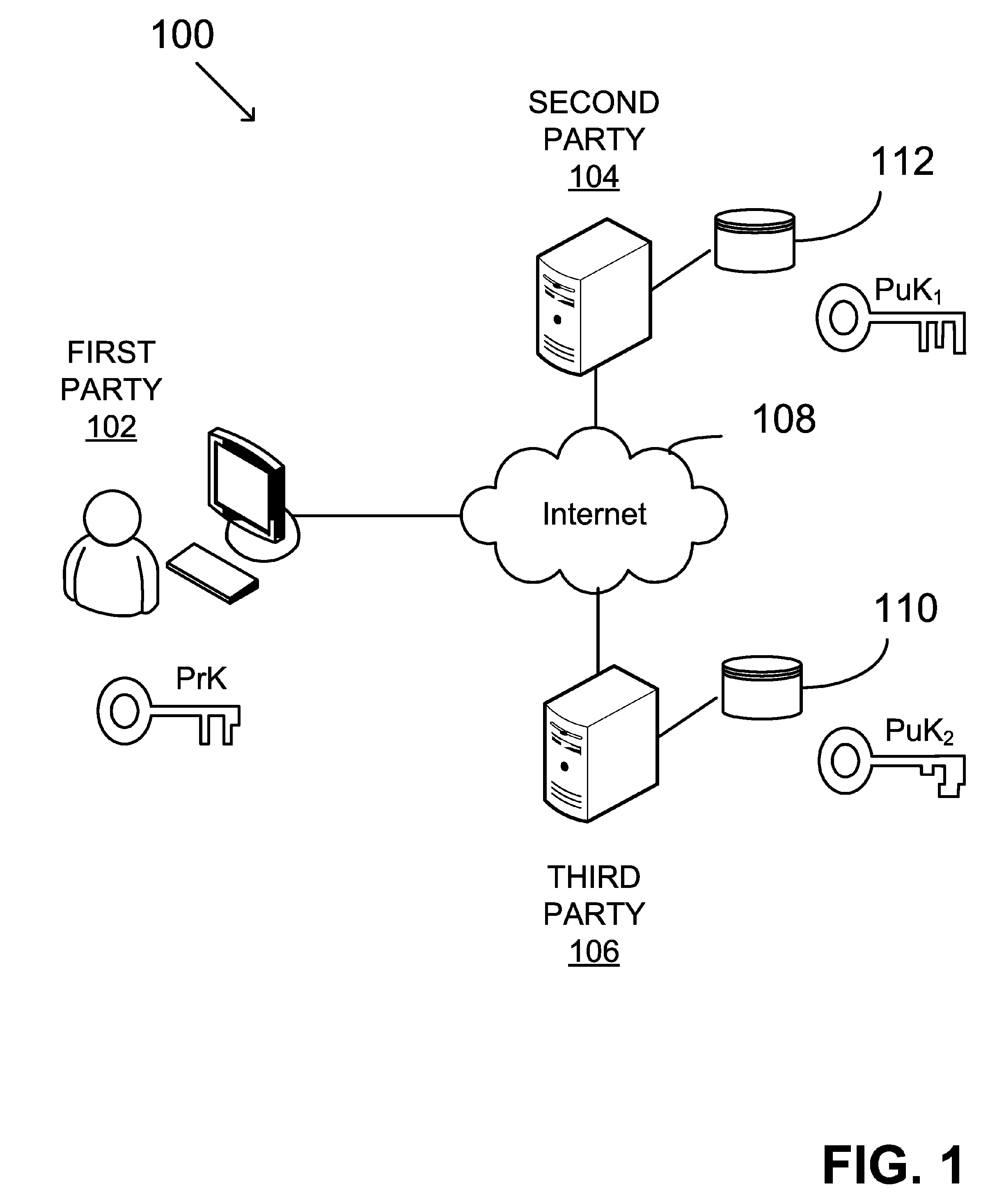
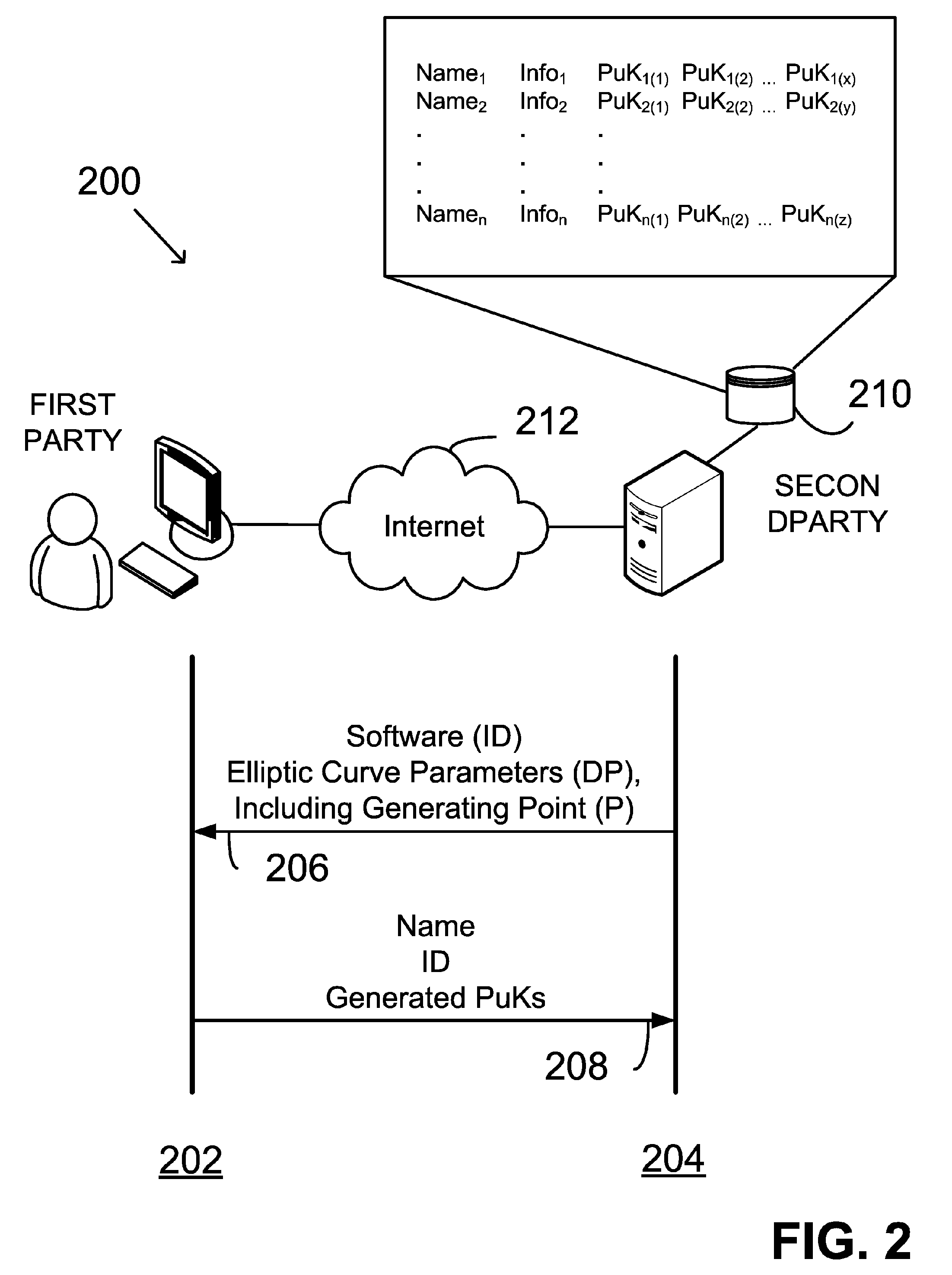
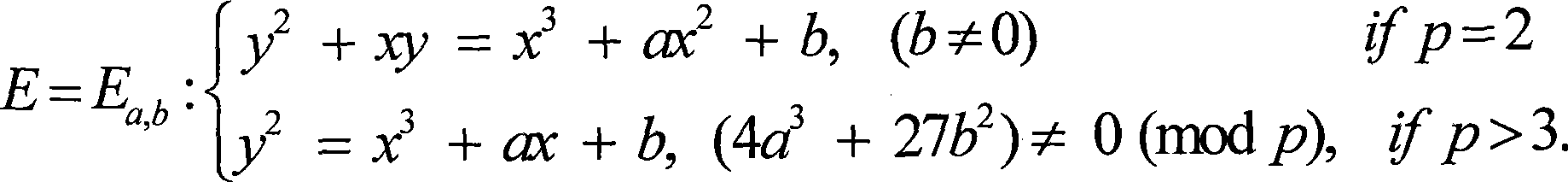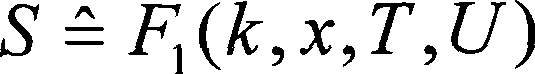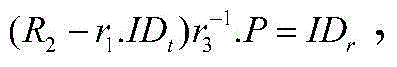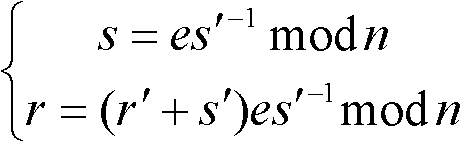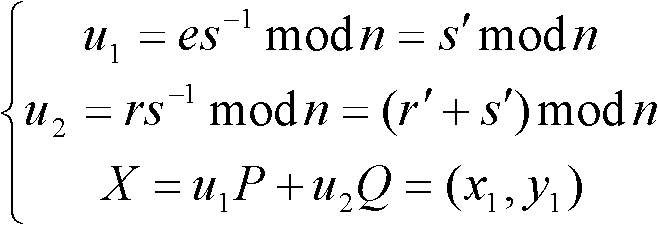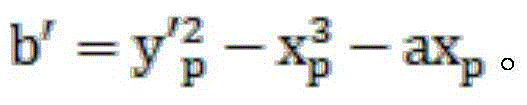Patents
Literature
54 results about "Elliptic Curve Digital Signature Algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
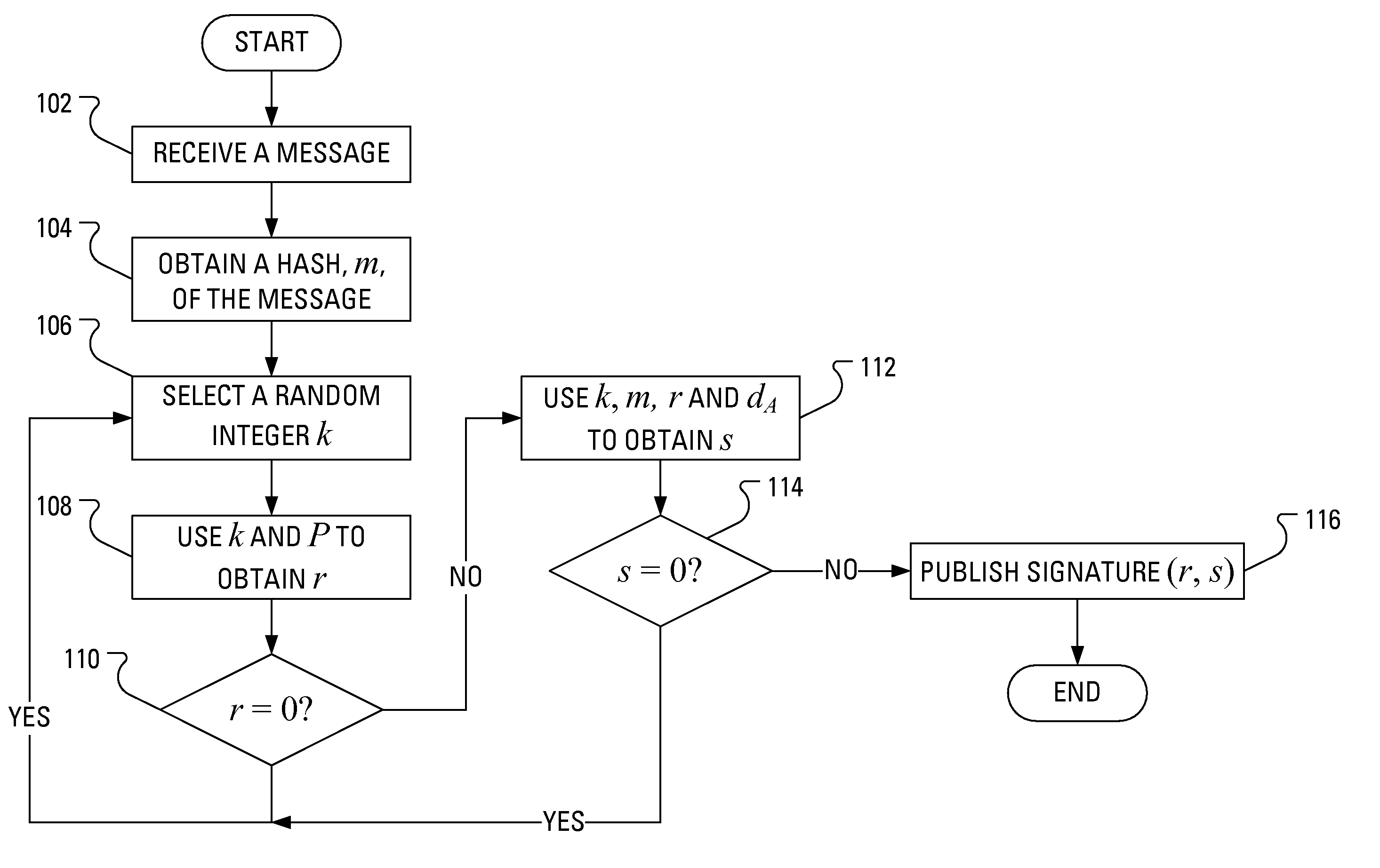
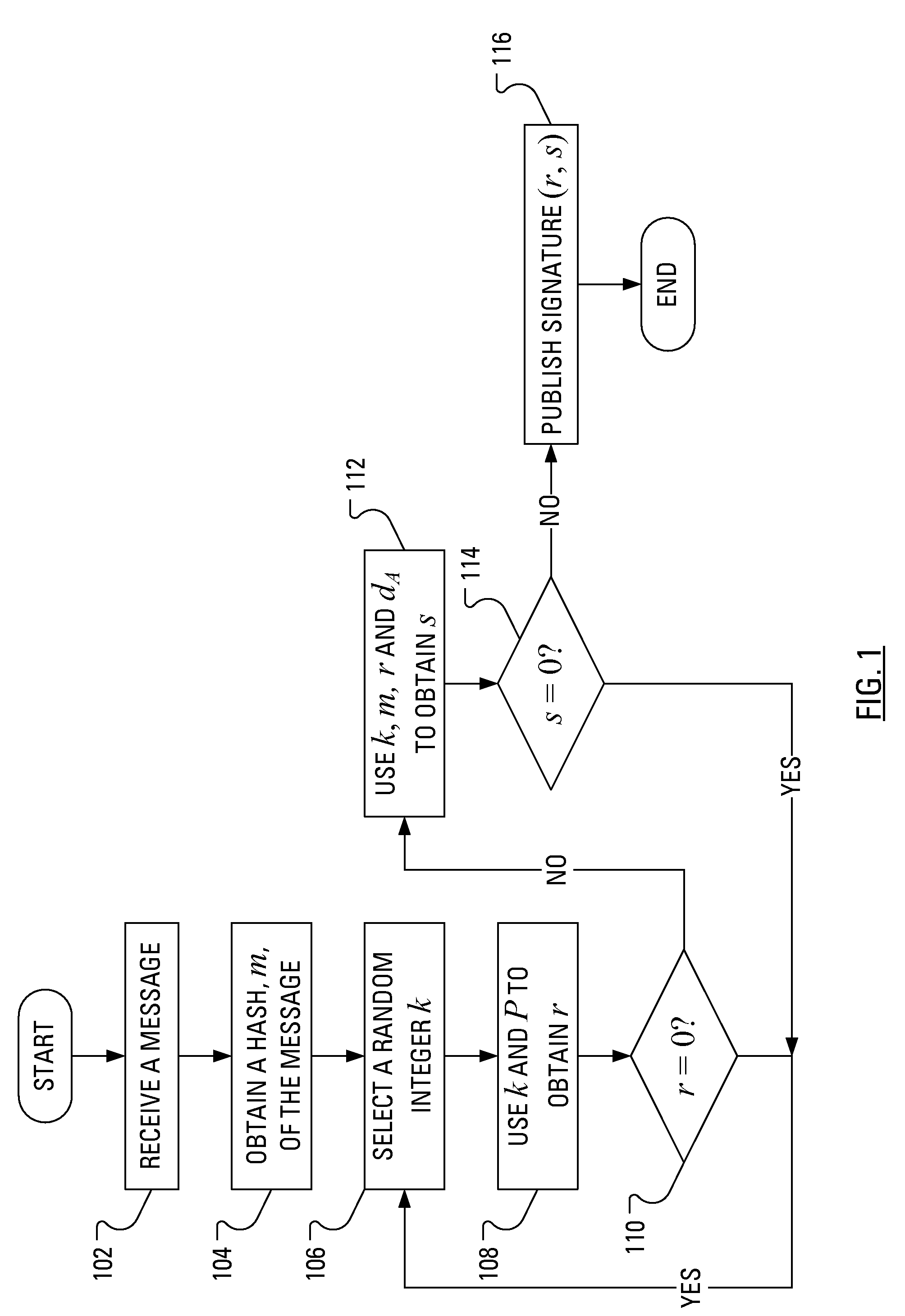
In cryptography, the Elliptic Curve Digital Signature Algorithm (ECDSA) offers a variant of the Digital Signature Algorithm (DSA) which uses elliptic curve cryptography.
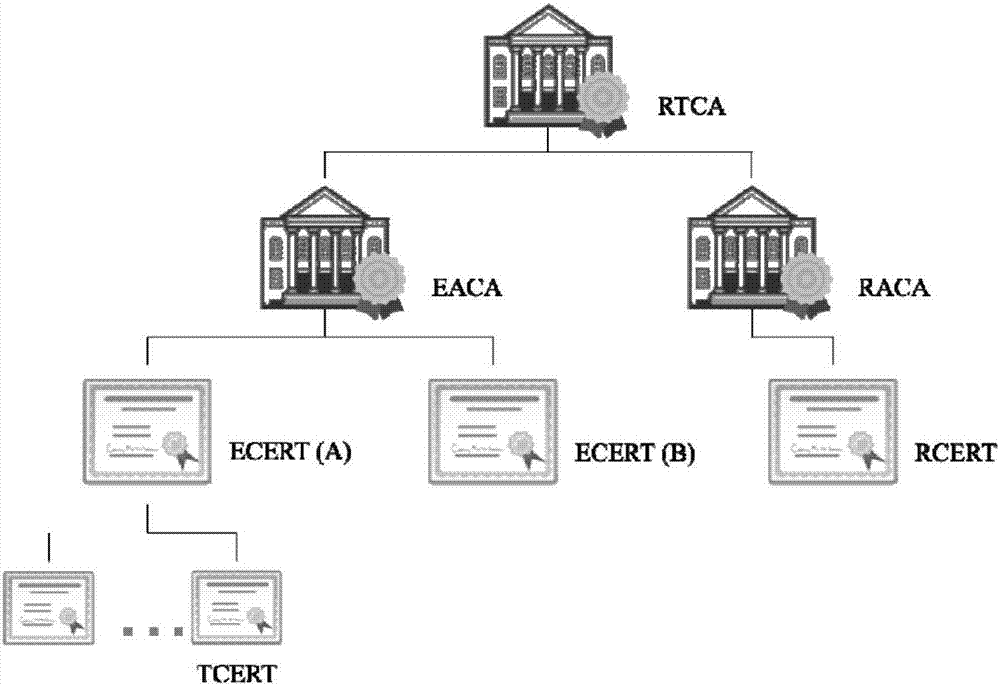
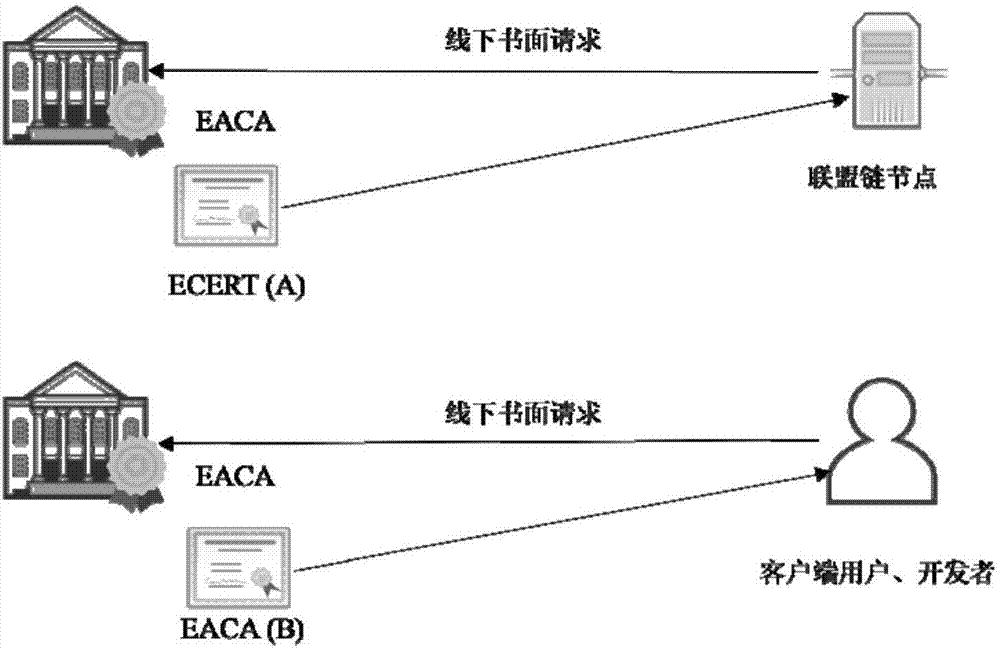
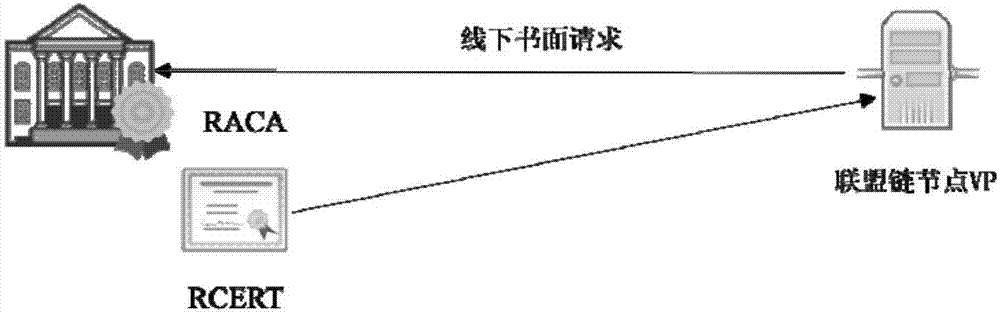
Consortium chain permission control method based on digital certificates and CA authentication system
ActiveCN107426157AProcess controlSecurityUser identity/authority verificationGranularityDigital Signature Algorithm
The invention discloses a consortium chain permission control method based on digital certificates and a CA authentication system. In a consortium chain, the enrollment control and automatic authorization of the consortium chain are realized through a layered digital certificate issuance system. The method of the invention pre-defines three kinds of permission mechanisms for respectively controlling enrollment permissions between consortium chain nodes, role permissions of the consortium chain nodes and access permissions of blockchain users. Three kinds of digital certificates including the enrollment certificate, role certificate and transaction certificate are used for respectively controlling the three permissions of node enrollment, role identification and client enrollment. An internationally accepted elliptic curve digital signature algorithm or a national crypto digital signature algorithm is used for achieving the generation of the digital certificates and secure message signature and validation, the defects of being large in permission granularity of a traditional blockchain or even having no enrollment functions and the like are overcome, the blockchain users are provided with anonymous transaction features, the security of blockchain transactions is improved, and the privacy needs of the users are met.
