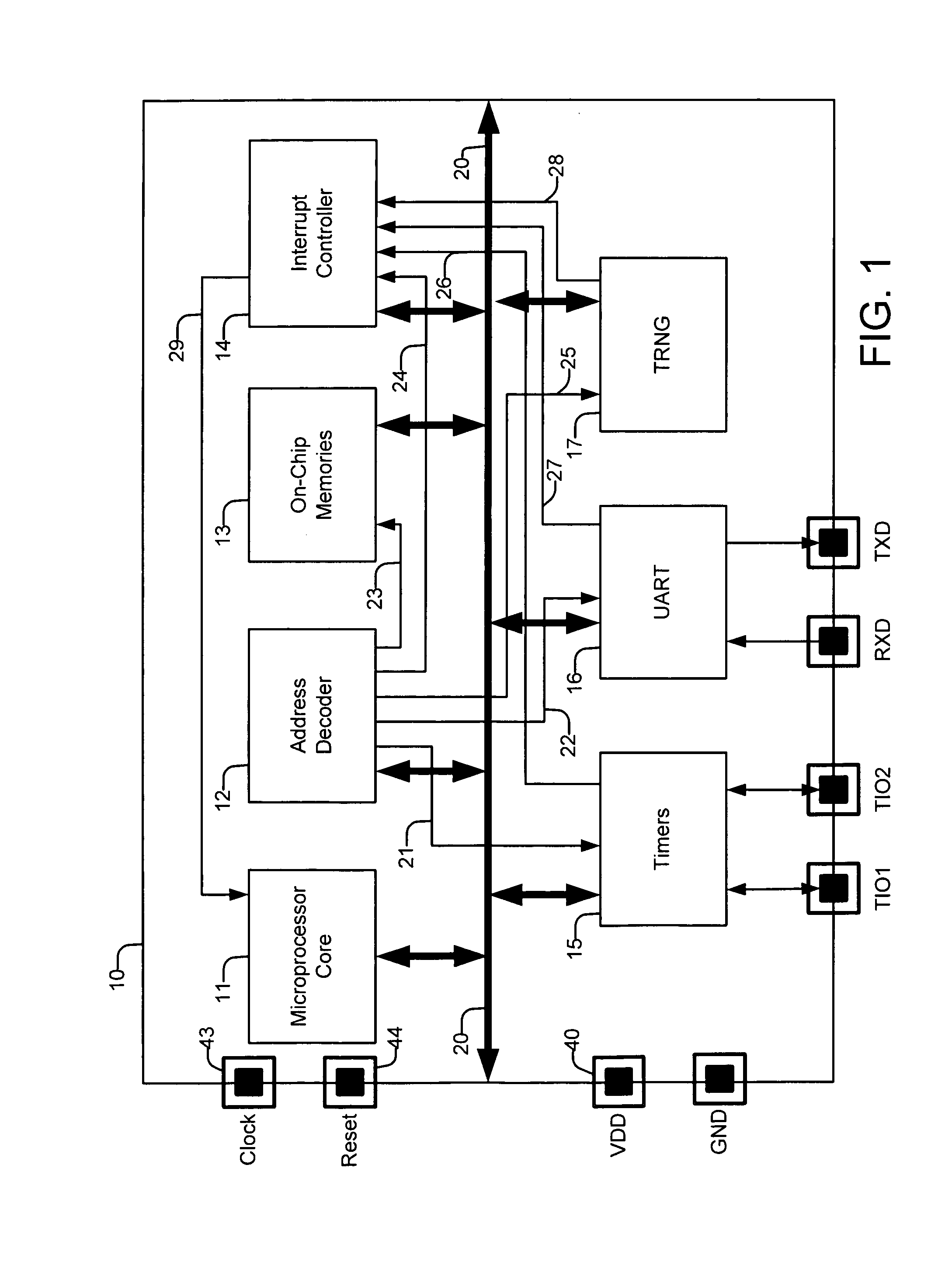
Credit card or portable identification cards containing smart card technology and electronic fuse (e-fuse) technology are combined with an LFSR pseudo random number generator to provide a secured method to prevent fraud and unauthorized use. Secure personalization via e-fuses, a pseudo-random number generator linear feedback shift register, free running clock oscillator, and power source embedded in the card provide a highly secured method to render a lost or stolen card useless. A unique card ID is permanently encoded within the card which requires a specific activation code to activate the card. A PIN number permits the card owner to activate the card for a predetermined length of time while processing a transaction. The card dynamically generates random code sequences and synchronization keys to secure a transaction.
Owner:KYNDRYL INC
Smart card with random temporary account number generation
The smart card with random temporary account number generation provides an authenticating system coupled with an access or transaction card, such as a credit card. The card includes first and second memory storage media, with the first memory medium containing a plurality of temporary account or authentication numbers. The card also has a biometric sensor, such as a fingerprint scanner, and the second memory stores the biometric parameters of the authorized user. A processor compares the biometric parameters with the measured biometric readings to enable the card. The processor has a random number generator, allowing for the randomized selection of one of the account numbers stored in the first memory, thus providing a temporary account number for the transaction. A remote site includes an identical random number generator and set of account numbers, allowing the temporary account number to be verified and then discarded, following the transaction.
Owner:HEWTON ALFRED
Smart card with random temporary account number generation
Owner:HEWTON ALFRED
Random number generator
InactiveUS7124157B2Promote generationStable structureRandom number generatorsDigital function generatorsAudio power amplifierNumber generator
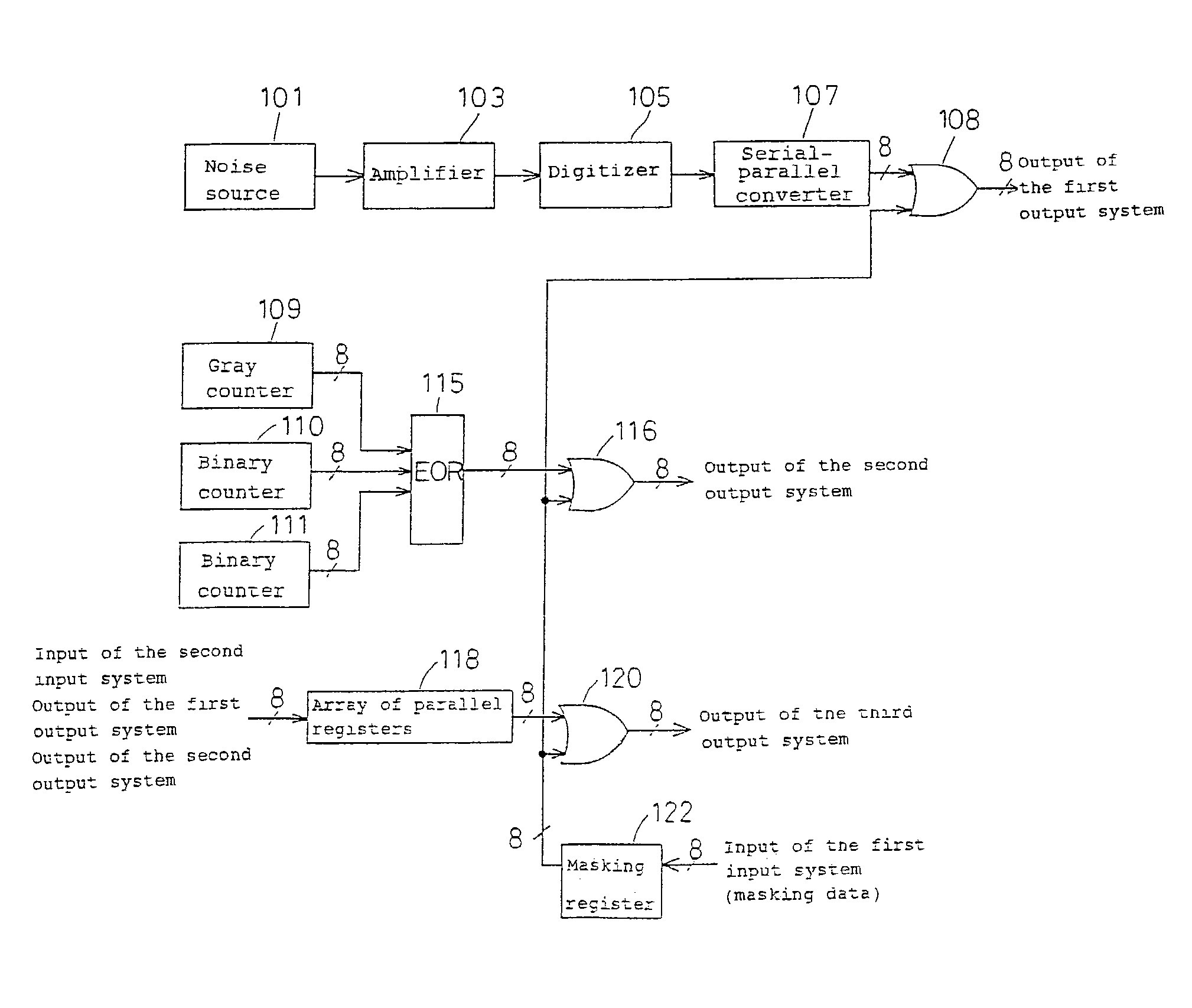
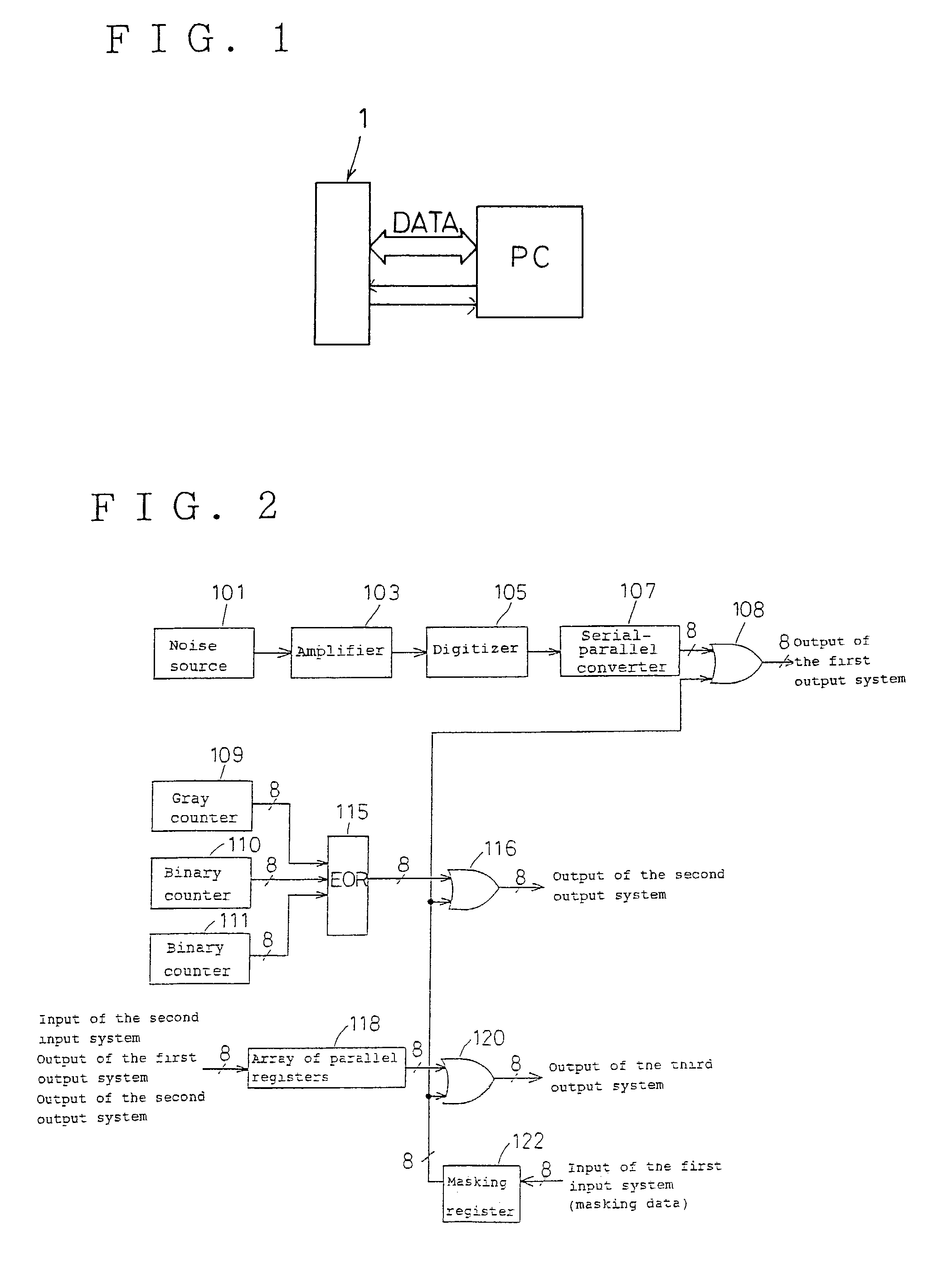
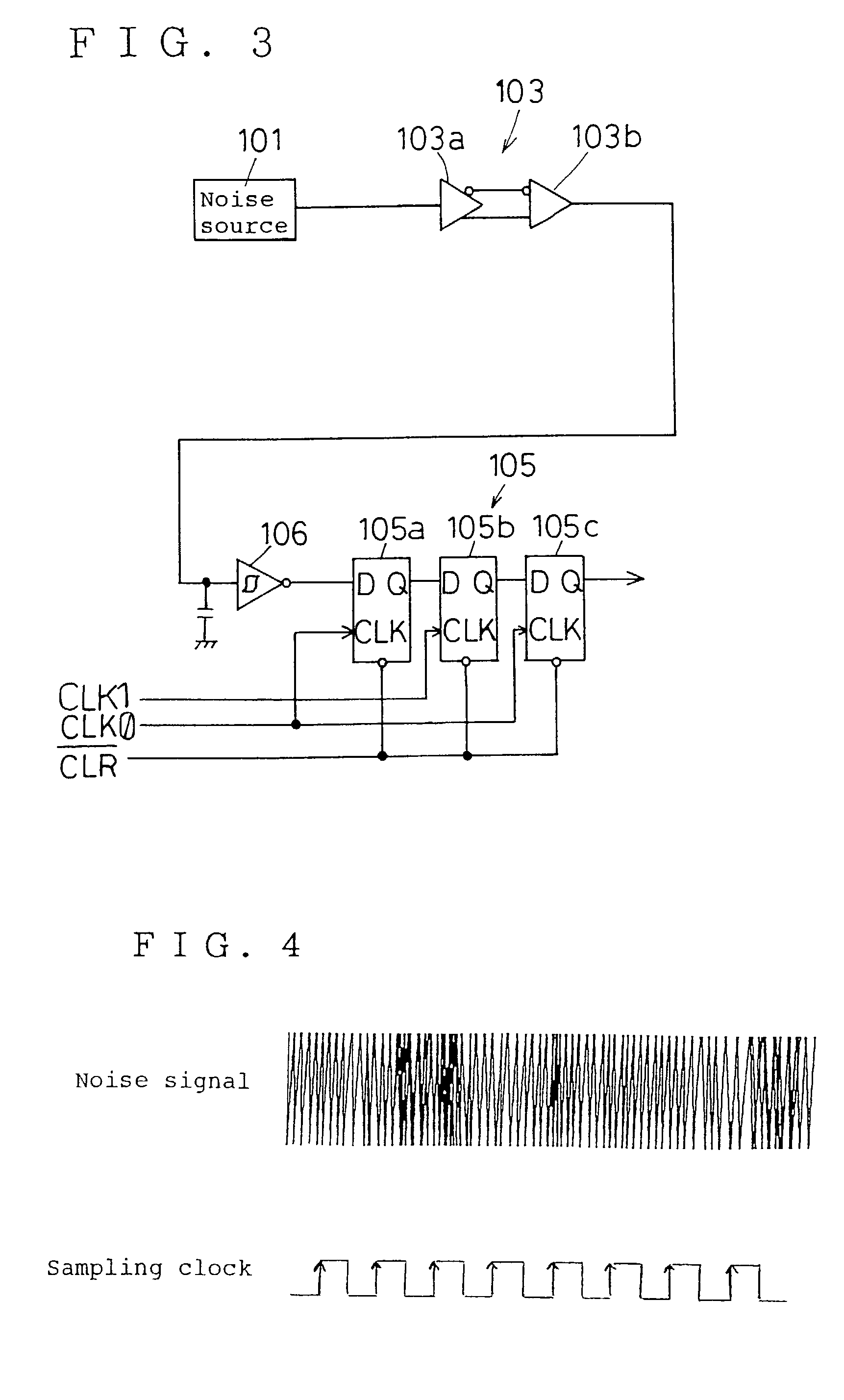
A random number generator having a simple construction which generates physical random numbers necessary for encryption. The random number generator has an amplifier to amplify noise signals generated from a noise source and digitizer to digitize the amplified noise signals. The digitizer includes a serial register.
Owner:HMI
Liquid crystal display unit having fine color control
InactiveUS6700559B1Reduced sensationImprove accuracyCathode-ray tube indicatorsPicture reproducers using solid-state color displayDigital dataPattern recognition
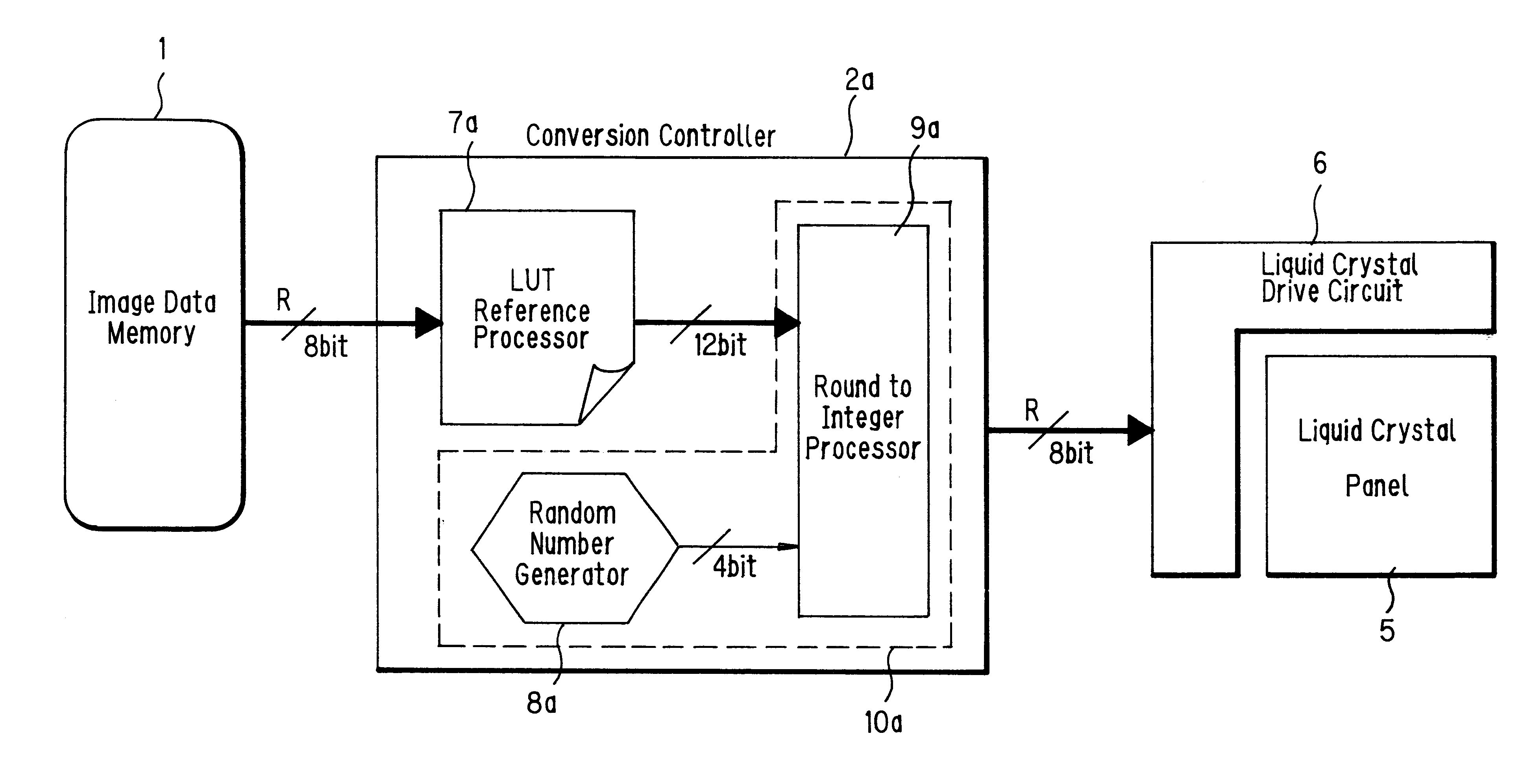
Eight-bit digital image data of R, G and B output from an image data memory are corrected by conversion controllers to meet characteristics of a liquid crystal panel. The corrected data are input to a liquid crystal drive circuit as digital image data, and an image is displayed on the liquid crystal panel. A LUT stored in a LUT reference processor stores data (addresses) by a number that makes it possible to refer to input image digital data at one to one. A random number generator is for generating random numbers and supplying the random numbers to a round-to-integer processor as threshold value data. The round-to-integer processor compares the data referred to by the LUT reference processor with the threshold data, and carries out a round-to-integer processing.
Owner:SHARP KK
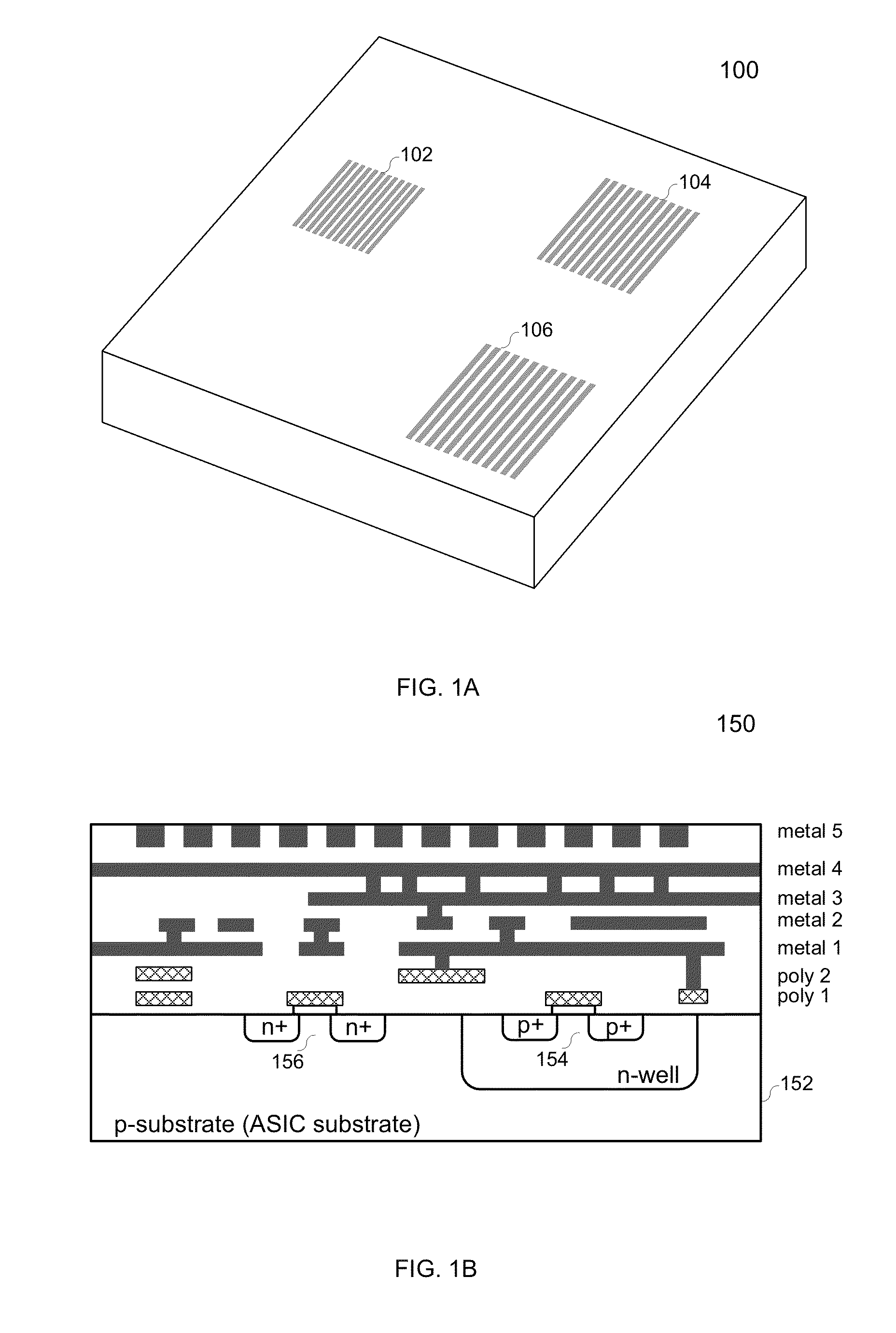
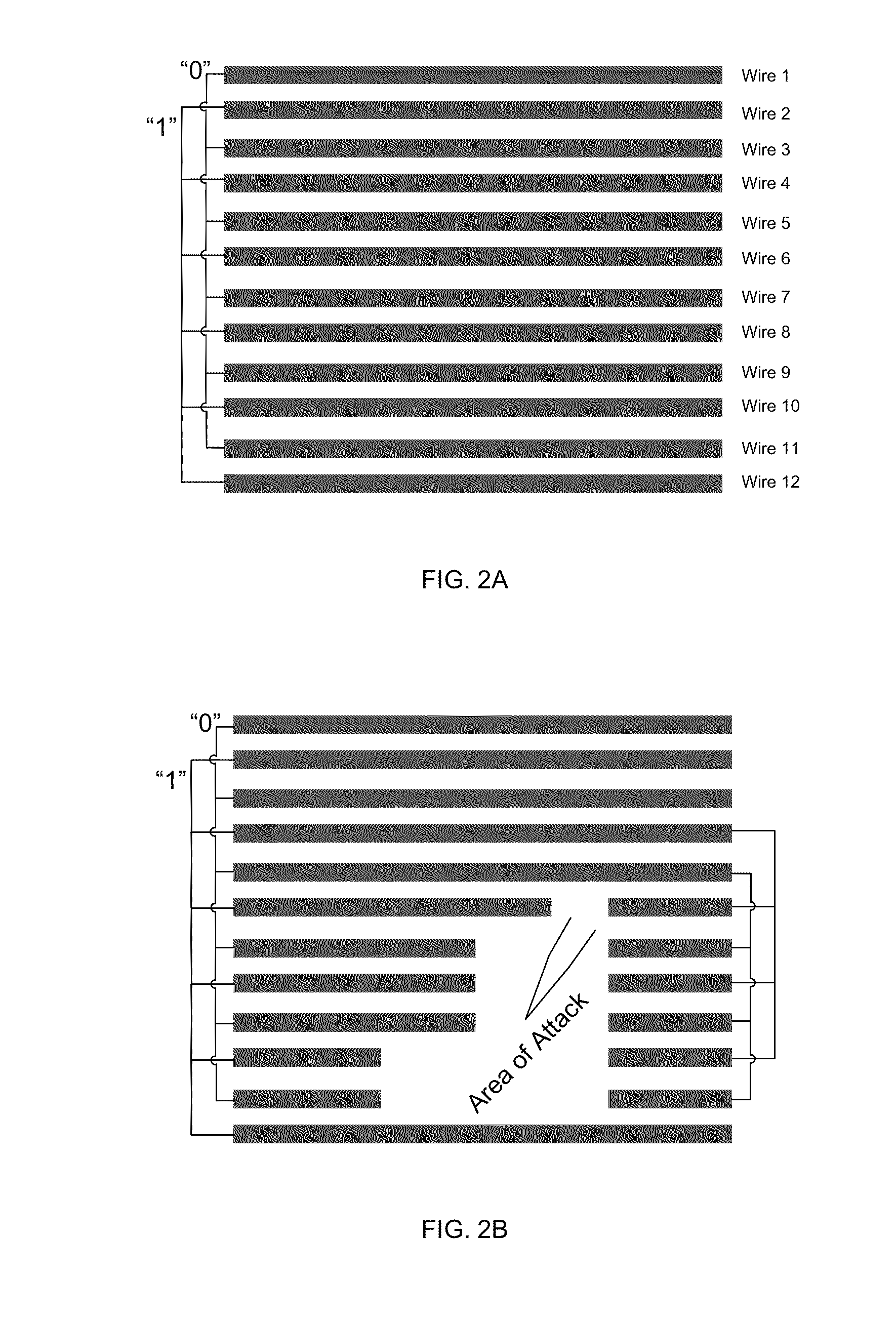
Tamper detection countermeasures to deter physical attack on a security asic
ActiveUS20130104252A1Error detection/correctionVolume/mass flow measurementCountermeasureNumber generator
Various embodiments of the present invention relates generally to an integrated circuit, and more particularly, to systems, devices and methods of incorporating a tamper detection countermeasure into a security ASIC to deter physical attacks. The tamper detection countermeasure architects an active mesh to cover a sensitive area in the security ASIC. A plurality of time-varying random numbers is generated by a random number generator (RNG), and the active mesh is driven and configured according to these random numbers. During tamper detection cycles, the active mesh is monitored with respect to the plurality of random numbers that is directly provided by the RNG. Upon a tampering attempt, a flag signal is generated and used to initialize subsequent anti-tampering actions. The active mesh may be controlled and monitored based on time-varying codes, and therefore, an adversary may not easily bypass the active mesh and attack the sensitive area.
