Realization method of elliptic curve cryptosystem for preventing side-channel attack
An elliptic curve cryptography and side-channel attack technology, applied in the field of cryptographic algorithms, can solve the problem that the attacker can no longer distinguish the point addition and the double point.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
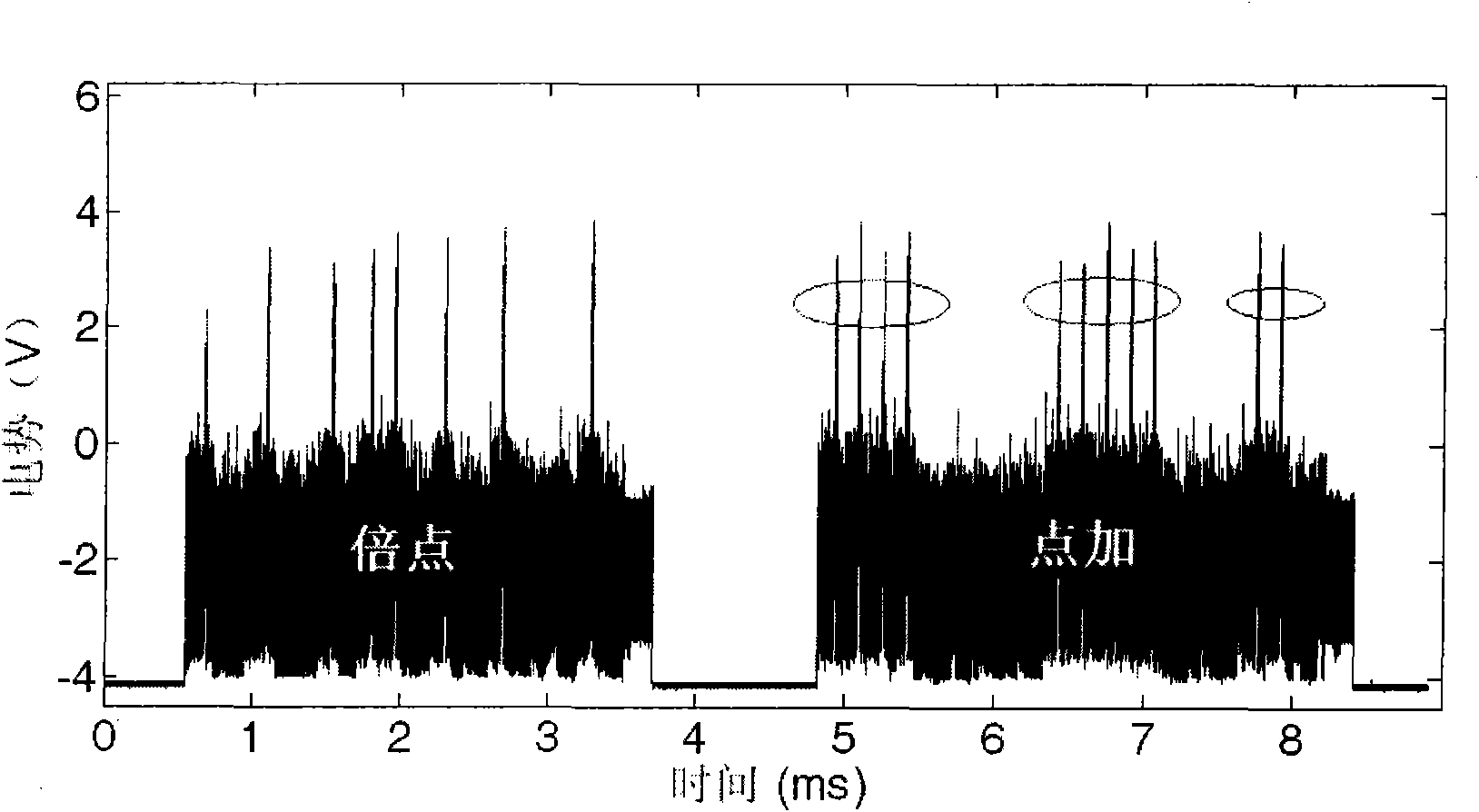
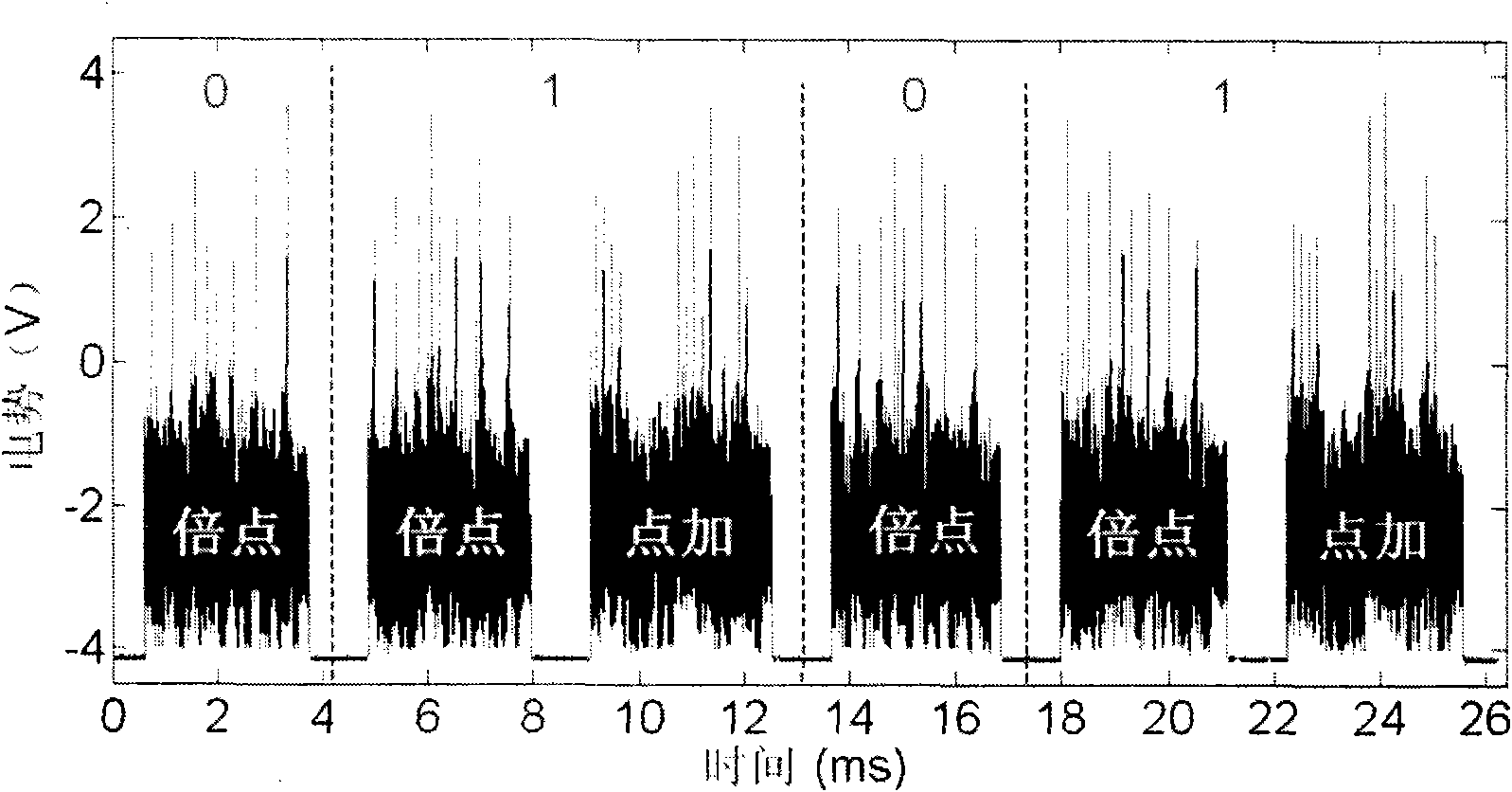
[0049] Taking the ECC on the prime number field under the projected coordinates in the international public key cryptography standard IEEE Std 1363-2000 as an example, the implementation method of the elliptic curve cryptosystem against side channel attack described in the present invention is further described.
[0050] like figure 1 As shown, the data transfer (DT), modular addition (MA), modular subtraction (MS), modular half (MH), modular multiplication (MM), and modular inversion (MI) are represented by different modules, namely figure 1 (a) means data transfer (DT), figure 1 (b) represents modulus addition (MA) and modulus subtraction (MS), figure 1 (c) represents the modular half (MH), figure 1 (d) means modular multiplication (MM) and figure 1 (e) represents the modular inverse (MI). And because some conditional judgment operations are unavoidably required in the calculation process, here you can use figure 1 The (f) block represents this operation.
[0051] Acco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com