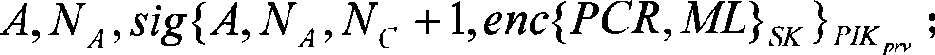Patents
Literature
419 results about "Man-in-the-middle attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography and computer security, a man-in-the-middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communications between two parties who believe they are directly communicating with each other. One example of a MITM attack is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within reception range of an unencrypted wireless access point (Wi-Fi) could insert themselves as a man-in-the-middle.
Online transactions systems and methods
InactiveUS20070043681A1Improve securityImprove computing powerAcutation objectsDigital data authenticationMan-in-the-middle attackInternet privacy
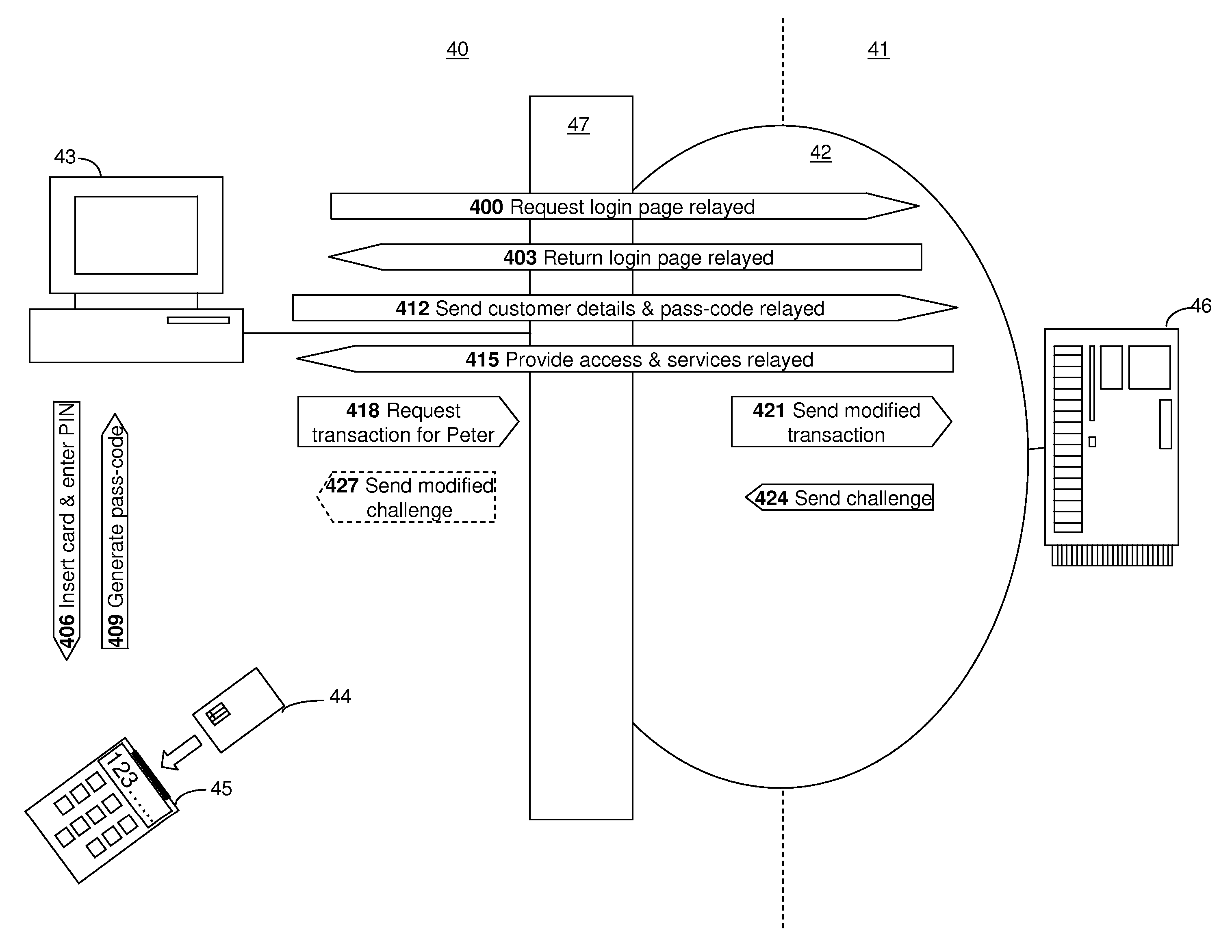
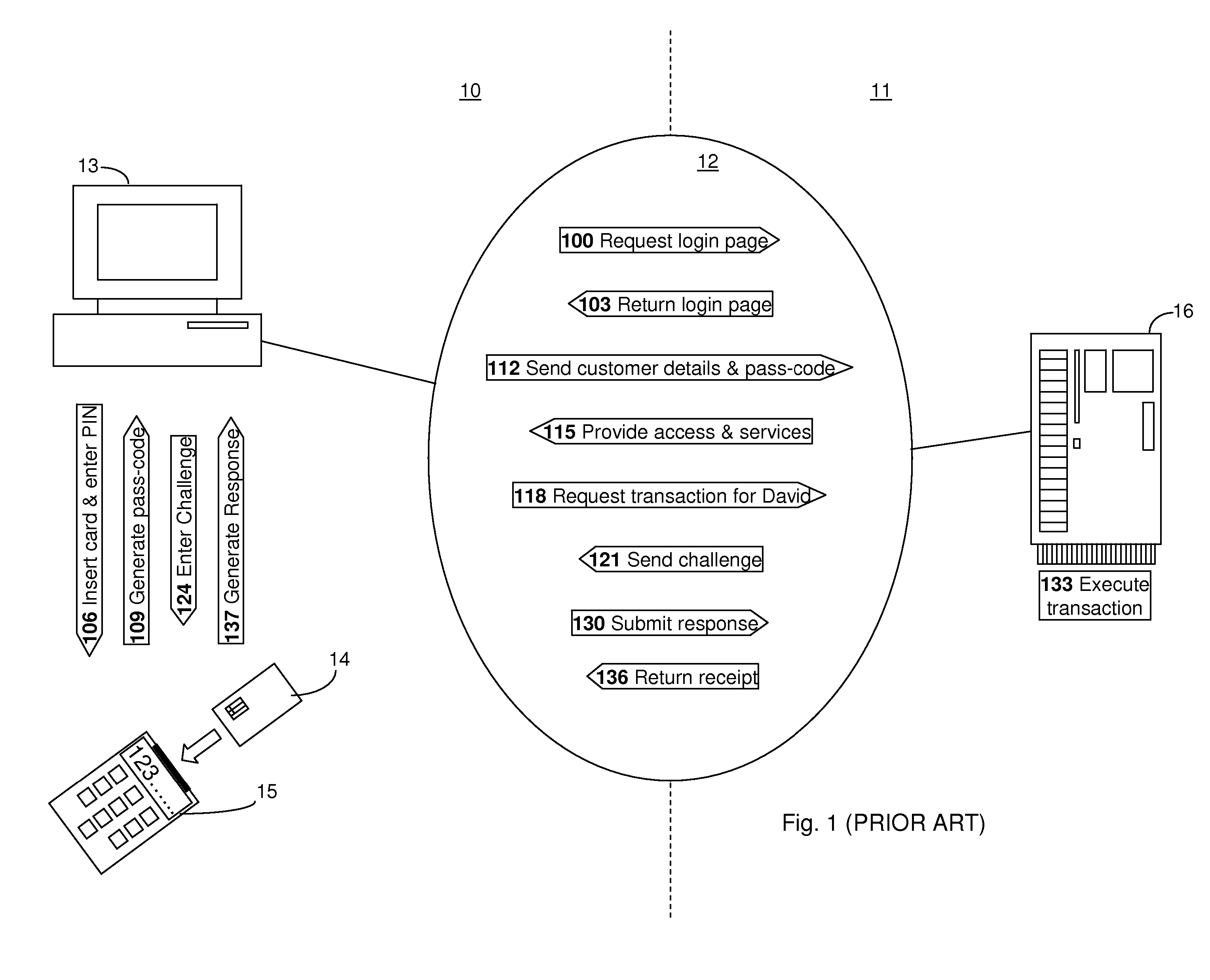
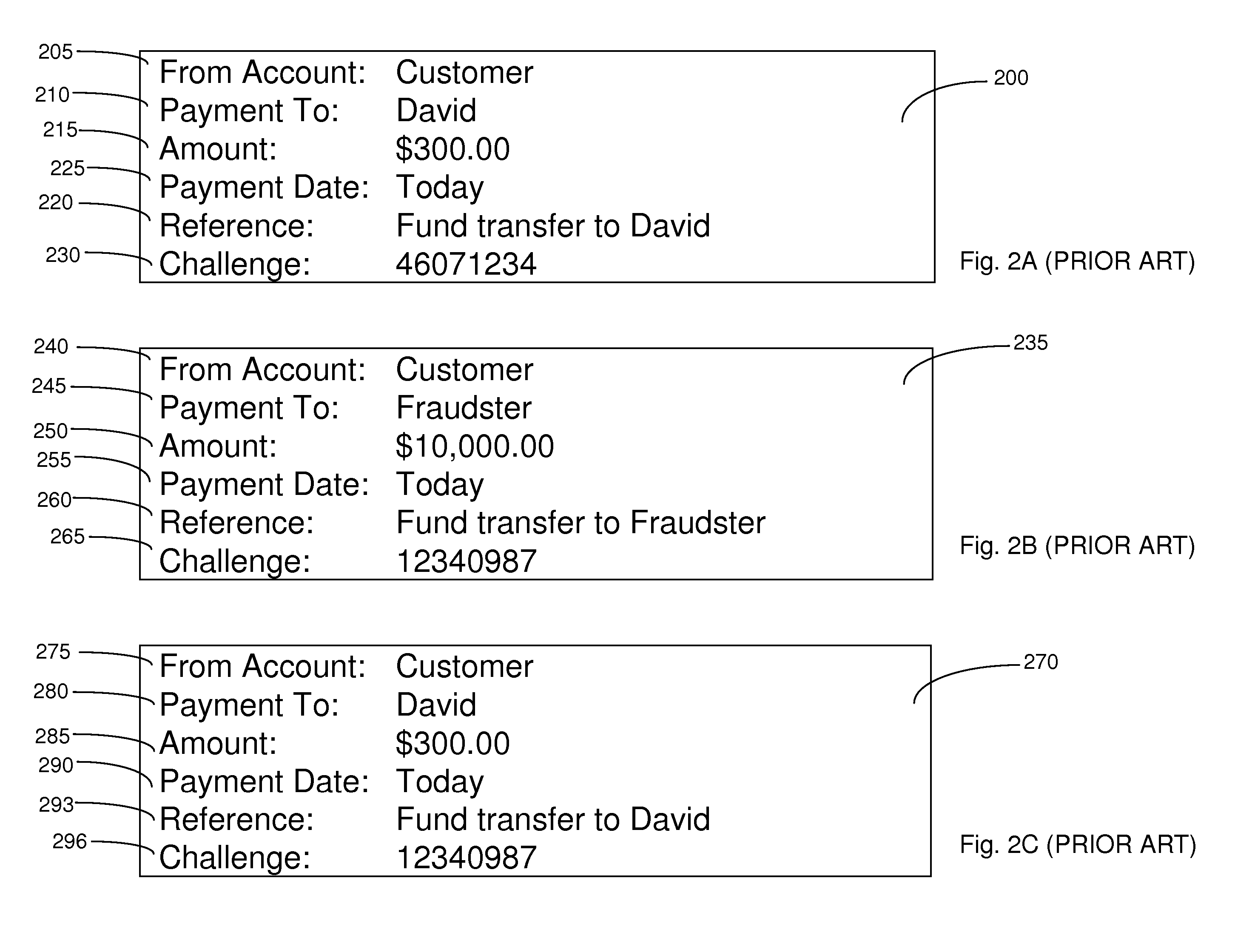
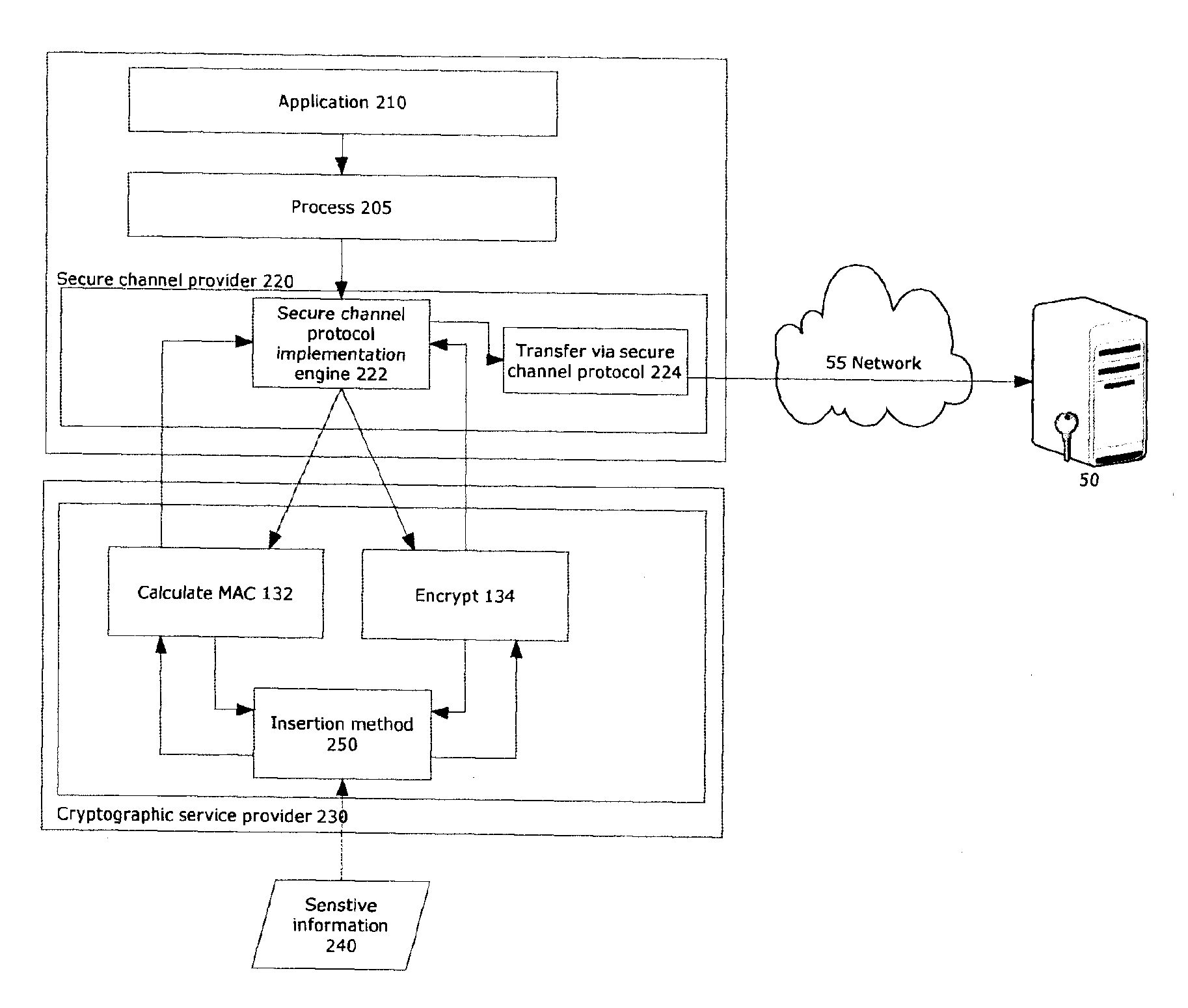
Embodiments of the present invention relate to an online transaction method enacted between a first party and a second party, for example a customer and a bank respectively. The method of the embodiment includes the steps of the first party transmitting a transaction request comprising transaction details and the second party receiving the transaction request and generating, for the first party, an authentication request, comprising transaction details and challenge data. In order to increase the security of the overall transaction, the authentication request is adapted so that it is difficult for an automated process to use or modify information therein to generate a replacement authentication request. Such a method finds application in reducing the potential for a man-in-the-middle attack, wherein an intermediate, subversive process can behave as a legitimate second party in order to steal money from the first party.
Owner:THE ROYAL BANK OF SCOTLAND PLC
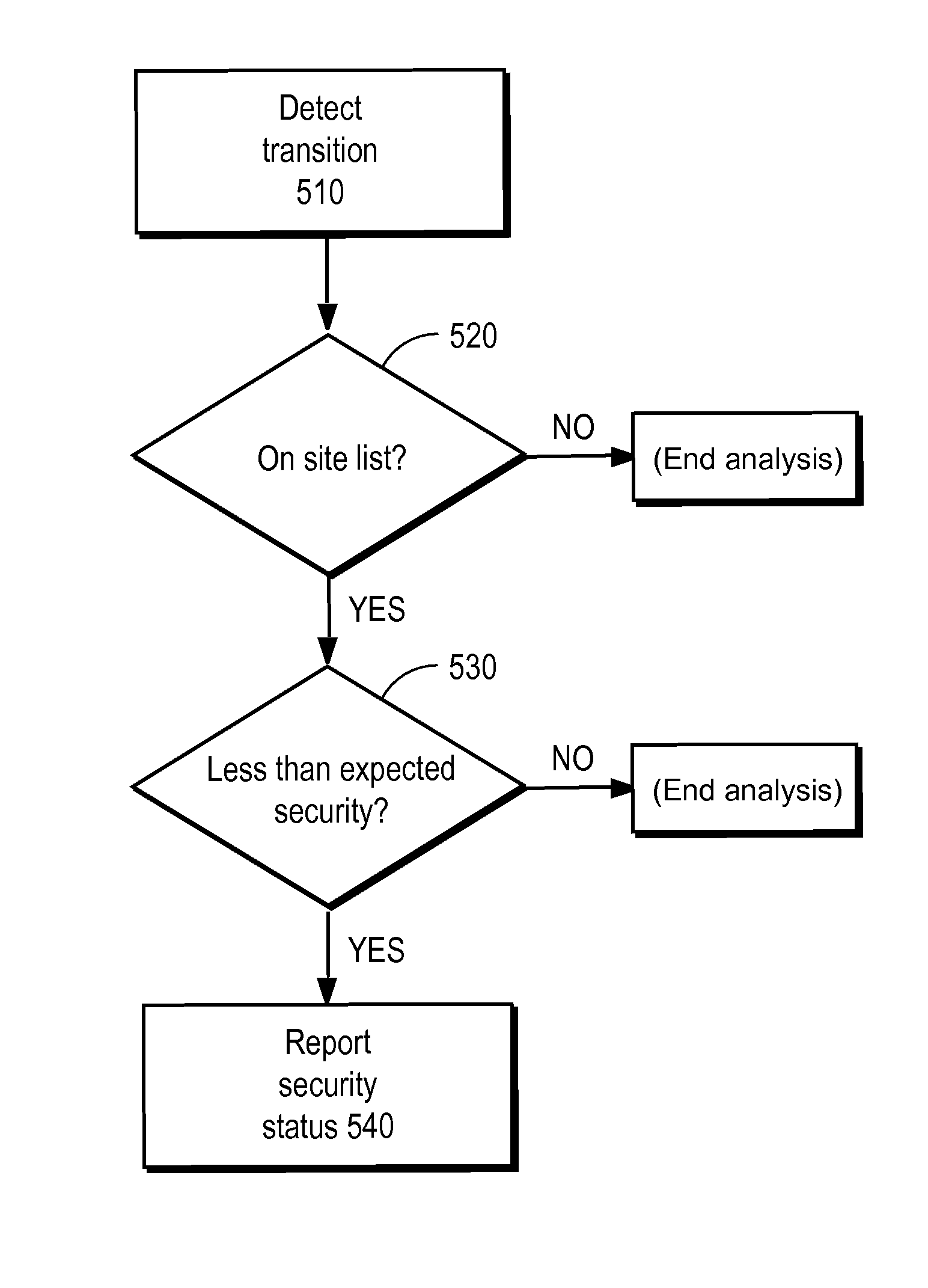
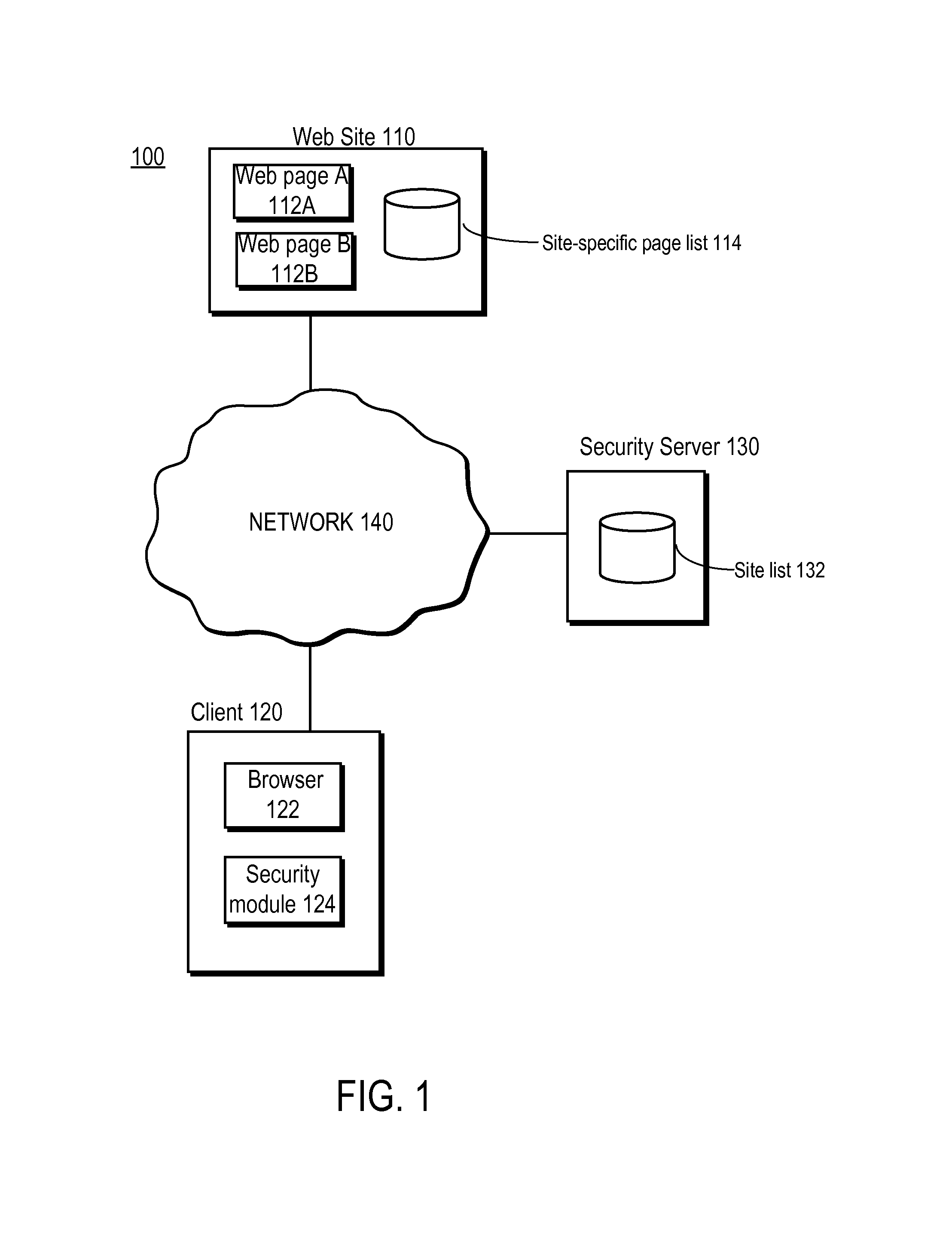
Detecting man-in-the-middle attacks via security transitions
ActiveUS8561181B1Memory loss protectionError detection/correctionMan-in-the-middle attackRemedial action
A page list comprising a list of transitions between network resources is established. Subsequently, a transition is detected between a first network resource and a second network resource. An expected security level associated with the transition is identified based on the page list. Responsive to the detected security level being determined to be lower than the expected security level, a remedial action is performed.
Owner:CA TECH INC
Protecting one-time-passwords against man-in-the-middle attacks
ActiveUS20070033642A1Key distribution for secure communicationDigital data processing detailsMan-in-the-middle attackKey authentication
To authenticate a user having an associated asymmetric crypto-key having a private / public key pair (D,E) based on a one-time-password, the user partially signs a symmetric session key with the first portion D1 of the private key D. The authenticating entity receives the partially signed symmetric session key via the network and completes the signature with the second private key portion D2 to recover the symmetric session key. The user also encrypts a one-time-password with the symmetric session key. The authenticating entity also receives the encrypted one-time-password via the network, and decrypts the received encrypted one-time-password with the recovered symmetric session key to authenticate the user.
Owner:VMWARE INC
Method and Devices For User Authentication
InactiveUS20080212771A1Effective protectionSecurity of the proposed method is not particularly underminedAcutation objectsDigital data processing detailsMan-in-the-middle attackData set
For authenticating a user using a communication terminal (1) to access a server (4) via a telecommunications network, a personal identification code is received from the user From secure session establishment protocol messages exchanged (S1, S2, S3) between the communication terminal (1) and the server (4), a data set is generated (S4). Based on the data set, a transaction authentication number is generated (S52) using the personal identification code. The transaction authentication number is transmitted (S54) from the communication terminal (1) to the server (4). In the server (4), the transaction authentication number received is verified (S20) based on the secure session establishment protocol messages exchanged with the communication terminal (1). The transaction authentication number enables session aware user authentication that protects online users against real-time man-in-the-middle attacks.
