Social video information security method and system
A video information and security technology, applied in the field of social video information security and systems, can solve problems such as the inability to guarantee the randomness of communication keys, the lack of user personal copyright protection, and the inability to verify user identities, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
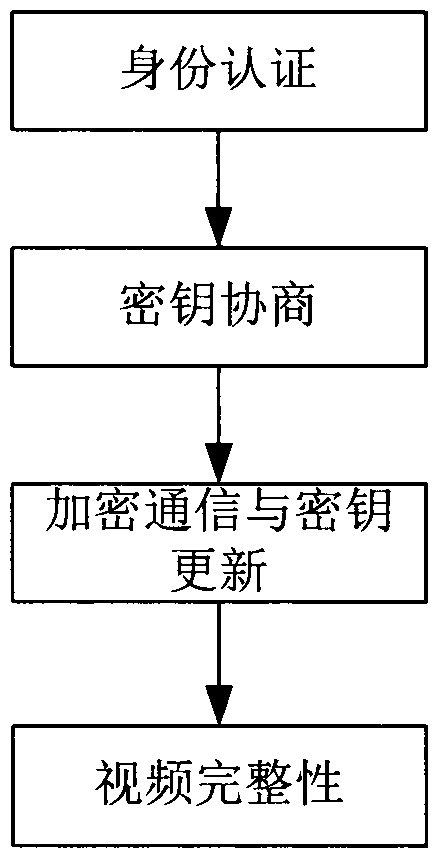
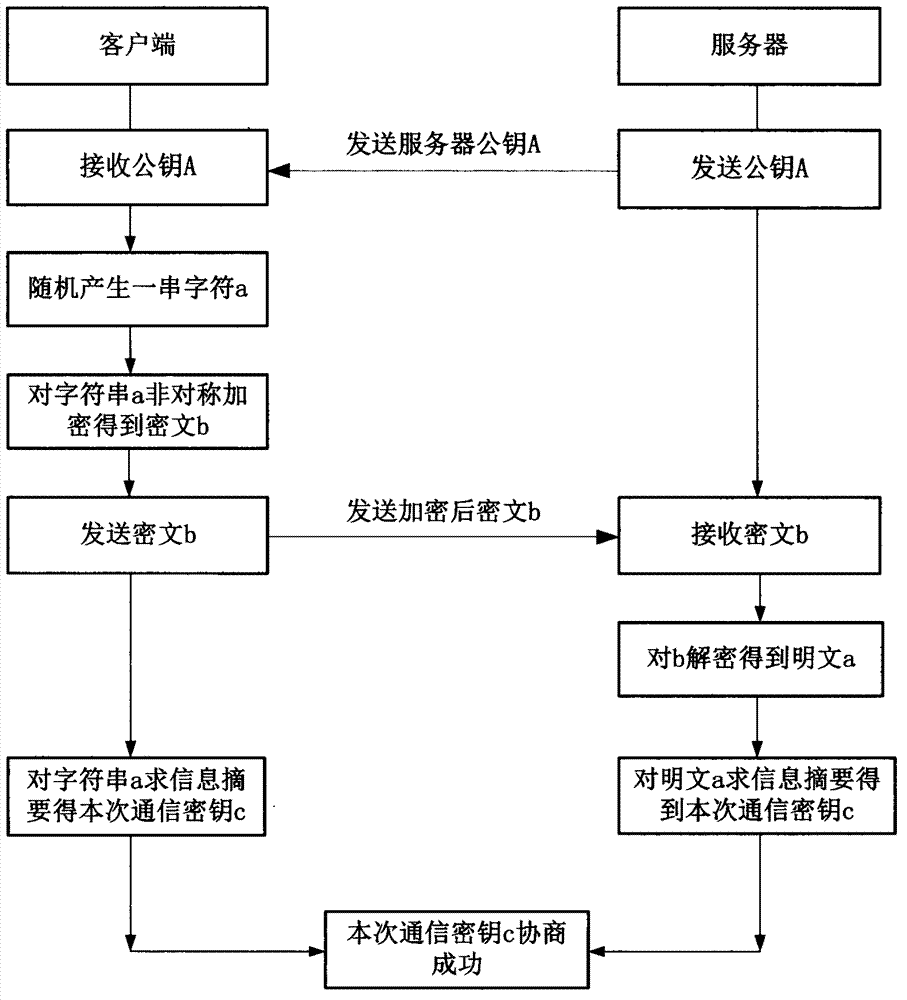
[0035] The present invention uses multiple data encryption methods, mainly including 128-bit block encryption AES algorithm; 1024-bit asymmetric encryption RSA algorithm; 64-bit stream encryption chaos pseudo-random sequence (CPRS Chaotic Pseudo-Random Sequence) algorithm and data summary Algorithm sha-1 algorithm, which mainly solves the following functional modules: (1) user identity authentication (2) key negotiation (3) media data encrypted transmission (4) key update (5) video integrity
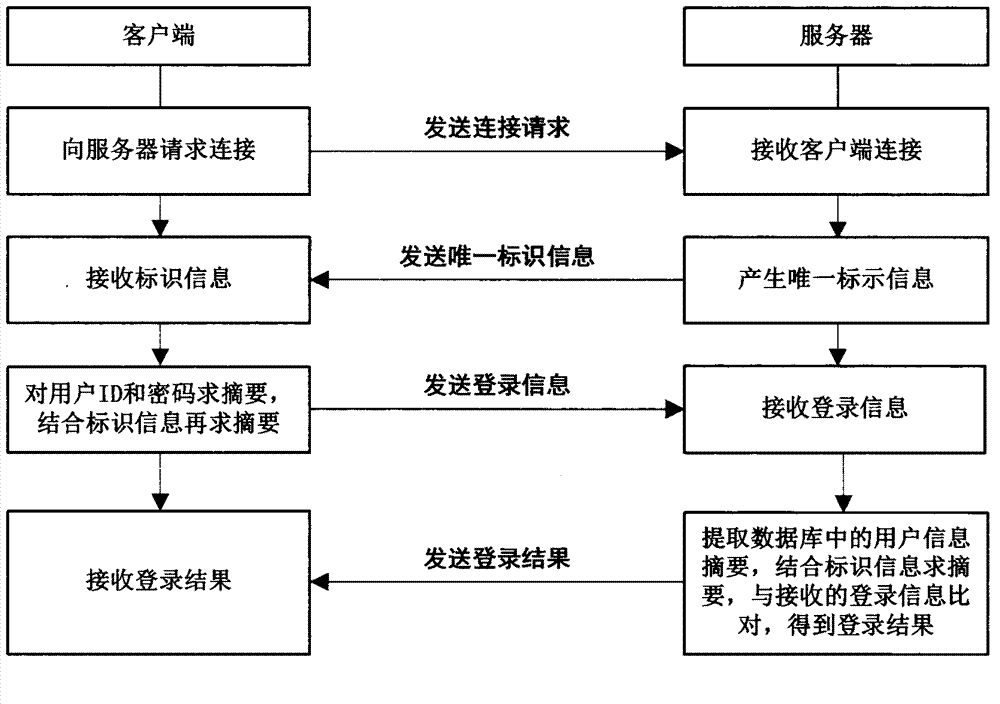
[0036] (1) User identity authentication
[0037] Before the two parties establish communication, the legitimacy of the client user must first be verified. Only with legitimate authenticated users, the server will establish a secure communication connection with it and provide services.
[0038]When the user requests a server connection, the server sends the server time, that is, the user login time, as the unique identification information to the user, and the user uses the personal ID ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com