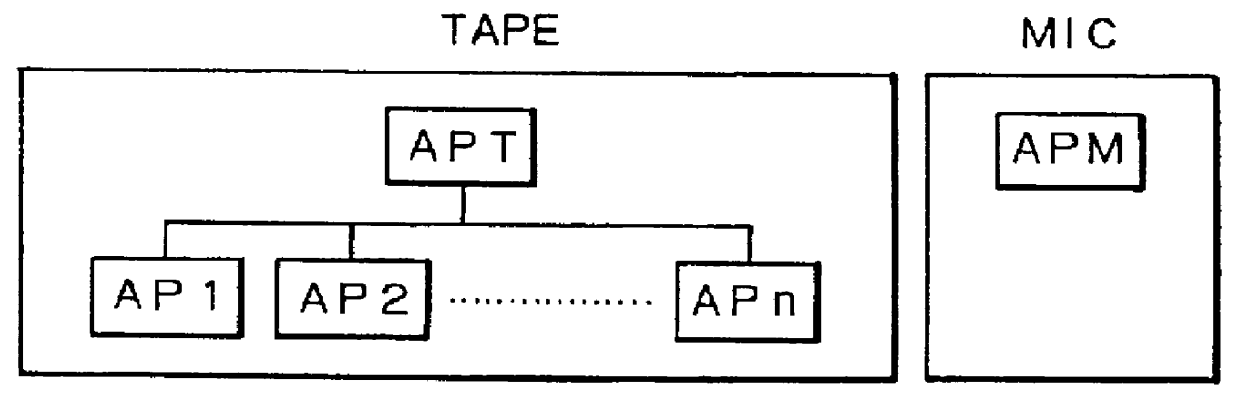
Patents
Literature
349results about How to "Secure performance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
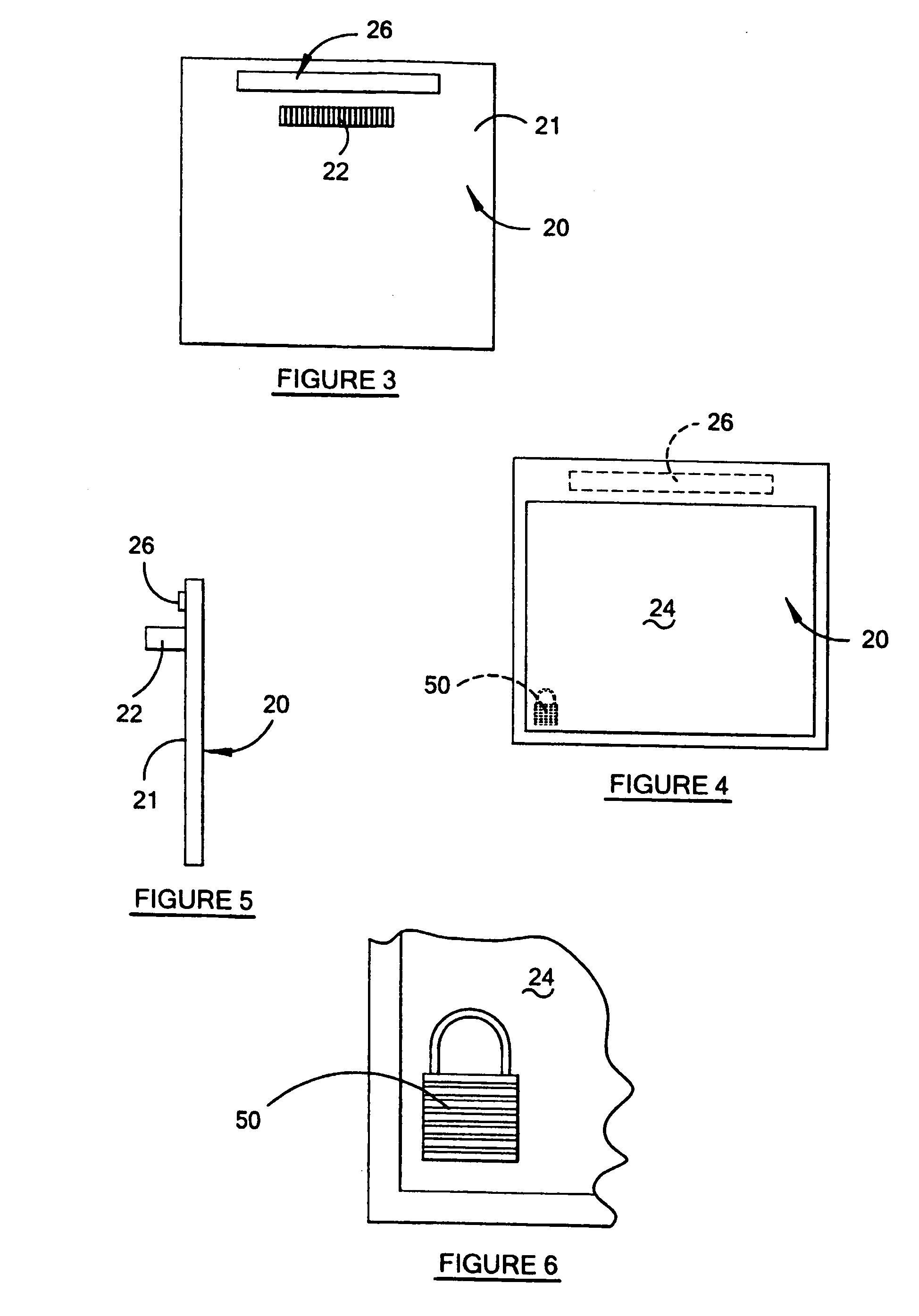
Semiconductor device and fabrication method for the same
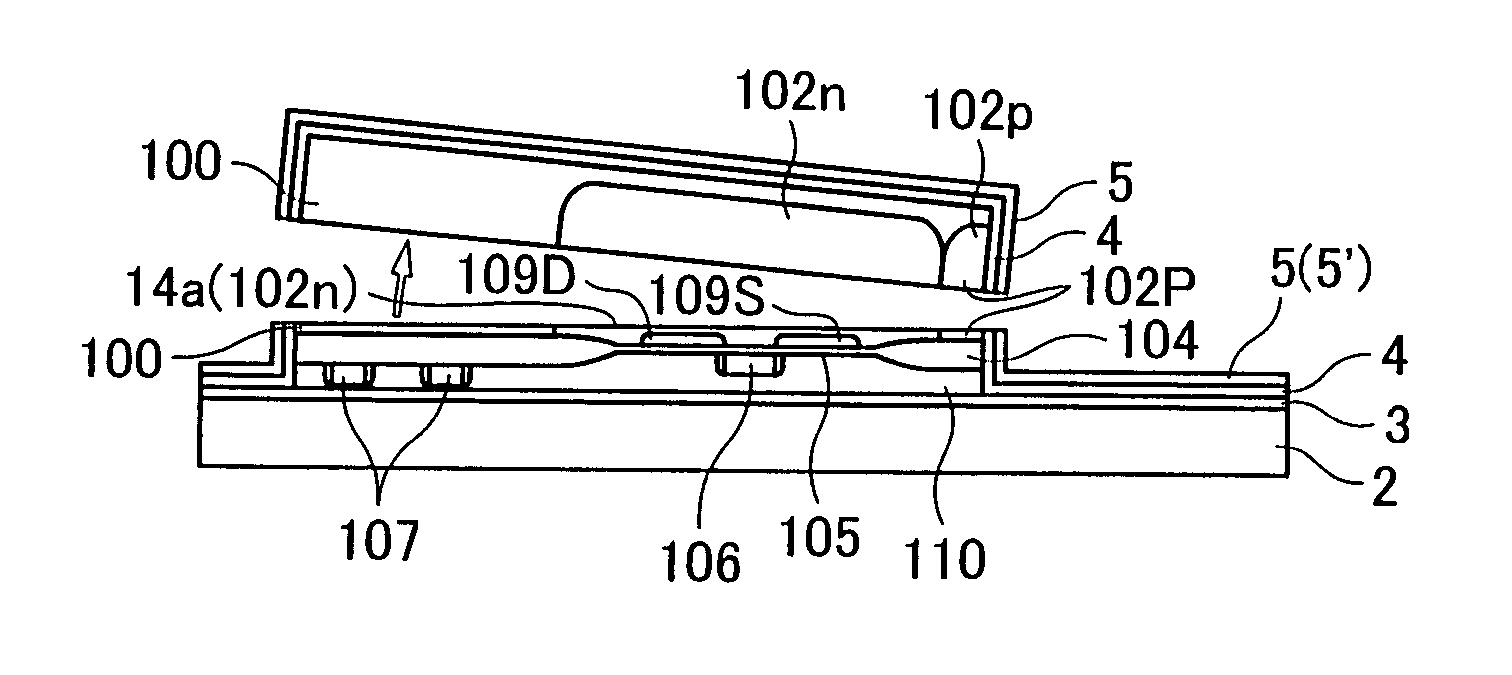
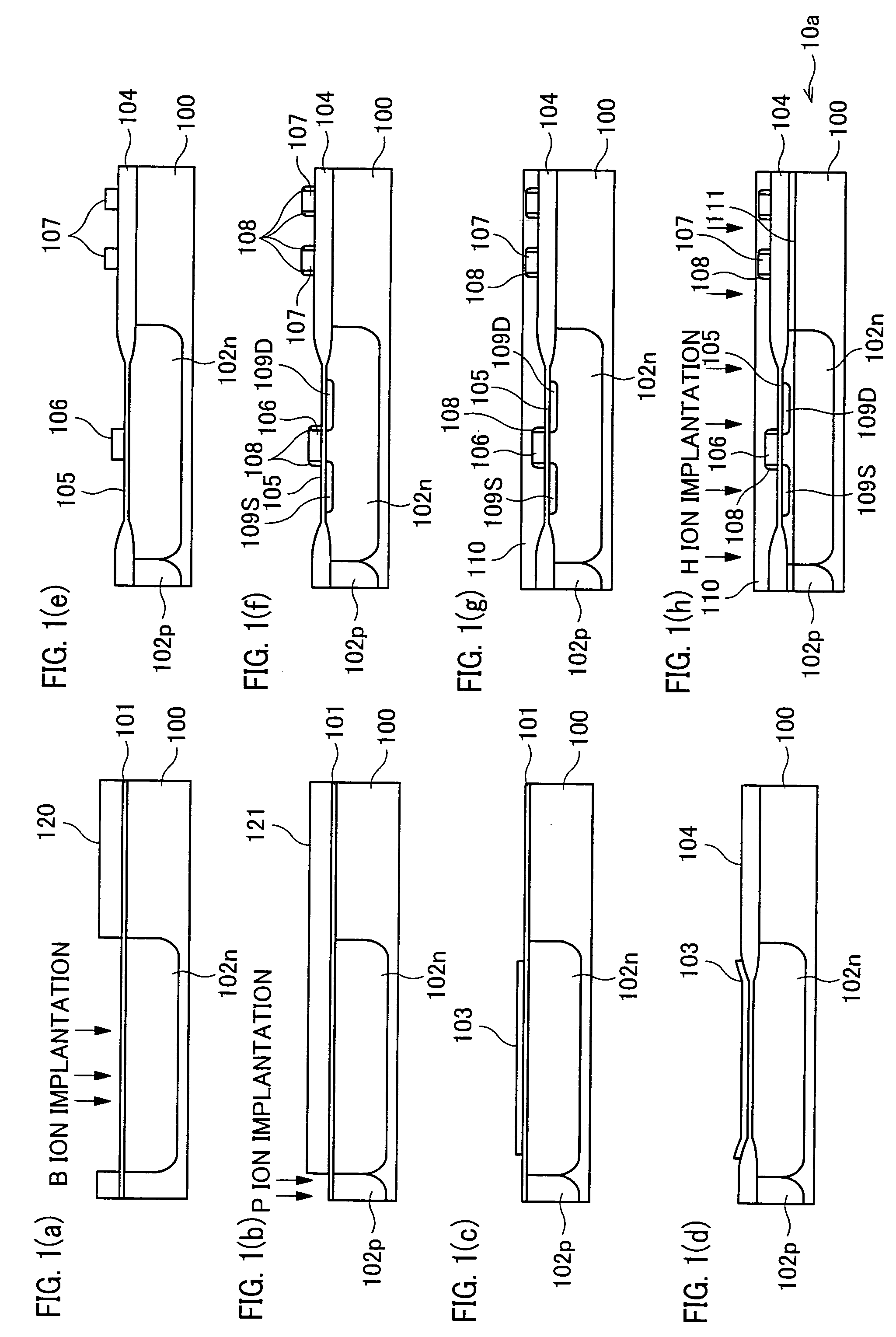
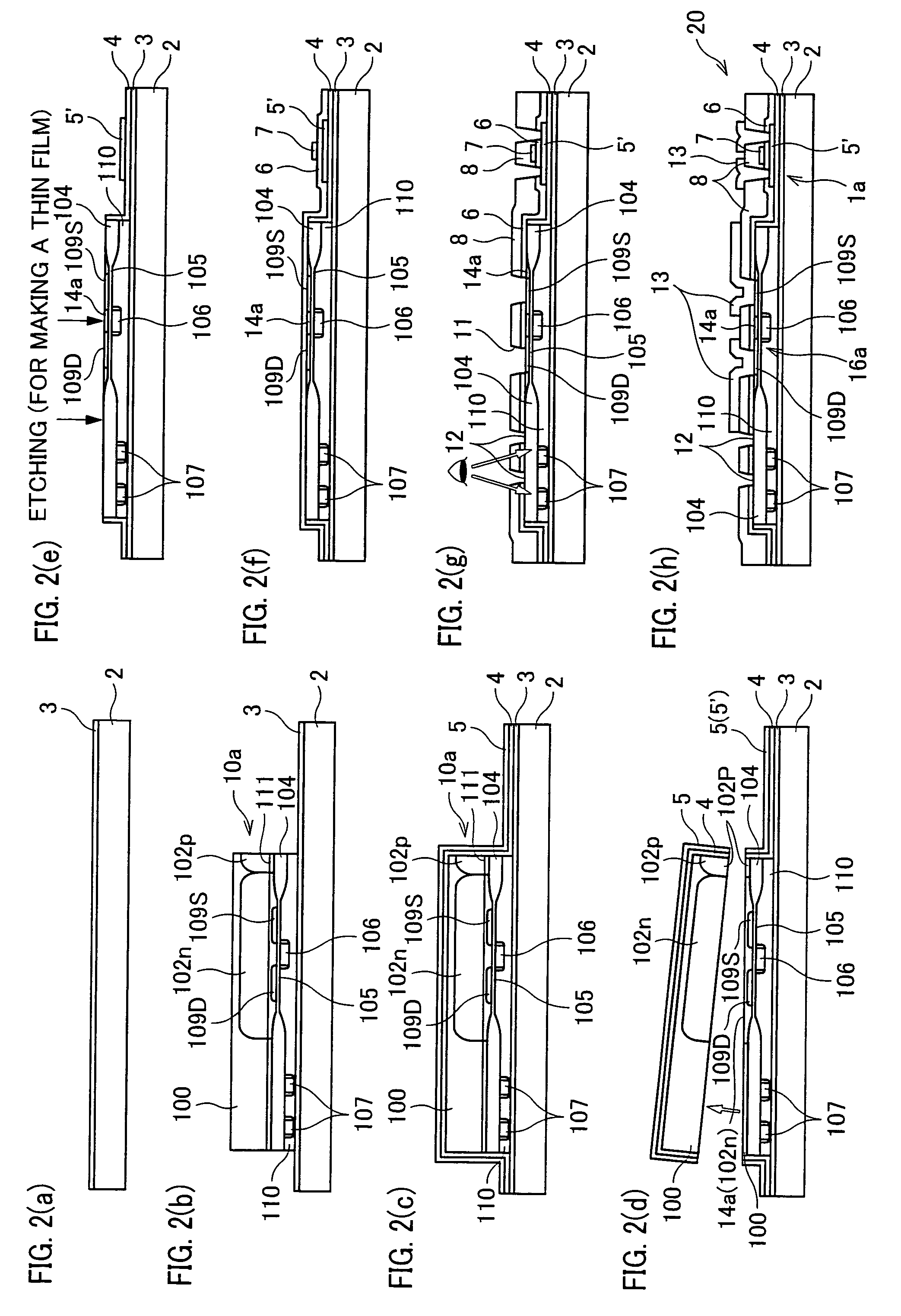
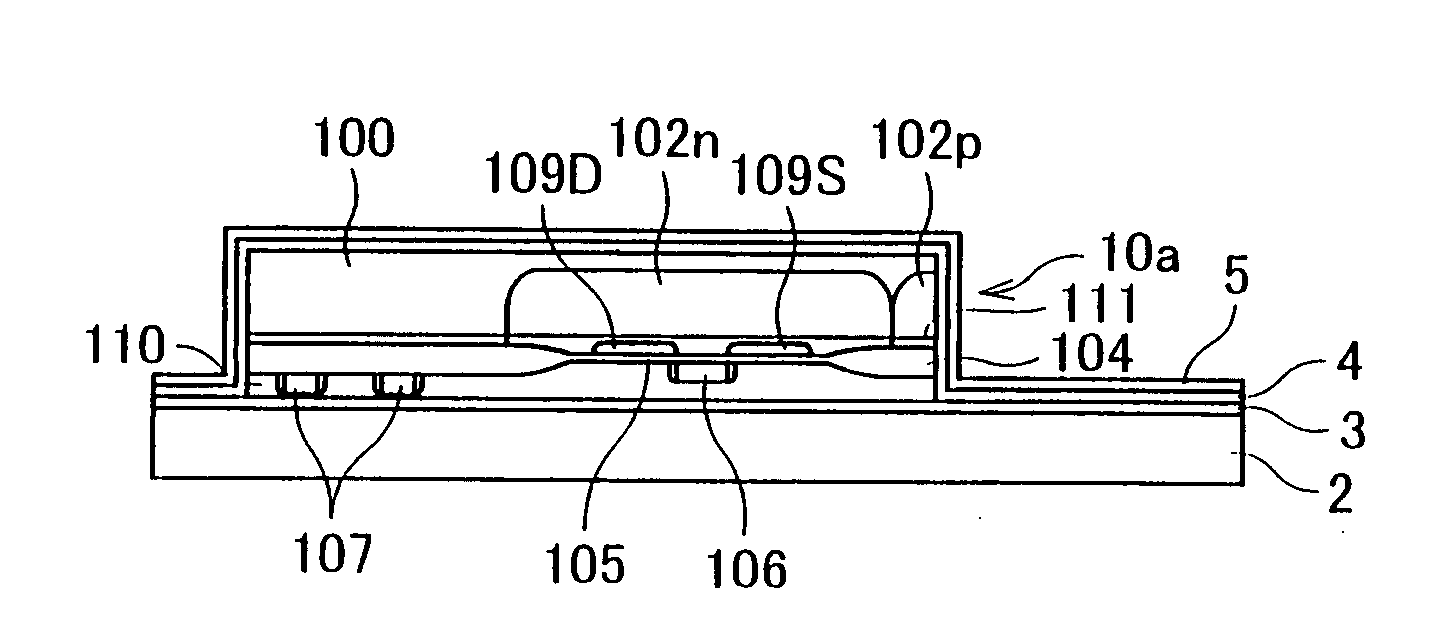
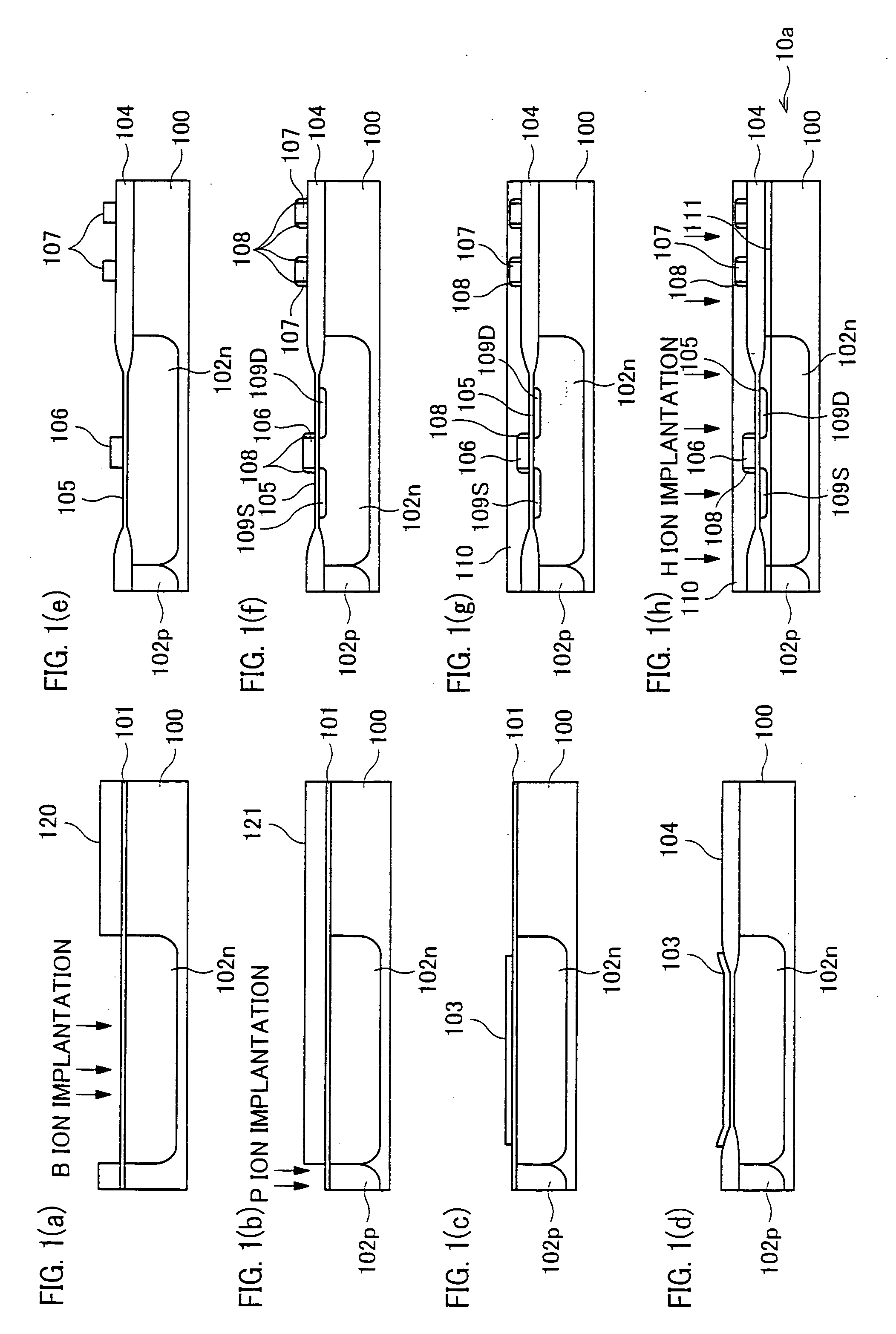
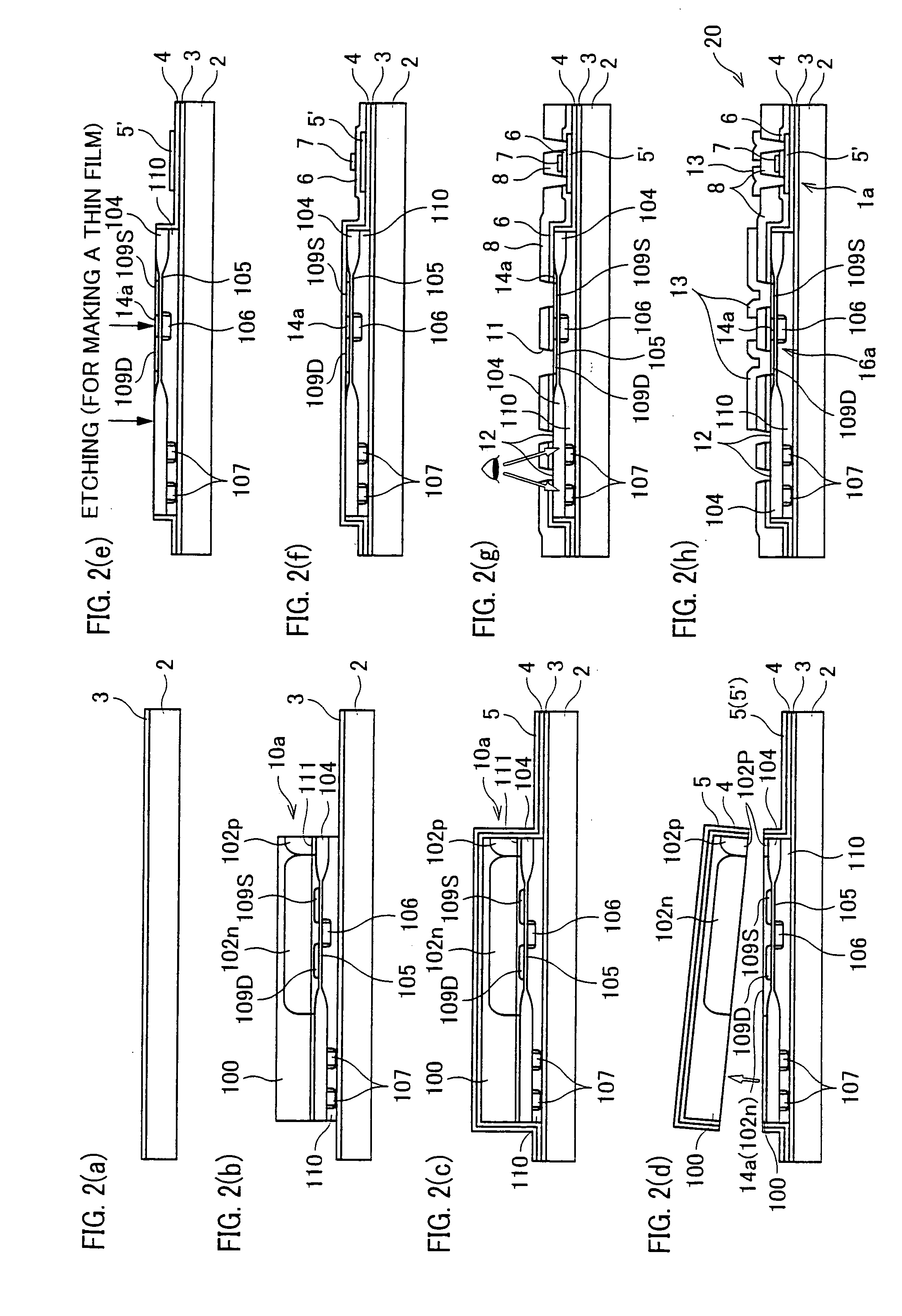
InactiveUS7205204B2Secure performanceImprove reliabilityTransistorSemiconductor/solid-state device detailsLOCOSSingle crystal
In a semiconductor device including a monocrystalline thin film transistor 16a that has been formed on a monocrystalline Si wafer 100 and then is transferred to a insulating substrate 2, LOCOS oxidization is performed with respect to the element-isolation region of the monocrystalline Si wafer 100 so as to create a field oxide film (SiO2 film) 104, and a marker 107 is formed on the field oxide film 104. With this structure, alignment of components may be performed based on a gate electrode 106 upon or after the transfer step.
Owner:SHARP KK
Semiconductor device and fabrication method for the same
InactiveUS20070108523A1Secure performanceImprove reliabilityTransistorSemiconductor/solid-state device detailsDevice materialLOCOS
In a semiconductor device including a monocrystalline thin film transistor 16a that has been formed on a monocrystalline Si wafer 100 and then is transferred to a insulating substrate 2, LOCOS oxidization is performed with respect to the element-isolation region of the monocrystalline Si wafer 100 so as to create a field oxide film (SiO2 film) 104, and a marker 107 is formed on the field oxide film 104. With this structure, alignment of components may be performed based on a gate electrode 106 upon or after the transfer step.
Owner:SHARP KK
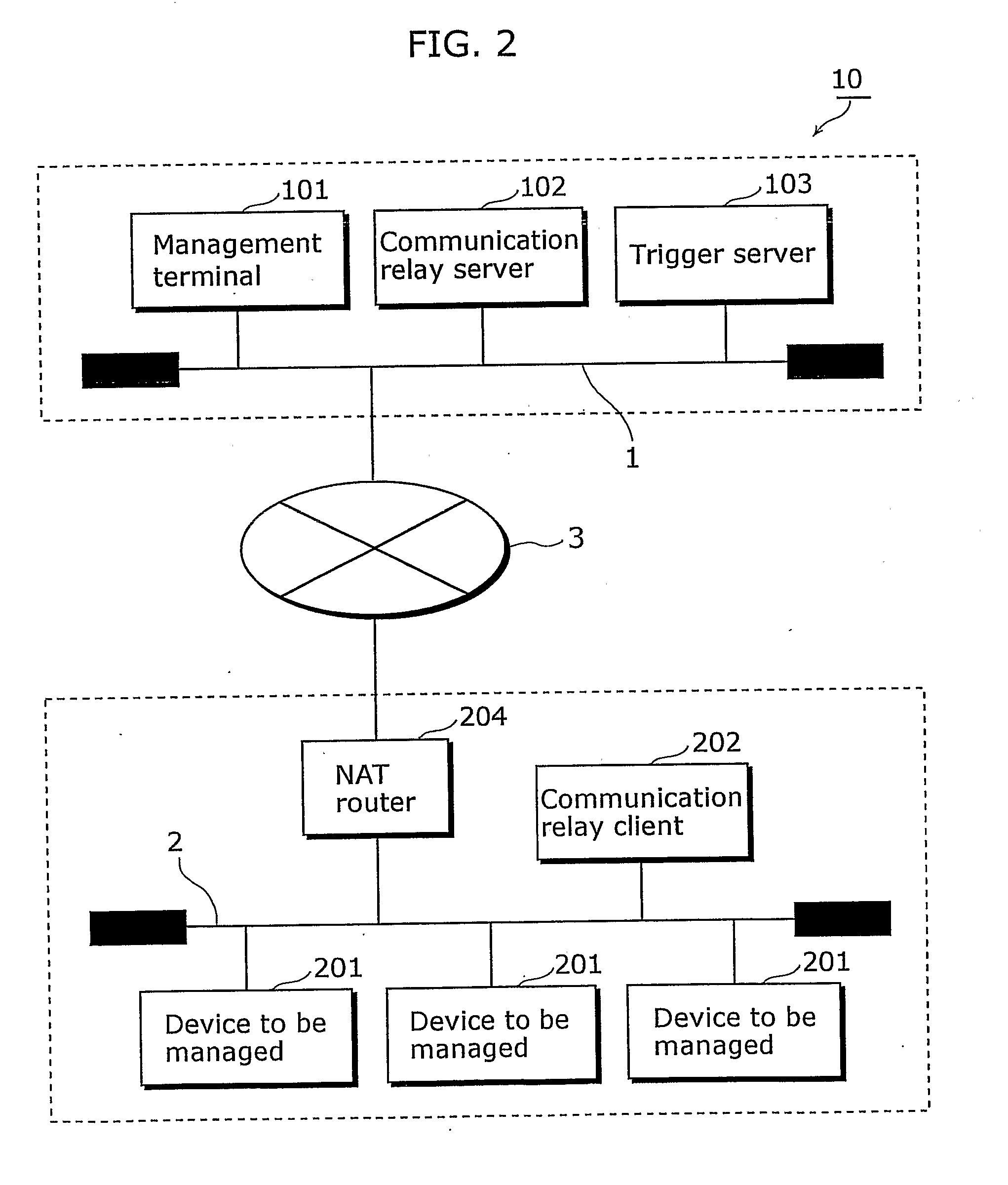
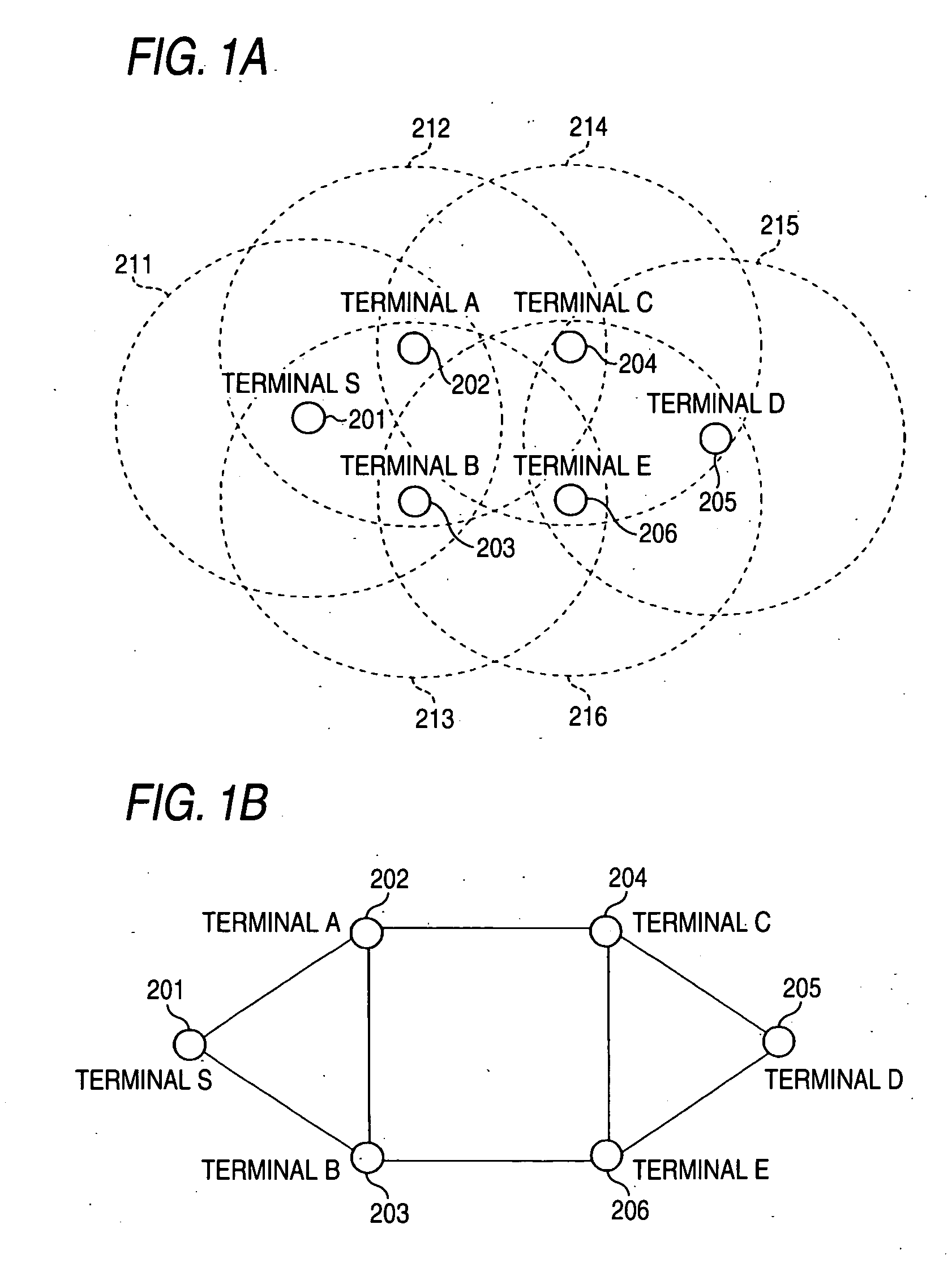
Communication network system and communication apparatus
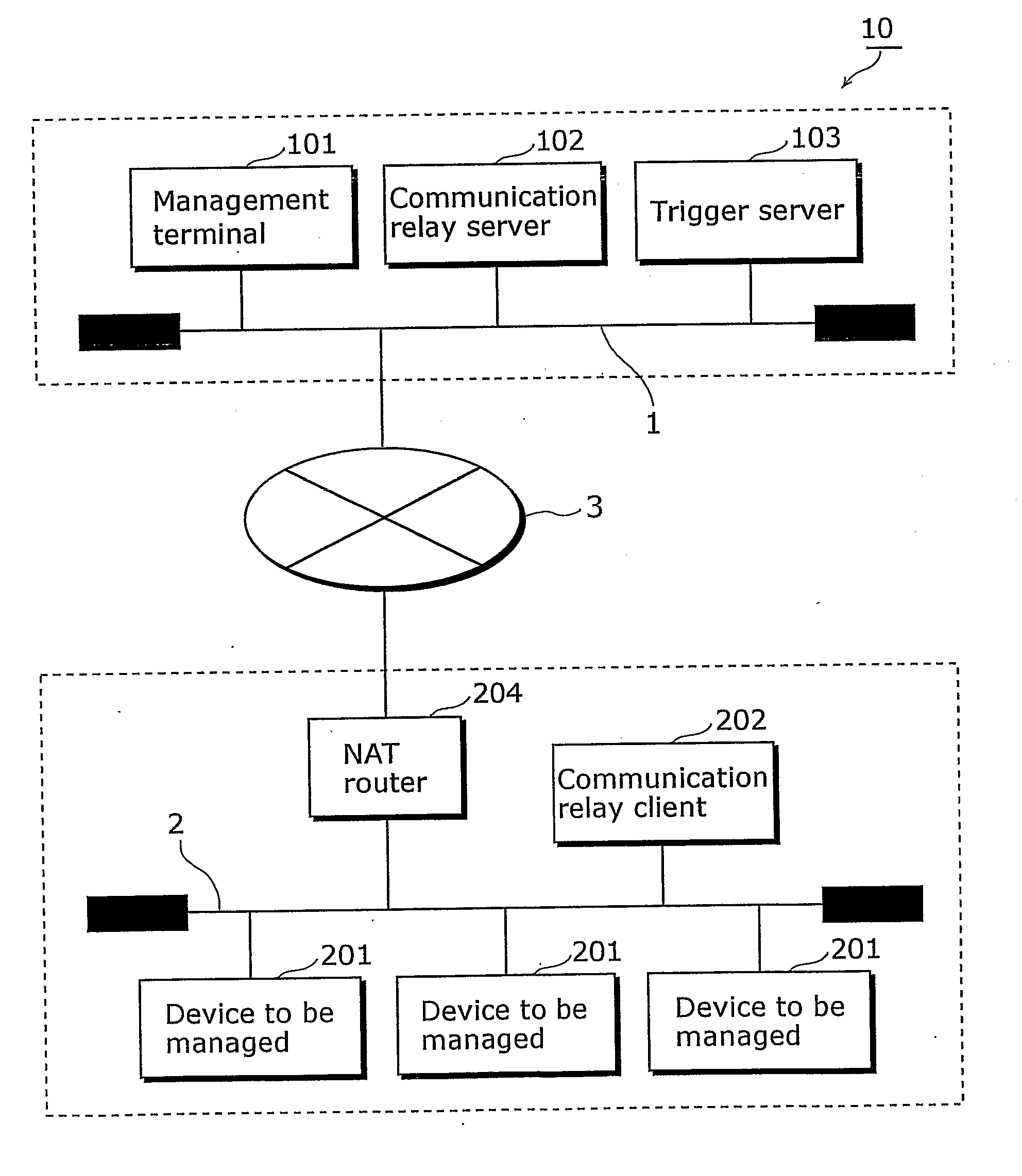
InactiveUS20070147419A1Secure performanceSpecial service provision for substationTime-division multiplexNetwork onNetworked system
The present invention provides a communication network system in which communication can be securely performed via a global network from an existing terminal apparatus to an existing device connected to a local network without needing a special gateway function in a router and without performing a special setting in the router. In the communication network system (10), a communication relay client (202) performs polling on a management center network (1) via a NAT router (204); a communication relay server (102) converts a packet transmitted from a management terminal (101); and the communication relay client (202) receives the converted packet as a response to the polling via the NAT router (204) from the side of the management center network (1). The communication relay client (202) converts the converted packet to the original packet, and transmits the original packet to a device to be managed (201).