Owner:PRIVASPHERE AG
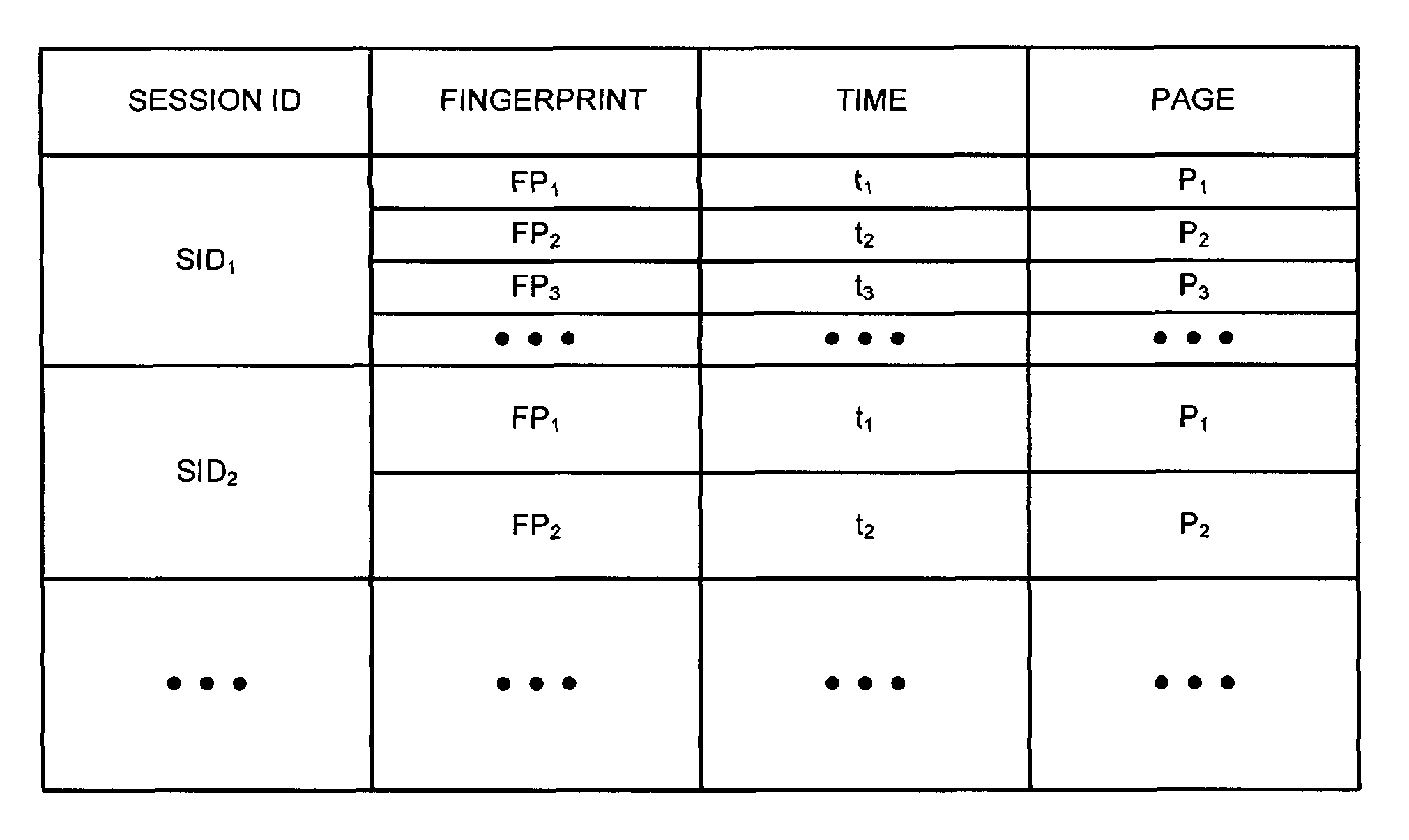
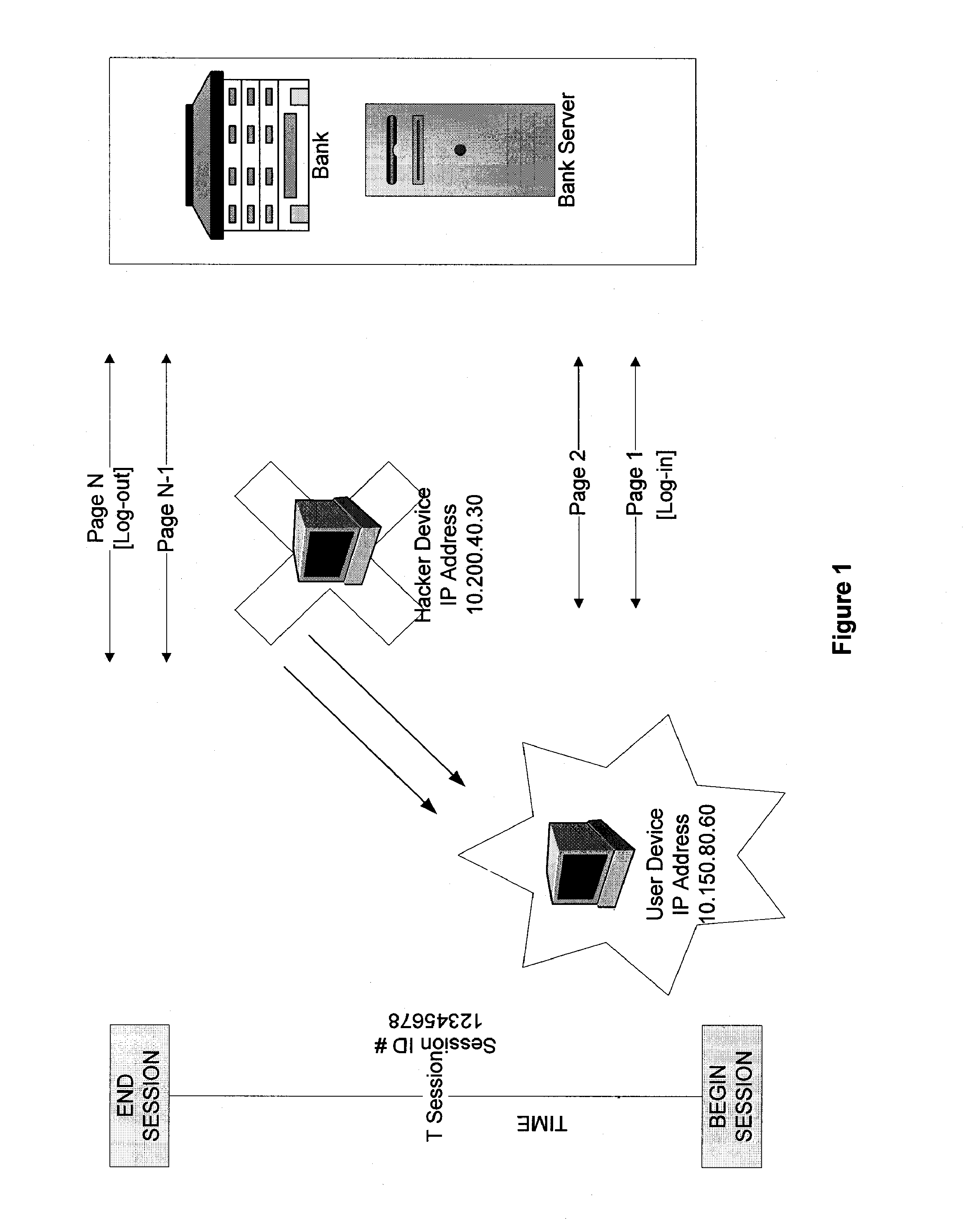
Systems and methods for detection of session tampering and fraud prevention
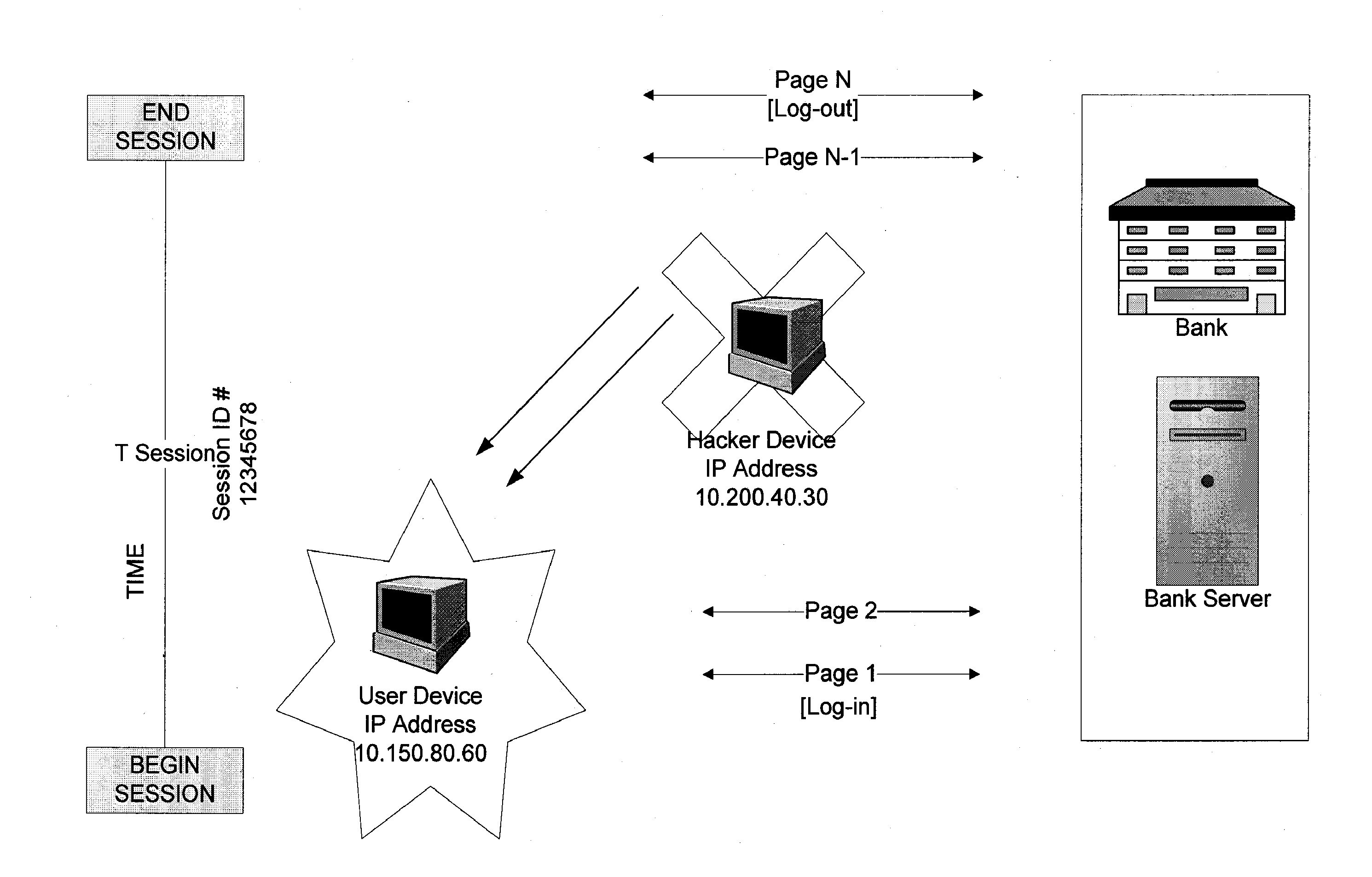
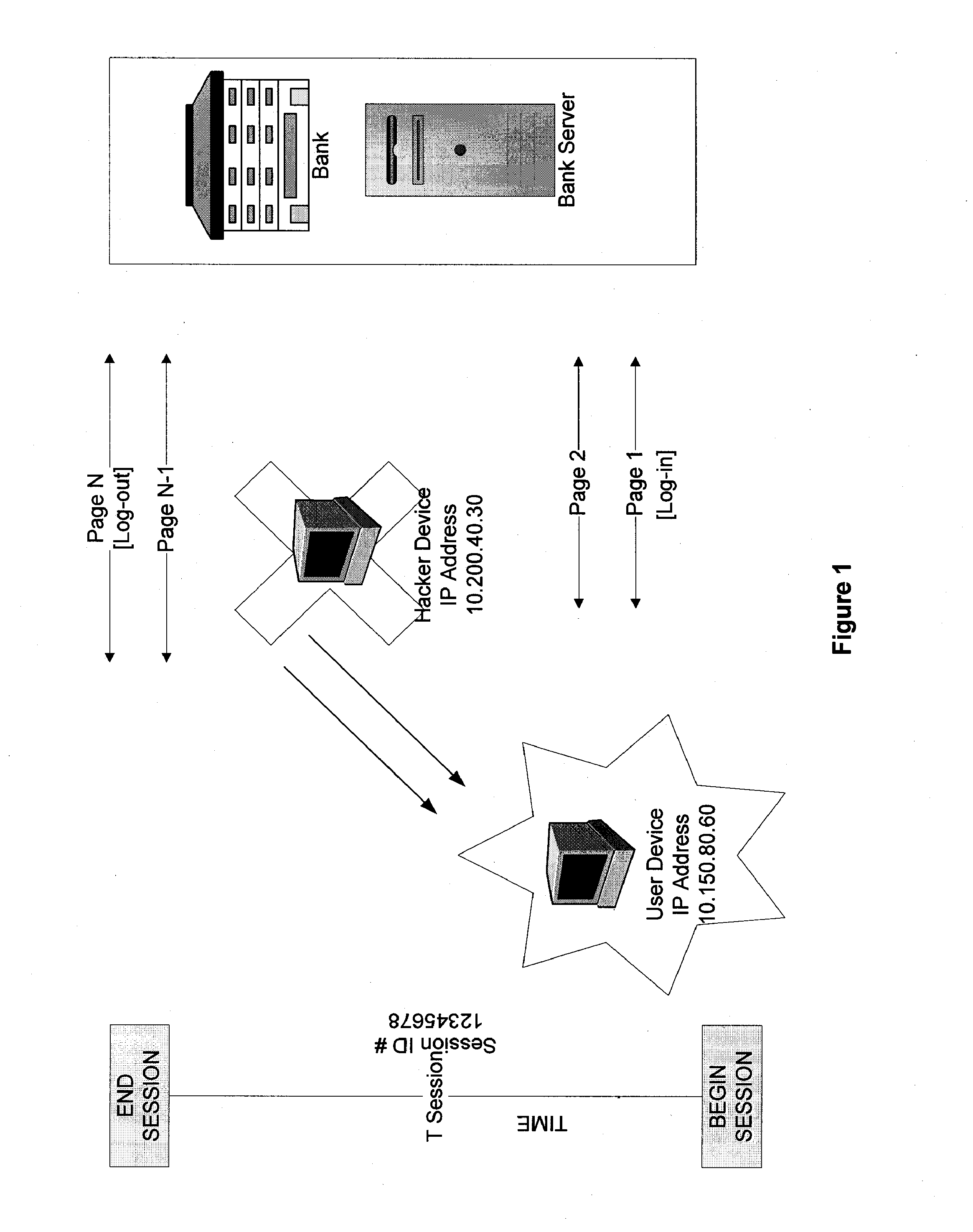
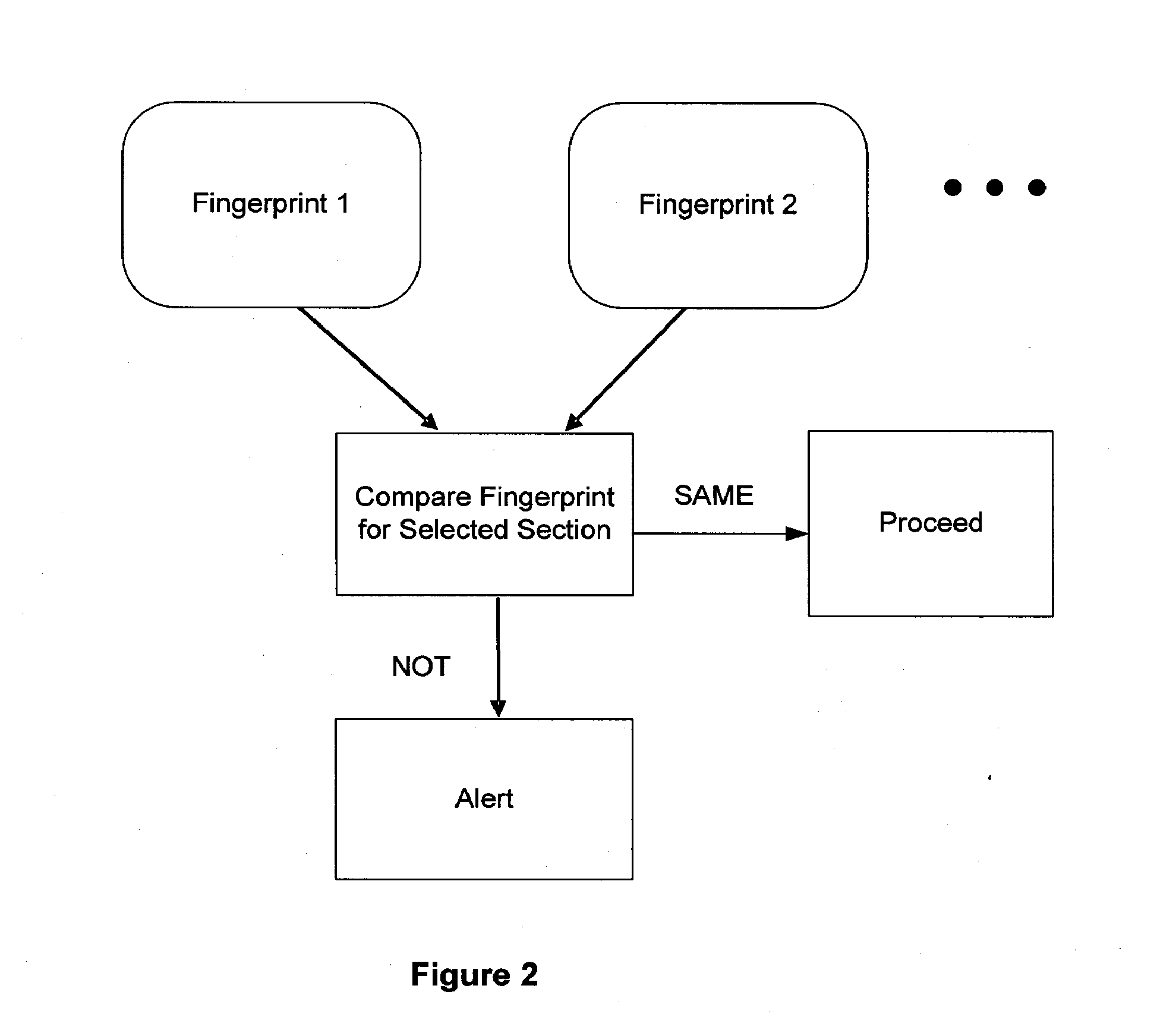
ActiveUS20070234409A1Secure performanceIdentify theftMemory loss protectionError detection/correctionMan-in-the-middle attackOperating system
The invention provides methods and apparatus for detecting when an online session is compromised. A plurality of device fingerprints may be collected from a user computer that is associated with a designated Session ID. A server may include pages that are delivered to a user for viewing in a browser at which time device fingerprints and Session ID information are collected. By collecting device fingerprints and session information at several locations among the pages delivered by the server throughout an online session, and not only one time or at log-in, a comparison between the fingerprints in association with a Session ID can identify the likelihood of session tampering and man-in-the middle attacks.
Owner:THE 41ST PARAMETER
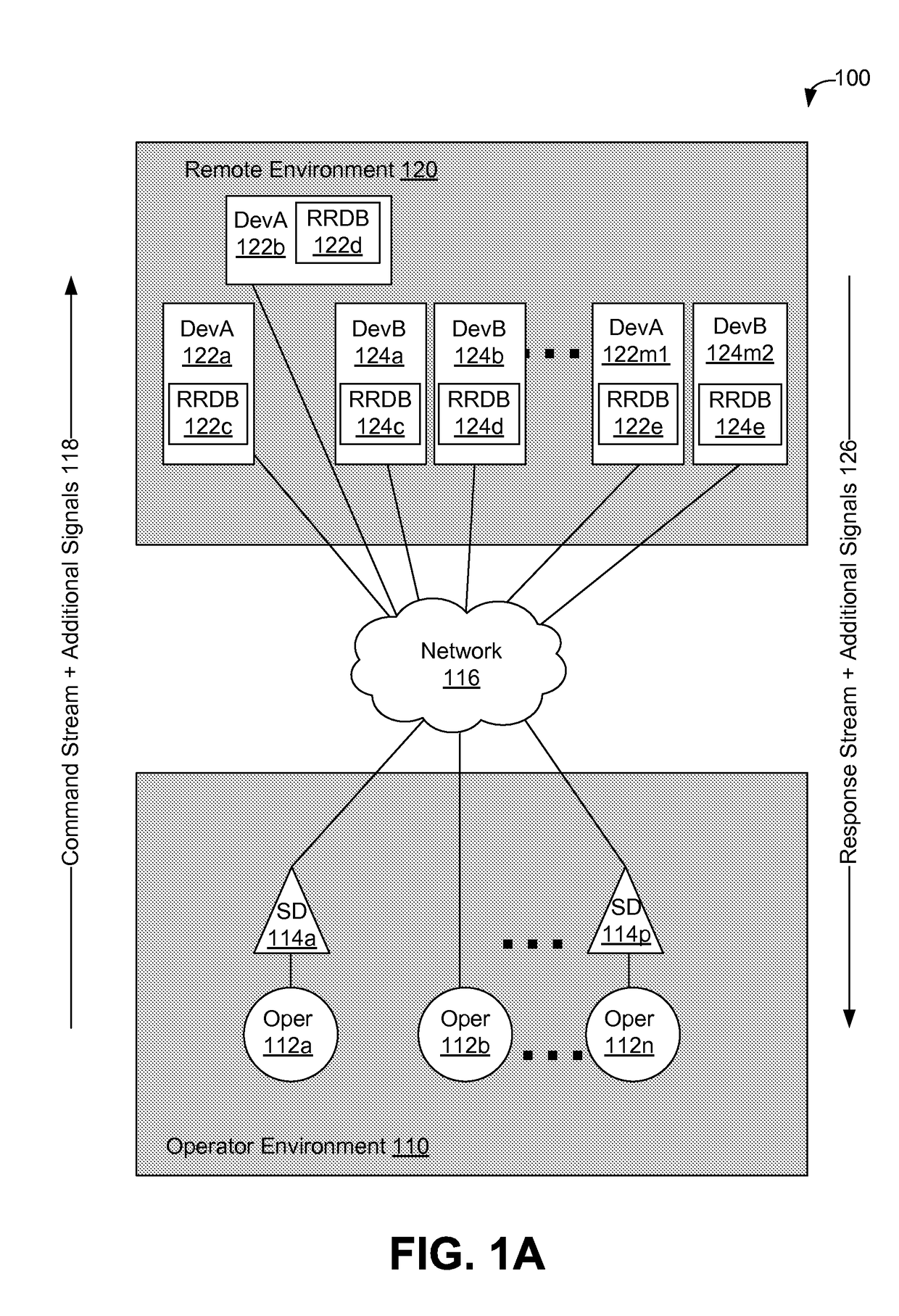
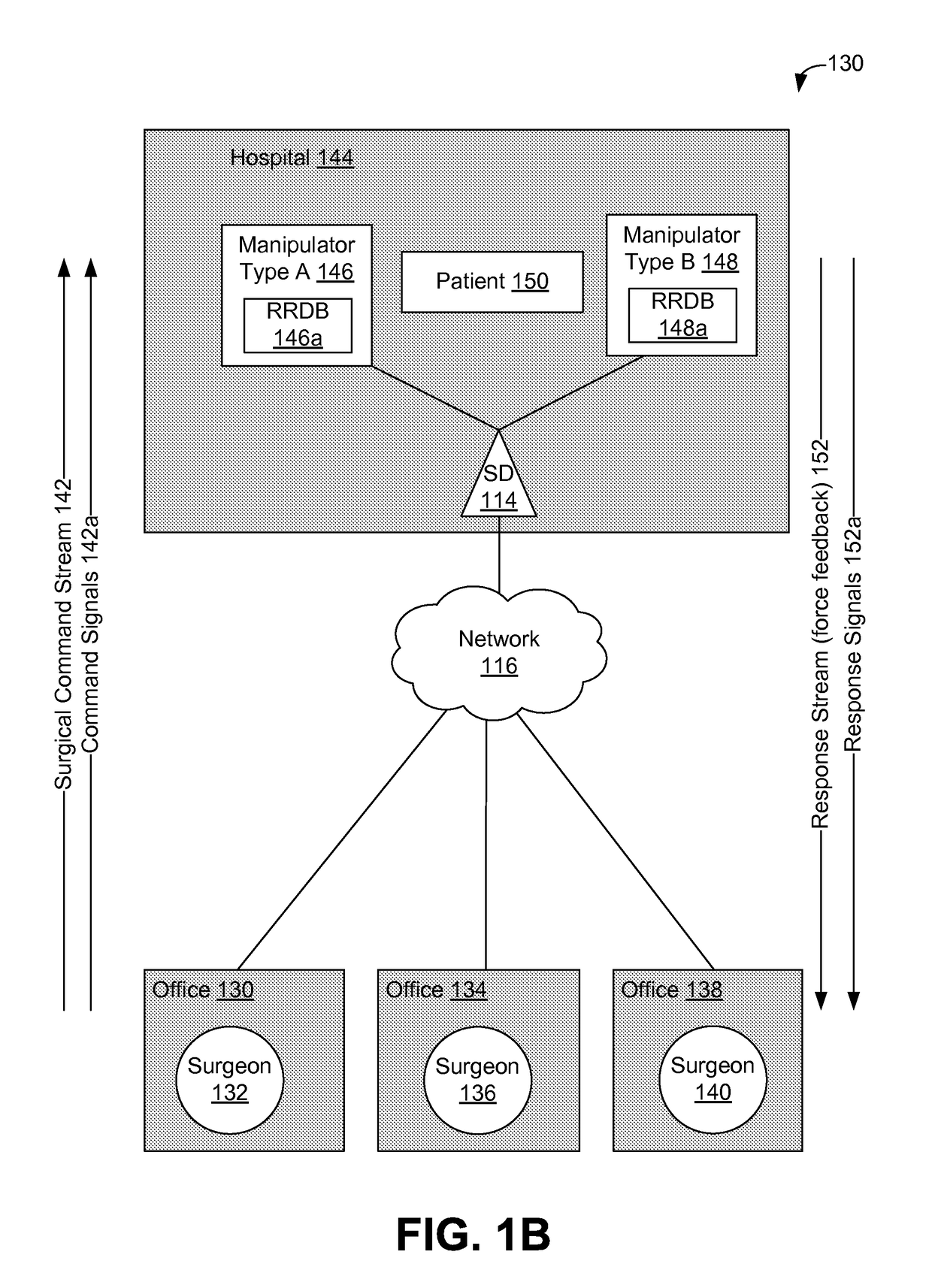
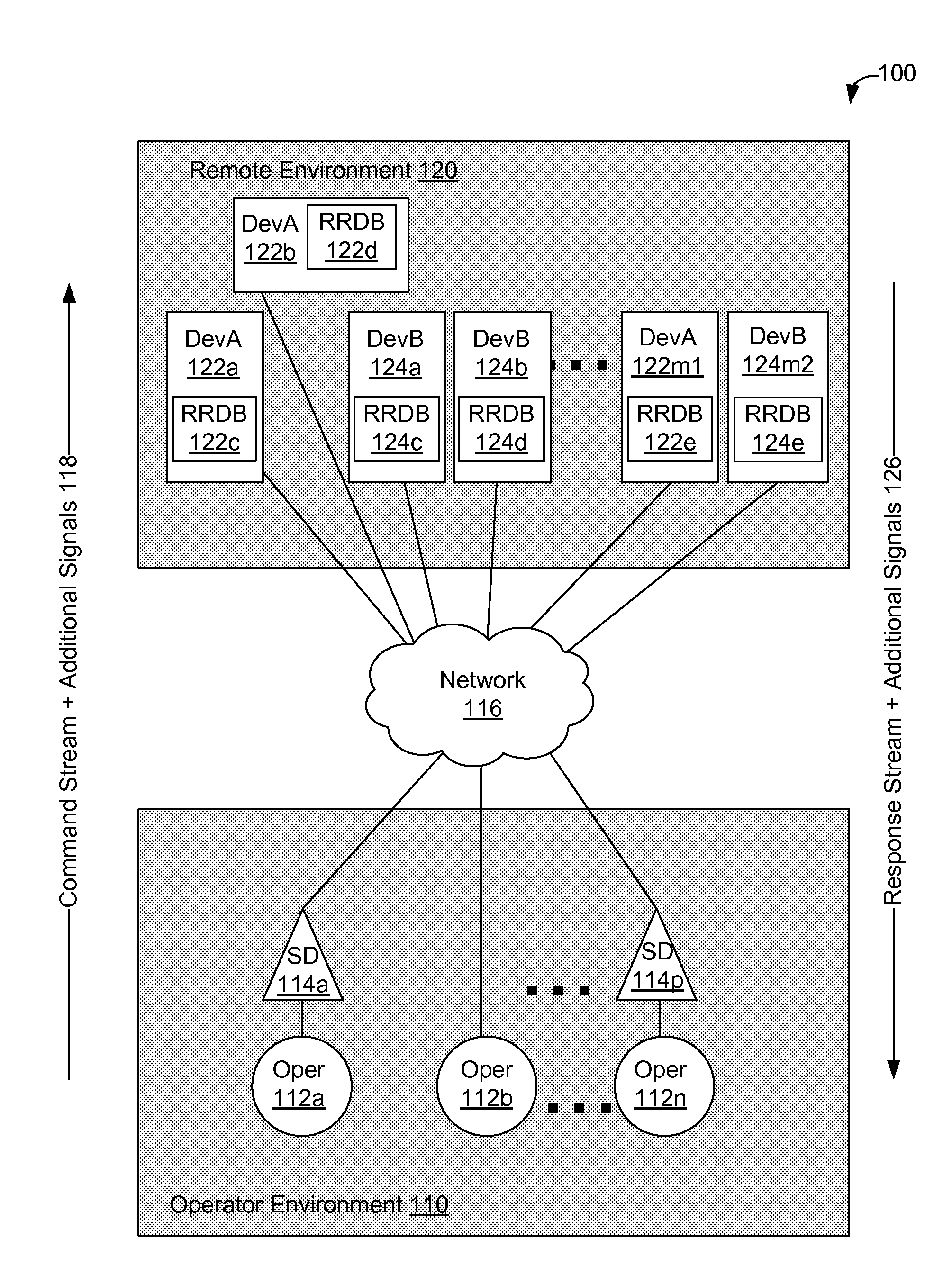
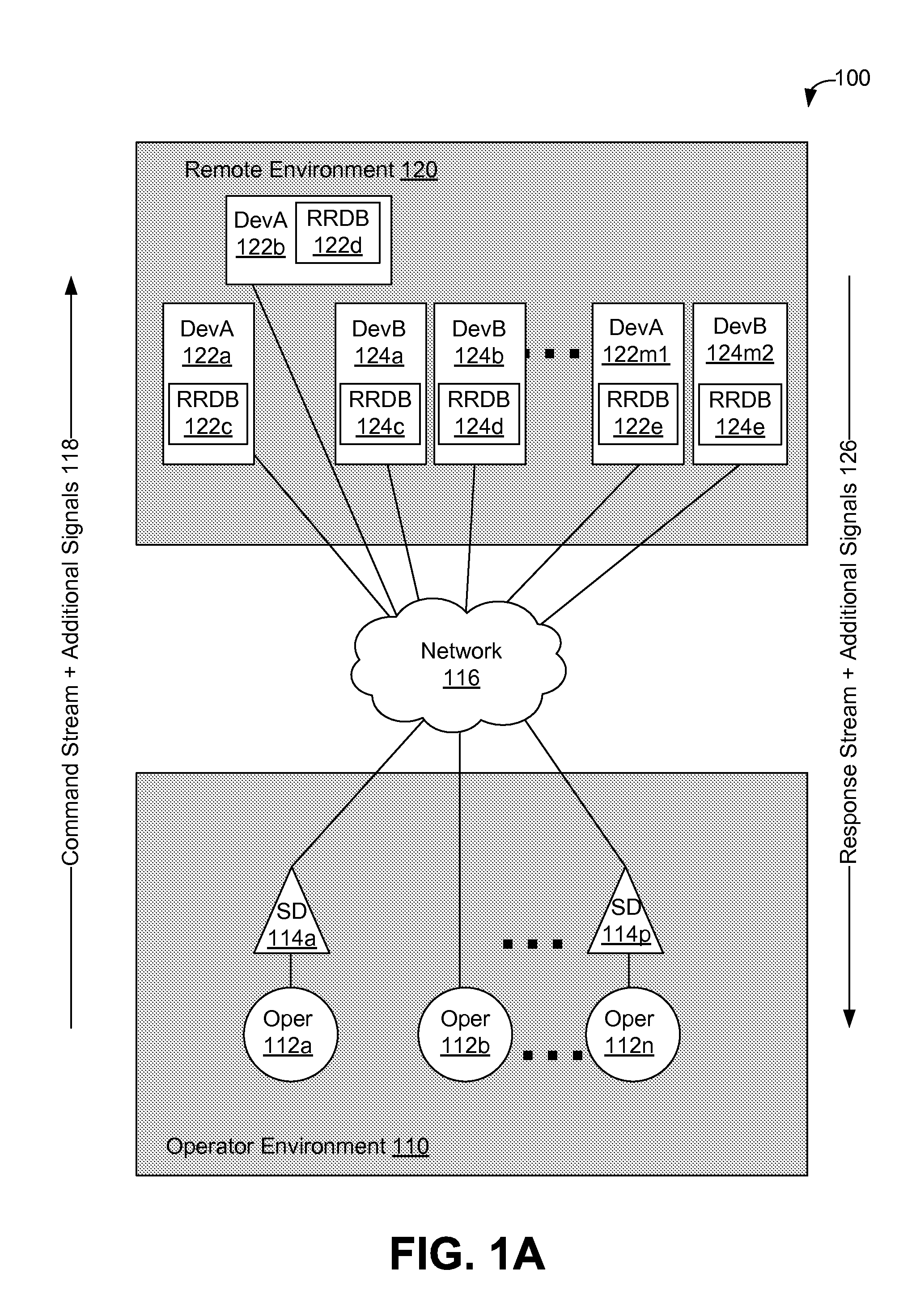
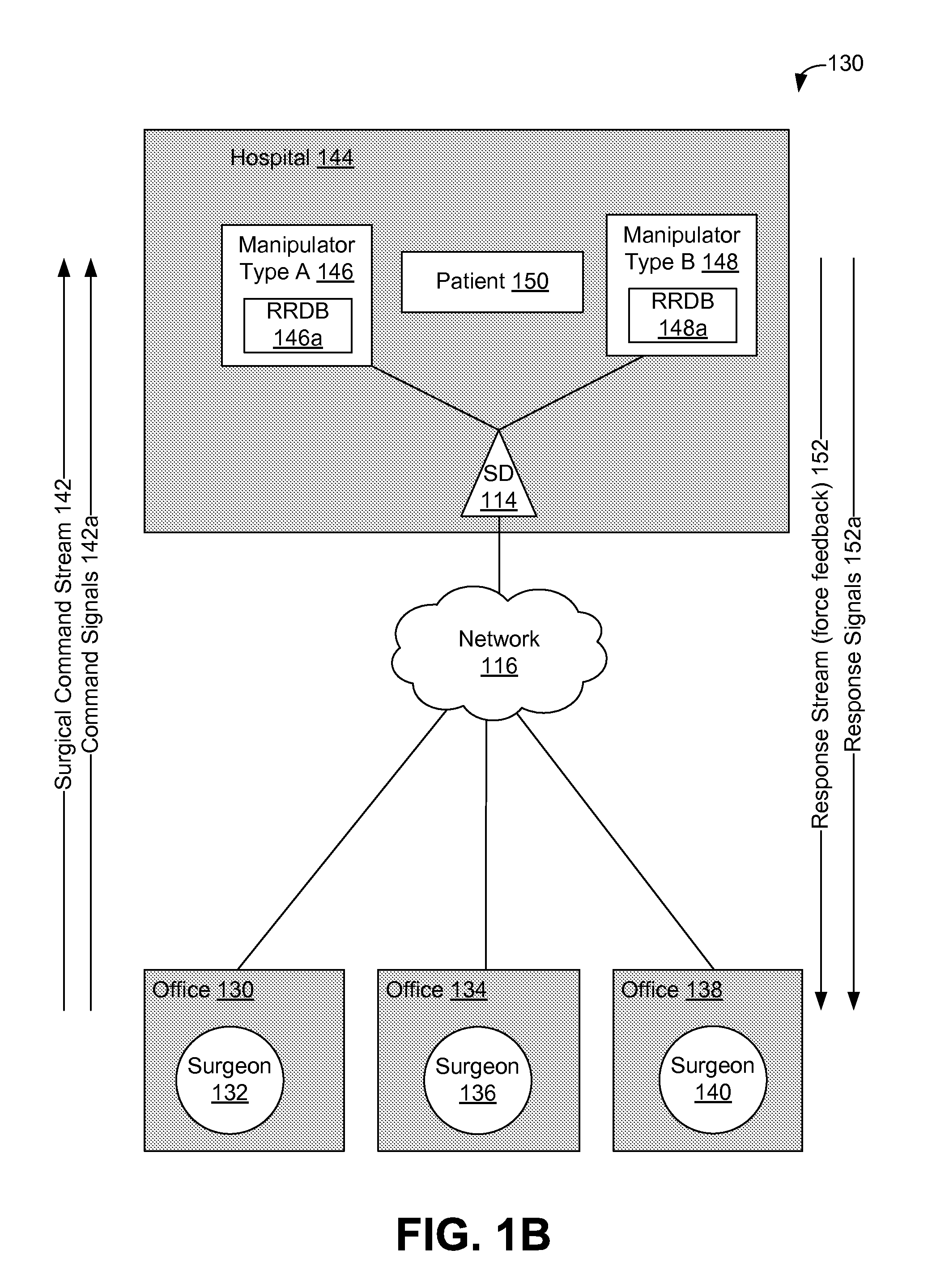
Using supplemental encrypted signals to mitigate man-in-the-middle attacks on teleoperated systems
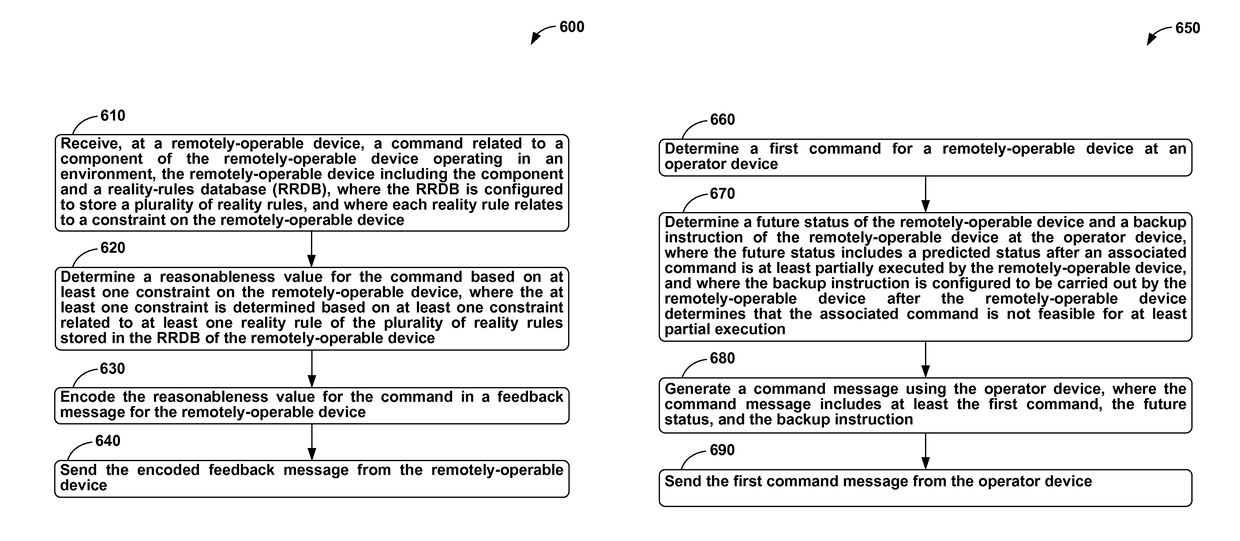
ActiveUS9686306B2Mechanical/radiation/invasive therapiesTelemedicineMan-in-the-middle attackOperational system
Methods and systems for securing remotely-operable devices are provided. A remotely-operable device can receive a command related to a component of the remotely-operable device operating in an environment. The remotely-operable device can include a reality-rules database (RRDB) that is configured to store a plurality of reality rules with each reality rule relating to a constraint on the remotely-operable device. The remotely-operable device can determine a reasonableness value for the command based on a constraint, where the constraint is determined based on a constraint related to at least one reality rule of the plurality of reality rules stored in the RRDB. The remotely-operable device can encode the reasonableness value for the command in a feedback message. The remotely-operable device can send the encoded feedback message from the remotely-operable device.