Owner:MAXIM INTEGRATED PROD INC
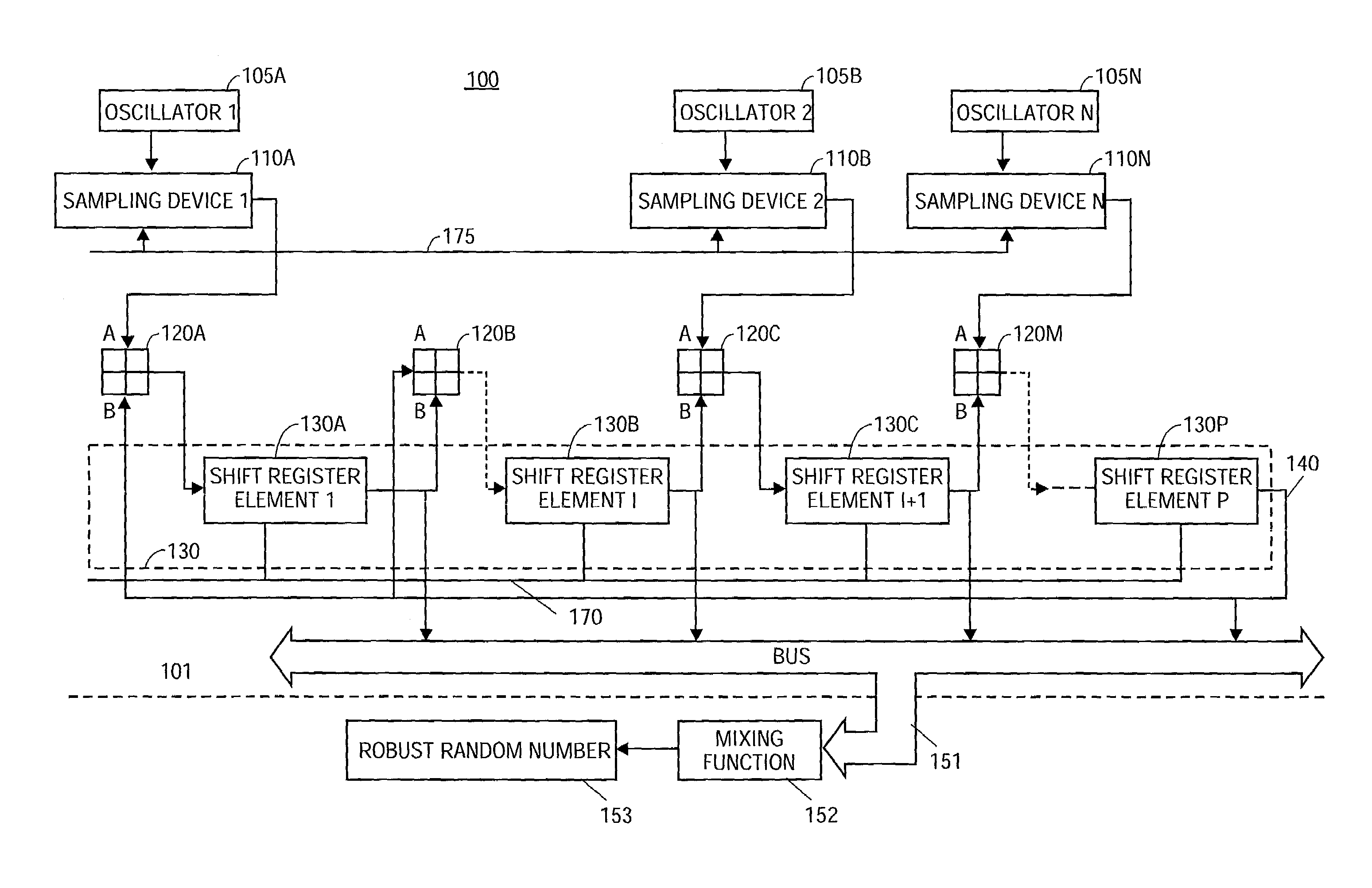
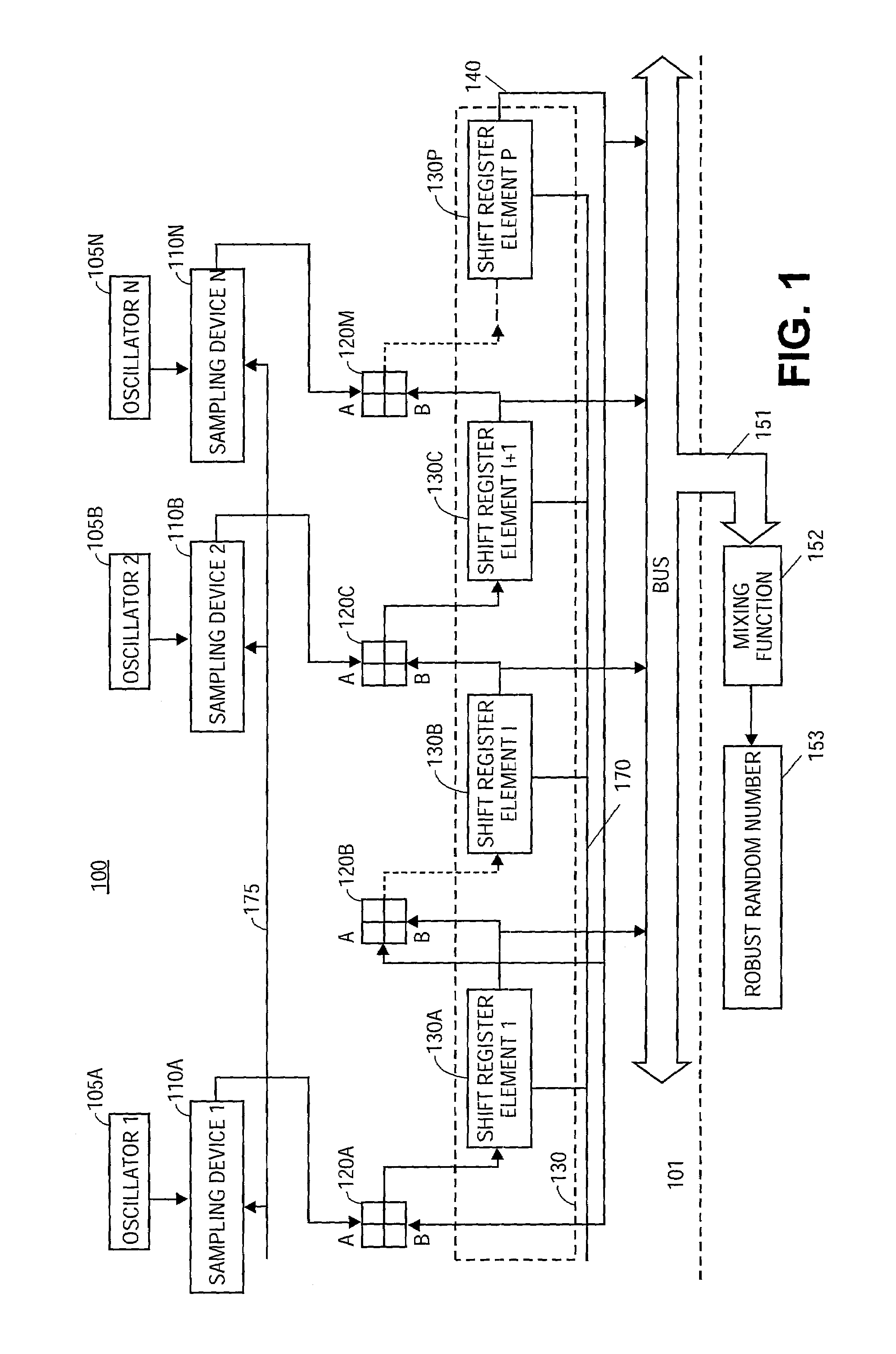
Random number generator
A random number generator comprising an oscillator with an output signal dependant upon a random source, a sampling device to sample the output signal from the oscillator to obtain a sampled oscillator output, and a fixed frequency clock driven linear feedback shift register (LFSR) communicatively coupled to the sampling device via a digital gate to receive the sampled oscillator output, and to provide a random number at an output of the LFSR. Additionally, the random number generator may comprise an optional mixing function communicatively coupled to the LFSR to read the random number, and to insert the random number into an algorithm to obtain a robust random number.
Owner:MARVELL ASIA PTE LTD
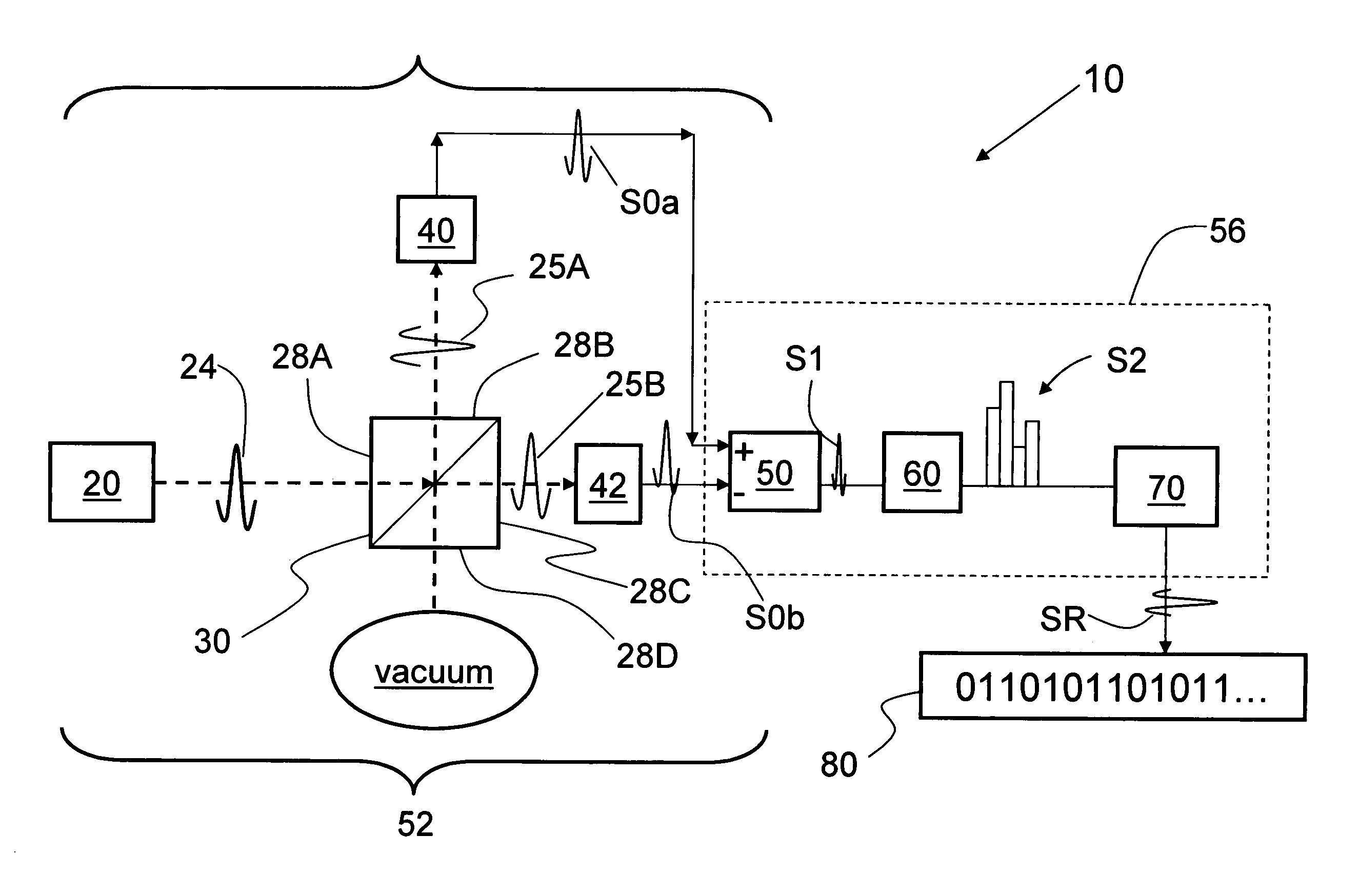
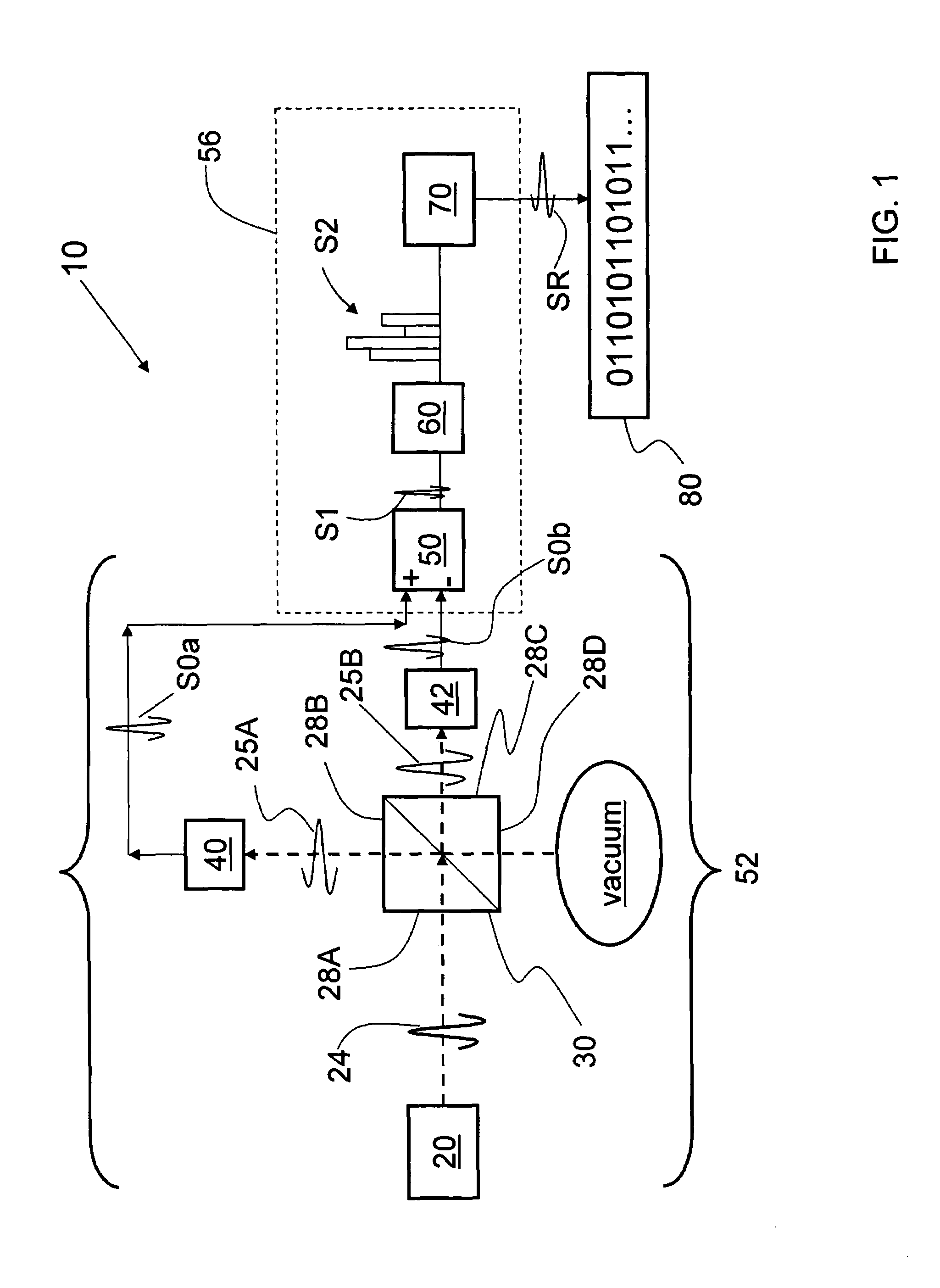
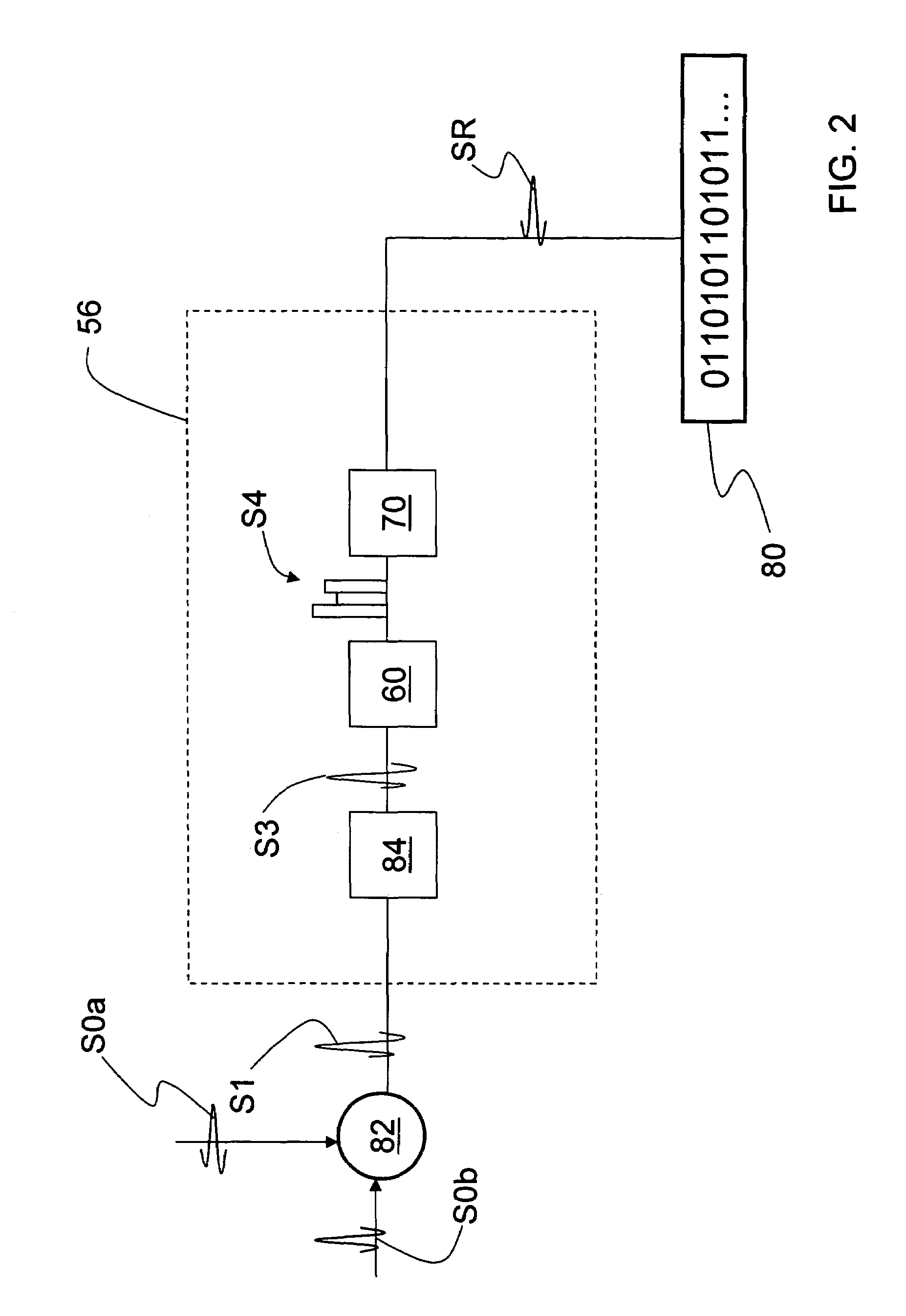
Quantum noise random number generator
A quantum noise random number generator system that employs quantum noise from an optical homodyne detection apparatus is disclosed. The system utilizes the quantum noise generated by splitting a laser light signal using a beamsplitter having four ports, one of which receives one of which is receives the laser light signal, one of which is connected to vacuum, and two of which are optically coupled to photodetectors. Processing electronics process the difference signal derived from subtracting the two photodetector signals to create a random number sequence. Because the difference signal associated with the two photodetectors is truly random, the system is a true random number generator.
