A method for generating commodity digital identity based on block chain
A digital identity and blockchain technology, applied in business, data processing applications, instruments, etc., can solve problems such as poor confidentiality, unfavorable index, easy to be cracked, etc., to reduce the possibility of adding effective digital identities, reduce The effect of repeating digital identities and facilitating digital management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
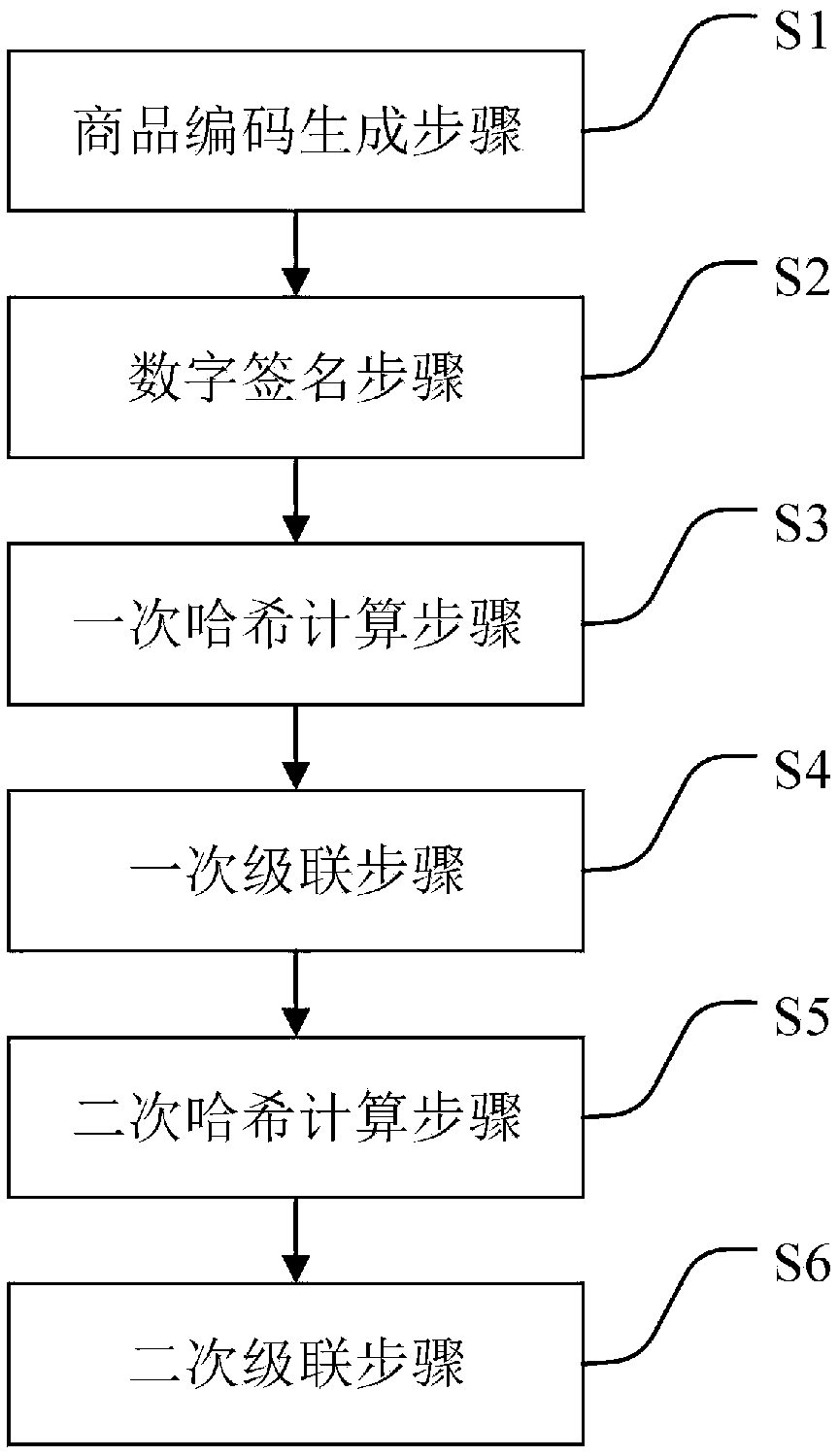
[0023] like figure 1 As shown, a method for generating a digital identity of a commodity based on a blockchain is suitable for a commodity anti-counterfeiting verification system based on a blockchain; the method for generating a digital identity for a commodity specifically includes the following steps:
[0024] Step S1, commodity code generating step: receive externally input commodity information; encode according to the preset coding rules according to the content of the commodity information, and generate a fixed-length character string code as the commodity code C.
[0025] In the commodity code generation step, the process of coding according to the preset coding rules according to the content of the commodity information specifically includes:
[0026] Obtain the content of the product information, including: product category, manufacturer name, category information, production time, and its own serial number;
[0027] Generate a fixed-length character string code, th...
specific example
[0029] Assuming that the product A to be coded is a wine product, its product information includes the type of product A, winery name, category information, production time, and its own serial number. For example, suppose the product information of product A is liquor, Anhui Bozhou Gujing tribute Liquor Co., Ltd., Gujing Niannian Puree 8 years, March 5, 2018 at 8:35, 43086983216.
[0030] The number corresponding to the category information of the commodity A is used as the initial character of the code C of the commodity A. The category information is divided into three types: white wine, red wine, and other wines; respectively corresponding to the numbers S, W, and O. At this time, the commodity A corresponds to code C as "S".
[0031] Completely describe the winery name of the product A in Chinese, and connect the obtained character string after the code C in the previous step. At this time, the code C is "S Anhui Bozhou Gujing Distillery Co., Ltd.".
[0032] Completely de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com