Owner:UNIV OF WASHINGTON CENT FOR COMMERICIALIZATION
Systems and methods for detection of session tampering and fraud prevention
ActiveUS8151327B2Memory loss protectionDigital data processing detailsMan-in-the-middle attackOperating system
The invention provides methods and apparatus for detecting when an online session is compromised. A plurality of device fingerprints may be collected from a user computer that is associated with a designated Session ID. A server may include pages that are delivered to a user for viewing in a browser at which time device fingerprints and Session ID information are collected. By collecting device fingerprints and session information at several locations among the pages delivered by the server throughout an online session, and not only one time or at log-in, a comparison between the fingerprints in association with a Session ID can identify the likelihood of session tampering and man-in-the middle attacks.
Owner:THE 41ST PARAMETER
Method for server-side detection of man-in-the-middle attacks
InactiveUS20090210712A1User identity/authority verificationMan-in-the-middle attackNetwork Communication Protocols
Problem The combination of a tendency towards permissivity when verifying certificate authenticity and the use of in-band client authentication opens up an opportunity for attackers to mount man-in-the-middle attacks on SSL connections.Solution The invention exposes any discrepancy between the intended recipient of the client credential and the actual recipient of the client credential by cryptographically including parameters that are uniquely linked to the channel (i.e., the communication session, as characterized by the parameters of the protocols that are being used), preferably the channel end points, in the calculation of the client credential. This links the process that provides the secure channel (e.g., the SSL protocol session) to the process that provides the authentication credential (e.g., the OTP token operation), thus exposing any attack that would break up the client-server channel. This is achieved without the requirement for an additional encrypted tunnel and allowing the continued use of existing components such as existing browsers.
Owner:VASCO DATA SECURITY INTERNATIONAL
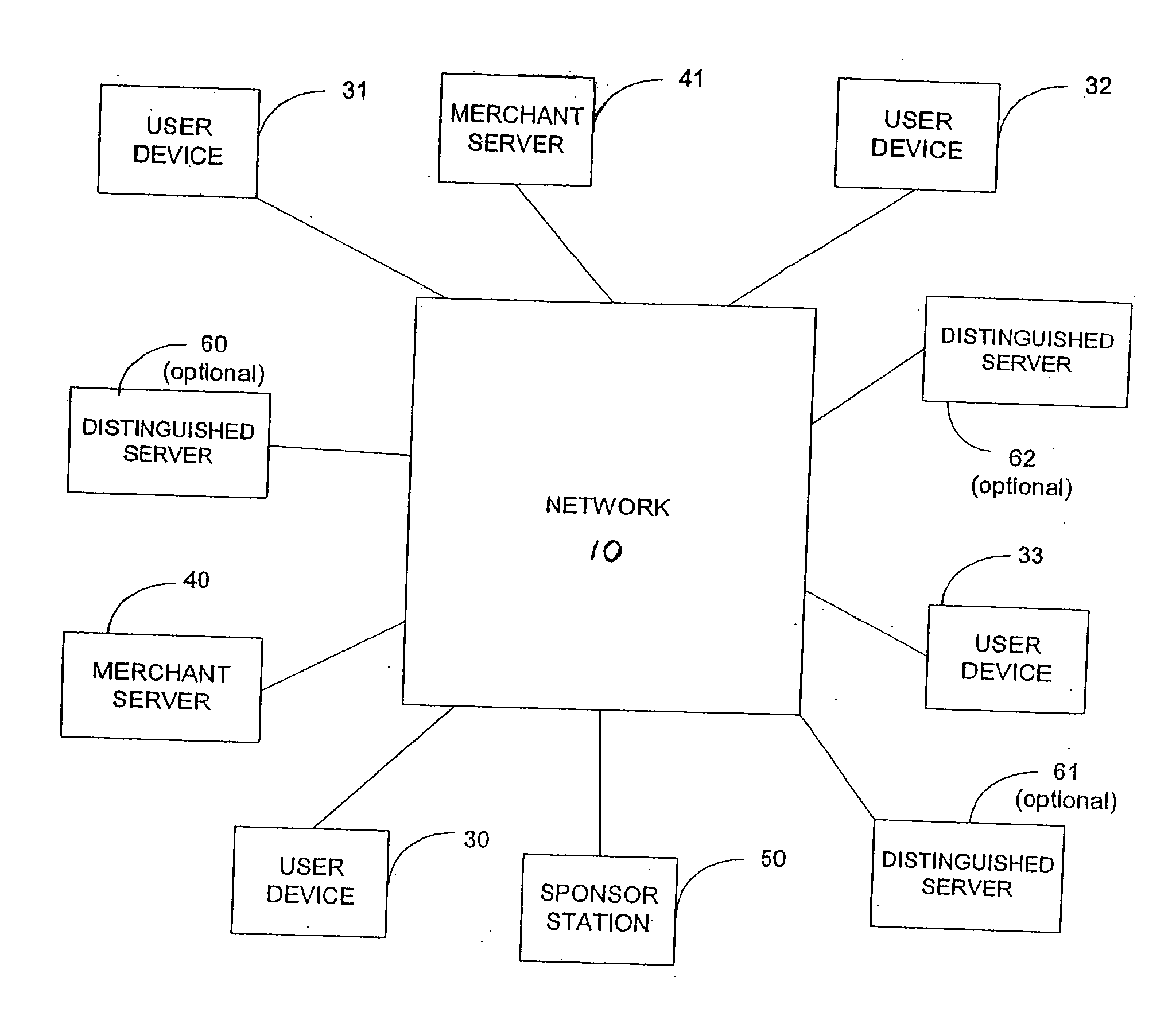
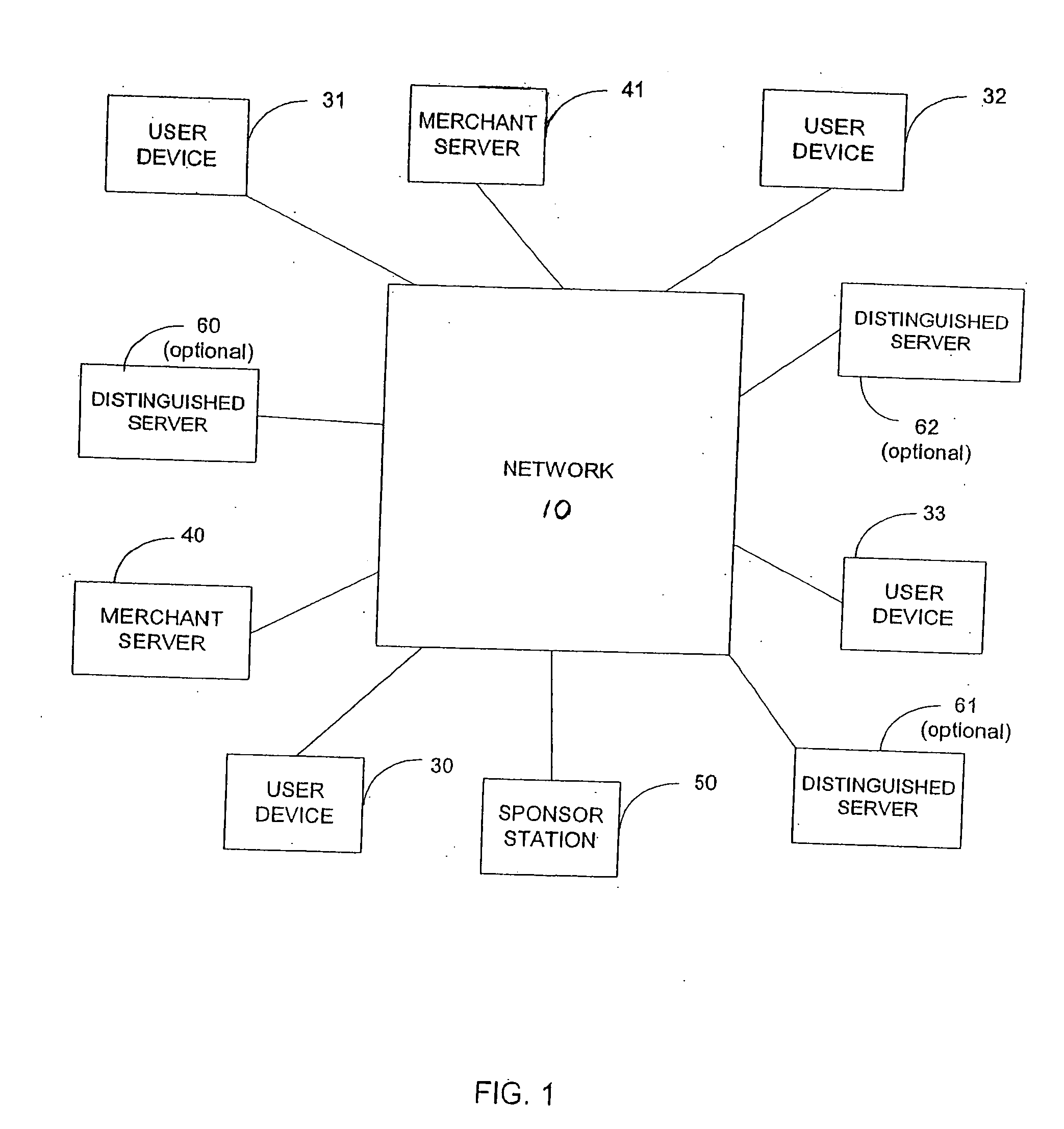
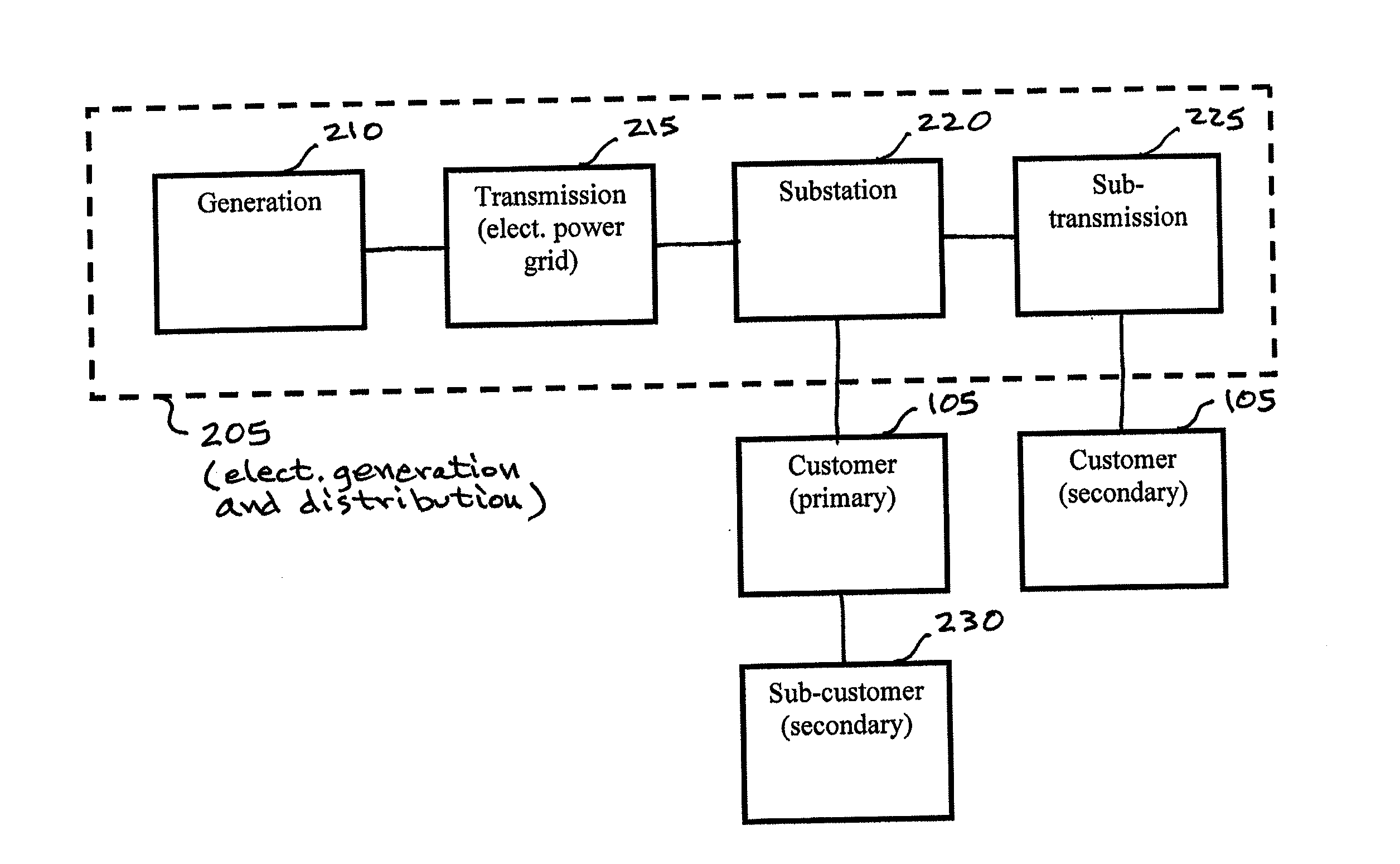
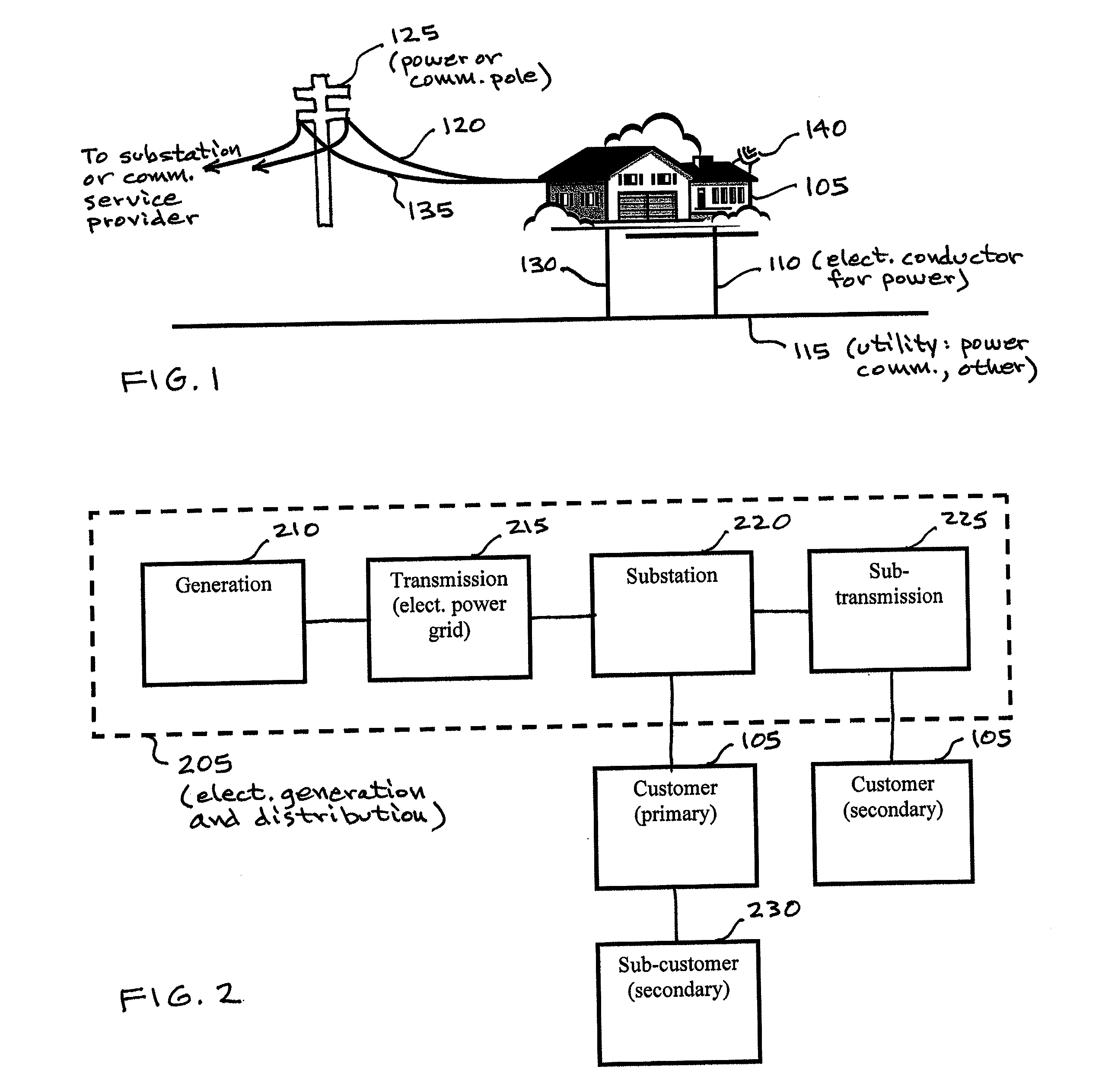
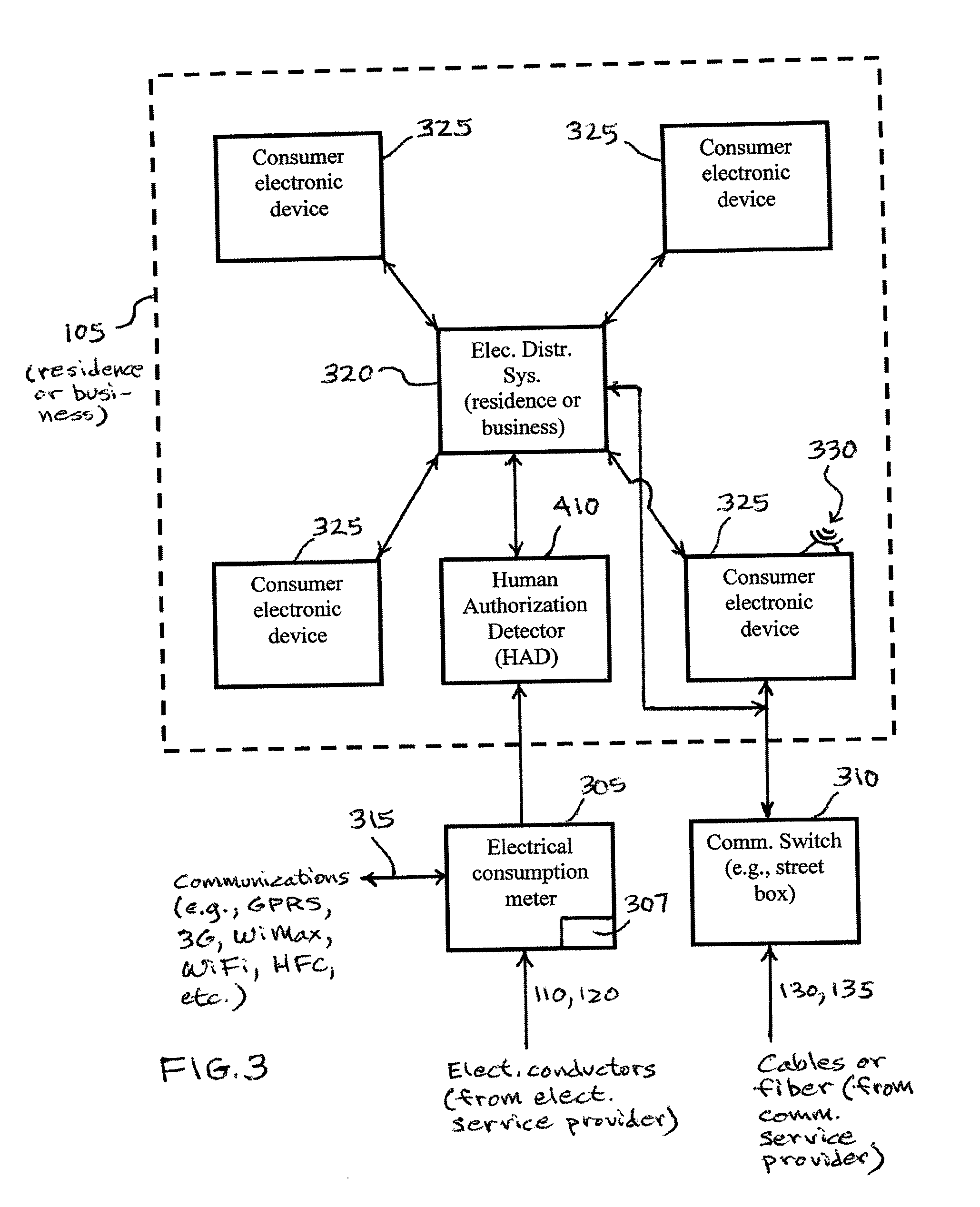
System, method, and apparata for secure communications using an electrical grid network
ActiveUS20100306533A1Fixes cost deployment costFixes cost marginal maintenance costLevel controlUser identity/authority verificationMan-in-the-middle attackSecure communication
A secure communications and location authorization system using a power line or a potion thereof as a side-channel that mitigates man-in-the-middle attacks on communications networks and devices connected to those networks. The system includes a power grid server associated with a substation, or curb-side distribution structure such as a transformer, an electric meter associated with a structure having electric service and able to communicate with the power grid server, a human authorization detector input device connected to the electric meter and the power grid server. The human authorization detector is able to receive an input from a user physically located at the structure and capable of communicating with the power grid server via the electric meter. The user's physical input into the device causing a request to be sent to the power grid server that then generates a location certificate for the user. Without the location certificate, access to the communications network and devices connected to those networks can be denied.
Owner:PHATAK DHANANJAY S
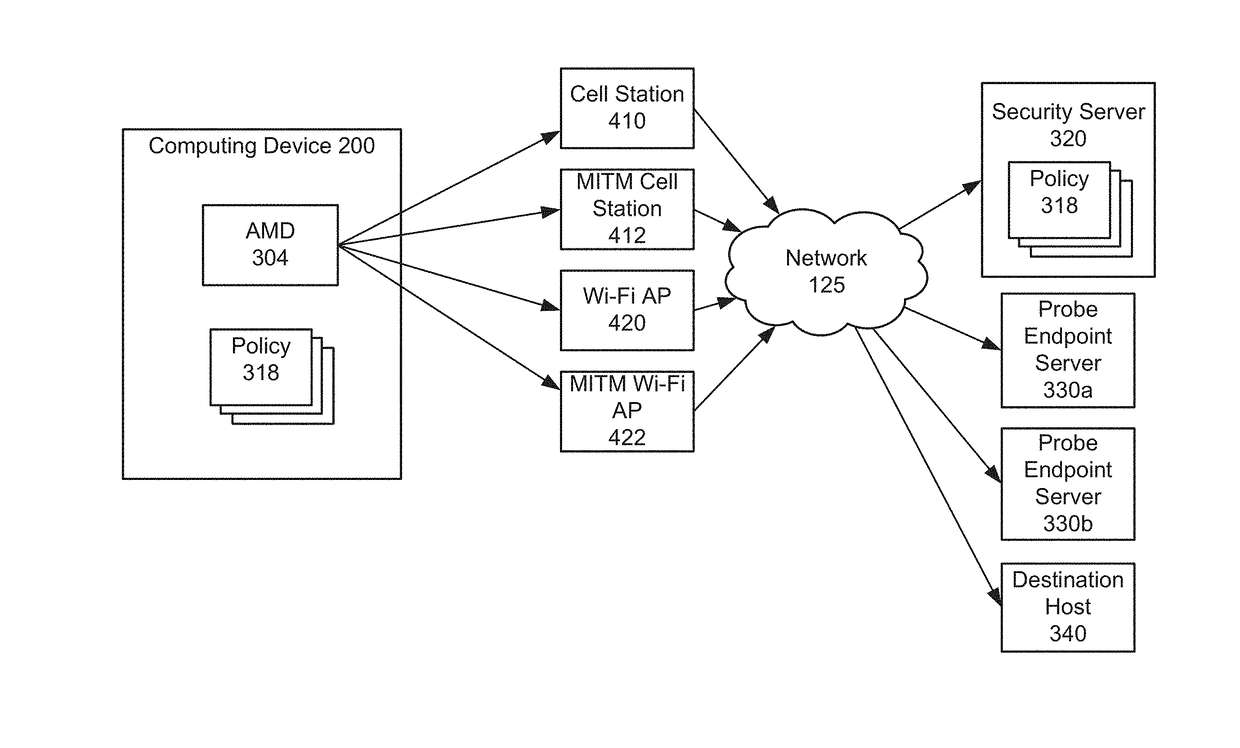
Methods and systems for detecting and preventing network connection compromise
ActiveUS20170346853A1Ensure safetyCompromise safetyPlatform integrity maintainanceData switching networksNetwork connectionMan-in-the-middle attack
The security of network connections on a computing device is protected by detecting and preventing compromise of the network connections, including man-in-the-middle (MITM) attacks. Active probing and other methods are used to detect the attacks. Responses to detection include one or more of displaying a warning to a user of the computing device, providing an option to disconnect the network connection, blocking the network connection, switching to a different network connection, applying a policy, and sending anomaly information to a security server.
Owner:LOOKOUT MOBILE SECURITY
System and Method of Mobile Anti-Pharming and Improving Two Factor Usage
InactiveUS20070174630A1Improve securityLow costRandom number generatorsUser identity/authority verificationPrivate networkSoftware
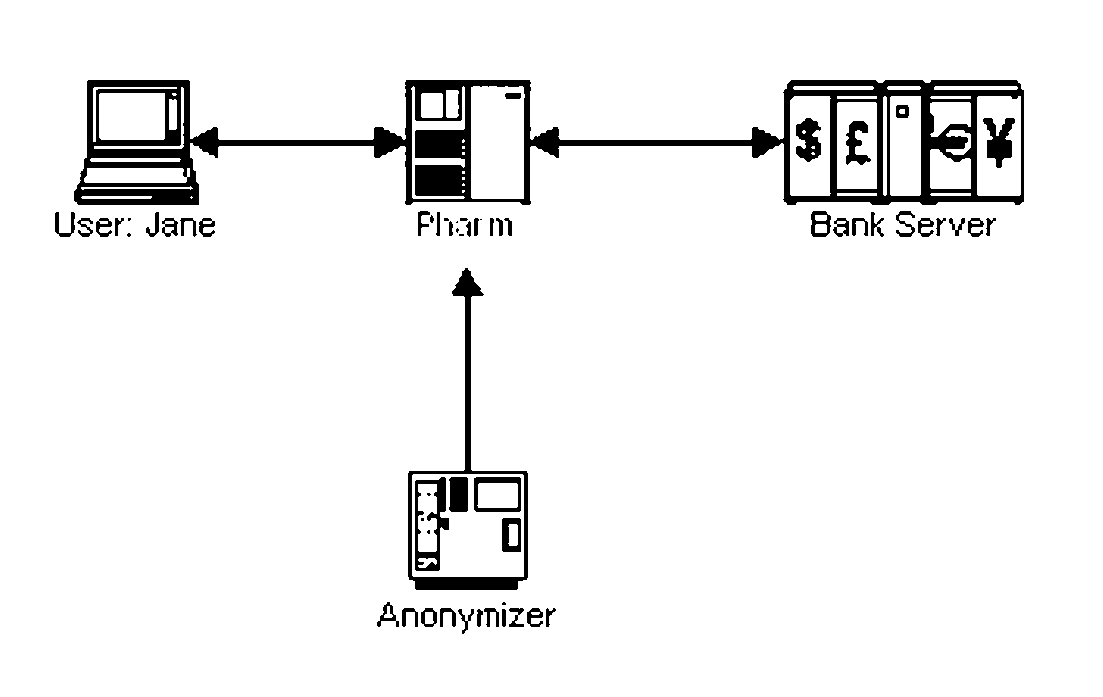
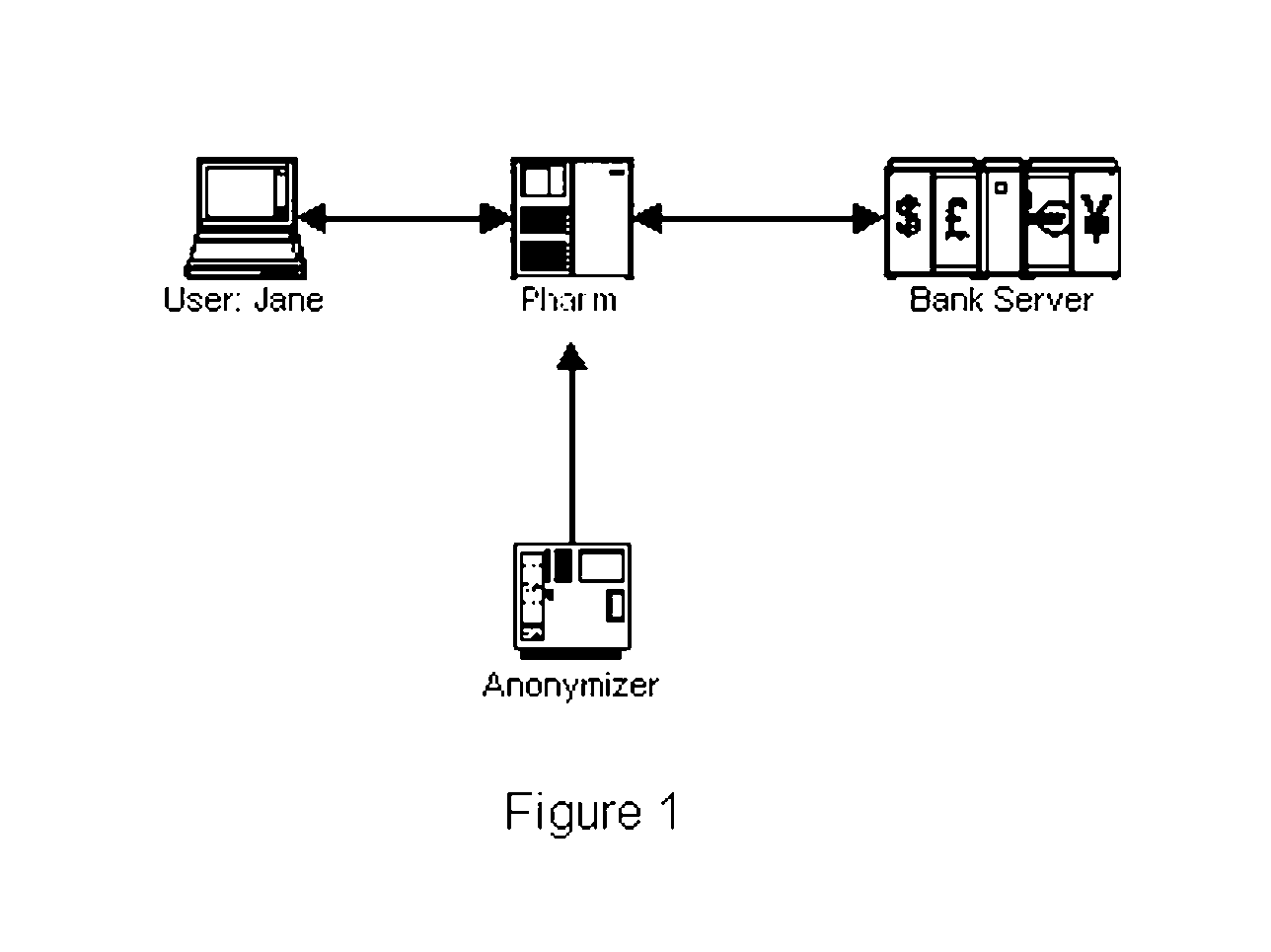
A variant of phishing involves subverting an Internet access point, often used for mobile computing. Malware can route user requests for bank websites into a phisher's private network, with fake bank websites (pharming). The user can have a “mobile password” at the bank. When she connects from an access point, she sends a hash, found from the password, starting at some position in it. The bank returns a hash, found from the same password, starting at another position in it. Each can verify the other. We protect both from a man in the middle attack. By hashing a web page and the mobile password, and inserting the hash into the page that is sent, the recipient can verify that the page is untampered. We use an anonymizer, external to the access point. A user pre-establishes a password with the anonymizer. At the access point, she and the anonymizer use a zero knowledge protocol to verify each other, based on the password. Then, the password encrypts communication between them. From the anonymizer, she logins elsewhere. The anonymizer is our man in the middle, to defeat a man in the middle attack. W extend earlier antiphishing methods, to attack pharms for non-existent banks, or that are unauthorized websites for actual companies. We show how to use a plug-in to let websites share several two factor implementations. This reduces the cost and inconvenience to consumers, who might otherwise have to carry and use a different two factor gadget, for each of their bank accounts or other corporate websites that mandates the usage of two factor authentication. By expanding the scope of two factor usage, we improve the security of e-commerce, without having to use a public key infrastructure.
