Ultra-chaos pseudo random sequence generator
A pseudo-random sequence and ultra-chaotic technology, which is applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of chaotic signals that are difficult to decipher and decipher
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
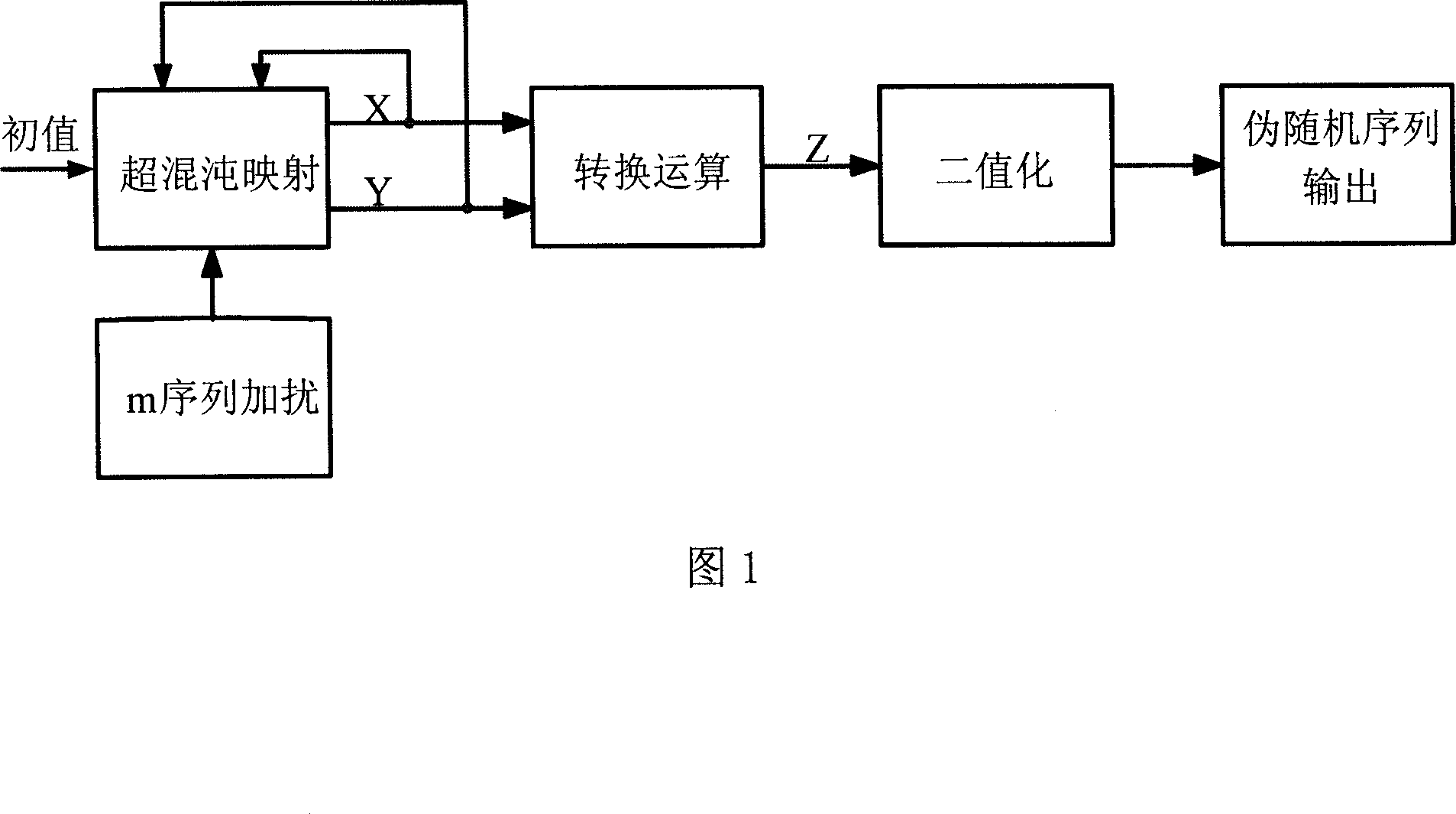
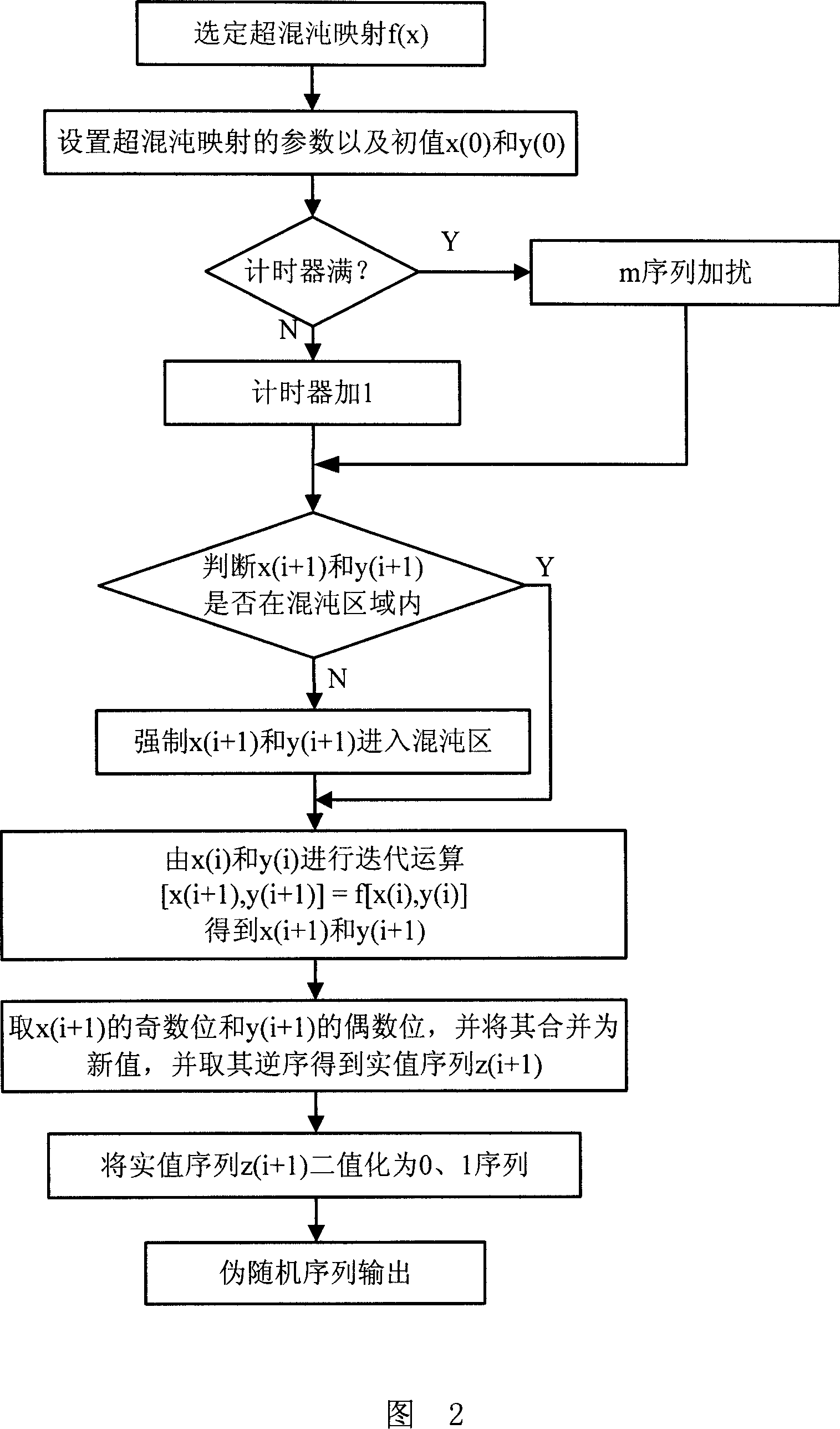
Image
Examples
example 1
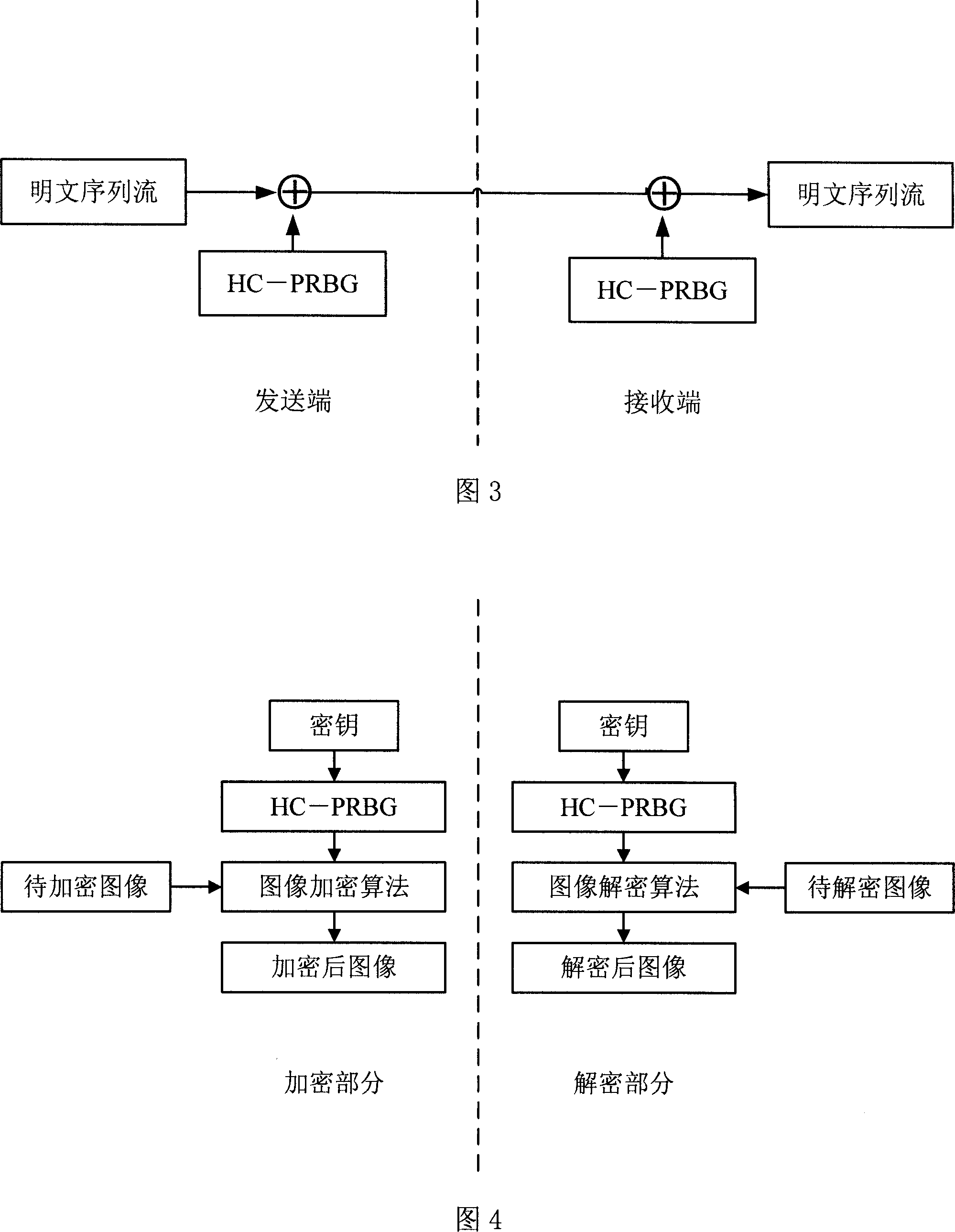
[0056] Let's take the application of HC-PRBG in image encryption as an example. In order to protect image data from being stolen, illegally copied and disseminated during transmission, various encryption schemes have been proposed to protect the security of image data. A common characteristic of these encryption technologies is that the encrypted data is transformed into a set of meaningless codes. Once interceptors spot code like this, they know they have very valuable information. In order to protect the security of image data and avoid exposing the value of image data, the information redundancy of images can be used to hide one image in another image. For image encryption, possible monitors or illegal interceptors