Owner:HANGZHOU QULIAN TECH CO LTD
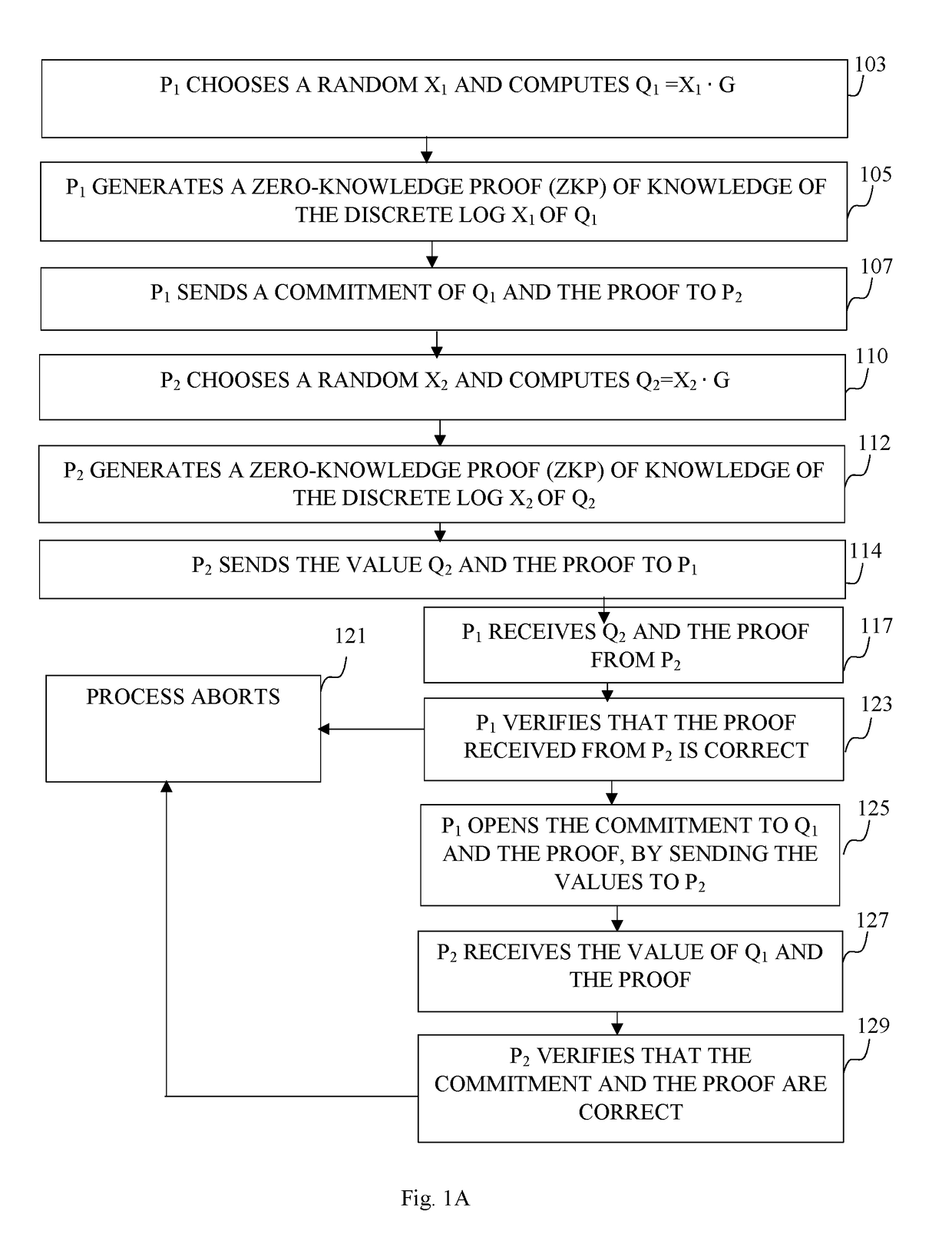
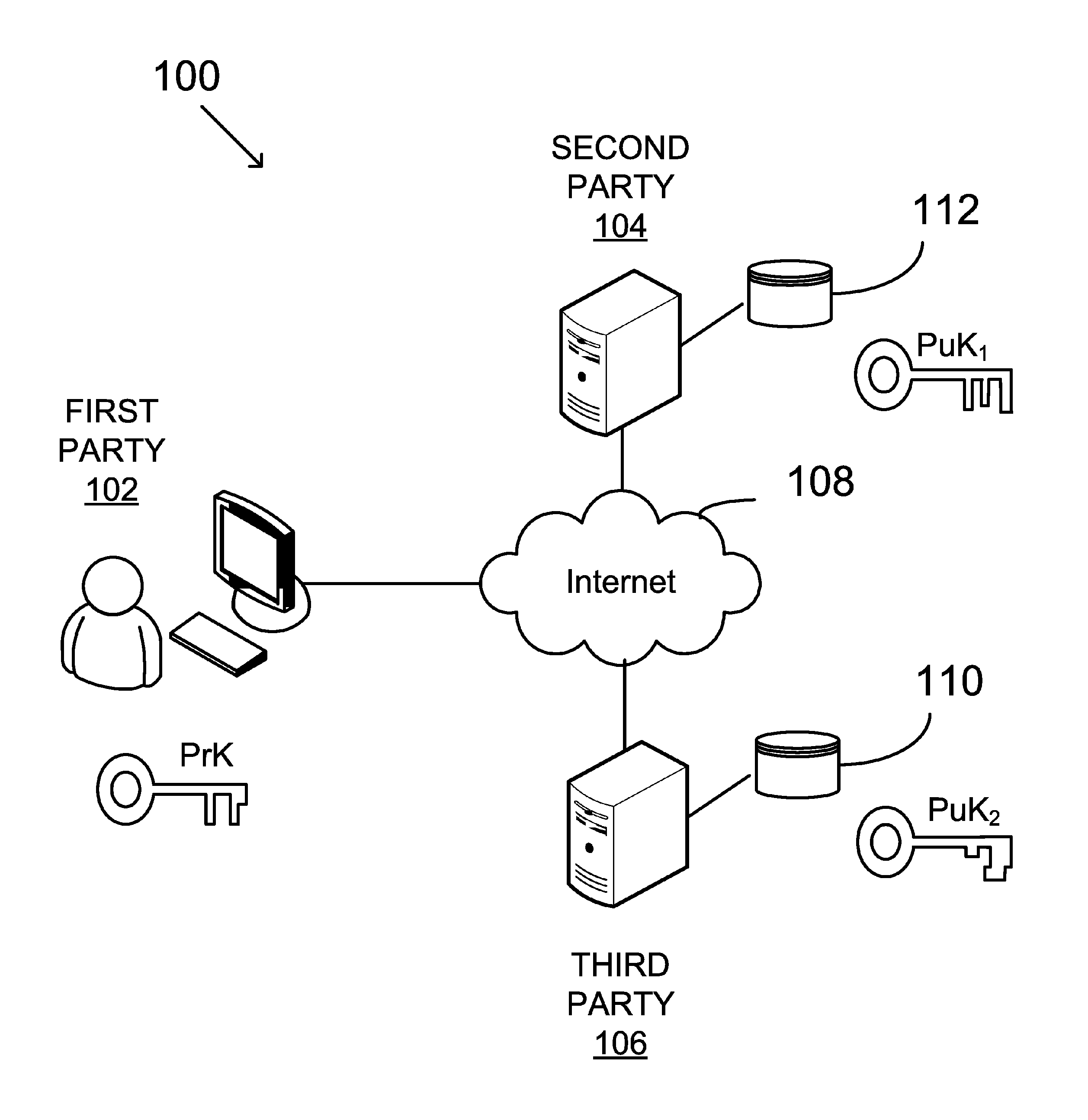
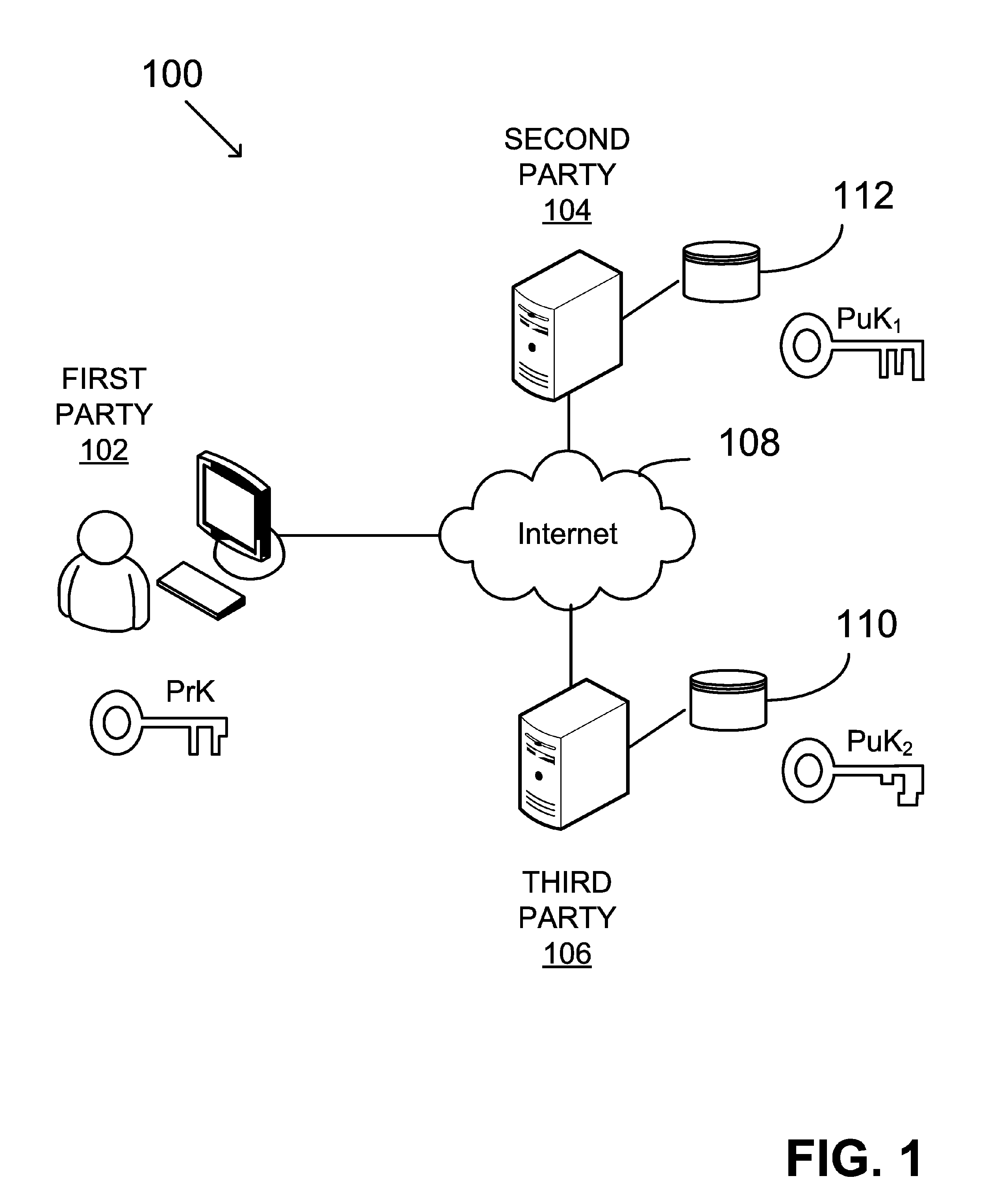
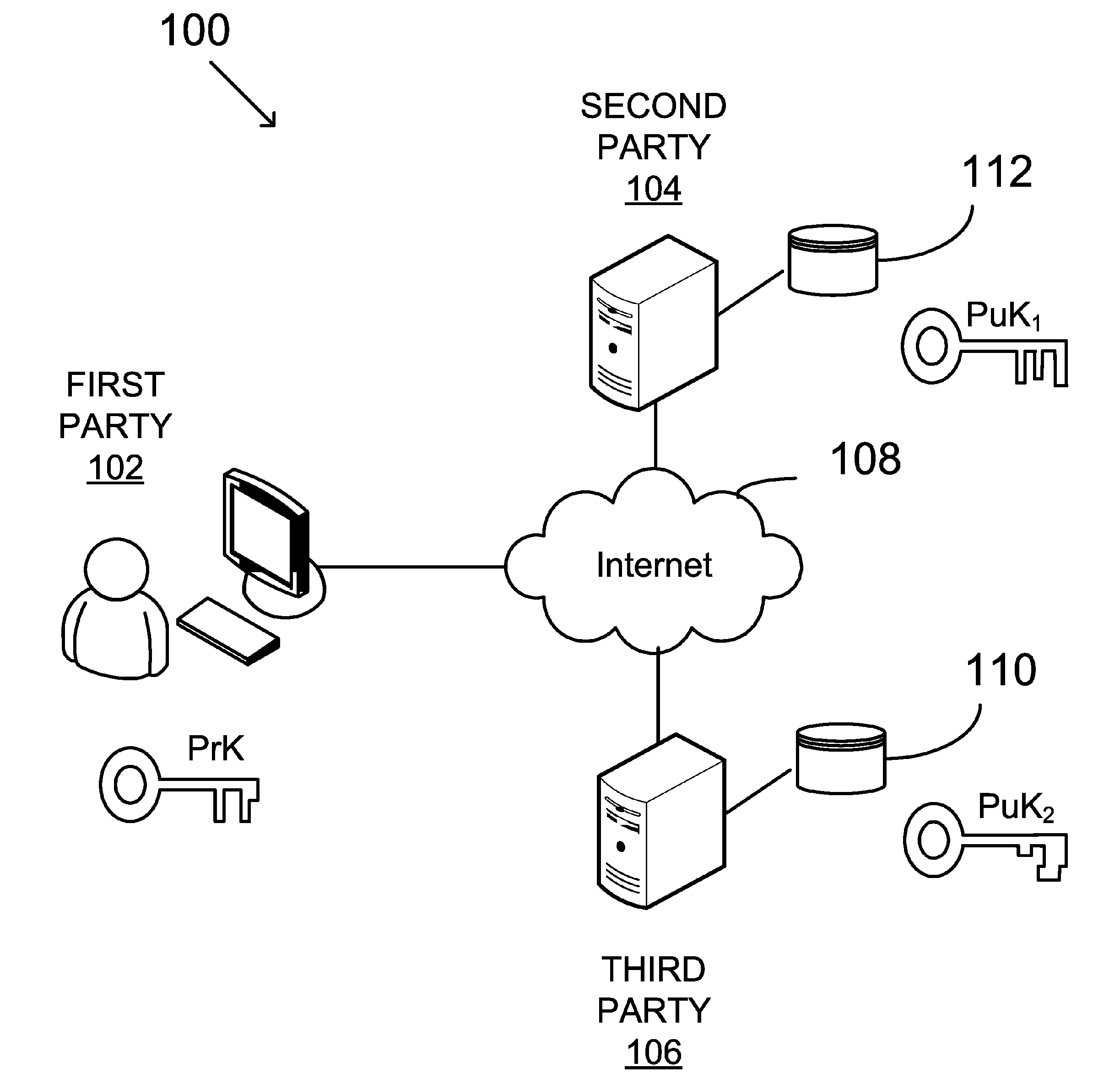
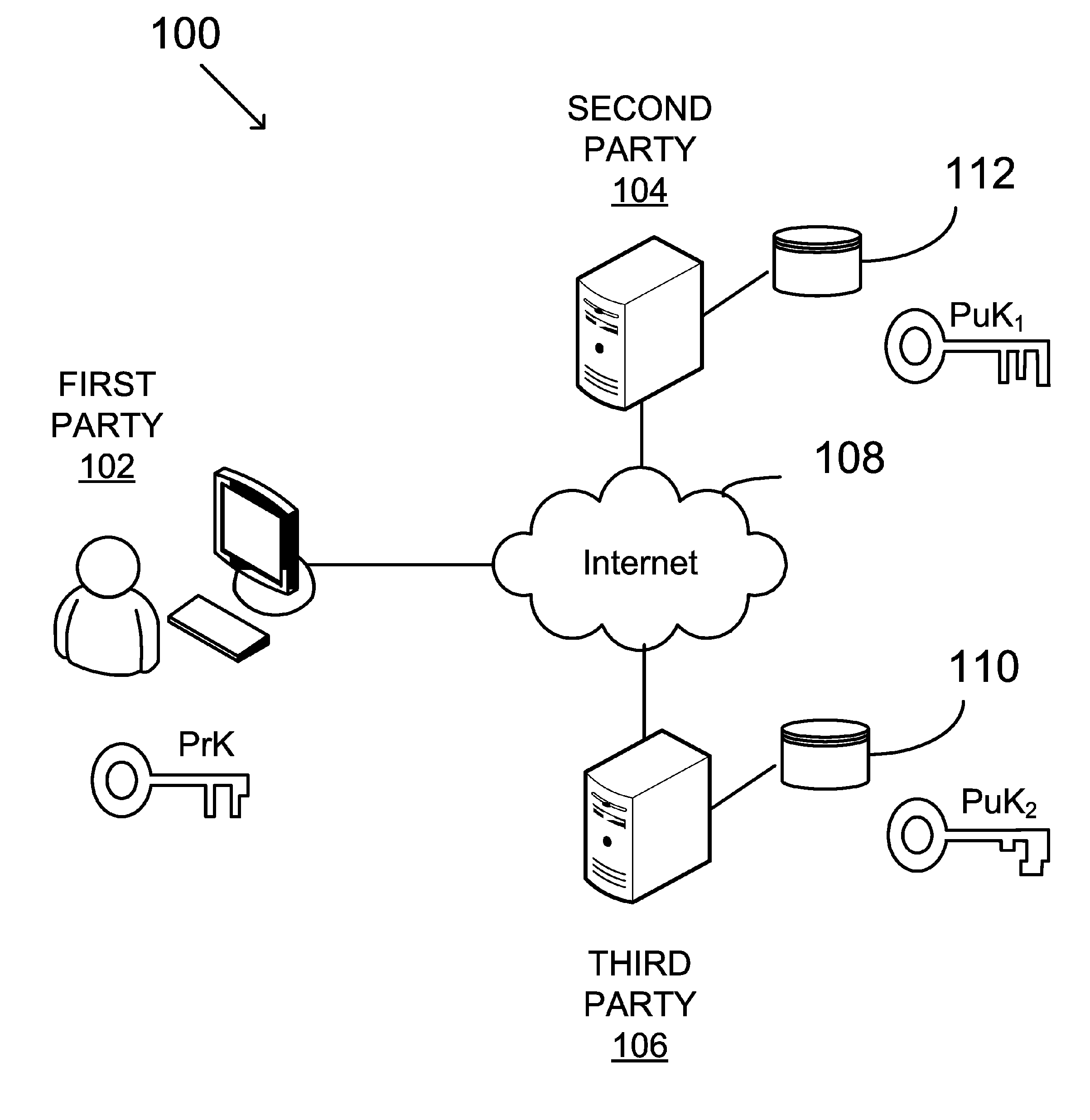
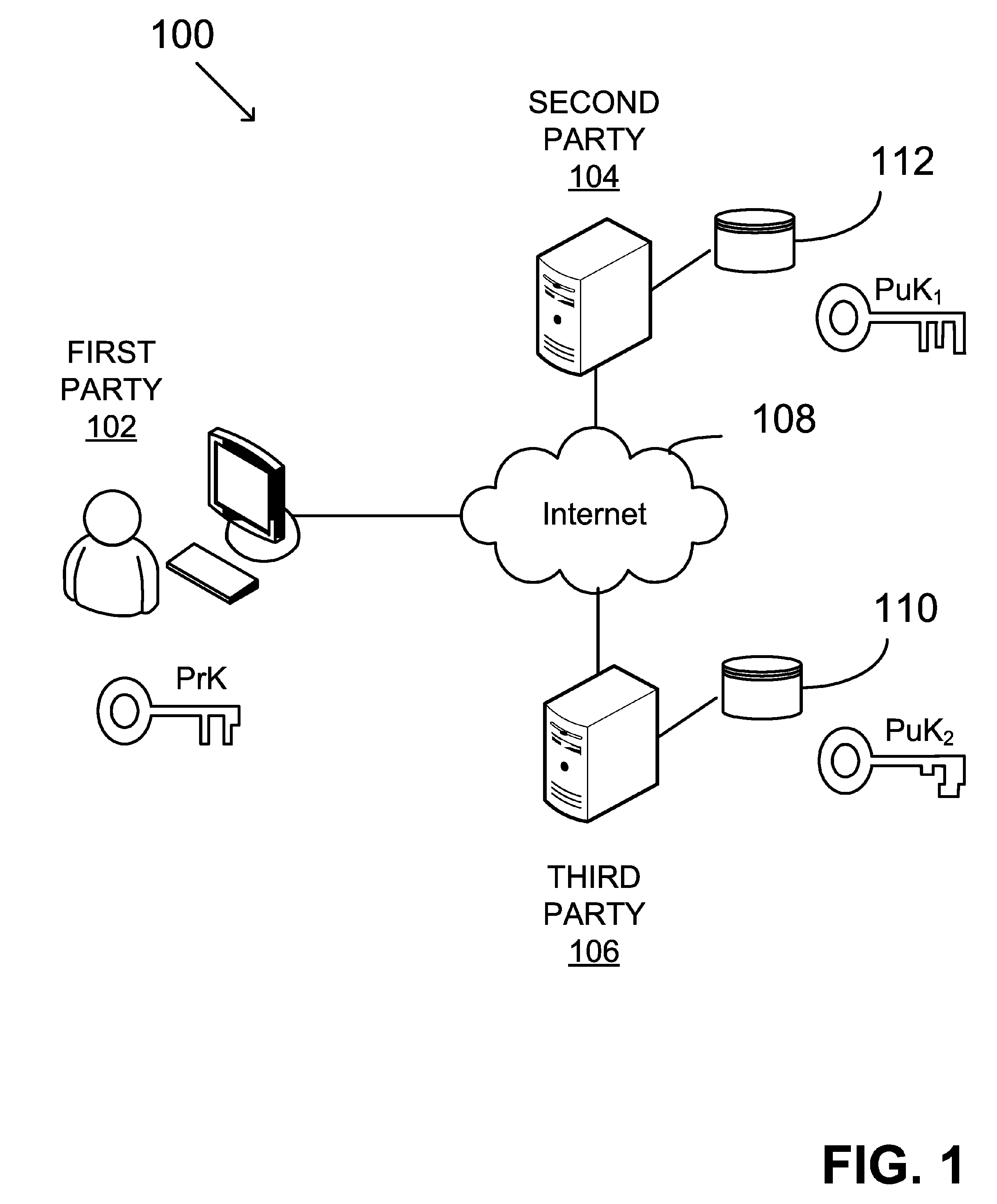
Digital signing by utilizing multiple distinct signing keys, distributed between two parties
ActiveUS20180359097A1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesThird partySystems design
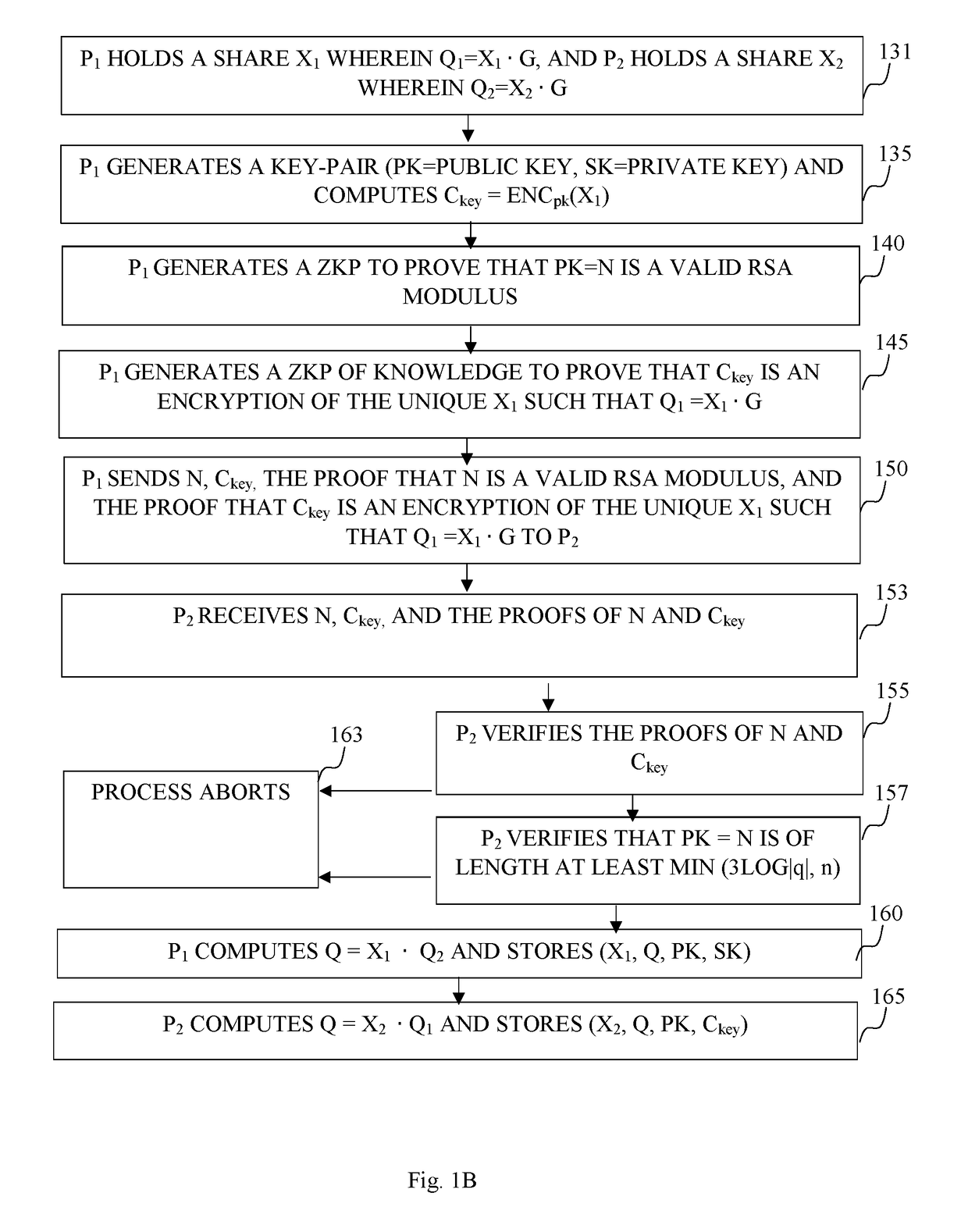
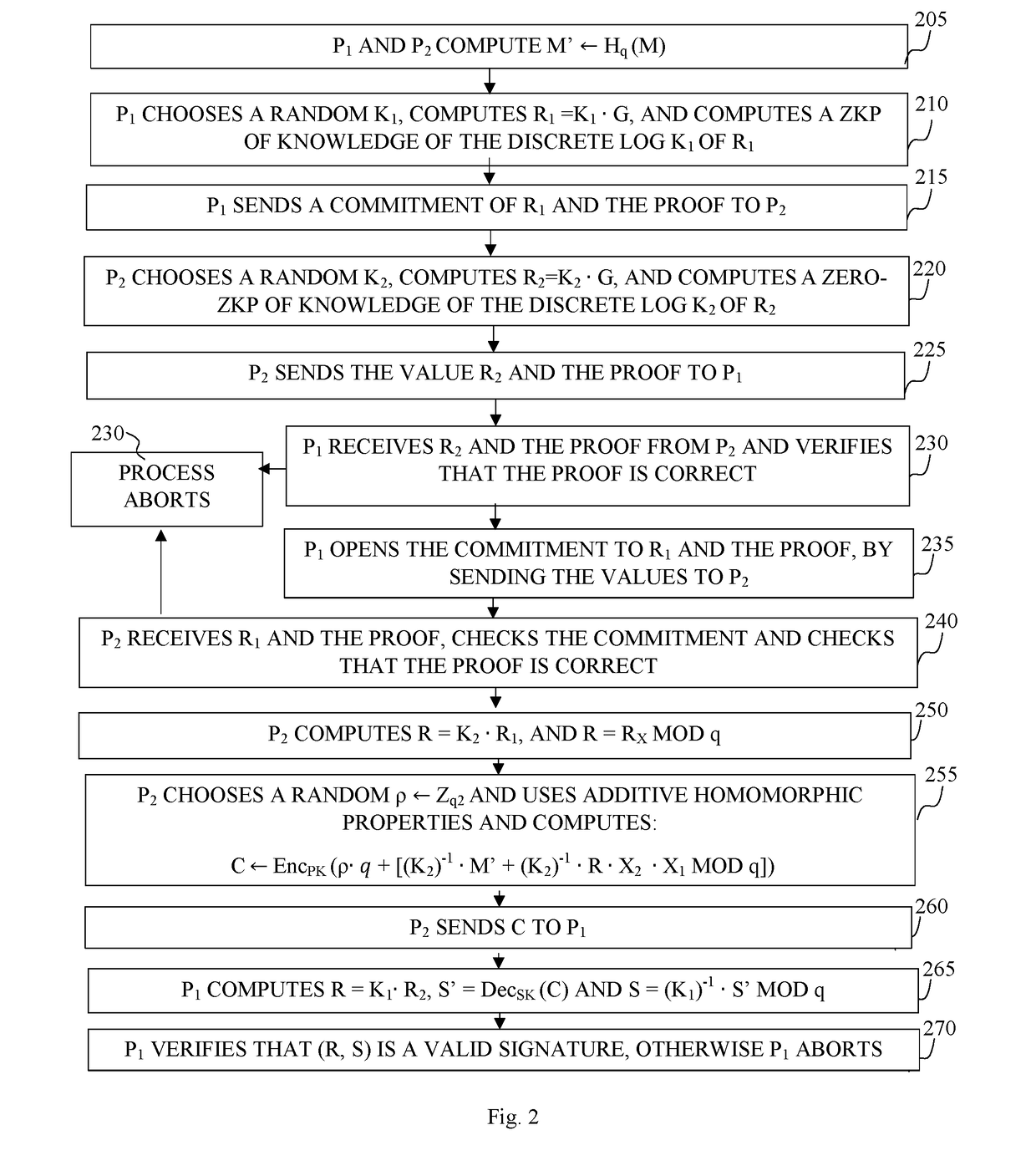
Described herein is a method and system for digital signing by utilizing Elliptic Curve Digital Signature Algorithm (ECDSA) with a group generator of an elliptic-curve group of order and an elliptic curve point Q. The method may be configured to receive a digital message and associated with a request from a third-party in order to sign the digital message. The system designed to sign such messages may comprise two parties denoted P1 and P2 configured to conduct a multiparty signing procedure by utilizing ECDSA. The digital signing procedure may follow preliminary steps configured to set the system with the necessary conditions for the multiparty signing procedure. Such preliminary steps may set the parties P1, and P2, in accordance with the configuration defined herein.
