Patents
Literature
44 results about "Implicit certificate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
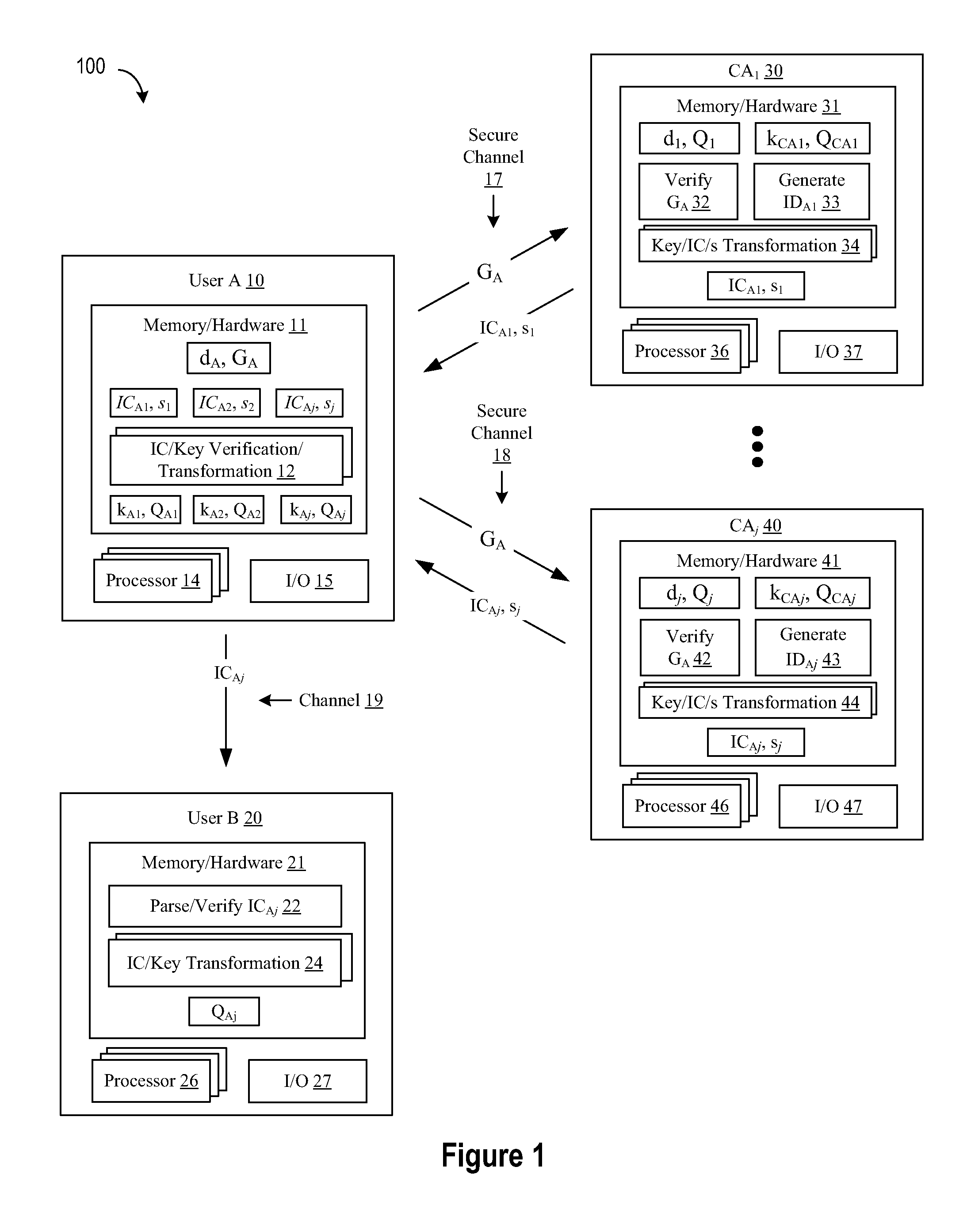
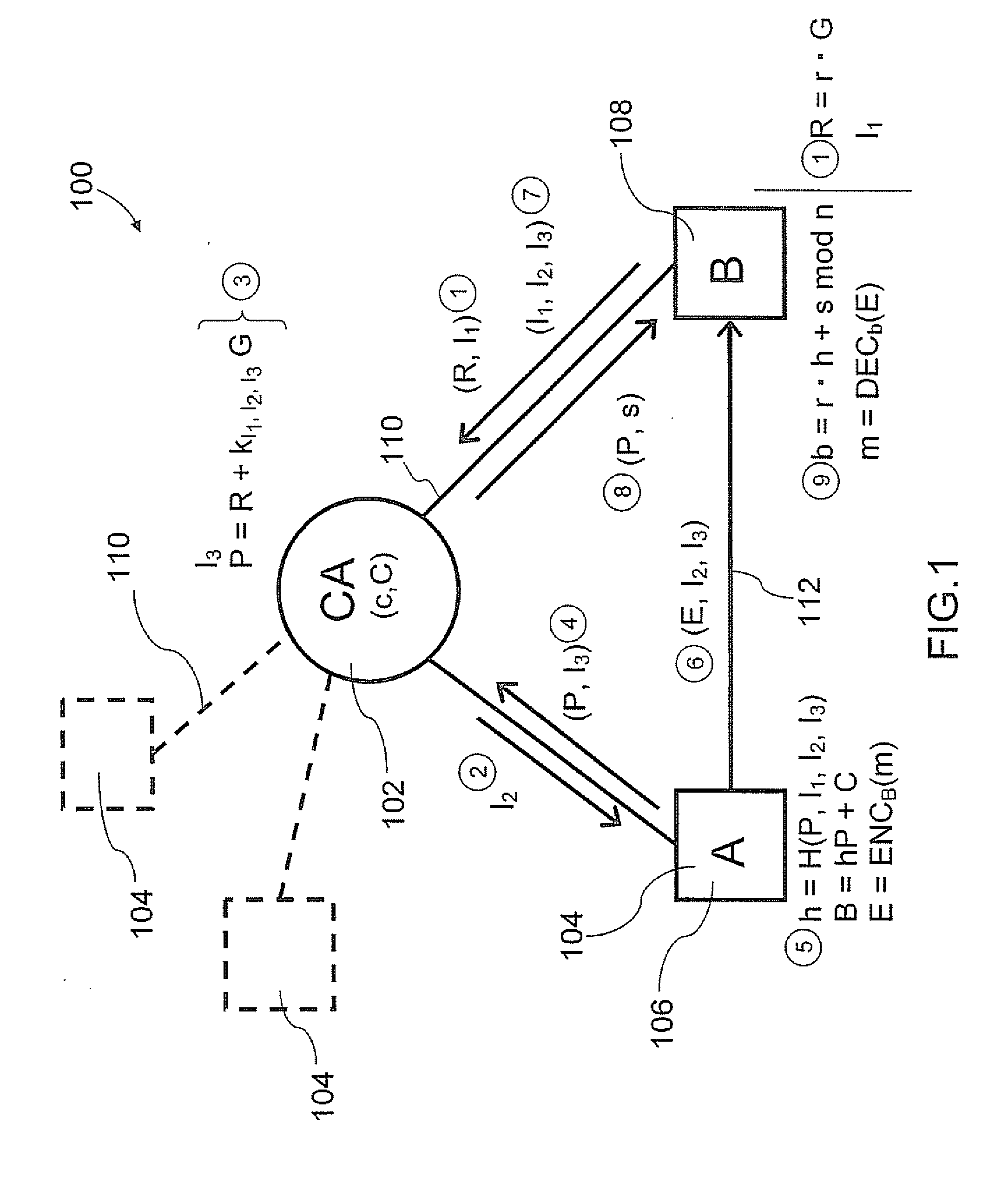
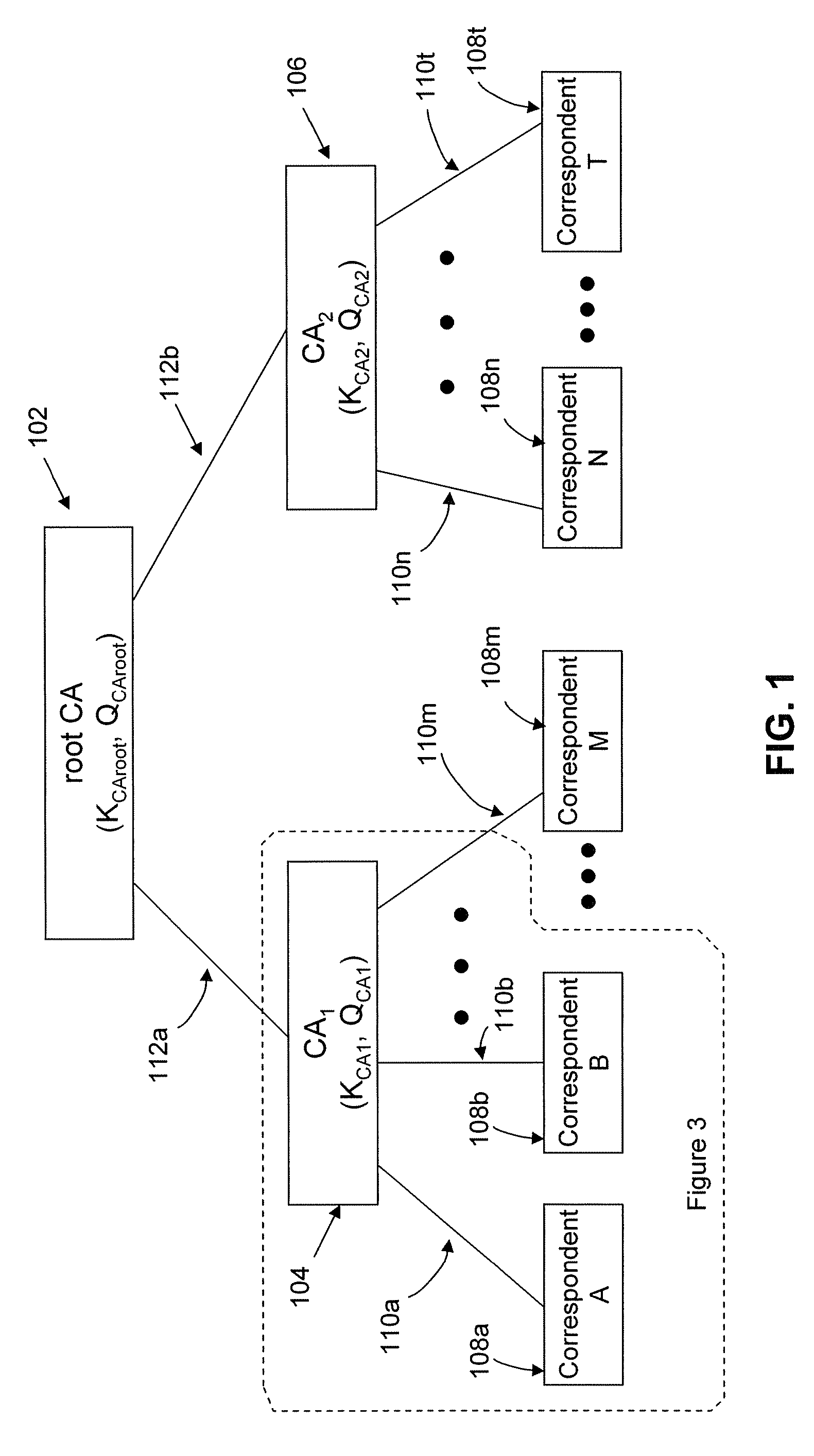
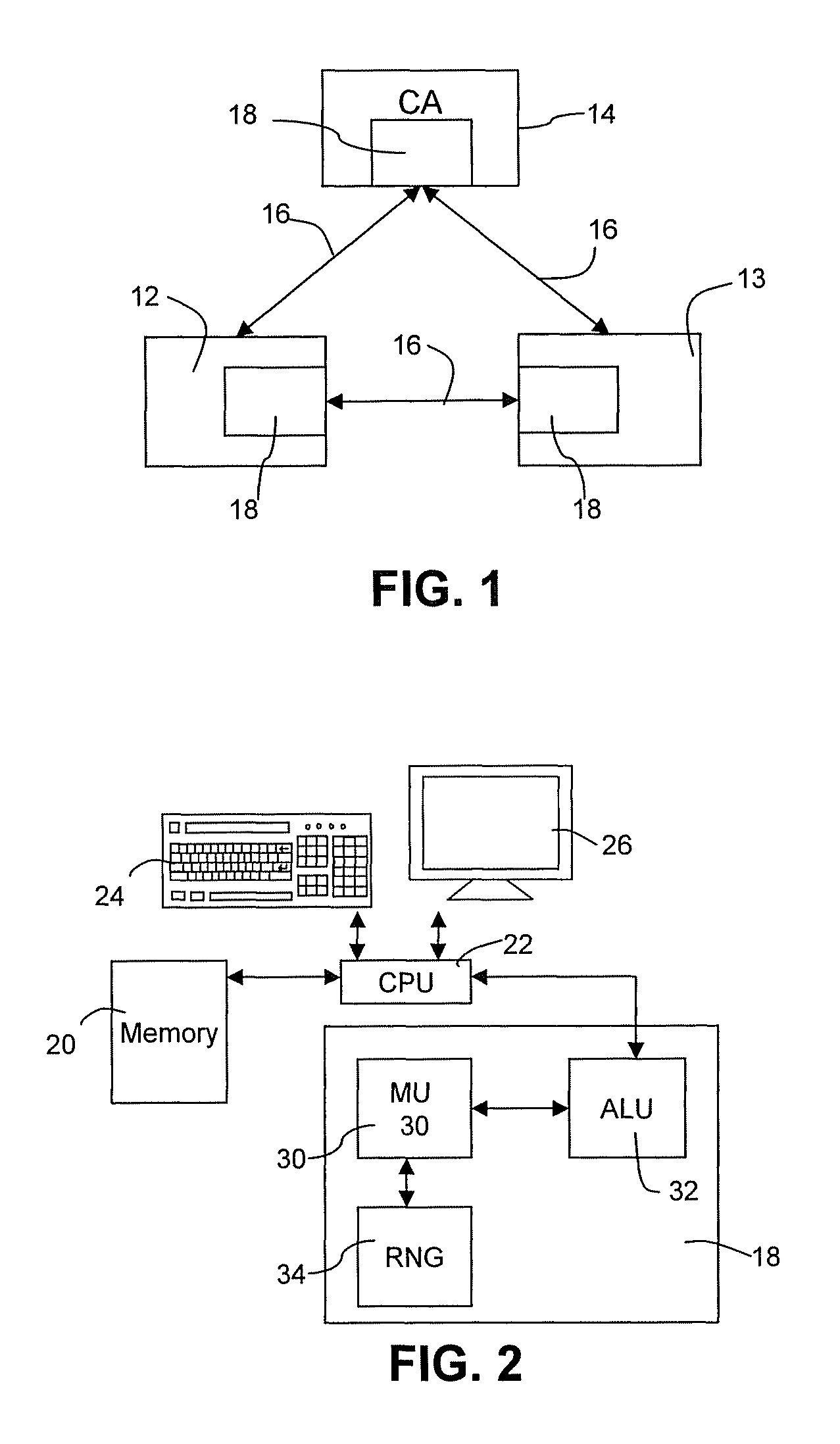
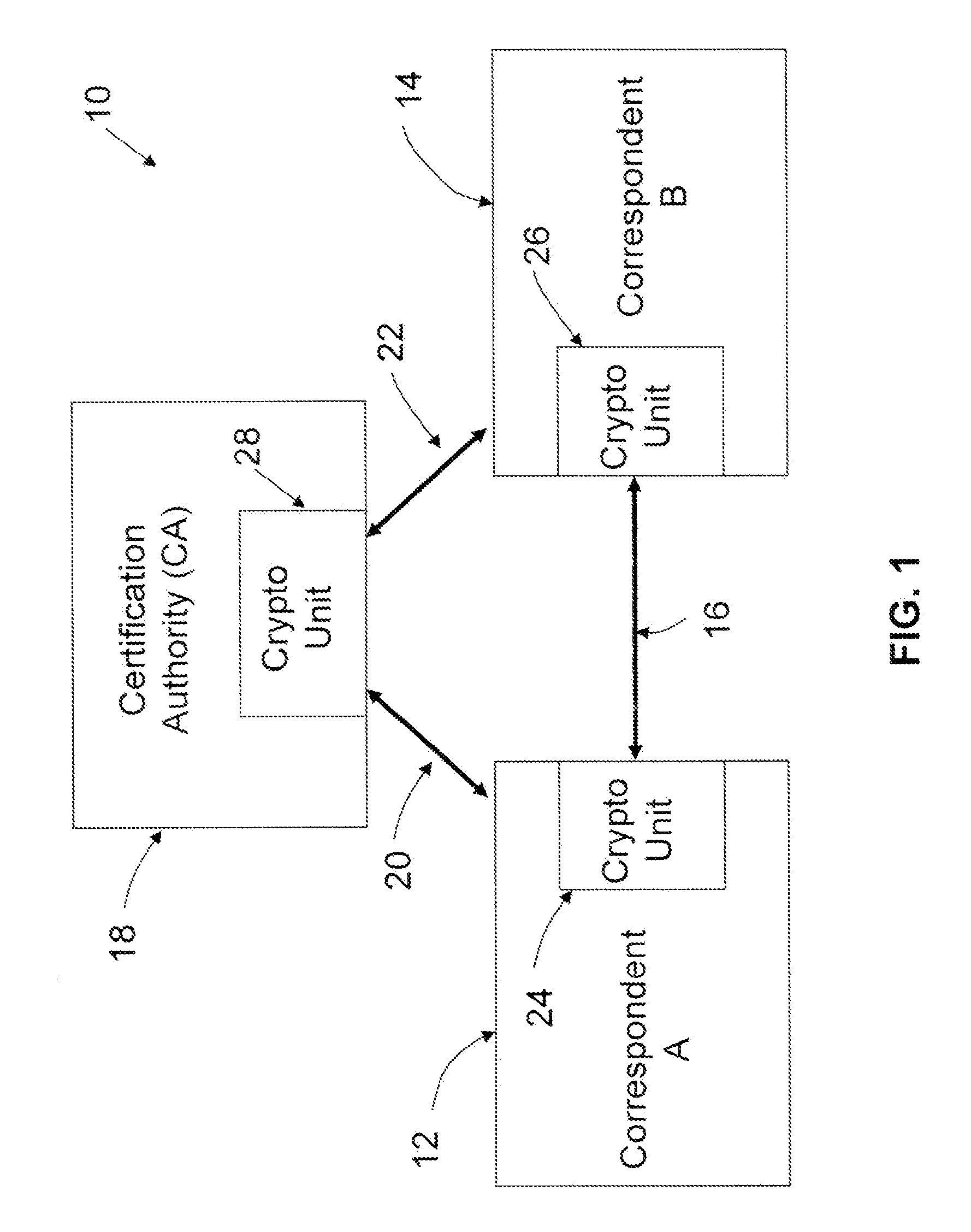
In cryptography, implicit certificates are a variant of public key certificate, such that a public key can be reconstructed from any implicit certificate, and is said then to be implicitly verified, in the sense that the only party who can know the associated private key is the party identified in the implicit certificate. This does not rule out the possibility that nobody knows the private key, but this possibility is not considered a major problem.
Implicit certificate verification
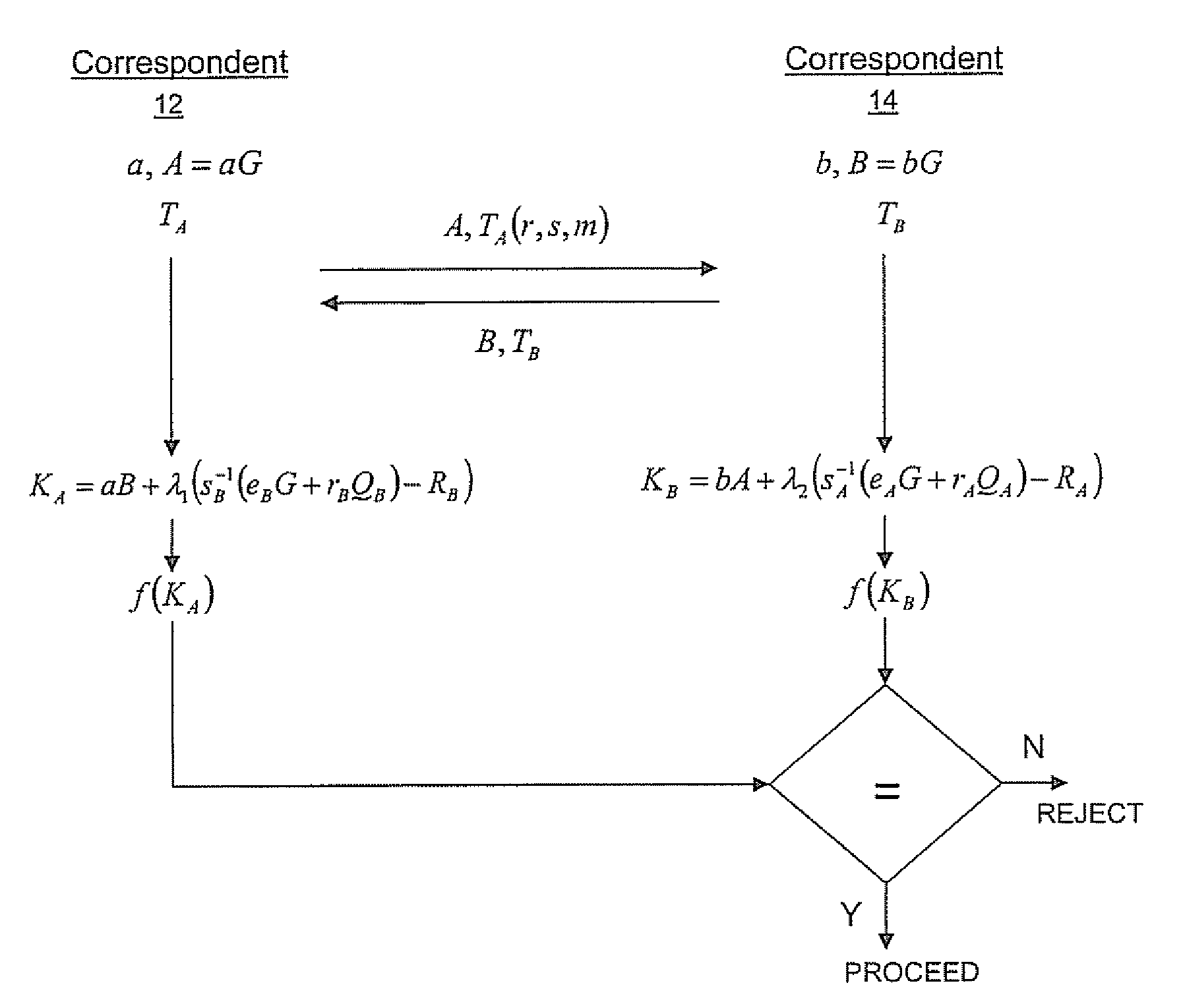
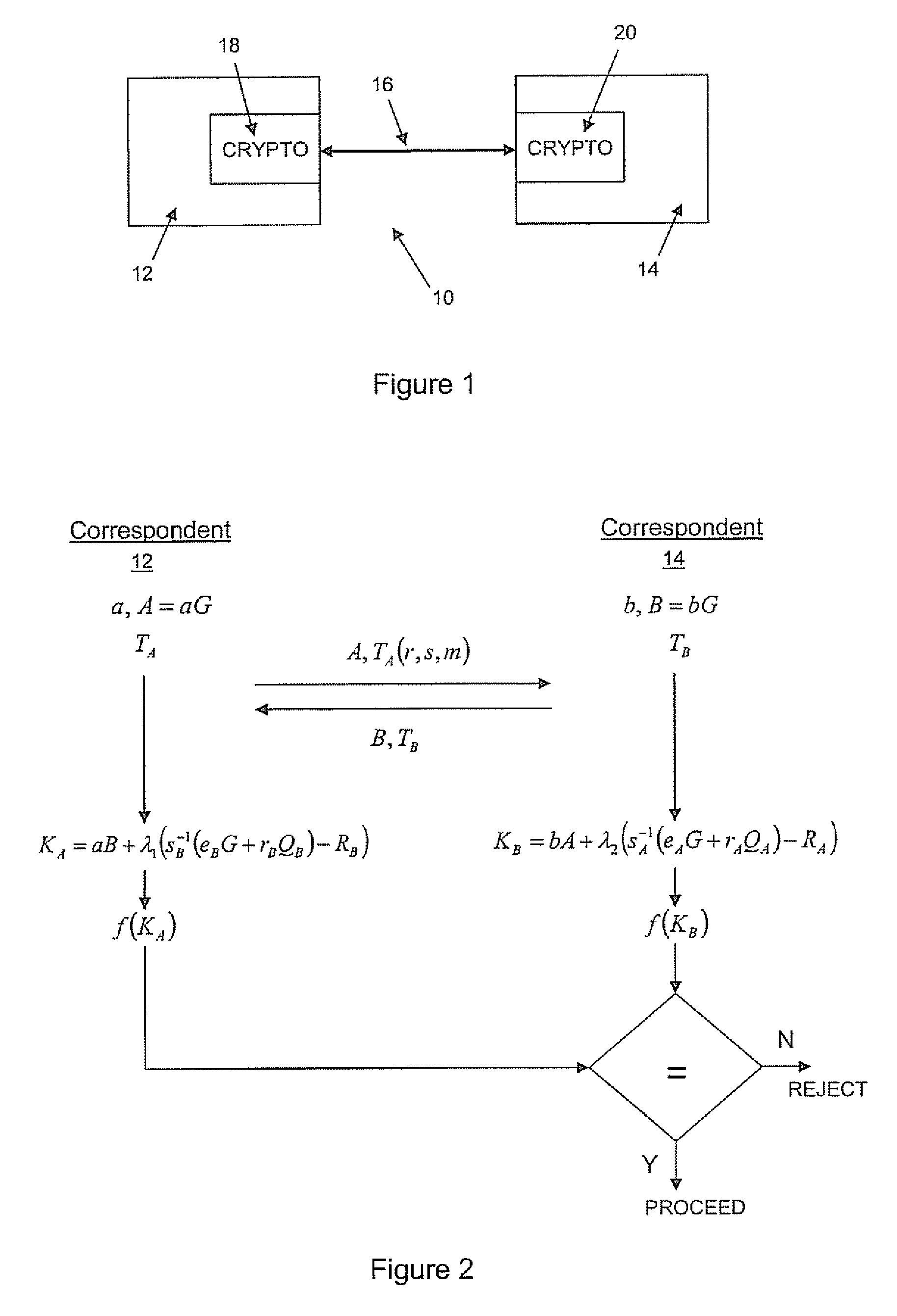
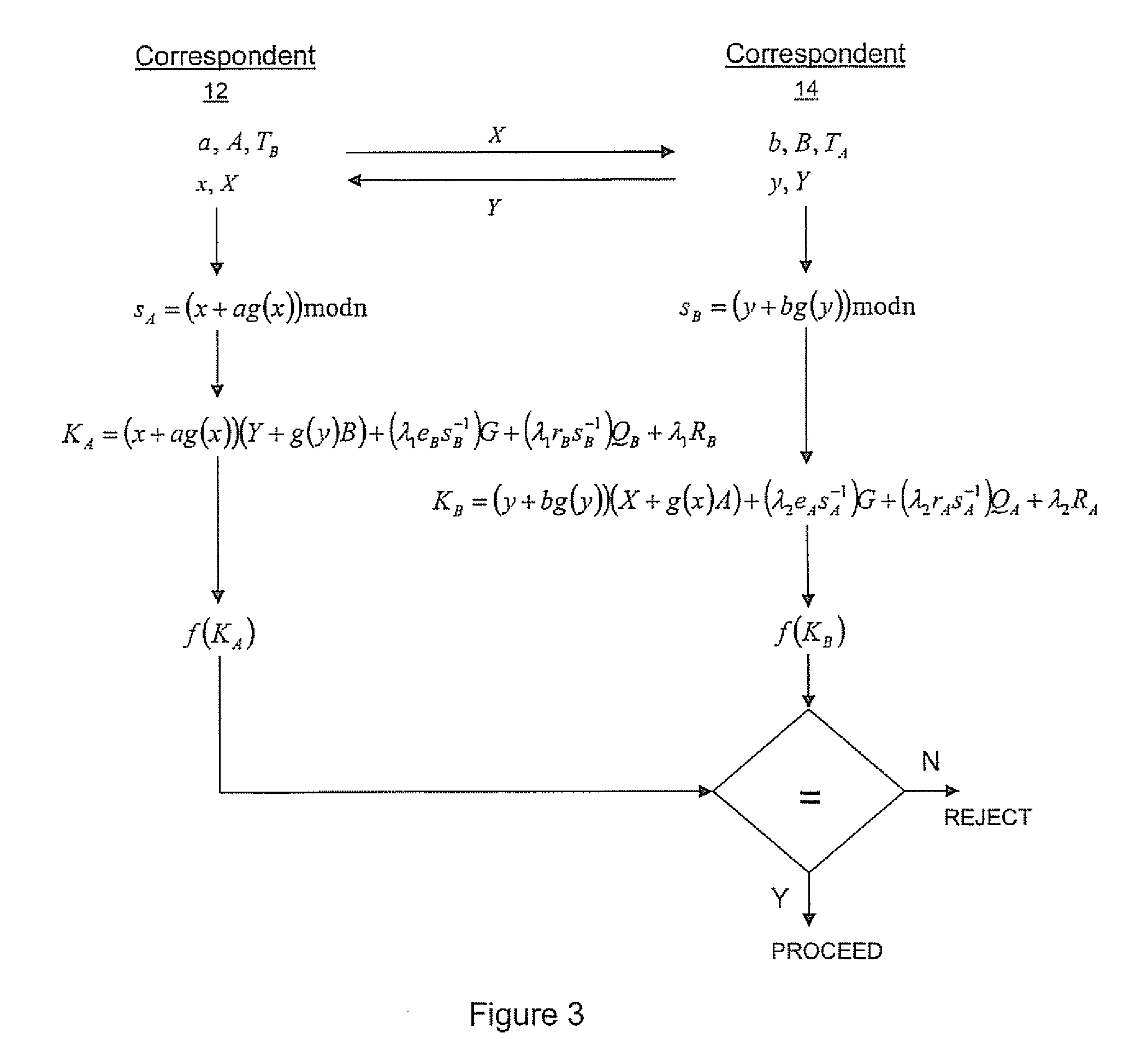
ActiveUS20100023771A1Heavy calculationPublic key for secure communicationDigital data processing detailsCryptographic key typesCryptographic nonce
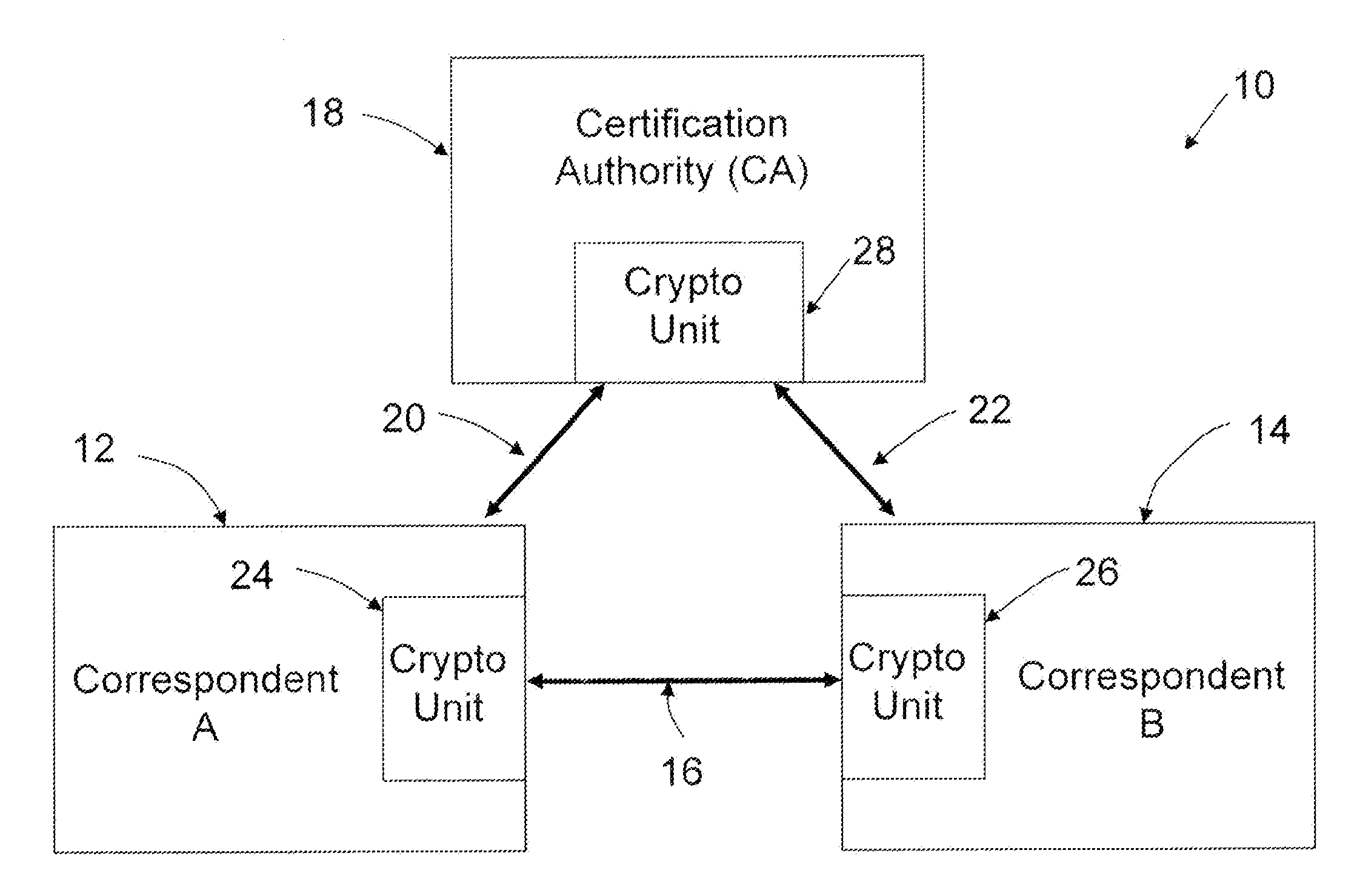
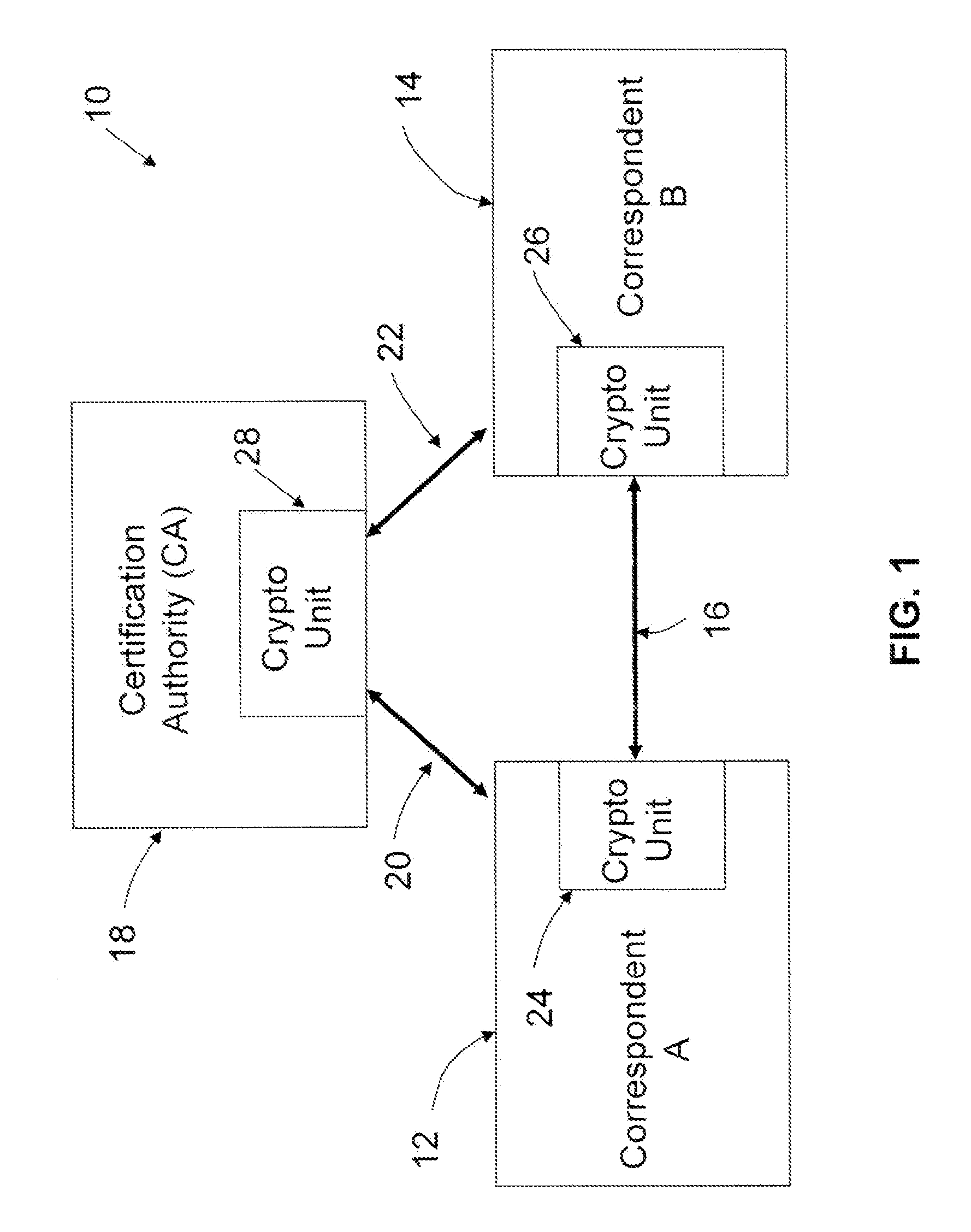
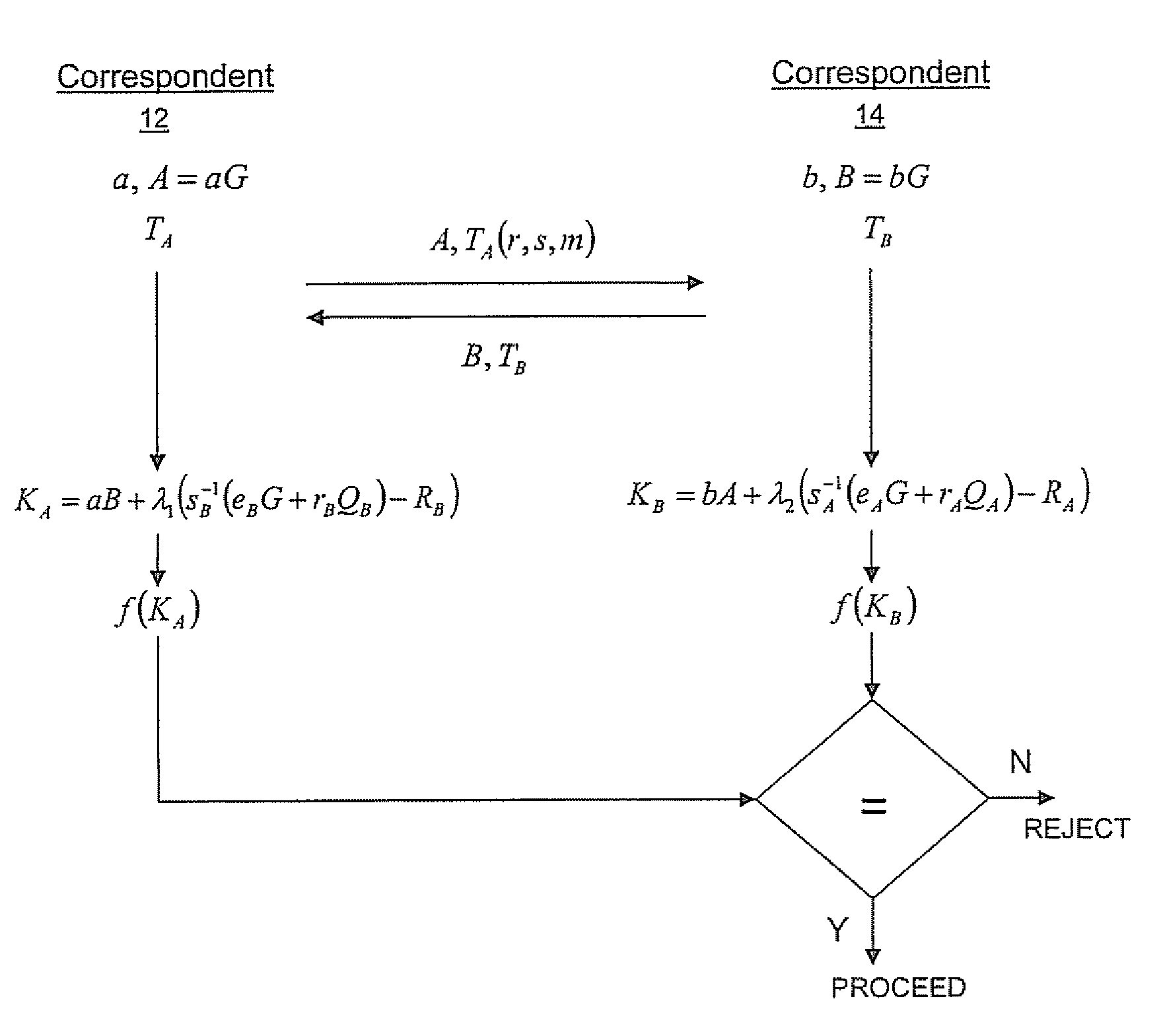
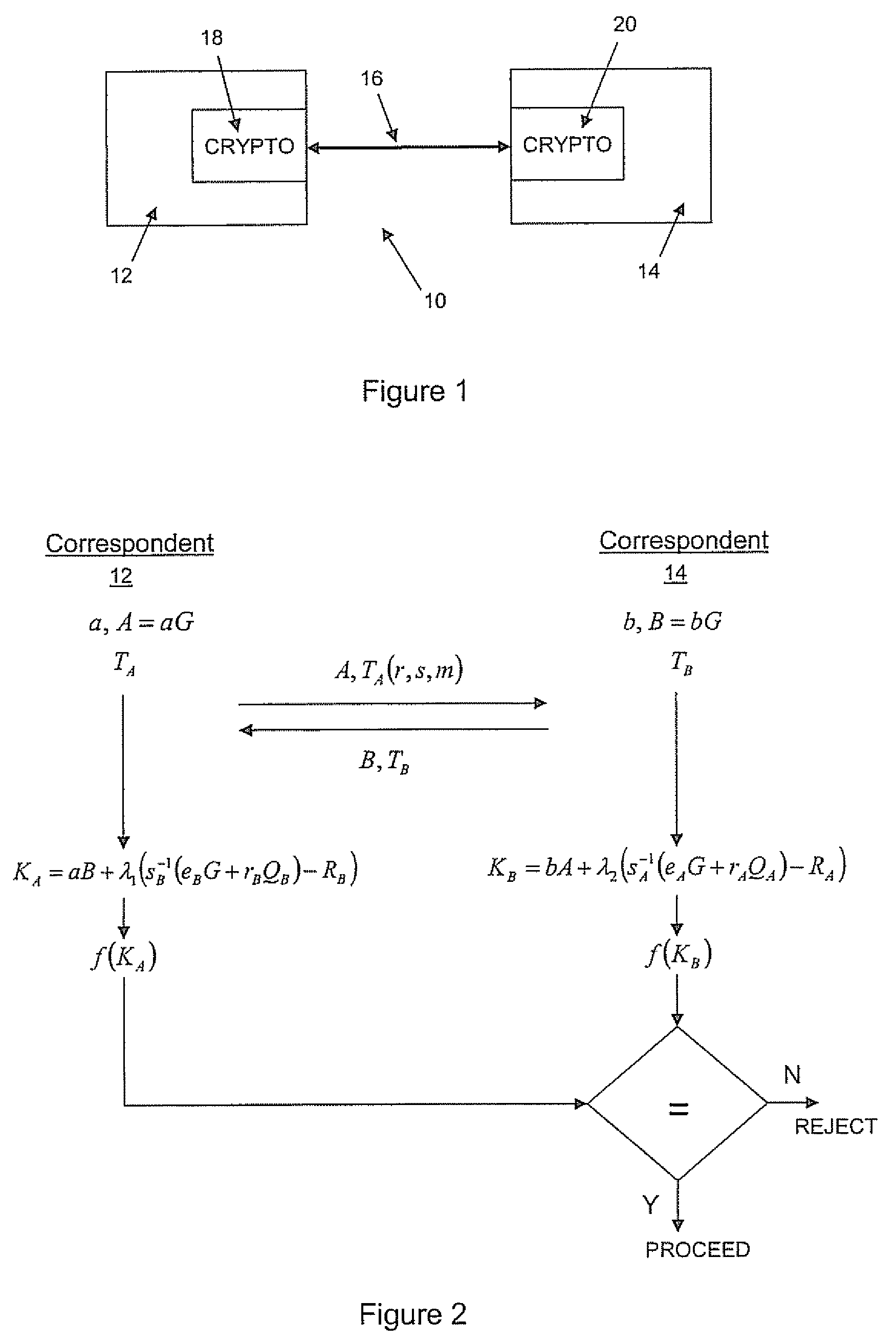
A method of computing a cryptographic key to be shared between a pair of correspondents communicating with one another through a cryptographic system is provided, where one of the correspondents receives a certificate of the other correspondents public key information to be combined with private key information of the one correspondent to generate the key. The method comprises the steps of computing the key by combining the public key information and the private key information and including in the computation a component corresponding to verification of the certificate, such that failure of the certificate to verify results in a key at the one corespondent that is different to the key computed at the other correspondent.
