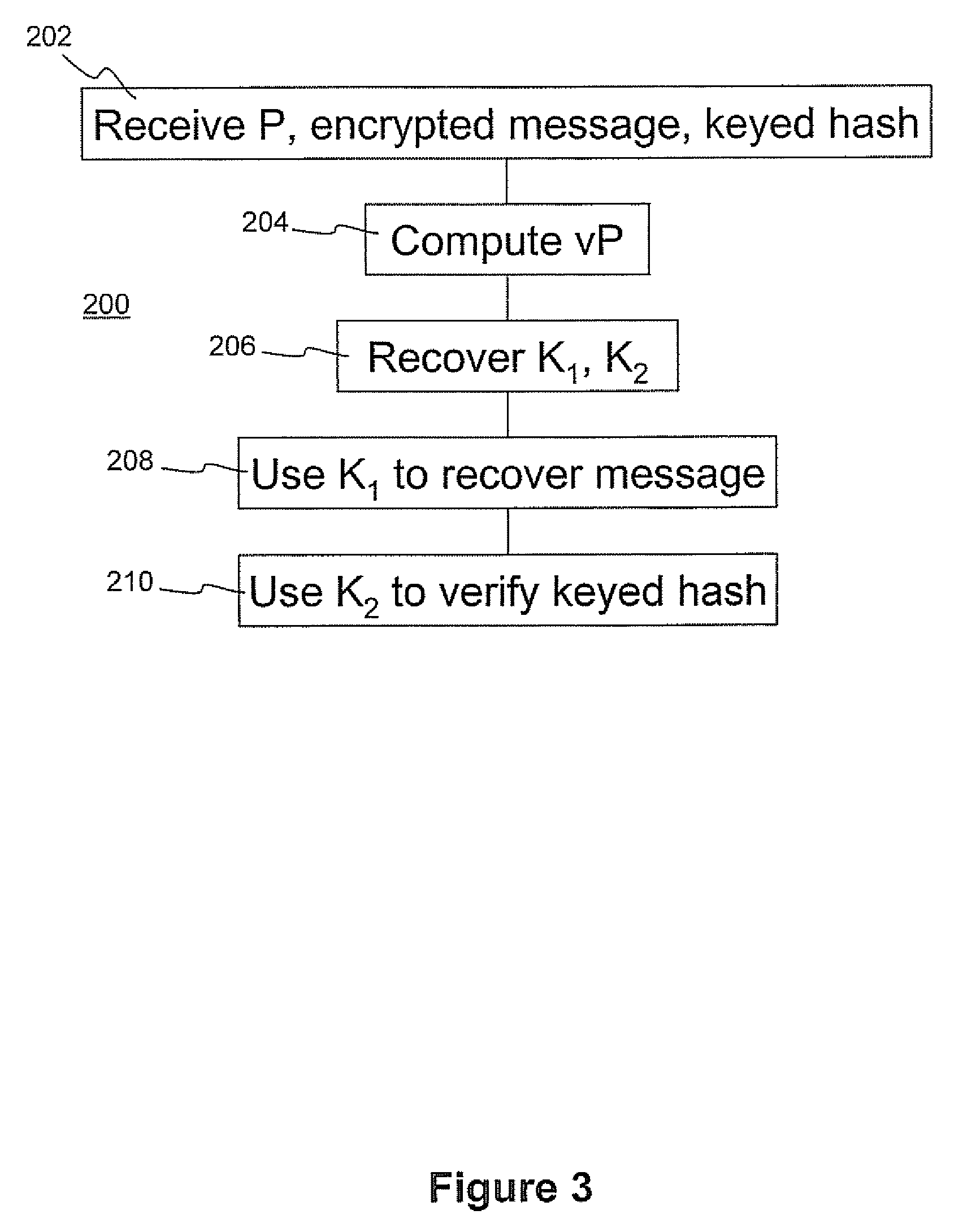
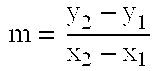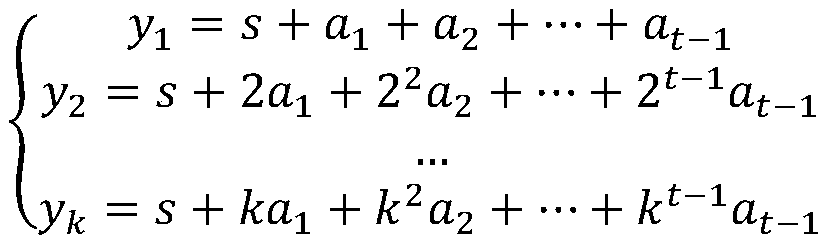Patents
Literature
81 results about "Elliptic curve cryptosystem" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Elliptic curve cryptosystem apparatus, elliptic curve cryptosystem method, elliptic curve cryptosystem program and computer readable recording medium storing the elliptic curve cryptosystem program
InactiveUS20060093137A1Increase speedProvide securityPublic key for secure communicationUnauthorized memory use protectionSoftware engineeringMechanical engineering
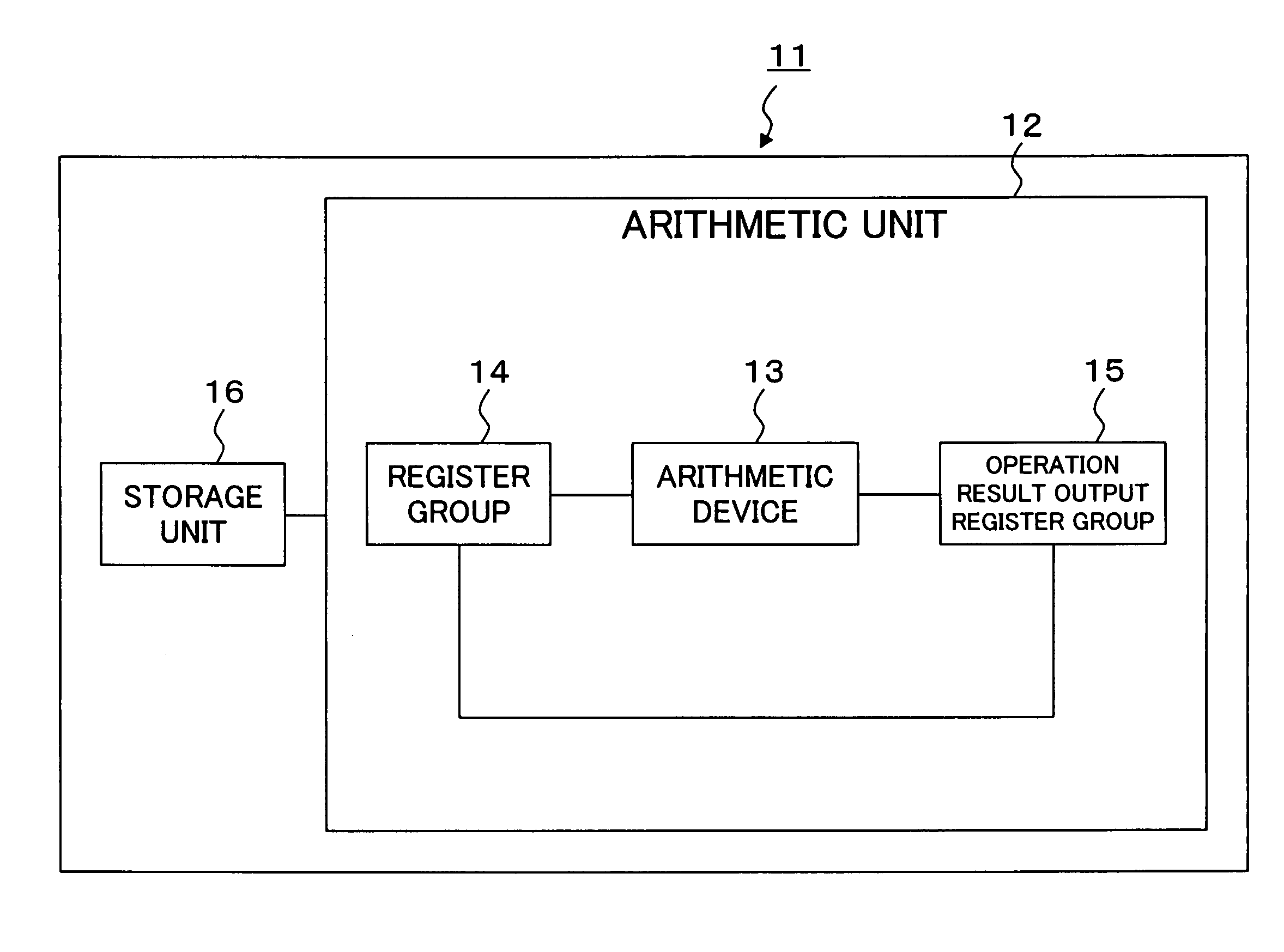
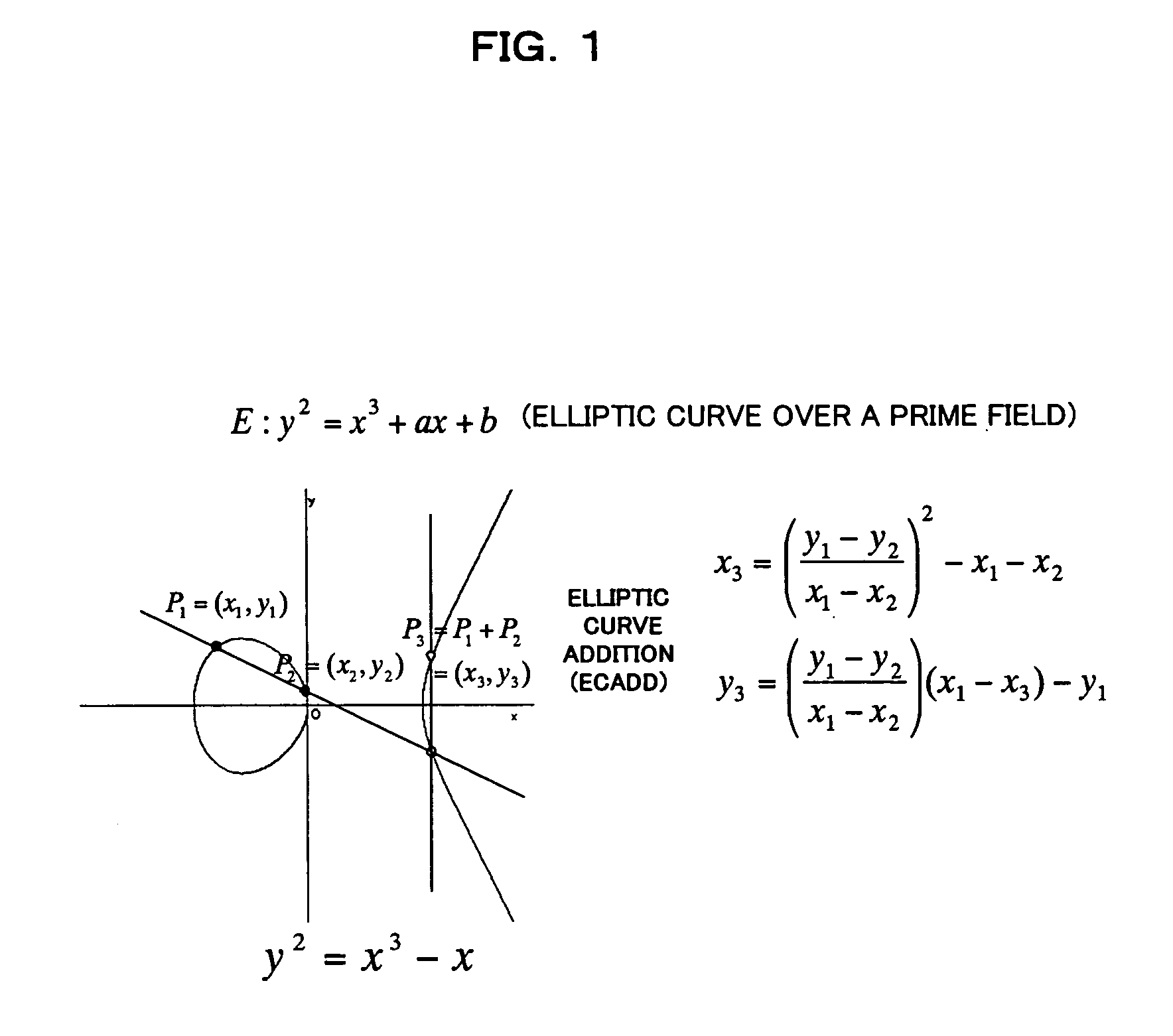
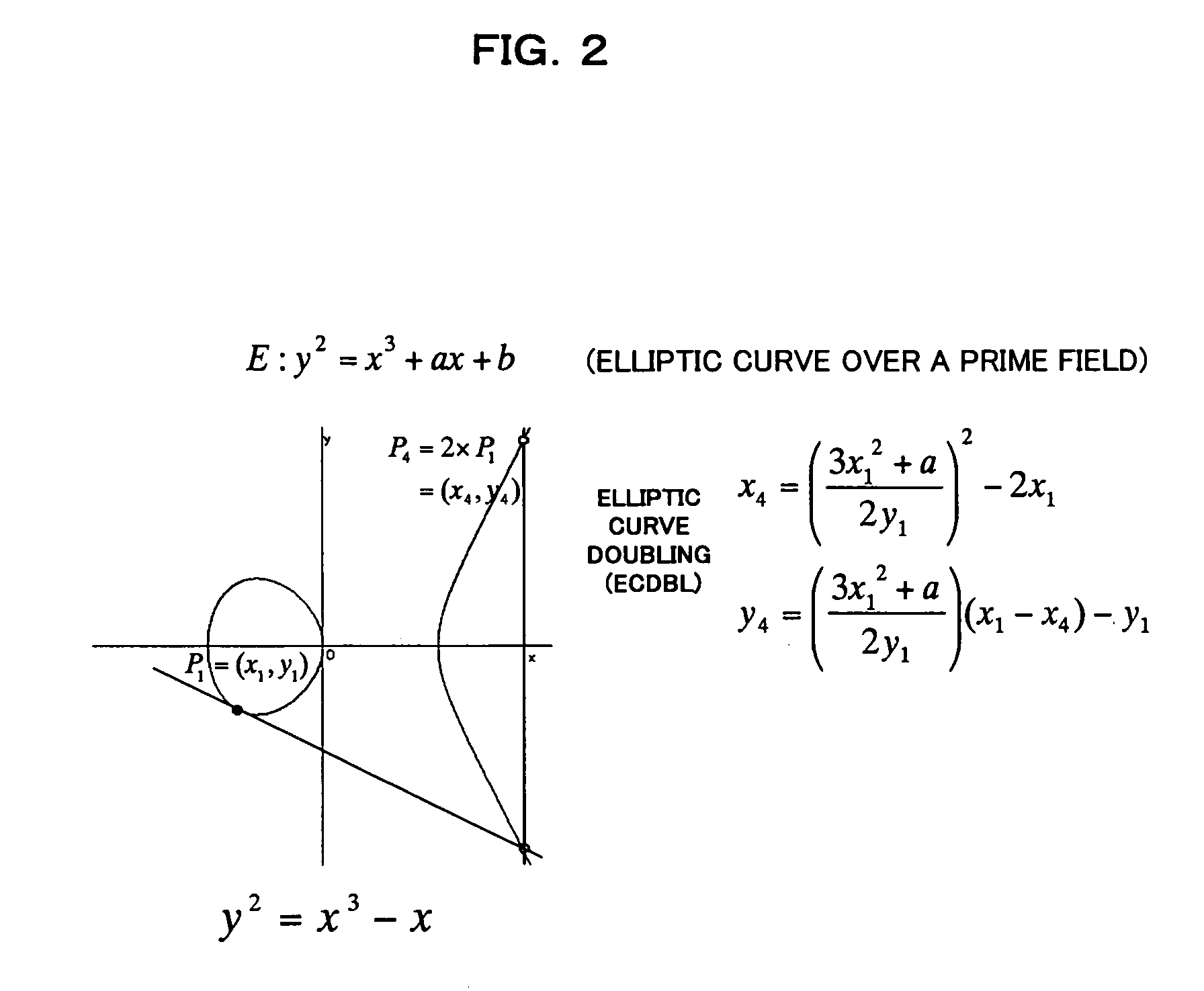
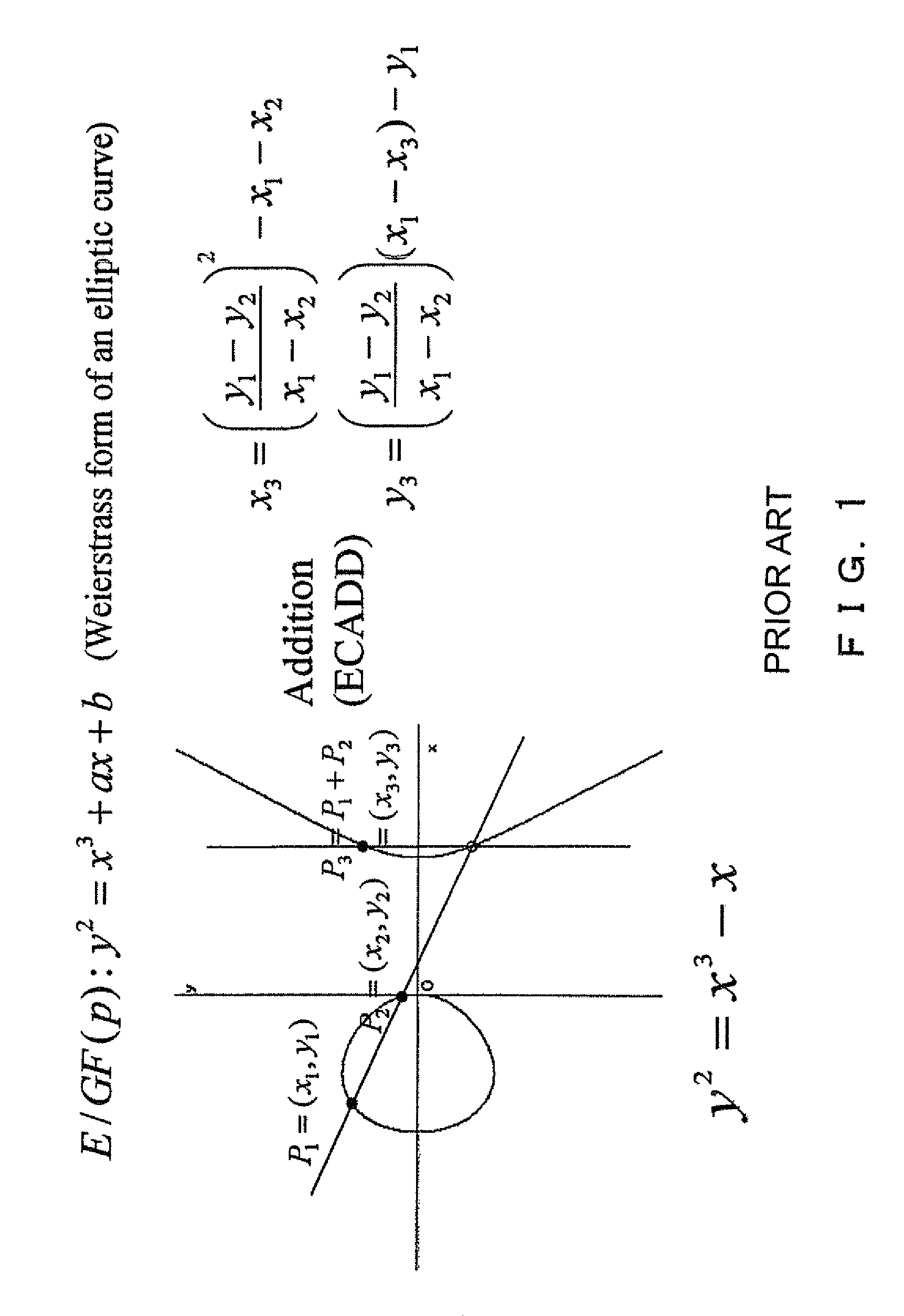
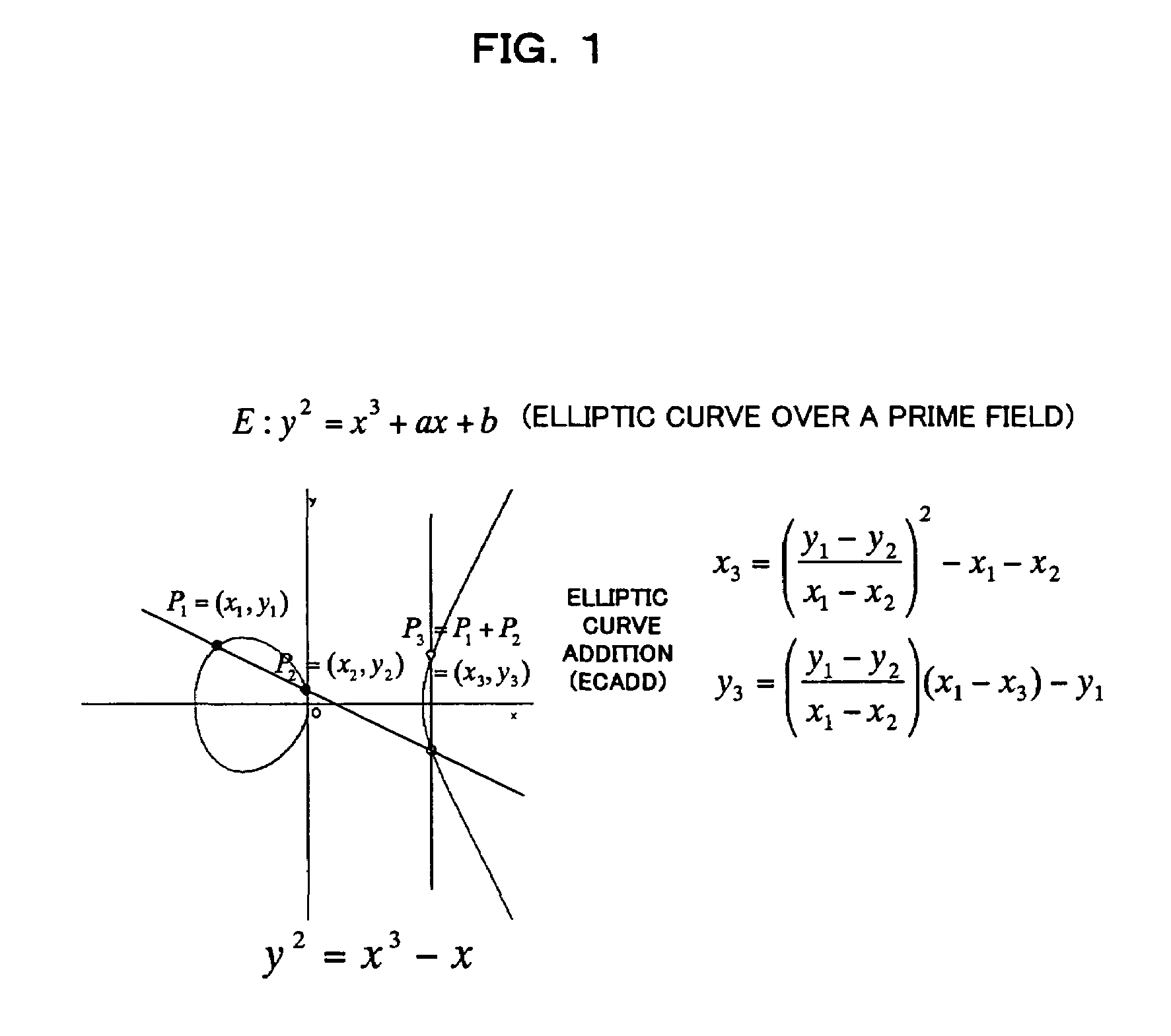
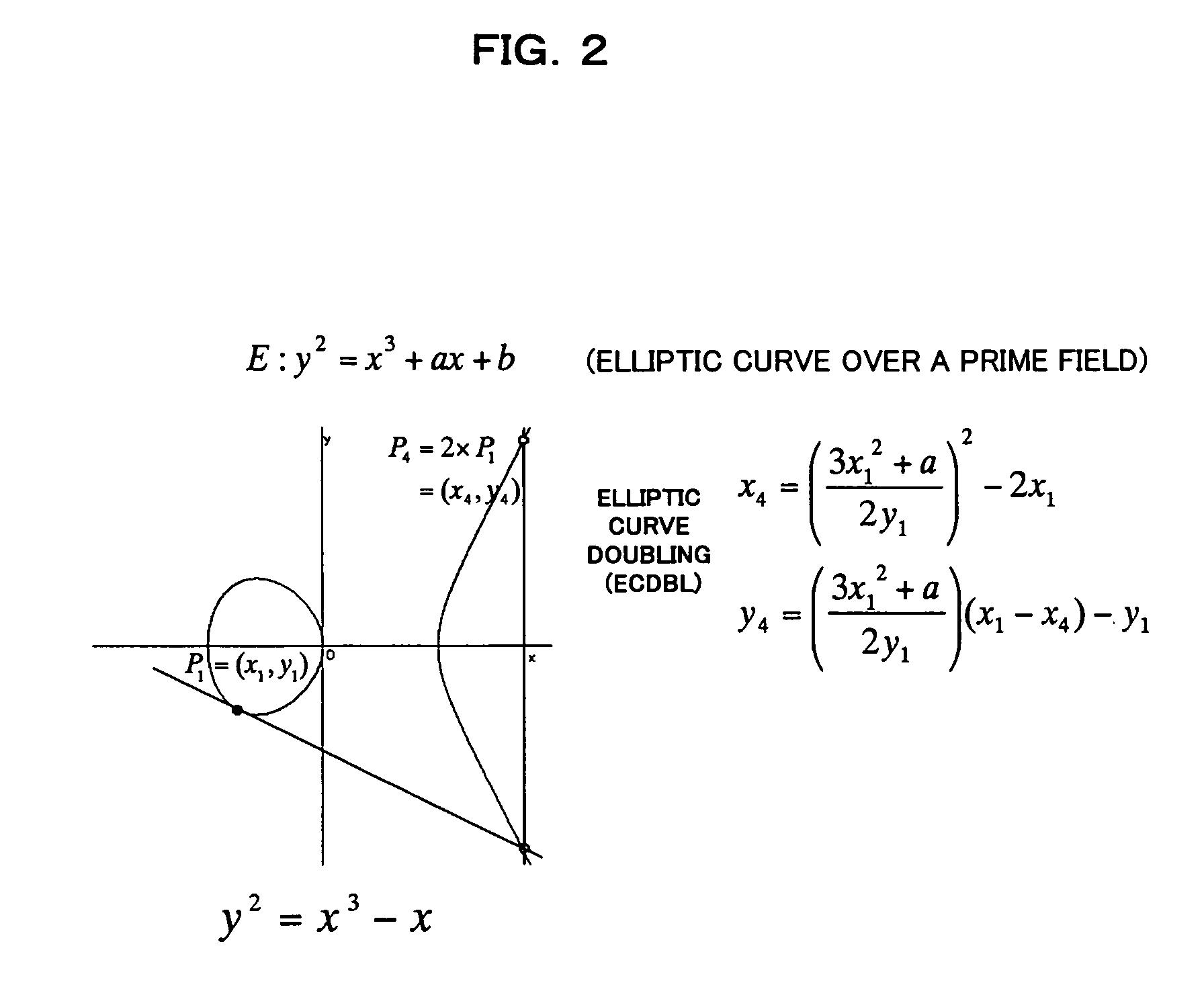
An elliptic curve cryptosystem apparatus performing an elliptic curve cryptosystem process has a coordinate transforming unit for transforming coordinates (X:Y:Z) on a point P on an elliptic curve over a finite field GF(pˆm) to coordinates (r1×(X−s1):r2×(Y−s2):r3×(Z−s3)) (where, p is a prime number, m is an integer not less than 1, r1, r2 and r3 are integers not less than 1 and not larger than (p−1), s1, s2 and s3 are integer not less than 0 and not larger than (p−1), and a code “ˆ” represents power), and a scalar multiplication operating unit for performing scalar multiplication on the point on the elliptic curve transformed by the coordinate transforming unit, wherein at least one of the parameters s1, s2 and s3 has a value other than 0. The apparatus can perform the scalar multiplication in the elliptic curve cryptosystem, with resistance to side channel attacks.
