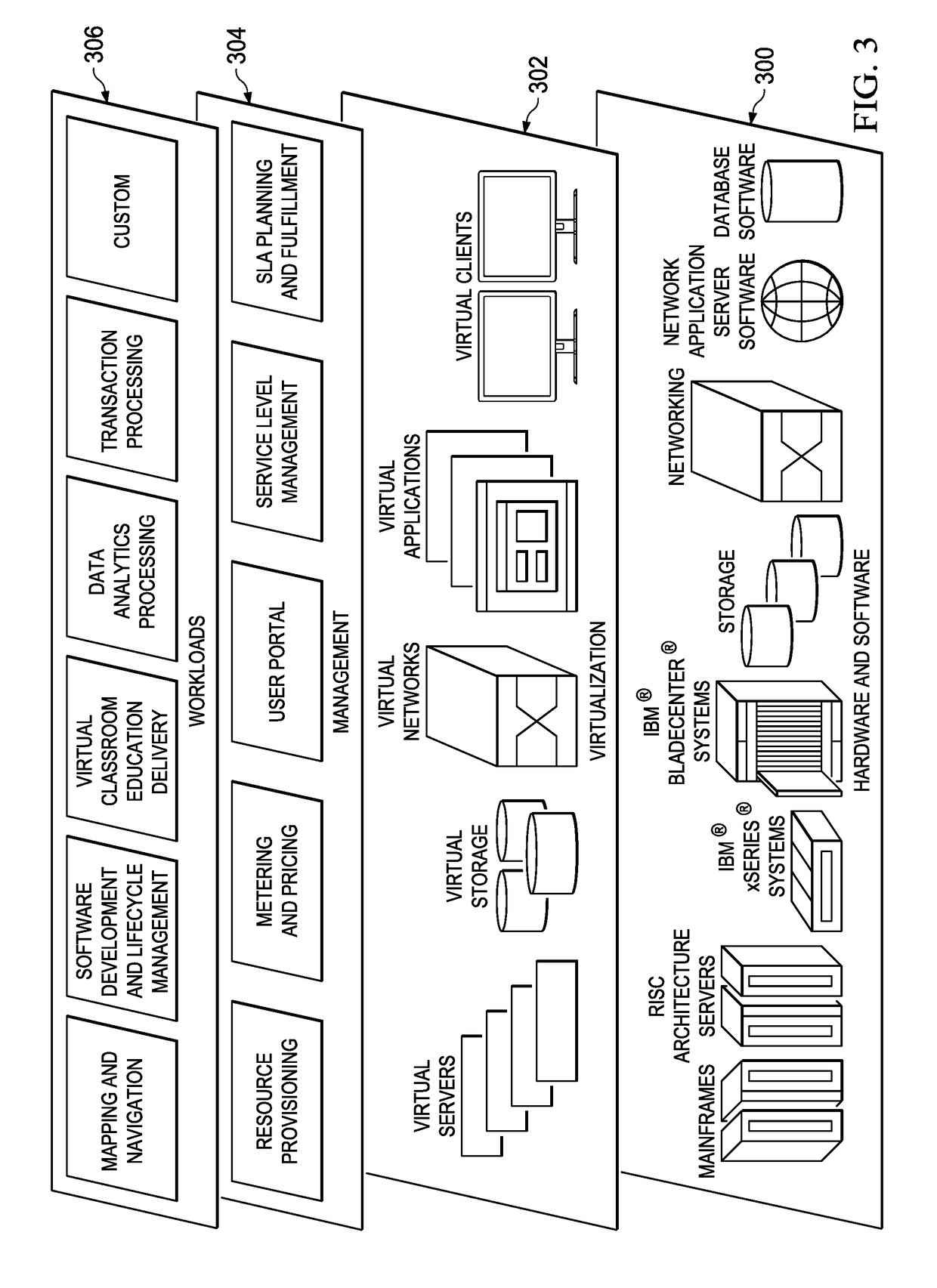
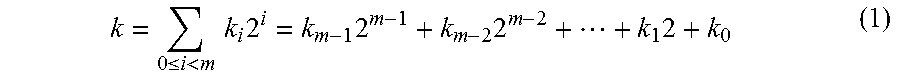Patents
Literature
81 results about "Power attack" patented technology
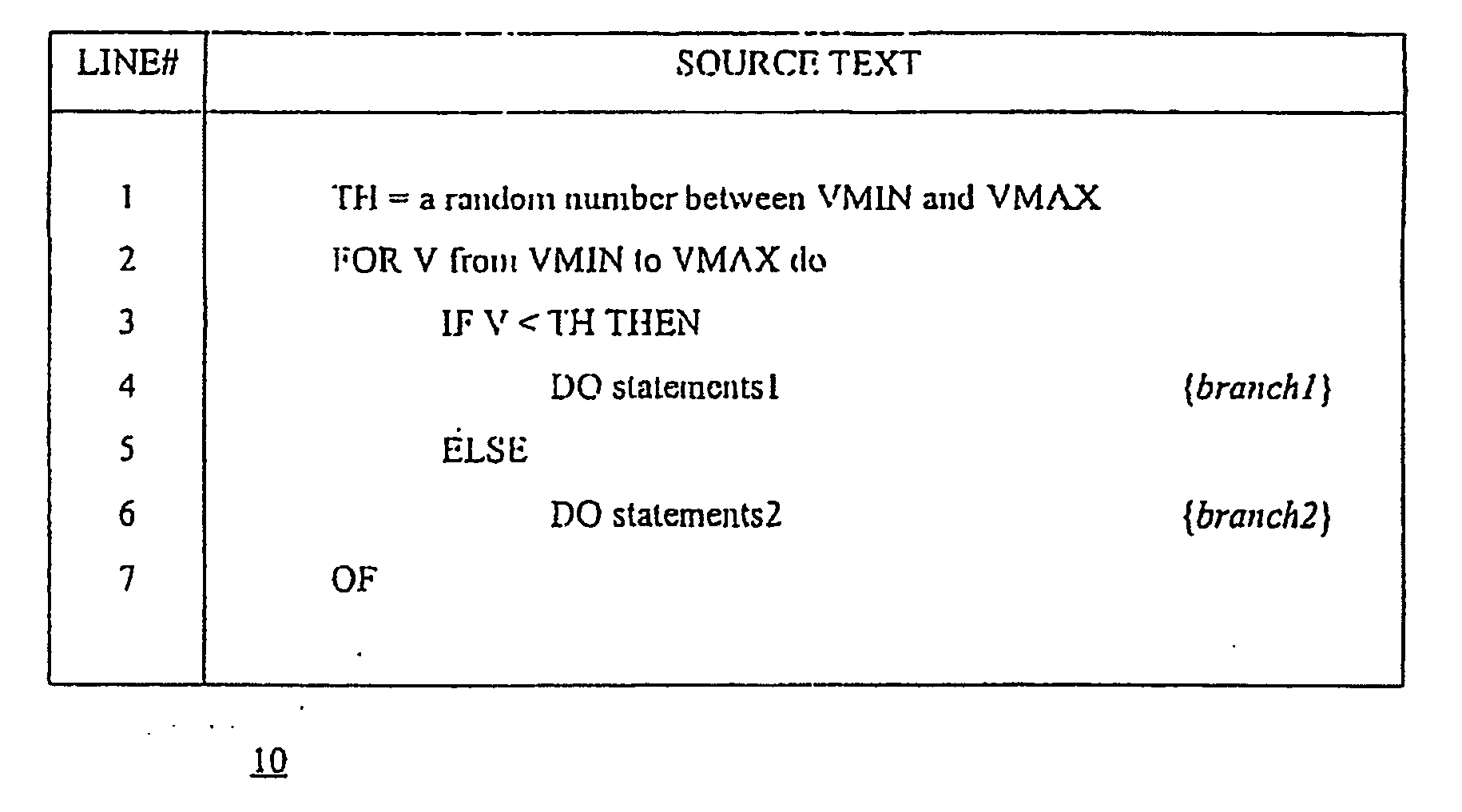
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
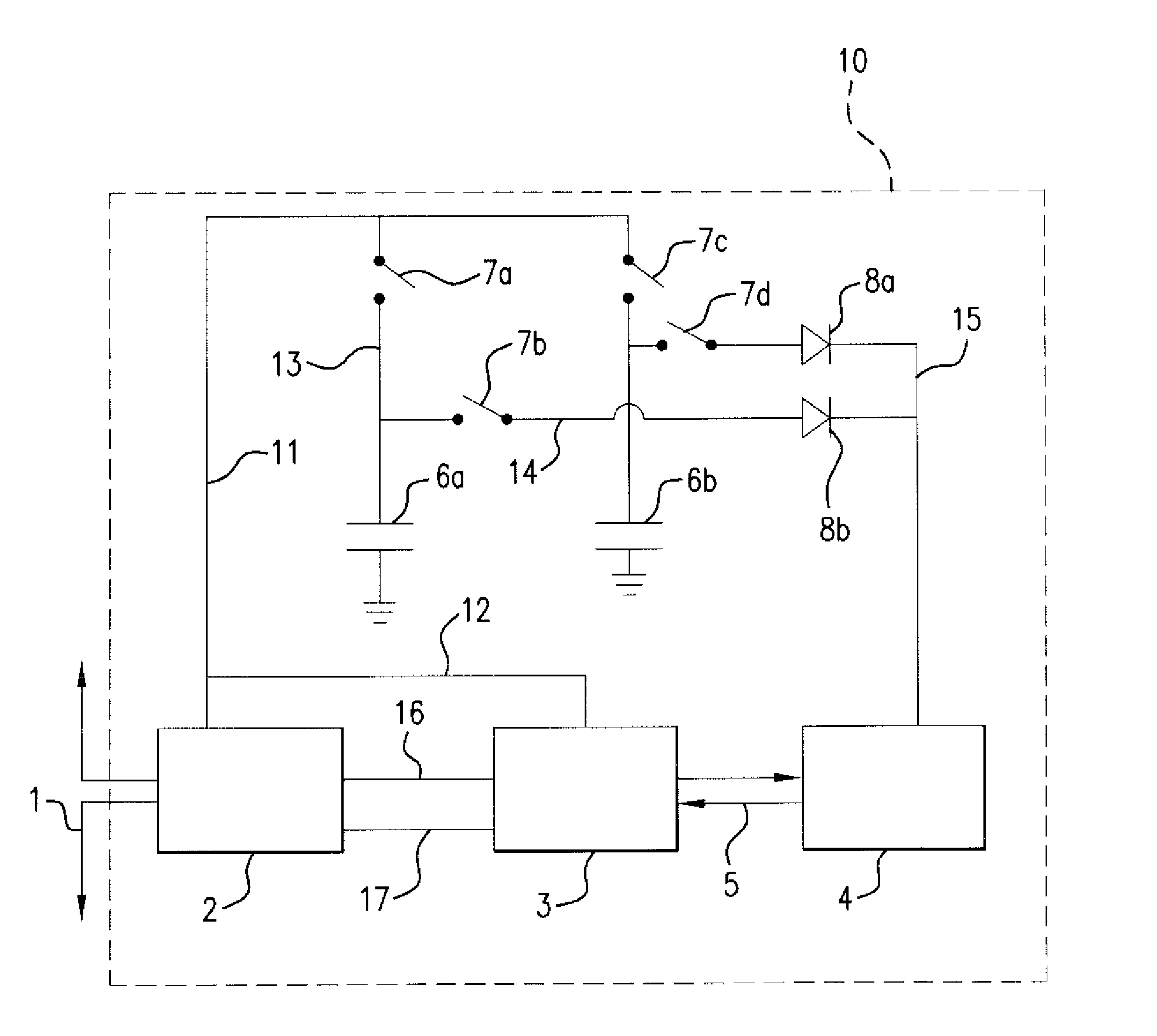
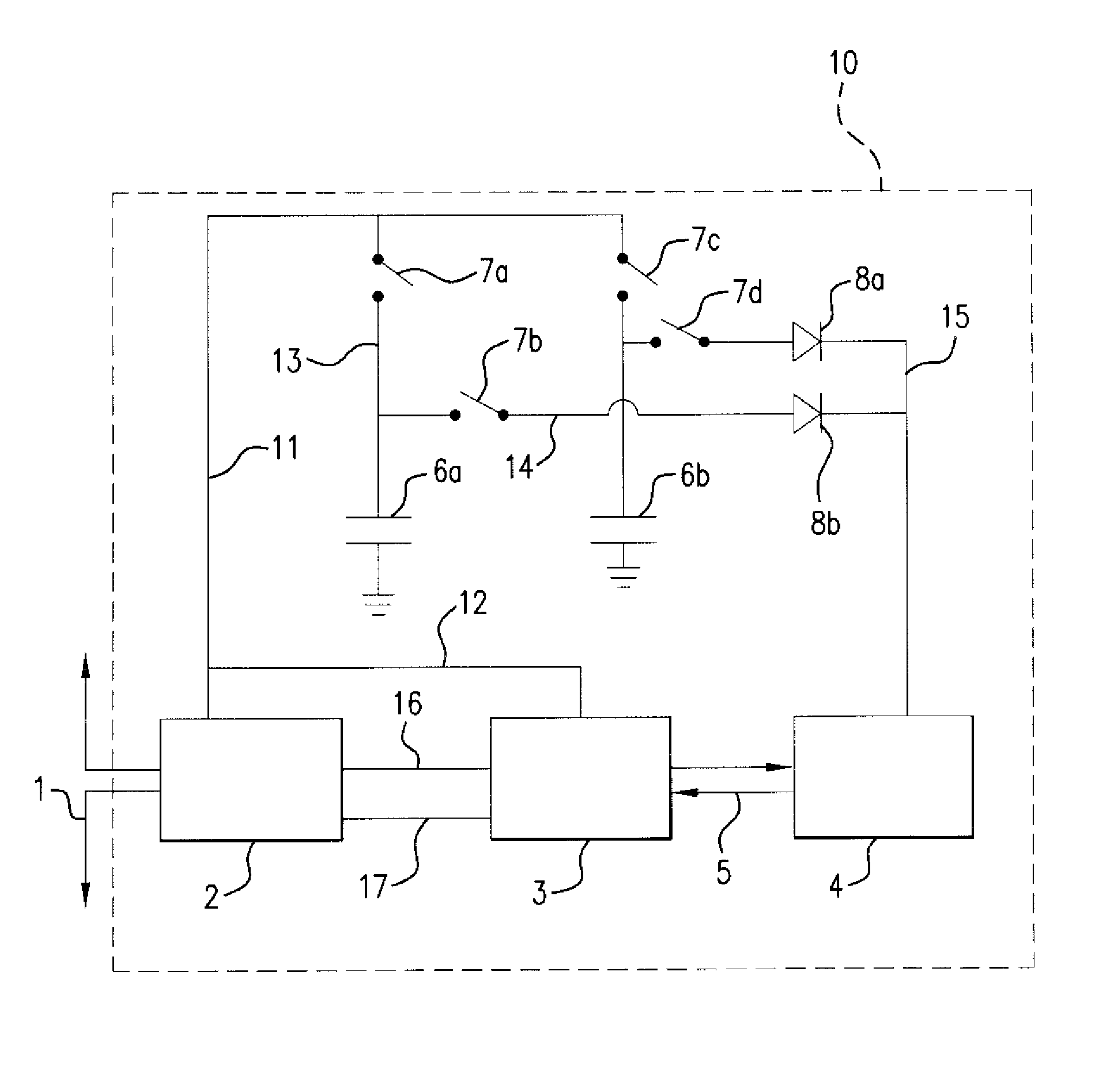
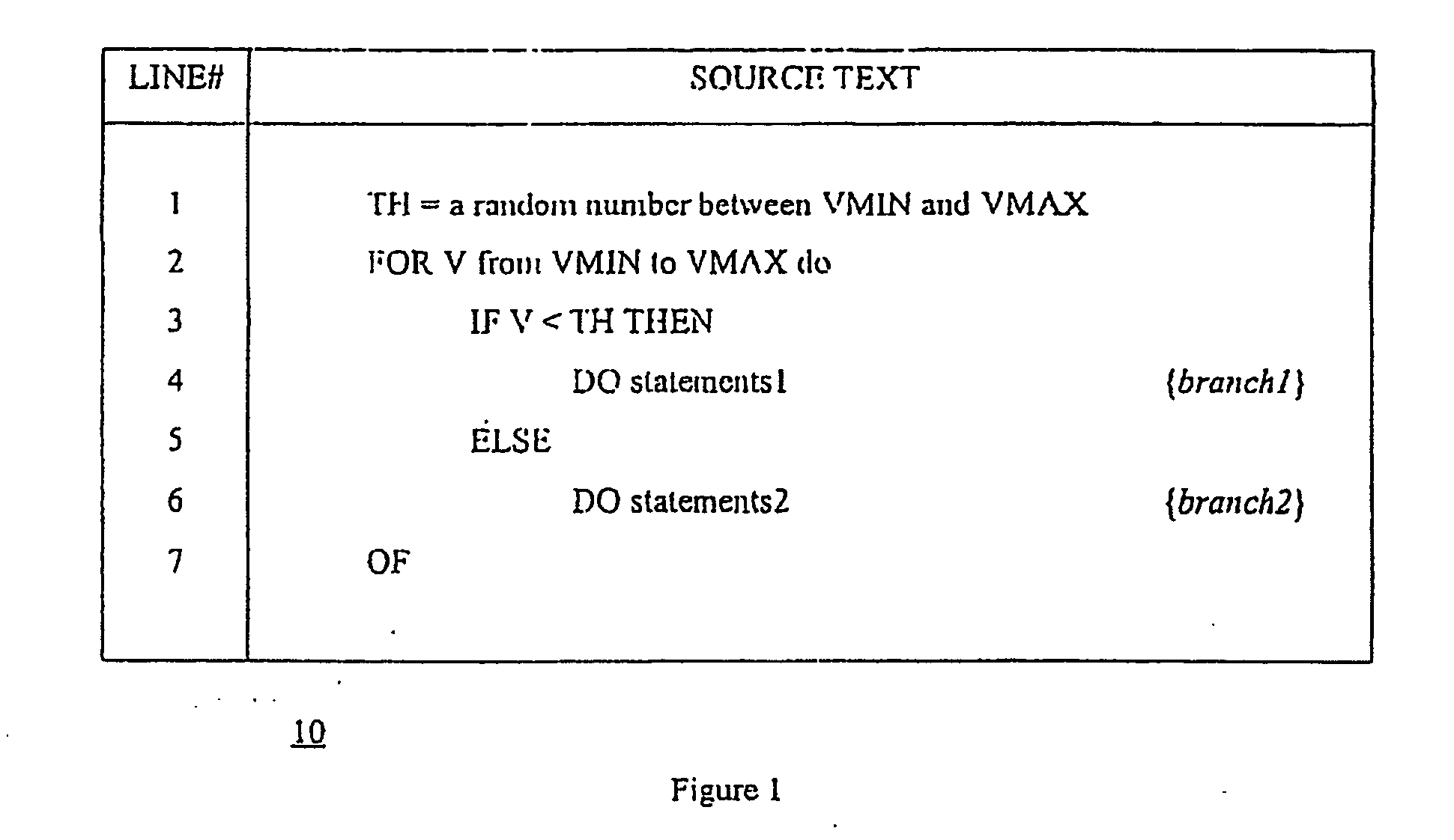
Method and apparatus for protecting RFID tags from power analysis
InactiveUS20100005533A1Cheap and effective solutionEliminate power consumption informationError detection/correctionVolume/mass flow measurementElectromagnetic fieldPower attack
RFID tags were believed to be immune to power analysis since they have no direct connection to an external power supply. However, recent research has shown that they s are vulnerable to such attacks, since it is possible to measure their power consumption remotely via a completely passive attack. The method and apparatus of the invention protects RFID tags against simple and differential power attacks. The invention is particularly useful regarding inventory control systems or secure documents such as epassports. The basic technique is to use two capacitors embedded in the RFID tag in lo such a way that at any given time one of them is storing energy that is being generated by the charge pump of the tag that sucks energy from the electromagnetic or magnetic field of a tag reader, and the other one is discharging and powering the computational element of the tag chip.