Owner:MALIKIE INNOVATIONS LTD
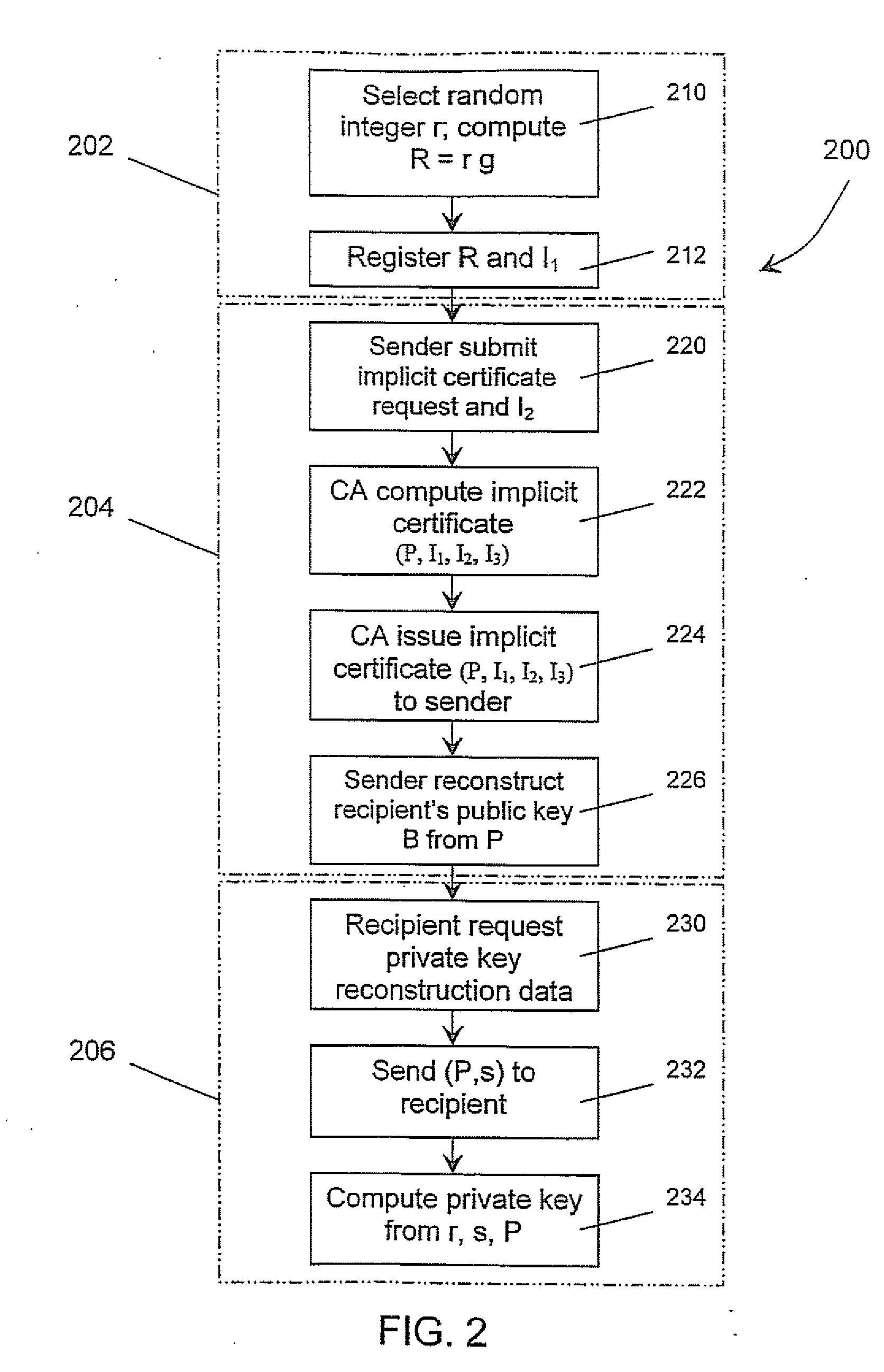
Using A Single Certificate Request to Generate Credentials with Multiple ECQV Certificates
A method and apparatus are disclosed for using a single credential request (e.g., registered public key or ECQV certificate) to obtain a plurality of credentials in a secure digital communication system having a plurality of trusted certificate authority CA entities and one or more subscriber entities A. In this way, entity A can be provisioned onto multiple PKI networks by leveraging a single registered public key or implicit certificate as a credential request to one or more CA entities to obtain additional credentials, where each additional credential can be used to derive additional public key-private key pairs for the entity A.
Owner:MALIKIE INNOVATIONS LTD
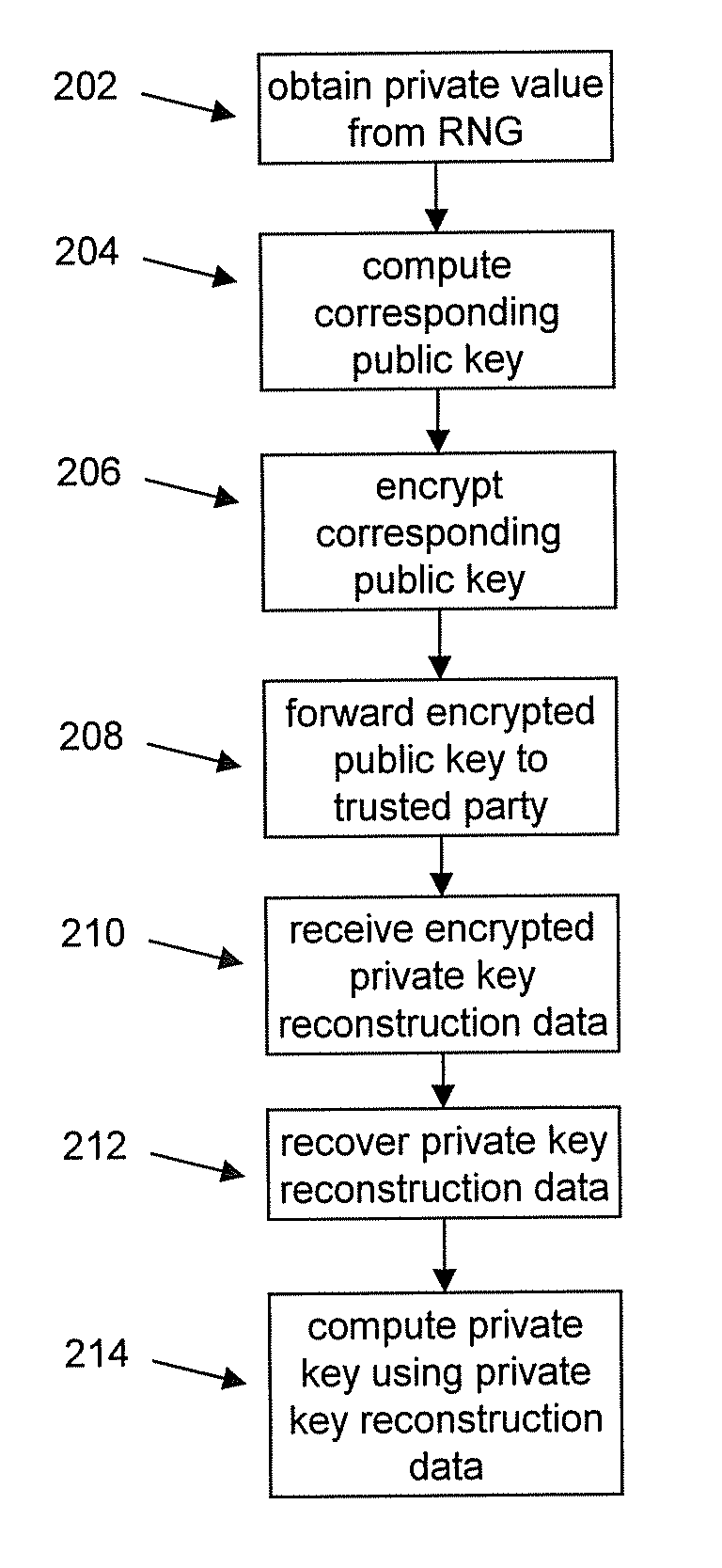
Masking the output of random number generators in key generation protocols
ActiveUS20110307698A1Key distribution for secure communicationPublic key for secure communicationDeterministic encryptionNumber generator
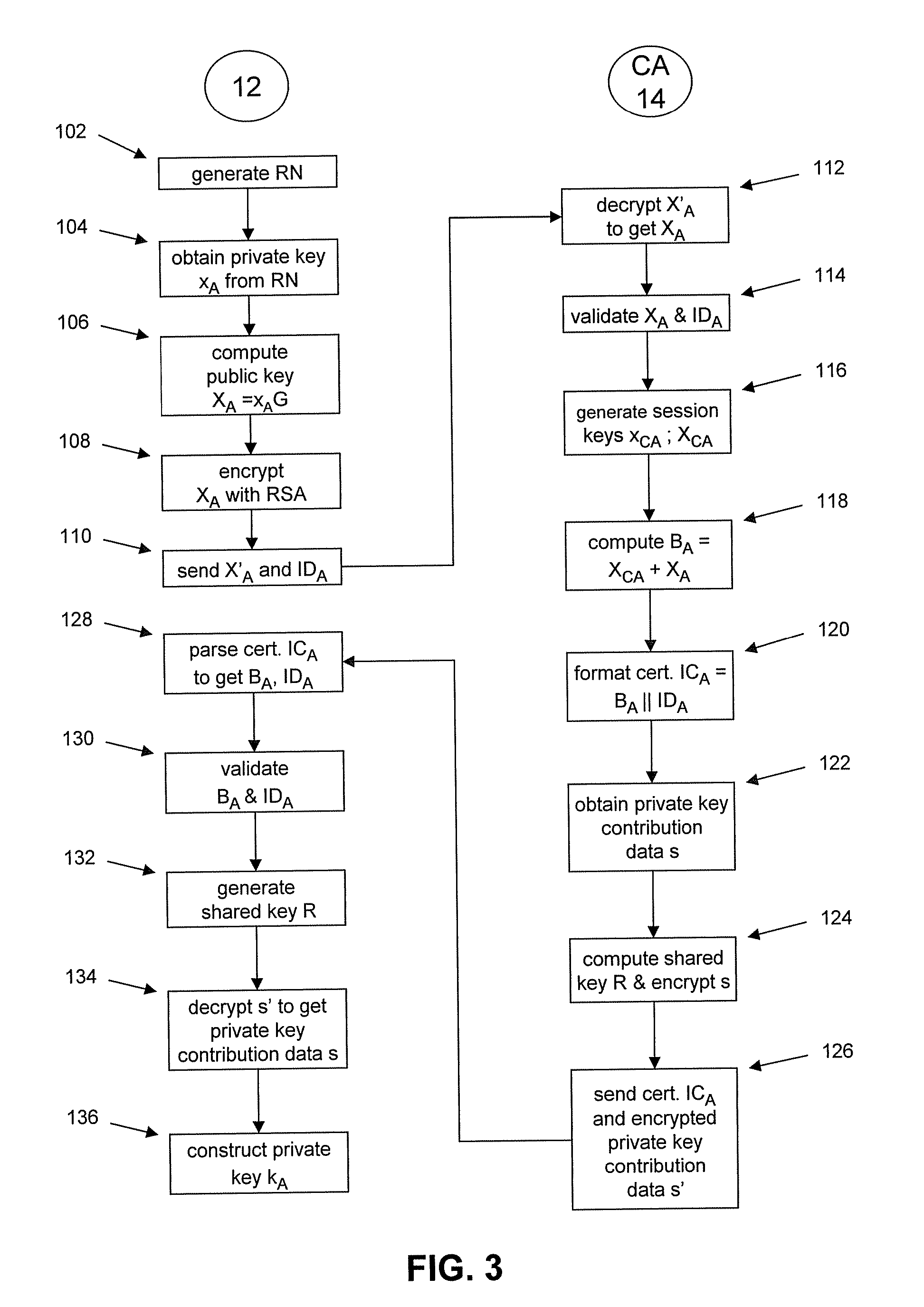
To mitigate the effects of a weak random number generator (RNG) in a public key cryptosystem, a public key obtained from the RNG is encrypted using a deterministic cryptographic scheme before being made publicly available. A trusted party receiving the encrypted public key can recover the public key and combine it with other information so it is not subject to direct scrutiny. In one embodiment, the trusted party incorporates the public key in a certificate, such as an implicit certificate, for use by the correspondents in other communications.