Owner:PANASONIC CORP
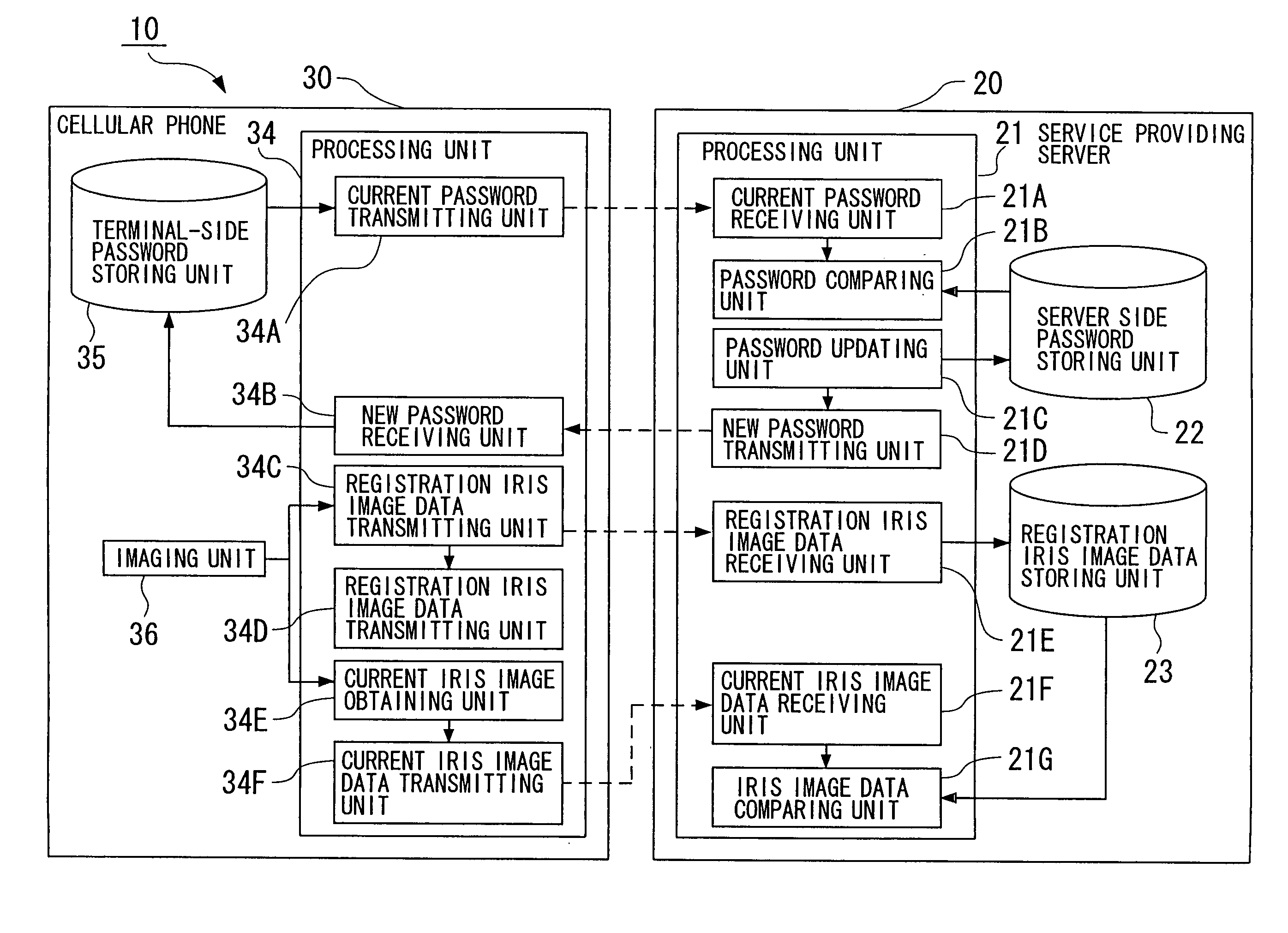
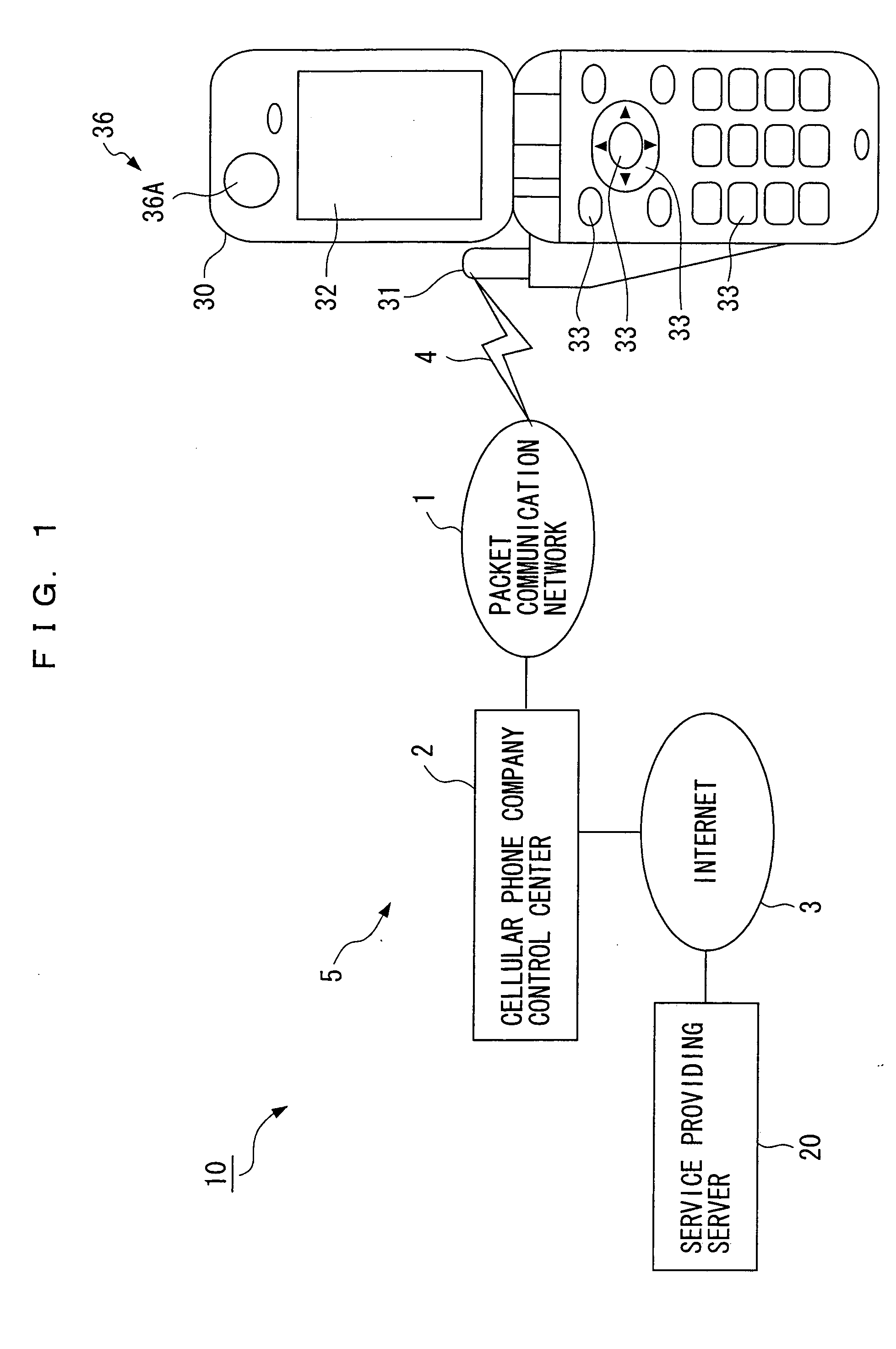
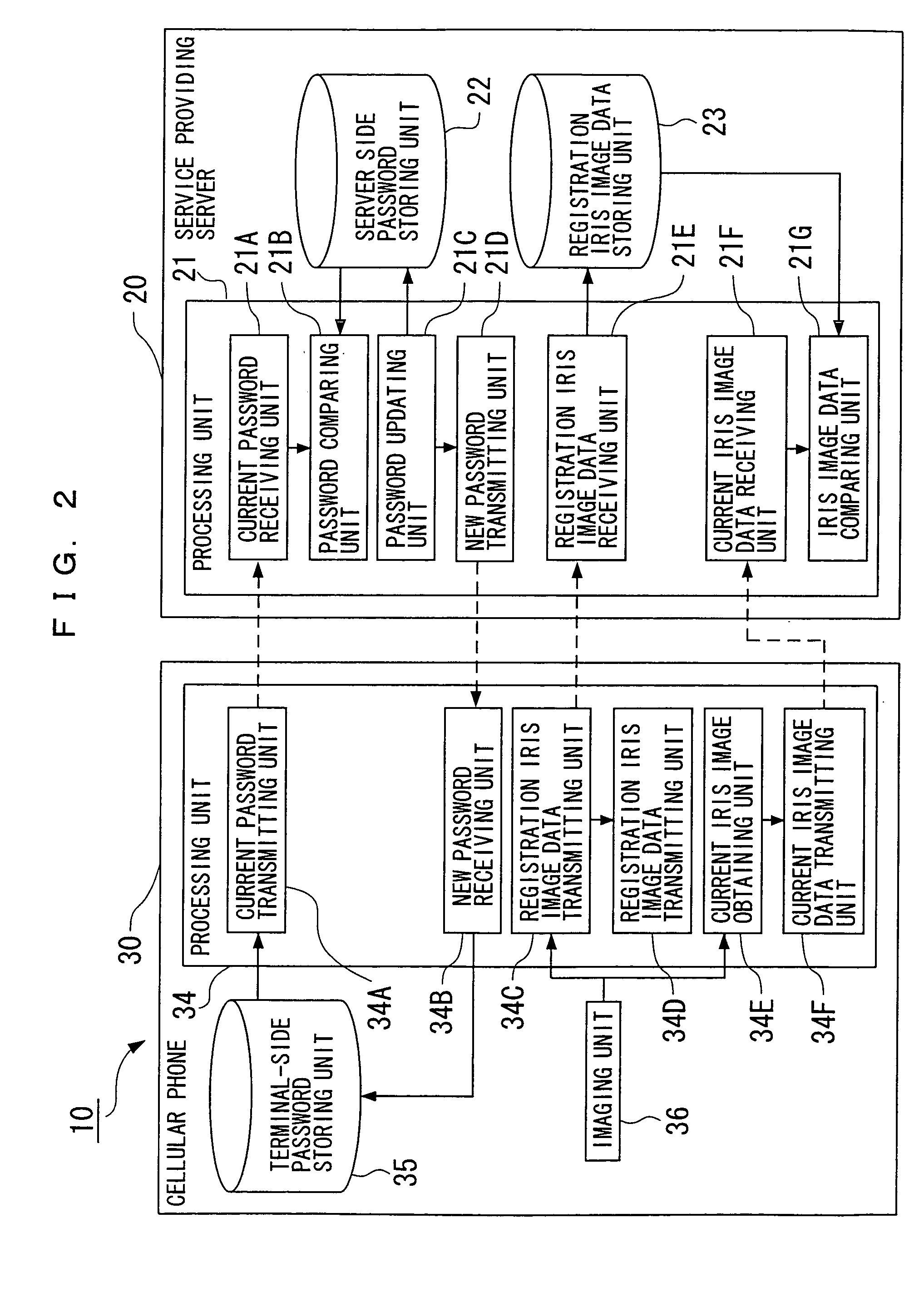
User authentication method and system, information terminal device and service providing server, subject identification method and system, correspondence confirmation method and system, object confirmation method and system, and program products for them
InactiveUS20050210267A1Secure performanceAvoid accessComputer security arrangementsSecret communicationUser authenticationSubject specific
An object of the present invention is to provide a user authentication method and system, an information terminal device and a service providing server, a subject identification method and system, a correspondence confirmation method and system, an object confirmation method and system, which are capable of assuring authentication and / or confirmation of a person, an animal and a plant, or an object and improving precision thereof, and program products for them. In order to perform user authentication when a user of an information terminal device 30 such as a cellular phone or the like receives a service from a service providing server 20 via a network, iris authentication is performed, and a password is automatically updated every time a service is provided to generate a new password to be used when a next service is provided, and the new password is stored in both the information terminal device 30 and the service providing server 20.
Owner:RIVERBELL
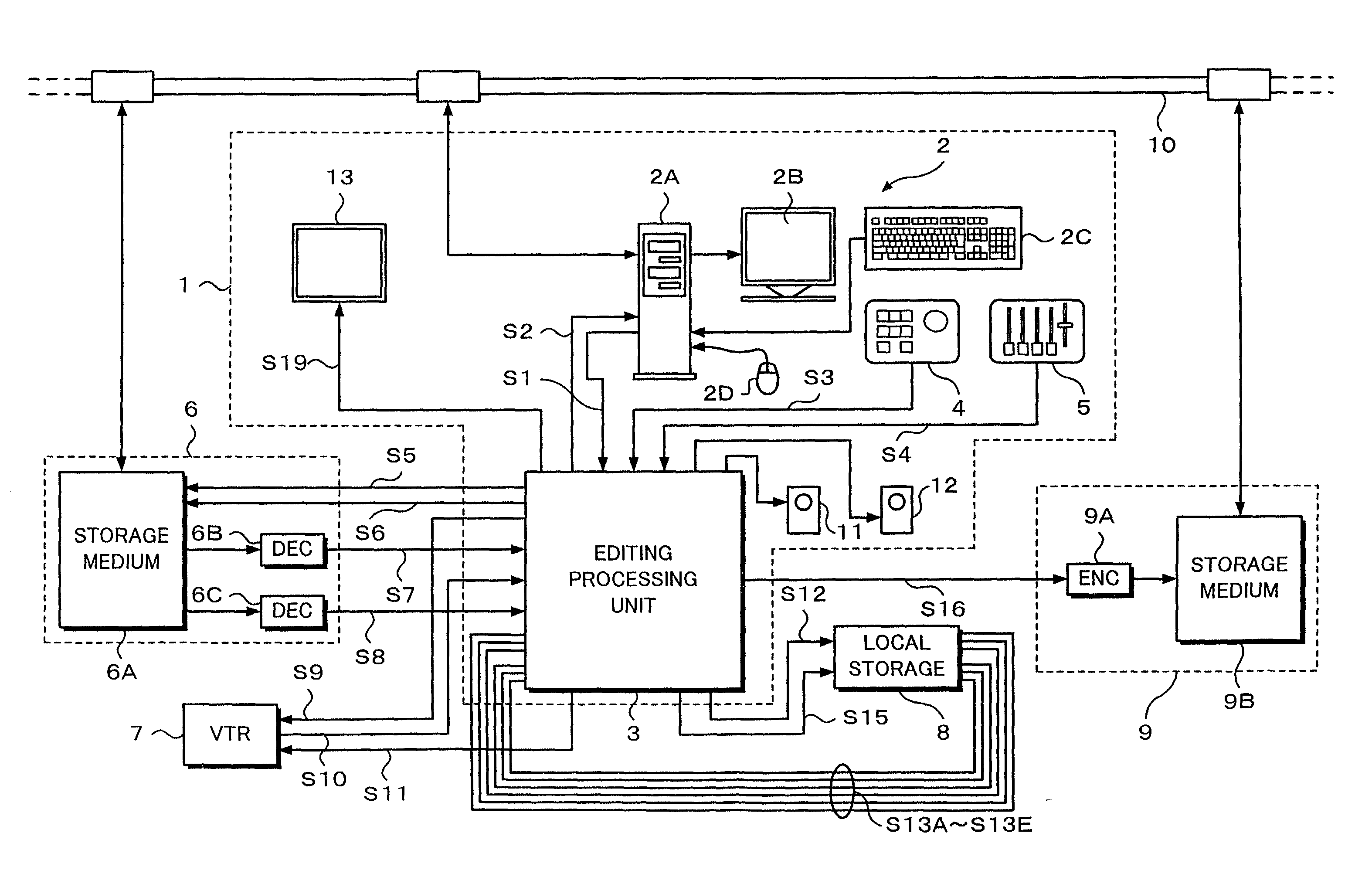
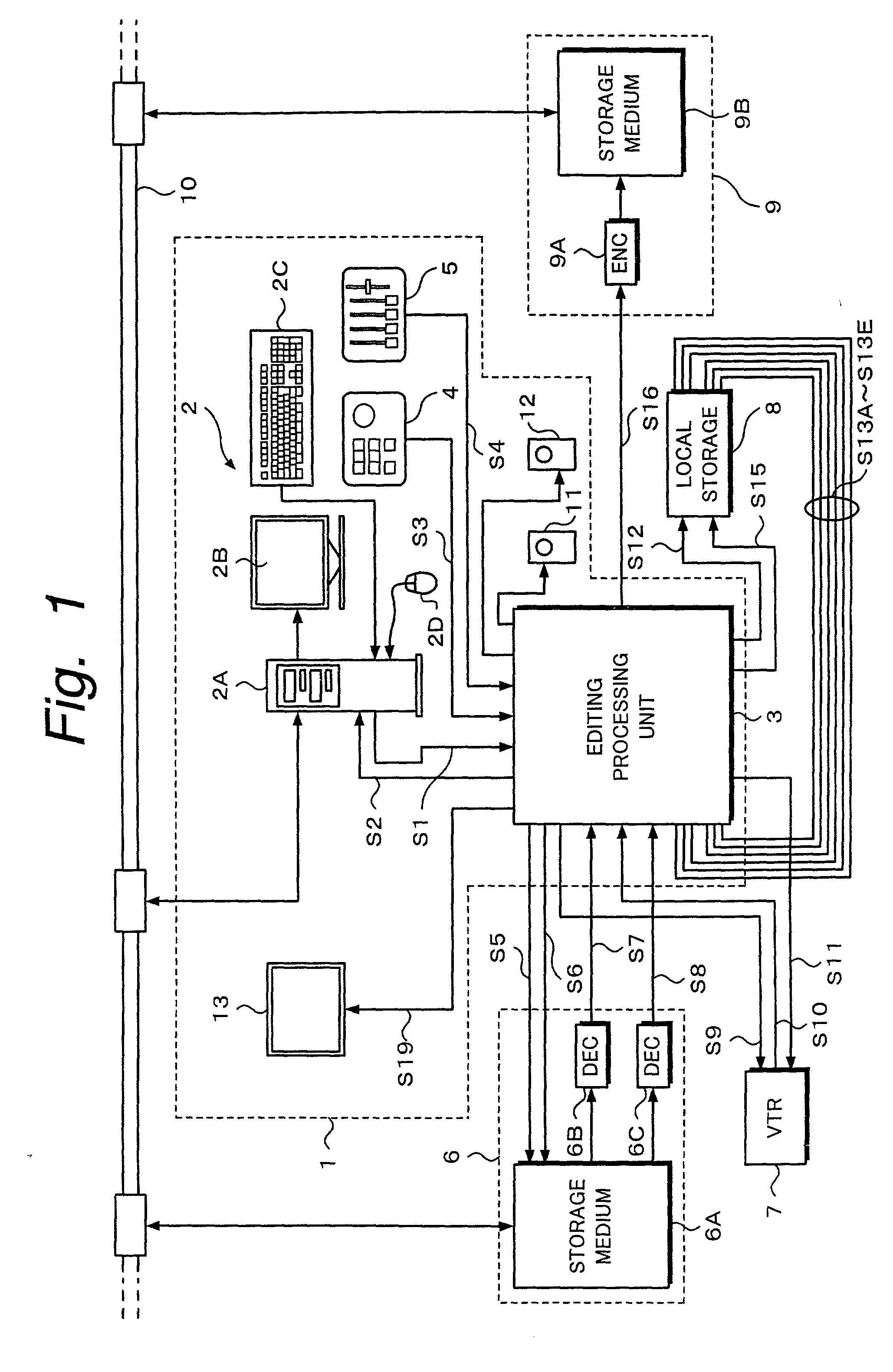
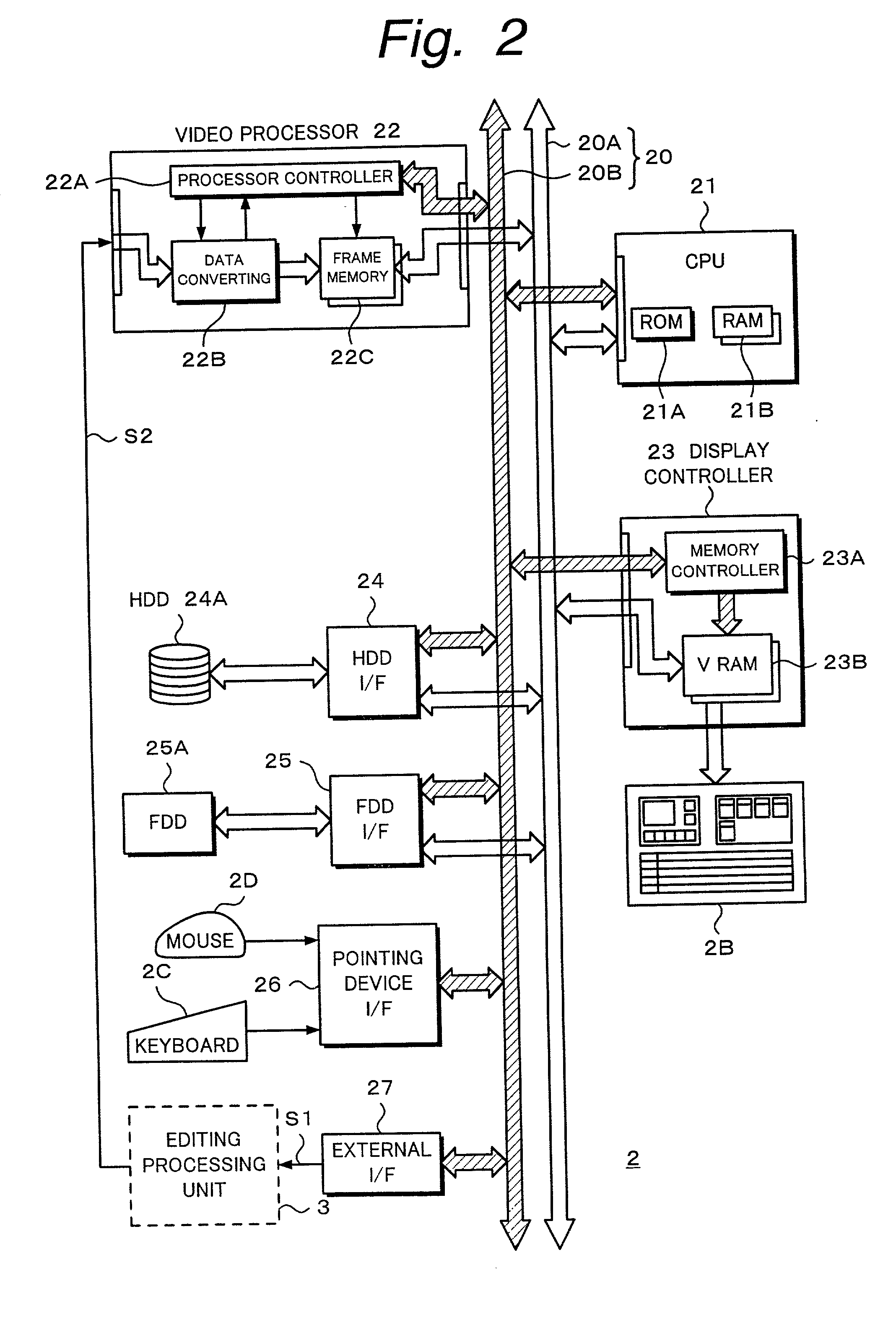
Editing device and editing method
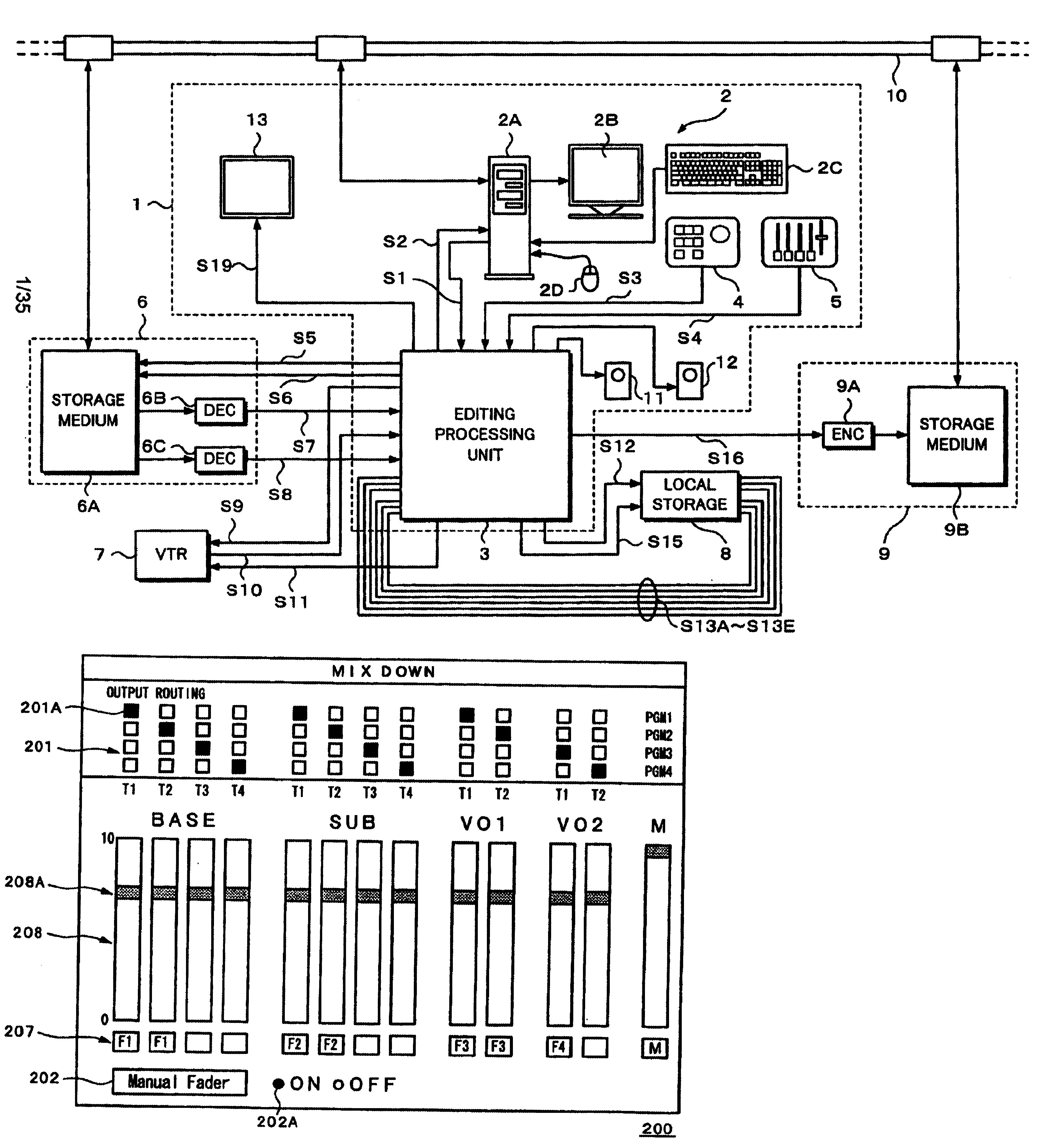
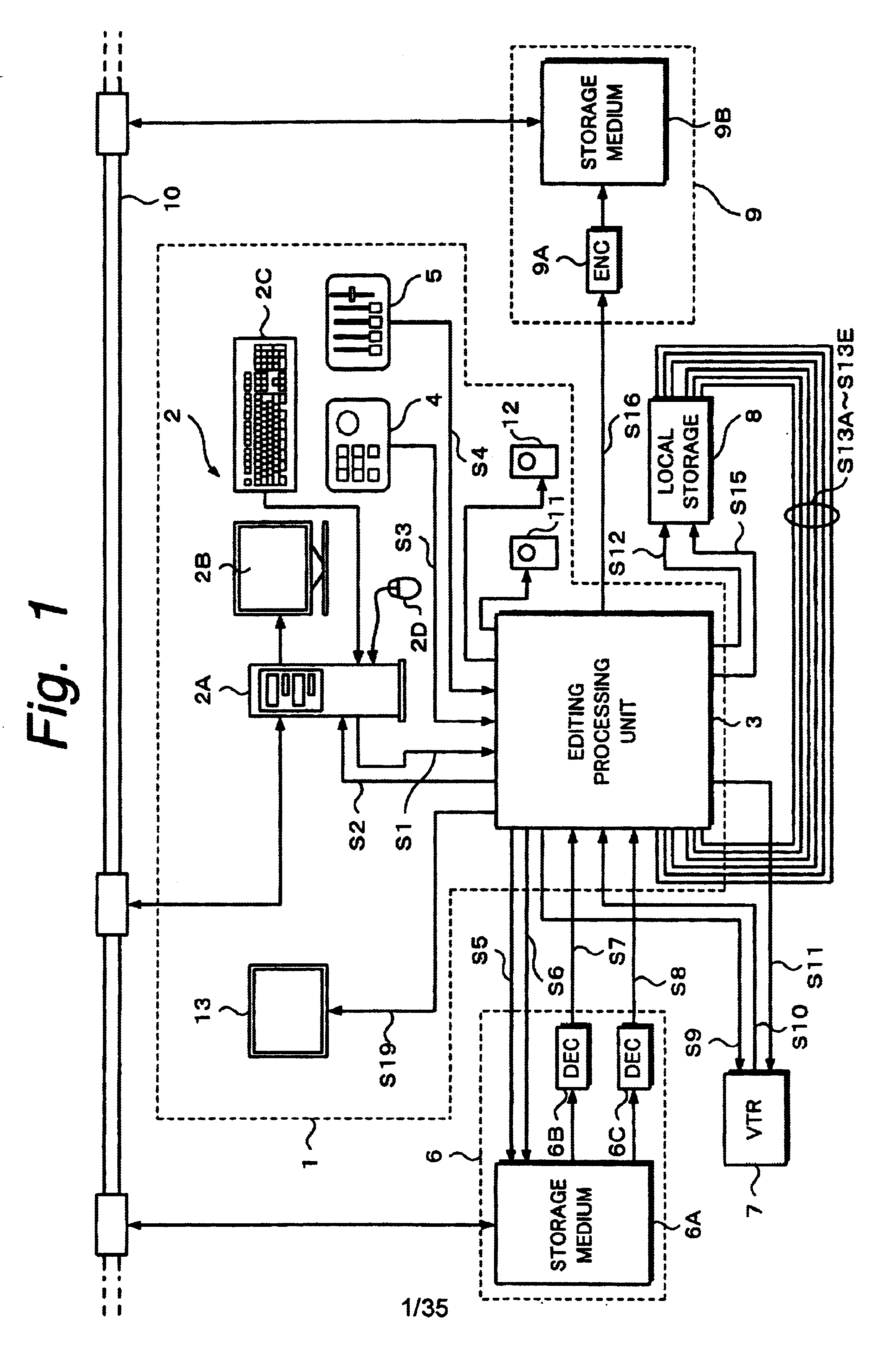
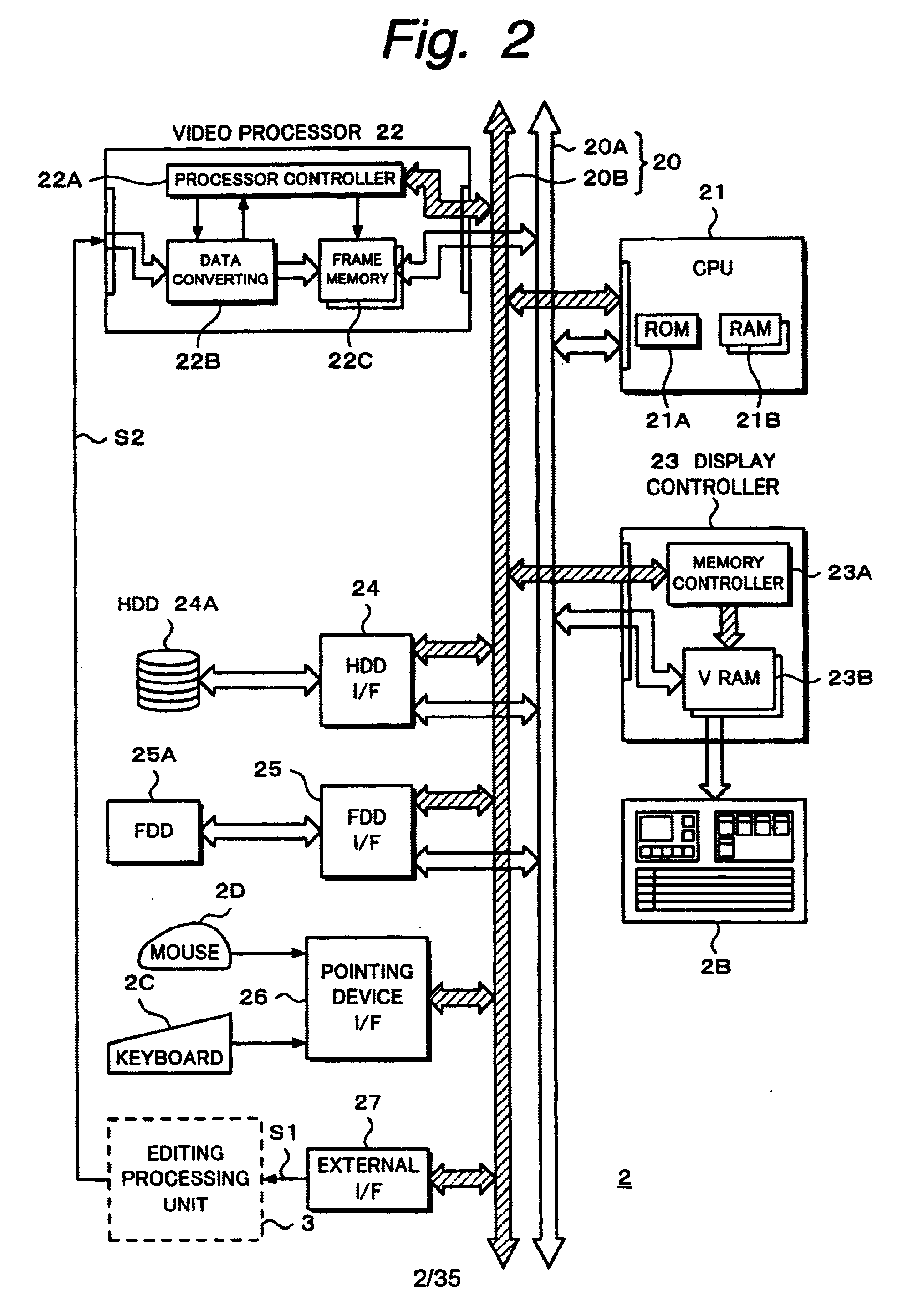
InactiveUS6674955B2Secure performanceRemove background noiseTelevision system detailsRedundant array of inexpensive disk systemsComputer graphics (images)Source material
An editing apparatus comprises an editing processing unit for processing a video signal and an audio signal supplied as source materials, and a computer for controlling the editing processing unit, wherein the computer comprises a controlling means for displaying a viewer window, a log window, and a program window on a display of the computer, the viewer window allowing the editing operator to decide an edit point while viewing a video image of a source material so as to produce an event, the log window displaying a clip image corresponding to an event that is set on the viewer window, the program window allowing the editing operator to arrange a plurality of events on a time line in a desired order so as to produce a program list, and wherein the controlling means displays an icon that represents by what source device each event arranged on the time line is produced.