Owner:METASWARM INC
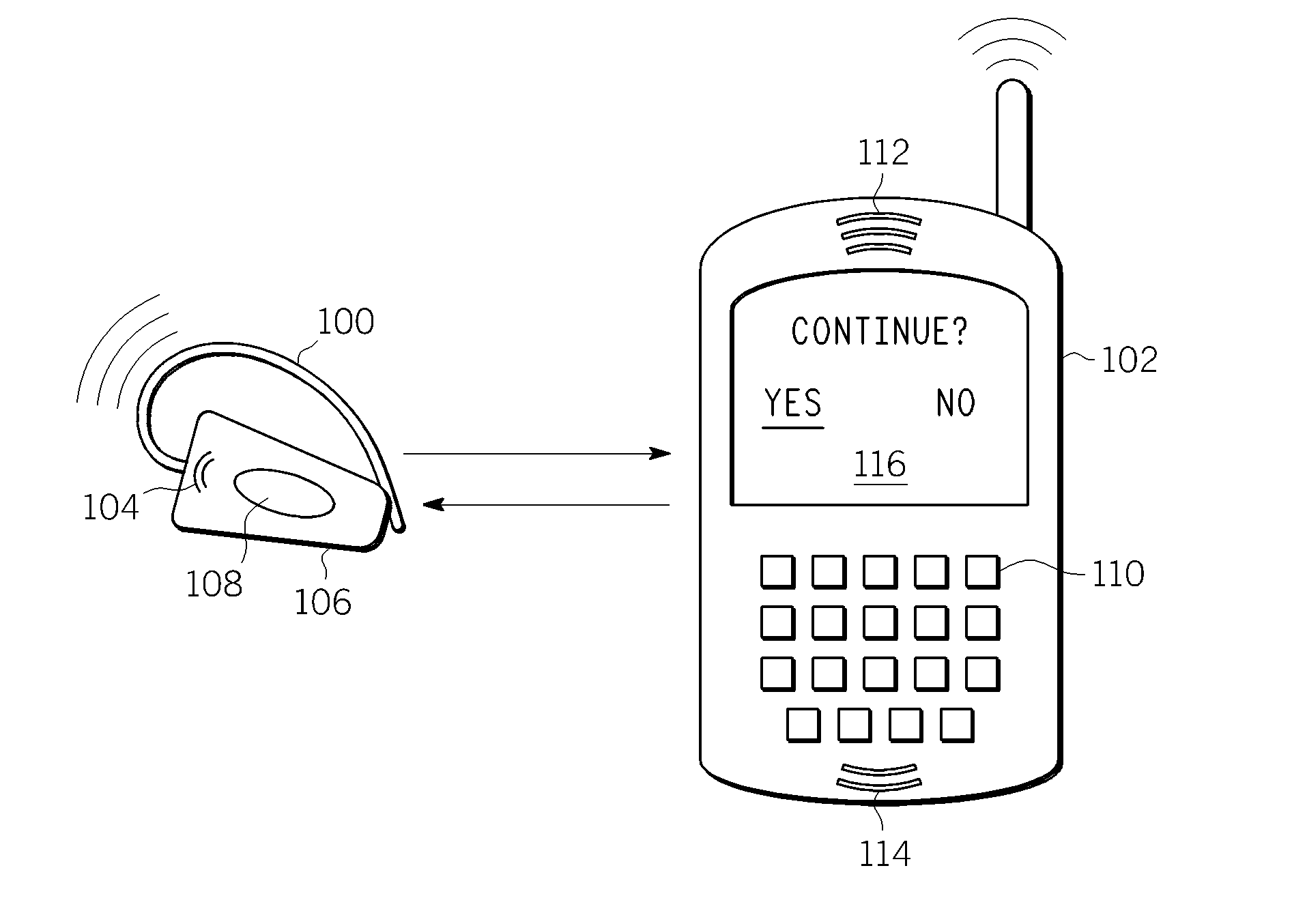
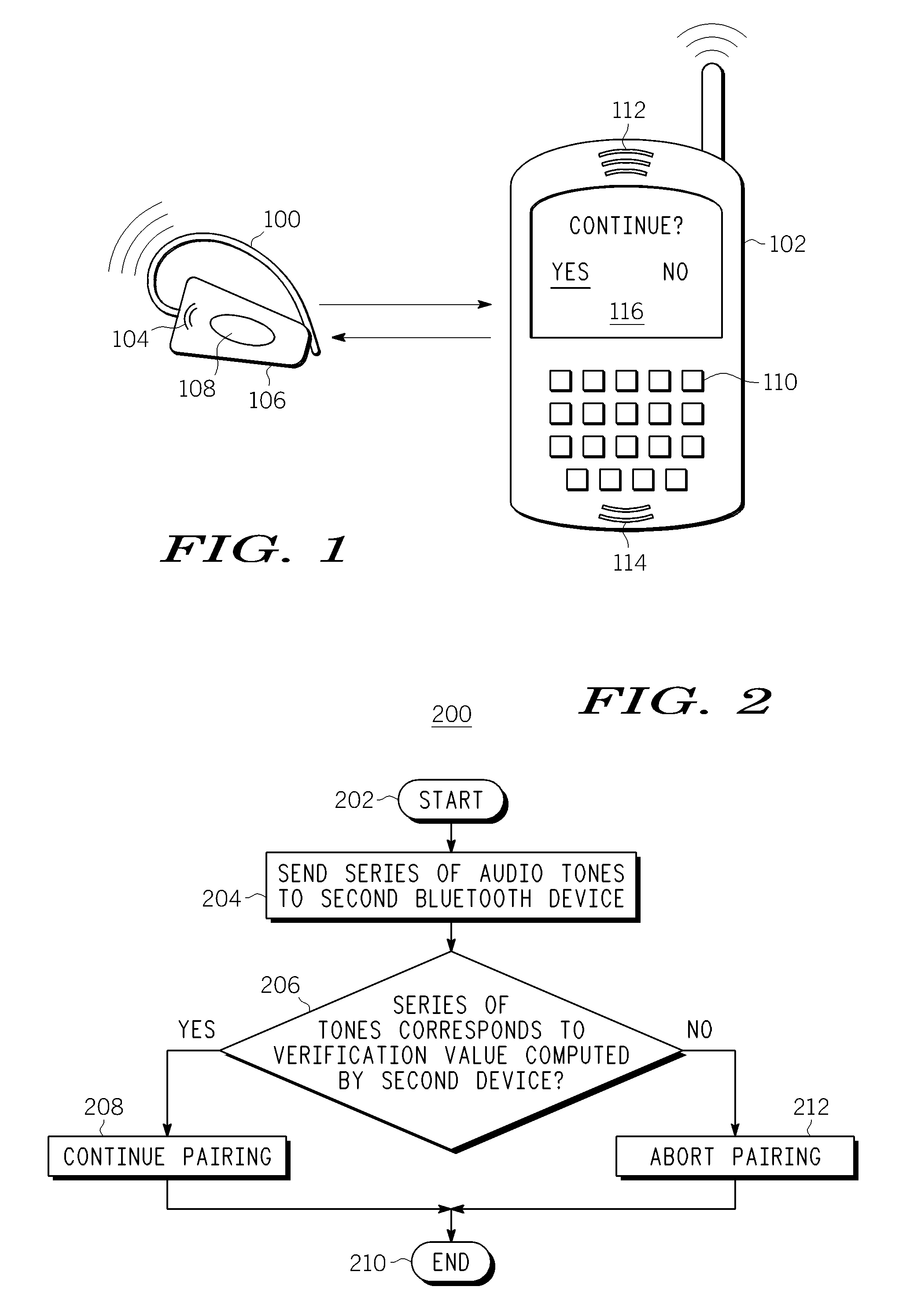
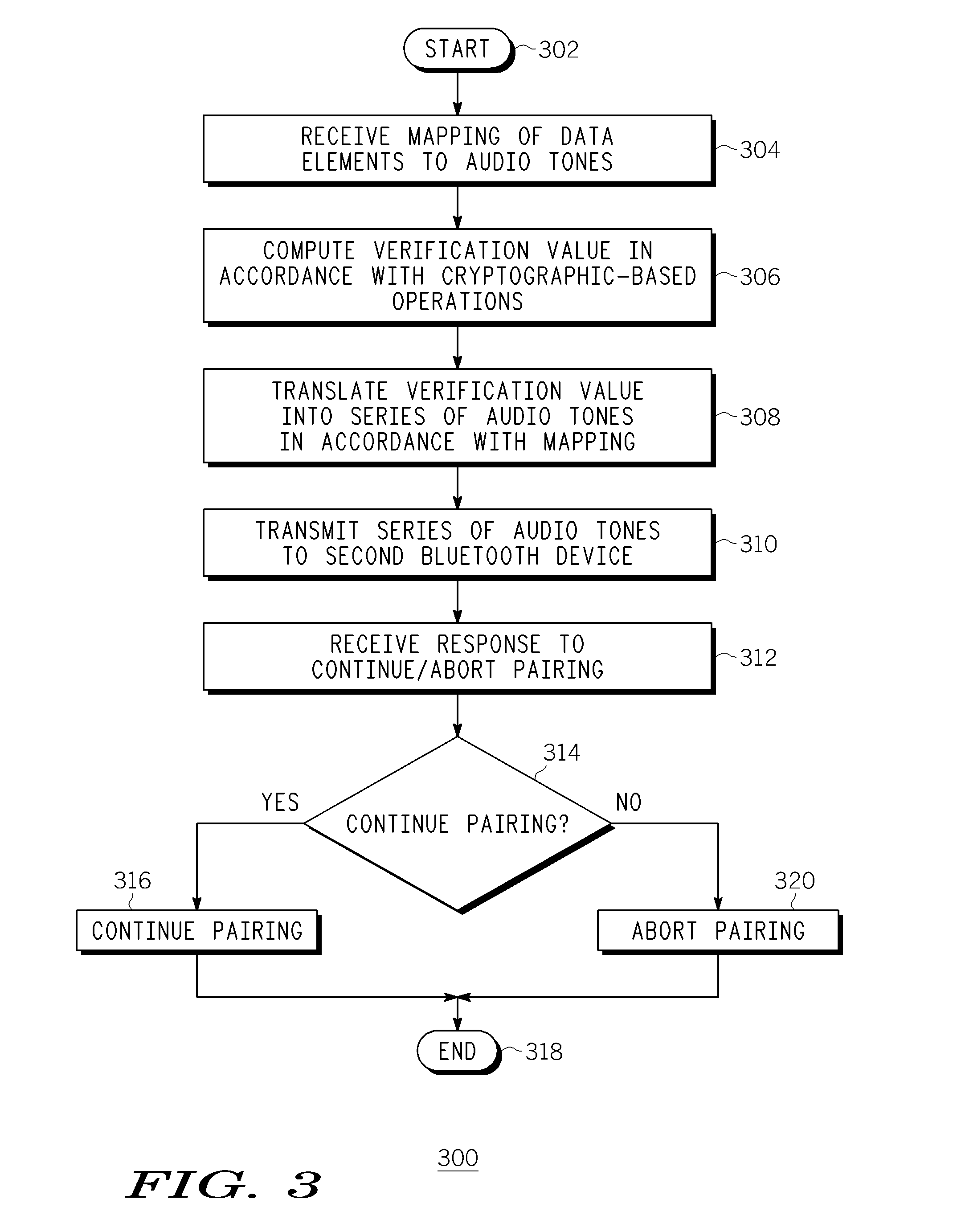
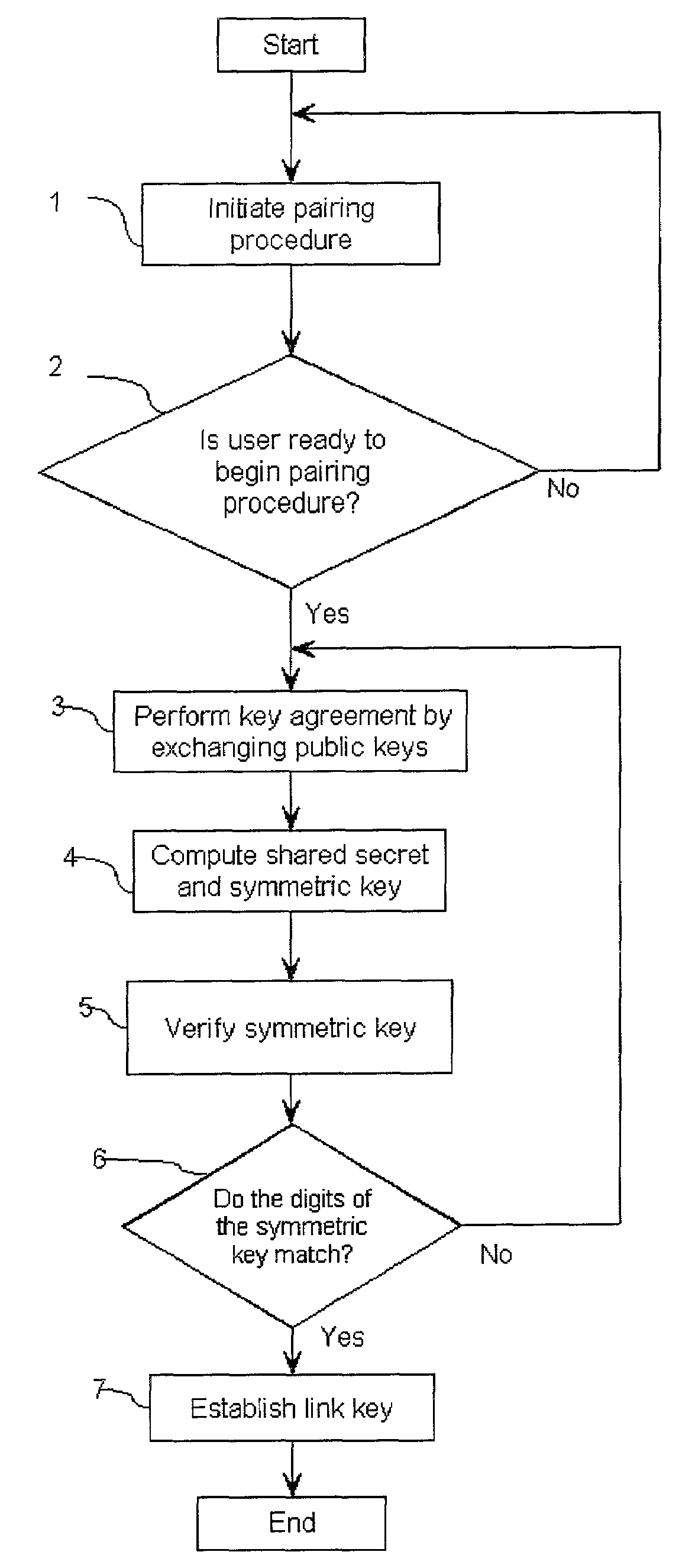
Method and Apparatus for Secure Pairing of Bluetooth Devices
Embodiments of the invention generally provide a method and apparatus for secure pairing of Bluetooth devices that supports the detection of man-in-the-middle attacks. One embodiment of a method for pairing a first Bluetooth device and a second Bluetooth device includes sending, by the first Bluetooth device, a series of audio tones to the second Bluetooth device, comparing the series of audio tones to a verification value computed by the second Bluetooth device and pairing with the second Bluetooth device if the verification value corresponds to the series of audio tones. Another embodiment of a method for pairing a first Bluetooth device and a second Bluetooth device includes receiving, at the second Bluetooth device, a series of audio tones from the first Bluetooth device, comparing the series of audio tones to a first verification value computed by the second Bluetooth device and pairing with the first Bluetooth device if the series of audio tones corresponds to the first verification value.
Owner:GENERAL INSTR CORP
Secure Communication Using Asymmetric Cryptography and Light-Weight Certificates
InactiveUS20110022835A1Communication securityEfficient managementPayment architectureSecuring communicationSecure communicationMan-in-the-middle attack
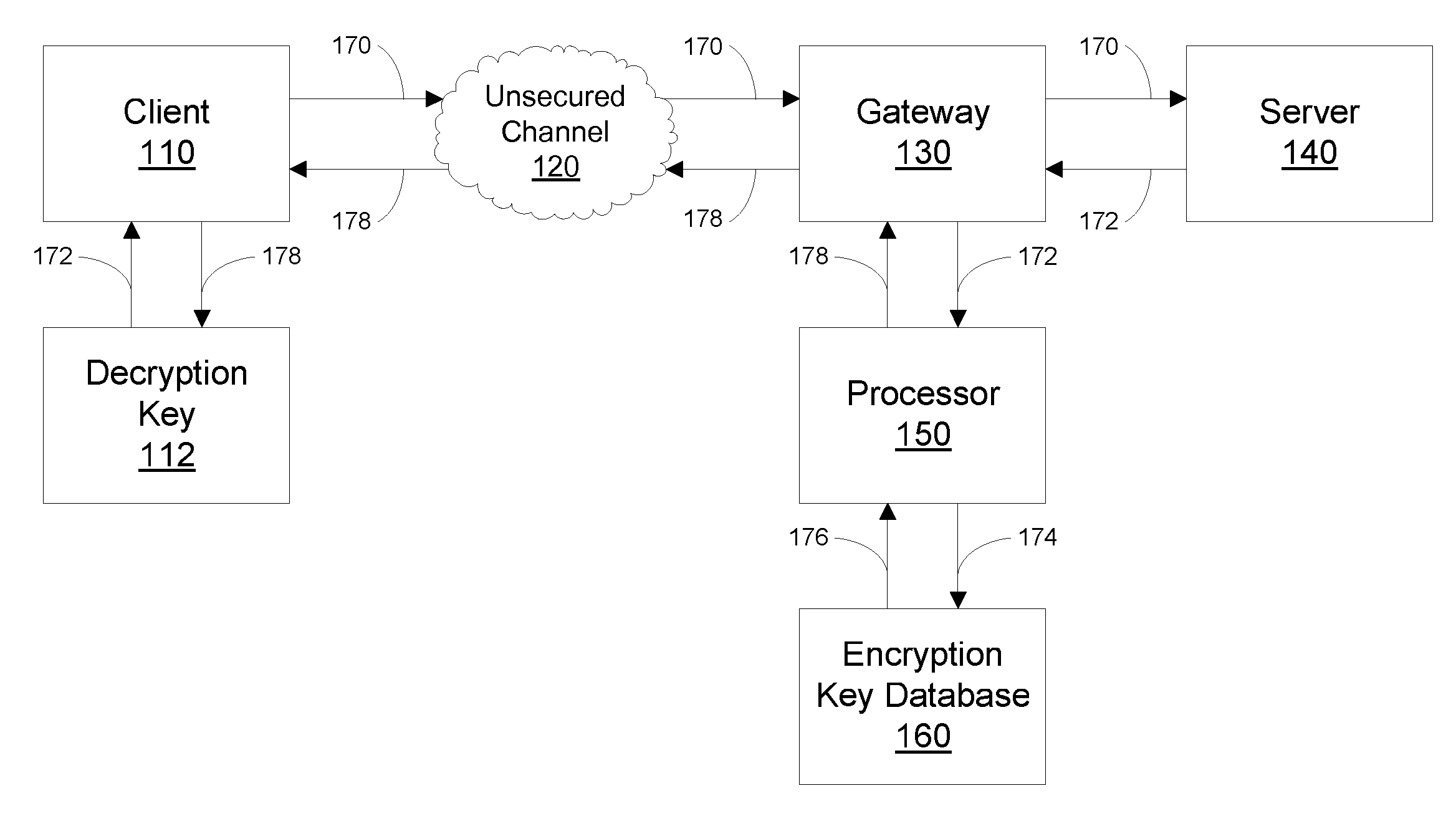
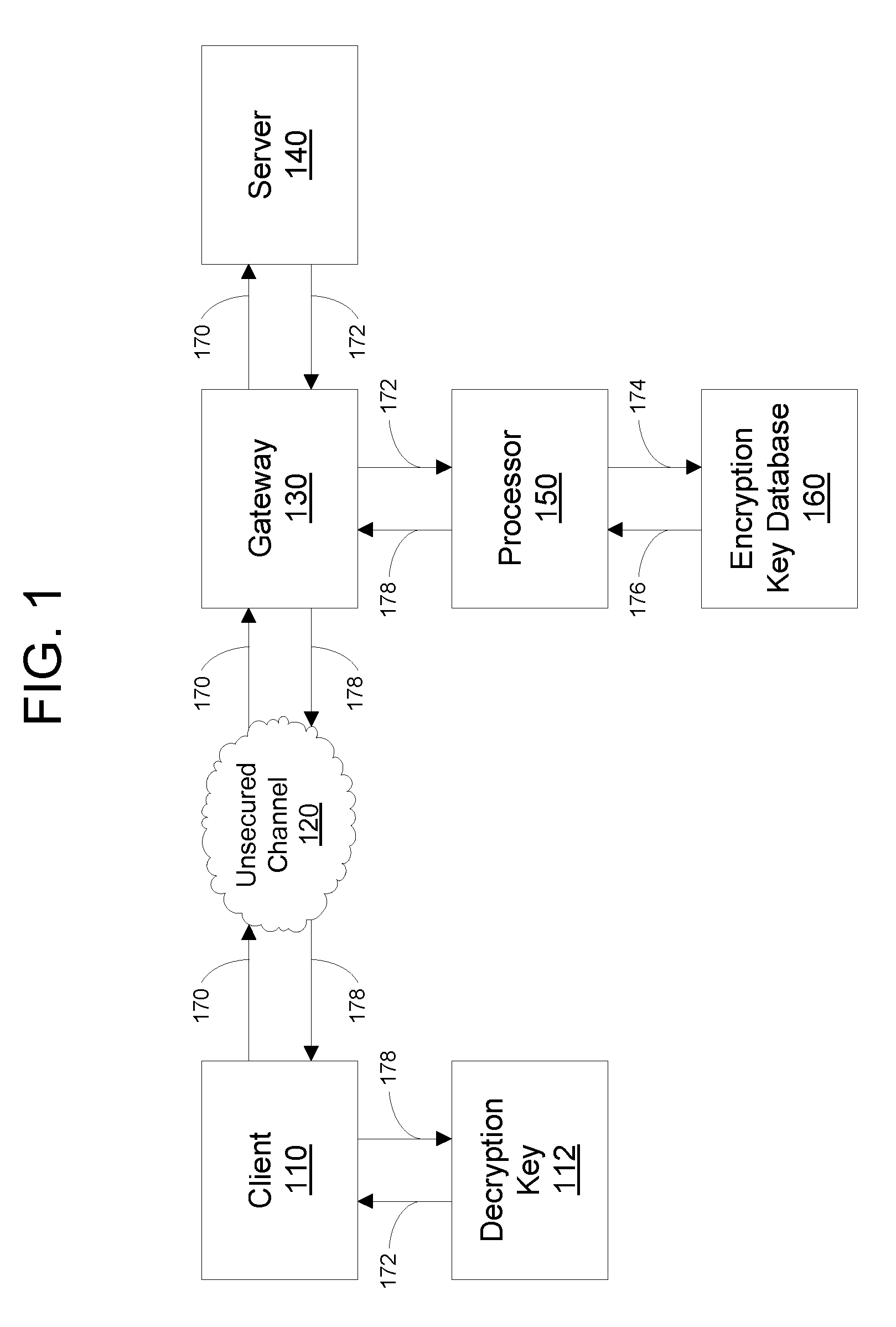
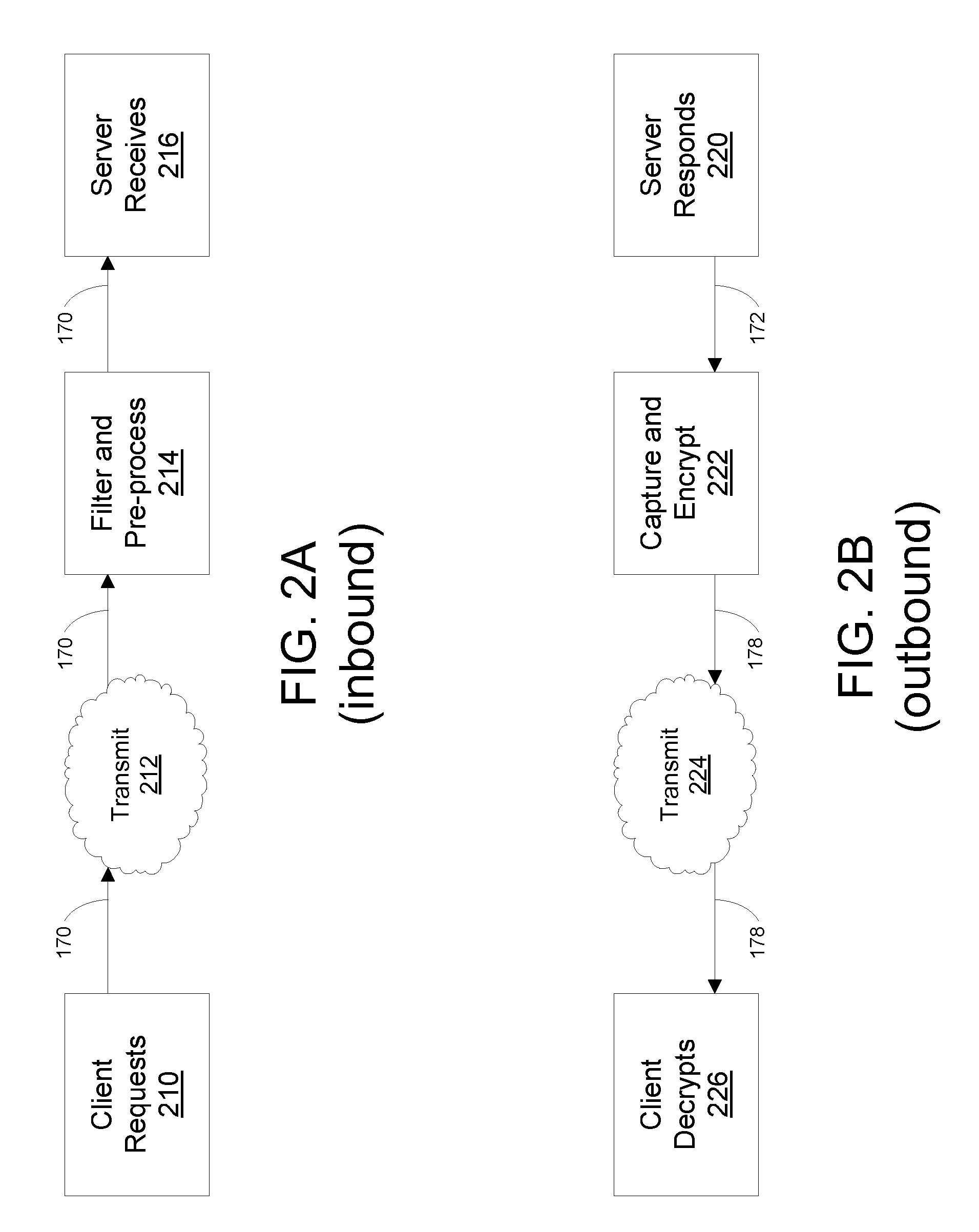
Encrypted communications between servers and client devices over an unsecured channel, such as the Internet, without using a public key infrastructure are disclosed. Messages to a client device are encrypted using an encryption key of an authorized individual, regardless of the identity of the user of the client device. Encryption is performed by a system that does not expose encryption keys to the client device or the server, thereby preventing man-in-the-middle attacks against the encryption key. Secure communications are combined with a two-factor protocol for authenticating the identity of an individual. An individual authenticates by generating a cipher using a light-weight certificate that has a shared secret but no other information identifying the individual. Separately, a server generates the same cipher using the shared secret, thereby authenticating the individual's identity to a relying party.