Owner:MALIKIE INNOVATIONS LTD
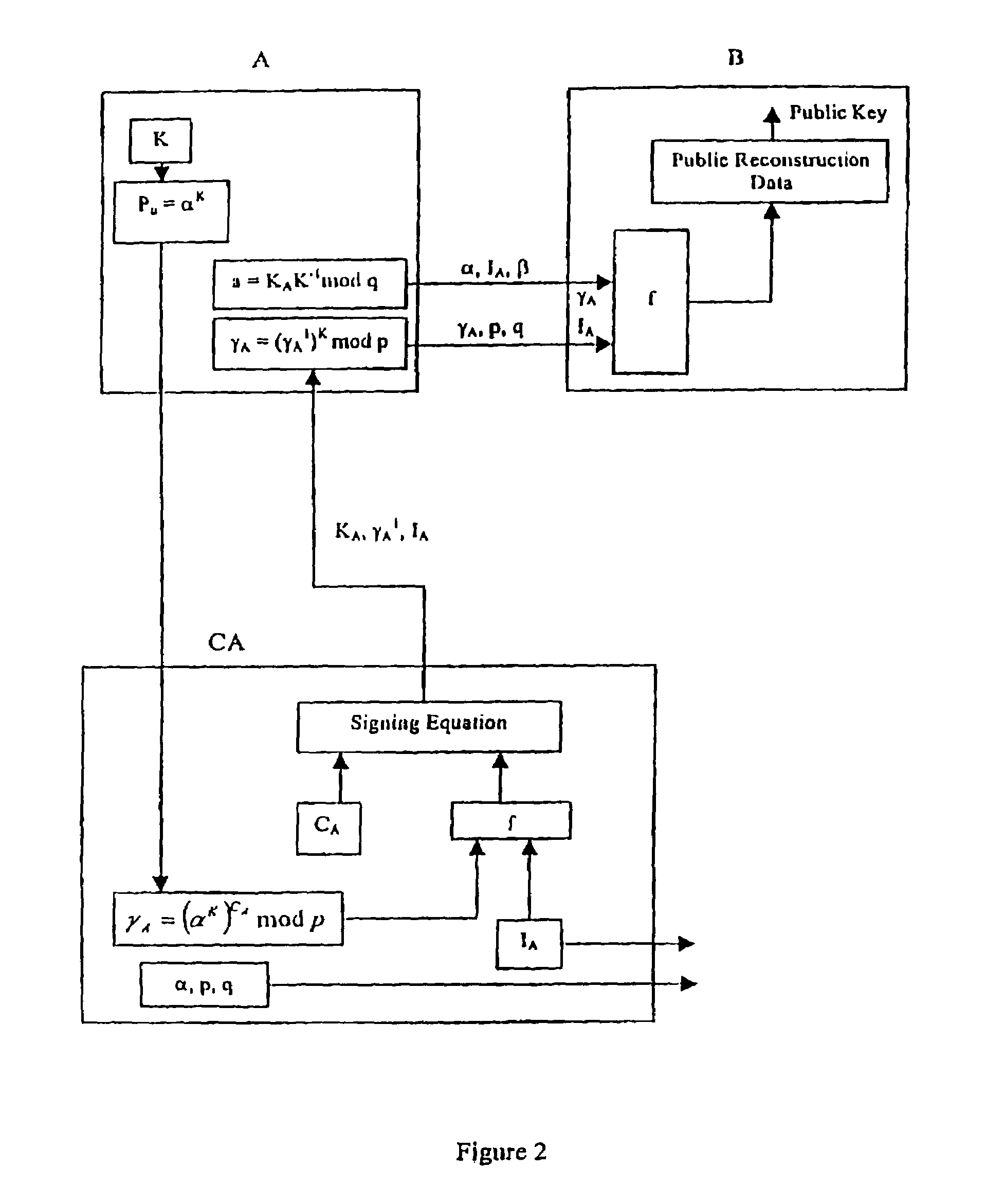
Implicit certificate scheme
InactiveUS20050114651A1Key distribution for secure communicationPublic key for secure communicationCommunications systemData entity
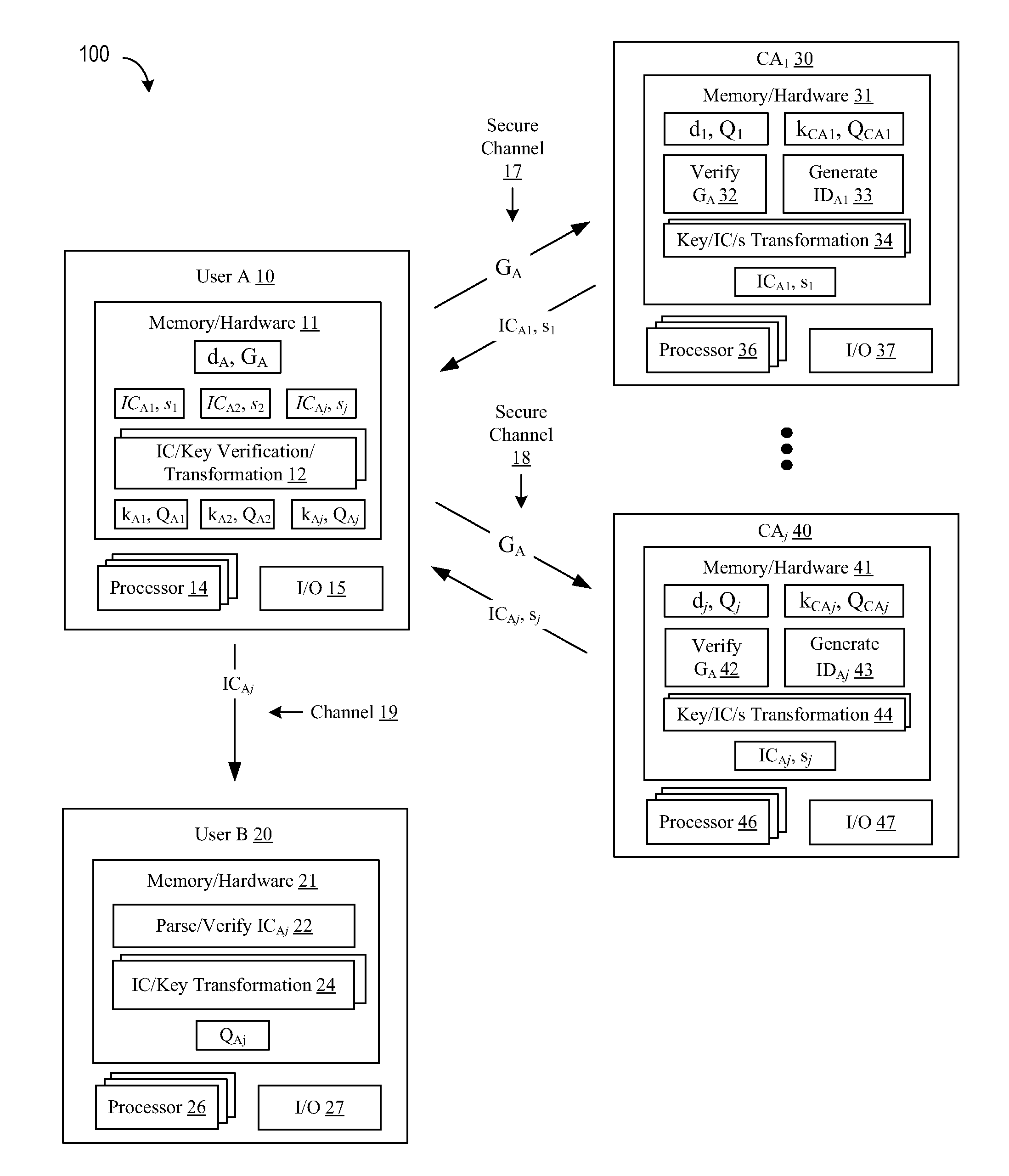
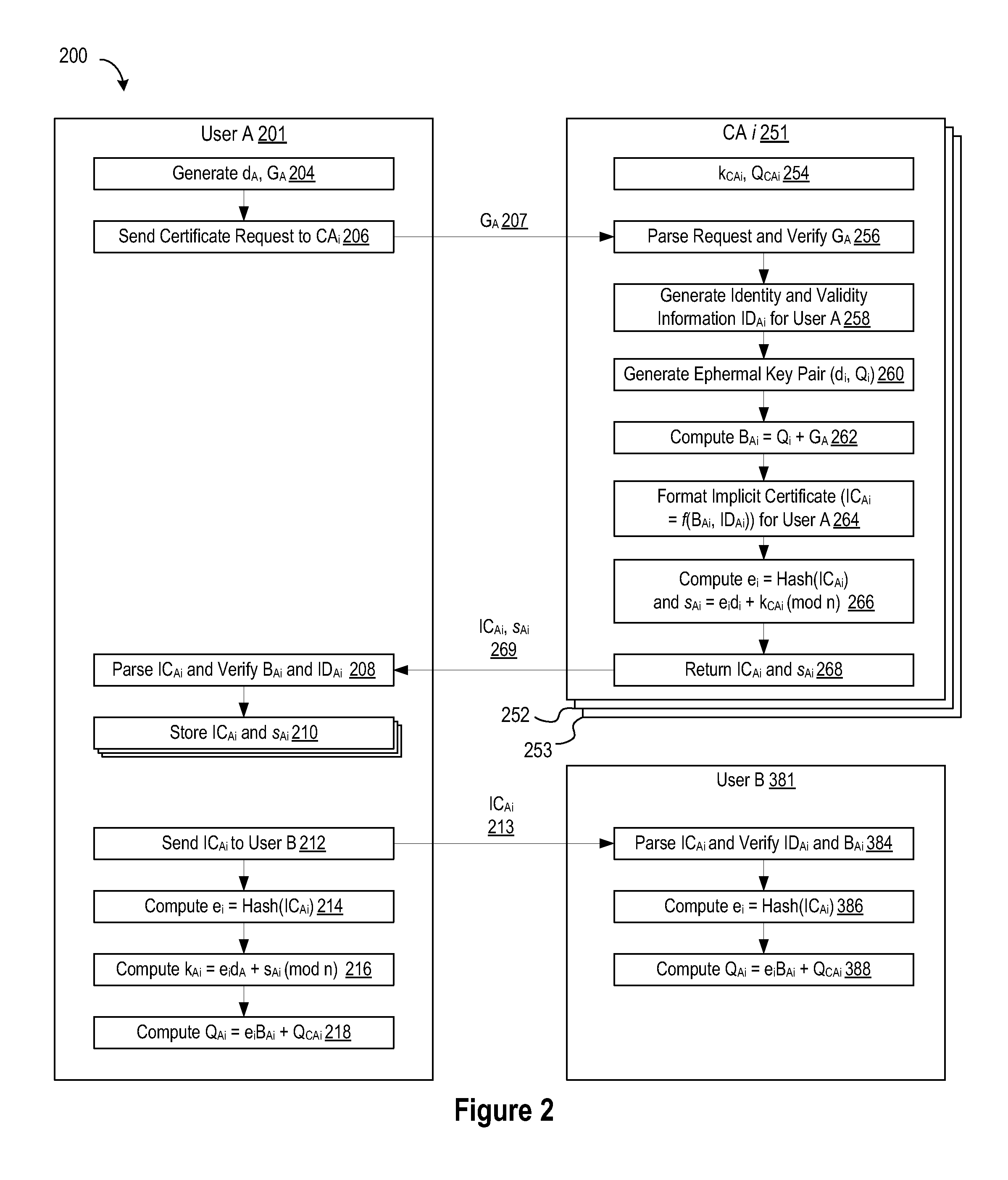
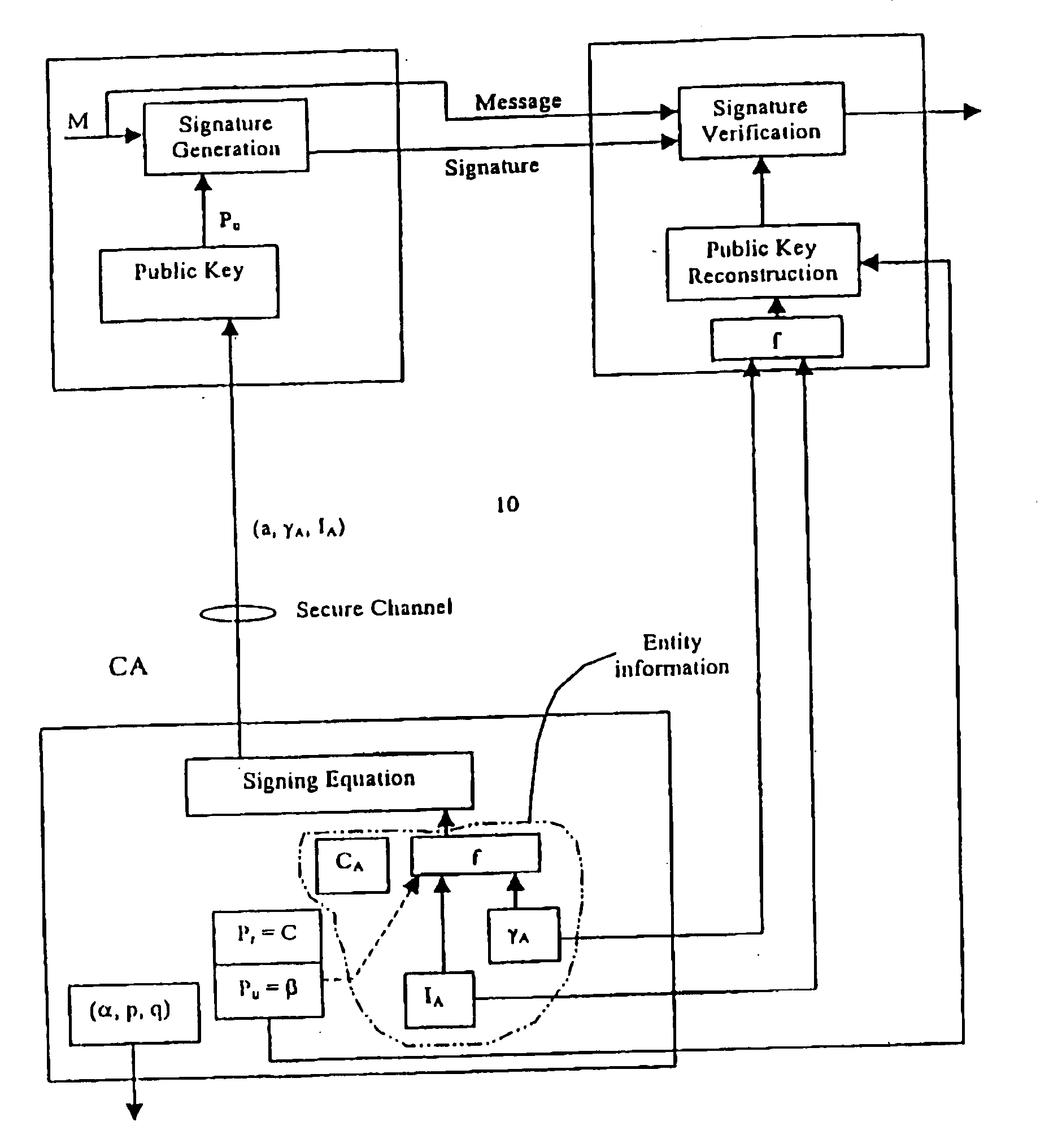
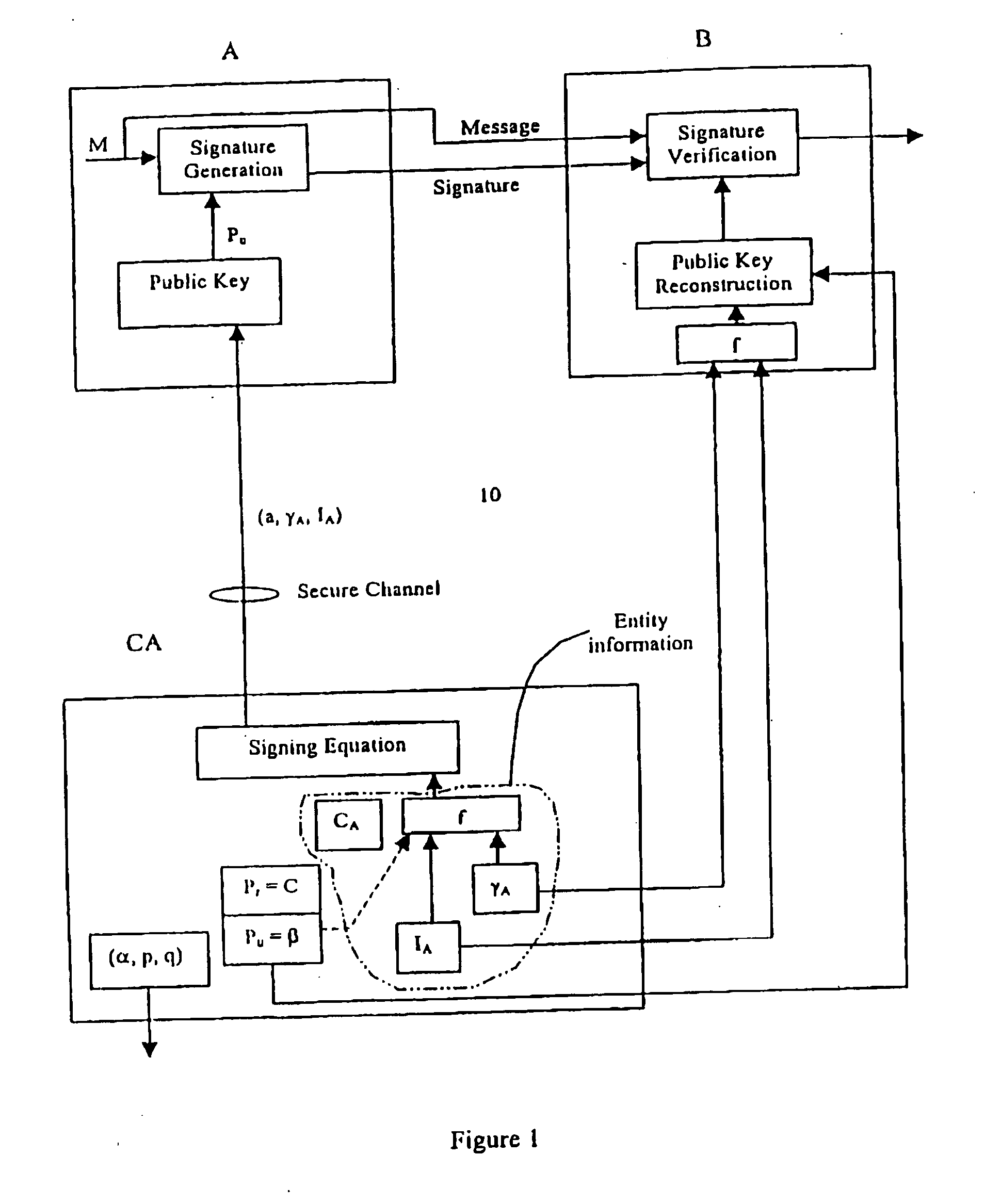
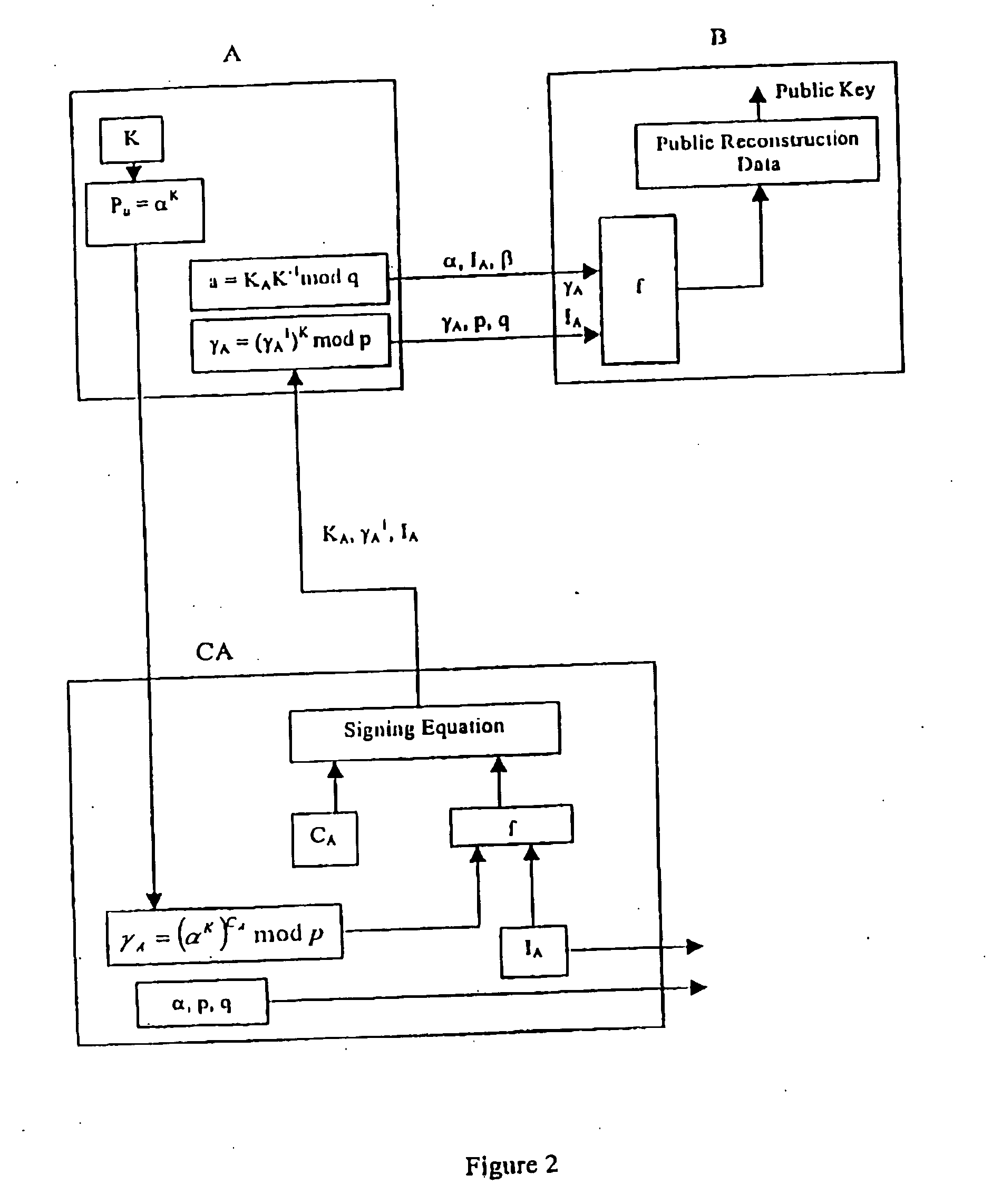
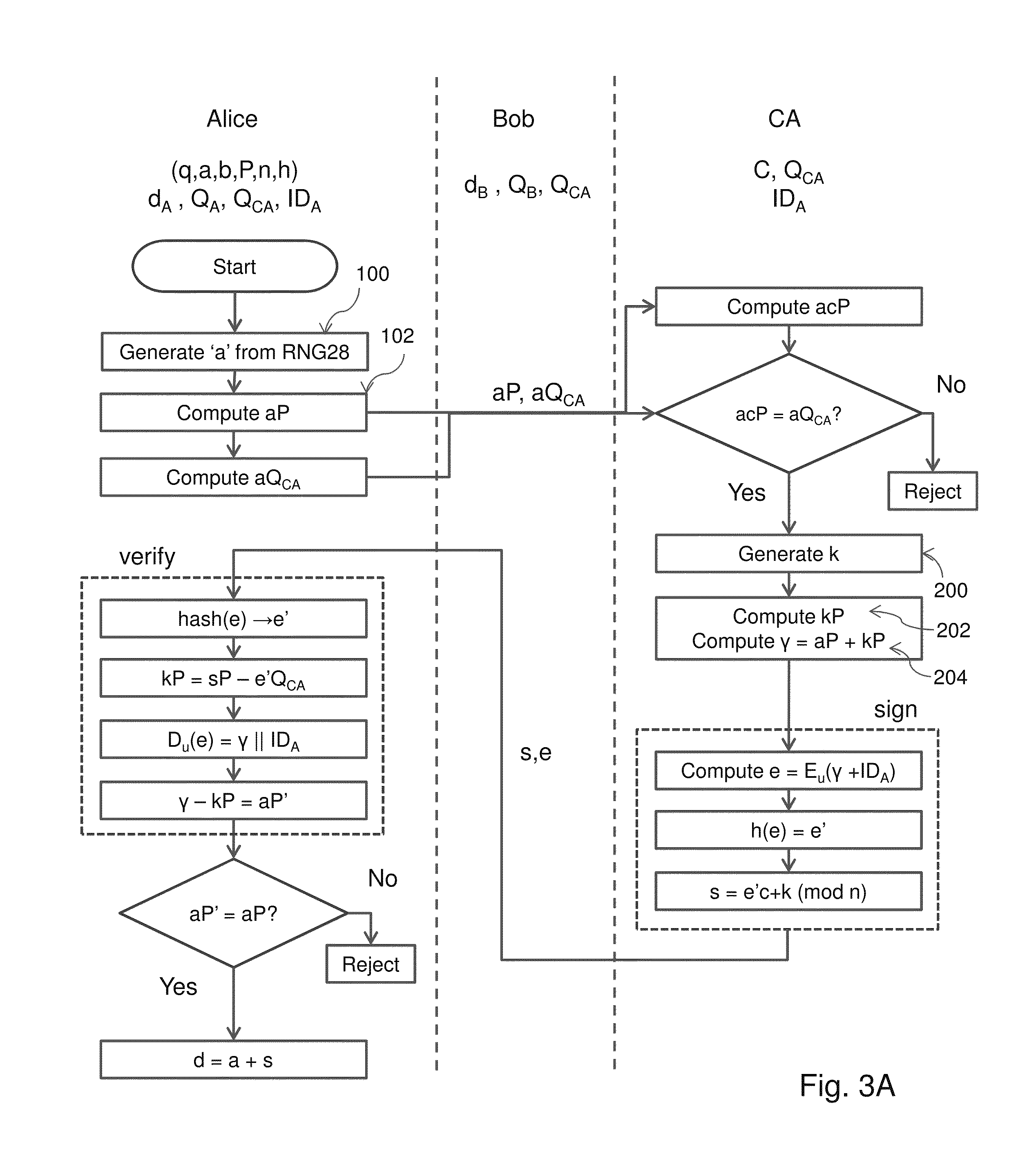
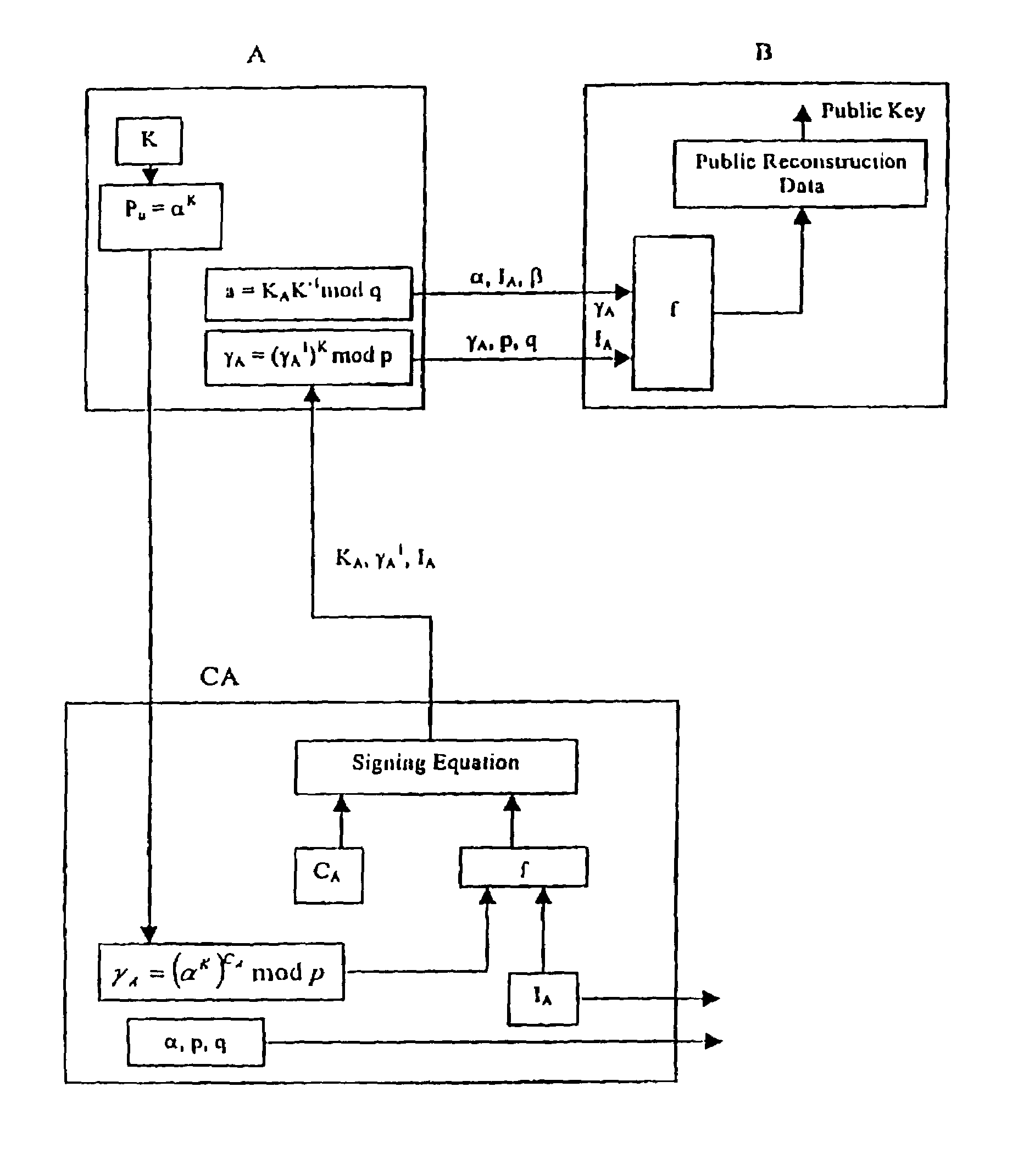
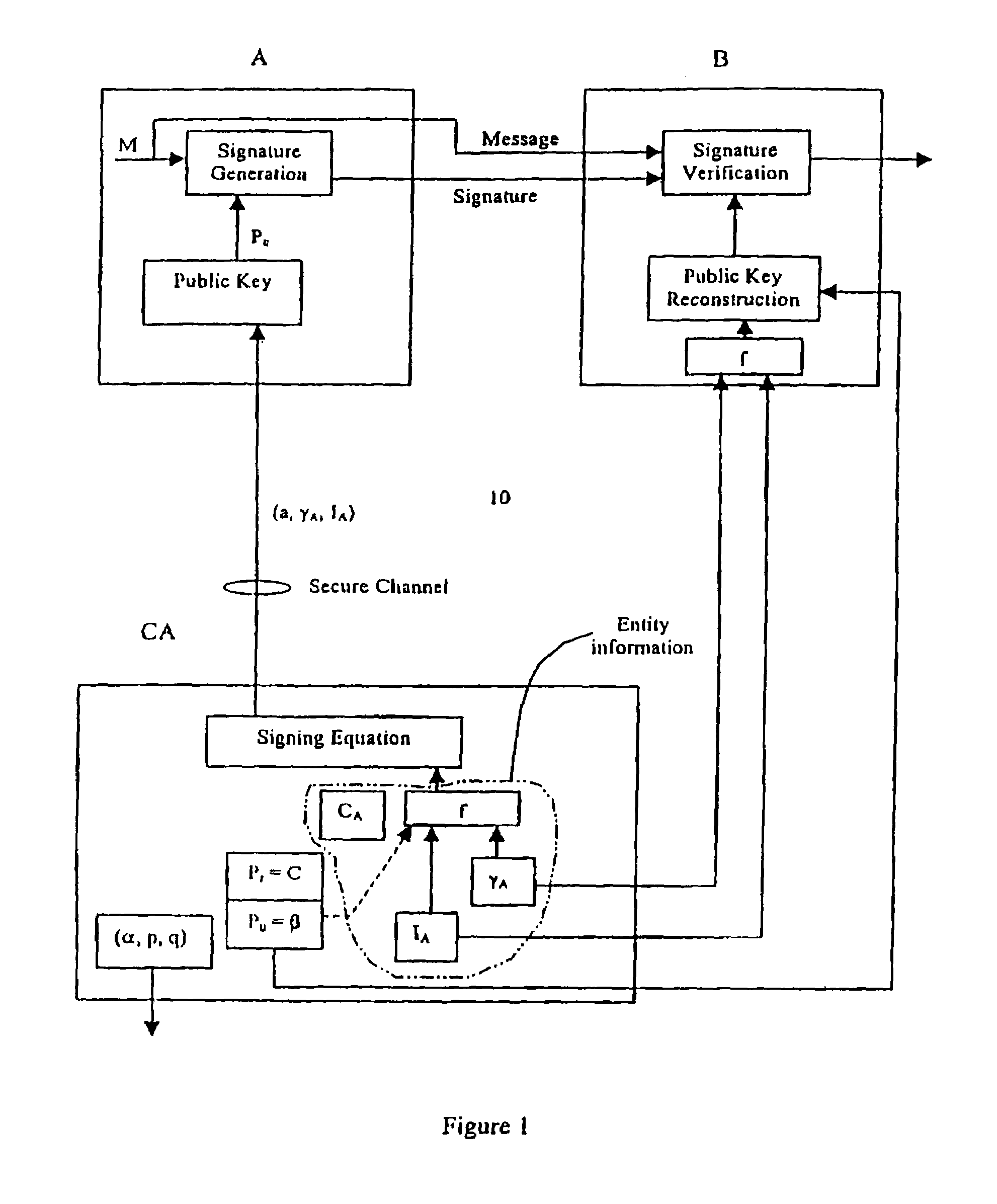
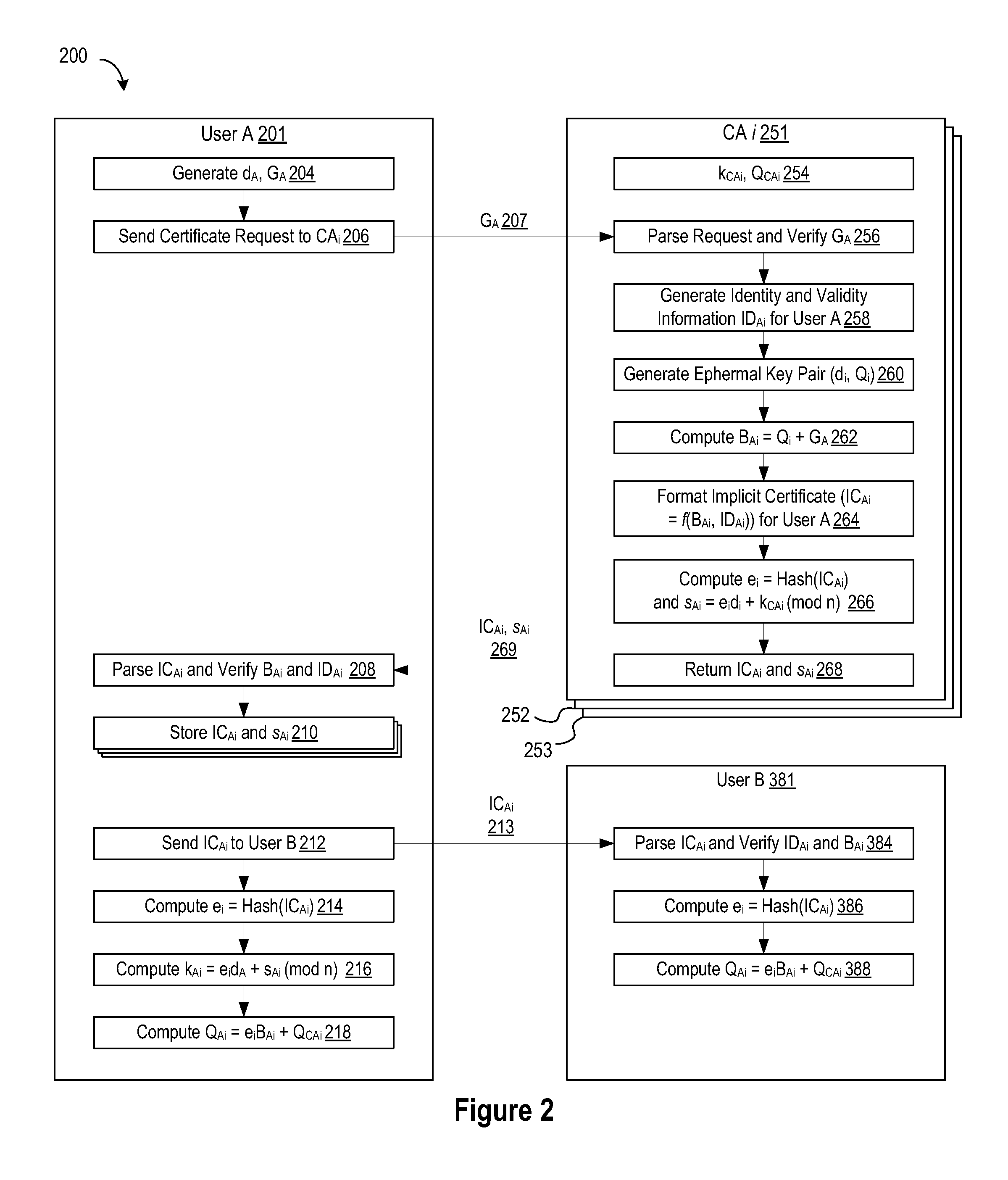
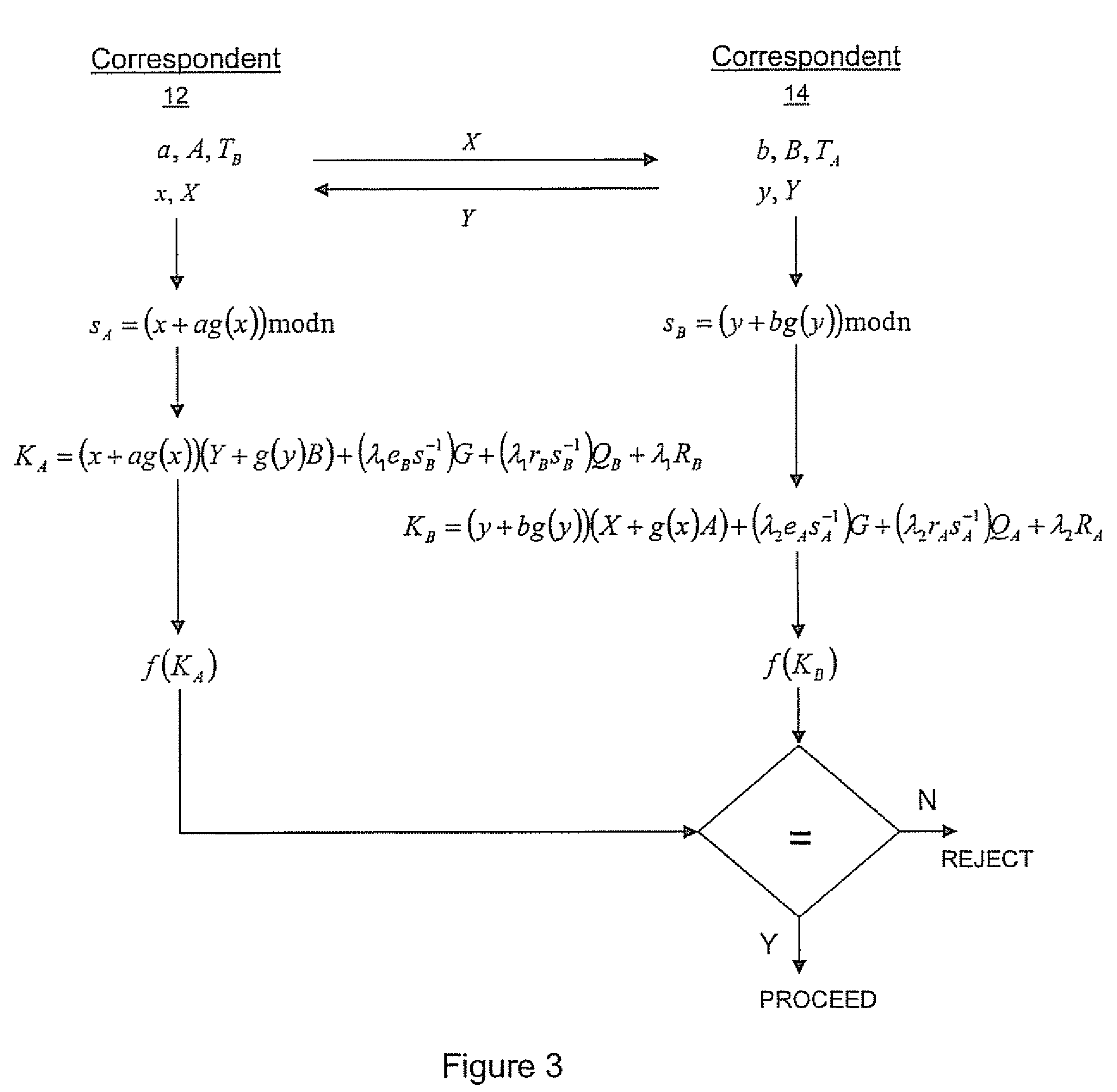
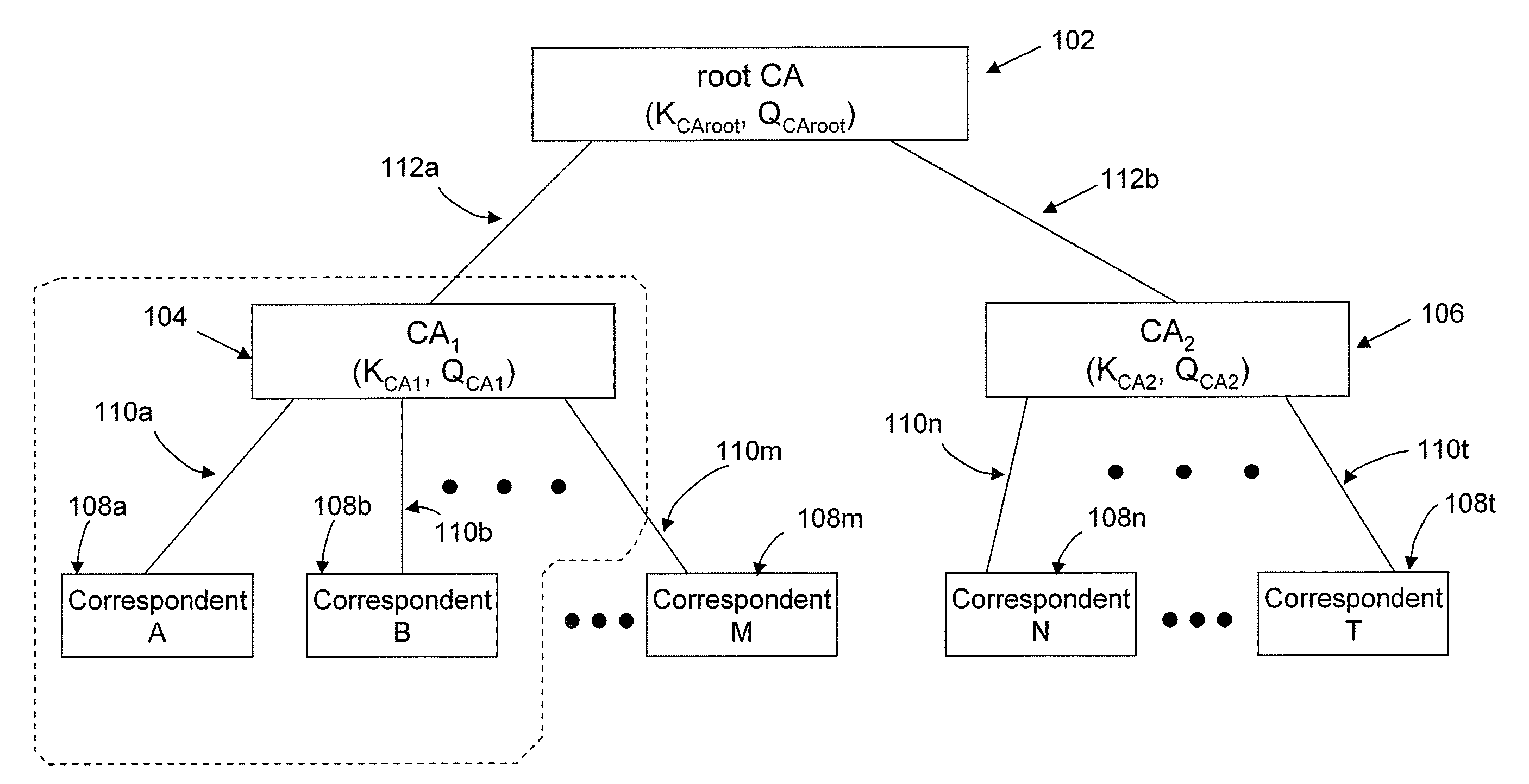
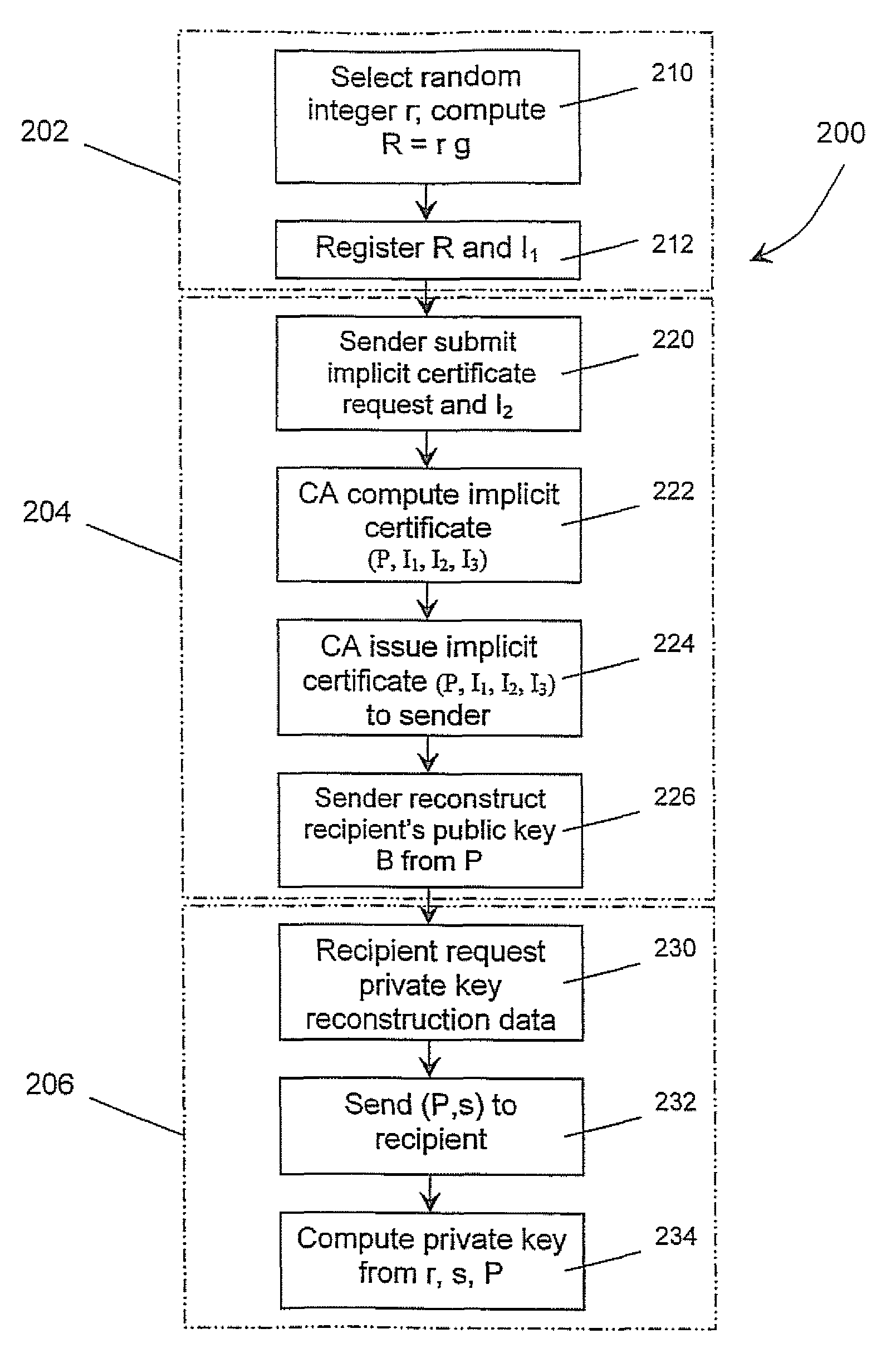
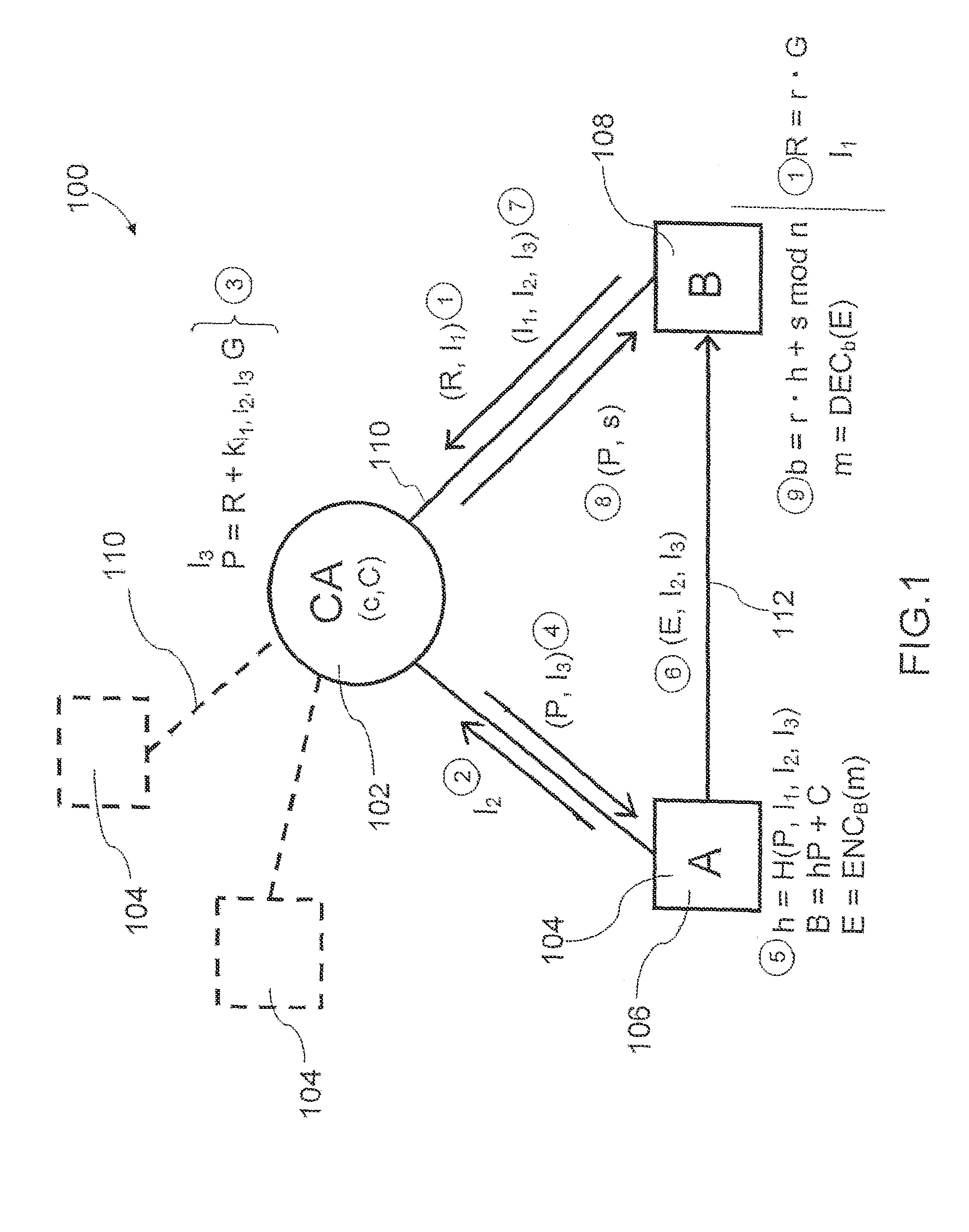
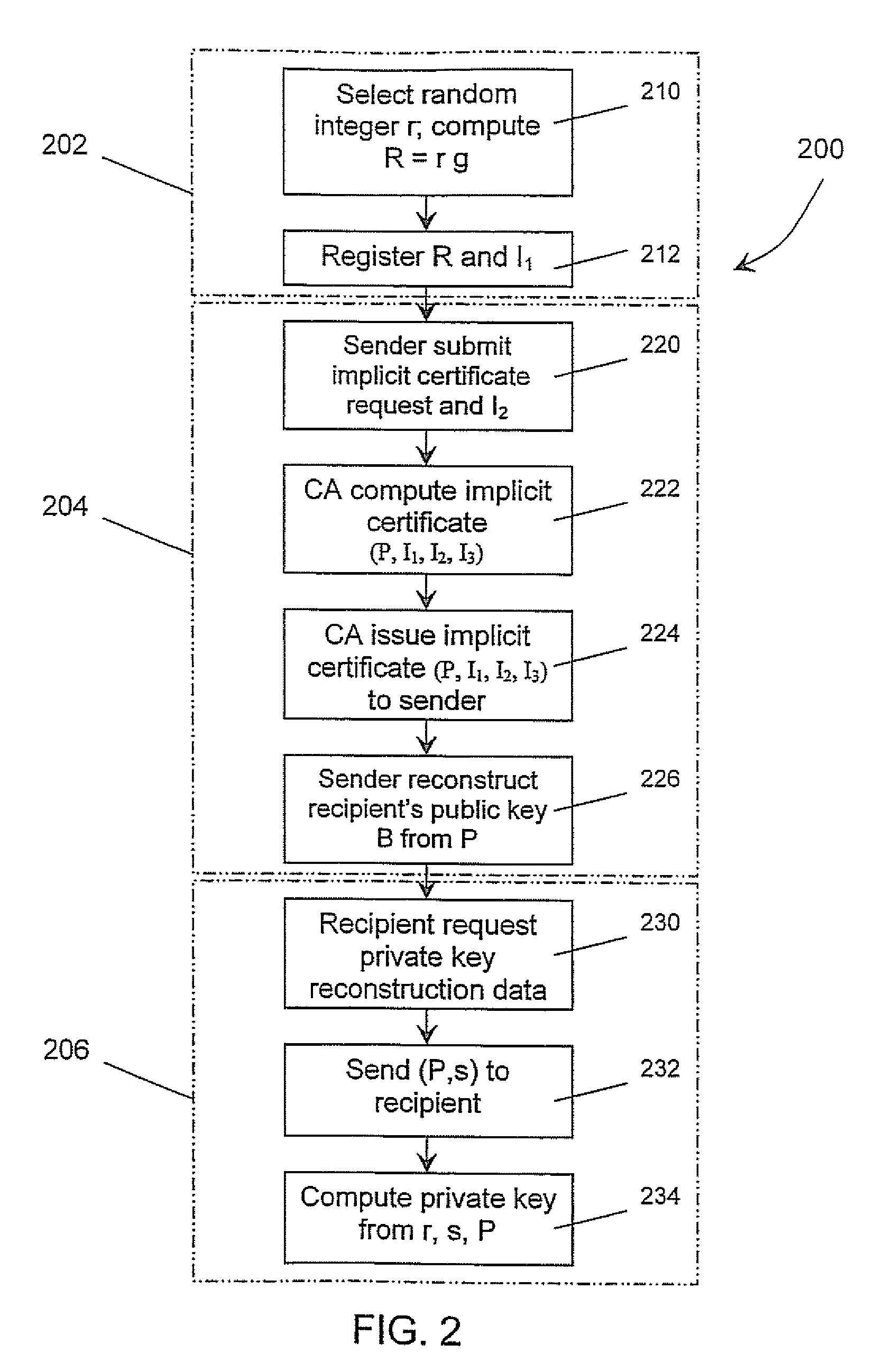
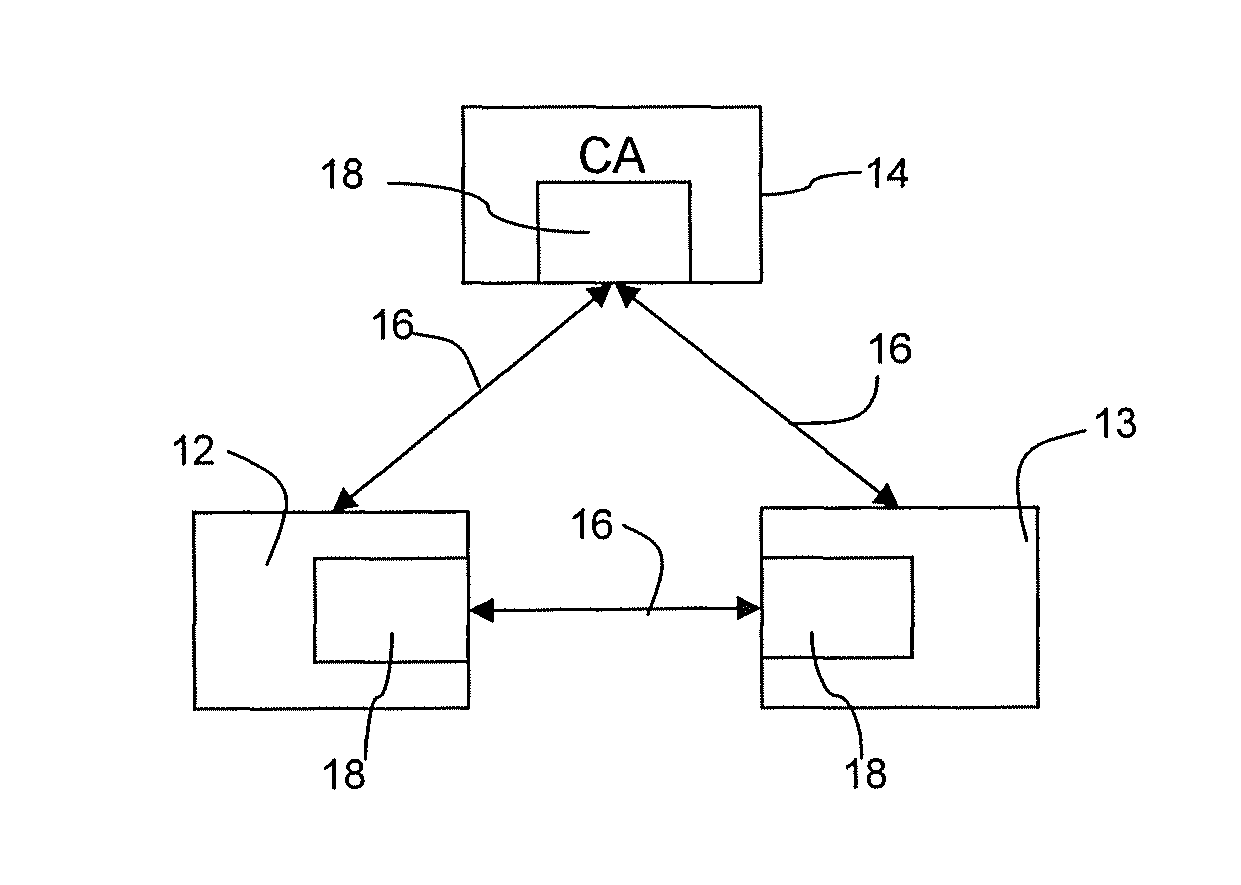
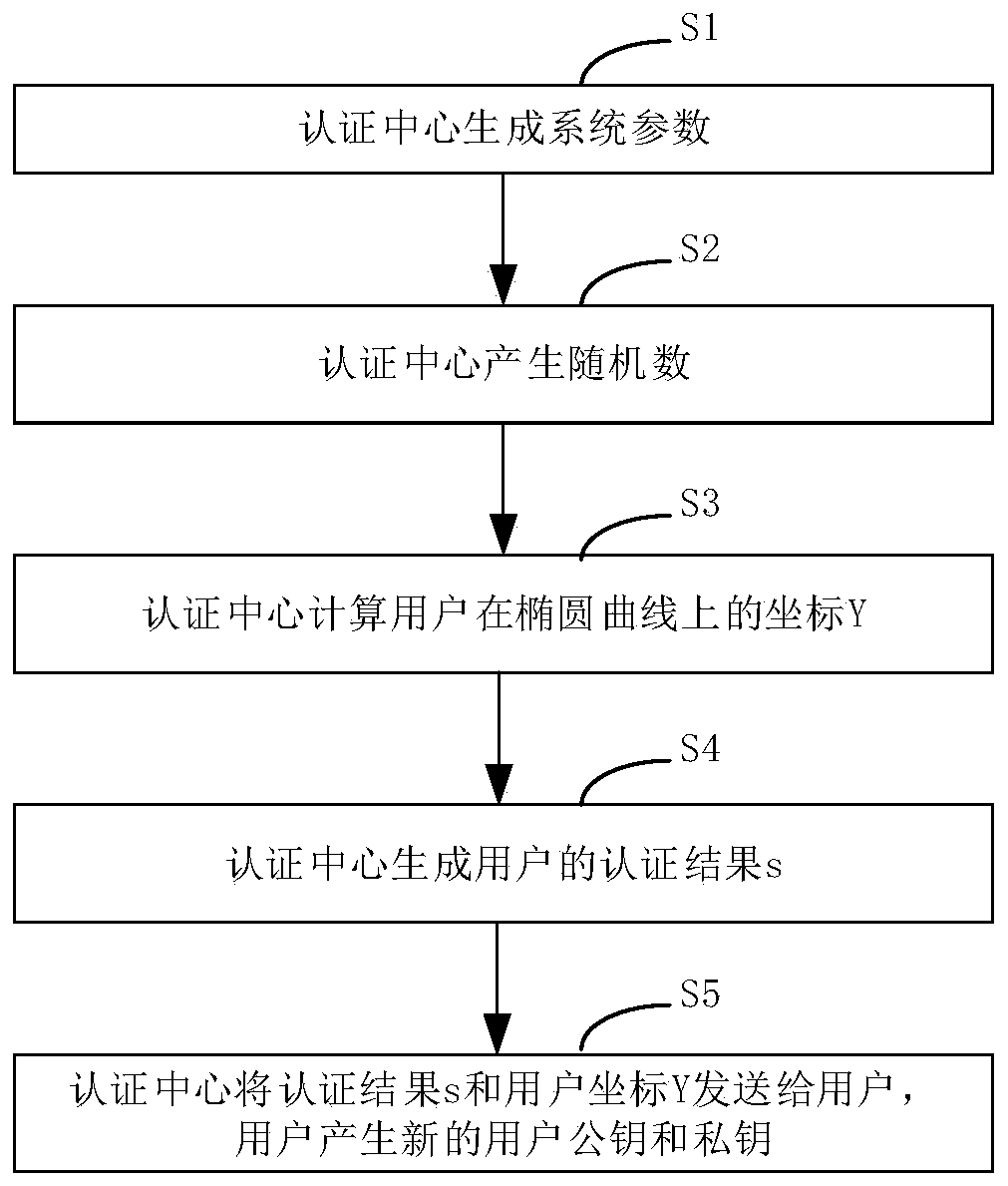
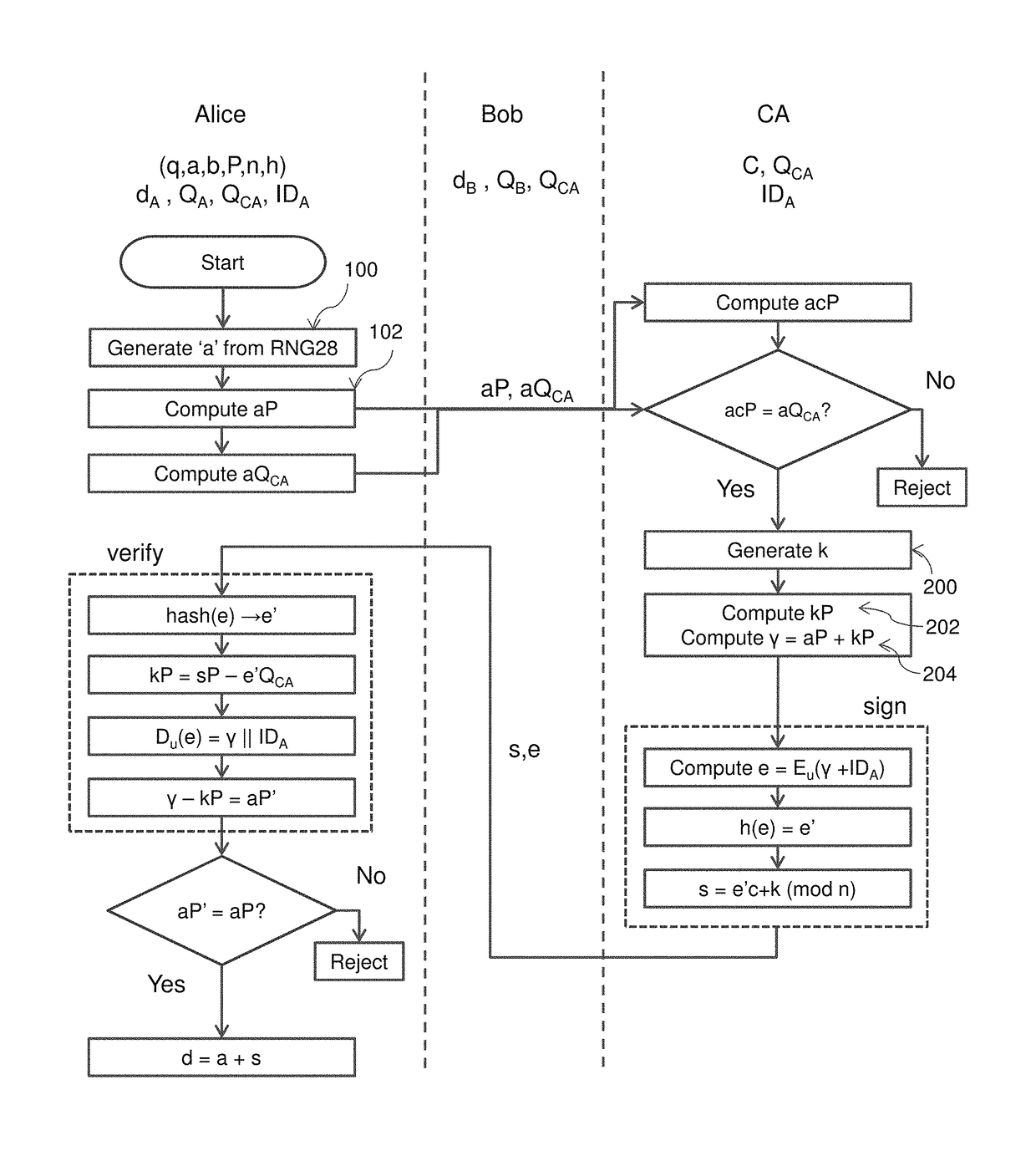
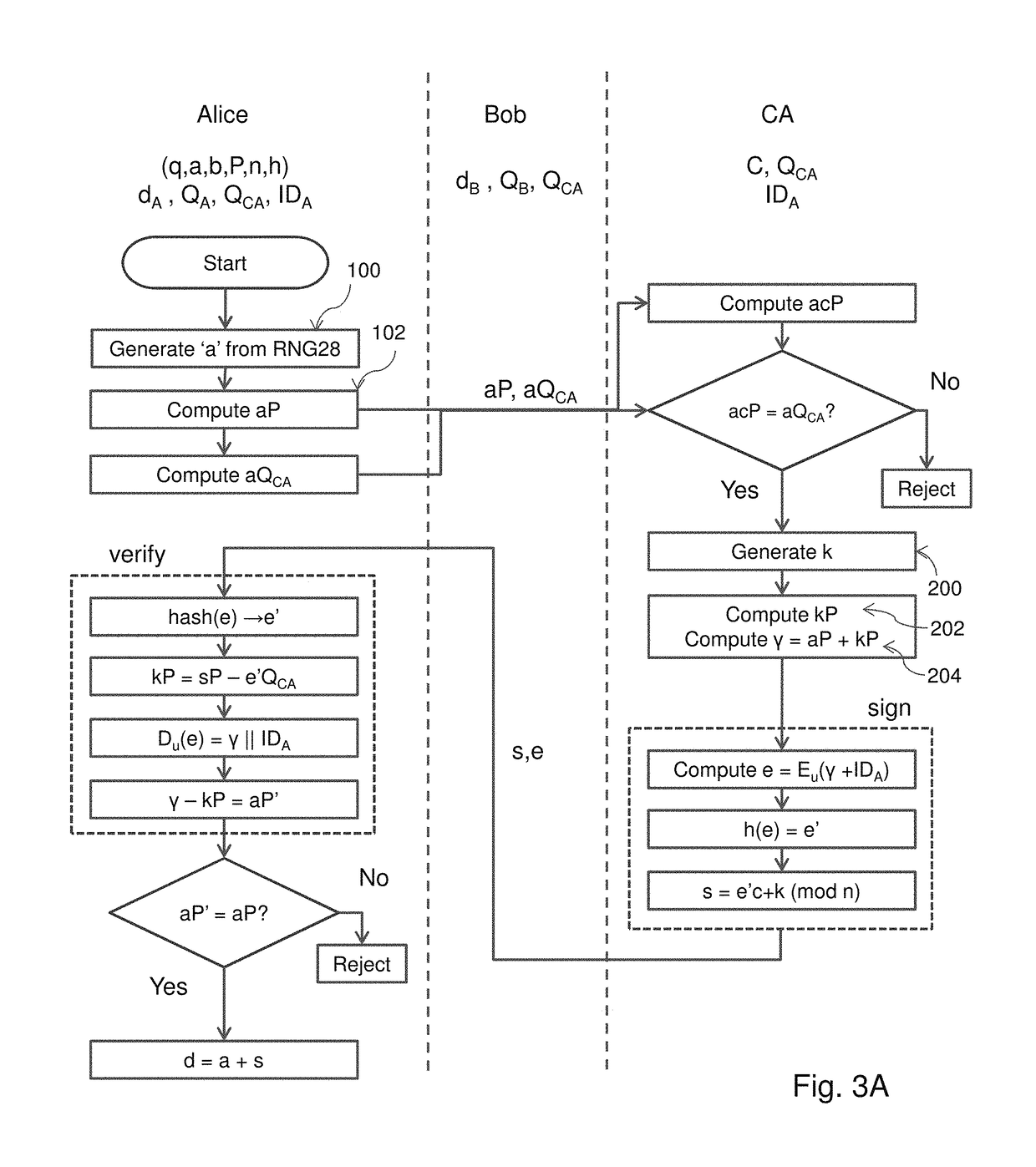
A method of generating a public key in a secure digital communication system, having at least one trusted entity CA and subscriber entities A. For each entity A, the trusted entity selects a unique identity distinguishing the entity A. The trusted entity then generates a public key reconstruction public data of the entity A by mathematically combining public values obtained from respective private values of the trusted entity and the entity A. The unique identity and public key reconstruction public data of the entity A serve as A's implicit certificate. The trusted entity combines the implicit certificate information with a mathematical function to derive an entity information ƒ and generates a value kA by binding with ƒ with private values of the trusted entity. The trusted entity transmits the value kA to the entity to permit A to generate a private key from kA, A's private value and A's implicit certificate. The entity A's public key information may be reconstructed from public information, and A's implicit certificate.