Owner:SONY CORP
Safety and management of computing environments that may support unsafe components
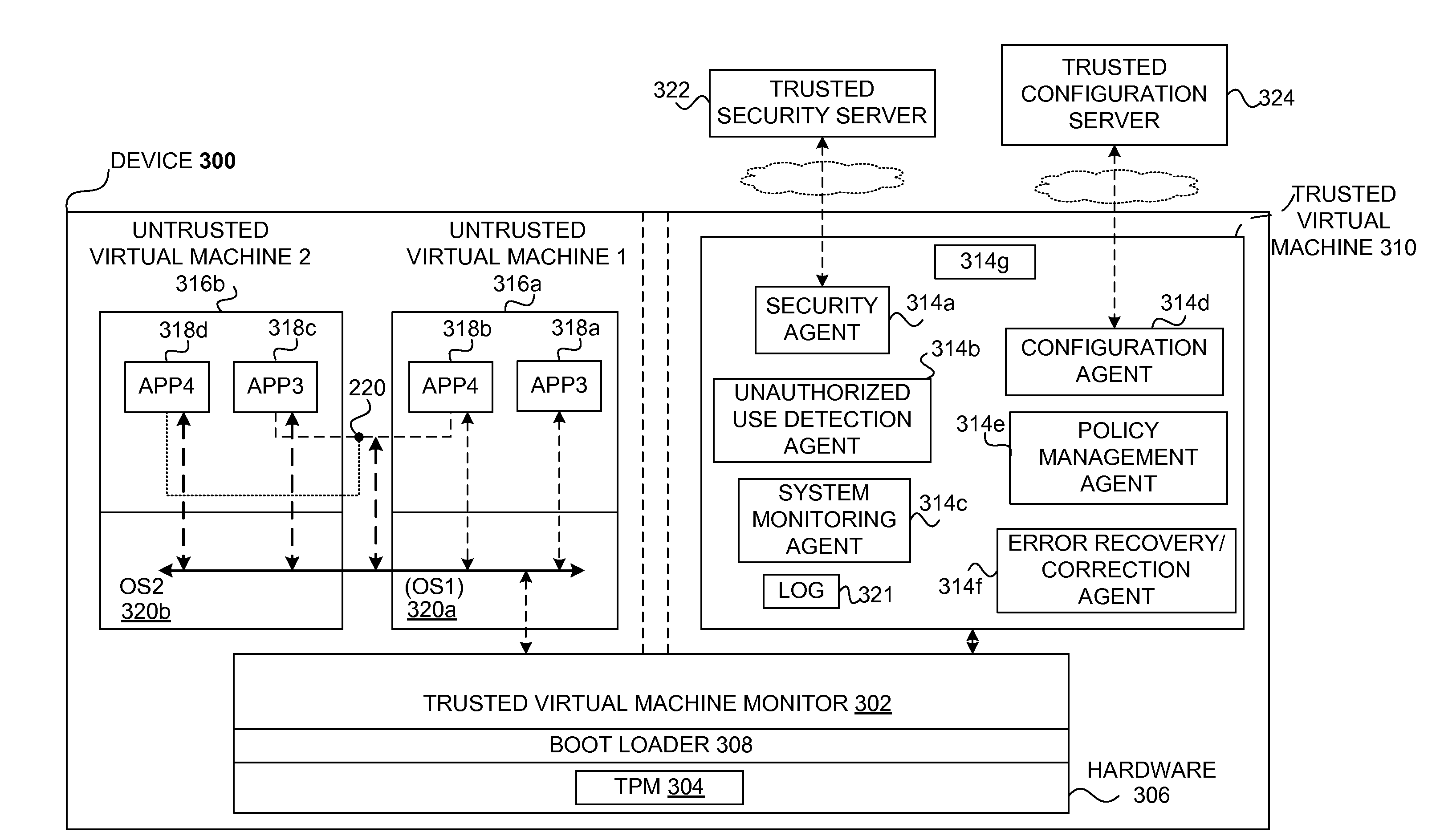
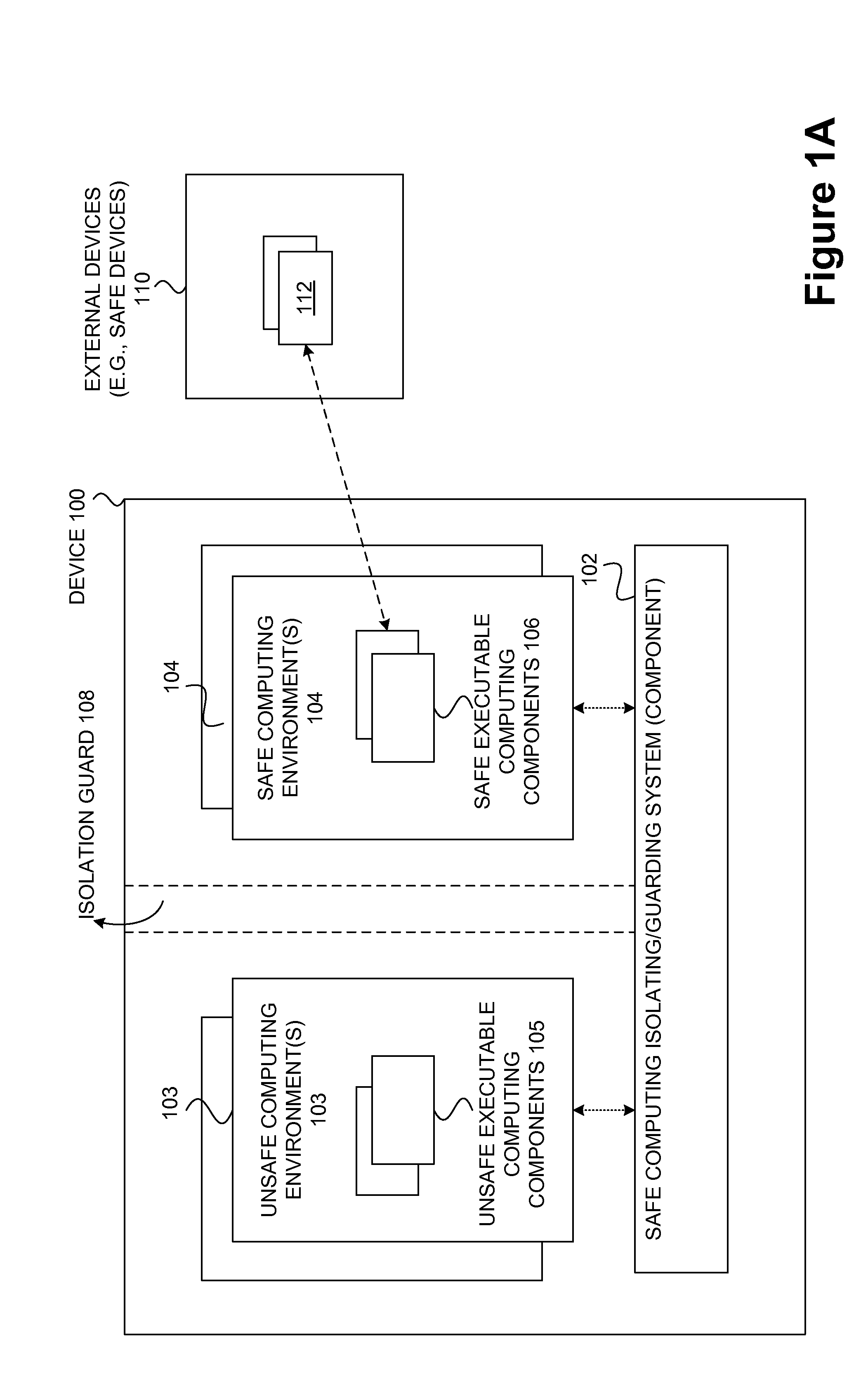
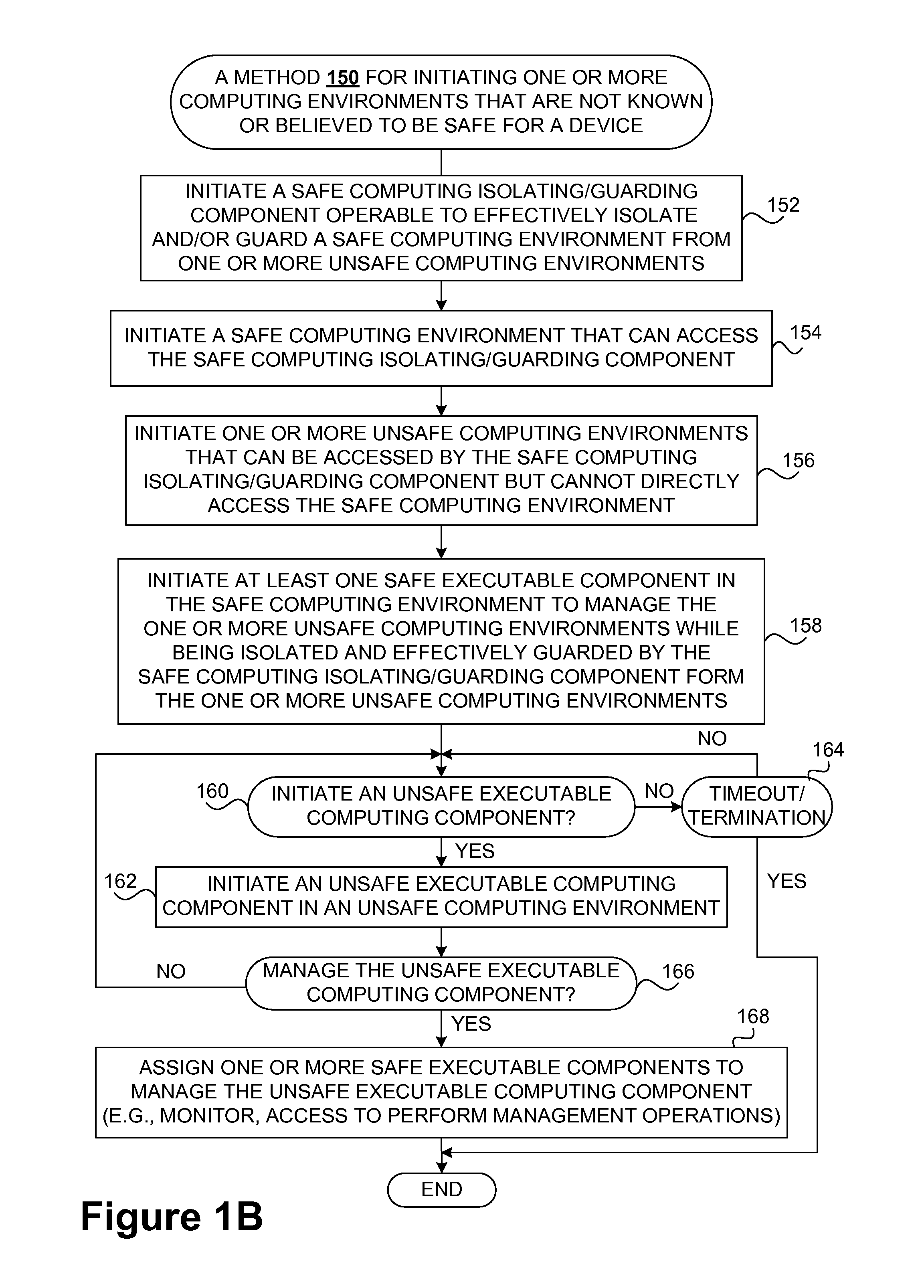
InactiveUS20090265756A1Effectively guardEffective isolationMemory loss protectionError detection/correctionTrusted componentsTrusted Computing
Techniques for managing and protecting computing environments are disclosed. A safe computing environment can be provided for ensuring the safety and / or management of a device. The safe computing environment can be secured by a safe component that isolates and protects it from unsafe computing environments which may also be operating. As a result, various security and management activities can be securely performed from a safe computing environment. A safe computing environment can, for example, be provided on a device as a safe virtual computing environment (e.g., a safe virtual machine) protected by a safe virtual computing monitor (e.g., a safe virtual machine monitor) from one or more other virtual computing environments that are not known or not believed to be safe for the device. It will also be appreciated that the safe components can, for example, be provided as trusted components for a device. As such, various trusted components (or agent) can operate in a trusted computing environment secured from interference by components that many not be trusted and perform various security and / or management tasks alone or in connection, for example, with other trusted components (e.g., trusted serves).
Owner:SAMSUNG ELECTRONICS CO LTD
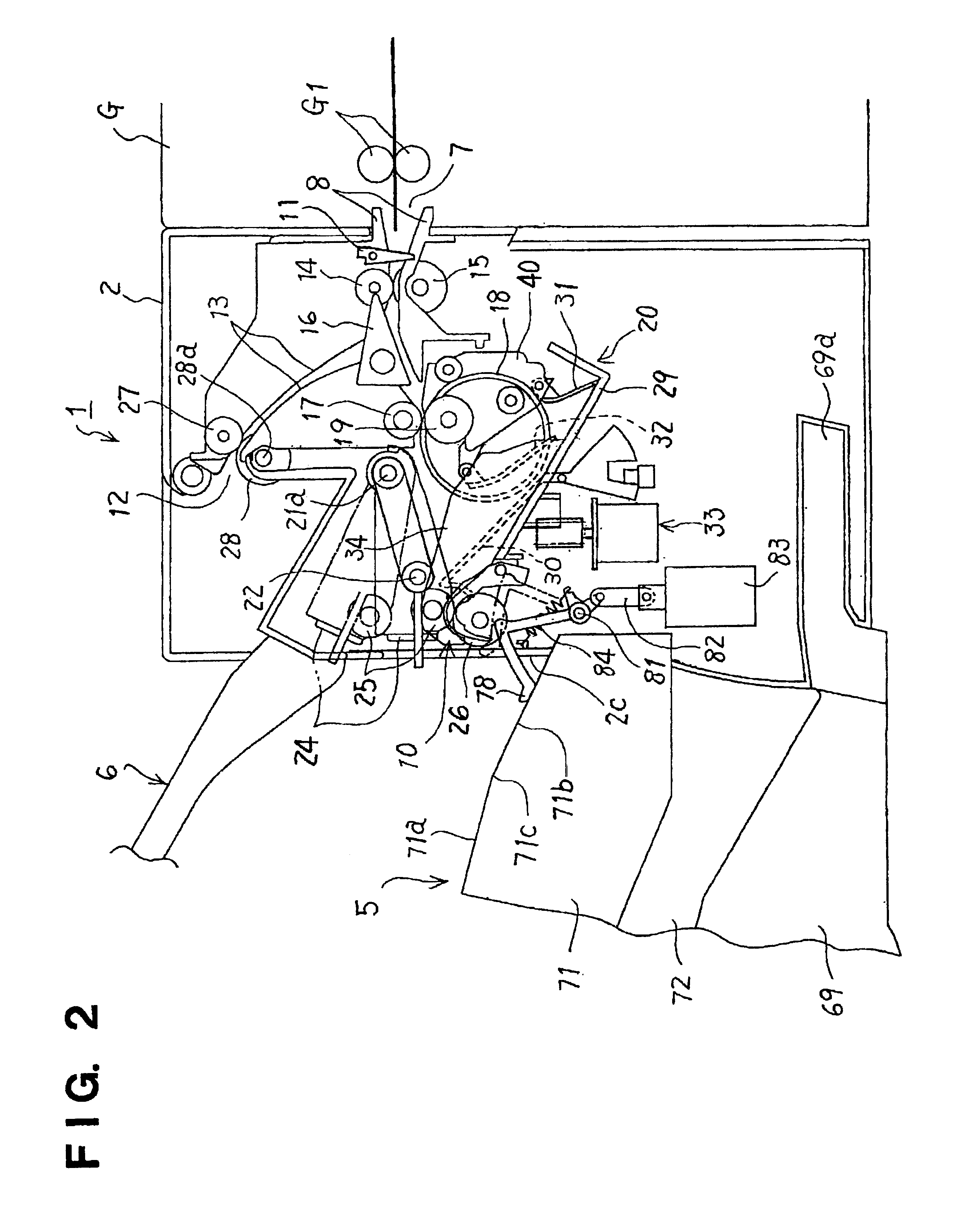
Sheet receiving apparatus
InactiveUS6412774B1Improve performanceAvoid unnecessaryFunction indicatorsPile receiversEngineeringSheet material
Owner:NISCA KK
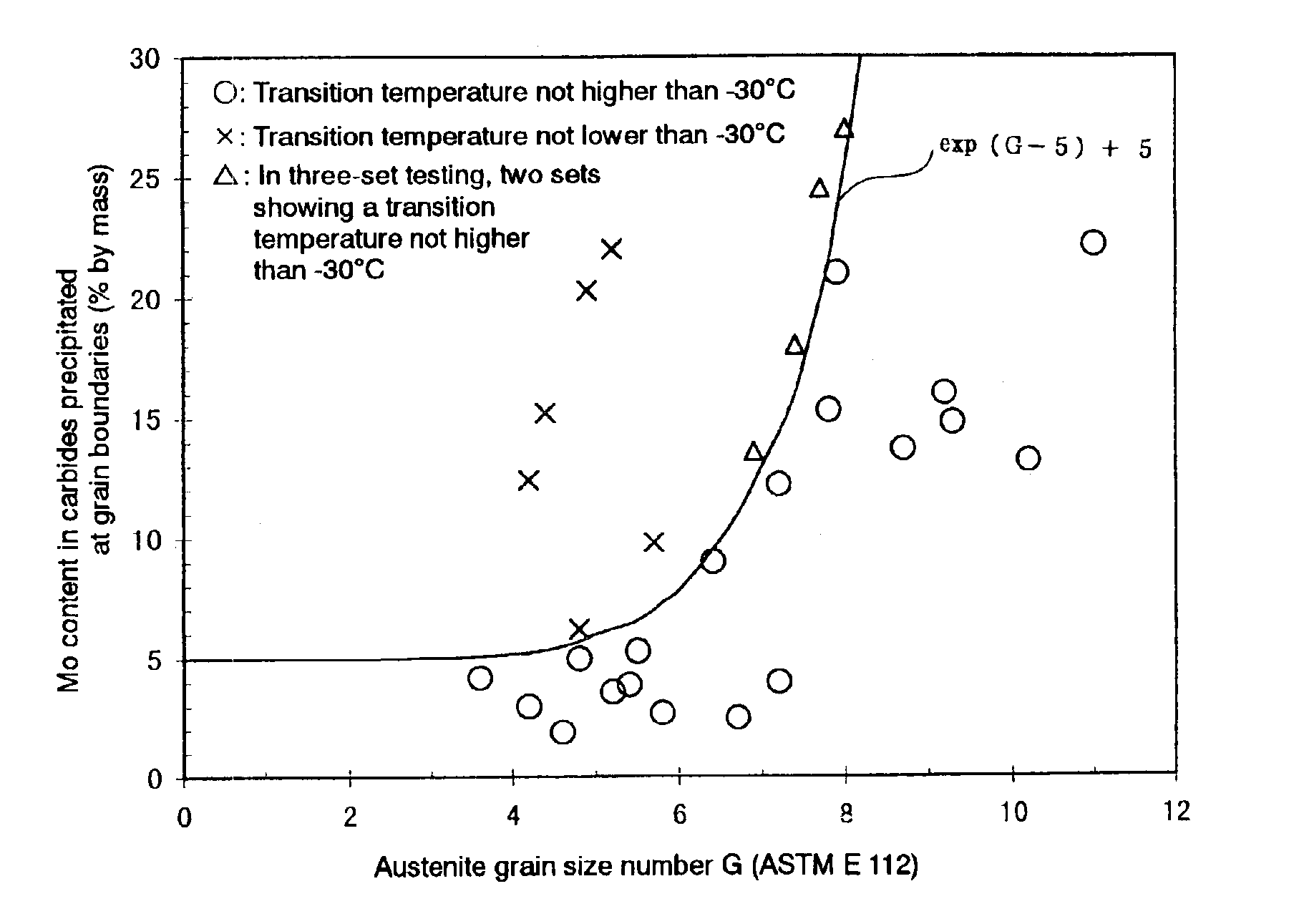
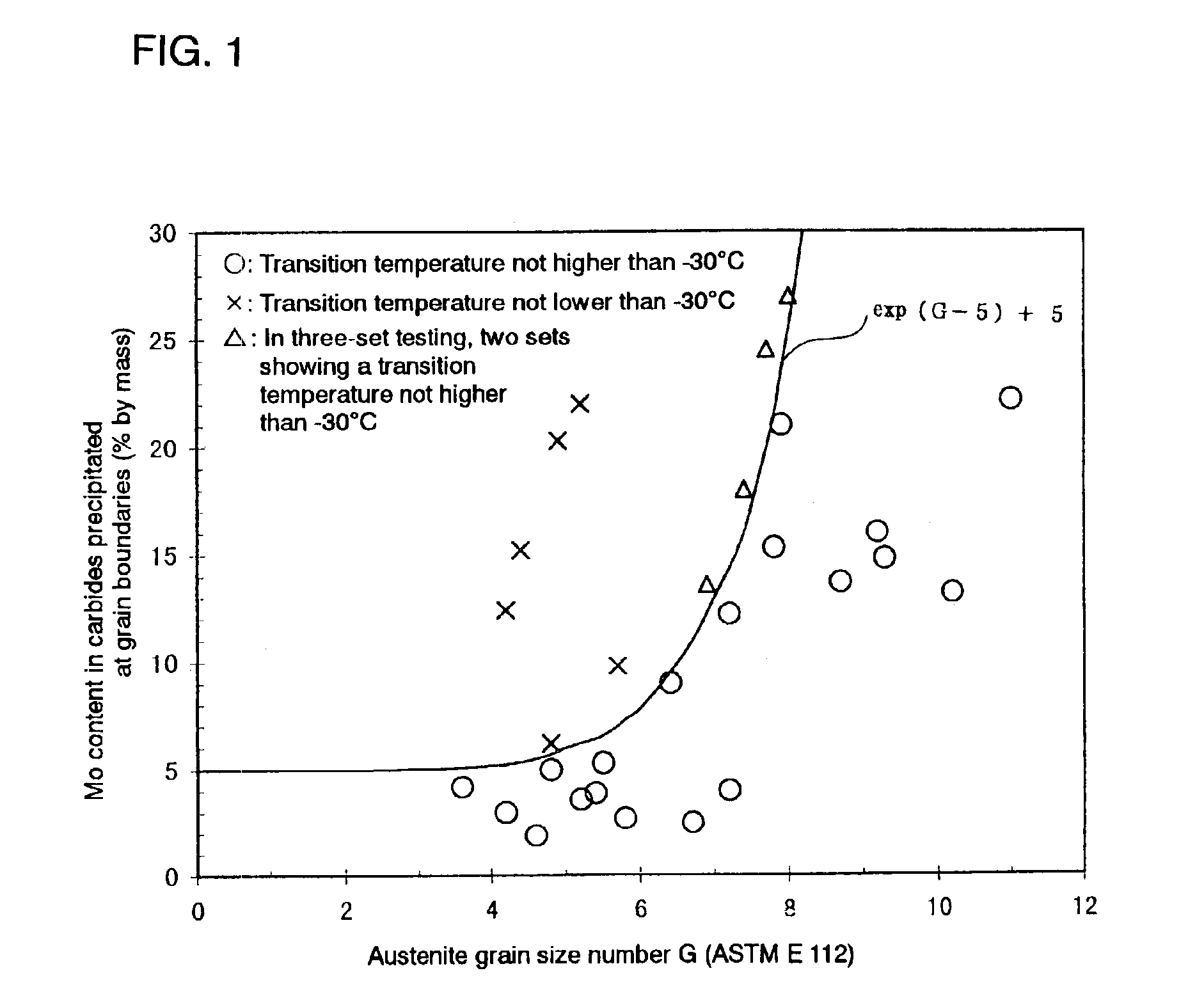
High toughness steel material and method of producing steel pipes using same
InactiveUS6958099B2Improve toughnessReduce hardenabilityFurnace typesHeat treatment furnacesProduction rateAustenite grain
A steel material and a steel pipe made by using the same are provided which are to be used in severe oil well environments. Such a highly tough oil well steel pipe can be produced by rolling the base material, quenching the rolling product from the austenite region and tempering the same so that the relationship between the content of Mo [Mo] in the carbides precipitated at austenite grain boundaries and the austenite grain size (according to ASTM E 112) can be defined by the formula (a) given below. In this manner, steel pipes suited for use even under oil well environments becoming more and more severe can be produced while satisfying the requirements that the cost should be rationalized, the productivity improved and energy saved.[Mo]≦exp(G−5)+5 (a)
Owner:NIPPON STEEL CORP
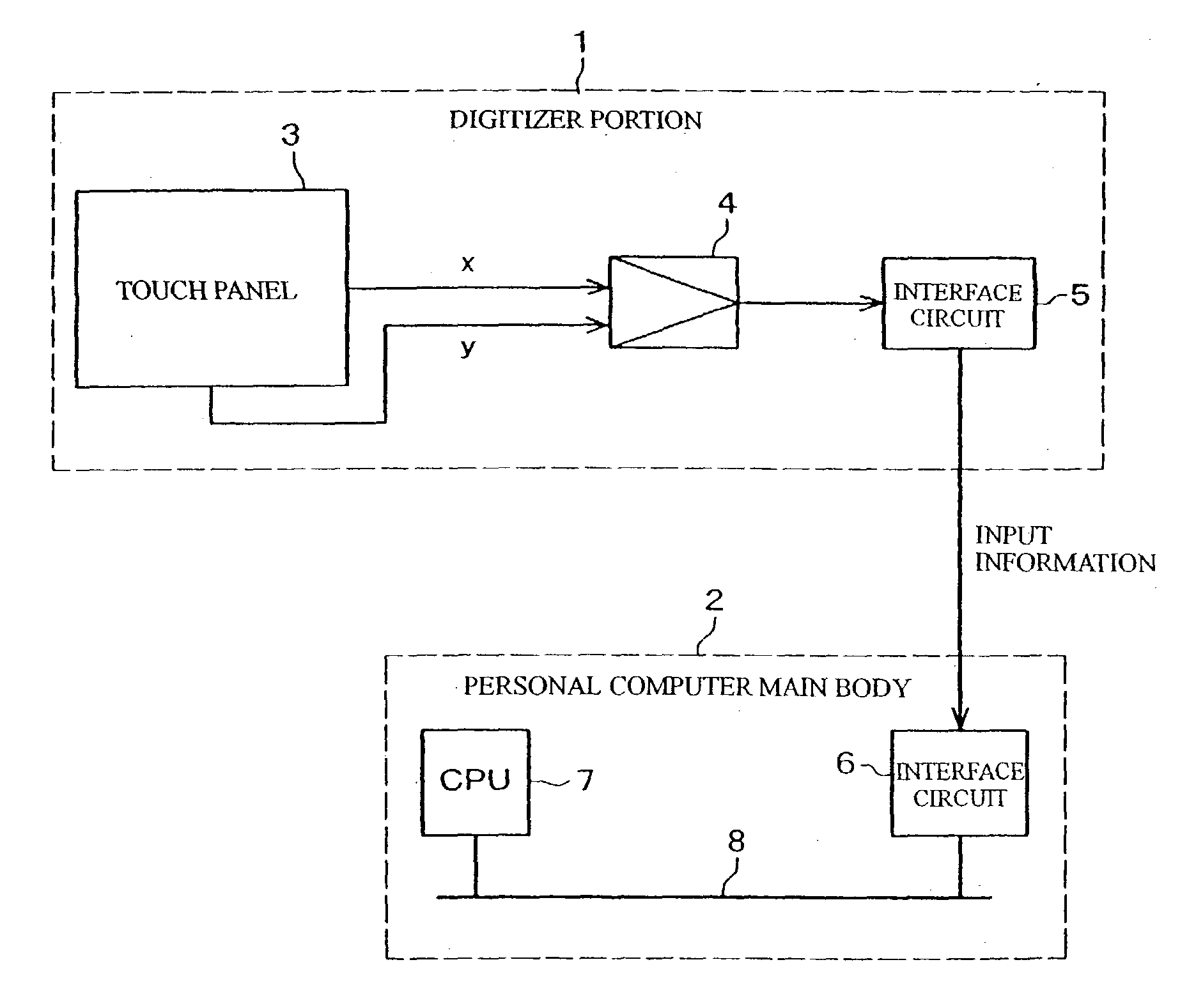
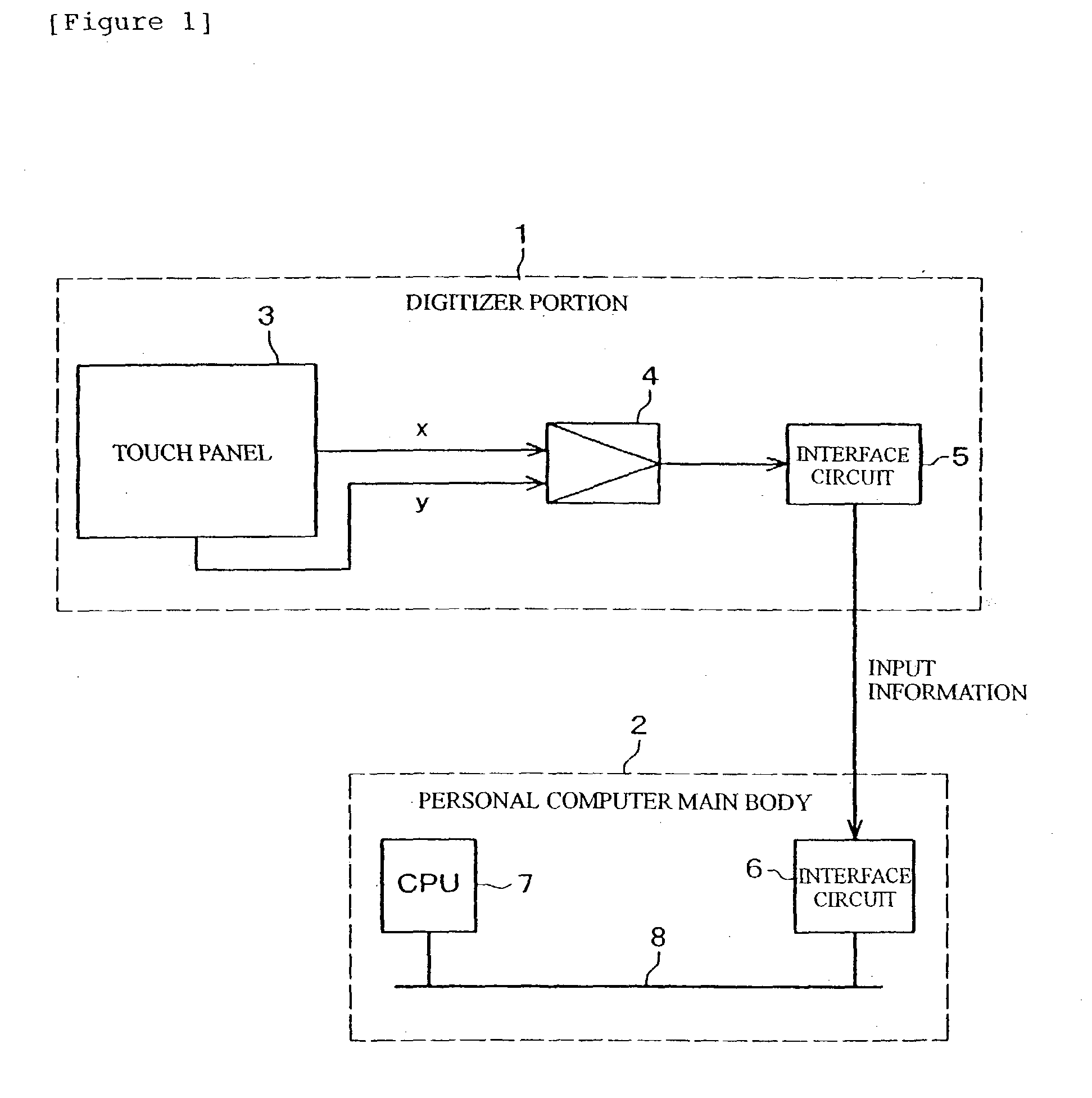
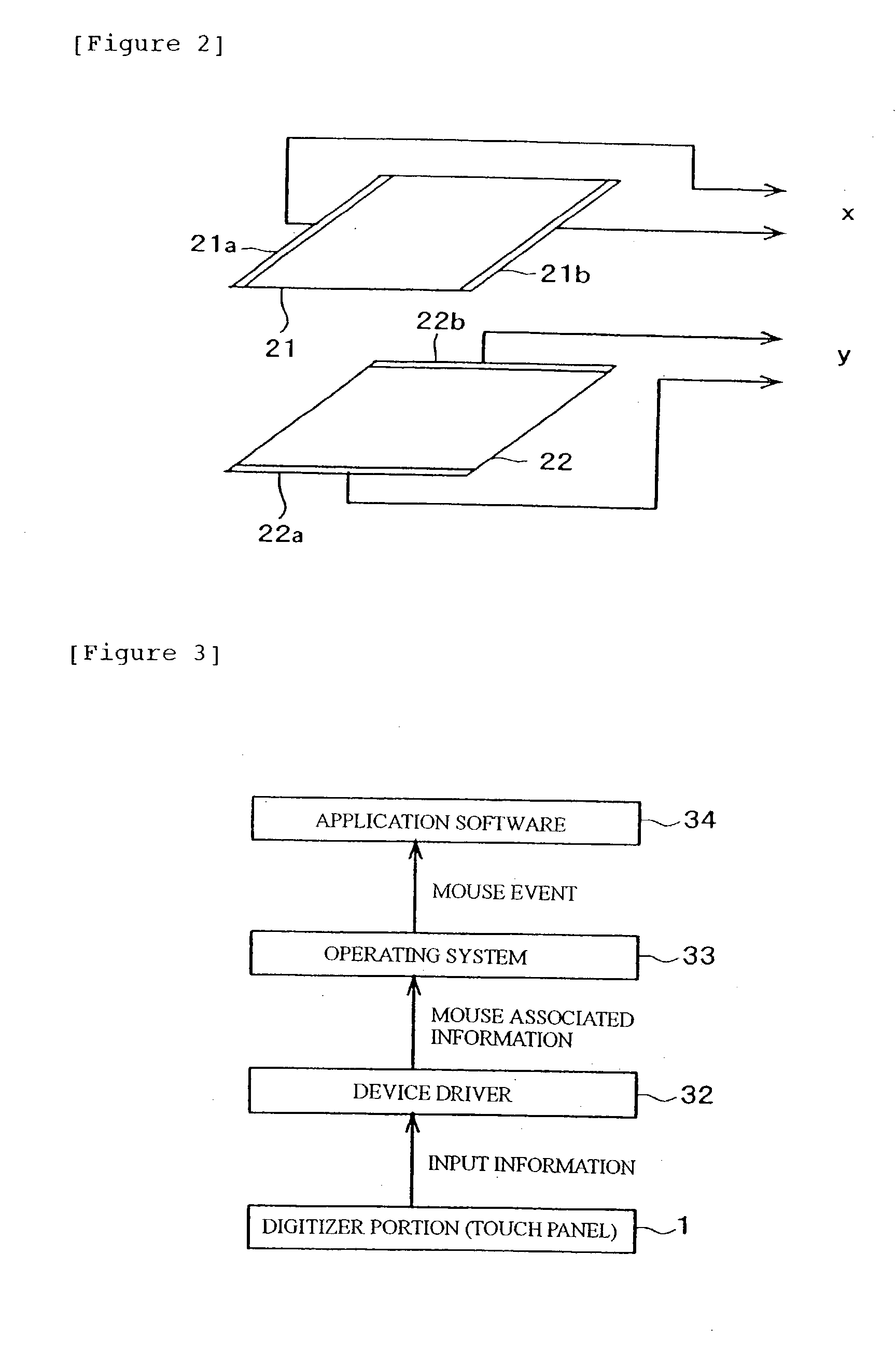
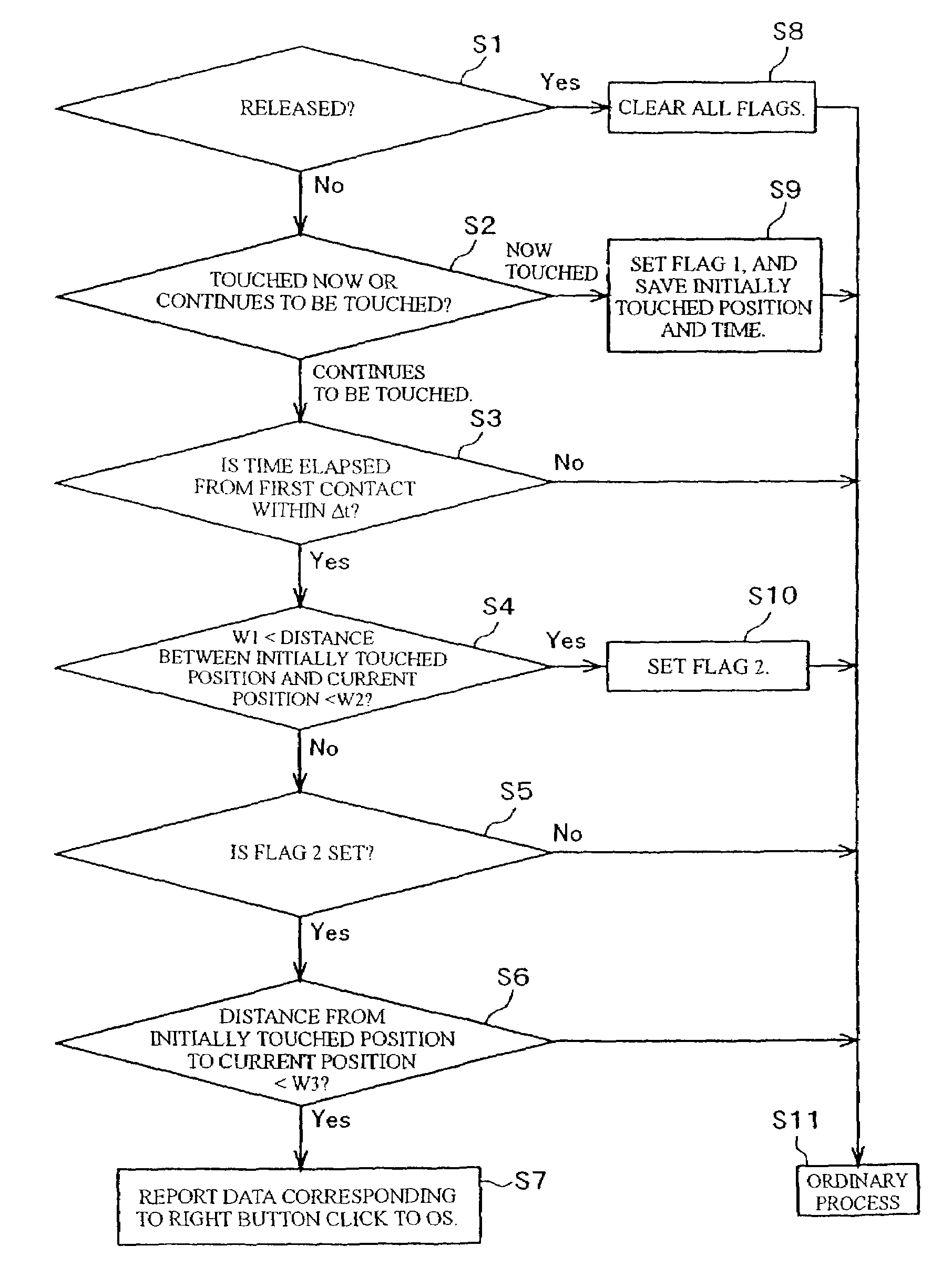
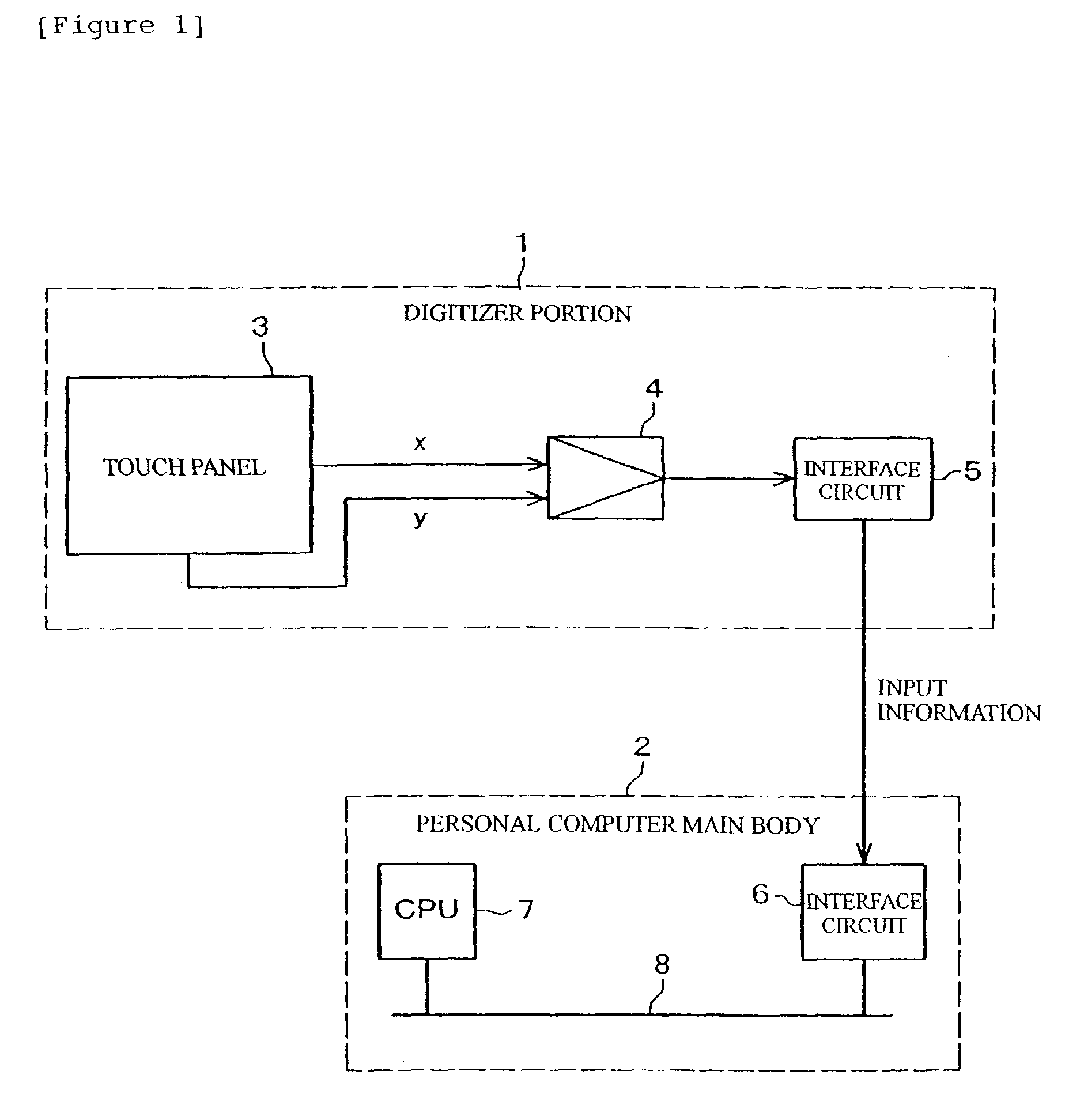
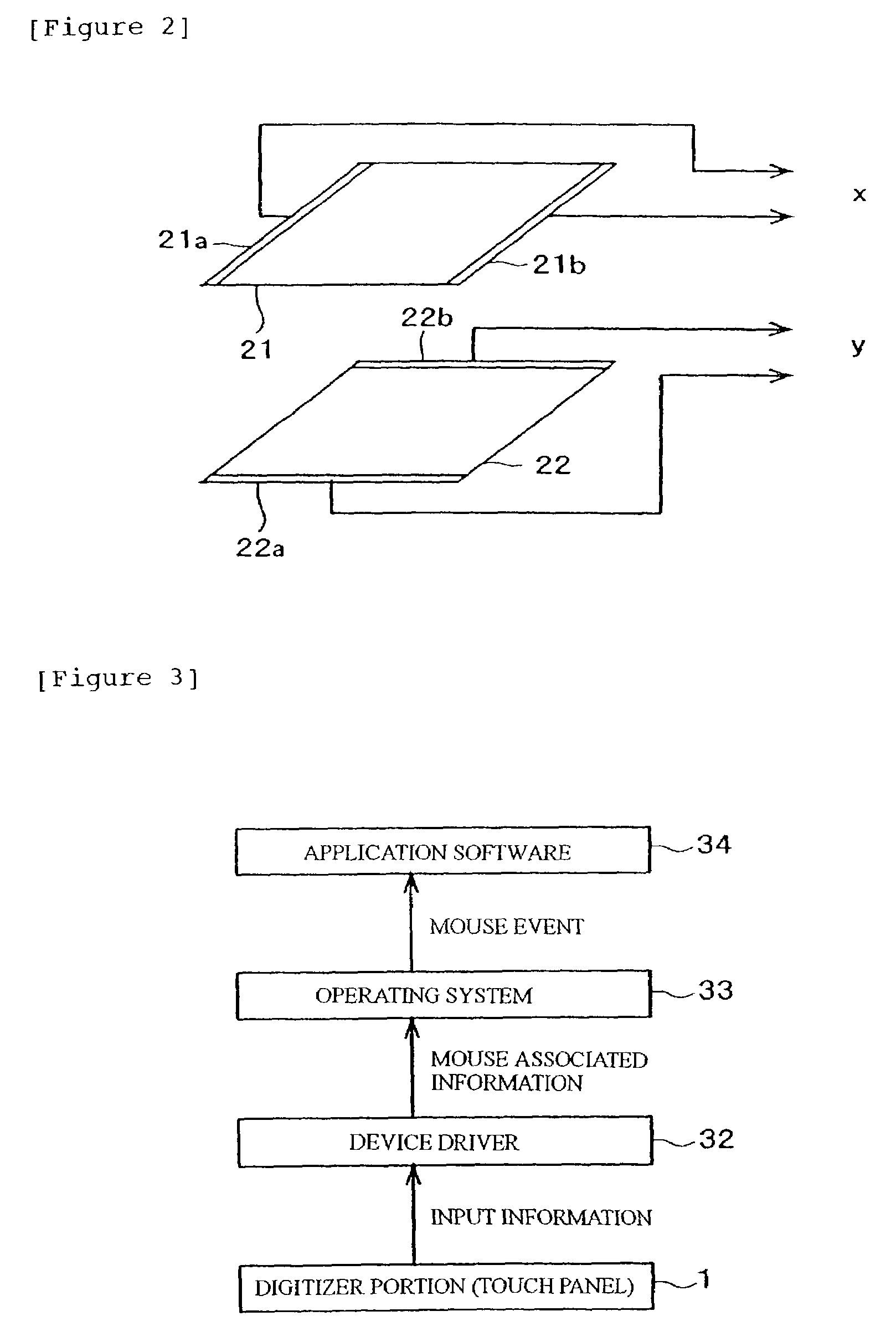
Information processing apparatus, program and coordinate input method
InactiveUS20030095112A1Easy inputPerformed easily and quicklyCathode-ray tube indicatorsInput/output processes for data processingComputational scienceInformation processing