Owner:SURIDX
Remote proving method in trusted computation environment
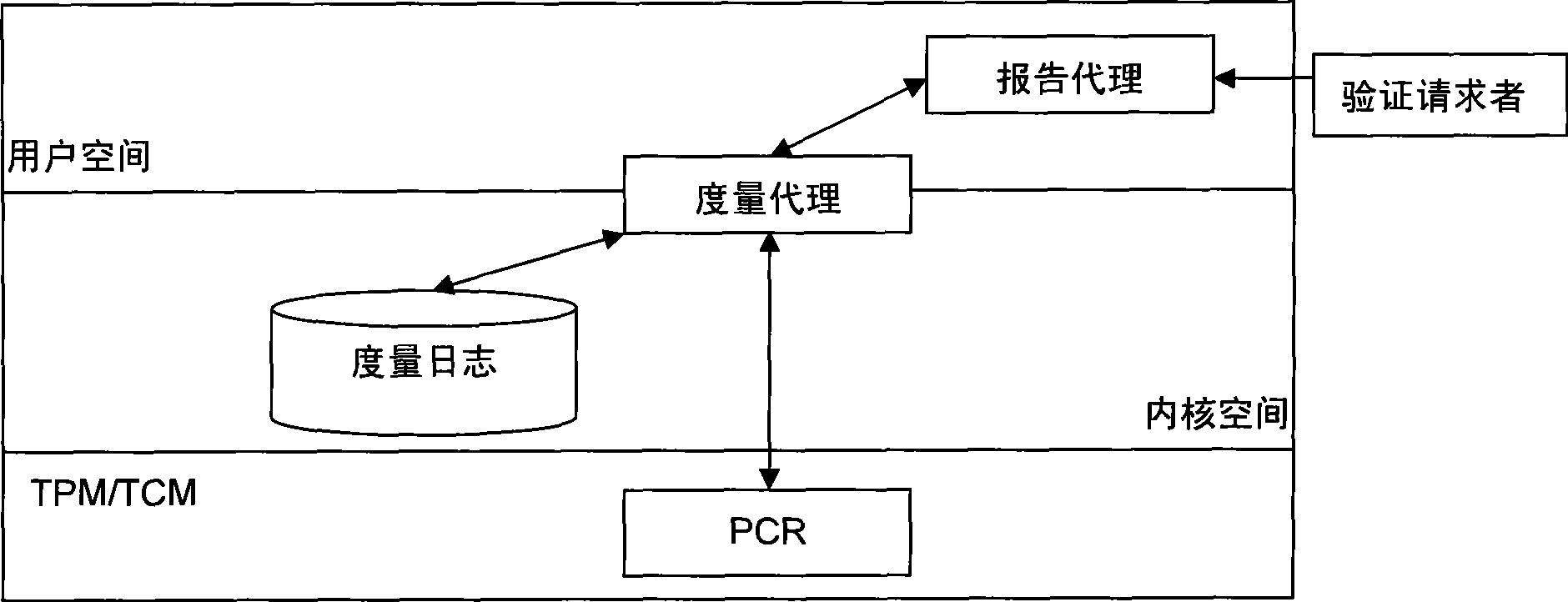
InactiveCN101477602AGuarantee authenticityGuaranteed privacyInternal/peripheral component protectionTransmissionMan-in-the-middle attackDigital signature
The invention provides a method for remote attestation in a trusted computing environment. The method is characterized in that secure session key is adopted for encrypting the metric value and the metric log of trusted platform to be verified, and signs for encryption result data. The method is based on a security chip TPM / TCM; the adopted remote attestation framework comprises three parts: an integrity measuring mechanism, a reporting mechanism and a validation mechanism, which are achieved by an integrity measuring agency, a report agency and a verification requestor, wherein, the measuring agency, the report agency and the verification requestor are installed in the trusted platform to be verified. The method ensures that the authenticity of the integrity measuring value and the measuring log and the privacy of the platform are kept; the replay attack, impersonation attack and man-in-the-middle attack are effectively prevented; the method is used for proving to the verification requestor that the running environment of the platform is credible, or used for self-test of the platform running environment; the method can be used for not only proving to the requestor that the platform running environment is credible, but also the self-test of the platform running environment; and the method is more suitable for a fair and open network environment.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Access control method and system for wireless local area network
ActiveCN101951603AAvoid blockingSave bandwidthSecurity arrangementMan-in-the-middle attackControl system
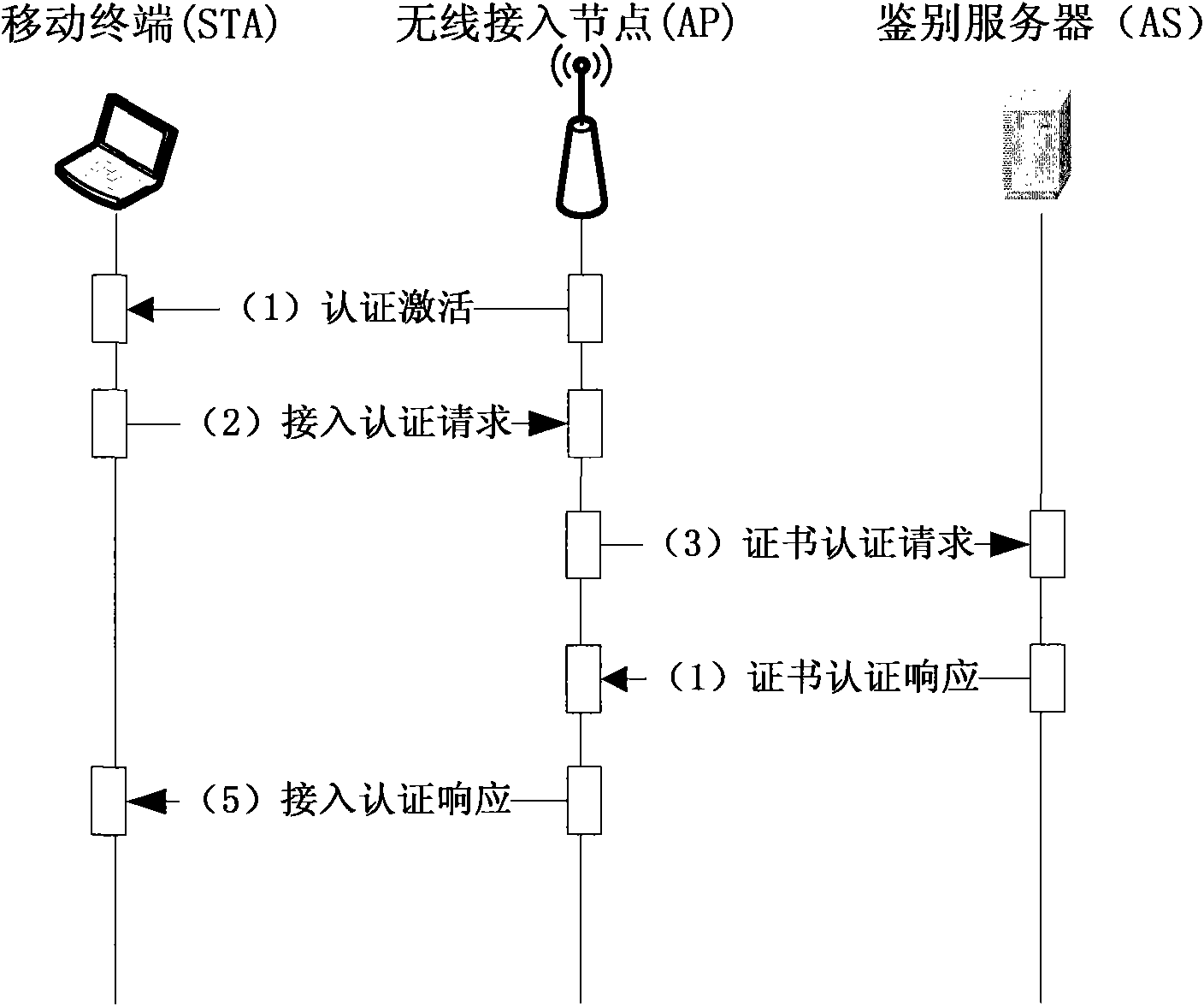
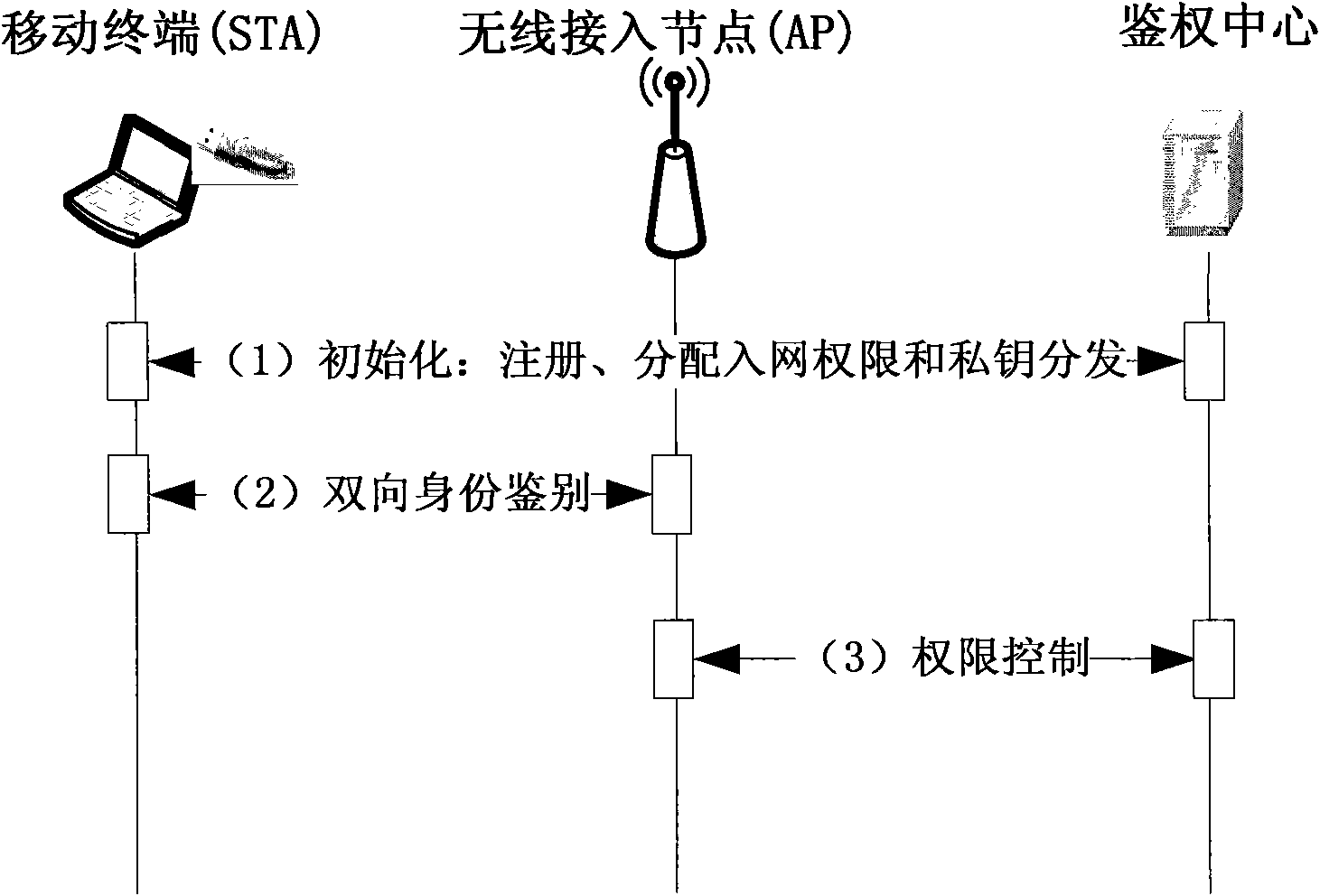
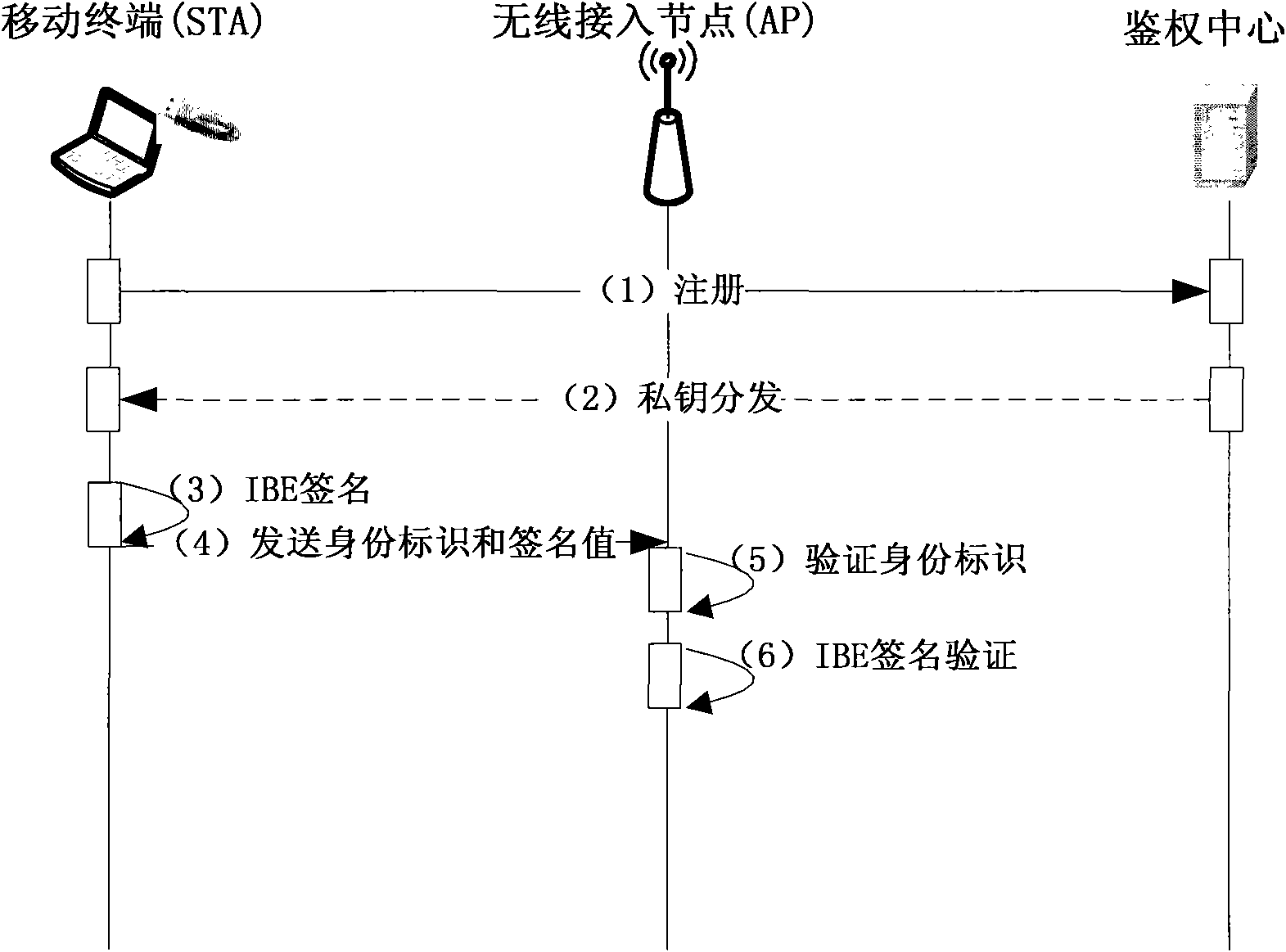
The invention discloses an access control method for a wireless local area network. The method comprises the following steps of: A, arranging a user identity token USB-KEY for storing an identity identifier and a private key on a mobile terminal and performing the operation of an IBE algorithm; B, performing identity authentication on the mobile terminal to be subjected to network entry by adopting the identity-based encryption technology, namely IBE technology, and if the authentication is not passed, not allowing users to access the network; and C, determining the resource access permissionof the mobile terminal, and controlling the network access action of the mobile terminal according to the resource access permission. The method introduces the authentication control of specific application resources accessed by the users, adapts to the development tendency of taking application as the center in the wireless local area network, and simultaneously, improves the safety of the access control scheme of the wireless local area network and avoids man-in-the-middle attack and the attack of denial of service. The invention also discloses a system for the access control of the wireless local area network correspondingly.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Apparatus and method to prevent man in the middle attack
InactiveUS20110154021A1Digital data processing detailsUser identity/authority verificationThird partyMan-in-the-middle attack
A system, peripheral device, and method for authenticating an encryption key before transmitting encrypted messages containing sensitive information are provided. Authentication of a client device during the coordination of data transfer among multiple computer devices is possible by providing a peripheral device that does not have a direct connection to a network, but rather, any message to be transmitted over the network must be relayed through a client device. Any sensitive information to be transferred to a remote device is inserted into a message, then the message is encrypted in the peripheral device. This prevents any process running on the client device from fooling the client device into communicating confidential information to a third party rather than the desired remote computer, because the client device never sees the sensitive information in an unencrypted form; only the peripheral device has access to the sensitive information in an unencrypted form.
Owner:NETABECURE INNOVATIONS
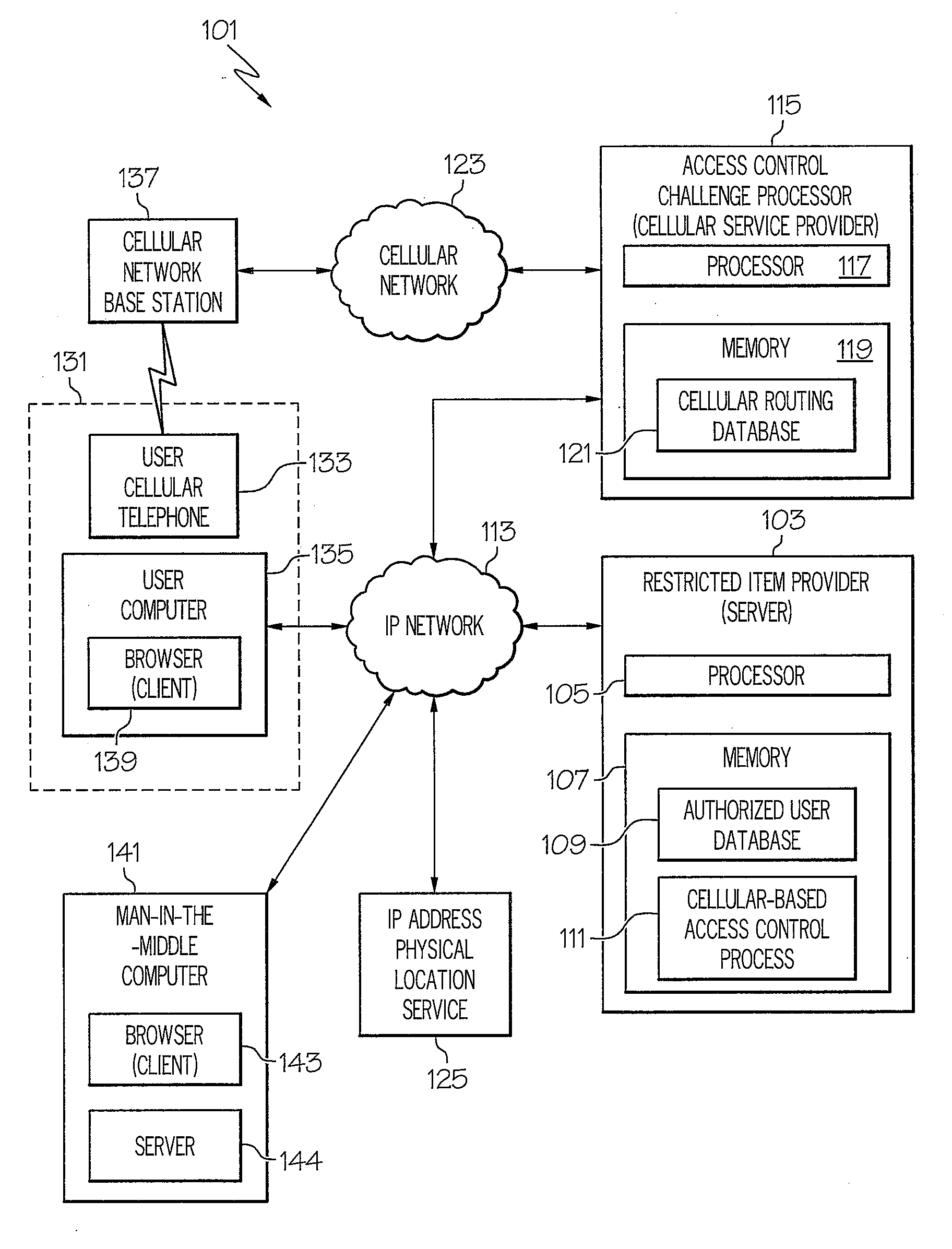
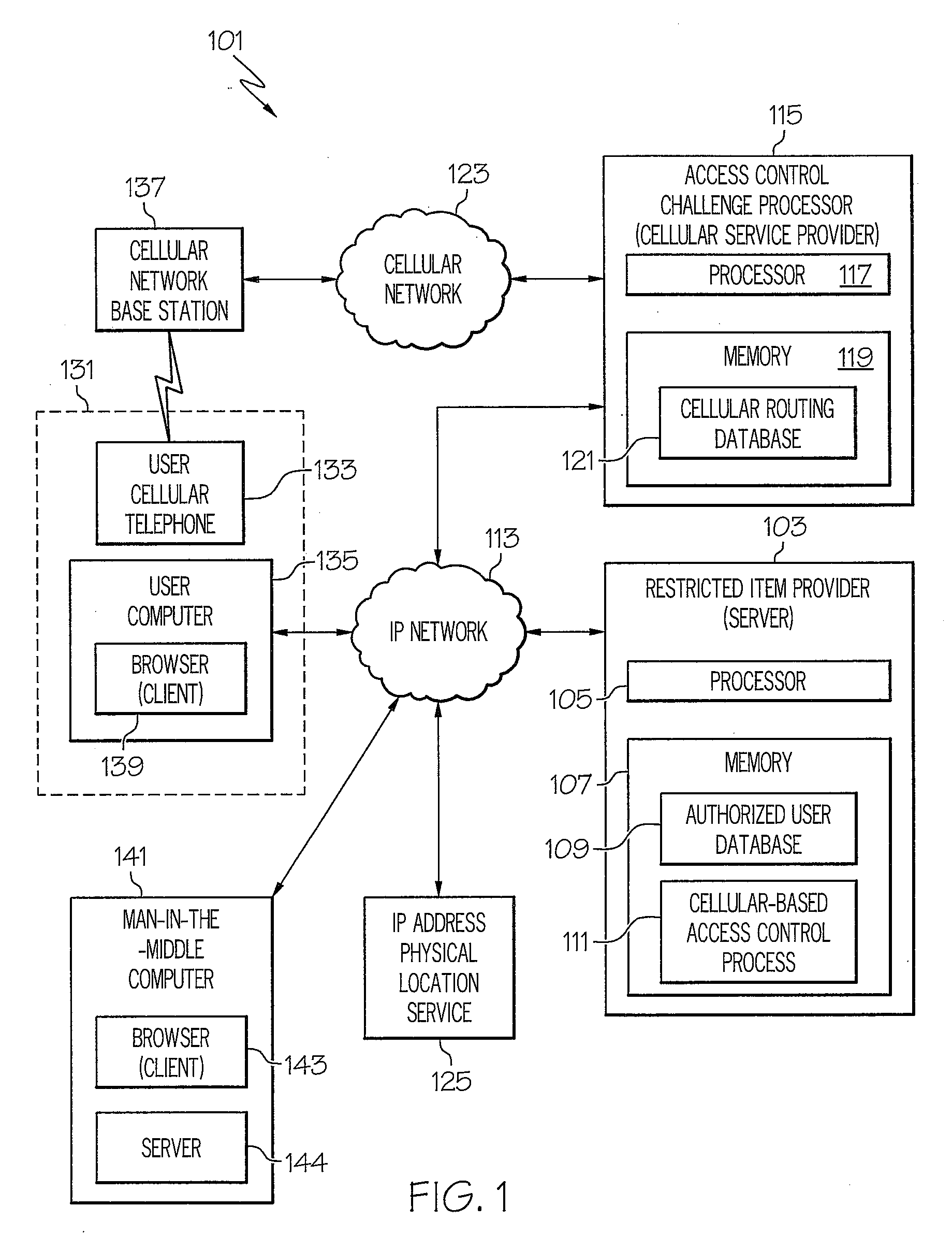
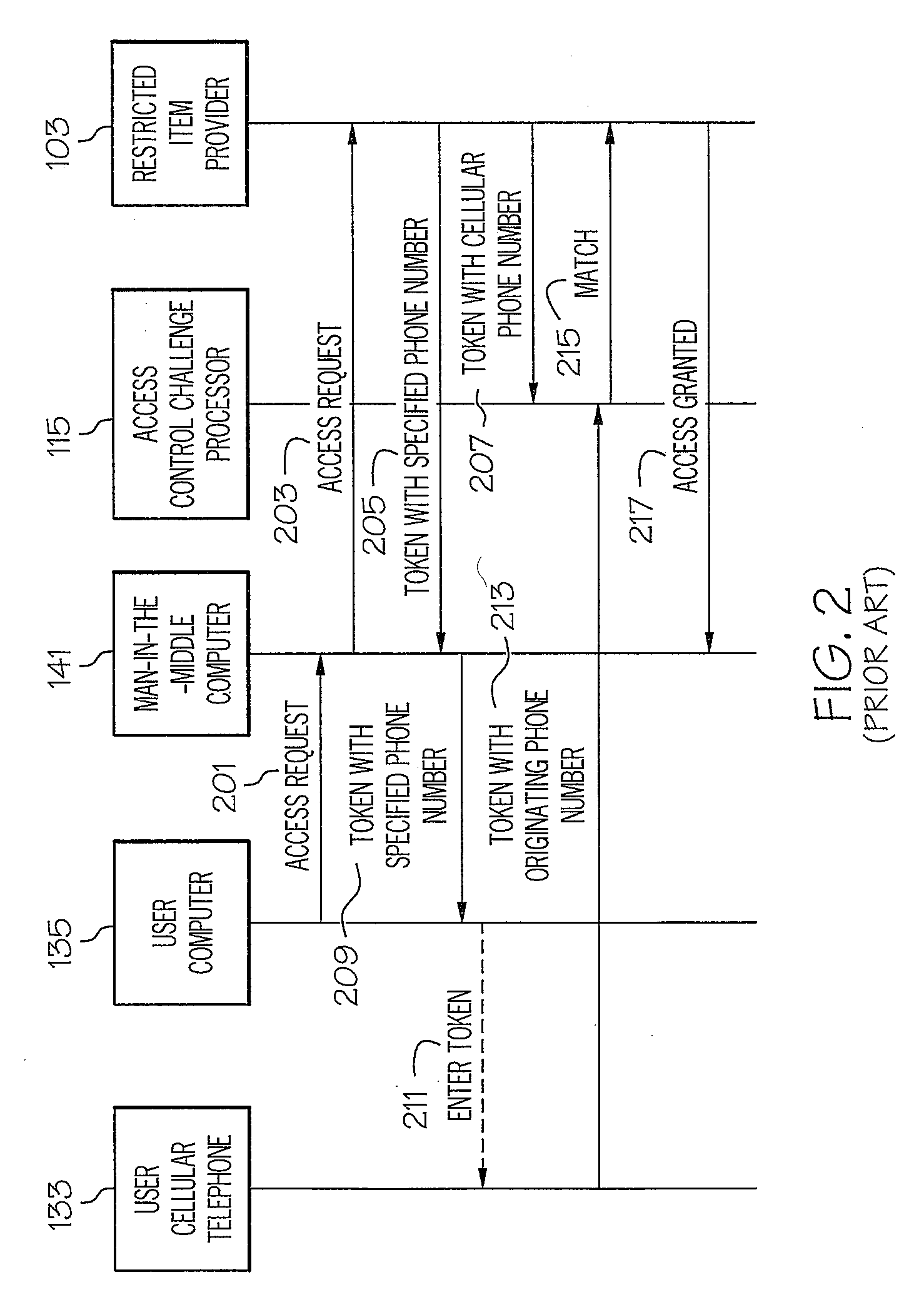
Method of and system for strong authentication and defense against man-in-the-middle attacks
InactiveUS20080318548A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMan-in-the-middle attackStrong authentication
A man-in-the-middle attack resistant method of and system for controlling access of a user to a restricted item receives a request from a user of a first device for access to a restricted item. The system determines the physical location of the first device. The system provides a token to the user and prompts the user to send the token to a recipient using a second device. The system denies the user access to the restricted item if the token is sent from a physical location not matching the physical location of the first device.