Owner:FUJITSU LTD
Method for Scalar Multiplication in Elliptic Curve Groups Over Prime Fields for Side-Channel Attack Resistant Cryptosystems
InactiveUS20090214025A1Secure performancePrevent internal leakageDigital data processing detailsSecret communicationEllipseElliptic curve cryptosystem
A method and device for transforming data with a secret parameter in an elliptic curve cryptosystem based on an elliptic curve defined over an underlying prime field, includes multiplying a point of the elliptic curve; representing the data to be transformed, by a scalar representing the secret parameter, wherein the multiplying includes performing at least one point addition operation and at least one point doubling operation on points of the elliptic curve; providing a representation in affine coordinates of the elliptic curve point to be multiplied and a representation in projective coordinates of intermediate elliptic curve points obtained during the multiplying; performing both the point addition operation and the point doubling operation by means of a sequence of elementary prime field operation types, the elementary prime field operation types including: a first type of prime field operations including field multiplication and field squaring of coordinates of the elliptic curve points and a second type of prime field operations including field addition, field doubling, and field subtraction of coordinates of the elliptic curve points.
Owner:TELECOM ITALIA SPA
Cryptographic method using construction of elliptic curve cryptosystem
InactiveUS6778666B1Simple calculationIncrease speedDigital data processing detailsPublic key for secure communicationEllipseTheoretical computer science
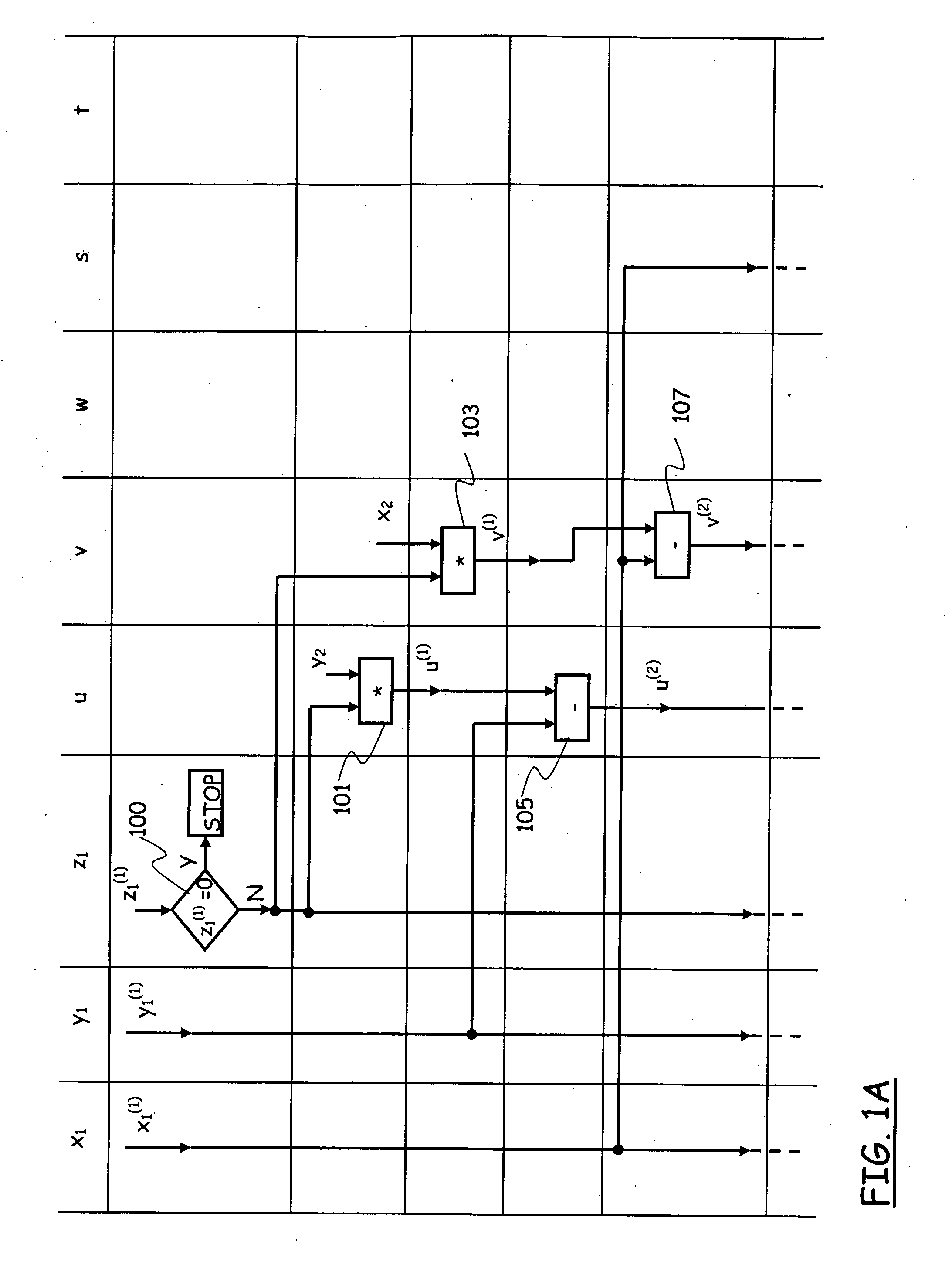
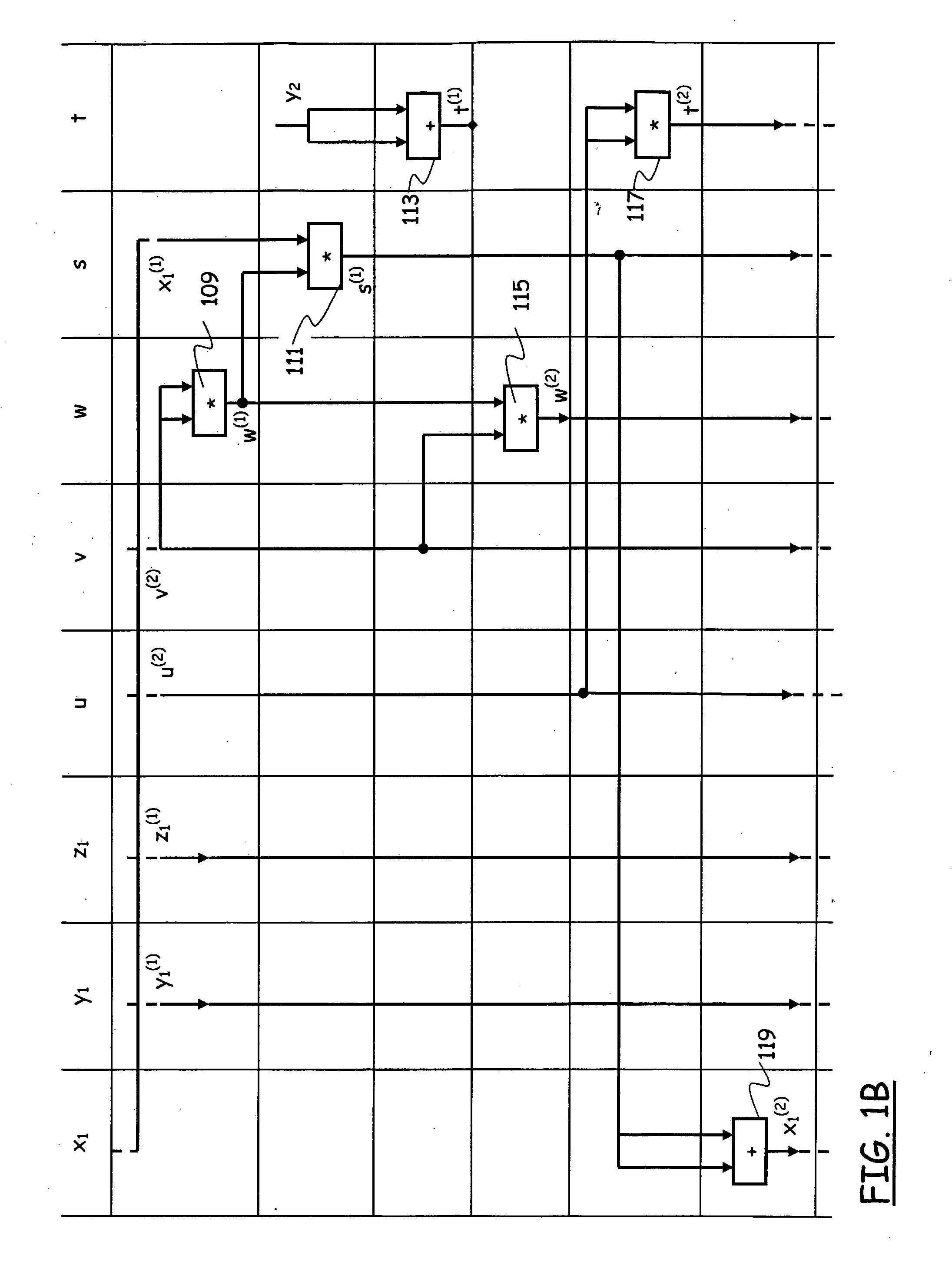
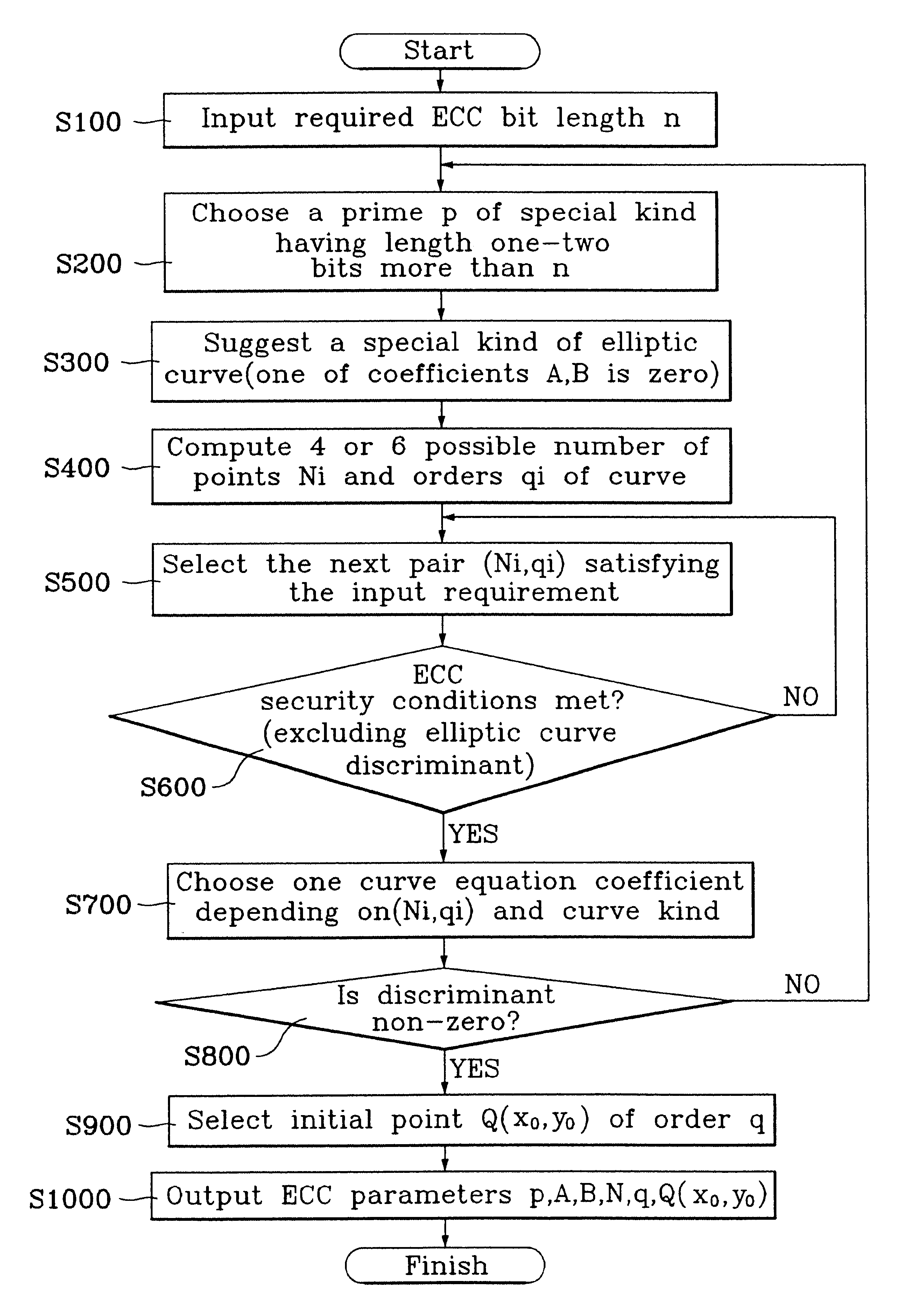
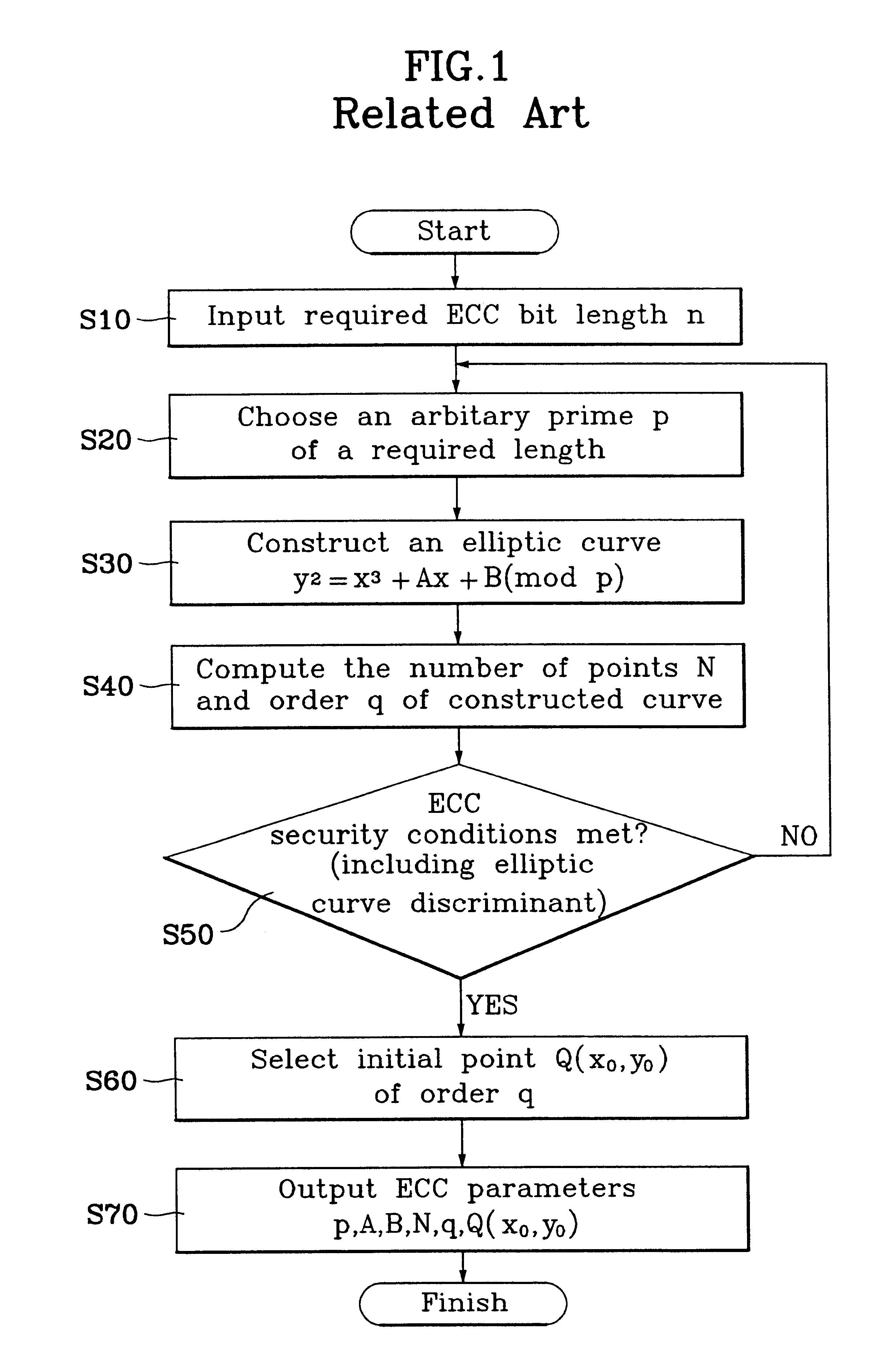
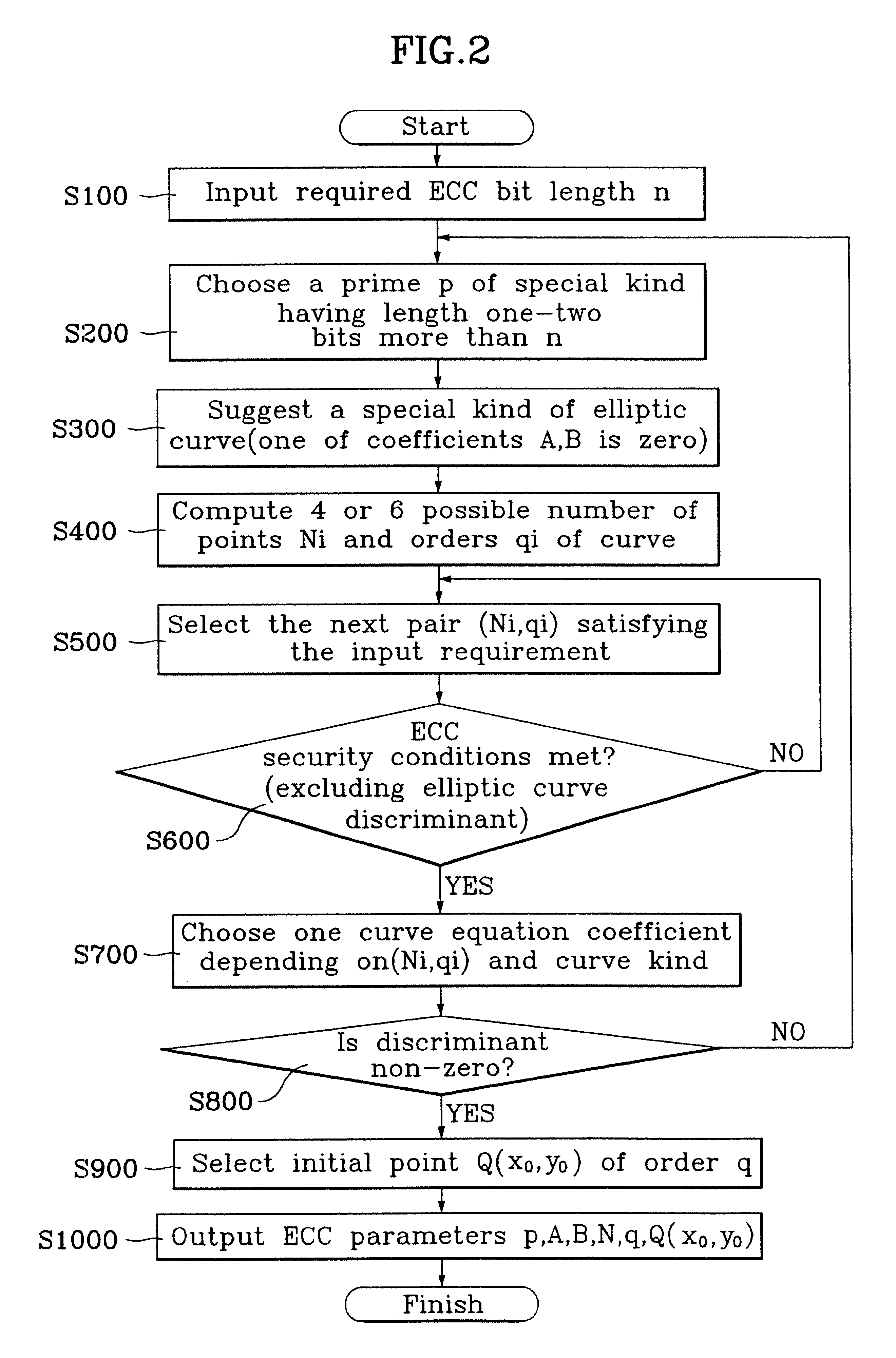
A method for a fast and efficient construction of an elliptic curve cryptosystem is disclosed. In the present invention, a prime p of a special kind is chosen which constructs a finite field underlying the elliptic curve cryptosystem. Accordingly, the selected prime p is utilized to construct a non-singular elliptic curve of a special kind, and the elliptic curve cryptosystem parameters can be easily chosen and computed. Using such procedure, the present invention allows a fast and easy construction of a large variety of elliptic cryptosystems used in telecommunications.