Owner:BLACKBERRY LTD
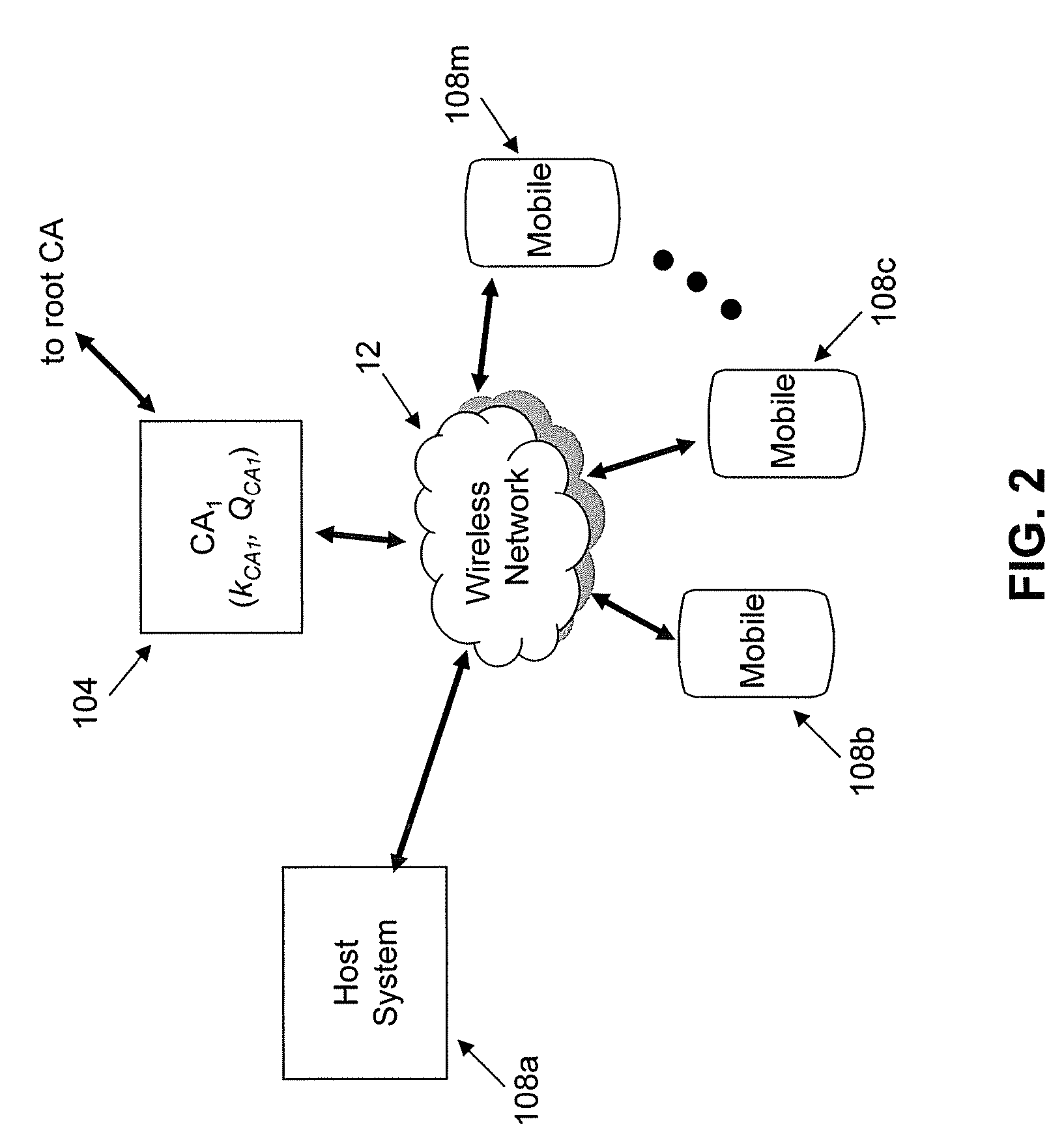
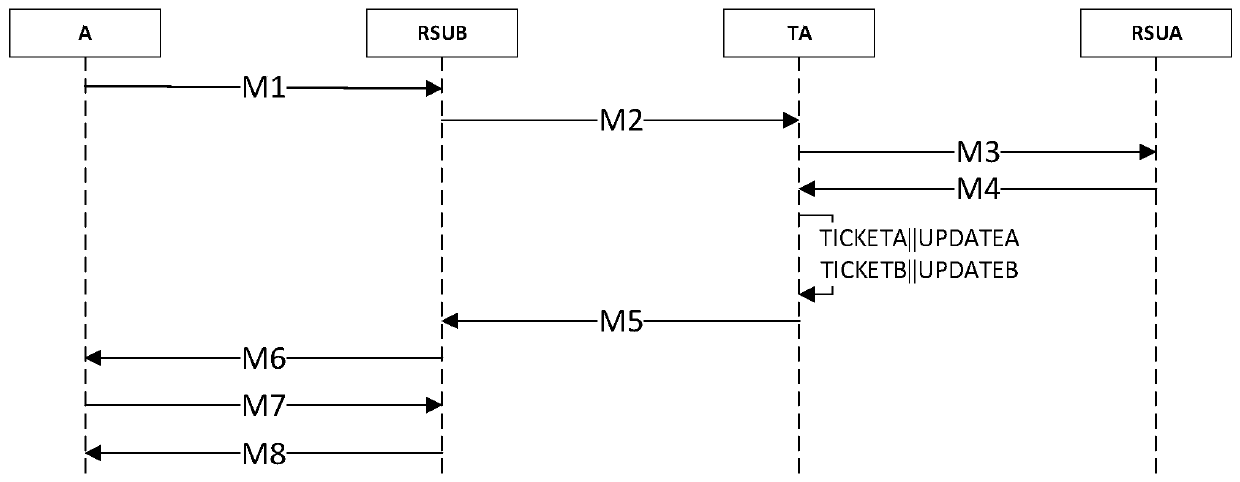
Light-weight authentication key negotiation method based on implicit certificate
ActiveCN106411528ACalculation speedReduce the probability of collisionKey distribution for secure communicationPublic key for secure communicationClient-sideSecure channel
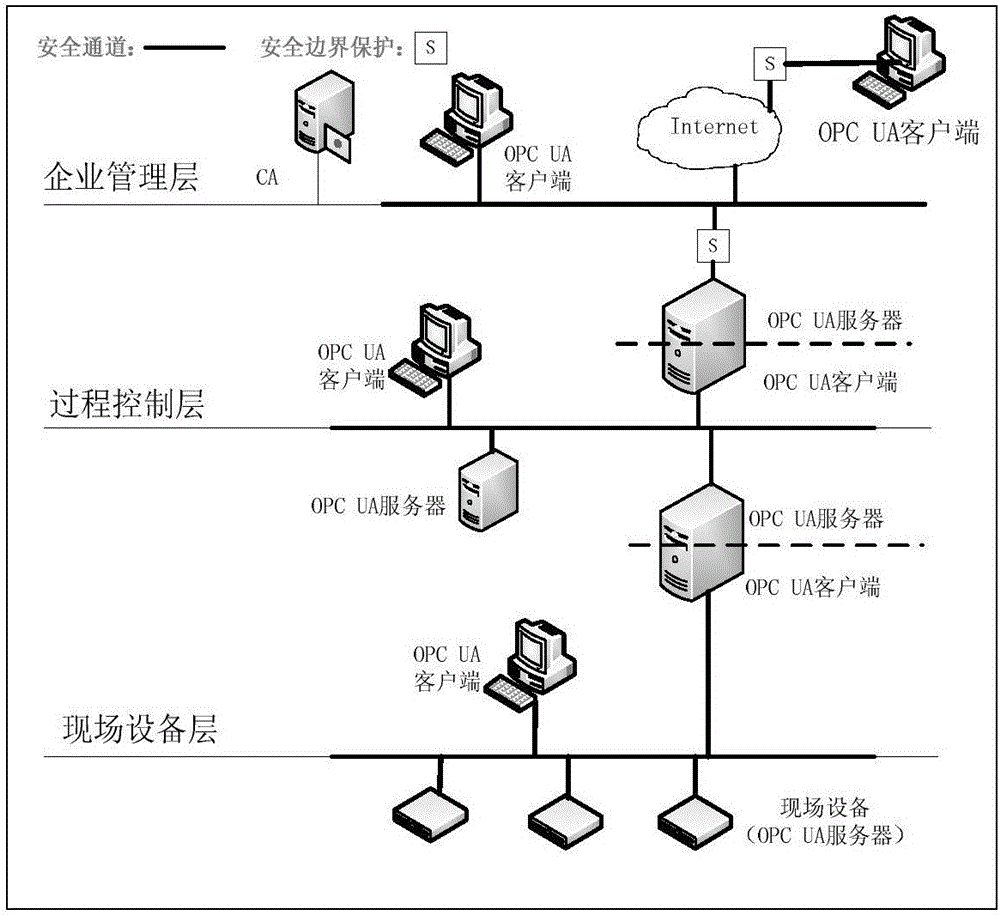
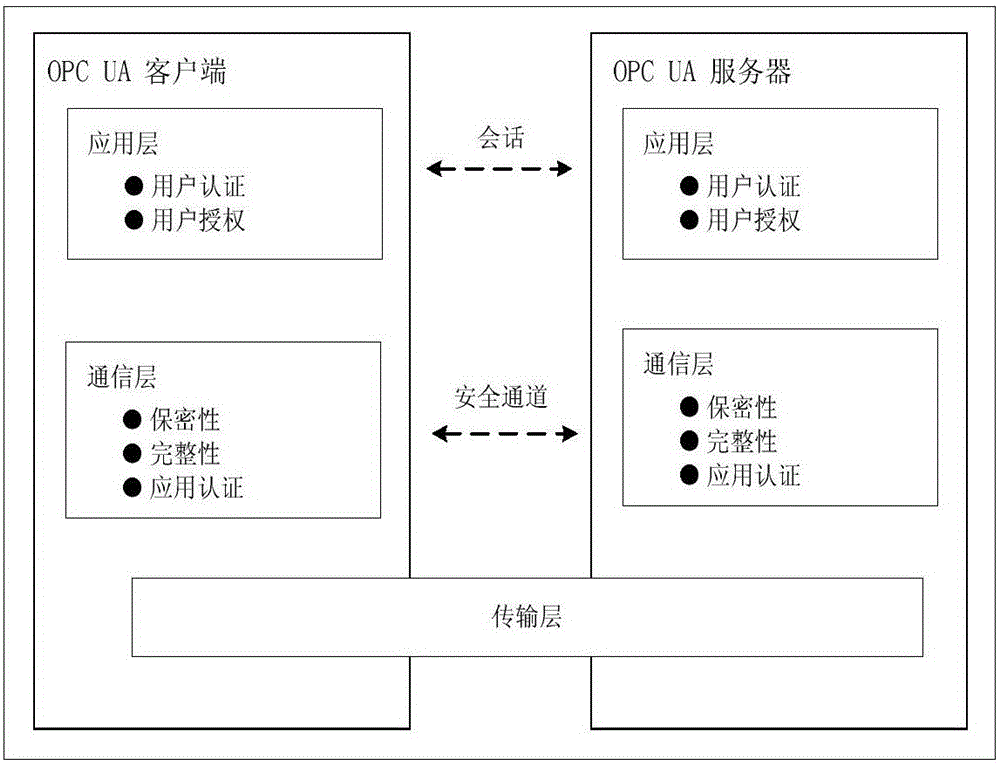
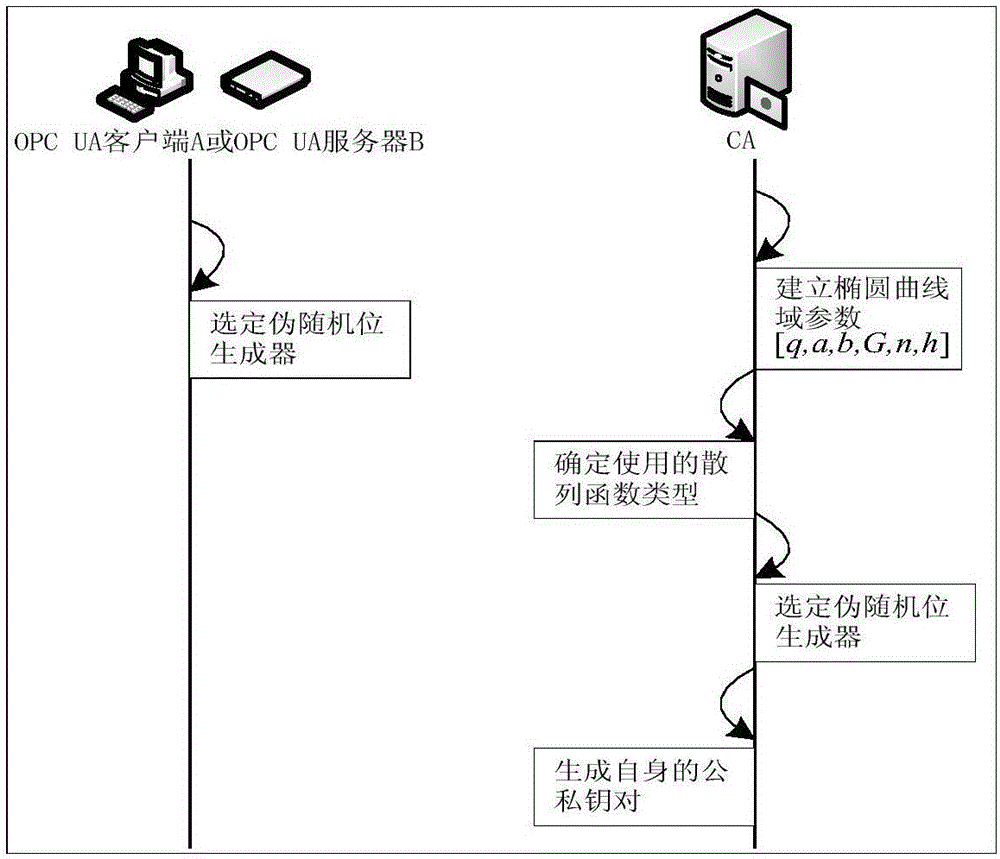
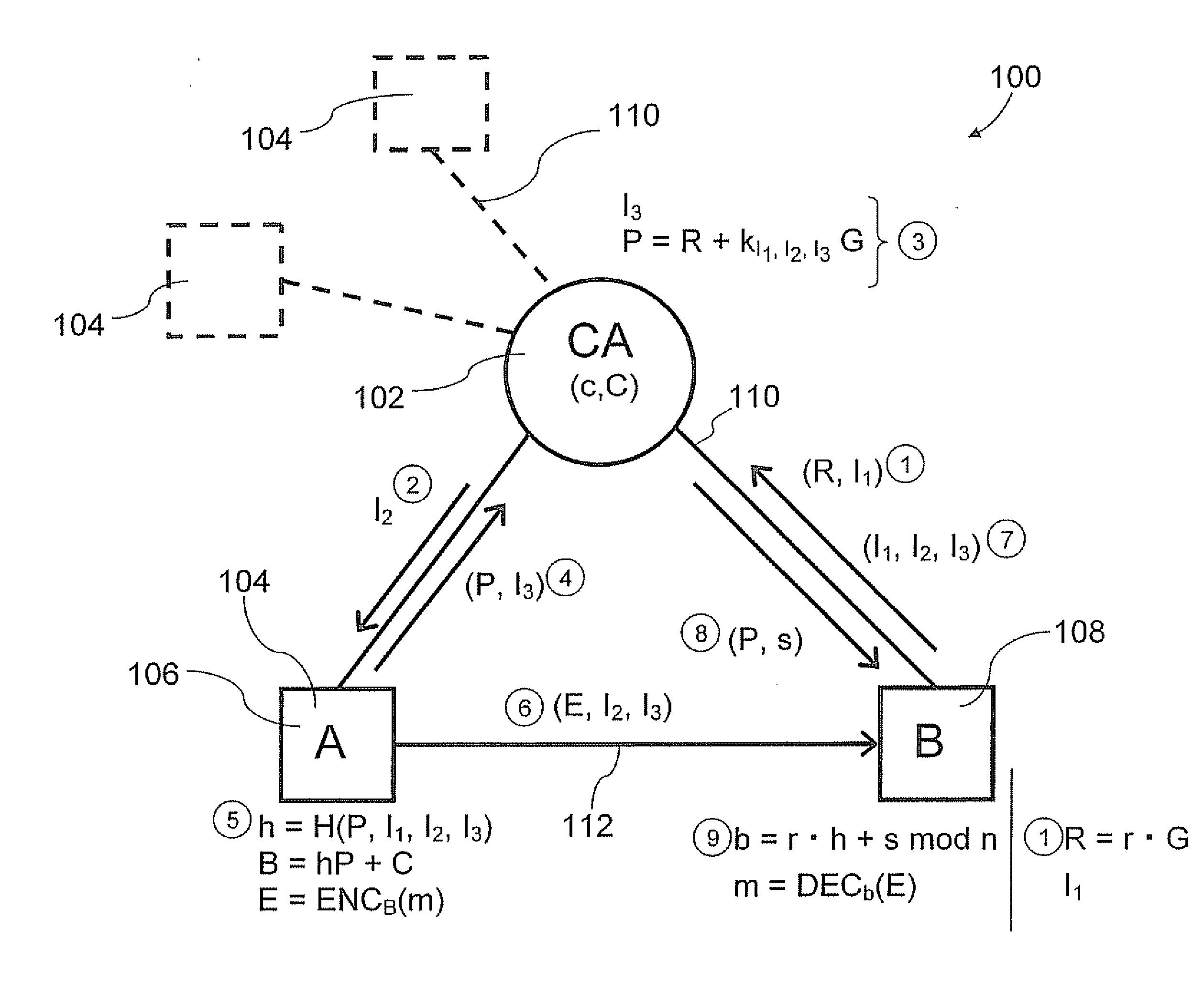
The invention relates to a light-weight authentication key negotiation method based on an implicit certificate, and belongs to the technical field of identity authentication. The method is used for establishing a secure channel between an OPC UA server and an OPC UA client and generating of a session key. Three entities, a credible certification authority (CA), the OPC UA client A and the OPC UA server B, are involved in an authentication key negotiation process. The OPC UA server B and the OPC UA client A acquire the own implicit certificates after the CA completes identity registration. Then the OPC UA server B and the OPC UA client A complete bidirectional authentication and key negotiation between the entities by using a light-weight algorithm. According to the method provided by the invention, the light-weight authentication key negotiation method based on the implicit certificate is provided aiming at the problem that an existing OPC UA security mechanism is not applicable to a resource-constrained communication environment. The method provided by the invention can be efficiently and safely applicable to an industrial network with a large amount of resource-constrained embedded OPC UA equipment.
Owner:KYLAND TECH CO LTD
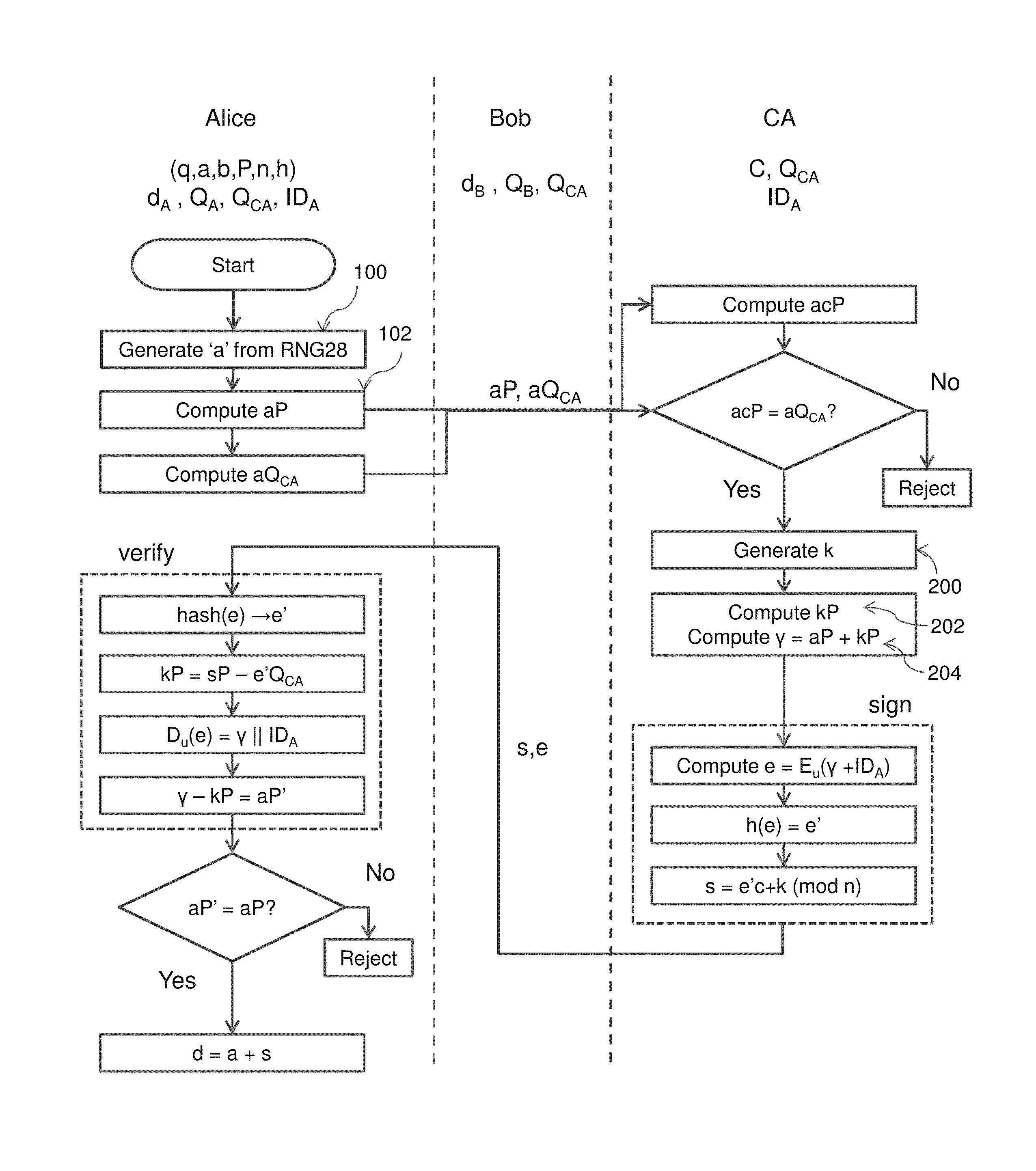
Method and system for generating implicit certificates and applications to identity-based encryption (IBE)
The invention relates to a method of generating an implicit certificate and a method of generating a private key from a public key. The method involves a method generating an implicit certificate in three phases. The public key may be an entity's identity or derived from an entity's identify. Only the owner of the public key possesses complete information to generate the corresponding private key. No authority is required to nor able to generate an entity's private key.
Owner:MALIKIE INNOVATIONS LTD
Verifiable Implicit Certificates
ActiveUS20150288527A1Key distribution for secure communicationPublic key for secure communicationCryptosystemImplicit certificate
An implicit certificate cryptosystem uses an implicit certificate that includes a pair of certificate components. One of the certificate components includes a public key reconstruction data that is the combination of ephemeral public keys of two entities, one of which is a trusted entity and the other of which is associated with the implicit certificate. The public key reconstruction data is then combined with the identity of the other entity and the combination encrypted to form a first certificate component. A second certificate component is generated by using the first certificate component as a message in a signature scheme and generating a signature of the trusted entity on the message. The two certificate components are provided to the other entity to permit the other entity to generate a private key using one of the certificate components. The corresponding public key can be derived from the remaining certificate component.
Owner:ETAS EMBEDDED SYST CANADA INC
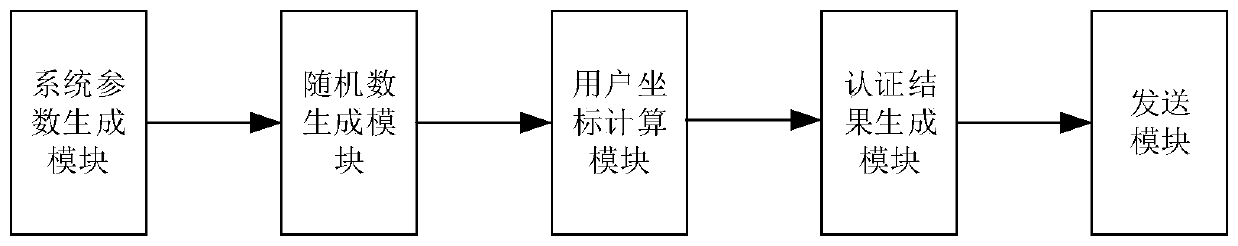
Implicit certificate key generation method based on SM2 digital signature
ActiveCN112367175AAvoid false binding attacksReduce overheadKey distribution for secure communicationPublic key for secure communicationComputer networkDigital signature
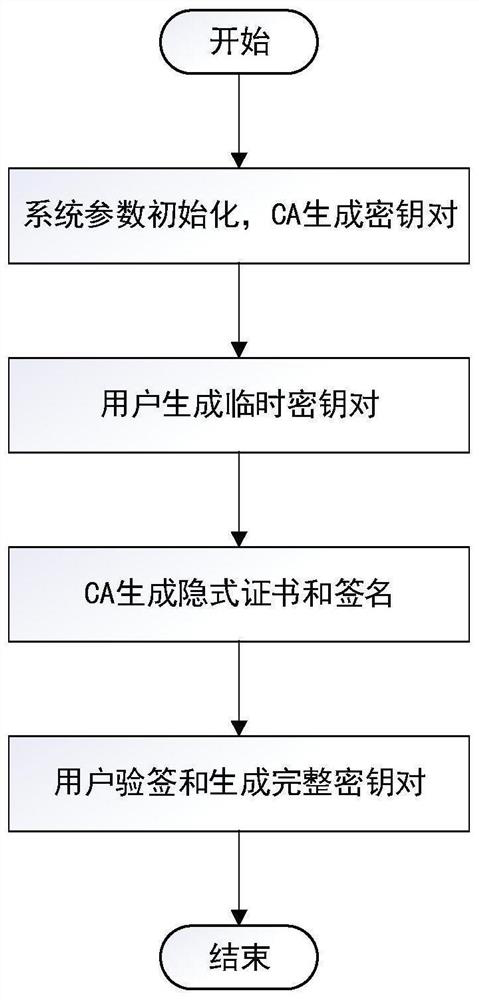
The invention discloses an SM2 digital signature-based implicit certificate key generation method, which mainly solves the problem that a user identity cannot correspond to a user public key in a public key cryptosystem in the prior art. According to the scheme, system parameters are set and initialized according to a standard cryptographic algorithm SM2; the certificate authority CA generates a key pair and sends a public key PCA to a user usr applying for a certificate; the user applying for the certificate generates a temporary key pair and sends an identity identifier IDA and a temporary public key X of the user to a certificate authority CA; the CA generates an implicit certificate cert and a signature s, and sends the cert and s to a user applying for the certificate; and the user generates a complete public key U and then verifies the complete public key U and the signature s to obtain a complete public and private key pair (u, U). The method conforms to the national cryptographic SM2 signature algorithm standard, is high in operation efficiency and short in bandwidth overhead, reduces the risk that a man-in-the-middle replaces a public key, and can be used for a resource-limited Internet of Things environment.
Owner:XIDIAN UNIV
Implicit certificate scheme
InactiveUS7391868B2Key distribution for secure communicationPublic key for secure communicationCommunications systemImplicit certificate
Owner:BLACKBERRY LTD
Acentric digital currency transaction method based on public and private key pair derivation
ActiveCN107784580AEnhanced anonymityStrong anonymityFinancePayment protocolsDigital currencyGeneration process
The invention relates to an acentric digital currency transaction method based on public and private key pair derivation; a receiver can scan on a public account book to calculate collection public and private key pairs according to the transfer time, thus reducing data storage; each transaction forms a new collection address, thus enhancing the digital currency anonymous property; only one time elliptical curve scalar multiplication calculation is added on the computational complexity in an implicit certificate generation process, thus easily reducing stronger anonymous property; a transaction initiator actively forms a new collection address in the process instead of using the new collection address issued by the receiver; each person only processes a long term public key, and new publicand private key pairs can be calculated according to the public messages on the public account book and the long term public and private key pairs, thus reducing the public and private key pair storage space; transaction graph analysis is hard to receive.
Owner:DATA COMM SCI & TECH RES INST +1
Using a single certificate request to generate credentials with multiple ECQV certificates
ActiveUS8701169B2Key distribution for secure communicationDigital data processing detailsCommunications systemInternet privacy
Owner:MALIKIE INNOVATIONS LTD
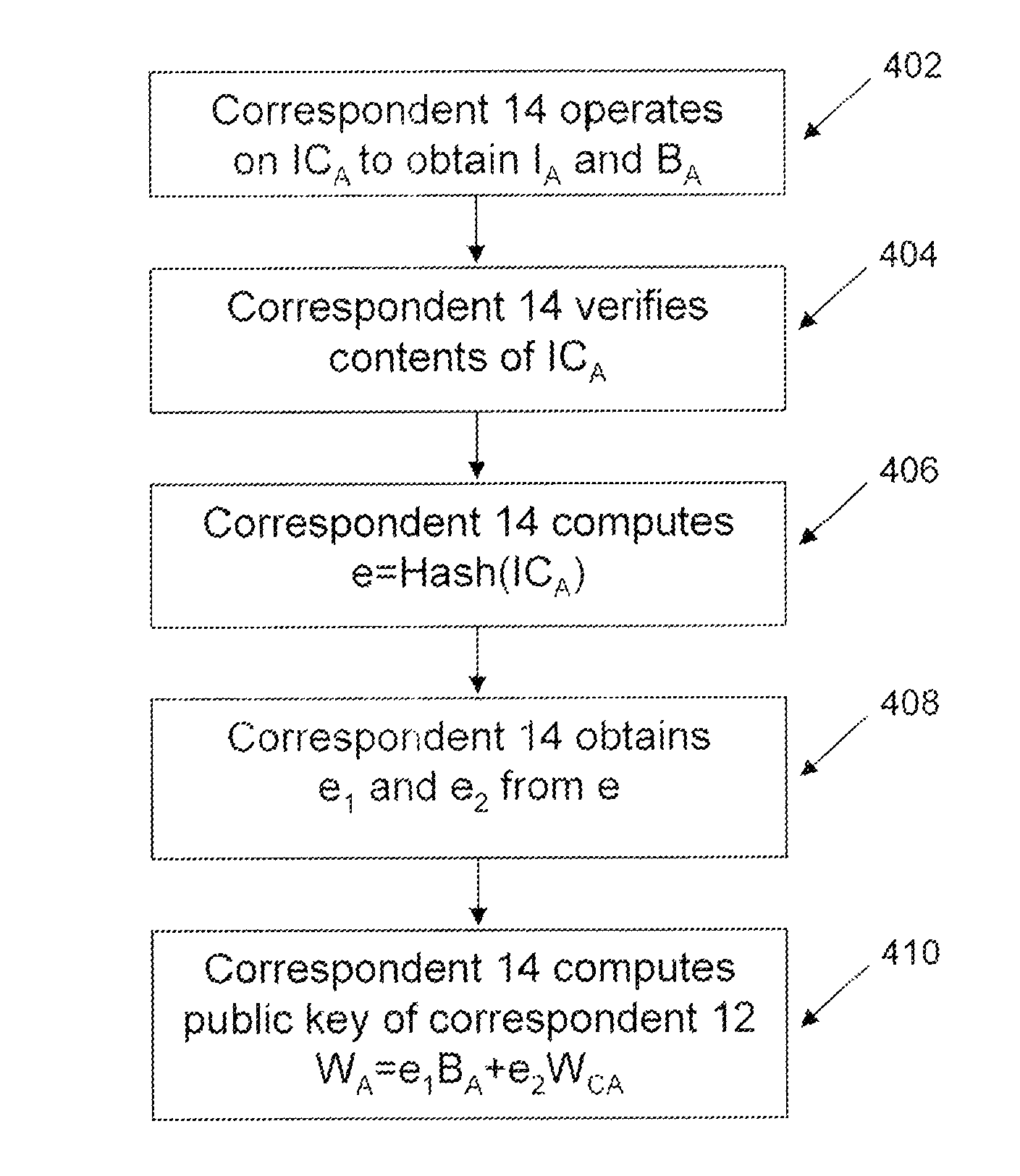
System and Method for Reducing Computations in an Implicit Certificate Scheme
ActiveUS20120221850A1Key distribution for secure communicationPublic key for secure communicationBit-lengthImplicit certificate
There are disclosed systems and methods for reducing the number of computations performed by a computing device constructing a public key from an implicit certificate associated with a certificate authority in an implicit certificate scheme. In one embodiment, the device first operates on the implicit certificate to derive an integer e. The device then derives a pair of integers (e1, e2) from the integer e, such that each of the pair of integers (e1, e2) has a bit length less than the bit length of the integer e, and such that the ratio of the pair of integers (e1, e2) corresponds to the integer e. The device then computes the public key by combining the integers e1 and e2 with public key contribution data derived from the implicit certificate and a public key of the certificate authority.
