Safety identification method in radio frequency distinguishing system
A radio frequency identification system and security authentication technology, which is applied in the authentication field between passive electronic tags and card readers, can solve the problem of high implementation cost of tag security authentication circuits, and achieve the effects of low power consumption, tracking prevention and low cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example
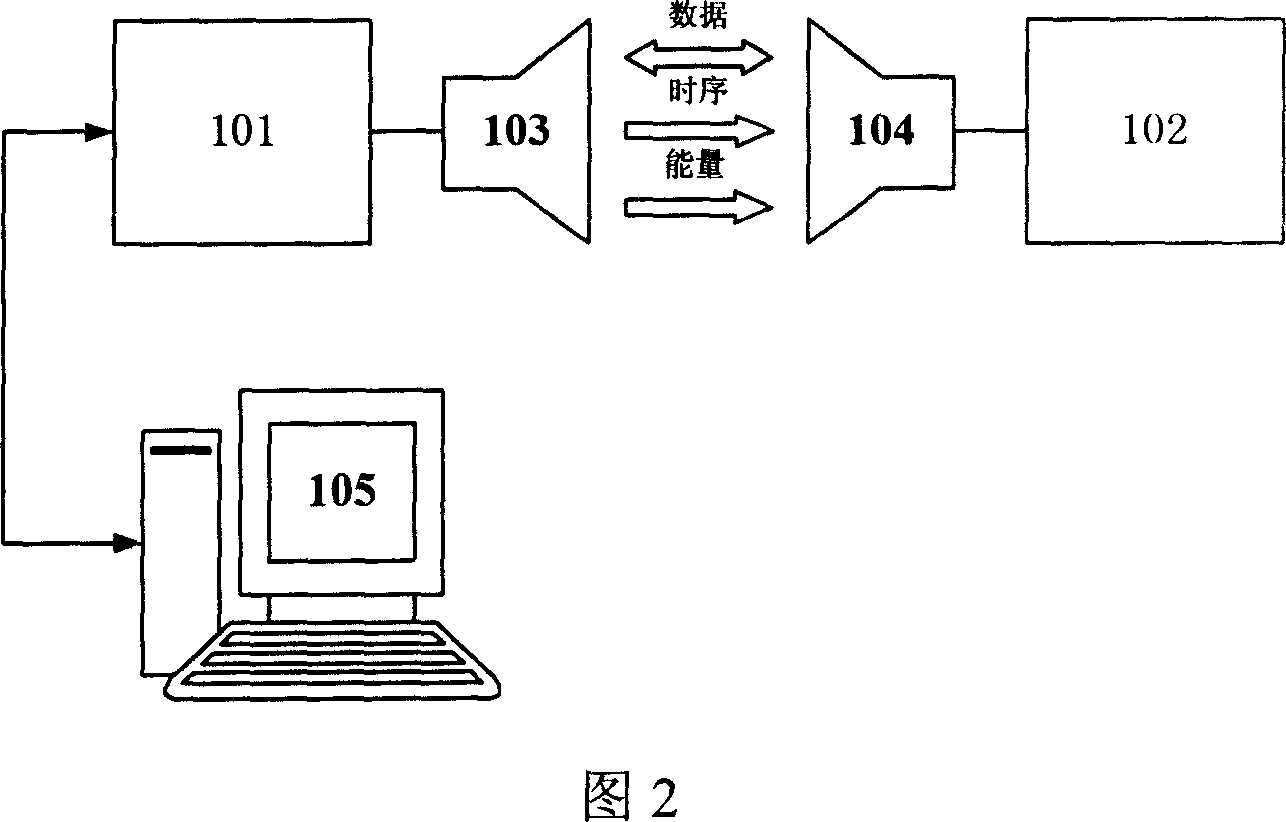
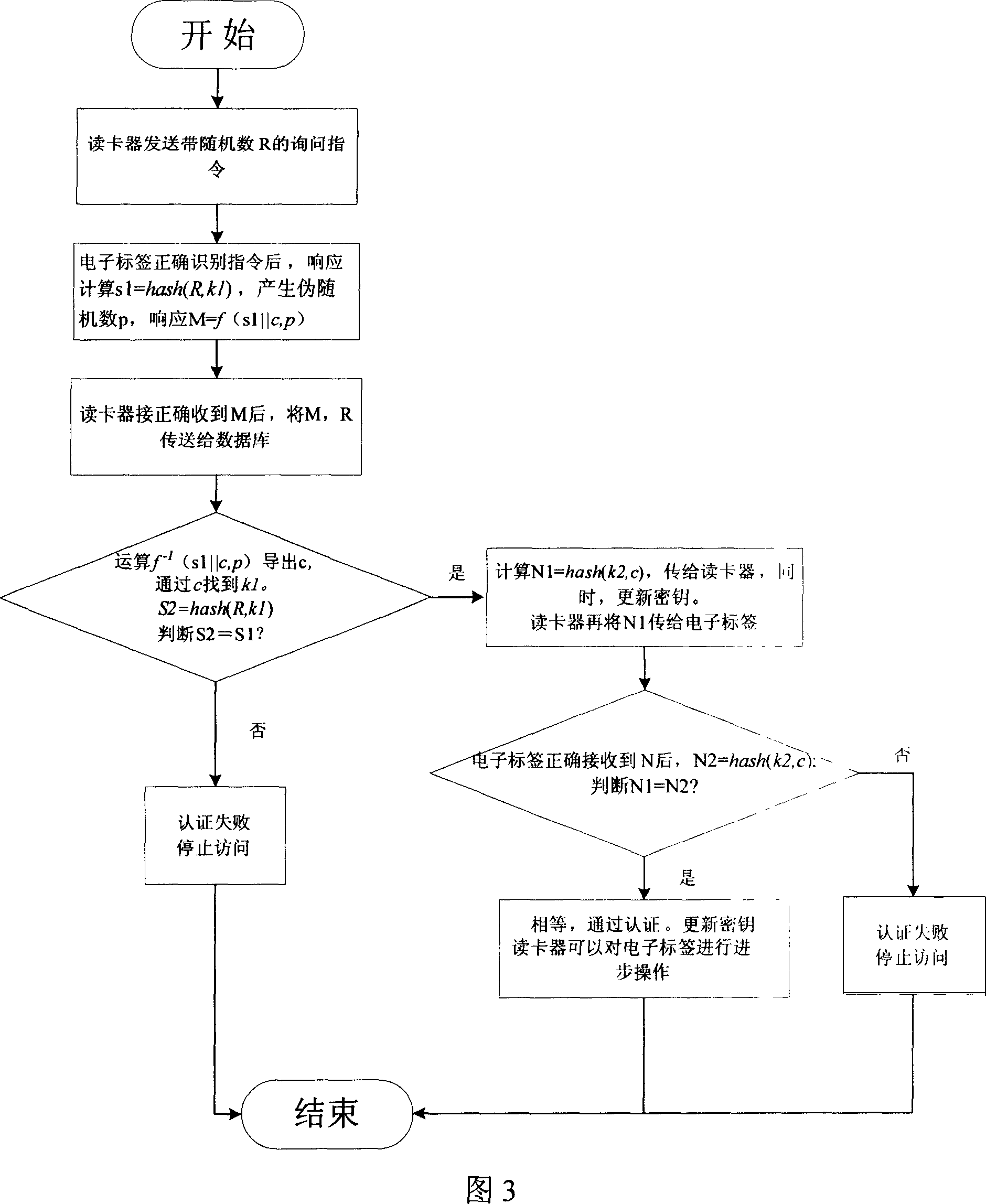