Owner:LG ELECTRONICS INC
Elliptic curve cryptosystem based on identity
ActiveCN103560882AReduce interventionReduce complexityKey distribution for secure communicationPublic key for secure communicationCryptosystemClient-side
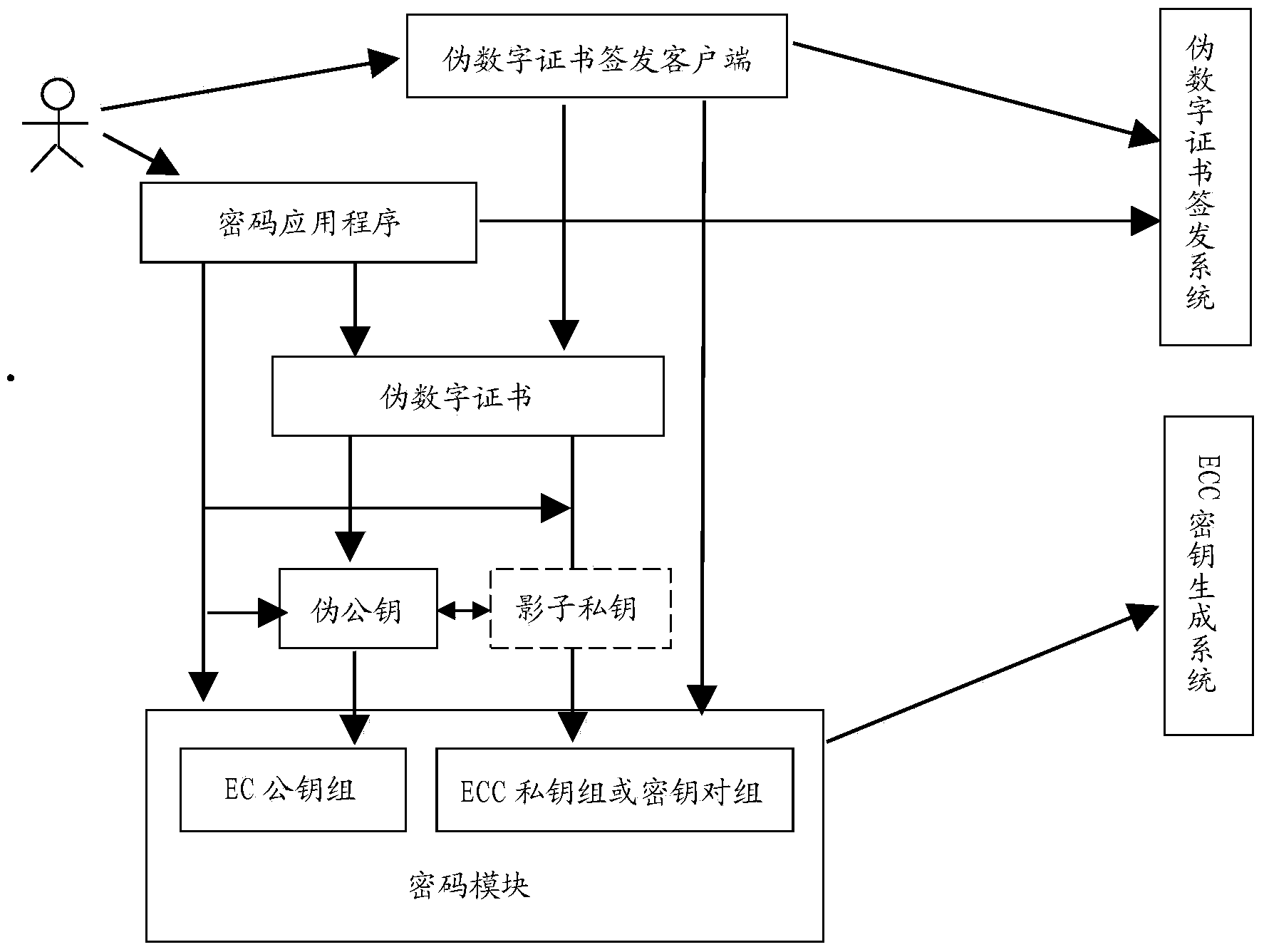
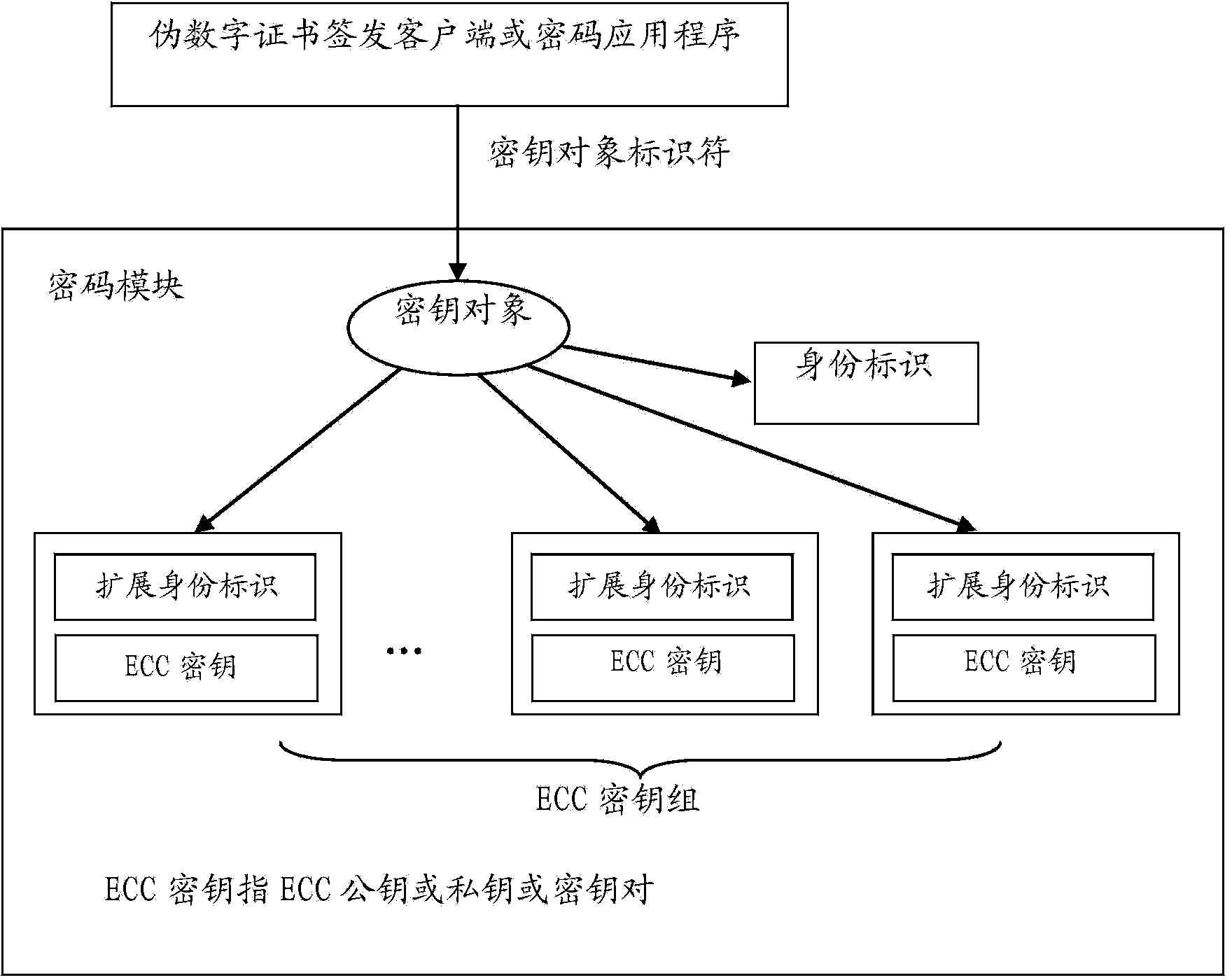
The invention relates to an elliptic curve cryptosystem based on an identity. The system comprises a pseudo public key, a pseudo digital certificate, an ECC key generation system, a pseudo digital certificate issuing system, a pseudo digital certificate issuing client-side, a crypto module and a crypto application program. According to the cryptosystem, the pseudo public key corresponding to one identity corresponds to an ECC public key set and an ECC private key set corresponding to the same identity in the crypto module, and therefore the crypto operation of the pseudo public key is automatically transformed into the operation of using a corresponding public key in the corresponding ECC public key set. The crypto operation of using a private key corresponding to the pseudo public key is automatically transformed into the operation of using a corresponding private key in the corresponding ECC private key set. When no corresponding ECC public key or private key exists, the corresponding ECC public key or private key is automatically acquired through the crypto module. The cryptosystem has part of advantages of an IBC, the crypto operation is easier than that of the IBC, the support of client-side crypto hardware is easily obtained, and the intervention of a user in the key updating process can be reduced.
Owner:嘉兴古奥基因科技有限公司
Realization method of elliptic curve cryptosystem for preventing side-channel attack
The invention relates to an elliptic curve cryptosystem (Elliptic Curve Cryptosystem, called ECC for short) for preventing side-channel attack (Side-Channel Attacks, called SCA for short), which belongs to the field of cryptographic algorithm. The realization method of the elliptic curve cryptosystem for preventing side-channel attack comprises the following steps: the operational step of dot multiplication is determined by a cryptographic key during the processes of encryption and decryption, and the dot multiplication step is finished through the operational combination of point addition and point double with balanced operational flow. By balancing the operational flow of the point addition and the point double, the operation time of the two are the same, and the consumed power is also the same, therefore, the difference of the side channel information leaked from the point addition and the point double is eliminated, and the side-channel attach method based on the difference of the point addition and the point double is failed to attack the ECC during the entire dot multiplication process.
Owner:SHENZHEN INST OF ADVANCED TECH
Method of countering side-channel attacks on elliptic curve cryptosystem
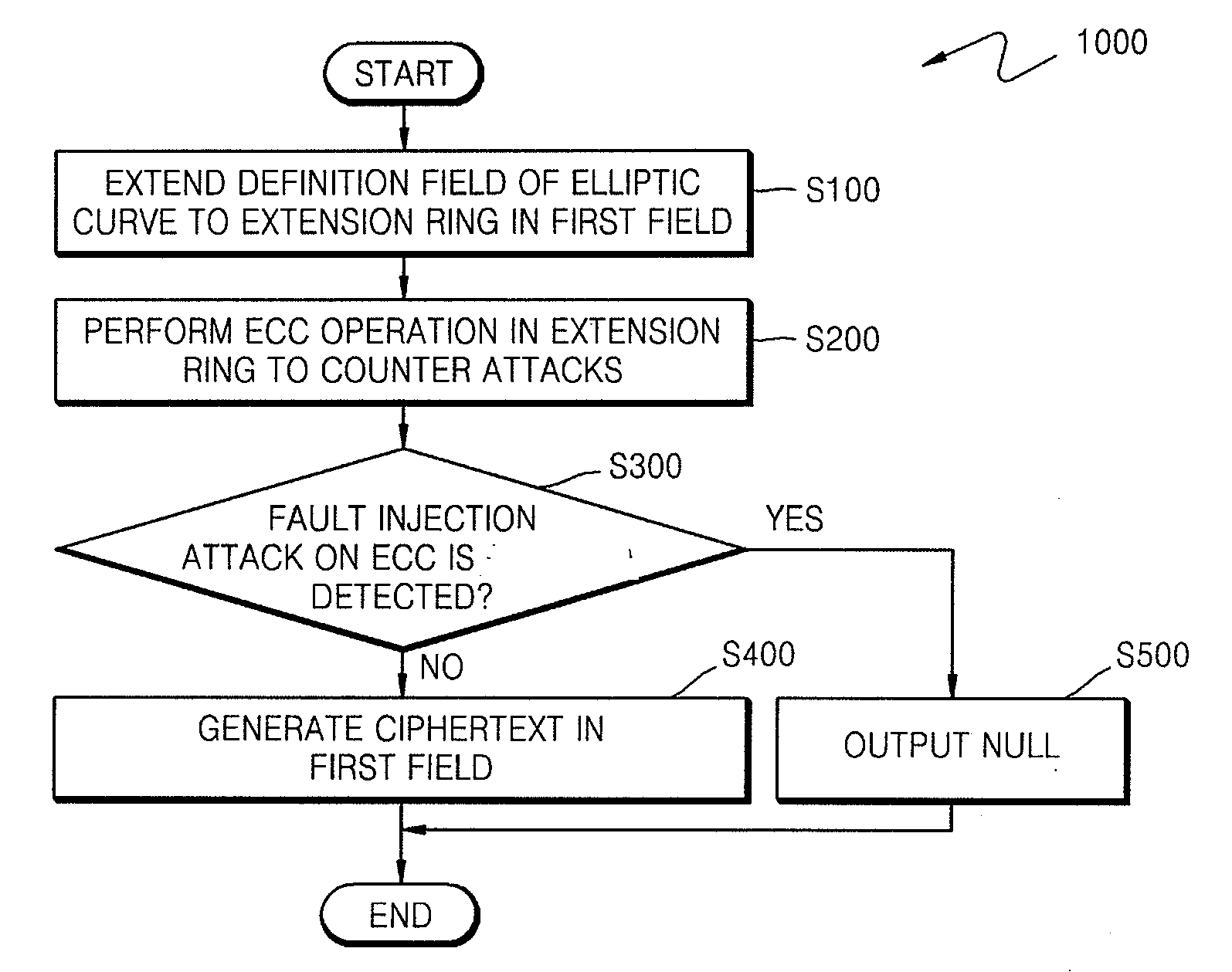
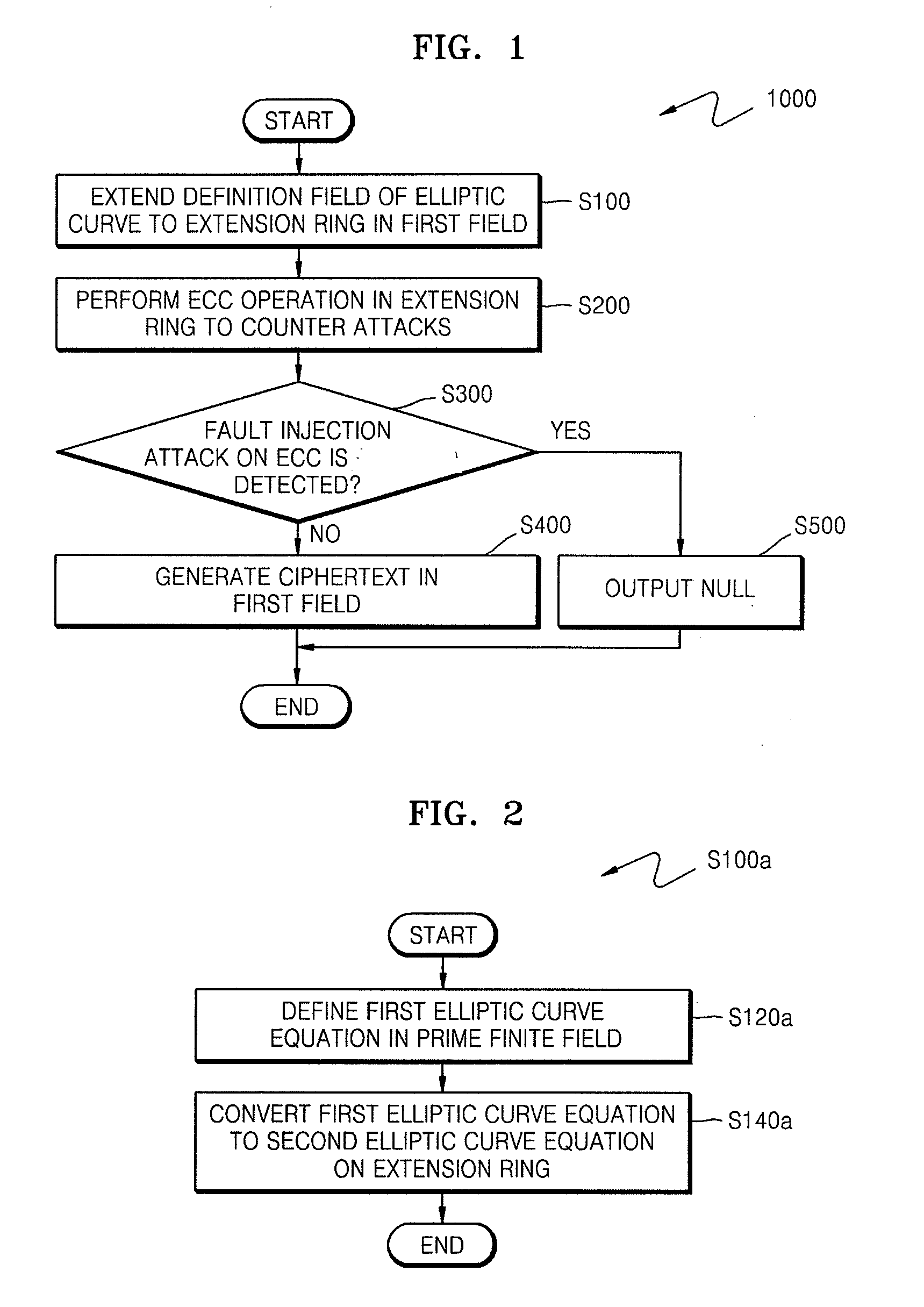
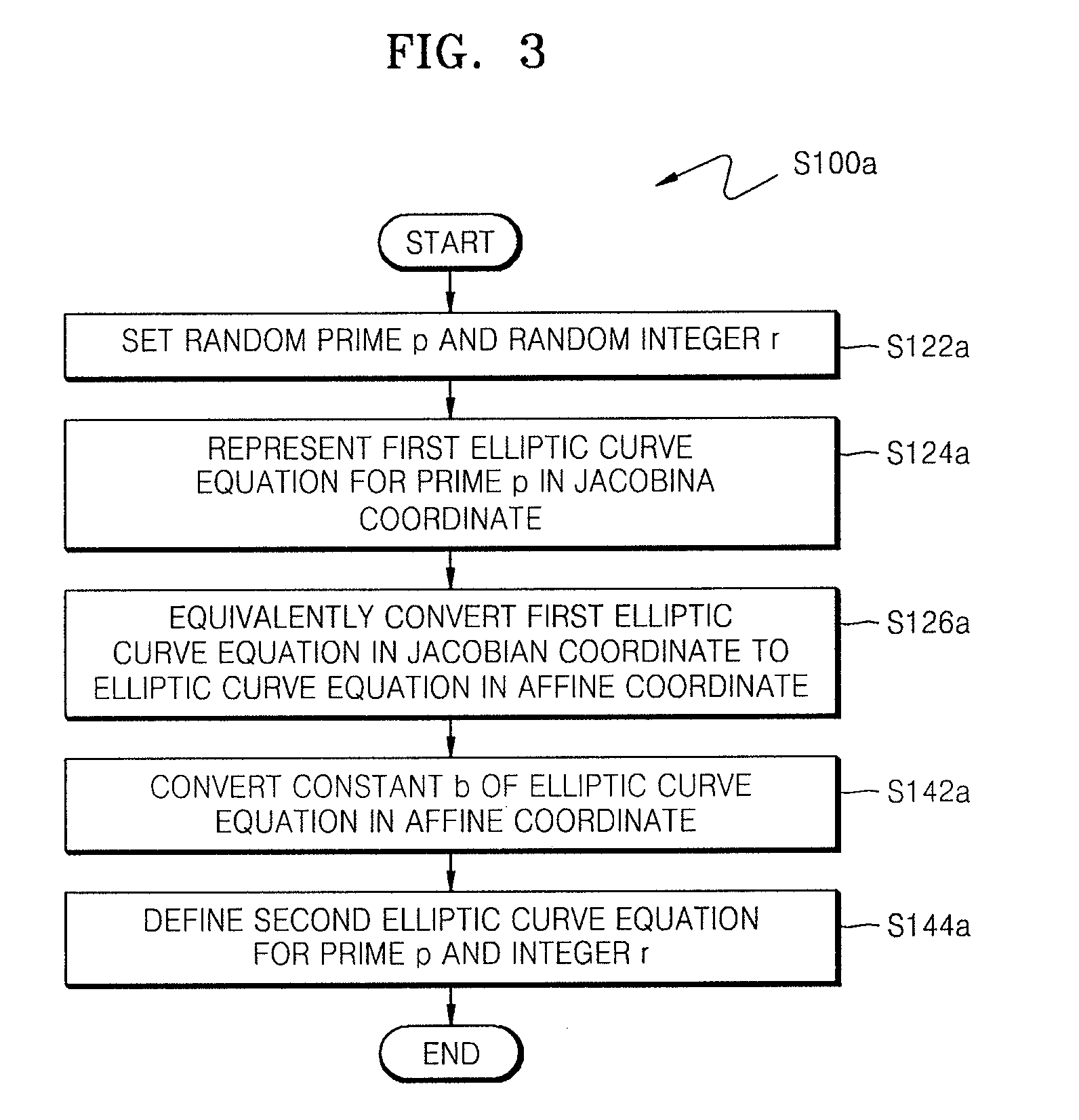
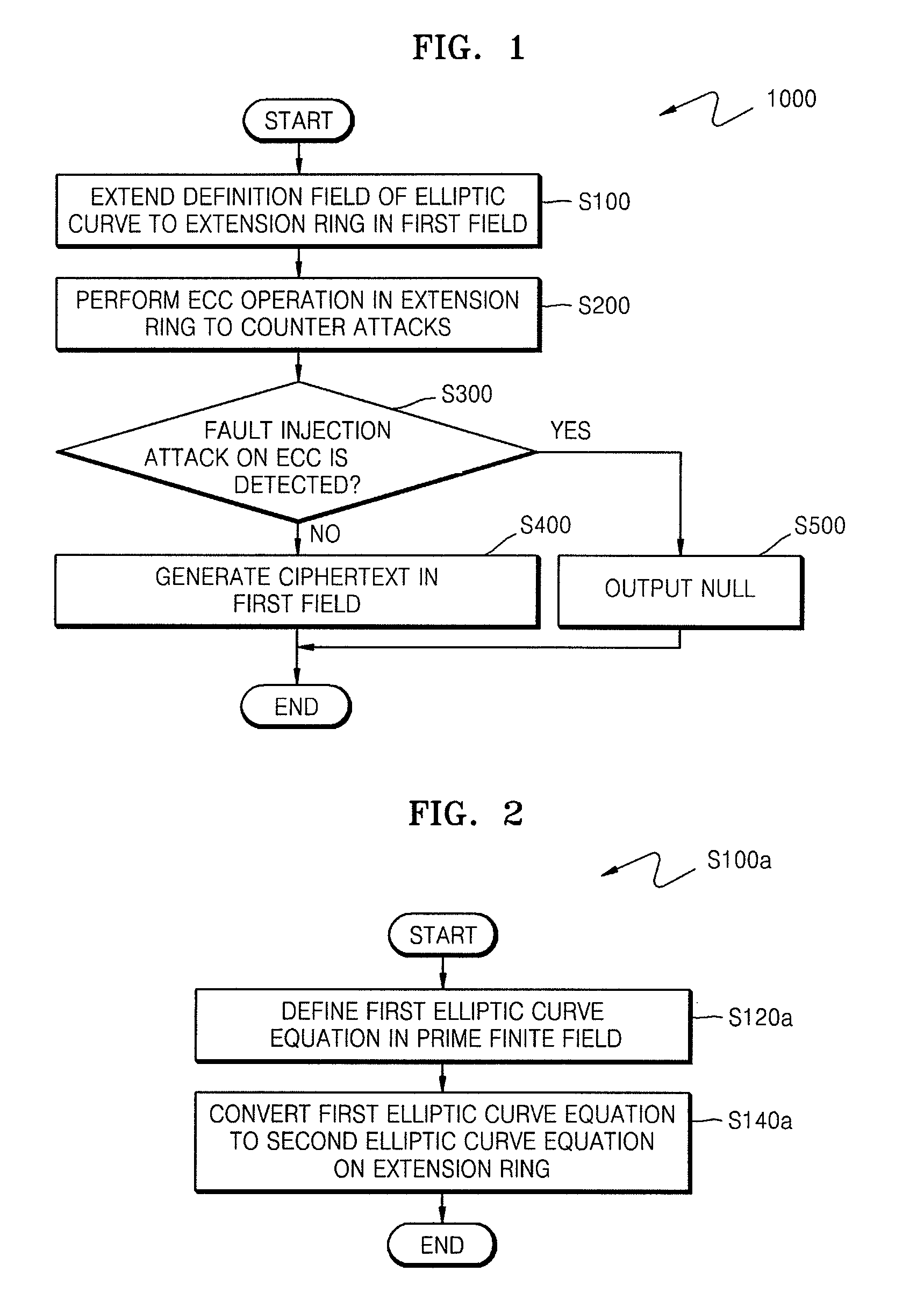
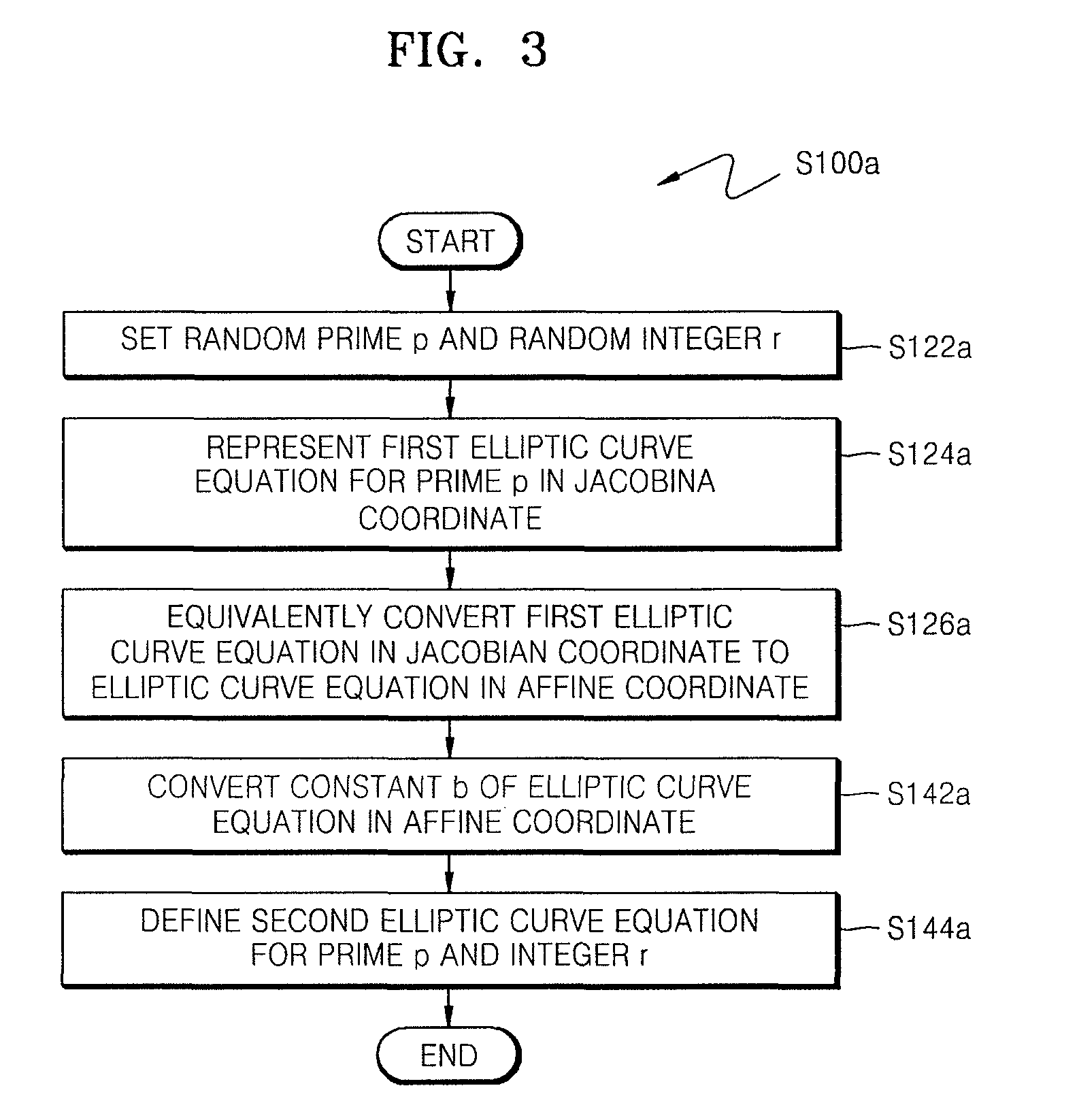
ActiveUS20090034720A1Improve securityEfficient fault attack countermeasureMultiple keys/algorithms usageData taking preventionFault detection algorithmCiphertext
A method of countering side-channel attacks on an elliptic curve cryptosystem (ECC) is provided. The method comprises extending a definition field of an elliptic curve of the ECC to an extension ring in a first field; generating a temporary ciphertext in the extension ring and countering attacks on the ECC; and generating a final ciphertext for the first field if a fault injection attack on the ECC is not detected. The countering of attacks on the ECC may comprise countering a power attack on the ECC. Checking if there is a fault injection attack on the ECC may be performed by determining if the temporary ciphertext satisfies a second elliptic curve equation. The fault detection algorithms takes place in a small subring of the extension ring, not in the original field, to minimize the computational overhead. The method can improve the stability of the ECC and reduce computational overhead of the ECC.