Owner:YEDA RES & DEV CO LTD
Block chain common recognition mechanism
InactiveCN106548397ASolve the problem of computing power attackImprove uniformityFinanceElectronic credentialsPattern recognitionPower attack
Owner:TIANJIN MIYOU TECH
Method and apparatus for minimizing differential power attacks on processors
InactiveUS7092523B2Minimizes attackMinimize their effectivenessEnergy efficient ICTPublic key for secure communicationComputer hardwarePower attack
Owner:MALIKIE INNOVATIONS LTD
Method of countering side-channel attacks on elliptic curve cryptosystem
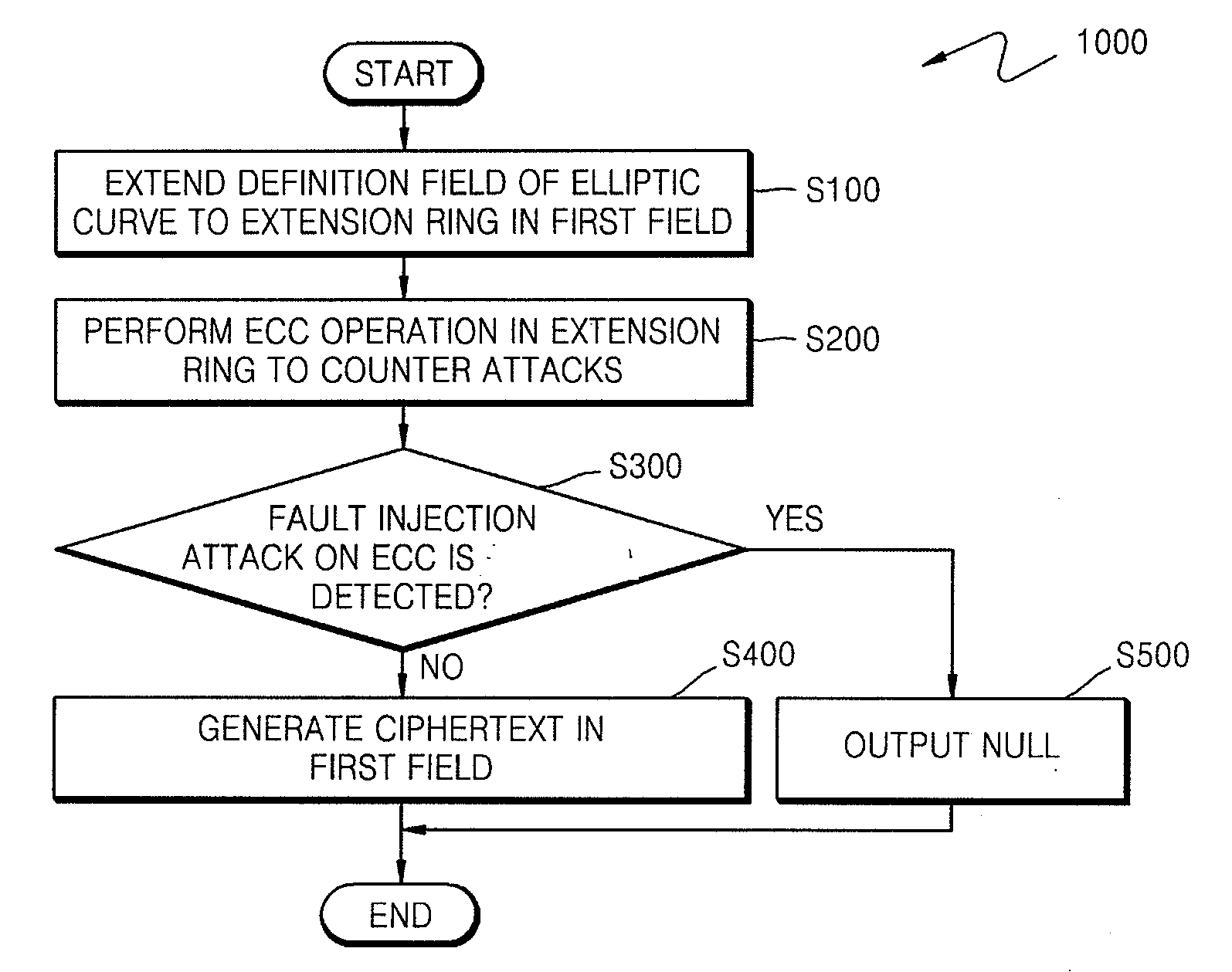
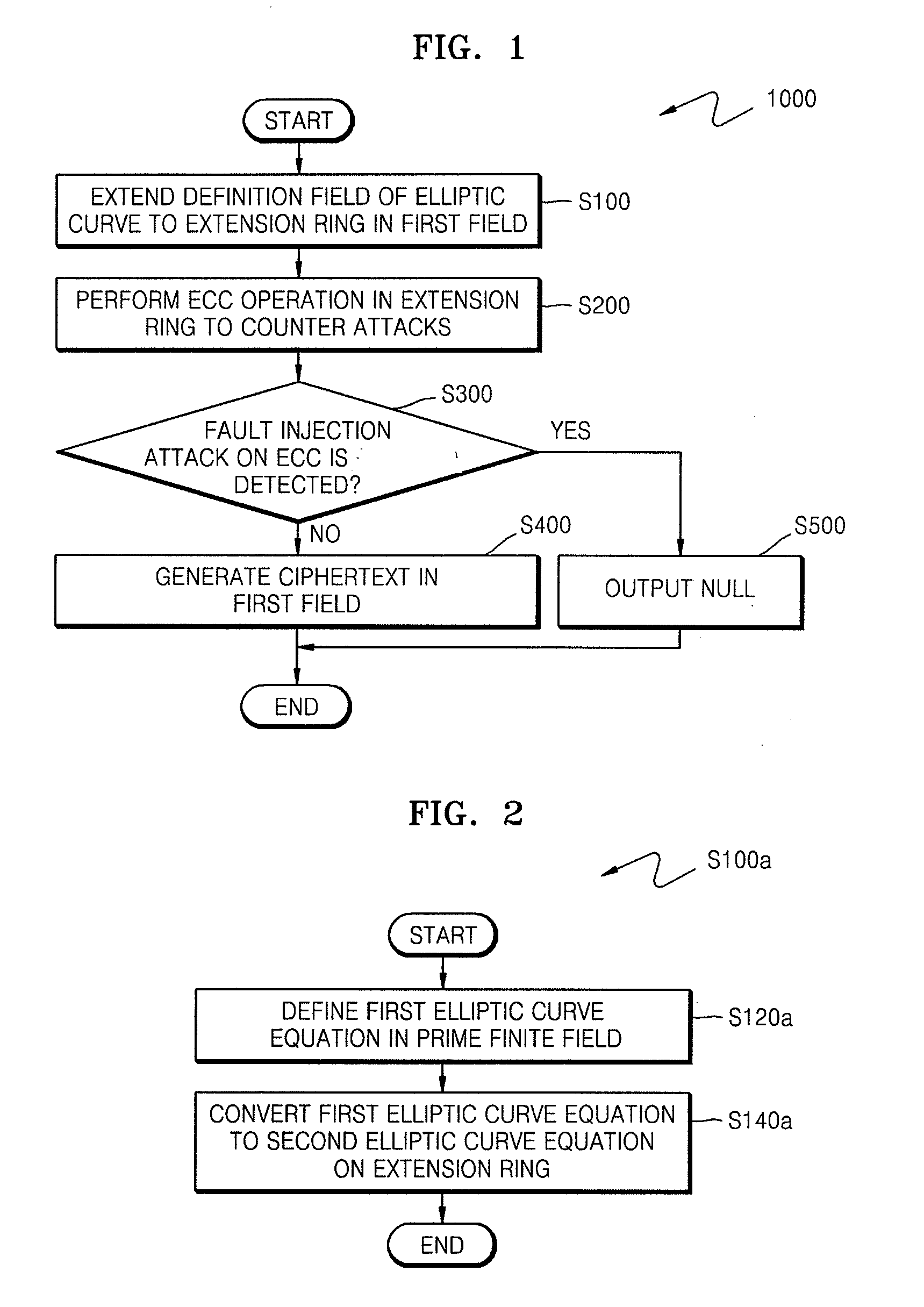
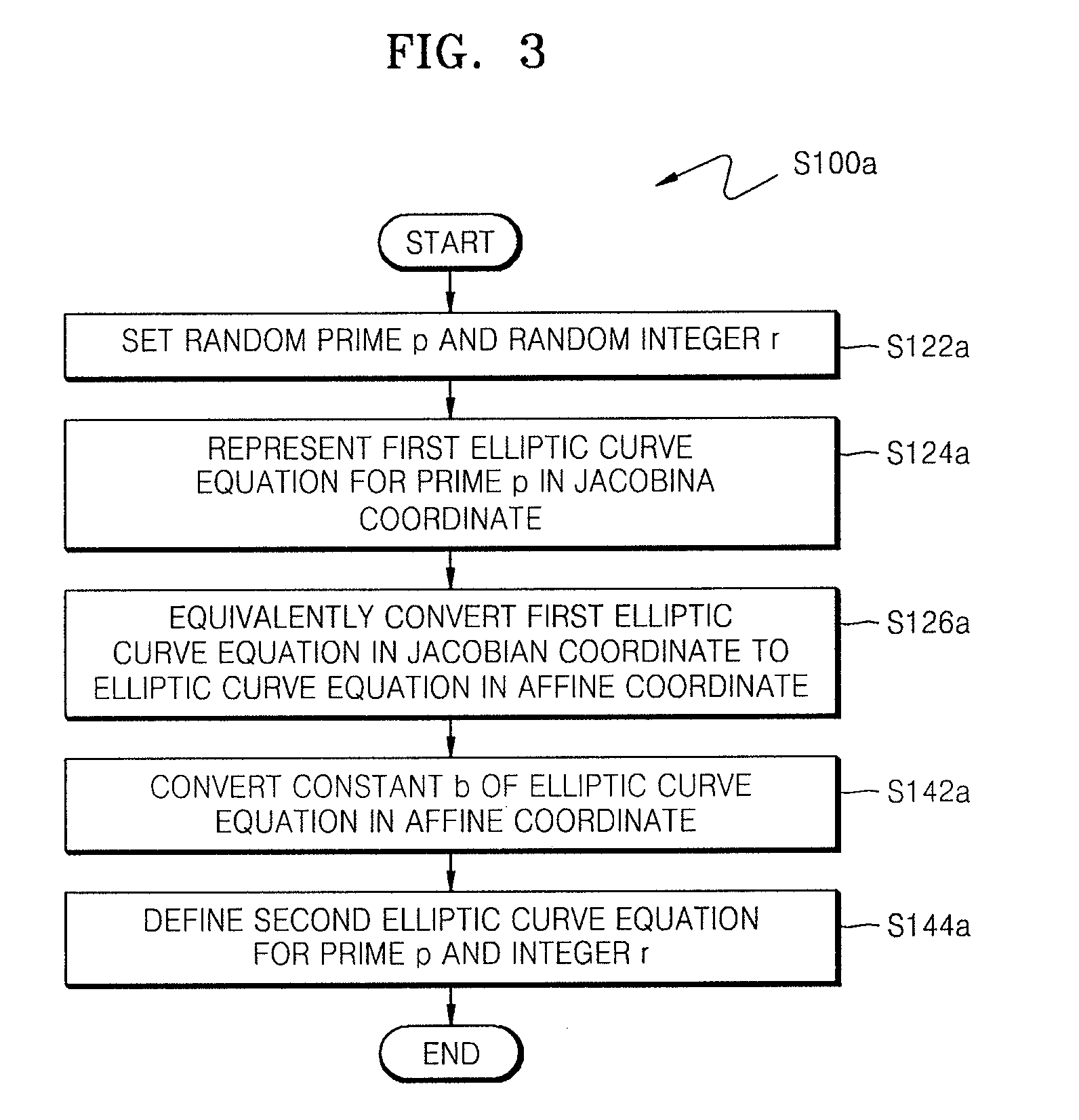
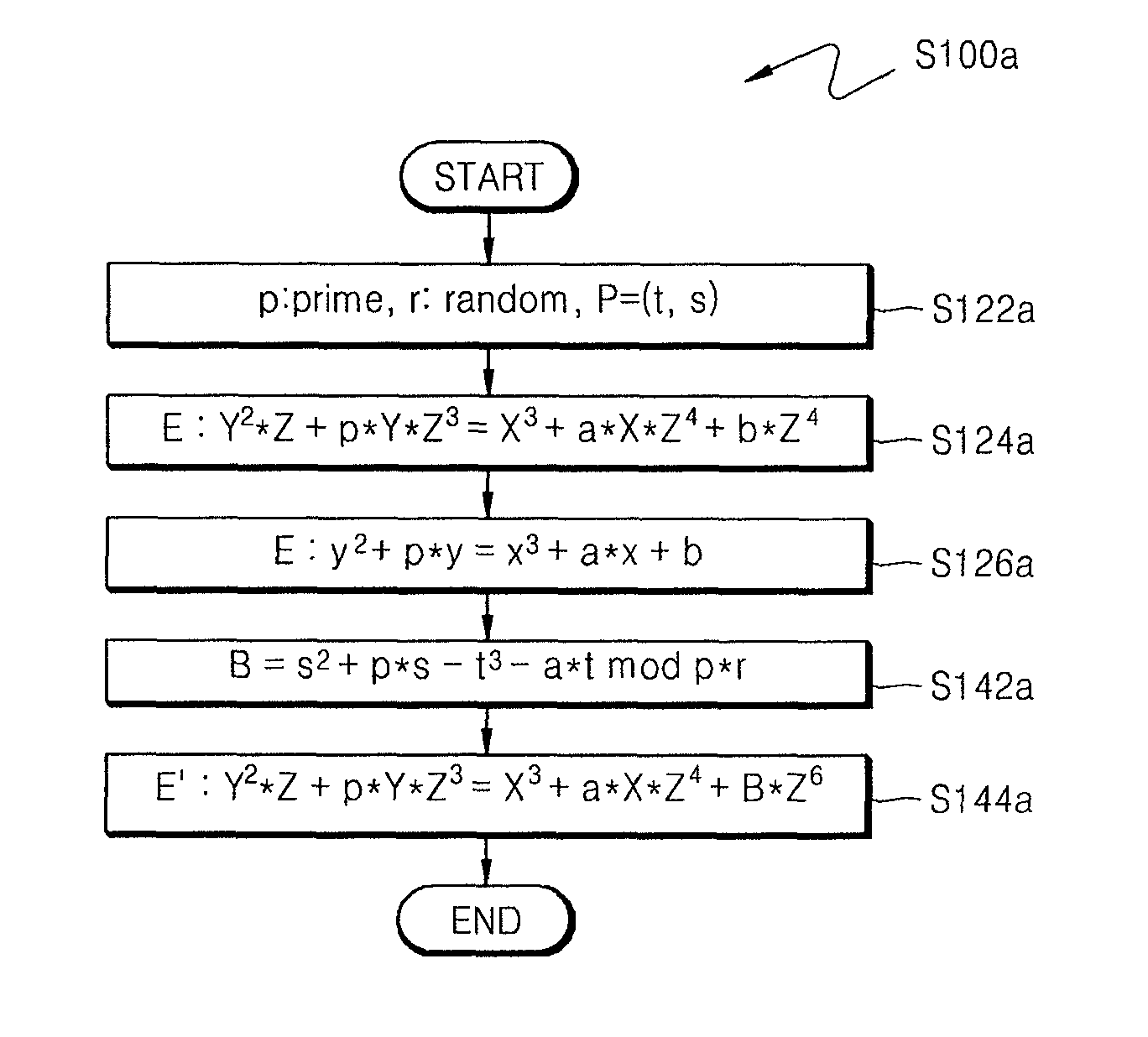
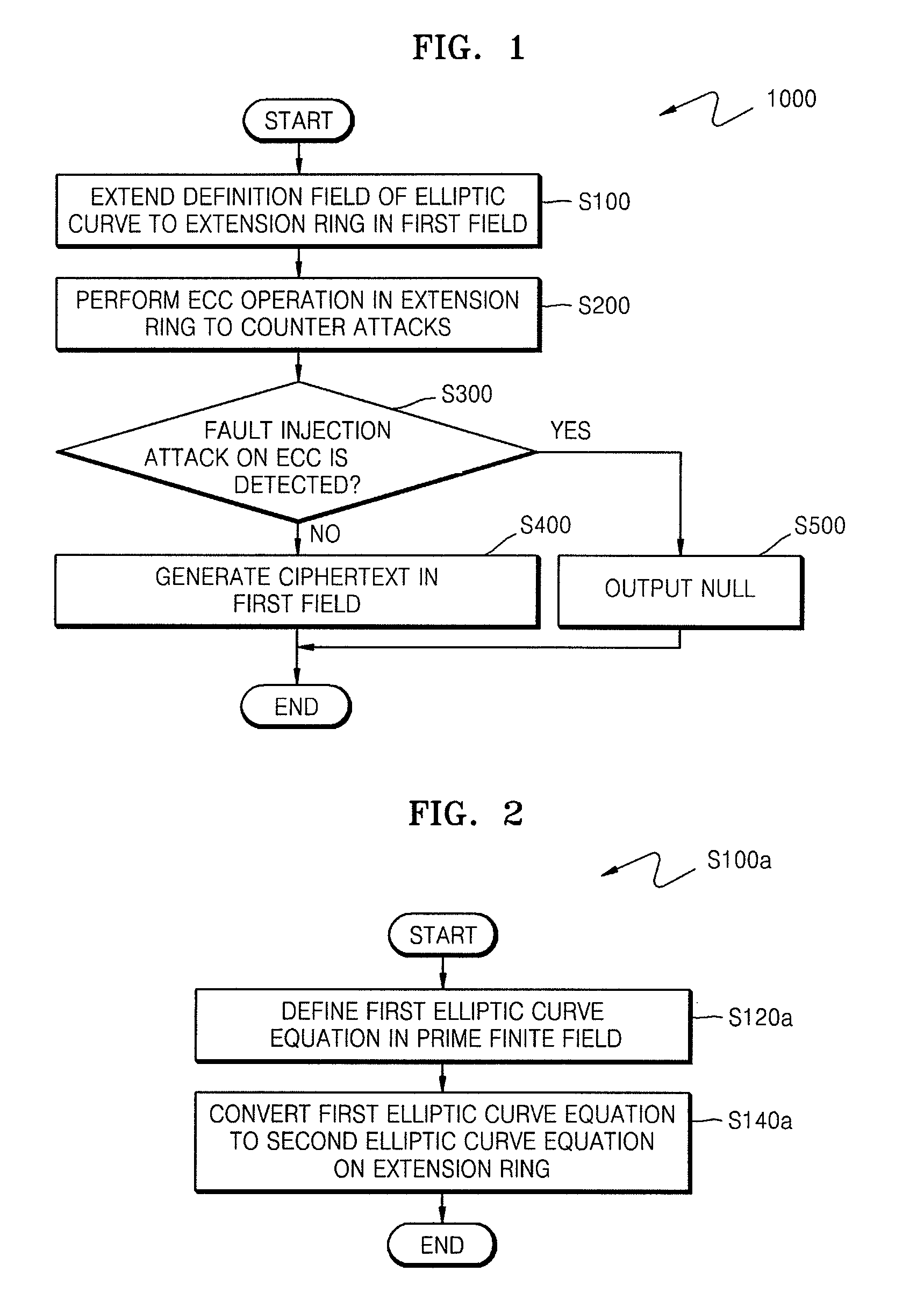
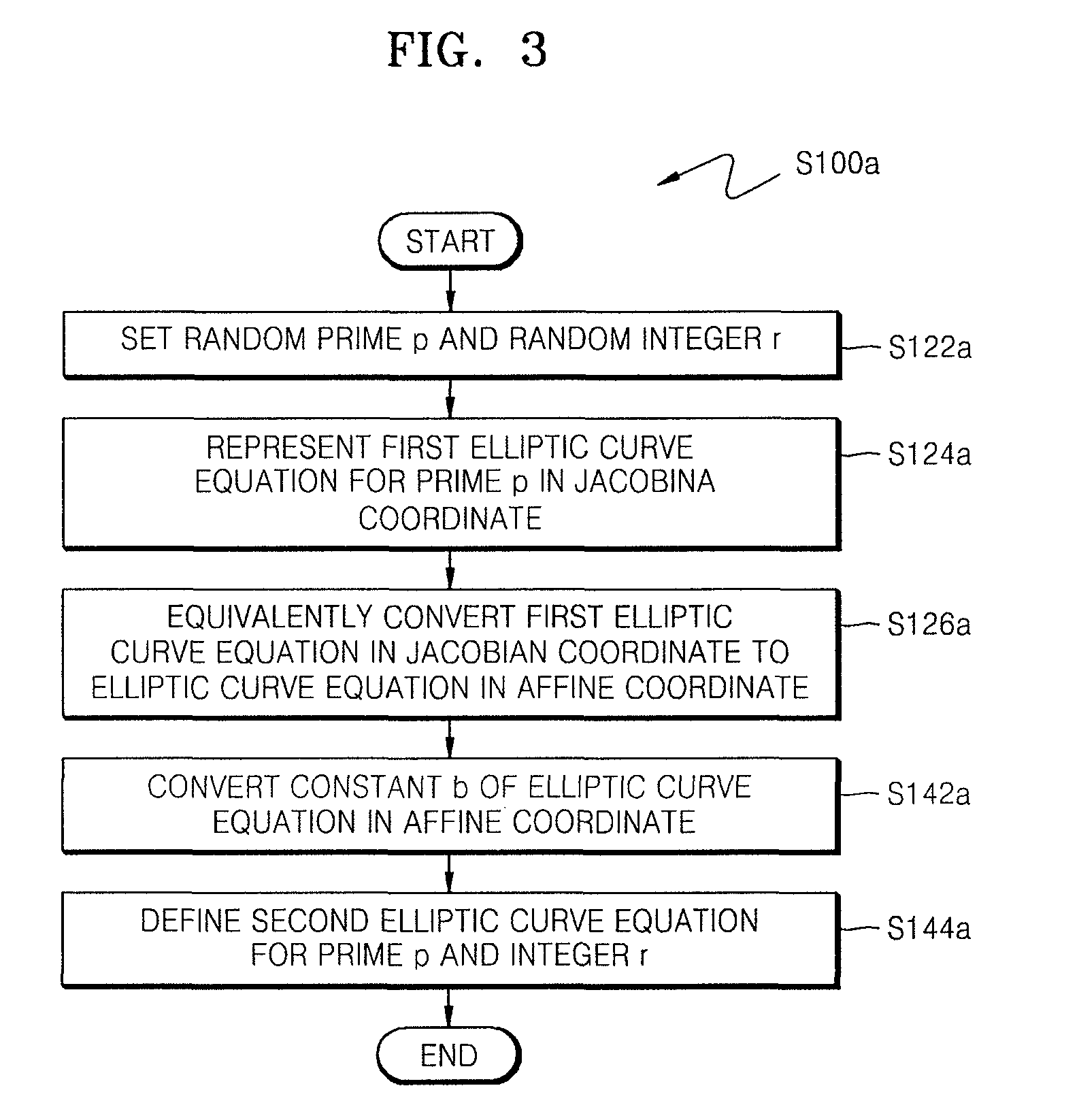
ActiveUS20090034720A1Improve securityEfficient fault attack countermeasureMultiple keys/algorithms usageData taking preventionFault detection algorithmCiphertext
A method of countering side-channel attacks on an elliptic curve cryptosystem (ECC) is provided. The method comprises extending a definition field of an elliptic curve of the ECC to an extension ring in a first field; generating a temporary ciphertext in the extension ring and countering attacks on the ECC; and generating a final ciphertext for the first field if a fault injection attack on the ECC is not detected. The countering of attacks on the ECC may comprise countering a power attack on the ECC. Checking if there is a fault injection attack on the ECC may be performed by determining if the temporary ciphertext satisfies a second elliptic curve equation. The fault detection algorithms takes place in a small subring of the extension ring, not in the original field, to minimize the computational overhead. The method can improve the stability of the ECC and reduce computational overhead of the ECC.
Owner:SAMSUNG ELECTRONICS CO LTD
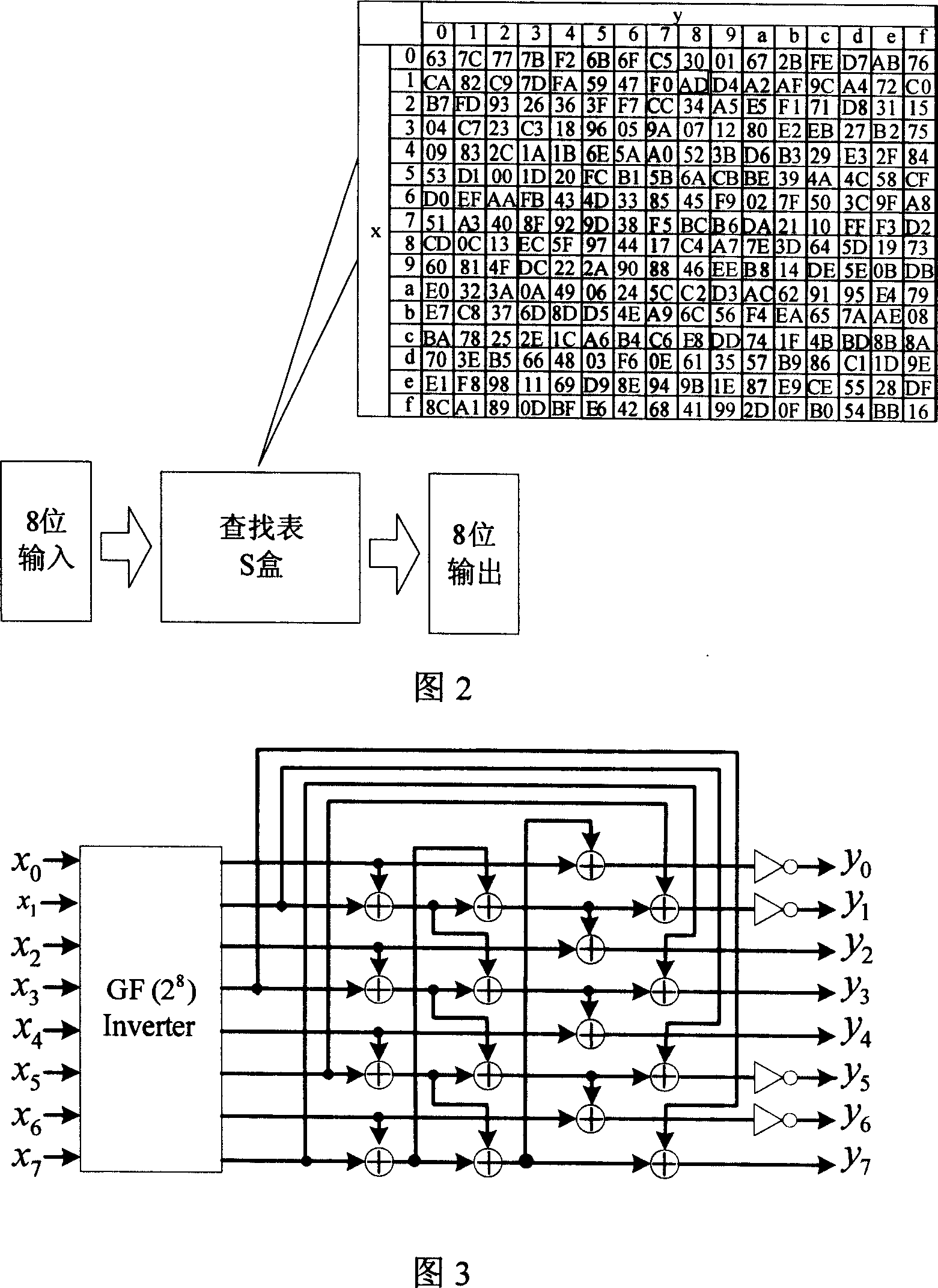
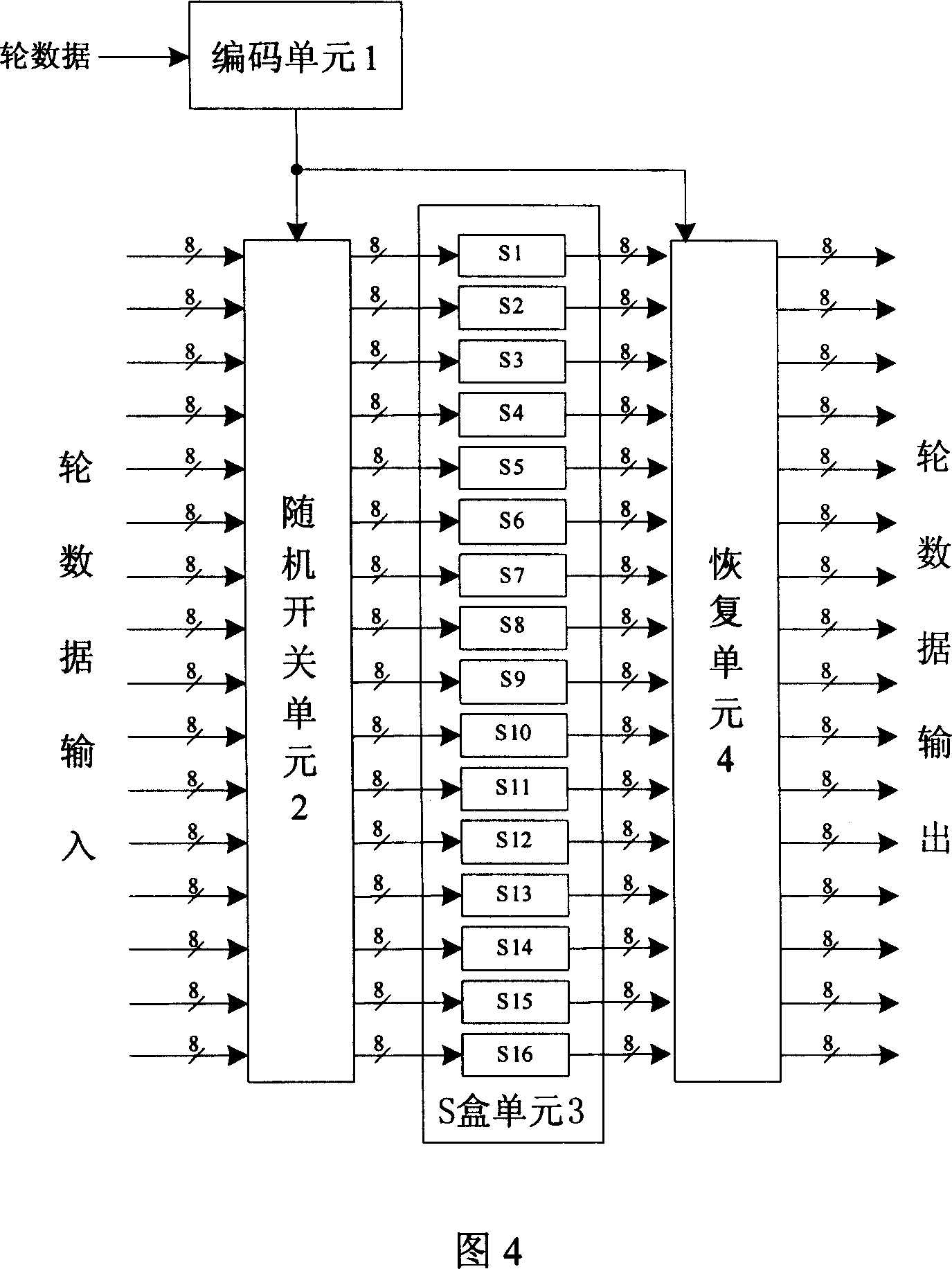
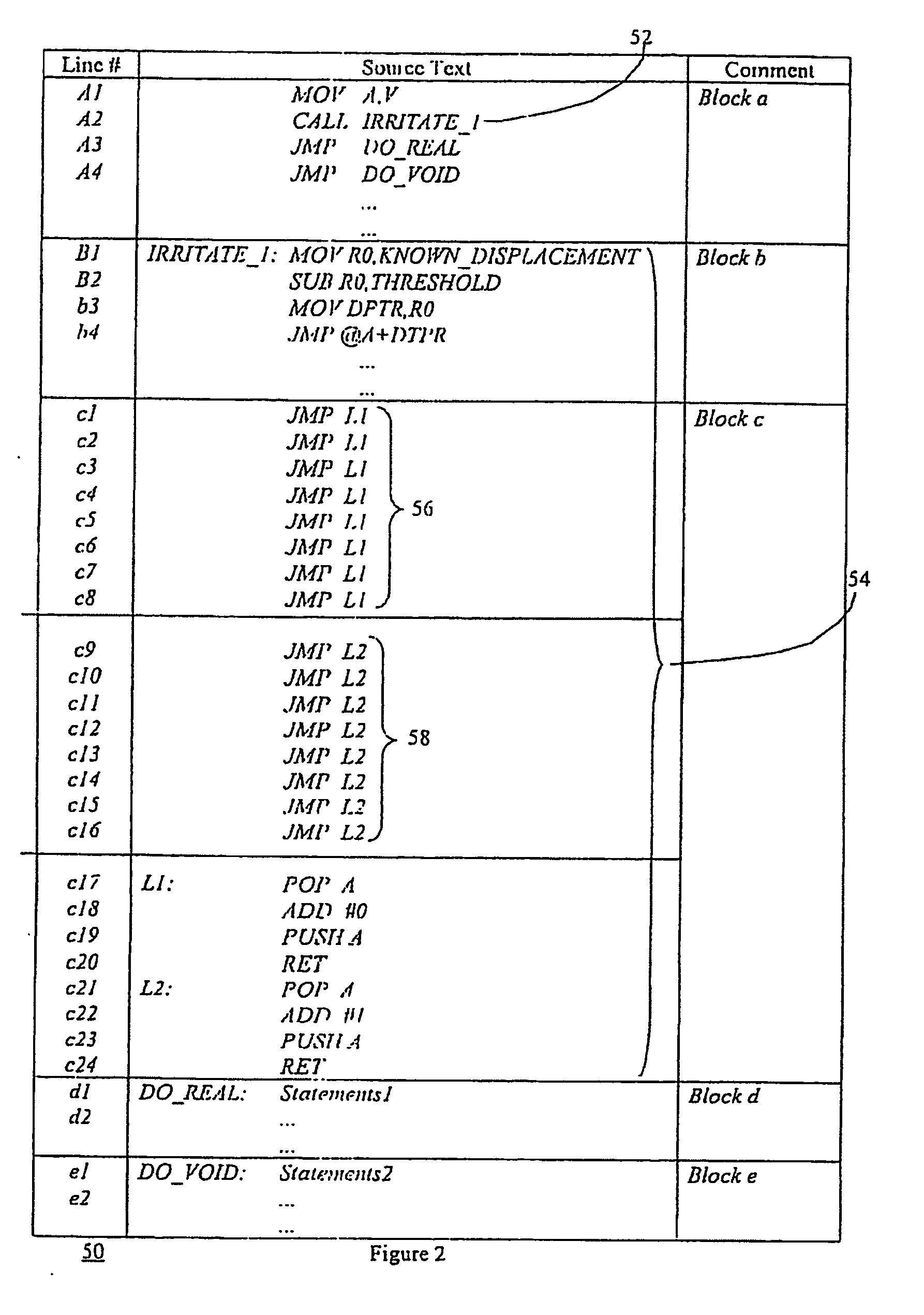
A byte replacement circuit for power consumption attack prevention
InactiveCN101009554AEnhanced anti-power attack featuresEncryption apparatus with shift registers/memoriesPlaintextS-box
The invention discloses a byte alternative circuit of anti power consumption attack that includes coding unit, random switching unit, S-box unit, and recovery unit. The S-box unit consists of 4-16 isomerous S-boxes. The invention adopts isomerous S-box unit to replace the traditional signal S-box, the switching unit is inserted in the input end of S-box unit, and the recovery unit is added behind the output end. When it is been attracting, the invention can select according to the input data of attack, and no need the additional random number generator. On the other hand, the method which adds the number of random plaintext is invalid for the circuit which is provided by the invention. The invention don't need to apply the special circuit and logical mode, and can be compatible with the presexisting AES enciphering circuit. The invention can improve the anti power consumption attack greatly with less expense, and it can cover the key when the hardware of AES is encrypting and decrypting to make the power attack not get the correct key.