Owner:IBM CORP
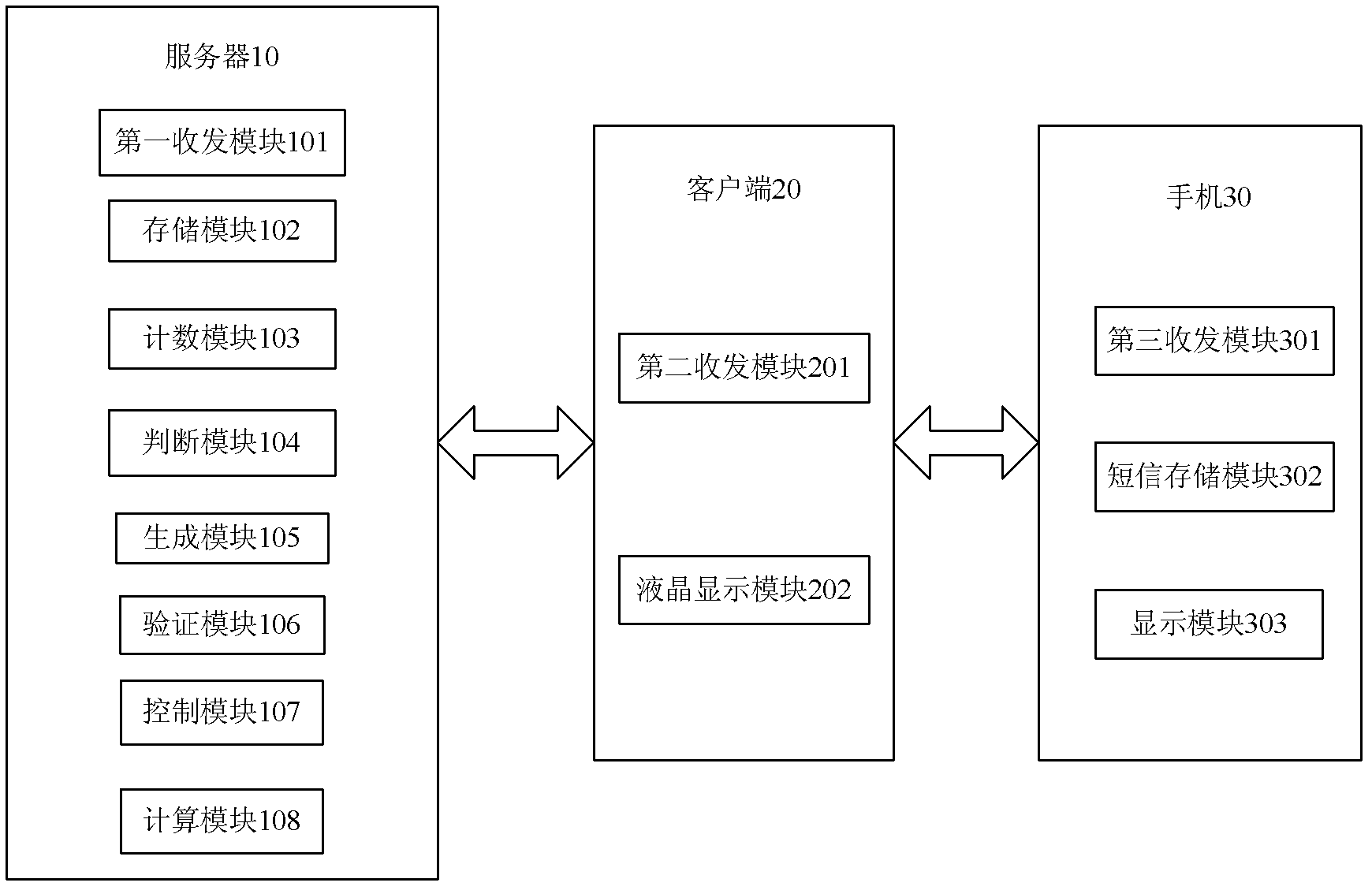
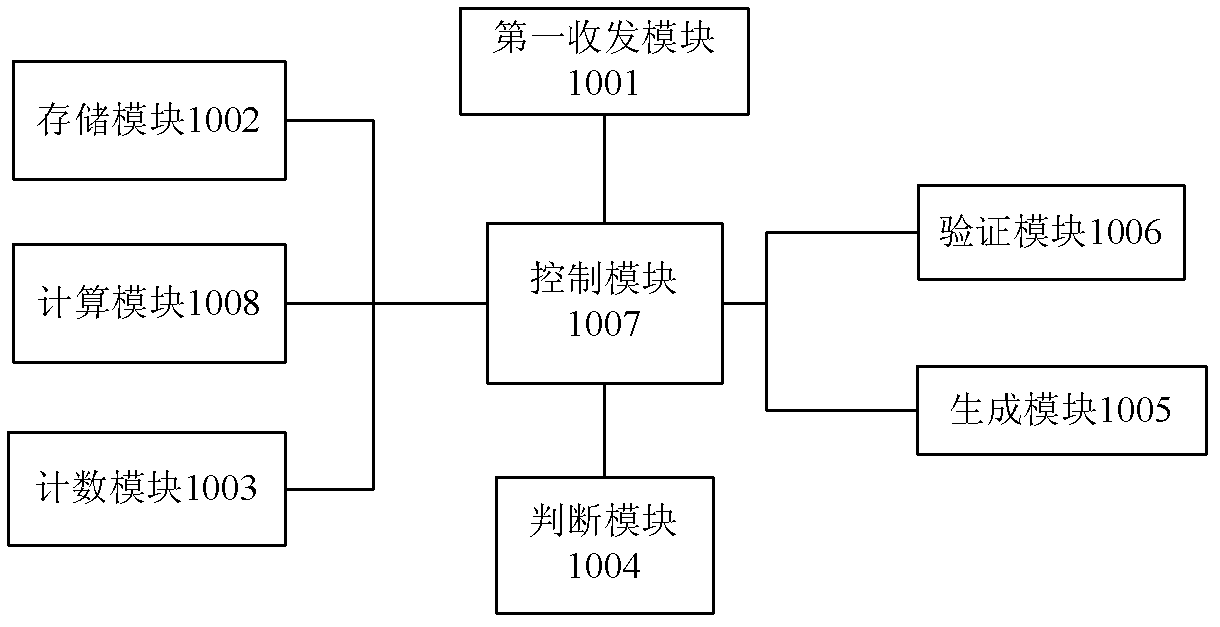
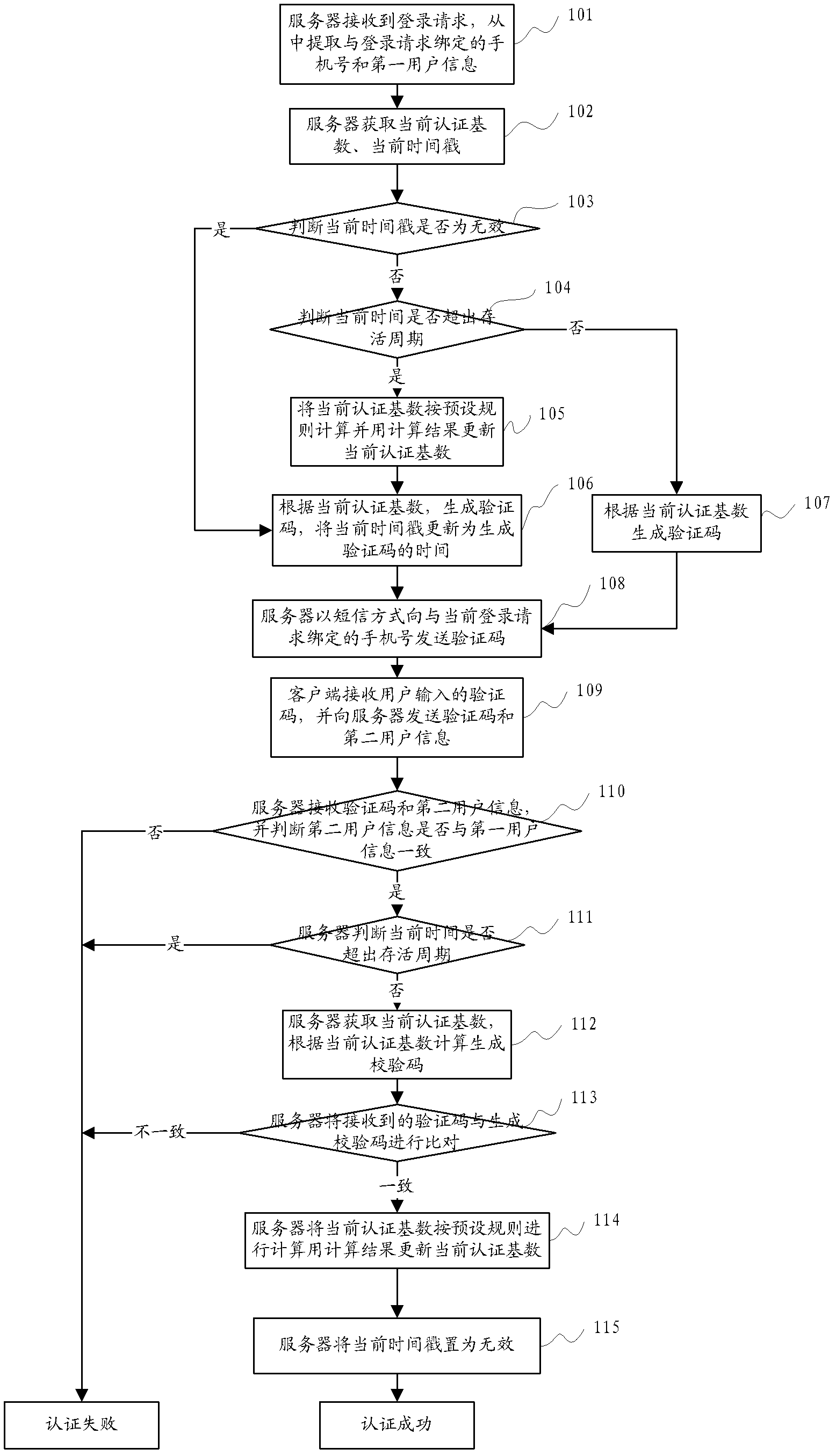
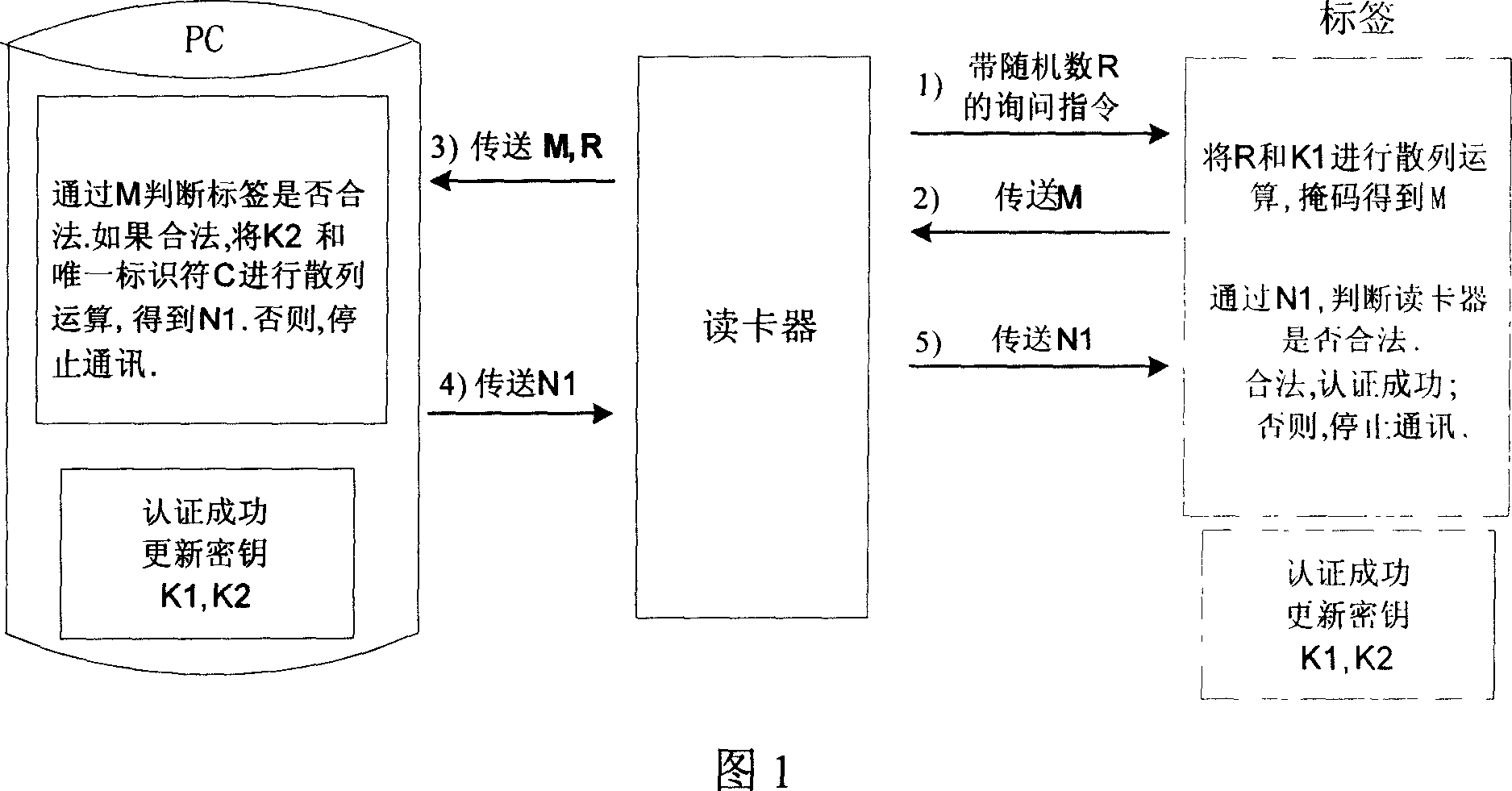
A SMS-based authentication method, system and device
ActiveCN102300182AAvoid attackTime-sensitiveUser identity/authority verificationMessaging/mailboxes/announcementsMan-in-the-middle attackUser input
The invention discloses a short-message-based authentication method, a short-message-based authentication system and a short-message-based authentication device, which relate to the technical field of network security. The authentication system comprises a server, a client and a mobile phone. The authentication device which is the server comprises a transmitting and receiving module, a storage module, a counting module, a judgment module, a generation module, an authentication module, a control module and a calculation module. In the short-message authentication method, the server generates an authentication code, records authentication code generation time, and transmits the generated authentication code to the mobile phone of a user in an out-of-band way; the user inputs the authentication code into the client; and the client transmits the authentication code to the server for authentication, so man-in-the-middle attacks can be prevented to a certain extent; moreover, the authentication code generated by the server has timeliness and may become invalid upon expiration.
Owner:FEITIAN TECHNOLOGIES
Device authentication in a PKI
ActiveUS7516325B2Minimizes attackAdvantageouslyKey distribution for secure communicationSynchronising transmission/receiving encryption devicesMan-in-the-middle attackPersonalization
A method for establishing a link key between correspondents in a public key cryptographic scheme, one of the correspondents being an authenticating device and the other being an authenticated device. The method also provides a means for mutual authentication of the devices. The authenticating device may be a personalized device, such as a mobile phone, and the authenticated device may be a headset. The method for establishing the link key includes the step of introducing the first correspondent and the second correspondent within a predetermined distance, establishing a key agreement and implementing challenge-response routine for authentication. Advantageously, man-in-the middle attacks are minimized.
Owner:BLACKBERRY LTD
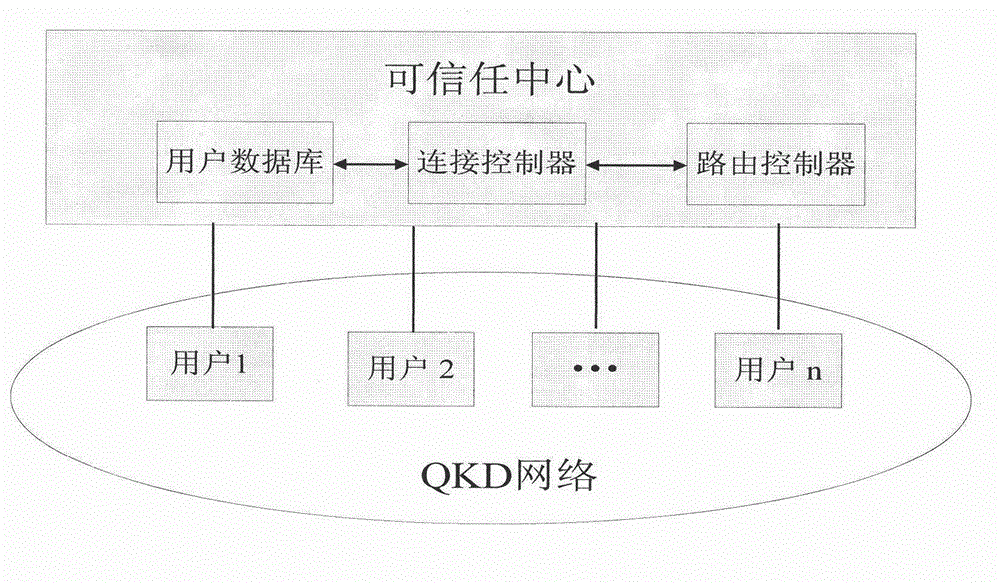
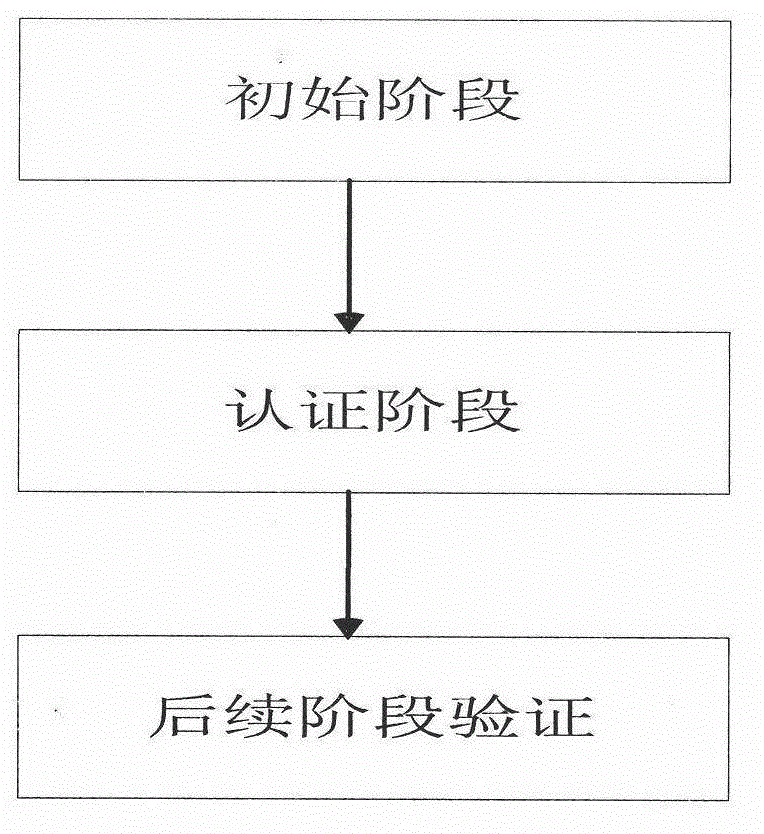
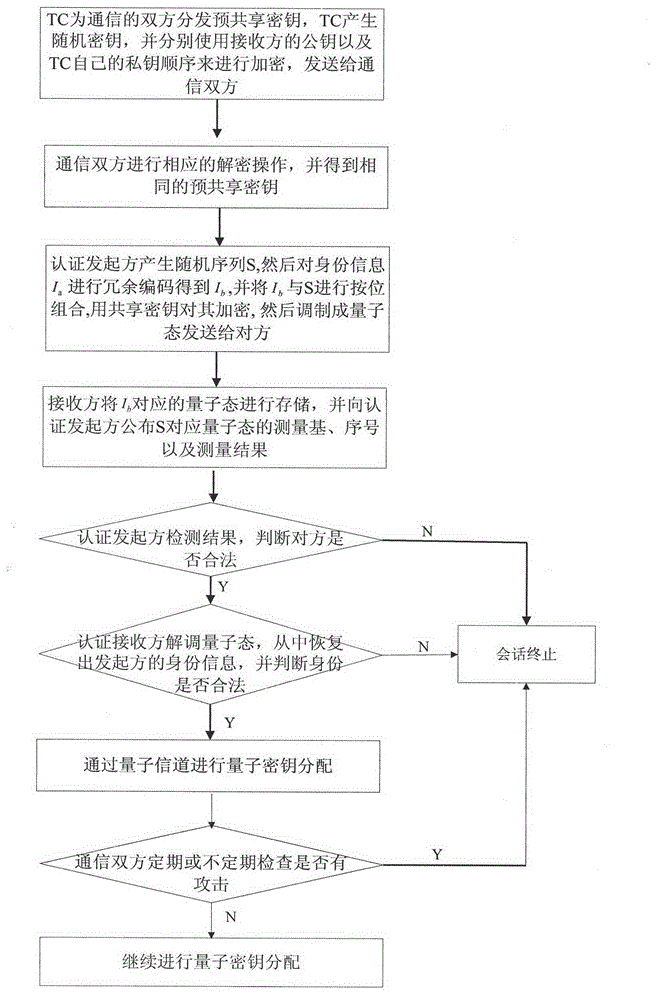
Model and method for user authentication for quantum key distribution network
ActiveCN102946313AAvoid Intermittent AttacksPrevent theftKey distribution for secure communicationUser identity/authority verificationCommunications securityMan-in-the-middle attack
The invention provides a model and a method for user authentication based on a trusted center in a quantum key distribution network, specifically, a user authentication model based on the trusted center is provided and an implementation method is described in detail, in order to realize the communication security between any two users in the network and prevent a man-in-the-middle attack. Based on the model, the invention further provides a method for user authentication, which comprises the following steps that: 1, any user requesting for communication in the network sends a connection request to the trusted center; 2, the trusted center sends a pre-shared key to the two communication parties respectively; 3, the two communication parties set up a quantum channel and are authenticated; and 4, the two parties are authenticated regularly or irregularly in the subsequent communication process. According to the invention, by fully considering the development status of the current quantum key distribution network and by combining with the actual requirement, a quantum communication channel can be set up securely between any two nodes in the network, so that the communication security between users can be realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Using Supplemental Encrypted Signals to Mitigate Man-in-the-Middle Attacks on Teleoperated Systems
ActiveUS20150295949A1Mechanical/radiation/invasive therapiesMemory loss protectionMan-in-the-middle attackHuman–computer interaction
Methods and systems for securing remotely-operable devices are provided. A remotely-operable device can receive a command related to a component of the remotely-operable device operating in an environment. The remotely-operable device can include a reality-rules database (RRDB) that is configured to store a plurality of reality rules with each reality rule relating to a constraint on the remotely-operable device. The remotely-operable device can determine a reasonableness value for the command based on a constraint, where the constraint is determined based on a constraint related to at least one reality rule of the plurality of reality rules stored in the RRDB. The remotely-operable device can encode the reasonableness value for the command in a feedback message. The remotely-operable device can send the encoded feedback message from the remotely-operable device.