Owner:SAMSUNG ELECTRONICS CO LTD
Method for realizing elliptic curve cryptosystem algorithm over prime field in integrated circuit
ActiveCN101547089AImprove efficiencySmall area overheadPublic key for secure communicationComputations using residue arithmeticCryptosystemIntegrated circuit
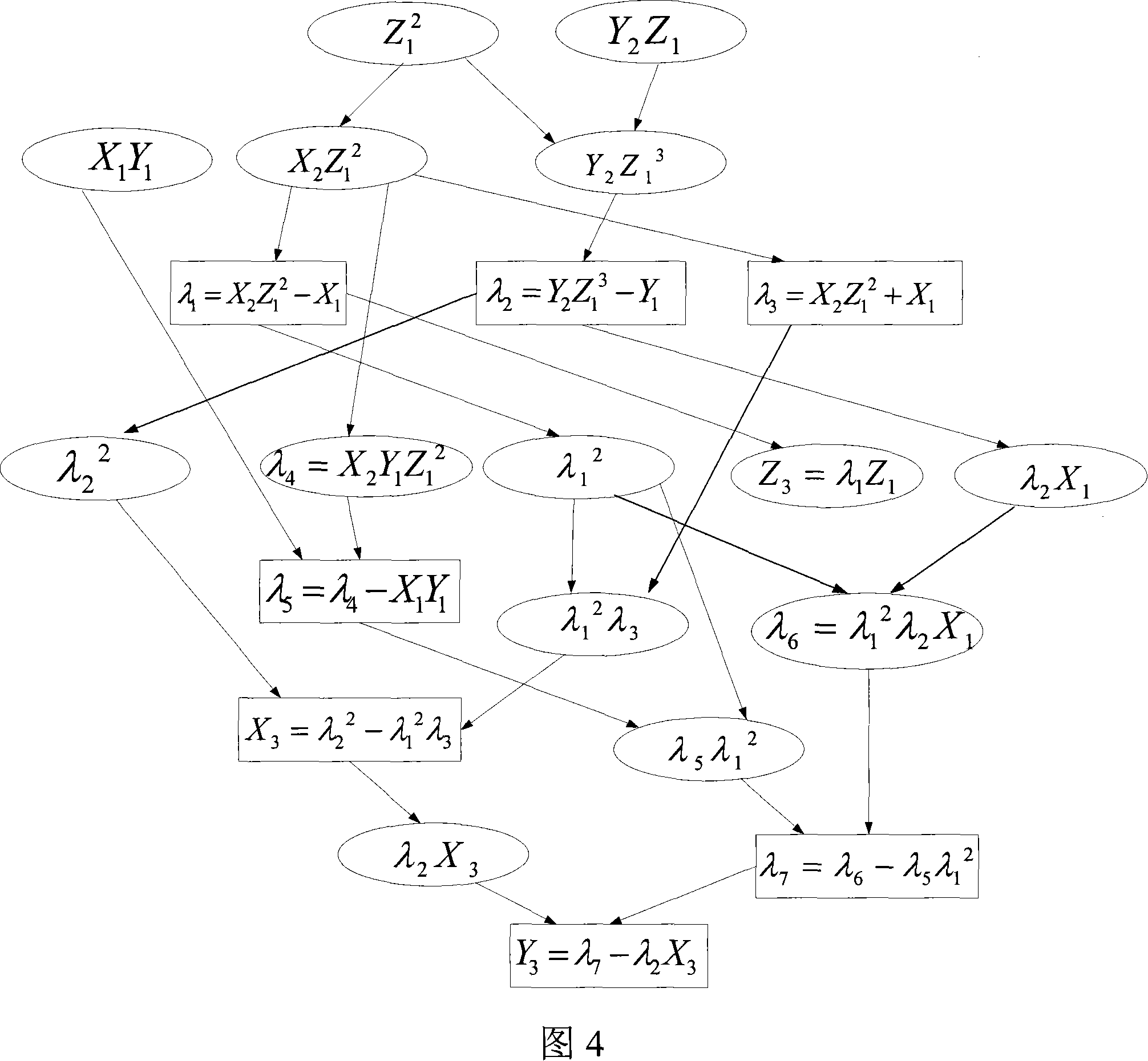
The invention provides a method for realizing an elliptic curve cryptosystem algorithm over a prime field in an integrated circuit, relates to the technical field of information encryption, and aims to solve the technical problem of the integrated circuit of a cryptosystem algorithm. The method comprises the flowing flows that: 1) a two-dimensional affine point (x, y) coordinate is mapped to a three-dimensional Jacobin projection coordinate (X, Y, Z); 2) the projection coordinate point is transformed to be expressed by Montgomery, and the transformation process is that (X, Y, Z) is transformed into (XR, YR, ZR), and the point coordinate in the form is applied with point operation operations comprising dot product, point double and point add to obtain the initial result of the point operation (XR, YR, ZR); 3) the projection coordinate result (XR, YR, ZR) is mapped back to an affine coordinate (xR, yR); and 4) the (xR, yR) expressed by the Montgomery is recovered into the (x, y) commonly expressed, wherein all big figures used in the operation are all stored into an SRAM. The method has the characteristics of convenient use, good performance, easy SoC integration, low cost, high performance and small area.
Owner:上海航芯电子科技股份有限公司
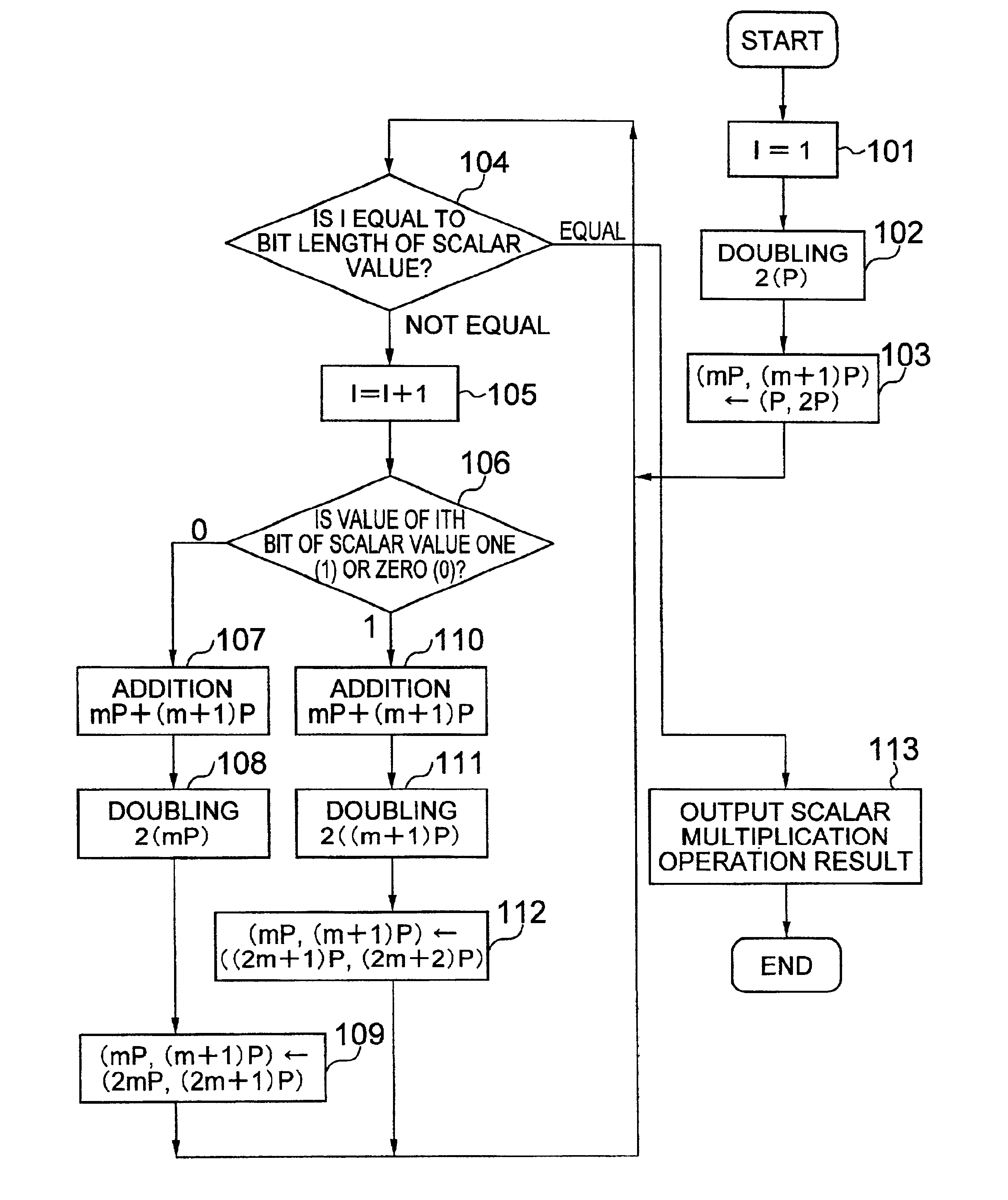
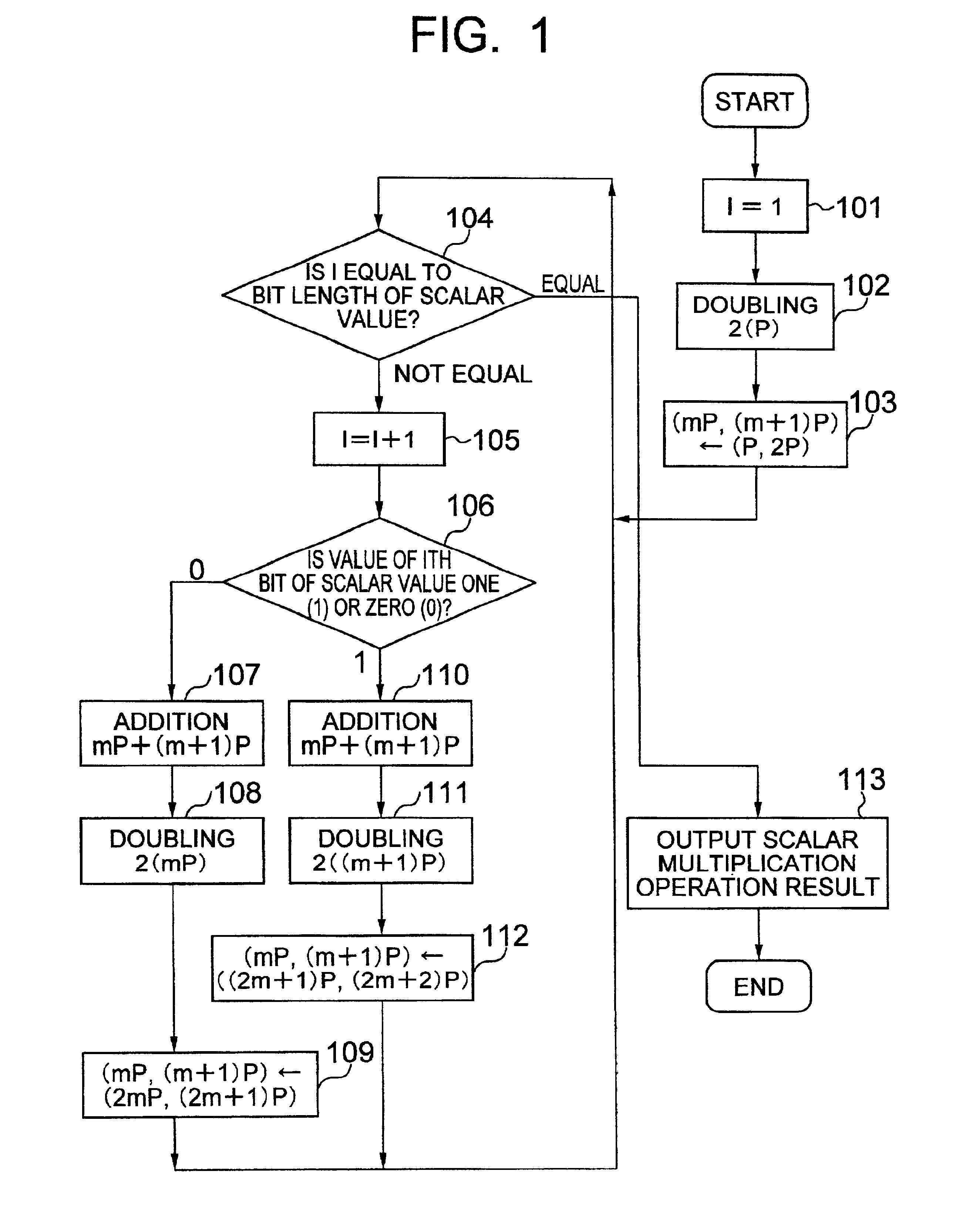
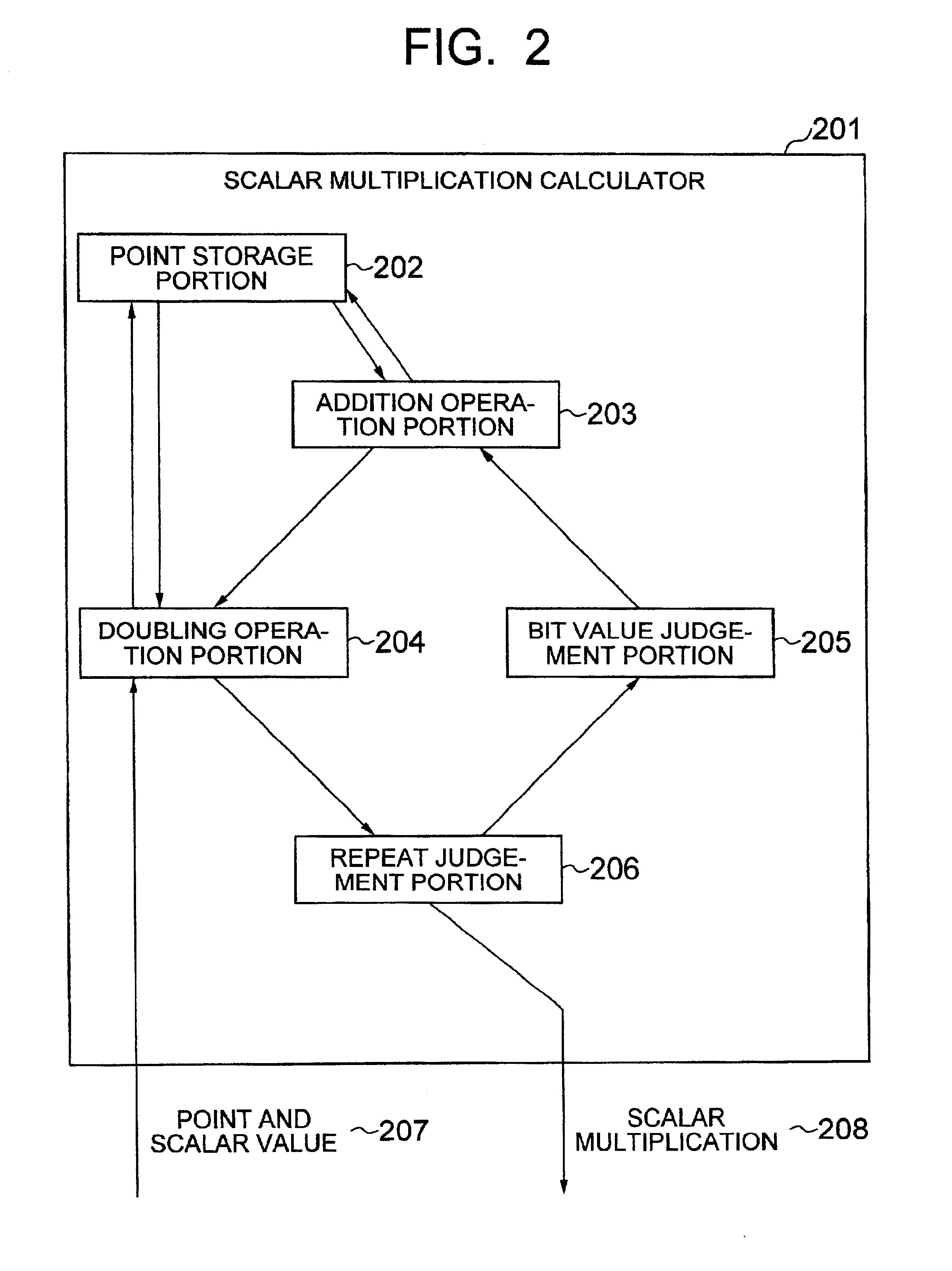
Method of calculating multiplication by scalars on an elliptic curve and apparatus using same and recording medium
InactiveUS7046801B2Increase speedCryptographic processing can be made in speedSecret communicationComputations using residue arithmeticComputer hardwareScalar Value
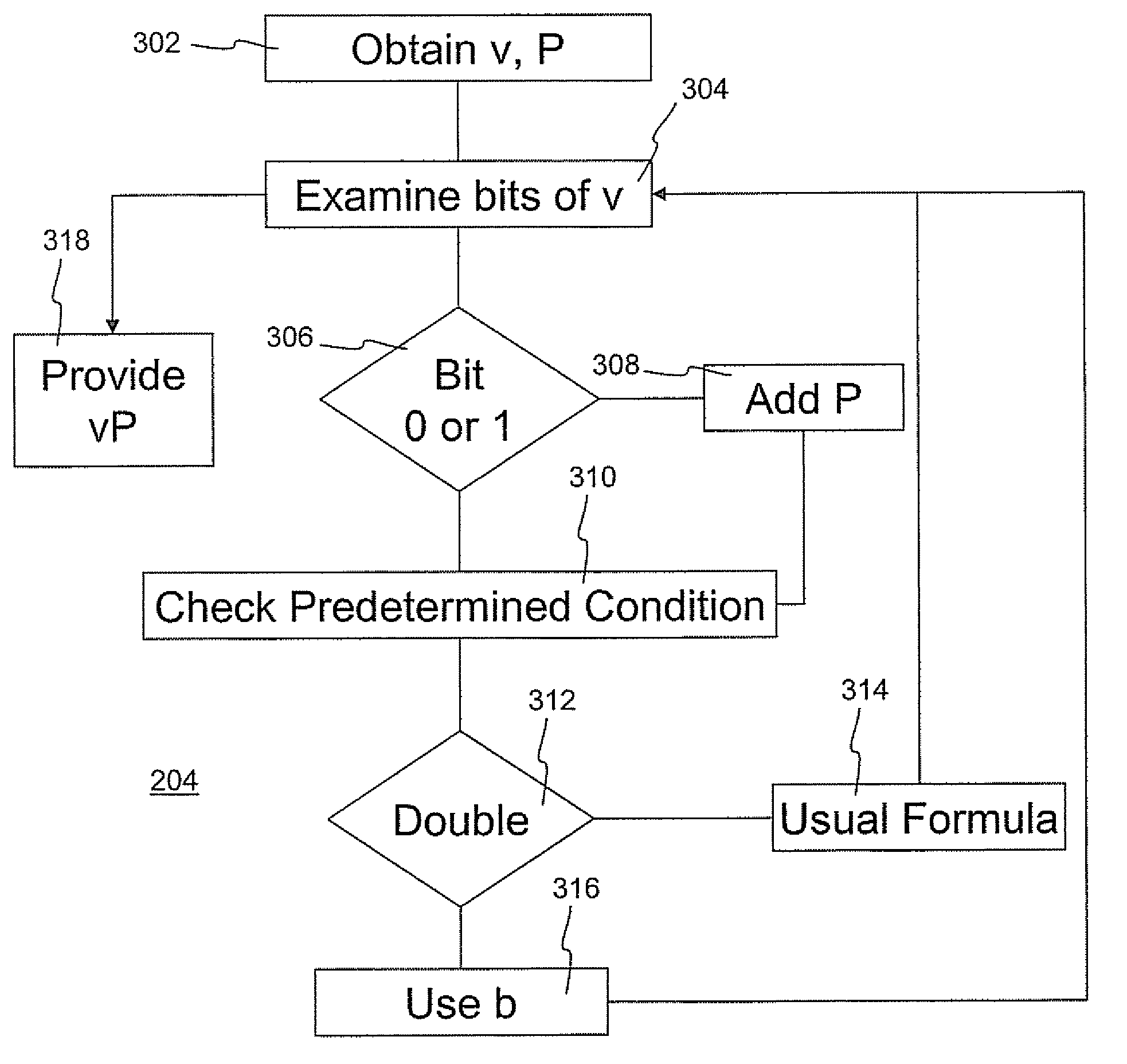
A cryptographic processing method in which dependence of cryptographic processing process and secret information on each other is cut off; and in which, when a scalar multiplied point is calculated from a scalar value and a point on an elliptic curve in an elliptic curve cryptosystem, a value of a bit of the scalar value is judged; and in which operations on the elliptic curve are executed a predetermined times and in a predetermined order without depending on the judged value of the bit.
Owner:HITACHI LTD
Method and system for atomicity for elliptic curve cryptosystems
InactiveUS20090046851A1Digital data processing detailsPublic key for secure communicationEllipseChannel analysis
A method and system are provided for atomicity for elliptic curve cryptosystems (ECC-systems). The method includes a side channel atomic scalar multiplication algorithm using mixed coordinates. The algorithm including repeating a sequence of field operations for each elliptic curve addition or doubling operation to provide an atomic block, wherein an atomic block appears equivalent by side-channel analysis. The mixed coordinates are chosen based on a ratio of I / M where I and M are the time required to execute an inversion and a multiplication in the ground field respectively. If the I / M ratio is less than 60, a mixture of affine and Jacobian coordinates are used during scalar multiplication. If the I / M ratio is 60 or more, a mixture of Chudnovsky-Jacobian and Jacobian coordinates are used during scalar multiplication. The method is optimized for elliptic curves over Fp defined by an equation of the form y2=x3+ax+b, where a, b ε Fp, having a=−3.