Owner:HUAZHONG UNIV OF SCI & TECH
Software mask defense scheme capable of preventing attack on advanced encryption standard (AES) algorithm based on power analysis
InactiveCN103795527AImprove securityResistance to high-order differential power attacksEncryption apparatus with shift registers/memoriesComputer hardwareAdvanced Encryption Standard
Owner:CHONGQING UNIV
AES (advanced encryption standard) algorithm circuit oriented method for testing differential power attack
InactiveCN103530474ASolve the technical difficulties of power consumption attack testingReduce risk of redesignSpecial data processing applicationsCorrelation coefficientDesign stage
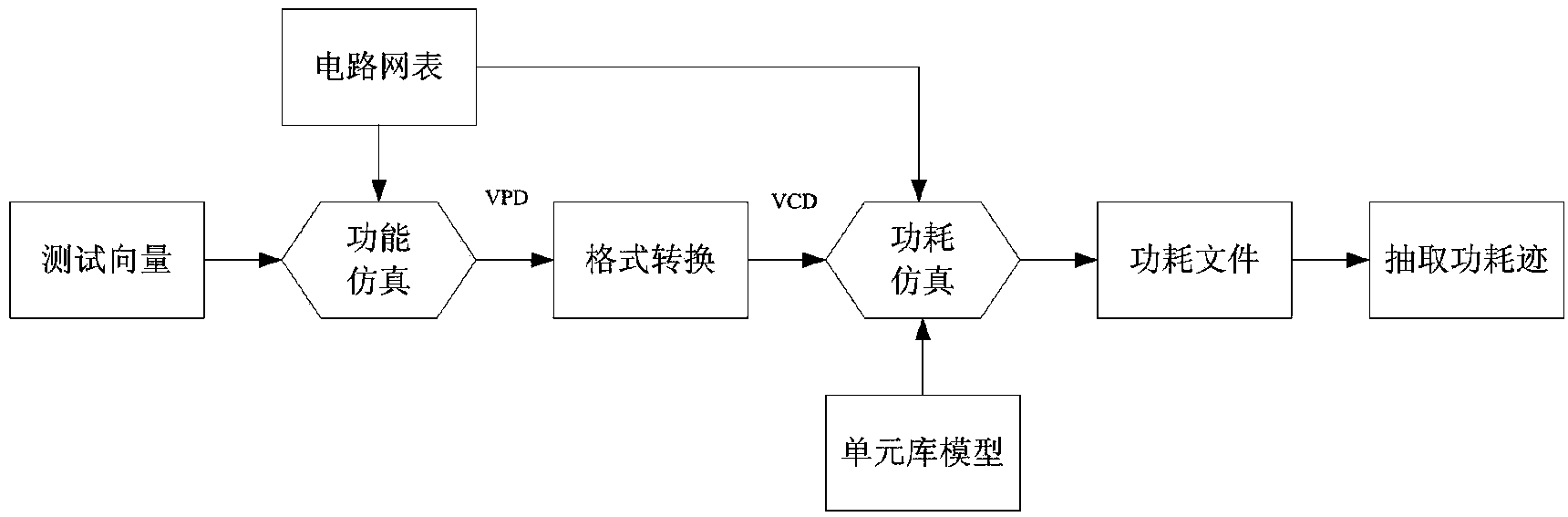
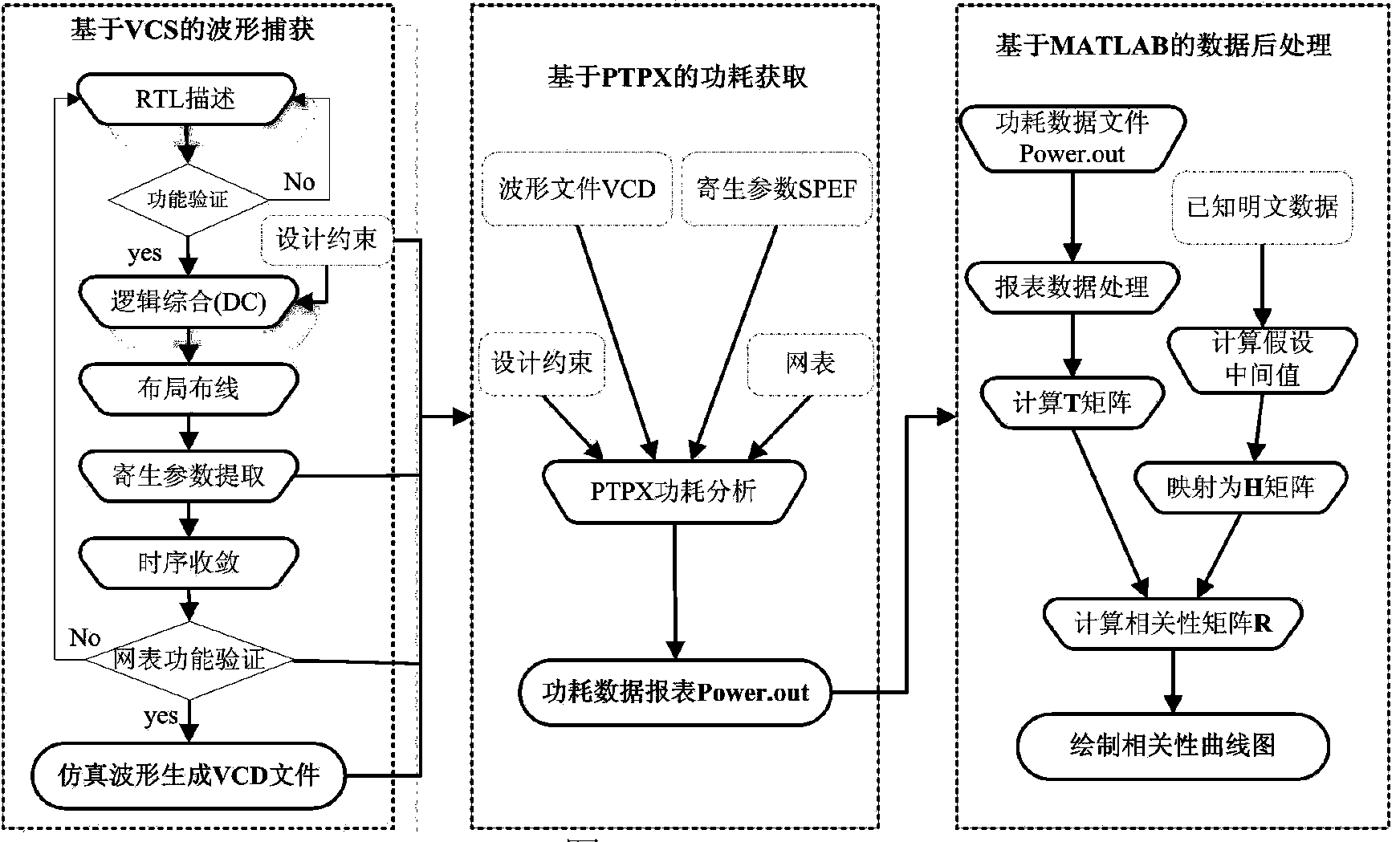
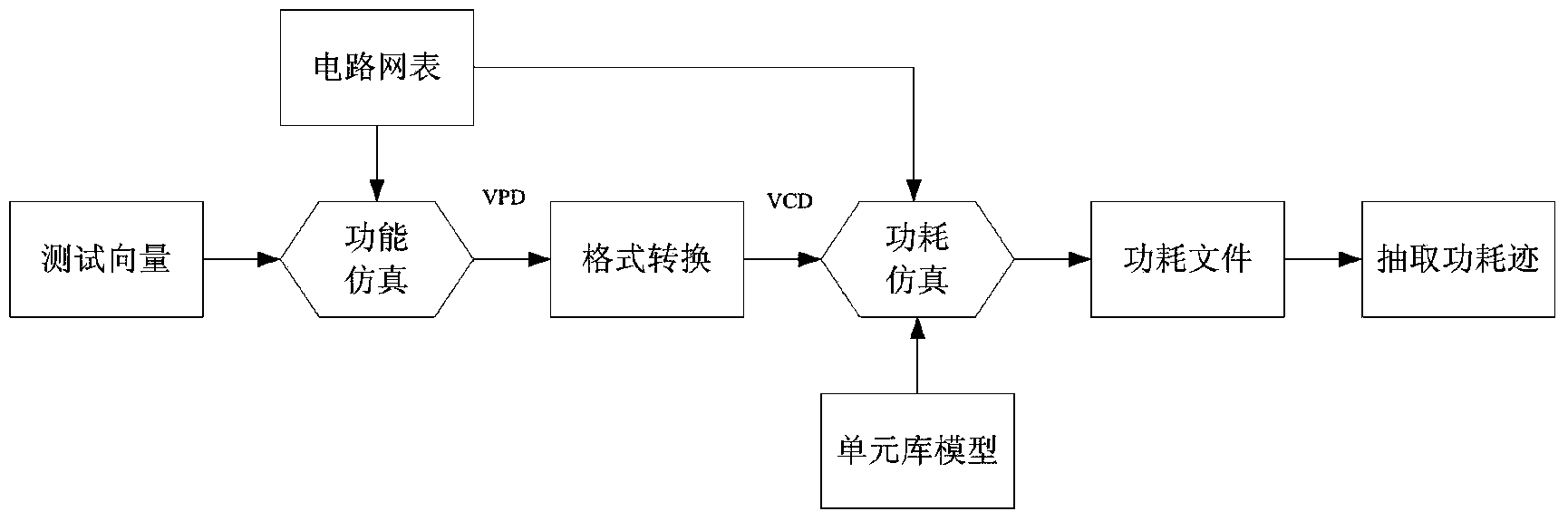
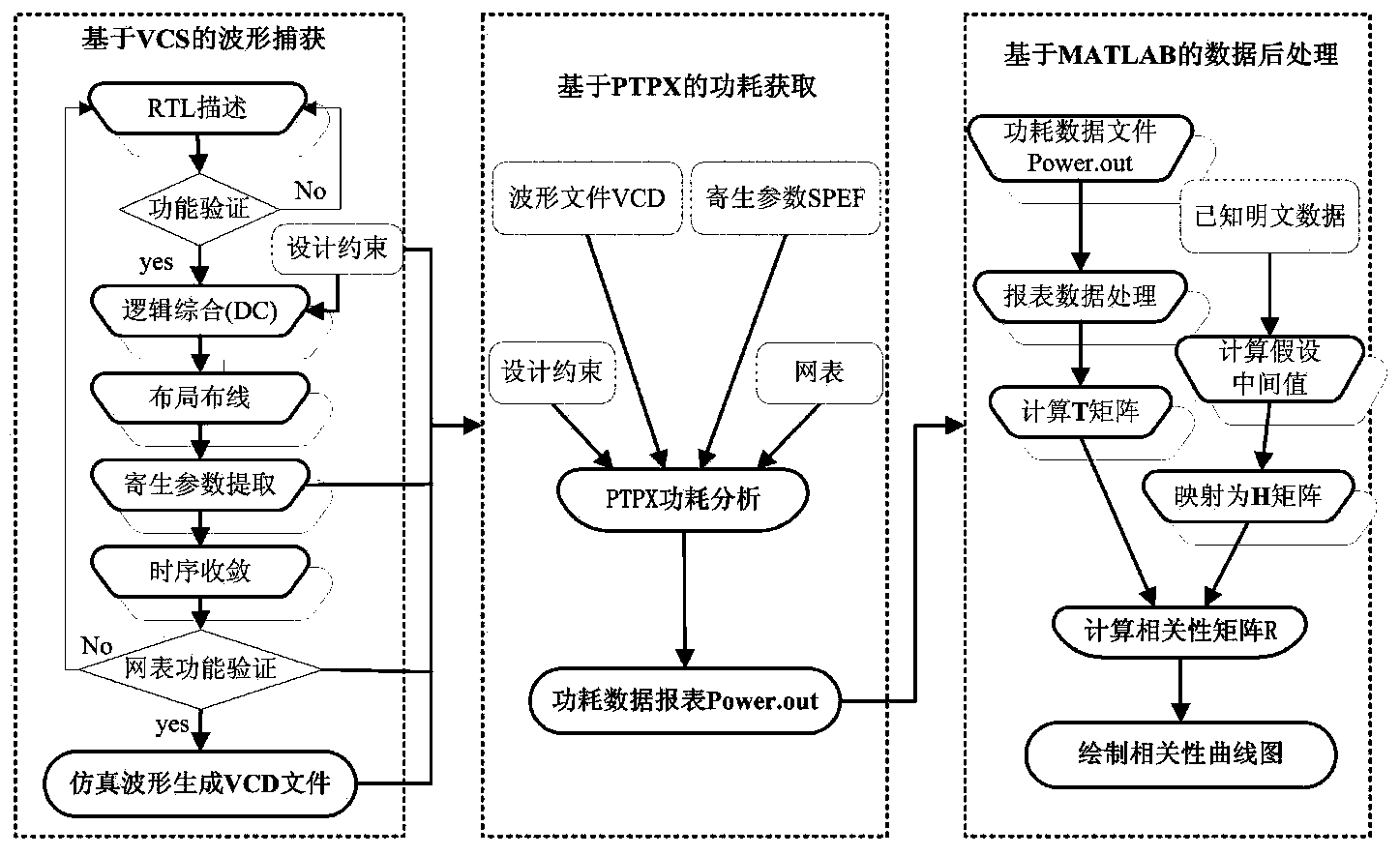
The invention discloses an AES (advanced encryption standard) algorithm circuit oriented method for testing differential power attack. An AES algorithm is a widely applied grouping symmetric cryptographic algorithm. The AES algorithm circuit oriented method is used for acquiring and processing power samples for tests for the differential power attack in a design stage of an AES cryptographic algorithm circuit and includes steps (1), carrying out functional simulation and acquiring power samples; (2), preprocessing the power samples; (3), acquiring hypothetical power samples; (4), computing correlation coefficients and analyzing attack results. The AES algorithm circuit oriented method has the advantages that only varied power points are sampled, so that large quantities of power sample data can be omitted, power attack computational complexity can be greatly reduced, the assess effectiveness and the speed are high, more importantly, the tests for the differential power attack can be carried out in the design stage of the circuit, the attack resistance of the cryptographic circuit can be assessed in advance, and tape-out risks of the AES circuit can be reduced.
Owner:SOUTHEAST UNIV
Differential power attack testing method for DES (data encryption standard) algorithm circuit
InactiveCN103532973ASolve the technical difficulties of power consumption attack testingReduce risk of redesignEncryption apparatus with shift registers/memoriesData switching networksCorrelation coefficientPassword
The invention discloses a differential power attack testing method for a DES algorithm circuit. A DES algorithm is a widely-applied grouping symmetric encryption algorithm. According to the method, a differential power attack test is performed on the DES algorithm circuit at a design stage, and the method comprises the steps as follows: (1), functional simulation and acquisition of a power consumption sample; (2), preprocessing of the power consumption sample; (3), acquisition of a hypothetical power consumption sample; and (4) calculation of correlation coefficients and analysis of attack results. According to the differential power attack testing method, only varying power consumption points are sampled, a large number of power consumption sample data are saved, the power attack calculation amount is reduced substantially, the method has the advantages of high evaluation efficiency and high speed, and above all, the power attack test can be performed at the circuit design stage, so that the anti-attack capability of a password circuit is evaluated in advance, and the redesign risk of the DES circuit after assembly line production of chips is reduced.
Owner:SOUTHEAST UNIV
Power attack prevention method oriented at AES algorithm and circuit achieving method thereof
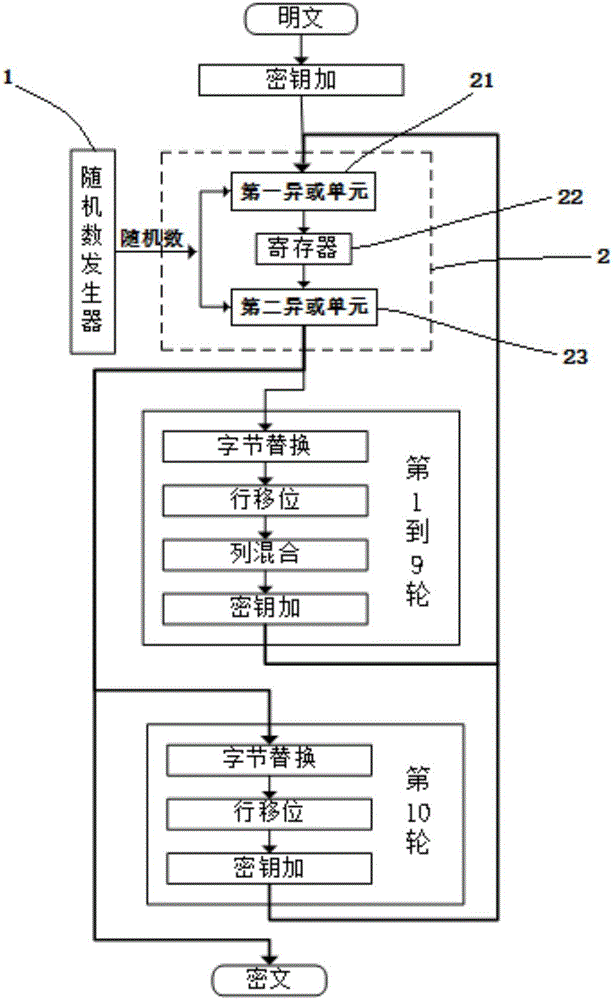
ActiveCN103916236APrevent leakageImprove the ability to resist power consumption attacksEncryption apparatus with shift registers/memoriesComputer hardwareProcessor register
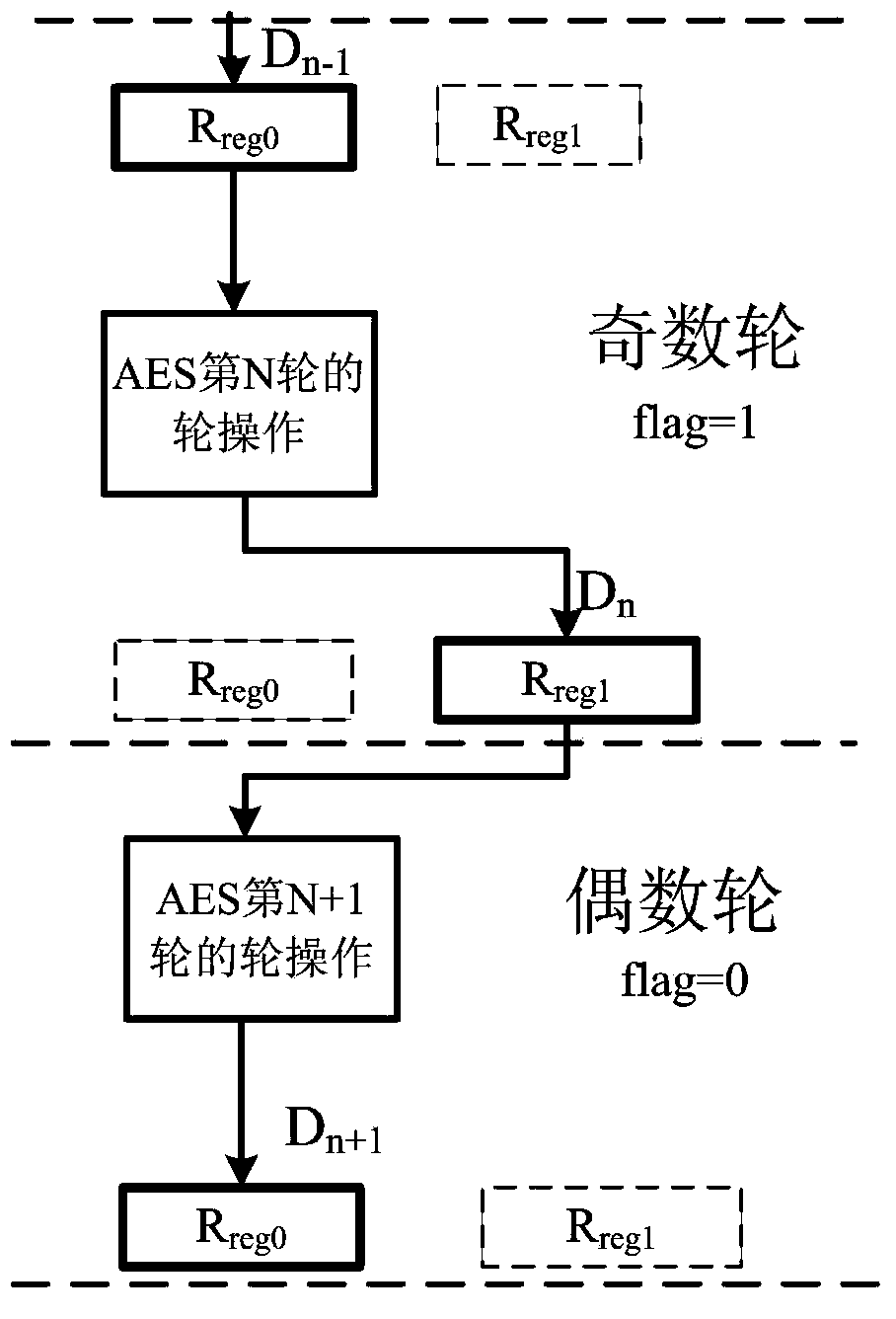
The invention provides a power attack prevention method oriented at an AES algorithm and a circuit achieving method of the power attack prevention method oriented at the AES algorithm. According to the basic principle, a control module and redundancy registers are added to an AES algorithm circuit. The AES algorithm selects the position of a register storing middle calculation data in each turn according to a zone bit generated by the control module, so that the middle data of each turn of encryption operation are alternatively stored in the different registers, the Hamming distance of the middle data of the AES algorithm is effectively hidden, and the AES algorithm can resist power analysis attacks based on a Hamming distance model. The power attack prevention method oriented at the AES algorithm and the circuit achieving method of the power attack prevention method oriented at the AES algorithm have the advantages of being high in flexibility, small in area cost, high in power attack resistance and the like, and provide a good resolution scheme for designing safe chips.