An apparatus, program product and method of detecting, within a predetermined time period after an input of a first coordinate, an input of a second coordinate being apart a predetermined distance or more from a first coordinate, or detecting, within a predetermined time period after an input of the first coordinate, an input of the second coordinate being apart a predetermined distance or more from the first coordinate and the following input of a third coordinate near the first coordinate, whereby a first processing in accordance with the first coordinate or a second processing in accordance with the first coordinate is performed depending on the detected result.
Owner:LENOVO PC INT
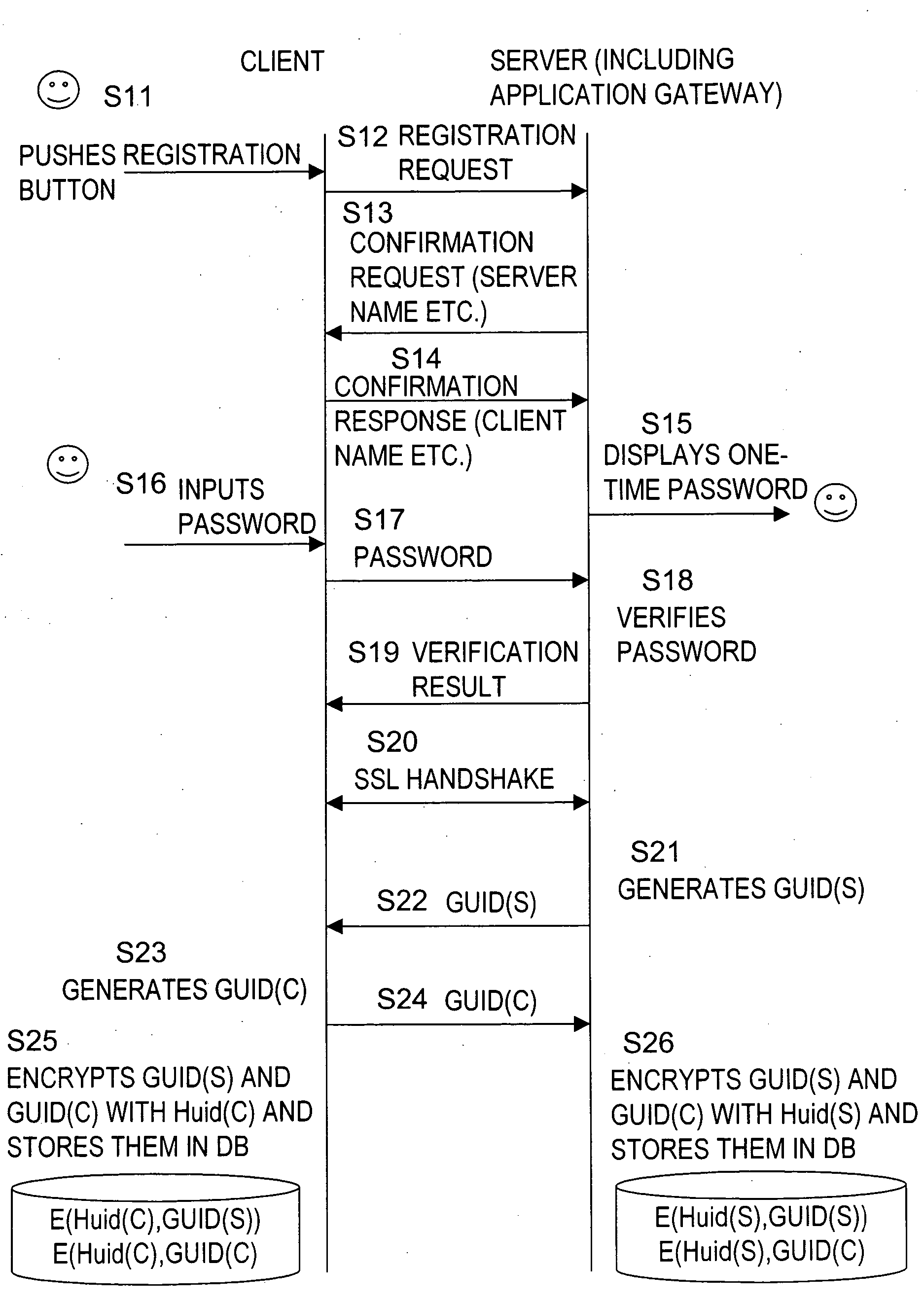
Access control processing method
ActiveUS20060168253A1Improve securityEasy accessUser identity/authority verificationDigital data protectionApplication softwareClient-side
The present invention provides a device and a method for accurately and efficiently controlling an access from an external network to an internal network. Both a client device connectable to the external network and an application gateway store shared secret information (Secret) including a client ID: GUID(C) as an ID generated by the client and a server ID: GUID(S) as an ID generated by the application gateway in respective storage units. In response to an access request from the client, the application gateway determines whether the client has appropriate shared secret information (Secret) so as to determine an access right. With this configuration, a right of access from the external network to the internal network, such as a home network, can be efficiently and accurately determined.
Owner:SONY CORP
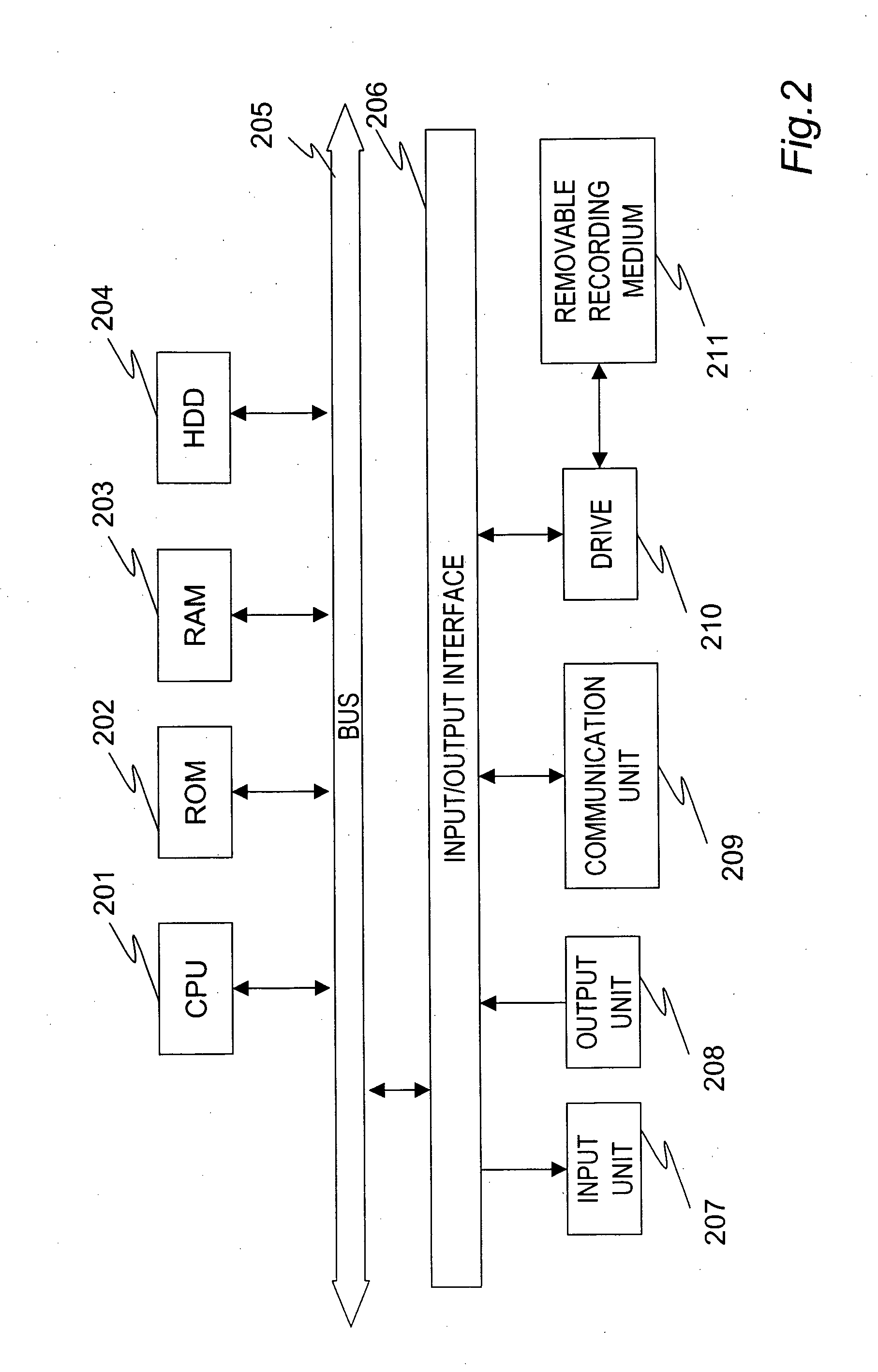
Editing apparatus having dedicated processing unit for video editing
InactiveUS20030086686A1Secure performanceRemove background noiseTelevision system detailsRedundant array of inexpensive disk systemsSource materialDisplay device
An editing apparatus is disclosed, that comprises an editing processing unit for processing a video signal and an audio signal supplied as source materials, and a computer for controlling the editing processing unit, wherein the computer comprises a controlling means for displaying a viewer window, a log window, and a program window on a display of the computer, the viewer window allowing the editing operator to decide an edit point while viewing a video image of a source material so as to produce an event, the log window displaying a clip image corresponding to an event that is set on the viewer window, the program window allowing the editing operator to arrange a plurality of events on a time line in a desired order so as to produce a program list, and wherein the controlling means displays an icon that represents by what source device each event arranged on the time line is produced.
Owner:SONY CORP
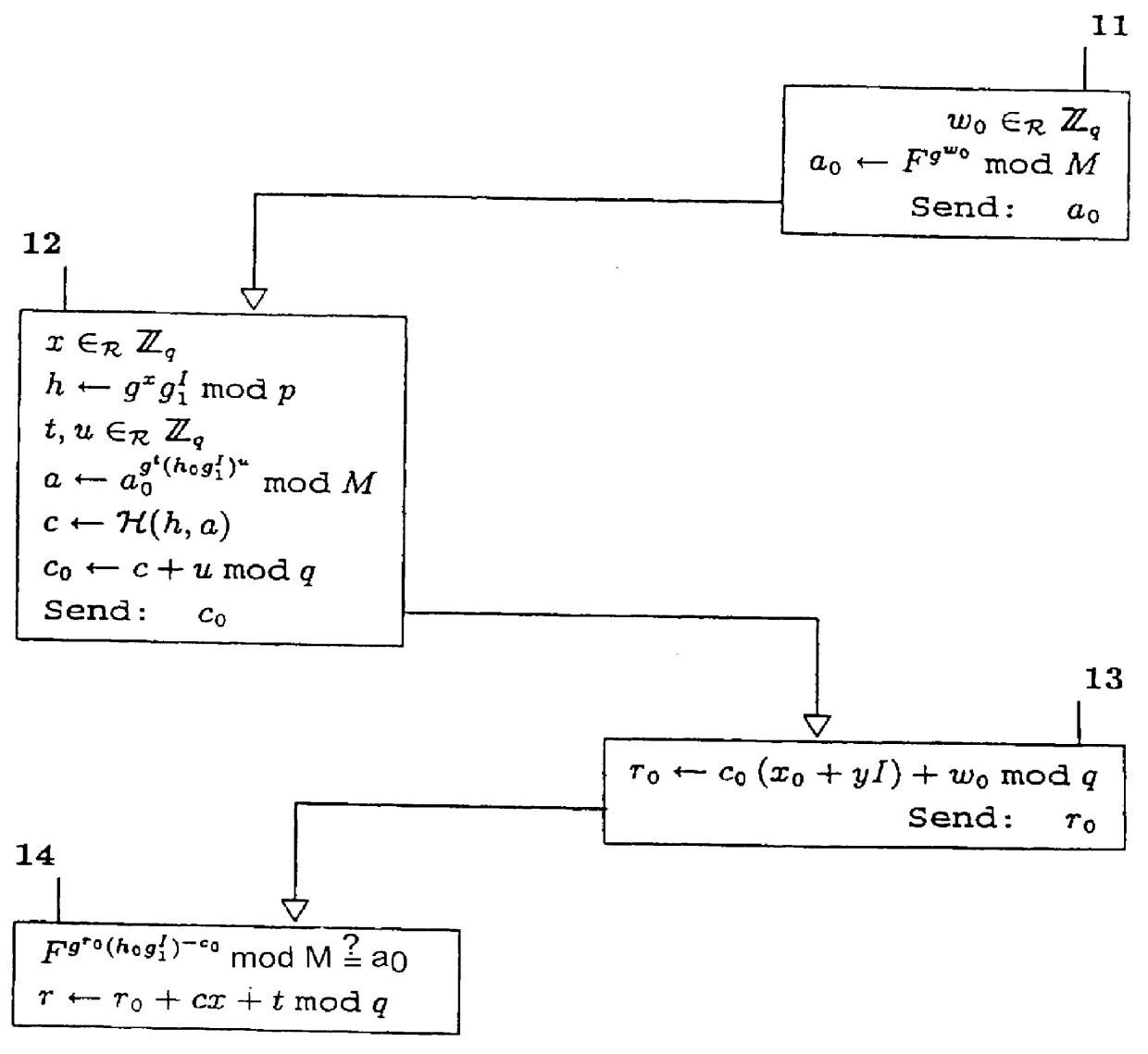
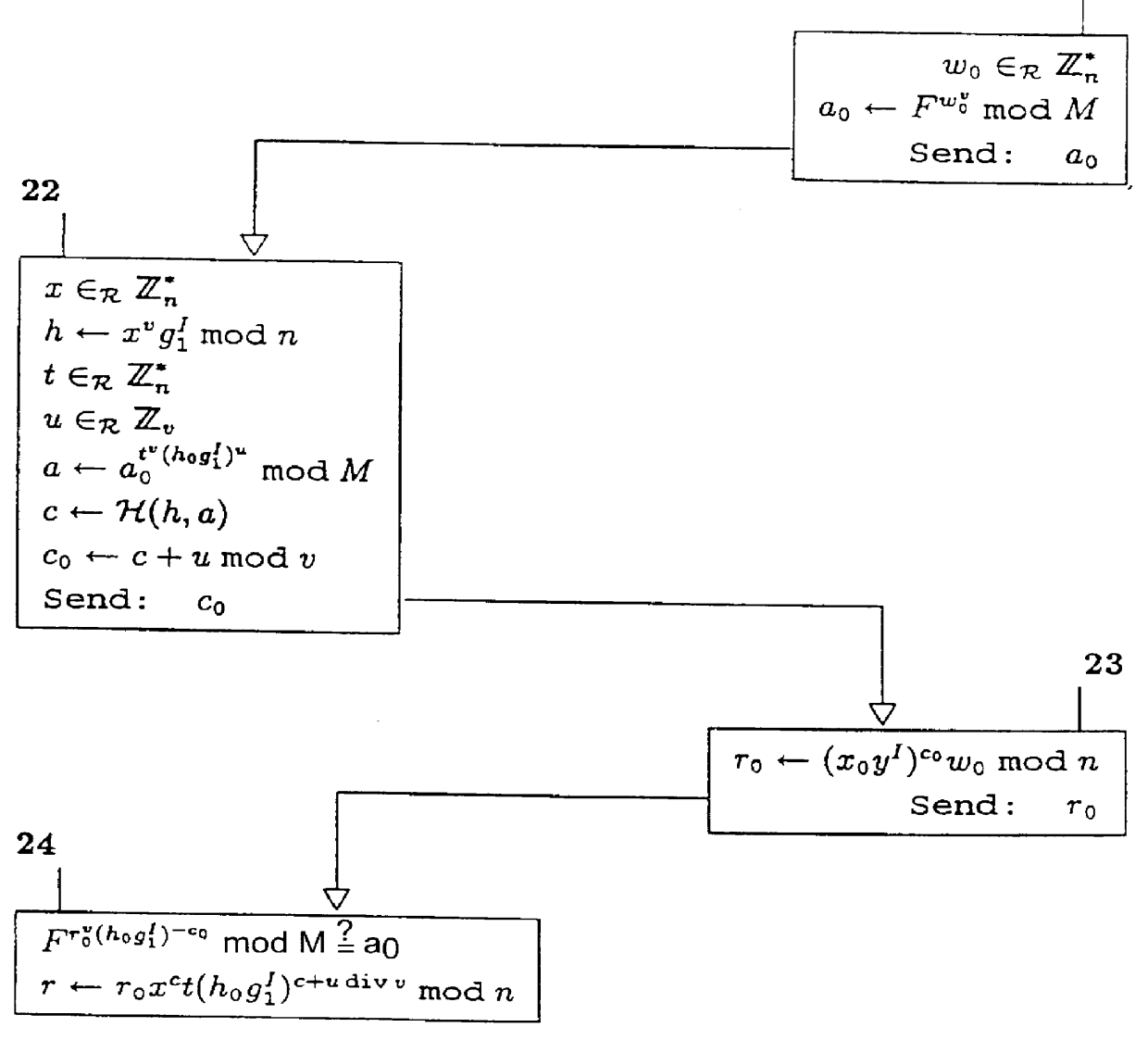
System for ensuring that the blinding of secret-key certificates is restricted, even if the issuing protocol is performed in parallel mode
InactiveUS6052467ASecure performanceImprove protectionKey distribution for secure communicationPublic key for secure communicationInternet privacyEngineering
PCT No. PCT / NL96 / 00129 Sec. 371 Date Feb. 19, 1998 Sec. 102(e) Date Feb. 19, 1998 PCT Filed Mar. 27, 1996 PCT Pub. No. WO96 / 31034 PCT Pub. Date Oct. 3, 1996A cryptographic method is disclosed that enables the issuer in a secret-key certificate issuing protocol to issue triples consisting of a secret key, a corresponding public key, and a secret-key certificate of the issuer on the public key, in such a way that receiving parties can blind the public key and the certificate, but cannot blind a predetermined non-trivial predicate of the secret key even when executions of the issuing protocol are performed in parallel.