Owner:DOORDASH INC
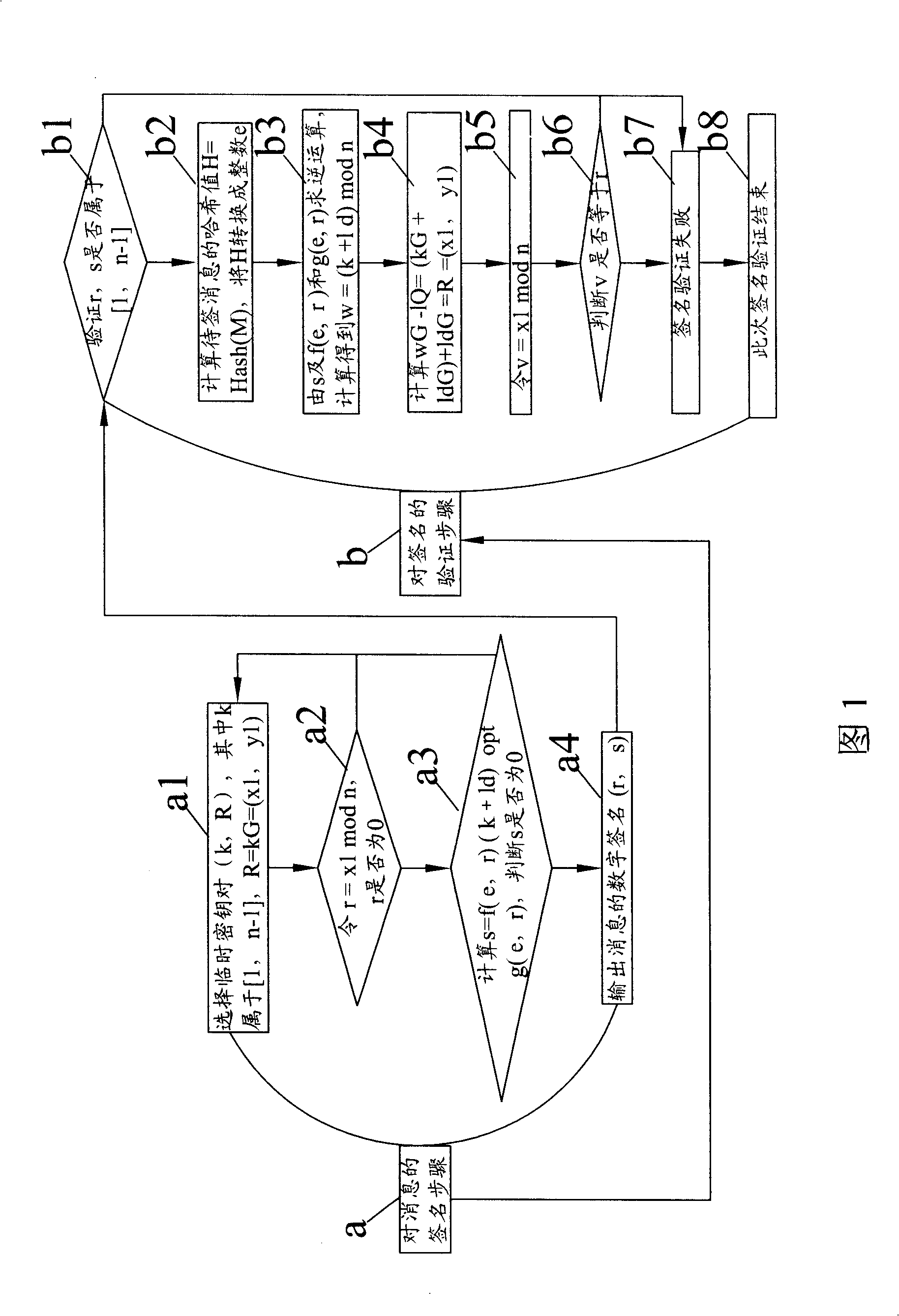
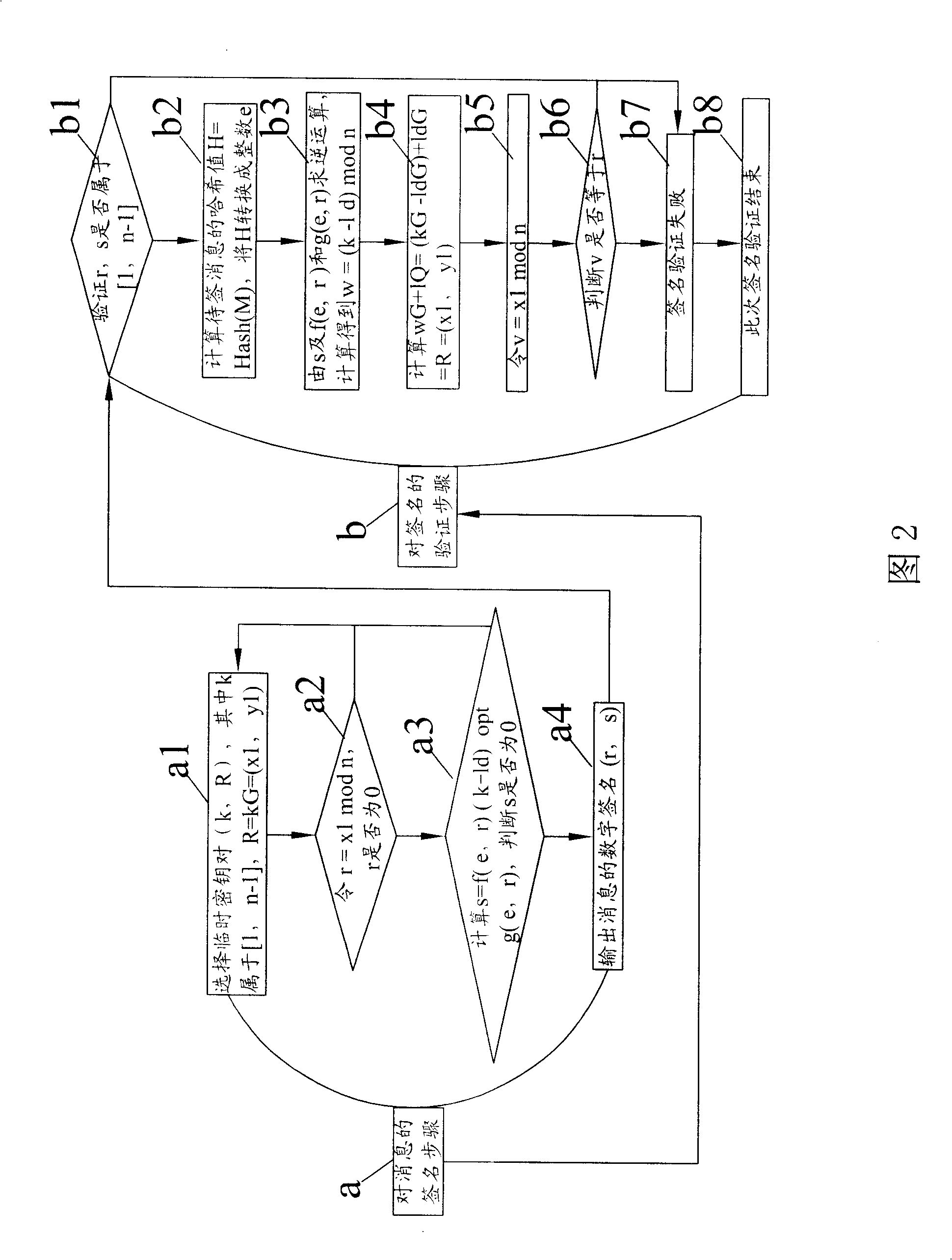
Method for improving digital signature check velocity of elliptic curve cipher system
InactiveCN101330385AShorten the timeUser identity/authority verificationInternational standardDigital signature
The invention is a method for increasing the speed of verifying digital signatures on an elliptic curve cryptosystem. The method is based on the ECDSA method of international standards, utilizes the deformation of signature formula in the digital signature verification step on the elliptic curve cryptosystem to change the twice dot product operation in the original verification step into one time dot product operation, thereby increasing the verification speed by one time compared with the ECDSA method of international standards.
Owner:AEROSPACE INFORMATION
Time point system for ellipse curve password system
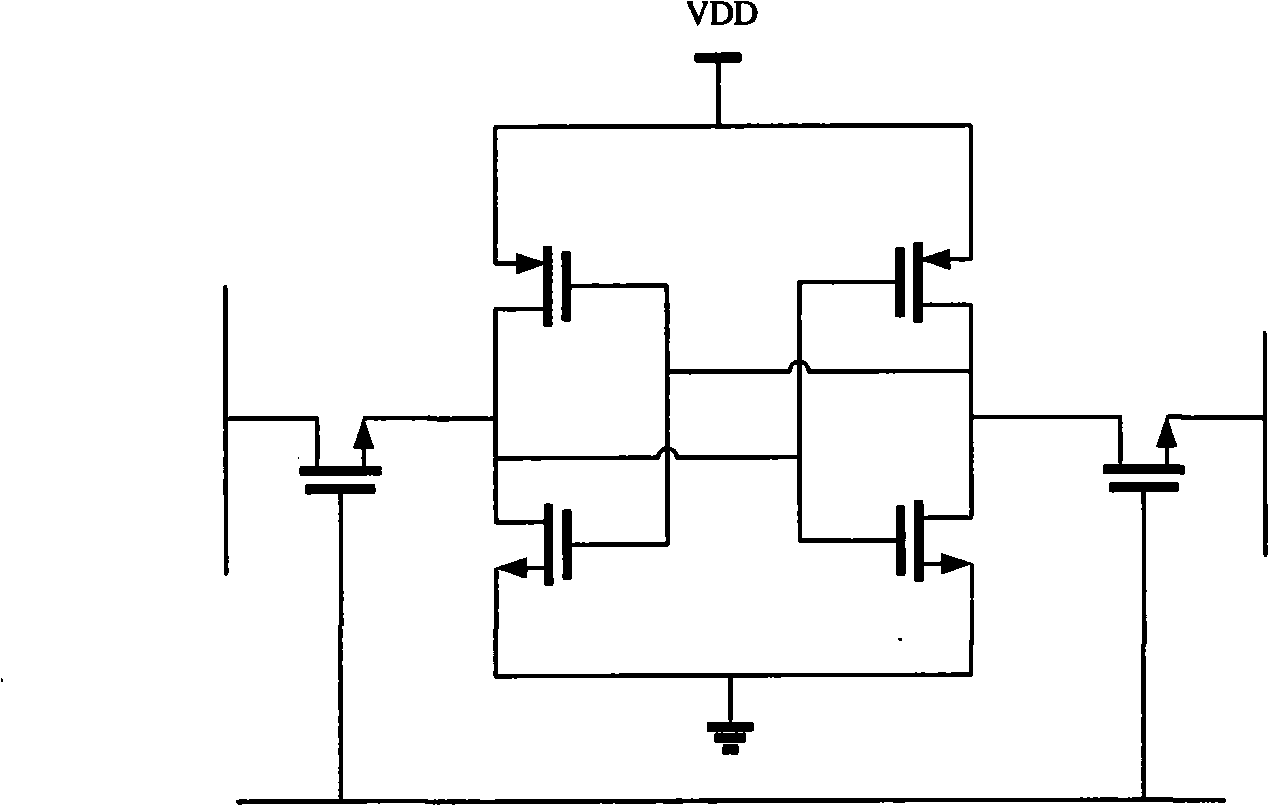
The invention relates to a point-timing system of an elliptic curve cryptosystem, which pertains to the point-timing technical field of an elliptic curve cryptosystem and is characterized in that: the invention includes a controller of a point-timing register, a point-timing multipath option controller, a first multipath selector group, a middle variable register group and a second multipath selector group; under gating control signals output by the point-timing multipath option controller and in the process of six production lines, point-timing algorithm for multipliers and addends of the second multipath selector group is carried out by a modular multiplier and a modular adder positioned outside the point-timing system. In each production line, under the control of the gating control signals, the modular multiplier and the modular adder respectively return intermediate data to the first and the second multipath selector groups; under the control of operation control signals output by the controller of the point-timing register, each multipath selector controlling the first multipath selector group outputs relevant multipliers and addends to the second multipath selector group by the middle variable register group. The point-timing system of an elliptic curve cryptosystem of the invention increases point-timing arithmetic speed, optimizes point- multiplying performance of elliptic curves under a basic level and improves data throughput rate.
Owner:TSINGHUA UNIV
Point addition system of elliptic curve cipher system
A point addition system for elliptic curve cryptosystem belongs to the elliptic curve cryptosystem point addition technical field. The present invention is characterized in that: the system comprises a point addition register controller, a point addition multi-channel selection controller, a first multi-channel selector group, an intermediate variable register group and a second multi-channel selector group; under the gating control signals output by the point addition multi-channel selection controller, in the process of six pipelines, point addition operation to the multipliers and addends output by the second multi-channel selector group is accomplished by a modular multiplier and a modular adder which are positioned outside the point addition system; in the process of each pipeline, under the control of the gating control signals, the modular multiplier and the modular adder respectively return intermediate data to the first multi-channel selector group and the second multi-channel selector group; under the control of operation control signals output by the point addition register controller, multi-channel selectors in the first multi-channel selector group are controlled to output corresponding multipliers and addends to the second multi-channel selector group through the intermediate variable register group. The present invention improves point addition operation speed, optimizes the point multiplication performance of elliptic curve in a basic aspect, and improves data throughput rate.
Owner:TSINGHUA UNIV
Remote protocol authentication method based on passwords
ActiveCN103905437ADefense against replay attacksResistant to Guessing AttacksUser identity/authority verificationPasswordSession key
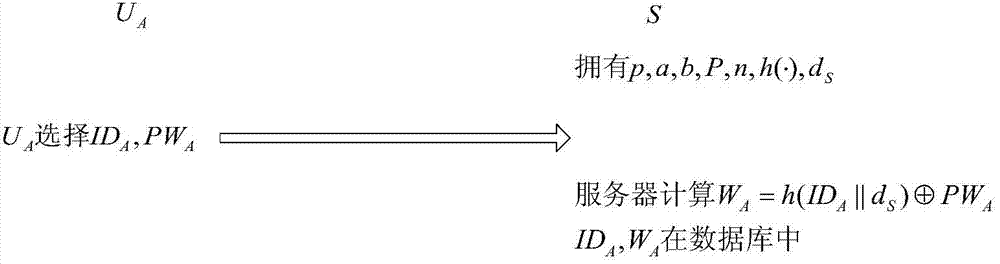
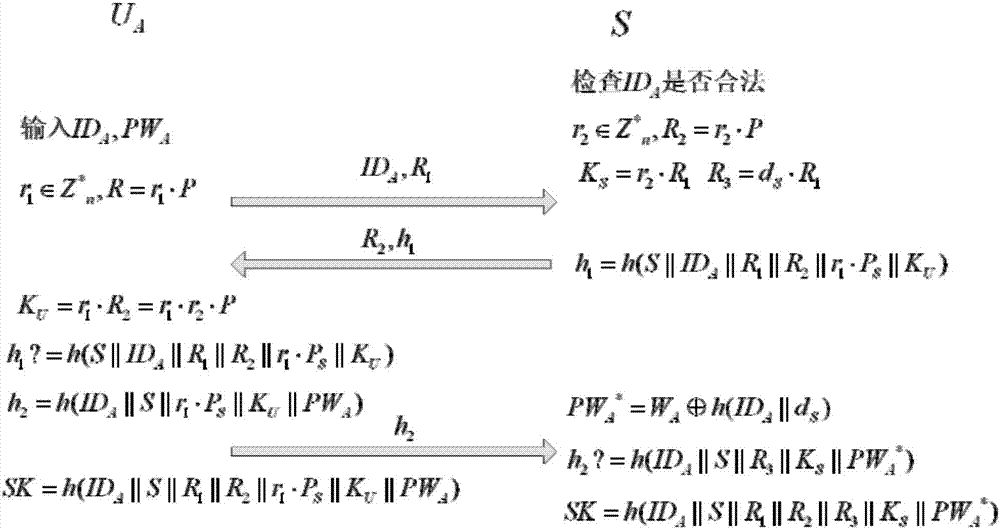
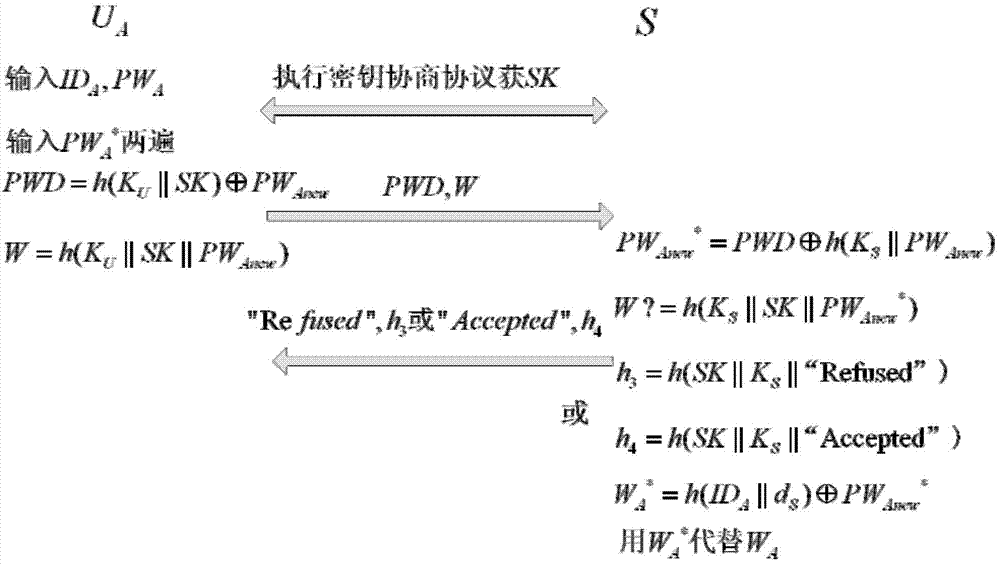
The invention relates to a remote protocol authentication method based on passwords. The method is characterized in that the method is achieved on the basis of the elliptic curve cryptographic algorithm, and the method includes the following steps that 1, in a system initialization sub-protocol, a user and a server negotiate elliptic curve cryptosystem parameters which need to be used in subsequent authentication; 2, a new user UA performs registration through a user registration sub-protocol and selects an identity label and a user password PWA; 3, when the user UA wants to login a system to perform session key negotiation, firstly the user UA inputs the identity label IDA and the user password PWA, then double-way authentication is conducted between the user UA and the server and secret keys used in subsequent communication are negotiated through identity authentication and a key negotiation sub-protocol.
Owner:HARBIN ENG UNIV
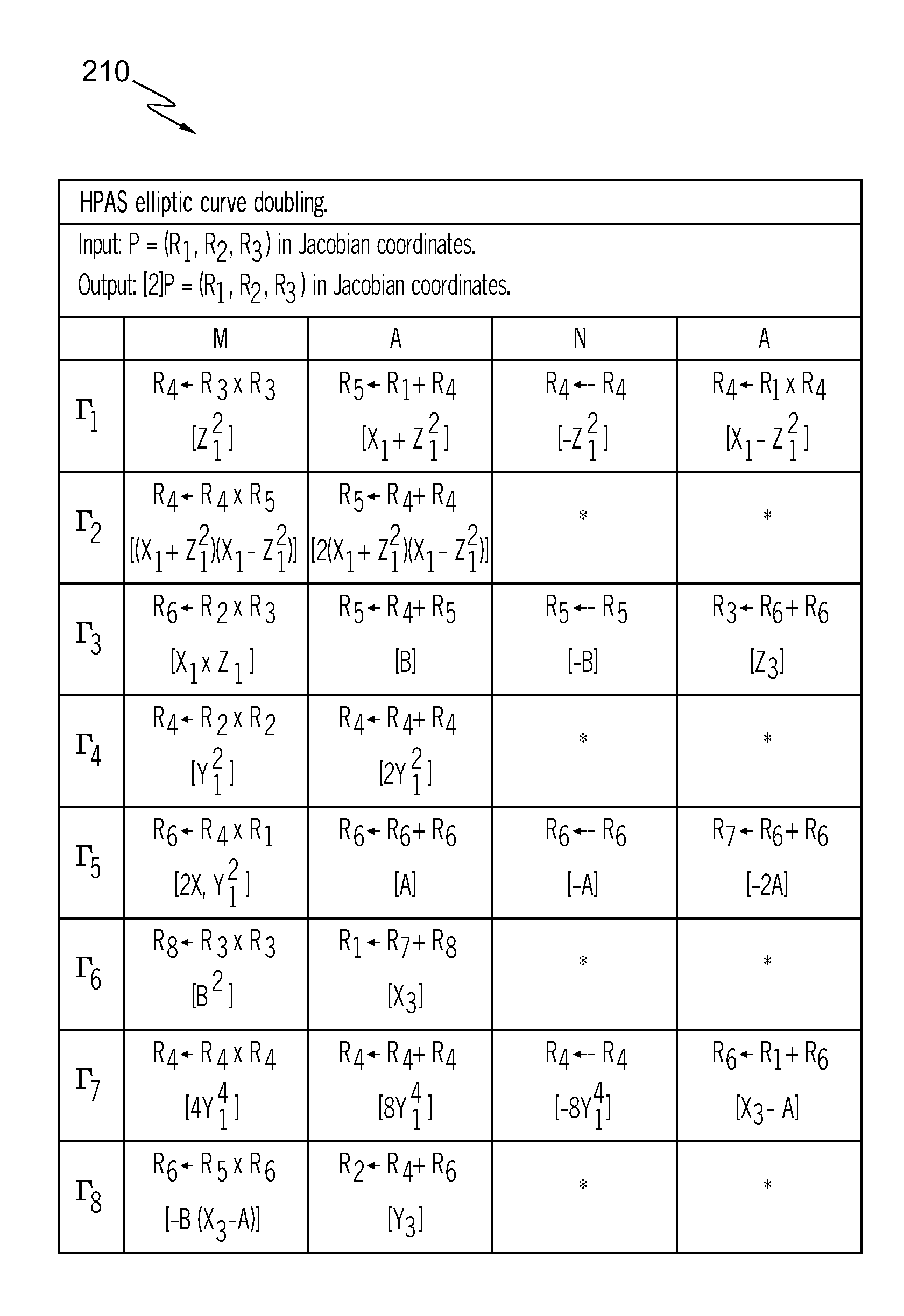
Method for elliptic curve scalar multiplication using parameterized projective coordinates
InactiveUS20080273695A1Protect scalar multiplication computationEnhance scalar multiplicationDigital data processing detailsPublic key for secure communicationEllipseScalar multiplication
The method for elliptic curve scalar multiplication in an elliptic curve cryptosystem implemented over an insecure communications channel includes the steps of: (a) selecting positive integers Lx and Ly, wherein Lx and Ly are not both equal to 1, and wherein Ly≠3 if Lx=2; (b) representing coordinates of a point P=(x,y) on an elliptic curve of the form F(x,y)=y2−x3−ax−b=0 defined over a finite field as projective coordinates according to transformsx=XZLxandy=YZLy,respectively; and (c) adding together K copies, K being a scalar, of the point P(X,Y) to obtain the scalar multiplication product KP. The scalar multiplication product is then converted from parameterized projective coordinates P(X,Y,Lx,Ly) to affine coordinates P(x,y). The method is optimized by restricting Ly so that Ly−Lx≧0 or, alternatively, so that Ly=Lx. The method may be carried out on a cryptographic device, which may be a computer, a (cellular) telephone, a smart card, an ASIC, or the like.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
Elliptic curve cryptosystem apparatus, storage medium storing elliptic curve cryptosystem program, and elliptic curve cryptosystem arithmetic method
InactiveUS7505587B2Reduce computing timeIncrease speedPublic key for secure communicationSecret communicationComputer hardwareEllipse
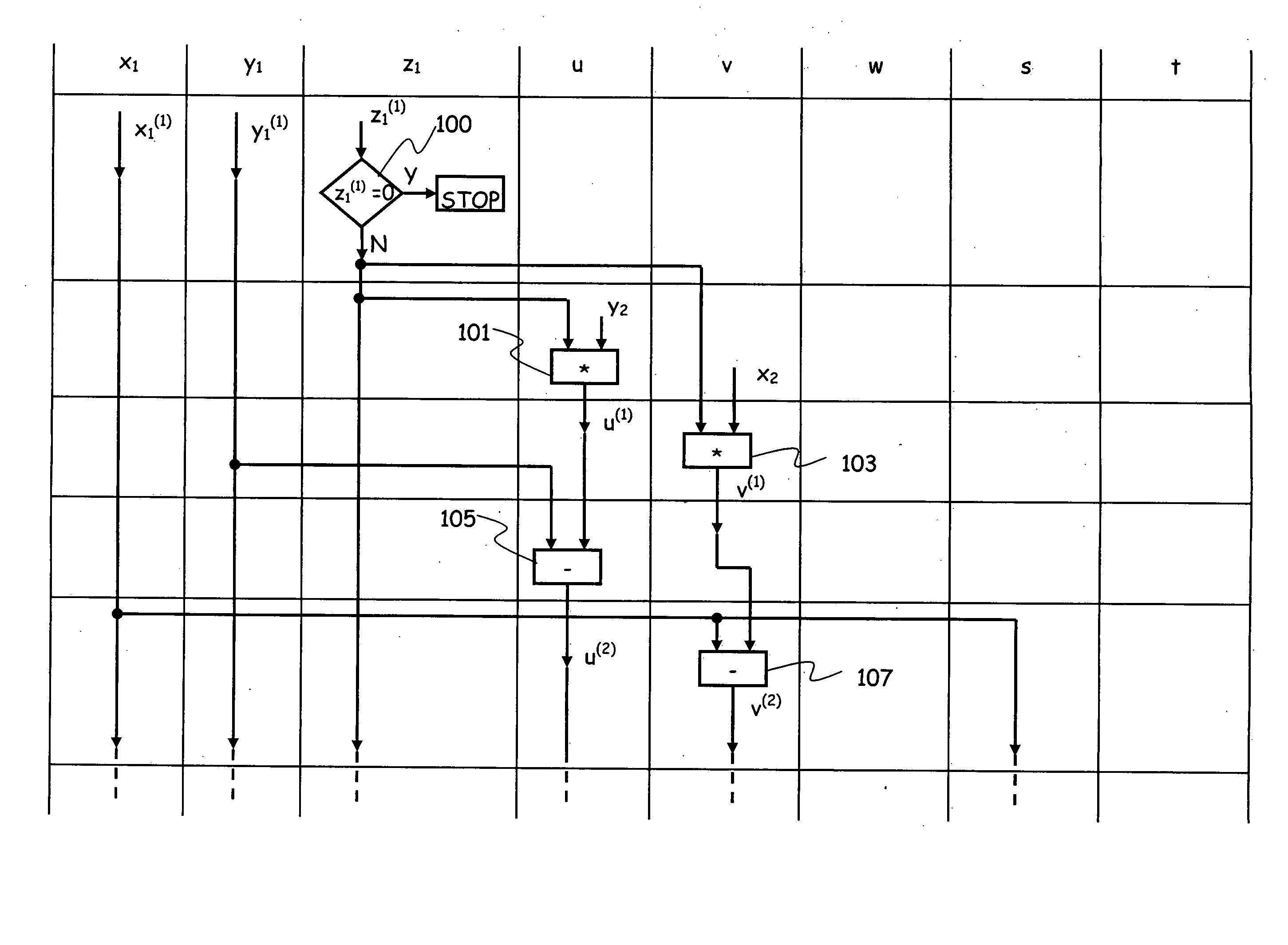
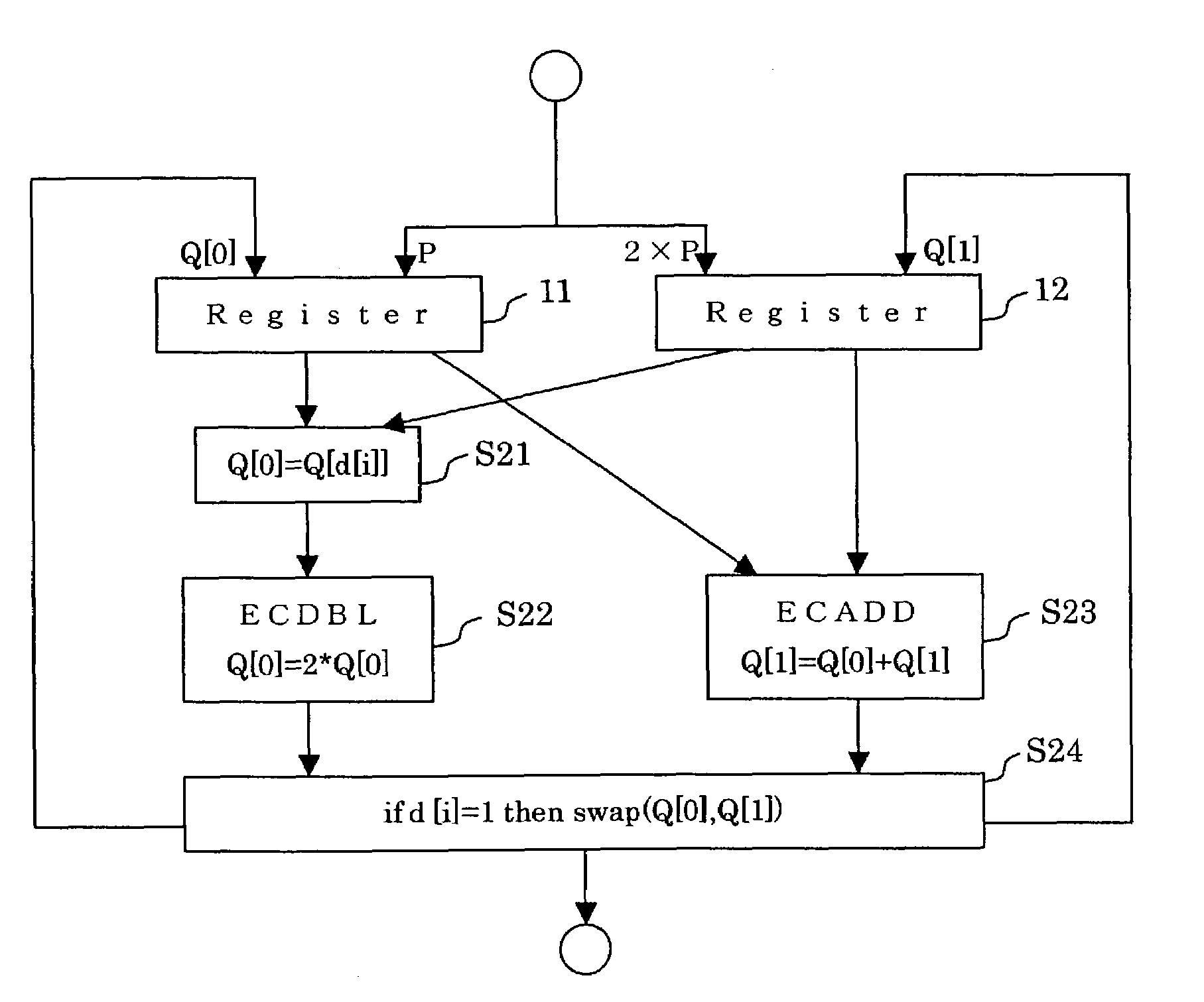
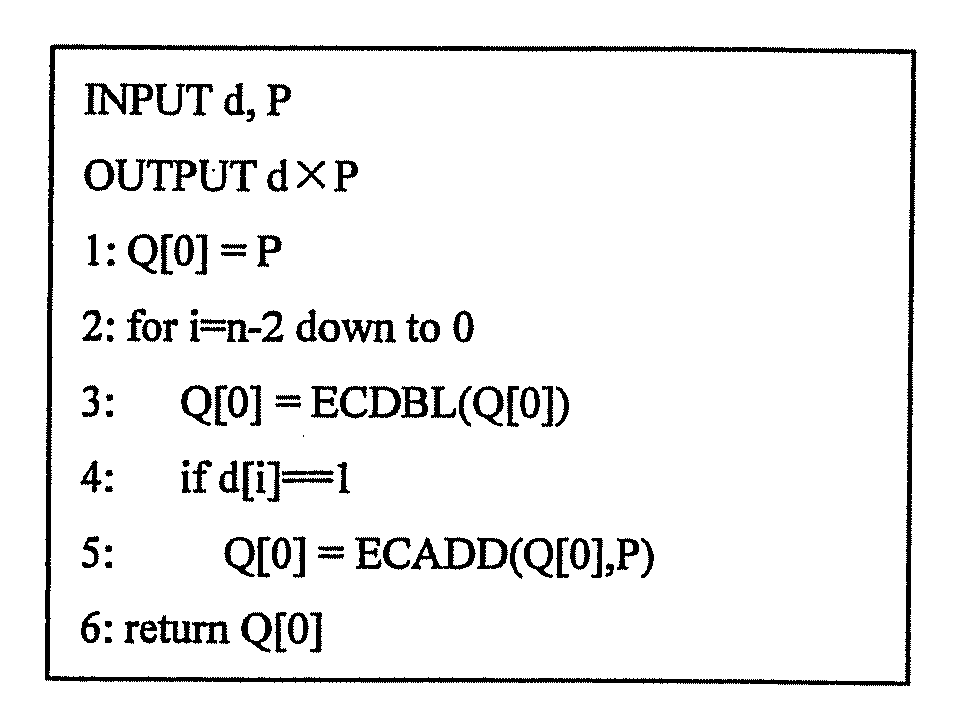
A scalar multiplication can be performed on an elliptic curve cryptosystem at a high speed. P is set as an initial value of Q[0], and 2×P is set as an initial value of Q[1]. An elliptic curve doubling ECDBL of Q[d[i]] is performed, and an arithmetic result is stored in Q[2]. An elliptic curve addition ECADD of Q[0] and Q[1] is performed, and an arithmetic result is stored in Q[1]. Q[2−d[i]] is stored in Q[0]. Q[1+d[i]] is stored in Q[1]. The elliptic curve addition ECADD and the elliptic curve doubling ECDBL are concurrently performed in the respective processors.