Owner:SOUTHEAST UNIV
AES (Advanced Encryption Standard) encryption method and power attack resisting method based on the same
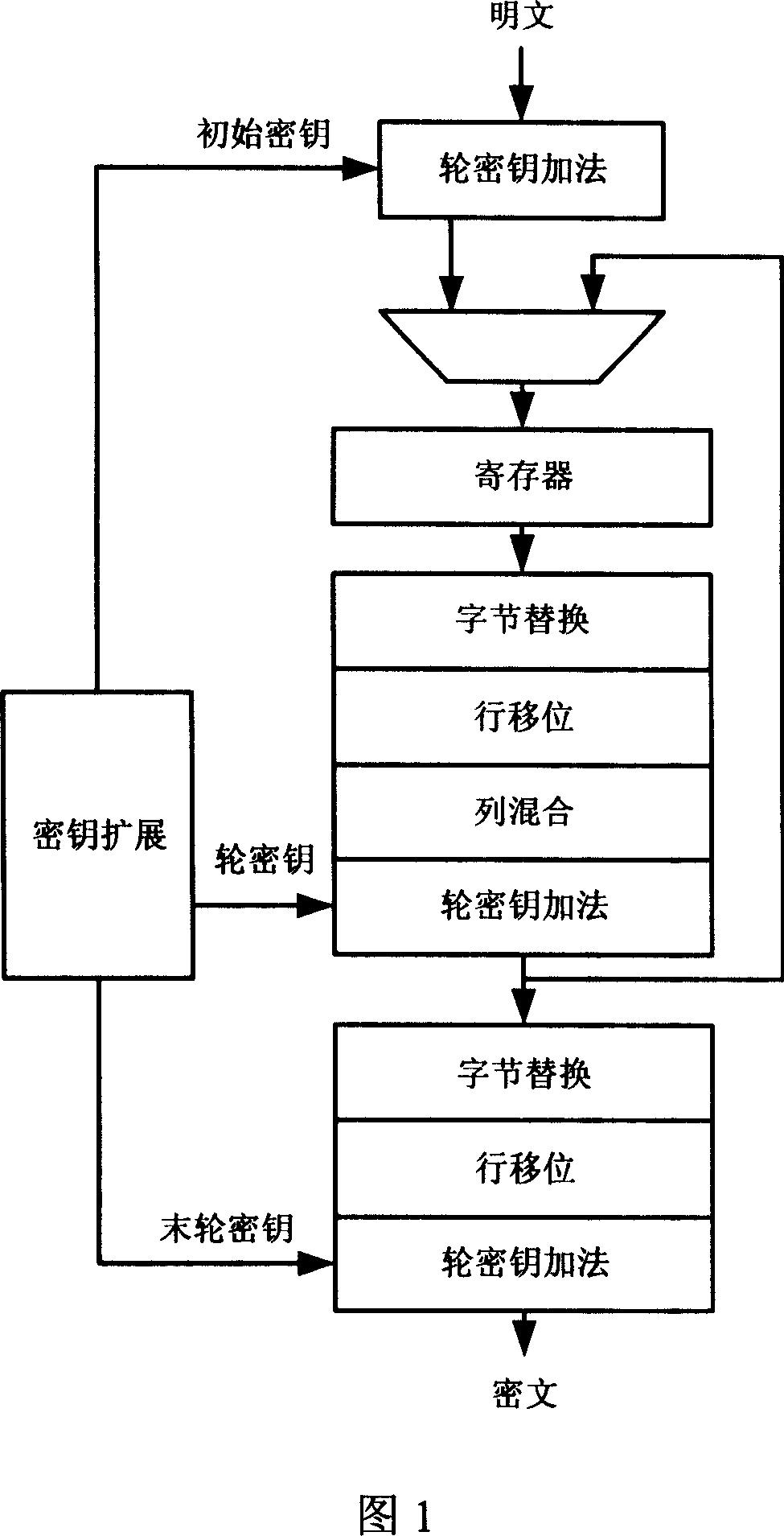
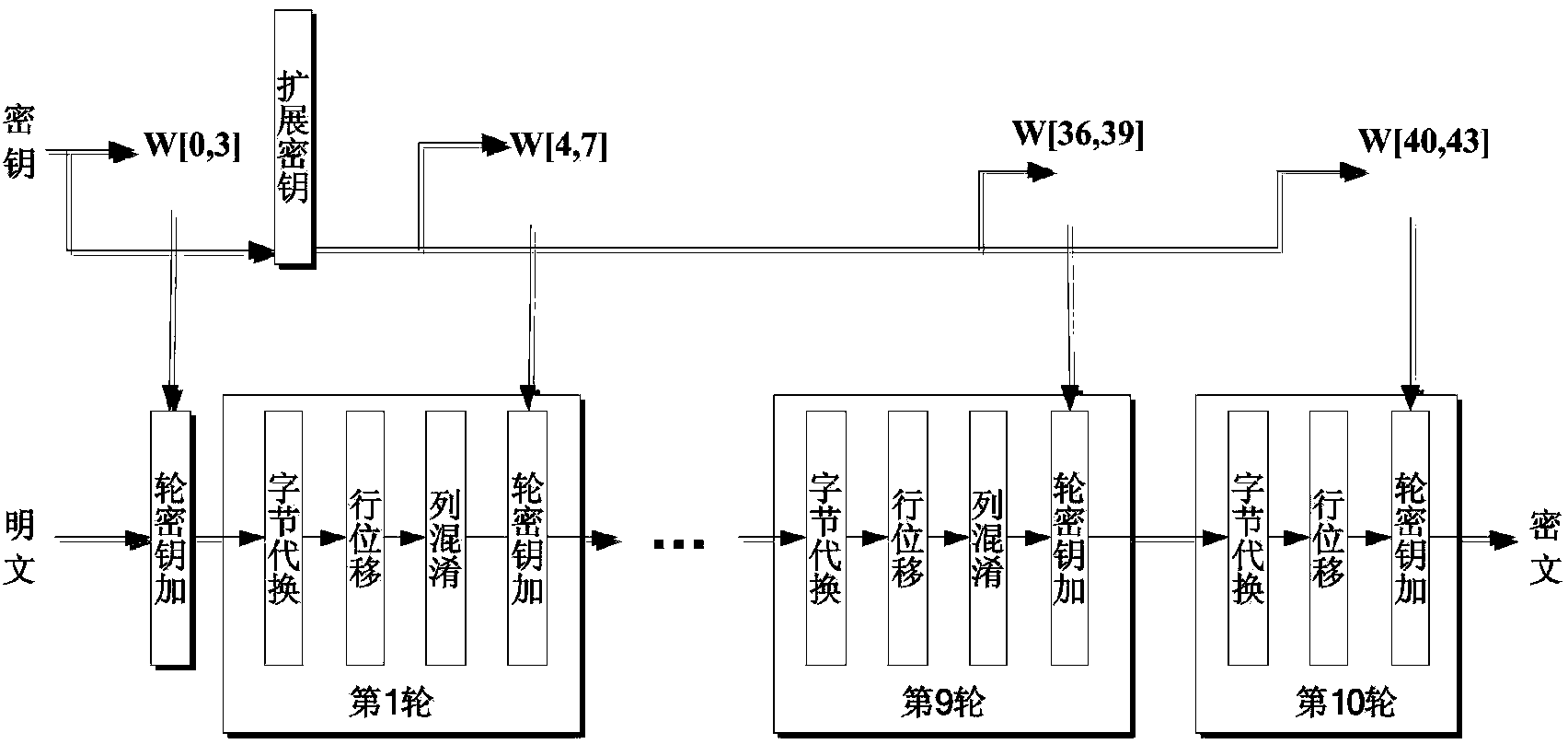
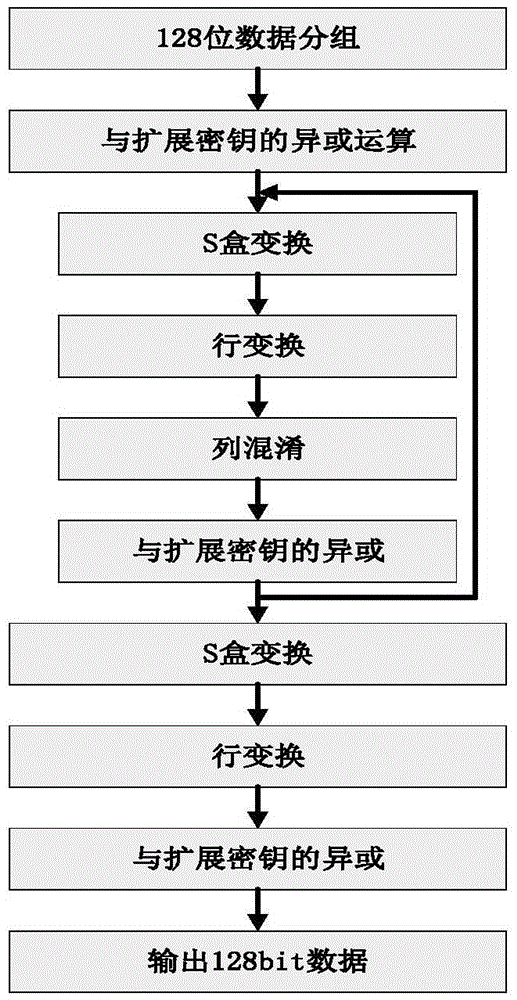
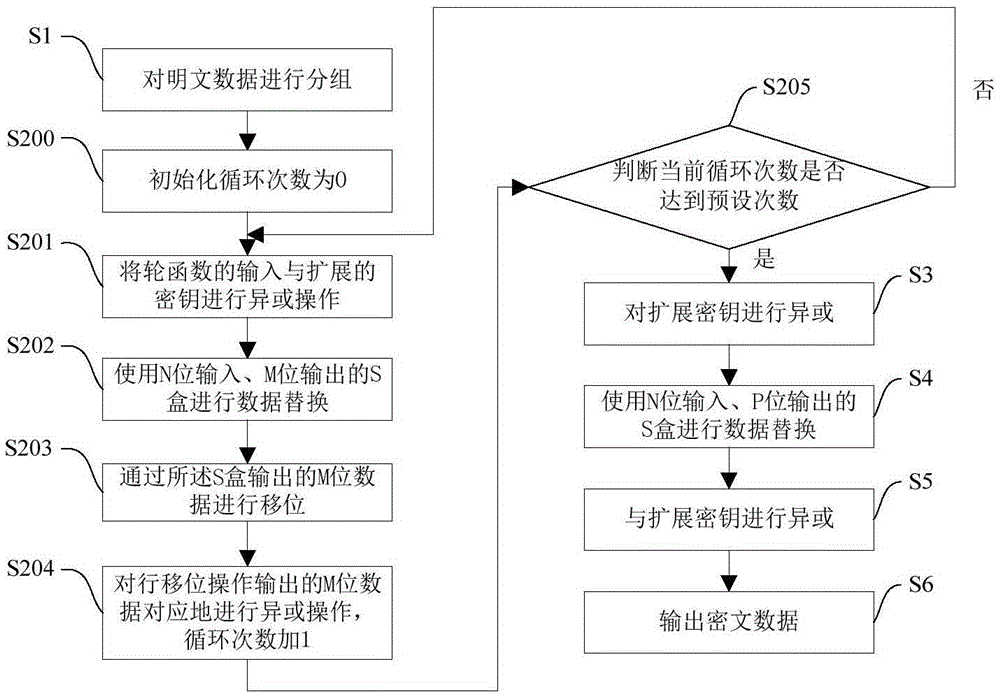
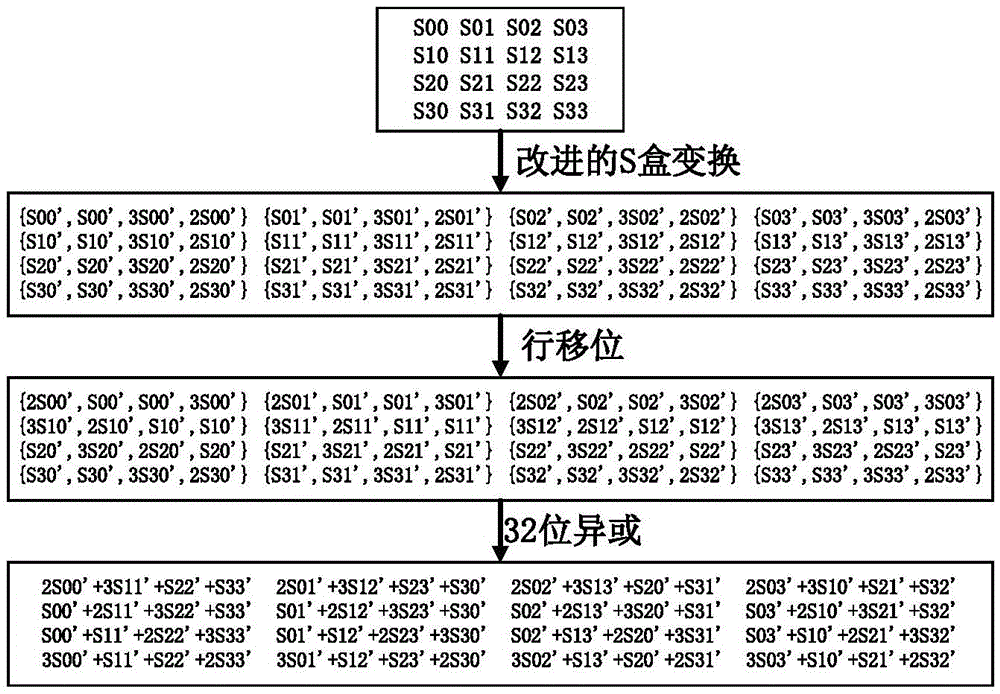
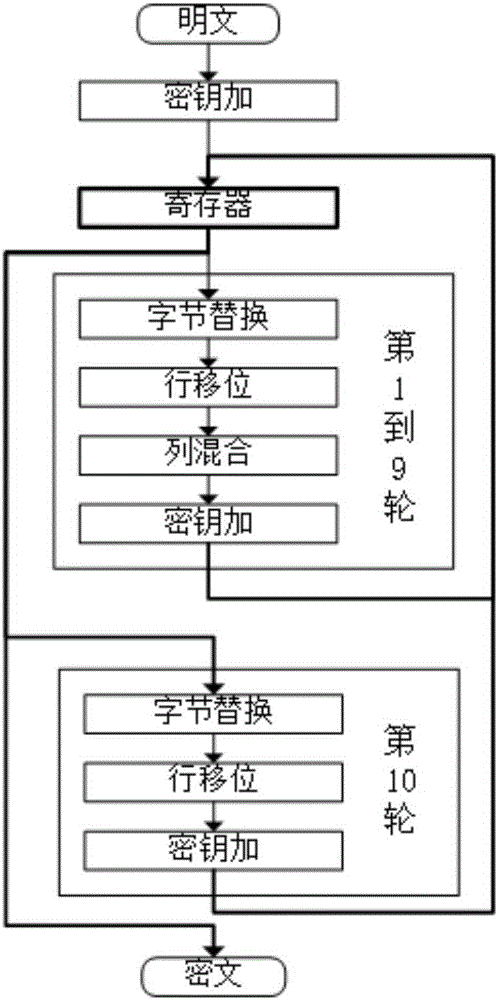
The invention discloses an AES (Advanced Encryption Standard) encryption method and a power attack resisting method based on the same; the AES encryption method comprises the following steps: grouping clear data; carrying out XOR operation on an input and an expanded secret key of a round function; carrying out data replacement with an S box having an 8-bit input and a 32-bit output; shifting 32-bit data output by the S box; carrying out the XOR operation correspondingly on the 32-bit data output by row shifting operation; carrying out the XOR operation on the expanded secret key; carrying out the data replacement with the S box having the 8-bit input and the 8-bit output; carrying out the XOR operation with the expanded secret key; and outputting encrypted data. The invention has the following advantages: the operations needed by each of the steps in the encryption method only have table look-up, shifting and XOR, so the logic implementation is relatively simple and efficient; and the power attack resisting method has mixcolumn, so the power attack resisting effect is good.
Owner:WUXI RES INST OF APPLIED TECH TSINGHUA UNIV
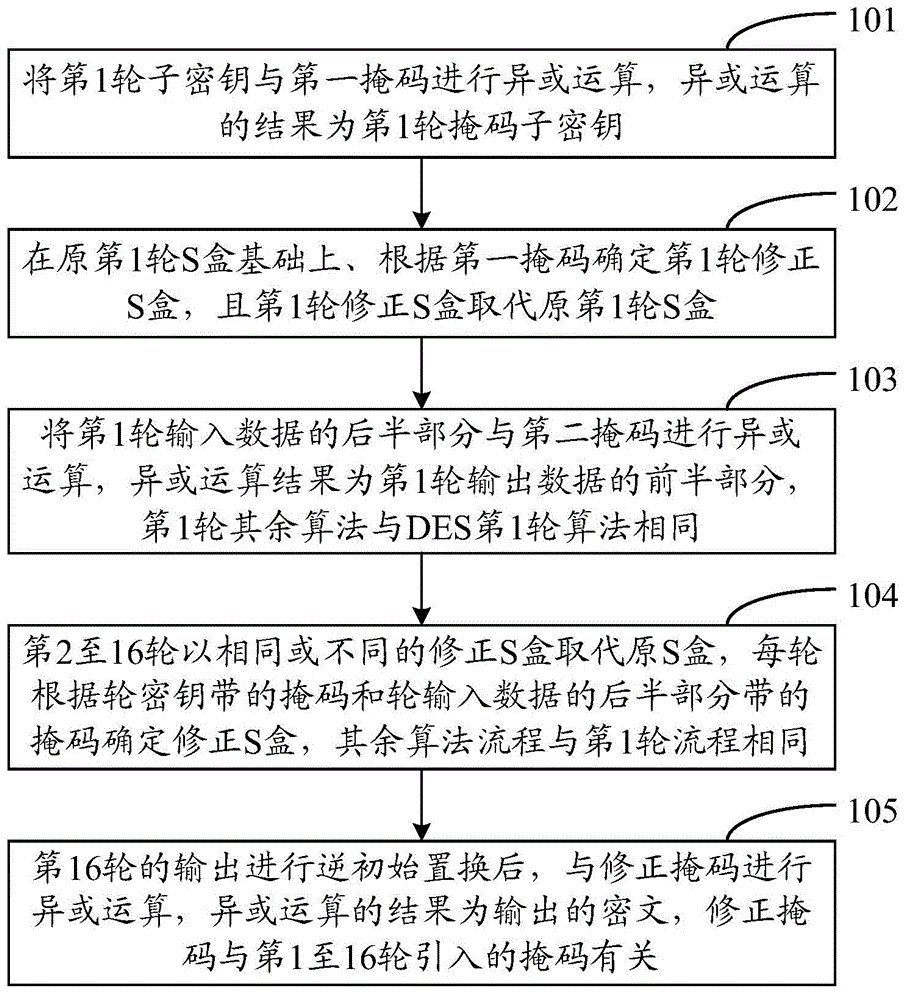
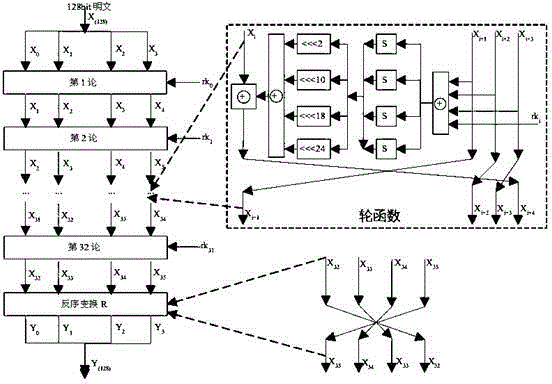
Mask method and device for resisting power attack in SM4 algorithm
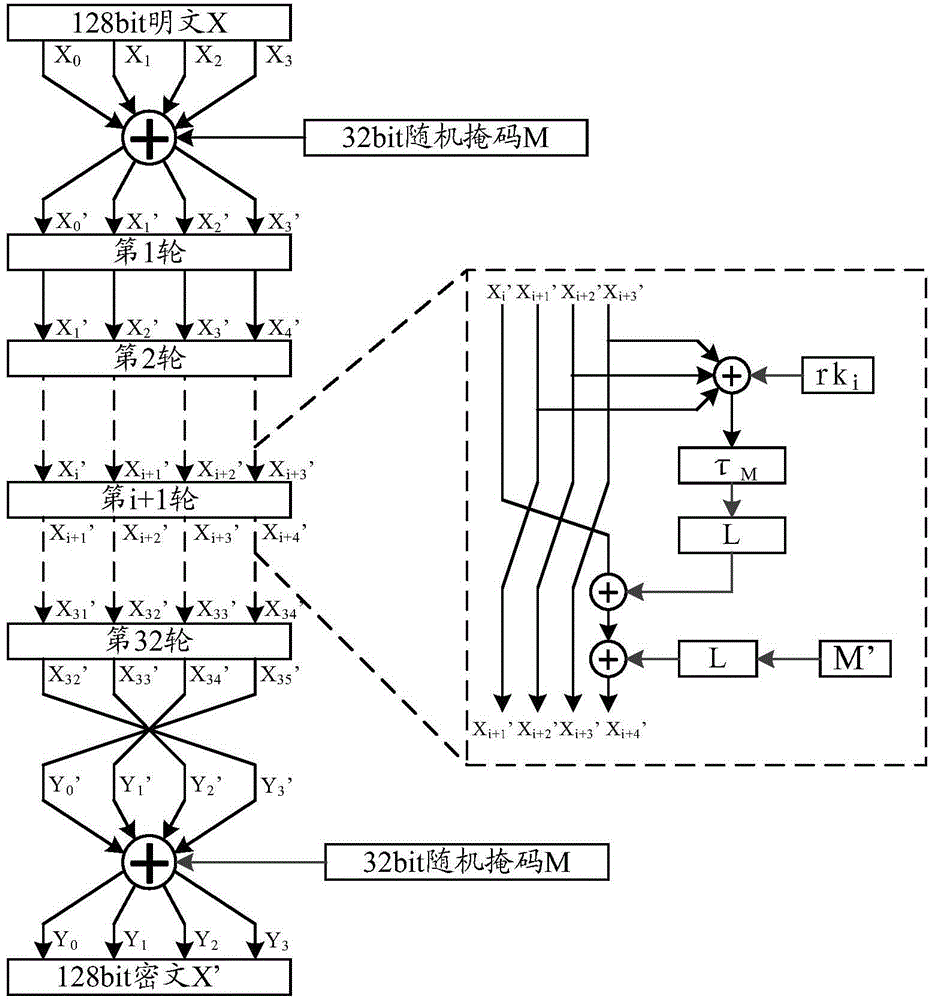
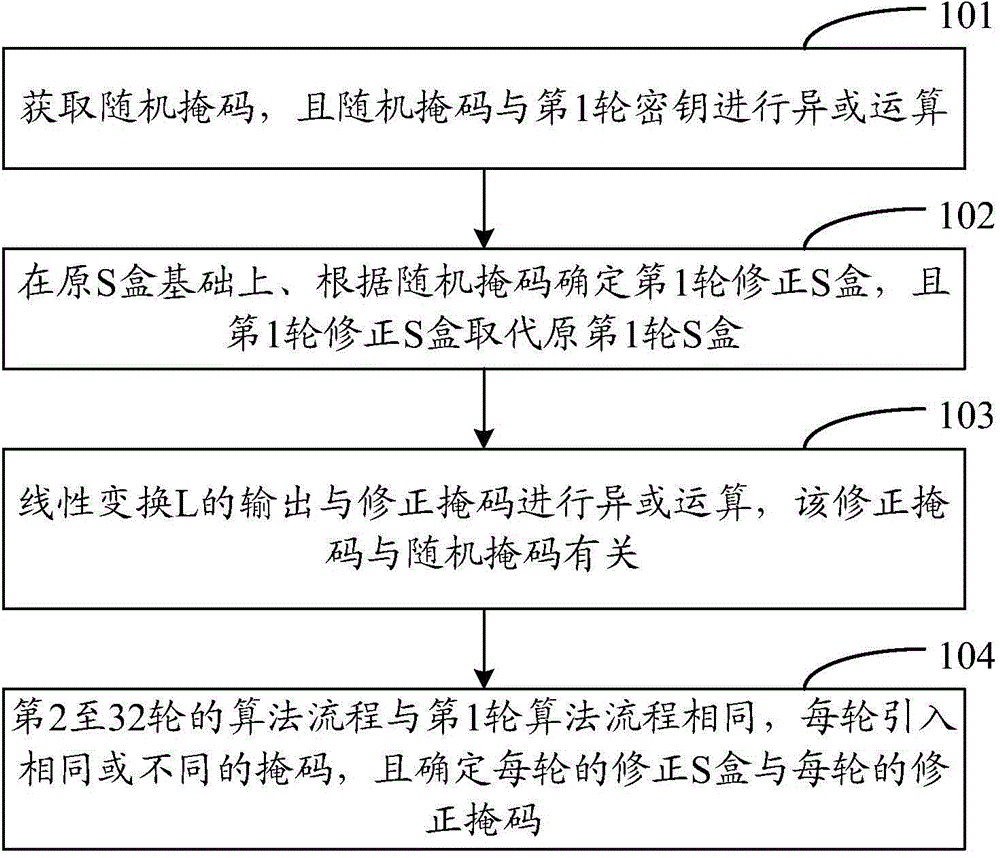
ActiveCN104639502AWon't leakEnergy attack resistanceKey distribution for secure communicationEncryption apparatus with shift registers/memoriesS-boxPower attack
The invention discloses a mask method and a device for resisting a power attack in an SM4 algorithm. The method comprises the following steps of obtaining a first random mask and carrying out OR operation on the first random mask and a first round of key; determining a first round of correction S box on the basis of the original first round of S box according to the first random mask and enabling the first round of correction S box to replace the original first round of S box; determining a first correction mask according to the first random mask and carrying out XOR operation on the outputs of the first correction mask and an L linear displacement; making the second to thirty-two rounds of the algorithm processes be the same as the first round of the algorithm process, introducing the same random mask or the different random masks into each round and determining the corresponding correction S box and the correction mask. Through introducing the same mask or the different masks into each round, mask values brought by intermediate results for vulnerable round operations are different, so that the power attack can be effectively resisted.
Owner:STATE GRID CORP OF CHINA +1
Encryption method and device using random clock based on chaos
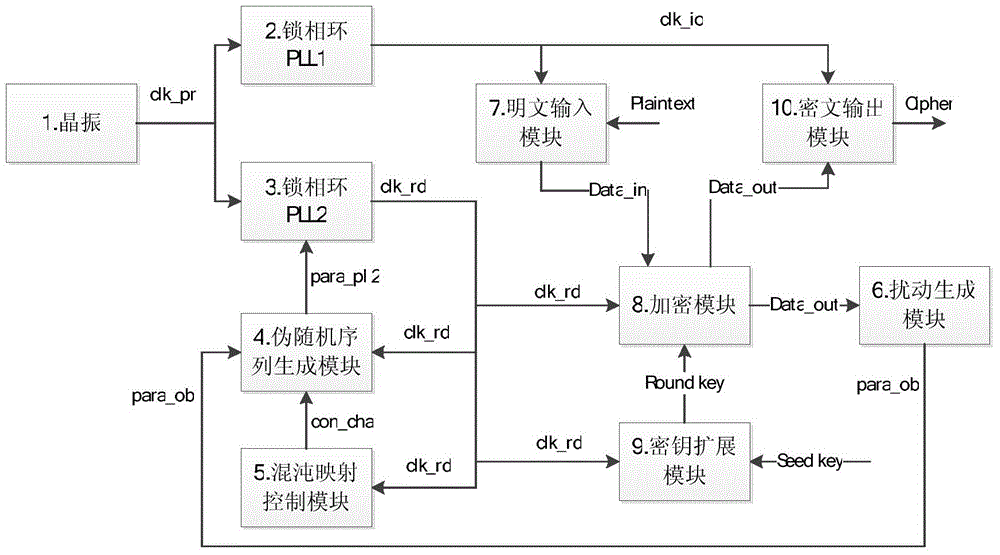
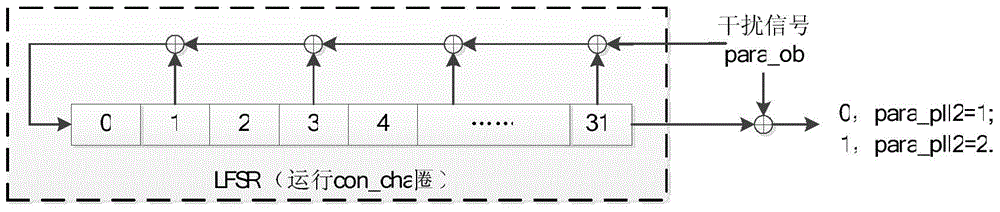
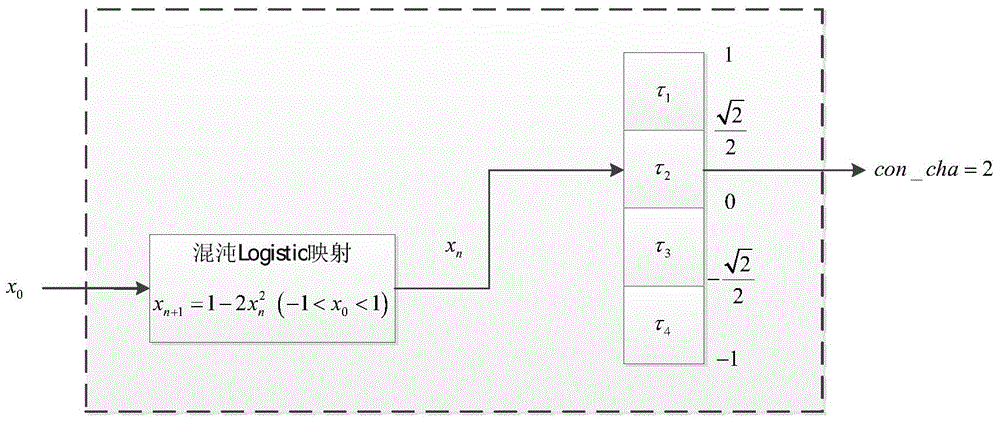
ActiveCN103560876AReduce resource requirementsImprove securityKey distribution for secure communicationSynchronising arrangementTelecommunications linkMicrowave
The invention provides an encryption method and device using a random clock based on chaos, and belongs to the field of information safety. According to the system, a design scheme which is integrated from top to bottom is adopted. The device is composed of a crystal oscillator, a PLL1, a PLL2, a pseudorandom sequence generating module, a chaotic mapping control module, a disturbance generating module, a clear text input module, an encryption module, a secret key extension module and a cipher text output module. According to the encryption method and device using the random clock based on chaos, a common linear feedback shift register, chaotic mapping control and cipher text feedback are combined to generate the random clock, the safety of the random clock is effectively improved, and power attack and electromagnetism attack can be effectively resisted. The encryption method and device using the random clock based on chaos can be applied to industrial and technical production of encrypted hardware storage device static encryption, microwave or photo-communication chains, and a receiving or transmitting port of a computer terminal and the like.