Owner:MAGIQ TECH INC
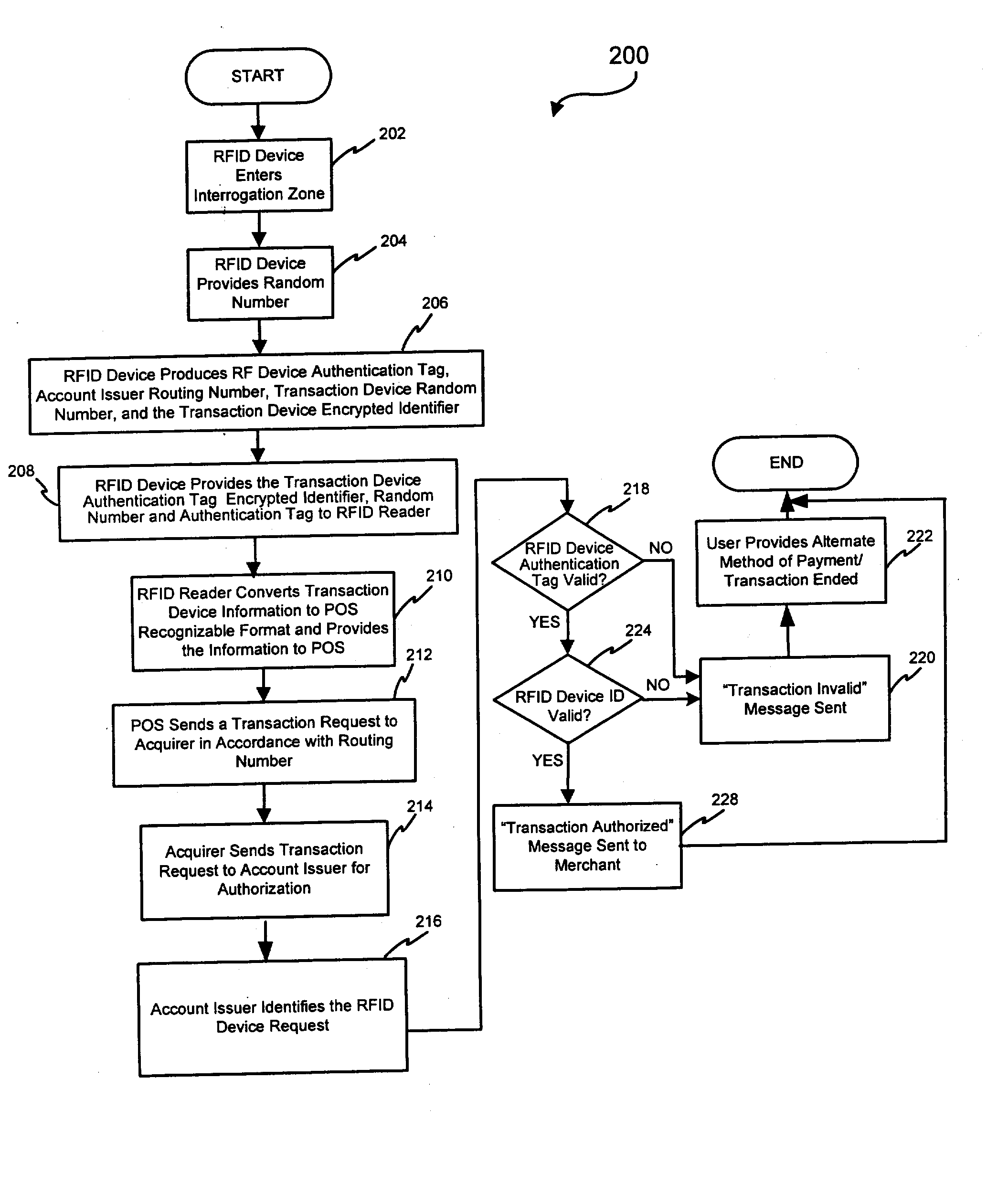
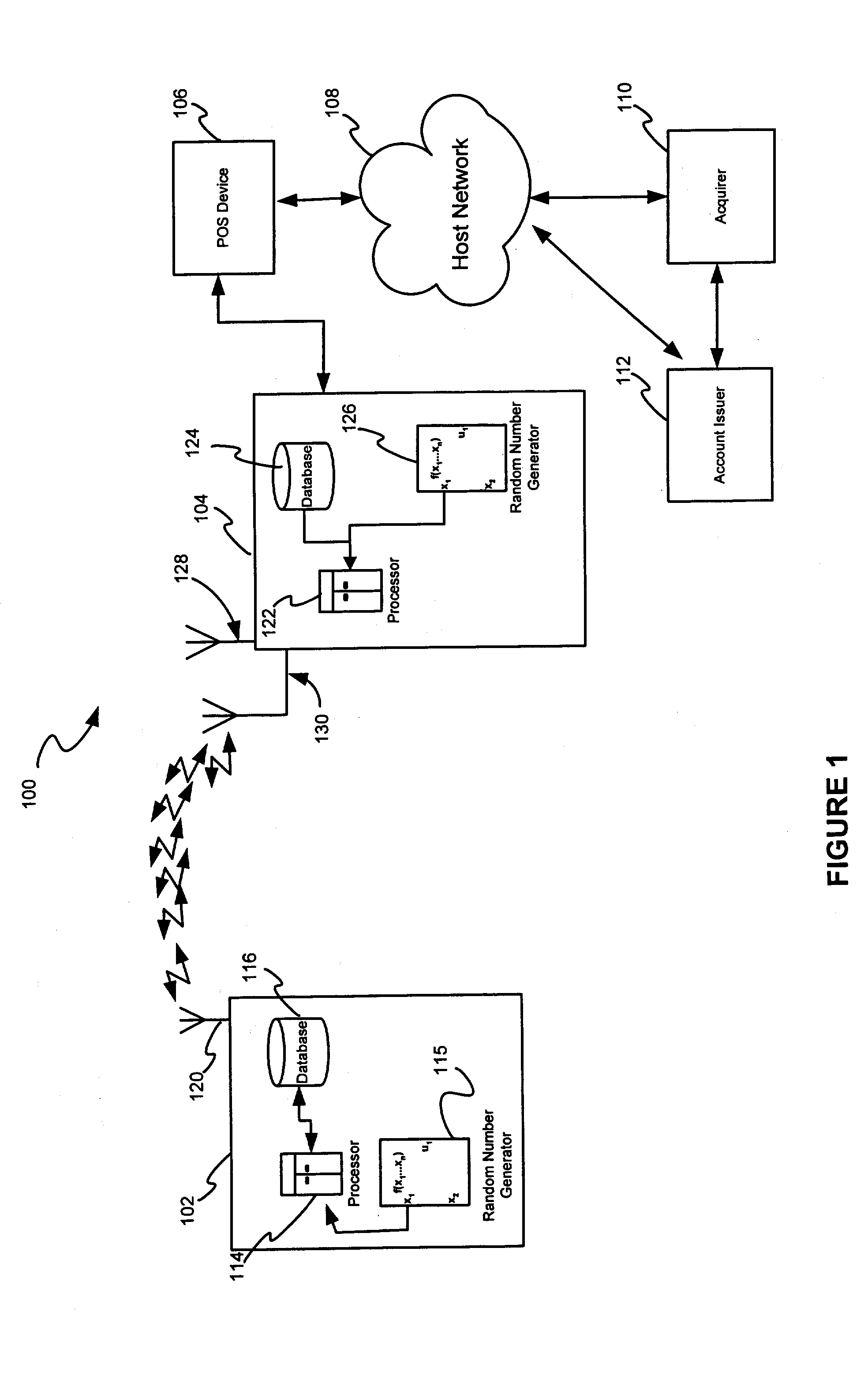
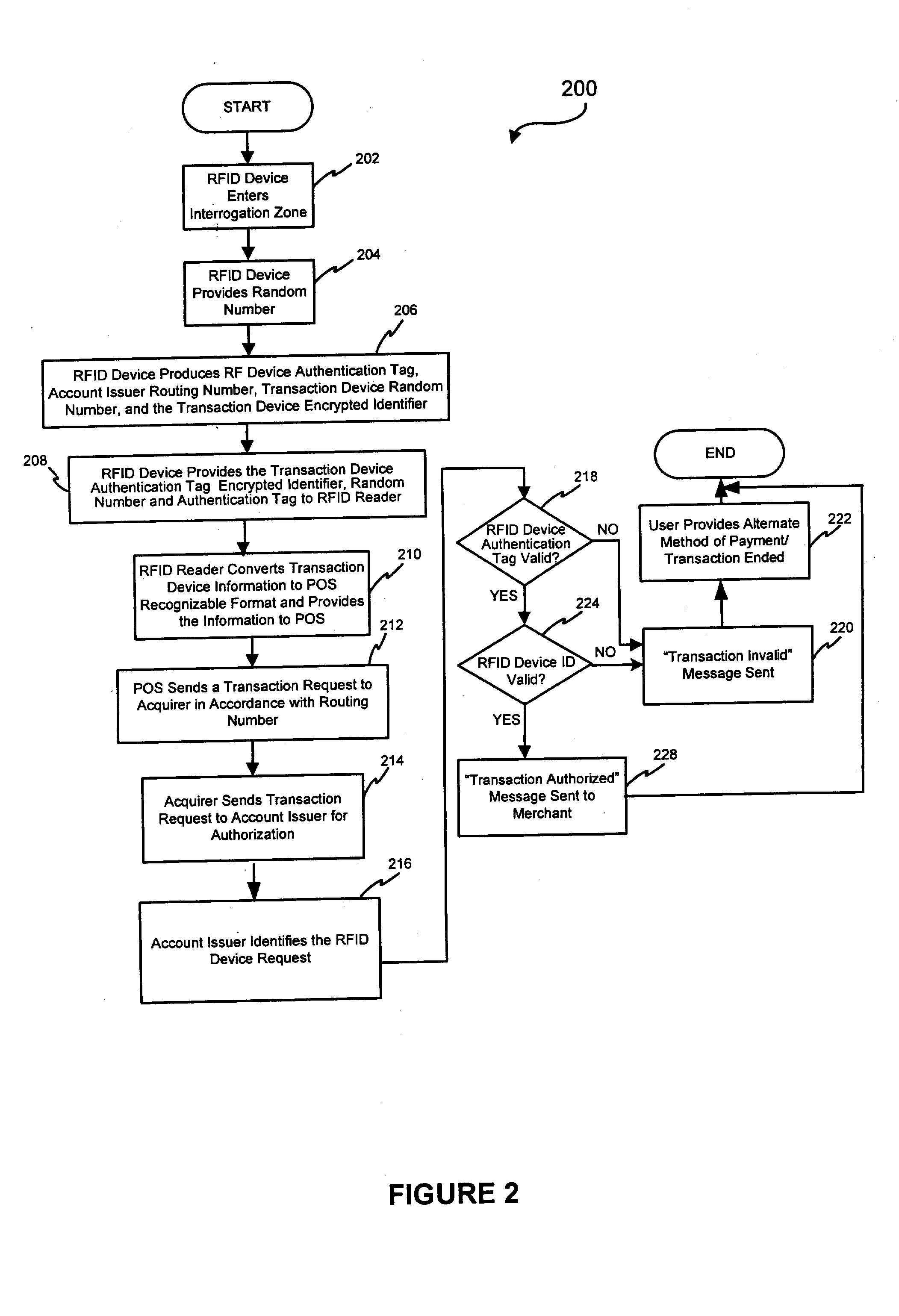
System and method for securing RF transactions using a radio frequency identification device including a random number generator
InactiveUS20050071231A1Individual entry/exit registersPayment circuitsIdentification deviceNumber generator
A system and method for securing a Radio Frequency (RF) transaction using a RF identification device (RFID) transaction device is provided. The method includes a RFID transaction device including a random number generator for generating a random number. The random number may be used by an account issuer to verify the validity of a RFID transaction device or RFID reader communicating on the RF transactions network. The authorizing agent may receive the random number and compare the random number to a device validating code.
Owner:LIBERTY PEAK VENTURES LLC
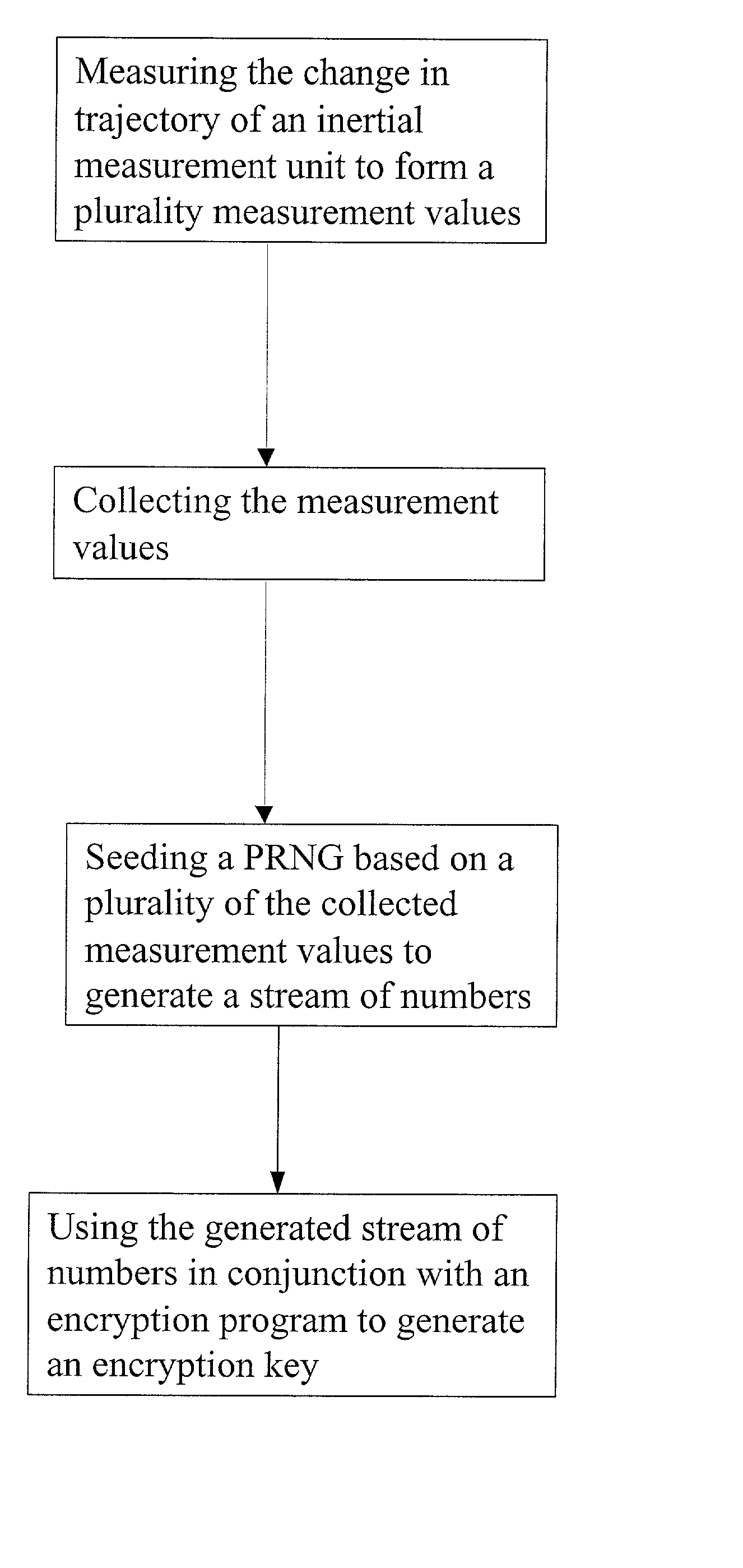
Entropy sources for encryption key generation
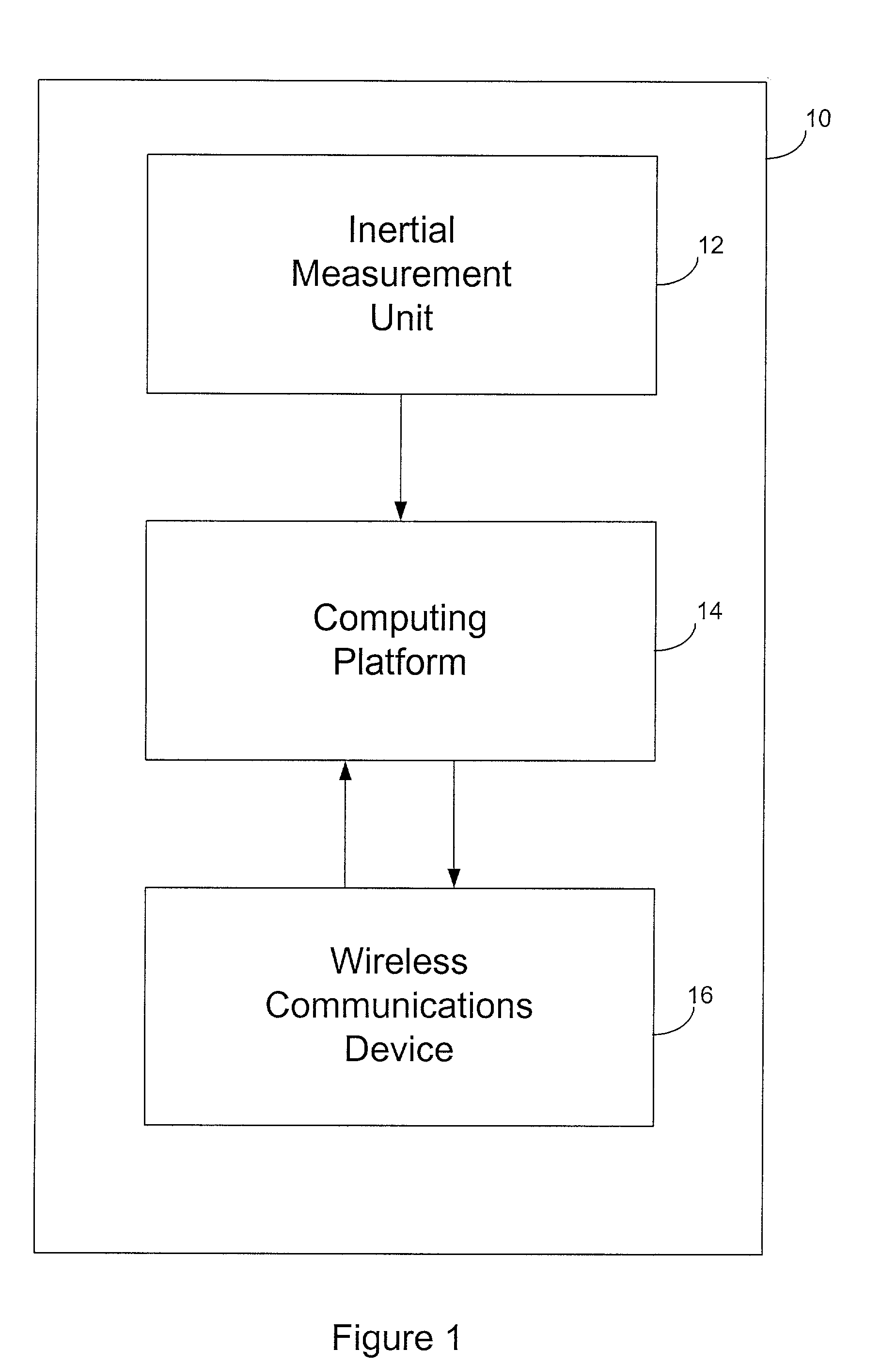
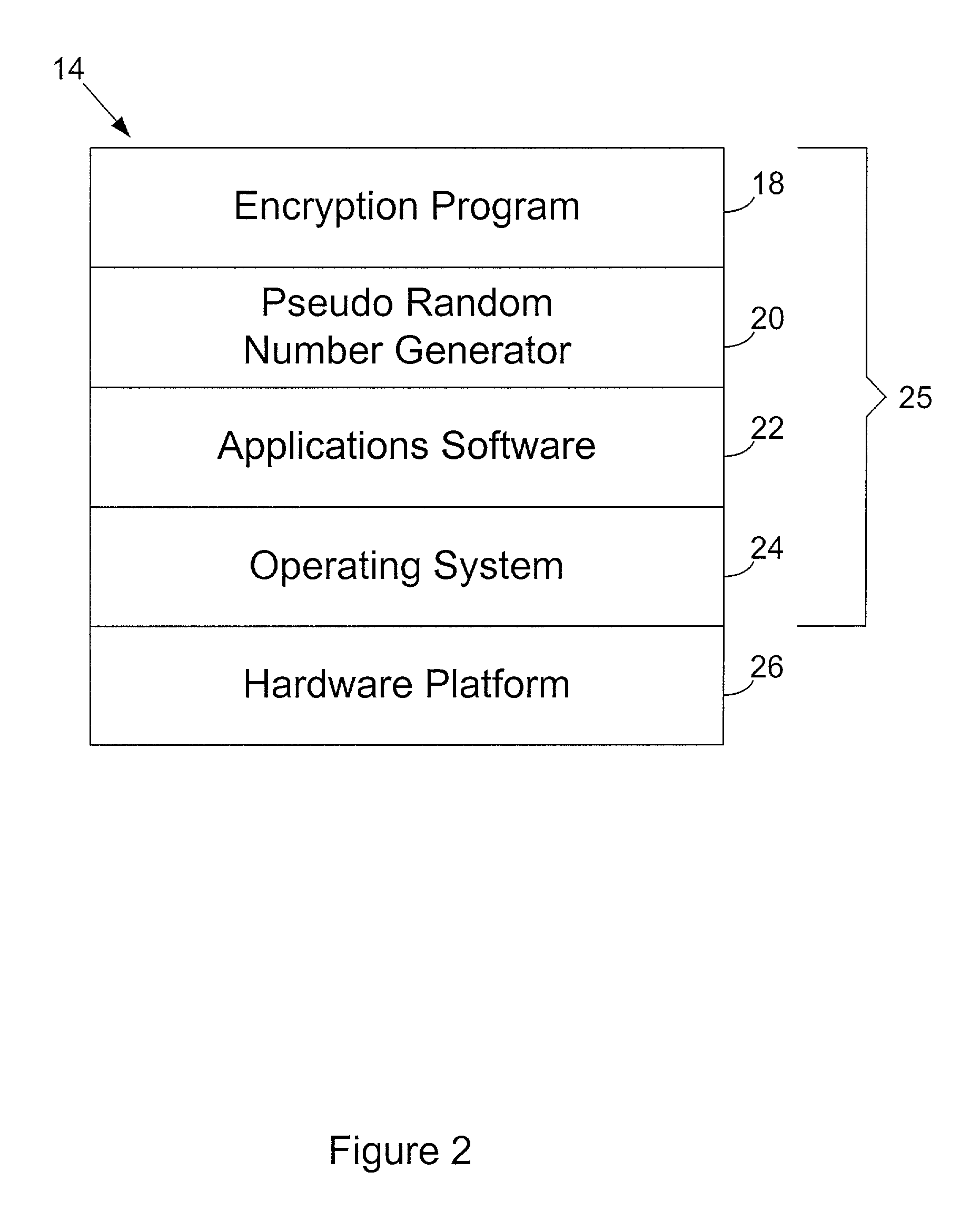
InactiveUS20020131592A1Maintain securityNecessary computer processing powerMechanically effected encryptionSecret communicationCryptographic key generationNumber generator
Inertial measurement units are subject to drift and noise characteristics that are normally distributed. While that drift and noise is problematic for inertial navigation, it is ideal for encryption key generation. The measurement values from an inertial measurement unit are random on several levels and can be used to effectively seed a pseudo random number generator for encryption key generation.
Owner:AIRBIQUITY INC
Random number generator and generation method
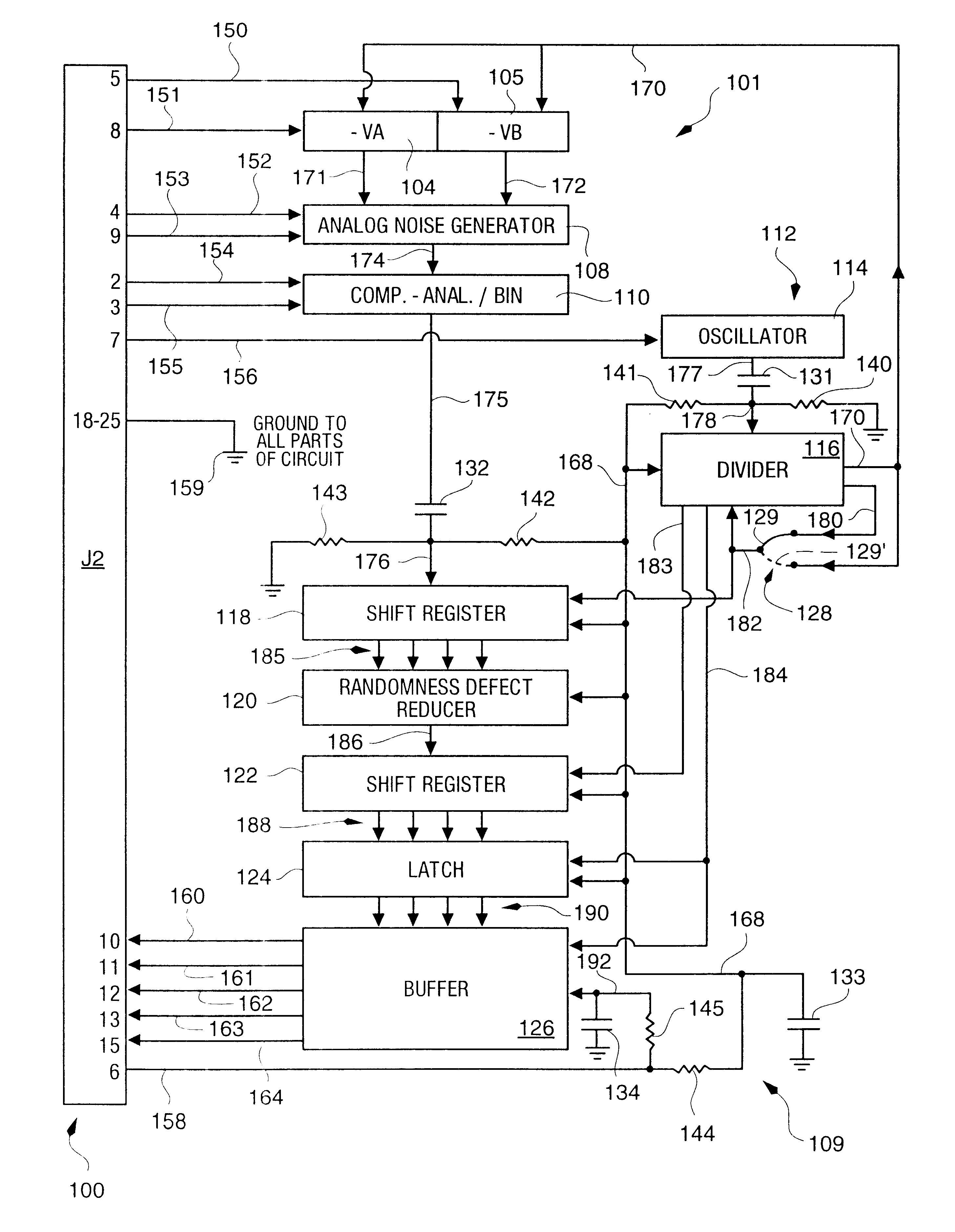
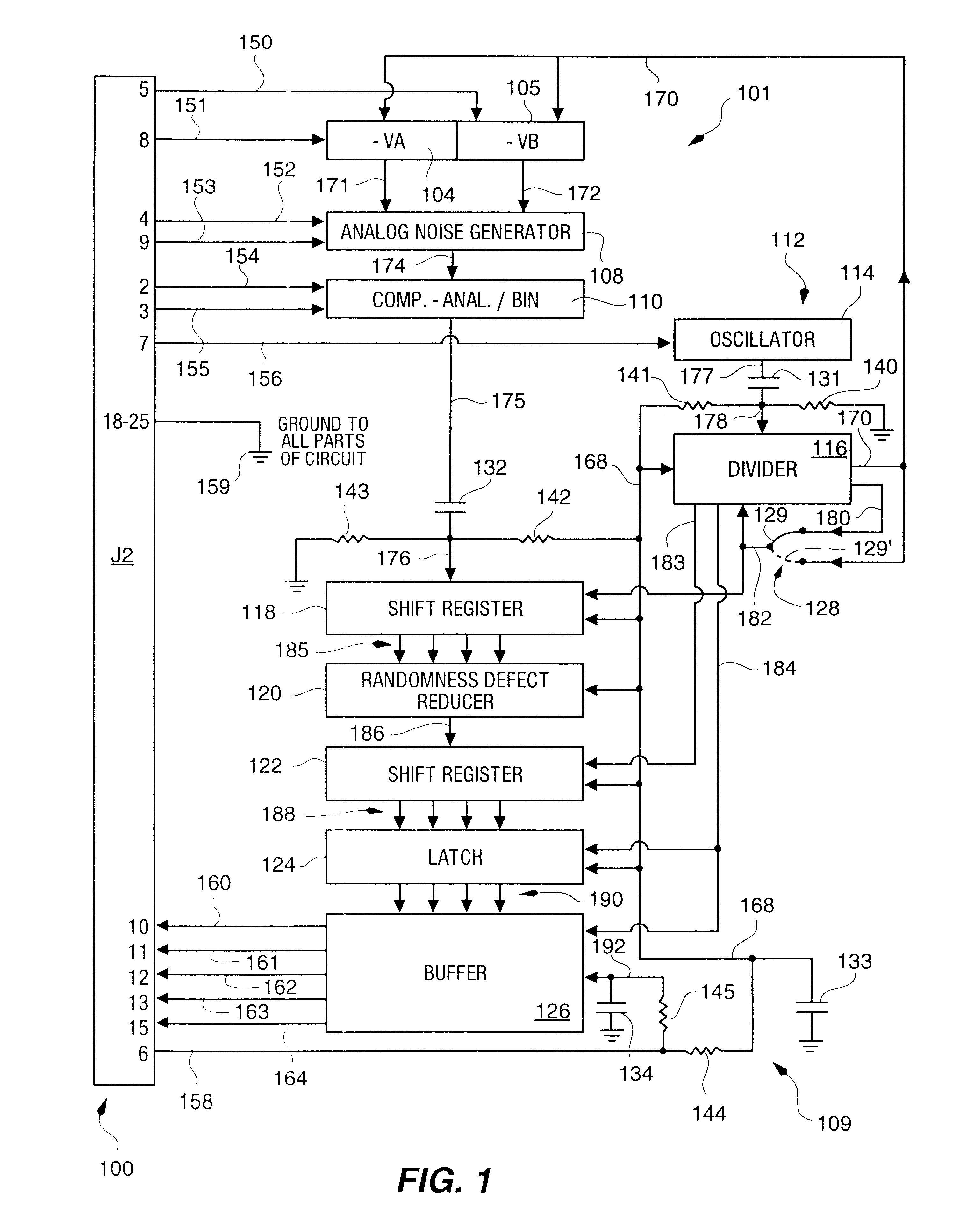
InactiveUS6324558B1Improve its ability to generateReduce defectsRandom number generatorsDigital function generatorsCmos comparatorShift register
An RNG circuit is connected to the parallel port of a computer. The circuit includes a flat source of white noise and a CMOS amplifier circuit compensated in the high frequency range. A low-frequency cut-off is selected to maintain high band-width yet eliminate the 1 / f amplifier noise tail. A CMOS comparator with a 10 nanosecond rise time converts the analog signal to a binary one. A shift register converts the serial signal to a 4-bit parallel one at a sample rate selected at the knee of the serial dependence curve. Two levels of XOR defect correction produce a BRS at 20 kHZ, which is converted to a 4-bit parallel word, latched and buffered. The entire circuit is powered from the data pins of the parallel port. A device driver interface in the computer operates the RNG. The randomness defects with various levels of correction and sample rates are calculated and the RNG is optimized before manufacture.