Owner:COINBASE IL RD LTD
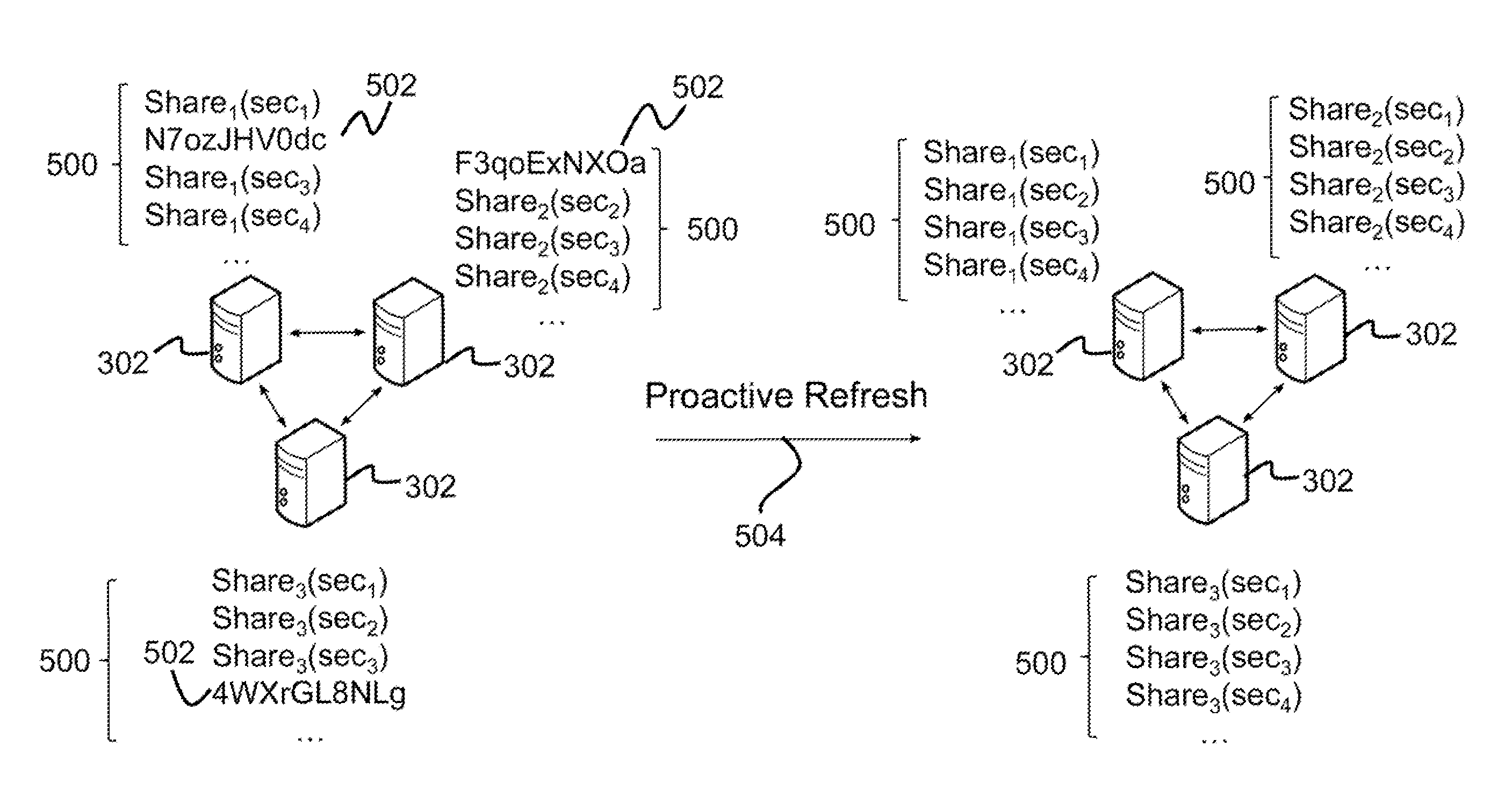
Method for secure and resilient distributed generation of elliptic curve digital signature algorithm (ECDSA) based digital signatures with proactive security
ActiveUS9489522B1User identity/authority verificationDigital data protectionActive safetySecret share
Described is system for generation of elliptic curve digital signature algorithm (ECDSA) based digital signatures. A Secret-Share protocol is initialized between a client and a set of servers to share a set of shares of a private key s among the set of servers. The set of servers initializes a protocol to generate a digital signature on a message using the set of shares of the private key s without reconstructing or revealing the private key s. The set of servers periodically initializes a Secret-Redistribute protocol on each share of the private key s to re-randomize the set of shares. A Secret-Open protocol is initialized to reveal the private key s to an intended recipient, wherein the private key s is used to compute the digital signature.