Owner:ZERO KNOWLEDGE SYST INT INC +1
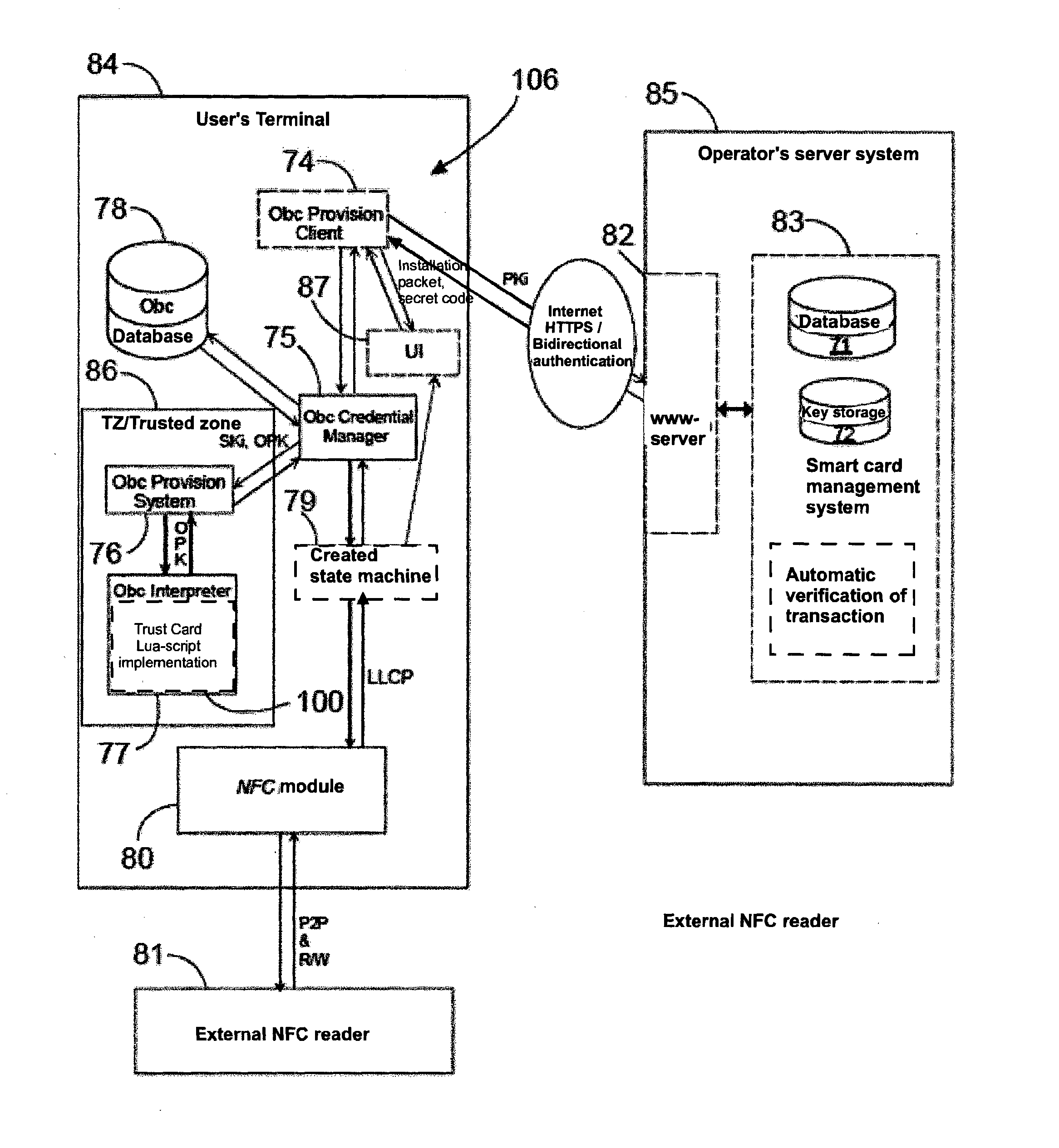
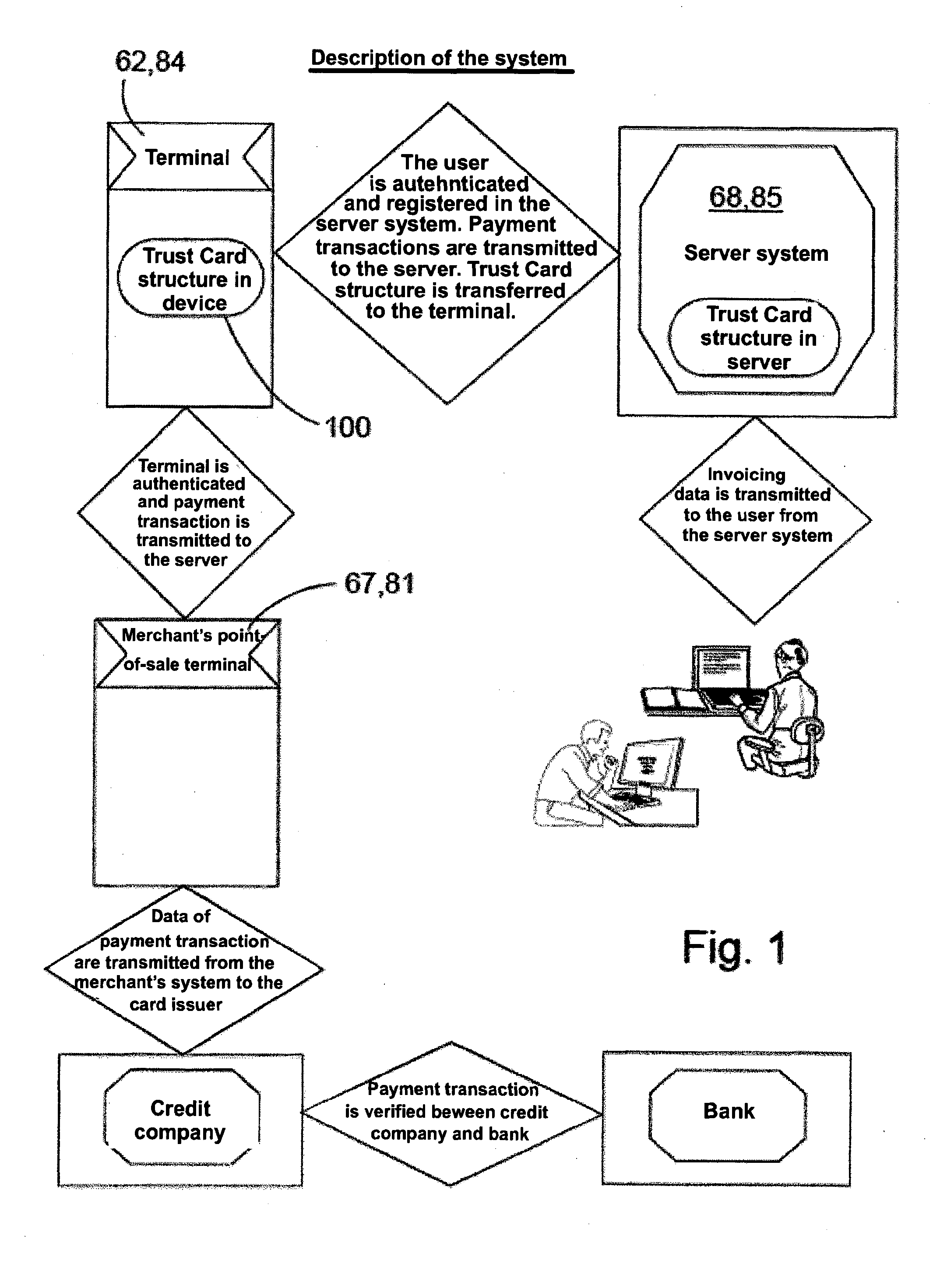
Payment system
ActiveUS20140236842A1Reduce riskIncrease safety and dynamicityFinancePoint-of-sale network systemsPayment transactionComputer hardware
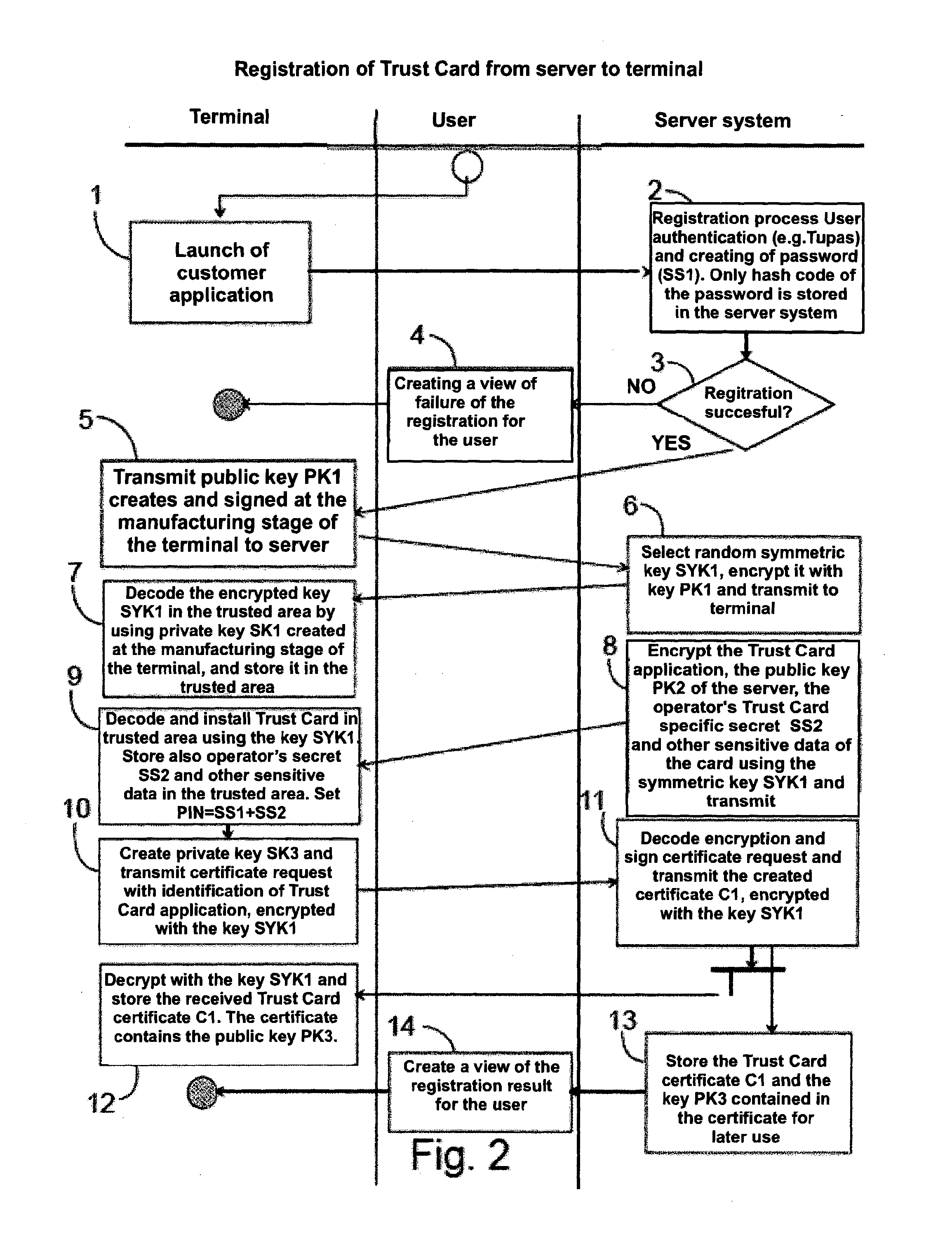
A method of making a payment in which payment data is received by a user's terminal from a point-of-sale terminal, a secret of a payment application is received by the terminal from the operator's server system, a trust card is activated in the user's terminal by utilizing said secret of the payment application, and data of the trust card is transmitted from the user's terminal to the point-of-sale terminal for making the payment transaction. A trust card is created in the server system, data of the trust card is transmitted to the terminal to be used for making the payment transaction, the secret of the payment application is formed in the server system, and access to the secret of the payment application is provided to the terminal for activating the trust card for making the payment transaction.
Owner:UNITO
System and method of performing electronic transactions
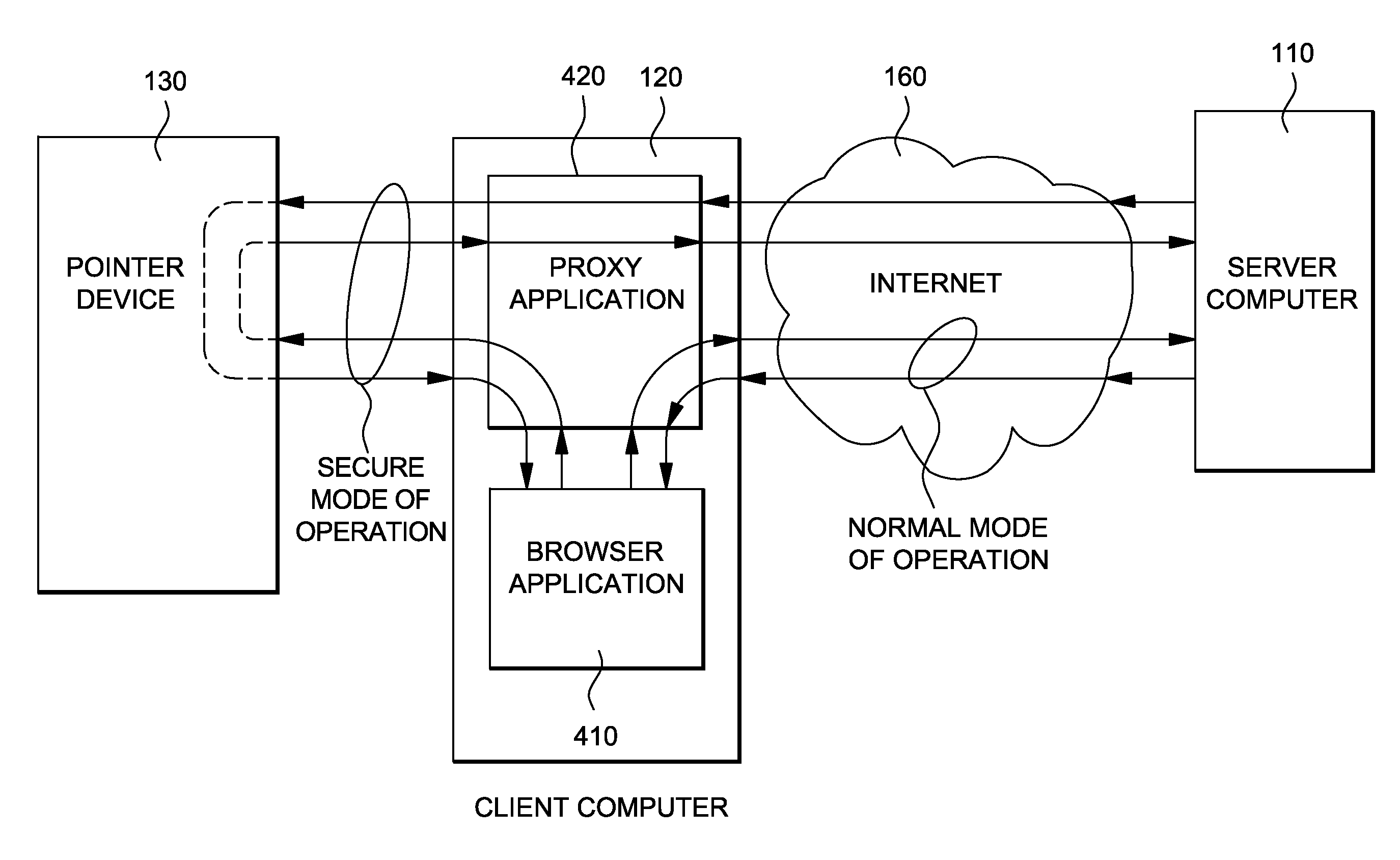
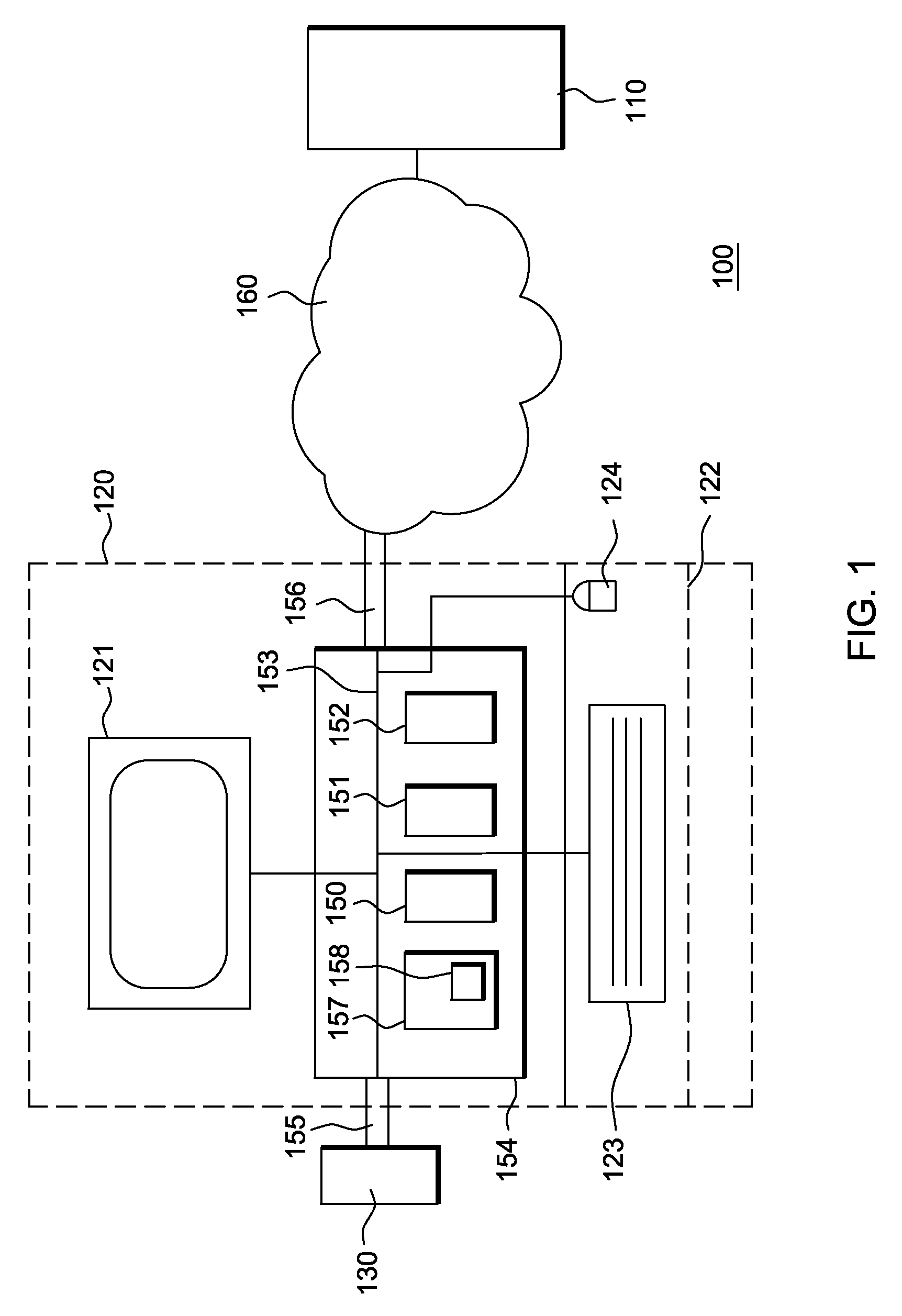
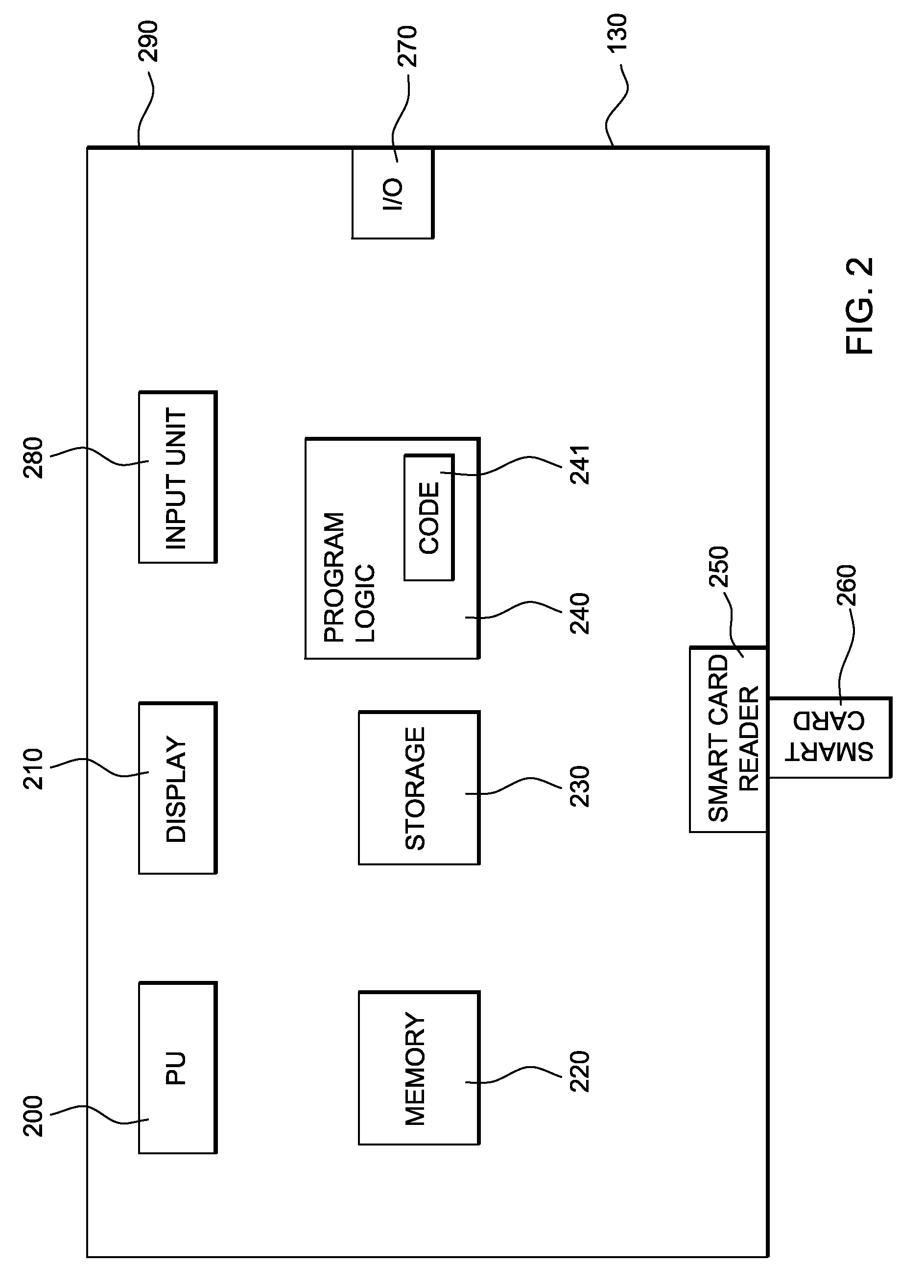
ActiveUS20100125729A1Improve usabilitySecure performanceMultiple digital computer combinationsPayment architectureDisplay deviceNetwork Communication Protocols
A system and method of performing electronic transactions between a server computer and a client computer. The method implements a communication protocol with encrypted data transmission and mutual authentication between a server and a hardware device via a network, performs a decryption of encrypted server responses, forwards the decrypted server responses from the hardware device to the client computer, displays the decrypted server responses on a client display, receives requests to be sent from the client computer to the server, parses the client requests for predefined transaction information by the hardware device, encrypts and forwards client requests, displays the predefined transaction information upon detection, forwards and encrypts the client request containing the predefined transaction information to the server if a user confirmation is received, and cancels the transaction if no user confirmation is received.
Owner:IBM CORP
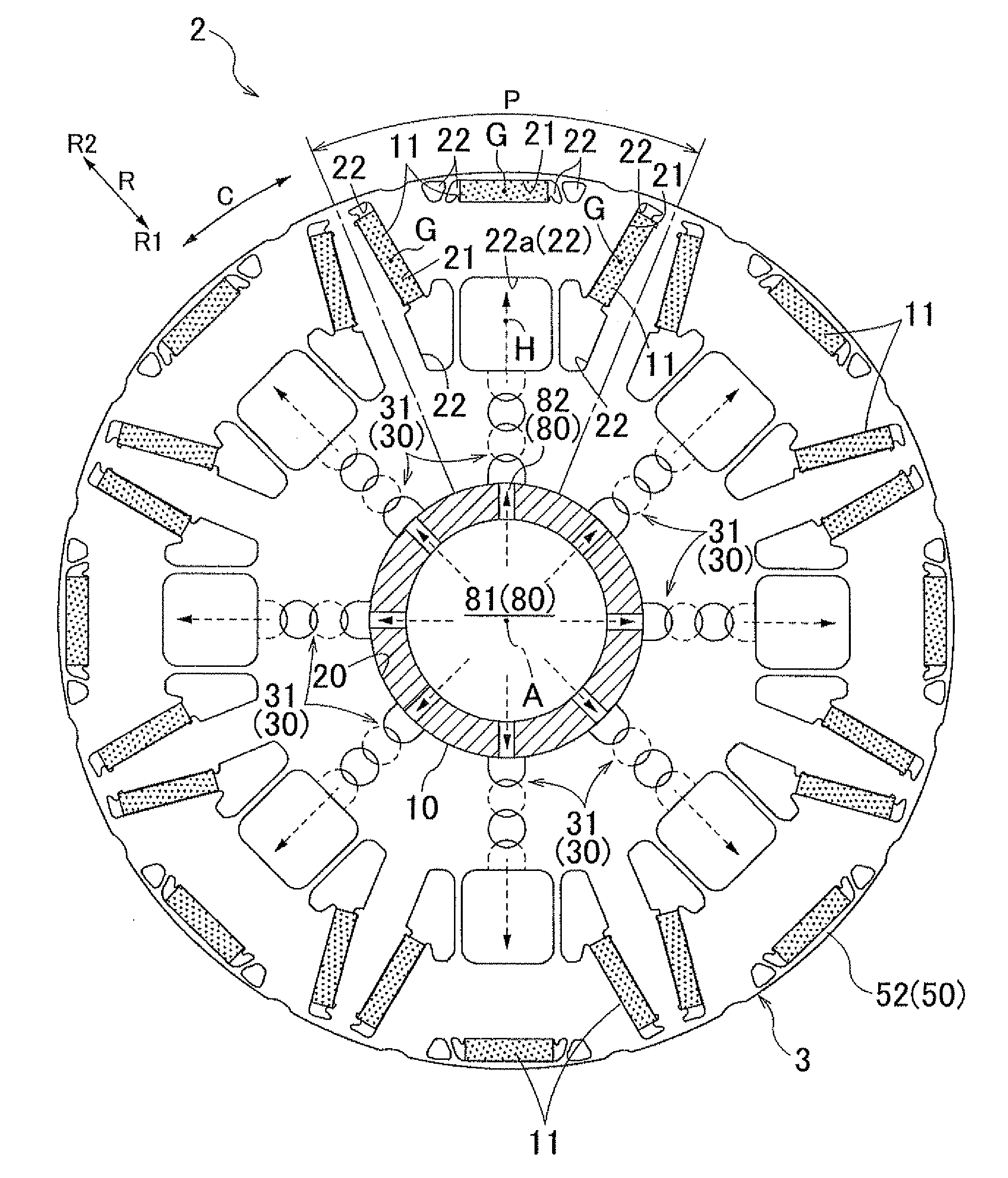
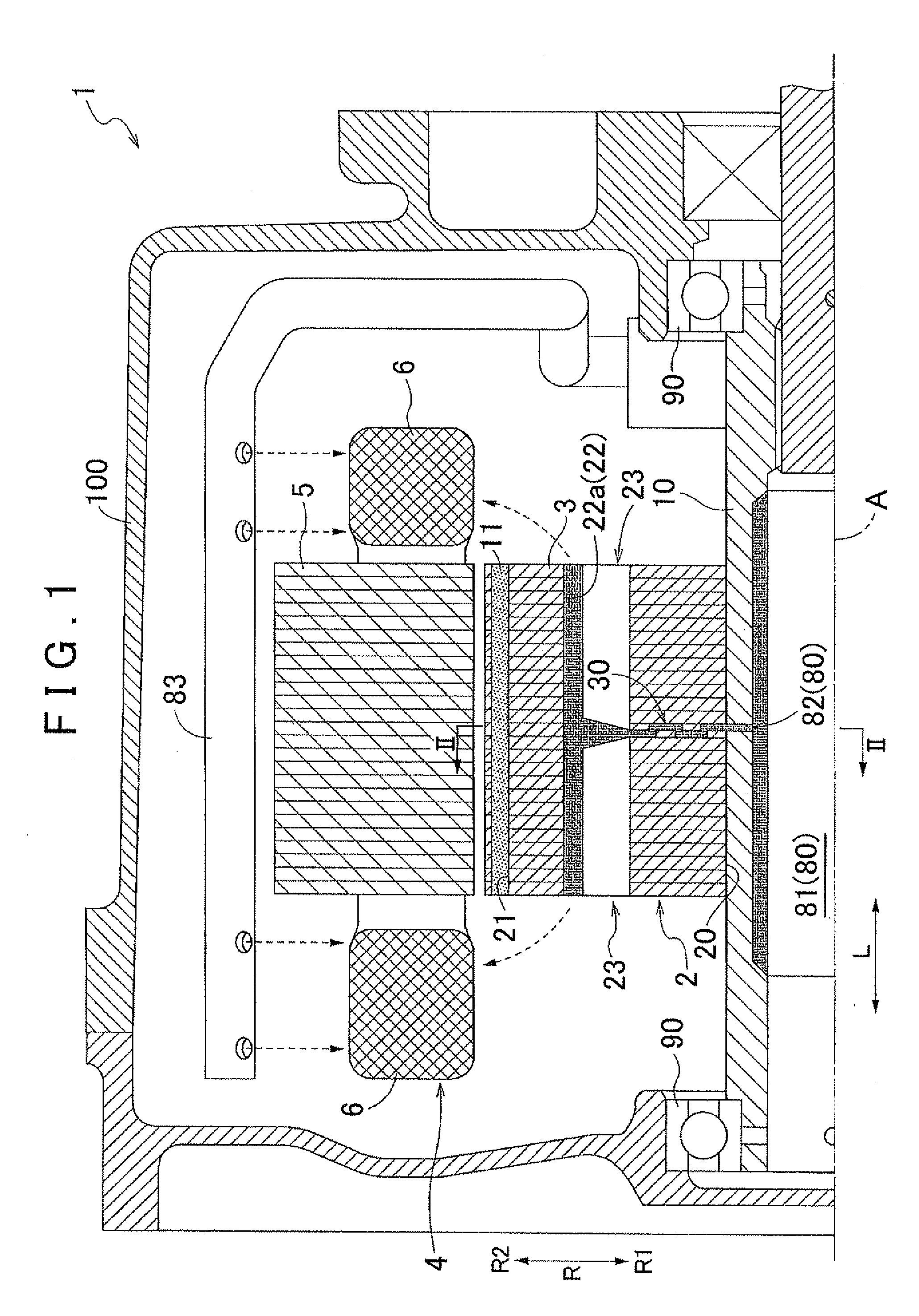
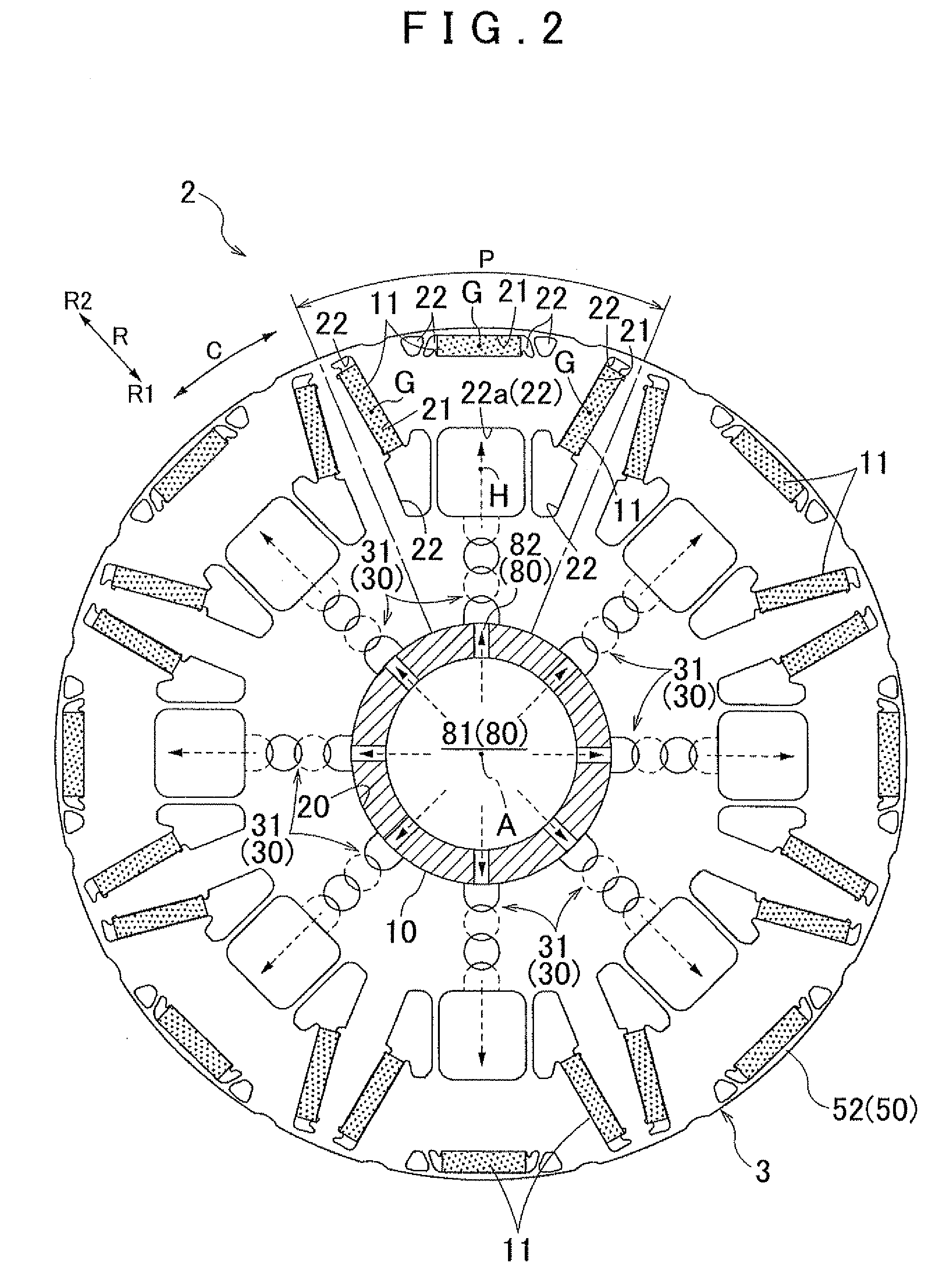
Rotating electrical machine
ActiveUS20130020889A1Improve cooling effectSecure performanceMagnetic circuit rotating partsCooling/ventillation arrangementRadial positionElectric machine
A rotating electrical machine includes a rotor which has a rotor core formed by stacking magnetic plates having an annular plate shape in an axial direction, a permanent magnet is inserted into a magnet insertion hole formed in the rotor core, and a rotor shaft is inserted into a shaft insertion hole surrounded by an inner peripheral surface of the rotor core; and a stator. A radial communication passage is formed by a communication penetration hole group that is formed by sequentially communicating a plurality of the penetration holes from a shaft insertion hole to a magnetic resistance hole in the radial direction. The plurality of the penetration holes are divided into at least two specific magnetic plates and formed such that the radial positions of the penetration holes are different from each other and the penetration holes partially overlap each other when viewed in the axial direction.
Owner:AISIN AW CO LTD
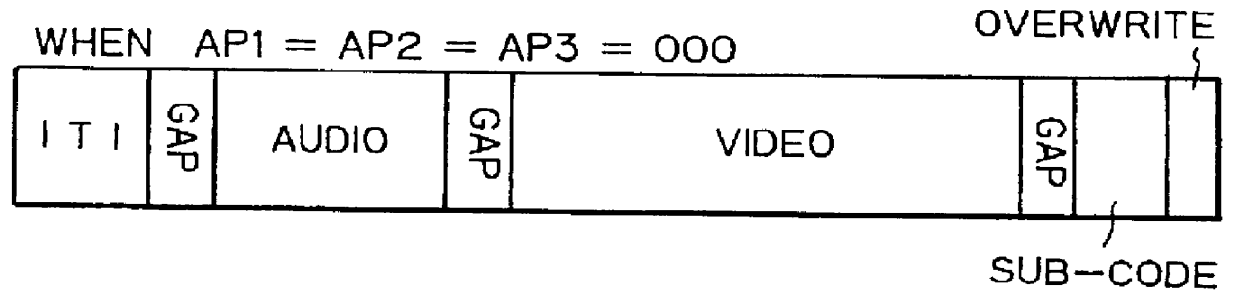
Digital audio signal transmission apparatus with data blocks of varying sizes
InactiveUS6097558AEasy loadingEasy to synthesizeTelevision system detailsStereophonic/quadraphonic recording circuitsComputer hardwareData segment
Digital audio signal transmission is provided for digitally processing, for transmission in a digital VCR format, audio signals from a plurality of channels into a digitized audio data segmented into blocks having a data size, each block reserved for audio data digitized from one of the channels. The audio data is converted from the channels into the blocks of digitized audio data by varying the data size of the blocks. The audio data is composed by scaling the audio data in at least one of the blocks and combining the scaled audio data with the audio data of another of the blocks into a block reserved for composite audio data.
