IPTV (Internet Protocol Television) user security terminal
A technology for secure terminals and users, applied in the field of IPTV security applications, can solve problems such as hidden dangers of IPTV user terminals, achieve good scalability, and protect the security of digital media content
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in further detail below through specific embodiments and in conjunction with the accompanying drawings.
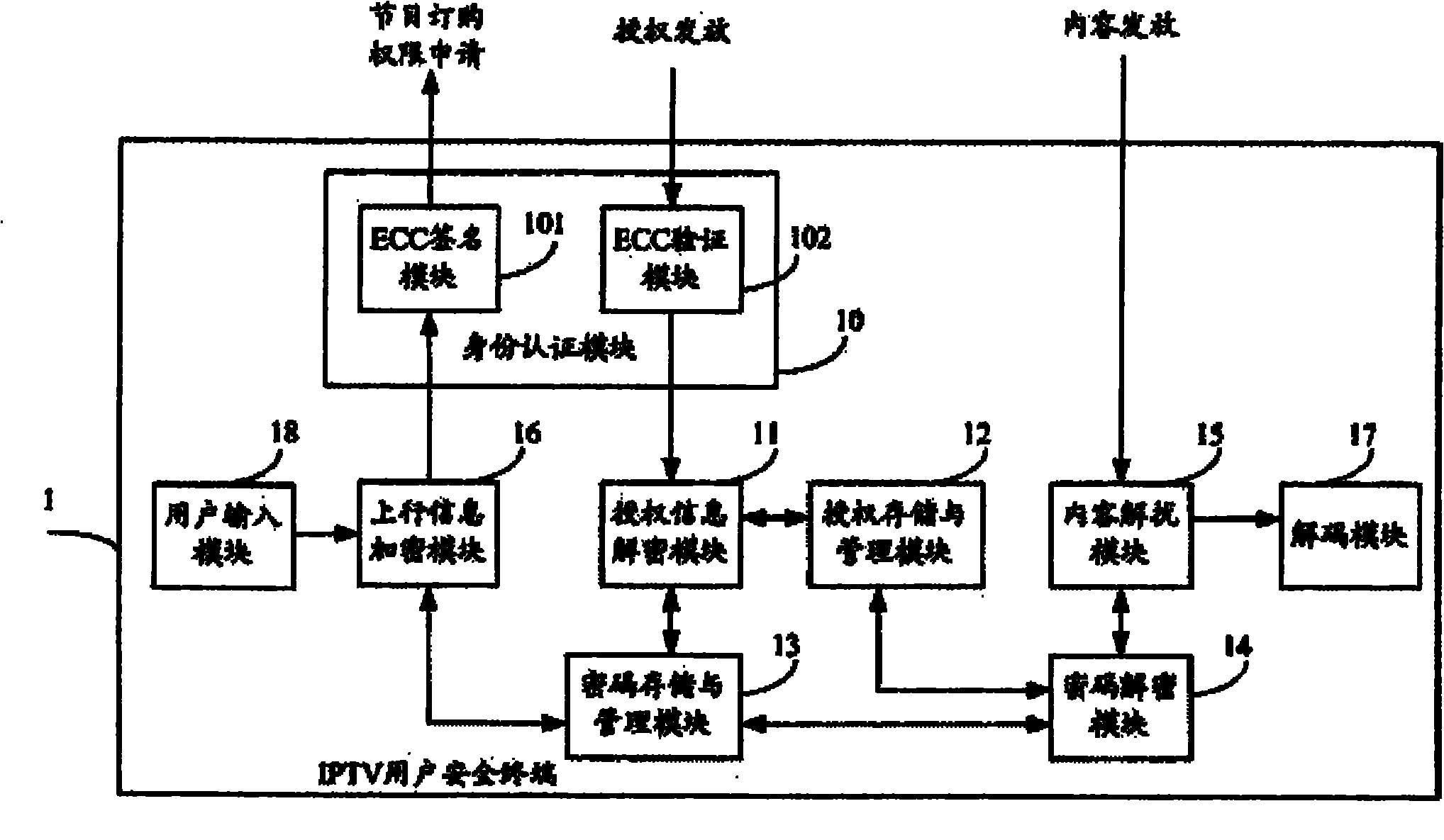
