Encryption method and device using random clock based on chaos
A random clock and clock technology, which is applied in the field of information security and can solve the problems of poor security performance of linear feedback shift registers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
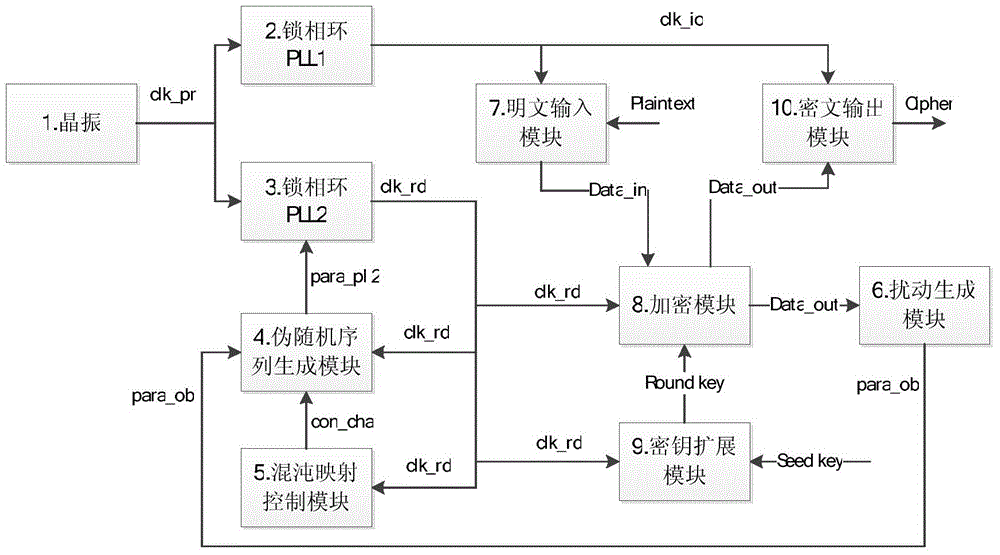
[0025] The specific implementation steps are as figure 1 The overall structure diagram and Figure 4 The method flow chart is as follows:
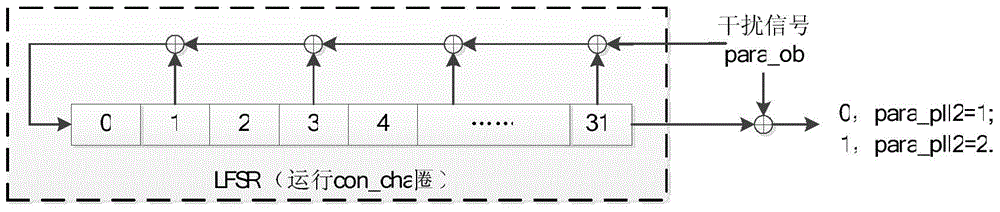
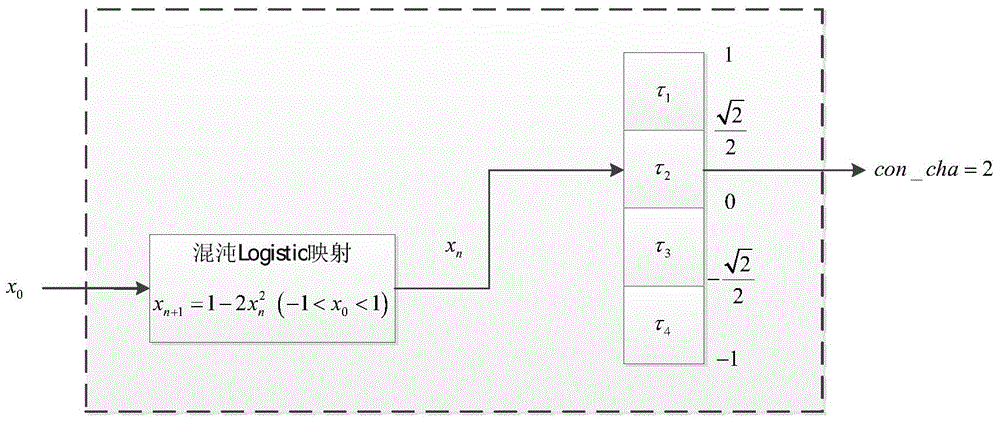
[0026] Step 1: Initialization of the chaotic map control module and the pseudo-random sequence generation module. First define the interference signal para_ob=0, give a certain initial value to the chaotic map control module and the pseudo-random sequence generation module, and then run 180 clocks respectively, so as to realize the initialization of the chaotic map control module and the pseudo-random sequence generation module procedure, go to step 2.
[0027] Step 2: Enter the seed key. There are two ways to enter the seed key. It can be entered manually or automatically generated by an external physical noise source. Go to step 3.
[0028] Step 3: The plaintext input module reads the plaintext and inputs it into the encryption module. The phase-locked loop PLL1 accepts the pre-calculated frequency division coefficient para_pll1, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com