[0033] The specific implementation of this authentication method is described with reference to FIG. 3 : the card reader in the handheld device has storage function and data calculation function, and the card reader 101 can be connected with the terminal PC105 in the fixed device. In this example, the card reader is set as a fixed device, and the authentication process is as follows:
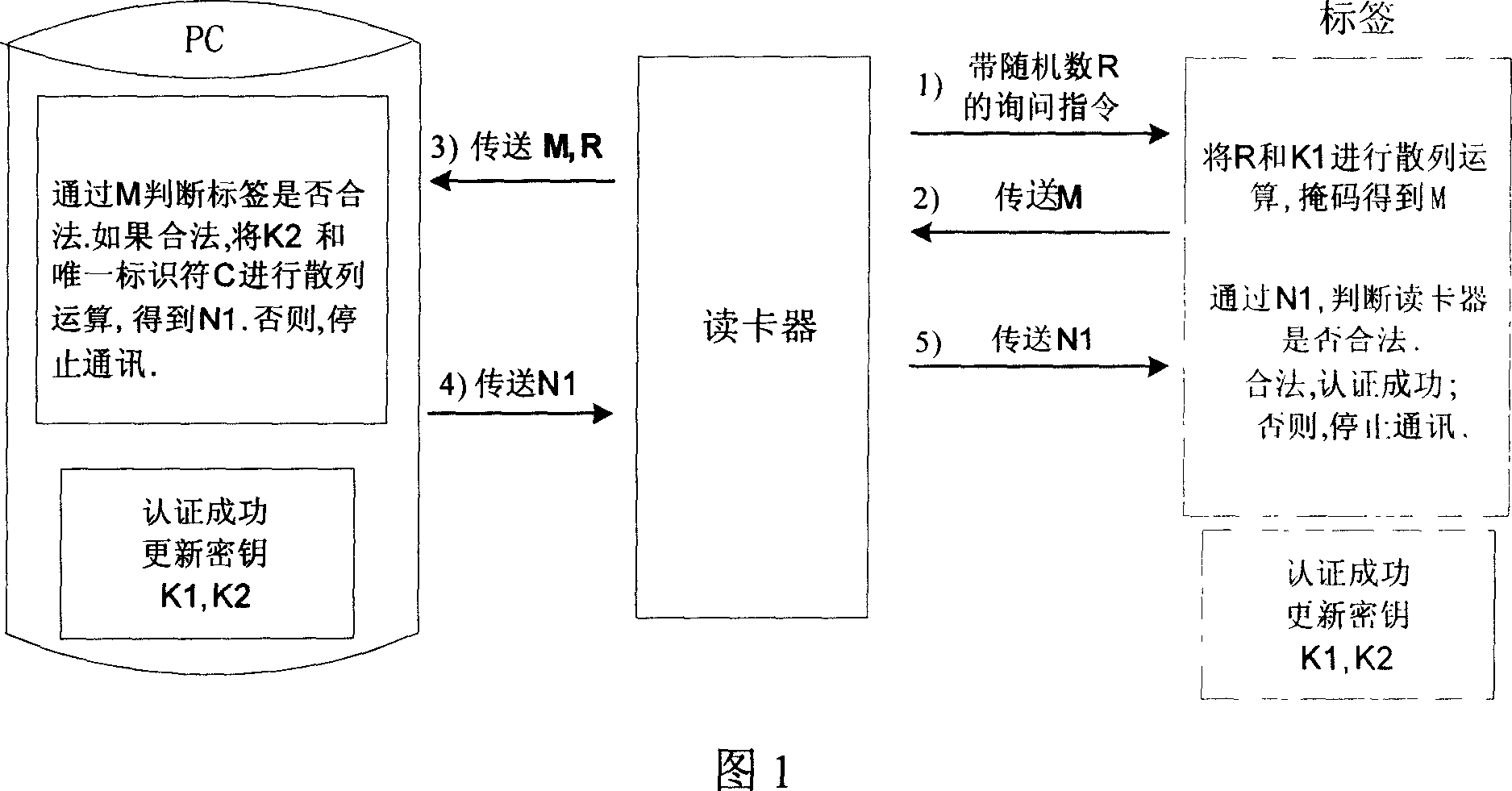
[0034] (1) First, the card reader sends an inquiry command with a pseudo-random number R.
[0035] (2) After the electronic tag receives the query command, it reads the key k1 from the EEPROM inside the tag chip, performs the operation S1=hash(R, k1), and returns M=f(s1∥c,p). Where f=(x, p) means to mask x with a random number p, and the symbol "∥" means a bit string.
[0036] (3) After the card reader correctly recognizes the information M of the electronic tag response through the anti-collision mechanism, it transmits M and the random number R to the terminal PC together.
[0037] (4) The t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com