Owner:QUANTUM WORLD
True random number generator and entropy calculation device and method
InactiveUS6862605B2Random number generatorsDigital function generatorsFrequency multiplierNumber generator
Owner:QUANTUM WORLD
Method for a Dynamic Perpetual Encryption Cryptosystem
A dynamic computer communication security encryption method or system using an initial seed key and multiple random number generators of a specific design, whereby a sequence of independent random entropy values is produced by one set of random number generators and encrypted along with the message stream using the initial seed key, or the output of a second set of random number generators initialized with the initial seed key, and following the subsequent transmission of the variable encrypted entropy / message block, the entropy values are used to symmetrically or identically augment or increase the current uncertainty or entropy of the cryptosystem at both the sender and the receiver, prior to the next encryption block operation. The encryption process effectively entailing the use of multiple encryption ciphers, and the entropy augmentation process entailing the encryption or application of various logical mathematical operations on the already dynamic but deterministic internal state values of the second set of random number generators, effectively altering their deterministic outputs in a random probabilistic manner.Random length message value sequences from one or more data sources is combined with one or more random length entropy value sequences from an independent source, following which the entropy “updates” may also be used to alter, or change any cryptosystem variable, value or component in a randomly determined manner. In addition, whilst ensuring synchronization, the random entropy sequences also serve to “pollute” the cipher-stream and thereby hinder most current forms of cryptanalysis, whilst simultaneously injecting additional entropy into the cryptographic system and allowing for its propagation to affect any connected system nodes, and thereby introducing unpredictable entropy into the system pseudorandom number generator outputs, and thereby ensuring the perpetual generation of unpredictable random numbers.Super-encryption mechanics are independent of the user data, simple, fast and efficient, and can incorporate compression, error correction and asymmetric encryption authentication routines. But most importantly, super-encryption ensures resistance to brute force attacks (not possible to verify if a message was even sent), an ability to exceed “perfect secrecy” requirements, and an improvement on previous super-encipherment design, since overhead can be dramatically reduced from 100% overhead.Communication links previously established by system nodes with central authorities may be used for secure node authentication and registration, whilst allowing the central authority to broker and synchronize communication channels and providing mutual authentication and other security functions between the system nodes.
Owner:FIGUEIRA HELDER SILVESTRE PAIVA
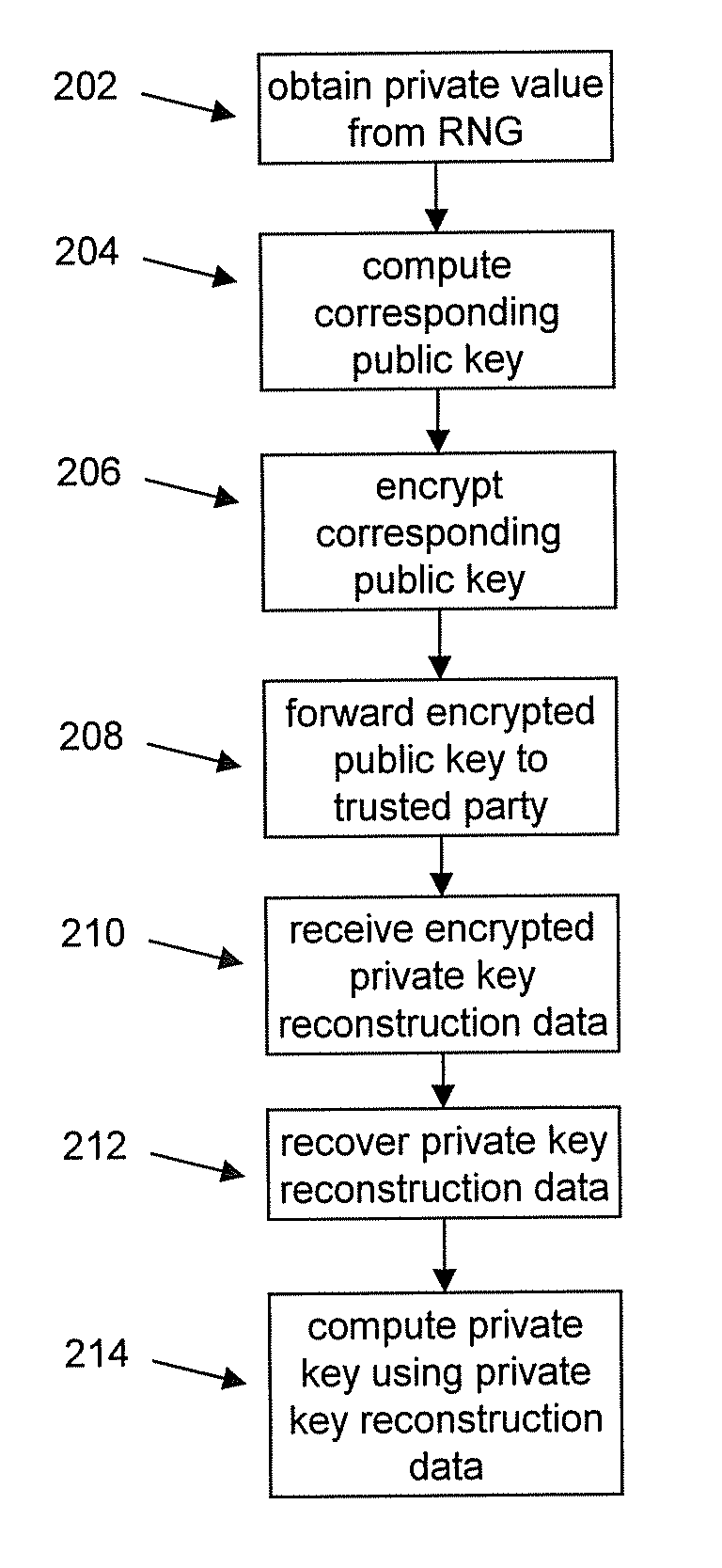
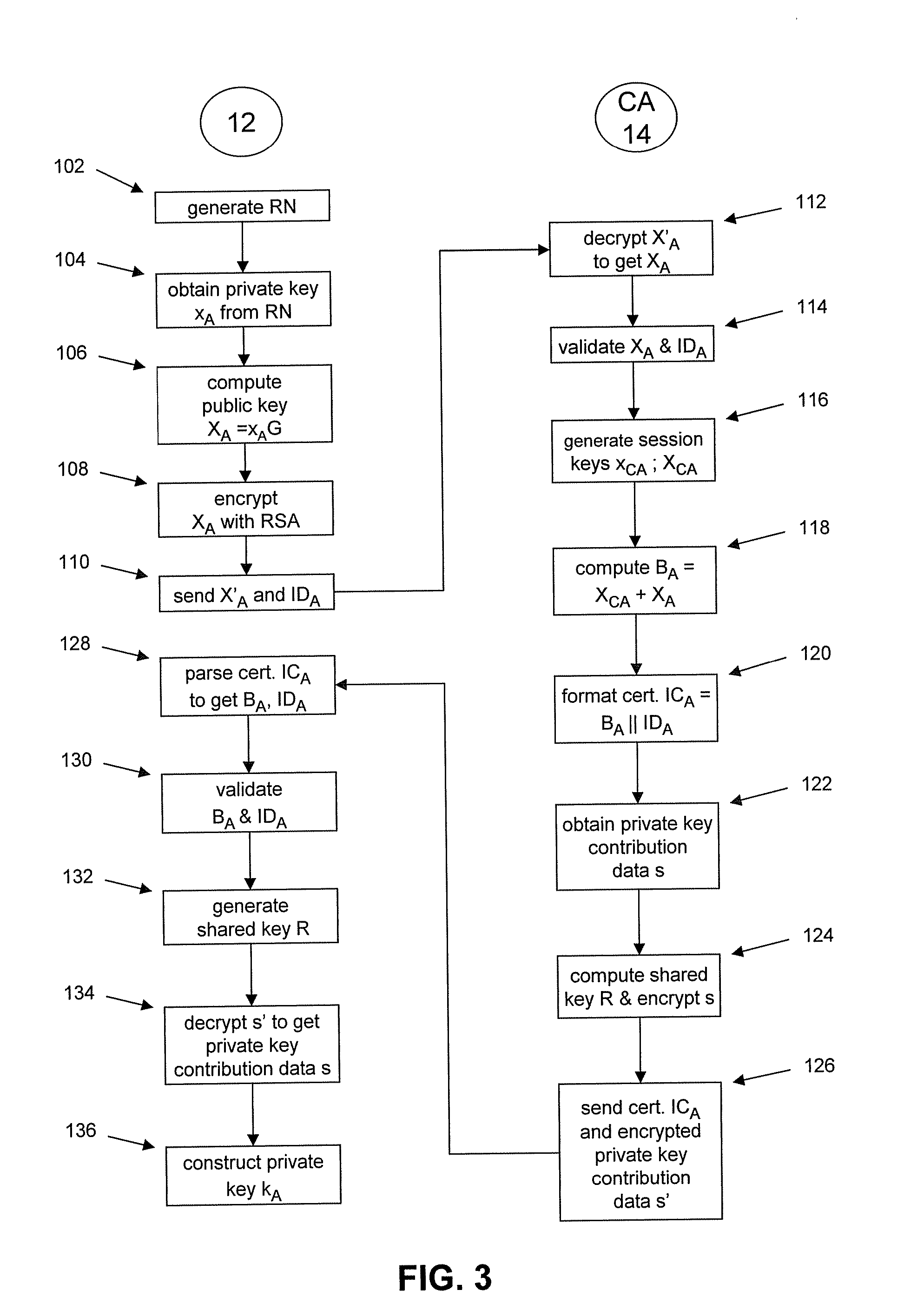
Masking the output of random number generators in key generation protocols
ActiveUS20110307698A1Key distribution for secure communicationPublic key for secure communicationDeterministic encryptionNumber generator
To mitigate the effects of a weak random number generator (RNG) in a public key cryptosystem, a public key obtained from the RNG is encrypted using a deterministic cryptographic scheme before being made publicly available. A trusted party receiving the encrypted public key can recover the public key and combine it with other information so it is not subject to direct scrutiny. In one embodiment, the trusted party incorporates the public key in a certificate, such as an implicit certificate, for use by the correspondents in other communications.
Owner:MALIKIE INNOVATIONS LTD
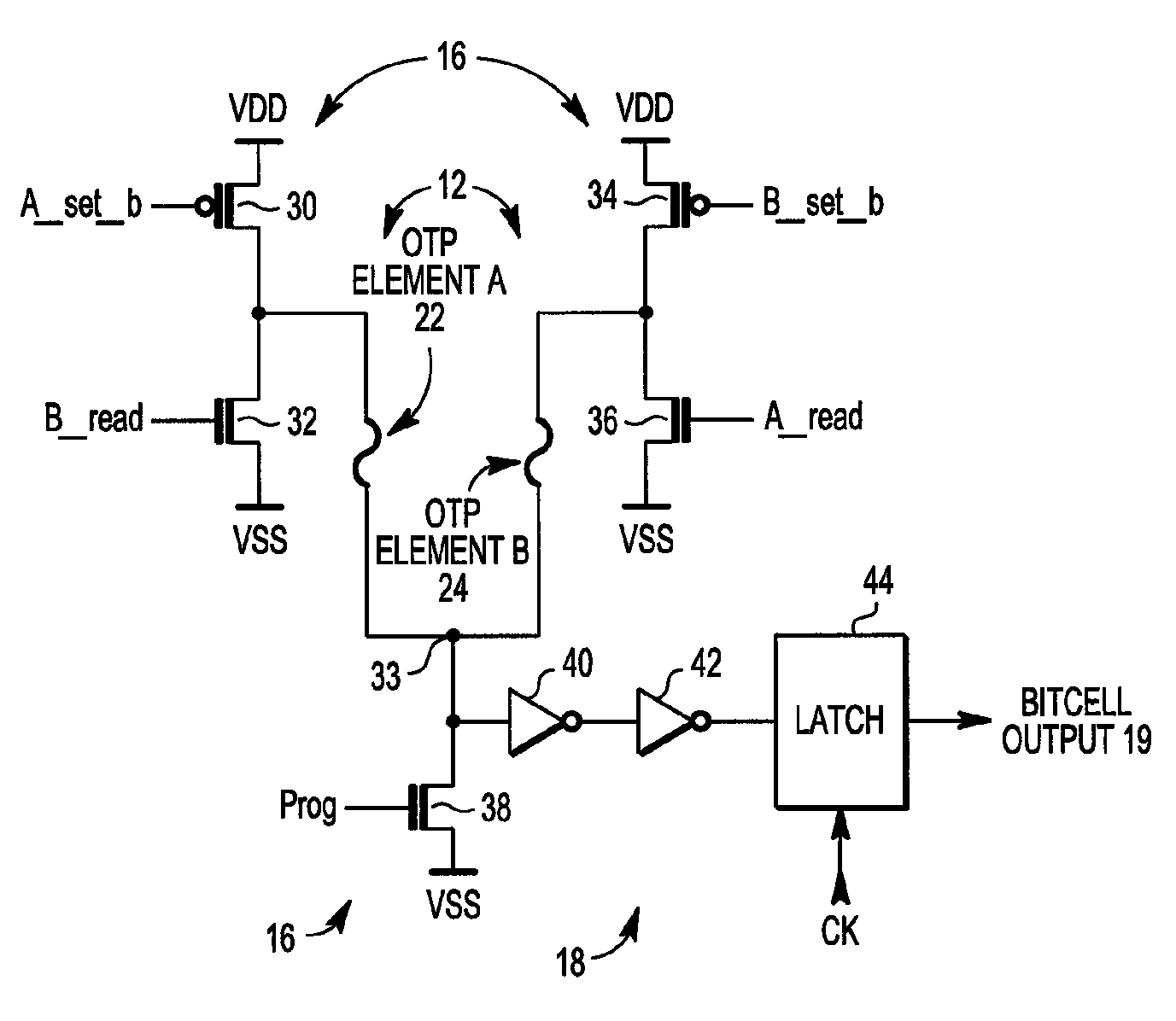
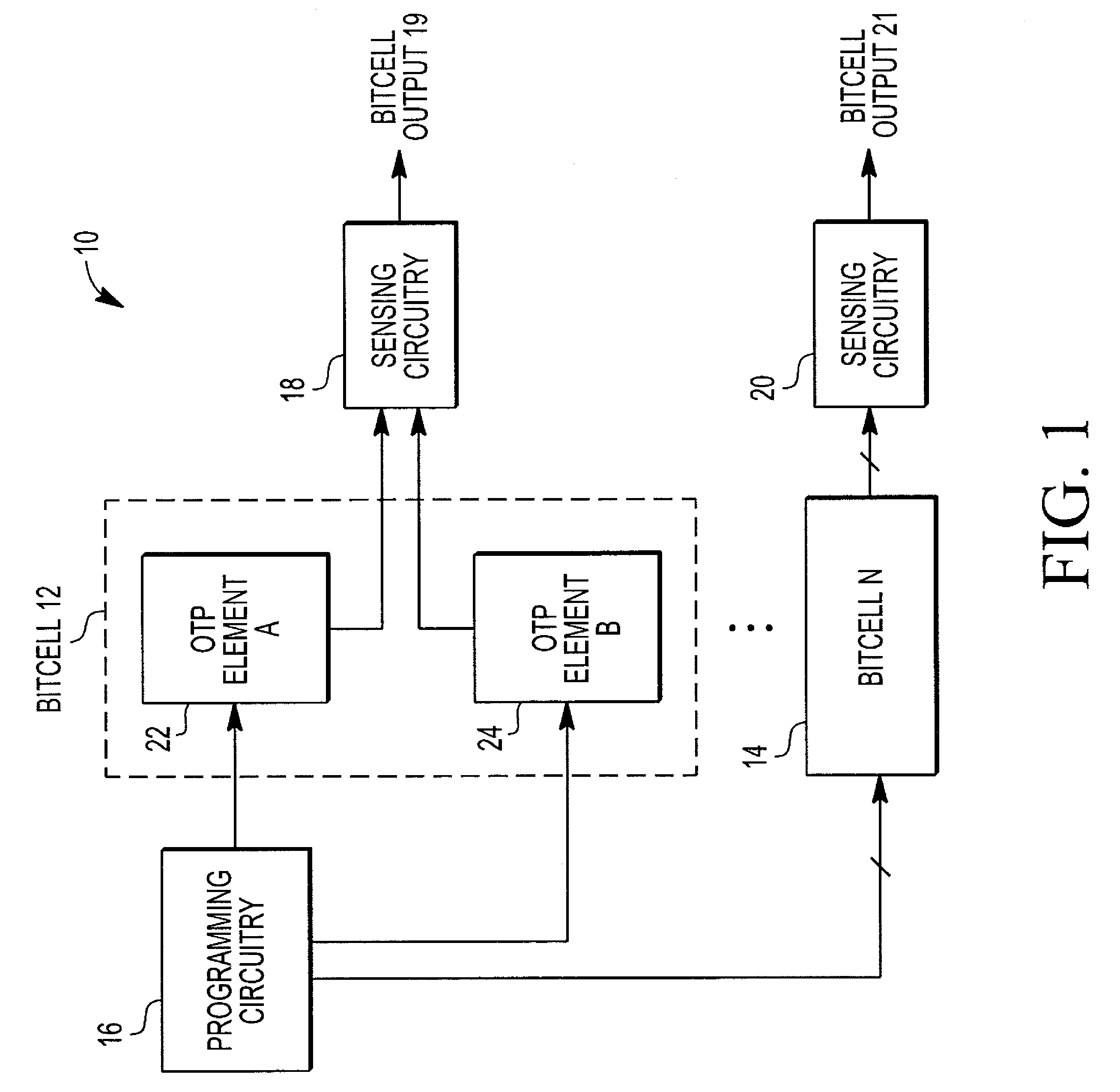
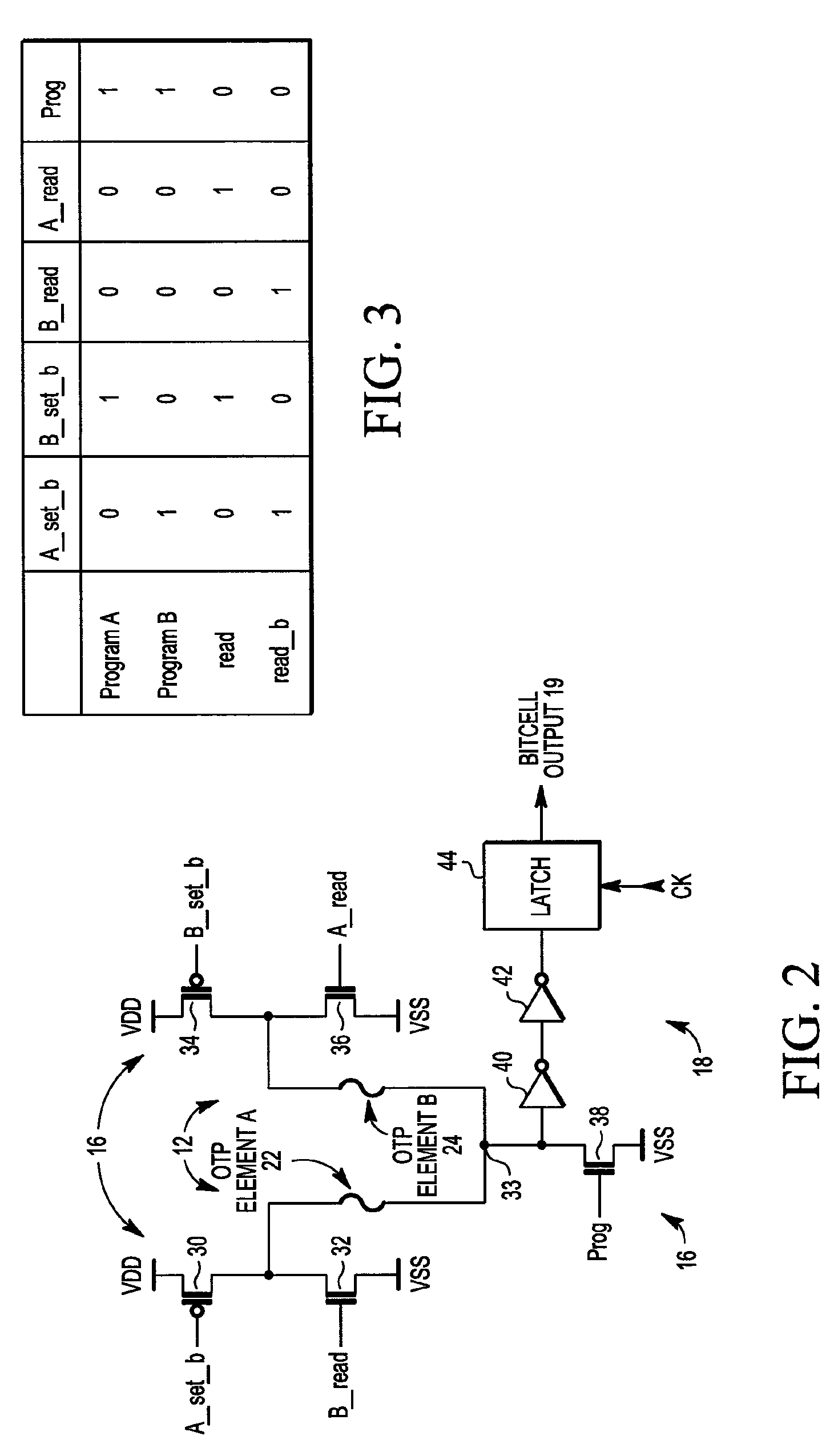
Random number generator
ActiveUS8380768B2Random number generatorsDigital function generatorsElectricityAudio power amplifier
A random number generator includes a first one time programmable (OTP) element and a second OTP element. The first OTP element and second OTP element have a first distribution of probable values for an electrical characteristic when unprogrammed and a second distribution of probable values when programmed. A programming circuit applies a programming signal to the first OTP element and to the second OTP element that causes the first OTP element to switch from being unprogrammed to being programmed and having a first value for its electrical characteristic and the second OTP element to switch from being unprogrammed to being programmed and having a second value for its electrical characteristic. A sense amplifier provides an output signal at a first logic state when the first value exceeds the second value and at a second logic state when the second value exceeds the first value.
Owner:NXP USA INC
Ultrafast quantum random number generation process and system therefore
ActiveUS20130036145A1Overcome limitationsShorten the construction periodRandom number generatorsDigital dataModulation bandwidthNumber generator
The invention is based on a process and system for producing random numbers by means of a quantum random number generator where the method comprises the steps of operating a laser in single mode and high modulation bandwidth by means of an electrical pulse driver, transforming the phase randomized optical pulses produced before in optical pulses with random amplitude and detecting the resulting random amplitude signals by means of a fast photodiode. The numbers thus produced are truly random.