Owner:UNIV OF WASHINGTON CENT FOR COMMERICIALIZATION
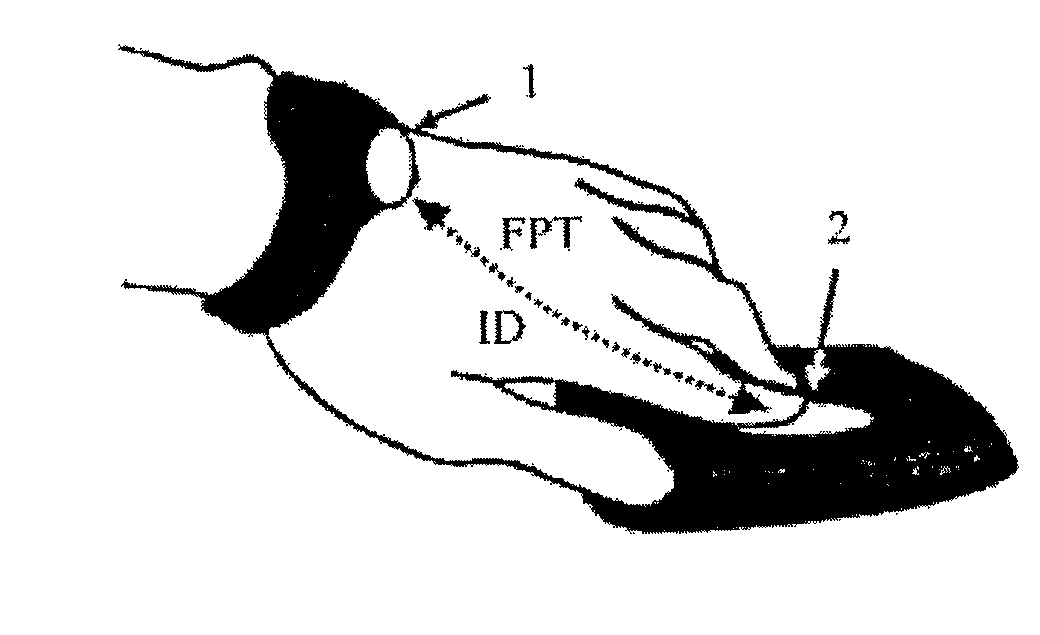
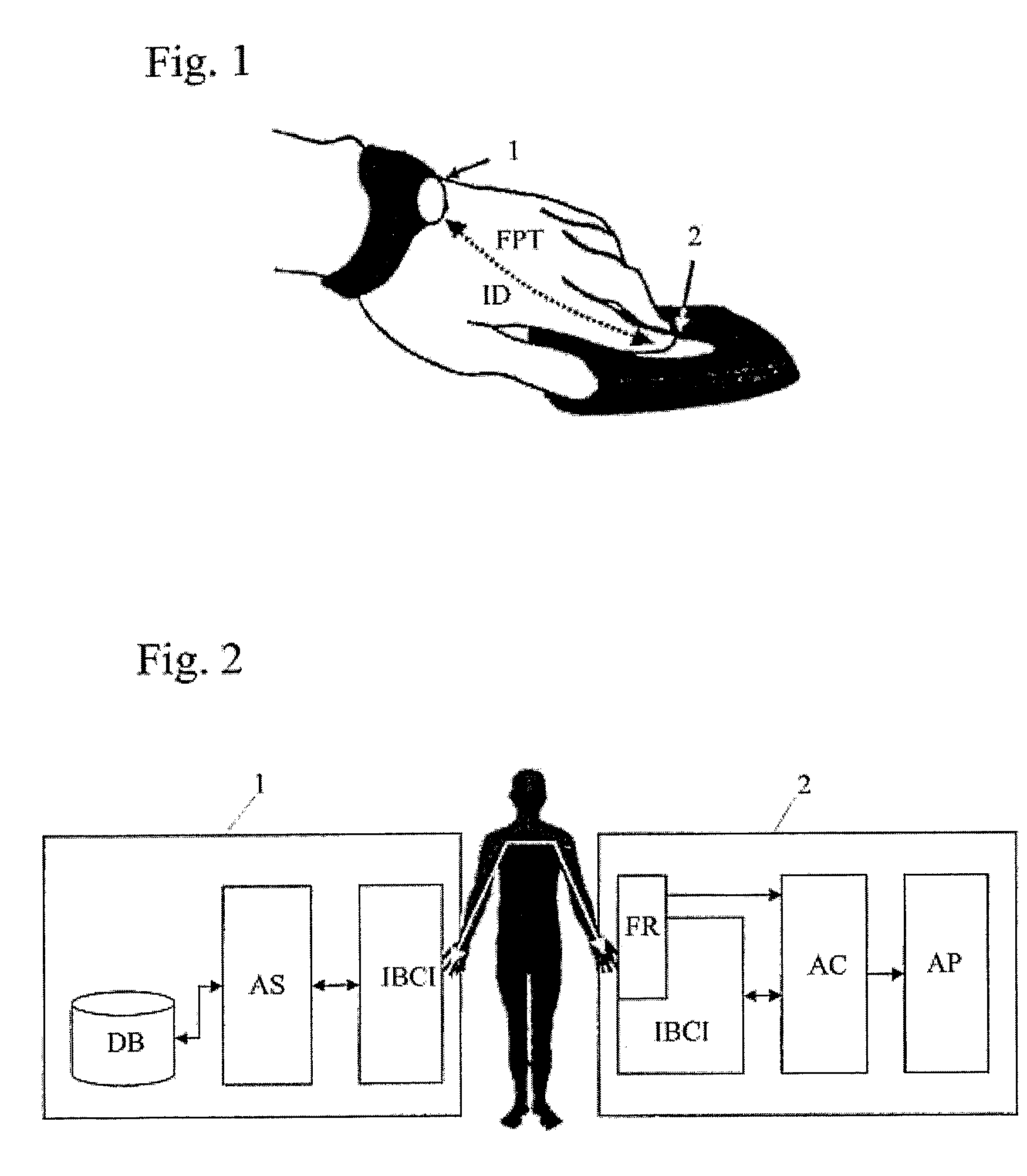
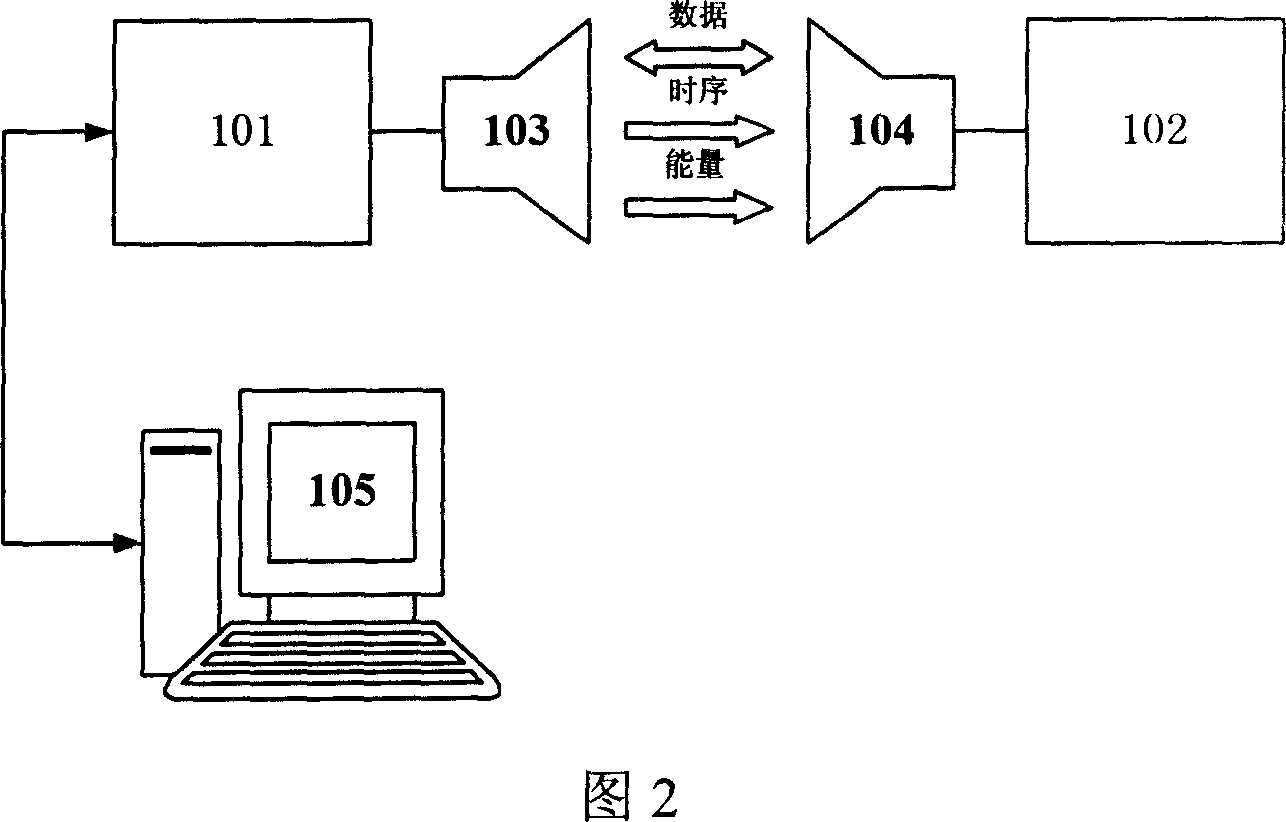
Identification system and method of operating same
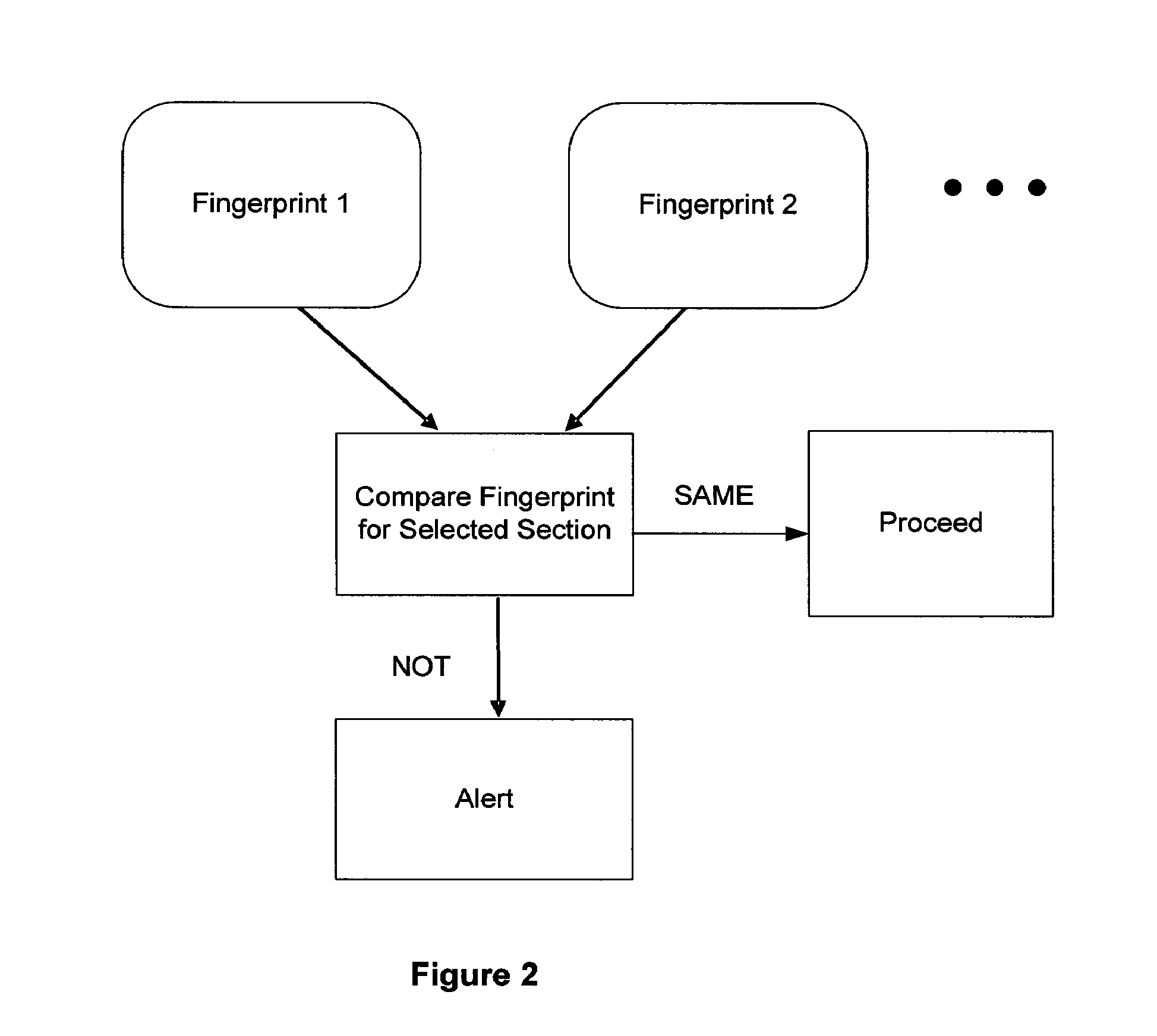
ActiveUS8098129B2Avoid disadvantagesElectric signal transmission systemsImage analysisMan-in-the-middle attackCommunication interface
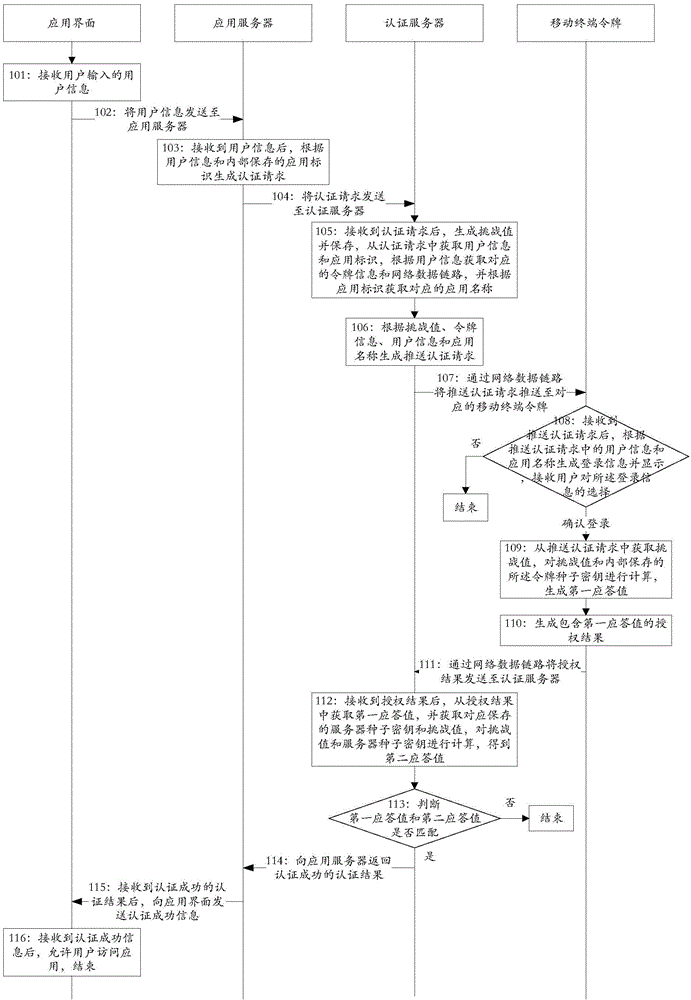
An identification system which is not prone to man-in-the-middle attacks and which is capable of intra-body communication includes at least one wearable electronic key (1). The electronic key includes an intra-body communication interface (IBCI) and a storage device (DB) in which user identification data (ID) are stored, and an authentication server (AS) for verification of a user's fingerprint. At least one reader (2) has an intra-body communication interface (IBCI) and a fingerprint reader.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
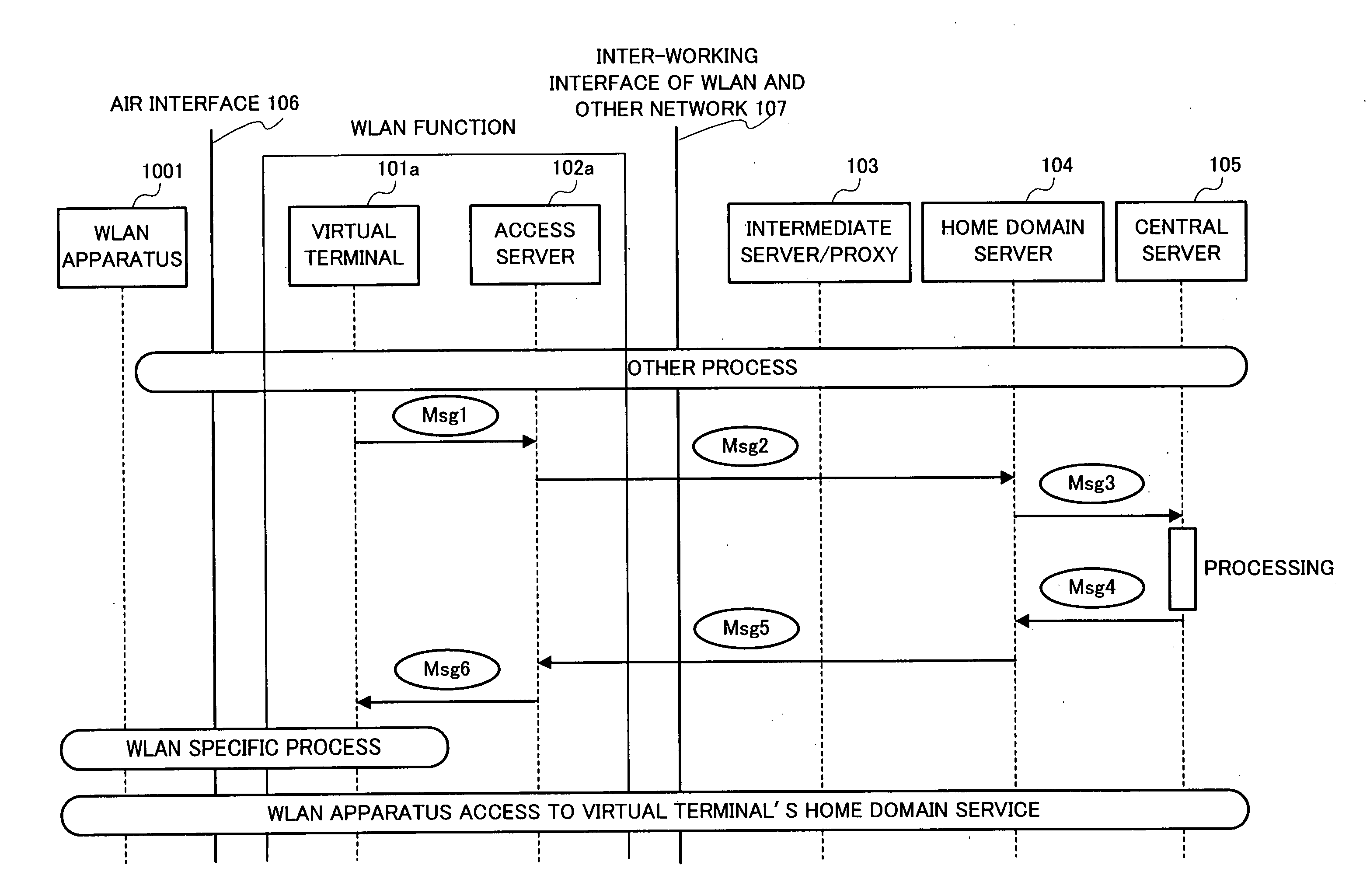
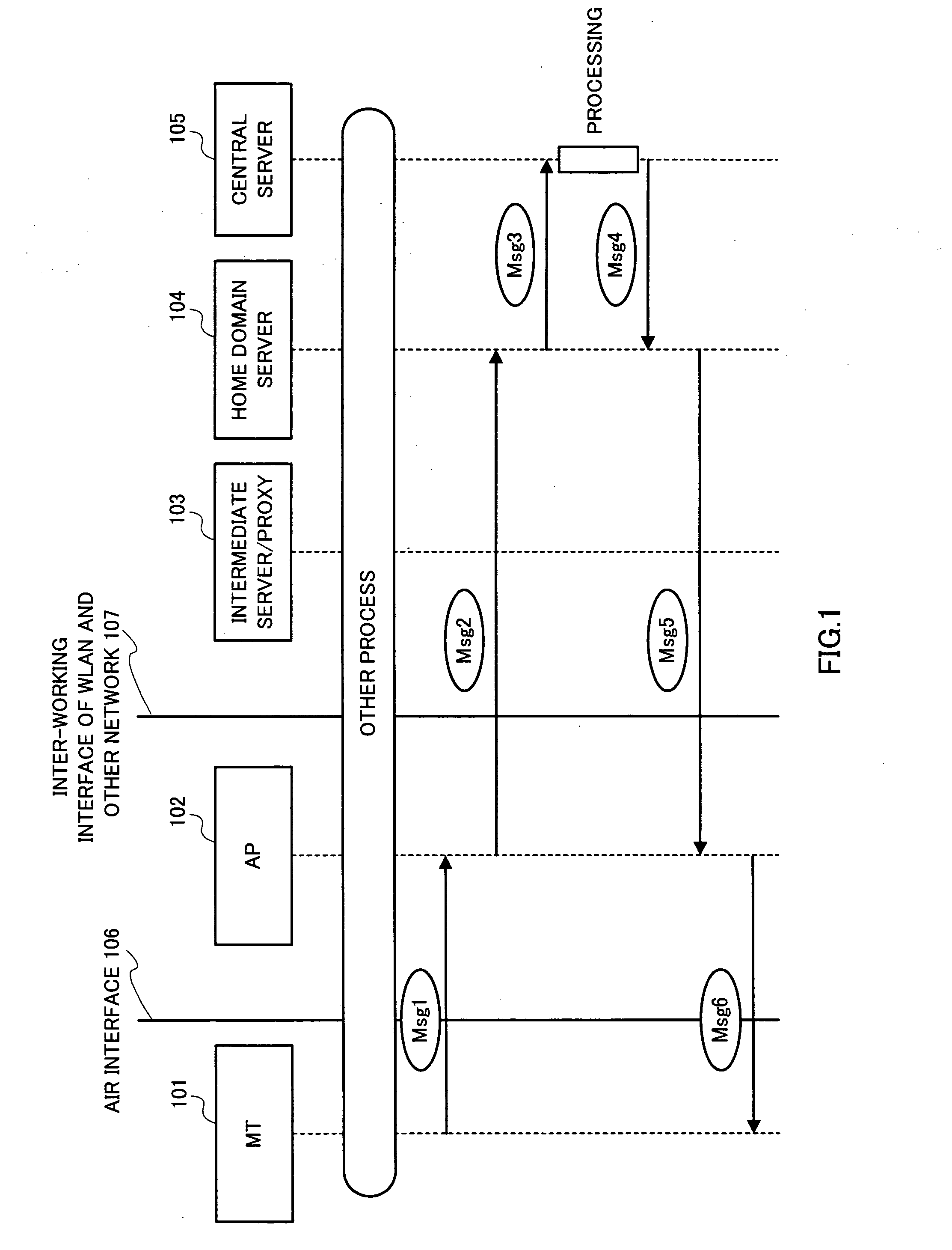
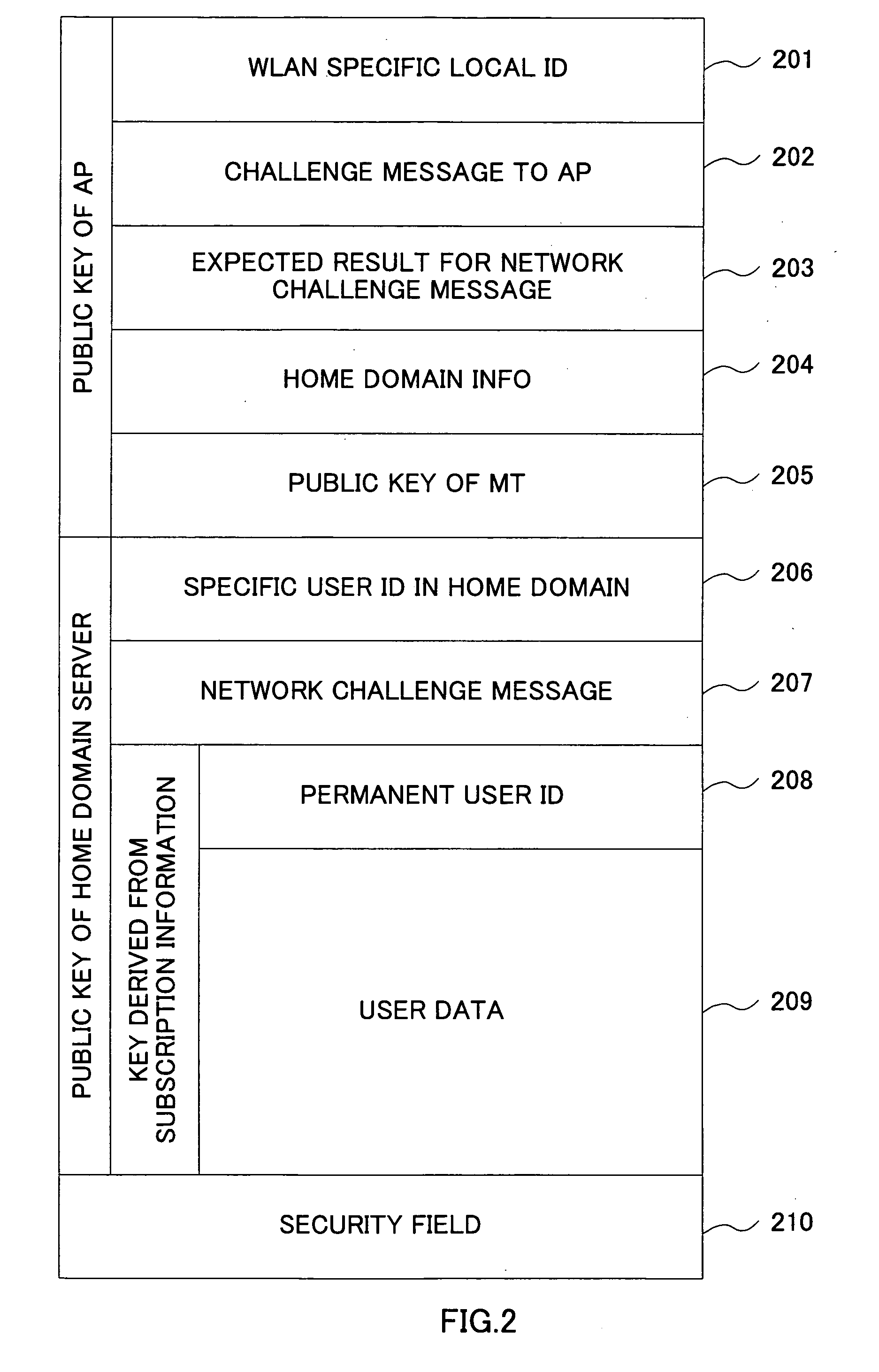
Identification information protection method in wlan inter-working
ActiveUS20060101273A1Save network resourcesAdd supportDigital data processing detailsUser identity/authority verificationMan-in-the-middle attackMessage switching
By introducing a hierarchical encryption scheme and the use of asymmetric cryptography, the critical information in message exchanges is concealed from unauthorized entities. This helps greatly in preventing man-in-the-middle attacks faced by inter-working. In addition, access control is conducted by introducing a network structure having a rule interpreter that is capable of mapping general rules to WLAN specific commands. It obviates the needs for mobile user's home network to understand information about every WLAN it is inter-worked with. A common interface independent of WLAN technologies could be used by the home network for all the WLANs. The above conception provides a solution to the problems of the protection of user identification information and access control in the inter-working of WLAN.
Owner:APPLE INC
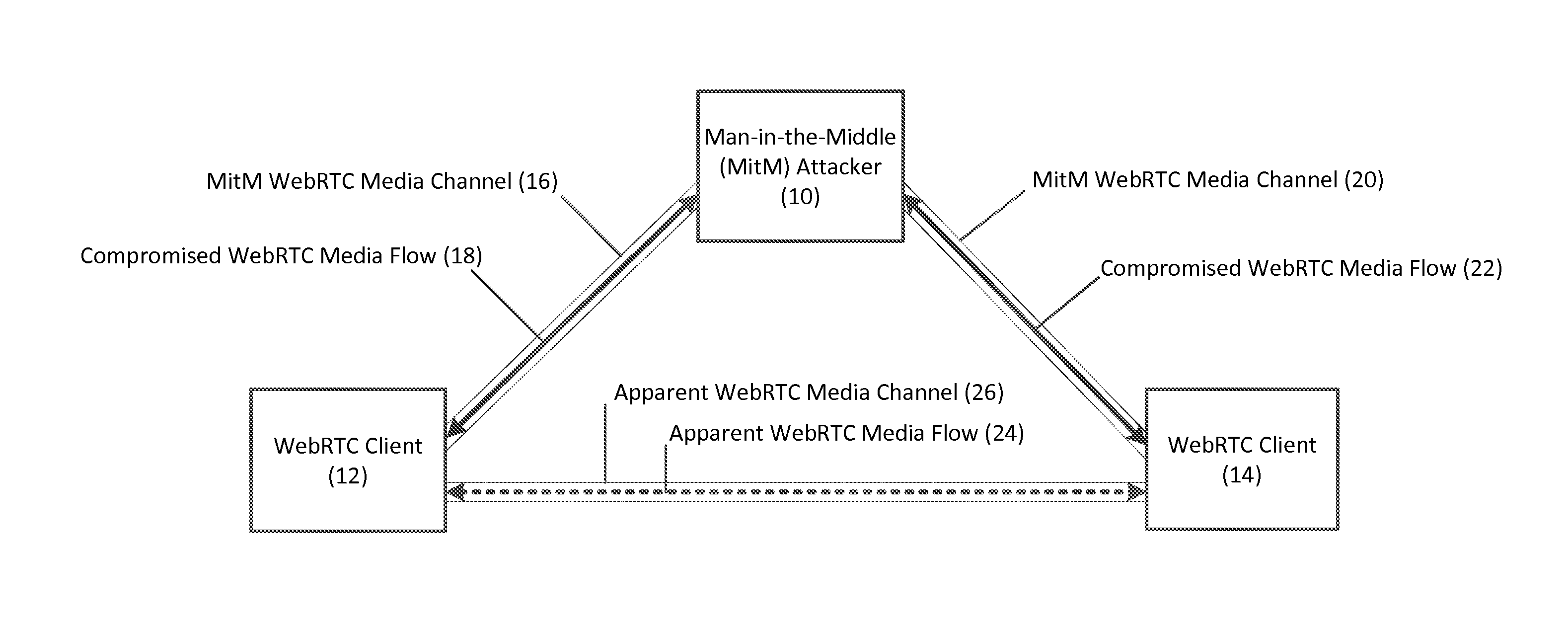
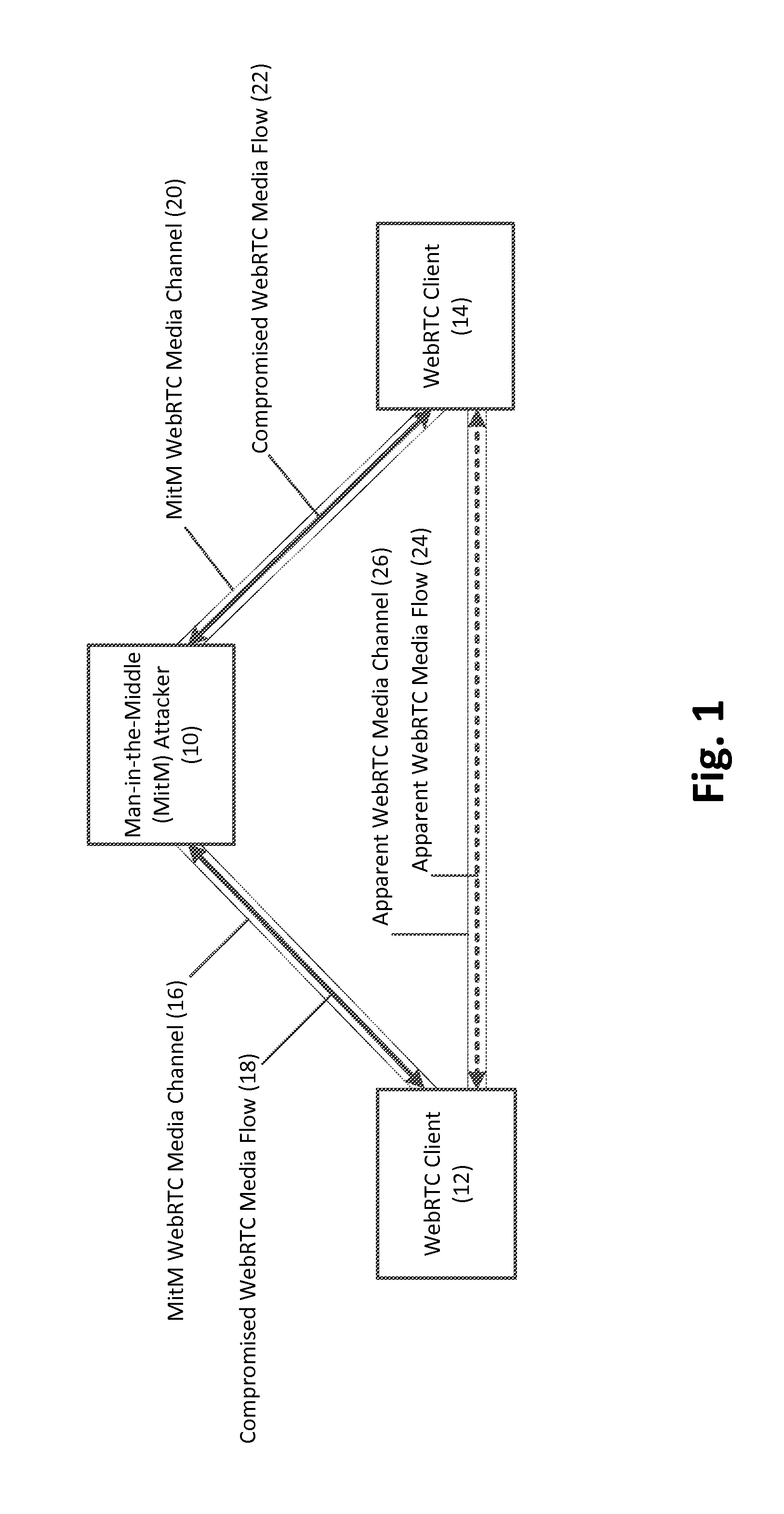
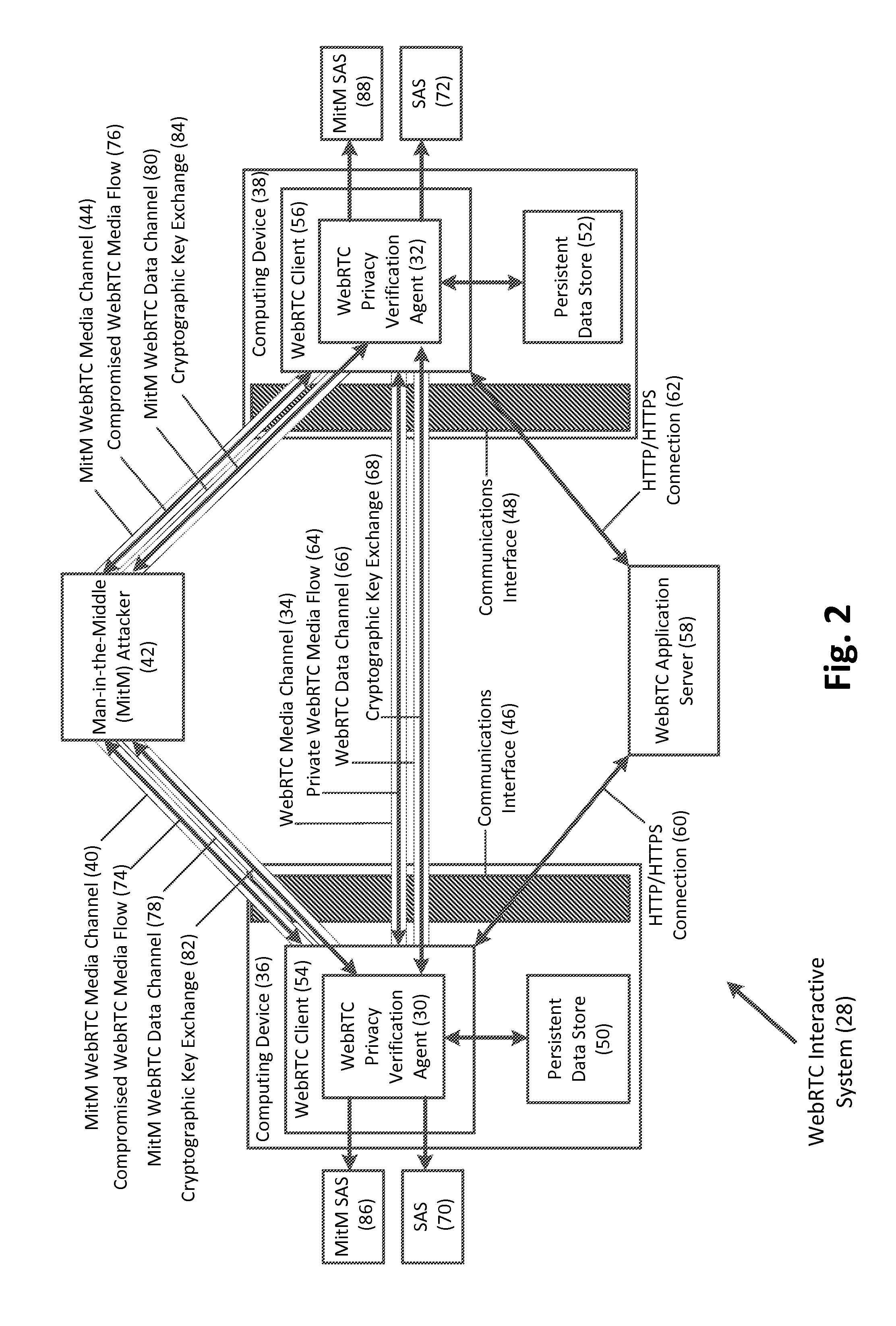
Verifying privacy of web real-time communications (webrtc) media channels via corresponding webrtc data channels, and related methods, systems, and computer-readable media
Verification of privacy of Web Real-Time Communications (WebRTC) media channels via corresponding WebRTC data channels, and related methods, systems, and computer-readable media are disclosed. In this regard, in one embodiment, a method for verifying privacy of a WebRTC media channel comprises establishing the WebRTC media channel between first and second WebRTC clients using a keying material. The method further comprises establishing a corresponding WebRTC data channel between the first and second WebRTC clients using the keying material, and negotiating, in the WebRTC data channel, a cryptographic key exchange. The method also comprises generating a first and a second Short Authentication String (SAS) based on the cryptographic key exchange in the WebRTC data channel. The method further comprises displaying the first SAS and the second SAS, such that a mismatch between the first SAS and the second SAS indicates an existence of a man-in-the-middle (MitM) attacker.
Owner:AVAYA INC
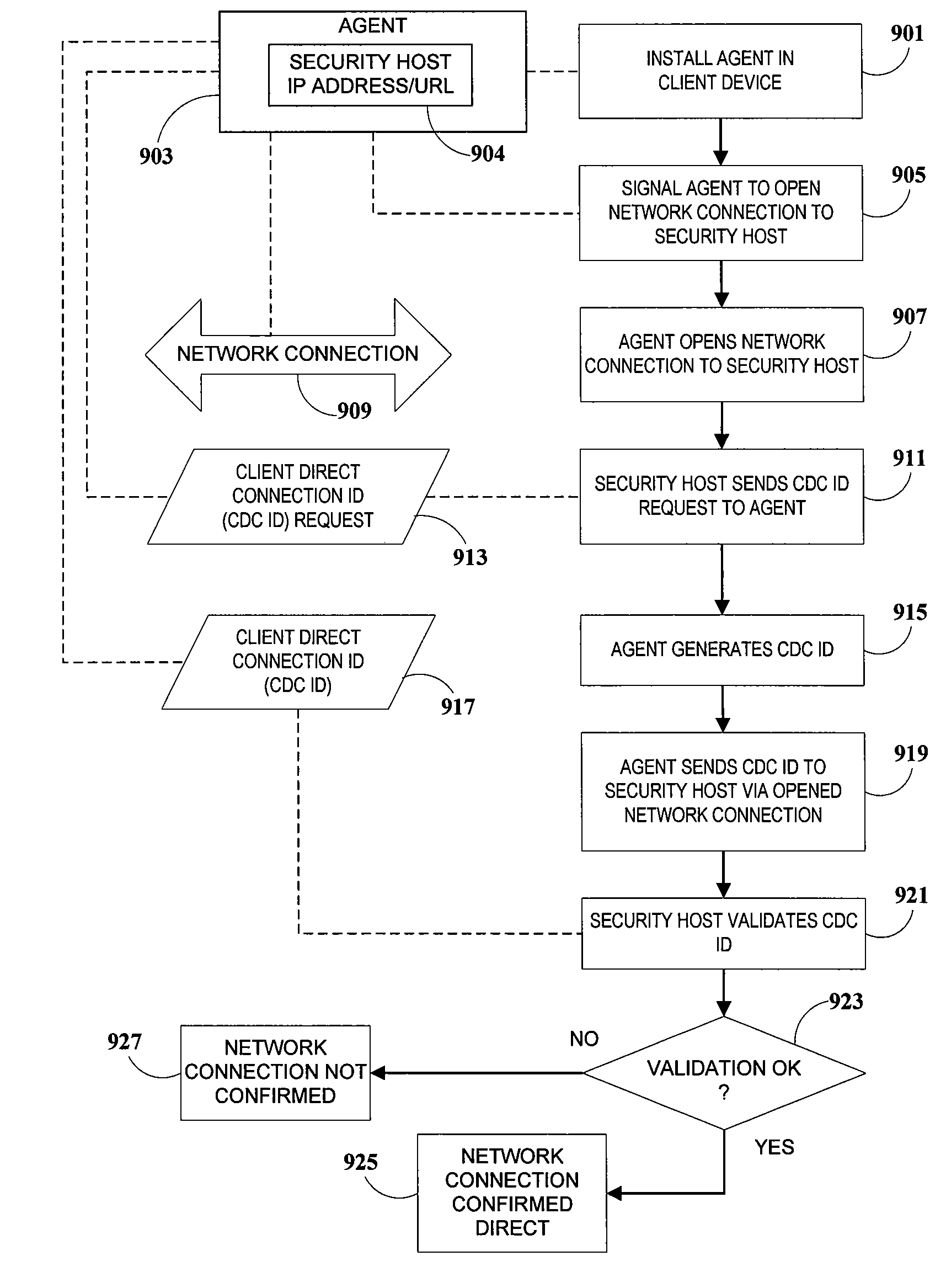
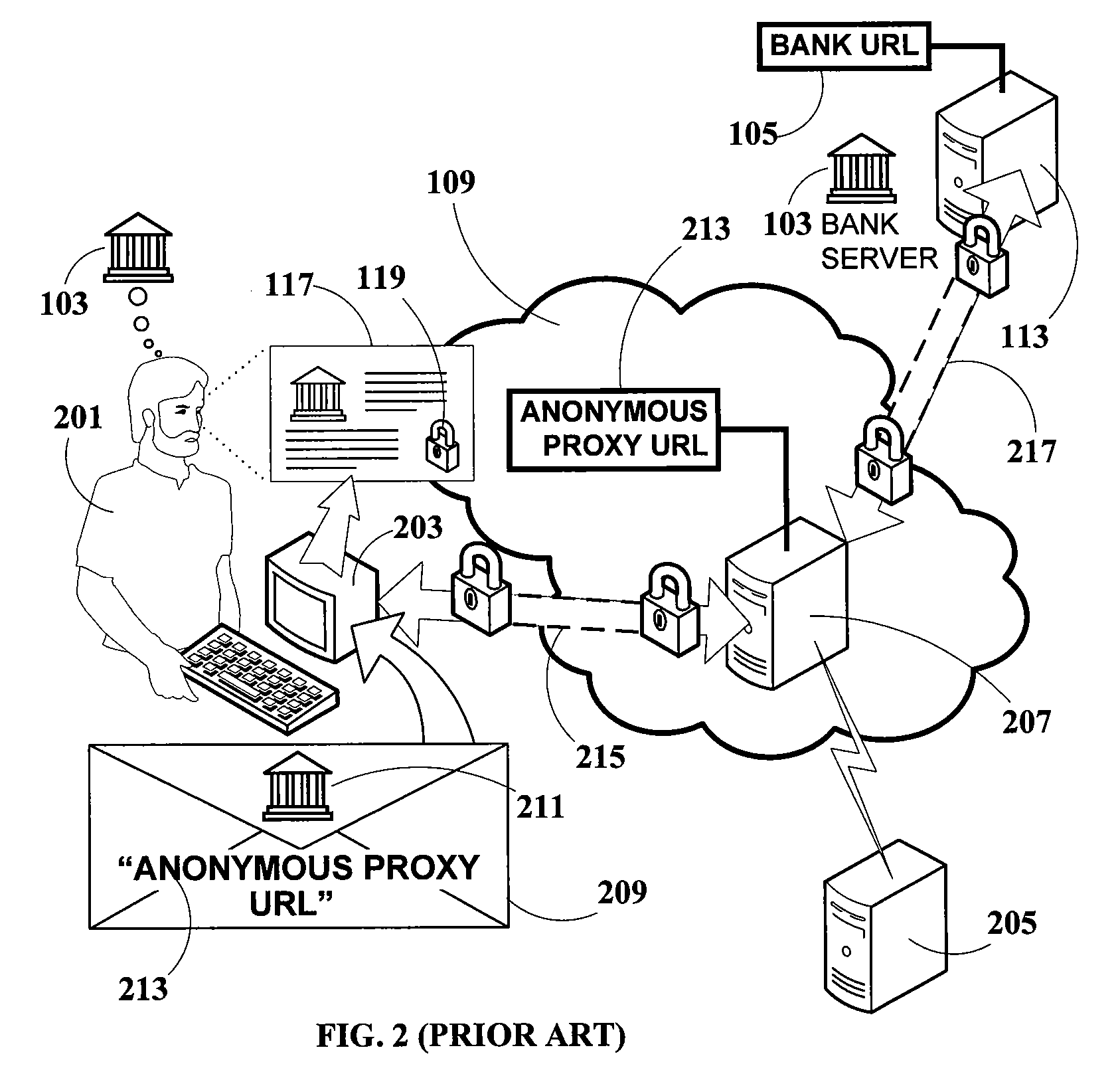
Method and system for detecting, blocking and circumventing man-in-the-middle attacks executed via proxy servers
InactiveUS20100088766A1Avoids user distressAvoids concernMemory loss protectionError detection/correctionThird partyMan-in-the-middle attack
A method for detecting and blocking a Man-in-the-Middle phishing attack carried out on a client connection which has been fraudulently routed through an anonymous proxy server. An agent downloaded to the client device opens a client direct connection to the security host protecting against the attack and sends a client direct connection ID to the security host for validation. By comparing IP addresses correlated via the validated client direct connection ID, the security host determines whether the original connection is direct (secure) or indirect (attack via phishing proxy). The detection and blocking can be performed by the service provider's server or by a third-party validation server handling all security without additional requirements on the service provider server. In addition to detecting and blocking such attacks, methods for client direct connection ID, as well as automatic transparent and seamless attack circumvention and preemptive circumvention are disclosed.