Owner:FUJITSU LTD +1
Method and Apparatus for Generating a Public Key in a Manner That Counters Power Analysis Attacks
ActiveUS20080219438A1Key distribution for secure communicationPublic key for secure communicationPower analysisCountermeasure
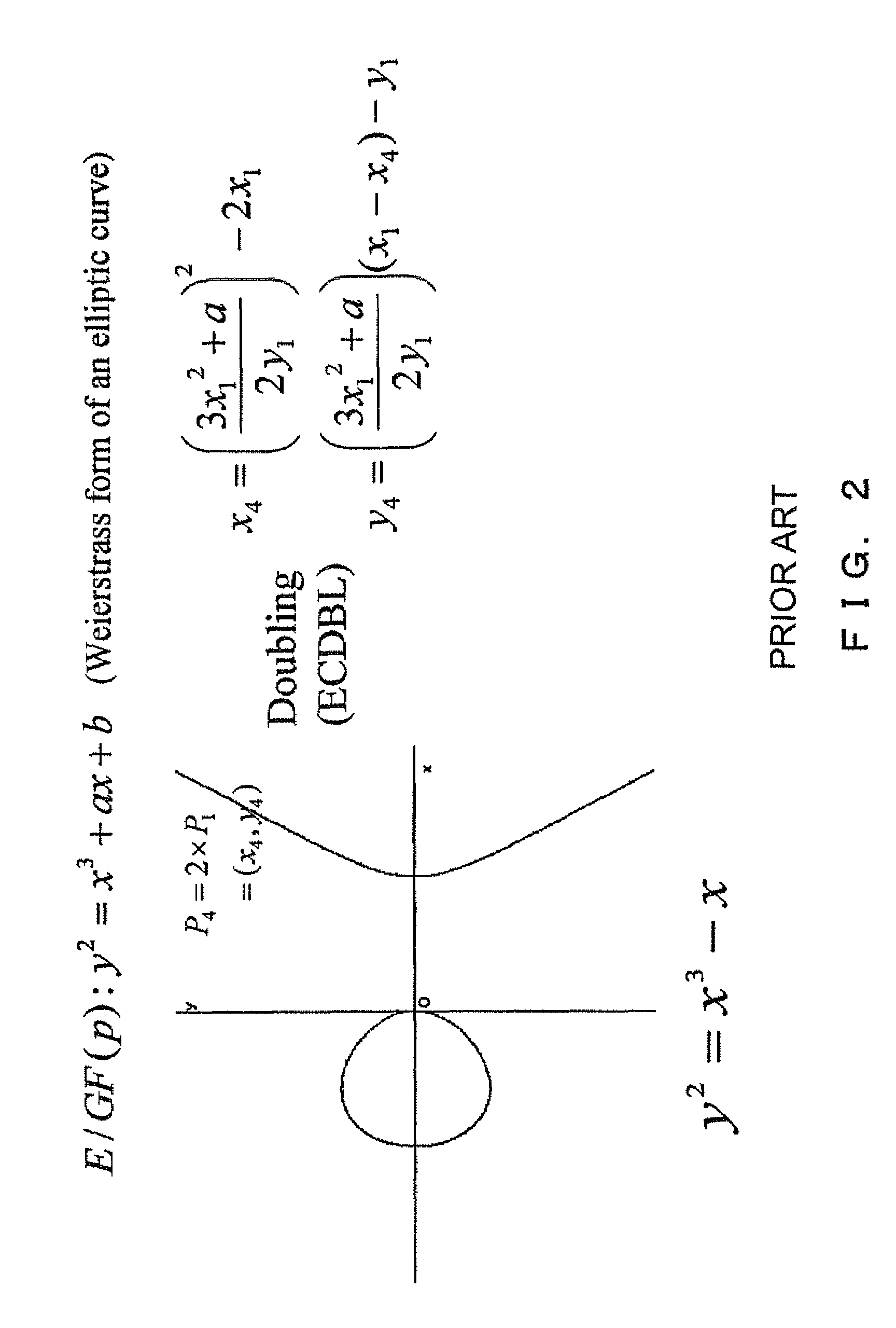
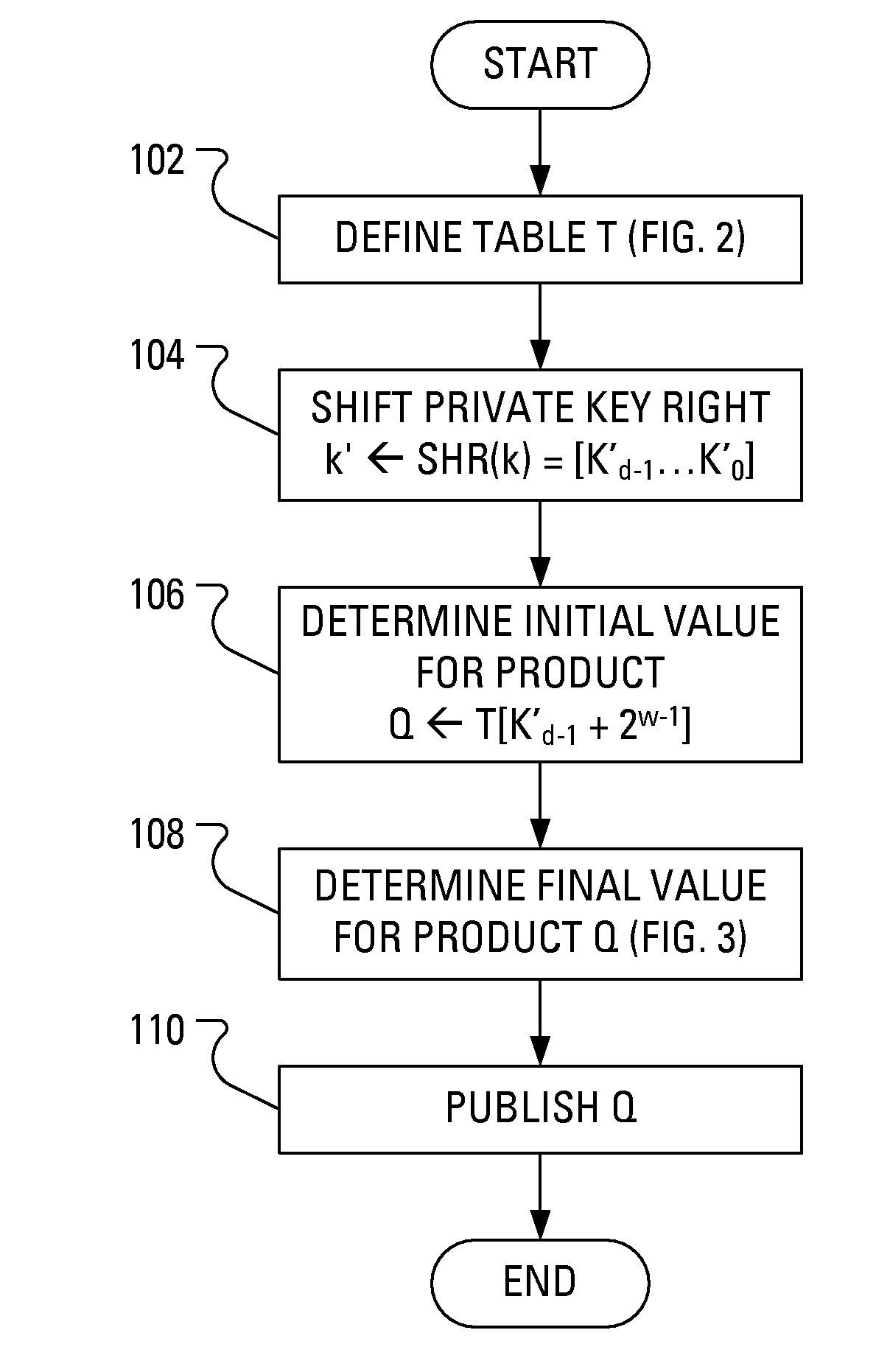
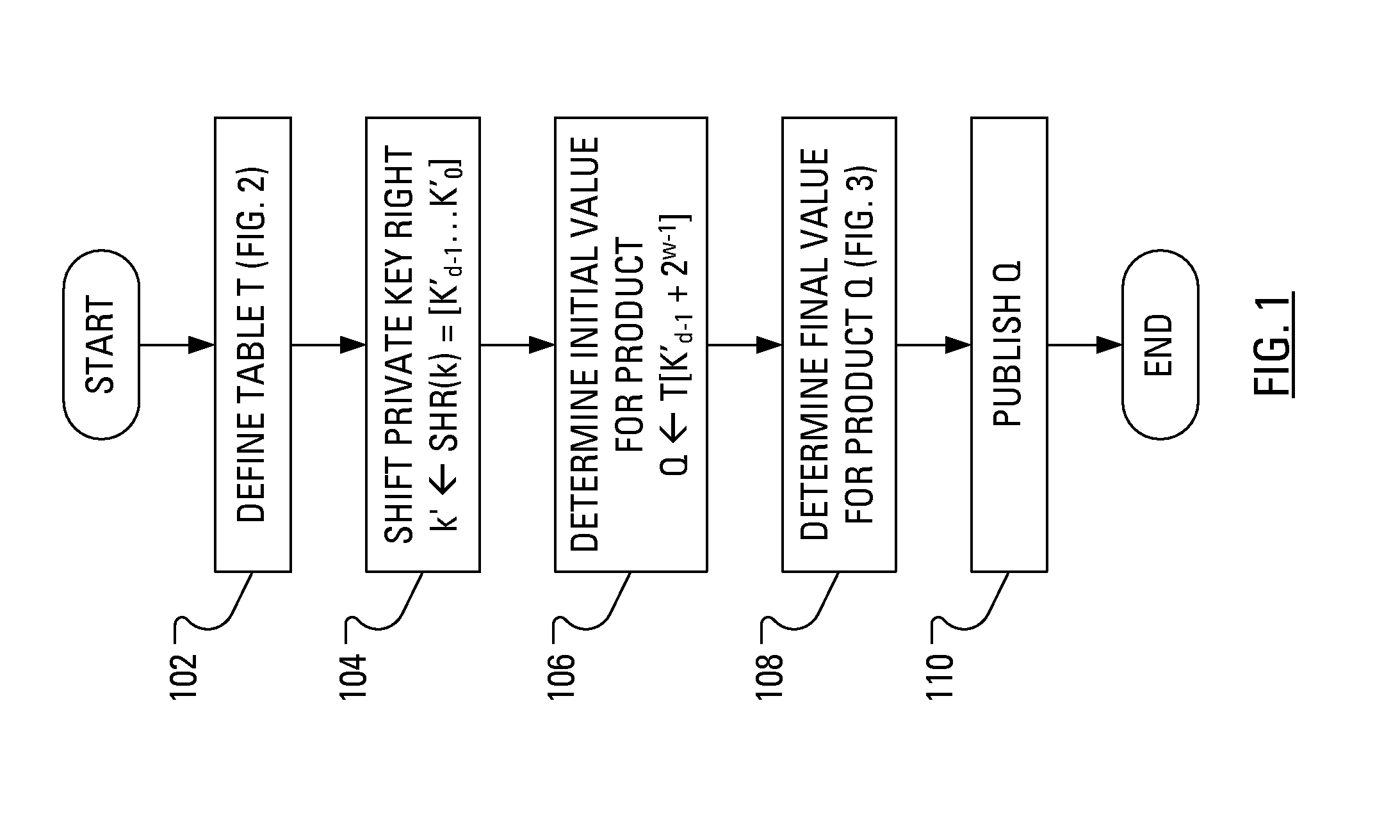
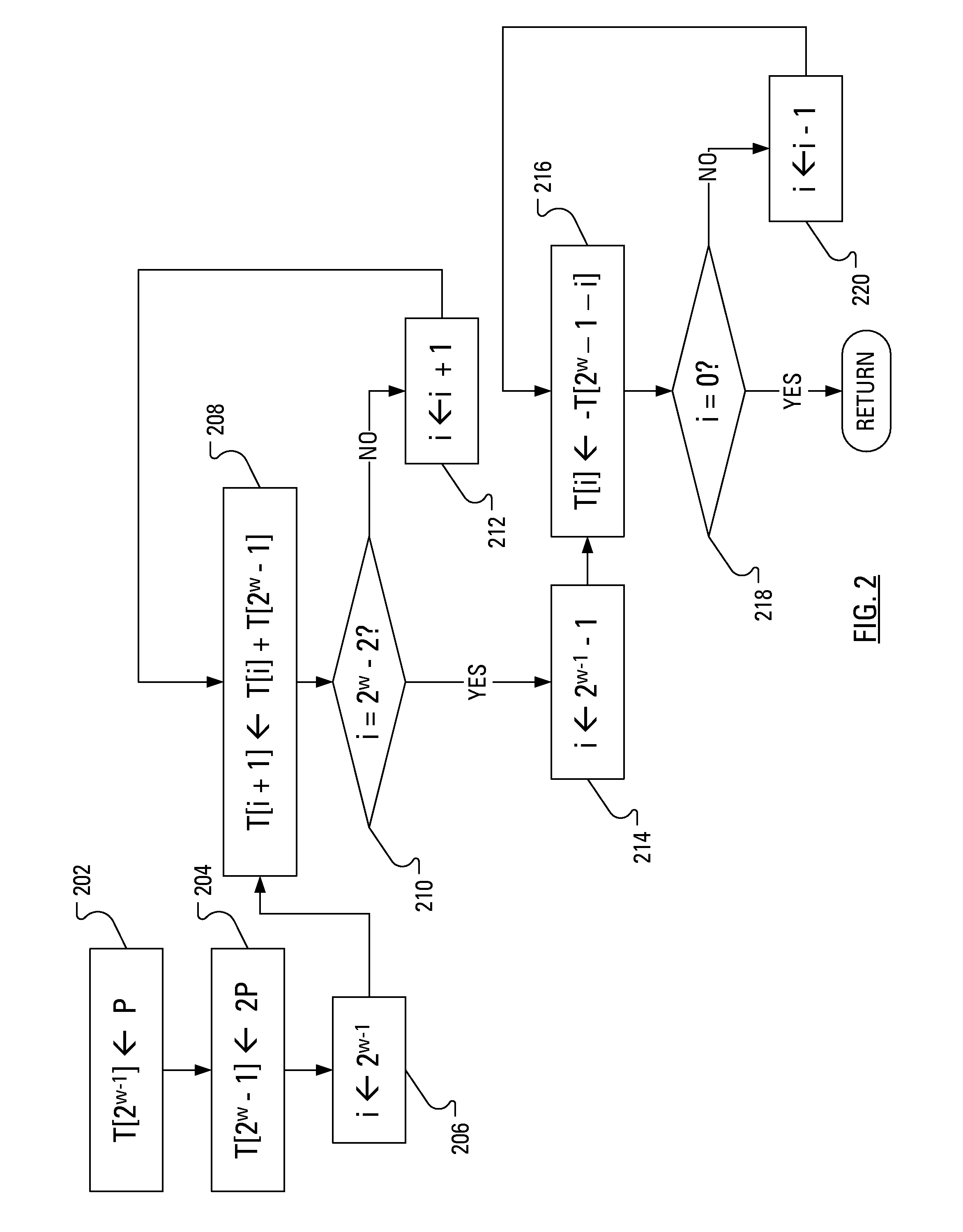
A public key for an Elliptic Curve Cryptosystem is generated in a manner that acts as a countermeasure to power analysis attacks. In particular, a known scalar multiplication method is enhanced by, in one aspect, performing a right shift on the private key. The fixed-sequence window method includes creation and handling of a translated private key. Conveniently, as a result of the right shift, the handling of the translated private key is made easier and more efficient.
Owner:MALIKIE INNOVATIONS LTD
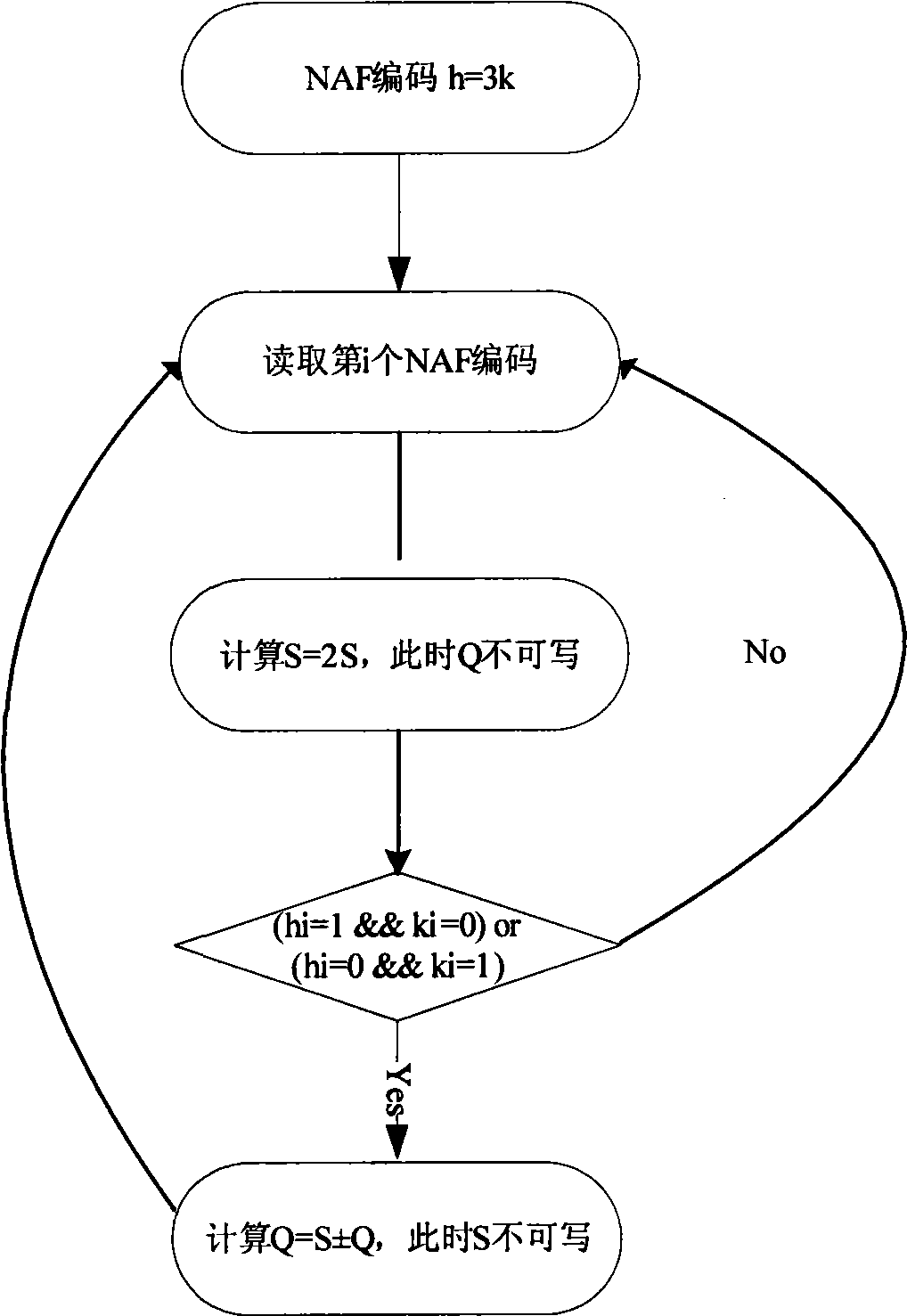
Implementation method for rapid scalar multiplication algorithm in elliptic curve cryptosystem
InactiveCN102393812AFast operationReduce the number of cyclesPublic key for secure communicationComputations using residue arithmeticCoordinate changeSymbol of a differential operator
The invention discloses an implementation method for a rapid scalar multiplication algorithm in an elliptic curve cryptosystem. The method at least comprises a scalar multiplication algorithm procedure of binary coding with the minimum Hamming weight and provided with symbols from left to right, and the method comprises the following steps of: arranging definitions on a finite prime number field, being arbitrary point, and being arbitrary integer; inputting'':''; outputting'':''; A. commanding '', ,''; B. decreasing progressively until, implementing: a. commanding; b. '', ,''; c. if, commanding; C. returning. The implementation method for the rapid scalar multiplication algorithm in the elliptic curve cryptosystem provided by the invention, the binary coding with the minimum Hamming weight and provided with the symbols from left to right is applied to the rapid scalar multiplication algorithm in the elliptic curve cryptosystem, a novel binary coding scalar multiplication algorithm with the symbols is created, which can be faster achieved. The novel binary coding scalar multiplication algorithm has the advantages that: arithmetic speed is high, additional memory plint space and coordinate change are not needed during calculation, calculation period is reduced, and the like.