Owner:MALIKIE INNOVATIONS LTD
Implicit certificate verification
ActiveUS8069346B2Digital data processing detailsUser identity/authority verificationCryptographic nonceImplicit certificate
Owner:MALIKIE INNOVATIONS LTD
Self-signed implicit certificates
There are disclosed systems and methods for creating a self-signed implicit certificate. In one embodiment, the self-signed implicit certificate is generated and operated upon using transformations of a nature similar to the transformations used in the ECQV protocol. In such a system, a root CA or other computing device avoids having to generate an explicit self-signed certificate by instead generating a self-signed implicit certificate.
Owner:MALIKIE INNOVATIONS LTD
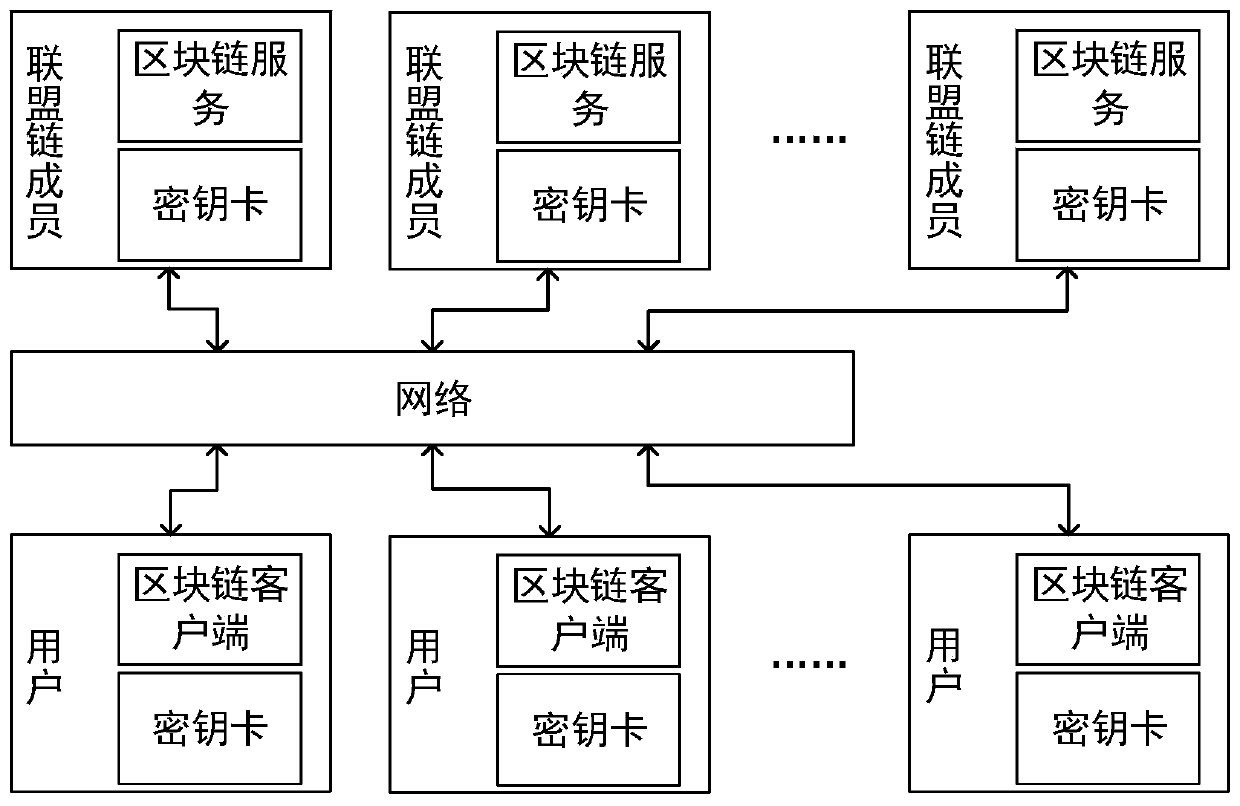
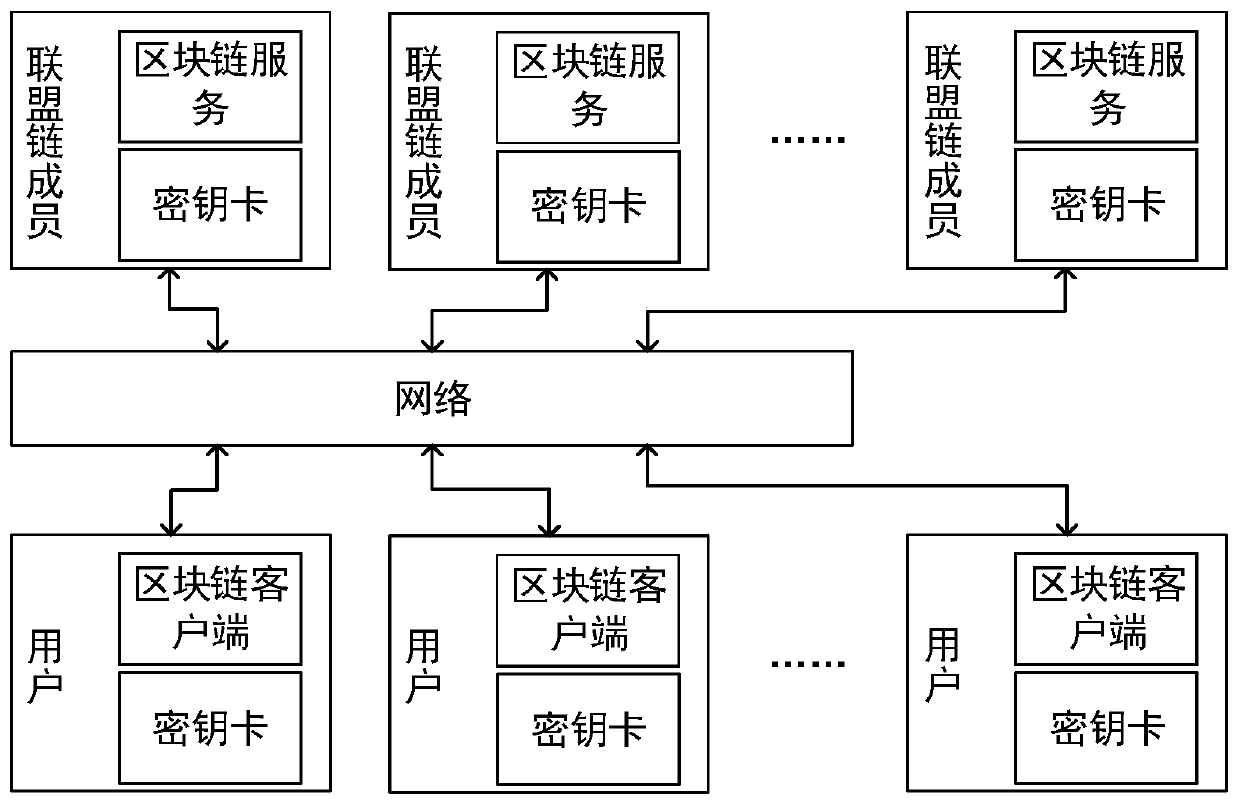
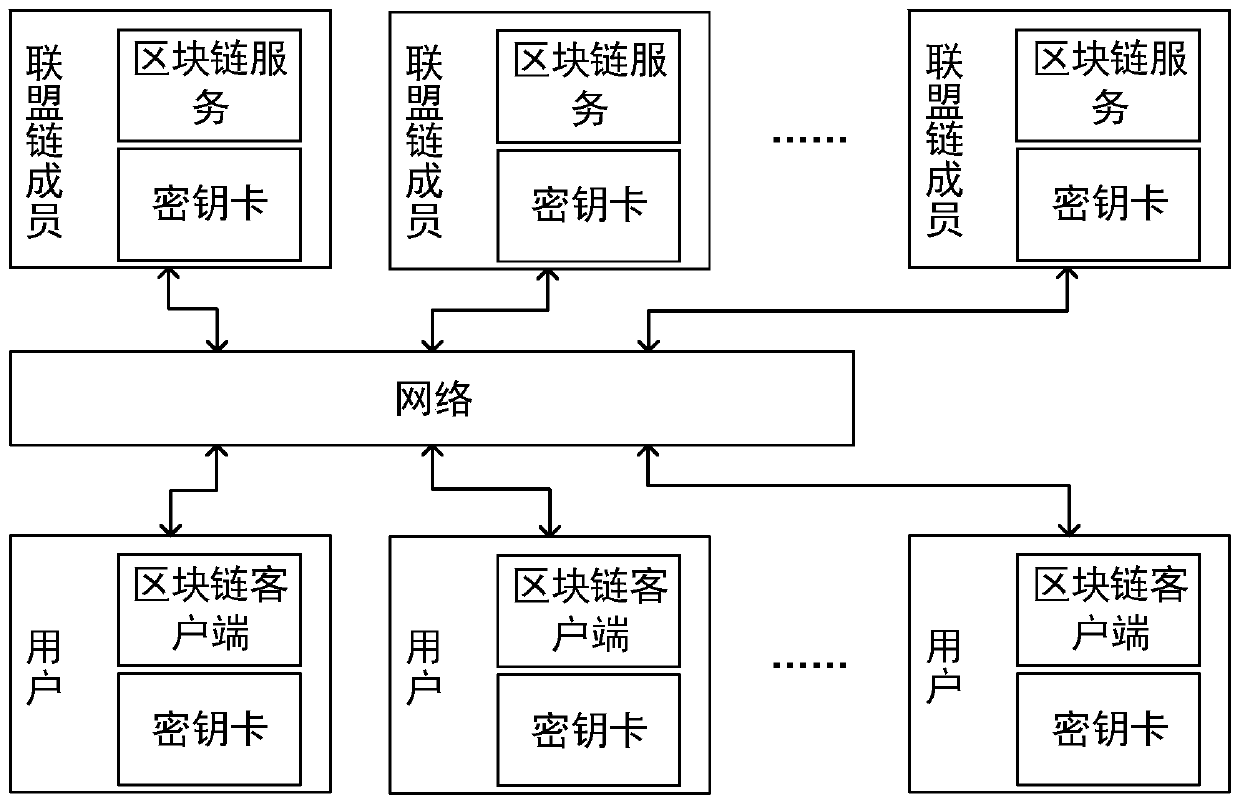
Anti-quantum computing implicit certificate issuing method and system based on alliance chain
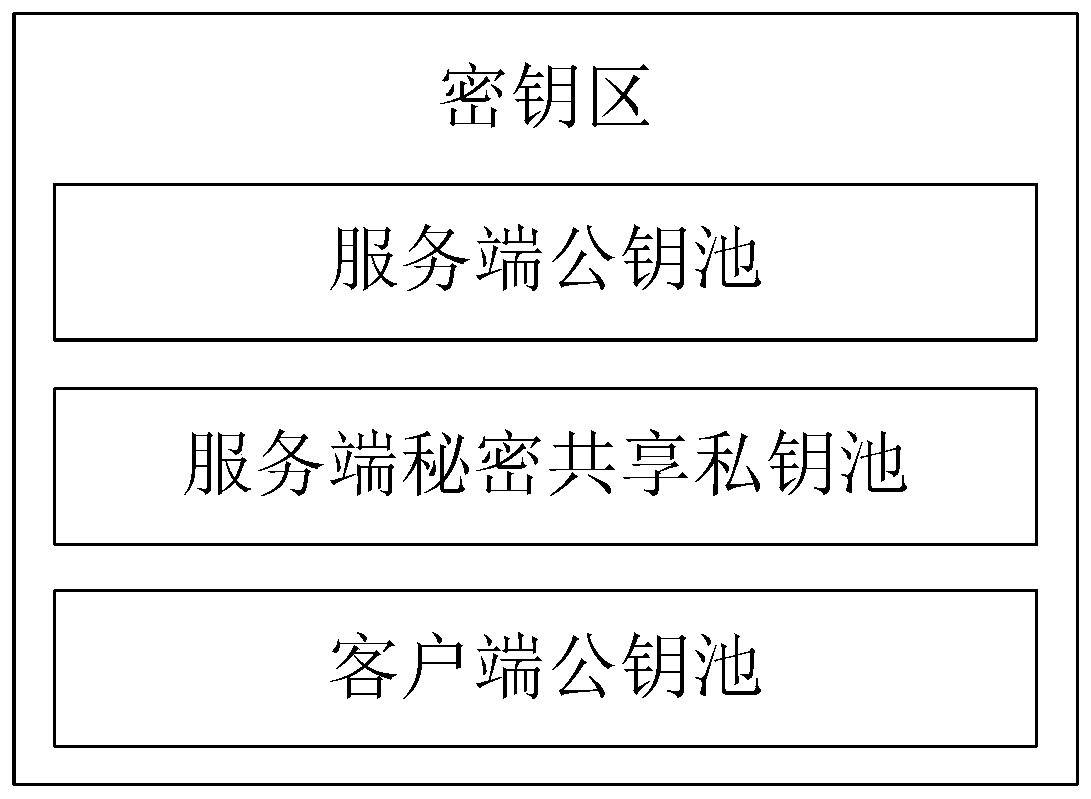
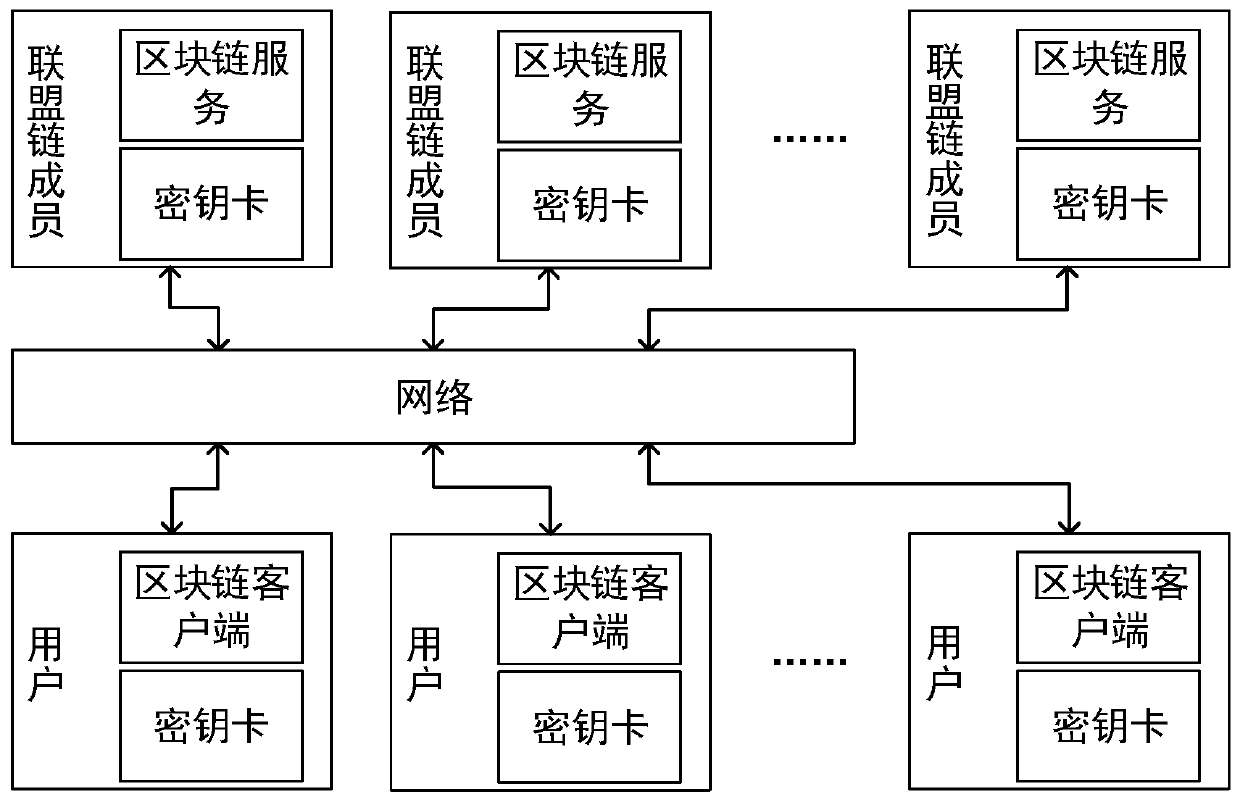
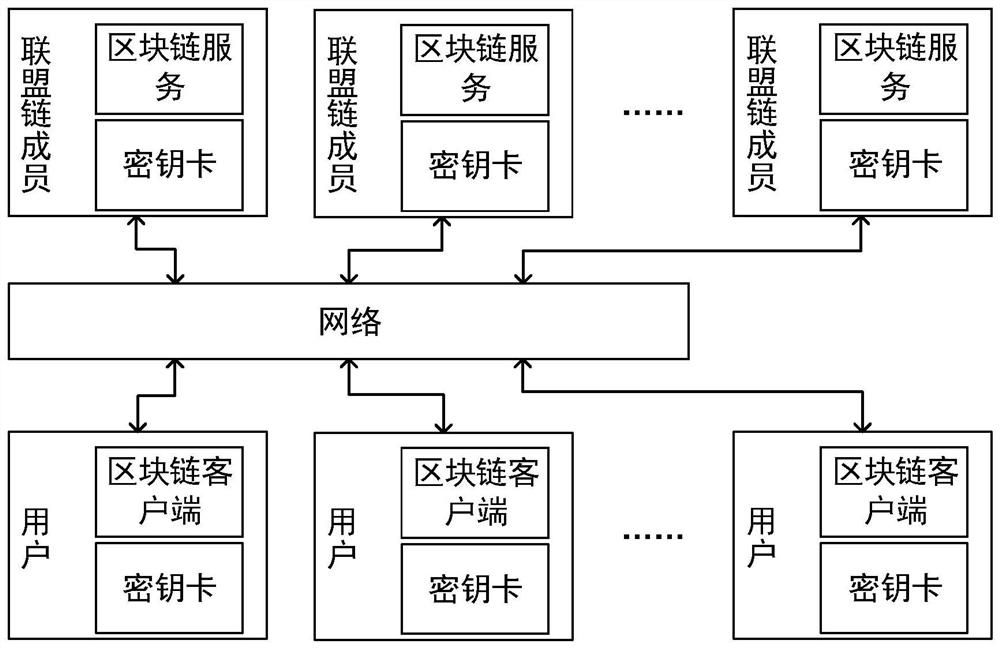
ActiveCN110661613AReduce the risk of theftImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSecret shareInternet privacy
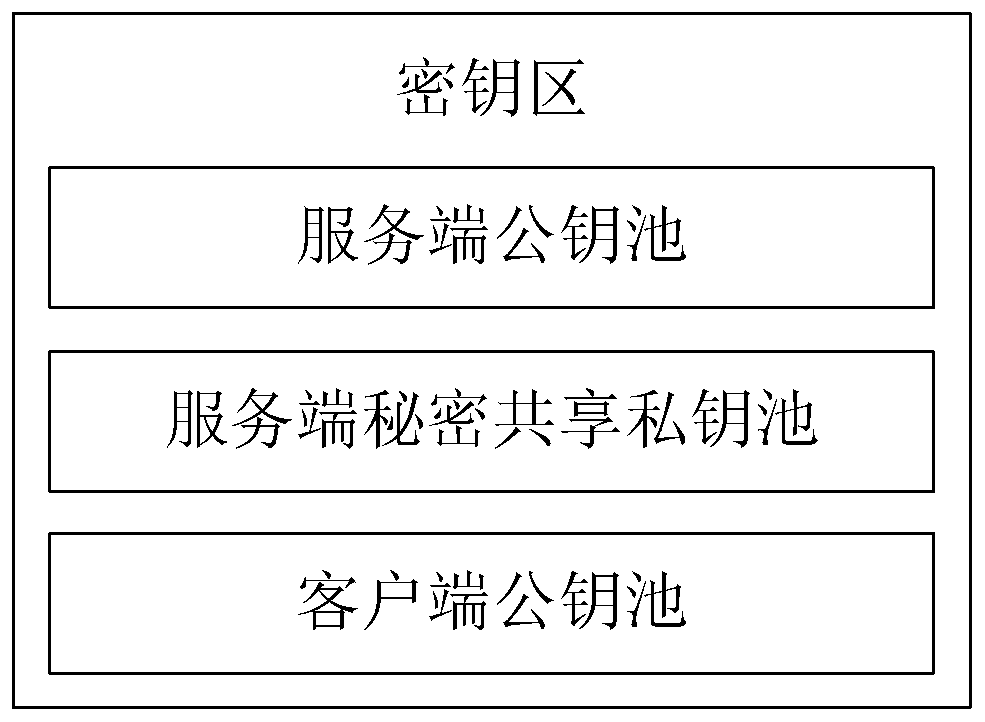
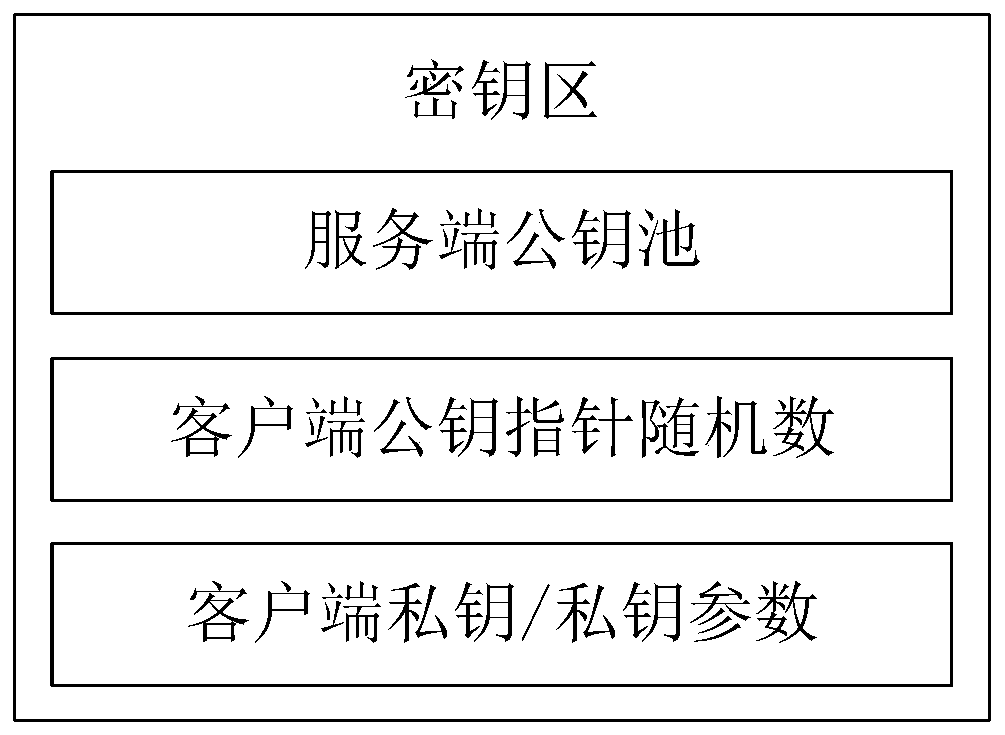
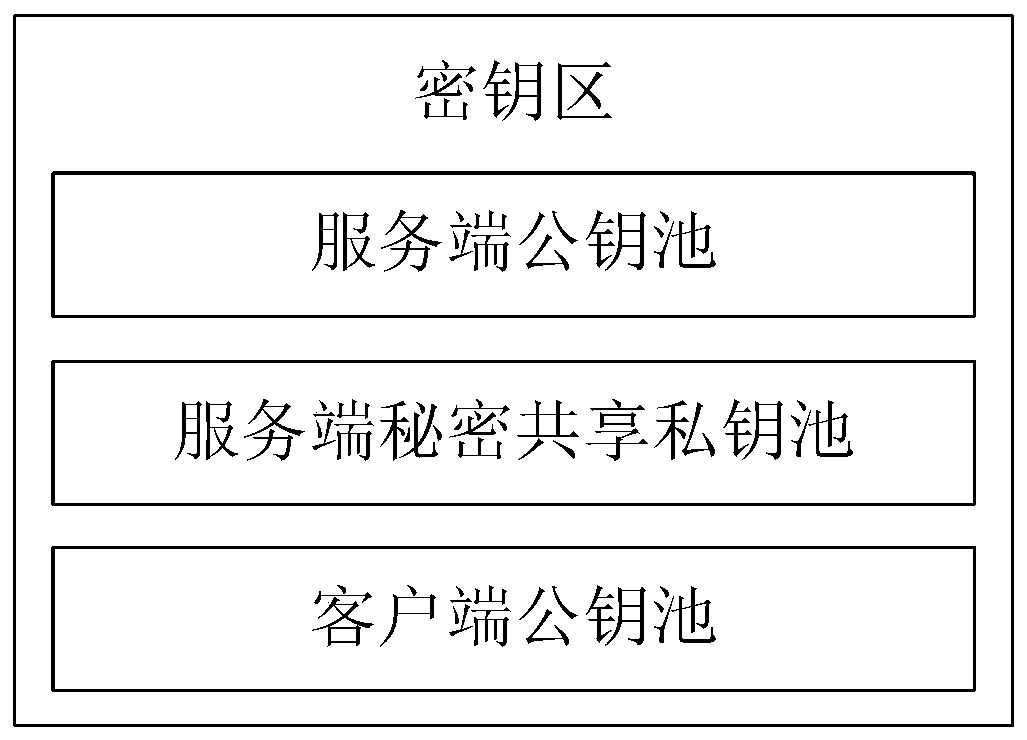
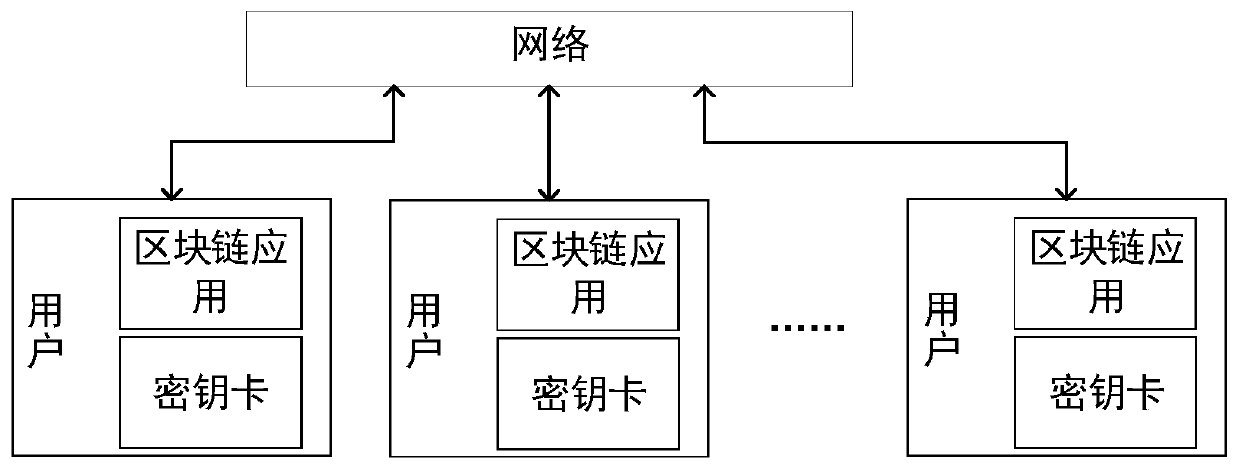
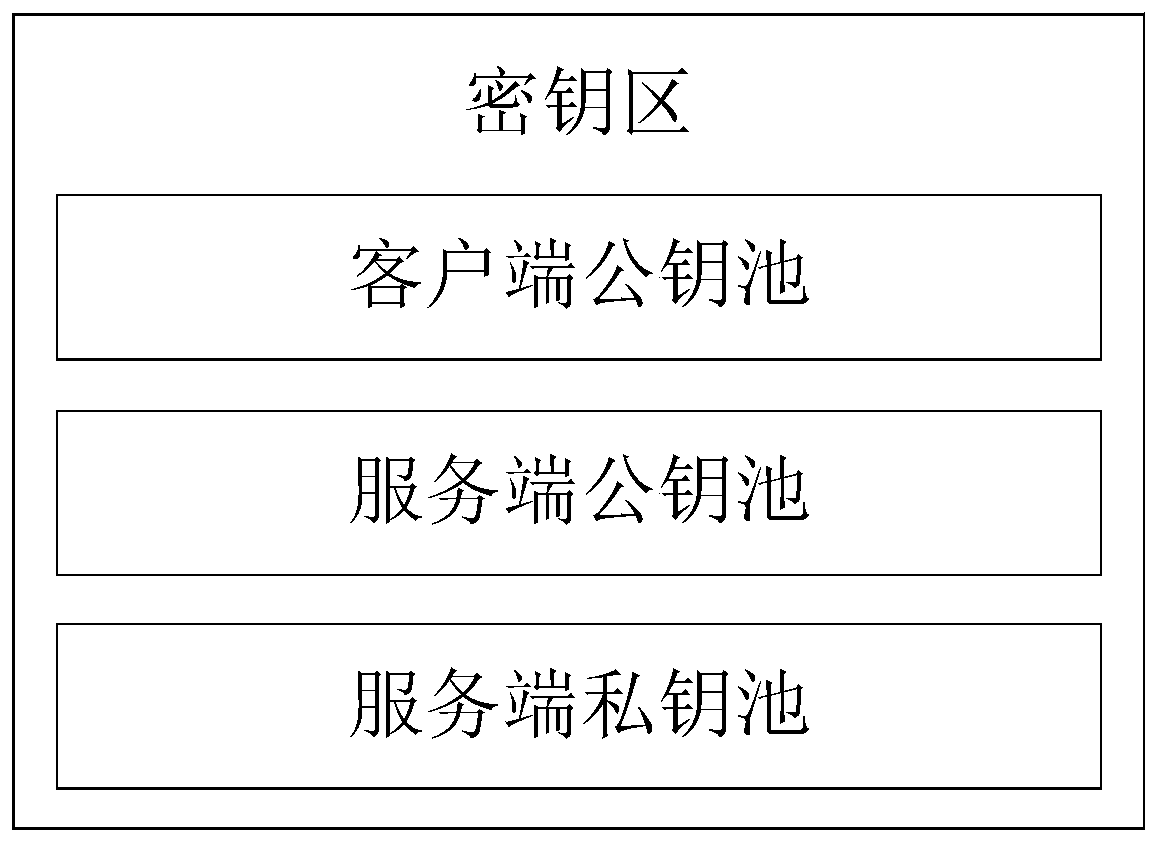
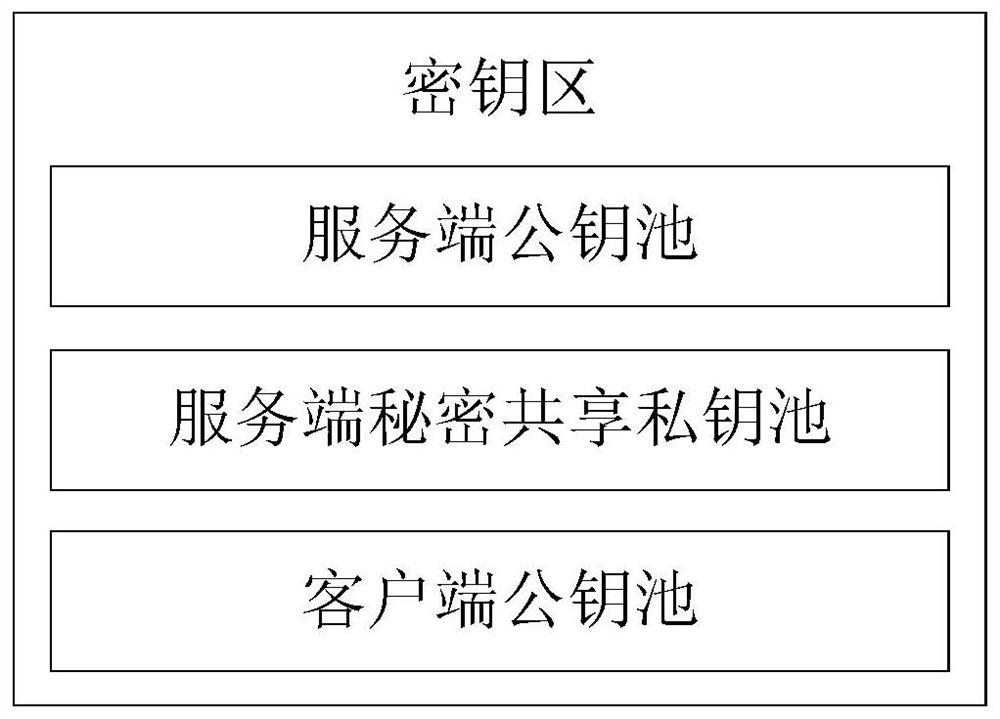
The invention relates to an anti-quantum computing implicit certificate issuing method and system based on an alliance chain implemented among alliance chain members communicating with each other. Thealliance member comprises a client and a server. The invention is characterized in that each party is configured with a key fob; algorithm parameters and server public key pools are stored in secretkey cards; the secret key cards of the server store a server secret sharing private key pool and a client public key pool. Client units in one-to-one correspondence with clients are stored in the client public key pool. Each client unit comprises a user name, an identity label, a public key updating state and an implicit certificate of the corresponding client, private key parameters are stored in a secret sharing mode, and safety is further improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
Method and system for generating implicit certificates and applications to identity-based encryption (IBE)
The invention relates to a method of generating an implicit certificate and a method of generating a private key from a public key. The method involves a method generating an implicit certificate in three phases. The public key may be an entity's identity or derived from an entity's identify. Only the owner of the public key possesses complete information to generate the corresponding private key. No authority is required to nor able to generate an entity's private key.