Owner:HRL LAB
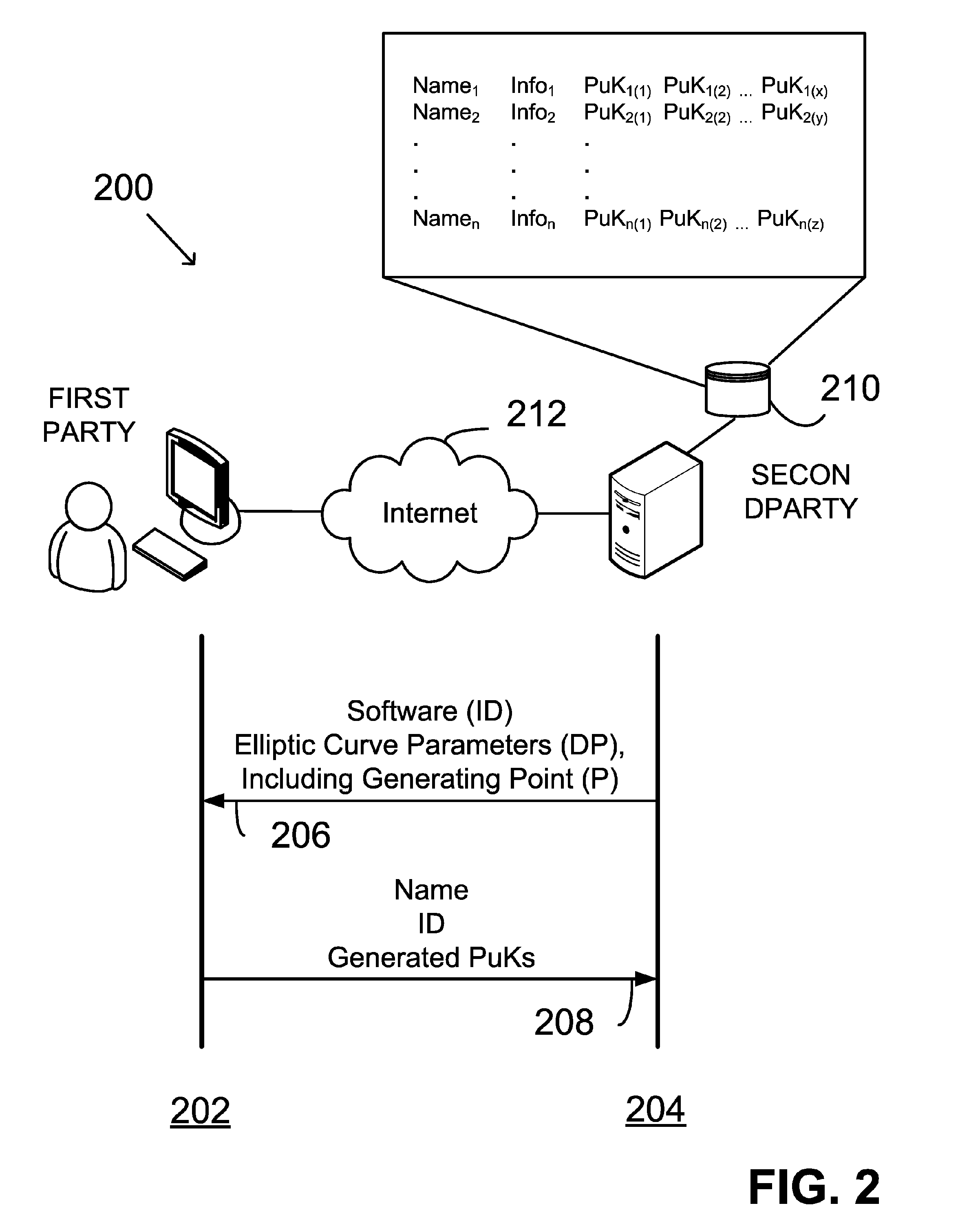
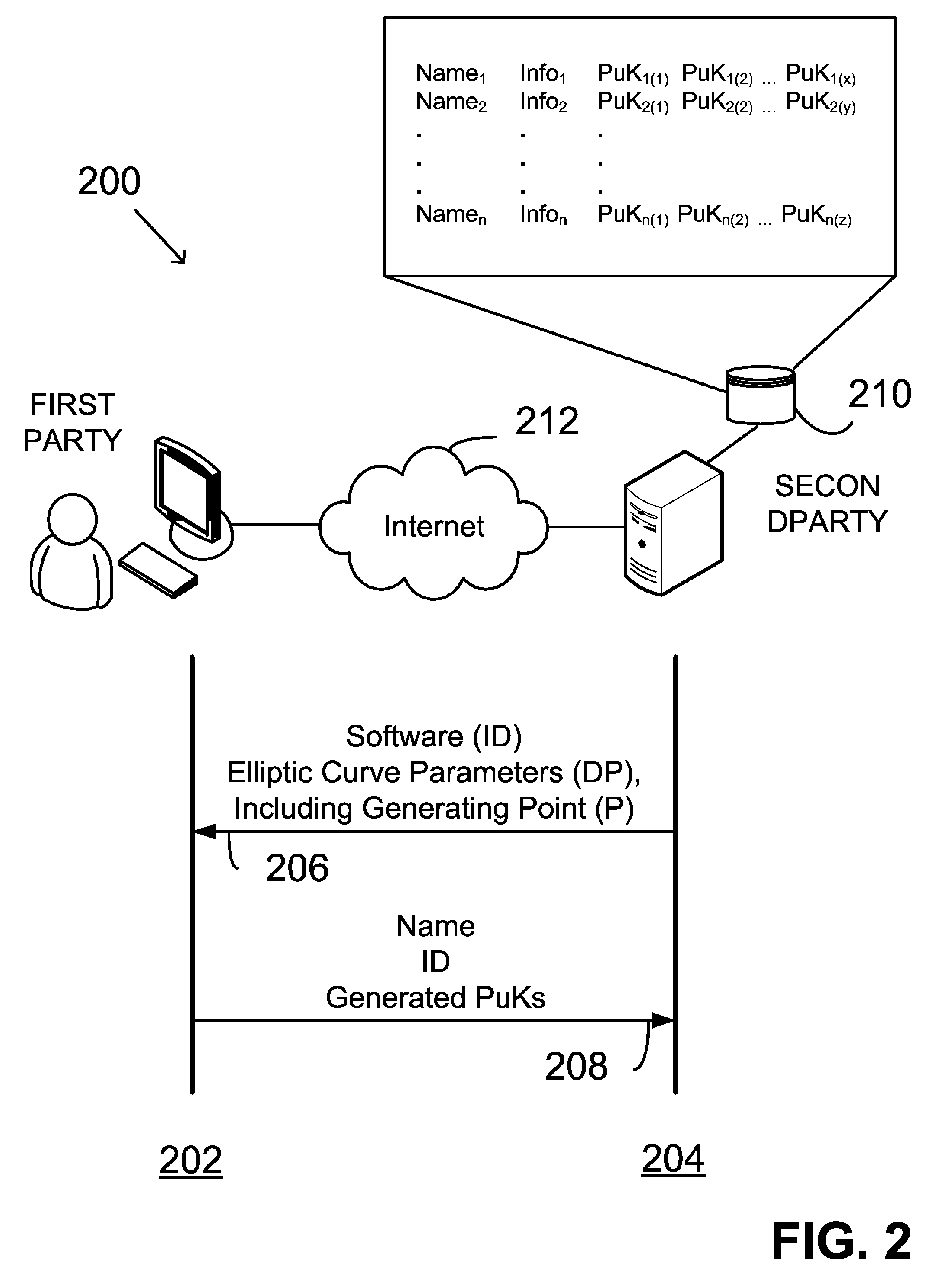
Providing digital signature and public key based on shared knowledge
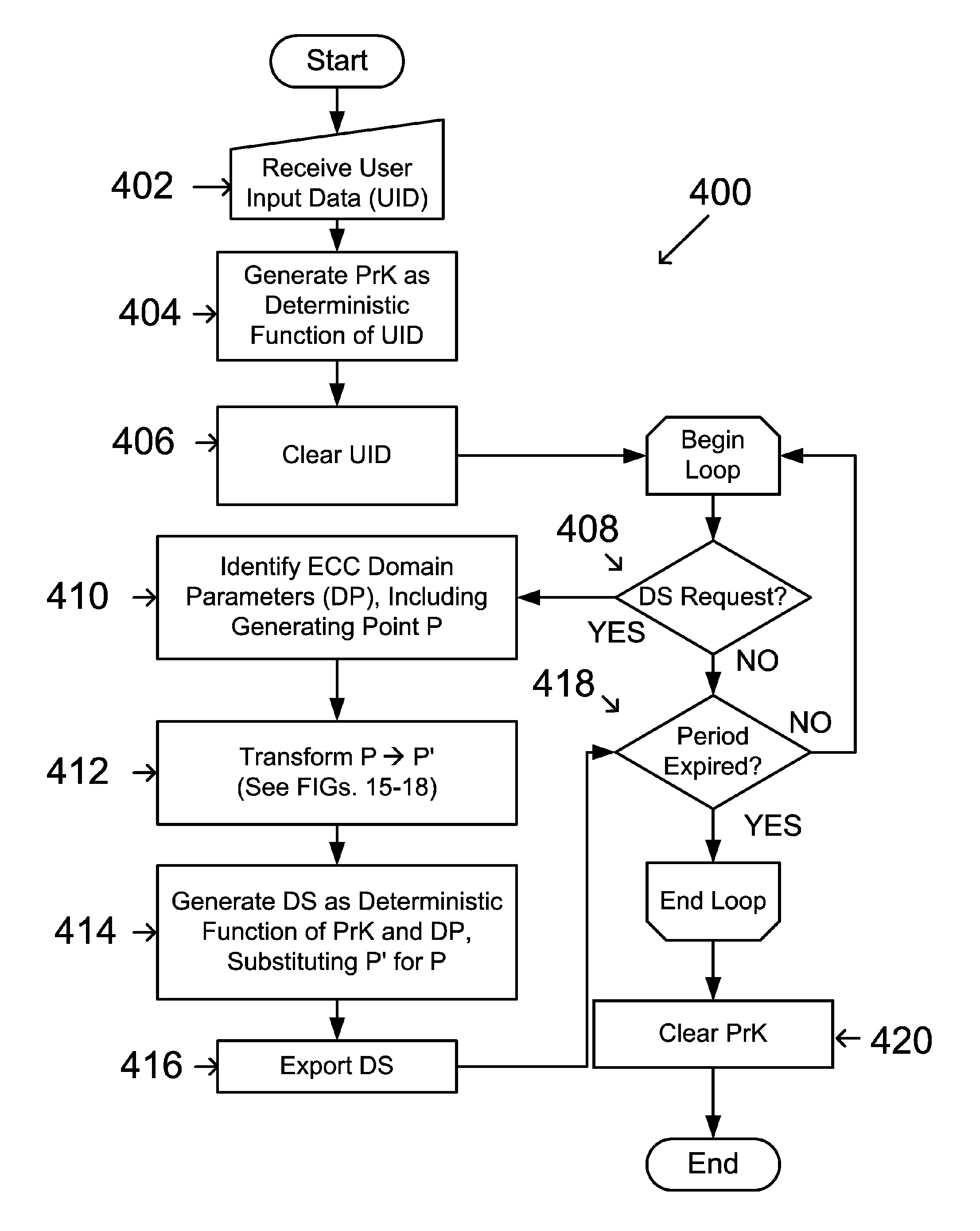
ActiveUS7593527B2Facilitating adoption and usePublic key for secure communicationUser identity/authority verificationDigital signatureDeterministic function
A public key and digital signature is provided using a private key of a public-private key pair in an elliptic curve digital signature algorithm (ECDSA) by: identifying domain parameters of an elliptic curve for use in elliptic curve cryptography, the domain parameters including an initial generating point; transforming the generating point into a new generating point as a deterministic function; generating the public key as a deterministic function of the private key and the domain parameters, in which the new generating point is substituted for the initial generating point; and generating the digital signature as a function of the private key and the domain parameters, in which the new generating point is substituted for the initial generating point.
Owner:FIRST DATA
Power Analysis Attack Countermeasure for the ECDSA
ActiveUS20080301458A1Encryption apparatus with shift registers/memoriesDigital data processing detailsPower analysisCountermeasure
Execution of the Elliptic Curve Digital Signature Algorithm (ECDSA) requires determination of a signature, which determination involves arithmetic operations. Some of the arithmetic operations employ a long term cryptographic key. It is the execution of these arithmetic operations that can make the execution of the ECDSA vulnerable to a power analysis attack. In particular, an attacker using a power analysis attack may determine the long term cryptographic key. By modifying the sequence of operations involved in the determination of the signature and the inputs to those operations, power analysis attacks may no longer be applied to determine the long term cryptographic key.
Owner:MALIKIE INNOVATIONS LTD
Providing digital signature and public key based on shared knowledge
ActiveUS20060153365A1Facilitating adoptionEasy to usePublic key for secure communicationUser identity/authority verificationDigital signatureDeterministic function
A public key and digital signature is provided using a private key of a public-private key pair in an elliptic curve digital signature algorithm (ECDSA) by: identifying domain parameters of an elliptic curve for use in elliptic curve cryptography, the domain parameters including an initial generating point; transforming the generating point into a new generating point as a deterministic function; generating the public key as a deterministic function of the private key and the domain parameters, in which the new generating point is substituted for the initial generating point; and generating the digital signature as a function of the private key and the domain parameters, in which the new generating point is substituted for the initial generating point.
Owner:FIRST DATA
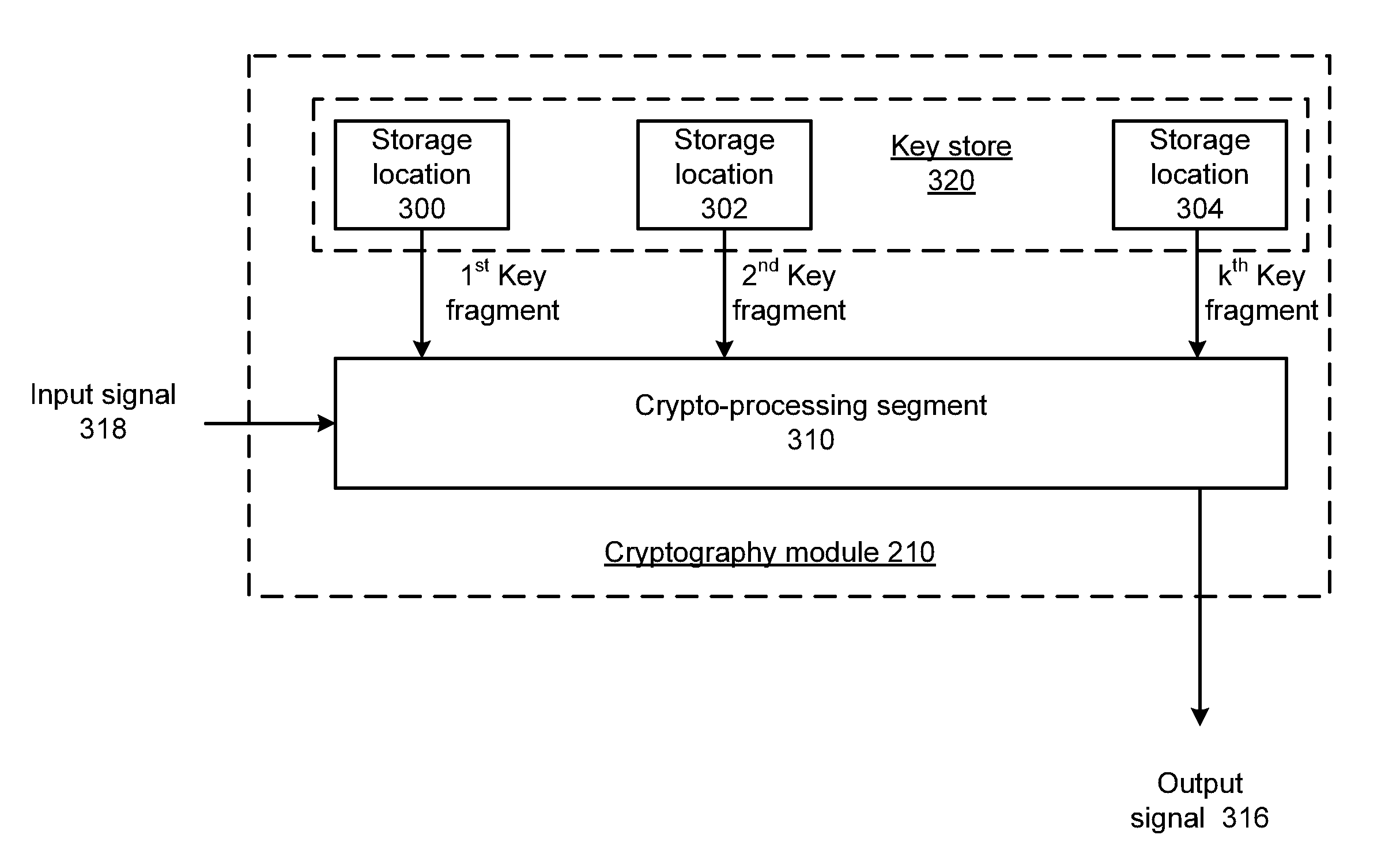
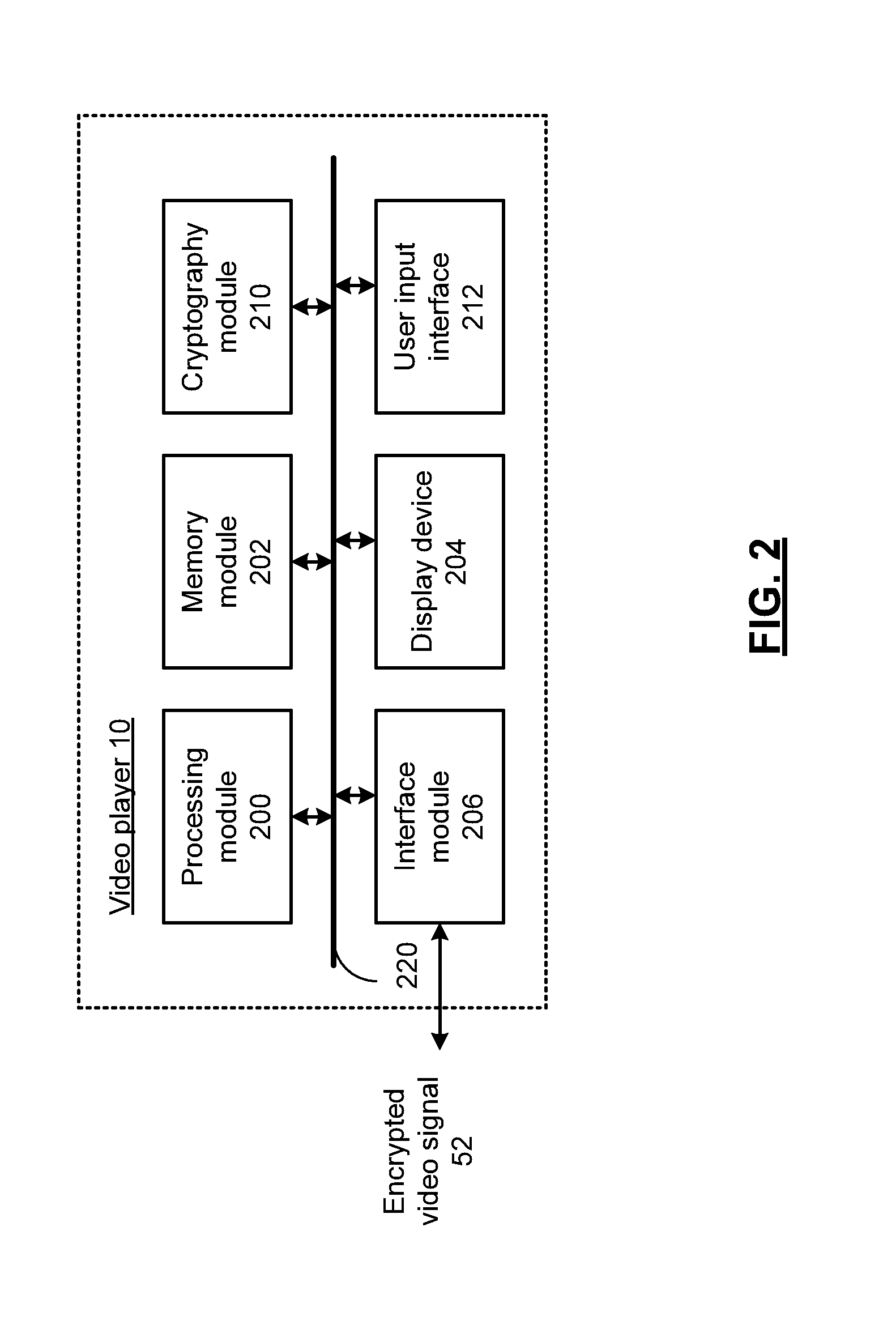
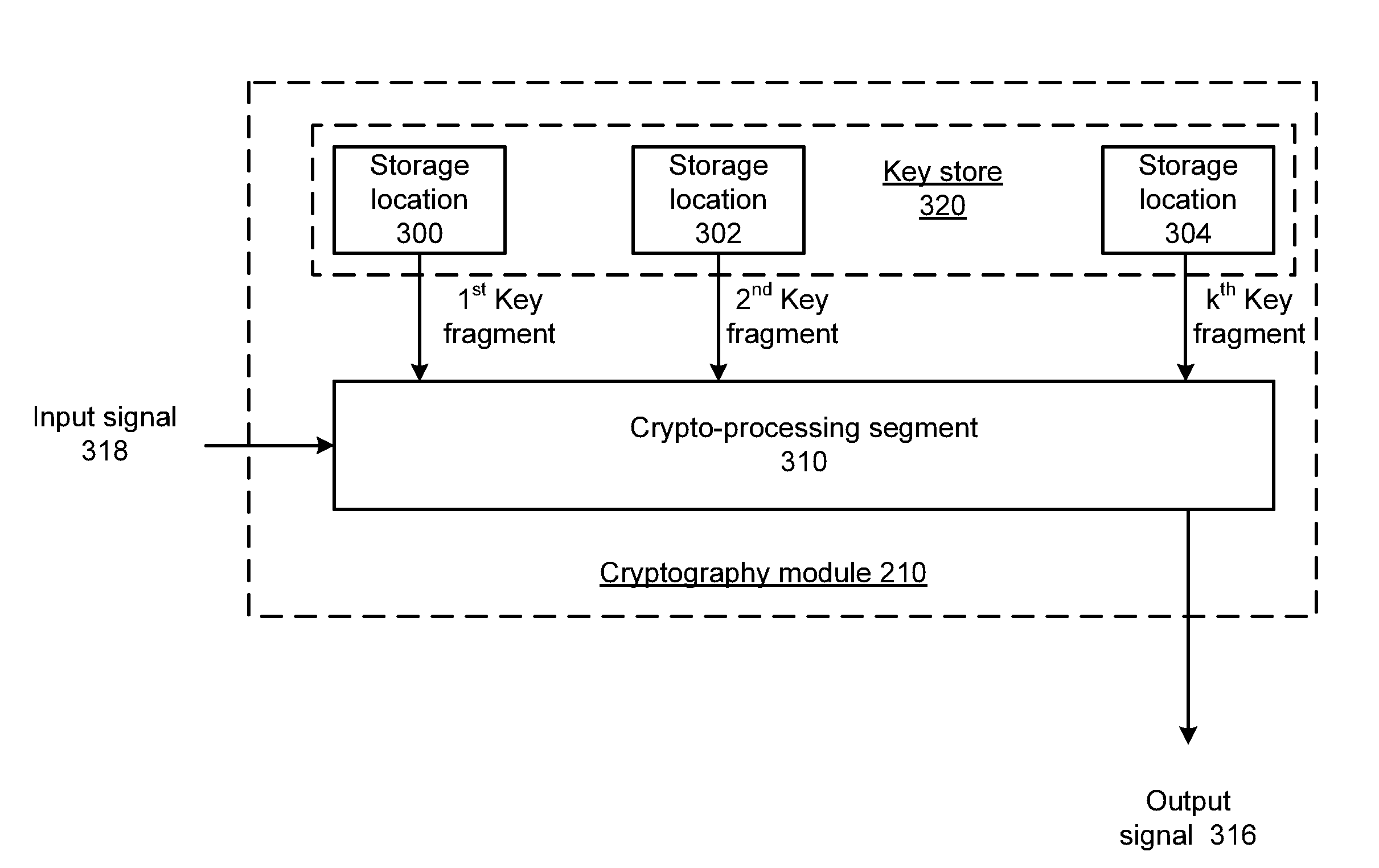
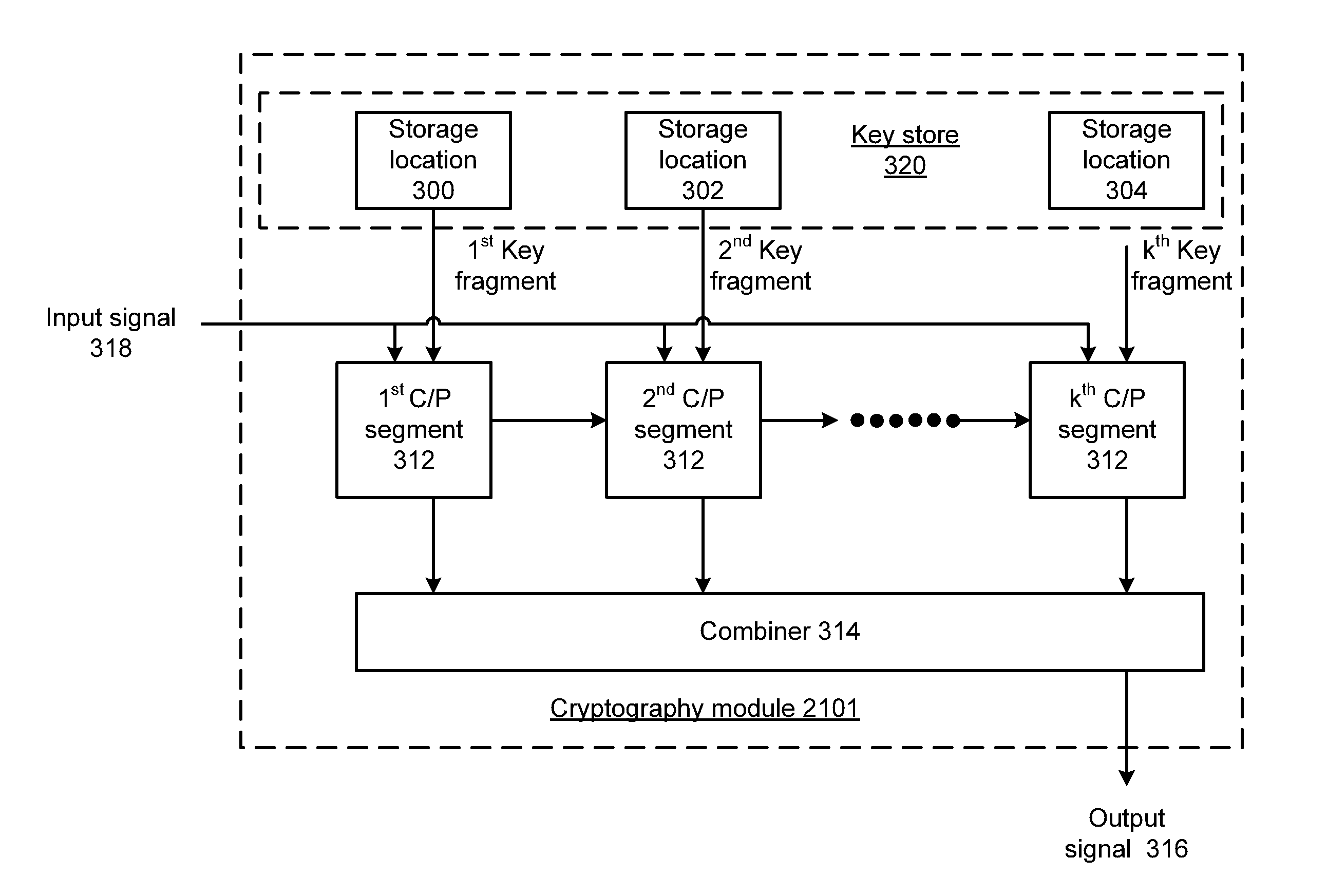
Elliptic curve cryptograhy with fragmented key processing and methods for use therewith
ActiveUS20120163581A1Internal/peripheral component protectionSecret communicationComputer hardwareElliptic Curve Digital Signature Algorithm
A cryptography module includes a key store having a plurality of storage locations for storing a private key as k key fragments. One or more crypto-processing segments each operate based on corresponding ones of the k key fragments to process a message in accordance with elliptic curve digital signature algorithm (ECDSA) to produce a signed message.