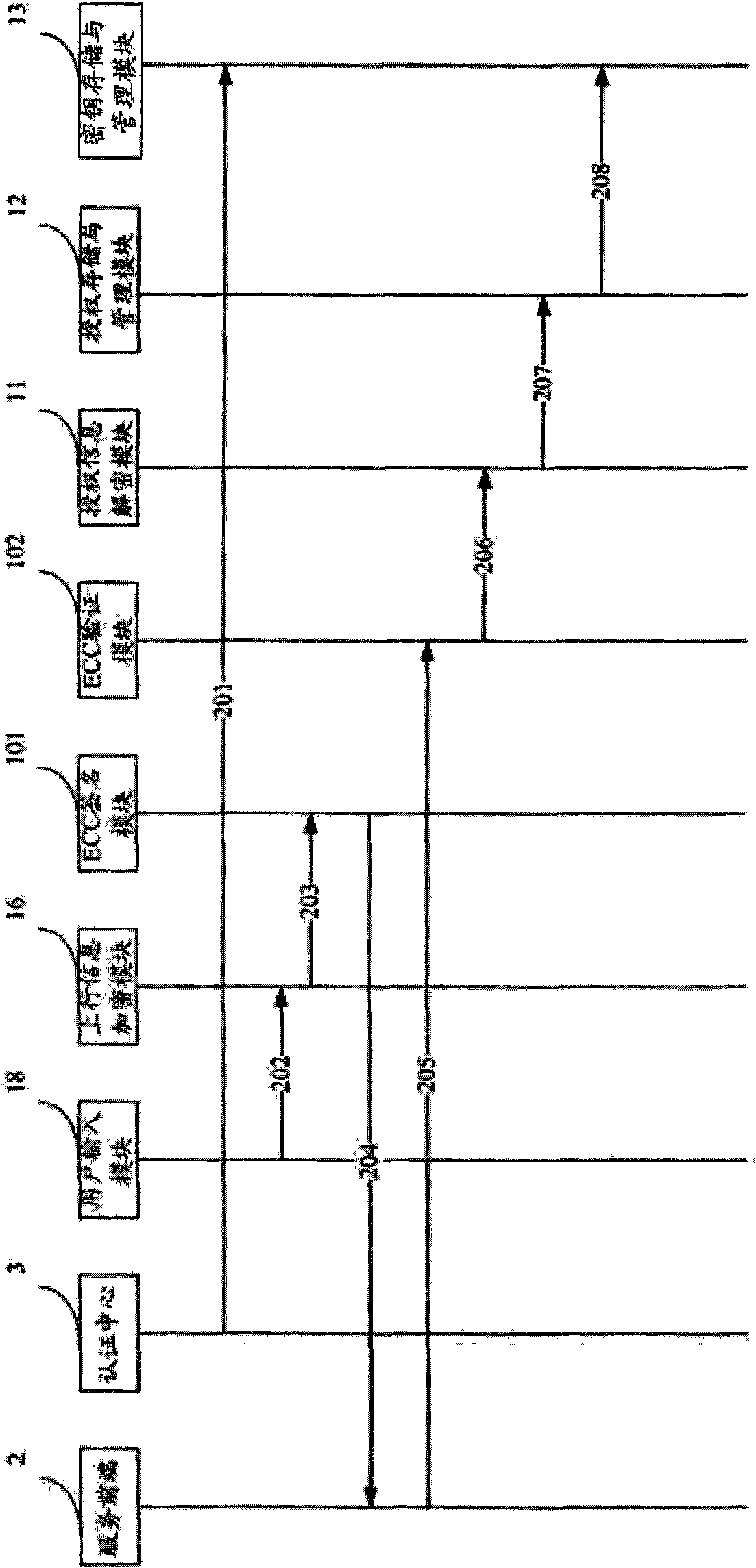
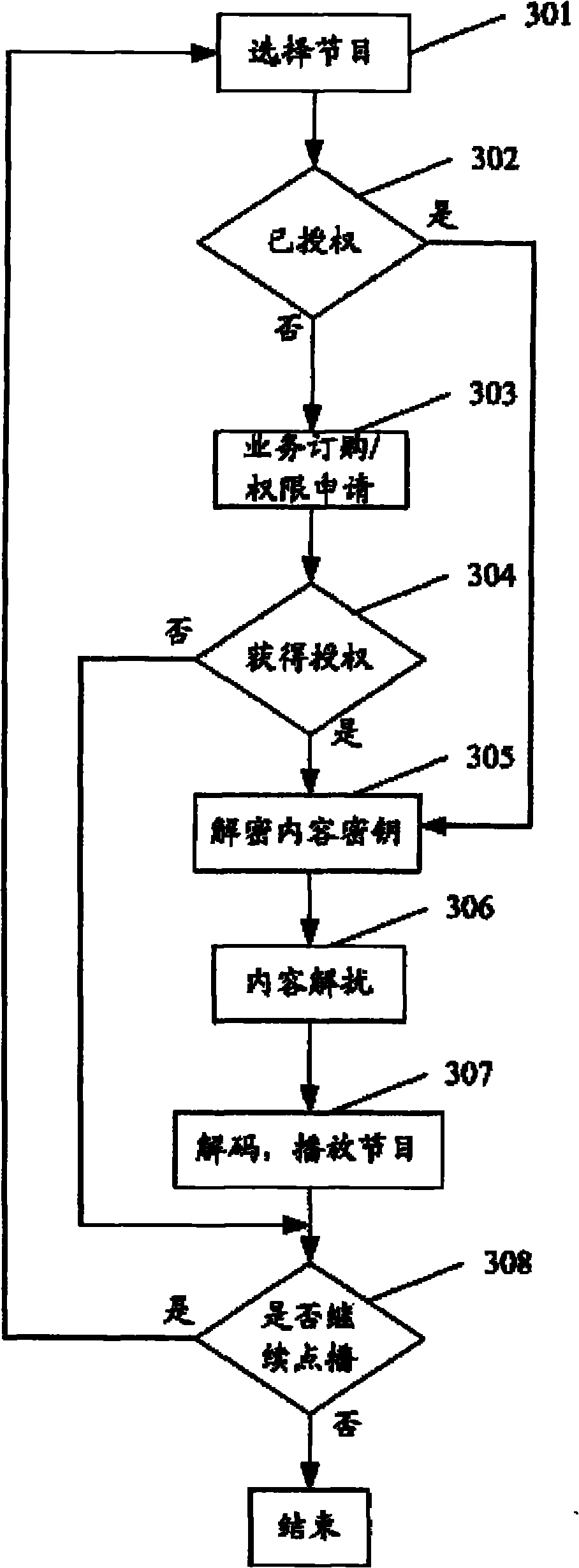
[0021] Such as figure 1 As shown, the IPTV user security terminal 1 provided by the present invention includes an identity authentication module 10, an authorization information decryption module 11, an authorization storage and management module 12, a key storage and management module 13, a key decryption module 14, and a content descrambling module 15 , an uplink information encryption module 16, a decoding module 17 and a user input module 18. Wherein, the identity authentication module 10 includes an ECC (Elliptic Curve Cryptosystems, Elliptic Curve Cryptosystem) signature module 101 and an ECC verification module 102 .
[0022] The ECC verification module 102 in the identity authentication module 10 is responsible for identity verification of the received authorization issuance information, and the ECC signature module 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com