Owner:MALIKIE INNOVATIONS LTD
Anti-quantum computing anonymous identity recognition method and system based on alliance chain and implicit certificate
ActiveCN110737915AImprove securityDigital data protectionInternal/peripheral component protectionSecret shareInternet privacy
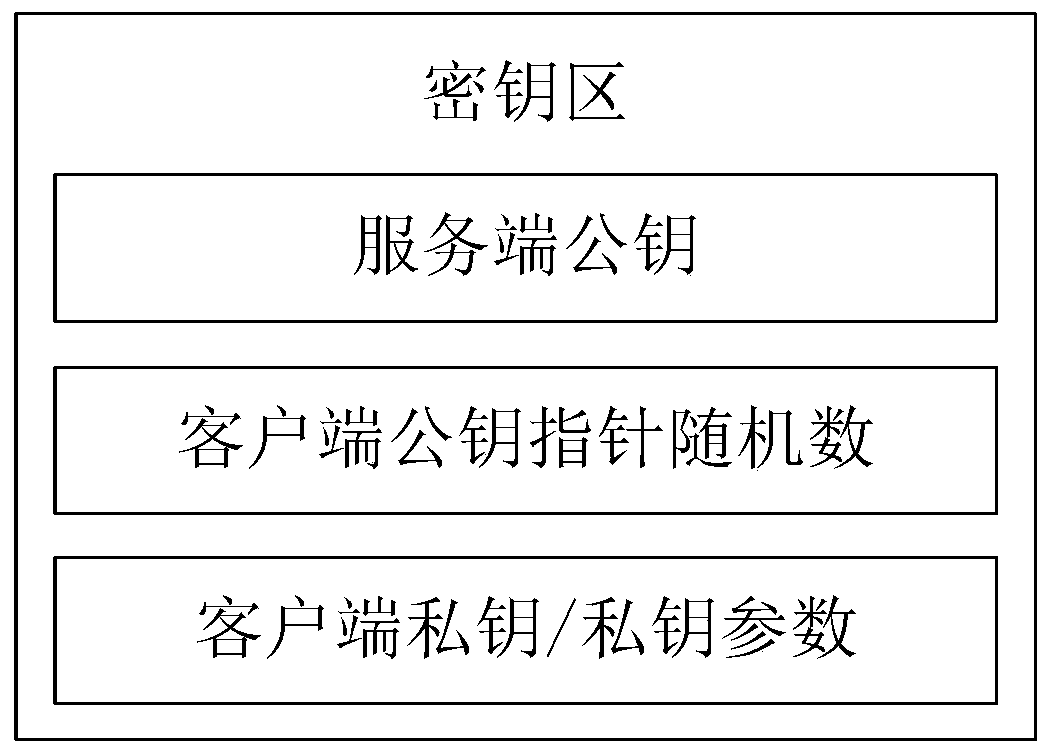
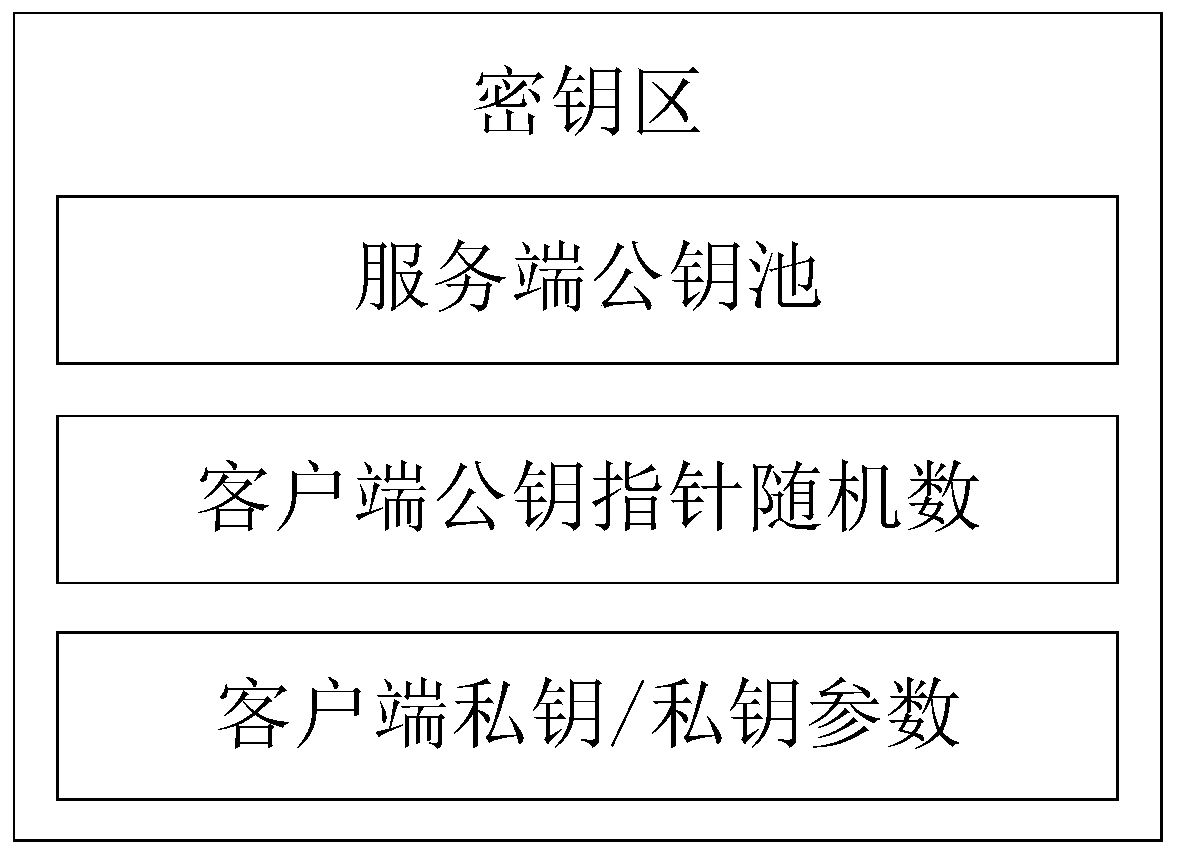
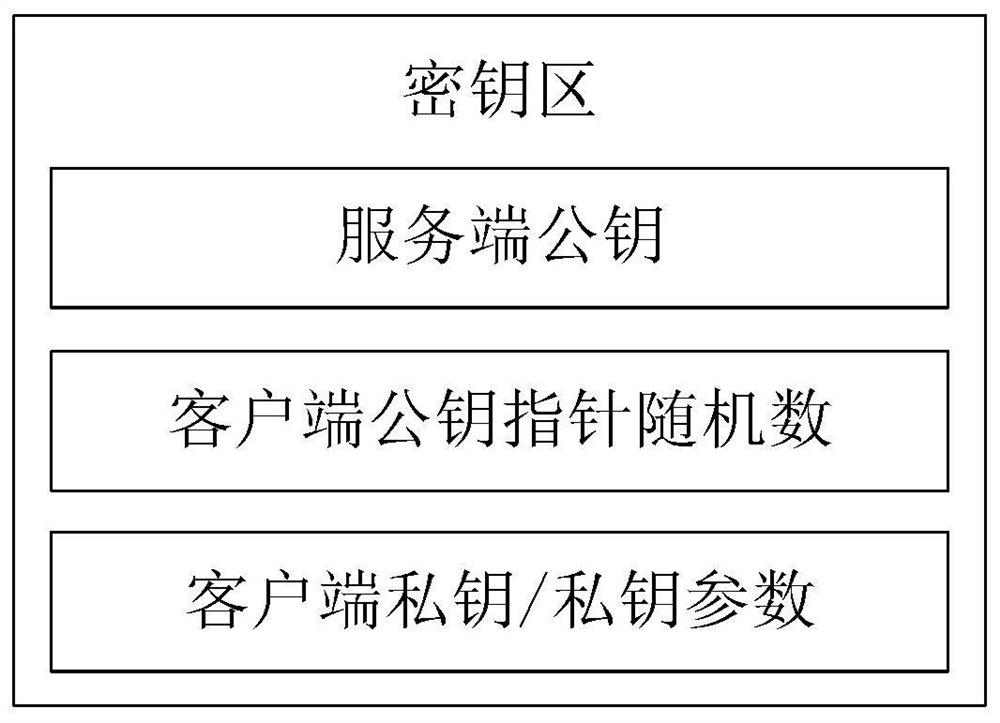
The invention relates to an anti-quantum computing anonymous identity recognition method and system based on an alliance chain and an implicit certificate. The method is implemented among alliance chain members communicating with each other, the alliance chain members include client members and server members, each party is configured with a key fob, and algorithm parameters and a server public key pool are stored in all the key fobs; a secret key card of the server stores a server secret sharing private key pool and a client public key pool. Client units in one-to-one correspondence with theclients are stored in the client public key pool, and each client unit comprises a user name, a true identity identifier, a public key updating state, an implicit certificate and a false identity identifier of the corresponding client; a client public key pointer random number, a client private key and a private key parameter are stored in a secret key card of the client, a message sent by a Userdoes not disclose an own real identity identifier, and a false identity identifier of the own is disclosed, so that the security of interaction of all parties is further improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
Anti-quantum calculation distributed Internet of Vehicles method and system based on identity secret sharing and implicit certificates
ActiveCN110830245AImprove securityKey distribution for secure communicationHigh level techniquesThird partyIdentity recognition
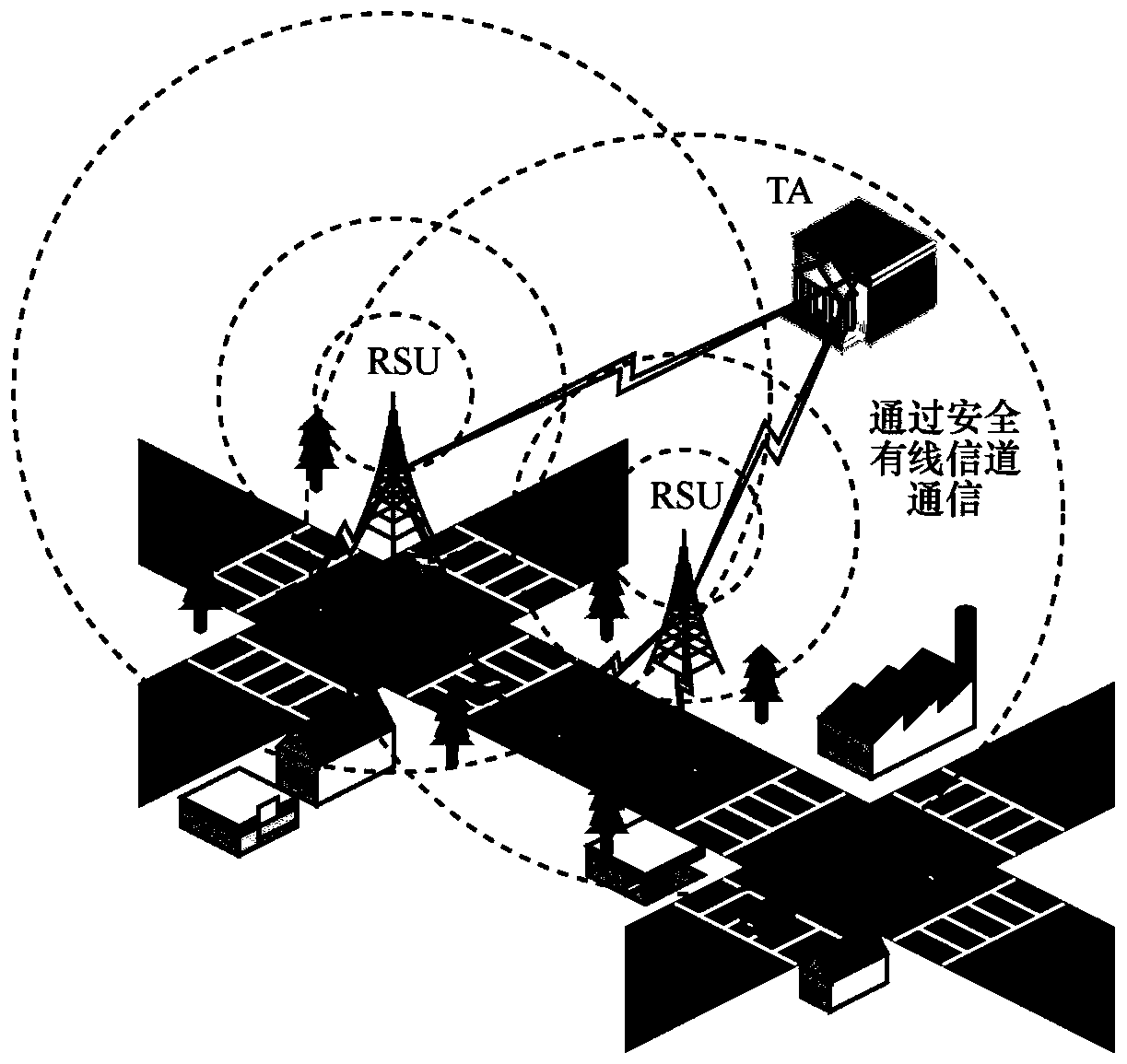
The invention relates to an anti-quantum calculation distributed Internet of Vehicles method and system based on identity secret sharing and an implicit certificate, wherein the client parts and the server parts communicate with each other. The server part comprises a third-party trust mechanism for providing corresponding services and a roadside unit, wherein the client part comprises a vehicle-mounted unit, and is characterized in that each party is configured with a key card, a public key, a private key and algorithm parameters of the own party are stored in all the key cards, and the server part is also configured with a key management server, so that the safety of the identity recognition of the vehicle-mounted unit in the communication process of each party in the Internet of Vehicles is further improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
Anti-quantum computing cloud storage method and system based on alliance chain and implicit certificate
PendingCN110930251AImprove securityPrevent leakageQuantum computersFinanceFile transmissionSecret share
The invention relates to an anti-quantum computing cloud storage method and system based on an alliance chain and an implicit certificate. The method is implemented among alliance chain members communicating with each other. The alliance chain members comprise client members and server members; the server side members comprise an Endorser, an Orderer and a Committer which are used for providing corresponding services; each party is configured with a key fob; a server public key pool, a server secret sharing private key pool and a client public key pool are stored in the server secret key card.Client private keys, private key parameters, server public keys and client public key pointer random numbers are stored in the client secret key cards; and an identity label and an implicit certificate are stored in the client secret key card. According to the method, file query is carried out on the cloud storage server based on the alliance chain and the implicit certificate, corresponding filetransmission is carried out according to the query result, the file transmission comprises uploading and downloading from the cloud storage server, and the file storage security is further improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
Blockchain method and system based on asymmetric key pool and implicit certificate
ActiveCN110545169AReduced risk of crackingEnsure communication securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital signatureQuantum computer
The invention relates to a blockchain method and system based on an asymmetric key pool and an implicit certificate. A quantum computer cannot crack a private key through signature information in a process that a user transmits the signature information to other members through employing a public key in a public key pool as an offset to encrypt the signature information; however, the conventionalmethod is that symmetric encryption calculation is performed on the signature, and the calculated amount is much higher than the offset calculation of the patent. Therefore, the offset calculation ofthe patent is a better anti-quantum calculation mode. In the blockchain system, digital signatures are numerous in calculation, so that the calculation amount of the whole blockchain system in the aspect of digital signature encryption and decryption can be greatly reduced.
Owner:RUBAN QUANTUM TECH CO LTD +1
Masking the output of random number generators in key generation protocols
ActiveUS8429408B2Key distribution for secure communicationPublic key for secure communicationDeterministic encryptionNumber generator
Owner:MALIKIE INNOVATIONS LTD
Implicit certificate distribution method and system
ActiveCN109978518AMuch recognitionEasy to useKey distribution for secure communicationPublic key for secure communicationDigital currencyEdwards curve
Owner:DATA COMM SCI & TECH RES INST +1
Batch authentication method for elliptic curve digital signature algorithm under implicit certificate
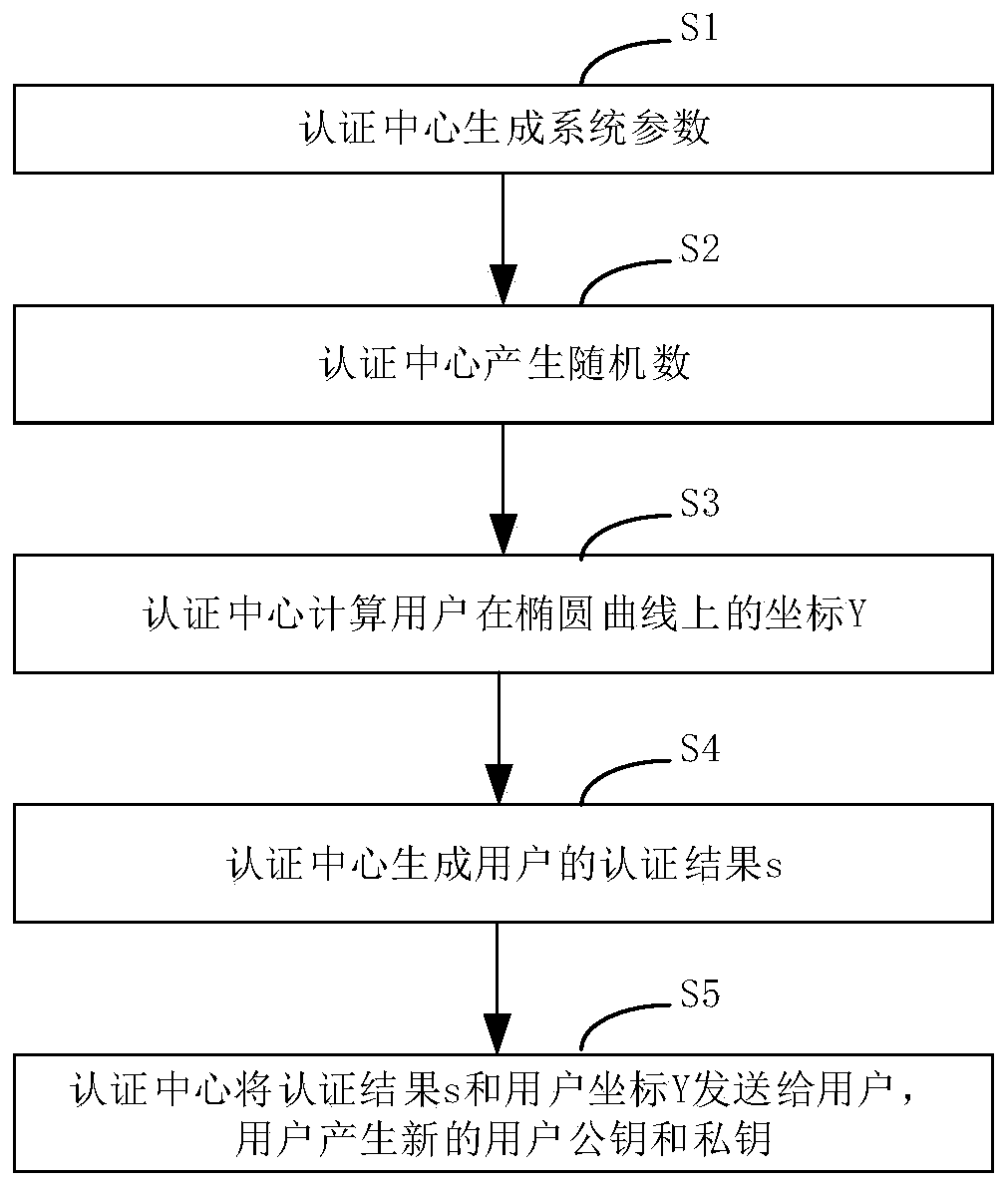
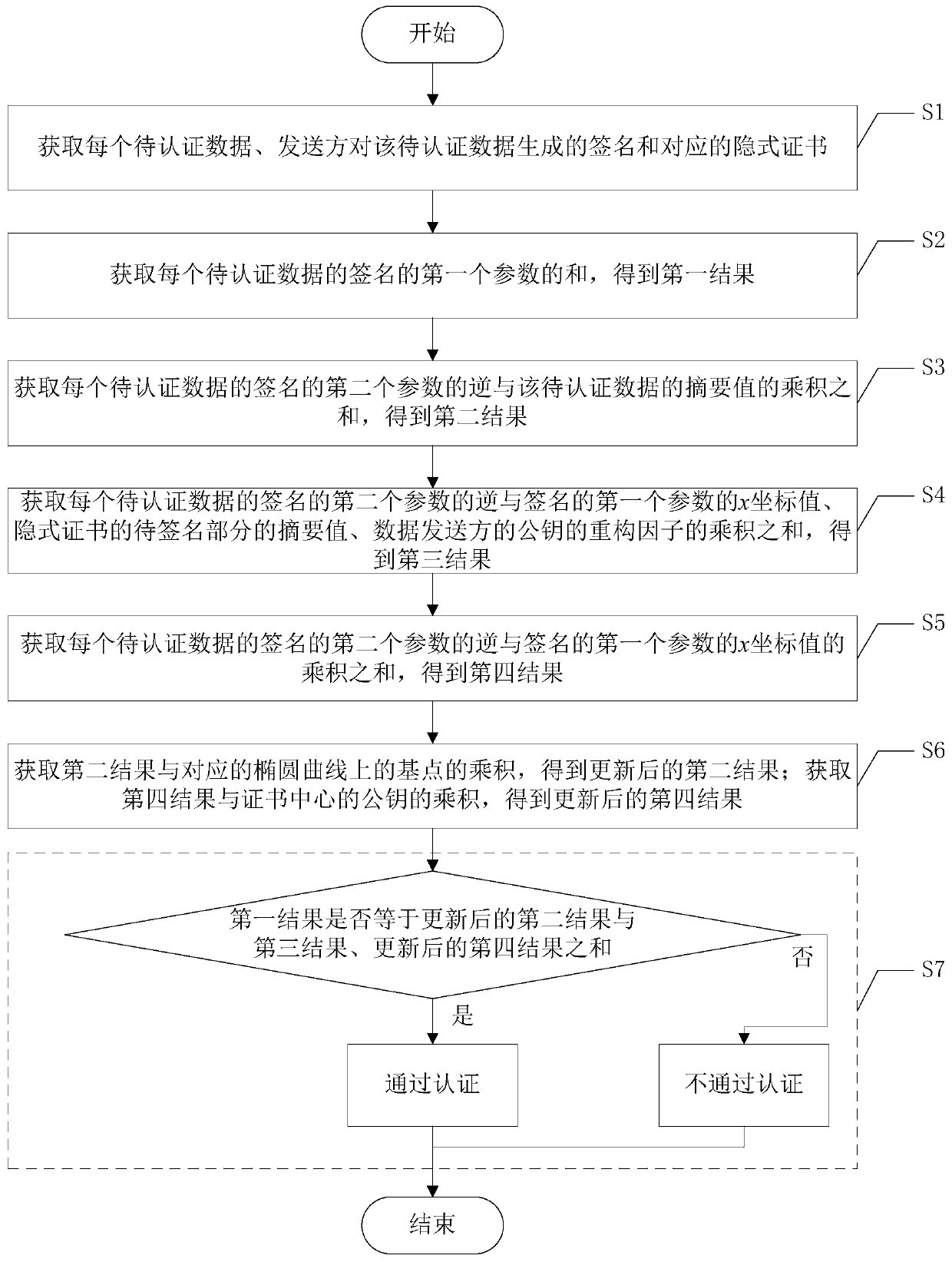
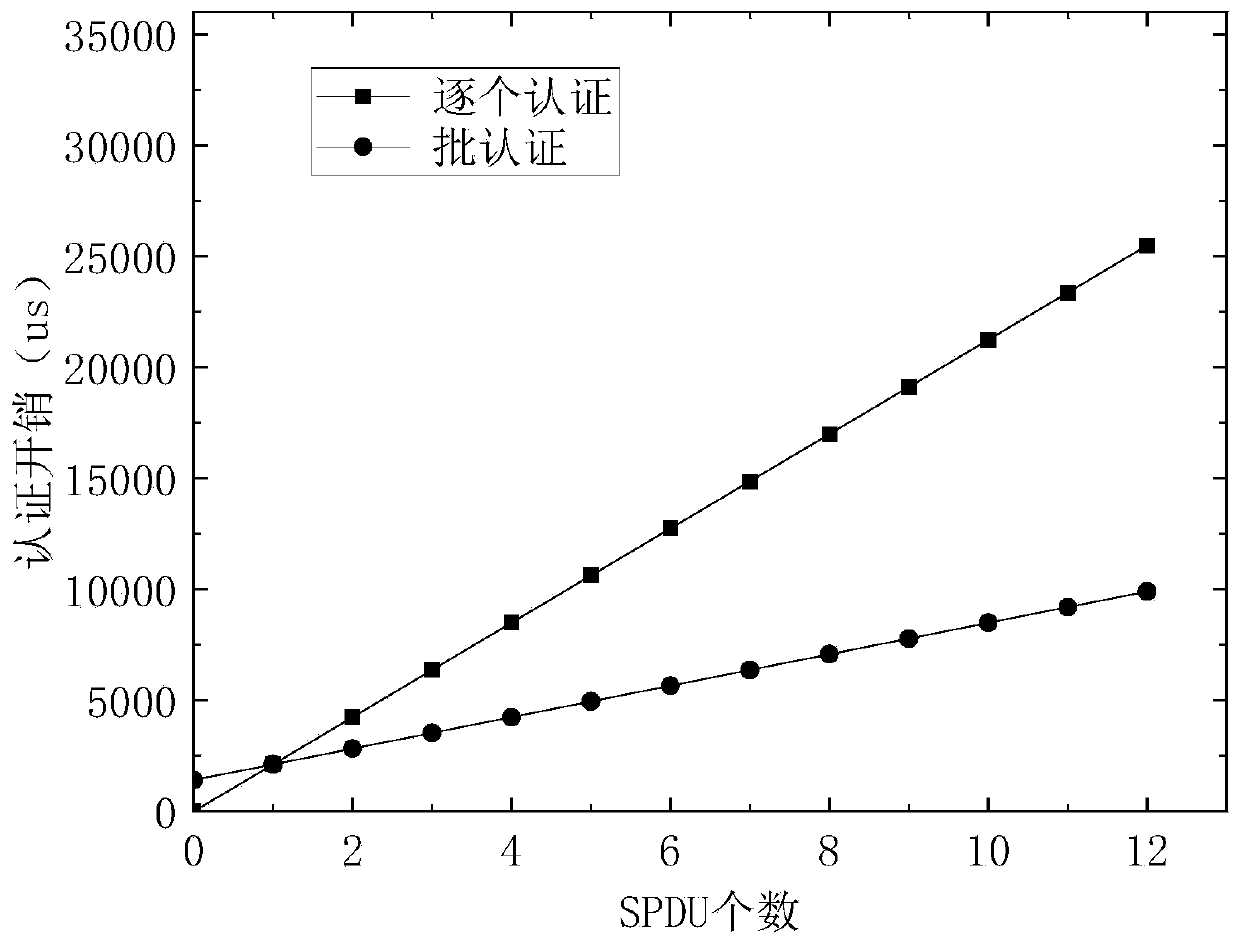
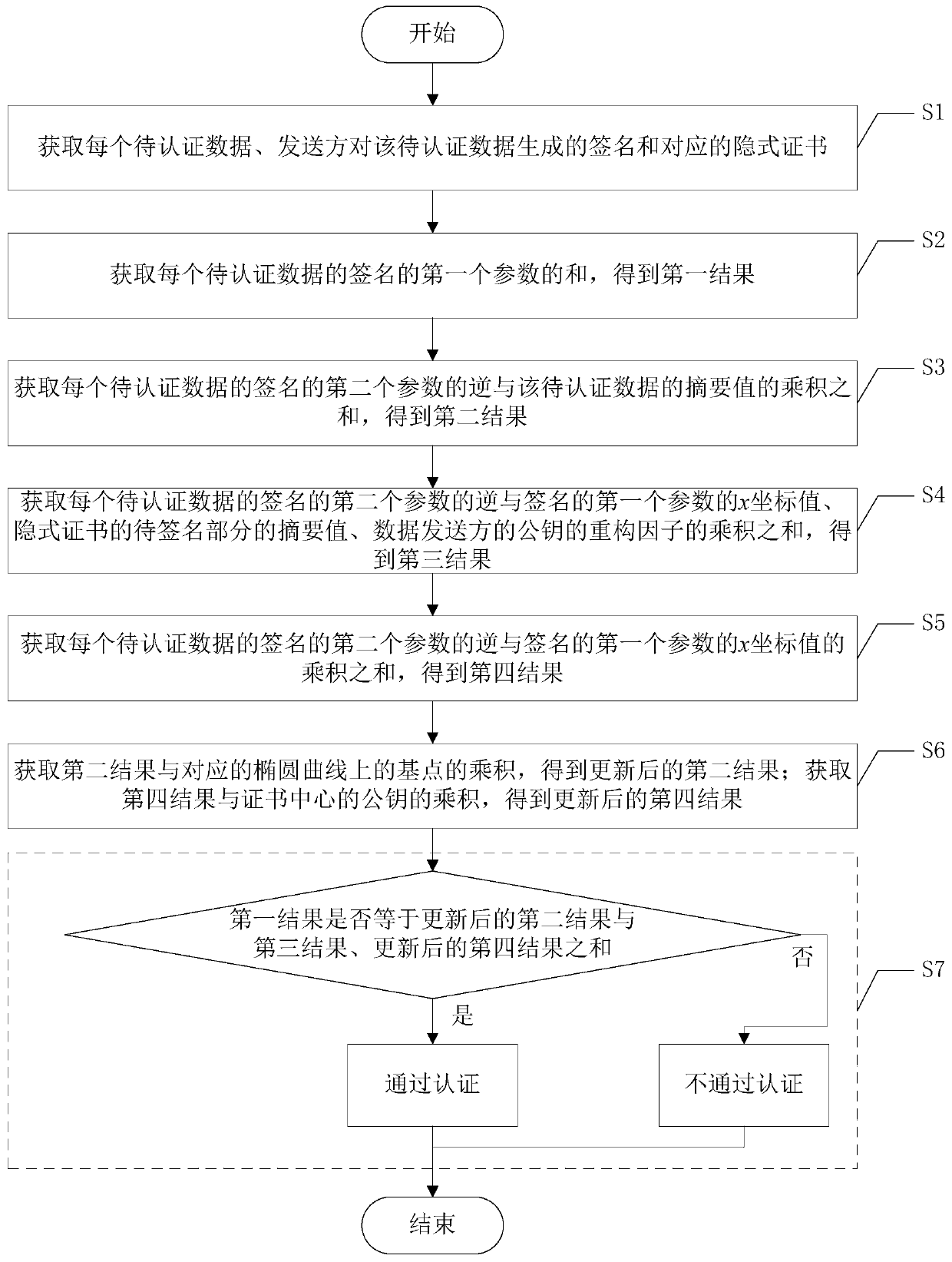
ActiveCN109981289AReduce authentication performance overheadReduce computational overheadMultiple keys/algorithms usagePublic key for secure communicationNetwork packetElliptic Curve Digital Signature Algorithm
The invention discloses a batch authentication method for an elliptic curve digital signature algorithm under an implicit certificate. The method mainly comprises the following steps: judging whetherthe sum of the first parameters of the signatures of the to-be-authenticated data is equal to the sum of the products of the inverse of the second parameters of the signatures of the to-be-authenticated data and the abstract values of the to-be-authenticated data and the products of the base points on the corresponding elliptic curves plus the inverse of the second parameters of the signatures ofthe to-be-authenticated data and the signatures; the sum of the product of the x coordinate value of the first parameter, the abstract value of the to-be-signed part of the implicit certificate and the reconstruction factor of the public key of the data sender plus the result obtained by the product of the sum of the product of the inverse of the second parameter of the signature of each piece ofto-be-authenticated data and the x coordinate value of the first parameter of the signature and the public key of the certificate center. if yes, the data packets of the batch are all legal and pass the authentication, otherwise, the authentication is not passed. The batch authentication method provided by the invention can obviously improve the throughput rate of the system.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
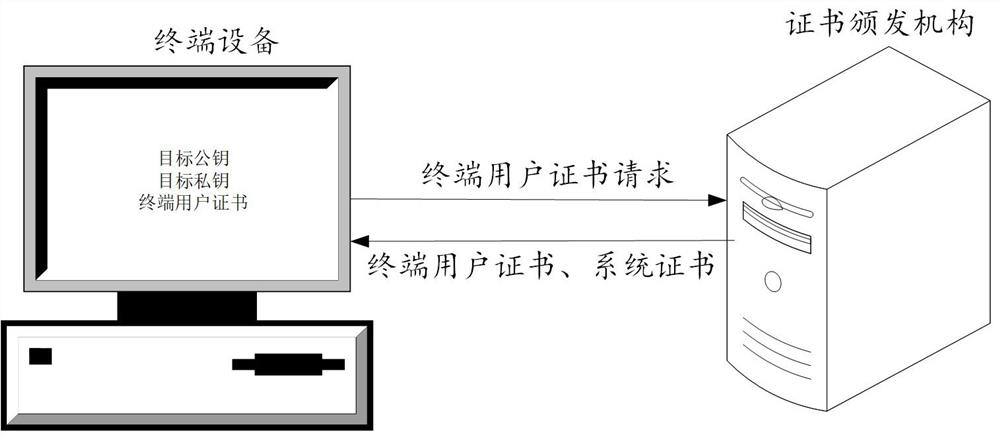
Digital identity authentication method and device, equipment and storage medium
ActiveCN114726546AMeet the establishmentSave storage spacePublic key for secure communicationUser identity/authority verificationDigital identityTerminal equipment
The embodiment of the invention provides a digital identity authentication method and device, equipment and a storage medium, and the method comprises the steps: obtaining a system certificate and a terminal user certificate issued by a certificate authority, the system certificate being a certificate of the certificate authority, the type of the system certificate being a display certificate, and the type of the terminal user certificate being the display certificate; the type of the terminal user certificate comprises an implicit certificate or a certificateless certificate. And obtaining an intermediate public key corresponding to the terminal user certificate based on a terminal user private key. And according to the intermediate public key and a system public key, a target public key is generated, the system public key is a public key corresponding to the system certificate, and the target public key is used for authenticating the digital identity of a terminal user. In the scheme, the advantages of the display certificate and other certificates are fused, the establishment of the existing public key infrastructure trust system can be effectively met, the storage space of the terminal equipment can be effectively reduced, the bandwidth overhead is reduced, and the communication efficiency is effectively improved.