Owner:AT&T INTPROP I L P
Signature generation method and a block chain account management method adopting the method
InactiveCN109257179AReduce space consumptionLow easy feeKey distribution for secure communicationUser identity/authority verificationFault toleranceDigital signature
The invention discloses a signature generation method and a block chain account management method adopting the method. The signature generation method is based on an elliptic curve digital signature algorithm and is different from the original ECDSA signature algorithm. The account private key and the random number participate in the ECDSA signature process in the form of multi-party calculation.Compared with the current block chain account management mode, the invention has the advantages of low space consumption, consistent occupation of space with the common digital signature, low cost, high fault tolerance, high stability, high success rate and high capacitance, and can be used for the management of any account adopting the ECDSA signature algorithm.
Owner:北京网录科技有限公司
Anti-spoofing method for Beidou second-generation system based on elliptic curve algorithm
InactiveCN109617693AImprove securityShort signature lengthUser identity/authority verificationSatellite radio beaconingDigital signatureAnti spoofing
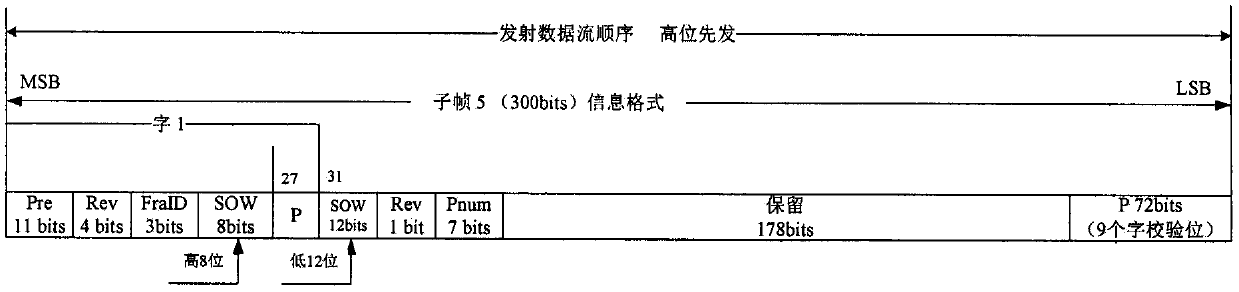
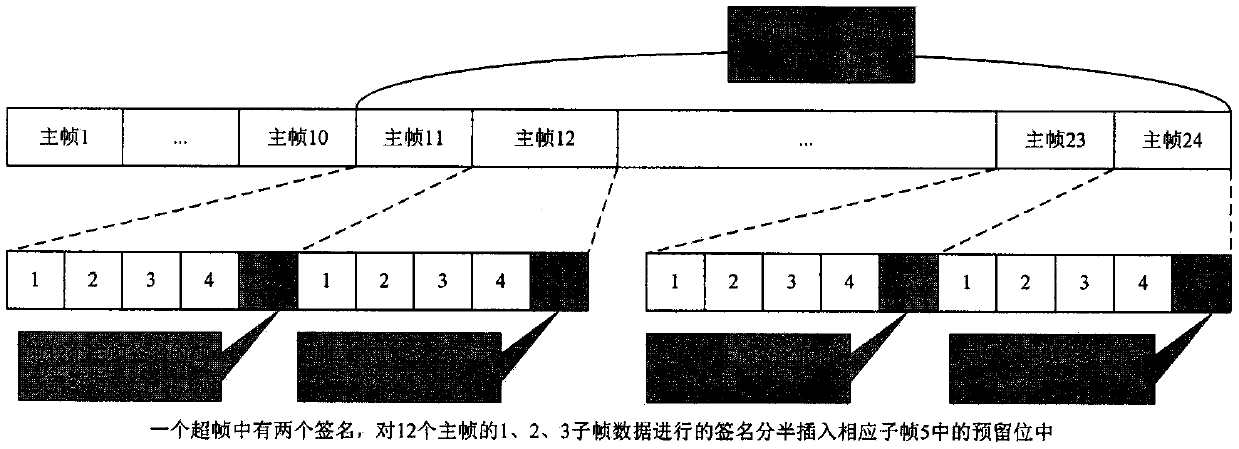
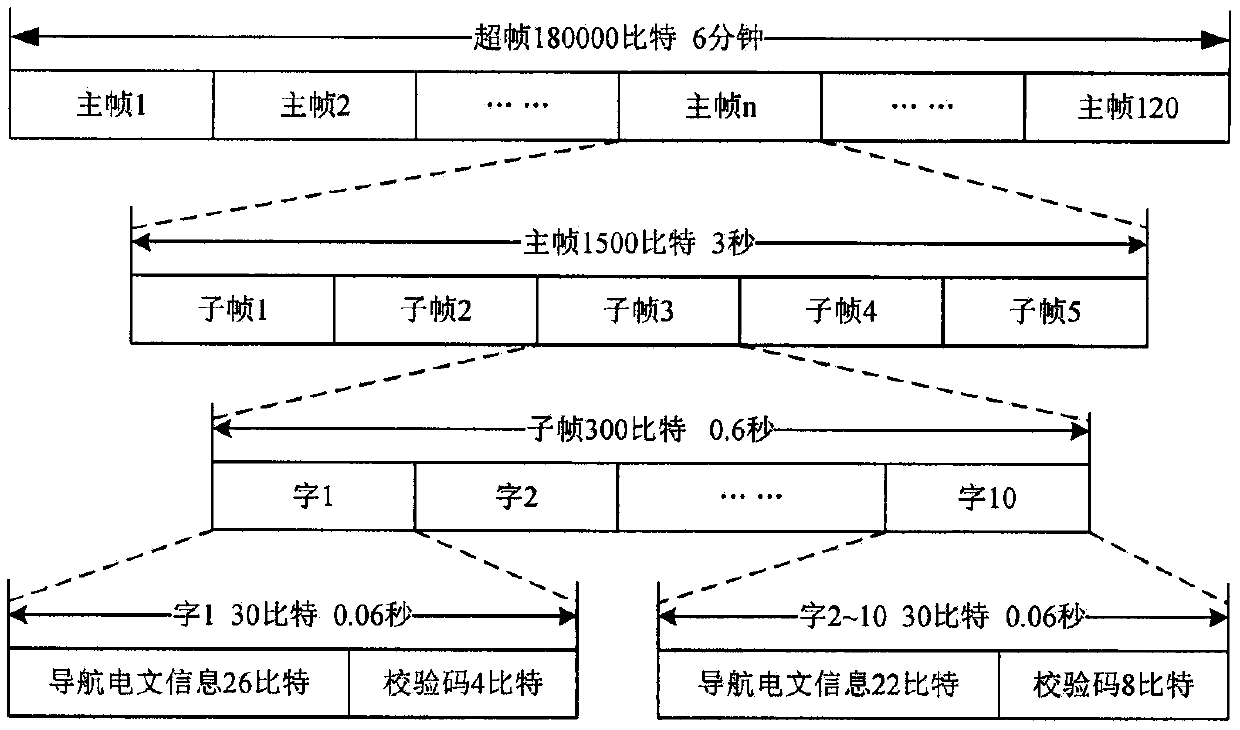
The invention relates to the technical field of information security, and designs an anti-spoofing scheme based on an Elliptic Curve Digital Signature Algorithm, ECDSA. Due to the transparency and predictability of a civil Beidou second-generation navigation signal, a Beidou civil satellite navigation system is easily threatened by spoofing attacks. Digital signature authentication information isinserted into reserved positions of Beidou D1 and D2 navigation messages, the authenticity and integrity of navigation data are verified, and then the purpose of resisting the spoofing attacks is achieved. The effectiveness, the security and the real-time performance of the anti-spoofing scheme are verified through a simulation experiment. An experimental result shows that the anti-spoofing schemecan effectively provide authentication for the Beidou second-generation navigation messages and enhance the ability of the civil satellite navigation system to resist the spoofing attacks.
Owner:CIVIL AVIATION UNIV OF CHINA
Security protection method for electric document digital signing based on elliptical curve
InactiveCN101441693AImprove securityEnsure safetyUser identity/authority verificationDigital data protectionDigital Signature AlgorithmDocumentation
The invention discloses an elliptic curve based safety protection method for digital signatures of electric documents. The method comprises the following steps: 1, generating system parameters: setting public parameters such as elliptic curve, mapping functions and a plurality of effectively computable functions; establishing a user cipher key; randomly selecting a private key for each signer, working out the corresponding public key, keeping the private key secret for signature by the signer, and verifying the signature by the disclosed the public key; 2, signing process: by utilizing the private key, generating the message signature and sending the message signature to a document receiver; and 3, verifying process: after the message and the signature are received, by utilizing the verification formula in the proposal for checking, verifying the signature if the verification formula is true, and ensuring that the message received by a verifier is sent by a sender keeping the private key corresponding to the public key. The digital signature method can generate a plurality of elliptic curve based digital signature algorithms for safety protection of integrality, trueness and non-repudiation during document transmission.
Owner:XIAN UNIV OF TECH
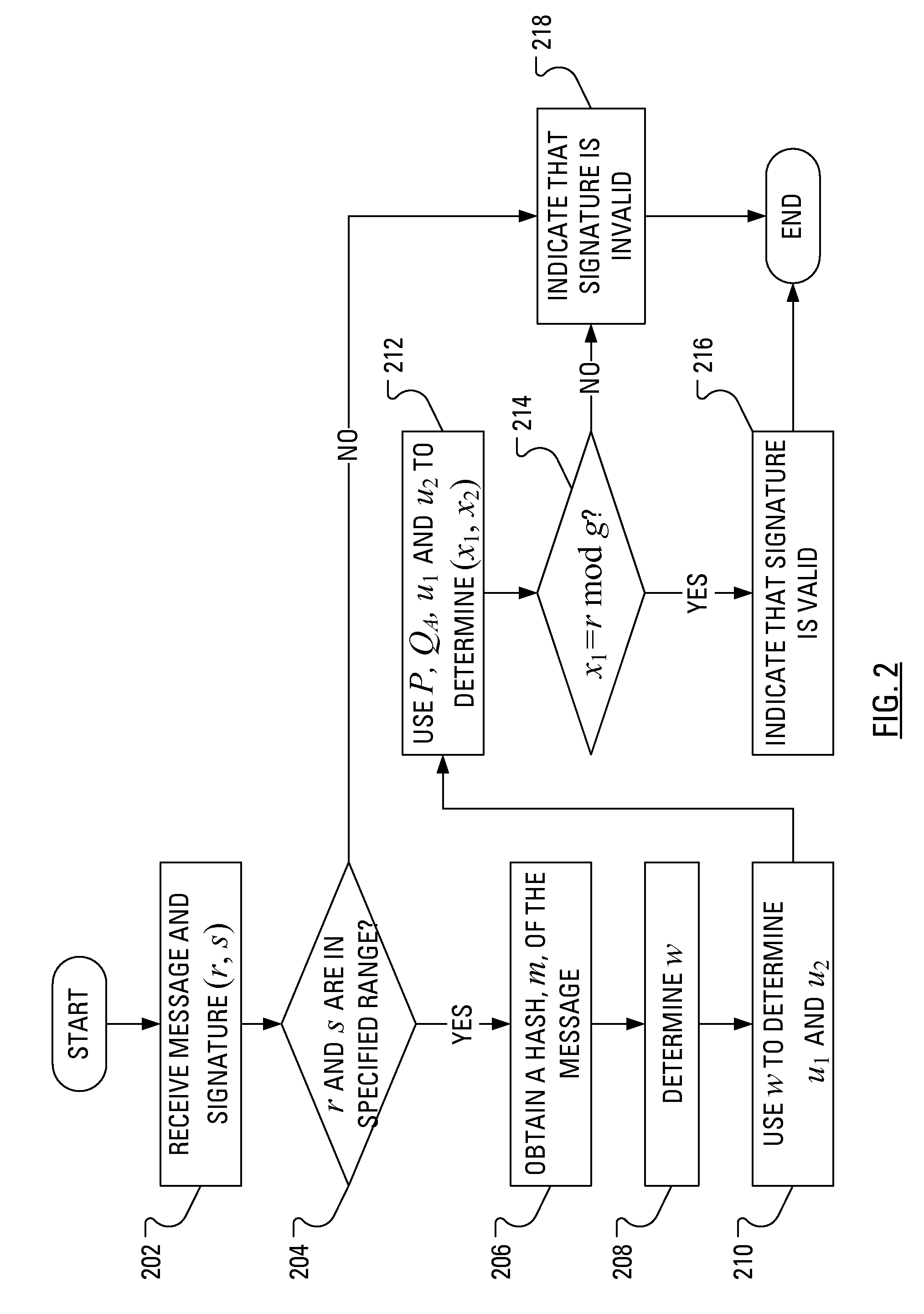
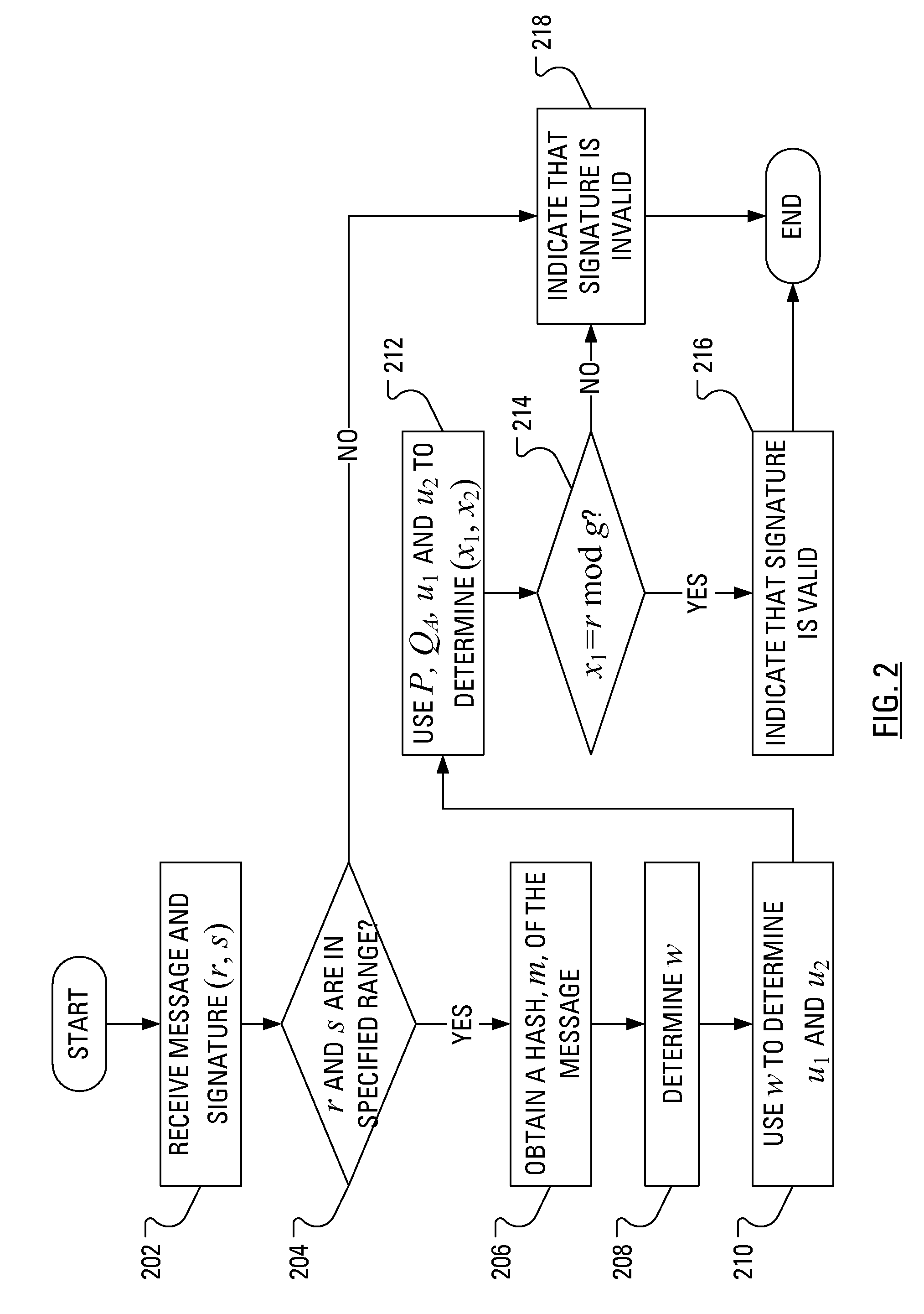
Verifying digital signature based on shared knowledge
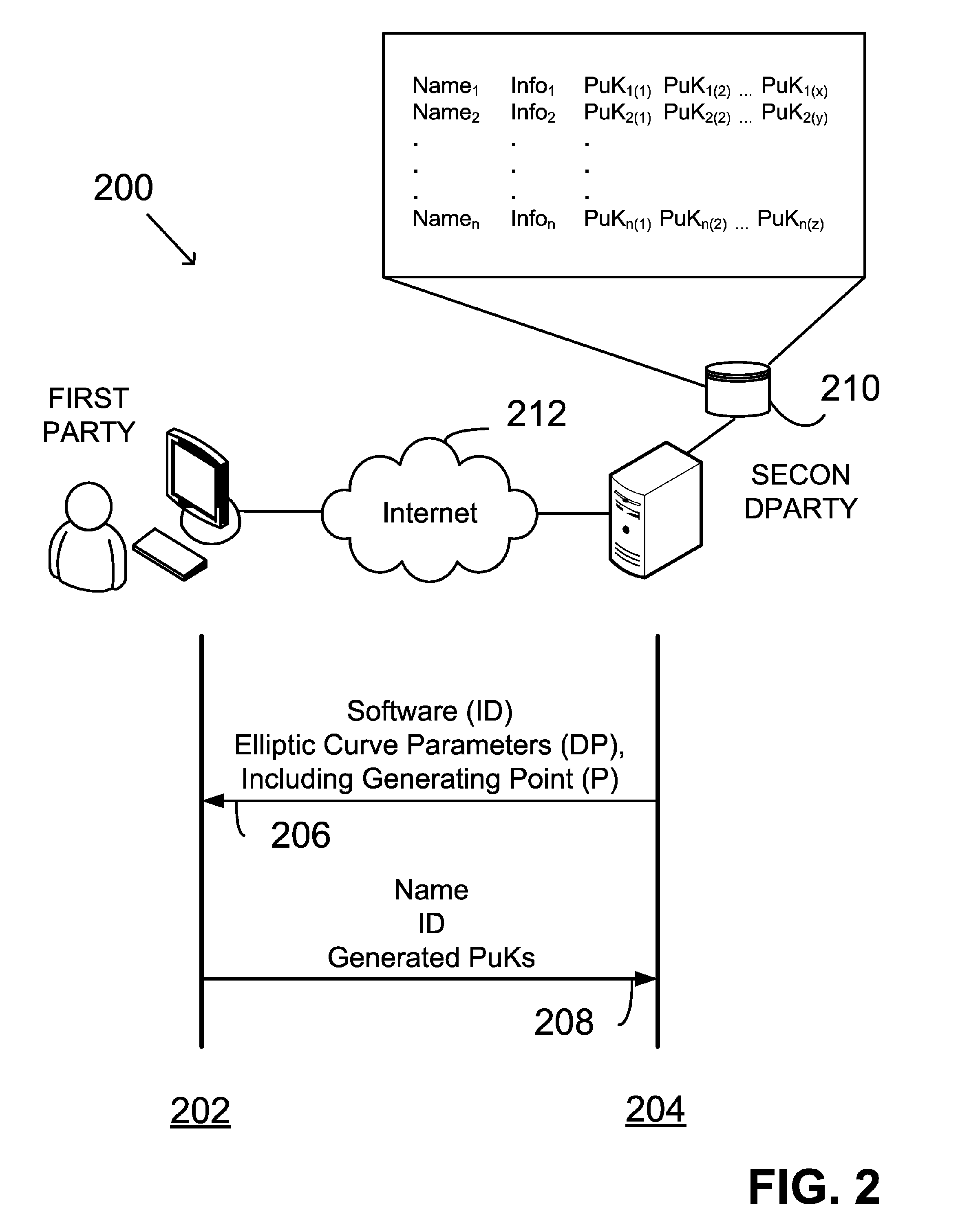
InactiveUS20060153366A1Facilitating adoptionEasy to useKey distribution for secure communicationPublic key for secure communicationDigital signatureDeterministic function
A method of verifying a digital signature of a first party that was generated using an elliptic curve digital signature algorithm (ECDSA) includes the steps of receiving a public key from the first party; receiving a digital signature from the first party, the digital signature being for an electronic message; identifying domain parameters of an elliptic curve used in elliptic curve cryptography, including identifying a generating point of the elliptic curve; transforming the identified generating point into a second generating point as a deterministic function of shared knowledge known to and between the first party and a second party; and verifying the received digital signature as a deterministic function of the received public key, the electronic message, and the identified domain parameters, in which the second generating point is substituted for the identified generating point.