Owner:四川卫士通信息安全平台技术有限公司
Elliptic curve cryptosystem apparatus, elliptic curve cryptosystem method, elliptic curve cryptosystem program and computer readable recording medium storing the elliptic curve cryptosystem program
InactiveUS7639808B2Provide securityPublic key for secure communicationUser identity/authority verificationSoftware engineeringCryptogram
An elliptic curve cryptosystem apparatus performing an elliptic curve cryptosystem process has a coordinate transforming unit for transforming coordinates (X:Y:Z) on a point P on an elliptic curve over a finite field GF(p^m) to coordinates (r1×(X−s1):r2×(Y−s2):r3×(Z−s3)) (where, p is a prime number, m is an integer not less than 1, r1, r2 and r3 are integers not less than 1 and not larger than (p−1), s1, s2 and s3 are integer not less than 0 and not larger than (p−1), and a code “^” represents power), and a scalar multiplication operating unit for performing scalar multiplication on the point on the elliptic curve transformed by the coordinate transforming unit, wherein at least one of the parameters s1, s2 and s3 has a value other than 0. The apparatus can perform the scalar multiplication in the elliptic curve cryptosystem, with resistance to side channel attacks.
Owner:FUJITSU LTD
Method and apparatus for performing elliptic curve arithmetic
ActiveUS7418099B2Avoid attackPublic key for secure communicationUser identity/authority verificationComputer hardwareElliptic curve cryptosystem
A method of performing a cryptographic operation on a point in an elliptic curve cryptosystem using an elliptic carve. The method comprises the steps of obtaining information that uniquely identifies the elliptic curve and performing computations on the point to obtain the result of the cryptographic operation. The computations use the information. The computations produce an incorrect result if the point is not on the elliptic curve.
Owner:BLACKBERRY LTD
Method for elliptic curve scalar multiplication using parameterized projective coordinates
InactiveUS20100322422A1Protect scalar multiplication computationEnhance scalar multiplicationDigital data processing detailsPublic key for secure communicationComputer hardwareEllipse
The method for elliptic curve scalar multiplication in an elliptic curve cryptosystem implemented over an insecure communications channel includes the steps of: (a) selecting positive integers Lx and Ly, where Lx and Ly are not both equal to 1, and where Ly≠3 if Lx=2; (b) representing coordinates of a point P=(x,y) on an elliptic curve of the form F(x,y)=y2−x3−ax−b=0 defined over a finite field as projective coordinates according to transformsx=XZLxandy=YZLy,respectively; and (c) adding together K copies, K being a scalar, of the point P(X,Y,ZL<sub2>x< / sub2>,ZL<sub2>y< / sub2>) to obtain the scalar multiplication product KP. The scalar multiplication product is then converted from parameterized projective coordinates P(X,Y,ZL<sub2>x< / sub2>,ZL<sub2>y< / sub2>) to affine coordinates P(x,y). The method is optimized by restricting Ly so that Ly−Lx≧0 or, alternatively, so that Ly=Lx. The method may be carried out on a cryptographic device, which may be a computer, a (cellular) telephone, a smart card, an ASIC, or the like.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
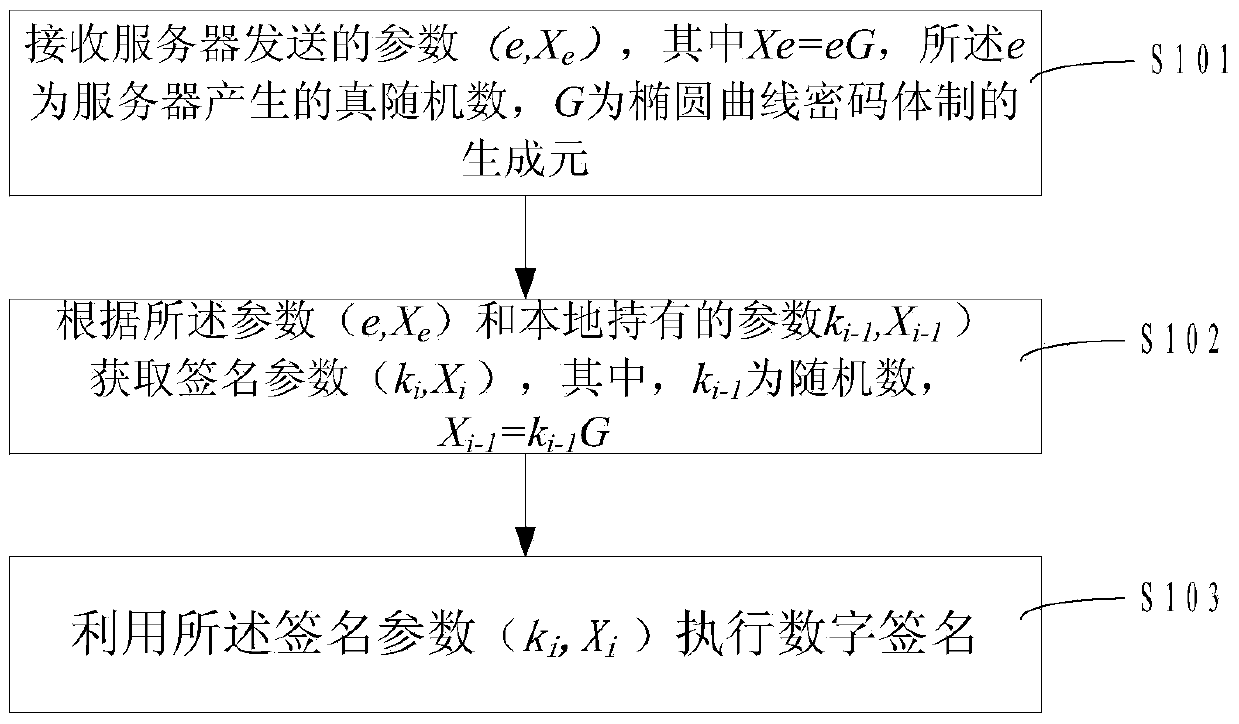
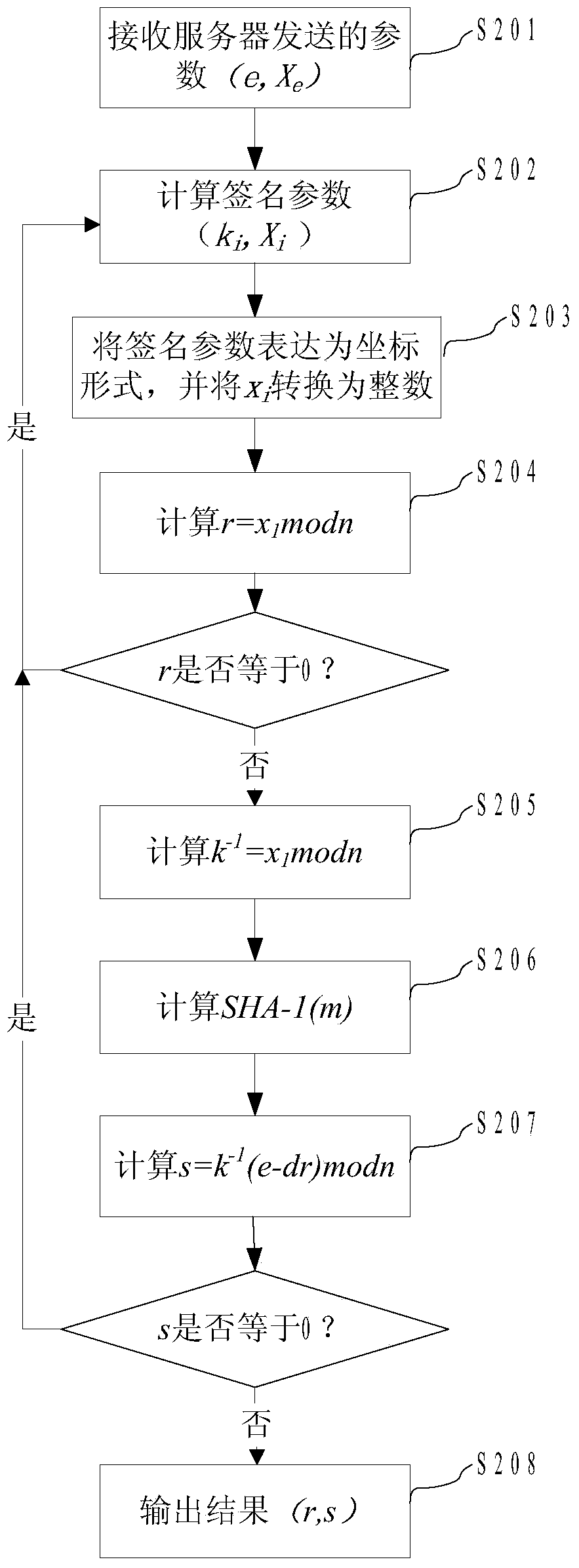
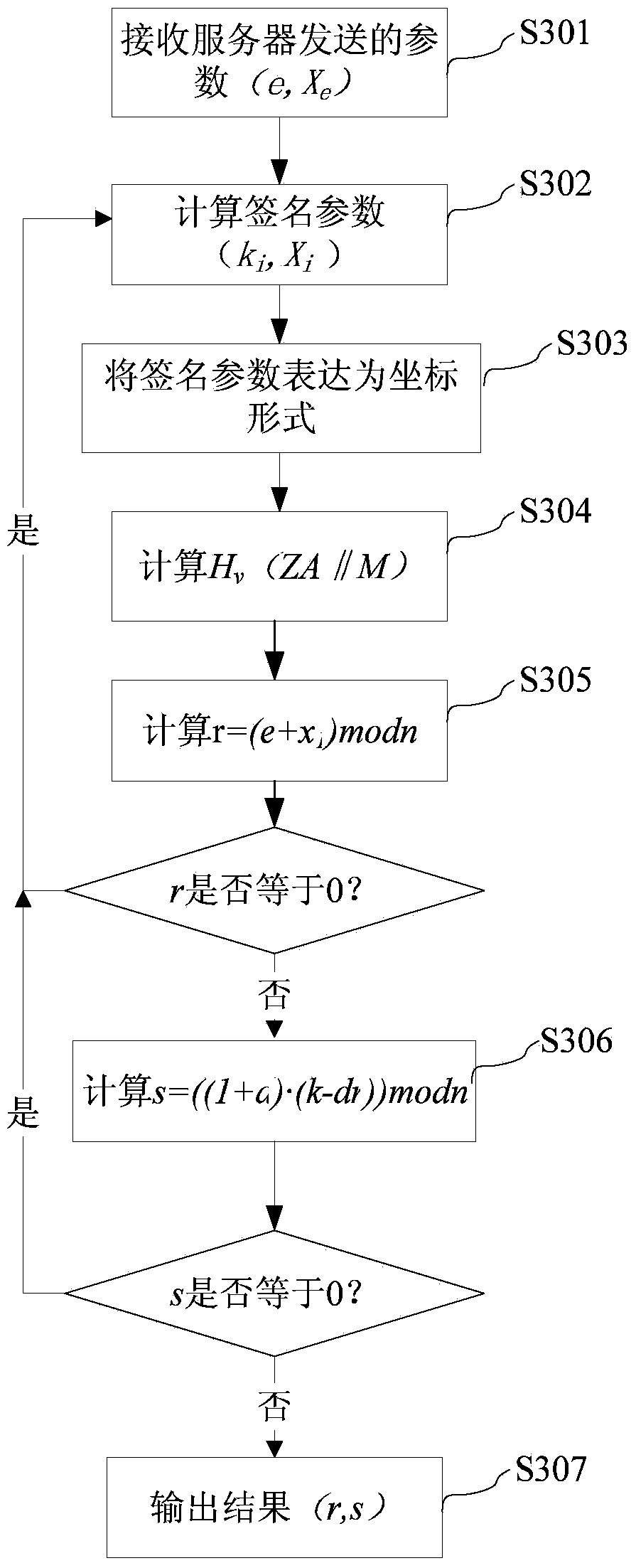
Digital signature method, digital signature equipment, password operation method in digital signature, and server
ActiveCN103475473AEnsure safetyGuaranteed privacyUser identity/authority verificationPasswordDigital Signature Algorithm
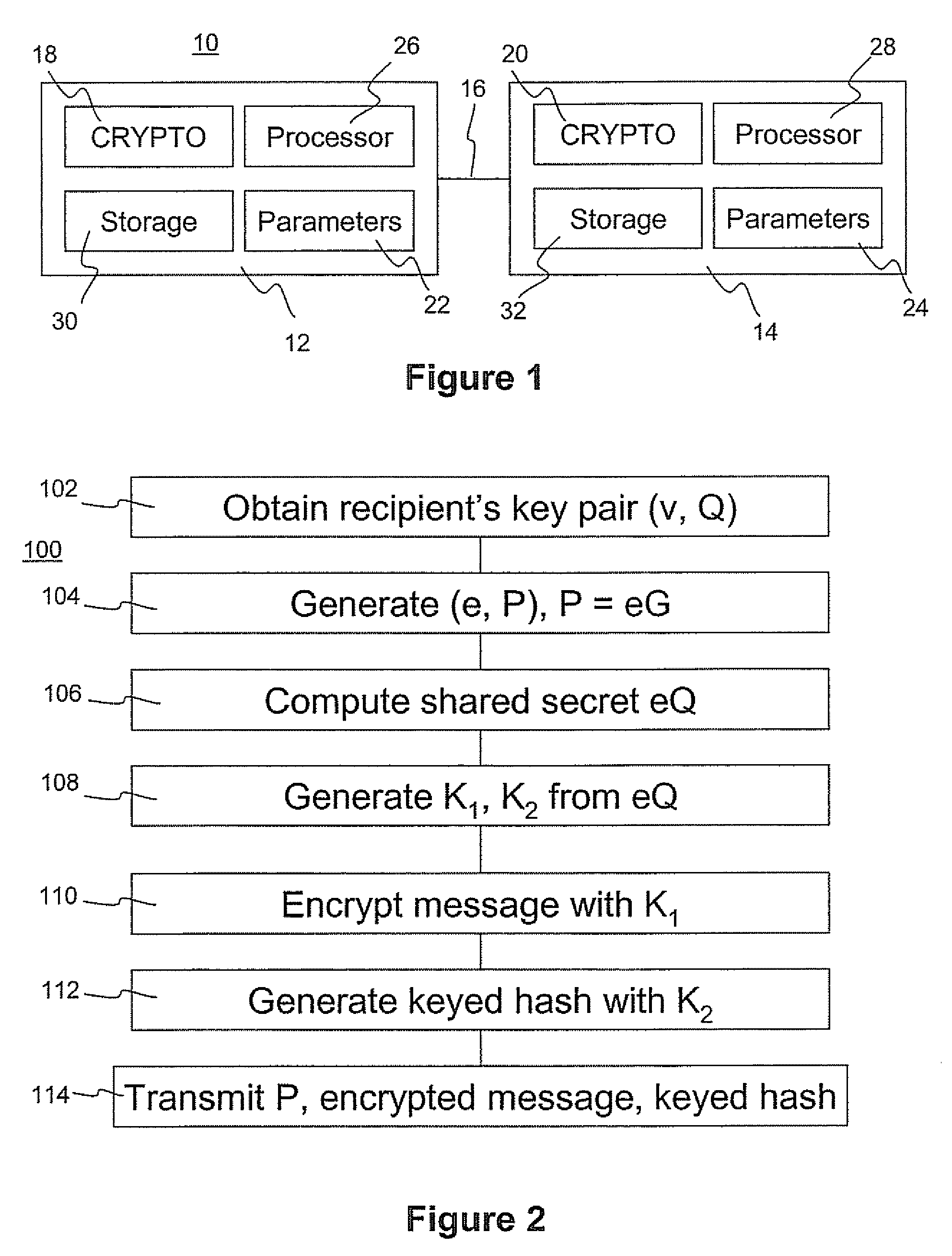
The invention provides a digital signature method and digital signature equipment. The method comprises the following steps: receiving parameters (e, Xe) transmitted by a server, wherein Xe is equal to eG, e is a true random number generated by the server, and G is a generator of an elliptic curve cryptosystem; acquiring signature parameters (ki, Xi) according to the parameters (e, Xe) and locally held parameters (ki-1, Xi-1), wherein Xi-1 is equal to ki-1G; executing digital signature by utilizing the signature parameters (ki, Xi). In addition, the invention also provides a password operation method in the digital signature and the server. The method comprises the following steps: generating the true random number e according to a preset cycle; calculating and storing the parameters (e, Xe), wherein Xe is equal to eG, and G is the generator of the elliptic curve cryptosystem; transmitting the parameters (e, Xe) to a client which executes the signature, wherein the client acquires the signature random number (ki, Xi) according to the parameters (e, Xe) and the parameters (ki-1, Xi-1) and executes the digital signature according to the (ki, Xi). By the technology disclosed by the invention, the leak of privacy that a service network acquires the password operation of a user when a digital signature algorithm is subjected to outsourcing process is avoided; the privacy of outsourcing password operation is guaranteed; the signature security is guaranteed.
Owner:GUANGDONG CERTIFICATE AUTHORITY
Systems and methods for operating secure elliptic curve cryptosystems
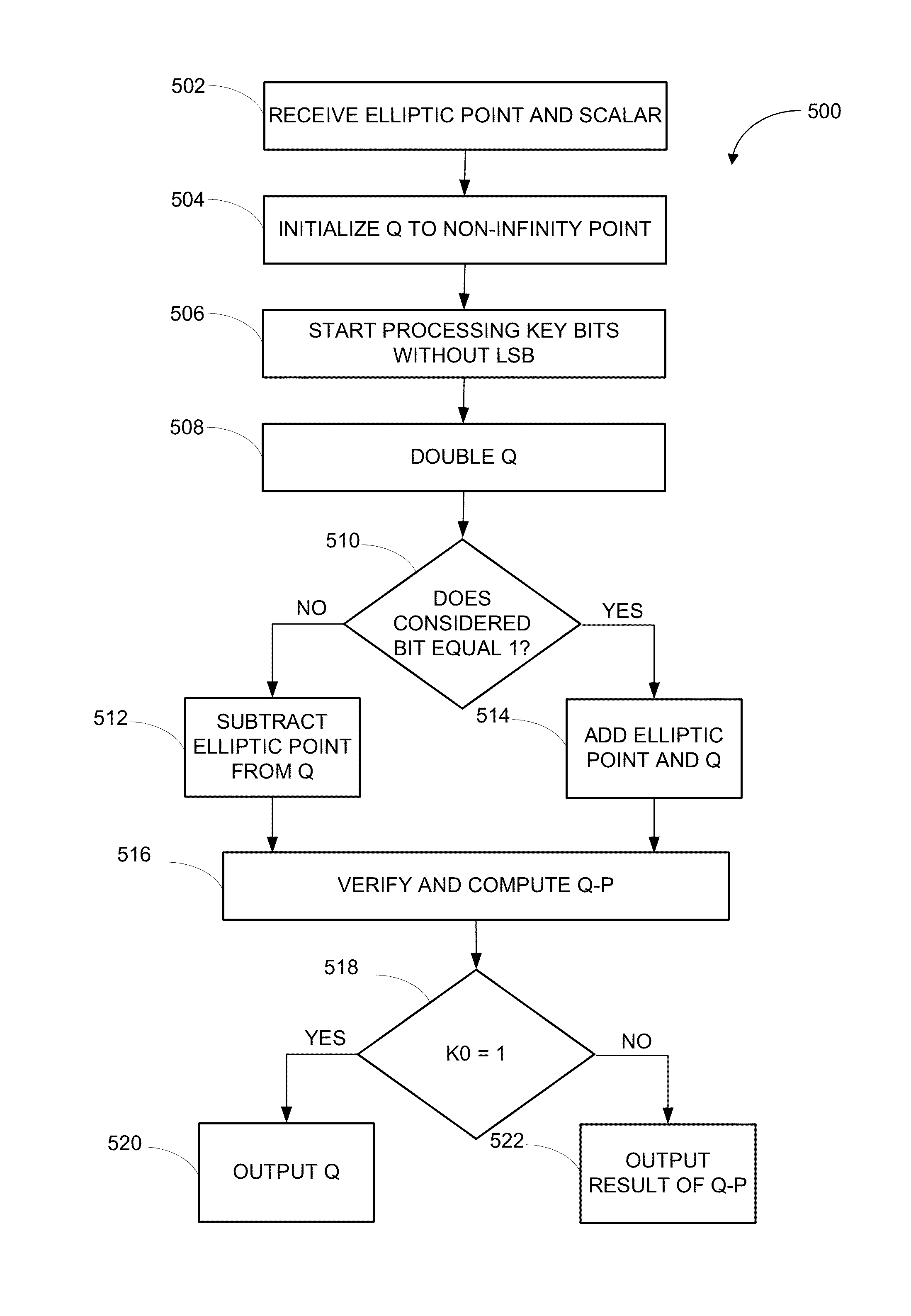
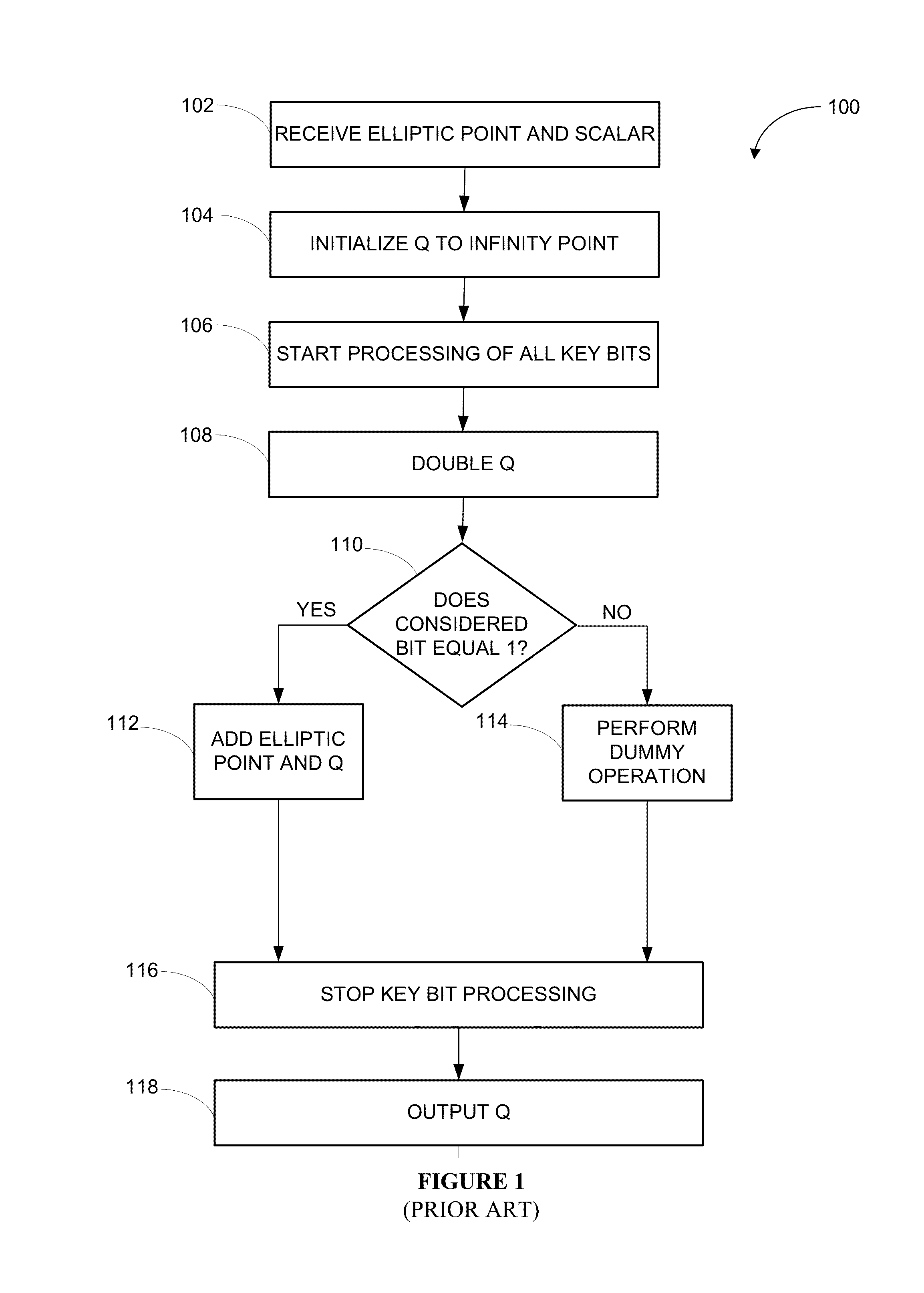
ActiveUS20160277178A1Digital data processing detailsInternal/peripheral component protectionPower analysisCountermeasure
Various embodiments of the invention implement countermeasures designed to withstand attacks by potential intruders who seek partial or full retrieval of elliptic curve secrets by using known methods that exploit system vulnerabilities, including elliptic operation differentiation, dummy operation detection, lattice attacks, and first real operation detection. Various embodiments of the invention provide resistance against side-channel attacks, such as sample power analysis, caused by the detectability of scalar values from information leaked during regular operation flow that would otherwise compromise system security. In certain embodiments, system immunity is maintained by performing elliptic scalar operations that use secret-independent operation flow in a secure Elliptic Curve Cryptosystem.
