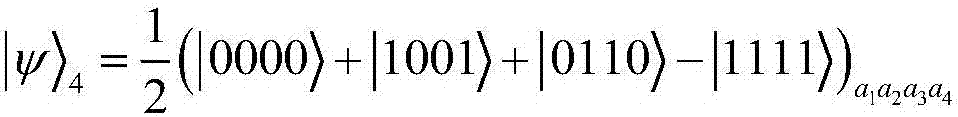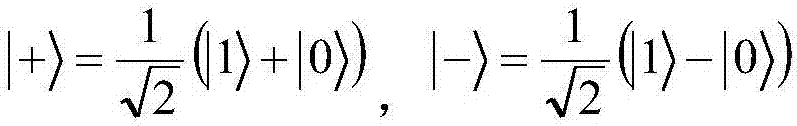Patents
Literature
489 results about "Pseudorandom sequence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
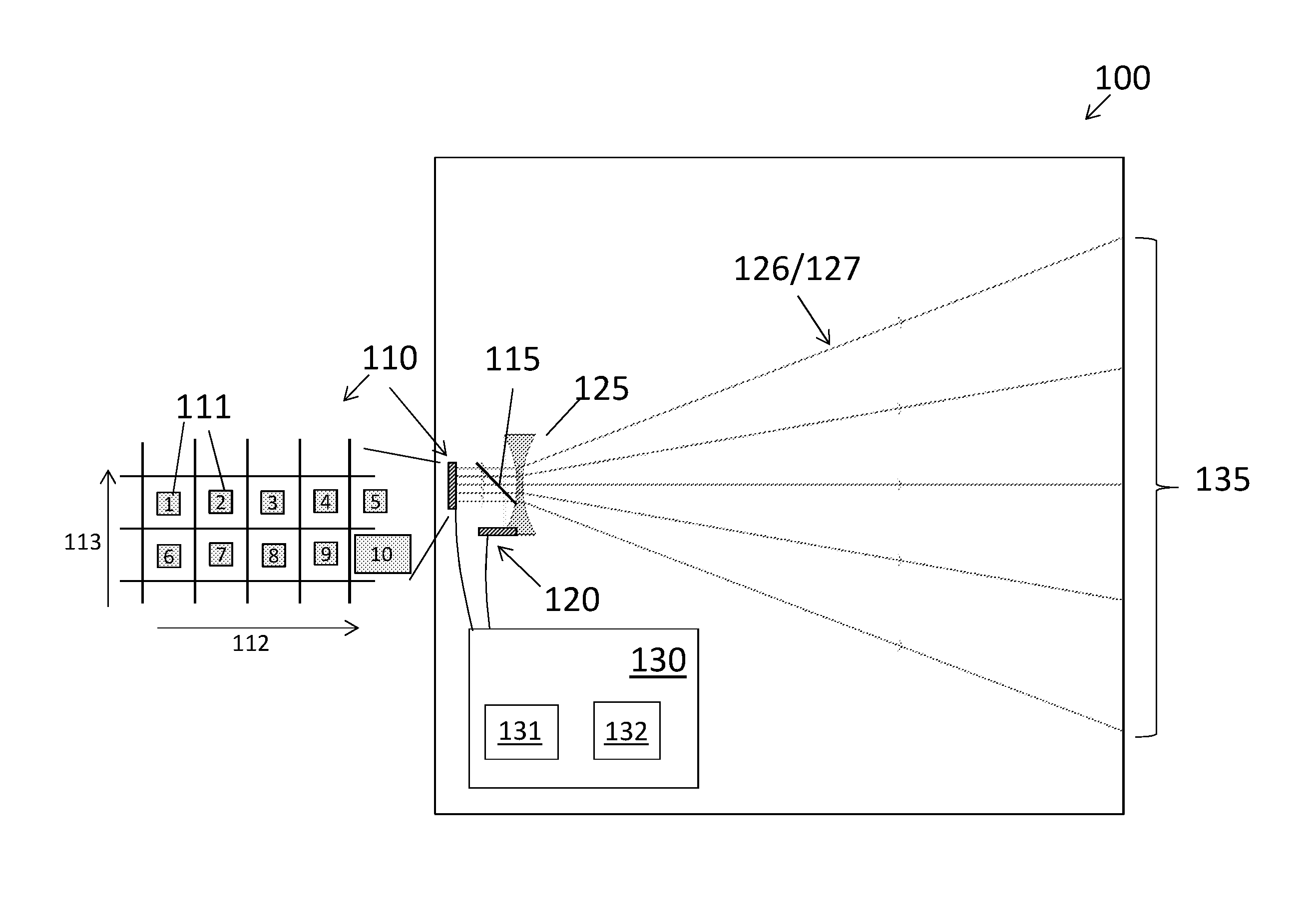
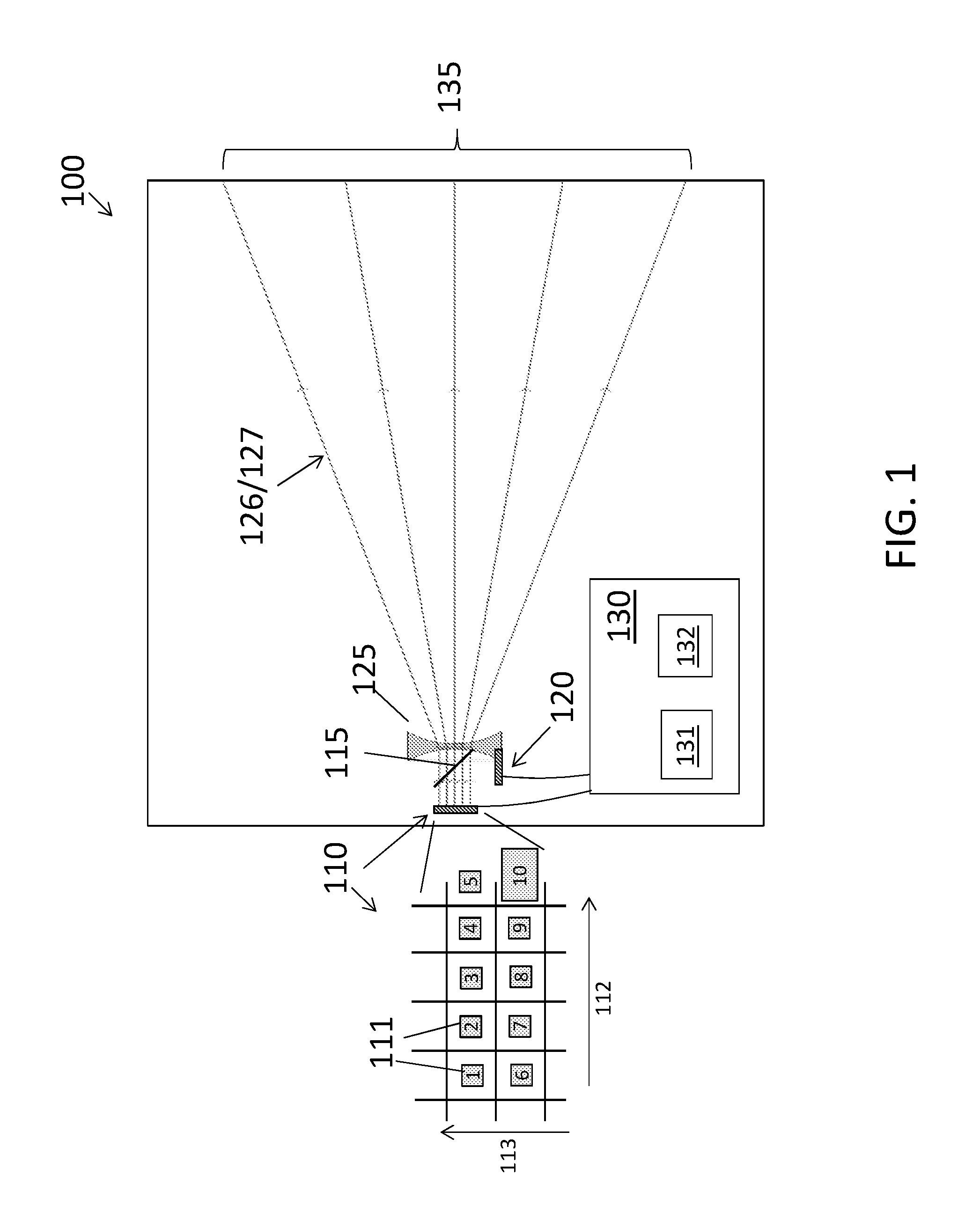
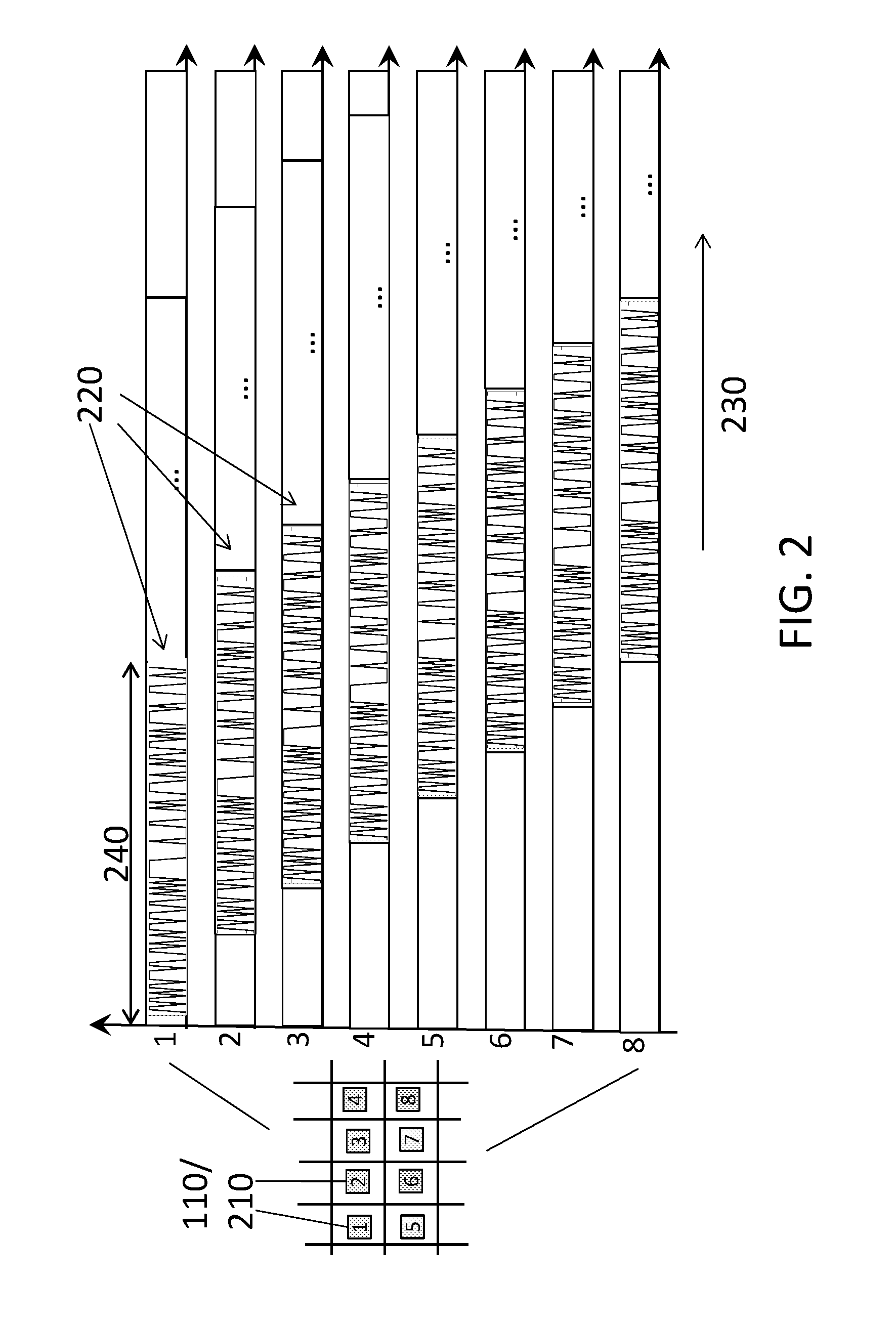
Pseudo-Random Sequence (Gold Sequence) This is not a specific physical channel, but this sequence (variation of the sequence) are used in many way to generate a specific sequence itself (e.g, Downlink Reference Signal) or to scramble the data of a specific channel.
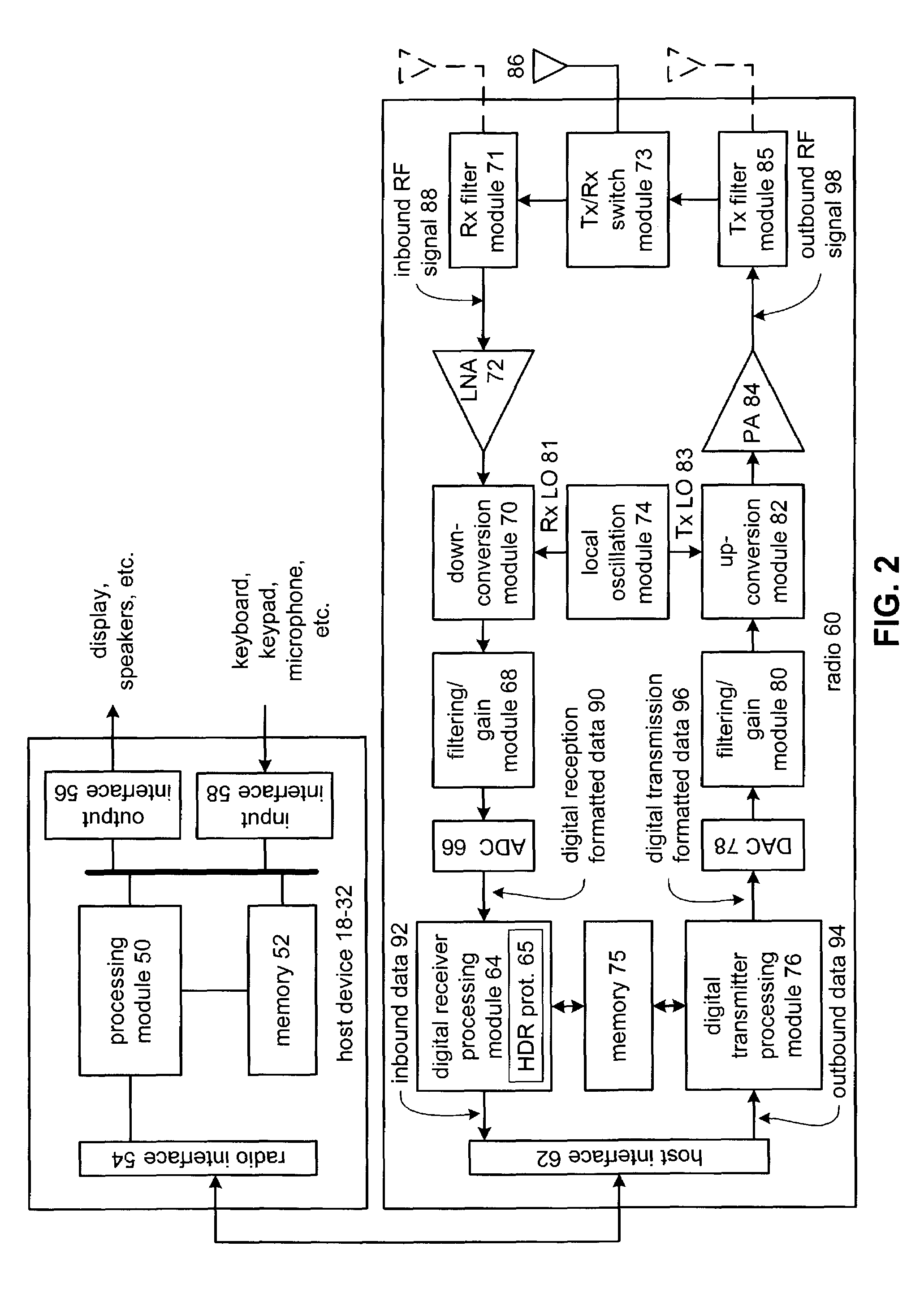
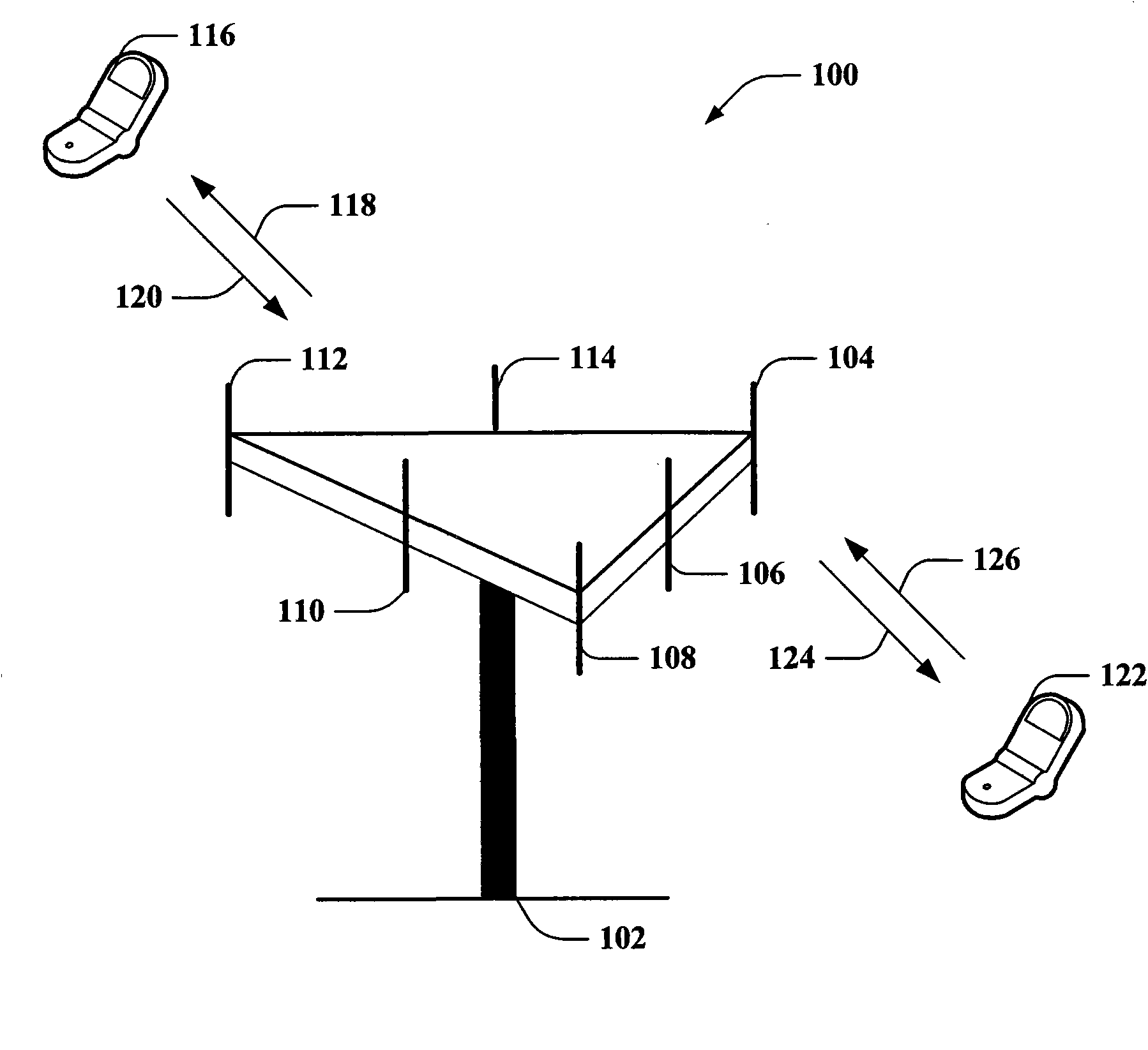
Wireless communication system and related methods
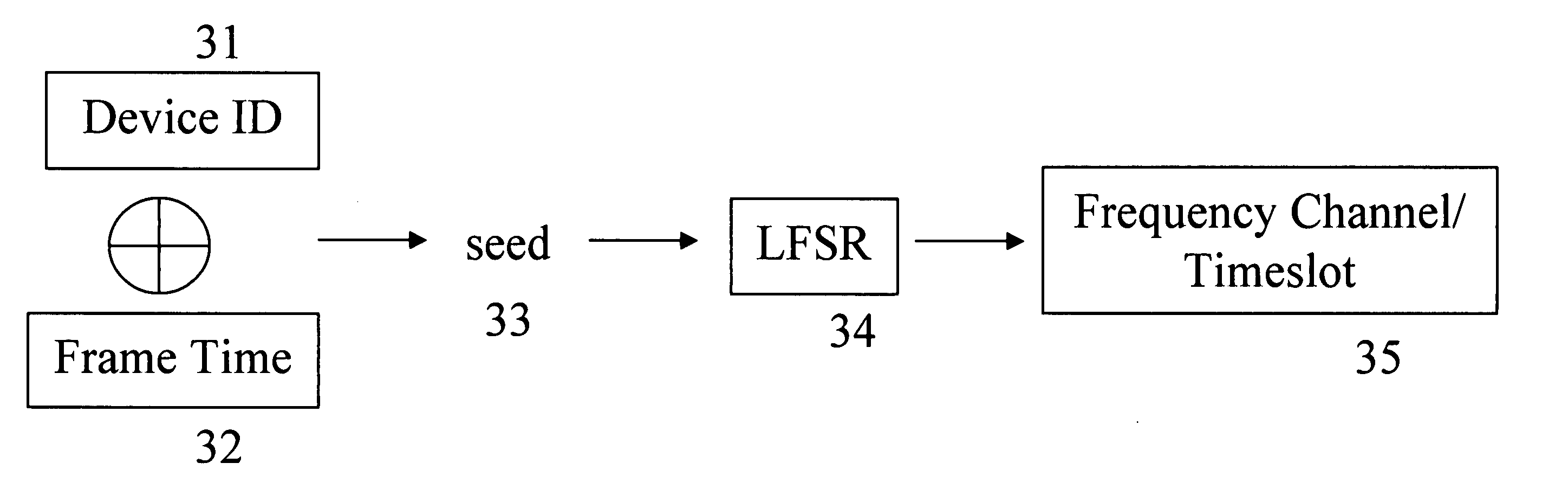
ActiveUS20060239333A1Error preventionFrequency-division multiplex detailsWireless mesh networkCommunications system
A method of operating a wireless mesh network comprises generating a pseudorandom sequence element in a transmitting device and a receiving device of the network using information shared by the transmitting and receiving devices. The pseudorandom sequence element is then used to calculate a communication channel / timeslot assignment for communication between the transmitting wireless device and the receiving wireless device.
Owner:ZENNER PERFORMANCE METERS
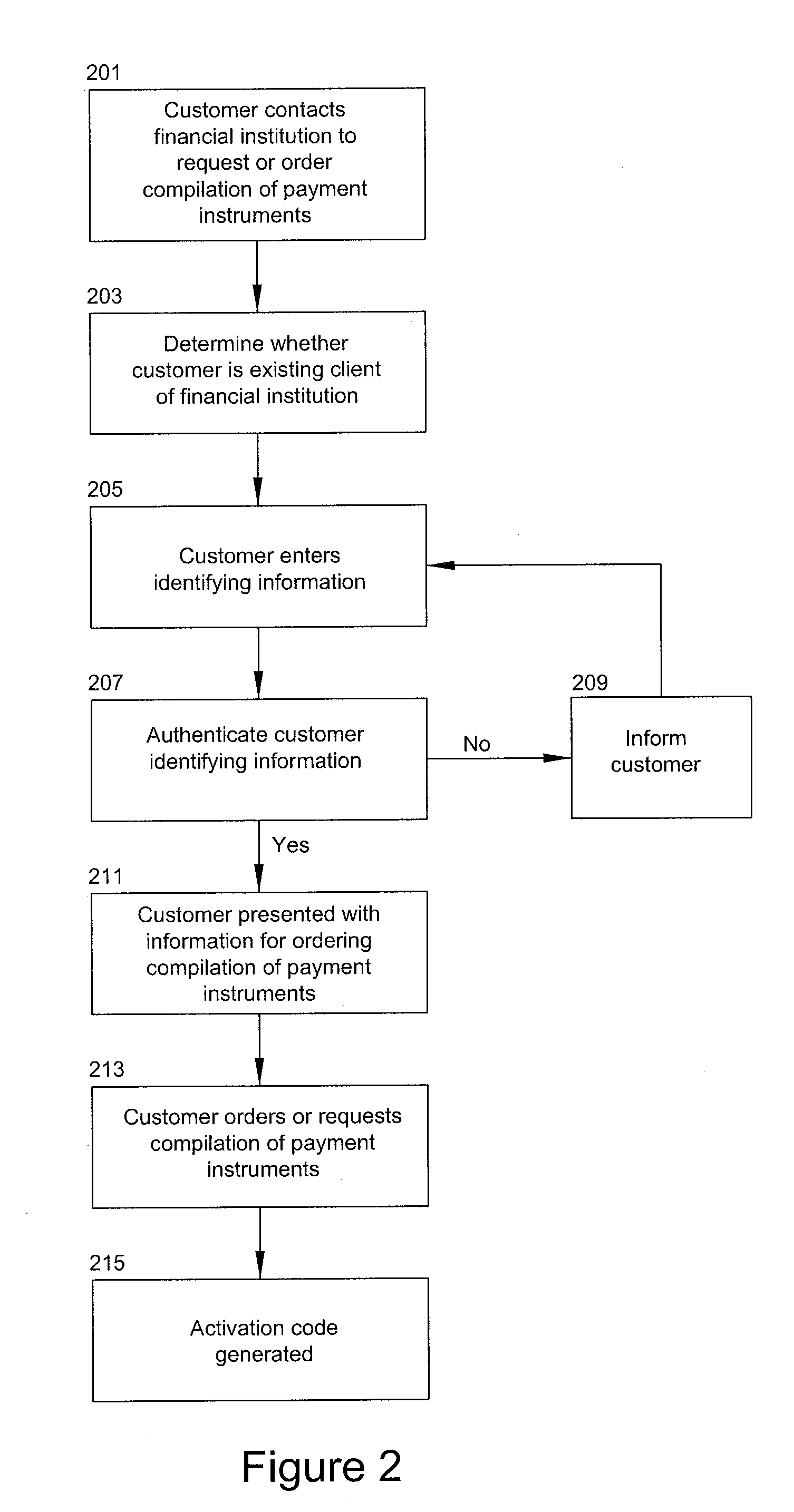
Method for authenticating financial instruments and financial transaction requests
A method for authenticating a check of a plurality of checks where the check was previously issued from a first party to a second party, including receiving first information from the first party, storing the first information in a file of a third party and receiving the check. The check has first party identifying information, a unique pseudorandom number of a pseudorandom sequence, and an amount. A status of activating the plurality of checks is determined. At least a portion of the first party identifying information included with the check, the unique pseudorandom number included with the check and the check amount included with the check are authenticated. The received check is authenticated if the first party, the unique pseudorandom number included with the check and the amount included with the check are authenticated and if the plurality of checks have been activated.