Owner:FIRST DATA
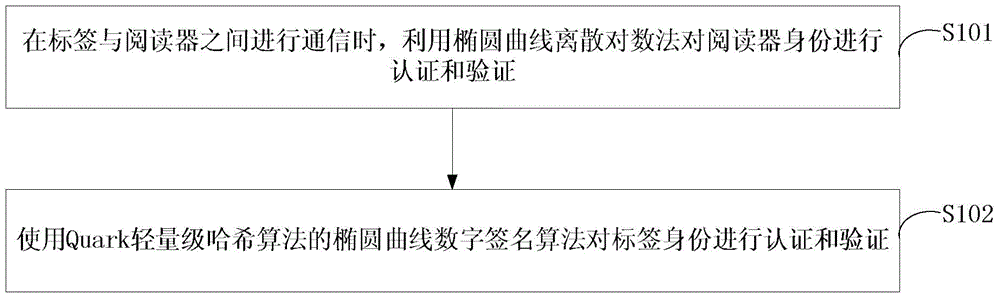
RFID system safety authentication method with ECC combining with lightweight Hash function
ActiveCN104901812AReduce overheadImprove security levelUser identity/authority verificationSensing record carriersComputer hardwareHash function
The invention discloses an RFID system safety authentication method with an ECC combining with a lightweight Hash function. When communication is performed between a label and a reader, first, an elliptic curve discrete logarithm method is used to perform authentication and verification on the identity of the reader, and then, an elliptic curve digital signature algorithm of a Quark lightweight Hash algorithm is used to perform authentication and verification on the identity of the label. Compared with a traditional scheme, the RFID system safety authentication method with the ECC combining with the lightweight Hash function has a higher security level, 48% of communication overhead is reduced, in the aspect of overall memory consumption, 24% of memory consumption is reduced, and performance in aspects of communication overhead and memory requirements is excellent.
Owner:SICHUAN UNIVERSITY OF SCIENCE AND ENGINEERING
Verifying digital signature based on shared knowledge
InactiveUS7936869B2Facilitating adoption and useKey distribution for secure communicationPublic key for secure communicationDigital signatureDeterministic function
A method of verifying a digital signature of a first party that was generated using an elliptic curve digital signature algorithm (ECDSA) includes the steps of receiving a public key from the first party; receiving a digital signature from the first party, the digital signature being for an electronic message; identifying domain parameters of an elliptic curve used in elliptic curve cryptography, including identifying a generating point of the elliptic curve; transforming the identified generating point into a second generating point as a deterministic function of shared knowledge known to and between the first party and a second party; and verifying the received digital signature as a deterministic function of the received public key, the electronic message, and the identified domain parameters, in which the second generating point is substituted for the identified generating point.
Owner:FIRST DATA
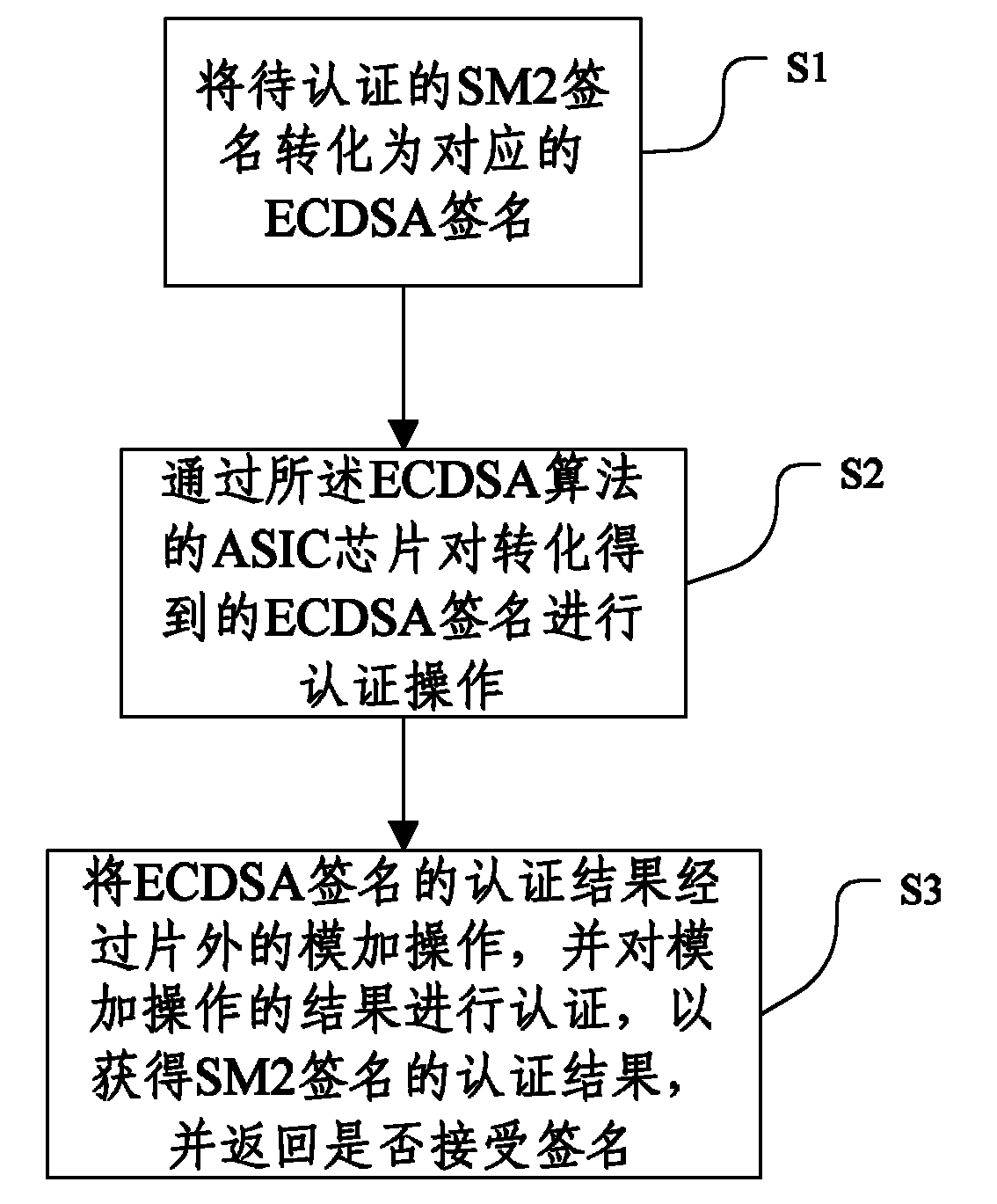
SM2 signature authentication method and system
InactiveCN102291240AShorten the development cyclePublic key for secure communicationUser identity/authority verificationDigital signatureApplication-specific integrated circuit
The invention discloses a method and system for authenticating an SM2 (Smart Media 2) signature, relating to the technical fields of digital signature and authentication technology. The method for authenticating the SM2 signature is implemented through an ASIC (Application Specific Integrated Circuit) chip in which an ECDSA (Elliptic Curve Digital Signature Algorithm) is adopted. The method comprises the following steps of: 1, converting an SM2 signature waiting to be authenticated into a corresponding ECDSA signature; 2, authenticating the ECDSA signature obtained by conversion by using the ASIC chip in which the ECDSA is adopted; and 3, performing out-chip modular addition operation on an authentication result of the ECDSA signature, authenticating a modular addition operation result toobtain an authentication result of the SM2 signature, and returning a result indicating whether the signature is received. In the method, the SM2 signature is converted into the ECDSA signature, and ECDSA authentication is performed on the ECDSA signature to obtain the authentication result of the SM2 signature, so that an SM2 algorithm can be directly realized by using the conventional ASIC chipfor realizing ECDSA signature authentication, a chip design special for SM2 signature authentication is not required, and the developing period is shortened.
Owner:TSINGHUA UNIV
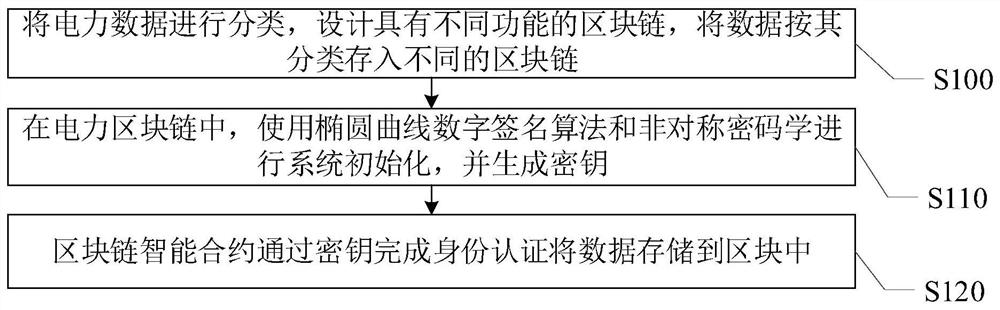
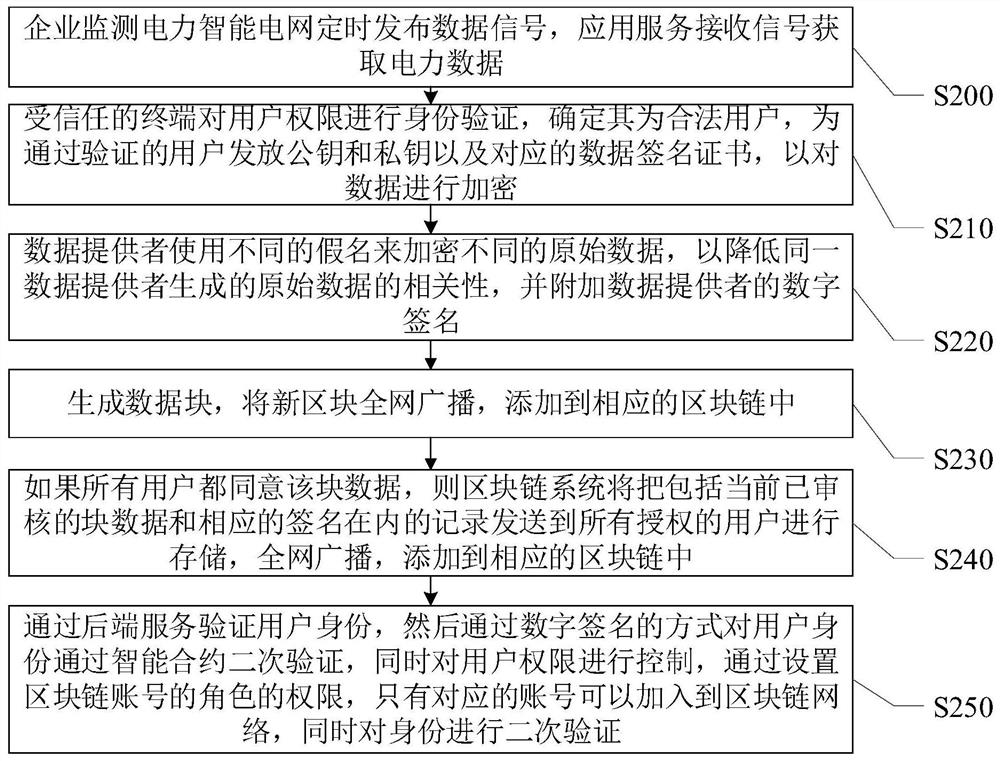
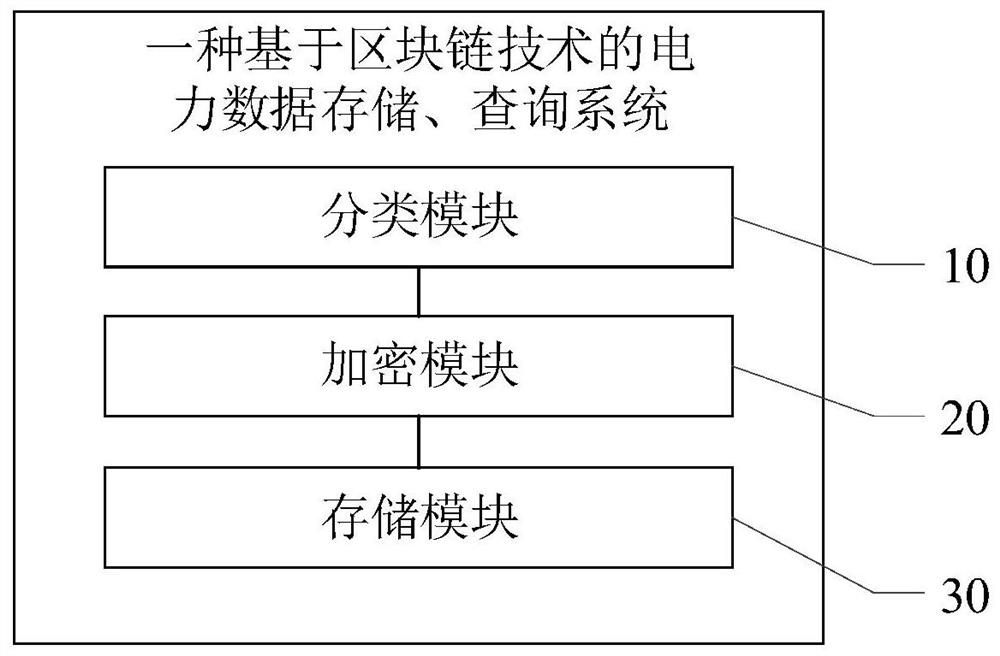
Electric power data storage and query method and system based on block chain technology
PendingCN113222595ARealize privacy protectionEnsure safetyFinanceProtocol authorisationKey (cryptography)Privacy protection
The invention provides a power data storage and query method and system based on a block chain technology, and relates to the field of block chains. The electric power data storage and query method based on the block chain technology comprises the following steps: classifying electric power data, designing block chains with different functions, and storing the data into different block chains according to the classification; in the power block chain, using an elliptic curve digital signature algorithm and asymmetric cryptography to carry out system initialization, and generating a key; and enabling the block chain smart contract to complete identity authentication through the key and store the data in the block. according to the method and system, only the corresponding account number can be added to the block chain network by setting the authority of the role of the block chain account number, and the identity is subjected to secondary verification, so that the privacy protection of the block chain data is realized, and the security of the block chain system is ensured. In addition, the invention further provides an electric power data storage and query system based on the block chain technology. The system comprises a classification module, an encryption module and a storage module.
Owner:上海和数软件有限公司 +2
Power analysis attack countermeasure for the ECDSA
ActiveUS8027466B2Digital data processing detailsUser identity/authority verificationPower analysisCountermeasure
Execution of the Elliptic Curve Digital Signature Algorithm (ECDSA) requires determination of a signature, which determination involves arithmetic operations. Some of the arithmetic operations employ a long term cryptographic key. It is the execution of these arithmetic operations that can make the execution of the ECDSA vulnerable to a power analysis attack. In particular, an attacker using a power analysis attack may determine the long term cryptographic key. By modifying the sequence of operations involved in the determination of the signature and the inputs to those operations, power analysis attacks may no longer be applied to determine the long term cryptographic key.
Owner:MALIKIE INNOVATIONS LTD
Reconfigurable rapid parallel multiplier
InactiveCN103942027AReduce computing timeReduce areaComputation using non-contact making devicesLimited resourcesBinary multiplier
The invention provides a reconfigurable rapid parallel multiplier. The reconfigurable rapid parallel multiplier comprises a control unit, a transient memory, two reconfigurable decomposition operand generating circuits, a secondary polynomial multiplier, a frequency adjustment circuit and an FPR circuit, wherein the control unit outputs a control vector S0, a control vector S1 and a control vector S2, the control vector S0 and the control vector S1 are used for controlling the two reconfigurable decomposition operand generating circuits so that i and i can be generated in the same way, the secondary polynomial multiplier is used for generating a control vector S2 which is used for controlling the frequency adjustment circuit to generate a D stored in the transient memory, i=0, 1, ..., and 5, and the FPR circuit is used for generating a final result C. Compared with an existing multiplier, the expandable multiplier has the advantages that the calculation time is shortened obviously, the area, the ADP and the power consumption are reduced obviously, and an analysis result provides a valuable reference for carrying out a pairing algorithm and an elliptic curve digital signature algorithm on an embedded system with limited resources and a smart phone.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL +1
Rapid ECDSA (Elliptic Curve Digital Signature Algorithm) based lightweight byzantine fault-tolerant routing of large-scale wireless sensor network
InactiveCN101969641AImplement security authenticationIncrease credibilitySecurity arrangementDigital signatureWireless sensor networking
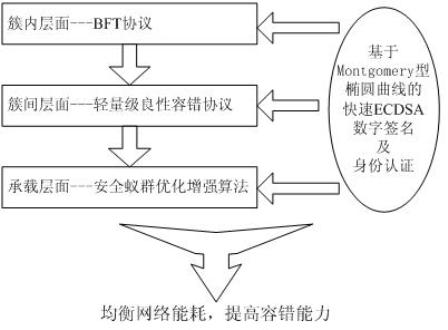
The invention relates to rapid ECDSA (Elliptic Curve Digital Signature Algorithm) based lightweight byzantine fault-tolerant routing of a large-scale wireless sensor network. The routing runs different fault-tolerant protocols aiming to different network layers, BFT (Byzantine Fault-Tolerant) protocols run in various clusters in a partial range, each piece of information transmitted in each cluster is signed by a threshold scheme (2f+1,3f+1) based on the lightweight optimization of the rapid ECDSA, messages transmitted outwards by all cluster heads carry digital signatures based on the rapid ECDSA, and lightweight virtuous fault-tolerant protocols run among all the clusters in the whole range. On the bearing layer of the whole network, an ant colony optimization and enhancement algorithm with added node authentication factors and confidence factors is adopted to rapidly and safely certify the nodes and search and establish reliable routing.