Owner:BEIHANG UNIV
Circuit structure for preventing power attacks on grouping algorithm
InactiveCN102970131AGuaranteed defense effectGuaranteed protective effectEncryption apparatus with shift registers/memoriesElectronic identificationSmart card
The invention provides technology which can effectively resist to attacks on modules, chips, smart card bodies and the like adopting a grouping encryption and decryption algorithm through power analysis (simple power analysis (SPA) and difference power analysis (DPA)) or electromagnetic radiation analysis (DEMA) to obtain encryption and decryption operation secret keys and a circuit implementation structure of the technology. In application of a high-safety smart card, including but not limited to application areas such as electronic identification cards, debit cards and social security cards, the circuit structure can effectively protect the grouping encryption modules, the chips, the smart card bodies and the like and prevent the encryption and decryption operation secret keys from decoding and obtaining by the power analysis or the electromagnetic radiation analysis. The circuit structure can improve efficiency of encryption operation in continuous encryption operation, improves safety protection strength on the grouping encryption modules, the chips, the smart card bodies and the like, guarantees execution efficiency of the encryption operation, and has good innovation, practical applicability and effectiveness.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
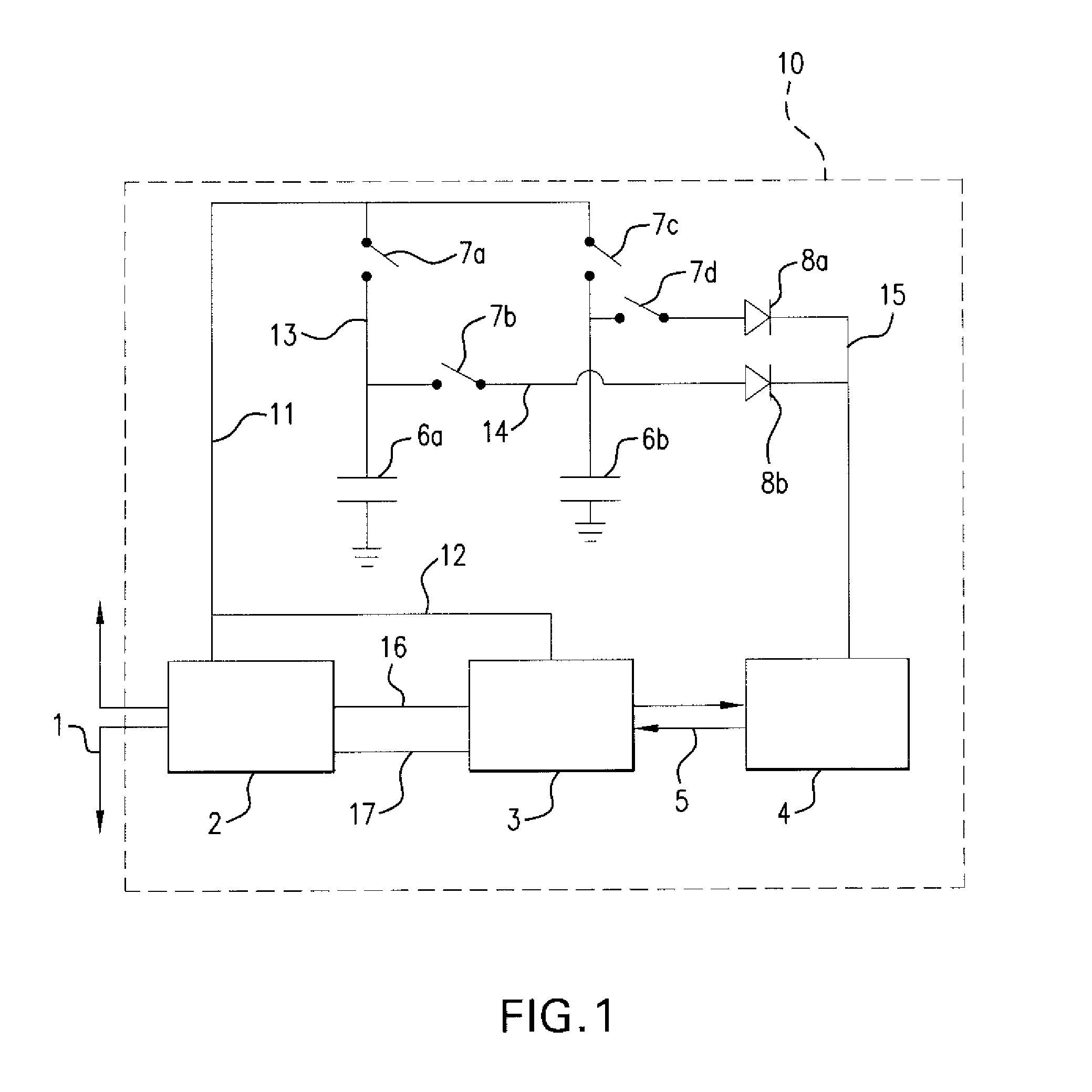
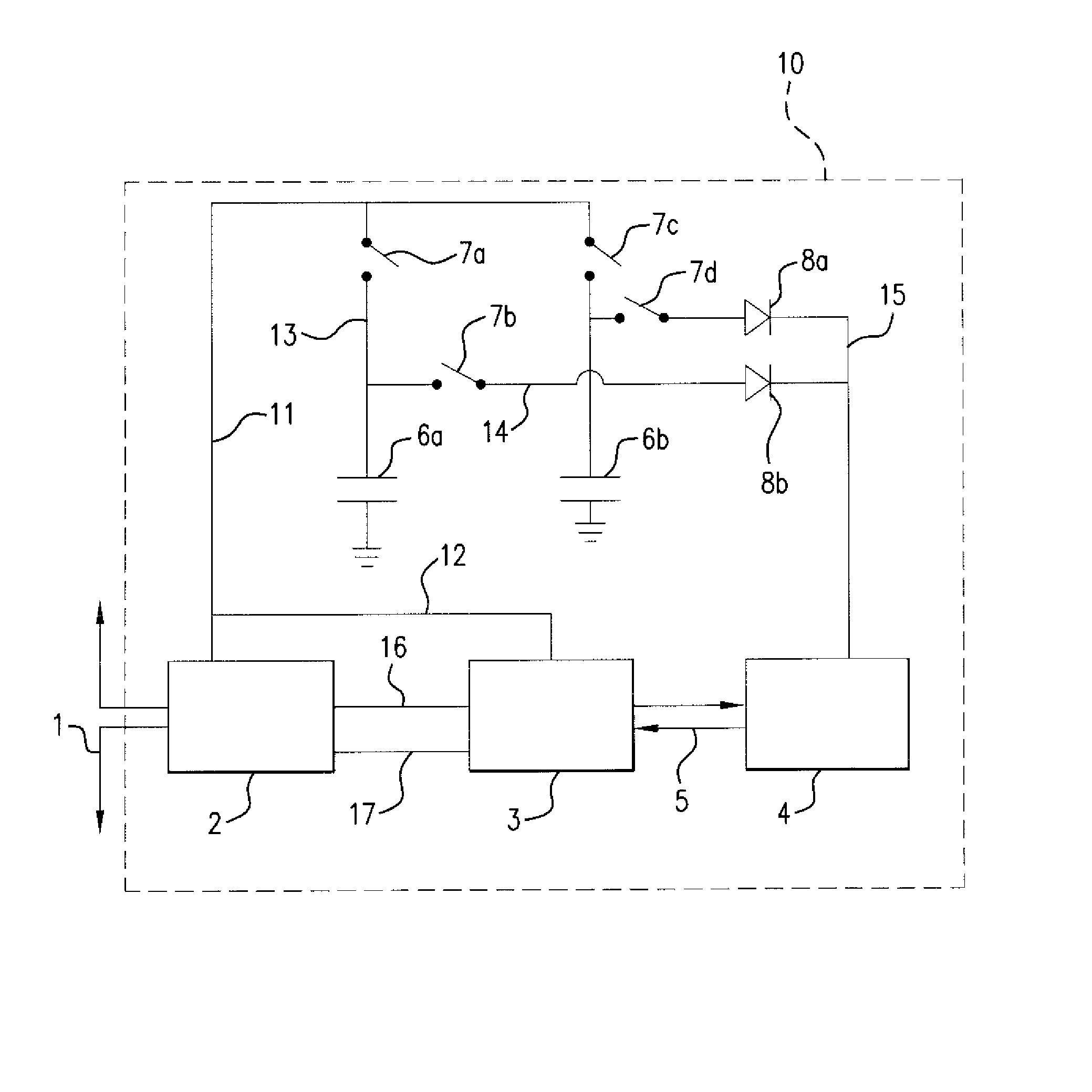
Method and apparatus for protecting RFID tags from power analysis
InactiveUS8365310B2Cheap and effectiveEliminate the power consumption informationError detection/correctionVolume/mass flow measurementHemt circuitsPower attack
Method and apparatus for protecting RFID tags against power attacks by embedding two capacitors in an RFID tag and coupling to the RFID power extraction and computational circuitry to be operated so that at any given time during normal operation of the RFID tag one of them is coupled to the power extraction circuitry of the RFID tag and is storing energy that is being generated by the charge pump of the tag by sucking energy from the electromagnetic or magnetic field of a tag reader, and the other one is uncoupled from the power extraction circuitry of the RFID tag and is discharging and powering the computational element of the tag chip.
Owner:YEDA RES & DEV CO LTD
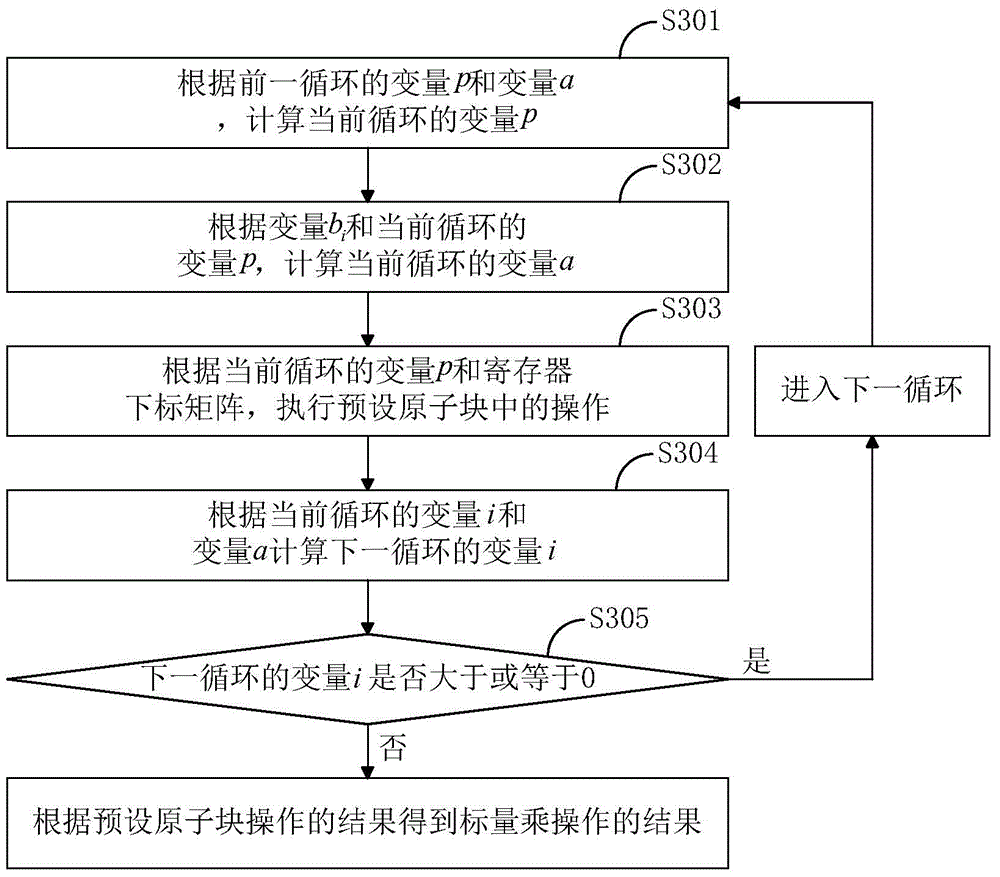
Key anti-power attack method
ActiveCN104917608AEasy to operateReduce computationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareInner loop
The invention discloses a key anti-power attack method. The method includes the step that a preset atomic block is utilized to perform point multiplying and / or point adding operation in scalar multiplication, wherein the preset atomic block contains modular multiplication operation, addition operation and subtraction operation. According to the method, the concept of the atomic algorithm is combined with the characteristics of a public key cryptographic algorithm, and therefore, the procedures of point adding operation and point multiplying operation can be optimized; an corresponding variables are adopted to control the internal loop of the scalar multiplication, and the scalar multiplication is converted to a modular multiplication-addition-subtraction atomic block loop. With the method of the invention adopted, computation burden required by the scalar multiplication can be greatly decreased, and the security of keys can be ensured, and the computation speed of the public key cryptographic algorithm can be improved.
Owner:TSINGHUA UNIV
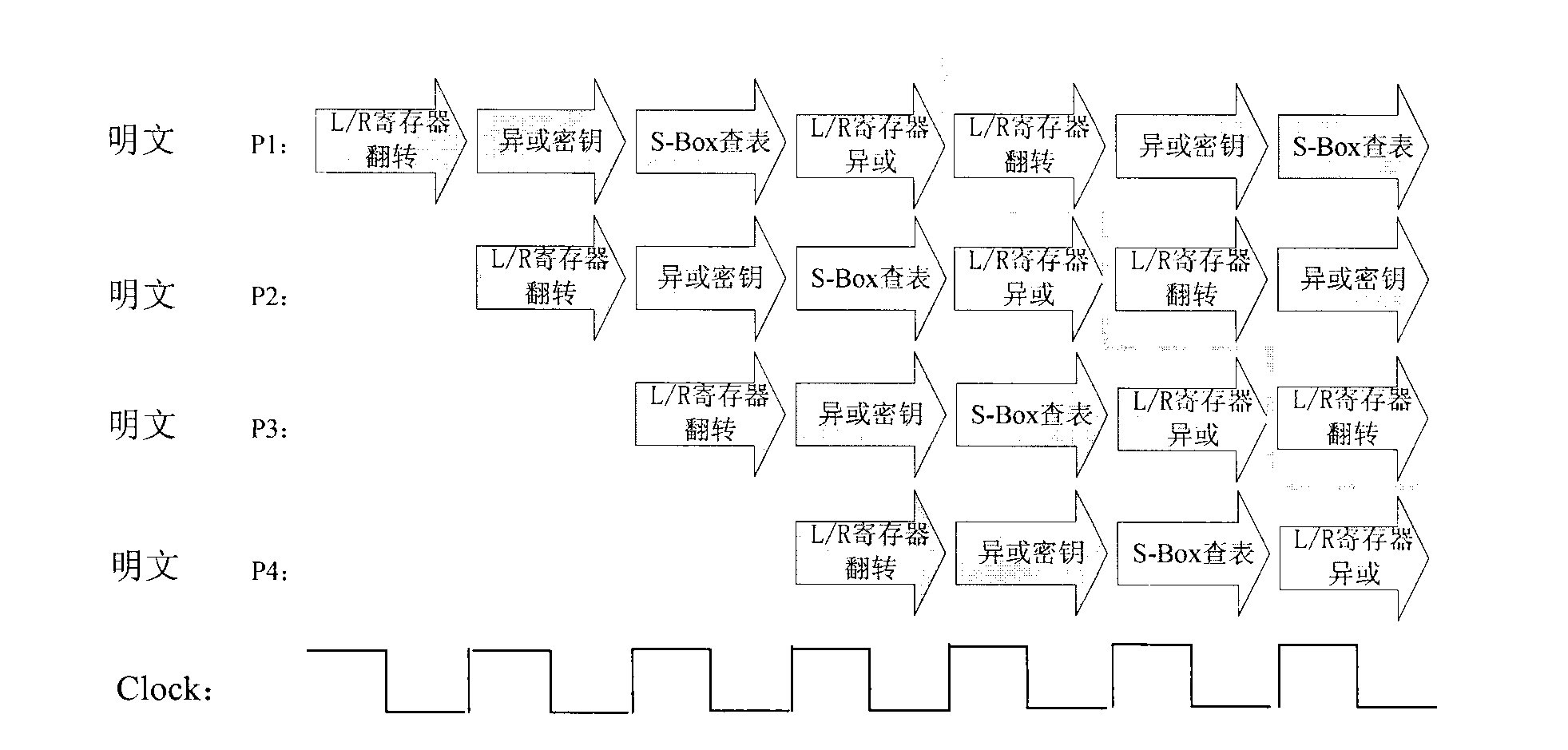
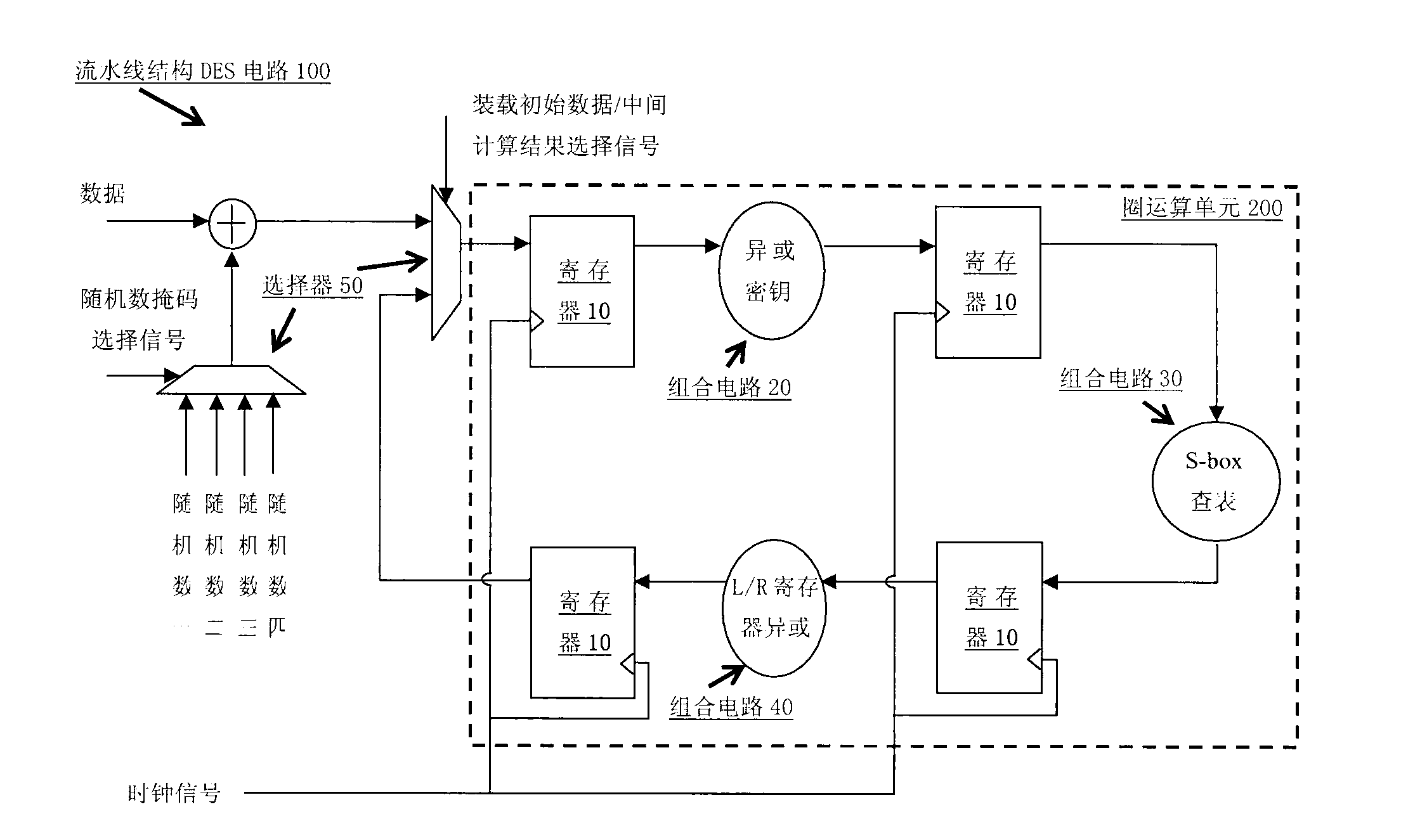
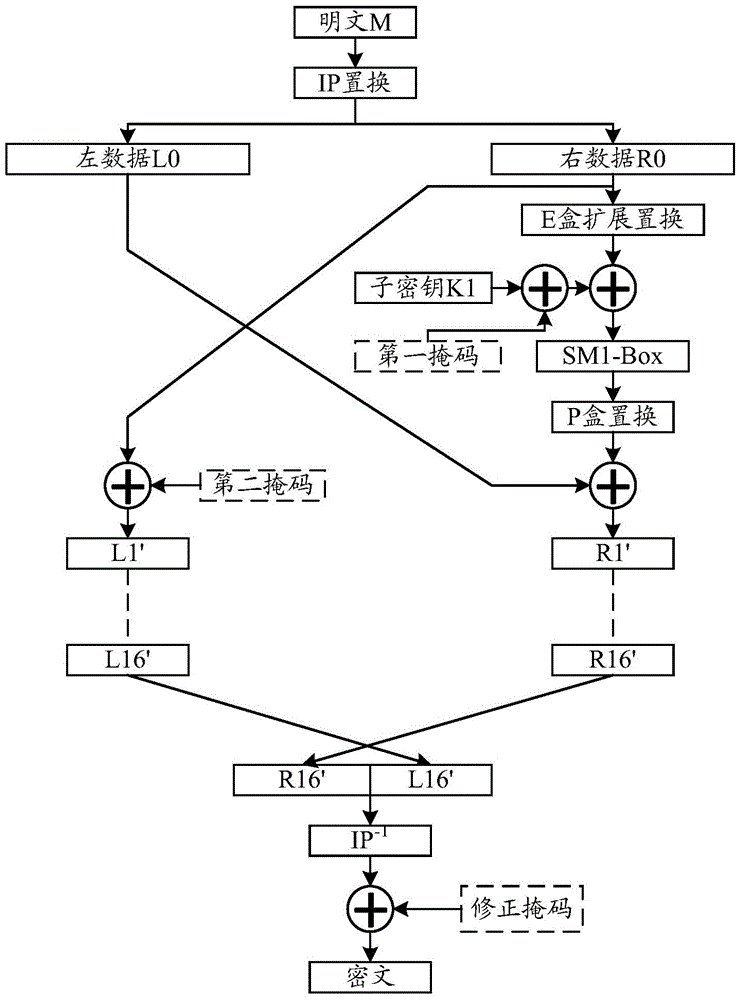
Anti-power-attack method and device for DES (Data Encrypt Standard) algorithm
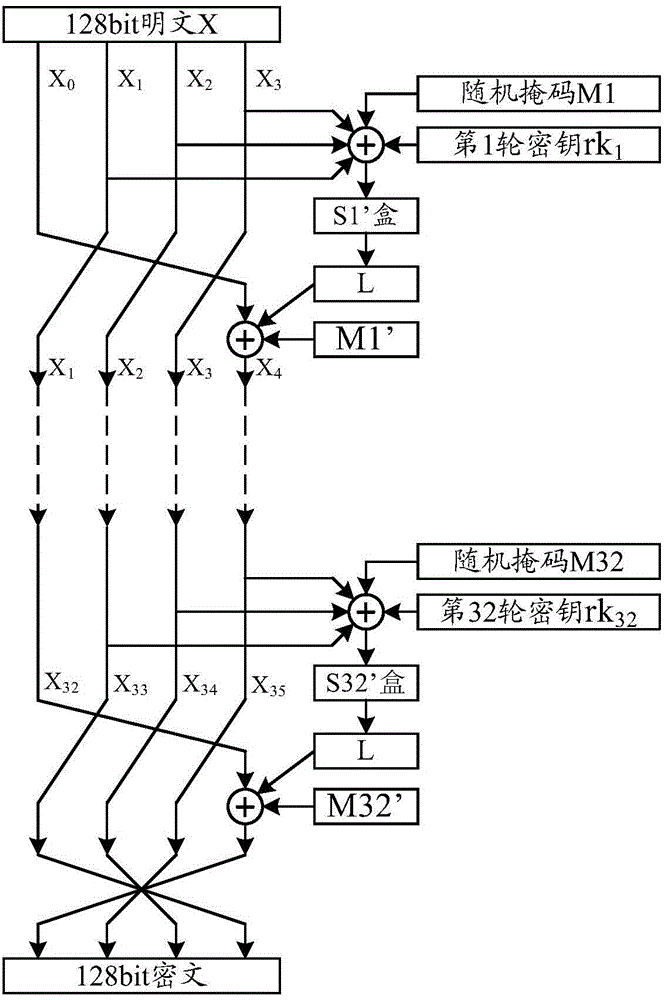
ActiveCN104639312AOvercome the flaw of leaking password informationEffective cover upEncryption apparatus with shift registers/memoriesS-boxCiphertext
The invention discloses an anti-power-attack method and device for a DES (Data Encrypt Standard) algorithm. The method comprises the following steps: performing exclusive-or operation on a first-round sub-key and a first mask; determining a first-round correction S-box according to the first mask on the basis of an original first-round S-box, and substituting the original first-round S-box; performing exclusive-or operation on the back half part of first-round input data and a second mask, wherein an exclusive-or operation result is the front half part of first-round output data; in second to sixteenth rounds, substituting the original S-box with identical or different correction S-boxes, and determining a correction S-box according to a mask carried by a wheel key and a mask carried by the back half part of wheel input data in each round, wherein other algorithm flows are the same as a first-round algorithm flow; and performing exclusive-or operation on a result obtained after the execution of reverse initial permutation on sixteenth-round output, wherein the result of the exclusive-or operation is an output cipher text. Through the anti-power-attack method for the DES algorithm provided by the invention, power attacks can be effectively resisted.
Owner:STATE GRID CORP OF CHINA +1
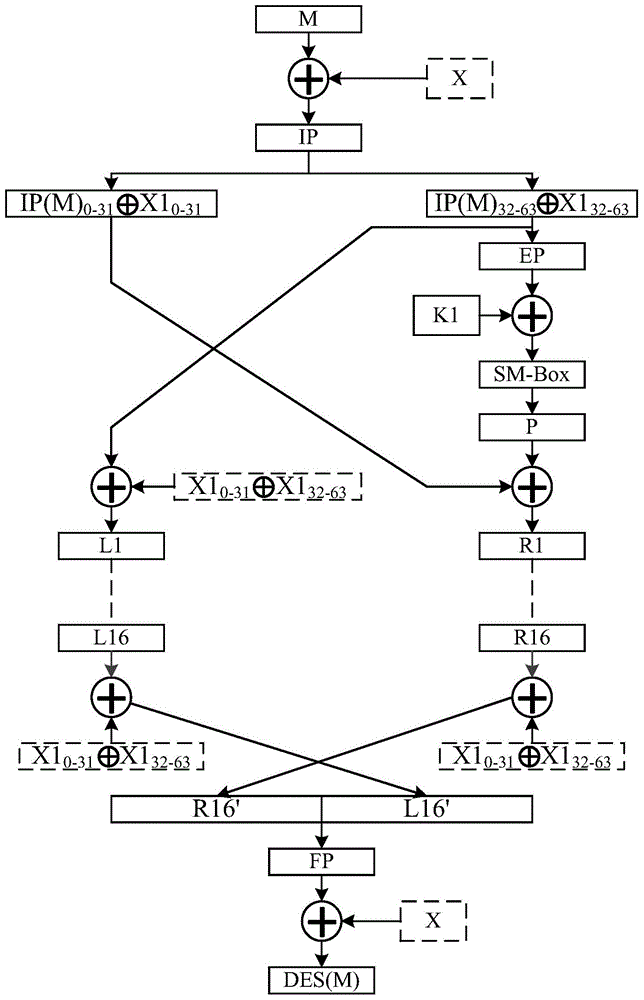
Password mask method for enhancing attack resistance ability
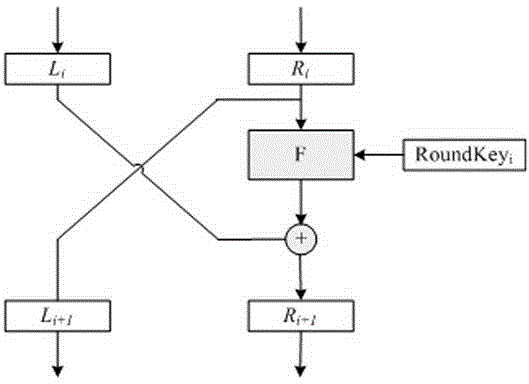
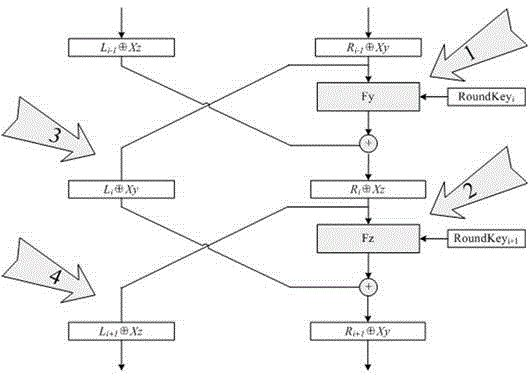
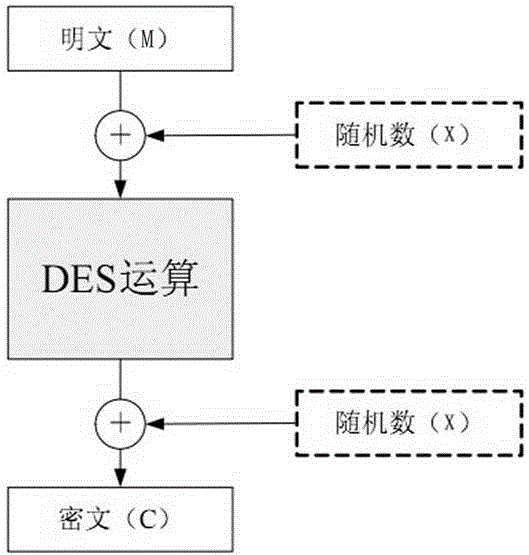
ActiveCN104618094AEnhanced resistance to differential power attacksSave hardware resourcesEncryption apparatus with shift registers/memoriesAlgorithmPassword
The invention discloses a password mask method for enhancing attack resistance ability. The password mask method for enhancing the attack resistance ability includes an encryption process. The encryption process includes steps: (1) introducing an original random number X, and performing exclusive-or operation on a clear text; (2) performing IP (internet protocol) initial displacement, and then dividing the clear text into an L portion and an R portion, and furthermore introducing random numbers Xy and Xz, generated in the middle process; (3) introducing F functions amended by mask codes, and performing n turns of F function operation; (4) combining the L portion with the R portion, and then performing an FP inverse initial permutation; (5) introducing the original random number X, and performing the exclusive-or operation so as to obtain a cipher text C. The password mask method for enhancing the attack resistance ability can achieve different effects of the mask codes by only using two types of the F functions amended by the mask codes during the whole encryption and decryption process, and only needs to achieve two types of SM-Box, and compared with other schemes with CPA attack resistance, the password mask method for enhancing the attack resistance ability can save a great number of hardware resources and reduce cost on the premise of substantially enhancing differential power attack and related power consumption attack resistance.