Owner:CAPITAL ONE SERVICES
Transmitter identification system
ActiveUS20050117070A1Television system detailsDirection finders using radio wavesSingle-frequency networkEngineering
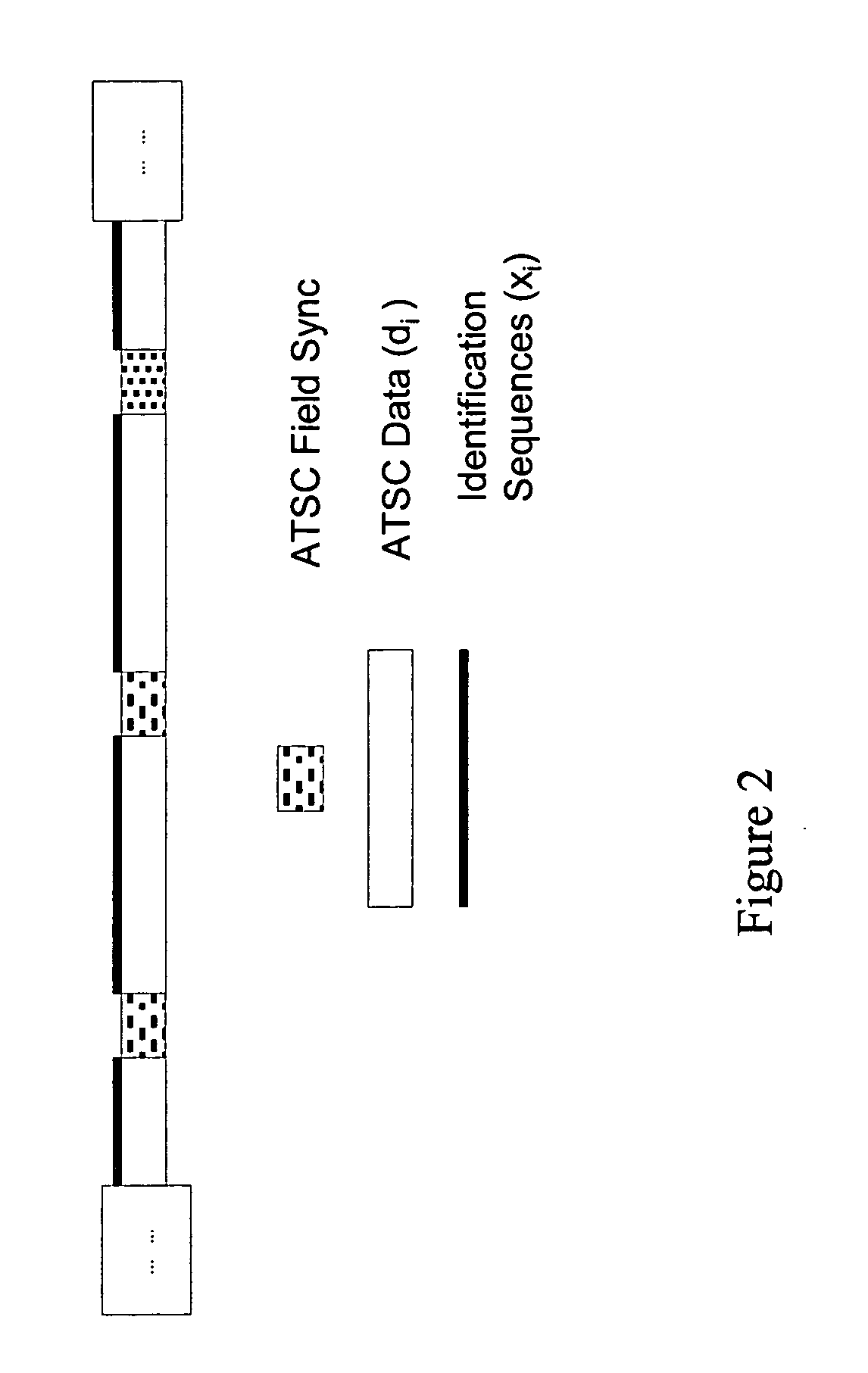
The invention relates to a transmitter identification system, which utilizes an identification signal embedded into a digital television signal, enabling the transmitter of origin to be identified at a receiving station. Ideally the identification signal is an orthogonal pseudo-random sequence time synchronized to the signal frame structure of the digital television signal. Particularly designed for single frequency networks, identification of the various transmitted signals enables the network to be tuned to eliminate or minimize multi-path effects at certain locations, which receive transmissions from various transmitters.
Owner:GULA CONSULTING LLC
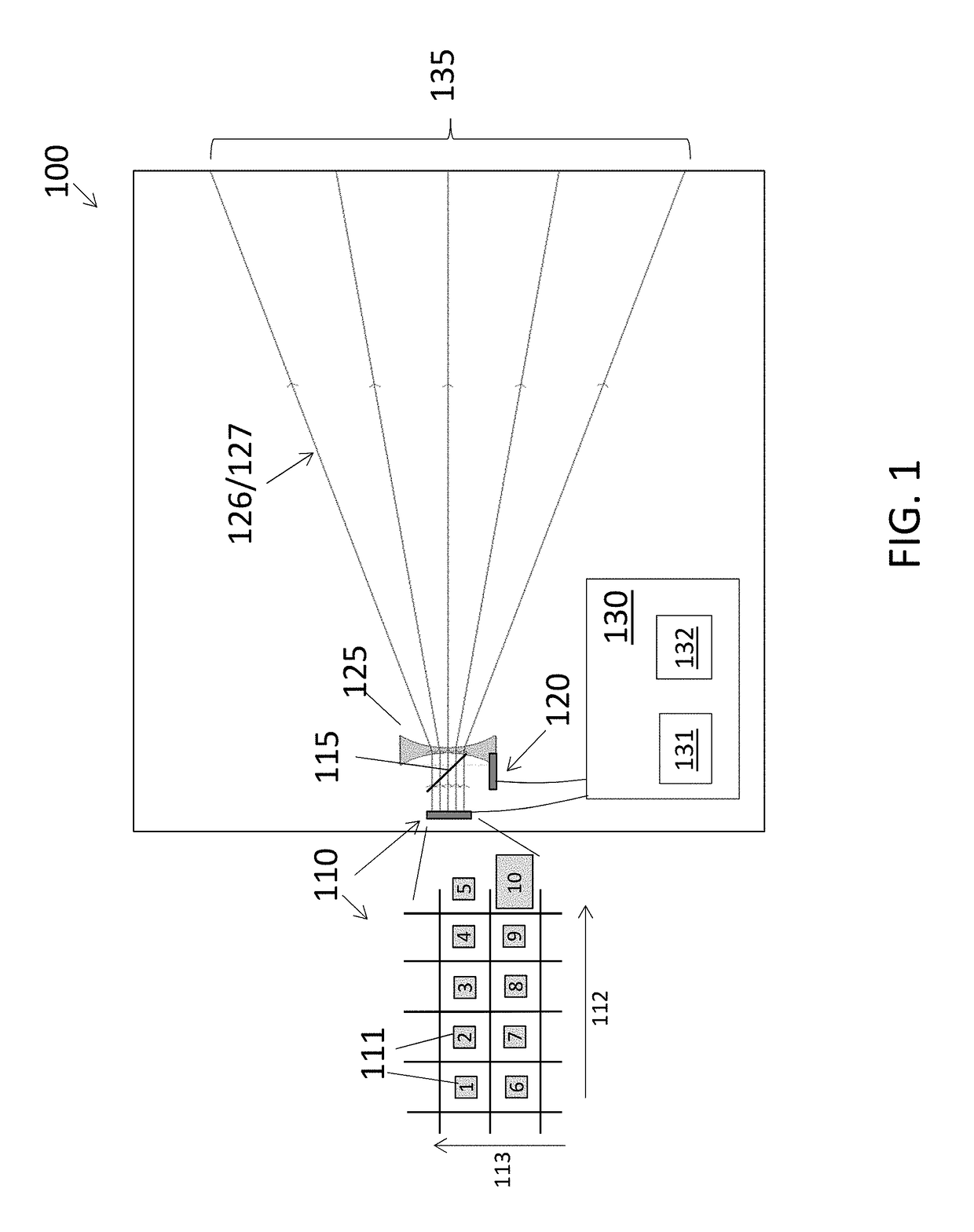
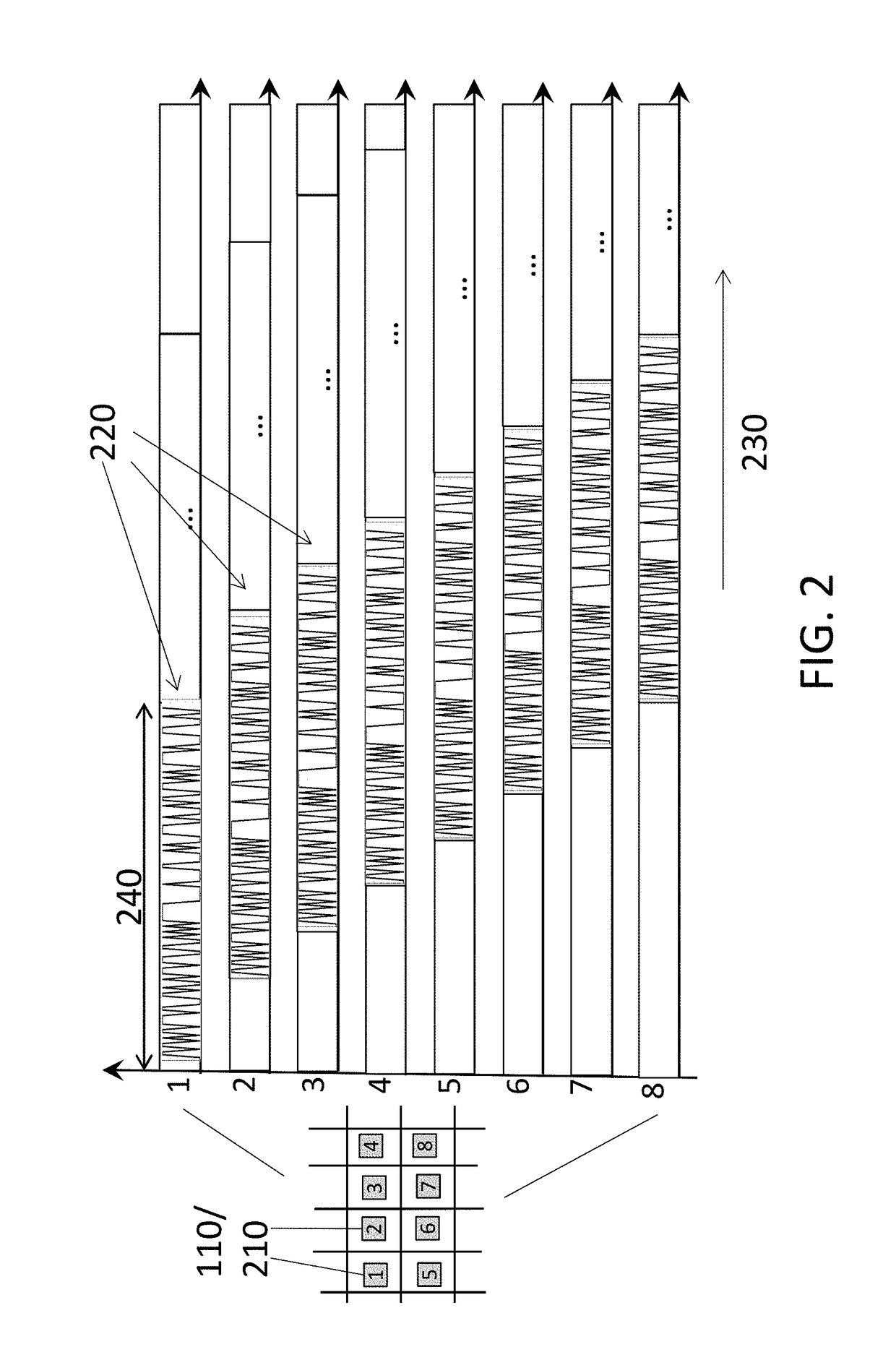
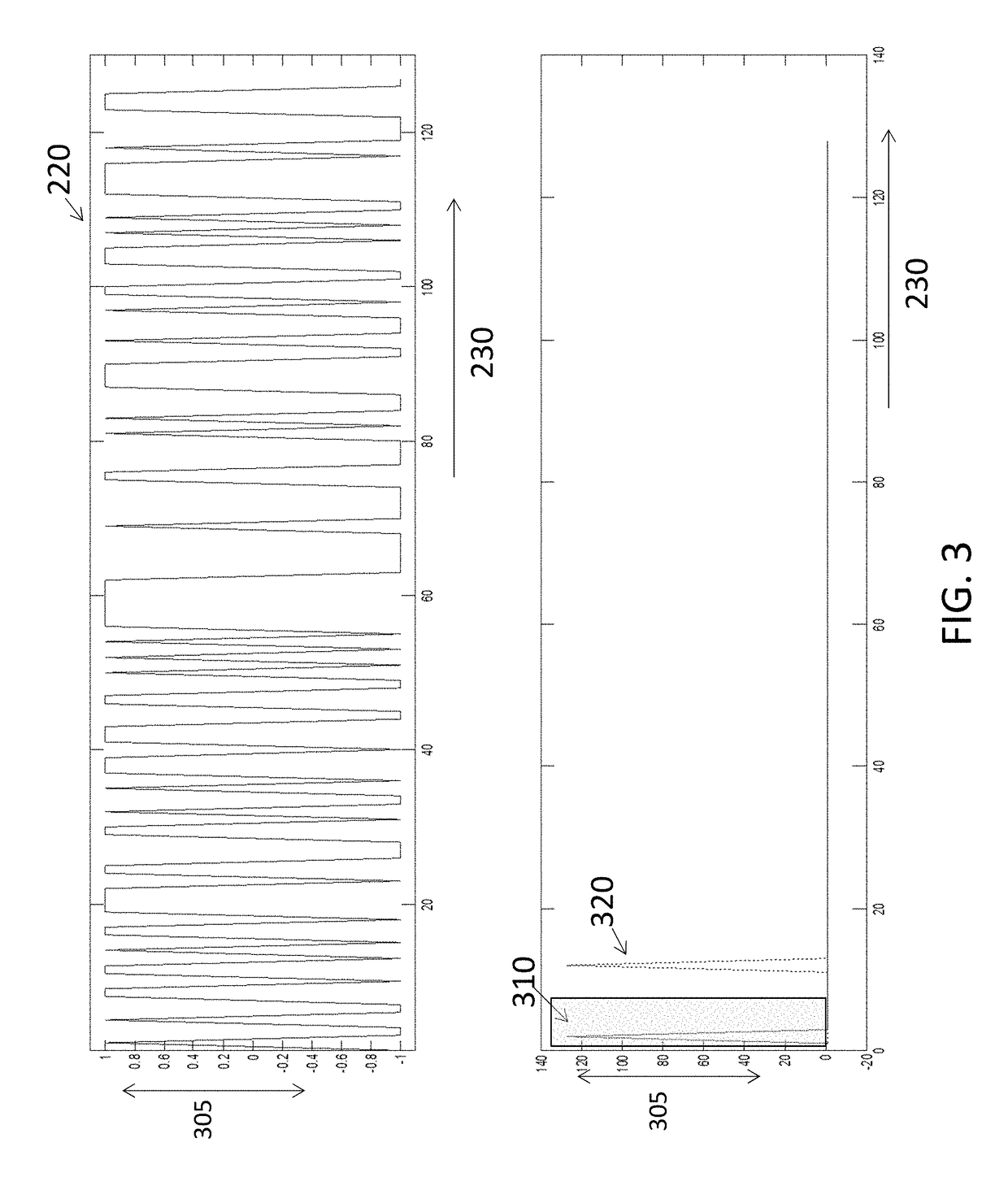
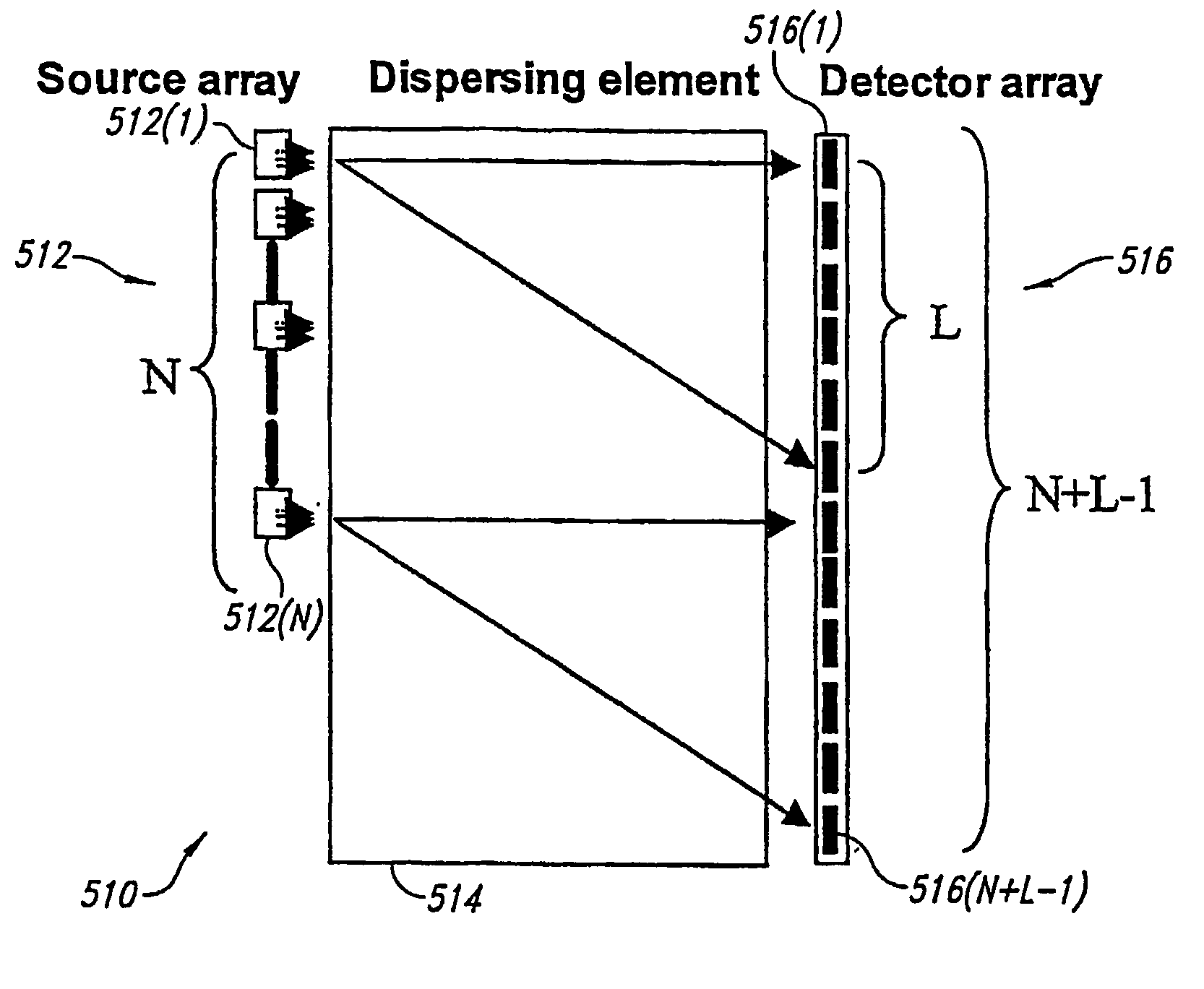
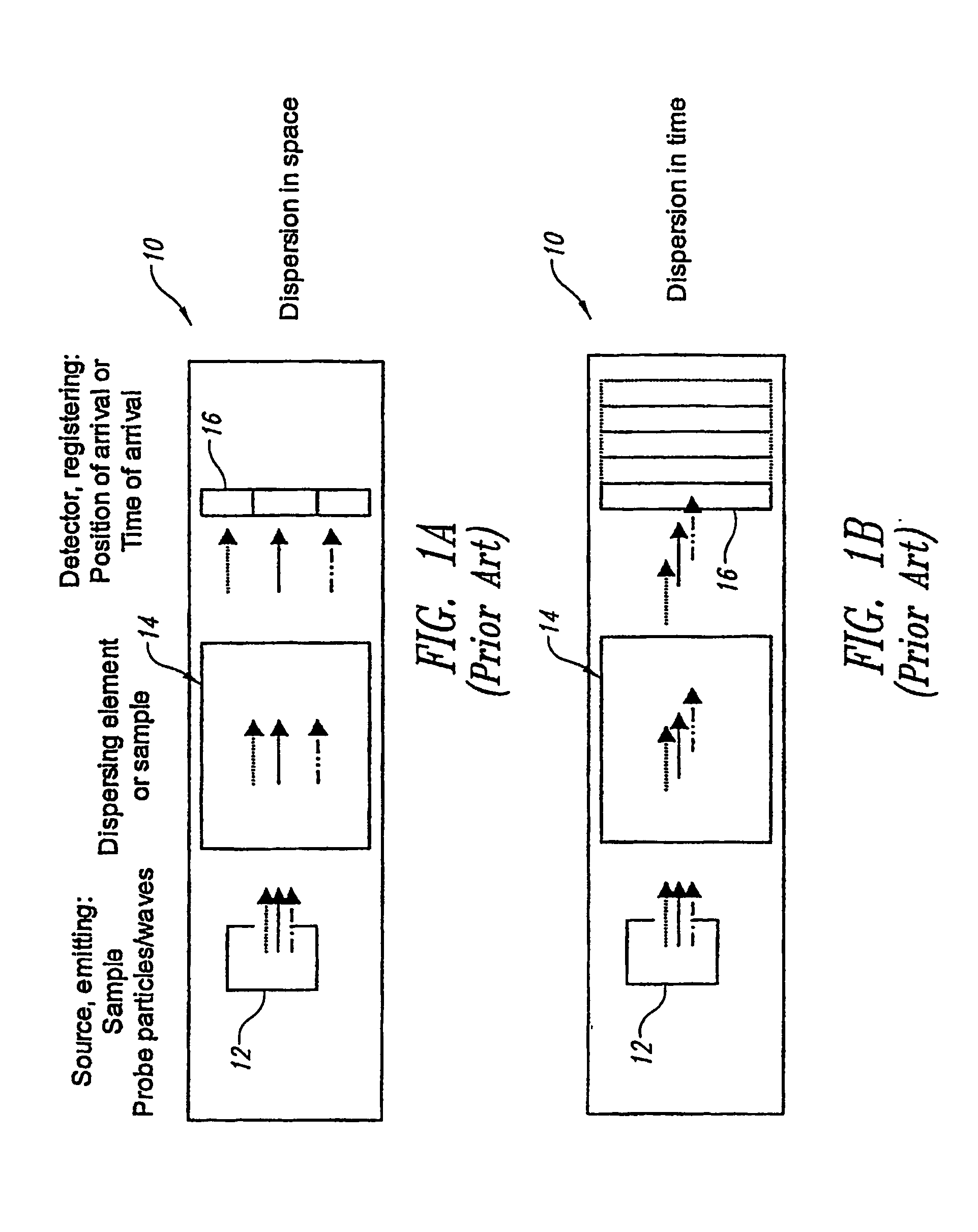
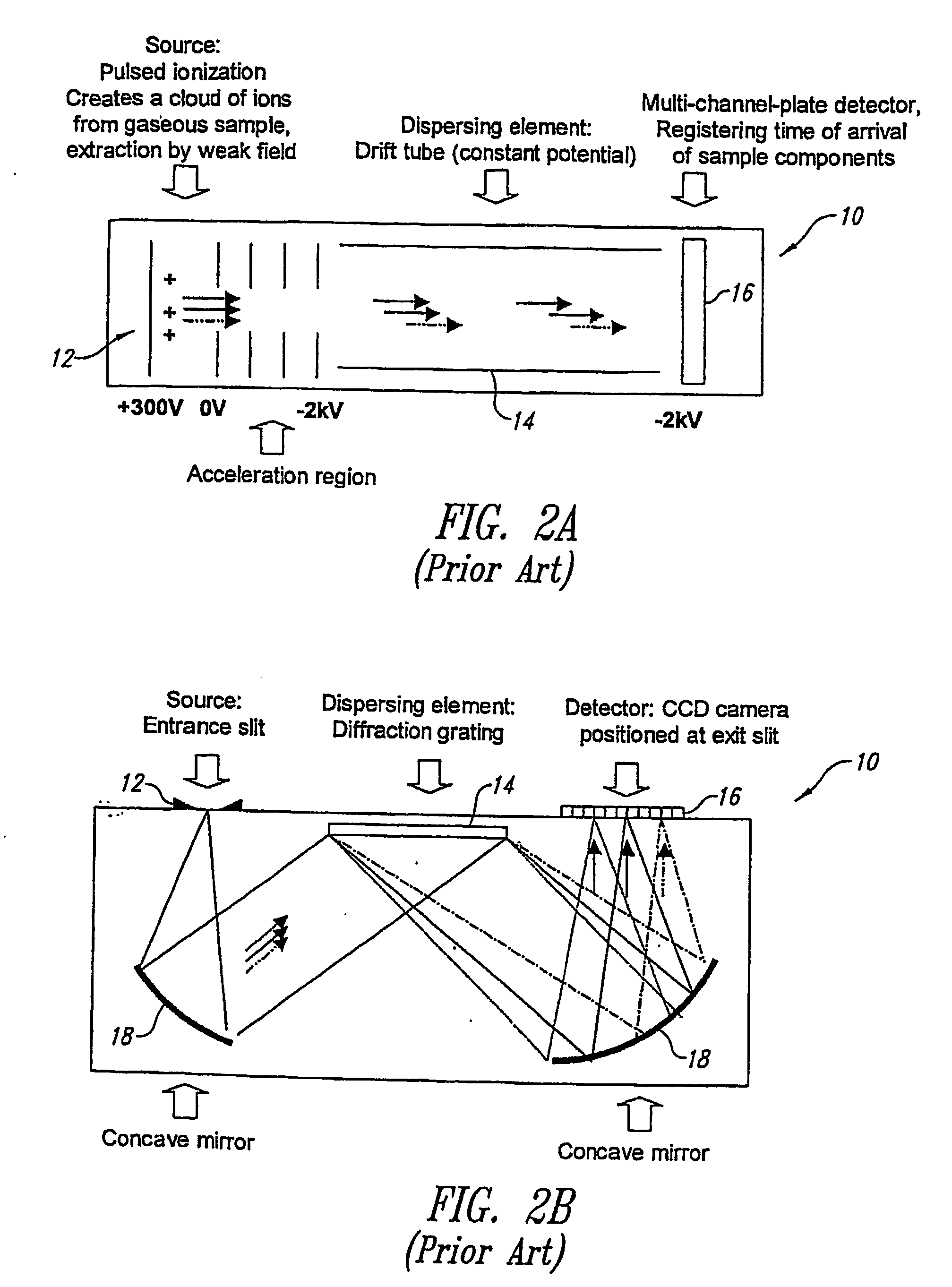
Analytical instruments using a pseudorandom array of sources, such as a micro-machined mass spectrometer or monochromator
InactiveUS7339521B2Maximize signalEnhanced signalParticle separator tubesAntenna arraysSignal-to-noise ratio (imaging)Signal on
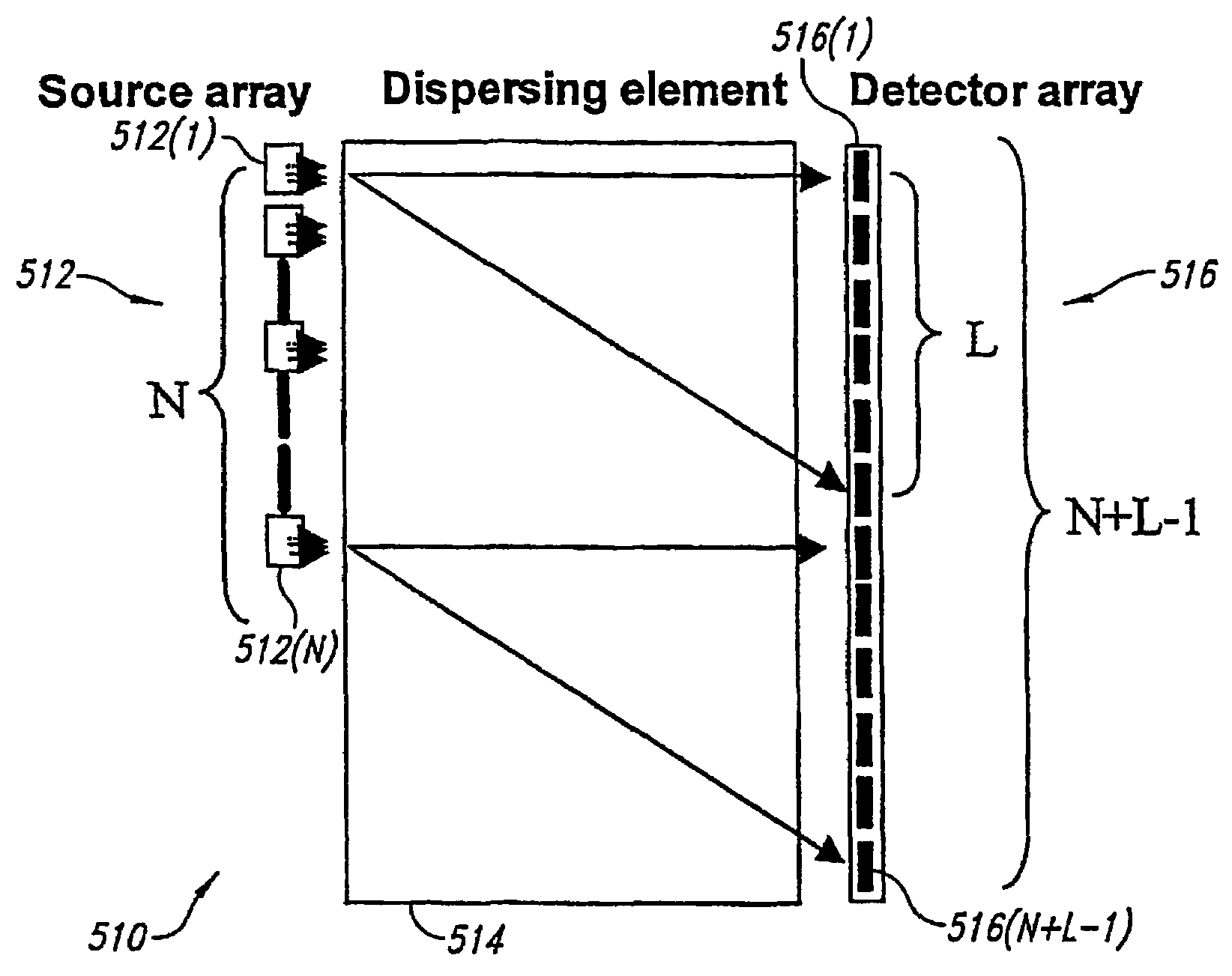
Novel methods and structures are disclosed herein which employ pseudorandom sequences to spatially arrange multiple sources in a pseudorandom source array. The pseudorandom source array can replace the single source in analytical instruments relying on spatial separation of the sample or the probe particles / waves emitted by the sources. The large number of sources in this pseudorandom source array enhances the signal on a position sensitive detector. A mathematical deconvolution process retrieves a spectrum with improved signal-to-noise ratio from the detector signal.
Owner:UNIV OF WASHINGTON
Pseudo random sequences in array lidar systems
A method of performing ranging and detection with an array lidar system and the array lidar system include a first illuminator to transmit a first pseudorandom binary sequence of pulses, the first pseudorandom sequence of pulses resulting in first reflections, and a second illuminator to transmit a second pseudorandom sequence of pulses, the second pseudorandom sequence of pulses being transmitted at least partly concurrently with transmission of the first pseudorandom sequence of pulses, the second pseudorandom sequence of pulses resulting in second reflections. A receiver receives the first reflections and the second reflections and associates the first reflections with the first illuminator based on a result of correlating the first reflections with the first pseudorandom sequence of pulses and a result of correlating the first reflections with the second pseudorandom sequence of pulses, the receiver includes an optical detector array and a processor.