Owner:SAFENET DATA SECURITY ISRAEL
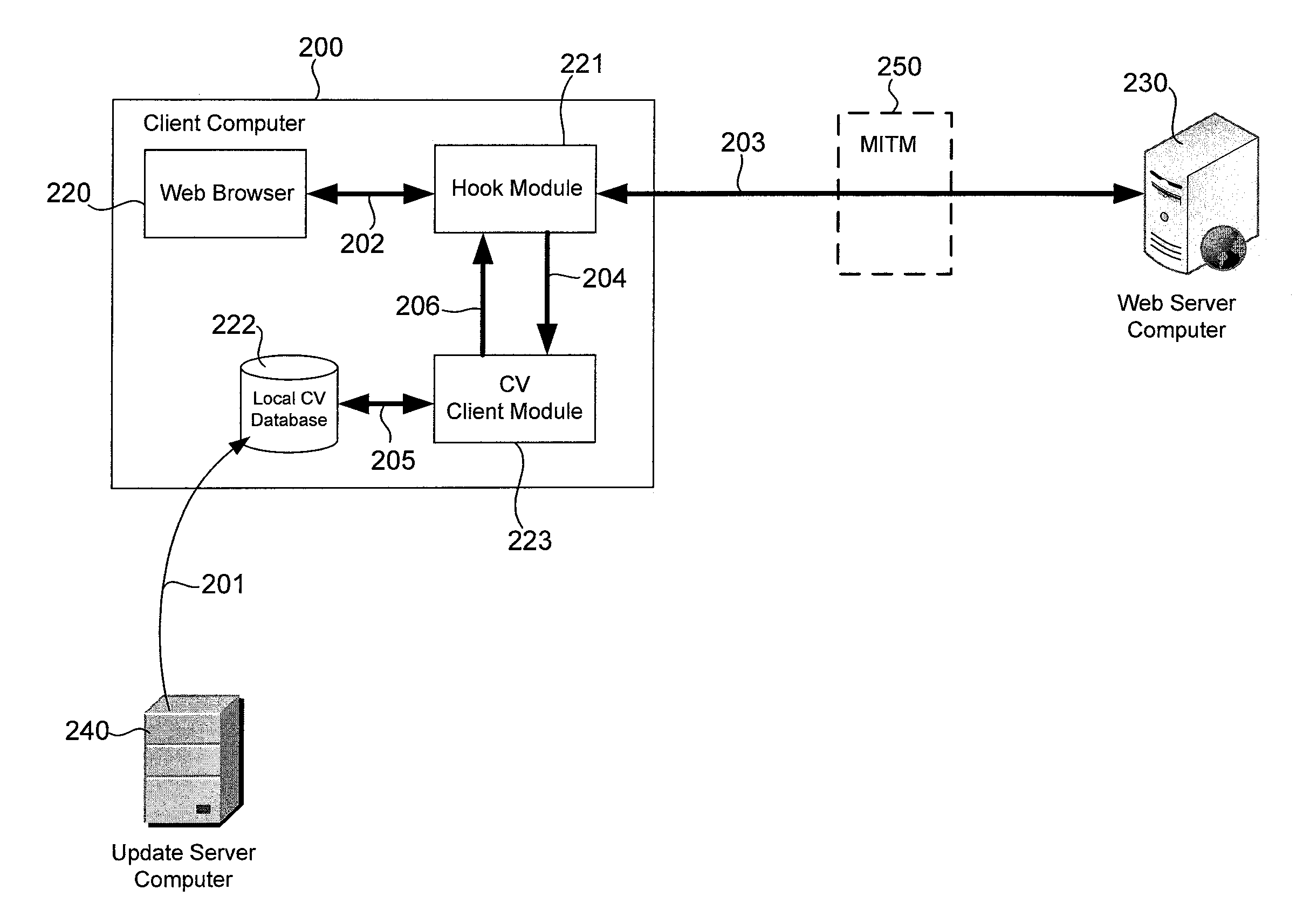
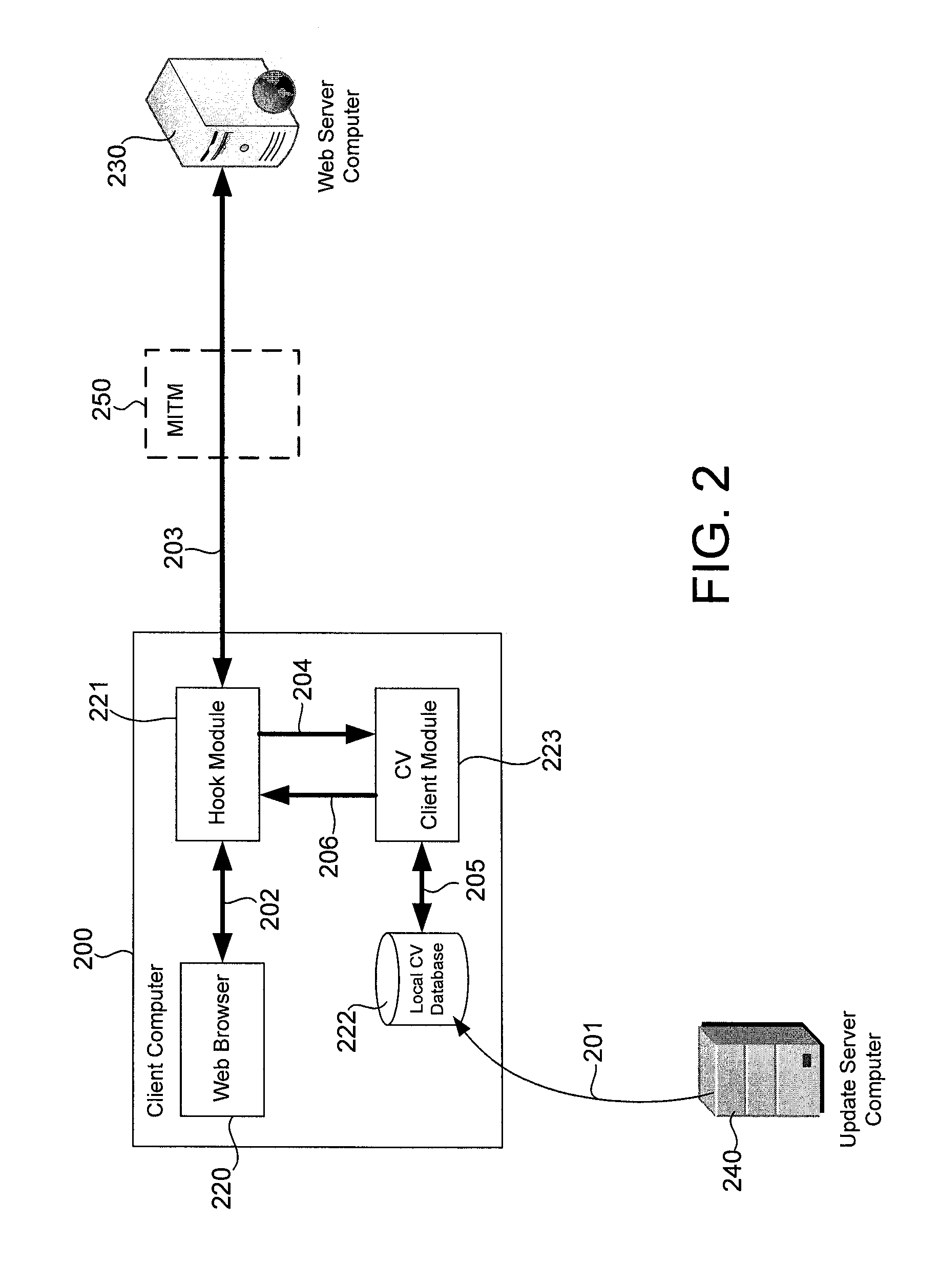
Verification of digital certificates used for encrypted computer communications
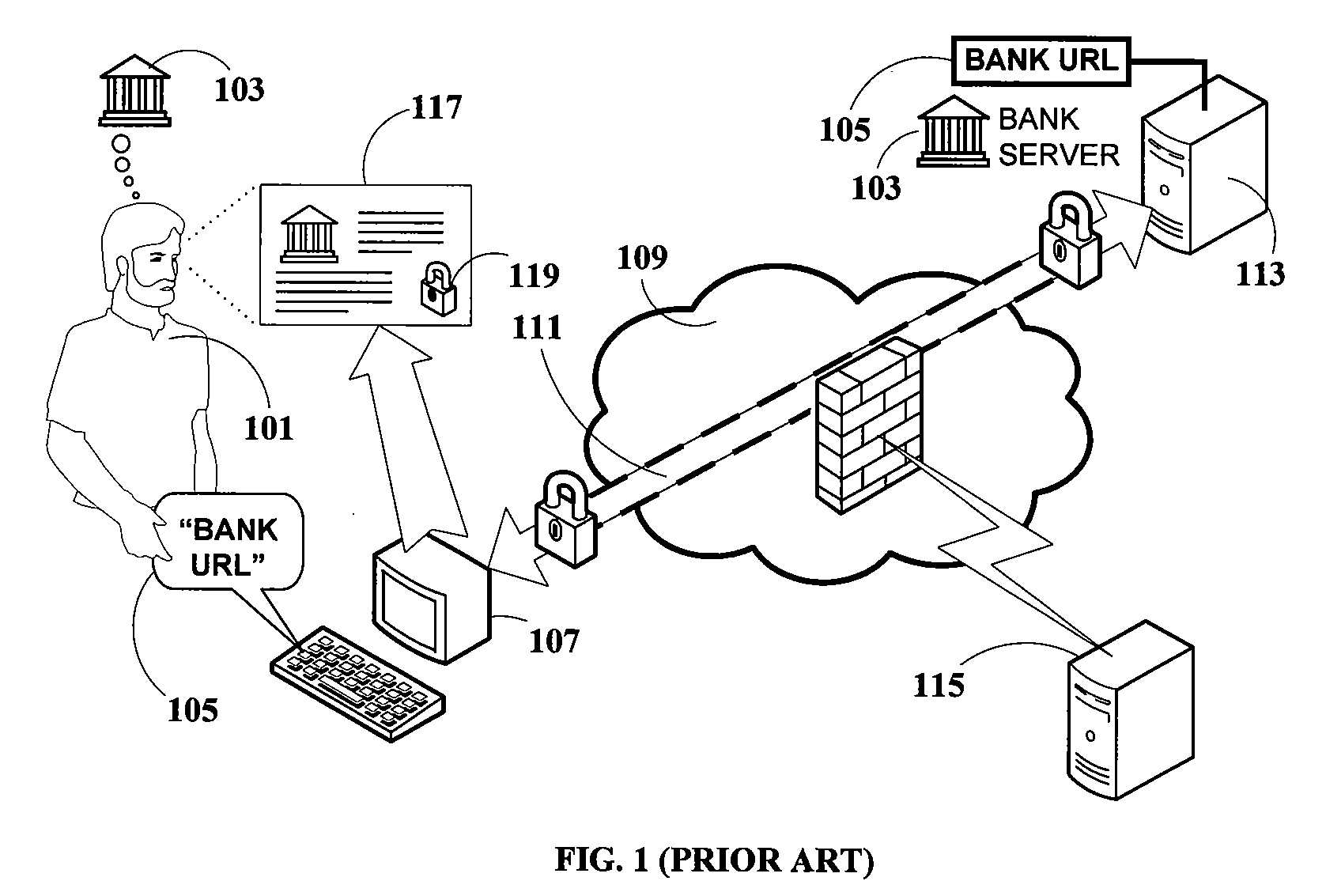
ActiveUS8677466B1Digital data processing detailsComputer security arrangementsMan-in-the-middle attackWeb site
A digital certificate may be extracted from communications between a web browser and a web server computer. The digital certificate may be verified independent of the web browser by comparing the digital certificate against contents of a database containing digital certificates of legitimate websites or by consulting a remotely located security server computer. For example, the digital certificate may be forwarded from a client computer running the web browser to the security server computer. The security server computer may obtain a digital certificate from the web server computer and compare it to the one received from the client computer to detect man-in-the-middle attacks, for example.
Owner:TREND MICRO INC
Work method of authentication pushing system and equipment
ActiveCN104639562AAvoid attackFast data transferUser identity/authority verificationMan-in-the-middle attackApplication server
The invention discloses a work method of an authentication pushing system and equipment, and belongs to the field of information security. The method comprises the following steps that an application interface receives user information and sends the user information to an application server, the application server sends the user information and an application identifier to an authentication server, the authentication server generates authentication pushing requests according to a generated challenge value, token information, the user information and the application name corresponding to the application identifier, and sends the authentication pushing requests to a mobile terminal token, the mobile terminal token generates login information according to the authentication pushing requests, when the user select the login confirm, a first response value is generated according to the challenge value and is sent to the authentication server, the authentication server generates a second response value according to the challenge value, and when the first response value and the second response value are identical, an authentication success result is returned to the application server. When the technical scheme is adopted, the data transmission speed of the traditional authentication is accelerated, the user does not need to take part in the password input, the man-in-the-middle attack is avoided, and the authentication security is improved.
Owner:FEITIAN TECHNOLOGIES
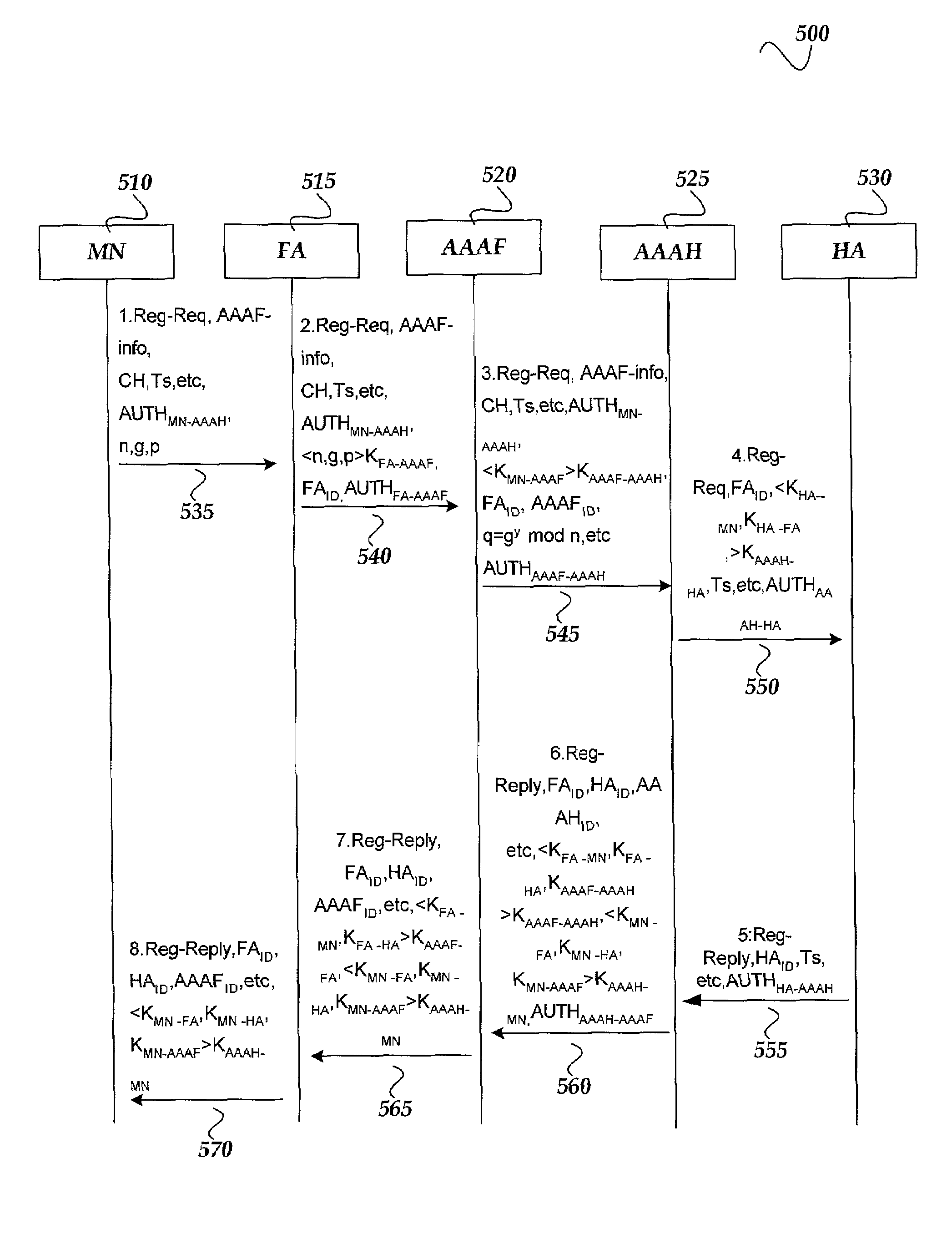
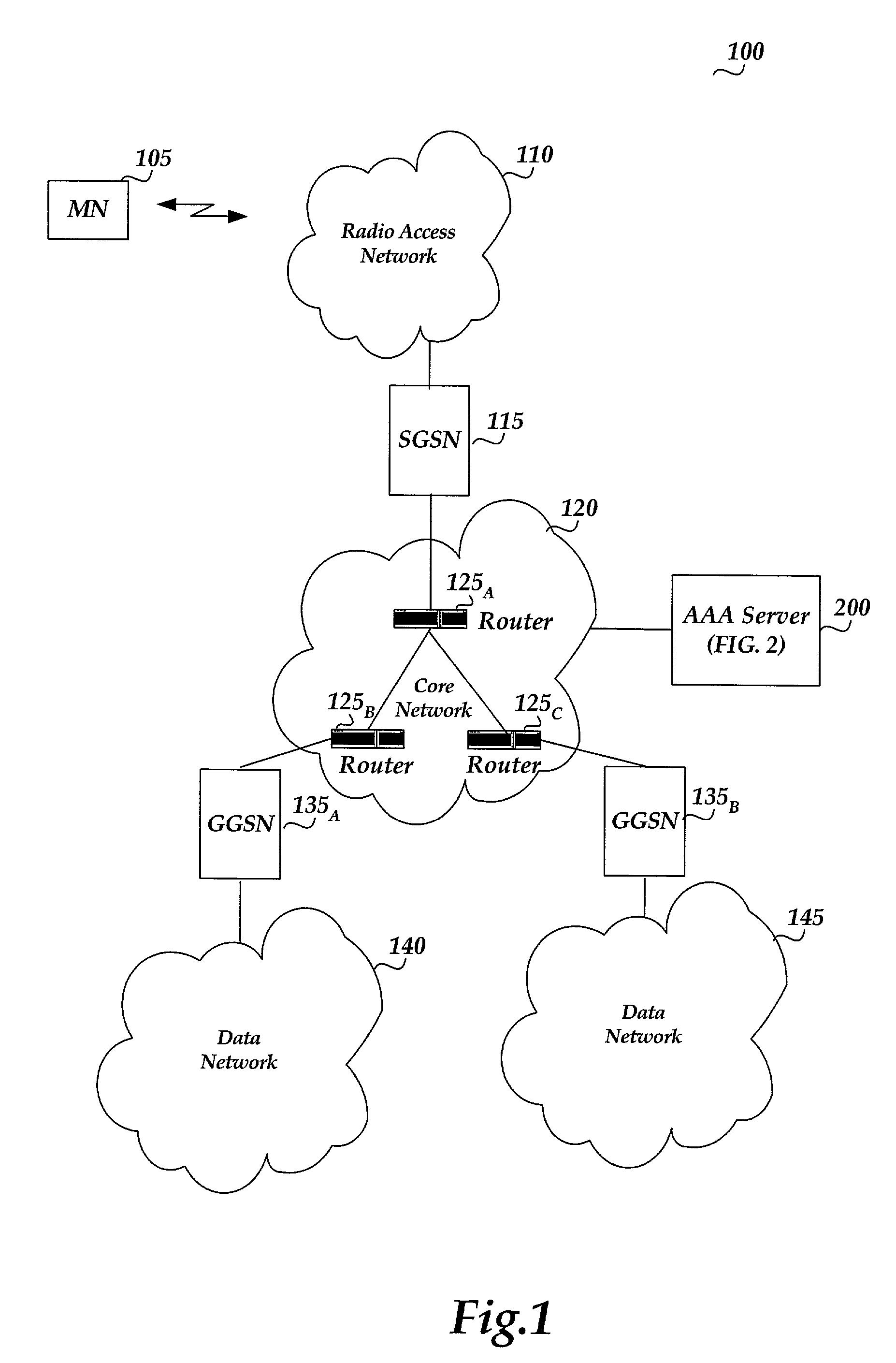
Secure key distribution protocol in AAA for mobile IP
InactiveUS7298847B2Enhances security and flexible and scalabilityKey distribution for secure communicationMultiple keys/algorithms usageMan-in-the-middle attackExtensibility
A security key distribution and authentication protocol in AAA for Mobile IP has been described. In order to guarantee the secure protocol, messages between the MN, FA, AAAF, AAAH, and HA are encrypted and signed using public / private keys. IPSEC or PKI infrastructure is not required to support the AAA secure key distribution. This protocol enhances the security, flexible, scalability of AAA, and aids in protecting the Diffie-Hellman algorithm from man-in-the-middle attacks. Through this protocol, it is easy to set up a secure registration path in AAA for Mobile IP. This secure registration path provides a secretive and secure key distribution function for AAA.
Owner:NOKIA INC
Safety identification method in radio frequency distinguishing system
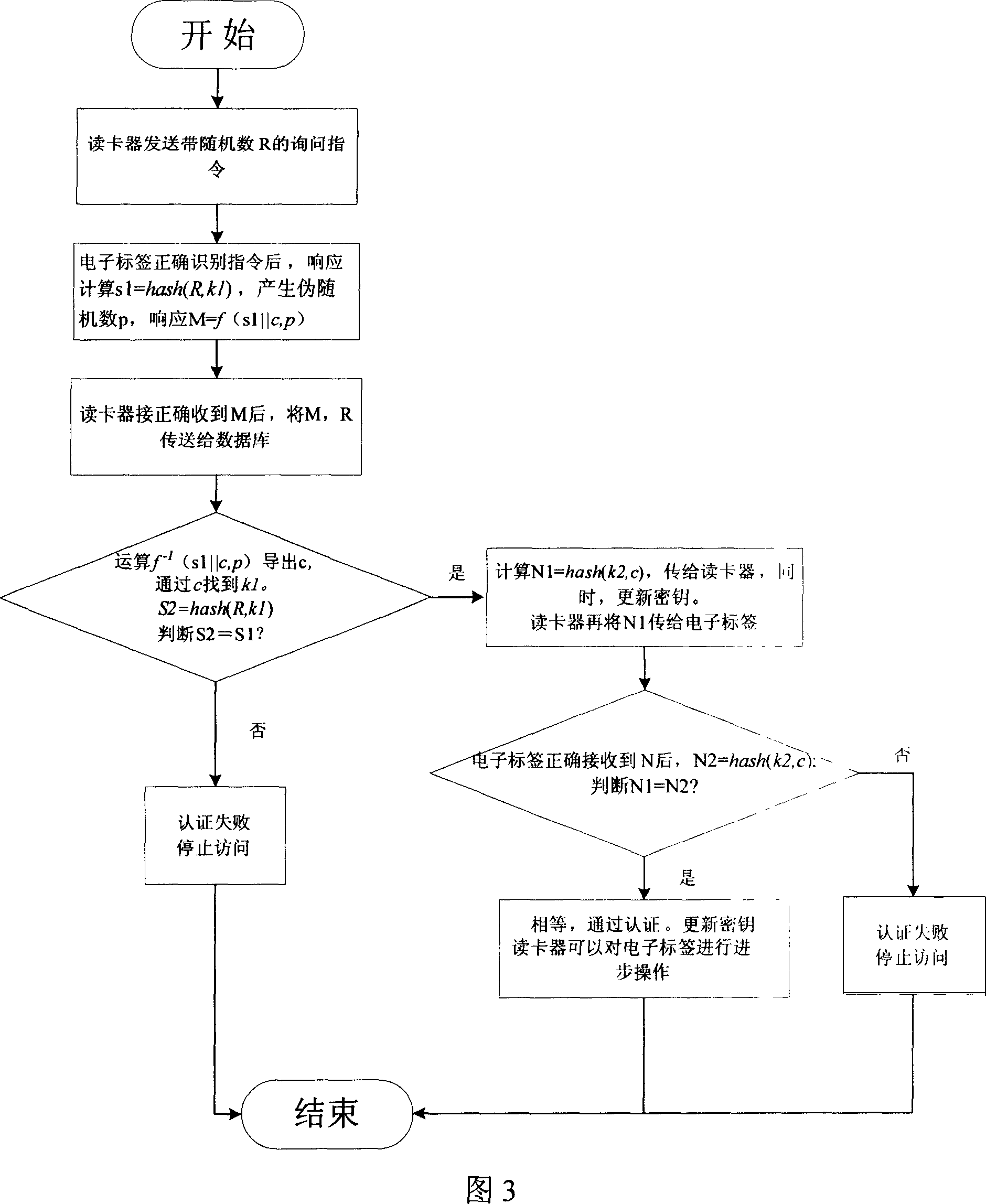
InactiveCN1932835AImprove the protective effectThe certification method has obvious advantagesMultiple keys/algorithms usageSensing record carriersUltra-widebandMan-in-the-middle attack
Owner:HUAZHONG UNIV OF SCI & TECH
Privacy leaking detecting method and system for android application network communication
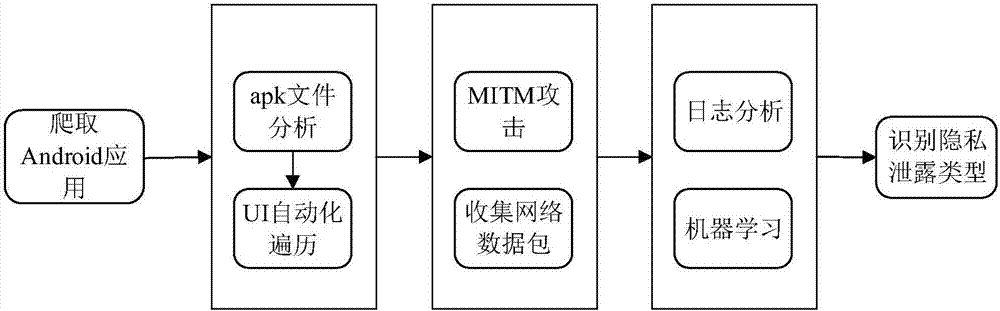
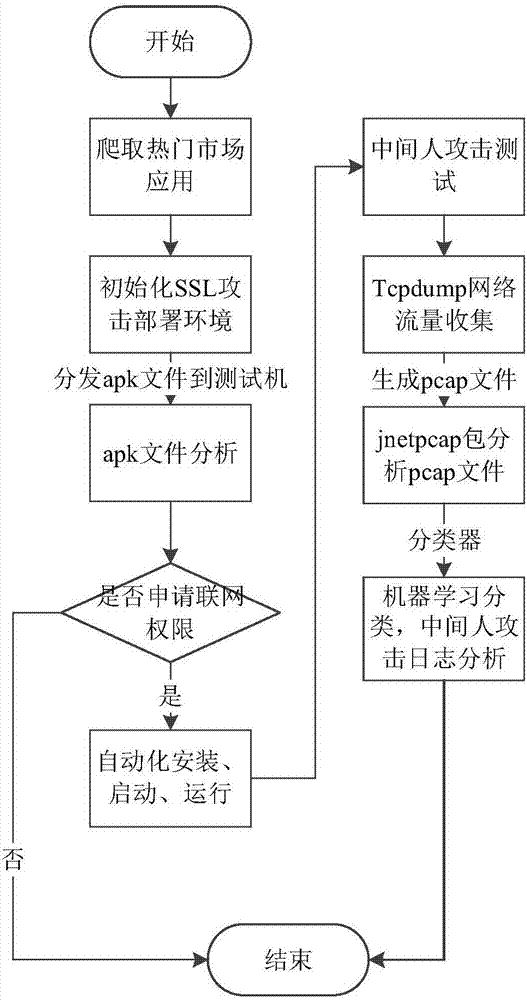
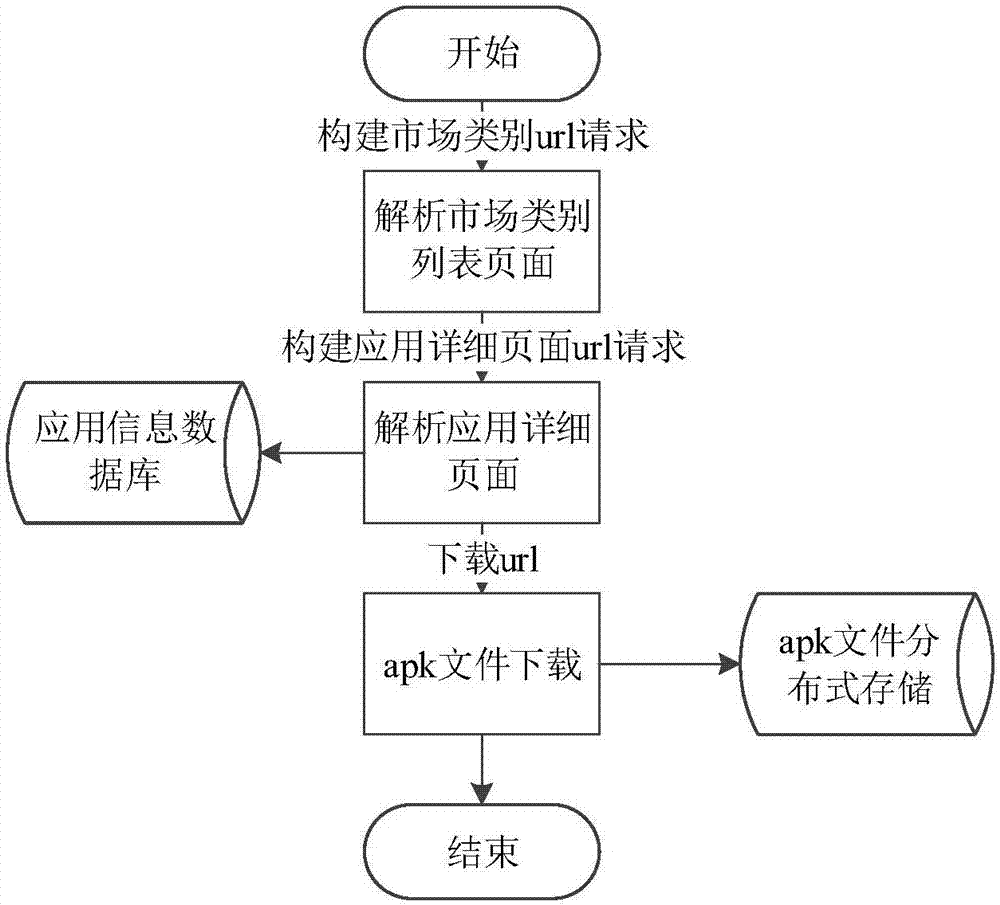
ActiveCN107133519AAccurate Privacy Leakage BehaviorAccurate detection of privacy leakage behaviorWeb data indexingPlatform integrity maintainanceMan-in-the-middle attackInternet privacy
The invention discloses a privacy leaking detecting method and system for android application network communication. The method comprises the following steps: crawling android application to be detected, and building an application set to be detected; building a main-in-the-middle attack server; initializing each tester environment; arranging a multi-tester distributive running scheduling system; analyzing APK files of the application to be detected; installing the application program corresponding to the APK file, and driving the application program to run; analyzing a log file created by the Burp Suite, and acquiring the application set with SSL man-in-the-middle attack; analyzing a network data pack file created in the running process of the collected application program; recognizing the privacy leaking type of the network data pack file according to the application set with the SSL man-in-the-middle attack. The method is flexible to use, and automatic in the whole process; the android system and the android application program structure are not modified; the privacy leaking behavior of the android application in the network communication process can be safely and accurately detected.
Owner:HUAZHONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com