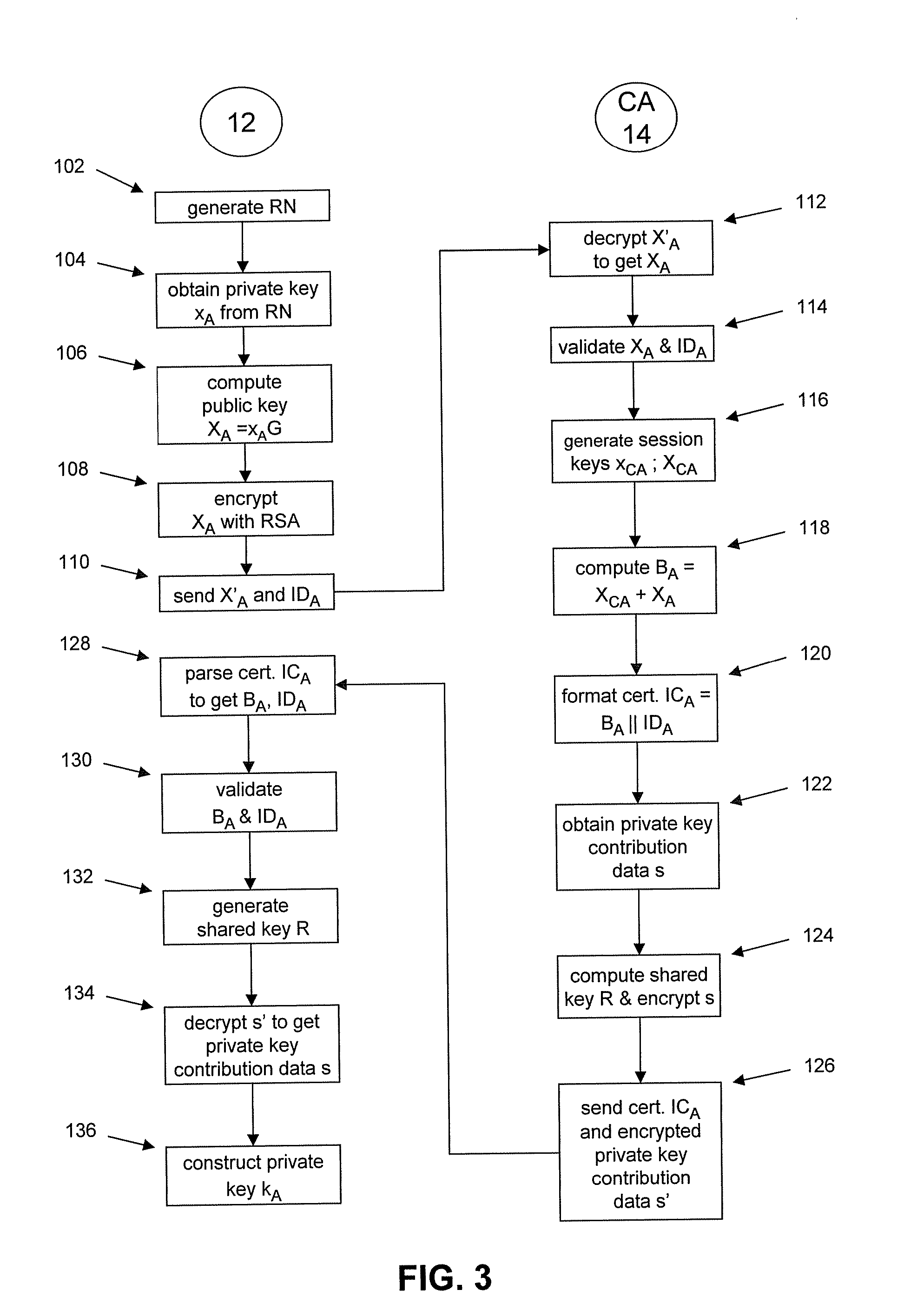
Owner:北京信安世纪科技股份有限公司
QKD network authentication key generation method and system based on alliance chain and implicit certificate
ActiveCN110880969AReduce workloadImprove securityKey distribution for secure communicationUser identity/authority verificationWeb authenticationSecret share
The invention relates to a QKD network authentication key generation method and system based on an alliance chain and an implicit certificate. The method is implemented among alliance chain members communicating with each other. The alliance chain members comprise client members and server members; it is characterized in that each member is configured with a key fob; a server public key pool, a server secret sharing private key pool and a client public key pool are stored in the server secret key card; client private keys, private key parameters, server public keys and client public key pointer random numbers are stored in the client secret key cards, and the server public keys comprise a first public key and a second public key; public key units in one-to-one correspondence with the client members are stored in the client public key pool, and identity identifiers and implicit certificates are stored in the public key units. During communication of each party, encryption communicationis carried out by using the key fob based on the alliance chain and the implicit certificate, so that the security is further improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
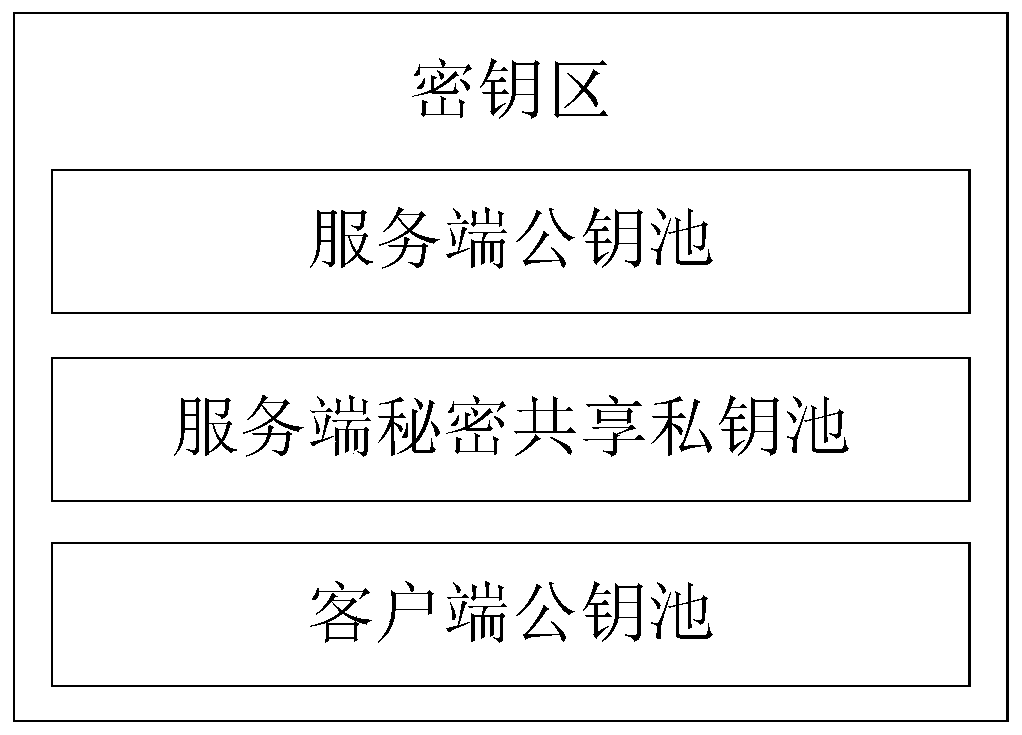
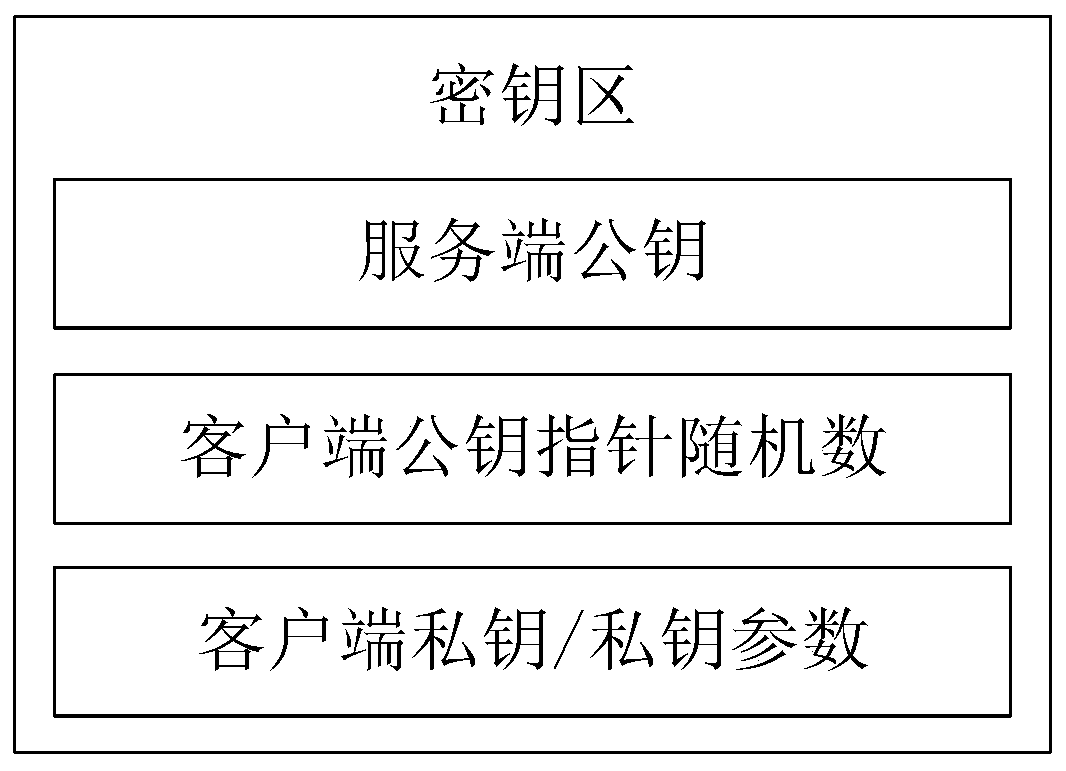
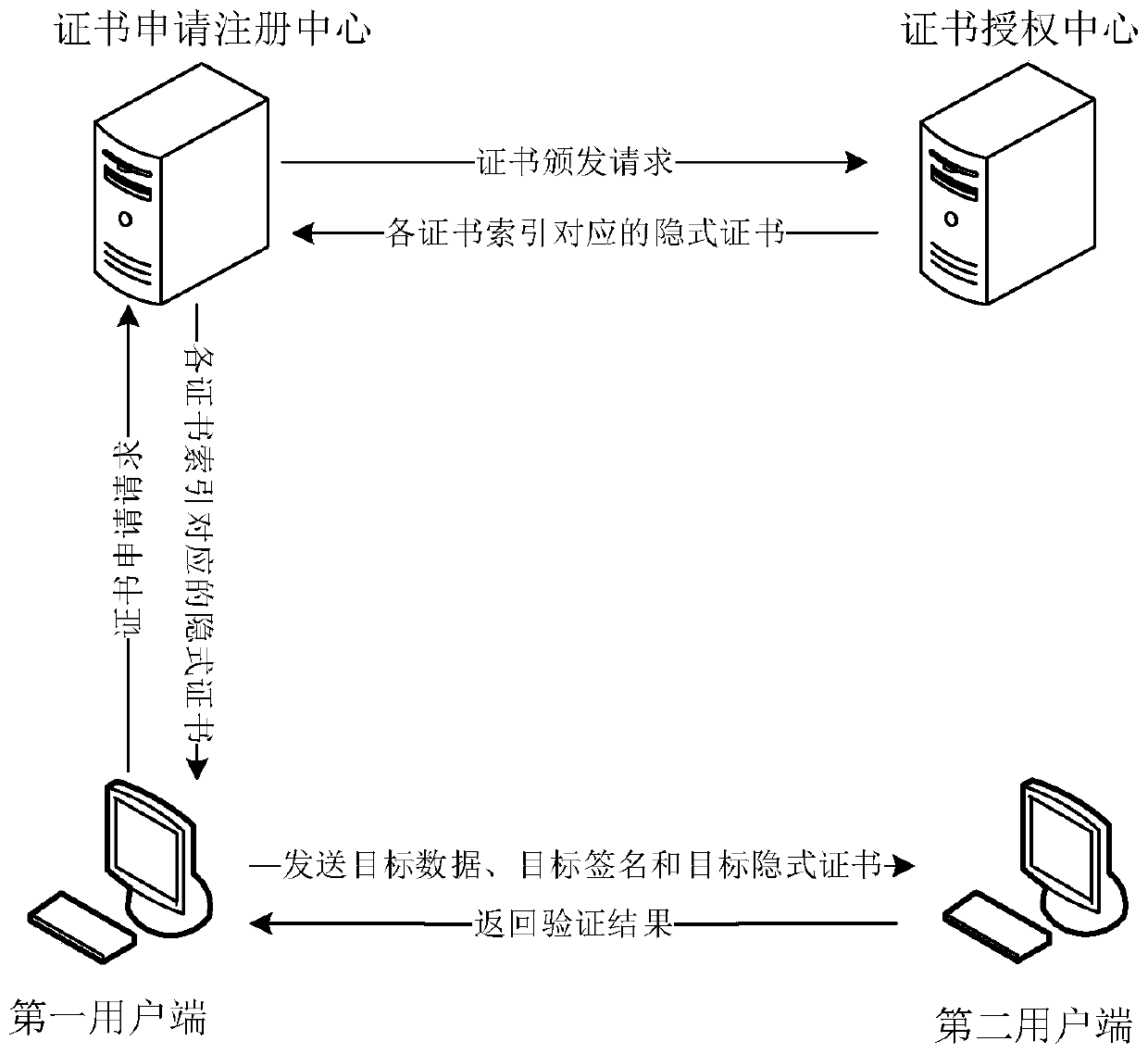
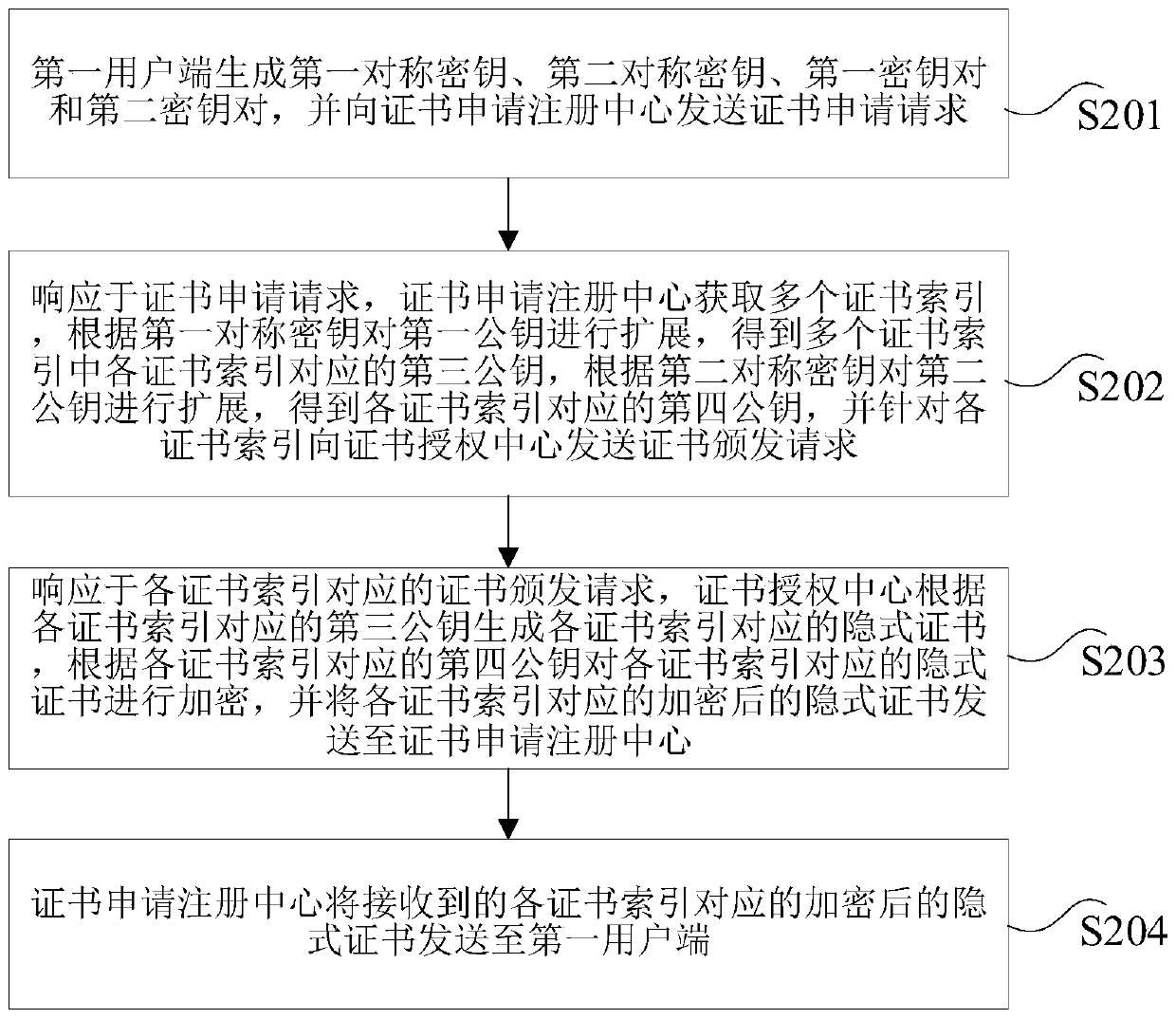
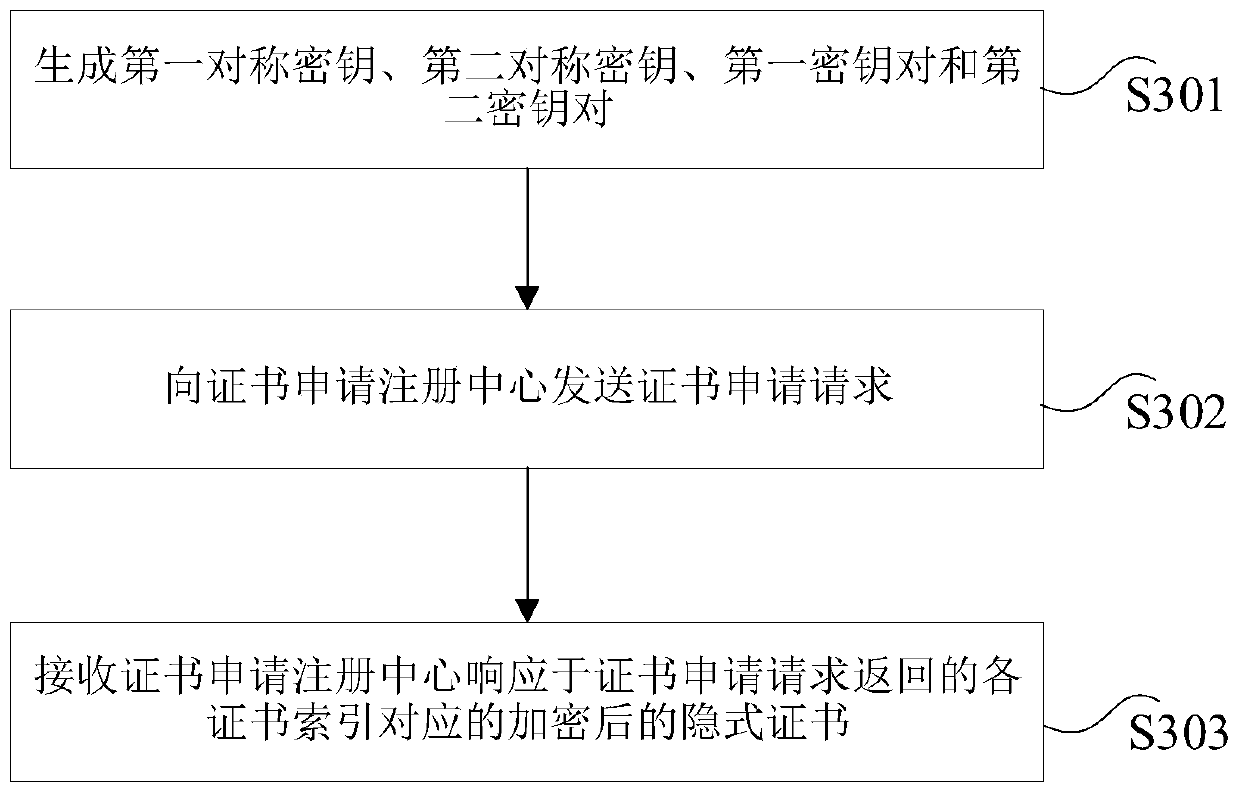
Implicit certificate key extension method and device
ActiveCN111064580AImprove production efficiencySave resourcesUser identity/authority verificationAuthorizationImplicit certificate
The invention provides an implicit certificate key expansion method and device, and the method comprises the steps that a first user side generates a first symmetric key, a second symmetric key, a first key pair and a second key pair, and transmits a certificate application request to a certificate application registration center; the certificate application registration center expands a first public key according to the first symmetric key and expands a second public key according to the second symmetric key to obtain a third public key and a fourth public key corresponding to each certificate index, and sends a certificate issuing request to a certificate authorization center for each certificate index; and the certificate authorization center generates a corresponding implicit certificate according to the third public key corresponding to each certificate index, encrypts the corresponding implicit certificate according to the fourth public key corresponding to each certificate index, and sends the encrypted implicit certificate corresponding to each certificate index to the certificate application registration center. According to the scheme, multiple implicit certificates can be obtained by sending the certificate application request once based on key extension, and the certificate generation efficiency is effectively improved.
Owner:晟安信息技术有限公司
System and method for reducing computations in an implicit certificate scheme
ActiveUS8572367B2Key distribution for secure communicationPublic key for secure communicationData combinationBit-length
There are disclosed systems and methods for reducing the number of computations performed by a computing device constructing a public key from an implicit certificate associated with a certificate authority in an implicit certificate scheme. In one embodiment, the device first operates on the implicit certificate to derive an integer e. The device then derives a pair of integers (e1, e2) from the integer e, such that each of the pair of integers (e1, e2) has a bit length less than the bit length of the integer e, and such that the ratio of the pair of integers (e1, e2) corresponds to the integer e. The device then computes the public key by combining the integers e1 and e2 with public key contribution data derived from the implicit certificate and a public key of the certificate authority.
Owner:MALIKIE INNOVATIONS LTD
Verifiable implicit certificates
ActiveUS9705683B2Key distribution for secure communicationPublic key for secure communicationCryptosystemImplicit certificate
An implicit certificate cryptosystem uses an implicit certificate that includes a pair of certificate components. One of the certificate components includes a public key reconstruction data that is the combination of ephemeral public keys of two entities, one of which is a trusted entity and the other of which is associated with the implicit certificate. The public key reconstruction data is then combined with the identity of the other entity and the combination encrypted to form a first certificate component. A second certificate component is generated by using the first certificate component as a message in a signature scheme and generating a signature of the trusted entity on the message. The two certificate components are provided to the other entity to permit the other entity to generate a private key using one of the certificate components. The corresponding public key can be derived from the remaining certificate component.
Owner:ETAS EMBEDDED SYST CANADA INC
Method and system for generating qkd network authentication key based on consortium chain and implicit certificate
ActiveCN110880969BReduce workloadImprove securityKey distribution for secure communicationUser identity/authority verificationWeb authenticationSecret share
This application relates to a QKD network authentication key generation method and system based on consortium chains and implicit certificates, implemented between consortium chain members communicating with each other, and the consortium chain members include client members and server members, and its features That is, each member is equipped with a key card, and the server key card stores a server public key pool, a server secret shared private key pool, and a client public key pool, and the client key card stores There are client private key, private key parameters, server public key and client public key pointer random number, the server public key includes the first public key and the second public key; the client public key pool stores A public key unit corresponding to each of the client members one by one, and an identity mark and an implicit certificate are stored in the public key unit. When all parties communicate, the key card is used to encrypt the communication based on the alliance chain and the implicit certificate, which further improves the security.
Owner:RUBAN QUANTUM TECH CO LTD +1
Implicit certificate calculation method suitable for Internet of Vehicles environment
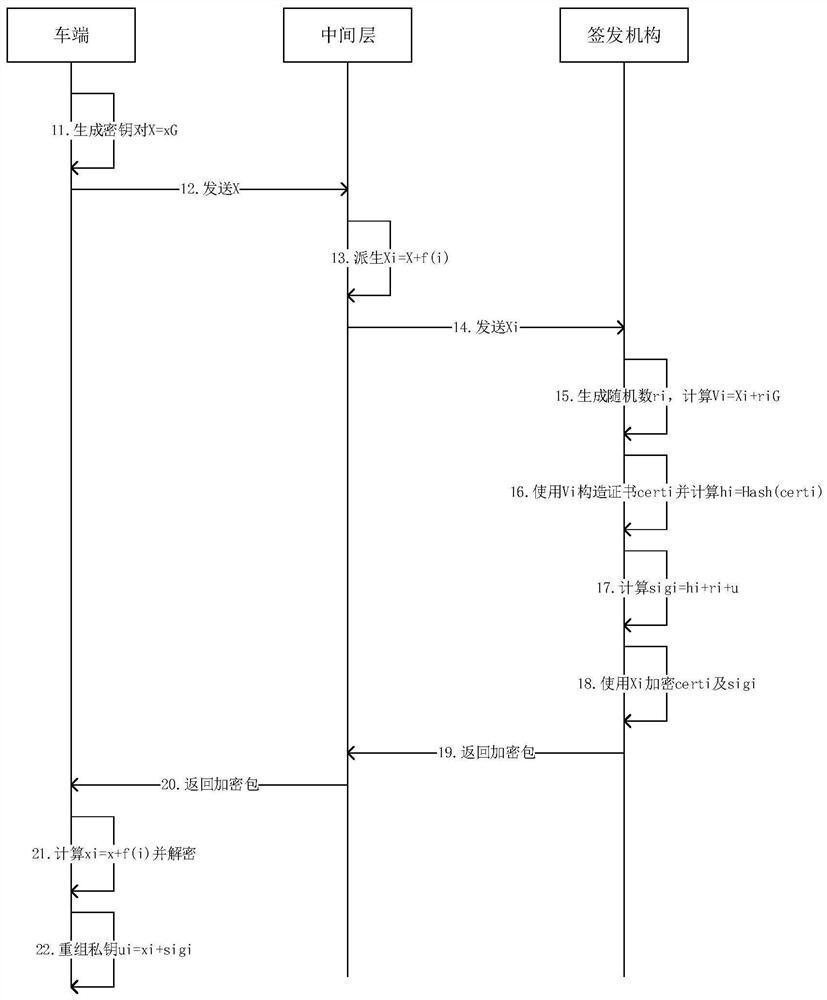
ActiveCN111600860BReduce computationKey distribution for secure communicationUser identity/authority verificationComputer networkThe Internet
The invention discloses an implicit certificate calculation method suitable for the environment of the Internet of Vehicles. Specifically, the issuing authority can use this method to issue an implicit certificate and reconstruct the key pair at the vehicle end. Moreover, moving some calculations from the issuing agency to the vehicle end greatly reduces the performance requirements of the issuing agency and eases the computing pressure on the issuing agency, thereby meeting the needs of a large number of vehicles in the Internet of Vehicles environment.
Owner:KOAL SOFTWARE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com