Owner:GM GLOBAL TECH OPERATIONS LLC
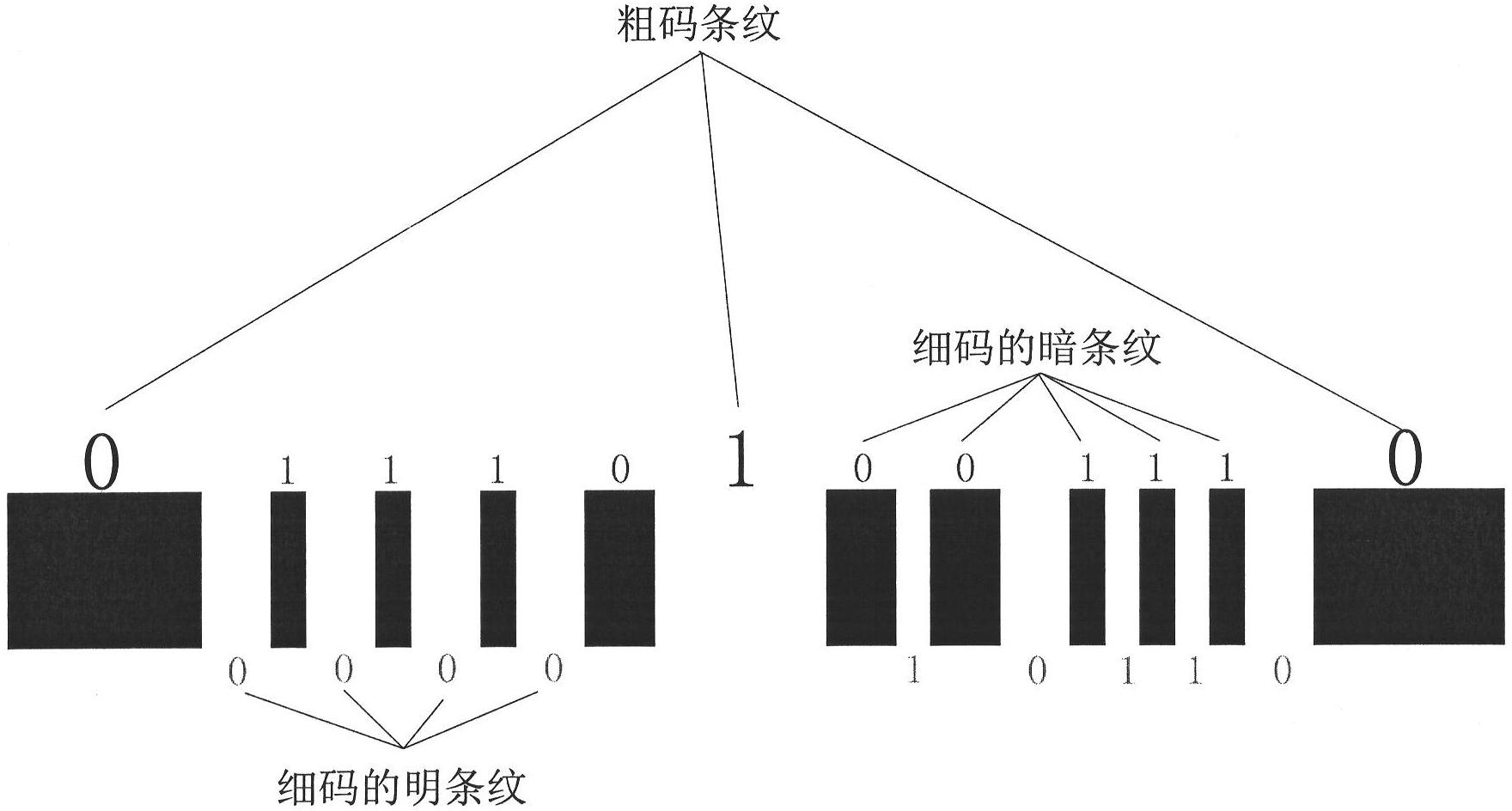
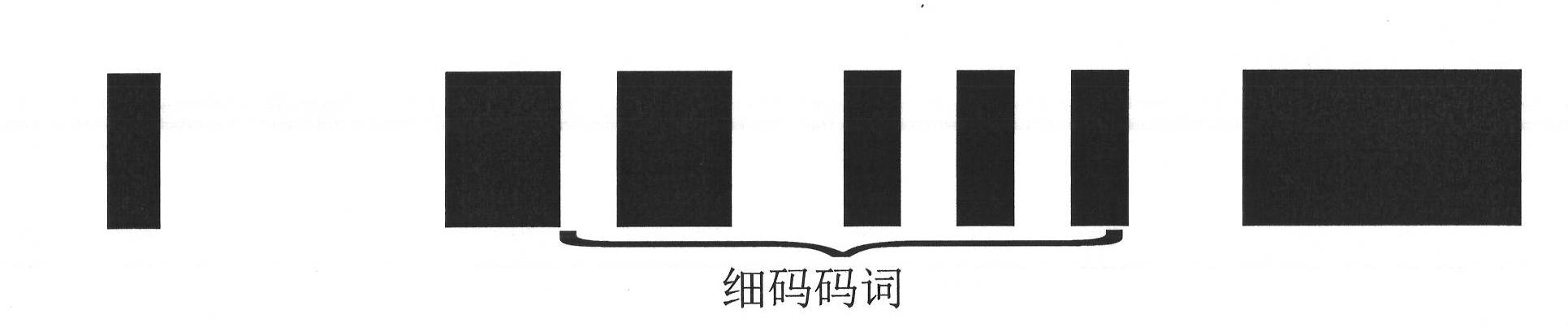
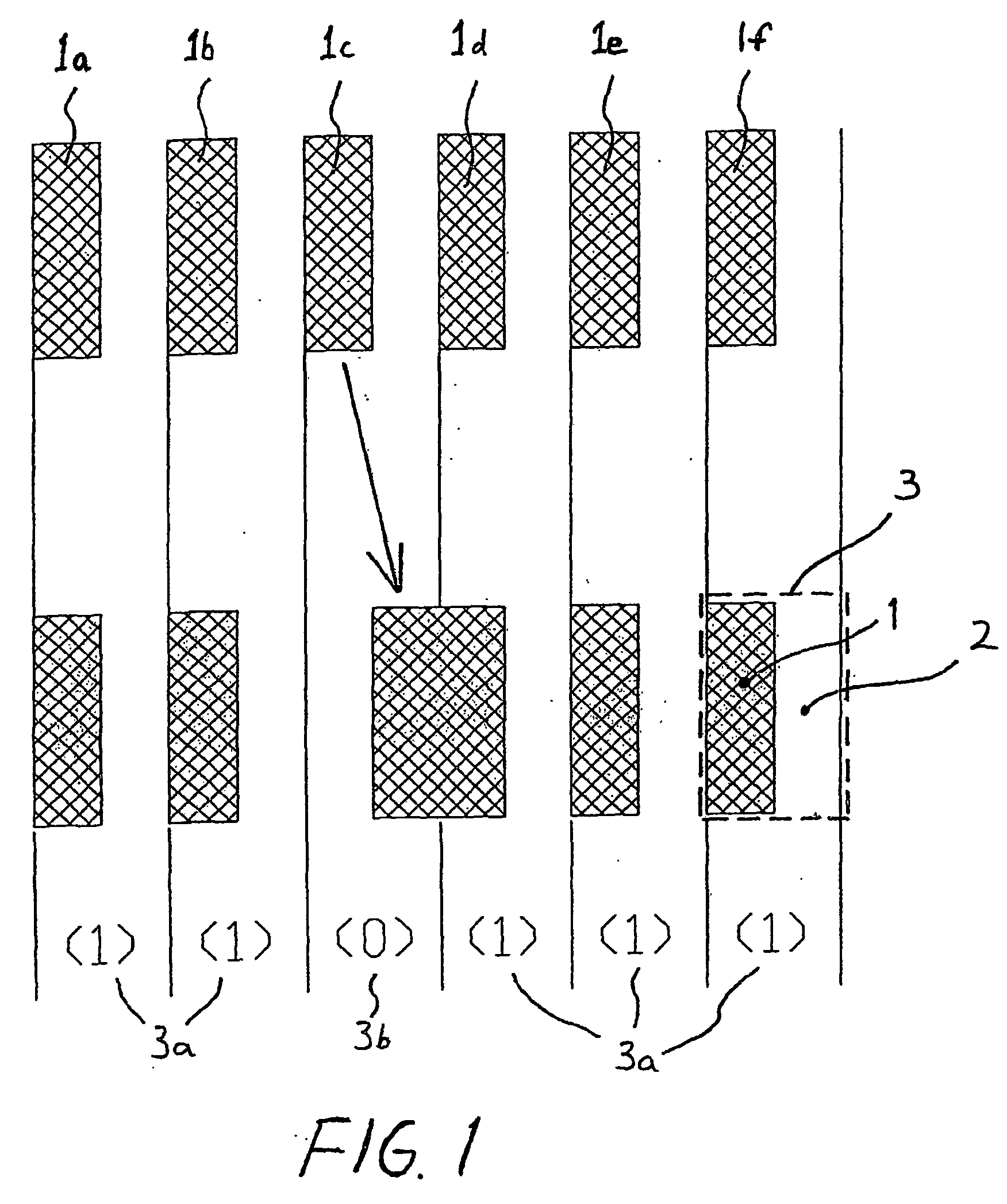
Pseudorandom bar code applied to digital level bar code ruler
InactiveCN102654400AIncrease profitSolve the problem of misjudgment as coarse codeSurveyor's staffsMovable markersEngineeringOperand
The invention discloses a pseudorandom bar code applied to a digital level bar code ruler, belonging to the technical field of manufacture of instruments of surveying and mapping. The pseudorandom bar code is formed by alternatively arranging a plurality of light and shade stripes with different widths, wherein the widths and light and shade changes of the strips are modulated by a plurality of pseudorandom sequences. The strips in the bar code comprise coarse code strips for remote measurement and thin code strips for close measurement. The thin code strips are formed by alternatively arranging light and shade strips with smaller widths, and the width changes of the light strips and shade strips are respectively modulated by a pseudorandom sequence. The coarse code strips are formed by arranging light and shade strips with bigger widths, and the widths and light and shade changes of the strips are modulated by a pseudorandom sequence. The coarse code strips are regularly embedded in the fine code strips to form a complete bar code. The pseudorandom bar code is characterized in that a plurality of pseudorandom sequences are alternatively coded for modulating the widths and light and shade changes of the strips. The pseudorandom bar code has the advantages of compatibility with remote measurement and close measurement, capability of forward measurement and backward measurement, simplicity in making a staff gauge, low requirement for a hardware system, small decoding operand, and rapidness and accuracy in identification.
Owner:丁梅 +3
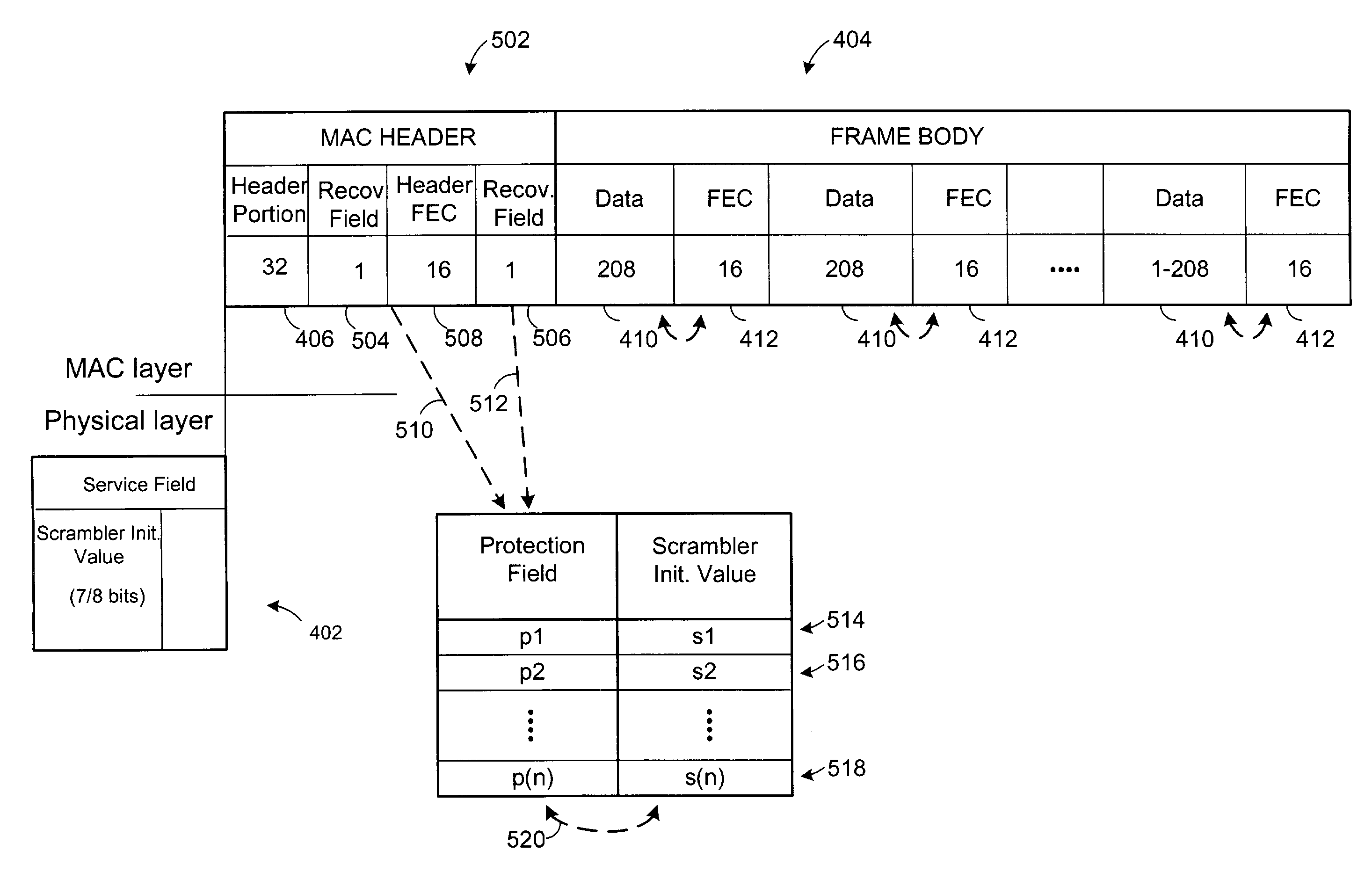
Scrambler initialization in a wireless local area network
InactiveUS7317735B1Accurate recoveryTime-division multiplexForward error control useTelecommunicationsPhysical layer
A method and system of the present invention includes the creation and transmission of a MAC header that includes a first MAC header portion and at least two scrambler recovery fields arranged on the two sides (before and after) of a header FEC portion. The invention includes determining whether a scrambler initialization field received at the physical layer was received in error, and if so, evaluating either one of the de-scrambled values of the two scrambler recovery fields in relation to a table to determine a pseudorandom sequence initialization value that corresponds to a given de-scrambled scrambler recovery field value. Once the corresponding pseudorandom sequence initialization value is determined, that value may be used to further de-scramble the data in the data frame to produce a correctly de-scrambled data frame.