Owner:SONY CORP
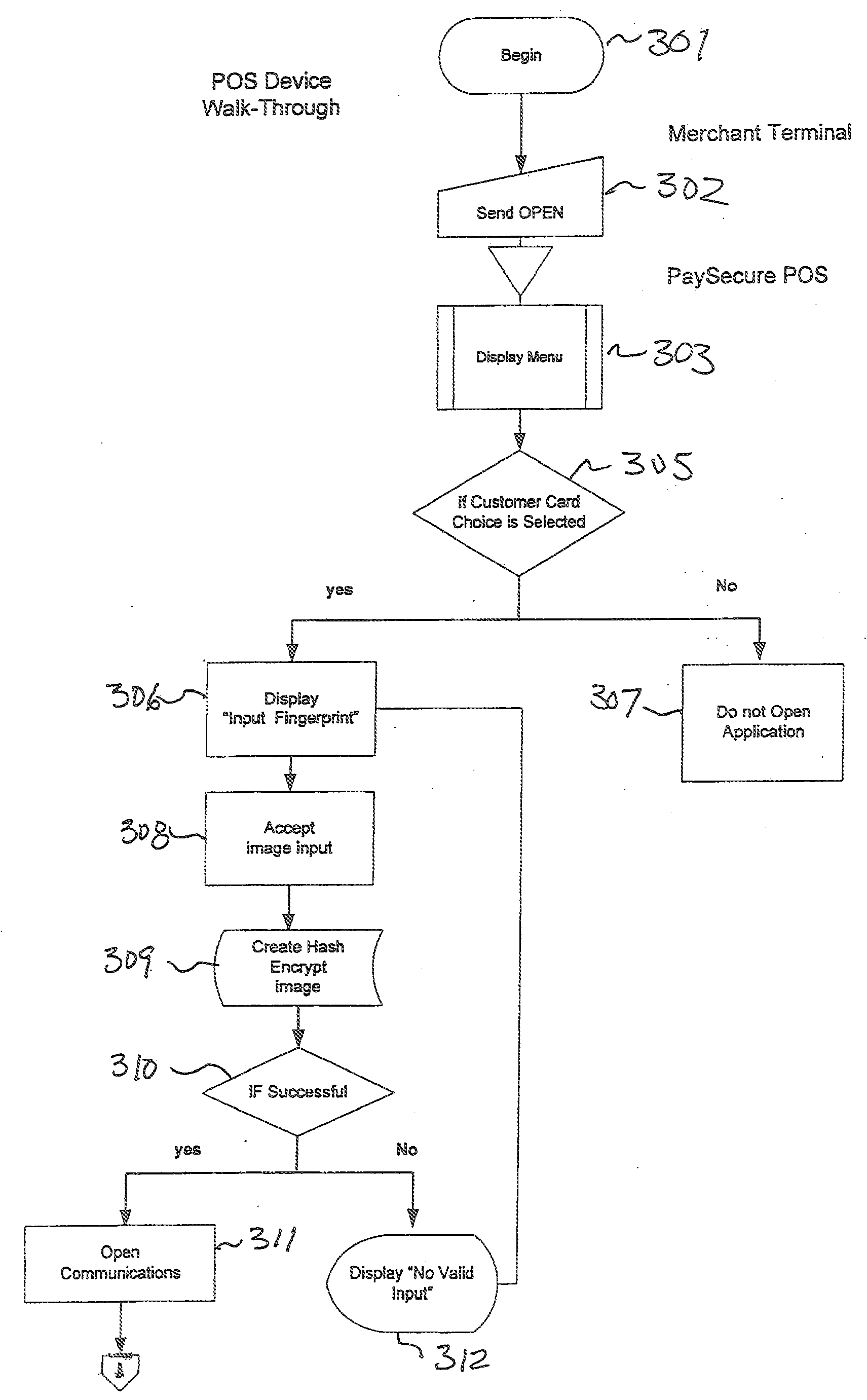
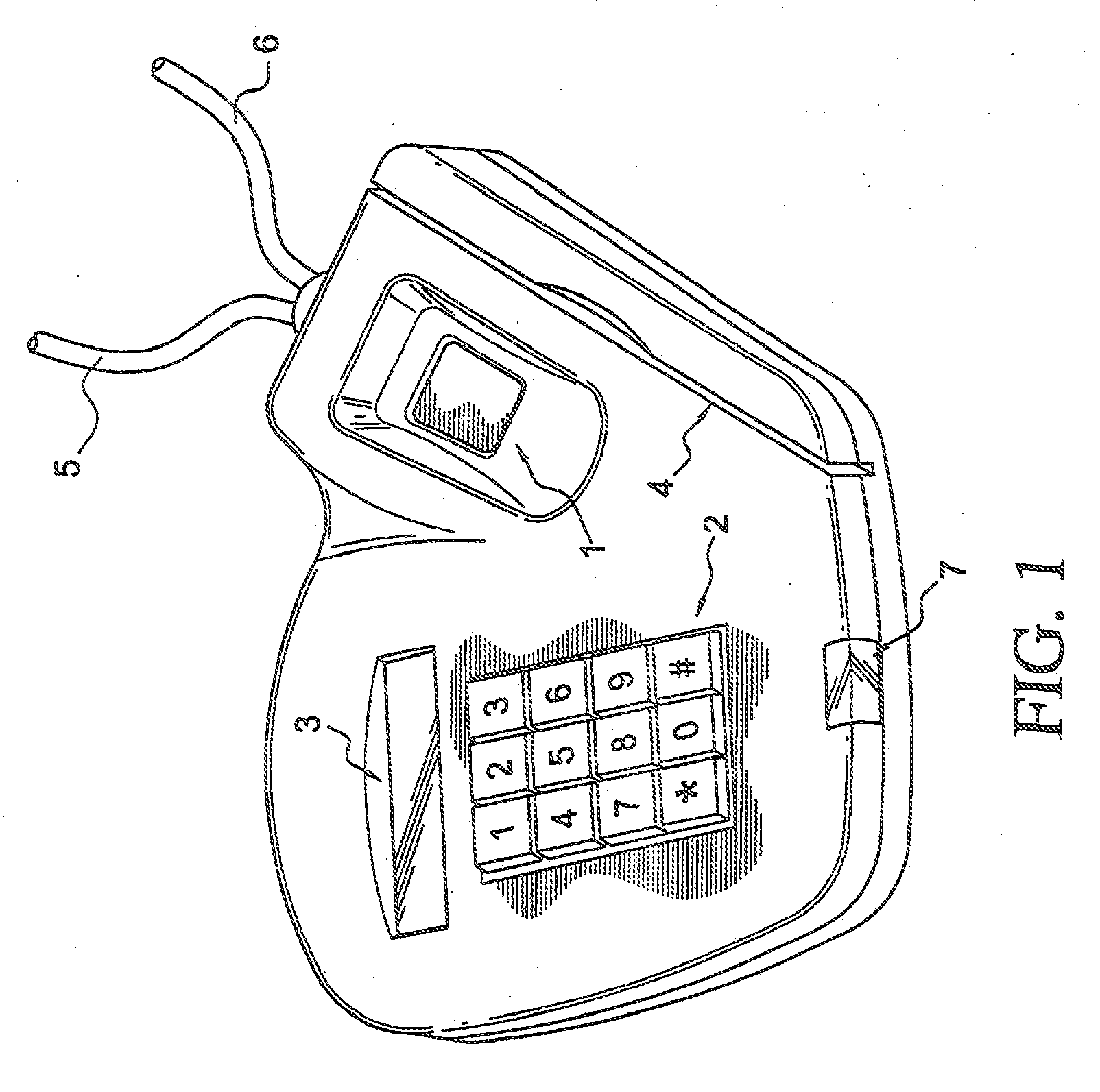
Secure point of sales biometric identification process and financial system for standalone and remote device transactions (paysecure)
InactiveUS20070005511A1Easy accessSecure performanceComplete banking machinesFinanceBiometric dataFinancial transaction
The present invention is an apparatus, method and system for secure point-of-sale (POS) and biometric data / finger print identification communications technology and systems processing methods in the area of financial merchant transactions. The present invention may use either or both standalone biometrics and biometric / fingerprinting technology with a touch screen device or a portable / mobile wireless device to securely process merchant POS financial transactions.
Owner:MARTINEZ PAMELA J
Method for Scalar Multiplication in Elliptic Curve Groups Over Prime Fields for Side-Channel Attack Resistant Cryptosystems
InactiveUS20090214025A1Secure performancePrevent internal leakageDigital data processing detailsSecret communicationEllipseElliptic curve cryptosystem
A method and device for transforming data with a secret parameter in an elliptic curve cryptosystem based on an elliptic curve defined over an underlying prime field, includes multiplying a point of the elliptic curve; representing the data to be transformed, by a scalar representing the secret parameter, wherein the multiplying includes performing at least one point addition operation and at least one point doubling operation on points of the elliptic curve; providing a representation in affine coordinates of the elliptic curve point to be multiplied and a representation in projective coordinates of intermediate elliptic curve points obtained during the multiplying; performing both the point addition operation and the point doubling operation by means of a sequence of elementary prime field operation types, the elementary prime field operation types including: a first type of prime field operations including field multiplication and field squaring of coordinates of the elliptic curve points and a second type of prime field operations including field addition, field doubling, and field subtraction of coordinates of the elliptic curve points.
Owner:TELECOM ITALIA SPA
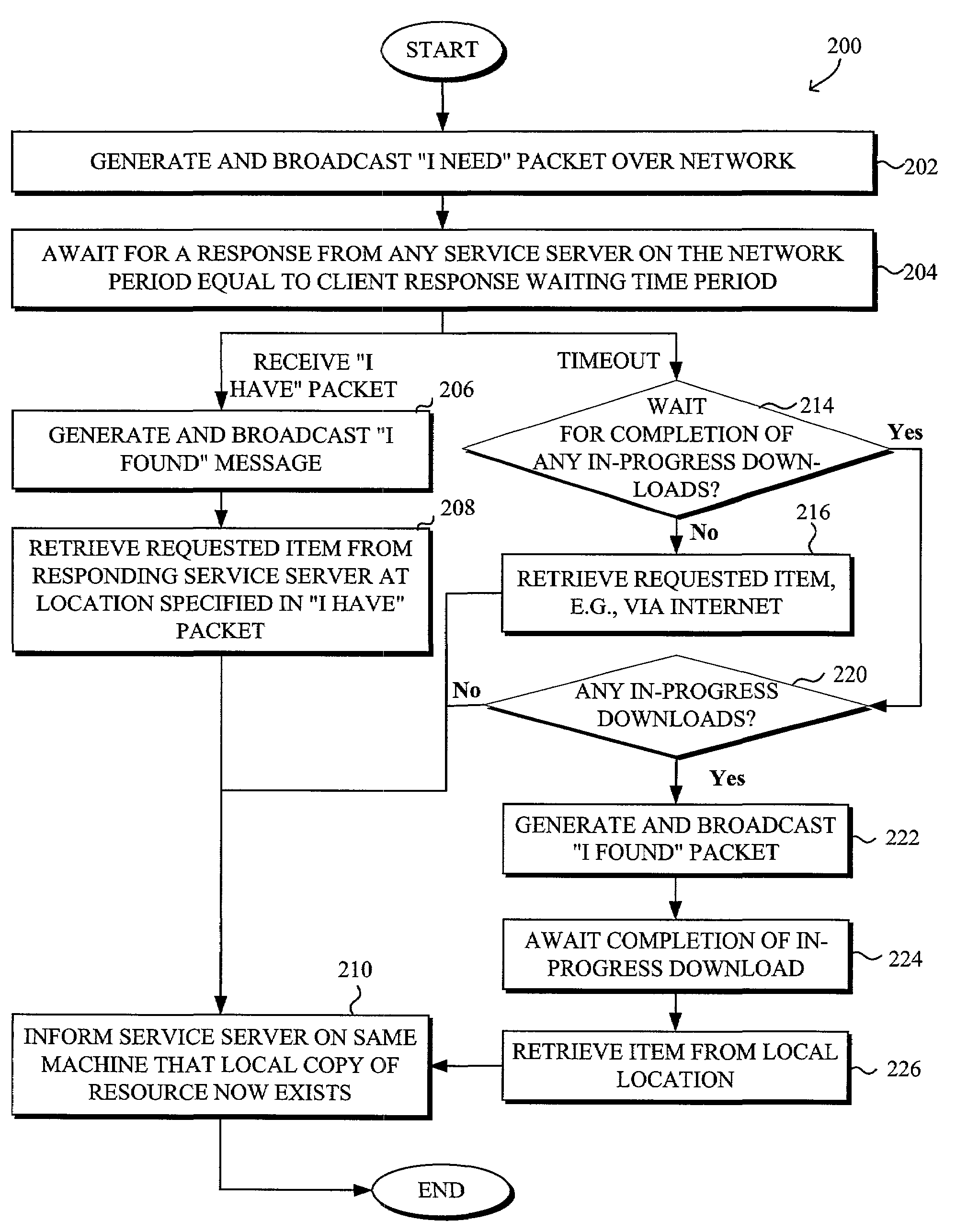
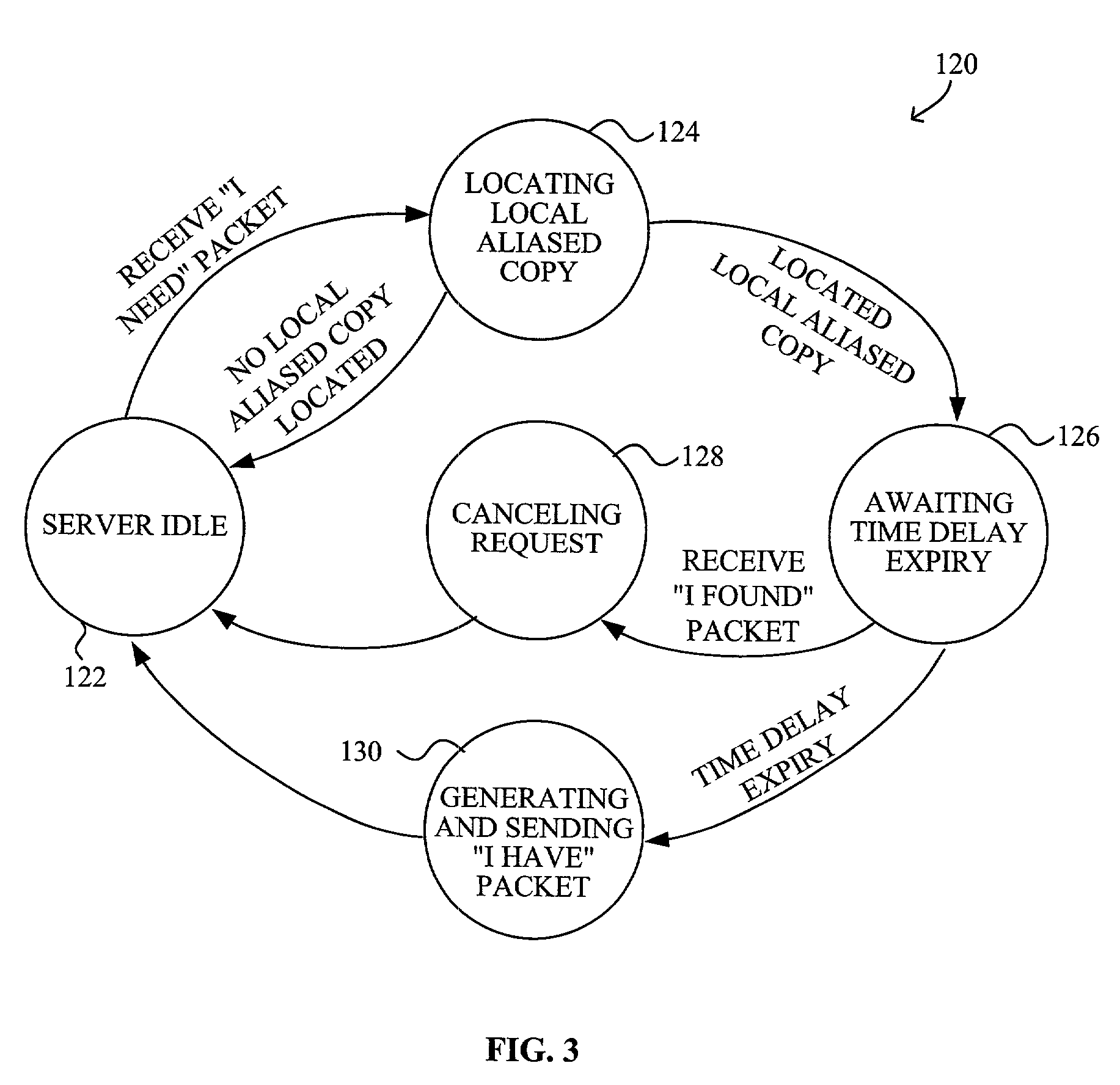
System and method to securely confirm performance of task by a peer in a peer-to-peer network environment
InactiveUS7181506B1Easy loadingSecure performanceMultiple digital computer combinationsTransmissionData packDigital signature
A system and method for securely confirming performance of a task by a peer in a peer-to-peer network environment using signed receipts are disclosed. The method generally comprises broadcasting a request over the network by a requesting peer for a task with respect to a remote non-local backend server, receiving a response containing a local alias URL pointing to a destination on a responding server node, forwarding the task to the local alias URL for performance by the responding server node, and verifying a digital signature of any receipt packet received from the responding server node to ensure that the receipt packet is from the remote non-local backend server. The method may also include placing the server node in a black list of the requesting peer if the verifying is unsuccessful.
Owner:MCAFEE LLC
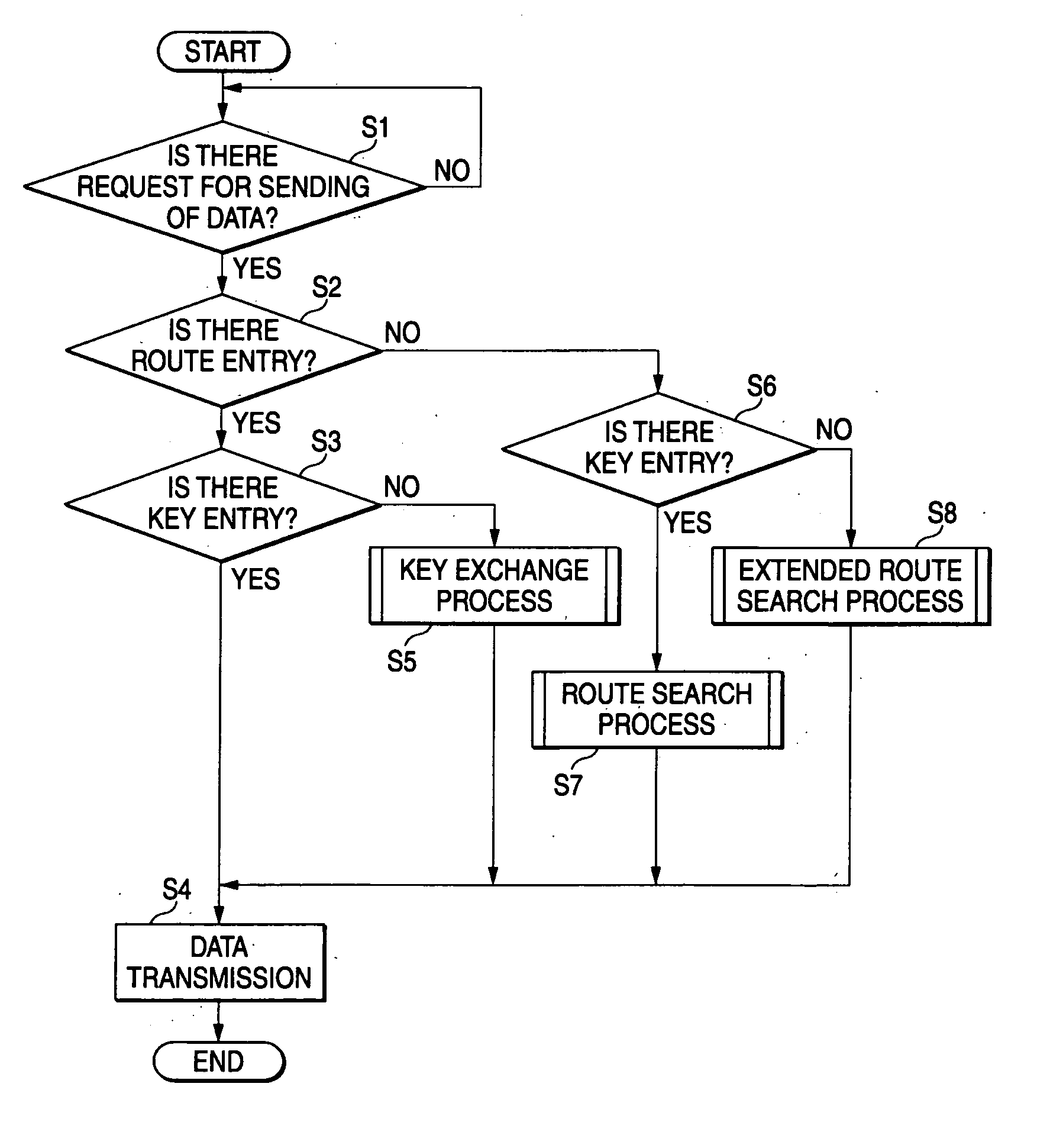
Wireless communication system, wireless communication device, method of wireless communication, and computer program
InactiveUS20070064950A1Short timeLow traffic loadKey distribution for secure communicationNetwork topologiesRoute searchComputer program
A wireless communication system includes plural wireless terminals between which multi-hop communications are performed; wherein processing for extended route search is activated to carry out route search and key exchange at the same time, the processing using a routing control protocol including a key exchange protocol.
Owner:SONY CORP
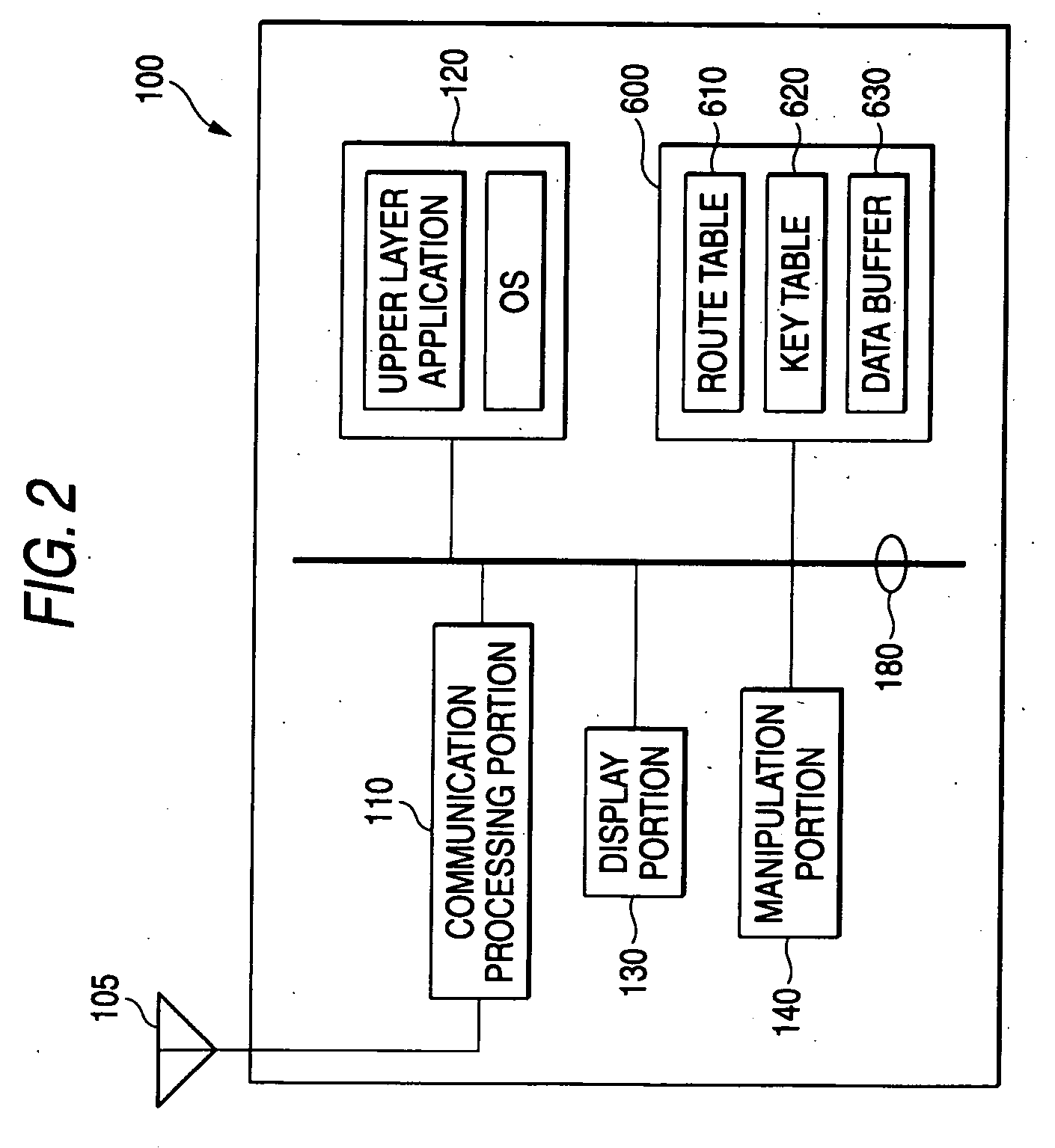
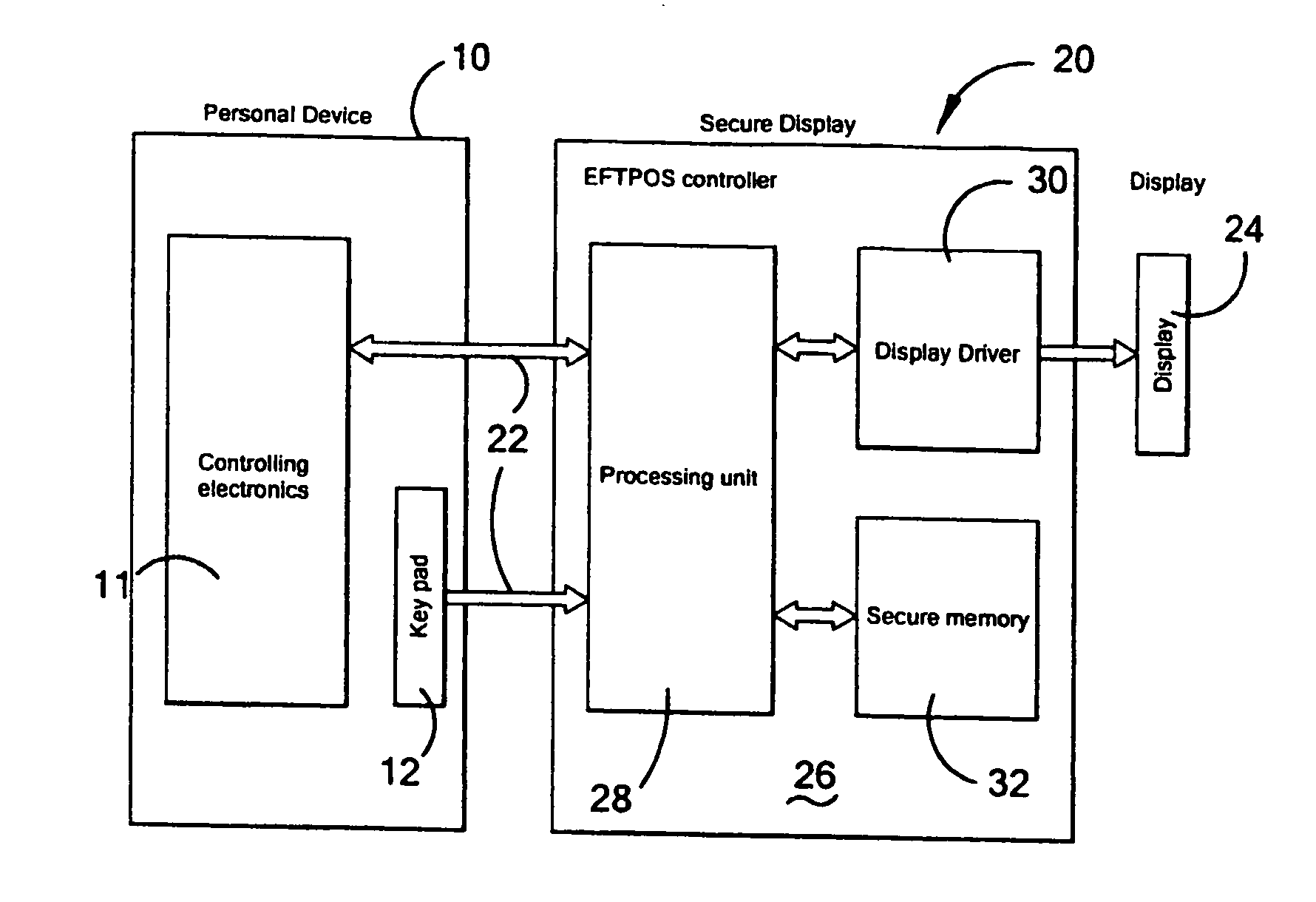
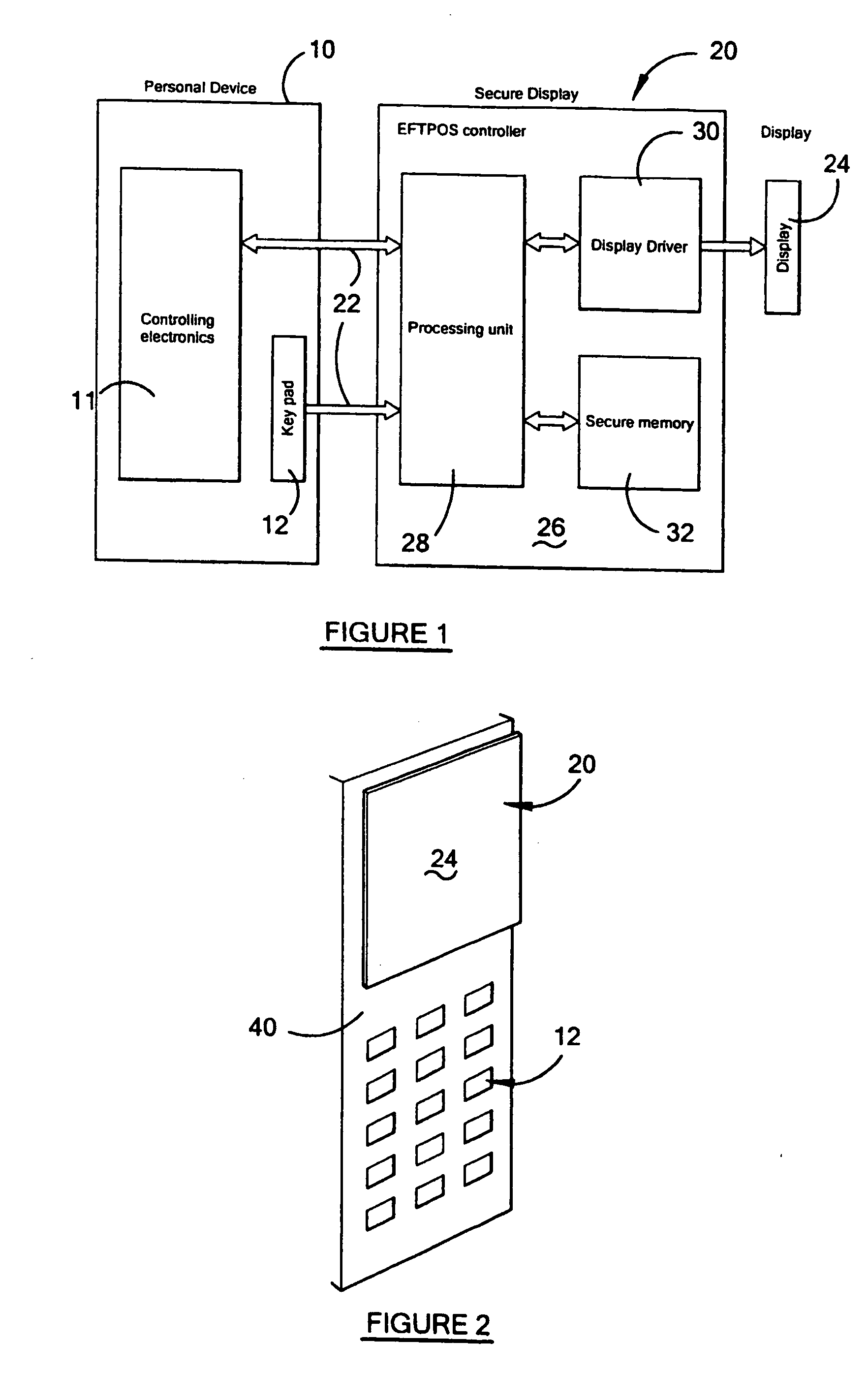
Display device and funds transaction device including the display device
InactiveUS20050222925A1Secure performanceProcess safetyFinancePoint-of-sale network systemsFinancial transactionComputer science
A display device is disclosed which may be used in a mobile telephone or other article which is intended to make secure transactions such as financial transactions, as well as other personal transactions such as telephone calls. The device includes a display (24) for displaying information, a financial transaction controller (26) including a processor (28), a display driver (30) for driving the display (24) and a secure memory (32). The financial transaction controller allows the display section (24), and an input keypad (12), to operate under the control of the device to enable personal functions other than financial transactions to be performed. However, in the event of a financial transaction, the financial transaction controller takes over control of the display section (24) and the input keypad (12) so that the financial transaction can be performed while the device is under the control of the financial transaction controller to thereby prevent tampering with or tapping off of data, and also the display of information other than under the control of the financial controller.