Owner:SHANDONG HUAYI MICRO ELECTRONICS
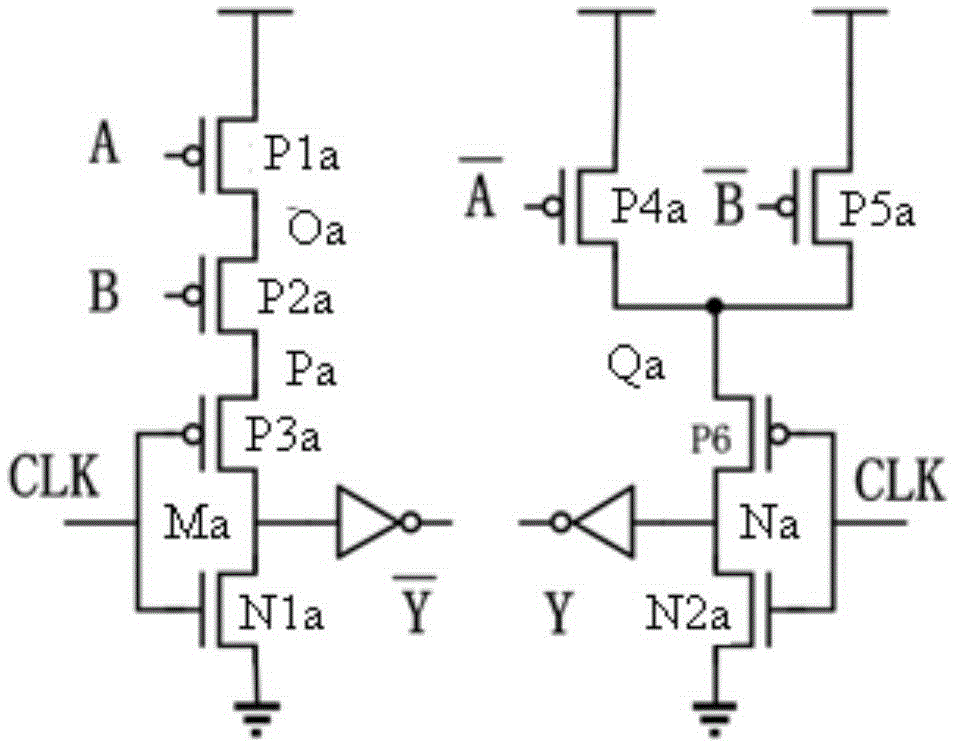
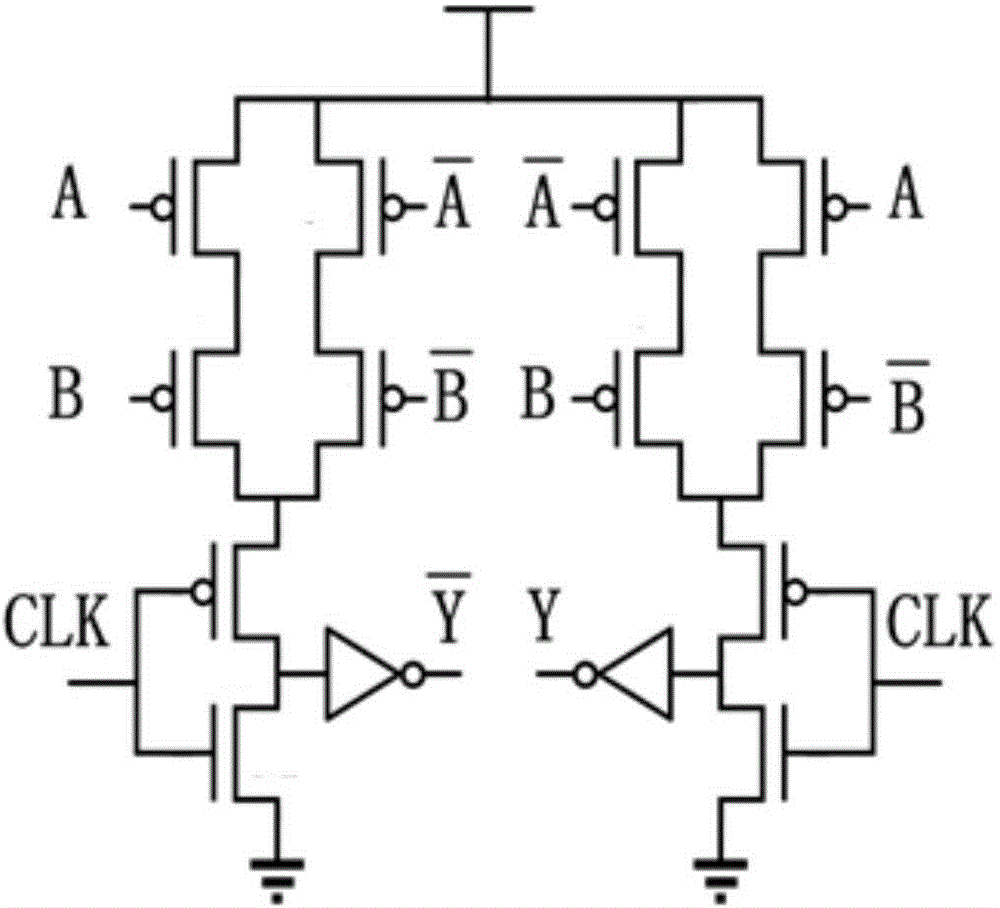
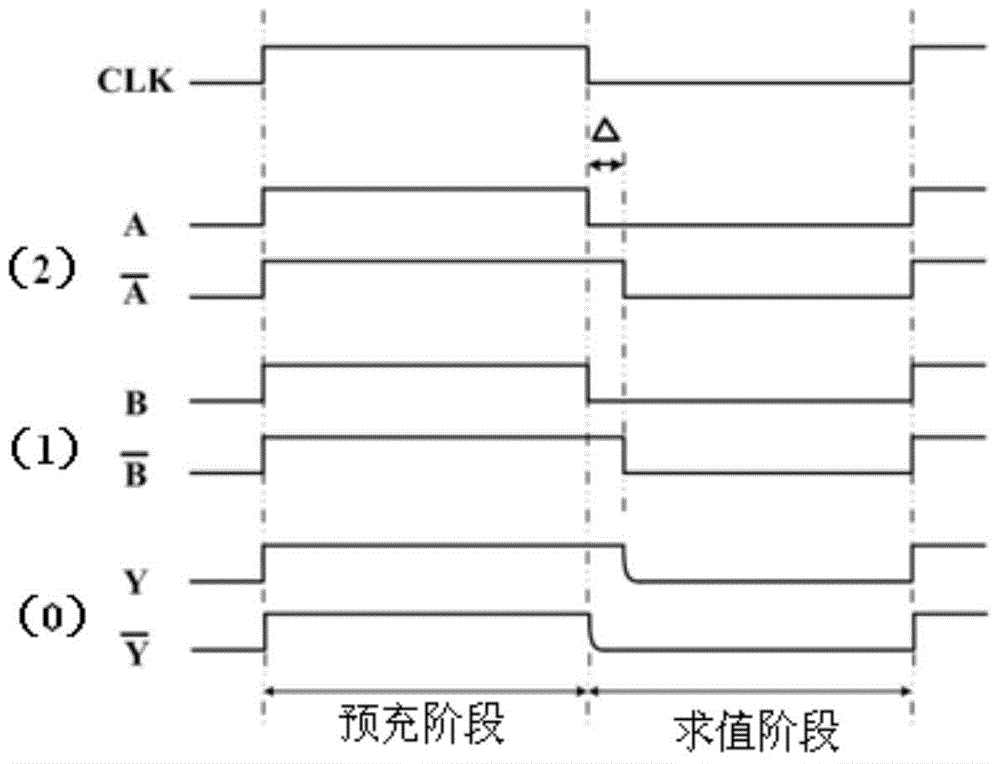
Time delay-based double-track pre-charge logic NAND gate circuit and Time delay-based double-track pre-charge logic exclusive or gate circuit
InactiveCN104682950AHigh speedIncrease power consumptionLogic circuits characterised by logic functionTime delaysPre-charge
The invention discloses a time delay-based double-track pre-charge logic NAND gate circuit and a time delay-based double-track pre-charge logic exclusive or gate circuit. By transforming positions of PMOS (P-channel metal oxide semiconductor) transistors or NMOS (N-channel metal oxide semiconductor) transistors in the time delay-based double-track pre-charge logic NAND gate circuit and the time delay-based double-track pre-charge logic exclusive or gate circuit in the prior art and increasing or decreasing the PMOS transistors or the NMOS transistors, the improvement of the NAND gate circuit and the exclusive or gate circuit is realized; the improved NAND gate circuit and the improved exclusive or gate circuit area capable of realizing more balanced power consumption, faster speed and lower power consumption, and can better resist differential power attack.
Owner:PEKING UNIV
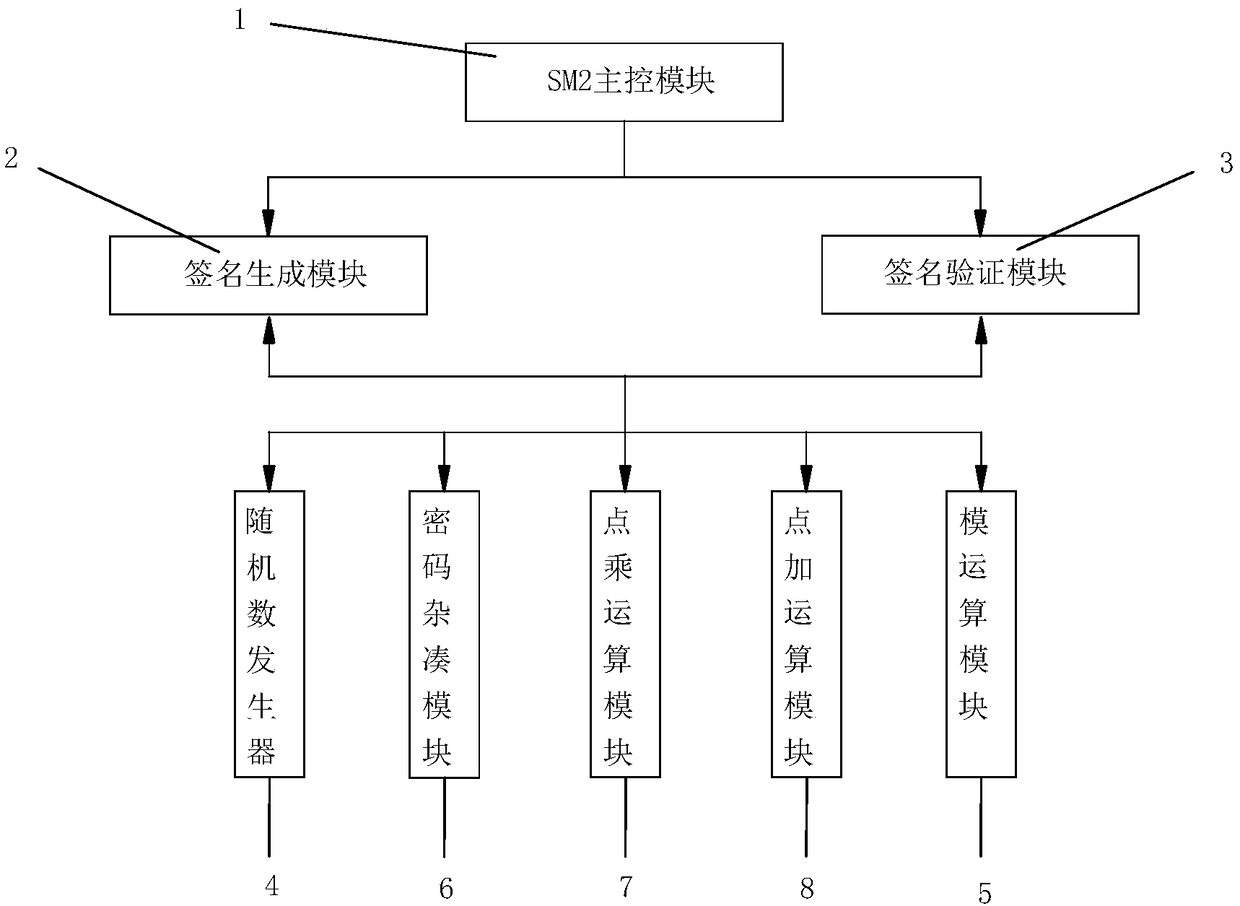
An SM2 elliptic curve signature verification hardware system and method resistant to differential power consumption attack
InactiveCN109214195AEnsure safetyGood anti-differential power attackDigital data protectionInternal/peripheral component protectionRandomizationPower attack
The invention relates to an SM2 elliptic curve signature verification hardware system and method for resisting differential power consumption attack, the anti-differential power consumption attack method of the invention is applied to scalar multiplication, by adding the improved randomized scalar method to the point multiplication operation, the correlation between the real key information and the power curve is destroyed, which makes it difficult for the power analysis to obtain the information to resist the power analysis, and ensures the security of the differential power attack, thus playing a very good role in resisting the differential power attack. And this method is simple and easy to implement, and can be integrated into a variety of encryption chips and other hardware devices.
Owner:GUANGDONG UNIV OF TECH
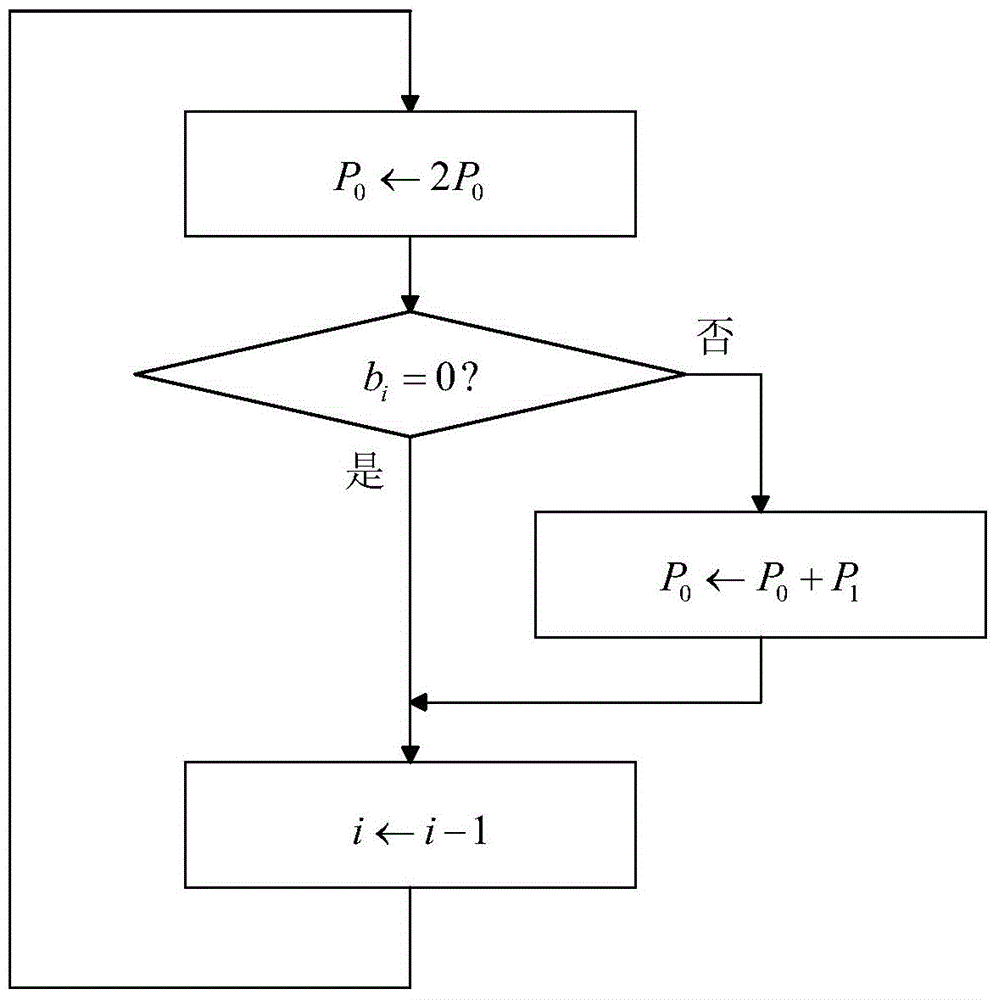
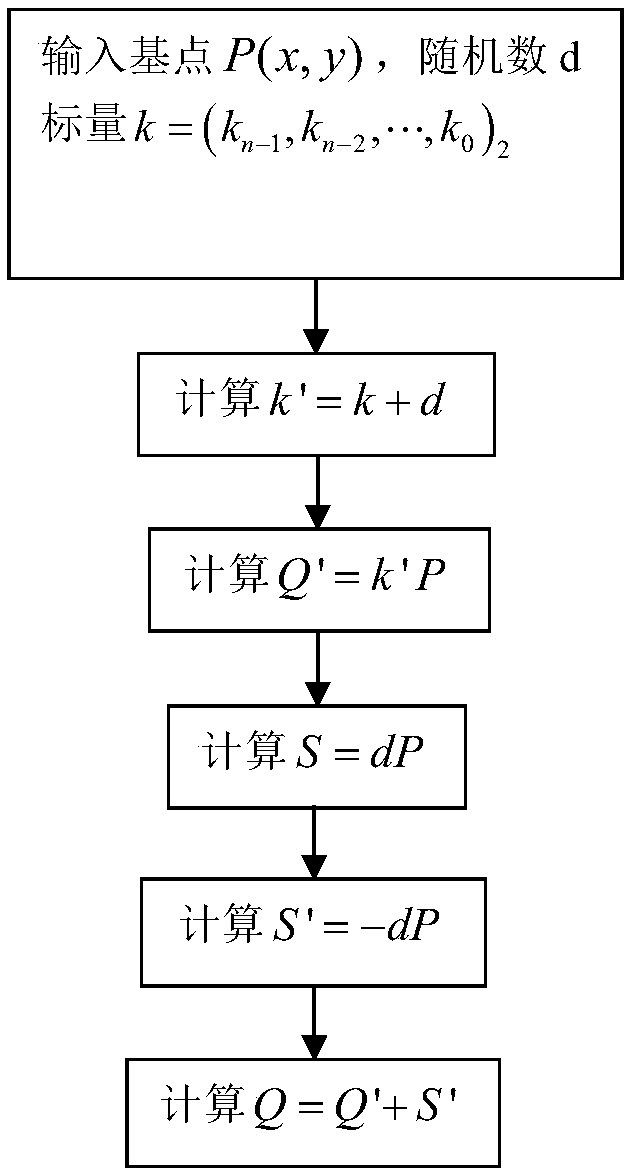
Method for efficiently protecting elliptic curve cryptography against simple power analysis attacks
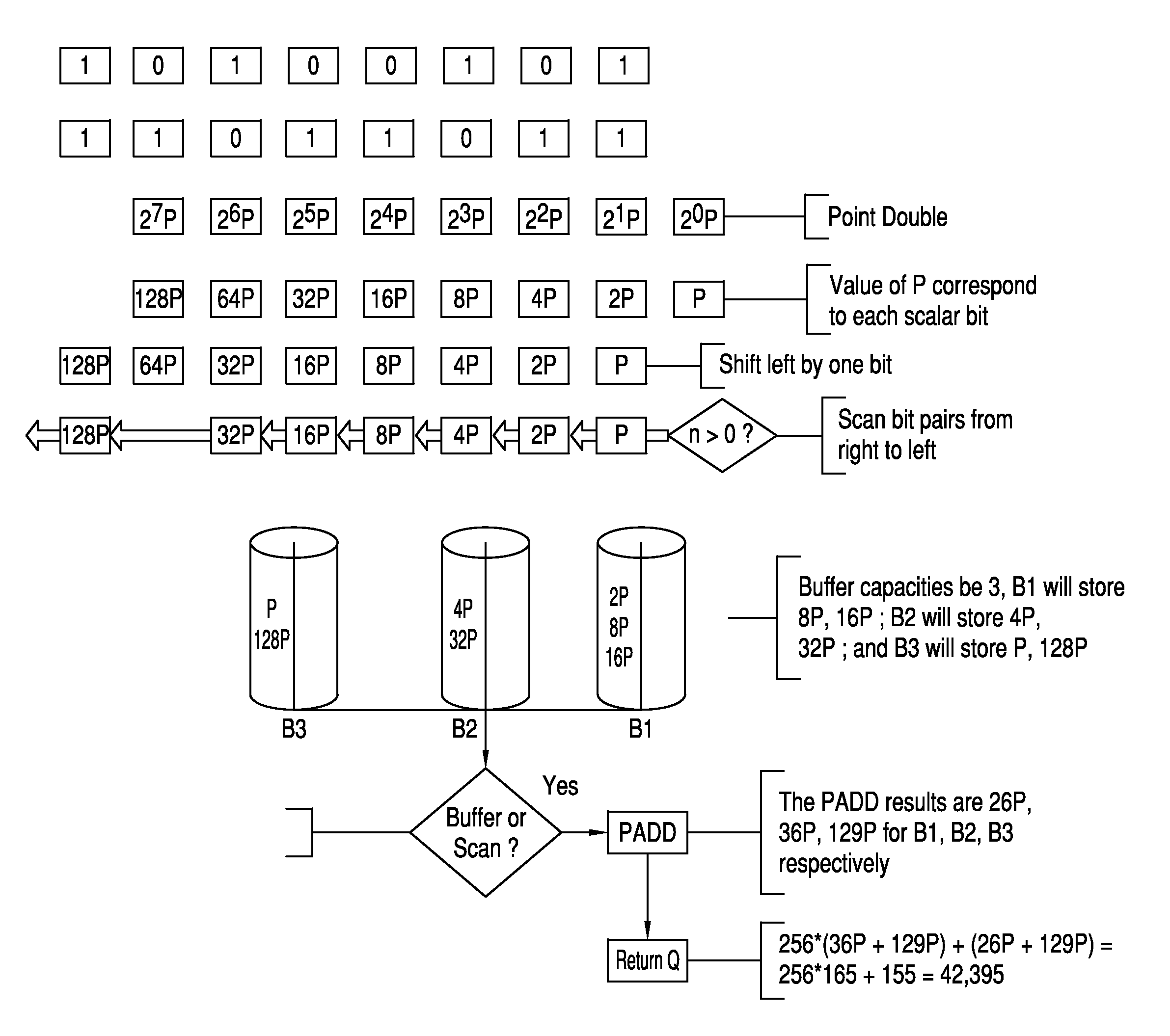
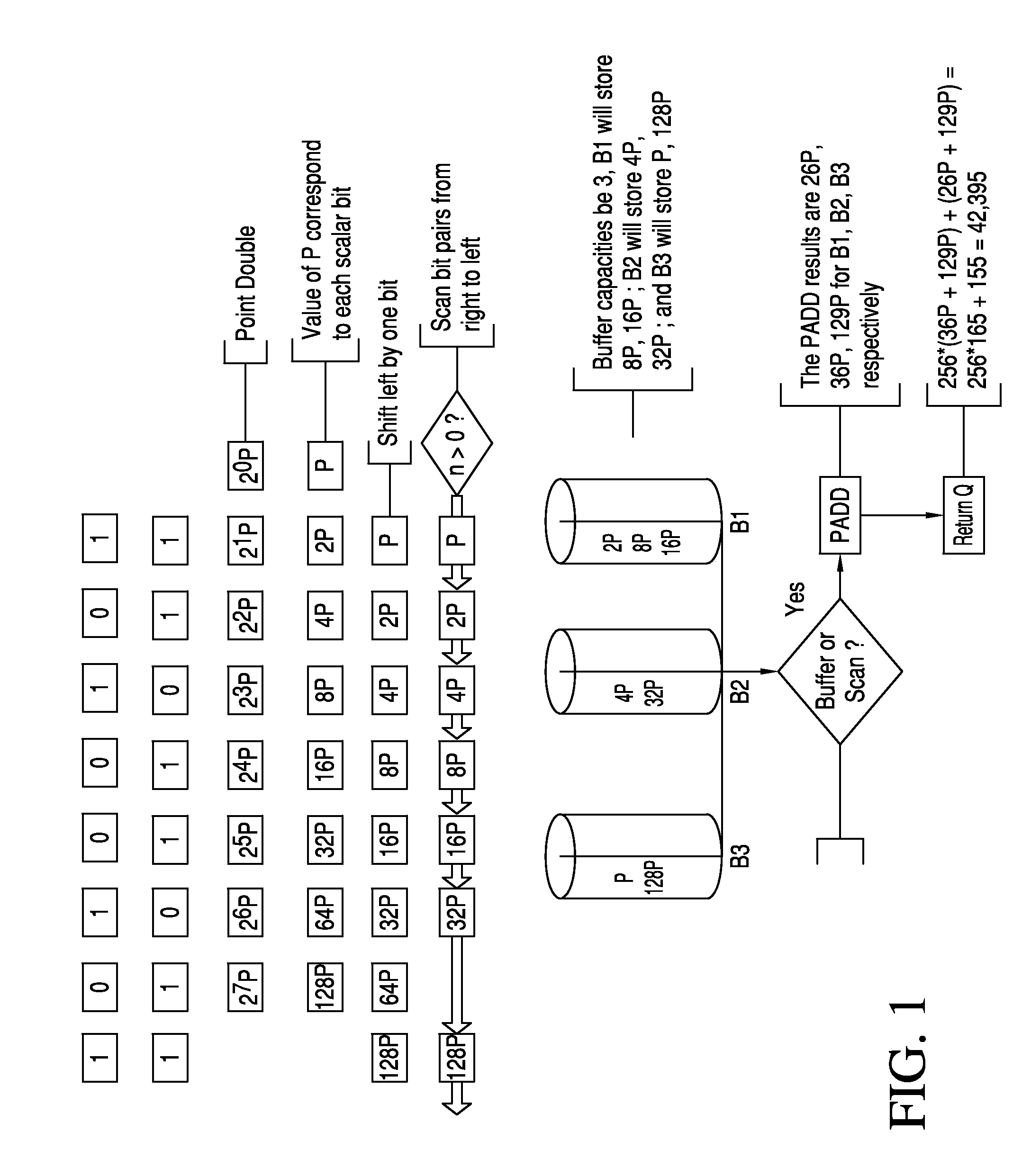
InactiveUS20160134417A1Improve efficiencyPublic key for secure communicationSecret communicationPower attackRight-to-left
A method and device for protecting elliptic curve cryptography against simple power attacks is disclosed. The method is based on a processor such as a computer equipped to encrypt and decrypt communications and selecting and entering a point P on an elliptic curve in the computer. The processor provides k copies of the point P (kP). The processor is used to divide a string of Ks into two equal length partitions that are scanned from right to left and performing point doubling operation and delay the point addition operation by storing the some doubled points in a buffer for later performing of addition operation.