Owner:BELL NORTHERN RES LLC
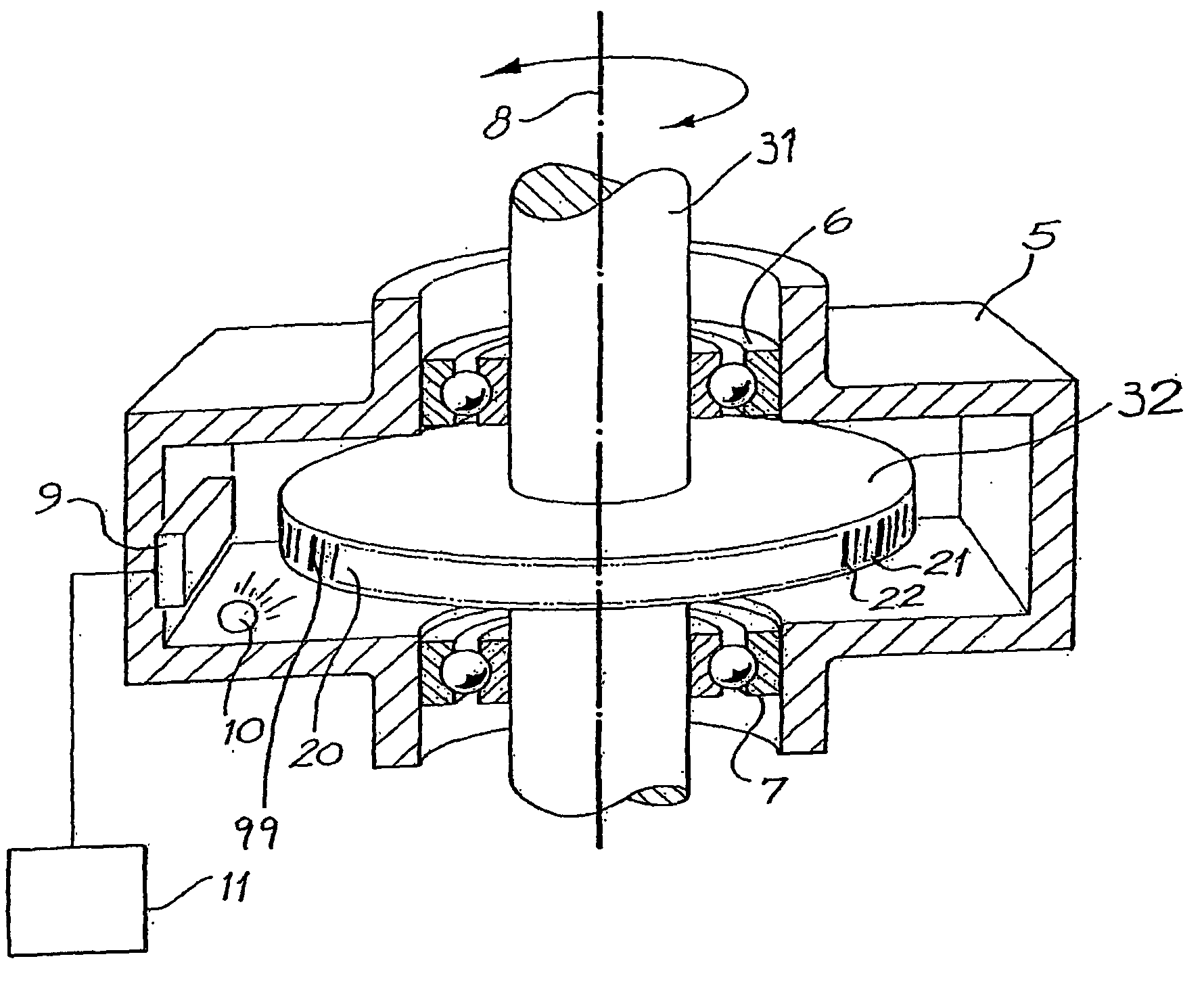
Position encoder using statistically biased pseudorandom sequence
InactiveUS20040015323A1Improve accuracyDigital computer detailsSpeed measurement using gyroscopic effectsManchester codeTransmittance
A position sensor encodes absolute position via n consecutive members of a pseudorandom sequence of bits, where each bit (30a-30k) comprises a region of high transmission or reflectivity adjacent to a region of low transmission or reflectivity. The pseudorandom sequence is chosen such that every series of n consecutive bits (30a-30k) in the sequence is predominantly formed from a predetermined bit value (1 or 0). The light transmitted or reflected from the series is therefore detected as a substantially periodic intensity pattern (42), which can be processed via Fourier analysis to yield an accurate interpolation of relative position. An example is given of a pseudorandom sequence, which can be represented as a cyclic Manchester code, in which at least 8 members of every series of 11 consecutive bits has a bit value of 1.
Owner:BISHOP INNOVATION PTY LTD
Pseudo random sequences in array lidar systems
A method of performing ranging and detection with an array lidar system and the array lidar system include a first illuminator to transmit a first pseudorandom binary sequence of pulses, the first pseudorandom sequence of pulses resulting in first reflections, and a second illuminator to transmit a second pseudorandom sequence of pulses, the second pseudorandom sequence of pulses being transmitted at least partly concurrently with transmission of the first pseudorandom sequence of pulses, the second pseudorandom sequence of pulses resulting in second reflections. A receiver receives the first reflections and the second reflections and associates the first reflections with the first illuminator based on a result of correlating the first reflections with the first pseudorandom sequence of pulses and a result of correlating the first reflections with the second pseudorandom sequence of pulses, the receiver includes an optical detector array and a processor.
Owner:GM GLOBAL TECH OPERATIONS LLC
Analytical instruments using a pseudorandom array of sources, such as a micro-machined mass spectrometer or monochromator
InactiveUS20050119868A1Maximize signalImprove signal-to-noise ratioAntenna arraysParticle separator tubesSignal-to-noise ratio (imaging)Signal on
Novel methods and structures are disclosed herein which employ pseudorandom sequences to spatially arrange multiple sources in a pseudorandom source array. The pseudorandom source array can replace the single source in analytical instruments relying on spatial separation of the sample or the probe particles / waves emitted by the sources. The large number of sources in this pseudorandom source array enhances the signal on a position sensitive detector. A mathematical deconvolution process retrieves a spectrum with improved signal-to-noise ratio from the detector signal.
Owner:UNIV OF WASHINGTON
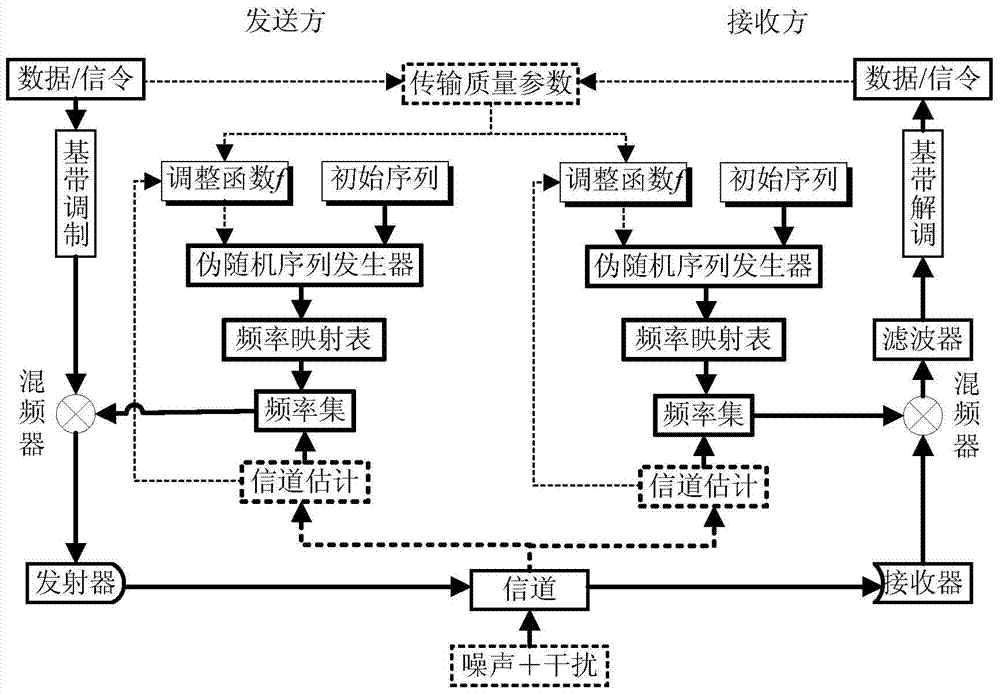
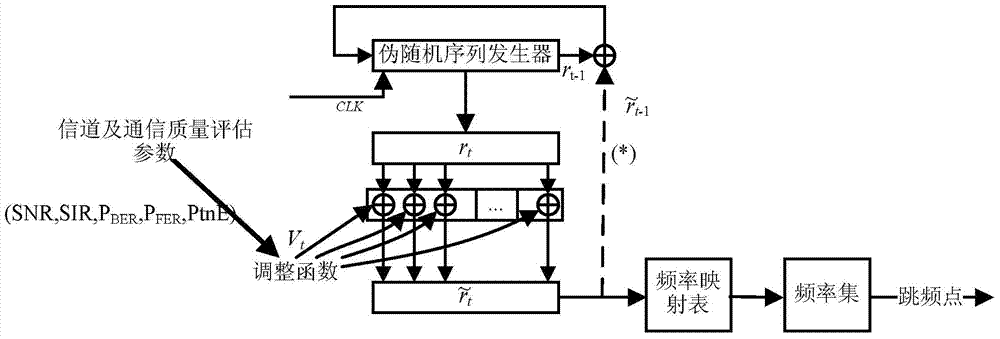
Self-adaptation frequency hopping pattern generation method
The invention discloses a self-adaptation frequency hopping pattern generation method. Both parties of communication obtain the same SNR and the same SIR through channel estimation, an adjustment factor Vt of a frequency hopping pattern is generated, an operation is performed on the adjustment factor Vt and a frequency hopping pattern control word rt generated by a pseudorandom sequence generator to obtain a frequency hopping pattern control word t, and the frequency hopping pattern control word t is used for generating the frequency hopping pattern. In the self-adaptation frequency hopping pattern generation method, channel estimation is used for generating the self-adaptation frequency hopping pattern based on channel dynamism, the channel dynamism utilized by the self-adaptation frequency hopping pattern is the special characteristic of the both parties of communication, any third party cannot copy the characteristic, and the interception resisting performance is further improved. More importantly, even if one device is cracked or obtained by the enemy, effective interception and interference cannot be performed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
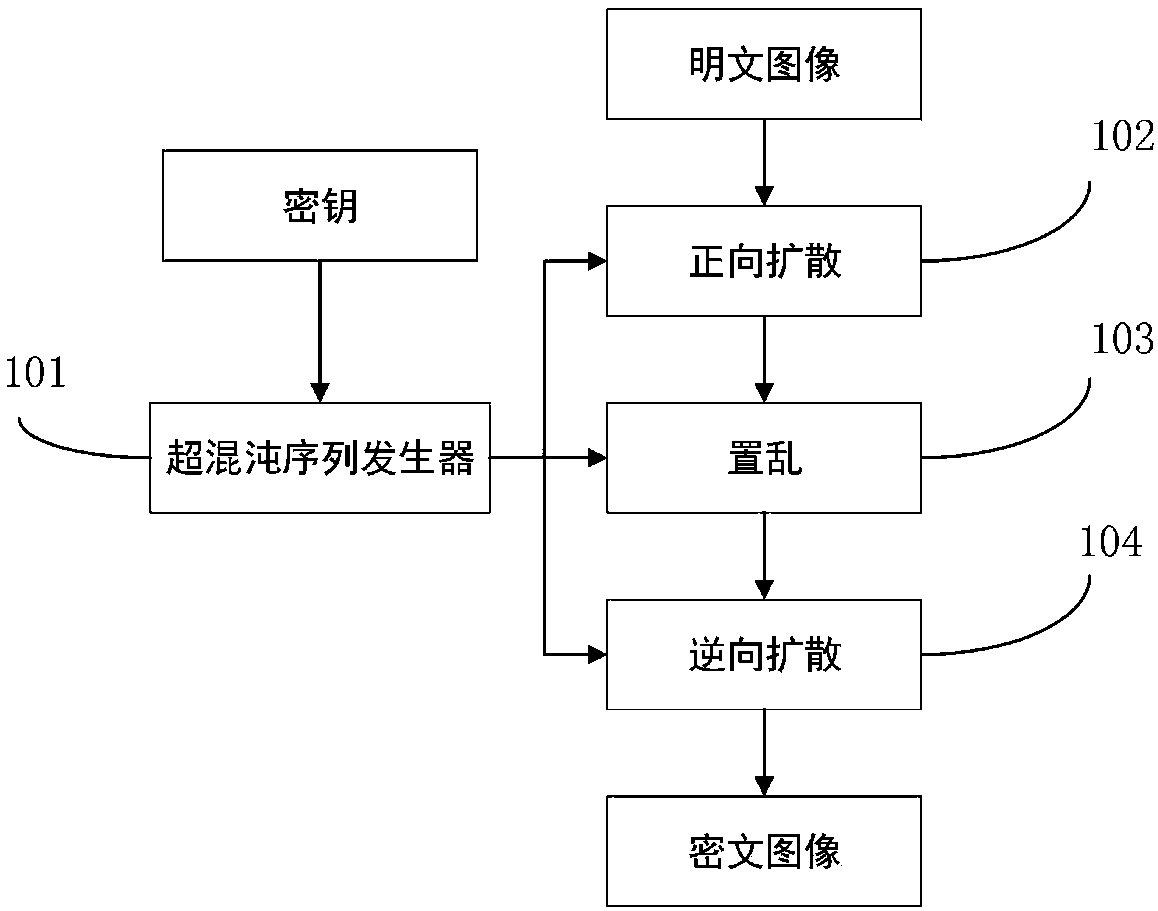
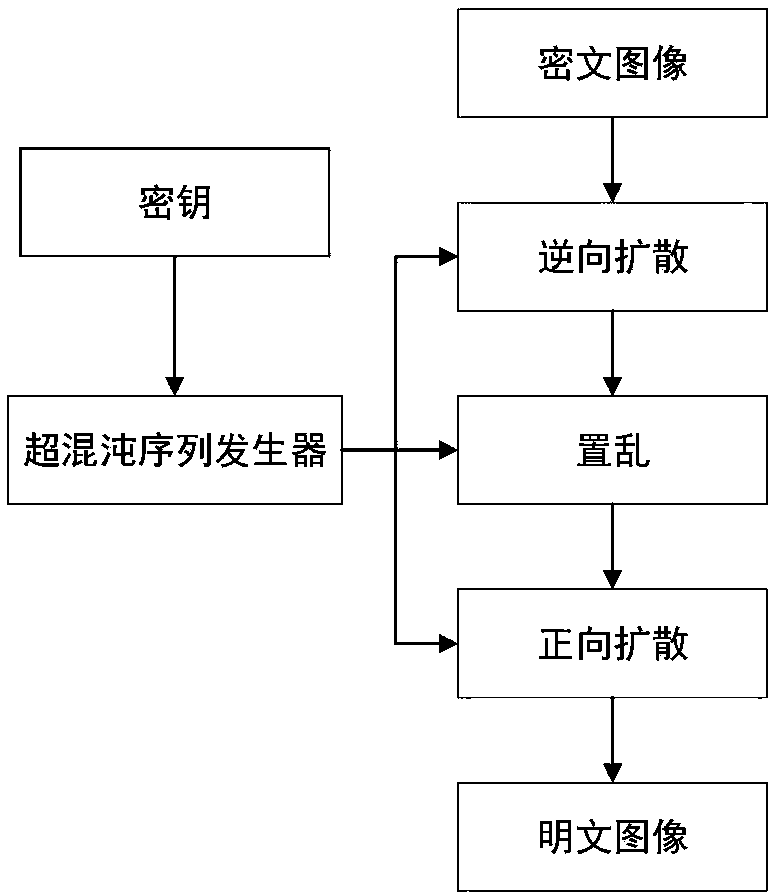
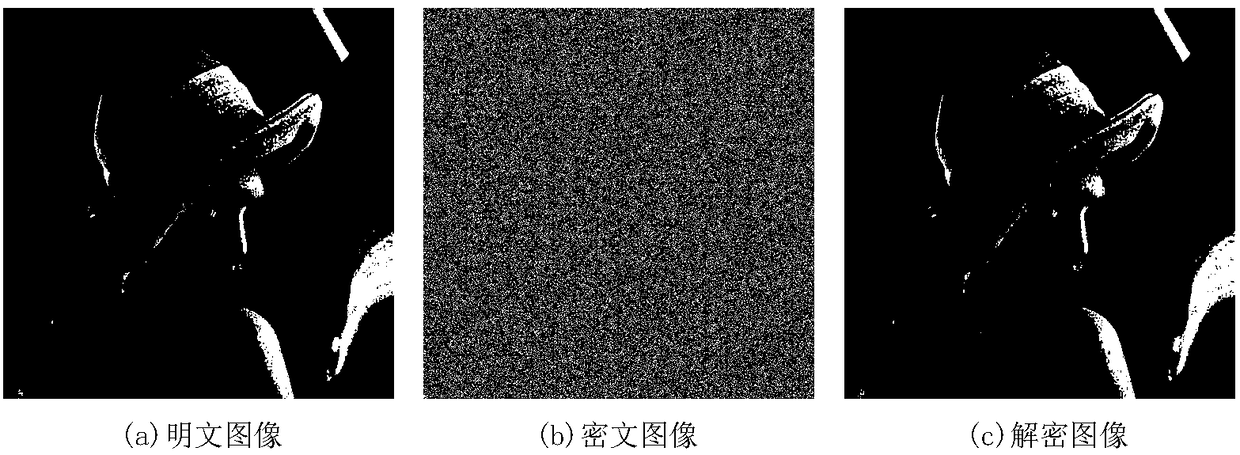
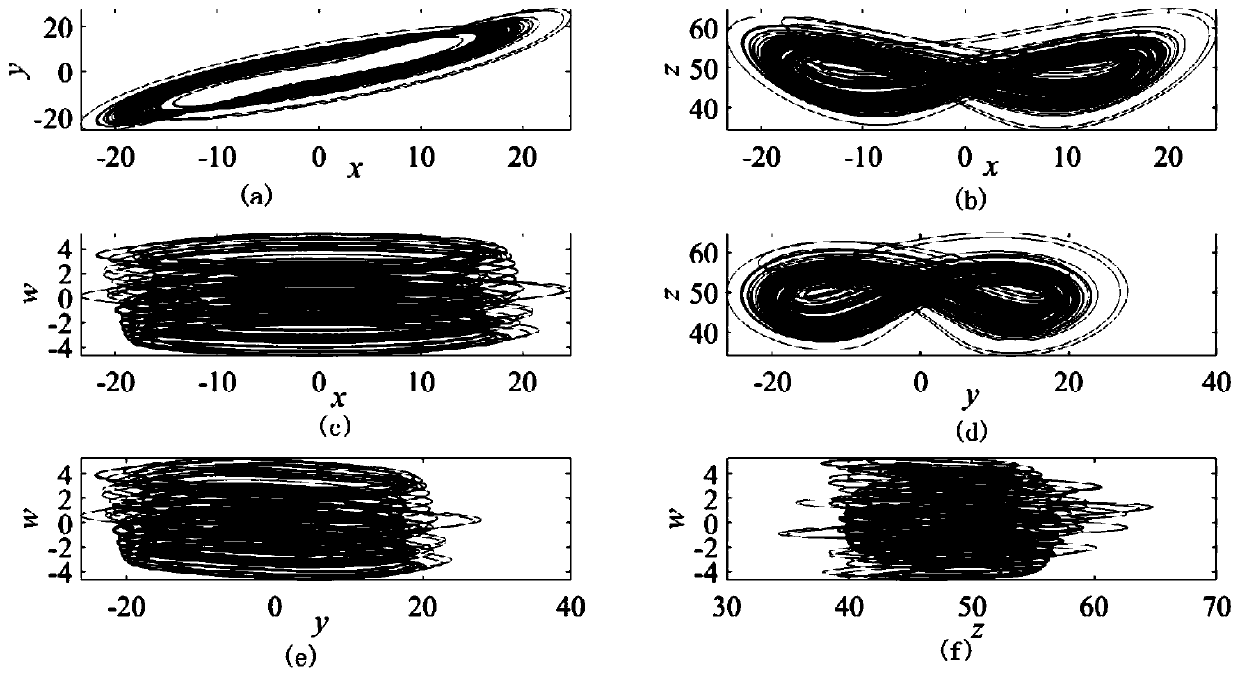
Plaintext associated image encryption algorithm based on hyperchaos Chen system
InactiveCN108234813AReduce the number of iterationsImprove the ability to resist known plaintext attacksKey distribution for secure communicationSecuring communication by chaotic signalsChosen-plaintext attackRelevant information
The invention relates to an image encryption algorithm based on a chaotic system, used for solving security problems that the image encryption algorithm is small in key space and poor in capacity of resisting to plaintext attacks. The algorithm comprises four modules such as a hyperchaos sequence generator, a forward diffusion module, a scrambling module and a reverse diffusion module. Firstly thehyperchaos Chen system is used for generating four chaotic pseudorandom sequences, a chaotic sequence and a plaintext image are used for performing forward diffusion operation to acquire a matrix A,then computation is performed in combination with the pseudorandom sequences and information related to the plaintext image to acquire a scrambled coordinate, the coordinate scrambling is performed onthe matrix A to acquire a matrix B, and at last the chaotic pseudorandom sequences and the matrix B are used for performing reverse diffusion operation to acquire a ciphertext image C. An experimentsimulation result expresses that the algorithm can improve the defect that the image encryption algorithm is small in key space, effectively resist to statistical attacks, differential attacks, and chosen-plaintext attacks, and achieve good encryption effect.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Ultra-chaos pseudo random sequence generator
InactiveCN101145901AImprove performanceSecuring communicationSecure communicationInformation security
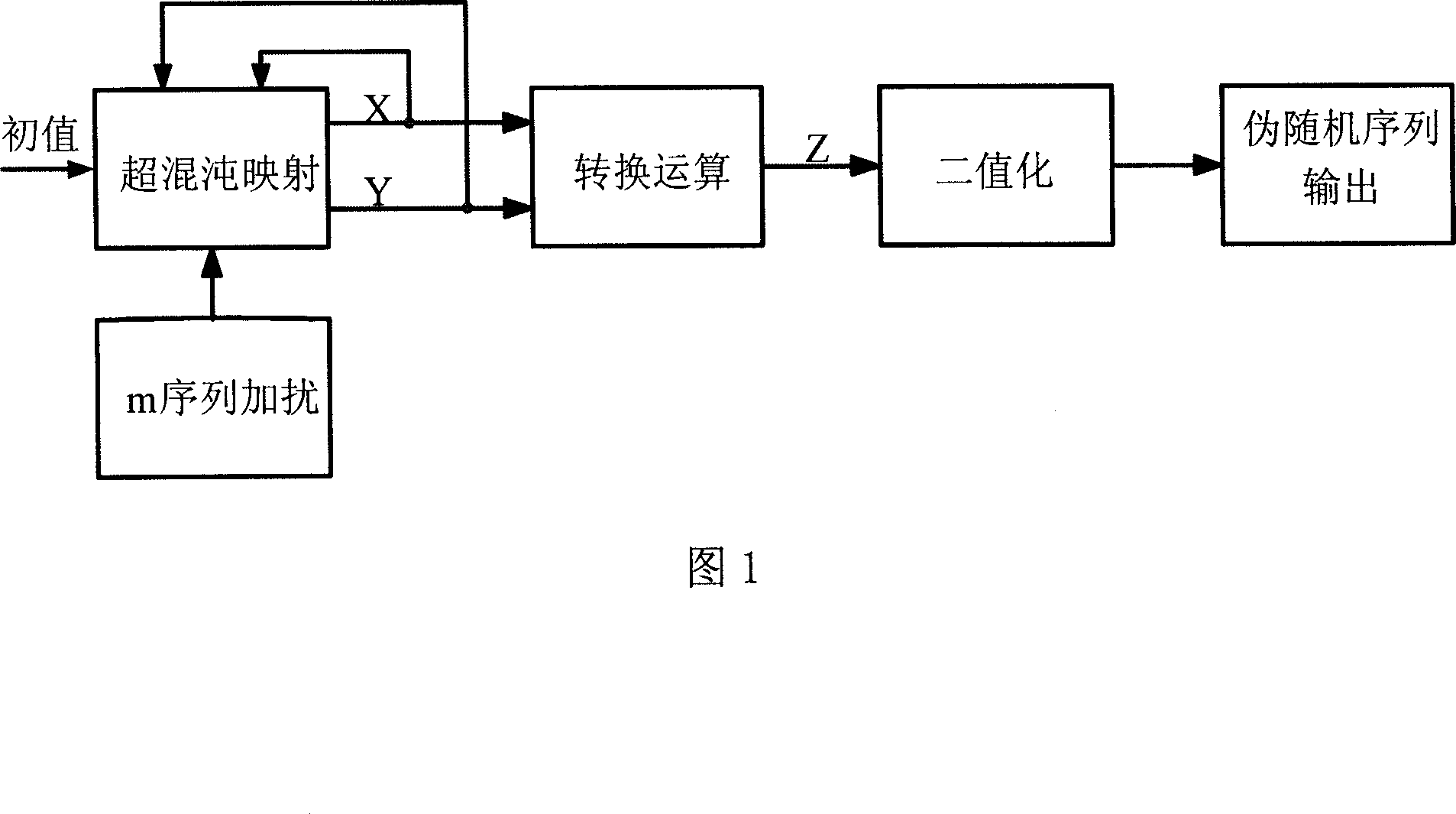
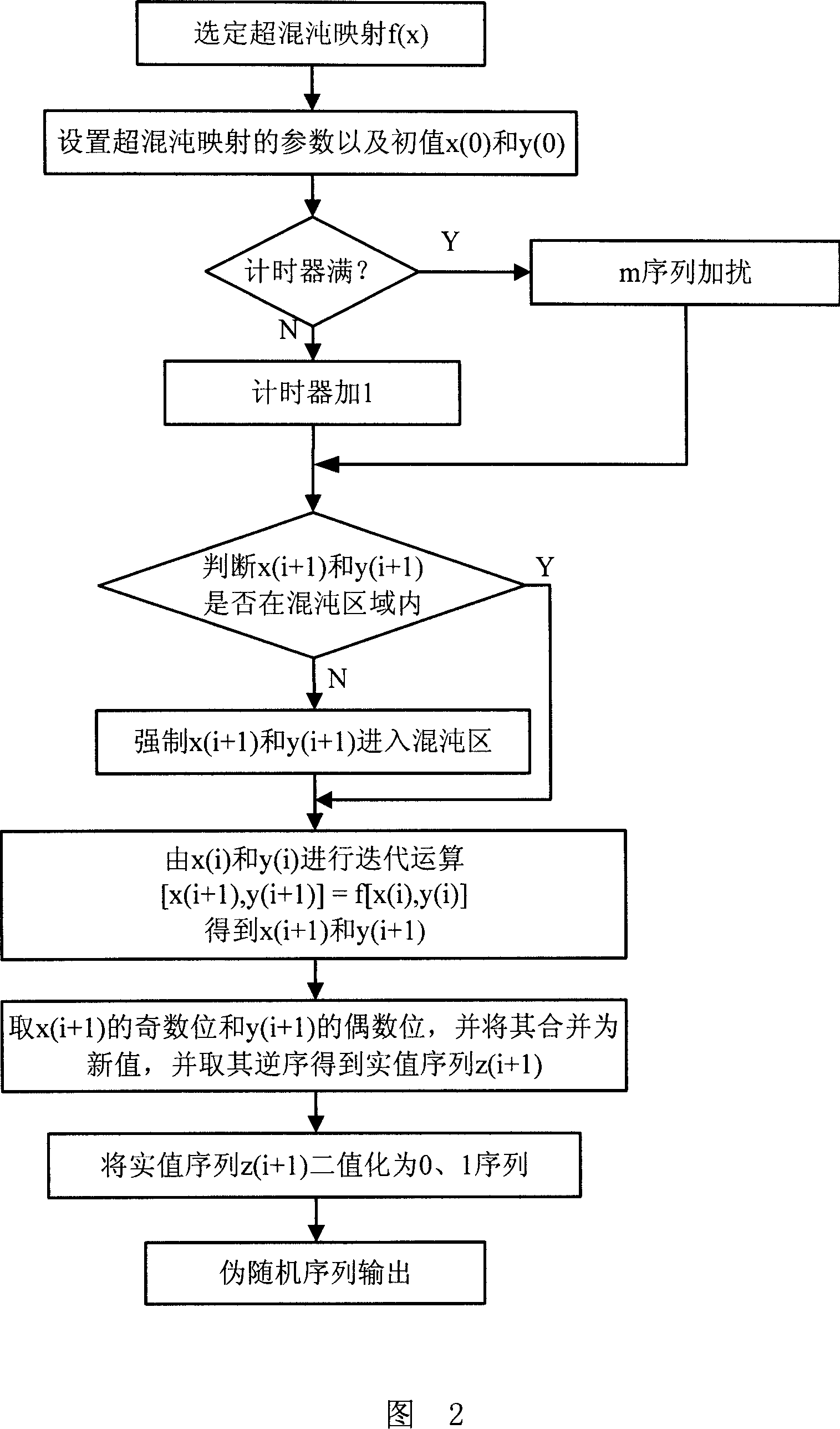
The invention provides a method of hyperchaos pseudorandom sequence generation. (1) select hyperchaos mapping and set initial values thereof x (0) and y(0); (2) carry out iterative computation by input values x(i) and y(i), and obtain output values x(i+1) and y(i+1); (3) undergo nonlinear transformation of x(i+1) and y(i+1), the transformation method is to take the odd bits of x(i+1) and the even bits of y(i+1) to be combined and then take the reverse sequence thereof as the value of the new sequence z(i+1), and at this time the sequence z(i+1) is a real-value sequence; (4) the real-value sequence z is binarized to be a 0-1 sequence, i.e. the pseudorandom sequence output is obtained. The hyperchaos pseudorandom sequence provided in the invention is characterized by strong safety and security, good random properties, simple and rapid generation, and a plurality of autocorrelation properties close to Delta function and cross correlation properties close to zero, being able to be widely applied to the fields like data encryption, secure communication and information safety and so on.
