Acentric digital currency transaction method based on public and private key pair derivation
A public-private key pair and digital currency technology, applied in the field of digital currency, can solve the problems of reduced computing efficiency and increased length of digital currency public ledgers, and achieve the effects of reducing space, strong anonymity, and enhanced anonymity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] Preferred embodiments of the present invention will be specifically described below in conjunction with the accompanying drawings, wherein the accompanying drawings constitute a part of the application and are used together with the embodiments of the present invention to explain the principles of the present invention.
[0049] A specific embodiment of the present invention discloses a centerless digital currency transaction method based on public-private key pair derivation.
[0050] The method for deriving the digital currency public-private key pair:
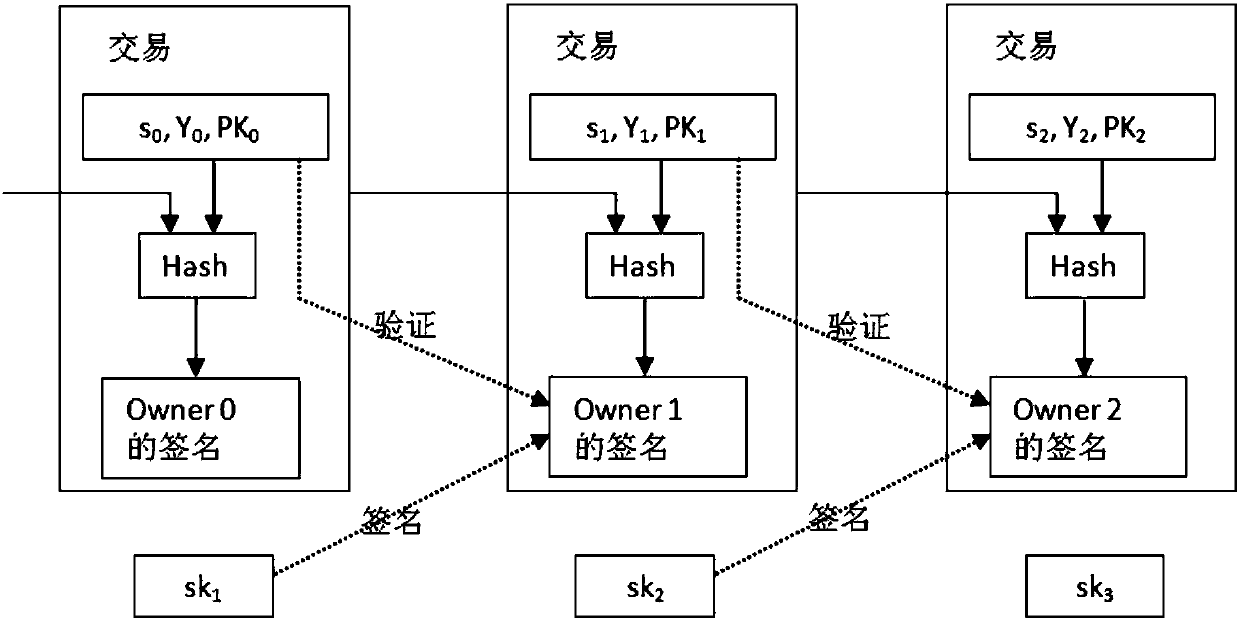
[0051] In the present invention, it is aimed at non-central digital currency, does not require a trusted CA to issue certificates to users, and does not require any trusted nodes to exist. Using the idea of implicit certificates, the payment user actively sends implicit authentication Result (s, Y), said s contains the private key of the paying user, said Y contains the public key of the receiving user, and implies th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com