Owner:SHANGHAI UNIV
ECDSA method for resisting error curve attack
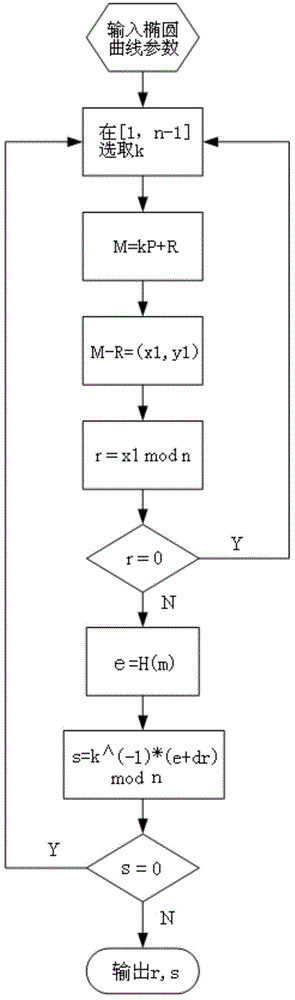
ActiveCN105610583AWon't wasteUser identity/authority verificationHash functionElliptic Curve Digital Signature Algorithm
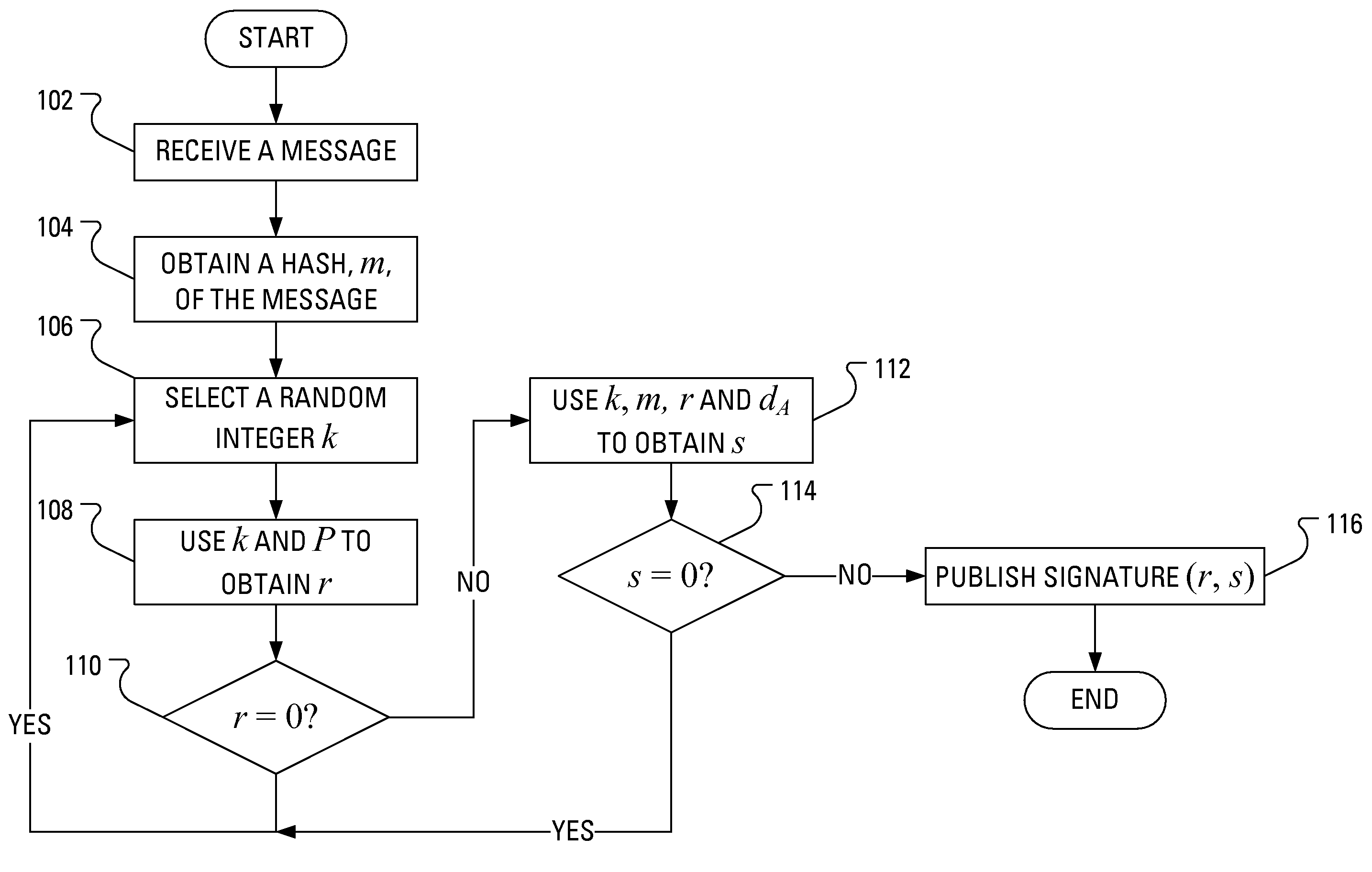
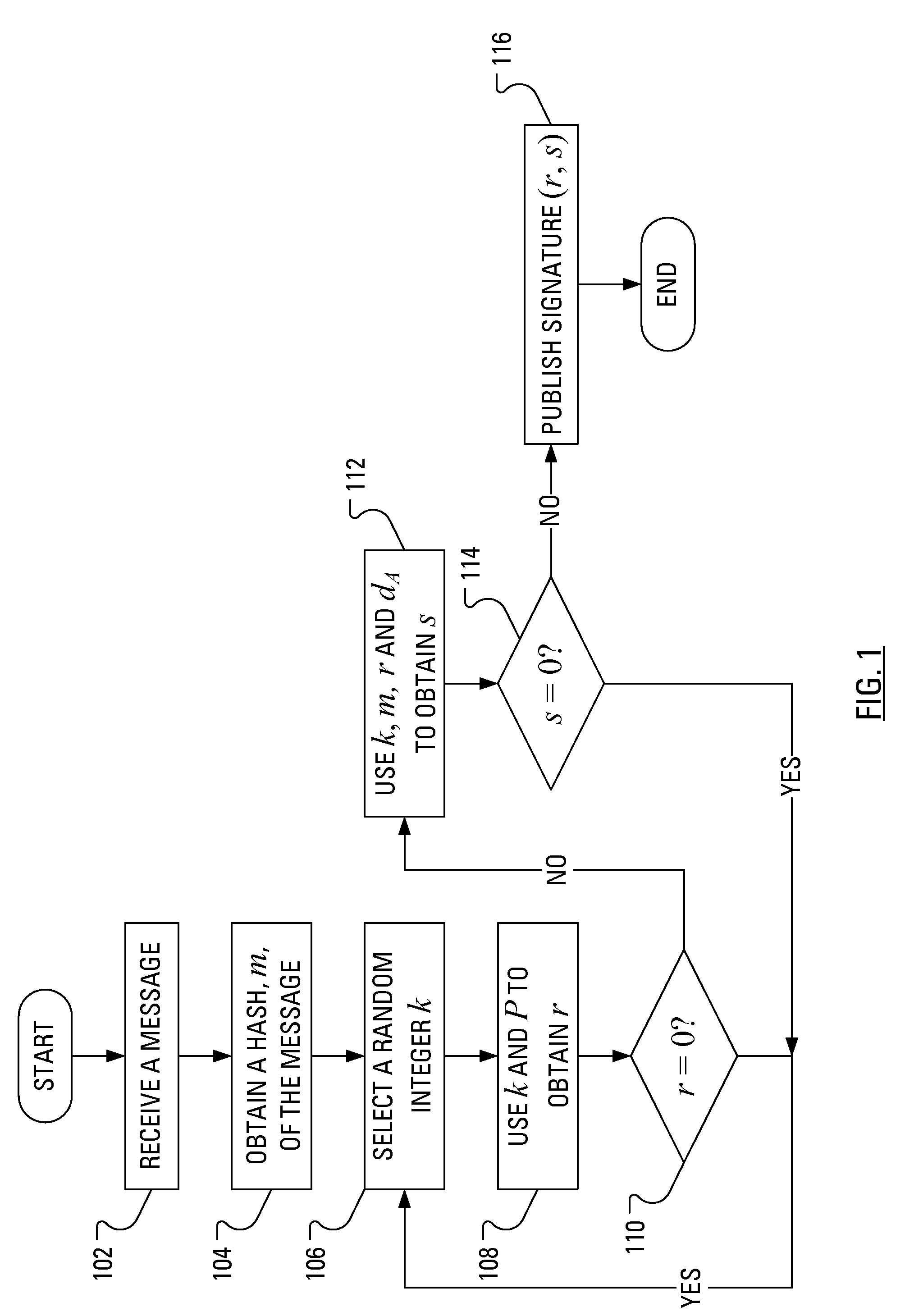
The invention discloses an ECDSA (Elliptic Curve Digital Signature Algorithm) method for resisting error curve attack, comprising the following steps: S1, randomly selecting k belonging to (1, n-1); S2, taking a random point R of an elliptic curve, and calculating M=R+kP; S3, calculating M-R=(x1,y1), and converting x1 into an integer; S4, calculating r=x1 mod n, and jumping back to S1 if r=0; S5, calculating e=H(m), wherein H(x) is a Hash function; S6, calculating s=k<1>(e+dr) mod n, and jumping back to S1 if s=0; and S7, outputting a signature pair (r, s). According to the invention, attackers can be effectively prevented from getting the private keys of users through error curve attack in the ECDSA.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
Two-party elliptic curve digital signature algorithm supporting key refreshing
ActiveCN111224783AKey distribution for secure communicationPublic key for secure communicationAlgorithmDigital signature
The invention belongs to the technical field of passwords, and particularly relates to a two-party elliptic curve signature algorithm supporting key refreshing. According to the algorithm, a functionof supporting key refreshing is added in a bipartite elliptic curve signature algorithm. In the secret key generation process of the two-party elliptic curve signature algorithm, two participants respectively generate a secret key share, a main secret key is composed of two secret key shares x1 and x2, and the main secret key x does not appear in the secret key generation and signature stage; theformula is as follows: x = x1 * x2mod q; the key refreshing process is participated by two parties, the key refreshing results are that the key shares x1 and x2 are changed into the key shares x '1 and x' 2, and the main key x is ensured to be unchanged; P1 and P2 are set as two parties, random numbers f1 and f2 are correspondingly generated, and finally respective calculation is performed to obtain x '1 and x' 2 through information communication of an interaction process; and after refreshing, x = x '1 * x' 2 = (x1 * f) * (x2 * f-1) mod q = x1 * x2 modq. The method provided by the invention provides high security for an elliptic curve signature algorithm.
Owner:FUDAN UNIV
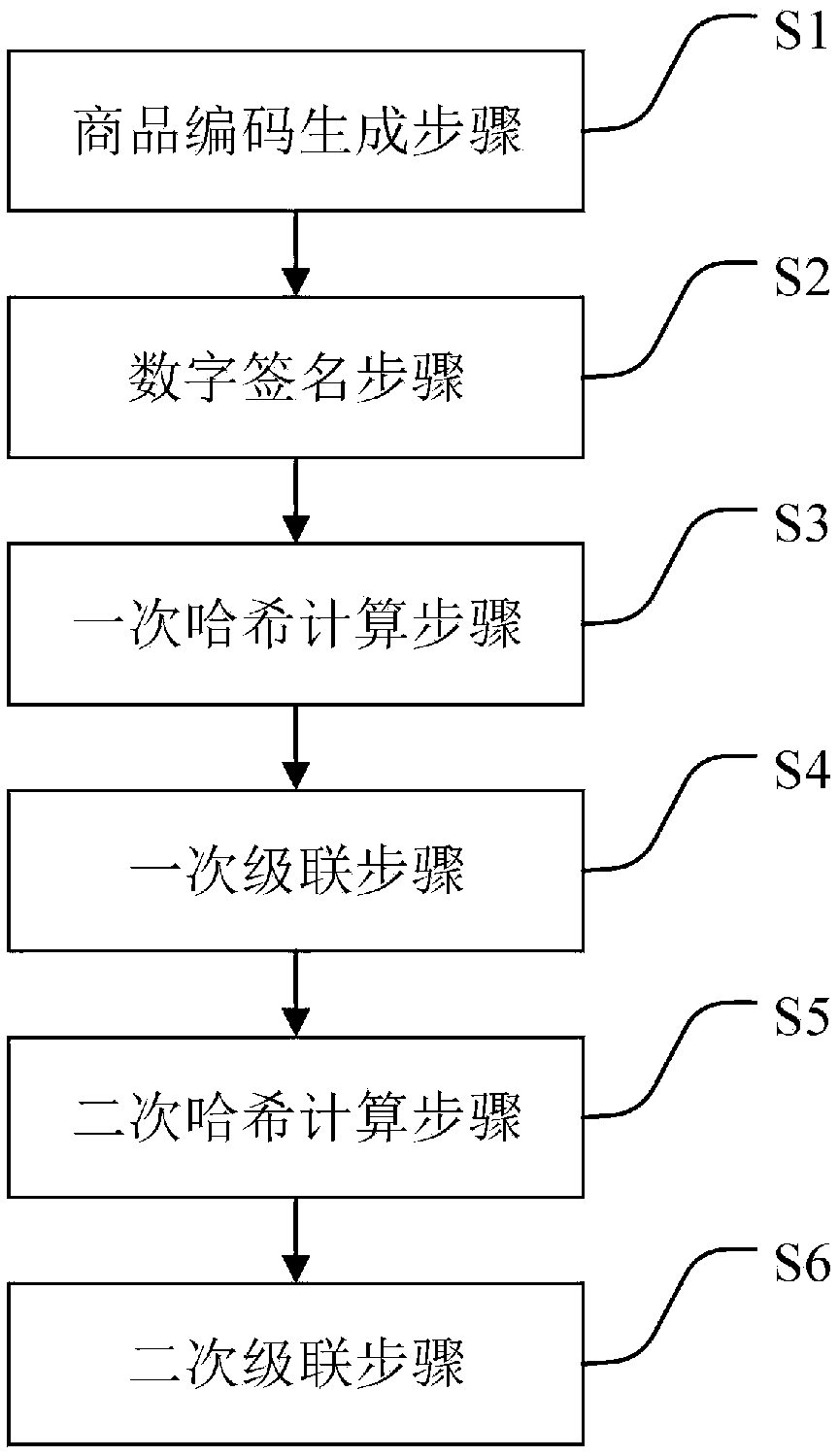
A method for generating commodity digital identity based on block chain
The invention provides a method for generating commodity digital identity based on a block chain. The method can shield the differences of the coding mode, coding length, manufacturer name length, commodity category information, etc. of different manufacturers, and finally obtain a fixed-length digital identity, which is convenient for the digital management of the products of the manufacturers, and also conducive to the comprehensive management of the products, without the need of distinguishing the different details of each manufacturer. Two different hashing algorithms are adopted, which toa certain extent reduces the possibility of duplicate digital identities in the same system using the method, and reduces the possibility of digital identity collision. The ECDSA algorithm of asymmetric cryptosystem is adopted, which is called the elliptic curve digital signature algorithm. If the key is not disclosed, other people cannot generate the same digital identity according to the same commodity information; generated digital identities do not collide, that is, do not duplicate; the identity can only be generated by a vendor that owns a private key and cannot be forged.
Owner:合肥高科创新科技有限公司
A method for secure and resilient distributed generation of elliptic curve digital signature algorithm (ecdsa) based digital signatures with proactive security
Described is system for generation of elliptic curve digital signature algorithm (ECDSA) based digital signatures. A. Secret-Share protocol is initialized between a client and a set of servers to share a set of shares of a private key s among the set of servers. The set of servers initializes a protocol to generate a digital signature on a message using the set of shares of the private key s without reconstructing or revealing the private key A. The set of servers periodically initialises a Secret-Redistribute protocol on each share of the private key A- to re- randomize the set of shares. A Secret-Open protocol is initialized to reveal the private key s to an intended recipient, wherein the private key A is used to compute the digital signature.
Owner:HRL LAB
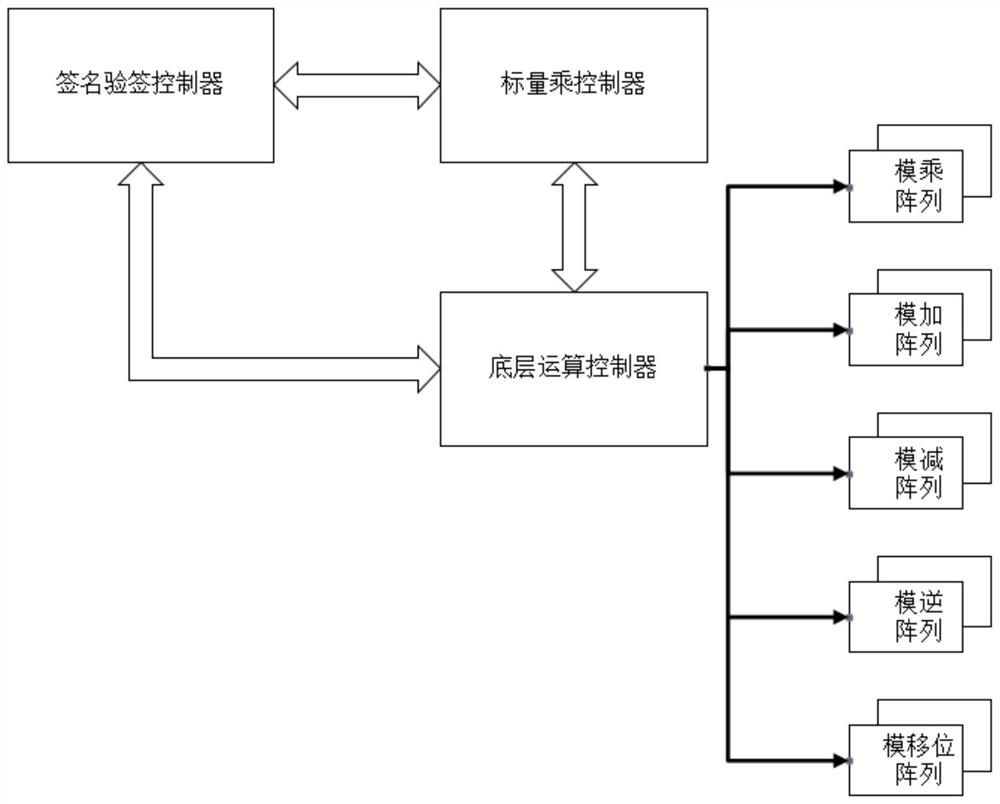
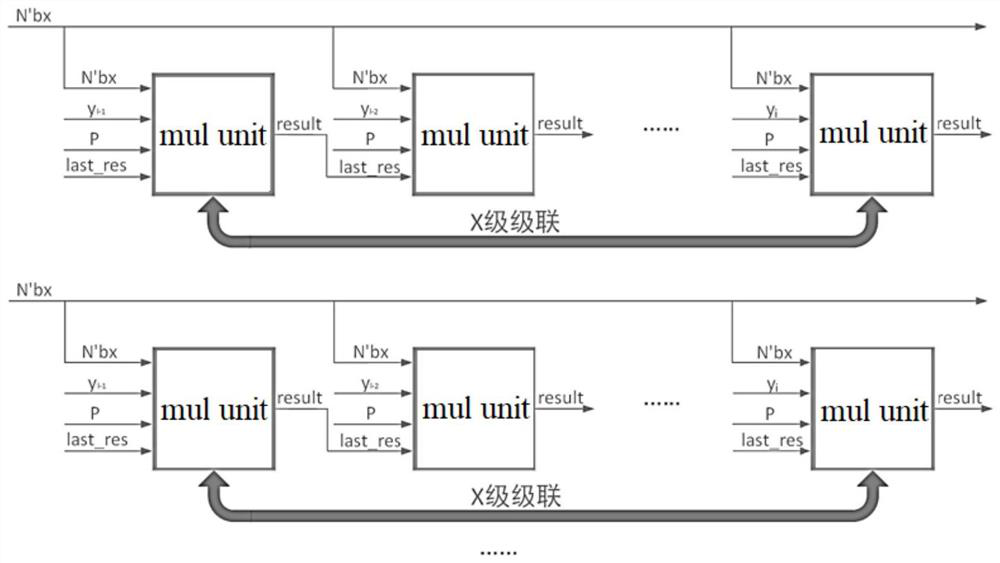
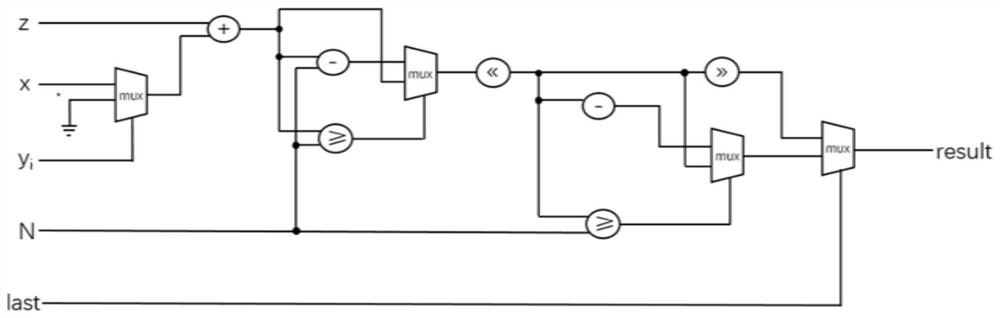
Hardware implementation method and system for elliptic curve digital signature and signature verification
PendingCN113783702AEasy to implementReduce overheadUser identity/authority verificationComputer hardwareDigital signature
The invention discloses a hardware implementation method and system for elliptic curve digital signature and signature verification, and belongs to the technical field of information security. In the prior art, the problems of high calculation complexity, insufficient hardware performance and high acceleration difficulty of an elliptic curve digital signature algorithm exist. In order to solve said problems, the hardware implementation method comprises the following steps: integrating point doubling, point addition, modular multiplication operation, modular addition operation, modular subtraction operation, modular inverse operation, modular shift operation and other bottom layer operations; building a new computing array structure, optimizing a scheduling method, and integrating and sharing computing resources. The calling times and the hardware resource consumption in the calculation process are reduced, the hardware performance and the scheduling sequence are improved, the system calculation time is shortened, the calculation efficiency is improved, the hardware resource use is reduced, and better performance is obtained.
Owner:南京宁麒智能计算芯片研究院有限公司
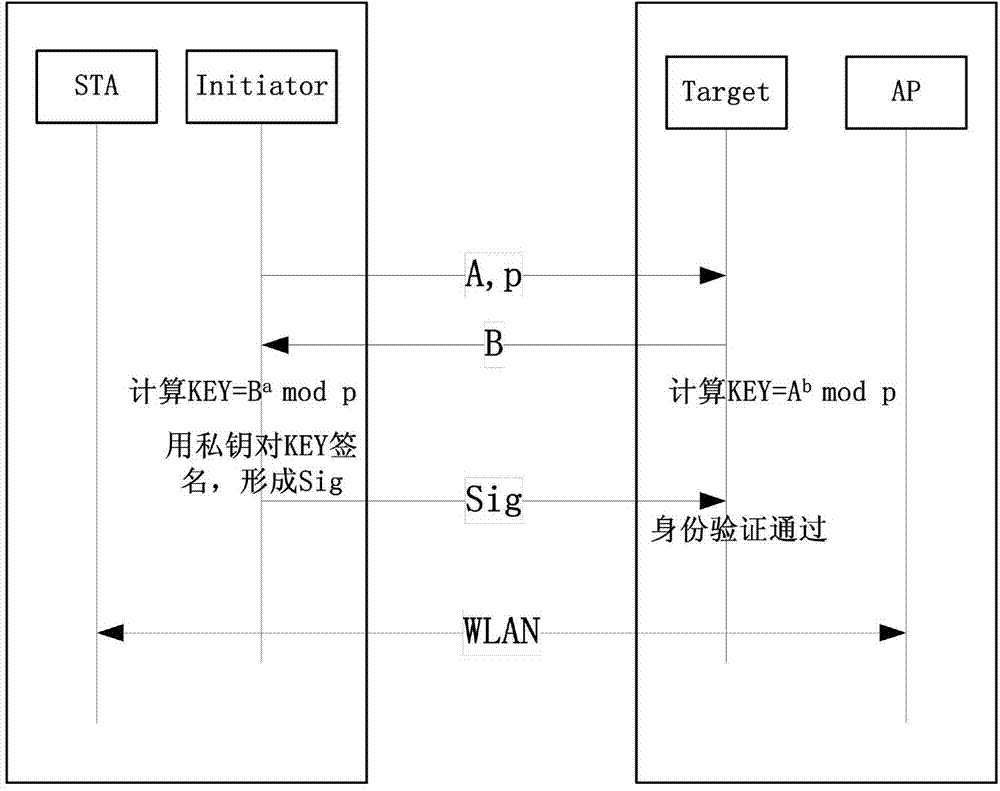
WLAN (wireless local area network) identity verification method
InactiveCN104780537AGuaranteed to be true and effectiveAvoid attackSecurity arrangementMan-in-the-middle attackValidation methods
Owner:TIANJIN UNIV
Elliptic curve cryptography with fragmented key processing and methods for use therewith
InactiveUS20140173288A1User identity/authority verificationInternal/peripheral component protectionElliptic Curve Digital Signature AlgorithmCryptography
A cryptography module includes a key store having a plurality of storage locations for storing a private key as k key fragments. One or more crypto-processing segments each operate based on corresponding ones of the k key fragments to process a message in accordance with elliptic curve digital signature algorithm (ECDSA) to produce a signed message.