Owner:UMM AL QURA UNIVERISTY
Method and apparatus for minimizing differential power attacks on processors
InactiveUS20070053509A1Minimizes attackMinimize their effectivenessEnergy efficient ICTPublic key for secure communicationComputer hardwarePower attack
Owner:MALIKIE INNOVATIONS LTD
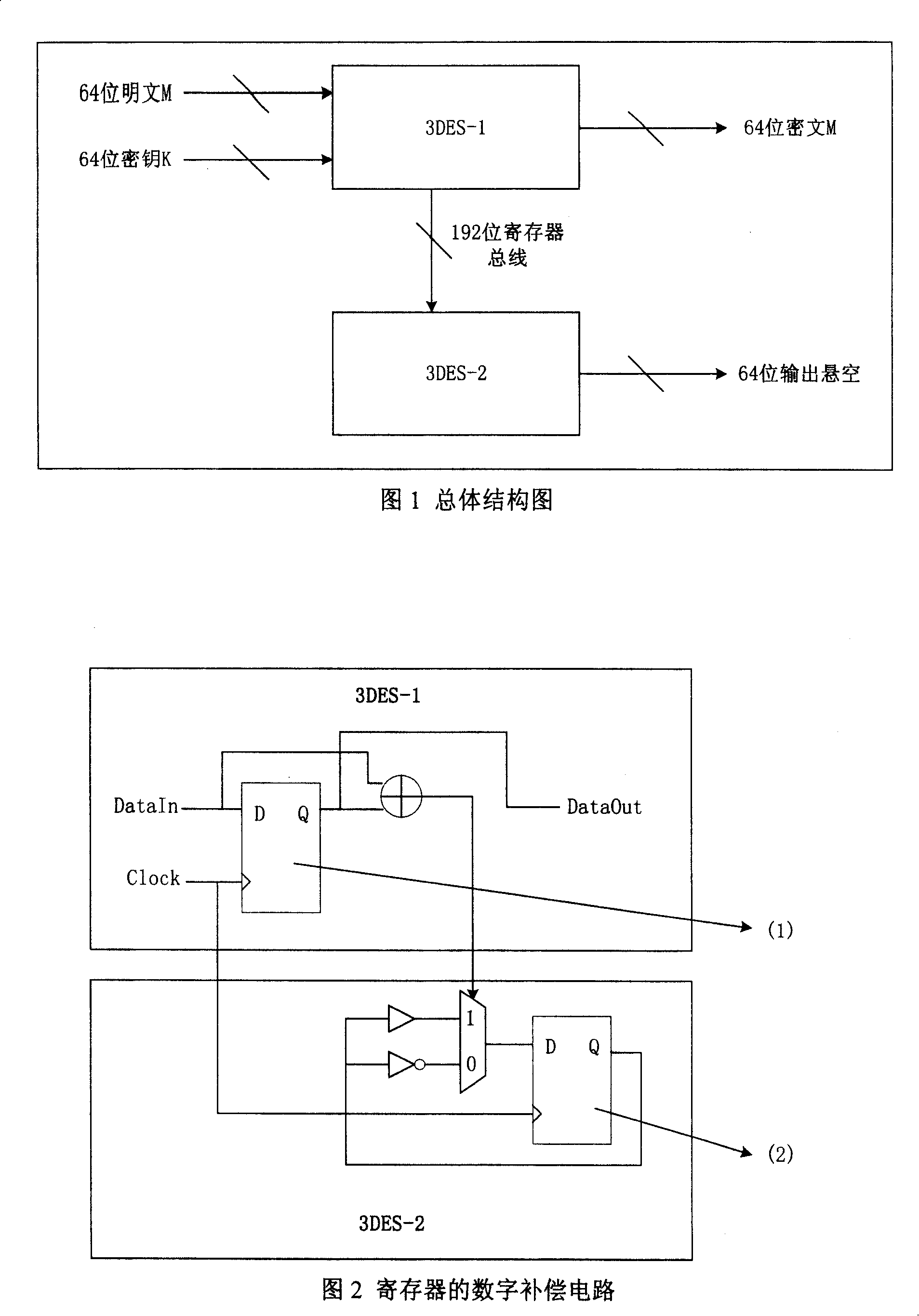
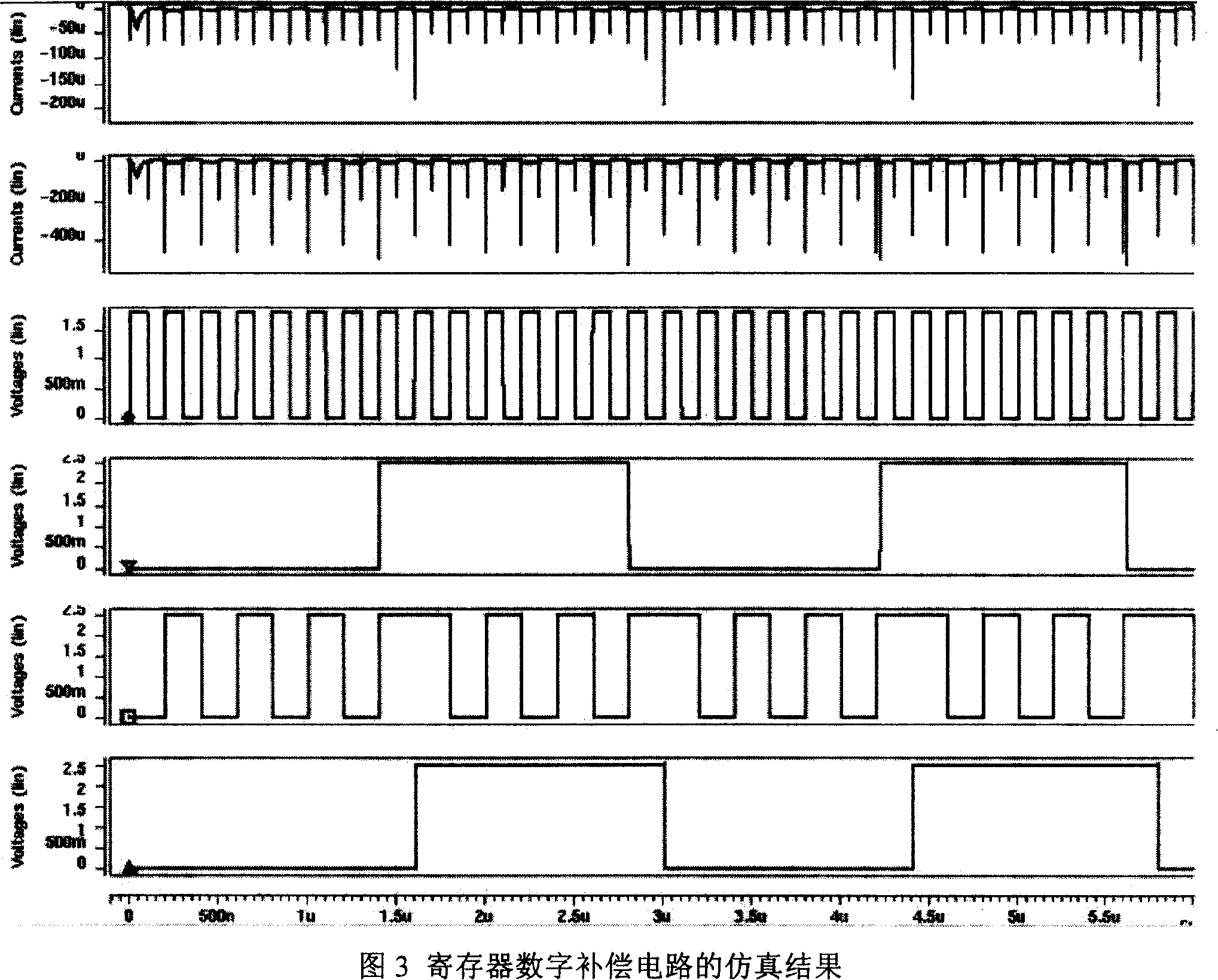
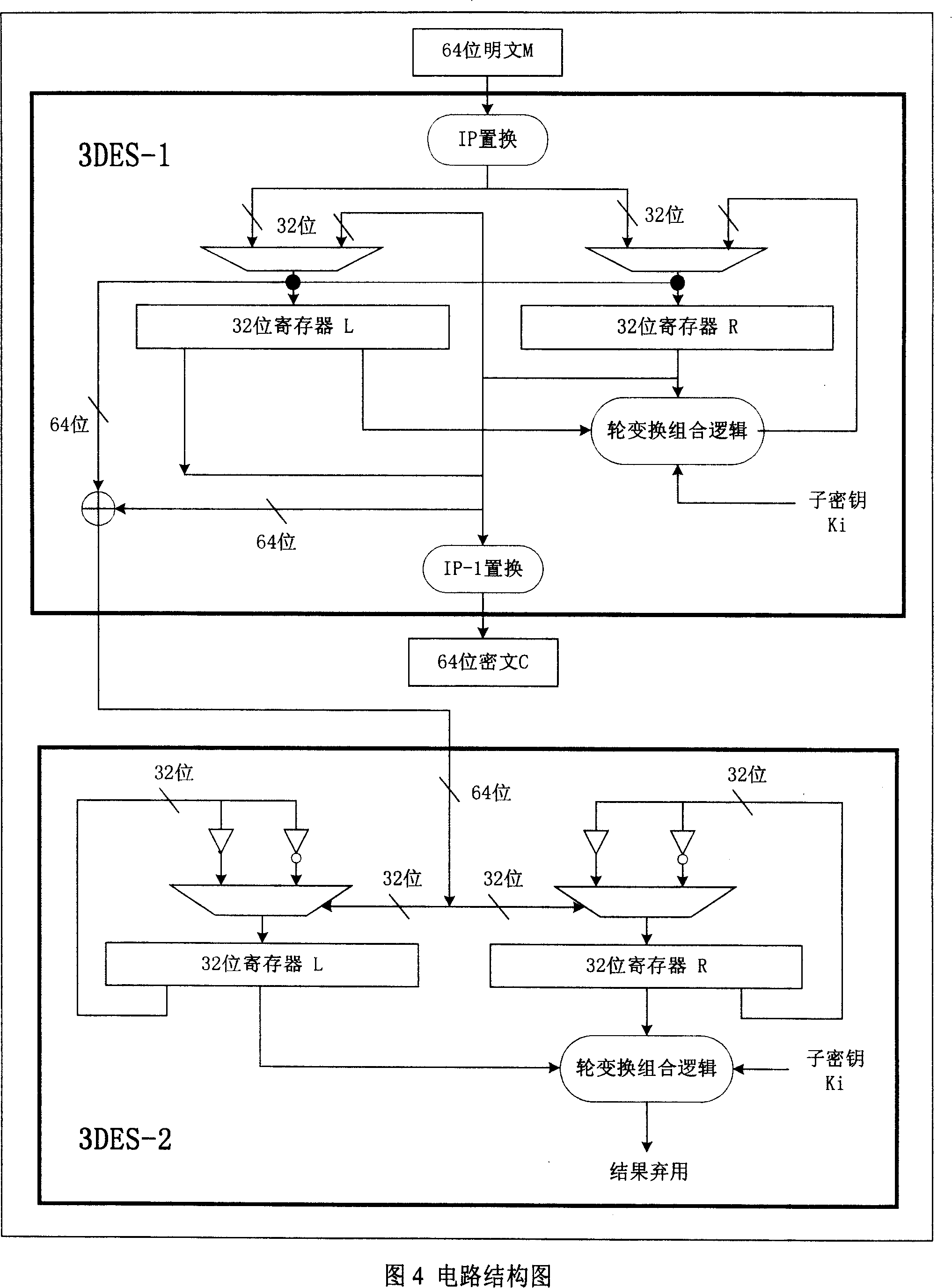
Hardware 3DES for using digital power consumption compensation to prevent from power consumption power attack
InactiveCN101150392AAchieve securityPrevent Power AttacksEncryption apparatus with shift registers/memoriesPower supply for data processingCoprocessorSmart card
This invention relates to a hardware 3DES preventing power loss attack by digital power loss compensation used in intelligent card chips of a safety applied field, which utilizes a method for digital circuit power loss compensation to design two symmetrical 3DEG hardware circuits, one for getting ciphering result and the other for compensaing power loss to a first 3DEG circuit only playing the role of a coprocessor of ciphered operation in an intellident card, which can prevent power loss attack in the intelligent card field at the same time when realizing 3DEG ciphered operation at high speed.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
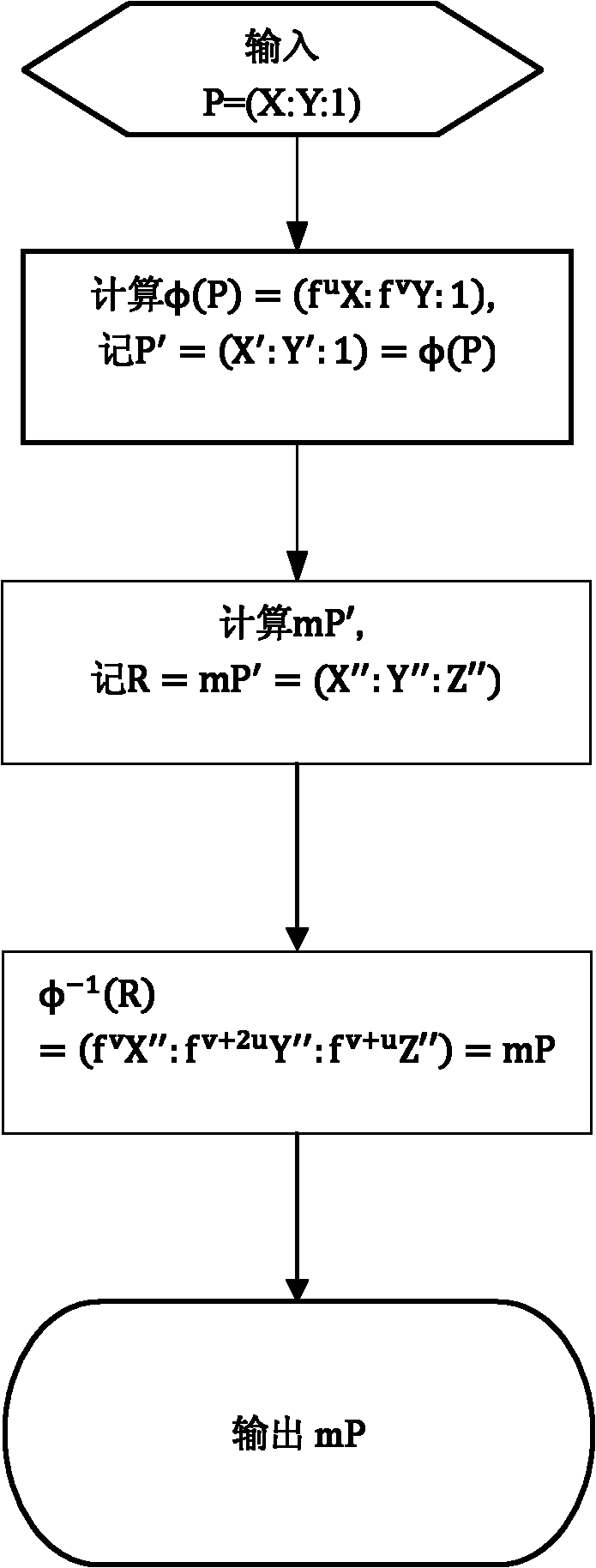
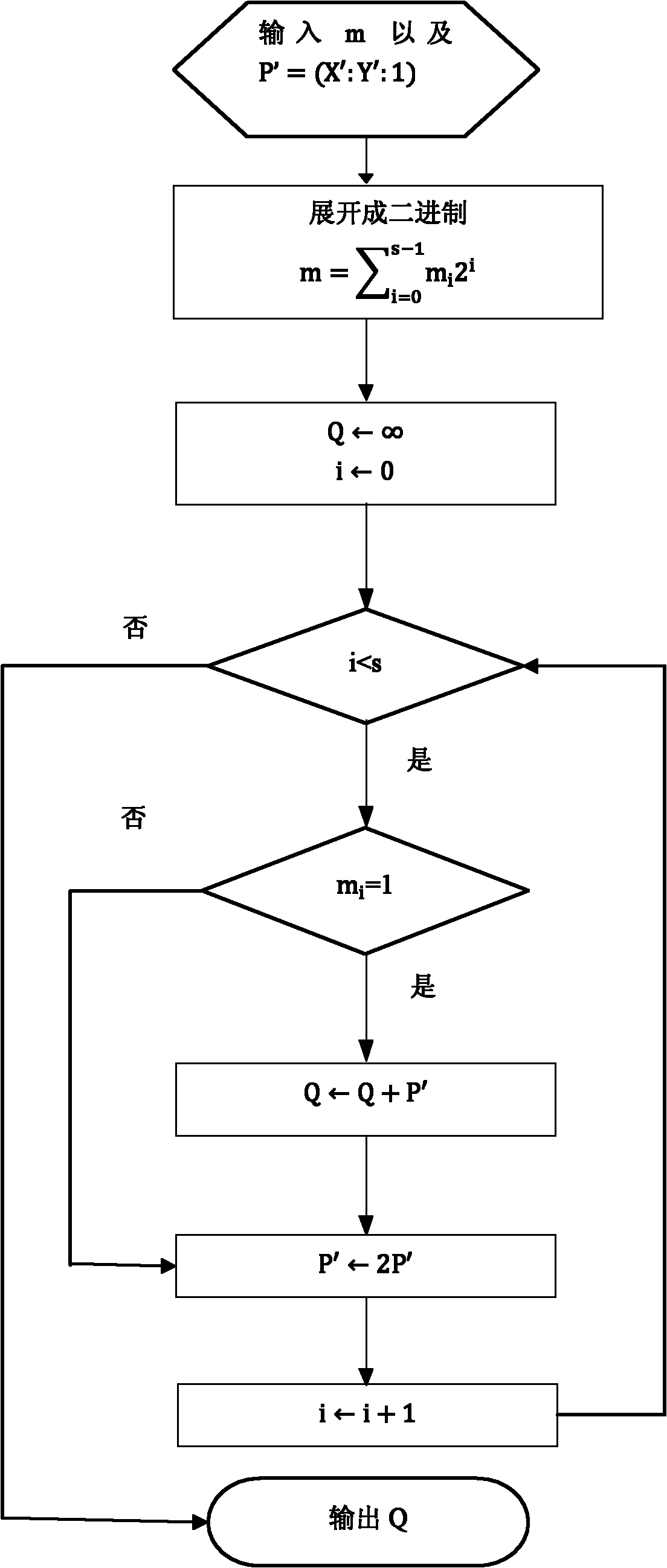
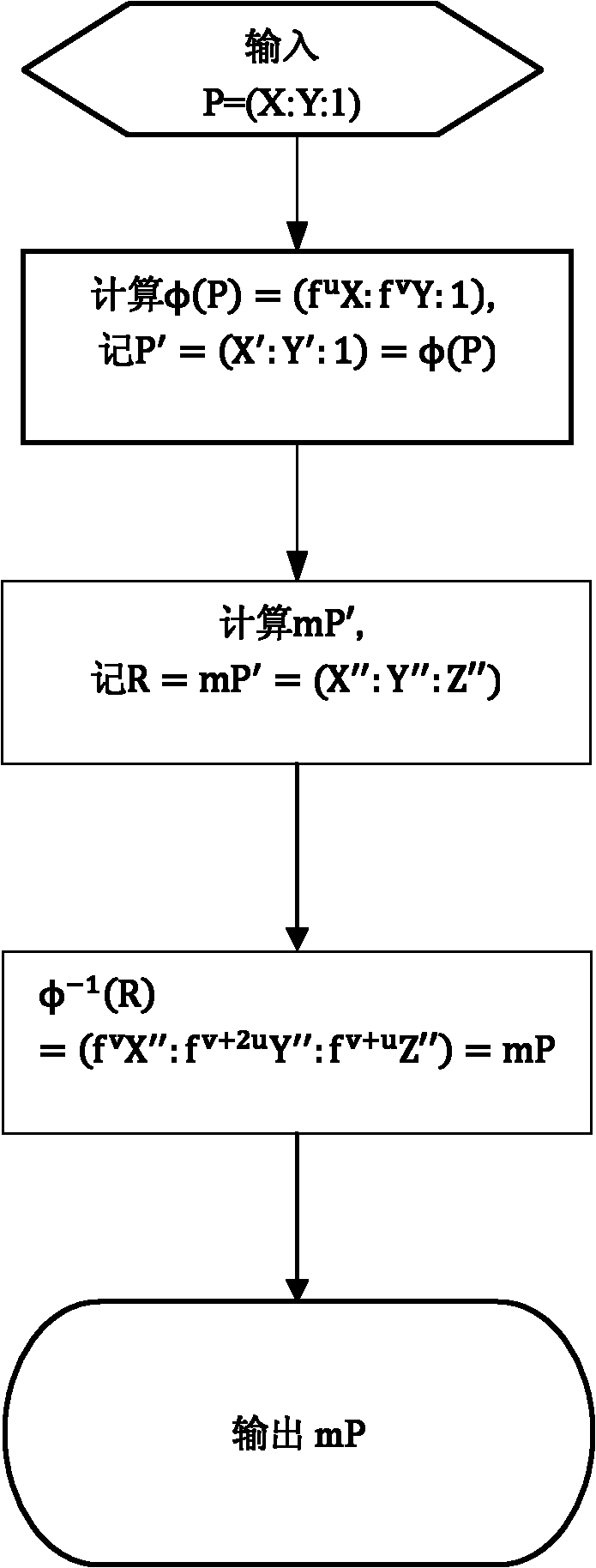
Method for enabling elliptic curve cryptography to defend differential power attack
The invention discloses a method for enabling elliptic curve cryptography to defend differential power attack. The method comprises the following steps: step 1) selecting a non-zero point P=(X:Y:1) on an elliptic curve E(F2<n>) and giving any integer m; step 2) calculating isomorphic mapping phi (P)=(fuX:fvY:1), recording P'=(X': Y': 1)=phi (P); step 3) calculating scalar multiplication mP', and recording a point R=mP'=(X'':Y'':Z''); and step 4), calculating isomorphic and inverse mapping phi<-1> (R)=(fvX'':fv+2uY'':fv+uZ'')=mP. The differential power attack can be defended with very low time cost by utilizing the method.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
AES algorithm oriented power attack resisting method based on register mask
ActiveCN106452725AReduce overheadWill not work with lower frequencyEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresProcessor registerPower attack
The invention discloses an AES algorithm oriented power attack resisting method based on a register mask. The method comprises the following steps: adding a random number generator and a register protection module in an AES algorithm, wherein the register protection module comprises a first XOR unit, a second XOR unit and a register; saving an intermediate result in the register after performing XOR on an intermediate result needing to be saved and a random number when updating the intermediate result in the register, and saving the random number at the same time; and reading a value in the register and performing the XOR on the value and the saved random number when reading the intermediate result in the register. Through the adoption of the method disclosed by the invention, the randomness of the storage value in the register is guaranteed, the Hamming distance leakage in the AES cryptographic algorithm is effectively hidden, and the power attack based on a Hamming distance model can be effectively resisted.
Owner:SOUTHEAST UNIV
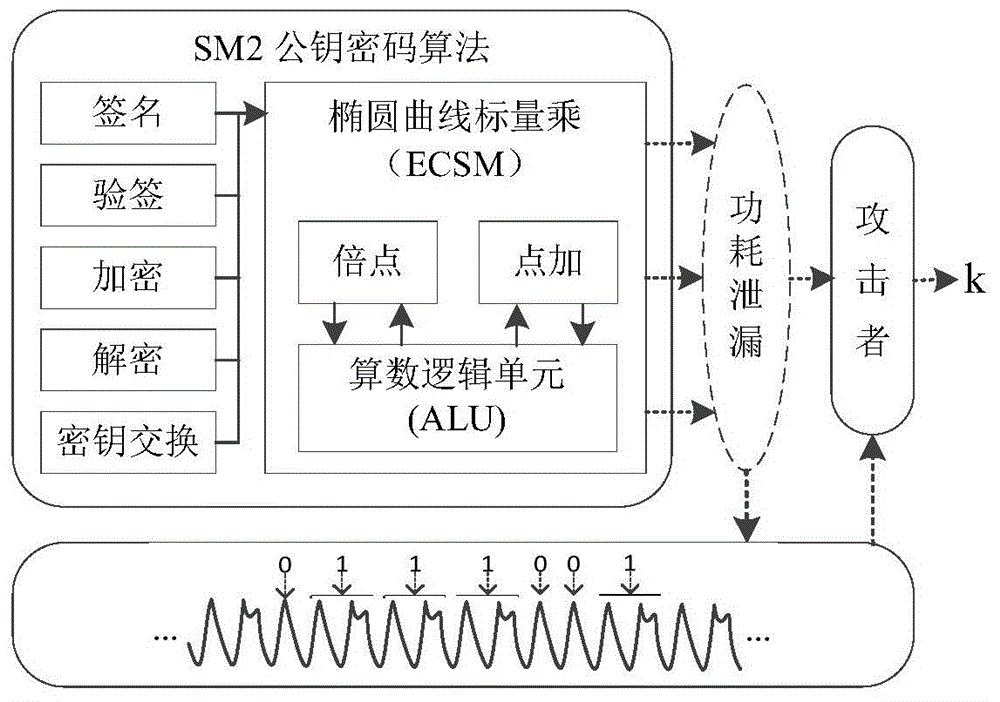
Side channel attack method for implementation of RSA (Rivest, Shamir and Adleman) cipher algorithms M-ary
ActiveCN104796250AEfficient analysisEasy to analyzeEncryption apparatus with shift registers/memoriesLinear correlationPower attack
The invention discloses a side channel energy analytical attack method by the aid of multiplication output during implementation of power residue computing algorithms M-ary in RSA (Rivest, Shamir and Adleman) cipher algorithms. A core of the side channel energy analytical attack method includes that multiplication output is used as an attack object to implement CPA (correlation power attack) when power residue computing is implemented by the aid of the algorithms M-ary. The method includes steps of (1), acquiring signals and building sampling matrixes; (2), selecting the multiplication output to be used as the attack object; (3), determining correlation models; (4), guessing circulation index values and acquiring intermediate value matrixes by means of computing; (5), acquiring simulation energy consumption matrixes by means of computing; (6), acquiring linear correlation coefficients among the matrixes determined in the steps (1) and (5) by means of computing and obtaining correct circulation indexes by means of attacking; (7), repeatedly carrying out steps (4), (5) and (6) to obtain all correct circulation indexes by means of attacking, and serially connecting all the correct circulation indexes with one another to obtain complete indexes. The side channel energy analytical attack method has the advantages that the RSA cipher algorithm analytical attack flexibility and effectiveness can be enhanced by the aid of the novel side channel attack method for the algorithms M-ary, and an RSA cipher algorithm analytical attack success rate can be increased by the aid of the novel side channel attack method for the algorithms M-ary.