Owner:FUNDACIO INST DE CIENCIES FOT NIQUES +2
Method and apparatus for controlling communication within a computer network
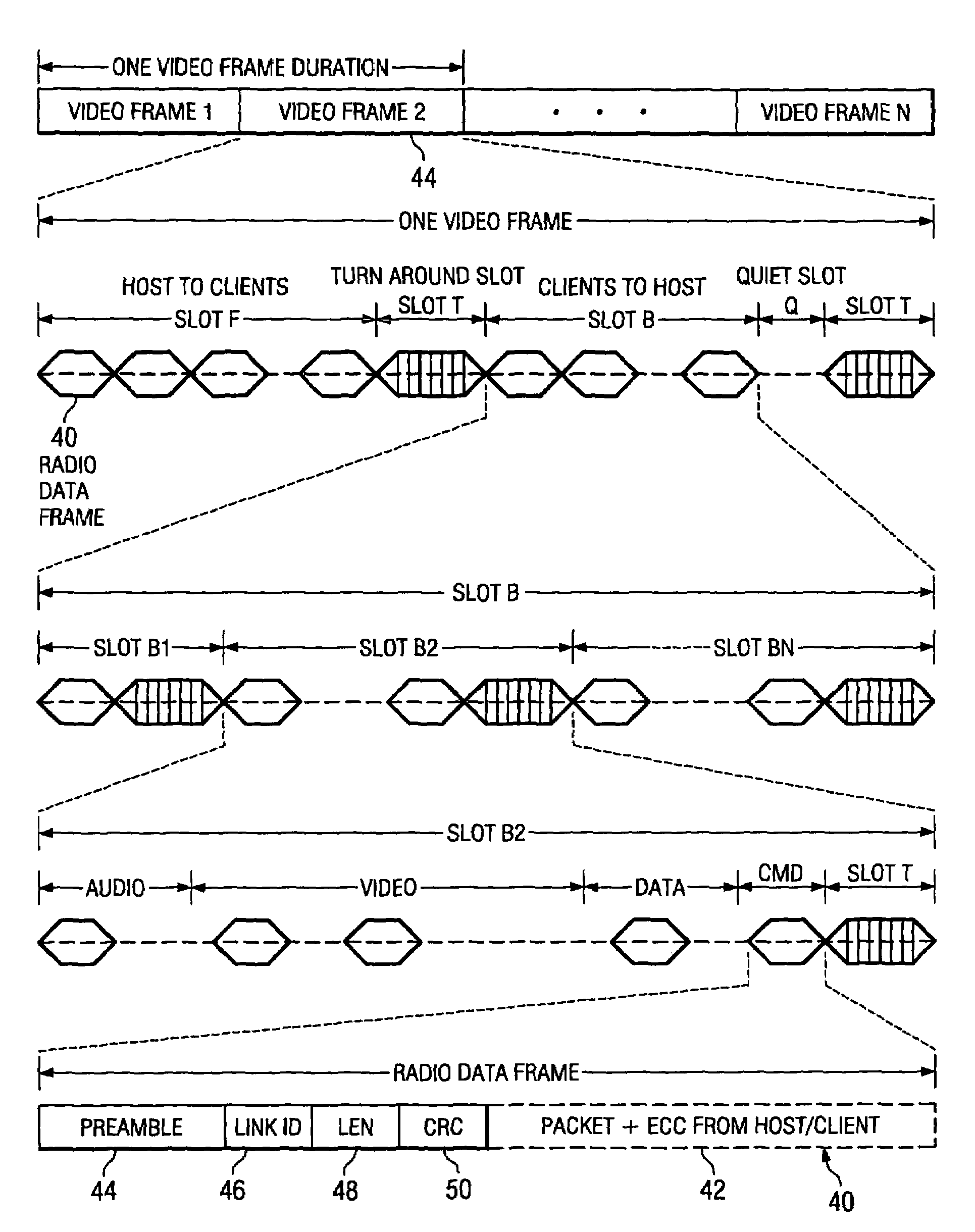
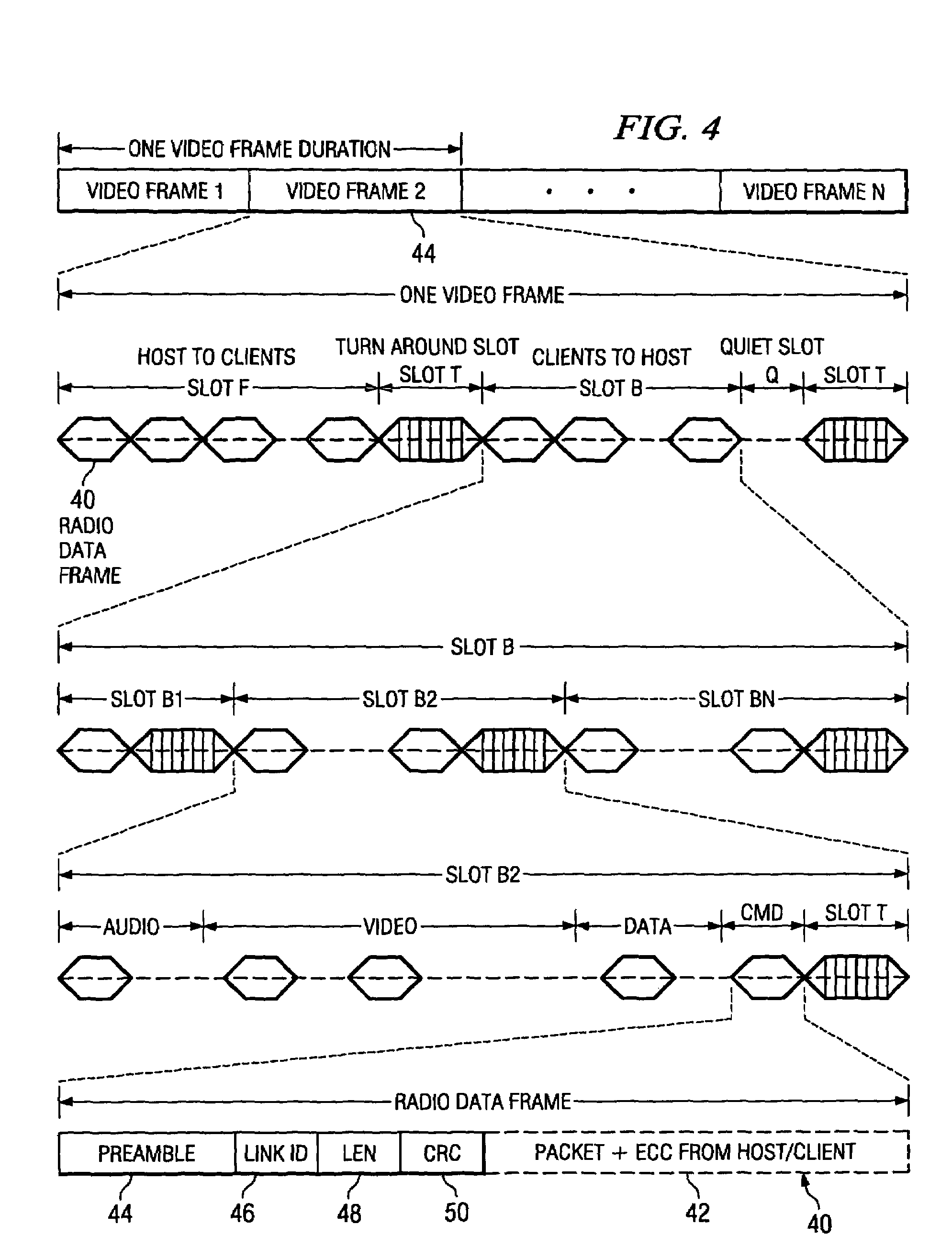
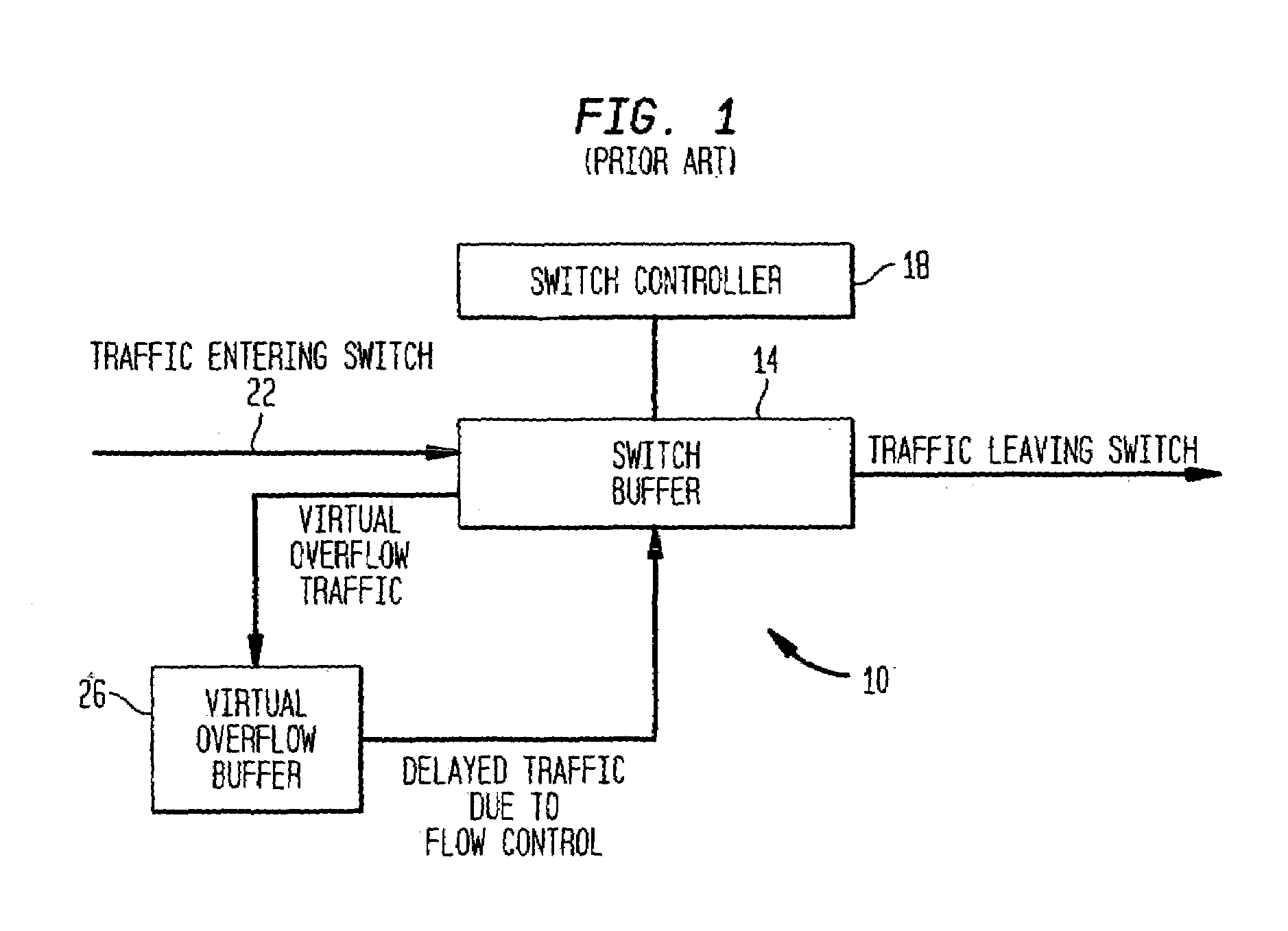
InactiveUS7251231B2Network traffic/resource managementNetwork topologiesReverse timeControl communications
A communication channel is controlled so as to dynamically accommodate network client requests for access thereto. The communication channel may be supported on a wireless link, such as a spread spectrum wireless link, and client requests for access thereto may be dynamically accommodated by allocating time slots for client transmissions on the wireless link. Providing a quiet time slot within which clients may request access to the communication channel may accommodate various client requests for access to the communication channel. These quiet slots may exist with other forward and reverse time slots which are superimposed on the communication channel, each forward and reverse time slot including one or more data frames. The forward and reverse time slots are preferably fixed, but negotiable, time periods. Each of the data frames may include a plurality of data packets, each of the data packets being variable in length. Preferably, each of the data packets includes error correction coding information as well as information which may be used to synchronize pseudo-random number generators of a transmitter and a receiver operating according to the communication protocol. Each of the data frames may further include link identification information that uniquely identifies a wireless link supporting the communication protocol.
Owner:CIRRUS LOGIC INC
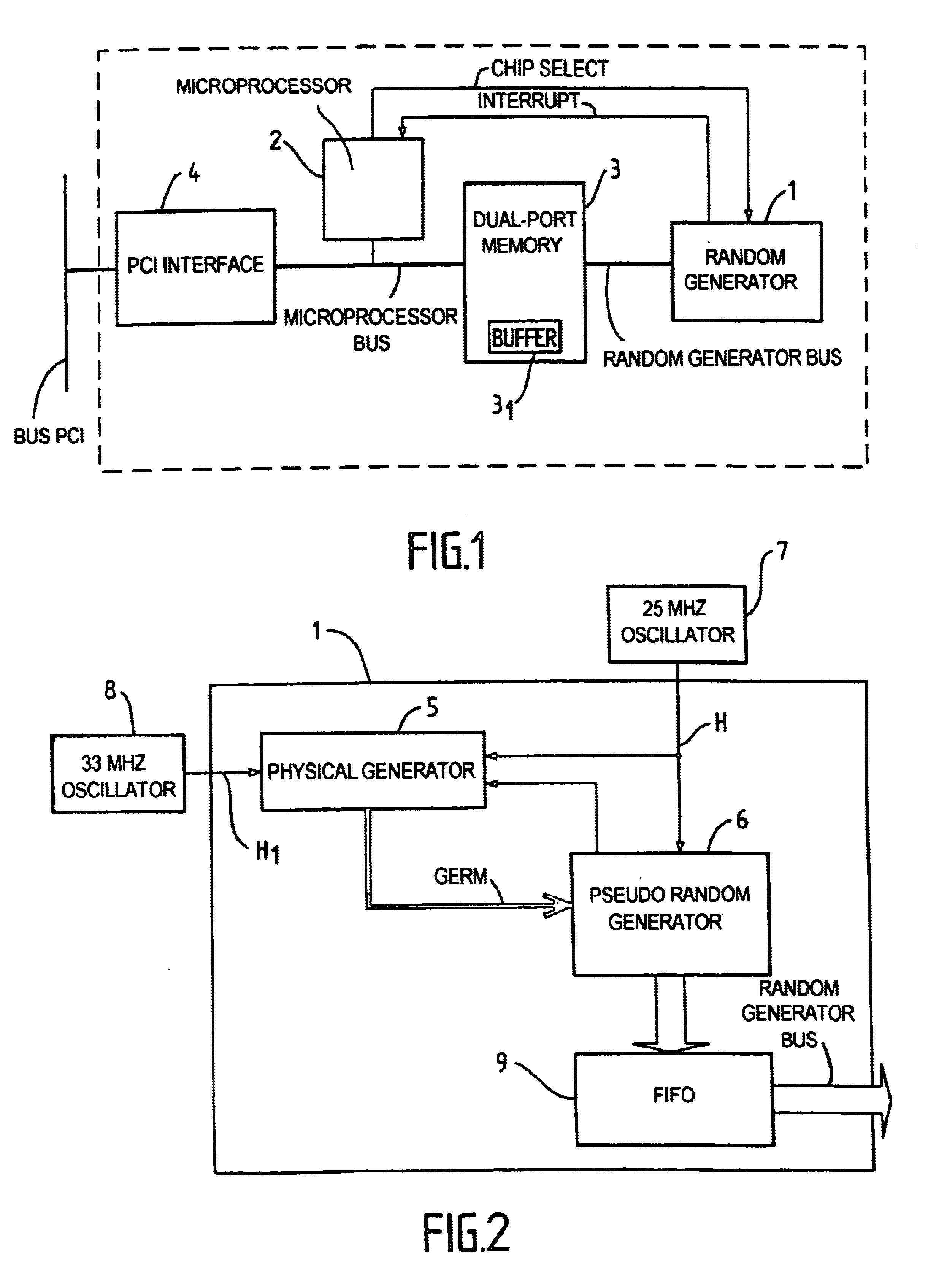
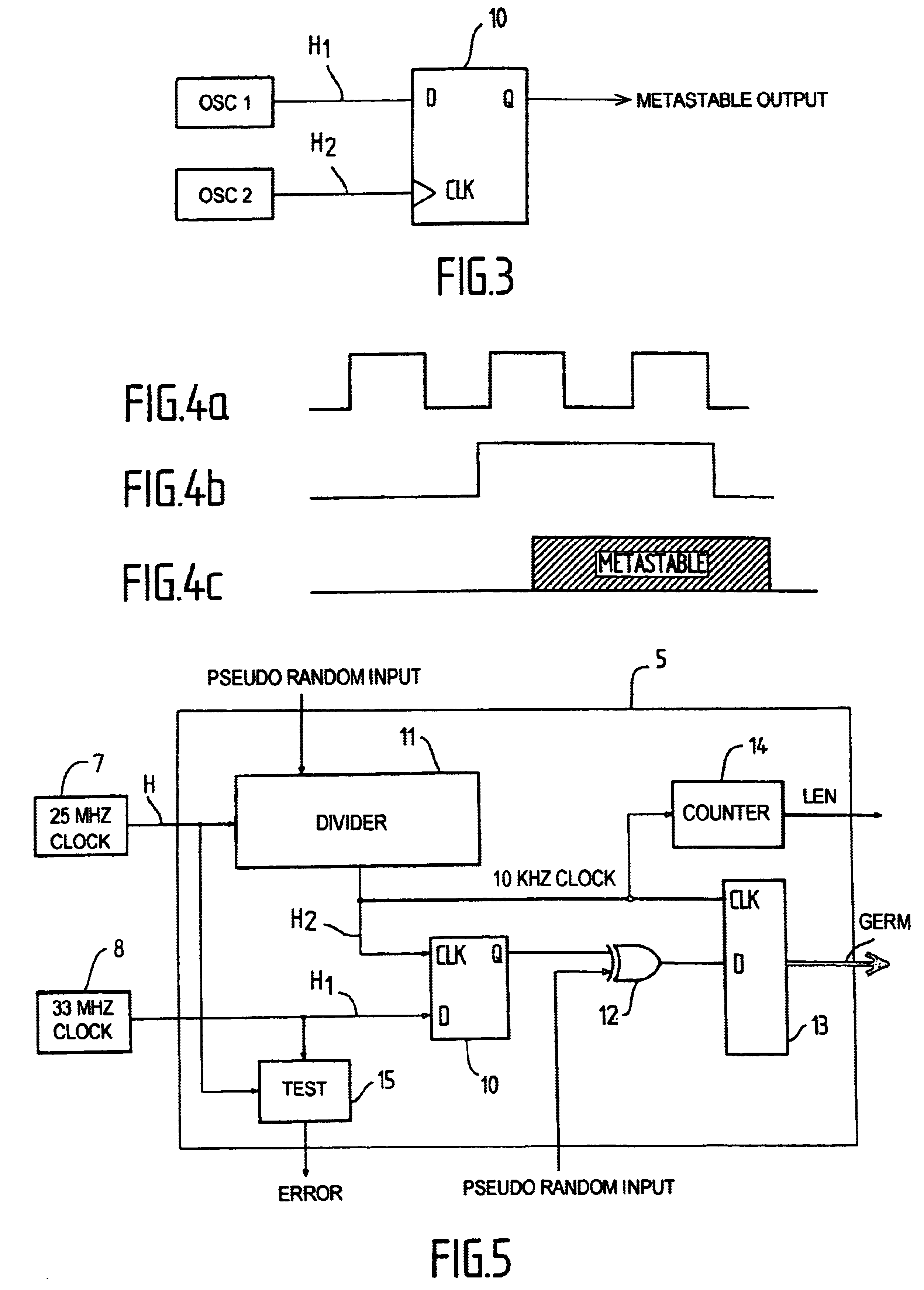
High speed random number generation
InactiveUS6714955B2Quality improvementReduce complexityRandom number generatorsDigital function generatorsInternal memoryPhase noise
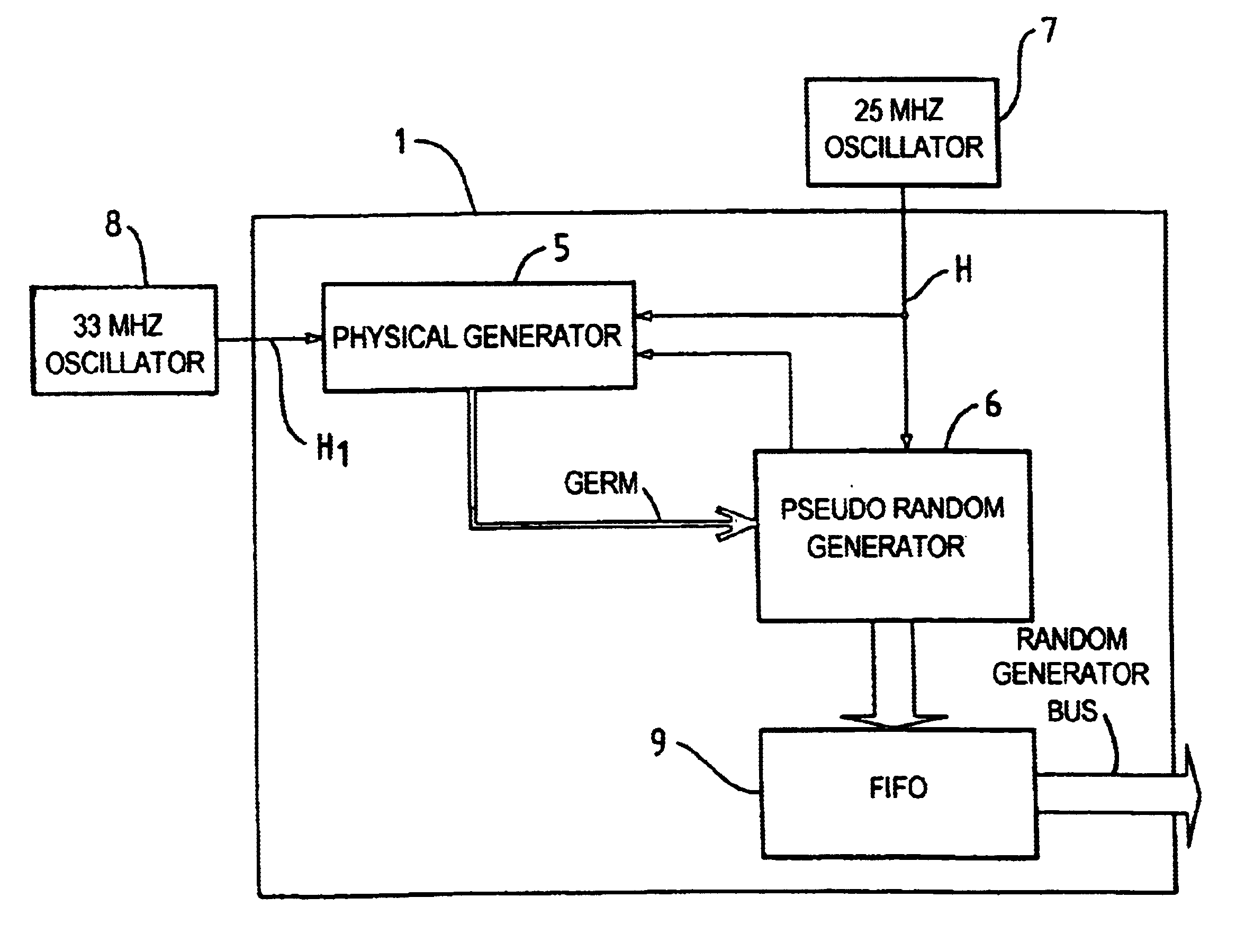
A high-speed random number generator (1) comprising a physical random number generator, having a data input, an output and a pseudo-random generator coupled to the output of the physical random generator. The pseudo-random generator has an input adapted to receive a germ delivered by the physical generator and deliver at an output a pseudo-random output signal. The physical generator comprises a logic circuit that includes at least a data input (D) and a clock input (CLK), the data input (D) receiving a first "high frequency" clock signal H1 and the clock input (CLK) receiving a second "low frequency" clock signal H2, with the "high frequency" signal H1 being sampled by the "low frequency" signal H2. The two clock signals H1 and H2 are of different frequencies respectively and issue from two different first (OSC1 and OSC2) operating asynchronously from one another and not adhering to the setup time of the logic circuit (10). The logic circuit is arranged to deliver at an output a signal in an intermediate state qualified as metastable between "0" and "1" and being constituted by a random number sequence. The metastability of the signal obtained as an output from the logic circuit (10) is accentuated by phase noise of the first oscillator (OSC1) generating the "high frequency" signal H1. The pseudo-random generator is arranged to re-inject part of the pseudo-random output signal into the physical generator. An internal memory stores the random numbers obtained as output signals from the pseudo-random generator. The two generators run on the same second "high frequency" clock H generated by the external oscillator (7).