Owner:HARBIN ENG UNIV
Wireless Communication System and Related Methods
ActiveUS20120106518A1Error preventionFrequency-division multiplex detailsCommunications systemWireless mesh network
A method of operating a wireless mesh network comprises generating a pseudorandom sequence element in a transmitting device and a receiving device of the network using information shared by the transmitting and receiving devices. The pseudorandom sequence element is then used to calculate a communication channel / timeslot assignment for communication between the transmitting wireless device and the receiving wireless device.
Owner:ZENNER PERFORMANCE METERS
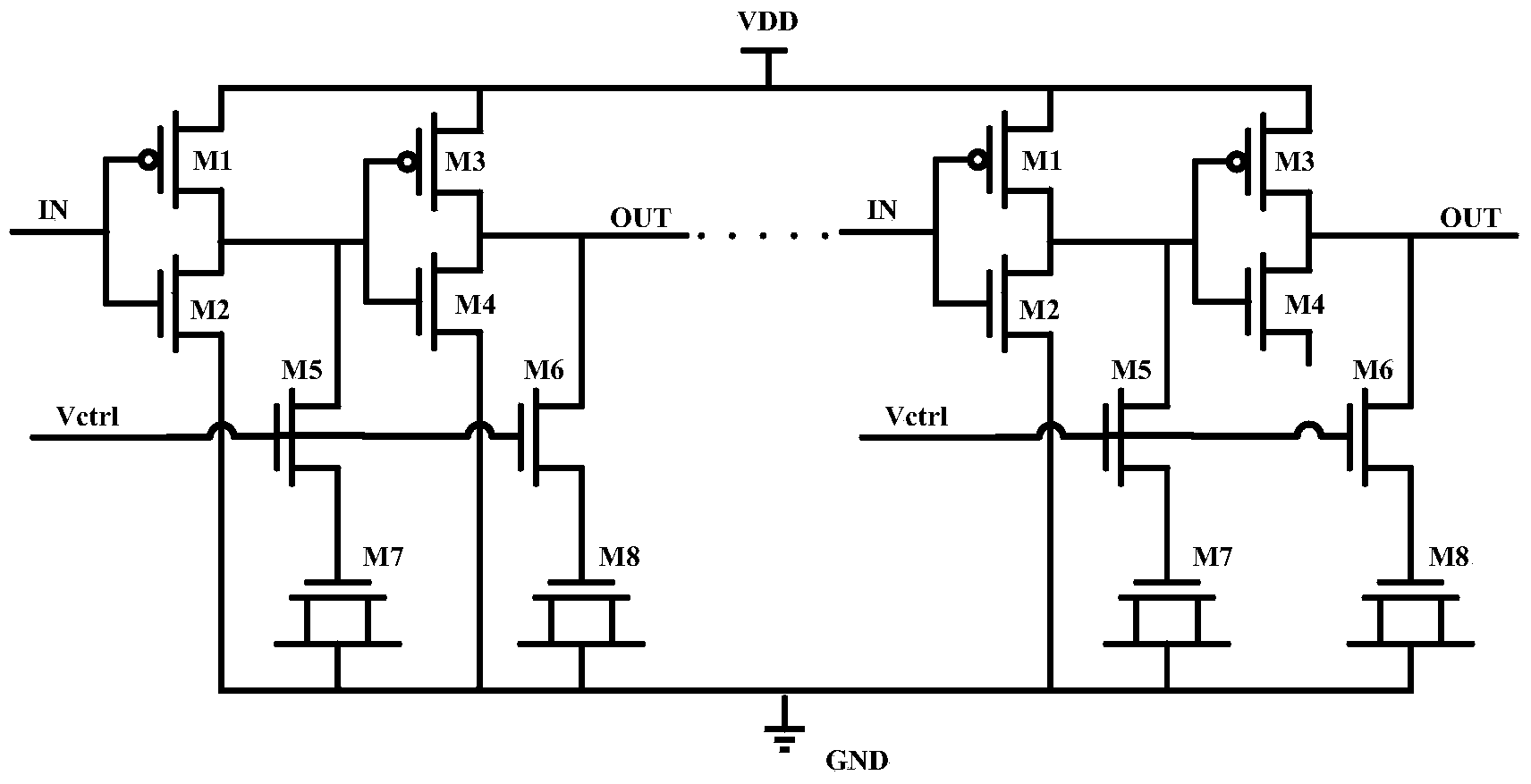
Voltage-control ring vibration type two-section type time digital conversion circuit based on DLL
The invention discloses a voltage-control ring vibration type two-section type time digital conversion circuit based on a DLL. TDC conversion with rough counting measuring and fine counting distinguishing is used in digital quantization of a tested time period. Delay time of a voltage-control delay unit is adjusted and controlled by the stage number a delay unit in a delay chain and the DLL. Under control of the DLL, a high-frequency stable clock is generated in a voltage-control ring vibration mode, multi-digit pseudorandom sequence LFSR counting is driven, and the function of rough counting measuring is achieved. High-section rough counting TDC has the effect of conversion range expanding, meanwhile, an N-stage voltage-control delay ring vibration structure is modulated by the DLL, by distinguishing of the evenly-distributed phases of nodes in a loop, rough measuring TDC quantization error time is subjected to fine quantization, and accordingly quantization accuracy is improved. A built-in identical-frequency redundancy coding processing mode is used in the low-band TDC, so that the common requirements of area lowering and data error code reducing are met at the same time.
Owner:SOUTHEAST UNIV
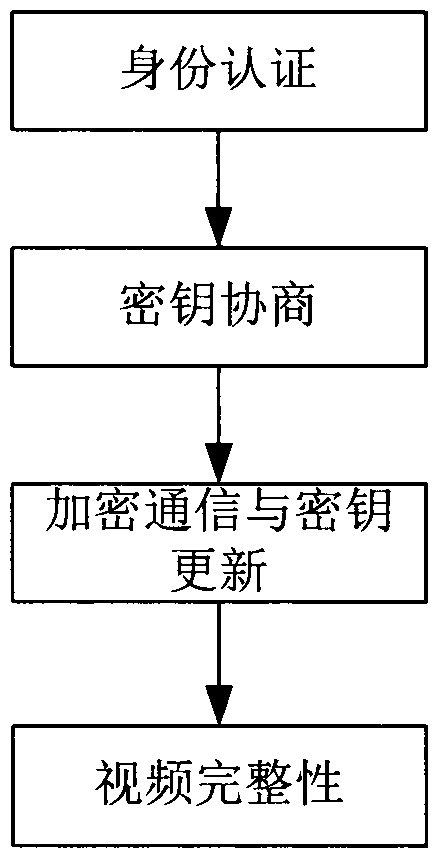
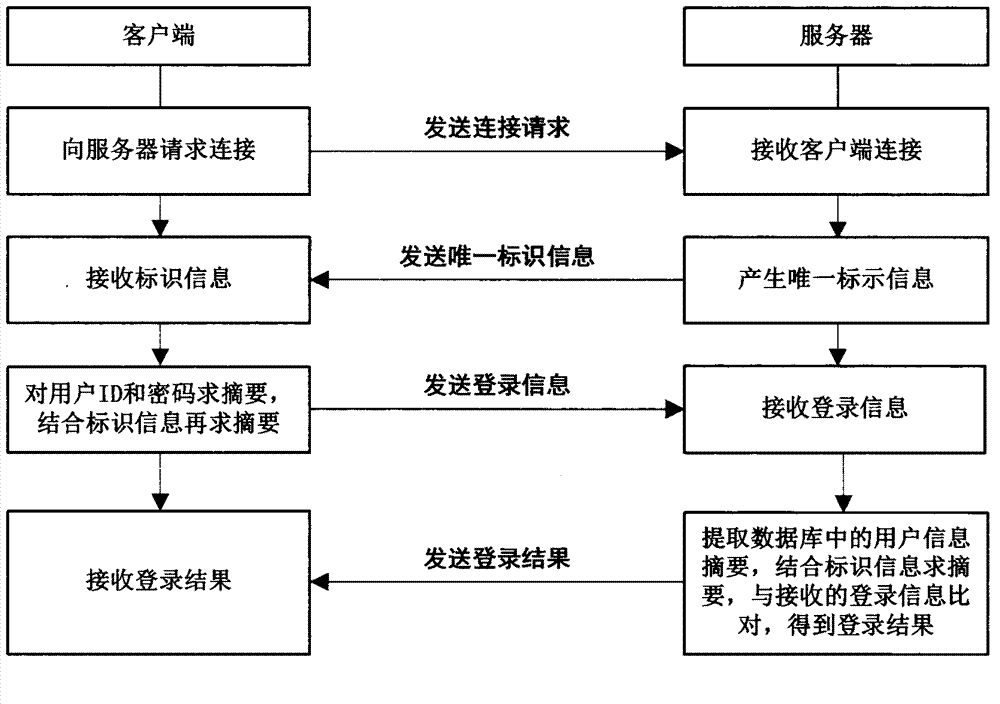
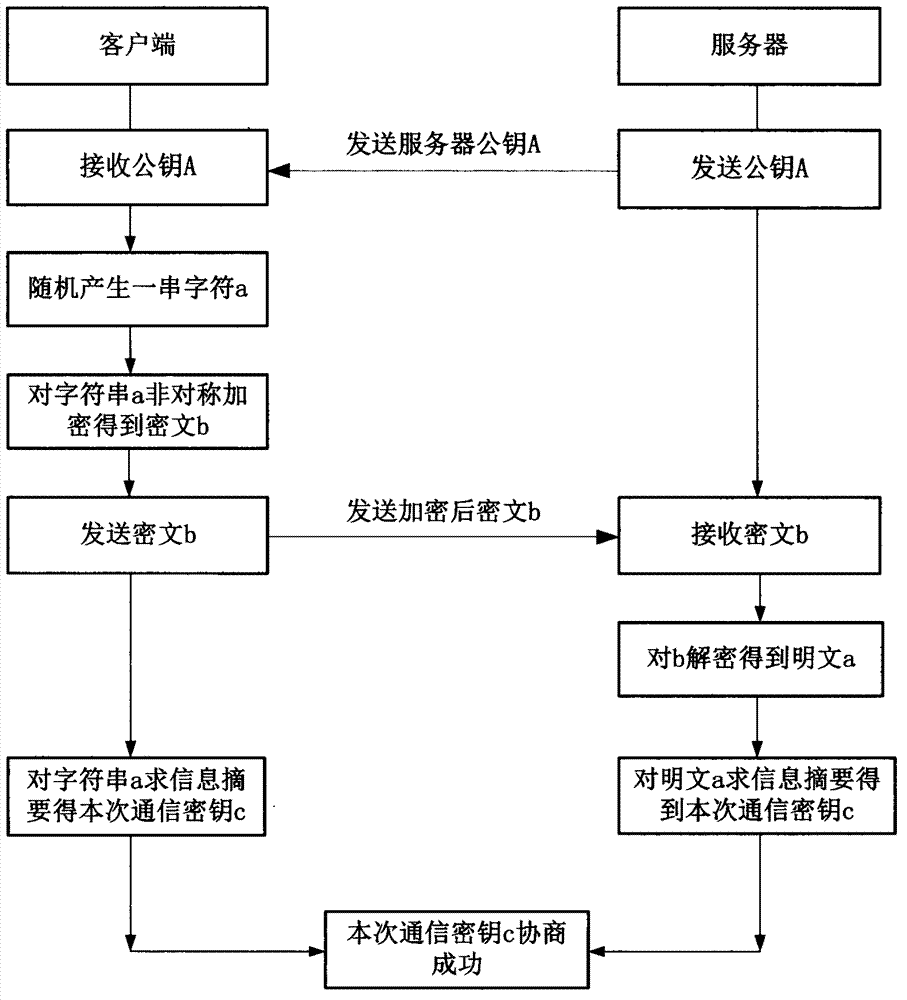
Social video information security method and system
InactiveCN102833246AIntegrity guaranteedGuaranteed randomnessKey distribution for secure communicationSelective content distributionData streamAttack
The invention discloses a social video information security method and a system. The method comprises the following four steps of identity authentication, key negotiation, encryption communication and rekeying and video integrity. The method comprises the following steps that a server carries out identity legitimacy authentication to connected users; two parties consult a post-communication key through asymmetric encryption and information digest algorithms; in the communication process, data streams are encrypted by using a chaotic pseudorandom sequence; and the server ensures that the video integrity is not damaged through two aspects of adding plaintext watermark and saving integrity information. The method and the system are applied, so that the user identity can be authenticated, imitation and attack are avoided, the randomness of every communication key is ensured, the personal information and the privacy of the users are prevented from being stolen, and the fact that the copyright of the videos shared by the users is not illegally infringed is effectively ensured. The technical scheme of the method and the system has a good development prospect.
Owner:NANJING UNIV
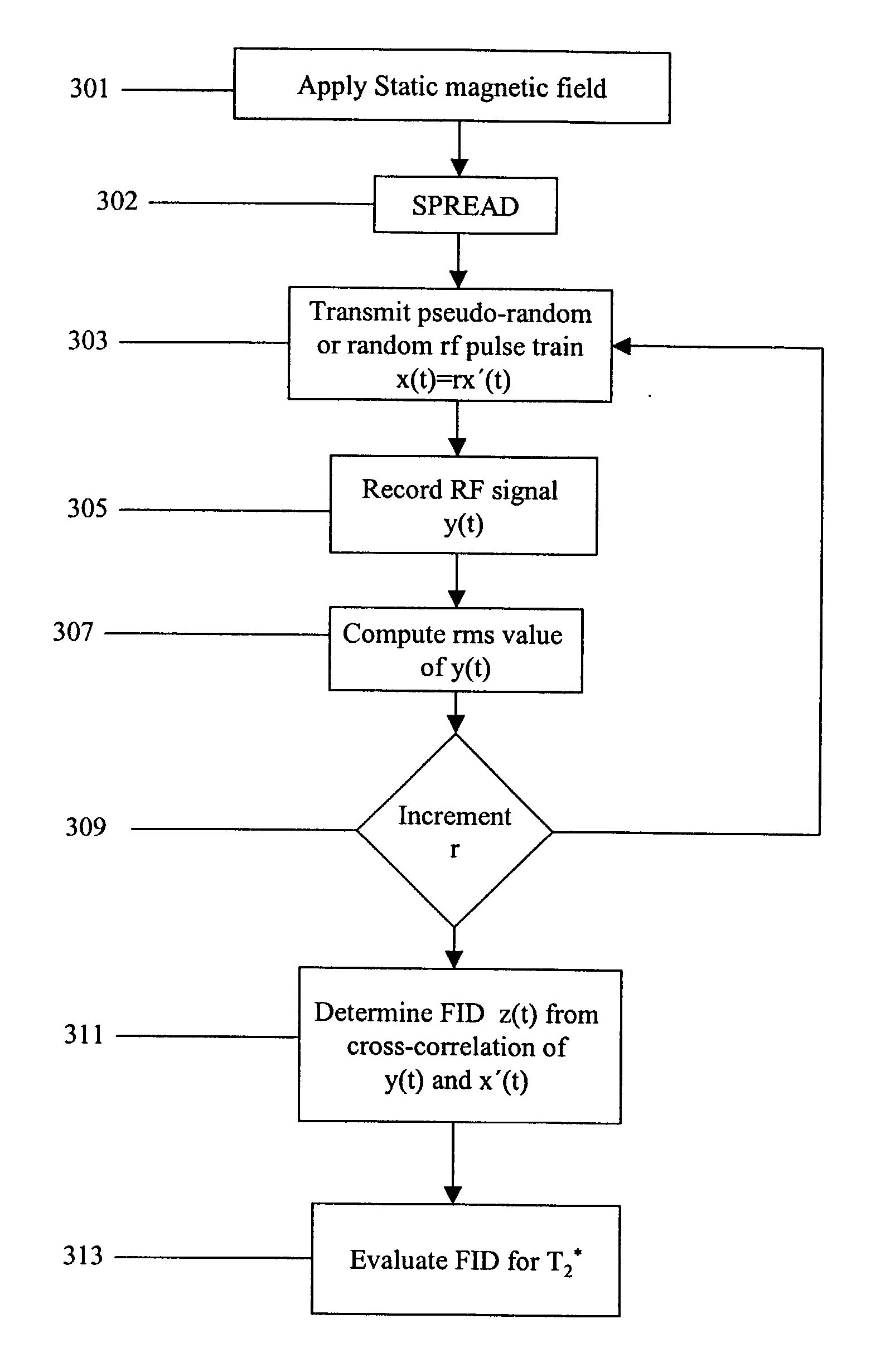
Stochastic NMR for downhole use
InactiveUS20040032258A1Electric/magnetic detection for well-loggingMeasurements using NMR imaging systemsSpinsPulse sequence
Stochastic pulsing using random or pseudo-random sequences is used for determination of nuclear spin properties of earth formations. This reduces the power requirements. Processing of the received signals may include linear or nonlinear cross-correlation with the excitation pulse sequence. Inversion of the results of the processing gives the desired nuclear spin property.
Owner:BAKER HUGHES INC
Environmental location system
InactiveUS6611758B1Easy to trackPrecise definitionAngle measurementNavigation by speed/acceleration measurementsInformation deviceAcoustic wave
A system and method for determining a location. The system employs encoded information devices dispersed through the environment, each having, a non-unique code associated therewith. The codes from the encoded information devices are acquired as a reading device passes nearby, and stored. The codes from a proximate set of information devices are correlated with a map or mapping relation to determine one or more consistent positions within the environment. The information devices are preferably passive acoustic wave transponders and the mapping relation may be a pseudorandom sequence or a defined map.
Owner:X CYTE
CP-EBPSK communication system for pseudorandom sequence phase modulation and communication method thereof
ActiveCN102739590AOccupies less bandwidthImprove spectrum utilizationPhase-modulated carrier systemsCommunications systemEngineering
The invention discloses a continue phase-extended binary phase shift keying (CP-EBPSK) communication system for pseudorandom sequence phase modulation and a communication method thereof. On the basis of a CP-EBPSK modulation mode, the CP-EBPSK communication system comprises a CP-EBPSK modulator of pseudorandom sequence phase modulation and a CP-EBPSK demodulator of pseudorandom sequence phase modulation. According to the CP-EBPSK modulator of pseudorandom sequence phase modulation, a pseudorandom sequence generator is added to an original CP-EBPSK modulator and the pseudo random number generated by the pseudorandom sequence generator is utilized to randomly select a symbol of the delta. And the CP-EBPSK demodulator of pseudorandom sequence phase modulation includes an impulse filter that is used for highlighting phase modulation information of a received signal and eliminating the polarity changes, so that the demodulation performance is not influenced by pseudorandom sequence modulation. According to the invention, advantages of narrow bandwidth occupied by the modulation signal, low interference, simple realization, wide code rate adaptive range and flexible application.