Owner:S AQUA SEMICONDUCTOR LLC
Information processing apparatus, program and coordinate input method
InactiveUS6992660B2Easy to switchWithout any changeTransmission systemsCathode-ray tube indicatorsComputational scienceInformation processing
Owner:LENOVO PC INT
Processing method of polymer crystal, processing system of polymer crystal, and observation system of polymer crystal
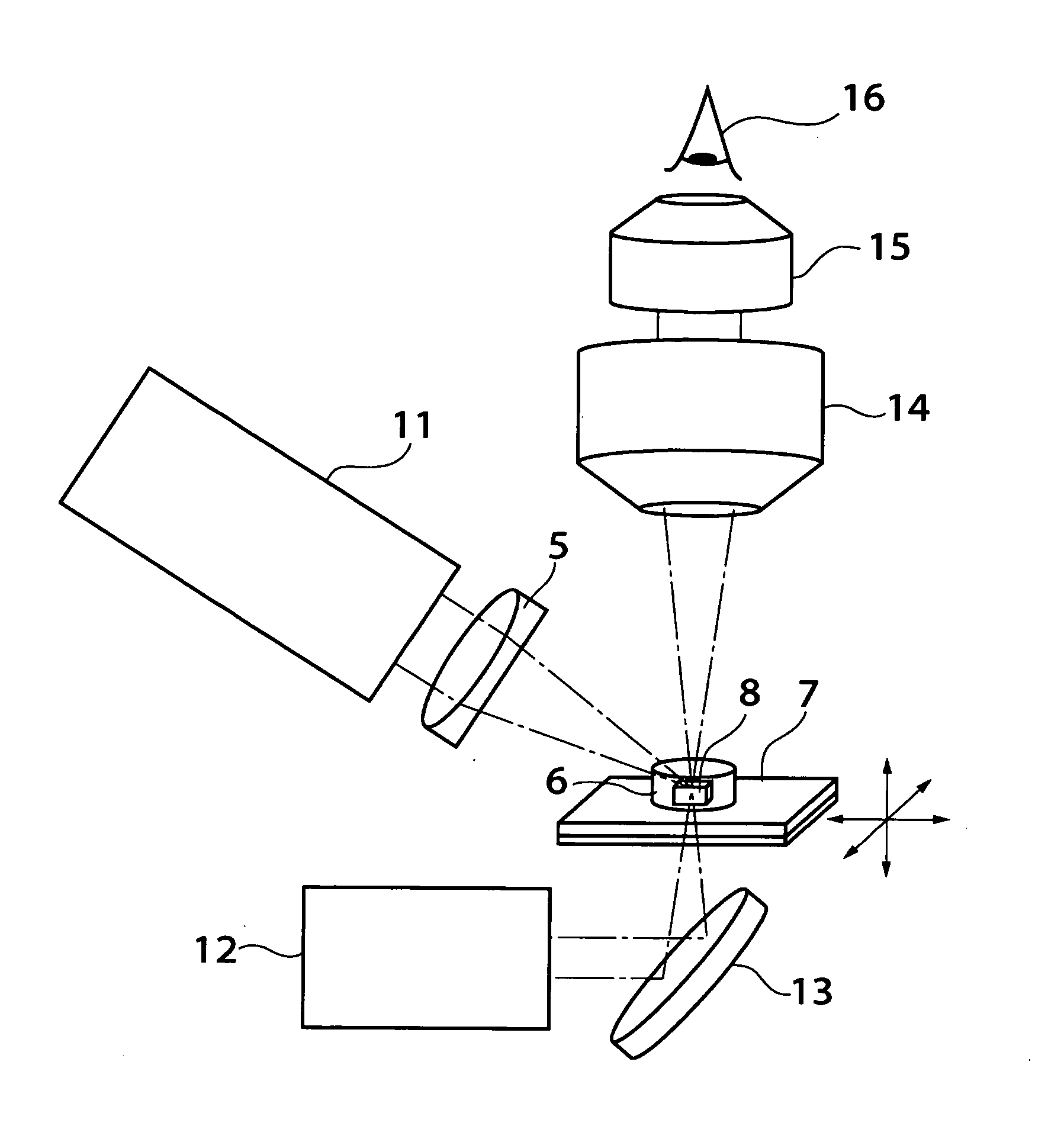
ActiveUS20060171656A1Accurately performAvoid damageCoupling light guidesWelding/soldering/cutting articlesPhysicsOrthogonal coordinates
The ultraviolet short-pulse laser light emitted from the ultraviolet short-pulse laser light source 1 is focused on and caused to irradiate a macromolecular crystal 8 contained in a sample container 6 via a shutter 2, intensity adjusting element 3, irradiation position control mechanism 4, and focusing optical system 5. The sample container 6 is carried on a stage 7, and can be moved in three dimensions along the directions of the x, y and z axes in an x-y-z orthogonal coordinate system with the direction of the optical axis being taken as the z axis; furthermore, the sample container 6 can be rotated about the z axis. Working of the macromolecular crystal is performed by means of ultraviolet short-pulse laser light that is focused on and caused to irradiate the surface of the macromolecular crystal 8. In this way, various types of working can be securely performed on macromolecular crystals with little damage and by means of a simple operation.
Owner:NIKON CORP +6
Internal-combustion-engine combustion condition detection apparatus and combustion condition detection method
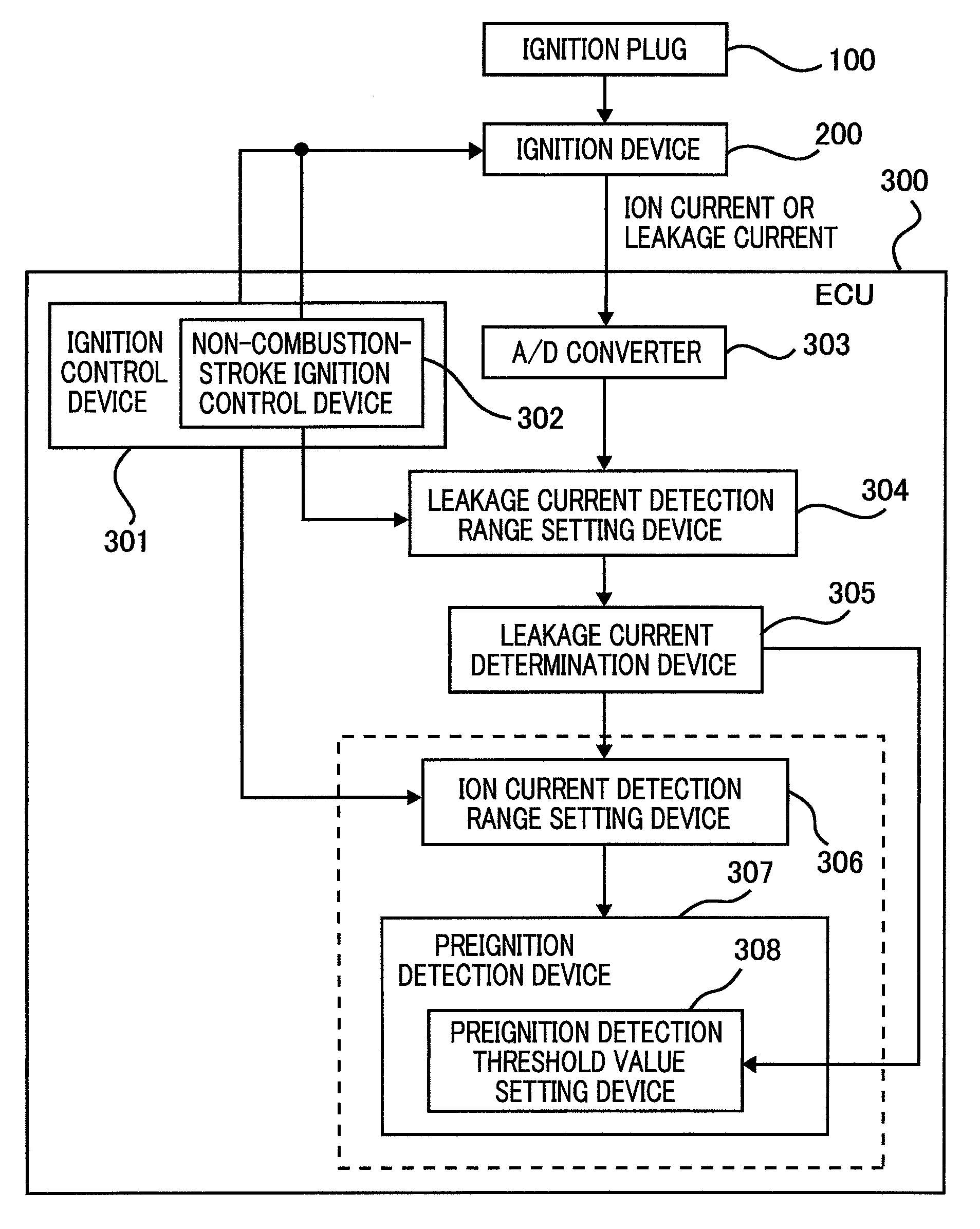
ActiveUS7673614B2High measurement accuracySecure performanceEngine testingMachines/enginesCombustionEngineering
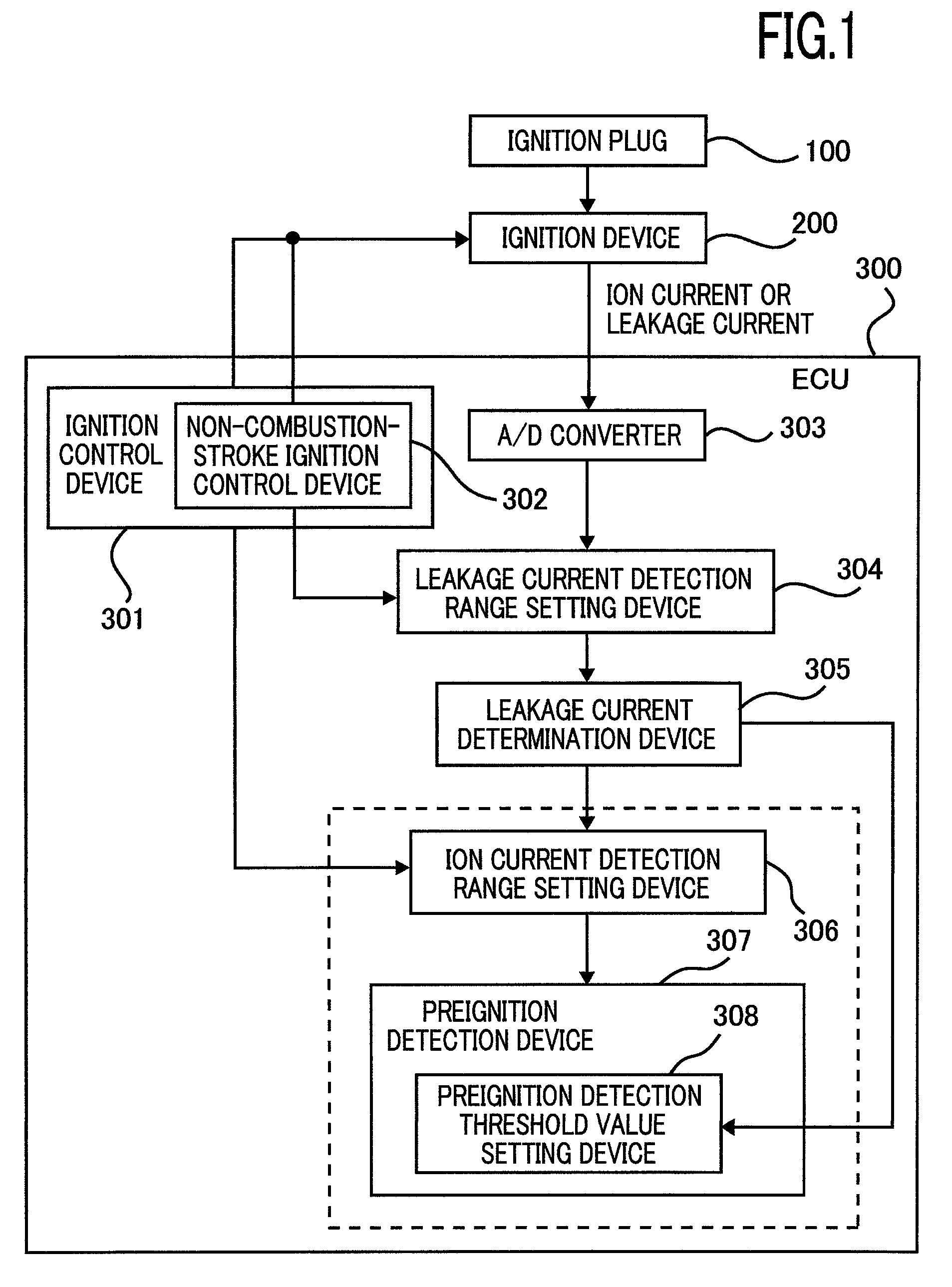
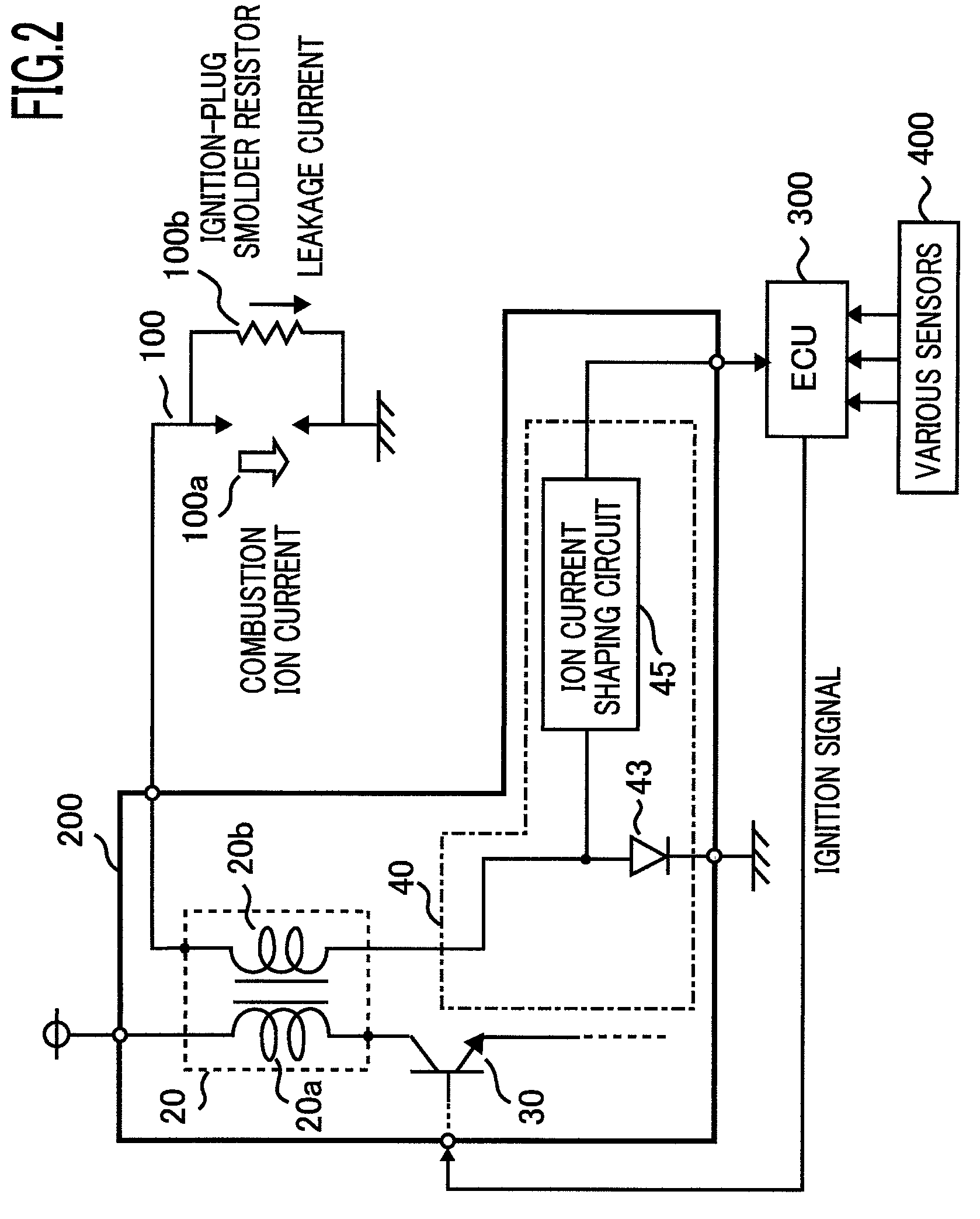
An internal-combustion-engine combustion condition detection apparatus is provided with an ignition means that makes an ignition plug ignite a fuel; an ignition control means that controls the operation of the ignition means; an ion-current detection means that detects an ion current generated; an ion current detection range setting means that sets an ion-current detection range; a preignition detection means that detects preignition within a detection range to be set; a leakage current detection range setting means that sets a leakage-current detection range; and a leakage current determination means that determines whether or not a smolder exists, based on a current detected, within a detection range to be set, by the ion-current detection means. The ignition control means includes a non-combustion-stroke ignition control means; the leakage-current detection range set by the leakage current detection range setting means is set within the non-combustion stroke.Accordingly, both a smolder detection and a preignition detection can securely be performed.
Owner:MITSUBISHI ELECTRIC CORP
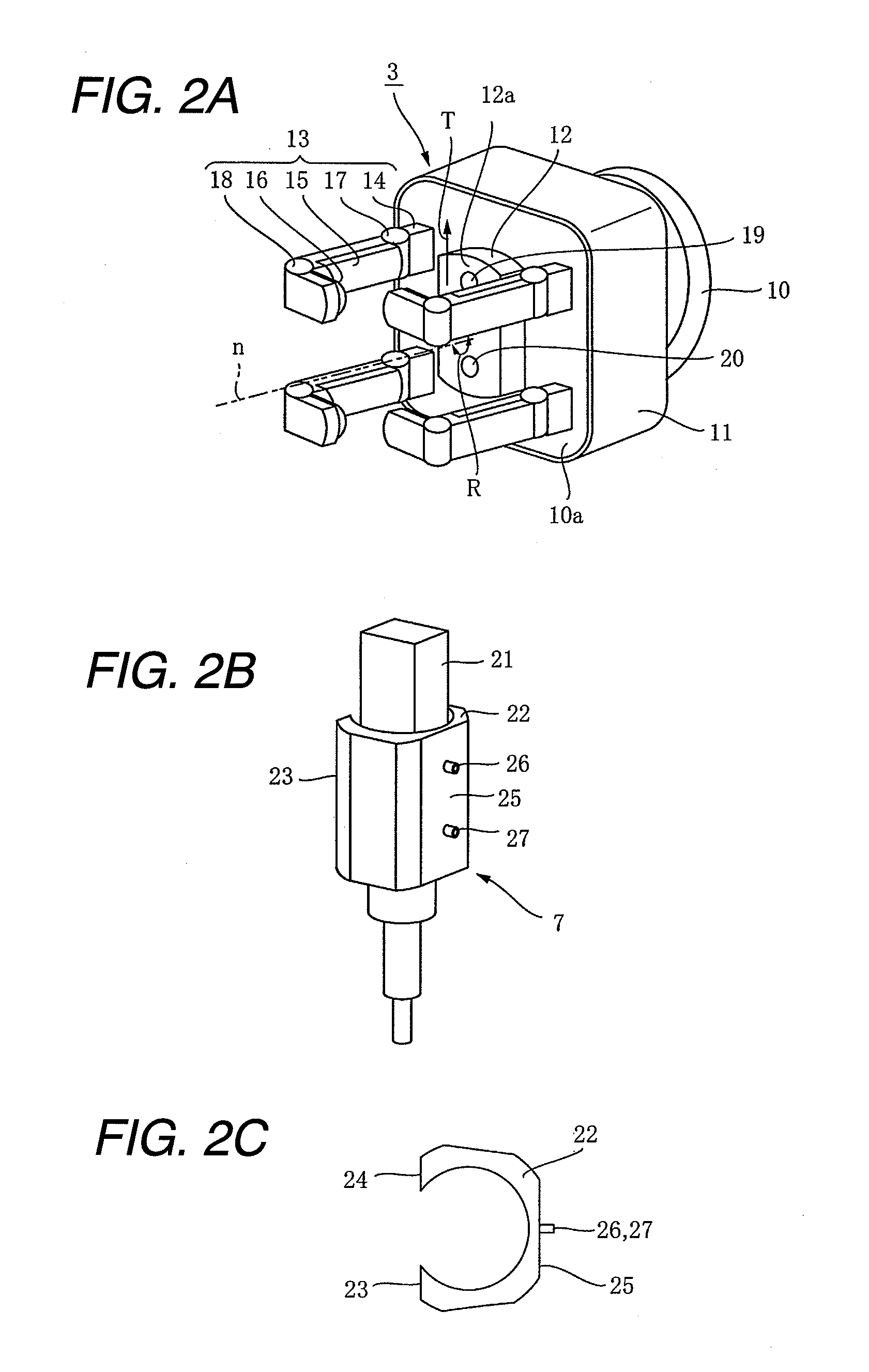
Gripping apparatus, robot system and gripping method
ActiveUS20120007374A1Promote reproductionExact reproductionGripping headsLoad-engaging elementsRobotic systemsSacroiliac joint
Owner:CANON KK
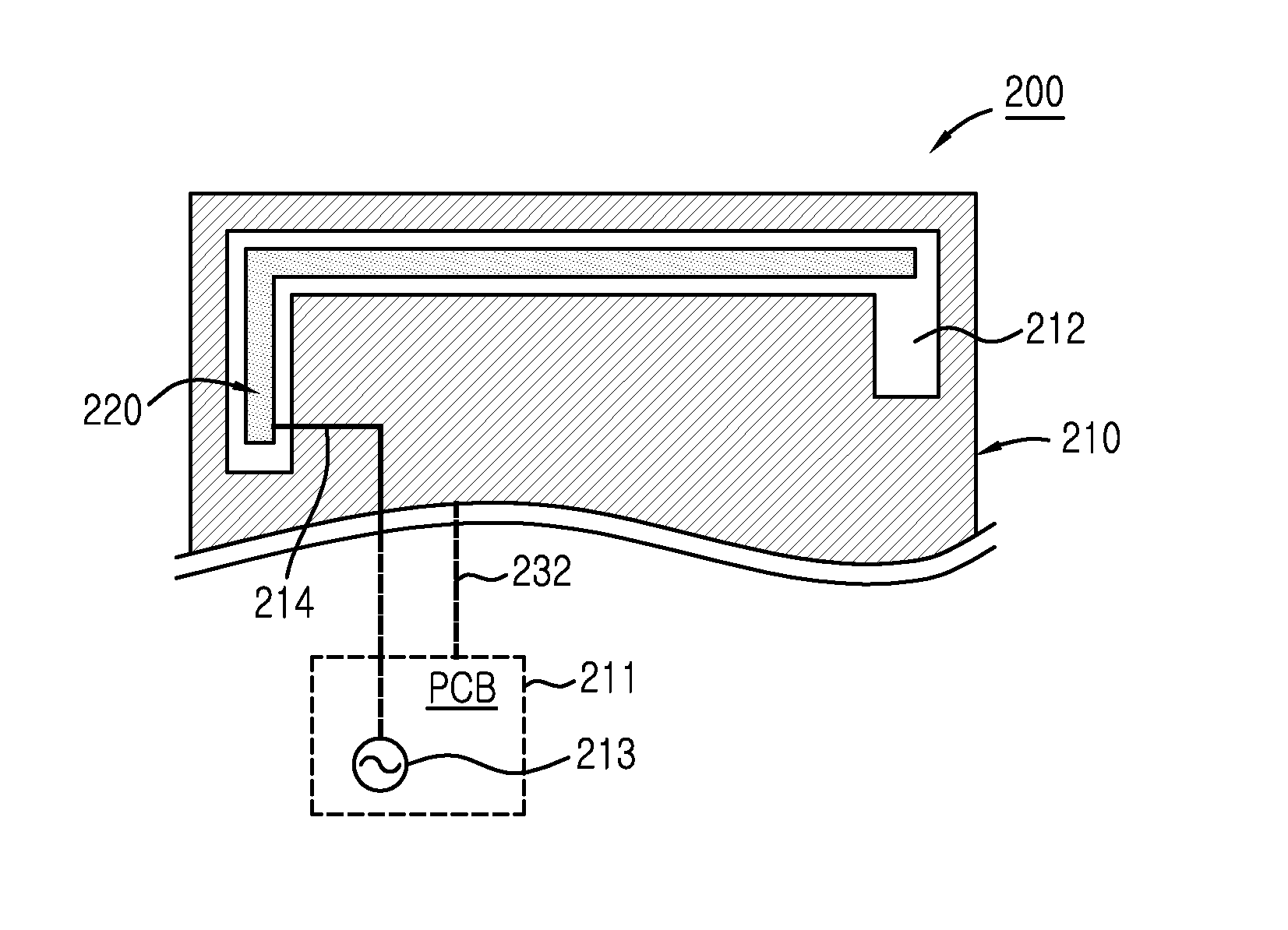
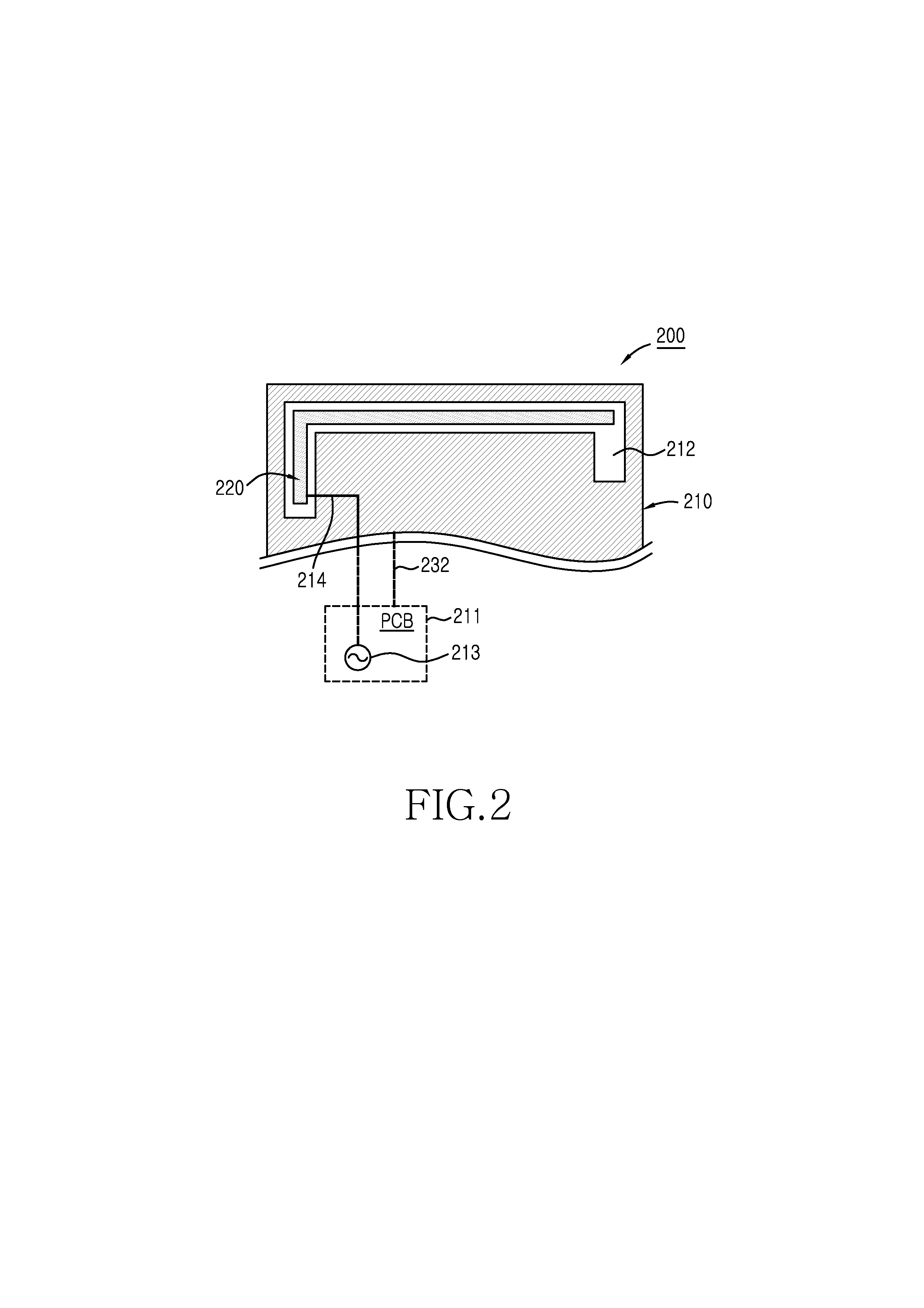
Antenna device for portable terminal
ActiveUS20130181871A1MiniaturizingSecure antenna performanceSimultaneous aerial operationsAntenna supports/mountingsElectromagnetic couplingElectricity
An antenna device for a portable terminal having a printed circuit board (PCB) is disclosed. The antenna device is comprised of first and second antenna elements. The first antenna element includes at least a portion of one or more metal members disposed within the portable terminal; is electrically connected with a ground surface of the PCB; and has a slot. The second antenna element, is disposed in proximity to the slot, spaced from and electromagnetically coupled to the first antenna element. The second antenna element receives RF power from the PCB and is configured to resonate at a frequency of the RF power.
Owner:SAMSUNG ELECTRONICS CO LTD
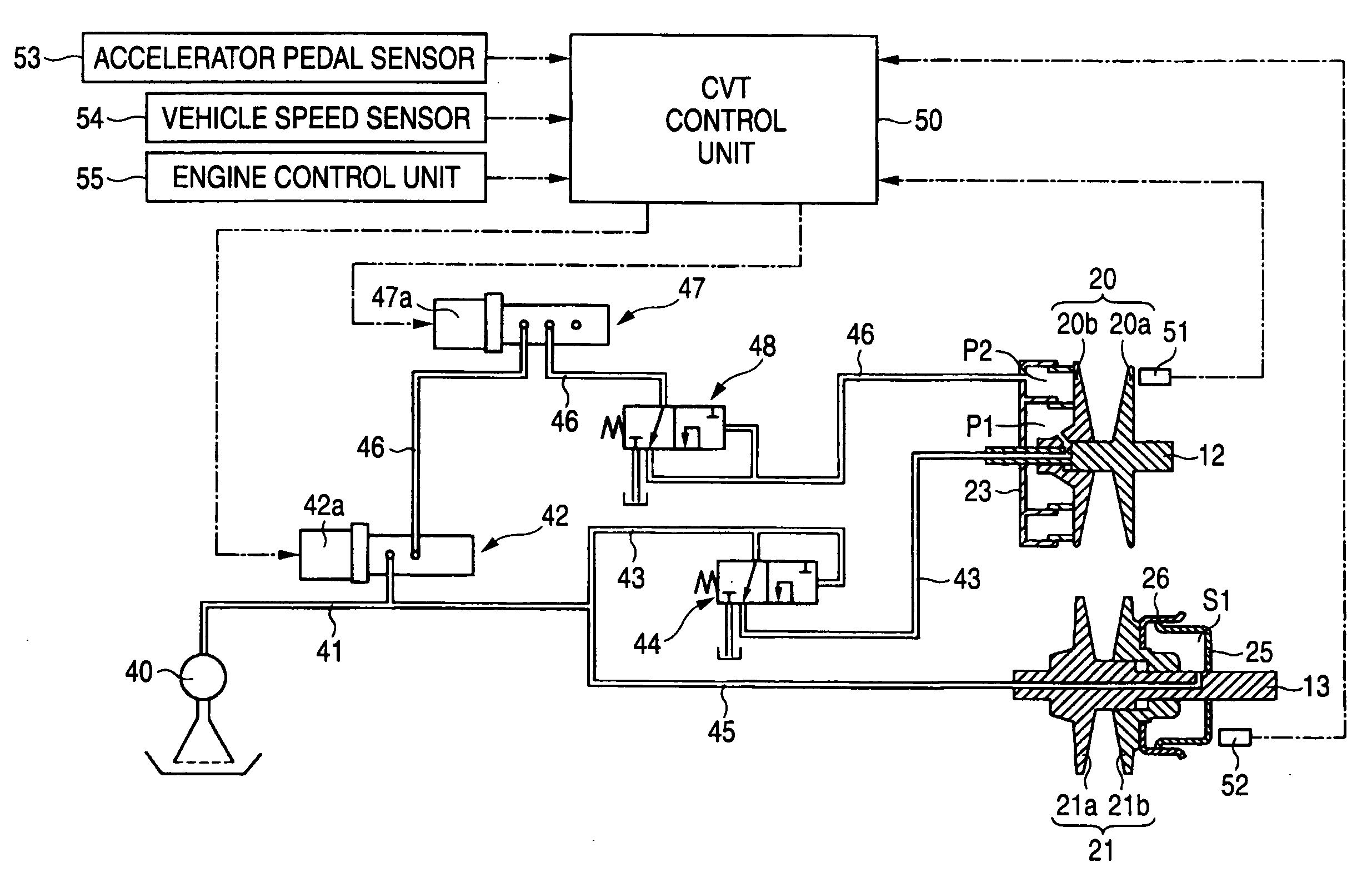
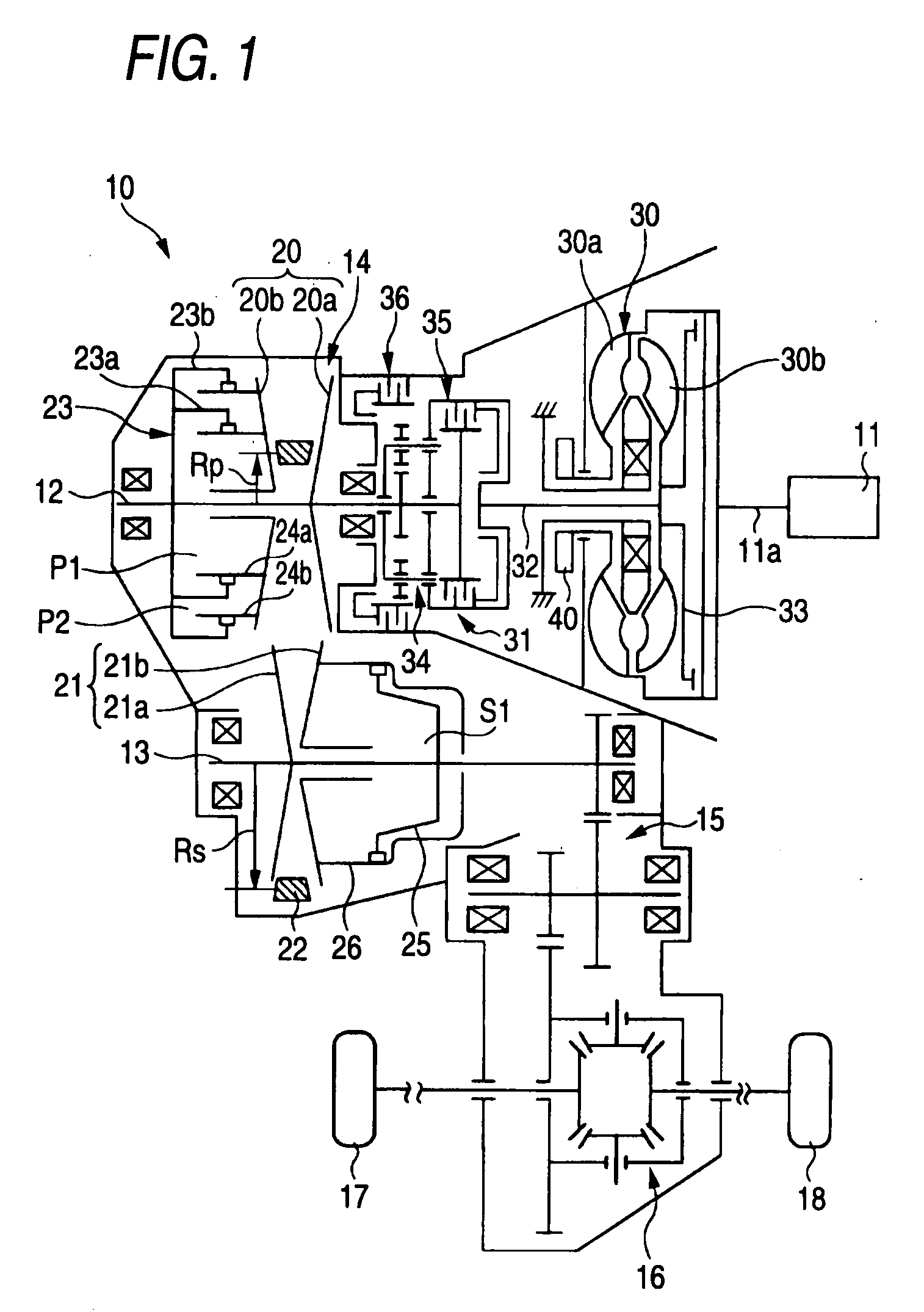
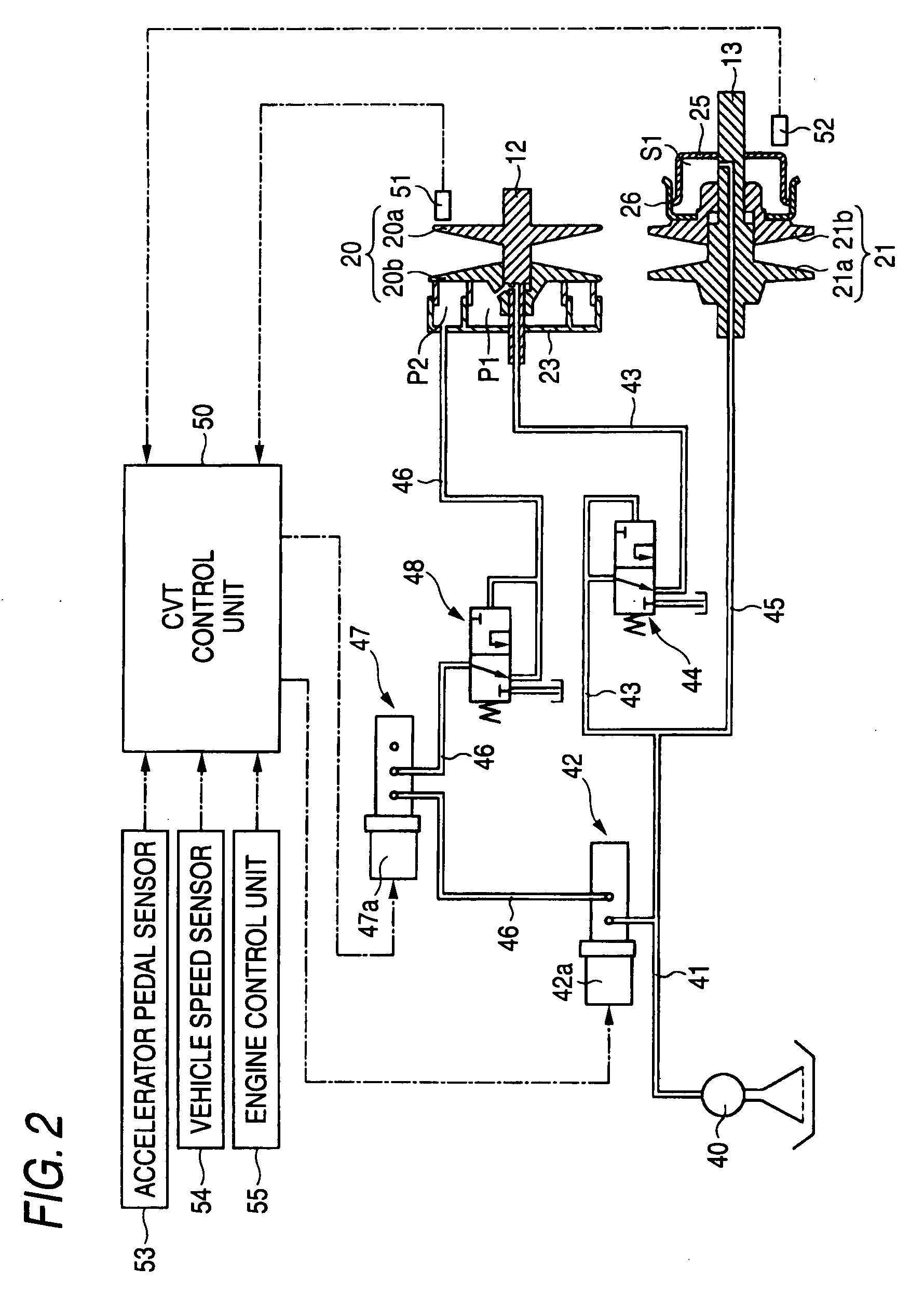
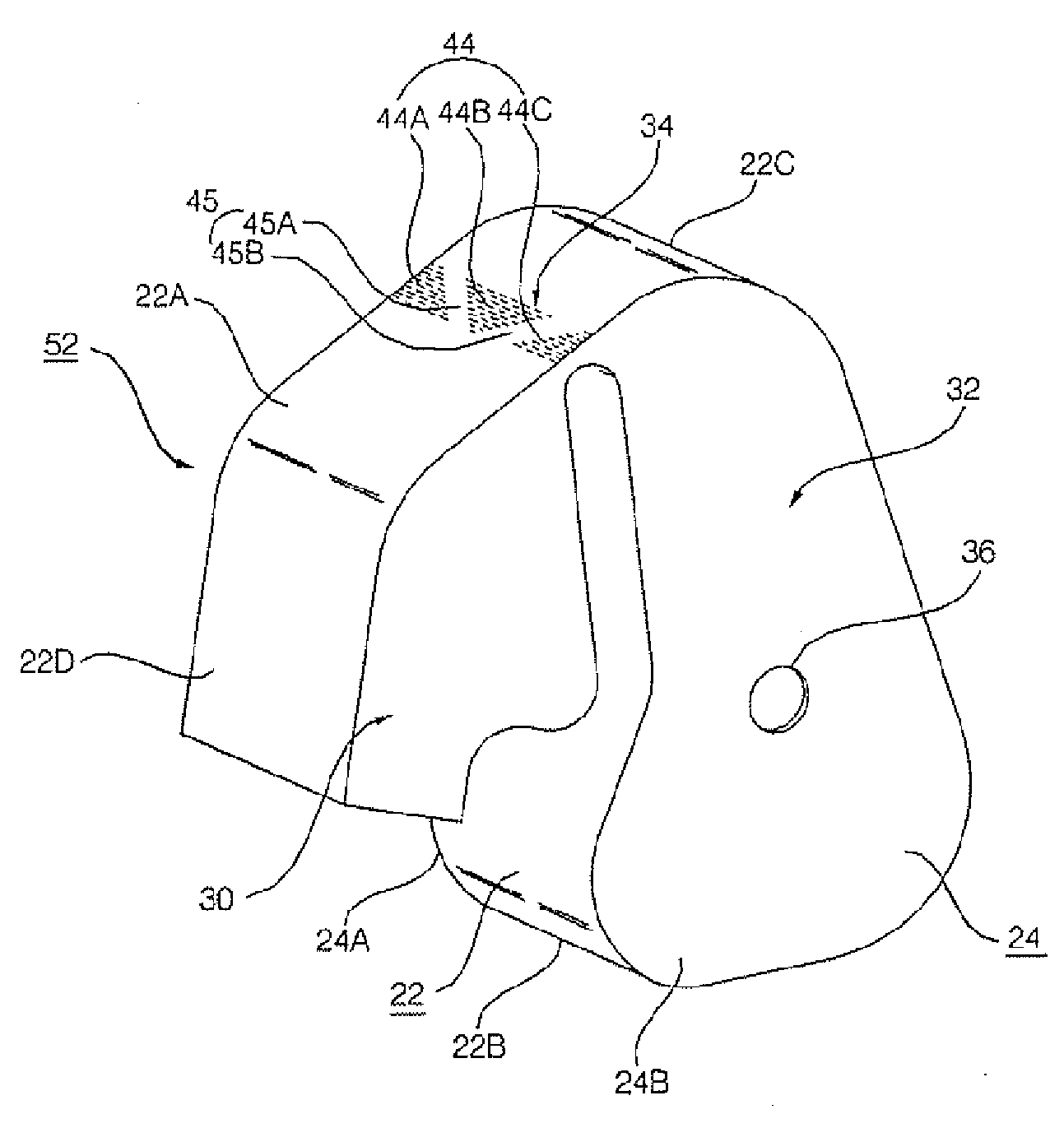
Control device for continuously variable transmission
Safety as well as the minimum driving performance is secured by preventing abrupt down-shifting if a line pressure valve or a primary pressure control valve fails. A line pressure path connected to an oil pump is connected with a line pressure control valve. A first primary pressure path branched from the line pressure path is connected with a hydraulic fluid chamber through a fail-safe valve, and a secondary pressure path branched from the line pressure path is connected to a hydraulic fluid chamber. The line pressure control valve is connected with a second primary pressure path in communication with a hydraulic fluid chamber, and this secondary primary pressure path is provided with a primary pressure control valve and a limiter valve. When the line pressure control valve and the primary pressure control valve fail and excess line pressure or primary pressure is output, the pressure in the hydraulic fluid chamber is reduced by the fail-safe valve, so that the pressure in the hydraulic fluid chamber is reduced by the limiter valve.