Owner:BULL SA
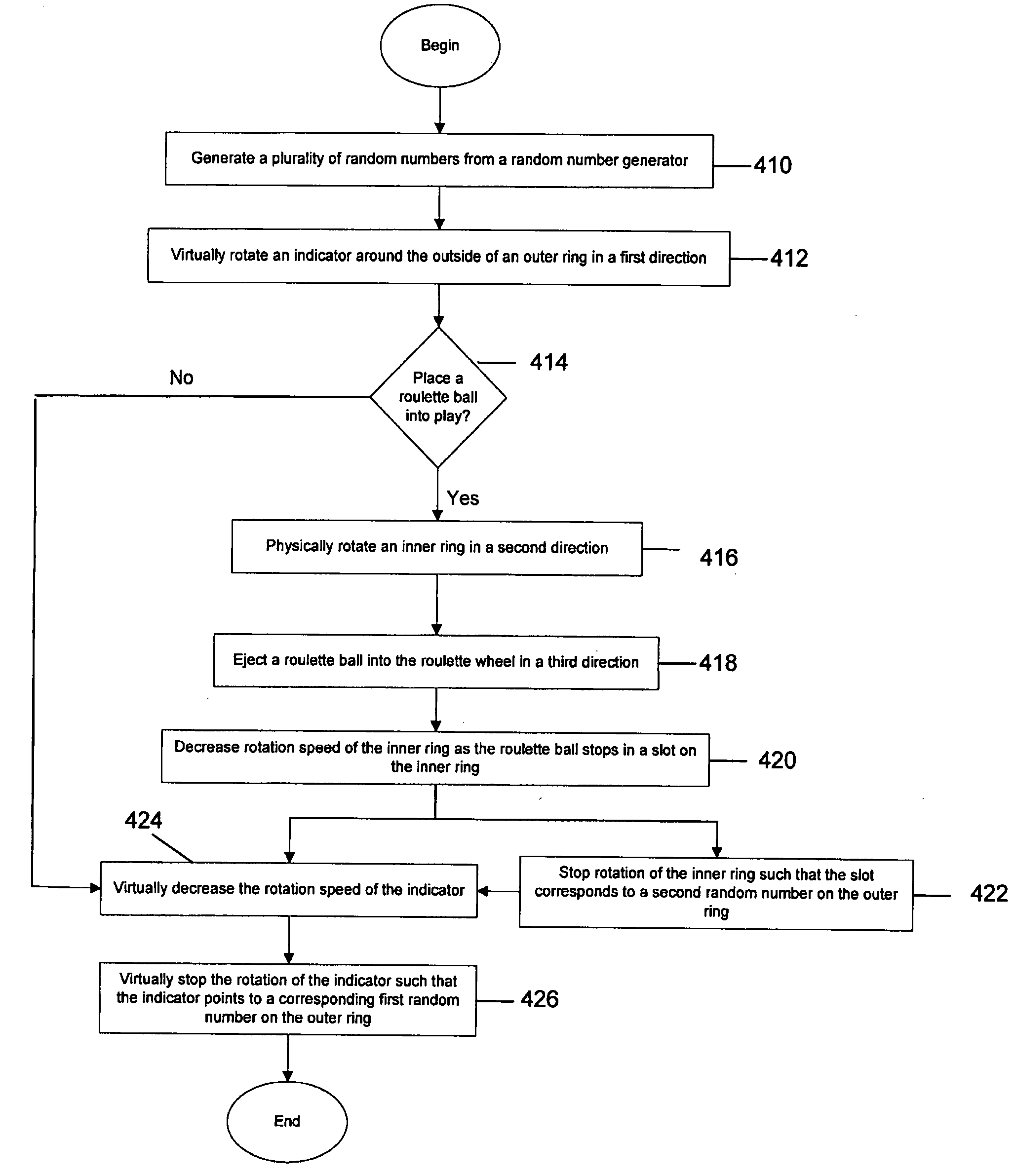
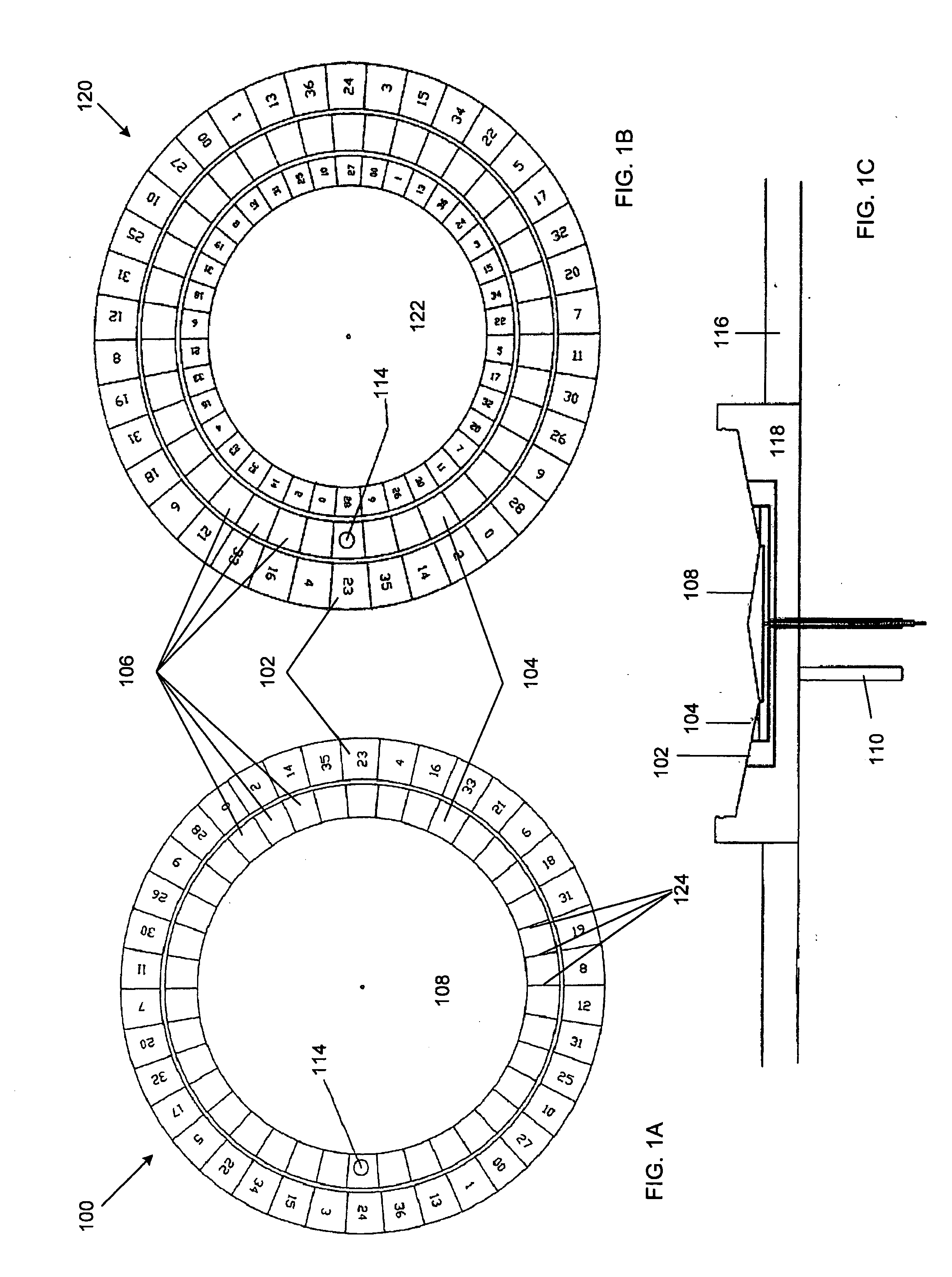
Random number generator based roulette wheel
The invention provides for the use of a random number generator in a roulette wheel to play a game of roulette. The gaming apparatus may have a random number generator, a roulette wheel, and means for controlling the roulette wheel to indicate a first winning number corresponding to a first random number generated by the random number generator. The roulette wheel may have a top ring, outer ring, separator ring, and an inner ring and each ring may be decoupled from each outer to spin in different directions.
Owner:IGT
Method for making seed value used in pseudo random number generator and device thereof
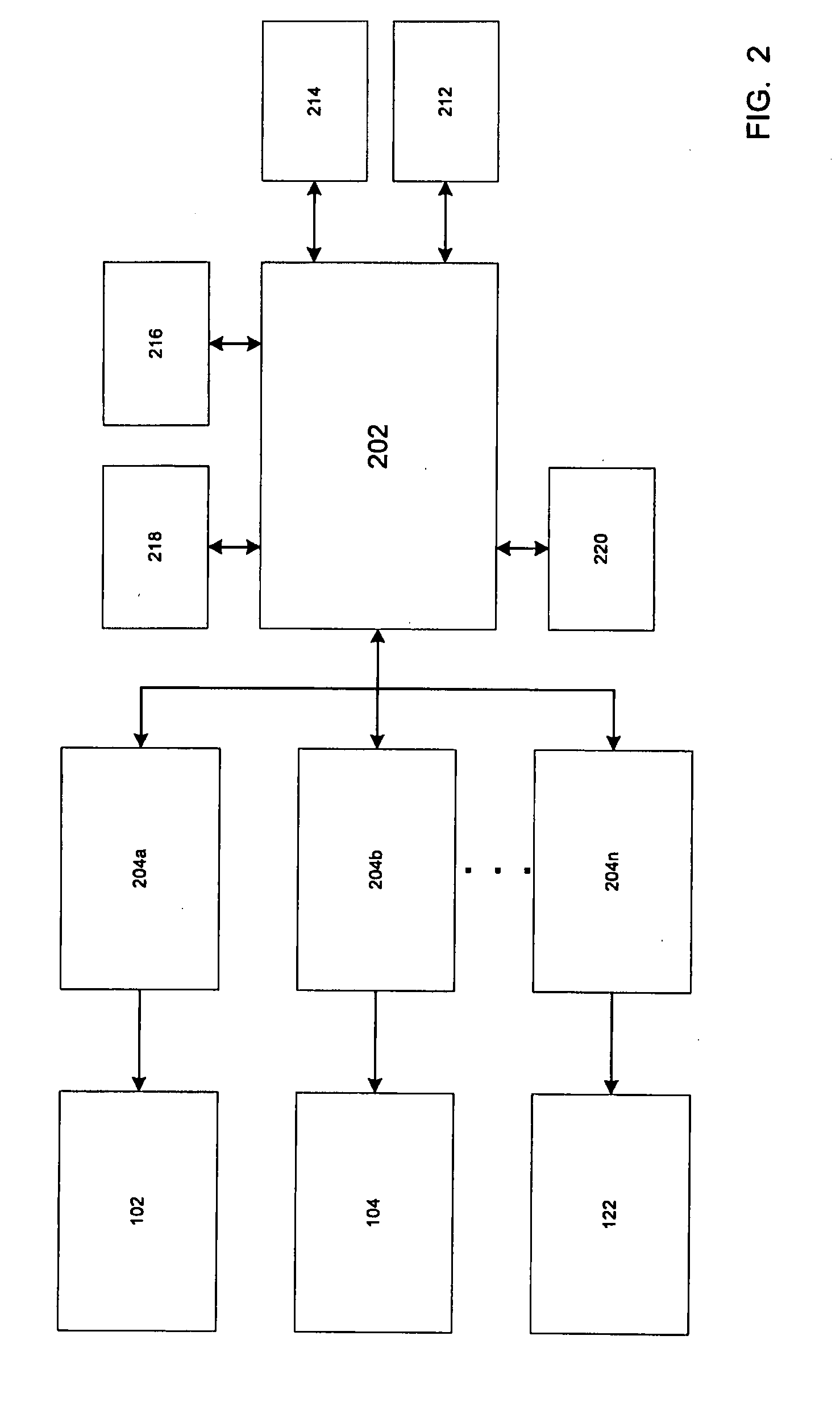
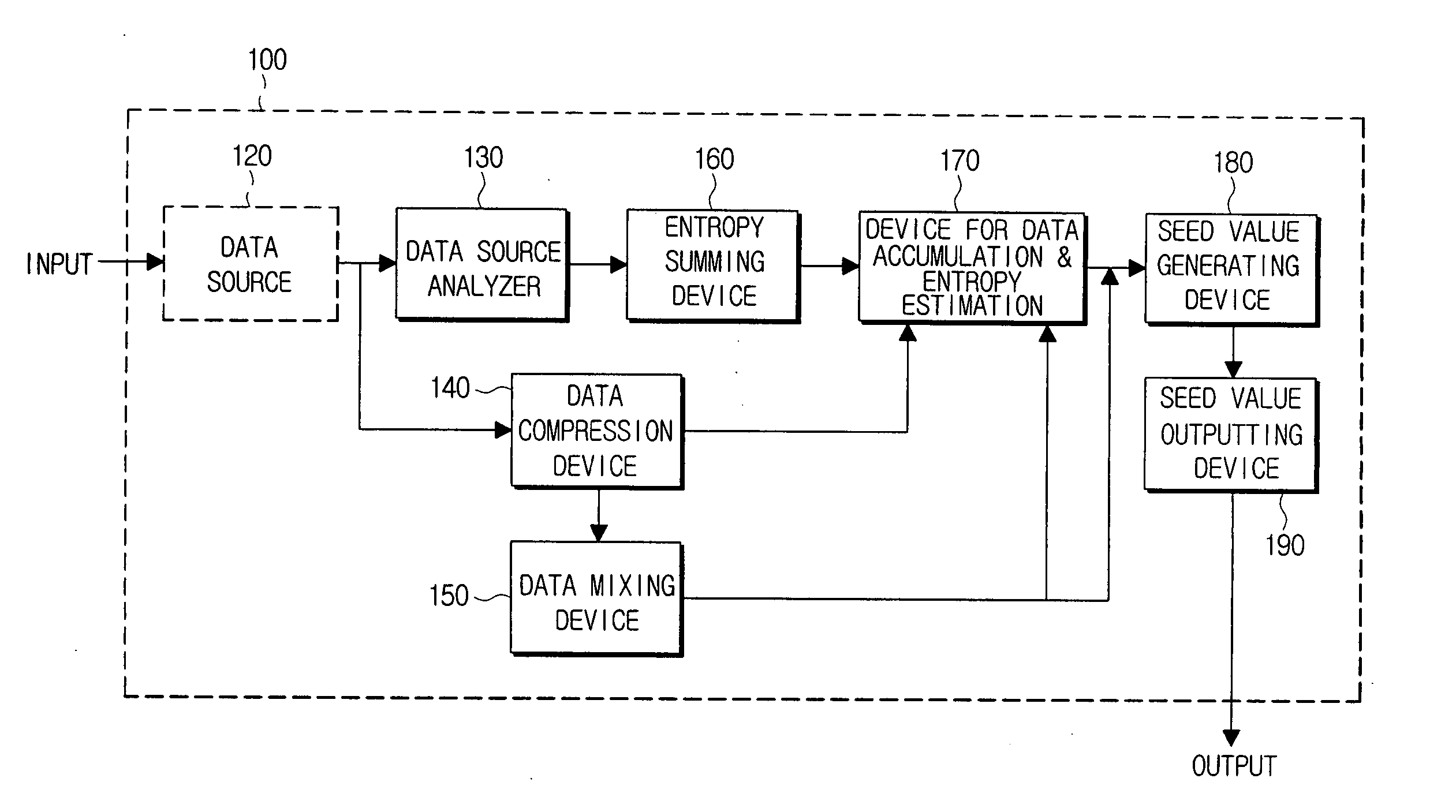
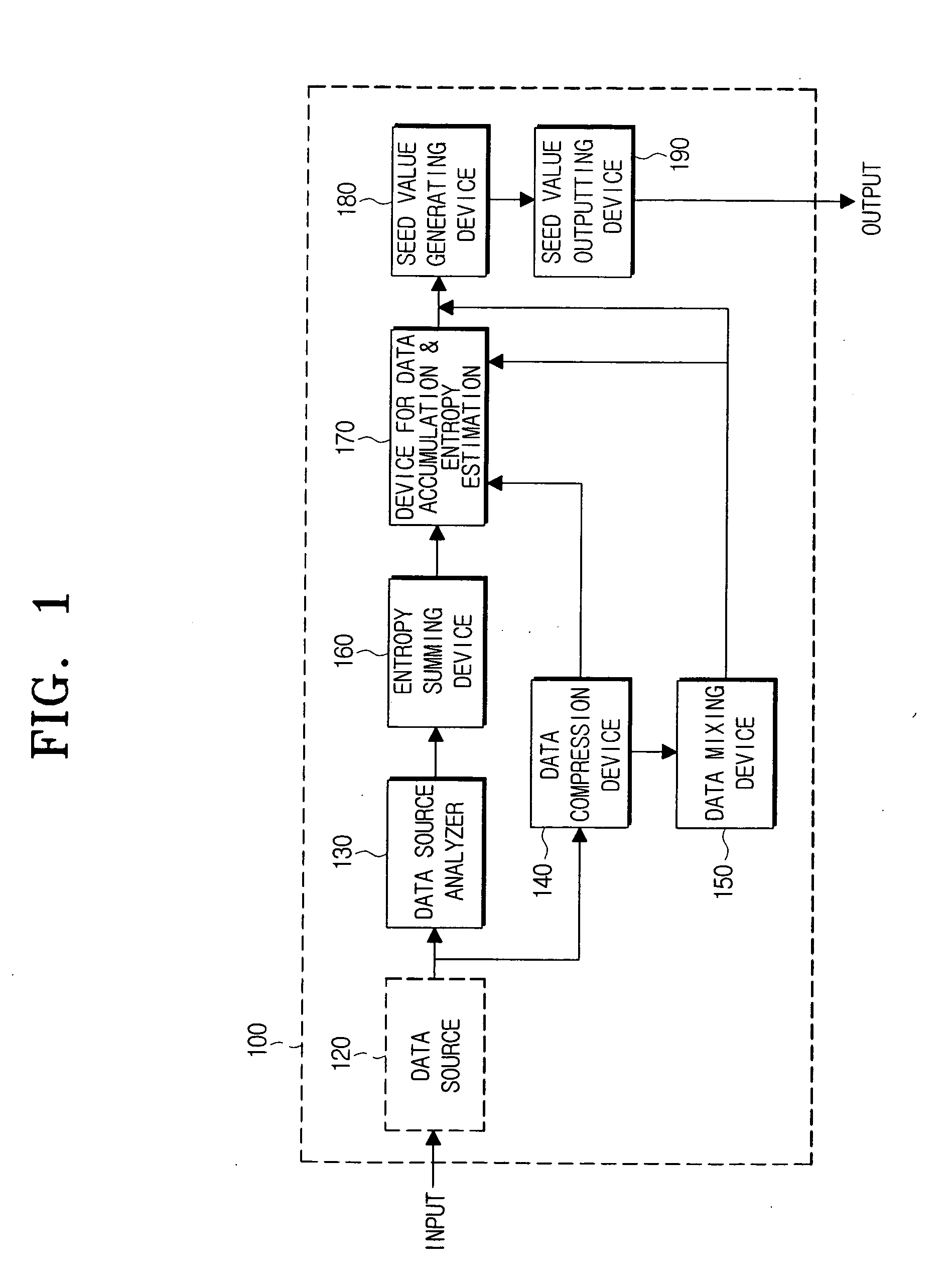
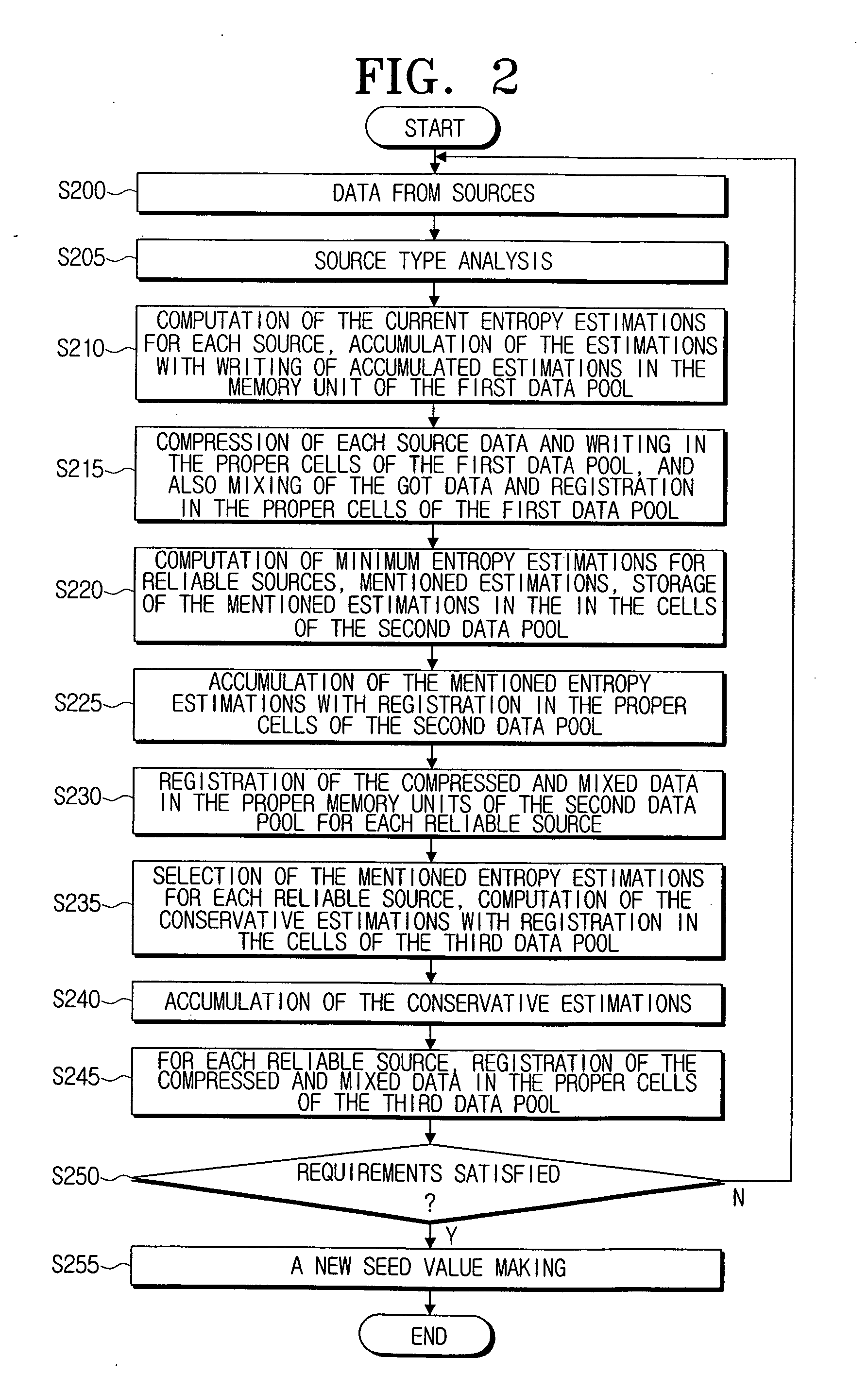
InactiveUS20060067527A1Computation using non-contact making devicesSecuring communicationSource typeData profiling
A seed value making method and device for a PRNG (Pseudo Random Number Generator) are provided. The seed value making method includes the steps of: accumulating in memory units of a First Data Pool data from various external sources, analyzing the data to determine a source type, computing entropy estimations for each of the external sources basing on the source type as determined, and generating a seed value by using the entropy estimations and the data accumulated in the memory units of the First Data Pool. Accordingly, in generating a seed value, dynamic estimation of random sources rate, and classification of sources on slow and fast ones, and reliable and unreliable ones, can be provided, and also, seed values can be made with taking in account rate and reliability of the sources.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for generating pseudo-random numbers
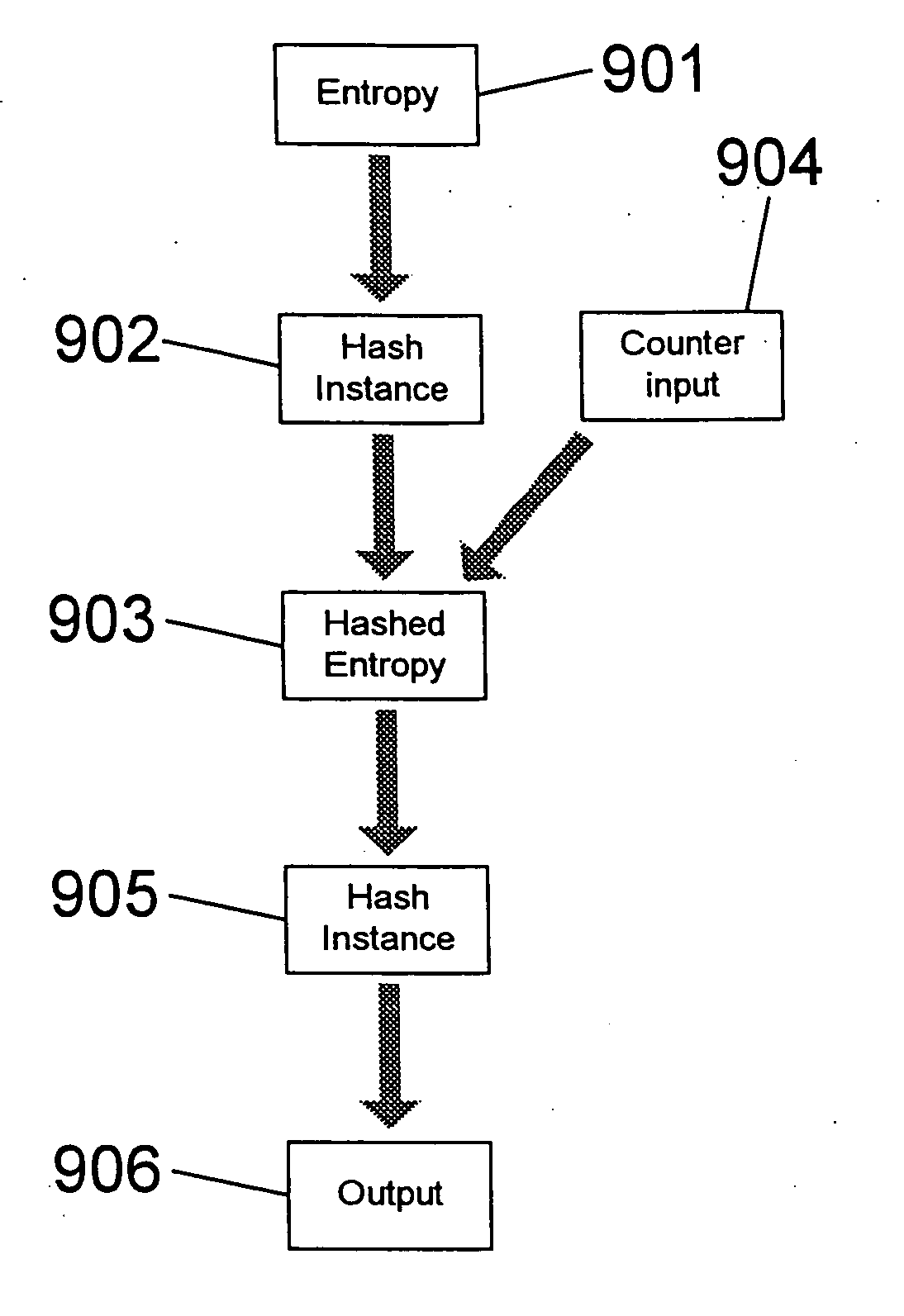
ActiveUS7894602B2Random number generatorsSecuring communicationCryptographic hash functionNumber generator
A process and system for generating a pseudo-random number is presented. Input data having entropy is gathered in an Entropy Pool and transformed once by a cryptographic hash function. The transformed data forms the internal state of the pseudo-random number generator. The generator forms the output by applying a second cryptographic hash function to this internal state. Finally, the generator updates the internal state by inputting the current internal state and data from the Entropy Pool into a third cryptographic hash function. The output of the third hash function forms the new internal state of the pseudo-random number generator.