Owner:苏州东奇信息科技股份有限公司
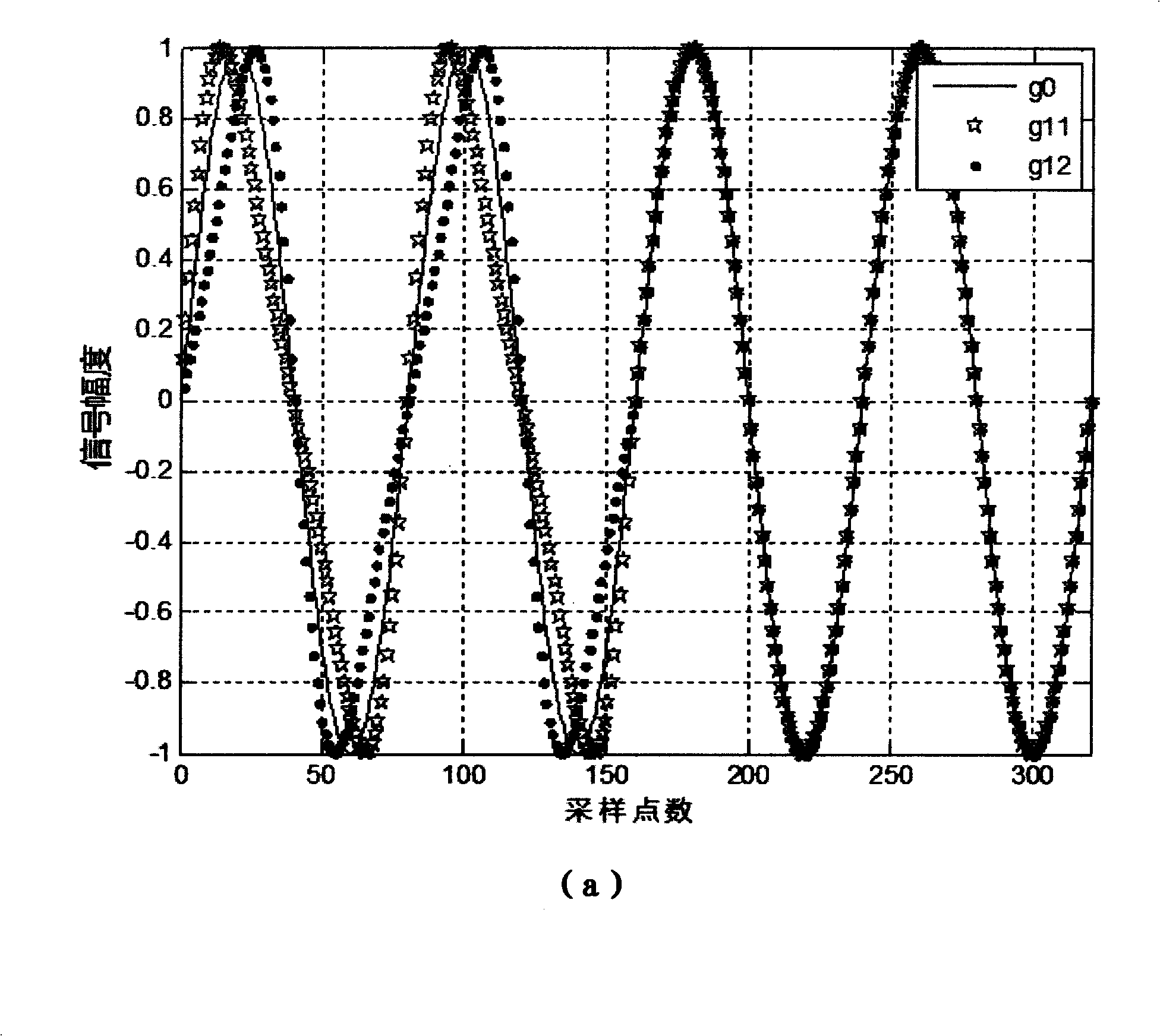
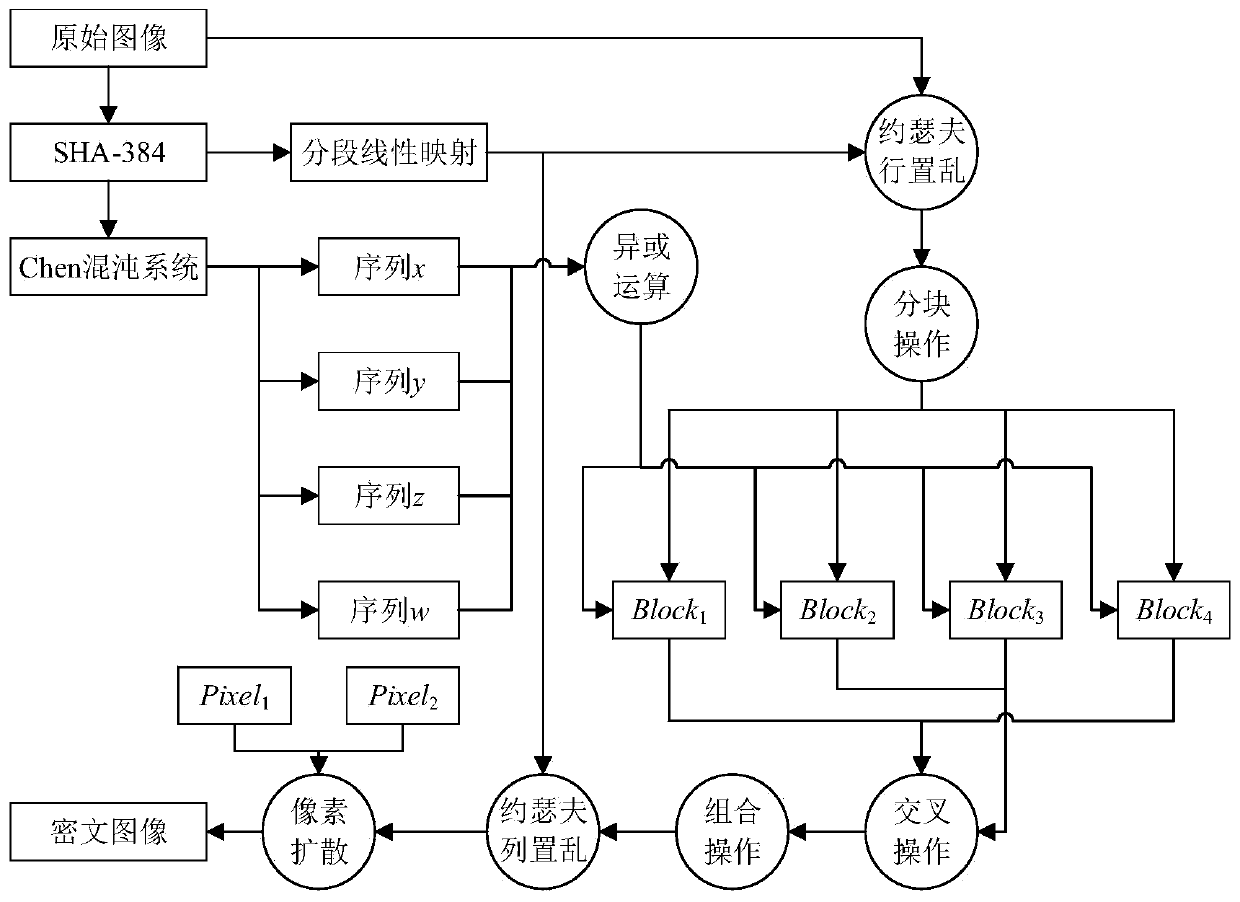
Josepher traversal and hyper-chaotic system image encryption method based on pixel value association
ActiveCN110086601AReduce the number of iterationsIncreased sensitivityEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsPlaintextHash function
The invention provides a Josepher traversal and hyper-chaotic system image encryption method based on pixel value association. The method comprises the following steps of inputting an original image into a hash function, and operating to obtain the initial values of the segmented linear mapping and a Chen hyper-chaotic system; obtaining a pseudorandom sequence U through the segmented linear mapping, and obtaining four pseudorandom sequences through the Chen hyper-chaotic system; taking the pseudorandom sequence U as an index value, and carrying out line scrambling on the original image by using a Josephv scrambling method associated with a pixel value to obtain a ciphertext image C1; respectively carrying out pixel replacement on equally divided ciphertext blocks of the ciphertext image C1by the four pseudorandom sequences to obtain a ciphertext image C2; taking the pseudorandom sequence U as an index value, and performing column scrambling on the ciphertext image C2 by using the Josephv scrambling method associated with the pixel value to obtain a ciphertext image C3; and performing pixel diffusion on the ciphertext image C3 by using the key pixel to obtain an encrypted ciphertext image. The method is strong in sensitivity to a secret key and a plaintext, and improves the security of the ciphertext image and the connection between the pixels.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
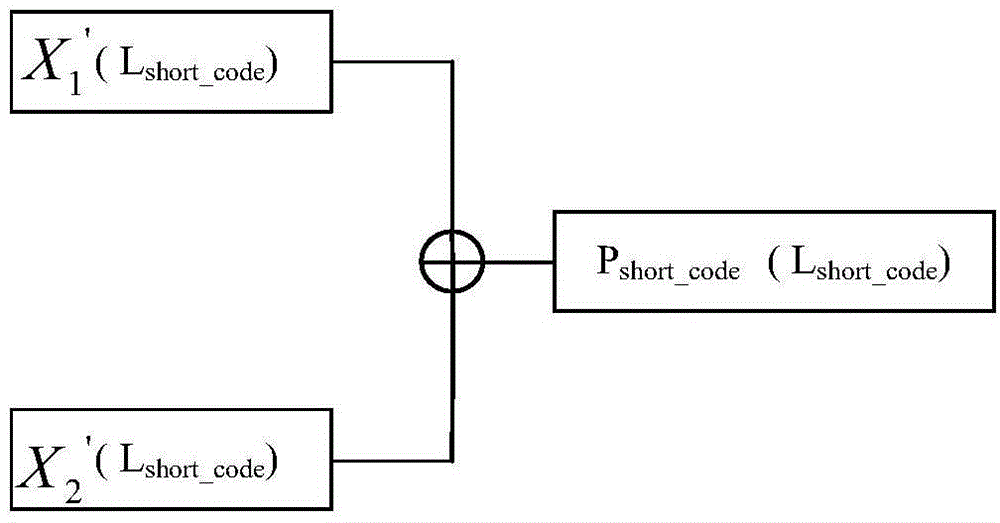
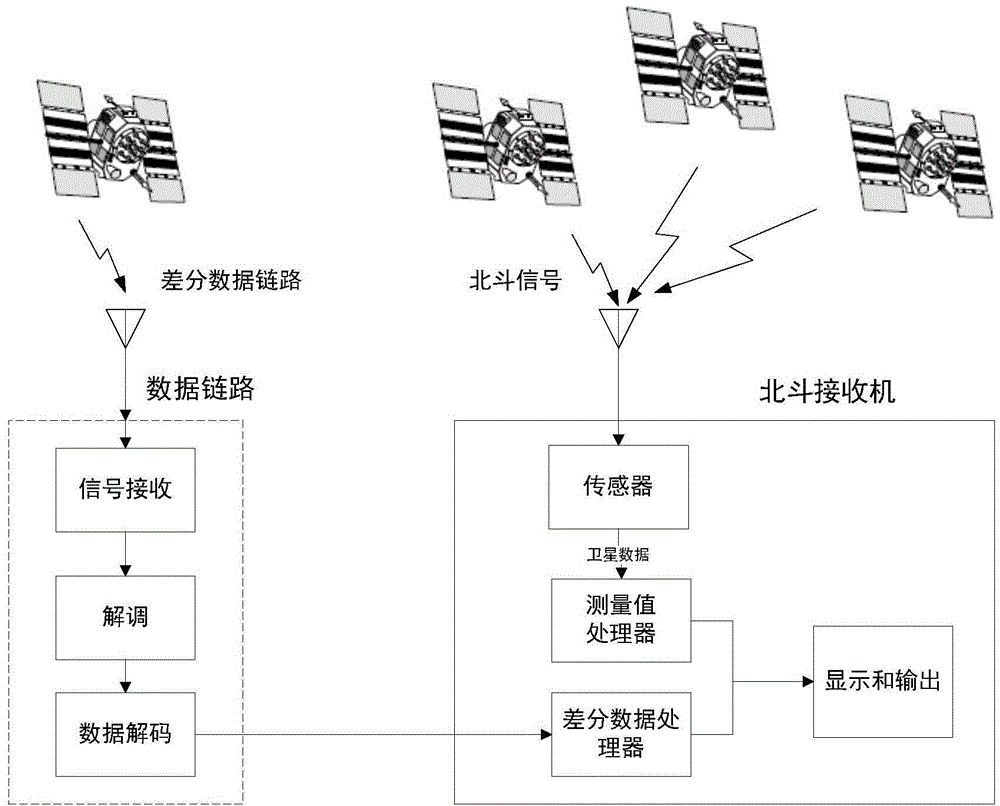
Beidou space-based high-precision real-time positioning method
InactiveCN104570024AImprove and enhance location services performanceEnhanced Location Services PerformanceSatellite radio beaconingSatellite observationCarrier signal
The invention provides a Beidou space-based high-precision real-time positioning method. The method comprises the following steps: firstly, generating difference revised data, then generating a difference broadcast telegraph text, adopting two pseudorandom sequences to generate a short precise code, and conducting spectrum spread and carrier modulation on the difference broadcast telegraph text and the short precise code so as to generate a difference broadcast signal; a user positioning terminal combines difference broadcast data of the difference broadcast signal and Beidou navigation satellite observation data to conduct positioning calculation so as to realize high-precision real-time positioning. The method can effectively realize decimeter-degree high-precision real-time positioning in the coverage area of a geosynchronous orbit satellite, and quickly improves and enhances the positioning service performance of a Beidou satellite navigation system.
Owner:NAT TIME SERVICE CENT CHINESE ACAD OF SCI
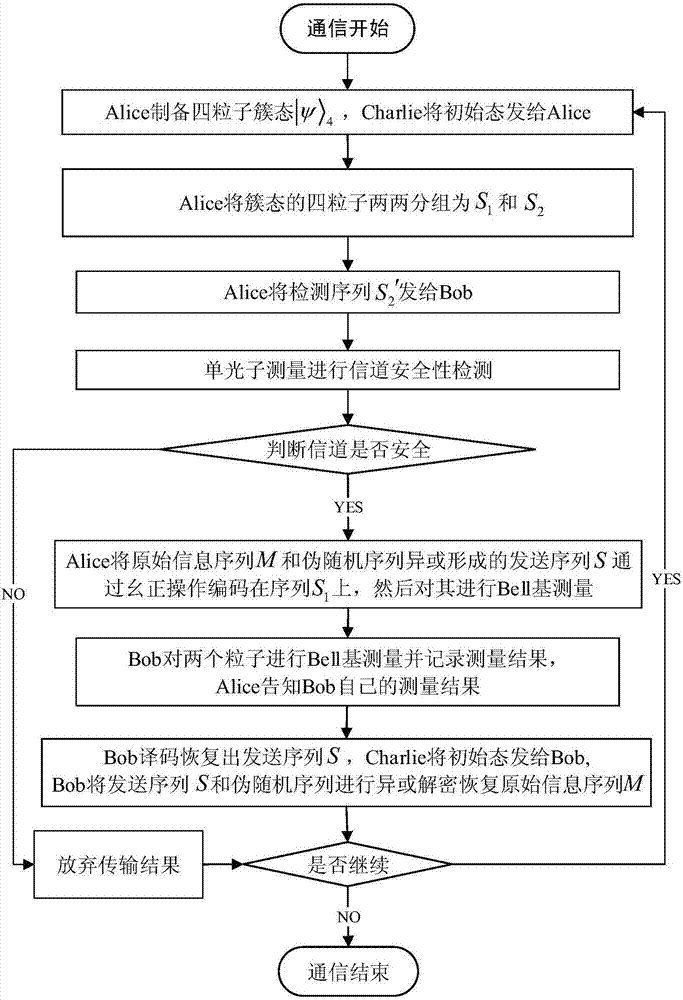
Controlled quantum security direct communication method based on four particle cluster states
ActiveCN107222307AMaintain entanglementLong cycleKey distribution for secure communicationPhotonic quantum communicationAlice and BobQuantum secure direct communication
The invention discloses a controlled quantum security direct communication method based on four particle cluster states. Alice and Bob respectively serve as a legal information sender and a legal information receiver during a quantum communication process, and Charlie serves as a credible scheme control party; information security is achieved by randomly inserting a single photon to perform measurement-based comparison detection, and communication starts after security detection; Alice uniformly divides the prepared four particle cluster states into two groups, after being subjected to an XOR operation with a pseudorandom sequence, the sent information is encoded on the two particles reserved by Alice via unitary transformation. Alice performs Bell-based measurement on reserved particles, and sends measurement information to Bob, and Bob recovers the original sequence via an initial state sent by Charlie after the measurement information is compared. The four particle cluster states used by the method has good entanglement, connectivity and damage resistance, only the receiver Bob in the method gets the permission of the controller Charlie, Bob can recover the original information, so that the information can be effectively prevented from being attacked during a transmission process, and an implementation process is simple.
Owner:NORTHWEST UNIV
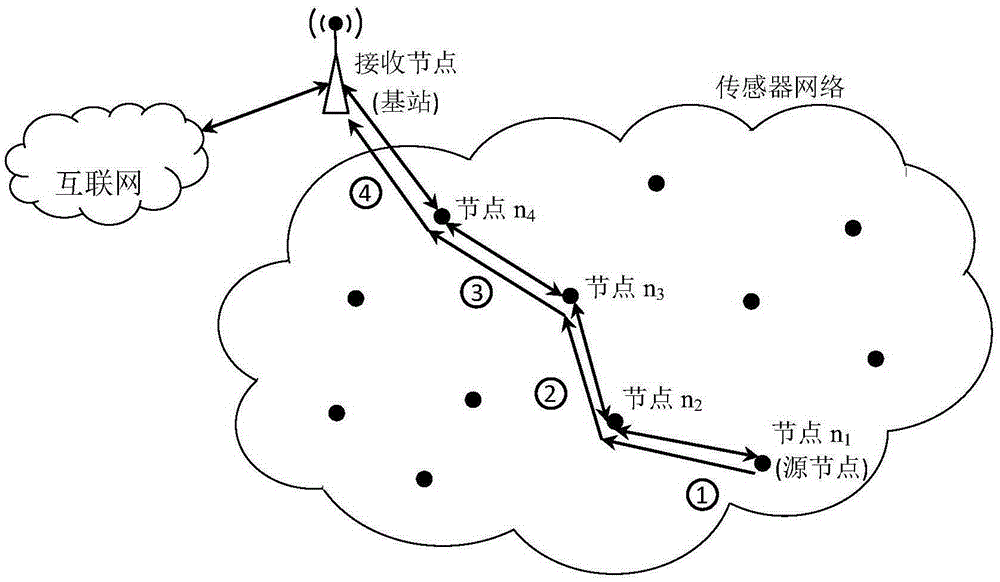
Wireless sensor network data traceablility method based on pseudorandom sequence
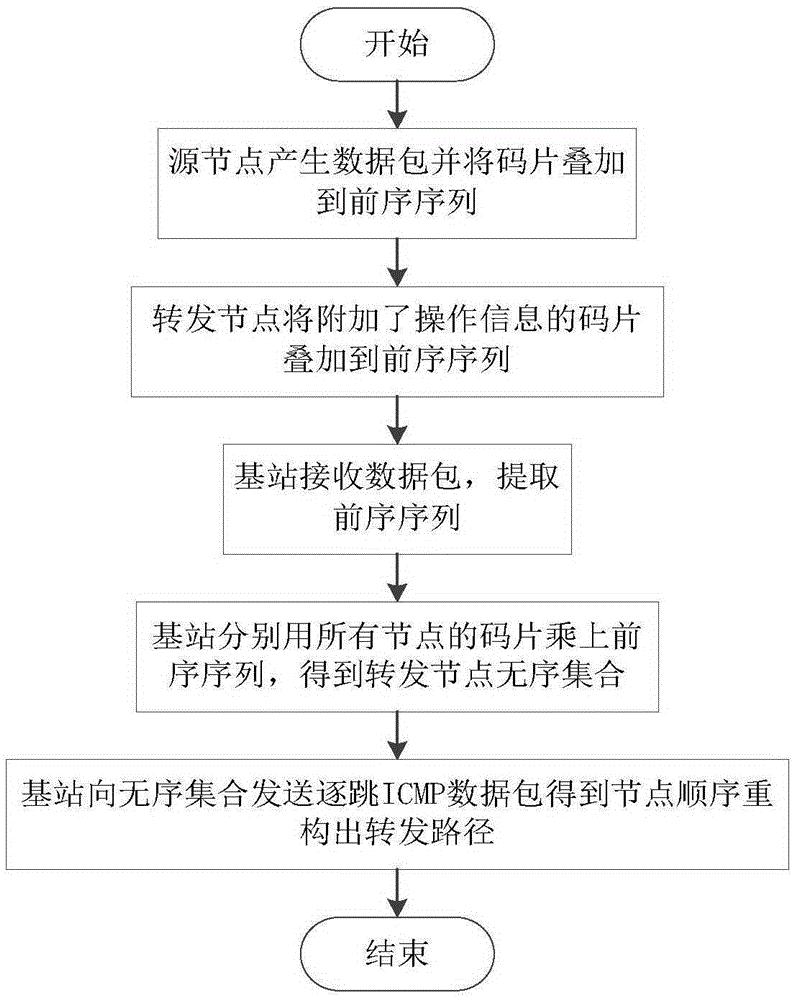
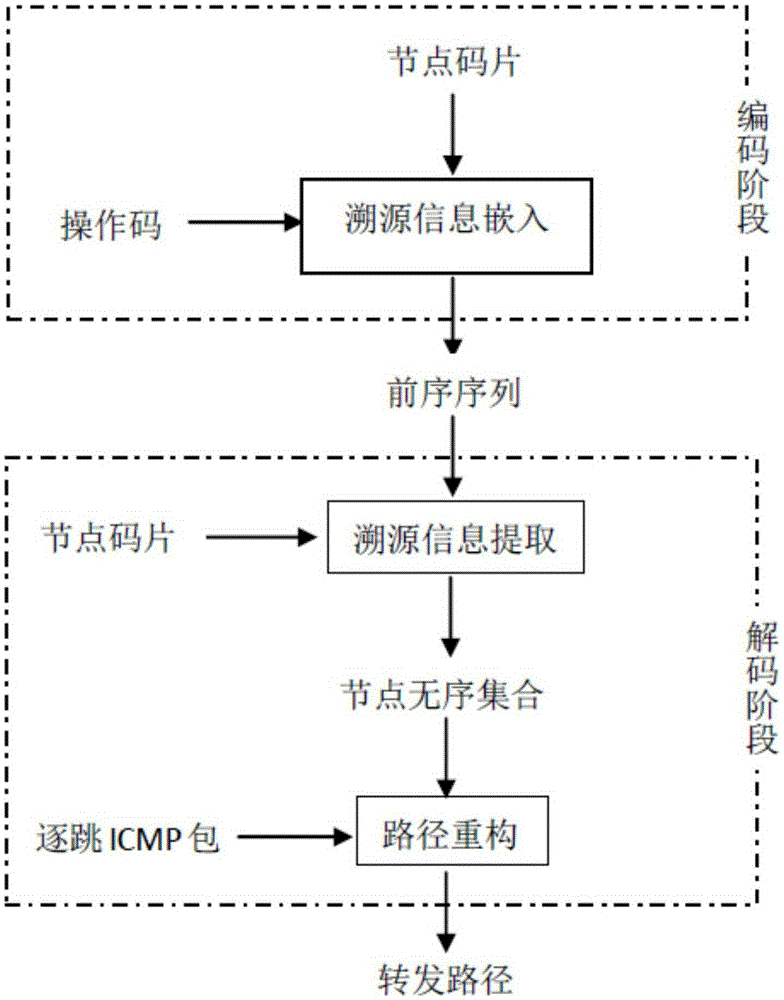
ActiveCN105338570APrevent degradationCutting costsNetwork traffic/resource managementNetwork topologiesInformation processingNetwork packet
The invention discloses a wireless sensor network data traceablility method based on a pseudorandom sequence. The method is characterized in that the method comprises a coding stage and a decoding state of traceablility information, wherein in the coding stage, a source node and a plurality of forwarding nodes enable orthogonal code pieces of themselves to serve as the traceablility information which is written to a preorder sequence of a data packet after being added, the code pieces are allocated autonomously by a base station during construction of the network, and after the data packet arrives at the base station, decoding starts; and in the decoding state, the base station enables the code pieces of all nodes managed thereby to calculate inner product with the preorder sequence of the data packet respectively, a forwarding path node unordered set is obtained according to the inner product result, and finally, the base station restores forwarding paths by sending a plurality of internet control message protocol messages having different time of live (TTL) values and obtaining the traceablility result. The pseudorandom sequence is utilized to realize reuse effect; and through extended operation codes, richer traceablility information is transmitted, thereby suppressing data degeneration, compressing the traceablility information to the largest degree, improving information processing speed in a wireless sensor network, and reducing traceablility cost.