Owner:SUBARU CORP
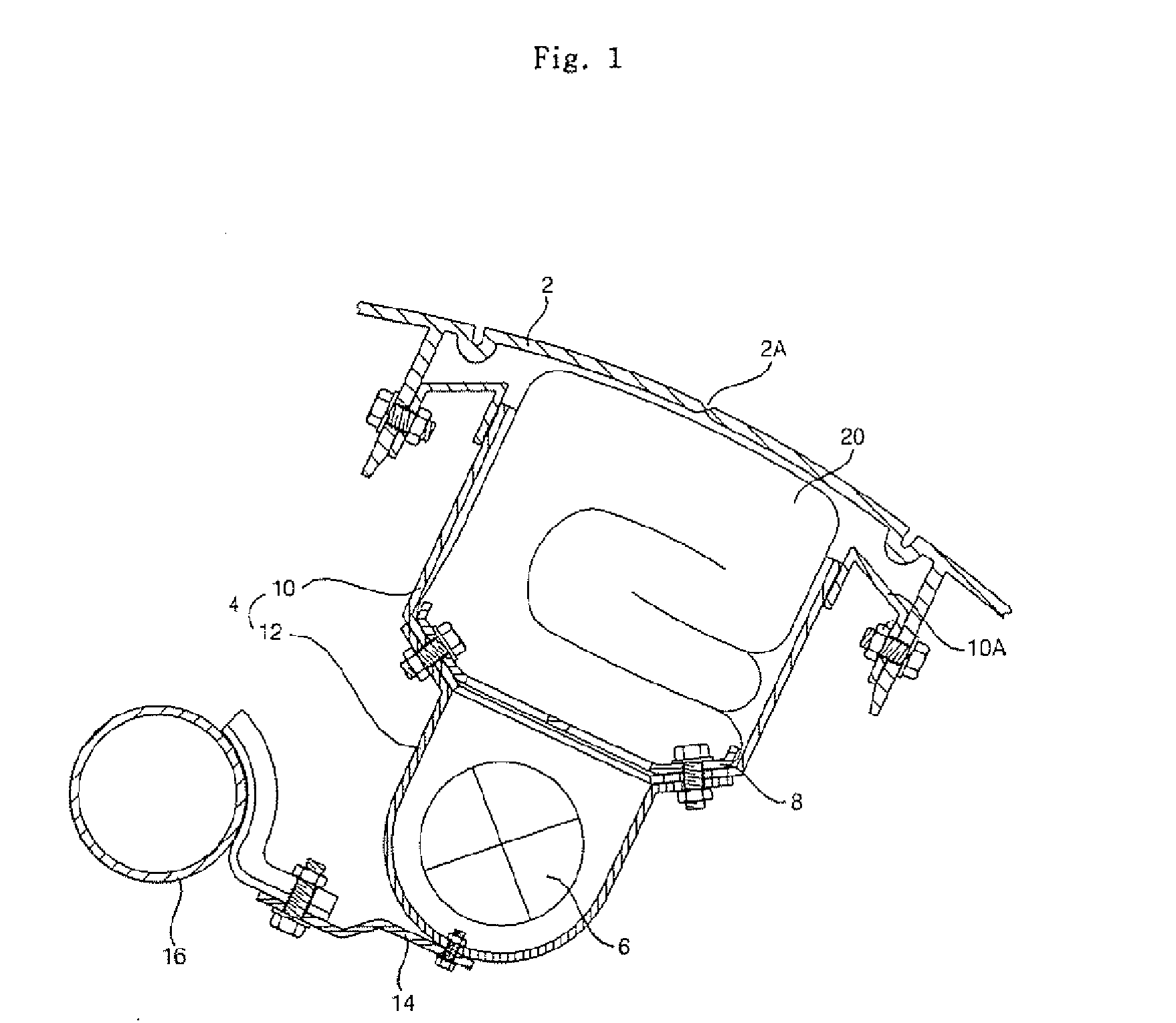
Cushion of air bag system
InactiveUS20070296186A1Avoid injurySecure performancePedestrian/occupant safety arrangementVehicle design optimisationOlder childEngineering
A cushion of an air bag system is provided. The cushion of the air bag system includes a first cushion deploying by a gas of an inflator, a second cushion formed in front of the first cushion to receive the gas from the first cushion and to deploy toward a rider, and a cushion connecting unit formed between the second cushion and the first cushion so that the second cushion is rotatably connected to the first cushion and that the internal gas of the first cushion flows into the second cushion. It is possible to prevent the rider in the OOP state from being injured and to secure the performance of protecting the rider in the normal position state. During the test of the performance of protecting the one year old child, the three year old child, and the six year old child in the OOP state of the air bag system, the injury reduction deployment of the cushion is satisfied. Since the passenger recognizing sensor and the plurality of flaps are omitted, it is possible to reduce the number, the cost, and the weight of parts of the air bag system.
Owner:LG ELECTRONICS INC
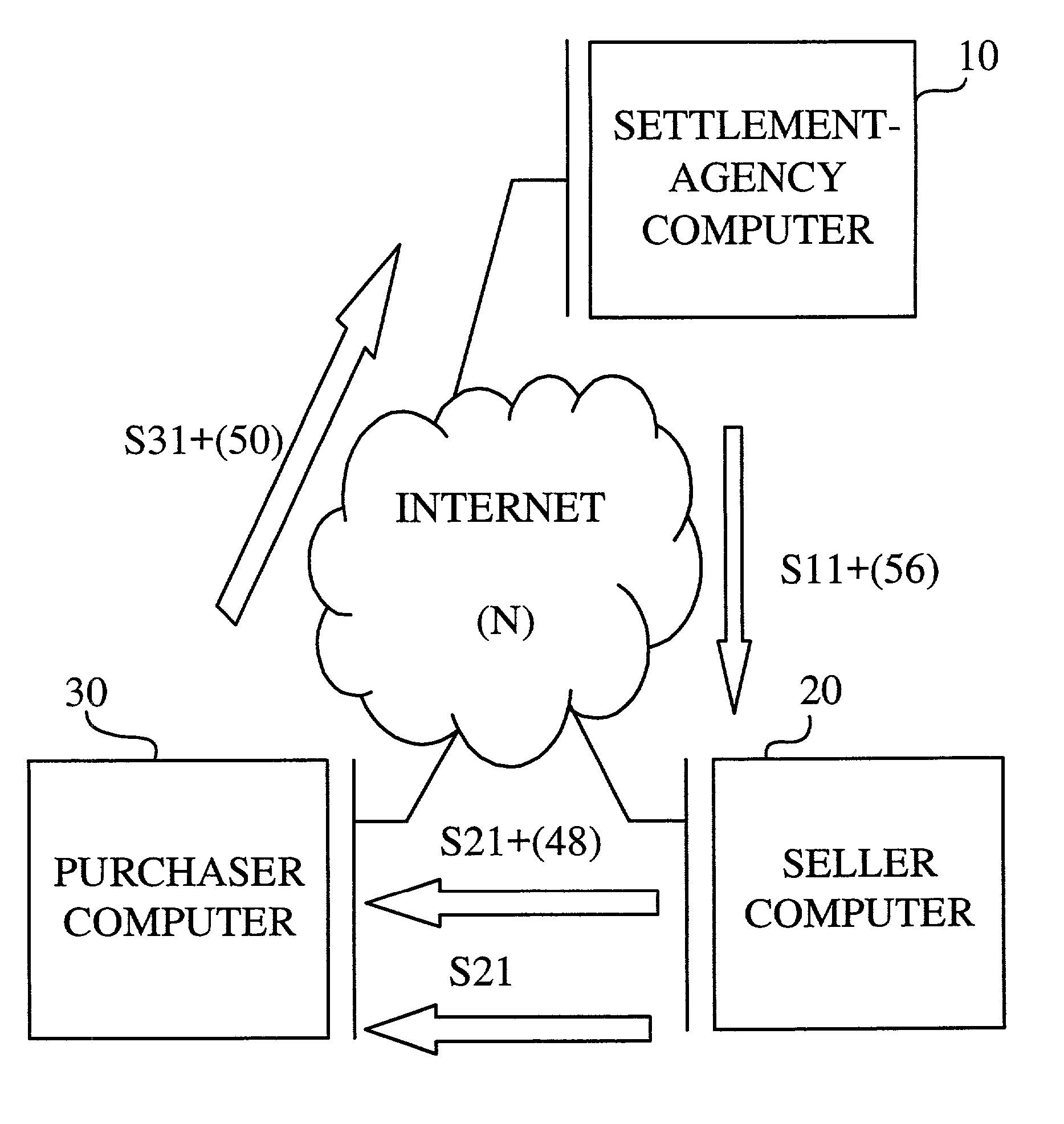
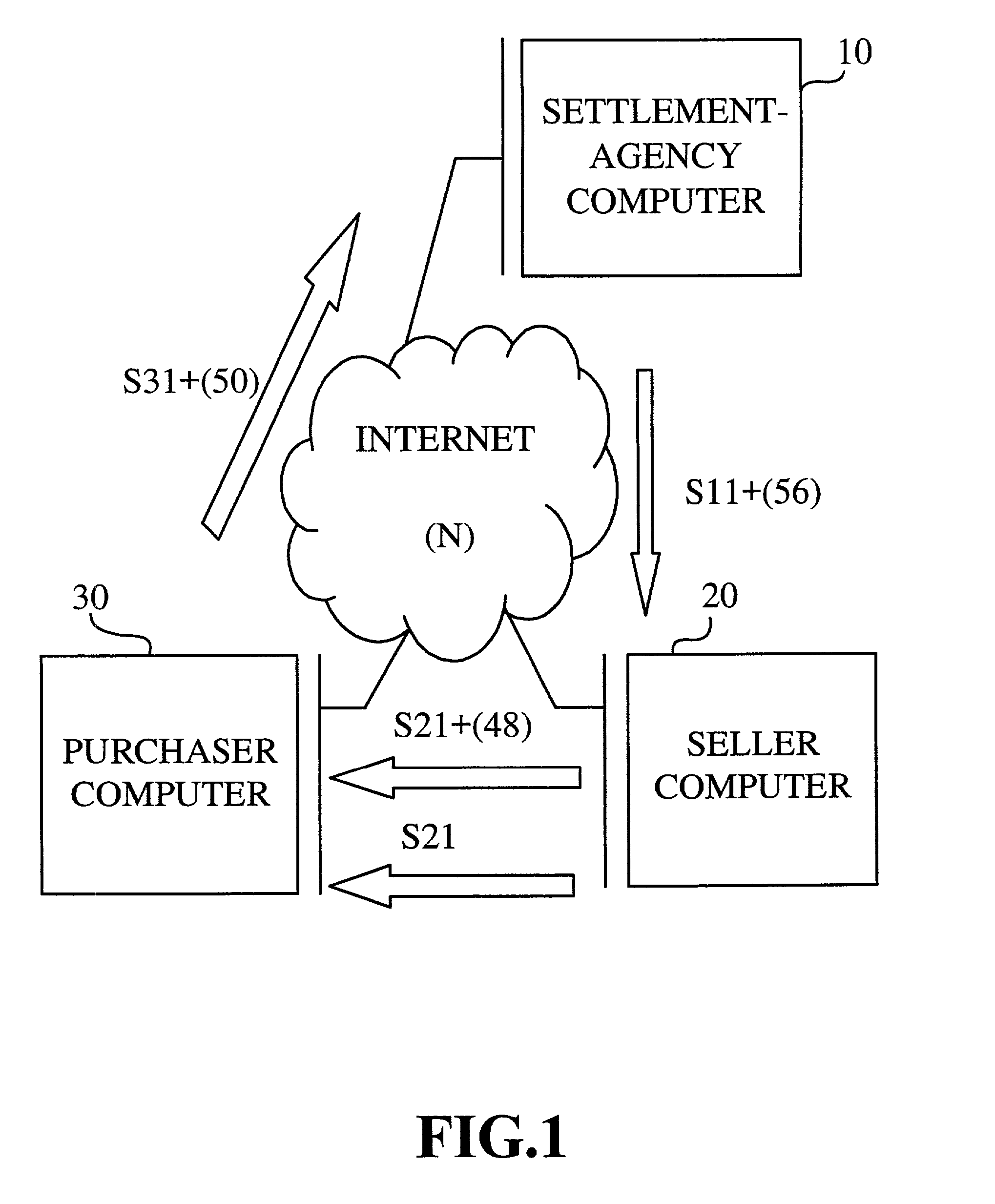
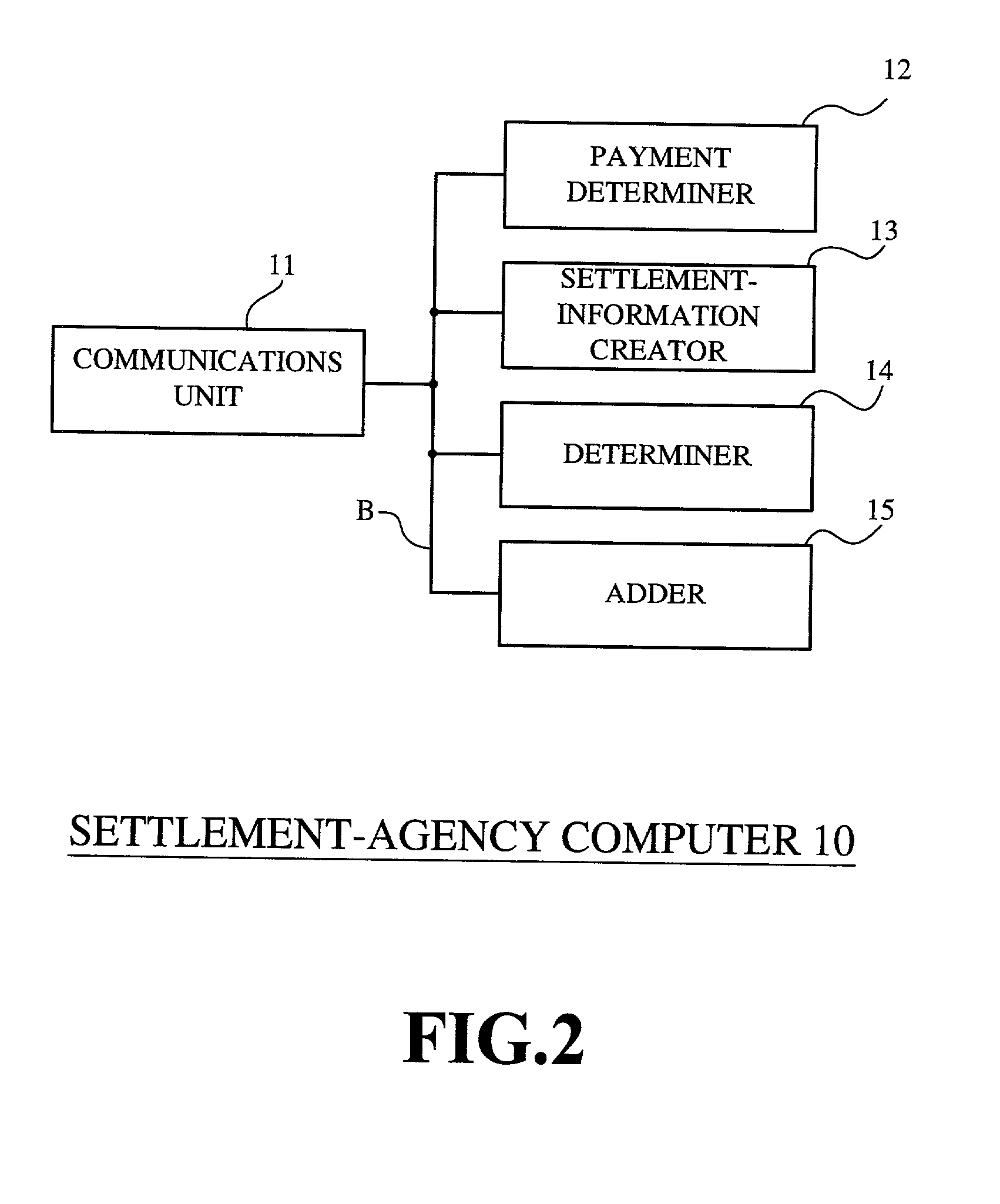
Electronic commerce system and electronic commerce method
A message, including ordering data regarding a price of a product that a purchaser wants to purchase and personal information including a credit card number of the purchaser, is given to a settlement agency computer from a purchaser computer used by the purchaser. The settlement agency computer determines whether to pay for the product for the purchaser, based on the ordering data and the personal information. In a case where it is determined to pay for the product for the purchaser, the settlement agency computer sends settlement permission information representing that payment can be made for the purchaser, to a seller computer used by a seller, while keeping the credit card number to be confidential. Hence, before delivering the product to the purchaser, the settlement is completed, and the credit card number of the purchaser is kept secret from the seller.
Owner:RICOH KK
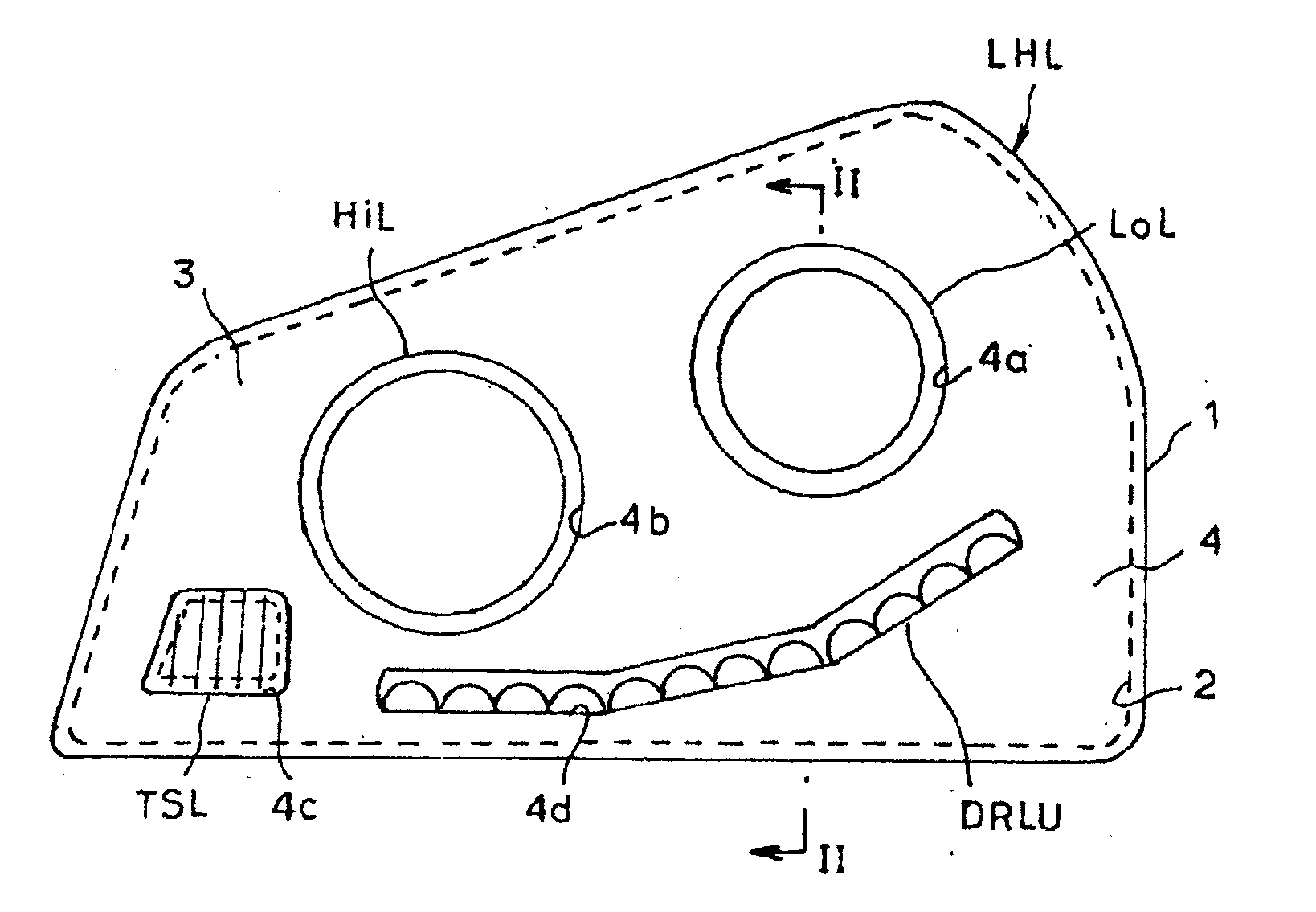
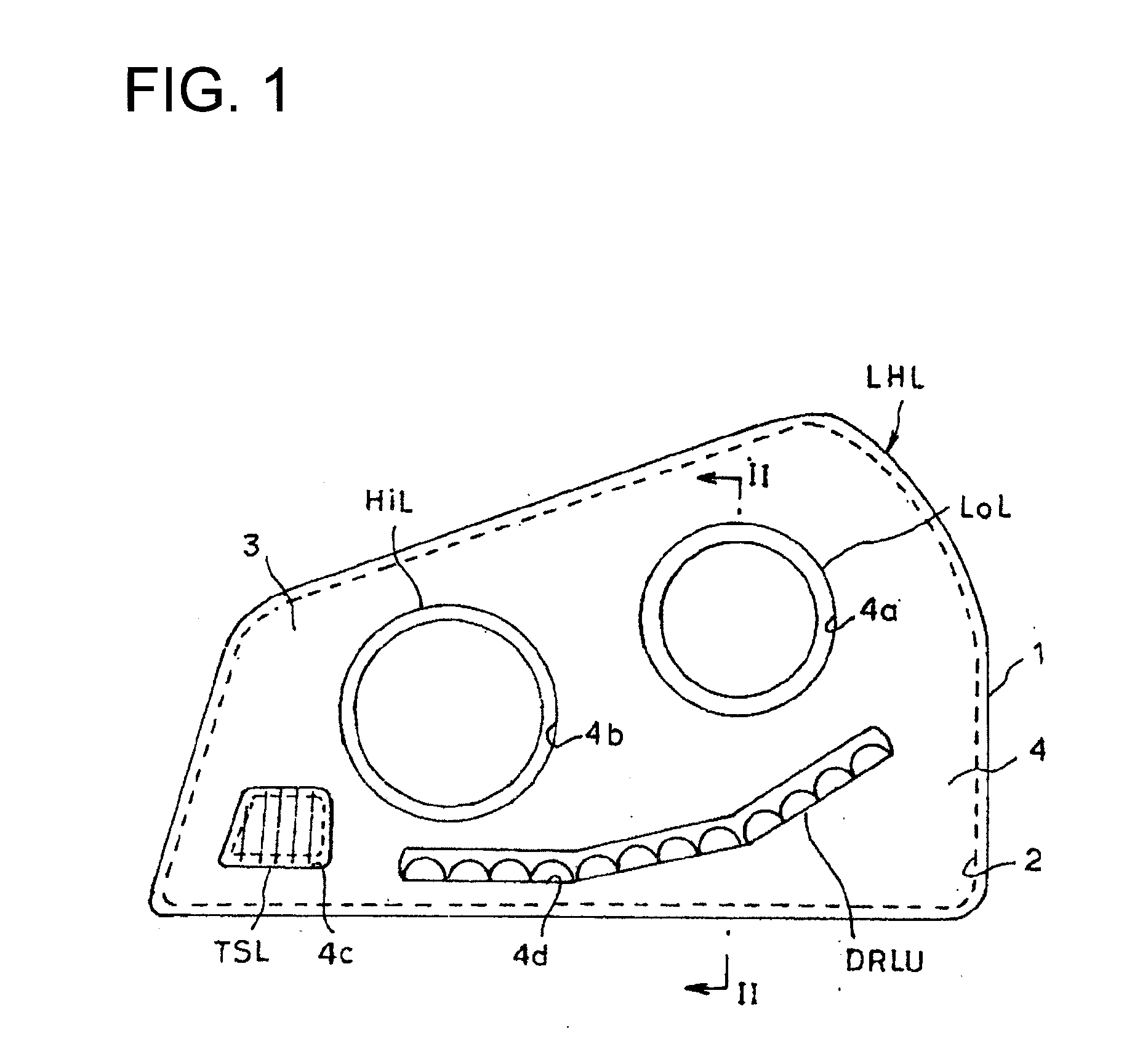
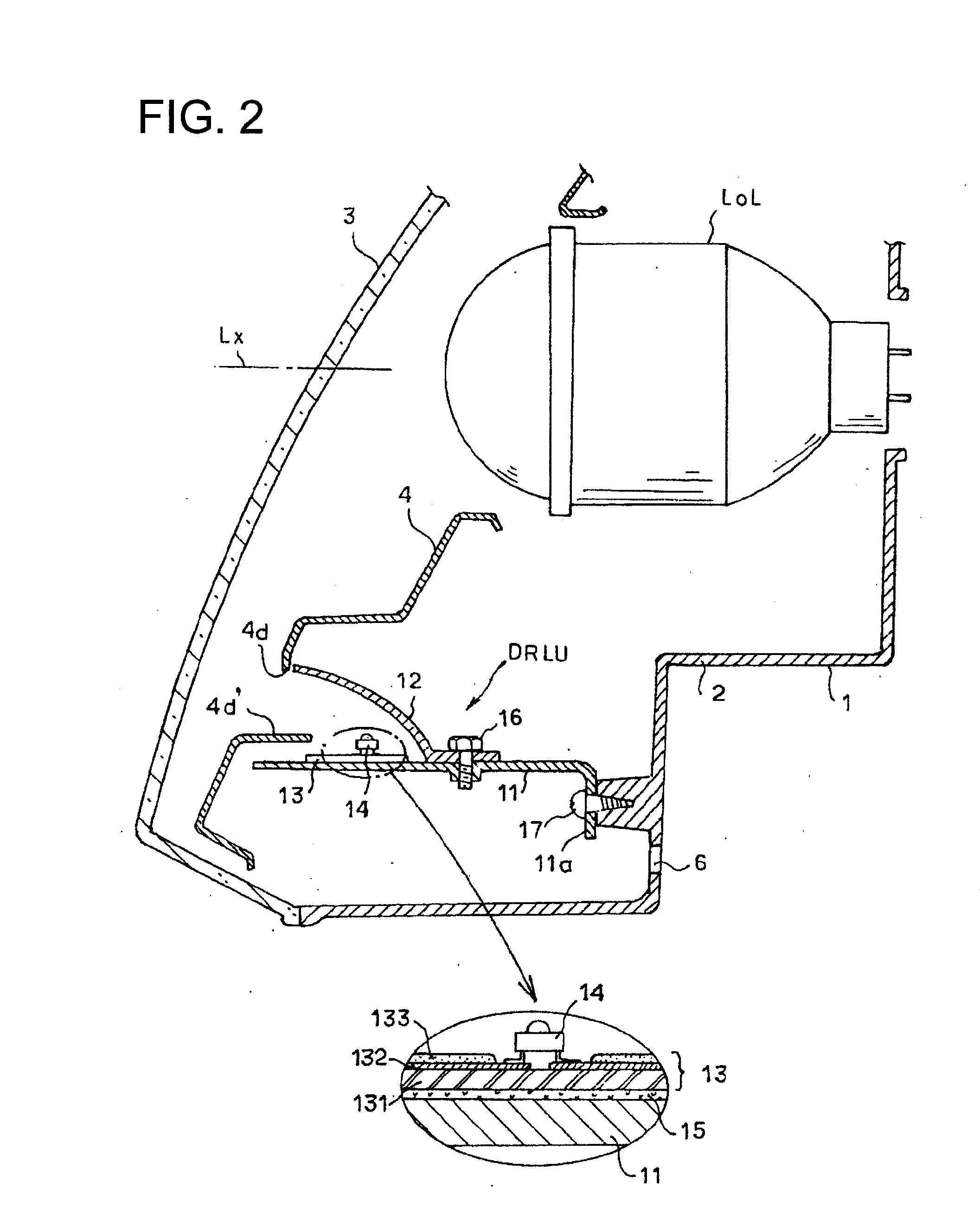
Vehicular lamp
InactiveUS20100290241A1Improve heat radiation performanceHeat radiation performance is degradedVehicle headlampsPoint-like light sourceThermal conductivityEngineering
A vehicular lamp including a light source unit including a light-emitting element inside a lamp housing; a planar wiring member on which the light-emitting element is mounted; and a support substrate having a flat portion that supports the planar wiring member. The support substrate is formed from a plate having high thermal conductivity, the planar wiring member is fixed to the flat portion of the support substrate, and a portion of the support substrate is fixedly supported inside the lamp housing.
Owner:KOITO MFG CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com