Owner:SAP AG
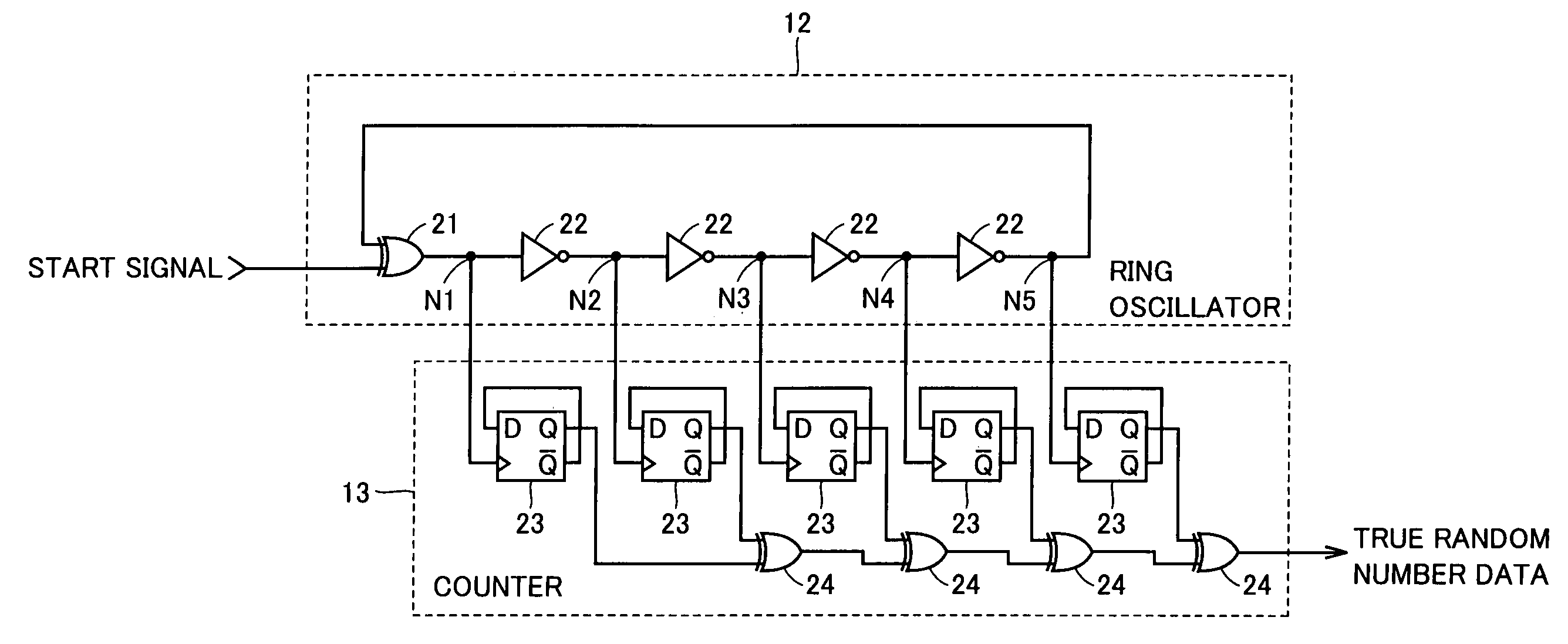
Random number generator with ring oscillation circuit
ActiveUS7424500B2Reduce power consumptionImprove performanceRandom number generatorsElectrical apparatusStable stateDelayed time
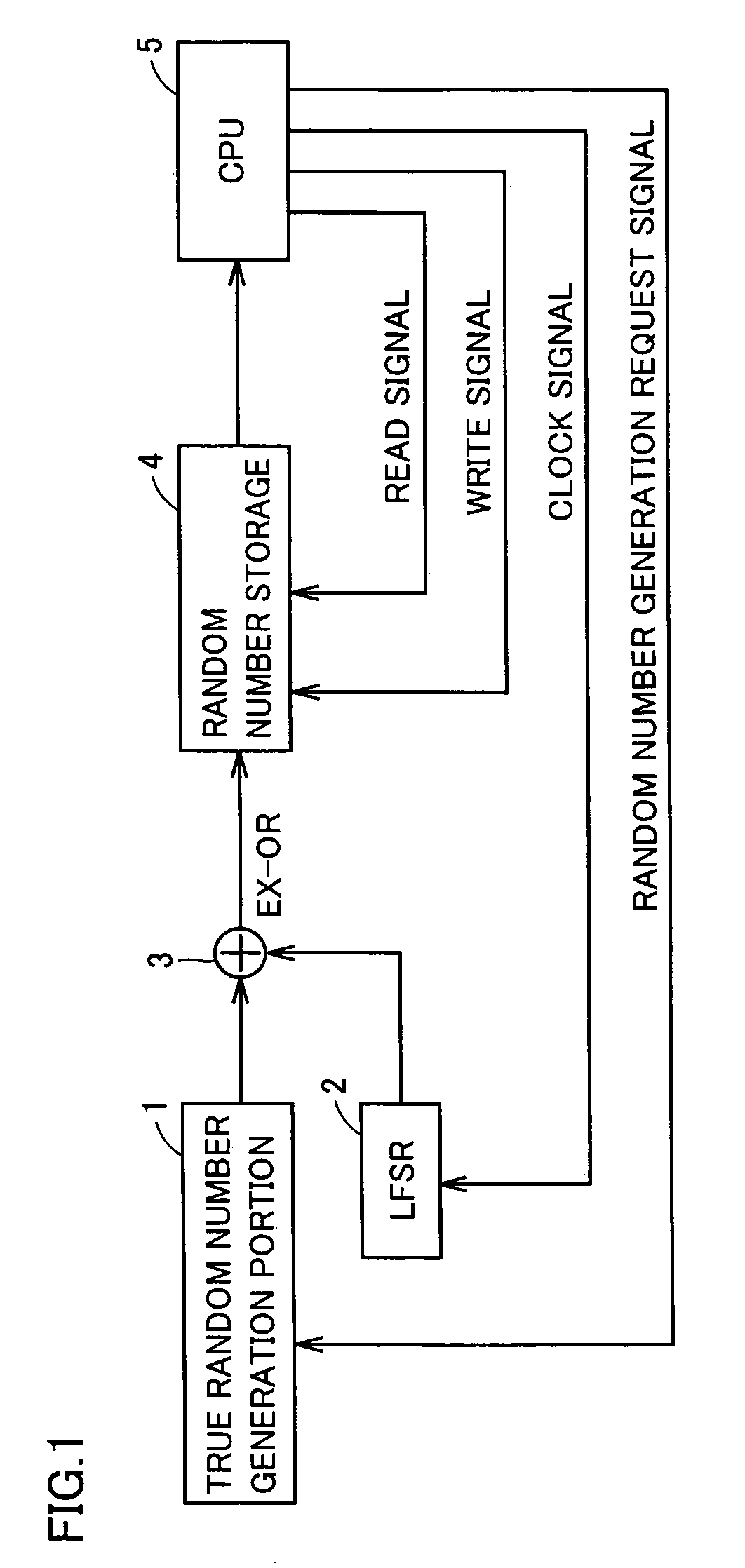
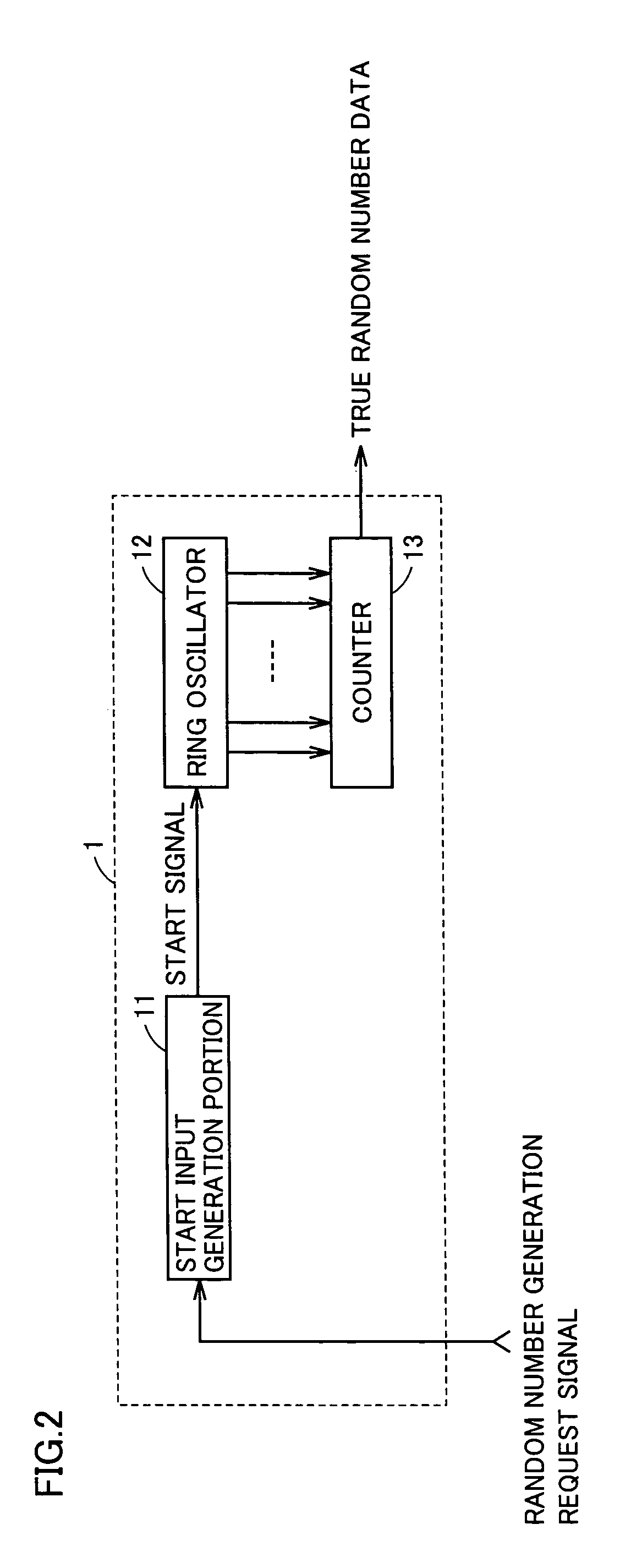
A random number generator includes a ring oscillator having an EX-OR gate and four inverters together forming a loop. This loop enters stable state for a start signal having the low level and oscillates for the start signal having the high level. When the start signal has a pulse of a width shorter than the loop's delay time, output nodes responsively, sequentially enter metastable state hovering between the high and low levels. The metastable waveform becomes smaller with time and finally disappears. As metastable state cannot be controlled in longevity, it disappears at any random number node. A counter thus outputs a signal serving as true random number data depending on the longevity of the metastable state. A random number generator miniaturized and having reduced power consumption, and of high performance can thus be implemented.
Owner:RENESAS LSI DESIGN CORP +1
Pseudo-random number generator
InactiveUS20040078576A1Efficient executionImprove efficiencyRandom number generatorsPublic key for secure communicationEngineeringPublic key cryptosystem
A pseudo-random number generator comprises: (a) a plurality of first-tier means each capable of receiving an entropy input and generating a respective hash output; and (b) a second-tier hashing means, which takes as input the respective first-tier hash outputs and generates as output a pseudo-random number. The generator of the present invention has particular application in cryptosystems, and particularly in public key cryptosystems where long sequences of data chosen from a large space of possible sequences need to be created quickly.
Owner:GEITINGER FELIX EGMONT
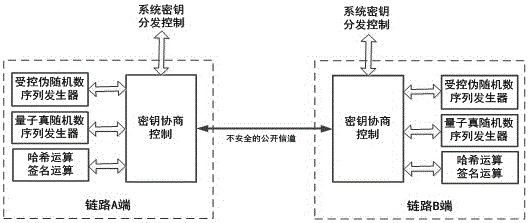
Negotiation system and negotiation method based on quantum truly random number negotiation secret key
ActiveCN106612176AEliminate channel eavesdropping attack vectorsKey distribution for secure communicationEavesdroppingComputer science
The invention provides a negotiation system and a negotiation method based on a quantum truly random number negotiation secret key. Based on a controlled pseudo random number sequence generator and a quantum truly random number sequence generator at both ends of a link, two groups of quantum truly random number sequences are exchanged mutually by a negotiation protocol; after carrying out hash value operation, each end of the link compares the quantum truly random number sequence exchanged from the opposite end with the group of quantum truly random number sequence of the local end, which is used for exchange, to acquire position marking information with the same bit value; and one group of pseudo random number sequence is read, according to the position marking information, taking out bit values of corresponding positions one by one to form an original material bit string of the secret key, and by hash operation, a shared secret key is obtained. Compared with the prior art, a channel-eavesdropping attack channel of an opponent can be completely eliminated, and in the secret key negotiating process, any information related to the original material of the secret key is not transferred, so that the opponent cannot acquire any information related to the generated shared secret key on the basis of a channel eavesdropping or decoding means.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
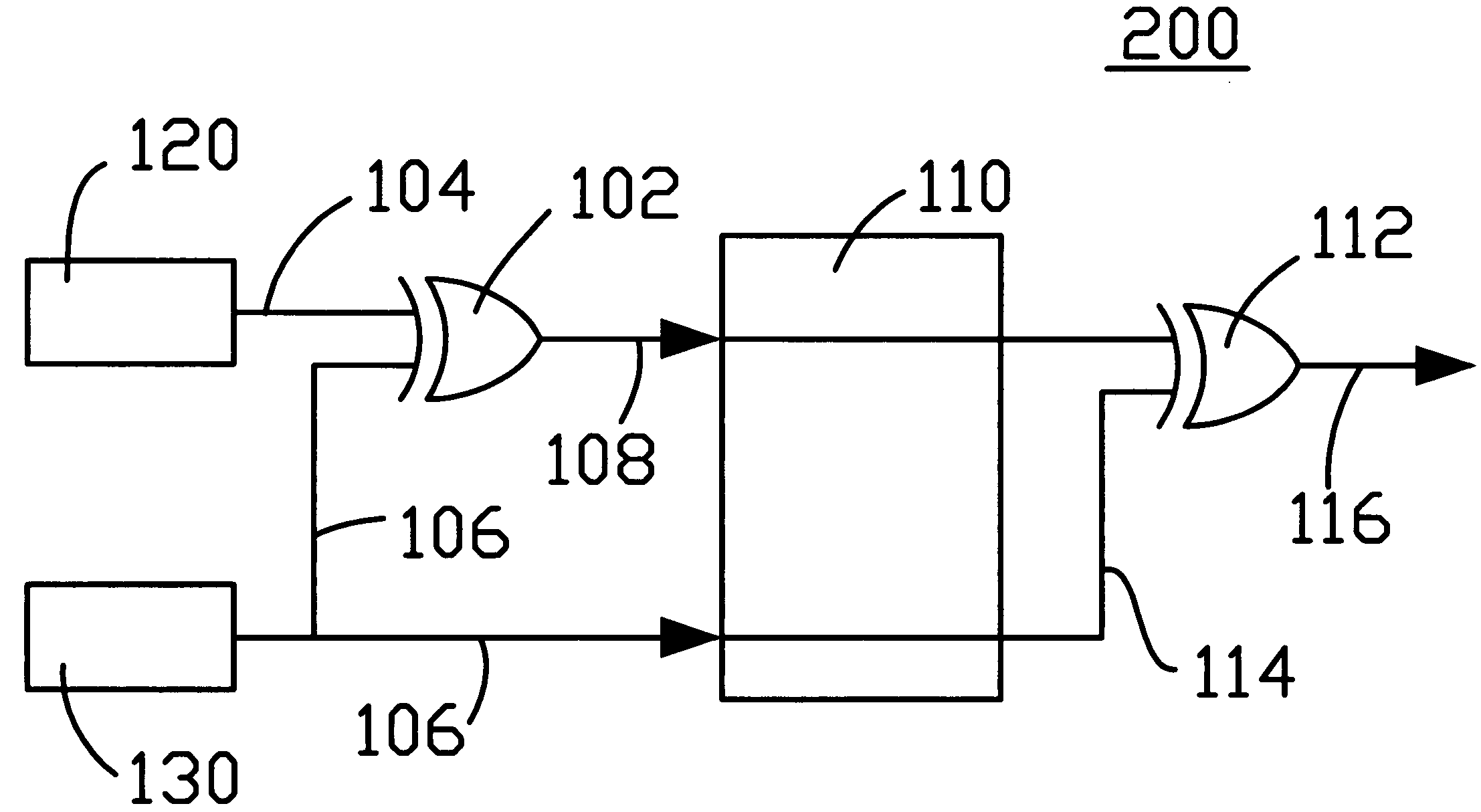
Power consumption stabilization system & method
InactiveUS20050078016A1Reduce maximum power consumptionLimiting designReliability increasing modificationsCode conversionNumber generatorComputer science
A source signal is provided. The source signal is XORed with a scrambling random signal to generate a scrambled signal. The scrambled signal is transmitted through the digital logic circuit. The scrambled signal is XORed with the descrambling random signal logically identical to the scrambling random signal to produce a descrambled signal identical to the source signal. In one embodiment, the scrambling random signal is transmitted through the digital logic circuit and used as the descrambling random signal. In another embodiment, the scrambling random signal and descrambling random signal are generated independently using pseudo-random number generators. In yet another embodiment, the scrambling random signal is self-synchronizing and is contained within the pattern of the scrambled signal.
Owner:AGILENT TECH INC
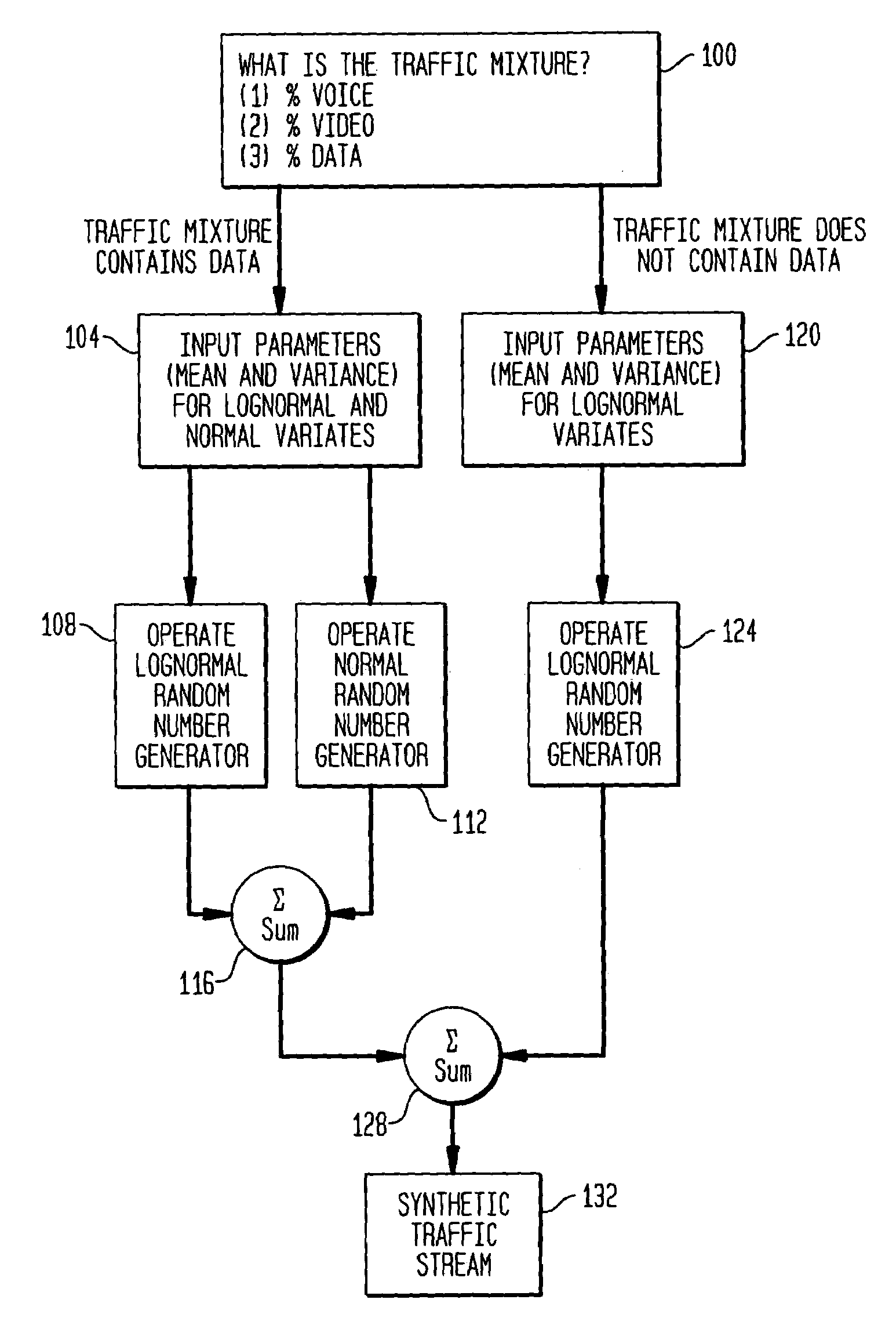
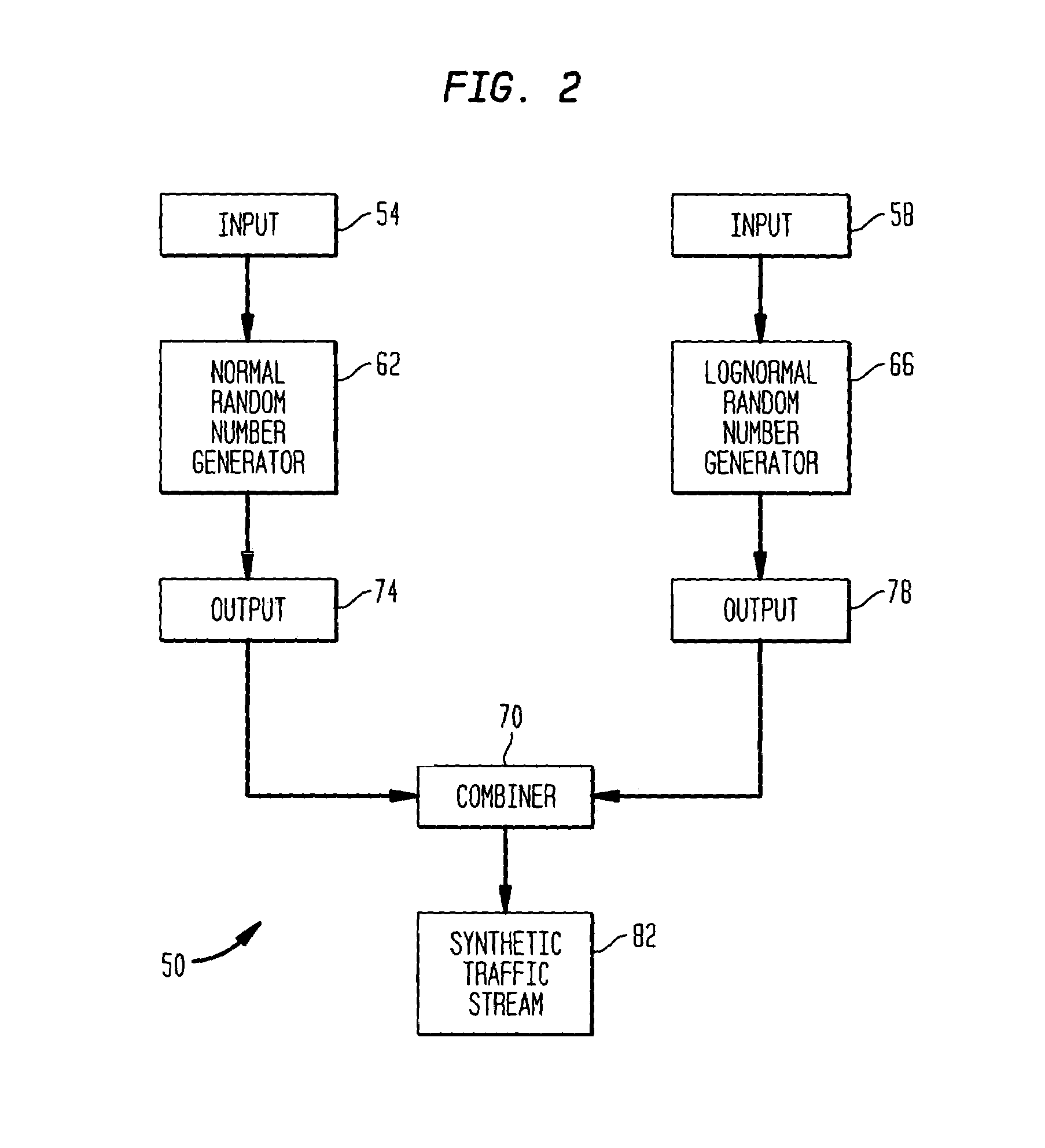
Traffic simulation algorithm for asynchronous transfer mode networks
InactiveUS7013255B1The effect is accurateAnalogue computers for electric apparatusDigital computer detailsTraffic capacityNetwork packet
The present invention is directed to a traffic simulation algorithm for an asynchronous transfer mode communications (ATM) network. The algorithm recognizes that packets in ATM networks can have interarrival times that are lognormally distributed or lognormally and normally distributed. Lognormal and, in some cases, normal random number generators are used to generate packet interarrival times of a synthetic traffic stream.
Owner:AVAYA INC
Radio frequency identification bidirectional authentication method based on hash function
InactiveCN103020671AUser identity/authority verificationCo-operative working arrangementsData synchronizationHash function
The invention provides a radio frequency identification bidirectional authentication method based on hash function. The mutual verification of identify between a tag and a reader is specifically as follows: the pre-allocated and stored tag information or shared information is read and verified by a rear-end system, the local time of the rear-end system is used as the identification tag information shared with the tag, the initial value is allocated to each tag by a rear-end database system, and the subsequent change is updated by the rear-end system according to the local system time of the tag in each verification process; the rear-end system stores the mark information and associated information of the tag and carries out hash calculation in each verification process; and the RFID (radio frequency identification) tag comprises a pseudo-random number generator, and carries out hash calculation and xor logic calculation. The method has excellent safety and privacy protection characteristic, and can protect content privacy and position privacy, resist replay attach, attach of denial of service and data synchronization attach and prevent fake.