Owner:SHANDONG UNIV
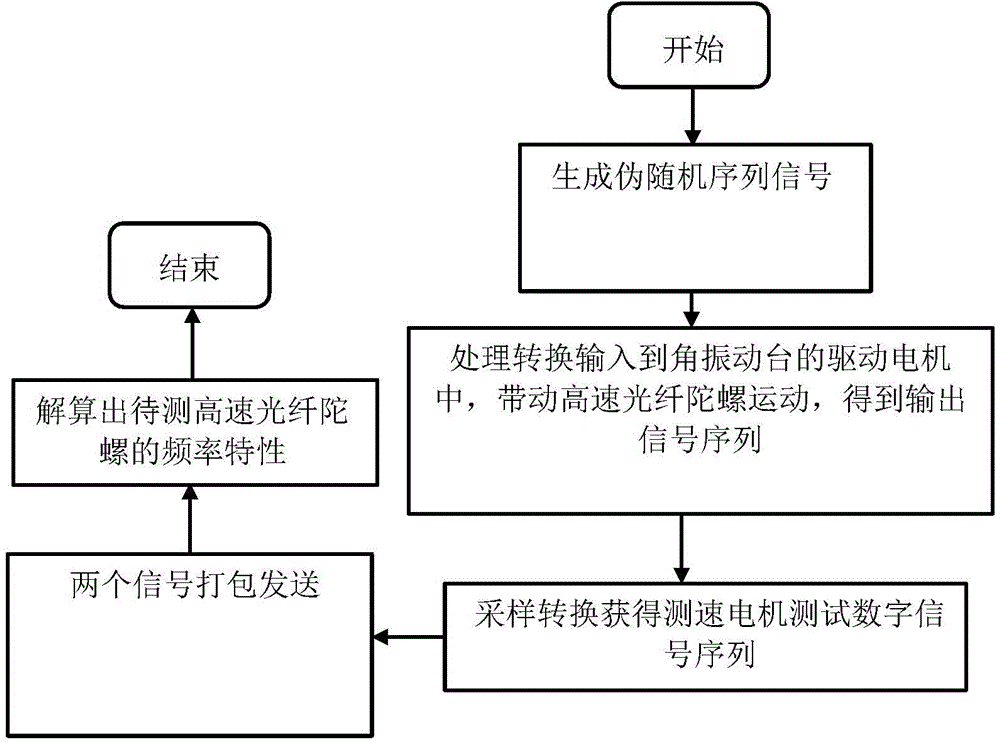
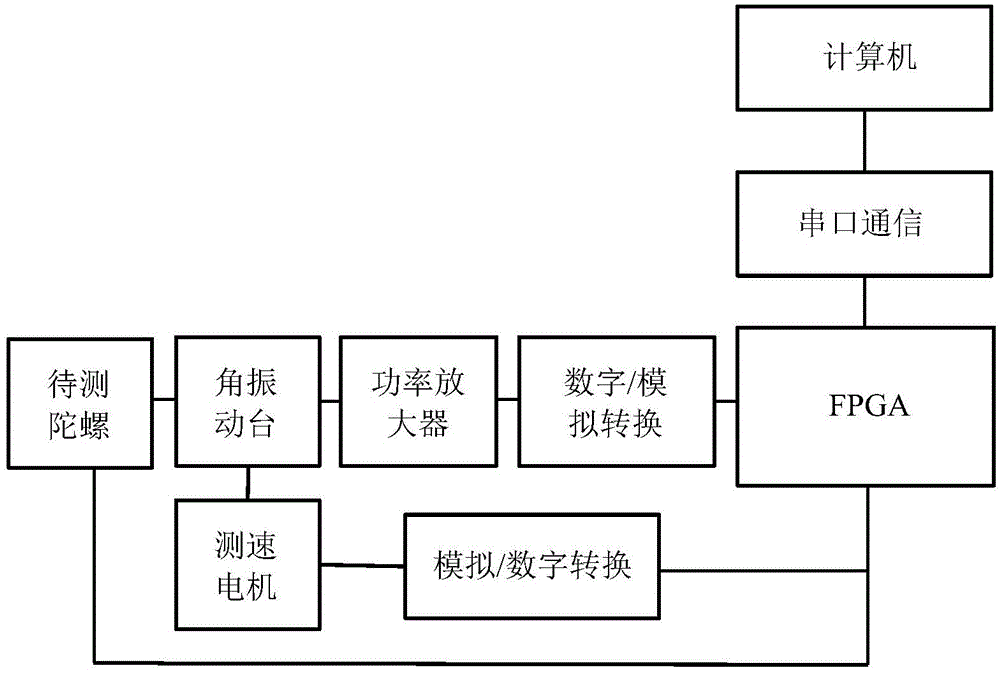
Method and system for measuring frequency characteristics of high-speed FOG (Fiber Optical Gyroscope)
InactiveCN104950169AEnhanced inhibitory effectReduce volumeSpectral/fourier analysisFrequency measurement arrangementDrive motorDigital signal
The invention discloses a method and a system for measuring frequency characteristics of a high-speed FOG (Fiber Optical Gyroscope). The method comprises the steps of logically generating a pseudorandom sequence test digital signal according to the generation of a pseudorandom sequence; processing and converting the pseudorandom sequence test digital signal into a pseudorandom sequence test analog signal, and inputting the pseudorandom sequence test analog signal to a driving motor of an angular vibration table to be used as a rotary input signal; enabling the angular vibration table to drive a to-be-measured high-speed FOG to run, and obtaining an output signal sequence of the to-be-measured high-speed FOG; collecting an angular speed analog signal of a speed measuring motor, and obtaining a digital signal sequence of the speed measuring motor; computing the output signal sequence of the to-be-measured high-speed FOG and the digital signal sequence of the speed measuring motor, and obtaining a frequency response function of the to-be-measured high-speed FOG, wherein the frequency response function comprises amplitude-frequency characteristics and phase-frequency characteristics; completing the measurement. The method disclosed by the invention can be used for quickly and accurately measuring the frequency characteristics of the high-speed FOG and has the characteristics that the frequency resolution is high, the measured frequency range is large, the amplitude-frequency characteristics and the phase-frequency characteristics of the high-speed FOG can be simultaneously measured, the noise suppression effect is good, the measuring speed is fast, and the like.
Owner:ZHEJIANG UNIV
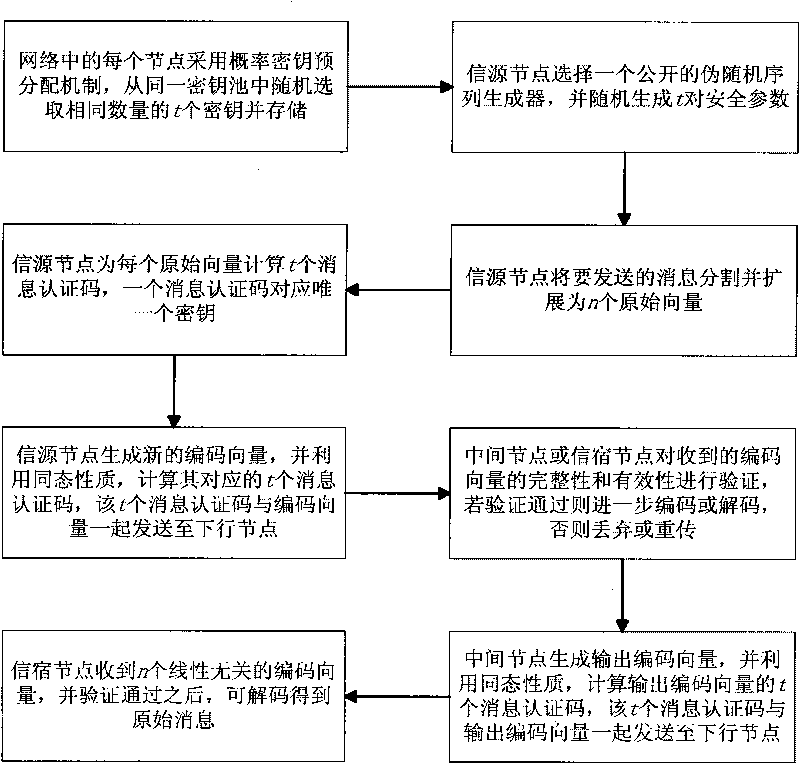
Anti-pollution network encoding method based on probability detection
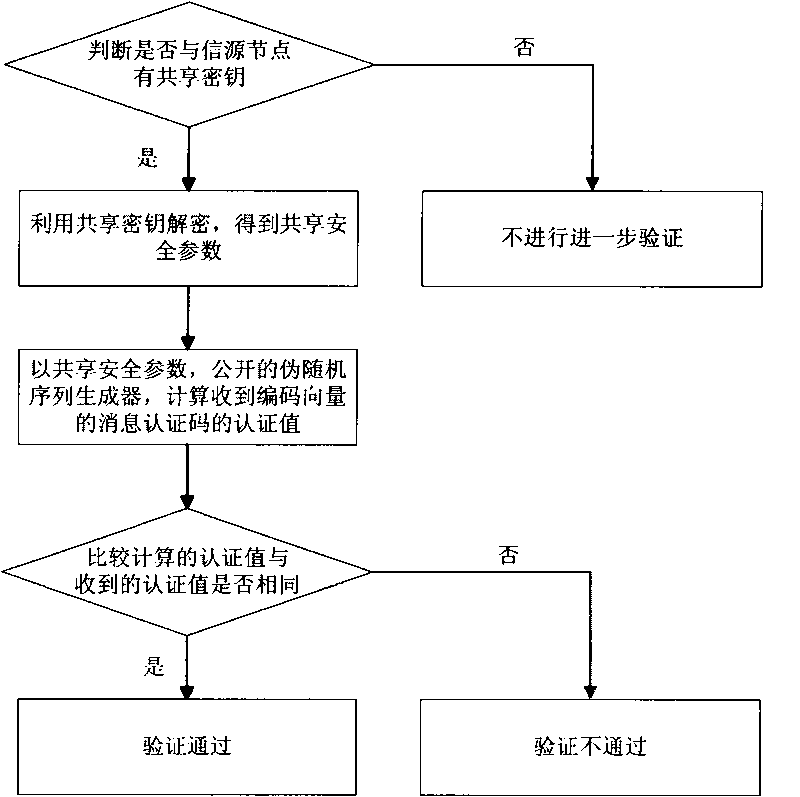
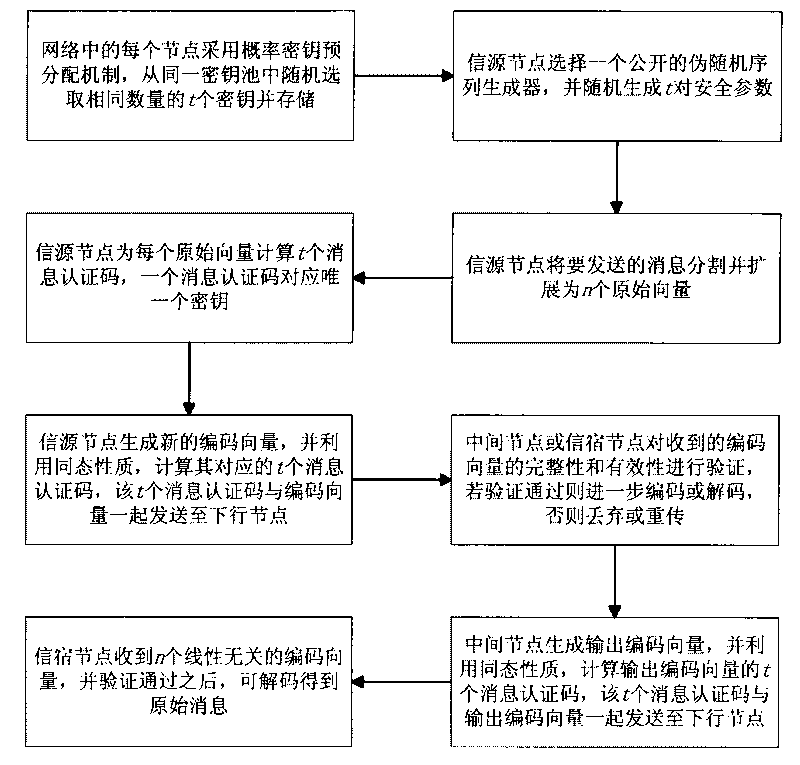
InactiveCN101714910AReduce overheadReduce computational complexityKey distribution for secure communicationError preventionNetwork codeMessage authentication code
The invention discloses an anti-pollution network encoding method based on probability detection, which comprises the following steps of: each node of the network randomly selects t keys from a key pool by adopting a probability key predistribution mechanism; an information source node cuts and expands information into n original vectors; the information source node selects t pairs of safety parameters and a pseudorandom sequence generator and computes t information authentication codes for each original vector by utilizing the t keys; the information source node or an intermediate node can compute t information authentication codes for new code vectors by utilizing homogeneity; the intermediate node or an information sink node authenticates the integrality and the effectiveness of received code vector data by utilizing shared keys of the intermediate node or the information sink node and the information source node; and the information sink node can decode to obtain original information after receiving n linearly independent code vectors and authenticating the n linearly independent code vectors. The invention has good safety property, high pollution detection probability, little communication overhead and fast authentication and is suitable for the safety application of network codes.
Owner:XIDIAN UNIV
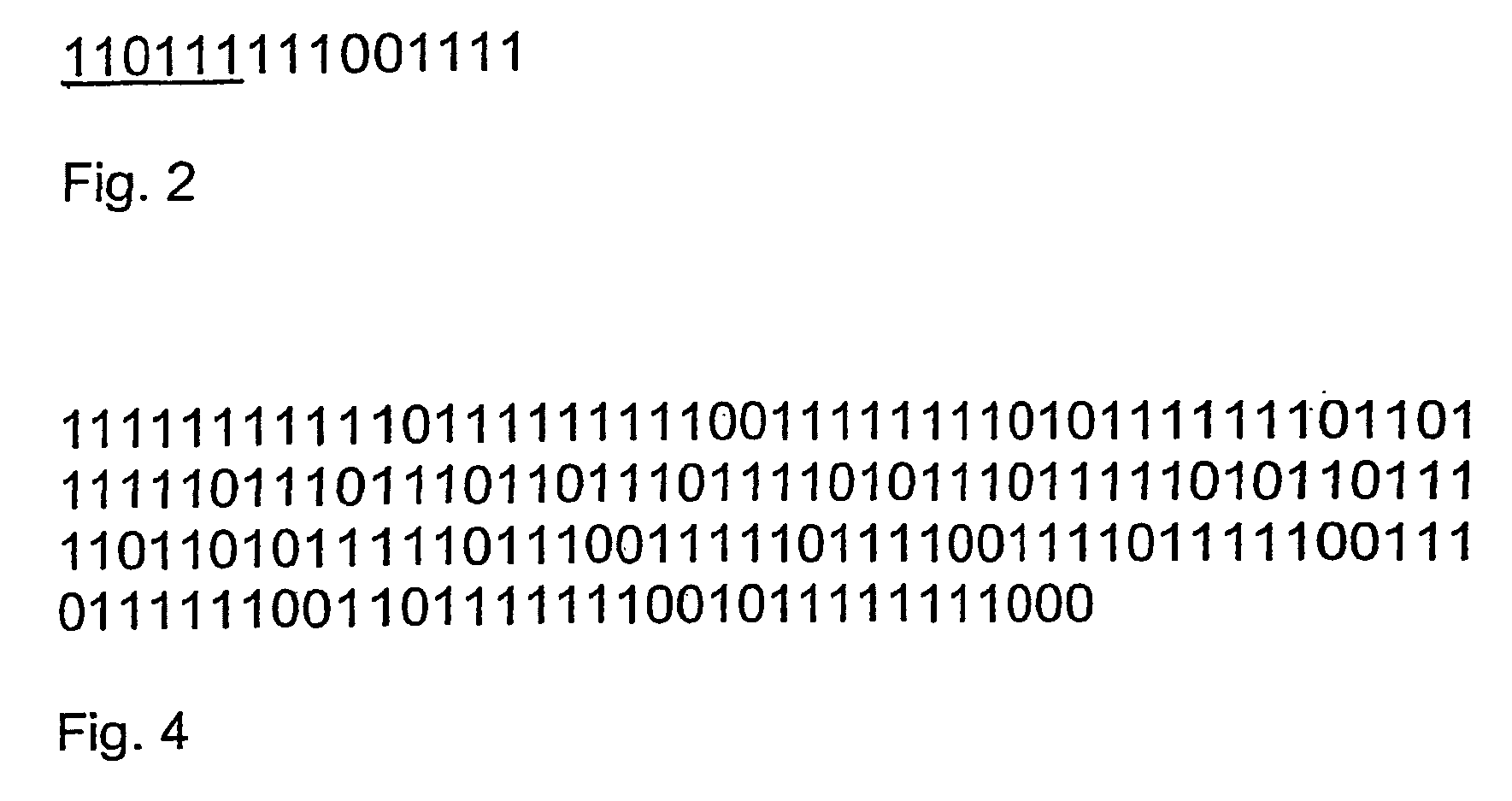
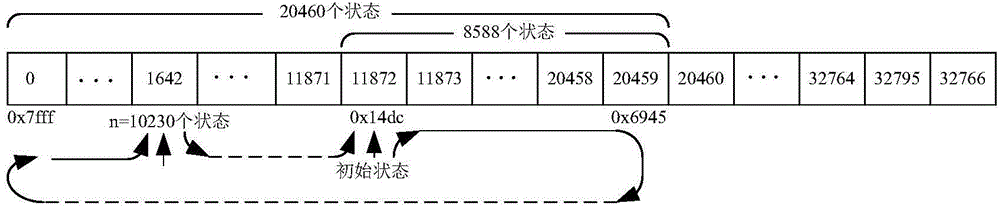
Pseudorandom sequence generating method
InactiveCN101132383APromote generationGenerate efficientlyRandom number generatorsPhase-modulated carrier systemsTime domainInitial sequence
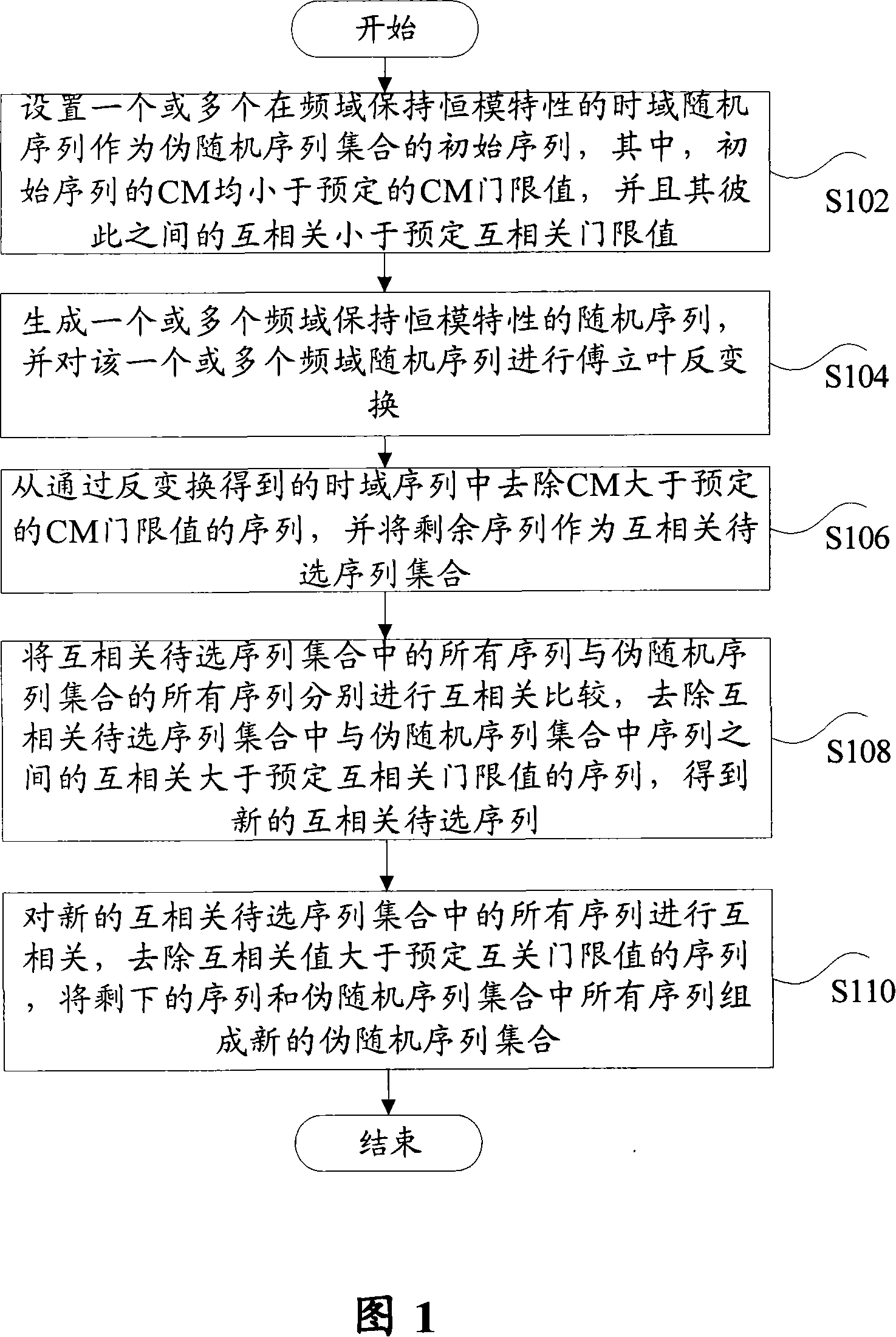
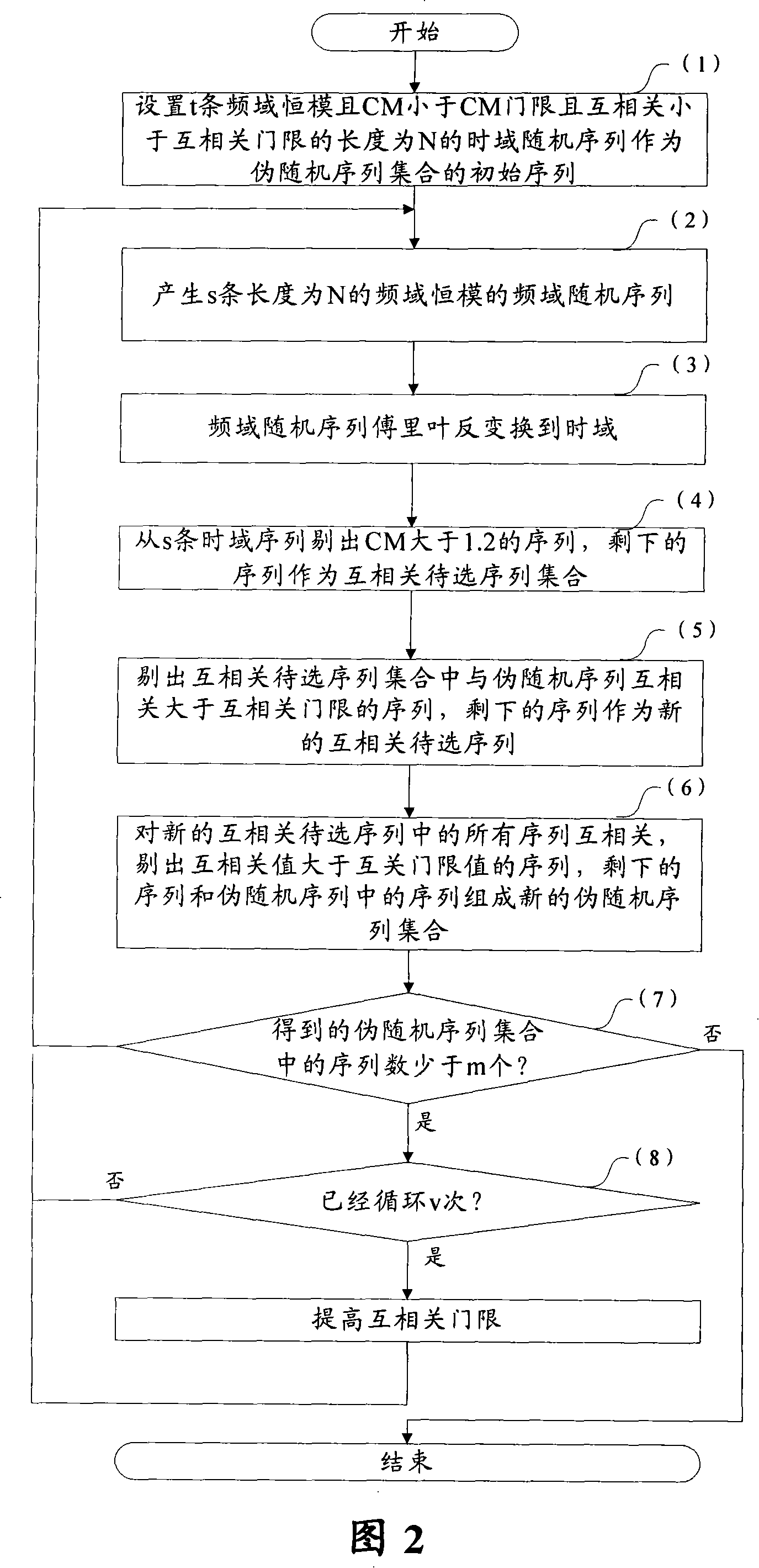
This invention relates to a method for generating false random sequences including: setting one or multiple time domain random sequences keeping constant mode property in the time domain as the intial sequences of a false random sequence set, generating one or multiple frequency domain random sequences of constant mode and making Fourier inversion to them, eliminating sequences with CM greater than a predesigned CM threshold value from the time domain sequences got by the inversion and taking the rest as the mutuallity set being selected and comparing them to eliminate sequences with the mutuality greater than a preset threshold value of mutuality among sequences from the being selected and the false random sequence set to get a new mutuality sequence to be selected to be corss correlated and eliminated sequences with the value greater than the preset threshold value of mutuality to form the rest sequences and those in the false random sequence set to a new false random sequence set.
Owner:ZTE CORP
Efficient system identification schemes for communication systems
Systems and methodologies are described that facilitate efficiently indicating parameter(s) associated with a base station utilizing synchronization signals in a wireless communication environment. For instance, relative locations of a PSC and a SSC in a radio frame can be a function of a parameter. Further, a PSC sequence utilized to generate PSCs can be selected based upon a parameter. Moreover, inclusion or exclusion of PSCs from a radio frame can be a function of a parameter. Additionally or alternatively, pseudo random sequence mappings (e.g., to cell IDs, tone locations) can be a function of a parameter. Example parameters can be whether the base station is part of a TDD or a FDD system, whether the radio frame employs FS1 or FS2, whether the base station is associated with a macro or a femto cell, or whether the base station is associated with a unicast or a multicast system.