Owner:AT&T INTPROP I LP
Certificate exchange mechanism for wireless networking
ActiveUS20170134170A1Public key for secure communicationUser identity/authority verificationCommunications systemWireless transmitter
A wireless communications system comprises a sector controller that includes a wireless transmitter, and a mobile subscriber station that includes a wireless receiver, and a memory. The wireless transmitter continuously transmitting frames. Each frame comprising a control field and the control field comprising a portion of an encryption certificate associated with the sector controller. The wireless receiver receives each frame and extracts the portion of the encryption certificate and stores the portion of an encryption certificate in the memory. The mobile subscriber station combines the portions of the encryption certificate stored in the memory and verifies that a complete encryption certificate has been received. After this the mobile subscriber station transmits its encryption certificate to the sector controller. The encryption certificates are based on an elliptic curve digital signature algorithm.
Owner:REDLINE COMM
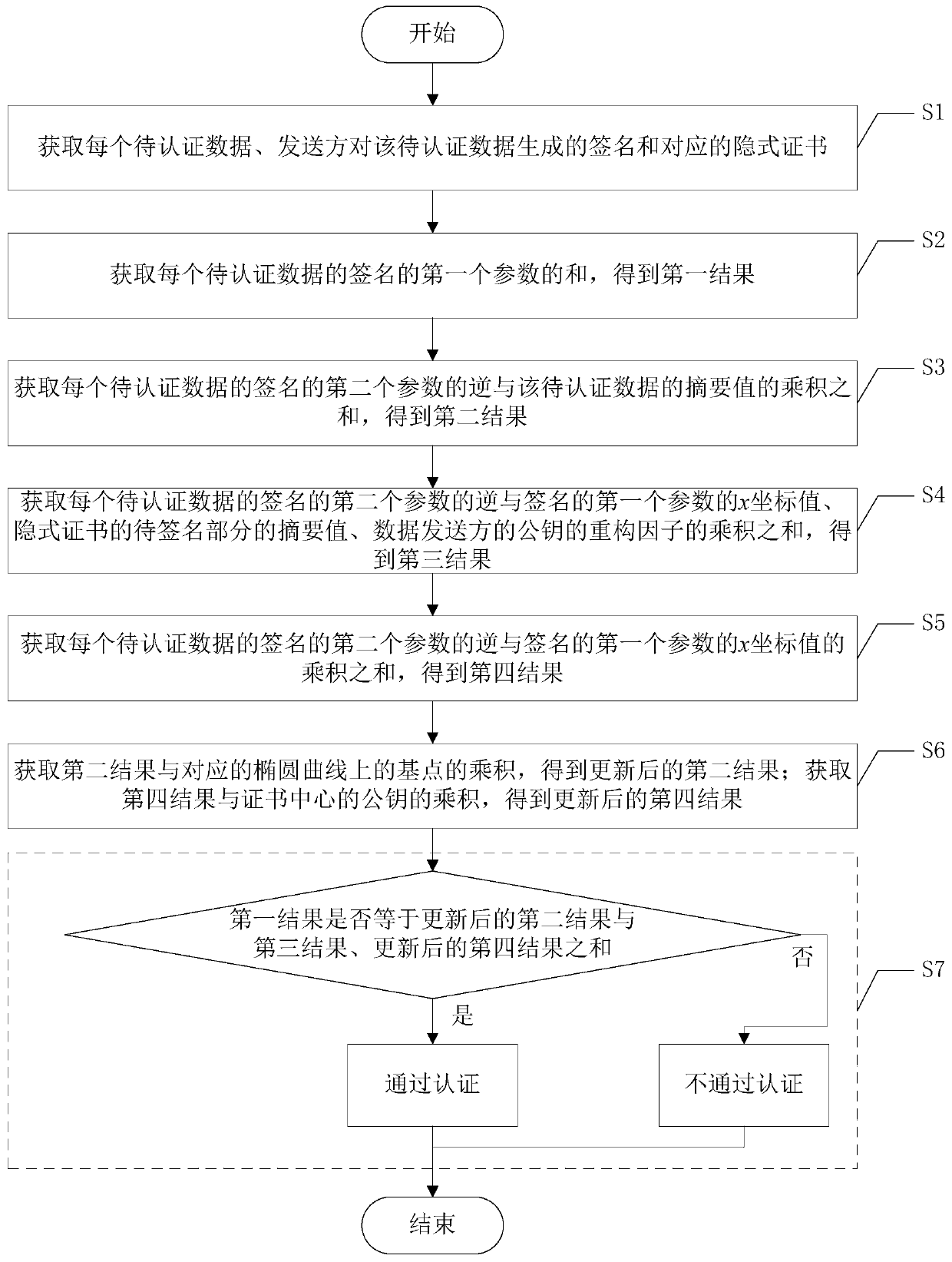
Batch authentication method for elliptic curve digital signature algorithm under implicit certificate
ActiveCN109981289AReduce authentication performance overheadReduce computational overheadMultiple keys/algorithms usagePublic key for secure communicationNetwork packetElliptic Curve Digital Signature Algorithm
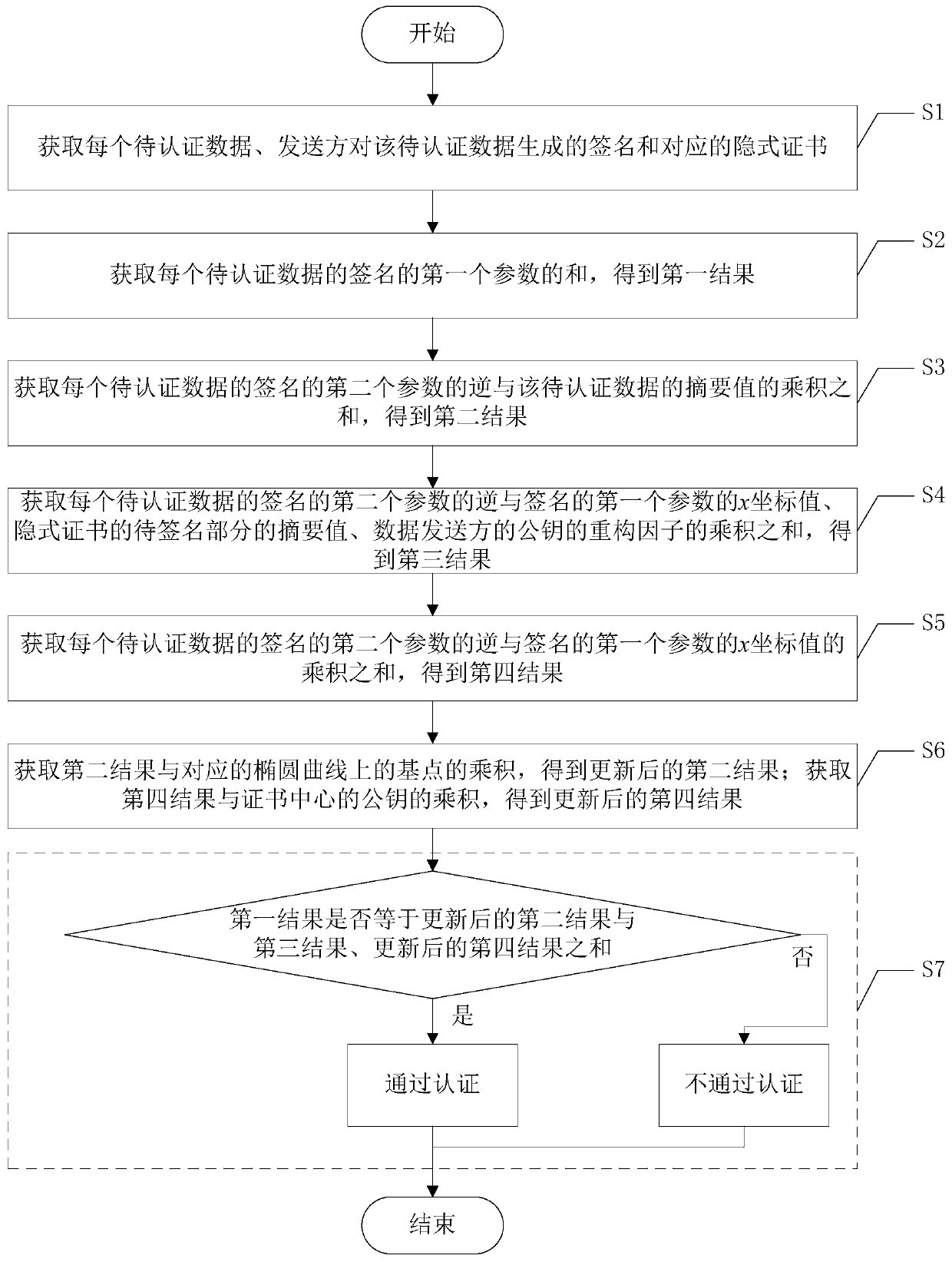
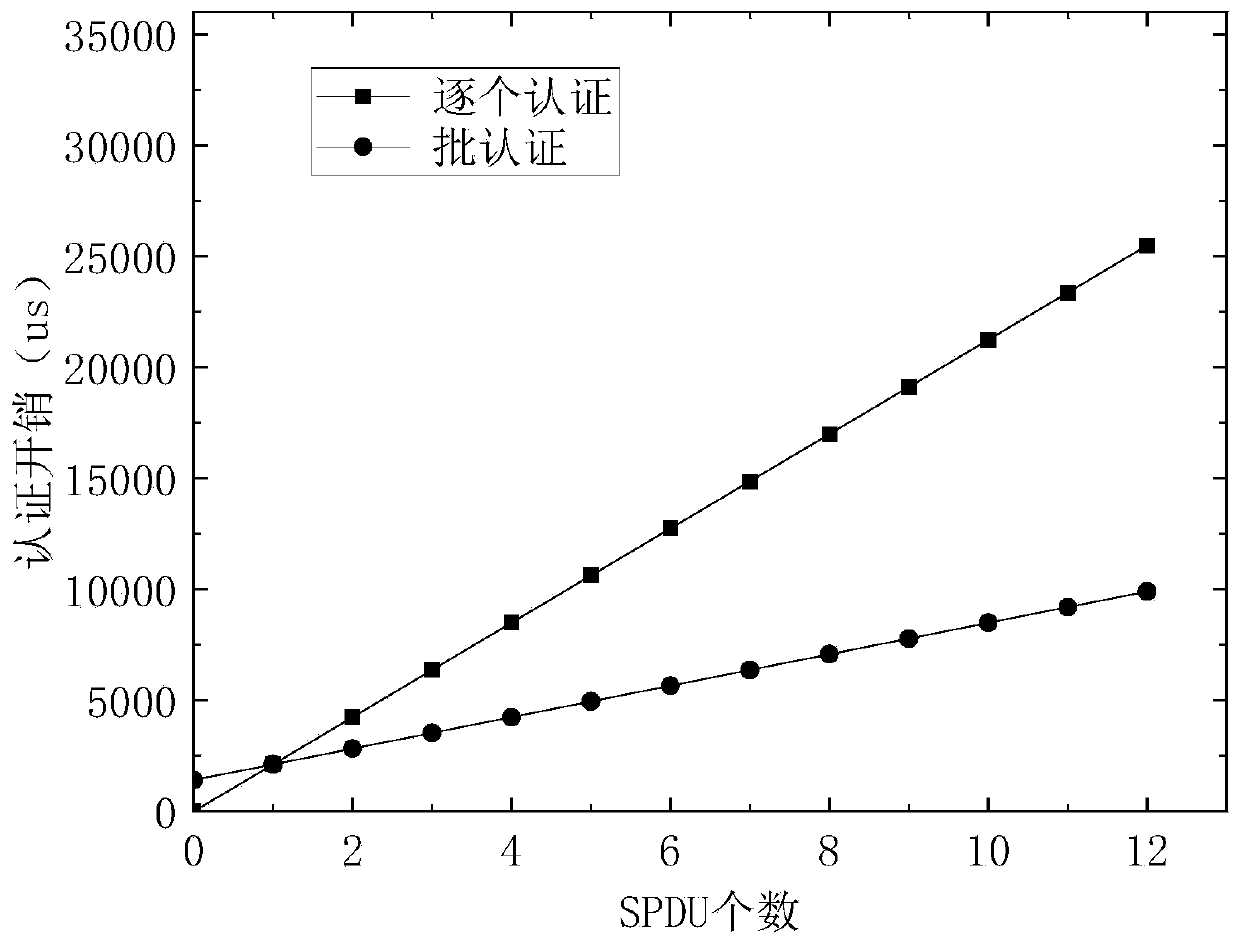
The invention discloses a batch authentication method for an elliptic curve digital signature algorithm under an implicit certificate. The method mainly comprises the following steps: judging whetherthe sum of the first parameters of the signatures of the to-be-authenticated data is equal to the sum of the products of the inverse of the second parameters of the signatures of the to-be-authenticated data and the abstract values of the to-be-authenticated data and the products of the base points on the corresponding elliptic curves plus the inverse of the second parameters of the signatures ofthe to-be-authenticated data and the signatures; the sum of the product of the x coordinate value of the first parameter, the abstract value of the to-be-signed part of the implicit certificate and the reconstruction factor of the public key of the data sender plus the result obtained by the product of the sum of the product of the inverse of the second parameter of the signature of each piece ofto-be-authenticated data and the x coordinate value of the first parameter of the signature and the public key of the certificate center. if yes, the data packets of the batch are all legal and pass the authentication, otherwise, the authentication is not passed. The batch authentication method provided by the invention can obviously improve the throughput rate of the system.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Elliptic curve cryptography with fragmented key processing and methods for use therewith
ActiveUS8705730B2Digital data processing detailsAnalogue secracy/subscription systemsElliptic Curve Digital Signature AlgorithmCipher
A cryptography module includes a key store having a plurality of storage locations for storing a private key as k key fragments. One or more crypto-processing segments each operate based on corresponding ones of the k key fragments to process a message in accordance with elliptic curve digital signature algorithm (ECDSA) to produce a signed message.
Owner:AT&T INTPROP I LP
Improved elliptic curve digital signature algorithm and signature verification method thereof
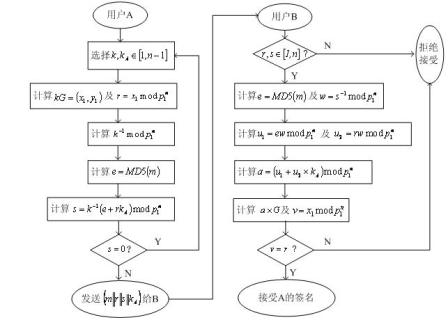
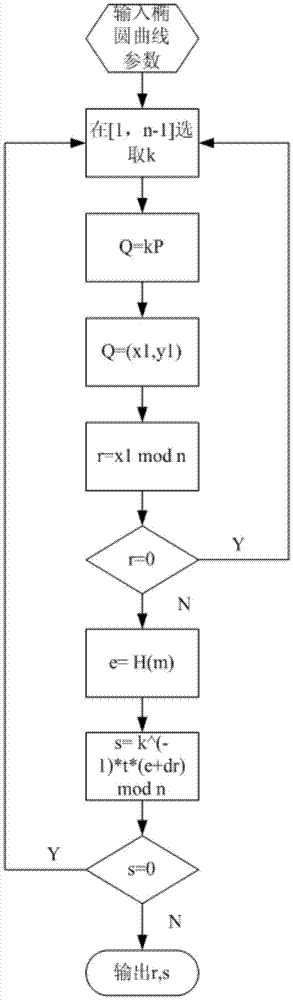
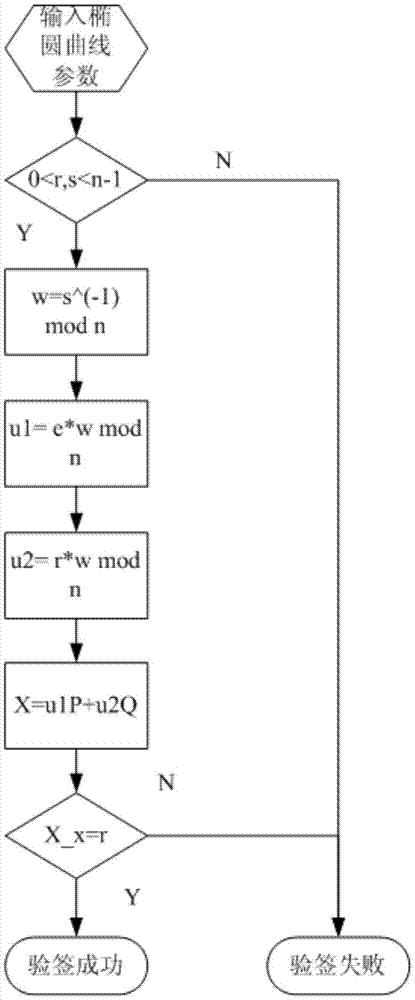
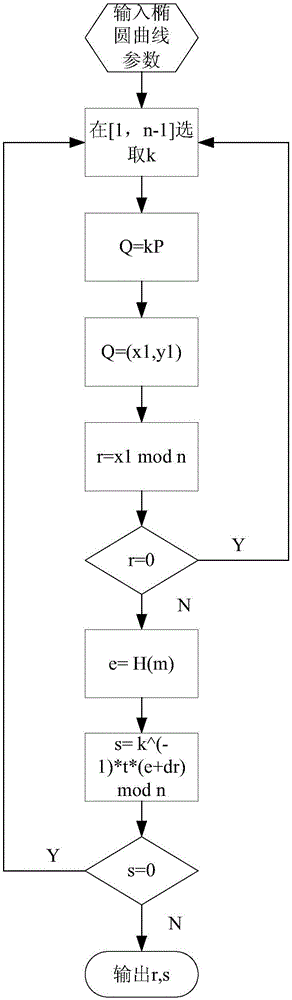
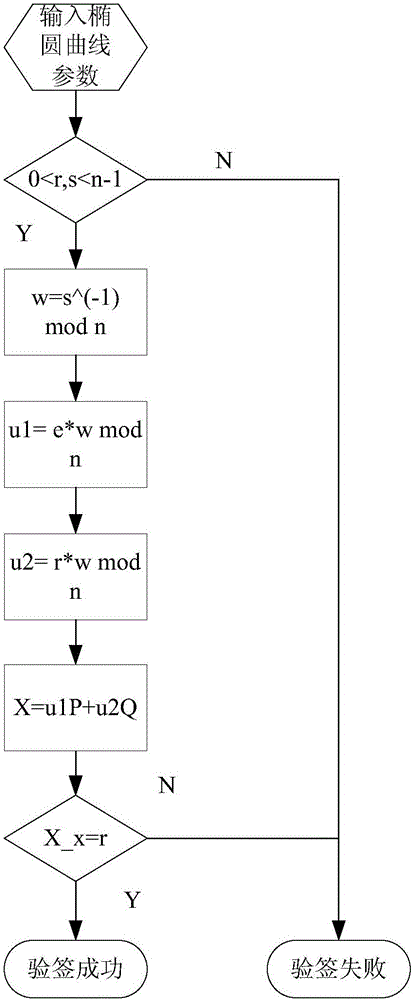
InactiveCN106856431ASolve the behavior of spoofing signaturesResolve lines that impersonate signaturesUser identity/authority verificationHash functionTrusted third party
The invention discloses an improved elliptic curve digital signature algorithm. Before identity identification, a signature side and a signature verification side obtains a time random number t from a trusted third party. The improved elliptic curve digital signature algorithm comprises: step one, a k belonging to [1, n-1] is selected randomly; step two, operation of kP=(x1,y1) is carried out and then the x1 is converted into an integer; step three, calculation is carried out based on a formula: r=x1mod n, wherein if the r is equal zero, the step one is carried out again and a random time number t is obtained from the trusted third party; step four, a formula e=H(m) is calculated, wherein the H(x) express a hash function; step five, calculation is carried out based on a formula: s=k<-1>t(e+dr)mod n, and if the s is equal to zero, the step one is carried out again and a random time number t is obtained from the trusted third party; and step six, a signature pair (r,s) is outputted. In addition, the invention also discloses a signature verification method based on the improved elliptic curve digital signature algorithm. Therefore, a behavior of signature countering by an intermediary can be avoided.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
Point-to-point elliptic-curve type digital signature algorithm and signature verification method based on the same
InactiveCN106533682ASolve the behavior of spoofing signaturesPublic key for secure communicationUser identity/authority verificationHash functionTheoretical computer science
The invention discloses an improved point-to-point elliptic-curve type digital signature algorithm. The algorithm comprises the following steps that: (1), a formula t=Hash(IDA||IDB||count)mod n is calculated, wherein the count is equal to 0X00000001; and if t is equal to 0, the count++ is realized and the t is calculated again; (2), k belonging to [1, n-1] is selected randomly; (3), a formula kP=(x1,y1) is operated and the x1 is transformed into an integer; (4), a formula r=x1 mod n is calculated; and if the r is equal to 0, the step (2) is carried out again; (5), an expression e=H(m) is calculated, wherein the H(x) is a hash function; (6), an expression s=k <1>t (e+dr) mod n is calculated; if the s is equal to 0, the step (2) is carried out again to obtain a random number; and (7), a signature pair (r,s) is outputted. In addition, the invention also discloses a signature verification method based on the improved point-to-point elliptic-curve type digital signature algorithm. A point-to-point signature verification behavior is realized.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com