Owner:CHENGDU UNIV OF INFORMATION TECH +3
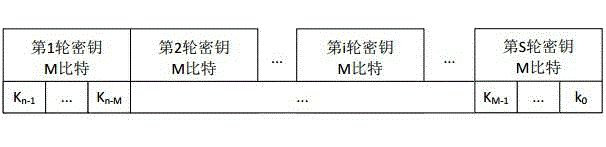
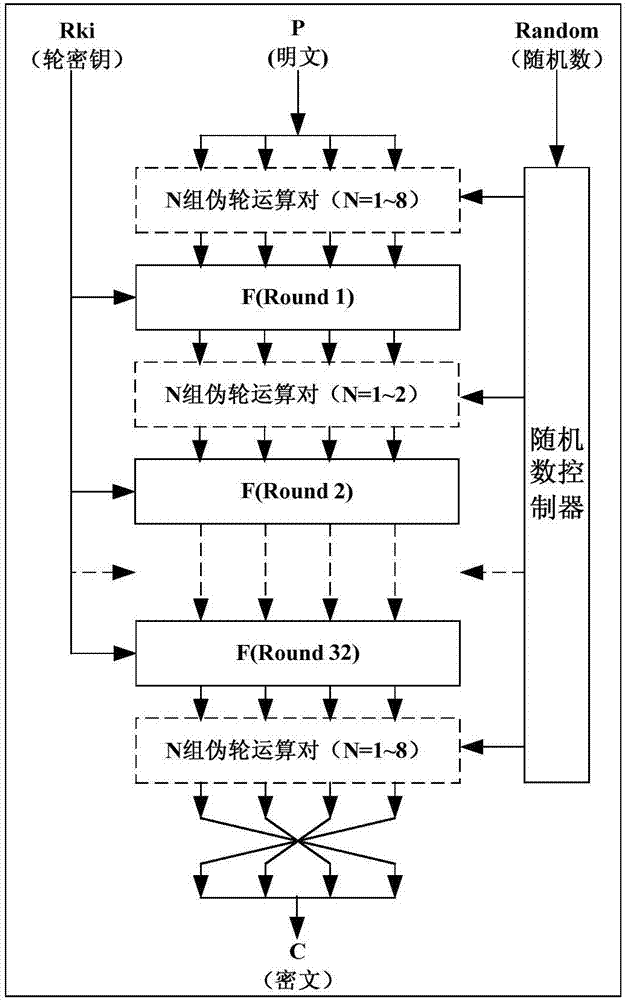
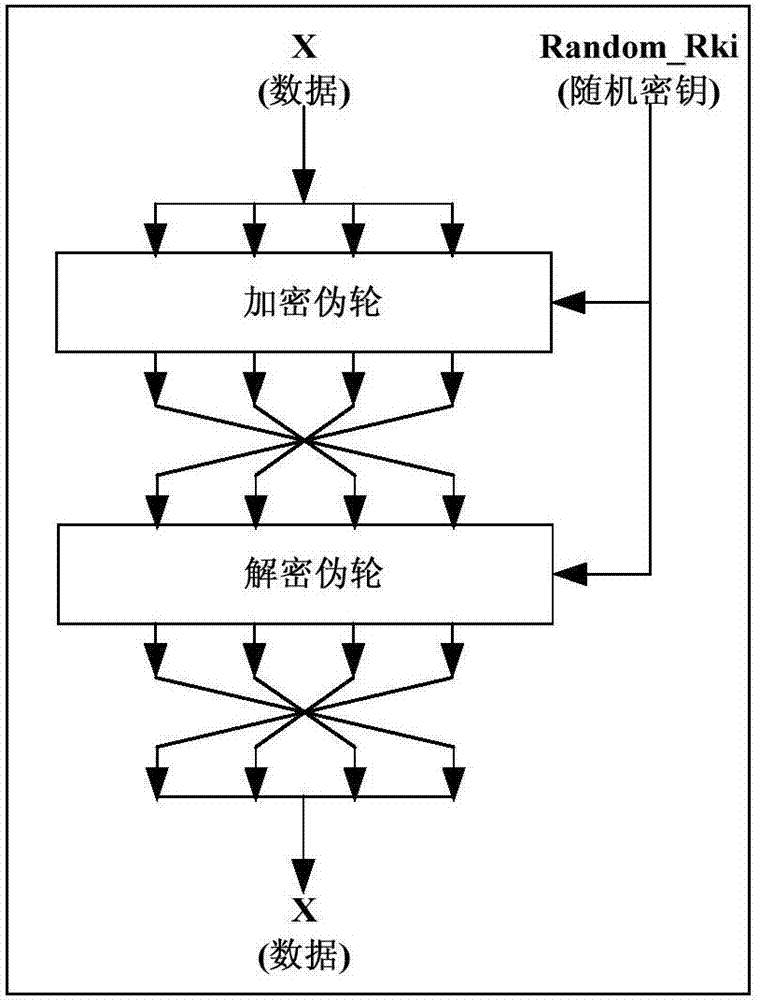
Power-attack-resistant SM4 algorithm hardware implementation system
InactiveCN107154843ADestroy associationPower consumption attack defenseEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresSmart cardHardware implementations
The invention discloses a power-attack-resistant SM4 algorithm hardware implementation system, and relates to the technical field of information safety. According to the system, a pseudo wheel operation pair module and a random number controller are added to an SM4 algorithm hardware circuit, thereby achieving the random insertion of a pseudo wheel operation pair between the wheel operations in the SM4 encryption process. The value of data passing through the pseudo wheel operation pair will not change, but the power consumption features of a circuit and the execution time sequence features of the circuit are disturbed. The correlation between the data and the power consumption is broken, and the power attack is effectively prevented. The system can be used in a safety chip of an intelligent card and a USBKey, and also can be suitable for various types of safety chips which need to prevent the power attack for the SM4.
Owner:北京万协通信息技术有限公司
Kernel-based power consumption and isolation and defense against emerging power attacks
ActiveUS20190004917A1Increase power consumptionHardware monitoringPower supply for data processingEngineeringPower usage
A system and method for achieving power isolation across different cloud tenants and workloads is provided. The system includes a model of per-workload power consumption and an approach for attributing power consumption for each container. It allows a cloud provider to detect abnormally high power usage caused by specific containers and / or tenants, and to neutralize the emerging power attacks that exploit information leakages in the public container cloud. The approach also enables the provider to bill tenants for their specific power usage. Thus, the technique herein provides a mechanism that operates to attribute power consumption data for each container to defend against emerging power attacks, as well as to make it feasible to develop a cloud billing model based on power usage. The mechanism defends against emerging power attacks in container cloud offerings by implementing in a power-based namespace workflow in an OS kernel. The namespace workflow partitions the power consumption information for each container.
Owner:IBM CORP
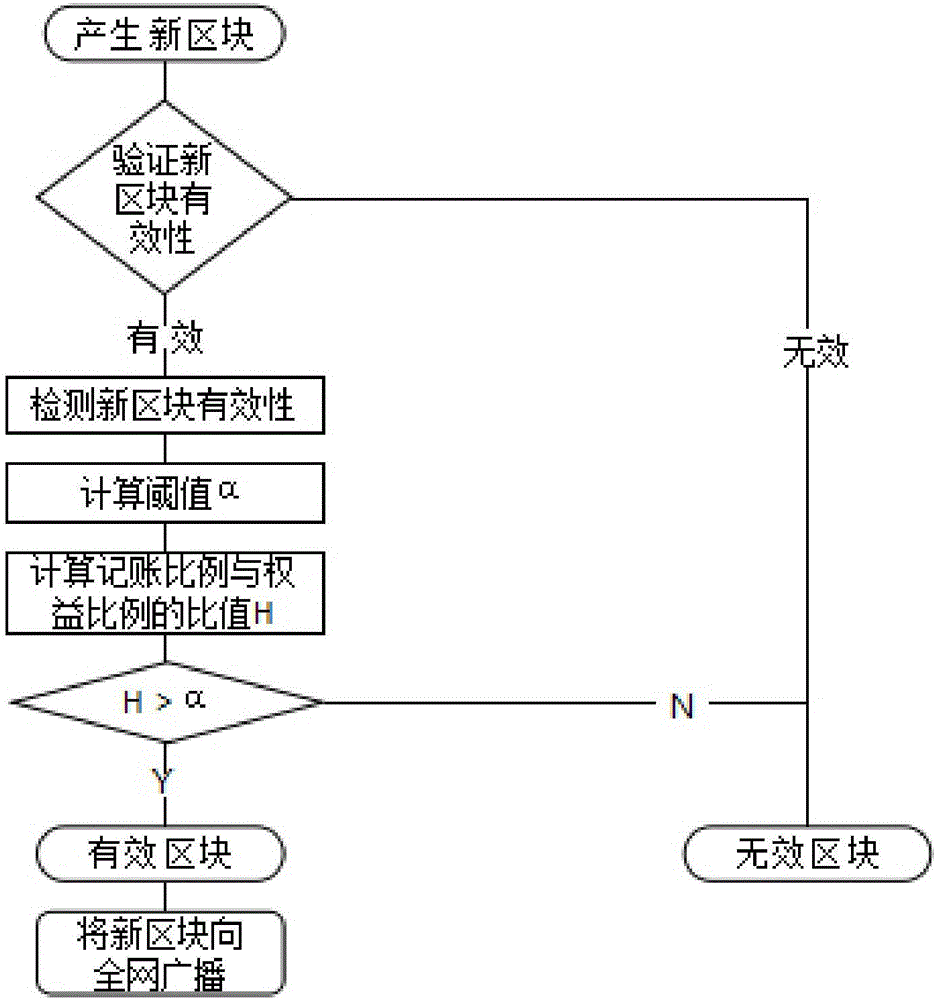
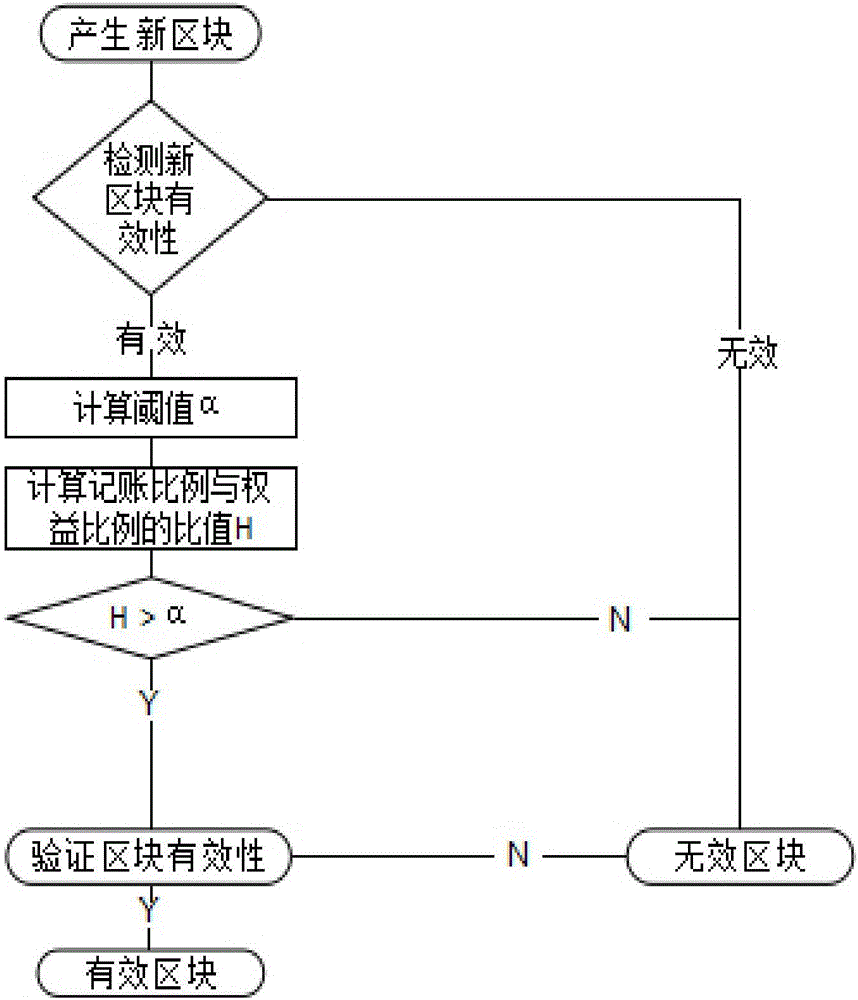
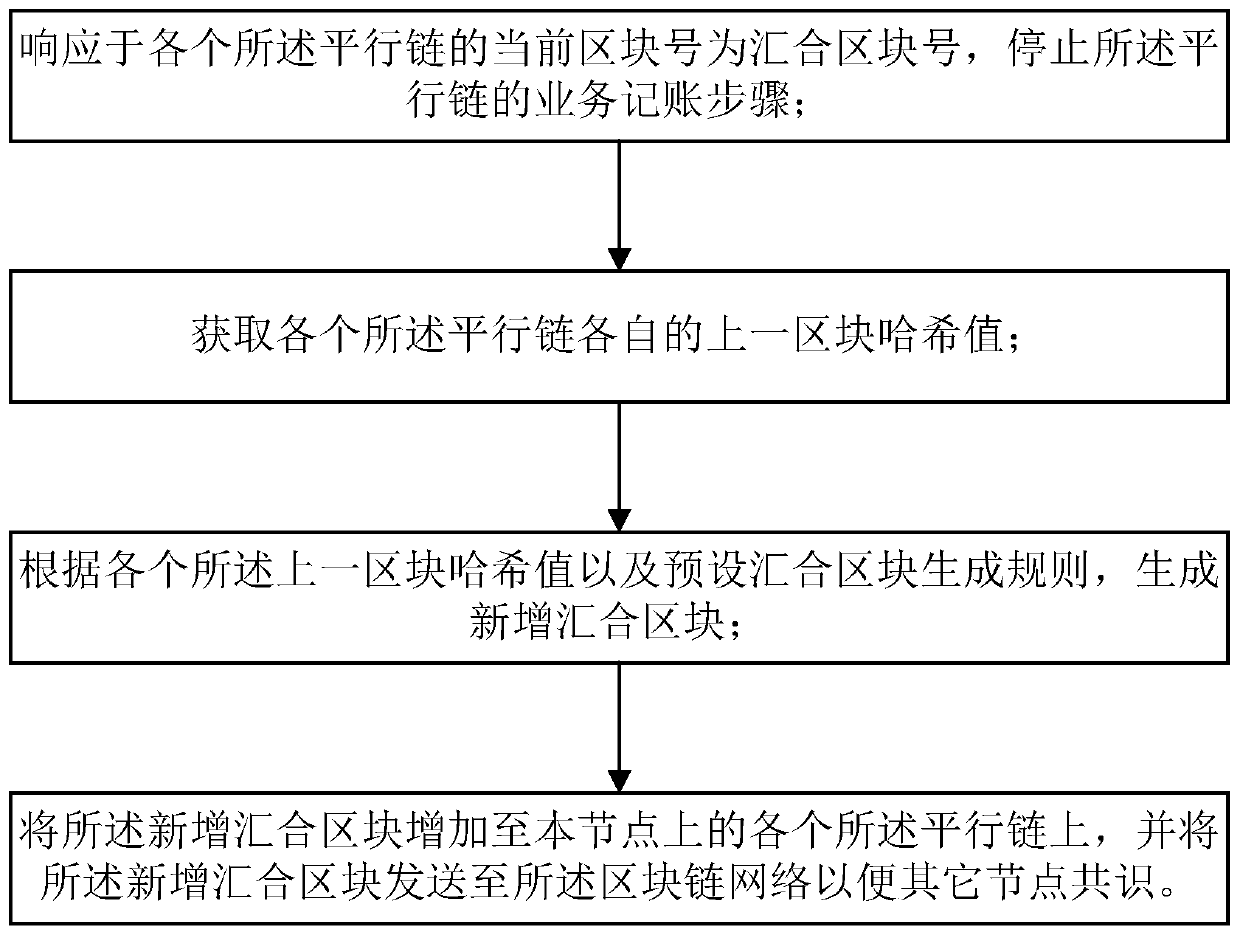
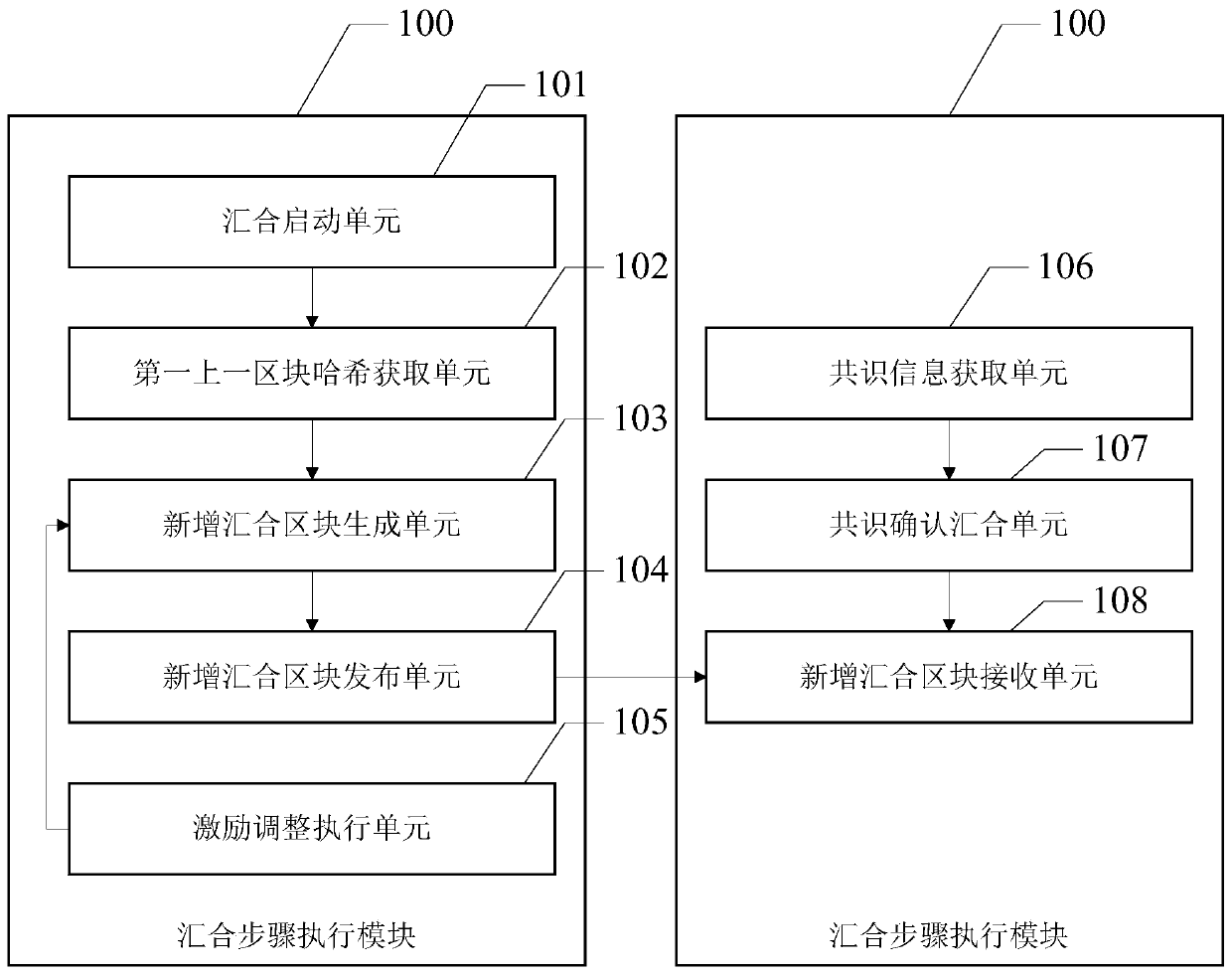
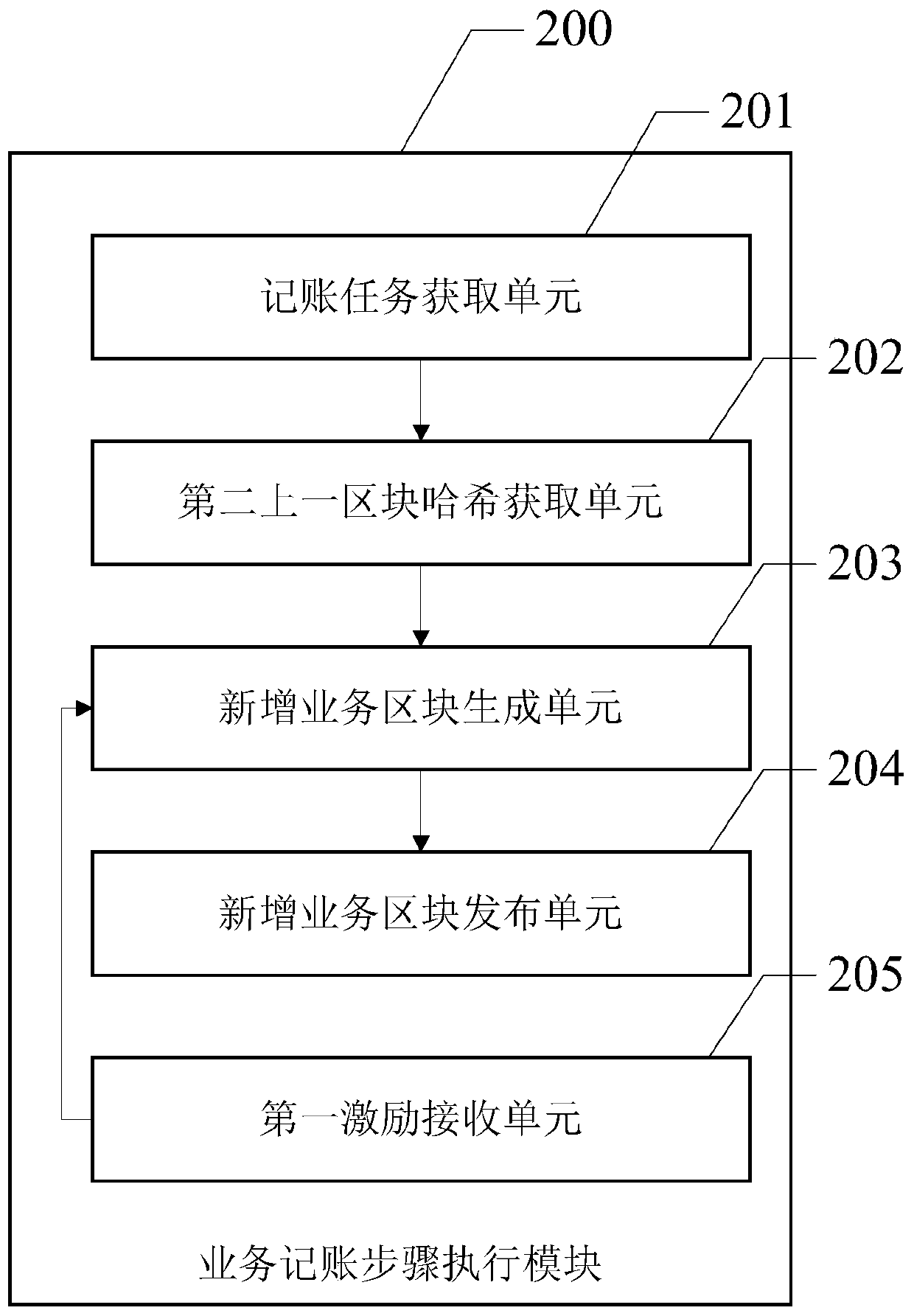
An account book accounting method of a block chain network with parallel chains periodically converged
ActiveCN109711842AReduce hardware costsImprove computing power offensive and defensive capabilitiesPayment protocolsPayment circuitsChain networkPower attack
The invention discloses an account book bookkeeping method of a blockchain network with parallel chains periodically converged, which relates to the field of blockchain and comprises a service bookkeeping step and a convergence step. The confluence step comprises the steps that firstly, in response to the fact that the current block number of each parallel chain is a confluence block number, stopping the service accounting step of the parallel chains; then, obtaining the Hash value of the previous block of each parallel chain; then, generating a newly added convergence block according to the hash value of each previous block and a preset convergence block generation rule; and finally, adding the newly-added convergence block to each parallel chain on the node, and sending the newly-added convergence block to the block chain network so as to facilitate consensus of other nodes. The block chain network comprises a plurality of parallel chains, the hardware cost at the initial stage of block chain project construction is reduced, meanwhile, a plurality of block chains are regularly crossed to form a convergence block, and the computing power attack defense capability of the whole block chain network is improved.
Owner:西安纸贵互联网科技有限公司
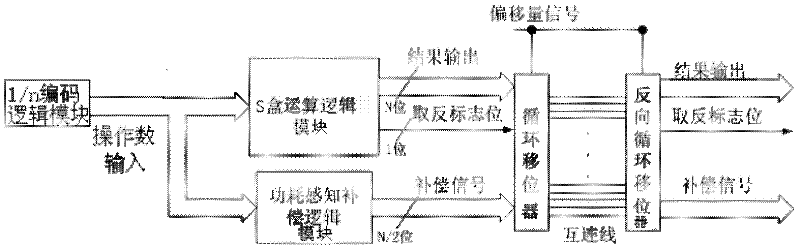
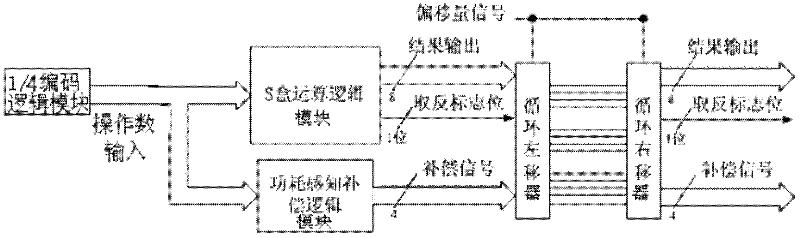
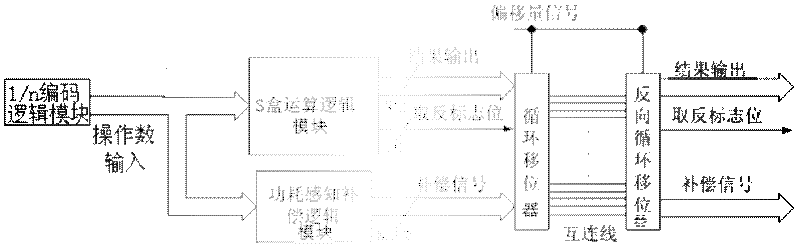
Power-aware power balancing S box unit circuit and application method thereof
ActiveCN102509145AReduce power overheadLower power consumption levelsEncryption apparatus with shift registers/memoriesRecord carriers used with machinesComputer modulePower balancing
The invention discloses a power-aware power balancing S box unit circuit and an application method thereof, belonging to the technical field of power attack resistance. The power-aware power balancing S box unit circuit comprises an S box arithmetic logic module, a power-aware compensation logic module, a cycling shifter and a backcycling shifter, wherein the S box arithmetic logic module and the power-aware compensation logic module are simultaneously driven by an operand input port, and the S box arithmetic logic module calculates output values at a result output port and output values at a negative flag bit output port in accordance with input data; and the power-aware compensation logic module calculates output values at a compensation signal output port in accordance with the input data. The invention reduces the power consumption of power balancing, and provides the implementation of equivalent load balancing of multiple data lines in a random exchange interconnection line manner for the load balancing problem of the multiple data lines.
Owner:TSINGHUA UNIV
Method of countering side-channel attacks on elliptic curve cryptosystem
ActiveUS8345863B2Improve securityEffective attackMultiple keys/algorithms usageData taking preventionElectric forceFault detection algorithm
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com