Owner:QUALCOMM INC
Systems and Methods for Improved Fault Coverage of LBIST Testing
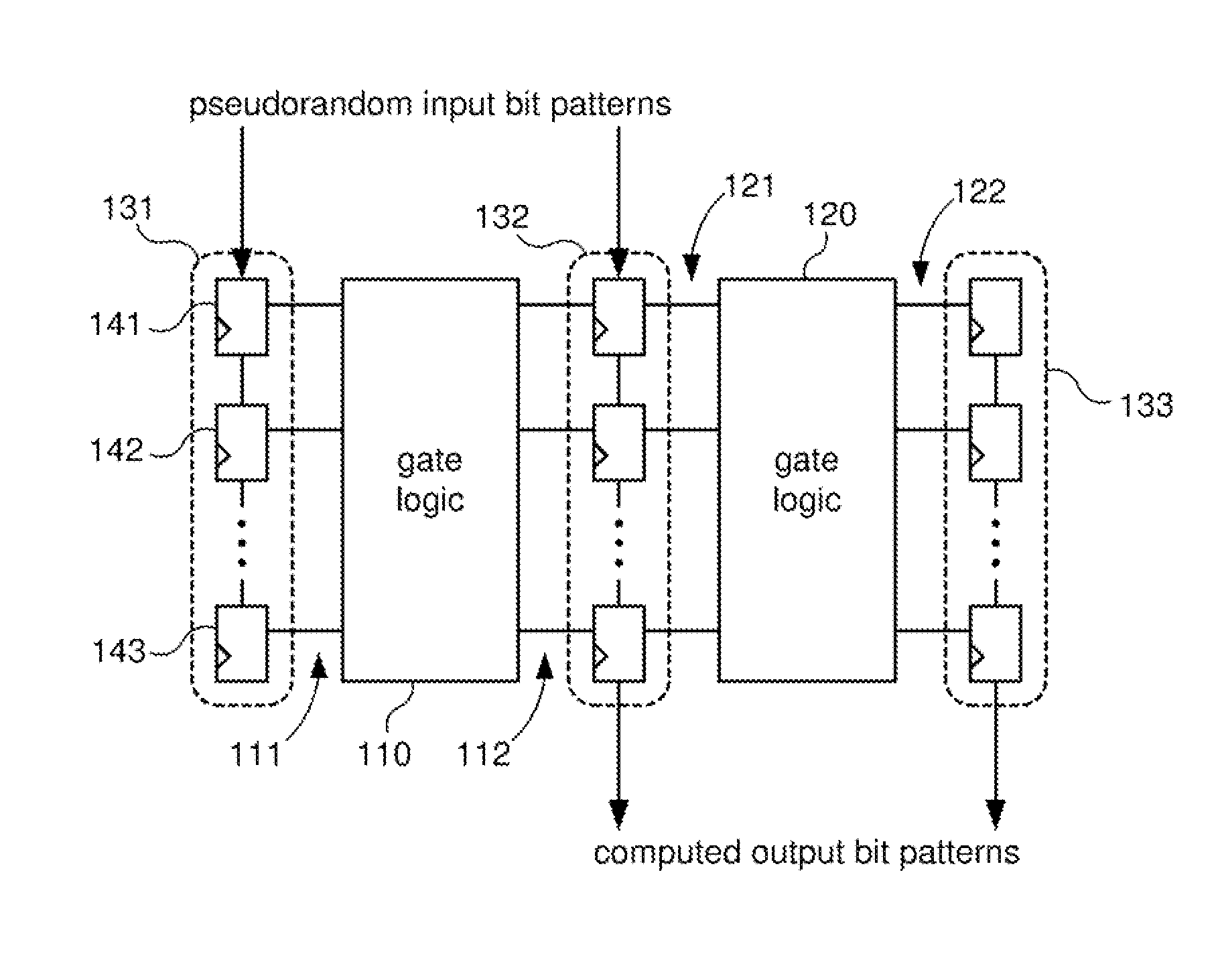
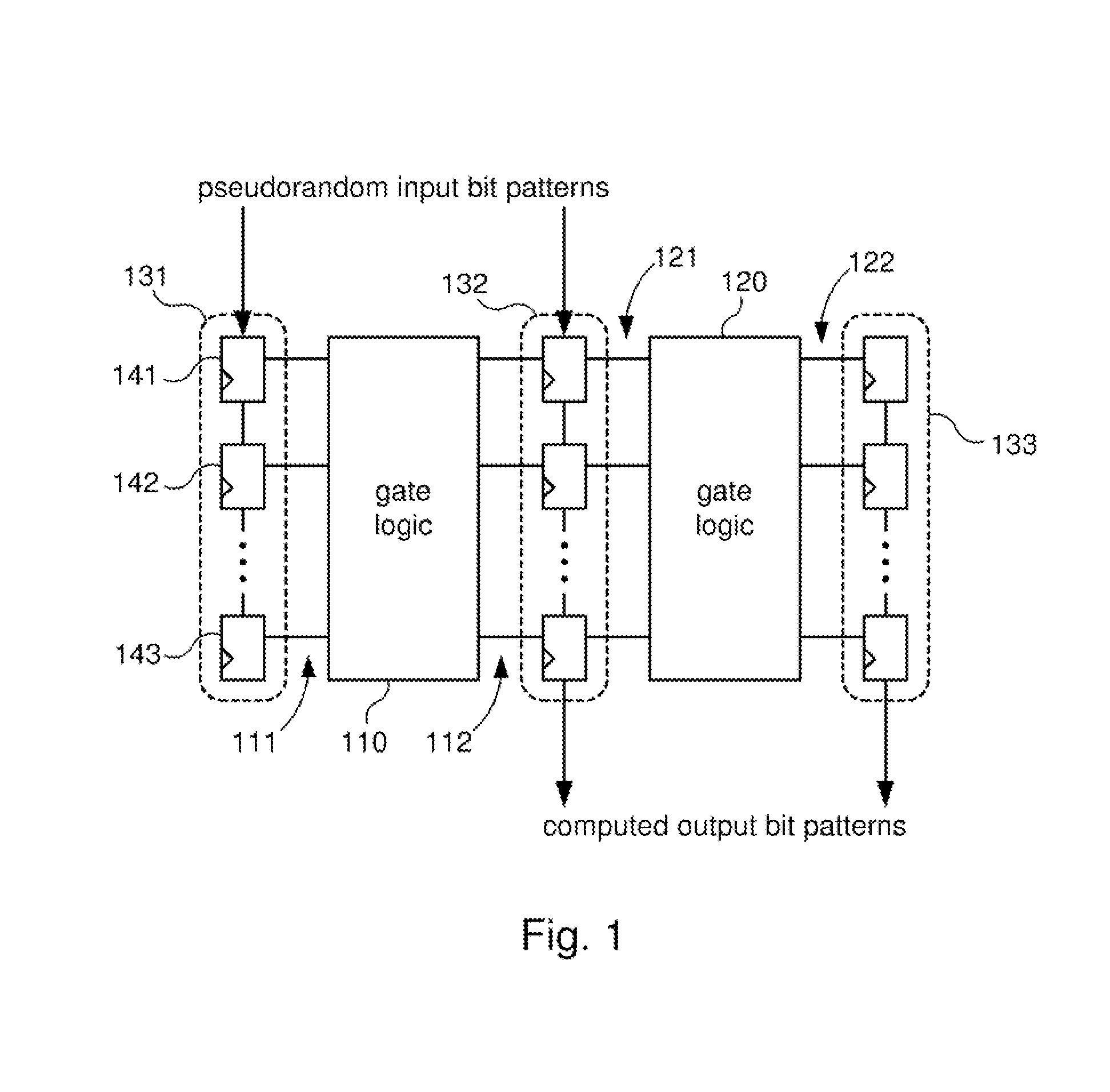
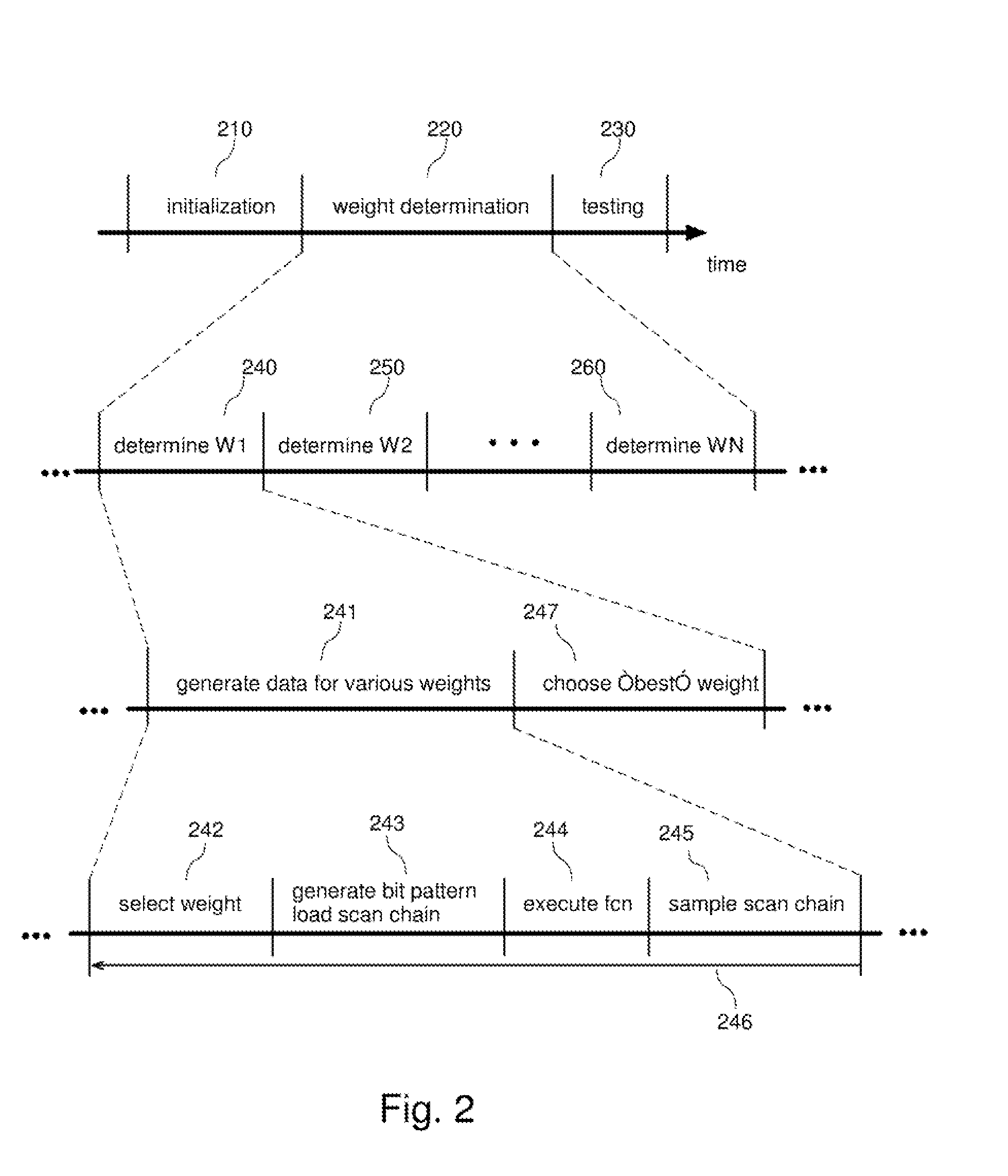
InactiveUS20070273401A1Improve fault coverageReduce in quantityElectronic circuit testingError detection/correctionFault coverageEngineering
Systems and methods for improved fault coverage of logic built-in-self-tests (LBISTs) in integrated circuits (ICs) by determining weighting and / or seed values to be used in generating pseudorandom test bit patterns for each channel to optimize fault coverage. In one embodiment, a method includes generating a pseudorandom sequence of bits, applying a weighting value to the sequence, propagating the weighted sequence through one or more levels of logic, and capturing the resulting data. Metrics are then applied to the captured data to determine the suitability or optimality of the weighting value, and an optimal weighting value is selected. This may be performed for a plurality of trial values for each of a number of channels to obtain a set of weighting values for the different LBIST channels. The method may also include determining a seed value for the pseudorandom bit pattern generator.
Owner:TOSHIBA AMERICA ELECTRONICS COMPONENTS
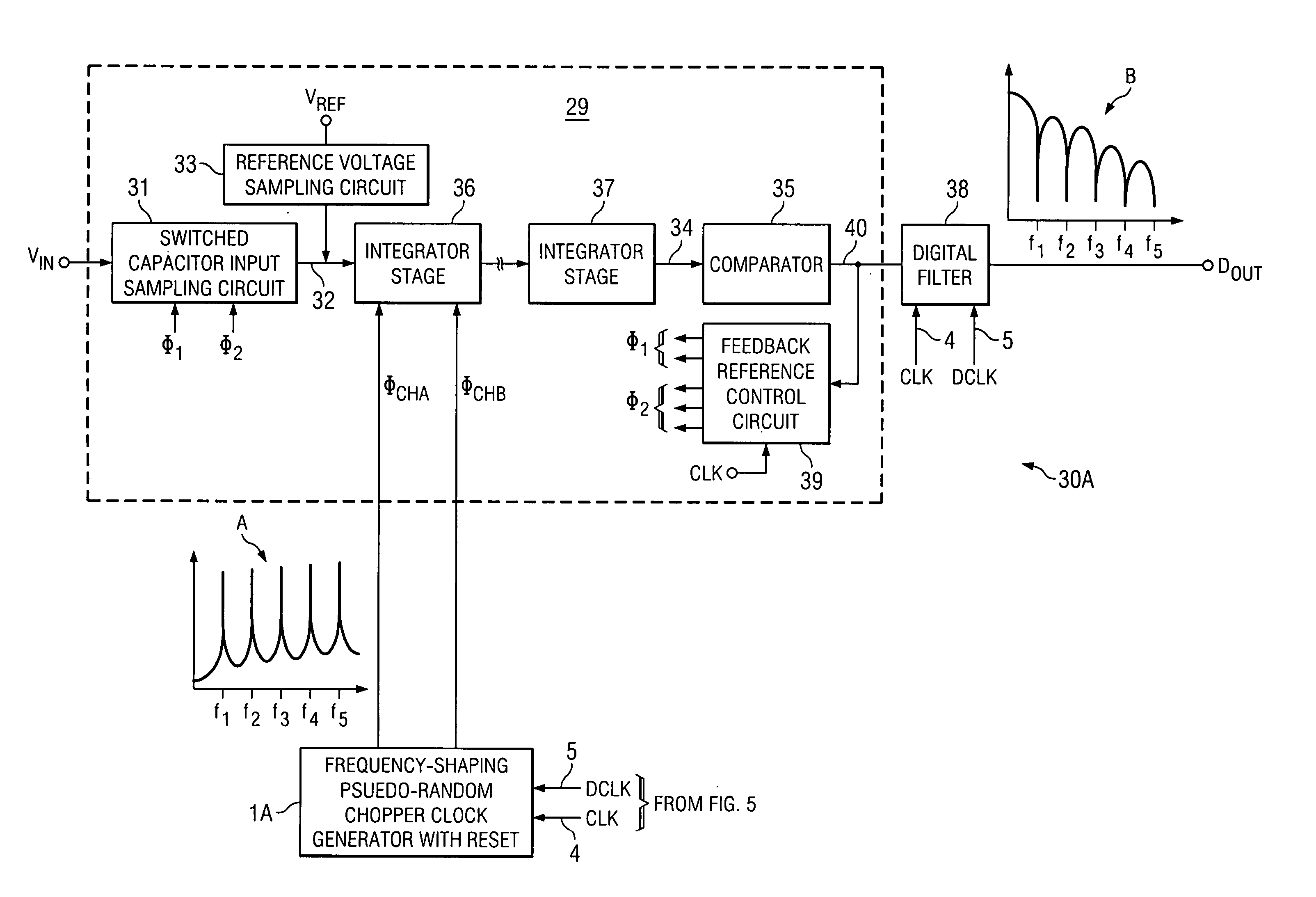
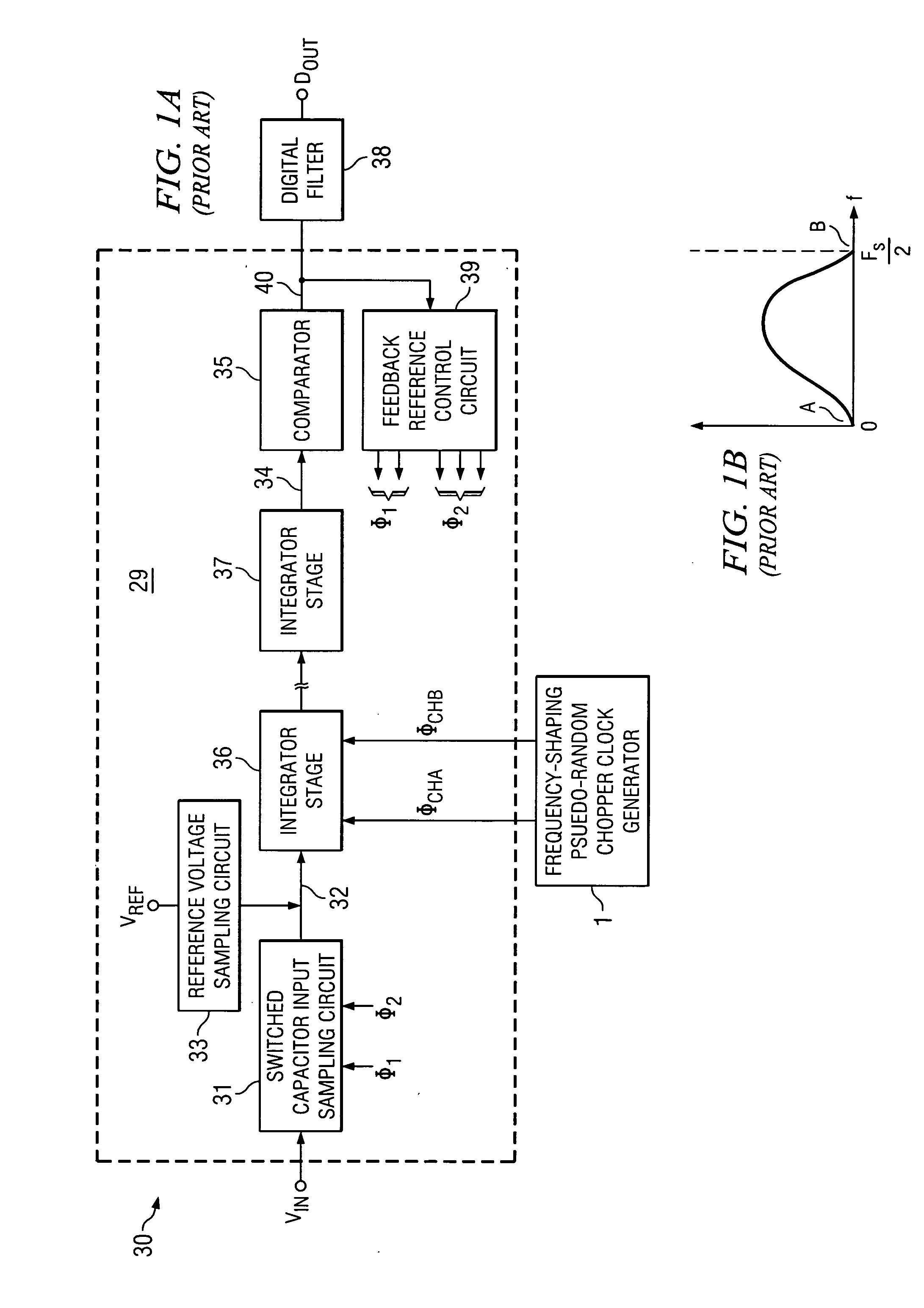
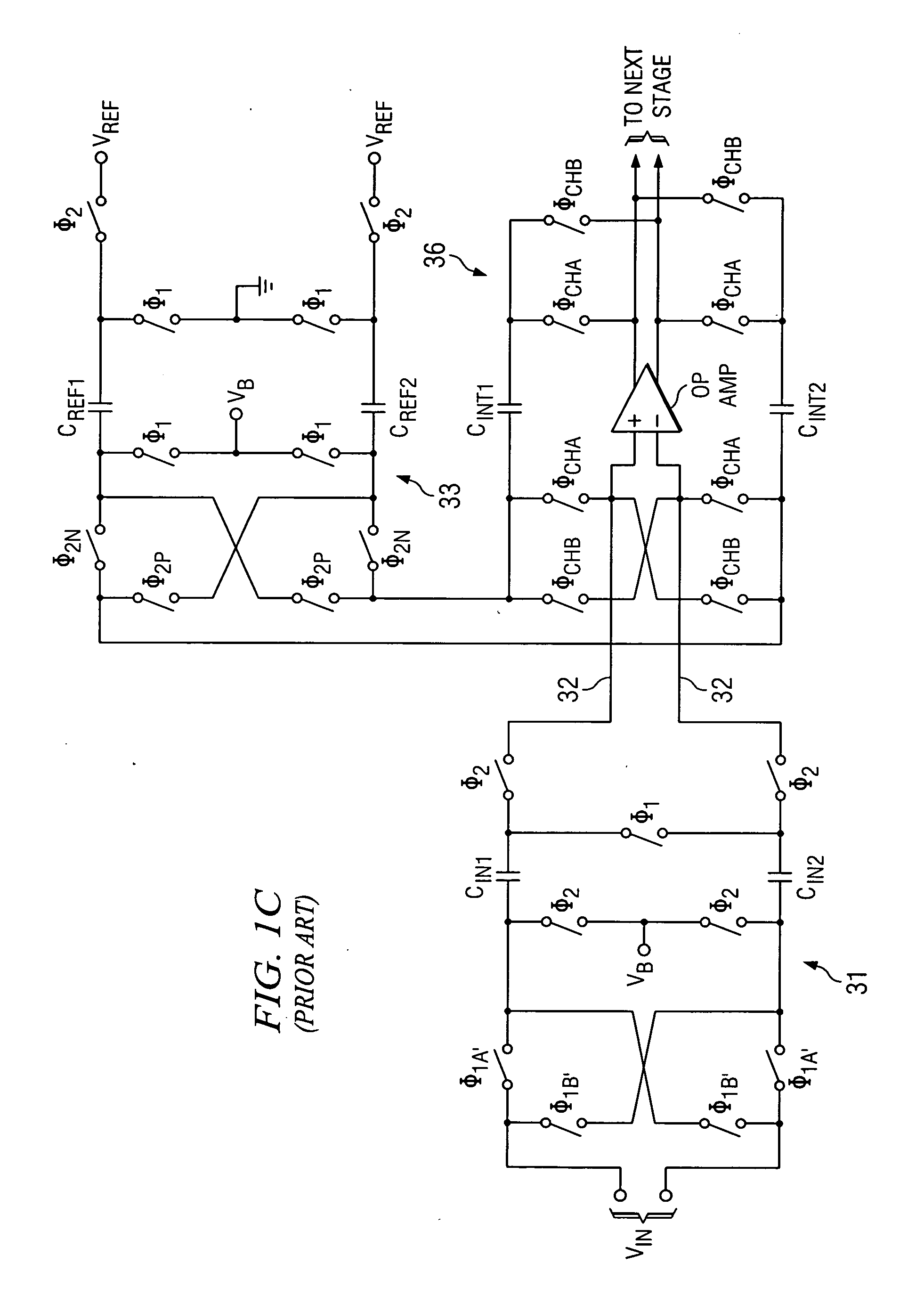
Oversampling analog-to-digital converter and method with reduced chopping residue noise
A delta-sigma modulator includes a chopper-stabilized integrator, a quantizer having an input coupled to an output of the integrator, an input signal acquiring circuit controlled by a switched reference feedback circuit and having an output coupled to the input of the integrator, and a frequency-shaped pseudo-random chopper clock signal generator circuit including a pseudo-random sequence generator and producing a frequency-shaped pseudo-random clock signal. Resetting circuitry is coupled to reset inputs of the pseudorandom sequence generator to reset it in synchronization with the digital output of the chopper-stabilized delta-sigma modulator to prevent noise caused by wrap-around operation of the pseudorandom sequence generator. A logic circuit produces chopper clock signals in response to the frequency-shaped pseudo-random clock signal and applies them to various input switches and output switches of the integrator.
Owner:TEXAS INSTR INC
Position encoder using statistically biased pseudorandom sequence
InactiveUS6789042B2Improve accuracyAngles/taper measurementsDigital computer detailsManchester codeTransmittance
A position sensor encodes absolute position via n consecutive members of a pseudorandom sequence of bits, where each bit (30a-30k) comprises a region of high transmission or reflectivity adjacent to a region of low transmission or reflectivity. The pseudorandom sequence is chosen such that every series of n consecutive bits (30a-30k) in the sequence is predominantly formed from a predetermined bit value (1 or 0). The light transmitted or reflected from the series is therefore detected as a substantially periodic intensity pattern (42), which can be processed via Fourier analysis to yield an accurate interpolation of relative position. An example is given of a pseudorandom sequence, which can be represented as a cyclic Manchester code, in which at least 8 members of every series of 11 consecutive bits has a bit value of 1.
Owner:BISHOP INNOVATION PTY LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com