Owner:NANJING UNIV OF POSTS & TELECOMM
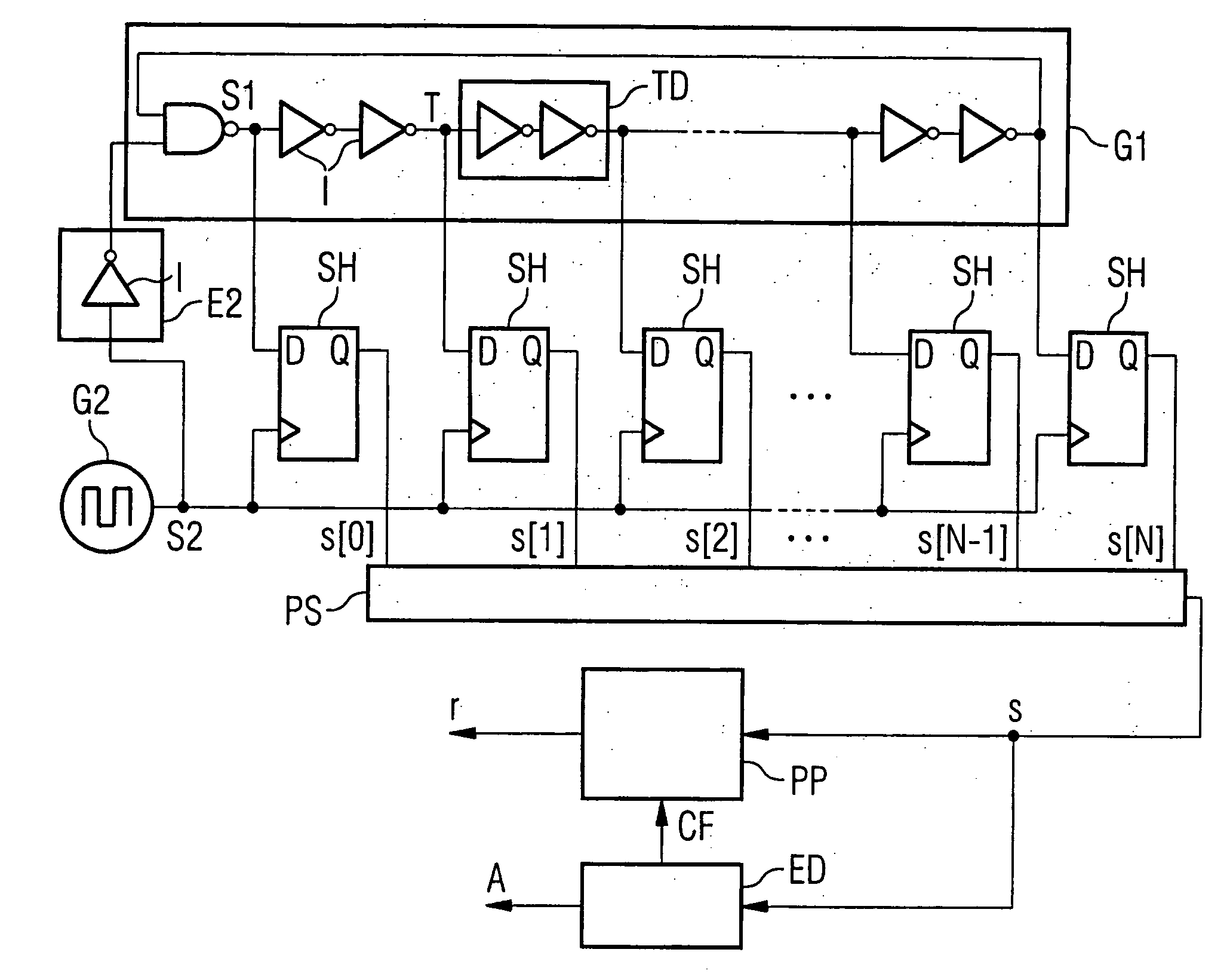
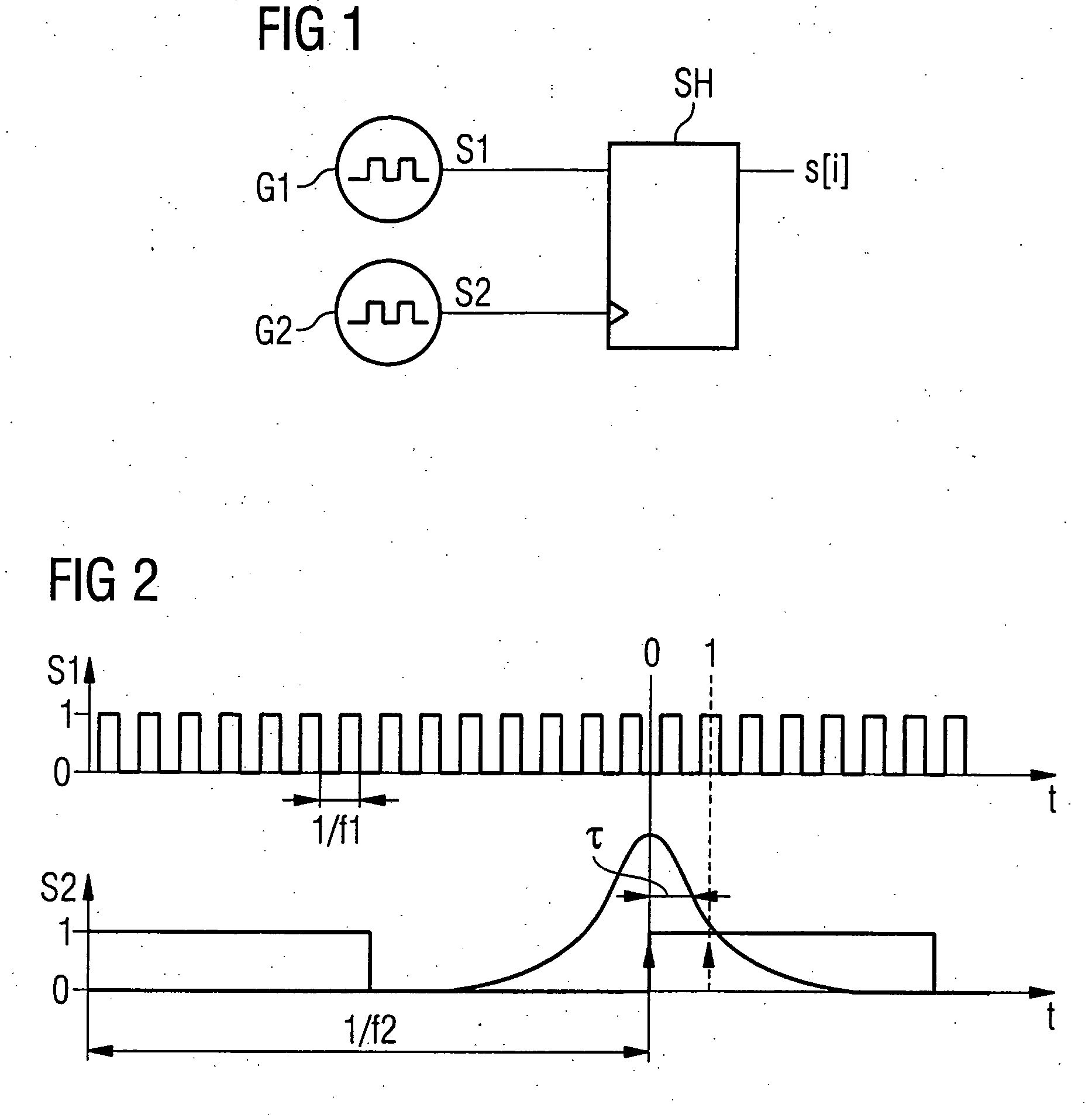
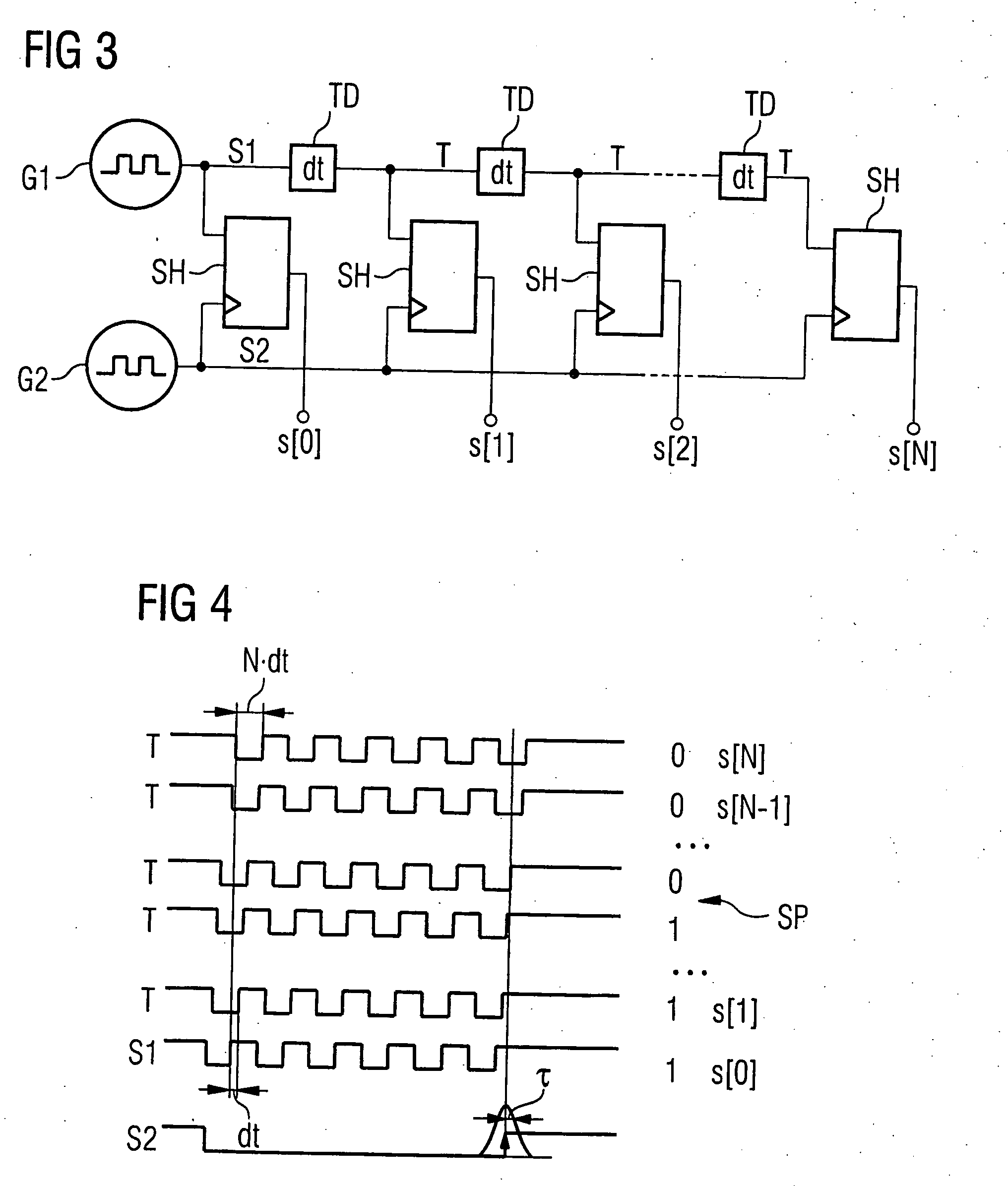
Random number generator and method for generating random numbers
ActiveUS20060173943A1Improved random stream qualityLow design costRandom number generatorsForms/shuttering/falseworksTime delaysNumber generator
Random number generator including a first signal source outputting a first signal having a first frequency, a second signal source outputting a second signal having a second frequency which is lower than the first frequency, and time delay elements, wherein the output signals are delayed by a time interval with respect to the input signal. The output of one time delay element is connected in series to the input of another time delay element. The input of the first time delay element is connected to the output of the first signal source. The output of the first signal source and the output of each of the time delay elements are connected to the data input of a corresponding sample and hold element. Clock signal inputs of the sample and hold elements are each connected to the output of the second signal source. Outputs of the sample and hold elements provide random values.
Owner:INFINEON TECH AG
Pseudo-random number generator
InactiveUS20050044119A1Random number generatorsDigital function generatorsTransition matricesPredictability
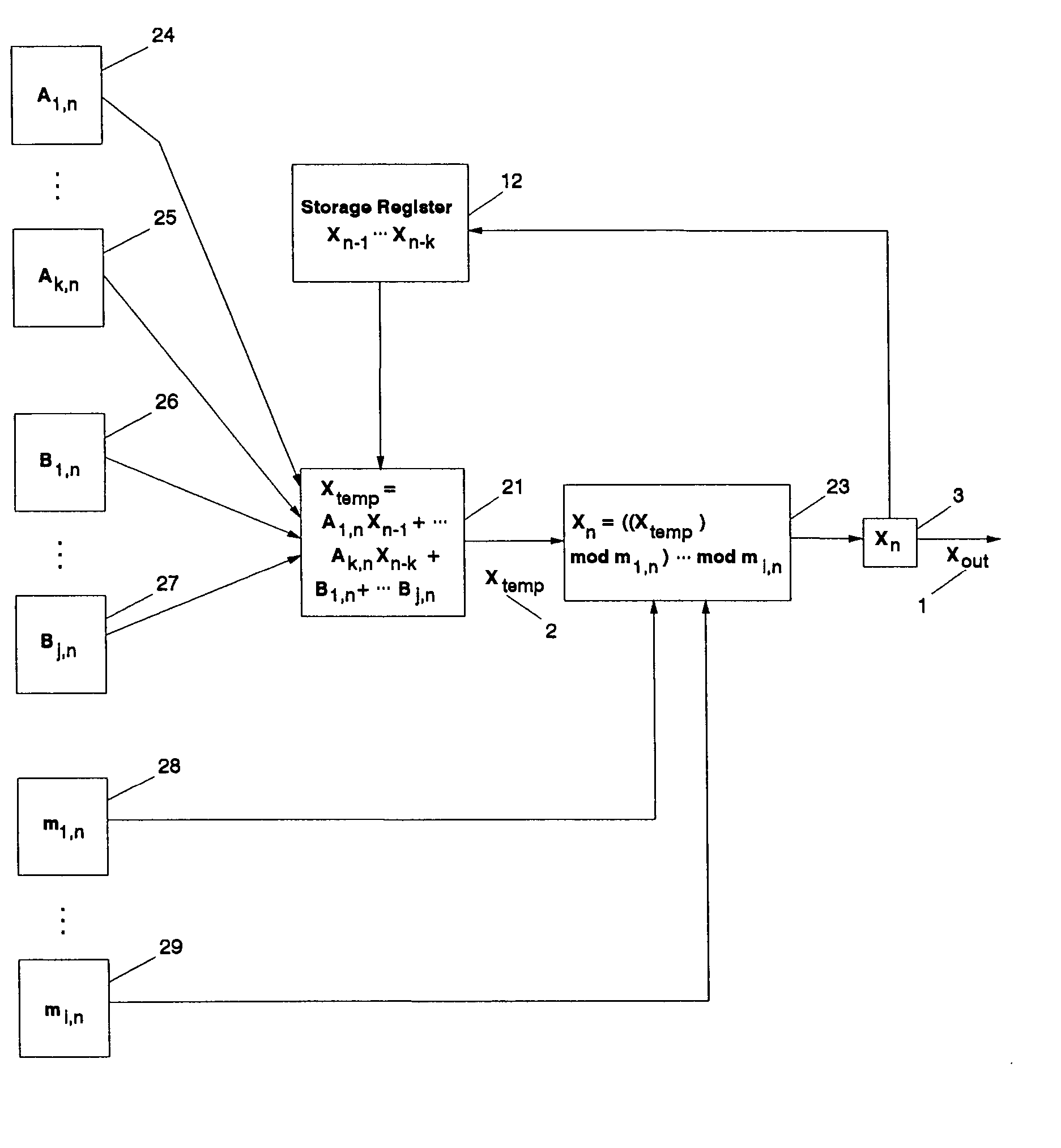
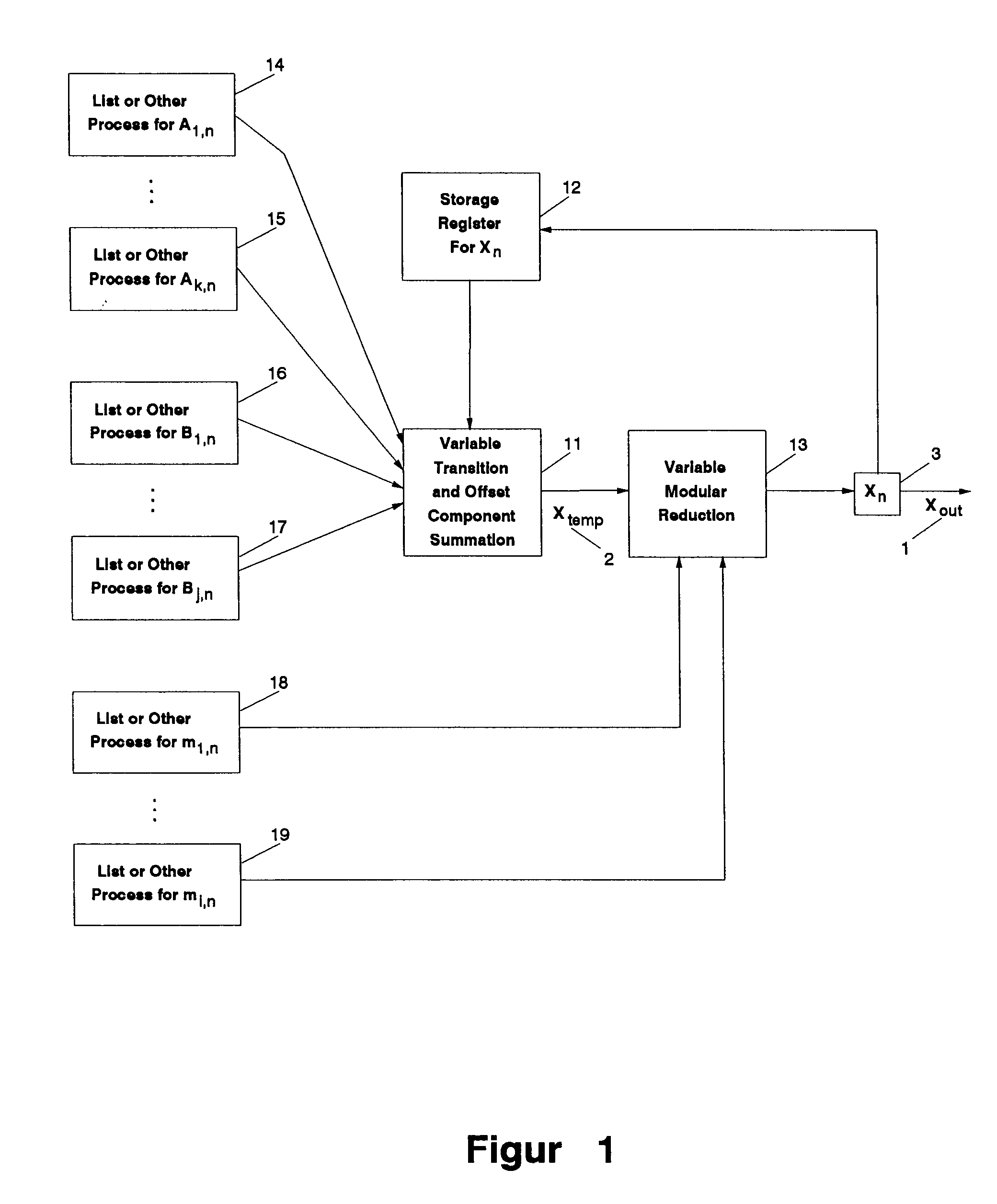
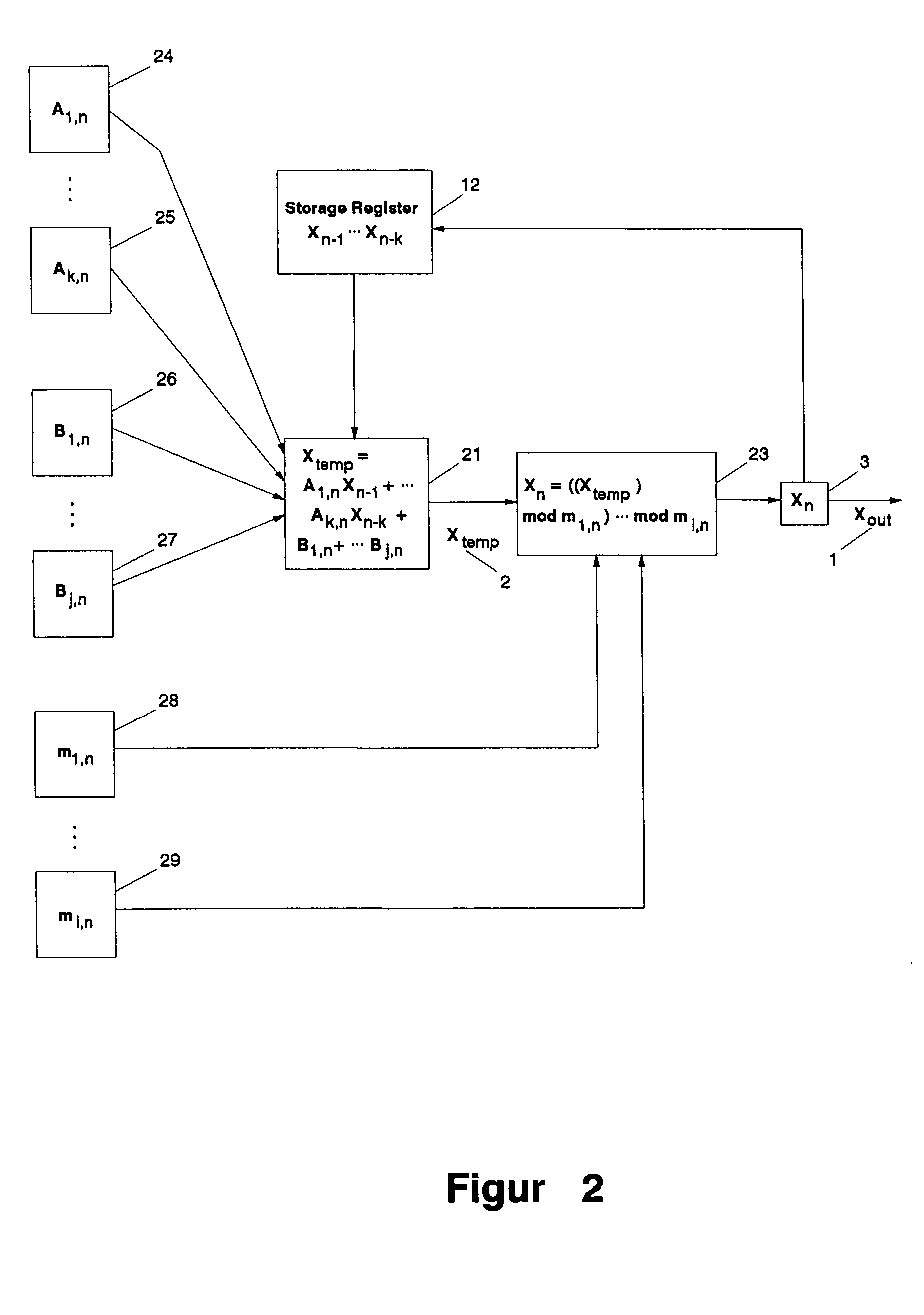
The present invention provides a method and an apparatus for generating pseudo-random numbers with very long periods and very low predictability. A seed random sequence is extended into a much longer sequence by successive iterations of matrix operations. Matrices of candidate output values are multiplied by non-constant transition matrices and summed with non-constant offset matrices; the result is then processed through one or more modulus operations, including non-constant modulus operators, to generate the actual output values. The invention also includes the possibility of introducing non-invertible matrices into the operations. The invention creates final results that are equidistributed over large samples. Secondary pseudo-random and other processes determine the non-constant transition matrices, offset matrices, and modulus operators.
Owner:LANGIN HOOPER JERRY JOE +1
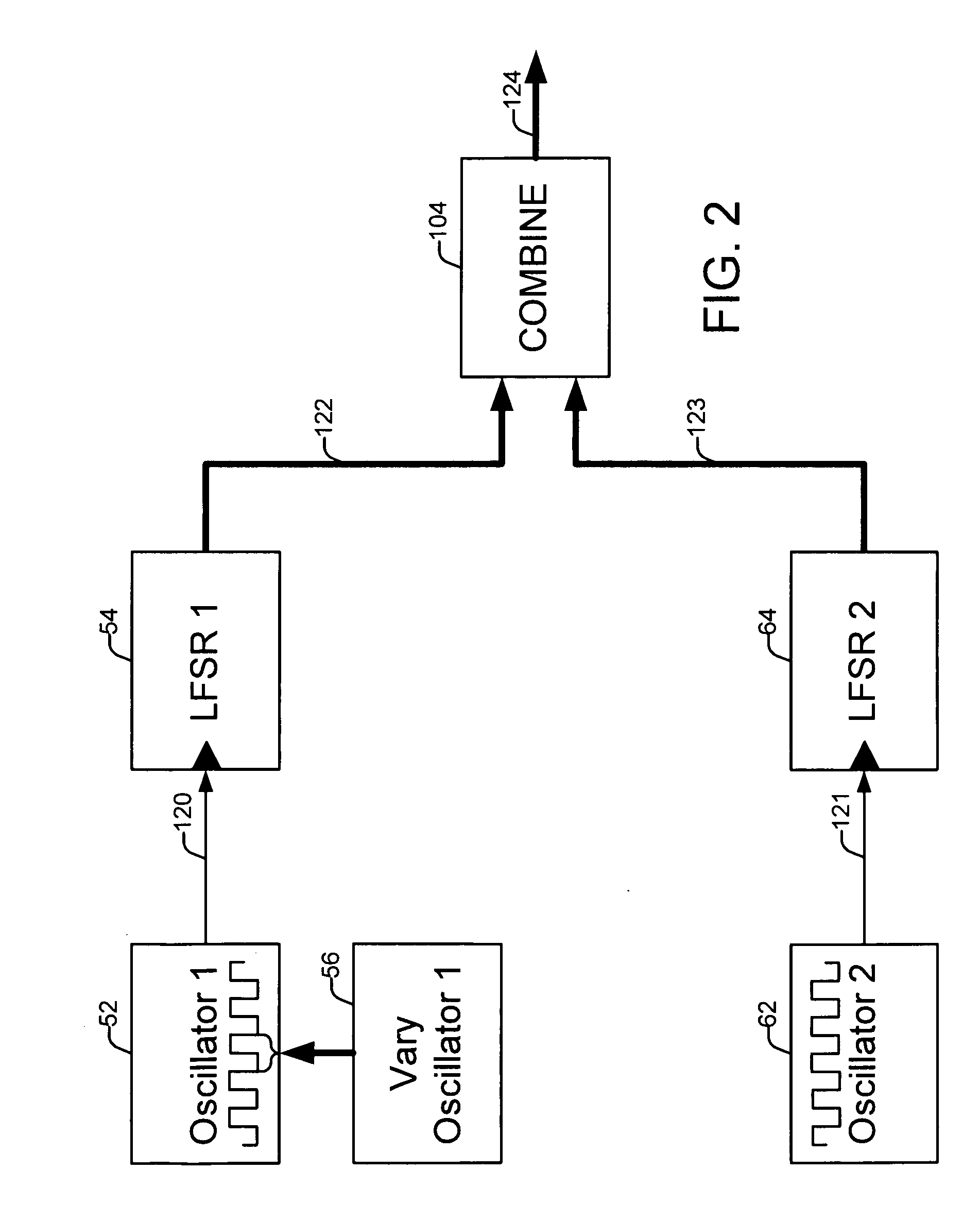
True random number generator
ActiveUS20090248771A1Random number generatorsSecuring communicationEngineeringPseudorandom number generator
True random number generation circuitry utilizes a pair of oscillators driving a pair of linear feedback shift registers, with their output being combined to generate random numbers. At least one of the oscillators is programmable with a variable frequency. One embodiment controls the variable frequency of oscillators with output from one or more sets of oscillators and linear feedback shift registers. In other embodiments, linear feedback shift register output is captured and used to control the frequency of oscillators.
Owner:ATMEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com