An Ad hoc network invasion detecting method and system based on trust model
A network intrusion detection and trust model technology, applied in the field of communication security, can solve problems such as one-sided evaluation of nodes, malicious nodes, and difficulties in intrusion detection, achieving good stability and security, low false alarm rate and false alarm rate, and good The effect of scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] Relevant technical content and detailed description of the present invention, now cooperate accompanying drawing to explain as follows:
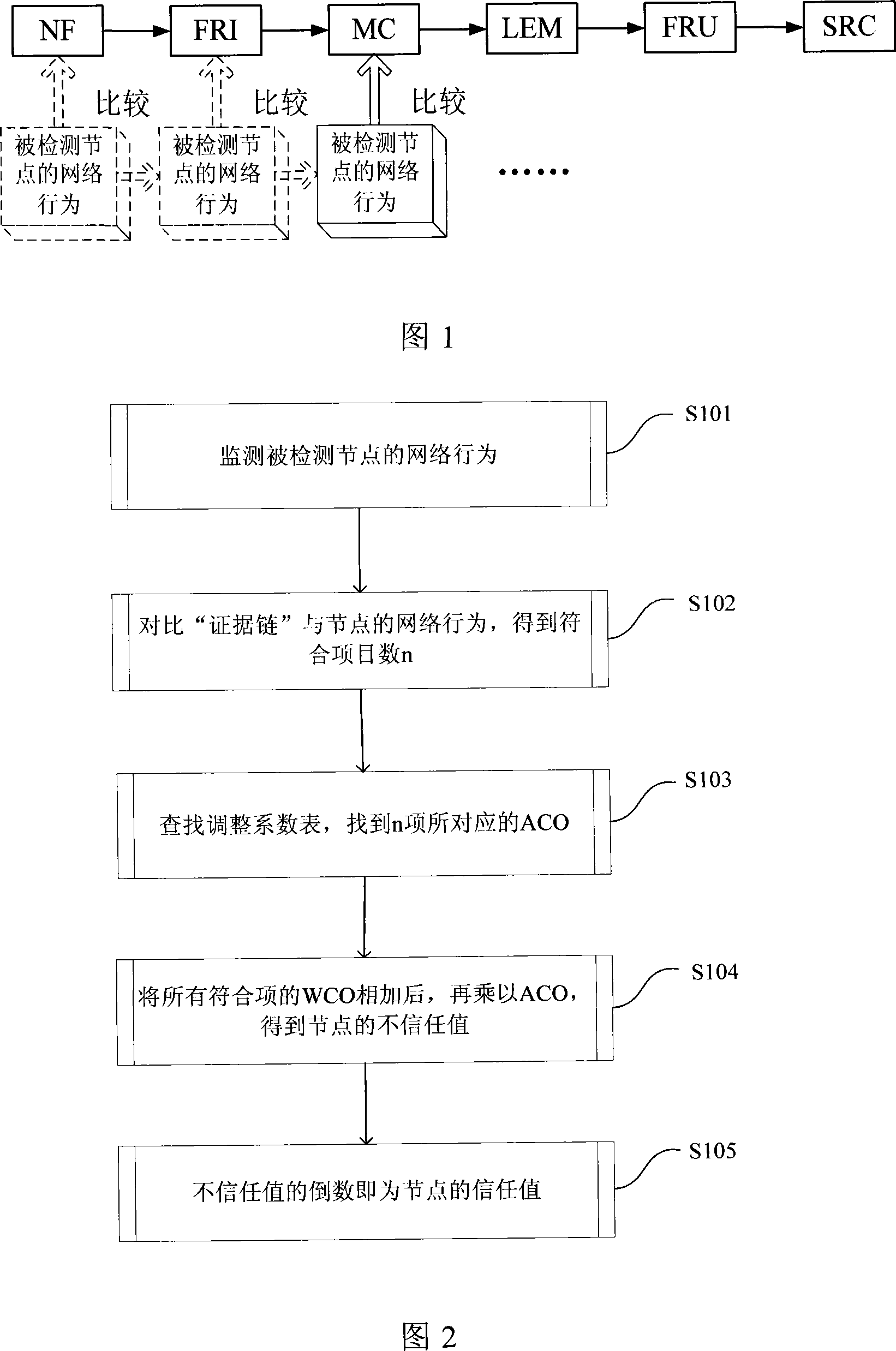
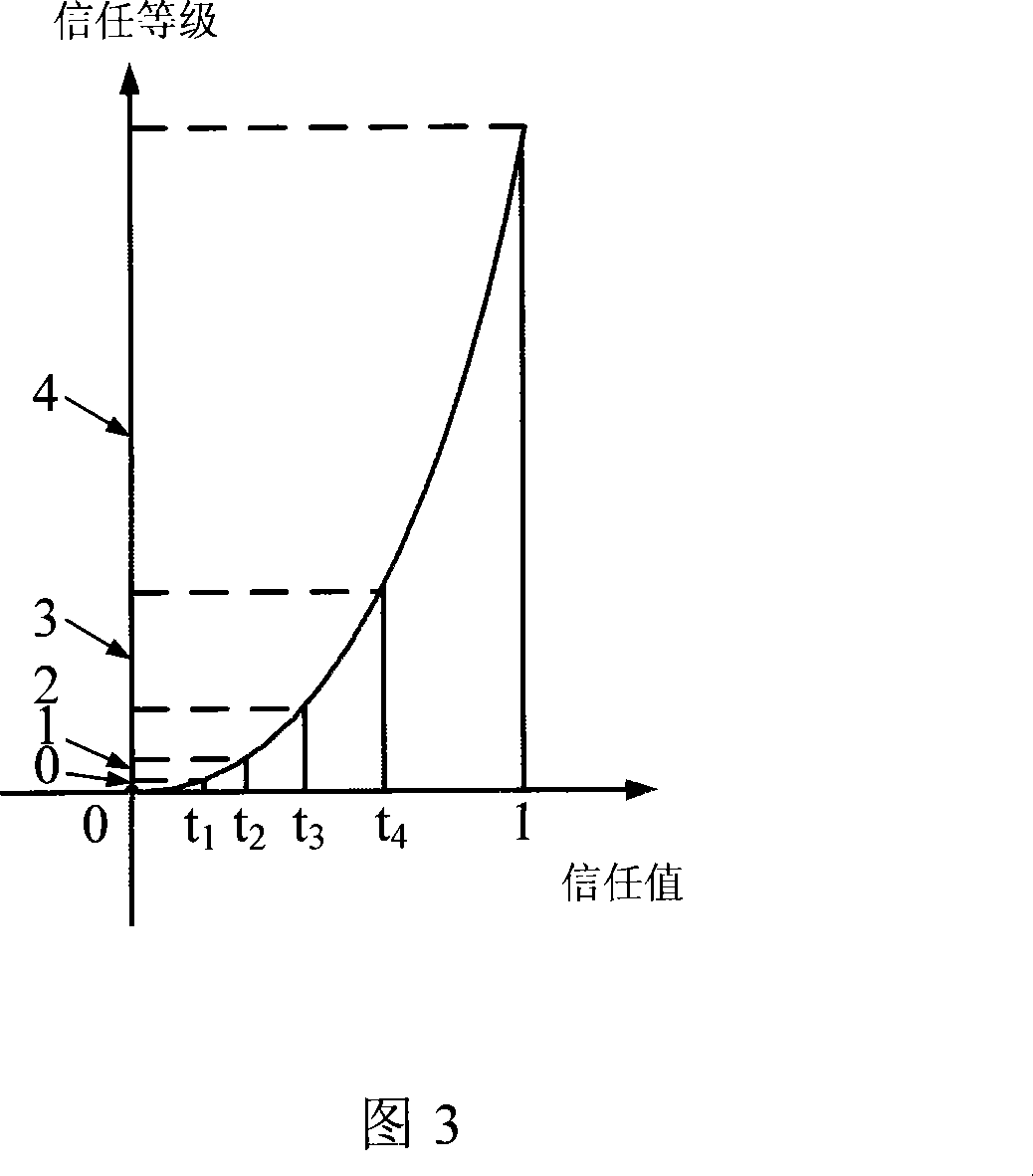
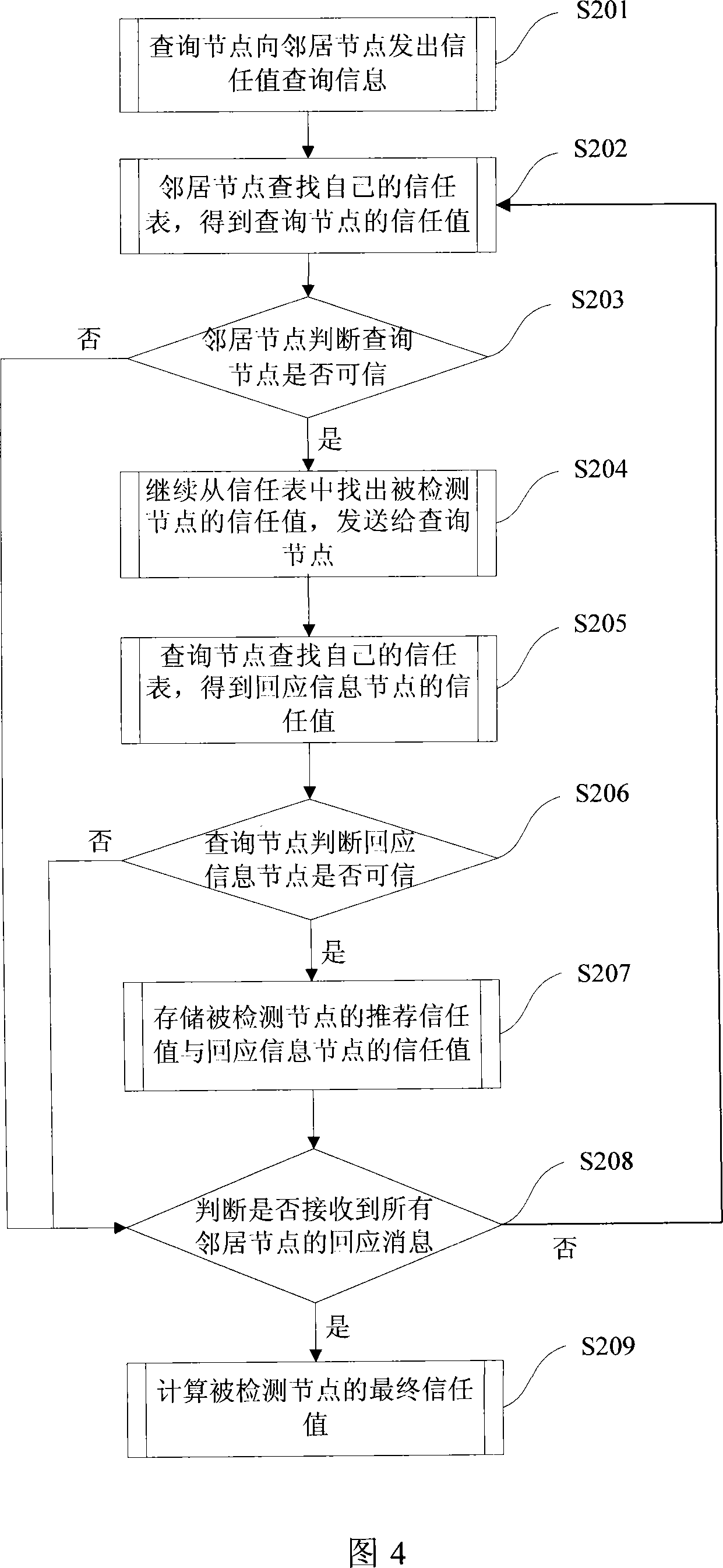
[0063] The present invention provides an Ad hoc network intrusion detection method based on a trust model, which detects several known types of attack behaviors through the means of node self-observation and mutual notification, and obtains a comprehensive evaluation of the node—trust value, so that Nodes in the network bypass possible malicious nodes when routing.
[0064] The present invention provides a method for detecting malicious nodes by way of "evidence chain". When the trust value of a node is lower than a certain threshold, other nodes will refuse to provide services to it, thereby excluding malicious nodes from the network. The invention compares the behavior of the node with a series of typical behaviors of malicious nodes specified in advance to obtain a local evaluation of the node. In addition, in order to avoid the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com