Owner:MAXIM INTEGRATED PROD INC
Remote sensing image encryption method based on elliptic curve cryptosystem
InactiveCN101582170ARealize visualizationFast encryptionWave based measurement systemsImage codingCryptosystemData file
The invention discloses a remote sensing image encryption method based on an elliptic curve cryptosystem, including the following steps: A, an original remote sensing image file is transformed into a data file in DAT format under support of an IDL / ENVI system; B, Montgomery type elliptic curve is utilized to fast encrypt MODIS remote sensing image, wherein, the DN value of the remote sensing image is encrypted mainly; C, the image is reconstructed under the support of the IDL / ENVI system to complete visualization of the encrypted image; D, after receiving the encrypted remote sensing image, An ECC private key of an authorized user is used to decrypt so as to obtain a remote sensing image with concrete physical meaning, thus the remote sensing decryption method based on ECC is completed. The method improves encryption speed of the mass remote sensing image, enhances safe intensity of the encrypted image, and meanwhile eliminates scrambling process in the traditional image encryption mode, thus remaining the readability of the remote sensing image.
Owner:SHANGHAI UNIV
Elliptic curve cryptosystem apparatus, storage medium storing elliptic curve cryptosystem program and elliptic curve cryptosystem arithmetic method
InactiveUS20090207997A1Increase speedImprove the immunityPublic key for secure communicationSecret communicationEllipseScalar multiplication
A scalar multiplication can be performed on an elliptic curve cryptosystem at a high speed. P is set as an initial value of Q[0], and 2×P is set as an initial value of Q[1]. An elliptic curve doubling ECDBL of Q[d[i]] is performed, and an arithmetic result is stored in Q[2]. An elliptic curve addition ECADD of Q[0] and Q[1] is performed, and an arithmetic result is stored in Q[1]. Q[2−d[i]] is stored in Q[0]. Q[1+d[i]] is stored in Q[1]. The elliptic curve addition ECADD and the elliptic curve doubling ECDBL are concurrently performed in the respective processors.
Owner:FUJITSU LTD +1
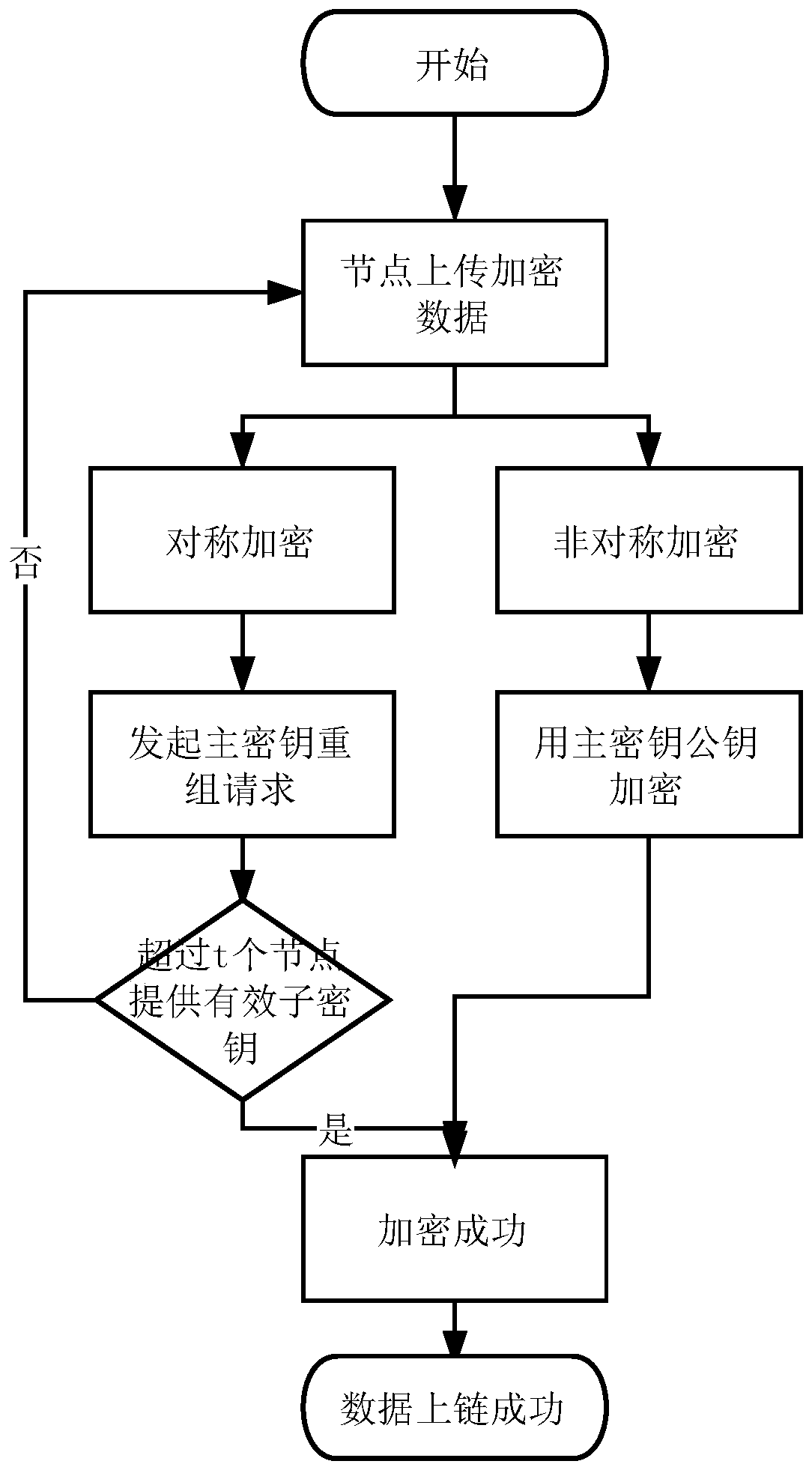
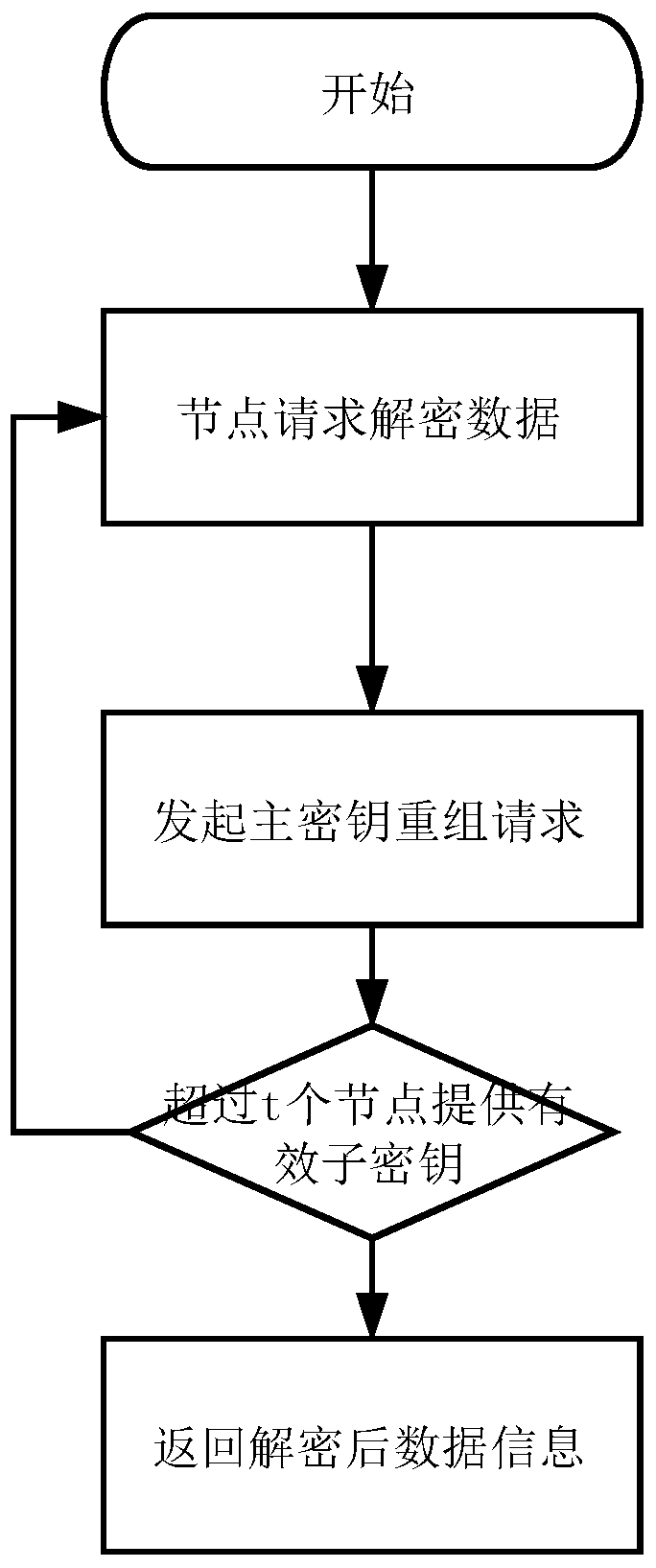
Blockchain key sharing and dynamic updating method based on an elliptic curve
InactiveCN109768863AEnsure safetySafe storageKey distribution for secure communicationPublic key for secure communicationSmart contractChain network
The invention discloses a blockchain key sharing and dynamic updating method based on an elliptic curve. The method comprises the steps of node key initialization, sub-key verification, main key synthesis, main key updating, sub-key addition and deletion and data encryption and decryption. Based on the idea of a threshold key sharing system, a linear equation set key sharing technology is proposedto distribute a block chain master key to each node, and the method can dynamically change the master key and add and delete the sub-keys on the premise of not changing node sub-keys, and is matchedwith a scene that the nodes in the block chain network are dynamically added and deleted. The purpose of the invention is to prevent fraud between nodes. According to the method, the sub-keys are distributed, an elliptic curve cryptosystem is combined, the method capable of identifying the authenticity of the sub-keys is also provided after the sub-keys are distributed, the trust problem between the nodes is guaranteed, the security of private data storage of the block chain is guaranteed, the credibility of the block chain system is enhanced, and related operations are defined in the smart contract and cannot be tampered.
Owner:HANGZHOU QULIAN TECH CO LTD
Method of countering side-channel attacks on elliptic curve cryptosystem
ActiveUS8345863B2Improve securityEffective attackMultiple keys/algorithms usageData taking preventionElectric forceFault detection algorithm
Owner:SAMSUNG ELECTRONICS CO LTD
Method for infinity point representation under affine coordinate system in elliptic curve cryptosystem
InactiveCN102104482AThe operation is implemented correctlyPublic key for secure communicationEllipseComputer science
The present invention discloses a method for infinity point representation under an affine coordinate system in an elliptic curve cryptosystem, including the step of adding a component z' in an existing affine coordinate system having two components, x and y, to form a new affine coordinate system. An ordinary point on an elliptical curve is represented as (x, y, 1) in the new affine coordinate system, i.e., coordinate point z'=1, wherein the ordinary point is represented as (x, y) in the existing affine coordinate system; and an infinity point on the elliptic curve is represented as (0, 0, 0) in the new affine coordinate system, i.e., coordinate point z'=0. The method for infinity point representation under the affine coordinate system in the elliptic curve cryptosystem enables an infinity point originally unable to be represented in the affine coordinate system, to be represented in the improved affine coordinate system, thereby being capable of distinguishing the infinity point from the ordinary point in the affine coordinate system, and enables the point operation of addition and multiplication relating to the affine coordinate system to be correctly realized.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
IPTV (Internet Protocol Television) user security terminal
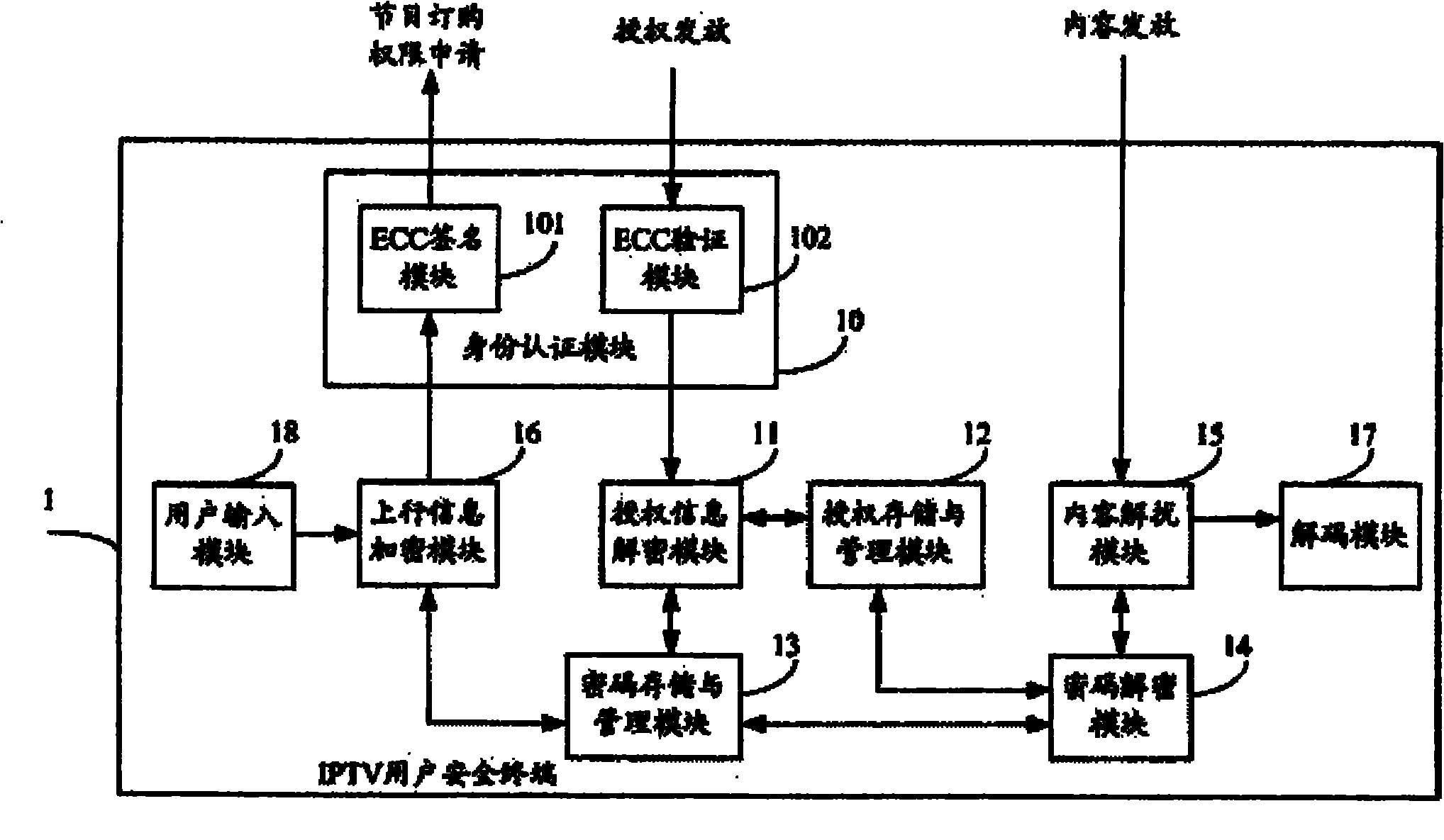
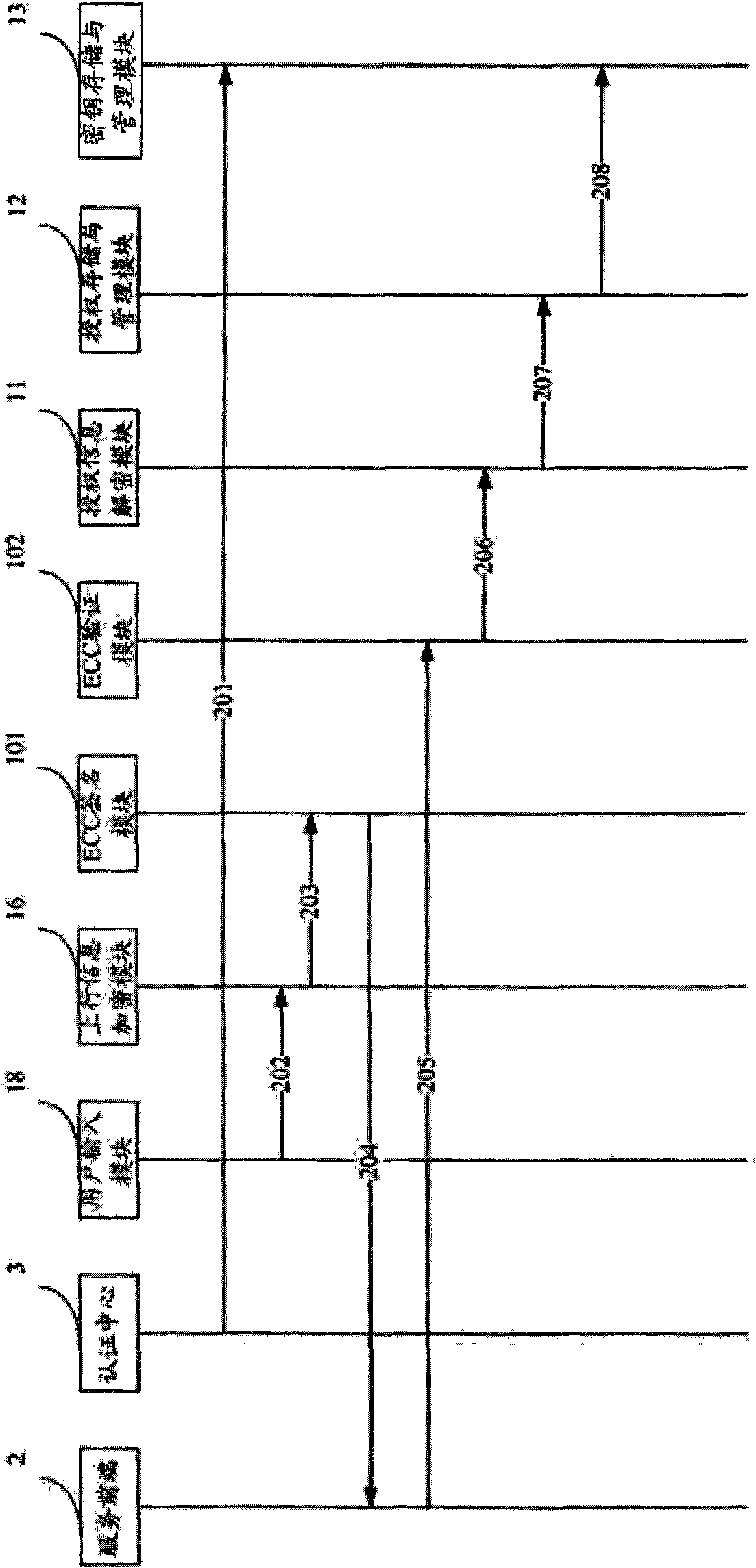
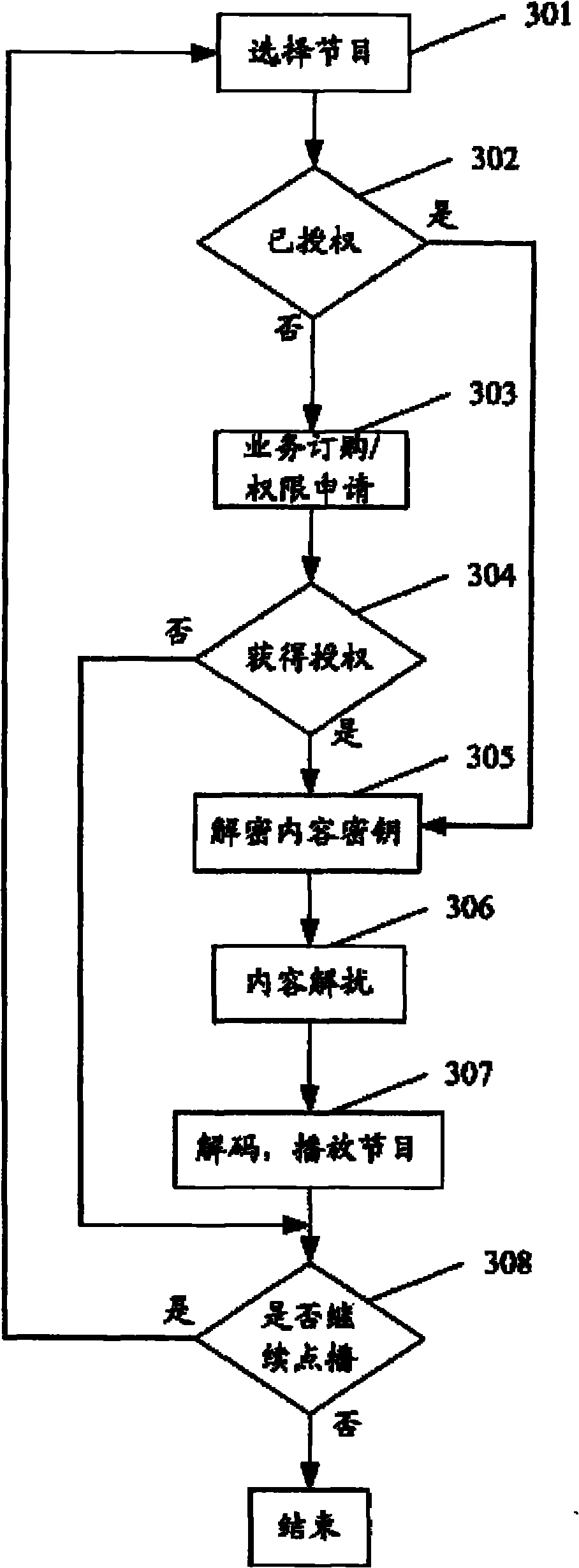
InactiveCN101895393AStrong scalabilityProtection securityTelevision system detailsPulse modulation television signal transmissionUser inputCryptosystem
The invention relates to an IPTV (Internet Protocol Television) user security terminal which comprises an identity authentication module, an authorization information decryption module, an authorization storage and management module, a key storage and management module, a key decryption module, a content descrambling module, an uplink information encryption module, a decoding module and a user input module, wherein the identity authentication module comprises an elliptic curve cryptosystem signature module and an elliptic curve cryptosystem verification module. The terminal ensures that only authorized users can watch programs based on good interactivity of the IPTV by means of identity authentication, authorization management, secret key encryption protection, content encryption protection and the like. The user security terminal has favorable expansibility, can satisfy live broadcast, VOD broadcast and other services of the IPTV, and can effectively protect the security of the digital media content of the IPTV.
Owner:AEROSPACE INFORMATION
ECC (elliptic curve cryptosystem) encryption hardware device with expandable parameter bit width
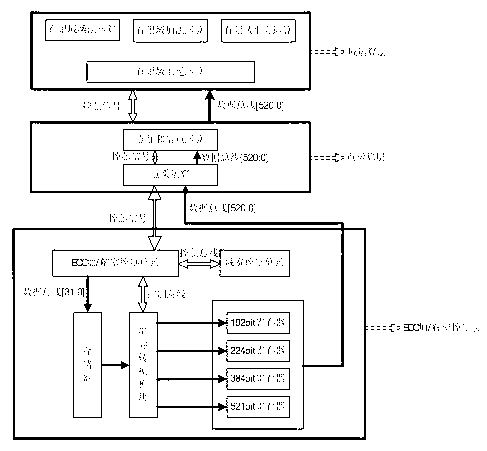
InactiveCN103023659AGuaranteed normal operationSolve the problem of scalable bit widthEncryption apparatus with shift registers/memoriesUser identity/authority verificationControl layerProcessor register
The invention discloses an ECC (elliptic curve cryptosystem) encryption hardware device with expandable parameter bit width. The device comprises an ECC encryption / decryption control layer, a point operation layer and a domain operation layer. The ECC encryption / decryption control layer comprises a domain width control unit, an ECC encryption / decryption control unit, a storage, a data serial-parallel conversion module and four register groups supporting multi-bit-width, namely a 192-bit register group, a 224-bit register group, a 384-bit register group and a 521-bit register group. The point operation layer comprises a point adding and point double operation module and a point multiplication module. The domain operation layer comprises an operation module for addition, multiplication, square and inversion of Galoias domain. By the device suitable for FPGA (field programmable gate array) or ASIC (application specific integrated circuit), bit width of prime domain register is expandable.
Owner:WUHAN UNIV
System and method for securing scalar multiplication against differential power attacks
InactiveUS20140177824A1Readily apparentDigital data processing detailsSecret communicationScalar multiplicationPower attack
The system and method for securing scalar multiplication against differential power attacks (DPAs) delays required point additions in elliptic curve cryptosystem scalar multiplication. A buffer is used to store the points that will be added later in a random manner. Then, a randomly selected one of the stored points in the buffer is added to the accumulation point, or several randomly selected points are added consecutively. This makes the power trace appear as a repeated sequence of consecutive point doubling followed by consecutive point additions, which makes it very difficult for an attacker to know the exact value of the inspected bit during the scalar multiplication process.
Owner:UMM AL QURA UNIVERISTY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com