Digital signature method, digital signature equipment, password operation method in digital signature, and server
A digital signature and server technology, applied in the field of cryptography, can solve problems such as difficulty in ensuring the privacy of operations, and achieve the effect of ensuring security, ensuring privacy, and avoiding privacy leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The specific implementation of the digital signature method of the present invention will be described in detail below in conjunction with the accompanying drawings.
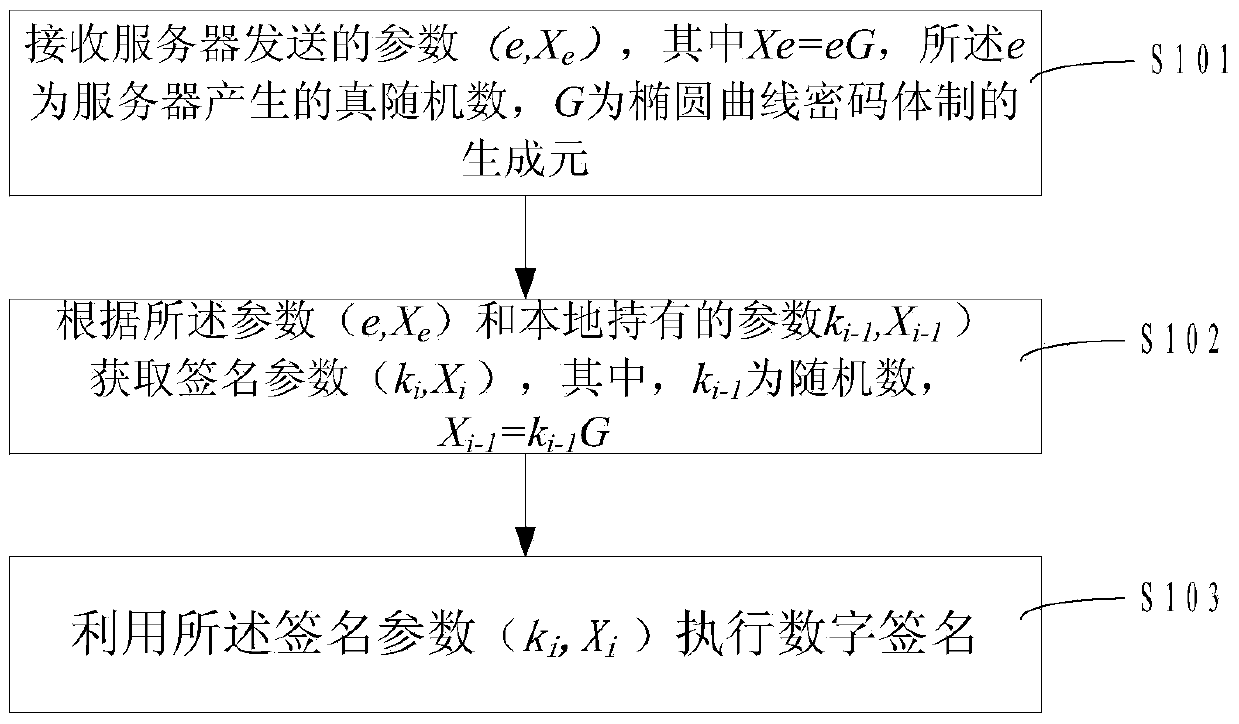
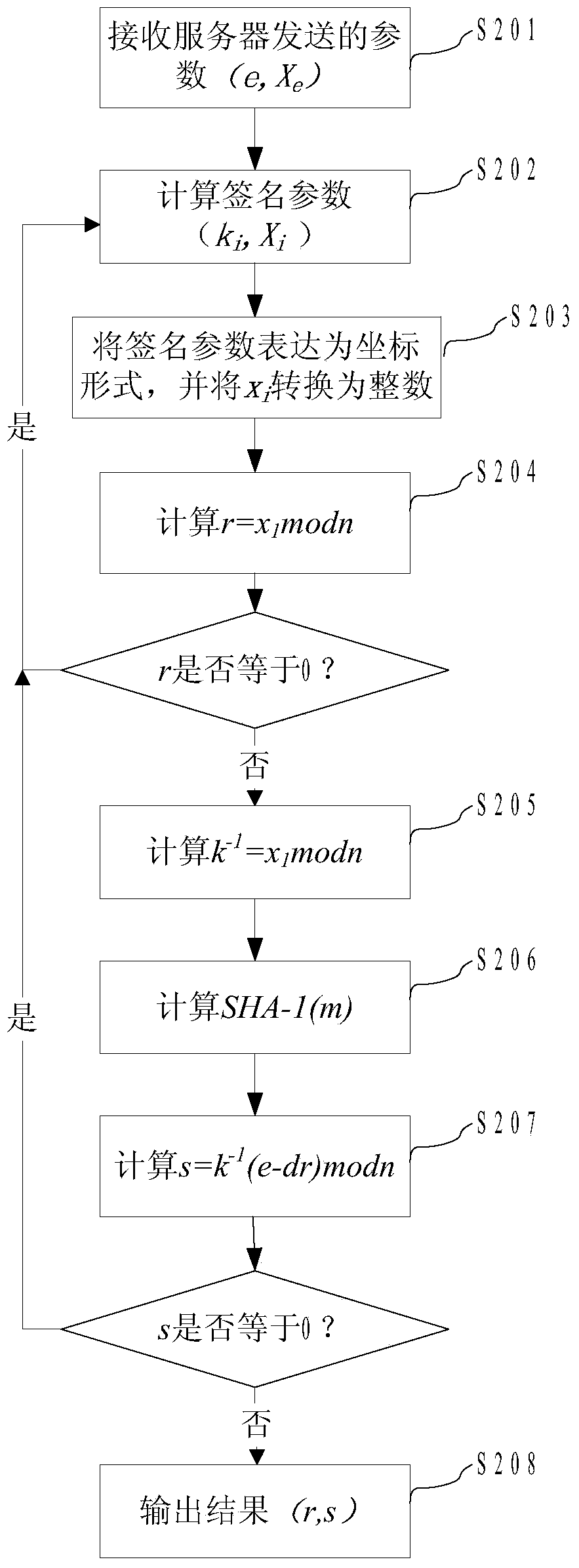
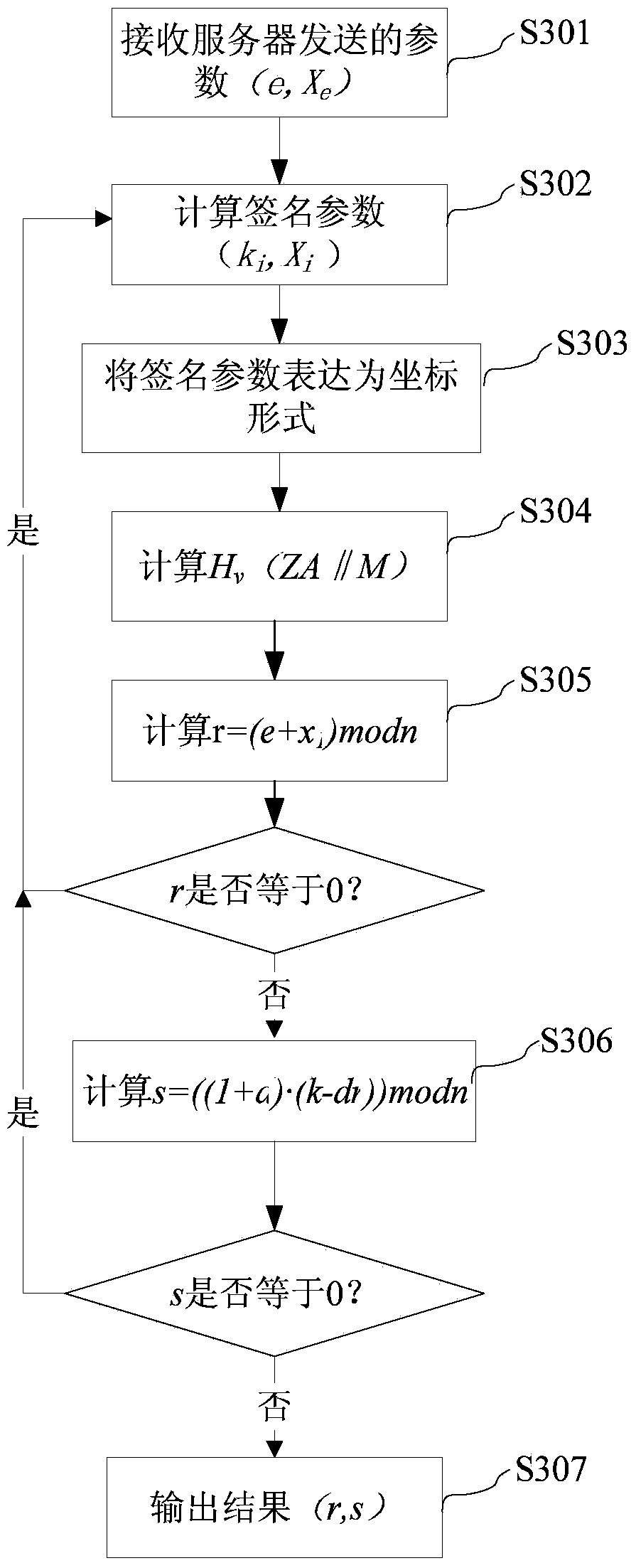
[0059] see figure 1 as shown, figure 1 It is a flow chart of the digital signature method of an embodiment, mainly including the following steps:
[0060] Step S101, receiving the parameters sent by the server (e, X e ), where X e =eG, the e is a true random number generated by the server, and G is the generator of the elliptic curve cryptosystem.
[0061] In this step, the server is a server that performs outsourced outsourced cryptographic operations, and the server can continuously generate a true random number e and calculate X e , when it is necessary to perform the signature calculation operation, submit an outsourcing application to the server. In the process, it can be set to only need to verify the identity, without submitting the request parameters, that is, you can receive the calculated an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com