can intercept and decipher the ciphertext, or destroy the ciphertext before sending it, thereby affecting the security of confidential information; but for image information hiding , it is difficult for a possible monitor or illegal interceptor to judge whether...
example 2
[0058] An important field of random sequence application is frequency hopping communication. The carrier frequency of the frequency hopping communication system is controlled by a set of code sequences. In a frequency band much wider than the information bandwidth, it randomly hops according to a certain rule. This hopping rule is called is the frequency hopping pattern. The code sequence that controls the frequency hopping pattern is called a frequency hopping sequence. Since there is no difference between the frequency hopping pattern and the frequency hopping sequence in essence, the two are no longer distinguished. The frequency hopping sequence is generally generated by a pseudo-random sequence. The most effective way to counter frequency hopping is to decipher the frequency hopping pattern, so as to realize tracking interference. A good frequency hopping sequence has better randomness, as long a period as possible, uniform distribution in the working frequency band, and ...
example 3
[0061] Ultra-wideband (UWB) technology is a new type of short-distance high-speed wireless communication technology that has attracted much attention. This technology has been used by the military for many years. After UWB is opened in the civilian field, it is expected to inject new vitality into the short-distance wireless access market by virtue of its advantages such as ultra-high transmission speed, low power, and low cost. Pulse radio vividly illustrates the characteristics of UWB transmitting narrow pulses directly for communication. In view of the relatively high requirements of the system on power efficiency, the modulation method of pulse radio generally adopts binary pulse phase modulation (PPM). In order to improve the confidentiality of communication, Chaotic Pulse Phase Modulation (CPPM) is adopted. This communication scheme is based on chaotic pulse sequences, and the time interval between pulses is determined by HC-PRBH. This pulse train with chaotic pulse s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com